Page 1
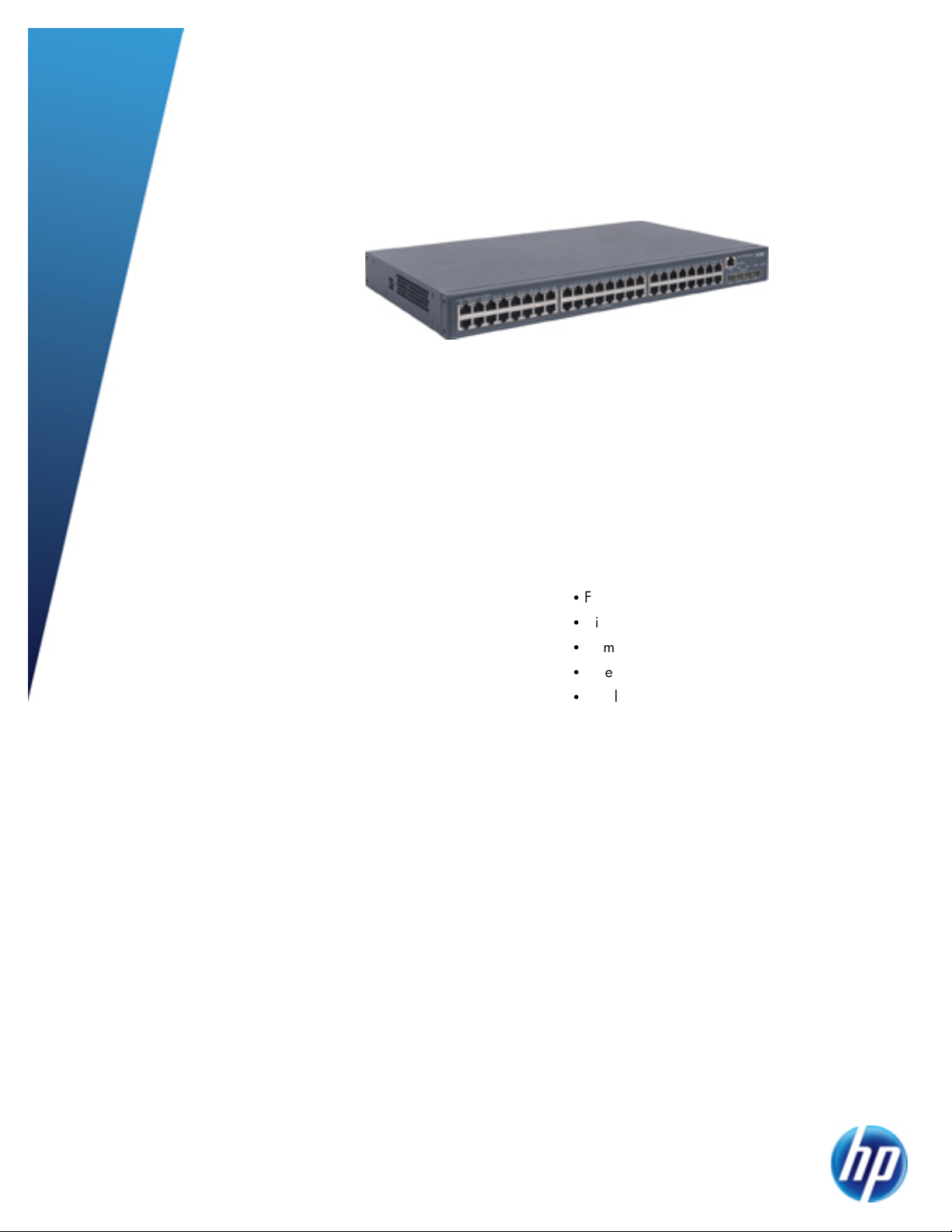
HP 5120 SI Switch Series
Data sheet
Product overview
The HP 5120 SI Switch Series are intelligent, fully
managed Gigabit Ethernet switches that provide high
performance, high port density and simplified
installation to maximize the value of your network
infrastructure investment. The 5120 SI is optimized for
the access layer in enterprise networks that require
Gigabit Ethernet to the desktop or at the distribution
layer in metropolitan area networks (MANs).
Wire-speed forwarding delivers optimal throughput
and the bandwidth necessary for mission-critical data
and high-speed communications. As part of their
comprehensive security control, they employ 802.1X
authentication to identify users who attempt to access
the network. These switches are highly reliable,
providing redundancy while eliminating loops in the
network. They also offer a range of management
protocols to simplify network administration.
Key features
b
Full wire-speed, multi-layer switching
b
High reliability with redundancy
b
Comprehensive security control policies
b
Diversified Quality of Service (QoS) policies
b
Excellent manageability
Page 2

Features and benefits
Quality of Service (QoS)
•
Broadcast control: allows limitation of broadcast
traffic rate to cut down on unwanted network
broadcast traffic
•
Powerful QoS feature: supports the following
congestion actions: strict priority (SP) queuing,
SDWRR, and SP+SDWRR
•
Advanced classifier-based QoS: classifies
traffic using multiple match criteria based on Layer
2, 3, and 4 information; applies QoS policies such
as setting priority level and rate limit to selected
traffic on a per-port basis
Management
•
Friendly port names: allow assignment of
descriptive names to ports
•
Remote configuration and management: is
available through a secure Web browser or a
command-line interface (CLI)
•
Manager and operator privilege levels:
enable read-only (operator) and read-write
(manager) access on CLI and Web browser
management interfaces
•
Command authorization: leverages RADIUS to
link a custom list of CLI commands to an individual
network administrator's login; also provides an audit
trail
•
Secure Web GUI: provides a secure, easy-to-use
graphical interface for configuring the module via
HTTPS
•
Dual flash images: provide independent primary
and secondary operating system files for backup
while upgrading
•
Multiple configuration files: can be stored to
the flash image
•
Complete session logging: provides detailed
information for problem identification and resolution
•
SNMPv1, v2c, and v3: facilitate centralized
discovery, monitoring, and secure management of
networking devices
•
Remote monitoring (RMON): uses standard
SNMP to monitor essential network functions;
supports events, alarm, history, and statistics group
plus a private alarm extension group
•
IEEE 802.1AB Link Layer Discovery Protocol
(LLDP): automated device discovery protocol
provides easy mapping by network management
applications
•
Management VLAN: segments traffic to and
from management interfaces, including CLI/telnet, a
Web browser interface, and SNMP
•
Device Link Detection Protocol (DLDP):
monitors cable between two switches and shuts
down the ports on both ends if the cable is broken,
this prevents network problems such as loops
Connectivity
•
Auto-MDIX: automatically adjusts for
straight-through or crossover cables on all
10/100/1000 ports
•
Flow control: using standard IEEE 802.3x, it
provides back pressure to reduce congestion in
heavy traffic situations
•
Jumbo packet support: supports up to 10k byte
frame size to improve performance of large data
transfers
•
High-density port connectivity: provides up to
48 fixed 10/100/1000BASE-T ports in an
entry-level static Layer 3 switch
•
Ethernet OAM: provides a Layer 2 link
performance and fault detection monitoring tool,
which reduces failover and network convergence
times
•
Power over Ethernet Plus (PoE+) support:
provides 30W power for connected devices,
simplifies deployment and dramatically reduces
installation costs by helping to eliminate the time
and cost involved in supplying local power at each
access point location
•
IPV6:
– IPV6 Host: enables switches to be managed and
deployed at the IPv6 network's edge
– Dual Stack (IPV4 and IPV6 using BIS):
allows IPV4 hosts to communicate with IPV6 hosts
– IPV6 ACL: for filtering IPV6 network traffic
Performance
•
Nonblocking architecture: up to 104 Gbps
nonblocking switching fabric provides wire-speed
switching with up to 77.4 million pps throughput
•
Hardware-based wire-speed access control
lists (ACLs): feature-rich ACL implementation
(TCAM based) helps ensure high levels of security
and ease of administration without impacting
network performance
2
Page 3

Resiliency and high availability
•
Separate data and control paths: increases
security and performance
•
Spanning Tree/MSTP, RSTP: provides
redundant links while preventing network loops
•
IEEE 802.3ad Link Aggregation Control
Protocol (LACP): supports up to 26 trunks, each
with 8 links per trunk; supports static or dynamic
groups
•
Smart link: allows 50 ms failover between links
•
Intelligent Resilient Framework (IRF): creates
virtual resilient switching fabrics, where two or more
switches perform as a single Layer 2 switch and
Layer 3 router; switches do not have to be
co-located and can be part of a disaster-recovery
system; servers or switches can be attached using
standard LACP for automatic load balancing and
high availability; simplifies network operation by
eliminating the complexity of Spanning Tree
Protocol, Equal-Cost Multipath (ECMP), or VRRP
Layer 2 switching
•
8K MAC address table: provides access to
many Layer 2 devices
•
VLAN support and tagging: support IEEE
802.1Q with 4,094 simultaneous VLAN IDs
•
IP multicast snooping: automatically prevents
flooding of IP multicast traffic
•
Internet Group Management Protocol
(IGMP) and Multicast Listener Discovery
(MLD) protocol snooping: effectively control
and manage the flooding of multicast packets in a
Layer 2 network
Layer 3 services
•
Address Resolution Protocol (ARP):
determines the MAC address of another IP host in
the same subnet; supports static ARPs; gratuitous
ARP allows detection of duplicate IP addresses
•
Dynamic Host Configuration Protocol
(DHCP): simplifies the management of large IP
networks; supports client; DHCP Relay enables
DHCP operation across subnets
•
Loopback interface address: defines an
address in Routing Information Protocol (RIP) and
OSPF that can always be reachable, improving
diagnostic capability
Layer 3 routing
•
Static IP routing: provides manually configured
routing for both IPv4 and IPv6 networks
Security
•
Access control lists (ACLs): provides IP Layer 2
to Layer 4 traffic filtering; supports global ACL,
VLAN ACL, port ACL, and IPv6 ACL
•
Identity-driven security and access control:
– Per-user ACLs: permits or denies user access to
specific network resources based on user identity
and time of day, allowing multiple types of users
on the same network to access specific network
services without risk to network security or
unauthorized access to sensitive data
– Automatic VLAN assignment: automatically
assigns users to the appropriate VLAN based on
their identities
•
Secure management access: securely encrypts
all access methods (CLI, GUI, or MIB) through
SSHv2, SSL, and/or SNMPv3
•
Secure FTP: allows secure file transfer to and from
the switch; protects against unwanted file
downloads or unauthorized copying of a switch
configuration file
•
Guest VLAN: similar to IEEE 802.1X, it provides a
browser-based environment to authenticated clients
•
Port isolation: secures and adds privacy, and
prevents malicious attackers from obtaining user
information
•
STP BPDU port protection: blocks Bridge
Protocol Data Units (BPDUs) on ports that do not
require BPDUs, preventing forged BPDU attacks
•
STP Root Guard: protects the root bridge from
malicious attacks or configuration mistakes
•
DHCP protection: blocks DHCP packets from
unauthorized DHCP servers, preventing
denial-of-service attacks
•
Dynamic ARP protection: blocks ARP
broadcasts from unauthorized hosts, preventing
eavesdropping or theft of network data
•
IP Source Guard: helps prevent IP spoofing
attacks
•
Endpoint Admission Defense (EAD): provides
security policies to users accessing a network
•
RADIUS/HWTACACS: eases switch management
security administration by using a password
authentication server
3
Page 4

•
Port security: allows access only to specified
MAC addresses, which can be learned or specified
by the administrator
•
MAC-based authentication: allows or denies
access to the switch based on client MAC address
Convergence
•
IEEE 802.1AB Link Layer Discovery Protocol
(LLDP): is an automated device discovery protocol
that provides easy mapping of network
management applications
•
LLDP-MED: is a standard extension that
automatically configures network devices, including
LLDP-capable IP phones
•
LLDP-CDP compatibility: receives and
recognizes CDP packets from Cisco's IP phones for
seamless interoperation
•
Voice VLAN: automatically assigns VLAN and
priority for IP phones, simplifying network
configuration and maintenance
•
IP multicast snooping (data-driven IGMP):
automatically prevents flooding of IP multicast traffic
•
Multicast VLAN: reduces network bandwidth
demand by eliminating multiple streams to each
VLAN
Additional information
•
Green IT and power: use the latest advances in
silicon development, shut off unused ports, and use
variable-speed fans to improve energy efficiency
•
Green initiative support: provides support for
RoHS and WEEE regulations
Warranty and support
•
Lifetime warranty: for as long as you own the
product with advance replacement and
next-business-day delivery (available in most
countries)†
•
Electronic and telephone support: limited
electronic and telephone support is available from
HP; refer to www.hp.com/networking/warranty for
details on the support provided and the period
during which support is available
•
Software releases: refer to
www.hp.com/networking/warranty for details on
the software releases provided and the period
during which software releases are available for
your product(s)
†Hardware warranties replacement for as long as you own the product, with next business day advance replacement (available in most countries). The disk drive included with HP
Alliance One Advanced Services and Services zl Modules, HP Threat Management Services zl Module, HP AllianceOne Ext zl Mod w/Rvrbd Stlhd, HP E-MSM765zl Mobility
Controller and HP Surv Brch Com zl Mod pwrby Msft Lync has a five-year hardware warranty. For details, refer to the Software license and hardware warranty statements at
www.hp.com/networking/warranty.
4
Page 5

HP 5120 SI Switch Series
Specifications
HP 5120-48G SI Switch (JE072A) HP 5120-24G SI Switch (JE074A) HP 5120-16G SI Switch (JE073A)
Ports
Physical characteristics
Dimensions
Weight
Memory and processor
Mounting
Performance
1000 Mb Latency
Throughput
Routing/Switching capacity
Routing table size
Environment
Operating temperature
Operating relative humidity
Nonoperating/Storage temperature
Nonoperating/Storage relative humidity
Electrical characteristics
Maximum heat dissipation
Voltage
Maximum power rating
Frequency
Notes
Safety
Emissions
Management
Services
48 RJ-45 autosensing 10/100/1000 ports (IEEE
802.3 Type 10BASE-T, IEEE 802.3u Type
100BASE-TX, IEEE 802.3ab Type 1000BASE-T);
Duplex: 10BASE-T/100BASE-TX: half or full;
1000BASE-T: full only
4 fixed Gigabit Ethernet SFP ports
1 RJ-45 serial console port
10.24(d) x 17.3(w) x 1.72(h) in. (26.01 x 43.94 x
4.37 cm) (1U height)
11.02 lb. (5 kg) 6.61 lb. (3 kg) 6.61 lb. (3 kg)
128 MB flash, 128 MB SDRAM; packet buffer size:
1 MB
Mounts in an EIA-standard 19 in. telco rack or
equipment cabinet (hardware included)
< 3 µs < 3 µs < 3 µs
77.4 million pps 41.7 million pps 29.8 million pps
104 Gbps 56 Gbps 40 Gbps
32 entries 32 entries 32 entries
32°F to 113°F (0°C to 45°C) 32°F to 113°F (0°C to 45°C) 32°F to 113°F (0°C to 45°C)
10% to 90%, noncondensing 10% to 90%, noncondensing 10% to 90%, noncondensing
-40°F to 158°F (-40°C to 70°C) -40°F to 158°F (-40°C to 70°C) -40°F to 158°F (-40°C to 70°C)
5% to 95%, noncondensing 5% to 95%, noncondensing 5% to 95%, noncondensing
189 BTU/hr (199.4 kJ/hr) 108 BTU/hr (113.94 kJ/hr) 76 BTU/hr (80.18 kJ/hr)
100-240 VAC 100-240 VAC 100-240 VAC
55.4 W 31.5 W 22.4 W
50/60 Hz 50/60 Hz 50/60 Hz
Maximum power rating and maximum heat
dissipation are the worst-case theoretical maximum
numbers provided for planning the infrastructure
with fully loaded PoE (if equipped), 100% traffic, all
ports plugged in, and all modules populated.
UL 60950-1; EN 60825-1 Safety of Laser
Products-Part 1; EN 60825-2 Safety of Laser
Products-Part 2; IEC 60950-1; CAN/CSA-C22.2
No. 60950-1; Anatel; ULAR; GOST; EN
60950-1/A11; FDA 21 CFR Subchapter J; NOM;
ROHS Compliance
FCC part 15 Class A; VCCI Class A; EN 55022
Class A; CISPR 22 Class A; ICES-003 Class A;
ANSI C63.4 2003; ETSI EN 300 386 V1.3.3;
AS/NZS CISPR22 Class A; EN 61000-3-2; EN
61000-3-3; EN 61000-4-2; EN 61000-4-3; EN
61000-4-4; EN 61000-4-5; EN 61000-4-6; EN
61000-4-11; EN 61000-3-2:2006; EN
61000-3-3:1995 +A1:2001+A2:2005; EMC
Directive 2004/108/EC; FCC (CFR 47, Part 15)
Class A
IMC - Intelligent Management Center; command-line
interface; Web browser; SNMP Manager
3-year, 4-hour onsite, 13x5 coverage for hardware
(UV858E)
3-year, 4-hour onsite, 24x7 coverage for hardware
(UV861E)
3-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 SW phone support and SW updates
(UV864E)
3-year, 24x7 SW phone support, software updates
(UV867E)
24 RJ-45 autosensing 10/100/1000 ports (IEEE
802.3 Type 10BASE-T, IEEE 802.3u Type
100BASE-TX, IEEE 802.3ab Type 1000BASE-T);
Duplex: 10BASE-T/100BASE-TX: half or full;
1000BASE-T: full only
4 fixed Gigabit Ethernet SFP ports
1 RJ-45 serial console port
6.3(d) x 17.3(w) x 1.72(h) in. (16 x 43.94 x 4.37
cm) (1U height)
128 MB flash, 128 MB SDRAM; packet buffer size:
0.5 MB
Mounts in an EIA-standard 19 in. telco rack or
equipment cabinet (hardware included)
Maximum power rating and maximum heat
dissipation are the worst-case theoretical maximum
numbers provided for planning the infrastructure
with fully loaded PoE (if equipped), 100% traffic, all
ports plugged in, and all modules populated.
UL 60950-1; EN 60825-1 Safety of Laser
Products-Part 1; EN 60825-2 Safety of Laser
Products-Part 2; IEC 60950-1; CAN/CSA-C22.2
No. 60950-1; Anatel; ULAR; GOST; EN
60950-1/A11; FDA 21 CFR Subchapter J; NOM;
ROHS Compliance
FCC part 15 Class A; VCCI Class A; EN 55022
Class A; CISPR 22 Class A; ICES-003 Class A;
ANSI C63.4 2003; ETSI EN 300 386 V1.3.3;
AS/NZS CISPR22 Class A; EN 61000-3-2; EN
61000-3-3; EN 61000-4-2; EN 61000-4-3; EN
61000-4-4; EN 61000-4-5; EN 61000-4-6; EN
61000-4-11; EN 61000-3-2:2006; EN
61000-3-3:1995 +A1:2001+A2:2005; EMC
Directive 2004/108/EC; FCC (CFR 47, Part 15)
Class A
IMC - Intelligent Management Center; command-line
interface; Web browser; SNMP Manager
3-year, 4-hour onsite, 13x5 coverage for hardware
(UV858E)
3-year, 4-hour onsite, 24x7 coverage for hardware
(UV861E)
3-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 SW phone support and SW updates
(UV864E)
3-year, 24x7 SW phone support, software updates
(UV867E)
16 RJ-45 autosensing 10/100/1000 ports (IEEE
802.3 Type 10BASE-T, IEEE 802.3u Type
100BASE-TX, IEEE 802.3ab Type 1000BASE-T);
Duplex: 10BASE-T/100BASE-TX: half or full;
1000BASE-T: full only
4 fixed Gigabit Ethernet SFP ports
1 RJ-45 serial console port
6.3(d) x 17.3(w) x 1.72(h) in. (16 x 43.94 x 4.37
cm) (1U height)
128 MB flash, 128 MB SDRAM; packet buffer size:
0.5 MB
Mounts in an EIA-standard 19 in. telco rack or
equipment cabinet (hardware included)
Maximum power rating and maximum heat
dissipation are the worst-case theoretical maximum
numbers provided for planning the infrastructure
with fully loaded PoE (if equipped), 100% traffic, all
ports plugged in, and all modules populated.
UL 60950-1; EN 60825-1 Safety of Laser
Products-Part 1; EN 60825-2 Safety of Laser
Products-Part 2; IEC 60950-1; CAN/CSA-C22.2
No. 60950-1; Anatel; ULAR; GOST; EN
60950-1/A11; FDA 21 CFR Subchapter J; NOM;
ROHS Compliance
FCC part 15 Class A; VCCI Class A; EN 55022
Class A; CISPR 22 Class A; ICES-003 Class A;
ANSI C63.4 2003; ETSI EN 300 386 V1.3.3;
AS/NZS CISPR22 Class A; EN 61000-3-2; EN
61000-3-3; EN 61000-4-2; EN 61000-4-3; EN
61000-4-4; EN 61000-4-5; EN 61000-4-6; EN
61000-4-11; EN 61000-3-2:2006; EN
61000-3-3:1995 +A1:2001+A2:2005; EMC
Directive 2004/108/EC; FCC (CFR 47, Part 15)
Class A
IMC - Intelligent Management Center; command-line
interface; Web browser; SNMP Manager
3-year, 4-hour onsite, 13x5 coverage for hardware
(UV858E)
3-year, 4-hour onsite, 24x7 coverage for hardware
(UV861E)
3-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 SW phone support and SW updates
(UV864E)
3-year, 24x7 SW phone support, software updates
(UV867E)
5
Page 6

HP 5120 SI Switch Series
Specifications (continued)
HP 5120-48G SI Switch (JE072A) HP 5120-24G SI Switch (JE074A) HP 5120-16G SI Switch (JE073A)
1-year, post-warranty, 4-hour onsite, 13x5 coverage
for hardware (HR584E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware (HR585E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware, 24x7 software phone support
(HR586E)
Installation with minimum configuration,
system-based pricing (UX116E)
Installation with HP-provided configuration,
system-based pricing (UX117E)
4-year, 4-hour onsite, 13x5 coverage for hardware
(UV859E)
4-year, 4-hour onsite, 24x7 coverage for hardware
(UV862E)
4-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV865E)
4-year, 24x7 SW phone support, software updates
(UV868E)
5-year, 4-hour onsite, 13x5 coverage for hardware
(UV860E)
5-year, 4-hour onsite, 24x7 coverage for hardware
(UV863E)
5-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV866E)
5-year, 24x7 SW phone support, software updates
(UV869E)
3 Yr 6 hr Call-to-Repair Onsite (UW963E) 3 Yr 6 hr Call-to-Repair Onsite (UW963E) 3 Yr 6 hr Call-to-Repair Onsite (UW963E)
4 Yr 6 hr Call-to-Repair Onsite (UW964E) 4 Yr 6 hr Call-to-Repair Onsite (UW964E) 4 Yr 6 hr Call-to-Repair Onsite (UW964E)
5 Yr 6 hr Call-to-Repair Onsite (UW965E) 5 Yr 6 hr Call-to-Repair Onsite (UW965E) 5 Yr 6 hr Call-to-Repair Onsite (UW965E)
1-year, 6 hour Call-To-Repair Onsite for hardware
(HR588E)
1-year, 24x7 software phone support, software
updates (HR587E)
1-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS682E)
1-year, 24x7 software phone support, software
updates + 4 hour hardware exchange (HS683E)
4-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS686E)
4-year, 24x7 software phone support, software
updates + 4 hour Hardware Exchange (HS687E)
5-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS688E)
Refer to the HP website at
www.hp.com/networking/services for details on the
service-level descriptions and product numbers. For
details about services and response times in your
area, please contact your local HP sales office.
1-year, post-warranty, 4-hour onsite, 13x5 coverage
for hardware (HR584E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware (HR585E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware, 24x7 software phone support
(HR586E)
Installation with minimum configuration,
system-based pricing (UX116E)
Installation with HP-provided configuration,
system-based pricing (UX117E)
4-year, 4-hour onsite, 13x5 coverage for hardware
(UV859E)
4-year, 4-hour onsite, 24x7 coverage for hardware
(UV862E)
4-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV865E)
4-year, 24x7 SW phone support, software updates
(UV868E)
5-year, 4-hour onsite, 13x5 coverage for hardware
(UV860E)
5-year, 4-hour onsite, 24x7 coverage for hardware
(UV863E)
5-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV866E)
5-year, 24x7 SW phone support, software updates
(UV869E)
1-year, 6 hour Call-To-Repair Onsite for hardware
(HR588E)
1-year, 24x7 software phone support, software
updates (HR587E)
1-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS682E)
1-year, 24x7 software phone support, software
updates + 4 hour hardware exchange (HS683E)
4-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS686E)
4-year, 24x7 software phone support, software
updates + 4 hour Hardware Exchange (HS687E)
5-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS688E)
Refer to the HP website at
www.hp.com/networking/services for details on the
service-level descriptions and product numbers. For
details about services and response times in your
area, please contact your local HP sales office.
1-year, post-warranty, 4-hour onsite, 13x5 coverage
for hardware (HR584E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware (HR585E)
1-year, post-warranty, 4-hour onsite, 24x7 coverage
for hardware, 24x7 software phone support
(HR586E)
Installation with minimum configuration,
system-based pricing (UX116E)
Installation with HP-provided configuration,
system-based pricing (UX117E)
4-year, 4-hour onsite, 13x5 coverage for hardware
(UV859E)
4-year, 4-hour onsite, 24x7 coverage for hardware
(UV862E)
4-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV865E)
4-year, 24x7 SW phone support, software updates
(UV868E)
5-year, 4-hour onsite, 13x5 coverage for hardware
(UV860E)
5-year, 4-hour onsite, 24x7 coverage for hardware
(UV863E)
5-year, 4-hour onsite, 24x7 coverage for hardware,
24x7 software phone (UV866E)
5-year, 24x7 SW phone support, software updates
(UV869E)
1-year, 6 hour Call-To-Repair Onsite for hardware
(HR588E)
1-year, 24x7 software phone support, software
updates (HR587E)
1-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS682E)
1-year, 24x7 software phone support, software
updates + 4 hour hardware exchange (HS683E)
4-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS686E)
4-year, 24x7 software phone support, software
updates + 4 hour Hardware Exchange (HS687E)
5-year, 24x7 software phone support, software
updates + Next Business Day Hardware Exchange
(HS688E)
Refer to the HP website at
www.hp.com/networking/services for details on the
service-level descriptions and product numbers. For
details about services and response times in your
area, please contact your local HP sales office.
6
Page 7

HP 5120 SI Switch Series
Specifications (continued)
HP 5120-48G SI Switch (JE072A) HP 5120-24G SI Switch (JE074A) HP 5120-16G SI Switch (JE073A)
Standards and protocols
(applies to all products in series)
General protocols
IEEE 802.1D MAC Bridges
IEEE 802.1p Priority
IEEE 802.1Q VLANs
IEEE 802.1s Multiple Spanning Trees
IEEE 802.1w Rapid Reconfiguration of Spanning
Tree
IEEE 802.1X PAE
IEEE 802.3ad Link Aggregation Control Protocol
(LACP)
IEEE 802.3x Flow Control
RFC 768 UDP
RFC 792 ICMP
RFC 793 TCP
RFC 826 ARP
RFC 854 TELNET
RFC 951 BOOTP
RFC 1350 TFTP Protocol (revision 2)
RFC 2131 DHCP
RFC 2865 Remote Authentication Dial In User
Service (RADIUS)
RFC 2866 RADIUS Accounting
IPv6
RFC 1350 TFTP
RFC 1886 DNS Extension for IPv6
RFC 1887 IPv6 Unicast Address Allocation
Architecture
RFC 1981 IPv6 Path MTU Discovery
RFC 2292 Advanced Sockets API for IPv6
RFC 2373 IPv6 Addressing Architecture
RFC 2460 IPv6 Specification
RFC 2461 IPv6 Neighbor Discovery
RFC 2462 IPv6 Stateless Address Auto-configuration
RFC 2463 ICMPv6
RFC 2464 Transmission of IPv6 over Ethernet
Networks
RFC 2465 Management Information Base for IP
Version 6: Textual Conventions and General
Group(partially support, only "IPv6 Interface
Statistics table")
RFC 2475 IPv6 DiffServ Architecture
RFC 2553 Basic Socket Interface Extensions for IPv6
RFC 2711 IPv6 Router Alert Option
RFC 2893 Transition Mechanisms for IPv6 Hosts
and Routers
RFC 2925 Definitions of Managed Objects for
Remote Ping, Traceroute, and Lookup Operations
(Ping only)
RFC 2925 Remote Operations MIB (Ping only)
RFC 3056 Connection of IPv6 Domains via IPv4
Clouds
RFC 3162 RADIUS and IPv6
RFC 3363 DNS support
RFC 3484 Default Address Selection for IPv6
RFC 3493 Basic Socket Interface Extensions for IPv6
RFC 3513 IPv6 Addressing Architecture
RFC 3542 Advanced Sockets API for IPv6
RFC 3587 IPv6 Global Unicast Address Format
RFC 3596 DNS Extension for IPv6
RFC 3736 Stateless Dynamic Host Configuration
Protocol (DHCP) Service for IPv6
RFC 4007 IPv6 Scoped Address Architecture
RFC 4022 MIB for TCP
RFC 4113 MIB for UDP
RFC 4251 SSHv6 Architecture
RFC 4252 SSHv6 Authentication
RFC 4253 SSHv6 Transport Layer
RFC 4254 SSHv6 Connection
RFC 4291 IP Version 6 Addressing Architecture
RFC 4293 MIB for IP
RFC 4419 Key Exchange for SSH
RFC 4443 ICMPv6
RFC 4541 IGMP & MLD Snooping Switch
RFC 4861 IPv6 Neighbor Discovery
RFC 4862 IPv6 Stateless Address Auto-configuration
RFC 5095 Deprecation of Type 0 Routing Headers
in IPv6
RFC 5722 Handling of Overlapping IPv6 Fragments
MIBs
IEEE8021-PAE-MIB
IEEE8023-LAG-MIB
RFC 1213 MIB II
RFC 1493 Bridge MIB
RFC 2011 SNMPv2 MIB for IP
RFC 2013 SNMPv2 MIB for UDP
RFC 2233 Interface MIB
RFC 2571 SNMP Framework MIB
RFC 2572 SNMP-MPD MIB
RFC 2573 SNMP-Target MIB
RFC 2618 RADIUS Authentication Client MIB
RFC 2620 RADIUS Accounting Client MIB
RFC 2665 Ethernet-Like-MIB
RFC 2668 802.3 MAU MIB
RFC 2674 802.1p and IEEE 802.1Q Bridge MIB
RFC 2819 RMON MIB
RFC 2925 Ping MIB
RFC 3414 SNMP-User based-SM MIB
RFC 3415 SNMP-View based-ACM MIB
RFC 3418 MIB for SNMPv3
RFC 4133 Entity MIB (Version 3)
LLDP-EXT-DOT1-MIB
LLDP-EXT-DOT3-MIB
LLDP-MIB
Network management
IEEE 802.1AB Link Layer Discovery Protocol (LLDP)
ANSI/TIA-1057 LLDP Media Endpoint Discovery
(LLDP-MED)
SNMPv1/v2c/v3
7
Page 8

HP 5120 SI Switch Series
Specifications (continued)
HP 5120-24G-HPoE SI Switch (JG091A) HP 5210-24G-PoE SI Switch (JG092A)
Ports
Physical characteristics
Dimensions
Weight
Memory and processor
Mounting
Performance
1000 Mb Latency
Throughput
Routing/Switching capacity
Routing table size
Environment
Operating temperature
Operating relative humidity
Nonoperating/Storage temperature
Nonoperating/Storage relative humidity
Electrical characteristics
Maximum heat dissipation
Voltage
DC voltage
Maximum power rating
PoE power
Frequency
Notes
Safety
Emissions
Management
Services
24 RJ-45 autosensing 10/100/1000 PoE+ ports (IEEE 802.3 Type 10BASE-T,
IEEE 802.3u Type 100BASE-TX, IEEE 802.3ab Type 1000BASE-T, IEEE 802.3at
PoE+); Duplex: 10BASE-T/100BASE-TX: half or full; 1000BASE-T: full only
4 fixed Gigabit Ethernet SFP ports
1 RJ-45 serial console port
16.54(d) x 17.32(w) x 1.72(h) in. (42 x 44.0 x 4.36 cm) (1U height) 16.54(d) x 17.32(w) x 1.72(h) in. (42 x 44.0 x 4.36 cm) (1U height)
15.43 lb. (7 kg) 15.43 lb. (7 kg)
128 MB flash, 128 MB SDRAM; packet buffer size: 0.5 MB 128 MB flash, 128 MB SDRAM; packet buffer size: 0.5 MB
Mounts in an EIA-standard 19 in. telco rack or equipment cabinet (hardware
included)
< 3 µs < 3 µs
41.7 million pps 41.7 million pps
56 Gbps 56 Gbps
32 entries 32 entries
32°F to 113°F (0°C to 45°C) 32°F to 113°F (0°C to 45°C)
10% to 90%, noncondensing 10% to 90%, noncondensing
-40°F to 158°F (-40°C to 70°C) -40°F to 158°F (-40°C to 70°C)
5% to 95%, noncondensing 5% to 95%, noncondensing
539 BTU/hr (568.65 kJ/hr) 290 BTU/hr (305.95 kJ/hr)
100-240 VAC 100-240 VAC
-52 to -55 VDC
832 W 255 W
720 W 170 W
50/60 Hz 50/60 Hz
Maximum power rating and maximum heat dissipation are the worst-case
theoretical maximum numbers provided for planning the infrastructure with fully
loaded PoE (if equipped), 100% traffic, all ports plugged in, and all modules
populated.
PoE Power is the power supplied by the internal power supply, it is dependent
on the type and quantity of power supplies and may be supplemented with the
use of a External Power Supply (EPS).
With AC input, the Max power consumption is 523W (370W for PoE)
UL 60950-1; EN 60825-1 Safety of Laser Products-Part 1; EN 60825-2 Safety
of Laser Products-Part 2; IEC 60950-1; CAN/CSA-C22.2 No. 60950-1; Anatel;
ULAR; GOST; EN 60950-1/A11; FDA 21 CFR Subchapter J; NOM; ROHS
Compliance
FCC part 15 Class A; VCCI Class A; EN 55022 Class A; CISPR 22 Class A;
ICES-003 Class A; ANSI C63.4 2003; ETSI EN 300 386 V1.3.3; AS/NZS
CISPR22 Class A; EN 61000-3-2; EN 61000-3-3; EN 61000-4-2; EN
61000-4-3; EN 61000-4-4; EN 61000-4-5; EN 61000-4-6; EN 61000-4-11;
EN 61000-3-2:2006; EN 61000-3-3:1995 +A1:2001+A2:2005; EMC
Directive 2004/108/EC; FCC (CFR 47, Part 15) Class A
IMC - Intelligent Management Center; command-line interface; Web browser;
SNMP Manager
3-year, 4-hour onsite, 13x5 coverage for hardware (UV858E) 3-year, 4-hour onsite, 13x5 coverage for hardware (UV858E)
3-year, 4-hour onsite, 24x7 coverage for hardware (UV861E) 3-year, 4-hour onsite, 24x7 coverage for hardware (UV861E)
3-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 SW phone support
and SW updates (UV864E)
3-year, 24x7 SW phone support, software updates (UV867E) 3-year, 24x7 SW phone support, software updates (UV867E)
4-year, 4-hour onsite, 13x5 coverage for hardware (UV859E) 4-year, 4-hour onsite, 13x5 coverage for hardware (UV859E)
4-year, 4-hour onsite, 24x7 coverage for hardware (UV862E) 4-year, 4-hour onsite, 24x7 coverage for hardware (UV862E)
4-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 software phone
(UV865E)
4-year, 24x7 SW phone support, software updates (UV868E) 4-year, 24x7 SW phone support, software updates (UV868E)
5-year, 4-hour onsite, 13x5 coverage for hardware (UV860E) 5-year, 4-hour onsite, 13x5 coverage for hardware (UV860E)
5-year, 4-hour onsite, 24x7 coverage for hardware (UV863E) 5-year, 4-hour onsite, 24x7 coverage for hardware (UV863E)
24 RJ-45 autosensing 10/100/1000 PoE+ ports (IEEE 802.3 Type 10BASE-T,
IEEE 802.3u Type 100BASE-TX, IEEE 802.3ab Type 1000BASE-T, IEEE 802.3at
PoE+); Duplex: 10BASE-T/100BASE-TX: half or full; 1000BASE-T: full only
4 fixed Gigabit Ethernet SFP ports
1 RJ-45 serial console port
Mounts in an EIA-standard 19 in. telco rack or equipment cabinet (hardware
included)
Maximum power rating and maximum heat dissipation are the worst-case
theoretical maximum numbers provided for planning the infrastructure with fully
loaded PoE (if equipped), 100% traffic, all ports plugged in, and all modules
populated.
PoE Power is the power supplied by the internal power supply, it is dependent
on the type and quantity of power supplies and may be supplemented with the
use of a External Power Supply (EPS).
UL 60950-1; EN 60825-1 Safety of Laser Products-Part 1; EN 60825-2 Safety
of Laser Products-Part 2; IEC 60950-1; CAN/CSA-C22.2 No. 60950-1; Anatel;
ULAR; GOST; EN 60950-1/A11; FDA 21 CFR Subchapter J; NOM; ROHS
Compliance
FCC part 15 Class A; VCCI Class A; EN 55022 Class A; CISPR 22 Class A;
ICES-003 Class A; ANSI C63.4 2003; ETSI EN 300 386 V1.3.3; AS/NZS
CISPR22 Class A; EN 61000-3-2; EN 61000-3-3; EN 61000-4-2; EN
61000-4-3; EN 61000-4-4; EN 61000-4-5; EN 61000-4-6; EN 61000-4-11;
EN 61000-3-2:2006; EN 61000-3-3:1995 +A1:2001+A2:2005; EMC
Directive 2004/108/EC; FCC (CFR 47, Part 15) Class A
IMC - Intelligent Management Center; command-line interface; Web browser;
SNMP Manager
3-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 SW phone support
and SW updates (UV864E)
4-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 software phone
(UV865E)
8
Page 9

HP 5120 SI Switch Series
Specifications (continued)
HP 5120-24G-HPoE SI Switch (JG091A) HP 5210-24G-PoE SI Switch (JG092A)
5-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 software phone
(UV866E)
5-year, 24x7 SW phone support, software updates (UV869E) 5-year, 24x7 SW phone support, software updates (UV869E)
3 Yr 6 hr Call-to-Repair Onsite (UW963E) 3 Yr 6 hr Call-to-Repair Onsite (UW963E)
4 Yr 6 hr Call-to-Repair Onsite (UW964E) 4 Yr 6 hr Call-to-Repair Onsite (UW964E)
5 Yr 6 hr Call-to-Repair Onsite (UW965E) 5 Yr 6 hr Call-to-Repair Onsite (UW965E)
Refer to the HP website at www.hp.com/networking/services for details on the
service-level descriptions and product numbers. For details about services and
response times in your area, please contact your local HP sales office.
Standards and protocols
(applies to all products in series)
General protocols
IEEE 802.1D MAC Bridges
IEEE 802.1p Priority
IEEE 802.1Q VLANs
IEEE 802.1s Multiple Spanning Trees
IEEE 802.1w Rapid Reconfiguration of Spanning
Tree
IEEE 802.1X PAE
IEEE 802.3ad Link Aggregation Control Protocol
(LACP)
IEEE 802.3x Flow Control
RFC 768 UDP
RFC 792 ICMP
RFC 793 TCP
RFC 826 ARP
RFC 854 TELNET
RFC 951 BOOTP
RFC 1350 TFTP Protocol (revision 2)
RFC 2131 DHCP
RFC 2865 Remote Authentication Dial In User
Service (RADIUS)
RFC 2866 RADIUS Accounting
IPv6
RFC 1350 TFTP
RFC 1886 DNS Extension for IPv6
RFC 1887 IPv6 Unicast Address Allocation
Architecture
RFC 1981 IPv6 Path MTU Discovery
RFC 2292 Advanced Sockets API for IPv6
RFC 2373 IPv6 Addressing Architecture
RFC 2460 IPv6 Specification
RFC 2461 IPv6 Neighbor Discovery
RFC 2462 IPv6 Stateless Address Auto-configuration
RFC 2463 ICMPv6
RFC 2464 Transmission of IPv6 over Ethernet
Networks
RFC 2465 Management Information Base for IP
Version 6: Textual Conventions and General
Group(partially support, only "IPv6 Interface
Statistics table")
RFC 2475 IPv6 DiffServ Architecture
5-year, 4-hour onsite, 24x7 coverage for hardware, 24x7 software phone
(UV866E)
Refer to the HP website at www.hp.com/networking/services for details on the
service-level descriptions and product numbers. For details about services and
response times in your area, please contact your local HP sales office.
RFC 2553 Basic Socket Interface Extensions for IPv6
RFC 2711 IPv6 Router Alert Option
RFC 2893 Transition Mechanisms for IPv6 Hosts
and Routers
RFC 2925 Definitions of Managed Objects for
Remote Ping, Traceroute, and Lookup Operations
(Ping only)
RFC 2925 Remote Operations MIB (Ping only)
RFC 3056 Connection of IPv6 Domains via IPv4
Clouds
RFC 3162 RADIUS and IPv6
RFC 3363 DNS support
RFC 3484 Default Address Selection for IPv6
RFC 3493 Basic Socket Interface Extensions for IPv6
RFC 3513 IPv6 Addressing Architecture
RFC 3542 Advanced Sockets API for IPv6
RFC 3587 IPv6 Global Unicast Address Format
RFC 3596 DNS Extension for IPv6
RFC 3736 Stateless Dynamic Host Configuration
Protocol (DHCP) Service for IPv6
RFC 4007 IPv6 Scoped Address Architecture
RFC 4022 MIB for TCP
RFC 4113 MIB for UDP
RFC 4251 SSHv6 Architecture
RFC 4252 SSHv6 Authentication
RFC 4253 SSHv6 Transport Layer
RFC 4254 SSHv6 Connection
RFC 4291 IP Version 6 Addressing Architecture
RFC 4293 MIB for IP
RFC 4419 Key Exchange for SSH
RFC 4443 ICMPv6
RFC 4541 IGMP & MLD Snooping Switch
RFC 4861 IPv6 Neighbor Discovery
RFC 4862 IPv6 Stateless Address Auto-configuration
RFC 5095 Deprecation of Type 0 Routing Headers
in IPv6
RFC 5722 Handling of Overlapping IPv6 Fragments
MIBs
IEEE8021-PAE-MIB
IEEE8023-LAG-MIB
RFC 1213 MIB II
RFC 1493 Bridge MIB
RFC 2011 SNMPv2 MIB for IP
RFC 2013 SNMPv2 MIB for UDP
RFC 2233 Interface MIB
RFC 2571 SNMP Framework MIB
RFC 2572 SNMP-MPD MIB
RFC 2573 SNMP-Target MIB
RFC 2618 RADIUS Authentication Client MIB
RFC 2620 RADIUS Accounting Client MIB
RFC 2665 Ethernet-Like-MIB
RFC 2668 802.3 MAU MIB
RFC 2674 802.1p and IEEE 802.1Q Bridge MIB
RFC 2819 RMON MIB
RFC 2925 Ping MIB
RFC 3414 SNMP-User based-SM MIB
RFC 3415 SNMP-View based-ACM MIB
RFC 3418 MIB for SNMPv3
RFC 4133 Entity MIB (Version 3)
LLDP-EXT-DOT1-MIB
LLDP-EXT-DOT3-MIB
LLDP-MIB
Network management
IEEE 802.1AB Link Layer Discovery Protocol (LLDP)
ANSI/TIA-1057 LLDP Media Endpoint Discovery
(LLDP-MED)
SNMPv1/v2c/v3
9
Page 10

HP 5120 SI Switch Series accessories
Transceivers
HP X120 1G SFP LC SX Transceiver (JD118B)
HP X120 1G SFP LC LX Transceiver (JD119B)
HP X125 1G SFP LC LH40 1310nm Transceiver (JD061A)
HP X120 1G SFP LC LH40 1550nm Transceiver (JD062A)
HP X125 1G SFP LC LH70 Transceiver (JD063B)
HP X120 1G SFP LC BX 10-U Transceiver (JD098B)
HP X120 1G SFP LC BX 10-D Transceiver (JD099B)
HP X120 1G SFP RJ45 T Transceiver (JD089B)
Cables
HP 0.5 m Multimode OM3 LC/LC Optical Cable (AJ833A)
HP 1 m Multimode OM3 LC/LC Optical Cable (AJ834A)
HP 2 m Multimode OM3 LC/LC Optical Cable (AJ835A)
HP 5 m Multimode OM3 LC/LC Optical Cable (AJ836A)
HP 15 m Multimode OM3 LC/LC Optical Cable (AJ837A)
HP 30 m Multimode OM3 LC/LC Optical Cable (AJ838A)
HP 50 m Multimode OM3 LC/LC Optical Cable (AJ839A)
NEW HP 0.5 m PremierFlex OM3+ LC/LC Optical Cable
(BK837A)
NEW HP 1 m PremierFlex OM3+ LC/LC Optical Cable
(BK838A)
NEW HP 2 m PremierFlex OM3+ LC/LC Optical Cable
(BK839A)
NEW HP 5 m PremierFlex OM3+ LC/LC Optical Cable
(BK840A)
NEW HP 15 m PremierFlex OM3+ LC/LC Optical Cable
(BK841A)
NEW HP 30 m PremierFlex OM3+ LC/LC Optical Cable
(BK842A)
NEW HP 50 m PremierFlex OM3+ LC/LC Optical Cable
(BK843A)
HP 3600 Switch SFP Stacking Kit (JD324B)
Power Supply
HP RPS1600 Redundant Power System (JG136A)
HP RPS1600 1600W AC Power Supply (JG137A)
Power cords
HP X290 1000 A JD5 2m RPS Cable (JD187A)
To learn more, visit www.hp.com/networking
© Copyright 2010-2011 Hewlett-Packard Development Company, L.P. The information contained herein is
subject to change without notice. The only warranties for HP products and services are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained
herein.
4AA3-0726ENW, Created August 2010; Updated February 2011, Rev. 1
 Loading...
Loading...