Page 1

HP iLO Chassis Management IPMI User Guide
Abstract
This document provides customers with information on the implementation of the Intelligent Platform Management Interface in
HP Moonshot iLO Chassis Management Firmware, including the available commands.
HP Part Number: 742544-003
Published: November 2014
Edition: 1
Page 2

© Copyright 2014
Notices
Confidential computer software. Valid license from HP required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions contained herein.
Page 3

Contents
1 Introduction and key concepts......................................................................7
Overview................................................................................................................................7
Sensor Data Model...................................................................................................................7
Sensor owner identification...................................................................................................7
Sensor type code.................................................................................................................8
System event log and event messages.....................................................................................8
SDR repository..................................................................................................................10
SDR formats.................................................................................................................10
Reading the SDR repository and device SDR repositories....................................................11
FRU......................................................................................................................................11
FRU inventory device..........................................................................................................12
Standardized timers................................................................................................................12
Watchdog timer................................................................................................................12
POH counter.....................................................................................................................12
Timestamp format...............................................................................................................12
2 The virtual topology of the Moonshot 1500 CM module................................14
3 Discovering managed entities using IPMITool................................................17
4 IPMItool..................................................................................................18
Moonshot IPMItool support — out of band.................................................................................18
Interfaces...............................................................................................................................19
System Interface.................................................................................................................19
LANPlus Interface...............................................................................................................19
Features................................................................................................................................20
Events...................................................................................................................................21
Inventory...............................................................................................................................22
Chassis management..............................................................................................................22
Synopsis................................................................................................................................22
IPMItool Raw command syntax and example..............................................................................24
5 Command specification.............................................................................25
Standard command specification..............................................................................................29
Global commands.............................................................................................................29
Get device ID command................................................................................................29
Cold reset command ....................................................................................................32
Warm reset command...................................................................................................33
Get self test results command .........................................................................................33
Get ACPI power state command .....................................................................................34
Broadcast get device ID command .................................................................................35
IPMI messaging support commands......................................................................................36
Set BMC global enables command .................................................................................36
Get BMC global enables command ................................................................................37
Clear message flags command ......................................................................................37
Get message flags command .........................................................................................38
Enable message channel receive command .....................................................................38
Get message command ................................................................................................39
Send message command...............................................................................................42
Get system GUID command ...........................................................................................44
Set system info parameters command ..............................................................................45
Get system info parameters command..............................................................................46
Master write-read command...........................................................................................49
Contents 3
Page 4

Get channel authentication capabilities command.............................................................50
Get Channel Cipher Suites Command.............................................................................52
Cipher suite records..................................................................................................54
Cipher suite ID numbers............................................................................................55
Set session privilege level command ...............................................................................56
Close session command.................................................................................................57
Get session info command ............................................................................................57
Get AuthCode command ..............................................................................................59
Set channel access command ........................................................................................60
Get channel access command .......................................................................................62
Get channel info command ...........................................................................................63
Set user access command..............................................................................................65
Get user access command..............................................................................................66
Set user name command ...............................................................................................68
Get user name command...............................................................................................68
Set user password command..........................................................................................69
RMCP+ support and payload commands..............................................................................70
Activate payload command............................................................................................71
Deactivate payload command........................................................................................73
Suspend/resume payload encryption command................................................................74
Set channel security keys command.................................................................................75
Get system interface capabilities command.......................................................................77
Get payload activation status command...........................................................................78
Get payload instance info command...............................................................................79
Set user payload access command..................................................................................79
Get user payload access command.................................................................................80
Get channel payload support command...........................................................................81
Get channel payload version command...........................................................................82
IPMI LAN Device Commands...............................................................................................83
Set LAN configuration parameters command....................................................................83
Get LAN configuration parameters command...................................................................83
SOL commands.................................................................................................................92
Set SOL configuration parameters command.....................................................................92
Get SOL configuration parameters command....................................................................93
MC watchdog timer commands...........................................................................................96
Watchdog timer actions.................................................................................................96
Watchdog timer use field and expiration flags..................................................................97
Using the timer use field and expiration flags...............................................................97
Watchdog timer event logging........................................................................................97
Pre-timeout interrupt.......................................................................................................98
Pre-timeout interrupt support detection.........................................................................98
BIOS support for watchdog timer................................................................................98
Reset watchdog timer command .....................................................................................98
Set watchdog timer command ........................................................................................98
Get watchdog timer command .....................................................................................100
Chassis commands..........................................................................................................102
Get chassis capabilities command ................................................................................102
Get chassis status command ........................................................................................103
Chassis control command ............................................................................................104
Chassis identify command ...........................................................................................105
Set power restore policy command ...............................................................................106
Set system boot options command ................................................................................107
Get system boot options command................................................................................107
Get POH counter command .........................................................................................111
Event commands..............................................................................................................112
4 Contents
Page 5

Set event receiver command.........................................................................................112
Get event receiver command........................................................................................113
Platform event message command.................................................................................113
SEL commands................................................................................................................114
SEL device commands..................................................................................................114
Get SEL info command............................................................................................114
Reserve SEL command............................................................................................115
Get SEL entry command..........................................................................................116
Add SEL entry command.........................................................................................116
Clear SEL...................................................................................................................117
SEL record type ranges................................................................................................117
Get SEL time command................................................................................................118
Set SEL time command.................................................................................................118
SDR repository device commands......................................................................................118
SDR record IDs...........................................................................................................118
Get SDR repository info command.................................................................................119
Get SDR repository allocation info command..................................................................120
Reserve SDR repository command.................................................................................120
Reservation restricted commands..............................................................................121
Reservation cancellation..........................................................................................121
Get SDR command......................................................................................................121
Add SDR command.....................................................................................................122
Delete SDR command..................................................................................................123
Clear SDR repository command....................................................................................123
Run initialization agent command..................................................................................124
FRU inventory device commands........................................................................................124
Get FRU inventory area info command...........................................................................125
Read FRU data command........................................................................................125
Write FRU data command.......................................................................................126
Sensor Device Commands.................................................................................................126
Get device SDR info command.....................................................................................126
Get device SDR command............................................................................................127
Reserve device SDR repository command.......................................................................128
Get sensor thresholds command....................................................................................128
Get sensor reading command.......................................................................................129
DCMI specific commands.................................................................................................130
Get DCMI capability info command..............................................................................131
Get asset tag command...............................................................................................133
Get DCMI sensor info command...................................................................................134
Set asset tag command................................................................................................135
Management controller ID string...................................................................................135
Get controller ID string command..................................................................................136
Set controller ID string command...................................................................................136
PICMG specific commands...............................................................................................137
Get PICMG properties command..................................................................................137
Get address info command..........................................................................................137
FRU inventory device lock control command....................................................................138
6 IPMI Messaging and Interfaces.................................................................140
System Interfaces..................................................................................................................140
Message interface description...........................................................................................141
IPMI Messaging Interfaces.................................................................................................141
Network function codes.........................................................................................................141
Completion codes.................................................................................................................142
Channel Model, Authentication, Sessions, and Users.................................................................144
Contents 5
Page 6

Channel numbers.............................................................................................................145
Logical channels..............................................................................................................145
Channel Privilege Levels....................................................................................................145
Users & Password support.................................................................................................146
IPMI sessions...................................................................................................................146
Session-less connections....................................................................................................147
Session inactivity timeouts.................................................................................................147
System interface messaging...................................................................................................147
Bridging..............................................................................................................................148
MC LUN 10b..................................................................................................................148
Send Message command with response tracking..................................................................149
Bridged Request Example..................................................................................................149
IPMB access via master write-read command.......................................................................151
MC IPMB LUNs................................................................................................................151
Sending Messages to IPMB from system software.................................................................152
Keyboard Controller Style Interface.........................................................................................153
KCS Interface/MC LUNs...................................................................................................153
KCS Interface-MC Request message format..........................................................................153
MC-KCS Interface Response Message format.......................................................................153
LAN Interface.......................................................................................................................154
Remote Management Control Protocol (RMCP).....................................................................154
RMCP port numbers....................................................................................................154
RMCP Message Format................................................................................................155
Serial Over LAN (SOL)..........................................................................................................156
7 Support and other resources....................................................................157
Information to collect before contacting HP...............................................................................157
How to contact HP................................................................................................................157
HP authorized resellers..........................................................................................................157
Related information...............................................................................................................157
A Command Assignments...........................................................................159
B Verbose output examples.........................................................................164
Glossary..................................................................................................186
Index.......................................................................................................188
6 Contents
Page 7

1 Introduction and key concepts
Overview
The term Intelligent Platform Management (IPMI), refers to autonomous monitoring and recovery
features implemented directly in platform management hardware and firmware. The key
characteristic of Intelligent Platform Management is that inventory, monitoring, logging, and recovery
control functions are available independently of the main processors, BIOS, and operating system.
Platform management functions are available even when the system is in a powered down state.
IPMI capabilities are a key component in providing enterprise-class management for HA systems.
Platform status information is obtained and recovery actions initiated under situations where system
management software and normal “in-band” management mechanisms are unavailable.
The independent monitoring, logging, and access functions available through IPMI provide a level
of manageability built-in to the platform hardware. This supports systems with no system management
software available for the particular operating system, or the end-user who elects not to load or
enable the system management software.
NOTE: The HP Moonshot-45G Switch Module does not support IPMI. Only the HP Moonshot iLO
Chassis Management Firmware supports IPMI.
Sensor Data Model
The IPMI Sensor Model provides access to monitored information including temperatures, voltages,
and fan status. Instead of providing direct access to the monitoring hardware, IPMI provides access
by abstracted sensor commands, such as the Get Sensor Reading command, implemented
via a management controller. This approach isolates software from changes in the platform
management hardware implementation. Sensors return analog or discrete readings and events
are either discrete or threshold-based. Sensors are classified according to:
• Type of readings
• Type of events
Event types, sensor types, and monitored entities are represented using numeric codes defined in
the IPMI specification. IPMI avoids reliance on strings for management information and using
numeric codes facilitates internationalization, automated handling by higher level software, and
reduces management controller code and data space requirements.
Sensor owner identification
The definition for the Request/Response identifier, Requester’s ID, and Responder’s ID are specific
to the particular messaging interface used. However, the SDR and SEL must contain information
to identify the owner of the sensor. For management controllers, a slave address and LUN identify
the owner of a sensor on the IPMB. For system software, a software ID identifies the sensor owner.
These fields are used in event messages, where events from management controllers or the IPMB
are identified by an eight-bit field where the upper 7 bits represent the slave address or the system
software ID. The least significant bit is 0 if the value represents a slave address and 1 if the value
represents a system software ID.
Sensor number is not part of the sensor owner ID, but is a separate field used to identify a particular
sensor associated with the sensor owner. This combination of sensor owner ID and sensor number
uniquely identify a sensor in the system.
Table 1 Sensor owner ID and sensor number field definition
System Sensor Owner IDIPMB Sensor Owner ID
system software ID (7 bits)7:1 slave address (7 bits)
Overview 7
Page 8
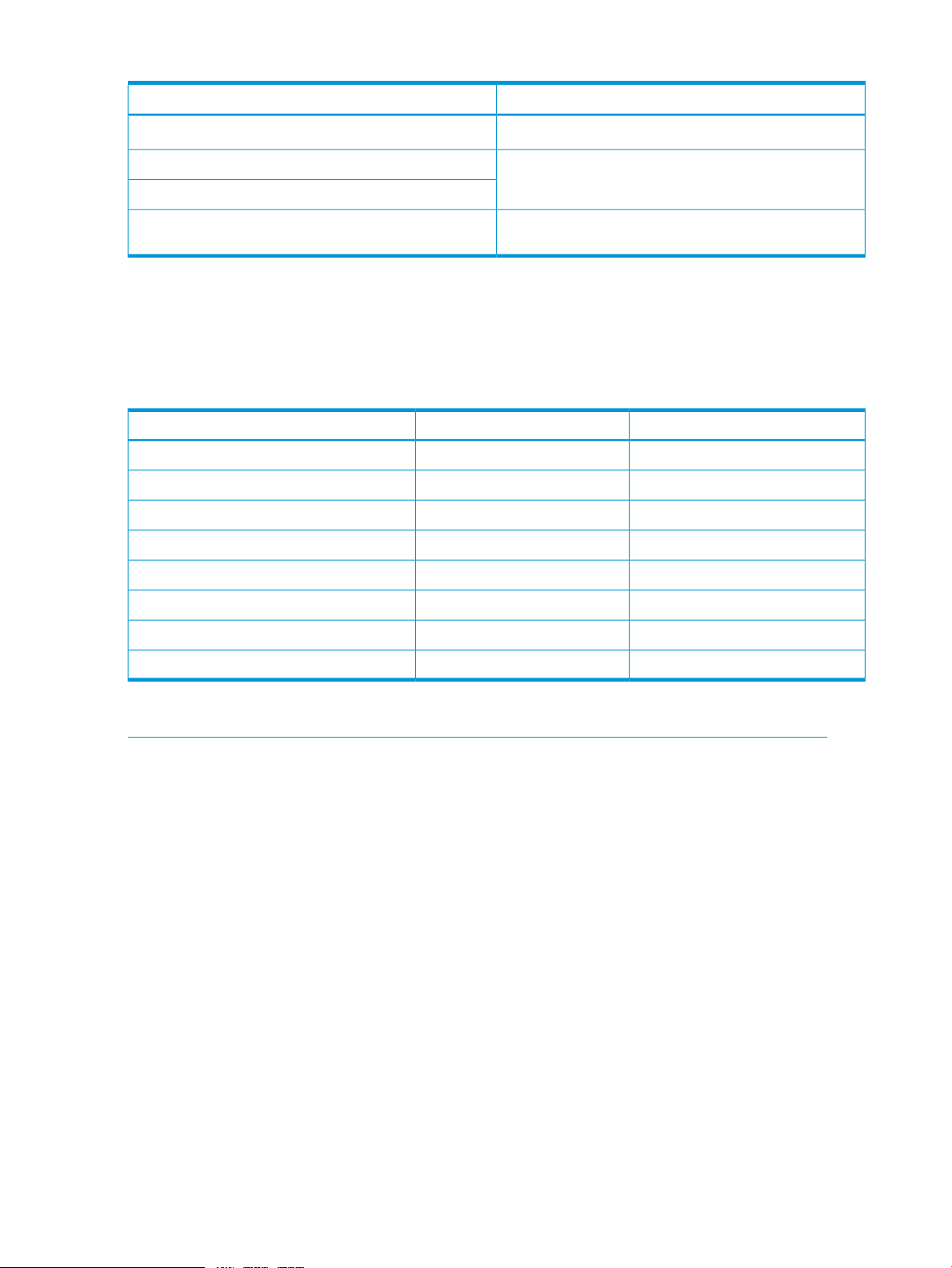
Table 1 Sensor owner ID and sensor number field definition (continued)
System Sensor Owner IDIPMB Sensor Owner ID
0 1b (ID is a software ID)0 0b (ID is a slave address)
sensor number (8 bits, FFh = reserved)LUN (2 bits)
sensor number (1 bit, FFh = reserved)
In Moonshot: 0x82 IPMB address
Sensor type code
Each sensor has a sensor type code and are defined in “Some Moonshot sensor type codes”
(page 8). Sensor type codes are used both in SDRs and event messages. An example of a sensor
type code is code 0x1, which indicates a temperature sensor.
Table 2 Some Moonshot sensor type codes
This only appears in the system node SEL, where the it is
logged by the host system
Reading type codeSensor type codeSensor type
0x10x1Temperature
0xA0x4Fan
0xB0x4Fan redundancy
0x6F0xF1PICMG IPMB0 Physical Link
0x710xC0Health LED
0x700xC0UID LED
0x6F0x8Power supply
0xB0x8Power supply redundancy
For a complete listing of sensor type codes, see the IPMI specification available at:
http://www.intel.com/content/www/us/en/servers/ipmi/second-gen-interface-spec-v2.html
System event log and event messages
The MC provides a centralized, non-volatile SEL. Having the SEL and logging functions managed
by the MC helps ensure that post-mortem logging information is available should a failure occur
that disables the systems processor(s).
A set of IPMI commands allows the SEL to be read and cleared, and for events to be added to the
SEL. The common request message used for adding events to the SEL is an event message. Event
messages are sent to the MC via the IPMB providing the mechanism for satellite controllers to detect
events and log them into the SEL. The controller that generates an event message to another
controller via IPMB is the IPMB Event Generator. The controller receiving event messages is the
IPMB Event Receiver.
In Moonshot, event messages are sent to the zone manager by each cartridge and chassis controller.
There are two event logs, the SEL and the IML. There are OEM specific commands for obtaining
and displaying these logs. For more information, see the related commands in “Command
specification” (page 25).
8 Introduction and key concepts
Page 9
Event messages are special messages sent by management controllers when they detect significant
or critical system management events. This includes messages for events such as:
• temperature threshold exceeded
• voltage threshold exceeded
• power fault
The event message generator notifies the system by sending an Event Request Message to
the event receiver device.
When the event receiver gets a valid event message, it sends a response message to the event
message generator which is typically transferred to the SEL. The event receiver does not interpret
event messages so that new event message types can be added into the system without impacting
event receiver implementation.
SEL commands — The SEL is a non-volatile repository for system events and some system
configuration information. The SEL device access the commands sent by the SEL. Event messages
when received by the event receiver device are written to the SEL.
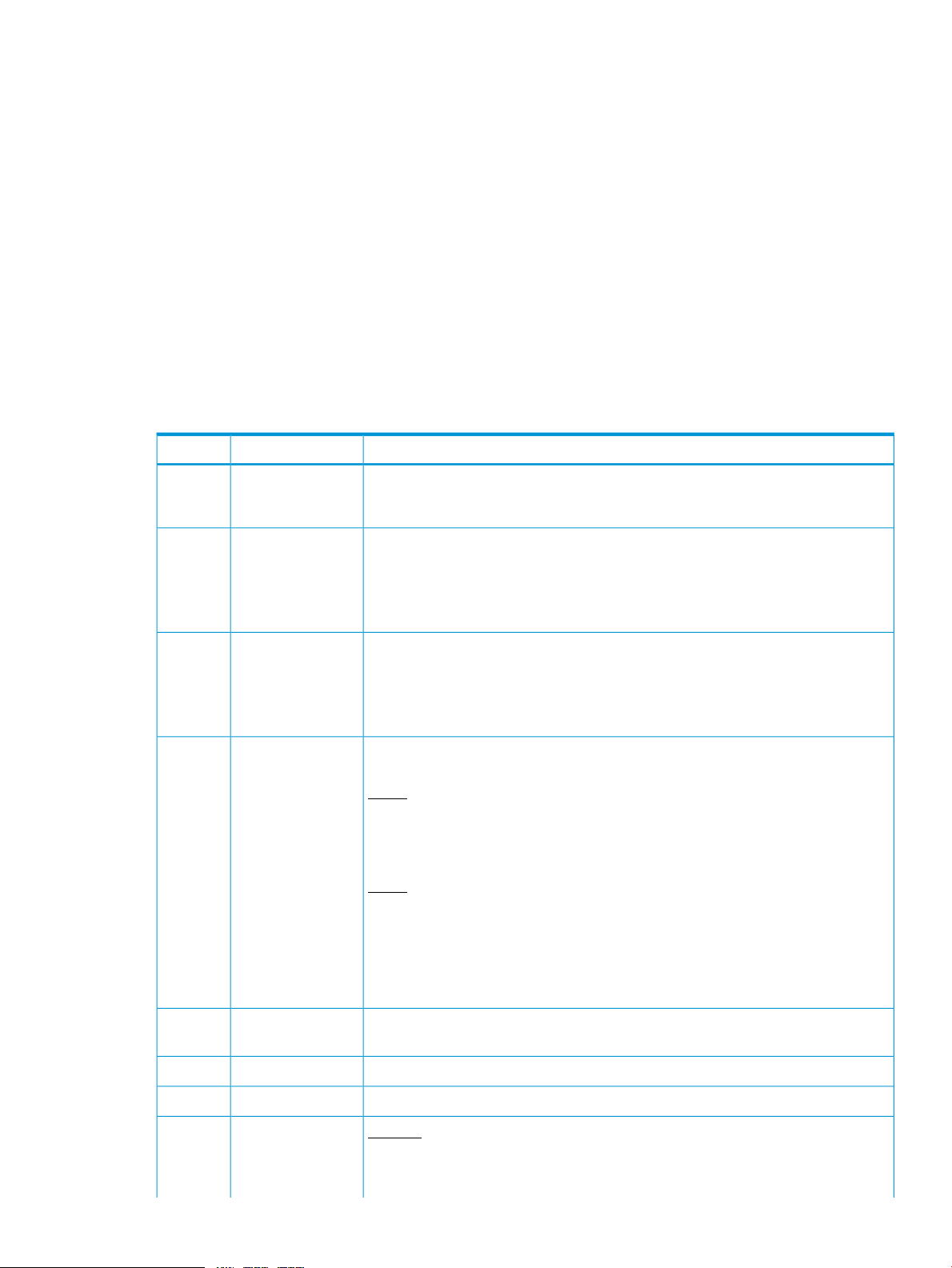
Table 3 SEL event records
DescriptionFieldByte
Record ID1
2
5
6
7
Generator ID8
9
ID used for SEL record access. The Record ID values 0000h and FFFFh have special
meaning in the Even Access commands and must not be used as Record ID values
for stored SEL event records.
[7:0] — Record typeRecord type3
02h = system event record
C0h-DFh = OEM timestamped, bytes 8–16 OEM defined
E0h-FFh = OEM non-timestamped, bytes 4–16 OEM defined
Time when event was logged. LS byte first.Timestamp4
RqSA & LUN if event was generated from IPMB. Software ID if event was generated
from system software.
Byte 1
[7:1] — 7–bit I2C. Slave address, or 7–bit system software ID
[0] 0b = ID is IPMB slave address
1b = System software ID
Byte 2
[7:4] — Channel number. Channel that received the event message 0h if the event
message was received via the system interface, primary IPMB, or internally generated
by the MC.
[3.2] — Reserved. Write as 00b.
[1.0] — IPMB device LUN if byte 1 holds slave address, otherwise 00b.
EvM Rev10
Event message format version (=04h for events in this specification, 03h for IPMI
v1.0 event messages).
Sensor type code for sensor that generated the event.Sensor type11
Number of sensor that generated the event.Sensor #12
Event dirEvent dir 113
[7] — 0b = Assertion event.Event type
1b = Deassertion event.
1
Sensor Data Model 9
Page 10

Table 3 SEL event records (continued)
1
The MC must accept Platform Event request messages that are in IPMI v1.0 format (EvM Rev=03h) and log them as IPMI
v1.5/v2.0 records by setting the EVMRev field to 04h and setting the channel number in the generator ID field
appropriately for the channel that received the event.
SDR repository
With IPMI’s extensibility and scalability each platform implementation can have a different
population of management controllers and sensors, and different event generation capabilities.
IPMI allows system management software to retrieve information from the platform and automatically
configure itself to the platform’s capabilities, enabling the use of plug and play, platform-independent
instrumentation software.
Information that describes the platform management capabilities is provided via two mechanisms:
DescriptionFieldByte
Event type
Type of trigger for the event, such as, a critical threshold going high or state asserted.
Also indicates class of the event. Example: discrete, threshold, or OEM. The event
type field is encoded using the event/reading type code.
Event request message, event data field contents.Event data 114
Event request message, event data field contents.Event data 215
Event request message, event data field contents.Event data 316
• Capability commands — these are commands within the IPMI command set that return
• SDRs — these contain information about the type and number of sensors in the platform, sensor
The primary purpose of SDRs is to describe the sensor configuration of the platform management
subsystem to system software. SDRs also include records describing the number and type of devices
connected to the system’s IPMB, records that describe the location and type of FRU Devices (devices
that contain field replaceable unit information).
SDRs are kept in a single, centralized, non-volatile storage area managed by the MC. This storage
area is the SDR repository. In Moonshot, the SDRR is kept by the zone manager; the remaining
controllers have device SDRs. Additional device SDRs are kept at the cartridge and system node
level. All SDR repositories provide a mechanism for information to be obtained independently from
the controller by the BIOS system management or remote management.
SDR formats
The general SDR format consists of three major components: the record header, record key fields,
and the record body. To save space, sensors that only generate events do not require SDRs, in
addition, generic system management software does not access sensors unless they are reported
by SDRs.
information on other commands and functions that the controller can handle.
threshold support, event generation capabilities, and sensor type readings.
10 Introduction and key concepts
Page 11
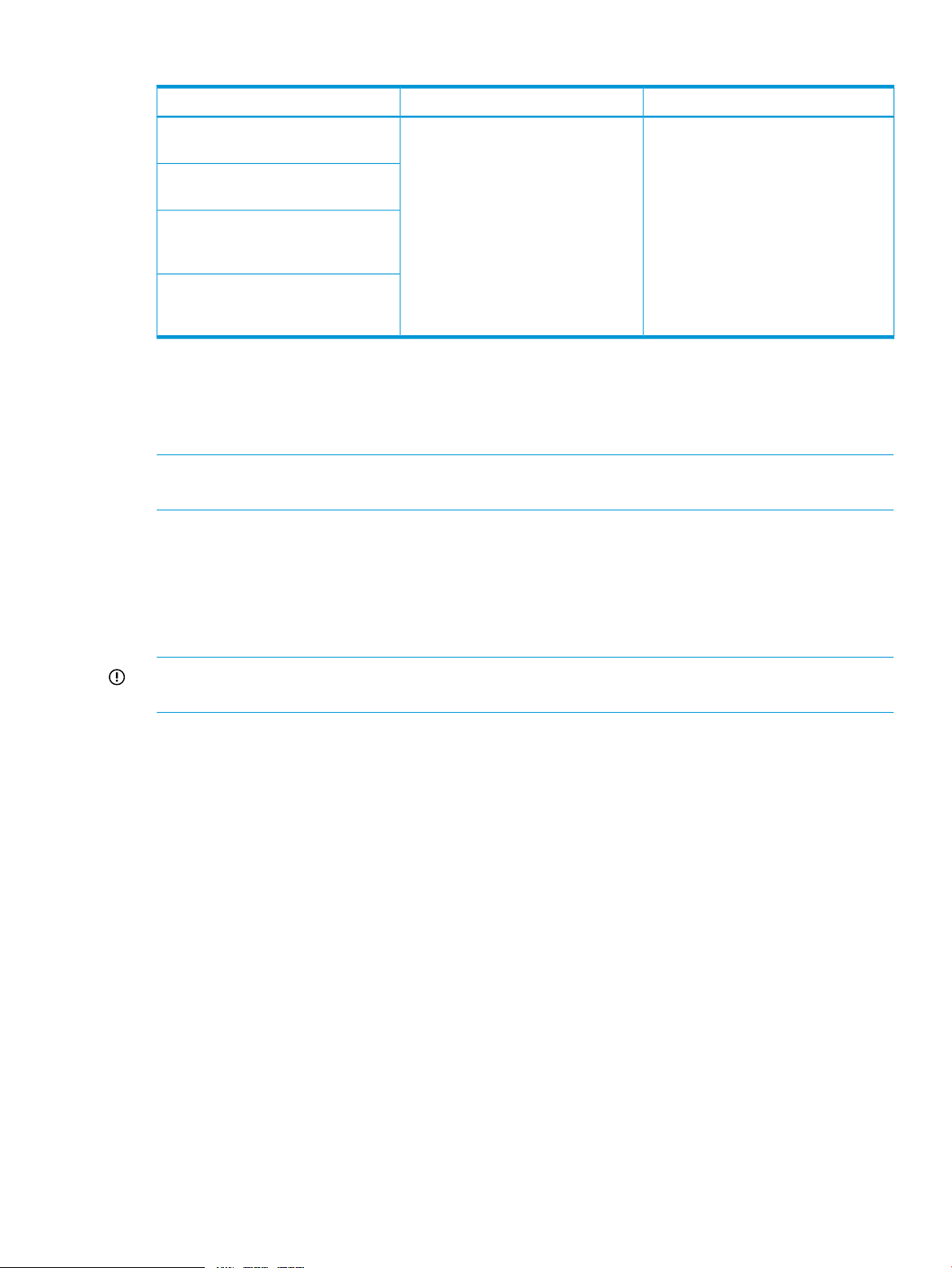
Table 4 Sensor data record formats
Record bodyRecord Key fieldsRecord header
Record ID — a value used for
accessing sensor data records.
SDR version — version number of the
SDR specification.
Record type — a number representing
the type of record. Example, 01h =
8–bit sensor with thresholds.
Record length — the number of bytes
of data following the record length
field.
The record key bytes are the
contiguous bytes following the record
header. The number of bytes vary
according to record type. Together,
they make up a set of unique fields for
a given record specifying location (for
example, slave address, LUN and Bus
ID) and sensor number.
Reading the SDR repository and device SDR repositories
An application that retrieves records from the SDR repository must first read them sequentially using
the Get SDR command. This command returns the requested record and the record ID of the next
SDR in sequence.
NOTE: Record IDs are not required to be sequential or consecutive and applications should not
assume that SDR record IDs follow any particular numeric ordering.
Retrieve succeeding records by issuing the Get SDR or Get device SDR command using the
next record ID returned in the previous response. This is continued until the End of Record ID
is encountered.
Once all the desired records have been read, the application can randomly access the records
according to their Record ID. An application that seeks to access records randomly must save a
data structure that retains the record key information according to the record ID.
Contains specific information to the
sensor data record
FRU
IMPORTANT: Record IDs may change with time, it is important for applications to first verify that
the Record Key information matches the record retrieved.
If the record ID is no longer valid for a record key, then, access the SDR records again as described
above until the record matches the record key.
An application can tell whether records have changed by examining the most recent addition
timestamp using the Get SDR repository info or Get device SDR repository info
command, depending on the zone in which the command is issued.
If the record information has changed, an application does not need to list out the entire contents
of all records. The Get SDR or Get device SDR allows a partial read of the SDR. Thus, an
application can search for a given Record Key by just retrieving that portion of the record.
The IPMI specifications include support for storing and accessing multiple sets of non-volatile FRU
data for different modules in the system. An enterprise-class system typically has FRU information
for each major system board such as the processor board, memory board or I/O board. FRU data
includes serial number, part number, model, and asset tag.
IPMI FRU information is accessible via the IPMB and management controllers. The information can
be retrieved at any time, independent of the main processor, BIOS, system software, or OS, via
out-of-band interfaces, such as the ICMB, a remote management card, or other device connected
to the IPMB. FRU information is still available when the system is powered down.
With these capabilities FRU information is available even under failure conditions when access
mechanisms that rely on the main processor are unavailable. This facilitates the creation of
automated remote inventory and service applications. IPMI does not seek to replace other FRU or
FRU 11
Page 12

inventory data mechanisms such as those provided by SM BIOS, and PCI vital product data. Rather,
IPMI FRU information is typically used to complement that information or provide information access
out-of-ban or under system down conditions.
IPMI provides FRU information in two ways: via a management controller, or via FRU SEEPROMs.
FRU information that is managed by a management controller is accessed using IPMI commands.
This isolates software from direct access to the non-volatile storage device, allowing the hardware
implementor to utilize whatever type of non-volatile storage required.
FRU inventory device
The FRU inventory device contains information such as the serial number, part number, asset tag,
and short descriptive string for the FRU. The contents of a FRU inventory record are specified in
the platform management FRU information storage definition.
The FRU inventory device is a logical device and is not necessarily implemented as a separate
physical device. This device contains the SDR repository device and typically holds FRU inventory
Information for the main system board and chassis. In addition, there may be a separate FRU
inventory device that provides access to the FRU information for a replaceable module such as a
memory module.
FRU devices can be located either behind a management controller or directly on the IPMB. The
sensor data records include a FRU device locator record that tells software where the device is
located and the type of commands required to access the FRU device. FRU devices can be located
in three types of location:
• Behind a management controller and accessed using Read/Write FRU data commands.
Multiple FRU devices can be behind a management controller.
• SEEPROM on a private bus behind a management controller. These devices are accessed
using Master Write-Read commands.
• SEEPROM on the IPMB. These devices are typically accessed using a Master Write-Read
command to the IPMB via the MC.
Standardized timers
Watchdog timer
IPMI provides a standardized interface for a system watchdog timer that can also be used for
BIOS, OS, and OEM applications. The timer can be configured to automatically generate selected
actions when it expires; including power off, power cycle, reset, and interrupt. The timer function
automatically logs the expiration event. Setting 0 for the timeout interval result causes the timeout
action to be initiated immediately. This provides a means for devices on the IPMB, such as remote
management cards, to use the watchdog timer to initiate emergency reset and other recovery
actions dependent on the capability of the timer.
In Moonshot, watchdog timers are implemented by the system node controllers.
POH counter
The standardized power-on hours (POH) counter is optional. It returns a counter value proportional
to the system operating power-on hours.
In Moonshot, the POH counter is implemented at the system node controller.
Timestamp format
A timestamp is a key component of event logging and tracking changes to the SDRs and the SDR
repository.
Time is an unsigned, 32–bit value representing the local time as the number of seconds from
00:00:00,January 1, 1970.
12 Introduction and key concepts
Page 13

The timestamps used for SDR and SEL records are specified in relative local time (that is, the
difference between the timestamp does not include the GMT offset). Converting the timestamp to
a GMT-based time requires adding the GMT offset for the system and is obtained from system
software level interfaces. IPMI commands do not store or return GMT offset for the system.
Applications may use ANSI C time standard library routines for converting the SEL timestamp into
other time formats.
Special timestamp values
0xFFFFFFFF indicates an invalid or unspecified time value.
0x00000000 through 0x20000000 indicate events that occur after initialization of the SEL device
up to when the timestamp is set with the system time value. These timestamp values are relative to
the completion of the SEL devices initialization, and not January 1, 1970.
Standardized timers 13
Page 14
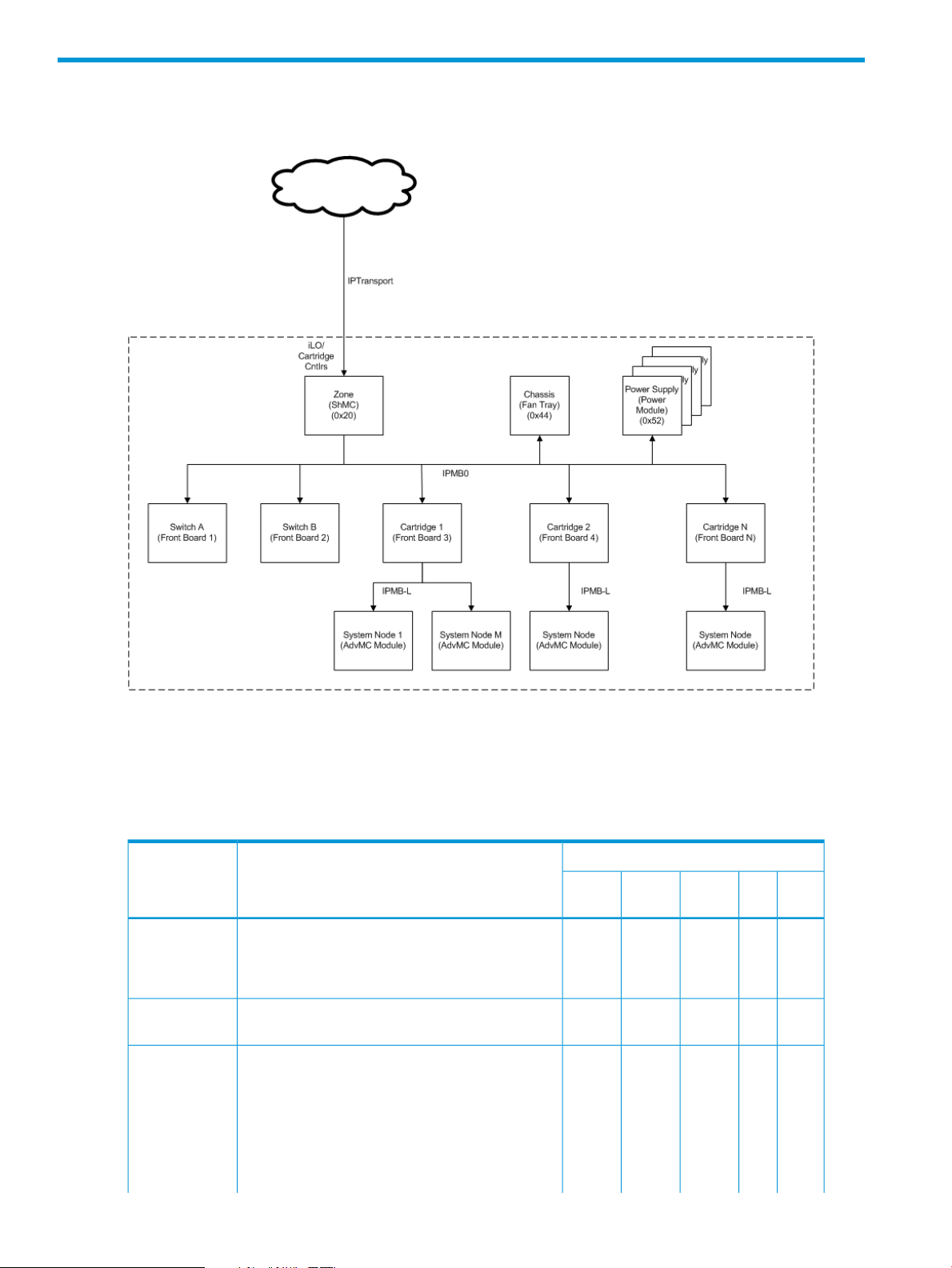
2 The virtual topology of the Moonshot 1500 CM module
Figure 1 Moonshot virtual IPMI topology
There are five virtual management controller (MC) entity types represented within the HP Moonshot
1500 Chassis Management module.
Table 5 (page 14) summarizes the various functions available in Moonshot and the virtual
management controllers to which they apply.
Table 5 Moonshot virtual management controller functions
Applicable Virtual Management ControllerDescriptionFunction
NodeCartPower
xxxxxThe MC must implement the mandatory IPM Device
xThe implementation must provide MC access via
IPM Device
System Interface
SDR Repository
ChassisZone
Supply
commands. If an IPMB is provided, the mandatory
commands must be accessible from the IPMB unless
otherwise noted.
one of the specified IPMI system interfaces.
xThe MC must provide a SDR Repository to hold
Sensor, Device Locator, and Entity Association
records for all sensors in the platform management
subsystem. This does not need to include SDRs for
sensors that only generate events. If the SDR
Repository is writable, it is recommended that at
least 20% additional space is provided for add-in
platform management extensions.
14 The virtual topology of the Moonshot 1500 CM module
Page 15
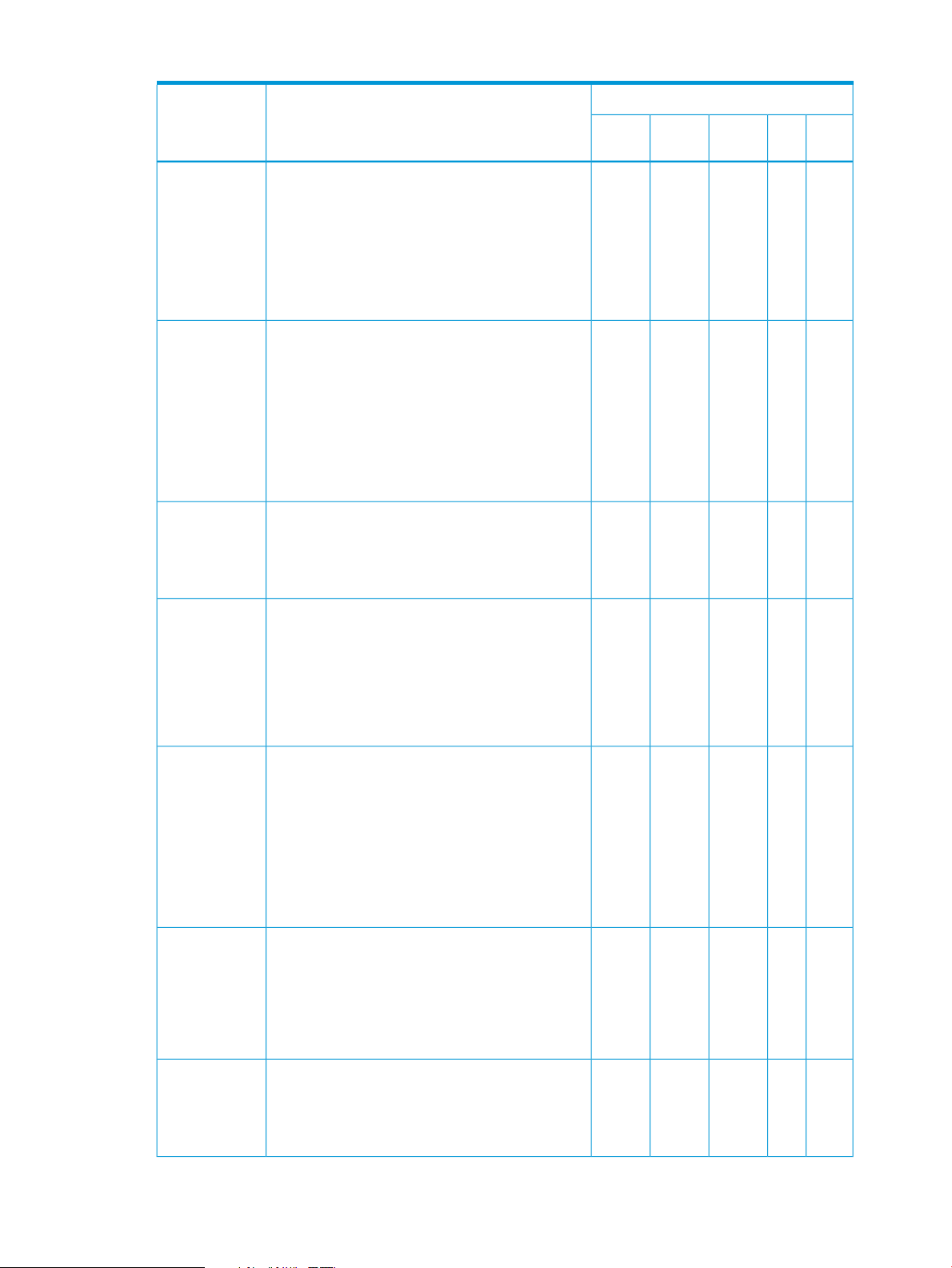
Table 5 Moonshot virtual management controller functions (continued)
Applicable Virtual Management ControllerDescriptionFunction
IPMB Interface
Watchdog
Timer
The SDR Repository must be accessible via the
system interface. If an IPMB is provided, the SDR
Repository must be readable via that interface as
well. SDR update via the IPMB interface is optional.
SDR Repository access when the system is powered
up or in ACPI ‘S1’ sleep is mandatory, but access
when the system is powered -down or in a >S1
sleep state is optional.
MC must provide the system interface to the IPMB.
If an IPMB is imp lemented, at least one of the
specified IPMB connectors must be provided. Refer
to the IPMB Protocol specification for connector
definition. In addition the MC must implement a
message channel that allows messages to be sent
from the IPMB to the system interface, and
vice-versa, and any other mandatory IPMB support
functions and commands.
Timer interface, with support for system reset action.
Certain functions within the Watchdog Timer are
optional. Refer to the sections on the Watchdog
Timer for information.
ChassisZone
Supply
NodeCartPower
xxxxxThe IPMB is highly recommended, but optional. The
xThe MC must provide the standardized Watchdog
Event Receiver
SEL Interface
FRU Inventory
Initialization
Agent
xxThe MC must implement an Event Receiver function
and accept Event Messages via the system interface.
If an IPMB is provided, the Event Receiver function
must also accept Event Messages from the IPMB.
Event Receiver operation while the system is
powered up or in ACPI ‘S1’ sleep is mandatory,
but operation when the system is powered down or
in a >S1 sleep state is optional.
xxThe MC must provide a System Event Log interface.
The event log must hold at least 16 entries. SEL
access must be provided via the system interface.
The SEL must be fully accessible via all mandatory
SEL commands through all supported interfaces to
the MC whenever the system is powered up or in
ACPI 'S1' sleep state. SEL read access is always
mandatory whenever the MC is accessible, and
through any interface that is operational, regardless
of system power state.
xxxxxThe MC must provide a logical Primary FRU
inventory device , accessible via the Write- and
Read FRU Data commands. The FRU
Inventory Device Info command must also
be supported. It is highly recommended that all other
management controllers also provide a Primary FRU
inventory device. (This was optional in IPMI v1.0.)
xxxxxThe initialization agent function is one where the
MC initializes event generation and sensors both
internally and on other management controllers
according to initialization settings stored in the SDR
for the sensor.
15
Page 16
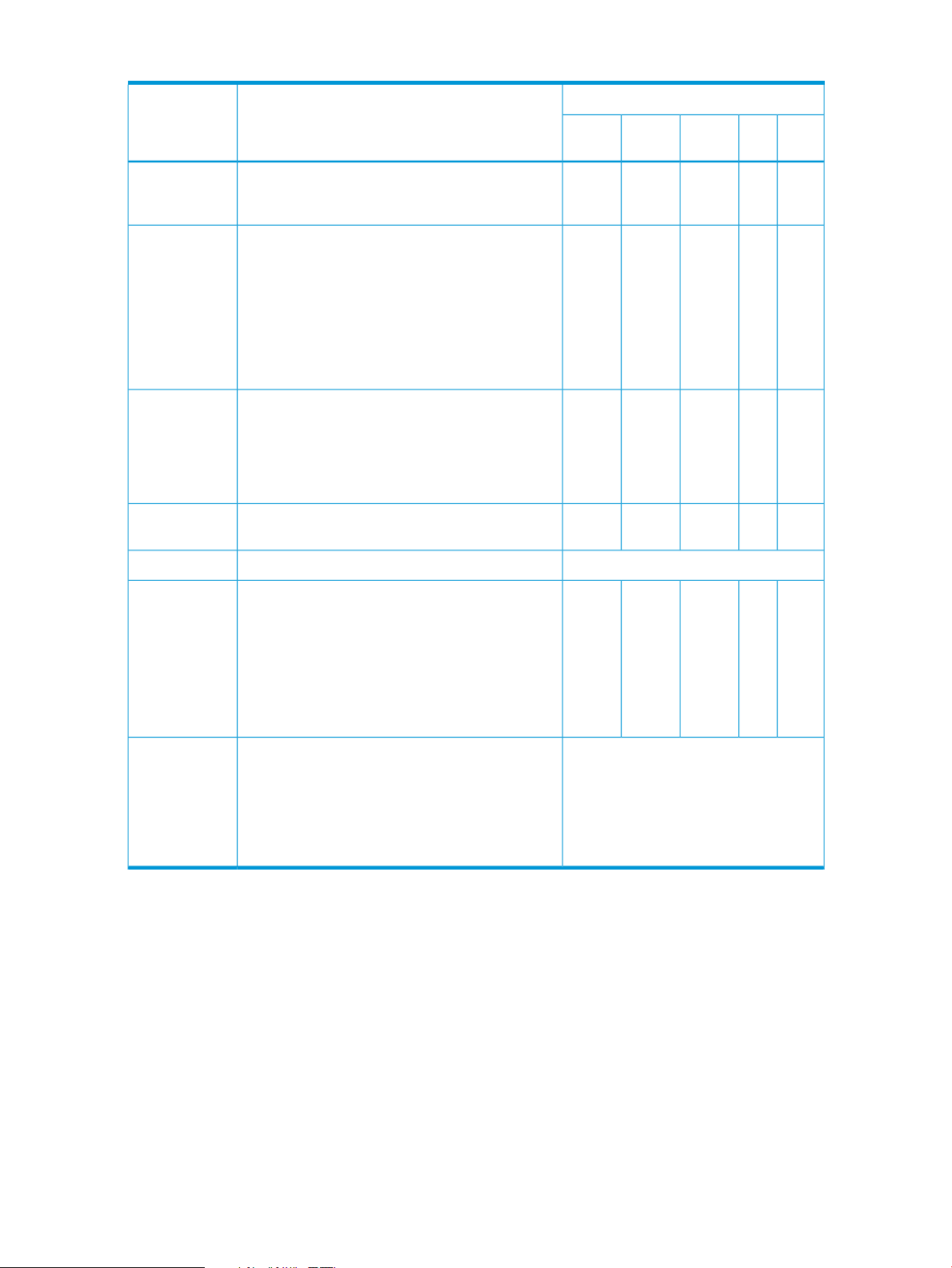
Table 5 Moonshot virtual management controller functions (continued)
Applicable Virtual Management ControllerDescriptionFunction
Sensors
Internal Event
Generation
External Event
Generation
LAN Messaging
would provide sensors for baseboard temperature,
voltage, and chassis intrusion monitoring.
Watchdog Timer. It is highly recommended that
sensors generate events to eliminate the need for
system management software to poll sensors, and
to provide “post -mortem” failure information in the
SEL. Internal event generation for sensors is optional,
but highly recommended - particularly for
‘environmental’ (e.g. temperature and voltage)
sensors.
Receiver command to allow it to be set as an IPMB
Event Generator and send its event messages to
another management controller. This would
primarily be used for development and test
purposes.
Messaging over LAN
ChassisZone
Supply
xAbility for the MC to send and receive IPMI
Not implemented yet.Ability to send an Alert over the LANLAN Alerting
NodeCartPower
xxxxxThe MC can provide sensors. A typical server MC
xxxxxThe MC must generate internal events for the
xxxThe MC could be designed to accept the Set Event
Bridging
Support
Platform Event
Filtering (PEF)
Policies optional. Refer to the sections on PEF for
messages between two interfaces connected to the
MC.
The following support is required if the
corresponding interfaces are supported:
• LAN <–> IPMB
• LAN <–> System Interface
n event. This capability is mandatory if paging or
alerting is supported. Certain actions within PEF areand Alert
information. The Alert action and Alert Policies are
mandatory if serial/modem or LAN alerting is
supported.
xxxxxThe ability to transfer IPMI request and response
Not implemented yet.Ability for MC to perform a selectable action on a
16 The virtual topology of the Moonshot 1500 CM module
Page 17

3 Discovering managed entities using IPMITool
Enter the IPMItool sdr list all command to show all management controller records, whether
you are querying an SDRR from the Virtual Zone MC or you are querying a device SDR for Virtual
Cartridge MC records. For example:
# ipmitool —l lanplus —H iloatx-gem-2c -U admin —P admin123 sdr list all
ZoMC | Static MC @ 20h | ok
254 | Log FRU @FEh f0.60 | ok
IPMB0 Phys Link | 0x00 | ok
ChasMgmtCtlr1 | Static MC @ 44h | ok
PsMgmtCtlr1 | Dynamic MC @ 52h | ok
PsMgmtCtlr2 | Dynamic MC @ 54h | ok
PsMgmtCtlr3 | Dynamic MC @ 56h | ok
PsMgmtCtlr4 | Dynamic MC @ 58h | ok
CaMC | Dynamic MC @ 82h | ok
CaMC | Dynamic MC @ A0h | ok
CaMC | Dynamic MC @ A6h | ok
CaMC | Dynamic MC @ DAh | ok
CaMC | Dynamic MC @ A4h | ok
Querying an SDRR from the Zone Management Controller
• Enter the sdr list all command to show all management controller records.
• Management controller records
Chassis controller – statically assigned, always should be present. Even though always
◦
assigned address 0x44, record should be parsed to learn address and channel number
(IPMB=0).
◦ Power supply controllers --- full complement of records always present. Dynamic indication
in record indicates to application that controller may or may not be present. When not
present, the controller will “nak”. Even though always assigned address 0x52-0x58,
records should be parsed to learn address and channel number (IPMB=0).
◦ Cartridge controllers are dynamically added/deleted to the SDRR upon cartridge
insertion/deletion. Possibility of “nak” condition during deletion transitions. Records
should be parsed to learn addresses and channel number (IPMB=0).
Querying a device SDR for a Cartridge Management Controller
• Management controller records
◦ System node controllers – statically assigned, always should be present. Number of system
node controllers is dependent on cartridge type. Some cartridges may not contain host
systems such as switches. Other cartridges may contain 1 or 4 system nodes. Records
should be parsed for addressing and channel number routing. System nodes routed on
channel 7 (IPMB-L).
You can learn the phsical locations of managed entities by entering the PICMG get address
info command. Use the IPMB address of the cartridge to get the physical address (slot number).
You can also learn the chassis topology through chassis FRU serial number for Zones with the same
chassis.
17
Page 18

4 IPMItool
IPMI tool is a simple command-line interface to systems that support the IPMI v1.5 specification. It
provides the ability to read the sensor data repository and print sensor values, display the contents
of the system event log, print field replaceable unit information, read and set LAN configuration
parameters, and perform remote chassis power control. It was originally written to take advantage
of IPMI-over-LAN interfaces but is also capable of using the system interface as provided by a
kernal device driver such as Open IPMI. IPMItool is available under a BSD-compatible license.
System Management Software is generally complex and makes platform management only part
of a much larger management picture. However, many system administrators and developers rely
on command-line tools that can be scripted and systems that can be micro-managed. IPMItool takes
a different approach to SMS and provides a completely command-line oriented tool. Therefore, it
is not designed to replace the Open IPMI library. Where possible, it supports printing
comma-separated values for output to facilitate parsing by other scripts or programs. It is designed
to run quick command response functions that can be as simple as turning the system on or off or
as complex as reading in the sensor data records and extracting and printing detailed sensor
information for each record.
Moonshot IPMItool support — out of band
Single-bridging out of band command
You must single-bridge out of band commands to reach specific chassis management controller or
cartridge management controller to discover management controller addresses.
Enter the sdr list all command at the zone management controller to discover chassis and
cartridge management controller addresses. For example,
• Chassis Controller
-b 0 -t 0x44
• Cartridge Controller Slot 1
-b 0 –t 0x82
• Cartridge Controller Slot 2
-b 0 –t 0x84
where:
• -b <ipmi channel number>
• -t <target slave address>
Double-bridging out of band commands
You must double-bridge out of band commands to reach specific system node management
controllers to discover system node management controller addresses.
Enter the sdr list all at the cartridge management controller to discover system node
management controller addresses. For example,
• –System Node Controller 2 (0x74) on Cartridge Controller Slot 1 (0x82)
-T 0x82 -B 0 –b 7 -t 0x74
• –System Node Controller 1 (0x72) on Cartridge Controller Slot 2 (0x84)
18 IPMItool
-T 0x84 -B 0 –b 7 -t 0x72
Page 19

where:
• –B <transit channel for bridged request (dual bridge)>
• –T <transit address for bridge request (dual bridge)>
• -b <ipmi channel number>
• -t <target slave address>
Interfaces
IPMItool supports dynamic loading of interfaces that correspond to low-level communication methods
for accessing IPMI systems. The most common of these are the System Interface provided by the
OpenIPMI Linux kernal driver and IPMI over LAN interfaces.
System Interface
There are multiple types of system interfaces, and they are all similar enough to enable a single
driver like OpenIPMI to support them all. They can be connected to any system bus such as ISA
or X-bus that allows the main processor to access I/O mapped locations and meet the timing
specifications. The varieties of system interfaces include KCS and SSIF. All of these are supported
in recent versions of the OpenIPMI driver for the Linux kernal. IPMItool uses this driver to access
the system interface through a character device node at /dev/ipmi0. To use this interface with
IPMItool provide the -l open parameter on the command line.
LANPlus Interface
The LANPlus interface communicates with the MC over an ethernet LAN connection using UDP
under IPv4. The LANPlus interface uses the RMCP+ protocol. RMCP+ facilitates improved
authentication and data integrity checks as well as encryption and the ability to carry multiple
types of payloads. Generic Serial Over LAN support requires RMCP+, so the IPMItool sol
activate command requires the use of LANPlus.
RMCP+ session establishment uses a symmetric challenge-response protocol called RAKP (Remote
Authenticated Key-Exchange Protocol) which allows the negotiation of many options.
NOTE: IPMItool does not allow the user to specify the value of every option, defaulting to the
most obvious settings marked as required in the v2.0 specification. Authentication and integrity
HMACS are produced with SHA1, and encryption is performed with AES-CBC-128. Role-level
logins are not yet supported.
IPMItool must be linked with the OpenSSL library in order to perform the encryption functions and
support the LANPlus interface. If the required packages are not found it will not be compiled and
supported.
ipmitool -I lanplus -H <hostname>[-U <username>][-P <password>]<command>
A hostname must be given on the command line in order to use the LAN interface with IPMItool.
The —C option allows the authentication integrity and encryption algorithms to be used for LANPlus
sessions based on the cipher suite ID found in IPMI v2.0. The default cipher suite is 3 which specifies
RAKP-HMAC-SHA1 authentication, HMAC-SHA1–96 integrity, and AES-CBC-128 encryption
algorithms.
Interfaces 19
Page 20

Example 1 Raw Get Device ID to chassis satellite controller over LAN
# ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L Administrator -b 0 -t 0x44 raw 6 1
15 01 02 01 02 29 0b 00 00 00 85 00 00 00 00
Example 2 Powering on C2N1 over LAN
# ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L Administrator -B 0 –T 0x84 –b 7 –t 0x72 chassis
power on
Chassis Power Control: Up/On
Example 3 Activating SOL on C2N1 over LAN
# ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L Administrator -B 0 –T 0x84 –b 7 –t 0x72 sol
activate
Activates SOL session for C2N1
Features
Instead of directly accessing the monitoring hardware for device entry, IPMI provides access to
sensor data through abstracted messaging commands. Some common types of sensors that can
be found in the system include baseboard and processor temperature sensors, processor and DIMM
presence sensors, fan speed and failure monitoring, and baseboard, processor and SCSI terminating
voltage sensors. The amount of data available for each sensor can be overwhelming, so by default
IPMItool only displays the sensor name, reading and status. Considerably more output can be seen
by enabling the verbose output option.
To facilitate discovery of features, IPMI includes a set of records called SDRs kept in a single
centralized non-volatile storage area. These records include software information such as how
many sensors are present, what type they are, their events, threshold info and more. This allows
software to interpret and present sensor data without any prior knowledge about the platform.
20 IPMItool
Page 21

Example 4 Output from sdr list all command
ZoMC | Static MC @ 20h | ok
254 | Log FRU @FEh f0.60 | ok
IPMB0 Phys Link | 0x00 | ok
ChasMgmtCtlr1 | Static MC @ 44h | ok
PsMgmtCtlr1 | Dynamic MC @ 52h | ok
PsMgmtCtlr2 | Dynamic MC @ 54h | ok
PsMgmtCtlr3 | Dynamic MC @ 56h | ok
PsMgmtCtlr4 | Dynamic MC @ 58h | ok
CaMC | Dynamic MC @ A6h | ok
CaMC | Dynamic MC @ A8h | ok
CaMC | Dynamic MC @ AAh | ok
CaMC | Dynamic MC @ ACh | ok
CaMC | Dynamic MC @ AEh | ok.
.
.
.
CaMC | Dynamic MC @ A4h | ok
Example 5 Output from sdr list all command at cartridge
01-Front Ambient | 21 degrees C | ok
02-CPU | 40 degrees C | ok
03-DIMM | 25 degrees C | ok
04-Cart Ctrlr | 24 degrees C | ok
05-CPU Zone | 29 degrees C | ok
06-LOM Zone | 36 degrees C | ok
CaMC | Dynamic MC @ A4h | ok
SnMC | Dynamic MC @ 72h | ok
SnMC 1 | Log FRU @01h c1.62 | ok
Events
See “Verbose output examples” (page 164) for an example of verbose output from the sdr list
all command.
Events are special messages sent by the management controller when they detect system
management events. Some examples of events are temperature threshold exceeded, voltage
threshold exceed, correctable ECC memory error, etc. These events are processed and usually
logged in the SEL. This is similar to the SDR in that it provides a centralized non-volatile storage
area for platform events that are logged autonomously by the MC or directly with event messages
sent from the host.
There is an abundance of information available from an event log entry. By default IPMItool displays
only the basic data for the event and the sensor that triggered it. Detailed information is available
with the verbose option.
Example 6 Output from sel list command
0 | 04/16/2013 | 20:22:01 | Power Supply #0x04 | Failure detected | Asserted
1 | 06/28/2013 | 20:36:17 | Power Supply #0x02 | Presence detected | Deasserted
2 | 07/28/2013 | 00:20:52 | Power Supply #0x02 | Failure detected | Asserted
3 | 08/04/2013 | 00:23:10 | Power Supply #0x02 | Presence detected | Deasserted
4 | 08/09/2013 | 14:34:48 | Fan #0x07 | Transition to Off Line | Asserted
5 | 08/09/2013 | 14:34:49 | Fan #0x07 | Transition to Running | Deasserted
See “Verbose output examples” (page 164) for an example of verbose output from the sel list
command.
Events 21
Page 22
Inventory
IPMI supports multiple sets of non-volatile FRU information for different parts in the system. This
provides access to data such as serial number, part number, asset tag, and other information for
major modules in the system including the baseboard, chassis, processors, memory, power supplies,
and even the management controller itself. This information is even available when the system is
powered down or non-operational, facilitating the creation of automated remote inventory and
service applications. IPMItool can read and display full FRU information for the system as well as
detailed descriptions of power supplies and full DIMM SPD data.
Example 7 Output from the fru print command
FRU Device Description : ChasMgmtCtlr1
Chassis Type : Rack Mount Chassis
Chassis Part Number : 700349-B21
Chassis Serial : 600012J0SD
Chassis Extra : d09701640003000000
Chassis Extra : d1110102000000
Board Mfg Date : Fri Dec 7 19:54:00 2012
Board Mfg : HP
Board Product : HP Moonshot 1500 Chassis Management Module
Board Serial : 1G24900006J0SE
Board Part Number : 712678-001
Board Extra : d25835
Board Extra : 700369-001
Product Manufacturer : HP
Product Name : HP Moonshot 1500 Chassis
Product Part Number : 700451-001
Chassis management
This feature provides standardized chassis status and control functions that allow a remote system
to be turned on/off or rebooted without manual intervention. It also provides commands for causing
the chassis to physically identify itself with an implementation dependant mechanism such as turning
on visible lights, displaying messages on an LCD, emitting beeps through a speaker, etc. IPMItool
fully supports the available chassis management commands and can eliminate trips to the data
center or server room to reset a frozen machine or help identify the single system in a rack that
must be removed.
Example 8 Sample chassis power commands
root@JSMITH-LX:/# ipmitool -I lanplus -H ILOH101GEMINI -U Administrator -P password sdr list all
(output)
root@JSMITH-LX:/# ipmitool -I lanplus -H ILOH101GEMINI -U Administrator -P password -t 0xa4 power status
Chassis Power is on
In all of the above examples only a portion of the available output is shown, the full output is much
richer and tells a full story about the system health and status; in addition verbose output options
are available which increase the output information. See “Verbose output examples” (page 164)
for examples of verbose output.
Synopsis
ipmitool [-chvV] [-Iopen <command>]
ipmitool [-chvV] -Ilan -H<hostname>
[-p<port>]
[-U<username>]
[-A<authtype>]
[-L<privlvl>]
[-aEPf<password>]
[-o<oemtype>]
22 IPMItool
Page 23

<command>
ipmitool [-chvV] -Ilanplus -H<hostname>
[-p<port>]
[-U<username>]
[-L<privlvl>]
[-aEPf<password>]
[-o<oemtype>]
[-C<ciphersuite>]
<command>
Description
This program allows management of IPMI functions of either the local system via a kernal device
driver or a remote system using IPMI v1.5 and IPMI v2.0. These functions include printing FRU
information, LAN configuration, sensor readings and remove chassis power control.
IPMI management of a local system interface requires a compatible IPMI kernel driver to be installed
and configured. On Linux this driver is called OpenIPMI and it is included in standard distributions.
Options
Prompt for the remote server password.—a
—A <authtype>
—C<ciphersuite>
—E
—f<password_file>
—H <address>
— I <interface>
—o<oemtype>
Specify the authentication type to use during IPMI v1.5 LAN session
activation. Supported types are NONE, PASSWORD, MD5 or OEM.
Present output in CSV format. Not available with all commands.—c
The remote server authentication, integrity, and encryption algoritms to
use for IPMI v2 lanplus connections. Default = 3 and specifies
RAKP-HMAC-SHA1 authentication, HMAC-SHA1–96 integrity, and
AES-CBC-128 encryption algorithms.
The remote server password is specified by the environment variable
ipmi_password.
Specifies a file containing the remote server password. If this option is
absent or if the <password_file> is empty the password defaults to
NULL.
Get basic usage help from the command line.—h
Remote server address can be IP address or hostname. This option
is required for LAN and LANPLUS interfaces.
Selects the IPMI interface. Supported interfaces display in the usage help
output.
Force session privilege level, defaults to admin.—L<privlvl>
Set the local IPMB address. Default = 0x20.—m<local address>
Select OEM type. Use —o list to see a list of currently supported OEM
types.
-P<password>
Remote server UDP port. Default = 623.-p<port>
Remote server password specified on the command line. It is not
recommended to specify a password on the command line.
NOTE: If no password method is specified, the IPMI tool prompts the
user for a password, if no password is entered, the remote server password
is set to NULL.
Bridge IPMI requests to the remote target address.—t<target address>
Remote server username. Default = NULL—U<username>
Synopsis 23
Page 24

—v
Increase verbose output level. May be specified multiple times to increase
levels of debug output, for example, specifying three times results in
hexdumps of all incoming and outgoing packets.
Display version information.—V
IPMItool Raw command syntax and example
1. Syntax — Target command towards specific virtual controller
• —b <ipmi channelnumber>
• —t <target slave address>
• -m <source slave address>
• Chassis controller —b 0 —t 0x44 —m 0x20
• Power supply A controller -b 0 -t 0x52 -m 0x20
• Power supply B controller -b 0 -t 0x54 -m 0x20
• Power supply C controller -b 0 -t 0x56 -m 0x20
• Power supply D controller -b 0 -t 0x58 -m 0x20
2. Examples:
• Raw Get Device ID to chassis satellite controller over LAN:
ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L
Administrator -b 0 -t 0x44 -m 0x20 raw 6 1
• Power on to C2N1 over LAN:
ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L
Administrator -B 0 –T 0x84 –b 7 –t 0x72 -m 0x20 chassis power on
• SOL to C2N1 over LAN
ipmitool -I lanplus -H 16.85.178.125 -U admin -P admin123 -L
Administrator -B 0 –T 0x84 –b 7 –t 0x72 -m 0x20 sol activate
24 IPMItool
Page 25
5 Command specification
IPMI provides standardized interfaces and commands for configuring the platform managemenet
subsystem. This enables cross-platform software to SDRs are an example of the interface for
configuring sensor population and behavior on a system. There are also commands for configuring
capabilities such as LAN and serial/modem remote protocols, user passwords and privilege levels,
platform event filtering, alert destinations, and others.
This section provides specifications for elements that apply to all requests and responses.
See “Completion codes” (page 142).
Unless otherwise noted, reserved bits and fields in commands (request messages) and responses
are written as 0. Applications must ignore the state of reserved bits when they are read.
Unless otherwise specified, commands that are listed as mandatory must be accessed via LUN
00b. An implementation may elect to make any command available on any LUN or channel as
long as it does not conflict with other requirements in this specification.
Command table notation
The following section includes command tables that list the data that is included in a request or a
response for each command. The completion code for a response is included as the first byte of
the response data field for each command. The NetFn and command byte values for each command
are specified in separate tables.
The following notation is used in the command tables.
Request data
Response data
4
5:7
(3)
DescriptionNotation
Identifies the portion of the table that lists the fields that are included in the data portion of a request
message for the given command.
Identifies the portion of the table that lists the fields that are included in the data portion of a response
message for the given command. The completion code is always listed as the first byte in the
response data field.
Single byte field. A single value in the byte column of a command table is used to identify a single
byte field. The value represents the offset to the field within the data portion of the message. In some
cases a single byte field follows a variable length field in which case the single byte offset is
represented with an alphabetic variable and number representing the single byte field’s location
relative to the end of the variable length field. For example: N+1.
Multi-byte field. The byte column indicates the byte offset(s) for a given field. For a multi-byte field,
the first value indicates the starting offset, the second value (following the colon) indicates the offset
for the last byte in the field. For example, 5:7 indicates a three-byte field spanning byte offsets 5,
6, and 7.
In some cases, multi-byte fields may be variable length, in which case an alphabetic variable is
used to represent the ending offset, for example: 5:N. Similarly, a field may follow a variable length
field. In this case the starting value is shown as an offset relative to the notation used for the previous
field, for example, if the previous field were 5:N, the next field would be shown starting at N+1.
A variable length field may follow a variable length field, in which case a relative starting offset is
shown with an alphabetic value indicating a relative ending offset, for example, N+1:M.
Optional Fields. When used in the byte column of the command tables, parentheses are used to
indicate optional data byte fields. These can be absent or present at the choice of the party
generating the request or response message. Devices receiving the message are required to accept
any legal combination of optional data byte fields.
Unless otherwise indicated, if an optional byte field is present, all prior specified byte fields must
also be present. Similarly, if an optional byte field is absent all following byte fields must also be
absent. For example, suppose a request accepts 4 data bytes. If data byte 3 was shown in
parentheses as (3), it would indicate that byte 3 and following were optional. A legal request could
consist of just bytes [1 and 2], bytes [1, 2, and 3,] or bytes [1, 2, 3 and 4]. A request which
eliminates byte 3, but includes byte 4. (a request with data bytes [1, 2, and 4]), is illegal.
25
Page 26
DescriptionNotation
Multi-byte fields that are shown as optional cannot be split. Either all bytes for the field are present
or absent. For example, if a four byte multi-byte field is listed as optional, it is illegal to include the
first two bytes, but not the second two bytes.
Table 6 (page 26) lists the available Moonshot IPMI commands and, where available, the equivalent
iLO Chassis Management CLI command. The IPMI commands and capabilities available for
Moonshot are not completely analogous to the commands available at the iLO Chassis Management
CLI, and so not every IPMI command has a CLI equivalent. Additionally, where there are analogous
commands, the responses offered by the two commands may not be equivalent.
Table 6 Moonshot IPMI commands and their iLO CM CLI equivalents
IPMI Device Global Commands
1
MC Watchdog Timer Commands
IPMI Messaging Support Commands
NetFnMoonshot IPMI Command
Code
0x01App (0x06)Get Device ID
0x01App (0x06)Broadcast ‘Get Device ID’
0x04App (0x06)Get Self Test Results
Moonshot iLO CM CLI command equivalentCommand
Show chassis info provides a partially
equivalent response.
Show chassis info provides a partially
equivalent response.
Reset CM0x02App (0x06)Cold Reset
Reset CM0x03App (0x06)Warm Reset
Show log IML provides a partially
equivalent response (specifically, failures
that were written to the iML)
show node power CxNy0x07App (0x06)Get ACPI Power State
IPMI specific0x22App (0x06)Reset Watchdog Timer
IPMI specific0x24App (0x06)Set Watchdog Timer
IPMI specific0x25App (0x06)Get Watchdog Timer
Capabilities
26 Command specification
IPMI specific0x2EApp (0x06)Set BMC Global Enables
IPMI specific0x2FApp (0x06)Get BMC Global Enables
IPMI specific0x30App (0x06)Clear Message Flags
IPMI specific0x31App (0x06)Get Message Flags
IPMI specific0x32App (0x06)Enable Message Channel Receive
IPMI specific0x33App (0x06)Get Message
IPMI specific0x34App (0x06)Send Message
0x37App (0x06)Get System GUID
0x59App (0x06)Get System Info Parameters
The physical node UUID is not shown in the
CLI.
Not supported in CLI.0x58App (0x06)Set System Info Parameters
Show node info returns the MAC
address; other parameters returned by the
IPMI command are IPMI specific.
IPMI specific0x38App (0x06)Get Channel Authentication
Page 27
Table 6 Moonshot IPMI commands and their iLO CM CLI equivalents (continued)
NetFnMoonshot IPMI Command
Code
Moonshot iLO CM CLI command equivalentCommand
IPMI specific0x3BApp (0x06)Set Session Privilege Level
IPMI specific0x3CApp (0x06)Close Session
IPMI specific0x3DApp (0x06)Get Session Info
IPMI specific0x3FApp (0x06)Get AuthCode
IPMI specific0x40App (0x06)Set Channel Access
IPMI specific0x41App (0x06)Get Channel Access
IPMI specific0x42App (0x06)Get Channel Info
Set user privilege0x43App (0x06)Set User Access
show user0x44App (0x06)Get User Access
add user0x45App (0x06)Set User Name
show user0x46App (0x06)Get User Name
set user password0x47App (0x06)Set User Password
IPMI specific0x48App (0x06)Activate Payload
IPMI specific0x49App (0x06)Deactivate Payload
Chassis Device Commands
IPMI specific0x4AApp (0x06)Get Payload Activation Status
IPMI specific0x4BApp (0x06)Get Payload Instance Info
IPMI specific0x4CApp (0x06)Set User Payload Access
IPMI specific0x4DApp (0x06)Get User Payload Access
IPMI specific0x4EApp (0x06)Get Channel Payload Support
IPMI specific0x4FApp (0x06)Get Channel Payload Version
No CLI equivalent0x52App (0x06)Master Write-Read
IPMI specific0x54App (0x06)Get Channel Cipher Suites
IPMI specific0x55App (0x06)Suspend/Resume Payload Encryption
IPMI specific0x56App (0x06)Set Channel Security Keys
IPMI specific0x57App (0x06)Get System Interface Capabilities
IPMI specific0x00Chassis (0x00)Get Chassis Capabilities
0x01Chassis (0x00)Get Chassis Status
show chassis status or show node
status
set node power0x02Chassis (0x00)Chassis Control
0x04Chassis (0x00)Chassis Identify
set chassis uid or set cartridge
uid
set chassis autopower0x06Chassis (0x00)Set Power Restore Policy
set node boot or set node bootonce0x08Chassis (0x00)Set System Boot Options
show node boot0x09Chassis (0x00)Get System Boot Options
No CLI equivalent0x0FChassis (0x00)Get POH Counter
27
Page 28
Table 6 Moonshot IPMI commands and their iLO CM CLI equivalents (continued)
Event Commands
Sensor Device Commands
NetFnMoonshot IPMI Command
Code
0x21S/E (0x04)Get Device SDR show chassis status
0x27S/E (0x04)Get Sensor Thresholds
0x2DS/E (0x04)Get Sensor Reading show chassis status
Moonshot iLO CM CLI command equivalentCommand
IPMI specific0x00S/E (0x04)Set Event Receiver
IPMI specific0x01S/E (0x04)Get Event Receiver
No CLI equivalent0x02S/E (0x04)Platform Event (Event Message)
IPMI specific0x20S/E (0x04)Get Device SDR Info
show chassis powersupply
show chassis temperature
show cartridge temperature
IPMI specific0x22S/E (0x04)Reserve Device SDR Repository
show chassis temperature and show
cartridge temperature
show chassis powersupply
show chassis temperature
show cartridge temperature
FRU Device Commands
SDR Device Commands
SEL Device Commands
IPMI specific0x10Storage (0x0A)Get FRU Inventory Area Info
show fru0x11Storage (0x0A)Read FRU Data
No CLI equivalent0x12Storage (0x0A)Write FRU Data
IPMI specific0x20Storage (0x0A)Get SDR Repository Info
IPMI specific0x21Storage (0x0A)Get SDR Repository Allocation Info
IPMI specific0x22Storage (0x0A)Reserve SDR Repository
0x23Storage (0x0A)Get SDR show chassis status
show chassis powersupply
show chassis temperature
show cartridge temperature
IPMI specific0x24Storage (0x0A)Add SDR
IPMI specific0x26Storage (0x0A)Delete SDR
IPMI specific0x27Storage (0x0A)Clear SDR Repository
IPMI specific0x2CStorage (0x0A)Run Initialization Agent
28 Command specification
IPMI specific0x40Storage (0x0A)Get SEL Info
IPMI specific0x42Storage (0x0A)Reserve SEL
show log IML0x43Storage (0x0A)Get SEL Entry
No CLI equivalent0x44Storage (0x0A)Add SEL Entry
clear log0x47Storage (0x0A)Clear SEL
Page 29

Table 6 Moonshot IPMI commands and their iLO CM CLI equivalents (continued)
LAN Device Commands
Serial/Modem Device Commands
DCMI Specific commands
NetFnMoonshot IPMI Command
Code
0x07DCGRP (0xDC)Get DCMI Sensor Info
Moonshot iLO CM CLI command equivalentCommand
show time0x48Storage (0x0A)Get SEL Time
set time0x49Storage (0x0A)Set SEL Time
set network0x01Transport (0x0C)Set LAN Configuration Parameters
show network0x02Transport (0x0C)Get LAN Configuration Parameters
IPMI specific0x21Transport (0x0C)Set SOL Configuration Parameters
IPMI specific0x22Transport (0x0C)Get SOL Configuration Parameters
IPMI specific0x01DCGRP (0xDC)Get DCMI Capability Info
show chassis asset0x06DCGRP (0xDC)Get Asset Tag
show chassis temperature and show
cartridge temperature
set chassis asset0x08DCGRP (0xDC)Set Asset Tag
IPMI specific0x09DCGRP (0xDC)Get Controller Id String
PICMG Specific commands
1
Only relevant to satellite controllers.
NOTE: The IPMI commands and capabilities available for Moonshot are not completely analogous
to those available to the iLO Chassis Management CLI, and so not every IPMI command has a CLI
equivalent.
Standard command specification
This section presents the commands that are common to all IPMI devices that follow this
specification’s message/command interface. This includes management controllers that connect
to the system via a compatible message interface, as well as IPMB devices.
Global commands
IPMI management controllers shall recognize and respond to these commands via LUN 0.
Get device ID command
IPMI specific0x0ADCGRP (0xDC)Set Controller Id String
IPMI specific0x00PICMG (0x00)Get PICMG Properties
IPMI specific0x01PICMG (0x00)Get Address Info
IPMI specific0x1FPICMG (0x00)Fru Inventory Device Lock Control
This command is available to MC, ChMC, and PSMC.
This command is used to retrieve the intelligent device’s hardware revision, firmware/software
revision, and sensor and event interface command specification revision information. The command
also returns information regarding the additional logical device functionality (beyond application
and IPM device functionality) that is provided within the intelligent device, if any.
Standard command specification 29
Page 30
While broad dependence on OEM-specific functionality is discouraged, two fields in the response
allow software to identify controllers for the purpose of recognizing controller specific functionality.
These are the device ID and the product ID fields. A controller that just implements standard IPMI
commands can set these fields to unspecified.
Table 7 Device ID command response data
Data fieldResponse data
byte number
Completion code1
Device ID. 00h = unspecified2
Device revision3
• [7] — 1=device provides device SDRs and 0=device does not provide device SDRs.
• [6:4) — Reserved. Return as 0.
• [3:0] — Device revision, binary encoded.
Firmware revision 14
• [7] — Device available: 0=normal operation, device firmware, SDR repository update or
self-initialization in progress. Firmware or SDR repository updates can be differentiated by issuing
a get SDR command and checking the completion code.
• [6:0] — Major firmware revision, binary encoded.
Firmware revision 2: minor firmware revision. BCD encoded.5
6
7
8:10
IPMI version. Holds IPMI command specification version. BCD encoded. 00h = reserved. Bits 7:4
hold the least significant digit of the revision, while bits 3:0 hold the most significant bits. For example,
a value of 51h indicates revision 1.5 functionality. 02h for implementations that provide IPMI v2.0
capabilities per this specification.
Additional device support (formerly called IPM device support) lists the IPMI logical device commands
and functions supported by the controller that are in addition to the mandatory IPM and application
commands.
• [7] — Chassis device
• [6] — Bridge (device responds to bridge NetFn commands)
• [5] — IPMB event generator. Device generates event messages (platform event request messages)
from the IPMB.
• [4] — IPMB event receiver. Device accepts event messages (platform event request messages) from
the IPMB.
• [3] — FRU inventory device
• [2] — SEL device
• [1] — SDR repository device
• [0] — Sensor device
manufacturer ID, LS byte first. The manufacturer ID is a 20-bit value that is derived from the IANA
private enterprise ID (see below). Most significant four bits = reserved (0000b).
000000h = unspecified. 0FFFFFh = reserved. This value is binary encoded. For example, the ID for
the IPMI forum is 7154 decimal, which is 1BF2h, and would be stored in this record as F2h, 1Bh,
00h for bytes 8 through 10, respectively.
11:12
(13:16)
30 Command specification
Product ID, LS byte first. This field can be used to provide a number that identifies a particular system,
module, add-in card, or board set. The number is specified according to the manufacturer given by
manufacturer ID (see below).
0000h = unspecified. FFFFh = reserved.
Auxiliary firmware revision information. This field is optional. If present, it holds additional information
about the firmware revision, such as boot block or internal data structure version numbers. The meanings
of the numbers are specific to the vendor identified by manufacturer ID (see below). When the
Page 31

Table 7 Device ID command response data (continued)
Data fieldResponse data
byte number
vendor-specific definition is not known, generic utilities should display each byte as 2-digit hexadecimal
numbers, with byte 13 displayed first as the most significant byte.
Additional specifications and descriptions for the device ID response fields:
Table 8 Additional device ID specifications
DescriptionDevice ID Specification
Device ID/Device instance
Device revision
Firmware revision 1
Specified by the manufacturer identified by the manufacturer ID field it allows
controller-specific software to identify the unique application command, OEM
fields, and functionality that are provided by the controller.
Controllers that have different application commands, or different definitions
of OEM fields, are expected to have different device ID values. Controllers
that implement identical sets of applications commands can have the same
device ID in a given system. Thus, a standardized controller could be produced
where multiple instances of the controller are used in a system, and all have
the same device ID value. (The controllers would still be differentiable by their
address, location, and associated information for the controllers in the SDRs.)
The device ID is typically used in combination with the product ID field such
that the device IDs for different controllers are unique under a given product
ID. A controller can optionally use the device ID as an instance identifier if
more than one controller of that kind is used in the system.
Binary encoded.
The least significant nibble is used to identify when significant hardware
changes have been made to the implementation of the management controller
that cannot be covered with a single firmware release. This field is used to
identify two builds off the same code firmware base, but for different board
fab levels. For example, device revision "1" might be required for fab X and
earlier boards, while device revision "2" would be for fab Y and later boards.
Binary encoded and unsigned.
Major revision of the firmware. 7-bits. It is incremented on major changes or
extensions of the functionality of the firmware, such as additions, deletions,
or modifications of the command set.
The device available bit is used to indicate whether normal command set
operation is available from the device, or if it is operating in a state where
only a subset of the normal commands are available. Typically because the
device is in a firmware update state. It may also indicate that full command
functionality is not available because the device is in its initialization phase
or an SDR update is in progress.
The revision information obtained when the device available bit is 1 is
indicative of the code version that is in effect. The version information may
vary with the device available bit state.
Binary encoded and unsigned.
Firmware revision 2
IPMI version
Minor revision of the firmware, incremented for minor changes such as bug
fixes.
BCD encoded.
The version of the IPMI specification in which the controller is compatible,
indicating conformance with this document including event message formats
and mandatory command support.
The value is 02h for implementations that provide IPMI v2.0 capabilities per
this specification.
BCD encoded with bits 7:4 holding the least significant digit of the revision
and bits 3:0 holding the most significant bits.
Standard command specification 31
Page 32

Table 8 Additional device ID specifications (continued)
DescriptionDevice ID Specification
Additional device support
Manufacturer ID
Indicates the logical device support that the device provides in addition to the
IPM and application logical devices.
Uses IANA (http://www.iana.org/). SMI network management private
enterprise codes (enterprise numbers) for identifying the manufacturer
responsible for the specification of functionality of the vendor (OEM) -specific
commands, codes, and interfaces used in the controller.
For example, an event in the SEL could have OEM values in the event record.
An application that parses the SEL could extract the controller address from
the event record contents and use it to send the get device ID command
and retrieve the manufacturer ID. A manufacturer-specific application could
then do further interpretation based on prior knowledge of the OEM field,
while a generic cross-platform application would typically just use the ID to
present the manufacturer’s name alongside uninterpreted OEM event values.
The manufacturer ID is for the manufacturer that defines the functionality of
the controller, which is not necessarily the manufacturer that created the
physical microcontroller. For example, vendor A may create the controller,
but it gets loaded with vendor B’s firmware. The manufacturer ID would be
for vendor B, since they defined the controller’s functionality.
The manufacturer ID value from the get device ID command does not
override manufacturer or OEM ID fields that are explicitly defined as part of
a command or record format.
If no vendor-specific functionality is defined, it is recommended that the field
be loaded with the manufacturer ID for the manufacturer that is responsible
for the controller's firmware, or the value FFFFh to indicate unspecified.
Binary encoded and unsigned.
Product ID
Auxiliary firmware revision information
Cold reset command
This command is available to the MC. This command is not required to return a response in all
implementations.
This command directs the responder's device to reinitialize its event, communication, and sensor
functions. This causes the default setting of interrupt enables, event message generation, sensor
scanning, threshold values, and other power up default state to be restored. If the device
incorporates a self test, the self test also runs at this time.
Table 9 Cold reset command response data
number
Used in combination with the manufacturer ID and device ID values to identify
the product-specific element of the controller-specific functionality. This number
is specified by the manufacturer identified by the manufacturer ID field.
Typically, a controller-specific application would use the product ID to identify
the type of board, module, or system that the controller is used in, instead of
using the data from the FRU information associated with the controller.
This field is optional. If present, it holds additional information about the
firmware revision, such as boot block or internal data structure version numbers.
The meanings of the numbers are specific to the vendor identified by
manufacturer ID. When the vendor-specific definition is not known, generic
utilities should display each byte as 2-digit hexadecimal numbers, with byte
13 displayed first as the most significant byte.
Data fieldResponse data byte
32 Command specification
Completion code1
Page 33

NOTE: The cold reset command is provided for platform development, test, and
platform-specific initialization and recovery actions. The system actions of the cold reset
command are platform specific. Issuing a cold reset command could have adverse effects on
system operation, particularly if issued during run-time. Therefore, the cold reset command
should not be used unless all the side-effects for the given platform are known.
It is recognized that there are conditions where a given controller may not be able to return a
response to a cold reset request message. Therefore, though recommended, the implementation
is not required to return a response to the cold reset command. Applications should not rely
on receiving a response as verification of the completion of a cold reset command.
Warm reset command
This command is available to the MC.
This command directs the responder's device to reset communications interfaces, but current
configurations of interrupt enables, thresholds, and so on are left alone. A warm reset does not
initiate the self test. The intent of the warm reset command is to provide a mechanism for cleaning
up the internal state of the device and its communication interfaces. A warm reset resets
communication state information such as sequence number and retry tracking, but does not reset
interface configuration information such as addresses, enables, and so on. An application may
try a warm reset if it determines a non-responsive communication interface, but it must also be
capable of handling the side effects.
Table 10 Warm reset command response data
Data fieldResponse data byte
number
Completion code1
Get self test results command
This command is available to MC, ChMC, and PSMC.
This command directs the device to return its self test results, if any. A device implementing a self
test normally runs that test on device power up as well as after cold reset commands. A device
is allowed to update this field during operation if it has tests that run while the device is operating.
Devices that do not implement a self test always return a 56h for this command.
While the self test only runs at particular times, the get self test results command can
be issued any time the device is in a ready for commands state.
Standard command specification 33
Page 34

Table 11 Get self test results command response data
Data fieldResponse data byte
number
Completion code.1
2
• 55h — No error. All self tests passed.
• 56h — Self test function not implemented in this controller.
• 57h — Corrupted or inaccessible data or devices.
• 58h — Fatal hardware error (system should consider MC inoperative). This indicates that
the controller hardware (including associated devices such as sensor hardware or RAM)
may need to be repaired or replaced.
• FFh — Reserved.
• All other — Device-specific internal failure. Refer to the particular device specification for
definition.
For byte 2 =:3
• 55h, 56h, FFh: 00h
• 58h, all other: Device-specific.
• 57h: self-test error bitfield. A return of 57h does not imply that all tests were run, just that
a given test has failed. For example, 1b means failed, 0b means unknown.
• [7] — 1b = Cannot access SEL device.
• [6] — 1b = Cannot access SDR repository.
• [5] — 1b = Cannot access MC FRU device.
• [4] — 1b = IPMB signal lines do not respond.
• [3] — 1b = SDR repository empty.
• [2] — 1b = Internal use area of MC FRU corrupted.
• [1] — 1b = Controller update boot block firmware corrupted.
• [0] — 1b = Controller operational firmware corrupted.
Get ACPI power state command
This command is available to the MC.
The command is used to retrieve the present power state information that has been set into the
controller. This is an independent setting from the system power state that may not necessarily
match the actual power state of the system. Unspecified bits and codes are reserved and returned
as 0.
Table 12 Get ACPI power state command response data
Data fieldResponse data
byte number
Completion code1
ACPI system power state2
[7] — Reserved
[6:0] — System power state enumeration
WorkingS0 / G000h
S101h
S202h
Hardware context maintained, typically equates to
processor/chip set clocks stopped
Typically equates to stopped clocks with processor/cache
context lost
34 Command specification
Page 35

Table 12 Get ACPI power state command response data (continued)
Data fieldResponse data
byte number
Typically equates to suspend-to-RAMS303h
Typically equates to suspend-to-diskS404h
Soft offS5 / G205h
Soft off, cannot differentiate between S4 and S5S4/S506h
Mechanical offG307h
Sleeping - cannot differentiate between S1-S3sleeping08h
Sleeping - cannot differentiate between S1-S4G1 sleeping09h
S5 entered by overrideOverride0Ah
ACPI device power state3
[7] — Reserved
[6:0] — Device power state enumeration
Broadcast get device ID command
This command is available to MC, ChMC, and PSMC. It is only relevant to satellite controllers.
This command is the broadcast version of the get device ID command which provides for the
discovery of intelligent devices on the IPMB only. Request is formatted as an entire IPMB application
request message, from the RsSA field through the second checksum, with the message prefixed
with the broadcast slave address, 00h. Response format is same as the regular get device ID
response.
The broadcast get device ID command is not bridged but can be delivered to the IPMB
using master write-read commands.
Legacy on20h
Unknown2Ah
D000h
D101h
D202h
D303h
Unknown02h
Legacy on (indicates on for system that does not support ACPI
or has ACPI capabilities disabled)
Legacy soft-offLegacy off21h
Power state has not been initialized, or device lost track of
power state
Power state has not been initialized, or device lost track of
power state
To perform a discovery, the command is repeatedly broadcast with a different rsSA slave address
parameter field specified in the command. The device that has the matching physical slave address
information shall respond with the same data it would return from a regular (non-broadcast) get
device ID command. Since an IPMB response message carries the responder’s slave address,
the response to the broadcast provides a positive confirmation that an intelligent device exists at
the slave address given by the rsSA field in the request.
An application driving discovery then cycles through the possible range of IPMB device slave
addresses to find the population of intelligent devices on the IPMB.
Standard command specification 35
Page 36

See “Get device ID command” (page 29) for information on the fields returned by the broadcast
get device ID command response. The IPMB message format for the broadcast get device
ID ID request exactly matches that for the get device ID command, with the exception that
the IPMB message is prefixed with the 00h broadcast address. The following illustrates the format
of the IPMB broadcast get device ID request message:
Figure 2 Broadcast get device ID request message
Addresses 00h-0Fh and F0h-FFh are reserved for I2C functions and not used for IPM devices on
the IPMB. These addresses can therefore be skipped if using the broadcast get device ID
command to scan for IPM devices. The remaining fields follow the regular IPMB definitions.
In order to speed the discovery process on the IPMB, a controller should drop off the bus as soon
as it sees that the rsSA in the command does not match its rsSA.
IPMI messaging support commands
This section defines the commands used to support the system messaging interfaces. This includes
control bits for using the MC as an event receiver and SEL device. SMM messaging and event
message buffer support is optional. Use of IPMI support for SMI and SMM messaging is deprecated.
Configuration interface support for enabling or disabling SMM messaging and corresponding SMI
has been removed from the specification. If SMM messaging were implemented using the IPMI
infrastructure, it would now be done as an OEM-proprietary capability.
System software that is not explicitly aware of the particular platform’s use of SMI messaging must
assume that the any SMI options have been pre-configured by the controller, system BIOS, or other
software. Therefore, runtime system software should not reconfigure SMI options, nor should it
access the event message buffer if it finds that event message buffer interrupt is mapped to SMI.
The effects of SMS accessing the event message buffer when it is configured for SMI are unspecified.
Set BMC global enables command
This command is available to the MC.
This command is used to enable message reception into message buffers, and any interrupt
associated with that buffer getting full. The OEM0, OEM 1, and OEM 2 flags are available for
definition by the OEM/system integrator. Generic system management software must not alter
these bits.
Table 13 Set BMC global enables command request and response data
Data fieldRequest data
byte number
1
This field is set to xxxx_100xb on power-up and system resets. If the implementation allows the receive
message queue interrupt to be enabled/disabled, the default for bit 0 should be 0b.
OEM 2 Enable[7]
OEM 1 Enable[6]
OEM 0 Enable[5]
Reserved[4]
1b =[3]
Generic system management software must do a ‘read-modifywrite’
using the get BMC global enables and set BMC global
enables commands to avoid altering this bit.
Enable system event logging (enables/disables logging of events to
the SEL - with the exception of events received over the system
interface. Event reception and logging via the system interface is
always enabled.) SEL logging is enabled by default whenever the
MC is first powered up. It is recommended that this default state also
be restored on system resets and power on.
36 Command specification
Page 37

Table 13 Set BMC global enables command request and response data (continued)
1b =[2]
1b =[0]
NOTE: If the event message buffer full or receive message queue interrupt are not supported, an
implementation can elect to return a CCh error completion code for the set BMC global enables
command if an attempt is made to enable the interrupt (this is the recommended implementation).
Alternatively, the implementation can accept the command, but must return 0b for the corresponding
bit in the get BMC global enables.
Data fieldResponse data
byte number
Completion code1
Get BMC global enables command
This command is available to the MC.
This command is used to retrieve the present setting of the global enables. The OEM0, OEM 1,
and OEM 2 flags are available for definition by the OEM/system integrator. Generic system
management software must ignore these bits.
Enable event message buffer. Error completion code returned if written
as 1 and the event message buffer not supported.
Enable event message buffer full interrupt.1b =[1]
Enable receive message queue interrupt (this bit also controls whether
KCS communication interrupts are enabled or disabled. An
implementation is allowed to have this interrupt always enabled.)
Table 14 Get BMC global enables command response data
Data fieldResponse data
byte number
Completion code1
If the receive message queue or event message full interrupts are not implemented the corresponding
interrupt enabled status bit must return as 0b.
Clear message flags command
This command is available to the MC.
This command is used to flush unread data from the receive message queue or event message
buffer. This will also clear the associated buffer full/message available flags. See “Get message
flags command ” (page 38).
OEM 2 enabled1b =[7]2
OEM 1 enabled1b =[6]
OEM 0 enabled1b =[5]
Reserved[4]
System event logging enabled1b =[3]
Event message buffer enabled1b =[2]
Event message buffer full interrupt enabled1b =[1]
1b =[0]
Receive message queue interrupt enabled (this bit also indicates whether
KCS communication interrupt is enabled or disabled.)
Standard command specification 37
Page 38

Table 15 Clear message flags command request and response data
Data fieldRequest data
byte number
Clear OEM 21b =[7]1
Clear OEM 11b =[6]
Clear OEM 01b =[5]
Reserved[4]
Clear watchdog pre-timeout interrupt flag1b =[3]
Reserved[2]
Clear event message buffer1b =[1]
Clear receive message queue1b =[0]
If the receive message queue or event message full interrupts are not implemented the corresponding
interrupt enabled status bit must return as 0b.
Data fieldResponse data
byte number
1
Completion code. Implementations are not required to return an error completion code if an attempt
is made to clear the event message buffer flag but the event message buffer is not supported.
Get message flags command
This command is available to the MC.
This command is used to retrieve the present message available states. The OEM0, OEM 1, and
OEM 2 flags are available for definition by the OEM/system integrator. Generic system
management software must ignore these bits.
Table 16 Get message flags command response data
Data fieldRequest data
byte number
Completion code1
Flags2
OEM 2 data available.1b =[7]
OEM 1 data available.1b =[6]
OEM 0 data available.1b =[5]
Reserved.[4]
Watchdog pre-timeout interrupt occurred.1b =[3]
Reserved.[2]
1b =[1]
1b =[0]
Event message buffer full. Return as 0 if event message buffer is not supported,
or when the event message buffer is disabled.
Receive message available. One or more messages ready for reading from
receive message queue.
Enable message channel receive command
This command is available to the MC.
This command is used to enable and disable message reception into the receive message queue
from a given message channel. The command provides a mechanism to allow SMS to only receive
38 Command specification
Page 39

messages from channels that it intends to process, and provides a disable mechanism in case the
receive message queue is being erroneously or maliciously flooded with requests on a particular
channel. It does not affect the ability for SMS to transmit on that channel. Only the SMS message
channel is enabled by default. All other channels must be explicitly enabled by BIOS or system
software, as appropriate. It is recommended that a destination unavailable completion code be
returned if a request message to SMS is rejected because reception has been disabled.
Table 17 Enable message channel receive command request and response data
Data fieldRequest data
byte number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
Channel state2
• [7:2] — Reserved
• [1:0]
◦ 00b = Disable channel
◦ 01b = Enable channel
◦ 10b = Gen channel enable/disable state
Data fieldResponse data
byte number
Completion code1
Channel number2
• [7:4] — Reserved
• [3:0] — Channel number
Channel state3
• [7:1] — Reserved
• [0]
Get message command
This command is available to the MC.
This command is used to get data from the receive message queue.
Software is responsible for reading all messages from the message queue even if the message is
not the expected response to an earlier send message. System management software is responsible
for matching responses up with requests.
The get message command includes an inferred privilege level that is returned with the message.
This can help avoid the need for software to implement a separate privilege level and authentication
mechanism. For example: A user activates a session with a maximum privilege level of Administrator
on a multi-session channel, and an MD5 authentication type was negotiated. That user-level
authentication is disabled. A user that has user or higher privilege can place messages into the
receive message queue by sending them to LUN 10b, or by using the send message command.
If the packet has authentication type = MD5, the packet is assigned an inferred privilege level
◦ 11b = Reserved
◦ 1b = Channel enabled
◦ 0b = Channel disabled
Standard command specification 39
Page 40

based the on the present operating privilege level for the user (set using the set session
privilege level command). If, before sending the packet, the user had set their privilege level
to Operator, the packet would be assigned an inferred privilege level of Operator. This means an
authenticated (signed) packet can be assigned different inferred privilege levels based on the
present operating privilege set by the set session privilege level command.) If the
message is received in a packet that has authentication type = none, the packet is assigned an
inferred privilege level of User, since that is the lowest privilege level for which that type of
authentication is accepted.
Now suppose that the remote user had used the receive message queue as a way to send a
message to system management software that requests a soft shutdown of the operating system.
The message would either have an inferred privilege level of Operator or User depending on
whether it was sent as an authenticated message or not. SMS can then use that inferred privilege
level as part of deciding whether to accept and process the message or not. For single-session
channels, the inferred privilege level is always set to the present operating privilege level. For
session-less channels, the inferred privilege level is set to none, indicating that there was no
IPMI-specified authentication operating on the channel from which the message was received.
Table 18 Get message command response data
Data fieldResponse data
byte number
Completion code.1
Generic, plus the command specific completion code: 80h = data not available (queue / buffer
empty). Implementation of this completion code is mandatory. The code eliminates the need for system
software to always check the message buffer flags to see if there is data left in the receive message
queue. If a non-OK, non-80h completion is encountered - software must check the message flags to
get the empty/non-empty status of the receive message queue.
Channel number2
• [7:4] Inferred privilege level for message.
When the MC receives a message for the receive message queue, it assigns an inferred privilege
level to the message as follows:
If the message is received from a session-based channel, it is initially assigned a privilege level
that matches the maximum requested privilege level that was negotiated via the activate
session command.
If per-message authentication is enabled, but user-level authentication is disabled, the MC assigns
a level of User to any messages that are received with an authentication type = none. (Per-message
and user-level authentication options only apply to multi-session channels).
The MC then lowers the assigned privilege limit, if necessary, based on the present session privilege
limit that was set via the set session privilege level command.
If the channel is session-less such as IPMB), the MC returns none for the privilege level.
◦ 0h = None (unspecified)
◦ 1h = Callback level
◦ 2h = User level
◦ 3h = Operator level
◦ 4h = Administrator level
◦ 5h = OEM proprietary level
40 Command specification
• [3:0] channel number
Message data. Maximum length and format dependent on protocol associated with the channel.3:N
Page 41

The following table indicates the contents of the Message Data field from the get message response
according to the channel type and channel protocol that was used to place the message in the
receive message queue.
Table 19 Get message data fields
Channel protocolOriginating channel
type
1
IPMB (I2C)1
5
Asynch. serial/modem
(RS-232)
IPMB
IPMB802.3 LAN4
IPMB (basic mode, terminal
mode, and PPP mode)
Message data for received requests (RQ) and
responses (RS)
RQ: netFn/rsLUN, chk1, rqSA, rqSeq/rqLUN, cmd,
<data>, chk2
RS: netFn/rqLUN, chk1, rsSA, rqSeq/rsLUN, cmd,
completion code, <data>, chk2
RQ: Session handle, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
RQ: Session handle, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
NOTE: When LUN 10b is used to deliver a
message to SMS from a terminal mode remote
console, the MC inserts fixed values for the SWIDs
and LUNs in the message. Messages from the
remote console are always returned as coming
from SWID 40h (81h) LUN 00b, and going to
SMS SWID 20h (41h) LUN 00b.
IPMBOther LAN6
IPMI-SMBusPCI SMBus7
SMBus v1.0/1.18
SMBus v2.09
BT, KCS, SMICSystem interface12
1
This message data matches the IPMB message format with the leading slave address omitted. The format includes
checksums. In order to verify those checksums, they must be calculated as if 20h (MC slave address) was the value that
was used as the slave address when the checksums were calculated per [IPMB]. 20h is always used for the checksum
RQ: Session handle, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
RQ: rsSA, Netfn(even)/rsLUN, 00h, rqSA,
rqSeq/rqLUN, CMD, <data>, PEC
RS: rqSA or rqSWID, NetFn(odd)/rqLUN, 00h,
rsSA or rsSWID, rqSeq/rsLUN, CMD, completion
code, <data>, PEC
n/an/aReserved for USB 1.x10
n/an/aReserved for USB 2.x11
RQ: Session handle, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
Standard command specification 41
Page 42

calculation for the receive message queue data whenever IPMB is listed as the originating bus and with IPMB as the
channel protocol.
Send message command
This command is available to the MC.
The send message command is used for bridging IPMI messages between channels, and between
the SMS and a given channel.
For IPMI v2.0 the send message command has been updated to include the ability to indicate
whether a message must be sent authenticated or with encryption (for target channels on which
authentication and/or encryption are supported and configured).
Table 20 Send message command request and response data
Data fieldRequest data
byte number
Channel number1
00b =[7:6]
01b =
10b =
No tracking. The MC reformats the message for the selected channel but does
not track the originating channel, sequence number, or address information.
This option is typically used when software sends a message from the system
interface to another media. Software will typically use no tracking when it
delivers sends a message from the system interface to another channel, such
as IPMB. In this case, the software formats the encapsulated message so that
when it appears on the other channel, it appears to have been directly
originated by MC LUN 10b. See “MC LUN 10b” (page 148) for more
information.
Track request. The MC records the originating channel, sequence number,
and addressing information for the requester, and then reformats the message
for the protocol of the destination channel. When a response is returned, the
MC looks up the requester’s information and format the response message
with the framing and destination address information and reformats the
response for delivery back to the requester. This option is used for delivering
IPMI request messages from non-SMS (non-system interface) channels. See
“Send Message command with response tracking” (page 149) for more
information.
Send raw (optional). This option is primarily provided for test purposes. It may
also be used for proprietary messaging purposes. The MC simply delivers the
encapsulated data to the selected channel in place of the IPMI message data.
If the channel uses sessions, the first byte of the message data field must be
a session handle. The MC must return a non-zero completion code if an attempt
is made to use this option for a given channel and the option is not supported.
It is recommended that completion code CCh be returned for this condition.
Reserved11b =
42 Command specification
1b =[5]
0b =
1b =[4]
0b =
Send message with encryption. MC returns an error completion code if this
encryption is unavailable.
Encryption not required. The message is sent unencrypted if that option is
available under the given session. Otherwise, the message is sent encrypted.
Send message with authentication. MC returns an error completion code if
this authentication is unavailable.
Authentication not required. Behavior is dependent on whether authentication
is used and whether the target channel is running an IPMI v1.5 or IPMI
v2.0/RMCP+ session, as follows:
• IPMI v1.5 sessions default to sending the message with authentication if
that option is available for the session.
• IPMI v2.0/RMCP+ sessions send the message unauthenticated if that option
is available under the session. Otherwise, the message is sent with
authentication.
Page 43

Table 20 Send message command request and response data (continued)
Channel number where to send the message[3:0]
Message data. Format dependent on target channel type.2:N
Data fieldRequest data
byte number
Completion code1
Generic, plus additional command-specific completion codes: 80h = Invalid session handle. The
session handle does not match up with any currently active sessions for this channel.
If channel medium = IPMB, SMBus, or PCI management bus (This status is recommended for applications
that need to access low-level I2C or SMBus devices).
• 81h = Lost arbitration
• 82h = Bus error
• 83h = NAK on write
Response data(2:N)
This data will only be present when using the send message command to originate requests from
IPMB or PCI management bus to other channels such as LAN or serial/modem. It is not present in the
response to a send message command delivered via the system interface.
NOTE: The MC does not parse messages that are encapsulated in a send message command
and does not know what privilege level should be associated with an encapsulated message. Thus,
messages that are sent to a session using the send message command are always output using
the authentication type that was negotiated when the session was activated.
The following table summarizes the contents of the message data field when the send message
command is used to deliver an IPMI message to different channel types. In most cases, the format
of message information the message data field follows are the same used for the IPMB, with two
typical exceptions:
• When the message is delivered to channels without physical slave devices, a SWID field takes
the place of the slave address field.
• When the message is delivered to a channel that supports sessions, the first byte of the message
data holds a session handle.
Table 21 Send message data fields
Target channel protocolTarget channel type
IPMBIPMB (I2C)1
IPMB+session header802.3 LAN4
Message data for sending requests (RQ) and
responses (RS)
RQ: rsSA, netFn/rsLUN, chk1, rqSA,
rqSeq/rqLUN, cmd, <data>, chk2
RS: rqSA, netFn/rqLUN, chk1, rsSA, rqSeq/rsLUN,
cmd, completion code, <data>, chk2
RQ: Session handle1, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle1, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
5
Asynch. serial/modem
(RS-232)
IPMB (basic mode, terminal
mode, and PPP mode)
RQ: Session handle1, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle1, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
Standard command specification 43
Page 44

Table 21 Send message data fields (continued)
Target channel protocolTarget channel type
IPMBOther LAN6
IPMI-SMBusPCI SMBus7
SMBus v1.0/1.18
SMBus v2.09
Message data for sending requests (RQ) and
responses (RS)
NOTE: Terminal mode has a single, fixed SWID
for the remote console. Software using send
message to deliver a message to a terminal mode
remote console should use their SWID or slave
address as the source of the request or response,
and the terminal mode SWID (40h) as the
destination.
RQ: Session handle1, rsSWID, netFn/rsLUN, chk1,
rqSWID or rqSA, rqSeq/rqLUN, cmd, <data>,
chk2
RS: Session handle1, rqSWID, netFn/rsLUN, chk1,
rsSWID or rsSA, rqSeq/rsLUN, cmd, completion
code, <data>, chk2
RQ: rsSA, netFn/rsLUN, chk1, rqSA,
rqSeq/rqLUN, cmd, <data>, chk2
RS: rqSA, netFn/rqLUN, chk1, rsSA, rqSeq/rsLUN,
cmd, completion code, <data>, chk2
n/an/aReserved for USB 1.x10
n/an/aReserved for USB 2.x11
System interface12
1
The session handle identifies a particular active session on the given channel. The MC assigns a different value to each
time a new session is activated. A typical implementation keeps track of the last value that was assigned and increment
it before assigning it to a new active session when the activate session command has been accepted. Software
must include this field for channels where the get channel info command indicates that the channel supports sessions.
Get system GUID command
This command is available to the MC.
This optional, though highly recommended, command can be used to return a GUID (also known
as a UUID), for the managed system to support the remote discovery process and other operations.
The format of the ID follows the octet format specified in [RFC 4122]. [RFC4122] specifies four
different versions of UUID formats and generation algorithms suitable for use for a GUID in IPMI.
• Time based — version 1 (0001b)
• Name based:
version 3 (0011b) MD5 hash◦
RQ: rsSA, netFn/rsLUN, chk1, rqSA,
rqSeq/rqLUN, cmd, <data>, chk2
RS: rqSA, netFn/rqLUN, chk1, rsSA, rqSeq/rsLUN,
cmd, completion code, <data>, chk2
NOTE: MC adds session handle information
when it puts the message into the receive message
queue .
◦ version 4 (0100b) Pseudo-random
◦ version 5 SHA1 hash
[SMBIOS] does not specify a particular specification or version for UUID generation. In general,
if it remains unspecified, the version 1 format is recommended by the IPMI specification for new
44 Command specification
Page 45

system implementations. However, versions 3, 4, or 5 formats are also allowed. A system GUID
should not change over the lifetime of the system.
If the MC is on a removable card that can be moved to another system, the vendor of the card or
system vendor should provide a mechanism for generating a new system GUID or retrieving the
SMBIOS UUID from the given system.
Since the GUID is typically permanently assigned to a system, an interface that would allow the
GUID to be configured or changed is not specified. For systems that support [SMBIOS], the system
GUID that is returned by the MC should match the UUID field value in the SMBIOS system
information (type 1) record.
The session header (session request data and session response data) values shown in the following
table illustrate the values that would be used to execute a get system GUID command outside
of an active session. The get system GUID is always accepted outside of an active session. The
get system GUID command can also be executed within the context of an active session
(providing the user is operating at higher than callback privilege). When the get system GUID
command is executed in the context of an active session, the session header fields must have correct
values according to the authentication, session ID, and session sequence number information that
was negotiated for the session.
Session header fields request and response data prior when used prior to session activation
authentication type = NONE
session seq# = null (0’s)
Session ID = null (0’s)
AuthCode = NOT PRESENT
Table 22 Get system GUID command response data
Data fieldResponse data
byte number
Completion code1
GUID bytes 1 through 16.2:17
Set system info parameters command
This command is available to the MC.
This command is used for setting system information parameters such as system name and
BIOS/system firmware revision information.
Table 23 Set system info parameters command request and response data
Data fieldRequest data
byte number
Parameter selector1
Configuration parameter data, per Table 25 (page 46)2:N
Data fieldResponse data
byte number
Completion dode1
• 80h = parameter not supported
• 81h = attempt to set the set in progress value (in parameter #0) when not in the set complete state.
(This completion code provides a way to recognize that another party has already claimed the
parameters).
• 82h = attempt to write read-only parameter
Standard command specification 45
Page 46

Get system info parameters command
This command is available to the MC.
This command is used for retrieving system information parameters from the set system info
parameters command.
Table 24 Get system info parameters command request and response data
Data fieldRequest data
byte number
[7]1
• 0b = get parameter
• 1b = get parameter revision only
[6:0] — reserved
Parameter selector2
3
byte number
The following data bytes are not returned when the get parameter revision only bit is 1b.
3:N
Set selector. Selects a given set of parameters under a given parameter selector value. 00h if
parameter does not use a set selector.
Block selector (00h if parameter does not require a block number)4
Data fieldResponse data
Completion code1
Generic codes, plus the command-specific completion code: 80h = parameter not supported.
[7:0] — Parameter revision. Format:2
• MSN = present revision
• LSN = oldest revision parameter that is backward compatible
• 11h for parameters in this specification
Configuration parameter data, per “System info parameters” (page 46). If the rollback feature is
implemented, the MC makes a copy of the existing parameters when the set in progress state becomes
asserted. (See the set in progress parameter #0). While the set in progress state is active, the MC
returns data from this copy of the parameters, plus any uncommitted changes that were made to the
data. Otherwise, the MC returns parameter data from non-volatile storage.
Table 25 System info parameters
#Parameter
Parameter data (non-volatile unless otherwise noted)
1
46 Command specification
0Set in progress (volatile)
Data 1 - This parameter is used to indicate when any of the following parameters
are being updated, and when the updates are completed. The bit is primarily
provided to alert software that some other software or utility is in the process
of making changes to the data.
An implementation can also elect to provide a rollback feature that uses this
information to decide whether to roll back to the previous configuration
information, or to accept the configuration change.
If used, the roll back restores all parameters to their previous state. Otherwise,
the change takes effect when the write occurs.
Reserved[7:2]
00b =[1:0]
Set complete. If a system reset or transition to
powered down state occurs while set in progress
is active, the MC goes to the set complete state.
If rollback is implemented, going directly to set
complete without first doing a commit write
causes any pending write data to be discarded.
Page 47

Table 25 System info parameters (continued)
#Parameter
Parameter data (non-volatile unless otherwise noted)
1
01b =
10b =
1System firmware version
System firmware version string in text. System firmware that requires multiple
strings to represent version information can separate those strings using 00h
as the delimiter for ASCII+LATIN1 and UTF-8 encoded string data, or 0000h
for UNICODE encoded string data. For IA32 and EMT64 utilizing non-EFI
system firmware, it is recommended that four blocks (64 bytes) of storage be
provided. For EFI-based systems, 256 bytes is recommended.
NOTE: System firmware may optionally include a routine that checks during
POST to see if this parameter is up-to-date with the present firmware version,
and if not, update it automatically. Other implementations may elect to
automatically update this parameter when system firmware updates occur.
Set in progress indicating that some utility or other
software is presently doing writes to parameter
data. It is a notification flag only, it is not a
resource lock. The MC does not provide any
interlock mechanism that would prevent other
software from writing parameter data while set
in progress value is present on these bits.
Commit write (optional). This is only used if a
rollback is implemented. The MC saves the data
that has been written since the last time the set
in progress and then go to the set in progress
state. An error completion code is returned if this
option is not supported.
Reserved11b =
Data 1 —
2:17 —
set selector = 16-byte data block number to access, 0 based. Two
data blocks (32-bytes) for string data required, at least three
recommended. Number of effective characters is dependent on the
encoding selected in string data byte 1.
16-byte block for system firmware name string dataData
For the first block of string data (set selector = 0), the first two bytes
indicate the encoding of the string and its overall length as follows:
String data byte 1:
• [7:4] — Reserved
• [3:0] — Encoding
◦ 0h = ASCII+Latin1
◦ 1h = UTF-8
◦ 2h = UNICODE
◦ All other = Reserved
String data byte 2:
• [7:0] - String length (in bytes, 1-based)
2System name
System name. A name for the overall system to be associated with the MC.
This may or may not match other names that are used for the system.
Data 1 —
set selector = 16-byte data block number to access, 0 based. Two
data blocks (32-bytes) for string data required, at least three
recommended. Number of effective characters will be dependent
on the encoding selected in string data byte 1.
2:17 -
16-byte block for system name string dataData
For the first block of string data (set selector = 0), the first two string
data bytes indicate the encoding of the string and its overall length
Standard command specification 47
Page 48

Table 25 System info parameters (continued)
#Parameter
Parameter data (non-volatile unless otherwise noted)
as follows. There is no required value to be set or used for any
bytes that are past the string length.
String data byte 1:
• [7:4] — Reserved
• [3:0] — Encoding
String data byte 2:
• [7:0] - String length (in bytes, 1-based)
1
◦ 0h = ASCII+Latin1
◦ 1h = UTF-8
◦ 2h = UNICODE
◦ All other = Reserved
name (non-volatile)
3Primary operating system
Primary operating system name. The OS that the system boots to for this MC
according to the default configuration of its system firmware. In systems that
may have multiple physical partitions, this reflects the OS for the partition that
holds the given MC. For systems that have virtual machine capability being
utilized (where more than one virtual systems may be sharing a physical MC),
it is recommended that this value hold the name of the virtual machine monitor
(VMM) software or VMM type).
Data 1
2:17
Set selector = 16-byte data block number to access, 0 based. Two
data blocks (32-bytes) for string data required, at least three
recommended. Number of effective characters will be dependent
on the encoding selected in string data byte 1.
16-byte block for system name string dataData
For the first block of string data (set selector = 0), the first two bytes
indicate the encoding of the string and its overall length as follows.
There is no required value to be set or used for any bytes that are
past the string length.
String data byte 1:
• [7:4] — Reserved
• [3:0] — Encoding
◦ 0h = ASCII+Latin1
◦ 1h = UTF-8 (ls-byte first)
◦ 2h = UNICODE (ls-byte first)
(volatile)
48 Command specification
◦ All other = Reserved
String data byte 2:
• [7:0] - string length (in bytes, 1-based)
4Operating system name
Present operating system name. The name of the operating system that is
presently running and able to access this MC’s system interface. The MC
automatically clears this value by zeroing out the string length on system power
cycles and resets.
In systems that may have multiple physical partitions, this reflects the OS for
the partition that holds the given MC. For systems that have virtual machine
capability being utilized (where more than one virtual systems may be sharing
a physical MC), it is recommended that this value hold the name of the virtual
machine monitor (VMM) software or VMM type.
Page 49

Table 25 System info parameters (continued)
#Parameter
Parameter data (non-volatile unless otherwise noted)
1
Data 1
2:17
Set selector = 16-byte data block number to access, 0 based. Two
data blocks (32-bytes) for string data required, at least three
recommended. Number of effective characters is dependent on the
encoding selected in string data byte 1.
16-byte block for system name string dataData
For the first block of string data (set selector = 0), the first two bytes
indicate the encoding of the string and its overall length as follows.
There is no required value to be set or used for any bytes that are
past the string length.
String data byte 1:
• [7:4] — Reserved
• [3:0] — Encoding
◦ 0h = ASCII+Latin1
◦ 1h = UTF-8
◦ 2h = UNICODE
◦ All other = Reserved
String data byte 2:
• [7:0] - String length (in bytes, 1-based)
OEM
255
1
Choice of system manufacturing defaults for non-volatile parameters is left to the system manufacturer unless otherwise
specified.
This range is available for special OEM system information parameters.192 …
Master write-read command
This command can be used for low-level I2C/SMBus write, read, or write-read access to the IPMB
or private busses behind a management controller. The command can also be used for providing
low-level access to devices that provide an SMBus slave interface.
NOTE: In Moonshot, this command is not available over LAN.
Table 26 Master write-read command request and response data
Data fieldIPMI request
data byte
number
Bus ID:1
Requested maximum privilege level2
Channel number (ignored when bus type=1b[7:4]
Bus ID, 0–based (always 000b for public bus ([bus type=0b])[3:1]
Bus type:[0]
0b =
Public (for example, IPMB or PIC Management) bus. The channel number
value is used to select the target bus.
Private bus (the bus ID value is used to select the target bus.)1b =
Slave address[7:1]
Reserved. Write a 0.[0]
Standard command specification 49
Page 50

Table 26 Master write-read command request and response data (continued)
3
4:N
data byte
number
(2:M)
Read count. Number of bytes to read, 1 based. 0 equals not bytes to read. The maximum read count
should be at least 34 bytes. This allows the command to be used for an SMBus Block Read. This is
required if the command provides access to an SMBus or IPMB. Otherwise, if FRU SEEPROM devices
are accessible, at least 31 bytes must be supported. Note than an implementation that supports fewer
bytes can be supported if none of the devices to be accessed can handle the recommended minimum.
Data to write. This command should support at least 35 bytes of write data. This allows the command
to be used for an SMBus Block Write with PEC. Otherwise, if FRU SEEPROM devices are accessible,
at least 31 bytes must be supported. Note that an implementation is allowed to support fewer bytes
if none of the devices to can handle the recommended minimum.
Data fieldIPMI response
Completion code1
A management controller shall return an error Completion Code if an attempt is made to access an
unsupported bus. This is a generic response but also may include the following command specific
codes:
• 81h—Lost arbitration
• 82h—Bus error
• 83h—NAK on write
• 84h—Truncated read
Bytes read from specified slave address. This field will be absent if the read count is 0. The controller
terminates the I2C transaction with a STOP condition after reading the requested number of bytes.
Get channel authentication capabilities command
This command is available to the MC.
This command is sent in unauthenticated (clear) format. This command is used to retrieve capability
information about the channel from which the message is delivered, or for a particular channel.
The command returns the authentication algorithm support for the given privilege level. When
activating a session, the privilege level passed in this command is normally the same requested
maximum privilege level that is used for a subsequent activate session command.
MC implementations of IP-based channels must support the get channel authentication
capabilities command using the IPMI v1.5 packet format. BMCs that support IPMI v2.0 RMCP+
must also support the command using the IPMI v2.0/RMCP+ format.
The get channel authentication capabilities command can also be used as a no-op
“ping” to keep a session from timing out.
Session header fields request and response data prior when used prior to session activation
authentication type = NONE/payload type = IPMI message
session seq# = null (0’s)
Session ID = null (0’s)
AuthCode = NOT PRESENT
Table 27 Get channel authentication capabilities command request and response data
data byte
number
50 Command specification
Data fieldIPMI request
Channel number1
Page 51

Table 27 Get channel authentication capabilities command request and response data (continued)
1b =[7]
0b =
Reserved[6:4]
Channel number[3:0]
Requested maximum privilege level2
Rreserved[7:4]
Requested privilege level[3:0]
Get IPMI v2.0+ extended data. If the given channel supports authentication
but does not support RMCP+ (such as a serial channel), then the response
data should return with bit [5] of byte 4 = 0b, byte 5 should return 01h,
Backward compatible with IPMI v1.5. Result response data only returns bytes
1:9, bit [7] of byte 3 (authentication type support) and bit [5] of byte 4 returns
as 0b, bit [5] of byte 5 returns 00h.
Channel numbers0hBh, Fh =
Retrieve information for the channel from which this request was issued.Eh =
Reserved0h =
Callback level1h =
User level2h =
Operator level3h =
Administrator level4h =
data byte
number
2
3
OEM proprietary level5h =
Data fieldIPMI response
Completion code1
Channel number on which the authentication capabilities is being returned. If the channel number in
the request was set to Eh, this returns the channel number for the channel where the request was
received.
Authentication type support. Returns the setting of the authentication type enable field from the
configuration parameters for the given channel that corresponds to the requested maximum privilege
level.
1b =[7]
Reserved[6]
IPMI v1.5 authentication type(s) enabled for given requested maximum privilege level.[5:0]
[5]
IPMI v2.0+ extended capabilities available. See Extended capabilities field
below.
IPMI v1.5 support only.0b =
1b = SupportedAll bits:
0b = Authentication type not available for use
OEM proprietary (per OEM identified by the IANA OEM ID in the RMCP ping
response)
Straight password / key[4]
Reserved[3]
MD5[2]
MD2[1]
Standard command specification 51
Page 52

Table 27 Get channel authentication capabilities command request and response data (continued)
None[0]
Reserved[7:6]4
[5]
Following bits apply to IPMI v1.5 and v2.0:
[2:0]
KG status (two-key login status). Applies to v2.0/RMCP+ RAKP authentication only.
Otherwise, ignore as reserved.
0b =
1b =
Per-message authentication status[4]
0b =
1b =
User level authentication status[3]
0b =
1b =
Anonymous login status. This parameter returns values that tells the remote console whether
there are users on the system that have ‘null’ usernames. This can be used to guide the way
the remote console presents login options to the user.
KG is set to default (all 0’s). User key KUID is used in place of KG in RAKP.
(Knowledge of KG not required for activating session.)
KG is set to non-zero value. (Knowledge of both KG and user password (if
not anonymous login) required for activating session.)
Per-message authentication is enabled. Packets to the MC must be authenticated
per authentication type used to activate the session, and the user level
authentication setting.
Per-message authentication is disabled. Authentication type none accepted
for packets to the MC after the session has been activated.
User level authentication is enabled. User level commands must be
authenticated per authentication type used to activate the session.
User level authentication is disabled. Authentication type none accepted for
user level commands to the MC.
[2]
[1]
[0]
For IPMI v1.5: - Reserved5
For IPMI v2.0+: - Extended capabilities
Reserved[7:2]
6:8
9
OEM ID. IANA enterprise number for OEM/Organization that specified the particular OEM
authentication type for RMCP. Least significant byte first. Return 00h, 00h, 00h if no OEM authentication
type available.
OEM auxiliary data. Additional OEM-specific information for the OEM authentication type for RMCP.
Return 00h if no OEM authentication type available.
Get Channel Cipher Suites Command
This command can be executed prior to establishing a session with the MC. The command is used
to look up what authentication, integrity, and confidentiality algorithms are supported. The algorithms
are used in combination as ‘Cipher Suites’. This command only applies to implementations that
support IPMI v2.0/RMCP+ sessions.
1b = Non-null usernames enabled. (One or more users are enabled that have
non-null usernames).
1b = Null usernames enabled. (One or more users that have a null username,
but non-null password, are presently enabled).
1b = Anonymous login enabled. (A user that has a null username and null
password is presently enabled).
Channel supports IPMI v2.0 connections1b =[1]
Channel supports IPMI v1.5 connections1b =[0]
52 Command specification
Page 53

The data is accessed 16-bytes at a time starting from List Index field value of 0 in the request and
then repeating the request incrementing the List Index field each time until fewer than 16-bytes of
algorithm data (or no algorithm data) is returned in the response, or the maximum List Index value
has been reached.
A given Cipher Suite may only be available for establishing a session at a particular maximum
privilege level or lower. For example, a Cipher Suite that has a privilege level of ‘Admin’ can
therefore be used for any privilege level, while a privilege level of User can only be used for
establish sessions with a Maximum Requested Privilege Level of User or Callback.
Because the authentication algorithm specifies the steps for authenticating the user, it is a necessary
part of session establishment. Therefore an authentication algorithm number is required for all
Cipher Suites. It is possible that a given Cipher Suite may not specify use of an integrity or
confidentiality algorithm. If the Cipher Suite has integrity and/or confidentiality of 'none', then all
the same steps for establishing a session are used (open session request/response, RAKP messages)
- but the integrity (AuthCode) and confidentiality fields will be absent in packets for that are sent
under the session.
Table 28 Get channel cipher suites command request and response data
Data fieldIPMI Request
Data Byte
Channel Number1
Reserved[7:4]
Data Byte
[3:0]
Payload Type.2
[7:6] - reserved
[5:0] - Payload Type number
Typically 00h (IPMI).
The Payload Type number is used to look up the Security Algorithm support when establishing a
separate session for a given payload type.
List Index.3
[5:0]
Data fieldIPMI Response
Channel number
0h-Bh, Fh = Channel numbers
Eh = retrieve information for channel this request was issued on.
1b = list algorithms by Cipher Suite[7]
0b = list supported algorithms
Reserved[6]
List index (00h-3Fh). 0h selects the first set of 16, 1h selects the next set of 16, and so
on.
00h = Get first set of algorithm numbers. The MC returns sixteen (16) bytes at a time per
index, starting from index 00h, until the list data is exhausted, at which point it will 0
bytes or <16 bytes of list data.
1
Completion Code1
Channel Number2
Channel number that the Authentication Algorithms are being returned for. If the channel number
in the request was set to Eh, this will return the channel number for the channel that the request was
received on.
Cipher Suite Record data bytes, per Table 22-18, Cipher Suite Record(3:18)
Standard command specification 53
Page 54

Table 28 Get channel cipher suites command request and response data (continued)
Format. Record data is ‘packed’; there are no pad bytes between records. It is possible that record
data will span across multiple List Index values.
The MC returns sixteen (16) bytes at a time per index, starting from index
00h, until the list data is exhausted, at which point it will 0 bytes or <16 bytes of list data.
1
When listing numbers for supported algorithms, the MC returns a list of the algorithm numbers for each algorithm that
the MC supports on a given channel. Each algorithm is listed consecutively and only listed once. There is no requirement
that the MC return the algorithm numbers in any specific order.
Cipher suite records
The data from the Get Channel Cipher Suites command is issued as Cipher Suite records. Tag bits
are used to delimit different fields in the record. Each record starts off with a “Start Of Record”
byte. This byte can be 30h or 31h, indicating that the Start Of Record byte is followed either by
an Cipher Suite ID, or by a OEM Cipher Suite ID plus OEM IANA.
Following the header bytes are algorithm number bytes for the different algorithms that form the
Cipher Suite. Each byte is tagged with the type of algorithm the number is for. Cipher Suite records
are required to list algorithms in the order: Authentication Algorithm number first, Integrity Algorithm
numbers next, and Confidentiality Algorithm numbers last.
If more than one algorithm of a given type is listed in the Cipher Suite Record, then any one of the
algorithms can be used in combination with the other types. For example, if a Cipher Suite response
returns both MD5 and MD2 as Authentication and Integrity algorithms, and xRC4 for confidentiality,
then the allowed combinations are [MD2, MD2, xRC4], [MD2, MD5, xRC4], [MD5, MD2, xRC4],
and [MD5, MD5, xRC4]. A remote console can negotiate for those combinations when establishing
a session.
Table 29 Cipher suite record format
Size
2 or 5
Tag bits
[7:6]
Tag bits
[5:0]
This field starts off with either a C0h or C1h "Start of Record" byte, depending on whether the
Cipher Suite is a standard Cipher Suite ID or an OEM Cipher Suite, respectively.
Standard cipher suite ID
• Byte 1:
[7:0] = 1100_0000b. Start of Record, Standard Cipher Suite.
• Byte 2 (Data following C0h (1100_0000b) start of record byte):
Cipher Suite ID—This value is used a numeric way of identifying the Cipher Suite on the platform.
It’s used in commands and configuration parameters that enable and disable Cipher Suites.
OEM cipher suite
• Byte 1:
[5:0] = 1100_0001b — Start of Record, OEM Cipher Suite.
• Byte 2 (Data following C1h (1100_0001) start of record byte):
OEM Cipher Suite ID
Byte 3:5 - OEM IANA
Least significant byte first. 3-byte IANA for the OEM or body that defined the Cipher
Suite.
54 Command specification
[5:0] = Authentication Algorithm Number.00b1
A Cipher Suite is only allowed to utilize one Authentication algorithm.
Page 55

Table 29 Cipher suite record format (continued)
Size
Tag bits
[7:6]
Tag bits
[5:0]
[5:0] = Integrity Algorithm Number(s).01bvar
[5:0] = Confidentiality Algorithm Number(s).10bvar
Cipher suite ID numbers
The following table provides the number ranges and assignments for Cipher Suite IDs. The Cipher
Suite ID values are used as a way to identify different Cipher Suites in configuration parameters
and IPMI commands.
The OEM IDs do not correspond to a particular Cipher Suite, but are handles that can be used to
identify the Cipher Suite on a particular implementation of a MC. I.e. the OEM Cipher Suite
corresponding to “80h” can be different from one MC to the next. These handles can, however,
be used in configuration parameters and commands the same way as the IPMI-defined Cipher
Suite IDs.
The Get Channel Cipher Suites command will return the algorithms used to form a given Cipher
Suite (those numbers can then be used by a remote console in the commands for establishing a
session). For OEM defined Cipher Suites, the Get Channel Cipher Suites command will also return
the IANA for the OEM or body that defined the Cipher Suite.
Table 30 Cipher suite ID numbers
Cipher SuiteCharacteristicsID
Algorithm
Integrity Algorithm(s)Authentication
Confidentiality
Algorithm(s)
BFh
NoneNoneRAKP-none00h, 00h, 00hno password0
NoneNoneRAKP-HMAC-SHA101h, 00h, 00hS1
NoneHMAC-SHA1-9601h, 01h, 00hS, A2
AES-CBC-12801h, 01h, 01hS, A, E3
xRC4-12801h, 01h, 02hS, A, E4
xRC4-4001h, 01h, 03hS, A, E5
NoneNoneRAKP-HMAC-MD502h, 00h, 00hS6
NoneHMAC-MD5-12802h, 02h, 00hS, A7
AES-CBC-12802h, 02h, 01hS, A, E8
xRC4-12802h, 02h, 02hS, A, E9
xRC4-4002h, 02h, 03hS, A, E10
NoneMD5-12802h, 03h, 00hS, A11
AES-CBC-12802h, 03h, 01hS, A, E12
xRC4-12802h, 03h, 02hS, A, E13
xRC4-4002h, 03h, 03hS, A, E14
OEM specifiedOEM specifiedOEM specifiedOEM specifiedOEM specified80h-
FFh
Key:
S = Authenticated session setup (correct role, username and password/key required to establish session.)
Standard command specification 55
----reservedC0h-
Page 56

Table 30 Cipher suite ID numbers (continued)
Cipher SuiteCharacteristicsID
A = Authenticated payload data supported.
E = Authentication and encrypted payload data supported.
Set session privilege level command
This command is available to the MC.
This command is sent in authenticated format. When a session is activated, the session is set to an
initial privilege level. A session that is activated at a maximum privilege level of callback is set to
an initial privilege level of callback and cannot be changed. All other sessions are initially set to
user level, regardless of the maximum privilege level requested in the activate session
command. The remote console must raise the privilege level of the session using this command in
order to execute commands that require a greater-than-user level of privilege.
This command cannot be used to set a privilege level higher than the lowest of the privilege level
set for the user (via the set user access command) and the privilege limit for the channel that
was set via the set channel access command. The specification allows a session to be used
across multiple channels. The maximum privilege limit and authentication are based on the user
privilege and channel limits. Since these can vary on a per channel basis, an implementation
cannot simply assign a single privilege limit to a given session but must authenticate incoming
messages according to the specific settings for the channel and the user on a per-channel basis.
Algorithm
Integrity Algorithm(s)Authentication
Confidentiality
Algorithm(s)
Table 31 Set session privilege level command request and response data
Data fieldIPMI request
data byte
number
Requested privilege level1
• [7:4] — Reserved
• [3:0] — Privilege level
◦ 0h — No change, just return present privilege level
◦ 1h — Reserved
◦ 2h — Change to user level
◦ 3h — Change to operator level
◦ 4h — Change to administrator level
◦ 5h — Change to OEM proprietary level
◦ All other = Reserved
Data fieldIPMI response
data byte
number
56 Command specification
Completion code. Generic, plus following command specific:1
• 80h = Requested level not available for this user
• 81h = Requested level exceeds channel and/or user privilege limit
• 82h = Cannot disable user level authentication
New privilege level (or present level if return present privilege level was selected.)2
Page 57

Close session command
This command is used to immediately terminate a session in progress. It is typically used to close
the session that the user is communicating over, though it can be used to terminate other sessions
in progress (provided that the user is operating at the appropriate privilege level, or the command
is executed over a local channel, such as the system interface).
Table 32 Close session command request and response data
Data fieldIPMI request
data byte
number
1:4
data byte
number
Session ID. For IPMI v2.0/RMCP+ this is the Managed System Session ID value that was generated
by the MC, not the ID from the remote console. If Session ID = 0000_0000h then an implementation
can optionally enable this command to take an additional byte of parameter data that allows a session
handle to be used to close a session.
Session Handle. Only present if Session ID = 0000_0000h.(5)
Data fieldIPMI response
Completion code.1
• 87h = Invalid session ID in request
• 88h = Invalid Session Handle in request
• 82h = Cannot disable user level authentication
Get session info command
This command is available to the MC.
This command is used to get information regarding which users presently have active sessions,
and, when available, addressing information for the party that has established the session. A
portion of the response is dependent on the type of channel.
For IPMI v2.0, a previously reserved field has been defined to hold a value indicating whether a
session operating on a channel of channel type = 802.3 LAN is presently using IPMI v1.5 or
v2.0/RMCP+ protocols.
Table 33 Get session info command request and response data
Data fieldIPMI request
data byte
number
1
Present if session index = FEh
Present if session index = FFh:
2:5
Session index. This value is used to select entries in a logical sessions table maintained by the
management controller. Information for all active sessions can be retrieved by incrementing the session
index from 1 to N, where N is the number of entries in the active sessions table.
• 00h = Return information for the active session associated with the session where this command
was received.
• N = Get information for Nth active session
• FEh = Look up session information according to the session handle passed in this request.
• FFh = Look up session information according to the session ID passed in this request.
Session handle. 00h = reserved.2
Session ID. ID of session to look up session information. For IPMI v2.0/RMCP+ this is the session ID
value that was generated by the MC, not the ID from the remote console.
Standard command specification 57
Page 58

Table 33 Get session info command request and response data (continued)
Data fieldIPMI response
data byte
number
Completion code1
2
3
The following parameters are returned only if there is an active session corresponding to the given session index:
Session handle presently assigned to active session. FFh = reserved. Return 00h if no active session
associated with given session index.
Number of possible active sessions. This value reflects the number of possible entries (slots) in the
sessions table.
• [7:6] — Reserved
• [5:0] — Session slot count. 1-based.
Number of currently active sessions on all channels on this controller.4
• [7:6] — Reserved
• [5:0] — Active session count. 1-based. 0=no currently active sessions.
User ID for selected active session.5
• [7:6] — Reserved
• [5:0] — User ID. 000000b = reserved.
Operating privilege level6
• [7:4] — Reserved
• [3:0] — Ppresent privilege level at which the user is operating.
[7:4] — Session protocol auxiliary data. For channel type = 802.3 LAN:7
• 0h = IPMI v1.5
• 1h = IPMI v2.0/RMCP+
Channel in which the session was activated.
[3:0] - Channel number
The following bytes 8:18 are optionally returned if channel type = 802.3 LAN:
8:11
12:17
18:19
The following bytes 8:13 are returned if channel type = asynch. serial/modem:
IP address of remote console (MS-byte first). Address that was received in the activate session
command that activated the session
MAC address (MS-byte first). Address that was received in the activate session command that
activated the session.
Port number of remote console (LS-byte first). Port number that was received in UDP packet that held
the activate session command that activated the session (for IPMI v1.5 packets) or that was
used for in the packet for RAKP Message 3 (for IPMI v2.0 / RMCP+ packets).
Session/channel activity type:8
• 0 = IPMI messaging session active
• 1 = Callback messaging session active
• 2 = Dial-out alert active
• 3 = TAP page active
Destination selector for active call-out session. 0 otherwise.9
• [7:4] - Reserved
• [3:0] - Destination selector. Destination 0 is always present as a volatile destination that is used
with the alert immediate command.
58 Command specification
Page 59

Table 33 Get session info command request and response data (continued)
If PPP connection, the IP address of the remote console. (MS-byte first). 00h, 00h, 00h, 00h otherwise.10:13
The following additional bytes 14:15 are returned if channel type = asynch. serial/modem and connection is PPP:
14:15
Port address of remote console (LS-byte first). Address that was received in the activate session
command that activated the session.
Get AuthCode command
This command is available to the MC.
This command is used to send a block of data to the MC, whereupon the MC returns a hash of
the data together concatenated with the internally stored password for the given channel and user.
This command allows a remote console to send an AuthCode and data block to system software
on a remote platform, whereby the system software can validate the AuthCode by comparing it
with the AuthCode returned by the MC. This enables the MC to serve as a validation agent for
remote requests that come through local system software instead of through a remote session directly
with the MC.
The following is an outline of potential use of this capability. Remote console software could request
that system software perform a particular operation. In response, local system software could deliver
a challenge string to the remote console, which would be required to hash it with the desired
password and return the AuthCode to the local system software. The local system software would
then perform the requested operation only if it found that the AuthCode matched the one returned
by the MC. The local software would typically implement mechanisms to bind the challenge string
to the requested operation to ensure that the challenge string and AuthCode combination only
applied to a given instance of the requested operation, and even from a particular remote console.
• Managed system delivers a random number token, S, to the console. In this example, the
console uses S to identify a particular request. The managed system tracks outstanding S
values, and expires them either because a valid message was received from a console that
used that token, or because the token was not used within a specified interval.
• Console determines: X = data to be authenticated
K1 = 16-byte signature of X and a sequence number = hash(X, S,
◦
SW_Authentication_Type). Where SW_Authentication_Type is any signature algorithm
management software wishes to use for providing a signature given X and S.
◦ K2 = 16-byte hash of K1 and the password = hash(K1, PWD, Authentication_Type).
Where Authentication_Type in this case is one of the supported authentication types for
the given MC.
• Console sends X, S, and K2 to software agents on the managed system.
• Software agent on the managed system calculates K1 from X and S that it received by locally
calculating K1=hash1(X, S, SW_Authentication_Type). The software also verifies that S is a
valid outstanding token.
• Managed system passes K1 to MC. MC internally looks up password based on the user ID
passed in the get authcode command and produces: K2
Authentication_Type).
• Managed system accepts data if software agents finds that K2 = K2
= hash(K1, PWD,
BMC
.
BMC
Standard command specification 59
Page 60

Table 34 Get AuthCode command request and response data
Data fieldIPMI request
data byte
number
[7:6] - Authentication type / Integrity algorithm number1
• 00b = IPMI v1.5 AuthCode algorithms
• 01b = IPMI v2.0/RMCP+ algorithm number
For [7:6] = 00b, IPMI v1.5 AuthCode number:
• [5:4] - Reserved
• [3:0] - Hash type
◦ 0h = Reserved
◦ 1h = MD2
◦ 2h = MD5
◦ 3h = Reserved
◦ 4h = Reserved (change from IPMI v1.5). This results in an error completion code.
◦ 5h = OEM proprietary
◦ All other = Reserved
For [7:6] = 01b, IPMI v2.0/RMCP+ Integrity algorithm number
• 5:0] - Integrity algorithm number. The user password is used as the starting key for the Integrity
algorithm, instead of session-dependent keys such as the session integrity key. The “none” Integrity
number (0) is illegal and results in an error completion code.
Channel number2
• [7:4] - Reserved
• [3:0] - Channel number
3
data byte
number
For IPMI v1.5 AuthCode number:
For IPMI v2.0 Integrity algorithm number
(2:21)
User ID. (Software will typically have to use the get user name command to look up the user ID
from a user name).
Data to hash (must be 16 bytes).4:19
Data fieldIPMI response
Completion code.1
AuthCode =2:17
Resultant hash, per selected Integrity algorithm. Up to 20 bytes. An implementation can elect to return
a variable length field based on the size of the hash for the given integrity algorithm, or can return a
fixed field where the hash data is followed by 00h bytes as needed to pad the data to 20 bytes.
Set channel access command
This command is available to the MC.
This command is used to configure whether channels are enabled or disabled, whether alerting is
enabled or disabled for a channel, and to set which system modes channels are available under.
This configuration is saved in non-volatile storage associated with the MC. The choice of factory
default setting for the non-volatile parameters is left to the implementer or system integrator.
60 Command specification
Page 61

The active (volatile) settings can be overwritten to allow run-time software to make temporary
changes to the access. The volatile settings are overwritten from the non-volatile settings whenever
the system is reset or transitions to a powered off state.
An implementation can elect to provide a subset of the possible access mode options. If a given
access mode is not supported, the command-specific completion code 83h (access mode not
supported) must be returned.
Table 35 Set channel access command request and response data
Data fieldRequest data
byte number
[7:4] — Reserved1
[3:0] — Channel number
Do not set or change channel access.00b =[7:6]2
Set non-volatile channel access according to bits [5:0].01b =
Set volatile (active) setting of channel access according to bits [5:0].10b =
Reserved.11b =
[5]
[4]
[3]
PEF alerting enable/disable. This bit globally gates whether PEF alerts can be issued from
the given channel. Setting this to enable PEF alerting is a necessary part of enabling alerts
for the channel, but for alerts to be generated, the PEF and channel configuration must
also be set to enable alerting. Setting this bit to enable does not alter the PEF configuration
or the alerting settings in the channel's configuration parameters. For example, if PEF is
not configured for generating an alert, enabling PEF alerting with this bit does not change
that configuration. Setting this bit to disable blocks PEF -generated alerts regardless of the
PEF and channel configuration parameters.
Enable PEF alerting.0b =
1b =
Per-message authentication enable/disable. This bit is ignored for channels (such as
serial/modem) that do not support per-message authentication.
1b =
User level authentication enable/disable. Optional. Return a CCh invalid data field error
completion code if an attempt is made to set this bit, but the option is not supported.
0b =
Disable PEF alerting on this channel. The alert immediate command
can still be used to generate alerts.
Enable per-message authentication.0b =
Disable per-message authentication. Authentication is required to activate
any session on this channel, but authentication is not used on subsequent
packets for the session.
Enable user level authentication. All user level commands are to be
authenticated per the authentication type that was negotiated when the
session was activated.
[2:0]
1b =
Access mode for IPMI messaging. (PEF alerting is enabled/disabled separately from IPMI
messaging, see bit 5).
001b =
Disable user level authentication. Allow user level commands to be executed
without being authenticated.
If the option to disable user level command authentication is accepted, the
MC will accept packets with authentication type set to none if they contain
user level commands.
For outgoing packets, the MC returns responses with the same authentication
type that was used for the request.
Disabled. Channel disabled for IPMI messaging.000b =
Pre-boot only. Channel only available when system is in a powered down
state or in BIOS before start of boot.
Standard command specification 61
Page 62

Table 35 Set channel access command request and response data (continued)
010b =
011b =
3
Channel privilege level limit. This value sets the maximum privilege level that can be accepted on
the specified channel.
Reserved.[5:4]
Channel privilege level limit.[3:0]
Always available. Channel always available for communication regardless
of system mode. BIOS typically dedicates the serial connection to the MC.
Shared. Same as always available, but BIOS typically leaves the serial port
available for software use.
Do not set or change channel privilege level limit.00b =[7:6]
Set non-volatile privilege level limit according to bits [3:0].01b =
Set volatile setting of privilege level limit according to bits [3:0].10b =
Reserved.11b =
Reserved.0h =
Callback level.1h =
User level.2h =
Operator level.3h =
Administrator level.4h =
Data fieldResponse data
byte number
Completion code. Generic, plus the following command-specific completion codes:1
Get channel access command
This command is available to the MC.
This command is used to return whether a given channel is enabled or disabled, whether alerting
is enabled or disabled for the entire channel, and under what system modes the channel can be
accessed.
Table 36 Get channel access command request and response data
Data fieldRequest data
byte number
[7:4] — Reserved1
[3:0] — Channel number
OEM proprietary level.5h =
Set not supported on selected channel (for example, channel is session-less).82h =
Access mode not supported.83h =
Reserved00b =[7:6]2
Response data
byte number
62 Command specification
Get non-volatile channel access01b =
Get present volatile (active) setting of channel access10b =
Reserved11b =
Reserved[5:0]
Data
field
Page 63

Table 36 Get channel access command request and response data (continued)
Completion code. Generic, plus the command-specific completion code:1
Command not supported for selected channel (for example, the channel is session-less.)82h =
Reserved.[7:6]2
Alerting enabled.0b =[5]
Alerting disabled.1b =
[4]
3
Channel privilege level limit. This value returns the maximum privilege level that can be accepted on
the specified channel.
Per-message authentication enable/disable. This bit is unspecified for channels (such as
serial/modem) that do not support per-message authentication.
Per message authentication enabled.0b =
Per message authentication disabled.1b =
User level authentication enable[3]
User level authentication enabled.0b =
User level authentication disabled.1b =
Access mode[2:0]
Disabled. Channel disabled for communication.0h =
1h =
2h =
3h =
Reserved.[7:4]
Pre-boot only. Channel only available when system is in a powered down
state or in BIOS before start of boot.
Always available. Channel always available for communication regardless
of system mode. BIOS typically dedicates the serial connection to the MC.
Shared. Same as always available, but BIOS typically leaves the serial port
available for software use.
Get channel info command
This command returns media and protocol information about the given channel. The channel
protocol may vary with changes to the configuration parameters associated with the channel.
Table 37 Get channel info command request and response data
Data fieldIPMI request
data byte
number
[7:4] — Reserved1
[3:0] — Channel number. Use Eh to get information about the channel from which this command is
being executed.
Channel privilege level limit.[3:0]
Reserved.0h =
Callback level.1h =
User level.2h =
Operator level.3h =
Administrator level.4h =
OEM proprietary level.5h =
Standard command specification 63
Page 64

Table 37 Get channel info command request and response data (continued)
Data fieldIPMI response
data byte
number
Completion code1
Reserved[7:4]2
[3:0]
Channel protocol type:4
Session support5
Number of sessions that have been activated on the given channel.
[5:0]
Actual channel number. This value typically matches the channel number passed in the
request, unless the request is for channel E, in which case the response returns the actual
channel number.
Reserved[7:4]3
7-bit channel medium type[6:0]
Reserved[7:5]
5-bit channel IPMI messaging protocol type[4:0]
Channel is session-less00b =[7:6]
Channel is single-session01b =
Channel is multi-session10b =
11b =
Active session count. 1-based. 00_0000b = no sessions have been activated on this
channel.
Channel is session-based (return this value if a channel could alternate
between single- and multi-session operation, as can occur with a
serial/modem channel that supports connection mode auto-detect)
6
Vendor ID (IANA enterprise number) for OEM/organization that specified the channel protocol.
Least significant byte first. Returns the IPMI IANA for IPMI-specification defined, non-OEM protocol
type numbers other than OEM.
The IPMI enterprise number is: 7154 (decimal). This gives the values F2h, 1Bh, 00h for bytes 6
through 8, respectively. This value is returned for all channel protocols specified in this document,
including PPP.
Auxiliary channel info9:10
For channel = Fh (system interface):
• Byte 1: SMS interrupt type
00h-0Fh = IRQ 0 through 15, respectively◦
◦ 10h-13h = PCI A-D, respectively
◦ 14h = SMI
◦ 15h = SCI
◦ 20h-5Fh = System interrupt 0 through 63, respectively
◦ 60h = Assigned by ACPI / Plug ‘n Play BIOS
◦ FFh = No interrupt / unspecified
◦ All other = Reserved
64 Command specification
• Byte 2: Event message buffer interrupt type. See values for byte 1.
Page 65

Table 37 Get channel info command request and response data (continued)
For OEM channel types: Byte 1:2 = OEM specified per OEM identified by vendor ID.
All other channel types: Byte 1:2 = reserved.
Set user access command
This command is available to the MC.
This command is used to configure the privilege level and channel accessibility associated with a
given user ID. If this command is not supported, then a single null user (User 1) per channel is
assumed and the privilege level and channel access are determined solely by the settings returned
by the get channel access limits command. If implemented, this command must support
at least the null user (User 1). The number of additional users supported is left to the implementer.
NOTE: The limits set using the set channel access command take precedence over the set
user access command settings. That is, if a given channel is limited to user level then all users
are limited to user level operation regardless of what their user access levels were set to using the
set user access command. Changes made to the user access and privilege levels may not
take affect until the next time the user establishes a session.
Table 38 Set user access command request and response data
Data fieldRequest data
byte number
[5]
[4]
Do not change any of the following bits in this byte.0b =[7]1
Enable changing the following bits in this byte.1b =
User restricted to callback[6]
0b =
1b =
User link authentication enable/disable (used to enable whether this user’s name and
password information will be used for link authentication, for example PPP CHAP) for
the given channel. Link authentication itself is a global setting for the channel and is
enabled/disabled via the serial/modem configuration parameters.
• 0b = disable user for link authentication
• 1b = enable user for link authentication
User IPMI messaging enable/disable (used to enable/disable whether this user’s name
and password information will be used for IPMI messaging. In this case, IPMI messaging
refers to the ability to execute generic IPMI commands that are not associated with a
particular payload type. For example, if IPMI messaging is disabled for a user, but that
user is enabled for activating the SOL payload type, then IPMI commands associated
with SOL and session management, such as get SOL configuration parameters
and close session are available, but generic IPMI commands such as get SEL
time are unavailable.)
• 0b = Disable user for IPMI messaging
• 1b = Enable user for IPMI messaging
User privilege limit is determined by the user privilege limit parameter,
below, for both callback and non-callback connections.
User privilege limit is determined by the user privilege limit parameter for
callback connections, but is restricted to callback level for non-callback
connections. Thus, a user can only initiate a callback when they call in to
the MC, but once the callback connection has been made, the user could
potentially establish a session as an operator.
Channel number[3:0]
Standard command specification 65
Page 66

Table 38 Set user access command request and response data (continued)
User ID2
• [7:6] — Reserved
• [5:0] — User ID. 000000b = Reserved.
User limits3
Reserved[7:4]
(4)
byte number
[3:0]
User session limit (optional). Sets how many simultaneous sessions can be activated with the username
associated with this user. If not supported, the username can be used to activate as many simultaneous
sessions as the implementation supports. Return a CCh invalid data field error completion code if
an attempt is made to set a non-zero value in this field, but the option is not supported.
[3:0]
Data fieldResponse data
Completion code.1
NOTE: An implementation does not return an error completion code if the user access level is set
higher than the privilege limit for a given channel. To bring attention to this condition, the software
must check the channel privilege limits set using the set channel access command and provide
notification of any mismatch.
User privilege limit. Determines the maximum privilege level that the user is allowed to
switch to on the specified channel.
Reserved0h =
Callback1h =
User2h =
Operator3h =
Administrator4h =
OEM proprietary5h =
No accessFh =
Reserved[7:4]
User simultaneous session limit. 1-based. 0h = only limited by the implementations
overall support for simultaneous sessions.
Get user access command
This command is available to the MC.
This command is used to retrieve channel access information and enabled/disabled state for the
given user ID. The command also returns information about the number of supported users.
Table 39 Get user access command request and response data
Data fieldRequest data
byte number
Data fieldResponse data
byte number
Completion code.1
66 Command specification
Reserved[7:4]1
Channel number[3:0]
Reserved[7:6]2
User ID. 000000b = reserved.[3:0]
Page 67

Table 39 Get user access command request and response data (continued)
NOTE: An implementation does not return an error completion code if the user access level is set
higher than the privilege limit for a given channel. To bring attention to this condition, the software
must check the channel privilege limits and provide notification of the mismatch.
2
3
4
Maximum number of user IDs. 1-based. Count includes User 1. A value of 1 indicates only User 1
is supported.
• [7:6] — Reserved
• [5:0] — Maximum number of user IDs on this channel.
Count of currently enabled user IDs (1-based). A value of 0 indicates that all users, including User
1, are disabled. This is equivalent to disabling access to the channel.
User ID cnable status (for IPMI v2.0 errata 3 and later implementations).[7:6]
00b =
[5:0]
Count of user IDs with fixed names, including User 1 (1-based). Fixed names in addition to User 1
are required to be associated with sequential user IDs starting from User ID 2.
• [7:6] — Reserved
• [5:0] — Count of user IDs with fixed names on this channel.
Count of currently enabled user IDs on this channel which indicates how many user ID
slots are presently in use.
User ID enable status unspecified. (For backward compatibility with pre-errata
3 implementations. IPMI errata 3 and later implementations should return
the 01b and 10b responses.)
User ID enabled via set user password command.01b =
User ID disabled via set user password command.10b =
Reserved.11b =
Channel access5
Reserved[7]
User access available during call-in or callback direct connection.0b =[6]
User access available only during callback connection.1b =
For pre- IPMI v2.0 errata 3 implementations: bits 5:4 are used for determining the count of currently
enabled user IDs in byte 3. Either bit being set to 1b represents an enabled user ID.
For IPMI v2.0 errata 3 and later implementations: the count of enabled User IDs is based on the user
IDs that are presently enabled as reflected in byte 3, bits [7:6], user ID enable status.
NOTE: Some pre- IPMI v2.0 errata 3 implementations may automatically clear bits [5:4], and may
also prevent them from being set, while the user ID is disabled. IPMI v2.0 errata 3 and later
implementations should not alter bits [5:4] based on whether or not a user ID is enabled.
User disabled for link authentication0b =[5]
User enabled for link authentication1b =
User disabled for IPMI messaging0b =[4]
User enabled for IPMI messaging1b =
User privilege limit for given channel[3:0]
Reserved0h =
Callback1h =
User2h =
Operator3h =
Standard command specification 67
Page 68

Table 39 Get user access command request and response data (continued)
Administrator4h =
OEM proprietary5h =
Set user name command
This command is available to the MC.
This command adds a new user ID. The names are stored as a logical array within non-volatile
storage associated with the management controller. Names are stored and retrieved using the user
ID as the index into the logical array. There is no configurable name for User ID 1. User ID 1 is
reserved for the null user name, User 1. Null user is not supported.
The management controller does not prevent duplicate user names from being enabled for the
same channel. It is the responsibility of configuration software to ensure that duplicate user names
are not enabled simultaneously for the same channel.
Having duplicate user names does not cause functional problems with the MC because the MC
uses the first username match that it finds. However, it could be confusing to the user if they have
duplicate user names enabled for a given channel, since only the settings for the first encountered
user name would be used by the MC.
This command is highly recommended for session-based channels. It is also recommended that the
implementation support multiple users with configurable user names.
Table 40 Set user name command request and response data
Data fieldRequest data
byte number
Fh =
No access. This value does not add to, or subtract from, the number of
enabled user IDs
User ID1
• [7:6] — Reserved
• [5:0] — User ID. 000000b = reserved. (User ID 1 is permanently associated with User 1, the
2:17
byte number
User name string in ASCII, 16 bytes, max. Strings with fewer than 16 characters are terminated with
a null (00h) character and 00h padded to 16 bytes. When the string is read back using the get
user name command, those bytes return as 0’s.
Data fieldResponse data
Completion code.1
Get user name command
This command is available to the MC.
This command is used to retrieve user name information that was set using the set user name
command. Configuration software can use this command to retrieve user names.
Table 41 Get user name command request and response data
Data fieldRequest data
byte number
User ID1
• [7:6] — Reserved
• [5:0] — User ID. 000000b = reserved.
null user name).
68 Command specification
Page 69

Table 41 Get user name command request and response data (continued)
Data fieldResponse data
byte number
Completion code.1
2:17
User name string in ASCII, 16 bytes, max. Strings with fewer than 16 characters are terminated with
null (00h) characters filling in the remaining bytes. MC does not check to see whether string data is
printable or not. Only character that MC interprets is null (00h).
Set user password command
This command is available to the MC.
This command is used to set and change user passwords and to enable and disable user IDs. If
no password protection is desired for a given user, the password must be stored as an ASCII
null-string. The management controller firmware forces the remaining fifteen bytes to 00h and stores
the password as sixteen bytes of 00h.
The password is stored as a 16-byte or 20-byte (for IPMI v2.0/RMCP+) octet string. All values
(0-255) are allowed for every byte. The management controller does not check the format or
interpret values that are passed in with this command.
Software is allowed to place additional restrictions on what passwords can be entered, in which
case it is the responsibility of configuration software and console software to stay in synch with
that definition. For example, remote console software could restrict passwords to the printable
ASCII character set in order to simplify direct keyboard entry. If this is done, any companion
configuration utility should ensure that the user does not configure the managed system with
non-printable passwords. Otherwise, it would be possible for the management controller to be
configured with passwords that could not be entered via the remote console utility.
Table 42 Set user password command request and response data
byte number
Data fieldRequest data
User ID1
For IPMI v2.0, the MC supports 20-byte passwords for all supported user IDs that have configurable
passwords. The MC maintains an internal tag that indicates whether the password was set as a
16-byte or as a 20-byte password.
A 16-byte password can be used in algorithms that call for a 20-byte password. In this case, the
16-byte password is padded with 0’s to 20- bytes.
The test password operation returns the test failed error completion code if an attempt is made to
test a password that was stored as a 20-byte password as a 16-byte password (per password size
bit 7), and vice versa. The test password operation can be used to determine whether a password
has been stored as 16-bytes or 20-bytes.
A password that has been stored as a 20-byte password cannot be used for establishing an IPMI
v1.5 session. If it is necessary to configure the same password for both IPMI v2.0 and IPMI v1.5
access, it must be set as a 16-byte password.1The password is padded with 0’s as necessary for
IPMI v2.0 / RMCP+ use.
Password size[7]
Set 20-byte user password/key.1b =
Set 16-byte user password/key (IPMI v1.5 backward compatible).0b =
Reserved[6]
[5:0]
User ID. 000000b = reserved. (User ID 1 is permanently associated with User 1, the null
user name).
Reserved[7:2]2
Operation[1:0]
Standard command specification 69
Page 70

Table 42 Set user password command request and response data (continued)
Disable user00b =
Enable user01b =
Set password10b =
11b =
For password size = 16 bytes:
3:18
For password size = 20 bytes:
3:22
byte number
1
The same user name can be used with different passwords on different channels. The MC scans user names until it finds
the first one that is enabled for a particular channel. Thus, it is possible for a MC implementation to be configured to
allow a 20-byte password on one channel, and a 16-byte password on another channel for the same user name. This
requires multiple user entries.
Password data. This is a required, fixed length field when used for the set and test password
operations. If the password is entered as an ASCII string, it must be null (00h) terminated and 00h
padded if the string is shorter than 16 bytes. This field is not needed if the operation is disable user
or enable user. If this field is present for those operations, the MC ignores the data.
Password data. This is a required, fixed length field when used for the set- and test password
operations. If the password is entered as an ASCII string, it must be null (00h) terminated and 00h
padded if the string is shorter than 20 bytes. This field is not needed if the operation is disable user
or enable user. If this field is present for those operations, the MC ignores the data.
Data fieldResponse data
Completion code. Generic, plus the command-specific completion codes:1
80h =
Mandatory. Password test failed. Password size is correct, but the password data does
not match the stored value.
Mandatory. Password test failed. Wrong password size was used.81h =
Test password. Compares the password data given in the request with the
presently stored password and returns an OK completion code if there is a
match. Otherwise, an error completion code is returned. (See the completion
code description in the response data.)
RMCP+ support and payload commands
This sections list the commands associated with discovering, enabling, and activating payloads
under IPMI v2.0/RMCP+ as well as updates and additions to IPMI commands to support IPMI
v2.0/RMCP+ sessions, authentication, and configuration.
70 Command specification
Page 71

NOTE: The following commands remain available for payloads if IPMI messaging payload type
is disabled:
• Deactivate payload
• Suspend/resume payload encryption (as defined for given payload)
• Get payload activation status
• Get channel payload version command
• Set session privilege level
• Close session
Table 43 (page 71) defines the payload type numbers and ranges for Payload Type Handles.
Table 43 Payload type numbers
TypeNumber
Standard Payload Types
Session Setup Payload Types
Activate payload command
This command is available to the MC.
This command is used for activating and deactivating a payload type under a given IPMI session.
The ability to execute this command is determined via the user’s privileges as assigned via the set
user payload access command.
Major format
version
Minor format
version
0h1hIPMI Message0h
0h1hSOL (serial over LAN)1h
0h1hRMCP+ Open Session Request10h
0h1hRMCP+ Open Session Response11h
0h1hRAKP Message 112h
0h1hRAKP Message 213h
0h1hRAKP Message 314h
0h1hRAKP Message 415h
The activate payload command may return a port number that is separate from the port
number for the session that the command was issued under. In this case, the remote console must
establish a session on the port number that the activate session command returned. The
remote console must then issue the activate payload command on that port number in order
to actually activate the payload. It is possible that the remote console already had a session active
on the given port number. If the privileges associated with that session are sufficient (this is typically
the case unless the remote console activated the session at a privilege level that was lower than
the maximum level for the user) the remote console can re-use the existing session and just use the
activate payload command to activate the new payload type.
BMCs may have limited resources for handling multiple sessions. It is highly recommended that a
remote console avoids creating multiple sessions and shares sessions for multiple payloads whenever
possible.
The activate payload command is only accepted over a channel on which payloads can be
activated. For example, the activate payload command cannot be executed from the IPMB.
Standard command specification 71
Page 72

Table 44 Activate payload command request and response data
Data fieldRequest data
byte number
1
3:6
• [7:6] — Reserved
• [5:0] — Payload type. IPMI message payloads do not need to be explicitly activated. A payload
that is required to be launched over a different port than that used to establish the initial IPMI
session is only required to support the IPMI commands needed by the particular payload type.
Payload instance2
• [7:4] — Reserved
• [3:0] — Payload instance. 1-based. 0h = reserved.
Auxiliary request data. Additional payload-specific parameters to configure behavior of the payload
when it becomes activated. Ignored if no auxiliary data is specified for a given payload type.
For payload type = SOL:
• Byte 1
[7] — Encryption activation. The encryption algorithms specified in this document must be
◦
used with authentication. The MC returns an error completion code if an attempt is made to
activate encryption without also activating authentication.
– 1b: Activate payload with encryption. All SOL payload data from the MC is encrypted, if
encryption was negotiated at the time of session activation.
– 0b: Activate payload without encryption. MC sends all SOL payload data unencrypted, if
that option is allowed. (An SOL configuration parameter allows a system to be configured
to require encryption for all SOL transfers).
◦ [6] — Authentication activation.
1b: Activate payload with authentication. All SOL payload data from the MC is
–
authenticated, if authentication was negotiated at the time of session activation
– 0b: Activate payload without authentication. MC sends all SOL payload data
unauthenticated, if that option is allowed. (An SOL configuration parameter allows a system
to be configured to require authentication for all SOL transfers).
◦ [5] — Test mode (optional). Enables DCD and DSR to be manually controlled by the remote
console and the reporting of RTS and DTR state via the SOL operation/status byte. This can
be used to facilitate software testing of the 16550 UART interface.
– 1b = Activate test mode. If test mode is not supported, bit [0] of the auxiliary response data
will be returned as 0b.
– 0b = Deactivate test mode.
◦ [4] — Reserved
◦ [3:2] — Shared serial alert behavior. The following settings determine what happens to serial
alerts if IPMI over serial and SOL are sharing the same baseboard serial controller.
– 11b: Reserved
– 10b: Serial/modem alerts succeed while SOL active.
– 01b: Serial/modem alerts deferred while SOL active.
– 00b: Serial/modem alerts fail while SOL active.
◦ [1] — SOL startup handshake
0b: MC asserts CTS and DCD/DSR to baseboard upon activation.–
– 1b: CTS and DCD/DSR remain deasserted after activation. Remote console must send an
SOL payload packet with control field settings to assert CTS and DCD/DSR. (This enables
72 Command specification
Page 73

Table 44 Activate payload command request and response data (continued)
the remote console to first alter volatile configuration settings before hardware handshake
is released).
◦ [0] — Reserved
• Byte 2:4 — Reserved, write a 00h
Data fieldResponse data
byte number
1
6:7
8:9
Completion code. Generic plus the command-specific completion codes: (An error completion code
should be returned if the payload type in the request is set to IPMI Message ( 0h ) ).
• 80h: Payload already active on another session (required). This will be returned any time an
attempt is made to activate a payload type when that type is already activated for another session,
and when the MC only supports one instance of that payload type running at a time.
• 81h: Payload type is disabled (optional). Given payload type is not configured to be enabled
for activation.
• 82h: Payload activation limit reached. Cannot activate given payload type because the maximum
number of simultaneous instances of that payload type are already running.
• 83h: Cannot activate payload with encryption.
• 84h: Cannot activate payload without encryption. MC requires encryption for all payloads for
given privilege level.
Auxiliary response data. LS-byte first. For payload = SOL:2:5
• [31:1] — Reserved. Return as 0s.
• [0]
◦ 0b = Test mode not supported / enabled.
◦ 1b = Test mode enabled.
Inbound payload size. Maximum size of payload data field from remote console to MC. Excludes
size of confidentiality header and trailer fields, if any. 1-based.
Outbound payload size. Maximum size of payload data field from MC to remote console. Excludes
size of confidentiality header and trailer fields, if any. 1-based.
10:11
Payload UDP port number. UDP port number through which the payload can be transferred. If the
port number is the same as the port that was used to establish the IPMI session, then SOL payload
transfers are now available under that IPMI session on that port. Otherwise, the remote console needs
to establish a separate IPMI session to the specified port number using the same IP address, username
and password/key information that was used to establish the IPMI session. SOL payload transfers
are then available over that session.
If the remote console already has an IPMI session established on that port for a different payload
type, the SOL payload type is also available over that session - provided that the session was
established at a privilege level that matches the privilege level and authentication required for SOL.
Otherwise, the remote console needs to close that session and reestablish it at the necessary privilege
level.
Payload VLAN number - FFFFh if VLAN addressing is not used.12:13
Deactivate payload command
This command is available to the MC.
This command is used to terminate use of a given payload on an IPMI session. This type of traffic
then becomes freed for activation by another session, or for possible re-activation under the present
session. The deactivate payload command does not cause the session to be terminated. The
close session command should be used for that purpose. A remote console application does
not need to explicitly deactivate payload(s) before terminating a session. When a session terminates,
all payloads that were active under that session are automatically deactivated by the MC.
Standard command specification 73
Page 74

Table 45 Deactivate payload command request and response data
Data fieldRequest data
byte number
1
3:6
byte number
1
• [7:6] — Reserved
• [5:0] — Payload type.
Payload instance2
• [7:4] — Reserved
• [3:0] — Payload instance. 1-based. 0h = reserved.
Payload auxiliary data. Additional parameters to configure behavior of the payload when it becomes
deactivated. Ignored if no auxiliary data is specified for given payload type.
For payload type = SOL, (no auxiliary data) write as 0000_0000h:
Data fieldResponse data
Completion code. Generic plus the command-specific completion codes: (An error completion code
should be returned if the payload type in the request is set to “IPMI Message” ( 0h ) ).
• 80h: Payload already deactivated.
• 81h: Payload type is disabled (optional). Given payload type is not configured to be enabled
for activation.
Suspend/resume payload encryption command
This command enables a remote console to control whether payload data from the MC is sent
encrypted or not. Since encryption can be a significant burden on software, this command provides
a mechanism to allow higher performance by operating without encryption and only activating
encryption when it is required for data confidentiality. The command can also trigger a regeneration
of the encryption Initialization Vector and re-initialization of the encryption state machine for
algorithms such as xRC4 that use the same initialization vector for multiple packets.
The extent at which this command can control encryption of data from the MC is dependent on
the payload definition. Some payload definitions may use a mix of encrypted and unencrypted
payload data transfers. For example, a payload may implement a ‘request/response’ protocol,
where the MC would return an encrypted or unencrypted response based on whether the request
from the remote console was encrypted or unencrypted. In this case, the command may only affect
data that is autonomously generated by the MC. Other payload definitions may just use whatever
encryption the session was activated with, and offer no ‘run-time’ control of encryption/decryption,
while other payload definitions may be ‘stream based’ where it is desirable for the remote console
to be able to select when payload data is from the MC is encrypted or not.
The Suspend/Resume Payload Encryption command is only accepted from the channel that the
payload was activated on.
Table 46 Payload-specific encryption behavior
Payload Type = IPMI Messaging
• Encrypted requests from the remote console will get encrypted responses from the MC.
• The Suspend/Resume Payload Encryption command controls whether asynchronous (unrequested) messages from
the MC are encrypted or not.
• PET Traps (which are actually separate from IPMI Messaging) are always sent unencrypted.
74 Command specification
Page 75

Table 46 Payload-specific encryption behavior (continued)
Payload Type = SOL
• The SOL configuration parameters allow configuring the system to require that SOL data be encrypted.
• The MC will transmit SOL payload data according to encryption settings that were selected when the payload was
activated unless over-ridden by SOL configuration parameters.
• The Suspend/Resume Payload Encryption command controls whether SOL Payload data is encrypted or not.
Table 47 Suspend/resume payload command request and response data
Data fieldIPMI
request
data byte
number
[7:6] - reserved1
[5:0] - payload type (See Table 13-16, Payload Type Numbers)
Payload Instance2
[7:4] - reserved
[3:0] - payload instance. 1-based. 0h = reserved.
[7:2] - reserved3
[4:0] - Operation
• 2h = Regenerate initialization vector. For xRC4 encryption, this causes the MC to reinitialize the xRC4
state machine, reset the data offset, and deliver a new Initialization Vector value in the next encrypted
packet it sends to the remote console. Because of processing delays and potential tasks in progress,
the remote console may receive additional packets from the MC that are encrypted using the prior
Initialization Vector before getting packets that use the new IV.
• 1h = Resume/Start encryption on all transfers of specified payload data from the MC.
• 0h = Suspend encryption on all transfers of specified payload messages from the MC.
Data fieldIPMI
response
data byte
number
Completion Code1
Generic plus the following command-specific completion codes:
• 80h: Operation not supported for given payload type.
• 81h: Operation not allowed under present configuration for given payload type.
• 82h: Encryption is not available for session that payload type is active under.
• 83h: The payload instance is not presently active.
Set channel security keys command
The Set Channel Security Keys command provides a standardized interface for initializing system
unique keys that are used for the pseudo-random number generator key (KR) and the key-generation
key (KG) used for RMCP+. Implementing the ability to set Kr is optional. The command is provided
mainly to offer a common interface for BMCs that are not pre-configured with a KR values, or which
may need their KR values to be restored if they are lost due to a data corruption or firmware update.
The command includes a mechanism that allows specified keys to be “locked”. Once locked, the
key value cannot be read back or rewritten via standard IPMI commands. It is possible, however,
that a firmware update or re- installation procedure may cause the keys to be cleared or unlocked.
Software utilities responsible for MC initial installation and setup should check to see whether keys
have been locked and if not, should initialize them appropriately and lock them.
Standard command specification 75
Page 76

If this command is not supported, it indicates that the keys are either permanently pre-configured,
or that they are only configurable via an OEM/MC-specific mechanism.
Data fieldRequest data
byte number
Channel Number1
[7:4] - reserved
[3:0] - Channel Number
NOTE: This command only applies to channels that support RMCP+, if the channel does not support
RMCP+ the command will return an error completion code.
Operation2
[7:2] - reserved
[1:0] - Operation
• 00b = read key
MC returns value of specified key, provided key has not yet been locked. Some BMCs may allow
the key to be re-written if it does not match the expected value. Other BMCs may only allow one
‘set’ operation. If the key value has not yet been initialized, the MC will return 0’s for the key value.
Utility software responsible for MC installation and initial setup can use this operation to also check
to see whether keys have been initialized and locked.
• 01b = set key
MC writes given key value to non-volatile storage.
(4:M)
byte number
• 10b = lock key
MC locks out modification or reading the key value. Once a key has been locked, it is not cannot
be rewritten or read via IPMI specified commands.
• 11b = reserved
Key ID3
[7:0] - key ID.
• 00h = RMCP+ “KR” key (20 bytes). The “KR” key is used as a unique value for random number
generation. Note: A MC implementation is allowed to share a single KR value across all channels.
A utility can set KR and lock it for one channel, and then verify it has been set and locked for any
other channels by using this command to read the key from other channels and checking the ‘lock
status’ field for each channel to see if it matches and is locked.
• 01h = RMCP+ “KG” key (20 bytes). “KG” key acts as a value that is used for key exchange for
the overall channel. This key is cannot be locked, to ensure a password/key configuration utility
can set its value. This value is used in conjunction with the user key values (passwords) in
RAKP-HMAC- SHA1 and RAKP-HMAC-MD5 authentication. I.e. the remote console needs to have
a-priori knowledge of both this key value and the user password setting, in order to establish a
session. KG must be individually settable on each channel that supports RMCP+.
• All other = reserved
Key value. Value for specified key. Used for “set” Operation only. Otherwise, this field is not used in
the request. The MC will ignore any bytes following the ‘Key ID’ byte.
Data fieldResponse data
76 Command specification
Completion Code. Generic, plus following command-specific completion codes:1
• 80h = Cannot perform set / confirm. Key is locked (mandatory)
• 81h = insufficient key bytes
• 82h = too many key bytes
• 83h = key value does not meet criteria for specified type of key
• 84h = KR is not used. MC uses a random number generation approach that does not require a
KR value.
Page 77

7:2 - reserved.2
1:0 - lock status
• 00b = key is not lockable.
• 01b = key is locked.
• 10b = key is unlocked.
• 11b = reserved
Key value.(3:N)
The MC returns the specified key value when the Operation is set to “read key”. Otherwise, the MC
returns no additional bytes past the completion code.
Get system interface capabilities command
This command can be used to determine whether the SSIF supports multi-part transactions, and
what size of IPMI messages can be transferred. The Get System Interface Capabilities command
is mandatory for BMCs that implement multi-part writes or reads. Thus, software can assume that
if the Get System Interface Capabilities command is not implemented, the interface only supports
single-part writes and reads.
Data fieldRequest
data byte
number
System Interface Type1
[7:4] - reserved
[3:0] - System Interface Type (For BT use the Get BT Interface Capabilities command)
• 0h = SSIF
• 1h = KCS
• 2h = SMIC
• all other = reserved
Data fieldResponse
data byte
number
Completion Code1
Reserved. Returned as 00h.2
For System Interface Type = SSIF:
[7:6] - Transaction support3
• 00b = only single-part reads/writes supported.
• 01b = multi-part reads/writes supported. Start and End transactions only.
• 10b = multi-part reads/writes supported. Start, Middle, and End transactions supported.
• 11b = reserved.
[5:4] - reserved.
[3] - PEC support.
• 1b = implements PEC. MC will start using PEC in read transactions after it receives any SSIF write
transaction that includes a valid PEC. The MC ceases using PEC if it receives an SSIF write transaction
that does not include PEC.
• 0b = does not support PEC. Note that a MC implementation may reject write transactions that include
a PEC byte.
Standard command specification 77
Page 78

[2:0] - SSIF Version
• 000b = version 1 (version defined in this specification).
Input message size in bytes. (1 based.)4
Number of bytes of IPMI message data that the MC can accept. This number does not include slave address,
SMBus length , PEC, or SMBus CMD bytes, just the IPMI message data. A MC that just supports single-part
writes would return 32 (20h) for this value. A MC that supports multi-part Start and End would return a
value from 33 to 64. A MC that supports multi-part with Middle transactions would return a value from 65
to 255.
Output message size in bytes. (1 based.)5
Maximum number of bytes of IPMI message data that can be read from the MC. This number does not
include slave address, SMBus length, PEC, SMBus CMD bytes, special bytes (such as the special bytes
following the length byte in the multi -part read middle and end transactions) just the IPMI message data.
A MC that just supports single-part reads would return 20h (32) for this value. A MC that supports multi-part
Start and End would return a value from 33 to 62 (the reason this is 62 instead of 64 is that there are two
special bytes after the length byte.) A MC that supports multi-part with Middle transactions would return a
value from 63 to 255.
For System Interface Type = KCS or SMIC
[7:3] - reserved3
[2:0] - System Interface Version
• 000b = version 1 (conformant with KCS or SMIC interface as defined in this specification).
Input maximum message size in bytes. (1 based.)4
Largest number of bytes that can be transferred in a KCS FFh means 255 or more.
Get payload activation status command
This command is available to the MC.
This command returns how many instances of a given payload type are presently activated, and
how many total instances can be activated.
Table 48 Get payload activation status command request and response data
Data fieldRequest data
byte number
1
byte number
Payload type number - number of the standard payload type or OEM payload handle from which
to retrieve status.
Data fieldResponse data
Completion code1
Instance capacity2
Reserved.[7:4]
[3:0]
Number of instances of a given payload type that can be simultaneously activated on
MC. 1-based. 0h = reserved.
Instance 8 is activated.1b =[7]3
Instance 8 is deactivated.0b =
78 Command specification
Instance 7 is activated.1b =[6]
Instance 7 is deactivated.0b =
...
Instance 1 is activated.1b =[0]
Page 79

Table 48 Get payload activation status command request and response data (continued)
...
Get payload instance info command
This command is available to the MC.
This command returns information about a specific instance of a payload type. It is primarily used
by software that may want to negotiate with an application that is presently using the given payload
type. It accomplishes this by using the session ID returned from this command with the get session
info command to look up the addressing information for the party that activated the payload.
The application may then use that information to establish a direct dialog with the application that
presently owns the payload (this inter-application communication is not defined in the IPMI
specifications).
Instance 1 is deactivated.0b =
Instance 16 is activated.1b =[7]4
Instance 16 is deactivated.0b =
Instance 15 is activated.1b =[6]
Instance 15 is deactivated.0b =
Instance 9 is activated.1b =[0]
Instance 9 is deactivated.0b =
Table 49 Get payload instance info command request and response data
Data fieldRequest data byte
number
1
byte number
1
2:5
Payload type number - number of the standard payload type or OEM payload handle from which
to retrieve status.
Payload instance. 1-based. 0h = reserved.2
Data fieldResponse data
Completion code. An error completion code should be returned if the payload type in the request
is set to IPMI message ( 0h ) .
Session ID - ID of session on which the instance is presently activated. (The managed system session
ID that the MC generated when the session was activated). 00_00_00_00h if the given instance
is not activated. Remote software can use this information with the get session info command
to identify the remote console that presently is using a given payload type.
Payload-specific information (8-bytes)6:13
For payload type = SOL:
• Byte 1: Port number, a number representing the system serial port that is being redirected.
1-based. 0h = unspecified. Used when more than one port can be redirected on a system.
• Byte 2: 8 = reserved.
Set user payload access command
This command is available to the MC.
This command controls whether the specified user has the ability to activate the specified payload
type on the given channel. The command uses bitfields to allow a configuration utility to use a
single command to set enable/disable multiple payloads at a time. Standard payloads are set
separately from OEM payload enables. The command would be issued at least once with standard
Standard command specification 79
Page 80

payloads selected to set the configuration for standard payloads, and then at least once with OEM
payloads selected to set the configuration for OEM payloads.
Table 50 Set user payload access command request and response data
Data fieldRequest data byte
number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
[7:6] - Operation2
• 00b = Enable. Writing a “1b” to enable/disable bit enables the corresponding payload.
Writing “0b” to bit causes no change to enabled/disabled state.
• 01b = Disable. Writing a “1b” to bit disables the corresponding payload. Writing ”0b” to bit
causes no change to enabled/disabled state.
• 10b, 11b = Reserved
[5:0] — User ID. 000000b = reserved.
Standard payload enables 13
• [7:2] — Reserved for standard payloads 2-7 enable/disable bits.
• [1] — Standard payload 1 (SOL) enable/disable
• [0] — Reserved. IPMI messaging is enabled/disabled for users via the set user access
command.
Standard payload enables 2 - reserved4
OEM payload enables 15
• [7] - OEM payload 7 enable/disable
• [6] - OEM payload 6 enable/disable
• [5] - OEM payload 5 enable/disable
• [4] - OEM payload 4 enable/disable
• [3] - OEM payload 3 enable/disable
• [2] - OEM payload 2 enable/disable
• [1] - OEM payload 1 enable/disable
• [0] - OEM payload 0 enable/disable
OEM payload enables 2 - reserved6
Data fieldResponse data
byte number
1
Completion code. An implementation will not return an error completion code if the user access
level is set higher than the privilege limit for a given channel. If it is desired to bring attention to
this condition, it is up to software to check the channel privilege limits set using the set channel
access command and provide notification of any mismatch.
Get user payload access command
This command is available to the MC.
The get user payload access command returns the user payload enable settings that were
set using the set user payload access command.
80 Command specification
Page 81

Table 51 Get user payload access command request and response data
Data fieldRequest data byte
number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
User ID2
• [7:6] — Reserved
• [5:0] - User ID. 000000b = reserved
Data fieldResponse data
byte number
Completion code1
Standard payload enables 12
• [7:2] — Reserved for standard payloads 2-7 enabled/disabled state.
• [1]
◦ 1b = Standard payload 1 enabled (SOL)
◦ 0b = Standard payload 1 disabled
• [0] — Reserved.
Standard payload enables 2 - reserved3
OEM payload enables 1. For each bit: 1b = payload enabled, 0b = payload disabled.4
• [7] - OEM payload 7 enabled/disabled
• [6] - OEM payload 6 enabled/disabled
• [5] - OEM payload 5 enabled/disabled
• [4] - OEM payload 4 enabled/disabled
• [3] - OEM payload 3 enabled/disabled
• [2] - OEM payload 2 enabled/disabled
• [1] - OEM payload 1 enabled/disabled
• [0] - OEM payload 0 enabled/disabled
OEM payload enables 2 - reserved5
Get channel payload support command
This command is available to the MC.
This command enables local and remote console software to determine what payloads are enabled
on the given MC. The command returns a bitfield indicating which payload type numbers can be
activated on the given channel.
Table 52 Get channel payload support command request and response data
Data fieldRequest data byte
number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
Data fieldResponse data
byte number
Standard command specification 81
Page 82

Table 52 Get channel payload support command request and response data (continued)
Completion code1
2
3
4
5
6
7
• [7] = Standard payload type #7 supported
• ...
• [0] = Standard payload type #0 supported
• [7] = Standard payload type #15 (0Fh) supported
• ...
• [0] = Standard payload type #8 supported
• [7] = Session setup payload type #7 supported
• ...
• [0] = Session setup payload type #0 supported
• [7] = Session setup payload type #15 (0Fh) supported
• ...
• [0] = Session setup payload type #8 supported
• [7] = Payload type 27h (OEM7) used
• ...
• [0] = Payload type 20h (OEM0) used
• [7] = Payload type 2Fh (OEM15) used
• ...
• [0] = Payload type 28h (OEM8) used
Reserved. Return as 0000h8:9
Get channel payload version command
This command is available to the MC.
This command returns version information for the given payload type. The version number has
major and minor parts. The major part of the version should only increment when there are
significant changes to the payload format, commands, or payload-specific protocols that break
backward compatibility with earlier versions. The minor part of the version increments when there
are extensions to the payload format that are significant but are backwards compatible with earlier
versions under the same major version number. An example of a major change would be a change
to the payload activation process that would prevent earlier applications from activating the given
payload type. An example of a minor format version change would be the definition of commands
for new functions that did not exist under the previous format, but if unused, do not interfere with
the operation of older applications.
Table 53 Get channel payload version command request and response data
Data fieldRequest data byte
number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
2
82 Command specification
Payload type number/payload type handle - number of the standard payload type or OEM payload
handle for which to retrieve status. See Table 43 (page 71).
Page 83

Table 53 Get channel payload version command request and response data (continued)
Data fieldResponse data
byte number
1
Completion code. Generic plus command-specific completion code: 80h — Payload type not
available on given channel.
Format version2
• [7:4] - Major format version. BCD encoded (0 to 9).
• [3:0] - Minor format version. BCD encoded (0 to 9). Software should present version data to
the user in the format “major.minor”. For example, 10h —>1.0.
The format version for the SOL payload implemented per this specification is 1.0 (10h).
IPMI LAN Device Commands
This section defines the configuration and control commands that are specific to LAN channels.
None of the commands in the following table are required unless a LAN channel is implemented.
See Table 125 (page 160) for the specification of the Network Function and Command (CMD)
values and privilege levels for these commands.
Set LAN configuration parameters command
This command is used for setting parameters such as the network addressing information required
fro IPMI LAN-operation.
Table 54 Set LAN configuration parameters request and response data
Data fieldRequest data byte
number
Channel number1
• [7:4] — Reserved
• [3:0] — Channel number
Parameter selector2
Configuration parameter data, per the table.3:N
Data fieldResponse data
byte number
Completion code.1
• 80h = parameter not supported.
• 81h = attempt to set the ‘set in progress’ value (in parameter #0) when not in the ‘set complete’
state. (This completion code provides a way to recognize that another party has already
‘claimed’ the parameters.)
• 82h = attempt to write read-only parameter.
• 83h = attempt to read write-only parameter.
Get LAN configuration parameters command
This command is used for retrieving the configuration parameters from the set LAN
configuration parameters command.
Standard command specification 83
Page 84

Table 55 Get LAN configuration parameters request and response data
Data fieldRequest data byte
number
[7]1
• 0b = Get parameter
• 1b = Get parameter revision only
[6:4] - Reserved
[3:0] - Channel number
Parameter selector2
3
byte number
The following data bytes are not returned when the ‘get parameter revision only’ bit is 1b.
3:N
Set Selector. Selects a given set of parameters under a given Parameter selector value. 00h
if parameter doesn’t use a Set Selector.
Block Selector (00h if parameter does not require a block number)4
Data fieldResponse data
Completion Code.1
Generic codes, plus following command-specific completion code(s):
80h = parameter not supported.
[7:0] - Parameter revision.2
Format: MSN = Present revision. LSN = Oldest revision with which the parameter is backward
compatible. 11h for parameters in this specification.
Configuration parameter data, per Table 56 (page 84). If the rollback feature is implemented,
the MC makes a copy of the existing parameters when the ‘set in progress’ state becomes
asserted (See the Set In Progress parameter #0). While the ‘set in progress’ state is active,
the MC will return data from this copy of the parameters, plus any uncommitted changes
that were made to the data. Otherwise, the MC returns parameter data from non-volatile
storage.
Table 56 LAN configuration parameters
Parameter Data (non-volatile unless otherwise noted)
#Parameter
1
(volatile)
84 Command specification
data 1 - This parameter is used to indicate when any of the following parameters
0Set In Progress
are being updated, and when the updates are completed. The bit is primarily
provided to alert software than some other software or utility is in the process of
making changes to the data. An implementation can also elect to provide a
‘rollback’ feature that uses this information to decide whether to ‘roll back’ to the
previous configuration information, or to accept the configuration change.
If used, the roll back shall restore all parameters to their previous state. Otherwise,
the change shall take effect when the write occurs.
[7:2] - reserved
[1:0] -
• 00b = set complete. If a system reset or transition to powered down state occurs
while ‘set in progress’ is active, the MC will go to the ‘set complete’ state. If
rollback is implemented, going directly to ‘set complete’ without first doing a
‘commit write’ will cause any pending write data to be discarded.
• 01b = set in progress. This flag indicates that some utility or other software is
presently doing writes to parameter data. It is a notification flag only, it is not
a resource lock. The MC does not provide any interlock mechanism that would
prevent other software from writing parameter data while.
• 10b = commit write (optional). This is only used if a rollback is implemented.
The MC will save the data that has been written since the last time the ‘set in
Page 85

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
progress’ and then go to the ‘set in progress’ state. An error completion code
will be returned if this option is not supported.
• 11b = reserved
This ‘read only’ field returns which possible Authentication Types (algorithms) can
1Authentication Type
Support (Read
Only)
be enabled for the given channel. The following Authentication Type Enables
parameter selects which Authentication Types are available when activating a
session for a particular maximum privilege level.
[7:6] -reserved
[5:0] -Authentication type(s) enabled for this channel (bitfield): All bits:
• 1b = supported
• 0b = authentication type not available for use.
[5] - OEM proprietary (per OEM identified by the IANA OEM ID in the RMCP Ping
Response)
[4] - straight password / key
[3] - reserved
[2] - MD5
[1] - MD2
[0] - none
1
Enables
This field is used to configure which Authentication Types are available for use
2Authentication Type
when a remote console activates an IPMI messaging connection to the MC for a
given requested maximum privilege level. Once the session has been activated,
the accepted authentication type will be the only one used for authenticated packets,
regardless of the present operating privilege level, or the privilege level associated
with the command.
Depending on configuration of per-message and user-level authentication disables,
unauthenticated packets (authentication type = none) may also be accepted. The
MC makes no attempt to check or ensure that stricter authentication types are
associated with higher requested maximum privilege levels. E.g. it is possible to
configure the MC so activating a session with a maximum privilege level of ‘User’
requires MD5 while ‘Admin’ requires ‘none’.
NOTE: An implementation that has fixed privilege and authentication type
assignments, in which case this parameter can be implemented as Read Only. It
is recommended that an implementation that implements a subset of the possible
authentication types returns a CCh error completion code if an attempt is made to
select an unsupported authentication type.
• byte 1: Authentication Types returned for maximum requested privilege =
Callback level.
◦ [7:6] -reserved
◦ [5:0] -Authentication type(s) enabled for this channel (bitfield):
◦ All bits:
– 1b = authentication type enabled for use at given privilege level
– 0b = authentication type not available for use at given privilege level.
◦ [5] - OEM proprietary (per OEM identified by the IANA OEM ID in the
RMCP Ping Response)
◦ [4] - straight password / key
◦ [3] - reserved
◦ [2] - MD5
Standard command specification 85
Page 86

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
◦ [1] - MD2
◦ [0] - none
• byte 2: Authentication Type(s) for maximum privilege = User level
(format follows byte 1)
• byte 3: Authentication Type (s) for maximum privilege = Operator level
(format follows byte 1)
• byte 4: Authentication Type (s) for maximum privilege = Administrator level
(format follows byte 1)
• byte 5: Authentication Type (s) for maximum privilege = OEM level
(format follows byte 1)
data 1:4 - IP Address3IP Address
MS-byte first.
data 14IP Address Source
[7:4] -reserved
[3:0] -address source
• 0h = unspecified
• 1h = static address (manually configured)
• 2h = address obtained by MC running DHCP
• 3h = address loaded by BIOS or system software
• 4h = address obtained by MC running other address assignment protocol
1
(can be Read Only)
Parameters
Port
Number (optional)
data 1:6 - MAC Address for messages transmitted from MC.5MAC Address
MS-byte first. An implementation can either allow this parameter to be settable, or
it can be implemented as Read Only.
data 1:4 - Subnet Mask. MS-byte first.6Subnet Mask
7IPv4 Header
• data 1 - Time-to-live. 1-based. (Default = 40h)
Value for time-to-live parameter in IP Header for RMCP packets and PET Traps
transmitted from this channel.
• data 2
◦ [7:5] - Flags. Sets value of bit 1 in the Flags field in the IP Header for packets
transmitted by this channel. (Default = 010b “don’t fragment”)
◦ [4:0] - reserved
• data 3
◦ [7:5] - Precedence (Default = 000b)
◦ [4:1] - Type of Service (Default = 1000b, “minimize delay”) [0] - reserved
data 1:2 - Primary RMCP Port Number, LSByte first.8Primary RMCP Port
Default = 26Fh (RMCP ‘Aux Bus Shunt’ port)Number (optional)
data 1:2 - Secondary Port Number, LSByte first.9Secondary RMCP
Default = 298h (RMCP ‘Secure Aux Bus’ port)
86 Command specification
Page 87

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
data 1 - MC-generated ARP control. Note: the individual capabilities for
10MC-generated ARP
control
(optional2)
interval (optional)
Address
MC-generated ARP responses and MC-generated Gratuitous ARPs are individually
optional. The MC should return an error completion code if an attempt is made to
enable an unsupported capability.
[7:2] - reserved
[1] -
• 1b = enable MC-generated ARP responses
• 0b = disable MC-generated ARP responses
[0] -
• 1b = enable MC-generated Gratuitous ARPs
• 0b = disable MC-generated Gratuitous ARPs
data 1 -11Gratuitous ARP
• Gratuitous ARP interval
• Gratuitous ARP interval in 500 millisecond increments. 0-based. Interval accuracy
is +/- 10%.
• If this configuration parameter is not implemented, gratuitous ARPs shall be
issued at a rate of once every 2 seconds.
data 1:4 - IP Address12Default Gateway
MS-byte first. This is the address of the gateway (router) used when the MC sends
a message or alert to a party on a different subnet than the one the MC is on.
1
MAC Address
Address
MAC Address
Destinations
(Read Only)
data 1:6 - MAC Address. MS-byte first.13Default Gateway
data 1:4 - IP Address14Backup Gateway
MS-byte first. This is the address of an alternate gateway (router) that can be
selected when a sending a LAN Alert.
data 1:6 - MAC Address. MS-byte first.15Backup Gateway
data 1:18 - Community String16Community String
Default = ‘public’. Used to fill in the ‘Community String’ field in a PET Trap. This
string may optionally be used to hold a vendor-specific string that is used to provide
the network name identity of the system that generated the event. Printable ASCII
string-. If a full 18 non-null characters are provided, the last character does not
need to be a null. 18 characters must be written when setting this parameter, and
18 will be returned when this parameter is read.
The null character, and any following characters, will be ignored when the
Community String parameter is placed into the PET. The MC will return whatever
characters were written. In other words, it will not set bytes following the null to
any particular value.
data 1 - Number of LAN Alert Destinations supported on this channel. (Read Only).
17Number of
At least one set of non-volatile destination information is required if LAN alerting
is supported. Additional non-volatile destination parameters can optionally be
provided for supporting an alert ‘call down’ list policy. A maximum of fifteen (1h
to Fh) non-volatile destinations are supported in this specification. Destination 0 is
always present as a volatile destination that is used with the Alert Immediate
command.
[7:4] - reserved.
[3:0] - Number LAN Destinations. A count of 0h indicates LAN Alerting is not
supported.
Standard command specification 87
Page 88

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
Sets the type of LAN Alert associated with the given destination. This parameter
18Destination Type
(volatile /
non-volatile - see
description)
is not present if the Number of Destinations parameter is 0.
• data 1 - Set Selector = Destination selector, 0 based.
[7:4] -reserved◦
◦ [3:0] -Destination selector. Destination 0 is always present as a volatile
destination that is used with the Alert Immediate command.
• data 2 - Destination Type
◦ [7] - Alert Acknowledge.
– 0b = Unacknowledged. Alert is assumed successful if transmission occurs
without error. This value is also used with Callback numbers.
– 1b = Acknowledged. Alert is assumed successful only if acknowledged
is returned. Note, some alert types, such as Dial Page, do not support
an acknowledge.
◦ [6:3] -reserved
◦ [2:0] -Destination Type
– 000b = PET Trap destination
– 001b - 101b = reserved
– 110b = OEM 1
– 111b = OEM 2
1
• data 3 - Alert Acknowledge Timeout / Retry Interval, in seconds, 0-based (i.e.
minimum timeout = 1 second).
This value sets the timeout waiting for an acknowledge, or the time between
automatic retries depending on whether the alert is acknowledge or not.
Recommended factory default = 3 seconds. Value is ignored if alert type does
not support acknowledge, or if the Alert Acknowledge bit (above) is 0b.
• data 4 - Retries
◦ [7:4] - Reserved
◦ [3] - Reserved
◦ [2:0] - Number of times to retry alert to given destination. 0 = no retries
(alert is only sent once). If the alert is acknowledged (Alert Acknowlege bit
= 1b) the alert will only be retried if a timeout occurs waiting for the
acknowledge. Otherwise, this value selects the number of times an
unacknowledged alert will be sent out. The timeout interval or time between
retries is set by the Alert Acknowledge Timeout / Retry Interval value (byte
3 of this parameter).
88 Command specification
Page 89

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
Sets/Gets the list of IP addresses that a LAN alert can be sent to. This parameter
19Destination
Addresses
is not present if the Number of Destinations parameter is 0.
• data 1 - Set Selector = Destination Selector.
[7:4] -reserved◦
◦ [3:0] -Destination selector. Destination 0 is always present as a volatile
destination that is used with the Alert Immediate command.
• data 2 - Address Format
◦ [7:4] - Address Format.
0h = IPv4 IP Address followed by DIX Ethernet/802.3 MAC Address
◦ [3:0] - Reserved
For Address Format = 0h:
• data 3 - Gateway selector
[7:1] - Reserved◦
◦ [0] -
– 0b = use default gateway
– 1b = use backup gateway
1
• data 4:7 - Alerting IP Address (MS-byte first)
• data 8:13 - Alerting MAC Address (MS-byte first)
Following parameters are introduced with IPMI v2.0 / RMCP+
VLAN configuration can be used with IPMI v1.5 and IPMI v2.0sessions. Parameters labeled “RMCP+” are
specific to IPMI v2.0 implementations that implement IPMI v2.0 / RMCP+ sessions.
20802.1q VLAN ID
(12-bit)
• data 1
[7:0] - Least significant 8-bits of the VLAN ID. 00h if VLAN ID not used.
• data 2
◦ [7] - VLAN ID enable.
– 0b = disabled
– 1b = enabled.
If enabled, the MC will only accept packets for this channel if they have
802.1q fields and their VLAN ID matches the VLAN ID value given in
this parameter.
◦ [6:4] - Reserved
◦ [3:0] - Most significant four bits of the VLAN ID
data 121802.1q VLAN
Priority
[7:3] - Reserved
[2:0] - Value for Priority field of 802.1q fields. Ignored when VLAN ID enable is
0b (disabled) - See 802.1q VLAN ID parameter, above. Setting is network
dependent. By default, this should be set to 000b.
Cipher Suite Entry
Support
This parameter provides a count of the number (16 max.) of Cipher Suites available
22RMCP+ Messaging
to be enabled for use with IPMI Messaging on the given channel.
Software can find out what security algorithms are associated with given Cipher
Suite ID by using the Get Channel Cipher Suites command. In addition, there are(Read Only)
Standard command specification 89
Page 90

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
Cipher Suite IDs assigned for standard Cipher Suites (see Table 22-19, Cipher
Suite IDs)
data 1
[7:5] - reserved
[4:0] - Cipher Suite Entry count. Number of Cipher Suite entries, 1-based, 10h
max.
This parameter contains zero to sixteen (16) bytes of Cipher Suite IDs for Cipher
23RMCP+ Messaging
Cipher Suite Entries
(Read Only)
Cipher Suite
Privilege Levels
Suites that can be used for establishing an IPMI messaging session with the MC.
The number of Cipher Suites that are supported is given in the preceding parameter.
• data 1 - Reserved
• data 2 - Cipher Suite ID entry A. data 3 - Cipher Suite ID entry B.
• ...
• data 17 - Cipher Suite ID entry P.
This parameter allows the configuration of which privilege levels are associated
24RMCP+ Messaging
with each Cipher Suite. The total number of nibbles supported (zero to sixteen)
matches the number of fixed Cipher Suite IDs.
• data 1 - Reserved
• data 2 - Maximum Privilege Level for 1st and 2nd Cipher Suites
1
VLAN TAGs
(can be READ
ONLY, see
description)
◦ [7:4] - Maximum Privilege Level for 2nd Cipher Suite
◦ [3:0] - Maximum Privilege Level for 1st Cipher Suite
– 0h = Unspecified (given Cipher Suite is unused)
– 1h = Callback level
– 2h = User level
– 3h = Operator level
– 4h = Administrator level
– 5h = OEM Proprietary level
• data 3 - Maximum Privilege Level for 3rd and 4th Cipher Suites data 4 -
Maximum Privilege Level for 5th and 6th Cipher Suites
• …
• data 9 - Maximum Privilege Level for 15th and 16th Cipher Suites
Sets/Gets the VLAN IDs (if any) addresses that a LAN alert can be sent to. This
25Destination Address
parameter is not present if the Number of Destinations parameter is 0, or if the
implementation does not support the use of VLAN IDs for alerts. Otherwise, the
number of VLAN TAG entries matches the number of Alert Destinations.
An implementation may only be able to send alerts using the same VLAN TAG
configuration as specified by parameters 20 and 21, in which case this parameter
is allowed to be READ ONLY, where data 3-4 reflects the settings of parameters
20 and 21, and data 2 [7:4] indicates that VLAN TAGs are being used for alerts.
If the implementation does support configurable VLAN TAGs for alert destinations,
90 Command specification
Page 91

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
it must support configuring unique TAG information for all destinations on the given
channel.
• data 1 - Set Selector = Destination Selector.
[7:4] -reserved◦
◦ [3:0] -Destination selector. Destination 0 is always present as a volatile
destination that is used with the Alert Immediate command.
• data 2 - Address Format
◦ [7:4] - Address Format.
– 0h = VLAN ID not used with this destination
– 1h = 802.1q VLAN TAG
◦ [3:0] - Reserved
For Address Format = 1h:
• data 3:-4 - VLAN TAG
◦ [7:0] - VLAN ID, least-significant byte
◦ [11:8] - VLAN ID, most-significant nibble
1
Threshold (optional)
◦ [12] - CFI (Canonical Format Indicator. Set to 0b) [15:13] - User priority
(000b, typical)
Sets/Gets the Bad Password Threshold. If implemented and non-zero, this value
26Bad Password
determines the number of sequential bad passwords that will be allowed to be
entered for the identified user before the user is automatically disabled from access
on the channel.
For example, a value of 3 indicates that 3 sequential attempts are allowed for the
given username on the particular channel. If the password for the third attempt is
not correct, the user will be disabled for the channel. If this value is zero (00h)
then there is no limit on bad passwords.
The effect of the disable is the same as if a Set User Access command were used
to remove the user's access from the channel.
Bad password attempts are tracked according to individual username on a per
channel basis. (Thus, a given username may be disabled on one channel, but still
enabled on another) Bad password attempts are not counted if integrity check or
other session parameters, such as session ID, sequence number, etc. are invalid.
That is, bad password attempts are not counted if there are any other errors that
would have caused the login attempt to be rejected even if the password was
valid. The count of bad password attempts is retained as long as the MC remains
powered and is not reinitialized.
Counting automatically starts over (is reset) under any one of the following
conditions:
• A valid password is received on any of the allowed attempts b) the Attempt
Count Reset Interval expires
• The user is re-enabled using the Set User Access command
• The user is automatically re-enabled when the User Lockout Interval expires.
• The Bad Threshold number parameter value is re-written or changed
Standard command specification 91
Page 92

Table 56 LAN configuration parameters (continued)
Parameter Data (non-volatile unless otherwise noted)
#Parameter
The Set User Access command is used to re-enable the user for the Channel.
• byte 1
[7:1] - reserved◦
◦ [0] -
– 0b = do not generate an event message when the user is disabled.
– 1b = generate a Session Audit sensor "Invalid password disable" event
message. byte 2
◦ 7:0 - Bad Password Threshold number.
• byte 3:4
◦ 15:0 - Attempt Count Reset Interval. The interval, in tens of seconds, for
which the accumulated count of bad password attempts is retained before
being automatically reset to zero. The interval starts with the most recent
bad password attempt for the given username on the channel. This interval
is allowed to reset if a MC power cycles or re-initialization occurs while the
interval is being counted.
0000h = Attempt Count Reset Interval is disabled. The count of bad password
attempts is retained as long as the MC remains powered and is not
reinitialized.
1
OEM Parameters
1
Choice of system manufacturing defaults is left to the system manufacturer unless otherwise specified.
2
This configuration parameter must be supported if the controller autonomously issues gratuitous ARPs or ARP responses.
SOL commands
• byte 5:6
◦ 15:0 - User Lockout Interval. The interval, in tens of seconds, that the user
will remain disabled after being disabled because the Bad Password
Threshold number was reached. The user is automatically re-enabled when
the interval expires. Note that this requires the MC implementation to track
that the user was disabled because of a Bad Password Threshold. This interval
is allowed to be restarted if a MC power cycle or re-initialization occurs
while the interval is being counted. Note that this requires an internal
non-volatile setting to be maintained that tracks when a particular user has
been temporarily disabled due to the Bad Password Threshold. This is
required to distinguish a user that was disabled automatically from a user
that is intentionally disabled using the Set User Access command.
0000h = User Lockout Interval is disabled. If a user was automatically
disabled due to the Bad Password threshold, the user will remain disabled
until re-enabled via the Set User Access command.
This range is available for special OEM configuration parameters. The OEM is
192
identified according to the Manufacturer ID field returned by the Get Device ID
:
command.
255
Set SOL configuration parameters command
This command is available to the MC.
This command is used for setting parameters such as the network addressing information required
for SOL payload operation. Parameters can be volatile or non-volatile.
92 Command specification
Page 93

Table 57 Set SOL configuration parameters command request and response data
Data fieldRequest data byte
number
1
byte number
• [7:4] — Reserved
• [3:0] — Channel number
Parameter selector2
Configuration parameter data. See Table 59 (page 94).3:N
Data fieldResponse data
Completion code.1
• 80h = Parameter not supported.
• 81h = Attempt to set the set in progress value (in parameter #0) when not in the set complete
state. (This completion code provides a way to recognize that another party has already
“claimed” the parameters).
• 82h = Attempt to write read-only parameter.
• 83h = Attempt to read write-only parameter.
Get SOL configuration parameters command
This command is available to the MC.
This command is used for retrieving the configuration parameters from the set sol
configuration parameters command.
Table 58 Get SOL configuration parameters command request and response data
Data fieldRequest data byte
number
1
• [7]
0b = Get parameter◦
◦ 1b = Get parameter revision only
• [6:4] — Reserved
• [3:0] — Channel number
Parameter selector2
3
byte number
1
The following data byte is not returned when the get parameter revision only bit is 1b.
Set selector. Selects a given set of parameters under a given parameter selector value. 00h if
parameter does not use a set selector.
Block selector (00h if parameter does not require a block number).4
Data fieldResponse data
Completion code. Generic codes, plus command-specific completion code: 80h = parameter not
supported.
[7:0] - Parameter revision. Format: MSN = present revision. LSN = oldest revision parameter in
which it is backward compatible. 11h for parameters in this specification.
3:N
Configuration parameter data, per Table 59: “SOL configuration parameters” (page 94) If the
rollback feature is implemented, the MC makes a copy of the existing parameters when the set in
progress state becomes asserted. (See the set in progress parameter #0). While the set in progress
state is active, the MC returns data from this copy of the parameters, plus any uncommitted changes
that were made to the data. Otherwise, the MC returns parameter data from non-volatile storage.
Standard command specification 93
Page 94

Table 59 SOL configuration parameters
#Parameter
Parameter Data (non-volatile unless otherwise noted)
1
0Set In Progress (volatile)
Data 1 - This parameter is used to indicate when any of the following parameters
are being updated, and when the updates are completed. The bit is primarily
provided to alert software that some other software or utility is in the process of
making changes to the data.
An implementation can also elect to provide a rollback feature that uses this
information to decide whether to roll back to the previous configuration
information, or to accept the configuration change.
If used, the roll back restores all parameters to their previous state. Otherwise,
the change takes effect when the write occurs.
Reserved[7:2]
00b =[1:0]
Set complete. If a system reset or transition to powered
down state occurs while set in progress is active, the MC
goes to the set complete state. If rollback is implemented,
going directly to set complete without first doing a commit
write causes any pending write data to be discarded.
01b =
Set in progress. This flag indicates that some utility or
other software is presently doing writes to parameter data.
It is a notification flag only, it is not a resource lock. The
MC does not provide any interlock mechanism that would
prevent other software from writing parameter data.
10b =
Commit write (optional). This is only used if a rollback is
implemented. The MC saves the data that has been written
since the last time it was set in progress and then goes to
the set in progress state. An error completion code will
be returned if this option is not supported.
Reserved11b =
Byte 1:1SOL enable
Reserved[7:1]
[0]
SOL enable. This controls whether the SOL payload type
can be activated. Whether an SOL stream can be
established is also dependent on the access mode and
authentication settings for the corresponding LAN channel.
The enabled/disabled state and access mode settings for
the serial/modem channel have no effect on SOL.
Enable SOL payload1b =
Disable SOL payload0b =
Byte 1: SOL authentication enable2SOL authentication
Force SOL payload encryption[7]
1b:
Force encryption. If the cipher suite for the session supports
encryption, this setting forces the use of encryption for all
SOL payload data.
0b:
Encryption controlled by remote console. Whether SOL
packets are encrypted or not is selected by the remote
console at the time the payload is activated (using the
activate payload command) and can be changed
during operation via the suspend/resume payload
encryption command.
94 Command specification
Force SOL payload authentication[6]
Page 95

Table 59 SOL configuration parameters (continued)
#Parameter
Parameter Data (non-volatile unless otherwise noted)
1
[3:0]
1b:
0b:
Reserved[5:4]
SOL privilege level. Sets the minimum operating privilege level that is
required to be able to activate SOL using the activate payload
command.
Force authentication. If the cipher suite for the session
supports authentication, this setting forces the use of
authentication on all SOL payload data.
Authentication controlled by remote software. For the
standard cipher suites, if encryption is used then
authentication must also be used. Therefore, while
encryption is being used, software is not be able to select
using unauthenticated payloads.
Reserved0h:
Reserved1h:
User level2h:
Operator level3h:
Administrator level4h:
OEM proprietary level5h:
ReservedAll other :
interval & character send
threshold
3Character accumulate
4SOL retry
• Byte 1: Character accumulate interval in 5 ms increments. 1-based. This sets
the typical amount of time that the MC waits before transmitting a partial SOL
character data packet. (Where a partial packet is defined as a packet that
has fewer characters to transmit than the number of characters specified by
the Send threshold parameter (see below). A packet is not sent.
00h = reserved
• Byte 2: Character send threshold. 1-based. The MC automatically sends an
SOL character data packet containing this number of characters as soon as
this number of characters (or greater) has been accepted from the baseboard
serial controller into the MC. This provides a mechanism to tune the buffer to
reduce latency to when the first characters are received after an idle interval.
In the degenerate case, setting this value to 1 would cause the MC to send
a packet as soon as the first character was received.
This can be useful if the character accumulate interval is large. If the MC is
waiting for an acknowledge from the previous packet, it ignores this threshold
and continues to collect data until it has a full packet’s worth.
• Byte 1: Retry count
[7:3] - Reserved◦
◦ [2:0] - Retry count. 1-based. 0 = no retries after packet is transmitted.
Packet is dropped if no ACK/NACK received by the time retries expire.
• Byte 2: Retry interval. 1-based. Retry interval in 10 ms increments. Sets the
time that the MC waits before the first retry and the time between retries when
sending SOL packets to the remote console.
(non-volatile)
◦ 00h: Retries sent back-to-back
5SOL non-volatile bit rate
This configuration parameter is not supported if the implementation does not
have a MC serial controller that can be potentially configured.
Serial communication with the MC when SOL is activated always occurs using
8 bits/character, no parity, 1 stop bit, and RTS/CTS (hardware) flow control.
Standard command specification 95
Page 96

Table 59 SOL configuration parameters (continued)
#Parameter
Parameter Data (non-volatile unless otherwise noted)
NOTE: If SOL is enabled for multiple LAN channels, the MC uses the serial
communication settings for the channel over which the activate sol command
was initially received. The settings for other channels are ignored.
Data 1
Reserved[7:4]
1
(volatile)
(optional, read only)
[3:0]
6SOL volatile bit rate
7SOL payload channel
Set volatile version of SOL serial settings. Data follows that for the SOL non-volatile
bit rate parameter.
This parameter indicates which IPMI channel is being used for the communication
parameters (such as IP address, MAC address) for the SOL payload. Typically,
these parameters come from the same channel that the activate payload
command for SOL was accepted.
Bit rate. 1-5h = reserved. Support for bit rates other than 19.2 kbps is
optional. The MC must return an error completion if a requested bit
rate is not supported. It is recommended that the parameter out-of-range
(C9h) code be used for this situation.
0h =
Use setting presently configured for IPMI over serial
channel. The setting is used even if the access mode for
the serial channel is set to disabled. IPMI specification
can allow more than one serial channel. If serial port
sharing is not implemented, this value is reserved. 6h:
9600 bps.
19.2 kbps7h =
38.4 kbps8h =
57.6 kbps9h =
115.2 kbpsAh =
ReservedAll other =
8SOL payload port number
(read only or read/write)
192:255OEM parameters
1
Choice of system manufacturing defaults is left to the system manufacturer unless otherwise specified.
MC watchdog timer commands
The MC implements a standardized watchdog timer that can be used for a number of system
timeout functions by system management software or by the BIOS. Setting a timeout value of 0
allows the selected timeout action to occur immediately. This provides a standardized means for
devices on the IPMB, such as remote management cards, to perform emergency recovery actions.
Watchdog timer actions
The following actions are available on expiration of the watchdog timer:
• System reset
• System power off
This parameter is read/write when the implementation allows the port number
over which the SOL payload can be activated to be configurable. Otherwise, it
is a read only parameter.
Data 1:2 - Primary RMCP port number, LS byte first.
This range is available for special OEM configuration parameters. The OEM is
identified according to the manufacturer ID field returned by the get device
id command.
96 Command specification
Page 97

• System power cycle
• Pre-timeout interrupt (optional)
The system reset on timeout, system power off on timeout, and system power cycle on timeout
action selections are mutually exclusive. The watchdog timer is stopped whenever the system is
powered-down. A command must be sent to start the timer after the system powers up.
Watchdog timer use field and expiration flags
The watchdog timer provides a timer use field that indicates the current use assigned to the watchdog
timer. The watchdog timer provides a corresponding set of timer use expiration flags that are used
to track the type of timeout that had occurred.
The timeout use expiration flags retain their state across system resets and power cycles, as long
as the MC remains powered. The flags are normally cleared solely by the set watchdog timer
command; with the exception of the don’t log flag, which is cleared after every system hard reset
or timer timeout.
The timer use fields indicate:
DescriptionTimer use field
BIOS FRB2 timeout
BIOS POST timeout
OS load timeout
SMS OS watchdog timeout
1
In a multiprocessor system, the bootstrap processor is defined as the processor that, on system power-up or hard reset,
is allowed to run and execute system initialization (BIOS POST) while the remaining processors are held in an idle state
awaiting startup by the multiprocessing OS.
An FRB-2 (fault-resilient booting, level 2) timeout has occurred indicating that the
last system reset or power cycle was due to the system timeout during POST,
presumed to be caused by a failure or hang related to the bootstrap processor.
In this mode, the timeout occurred while the watchdog timer was being used by
the BIOS for some purpose other than FRB-2 or OS load watchdog.
The last reset or power cycle was caused by the timer being used to watchdog
the interval from boot to OS up and running. This mode requires system
management software, or OS support. BIOS should clear this flag if it starts this
timer during POST.
Indicates that the timer was being used by SMS. During run-time, SMS starts the
timer, then periodically resets it to keep it from expiring. This periodic action
serves as a heartbeat that indicates that the OS (or at least the SMS task) is still
functioning. If SMS hangs, the timer expires and the MC generates a system
reset. When SMS enables the timer, it should make sure the SMS bit is set to
indicate that the timer is being used in its OS watchdog role.
Indicates that the timer was being used for an OEM-specific function.OEM
Using the timer use field and expiration flags
The software that sets the timer use field is responsible for managing the associated timer use
expiration flag. For example, if SMS sets the timer use to SMS/OS watchdog, then that same SMS
is responsible for acting on and clearing the associated timer use expiration flag.
In addition, software should only interpret or manage the expiration flags for watchdog timer uses
that it set. For example, BIOS should not report watchdog timer expirations or clear the expiration
flags for non-BIOS uses of the timer. This is to allow the software that did set the timer use to see
that a matching expiration occurred.
1
Watchdog timer event logging
By default, the MC automatically logs the corresponding sensor-specific watchdog sensor event
when a timer expiration occurs. A don’t log bit is provided to temporarily disable the automatic
logging. The don’t log bit is automatically cleared (logging re-enabled) whenever a timer expiration
occurs.
Standard command specification 97
Page 98

Pre-timeout interrupt
The watchdog timer offers a pre-timeout interrupt option. This option is enabled whenever the
interrupt on timeout option is selected along with any of the other watchdog timer actions. If this
option is enabled, the MC generates the selected interrupt a fixed interval before the timer expires.
This feature can be used to allow an interrupt handler to intercept the timeout event before it actually
occurs. The default pre-timeout interrupt interval is one (1) second.
The watchdog timeout action and the pre-timeout interrupt functions are individually enabled. Thus,
the watchdog timer can be configured so that when it times out it provides just an interrupt, just
the selected action, both an interrupt and selected action, or none.
If the pre-timeout interval is set to zero, the pre-timeout action occurs concurrently with the timeout
action. If a power or reset action is selected with a pre-timeout interval of zero, there is no guarantee
that a pre-timeout interrupt handler would have time to execute, or to run to completion.
Pre-timeout interrupt support detection
An application that wishes to use a particular pre-timeout interrupt can check for its support by
issuing a set watchdog timer command with the desired pre-timeout interrupt selection. If the
controller does not return an error completion code, then a get watchdog timer command
should be issued to verify that the interrupt selection was accepted.
While it can be assumed that a controller that accepts a given interrupt selection supports the
associated interrupt, it is recommended that, if possible, an application also generate a test interrupt
and verify that the interrupt occurs and the handler executes correctly.
BIOS support for watchdog timer
If a system warm reset occurs, the watchdog timer may still be running while BIOS executes
POST. Therefore, BIOS should take steps to stop or restart the watchdog timer early in POST.
Otherwise, the timer may expire later during POST or after the OS has booted.
Reset watchdog timer command
This command is used for starting and restarting the watchdog timer from the initial countdown
value that was specified in the set watchdog timer command. If a pre-timeout interrupt has
been configured, the reset watchdog timer command is not restart the timer once the
pre-timeout interrupt interval has been reached. The only way to stop the timer once it has reached
this point is via the set watchdog timer command.
Table 60 Reset watchdog timer command response data
Data fieldResponse data
byte number
1
Completion code. Generic plus command-specific completion code: 80h — Attempt to start
un-initialized watchdog. It is recommended that a MC implementation return this error completion
code to indicate to software that a set watchdog timer command has not been issued to
initialize the timer since the last system power on, reset, or MC reset. Since many systems may
initialize the watchdog timer during BIOS operation, this condition may only be seen by software
if a MC gets re-initialized during system operation (as might be the case if a firmware update
occurred, for example).
Set watchdog timer command
This command is used for initializing and configuring the watchdog timer. The command is also
used for stopping the timer.
98 Command specification
Page 99

If the timer is already running, the set watchdog timer command stops the timer (unless the
don’t stop bit is set) and clears the watchdog pre-timeout interrupt flag. MC hard resets, system
hard resets, and the cold reset command also stop the timer and clear the flag.
• Byte 1 is used for selecting the timer use and configuring whether an event will be logged on
expiration.
• Byte 2 is used for selecting the timeout action and pre-timeout interrupt type.
• Byte 3 sets the pre-timeout interval. If the interval is set to zero, the pre-timeout action occurs
concurrently with the timeout action.
• Byte 4 is used for clearing the timer use expiration flags. A bit set in byte 4 of this command
clears the corresponding bit in byte 5 of the get watchdog timer command.
• Bytes 5 and 6 hold the least significant and most significant bytes, respectively, of the
countdown value. The watchdog timer decrement is one count/100 ms. The counter expires
when the count reaches zero. If the counter is loaded with zero and the reset watchdog
command is issued to start the timer, the associated timer events occur immediately.
Table 61 Set watchdog timer command request and response data
Data fieldRequest data
byte number
Timer use1
Don't log1b =[7]
1b =[6]
0b =
Reserved[5:3]
Timer use (logged on expiration when don't log bit = 0b)[2:0]
-111b =
Timer actions2
Reserved[7]
Don't stop the timer on set watchdog timer command. New parameters
take effect immediately. If the timer is already running, the countdown value
gets set to the given value and the countdown continues from that point. If the
timer is already stopped, it remains stopped. If the pre-timeout interrupt bit is
set, it is cleared.
Timer stops automatically when the set watchdog timer command is
received.
Reserved000b =
BIOS FRB2001b =
BIOS/POST010b =
OS Load011b =
SMS/OS100b =
OEM101b =
Reserved110b
1
Pre-timeout interrupt (logged on expiration when don’t log bit = 0b)[6:4]
011b =
None000b =
SMI (optional)001b =
NMI / diagnostic interrupt (optional)010b =
Messaging interrupt (this is the same interrupt as allocated to the messaging
interface, if communications interrupts are supported for the system interface).
Standard command specification 99
Page 100

Table 61 Set watchdog timer command request and response data (continued)
Reserved100b,111b
=
Reserved[3]
Timeout action[2:0]
No action000b =
Hard reset001b =
Power down010b =
Power dycle011b =
Reserved100b,111b
=
Pre-timeout interval in seconds. 1 based.3
Timer use expiration flags clear. (0b = leave alone, 1b = clear timer use expiration bit).4
Reserved[7]
Reserved[6]
OEM[5]
SMS/OS[4]
Initial countdown value, LS byte (100 ms/count)5
Initial countdown value, MS byte6
Data fieldResponse data
byte number
Completion code1
1
Potential race conditions exist with implementations of this option. If the set watchdog timer command is sent just
before a pre-timeout interrupt or timeout is set to occur, the timeout could occur before the command is executed. To
avoid this condition, it is recommended that software set this value no closer than 3 counts before the pre-timeout or
timeout value is reached.
Get watchdog timer command
This command retrieves the current settings and present countdown of the watchdog timer. The
timer use expiration flags in byte 5 retain their states across system resets and system power cycles.
With the exception of bit 6 in the timer use byte, the timer use expiration flags are cleared using
the set watchdog timer command. They may also become cleared because of a loss of MC
power, firmware update, or other cause of MC hard reset. Bit 6 of the timer use byte is automatically
cleared to 0b whenever the timer times out, is stopped when the system is powered down, enters
a sleep state, or is reset.
OS load[3]
BIOS/POST[2]
BIOS FRB2[1]
Reserved[0]
Table 62 Get watchdog timer command response data
byte number
100 Command specification
Data fieldResponse data
Completion code1
 Loading...
Loading...