Page 1

Notebook PC
User Guide
Page 2

© Copyright 2010 Hewlett-Packard
Development Company, L.P.
Bluetooth is a trademark owned by its
proprietor and used by Hewlett-Packard
Company under license. Intel is a trademark
of Intel Corporation in the U.S. and other
countries or regions. Java is a U.S.
trademark of Sun Microsystems, Inc.
Microsoft and Windows are U.S. registered
trademarks of Microsoft Corporation. SD
Logo is a trademark of its proprietor.
The information contained herein is subject
to change without notice. The only
warranties for HP products and services are
set forth in the express warranty statements
accompanying such products and services.
Nothing herein should be construed as
constituting an additional warranty. HP shall
not be liable for technical or editorial errors
or omissions contained herein.
First Edition: March 2010
Document Part Number: 601867-001
Product notice
This user guide describes features that are
common to most models. Some features
may not be available on your computer.
Page 3

Safety warning notice
WARNING! To reduce the possibility of heat-related injuries or of overheating the computer, do not
place the computer directly on your lap or obstruct the computer air vents. Use the computer only on a
hard, flat surface. Do not allow another hard surface, such as an adjoining optional printer, or a soft
surface, such as pillows or rugs or clothing, to block airflow. Also, do not allow the AC adapter to contact
the skin or a soft surface, such as pillows or rugs or clothing, during operation. The computer and the
AC adapter comply with the user-accessible surface temperature limits defined by the International
Standard for Safety of Information Technology Equipment (IEC 60950).
iii
Page 4

iv Safety warning notice
Page 5

Table of contents
1 Features ........................................................................................................................................................... 1
Identifying hardware ............................................................................................................................. 1
Top components .................................................................................................................. 1
TouchPad ............................................................................................................ 1
Lights ................................................................................................................... 3
Buttons, switch, and speaker .............................................................................. 4
Keys .................................................................................................................... 6
Front components ................................................................................................................ 7
Right-side components ........................................................................................................ 8
Left-side components .......................................................................................................... 9
Bottom components ............................................................................................................. 9
Multimedia components ..................................................................................................... 11
Wireless antennas (select models only) ............................................................................ 12
Additional hardware components ...................................................................................... 13
Identifying the labels ........................................................................................................................... 13
2 Networking .................................................................................................................................................... 15
Using wireless devices (select models only) ...................................................................................... 15
Identifying wireless and network icons .............................................................................. 15
Using the wireless controls ................................................................................................ 16
Using the wireless key ....................................................................................................... 16
Using operating system controls ........................................................................................ 16
Using a WLAN .................................................................................................................................... 17
Setting up a WLAN ............................................................................................................ 17
Protecting your WLAN ....................................................................................................... 17
Connecting to a WLAN ...................................................................................................... 19
Roaming to another network .............................................................................................. 19
Using Bluetooth wireless devices (select models only) ...................................................................... 20
Bluetooth and Internet Connection Sharing (ICS) ............................................................. 20
Troubleshooting wireless connection problems ................................................................................. 21
Cannot create a WLAN connection ................................................................................... 21
Cannot connect to a preferred network ............................................................................. 22
Network icon is not displayed ............................................................................................ 22
Current network security codes are unavailable ................................................................ 22
v
Page 6

WLAN connection is very weak ......................................................................................... 23
Cannot connect to the wireless router ............................................................................... 23
Using the modem (select models only) .............................................................................................. 24
Connecting a modem cable (purchased separately) ......................................................... 24
Connecting a country-specific modem cable adapter (purchased separately) .................. 25
Selecting a location setting ................................................................................................ 25
Viewing the current location selection ............................................................... 25
Adding new locations when traveling ................................................................ 26
Solving travel connection problems .................................................................. 27
Using preinstalled communication software ...................................................... 28
Connecting to a local area network (LAN) .......................................................................................... 29
3 Pointing devices and keyboard ................................................................................................................... 30
Using pointing devices ....................................................................................................................... 30
Setting pointing device preferences ................................................................................... 30
Using the TouchPad .......................................................................................................... 30
Connecting an external mouse .......................................................................................... 30
Using the keyboard ............................................................................................................................ 30
Using hotkeys .................................................................................................................... 30
Displaying system information .......................................................................... 32
Opening Help and Support ................................................................................ 33
Decreasing screen brightness ........................................................................... 33
Increasing screen brightness ............................................................................ 33
Switching the screen image .............................................................................. 33
Initiating Standby (fn+f5) ................................................................................... 34
Initiating QuickLock (fn+f6) (select models) ...................................................... 34
Launching Web browser (fn+f7) (select models) ............................................... 34
Launching printer (fn+f8) (select models) .......................................................... 34
Muting speaker sound (fn+f7) (select models) .................................................. 34
Decreasing speaker sound (fn+f8) (select models) ........................................... 34
Increasing speaker sound (fn+f9) (select models) ............................................ 35
Playing the previous track or section of an audio CD or a DVD (fn+f10) (select
models) ............................................................................................................. 35
Playing, pausing, or resuming an audio CD or a DVD (fn+f11) (select
models) ............................................................................................................. 35
Playing the next track or section of an audio CD or a DVD (fn+f12) (select
models) ............................................................................................................. 35
Using the embedded numeric keypad ................................................................................................ 36
Enabling and disabling the embedded numeric keypad .................................................... 36
Switching key functions on the embedded numeric keypad .............................................. 36
Using an optional external numeric keypad ....................................................................................... 37
4 Multimedia ..................................................................................................................................................... 38
Multimedia features ............................................................................................................................ 38
vi
Page 7

Identifying your multimedia components ........................................................................... 38
Adjusting the volume ......................................................................................................... 40
Multimedia software ........................................................................................................................... 41
Opening preinstalled multimedia software ......................................................................... 41
Using multimedia software ................................................................................................. 41
Installing multimedia software from a disc ......................................................................... 42
Audio .................................................................................................................................................. 43
Connecting external audio devices .................................................................................... 43
Checking your audio functions ........................................................................................... 43
Video .................................................................................................................................................. 45
Connecting an external monitor or projector ...................................................................... 45
Using the external monitor port ......................................................................... 45
Using the HDMI port .......................................................................................................... 45
Configuring audio for HDMI ............................................................................................... 46
Optical drive (select models only) ...................................................................................................... 47
Identifying the installed optical drive .................................................................................. 47
Using optical discs (CDs, DVDs, and BDs) ....................................................................... 47
Selecting the right disc (CDs, DVDs, and BDs) ................................................................. 47
CD-R discs ........................................................................................................ 48
CD-RW discs ..................................................................................................... 48
DVD±R discs ..................................................................................................... 48
DVD±RW discs ................................................................................................. 48
LightScribe DVD+R discs .................................................................................. 48
Blu-ray Discs (BDs) ........................................................................................... 48
Playing a CD, DVD, or BD ................................................................................................. 49
Configuring AutoPlay ......................................................................................................... 49
Changing DVD region settings .......................................................................................... 50
Observing the copyright warning ....................................................................................... 50
Copying a CD or DVD ........................................................................................................ 50
Creating (burning) a CD or DVD ........................................................................................ 51
Removing an optical disc (CD, DVD, or BD) ..................................................................... 51
Troubleshooting ................................................................................................................. 52
The optical disc tray does not open for removal of a CD, DVD, or BD ............. 52
The computer does not detect the optical drive ................................................ 53
Preventing playback disruptions ....................................................................... 54
A disc does not play .......................................................................................... 54
A disc does not play automatically .................................................................... 55
A movie stops, skips, or plays erratically .......................................................... 55
A movie is not visible on an external display ..................................................... 55
The process of burning a disc does not begin, or it stops before
completion ......................................................................................................... 55
A device driver must be reinstalled ................................................................... 56
Obtaining the latest HP device drivers ............................................. 56
Obtaining Microsoft device drivers ................................................... 56
vii
Page 8

Webcam ............................................................................................................................................. 57
Webcam tips ...................................................................................................................... 57
Adjusting webcam properties ............................................................................................. 57
5 Power management ...................................................................................................................................... 59
Setting power options ......................................................................................................................... 59
Using power-saving states ................................................................................................. 59
Initiating and exiting Standby ............................................................................ 59
Initiating and exiting Hibernation ....................................................................... 60
Using the Power Meter ...................................................................................................... 60
Using power schemes ....................................................................................................... 61
Viewing the current scheme .............................................................................. 61
Selecting a different power scheme .................................................................. 61
Customizing power schemes ............................................................................ 62
Setting password protection upon exiting Standby ............................................................ 62
Using external AC power .................................................................................................................... 62
Connecting the AC adapter ............................................................................................... 63
Using battery power ........................................................................................................................... 63
Displaying the remaining battery charge ........................................................................... 64
Inserting or removing the battery ....................................................................................... 64
Charging a battery ............................................................................................................. 66
Maximizing battery discharge time .................................................................................... 66
Managing low battery levels .............................................................................................. 66
Identifying low battery levels ............................................................................. 67
Resolving a low battery level ............................................................................. 67
Resolving a low battery level when external power is available ....... 67
Resolving a low battery level when a charged battery is
available ........................................................................................... 67
Resolving a low battery level when no power source is
available ........................................................................................... 67
Resolving a low battery level when the computer cannot exit
Hibernation ....................................................................................... 67
Calibrating a battery ........................................................................................................... 68
Step 1: Fully charge the battery ........................................................................ 68
Step 2: Disable Hibernation and Standby ......................................................... 68
Step 3: Discharge the battery ............................................................................ 69
Step 4: Fully recharge the battery ..................................................................... 69
Step 5: Reenable Hibernation and Standby ...................................................... 69
Conserving battery power .................................................................................................. 69
Storing a battery ................................................................................................................ 70
Disposing of a used battery ............................................................................................... 70
Replacing the battery ......................................................................................................... 70
Testing an AC adapter ....................................................................................................................... 71
Shutting down the computer ............................................................................................................... 71
viii
Page 9

6 Drives ............................................................................................................................................................. 72
Identifying installed drives .................................................................................................................. 72
Handling drives ................................................................................................................................... 72
Improving hard drive performance ..................................................................................................... 74
Using Disk Defragmenter ................................................................................................... 74
Using Disk Cleanup ........................................................................................................... 74
Using external drives .......................................................................................................................... 75
Using optional external devices ......................................................................................... 75
Replacing the hard drive .................................................................................................................... 76
7 External devices ............................................................................................................................................ 80
Using a USB device ........................................................................................................................... 80
Connecting a USB device .................................................................................................. 80
Stopping and removing a USB device ............................................................................... 80
Using USB legacy support ................................................................................................. 81
Using external drives .......................................................................................................................... 82
Using optional external devices ......................................................................................... 82
8 External media cards .................................................................................................................................... 83
Using Media Card Reader cards ........................................................................................................ 83
Inserting a digital card ........................................................................................................ 83
Removing a digital card ..................................................................................................... 84
Using ExpressCards (select models only) .......................................................................................... 85
Configuring an ExpressCard .............................................................................................. 85
Inserting an ExpressCard .................................................................................................. 85
Stopping and removing an ExpressCard ........................................................................... 86
9 Memory modules .......................................................................................................................................... 88
Adding or replacing a memory module in the expansion memory module slot .................................. 89
Upgrading a memory module in the primary memory module slot ..................................................... 93
10 Security ........................................................................................................................................................ 97
Protecting the computer ..................................................................................................................... 97
Using passwords ................................................................................................................................ 98
Setting passwords in Windows .......................................................................................... 98
Setting passwords in Computer Setup .............................................................................. 98
BIOS administrator password ............................................................................................ 99
Managing a BIOS administrator password ........................................................ 99
Entering a BIOS administrator password ........................................................ 100
Using Computer Setup DriveLock ................................................................................... 100
Setting a DriveLock password ......................................................................... 101
Entering a DriveLock password ...................................................................... 101
Changing a DriveLock password .................................................................... 101
ix
Page 10

Removing DriveLock protection ...................................................................... 102
Using Computer Setup Auto DriveLock ........................................................................... 102
Entering an Automatic DriveLock password ................................................... 103
Removing Automatic DriveLock protection ..................................................... 103
Using Computer Setup security features .......................................................................................... 104
Securing system devices ................................................................................................. 104
Viewing Computer Setup System Information ................................................................. 104
Using Computer Setup System IDs ................................................................................. 105
Using antivirus software ................................................................................................................... 106
Using firewall software ..................................................................................................................... 107
Installing critical updates .................................................................................................................. 108
Using HP ProtectTools Security Manager (select models only) ....................................................... 109
Installing a security cable ................................................................................................................. 110
11 Software updates ...................................................................................................................................... 111
Updating software ............................................................................................................................ 111
Updating the BIOS ........................................................................................................................... 113
Determining the BIOS version ......................................................................................... 113
Downloading a BIOS update ........................................................................................... 114
Updating programs and drivers ........................................................................................................ 116
Using SoftPaq Download Manager .................................................................................................. 117
12 Backup and recovery ................................................................................................................................ 118
Backing up your information ............................................................................................................. 119
Performing a recovery ...................................................................................................................... 120
Recovering your information ............................................................................................ 120
Recovering the operating system and programs ............................................................. 120
13 Computer Setup ........................................................................................................................................ 121
Starting Computer Setup .................................................................................................................. 121
Using Computer Setup ..................................................................................................................... 121
Navigating and selecting in Computer Setup ................................................................... 121
Restoring factory settings in Computer Setup ................................................................. 122
Computer Setup menus ................................................................................................................... 122
File menu ......................................................................................................................... 123
Security menu .................................................................................................................. 123
System Configuration menu ............................................................................................ 124
14 MultiBoot ................................................................................................................................................... 129
About the boot device order ............................................................................................................. 129
Enabling boot devices in Computer Setup ....................................................................................... 131
Considering boot order changes ...................................................................................................... 132
Choosing MultiBoot preferences ...................................................................................................... 133
x
Page 11

Setting a new boot order in Computer Setup ................................................................... 133
Dynamically choosing a boot device using the F9 prompt ............................................... 133
Setting a MultiBoot Express prompt ................................................................................ 134
Entering MultiBoot Express preferences ......................................................................... 134
15 Management and printing ........................................................................................................................ 135
Using Client Management Solutions ................................................................................................ 135
Configuring and deploying a software image ................................................................... 135
Managing and updating software ..................................................................................... 136
HP Client Manager for Altiris (select models only) .......................................... 136
HP Client Configuration Manager (CCM) (select models only) ....................... 137
HP System Software Manager (SSM) ............................................................. 137
16 Cleaning guidelines .................................................................................................................................. 139
Cleaning products ............................................................................................................................ 139
Cleaning procedures ........................................................................................................................ 140
Cleaning the display ........................................................................................................ 140
Cleaning the sides and cover .......................................................................................... 140
Cleaning the TouchPad and keyboard ............................................................................ 140
Cleaning a tablet PC pen and pen holder ........................................................................ 140
Index ................................................................................................................................................................. 141
xi
Page 12

xii
Page 13
1Features
Identifying hardware
To see a list of hardware installed in the computer:
1. Select Start > My Computer.
2. In the left pane of the System Tasks window, select View system information.
3. Select Hardware tab > Device Manager.
You can also add hardware or modify device configurations using Device Manager.
Top components
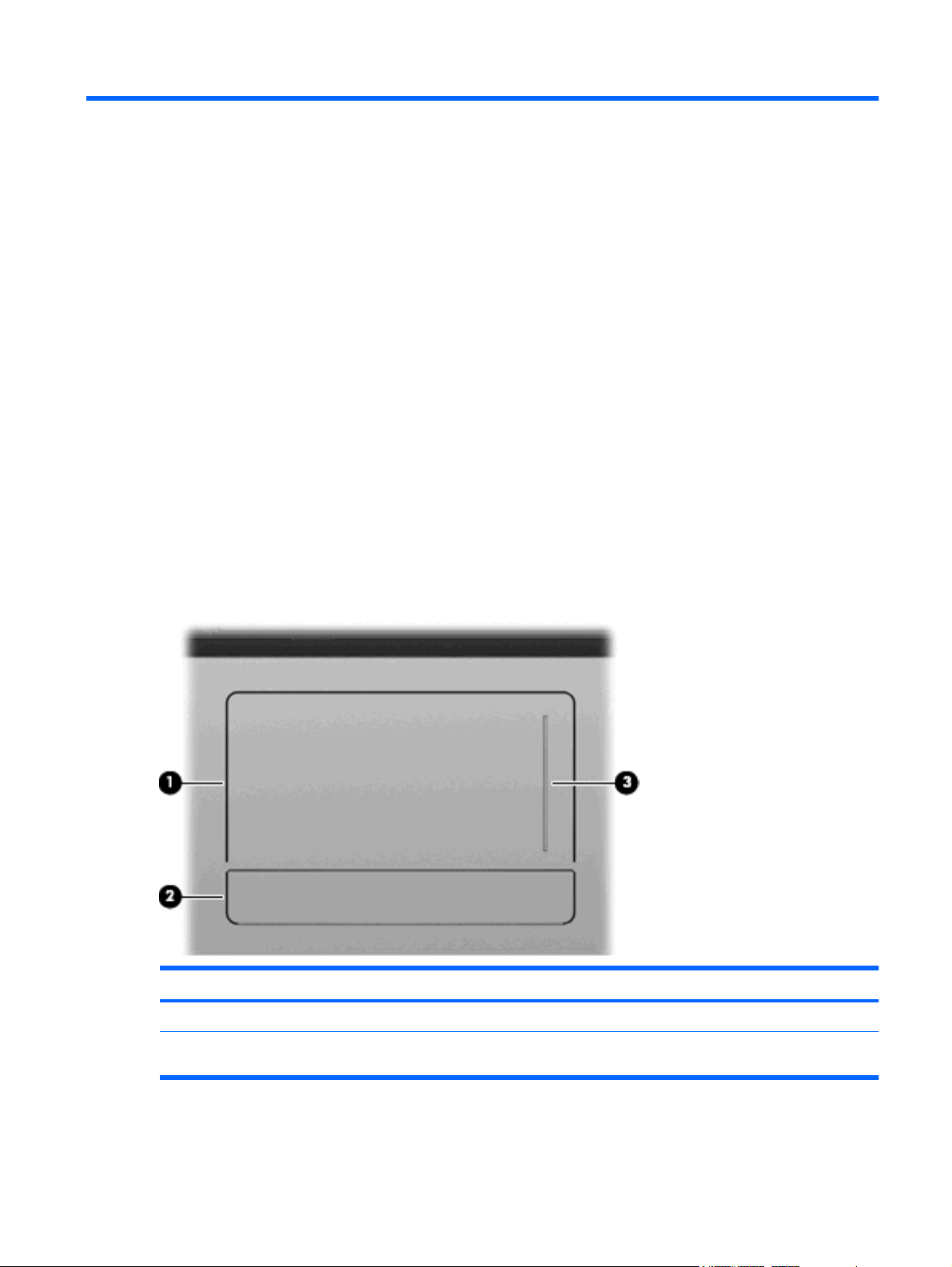
TouchPad
Component Description
(1) TouchPad* Moves the pointer and selects or activates items on the screen.
(2) TouchPad button* The left and right sides of the single button function like the left and
right buttons on an external mouse.
Identifying hardware 1
Page 14
Component Description
(3) TouchPad scroll zone Scrolls up or down.
*This table describes factory settings. To view or change pointing device preferences, select Start > Control Panel > Printers
and Other Hardware > Mouse.
2 Chapter 1 Features
Page 15
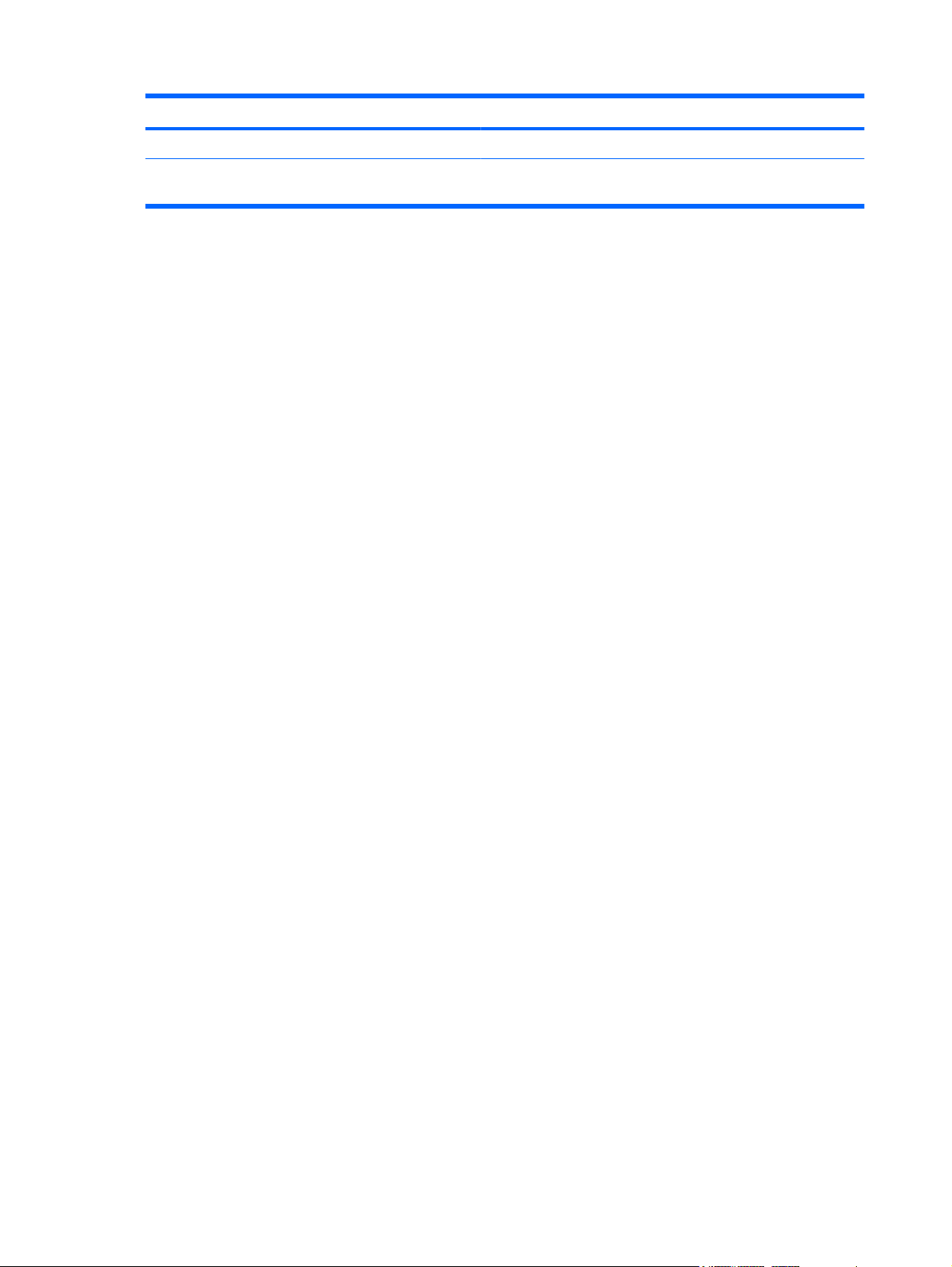
Lights
NOTE: Refer to the illustration that most closely matches your computer.
Component Description
(1) Caps lock light On: Caps lock is on.
Identifying hardware 3
Page 16

Component Description
(2) Power light
(3) Wireless light
Buttons, switch, and speaker
On: The computer is on.
●
Blinking: The computer is in Standby.
●
Off: The computer is off or in Hibernation.
●
White: An integrated wireless device, such as a wireless local
●
area network (WLAN) device and/or a Bluetooth® device, is
on.
Amber: All wireless devices are off.
●
Component Description
(1) Speaker Produces sound.
4 Chapter 1 Features
Page 17

Component Description
(2) Internal display switch Turns off the display if the panel lid is closed while the power is on.
(3) Power button
When the computer is off, press the button to turn on the
●
computer.
When the computer is on, press the button to shut down the
●
computer.
When the computer is in Standby, press the button briefly to
●
exit Standby.
When the computer is in Hibernation, press the button briefly
●
to exit Hibernation.
If the computer has stopped responding and Windows shutdown
procedures are ineffective, press and hold the power button for at
least 5 seconds to turn off the computer.
To learn more about your power settings, select Start > Control
Panel > Performance and Maintenance > Power Options.
Identifying hardware 5
Page 18

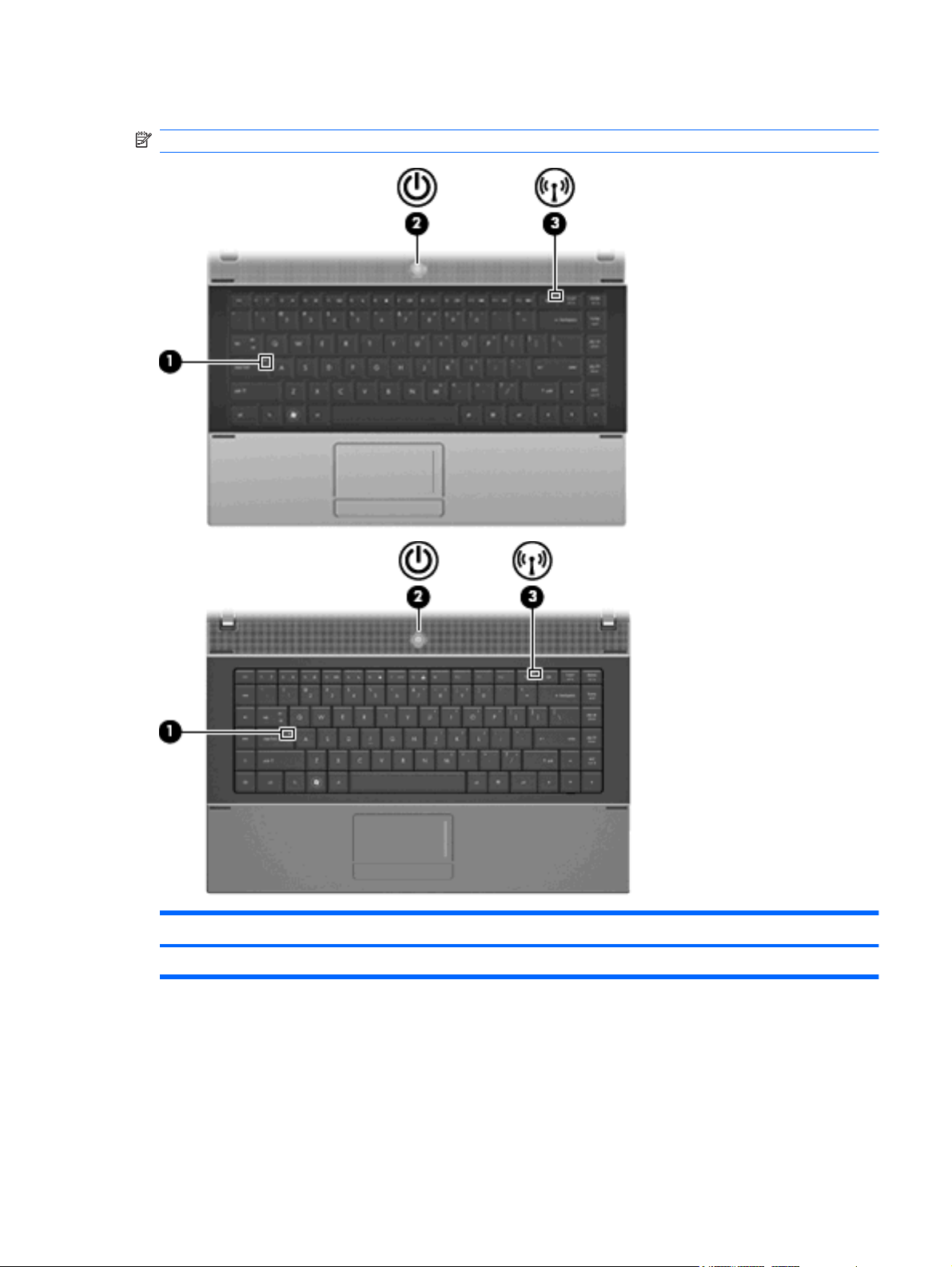
Keys
NOTE: Refer to the illustration and table that most closely matches your computer.
Component Description
(1) esc key Displays system information when pressed in combination with the
fn key.
(2) fn key Executes frequently used system functions when pressed in
(3) Windows logo key Displays the Windows Start menu.
(4) Windows applications key Displays a shortcut menu for items beneath the cursor.
(5) Embedded numeric keypad keys Can be used like the keys on an external numeric keypad when
(6) Function keys Execute frequently used system functions when pressed in
(7) Wireless key Because the wireless devices are enabled at the factory, use the
combination with a function key or the esc key.
pressed in combination with the fn and num lk keys.
combination with the fn key.
wireless key to turn on or turn off the wireless devices
simultaneously.
6 Chapter 1 Features
Page 19
Component Description
(1) esc key Displays system information when pressed in combination with the
fn key.
(2) fn key Executes frequently used system functions when pressed in
(3) Windows logo key Displays the Windows Start menu.
(4) Windows applications key Displays a shortcut menu for items beneath the cursor.
(5) Embedded numeric keypad keys Can be used like the keys on an external numeric keypad when
(6) Wireless key Because the wireless devices are enabled at the factory, use the
(7) Function keys Execute frequently used system functions when pressed in
Front components
combination with a function key or the esc key.
pressed in combination with the fn and num lk keys.
wireless key to turn on or turn off the wireless devices
simultaneously.
combination with the fn key.
Identifying hardware 7
Page 20

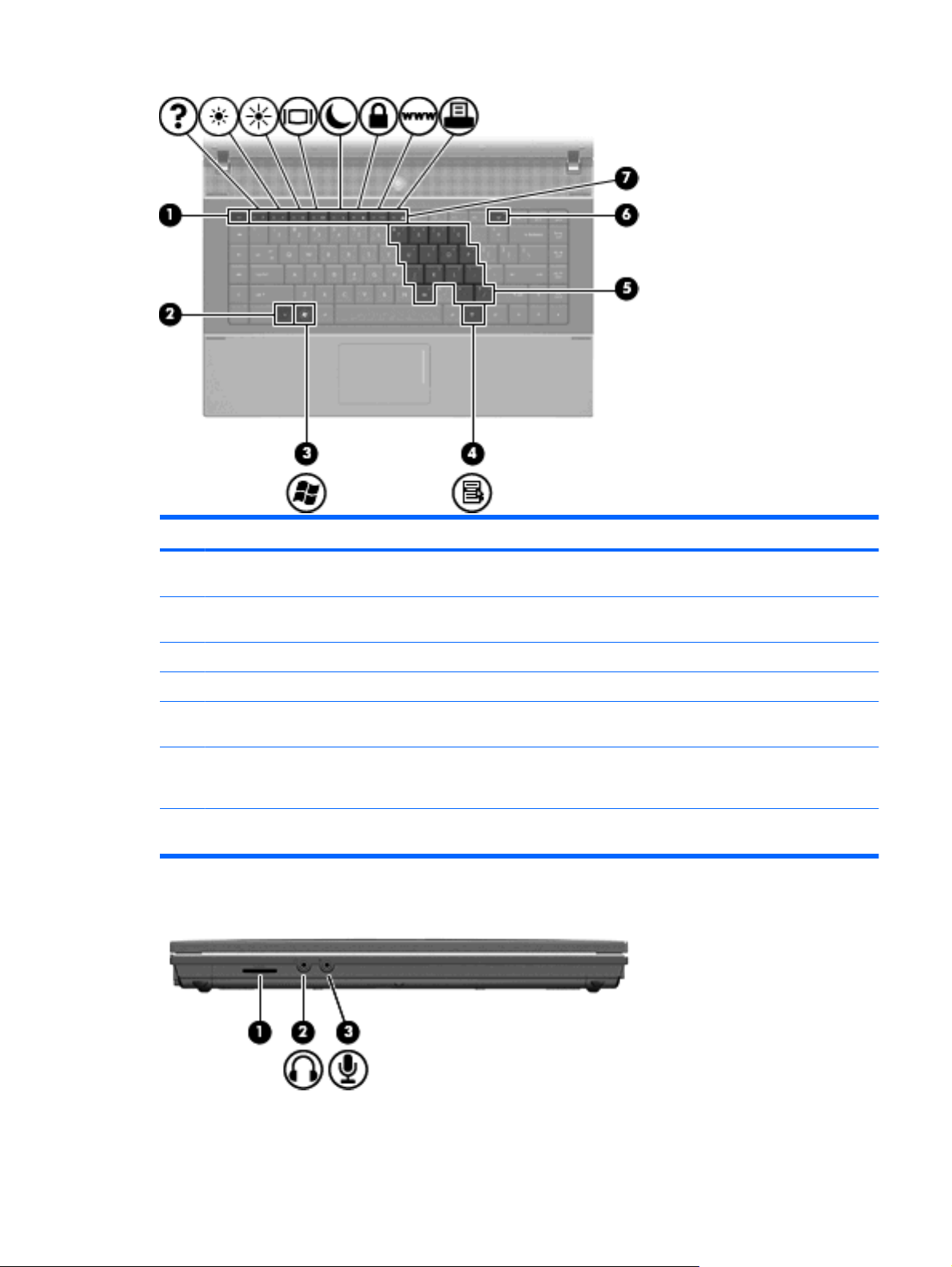
Component Description
(1) SD Card Reader Supports the following optional digital card formats:
(2) Audio-out (headphone) jack Produces sound when connected to optional powered stereo
(3) Audio-in (microphone) jack Connects an optional computer headset microphone, stereo array
Right-side components
MultiMediaCard (MMC)
●
MultiMediaCard 4.2 (MMC Plus, including MMC Plus HC)
●
Secure Digital (SD) Memory Card
●
Secure Digital High Capacity (SDHC) Memory Card
●
Secure Digital High Speed (SDHS) Memory Card
●
speakers, headphones, ear buds, a headset, or television audio.
NOTE: When a device is connected to the headphone jack, the
computer speakers are disabled.
microphone, or monaural microphone.
Component Description
(1) USB ports (2) Connect optional USB devices.
(2) RJ-11 (modem) jack (select models only) Connects a modem cable.
(3) Optical drive (select models only) Reads optical discs and, on select models, also writes to optical
(4) Optical drive light (select models only) Blinking: The optical drive is being accessed.
(5) Optical drive button (select models only) Opens optical drive tray.
discs.
8 Chapter 1 Features
Page 21

Left-side components
Component Description
(1) ExpressCard slot Supports optional ExpressCards.
(2) Security cable slot Attaches an optional security cable to the computer.
(3) Vent Enables airflow to cool internal components.
NOTE: The security cable is designed to act as a deterrent, but
it may not prevent the computer from being mishandled or stolen.
NOTE: The computer fan starts up automatically to cool internal
components and prevent overheating. It is normal for the internal
fan to cycle on and off during routine operation.
(4) External monitor port Connects an external VGA monitor or projector.
(5) Battery light
(6) Power connector Connects an AC adapter.
(7) RJ-45 (network) jack Connects a network cable.
(8) HDMI port Connects an optional HDMI device.
(9) USB port (1) Connect optional USB devices.
Amber: A battery is charging.
●
Turquoise: A battery is close to full charge capacity.
●
Blinking amber: A battery that is the only available power
●
source has reached a low battery level. When the battery
reaches a critical battery level, the battery light begins blinking
rapidly.
Off: If the computer is plugged into an external power source,
●
the light turns off when all batteries in the computer are fully
charged. If the computer is not plugged into an external power
source the light stays off until the battery reaches a low battery
level.
Bottom components
NOTE: Refer to the illustration that most closely matches your computer.
Identifying hardware 9
Page 22
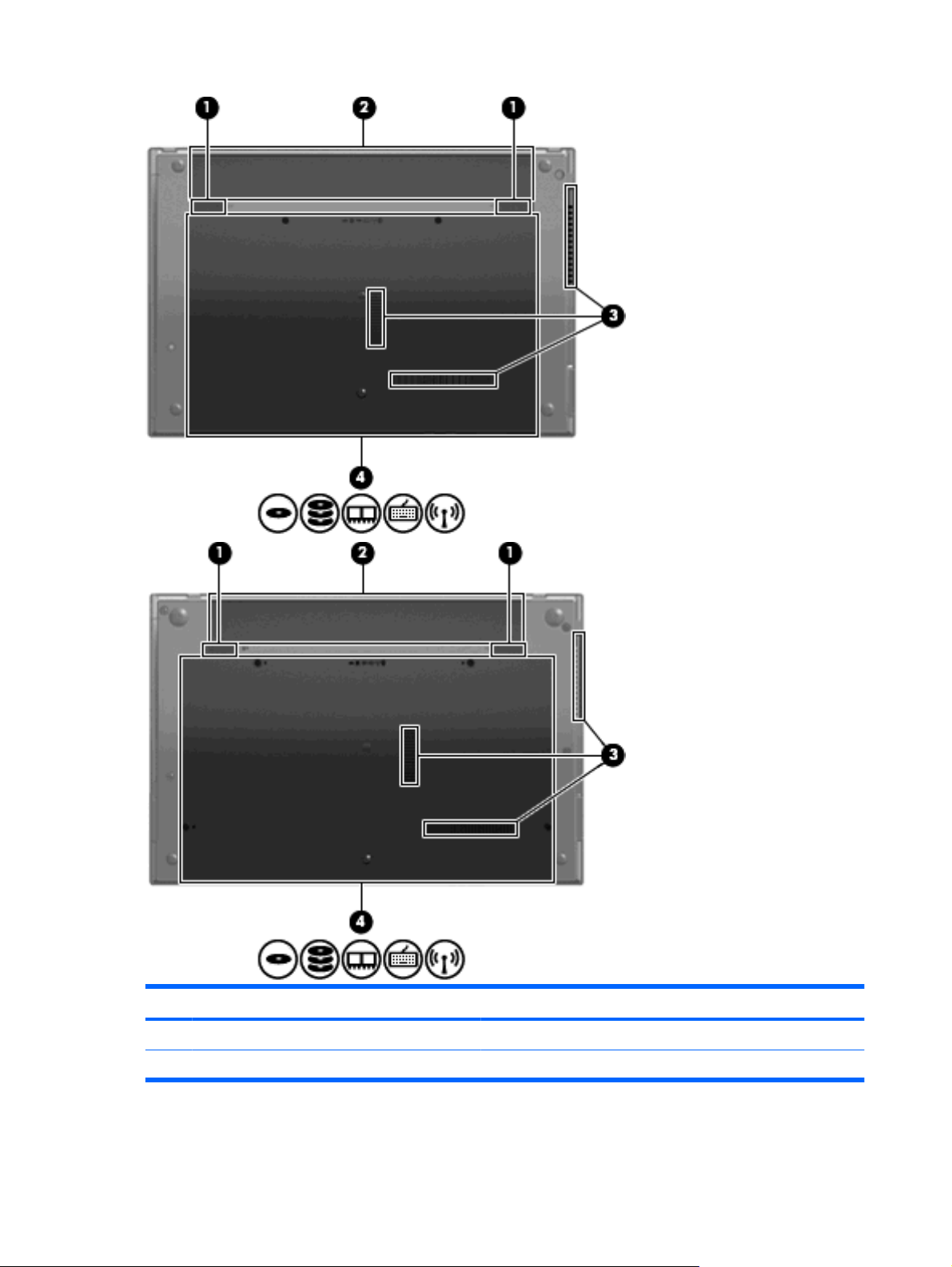
Component Description
(1) Battery release latches (2) Release the battery from the battery bay.
(2) Battery bay Holds the battery.
10 Chapter 1 Features
Page 23

Component Description
(3) Vents (3) Enable airflow to cool internal components.
(4) Memory module compartment Contains the memory module slots.
WLAN module compartment Contains the wireless LAN module slot.
Hard drive bay Holds the hard drive and a Bluetooth device.
Multimedia components
NOTE: The computer fan starts up automatically to cool internal
components and prevent overheating. It is normal for the internal
fan to cycle on and off during routine operation.
CAUTION: To prevent an unresponsive system and the display
of a warning message, replace the WLAN module with only a
module authorized for use in the computer by the governmental
agency that regulates wireless devices in your country. If you
replace the module and then receive a warning message, remove
the module to restore computer functionality, and then contact
technical support through Help and Support.
Component Description
(1) Webcam light (select models only) On: The webcam is in use.
(2) Webcam (select models only) Records video and captures still photographs.
Identifying hardware 11
Page 24

Component Description
(3) Integrated microphone Records sound.
(4) Audio-out (headphone) jack Produces sound when connected to optional powered stereo
speakers, headphones, ear buds, a headset, or television audio.
NOTE: When a device is connected to the headphone jack, the
computer speakers are disabled.
(5) Audio-in (microphone) jack Connects an optional computer headset microphone, stereo array
(6) Speaker Produces sound.
Wireless antennas (select models only)
On select computer models, at least 2 antennas send and receive signals from one or more wireless
devices. These antennas are not visible from the outside of the computer.
microphone, or monaural microphone.
NOTE: For optimal transmission, keep the areas immediately around the antennas free from
obstructions.
To see wireless regulatory notices, refer to the section of the Regulatory, Safety and Environmental
Notices that applies to your country or region. These notices are located in Help and Support.
12 Chapter 1 Features
Page 25

Additional hardware components
Component Description
(1) Power cord* Connects an AC adapter to an AC outlet.
(2) AC adapter Converts AC power to DC power.
(3) Battery* Powers the computer when the computer is not plugged into
*Modem cables, batteries, modem cable adapters, and power cords vary in appearance by country or region.
Identifying the labels
The labels affixed to the computer provide information you may need when you troubleshoot system
problems or travel internationally with the computer:
Service tag—Provides important information, including the following:
●
Product name (1). This is the product name affixed to the front of your notebook.
◦
Serial number (s/n) (2). This is an alphanumeric identifier that is unique to each product.
◦
Part number/Product number (p/n) (3). This number provides specific information about the
◦
product's hardware components. The part number helps a service technician to determine
what components and parts are needed.
external power.
Identifying the labels 13
Page 26

Model description (4). This is the number you use to locate documents, drivers, and support
◦
for your notebook.
Warranty period (5). Describes the duration of the warranty period for this computer.
◦
Have this information available when you contact technical support. The service tag label is affixed
to the bottom of the computer.
Microsoft® Certificate of Authenticity—Contains the Windows Product Key. You may need the
●
Product Key to update or troubleshoot the operating system. This certificate is affixed to the bottom
of the computer.
Regulatory label—Provides regulatory information about the computer. The regulatory label is
●
affixed to the bottom of the computer.
Modem approval label—Provides regulatory information about the modem and lists the agency
●
approval markings required by some of the countries in which the modem has been approved for
use. You may need this information when traveling internationally. The modem approval label is
affixed to the bottom of the computer.
Wireless certification label(s) (select models only)—Provide information about optional wireless
●
devices and the approval markings of some of the countries in which the devices have been
approved for use. An optional device may be a WLAN device or a Bluetooth device. If your computer
model includes one or more wireless devices, one or more certification labels are included with
your computer. You may need this information when traveling internationally. Wireless certification
labels are affixed to the bottom of the computer.
14 Chapter 1 Features
Page 27
2Networking
Using wireless devices (select models only)
Wireless technology transfers data across radio waves instead of wires. Your computer may be
equipped with one or more of the following wireless devices:
WLAN device—Connects the computer to wireless local area networks (commonly referred to as
●
Wi-Fi networks, wireless LANs, or WLANs) in corporate offices, your home, and public places such
as airports, restaurants, coffee shops, hotels, and universities. In a WLAN, each mobile wireless
device communicates with a wireless router or a wireless access point.
Bluetooth device—Creates a personal area network (PAN) to connect to other Bluetooth-enabled
●
devices such as computers, phones, printers, headsets, speakers, and cameras. In a PAN, each
device communicates directly with other devices, and devices must be relatively close together—
typically within 10 meters (approximately 33 feet) of each other.
Computers with WLAN devices support one or more of the following IEEE industry standards:
802.11b, the first popular standard, supports data rates of up to 11 Mbps and operates at a
●
frequency of 2.4 GHz.
802.11g supports data rates of up to 54 Mbps and operates at a frequency of 2.4 GHz. An 802.11g
●
WLAN device is backward compatible with 802.11b devices, so they can operate on the same
network.
802.11a supports data rates of up to 54 Mbps and operates at a frequency of 5 GHz.
●
NOTE: 802.11a is not compatible with 802.11b and 802.11g.
802.11n supports data rates of up to 450 Mbps and may operate at 2.4 GHz or 5 GHz, making it
●
backward compatible with 802.11a, b, and g.
NOTE: The specifications for the 802.11n WLAN are draft specifications and are not final. If the
final specifications differ from the draft specifications, it may affect the ability of the computer to
communicate with other 802.11n WLAN devices.
For more information on wireless technology, refer to the information and Web site links provided in
Help and Support.
Identifying wireless and network icons
Icon Name Description
Wireless (connected) Identifies the location of the wireless lights and the wireless switch on
the computer.
Using wireless devices (select models only) 15
Page 28

Wireless
(disconnected)
Indicates that all of the wireless devices are off.
Network status
(connected)
Network status
(disconnected)
Using the wireless controls
You can control the wireless devices in your computer using these features:
Wireless key or wireless button (referred to in this guide as the wireless key)
●
Operating system controls
●
Using the wireless key
The computer has a wireless key, one or more wireless devices, and one wireless light, All of the wireless
devices on your computer are enabled at the factory, so the wireless light is on (white) when you turn
on the computer.
The wireless light indicates the overall power state of your wireless devices, not the status of individual
devices. If the wireless light is white, at least one wireless device is on. If the wireless light is amber, all
wireless devices are off.
Indicates that one or more of your network drivers are installed and one
or more network devices are connected to the network.
Indicates that one or more of your network drivers are installed but no
network devices are connected to the network.
Because the wireless devices are enabled at the factory, you can use the wireless key to turn on or turn
off the wireless devices simultaneously. Individual wireless devices can be controlled through Wireless
Assistant software (select models only) or through Computer Setup.
NOTE: If the wireless devices are disabled by Computer Setup, the wireless key will not work until you
reenable your devices.
Using operating system controls
Some operating systems also offer a way to manage integrated wireless devices and the wireless
connection. For more information, refer to the operating system documentation.
16 Chapter 2 Networking
Page 29
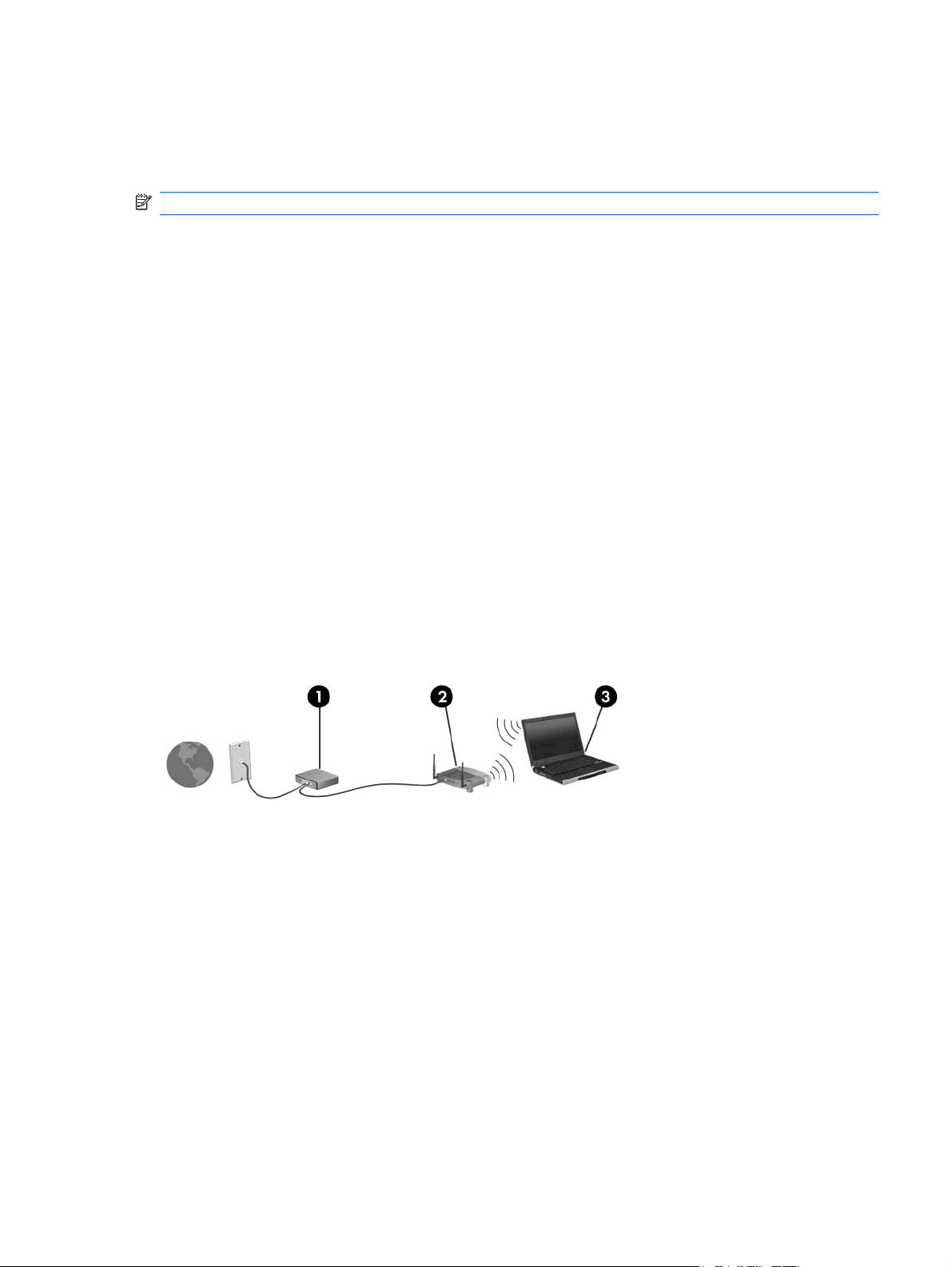
Using a WLAN
With a WLAN device, you can access a wireless local area network (WLAN), which is composed of other
computers and accessories that are linked by a wireless router or a wireless access point.
NOTE: The terms wireless router and wireless access point are often used interchangeably.
A large-scale WLAN, such as a corporate or public WLAN, typically uses wireless access points
●
that can accommodate a large number of computers and accessories and can separate critical
network functions.
A home or small office WLAN typically uses a wireless router, which allows several wireless and
●
wired computers to share an Internet connection, a printer, and files without requiring additional
pieces of hardware or software.
To use the WLAN device in your computer, you must connect to a WLAN infrastructure (provided through
a service provider or a public or corporate network).
Setting up a WLAN
To set up a WLAN and connect to the Internet, you need the following equipment:
A broadband modem (either DSL or cable) (1) and high-speed Internet service purchased from an
●
Internet service provider (ISP)
A wireless router (purchased separately) (2)
●
The wireless computer (3)
●
The illustration below shows an example of a wireless network installation that is connected to the
Internet.
As your network grows, additional wireless and wired computers can be connected to the network to
access the Internet.
For help in setting up your WLAN, refer to the information provided by your router manufacturer or your
ISP.
Protecting your WLAN
Because the WLAN standard was designed with only limited security capabilities—basically to foil casual
eavesdropping rather than more powerful forms of attack—it is essential to understand that WLANs are
vulnerable to well-known and well-documented security weaknesses.
WLANs in public areas, or “hotspots,” like coffee shops and airports may not provide any security. New
technologies are being developed by wireless manufacturers and hotspot service providers that make
the public environment more secure and anonymous. If you are concerned about the security of your
computer in a hotspot, limit your network activities to noncritical e-mail and basic Internet surfing.
Using a WLAN 17
Page 30

When you set up a WLAN or access an existing WLAN, always enable security features to protect your
network from unauthorized access. The common security levels are Wi-Fi Protected Access (WPA) and
Wired Equivalent Privacy (WEP). Because wireless radio signals travel outside the network, other WLAN
devices can pick up unprotected signals and either connect to your network (uninvited) or capture
information being sent across it. However, you can take precautions to protect your WLAN:
Use a wireless transmitter with built-in security
●
Many wireless base stations, gateways, and routers provide built-in security features such as
wireless security protocols and firewalls. With the correct wireless transmitter, you can protect your
network from the most common wireless security risks.
Work behind a firewall
●
A firewall is a barrier that checks both data and requests for data that are sent to your network and
then discards any suspicious items. Firewalls are available in many varieties, both software and
hardware. Some networks use a combination of both types.
Use wireless encryption
●
A variety of sophisticated encryption protocols is available for your WLAN. Find the solution that
works best for your network security:
Wired Equivalent Privacy (WEP) is a wireless security protocol that uses a WEP key to
◦
encode or encrypt all network data before it is transmitted. Usually, you can allow the network
to assign the WEP key. Alternatively, you can set up your own key, generate a different key,
or choose other advanced options. Without the correct key, others will not be able to use the
WLAN.
WPA (Wi-Fi Protected Access), like WEP, uses security settings to encrypt and decrypt data
◦
that is transmitted over the network. However, instead of using one static security key for
encryptions as WEP does, WPA uses temporal key integrity protocol (TKIP) to dynamically
generate a new key for every packet. It also generates different sets of keys for each computer
on the network.
Close your network
●
If possible, prevent your network name (SSID) from being broadcast by the wireless transmitter.
Most networks initially broadcast the name, telling any computer nearby that your network is
available. By closing the network, other computers are less likely to know that your network exists.
NOTE: If your network is closed and the SSID is not broadcast, you will need to know or remember
the SSID to connect new devices to the network. Write down the SSID and store it in a secure
place before closing the network.
18 Chapter 2 Networking
Page 31

Connecting to a WLAN
To connect to the WLAN, follow these steps:
1. Be sure that the WLAN device is on. If it is on, the wireless light is on. If the wireless light is amber,
slide the wireless switch.
2. Select Start > Connect To.
3. Select your WLAN from the list, and then type the network security key, if required.
If the network is unsecured, meaning that anyone can access the network, a warning is
●
displayed. Click Connect Anyway to accept the warning and complete the connection.
If the network is a security-enabled WLAN, you are prompted to enter a network security key,
●
which is a security code. Type the code, and then click Connect to complete the connection.
NOTE: If no WLANs are listed, you are out of range of a wireless router or access point.
NOTE: If you do not see the network you want to connect to, click Show all connections. A list
of options will appear that includes creating a new network connection, as well as troubleshooting
connection issues.
After the connection is made, place the mouse pointer over the network status icon in the notification
area, at the far right of the taskbar, to verify the name and status of the connection.
NOTE: The functional range (how far your wireless signals travel) depends on WLAN implementation,
router manufacturer, and interference from other electronic devices or structural barriers such as walls
and floors.
More information about using a WLAN is available through the following resources:
Information from your ISP and the manufacturer's instructions included with your wireless router
●
and other WLAN equipment
Information and Web site links provided in Help and Support
●
For a list of public WLANs near you, contact your ISP or search the Web. Web sites that list public
WLANs include Cisco Internet Mobile Office Wireless Locations, Hotspotlist, and Geektools. Check with
each public WLAN location for cost and connection requirements.
For additional information on connecting your computer to a corporate WLAN, contact your network
administrator or IT department.
Roaming to another network
When you move your computer within range of another WLAN, Windows attempts to connect to that
network. If the attempt is successful, your computer is automatically connected to the new network. If
Windows does not recognize the new network, follow the same procedure you used initially to connect
to your WLAN.
Using a WLAN 19
Page 32

Using Bluetooth wireless devices (select models only)
A Bluetooth device provides short-range wireless communications that replace the physical cable
connections that traditionally link electronic devices such as the following:
Computers (desktop, notebook, PDA)
●
Phones (cellular, cordless, smart phone)
●
Imaging devices (printer, camera)
●
Audio devices (headset, speakers)
●
Bluetooth devices provide peer-to-peer capability that allows you to set up a personal area network
(PAN) of Bluetooth devices. For information on configuring and using Bluetooth devices, refer to the
Bluetooth software Help.
Bluetooth and Internet Connection Sharing (ICS)
HP does not recommend setting up one computer with Bluetooth as a host and using it as a gateway
through which other computers may connect to the Internet. When two or more computers are connected
using Bluetooth, and Internet Connection Sharing (ICS) is enabled on one of the computers, the other
computers may not be able to connect to the Internet using the Bluetooth network.
The strength of Bluetooth is in synchronizing information transfers between your computer and wireless
devices including cellular phones, printers, cameras, and PDAs. The inability to consistently connect
two or more computers to share the Internet through Bluetooth is a limitation of Bluetooth and the
Windows operating system.
20 Chapter 2 Networking
Page 33

Troubleshooting wireless connection problems
Some possible causes for wireless connection problems include the following:
Wireless device is not installed correctly or has been disabled.
●
Wireless device or router hardware has failed.
●
Network configuration (SSID or security) has been changed.
●
Wireless device encountered interference from other devices.
●
NOTE: Wireless networking devices are included with select computer models only. If wireless
networking is not listed in the feature list on the side of the original computer package, you may add
wireless networking capability to the computer by purchasing a wireless networking device.
Before working your way through the sequence of possible solutions to your network connection
problem, be sure that device drivers are installed for all wireless devices.
Use the procedures in this chapter to diagnose and repair a computer that does not connect to the
network you want to use.
Cannot create a WLAN connection
If you have a problem connecting to a WLAN, confirm that the integrated WLAN device is properly
installed on your computer:
1. Select Start > My Computer.
2. Right-click in the My Computer window.
3. Select Properties > Hardware > Device Manager > Network Adapters.
4. Identify the WLAN device from the Network adapters list. The listing for a WLAN device may include
the term wireless, wireless LAN, WLAN, or 802.11.
If no WLAN device is listed, either your computer does not have an integrated WLAN device, or
the driver for the WLAN device is not properly installed.
For more information on troubleshooting WLANs, refer to the Web site links provided in Help and
Support.
Troubleshooting wireless connection problems 21
Page 34

Cannot connect to a preferred network
Windows can automatically repair a corrupted WLAN connection:
If there is a network status icon in the notification area, at the far right of the taskbar, right-click the
●
icon, and then click Repair from the menu.
Windows resets your network device and attempts to reconnect to one of the preferred networks.
If an “x” is superimposed over the network status icon, one or more of your WLAN or LAN drivers
●
are installed, but the computer is not connected.
If there is no network status icon in the notification area, follow these steps:
●
1. Click Start > Control Panel > Network and Internet Connections > Network
Connections.
2. Click on one of the connections.
3. In the left pane, click Repair this connection.
The Network connections window is displayed, and Windows resets your network device and
attempts to reconnect to one of the preferred networks.
Network icon is not displayed
If the network icon is not displayed in the notification area after you configure the WLAN, the software
driver is either missing or corrupted. A Windows “Device not Found” error message may also be
displayed. The driver must be reinstalled.
To get the latest version of the WLAN device software for your computer, follow these steps:
1. Open your Internet browser and go to
2. Select your country or region.
3. Click the option for software and driver downloads, and then type your computer model number in
the Search box.
4. Press enter, and then follow the on-screen instructions.
NOTE: If the WLAN device you are using was purchased separately, consult the manufacturer's Web
site for the latest software.
http://www.hp.com/support.
Current network security codes are unavailable
If you are prompted for a network key or an SSID when connecting to a WLAN, the network is protected
by security. You must have the current codes to make a connection on a secure network. The SSID and
network key are alphanumeric codes that you enter into your computer to identify your computer to the
network.
For a network connected to your personal wireless router, review the router user guide for
●
instructions on setting up the same codes on both the router and the WLAN device.
For a private network, such as a network in an office or at a public Internet chat room, contact the
●
network administrator to obtain the codes, and then enter the codes when prompted to do so.
Some networks change the SSID or network keys used in their routers or access points on a regular
basis to improve security. You must change the corresponding code in your computer accordingly.
22 Chapter 2 Networking
Page 35

If you are provided with new wireless network keys and SSID for a network, and if you have previously
connected to that network, follow the steps below to connect to the network:
1. Select Control Panel > Network and Internet Connections > Network Connections.
A list showing the available WLANs is displayed. If you are in a hotspot where several WLANs are
active, several will be displayed.
2. Right-click the network, and then click Properties.
3. Click the Wireless Networks tab.
4. Select the network, and then click Properties.
NOTE: If the network you want is not listed, check with the network administrator to be sure that
the router or access point is operating.
5. Click the Association tab, and then enter the correct wireless encryption data into the Network
key field.
6. Click OK to save these settings.
WLAN connection is very weak
If the connection is very weak, or if your computer cannot make a connection to a WLAN, minimize
interference from other devices, as follows:
Move your computer closer to the wireless router or access point.
●
Temporarily disconnect wireless devices such as a microwave, cordless phone, or cellular phone
●
to be sure that other wireless devices are not interfering.
If the connection does not improve, try forcing the device to reestablish all connection values:
1. Select Control Panel > Network and Internet Connections > Network Connections.
2. Right-click the network, and then click Properties.
3. Click the Wireless Networks tab.
A list showing the available WLANs is displayed. If you are in a hotspot where several WLANs are
active, several will be displayed.
4. Select a network, and then click Remove.
Cannot connect to the wireless router
If you are trying to connect to the wireless router and are unsuccessful, reset the wireless router by
removing power from the router for 10 to 15 seconds.
If the computer still cannot make a connection to a WLAN, restart the wireless router. For details, refer
to the router manufacturer's instructions.
Troubleshooting wireless connection problems 23
Page 36

Using the modem (select models only)
The modem must be connected to an analog telephone line using a 6-pin, RJ-11 modem cable
(purchased separately). In some countries, a country-specific modem cable adapter (purchased
separately) is also required. Jacks for digital PBX systems may resemble analog telephone jacks, but
they are not compatible with the modem.
WARNING! Connecting the internal analog modem to a digital line can permanently damage the
modem. Immediately disconnect the modem cable if you accidentally connect it to a digital line.
If the modem cable contains noise suppression circuitry (1), which prevents interference from TV and
radio reception, orient the circuitry end (2) of the cable toward the computer.
Connecting a modem cable (purchased separately)
WARNING! To reduce the risk of electric shock, fire, or damage to the equipment, do not plug a modem
cable (purchased separately) or telephone cable into the RJ-45 (network) jack.
To connect a modem cable:
1. Plug the modem cable into the modem jack (1) on the computer.
2. Plug the modem cable into the RJ-11 telephone wall jack (2).
24 Chapter 2 Networking
Page 37

Connecting a country-specific modem cable adapter (purchased separately)
Telephone jacks vary by country. To use the modem and the modem cable (purchased separately)
outside the country in which you purchased the computer, you must obtain a country-specific modem
cable adapter (purchased separately).
To connect the modem to an analog telephone line that does not have an RJ-11 telephone jack, follow
these steps:
1. Plug the modem cable into the modem jack (1) on the computer.
2. Plug the modem cable into the country-specific modem cable adapter (2).
3. Plug the country-specific modem cable adapter (3) into the telephone wall jack.
Selecting a location setting
Viewing the current location selection
To view the current location setting for the modem, follow these steps:
1. Select Start > Control Panel.
2. Click Date, Time, Language, and Regional Options.
3. Click Regional and Language Options.
4. Your location is displayed under Location.
Using the modem (select models only) 25
Page 38

Adding new locations when traveling
By default, the only location setting available to the modem is a location setting for the country in which
you purchased the computer. As you travel to different countries, set the internal modem to a location
setting that meets the operating standards of the country in which you are using the modem.
As you add new location settings, they are saved by the computer so that you can switch among settings
at any time. You can add multiple location settings for any country.
CAUTION: To prevent losing your home country settings, do not delete your current modem country
settings. To enable modem use in other countries while preserving your home country configuration,
add a new configuration for each location in which you will use the modem.
CAUTION: To prevent configuring the modem in a way that violates the telecommunications
regulations and laws of the country you are visiting, select the country in which the computer is located.
The modem may not function properly if the correct country selection is not made.
To add a location setting for the modem, follow these steps:
1. Select Start > Control Panel > Network and Internet Connections.
2. In the left-side panel, click Phone and Modem Options.
3. Click the Dialing Rules tab.
4. Click New. (The New Location window is displayed.)
5. In the Location name box, type a name (such as “home” or “work”) for the new location setting.
6. Select a country or region from the Country/region drop-down list. (If you select a country or region
that is not supported by the modem, the Country/region selection for USA or UK is displayed by
default.)
7. Click OK to save your new location setting. (The Phone and Modem Options window is displayed.)
8. Do one of the following:
To set your new location setting as the current location, click OK.
●
To select another location setting as the current location setting, select your preference from
●
the settings in the Location list, and then click OK.
NOTE: You can use the preceding procedure to add location settings for places within your own
country as well as in other countries. For example, you could add a setting named “Work” that
includes dialing rules for accessing an outside line.
26 Chapter 2 Networking
Page 39

Solving travel connection problems
If you experience modem connection problems when using the computer outside of the country in which
you purchased it, try the following suggestions:
Check the telephone line type.
●
The modem requires an analog, not a digital, telephone line. A line described as a PBX line is
usually a digital line. A telephone line described as a data line, fax machine line, modem line, or
standard telephone line is usually an analog line.
Check for pulse or tone dialing.
●
An analog telephone line supports one of two dialing modes: pulse dialing or tone dialing. These
dialing mode options are selected in the Phone and Modem Options settings. The dialing mode
option selected must match the dialing mode supported by the telephone line in your location.
To determine the dialing mode supported by a telephone line, dial a few digits on the telephone,
and then listen for clicks (pulses) or tones. Clicks indicate that the telephone line supports pulse
dialing. Tones indicate that the telephone line supports tone dialing.
To change the dialing mode in your current modem location setting, follow these steps:
1. Select Start > Control Panel > Network and Internet Connections.
2. In the left-side panel, click Phone and Modem Options.
3. Click the Dialing Rules tab.
4. Select your modem location setting.
5. Click Edit.
6. Click either Tone or Pulse.
7. Click OK twice.
Check the telephone number you are dialing and the response of the remote modem.
●
Dial a telephone number, make sure there is a response from the remote modem, and then hang
up.
Set the modem to ignore dial tones.
●
If the modem receives a dial tone it does not recognize, it does not dial and displays a “No Dial
Tone” error message.
To set the modem to ignore all dial tones before dialing, follow these steps:
1. Select Start > Control Panel > Network and Internet Connections.
2. In the left-side panel, click Phone and Modem Options.
3. Click the Modems tab.
4. Click the listing for the modem.
5. Click Properties.
6. Click Modem.
Using the modem (select models only) 27
Page 40

7. Clear the check box for Wait for dial tone before dialing.
8. Click OK twice.
Using preinstalled communication software
To use preinstalled modem software for terminal emulation and data transfer:
1. Select Start > All Programs > Accessories > Communications.
2. Click a fax or terminal emulation program or Internet connection wizard.
28 Chapter 2 Networking
Page 41

Connecting to a local area network (LAN)
Connecting to a local area network (LAN) requires an 8-pin, RJ-45 network cable (not included). If the
network cable contains noise suppression circuitry (1), which prevents interference from TV and radio
reception, orient the circuitry end of the cable (2) toward the computer.
To connect the network cable:
1. Plug the network cable into the network jack (1) on the computer.
2. Plug the other end of the cable into a network wall jack (2).
WARNING! To reduce the risk of electric shock, fire, or damage to the equipment, do not plug a
modem or telephone cable into the RJ-45 (network) jack.
Connecting to a local area network (LAN) 29
Page 42

3 Pointing devices and keyboard
Using pointing devices
Setting pointing device preferences
Use Mouse Properties in Windows to customize settings for pointing devices, such as button
configuration, click speed, and pointer options.
To access Mouse Properties, select Start > Control Panel > Printers and Other Hardware >
Mouse.
Using the TouchPad
To move the pointer, slide your finger across the TouchPad surface in the direction you want the pointer
to go. Use the TouchPad buttons like the corresponding buttons on an external mouse. To scroll up and
down using the TouchPad vertical scroll zone, slide your finger up or down over the lines.
NOTE: If you are using the TouchPad to move the pointer, you must lift your finger off the TouchPad
before moving it to the scroll zone. Simply sliding your finger from the TouchPad to the scroll zone will
not activate the scrolling function.
Connecting an external mouse
You can connect an external USB mouse to the computer using one of the USB ports on the computer.
A wireless Bluetooth mouse can be used only on Bluetooth-enabled computers (select models only);
follow the instructions provided with the device. A USB device can be added by connecting the device
to a USB port on the computer or on an optional docking device (select models only).
Using the keyboard
Using hotkeys
Hotkeys are combinations of the fn key (1) and either the esc key (2) or one of the function keys (3).
The icons on the f1 through f12 keys represent the hotkey functions. Hotkey functions and procedures
are discussed in the following sections.
NOTE: Refer to the illustration that most closely matches your computer.
30 Chapter 3 Pointing devices and keyboard
Page 43

Function Hotkey
Display system information. fn+esc
Open Help and Support. fn+f1
Decrease screen brightness. fn+f2
Increase screen brightness. fn+f3
Switch the screen image. fn+f4
Initiate Standby. fn+f5
Initiate QuickLock. fn+f6
Mute speaker sound. fn+f7
Decrease speaker sound. fn+f8
Increase speaker sound. fn+f9
Play previous track. fn+f10
Play, pause, or resume a CD, DVD, or BD. fn+f11
Play next track. fn+f12
Using the keyboard 31
Page 44

Function Hotkey
Display system information. fn+esc
Open Help and Support. fn+f1
Decrease screen brightness. fn+f2
Increase screen brightness. fn+f3
Switch the screen image. fn+f4
Initiate Standby. fn+f5
Initiate QuickLock fn+f6
Launch Web browser. fn+f7
Launch printer. fn+f8
To use a hotkey command on the computer keyboard, follow either of these steps:
Briefly press the fn key, and then briefly press the second key of the hotkey command.
●
– or –
Press and hold down the fn key, briefly press the second key of the hotkey command, and then
●
release both keys at the same time.
Displaying system information
Press fn+esc to display information about system hardware components and the system BIOS version
number.
In the Windows fn+esc display, the version of the system BIOS (basic input-output system) is displayed
as the BIOS date. On some computer models, the BIOS date is displayed in decimal format. The BIOS
date is sometimes called the system ROM version number.
32 Chapter 3 Pointing devices and keyboard
Page 45

Opening Help and Support
Press fn+f1 to open Help and Support.
In addition to providing information about your Windows operating system, Help and Support provides
the following information and tools:
Information about your computer, such as model and serial number, installed software, hardware
●
components, and specifications
Answers to questions about using your computer
●
Tutorials to help you learn to use the computer and Windows features
●
Updates for the Windows operating system, drivers, and the software provided on your computer
●
Checkups for computer functionality
●
Automated and interactive troubleshooting, repair solutions, and system recovery procedures
●
Links to support specialists
●
Decreasing screen brightness
Press fn+f2 to decrease screen brightness. Hold down the hotkey to decrease the brightness level
incrementally.
Increasing screen brightness
Press fn+f3 to increase screen brightness. Hold down the hotkey to increase the brightness level
incrementally.
Switching the screen image
Press fn+f4 to switch the screen image among display devices connected to the system. For example,
if a monitor is connected to the computer, pressing fn+f4 alternates the screen image from computer
display to monitor display to simultaneous display on both the computer and the monitor.
Most external monitors receive video information from the computer using the external VGA video
standard. The fn+f4 hotkey can also alternate images among other devices receiving video information
from the computer.
The following video transmission types, with examples of devices that use them, are supported by the
fn+f4 hotkey:
LCD (computer display)
●
External VGA (most external monitors)
●
HDMI (televisions, camcorders, DVD players, VCRs, and video capture cards with HDMI ports)
●
Composite video (televisions, camcorders, DVD players, VCRs, and video capture cards with
●
composite-video-in jacks)
NOTE: Composite video devices can be connected to the system only by using an optional
docking device or optional expansion product
Using the keyboard 33
Page 46

Initiating Standby (fn+f5)
CAUTION: To reduce the risk of information loss, save your work before initiating Standby.
Press fn+f5 to initiate Standby.
When Standby is initiated, your information is stored in system memory, the screen is cleared, and power
is conserved. While the computer is in Standby, the power lights blink.
The computer must be on before you can initiate Standby.
NOTE: If a critical battery level occurs while the computer is in Standby, the computer initiates
Hibernation and the information stored in memory is saved to the hard drive. The factory setting for
critical battery action is Hibernate, but this setting can be changed using Power Options in Windows
Control Panel.
To exit Standby, briefly press the power button.
The function of the fn+f5 hotkey can be changed. For example, you can set the fn+f5 hotkey to initiate
Hibernation instead of Standby.
NOTE: In all Windows operating system windows, references to the sleep button apply to the fn+f5
hotkey.
Initiating QuickLock (fn+f6) (select models)
Press fn+f6 to initiate the QuickLock security feature.
QuickLock protects your information by displaying the operating system Log On window. While the Log
On window is displayed, the computer cannot be accessed until a Windows user password or a Windows
administrator password is entered.
NOTE: Before you can use QuickLock, you must set a Windows user password or a Windows
administrator password. For instructions, refer to Help and Support.
To use QuickLock, press fn+f6 to display the Log On window and lock the computer. Then follow the
instructions on the screen to enter your Windows user password or your Windows administrator
password and access the computer.
Launching Web browser (fn+f7) (select models)
To launch your default Web browser, press fn+f7.
Launching printer (fn+f8) (select models)
To print the item displayed, press fn+f8 to activate your printer.
Muting speaker sound (fn+f7) (select models)
Press fn+f7 to mute speaker sound. Press the hotkey again to restore speaker sound.
Decreasing speaker sound (fn+f8) (select models)
Press fn+f8 to decrease speaker volume. Hold down the hotkey to decrease speaker volume
incrementally.
34 Chapter 3 Pointing devices and keyboard
Page 47

Increasing speaker sound (fn+f9) (select models)
Press fn+f9 to increase speaker volume. Hold down the hotkey to increase speaker volume
incrementally.
Playing the previous track or section of an audio CD or a DVD (fn+f10) (select models)
While an audio CD or a DVD is playing, press fn+f10 to play the previous track of the CD or the previous
section of the DVD.
Playing, pausing, or resuming an audio CD or a DVD (fn+f11) (select models)
The fn+f11 hotkey functions only when an audio CD or a DVD is inserted.
If the audio CD or the DVD is not playing, press fn+f11 to begin or resume the play.
●
If the audio CD or the DVD is playing, press fn+f11 to pause the play.
●
Playing the next track or section of an audio CD or a DVD (fn+f12) (select models)
While an audio CD or a DVD is playing, press fn+f12 to play the next track of the CD or the next section
of the DVD.
Using the keyboard 35
Page 48

Using the embedded numeric keypad
The 15 keys of the embedded numeric keypad can be used like the keys on an external keypad. When
the embedded numeric keypad is turned on, each key on the keypad performs the function indicated by
the icon in the upper-right corner of the key.
Enabling and disabling the embedded numeric keypad
Press fn+num lk to enable the embedded numeric keypad. Press fn+num lk again to return the keys to
their standard keyboard functions.
NOTE: The embedded numeric keypad will not function while an external keyboard or numeric keypad
is connected to the computer.
Switching key functions on the embedded numeric keypad
You can temporarily alternate the functions of keys on the embedded numeric keypad between their
standard keyboard functions and their keypad functions by using the fn key or the fn+shift key
combination.
To change the function of a keypad key to keypad functions while the keypad is off, press and hold
●
the fn key while pressing the keypad key.
To use the keypad keys temporarily as standard keys while the keypad is on:
●
Press and hold the fn key to type in lowercase.
◦
Press and hold fn+shift to type in uppercase.
◦
36 Chapter 3 Pointing devices and keyboard
Page 49

Using an optional external numeric keypad
Keys on most external numeric keypads function differently according to whether num lock is on or off.
(Num lock is turned off at the factory.) For example:
When num lock is on, most keypad keys type numbers.
●
When num lock is off, most keypad keys function like the arrow, page up, or page down keys.
●
When num lock on an external keypad is turned on, the num lock light on the computer is turned on.
When num lock on an external keypad is turned off, the num lock light on the computer is turned off.
To turn num lock on or off on an external keypad as you work:
Press the num lk key on the external keypad, not on the computer.
▲
Using an optional external numeric keypad 37
Page 50

4Multimedia
Multimedia features
Your computer includes multimedia features that allow you to listen to music, watch movies, and view
pictures. Your computer may include the following multimedia components:
Optical drive for playing audio and video discs
●
Integrated speakers for listening to music
●
Integrated microphone for recording your own audio
●
Integrated webcam that allows you to capture and share video
●
Preinstalled multimedia software that allows you to play and manage your music, movies, and
●
pictures
Hotkeys that provide fast access to multimedia tasks
●
NOTE: Your computer may not include all of the components listed.
The following sections explain how to identify and use the multimedia components included with your
computer.
Identifying your multimedia components
The following illustration and table describe the multimedia features of the computer.
NOTE: Your computer may look slightly different from the illustration in this section.
38 Chapter 4 Multimedia
Page 51

Component Description
(1) Webcam light (select models only) On: The webcam is in use.
(2) Webcam Records video and captures still photographs.
(3) Integrated microphone Records sound.
(4) Audio-out (headphone) jack Produces sound when connected to optional powered stereo
(5) Audio-in (microphone) jack Connects an optional computer headset microphone, stereo array
(6) Speaker Produce sound.
speakers, headphones, ear buds, a headset, or television audio.
NOTE: When a device is connected to the headphone jack, the
computer speakers are disabled.
microphone, or monaural microphone.
Multimedia features 39
Page 52

Adjusting the volume
You can adjust the volume using the following controls:
Computer volume keys: (select models only)
●
To mute or restore volume, press and hold the fn key (1), and then press the mute key f7
◦
(2).
To decrease volume, press and hold the fn key (1), and then tap the volume down key f8
◦
(3) until the desired volume level is reached.
To increase volume, press and hold the fn key (1), and then tap the volume up key f9 (4) until
◦
the desired volume level is reached.
Windows volume control:
●
a. Click the Volume icon in the notification area, at the far right of the taskbar.
b. Increase or decrease the volume by moving the slider up or down. Select the Mute check box
to mute the volume.
– or –
a. Double-click the Volume icon in the notification area.
b. In the Speakers column, you can increase or decrease the volume by moving the Volume
slider up or down. You can also adjust the balance or mute the volume.
If the Volume icon is not displayed in the notification area, follow these steps to add it:
a. Select Start > Control Panel > Sounds, Speech, and Audio Devices > Sounds and Audio
Devices > Volume tab.
b. Select the Place volume icon in the taskbar check box.
c. Click Apply.
Program volume control:
●
40 Chapter 4 Multimedia
Page 53

Volume can also be adjusted within some programs.
Multimedia software
The computer includes preinstalled multimedia software. Some computer models also include additional
multimedia software on an optical disc.
Depending on the hardware and software included with the computer, the following multimedia tasks
may be supported:
Playing digital media, including audio and video CDs, DVDs, and BDs, and Internet radio
●
Creating or copying data CDs
●
Creating, editing, and burning audio CDs
●
Creating, editing, and burning a video or movie to a DVD or video CD
●
CAUTION: To prevent loss of information or damage to a disc, observe the following guidelines:
Before writing to a disc, connect the computer to a reliable external power source. Do not write to a disc
while the computer is running on battery power.
Before writing to a disc, close all open programs except the disc software you are using.
Do not copy directly from a source disc to a destination disc or from a network drive to a destination
disc. Instead, copy from a source disc or network drive to your hard drive, and then copy from your hard
drive to the destination disc.
Do not use the computer keyboard or move the computer while the computer is writing to a disc. The
write process is sensitive to vibration.
NOTE: For information about using software included with the computer, refer to the software
manufacturer's instructions that may be provided on disc, as online Help files, or on the software
manufacturer's Web site.
Opening preinstalled multimedia software
1. Select Start > All Programs.
2. Click the program that you want to open.
Using multimedia software
1. Select Start > All Programs, and then open the multimedia program you want to use. For example,
if you want to use Windows Media Player to play an audio CD, click Windows Media Player.
NOTE: Some programs may be located in subfolders.
2. Insert the media disc, such as an audio CD, into the optical drive.
3. Follow the instructions on the screen.
Multimedia software 41
Page 54

– or –
1. Insert the media disc, such as an audio CD, into the optical drive.
An AutoPlay dialog box opens.
2. Click a multimedia task from the list of tasks.
Installing multimedia software from a disc
1. Insert the disc into the optical drive.
2. When the installation wizard opens, follow the on-screen instructions.
3. Restart the computer if prompted to do so.
42 Chapter 4 Multimedia
Page 55

Audio
Your computer enables you to use a variety of audio features:
Play music using your computer speakers and/or connected external speakers
●
Record sound using the internal microphone or connect an external microphone
●
Download music from the Internet
●
Create multimedia presentations using audio and images
●
Transmit sound and images with instant messaging programs
●
Stream radio programs (select models only) or receive FM radio signals
●
Create or “burn” audio CDs (select models only)
●
Connecting external audio devices
WARNING! To reduce the risk of personal injury, adjust the volume before putting on headphones,
earbuds, or a headset. For additional safety information, refer to the Regulatory, Safety and
Environmental Notices.
To connect external devices such as external speakers, headphones, or a microphone, refer to the
information provided with the device. For best results, remember the following tips:
Be sure that the device cable is securely connected to the correct jack on your computer. (Cable
●
connectors are normally color-coded to match the corresponding jacks on the computer.)
Be sure to install any drivers required by the external device.
●
NOTE: A driver is a required program that acts like a translator between the device and the
programs that use the device.
Checking your audio functions
To check the system sound on your computer, follow these steps:
1. Select Start > Control Panel.
2. Select Sounds, Speech, and Audio Devices > Sounds and Audio Devices.
3. When the Sounds and Audio Devices Properties window opens, click the Sounds tab. Under
Program events, select any sound event, such as a beep or alarm, and then click the right arrow
icon next to the listed sound.
You should hear sound through the speakers or through connected headphones.
To check the record functions of the computer, follow these steps:
1. Select Start > All Programs > Accessories > Entertainment > Sound Recorder.
2. Click Record and speak into the microphone. Save the file to your desktop.
3. Open Windows Media Player and play back the sound.
Audio 43
Page 56

NOTE: For best results when recording, speak directly into the microphone and record sound in a
setting free of background noise.
To confirm or change the audio settings on your computer, right-click the Sound icon on the
▲
taskbar, or select Start > Control Panel > Sounds, Speech, and Audio Devices > Sounds and
Audio Devices.
44 Chapter 4 Multimedia
Page 57

Video
Your computer enables you to use a variety of video features:
Watch movies
●
Play games over the Internet and offline
●
Edit pictures and video to create presentations
●
Connect external video devices
●
Connecting an external monitor or projector
Your computer has an external monitor port that allows you to connect external monitors and projectors.
Using the external monitor port
The external monitor port connects an external display device, such as an external monitor or a projector,
to the computer.
To connect a display device, connect the device cable to the external monitor port.
▲
NOTE: If a properly connected external display device does not display an image, press fn+f4 to
transfer the image to the device. Repeatedly pressing fn+f4 alternates the screen image between the
computer display and the device.
Using the HDMI port
Select computer models include an HDMI (High Definition Multimedia Interface) port. The HDMI port
connects the computer to an optional video or audio device, such as a high-definition television, or any
compatible digital or audio component.
The computer can support one HDMI device connected to the HDMI port, while simultaneously
supporting an image on the computer display or any other supported external display.
NOTE: To transmit video signals through the HDMI port, you need an HDMI cable (purchased
separately), available from most electronics retailers.
Video 45
Page 58

To connect a video or audio device to the HDMI port:
1. Plug one end of the HDMI cable into the HDMI port on the computer.
2. Connect the other end of the cable to the video device, according to the device manufacturer's
instructions.
3. Press fn+f4 to switch the image between the display devices connected to the computer.
Configuring audio for HDMI
To configure HDMI audio, first connect an audio or video device, such as a high-definition TV, to the
HDMI port on your computer. Then configure the default audio playback device as follows:
1. Right-click the Speaker icon in the notification area, at the far right of the taskbar, and then click
Playback devices.
2. On the Playback tab, click either Digital Output or Digital Output Device (HDMI).
3. Click Set Default, and then click OK.
To return audio to the computer speakers, follow these steps:
1. Right-click the Speaker icon in the notification area, at the far right of the taskbar, and then click
Playback devices.
2. On the Playback tab, click Speakers.
3. Click Set Default, and then click OK.
46 Chapter 4 Multimedia
Page 59

Optical drive (select models only)
Depending on the type of optical drive and software installed in your computer, the optical drive plays,
copies, and creates CDs, DVDs, or BDs.
Identifying the installed optical drive
Select Start > Computer.
▲
You will see a list of all the devices installed on your computer, including your optical drive. You may
have one of the following types of drives:
DVD-ROM Drive
●
DVD±R SuperMulti DL LightScribe Drive
●
NOTE: Both drives listed above may not be supported by your computer.
Using optical discs (CDs, DVDs, and BDs)
An optical drive, such as a DVD-ROM drive, supports optical discs (CDs and DVDs). These discs store
information, such as music, photos, and movies. DVDs have a higher storage capacity than CDs.
Your optical drive can read standard CD and DVD discs. If your optical drive is a Blu-ray Disc (BD) drive,
it can also read BDs.
NOTE: Some of the optical drives listed may not be supported by your computer. The listed drives are
not necessarily all of the supported optical drives.
Some optical drives can also write to optical discs, as described in the following table.
Optical drive type Write to CD-RWWrite to
DVD±RW/
R
DVD-ROM Drive No No No No No
DVD±R SuperMulti DL
LightScribe Drive*
*Double-layer discs can store more data than single-layer discs. However, double-layer discs burned with this drive may not
be compatible with many single-layer DVD drivers and players.
†
LightScribe discs must be purchased separately. LightScribe creates a grayscale image similar to black-and-white
photography.
†
Yes Yes Yes Yes No
Write to DVD±R DL Write label to
CAUTION: To prevent possible audio and video degradation, loss of information, or loss of audio or
video playback functionality, do not initiate Standby or Hibernation while reading a CD, DVD, or BD, or
writing to a CD or DVD.
Selecting the right disc (CDs, DVDs, and BDs)
Write to BD R/RE
LightScribe CD or
DVD ±RW/R
An optical drive supports optical discs (CDs and DVDs, and BDs). CDs, used to store digital data, are
also used for commercial audio recordings and are convenient for your personal storage needs. DVDs
and BDs are used primarily for movies, software, and data backup purposes. DVDs and BDs are the
same form factor as CDs, but have a much higher storage capacity.
Optical drive (select models only) 47
Page 60

NOTE: The optical drive on your computer may not support all the types of optical discs discussed in
this section.
CD-R discs
Use CD-R (write-once) discs to create permanent archives and to share files with virtually anyone.
Typical uses include the following:
●
●
●
●
●
After data is recorded, it cannot be erased or written over.
CD-RW discs
Use a CD-RW disc (a rewritable version of a CD) to store large projects that must be updated frequently.
Typical uses include the following:
●
Distributing large presentations
Sharing scanned and digital photos, video clips, and written data
Making your own music CDs
Keeping permanent archives of computer files and scanned home records
Offloading files from your hard drive to free up disk space
Developing and maintaining large documents and project files
Transporting work files
●
Making weekly backups of hard drive files
●
Updating photos, video, audio, and data continuously
●
DVD±R discs
Use blank DVD±R discs to permanently store large amounts of information. After data is recorded, it
cannot be erased or written over.
DVD±RW discs
Use DVD±RW discs if you want to be able to erase or write over data that you saved earlier. This type
of disc is ideal for testing audio or video recordings before you burn them to a CD or DVD that cannot
be changed.
LightScribe DVD+R discs
Use LightScribe DVD+R discs for sharing and storing data, home videos, and photos. These discs are
read-compatible with most DVD-ROM drives and DVD video players. With a LightScribe-enabled drive
and LightScribe software, you can write data to the disc and then add a designer label to the outside of
the disc.
Blu-ray Discs (BDs)
BD is a high-density optical disc format for the storage of digital information, including high-definition
video. A single-layer Blu-ray Disc can store 25 GB, over 5 times the storage capacity of a single-layer
DVD at 4.7 GB. A dual-layer Blu-ray Disc can store 50 GB, almost 6 times the storage capacity of a
dual-layer DVD at 8.5 GB.
48 Chapter 4 Multimedia
Page 61

Typical uses include the following:
Storage of large amounts of data
●
High-definition video playback and storage
●
Video games
●
NOTE: As Blu-ray is a new format containing new technologies, certain disc, digital connection,
compatibility and/or performance issues may arise, and do not constitute defects in the product. Flawless
playback on all systems is not guaranteed.
Playing a CD, DVD, or BD
1. Turn on the computer.
2. Press the release button (1) on the drive bezel to release the disc tray.
3. Pull out the tray (2).
4. Hold the disc by the edges to avoid touching the flat surfaces and position the disc label-side up
over the tray spindle.
NOTE: If the tray is not fully accessible, tilt the disc carefully to position it over the spindle.
5. Gently press the disc (3) down onto the tray spindle until the disc snaps into place.
6. Close the disc tray.
If you have not yet configured AutoPlay, as described in the following section, an AutoPlay dialog box
opens. It prompts you to select how you want to use the media content.
NOTE: For best results, be sure that your AC adapter is plugged into an external power source while
playing a BD.
Configuring AutoPlay
1. Select Start > My Computer.
2. Right-click the device (such as CD-ROM drive), and then click Properties.
Optical drive (select models only) 49
Page 62

3. Click the AutoPlay tab, and then select one of the available actions.
4. Click OK.
NOTE: For more information about AutoPlay, select Start > Help and Support.
Changing DVD region settings
Most DVDs that contain copyrighted files also contain region codes. The region codes help protect
copyrights internationally.
You can play a DVD containing a region code only if the region code on the DVD matches the region
setting on your DVD drive.
CAUTION: The region settings on your DVD drive can be changed only 5 times.
The region setting you select the fifth time becomes the permanent region setting on the DVD drive.
The number of region changes remaining is displayed on the DVD Region tab.
To change settings through the operating system:
1. Select Start > My Computer.
2. Right-click in the window and select Properties > Hardware tab > Device Manager.
3. Click the plus sign (+) next to DVD/CD-ROM drives, right-click the DVD drive for which you want
to change region settings, and then click Properties.
4. Make the desired changes on the DVD Region tab.
5. Click OK.
Observing the copyright warning
It is a criminal offense, under applicable copyright laws, to make unauthorized copies of copyrightprotected material, including computer programs, films, broadcasts, and sound recordings. Do not use
this computer for such purposes.
NOTE: For details about using software included with the computer, refer to the software
manufacturer's instructions. These instructions may be provided with the software, on disc, or on the
manufacturer's Web site.
Copying a CD or DVD
1. Select Start > All Programs > Roxio > Creator Business.
NOTE: If this is the first time you have used Roxio, you must accept the program license
agreement before you can complete this process.
2. In the right pane, click Copy Disc.
3. Insert the disc you want to copy into the optical drive.
4. Click Copy Disc at the bottom right of the screen.
50 Chapter 4 Multimedia
Page 63

Creator Business reads the source disc and copies the data to a temporary folder on your hard
drive.
5. When prompted, remove the source disc from the optical drive and insert a blank disc into the drive.
After the information is copied, the disc you created is ejected automatically.
Creating (burning) a CD or DVD
CAUTION: Observe the copyright warning. It is a criminal offense, under applicable copyright laws,
to make unauthorized copies of copyright-protected material, including computer programs, films,
broadcasts, and sound recordings. Do not use this computer for such purposes.
If your optical drive is a CD-RW, DVD-RW, or DVD±RW optical drive, you can use software such as
Windows Media Player to burn data and audio files, including MP3 and WAV music files.
Observe the following guidelines when burning a CD or DVD:
Before burning a disc, save and close any open files and close all programs.
●
A CD-R or DVD-R is usually best for burning audio files because after the information is copied, it
●
cannot be changed.
Because some home and car stereos will not play CD-RWs, use CD-Rs to burn music CDs.
●
A CD-RW or DVD-RW is generally best for burning data files or for testing audio or video recordings
●
before you burn them to a CD or DVD that cannot be changed.
DVD players used in home systems usually do not support all DVD formats. Refer to the user guide
●
that came with your DVD player for a list of supported formats.
An MP3 file uses less space than other music file formats, and the process for creating an MP3
●
disc is the same as the process for creating a data file. MP3 files can be played only on MP3 players
or on computers with MP3 software installed.
To burn a CD or DVD, follow these steps:
1. Download or copy the source files into a folder on your hard drive.
2. Insert a blank disc into the optical drive.
3. Select Start > All Programs and the name of the software you want to use.
4. Select the kind of disc you want to create—data, audio, or video.
5. Right-click Start, click Explore, and then navigate to the folder where the source files are stored.
6. Open the folder, and then drag the files to the drive that contains the blank disc.
7. Initiate the burning process as directed by the program you have selected.
For specific instructions, refer to the software manufacturer's instructions. These instructions may be
provided with the software, on disc, or on the manufacturer's Web site.
Removing an optical disc (CD, DVD, or BD)
1. Press the release button (1) on the drive bezel to release the disc tray, and then gently pull out the
tray (2) until it stops.
Optical drive (select models only) 51
Page 64

2. Remove the disc (3) from the tray by gently pressing down on the spindle while lifting the outer
edges of the disc. Hold the disc by the edges and avoid touching the flat surfaces.
NOTE: If the tray is not fully accessible, tilt the disc carefully as you remove it.
3. Close the disc tray and place the disc in a protective case.
Troubleshooting
The following sections describe several common issues and resolutions.
The optical disc tray does not open for removal of a CD, DVD, or BD
1. Insert the end of a paper clip (1) into the release access in the front bezel of the drive.
2. Press in gently on the paper clip until the disc tray is released, and then pull out the tray (2) until it
stops.
52 Chapter 4 Multimedia
Page 65

3. Remove the disc (3) from the tray by gently pressing down on the spindle while lifting the outer
edges of the disc. Hold the disc by the edges and avoid touching the flat surfaces.
NOTE: If the tray is not fully accessible, tilt the disc carefully as you remove it.
4. Close the disc tray and place the disc in a protective case.
The computer does not detect the optical drive
If Windows does not detect an attached device, the device driver software may be missing or corrupted.
If you suspect that the DVD/CD-ROM drive is not being detected, verify that the optical drive is listed in
the Device Manager utility.
1. Remove any discs from the optical drive.
2. Select Start > My Computer.
3. In the Device Manager window, click the plus sign (+) next to Discs Drives or DVD/CD-ROM
drives, unless a minus sign (-) is already showing. Look for an optical drive listing.
4. Right-click the optical device listing to perform the following tasks:
Update the driver.
●
Uninstall the device.
●
Scan for hardware changes. Windows scans your system for installed hardware and installs
●
any required default drivers.
Click Properties to see if the device is working properly.
●
Click Troubleshoot to fix problems.
◦
Click the Driver tab to update, disable, or uninstall drivers for this device.
◦
Optical drive (select models only) 53
Page 66

Preventing playback disruptions
To reduce the possibility of playback disruption:
Save your work and close all open programs before playing a CD, DVD, or BD.
●
Do not connect or disconnect hardware while playing a disc.
●
Do not initiate Hibernation or Standby while playing a disc. Otherwise, you may see a warning message
asking if you want to continue. If this message is displayed, click No. After you click No, the computer
may behave in either of the following ways:
Playback may resume.
●
– or –
The playback window in the multimedia program may close. To return to playing the CD, DVD, or
●
BD, click the Play button in your multimedia program to restart the disc. In rare cases, you may
need to exit the program and then restart it.
A disc does not play
Save your work and close all open programs before playing a CD, DVD, or BD.
●
Log off the Internet before playing a CD, DVD, or BD.
●
Be sure that you insert the disc properly.
●
Be sure that the disc is clean. If necessary, clean the disc with filtered water and a lint-free cloth.
●
Wipe from the center of the disc to the outer edge.
Check the disc for scratches. If you find scratches, treat the disc with an optical disc repair kit
●
available at many electronics stores.
Disable Standby before playing the disc.
●
Do not initiate Hibernation or Standby while playing a disc. Otherwise, you may see a warning
message asking if you want to continue. If this message is displayed, click No. After you click No,
the computer may behave in either of the following ways:
Playback may resume.
◦
– or –
The playback window in the multimedia program may close. To return to playing the disc, click
◦
the Play button in your multimedia program to restart the disc. In rare cases, you may need
to exit the program and then restart it.
Increase system resources:
●
Turn off external devices such as printers and scanners. Disconnecting these devices frees up
valuable system resources and results in better playback performance.
Change desktop color properties. Because the human eye cannot easily tell the difference between
colors beyond 16 bits, you should not notice any loss of color while watching a movie if you lower system
color properties to 16-bit color, as follows:
1. Right-click anywhere on the desktop except on an icon, and then select Properties > Settings.
2. Set Color quality to Medium (16 bit).
54 Chapter 4 Multimedia
Page 67

A disc does not play automatically
1. Click Start > My Computer.
2. Right-click the device (such as CD-ROM drive), and then click Properties.
3. Click the AutoPlay tab, and then select one of the available actions.
4. Click OK.
A CD, DVD, or BD should now start automatically when it is inserted into the optical drive.
A movie stops, skips, or plays erratically
Clean the disc.
●
Conserve system resources by trying the following suggestions:
●
Log off the Internet.
◦
Change the color properties of the desktop:
◦
1. Right-click on a blank area of the computer desktop, and then select Properties >
Settings.
2. Set Color quality to Medium (16 bit), if this setting is not already selected.
Disconnect external devices, such as a printer, scanner, camera, or handheld device.
◦
A movie is not visible on an external display
1. If both the computer display and an external display are turned on, press fn+f4 one or more times
to switch between the two displays.
2. Configure the monitor settings to make the external display primary:
a. Right-click on a blank area of the computer desktop, and then select Properties >
Settings.
b. Specify a primary display and a secondary display.
NOTE: When using both displays, the DVD image will not appear on any display designated as
the secondary display.
To get information about a multimedia question not covered in this guide, select Start > Help and
Support.
The process of burning a disc does not begin, or it stops before completion
Be sure that all other programs are closed.
●
Turn off Standby mode and Hibernation.
●
Be sure that you are using the right kind of disc for your drive. See your user guides for more
●
information about disc types.
Be sure that the disc is inserted properly.
●
Select a slower write speed and try again.
●
Optical drive (select models only) 55
Page 68

If you are copying a disc, save the information on the source disc to your hard drive before trying
●
to burn the contents to a new disc, and then burn from your hard drive.
Reinstall the disc-burning device driver located in the DVD/CD-ROM drives category in Device
●
Manager.
A device driver must be reinstalled
Obtaining the latest HP device drivers
Follow either of the following procedures to obtain HP device drivers.
To use the HP Update Utility:
1. Select Start > All Programs > HP > HP Update.
2. On the HP Welcome screen, click Settings, and then select a time when the utility should check
for software updates on the Web.
3. Click Next to immediately check for HP software updates.
To use the HP Web site to obtain HP device drivers:
1. Open your Internet browser, go to
region.
2. Click the option for software and driver downloads, and then type your computer model number in
the product box.
3. Press enter, and then follow the on-screen instructions.
Obtaining Microsoft device drivers
You can obtain the latest Windows device drivers by using Microsoft® Update. This Windows feature
can be set to automatically check for and install updates for your hardware drivers, as well as for the
Windows operating system and other Microsoft products.
To use Microsoft Update:
1. Open your Internet browser, go to
2. Click Microsoft Update to get the latest updates for your computer operating system, programs,
and hardware.
3. Follow the on-screen instructions to install Microsoft Update.
4. Click Change settings, and then select a time for Microsoft Update to check for updates to the
Windows operating system and other Microsoft products.
5. If prompted to do so, restart your computer.
http://www.hp.com/support, and then select your country or
http://www.microsoft.com, and click Security & Updates.
56 Chapter 4 Multimedia
Page 69

Webcam
NOTE: This section describes features that are common to most models. Some features may not be
available on your computer.
Your computer includes an integrated webcam, located at the top of the display. With the preinstalled
software, you can use the webcam to take a photo, record a video, or make an audio recording. You
can preview the photo, video recording, or audio recording, and save it on your computer hard drive.
To access the webcam and HP Webcam software, select Start > All Programs > HP >HP Webcam.
The webcam software enables you to experiment with the following features:
Video—Record and play back webcam video.
●
Audio—Record and play back audio.
●
Streaming video—Use with instant message software solutions that support UVC (Universal Video
●
Class) cameras.
Snapshots—Take still photos.
●
Webcam tips
For optimum performance, observe the following guidelines while using the webcam:
Be sure that you have the latest version of an instant message program before starting a video
●
conversation.
The webcam may not work properly across some network firewalls.
●
NOTE: If you are having trouble viewing or sending multimedia files to someone on another LAN
or outside your network firewall, temporarily disable the firewall, perform the task you want to
perform, and then reenable the firewall. To permanently resolve the problem, reconfigure the
firewall as necessary, and adjust the policies and settings of other intrusion detection systems. For
additional information, contact your network administrator or IT department.
Whenever possible, place bright light sources behind the webcam and out of the picture area.
●
NOTE: For details about using your webcam, click the Help menu in the webcam software Help.
Adjusting webcam properties
You can adjust webcam properties using the Properties dialog box, which is accessible from various
programs that use the integrated webcam, usually from a configuration, settings, or properties menu:
Brightness—Controls the amount of light that is incorporated into the image. A higher brightness
●
setting creates a brighter image; a lower brightness setting creates a darker image.
Contrast—Controls the difference between lighter and darker areas on the image. A higher
●
contrast setting intensifies the image; a lower contrast setting maintains more of the original
information’s dynamic range, but leads to a flatter image.
Hue—Controls the aspect of color that distinguishes it from another color (what makes a color red,
●
green, or blue). Hue is distinct from saturation, which measures the intensity of the hue.
Saturation—Controls the strength of color in the final image. A higher saturation setting creates a
●
bolder image; a lower saturation setting creates a more subtle image.
Webcam 57
Page 70

Sharpness—Controls the definition of edges in an image. A higher sharpness setting creates a
●
more defined image; a lower sharpness setting creates a softer image.
Gamma—Controls the contrast affecting the mid-level grays or midtones of an image. Adjusting
●
the gamma of an image allows you to change the brightness values of the middle range of gray
tones without dramatically altering the shadows and highlights. A lower gamma setting makes
grays look black, and makes dark colors even darker.
For information about using the webcam, select Start > Help and Support.
58 Chapter 4 Multimedia
Page 71

5 Power management
Setting power options
Using power-saving states
The computer has two power-saving states enabled at the factory: Standby and Hibernation.
When Standby is initiated, the power lights blink and the screen clears. Your work is saved to memory.
Exiting Standby is faster than exiting Hibernation. If the computer is in Standby for an extended period
or if the battery reaches a critical battery level while in Standby, the computer initiates Hibernation.
When Hibernation is initiated, your work is saved to a hibernation file on the hard drive and the computer
turns off.
CAUTION: To prevent possible audio and video degradation, loss of audio or video playback
functionality, or loss of information, do not initiate Standby or Hibernation while reading from or writing
to a disc or an external media card.
NOTE: You cannot initiate any type of networking connection or perform any computer functions while
the computer is in Standby or in Hibernation.
NOTE: When HP 3D DriveGuard has parked a drive, the computer will not initiate Standby or
Hibernation, and the display will be turned off.
Initiating and exiting Standby
The system is set at the factory to initiate Standby after 10 minutes of inactivity when running on battery
power and 25 minutes of inactivity when running on external power.
Power settings and timeouts can be changed using Power Options in Windows® Control Panel.
With the computer on, you can initiate Standby in any of the following ways:
Press f5.
●
Click Start > Turn Off Computer > Stand By.
●
If Stand by is not displayed, follow these steps:
a. Click the down arrow.
b. Select Stand by from the list.
c. Click OK.
Setting power options 59
Page 72

To exit Standby:
Briefly press the power button.
▲
When the computer exits Standby, the power lights turn on and your work returns to the screen
where you stopped working.
NOTE: If you have set a password to be required when the computer exits Standby, you must enter
your Windows password before your work will return to the screen.
Initiating and exiting Hibernation
The system is set at the factory to initiate Hibernation after 30 minutes of inactivity when running on
battery power or when the battery reaches a critical battery level.
NOTE: The system will not initiate Hibernation when running on external power.
Power settings and timeouts can be changed using Power Options in Windows Control Panel.
To initiate Hibernation:
1. Select Start > Turn Off Computer.
2. Hold down the shift key and select Hibernate.
If Hibernate is not displayed, follow these steps:
a. Click the down arrow.
b. Select Hibernate from the list.
c. Click OK.
To exit Hibernation:
Briefly press the power button.
▲
The power lights turn on and your work returns to the screen where you stopped working.
NOTE: If you have set a password to be required when the computer exits Hibernation, you must enter
your Windows password before your work will return to the screen.
Using the Power Meter
The Power Meter is located in the notification area, at the far right of the taskbar. The Power Meter
allows you to quickly access power settings and view the remaining battery charge.
To access Power Options, right-click the Power Meter icon and select Adjust Power
●
Properties.
To display the percentage of remaining battery charge, double-click the Power Meter icon.
●
Different battery meter icons indicate whether the computer is running on battery or external power.
To remove the Power Meter icon from the notification area, follow these steps:
1. Right-click the Power Meter icon in the notification area, and then click Adjust Power
Properties.
2. Click the Advanced tab.
60 Chapter 5 Power management
Page 73

3. Clear the Always show icon on the taskbar check box.
4. Click Apply, and then click OK.
To show the Power Meter icon in the notification area, follow these steps:
1. Select Start > Control Panel > Performance and Maintenance > Power Options.
2. Click the Advanced tab.
3. Select the Always show icon on the taskbar check box.
4. Click Apply, and then click OK.
NOTE: If you cannot see an icon you have placed in the notification area, click the Show Hidden
Icons icon (< or <<) in the notification area.
Using power schemes
A power scheme is a collection of system settings that manages how the computer uses power. Power
schemes can help you conserve power and maximize computer performance.
The following power schemes are available:
Portable/Laptop (recommended)
●
Home/Office Desk
●
Presentation
●
Always On
●
Minimal Power Management
●
Max Battery
●
You can change the settings of these power plans through Power Options.
Viewing the current scheme
Click the Power Meter icon in the notification area, at the far right of the taskbar.
▲
– or –
Select Start > Control Panel > Performance and Maintenance > Power Options.
Selecting a different power scheme
Click the Power Meter icon in the notification area, at the far right of the taskbar, and then select
▲
a power scheme from the list.
– or –
a. Select Start > Control Panel > Performance and Maintenance > Power Options.
b. Select a power scheme from the Power schemes list.
c. Click OK.
Setting power options 61
Page 74

Customizing power schemes
1. Select Start > Control Panel > Performance and Maintenance > Power Options.
2. Select a power scheme from the Power schemes list.
3. Modify the Plugged in and Running on batteries settings as needed.
4. Click OK.
Setting password protection upon exiting Standby
To set the computer to prompt for a password when the computer exits Standby, follow these steps:
1. Right-click the Power Meter icon in the notification area, and then click Adjust Power
Properties.
2. Click the Advanced tab.
3. Select the Prompt for password when computer resumes from standby check box.
4. Click Apply.
Using external AC power
External AC power is supplied through one of the following devices:
WARNING! To reduce potential safety issues, use only the AC adapter provided with the computer,
a replacement AC adapter provided by HP, or a compatible AC adapter purchased from HP.
Approved AC adapter
●
Optional docking device or optional expansion product
●
Connect the computer to external AC power under any of the following conditions:
WARNING! Do not charge the computer battery while you are onboard aircraft.
When you are charging or calibrating a battery
●
When you are installing or modifying system software
●
When you are writing information to a CD or DVD
●
When you connect the computer to external AC power, the following events occur:
The battery begins to charge.
●
If the computer is turned on, the battery meter icon in the notification area changes appearance.
●
When you disconnect external AC power, the following events occur:
The computer switches to battery power.
●
The display brightness is automatically decreased to save battery life. To increase display
●
brightness, press the f4 key or reconnect the AC adapter.
62 Chapter 5 Power management
Page 75

Connecting the AC adapter
WARNING! To reduce the risk of electric shock or damage to the equipment:
Plug the power cord into an AC outlet that is easily accessible at all times.
Disconnect power from the computer by unplugging the power cord from the AC outlet (not by
unplugging the power cord from the computer).
If provided with a 3-pin attachment plug on the power cord, plug the cord into a grounded (earthed) 3pin outlet. Do not disable the power cord grounding pin, for example, by attaching a 2-pin adapter. The
grounding pin is an important safety feature.
To connect the computer to external AC power, follow these steps:
1. Plug the AC adapter into the power connector (1) on the computer.
2. Plug the power cord into the AC adapter (2).
3. Plug the other end of the power cord into an AC outlet (3).
Using battery power
When a charged battery is in the computer and the computer is not plugged into external power, the
computer runs on battery power. When the computer is plugged into external AC power, the computer
runs on AC power.
If the computer contains a charged battery and is running on external AC power supplied through the
AC adapter, the computer switches to battery power if the AC adapter is disconnected from the
computer.
NOTE: The display brightness is decreased to save battery life when you disconnect AC power. To
increase display brightness, use the f3 key or reconnect the AC adapter.
You can keep a battery in the computer or in storage, depending on how you work. Keeping the battery
in the computer whenever the computer is plugged into AC power charges the battery and also protects
your work in case of a power outage. However, a battery in the computer slowly discharges when the
computer is off and unplugged from external power.
Using battery power 63
Page 76

WARNING! To reduce potential safety issues, use only the battery provided with the computer, a
replacement battery provided by HP, or a compatible battery purchased from HP.
Computer battery life varies, depending on power management settings, programs running on the
computer, display brightness, external devices connected to the computer, and other factors.
Displaying the remaining battery charge
Double-click the Power Meter icon in the notification area, at the far right of the taskbar.
▲
– or –
Select Start > Control Panel > Performance and Maintenance > Power Options > Power
Meter tab.
Most charge indicators report battery status as both a percentage and as the number of minutes of
charge remaining:
The percentage indicates the approximate amount of charge remaining in the battery.
●
The time indicates the approximate running time remaining on the battery if the battery continues
●
to provide power at the current level. For example, the time remaining will decrease when a DVD
is playing and will increase when a DVD stops playing.
When a battery is charging, a lightning bolt icon may be superimposed over the battery icon on the
Power Meter screen.
Inserting or removing the battery
CAUTION: Removing a battery that is the sole power source can cause loss of information. To prevent
loss of information, initiate Hibernation or shut down the computer through Windows before removing
the battery.
To insert the battery:
1. Turn the computer upside down on a flat surface, with the battery bay toward you.
64 Chapter 5 Power management
Page 77

2. Insert the battery into the battery bay (1) and push in until it is seated.
The battery release latches (2) automatically lock the battery into place.
To remove the battery:
1. Turn the computer upside down on a flat surface, with the battery bay toward you.
2. Slide the battery release latches (1) to release the battery.
3. Remove the battery (2) from the computer.
Using battery power 65
Page 78

Charging a battery
WARNING! Do not charge the computer battery while you are onboard aircraft.
The battery charges whenever the computer is plugged into external power through an AC adapter, an
optional power adapter, an optional expansion product, or an optional docking device.
The battery charges whether the computer is off or in use, but it charges faster when the computer is
off.
Charging may take longer if a battery is new, has been unused for 2 weeks or more, or is much warmer
or cooler than room temperature.
To prolong battery life and optimize the accuracy of battery charge displays, follow these
recommendations:
If you are charging a new battery, charge it fully before turning on the computer.
●
Charge the battery until the battery light turns off.
●
NOTE: If the computer is on while the battery is charging, the battery meter in the notification
area may show 100 percent charge before the battery is fully charged.
Allow the battery to discharge below 5 percent of a full charge through normal use before charging
●
it.
If the battery has been unused for one month or more, calibrate the battery instead of simply
●
charging it.
The battery light displays charge status:
On: The battery is charging.
●
Blinking: The battery has reached a low battery level or critical battery level and is not charging.
●
Off: The battery is fully charged, in use, or not installed.
●
Maximizing battery discharge time
Battery discharge time varies, depending on the features you use while on battery power. Maximum
discharge time gradually shortens as the battery storage capacity naturally degrades.
Tips for maximizing battery discharge time:
Lower the brightness on the display.
●
Remove the battery from the computer when it is not being used or charged.
●
Store the battery in a cool, dry location.
●
Managing low battery levels
The information in this section describes the alerts and system responses set at the factory. Some lowbattery alerts and system responses can be changed using Power Options in Windows Control Panel.
Preferences set using Power Options do not affect lights.
66 Chapter 5 Power management
Page 79

Identifying low battery levels
When a battery that is the sole power source for the computer reaches a low battery level, the battery
light blinks.
If a low battery level is not resolved, the computer enters a critical battery level, and the battery light
blinks rapidly.
The computer takes the following actions for a critical battery level:
If Hibernation is enabled and the computer is on or in Standby, the computer initiates Hibernation.
●
If Hibernation is disabled and the computer is on or in Standby, the computer remains briefly in
●
Standby, and then shuts down and loses any unsaved information.
Resolving a low battery level
CAUTION: To reduce the risk of losing information when the computer reaches a critical battery level
and has initiated Hibernation, do not restore power until the power lights turn off.
Resolving a low battery level when external power is available
Connect one of the following devices:
▲
AC adapter
●
Optional expansion product or docking device
●
Optional power adapter
●
Resolving a low battery level when a charged battery is available
1. Turn off the computer or initiate Hibernation.
2. Remove the discharged battery, and then insert a charged battery.
3. Turn on the computer.
Resolving a low battery level when no power source is available
Initiate Hibernation.
▲
– or –
Save your work and shut down the computer.
Resolving a low battery level when the computer cannot exit Hibernation
When the computer lacks sufficient power to exit Hibernation, follow these steps:
1. Insert a charged battery or plug the computer into external power.
2. Exit Hibernation by briefly pressing the power button.
Using battery power 67
Page 80

Calibrating a battery
Calibrate a battery under the following conditions:
When battery charge displays seem inaccurate
●
When you observe a significant change in battery run time
●
Even if a battery is heavily used, it should not need to be calibrated more than once a month. It is also
not necessary to calibrate a new battery.
Step 1: Fully charge the battery
WARNING! Do not charge the computer battery while you are onboard aircraft.
NOTE: The battery charges whether the computer is off or in use, but it charges faster when the
computer is off.
To fully charge the battery:
1. Insert the battery into the computer.
2. Connect the computer to an AC adapter, optional power adapter, optional expansion product, or
optional docking device, and then plug the adapter or device into external power.
The battery light on the computer turns on.
3. Leave the computer plugged into external power until the battery is fully charged.
The battery light on the computer turns off.
Step 2: Disable Hibernation and Standby
1. Right-click the Power Meter icon in the notification area, at the far right of the taskbar, and then
click Adjust Power Properties.
– or –
Select Start > Control Panel > Performance and Maintenance > Power Options.
2. Record the 4 settings listed in the Running on batteries and Plugged in columns so that you can
reset them after the calibration.
3. Set the 4 options to Never.
4. Click OK.
68 Chapter 5 Power management
Page 81

Step 3: Discharge the battery
The computer must remain on while the battery is being discharged. The battery can discharge whether
or not you are using the computer, but the battery will discharge faster while you are using it.
If you plan to leave the computer unattended during the discharge, save your information before
●
beginning the discharge procedure.
If you use the computer occasionally during the discharge procedure and have set energy-saving
●
timeouts, expect the following performance from the system during the discharge process:
The monitor will not turn off automatically.
◦
Hard drive speed will not decrease automatically when the computer is idle.
◦
System-initiated Hibernation will not occur.
◦
To discharge a battery:
1. Unplug the computer from its external power source, but do not turn off the computer.
2. Run the computer on battery power until the battery is discharged. The battery light begins to blink
when the battery has discharged to a low battery level. When the battery is discharged, the battery
light turns off and the computer shuts down.
Step 4: Fully recharge the battery
To recharge the battery:
1. Plug the computer into external power and maintain external power until the battery is fully
recharged. When the battery is recharged, the battery light on the computer turns off.
You can use the computer while the battery is recharging, but the battery will charge faster if the
computer is off.
2. If the computer is off, turn it on when the battery is fully charged and the battery light has turned
off.
Step 5: Reenable Hibernation and Standby
CAUTION: Failure to reenable Hibernation after calibration may result in a full battery discharge and
information loss if the computer reaches a critical battery level.
1. Select Start > Control Panel > Performance and Maintenance > Power Options.
2. Reenter the settings that you recorded for the items in the Plugged in column and the Running
on batteries column.
3. Click OK.
Conserving battery power
Select low power-use settings through Power Options in Windows Control Panel.
●
Turn off wireless and local area network (LAN) connections and exit modem applications when you
●
are not using them.
Disconnect external devices that are not plugged into an external power source, when you are not
●
using them.
Using battery power 69
Page 82

Stop, disable, or remove any external media cards that you are not using.
●
Use the f2 and f3 keys to adjust screen brightness as needed.
●
If you leave your work, initiate Standby or Hibernation, or shut down the computer.
●
Storing a battery
CAUTION: To prevent damage to a battery, do not expose it to high temperatures for extended periods
of time.
If a computer will be unused and unplugged from external power for more than 2 weeks, remove the
battery and store it separately.
To prolong the charge of a stored battery, place it in a cool, dry place.
NOTE: A stored battery should be checked every 6 months. If the capacity is less than 50 percent,
recharge the battery before returning it to storage.
Calibrate a battery before using it if it has been stored for one month or more.
Disposing of a used battery
WARNING! To reduce the risk of fire or burns, do not disassemble, crush, or puncture; do not short
external contacts; do not dispose of in fire or water.
Refer to the Regulatory, Safety and Environmental Notices for battery disposal information.
Replacing the battery
Computer battery life varies, depending on the power management settings, programs running on the
computer, display brightness, external devices connected to the computer, and other factors.
NOTE: To ensure that you always have battery power when you need it, HP recommends purchasing
a new battery when the storage capacity indicator turns green-yellow.
70 Chapter 5 Power management
Page 83

Testing an AC adapter
Test the AC adapter if the computer exhibits any of the following symptoms:
The computer will not turn on when connected to the AC adapter.
●
The display does not turn on when the computer is connected to the AC adapter.
●
The power light is off when the computer is connected to the AC adapter.
●
To test the AC adapter:
1. Remove the battery from the computer.
2. Connect the AC adapter.
3. Turn on the computer.
If the power light turns on, the AC adapter is functioning properly.
●
If the power light remains off, the AC adapter is not functioning and should be replaced.
●
Contact technical support for information on obtaining a replacement AC power adapter by
selecting Start > Help and Support.
Shutting down the computer
CAUTION: Unsaved information will be lost when the computer is shut down.
The Shut Down command closes all open programs, including the operating system, and then turns off
the display and computer.
Shut down the computer under any of the following conditions:
When you need to replace the battery or access components inside the computer
●
When you are connecting an external hardware device that does not connect to a USB port
●
When the computer will be unused and disconnected from external power for an extended period
●
To shut down the computer, follow these steps:
NOTE: If the computer is in Standby or in Hibernation, you must first exit Standby or Hibernation before
shutdown is possible.
1. Save your work and close all open programs.
2. Select Start > Turn Off Computer > Turn Off.
If the computer is unresponsive and you are unable to use the preceding shutdown procedures, try the
following emergency procedures in the sequence provided:
Press ctrl+alt+delete. Then, select Shut Down > Turn Off.
●
Press and hold the power button for at least 5 seconds.
●
Disconnect the computer from external power and remove the battery.
●
Testing an AC adapter 71
Page 84

6 Drives
Identifying installed drives
To view the drives installed on the computer, select Start > My Computer.
On models with a secondary hard drive (drive D), the optical drive becomes drive E. The next drive
added to the system, such as a new USB drive, will be assigned the next available drive letter.
Handling drives
Drives are fragile computer components that must be handled with care. Refer to the following cautions
before handling drives. Additional cautions are included with the procedures to which they apply.
72 Chapter 6 Drives
Page 85

CAUTION: To reduce the risk of damage to the computer, damage to a drive, or loss of information,
observe these precautions:
Before you move a computer that is connected to an external hard drive, initiate Standby and allow the
screen to clear, or properly disconnect the external hard drive.
Before handling a drive, discharge static electricity by touching the unpainted metal surface of the drive.
Do not touch the connector pins on a removable drive or on the computer.
Handle a drive carefully; do not drop a drive or place items on it.
Before removing or inserting a drive, shut down the computer. If you are unsure whether the computer
is off, in Standby, or in Hibernation, turn the computer on and then shut it down through the operating
system.
Do not use excessive force when inserting a drive into a drive bay.
Do not type on the keyboard or move the computer while an optional optical drive is writing to a disc.
The write process is sensitive to vibration.
When the battery is the only source of power, be sure that the battery is sufficiently charged before
writing to media.
Avoid exposing a drive to temperature or humidity extremes.
Avoid exposing a drive to liquids. Do not spray the drive with cleaning products.
Remove media from a drive before removing the drive from the drive bay, or traveling with, shipping, or
storing a drive.
If a drive must be mailed, place the drive in a bubble-pack mailer or other suitable protective packaging
and label the package “FRAGILE.”
Avoid exposing a drive to magnetic fields. Security devices with magnetic fields include airport walkthrough devices and security wands. The airport security devices that check carry-on luggage, such as
conveyor belts, use X-rays instead of magnetism and will not damage a drive.
Handling drives 73
Page 86

Improving hard drive performance
Using Disk Defragmenter
As you use the computer, files on the hard drive become fragmented. Disk Defragmenter consolidates
the fragmented files and folders on the hard drive so that the system can run more efficiently.
To run Disk Defragmenter:
1. Select Start > All Programs > Accessories > System Tools > Disk Defragmenter.
2. Under Volume, click the listing for the hard drive, usually listed as (C:), and then click
Defragment.
For additional information, access the Disk Defragmenter online Help.
Using Disk Cleanup
Disk Cleanup searches the hard drive for unnecessary files that you can safely delete to free up disk
space and help the computer to run more efficiently.
To run Disk Cleanup:
1. Select Start > All Programs > Accessories> System Tools > Disk Cleanup.
2. Follow the on-screen instructions.
74 Chapter 6 Drives
Page 87

Using external drives
Removable external drives expand your options for storing and accessing information. A USB device
can be added by connecting the device to a USB port on the computer or on an optional docking device
(select models only).
USB drives include the following types:
1.44-megabyte diskette drive
●
Hard drive module (a hard drive with an adapter attached)
●
DVD-ROM Drive
●
DVD+/-RW SuperMulti Double-Layer LightScribe Drive
●
Blu-ray ROM DVD+/-RW SuperMulti Double-Layer LightScribe Drive
●
Using optional external devices
NOTE: For more information about required software and drivers, or to learn which computer port to
use, refer to the manufacturer's instructions.
To connect an external device to the computer:
CAUTION: To reduce the risk of damage to the equipment when connecting a powered device, be
sure that the device is turned off and the AC power cord is unplugged.
1. Connect the device to the computer.
2. If you are connecting a powered device, plug the device power cord into a grounded AC outlet.
3. Turn on the device.
To disconnect an unpowered external device, turn off the device, and then disconnect it from the
computer. To disconnect a powered external device, turn off the device, disconnect it from the computer,
and then unplug the AC power cord.
Using external drives 75
Page 88

Replacing the hard drive
CAUTION: To prevent information loss or an unresponsive system:
Shut down the computer before removing the hard drive from the hard drive bay. Do not remove the
hard drive while the computer is on, in Standby, or in Hibernation.
If you are not sure whether the computer is off or in Hibernation, turn the computer on by pressing the
power button. Then, shut down the computer through the operating system.
To remove a hard drive:
1. Save your work.
2. Shut down the computer and close the display.
3. Disconnect all external hardware devices connected to the computer.
4. Unplug the power cord from the AC outlet.
5. Turn the computer upside down on a flat surface, with the hard drive bay toward you.
6. Remove the battery from the computer.
7. Loosen the bottom door screws (1).
8. Slide the bottom door forward (2), and then lift it away from the computer (3).
NOTE: Refer to the illustration that most closely matches your computer.
9. Remove the 2 screws securing the rear of the drive (1).
76 Chapter 6 Drives
Page 89

10. Loosen the hard drive screw (2).
11. Pull the hard drive tab (3) to the left to disconnect the hard drive.
12. Lift the hard drive (4) out of the hard drive bay.
To install a hard drive:
1. Insert the hard drive into the hard drive bay (1).
2. Pull the hard drive tab (2) to the right to connect the hard drive.
3. Tighten the hard drive screw (3).
Replacing the hard drive 77
Page 90

4. Replace and secure the 2 screws at the rear of the drive.
5. Replace the bottom door (1) sliding it securely into place (2).
78 Chapter 6 Drives
Page 91

6. Tighten the bottom door screws (3).
NOTE: Refer to the illustration that most closely matches your computer.
Replacing the hard drive 79
Page 92

7 External devices
Using a USB device
Universal Serial Bus (USB) is a hardware interface that can be used to connect an optional external
device, such as a USB keyboard, mouse, drive, printer, scanner, or hub.
Some USB devices may require additional support software, which is usually included with the device.
For more information about device-specific software, refer to the manufacturer's instructions.
Your computer model has 4 USB ports, which support USB 1.0, USB 1.1, and USB 2.0 devices. A USB
hub provides additional USB ports that can be used with the computer.
Connecting a USB device
CAUTION: To prevent damage to a USB connector, use minimal force to connect a USB device.
To connect a USB device to the computer, connect the USB cable for the device to the USB
▲
port.
You will hear a sound when the device has been detected.
NOTE: The first time you connect a USB device, a message is displayed in the notification area to let
you know the device is recognized by the computer.
Stopping and removing a USB device
CAUTION: To prevent loss of information or an unresponsive system, stop a USB device before
removing it.
80 Chapter 7 External devices
Page 93

CAUTION: To prevent damage to a USB connector, do not pull on the cable to remove the USB device.
To stop and remove a USB device:
1. Double-click the Safely Remove Hardware icon in the notification area, at the far right of the
taskbar.
NOTE: To display the Safely Remove Hardware icon, click the Show Hidden Icons icon (< or
<<) in the notification area.
2. Click the name of the device in the list.
NOTE: If the USB device is not listed, you do not have to stop the device before you remove it.
3. Click Stop, and then click OK.
4. Remove the device.
Using USB legacy support
USB legacy support (enabled by default) permits the following actions:
Using a USB keyboard, mouse, or hub connected to a USB port on the computer during startup or
●
in an MS-DOS-based program or utility
Starting or restarting from an optional external MultiBay or an optional USB bootable device
●
USB legacy support is enabled at the factory. To disable or enable USB legacy support:
1. Open Computer Setup by turning on or restarting the computer, and then pressing f10 while the
“F10 = ROM Based Setup” message is displayed in the lower-left corner of the screen.
2. Use the arrow keys to select System Configuration > Device configurations, and then press
enter.
3. Use the arrow keys to enable or disable USB legacy support, and then press f10.
4. To save your preferences and exit Computer Setup, use the arrow keys to select File > Save
changes and exit. Then follow the instructions on the screen.
Your preferences go into effect when the computer restarts.
Using a USB device 81
Page 94

Using external drives
Removable external drives expand your options for storing and accessing information. A USB drive can
be added by connecting the drive to a USB port on the computer.
USB drives include the following types:
1.44-megabyte diskette drive
●
Hard drive module (a hard drive with an adapter attached)
●
DVD-ROM Drive
●
DVD+/-RW SuperMulti DL LightScribe Drive
●
Blu-ray ROM DVD+/-RW SuperMulti DL LightScribe Drive
●
Using optional external devices
NOTE: For more information about required software and drivers, or to learn which computer port to
use, refer to the manufacturer's instructions.
To connect an external device to the computer:
CAUTION: To reduce the risk of damage to the equipment when connecting a powered device, be
sure that the device is turned off and the AC power cord is unplugged.
1. Connect the device to the computer.
2. If you are connecting a powered device, plug the device power cord into a grounded AC outlet.
3. Turn on the device.
To disconnect an unpowered external device, turn off the device, and then disconnect it from the
computer. To disconnect a powered external device, turn off the device, disconnect it from the computer,
and then unplug the AC power cord.
82 Chapter 7 External devices
Page 95

8 External media cards
Using Media Card Reader cards
Optional digital cards provide secure data storage and convenient data sharing. These cards are often
used with digital media-equipped cameras and PDAs, as well as with other computers.
The Digital Media Slot supports the following digital card formats:
MultiMediaCard (MMC)
●
MultiMedia Card 4.2
●
Secure Digital (SD) Memory Card
●
Secure Digital High Capacity (SDHC) Memory Card
●
Secure Digital High Speed (SDHS) Memory Card
●
Inserting a digital card
CAUTION: To avoid damaging the digital card or the computer, do not insert any type of adapter into
the SD Card Reader.
CAUTION: To prevent damage to the digital card connectors, use minimal force to insert a digital card.
1. Hold the digital card label-side up, with the connectors facing the computer.
2. Insert the card into the Media Card Reader, and then push in on the card until it is firmly seated.
You will hear a sound when the device has been detected, and a menu of available options may
be displayed.
Using Media Card Reader cards 83
Page 96

Removing a digital card
CAUTION: To prevent loss of data or an unresponsive system, use the following procedure to safely
remove the digital card.
Save your information and close all programs associated with the digital card.
NOTE: To stop a data transfer, click Cancel in the operating system Copying window.
To remove a digital card:
To eject the digital card, press in on the card (1), and then remove it from the slot (2).
▲
84 Chapter 8 External media cards
Page 97

Using ExpressCards (select models only)
An ExpressCard is a high-performance PC Card that is inserted into the ExpressCard slot.
Like standard PC Cards, ExpressCards are designed to conform to the standard specifications of the
Personal Computer Memory Card International Association (PCMCIA).
Configuring an ExpressCard
Install only the software required for your device. If you are instructed by the ExpressCard manufacturer
to install device drivers:
Install only the device drivers for your operating system.
●
Do not install other software, such as card services, socket services, or enablers, supplied by the
●
ExpressCard manufacturer.
Inserting an ExpressCard
CAUTION: To prevent damage to the computer and external media cards, do not insert a PC Card
into an ExpressCard slot.
CAUTION: To prevent damage to the connectors:
Use minimal force when inserting an ExpressCard.
Do not move or transport the computer when an ExpressCard is in use.
The ExpressCard slot may contain a protective insert. To remove the insert:
1. Press in on the insert (1) to unlock it.
2. Pull the insert out of the slot (2).
To insert an ExpressCard:
1. Hold the card label-side up, with the connectors facing the computer.
Using ExpressCards (select models only) 85
Page 98

2. Insert the card into the ExpressCard slot, and then push in on the card until it is firmly seated.
You will hear a sound when the device has been detected, and a menu of options may be displayed.
NOTE: The first time you insert an ExpressCard, a message is displayed in the notification area
to let you know the device is recognized by the computer.
NOTE: An inserted ExpressCard uses power even when idle. To conserve power, stop or remove an
ExpressCard when it is not in use.
Stopping and removing an ExpressCard
CAUTION: To prevent loss of data or an unresponsive system, stop an ExpressCard before removing
it.
1. Save your information and close all programs associated with the ExpressCard.
NOTE: To stop a data transfer, click Cancel in the operating system Copying window.
2. Stop the ExpressCard:
a. Double-click the Safely Remove Hardware icon in the notification area, at the far right of the
taskbar.
NOTE: To display the Safely Remove Hardware icon, click the Show Hidden Icons icon
(< or <<) in the notification area.
b. Click the name of the ExpressCard in the list.
c. Click Stop, and then click OK.
NOTE: If the ExpressCard is not listed, you do not have to stop the card before you remove
it.
3. Release and remove the ExpressCard:
a. Gently press in on the ExpressCard (1) to unlock it.
b. Pull the ExpressCard out of the slot (2).
86 Chapter 8 External media cards
Page 99

Using ExpressCards (select models only) 87
Page 100

9 Memory modules
The computer has one memory module compartment, which is located on the bottom of the computer.
The memory capacity of the computer can be upgraded by adding a memory module to the vacant
expansion memory module slot or by upgrading the existing memory module in the primary memory
module slot.
All memory modules installed in the computer must be the same type. When upgrading memory
capacity, verify that the upgrade modules are the same type as those already installed in the computer.
WARNING! To reduce the risk of electric shock and damage to the equipment, unplug the power cord
and remove all batteries before installing a memory module.
CAUTION: Electrostatic discharge (ESD) can damage electronic components. Before beginning any
procedure, touch a grounded metal object to be sure that you are discharged of static electricity.
88 Chapter 9 Memory modules
 Loading...
Loading...