Page 1

900 Series HP 3000 Computer Systems
Getting Started as an
MPE/iX Programmer
Programmer's Guide
ABCDE
HP Part No. 32650-90008
Printed in U.S.A. 1992
Second Edition
E0692
Page 2

The information contained in this document is sub ject to change
without notice.
Hewlett-Packard makes no warrantyofany kind with regard to this
material, including, but not limited to, the implied w
merchantability or tness for a particular purpose. Hewlett-P
shall not be liable for errors con
special, incidental or consequential damages in connection with the
furnishing or use of this material.
Hewlett-Packard assumes no responsibility for the use or reliability of
its software on equipment that is not furnished by Hewlett-Packard.
This document contains proprietary information which is protected
by copyright. All rights are reserved. Reproduction, adaptation, or
translation without prior written permission is prohibited, except as
allowed under the copyrightlaws.
c
Copyright
Use, duplication, or disclosure by the U.S. Government is sub ject
to restrictions as set forth in subparagraph (c) (1) (ii) of the
Rights in Technical Data and Computer Software clause at DFARS
252.227-7013. Rights for non-DoD U.S. Government Departments and
agencies are as set forth in FAR 52.227-19 (c) (1,2).
tained herein or for direct, indirect,
1992 by Hewlett-Packard Company
arranties of
ackard
Hewlett-Packard Company
3000 Hanover Street
Palo Alto, CA 94304 U.S.A.
Restricted Rights Legend
Page 3
Printing History
The following table lists the prin
dates for each edition. The softw
at the time this documen
document. Therefore, do not expect a one-to-one corresp ondence bet
and document editions.
Edition Date Software Version
First Edition November 1987 A.01.00
Update 1 July 1988 A.10.00
Update 2 December 1988 A.20.00
Second Edition June 1992 B.40.00
twas issued. Many product releases do not require c
tings of this documen
are version indicates the version of the softw
t, together with the respectiv
ween product releases
e release
are product
hanges to the
iii
Page 4

iv
Page 5

Preface
Note
MPE/iX, Multiprogramming Executive with Integrated POSIX, is the latest
in a series of forward-compatible operating systems for the HP 3000 line of
computers.
In HP do cumentation and in talking with HP 3000 users, y
ou will encounter
references to MPE XL, the direct predecessor of MPE/iX. MPE/iX
is a sup erset of MPE XL. All programs written for MPE XL will run
without change under MPE/iX You can continue to use MPE XL system
documentation, although it may not refer to features added to the op erating
system to support POSIX (for example, hierarc
Finally,you may encounter references to MPE V, whic
system for HP 3000s, not based on P
can be run on the P
compatibility mode
A-RISC (Series 900) HP 3000s in what is kno
.
Getting Started as an MPE/iX Programmer
A-RISC architecture. MPE V softw
is a manual designed to introduce a programmer
hical directories).
h is the operating
wn as
to the Hewlett-Packard MPE/iX operating system, which runs on 900 Series HP 3000
computers. It provides:
An overview of the op erating system architecture, features, and facilities, explaining the
concepts necessary for a programmer to obtain a working knowledge of the system.
References to other manuals for detailed information, syntax, and advanced concepts.
are
As a prerequisite, you should review the self-paced training course
Advanced Skills
Getting Started as an MPE/iX Programmer
consists of the
(32650-60039).
is part of the Programmer's Series. This series
MPE/iX Intrinsics Reference Manual
(32650-90028) and a set of task-oriented
HP 3000 Series 900
user's guides.
How to Use this Manual
If you are new to the subject of programming on the MPE/iX operating system, y
read chapter 1 rst. If you are familiar with MPE/iX, turn directly to the c
hapter that
contains the information you need.
For information on additional programming manuals refer to the
Guide
(32650-90144).
MPE/iX Documentation
ou should
v
Page 6

Organization of this Manual
The guide contains the following chapters:
Chapter 1 Overview
covers the basics of programming on MPE/iX. It in
900 Series HP 3000, HP-P
describes the following topics on a high lev
programming purposes: MPE/iX operating system features and
fundamentals, user interface, accounting structure, migration from the MPE
V/E operating system, and data con
Chapter 2 Utilities and Tools
covers programmatic access to the MPE/iX Command
Interpreter and many other MPE/iX subsystems and utilities.
Chapter 3 Program Development
running a program on MPE/iX. It discusses the m
environment, error detection, and control co des.
Chapter 4 Link Editor
covers HP Link Editor/XL, whic
used to bring pieces of code together in
maintain libraries of sharable code.
Chapter 5 Optimizing a Program
improves program performance.
Chapter 6 File System
describes the MPE/iX File System, including le and record
structure, File System services, le specications, le domains, data
transfer, and le security.
Chapter 7 Data Management
covers data management concepts and subsystems on
MPE/iX, including KSAM, ALLBASE/SQL, TurboIMAGE, and QUERY.
troduces the
A architecture, and MPE operating systems. It
el, suitable for management and
version from MPE V/E.
covers writing, compiling, linking, loading, and
ultiprogramming
h is a subsystem of MPE/iX
to executable program les and
covers the Optimizer subsystem of MPE/iX, which
vi
Page 7

Conventions
UPPERCASE
In a syntax statement, commands and keywords are shown in
uppercase characters. The characters must b e entered in the order
shown; however, you can enter the characters in either upp ercase or
lowercase. For example:
COMMAND
can be entered as any of the following:
command Command COMMAND
It cannot, however, b e en
tered as:
comm com_mand comamnd
italics
In a syntax statement or an example, a w
ord in italics represents a
parameter or argument that you must replace with the actual v
In the following example, you must replace
lename
with the name
alue.
of the le:
bold italics
COMMAND
In a syntax statement, a word in bold italics represents a parameter
lename
that you must replace with the actual value. In the following
example, you must replace
COMMAND(
lename
)
lename
with the name of the le:
punctuation In a syntax statement, punctuation characters (other than brackets,
braces, vertical bars, and ellipses) must be entered exactly as shown.
In the following example, the parentheses and colon must be entered:
(
lename
):(
lename
)
underlining Within an example that contains interactive dialog, user input and
user responses to prompts are indicated by underlining. In the
following example, yes is the user's response to the prompt:
Do you want to continue? >> yes
{ }
In a syntax statement, braces enclose required elements. When
several elements are stacked within braces, you must select one. In
[ ]
the following example, you must select eitherONor
COMMAND
ON
OFF
In a syntax statement, brackets enclose optional elements. In the
following example,
COMMAND
OPTION
lename
can be omitted:
[OPTION]
OFF
:
When several elements are stacked within brackets, you can select
one or none of the elements. In the following example, you can select
OPTIONorparameter
COMMAND
lename
or neither. The elements cannot be repeated.
OPTION
parameter
vii
Page 8

Conventions (continued)
[
...
]
In a syntax statement, horizontal ellipses enclosed in brackets
indicate that you can repeatedly select the elemen
within the immediately preceding pair of brac
example below, you can select
instance of
[,
parameter
parameter
][...]
parameter
must b e preceded b
t(s) that appear
kets or braces. In the
zero or more times. Eac
y a comma:
h
In the example b elo
parameter
of
parameter
[
|
...
|
In a syntax statement, horizontal ellipses enclosed in v
is repeated; no comma is used before the rst o ccurrence
:
parameter
indicate that you can select more than one elemen
w, you only use the comma as a delimiter if
][,...]
ertical bars
t within the
immediately preceding pair of brackets or braces. However, each
particular element can only be selected once. In the follo
example, you must select
A, AB, BA
,orB. The elements cannot be
wing
repeated.
A
|
...
B
|
... In an example, horizontal or vertical ellipses indicate where p ortions
of an example have been omitted.
1
In a syntax statement, the space symbol1shows a required blank.
In the follo wing example,
parameter
and
parameter
must b e
separated with a blank:
(
4 5
parameter
The symbol
4
RETURN
)1(
parameter
4 5
indicates a key on the keyboard. For example,
5
represents the carriage return key or
)
4
Shift
5
represents the
shift key.
viii
4
CTRL
5
character
4
CTRL
5
character
indicates a control character. For example,
4
CTRL
5
means that you press the control key and the Y key simultaneously.
Y
Page 9

Contents
1. OVERVIEW
Introduction to the HP 3000
900 Series HP 3000 . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
HP Precision Architecture (HP-PA) . . . . . . . . . . . . . . . . . . 1-1
MPE Operating Systems .
MPE/iX and MPE V/E Op erating Systems
Naming Conventions for HP 3000 Systems and Soft
Native Mode and Compatibilit
MPE/iX Mixed Mo des . . . . . . . . . . . . . . . . . . . . . . . 1-5
900 Series Migration . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Object Code Translator . . . . . . . . . . . . . . . . . . . . . . . 1-6
Native Mode Compilers . . . . . . . . . . . . . . . . . . . . . . . 1-6
Data Base Manipulations . . . . . . . . . . . . . . . . . . . . . . 1-6
Migration Restrictions . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Cross-family Application Development. . . . . . . . . . . . . . . . . 1-7
MPE/iX Features . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Multiprogramming . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Interactive and Batch Processing . . . . . . . . . . . . . . . . . . . 1-8
MPE/iX Information Management . . . . . . . . . . . . . . . . . . . 1-8
Self-adjusting System Tables . . . . . . . . . . . . . . . . . . . . . 1-9
On-line Diagnostics for Peripherals . . . . . . . . . . . . . . . . . . 1-9
Disc Failure Tolerance . . . . . . . . . . . . . . . . . . . . . . . . 1-9
Automatic Power Fail Recovery . . . . . . . . . . . . . . . . . . . . 1-9
MPE/iX Transaction ManagementFacility. . . . . . . . . . . . . . . . 1-10
Transaction Locking . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
Transaction Logging and Recovery . . . . . . . . . . . . . . . . . . 1-10
Simplifying a Program . . . . . . . . . . . . . . . . . . . . . . . . 1-11
DEBUG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-11
MPE/iX User Interface . . . . . . . . . . . . . . . . . . . . . . . . 1-12
MPE/iX System Performance . . . . . . . . . . . . . . . . . . . . . 1-13
Mapped Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-13
Directory Entries . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Native Mode System Comp onents . . . . . . . . . . . . . . . . . . . . 1-14
Terminal Keyboard Layouts . . . . . . . . . . . . . . . . . . . . . . 1-15
Giving Commands to MPE/iX . . . . . . . . . . . . . . . . . . . . . 1-16
MPE/iX Commands . . . . . . . . . . . . . . . . . . . . . . . . 1-16
MPE/iX Command Parameters . . . . . . . . . . . . . . . . . . . 1-17
Continuing an MPE/iX Command to Another Line . . . . . . . . . . 1-18
On-line Help in Using an MPE/iX Command . . . . . . . . . . . . . 1-18
Correcting or Mo difying an MPE/iX Command . . . . . . . . . . . . 1-18
Referring to Several Files at Once . . . . . . . . . . . . . . . . . . 1-18
Command Files and User-dened Command Files . . . . . . . . . . . . 1-19
. . . . . . . . . . . . . . . . . . . . . . 1-1
. . . . . . . . . . . . . . . . . . . . . . . 1-2
. . . . . . . . . . . . . . 1-3
ware . . . . . . . . . 1-4
yMode . . . . . . . . . . . . . . . . . 1-5
Contents-1
Page 10

Break Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-21
Echo On/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-23
Accounting Structure Overview . . . . . . . . . . . . . . . . . . . . . 1-23
Logon and Logo . . . . . . . . . . . . . . . . . . . . . . . . . . 1-23
Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-23
User . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-24
Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-25
File Specications . . . . . . . . . . . . . . . . . . . . . . . . . . 1-26
Referring to a File in a Dieren
Referring to a File in a Dieren
t Group . . . . . . . . . . . . . . . 1-27
t Account . . . . . . . . . . . . . . 1-27
Session and Batch Mo des . . . . . . . . . . . . . . . . . . . . . . . 1-27
Converting Data Files from MPE V/E to MPE/iX
. . . . . . . . . . . . 1-29
Data Alignment Dierences . . . . . . . . . . . . . . . . . . . . . 1-29
Converting Files . . . . . . . . . . . . . . . . . . . . . . . . . . 1-32
Data Communications . . . . . . . . . . . . . . . . . . . . . . . . . 1-33
Network File Transfer (NFT) . . . . . . . . . . . . . . . . . . . . . 1-33
Remote Process Management (RPM) . . . . . . . . . . . . . . . . . 1-33
Local Area Network (LAN) . . . . . . . . . . . . . . . . . . . . . 1-34
Remote File Access . . . . . . . . . . . . . . . . . . . . . . . . . 1-34
Remote Terminal Access . . . . . . . . . . . . . . . . . . . . . . . 1-34
Remote Data Base Access . . . . . . . . . . . . . . . . . . . . . . 1-34
2. Utilities and Tools
Programmatic Access to the Command Interpreter . . . . . . . . . . . . 2-1
Concatenating Strings and String Substitution . . . . . . . . . . . . . 2-2
Expression Evaluation . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Using Job Control Words (JCWs) . . . . . . . . . . . . . . . . . . . 2-2
Job Control Word Name and Type . . . . . . . . . . . . . . . . . 2-2
Changing the Value of a JCW . . . . . . . . . . . . . . . . . . . 2-2
JCW and CIERROR . . . . . . . . . . . . . . . . . . . . . . . 2-3
Reserved-word Prexes . . . . . . . . . . . . . . . . . . . . . . 2-3
Help Facility . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
Toolset/XL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Useful Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Forms Design and Screen Handling Tools . . . . . . . . . . . . . . . 2-5
Source Data Entry . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Transaction Pro cessing . . . . . . . . . . . . . . . . . . . . . . 2-5
VPLUS/V Features . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Report Generation Tools . . . . . . . . . . . . . . . . . . . . . . . 2-6
Business Report Writer/XL . . . . . . . . . . . . . . . . . . . . 2-6
Report/V . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-6
HP Visor . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-6
System Dictionary/XL . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Editor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
SORT-MERGE/XL . . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Ordering Sequence . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Collating Sequence . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
DISCFREE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
FCOPY/XL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Contents-2
Page 11

3. Program Development
Writing a Program . . . . . . . . . . . . . . . . . . . . . . . . . . 3-2
How to Use Intrinsics . . . . . . . . . . . . . . . . . . . . . . . . 3-2
Compiling a Program . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
Compiler Input . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
Compiler Output . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
Compiler Operation .
. . . . . . . . . . . . . . . . . . . . . . . . 3-4
Compiled Co de . . . . . . . . . . . . . . . . . . . . . . . . . . 3-6
Data Variables Information . . . . . . . . . . . . . . . . . . . . . 3-6
Unresolved References . . . . . . . . . . . . . . . . . . . . . . . 3-6
Compiler Libraries . . . . . . . . . . . . . . . . . . . . . . . . 3-6
Command to Compile Only . . . . . . . . . . . . . . . . . . . . 3-6
Compiler Control . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Linking a Program . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Creating Executable Program Files . . . . . . . . . . . . . . . . . . 3-9
Symbol Listing . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Loading and Running a Program
. . . . . . . . . . . . . . . . . . . . 3-13
Program Auxiliary Header . . . . . . . . . . . . . . . . . . . . . . 3-13
Using Executable Libraries . . . . . . . . . . . . . . . . . . . . . . 3-14
Searching Executable Libraries . . . . . . . . . . . . . . . . . . . . 3-14
UNSAT Procedure . . . . . . . . . . . . . . . . . . . . . . . . . 3-14
System Libraries . . . . . . . . . . . . . . . . . . . . . . . . . . 3-15
Mixing Execution Mo des . . . . . . . . . . . . . . . . . . . . . . . 3-15
Virtual Memory and Demand Paging . . . . . . . . . . . . . . . . . 3-16
LMAP: Load MAP . . . . . . . . . . . . . . . . . . . . . . . . . 3-16
Load-time Binding Sequence . . . . . . . . . . . . . . . . . . . . . 3-16
Running a Program . . . . . . . . . . . . . . . . . . . . . . . . . 3-16
Multi-programming Environment . . . . . . . . . . . . . . . . . . . . 3-17
Priority Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-17
Linear Subqueues . . . . . . . . . . . . . . . . . . . . . . . . . 3-17
Circular Subqueues . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Error Detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Command Interpreter Errors . . . . . . . . . . . . . . . . . . . . . 3-18
File System Errors . . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Compiler, Link Editor, and Loader Errors . . . . . . . . . . . . . . . 3-18
Run-time Errors . . . . . . . . . . . . . . . . . . . . . . . . . . 3-19
Abort Message Information . . . . . . . . . . . . . . . . . . . . . 3-19
Typical Causes of Program Ab orts . . . . . . . . . . . . . . . . . . 3-20
File Information Display (Tombstone) . . . . . . . . . . . . . . . . . 3-20
Control Codes (JCWs) . . . . . . . . . . . . . . . . . . . . . . . . 3-21
System JCW . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21
JCW Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-22
Using a System JCW . . . . . . . . . . . . . . . . . . . . . . . . 3-23
User-dened JCWs . . . . . . . . . . . . . . . . . . . . . . . . . 3-24
Using a User-dened JCW . . . . . . . . . . . . . . . . . . . . . . 3-24
Contents-3
Page 12

4. HP Link Editor/XL
Common Uses of HP Link Editor/XL
Linking a Relocatable Object File .
Comparison of HP Link Editor/XL and MPE V/E Segmen
How HP Link Editor/XL W
orks . . . . . . . . . . . . . . . . . . . . 4-4
. . . . . . . . . . . . . . . . . . 4-3
. . . . . . . . . . . . . . . . . . . 4-3
ter . . . . . . . 4-4
Files Used by HP Link Editor/XL . . . . . . . . . . . . . . . . . . . . 4-4
HP Link Editor/XL Commands .
. . . . . . . . . . . . . . . . . . . . 4-6
Case Sensitivity. . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
Keyword and Positional Parameters . . . . . . . . . . . . . . . . . . 4-7
Using an Indirect File . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
Starting and Ending HP Link Editor/XL
Creating an Executable Program File
Comparison of Executable and Relocatable Libraries
Using a Relocatable Library
. . . . . . . . . . . . . . . . . . . . . . 4-12
. . . . . . . . . . . . . . . . 4-8
. . . . . . . . . . . . . . . . . . 4-9
. . . . . . . . . . . 4-11
Using an Executable Library . . . . . . . . . . . . . . . . . . . . . . 4-13
5. Optimizing a Program
Optimizer Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Use of MPE/iX Optimizer with Languages . . . . . . . . . . . . . . . . 5-3
Optimizer Assumptions . . . . . . . . . . . . . . . . . . . . . . . . 5-3
Coding for Performance and Optimization . . . . . . . . . . . . . . . . 5-4
Reduce Aliasing . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
Use Optimal Data Types . . . . . . . . . . . . . . . . . . . . . . . 5-4
Eliminate Common Subexpressions . . . . . . . . . . . . . . . . . . 5-5
Instructions Required for Operations on Simple Data T
ypes . . . . . . . 5-6
Optimize Arrays . . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Reduce Pro cedure Calls . . . . . . . . . . . . . . . . . . . . . . . 5-7
Expand Small Pro cedures In-line . . . . . . . . . . . . . . . . . . . 5-7
Extract Procedure Calls from Loops . . . . . . . . . . . . . . . . . . 5-8
Avoid Non-native Alignment . . . . . . . . . . . . . . . . . . . . . 5-8
Optimize HP COBOL II/XL Data Types . . . . . . . . . . . . . . . 5-9
Optimize HP COBOL II/XL Data Types . . . . . . . . . . . . . . . 5-9
6. File System
Records and Files in the File System . . . . . . . . . . . . . . . . . . 6-2
Device Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Disc Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-3
Disc File Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-4
File Directory Structure . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Domains . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
File Specications . . . . . . . . . . . . . . . . . . . . . . . . . . 6-8
File Designators . . . . . . . . . . . . . . . . . . . . . . . . . . 6-9
User-dened Files . . . . . . . . . . . . . . . . . . . . . . . . . . 6-11
System Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-12
Contents-4
NEW Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
TEMP Files . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
PERMANENT Files . . . . . . . . . . . . . . . . . . . . . . . 6-7
Eect of File Domain on Operations . . . . . . . . . . . . . . . . . 6-7
Changing Domains . . . . . . . . . . . . . . . . . . . . . . . . 6-8
Backreferencing a File . . . . . . . . . . . . . . . . . . . . . . . 6-10
File Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-11
Page 13

Input/Output Sets . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
Passed Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-15
Searching File Directories . . . . . . . . . . . . . . . . . . . . . . 6-16
Finding Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-16
Types of Operations Allow
ed on Files . . . . . . . . . . . . . . . . . 6-16
Opening a File . . . . . . . . . . . . . . . . . . . . . . . . . . 6-16
Closing a File . . . . . . . . . . . . . . . . . . . . . . . . . . 6-17
Using Files at Run Time .
. . . . . . . . . . . . . . . . . . . . . . . 6-20
Hierarchy of File Overrides . . . . . . . . . . . . . . . . . . . . . . . 6-21
Record Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-22
Storage Format . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-22
Record Types . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-22
Specifying a Record Size .
. . . . . . . . . . . . . . . . . . . . . . 6-24
File Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-25
File Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-25
File Codes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-26
Creating a File . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-27
HPFOPEN and FOPEN Intrinsics . . . . . . . . . . . . . . . . . 6-27
The :BUILD Command . . . . . . . . . . . . . . . . . . . . . . 6-28
Deleting Files . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-28
Renaming Files . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-28
Saving Temporary Files . . . . . . . . . . . . . . . . . . . . . . . 6-28
Listing File Characteristics . . . . . . . . . . . . . . . . . . . . . . 6-29
The :FILE Command . . . . . . . . . . . . . . . . . . . . . . . . 6-29
Record Selection and Data Transfer . . . . . . . . . . . . . . . . . . . 6-30
Record Pointers . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-30
Pointer Initialization . . . . . . . . . . . . . . . . . . . . . . . . 6-30
Record Selection . . . . . . . . . . . . . . . . . . . . . . . . . . 6-30
Mapped Access to Disc Files . . . . . . . . . . . . . . . . . . . . . 6-31
Multiple Record Transfers . . . . . . . . . . . . . . . . . . . . . . 6-31
Data Transfer Control Operations . . . . . . . . . . . . . . . . . . . 6-32
Reading from a File . . . . . . . . . . . . . . . . . . . . . . . . . 6-32
Writing to a File . . . . . . . . . . . . . . . . . . . . . . . . . . 6-33
Updating a File . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-33
Using Mapped Access to a File . . . . . . . . . . . . . . . . . . . . 6-34
Device File Buers . . . . . . . . . . . . . . . . . . . . . . . . . 6-34
Sharing a File . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-35
Maintaining File Security . . . . . . . . . . . . . . . . . . . . . . . 6-37
Lockwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-38
MPE/iX File Access System . . . . . . . . . . . . . . . . . . . . . 6-38
Specifying and Restricting File Access by Access Mo de . . . . . . . . 6-38
Specifying File Access byType or User . . . . . . . . . . . . . . . 6-39
Access Control Denitions (ACDs) . . . . . . . . . . . . . . . . . . 6-42
Specifying and Restricting File Access . . . . . . . . . . . . . . . . 6-42
Managing ACDs with Commands and Intrinsics . . . . . . . . . . . 6-42
Changing Disc File Security Provisions . . . . . . . . . . . . . . . 6-43
Suspending and Restoring Security Provisions . . . . . . . . . . . . 6-44
Contents-5
Page 14

7. Data Management
Data Management Subsystems . . . . . . . . . . . . . . . . . . . . . 7-1
KSAM/V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-2
FCOPY (KSAM Options) . . . . . . . . . . . . . . . . . . . . . . 7-3
KSAM procedures . . . . . . . . . . . . . . . . . . . . . . . . . 7-5
ALLBASE/SQL . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
HP SQL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-7
Logical Transaction . . . . . . . . . . . . . . . . . . . . . . . . . 7-7
Concurrency . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-8
Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-8
Database Creation . . . . . . . . . . . . . . . . . . . . . . . . . 7-8
Database Restructuring . . . . . . . . . . . . . . . . . . . . . . . 7-9
TurboIMAGE/XL Data Base . . . . . . . . . . . . . . . . . . . . . . 7-11
Master Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-12
Chain Head . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-12
Automatic Master Set . . . . . . . . . . . . . . . . . . . . . . . 7-13
Manual Master Set . . . . . . . . . . . . . . . . . . . . . . . . 7-13
TurboIMAGE/XL and QUERY/V . . . . . . . . . . . . . . . . . . . 7-14
Creating a Schema . . . . . . . . . . . . . . . . . . . . . . . . . 7-14
Creating a Ro ot File . . . . . . . . . . . . . . . . . . . . . . . 7-14
DBUTIL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-15
Creating a Data Base . . . . . . . . . . . . . . . . . . . . . . . 7-16
TurboIMAGE/XL Pro cedures . . . . . . . . . . . . . . . . . . . . 7-16
Backing Up or Restructuring a Data Base . . . . . . . . . . . . . . 7-17
Changing an Existing Data Base Design . . . . . . . . . . . . . . . 7-17
Recovering a Data Base . . . . . . . . . . . . . . . . . . . . . . 7-18
QUERY/V . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-18
TurboIMAGE DBchange/V . . . . . . . . . . . . . . . . . . . . . . 7-20
Key DBchange/V Features . . . . . . . . . . . . . . . . . . . . . . 7-20
DICTDBA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-21
DICTDBU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-21
DICTDBL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-21
Index
Contents-6
Page 15

Figures
1-1. MPE/iX On-line Access Capabilities . . . . . . . . . . . . . . . . . 1-2
1-2. 900 Series HP 3000 High-lev
el Tools . . . . . . . . . . . . . . . . . . 1-3
1-3. HP 3000 Software Naming Conventions Example . . . . . . . . . . . . 1-4
1-4. Commanding MPE/iX . . . . . . . . . . . . . . . . . . . . . . . . 1-16
1-5. UDC File Example . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
1-6. Accounts Example . . . . . . . . . . . . . . . . . . . . . . . . . 1-24
1-7. User Example . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-25
1-8. Groups Example . . . . . . . . . . . . . . . . . . . . . . . . . . 1-26
1-9. Session and Job Commands
1-10. Session and Job Characteristics .
. . . . . . . . . . . . . . . . . . . . . 1-28
. . . . . . . . . . . . . . . . . . . 1-28
1-11. HP FORTRAN 77/iX COMMON Block Data Alignment Example . . . . 1-30
1-12. IEEE Single-precision Real Number Format . . . . . . . . . . . . . . 1-31
1-13. IEEE Double-precision Real Number Format . . . . . . . . . . . . . . 1-32
3-1. MPE/iX Program Development. . . . . . . . . . . . . . . . . . . . 3-1
3-2. Compiler Producing Relocatable Ob ject Mo dules
. . . . . . . . . . . . 3-5
3-3. Linking and Using User Libraries . . . . . . . . . . . . . . . . . . . 3-8
3-4. UNSAT Procedure Example . . . . . . . . . . . . . . . . . . . . . 3-15
3-5. Job Control Word (JCW) Structure . . . . . . . . . . . . . . . . . . 3-21
3-6. JCW Notation Examples . . . . . . . . . . . . . . . . . . . . . . 3-23
4-1. :LINK and HP Link Editor/XL on MPE/iX
. . . . . . . . . . . . . . 4-2
4-2. Files Used by HP Link Editor/XL . . . . . . . . . . . . . . . . . . . 4-5
4-3. Creating an Executable Program File . . . . . . . . . . . . . . . . . 4-9
4-4. Linking to Create an Executable Program File
. . . . . . . . . . . . . 4-10
4-5. Executable Program File Commands . . . . . . . . . . . . . . . . . 4-11
5-1. Reducing Aliasing . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
5-2. Eliminating Common Subexpressions . . . . . . . . . . . . . . . . . 5-5
5-3. Instructions Operations on Simple Data Types . . . . . . . . . . . . . 5-6
5-4. Optimizing Arrays . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
5-5. Reducing Procedure Calls . . . . . . . . . . . . . . . . . . . . . . 5-7
5-6. Expanding Small Pro cedures In-line . . . . . . . . . . . . . . . . . . 5-7
5-7. Extracting Calls from Loops . . . . . . . . . . . . . . . . . . . . . 5-8
5-8. Avoiding Non-native Alignment. . . . . . . . . . . . . . . . . . . . 5-8
6-1. File System Interface . . . . . . . . . . . . . . . . . . . . . . . . 6-1
6-2. Records and Files Relationship . . . . . . . . . . . . . . . . . . . . 6-2
6-3. Specifying Device File Characteristics . . . . . . . . . . . . . . . . . 6-3
6-4. Identifying a Disc File using File Designators . . . . . . . . . . . . . . 6-10
6-5. Backreferencing a Previously Identied File . . . . . . . . . . . . . . 6-11
6-6. System Files in Use . . . . . . . . . . . . . . . . . . . . . . . . . 6-13
6-7. Using a System File . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
6-8. Passing Files between Program Runs . . . . . . . . . . . . . . . . . 6-15
6-9. Directories Searched Based on File Domain . . . . . . . . . . . . . . . 6-19
6-10. Nested HPFOPEN/FOPEN and FCLOSE Pairs . . . . . . . . . . . . 6-20
Contents-7
Page 16

6-11. File System HierarchyofOv
6-12. Record Types . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-23
6-13. Odd-byte Record Sizes . . . . . . . . . . . . . . . . . . . . . . . . 6-25
6-14. Creating a File . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-27
6-15. Actions Resulting from Multiaccess of Files
6-16. Security Level for File Access .
7-1. Building a KSAM File .
7-2. Loading a KSAM File .
7-3. Reorganizing a KSAM File .
7-4. TurboIMAGE/XL Data Set Organization Example
7-5. Example of Creating a Ro ot File
7-6. Creating a Data Base
errides . . . . . . . . . . . . . . . . . . 6-21
. . . . . . . . . . . . . . 6-37
. . . . . . . . . . . . . . . . . . . . 6-40
. . . . . . . . . . . . . . . . . . . . . . . 7-2
. . . . . . . . . . . . . . . . . . . . . . . 7-4
. . . . . . . . . . . . . . . . . . . . . 7-5
. . . . . . . . . . . 7-13
. . . . . . . . . . . . . . . . . . . 7-15
. . . . . . . . . . . . . . . . . . . . . . . . 7-16
Contents-8
Page 17

Tables
1-1. Word and Integer Conversions . . . . . . . . . . . . . . . . . . . . 1-31
6-1. New, Temporary, and Permanent File Features . . . . . . . . . . . . . 6-6
6-2. Valid File Domains . . . . . . . . . . . . . . . . . . . . . . . . . 6-6
6-3. Input Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
6-4. Output Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-15
6-5. Comparison of Logical Record F
6-6. Standard Default Record Sizes
6-7. File Sharing Restriction Options . . . . . . . . . . . . . . . . . . . 6-36
6-8. File Access Mo de T
6-9. User Type Denitions . . . . . . . . . . . . . . . . . . . . . . . . 6-40
7-1. ALLBASE/SQL Specications . . . . . . . . . . . . . . . . . . . . 7-10
7-2. Data Base Terminology . . . . . . . . . . . . . . . . . . . . . . . 7-11
7-3. Data Management Considerations . . . . . . . . . . . . . . . . . . . 7-19
ypes . . . . . . . . . . . . . . . . . . . . . . . 6-39
ormats . . . . . . . . . . . . . . . . 6-24
. . . . . . . . . . . . . . . . . . . . 6-24
Contents-9
Page 18

Page 19

1
OVERVIEW
This chapter introduces the 900 Series HP 3000 and the MPE/iX operating system, describing
how they t into the HP 3000 family of computers and MPE operating systems, in general.
It describes hardw
are and software naming conventions and provides a brief overview of
migration to the 900 Series from MPE V/E-based systems. It describes MPE/iX dual
operating mo des, features, and ma jor subsystems.
It provides an overview of MPE/iX accoun
execute MPE/iX commands, and the considerations necessary to con
ting structure, session and batc
vert les to MPE/iX.
h modes, howto
Introduction to the HP 3000
The HP 3000 is a general-purpose multiprogramming machine, designed for the interactive,
transaction processing environment of business and industry. The HP 3000 family of
computers includes several mo dels of the machine, each with a dierent series number.
900 Series HP 3000
The newest high performance members of the 900 Series HP 3000 family are based on HP
Precision Architecture (HP-PA), a highly exible computer design that can meet curren
t user
requirements and requirements arising during future growth.
HP Precision Architecture (HP-PA)
HP Precision Architecture (HP-PA) is based on Reduced Instruction Set Computer (RISC)
concepts with added extensions for a complete system. This increases computer performance
by reducing and simplifying the computer instruction set. HP-PA eliminates system overhead
associated with conventional computer micro code by directly implementing computer
instructions in hardware. The uniformity of HP-PA instructions enhances pipelining,
providing higher performance byoverlapping execution of multiple instructions. Many
technologies can implement HP-PA; highly integrated VLSI designs can be achieved by
eliminating the chip space required for microco de.
High performance from HP-PA architecture results from the memory hierarchy design and the
use of optimizing compilers. Pro cessor waiting time for memory accesses is minimized due to
the following architectural characteristics:
Frequently used instructions and data are stored in a large number of CPU registers.
High-speed buering of code and data occurs.
Optimizing compilers generate ecient ob ject code, allocate registers, and schedule
instruction sequences to maintain ecient pipeline operation.
OVERVIEW 1-1
Page 20
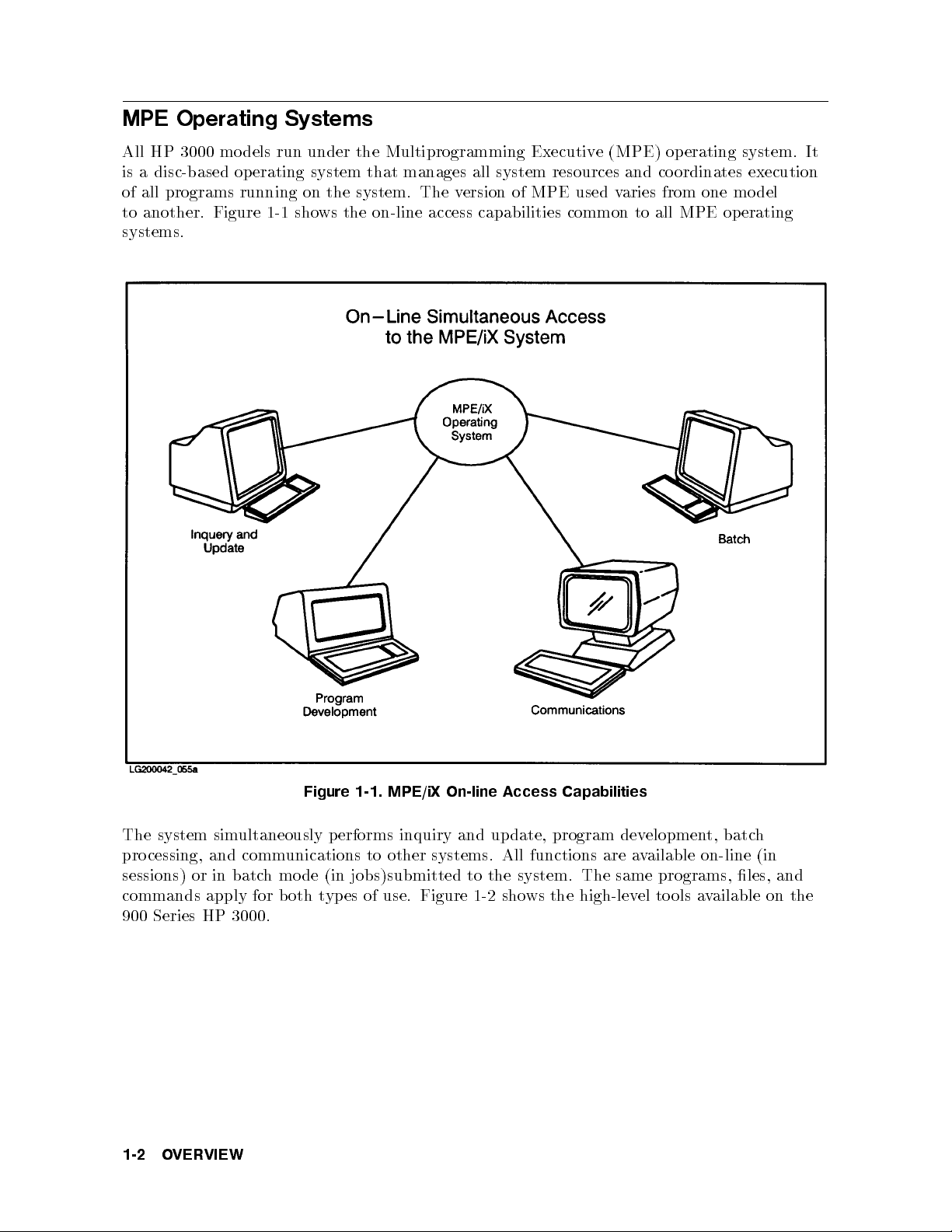
MPE Operating Systems
All HP 3000 models run under the Multiprogramming Executiv
is a disc-based operating system that manages all system resources and co ordinates execution
of all programs running on the system. The v
to another. Figure 1-1 shows the on-line access capabilities common to all MPE operating
systems.
ersion of MPE used varies from one model
e (MPE) op erating system. It
Figure 1-1. MPE/iX On-line Access Capabilities
The system simultaneously p erforms inquiry and up date, program dev
processing, and communications to other systems. All functions are available on-line (in
sessions) or in batch mo de (in jobs)submitted to the system. The same programs, les, and
commands apply for both types of use. Figure 1-2 shows the high-level to ols available on the
900 Series HP 3000.
1-2 OVERVIEW
elopment, batch
Page 21
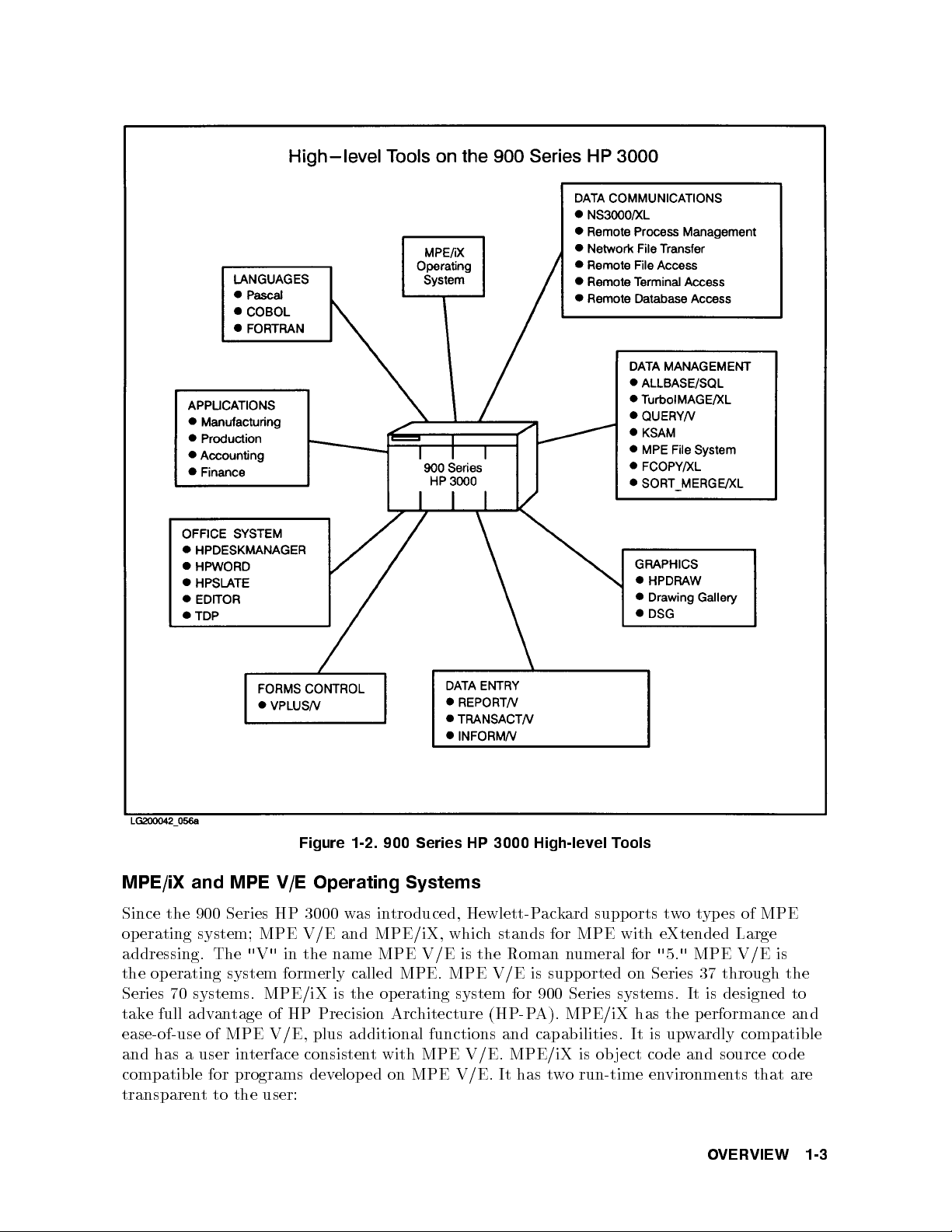
Figure 1-2. 900 Series HP 3000 High-level Tools
MPE/iX and MPE V/E Operating Systems
Since the 900 Series HP 3000 was introduced, Hewlett-Packard supports twotypes of MPE
operating system; MPE V/E and MPE/iX, which stands for MPE with eXtended Large
addressing. The"V"in the name MPE V/E is the Roman numeral for"5."MPE V/E is
the operating system formerly called MPE. MPE V/E is supported on Series 37 through the
Series 70 systems. MPE/iX is the operating system for 900 Series systems. It is designed to
take full advantage of HP Precision Architecture (HP-PA). MPE/iX has the performance and
ease-of-use of MPE V/E, plus additional functions and capabilities. It is upwardly compatible
and has a user interface consistent with MPE V/E. MPE/iX is object co de and source code
compatible for programs developed on MPE V/E. It has two run-time environments that are
transparent to the user:
OVERVIEW 1-3
Page 22
Compatibility Mo de (CM), which provides ob ject-code compatibility with MPE V/E-based
applications.
Native Mode (NM), whic
h provides full performance benets and adv
anced capabilities of
HP-PA.
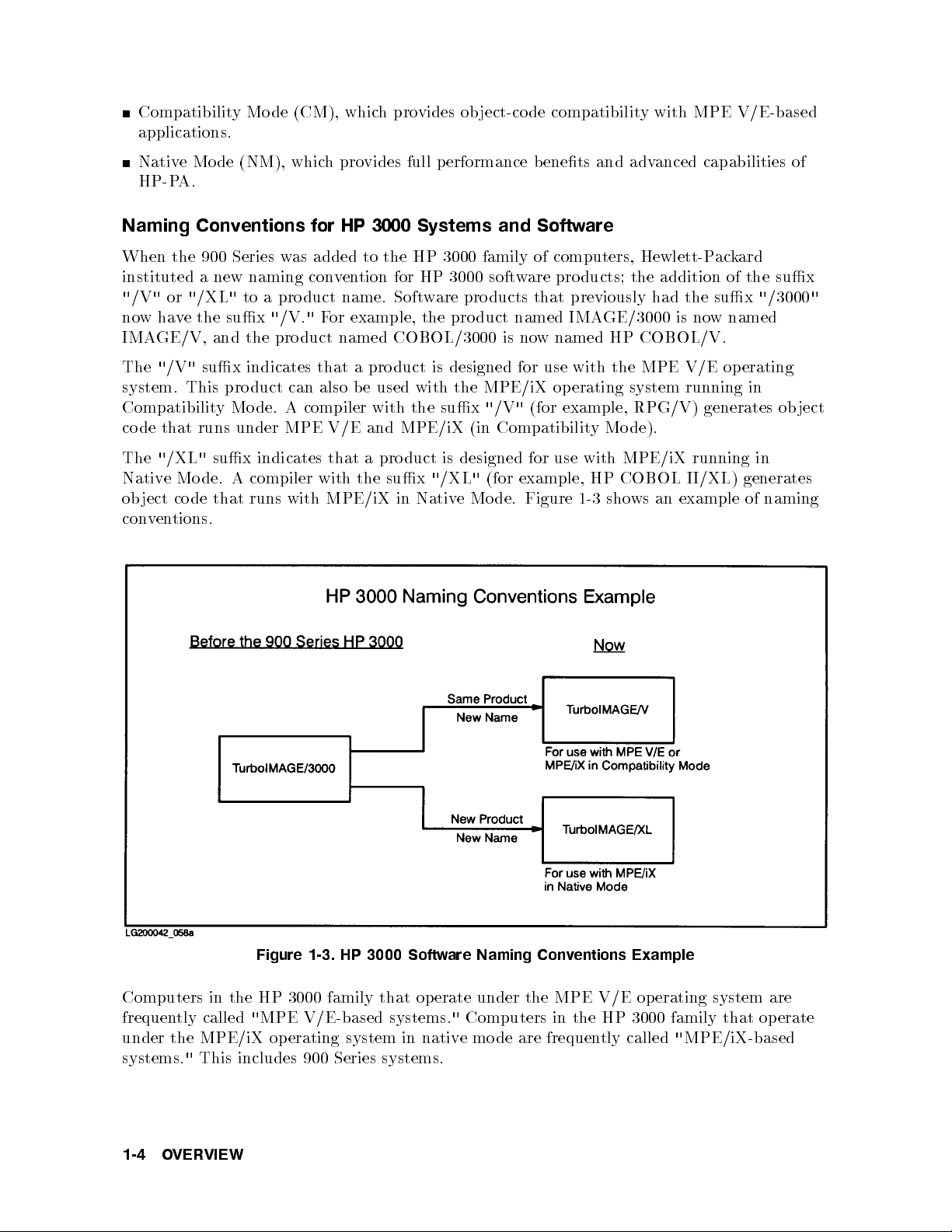
Naming Conventions for HP 3000 Systems and Softw
When the 900 Series w
instituted a new naming convention for HP 3000 softw
"/V"or"
/XL"to a pro duct name. Soft
as added to the HP 3000 family of computers, Hewlett-P
are products; the addition of the sux
ware pro ducts that previously had the sux
nowhave the sux"/V."For example, the pro duct named IMA
IMAGE/V, and the pro duct named COBOL/3000 is no
w named HP COBOL/V.
are
ackard
GE/3000 is now named
"
/3000
The"/V"sux indicates that a pro duct is designed for use with the MPE V/E operating
system. This product can also be used with the MPE/iX operating system running in
Compatibility Mode. A compiler with the sux
code that runs under MPE V/E and MPE/iX (in Compatibilit
"/V"
(for example, RPG/V) generates ob ject
y Mode).
The"/XL"sux indicates that a pro duct is designed for use with MPE/iX running in
Native Mode. A compiler with the sux
ob ject co de that runs with MPE/iX in Native Mo de. Figure 1-3 sho
"
/XL"(for example, HP COBOL I I/XL) generates
ws an example of naming
conventions.
"
Figure 1-3. HP 3000 Software Naming Conventions Example
Computers in the HP 3000 family that operate under the MPE V/E operating system are
frequently called"MPE V/E-based systems."Computers in the HP 3000 family that operate
under the MPE/iX operating system in native mode are frequently called"MPE/iX-based
systems."This includes 900 Series systems.
1-4 OVERVIEW
Page 23

Native Mode and Compatibility Mode
MPE/iX provides two run-time execution environments: Native Mode (NM) and
Compatibility Mo de (CM). MPE/iX dynamically and transparen
modes as required b
y applications.
tly coordinates and c
hanges
NM is the native MPE/iX run-time environment. Source co de has been compiled in
Series native instruction set. NM is the preferred en
vironment for the 900 Series and pro
to the 900
vides
the highest p erformance from the systems through the use of demand paged virtual memory
and memory mapp ed les.
CM provides ob ject code compatibilit
ybetween MPE V/E based systems and 900 Series
computers. CM allows you to move applications and data to 900 Series computers without
changes or recompilation.
MPE/iX is a compatible sup erset of MPE V/E. CM pro
environment, including MPE V/E code and stac
k structures and most callable MPE V/E
vides a working MPE V/E
system intrinsics.
MPE/iX Mixed Modes
Applications can run partly in Native Mo de (NM) and partly in Compatibility Mo de (CM).
MPE/iX transparently switches between modes for system routines. MPE/iX has a Switc
Subsystem that determines if code is in NM or CM and automatically switc
hes between them,
h
as needed, while the routine is running. When the called routines are in the other mode, users
must write their own switching routines.
900 Series Migration
The use of Compatibility Mo de (CM) and migration utilities pro
migration to 900 Series systems. The high degree of ob ject code compatibility bet
V/E and MPE/iX operating in CM allo ws y
ou to store any MPE V/E based application
vides smooth, exible
ween MPE
ob ject co de program written in a language supported on MPE V/E, restore it on a 900 Series
system, and run it in MPE/iX Compatibility Mo de. You can move data bases to a 900 Series
system in the same way.
900 Series systems are fully upward compatible with other systems in the HP 3000 family
.
Migration tools are provided to facilitate upgrading to the 900 Series in stages, as your
schedule permits, without interruption of operations. Migration to the 900 Series provides:
Object code compatibility: a simple store/restore procedure allows you to move MPE V/E
applications and data to the 900 Series. You can back up applications and databases on a
tape and restore them on a 900 Series system without mo dication. The applications and
databases run on the 900 Series in CM.
Source code compatibility: you can recompile applications for maximum p erformance
by using Native Mo de (NM) optimizing compilers, which improve performance. You can
achieve maximum database performance by using software utilities to transform databases
into NM.
OVERVIEW 1-5
Page 24

Migration exibility: upgrading to the 900 Series is extremely exible because applications
and databases can access and comm
modes (in other w
ords, when one is in CM and the other is in NM).
unicate with each other when they are in dieren
t
Operational exibility: MPE/iX is a functional superset of MPE V/E. They are nearly
identical in terms of user in
terface, system management, accounting, and security.
Peripheral compatibilit y: Because of common I/O mec
many of the same peripherals and w
orkstations as other HP 3000 systems do.
hanisms, the 900 Series supp orts
Cross-family development: CM allows you to develop applications on the 900 Series that
can also be run on MPE V/E-based systems.
Migration to the 900 Series is exible because y
ou can move some applications to NM and
move others to CM. Both kinds of applications can access the same database, and it can be
in CM or NM. Y
migrate applications to NM at con
ou can immediately move all your applications and databases to CM and can
venient times.
Object Code Translator
MPE/iX provides an Ob ject Code Translator (OCT) that can be used to translate MPE V/E
ob ject co de into native instructions for the 900 Series. This improves performance over that of
the MPE V/E object co de.
Native Mode Compilers
To take full advantage of 900 Series performance capabilities, y
based applications using Native Mo de (NM) compilers for the 900 Series. They pro
code compatibility with the rest of the HP 3000 family of computers. Usually
require little or no code mo dication. The NM compilers a
ou can recompile MPE V/E
vide source
, applications
vailable on MPE/iX include:
HP C/iX
COBOL II/XL
HP Pascal/iX
HP FORTRAN 77/iX
Data Base Manipulations
For improved performance of database manipulations, you can move to ALLBASE/SQL, the
Native Mode Database Management System for the 900 Series. Utilities are available for
converting to ALLBASE/SQL from TurboIMAGE/XL.
Migration Restrictions
Minor restrictions may apply to migrating MPE V/E-based applications to a 900 Series
system. An application may require modication if it uses:
Undocumented intrinsics
Privileged machine instructions
Unsupported hardware
Architecture-dependent information
Applications written in SPL/V, the systems programming language for MPE V/E-based
systems, can run in Compatibilit y Mo de (CM) on a 900 Series system, but cannot migrate to
1-6 OVERVIEW
Page 25

Native Mode (NM) because SPL/V has a high dependence on the MPE V/E-based HP 3000
architecture. However, you can improve the performance of an SPL/V application running in
CM by using the MPE V/E Ob ject Code T
ranslator.
If you require NM performance, these applications should be rewritten in HP C/iX or HP
Pascal/iX, which are systems programming languages for MPE/iX. If an application written
in a high-level language calls SPL/V procedures, y
and uses a user-supplied mode switc
hing procedure to switc
ou can recompile it in NM. It runs in NM
h to CM to call SPL procedures.
For information on less frequently encountered exceptions, refer to the
manuals. For information on switching, refer to
Switch Programming Guide
Migration Series
(32650-90014).
of
Cross-family Application Development
You can develop applications on a 900 Series system for use on HP 3000 systems that use HP
Precision Architecture (HP-PA) by using a 900 Series for cen
tralized development. You can
compile the source code for programs written to run on a Native Mo de compiler on the 900
Series system and compile it to run on MPE V/E-based systems.
Similarly,you can compile source code written to run in Compatibility Mo de on the 900 Series
and compile it to run on MPE V/E-based systems. The MPE V Segmen
ter is supplied with
MPE/iX to facilitate cross-family development in these languages.
MPE/iX Features
The main features of the MPE/iX op erating system on a 900 Series computer include:
Multiprogramming: concurrent transaction processing, data communications, on-line
program development, and batch processing.
Extended large addressing: 48-bit virtual addressing.
Demand paged virtual memory, which transparently manages virtual memory and
eliminates the need for program segmentation.
Mapped disc les, which eliminates the need for File System buering for disc les. This
increases system p erformance for I/O-intensive applications.
Concurrentmultilingual capability, including HP-extended versions of C, COBOL, RPG,
FORTRAN, BASIC, and Pascal.
File System, which includes le backup, user logging, security, and interpro cess
communication (IPC).
Access security and complete accounting resources.
Command interpreter, which includes user-dened commands (UDCs), command les,
conditional job control, extensive on-line help facility, and descriptive error messages.
Device and le independence, which simplies application development and maintenance.
I/O System, which provides input/output sp ooling and a tape label facility.
Complete, automatic lo cal and remote terminal management.
Power fail/automatic restart.
OVERVIEW 1-7
Page 26

Interactive Debug facility, which provides windows that allowyou to simultaneously see
the environment of the program being tested. It supports breakpoin
ts, single stepping,
calculation of expressions, macros, and command les.
Multiprogramming
MPE/iX supports m
ultiprogramming, the concurrent execution of multiple programs. All
system resources are available to you as if you were the only user on the system. While
one program is waiting for input, the system shifts con
program in the queue. In this w
ay, activities such as transaction processing, on-line program
trol of the CPU to the next highest
development, interactive data entry, data communications, and batch pro cessing can be
concurrently performed.
MPE/iX is a multiprogramming, multiuser system. On this kind of a system, m
can share code. F
process is created for eac
interpreter on the system), but eac
MPE/iX completely protects one program execution from in
or example, when multiple users access the BASIC/V in
h one. They all use the same code (b ecause there is only one BASIC
h user has a unique en
vironment created by MPE/iX.
terfering with another.
terpreter, a separate
ultiple users
Interactive and Batch Processing
MPE/iX provides interactive and batch processing. An interactive process is called a session.
A batch process is called a job.
In a session, you enter commands and data at a terminal and receiv
e an immediate resp onse.
This is especially useful for data entry and retrieval, program development, text editing, and
any application that is expedited by direct dialogue with the computer.
In batch processing, you submit a job to the computer. A job is a single unit comp osed of
commands that request various operations, such as program compilation and execution, le
manipulation, or utility functions. While a job is processing, there is no user in
the computer unless the job is set up to request information. Jobs can b e sc
teraction with
heduled to run
at lower priorities than interactive sessions and at sp ecic times (for example, when system
activities are low).
MPE/iX Information Management
Commercial applications primarily use database applications. The 900 Series provides
ALLBASE/SQL, which includes TurboIMAGE/XL, a network database management
product, and HP SQL, which has a relational interface to data. ALLBASE/SQL provides a
TurboIMAGE/XL cross-developmentenvironment. The relational interface, HP SQL, is fully
compatible with the version of SQL in most common use. It provides relational access for
increased exibility.
ALLBASE/SQL and other tools form Hewlett-Packard's information management framework.
These include:
Programming languages and tools.
Reporting and presentation to ols that allow access to information without programming.
1-8 OVERVIEW
Page 27

A common data dictionary that pro
vides the integration necessary to tie the system
together.
The products that meet these needs on the 900 Series are:
System Dictionary/XL, which provides programmers and system administrators with
a single source for documen
conguration information. This cen
ting all asp ects of the system, from data denitions to
tral source of information aids in dev
eloping and
maintaining applications and eectively managing system resources. The System
Dictionary/XL has programmatic interfaces for easy integration with other softw
can customize System Dictionary/XL to meet y
our needs.
Optimizing compilers, which use HP Precision Architecture (HP-PA) to allo w all
programming on the 900 Series computers to be done in high-lev
are integrated with MPE/iX to pro
vide convenient access to ALLBASE/SQL and other
el languages. The compilers
information managements subsystems.
VPLUS/V, which is a forms design and screen-handling tool for programmers.
are. You
Toolset/XL, which includes facilities for full screen editing, sym
and version management of source code. It pro
vides a high-productivity,integrated
bolic source-level debugging,
environment for application development.
Transact/XL, which is a pro cedural, high-level programming language for transaction
processing applications. It provides the functions of a high-level language, such as COBOL,
combined with a comprehensive set of p owerful verbs that can perform several functions in a
single call.
Self-adjusting System Tables
Most system tables in MPE/iX are self-adjusting. MPE/iX con
tables to t the workload. Usually, the system manager can do this without sh
tinuously monitors and adjusts
utting down the
system.
On-line Diagnostics for Peripherals
Hewlett-Packard Customer Engineers (CEs) are equipped with on-line diagnostic to ols for
many HP peripheral devices. A CE can remotely run diagnostics without sh
utting down the
system.
Disc Failure Tolerance
MPE/iX allows any system disc not critical to the functioning of the op erating system to go
o-line without aecting the system. Users cannot access les on o-line discs.
Automatic Power Fail Recovery
MPE/iX and the 900 Series hardware provide automatic power fail recovery. When a p ower
failure starts, the system initiates a power failure pro cedure to preserve the op erating
environment before the complete loss of power. A battery pack ensures the validity of main
memory for a minimum of 15 minutes. If p ower is restored within 15 minutes, the system
automatically resumes pro cessing from the p oint at which the power failure occurred, and jobs
continue from the pointofinterrupt.
OVERVIEW 1-9
Page 28

MPE/iX Transaction Management F
acility
The MPE/iX Transaction ManagementFacility provides the following functions for
transaction-oriented applications:
Automatic transaction lo cking
Automatic transaction logging
Automatic rollback recovery from"soft"failures
Semi-automatic rollforward recovery from"hard"failures
These functions are described in detail in the subsections b elo
w.
Transaction Locking
A transaction is a series of data updates that m
consistency; either all or none of the updates in the series m
transaction may appear to b e a single c
manychanges to records in sev
eral les or data sets.
hange. However, internal to the system, it ma
For example, if you enter a customer order on the system with a simple command, it ma
ust be entirely completed to obtain logical
ust be done. T
o the user, a
y require
y
internally require updating several les containing data on orders, customers, and inventory
requirements. The multiple changes, all of which are required for logical consistency, form one
transaction.
The MPE/iX Transaction ManagementFacility ensures data consistency and integrityby
providing automatic transaction lo cking. Transaction lo cking meets two criteria:
Only one transaction at a time is allowed to update a given portion of data.
All changes that are part of a transaction must be completed b efore the changes are
committed to disc (permanently recorded). When a transaction is abnormally terminated
before it is completed, the changes made up to that point are not committed.
MPE/iX transaction lo cking is based on page-level protection of the system architecture and
does not require signicant CPU overhead.
Transaction Logging and Recovery
The Transaction ManagementFacility automatically generates and maintains a transaction log
le that records all transaction updates. Maintaining a log le facilitates recovery from the
abnormal end of transactions and system failures. In these cases, les can be restored to a
consistent state by copying the contents of the log le into the data le. This"undoes"the
actions of partially committed transactions.
System failures are either hard or soft. When a soft failure occurs, data is not altered or lost,
but some incomplete transactions may exist. In this case, the Recovery Manager portion of
the Transaction ManagementFacility is automatically invoked to perform recovery of the
data le when the system is restarted. Files are restored to their original state by copying the
"
before image"of data from the log le for incomplete transactions. This is called rollback
recovery. Recovery from a soft failure is ecient and takes a maximum of only a few minutes.
Rollback recovery is automatically performed for abnormally ended transactions.
When a hard failure occurs (for example, a disc media failure), data is lost. At system
restart, you must mount a backup tap e and issue the MPE/iX command
:RECOVER
. The
1-10 OVERVIEW
Page 29

Transaction ManagementFacility returns data to a consisten
committed transactions in the log le to the c
called"rollforward recovery.
"
heckpoint presented by the backup tape. This is
t state by reapplying all
Transaction logging requires little CPU o
verhead b ecause it is designed as an in
tegral part of
the MPE/iX File System, utilizing the addressing and protection features of HP Precision
Architecture (HP-PA).
Simplifying a Program
The Transaction ManagementFacility simplies development and maintenance of
transaction-oriented applications by:
Maintaining recovery routines, so a programmer does not ha
ve to develop and maintain
custom ones.
Simplifying the programming task of ensuring data in
tegrity and increasing its eciency
.
Providing locking and logging, thus requiring the programmer to mark only the beginning
and end of transactions.
DEBUG
DEBUG is a low-level assembly language debugger, requiring some knowledge and familiarity
in the following areas to utilize:
Assembly code
Procedure calling conventions
Parameter passing conventions
HP3000 and HP Precision Architecture (HP-PA)
Hewlett-Packard oers two source level, symbolic debuggers, SYMBOLIC DEBUG/XL and
Toolset/XL, whichyou can use if you do not require assembly language debugger features.
DEBUG is an intrinsic procedure, providing privileged and non-privileged users with an
interactive debugging facility for checking out their operating environments. Using DEBUG, it
is possible to:
Set, delete, and list breakpoints in a program. The program executes until a breakpoint
is reached, then stops and passes control to the user. When you set breakp oints, you can
specify a list of commands that will automatically b e executed when the breakp oint is hit.
Single step (multiple steps) through a program.
Display and/or mo dify the contents of memory locations. A full set of addressing modes is
oered, including:
- absolute CM memory
- code segment relative
- data segment relative
- S relative
- Q relative
- DB relative
- HP-PA virtual addresses
- HP-PA real memory addresses
OVERVIEW 1-11
Page 30

Display a symbolic procedure stac
(NM) and Compatibility Mo de (CM) calls. Y
k trace, optionally displaying interleaved Native Mode
ou can also temp orarily set the curren
environment back to the environment that existed at an
t debug
y marker in the stack.
Calculate the value of expressions to determine the correct v
point in a program. V
alues can b e custom formatted in sev
alues of variables at a given
eral bases.
Use full screen displays (windows) that allowyou to inspect registers, program code, the
current stack frame, and the top of stac
important data blo c
ks to dynamically monitor c
Display on-line help for all commands, predened functions, and en
Create and reference user-dened v
k. Groups of custom user windo
hanging values.
ariables.
ws can b e aimed at
vironmentvariables.
Dene powerful, parameterized macros. You can invoke macros as new commands to
perform sequences of commands or as functions within expressions that return single v
alues.
Dene aliases for command and macro names.
Execute commands from a le, record all user input to a logle, and record all DEBUG
output to a listle.
MPE/iX User Interface
MPE/iX has a user interface that includes a command language, on-line HELP facility
,
user-dened commands (UDCs), and command les.
The MPE/iX command language is processed by the Command Interpreter. It contains all
necessary commands to direct and control the system.
You can enter identical MPE/iX commands during a session or through a job; MPE/iX has no
separate control language for jobs. You can also issue MPE/iX commands in a command le.
Actions MPE/iX commands can p erform include:
Initiate and terminate jobs and sessions.
Run system programs and utilities.
Compile, link, load, run, and debug programs.
Create, maintain, and delete les.
Display le information.
Display job, session, or device status.
Transmit messages.
Establish communication with lo cal and remote computers.
Control and manage system resources.
If the command interpreter (CI) detects an error in command syntax in interactivemode
(during a session), it provides a descriptive error message specifying the erroneous parameter
and prompts you to correctly reenter the command. If it detects a syntax error while running,
it lists the error on the output device and halts the job.
1-12 OVERVIEW
Page 31

You can use the command language to create batc
h les (also called stream jobs) that con
control statements and variables. Execution of the commands in the le can be altered at
execution time by using these control statements.
MPE/iX System Performance
tain
MPE/iX provides ecient performance through use of the mapped le tec
concurrent directories described in the follo
wing subsections.
hnique and
Mapped Files
MPE/iX employs the mapp ed le tec
version of the disc cac
hing-capability of MPE V/E. File access eciency is impro
code and data portions of les required for processing reside in memory
faster than performing physical disc I/O operations. The mapp ed le tec
system buering and optimizes global system memory managemen
File mapping is based on MPE/iX demand paged virtual memory
hnique for performing le access. It is an impro
ved when
. Accessing memory is
hnique eliminates le
t.
, which uses to advantage
ved
the large amount of virtual memory on the system. When a le is opened, it is logically
mapped into virtual memory. An open le and its contents are referenced by virtual
addresses. Eachbyte of each op ened le has a unique virtual address.
File mapping improves I/O p erformance without imposing additional CPU o
verhead or
sacricing data integrity and protection. Traditional disc caching schemes for increasing
I/O performance impose a CPU o
architecture allo w MPE/iX to perform le mapping without incurring this penalt
verhead p enalty. The 900 Series hardware and system
y. System
hardware p erforms the virtual to physical address translations for locating p ortions of the
mapped les, thus eliminating CPU overhead for this function.
If the required pages are not in memory
directly from disc and places them in the user's area in memory
, the MPE/iX Memory Manager fetches them
. This eliminates File System
buering. Pages are"prefetched"to reduce the amountofphysical disc I/O. Prefetching
means that the page specied for fetching and the group of pages surrounding it are a fetc
hed
all at once. This improves eciency b ecause the processor is likely to require pages that are
located near each other. Two benets of this are:
Eliminating unnecessary data movement in memory improves system p erformance.
Memory space usage is optimized.
MPE/iX le system access intrinsics are built on the mapp ed le technique. Programs using
le access metho ds supported by MPE le types and intrinsics obtain the benets of le
mapping without requiring changes.
You can directly access mapped les when programming in languages with p ointers. For
example, you can obtain the advantage of File System naming and data protection for
accessing array type structures and developing sp ecialized access metho ds.
You can write programs that address les through virtual memory, instead of calling File
System intrinsics for disc reading and writing. The le interface provides opening and closing
of user mapp ed les with normal naming and security, but with improved
LOAD
and
STORE
speed on le references.
OVERVIEW 1-13
Page 32

Directory Entries
On operating systems that ha
directory services for les on an
directory. In other words, they must o ccur one at a time. A
a bottleneck due to physical contention for one disc and logical con
ve the system directory cen
tralized on one disc, access to
y disc on the system requires serial access to the system
t peak usage times, this creates
tention for one directory
user.
The space for the directory structure is spread across the v
olume set, not necessarily located
on one volume. The lo cking mechanism allows multiple readers and ensures that the proper
locks for sp ecic c
MPE/iX uses directory entries that are spread across all mem
speed up le access and eliminate the ph
hanges in the directory structure, suc
ysical or logical serialization imposed b
h as le name insertions and deletions.
bers of the system v
olume set to
y a centralized
directory.
With MPE/iX, each disc in a system v
user requests automatically go through the directories and arriv
the requested les without going through a cen
simultaneously access a system directory
On nonsystem volume sets, the directory is restricted to the MASTER v
olume set has a directory of les located on it. Th
e at the disc con
taining
tralized directory. Multiple users can
.
olume of the set, so
us,
that it is not necessary to mount the entire set at one time.
Native Mode System Components
This section describ es the MPE/iX op erating system subsystems imp ortant for programming
only in Native Mo de (NM). For programming information on MPE/iX operating in
Compatibility Mode (CM), refer to the Migration Series of man
System (FOS) is the name for the MPE/iX operating system and asso ciated softw
in a standard 900 Series HP 3000 installation. The softw
are that automatically comes with
uals. Fundamental Operating
are included
MPE/iX is a collection of high-level tools that make the system easier to use. In addition,
other high-level to ols are optionally available for use with MPE/iX. Collectively, these tools
include:
MPE/iX operating system
Languages:
HP C/iX
COBOL II/XL
HP Pascal/iX
HP FORTRAN 77/iX
HP Business BASIC/V (CM only)
SPL/V (CM only)
RPG/V (CM only)
Forms design and screen handling:
- forms control
- VPLUS/V (formatted data entry application)
1-14 OVERVIEW
Page 33

Oce systems:
- TDP (text editor and formatting application)
- HPSLATE
- HPDESKMANAGER (electronic mail application)
- HPWORD
- Editor (text editor application)
Development aids:
- System Dictionary/XL
-Transact/V
- Inform/V
- Report/V
Data Management:
- ALLBASE/SQL
-TurboIMAGE/XL
- Query/V (subsystem for v
erifying and mo difying data)
- Keyed Sequential Access Management (KSAM)
- MPE/iX File System
- SORT-MERGE/XL (utility for ordering records in a le and merging records in sorted
les. It can sort anycharacter sequence using any data type.)
MPE/iX also provides sp ecial purpose utilities for system administration tasks.
For example, the MPE/iX Tape Labeling Facility allows you to place labels on magnetic
tapes for identication and protection.
MPE/iX provides utilities to facilitate migration of applications and databases to the 900
Series systems.
Terminal Keyboard Layouts
Hewlett-Packard terminals contain keys for the entire ASCII character set. These characters
can be displayed on the CRT screen and printed on a printer. HP terminals have three mo des
of operation:
Local (not connected to the HP 3000 system)
Remote character mode
Remote blo ckmode
Non-printable keys include the SHIFT, BACKSPACE, RETURN, and TAB keys. The
5
(escape) and
4
(control) keys generate special codes for terminal operation. The most
CTRL
4
ESC
5
frequently used codes are the following key combinations (not case sensitive):
4
CTRL
4
CTRL
5-4
Y
5-4S5
5
stop subsystem activity
suspend output
4
CTRL
5-4Q5
resume output
OVERVIEW 1-15
Page 34

Terminals come with various memory amoun
can access at one time. When eac
room for a new line at the b ottom. This con
point, information will be lost from view when y
up at the top of the memory buer is no longer a
Giving Commands to MPE/iX
There are several ways to command MPE/iX: commands, command les, and user-dened
commands (UDCs). These alternatives are described in the subsections b elo
Figure 1-4.
h line of the screen is lled, the top line scrolls up to mak
ts. This aects the amount of information you
tinues until terminal memory is lled. A
ou enter another line b ecause the line scrolled
vailable.
w and shown in
t this
e
Figure 1-4. Commanding MPE/iX
MPE/iX Commands
MPE/iX commands p erform many dierent functions: managing les, compiling programs,
executing programs, and so on. Many commands actually invoke subsystems, causing other
programs to run. Some commands require that you have capabilities on the system beyond
that of the normal user. For example, they may require Account Manager (AM), System
Manager (SM), or System Sup ervisor (OP) capability.
In a session, the command interpreter uses a leading colon (:) as a prompt character to
indicate that it is expecting you to enter an MPE/iX command. In jobs, you enter the leading
colon before an MPE/iX command to identify it. In b oth cases, the system disregards blanks
between the leading colon and the MPE/iX command.
1-16 OVERVIEW
Page 35

The list below shows some common MPE/iX commands grouped according to similar
function.
:HELLO
:BYE
:BUILD
:FILE
:LINK
:RUN
:COPY
:RENAME
:LISTF
:PURGE
:SHOWJOB
:SHOWME
:HELP
:REDO
:TELL
:TELLOP
:SETMSG
:CCXL
:COB85XL
:PASXL
:FTNXL
:RESUME
:ABORT
BREAK key
For detailed information, refer to the
MPE/iX Commands Reference Manual Volumes 1 and 2
(32650-90003 and 32650-90364).
MPE/iX Command Parameters
Some commands require or can accept parameters. Parameters given in command syntax can
havetwo components:
Literal information that you must enter exactly as shown in documentation. For example, in
the command
:SHOWJOB JOB=@J
JOB=
is literal information.
User-supplied variable information that is specic for the currentinvocation of the
command. For example, in the command ab ove,@Jis a user-supplied variable.
For detailed information on the conventions for documenting command syntax (including
parameters), refer to"Notation Conventions"in the front of this manual.
OVERVIEW 1-17
Page 36

MPE commands can have positional or k
positional parameter list are:
eyword parameter lists. The c
haracteristics of a
Location of a parameter in the list is signican
Each parameter is separated b
y a comma (,).
If a parameter is omitted from the list, a place-holding comma m
t.
ust replace it, unless the
parameter is at the end of the list.
For example:
:COBOLII SOURCE,,LISTOUT
The characteristics of a keyword parameter list are:
Location of a parameter in the list is not signican
Each parameter is preceded b
y a semicolon (;).
t.
It can have a positional subparameter list.
For example,
:FILE OUTFILE;DEV=LP;CCTL
is the same as
:FILE OUTFILE;CCTL;DEV=LP
Continuing an MPE/iX Command to Another Line
The maximum number of characters in a command is 256. You can continue a command on
more than one line byentering an amp ersand (&) as the last nonblank character on the line
to be continued. Enter the ampersand immediately b efore or after a delimiter (
,;.=/
or
blank).
For example:
:BUILD MYFILE;DEV=DISC &
:REC=-80
On-line Help in Using an MPE/iX Command
MPE/iX provides an on-line help facility to aid you in using MPE/iX commands. You can
easily experiment with it bytyping
HELP
at the colon (:) prompt.
Correcting or Modifying an MPE/iX Command
MPE/iX provides a correction facility to correct the previous MPE/iX command or modify it
to use again. The
:REDO
command allows you to modify the previously displayed command
without having to retype the entire command. It does not cancel any action p erformed by the
previously displayed command.
Referring to Several Files at Once
Several generic characters can b e used like wildcards in specifying a le set or volume set.
This is especially useful in listing operations, to avoid entering exact names when you are
performing the op eration on many les with similar names. Generic characters allow you to
process an entire set of les in one MPE/iX command, by specifying a string or character that
1-18 OVERVIEW
Page 37

is common to all members of the set. Y
commands.
ou can use generic c
haracters with some MPE/iX
The generic characters (or portions of names) are described as follo
@ All strings up to eigh
tcharacters long, including a n
? A single alphanumeric character.
# A single numeric character.
Examples of wildcard use are:
@A@
All lenames (in the logon accoun
t and group) that include an
example, it could include the lenames:
AARDVARK
DELTA
BACCUS
@.@.PRR
All lenames in all groups of the
PROG
account. For example, it could include
the lenames:
CONTENTS.PUB.PROG
CONTENTS.MKT.PROG
CONTENTS.ENG.PROG
ABC?
All lenames (in the logon account and group) starting with
with any single alphanumeric character. For example, it could include the
lenames:
ABCX
ABCY
ABCZ
ws:
ull string.
A
.For
ABC
and ending
XYZ#@
All lenames (in the logon account and group) starting with
XYZ
, followed
by a single numeric character, and possibly ending in other characters. For
example, it could include the lenames:
XYZ1
XYZ23
XYZ2AAA
Command Files and User-defined Command Files
Command les and user-dened commands (UDCs) are les that allow programmers to
customize their environment. MPE/iX accepts numbered and unnumbered les composed of
commands. The commands can consist of anynumber of MPE/iX commands. Each command
line can b e a maximum of 279 characters long. To continue a line, place an ampersand (&)at
the end of the line, after the last nonblank character. A command line can be continued up
to a maximum of ten lines, not exceeding a total of 279 characters. The maximum number of
characters on a line is 80.
A Command File is a le that contains a single command denition. It is executed by
specifying its le name. A Command File do es not have a command name and is not entered
in a catalog directory.For example, entering
:COB85XL
, followed by a source le name,
executes a command denition that invokes the COBOL II/XL compiler.
OVERVIEW 1-19
Page 38

A User-Dened Command (UDC) le is a text le that con
denitions and with a name for eac
h denition. Each denition is a UDC. Y
to perform several MPE/iX commands in succession b
tains one or more command
y issuing only the name of the UDC.
You can also use a UDC to disable an MPE/iX command. Y
using Editor or TDP.
ou can use a UDC
ou can create the UDC le b
y
Each UDC le command denition in a UDC has the following componen
Head: name of the UDC (required) and parameters and defaults (optional).
Options (this portion is optional):
LIST
, which lists all commands executable when the UDC is in
LOGON
, which immediately executes the UDC at log on.
NOBREAK
NOHELP
Body: one or more MPE/iX commands con
Separator: one or more asterisks (
, which disables the BREAK k
, which disables
:HELP
for UDC execution (normally
*
ey for UDC execution.
tained in this UDC.
) alone on a line, separating command denitions.
voked.
:HELP
lists the entire UDC le).
Figure 1-5 shows an example of a UDC le containing two UDCs.
ts:
Figure 1-5. UDC File Example
This UDC le denes two UDCs that accept parameters when executed. The rst UDC
purges one or more les. The second one runs a program. The following rules apply to
parameter specications:
Parameters can haveany name that starts with an alphabetic character and has no special
characters, such as $ or %.
A parameter without a default value is required to execute the UDC.
An exclamation point(!) indicates that the following string is a parameter. If no
exclamation point appears, MPE/iX processes the string as part of the command.
If the default value specied for a parameter contains a special character other than$or#,
the default must be delimited by double quotation marks (").
1-20 OVERVIEW
Page 39

If a UDC calls another UDC, the called UDC m
ust be dened in the UDC catalog (see
below) after the calling UDC unless recursion is sp ecically enabled.
To activate the UDCs in a UDC le, the le m
the
:SETCATALOG
command to catalog a UDC le. Eac
specied le becomes the only enabled UDC le, unless y
appended. An enabled UDC le is frequen
Executing
disable the UDC catalog to sa
want to disable the UDC catalog, y
Executing
:SETCATALOG
:SHOWCATALOG
without any le names disables all UDC catalogs. Y
ve a new version of a it to the same le name. If y
ou can save a new version of it under a dieren
shows a list of all UDC catalogs (enabled UDC les) and the UDCs
ust be iden
tied to MPE/iX as a catalog. Use
h time you execute
ou specify that more les should be
tly called a UDC catalog.
:SETCATALOG
ou must rst
ou do not
t le name.
, the
within them.
The le named
COMMAND.PUB.SYS
contains a table of UDC users and catalogs. Purging or
putting a lo ckword on this le disables all UDCs.
When you use a UDC, catalogs are searc
hed for the sp ecied command name in the follo
wing
order of catalogs set at:
User level (Us)
Account level (Ac)
System level (Sy)
The order in which UDC catalogs are searched within a level is determined by the order
in which they were specied in the
:SETCATALOG
command. Command denitions are
sequentially searched for execution in order of appearance in a UDC catalog.
System resources are required to manage UDCs for eac
h session in which they are enabled.
UDCs that are automatically executed at log on cause an increase in the time required to
complete the log on. A situation where many users have several UDC catalogs (enabled UDC
les) can have a severe negative impact on system performance.
For detailed information on command les and UDCs, refer to
and Variables Programmer's Guide
(32650-90011).
Command Interpreter Access
Break Mode
When a pro cess is in control, it reads user input and acts according to its o
wn rules and
conventions. It is p ossible to temporarily interrupt the process to go back to the command
interpreter (CI) without exiting the process and having to restart it. When this o ccurs, the CI
is executing in break mo de.
Activating the BREAK key interrupts the data communication function of the terminal. This
can suspend or terminate the process currently executing (for example, a subsystem or user
program). The program currently running is interrupted, not the actual MPE/iX command
that started execution of the program; this command mayhave already completed execution.
In break mo de, you can enter MPE/iX commands and user-dened commands (UDCs). When
you press the BREAK key, the colon prompt (:) app ears, indicating that your session is in
break mode.
The following MPE/iX commands can be interrupted by pressing the BREAK key. This
action aborts the output of the command, not its action:
OVERVIEW 1-21
Page 40

:BYE
:HELLO
:HELP
:LISTF
:LISTVS
:REDO
:REMOTE HELLO
:REPORT
:SHOWDEV
:SHOWIN
:SHOWJCW
:SHOWJOB
:SHOWME
:SHOWOUT
:STREAM
The following MPE/iX commands can byinterrupted by pressing the BREAK k
ey. This
action temp orarily suspends execution of the command; execution can b e resumed b
:RESUME
.
:CCXL
:CCXLG
:CCXLK
:COB74XL
:COB74XLG
:COB74XLK
:COB85XL
:COB85XLG
:COB85XLK
:EDITOR
:FTNXL
:FTNXLGO
:FTNXLLK
:LINK
:LINKEDIT
:PASXL
:PASXLGO
:PASXLLK
:RESTORE
:RUN
:STORE
yentering
1-22 OVERVIEW
Page 41

Echo On/Off
Normally,everything you type on the k
screen echoes your typing. However, in some situations, y
eyboard is shown on the screen. In other w
ou may not want to see your typing
appear. For example, when you are typing a password, someone looking o
may see it or observ
the password does not appear on the screen. Y
does not appear, b
e it on the screen if y
yentering
ou leave the terminal. It pro
ou can turn o the ec
vides better securit
ho feature, so your typing
:SET ECHO=OFF
You can turn on the ec
ho feature, so you can see what y
ou type, byentering
:SET ECHO=ON
Accounting Structure Overview
For programming on the 900 Series HP 3000, it is imp ortant that y
ou understand the
accounting structure. Its ma jor comp onents are:
Accounts
Users
Groups
Files
ords, the
ver your shoulder
yif
The accounting structure on the HP 3000 family of computers is designed for business
and industrial purposes. The ability to account for system use on a department level is a
fundamental element in business accounting. HP 3000 systems record on an account basis
the amount of CPU time, elapsed time (connect time), and disc space used. An HP 3000
computer must have a system account named
SYS
. This is used to store the information
necessary to running the op erating system. You can add more accounts for other purposes.
A user name identies a valid user for an account. A group is a partition in an accoun
t for
storing les that are logically related.
Logon and Logoff
If you are not familiar with the HP 3000 accounting structure, you can still log on and o
the system for simple use while you are learning ab out the accounting structure. Simple
instructions for logging on the system are provided in To log o the system, simply enter the
MPE/iX command
:BYE
.
Account
An account on the 900 Series HP 3000 provides a billable entity for accounting purposes.
Accounts can be added to or removed from a system, as needed. A system always has a
SYS
account, containing op erating system software, subsystem software, and system data. A
SUPPORT
proper system support. The
account contains troublesho oting information useful for providing information for
SYS
and
SUPPORT
accounts are part of the system when it is
delivered. On an account basis, the system can limit:
OVERVIEW 1-23
Page 42

Amount of CPU time
Elapsed connect time
Disc space used
An account name can be from one to eigh
alphabetic character. Following is an example of a logon for user John in the accoun
t alphanumeric characters long, starting with an
tPROG.
:HELLO JOHN.PROG
As a security provision, you can assign an accoun
has a password, MPE/iX prompts you to enter it after you enter the
you enter a password in response to this prompt, it is not ec
As a short cut, y
for MPE/iX to prompt y
ou can enter the account password in the
ou for it. To do this, t
t password to an account. When an account
:HELLO
hoed on the screen as y
:HELLO
command instead of w
command. When
ou type it.
aiting
ype the account password after the account
name, separated by a slash (/). When you enter a password in this way, as part of the log on
line, it is echoed on the screen as y
visible. For example, if the accoun
wait for the password prompt or log on b
ou type it and ma
y reduce system security because it is
tPROG has an account password of
yentering:
XYZ
you can either
:HELLO JOHN.PROG/XYZ
Figure 1-6 shows an example of the types of accounts a company mighthave on a system.
Figure 1-6. Accounts Example
User
Each account can have many users. A valid user name is required to log onto an account. At
least one user must be designated for an account in order to log onto it. The
automatically comes with the user name
MANAGER
. User names can be added to or removed
SYS
account
from an account, as needed. An example of a logon for a user MARY in the FINANCE
account follows:
:HELLO MARY.FINANCE
1-24 OVERVIEW
Page 43

As a security provision, you can assign a user passw
ord to a user. When a user has a
password, MPE/iX prompts you to enter it after you enter the
account password, if one exists. When y
not echoed on the screen as y
ou type it.
ou enter a password in response to this prompt, it is
:HELLO
command and the
As a short cut, y
for MPE/iX to prompt y
ou can enter the user password in the
ou for it. To do this, type the user passw
:HELLO
command instead of waiting
ord after the user name,
separated by a slash (/). When you enter a password in this way, as part of the log on line,
it is echoed on the screen as y
For example, if the user JOHN has a user passw
password prompt or log on as follo
ou type it and may reduce system security because it is visible.
ord of
BDATA
you can either w
ait for the
ws:
:HELLO JOHN/BDATA.PROG/XYZ
Figure 1-7 shows an example of sev
eral users on an accoun
t.
Figure 1-7. User Example
Group
A group in an account allows you to store sets of les that have something in common. You
can think of a group as a le folder holding any les you wish to keep together. Groups
partition sets of les in an account. You can execute the MPE/iX command
:REPORT
to see a
list of all groups in the logged on account.
When an account is created, it automatically has a group named
PUB
. Groups can be added
to or removed from an account, as needed. As a convenience, a user can be set up to have
a home group. If you have a home group, you need not sp ecify the group when you log on.
Otherwise, you must specify the group at log on, or you will be logged onto the
PUB
group, by
default.
Following is an example of a logon to the group PROJ1:
:HELLO JOHN.PROG,PROJ1
As a security provision, you can assign a user password to a group. When a group has a
password, MPE/iX prompts you to enter it after you enter the
:HELLO
command and the
OVERVIEW 1-25
Page 44

account and user passwords, if they exist. When y
prompt, it is not ec
hoed on the screen as y
ou type it.
ou enter a password in response to this
As a short cut, y
for MPE/iX to prompt you for it. To do this, t
ou can enter the group password in the
ype the group passw
:HELLO
command instead of waiting
ord after the group name,
separated by a slash (/). When you enter a password in this way, as part of the log on line,
it is echoed on the screen as y
For example, if the
PROJ1
wait for the password prompt or log on b
ou type it and ma
y reduce system securit
group shown above has a group passw
yentering the password as part of your logon:
ord of
y because it is visible.
MINE
you can either
:HELLO JOHN.PROG,PROJ1/MINE
The following gure shows an example of sev
eral groups and several users on an account.
Figure 1-8. Groups Example
File Specifications
You must use a standard le reference format to refer to a le. If y
ou are logged into the
account and group where the le resides, only the le name and lockword (if it has one) are
required. A lo ckword is an optional, additional security provision that the MPE/iX File
System provides for individual les. le level. If a le has a lockword, you must specify the
le name and lo ckword to refer to the le, using the following format:
lename/lockword
where
associated with the le. For example, you can refer to a le named
MY
lename
by specifying:
is a valid le name (refer to Chapter 7) and
lockword
is the lo ckword
STATUS
with the lo ckword
STATUS/MY
1-26 OVERVIEW
Page 45

Referring to a File in a Different Group
To refer to a le in a dieren
t group in the accoun
standard le reference format:
lename/lockword.groupname
where
to the le described in the example abo
groupname
is the name of the group where the le resides. F
ve, residing in a group named
STATUS/MY.SEPT
Referring to a File in a Different Account
To refer to a le in a dieren
t account than the one y
standard le reference format:
lename/lockword.groupname.accountname
where
accountname
is the name of the accoun
refer to the le describ ed in the example abo
specifying:
STATUS/MY.SEPT.MANU
Session and Batch Modes
tyou are logged onto, use the following
or example, you can refer
SEPT
,by specifying:
ou are logged onto, use the following
t where the le resides. F
ve, residing in an accoun
or example, you can
t named
MANU
,by
This section describes how to use sessions and jobs on a 900 Series HP 3000. A detailed
description of the steps involved in program development are given in Chapter 3"Program
Development.
The twoways to perform tasks on a Series 900 HP 3000 system are session mo de and batc
"
h
mode. Session mo de is interactive. In other words, you log on to the system, it prompts you
with information displayed on the screen to determine what you want to do (or tell you what
it has done), you enter information telling it what you want to do, and the system executes
your commands. Session mode is dynamic; y
ou can submit commands that can alter the
outcome of your task, as you go.
Batch mode requires that you set up a job that you can submit all at once to the system for
processing. The job contains all the information necessary for the system to perform y
task: a log on, a list of commands to execute, and an end-of-job signal. When y
ou submit a
our
job in batch mo de, you cannot alter the outcome of the task. The job will run to completion
(assuming it do es not end abnormally) without any opp ortunity for you to change the
commands in the job.
You can use the MPE/iX command
:STREAM
to initiate a job, once you have placed all the
instructions for the job in a le. This job stream is indep endent of the session or job that
originated the le. You can use it to initiate a job directly from a current session or from a
disc le.
Almost all MPE/iX commands execute in either mode. Some give slightly dierent
information depending on the mode in which they are executed, and some are totally
interactive and are ignored in batch mode.
Figure 1-9 shows a comparison of the commands that begin and end a session and job.
OVERVIEW 1-27
Page 46

Figure 1-9. Session and Job Commands
Figure 1-10 shows a comparison of c
be familiar with all of the terms used, but y
dierences and refer to this gure again when y
3000.
Figure 1-10. Session and Job Characteristics
You can identify sessions and jobs currently running on the system by using the MPE/iX
command
(sessions start with#S, jobs start with#J), gives their state of execution, input priorit y, and
other pertinent information.
:SHOWJOB
. This lists all sessions and jobs, identies them with a unique number
haracteristics of a session and a job. Y
ou can get a general idea of the similarities and
ou are more familiar with the 900 Series HP
ou may not yet
1-28 OVERVIEW
Page 47

Converting Data Files from MPE V/E to MPE/iX
When converting les from MPE V/E to MPE/iX, y
ou must consider several dierences in
data storage, including:
Floating point dierences
Floating point, single precision dierences
Floating point, double precision dierences
Floating point conversion intrinsic
HP FORTRAN 77/iX native alignment
HP Pascal/iX allo cation alignment of independentvariables
COBOL II/XL native alignment
MPE/iX has many data type dierences from MPE V/E, in terms of concepts of data storage,
dierences in data storage tec
them. For an overview of data conversion, refer to
Programmers
(30367-90005). For detailed information on MPE/iX data types, refer to
Types Conversion Programmer's Guide
hniques, and implications for the programmer in handling
Introduction to MPE/iX for MPE V
(32650-90015). It describes the utilities for con
Data
verting
MPE V/E binary data les to MPE/iX native mode format.
Dierences integral to the conversion of MPE V/E data les to MPE/iX are:
MPE V/E and MPE/iX data variables and data structures are dierent. MPE V/E has a
16-bit nativeword length and MPE/iX has a 32-bit w
ord length.
MPE V/E and MPE/iX oating point formats dier.
MPE/iX is the same as MPE V/E for most data con
numbers. An intrinsic called
HPFPCONVERT
, included in MPE/iX, converts oating-point
versions, except for oating-p oint decimal
decimal number formats.
Data alignment and real number storage formats dier in MPE/iX from their MPE V/E
implementations.
Data Alignment Differences
MPE V/E and MPE/iX eachhave a dierentword size; MPE/iX has a 32-bit word size, and
MPE V/E has a 16-bit word size. Therefore, applications to be compiled on MPE/iX to run
in Native Mode using MPE V/E-compatible data les, mayhave to select the HP3000_16
compiler directive that is provided with Native Mo de compilers. This option causes the
compiler to:
Align data in records on 16-bit b oundaries (as in MPE V/E), instead of 32-bit boundaries.
Selects the MPE V/E representation mo de for real numbers.
Many data structures that are aligned on 16-bit boundaries on MPE V/E are aligned
on 32-bit boundaries on MPE/iX. On MPE/iX, 32-bit data types are aligned on 32-bit
boundaries, by default, to improve performance. Figure 1-11 shows the dierences in data
alignmentbetween MPE V/E and MPE/iX with an HP FORTRAN 77/iX example.
OVERVIEW 1-29
Page 48

Figure 1-11. HP FORTRAN 77/iX COMMON Block Data Alignment Example
Native alignment for some HP Pascal/iX, COBOL I I/XL, and HP FORTRAN 77/iX
data types is dierent than that used by languages running on MPE V/E. For tables
comparing alignmentby data type, refer to
Introduction to MPE/iX for MPE V Programmers
(30367-90005).
If an application uses both native aligned data les and MPE V/E aligned data les, an
alignment directive should be sp ecied in the program record denitions to force MPE/iX
or MPE V/E-aligned records on a structure-by-structure basis. MPE/iX compilers oer two
directives to specify MPE/iX or MPE V/E alignment, HP3000_32 and HP3000_16. For more
information on these directives, refer to the programmer's guide for the appropriate language
in the
Language Series
.
Note
The HP3000_16 compiler directive maintains data alignment and format
compatibility with MPE V/E and impacts the abilit
(NM) data structures. Unless specied otherwise, all data elemen
mode of the program or as specied b
y the compiler options in eect.
y to use Native Mo de
ts are in the
For example, to maintain Compatibility Mode (CM) data alignment and
format and create NM data structures, you should explicitly dene the
individual structures to b e in NM format as HP3000_32 while operating
under the HP3000_16 compiler directive. The other alternative is to create a
program that will read data in one mode and write it in the other.
Native Mode (NM) words and integers are dierent from Compatibility Mode (CM) words.
Table 1-1 shows the proper conversions. In this manual, NM words are implied, unless a CM
prex is added to a term.
1-30 OVERVIEW
Page 49

Table 1-1. Word and Integer Conv
ersions
Bits Native Mode (NM) Compatibility Mo de (CM)
16 1 halfword or shortint 1CMword or integer
32 1word or integer 2CMwords, double integers, or
double words
64 2words 4CMwords
Integers in MPE/iX can be 16 or 32 bits long, signed, or unsigned. Signed in
complement form. Halfword in
and word integers (32-bit) at addresses divisible b
Real numbers in MPE/iX are stored in one of t
of storing oating-p oin
tnumbers in the MPE/iX en
tegers (16-bit) are stored in memory at ev
y four.
wo oating-p oint formats. The two methods
vironment are: HP 3000 format, and
according to IEEE Task P854. The default MPE/iX Native Mode (NM) real n
representation conforms to IEEE T
than that used in MPE V/E-based HP 3000 systems. The real n
application can b e forced to the HP 3000 represen
ask P854. This standard species a storage format dieren
umber format for a particular
tation by sp ecifying the HP3000
tegers are in twos
en byte addresses,
umber
16
compiler directive. Since this compiler directive selects b oth MPE V/E alignment and real
number format, native aligned data must then be aligned on a per record basis.
A single source module can use only one real n
umber format, but the
HPFPCONVERT
intrinsic
converts real numbers between the various formats. Separate (external) procedures may use
dierent formats. The formats have dierent precisions and ranges for both single-precision
and double-precision real numbers.
Because of accuracy dierences b etween IEEE and HP 3000 double real numbers, the least
signicant digit may be lost in 16-digit real numbers. Since the HP 3000 double precision
range is smaller than the IEEE double real range, con
version from a very large or small one in
IEEE to one in HP 3000 may cause an overow or underow.
For a comparison of the real number representation on MPE V/E and MPE/iX, refer to
Introduction to MPE/iX for MPE V Programmers
(30367-90005).
t
Figure 1-12 and Figure 1-13 show the internal representation for oating-p ointnumbers on
MPE/iX.
Figure 1-12. IEEE Single-precision Real Number Format
OVERVIEW 1-31
Page 50

Figure 1-13. IEEE Double-precision Real Number Format
Conversion from HP 3000 format to IEEE format for a single-precision real n
present a range problem, because the IEEE range is smaller. Th
performing either of the follo
wing conversions:
us, overow can o ccur in
From an HP 3000 single-precision real number to an IEEE single-precision real n
umber can
umber.
From an IEEE double-precision real number to an IEEE single-precision real number.
You mayhave to develop new error handling co de to prev
entoverow.
The mantissa of an HP 3000 double-precision real number provides enough bits for 16 digits
of accuracy. The mantissa of an IEEE double-precision real number provides for 15.9 digits
of accuracy.Thus, converting double-precision real numbers from HP 3000 to IEEE format
can incur an extremely small loss of numeric precision. However, if the requirements of an
application depend on the ASCII representation of oating-point results, the eect of this
accuracy dierence can be important.
For example, if a program assumes 16-digit accuracy and requests 16 digits for formatting
output, with trailing zero suppression, the number 64.4 appears as 64.4 when the system is
running in Compatibility Mode (CM) and 64.40000000000001 when the system is running in
Native Mode (NM).
Rounding is frequently necessary when formatting output. In HP 3000 format, a n
umber
equidistant from two adjacentintegers rounds to the integer of greater magnitude. For
example, 1.5 rounds to 2, and 2.5 rounds to 3. In IEEE format, a n
umber equidistant from
two adjacentintegers rounds to the integer that has a least signicant bit of zero (in other
words, the even integer). For example, 1.5 rounds to 2, and 2.5 also rounds to 2.
Converting Files
General procedures for converting data les from MPE V/E to MPE/iX are describ ed
below. For detailed information on conversion, refer to
Programmers
(30367-90005) or the appropriate language manual in the
Introduction to MPE/iX for MPE V
Migration Series
The pro cedure for converting HP FORTRAN 77 binary les from MPE V/E to MPE/iX
format is as follows:
1. Read data from le in a subroutine with
2. Pass the data to a subroutine that has
$HP3000_16 ON
$HP3000_16 OFF
.
.
1-32 OVERVIEW
.
Page 51

3. Call the intrinsic
HPFPCONVERT
format.
4. Write the data out to a new le.
to convert
REALs
from MPE V/E to MPE/iX oating p oin
t
Note
A subroutine that has
Pascal on MPE V/E and MPE/iX has the follo
MPE V/E and IEEE oating poin
$HP3000_16 ON
wing incompatibilities due to data alignmen
t format
cannot call the
HPFPCONVERT
intrinsic.
t:
Data alignment of simple variables and record elements
String format
Pointers
COBOL II on MPE V/E and MPE/iX has incompatible indexed and sync
hronized data items.
Data Communications
Hewlett-Packard's networked, data communications and data management products are called
HP AdvanceNet. AdvanceNet provides network services (NS) software products, including
interactive and programmatic services. NS enables Hewlett-Packard and multivendor
computer systems to communicate with each other and share resources. For detailed
information, refer to
NS3000/XL User/Programmer Reference Manual
(36920-90001).
Network File Transfer (NFT)
Network File Transfer (NFT) is the network service that copies disc les from one computer
system in a network to another. NFT can transfer a le bet
ween anytwo systems in a lo cal
area network. NFT can transfer les b etween two systems remote from your own or perform
local transfers on a single HP 3000. You can use NFT interactively or programmatically.
Remote Process Management (RPM)
Remote Process Management (RPM) provides intrinsics that allow a pro cess to create and kill
other processes (that is, initiate and terminate their execution). A created pro cess ma
yor
may not be dependent on the creator. If it is independent, it can continue to execute after
the creator has expired. RPM permits a pro cess to create a process and send information
to it in the same intrinsic call. You can use RPM in conjunction with Network Interprocess
Communication (NetIPC) to manage distributed applications. For detailed information on
NetIPC, refer to
NetIPC 3000/XL Programmers Reference Manual
(5958-8600).
OVERVIEW 1-33
Page 52

Local Area Network (LAN)
NS 3000/XL is Hewlett-Packard's local area network (LAN) software services for linking
multivendor computer equipment, including MPE/iX based HP 3000 processors. These
network services (NS) run in conjunction with either of the HP Adv
anceNet link pro ducts
ThinLAN3000/XL Link and StarLAN/3000 Link. The LAN link supports the NS pro duct and
consists of b oth hardw
these link pro ducts com
are and software components. NS3000/XL software services and one of
bine to form a high-sp eed, shared-access, IEEE 802.3 LAN.
Remote File Access
The Remote File Access service (RF
A) allows access to remote les and devices. Using RF
A,
you can create, op en, read, write, close, and perform other manipulations on a le residing on
a remote HP 3000 system. Since a le can b e a peripheral device, y
from a tap e moun
The RFA uses the same MPE/iX File System in
ted on a remote system or prin
t local data on a remote prin
trinsics used on a local system. They are sen
ou can, for example, read
ter.
to the remote environment and executed there. A lo cal program can call them explicitly or
use the I/O procedures specic to the language in whic
You can interactively access a remote le or device if you have previously issued a
command that sp ecies the remote lo cation of the le. Y
h the program is written.
:FILE
ou cannot directly indicate the
location in the MPE/iX or subsystem command that accesses the le.
You can programmatically access a remote le from a lo cal application program once y
ou have
established an environment on the remote node by doing one of the following:
Calling standard MPE/iX File System intrinsics.
Using I/O pro cedures sp ecic to the language in whic
issued a
then an
formaldesignator
:FILE
command specifying a formal le designator for a remote le or device,
HPFOPENorFOPEN
parameter.
call in a local program can use this formal le designator in the
h the program is written. If you have
Remote Terminal Access
You can use the Virtual Terminal (VT) and Remote File Access (RFA) services to access
remote terminals. Use a
:FILE
command or an
HPFOPENorFOPEN
call to indicate that the
le you wish to access is actually a remote terminal. The remote terminal functions as a
non-session I/O device.
t
Remote Data Base Access
TurboIMAGE/XL is a Hewlett-Packard database management system. You can use
TurboIMAGE/XL intrinsics and utilities to access a TurboIMAGE/XL database residing on a
remote HP 3000. TurboIMAGE/XL intrinsics are sent to the remote node and executed in the
remote environment. The database should reside on an HP 3000, since other TurboIMAGE
products are not fully compatible with TurboIMAGE/XL. The database must b e located
entirely on a single node.
You can obtain the information required to op en a remote TurboIMAGE/XL database in a
program in three ways:
1-34 OVERVIEW
Page 53

Identify the database as a remote le in a previously executed
:FILE
command.
Use the
Create a database-access le to supply
COMMAND
intrinsic to include
:FILE
information in a program.
:FILE,:DSLINE
, and
:REMOTE HELLO
commands.
OVERVIEW 1-35
Page 54

Page 55

Utilities and Tools
2
This section describes the MPE/iX user in
programmatically access MPE/iX features and pro
The information is presen
on programmatic access, refer to
Guide
(32650-90011).
ted as an overview on a conceptual lev
Command Interpreter Access and Variables Programmer's
Programmatic access to MPE/iX allo
program without having to enter break mode. With the a
sophisticated, automated subsystems to run under MPE/iX. The tec
terface to showhow user programs can
vides an introduction to utilities and to ols.
el. For detailed information
ws you to use command in
terpreter (CI) features in a
vailable techniques, you can develop
hniques include:
Using MPE/iX programmatic interfaces, command les, and user-dened commands
(UDCs).
Performing variable dereferencing, concatenation, string substitution, recursive
dereferencing, and expression evaluation.
Using Job Control Words (JCWs) and variables.
Using the MPE/iX Help facility for commands, command les, and UDCs.
Programmatic Access to the Command Interpreter
Three intrinsics,
COMMAND,HPCICOMMAND
, and
MYCOMMAND
, allow programmatic use of the
MPE/iX command interpreter (CI). They allow a program other than the CI to:
Perform system services (for example, building and purging les).
Use the entire MPE/iX CI command set, command les, and UDCs.
Parse MPE/iX commands.
Some interactive subsystems can programmatically perform these functions without rst
having to exit their specic subsystem environment (that is, enter break mode).
The intrinsics for programmatic use of the CI are:
COMMAND
HPCICOMMAND
, which provides access to the MPE V/E subset of CI commands.
, which provides programmatic access to most of the MPE/iX CI command
set, command les, and UDCs.
MYCOMMAND
, which provides a programmatic ability to parse a line and return one or more of
its parameters.
Command les and user-dened commands (UDCs) are les that allow programmers to
develop their own environment. These are discussed in Chapter 1. For detailed information on
command les and UDCs, refer to
Guide
(32650-90011).
Command Interpreter Access and Variables Programmer's
Utilities and Tools 2-1
Page 56

Concatenating Strings and String Substitution
You can concatenate a string with a prex or sux. String substitution in a Command File or
a UDC parameter tak
es precedence over substitution of Command In
terpreter-level variables.
For example,
:SETVAR x 1
:WHILE x < 10 DO
:PURGE ACCT!x
:SETVAR x x+1
:ENDWHILE
:DELETEVAR x
purges les
ACCT1,ACCT2
,... ,
ACCT9
.
Expression Evaluation
You can specify an expression in a Command File or a UDC parameter and an appropriate
value will be assigned to it.
Using Job Control Words (JCWs)
A Job Control Word (JCW) is one type of predened variable. On MPE/iX, JCWs are a
subset of session-level variables, restricted byvalues and naming conventions. MPE/iX stores
JCWs as integers in the session-level variable table. You can manipulate JCWs with
JCW commands and intrinsics
Variable commands and intrinsics
IF
command
The commands
on standard variables.
correspond to the intrinsics
distinguishes between the table entries created by the
intrinsic) and those created by the
JCW commands and intrinsics usually function like the corresponding v
intrinsics, with a few exceptions, described belo
SETJCW
and
SHOWJCW
DELETEVAR
HPCIGETVAR
correspond to the commands
SETVAR
is used to delete JCWs. The intrinsics
and
SETVAR
HPCIPUTVAR
command (or the
used on CI variables. MPE/iX
SETJCW
command (or the
HPCIPUTVAR
w.
and
GETJCW
SHOWVAR
and
used
PUTJCW
PUTJCW
intrinsic).
ariable commands and
Job Control Word Name and Type
A JCW name can be a maximum of 255 characters long. The rst character must be
alphabetic. Other characters can be alphabetic or numeric. A JCW name cannot contain the
underscore (_) or the wildcard parameters (#, ?, [, and ]). A JCW must be of type integer,
with a value in the range 0 to 65535. This is the only dierence between JCW names and
variable names. For detailed information on naming and dereferencing variables, refer to
Command Interpreter Access and Variables Programmer's Guide
(32650-90011).
Changing the Value of a JCW
Once created, you can change the value of a JCW by using variable or JCW commands
and intrinsics. If you assign a value to a JCW that is outside the valid JCW range, then
MPE/iX reclassies it as a standard variable when you assign such a string value to it. You
can no longer use JCW commands and intrinsics on it; you must use variable commands and
2-2 Utilities and Tools
Page 57

intrinsics to display,change, or delete it. Y
ou can force reclassication of a JCW b
it a large numeric value. For example,
SETJCW X 99
denes a variable namedXas a JCW with value 99.
The statement:
SETVAR X 400
y assigning
givesXthe new value of 400, butXremains a JCW. However, when you assign a string v
ABCtoX
with the statement:
alue
SETVAR X "ABC"
thenXbecomes a variable and not a JCW. MPE/iX informs y
ou of the change with the
message:
JCW HAS BEEN RE-CLASSIFIED AS A STANDARD VARIABLE
JCW and CIERROR
Two special session-level JCWs named
JCW
and
CIERROR
are also system JCWs. Therefore,
they cannot b e reclassied as session-level variables or deleted. You can change their values
with the
SETVAR
and
HPCIPUTVAR
commands, but only to assign a new v
alue in the legal range
for JCWs. If you attempt to assign a value outside the range, MPE/iX issues the message:
THE VALUE MUST BE AN INTEGER IN THE RANGE 0...65535
and the initial value remains unchanged.
Reserved-word Prefixes
JCWs with reserved-word prexes and numeric values are:
SYSTEM 49152
FATAL 32768
WARNING 16384
OK 0
Help Facility
The MPE/iX Help facilityis available for commands, User-Dened Commands (UDCs),
command les, and program les. Command les and UDCs havetwo special options for
the Help facility:
security for UDCs and command les. When
Command File, but cannot display its contents.
information on this topic, refer to
Guide
(32650-90011).
HELP
and
NOHELP.NOHELP
disables the Help facility to provide increased
NOHELP
is active, you can execute a UDC or
HELP
is the default option. For detailed
Command Interpreter Access and Variables Programmer's
Utilities and Tools 2-3
Page 58

Toolset/XL
The Toolset/XL Program Development System is a product that pro
programming environment for use with COBOL I I/XL, HP F
Pascal/iX on the 900 Series HP 3000. It com
to facilitate all phases of program dev
elopment, from source co de creation and mo dication
bines an integrated set of programming tools
ORTRAN 77/iX, and HP
to program compilation, execution, and testing for COBOL I I/XL and HP P
HP FORTRAN 77/iX, it provides programming tools for program testing on the sym
vides a uniform
ascal/iX. For
bolic
debugging level.
The ma jor features of T
oolset/XL are:
User interface provides easy access to all programming to ols.
Workspace File Manager allows y
ou to generate versions of source les requiring a minim
of disc utilization. It stores source les using data compression to eliminate unnecessary
trailing blanks.
Full screen editor allows y
ou to enter and modify source co de on the screen.
Program Translation Management simplies program compilation and execution. The
latest compile listing is saved on-line, compile time errors are lo cated in the compile listing
by using a \p oint and push" technique, and the source le can be immediately edited b
accessing the full screen editor.
Symbolic Debug signicantly reduces time required to lo cate run-time errors. Y
symbolically reference variables and lo cations using names in the program. Y
clear program breakpoints with optional frequency and proceed coun
ts, edit source le at a
ou can
ou can set and
breakpoint, displayvalues and move new values to any data item, trace and retrace program
ow, and trace changes in data item values between paragraphs.
um
y
COBOL II/XL COPY Library Editing and Managemen
t provides a reusable code feature.
COBOL II/XL and HP Pascal/iX Data Denition Extractor allowyou to extract denitions
from Dictionary/V and use them to generate data declarations.
In addition to the features described above, Toolset/XL provides an on-line help facility,
a recovery feature for system failure, and the ability to directly access man
y MPE/iX
commands.
2-4 Utilities and Tools
Page 59

Useful Tools
Several useful programming to ols are a
administrators, programmers, and general users. Y
vailable to facilitate tasks common to system
ou can reduce the tedious asp ects of man
repetitious tasks by using Hewlett-Packard to ols to expedite forms design, screen handling,
report generation, and system dictionaries, as described belo
Forms Design and Screen Handling T
ools
w.
VPLUS/V is a comprehensive software system that implements and controls source data
entry. It also provides an interface between a terminal and an
y transaction processing
program.
Source Data Entry
As a source data en
validation built into the forms. It also pro
ENTRY that you can use to en
to browse the entered data and modify it as it is en
Thus, source data entry through VPLUS/V can be done without programming b
try system, VPLUS/V pro
vides a ready-to-use data en
ter data without any programming eort. ENTR
vides easy forms design with data editing and
try program called
Y allows you
tered.
y simply
using ENTRY. However, if you need additional or dierent capabilities, you can write your
own application incorporating VPLUS/V intrinsics.
Transaction Processing
y
As an interface to transaction pro cessing applications, VPLUS/V provides a set of intrinsics
that allows you to control forms and data on a terminal from an application program. These
intrinsics are available to programs written in any of the supported programming languages.
VPLUS/V also provides a reformatting capability.You can enter specications to control how
entered data is to be reformatted and then run a program to actually reformat the data.
VPLUS/V intrinsics and the reformatting capability, either singly or in combination, provide
a \front end" to existing transaction processing applications. Th
concentrate on processing problems rather than on editing data or con
us, VPLUS/V allows you to
trolling the terminal.
VPLUS/V Features
The main features of the VPLUS/V system are:
Forms design program called FORMSPEC that allo ws quick and easy forms design by using
menus at a terminal.
Batch mode management of forms les (through FORMSPEC) that allows a forms le to be
updated, compiled, and listed without tying up a terminal.
Advanced forms design (through FORMSPEC) that edits, formats, moves, and computes
data when the form is executed. It uses the user's native language for alphabetic
information and the local customs for numeric and date information.
Ready-to-run data entry program called ENTRY that provides immediate data entry and
modication with no programming eort.
Flexible data reformatting design program called REFSPEC that sp ecies reformatting of
entered data.
Utilities and Tools 2-5
Page 60

Batch program called REFORMAT that reformats the data according to the REFSPEC
formatting specications and writes it to a le for use b
y an application.
Set of intrinsics that provides a powerful programming language interface to terminals,
using FORMSPEC denitions, from applications written in an
y of the supported
programming languages.
Report Generation Tools
Several useful report generation to ols are a
vailable. These are described in the subsections
below.
Business Report Writer/XL
Business Report W
report writing system designed to streamline the dev
riter/XL facilitates rep ort dev
elopment and execution. It is a men
elopment and maintenance of large
u-driven
production rep orts.
Its capabilities include on-line report formatting, rotational views of data, m
advanced calculations, and performance tuning. It pro
databases, MPE les, and KSAM les. Business Report W
vides access to TurboIMAGE/XL,
riter/XL, together with System
ultipass reporting,
Dictionary/XL or Dictionary/V transparently resolve data denitions, structures, and access
paths.
Business Report Writer/XL execution programs are part of the MPE XL F
undamental
Operating System (FOS). Rep orts developed on Business Rep ort Writer/XL can be run on
other HP 3000 systems without access to Business Rep ort W
riter/XL or a dictionary.By
using intrinsics with user-specied parameter values, you can run reports from applications
written in other languages. Business Report W
riter/XL contains a conversion utilityto
automatically translate Report/V programs into Business Report Writer/XL. For detailed
information, refer to
Business Report Writer/XL Reference Manual.
Report/V
Report/V is a non-procedural report writing language operative only when MPE/iX is in
Compatibility Mode. It includes a high-level language that creates reports, a compiler, and a
processor to execute the reports. It provides access to TurboIMAGE/XL databases, MPE
les, and KSAM les. More advanced reporting capabilities are available in Native Mode
through Business Rep ort Writer/XL, which can automatically translate Report/V programs.
For detailed information, refer to
Report V Reference Manual
(32245-90001).
HP Visor
HP Visor is a terminal-based interface to HP SQL/V and ALLBASE/XL (HP SQL)
databases. It allows end users or database administrators to perform queries and generate
their own reports, without involving a programmer. It provides facilities for programmers to
use in preconguring complex tasks or to improve productivity when working with HP SQL
databases.
HP Visor has a forms-based interface that allows the user to mark boxes and press function
keys to step through tasks such as queries or custom report generation. It also provides
additional capabilities for experienced users to directly enter HP Visor or SQL commands.
Three mo dules are integrated with the HP Visor interface.
2-6 Utilities and Tools
Page 61

EZAccess, which enables new or infrequen
t users of the database to generate queries.
SQLAccess, which enables users familiar with HP SQL to use a screen-based editor to
formulate SQL queries and perform man
y other database operations.
EZReport, which formats and displays query results from EZAccess or SQLAccess and
allows users to customize report formats and calculate additional statistcs using the data
retrieved by the query.
System Dictionary/XL
System Dictionary/XL provides programmers and system administrators with a single source
for documenting all aspects of the system, including:
Data denitions.
Descriptions of databases, application systems, accoun
ting structures.
Conguration information.
It ensures that the information is en
tered in a standard format, stored in an organized
structure, and easily available to users and programs. This central source of information aids
in developing and maintaining applications and eectively managing system resources. System
Dictionary/XL has a programmatic interface for easy integration with other software. You can
customize it to meet your needs. Ma jor System Dictionary/XL features are:
Entity-relationship mo del provides a documentation structure closely matching the user's
conceptual mo del.
Extensibility allows customized documentation structure.
Programmatic access for automatic access and update.
Domains eliminate name conicts.
Separate test, production, and archival versions.
Uses synonyms and aliases to provide alternative names in the dictionary from those used
by external systems.
Interactive or batchmodeinterface.
Accepts macros and include les.
Reports on dictionary contents.
Input, output, and all dictionary names can be converted to lo cal languages.
Security provides restricted access to domains and dictionary ob jects and denes user
capabilities.
Automates conversion from Dictionary/V to System Dictionary.
Creates IMAGE schemas and ro ot les from dictionary denitions and produces dictionary
denitions from an IMAGE ro ot le.
Loads information ab out VPLUS/V forms les into the dictionary.
Generates denitions for HP COBOL II/XL COPY libraries from System Dictionary
denitions (this is part of a separate product called COBOL II/XL Denition Extractor).
Utilities and Tools 2-7
Page 62

A data dictionary is not an alternativ
e to a database managemen
t system (DBMS). A
dictionary manages information about data on the system, while a DBMS manages the data
itself. A DBMS schema may contain some information on the format and usage of the data.
However, dictionary information is more extensiv
e and easily usable.
In addition to documen
KSAM les, VPLUS/V forms les, programs, net
components. It can also documen
For detailed information, refer to one of the follo wing man
HP System Dictionary/XL COBOL Denition Extr
HP System Dictionary/XL General Reference Manual (Volumes 1 and 2)
ting IMAGE databases, System Dictionary can describe MPE les,
work device congurations, and other system
t the relationships among componen
ts.
uals in the Tools Series:
actor Reference Manual
(32256-90001).
(32256-90004 and
32256-90005).
HP System Dictionary/XL Intrinsics R
HP System Dictionary/XL SDMAIN R
HP System Dictionary/XL Utilities Reference Manual
eference Manual
eference Manual
(32256-90002).
(32256-90001).
(32256-90003).
Editor
The Editor is an HP 3000 subsystem that runs on MPE operating systems. It is a
line-oriented text editor used to create and manipulate ASCII les. Files can be source
programs, job streams, or text material.
You enter commands and lines of text through an input le. The Editor sends messages and
prompts in an interactive session by writing to an output le. You issue Editor commands
that operate on an Editor work le, which is a temporary le especially created for this
purpose. Each operation performed in the Editor manipulates the w
le is created as the result of sa
ving the work le. Until you keep the contents of the work le,
no permanent text le exists. If you are up dating an existing text le, it remains unc
ork le. A permanent text
hanged
while you make the changes on the temp orary work le copy. The original p ermanent text le
is overwritten only when you save the work le.
The work le is created as a temp orary le and is deleted when y
ou make a normal, orderly
exit from the Editor. If your edit session ends abnormally, the temp orary work le is saved
as a sp ecially named le and is still a
vailable. This is called a \K" le; the le name has the
form
Kdddhhmm
where
ddd
is the Julian day,hhis the hour, andmmis the minute at which the session
abnormally ended.
You can use the Editor command
VERIFY
to determine all aspects of the Editor's op erating
environment, including the location of the work le pointer. For example, you can determine
the increment for line numbers, page margins, record length, total length of work le,
format, tabs, and other attributes of the environment. Editor is described in the
Reference Manual
(03000-90012).
EDIT/3000
2-8 Utilities and Tools
Page 63

SORT-MERGE/XL
SORT-MERGE/XL is an MPE/iX subsystem that allo
merge several sorted les to form one le in a specied sequence. SOR
the order of the records from the input le according to y
ws you to sort one or more les or
T-MERGE/XL changes
our specications and writes them to
the output le.
You can use SORT-MERGE/XL interactively or programmatically
intrinsics for programmatic use. Y
ou must specify the input and output les and the sorting
(or merging) keys. The collating sequence defaults to ASCII unless y
detailed information on SORT-MERGE/XL, refer to
SORT-MERGE/XL Programmer's Guide
. Use the
SORT-MERGE/XL
ou specify otherwise. F
(32650-90080).
Key
Akey is the section of the record that SOR
which input records are to be rearranged for output. It is a record eld y
the position of the rst b
yte and the n
portion of a record for each record in a le. The data format for that portion m
T-MERGE/XL uses to determine the order in
ou specify by stating
umber of bytes in the eld. The k
ey applies to the same
ust be of the
same type in all records.
You can specify multiple keys. The rst one you enter becomes the ma jor key. SORT-
MERGE/XL uses the ma jor key to rearrange the records. If the contentoftwo records is
the same in a key eld, SORT-MERGE/XL uses the content of the next specied key to
determine which is written to the output le rst. If the con
tent of all the key elds for two
records is identical, then SORT-MERGE/XL preserves the order found in the input le when
it writes to the output le.
or
Ordering Sequence
SORT-MERGE/XL arranges records in the output le according to an ordering sequence
based on the value of data in the keys. The individual bytes in the key denitions determine
these values, based on their positions in a collating sequence.
Collating Sequence
The collating sequence can b e ASCII, EBCDIC, a nativ
EBCDIC are the basic collating sequences. Native language collating sequences apply to k
of type
CHARACTER
.You can specify the rearrangement to be in ascending or descending order,
e language, or user-dened. ASCII and
eys
based on the appropriate collating sequence.
Utilities and Tools 2-9
Page 64

DISCFREE
DISCFREE is a utility that reduces the amoun
a term used to describe the exten
t to which les are physically divided up on a disc. As disc
space becomes fragmented, smaller and smaller amoun
les must be broken into smaller and smaller pieces to t. F
t of fragmentation on a disc. F
ts of contiguous space are available, and
ragmentation has a negative eect
ragmentation is
on system p erformance and is highly undesirable.
You can use DISCFREE to:
Determine free space on the disc.
Perform a
START NORECOVERY
to correct fragmentation.
Obtain a detailed format of free space (HISTOGRAM) or free space allocation
(ALLOCATION) on discs.
For more information on using DISCFREE, refer to
Volume Management
(32650-90045).
FCOPY/XL
FCOPY/XL is a utility program on MPE/iX that allows you to copy data from one le to
another. You can copy the contentofanentire le or a selected portion of a le from an
y
supported input device to any supported output device. Supported input devices are disc,
magnetic tap e, terminal, and tap e cartridge. Supported output devices are disc, magnetic
tape, terminal, tape cartridge, and line prin
ter.
FCOPY/XL's basic functions include:
Making multiple copies of les
Making account-independent magnetic tap e copies of disc les
Transferring programs or data from one medium to another (for example, from magnetic
tape to disc)
FCOPY/XL has many features that expedite le manipulation. These include:
FCOPY/XL code translating function, which converts data from one computer code system
to another as part of a copying operation. FCOPY/XL can translate les between ASCII
and EBCDIC or BCDIC formats. You can use this feature to prepare magnetic tapes to
be used at dierent computer installations or to incorp orate magnetic tapes from other
installations into your 900 Series HP 3000 system. FCOPY/XL can translate b etween
uppercase and lowercase alphabetic characters. This is useful for a peripheral that has only
an uppercase character set.
FCOPY/XL subset function, which allows you to perform operations using a specied
portion of a le. You can designate the le subset as a range of contiguous records or as all
records containing a sp ecied data item in specied columns. This is useful for separating a
le into several separate les or copying or displaying only sp ecic records of a le.
FCOPY/XL skip end-of-le function, which allows you to position magnetic tap e to the
exact le where you want to read or write.
2-10 Utilities and Tools
Page 65

FCOPY/XL display functions, which shownumeric codes and corresponding c
symbols, thus allowing you to examine the con
tents of les at a terminal or on a prin
haracter
ter list.
You can also op erate on m
FCOPY/XL. For detailed information on using F
Reference Manual
(03000-90064).
ultiple les and multiple tap es. You can interactively invoke
COPY/XL and syntax, refer to
FCOPY
Utilities and Tools 2-11
Page 66

Page 67

Program Development
The required elements for running a program are:
Data space (for input, output, and computations)
3
Instructions (machine readable co de and constan
System routines (for example, input and output)
Program development is a term for taking a program design, on paper, to the poin
machine readable and functions reliably
Program components are data and code. When a program is running, instructions and data
are fetched from main memory to the CPU; data ma
for later use. Co de and data must be in main memory when required for execution. CPU
registers keep track of the location of such information as:
Next instruction to execute
Program status
Data calculations
The ma jor steps for developing a program are:
1. Writing: design the program and enter the source code in a text le.
2. Compiling: translate source co de to mac
3. Linking: bind all resources necessary for the program's code to run the program.
4. Run: execute the program.
These steps are described in detail in the subsections b elo
these steps.
.
hine readable instructions.
ts)
t where it is
y be stored backinto main memory
w. Figure 3-1 shows a summary of
Figure 3-1. MPE/iX Program Development
Program Development 3-1
Page 68

Writing a Program
You can write a program with an
y text editor or word pro cessor. MPE/iX pro
vides two
facilities for entering text that you can use to create a source le for a program: Editor and
Toolset/XL. For an overview of Editor and T
Tools."Since these facilities can be used for writing documen
oolset/XL, refer to Chapter 2,
ts, memos, and programs, the
"
Utilities and
output is called text les. Although the source code for a program is a text le, this guide
refers to it as a source le for program dev
elopment purposes.
How to Use Intrinsics
Many programs use low-level, system supplied procedures or subroutines to handle recurring
tasks. On MPE/iX, these are performed through a set of procedures called in
are an integral part of the operating system. In
on the system and allo
w a program to gain access to system services. T
trinsics are always available to any pro cess
trinsics, which
asks that intrinsics
provide include:
Accessing and alteration of les (for example, writing to a le)
Requesting of utility functions (for example, perform ASCII/binary n
umber conversion)
Access to system resources (for example, obtain system timer information)
You can manipulate and manage pro cesses and system resources b
y means of intrinsics,
provided you have the required execution privileges. Manyintrinsics return values to the
caller. Most do this through parameters; some, through functional returns. Most in
trinsics
are coded in HP Pascal/iX (one of the systems programming languages for the 900 Series HP
3000) and are dened by a procedure declaration consisting of:
Procedure header, containing the pro cedure name and typ e, pro cedure denitions, and other
information about the pro cedure.
Procedure bo dy, containing executable statements and declarations local to this pro cedure.
Intrinsics work like user-written procedures, except that the details of p erforming the task are
invisible to you.
Note
Most intrinsics are callable from any language supported on MPE/iX.
The MPE/iX intrinsic mechanism provides exible and convenient access to intrinsic routines
from various languages. In some programming languages, you need not (or cannot) give
descriptions for pro cedures that are external to your program. When you designate that an
external routine is an intrinsic, the compiler uses the Intrinsic Mechanism to correctly invoke
the routine by:
Providing a consistentintrinsic interface
Ensuring proper data type conversion
Generating proper reference parameter addresses
Ensuring that the intrinsic is properly called
3-2 Program Development
Page 69

Although intrinsics usually refer to system routines, y
to access as if they w
ere intrinsics and then place them in new or existing in
libraries.
ou can dene routines that y
trinsic les and
ou want
You invokeanintrinsic by calling it from within a program. In HP C/iX, HP P
COBOL II/XL, and HP F
Intrinsics Mechanism facilitates the declaration of system in
processed as external pro cedures b
Before you can call an in
ORTRAN 77/iX programs, you explicitly call an in
trinsics. All MPE/iX intrinsics are
y user programs.
trinsic from a program, y
ou must declare it in all languages b
ascal/iX,
trinsic. The
y using
an intrinsic declaration statement. The format varies depending on the language. Refer to the
appropriate language programming guides for details on ho
information on intrinsics and intrinsic declarations, refer to
Manual
(32650-90028).
w to call intrinsics. For detailed
MPE/iX Intrinsics Reference
Compiling a Program
When you havesaved the program source code in a le, it m
ust be compiled; translated
into machine readable instructions in a program le. The MPE/iX Native Mode language
compilers available for this purpose are HP C/iX, HP P
ascal/iX, HP COBOL I I/XL, and HP
FORTRAN 77/iX. Commands are available to:
Compile, link, and execute a program, in one command
Compile and link a program, in one command
Compile a program
An overview of these commands is given later in this section. For detailed information on
them, refer to :
HP C/iX Reference Manual Supplement
HP Pascal Programmer's Guide
(31502-90002).
HP COBOL II/XL Programmer's Guide
HP FORTRAN 77/iX Programmer's Guide Supplement
(31506-90001).
(31500-90002).
(31501-90002).
Compiler Input
Follow the appropriate instructions for the language you are using; HP C/iX, HP Pascal/iX,
HP COBOL II/XL, or HP FORTRAN 77/iX. For example, to compile a program named
MYPROG
in HP Pascal/iX, enter:
:PASXL MYPROG
For further instructions on compiling, refer to:
HP C/iX Reference Manual Supplement
HP Pascal Programmer's Guide
(31502-90002).
HP COBOL II/XL Programmer's Guide
HP FORTRAN 77/iX Programmer's Guide Supplement
(31506-90001).
(31500-90002).
(31501-90002).
MPE/iX Commands Reference Manual Volumes 1 and 2
(32650-90003 and 32650-90364).
Program Development 3-3
Page 70

Compiler Output
The compiler can write compiled code in a relocatable ob ject le, generate a source code
listing, and generate an error list. Unless y
le to the standard le
and
$NEWPASS
is closed. The compiler writes the source co de and error list to
$NEWPASS
, which is renamed
ou specify dierently, the compiler writes the ob ject
$OLDPASS
when the compile is completed
$STDLIST
.
Compiler Operation
The compiler reads a source le as input, p erforms a translation to object co de, and writes
the resulting compiled code in relo catable ob ject mo dules. The n
umber of mo dules in a le is
compiler dependent. MPE/iX compilers usually produce one relocatable ob ject module in a
relocatable ob ject le. The in
ternal structure of a relo catable ob ject mo dule is common to all
compilers that generate Hewlett-Packard Precision Architecture (HP-PA) code. A relocatable
ob ject mo dule con
tains a combination of code and data for all procedures in the source
le that was the compilation unit. A relocatable object mo dule is the smallest unit that a
compiler can pro duce or the Link Editor can manipulate.
A source le with sev
eral pro cedures in it compiles all of them in
to one relo catable ob ject
module. The pro cedures within the relo catable ob ject mo dule cannot be replaced or purged
individually.
When a large program is divided into several source les, each one can refer to external
procedures (subroutines or variables that are dened in another le). Because MPE/iX
compilers pro cess only one source le at a time, external procedure references cannot b e
resolved at compile time. They are resolved at link time, when all of the program componen
are brought together. The compiler simply assigns a x-up request (frequen
tly called a
relocatable address) to each external reference, indicating the relative p osition of each
subroutine or variable in the relocatable ob ject module.
Note
A relocatable object mo dule on MPE/iX corresponds to a relo catable binary
module (RBM) on MPE V/E, with the following exceptions:
A relocatable object mo dule can con
tain zero, one, or several pro cedures,
while an RBM represents only one.
A relocatable object mo dule is complete in itself and can stand alone as an
independent le, while an RBM can exist only as part of an MPE V/E user
subprogram library (USL) or a relo catable library (RL).
To separate relocatable ob ject modules for two procedures into dierent relo catable ob ject
les, you must put the procedures in separate source les and compile them individually.You
can gather them together at link time. Figure 3-2 shows an MPE/iX Native Mode compiler
producing a relo catable ob ject module.
ts
3-4 Program Development
Page 71

Figure 3-2. Compiler Producing Relocatable Object Modules
A relocatable object mo dule is an independen
relocatable libraries (RLs) and links to other relo catable ob ject mo dules, although these are
made, when necessary, at link time. External resources (usually system routines) are acquired
at run time.
A relocatable object mo dule contains the following information, described in detail in the
subsections below:
Compiled code (machine instructions) for all procedures in the source le
Information on data variables to be used
External references (resources required to run the program)
The compiler generates a symbol table in each relo catable ob ject mo dule. It lists all the
procedures and variables that are dened in the mo dule and may be required by other
modules at link time and all those that are referenced in the module, but not dened there.
t le. It may not require resources suchas
Program Development 3-5
Page 72

The compiler assigns a x-up address to eac
h dened subroutine or variable symbol, indicating
its position relative to the beginning of the mo dule.
Compiled Code
A compiler segregates code and data in
individual compiler determines how compiled code is organized within it and the con
to separate areas in a relocatable ob ject mo dule. The
tentis
compiler dependent. Data constants are stored in the relocatable ob ject module along with
code and, th
us, are non-modiable. T
ochange compiled code, y
ou must recompile the entire
relocatable ob ject mo dule.
Data Variables Information
A relocatable object mo dule con
data types and required data space. The exact t
It is used when initialization of v
tains information on data requiremen
ype of information is compiler dependen
ts. Usually, it describ es
t.
ariables is requested or when the data space has a common
variable, whichisa variable that several pieces of code can share.
Unresolved References
Because a compiler processes one source le at a time, it cannot resolv
determine parameter compatibility with them, or analyze actual data. This m
e external references,
ust be resolved
at link time or run time. The compiler simply lists external references required for execution
in a symbol table lo cated in the relo catable ob ject mo dule, allowing y
ou to compile a program
in several pieces by separately compiling several source les. The symbol table lists all
subroutines and variable names that are dened by the relocatable ob ject mo dule.
Compiler Libraries
Compiler libraries are used at run time byevery program. On MPE/iX, they are stored in a
library named
XL.PUB.SYS
.
Command to Compile Only
The command to compile a program (without linking, loading, and running it) is the
command, followed by an optional list of le names. The commands are:
:CCXL
:COB85XL
:FTNXL
:PASXL
If you omit a le from the list, a standard default le is used. The standard default les are:
$STDIN
$NEWPASS
$STDLIST
If you fail to supply a relocatable ob ject module, a compiler opens a new le named
and designates it to b e a relo catable ob ject mo dule. At the end of the compilation,
is automatically renamed
textle
objectle
listle
$OLDPASS
$NEWPASS
$NEWPASS
and saved. Unless you designate dierently, the compiler
listing produced by the compilation is output to your job or session list device, so you can see
any errors.
3-6 Program Development
Page 73

You can obtain twotypes of output from a compiler, aside from the compiler listing of errors:
Source code translation of the output to a relocatable object mo dule.
Source listing, with various map and table options.
Compiler Control
If you wish only to compile a program, without linking and running it, y
"
compile only"command for the appropriate language. These commands allow y
ou can use the
ou to provide
several optional parameters that specify the name of the textle (source le), ob jectle
(relocatable ob ject module), and listle. The text le con
program. The relo catable ob ject module will con
listle, which is usually on a terminal or prin
tain the output from the compile. The
ter, will reect the progress of the compile.
When source co de has been successfully compiled and y
ob ject mo dule, y
relocatable ob ject mo dules. A softw
ou are ready to link a program le from information in one or more
are product called Link Editor performs this op eration.
tains the source code for the
ou have an error-free relo catable
Linking a Program
Many executable programs are originally generated from more than one source le. On
MPE/iX, each source le is compiled separately to produce a relocatable ob ject mo dule.
The linking phase of program development makes a relocatable ob ject le into an executable
program le. It can also bring together separately compiled relocatable object modules in
to
an executable program le.
Use the MPE/iX command
:LINK
to automatically access Link Editor to create an executable
program le from one or more relo catable ob ject mo dules.
Note
Link Editor on MPE/iX replaces Segmenter on MPE V/E. You can still use
Segmenter in MPE/iX Compatibility Mode. For detailed information, refer
to
MPE Segmenter Reference Manual
the dierences b etween Link Editor and Segmenter, refer to
Reference Manual
(32650-90030).
(30000-90011). For an explanation of
Link Editor/XL
:LINK
is the MPE/iX counterpart to
:PREP
on MPE V/E systems. However, it operates dierently and has dierent
options. For an explanation of the dierences between
to
Link Editor/XL Reference Manual
of
:LINK
and Link Editor in MPE/iX.
(32650-90030). Figure 3-3 shows the role
:LINK
and
:PREP
, refer
Program Development 3-7
Page 74

Figure 3-3. Linking and Using User Libraries
:LINK
operates on one or more relo catable ob ject mo dules created b
y a native compiler to
perform the following tasks:
Search one or more relo catable libraries (RLs) and resolv
e references to them in any of the
relocatable ob ject modules being linked.
Resolve references among the relo catable ob ject mo dules.
Merge all the relocatable ob ject modules asso ciated with one program to create an
executable program le.
If you use language commands that compile, link, and execute in one command (for example,
:PASXLGO
:FTNXLLK
command
to use values dierent from standard Link Editor defaults.
passes the specied parameters to it. (An analogous
MPE/iX command
and
:COB85XLG
) or compile and link in one command (for example,
:PASXLLK
and
), then linking is automatic. When you compile separately,you can use the MPE/iX
:LINK
to produce an executable program le. Use this metho d when you want
:LINK
LINK
simply provides a short cut.)
:LINK
command exists in Link Editor; the
invokes Link Editor and
3-8 Program Development
Page 75

Creating Executable Program Files
The MPE/iX command
:LINK
command invokes Link Editor, which is an MPE/iX subsystem that prepares compiled
programs for execution and main
resolves external references in relocatable ob ject modules b
modules to produce an executable program le con
:LINK
creates a load module (an executable program le). The
tains libraries. When invoked by using
:LINK
, Link Editor
y merging relo catable ob ject
taining all of the co de and data that w
as in
the relocatable object mo dules.
It assigns nal addresses to eac
h symbol (for a variable or procedure) to ensure that none
overlap each other in the executable program le. These addresses are called virtual addresses,
because they are still subject to a nal relocation when the program is loaded in
memory. Once virtual addresses are determined, Link Editor can resolv
references that could not b e resolv
the relocatable object mo dules ha
libraries to search for unresolved references at link time. An
ed at compile time, because the sym
ve been merged to one table. Y
ou can specify the relo catable
y remaining external calls m
e many of the
bol tables from all of
to physical
ust be
resolved at load time.
:LINK
le. For example, in the
parameters can sp ecify indirect les. An indirect le is a le list con
:LINK
command, an indirect le can be used to specify one of the
tained in an ASCII
following lists:
Files to link
Relocatable libraries (RLs) to merge
Executable libraries (XLs) names to put in a program header
For an overview of Link Editor, refer to Chapter 4. F
Link Editor, refer to
Link Editor/XL Reference Manual
or detailed information on
(32650-90030).
You can request options at link time to:
Produce a program le map.
Search specied relo catable libraries (RLs) for an
y required co de not found in the
relocatable object module.
Give the executable program le certain privileges and capabilities.
Symbol Listing
Example 3-1 shows a source le named
for
EX1SRC
named
EX1PROG
.
EX1SRC
. An executable program le has been created
:LINK
and
Program Development 3-9
Page 76

IDENTIFICATION DIVISION.
PROGRAM-ID. EX1
ENVIRONMENT DIVISION.
INPUT-OUTPUT DIVISION.
FILE-CONTROL.
SELECT IFILE ASSIGN "IFILE".
SELECT PFILE ASSIGN "PFILE".
DATA DIVISION.
FILE SECTION.
FD IFILE.
01 IREC.
05 NAME PIC X(30).
05 SOC-SEC PIC X(9).
05 HIRE-DATE.
10 MO PIC XX.
10 DA PIC XX.
10 YR PIC XX.
05 SALARY PIC S9(6).
05 PIC X(29).
FD PFILE.
01 PREC.
05 SOC-SEC PIC X(9).
05 PIC XX.
05 NAME PIC X(30).
05 PIC XX.
05 HIRE-DATE.
10 MO PIC XX.
10 PIC X.
10 DA PIC XX.
10 PIC X.
10 YR PIC XX.
05 PIC X(81).
01 HREC.
05 HSOC-SEC PIC X(11).
05 HNAME PIC X(32).
05 HHIRE-DATE PIC X(89).
Example 3-1. Source File Example (page 1 of 2)
3-10 Program Development
Page 77

WORKING STORAGE SECTION.
01 LNCNT PIC S9(4) BINARY VALUE 60.
01 W-DATE.
05 WYR PIC XX.
05 PIC X(4).
PROCEDURE DIVISION.
P1.
ACCEPT W-DATE FROM DATE.
OPEN INPUT IFILE OUTPUT PFILE.
PERFORM WITH TEST AFTER UNTIL SOC-SEC OF IREC = ALL "9"
READ IFILE
AT END MOVE ALL "9" TO SOC-SEC OF IREC
NOT AT END
IF WYR = YR OF IREC THEN
ADD 1 TO LNCNT
IF LNCNT > 50 PERFORM HEADINGS END-IF
MOVE SPACES TO PREC
MOVE CORR IREC TO PREC
WRITE PREC AFTER ADVANCING 1 LINE
END-IF
END-READ
END PERFORM
CLOSE IFILE PFILE
STOP RUN.
HEADINGS.
MOVE "SOC-SEC" TO HSOC-SEC.
MOVE "NAME" TO HNAME.
MOVE "HIRE DATE" TO HHIRE-DATE.
WRITE PREC AFTER ADVANCING PAGE.
MOVE 0 TO LNCNT.
Example 3-1. (page 2 of 2)
Program Development 3-11
Page 78

The commands
:LINKEDIT
LinkEd> LISTPROG EX1PROG
invoke HP Link Editor/XL and create a program map displa
ying the symbols in
shown in the following example:
PROGRAM : EX1PROG
XL LIST
CAPABILITIES : BA, IA
HEAP SIZE :
STACK SIZE :
VERSION : 85082112
Sym C H X P Sym
Sym Sym Lset
Name Type Scope Value Name
---- - - - - ---- ----- ----- ----
$START 0 3 3 sec_p univ 000059B7
_start 0 3 3 sec_p univ 00005A07
ex1 0 3 3 pri_p univ 000059EB
M$1 0 data local dp+00000000
In this program map, the portion preceding the sym
bol table is the header, which provides
general information ab out the executable program le:
PROGRAM
XL LIST
names the executable program le.
shows the names of executable libraries specied in the
command.
XL
parameter of the
EX1PROG
LINK
,as
CAPABILITIES
LINK
command.
HEAP SIZE
STACK SIZE
VERSION
shows the capabilities assigned to the program in the
shows the value specied in the
shows the value specied in the
NMHEAP
NMSTACK
parameter of the
parameter of the
shows the executable program le format version.
CAP
parameter of the
LINK
command.
LINK
command.
The header information is follo wed by a list of symbols in the executable program le. F
information on understanding the symbol listing, refer to
Link Editor/XL Reference Manual
(32650-90030).
or
3-12 Program Development
Page 79

Loading and Running a Program
The loader p erforms the follo
Loads the executable mo dule in
wing tasks:
to virtual memory lo cations.
Updates addresses contained in an executable object mo dule with the actual memory
addresses.
Resolves unsatised external references to executable libraries. If an
y unsatised external
references remain, the loader aborts.
The loader loads executable libraries to resolv
requests of the unresolved reference to an export denition con
library. The actual link is made b
executable library can ha
ve access to the caller's data without passing parameters.
y pointer reference to shared code. No ob ject mo dule in an
e external references b
tained in the executable
y linking the import
The rst step in running a program is to load it. The MPE/iX Loader performs the nal step
in preparing a le for execution in Native Mode and Compatibilit
in Compatibility Mode, the loader sim
ulates the MPE V/E Loader, with only the c
y Mode. When op erating
hanges
necessary to make it run.
MPE/iX Loader input consists of an executable program le and an optional set of executable
libraries.
The loader initializes code and data to create table en
tries needed to execute or access the
code and data and creates links to connect program references to executable libraries.
A program load performs the following tasks:
Maps executable module into virtual memory by converting the co de relative addresses to
absolute addresses. (Co de relative addresses are those which are relative to the beginning of
the executable program le.)
Changes the access rights of pages that contain code. Code is executed without copying it;
it is mapped to virtual memory.Write access to program co de is not necessary on MPE/iX;
only read and execute access is granted to code pages.
Creates global data areas for the program and eac
h module in referenced executable
libraries.
Copies global data initialization information into process data space and sets the
appropriate register to point to it.
Generates external reference list and attempts to locate all entries in the list.
Program Auxiliary Header
The MPE/iX program auxiliary header resides in an executable program le, is generated by
HP Link Editor/XL, and is used by the loader. It species the following information:
Primary entry point name
UNSAT
XL LIST
procedure name
(the list of XLs sp ecied at link time)
Program capabilities
Maximum stack and heap sizes
Program Development 3-13
Page 80

MPE/iX allows you to change the specications listed ab o
entry point name and program capabilities. An
y information you sp ecify at run time o
the specications given by HP Link Editor/XL.
ve at load time, except the primary
verrides
If the program auxiliary header is not specied, the loader uses the default v
command. Libraries specied at run time tak
e precedence over those specied at link time.
alues for the
:RUN
Using Executable Libraries
On MPE/iX, you can run a Native Mode program and specify the use of m
ultiple libraries
with dierent names, rather than just one executable library (XL) at a time.
The syntax for running a program that utilizes one or more executable libraries is as follows:
:RUN prog; XL = "
In this syntax,
execute and
prog
You can specify an
xlib1[,xlib2
xlib1,xlib2,xlib3
][,
,...
xlib3
]...
"
are replaced by the names of the libraries y
is a Native Mo de program name.
ynumber of XLs, up to a maximum limit of 288 c
ou wantto
haracters for the
complete command. You can use anyvalid le name for an XL. The system library is added
to the end of the list by default. However, if you specify it, you must make it the last library
listed. XLs that you sp ecify at run time override those sp ecied at link time.
Searching Executable Libraries
The following guidelines apply to searching executable libraries (XLs):
The library list can b e specied at Link time, but is not actually used un
til run time.
Run-time libraries can app ear only once in the
:RUN
command.
You must list libraries in order of increasing privilege level.
If the system library is not specied, the system automatically adds
NL.PUB.SYS
as the last libraries to search.
XL.PUB.SYS
and
UNSAT Procedure
You can load a program that has one or more referenced external procedures that cannot
be lo cated by specifying an UNSAT procedure. This is a dummy pro cedure specied in the
UNSAT
parameter of the
:LINK
command. This procedure is substituted for the missing library
routine. You can set up the procedure to contain statements that facilitate program execution
in the absence of the real routine. For example, the execution of the UNSAT pro cedure could
print a statement informing you that it was called.
Note
The content of an UNSAT pro cedure determines whether or not a program
can continue to run after the UNSAT procedure is called.
When the loader encounters an UNSAT procedure, it uses it to resolve all remaining
unresolved references. The UNSAT pro cedure iself may be written in any language; however,
it must be compiled and put into one of the executable libraries that is specied at run time.
Figure 3-4 shows an example of using an
UNSAT
procedure in a program.
3-14 Program Development
Page 81

Figure 3-4. UNSAT Procedure Example
System Libraries
System library characteristics include the following:
They are loaded in system space.
Processes using the same object mo dule share co de, global data, and binding.
Object modules can reference only themselves or other system library ob ject mo dules.
Cannot use
UNSAT
procedures.
System libraries are the only libraries that can contain b oth system and nonsystem ob ject
modules. (A nonsystem ob ject module shares only the co de with other pro cesses. Its data
and binding are unique to each pro cess that references it. A nonsystem ob ject mo dule
is loaded once for each pro cess that uses it.) The Native Mo de system library is named
NL.PUB.SYS
. The Compatibility Mo de system library is named
SL.PUB.SYS
.
Mixing Execution Modes
While the op erating system is executing for a process, the process may switch execution
modes. It can alternate rep eatedly between Native Mode (NM) and CompatibilityMode
(CM). MPE/iX provides switch stubs to allow NM programs to access CM intrinsics. The
operating system intrinsic call determines when to use the NM Executable Library (NL) or
the CM Segmented Library (SL).
The NM intrinsic le is
SYSINTR.PUB.SYS
; the CM intrinsic le is
SPLINTR.PUB.SYS
.
You can set up a Native mo de program to call procedures that are in a CM Segmented
Library (SL) by using the switchintrinsics. This requires that the program specify the switch
stub. The switchintrinsic uses the
LOADPROC
procedure to nd the CM procedure. For
Program Development 3-15
Page 82

detailed information on the switch subsystem and programmatic access through switc
refer to
Switch Programming Guide
(32650-90014).
h stubs,
Virtual Memory and Demand P
When a program is running, only part of it is needed at an
memory, MPE/iX brings pieces of a program in, as needed for curren
aging
y one time. Tosave space in main
t execution. It divides a
program into xed-length pieces called pages (for a description of pages, refer to Chapter 1).
The remainder of the program can b e stored on a high-speed device (for example, a disc) that
can act as an extension of real memory
virtual memory reduces to a minim
available memory size, because it eliminates the requiremen
. This extension is called virtual memory
. The use of
um the problem of application program size compared to
t for loading all code and data in
main memory at once.
LMAP: Load MAP
An
LMAP
facilitates code managementby listing a loaded program. It describes the spaces
loaded for a pro cess and the link
ages used to connect the external references of the process for
the program and each library sp ecied by the user. To pro duce a load map (map of a loaded
program), specify the
to dene the le with the formal le designator
detailed information refer to the
(32650-90003 and 32650-90364). A load map can also help to determine if y
goo d lo calization. An
LMAP
parameter of the
LMAP
shows:
:RUN
command. To printan
LOADLIST
as a line printer device le. For
LMAP
, use
:FILE
MPE/iX Commands Reference Manual Volumes 1 and 2
ou haveachieved
File name and type of le (program or library)
Number of external references a program le mak
es
Type of library from which each call is resolved
to
Load-time Binding Sequence
The loader assigns virtual addresses and makes an executable program le into a runnable
process.
Running a Program
When a program has been successfully linked, you can load it and execute the
:RUN
command.
At this stage of operation, the program is called a process. A process is a unique execution of
a particular program by a particular user at a particular time. If you change even one element
of a program, it becomes a dierent process than it was before.
When you execute a program, a piece of software called the LOADER starts the pro cess
on the system. The loader must resolveany external references in the program by using
executable libraries.
MPE/iX is a multiprogramming operating system, which has many processes competing for
CPU time. Only one process can execute at a given instant in time. When a program has had
external references resolved it is ready to execute. It can now compete with other pro cesses
for the resources of main memory and CPU time.
The
:RUN
command requires you to specify the lename of the program and allows you to
specify many other options, such as obtaining a program load map. You can specify values for
process stack and heap size to override values specied at the link stage. There are facilities
3-16 Program Development
Page 83

for passing information to a program at run time and determining whic
to resolve external references.
Multi-programming Environment
h libraries are searched
MPE/iX is a multiprogramming environment in which one pro cess has con
any given instant. All other processes are suspended to allo
w time for this to occur, and the
processes take turns. The frequency and duration of a turn is determined b
Dispatcher and is dependen
suspend for many reasons. For example, a process ma
t on the priorit y assigned to the pro cess. Processes can v
y suspend because it is w
or output. The co de and data for suspended processes is retained in memory un
trol of the CPU at
y the MPE/iX
oluntarily
aiting for input
til space is
needed by the executing process.
Priority Levels
A prioritynumber identies the priority lev
the priority. Priorities range from 1 to 255. MPE/iX uses a mec
el for a process. The lo
hanism of subqueues to
wer the number, the higher
determine when to change the priority level of a pro cess, if at all. Operating system processes
are given the highest priority to promptly service requests. The AS subqueue (used for most
operating system processes) receives the highest priorities, followed by the BS subqueue
(usually used for special user pro cesses). The CS, DS, and ES subqueues (used for the
Command Interpreter, Editor, compilers, and standard user pro cesses), as a group receiv
e the
lowest priorities.
Operating system processes are given the highest priority to promptly service requests. At the
user level, processes are queued and given CPU control based on rules for the types of queue
used at the particular level of the process. The op erating system alwa
priority pro cess that is ready to execute. A system manager can assign to users and accoun
privileges or restrictions of one subqueue o
ver another. A system sup ervisor has some con
ys runs the highest
ts
trol
over the priority levels in CS, DS, and ES.
Linear Subqueues
The AS and BS subqueues are linear queues. The c
haracteristics of a linear queue are:
MPE/iX do es not change the priorit y level of a process.
Processes at a given priority level execute on a rst come, rst served basis.
An executing pro cess controls the CPU until it voluntarily suspends or receives a higher
priority interrupt.
The AS sub queue should be reserved for operating system processes. A user process running
in AS can severely impair the op erating system's ability to function. The BS subqueue is
for special high priorit y user pro cesses. It is a recommended practice to run a special user
process at a priority of 140 or lower to avoid preempting important MPE/iX functions, such
as spo oler operation.
Program Development 3-17
Page 84

Circular Subqueues
The CS, DS, and ES subqueues are circular queues. The c
haracteristics of a circular queue
are:
Priority levels are cycled.
An executing process con
priorityinterrupt, or reaches the end of its quan
A circular queue lowers the priority of a process at the end of its quan
trols the CPU until it voluntarily suspends, receives a higher
tum (time slice).
tum. After the drop,
the process eventually gets another opp ortunity to execute. The CS, DS, and ES subqueues
dier in howlow a priority can be dropped.
Error Detection
The types of errors that can o ccur on the MPE/iX operating system are in the categories
given below, along with suggested actions:
Command Interpreter Errors
Errors in using Command Interpreter (CI) are usually the simplest errors to detect. They
include typing errors and syntax mistakes. For correcting typing errors, use the :REDO
command. For syntax errors or misunderstandings in how the command works, use the
:HELP
command or refer to the
MPE/iX Commands Reference Manual Volumes 1 and 2
(32650-90003 and 32650-90364).
File System Errors
File System errors are common at all lev
els of user interface because le access aects almost
every kind of op eration. When you are unable to open, access, or close a le, consider the
rules governing the le's domain, access, and security.For detailed information, refer to
Accessing Files Programmer's Guide
(32650-90017).
Compiler, Link Editor, and Loader Errors
You mayhave exceeded a congured system limit with program les; ask the system manager
for information. If a program load fails, it is probably marked unrunnable, in which case you
must link it again or restore the le.
Unresolved externals do not mark the le unrunnable. If this problem occurs, check for errors
in the subprogram names and
XL=
names. Determine if the routines you requested actually
reside in the Executable Libraries you searched.
For errors reported by a compiler, refer to compiler information in the appropriate language
manual.
3-18 Program Development
Page 85

Run-time Errors
Run-time errors presentachallenging problem, frequently causing the program to end
abnormally (abort). T
o determine the answer to a run-time error, y
ou must consider the
following aspects of the problem:
What is the cause or source?
What is the mec
hanism of the abort?
What information is provided to help trace and correct the problem?
What are typical ab ort situations?
The decision to abort a pro cess can be made b
y:
User program
Library routine
MPE/iX intrinsic
MPE/iX op erating system
A program's design can cause it to abort if bad input or some unreco
The program can call the
QUIT
intrinsic or an equivalent compiler-determined statement.
verable situation o ccurs.
In this case, the unrecoverable situation is by design; the programmer must provide code to
handle the problem or ab ort the program.
A process can abort b ecause a subsystem library routine encoun
example, if an HP FORTRAN 77/iX program p erforms a
tered a problem. For
READ
statement, an HP FORTRAN
77/iX library routine is called to perform the necessary I/O. If an end-of-le condition is
encountered, a data format problem occurs. If the library routine cannot complete the
operation, it may abort the program.
An MPE/iX intrinsic can abort a program, depending on the individual in
trinsic's
requirements. For example, it may encounter a missing parameter, an unusable parameter
value, or an unusable address. The intrinsic might require that the program le have a sp ecial
capability to use the intrinsic.
900 Series HP 3000 hardware or software can detect errors. For example, if an arithmetic
operation exceeds a data value maximum, computer hardware detects an overow problem.
It may also detect a bad instruction or invalid address for code or data. MPE/iX aborts a
program when a stack requires more room than is available. This alerts you to a potential
problem with recursive calls and lo ops.
Abort Message Information
When MPE/iX carries out an abort for any reason, the process must terminate cleanly
(complete the op erations it would have completed if it had ended normally). However,
because the termination is unexpected, information may b e lost. For example, NEW les
may not be retained. A message indicating the type of abort is printed before termination.
After termination, Command Interpreter prints the nal message line. The information in the
message helps to identify the cause and guide you toward a solution to the problem.
An abort message appears in a standard format providing:
Program le name
Location at which the abort occurred in the program le
Message text describing the type of abort
Program Development 3-19
Page 86

If the ab ort o ccurred during execution of an in
library routine, then the lo cation is giv
location indicates the location from whic
en within the appropriate routine and the program le
h the routine was called in the user's program.
trinsic, a subsystem library routine, or a user
For detailed information on reading an abort message, refer to
Manual
(32650-90028)jor the
MPE/iX Commands Reference Manual Volumes 1 and 2
MPE/iX Intrinsics Reference
(32650-90003 and 32650-90364).
Typical Causes of Program Aborts
Two causes of ab ort that occur frequen
tly are data memory protection traps and aborts in
library routines.
A data memory protection trap occurs when a program attempts to address outside the
bounds of the code/data area. This can b e caused b
subscript. For example, a parameter address ma
y a faulty address or index used for a
y be passed as a b
yte address, rather than a
word-aligned address expected by the called routine. Address corruption can occur if an array
subscript goes out of the b ounds of the array
When an ab ort occurs in a library routine, the problem is most frequen
program. Examine the program for le equations that y
, but is still inside the bounds of the stac
tly in the user
ou mayhaveoverlooked. It is
k.
possible, although considerably less frequent, that a bug actually exists in the library routine
itself.
File Information Display (Tombstone)
It is frequently necessary to obtain status information on a le to determine the cause of an
error. A le information display is frequently called a tombstone. It provides:
Actual physical and operational le characteristics.
Current le information, pertaining to end of le, record poin
ter, and logical and physical
transfer count.
Information on the last error for the le and the last
When a le is opened, the nal c
because of defaults, overrides,
You can use the
PRINTFILEINFO
haracteristics may be dierent from those originally requested
:FILE
commands, and the le lab el.
intrinsic to print a tombstone. It requires that you sp ecify
the le number returned when the le is opened b
HPFOPENorFOPEN
y
HPFOPEN or FOPEN
error.
. The tombstone can
display either a full or short format. If the le is op en, it provides a full display. Otherwise, it
provides a short display. Calling this intrinsic does not automatically abort the program.
You can call the
PRINTFILEINFO
intrinsic from programs written in COBOL II/XL and HP
FORTRAN 77/iX. When calling from COBOL II/XL, use the FD lename. You can call the
name
PRINTFILEINFO
required le number by using the
directly from HP FORTRAN 77/iX programs. You can obtain the
FNUM
intrinsic.
3-20 Program Development
Page 87

Control Codes (JCWs)
A Job Control Word (JCW) is one w
ord (16 bits) of memory used to pass information
between job steps and to determine the status of the previous job step. Figure 3-5 sho
structure of a JCW. It is composed of a 2-bit t
The space allowed for JCWs is determined b
le equations, temp orary les, and data space is tak
one user-dened JCW named
You can dene as man
y user-dened JCWs as remaining space allo
You can use the MPE/iX command
CIERROR
:SHOWJCW
that is actually dened b
dened any JCWs of your own, this shows only the value of the system JCW and
ype and a 14-bit modier.
y the space allowed for your session or job after
en. There is alwa
ys one system JCW and
y Command Interpreter (CI).
ws.
to see the value of JCWs. If y
ou have not
CIERROR
ws the
.
Figure 3-5. Job Control Word (JCW) Structure
System JCW
The system JCW is set by MPE/iX and some subsystems. You can set the system JCW
programmatically by using intrinsics or interactively at the Command Interpreter (CI) level by
using the
:SETJCW
command.
MPE/iX checks the system JCW before each step (process) in a session or job is executed.
Based on the system JCW value, MPE/iX may abort the session or job. You can interactively
check the system JCW at the CI level by using the
programmatically checkbyintrinsics (calling
:ENDIF
construct.
:FINDJCW
:SHOWJCW
command. You can
)orby using an
:IF/THEN,:ELSE
,
The system JCW type provides information on the severity of an error. The modier can be
set to identify the cause or to pass information to subsequent job steps. However, information
placed there by the user may not be preserved, because MPE/iX can change it. Thus it is
frequently expedient to place information that you want preserved in a user-dened JCW
Program Development 3-21
Page 88

instead of in the system JCW. When set b
MPE/iX. The types are the bit settings giv
descriptions.
y the user, the modier ma
y be mo died b
y
en b elow, accompanied by their keywords, and
00:OK
01:WARN
10:FATAL
11:SYSTEM
The mo dier can be set to an
up for use by each of the four t
No error occurred in the previous step.
An unusual event o ccurred, but not necessarily fatal.
Program aborts, under its o
wn control.
System aborts user process due to a problem outside
the pro cess's direct con
trol.
ynumber from 0 to 65535, inclusiv
ypes given ab ove:
e. These numbers are divided
OK 0-16383
WARN 16384-32767
FATAL 32768-49151
SYSTEM 49152-65535
JCW Notation
A JCW value can be described with three kinds of notation:
Akeyword, followed by a constant. The constant is the decimal equivalent of the o ctal
number in the modier.
Modier app ended to the type to form one constant.
The numerical value of the modier.
Figure 3-6 shows examples of JCW notations.
3-22 Program Development
Page 89

Figure 3-6. JCW Notation Examples
Using a System JCW
The following job shows an example of using a system JCW:
:JOB STUDENT.INTRO/PASSWORD
:CONTINUE
:FTNXL ABC
:IF JCW<FATAL THEN
: LINK $OLDPASS,ABCPROG
: SAVE ABCPROG
: RUN ABCPROG
:ELSE
: SAVE $OLDPASS,ABCOBJ
:ENDIF
:SHOWJCW
:EOJ
This job compiles an HP FORTRAN 77/iX program. If it works, you want to link the ob ject
le to your program le and run the program. If a problem occurs during the compile, you
wantto save the le and end the job.
If an error occurs, HP FORTRAN 77/iX sets
JCW against the value
command causes the job to proceed even if the
FATAL(FATAL
is the same as
JCW = FATAL
FATAL0or32768
, so the job tests the value of the
). The
Program Development 3-23
:CONTINUE
Page 90

next step produces an error. The
decision based on the JCW v
that CI creates is called
CIERROR
:IF/THEN,:ELSE,:ENDIF
alue following the
. CI sets the JCW modier to the last CI error n
Sometimes, CI ab orts a job based on the v
User-defined JCWs
:FTNXL
alue of the
structure allows you to makea
job step. The system-dened JCW
umber.
CIERROR
modier.
User-dened JCWs allowyou to supply input to programs b
y using Command Interpreter
(CI) and get status from programs that can be examined in CI. Characteristics of user-dened
JCWs include:
Available to each pro cess in the same session or job.
Have names dierent from
Are created and set in
JCWorCIERROR
teractively with
.
:SETJCW
or programmatically with the
PUTJCW
intrinsic.
Can be examined interactively with
:SHOWJCW
or programmatically with the
FINDJCW
intrinsic.
MPE/iX does not examine user-dened JCWs. The v
only to the user. Keywords and denitions assigned to the typ e and modier can be iden
alue of a user-dened JCW has meaning
tical
to those assigned to system JCWs or dierent. You determine what action to take based on
your own denitions.
Using a User-defined JCW
The following job shows an example of using a user-dened JCW.
:JOB STUDENT.INTRO/PASSWORD
:SETJCW UPDATE=OK
:RUN UPDATEDB
:IF UPDATE=OK THEN
: RUN REPORT
:ELSE
: SHOWJCW
: TELLOP REPORT NOT RUN
: TELLOP TOO MANY INPUT ERRORS
:ENDIF
:EOJ
In this example, the job stream begins by dening and setting a user-dened JCW called
UPDATE
edits a database. If too many errors o ccur,
the
to the valueOK(OKis the same as
PUTJCW
intrinsic. The
:IF/THEN,:ELSE
OK0or0
UPDATEDB
). Running the program named
changes the value of
structure tests the value of
UPDATE
UPDATE
UPDATEDB
by using
. If the program
is successful (in other words, if there are not too many errors), it runs another program called
REPORT
. If to o many errors did occur in the
UPDATEDB
program, the job shows the JCW
values, sends two messages to the console operator, and ends.
3-24 Program Development
Page 91

HP Link Editor/XL
4
HP Link Editor/XL is a soft
Series 900 HP 3000 computers and allows y
ware tool that prepares compiled programs for execution on
ou to create and main
tain libraries containing
subprograms that you frequently use.
Most MPE/iX compilers let you compile, link, and execute a program, all in one step, or just
compile and link in one step. In these cases, y
to perform the linking function; it is executed automatically
This chapter describes the basic function of HP Link Editor/XL. F
how to use HP Link Editor/XL, refer to
HP Link Editor/XL uses one or more relocatable object mo dules produced b
native compilers to create one of the follo
ou do not directly execute HP Link Editor/XL
.
or detailed information on
Link Editor/XL Reference Manual
(32650-90030).
y one or more
wing les:
Relocatable library (RL), which is a collection of relocatable ob ject mo dules that can be
used by many programs at link time.
Executable library (XL), which is a collection of executable modules that can be shared b
many programs at run time.
Executable program le, which is the result of merging all relocatable ob ject modules
associated with one program.
It can also operate on an existing RL or XL to update it. Figure 4-1 sho
ws the role of
:LINK
and HP Link Editor/XL on the MPE/iX operating system.
y
HP Link Editor/XL 4-1
Page 92

Figure 4-1. :LINK and HP Link Editor/XL on MPE/iX
You automatically enter HP Link Editor/XL for the purpose of manipulating relocatable
ob ject mo dules into an executable program le by using the MPE/iX command
command is esp ecially useful in program development, when you must link a large program
that calls many separately compiled routines or when you want to use values dierent from
standard HP Link Editor/XL defaults for this process. F
"
Linking a Program"subsection of Chapter 3. For detailed information on linking, refer to
Link Editor/XL Reference Manual
You can enter HP Link Editor/XL to:
Create an executable program le (the executable form of a program), which includes
several dierent mo dules that have been compiled separately.
Change one or more of the default parameters associated with the program. For example,
you may need to change the execution stack size.
Use one or more library routines in your program. HP Link Editor/XL creates and
maintains two kinds of libraries: relo catable libraries and executable libraries. Routines in
relocatable libraries are in their compiled format. Routines in executable libraries are in
executable form. Libraries minimize duplication of programming eort, promote consistency
and standardization in a programming organization, and help to produce easily maintained
programs.
(32650-90030).
or a
:LINK
overview, refer to the
:LINK
. This
4-2 HP Link Editor/XL
Page 93

Common Uses of HP Link Editor/XL
The most common ways to use HP Link Editor/XL are to:
Link one or more relocatable ob ject les.
Link relo catable ob ject mo dules from a relo catable library
Name executable mo dules from an executable library to b e searc
Obtain program le information b
y using the
LISTPROG
.
hed at load time.
command.
Linking a Relocatable Object File
When you want to use le names or run-time defaults that v
the compiler, link a relocatable ob ject le y
ourself, rather than ha
ary from the defaults pro
ve it automatically linked.
vided by
(Run-time defaults include type checking levels, capability-class attributes, stack size, and
heap size.)
For example, you can compile, link, and execute a COBOL II/XL program named
EX1SRC
using the command
:COB85XLG EX1SRC
This command is equivalenttoinvoking the following three commands:
:COB85XL EX1SRC
:LINK
:RUN $OLDPASS
,by
Both of the methods given above use
$OLDPASS
for the relo catable ob ject le and for the
executable program le.
The example below shows how to compile and link the COBOL II/XL source le, EX1SR
using a dierent relo catable ob ject le and a dieren
creates the relo catable ob ject le named
LINK
uses to create the executable program le named
EX1OBJ
t executable program le. The compiler
, which the HP Link Editor/XL command
EX1PROG
. The second line of this
example is the HP Link Editor/XL command line.
:COB85XL EX1SRC,EX1OBJ
:LINK FROM=EX1OBJ;TO=EX1PROG
For a listing of the source le named
ob ject les at once, refer to
Link Editor/XL Reference Manual
EX1PROG
and examples of linking several relo catable
(32650-90030).
C,
HP Link Editor/XL 4-3
Page 94

Comparison of HP Link Editor/XL and MPE V/E Segmenter
HP Link Editor/XL on MPE/iX corresponds to Segmen
ter on an MPE V/E op erating system,
with a few dierences. The primary dierences are:
A source le must be recompiled to c
You can create a relo catable library (RL) that con
or you can create RLs that con
hange any part of a relocatable ob ject mo dule.
tains one large relocatable ob ject module;
tain several relo catable ob ject modules, whic
h can b e
independently added, copied, or purged.
An executable library (XL) is similar to a segmen
ted library (SL), except that it do es not
require segmenting as it grows.
You can create an XL that con
XLs that contain several executable object mo dules, whic
tains one large executable ob ject mo dule; or y
h can b e independen
ou can create
tly added,
copied, or purged.
For a detailed description of the dierences bet
Segmenter on MPE V/E, refer to
Link Editor/XL Reference Manual
ween HP Link Editor/XL on MPE/iX and
(32650-90030).
How HP Link Editor/XL Works
HP Link Editor/XL processes ob ject co de produced b
as COBOL I I/XL. Object code is sa
ved in relocatable ob ject les. HP Link Editor/XL links
y high-level language compilers, such
relocatable ob ject les for execution by assigning actual memory locations to them and to an
external subroutines that they use.
y
In addition to creating executable program les, you can use HP Link Editor/XL to create
and maintain relocatable and executable libraries.
When you invoke the MPE/iX command
linking is completed, and HP Link Editor/XL is exited. Information required b
Editor/XL is passed to it as
:LINK
parameters.
:LINK
, HP Link Editor/XL is automatically entered,
y HP Link
Files Used by HP Link Editor/XL
HP Link Editor/XL can use three types of input les:
Relocatable ob ject les.
Command input le, containing commands for processing.
Relocatable library (RL) les to b e searched or manipulated
The command input le is the standard le
For batch jobs,
STDIN
option of the MPE/iX command
$STDINX
is the job le. You can redirect
$STDINX
:RUN
.For example, to use the le named
.For sessions,
$STDINX
$STDINX
to another le by using the
is the terminal.
SCRIPT
the standard input le, enter the command
:RUN LINKEDIT.PUB.SYS;STDIN=SCRIPT
You can send one input command through the"INFO=
command
:RUN
instead of using
$STDINX
. This starts HP Link Editor/XL, executes the
string"parameter of the MPE/iX
as
4-4 HP Link Editor/XL
Page 95

command you specied, and exits HP Link Editor/XL. Figure 4-2 sho
Link Editor/XL.
ws the les used b
yHP
Figure 4-2. Files Used by HP Link Editor/XL
Note
Types of HP Link Editor/XL output les are:
$STDLIST
unless you redirect it, as discussed below.
LINKLIST
An executable program le.
An executable library le (XL).
A relo catable library le (RL).
A relo catable ob ject le.
A relo catable ob ject le pro duced b
one relo catable ob ject mo dule.
, which is the terminal during a session and the output spool le from a batc
, which is a list le.
y one of the MPE/iX compilers contains
h job,
HP Link Editor/XL 4-5
Page 96

You can redirect
command
:RUN
$STDLIST
to another device b
.For example, the following commands send HP Link Editor/XL output to the
printer and runs HP Link Editor/XL:
:FILE LINKOUT;DEV=LP
:RUN LINKEDIT.PUB.SYS;STDLIST=*LINKOUT
y using the
STDLIST
option of the MPE/iX
LINKLIST
LINKLIST
Symbol map pro duced b
Listing produced by the
Listing produced by the
Listing produced by the
Listing produced by the
Listing produced by the
HP Link Editor/XL creates a list le named
amounts of information. It usually writes the information to the
can redirect
:FILE
.For example, the following commands send the listing of a relocatable library named
LIBRL
information is sent to the
contains:
LINKLIST
to a dierent device by using the
to a line printer:
y the
MAP
LISTPROG
LISTOBJ
LISTRL
MAP
option of the
LISTXL
$STDLIST
option of the
command.
command.
command.
command.
device by default.
LINK
command.
ADDXL
LINKLIST
command.
for commands that generate large
$STDLIST
DEV
option of the MPE/iX command
device, but you
:FILE LINKLIST;DEV=LP
:LINKEDIT
:LinkEd> LISTRL RL=LIBRL
:LinkEd> EXIT
HP Link Editor/XL Commands
HP Link Editor/XL commands that create and display executable program les and display
symbols in a relo catable object le are:
LINK
, which creates an executable program le.
LISTOBJ
LISTPROG
, which displays symbols in a relo catable ob ject le.
, which displays symbols in an executable program le.
Other HP Link Editor/XL commands manage relo catable and executable libraries. They
allow you to add relocatable object modules to an RL or XL, purge modules from an RL or
XL, copy modules between two RLs or two XLs. Some frequently used HP Link Editor/XL
commands are:
COPYRL
EXTRACTRL
, which copies modules from one relocatable library to another.
, which extracts a relocatable ob ject mo dule or a group of ob ject mo dules from a
relocatable library.
SHOWRL
LISTPROG
For detailed information, refer to
and
SHOWXL
, which display the name of the current (or working) library.
, which displays a symbol listing on
Link Editor/XL Reference Manual
LINKLIST
.
(32650-90030).
4-6 HP Link Editor/XL
Page 97

Case Sensitivity
HP Link Editor/XL reads commands from the standard input le
sensitive in commands or le names. Ho
sensitive. For example, the
ENTRY
name, which is case sensitive. This name m
the entry name in the sym
COPY,EXTRACT
bol table, which indicates the name used in the relocatable ob ject
wever, entry point (pro cedure) names are case
, and
PURGE
commands allowyou to specify an
ust correspond, character for character, to
module. Usually, a case-insensitive language compiler converts a pro cedure name to lo
For relo catable ob ject modules compiled in these languages, specify lo
$STDINX
. It is not case
wercase entry p oint
wercase.
names.
Keyword and Positional Parameters
Most HP Link Editor/XL commands ha
These types of parameters are briey discussed in Chapter 1,
ve one or more k
eyword or positional parameters.
"
Overview."For a complete
discussion of keyword and positional parameters in HP Link Editor/XL commands, refer to
Link Editor/XL Reference Manual
Note
When specifying positional parameters, use only one le name rather than a
(32650-90030).
le name list, even if the command syntax p ermits a list. (For example, the
ADDRL
command syntax allows a le name list in the
FROM=
parameter.) To
obtain a le name list, you must either sp ecify keyword parameters or use an
indirect le.
Using an Indirect File
An indirect le is an ASCII le containing a list of names. You can use indirect le names
in HP Link Editor/XL commands instead of individually en
tering each name contained in
the le. You can also mix indirect and regular le names in commands. Indirect les are
a convenientwaytoenter a long list of names for commands that y
can use indirect les only with the follo wing commands in the specic parameters giv
ou use frequently.You
en in
parentheses.
LINK (FROM=, RL=, and XL=)
ADDRL (FROM= and RL=)
COPYRL (ENTRY=, MODULE=, and LSET=)
EXTRACTRL (ENTRY=, MODULE=, and LSET=)
LISTRL (ENTRY=, MODULE=, and LSET=)
PURGERL (ENTRY=, MODULE=, and LSET=)
ADDXL (FROM=, RL=, ENTRY=, MODULE=, and LSET=)
COPYXL (ENTRY=, MODULE=, and LSET=)
LISTXL (ENTRY=, MODULE=, and LSET=)
PURGEXL (ENTRY=, MODULE=, and LSET=)
When you create an indirect le, enter one or more names on each line, using as many lines as
necessary. Use a space or a comma to separate each name on a line. Make sure that HP Link
Editor/XL has read access to the le.
To use an indirect le in a command, precede its name by a caret.
HP Link Editor/XL 4-7
Page 98

For example, if an ASCII le named
LIB1OBJ
LIB2OBJ
LIB3OBJ
LIB4OBJ
LIB5OBJ
OBJLIST
contained the lines
you can use the indirect le
ob ject les named in
OBJLIST
OBJLIST
in the following commands to add the v
to the relo catable library named
LIBRL
e relocatable
:
:LINKEDIT
LinkEd> BUILDRL LIBRL
LinkEd> ADDRL FROM=JLIST
LinkEd> EXIT
Starting and Ending HP Link Editor/XL
You automatically use HP Link Editor/XL when you execute one of the MPE/iX commands
that compiles and links a program in one step or compiles, links, and executes a program in
one step. You can directly start HP Link Editor/XL in one of the follo
Enter the
:LINKEDIT
command at the MPE/iX prompt:
wing ways:
:LINKEDIT
HP Link Editor/XL displays its command line prompt
command. Each time you enter a link editor command, it is executed and y
to enter another. This continues until you end HP Link Editor/XL with the
Enter a
:LINK
command at the MPE/iX prompt:
LinkEd>
, and waits for you to enter a
ou are prompted
EXIT
command.
:LINK FROM=EX1OBJ;TO=EX1PROG;RL=LIBRL
The link editor performs the link operation, then ends. The
:LINK
command is discussed
in Chapter 3 and has the same syntax when used at the MPE/iX command level as when
entered at the link editor prompt.
Enter a
Enter an
:RUN
INFO
or a
:LINKEDIT
command, with an
INFO
string, at the MPE/iX prompt.
string that contains one link editor command:
:RUN LINKEDIT.PUB.SYS;INFO="LISTRL;RL=LIBRL"
Or you can use the short form:
:LINKEDIT "LISTRL;RL=LIBRL"
The command in the
INFO
string is executed and HP Link Editor/XL ends. You can execute
any link editor command in this manner.
4-8 HP Link Editor/XL
Page 99

There are three situations that terminate HP Link Editor/XL:
When you explicitly end HP Link Editor/XL b
yentering the
EXIT
command:
LinkEd> EXIT
You can abbreviate the
EXIT
command asE,EX,or
EXI
. The commands
QUIT,Q
, and
BYE
also
terminate HP Link Editor/XL.
When end-of-le in
When an error occurs in a batc
$STDINX
is encountered.
h job. An error message is prin
ted, the system Job Con
trol
Word (JCW) is set to indicate a fatal error, and HP Link Editor/XL ends.
Creating an Executable Program File
HP Link Editor/XL creates executable program les from relo catable ob ject les and
relocatable libraries in the following w
and libraries into one module and resolv
ay. First, it merges selected relocatable ob ject les
es inter-module references. Then, it searc
hes selected
relocatable libraries, resolving external references to symbols undened after the merge
operation. When a relocatable ob ject module in the library resolv
es an external reference,
the module is merged into the executable program le that is b eing built. In the last step,
HP Link Editor/XL assigns virtual addresses to all sym
bols, binds references to the known
symbols within each relo catable ob ject mo dule, and puts the resulting executable program in
a form that the loader can process. Figure 4-3 sho
ws the les HP Link Editor/XL uses when
it creates an executable program le.
Figure 4-3. Creating an Executable Program File
HP Link Editor/XL 4-9
Page 100

An executable program le contains only one program en
instruction where execution begins. Eac
example, HP FORTRAN 77/iX uses the main program as the en
uses a program's outer bloc
HP Link Editor/XL separates code and data areas, as sho
k as the entry p oint. When creating an executable program le,
h language denes its o
try point, which marks the
wn in Figure 4-4.
wn program entry point. For
try point, while HP Pascal/iX
The functions of the
Binding
Merging relocatable object mo dules
Searching relocatable libraries (RLs)
LINK
command are:
Figure 4-4. Linking to Create an Executable Program File
4-10 HP Link Editor/XL
 Loading...
Loading...