Page 1

HP-UX Bastille Version B.3.3 User Guide
HP Part Number: 5900-0871
Published: June 2010
Edition: 1
Page 2

© Copyright 2010 Hewlett-Packard Development Company, L.P.
Confidential computersoftware. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standardcommercial license.The informationcontained hereinis subject to change without notice. The only warranties forHP products
and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. UNIX is a registered
trademark of The Open Group.
Trademark Acknowledgments
UNIX® is a registered trademark of The Open Group.
Intel® Itanium® is a trademark of Intel Corporation in the U.S. and other countries.
Page 3

Table of Contents
1 About this product..........................................................................................................7
1.1 Features and benefits.........................................................................................................................7
1.2 Compatibility....................................................................................................................................8
1.3 Performance.......................................................................................................................................8
1.4 Support..............................................................................................................................................8
2 Installing HP-UX Bastille.................................................................................................9
2.1 Installation requirements..................................................................................................................9
2.2 Installation.........................................................................................................................................9
3 Using HP-UX Bastille....................................................................................................11
3.1 Creating a security configuration profile........................................................................................11
3.2 Configuring a system......................................................................................................................13
3.3 Assessing a system..........................................................................................................................13
3.3.1 Using scored reports ...............................................................................................................14
3.4 Reverting.........................................................................................................................................16
3.5 Monitoring drift...............................................................................................................................17
3.6 Locating files ...................................................................................................................................17
4 Removing HP-UX Bastille..............................................................................................19
5 Troubleshooting............................................................................................................21
5.1 Diagnostic tips.................................................................................................................................21
5.2 General use tips...............................................................................................................................21
5.3 Known issues and workarounds.....................................................................................................21
5.3.1 Changes made by HP-UX Bastille might cause other software to stop working...................21
5.3.2 Cannot use X because $DISPLAY is not set............................................................................22
5.3.3 System is in original state........................................................................................................22
5.3.4 HP-UX Bastille must be run as root........................................................................................22
5.3.5 Problems opening, copying, or reading files..........................................................................22
5.3.6 Errors related to individual configuration files......................................................................22
5.3.7 HP Secure Shell locks you out of your system immediately when passwords expire...........22
5.3.8 HP-UX Bastille configures a firewall using IPFilter................................................................22
5.3.9 Security Patch Check...............................................................................................................22
5.3.10 Rerun HP-UX Bastille after installing new software or applying new patches....................22
6 Support and other resources.......................................................................................23
6.1 Contacting HP.................................................................................................................................23
6.1.1 Before you contact HP.............................................................................................................23
6.1.2 HP contact information...........................................................................................................23
6.1.3 Subscription service.................................................................................................................23
6.1.4 Documentation feedback.........................................................................................................23
6.2 Related information.........................................................................................................................23
6.3 Typographic conventions................................................................................................................24
Table of Contents 3
Page 4

A Install-Time Security (ITS) using HP-UX Bastille..........................................................27
A.1 Choosing security levels.................................................................................................................27
A.2 Choosing security dependencies....................................................................................................30
A.3 Selecting security levels during installation...................................................................................30
B Configuring HP-UX Bastille for use with Serviceguard.............................................31
B.1 Configuring Sec20MngDMZ or Sec30DMZ security levels............................................................31
B.2 Configuring Sec10Host level...........................................................................................................31
C Question modules........................................................................................................33
D Sample weight files......................................................................................................63
D.1 all.weight........................................................................................................................................63
D.2 CIS.weight......................................................................................................................................64
E CIS mapping to HP-UX Bastille...................................................................................67
Index.................................................................................................................................71
4 Table of Contents
Page 5

List of Figures
3-1 HP-UX Bastille user interface........................................................................................................12
3-2 Standard assessment report..........................................................................................................14
3-3 Scored assessment report..............................................................................................................15
3-4 Assessment report score................................................................................................................16
A-1 Security software dependencies....................................................................................................30
5
Page 6

List of Tables
3-1 Question modules.........................................................................................................................12
A-1 Security levels................................................................................................................................27
A-2 Host-based Sec10Host, Sec20MngDMZ, and Sec30DMZ security settings..................................28
A-3 Additional Sec20MngDMZ security settings................................................................................29
A-4 Additional Sec30DMZ security settings........................................................................................29
6 List of Tables
Page 7

1 About this product
HP-UX Bastille is a system hardening and reporting program that enhances the security of the
HP-UX operating system by consolidating essential hardening and lock-down checklists from
industry and government security organizations, and making them accessible to administrators
in an easy to use package. The HP-UX Bastille GUI interface guides users through creating a
custom security configuration profile. The policy configuration engine hardens HP-UX to
specification by locking down each selected security item. Security items include:
• Configuring daemons, services, firewalls, and client software to use more secure settings
• Disabling unused or unneeded inetd services
• Creating chroot jails for commonly used server programs
• Assessing the current HP-UX system against all relevant lock-down items with the reporting
feature
• Applying saved configuration profiles to multiple similar machines with a command-line
batch mode
These HP-UX Bastille features ease compliance with regulatory requirements and
industry-consensus security benchmarks like the Center for Internet Security (CIS) benchmark.
HP-UX Bastille also facilitates internal and external security audits.
NOTE: HP-UX Bastille is built from the open-source, cross-platform software program Bastille.
HP made significant contributions to the open-source Bastille software over many years. The
original Linux version is now named Bastille-Linux to avoid confusion with other cross-platform
implementations, and is not covered by this document.
1.1 Features and benefits
HP-UX Bastille provides the following features and benefits:
• Locks down the system
— Increases security by configuring daemons and system settings
— Turns off unnecessary services such as pwgrd
— Assists with creation of chroot jails to partially limit the vulnerability of common
internet services such as web servers and DNS
— Configures automatic runs of Software Assistant (SWA) or Security Patch Check
— Configures an IPFilter-based firewall
• Provides an interactive, wizard-style GUI interface
— Guides users to optimize the trade off between security, usability, and functionality
— Explanatory text helps less experienced administrators make appropriate security
decisions
• Reports security configuration state
— Generates reports in HTML, text, and config file format
— Establishes a baseline for comparison to later configuration differences with the
bastille_drift command
• Returns the security configuration to the state before HP-UX Bastille was run with the revert
-r feature.
— Provides a safety net in case of unexpected incompatible changes when hardening
running systems
• Integrates with HP Systems Insight Manager (SIM)
— Locks down and reporting available from SIM menus
— SIM.config pretested configuration for SIM server lock down
1.1 Features and benefits 7
Page 8

• Install-time Security (ITS) for Ignite-UX and Update-UX
— Applies predefined HP-UX Bastille security configuration profile during first system
boot
— Enables out-of-the-box security by avoiding any vulnerability window after initial install
1.2 Compatibility
There are no differences between the Intel Itanium-based and PA-RISC implementation. Some
products depend on services, system settings, or network ports that HP-UX Bastille secures. In
cases where products depend on out-of-the-box settings that HP-UX Bastille might change,
dependencies are documented.
HP-UX Bastille is available for the following operating systems:
• HP-UX 11i v1 (11.11)
• HP-UX 11i v2 (11.23)
• HP-UX 11i v3 (11.31)
NOTE: HP-UX Bastille for 11i v1 is still supported, but no longer being developed.
For more information about HP-UX Bastille compatibility with Serviceguard, see Appendix B
(page 31) and the Serviceguard documentation available at http://docs.hp.com/en/netsys.html.
1.3 Performance
Although HP-UX Bastille does not directly affect performance, IPFilter settings such as host-based
firewall can cause a slight decrease in network performance. Install Time Security (ITS) does not
affect performance, but if the DMZ or MngDMZ security levels are used, network performance
might slow IPFilter packet filtering.
1.4 Support
For customers with an HP-UX support agreement, technical support is available through the HP
World Wide Response Centers at www.hp.com/support. Support is also offered through the IT
Resource Center at www.itrc.hp.com.
For the HP-UX discussion forum, from the ITRC home page click Forums→HP-UX→Security.
Or, the direct link is ITRC Forums Security.
If you find a security vulnerability associated with HP-UX Bastille, report it at:
http://welcome.hp.com/country/us/en/sftware_security.html.
HP-UX Bastille makes changes that can potentially affect the functionality of other software. If
you experience problems after applying HP-UX Bastille changes to your system, be sure your
support contact knows that you run HP-UX Bastille on your system.
8 About this product
Page 9
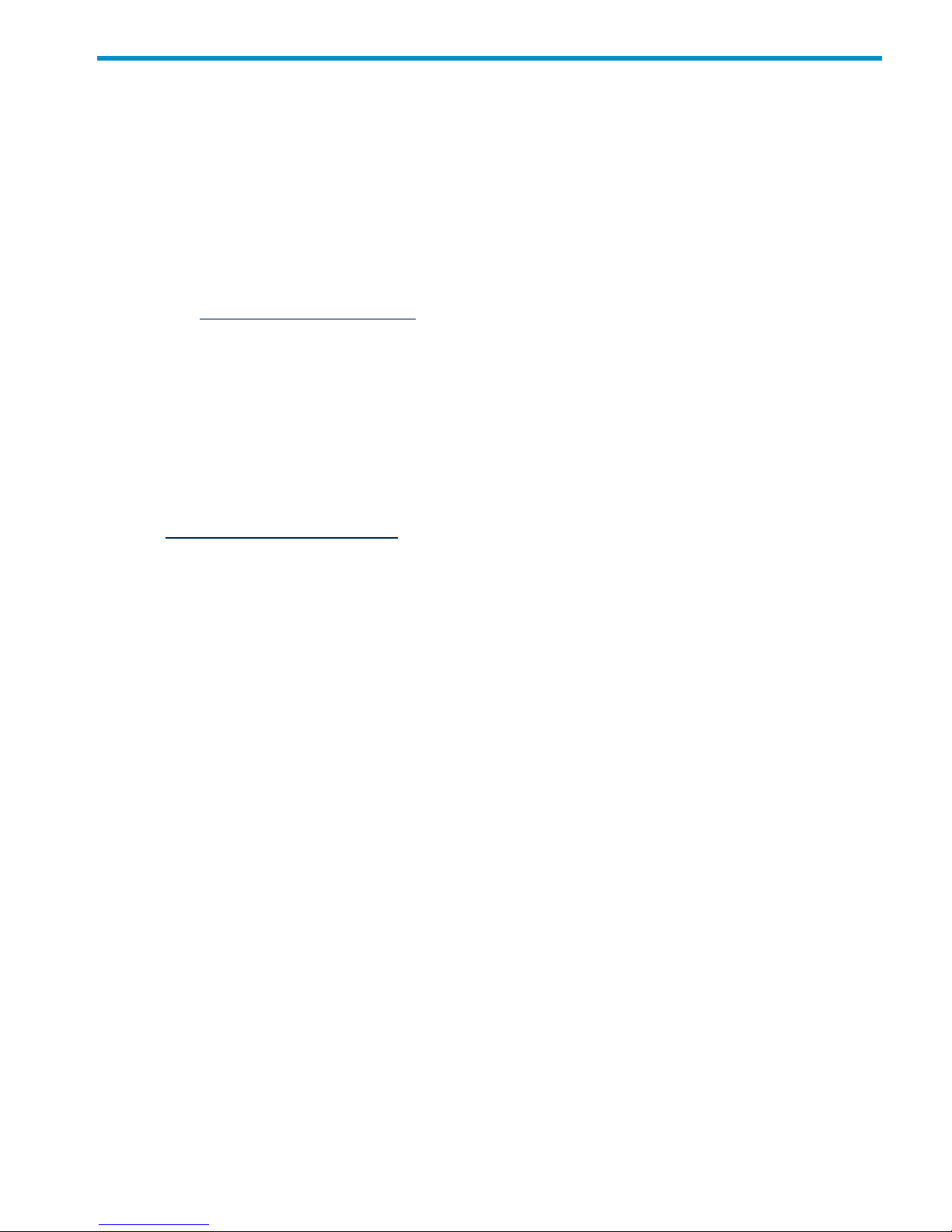
2 Installing HP-UX Bastille
2.1 Installation requirements
The following prerequisites are required to install HP-UX Bastille:
• Root access
• Perl dependencies:
— HP-compiled version of Perl D.5.8.0.D or later
— Perl/Tk version 8.00.23 or later
Perl is available for download at:
https://www.hp.com/go/perl
• For operating system compatibility, see “Compatibility” (page 8).
• 1 MB disk space
2.2 Installation
HP-UX Bastille is included as recommended software on the Operating Environment media and
can be installed and run with Ignite-UX or Update-UX. HP-UX Bastille is installed by default,
and a manual installation is only necessary to obtain the latest version from the web.
To download the latest version of HP-UX Bastille, see the following website:
http://www.hp.com/go/bastille
Installation command:
# swinstall -s <path to depot> HPUXBastille
2.1 Installation requirements 9
Page 10

10
Page 11

3 Using HP-UX Bastille
HP-UX Bastille provides three main services:
• Creating a security configuration profile for a system
An X Window GUI user interface presents a series of questions that explain a security issue
and describe the resulting action needed to lock down the HP-UX system. Each question
also describes the high-level cost and benefit of each decision. The user decides how HP-UX
Bastille handles the issues during lock down. After answering all questions, HP-UX Bastille
presents the option to save the security configuration profile information in a default
configuration file, and use the configuration file to lock down the system. Alternatively, the
user can choose to save the security configuration profile in a custom-named configuration
file without continuing to lock down the system.
• Configuring a system (hardening/lock down)
Reading from a configuration file, the HP-UX Bastille configuration-policy engine
automatically completes each lock-down step and produces a list of the remaining actions
that the user must manually perform to complete the lock-down process. Log files are
produced to record all actions taken and any errors encountered during the configuration
process. The configuration service is invoked either during the interactive session to create
a configuration file (see above), or from the command line using the batch-mode option.
The command-line mode is useful for replicating a security configuration to multiple
machines, or when using one of the predefined configuration files supplied with HP-UX
Bastille. In these cases, an alternative configuration file is specified by using the -f option.
• Assessing a system
HP-UX Bastille assesses the existing security configuration state of an HP-UX system by
testing the system against each security issue. A reporting module creates files that contain
an itemized summary of the current security status of the system configuration. Files are
produced in HTML, text, and configuration formats. The percentage of weight items secured
properly is generated. This service can be used to audit a large number machines that have
the same operating system and applications installed. Scored assessment reports can be used
to select only a subset of the security issues.
The most common use of HP-UX Bastille is on a single machine, using the GUI interface to
create and apply a customized security configuration profile in the same session. Only the
default configuration file is used. If modifications are required later, the HP-UX Bastille GUI
interface is invoked again to make changes and apply them in the same session.
If multiple machines or configuration files must be managed, the creation and application
of security configuration profiles are usually independent operations and scripted. In that
case, non-interactive command-line options may be more useful when configuring a system.
For example, with a set of similar HP-UX servers, a single initial "golden" configuration file
can be created on one machine with the GUI interface, then copied and applied to all the
other machines with the batch-mode option. Similarly, if multiple configuration files are
needed, then scripts using the -f option are frequently used.
3.1 Creating a security configuration profile
1. Change to root user.
2. If using a remote X server, ensure that it is running, and that the local $DISPLAY variable
is set correctly. Test using xterm or xclock.
3. Start HP-UX Bastille. If HP-UX Bastille is installed, the PATH environment variable has been
updated. In this case, use:
# bastille
3.1 Creating a security configuration profile 11
Page 12
If the PATH environment variable has not been updated, use:
# /opt/sec_mgmt/bastille/bin/bastille
Figure 3-1 shows the main screen of the HP-UX Bastille user interface.
Figure 3-1 HP-UX Bastille user interface
4. Answer the questions that appear on screen. The questions are categorized by function.
Check marks are used as completion indicators to track your progress through the program.
Only questions that apply to your operating system and relate to installed tools appear.
Each question explains a security issue and describes the resulting action needed to lock
down the HP-UX system. Each question also describes the high-level cost and benefit of
each decision.
Use the Explain More/Explain Less button for more or less verbose explanations. Not all
questions have both long and short answers. For a complete list of questions with detailed
information about each item, see Appendix C (page 33).
Table 3-1 Question modules
DescriptionQuestion module
Installs and configures applications for security bulletin compliance checkingPatches
Performs SUID and other permission tuningFilePermissions
Configures login settings and access to cron
AcountSecurity
Disables unrequired inetd services
Secureinetd
Turns off services that are often unrequired or a security riskMiscellaneousDaemons
Disables or configures mail securitySendmail
Disables or configures DNS securityDNS
Configures Apache web server securityApache
Configures FTP securityFTP
12 Using HP-UX Bastille
Page 13

Table 3-1 Question modules (continued)
DescriptionQuestion module
Configures security services that are unique to the HP-UX platformHP-UX
Creates an IPFilter-based firewallIPFilter
5. After you answer all the questions, the Save/Apply button appears. If you want to proceed
to configuring the system, click the Save/Apply button to save and apply your configuration.
HP-UX Bastille applies the changes as described in “Configuring a system” (page 13).
NOTE: You can use the menu bar to save or load a configuration file at any time during
the process. However, your configuration file contains additional questions that might be
irrelevant to the target system unless the file is saved with the Save/Apply button. This
button is at the end of the question list and only available after all the questions are complete.
The Save/Apply mechanism always saves a copy in the default location /etc/opt/
sec_mgmt/bastille/config. To save your configuration file in the location of your
choice, use the menu bar File item.
3.2 Configuring a system
1. Depending on the mode you are using:
• If you are running HP-UX Bastille in batch mode to make configuration changes:
— If you are using the default configuration file path /etc/opt/sec_mgmt/
bastille/config:
# bastille -b
— Otherwise, specify the path to the configuration file explicity with the -f option:
# bastille -b -f file
• If you are continuing from an HP-UX Bastille GUI session that is creating or modifying
the configuration file (see “Creating a security configuration profile” (page 11)), status
messages from the configuration process appear in the GUI box.
2. Review log files. To view the logs in real time:
# tail -f <log file>
The action log contains the steps performed when the system was changed. It is only created
if the changes are applied to the system. Action log files appear in /var/opt/sec_mgmt/
bastille/log/action-log.
The error log contains any errors encountered when the system was changed. It is only
created if errors occur during execution. Error log files appear in /var/opt/sec_mgmt/
bastille/log/error-log.
3. Complete the items in the TODO.txt file. This list is located in /var/opt/sec_mgmt/
bastille/TODO.txt.
NOTE: Changes must be applied to the system to create the TODO.txt file.
The configuration is secure after the items in the TODO.txt file are completed.
3.3 Assessing a system
HP-UX Bastille can assess the status of a system with the --assess or --assessnobrowser
options. The --assess option displays the report in a local browser.
The --assessnobrowser option saves the report in the following file locations:
3.2 Configuring a system 13
Page 14

/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report.html
/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report.txt
/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report-log.txt
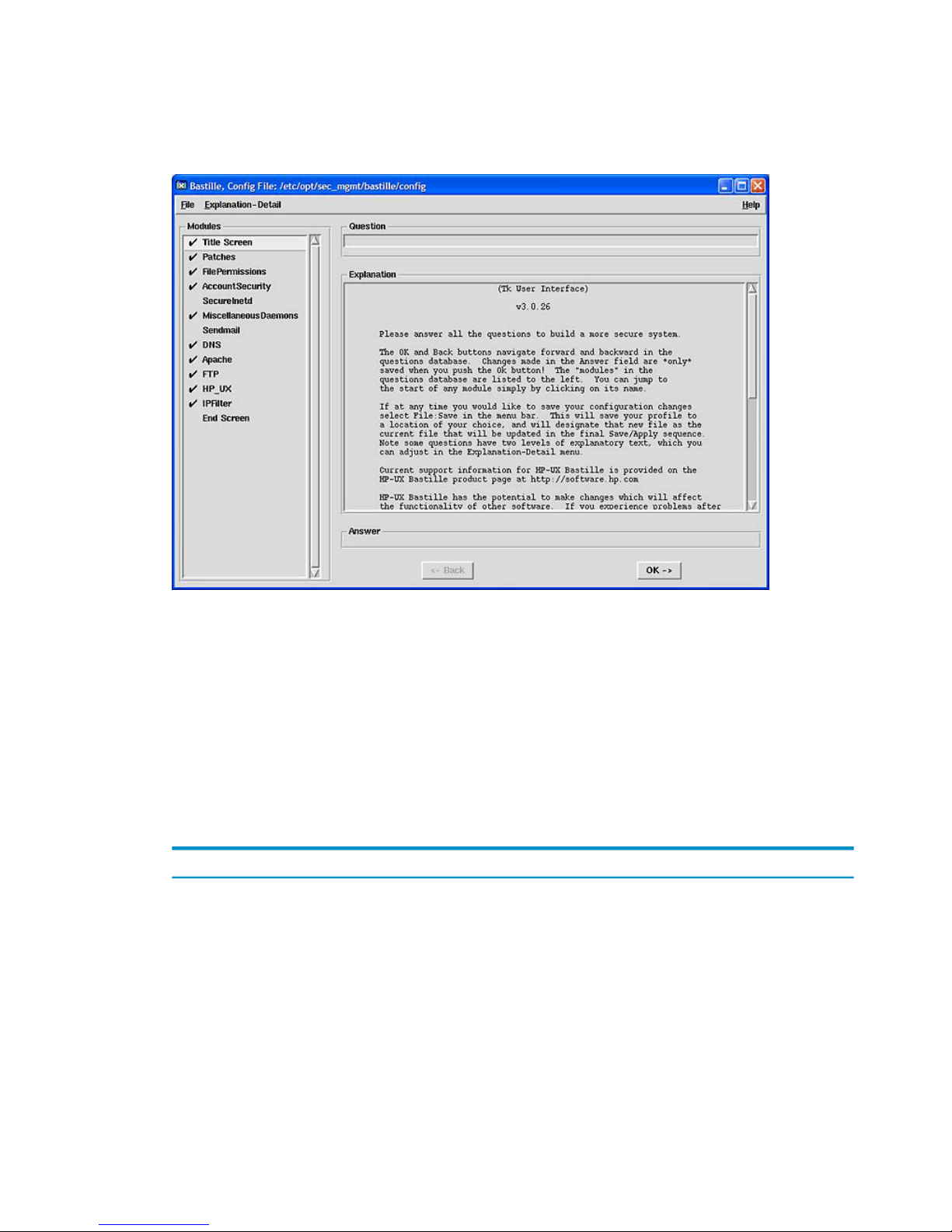
Figure 3-2 Standard assessment report
For each question, the standard report lists one of the following results:
Yes The associated HP-UX Bastille lock down is applied to the
product or service shipped with HP-UX. The status of
products or services that are not shipped with the HP-UX OE
is not always detected. HP-UX Bastille might not detect all
variations of ways to disable or enable a service or feature.
Accepted standard configurations are detected.
No The configuration for the corresponding question is not
applied.
<Set to value> Displays the non-Boolean setting corresponding to the
question.
Not Defined A non-Boolean setting is defined, but is not set. The system
default settings apply.
N/A: S/W Not Installed The relevant software is not installed, so lock down for this
item is not necessary.
3.3.1 Using scored reports
HP-UX Bastille assessment reports can be scored to show the percentage of selected lock-down
items that are properly secured on the system. This provides a single indicator to judge the initial
security configuration state of a system, or to gauge the hardening progress when incrementally
aligning a system to a security configuration goal.
For example, a weights file can be prepared to select only HP-UX Bastille lock-down items that
match equivalent items in an industry-consensus security benchmark. By reviewing scored
reports using this file on all similar HP-UX servers in the datacenter, a systems manager can
evaluate the resources required to bring these servers into compliance with the benchmark.
14 Using HP-UX Bastille
Page 15

Enable scored reports by creating the /etc/opt/sec_mgmt/bastille/HPWeights.txt file,
and populating it with an entry for each HP-UX Bastille lock-down item to be considered in the
final score. The HPWeights.txt file format is similar to an HP-UX Bastille configuration file,
except only entries for items to be scored are present, and the item value is always set to "1".
HP-UX Bastille detects the HPWeights.txt file when generating an assessment, and adds
Weight and Score columns to the report. The final score is a percentage calculated from the
number of the weighted items that have a result equal to "Yes".
Figure 3-3 Scored assessment report
The assessment report contains the following columns in addition to the columns contained in
the standard report:
Weight The weight column indicates the item was selected in the weights file.
Score The score column displays a 1.00 if the item was both weighted and secured properly.
3.3 Assessing a system 15
Page 16
Figure 3-4 Assessment report score
The percentage of weight items secured properly is displayed at the end of the .txt report and
in the header row of the .html report. For example, see Figure 3-4
Sample weight files that match the default configuration files are provided in /etc/opt/
sec_mgmt/bastille/configs/defaults. This directory also includes the template file
all.weight which contains all possible HP-UX question items as selected. For sample files,
see Appendix D (page 63).
3.4 Reverting
If you want to revert the system files to the state they were in before HP-UX Bastille was run,
use the revert option:
# bastille -r
IMPORTANT: Before using the revert feature, read the revert-actions script to ensure
changes do not disrupt your system. This file appears in /var/opt/sec_mgmt/bastille/
revert/revert-actions.
If changes were made to the system after HP-UX Bastille was run, either manually or by other
programs, review those changes to verify they still work and have not broken the system or
compromised its security. Certain firewall options and reverting the system can make a system
less secure.
After running the revert option, look at the TOREVERT.txt file to ensure that the tasks needed
to finalize the revert process are complete. The file is located in /var/opt/sec_mgmt/
bastille/TOREVERT.txt.
16 Using HP-UX Bastille
Page 17
IMPORTANT: When reverting to the configuration prior to the use of HP-UX Bastille, security
configuration changesare undone temporarily. Other manual configuration changes or additional
software installed after HP-UX Bastille was initially run might require a manual merge of
configuration settings.
3.5 Monitoring drift
The bastille_drift program creates HP-UX Bastille configuration baselines and compares
the current state of the system to a saved baseline. This enables the user to compare changes, if
any, against a saved baseline.
NOTE: When first run successfully, HP-UX Bastille automatically saves a baseline in the default
location /var/opt/sec_mgmt/bastille/baselines.
You can use HP-UX Bastille to monitor drift as follows:
• To save a baseline:
# bastille_drift --save_baseline baseline
• To compare the current state of the system to a saved baseline:
# bastille_drift --from_baseline baseline
Run the bastille_drift utility when new software or patches are installed to check for
changes in the system. The bastille_drift utility also identifies system changes when
swverify is run using -x fix=true or the -F option for vendor-specific fix scripts.
For more information, see bastille_drift(1M).
3.6 Locating files
This section describes the location of important files.
The configuration file contains the answers to the most recently saved session.
/etc/opt/sec_mgmt/bastille/config
The error log contains any errors HP-UX Bastille encountered while making changes to the
system.
/var/opt/sec_mgmt/bastille/log/error-log
The action log contains the specific steps that HP-UX Bastille performed when making changes
to the system.
/var/opt/sec_mgmt/bastille/log/action-log
The TODO.txt file list contains the tasks the must be completed to ensure the system is secure.
/var/opt/sec_mgmt/bastille/TODO.txt
The revert-actions script is part of the revert feature. It returns the changed files to the state
they were in before HP-UX Bastille was run.
/var/opt/sec_mgmt/bastille/revert/revert-actions
The TOREVERT.txt file contains the tasks that must be completed to finish reverting the machine
to the state it was in before HP-UX Bastille was run.
/var/opt/sec_mgmt/bastille/TOREVERT.txt
The assessment reports are available as HTML, text, and a configuration file.
/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report.html
/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report.txt
/var/opt/sec_mgmt/bastille/log/Assessment/assessment-report-log.txt
3.5 Monitoring drift 17
Page 18

The Drift file contains information about any configuration drift experienced since the last
HP-UX Bastille run. This file is only created when an earlier HP-UX Bastille configuration was
applied to the system.
/var/opt/sec_mgmt/bastille/log/Assessment/Drift.txt
18 Using HP-UX Bastille
Page 19

4 Removing HP-UX Bastille
Use the swremove command to remove HP-UX Bastille from an HP-UX machine. When HP-UX
Bastille is removed, the system does not revert to the state it was in before HP-UX Bastille was
installed. HP-UX Bastille removal leaves behind the revert-actions script. This script enables
the administrator to revert the configuration files that HP-UX Bastille modified without an HP-UX
Bastille installation. In most cases, HP-UX Bastille changes are recorded at the file level, so the
revert-actions script only reverts the modified files. Other changes can be reverted
programmatically, even if you made intervening changes in the same file. For example, the
permissions file can be reverted to its original form even if you modified the file.
To revert changes on a system where HP-UX Bastille is removed:
1. # cd /var/opt/sec_mgmt/bastille/revert/
2. # chmod 0500 revert-actions
3. # ./revert-actions
4. # mv revert-actions revert-actions.last
5. Check for a TOREVERT.txt file.
/var/opt/sec_mgmt/bastille/TOREVERT.txt
If the file exists, complete the actions listed.
19
Page 20

20
Page 21
5 Troubleshooting
5.1 Diagnostic tips
When troubleshooting issues with HP-UX, remember these tips:
• To revert changes:
# bastille -r
• To list the current config file:
# bastille -l
• Locate the list of all actions performed by HP-UX Bastille at /var/opt/sec_mgmt/
bastille/log/action-log
• Use the following files to help diagnose problems:
— /var/opt/sec_mgmt/bastille/log/action-log
— /var/opt/sec_mgmt/bastille/log/error-log
— /etc/opt/sec_mgmt/bastille/config
5.2 General use tips
• Changes made by HP-UX Bastille can potentially to cause other software to stop working.
HP recommendsmaking changes in a non-production environment. Fully test all production
applications after HP-UX Bastille is applied before putting the systems into production.
• On HP-UX systems, do not run HP-UX Bastille during a Software Distributor operation
such as swinstall and swremove because file-lock errors might occur.
• On HP-UX machines, do not run HP-UX Bastille during heavy use of the system, or when
running applications that modify the system configuration. During these times, HP-UX
Bastille might not be able to get exclusive access to some of the necessary files. If this happens,
run bastille -b when the machine is quiet to reapply the changes.
• Install the latest patches on your system to ensure that it is as secure. If current patches are
not applied, your system can be compromised even though you use this program. HP-UX
uses the Security Patch Check tool to help with this process. HP-UX Bastille will help with
the installation of the Security Patch Check tool.
NOTE: Because some patches and software can return settings to default values, rerun
HP-UX Bastille to maintain system security.
• Rerun HP-UX Bastille:
— When new software is installed
— When the OS is revised
— When patches are installed
— When system customizations are made that might affect security
— On HP-UX if swverify is used with the -x fix=true option or the -F option to run
vendor-specific fix scripts
5.3 Known issues and workarounds
5.3.1 Changes made by HP-UX Bastille might cause other software to stop working
To revert the system to the state it was in before you ran HP-UX Bastille:
# bastille -r
This command also confirms that the problem is eliminated.
5.1 Diagnostic tips 21
Page 22

5.3.2 Cannot use X because $DISPLAY is not set
You request the X interface, but the $DISPLAY environment variable is not set. Set the environment
variable to the desired display to correct the problem.
5.3.3 System is in original state
You attempt to revert changes with the -r option, but there are no changes to revert.
5.3.4 HP-UX Bastille must be run as root
HP-UX Bastille must be run as the root user because the changes affect system files.
5.3.5 Problems opening, copying, or reading files
Error messages citing problems performing these operations are usually related to NFS file
systems that do not trust the root user on the local machine. Consult the options section in the
fstab(4) manpage for details.
5.3.6 Errors related to individual configuration files
Errors about individual configuration files indicate:
• That a system is too heavily modified for HP-UX Bastille to make effective changes.
• That the files, locations, or permissions of the HP-UX Bastille installation directories have
been changed.
5.3.7 HP Secure Shell locks you out of your system immediately when passwords
expire
You might need PAM patch: PHCO_24839 (HP-UX 11.11) available atthe HP IT Resource Center:
https://www2.itrc.hp.com/service/patch/mainPage.do
5.3.8 HP-UX Bastille configures a firewall using IPFilter
The most common conflicts are with firewalls. When a network service is not working, and it is
not turned off by HP-UX Bastille, verify the firewall rules pass the ports needed. For more
information, see ipfstat(8) and ipmon(8).
5.3.9 Security Patch Check
Security Patch Check is being deprecated in favor of SWA.
5.3.10 Rerun HP-UX Bastille after installing new software or applying new patches
Installing new software or applying new patches might change the system state. On HP-UX, if
vendor-specific fix scripts are run with swverify using either the -x fix=true option or the
-F option, then rerun HP-UX Bastille.
22 Troubleshooting
Page 23

6 Support and other resources
6.1 Contacting HP
6.1.1 Before you contact HP
Be sure to have the following information available before you contact HP:
• Technical support registration number (if applicable)
• Product serial number
• Product identification number
• Applicable error message
• Add-on boards or hardware
• Third-party hardware or software
• Operating system type and revision level
6.1.2 HP contact information
For the name of the nearest HP authorized reseller:
• See the Contact HP worldwide (in English) webpage (http://welcome.hp.com/country/us/
en/wwcontact.html).
For HP technical support:
• In the United States, for contact options see the Contact HP United States webpage (http://
welcome.hp.com/country/us/en/contact_us.html). To contact HP by phone:
— Call 1-800-HP-INVENT (1-800-474-6836). This service is available 24 hours a day, 7 days
a week. For continuous quality improvement, calls may be recorded or monitored.
— If you have purchased a Care Pack (service upgrade), call 1-800-633-3600. For more
information about Care Packs, refer to the HP website (http://www.hp.com/hps).
• In other locations, see the Contact HP worldwide (in English) webpage (http://
welcome.hp.com/country/us/en/wwcontact.html).
6.1.3 Subscription service
HP recommends that you register your product at the Subscriber's Choice for Business website:
http://www.hp.com/country/us/en/contact_us.html
After registering, you will receive email notification of product enhancements, new driver
versions, firmware updates, and other product resources.
6.1.4 Documentation feedback
HP welcomes your feedback. To make comments andsuggestions about product documentation,
go to http://www.hp.com/bizsupport/feedback/ww/webfeedback.html. Include the document
title and manufacturing part number. All submissions become the property of HP.
6.2 Related information
The HP-UX Bastille website:
http://www.hp.com/go/bastille
HP-UX Bastille manpages:
• bastille(1M) in HP-UX 11i v3 Reference 1M System at:
http://docs.hp.com/en/hpuxman_pages.html
6.1 Contacting HP 23
Page 24

• bastille_drift(1M) in HP-UX 11i v3 Reference 1M System at:
http://docs.hp.com/en/hpuxman_pages.html
The HP-UX Security Forum is offered through the HP IT Resource Center (ITRC) at:
ITRC Forums Security
Product specifications and download:
http://h20392.www2.hp.com/portal/swdepot/displayProductInfo.do?productNumber=B6849AA.
For moreinformation about HP-UX Bastillecompatibility with Serviceguard, see the Serviceguard
documentation available at:
http://www.hp.com/go/hpux-serviceguard-docs.
The IPFilter-SG rules are documented in the HP-UX IPFilter Version 17 Administrator's Guide.
IPFilter documentation is available at:
http://www.hp.com/go/hpux-security-docs
6.3 Typographic conventions
This document uses the following typographical conventions:
%, $, or #
A percent sign represents the C shell system prompt. A dollar
sign represents the system prompt for the Bourne, Korn, and
POSIX shells. A number sign represents the superuser prompt.
audit(5) A manpage. The manpage name is audit, and it is located in
Section 5.
Command
A command name or qualified command phrase.
Computer output
Text displayed by the computer.
Ctrl+x A key sequence. A sequence such as Ctrl+x indicates that you
must hold down the key labeled Ctrl while you press another
key or mouse button.
ENVIRONMENT VARIABLE The name of an environment variable, for example, PATH.
[ERROR NAME]
The name of an error, usually returned in the errno variable.
Key The name of a keyboard key. Return and Enter both refer to the
same key.
Term The defined use of an important word or phrase.
User input
Commands and other text that you type.
Variable
The name of a placeholder in a command, function, or other
syntax display that you replace with an actual value.
[] The contents are optional in syntax. If the contents are a list
separated by |, you must choose one of the items.
{} The contents are required in syntax. If the contents are a list
separated by |, you must choose one of the items.
... The preceding element can be repeated an arbitrary number of
times.
Indicates the continuation of a code example.
| Separates items in a list of choices.
WARNING A warning calls attention to important information that if not
understood or followed will result in personal injury or
nonrecoverable system problems.
24 Support and other resources
Page 25

CAUTION A caution calls attention to important information that if not
understood or followed will result in data loss, data corruption,
or damage to hardware or software.
IMPORTANT This alert provides essential information to explain a concept or
to complete a task.
NOTE A note contains additional information to emphasize or
supplement important points of the main text.
6.3 Typographic conventions 25
Page 26

26
Page 27

A Install-Time Security (ITS) using HP-UX Bastille
Install-Time Security (ITS) adds a security step to the installation or update process. This additional
step allows the HP-UX Bastille security lock-down engine to run during system installation with
one of four configurations ranging from default security to DMZ. ITS includes the following
bundles:
• Sec00Tools (recommended software bundle)
• Sec10Host (optional software bundle)
• Sec20MngDMZ (optional software bundle)
• Sec30DMZ (optional software bundle)
A.1 Choosing security levels
At cold install or update time, you can choose one of the security levels listed in Table A-1. Each
level provides incrementally higher security.
Table A-1 Security levels
Description
Configuration file name
1
Security level
The Install Time Security infrastructure. No security changes.
Not applicable
Sec00Tools
2
Host-based lockdown with firewall pre-enablement.Some common
clear-text services are turned off, excluding Telnet and FTP.
HOST.config
Sec10Host
3
Lock down that allows secure management. IPFilter firewall blocks
incoming connectionsexcept common, relatively safe, management
protocols.
MANDMZ.config
Sec20MngDMZ
3
Network-DMZ lock down. IPFilter blocks all incoming connections
except HP-UX Secure Shell.
DMZ.config
Sec30DMZ
3
1
Configuration files are installed in /etc/opt/sec_mgmt/bastille/configs/defaults.
2 Sec00Tools is installed by default.
3 Sec10Host, Sec20MngDMZ, and Sec30DMZ are selectable.
NOTE: When you select either the Sec20MngDMZor Sec30DMZsecurity level, IPFilter restricts
inbound network connections. For more information on how to add inbound ports to your /etc/
opt/ipf.customerrules file, see the HP-UX IPFilter (Version A.03.05.09 and later)
Administrator's Guide and the HP-UX System Administrator's Guide.
Using one of these security levels applies a default security profile, simplifying the lock-down
process. The following tables list the services and protocols affected by each security level.
A.1 Choosing security levels 27
Page 28

IMPORTANT: Review these tables carefully. Some locked-down services and protocols might
be used by other applications and have adverse effects on the behavior or functionality of these
applications. You can change these security settings after installing or updating your system.
Table A-2 Host-based Sec10Host, Sec20MngDMZ, and Sec30DMZ security settings
ActionCategory
Deny login unless home directory exists
Deny non-root logins if /etc/nologin file exists
Set a default path for su command
Deny root logins from network tty
Hide encrypted passwords
Deny ftp system account logins
Deny remote X logins
Logins and passwords
Modify ndd settings1,
2
Restrict remote access to swlist
Set default umask
Enable kernel-based stack execute protection
File system, network, and kernel
Disable ptydaemon
Disable pwgrd
Disable rbootd
Disable NFS client daemons
Disable NFS server
Disable NIS client programs
Disable NIS server programs
Disable SNMPD
Daemons
Disable bootp
Disable inetd built-in services
Disable CDE helper services
Disable finger
Disable ident
Disable klogin and kshell
Disable ntalk
Disable login, shell, and exec services
Disable swat
Disable printer
Disable recserv
Disable tftp
Disable time
Disable uucp
Disable Event Monitoring Services (EMS) network
communication
Enable logging for all inetd connections
inetd services
Run sendmail via cron to process queue
Stop sendmail from running in daemon mode
Disable vrfy and expn commands
sendmail
Disable HP Apache 2.x Web Server
3
Set up cron job to run SWA
1
Other settings
28 Install-Time Security (ITS) using HP-UX Bastille
Page 29

1
Manual action may be required to complete configuration. For more information, see /etc/opt/sec_mgmt/
bastille/TODO.txt after update or installation.
2
The following ndd changes are made:
ip_forward_directed_broadcasts=0
ip_forward_src_routed=0
ip_forwarding=0
ip_ire_gw_probe=0
ip_pmtu_strategy=1
ip_send_source_quench=0
tcp_conn_request_max=4096
tcp_syn_rcvd_max=1000
3 Settings applied only if software is installed.
Table A-3 Additional Sec20MngDMZ security settings
1
ActionCategory
inetd services
Includes all disabled inetd services in Table A-2
Disable ftp
Disable telnet
Restrict syslog daemon to local connections
IPFilter configuration
2
Block incoming DNS query connections
Block incoming HIDS administration connections3,
4
Configure IPFilter to allow outbound traffic
Configure IPFilter to block incoming traffic with IP
options set
Configure IPFilter to block all other traffic except for
HP-UX Secure Shell, HIDS agent, WBEM, web admin,
web admin autostart,5and ICMP echo
1 Applies all security configuration settings in Table A-2.
2
Additional IPFilter rules may be applied with a custom rules file located at /etc/opt/sec_mgmt/bastille/
ipf.customrules.
3 HP-UX Host IDS is a selectable software bundle and only available for commercial servers.
4 Settings applied only if software is installed.
5
Manual action may be required to complete configuration. For more information, see /var/opt/sec_mgmt/
bastille/TODO.txt after installation or update.
Table A-4 Additional Sec30DMZ security settings
1
ActionCategory
IPFilter configuration
2
Includes all IPFilter settings in Table A-3
Block incoming HIDS agent connections3,
4
Block incoming WBEM connections
5
Block incoming web admin connections
Block incoming web admin autostart connections
Block all traffic except HP-UX Secure Shell
Block ICMP echo
1 Applies all security configuration settings in Table A-2 and Table A-3.
2
Additional IPFilter rules may be applied with a custom rules file located at /etc/opt/sec_mgmt/bastille/
ipf.customrules.
3 Settings applied only if software is installed.
4 HP-UX Host IDS is a selectable software bundle and only available for commercial servers.
5 WBEM is required for several HP management applications including HP Systems Insight Manager (SIM) and
ParMgr.
A.1 Choosing security levels 29
Page 30

A.2 Choosing security dependencies
The Sec00Toolssecurity levelis installed by default but does not implement any security changes
when you install or update HP-UX Bastille. The Sec00Tools security level has the following
benefits:
• Ensures that the required software is installed.
• Contains the prebuilt configuration files that are used to create a security level.
• Can be used as a template to create a custom security configuration.
• Ensures that the software needed by other security levels is present.
NOTE: The three selectable security levels depend on Sec00Tools to installthe necessary software
to secure the system.
Figure A-1 Security software dependencies
A.3 Selecting security levels during installation
From the Ignite-UX GUI Installation and Configuration dialog box, click the System tab . The
System tab enables you to customize information such as security levels, hostname, IP address,
root password, and the time zone.
1. Click the System tab to select the security level appropriate for your deployment.
• If you are using the Ignite-UX GUI, select Security Choices.
• If you are using the Ignite Install HP-UX Wizard, navigate to the Additional Software
screen and select Security Choices.
2. The security levels appear. By default, Sec00Tools is selected. Select the security level
appropriate for your deployment. See Table A-1 for more information.
3. Click OK.
30 Install-Time Security (ITS) using HP-UX Bastille
Page 31

B Configuring HP-UX Bastille for use with Serviceguard
B.1 Configuring Sec20MngDMZ or Sec30DMZ security levels
Serviceguard uses dynamic ports. To enable operation, the possible-SG port range must be
opened. Opening the port range is not consistent with the security goals of Sec20MngDMZ
MANDMZ.config and Sec30DMZ DMZ.config because multipleservices (including applications
similar to rcp), might also listen to this same port range. At these security levels, the firewall
provides security benefits consistent with the Serviceguard security deployment model.
For moreinformation about HP-UX Bastillecompatibility with Serviceguard, see the Serviceguard
documentation available at:
http://docs.hp.com/en/netsys.html.
Before you open the Serviceguard port range, review the required IPFilter-SG rules. IPFilter
documentation is available at:
http://docs.hp.com/en/internet.html
When the Serviceguard security patch of 2004 is installed, Serviceguard requires identd. To
enable identd:
1. Edit the HP-UX Bastille /etc/opt/sec_mgmt/bastille/config configuration file by
changing the answer to the question:
Should Bastille ensure inetd's ident service does not run on this
system?
Change the answer from Y to N.
SecureInetd.deactivate_ident=N
2. Apply the configuration file changes.
• If you have not made any configuration changes to the system since the last time HP-UX
Bastille was used, use HP-UX Bastille to apply the changes.
a. Revert to the previous HP-UX Bastille configuration:
# bastille -r
b. Apply the new HP-UX Bastille configuration:
# bastille -b
• If the you have applied configuration changes to the system since the last time HP-UX
Bastille was used, apply the changes manually.
a. Remove the # from the /etc/inetd.conf file line:
#auth stream tcp6 wait bin /usr/lbin/identd identd
b. Force inetd to read the configuration:
# inetd -c
B.2 Configuring Sec10Host level
If HP-UX Bastille is started using Sec10Host host.config level security, change the following
line:
SecureInetd.deactivate_ident=Y
Change the Y to N:
SecureInetd.deactivate_ident=N
If you are using the Serviceguard SNMP subagent, set:
MiscellaneousDaemons.snmpd=N
B.1 Configuring Sec20MngDMZ or Sec30DMZ security levels 31
Page 32

32
Page 33

C Question modules
AccountSecurity.ABORT_LOGIN_ON_MISSING_HOMEDIR
Headline Do not allow logins unless the home directory exists.
Default N
Description
The ABORT_LOGIN_ON_MISSING_HOMEDIR parameter controlslogin behavior
if a user's home directory does not exist.
Actions
Set ABORT_LOGIN_ON_MISSING_HOMEDIR=1 in /etc/security.
AccountSecurity.atuser
Headline
Restrict the use of at to administrative accounts.
Default N
Description
The at command allows users to submit jobs for the system to run at a
particular time. Administrators can use at to defer jobs to run when the system
is otherwise unused. However, executing jobs later or automatically represents
a privilege that can be abused and makes actions slightly harder to track. Many
sites chooseto restrict the at command to administrative accounts. HPsuggests
restricting permission to new administrators until they understand how it can
be abused and which users need access. Create the /etc/at.allow file of
users with permission. This file can be edited later. If this file is not created,
all users have permission to use the at command.
Actions
Delete the file at.deny
Create or replace the file at.allow with a single entry for user root
Set permissions to 0400
Change ownership to root:sys
AccountSecurity.AUTH_MAXTRIES
Headline Lock account after too many consecutive authentication failures.
Default N
Description
The AUTH_MAXTRIES parameter controls whether an account is locked after
too many consecutive authentication failures. It does not apply to trusted
systems. This parameter is supported for users in all name server switch
repositories, such as local, NIS, and LDAP.
Actions
Set AUTH_MAXTRIES=1 in /etc/security.
AccountSecurity.block_system_accounts
Headline Disable login access to the system accounts.
Default N
Description System accounts are provisioned on a new system, for example bin, sys, uucp,
et-cetera. These accounts (except for root) exist to own files, processes, or
system resources but are not generally logged into. Because these accounts
have broad access to the system, HP recommends disabling them. This item
disables default system accounts.
Actions
Lock the account and change the user shell to /bin/false for the following
users: www sys smbnull iwww owww sshd hpsmh named uucp nuucp adm
daemon bin lp nobody noaccess hpdb useradm.
AccountSecurity.create_securetty
Headline Disallow root logins from network TTYs.
33
Page 34

Default N
Description HP-UX Bastille can restrict root from logging into a tty over the network. This
forces administrators to log in first as a non-root user, then su to become root.
Root logins are still permitted on the console and through services that do not
use tty's like HP-UX Secure Shell.
Actions
Create or replace the file /etc/securetty with the single entry console.
AccountSecurity.crontabs_file
Headline
Ensure the crontab files are only accessible by root.
Default Y
Description Because a variety of administrators, scripts, and users edit crontab files,
sometimes these files contain incorrect permissions. HP-UX Bastille ensures
these files can only be read and changed by the root user. Perform this task
to ensure these files can only be read and written-to by root, with the crontab
command.
Actions Change ownership and permissions for all crontab files permitting access only
to root.
AccountSecurity.cronuser
Headline
Restrict the use of cron to administrative accounts.
Default N
Description
The cron function allows you to schedule jobs to run automatically at a certain
time, possibly recurring. Administrators can use cron to check the system
logs every night at midnight or confirm file integrity every hour. However,
executing jobs later or automatically represents a privilege that can be abused
and makes actions slightly harder to track.
Actions
Delete the file cron.deny
Create or replace the file cron.allow with a single entry for user root
Set permissions to 0400
Change ownership to root:sys
AccountSecurity.gui_login
Headline Disable the local graphical login.
Default Y
Description Most servers do not have a graphics console directly attached, and do not run
a graphics login. Disabling this feature reduces targets for hackers and saves
system resources for systems that do not have a graphics console.
Actions
In the /etc/rc.config.d/xfs file, set RUN_X_FONT_SERVER=0.
In the /etc/rc.config.d/audio file, set AUDIO_SERVER=0.
In the /etc/rc.config.d/slsd file, set SLSD_DAEMON=0.
In the /etc/rc.config.d/desktop file, set DESKTOP=0.
Terminate the following daemon processes if running: xfs, Aserver, SLSd,
dtlogin, dtrc.
AccountSecurity.hidepasswords
Headline Hide the encrypted passwords on this system.
Default N
34 Question modules
Page 35

Description
HP-UX storesthe encrypted password string for eachuser in the /etc/passwd
file. These encrypted strings are viewable by anyone with access to the /etc/
file system, typically all users. Using the encrypted string, an attacker can find
valid passwords for your system.
Actions Convert system to trusted mode or use shadowed passwords (dependent on
OS version).
AccountSecurity.lock_account_nopasswd
Headline Lock the local accounts with no password.
Default Y
Description Accounts with no passwords allow any user to execute arbitrary actions on
your server and invite attack. Passwordless accounts should always be against
policy. This item disables accounts with no password.
Actions
Lock all local accounts that do not have a password with the passwd -l
command.
AccountSecurity.mesgn
Headline
Set mesg n for all users.
Default N
Description
The mesg n command forbids messages through write by revoking write
permission to users without appropriate privilege on the user's terminal. For
a description of mesg, see write(1). Disabling this feature prevents untrusted
users from contacting users to solicit credentials or other sensitive data.
Actions Append the line "mesg n" to the files profile, csh.login, d.profile, and d.login
in /etc.
AccountSecurity.MIN_PASSWORD_LENGTH
Headline Set the minimum length of new passwords.
Default 8
Description
The MIN_PASSWORD_LENGTH parameter controls the minimum length of new
passwords. This policy is not enforced for the root user on an untrusted system.
Actions
In the /etc/default/security file, set the parameter
MIN_PASSWORD_LENGTH.
AccountSecurity.NOLOGIN
Headline
Non-root users are not allowed to log in if /etc/nologin exists.
Default N
Description
The NOLOGIN parameter controls non-root login with the /etc/nologin
file.
Actions
Sets the parameter NOLOGIN=1 in the /etc/default/security file.
AccountSecurity.NUMBER_OF_LOGINS_ALLOWED
Headline Enter the maximum number of logins per user.
Default 1
Description
The NUMBER_OF_LOGINS_ALLOWED parameter controls the number of
simultaneous sessions allowed per user. This is applicable only for non-root
users. This limits user accounts sharing and alerts users to a compromised
account.
Actions
Sets the parameter NUMBER_OF_LOGINS_ALLOWED in the /etc/default/
security file.
35
Page 36

AccountSecurity.NUMBER_OF_LOGINS_ALLOWEDyn
Headline Set a maximum number of logins per user.
Default N
Description
Sets the NUMBER_OF_LOGINS_ALLOWEDyn parameter.
Actions None.
AccountSecurity.PASSWORD_HISTORY_DEPTH
Headline Set the password history depth.
Default 3
Description
The PASSWORD_HISTORY_DEPTH parameter controls the password history
depth. A new password is checked against the number of most recently used
passwords stored in password history for a particular user. Users are not
allowed to reuse a stored, previously used password.
Actions
Sets the parameter PASSWORD_HISTORY_DEPTH in the /etc/default/
security file.
AccountSecurity.PASSWORD_HISTORY_DEPTHyn
Headline Set a password history depth.
Default N
Description
Sets the PASSWORD_HISTORY_DEPTHyn parameter.
Actions None.
AccountSecurity.PASSWORD_MAXDAYS
Headline Set the maximum number of days between password changes.
Default 182
Description This parameter controls the default maximum number of days that passwords
are valid. For systems running HP-UX 11.11and HP-UX 11.0, setting this value
requires conversion to trusted mode. For HP-UX 11.22 and later, shadowed
password conversion is required. This parameter applies only to local non-root
users.
Actions
Sets the parameter PASSWORD_MAXDAYS in the /etc/default/security
file.
AccountSecurity.PASSWORD_MINDAYS
Headline Set the minimum number of days between password changes.
Default 7
Description This parametercontrols the default minimum number of days until a password
can be changed. For systems running HP-UX 11.11 and HP-UX 11.0, setting
this value requires conversion to trusted mode. For HP-UX 11.22 and later,
shadowed password conversion is required. This parameter applies only to
local non-root users. When used with password aging, prevents users from
immediately resetting expired passwords.
Actions
Sets the parameter PASSWORD_MINDAYS in the /etc/default/security
file.
AccountSecurity.PASSWORD_WARNDAYS
Headline Set the number of days a user will be warned that their password will expire.
Default 28
36 Question modules
Page 37

Description This parametercontrols the default numberof days before password expiration
that a user is warned that the password must be changed. For systems running
HP-UX 11.11 and HP-UX 11.0, setting this value requires conversion to trusted
mode. For HP-UX 11.22 and later, shadowed password conversion is required.
This parameter applies only to local non-root users.
Actions
Sets the parameter PASSWORD_WARNDAYS in the/etc/default/security
file.
AccountSecurity.passwordpolicies
Headline Set up password policies.
Default N
Description Set up password policies.
Actions None.
AccountSecurity.restrict_home
Headline Restrict the home directory permissions.
Default N
Description Home directories should not be world-writable or world-readable. This item
removes world-visibility and group-write from the local account directories,
similar to executing chmod o-rwx,g-w <dir>.
Actions Remove world visibility and group write from the local account home
directories, similar to executing chmod o-rwx,g-w <home dir>.
AccountSecurity.root_path
Headline Remove the dot from the root path.
Default N
Description A dot in the root path instructs the shell to look in the current directory for
an executable. This can cause a local command to either override a common
administrative command, or cause an incorrectly typed command to execute
a local command. This allows malicious users to plant rogue commands that
could potentially run malicious software as root. This item removes the current
working directory, "dot" from the root path startup scripts.
Actions Remove the current working directory "." or any group/world-writable
directory from the root $PATH.
AccountSecurity.serial_port_login
Headline Disable all serial ports except the console.
Default Y
Description The ability to login on a serial port except the console is a rare need.
Historically, these were used for terminal devices or modems, but it is unlikely
that a site would need this capability. This item turns off the process that
listens to the tty devices.
Actions
Comment out serial port tty entries in the /etc/inittab file and invoke
init to reread the file.
AccountSecurity.single_user_password
Headline Password protect single-user mode.
Default N
Description Password protecting single-user mode provides limited protection against
anyone who has physical access to the machine, because they cannot reboot
and have root access without typing the password. However, if an attacker
37
Page 38

has physical access to the machine and enough time, there is very little you
can do to prevent unauthorized access. This may be more problematic when
an authorized administrator can't remember the password. Note: For HP-UX
11.22 and prior, this requires conversion to trusted mode. HP-UX Bastille will
automatically do the conversion if you select this option. Trusted mode is
incompatible with LDAP-UX client services prior to version 3.0 and can cause
other incompatibility issues with applications which do their own
authentication.
Actions
Sets the parameter BOOT_AUTH=1 in the /etc/default/security file. For
HP-UX 11.22and prior, convert to trusted mode, and set ensure bootpw=YES
with modprdef.
AccountSecurity.SU_DEFAULT_PATH
Headline
Set the new PATH at su .
Default
/sbin:/usr/sbin:/bin:/usr/bin
Description
The SU_DEFAULT_PATH parameter defines a new default PATH environment
value to be set when su to a non-superuser account is executed. Refer to su(1).
Set SU_DEFAULT_PATH=new_PATH. This ensures that an su session will
always have a default PATH value, preventing the inheritance of a poisoned
PATH variable fromyour current login session. The PATH environment variable
is set to new_PATH when the su command is invoked. Other environment
values are not changed. The PATH value is not validated. This parameter does
not apply to a superuser account, and is applicable only when the "-" option
is not used along with the su command.
Actions
Sets the parameter SU_DEFAULT_PATH in the /etc/default/security
file.
AccountSecurity.SU_DEFAULT_PATHyn
Headline
Set a default path for the su command.
Default Y
Description
Set the SU_DEFAULT_PATHyn parameter.
Actions None.
AccountSecurity.system_auditing
Headline Basic system security auditing enabled.
Default N
Description Enabling basic system security auditing logs a subset of system calls. This
logging produces system overhead. If this system is in a performance sensitive
role, the risk of not logging may be less than the risk of incurring a small
amount of overhead.
Actions Configure and start auditing and acct programs. Convert to trusted mode if
necessary.
AccountSecurity.umask
Headline
Set umask for all users on the system.
Default 77
Description
The umask utility sets a default permission for files that you create. HP-UX
Bastille can set one of several umasks. Select one of the following or create
your own: 002–Everyone can read your files and people in your group can
alter them. 022–Everyone can read your files, but no one can write to them.
027–Only people in your group can read your files, but no one can write to
them. 077–No one on the system can read or write your files. In addition to
38 Question modules
Page 39

configuring a umask for all of the user shells, HP-UX 11.22 and later have an
option in the /etc/default/security file to set the default system umask.
This parameter controls umask(2) of all sessions initiated with pam_unix(5)
which can then be overridden by the shell. NOTE: If your system is converted
to trusted mode, this parameter will be overridden by the trusted system
default umask, which is 077.
Actions
Set the selected umask in all known shell startup scripts.
AccountSecurity.umaskyn
Headline
Set the default umask.
Default N
Description
Set the default umask.
Actions None.
AccountSecurity.unowned_files
Headline Assign unowned files to the bin user.
Default N
Description Do not leave files owned by users or groups that do not have meaning to the
system. If a user or group is later defined with the uid or gid that owns that
file, the data could be exposed to potentially unauthorized access. This can
happen when a user is deleted without cleaning up the file system. This item
will look for files that are not owned by a defined system user or group and
assign those files to bin.
Actions Find all local files that are not owned by a defined system user and/or group.
Assign those files to bin. Remove world-writable, suid and sgid bits from
these files.
AccountSecurity.user_dot_files
Headline Remove world-write permission from local user account dot files.
Default Y
Description Dot files, or those that begin with a "." are hidden from standard file lists and
are often used for configuration. The combination of being less visible and
being used to change the behavior of the user account means that if an incorrect
permission is set (perhaps with a loose umask), the account could be subject
to attack. This item reviews the local user account store, finds the local home
directories, and removes the world-writeable bit, if any. This is a simple, and
relatively safe operation.
Actions Find all local non-root login home directories and ensure that any "dot" files
within those directories do not have world-writable permissions.
AccountSecurity.user_rc_files
Headline
Delete .shosts, .rhosts, and .netrc from the local user accounts
Default Y
Description .shosts, .rhosts, and .netrc are files that sit in the home directories of users and
are used to create trust relationships between given users on a system and
other systems. Such non-interactive trust is dangerous as it creates the potential
for an attacker to leverage those trust relationships if they manage to expose
an account. If there is no business need for static trust, delete these files.
Actions Find all local non-root login home directories, and delete the files .shosts,
.rhosts, and .netrc if found within those directories.
39
Page 40

Apache.chrootapache
Headline
Applies chroot to your HP Web Services Apache Server.
Default N
Description The HP Web Services versions of the Apache web server for HP-UX is available
free for download at www.hp.com/go/softwaredepot. A chroot script is built
into the distribution. This script makes a copy of Apache and related binaries
and libraries and places them inside of a chroot jail. This allows Apache to
run with limited file system access. If you are not currently running the Apache
web server, answer no to this question. The Apache server, httpd, is given
access to several compilers and system libraries so it can process cgi's, login
attempts, and so forth. One way to lessen the risk presented by this special
status is to lock the daemon (httpd) into a "chroot jail." In this case, the daemon
has access to only a small segment of the file system, a directory created
specifically for the purpose of giving the daemon access to only the files it
needs. The adjective "chroot'ed" is derived from "change root", since HP-UX
Bastille sets the daemon's root directory ( / ) to some child node in the directory
tree. A root process can break out of a chroot jail, but this is still an effective
deterrent sinceHP-UX Bastille limits the number of common rootattack vectors
within the jail. If a security vulnerability is found in one of the files that has
been placed inside of the "chroot jail", that file must be manually patched by
copying the fixed file(s) into the jail. This chroot script was written to provide
for a fully functional web server inside of a chroot'ed environment. For
additional security, remove unneeded libraries and compilers that are not
used by your Apache server.
IMPORTANT: Manual action is required to complete this configuration. See
the TODO.txt file for details.
Actions Makes a copy of Apache and related binaries and libraries and places them
inside of a chroot jail.
Apache.deactivate_hpws_apache
Headline Deactivate the HP Web Services Apache Web Server.
Default Y
Description If you do not plan to use this system as a web server, HP recommends that
you deactivate your Apache web server. Programs that require an Apache
server installation but do not bind to port 80 can still start their own instances
of the web server. If you do not plan to use your Apache server immediately,
then you should deactivate it until needed. This item does not turn off copies
of Apache or other web servers if they are supplied with individual products,
nor does it disable APACHE_SSL.
Actions
Stop the Apache server if it is running. Set HPWS_APACHE_START=0 in the
/etc/rc.config.d/hpws_apacheconf file.
DNS.chrootbind
Headline
Names and sets chroot to run as a non-root user.
Default N
Description The name server "named" usually runs with privileged access. This allows
"named" to function correctly, but increases the security risk if any
vulnerabilities are found. Decrease this risk by running "named" as a
non-privileged user and by putting its files in a restricted file system called a
chroot jail. If a security vulnerability is found in one of the files that has been
placed inside of the chroot jail, that file must be manually patched by copying
the fixed file(s) into the jail. For security reasons, restrict every process which
40 Question modules
Page 41

is listening to untrusted data as much as possible. This is especially true of
network daemons, such as bind. If a vulnerability is found in the daemon,
then a chroot jail contains any intrusions. Only a root process can break out
of a chroot jail. HP-UX Bastille ensures that "named" is not running as root.
A successful attack on "named" in a chroot jail running as a non-privileged
user allows the attacker to modify only files owned or writeable by that
non-privileged user and protects the rest of the system.
IMPORTANT: On HP-UX, the general structure of the jail is created but several
entries are added to the HP-UX Bastille generated TODO.txt file which require
manual action on your part. HP-UX does not ship with a name server
configured by default, so much of this depends on how your system's name
server is configured. Manualaction is required to complete this configuration.
See the TODO.txt file for details.
Actions Make a copy of BIND and related binaries and libraries and place them inside
of a chroot jail.
FilePermissions.world_writeable
Headline Scan for world-writeable directories.
Default N
Description HP-UX Bastille can scan your system for world-writeable directories, including
base OS, 3rd party applications, and user directories. A script is created which
can be edited to suit your needs and run to tighten these permissions. Changing
the permissions of directories in this way has the potential to break
compatibility withsome applications and requirestesting in your environment.
Note: The changes made by this script are NOT supported by HP. They have
a low likelihood of breaking things in a single purpose environment, but are
known to break some applications in very subtle ways in a general purpose
environment For example, applications which rely on unique process id's in
/tmp when run by different users can break when the process id's are recycled,
or programs which are run by different users but create logs in a common
directory might fail. Other examples are listed in the long explanation. As you
run the script, a revert-directory-perms.sh script is created which
allows you to revert to a supported state,independent of other HP-UX Bastille
configurations which are supported. Running bastille -r reverts allHP-UX
Bastille changes including running the revert-directory-perms.sh
script.
IMPORTANT: Manual action is required to complete this configuration. See
the TODO.txt file for details.
Actions Scan the system for world-writeable directories. Create a script to tighten these
permissions. HP-UX Bastille does not run this script, but offers it as a starting
point for users to review and modify.
FTP.ftpbanner
Headline Present an ftpd banner upon login to FTP.
Default N
Description
ftpbanner provides for a login banner to be presented upon the initial access
to the FTP server.
Actions
Append suitable banner line to ftpaccess file.
FTP.ftpusers
Headline
Disallow system account logins through ftpd.
41
Page 42

Default N
Description
The ftpusers file allows the administrator to set accounts that shall not be
allowed to log in through the ftpd. Default system users should not be allowed
access to the system through the ftpd because it sends the username and
password in clear text over the network. HP-UX Bastille disallows ftp logins
to a WU-FTPD server from the following users: root, daemon, bin, sys, adm,
uucp, lp, nuucp, hpdb, and guest. If you have a compelling reason to allow
these users ftp access, then answer no to this question. Use this as a secondary
measure if you deactivated the ftp server.
Actions
Add the following user names to the /etc/ftpd/ftpusers file: root,
daemon, bin, sys, adm, uucp, lp, nuucp, hpdb, and guest.
HP_UX.gui_banner
Headline Set up a login banner for graphical login.
Default N
Description Setting a GUI login banner notifies users that they may use the system, but
they are subject to local policy and monitoring. It also serves as notification
that the system is not for public use. This helps eliminate the claims of "I
thought anyone could use it."
Actions
For all Xresources files in /usr/dt/config/* directories, modify the
matching /etc/dt/config/*/Xresources file by adding the following
lines:
Dtlogin*greeting.labelString: "Authorized users only. All activity may be monitored and
reported."
Dtlogin*greeting.persLabelString: "Authorized users only. All activity may be monitored
and reported."
Create the matching /etc/dt/config/*/Xresources files if not present.
HP_UX.mail_config
Headline
Allow mailing of your configuration and TODO.txt files to HP.
Default N
Description The HP-UX Bastille development team would like to know how you use
HP-UX Bastille. Based on how you answer these questions, HP can meet your
needs better. You can help by sending your configuration and TODO.txt files
back to HP. Answering yes to this question does that automatically. If you
feel that your hostname or your security configuration is confidential,
answerno. The information is sent unencrypted over the public Internet. If
outbound mail is unable to reach the Internet from this machine, answer no.
If you have suggestions for improvements, new questions, code, or tests,
discuss these on the Bastille Linux discussion list at: http://lists.sourceforge.net/
mailman/listinfo/bastille-linux-discuss. You can provide feedback concerning
HP-UX Bastille directly to the IT Resource Center at http://itrc.hp.com, using
the System Administration or Security forum. Please send all comments. We
want to hear from you.
Actions
Mail the /etc/opt/sec_mgmt/bastille/config and /var/opt/
sec_mgmt/bastille/TODO.txt files to HP so we can improve HP-UX
Bastille.
HP_UX.ndd
Headline
Make suggested ndd changes.
Default N
Description
The ndd utility gets and sets network device parameters. The following is a
list of ndd changes HP-UX Bastille sets:
42 Question modules
Page 43

arp_cleanup_interval–60000•
• ip_forward_directed_broadcasts–0
• ip_forward_src_routed–0
• ip_forwarding–0
• ip_ire_gw_probe–0
• ip_pmtu_strategy–1
• ip_respond_to_echo_broadcast–0
• ip_respond_to_timestamp–0
• ip_respond_to_timestamp_broadcast–0
• ip_send_redirects–0
• ip_send_source_quench–0
• tcp_conn_request_max–4096
• tcp_syn_rcvd_max–4096
For more information on each of these parameters, run ndd -h
NOTE: If you already have some non-default, non-HP-UX Bastille settings
in effect, you must merge the settings manually. A reminder is added to your
TODO.txt file.
IMPORTANT: Manual action may be required to complete this configuration.
See the TODO.txt file for details.
Actions
If the /etc/rc.config.d/nddconf file has no entries, the following
parameters are set:
ip_forward_directed_broadcasts=0
ip_forward_src_routed=0
ip_forwarding=0
ip_ire_gw_probe=0
ip_pmtu_strategy=1
ip_respond_to_echo_broadcast= 0
ip_send_redirects= 0
ip_send_source_quench=0
tcp_conn_request_max=4096
tcp_syn_rcvd_max=4096
arp_cleanup_interval= 60000
ip_respond_to_timestamp= 0
ip_respond_to_timestamp_broadcast= 0
Otherwise, an item is created in the TODO.txt file for you to manually
integrate the parameter changes.
HP_UX.other_tools
Headline Provide information about other security tools that HP has to offer.
Default N
Description Although HP-UX Bastille helps to configure most of the security-relevant
features of your operating system, it is not a substitute for a complete security
solution. Such a solution includes properly configured firewalls, network
topologies, intrusion detection, policies, and user education. Hewlett-Packard
has tools and resources to help with most aspects of system security.
43
Page 44

Actions
Adds a summary description of HP security and services to the TODO.txt
file for user reference.
HP_UX.restrict_swacls
Headline
Restrict remote access to swlist.
Default N
Description
The swagentd daemon allows remote access to list and install software on
your system. This feature is convenient for remote administration. Security
Patch Check can use this to query remote machines. It can also be a security
risk because patch and other critical system information is available to anyone
inside that system's firewall. HP recommends that you disallow the swagentd
default, remote read access.
Actions
If the swagentd daemon is running, use swacl to remove remote read access:
swacl -l host -D any_other
swacl -l root -D any_other
Otherwise, an item is created in the TODO.txt file to remind you to run HP-UX
Bastille again when the daemon is up.
HP_UX.scan_ports
Headline
Provide instructions in your TODO.txt file on how to run a port scan.
Default N
Description One of the final steps in lock down is to verify that only the services you need
are still running. Several tools do this, including netstat which is included
with HP-UX, and lsof (List OpenFiles) which is a free downloadable tool.
The lsof tool provides information about all the processes running on your
system. If there are processes running that you don't recognize, take this
opportunity to do some research and learn about them.
IMPORTANT: Manual action required to complete this configuration. See
the TODO.txt file for details.
Actions
Provide instructions in your TODO.txt file on how to run a port scan.
HP_UX.screensaver_timeout
Headline Set the GUI screen-saver timeout to 10 minutes.
Default N
Description The GUI login screen-saver timeout varies from 10 to 30 minutes depending
on the HP-UX version. This item ensures the value is set at a consistent 10
minutes. Setting a short timeout ensures that extended absences don't leave
a console unnecessarily open.
Actions
For all sys.resources files in /usr/dt/config/* directories, modify the
matching /etc/dt/config/*/sys.resources file by adding the following
lines:
dtsession*saverTimeout: 10
dtsession*lockTimeout: 10
Create the matching /etc/dt/config/*/sys.resources files if not
present.
HP_UX.stack_execute
Headline Enable kernel-based stack-execute protection.
44 Question modules
Page 45

Default Y
Description A common way to gain privileged access is to provide some type of
out-of-bounds input that is not checked by a program. This input can be used
to overflow the stack in a way that leaves some cleverly written instructions
stored in a place that will be executed by the program. The HP-UX kernel is
able to disallow execution of commands from the stack. This contains many
of these types of attacks, making them ineffective. Because this is done at the
kernel level, it is independent of any application which may have a
vulnerability of this type. This will break some applicationsdesigned to execute
code off the stack, for example Java 1.2 programs using JDK/JRE 1.2.2 versions
older than 1.2.2.06. However, you can run chatr +es <executable file>
to override this for individual broken programs.
Actions
Invokes kctune -K executable_stack=0 to disable stack execution.
HP_UX.tcp_isn
Headline Make TCP ISN RFC 1948 compliant.
Default N
Description The use of random sequence numbers makes TCP traffic difficult to spoof off
network. By setting the TCP stack to use RFC 1948-compliant sequence
numbers, you raise the difficulty level for a successful off-network attack. This
setting does not prevent a "man in the middle" style attack where the attacker
has access to a network that is along the routing path between two
communicating nodes. TCP does not offer protections for this case without
adding additional layers like IPSec.
Actions Make TCP ISN RFC 1948 compliant.
IPFilter.block_cfservd
Headline
BLOCK incoming cfrun requests with IPFilter.
Default Y
Description
The cfengine utility provides policy-based configuration management for
groups of systems and Serviceguard clusters. A central "policy host" acts as a
repository for the configuration policy files and reference files that are
distributed to managed clients. Typically managed clients perform
synchronization runs at administrator defined intervals, for example with a
cron job on the managed client. The cfrun utility can also be used by the
administrator on the policy host to contact each managed client and request
an immediate or "on-demand" synchronization run. If this system should
allow on-demand synchronization requests, answer no to this question.
Otherwise, answer yes.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow cfservd incoming connections
pass in quick proto tcp from any to any port = 5308 flags S keep state keep
frags
IPFilter.block_DNSquery
Headline BLOCK incoming DNS query connections with IPFilter.
Default Y
Description DNS queryconnections should only be allowed on DNSservers. If this machine
is a DNS server for other machines, you should answer "No" to this question.
Otherwise, you should block DNS queries by answering "Yes".
45
Page 46

Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow DNSquery incoming connections
pass in quick proto udp from any to any port = domain keep
state"
IPFilter.block_hpidsadmin
Headline BLOCK incoming connections to the HIDS GUI with IPFilter.
Default Y
Description The HP-UX Host IntrusionDetection System(HIDS) Management GUIlistens
on port 2984 for incoming connections initiated by HIDS agents on each
configured host. If you are not running the HP-UX Host HIDS GUI on this
hos, answer yes. If you are running the HP-UX Host HIDS GUI on this host,
and it only manages one LOCAL HIDS agent running on this host (i.e., you
are not managing any HIDS agents on any remote hosts using this GUI),
answer yes. If you are running an HP-UX Host HIDS GUI on this host and
you are managing some remote HIDS agents, answer no.
NOTE: Install and configure HIDS separately from HP-UX Bastille. For more
information, see http://www.hp.com/security.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow hpidsadmin incoming connections
pass in quick proto tcp from any to any port = hpidsadmin flags S keep state
keep frags
IPFilter.block_hpidsagent
Headline BLOCK incoming HIDS agent connections with IPFilter.
Default N
Description HP-UX HIDS enhances host-level security with near realtime automatic
monitoring of each configured host for signs of potentially damaging
intrusions. HIDS contains a System Management GUI that allows the
administrator to configure, control, and monitor the HIDS system, and a
host-based agent which is an intrusion detection sensor, that gathers system
data, monitors system activity, and issues intrusion alerts. The communication
between the GUI and agents is encrypted. The agent listens on port 2985 for
incoming connections initiated by the GUI. If you are not running the HP-UX
Host Intrusion Detection System (HIDS) agent on this host, answer yes. If you
are running the HP-UX Host HIDS agent on this host but you are running the
HP-UX HostHIDS GUI locally onthis host (i.e., you are not remotely managing
this agent by running the GUI on a remote host, answer yes. If you are running
an HP-UXHost HIDS agent locally on this host and you are remotely managing
this agent with aremote HP-UXHost HIDS SystemManagement GUI,answer
no.
NOTE: You must install and configure HIDS separately from HP-UX Bastille.
For more information, see http://www.hp.com/security.
HIDS does not:
• Replace comprehensive security policies and procedures. You must define
and implementsuch security policies and procedures and configure HIDS
to enforce them. A lack of such policies, procedures, and configuration
46 Question modules
Page 47

can result in attacks that go undetected and reports of many false alerts.
HIDS will work but your system may still be vulnerable.
• Prevent the onset of attacks. If your system is vulnerable to attacks, those
vulnerabilities will remain even after HIDS is installed.
• Find static security flaws on a system. For example, if the password file
contained an illegitimate account before HIDS was installed, that
illegitimate account remains a vulnerability even after HIDS is installed
and operational. Furthermore, HIDS cannot authenticate users of a valid
account. For example, if users share password information, HIDS cannot
ascertain the identity of an unauthorized user gaining access to a system
via a legitimate account login.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow hpidsagent incoming connections
pass in quick proto tcp from any to any port = hpidsagent flags S keep state
keep frags
IPFilter.block_netrange
Headline Allow additional incoming network traffic from a select list of IP addresses.
Default 192.168.1.0/255.255.255.0 10.10.10.10
Description The basic IPFilter rules setup by HP-UX Bastille only allow network traffic for
services associated with software that HP-UX Bastille recognizes as installed
on the system. All other incoming traffic is blocked by default. To allow
additional incoming traffic based on the IP address of the sending host, enter
specific IP addresses here with an optional netmask. Otherwise, answer 'N'.
Actions Enable incoming network traffic for select hosts by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# Allow incoming connections from the following select IP
addresses:
pass in quick from <ip>/<netmask> to any
IPFilter.block_ping
Headline BLOCK incoming ICMP echo requests with IPFilter.
Default Y
Description
ICMP echo or ping is used for device discovery for a number of applications,
including System Insight Manager, and OpenView Network node manager.
Though this is commonly used by hackers to discover hosts, the information
returned to them is minimal. Past vulnerablities of ping are patched. For this
reason, you should block incoming icmp-echo requests if you do not need
management applications to discover the device.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow ping incoming connections
pass in quick proto icmp from any to any icmp-type
IPFilter.block_SecureShell
Headline BLOCK incoming Secure Shell connections with IPFilter.
Default N
Description Secure Shell is the best replacement for Telnet, remote shell, and FTP. It is
authenticated and encrypted. If you want remote access to your machine, this
47
Page 48

is the best way to do it. You should only block Secure Shell access if you have
an alternate, secure method to manage your machine (such as physical access
to the console or a secure terminal server) or if you do not use Secure Shell.
Otherwise, answer no to this question.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow SecureShell incoming connections
pass in quick proto tcp from any to any port = 22 flags S keep state
keep frags
IPFilter.block_wbem
Headline BLOCK incoming WBEM https connections with IPFilter.
Default N
Description Web-Based Enterprise Management (WBEM) is a Distributed Management
Task Force (DMTF) industry standard, http(s)-based management protocol
which features encryption and authentication. It is much better than SNMP,
which has a history of security issues and is by default a clear-text,
unauthenticated protocol. Like SNMP, WBEM can be a powerful aid in
managing multiple machines and it is by default much more secure. However,
any service can be a security risk, so you should block it if you are not going
to use it.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow wbem incoming connections
pass in quick proto tcp from any to any port = 5989 flags S keep state keep
frags
IPFilter.block_webadmin
Headline BLOCK incoming web admin connections with IPFilter.
Default Y
Description Port 1188 is used by web-based tools that are replacements for areas of SAM.
The listener on this port is the HP release of Apache with a custom
configuration file that loads only a minimum set of modules. It is also restricted
to use https for all communication and can only be used to run the system
management tools. In general, this web server is running only when in use.
It exits after a period of inactivity. Disabling this port means that some system
administration functions are only available using the command line.
Actions Enable incoming network traffic for this service by adding the following lines
to the /etc/opt/ipf/ipf.conf file when actively managed by HP-UX
Bastille:
# do allow webadmin incoming connections
pass in quick proto tcp from any to any port = 1188 flags S keep state keep
frags
# do allow webadminautostart incoming connections
pass in quick proto tcp from any to any port = 1110 flags S keep state keep
frags
IPFilter.configure_ipfilter
Headline Set up basic firewall rules with these properties.
Default N
Description Firewalls generally make up the first line of defense in any network security
architecture. IPFilter is a free, host-based firewall which is available for HP-UX.
It looks like you have IPFilter installed, but that does not mean that it has been
48 Question modules
Page 49

configured. HP-UX Bastille cannot detect whether the rule-set is appropriate
for your needs. HP-UX Bastille can create a very basic firewall configuration.
WARNING! Firewalls are designed to keep people out of your machine.
Therefore, the features in this section have the ability to keep you out too.
Blocked communication can include traffic from management applications
like Serviceguard, System Insight Manager, OpenView, System Management
Homepage, and others. To use communication from any application that is
not explicitly allowed in one of the follow-up questions, please see that
application's Firewall- or Bastille-interaction documentation for which ports
to accept with the ipf.customrules file described below. The HP-UX
Networking Ports Reference Guide is also helpful. The most problematic
communications are externally-initiated, UDP, or RPC-based. Be careful when
answering these questions. Verify that you can still log in to your machine
remotely (and have physical access just in case) before logging out.
WARNING! IPFilter is only able to block traffic which is processed by the
kernel. Network cards exist which take the processing of this traffic out of the
kernel for performance reasons. This is referred to as TOE or TCP offload
engine. If you are using such a card (can be used for iSCSI and 10Gb Ethernet),
configuring an IPFilter-based firewall will have no effect for traffic processed
by that card. Also, local traffic is not processed.
WARNING! This overwrites any existing firewall rules. If you already have
sufficiently secure firewall rules in place, then say no to this question.
Answering yes to this question creates and applies firewall rules that:
• Block incoming traffic with ip options set. These options are used
frequently by attackers and infrequently for any other purpose.
• Apply a custom rule-set from /etc/opt/sec_mgmt/bastille/
ipf.customrules. This file as delivered with HP-UX Bastille allows
all outgoing connections and keeps track of them so that traffic which
corresponds to those connections is allowed back in. This custom rule-set
also contains rules to not log netbios nameserver, netbios datagram, and
RPC portmap network traffic, all of which can fill up your logs rather
quickly on a large network.
This basic configuration allows most local applications to operate properly
without allowing attackers in through ports you don't use. You can addcustom
rules which better fit the specific needs of your environment. If you modify
the custom file, rerun the HP-UX Bastille back-end (bastille -b) to apply
the new rule-set.
IMPORTANT: Changing this file has the ability to either increase or decrease
the security of your system. After applying this custom configuration, be sure
to verify the active rule-set and the ipf.conf file to make sure the result is
what you intended.
WARNING! If IPFilter is not enabled on your system,HP-UX Bastille enables
it. This can bring down the network stack for about 10-15 seconds. All
connections should be restored at that point, but all connections will suspend
and some may be lost (including HP-UX Bastille's UI).
If your HP-UX Bastille connection is lost, check the results by running
bastille -l to see if HP-UX Bastille correctly applied your configuration,
or the action log for more detail. You can also save the HP-UX Bastille
configuration file and run bastille -b on a console to check for HP-UX
Bastille's full output real-time.
49
Page 50

Block anything you are not asked about explicitly, including all incoming
traffic. If this is the first time you are using HP-UX Bastille to configure your
firewall, you will be asked about several service specific options if the
applicable software appears to be installed. If you have already configured a
firewall using HP-UX Bastille, you will only be asked about protocols which
are currently allowed by the HP-UX Bastille configuration.
IMPORTANT: Manual action required to complete this configuration. See
the TODO.txt file for details.
Actions Setup a basic default-deny firewall configuration.
IPFilter.install_ipfilter
Headline Provide information on how to get a copy of IPFilter.
Default Y
Description Firewalls generally make up the first line of defense in any network security
architecture. IPFilter is a free host-based firewall which is available for HP-UX.
It looks like you have IPFilter installed, but that does not mean that it is
configured. HP-UX Bastille cannot detect whether the rule-set is appropriate
for your needs.
Actions
Provide information on how to get a copy of IPFilter in TODO.txt.
MiscellaneousDaemons.configure_ssh
Headline Configure the HP-UX Secure Shell daemon to use generally-accepted defaults.
Default N
Description Secure Shell is one of the most important tools in the administrator security
toolkit. It enables remote secure login and command execution, and can wrap
otherwise-unauthenticated and non-protected X11 traffic in a secure SSL
tunnel. This item configures SSH to conform with some generally-accepted
best practices. This item configures:
• Use only protocol 2, a protocol generally considered more secure
• Ignore rhosts, to avoid trusting remote hosts to assert user id without
user-based authentication
• Forward X11 traffic, if any, in a secure SSL tunnel
• Block use of accounts with empty passwords
• Use the contents of /etc/issue (also set in HP-UX Bastille) as the login
banner
Actions
Set the following parameters in /etc/opt/ssh/sshd_config:
• Protocol–2
• X11Forwarding–yes
• IgnoreRhosts–yes
• RhostsAuthentication–no
• RhostsRSAAuthentication–no
• PermitRootLogin–no
• PermitEmptyPasswords–no
• Banner– /etc/issue
MiscellaneousDaemons.diagnostics_localonly
Headline Restrict the diagnostic daemon to local connections.
Default N
50 Question modules
Page 51

Description The HP-UX diagnostics daemon can listen on a network port. The diagnostics
GUI can be run remotely for administrators and support personnel to find
and fix hardware problems. Later versions of this daemon have the option to
only listen to local UNIX domain sockets. This way, the GUI can still be run
locally to diagnose hardware problems, but it does not allow a network attacker
to take advantage of any vulnerabilities that might be found in the future.
Actions Stop the diagnostics daemon.
Create the /var/stm/config/sys/local_only file.
Start the daemon.
MiscellaneousDaemons.disable_bind
Headline Disable the Bind/DNS server on this system.
Default Y
Description The DNS server, Bind, is a useful but easily spoofed infrastructure for mapping
IP addresses to their associated host names. If this system is not a DNS server,
disable to reduce the risk to this system if an exploit is discovered.
Actions
If running, stop process named.
Set NAMED=0 in /etc/rc.config.d/namesvrs.
MiscellaneousDaemons.disable_ptydaemon
Headline
Disable both the ptydaemon and vtdaemon.
Default N
Description
The ptydaemon is used by the shell layers (shl) software. The shl utility is
an alternative to job control. If no one on your system is going to use shl, you
can safely turn the ptydaemon off.
Actions
If running, stop process ptydaemon.
Set PTYDAEMON_START=0 in /etc/rc.config.d/ptydaemon.
MiscellaneousDaemons.disable_pwgrd
Headline
Disable pwgrd.
Default N
Description
The pwgrd utility is the Password and Group Hashing and Caching daemon.
The pwgrd utility provides accelerated lookup of password and group
information for libc routines such as getpwuid and getgrname. However,
on systems with normal sized (less than 50 entries) password files, pwgrd
slows lookups due to UNIX domain sockets overhead. The security benefit of
turning this service off is also based on the principle of minimalism. This
daemon runs as root and accepts input from non-privileged users.
Actions
If running, stop process pwgrd.
Set PWGR=0 in /etc/rc.config.d/pwgr.
MiscellaneousDaemons.disable_rbootd
Headline
Deactivate rbootd.
Default Y
Description
The rbootd daemon is used for the RMP protocol, which is a predecessor to
the "bootp" protocol which serves DHCP. Unless you are using this machine
to serve dynamic IP addresses to very old HP-UX systems (prior to 10.0, or
older than s712), you have no reason to run this.
51
Page 52

Actions
If running, stop process rbootd.
Set START_RBOOTD=0 in /etc/rc.config.d/netdaemons.
MiscellaneousDaemons.disable_smbclient
Headline Disable the HP-UX CIFS client.
Default Y
Description CIFS can be used to share files and other resources between computers. The
CIFS product suite integrates HP-UX with Microsoft Windows environments
by providing remote file sharing, printer access and authentication services
between HP-UX and Windows systems.
Actions
If running. stop process cifsclient.
Set RUN_CIFSCLIENT=0 in /etc/rc.config.d/cifsclient.
MiscellaneousDaemons.disable_smbserver
Headline Disable the HP-UX CIFS (Samba) Server.
Default N
Description CIFS can be used to share files and other resources between computers. The
CIFS product suite integrates HP-UX with Microsoft Windows environments
by providing remote file sharing, printer access, and authentication services
between HP-UX and Windows systems.
Actions
If running, stop processes smbd and nmbd.
Set RUN_SAMBA=0 in /etc/rc.config.d/samba.
MiscellaneousDaemons.nfs_core
Headline Disable the NFS and RPC infrastructure.
Default N
Description RPC is atraditional part of UNIX used in avariety of UNIX services, including
NIS, NFS, and others. If you are sure you are not using a service that is affected,
you may disable RPC. RPC has had security issues in the past and by default
does not support a strong authentication mechanism. If you disable the core
NFS infrastructure, HP-UX Bastille disables NIS, NIS+ and NFS.
Actions Stop and disable NIS/NIS+ Server and Client.
Stop and disable NFS Server and Client.
Set NFS_CORE=0 in /etc/rc.config.d/nfsconf.
MiscellaneousDaemons.nobody_secure_rpc
Headline Disable the nobody user in the ONC Secure RPC
Default N
Description Secure RPC is a cryptographically authenticated means to communicate with
a system. By configuring keyserv to prevent the use of default keys for the
nobody user, other users are prevented from accessing the nobody user with
default credentials. This is a safer way to operate Secure RPC.
Actions
Add the -d flag to the KEYSERV_OPTIONS= parameter line in /etc/
rc.config.d/namesvrs.
MiscellaneousDaemons.snmpd
Headline Disable SNMPD.
Default N
52 Question modules
Page 53

Description The simple network management protocol (SNMP) aids in the management
of machines over the network. This can be a powerful method of monitoring
and administering a set of networked machines. If you use network
management software to maintain the computers on your network, you should
audit the way in which SNMP is used by that software.
• Use SNMPv3 wherever possible.
• Set restrictive access control lists.
• Block SNMP traffic at your firewall.
• Disable the SNMP daemons.
The average home user or standalone server has no reason to run these
daemons. Depending on their default configuration, these deamons could be
a major security risk. However, if configured correctly and used in conjunction
with management software, these daemons can dramatically improve
accessibility and response time to problems when they occur. If this is disabled,
network management software such as HP Openview which relies on SNMP
does not work.
Actions
If running stop process snmpdm.
Set SNMP_HPUNIX_START=0 in /etc/rc.config.d/Hpunix.
Set SNMP_MASTER_START=0 in /etc/rc.config.d/Master.
Set SNMP_MIB2_START=0 in /etc/rc.config.d/Master.
Set SNMP_TRAPDEST_START=0 in /etc/rc.config.d/TrpDst.
MiscellaneousDaemons.syslog_localonly
Headline Restrict the system logging daemon to local connections.
Default N
Description
The system logging daemon syslogd listens on network ports to support
remote logging facilities. Remote logging can be helpful for security reasons
because if an attacker gains access to a single machine, he can probably modify
or delete the logs on that machine. Storing the logs on another machine can
help with forensics and incidence response,even if the logs have been tampered
with on the local machine.
Actions
Add the -N flag to the SYSLOGD_OPTS= parameter line in /etc/
rc.config.d/syslogd.
MiscellaneousDaemons.xaccess
Headline Disallow remote X logins.
Default N
Description XDMCP is an unencrypted protocol that allows remote connections to an X
server. This protocol is commonly used by dumb graphics terminals and
PC-based X-emulation software to bring up a remote login and desktop.
Actions
If the /etc/dt/config/Xconfig file does not exist, create it from /usr/
dt/config/Xconfig.
Append the Dtlogin.requestPort:0 line in the /etc/dt/config/
Xconfig file.
other_boot_serv
Headline Deactivate uncommon legacy boot services.
Default Y
Description
The services mrouted, rwhod, ddfs, rarpd, rdpd, and snaplus2 are not
usually used on standalone or specific-purpose servers. These services are
53
Page 54

sometimes configured to provide network services to other systems. Disable
these services unless you know of a specific reason to leave them enabled.
Actions
Kill processes: mrouted, rwhod, rarpd, rdpd, snapdaemon
Set MROUTED=0 in /etc/rc.config.d/netdaemons
Set RWHOD=0 in /etc/rc.config.d/netdaemons
Set RARPD=0 in /etc/rc.config.d/netconf
Set RDPD=0 in /etc/rc.config.d/netconf
Set START_SNAPLUS=0 in /etc/rc.config.d/snaplus2
Patches.spc_cron_run
Headline
Set up a cron job to run SWA or SPC.
Default Y
Description HP-UX Bastille can configure Software Assistant (SWA), or Security Patch
Check (SPC)to run daily using the cron scheduling daemon. Keeping a system
secure requires constant vigilance. Staying up-to-date on security bulletins
issued by Hewlett-Packard is critical. These tools are the easiest way to make
sure this system is compliant with the steps required in HP security bulletins.
A subscription to the HP security bulletin mailing list provides the latest
security fixes from HP.
NOTE: This question is asked whether or not you have Software Assistant,
or Security Patch Check installed so that HP-UX Bastille can pre-configure
cron to run these applications after they are installed.
NOTE: HP recommends SWA. SPC uses FTP, a clear-text, unauthenticated
protocol.
Register for notification of all HP security bulletins at http://www.itrc.hp.com.
Click on Maintenance and Support for HP Products then select Support
Information Digests.
Actions
Set a daily cron job to run SWA or SPC.
Patches.spc_cron_time
Headline Set hour for a security bulletin compliance report.
Default 11
Description Specify a number between 0 and 23, corresponding to the hour in your time
zone that is most convenient to run a security bulletin compliance report. For
example, if you specify 0, Security Patch Check runs between 12:00 A.M. and
12:59 A.M. in your local time zone. If you specify 23, the security bulletin
compliance report runs between 11:00 P.M. and 11:59 P.M.
Actions Parameter only.
Patches.spc_proxy_yn
Headline
Does this machine require a proxy to ftp to the Internet?
Default N
Description
Sets spc_proxy_yn.
Actions None.
Patches.spc_run
Headline Run SWA/SPC.
Default Y
Description Patching, updating, and configuring software to address known security
vulnerabilities is important for securing a system. SWA and SPC are tools
54 Question modules
Page 55

which analyze the software installed on the system. HP-UX Bastille runs SWA
version C.01.01 or later. Otherwise, SPC is used to create a security-compliance
report. The security compliance report lists:
• Installed patches that have warnings (recalls) issued by HP.
• Security patches announced by HP that will fix installed software but
have not been applied.
• Currently installed patches not properly configured.
• Software that needs to be removed or updated to comply with a bulletin.
• Manual actions necessary to bring the server to bulletin compliance.
SWA and SPC can work through a proxy-type firewall to download current
catalogs from HP with security and patch-warning information. Bulletin
compliance requires vigilance. New vulnerabilities are found and fixed on a
regular basis. HP recommends running one of these tools frequently, such as
in a nightly cron job.(A separate question will cover this). HP recommends
that you subscribe to the HP Security Bulletin mailing list.
NOTE: SPC uses clear-text protocols FTP or HTTP if a link can not be
established with https. The output of this tool is appended to the HP-UX
Bastille generated TODO.txt file so that you can apply the necessary patches.
IMPORTANT: Manual action required to complete this configuration. See
TODO.txt file for details.
Actions HP-UX Bastille runs SWA or SPC.
Printing.printing
Headline Disable printing.
Default N
Description If this machine does not print, stop the print scheduler and disable the
associated print daemon utilities. On Linux, this includes the restriction of the
daemon file permissions. On HP-UX, this includes the disablement of the
xprintserver and pd client services where applicable.
Actions
If running, stop processes lpsched pdclientd.
Set XPRINTSERVERS= in /etc/rc.config.d/tps.
Set LP=0 in /etc/rc.config.d/lp.
Set PD_CLIENT=0 in /etc/rc.config.d/pd.
SecureInetd.banners
Headline Display "Authorized Use" messages at login time.
Default N
Description You can create "Authorized Use Only" messages for your site. These can be
helpful in prosecuting system crackers you catch trying to break into your
system. HP-UX Bastille makes default messages that you can edit. This is like
an "anti-welcome mat" for your system.
Actions
Create default login banner messages in the /etc/motd and /etc/issue
files.
Modify the entries for rlogind and telnetd in the /etc/inetd.conf file
to use /etc/issue banner.
SecureInetd.deactivate_bootp
Headline
Ensure that the inetd bootp service does not run on this system.
55
Page 56

Default Y
Description
The bootpd daemon implements three functions; a DHCP server, an Internet
Boot Protocol(BOOTP) server, and a DHCP/BOOTP relay agent. If this system
is not a BOOTP/DHCP server or a DHCP/BOOTP relayagent, HP recommends
disabling this service.
Actions
Comment out the entry for bootp in the /etc/inetd.conf file.
SecureInetd.deactivate_builtin
Headline
Ensure that the inetd built-in services do not run on this system.
Default N
Description
The inetd built-in services include chargen, daytime, discard, and echo.
These services are rarely used and when they are it is generally for testing.
The UDP versions of these services can be used in a Denial of Service attack
and therefore HP recommends disabling these services.
The daytime service sends the current date and time as a human-readable
character string (RFC 867). The discard service throws away anything that
is sent to it, similar to /dev/null (RFC 863). The chargen service character
generator sends a stream of some undefined data, preferably data in some
recognizable pattern (RFC 862). The echo service returns the packets sent to
it (RFC 862).
Actions
Comment out the entries for daytime, echo, discard, and chargen in the
/etc/inetd.conf file.
SecureInetd.deactivate_dttools
Headline
Ensure the inetd CDE helper services do not run on this system.
Default N
Description
The dtspcd, ttdbserver, and cmsd services are used by CDE. Each service
has merits, but they are all rarely used and mostly deprecated.
Actions
In the /etc/inetd.conf file, comment out the entries for:
• dtspc stream tcp nowait root /usr/dt/bin/dtspcd
/usr/dt/bin/dtspcd
• rpc xti tcp swait root /usr/dt/bin/rpc.ttdbserver
100083 1 /usr/dt/bin/rpc.ttdbserver
• srpc dgram udp wait root /ur/dt/bin/rpc.cmsd 100068
2-5 rpc.cmsd
SecureInetd.deactivate_finger
Headline
Ensure the inetd finger service does not run on this system.
Default Y
Description
The server for the RFC 742 Name/Finger protocol is fingerd. It provides a
network interface to finger, which gives a status report of users currently
logged in the system or a detailed report about a specific user. For more
information aboutthe finger command, see finger(1). HP recommends disabling
the service because fingerd provides local system user information to remote
sources andthis can be useful to someone attempting to break into your system.
Actions
In the /etc/inetd.conf file, comment out the entry for finger.
SecureInetd.deactivate_ftp
Headline
Ensure that the inetd FTP service does not run on this system.
Default N
56 Question modules
Page 57

Description FTP is a legacy protocol. It is a clear-text protocol, like Telnet, and allows an
attacker to eavesdrop on sessions and steal passwords. This also allows an
attacker to take over an FTP session, using a clear-text-takeover tool like Hunt
or Ettercap. It can make effective firewalling difficult because of the way FTP
requires many ports to stay open. Every major FTP daemon has had a long
history of security vulnerability. They represent one of the major successful
attack vectors for remote root attacks.
Actions
In the /etc/inetd.conf file, comment out the entry for ftp.
SecureInetd.deactivate_ident
Headline
Ensure that the inetd ident service does not run on this system.
Default N
Description
The ident service implements the TCP/IP proposed standard IDENT user
identification protocol as specified in the RFC 1413 document. The identd
service operates by looking up specific TCP/IP connections and returning the
user name of the process owning the connection. This service can be used to
determine user information on a given machine inpreparation for a brute-force
password attack like a dictionary attack. HP recommends disabling this service
unless compelled by application specific needs.
Actions
In the /etc/inetd.conf file, comment out the entry for auth or ident.
SecureInetd.deactivate_ktools
Headline
Ensure that the inetd klogin and kshell services do not run on this
system.
Default N
Description
The kshell and klogin services use Kerberos authentication protocols. If
this machine is not using the Kerberos scheme, HP recommends disabling
these services. Any service or daemon running on the system that is not needed
or used should be disabled.
Actions
In the /etc/inetd.conf file, comment out the entry for kshell and
klogin.
SecureInetd.deactivate_ntalk
Headline
Ensure that the inetd ntalk service does not run on this system.
Default N
Description
The ntalk service is a visual communication program that predates instant
messaging applications and copies lines from your terminal to another user's
terminal. The ntalk service is considered a light security hazard, but should
be disabled if not used on this machine.
Actions
In the /etc/inetd.conf file, comment out the entry for ntalk.
SecureInetd.deactivate_printer
Headline
Ensure the inetd printer service does not run on this system.
Default N
Description
The printer service is a line printer daemon that accepts remote spool
requests. It uses the rlp daemon to process remote print requests and displays
the queue and removes jobs from the queue upon request. If this machine is
not used as a remote print spooler, this service should be disabled.
Actions
In the /etc/inetd.conf file, comment out the entry for printer.
57
Page 58

SecureInetd.deactivate_recserv
Headline
Ensure the inetd recserv service does not run on this system.
Default N
Description HP SharedX Receiver Service receives shared windows from another machine
in X without explicitly performing any xhost command. This service is
required for MPower remote windows. If you use MPower, leave this service
running on your system. The SharedX Receiver Service is an automated
wrapper around the xhost command. For more information about the xhost
command, seexhost(1). This service shouldbe disabled unless shared windows
are viewed often on this machine. The xhost command is generally the more
secure solution because it makes all sharing of windows explicit.
Actions
In the /etc/inetd.conf file, comment out the entry for recserv.
SecureInetd.deactivate_rquotad
Headline
Ensure the inetd rquotad service does not run on this system.
Default Y
Description
The rquotad server is an RPC server that returns quotas for a user of a local
file system mounted remotely through NFS. This service should be disabled
if not using quotas with NFS.
Actions
In the /etc/inetd.conf file, comment out the entry for rpc.rquotad.
SecureInetd.deactivate_rtools
Headline
Ensure that the login, shell, and exec services do not run on this system.
Default N
Description
The login, shell, and exec services use the r-tools: rlogind, remshd, and
rexecd respectively, which use IP-based authentication. This form of
authentication can be easily defeated with forging packets that suggest the
connecting machine is a trusted host when in fact it may be an arbitrary
machine on the network. Administrators in the past have found these services
useful, but many are unaware of the security ramifications of leaving these
services enabled.
Actions
In the /etc/inetd.conf file, comment out the entries for login, shell,
and exec.
SecureInetd.deactivate_swat
Headline
Ensure the inetd swat service does not run on this system.
Default N
Description
The swat service allows a Samba administrator to configure Samba through
a web browser. The swat service allows administrators to view, change, and
affect the change through the web. The drawback from a security standpoint
comes from the authentication method used for the Samba administrator.
Clear-text passwords are passed through the network if a connection is initiated
from an outside source. This form of authentication is easily defeated and HP
recommends not running the swat service on this machine.
Actions
In the /etc/inetd.conf file, comment out the entry for swat.
SecureInetd.deactivate_telnet
Headline
Ensure that the telnet service does not run on this system.
Default N
Description Telnet is not secure. Telnet is shipped on most operating systems for backward
compatibility. Do not use it in an untrusted network. Telnet is a clear-text
58 Question modules
Page 59

protocol. Any data transferred, including passwords, can be monitored by
anyone else on your network even if you use a switching router. Switches
were designed for performance, not security and can be made to broadcast.
Other networks can monitor this information too if the Telnet session crosses
multiple LANs. There are also other more active attacks. For example, anyone
who can eavesdrop can usually take over your Telnet session using a tool like
Hunt or Ettercap. The standard practice among security-conscious sites is to
migrate as rapidly as practical from Telnet to Secure Shell (command: ssh).
HP recommends to make this move as soon as possible. Secure shell
implementations are available from openssh.org andssh.com. Mostoperating
system vendors also distribute a version of secure shell. Check with your
vendor first to see if there is a version that has been tested with your OS.
NOTE: Deactivating the telnetd service will not affect your Telnet client.
Actions
In the /etc/inetd.conf file, comment out the entry for telnet.
SecureInetd.deactivate_tftp
Headline
Ensure the inetd TFTP service does not run on this system.
Default Y
Description The Trivial File Transfer Protocol (TFTP) is often used to download operating
system images and configuration data to diskless hosts. TFTP is a UDP-based
file-transfer program that provides little security. If this machine is not a boot
server for diskless host/appliances or an Ignite-UX server, TFTP should be
disabled.
Actions
In the /etc/inetd.conf file, comment out the entry for tftp.
SecureInetd.deactivate_time
Headline
Ensure the inetd time service does not run on this system.
Default N
Description
The time service built into inetd produces machine-readable time in seconds
since midnight on 1 January 1900 (RFC 868). It is used for clock
synchronization, but it lacks the ability to be configured securely. HP
recommends disabling the time service for this machine. Use the Network
Time Protocolto synchronize clocks becauseXNTP can be configured securely.
For more information on XNTP, xntpd(1).
Actions
In the /etc/inetd.conf file, comment out the entry for time.
SecureInetd.deactivate_uucp
Headline
Ensure the inetd uucp service does not run on this system.
Default Y
Description
UNIX to UNIX Copy (UUCP) copies files named by the source_files
argument tothe destination identified by the destination_file argument.
UUCP uses clear-text transport for authentication. It is not commonly used.
HP recommends disabling this service and using a more secure file transfer
program such as scp.
Actions
In the /etc/inetd.conf file, comment out the entry for uucp.
SecureInetd.ftp_logging
Headline Enable logging for FTP connections.
Default N
59
Page 60

Description Logging FTP connection and command activity is recommended. The only
reason not to do this is the frequency of logging from FTP fills logs more
quickly, particularly if FTP services are heavily used on this machine.
Actions
In the /etc/inetd.conf file, add the -l flag to the entry for ftpd.
SecureInetd.inetd_general
Headline
Reminder to disable unneeded inetd services in the TODO.txt file.
Default N
Description
Disable unneeded inetd services. Leave only those services running that are
critical to the operation of this machine. This is an example of the frequent
trade off between security and functionality. The most secure machine is not
very useful. For the most secure but useful system, enable only those services
which this system needs to fulfill its intended purpose. You can further restrict
access using the inetd.sec file or a program like tcpwrappers. If you
answer Y to this question, HP-UX Bastille also points you to information on
how to configure these tools.
IMPORTANT: Manual action required to complete this configuration. See
TODO.txt file for details.
Actions
Instructions for manual actions provided in TODO.txt list.
SecureInetd.log_inetd
Headline
Enable logging for all inetd connections.
Default N
Description
Logging connectionattempts to inetd services is a good idea. The only reason
not to do this is the frequency of logging from inetd fills logs more quickly,
particularly if inetd services are heavily used on this machine.
Actions
In the /etc/rc.config.d/netdaemons file, add the -l flag to the
INETD_ARGS= parameter.
SecureInetd.owner
Headline Who is responsible for granting authorization to use this machine?
Default The owner
Description HP-UX Bastille makes the banner more specific by telling the user who is
responsible for this machine. This will state explicitly who the user needs to
obtain authorization from to use this machine. Fill in the name of the company,
person, or other organization who owns or is responsible for this machine.
Actions Parameter for default banner. No action.
Sendmail.sendmailcron
Headline
Run sendmail via cron to process the queue.
Default Y
Description
Should sendmail run every 15 minutes to process the mail queue by
processing and sending out email? If this machine does not run sendmail in
daemon mode, you might want to enable this to make your outbound mail
more reliable.
In most cases, mail queue processing is not required because most mailer
programs activate sendmail to process their particular message. A message
usually only gets written to the queue (and thus needs a cron entry) if
sendmail has trouble delivering it. For example if the receiving mail server
is down.
60 Question modules
Page 61

NOTE: While processing the mail queue, sendmail does not accept inbound
connections.
NOTE: The 15 minute interval can be changed later. See crontab(1).
Actions
Set a cron job to run /usr/sbin/sendmail -q every 15 minutes.
Sendmail.sendmaildaemon
Headline
Stop sendmail from running in daemon mode.
Default Y
Description
To send and receive mail, sendmail does not need to be running in daemon
mode. Unless you have a constant network connection, you cannot run
sendmail in daemon mode. Daemon mode means that sendmail is
constantly listening on a network connection waiting to receive mail. If you
disable daemonmode, HP-UX Bastille asksif you would like to run sendmail
every few minutes to process the queue of outgoing mail. Most programs send
mail immediately, and processing the queue takes care of transient errors. If
you receive all of your email through a POP/IMAP mailbox provided by your
ISP, you may not need daemon-mode sendmail, unless you run a special
fetchmail-style POP/IMAP-based retrieval program. For example, if you read
your mail with the Netscape common POP/IMAP read functionality, turn
daemon mode off. The only reason to run sendmail in daemon mode is if
you run a mail server.
Actions
In the /etc/rc.config.d/mailservs file, set SENDMAIL_SERVER=0.
Sendmail.vrfyexpn
Headline
Disable the VRFY and EXPN sendmail commands.
Default Y
Description
An attacker canuse the sendmail vrfy (verify recipient existence) and expn
(expand recipient alias/list contents) commands to learn more about accounts
on the system. For example, the expn command can be used to findout where
the postmaster and abuse aliases are redirected. This identifies which user
account belongs to the system administrator. These sendmail commands
can be disabled without breaking anything and make the system cracker's job
more difficult. The only reasons to leave them on are because you run an
old-fashioned friendly site, you use them to debug your own mail server, or
some software you use relies on this.
Actions
In the sendmail configuration file /etc/mail/sendmail.cf, append the
O PrivacyOptions=goaway line.
61
Page 62

62
Page 63

D Sample weight files
D.1 all.weight
The weight file below is located in /etc/opt/sec_mgmt/bastille/configs/defaults.
This template file contains all possible HP-UX question items as selected.
AccountSecurity.ABORT_LOGIN_ON_MISSING_HOMEDIR=1
AccountSecurity.AUTH_MAXTRIES=1
AccountSecurity.MIN_PASSWORD_LENGTH=1
AccountSecurity.NOLOGIN=1
AccountSecurity.NUMBER_OF_LOGINS_ALLOWED=1
AccountSecurity.PASSWORD_HISTORY_DEPTH=1
AccountSecurity.PASSWORD_MAXDAYS=1
AccountSecurity.PASSWORD_MINDAYS=1
AccountSecurity.PASSWORD_WARNDAYS=1
AccountSecurity.SU_DEFAULT_PATH=1
AccountSecurity.atuser=1
AccountSecurity.block_system_accounts=1
AccountSecurity.create_securetty=1
AccountSecurity.crontabs_file=1
AccountSecurity.cronuser=1
AccountSecurity.gui_login=1
AccountSecurity.hidepasswords=1
AccountSecurity.lock_account_nopasswd=1
AccountSecurity.mesgn=1
AccountSecurity.restrict_home=1
AccountSecurity.root_path=1
AccountSecurity.serial_port_login=1
AccountSecurity.single_user_password=1
AccountSecurity.system_auditing=1
AccountSecurity.umask=1
AccountSecurity.unowned_files=1
AccountSecurity.user_dot_files=1
AccountSecurity.user_rc_files=1
Apache.chrootapache=1
Apache.deactivate_hpws_apache=1
DNS.chrootbind=1
FTP.ftpbanner=1
FTP.ftpusers=1
FilePermissions.world_writeable=1
HP_UX.gui_banner=1
HP_UX.mail_config=1
HP_UX.ndd=1
HP_UX.other_tools=1
HP_UX.restrict_swacls=1
HP_UX.scan_ports=1
HP_UX.screensaver_timeout=1
HP_UX.stack_execute=1
HP_UX.tcp_isn=1
IPFilter.block_DNSquery=1
IPFilter.block_SecureShell=1
IPFilter.block_cfservd=1
IPFilter.block_hpidsadmin=1
IPFilter.block_hpidsagent=1
IPFilter.block_netrange=1
IPFilter.block_ping=1
IPFilter.block_wbem=1
IPFilter.block_webadmin=1
IPFilter.configure_ipfilter=1
IPFilter.install_ipfilter=1
MiscellaneousDaemons.configure_ssh=1
MiscellaneousDaemons.diagnostics_localonly=1
D.1 all.weight 63
Page 64

MiscellaneousDaemons.disable_bind=1
MiscellaneousDaemons.disable_ptydaemon=1
MiscellaneousDaemons.disable_pwgrd=1
MiscellaneousDaemons.disable_rbootd=1
MiscellaneousDaemons.disable_smbclient=1
MiscellaneousDaemons.disable_smbserver=1
MiscellaneousDaemons.nfs_client=1
MiscellaneousDaemons.nfs_core=1
MiscellaneousDaemons.nfs_server=1
MiscellaneousDaemons.nis_client=1
MiscellaneousDaemons.nis_server=1
MiscellaneousDaemons.nisplus_client=1
MiscellaneousDaemons.nisplus_server=1
MiscellaneousDaemons.nobody_secure_rpc=1
MiscellaneousDaemons.other_boot_serv=1
MiscellaneousDaemons.snmpd=1
MiscellaneousDaemons.syslog_localonly=1
MiscellaneousDaemons.xaccess=1
Patches.spc_cron_run=1
Patches.spc_run=1
Printing.printing=1
SecureInetd.banners=1
SecureInetd.deactivate_bootp=1
SecureInetd.deactivate_builtin=1
SecureInetd.deactivate_dttools=1
SecureInetd.deactivate_finger=1
SecureInetd.deactivate_ftp=1
SecureInetd.deactivate_ident=1
SecureInetd.deactivate_ktools=1
SecureInetd.deactivate_ntalk=1
SecureInetd.deactivate_printer=1
SecureInetd.deactivate_recserv=1
SecureInetd.deactivate_rquotad=1
SecureInetd.deactivate_rtools=1
SecureInetd.deactivate_swat=1
SecureInetd.deactivate_telnet=1
SecureInetd.deactivate_tftp=1
SecureInetd.deactivate_time=1
SecureInetd.deactivate_uucp=1
SecureInetd.ftp_logging=1
SecureInetd.log_inetd=1
SecureInetd.owner=1
Sendmail.sendmailcron=1
Sendmail.sendmaildaemon=1
Sendmail.vrfyexpn=1
D.2 CIS.weight
The sample weight file below aligns with the CIS standard.
AccountSecurity.AUTH_MAXTRIES=1
AccountSecurity.MIN_PASSWORD_LENGTH=1
AccountSecurity.PASSWORD_HISTORY_DEPTH=1
AccountSecurity.PASSWORD_MAXDAYS=1
AccountSecurity.PASSWORD_MINDAYS=1
AccountSecurity.PASSWORD_WARNDAYS=1
AccountSecurity.atuser=1
AccountSecurity.block_system_accounts=1
AccountSecurity.create_securetty=1
AccountSecurity.crontabs_file=1
AccountSecurity.cronuser=1
AccountSecurity.gui_login=1
AccountSecurity.hidepasswords=1
AccountSecurity.lock_account_nopasswd=1
AccountSecurity.mesgn=1
64 Sample weight files
Page 65

AccountSecurity.restrict_home=1
AccountSecurity.root_path=1
AccountSecurity.serial_port_login=1
AccountSecurity.system_auditing=1
AccountSecurity.umask=1
AccountSecurity.unowned_files=1
AccountSecurity.user_dot_files=1
AccountSecurity.user_rc_files=1
Apache.deactivate_hpws_apache=1
FTP.ftpbanner=1
FTP.ftpusers=1
HP_UX.gui_banner=1
HP_UX.ndd=1
HP_UX.screensaver_timeout=1
HP_UX.stack_execute=1
HP_UX.tcp_isn=1
MiscellaneousDaemons.configure_ssh=1
MiscellaneousDaemons.disable_bind=1
MiscellaneousDaemons.disable_ptydaemon=1
MiscellaneousDaemons.disable_rbootd=1
MiscellaneousDaemons.disable_smbclient=1
MiscellaneousDaemons.disable_smbserver=1
MiscellaneousDaemons.nfs_client=1
MiscellaneousDaemons.nfs_core=1
MiscellaneousDaemons.nfs_server=1
MiscellaneousDaemons.nis_client=1
MiscellaneousDaemons.nis_server=1
MiscellaneousDaemons.nisplus_client=1
MiscellaneousDaemons.nisplus_server=1
MiscellaneousDaemons.nobody_secure_rpc=1
MiscellaneousDaemons.other_boot_serv=1
MiscellaneousDaemons.snmpd=1
MiscellaneousDaemons.syslog_localonly=1
MiscellaneousDaemons.xaccess=1
Printing.printing=1
SecureInetd.banners=1
SecureInetd.deactivate_bootp=1
SecureInetd.deactivate_builtin=1
SecureInetd.deactivate_dttools=1
SecureInetd.deactivate_finger=1
SecureInetd.deactivate_ftp=1
SecureInetd.deactivate_ident=1
SecureInetd.deactivate_ktools=1
SecureInetd.deactivate_ntalk=1
SecureInetd.deactivate_printer=1
SecureInetd.deactivate_recserv=1
SecureInetd.deactivate_rquotad=1
SecureInetd.deactivate_rtools=1
SecureInetd.deactivate_telnet=1
SecureInetd.deactivate_tftp=1
SecureInetd.deactivate_time=1
SecureInetd.deactivate_uucp=1
SecureInetd.log_inetd=1
SecureInetd.owner=1
Sendmail.sendmailcron=1
Sendmail.sendmaildaemon=1
D.2 CIS.weight 65
Page 66

66
Page 67

E CIS mapping to HP-UX Bastille
Mapping to HP-UX BastilleLevel 1 benchmark for HP-UX 11i (v1.5.0)CIS
HP-UX Bastille lock down itemsCIS benchmark sectionCIS ID
Patches and Additional Software1.1
Not ScorableApply latest OS patches1.1.1
MiscellaneousDaemons.configure_sshInstall and configure SSH1.1.2
Not ScorableInstall and Run Bastille1.1.3
Minimize inetd network services1.2
SecureInetd.deactivate_builtin
SecureInetd.deactivate_finger
SecureInetd.deactivate_ident
SecureInetd.deactivate_ntalk
SecureInetd.deactivate_recserv
SecureInetd.deactivate_time
SecureInetd.deactivate_uucp
SecureInetd.deactivate_telnet
SecureInetd.deactivate_ftp
SecureInetd.deactivate_rtools
SecureInetd.deactivate_tftp
SecureInetd.deactivate_printer
SecureInetd.deactivate_rquotad
SecureInetd.deactivate_dttools
SecureInetd.deactivate_ktools
SecureInetd.deactivate_bootp
Disable Standard Services1.2.1
Not ApplicableOnly enable telnet1.2.2
Not ApplicableOnly enable FTP1.2.3
Not ApplicableOnly enable rlogin/remsh/rcp1.2.4
Not ApplicableOnly enable TFTP1.2.5
Not ApplicableOnly enable printer service1.2.6
Not ApplicableOnly enable rquotad1.2.7
Not ApplicableOnly enable CDE-related daemons1.2.8
Not ApplicableOnly enable Kerberos-related daemons1.2.9
Not ApplicableOnly enable BOOTP/DHCP daemon1.2.10
Minimize boot services1.3
AccountSecurity.serial_port_loginDisable login: prompts on serial ports1.3.1
MiscellaneousDaemons.nis_client
MiscellaneousDaemons.nis_server
MiscellaneousDaemons.nisplus_server
MiscellaneousDaemons.nisplus_client
Disable NIS/NIS+ related processes1.3.2
Printing.printingDisable printer daemons1.3.3
AccountSecurity.gui_loginDisable GUI login1.3.4
Sendmail.sendmaildaemon
Sendmail.sendmailcron
Disable email server1.3.5
MiscellaneousDaemons.snmpdDisable SNMP and OpenVIew1.3.6
67
Page 68

Mapping to HP-UX BastilleLevel 1 benchmark for HP-UX 11i (v1.5.0)CIS
MiscellaneousDaemons.disable_rbootd
MiscellaneousDaemons.nfs_server
MiscellaneousDaemons.nfs_client
MiscellaneousDaemons.disable_ptydaemon
Apache.deactivate_hpws_apache
MiscellaneousDaemons.snmpd
MiscellaneousDaemons.nfs_core
MiscellaneousDaemons.other_boot_serv
MiscellaneousDaemons.disable_smbclient
MiscellaneousDaemons.disable_smbserver
MiscellaneousDaemons.disable_bind
Disable other standard boot services1.3.7
Not ApplicableOnly enable Windows-compatibility server processes1.3.8
Not ApplicableOnly enable Windows-compatibility client processes1.3.9
Not ApplicableOnly enable NFS server processes1.3.10
Not ApplicableOnly enable NFS client processes1.3.11
Not ApplicableOnly enable RPC-based services1.3.12
Not ApplicableOnly enable Web server1.3.13
Not ApplicableOnly enable BIND DNS server1.3.14
Kernel Tuning1.4
HP_UX.stack_executeEnable stack protection1.4.1
HP_UX.nddNetwork parameter modifications1.4.2
HP_UX.tcp_isnUse better TCP sequence numbers1.4.3
HP_UX.nddAdditional network parameter modifications1.4.4
File/Directory Permissions/Access1.5
Not ScorableSet Sticky Bit on World Writable Directories1.5.1
Not Scorable
Find unauthorized world-writable files and SUID/SGID
executables1.5.2
AccountSecurity.unowned_filesFind 'unowned' files and directories1.5.3
System Access, Authentication, and Authorization1.6
AccountSecurity.hidepasswordsEnable Hidden Passwords1.6.1
FTP.ftpusersRestrict users who can access to FTP1.6.2
MiscellaneousDaemons.syslog_localonlyPrevent Syslog from accepting messages from the network1.6.3
MiscellaneousDaemons.xaccessDisable XDMCP port1.6.4
HP_UX.screensaver_timeoutSet default-lock screensaver timeout1.6.5
Not ScorableConfigure IPFilter to allow only select communication1.6.6
AccountSecurity.cronuser
AccountSecurity.atuser
Restrict at/cron to authorized users1.6.7
AccountSecurity.crontabs_fileRestrict crontab file permissions1.6.8
AccountSecurity.create_securettyRestrict root logins to system console1.6.9
AccountSecurity.AUTH_MAXTRIESSet retry limit for account lockout1.6.10
MiscellaneousDaemons.nobody_secure_rpcDisable 'nobody' access for secure RPC1.6.11
Logging1.7
68 CIS mapping to HP-UX Bastille
Page 69

Mapping to HP-UX BastilleLevel 1 benchmark for HP-UX 11i (v1.5.0)CIS
AccountSecurity.system_auditingEnable kernel-level auditing1.7.1
SecureInetd.log_inetdEnable logging from inetd1.7.2
SecureInetd.ftp_loggingTurn on additional logging for FTP daemon1.7.3
User Accounts and Environment1.8
AccountSecurity.block_system_accountsBlock system accounts1.8.1
AccountSecurity.lock_account_nopasswdVerifythat there are no accounts with empty password fields1.8.2
AccountSecurity.PASSWORD_MAXDAYS
AccountSecurity.PASSWORD_MINDAYS
AccountSecurity.PASSWORD_WARNDAYS
Set account expiration parameters on active accounts1.8.3
AccountSecurity.PASSWORD_HISTORY_DEPTH
AccountSecurity.MIN_PASSWORD_LENGTH
Set strong password enforcement policies1.8.4
MiscellaneousDaemons.nis_clientVerify no legacy '+' entries exist in passwd and group files1.8.5
AccountSecurity.root_pathNo '.' or group/world-writable directory in root $PATH1.8.6
AccountSecurity.restrict_home
User home directories should be mode 750 or more
restrictive1.8.7
AccountSecurity.user_dot_filesNo user dot-files should be group/world writable1.8.8
AccountSecurity.user_rc_filesRemove user .netrc, .rhosts and .shosts files1.8.9
AccountSecurity.umaskSet default umask for users1.8.10
AccountSecurity.mesgnSet "mesg n" as default for all users1.8.11
Warning Banners1.9
SecureInetd.bannersCreate warning banners for terminal-session logins1.9.1
HP_UX.gui_bannerCreate warning banners for GUI logins1.9.2
FTP.ftpbannerCreate warning banners for FTP daemon1.9.3
69
Page 70

70
Page 71

Index
A
assessing, 11
C
compatibility, 8
configuration
batch mode, 13
creating, 11
replicating, 11
Serviceguard, 31
D
drift, 17
F
features, 7
file locations, 17
I
installation requirements, 9
installing, 9
ITS, 27
K
known issues, 21
P
performance, 8
Q
question modules, 33
R
related information, 23
removing, 19
reporting, 13
reverting, 16
S
scored assessment report, 14
security
dependencies, 30
levels, 27, 30
support, 8, 23
T
tips
diagnostic, 21
general use, 21
issues and workarounds, 21
troubleshooting, 21
U
using, 11
W
weight files
samples, 63
workarounds, 21
71
Page 72

 Loading...
Loading...