Client Configuration Area
Each user account needs to define the protocol and the credentials used to authenticate a user. Because Windows Mobile
devices are usually small devices with a single NIC and, usually, a single user, the initial configuration is usually the only time
the software needs to be set up. The Client will need to be reconfigured if the device is used on multiple networks, or if different
users share the computer.
Note: Fields are be grayed out if not relevant to the selected protocol.
Accessing the Client Configuration Area
On the main screen, tap Client > Configure (see Client Menu on page 9-17). The Client Configuration screen opens displaying
the User tab.
On this tab, You…
User Settings Tab Configure authentication credentials and profiles.
System Settings Tab Set the level of detail that the Client will provide in the system log and zero-config options.
Server Identity Tab Control how the Client authenticates the server that handles the 802.1X protocol on the network side.
This applies only to the TLS, TTLS, and PEAP authentication methods and is used to tell the Client
what server credentials to accept from the authentication server to verify the server.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 21
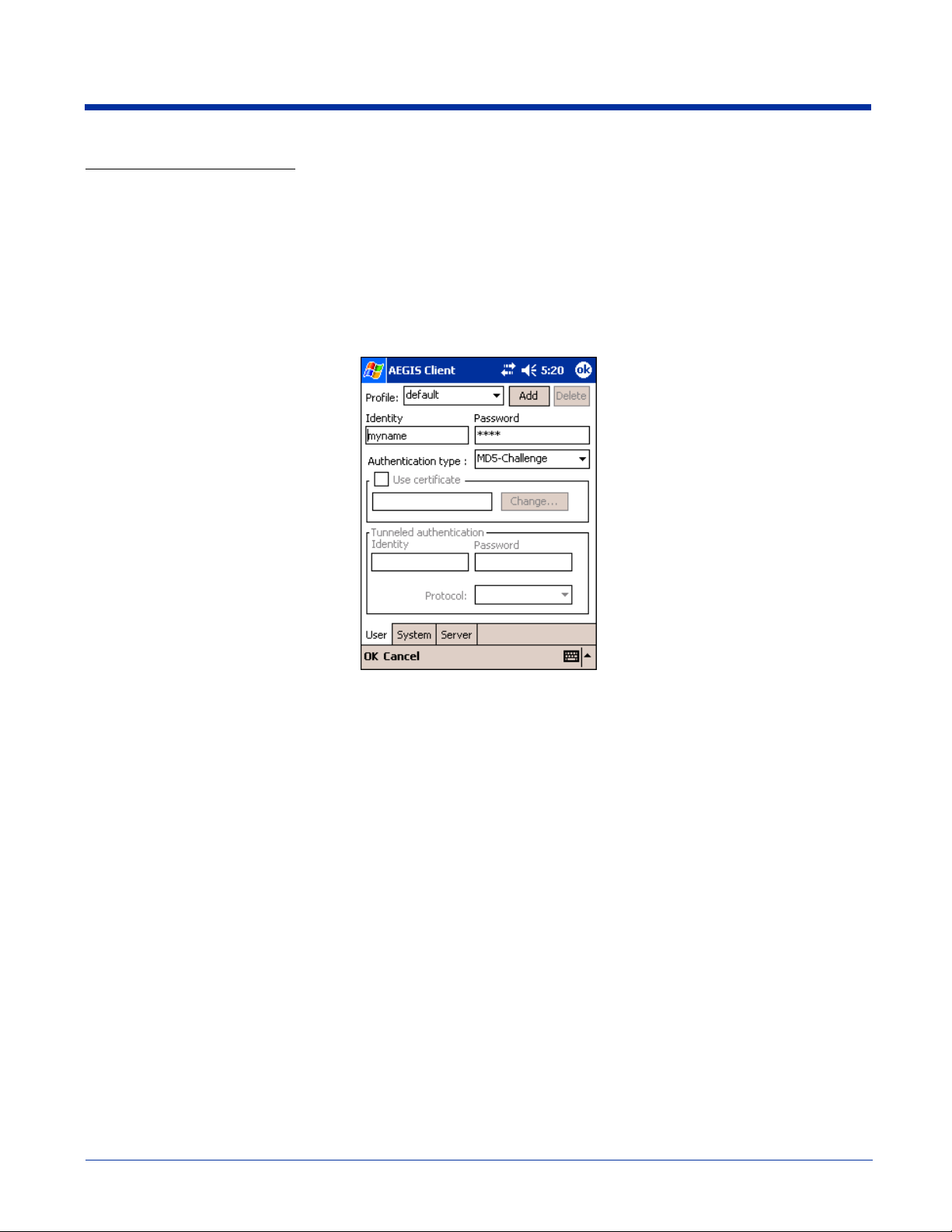
User Tab
The User settings tab defines the protocol and the credentials used to authenticate a user.
Field Description
Profile
Multiple user credential profiles can be created for use when the user roams from one network to another.
The drop-down list contains existing authentication credential profiles. Select a profile from the list to edit
it in the fields that follow.
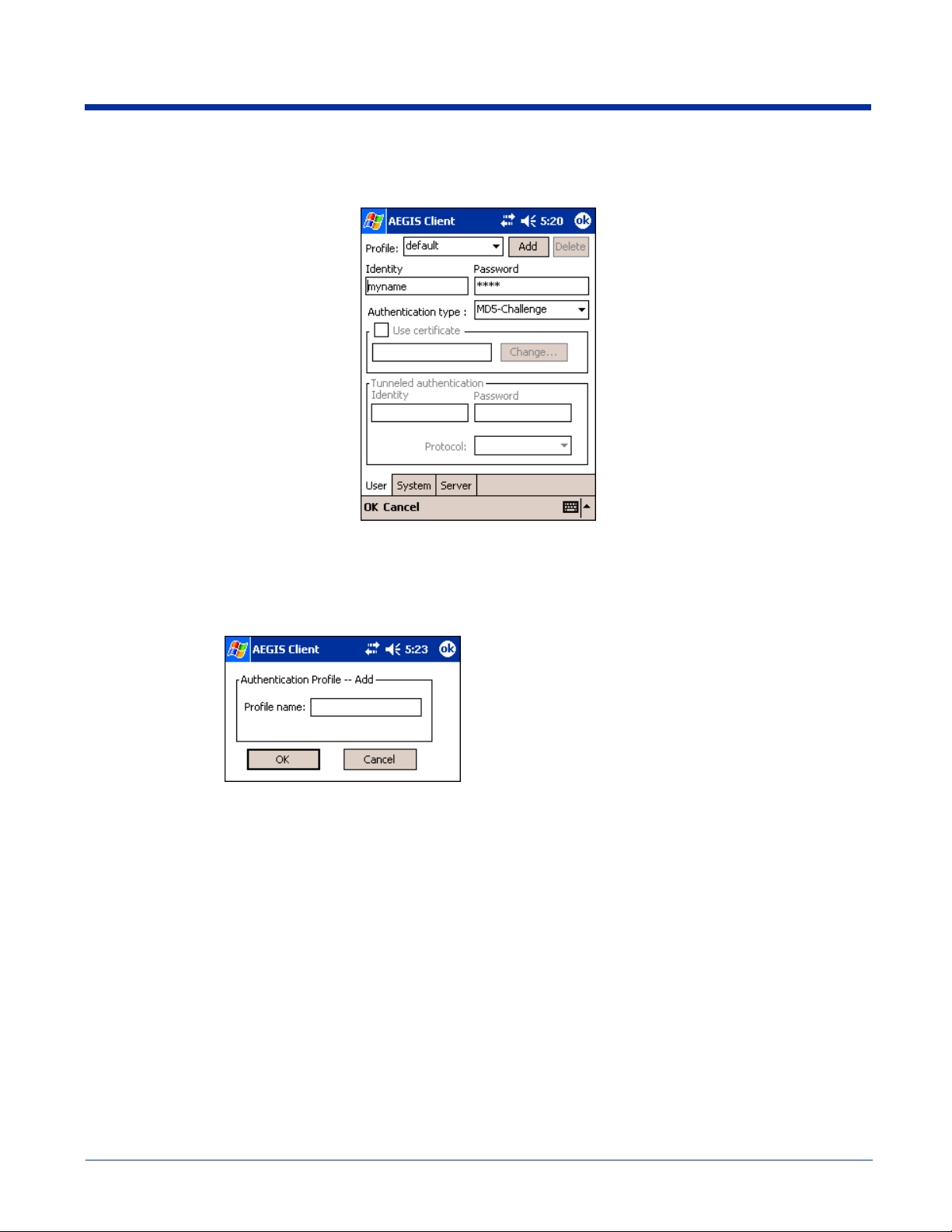
Tapping Add permits new profiles to be added to the list. A
screen appears where you can enter a name for the new
profile.
Enter a Profile name and tap OK. The name entered appears
in the Profile drop-down list.
Tapping Delete deletes authentication profiles. To be deleted,
a profile cannot be assigned to a configured network.
Identity
This is the 802.1X identity supplied to the authenticator. The identity value can be up to 63 ASCII
characters and is case-sensitive.
For tunneled authentication protocols such as TTLS and PEAP, this identity (called the Phase 1 identity)
is sent outside the protection of the encrypted tunnel. Therefore, it is recommended that this field not
contain a true identity, but instead the identity “anonymous” and any desired realm (e.g.
anonymous@myrealm.com). For TTLS and PEAP, true user credentials (Phase 2 identity) are entered
in the Tunneled authentication section.
Note: When used with PEAP and the .NET Enterprise Server Version 5.2, this field must contain the
identity used in both Phase I and Phase II. The Phase II identity field is ignored.
Password
Authentication
type
This is the password used for MD5-Challenge or LEAP authentication. It may contain up to 63 ASCII
characters and is case-sensitive. Asterisks appear instead of characters for enhanced security.
This is the authentication method to be used - MD5-Challenge, LEAP, PEAP, TLS, or TTLS.
Your network administrator should let you know the protocols supported by the RADIUS server. The
RADIUS server sits on the network and acts as a central credential repository for Access Servers that
receive the radio signals and ultimately block or allow users to attach to the network.
9 - 22 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Field Description
Use certificate
This is the certificate to be used during authentication. A certificate is required for TLS, optional for TTLS
and PEAP, and unused by MD5 and LEAP. Therefore, this option becomes active only when TLS, TTLS,
or PEAP is selected as the Authentication type.
If Use certificate is enabled, the client certificate displayed in the field is the one that is passed to the
server for verification.
To select a client certificate, tap Change and select the
certificate from the list that appears.
To appear in this list, certificates must be installed in the
system, for a description of this process see Installing
Certificates with CertAdd on page 9-32.
The Issued to field should match the Identity field and the user
ID on the authentication server (i.e., RADIUS server) used by
the authenticator.
Your certificate must be valid with respect to the authentication server. This generally means that the
authentication server must accept the issuer of your certificate as a Certificate Authority.
Note: When obtaining a client certificate, do not enable strong private key protection. If you enable
strong private key protection for a certificate, you will need to enter an access password for the
certificate each time this certificate is used.
Tunneled authentication area
Tunneled authentication parameters are used by only by TLS, TTLS and PEAP protocols, in Phase 2 of authentication, and
after the secure tunnel has been established. The fields in this section are active only if the TLS, TTLS, or PEAP is selected
as the Authentication type.
Identity
The user identity used in Phase 2 authentication. The identity specified may contain up to 63 ASCII
characters, is case-sensitive and takes the form of a Network Access Identifier, consisting of <name of
the user>@<user’s home realm>. The user’s home realm is optional and indicates the domain to which
the tunneled transaction is to be routed.
Note: Because Microsoft .NET Enterprise Server Version 5.2 does not use this parameter for PEAP,
This field will have no effect for PEAP at this time. Phase 1 identity is used instead.
Password
Protocol
The password used for the tunneled authentication protocol specified. It may contain up to 63 ASCII
characters and is case-sensitive. Asterisks appear instead of characters for enhanced security.
This parameter specifies the authentication protocol operating within the secure tunnel.
The following protocols are currently supported for TTLS: EAP-MD5, CHAP, PAP, MS-CHAP and MS-
CHAP-V2.
The following protocols are currently supported for PEAP: EAP-MS-CHAP-V2, TLS/SmartCard, and
Generic Token Card (EAP-GTC).
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 23
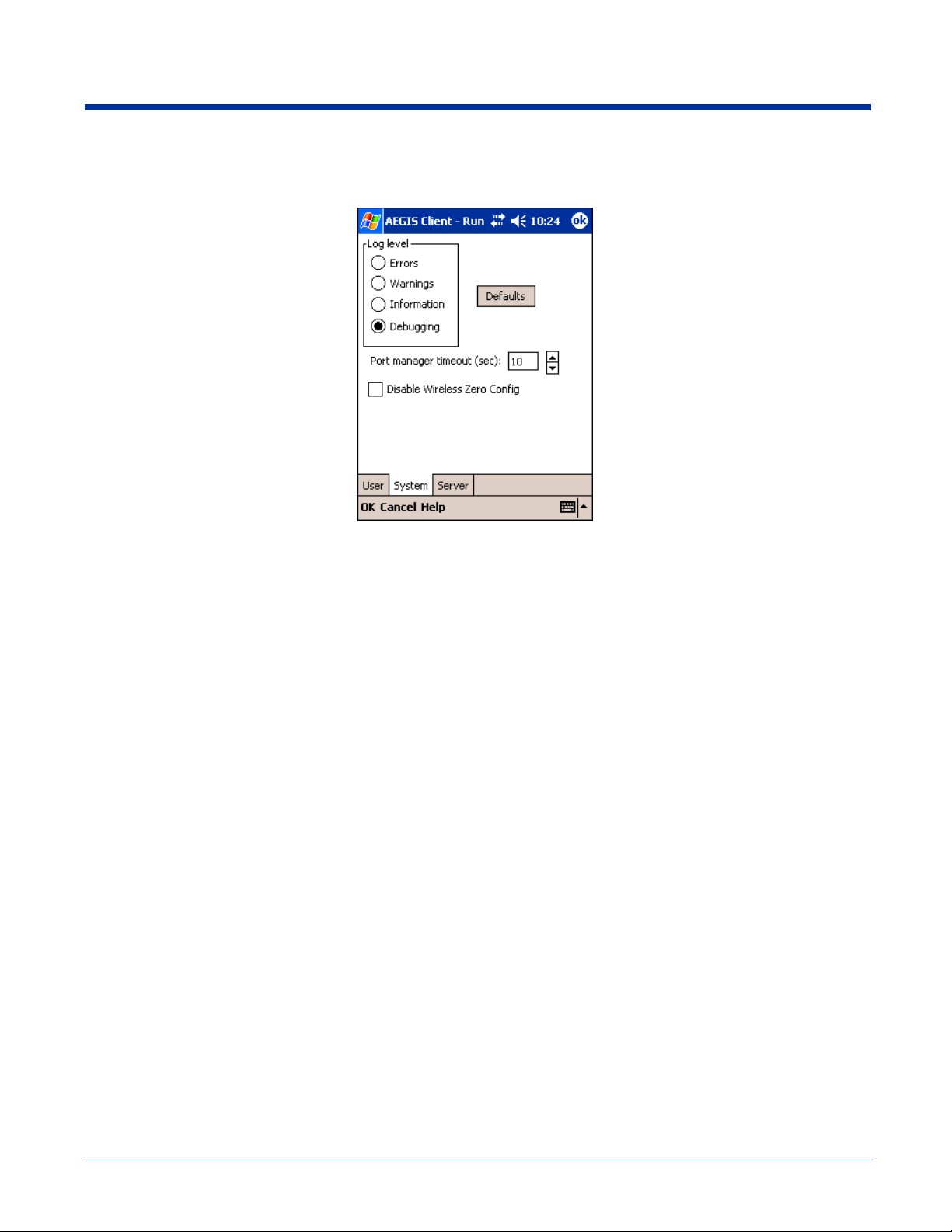
System Tab
The System Settings tab controls logging and the port manger timeout period.
Field Description
Log Level
Defaults Tap this button to return log settings to the default settings.
Disable Wireless
Zero Config
Port Manager
Timeout
These settings control the detail of the log messages generated by the Client. Each level is cumulative.
By default, all errors, warnings, and information events are logged. Each entry records a severity code
(of one [debug message] to four [error] asterisks), a time stamp, and a message.
Errors - only the most severe conditions are logged.
Warnings - less severe conditions are logged.
Information - all errors, warnings, and information events are logged. This is the default setting.
Debugging - creates a log message each time the Client detects or reacts to an event. Be advised
that log entries fill memory quickly if the Debugging level is chosen. Do not use the Debugging option
for a significant length of time because most internal operations generate messages.
Use this option only as directed by technical support.
Selecting this option disables other wireless utilities whether the Client is running or not. If not selected,
other wireless utilities cannot apply their settings to the wireless card while the Client is running
(although their status displays are usually unaffected). You will need to perform a soft reset whenever
this setting is changed.
The interval at which the client polls the ports. This is used under different circumstances, for instance
after physical changes such as card removal or insertion have been detected. This value should not
be changed from the 10-second default unless so advised by technical support.
9 - 24 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
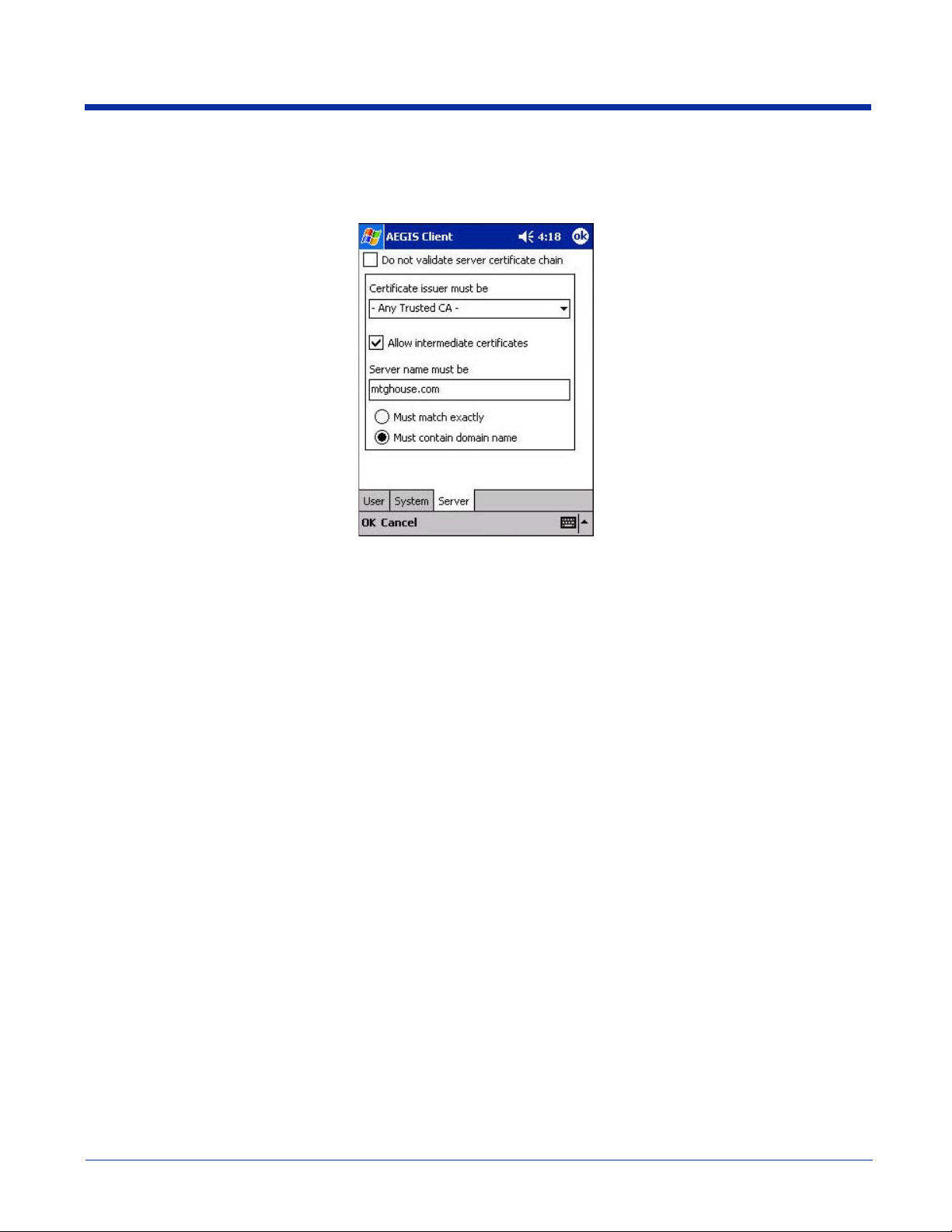
Server Tab
The Server identity tab defines the credentials the client uses to authenticate the server during TLS/TTLS/PEAP authentication
message exchange. The Client uses this information to verify that the Client is communicating with a trusted server.
Field Description
Do not validate server
certificate chain
Certificate issuer
must be
If this option is selected, the server certificate received during the TLS/TTLS/PEAP message
exchange is not validated.
This is the certificate authority used during TLS/TTLS/PEAP message exchange. Any Trusted
CA is the default selection and means that any certificate authority can be used during
authentication.
Allow intermediate
certificates
Server name must be
Must match exactly
Must contain domain
name
Both trusted intermediate certificate authorities and root authorities whose certificates exist in
the system store are available for selection in the drop-down list.
This option is selected by default and enables unspecified certificates to be in the server
certificate chain between the server certificate and the certificate authority selected in the
Certificate issuer must be field.
When selected, this option allows the server certificate received during negotiation to be issued
directly by the certificate authority or by one of its intermediate certificate authorities.
If disabled, then the selected Certificate issuer must have directly issued the server certificate.
This is either the server name or the domain the server belongs to, depending on which option
is selected below the text field.
During authentication, this name will be compared to the server certificate’s Subject: CN field.
When selected, the server name entered must match the server name found on the certificate
exactly.
When selected, the server name field identifies a domain and the certificate must have a server
name belonging to this domain or to one of its sub-domains (e.g., zeelans.com, where the
server is blueberry.zeelans.com).
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 25
Port Settings Area
In the Port Settings area, you configure network parameters for each port listed on the main screen; see Main Screen on page
9-17.
1. On the main screen, tap and hold on a port. The Port popup menu appears; see Port Menu on page 9-20.
2. Tap Configure. The Port Settings Configuration screen opens displaying the Wireless Networks tab.
On this tab, You…
Wireless Networks Tab Set the parameters for Network APs and underlying protocol.
Protocol Tab Configure common protocols that apply to any network the port connects to.
9 - 26 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
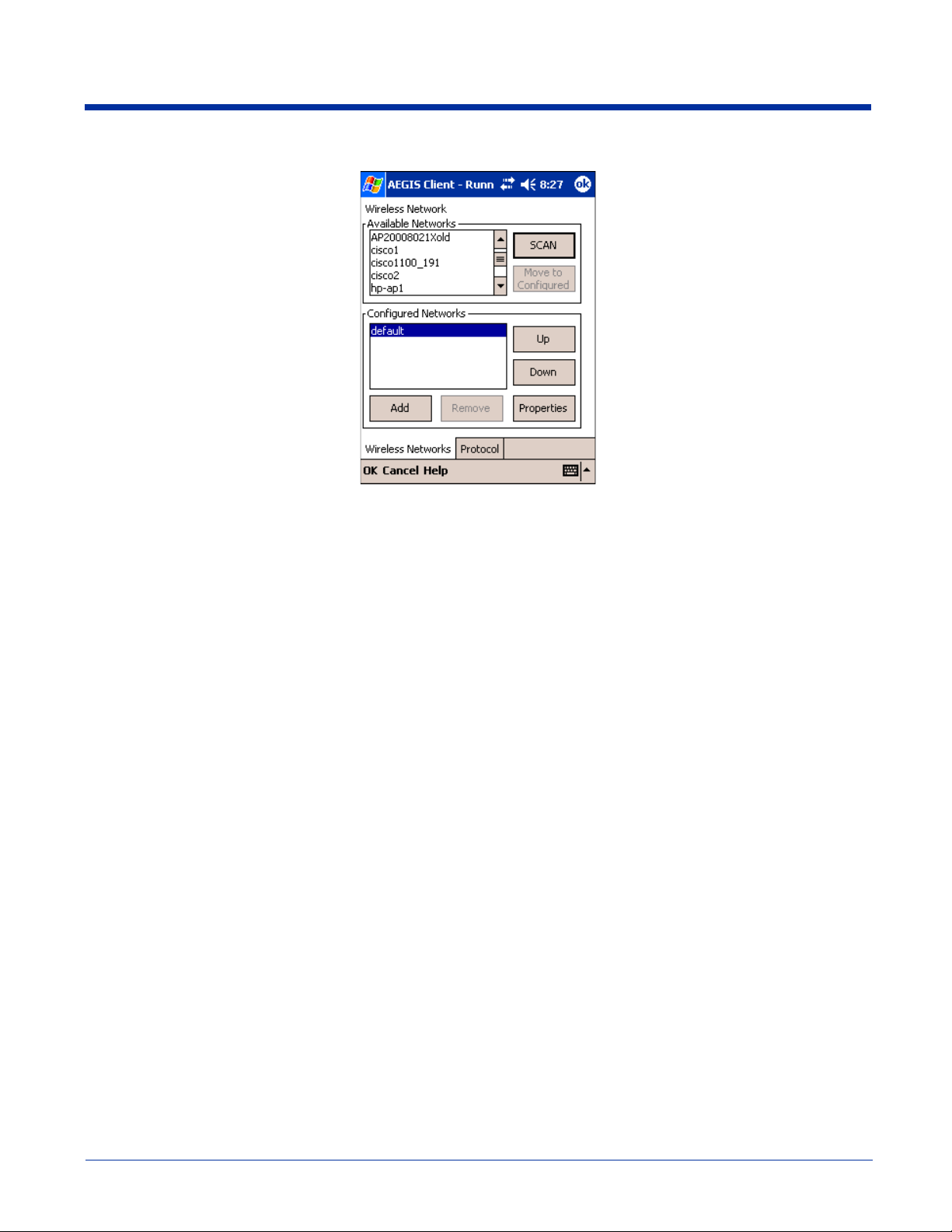
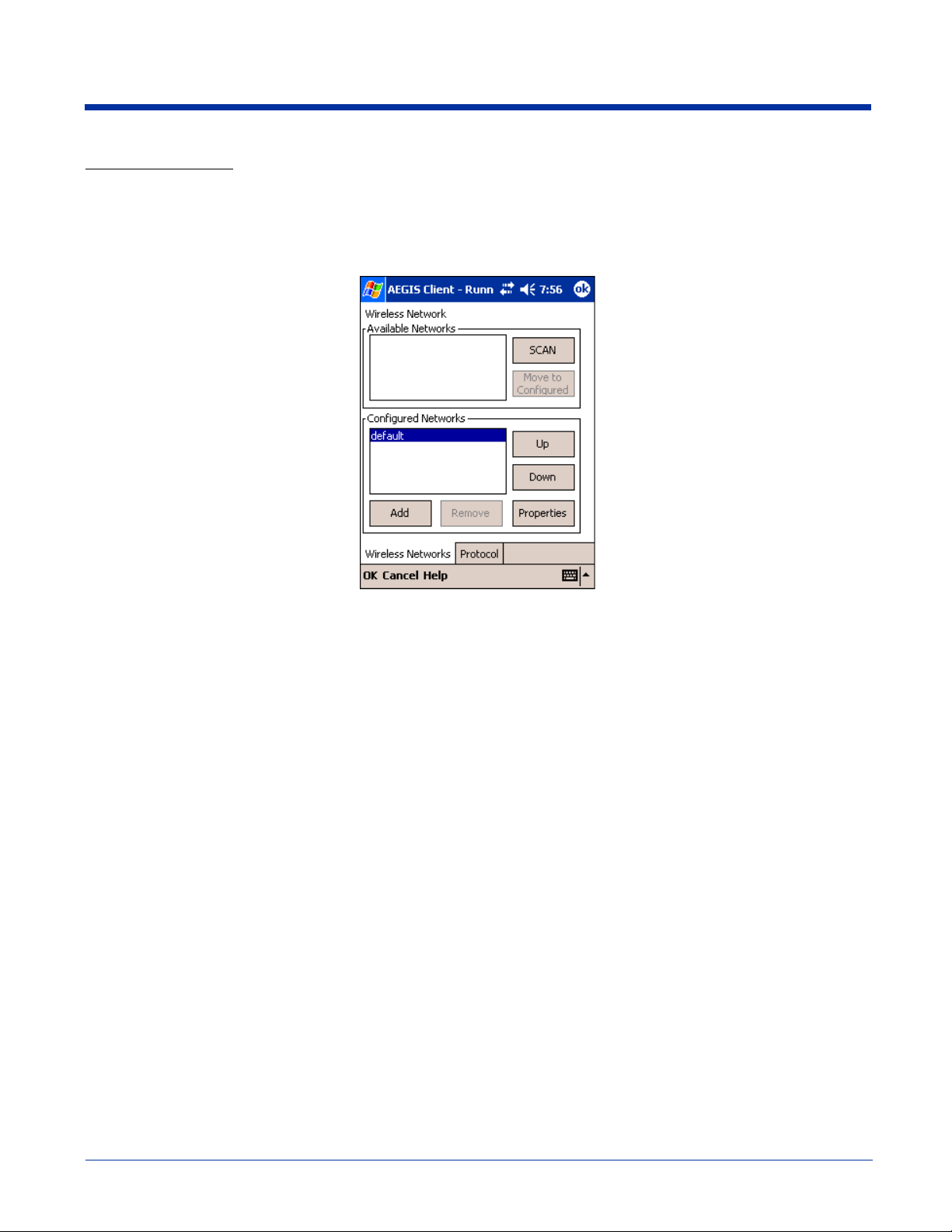
Wireless Networks Tab
Field Description
Available Networks Section
This section displays the networks the terminal recognizes as available to connect to. When the Client is first installed, there
are no entries in the Available Networks list.
Scan
Tap this button to see a list of networks broadcasting their availability.
Note: You can also attach to networks who are not broadcasting.
Move to
Configured
Configured Networks section
This section displays the networks your terminal is connected to. This section enables you to add or remove networks as well
as review and edit the properties of existing configured networks.
Default
Up Tapping this button moves a selected network up one place in the list.
This button activates only after Scan has been tapped and available networks have been retrieved.
In the list of networks retrieved, select the network you wish to connect to, and tap Move to Configured.
This selects the network, which now appears in the Configured Networks section.
When the Client is first installed, there is a Configured Network named "default" in the list. This profile has
Associate with any network selected in its Properties selection screen.
If you are going to be in a location with only one AP (or more than one AP that attaches to the same
network), the default profile may be sufficient for you needs, without necessitating the selection of a specific
network or networks.
If default is last in the list, it can act as a wildcard should you be out of the range of your primary networks
(which are listed first). Do not place default at the top or middle of the list because, if it is, connection to the
other list entries will never be attempted.
Down Tapping this button moves a selected network down one place in the list.
Note: The order of the networks in this list is the exact order that connections will be attempted. The
network listed first will be attempted first and so on. Place your primary networks first.
Add
Remove Tap this button to remove a selected network in the list.
Tap this button to manually add a network to the Configured Networks list if
• the AP does not broadcast its SSID or
• you are pre-configuring the client for an AP that is not currently in range.
For more information, see Adding a Wireless Network Configuration on page 9-29.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 27
Field Description
Properties
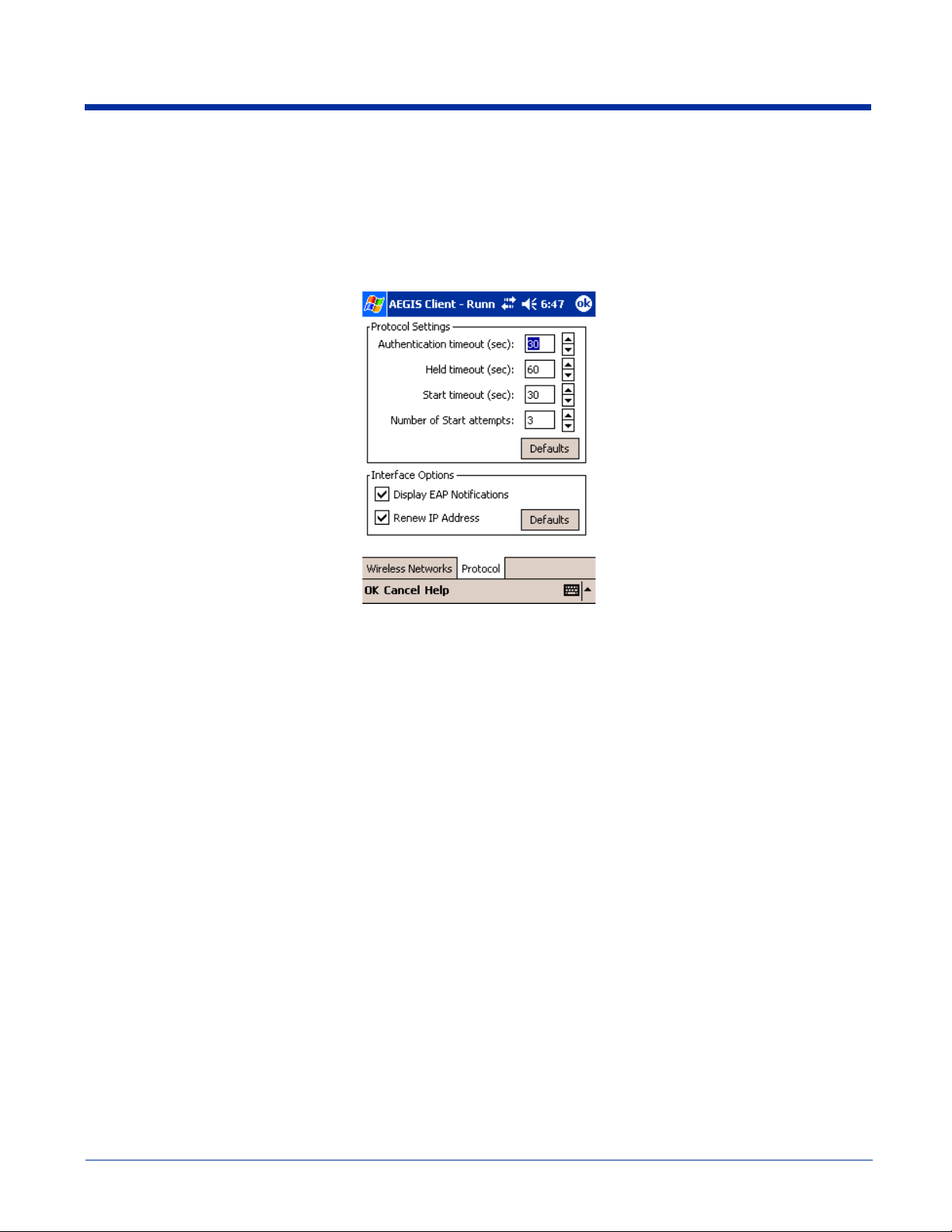
Protocol Tab
The Protocol tab enables you to configure parameters that will apply to all the networks the selected port connects to.
Tap this button to review the properties of a network selected in the list. This button opens the same network
configuration screen as the Add button does; use it to edit network configuration properties.
Field Description
Protocol
Settings
Display EAP
notifications
Renew IP
address
These are the timer intervals and retry settings defined in the 802.1X standard. They determine how long
the supplicant state machine will wait in a given state. These parameters shouldn’t be modified without
an understanding of the supplicant state machine. For more information about the supplicant state
machine, obtain its 802.1X protocol specification.
The parameters are:
• Authentication Timeout - The period of time the Client remains in the authenticating or acquired
state without receiving a response from the AP or switch.
• Held Timeout - The period of time the Client remains in the held state after failing authentication.
• Start Timeout - The period of time the Client remains in the connecting state before restarting when
there is no response.
• Number of Start Attempts - The number of times the Client restarts before giving up. At that point,
the Client then defaults to the authenticated state, but there will be no network connectivity because
the protocol exchange was never completed.
This option specifies that the EAPOL notification message will be displayed to the user. An authenticator
may use such notification to inform you, for example, about a near password expiration. However, some
authenticators send chatty and annoying notifications that may, for the convenience of the user, be
suppressed. Note that all notifications are written to the event log even if they are not displayed.
Select this option to initiate a DHCP request to obtain a dynamic IP address after a successful
authentication, but only if the client detects that the connected network (the SSID) has changed. The
result is that renewal should not occur upon re-authentication, but does occur at boot or when connecting
to a different network. If you have a slow authenticator, you may wish to enable this option when
configuring the service because a slow authenticator may prevent you from getting a DHCP-assigned IP
address upon boot-up. This option is ignored if the given adapter has a static IP address.
9 - 28 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
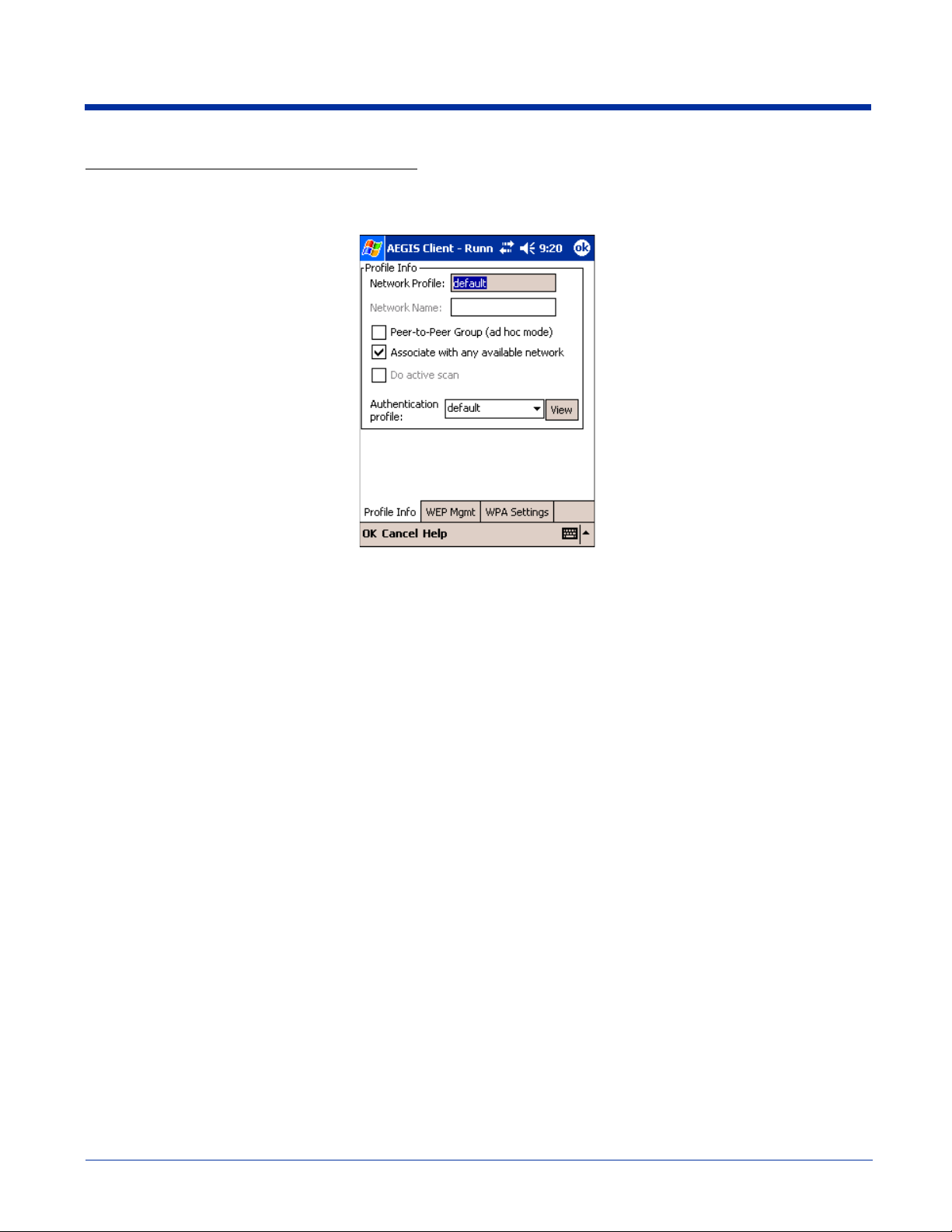
Adding a Wireless Network Configuration
To add a wireless network configuration, on the main screen, tap and hold on the port, tap Configure on the Port popup menu,
then tap Add in the Network Configurations section of the Wireless Networks tab. The Network Profile screen opens displaying
the Profile Info tab.
Profile Info Tab
Field Description
Network Profile
Network Name
Peer-to-Peer
Group (ad hoc
mode):
Do active scan
Authentication
Profile
Enter the name of this record. This is the name that appears in the Configured Networks list and, by
default, is the same as the broadcast SSID. Note that there is nothing special about the name "default".
You could configure any other record similarly and it would behave the same way.
This is the SSID of the AP. If the AP broadcasts its SSID, then this value may be derived from the
Available Networks list. If the SSID does not broadcast, then you must manually enter the value here.
Select this option to have two or more client workstations communicate with each other without the
benefit of an AP. You should also select Do Active Scan and, in the WEP Management page, enable
Use key for data encryption while entering a common key for both sides . WPA is not supported in this
mode.
Select this option whenever the AP (or client, for ad hoc mode) is not broadcasting its SSID.
Select the Client Configuration (user) profile associated with this network. The drop-down list contains
client profile names created in the User tab of the Client Configuration Area; see User Tab on page 9-
22.
To open the selected profile, select it in the drop-down list and tap View. The User tab opens displaying
the profile details. If you tap OK (to save changes) or Cancel, you are returned to the Profile Info tab.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 29
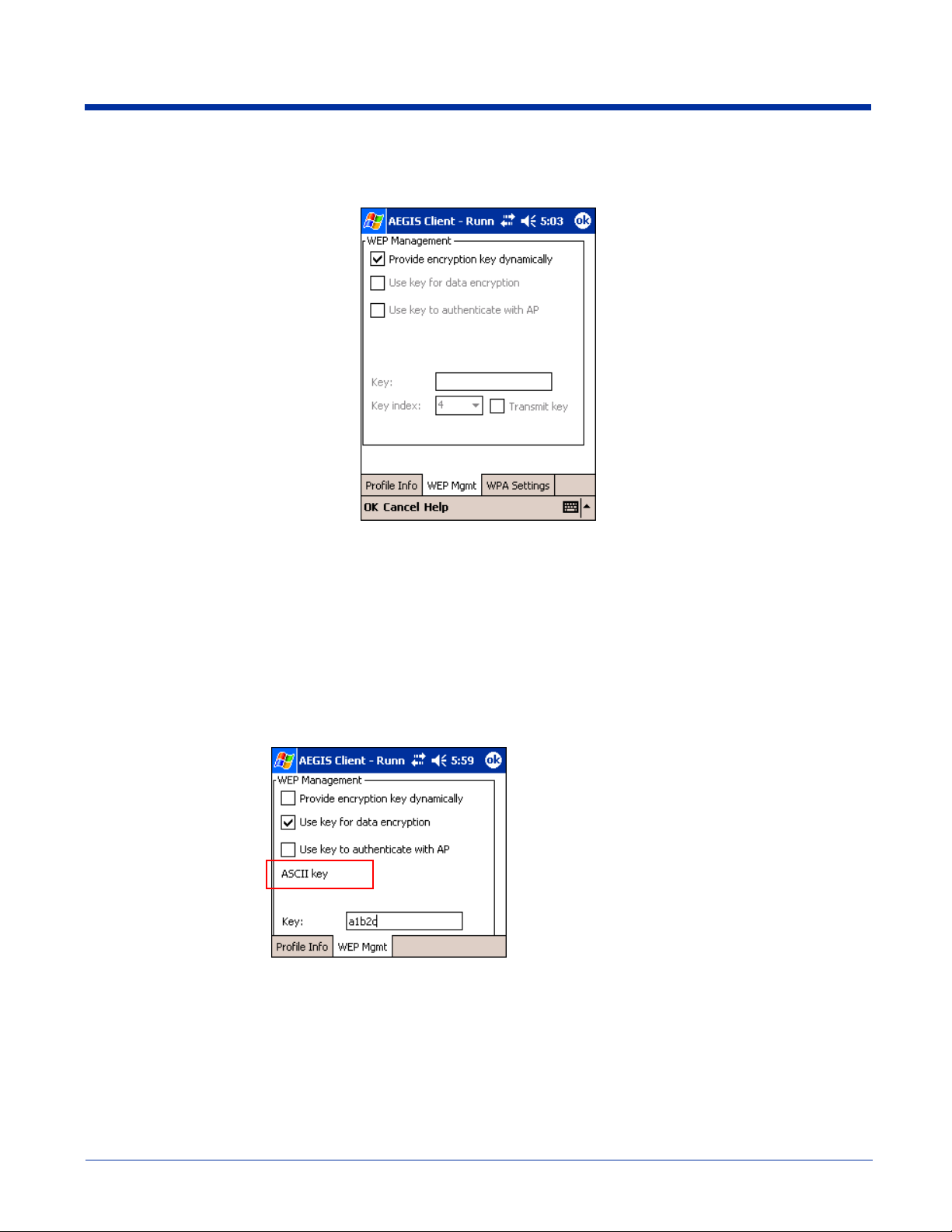
WEP Mgmt Tab
The WEP Mgmt tab enables you to set WEP parameters for each port.
Note: The settings on this tab window are interrelated. This means that selecting one may disable access to others.
Field Description
Provide encryption
key dynamically
Use key for data
encryption
Use key to
authenticate with AP
Key
Key Index/Transmit
Key
This option is selected by default. If this option is selected, the other WEP settings on this page
are disabled. To enter a custom WEP, de-select this option. The other fields become active.
Select this option to manually enter a WEP key to encrypt your data to the AP. You enter that
key in the Key field below.
Select this option if your network does not support 802.1x authentication and you need to
connect to the AP without username and password authentication. The key entered below is
used to authenticate instead.
In this field, enter the WEP key:
ASCII - 5 or 13 characters
Hexadecimal - 10 or 26 characters.
When the key entered is in the correct format, the
screen changes to display the type - ASCII or
Hexadecimal.
The Key Index drop-down list contains the available keys. You may enter up to four keys for
reception; the Client will try all four to find one that works with the AP.
From the drop-down list, select the key to be used for transmission as well. If the key selected is
the transmit key, the Transmit key box is checked.
To change the transmit key, select another key and check the Transmit key box. The check box
of the original transmit key will be automatically de-selected.
9 - 30 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
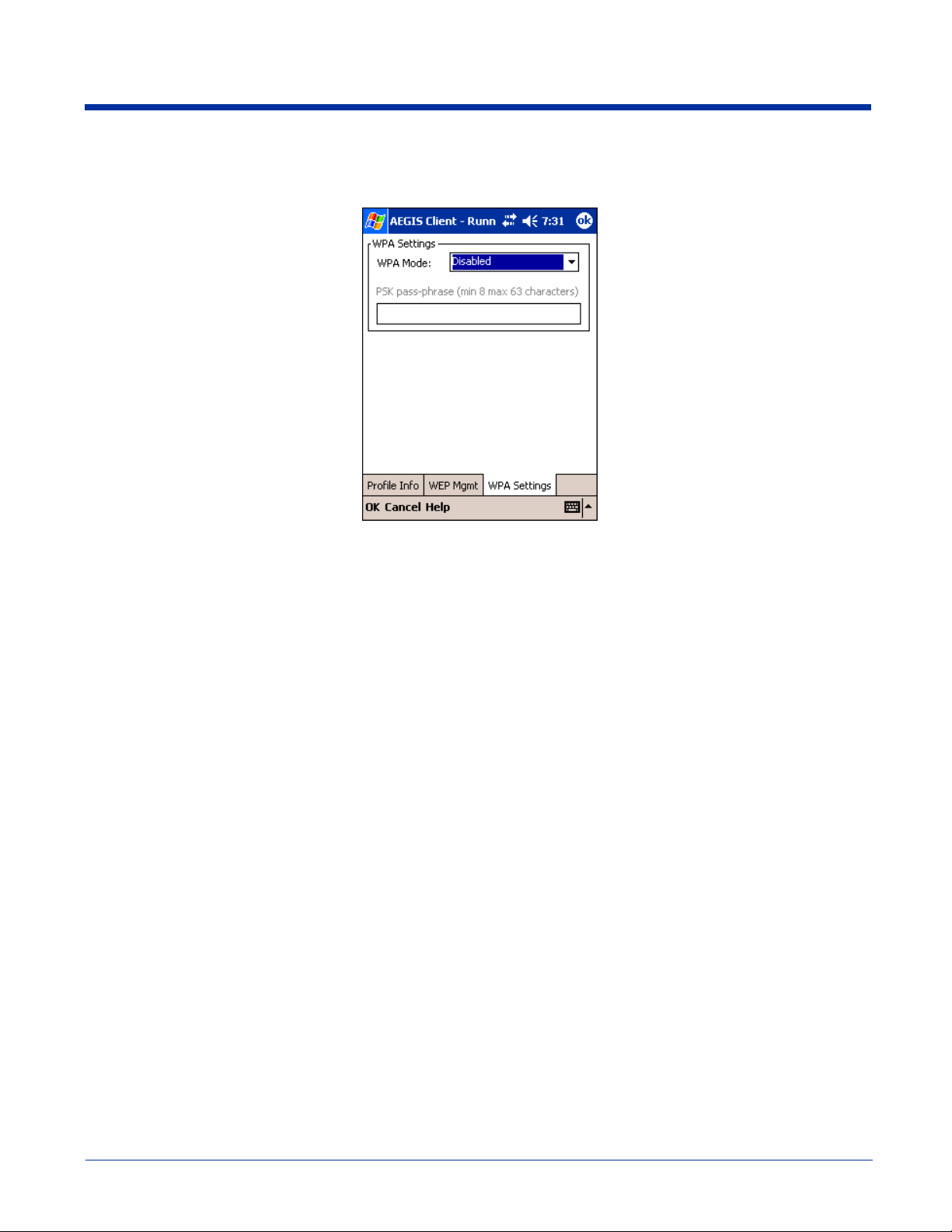
WPA Settings Tab
The WPA Settings tab enables you to configure WPA settings.
Field Description
WPA Mode
PSK pass-phrase
This drop-down list contains the following options:
• Disabled - Do not enable WPA mode. This is the default selection.
• WPA 802.1x - Enable WPA and obtain key information through the 802.1x protocol.
• WPA PSK - Enable WPA with Pre-Shared Key (PSK) information entered in the field below.
This mode is used if the 802.1x protocol is not being used for authentication.
This field activates if you select WPA PSK in the WPA Mode drop-down list.
Enter between 8 and 63 characters for your pass phrase. Asterisks appear as you type for
increased security.
Logging
The event log is an ASCII text file named “LOG8021X.TXT” located in the directory defined by the WINDIR environment variable
(usually the Windows directory). The information the log records is determined by the log settings on the System tab of the Client
Configuration Area; see System Tab on page 9-24.
The format of the entries is
Time Stamp Message Text
The Refresh button at the bottom of the screen is used to update the log file while you are reading it. If the file gets too large, old
entries are automatically deleted.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 31
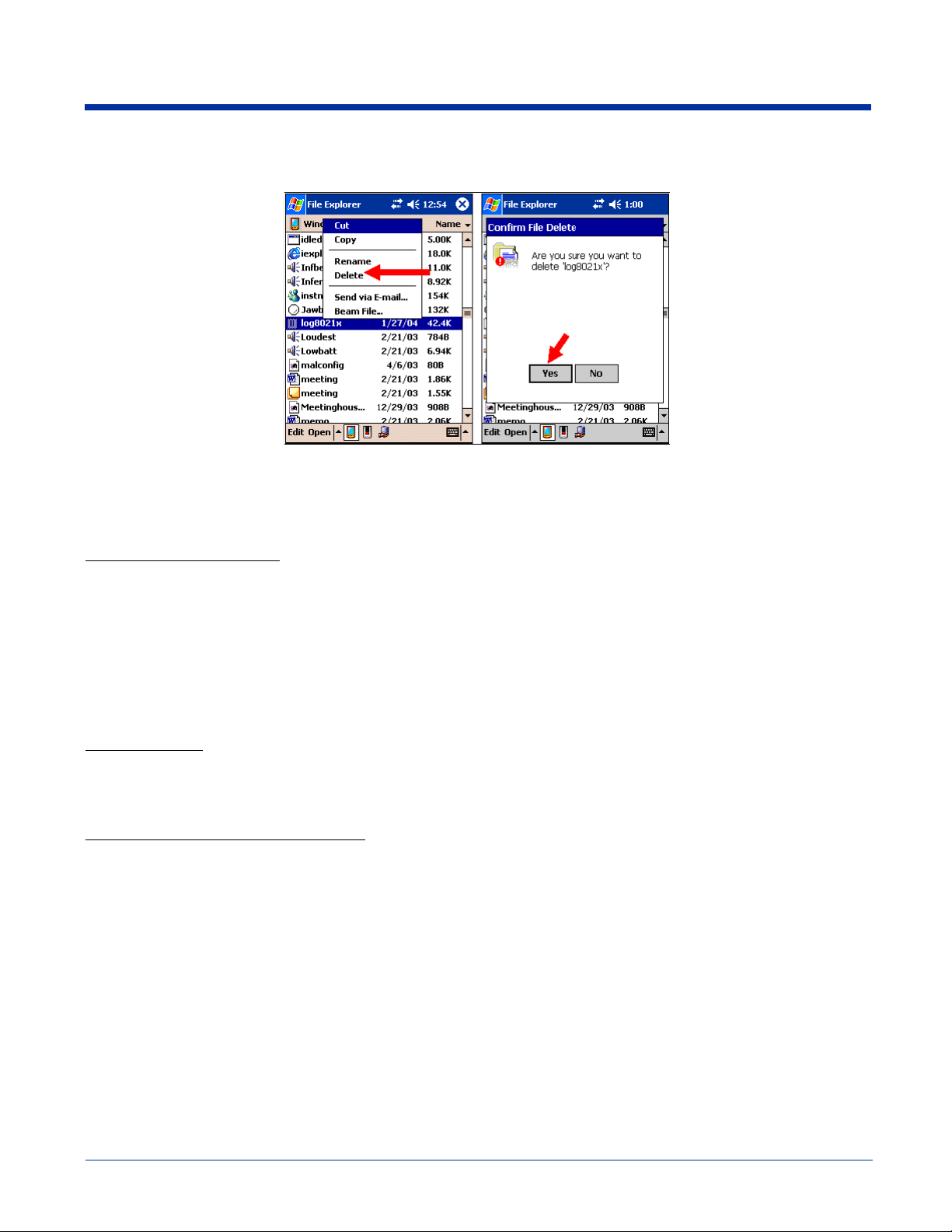
If you wish to start with a blank file, exit from the Client (so the icon no longer appears at the lower right of the screen) and delete
the log file (log8021x) in File Explorer; see Finding and Organizing Information on page 4-12.
When you restart the Client, a new log file is created.
Installing Certificates with CertAdd
Certificate Requirements
During configuration, you may have specified one or two certificates to use during the authentication process. The specified
identity should match the Issued to field in the certificate and should be registered on the authentication server (i.e., RADIUS
server) that is used by the authenticator. In addition, your certificate must be valid on the authentication server. This requirement
depends on the authentication server and generally means that the authentication server must know the issuer of your certificate
as a trusted Certificate Authority.
If the selected certificate does require a password or pass phrase to decode the private key, enter this value in the “Certificate
Pass Phrase” field. This value will be encrypted when the configuration is saved. However, on some systems, there may not be
a certificate. If that is the case, you can use the section below as a primer on OS X certificate management.
About CertAdd
CertAdd is a stand-alone utility included with the Client that allows certificates to be selected and installed on a Windows Mobile
device.
Installing Certificates with CertAdd
Client or Certificate Authority (CA) certificates can be imported from *.cer (same as *.der), *.p7b, or *.pfx files.
1. Download the certificate file to the My Documents folder. The location isn’t critical, although you may want to create a standard folder for consistency.
9 - 32 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
2. Go to Start > Programs > Meetinghouse Certificate Installer. The opening screen is displayed. All valid certificate file
types located in the My Documents folder appear in the list.
3. Tap and hold on a certificate in the list. A pop-up appears asking if you want to install the certificate.
4. Tap OK. The certificate is loaded into the correct certificate store.
Advice and Workarounds
Issue Possible Causes and Solutions
The Client will not start on the device with an
error message about missing files.
The wireless network interface (port) does not
appear in the main AEGIS screen.
The wireless network interface appears, but
when I select it and go to the "configure" menu,
the Scan button is disabled.
The client is not attaching to the correct AP. The default network profile instructs the client to attach to the first
Perform a soft reset.
• The license is not valid (If you have entered a time-limited license, is
your clock on the device correct?).
• Restart the client - on the main screen tap Client > Restart.
• Perform a soft reset.
• If the radio is turned off or the radio card is not present, this will
sometimes cause the port name to not appear.
• If the radio driver is very old and does not support NDIS 5.1
commands, the Client may not be able to detect it.
Power up the radio; see Enabling Radios and Radio Combinations on
page 4-7.
available AP. You must select a network, move it to the Configured
Networks list, and then move it above default in the list using the up
arrow buttons.
For more information, see Wireless Networks Tab on page 9-27.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 33
Advice and Workarounds
Issue Possible Causes and Solutions
The Client is failing authentication even though
all my information was entered correctly.
My AP does not broadcast its SSID. Even
though I have manually configured an AP with
that name, the Client won't associate with it.
I am authenticated, but I don't get an IP
address through DHCP.
I cannot attach to my old network that does not
support 802.1x authentication, but is using
WEP encryption.
I made changes, but they do not appear to ha ve
taken effect.
How do I enable peer-to-peer (ad-hoc) mode to
have two clients communicate without an AP?
1. Verify that the network profile for the AP corresponds to the authenti-
cation profile you created for it.
• Select the network profile in the Configured Networks list.
•Tap Properties. The Profile Info tab opens - see page 9-29.
• In the Authentication profiles drop-down list, select the profile
you want to review.
•Tap View. The User tab appears displaying the profile’s
information.
2. Verify that you have configured the identity and password into the
correct fields on the User tab (page 9-29) in the authentication
profile. If you are using PEAP or TTLS, the username and password
are entered in the Tunneled authentication section.
• Make sure that the desired SSID is listed as the Network Name, not
the Network Profile (which is a screen label)
• Verify that Do Active Scan is selected on the Profile Info tab; see Do
active scan on page 9-29. Otherwise, the Client will not attempt to find
the AP.
On the main screen, tap and hold on your AP, tap Configure on the
popup menu, and select the Protocol tab. Verify that Renew IP Address
is selected; see Renew IP address on page 9-28.
• Verify that you can see your SSID in the Available Networks list on the
Wireless Networks tab. Move the SSID to the top of the Configured
Networks list so that it is accessed first. If the SSID is not there, you
can add it manually and enter the SSID as the network name - page
9-27
• Select the SSID and tap Properties.
• On the Profile Info tab, select Do active scan if your AP does not
broadcast its SSID.
• On the WEP Mgmt tab, select Use key for data encryption and Use
key to authenticate with AP.
• Enter the WEP Key - see Key on page 9-30.
• On the Protocol tab, select Renew IP Address (unless you have
entered one manually separate from the Client)
• Note that the port status indicator in the main screen reads
"Associated," not "Authenticated" when the connection is complete;
although the log file will indicate "Entered AUTHENTICATED state."
Always tap OK before exiting a screen you have changed. Then restart
the Client from the Client menu on the main screen.
• On the Wireless Networks tab, add a new profile to the Configured
Network list.
• On the Profile Info tab, give each side the same network name (SSID).
•Select Peer-to-Peer Group (ad hoc mode) and Do active scan.
• On the WEP management section, select Use key for data encryption
and enter an identical key for both clients.
• Verify that this network profile is the first (or only) one in the
Configured Network list and try to restart both clients at roughly the
same time.
9 - 34 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
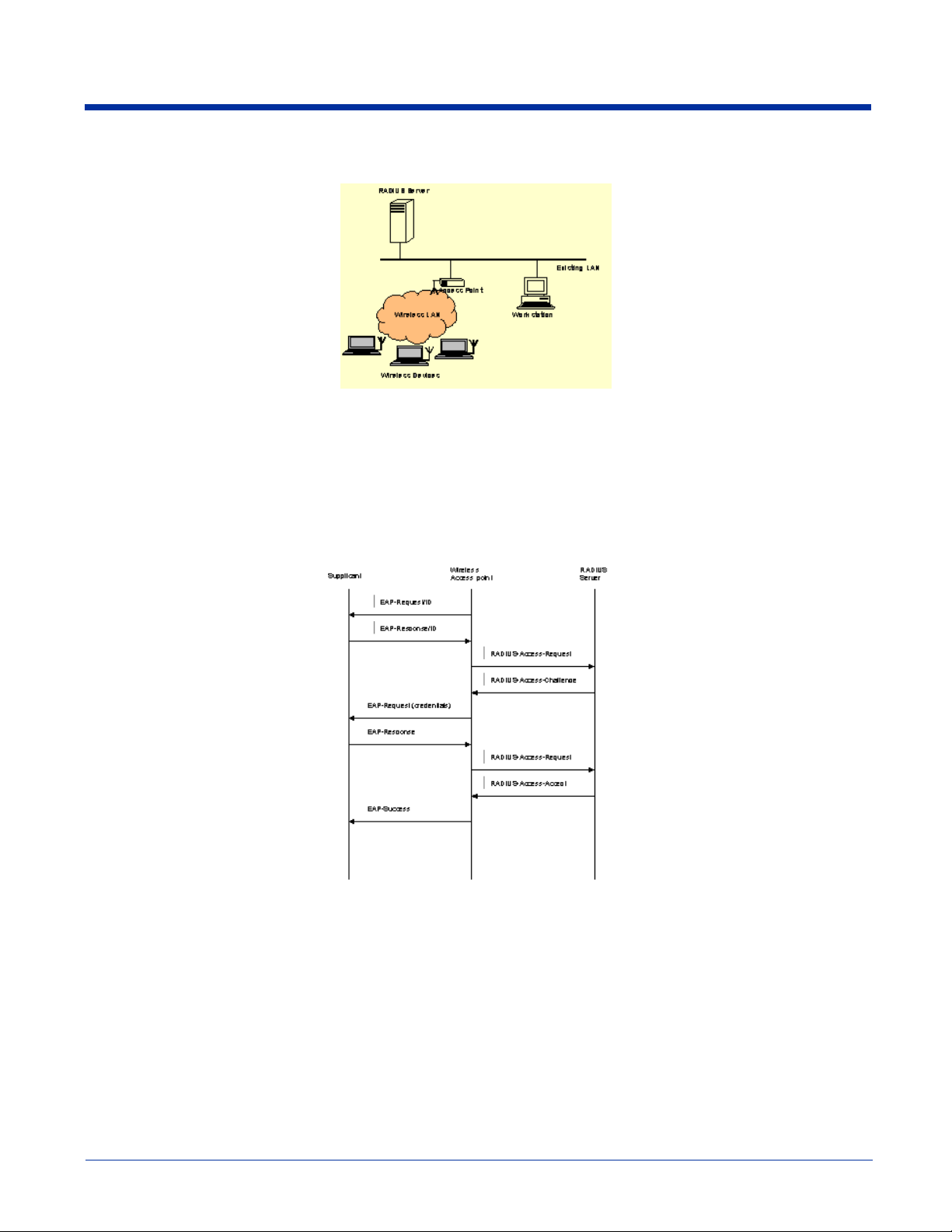
How 802.1X Works
The network elements in the above graphics are those involved in a typical wireless LAN. When 802.1X is running, a wireless
device must authenticate itself with the AP in order to get access to the Existing LAN. With respect to the terms used in the 802.1X
standard, APs (APs) function as authenticators and wireless devices function as supplicants. The authenticator keeps a control
port status for each Client it is serving. If a Client has been authenticated, its control port status is said to be Authorized, and the
Client can send application data to the LAN through the AP. Otherwise, the control port status is said to be Unauthorized, and
application data cannot traverse the AP.
Typical Message Exchange Using MD5 or TLS
The above graphic displays the typical message exchange when the device and the AP support 802.1X. When an AP acting as
an authenticator detects a wireless station on the LAN, it sends an EAP-Request for the user's identity to the terminal. In turn,
the terminal responds with its identity, and the AP relays this identity to an authentication server, which is typically an external
RADIUS server.
The RADIUS server can then act as a central repository of user profile information. Such use of a centralized authentication
server allows the user to access wireless LANs at many different points, but still be authenticated against the same server. In
response to the Access-Request, the RADIUS server sends an Access-Challenge to the AP, which is then relayed in the form of
an EAP-Request to the device. The device sends its credentials to the AP, which in turn relays them to the RADIUS server. The
RADIUS server determines whether access to the network is accepted or denied based on the Client's credentials.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 35
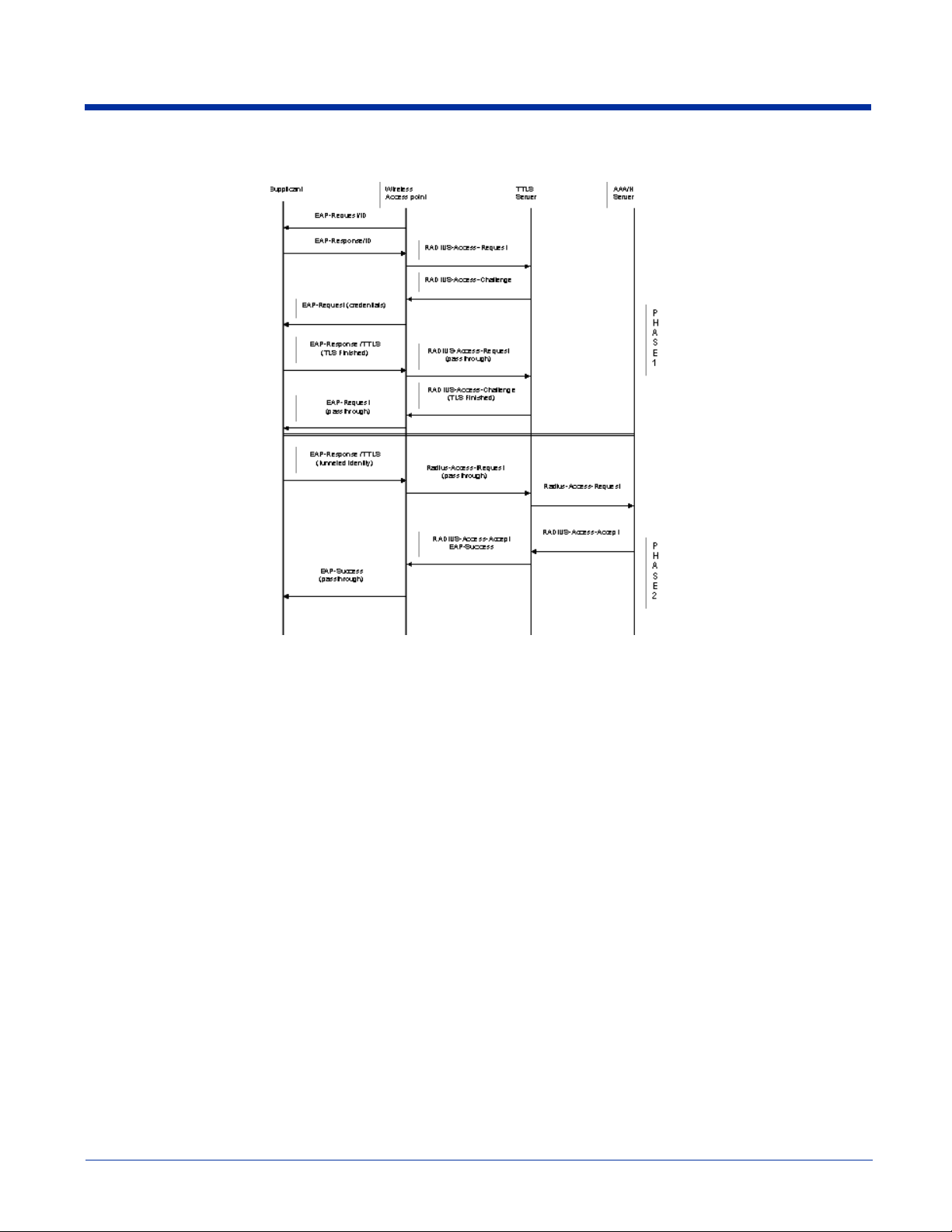
Typical Message Exchange Using TTLS and PEAP
The above graphic shows a typical message flow for a TTLS transaction. TTLS authentication comprises two phases. In Phase
1, TLS is used to authenticate the TTLS server to the client. The TTLS server may optionally request authentication of the client's
certificate, but by default the client verifies only the server's certificate. The TLS handshake is negotiated between the client and
the TTLS server. Following the TLS handshake, Phase 2 may proceed using a secure channel (tunnel) provided by the TLS
record layer. The secure tunnel is then used to exchange information for the negotiation of the following legacy protocols: EAPMD5, PAP, CHAP, MS-CHAP, or MS-CHAPV2 (subject to support by the AAA server). A TTLS server may perform the
authentication, or the information may be de-tunneled and passed on to an AAA server. The AAA server is the server in the user's
home domain where authentication and authorization are administered.
PEAP works in the same manner as TTLS. However, supports different legacy protocols within the encrypted Phase 2 tunnel.
Currently the tunneled protocols are EAP-MSChapV2 and EAP-TLS/SmartCard. Like TTLS, the use of a client certificate is
optional, if one is used, the same certificate is used for Phase 1 and Phase 2. The client certificate is optional for both phases.
Benefits of 802.1X
Central User Administration
The Client allows network administrators to continue to use RADIUS or another AAA server as their centralized authentication
server. In 802.11b, where authentication took place between the AP and the station, there was no concept of passing credentials
from the AP to an authentication server. For LANs this was fine. However, as users began to use their devices in remote
locations, the security provided became inadequate. 802.1X solves this problem by allowing APs to pass client credentials to the
appropriate authentication server.
9 - 36 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
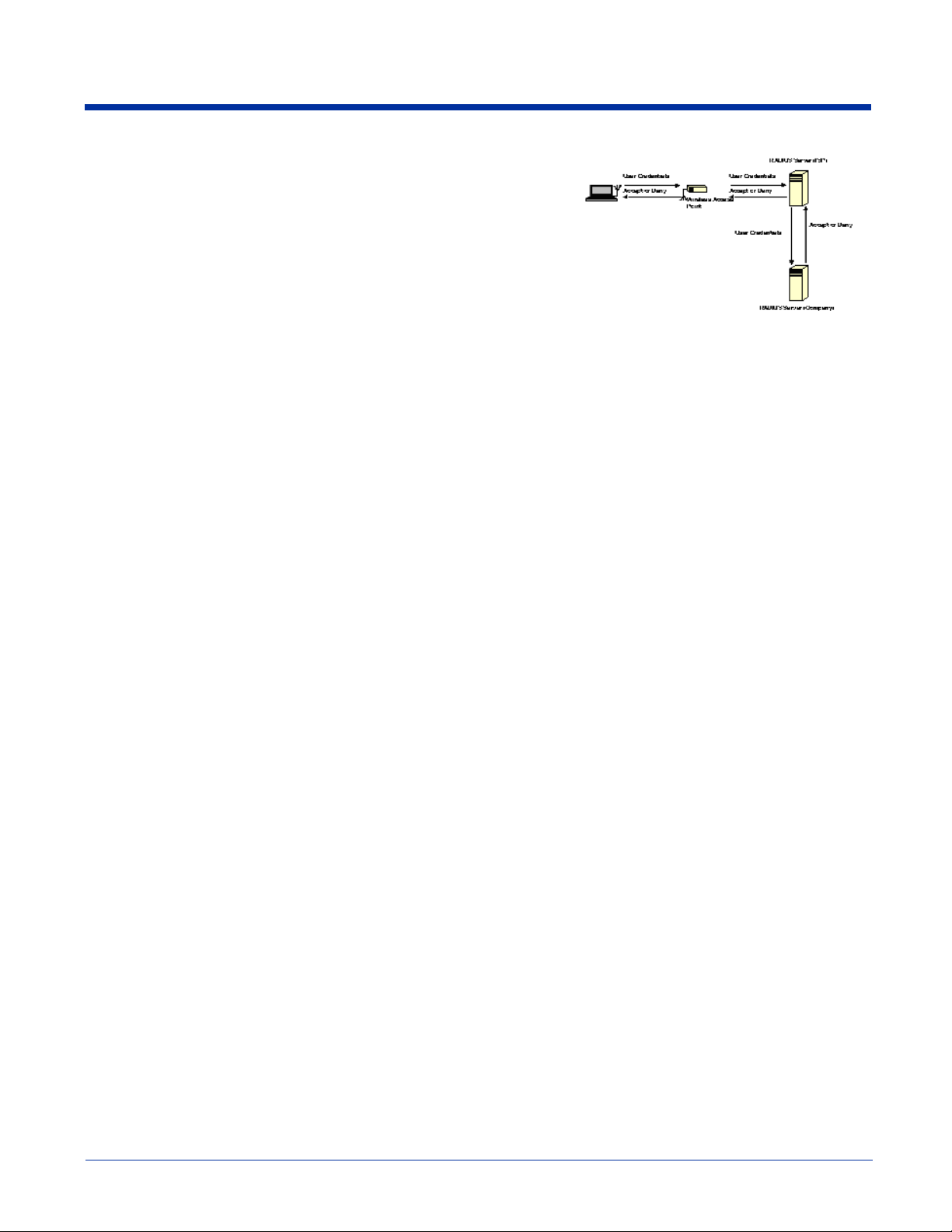
For example, the following graphic displays the authentication flow for a mobile
user who wishes to create a virtual private network with his home office.
By using the Client, the user can associate with a wireless network provided by
a third party, in this case the ISP. We assume that the company and the ISP
have established a service relationship beforehand. When the ISP receives the
user's credentials, the ISP proxies the credentials to the company's AAA server,
which returns a message telling the ISP to either accept or deny the user
access. This response is then propagated to the remote user.
Dynamic Session Specific Wireless Encryption Keys
There have been many published reports recently about the lack of security provided by the Wired Equivalent Privacy (WEP)
protocol. One of the problems with WEP is that the shared key used by the station and the AP is inherently static. That is, this
shared key will only change if it is manually reconfigured on both devices. The Client remedies this by supporting the Transport
Layer Security (TLS) protocol. TLS ensures that a new shared key is generated each time a station associates itself with an AP.
TLS has proven itself an excellent authentication and encryption protocol in commercial environments. The Client also supports
the MD5 and TTLS security protocols.
Additional Advantages of TTLS and PEAP
The Client provides the advantage of Tunneled TLS (TTLS) and PEAP support. These protocols provide the security of TLS
with greatly reduced administrative load. Security is enhanced by never passing user ID and password in the clear. No "real" user
ID or password is required in Phase 1. After the secure tunnel is established, Phase 2, user credentials are passed in safe,
encrypted form. To further enhance security, the WEP keys, which encrypt the data between the wireless card and the AP, may
be automatically changed on a per-session basis, limiting the time available to an unauthorized sniffer to crack the keys. By
limiting the session time (the reauthentication period), the keys can essentially be made uncrackable.
Administration is eased by greatly reduced certificate requirements in comparison to TLS. In TLS, each client must have a client
certificate to pass to the server, and a CA certificate with which to verify a server certificate, while the server must have a client
certificate from each user and CA certificates for each possible CA chain and its own server certificate. TTLS and PEAP require
only that a single server certificate be created for the server to present to the client, and that the client have a CA certificate to
verify the server. Because these are the same for each client on the network, they are easily managed, unlike TLS, where every
client certificate is unique. TTLS and PEAP thus provide the security of a TLS channel without the need for managers to distribute
and manage client certificates. Lastly, TTLS allows for the use of existing legacy authentication protocols. Administrators may
continue to use established authentication databases.
Cisco LEAP
The message exchange used by Cisco LEAP is proprietary. This protocol is not a standard EAP type, but is supported by the
Client through a licensing arrangement with Cisco.
Relative Merits of Authentication Protocols
MD5 is the least secure of the EAP protocols as it only does a one-way authentication, and does not support automatic
distribution and rotation of WEP keys, increasing the administrative burden of manual WEP key maintenance.
TLS, while the most secure EAP protocol, requires client certificates to be installed on each wireless client. Establishing and
maintaining this PKI infrastructure is normally a burden most administrators do not feel is worth the extra level of security gained.
TTLS and PEAP bypassed the certificate issue by tunneling TLS, and thus eliminating the need for a certificate on the client side.
PEAP supports only EAP-compliant authentication protocols within the tunnel structure, and is rapidly becoming the most widely
supported of the EAP methods. TTLS supports pre-EAP authentication protocols within the tunnel structure, and should be used
in those circumstances when pre-EAP interior protocols are desirable.
LEAP is a pre-EAP, Cisco-proprietary protocol, with many of the features of EAP protocols. Cisco controls the ability of other
vendors to implement this protocol, so it should be selected for use only when limited vendor choice for client, access-point, and
server products is not a concern.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 9 - 37

Differences Between Protocols
Security Feature MD5
Challenge
Client -side certificate required? No Yes No No No
Server-side certificate required? No Yes No Yes No
Dynamic WEP Re-keying No Yes Yes Yes Yes
Mutual or One-way Authentication? One-way Mutual Mutual Mutual Mutual
Support of non-EAP protocols within
a secure tunnel?
Relative Deployment Complexity Simple Difficult Moderate Moderate Moderate
Relative Security Poorest Highest High High High
N/A N/A Yes No N/A
TLS TTLS PEAP LEAP
9 - 38 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

10
Wireless PAN Communications with Bluetooth
Overview
Dolphin 7900 terminals are available with a Bluetooth radio for WPAN (Wireless Personal Area Network) usage. When the mobile
computer is first initialized, the *.cab file and module for Bluetooth are installed.
Enabling the Bluetooth Radio Driver
Before using the radio, make sure that the Bluetooth radio is enabled. When the radio driver is enabled, the Bluetooth icon
appears in the task tray on the Today screen.
Radios are enabled in the Radio Manager utility; see Enabling Radios and Radio Combinations on page 4-7.
Setting Up Your Bluetooth Card
Note: If you use the Get Connected! Wizard, which is recommended for normal usage, then this step is not necessary. This step
would be used to change the friendly name of your mobile computer.
1. Tap the Bluetooth icon that appears in the task tray on the Today screen.
2. In the pop-up menu, select Advanced Features, then My Bluetooth Device. (If you installed OBEX, the menu also lists
Transfer via Bluetooth.)
3. In the My Bluetooth Device screen, you can modify the Friendly Name and make any desired configuration changes.
When done, tap OK.
• In normal phone connect operation, Discoverable mode is not needed and should be disabled.
• If you do enable Discoverable mode (e.g., for ActiveSync), note that it does not shut off by itself. To save power, remember
to disable it when not needed.
• Connectable, Use Authentication, and Use Encryption are also not required for printing or dial-up networking applications.
• Check Use Authentication to enable the Use Encryption option.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 1
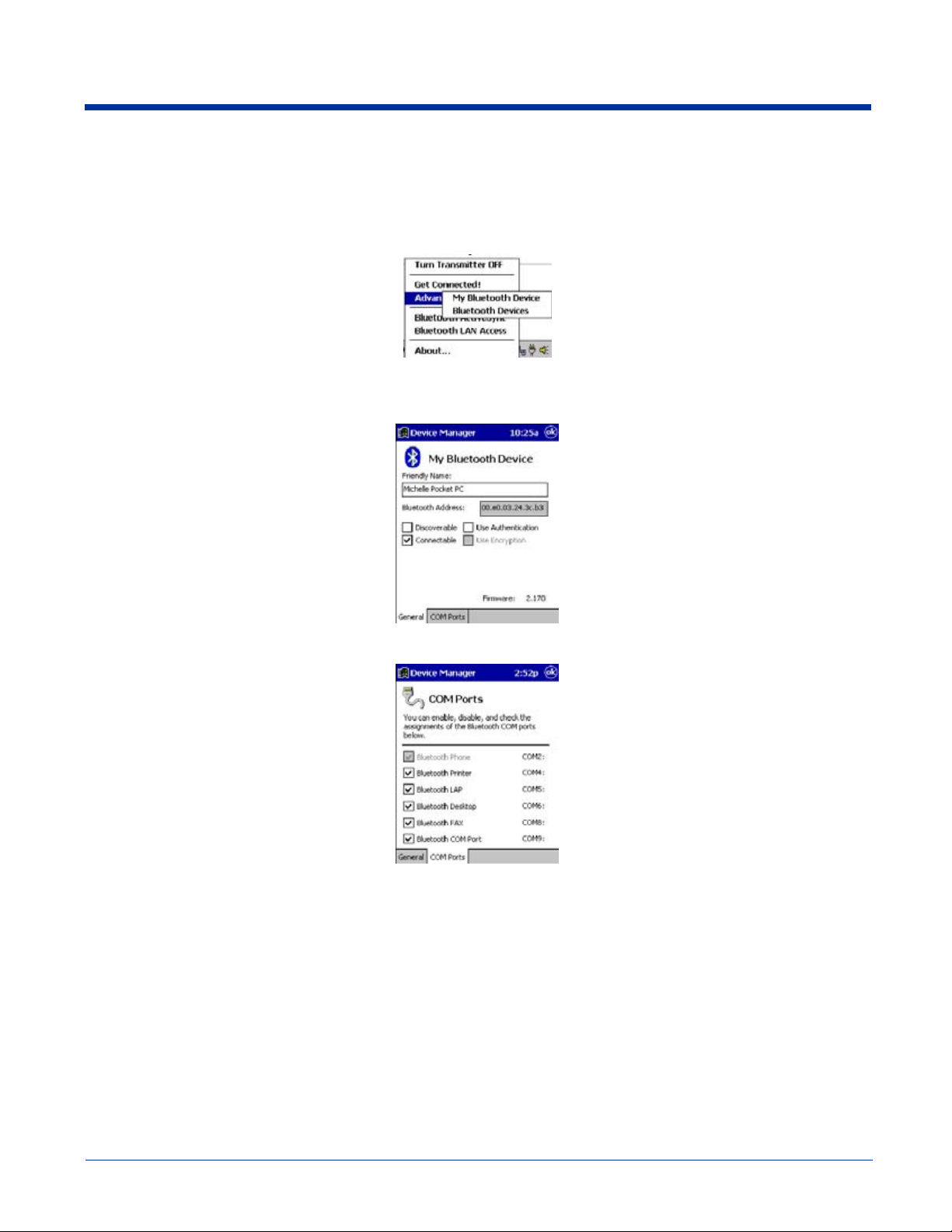
Assign COM Ports
Follow these steps to view and/or modify the Bluetooth COM ports. If you are not going to use the IrDA port, you can disable it
to free up a port for Bluetooth devices; see Using Infrared on page 8-5.
1. Tap on the Bluetooth icon on the Today screen. Select Advanced Features then My Bluetooth Device.
Note: If you installed OBEX, the menu also lists Transfer via Bluetooth.
2. The My Bluetooth Device screen appears. Tap on the COM Ports tab.
3. As needed, view and/or enable/disable the Bluetooth COM port assignments. Tap OK.
Note: The Bluetooth Phone port cannot be disabled. For more information about COM ports, see Com Port Assignment Table
on page 7-20.
Discover Bluetooth Device(s)
Follow these steps to discover other Bluetooth devices nearby, including non-phone devices. The Device Discovery Wizard is a
more detailed alternative to using the Bluetooth “Get Connected!” Wizard or Bluetooth ActiveSync or Bluetooth LAN Access
options. The Device Discovery Wizard allows you to discover any type of Bluetooth device.
1. If not open, launch the Bluetooth Devices folder. Tap on the Bluetooth icon on the Today screen. Select Advanced Fea-
tures then Bluetooth Devices.
2. In the Bluetooth Devices Folder, tap on the Device Discovery icon. Or you can tap on Tools. In the pop-up menu, select
Device Discovery.
10 - 2 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

3. Follow the Bluetooth Device Discovery Wizard to search for Bluetooth devices nearby. When prompted, select the device
type you seek.
4. When the search is complete, a screen reports the discovered Bluetooth devices. Check the box next to any device you
wish to save information about, (i.e., any devices you wish to connect to). Tap Next.
5. A service discovery phase begins, 5-10 seconds per chosen device.
6. In the next screen, tap Finish.
Bond With Discovered Device(s)
Follow these steps to bond with an already discovered Bluetooth device. In most cases, bonding is for establishing secure
communications with a Bluetooth-enabled phone. This is a more detailed alternative to using the Bluetooth “Get Connected!
Wizard.”
Important!
• Do not try to bond with a Motorola Timeport 270C or Nokia 6310!
• Do not use this method to bond with a printer! The third-party printing software included on the installation CD also handles
bonding.
1. If not open, launch the Bluetooth Devices folder. Tap on the Bluetooth icon in the Today screen. Select Advanced Fea-
tures, then Bluetooth Devices.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 3
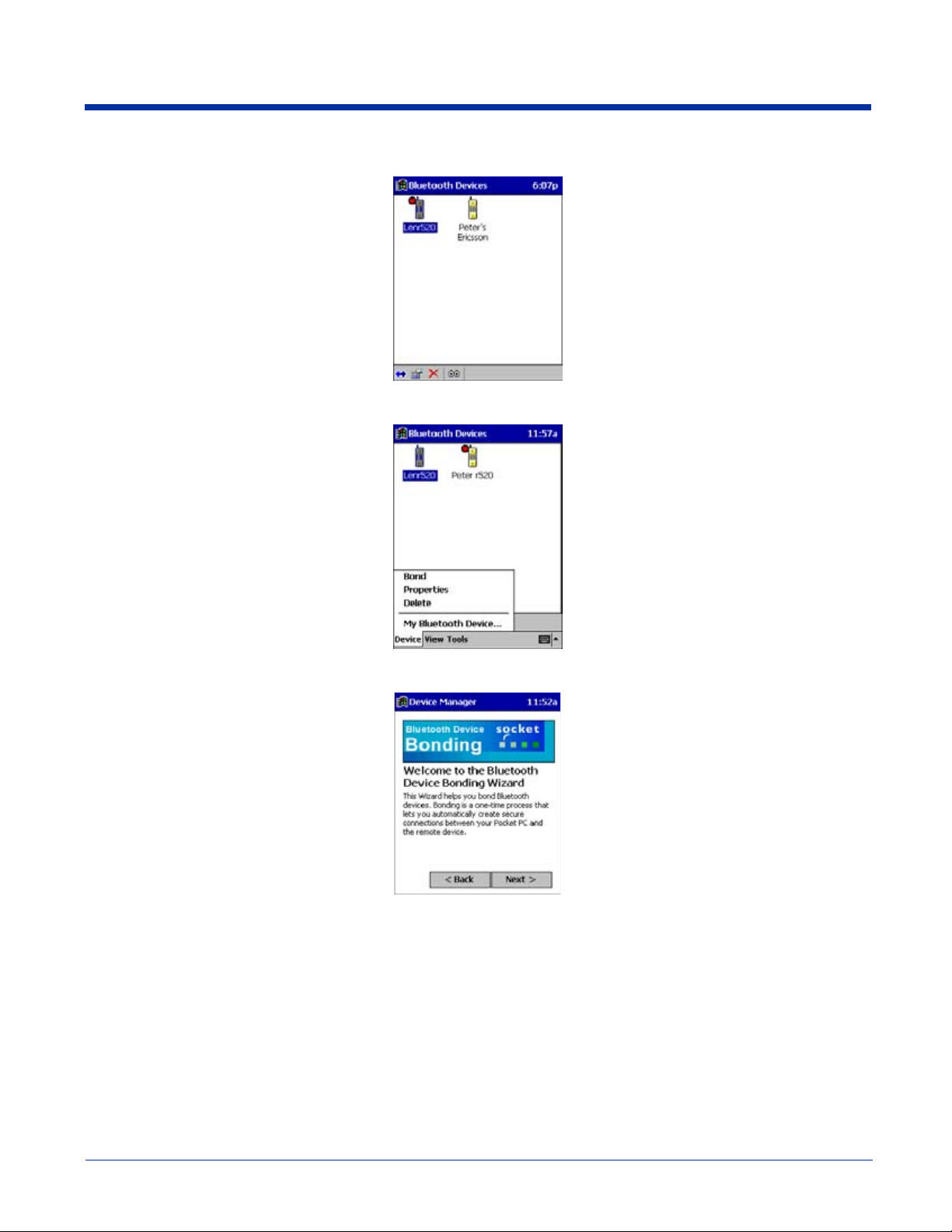
2. Tap and hold your stylus on the Bluetooth device you want to bond with. In the pop-up menu, select Bond.
3. Alternatively, after selecting a device, tap on the Bond icon. Or tap on Device, then select Bond.
4. The Bluetooth Device Bonding Wizard launches. Follow the wizard to bond with your selected device.
10 - 4 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
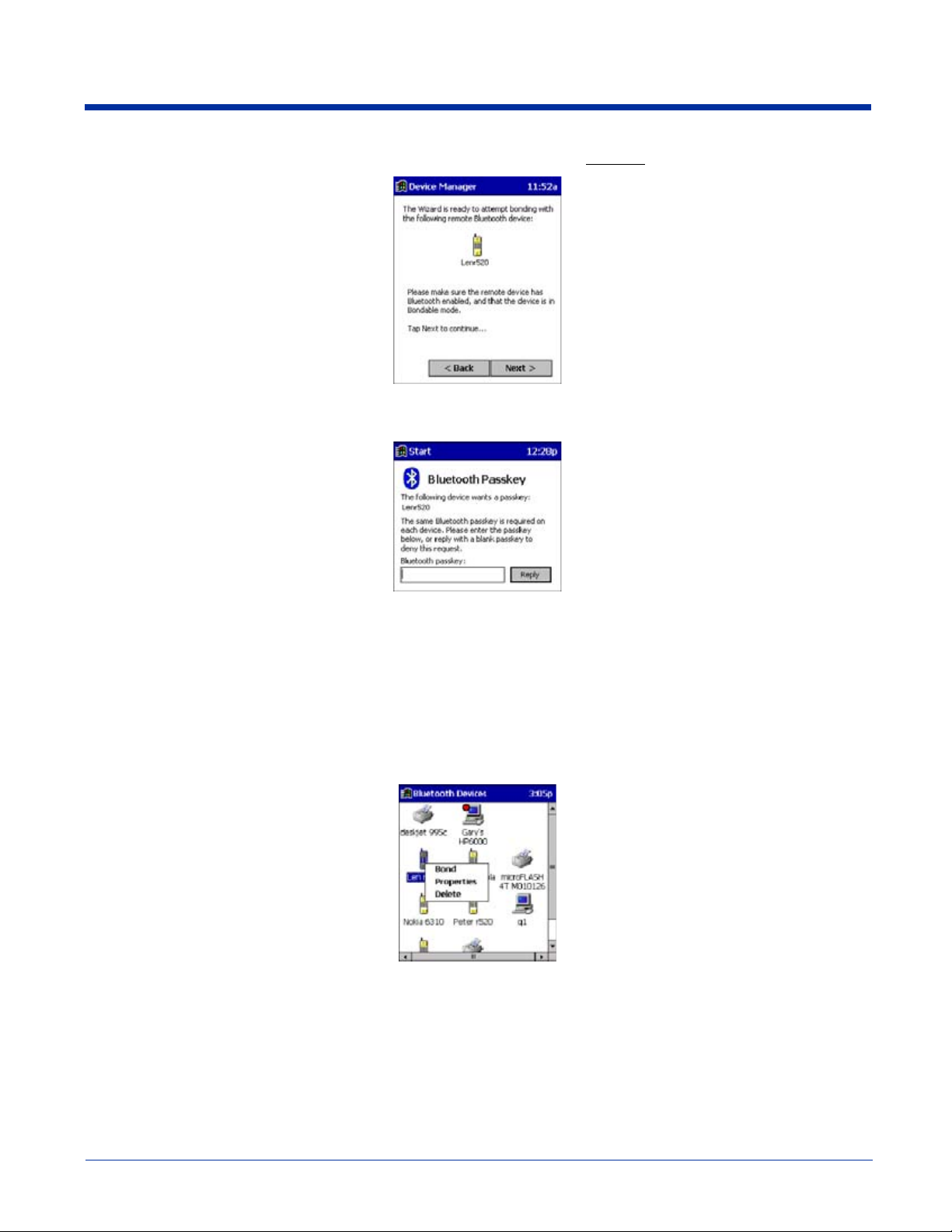
5. As prompted, make sure the Bluetooth device that you want to bond with is in
6. If the remote device is set up to accept bonding, a Bluetooth Passkey screen appears. To continue bonding, enter the
correct passkey and tap Reply.
Bondable
mode.
7. When you have successfully bonded with the other device, tap Finish.
View Device Properties
Follow these steps to view the properties of an already discovered device.
1. If not open, launch the Bluetooth Devices folder. Tap on the Bluetooth icon on the Today screen. Select Advanced Fea-
tures then Bluetooth Devices.
2. Select a device. Tap on the Properties icon, or tap on Device then select Properties. Alternatively, you can tap and hold
your stylus on the Bluetooth device you want to view information about. In the pop-up menu, select Properties.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 5
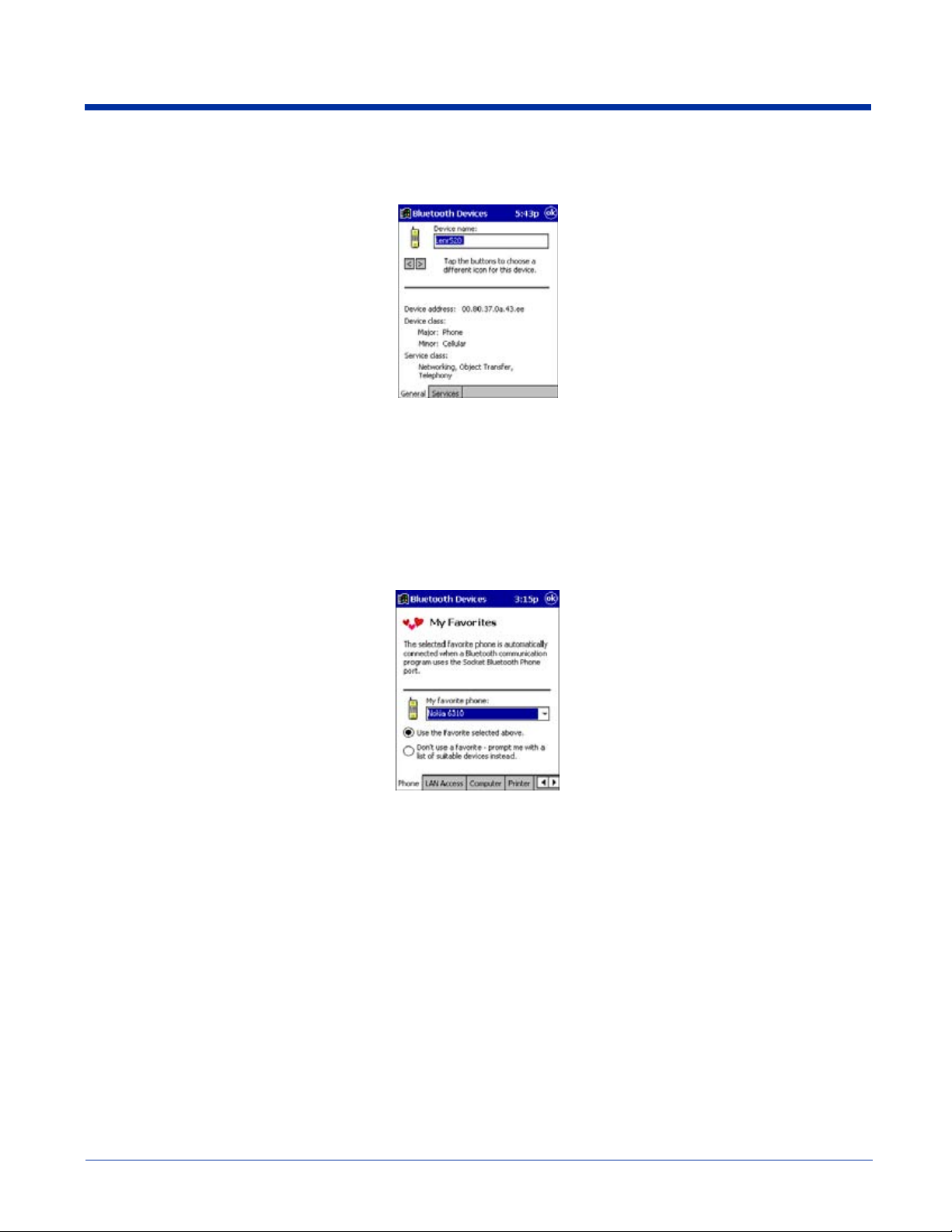
3. Use the General and Services screens to research device properties. If needed, assign a new device type icon by tapping
on the arrow buttons in the General screen. You can also use the Device name field to rename the device. When done, tap
OK for the setting to take effect.
Set Up Your Favorite Device
Follow these steps to set up default devices in the Bluetooth Devices folder. Please note that the Get Connected! Wizard
automatically assigns the favorite phone.
Complete these steps:
1. Tap on Tools and select My Favorites.
2. Tap on the tab for the type of device you would like to set a favorite for. If needed, use the arrow buttons to scroll and find the
tab you need.
Note: Tabs appears only for COM ports you have enabled. To enable a port, refer to the “Assign COM Ports” section earlier in
this chapter.
3. To select a favorite device, select Use the favorite selected above. In the drop-down list, select your device. Tap OK.
4. After setting a device as your favorite, its icon appears in the Bluetooth Devices folder with a heart next to it.
Change Views
You can switch between the Large Icons or Details views for the Bluetooth Devices folder.
1. In Bluetooth Devices, tap on View.
10 - 6 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
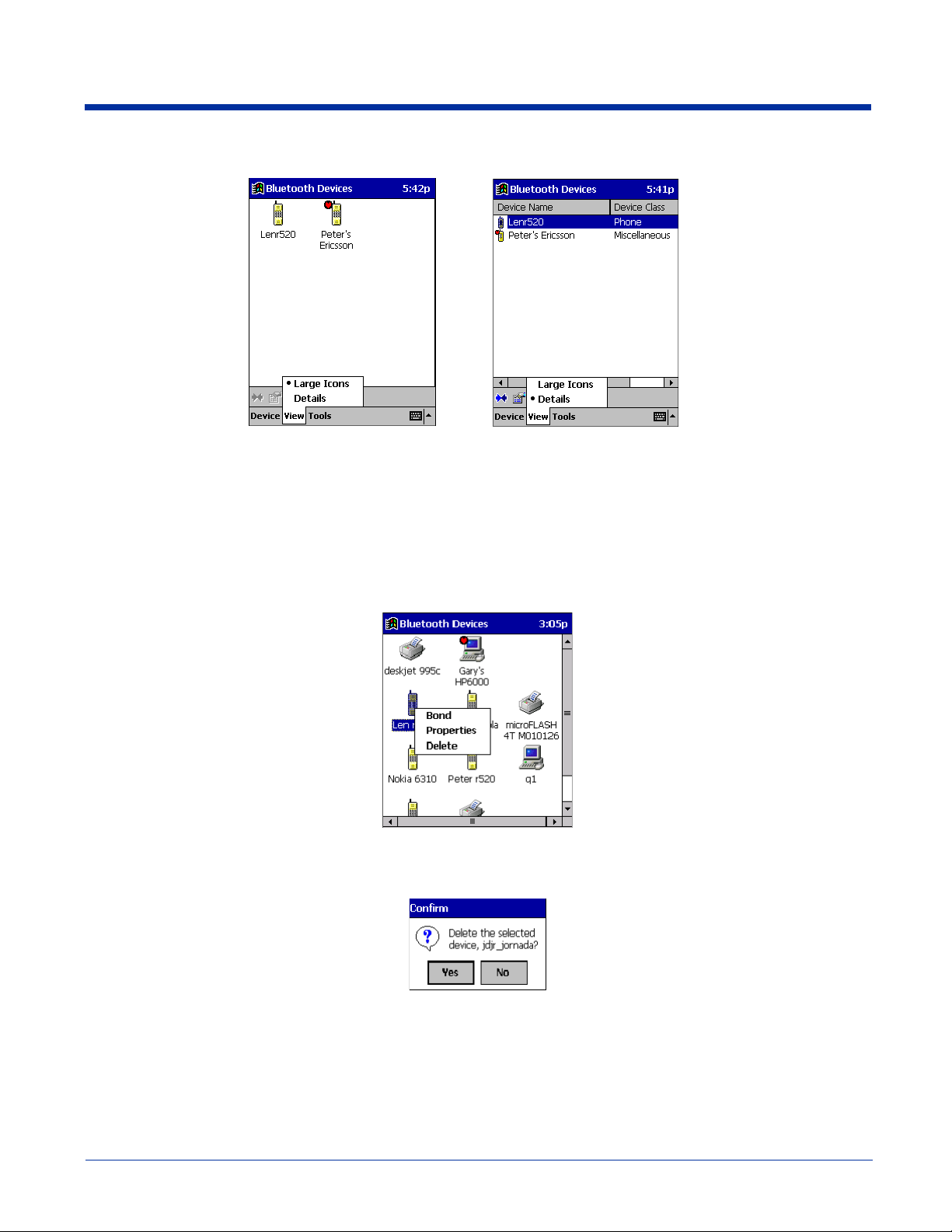
2. In the pop-up menu, choose between Large Icons or Details.
Large Icons Details
Note: In Details view, you can see the Device Class and scroll right to see the current Bonded status.
Delete a Device From the Folder
If you no longer plan to connect with it, you can delete a device from the Bluetooth Devices folder.
1. If not open, launch the Bluetooth Devices folder.
2. Tap and hold your stylus on the device you wish to delete. In the pop-up menu, select Delete.
3. Alternatively, after selecting a device, tap on the Delete icon. Or tap on Device then select Delete.
4. A Confirm screen appears. Tap Yes.
Turn Radio Transmitter ON/OFF
You may want to turn off the radio transmitter to save power or if you are entering an area with radio restrictions (e.g., an airplane).
1. The Bluetooth icon should appear in the task tray on the Today screen. Tap on the icon.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 7

2. In the pop-up menu, select Turn Transmitter OFF.
3. The Bluetooth Card radio transmitter shuts off. The Bluetooth icon in the task tray becomes gray, as well as relevant menu
options (e.g., Get Connected!).
4. To turn the radio transmitter back on, tap on the gray Bluetooth icon. In the pop-up-menu, select Turn Transmitter ON.
Bluetooth ActiveSync
This section explains how to use the Bluetooth ActiveSync feature. It helps you quickly and easily ActiveSync to a notebook or
desktop computer with ActiveSync v3.x installed.
1. Tap on the Bluetooth icon. In the pop-up menu, select Bluetooth ActiveSync.
2. The next screens varies depending on if your Bluetooth Devices folder contains any computers, and if one is chosen as your
favorite. Please refer to the appropriate scenario:
SCENARIO #1: Your Bluetooth Devices folder contains a favorite desktop computer.
(a) When you tap Bluetooth ActiveSync, your mobile computer automatically tries to connect to your favorite computer.
(b) The Connect To screen appears, reporting that it is trying to connect to Wireless ActiveSync.
(c) After a successful connection is made, the status screen reports Connected. Now you are ready to synchronize files, if
desired.
SCENARIO #2: Your Bluetooth Devices folder contains no favorite desktop computer.
10 - 8 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
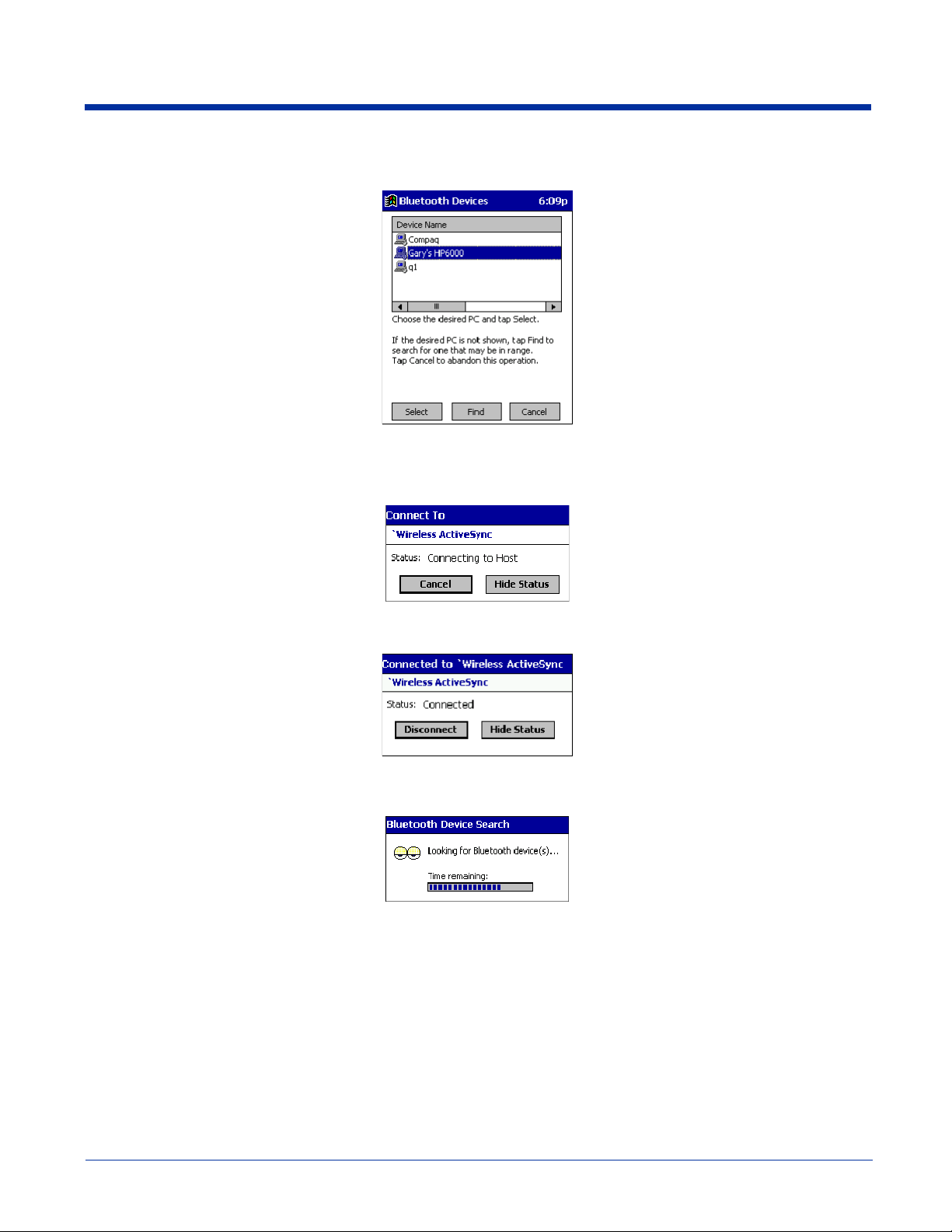
(a) When you tap on Bluetooth ActiveSync, a screen appears that allows you to choose which computer to connect to in
your Bluetooth Devices folder. Choose a computer from the list and tap Select, or tap Find to search for another computer.
Note: If the computer you want to connect to is not listed, tap
Find
to begin a search. Proceed as described in Scenario #3 on
page 10-9.
(b) Your mobile computer attempts to connect to your selected computer.
(c) After a successful connection is made, the status screen reports Connected. Now you are ready to synchronize files, if
desired.
SCENARIO #3: Your Bluetooth Devices folder contains no computers.
(a) When you tap on Bluetooth ActiveSync, a Bluetooth Device Search automatically begins.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 9
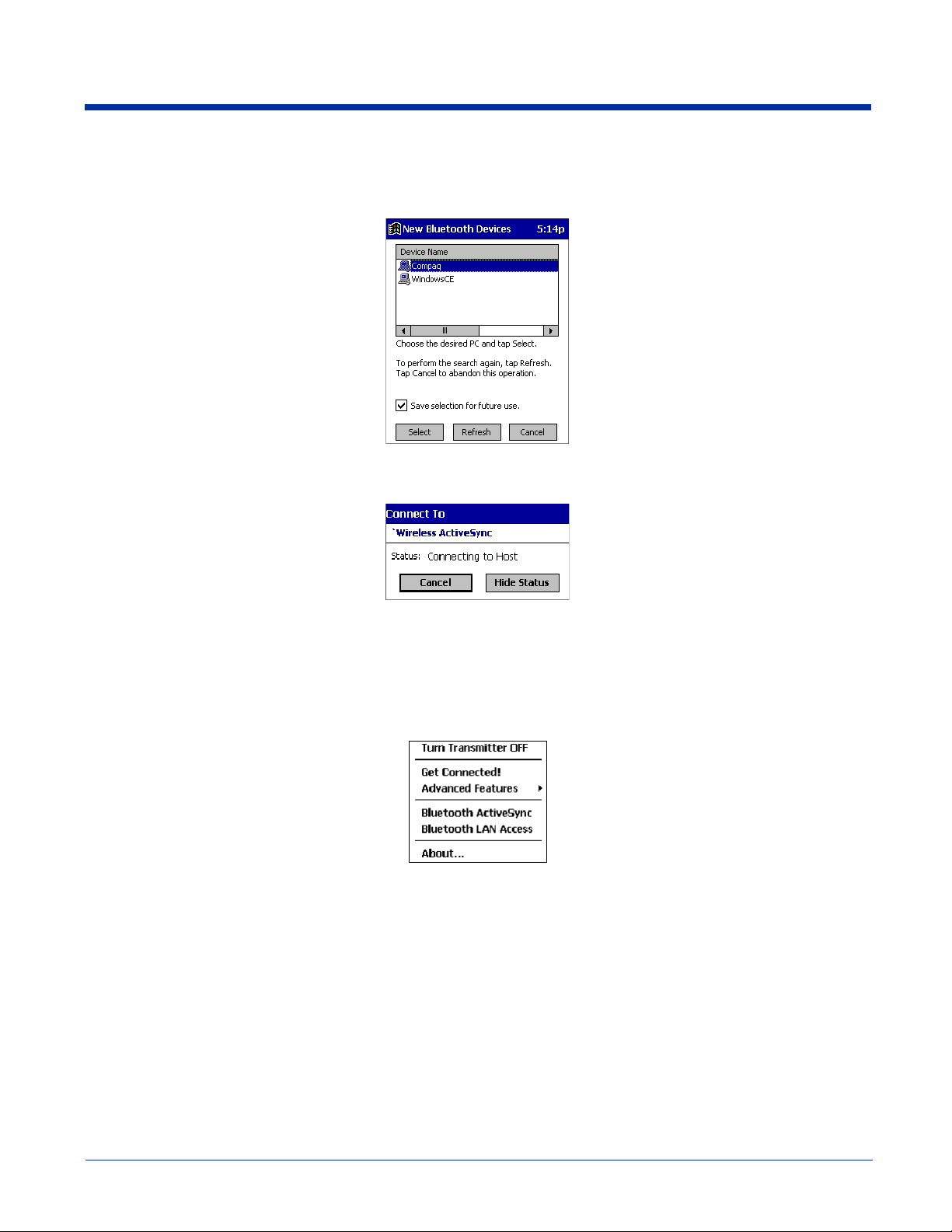
Note: You can also start the device search by tapping Find in the Bluetooth Devices screen.
(b) After the search is complete, select the computer you wish to ActiveSync with and tap Select. If the computer is not listed,
make sure the computer is discoverable and tap Refresh to search again.
(c) After you tap Select, a service discovery phase begins.
(d) The Connect To screen appears, reporting that it is trying to connect to Wireless ActiveSync.
(e) After a successful connection is made, the status screen reports Connected. Now you are ready to synchronize, if desired.
Bluetooth LAN Access
This section explains how to use the Bluetooth LAN Access feature to quickly and easily connect to a Bluetooth-enabled LAN AP.
1. Tap on the Bluetooth icon. In the pop-up menu, select Bluetooth LAN Access.
2. The next screens varies depending on if your Bluetooth Devices folder contains any APs, and if one is chosen as your
favorite. Please refer to the appropriate scenario:
SCENARIO #1: Your Bluetooth Devices folder contains no favorite AP.
10 - 10 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
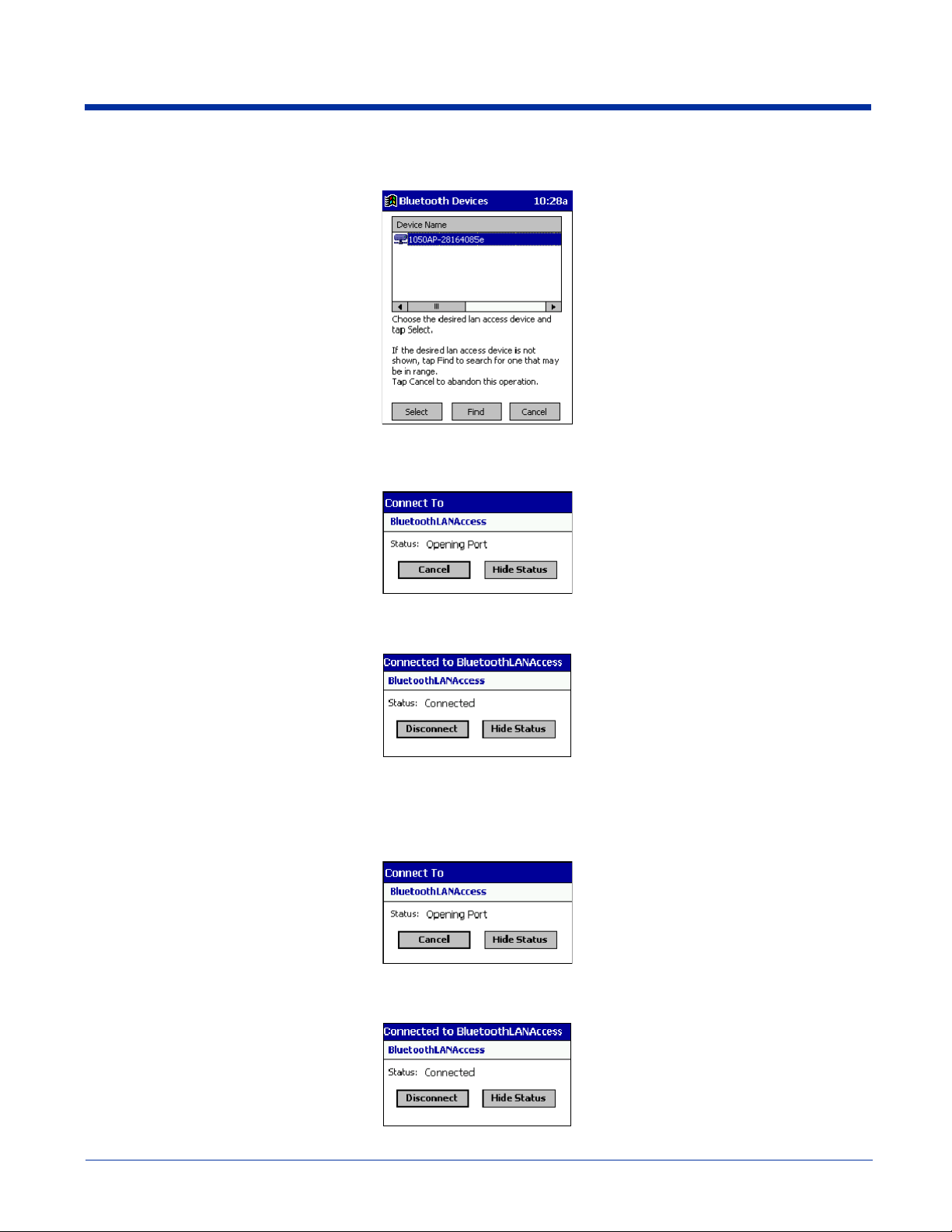
(a) When you tap Bluetooth LAN Access, a screen appears that allows you to choose which AP to connect to in your
Bluetooth Devices folder. Choose an AP from the list and tap Select.
Note: If your AP is not listed, tap Find and proceed as described in Scenario #3.
(b) Your mobile computer tries to connect to the selected AP.
(c) If your LAN requires a passkey, a screen appears asking for the passkey. Enter the passkey, then tap OK.
(d) After a successful connection is made, the status screen reports Connected.
(e) Now you are ready to access your LAN for Internet access, files, etc.
SCENARIO #2: Your Bluetooth Devices folder contains a favorite AP.
(a) When you tap Bluetooth LAN Access, your mobile computer automatically tries to connect with your favorite AP.
(b) If your LAN requires a passkey, a screen appears, asking for the passkey. Enter the passkey, then tap OK.
(c) After a successful connection is made, the status screen reports Connected.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 11
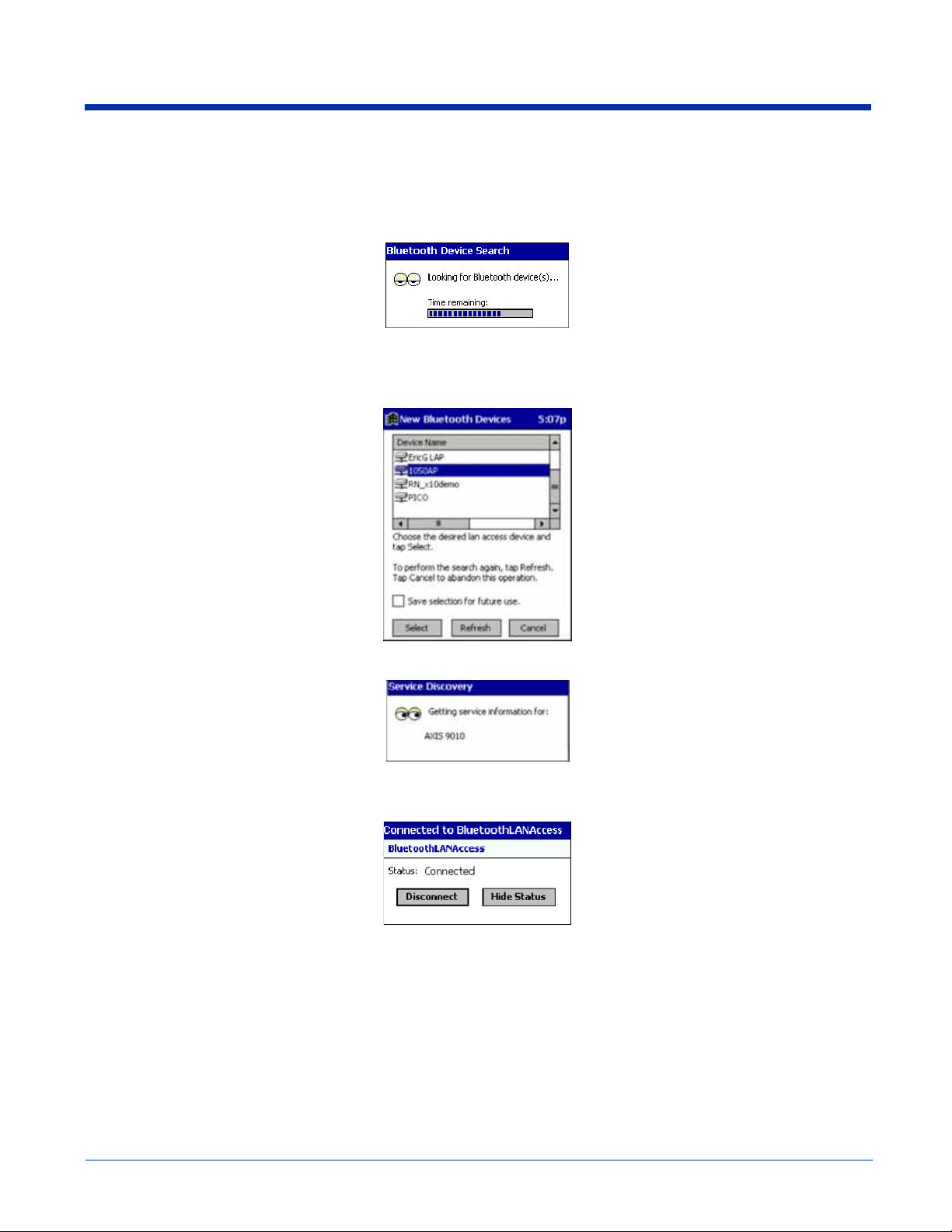
(d) Now you are ready to access your LAN for Internet access, files, etc.
SCENARIO #3: Your Bluetooth Devices folder has no APs.
(a) When you tap Bluetooth LAN Access, the mobile computer automatically begins to search for new Bluetooth devices.
Note: You can also start the device search by tapping Find in the Bluetooth Devices screen. See Scenario #2 on page 10-8.
(b) After the search is complete, select the AP you wish to connect to. Tap Select. If the AP is not listed, tap Refresh to
search again.
(c) After you tap Select, a service discovery phase begins.
(d) If the LAN requires a Passkey, a screen appears, asking for the Passkey. Enter the passkey, then tap OK.
(e) After a successful connection is made, the screen reports Connected.
(f) Now you are ready to access your LAN for Internet access, files, etc.
OBEX
This section explains how to use the OBEX (object exchange) application to trade business cards, contacts or files with another
Bluetooth device that supports OBEX.
Bluetooth OBEX application supports five operations:
• Exchange Business Cards
• Send a Contact
• Send a File
10 - 12 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

• Browse Remote Device
• Receive Contact or File
• Enable File Sharing
The first four operations - exchange business cards, send a contact, send a file, and browse remote device - are client-oriented.
They involve initiating an object exchange.
The last two operations - receive contact or file and enable file sharing - are server-oriented. They involve accepting objects in
an exchange initiated by another Bluetooth device.
Exchange Business Cards
1. Make sure both Bluetooth devices have a business card assigned to them.
Note: If each device does not have a business card assigned to it, you cannot exchange business cards.
To assign a business card to your mobile computer, do the following:
• Tap on the Bluetooth icon. In the pop-up menu, tap Advanced Features > My Bluetooth Device.
• Tap on the Object Sharing tab. Under My business card, tap Assign
• In the next screen, select your business card and tap OK. If your business card is not listed, tap Contacts to create one.
When you return to the Object Sharing screen, tap OK.
2. Make sure the other Bluetooth device is set up to receive a contact. The device must support the OBEX Object Push profile.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 13

Note: If the other device is also using the Bluetooth Connection Kit, you can set it up to receive a contact by tapping the
Bluetooth
3. Now you are ready to exchange business cards. Tap on the Bluetooth icon. In the pop-up menu, tap Transfer via
Bluetooth > Exchange Business Cards.
4. If your mobile computer has no devices in the Bluetooth Devices Folder, then it begins to search for Bluetooth devices
nearby.
5. Select the Bluetooth device you wish to exchange business cards with. If the device is not listed, tap Find.
icon. In the pop-up menu, tap
Transfer via Bluetooth
>
Receive Contact or File
.
6. Your mobile computer begins to exchange business cards. After the exchange, the new business card should appear in your
Contacts list.
Send a Contact
1. Make sure the other Bluetooth device is set up to receive a contact. It must support the OBEX Object Push server profile.
Refer to the documentation that came with the device for instructions.
Note: If the other device is also using the Bluetooth Connection Kit, you can set it up to receive a contact by tapping the
Bluetooth
2. Now you are ready to send a contact. Go to your Contacts folder.
icon. In the pop-up menu, tap
Transfer via Bluetooth
>
Receive Contact or File
.
10 - 14 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

3. Tap and hold your stylus on the contact(s) you would like to send. In the pop-up menu, select Send Via Bluetooth.
4. If your mobile computer has no devices in the Bluetooth Devices Folder, then it begins to search for Bluetooth devices
nearby.
5. Select the Bluetooth device you wish to send the contact(s) to. If the desired device is not listed, tap Find.
6. Your mobile computer processes and send the contact(s).
Send a File
1. Make sure the other Bluetooth device is set up to receive a file. It must support the OBEX Object Push server profile. Refer
to the documentation that came with the device for instructions.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 15

Note: If the other device is also using the Bluetooth Connection Kit, you can set it up to receive a file by tapping the
icon. In the pop-up menu, tap
2. Now you are ready to send a file. Tap on the Bluetooth icon. In the pop-up menu, tap Transfer via Bluetooth > Send a
File.
3. If your mobile computer has no devices in the Bluetooth Devices Folder, then it begins to search for Bluetooth devices
nearby.
4. Select the Bluetooth device you wish to send a file. If the desired device is not listed, tap Find.
Transfer via Bluetooth > Receive Contact or File
.
Bluetooth
5. In the next screen, tap on the file you wish to send. You can use the Folder and Type drop-down menus to search for your
file. Also, you can scroll horizontally to view the folder, date, size, type, and location of each file.
10 - 16 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

6. Your mobile computer sends the file.
Browse Remote Device
The Bluetooth File Explorer lets your mobile computer share files with another Bluetooth device. The other device must support
the OBEX File Transfer server profile.
This section covers the following file transfer operations:
• Prepare for file transfer
• Send/receive file(s) or folder(s)
• Create a folder
• Delete file(s) or folder(s)
• Refresh remote view
• Connect/disconnect
• Exit the program
Note: “Local device” refers to the mobile computer you are running the OBEX from. “Remote device” refers to the Bluetooth
device you are trying to transfer files with.
Prepare for File Transfer
1. Make sure the remote device has file sharing enabled. It must support the OBEX File Transfer server profile.
Note: If the other device is also using the Bluetooth Connection Kit, you can enable file sharing by tapping the
In the pop-up menu, tap
2. Now you are ready to browse the remote device. Tap on the Bluetooth icon. In the pop-up menu, tap Transfer via
Bluetooth > Browse Remote Device.
3. If your mobile computer has no devices in the Bluetooth Devices Folder that supports OBEX File Transfer, then it begins to
search for Bluetooth devices nearby.
Transfer via Bluetooth
>
Enable File Sharing
.
Bluetooth
icon.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 17

4. Select the Bluetooth device you wish to browse. If the desired device is not listed, tap Find.
5. Your mobile computer begins to establish a file sharing connection.
6. After the devices successfully connect, the Bluetooth File Explorer appears. Half of the screen shows contents of the remote
device, while the other half shows contents of your device (the local device). The very bottom of the screen reports the
connection status.
Send/Receive File(s) or Folder(s)
• Single-tap items to select them for transfer.
• Double-tap on a folders to open it and see its contents.
10 - 18 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

1. Select the file(s) or folder(s) that you wish to transfer. You can select items from only one device per transfer session.
2. There are two different ways to initiate the transfer:
• Tap on the File menu. Select Send to remote or Get from remote, as applicable. The inappropriate option should be gray.
• Tap on the Send to remote icon or Get from remote icon, as applicable. The inappropriate icon should be gray.
3. A screen reports the status of the transfer.
4. After the transfer, a copy of each selected item should appear in the other device.
Create a Folder
1. Tap on the File menu. Select Remote device or Local device, wherever you want to create a folder, then tap Create
remote folder or Create local folder, as applicable.
2. You can also tap and hold your stylus on an item in either the remote or local device that you wish to put in a new folder. In
the pop-up menu, select Create folder.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 19

3. In the next screen, enter a name for your new folder. Tap OK.
4. The new folder should be listed under the appropriate device.
Delete File(s) or Folder(s)
1. Select item(s) that you wish to delete. You can only delete item(s) from one device at a time.
2. Tap on the File menu. Select Remote device or Local device, wherever the item(s) are located, then tap Delete remote
item(s) or Delete local item(s), as applicable.
3. Tap and hold your stylus an item in either the remote or local device that you wish to put in a new folder. In the pop-up menu,
select Delete folder.
4. In the Confirm screen, tap Yes.
Refresh Remote View
1. Tap on the Device menu. Select Refresh remote view.
2. Your local device begins to read the contents of the remote device.
3. After a few seconds, the contents view of the remote device is refreshed.
Connect/Disconnect
To connect to the remote device, do the following:
1. Make sure the remote device has file sharing enabled.
10 - 20 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

2. Start the connection process by either of two methods:
• Tap on the Device menu. Select Connect.
• Tap on the Connect icon.
3. In the next screen, select the device you wish to connect to. Tap Select. Your mobile computer attempts to connect to the
device selected.
To disconnect from the remote device, do the following:
1. Start the disconnection process by either of two methods:
• Tap on the Device menu. Select Disconnect.
• Tap on the Connect icon.
2. Your mobile computer disconnects from the remote device. Afterwards, no contents are listed for the remote device.
Exit Bluetooth File Explorer
To exit the Bluetooth File Explorer, tap File > Exit.
Receive Contact or File
1. Tap on the Bluetooth icon. In the pop-up menu, tap Transfer via Bluetooth > Receive Contact or File.
2. The Receive Contact or File status screen appears. Your mobile computer waits two minutes for the contact or file.
3. After successfully connecting to the remote device, the screen reports Connected then disappear. The new contact or file
should now be on your device.
4. If two minutes passes before you receive the item, tap Wait Again.
5. After you receive the file or contact, the “Receive Contact or File” feature is automatically disabled.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 21

Enable File Sharing
1. Tap on the Bluetooth icon. In the pop-up menu, tap Transfer via Bluetooth > Enable File Sharing.
2. The Enable File Sharing status screen appears. Your mobile computer waits two minutes for the remote device to connect.
3. After successfully connecting to the remote device, the screen report Connected.
4. If two minutes passes before you connect, tap Wait Again.
5. File sharing is enabled until you end it by tapping Cancel.
Using the Dialer
This section explains how to assign a dialing prefix and use the Dialer to dial a number directly from your Contacts list. The Dialer
makes it quick and easy to perform dial-up networking.
Note: The Dialer has been verified to work with Nokia and Ericcson phones and is known not to work with the Motorola 270c,
NTT Docomo Paldio 633S or Sony au C413S phone. Results may vary with other phones that are not listed as being supported
by the Bluetooth system.
Assign a Dialing Prefix
If you have not already assigned a dialing prefix during the install process, you can do so by following these steps:
1. Go to Start > Settings > System tab. Tap on Dialer.
2. Select the appropriate Dialing Prefix, then tap OK.
Using the Dialer
1. To use the dialer, the mobile computer must already be connected to the Bluetooth phone. You can use the Get Connected!
Wizard to do this. Also, the Bluetooth phone must be selected as your favorite.
2. Go to Start > Contacts.
10 - 22 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

3. Tap and hold your stylus on the contact you wish to dial to. In the pop-up menu, select Dial Contact. Alternatively, you can
tap on Tools and select Dial Contact.
4. If you have multiple phone numbers for a contact, a screen appears listing them, including any dialing prefix you may have
assigned. Select the phone number you wish to dial.
5. Your mobile computer connects to your phone and begins dialing.
The Dialer can dial a phone number containing any of the following non-numeric characters:
*#+./!@-\space A B C D T P W
The following string can also be included in a phone number: (',')
The Dialer cannot dial a phone number containing non-numeric characters other than those listed above. Hand Held Products
recommends that you follow the standard Microsoft Outlook format for phone numbers.
Get Connected Wizard
The Get Connected! Wizard guides you through a one-time setup process that prepares the mobile computer and phone for
Bluetooth connections. The wizard varies depending on what phone you want to connect to.
Ericcson, Nokia 6210, NTT DoCoMo, Sony Phones
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 23

1. Tap on the Bluetooth task tray icon. In the pop-up menu, select Get Connected!
2. Follow the Bluetooth “Get Connected!” Wizard. In the second screen, use the drop-down list to select your Bluetooth phone.
The wizard provides tailored instructions based on your selection.
3. Follow the next screen(s) to prepare your specific phone for Bluetooth connections. You may need to do 1, 2 or all of the
following steps:
(a) Naming your Bluetooth phone
(b) Setting your Bluetooth phone in Discoverable mode
(c) Preparing your Bluetooth passkey.
1. When the search is complete, a list of the discovered Bluetooth phones appears. Choose the phone you wish to connect to,
and tap Select. A service discovery phase begins, about 5-10 seconds.
2. As prompted in the next screen, prepare your phone for bonding. For instructions on setting your phone to “Bondable” or
“Pairable” mode, refer to your phone manual. Have your passkey ready, then tap Next>.
10 - 24 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

3. In the next screen, enter the passkey. Tap Reply.
4. The mobile phone may then either automatically accept the passkey or ask you to enter one. If prompted for a passkey, use
the same one you entered on the mobile computer.
Ericsson T68/T68i only: When the phone asks you if you want to bond, select 2: Add to paired devices. Do not tap ACCEPT.
5. Tap Finish. After successfully connecting, the phone appears in the Bluetooth Devices folder. On the Today screen, the
Bluetooth icon blinks. You do not need to run the Get Connected! Wizard again unless you plan to switch between different
phones.
Note: You may also switch between different phones by assigning a new “favorite phone” in the Bluetooth Devices folder.
Motorola Timeport 270C, Nokia 3650/6310/7650/8910/8910i
1. Tap on the Bluetooth task tray icon. In the pop-up menu, select Get Connected!
2. Follow the Bluetooth “Get Connected!” Wizard. In the second screen, use the drop-down list to select your Bluetooth phone.
The wizard provides tailored instructions for your phone.
Note: The screens below are for the Nokia 7650.
3. As directed on the next two screens, assign the phone a unique name, set the phone to Discoverable mode, and tap Next.
4. The mobile computer searches for the phone. When the search is over, a list of the discovered Bluetooth phones appears.
5. Choose the phone you want to connect to, and tap Select. A service discovery phase begins, about 5-10 seconds.
6. The next two screens describe procedures you complete outside of the wizard. Read through each screen but do not
complete the described procedures until you exit the wizard.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 25

Bonding with your phone - This must be completed to establish the Bluetooth connection and involves dial-up
networking.
Automatic Connections - This procedure is optional but makes future Bluetooth connections more convenient.
7. Continue to the last screen of the wizard and tap Finish. Now proceed to STEP 6 to complete the bonding process and, if
desired, set up automatic connections.
Dial Up to Your Network
Complete the following steps to create a new Bluetooth internet connection. Before setting up dial-up networking, prepare
yourself with dial-up information and other necessary settings from your office network or ISP.
Note: For more information about modem connections, see Creating an External Modem Connection to an ISP on page 7-21.
1. Go to Start > Settings > Connections tab > Connections.
2. In the top field, select Internet Settings and tap Modify. Then, tap New.
10 - 26 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

3. Enter a name for the connection. Remember what you name the connection. In the future, you will need to select it to start
the connection.
For the modem, select Bluetooth Phone.
For the Baud Rate, select 115200.
If you want to configure Port Settings, TCP/IP, or Name Server settings, navigate to the setting and tap Advanced.
4. Tap Next.
5. In the Phone number field, enter the dial-up number. Tap Next.
6. Uncheck Wait for dial tone before dialing. Tap Finish.
7. Now you are ready to start the connection. In the Connections screen, under Internet Settings, tap Connect. In Network Log
On, verify the dialing settings. Tap OK.
ONLY FOR MOTOROLA TIMEPORT 270C OR NOKIA 3650/6310/7650/8910/8910i:
h) After you tap Connect for the first time, the phone displays a message asking if you want to bond. On Motorola, enter
GRANT; on Nokia, enter ACCEPT.
i) Make up a 4-16 digit passkey, enter it on the phone, then enter it on the terminal.
Note: The Bluetooth icon on the Today screen blinks to indicate a connection.
j) After successfully bonding, you can set up the phone to automatically connect to your Dolphin 7900 without a passkey.
Automatic Connections for Motorola Timeport 270C:
• On the phone, press MENU.
• Scroll to Settings, then press SELECT.
• Scroll to Connection, then press ON.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 10 - 27

• On Bluetooth Link, press SELECT.
• Scroll to Devices, then press SELECT.
• Choose your mobile computer, then press EDIT.
• Scroll to Access:Ask, then press CHANGE.
• Scroll to Automatic, then press SELECT. Press DONE.
Automatic Connections for Nokia 3650/7650:
• On the phone, press MENU.
• Scroll to Connectivity, then press OPTIONS.
• The Open option should be highlighted. Press SELECT.
• The Bluetooth option should be highlighted. Press OPTIONS.
• The Open option should be highlighted. Press SELECT.
• Scroll to the right tab to access the Paired devices list. Highlight your mobile computer, then press OPTIONS.
• Scroll to Set as authorized, then press SELECT.
• In the confirmation screen, press YES.
Automatic Connections for Nokia 6310/8910/8910i:
• On the phone, press MENU.
• Scroll to 10 Bluetooth, then press SELECT.
• Scroll to 4 View Paired Devices, then press SELECT.
• Highlight the Dolphin 7900, then press OPTIONS.
• Scroll to 3 Request Connection Authorization, then press NO.
To use a different Bluetooth phone for dial-up networking, you can use the same connection setup, but you must make the new
phone your favorite. Just run the Get Connected! Wizard again, select the new phone, and make it your new Favorite when
prompted.
10 - 28 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

11
Wireless WAN Communications with GSM/GPRS
Overview
Dolphin 7900 terminals can be configured with a Wireless Wide Area Network (WWAN) via an integrated Siemens® GSM/GPRS
tri-band radio module.
GSM GSM stands for Global System for Mobile communications. It is an open, non-proprietary wireless
GPRS GPRS stands for General Packet Radio Service. It is a non-voice value added service that allows
Enabling the GSM/GPRS Radio Driver
When the mobile computer is first initialized, the radio driver for the GSM module is installed. Before using the radio, make sure
that the GSM radio is enabled. For more information, see Radio Manager on page 4-6.
Frequencies
A Dolphin 7900 terminal can support the MC-45 or MC-46 frequency.
MC-45 Supports 900/1800/1900 MHz frequencies in Europe, Middle East, and Asia. Dolphin terminals with
MC-46 Supports 850/1800/ 1900 MHz frequencies in US, Latin America, and Canada. Dolphin terminals with
With the exception of two-way voice communication, which applies only to the MC-45 radio, the features described in this chapter
apply to both the MC-45 and MC-46.
wide area networking system that is constantly evolving and growing. One of its great strengths is
international roaming capability, which provides standardized dialing in more than 170 countries.
packet switched data and information to be instantly sent and received across a network.
an MC-45 radio have two-way voice and data communication.
an MC-46 radio have two-way data communication only.
Tri-Band Antenna
Dolphin 7900 terminals configured with an MC-45 or MC-46 radio feature a tri-band antenna..
Requirements
Using GMS/GPRS on a Dolphin 7900 terminal requires:
• a network subscription to a GSM/GPRS network (you need to know what service providers are in your geographic area), and
• a SIM card installed on the terminal ((see SIM Card on page 11-2).
Capabilities
Dolphin 7900 computers with integrated GSM/GPRS radios are optimized for the following two-way voice and data
communications:
• GSM voice data ("dial-up")
• Short Message Service (SMS) text messages
• GPRS Class 10 - data transmissions average. 40-60 Kbps (the speed is dependent on the wireless network carrier)
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 1

SIM Card
SIM stands for Subscriber Information Module. A SIM card stores the subscriber's personal information, GSM/GPRS radio
settings, security key, contacts, etc. SIM cards can be installed and removed from compatible mobile devices, enabling you to
switch devices without losing your personal information. SIM cards are obtained and activated by the network provider that
supports your GSM/GPRS network.
SIM Card Requirements
Before installing the SIM card:
•The SIM card must be activated by the service provider.
• The terminal must be powered down.
To Install a SIM Card
For detailed instructions, see Opening the Access Door on page 3-6.
If the SIM card is not installed properly, the Dialler screen (page 11-5) will indicate that no SIM card is installed.
Note: If no SIM card is installed, you can still make emergency phone calls such as 9-1-1, for example.
11 - 2 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Using uPhone
The uPhone Application Suite contains three programs that function together to provide a complete voice, data, and text
messaging solution for a mobile device fitted with a radio modem:
• Dialler emulates a mobile phone and is used to make and receive telephone calls - Using the Dialler, page 11-5.
• Call Log enables you to view and manipulate a list of the most recent calls - Call Log, page 11-14.
• SMS Manager provides a text message handler similar to many email programs - SMS Manager, page 11-16.
Note: Because the uPhone application operates two-way voice communication for the GSM radio, you cannot use uPhone for
anything but emergency phone calls with the MC-46 radio.
Accessing uPhone
Go to Start > Programs > uPhone. Tap one of the icons to launch the program.
Navigation Bar
When the Dialler or SMS Manager applications are not open, the icons in the Navigation bar at the top of the screen indicates
the status of the phone and messaging system. Each icon indicates s specific action and, when tapped, displays a bubble window
that lets you know what is happening.
Status Icons and Bubble Options
Icon This icon means… Tapping this icon displays this bubble: Bubble Options
The phone is off. Tap Power Phone On to turn the
The phone can only make
emergency calls. This
usually means there is no
SIM card installed or PIN
number established.
The phone is registering
on the network.
phone on and close the bubble.
Tap Hide to leave the phone off
and close the bubble.
Tap Hide to dismiss the bubble.
This icon will appear in the
Navigation bar until a SIM card is
installed or a PIN is entered.
Tap Hide to dismiss the bubble.
This is a temporary state. This
icon appears only until the phone
is registered on the network.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 3

Status Icons and Bubble Options
Icon This icon means… Tapping this icon displays this bubble: Bubble Options
The phone is on and
registered.
To the right of the phone is
a bar that indicates signal
strength.
Indicates medium signal strength.
Indicates good signal strength.
Indicates full signal strength.
Tap Hide to dismiss the bubble.
Tap Power Phone Off to turn off
the phone. The icon in the
Navigation bar changes to
indicate the phone is now off.
Incoming SMS message
available.
A new voicemail message
is available.
There is a call in progress
to the name or number
shown in the bubble.
(This icon is showing full
signal strength; the icon
will change according to
the current signal
strength.)
This bubble appears automatically when a
new SMS message is received. It contains
the sender’s information and the first line of
the text message.
This bubble appears automatically when a
voicemail notification is received.
Tap View to display the full
message in SMS Manager.
Tap Reply to switch to the SMS
Manager Compose screen. The
'To:' field is auto-filled with the
sender’s address.
Tap Save to put the message in
the SMS Manager Inbox.
Tap Delete to delete the
message.
Tapping each button closes the
bubble.
Tap Call Answerphone to dial
the Answerphone service and
retrieve voicemail messages. To
set up Answerphone, see,
uPhone Configuration, General
Tab, page 11-21.
Tap Hide to close the bubble.
Tap Hide to close the bubble.
Tap End to end the call.
11 - 4 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Status Icons and Bubble Options
Icon This icon means… Tapping this icon displays this bubble: Bubble Options
This icon appears when
there is a call coming in or
going out.
A different bubble displays
for each circumstance.
If the incoming call is a
conference call, a different
bubble displays.
For a call going out Tap Hide to close the bubble.
Tap End to end the call.
When a call is coming in, this bubble displays
while the ringtone sounds.
If the caller is in the Phonebook,
the name displays. If not in the
Phonebook, the caller’s number
displays; if the number can’t be
read, “no number” displays.
Tap Answer to answer the call;
this places any current call on
hold.
Tap Reject to reject the call.
Using the Dialler
The Dialler is the is the program that manages your GSM/GPRS cell phone calls.
To launch the Dialler, tap Start > Programs > uPhone > Dialler. The program launches and the uPhone Dialler screen opens:
Dialler screen
Signal Strength
Tap to send (make) a call or
accept an incoming call
Three information lines:
Network Operator name of service provider.
Number/Name - number/ name of dialed,
incoming, and outgoing calls.
Status - displays the status of the phone.
Tap to end a call
Tap to clear the Dialler
Phone keypad - tap the numbers to dial
interactive voice systems; also
Tap * and # buttons for
known as touchtones.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 5

Making a Call
To Enter a Number
Cingular
You can:
• Enter the numbers manually using the phone keypad on the Dialler screen, the SIP, or the Dolphin keyboard.
As you enter each number, the digits appears on the Dialler screen in the Name/Number line. If a contact matching
the entered number is found in the Phonebook, the name of the contact appears in the Name/Number line as you
type; tapping on the name enters the rest of the number automatically.
• Use the Phonebook - Phonebook, page 11-9 - to
• Select an existing contact.
Tap Tools > Phonebook, select a name or number in the list, and tap OK (you can also tap and hold on the entry).
The number is automatically entered in the Dialler and appears on the screen.
• Use speed dial.
Tap and hold on the list to see a popup menu of speed dial numbers.
• Use the Call Log - Call Log, page 11-14.
When the phone is in Idle status, you can tap the Send button on the screen , press the OK key, or tap
Tools > Call Log to see a list of the last 20 calls made or received. Tap and hold on an entry in the list and select
Dial.
Pressing the Send button or OK key performs this function only when the phone is in an Idle Status.
To Send a Call To a Dialed Number
You can:
• Tap the Send button .
• Press the OK key on the keyboard.
• Press the appropriate key combination on the keyboard - Keyboard Combinations for Calls, page 11-8.
When the call is connected, the three information lines display the following:
Joe Smith
Network Operator Displays the name of the service provider you are using.
Name/Number Displays the name and/or number you called. If the number is from your Phonebook, that entry
Status The status of the call.
0:00 The numbers in the lower, right corner display the minutes:seconds that have elapsed.
displays in the Number/Name (2nd) line.
Idle - means no calls are incoming or outgoing.
In Call - means a phone call is in progress.
Incoming Call - means that a a call is coming in.
11 - 6 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Receiving a Call
When the Dialler screen is open and an incoming call is detected, text is displayed on the Dialler screen. If the Dialler is not visible
at the time of the incoming call, a Navigation Bar notification appears; see Status Icons and Bubble Options on page 11-3.
When a call is coming in, the ringtone sounds and the three information lines on the Dialler screen display the following:
Network Operator Displays the name of the service provider you are using.
Name/Number Displays the name and/or number calling in. If the number is in your Phonebook, that entry displays.
Status Incoming Call.
To Answer a Call
To answer a call, you can:
• Tap the Send button .
• Press the OK key on the keyboard.
• Press the appropriate key combination on the keyboard - Keyboard Combinations for Calls, page 11-8.
To Reject a Call
You can:
• Tap the End button .
• Press the appropriate key combination on the keyboard - Keyboard Combinations for Calls, page 11-8.
Call Waiting
If call waiting is enabled, a second incoming call can be received while a first call is in progress. The second incoming call uses
a different ringtone but displays the same incoming call notification.
If a second call is coming in, answering it (see To Answer a Call on page 11-7) automatically places the first call on hold. You
can also reject the second call; see To Reject a Call on page 11-7.
Ending a Call
To end or reject a call, you can:
• Tap the End button .
• Press the appropriate key combination on the keyboard.
Call Waiting If two calls are in progress, the above options end the active call and place the other on hold.
To activate the call on hold, tap Send or press OK or the key combination to send calls.
To end the call on hold, tap End or press the key combination to end calls on the keyboard.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 7

Conference Call If a conference call is in progress, tap End or the key combination to end calls.
Keyboard Combinations for Calls
Each keyboard option contains a Blue modifier key combination to send and end a call.
Keyboard To Send, Press… To End (reject), Press…
25-key keyboard Blue + Left Arrow Blue + Right Arrow
36-key keyboard Blue + Left Arrow Blue + Right Arrow
For more information about Dolphin 7900 keyboards, see Using the Keyboards on page 6-1.
Call Waiting
The uPhone Dialler supports call waiting functionality. This means that you can receive a second call while on a first call.
Placing a Current Call on Hold
When a second call is coming in, to place the current call on hold
• Tap the Send button .
• Press the OK key on the keyboard.
• Press the key combination for sending calls on the keyboard.
The Status line of the first call changes to Call on Hold.
Tapping Send again restores the call on hold.
Making a Second Call To make a second call, place the current call on hold, then dial the second number. When there are
Switching Between Calls To switch between the active and held call, tap Send , press OK, or the appropriate key
two calls (one active and one held) the status line displays In Call, Call on Hold.
combination to send calls. The display is updated to show the active call details, and that the other
call is on hold.
Making Conference Calls
In addition to supporting call waiting functionality, the uPhone Dialler enables you to join two calls into a conference call.
11 - 8 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

When two calls are in progress, tap the phone icon on the Navigation bar. This opens a bubble dialog that enables you to
conference both calls into one.
Button Tapping this button…
Swaps between the currently held and active calls.
Hold Active and Accept Held
End Active and Accept Held
Join Held in Conference Call
End Held
Tapping Send , or pressing OK performs the same function without opening this
bubble dialog.
Drops the current active call and connects the held call.
Connects the held call and the currently active call in a three-way conference call.
More than three parties can join a conference call via networking; each of the other
parties can add another call to the conference, and so on.
Drops the held call, and continues with the currently active call.
Hide
Closes the bubble.
Touchtones
To transmit touchtones for interactive voice systems while in a call, you can
• Tap the 0-9, *, and # buttons on the uPhone Dialler screen.
• Press 0-9 keys on the Dolphin keyboard; use the uPhone Dialler screen buttons for * and #.
Volume Control
Use the Dolphin keyboard to manually adjust the speaker volume.
To raise the volume, press the Blue modifier key + Up arrow.
To lower the volume, press the Blue modifier key + Down arrow.
Phonebook
The Phonebook contains the contacts from the SIM card and Pocket Contacts. If fixed dialing is set in the SIM, then only those
numbers in the fixed dialing list are shown in the Phonebook, and only these numbers can be called from the Dialler.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 9

You can access the Phonebook manually by opening the Dialler and going to Tools > Phonebook. When you tap and hold on
an entry, a popup menu displays.
Dial Opens the Dialler with the number entered ready for dialing.
Send SMS Opens the SMS Manager in the Compose screen with the 'To:' field populated with the number.
Speed Dial 2-9 These eight slots are used to assign the Dialler Speed Dial keys. To assign a number to a Speed Dial
slot, tap on an entry to assign the number.
Tapping and holding the associated button when in Dialler will automatically dial the assigned
contact.
Tools Menu
The Tools menu provides the following options:
Select this item To…
Phonebook Display the Phonebook.
Call Log Switch to the Call Log.
SMS Manager Switch to the SMS Manager Inbox.
Select Skin Allow selection of a new skin for the uPhone Dialler application.
Configuration Open the uPhone Configuration control panel
Ringtones Switch to the ring tone selection control panel.
Exit Exit the uPhone Dialler.
11 - 10 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Settings Menu
The Settings menu provides the following options:
Speakerphone Toggles speakerphone mode on and off. When an audio plug (for a headset) is inserted into the audio
Mic mute Toggles microphone mute on and off (the other party cannot hear a private conversation when the
A checkmark to the left of the entry indicates that the mode is active. When the entry is grayed-out, it is unavailable and cannot
be selected.
jack (2.5mm), Speakerphone is inactive on this menu.
microphone is muted). This mode is active only during a call and automatically cancelled at the end
of a call.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 11

Audio Modes
The back panel of the Dolphin 7900 contains both a speaker and a microphone that you can use to send and receive audio
signals over the GSM network. For details about the microphone and speaker on the back panel of the Dolphin 7900, see Back
Panel Features on page 3-4.
There are three audio modes:
1. Handset
2. Headset
3. Speakerphone
Handset
Handset mode is when you use the use the back panel of the terminal just as you would a cell phone, holding the speaker to your
ear to receive audio information and the your mouth over the microphone to send audio information.
This is the default audio mode.
Headset
Headset mode is when you plug a headset into the audio jack and speak into the microphone. You must use a 2.5mm plug; no
other audio plug will fit.
Speakerphone
Use the microphone on the front panel (Microphone, page 3-3) as a speakerphone.
To switch the front panel to speakerphone, in the Dialler, tap Settings > Speakerphone. The audio levels adjust appropriately
for speakerphone use. For more information, see Settings Menu on page 11-11.
11 - 12 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Ringtone Configuration
Different ringtones, with individual volume settings, can be set for the following:
Ring Tone Sounds on an incoming call.
Message Tone Sounds on an incoming SMS or Voicemail notification.
Call Waiting Tone Sounds to indicate an incoming call while you are already on a voice call.
Accessing Ringtone Configuration
You can access Ringtones two ways:
1. Go to Start > Settings > Personal tab > Ringtones icon OR
2. Open the Dialler (tap Start > Programs > uPhone > Dialler) and go to Tools > Ringtones.
The Ringtones screen opens displaying the current settings.
Select the desired ringtone for each type of tone in the drop-down lists. Tapping OK saves any changes. Opening another screen
without tapping OK discards any changes.
WAV Files
You can customize your ringtones with *.wav files installed on your terminal. To appear here, *.wav files must be stored in the
Programs Files > uPhone >Ring Tones folder.
Previewing Tones
You can preview each tone by selecting the *.wav file in the drop-down list and tapping the Preview button. Use the slider to set
the volume for each tone.
While the tone is playing, the Preview button changes to a Stop button; tap it to stop the preview.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 13

Call Log
The Call Log maintains a list of the last 20 calls made or received in each of the following categories:
•Voice Calls In
•Voice Calls Out
• Voice Calls Missed
•GPRS Data
Voice Call In is the default display whenever the Call Log is opened.
Call Log Options
Select the option you want to view. To see everything, select All Calls.
Opening the Call Log
You can access the Call Log two ways:
1. Go to Start > Programs > uPhone > Call Log) OR
2. Open the Dialler (go to Tools > Call Log).
The Call Log opens displaying the last few Voice Calls In; the most recent call always appears at the top.
This column Displays the …
Name The phone number or the name if the call was from or to a matching entry in the Phonebook.
Time Time and date the call started. This is the local time and date.
Duration Duration of the call (hours:minutes:seconds). The clock starts when the call connects, not when
dialed.
11 - 14 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Tools Menu
The Tools menu in the Call Log provides the following options:
Select this menu option To…
Clear Delete the entire Call Log.
Exit Close the Call Log.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 15

SMS Manager
Abbreviated for Short Message Service, SMS enables the transmission of short messages (140-160 characters) to and from a
cell phone. SMS messages travel over the system's control channel, which is separate from the voice channel.
The SMS Manager on the Dolphin 7900 supports creation, sending, receiving, and storing of SMS text messages. Text
messages sent or received can be up to 160 characters long.
Opening the SMS Manager
You can access the SMS Manager two ways:
1. Go to Start > Programs > uPhone > SMS Manager, OR
2. Open the Dialler (Start > Programs > uPhone > Dialler) and go to Tools > SMS Manager. The SMS Manager opens to the
Inbox, which displays a list of your most recent text messages.
Folders
There are three folders: Inbox, Sent, and Outbox. Tap the Inbox folder to see all three folders. The name of the folder appears
in the gray bar just under the title bar.
Tap here
Note: Click the SMS box to expand and collapse the folders.
11 - 16 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Inbox
The Inbox folder displays received text messages. Received messages have an envelope icon to the left. The Inbox folder also
receives error messages from text messages that could not transmit successfully.
When the Inbox folder is selected, received messages appear in the list.
To Do this…
Open a message Tap on the message and the content of the message appears.
Delete a message Tap and hold on the message. A popup menu appears that enables you to delete the message. Tap
Delete.
Sent Folder
The Sent folder displays sent messages.
Outbox Folder
The Outbox folder displays text messages waiting to be sent.
Sending an SMS Message
1. In the task tray at the bottom of the screen, tap New. The new message screen opens with the cursor active in the text area.
2. Tap inside the To: field. To add the number, you can type it in or tap To:
• You must type a number that is in the appropriate international ISDN format for the country you are dialing. However,
you can dial a local number without the country code.
• Destination numbers
can
start with a “+” sign.
to select an entry from your Phonebook.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 17

3. Tap inside the text area. To write a message, you can use the SIP or the terminal keyboard.
The Remaining characters field displays how many characters you can type in a message. Because 160 is the maximum
number of characters per message, the number portion of the field counts backwards from160 as you type.
4. When finished typing, tap the Send icon to transmit the message .
If you tap OK before tapping Send, the program requests confirmation before discarding the message.
5. The Sending message box appears over the message.
6. When the message has been sent, the Message sent box appears.
Icons at the Top of the Message Screen
Tap this icon To…
At the top of the window:
Copy selected text.
Cut selected text.
Paste text.
Undo the previous action.
11 - 18 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Icons at the Top of the Message Screen
This icon appears only in a message that has been
sent. Tapping this button will re-send the message.
In the task tray at the bottom of the window:
Send all messages in the Outbox.
Edit Menu
The Edit menu in the command bar provides the same options as the icons at the top of the screen, with the following additional
options:
Select All Selects all text in the active message section.
Clear Selection De-selects all text in the active message section.
Online Help
Tapping Help > About provides information about the uPhone applications.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 19

uPhone Configuration
uPhone Settings enable you to establish the normal operating parameters for uPhone applications.
Accessing
You can access uPhone Settings two ways:
1. Go to Start > Settings > System tab > uPhone icon.
2. In the Dialler application, selecting Tools > Configuration.
3. The configuration utility opens displaying the General Tab (page 11-21).
Requirements
Because you will be adjusting network settings, the GSM radio must be enabled, and a SIM must be installed for it to open
correctly. If not, you will receive a notification message when you try to open the control panel.
If the radio is enabled and a SIM installed, the following message displays while the system accesses the network:
“Settings on the Network are being accessed. Please wait…”
If there is no response from the network within 60 seconds, this message times-out and the control panel closes. Otherwise, the
uPhone Settings screen displays; the General tab appears first by default.
Tab Windows
uPhone Settings consists of five tabs: General, Network, Divert, Bar, Messaging, and Other.
Tapping OK accepts any changes and exits the uPhone Settings.
11 - 20 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

General Tab
Field Description
Phone Number This is the phone number stored on the SIM. It is displayed here for information only.
Answerphone This is the number to dial to retrieve voicemail messages. To enter a new number, tap on this field
Call waiting Select On or Off to enable or disable call waiting functionality. Call waiting must be set to On for
PIN protection Select On or Off to enable or disable PIN protection. If enabled, a PIN number is requested when the
Change PIN This button is active only if PIN protection is set to On. Otherwise, the button is grayed-out.
and enter the digits.
conference calls.
phone is switched on.
If you tap Change PIN, a dialog box appears enabling you to change the PIN.
In the Old PIN field, enter the current PIN, then enter the new PIN in the New PIN and Confirm PIN
fields. Tap OK to save the change. If you do not tap OK, the old PIN remains in effect.
While typing, the numbers appear as asterisks to protect the number from observation by third
parties.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 21

Network Ta b
The Network tab provides the ability to choose between Automatic and Manual network selection.
If you choose Manual network selection, the drop-down list of available networks activates. Choose a network from this list and
tap OK. A wait icon appears while the system accesses the selected network.
11 - 22 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Divert Tab
The divert tab enables you to select divert options for incoming calls when you are unavailable to answer; e.g., when the phone
is off, you are out of network coverage, busy, or not able to answer.
Select an option from the All Calls drop-down list to divert all incoming calls automatically.
Select an option from the Unavailable drop-down list to divert incoming calls when you are unavailable.
The options in both lists are as follows:
Not Diverted Select this option to not divert calls. This is the default setting.
Answerphone Select this option to divert calls to voicemail.
To number Select this option to forward incoming calls to another number. Enter that number in the field below
the drop-down list.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 23

Bar Tab
The Bar tab sets enables you to block both incoming and outgoing calls.
Bar outgoing calls Select one of the following options from the drop-down list:
Not barred No restrictions on outgoing calls.
International calls Bar international calls.
International except to
home country
All outgoing calls Bar all outgoing calls.
Only international calls to the home country designated on the SIM
card can be made.
Bar incoming calls Select one of the following options from the drop-down list:
Not barred No restrictions on incoming calls.
Incoming calls when
roaming
All incoming calls Bar all incoming calls.
Change barring code Tap this button to change the barring code. A dialog box appears that enables you to change the
barring code.
In the Old code field, enter the current code, and enter the new code in the New code and the
Confirm code fields. Tap OK to save the change. While typing, the numbers appear as asterisks to
protect the number from observation by third parties. To save the barring options, tap OK. The system
displays a dialog requesting the barring password before sending the updated settings to the network.
Type in the password and tap OK.
Bar incoming calls when the network coverage is in roaming status.
11 - 24 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Messaging Tab
The Messaging tab enables you to adjust the default SMS settings.
Request Delivery Reports By default, the SMS manager receives a confirmation report that each SMS message has been
sent. For details, see Sent Folder on page 11-17.
These confirmation reports can take up valuable space and memory. Therefore, you can cancel
these reports on this tab by selecting Off and tapping OK.
SMS number of retries This setting enables you to control the number of times the system will try to send an SMS
message until the message is sent. Nine is the default number. To change the default, enter
the number in the field and tap OK.
Other Ta b
The Other tab contains settings that apply only to an MC-46 GSM radio.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 25

GPRS Settings
After subscribing to a GPRS network and installing your SIM card, you can load the parameters of your GPRS subscription into
the terminal. However, some subscriptions load automatically when you install your SIM card. If the GPRS settings do not load
automatically, you must enter them manually.
Because GSM/GPRS technology uses a network connection, you need to configure those settings in the Connection Manager
(see Connections Tab on page 7-19). uPhone does include a pre-configured GPRS connection for Internet settings, but you can
also configure GPRS settings for browsing the web via a VPN or Proxy Server.
Requirements
You must select or create GPRS settings prior to making a GPRS call for the first time. Make sure that you are not using
ActiveSync when configuring the connection settings.
To establish a GPRS connection, you need to use the information from your network service provider. Given that there can be
so many different configurations, such as VPN or Proxy Server connections, see Connections Tab on page 7-19 for instruction
about how to set up each kind of connection.
To Select the Pre-Configured GPRS Settings
1. Go to Start > System > Connections tab > uPhone GPRS. The GPRS Settings screen appears displaying the default
GPRS settings.
The Current Profile drop-down list contains a number of pre-configured connection profiles.
2. If the profile associated with your account appears in the Current Profile list, select it. If your account profile does not appear
in the list, you need to create one. For details, see To Add a GPRS Setting on page 11-27.
3. In the Details section,
• Type in the APN number and the IP address
• Select the Protocol
4. Tap OK to save.
Note: Select
Reset security settings
11-27.
to reset the username and password for your profile; see To Add a GPRS Setting on page
11 - 26 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

To Add a GPRS Setting
1. On the GPRS Settings screen, in the Current Profile drop-down list, select Add new.
2. Type in the Profile Name, APN, IP Address, and select the Protocol.
3. Tap OK. You return to the settings screen. The Profile Name you selected now appears in the Current Profiles list.
GPRS Connection
When a GPRS connection is required - e.g., by navigating to a web site - a Network Log On screen is automatically displayed.
Enter the Password and Domain, then tap OK to connect.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 11 - 27

You have the option of disconnecting by tapping on the GPRS connection icon in the navigation bar and tapping End.
11 - 28 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

12
Applications
Dolphin 7900 terminals ship with the following Microsoft applications installed:
• Calendar (page 12-1)
• Contacts (page 12-3)
• Tasks (page 12-6)
• Notes (page 12-7)
• Messaging (page 12-8)
• Pocket Internet Explorer (page 12-11)
• Pocket Word (page 12-14)
• Pocket Excel (page 12-16)
• Windows Media Player for Pocket PC (page 12-18)
• MSN Messenger (page 12-19)
• Pictures (page 12-20)
Note: Microsoft® Money, Microsoft® Reader are NOT installed on the Dolphin 7900 when shipped but may be installed from the
Microsoft Companion CD.
Calendar
Use Calendar to schedule appointments, including meetings and other events. You can check your appointments in one of
several views (Agenda, Day, Week, Month, and Year) and easily switch views by using the View menu.
Note: You can customize the Calendar display, such as changing the first day of the week, by tapping the Tools menu.
Creating an Appointment
1. If you are in Day or Week view, tap the desired date and time for the appointment.
2. Tap New.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 1

3. Using the input panel, enter a description and a location. Tap first to select the field.
4. If needed, tap the date and time to change them.
5. Enter other desired information. To see all available fields, hide the input panel.
6. To add notes, tap the Notes tab. You can enter text, draw, or create a recording.
For more information on creating notes, refer to Notes on page 12-7.
7. When finished, tap OK to return to the calendar.
Note: If you select Remind me in an appointment, you will be reminded according to the options set in
Personal tab > Sounds & Reminders.
Using the Summary Screen
When you tap an appointment in Calendar, a summary screen displays the details of the appointment.
Start
> Settings >
12 - 2 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Creating Meeting Requests
You can use Calendar to set up meetings with users of Outlook or Pocket Outlook. The meeting request is created automatically
and sent either when you synchronize Inbox or when you connect to your e-mail server. Indicate how you want meeting requests
sent by tapping Tools and then Options. If you send and receive e-mail messages through ActiveSync, select ActiveSync.
Scheduling a Meeting
1. Create an appointment.
2. In the appointment details, hide the input panel, and then tap Attendees.
3. From the list of e-mail addresses you’ve entered in Contacts, select the meeting attendees. The meeting notice is created
automatically and placed in the Outbox folder.
For more information on sending and receiving meeting requests, see Calendar Help and Inbox Help.
Contacts
Contacts maintains the contact information - phone numbers, e-mails, addresses, etc. - you need on your terminal.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 3
Note: To change the way information is displayed in the list, tap
Tools
>
Options
.
Creating a Contact
1. On the Contacts screen, tap New.
2. Using the SIP or Dolphin keyboard, enter the contact’s information. Scroll down to see all available fields.
3. To assign the contact to a category, scroll to and tap Categories, then select a category from the list.
(In the contact list, you can display contacts by category.)
4. To add notes about this contact, tap the Notes tab. For more information on creating notes, refer to Notes on page 12-7.
5. When finished, tap OK to return to the contact list.
Searching for Contacts
There are four ways to find a contact:
• In the contact list, enter a contact name in the box under the navigation bar. To show all contacts again, clear text from the
box or tap the button to the right of the box.
• In the contact list, tap the category list (labeled All Contacts by default) and select the type of contact that you want displayed.
To show all contacts again, select All Contacts. To view a contact not assigned to a category, select None.
• To view the names of companies your contacts work for, in the contact list, tap View > By Company. The number of contacts
that work for that company are displayed to the right of the company name.
•Tap Start > Find, enter the contact name, select Contacts for the type, and then tap Go.
12 - 4 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Using the Summary Screen
When you tap a contact in the contact list, a summary screen displays their information.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 5

Tasks
Note: To change the way information is displayed in the list, tap Tools > Options.
Creating a Task
1. Tap New.
2. Using the SIP or Dolphin keyboard, enter the task information.
If the input panel is open, you need to hide it to see all available fields.
3. Tap Starts to enter a start date and/or Due to enter a due date for the task.
4. To assign the task to a category, tap Categories and select a category from the list.
In the task list, you can display tasks by category.
5. To add notes, tap the Notes tab.
For more information on creating notes, refer to Notes on page 12-7.
6. When finished, tap OK to return to the task list.
12 - 6 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Note: To quickly create a task with only a subject, tap
enter your task information.
Entry Bar
on the
Tools
menu. Then, tap Tap here to add a new task and
Using the Summary Screen
When you tap a task in the task list, a summary screen displays the task information.
Notes
Quickly capture thoughts, reminders, ideas, drawings, and phone numbers with Notes. If a note is open when you create the
recording, it will be included in the note as an icon.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 7

Creating a Note
1. Tap New.
2. Type your note using the SIP or the Dolphin keyboard.
Messaging
Use Messaging to send and receive e-mail messages; this is your email Inbox. To use e-mail, you can:
• Synchronize e-mail messages with Microsoft Exchange or Microsoft Outlook on your desktop computer.
• Send and receive e-mail messages by connecting directly to an e-mail server through an ISP or a network.
Synchronizing E-mail Messages
E-mail messages can be synchronized as part of the general synchronization process. You need to enable Inbox synchronization
in ActiveSync. For information on enabling Inbox synchronization, see ActiveSync Help on the desktop computer.
During synchronization:
• Messages are copied from the mail folders of Exchange or Outlook on your desktop computer to the ActiveSync folder in Inbox
on the terminal. By default, you will receive messages from the past three days only, the first 100 lines of each message, and
file attachments of less than 100 KB in size.
• E-mail messages in subfolders must be selected in ActiveSync on your desktop computer to be transferred.
• E-mail messages in the Outbox folder on the terminal are transferred to Exchange or Outlook, and then sent from those
programs.
Note: You can also synchronize e-mail messages with your desktop computer from a remote location. For more information,
see Chapter 7.
Connecting Directly to an E-mail Server
In addition to synchronizing e-mail messages with your desktop computer, you can send and receive e-mail messages by
connecting to an e-mail server. When you connect the terminal to the e-mail server, new messages are downloaded to the Inbox
folder, messages in the Outbox folder are sent, and messages that have been deleted on the e-mail server are removed from
the Inbox folder.
Messages received directly from an e-mail server are linked to your e-mail server rather than your desktop computer. When you
delete a message on the terminal, it is also deleted from the e-mail server the next time you connect the terminal to the e-mail
server according to the settings selected in ActiveSync.
You can work online or offline. When working online, you read and respond to messages while connected to the e-mail server.
Messages are sent as soon as you tap Send, which saves space on the terminal. When working offline, after you’ve downloaded
new message headers or partial messages, you can disconnect from the e-mail server and then decide which messages to
download completely. The next time you connect, Inbox downloads the complete messages you’ve marked for retrieval and
sends the messages you’ve composed.
12 - 8 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Receiving Messages
When you connect to your e-mail server or synchronize with your desktop computer, by default, you’ll receive messages from
the last five days only, the first 100 lines of each new message, and file attachments of less than 100 KB in size. The original
messages remain on the e-mail server or your desktop computer.
You can mark the messages that you want to retrieve in full during your next synchronization or e-mail server connection. In the
message list, tap and hold the message you want to retrieve. On the pop-up menu, tap Mark for Download. The icons in the
Inbox message list give you visual indications of message status.
You specify your downloading preferences when you set up the service or select your synchronization options. You can change
them at any time:
• Change options for Inbox synchronization using ActiveSync options. For more information, see ActiveSync Help.
• Change options for direct e-mail server connections in Inbox on the terminal. Tap Tools and then tap Options. On the Service
tab, tap the service you want to change. Tap and hold the service and select Delete to remove a service.
Using the Message List
Messages you receive are displayed in the message list. By default, the most recently received messages are displayed first in
the list and unread messages are displayed in bold type.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 9

When you tap on a message to open it, the following screen appears:
Composing Messages
1. Tap New.
2. In the To field, enter the e-mail or SMS address of one or more recipients, separating them with a semicolon (;), or select a
name from the contact list by tapping the Address Book button.
All e-mail addresses entered in the e-mail fields in Contacts appear in the Address Book.
3. Compose your message. To enter preset or frequently used messages, tap My Text and select a message.
4. Tap Send when you’ve finished the message.
If you are working offline, the message is moved to the Outbox folder and will be sent the next time you connect.
5. If you are sending an SMS message and want to know if it was received, tap Edit, Options, and select Request SMS text
message delivery notification before sending the message.
Managing E-mail Messages and Folders
Messages are displayed in one of five folders for each service you have created: Inbox, Deleted Items, Drafts, Outbox, and Sent
Items.
The Deleted Items folder contains messages that have been deleted on the device. The behavior of the Deleted and Sent Items
folders depends on the selected options. To select these options, tap Tools > Options > Message tab.
To move a message to another folder, in the message list, tap and hold the message, tap Move to on the pop-up menu, and
select the desired folder.
To create additional folders, tap Tools > Manage Folders.
12 - 10 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Folder Behavior with a Direct Connection to an E-mail Server
The behavior of the folders you create depends on whether you are using ActiveSync, SMS, POP3, or IMAP4.
ActiveSync
If you use ActiveSync, e-mail messages in the Inbox folder in Outlook on your desktop computer are automatically synchronized
with the terminal. You can select to synchronize additional folders by designating them for ActiveSync. The folders you create
and the messages you move will then be mirrored on the server.
For example, if you move two messages from the Inbox folder to a folder named Family, and you have designated Family for
synchronization, the server creates a copy of the Family folder and copies the messages into that folder. You can then read the
messages while away from your desktop computer.
SMS
If you use SMS, messages are stored in the Inbox folder.
POP3
If you use POP3 and you move e-mail messages to a folder you created, the link is broken between the messages on the terminal
and their copies on the mail server. The next time you connect, the mail server will see that the messages are missing from the
terminal Inbox and delete them from the server. This prevents you from having duplicate copies of a message, but it also means
that you will no longer have access to messages that you move to folders created from anywhere except the terminal.
IMAP4
If you use IMAP4, the folders you create and the e-mail messages you move are mirrored on the server. Therefore, messages
are available to you anytime you connect to your mail server, whether it is from the terminal or desktop computer. This
synchronization of folders occurs whenever you connect to your mail server, create new folders, or rename/delete folders when
connected.
Pocket Internet Explorer
Use Microsoft Pocket Internet Explorer to view Web or WAP pages. You can use the following methods:
• During synchronization with your desktop computer, download your favorite links and mobile favorites that are stored in the
Mobile Favorites subfolder in Internet Explorer on the desktop computer.
• Connect to an ISP or network and browse the Web. When connected to an ISP or network, you can also download files and
programs from the Internet or intranet.
Accessing Pocket Internet Explorer
To open Pocket Internet Explorer, tap Start and then Internet Explorer.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 11

You can use Pocket Internet Explorer to browse Mobile Favorites and channels that have been downloaded without connecting
to the Internet. You can also connect to the Internet through an ISP or a network connection and browse the Web.
Browse the Internet on Your Terminal
Note: You must set up a connection to your ISP or corporate network using Connections before browsing; see Using an ISP on
page 8-8. If you select Pocket Internet Explorer before setting up the network connections, a screen may appear allowing
you to proceed to the connection settings screen.
1. Open Internet Explorer (Start > Internet Explorer).
2. To connect and start browsing, tap View and then Address Bar.
3. In the address bar that appears at the top of the screen, enter the Web address you want to visit and then tap Go.
4. Tap the arrow to choose from previously entered addresses. If Mobile Favorites have been set up, you can tap one of them
to start browsing. See Mobile Favorites Folder on page 12-12.
View Options
You can switch to a One Column view, which condenses web content into a single column so that you do not have to scroll right
to see the entire page. Tap View > Layout > One Column.
Default View One Column View
Mobile Favorites Folder
Purpose
The Mobile Favorites folder was created on your desktop computer when you installed ActiveSync. It enables you to create
Favorite Links on your desktop computer that you can transfer to your Dolphin terminal. Those Favorite Links are then available
when browsing the internet on your terminal.
Process
First, you create your Favorite Links in the Mobile Favorites folder on your desktop computer. Then, the next time you sync your
desktop computer with your terminal, those Mobile Favorites are transferred to the Mobile Favorites folder on to your terminal.
Only items stored in the Mobile Favorites subfolder in the Favorites folder in Internet Explorer on your desktop computer are
synchronized with the Mobile Favorites folder on your terminal.
12 - 12 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Note: Unless you mark a Favorite Link as a mobile favorite, only the link downloads to your terminal, and you will need to connect
to your ISP or network to view the content. For more information on synchronization, see ActiveSync Help on the desktop
computer.
Creating and Synchronizing Mobile Favorites
If you are using Microsoft Internet Explorer 5.0 or later on your desktop computer, you can download Mobile Favorites to the
terminal. Synchronizing mobile favorites downloads Web content to your device so that you can view pages while you are
disconnected from your ISP and desktop computer.
Use the Internet Explorer plug-in installed with ActiveSync to create mobile favorites
1. On your desktop computer, open Internet Explorer, click Tools > Create Mobile Favorite.
2. To change the link name, enter a new name in the Name box.
3. Optionally, in Update, select a desired update schedule.
4. Tap OK. Internet Explorer downloads the latest version of the page to your desktop computer.
5. If you want to download the pages that are linked to this mobile favorite, in Internet Explorer on the desktop computer, rightclick the mobile favorite and then click Properties. On the Download tab, specify the number of links down that you want to
download. To conserve memory, go only one level down.
6. Synchronize the terminal and desktop computer. Mobile favorites that are stored in the Mobile Favorites folder in Internet
Explorer are downloaded to the terminal.
If you did not specify an update schedule in Step 3, you will need to manually download content to keep the information updated
on your desktop computer and terminal. Before synchronizing, in Internet Explorer on your desktop computer, click Tools and
then Synchronize. You will see the last time content was downloaded to the desktop computer, and you can manually download
content if needed.
You can add a button to the Internet Explorer toolbar for creating mobile favorites. In Internet Explorer on your desktop computer,
click View, Toolbars, and then Customize.
Using Mobile Favorites and Channels
1. Open Pocket Internet Explorer.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 13

2. Tap the Favorites button to display your list of favorites .
3. Tap the page you want to view.
You’ll see the page that was downloaded the last time you synchronized with your desktop computer. If the page is not on the
terminal, the favorite will be dimmed. You will need to synchronize with your desktop computer again to download the page to
the terminal, or connect to the Internet to view the page.
Mobile favorites take up storage memory on the terminal. To minimize the amount of memory used:
• In the settings for the Favorites information type in ActiveSync options, turn off pictures and sounds, or stop specific
mobile favorites from being downloaded to the terminal. For more information, see ActiveSync Help.
• Limit the number of downloaded linked pages. In Internet Explorer on the desktop computer, right-click the mobile
favorite you want to change and then Properties. On the Download tab, specify 0 or 1 for the number of linked pages
you want to download.
Using AvantGo® Channels
AvantGo is a free interactive service that provides access to personalized content and thousands of popular web sites. Subscribe
to AvantGo channels directly from the terminal. For more information, visit: http://avantgo.com/frontdoor/index.html.
1. In ActiveSync options on the desktop computer, turn on synchronization for the AvantGo information type.
2. In Pocket Internet Explorer, tap the Favorites button to display your list of favorites .
3. Tap the AvantGo Channels link.
4. Tap Activate and follow the directions on the screen. Synchronize the terminal with your desktop computer and then tap the
My Channels button to complete the AvantGo setup.
5. When synchronization is complete, tap the AvantGo Channels link in your list of favorites to see a few of the most popular
channels. To add or remove channels, tap the Add or Remove link.
Pocket Word
Pocket Word works with Microsoft Word on your desktop computer to give you easy access to copies of your documents. You
can create new documents on the terminal, or you can copy and paste documents from your desktop computer. Synchronize
documents between your desktop computer and your device so that you have the most up-to-date content in both locations.
You can open only one document at a time; when you open a second document, you’ll be asked to save the first. You can save
a document you create or edit in a variety of formats, including Word (.doc), Pocket Word (.psw), Rich Text Format (.rtf), and
Plain Text (.txt).
12 - 14 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Using Pocket Word
Pocket Word contains a list of the files stored on the terminal. Tap a file in the list to open it. To delete, make copies of, and send
files, tap and hold a file in the list. Then, select the appropriate action on the pop-up menu.
You can change the zoom magnification by tapping View > Zoom, and then selecting the percentage you want. Select a higher
percentage to enter text and a lower one to see more of your document. If you’re opening a Word document created on a desktop
computer, select Wrap to Window on the View menu so that you can see the entire document.
Creating a Word File
To create a new file, tap Start > Programs > Pocket Word > New. A blank document appears. If you’ve selected a template for
new documents in the Options dialog box, that template appears with appropriate text and formatting already provided.
You can enter information in Pocket Word in one of two modes (typing on the SIP or keyboard and drawing), which are displayed
on the View menu.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 15

Typing Mode
Using the SIP or Dolphin keypad, enter typed text into the document.
To format existing text and to edit text, first select the text. You can select text as you do in a Word document, using your stylus
instead of the mouse to drag through the text you want to select. You can search a document to find text by tapping Edit and
then Find/Replace.
Drawing Mode
In drawing mode, use your stylus to draw on the screen. Gridlines appear as a guide. When you lift your stylus off the screen
after the first stroke, you’ll see a drawing box indicating the boundaries of the drawing. Every subsequent stroke within or touching
the drawing box becomes part of the drawing.
For more information on using Pocket Word, tap Start and then Help.
Pocket Excel
Pocket Excel works with Microsoft Excel on your desktop computer to give you easy access to copies of your workbooks. You
can create new workbooks on the terminal, or you can copy and paste workbooks from your desktop computer. Synchronize
workbooks between your desktop computer and the terminal so that you have the most up-to-date content in both locations.
You can open only one workbook at a time; when you open a second workbook, you’ll be asked to save the first. You can save
a workbook you create or edit in a variety of formats, including Pocket Excel (.pxl) and Excel (.xls).
Pocket Excel contains a list of the files stored on your device. Tap a file in the list to open it. To delete, make copies of, and send
files, tap and hold a file in the list. Then select the appropriate action from the pop-up menu. Pocket Excel provides fundamental
spreadsheet tools, such as formulas, functions, sorting, and filtering. To display the toolbar, tap View > Toolbar.
12 - 16 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Creating an Excel File
To create a new file, tap Start > Programs > Pocket Excel > New. A blank workbook appears. If you’ve selected a template for
new workbooks in the Options dialog box, that template appears with appropriate text and formatting already provided.
If your workbook contains sensitive information, you can protect it with a password. To do so, open the workbook, tap Edit, and
then Password. Every time you open the workbook, you will need to enter the password, so choose one that is easy for you to
remember but hard for others to guess.
Tips for Working in Pocket Excel
• View in full-screen mode to see as much of your worksheet as possible. Tap View and then Full Screen. To exit full-screen
mode, tap Restore.
• Show and hide window elements. Tap View and then tap the elements you want to show or hide.
• Freeze panes on a worksheet. First select the cell where you want to freeze panes. Tap View > Freeze Panes. You might
want to freeze the top and left-most panes in a worksheet to keep row and column labels visible as you scroll through a sheet.
• Split panes to view different areas of a large worksheet. Tap View > Split. Then drag the split bar to where you want it. To
remove the split, tap View > Remove Split.
• Show and hide rows and columns. To hide a hidden row or column, select a cell in the row or column you want to hide. Then
tap Format,> Row or Column > Hide. To show a hidden row or column, tap Tools > Go To, and then type a reference that
is in the hidden row or column. Then tap Format > Row or Column > Unhide.
For more information on using Pocket Excel, tap Start > Help.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 17

Windows Media Player for Pocket PC
Use Microsoft Windows Media Player (WMP) for Pocket PC to play digital audio and video files stored on the terminal. To switch
to Windows Media Player for Pocket PC, tap Start > Windows Media.
After a media file has been loaded, you can play, pause, stop, song advance/reverse, mute sound, or adjust volume.
This slider indicates the
progress of media playback.
Tools Menu
The tools menu allows you to perform several important functions.
About gives you information about the codecs used in your version of WMP.
12 - 18 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Settings allows you to configure several important aspects of WMP.
Properties gives a detailed listing of a media file's attributes.
Open URL allows you to open WMP-compliant media from a network or Internet resource.
Add Web Favorite adds a streaming media file that is currently playing to web favorites.
Repeat plays a playlist repeatedly.
Shuffle plays items in a playlist in a random order.
MSN Messenger
MSN Messenger is an instant messaging program that lets you:
• See who is online.
• Send and receive instant messages.
• Have instant message conversations with groups of contacts.
Note: To use MSN Messenger, you must have a Microsoft Passport™ account or a Microsoft Exchange e-mail account. You
must have a Passport to use MSN Messenger Service. If you have a Hotmail or MSN account, you already have a
Passport account. Sign up for a Microsoft Passport account at www.passport.com.
Setting Up
Before you can connect for the first time, you must enter the information from your Passport or Exchange account. After you set
up your account information on the terminal for the first time, you will go directly to login when you access MSN Messenger.
Note: Ensure that you are connected to the Internet (see Connections Tab on page 7-19).
1. Tap Start > Programs > MSN Messenger
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 12 - 19

2. Tap Tools > Options > Account tab.
3. In the Accounts tab, enter your Passport or Exchange account information.
Be sure to indicate the service you’re using to connect - Messenger or Exchange.
4. When complete, tap OK. You are returned to the sign-in screen.
5. To sign in, tap the sign-in screen and enter your e-mail address and password.
Note: If you already use MSN Messenger, your contacts will show up on your device without being added again.
Pictures
Use Pictures to view JPEG pictures stored on the terminal or storage card.
To begin, tap Start > Programs > Pictures.
Choose to view main memory or storage card contents. By tapping and holding on an image, you can create a clone of that file,
delete that file, select all files, send file via e-mail, beam picture, or rename the image.
12 - 20 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

13
Dolphin 7900 HomeBase
Overview
As the hub of your Dolphin 7900 system, the Dolphin HomeBase charging and communication cradle supports both RS-232 and
USB communications, which make it able to interface with the majority of PC-based enterprise systems. When a terminal is
seated in the HomeBase, its main battery pack charges in less than four hours.
Power
The HomeBase completes a full charge of the main battery pack in less than four hours. The HomeBase also provides power to
the intelligent battery charging system in all Dolphin terminals that senses when a full charge has been achieved and switches
to a trickle charge to maintain the full charge.
Communications
Reliable data communications at speeds of up to 115k baud can be transmitted by the HomeBase through the RS-232 serial
port. Using the full-speed USB port, the data transmission rate goes up to 12 Mbps. HomeBases cannot be physically connected
to each other - sometimes referred to as “daisy-chained” - but can be networked together via serial or USB hub.
Convenient Storage
Intelligent battery charging makes the Dolphin HomeBase a safe and convenient storage receptacle for your Dolphin terminal.
Capacity
The Dolphin HomeBase holds one terminal and features an auxiliary battery well behind the terminal well that can charges a
battery pack independently of the terminal well. This means that one HomeBase can charge two battery packs: the one installed
in the terminal and a spare.
Use only the peripherals, power cables, and power adapters from Hand Held Products. Use of peripherals, cables, or
power adapters not sold/manufactured by Hand Held Products will void the warranty and may damage the terminal.
!
Use only the Li-ion battery packs provided by Hand Held Products. The use of any battery pack not sold/manufactured
by Hand Held Products in a Dolphin terminal will void your warranty and may result in damage to the Dolphin terminal
!
or battery.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 13 - 1

Dolphin 7900 HomeBase Parts and Functions
Front Panel
Terminal Well
Terminal Well
Place the Dolphin terminal in this well to communicate with a host device, power the terminal, and charge its battery
pack. If the host device is a desktop computer that uses ActiveSync, synchronization begins immediately. While
seated in the terminal well, the main battery installed in the terminal charges. The HomeBase completely charges
a battery pack in less than four hours.
DOCK LED
Turns solid green when the Dolphin terminal is properly seated in the Dolphin HomeBase. When this light is on, the
terminal is connected to the base.
AUX Battery LED
Indicates status of the battery charging in the auxiliary battery well.
This color… means…
Orange
Green
For information about charging a battery in the auxiliary battery well, see page 13-5
COMM LED
DOCK
LED
The auxiliary battery is charging.
The auxiliary battery has completed charging and is ready for use.
AUX
Battery
LED
COMM
LED
This is the communication LED. It indicates the status of data transfer between the Dolphin terminal and the host
device. The color of this LED differs if the HomeBase is using the serial or USB port connection.
If using the serial port
This color… means…
Red
Green
Serial data is being sent from the host device to the Dolphin HomeBase.
Serial data is being sent from the Dolphin HomeBase to the host device.
13 - 2 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

If using the USB port
Back Panel
Orange
This color… means…
Green LED
Serial data is being sent at high data rates.
A USB connection is established with the host computer.
Auxiliary Battery Well
Auxiliary Battery Well
The HomeBase enables you to charge an additional Li-ion battery pack independently of the terminal well. This
feature ensures that you can always have a fully-charged battery for your Dolphin terminal; see Charging a Spare
Battery in the Auxiliary Battery Well on page 13-5.
USB Port
This USB Port is full-speed and 2.0 compliant. Using a USB cable, you can connect the HomeBase to a peripheral
device, such as a desktop computer or printer. When the Dolphin terminal is seated in the terminal well, it is
connected to the peripheral device via the HomeBase. The USB port requires that you use ActiveSync 3.7 or higher.
RS-232 Port
Use a 9-pin, RS-232 cable from Hand Held Products to connect this port to a peripheral device for RS-232 data
communication. For more information, see HomeBase Serial Connector on page 13-4.
DC Power Jack
Use a power cable from Hand Held Products to supply power to this power jack. For more information, see Powering
the HomeBase on page 13-4.
DC Power JackRS-232 PortUSB Port
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 13 - 3

Powering the HomeBase
The terminal requires 9.5 Volts DC input for communications and battery charging; the Hand Held Products power cable contains
a power adapter that converts the power source voltage accordingly. Only the power adapter cable from Hand Held Products
converts the voltage appropriately.
We recommend that you leave the Dolphin HomeBase connected to its power source at all times, so that it is always ready to use.
1. Connect the power cable to the DC jack on the rear panel of the HomeBase.
2. Connect the power cable to the power adapter.
3. Plug the power adapter cable into the power source.
4. The Dolphin HomeBase is now powered.
HomeBase Serial Connector
The following diagram displays the pin diagram of the serial connector of the HomeBase.
Pin # Description
1 Internal Jumper to Pin 6
2 TXD
3 RXD
4 DSR
5 GND
6 DTR
7 CTS
8RTS
9RI
Note: Signals referenced are for a DTE device. The HomeBase is at a right-angle to the printed circuit board (PCB). The ninth
pin has a ring indicator (RI).
13 - 4 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05

Charging the Main Battery
The Dolphin HomeBase powers the terminal and fully charges its main battery pack in less than four hours. The HomeBase
contains an intelligent battery charging system that protects the battery from being damaged by overcharging; the unit senses
when a battery pack is fully charged and automatically switches to a trickle charge that maintains the battery at full capacity.
Therefore, Dolphin terminals may be stored in the HomeBase without damage to the terminals, battery packs, or peripherals.
To check battery power, use the Power system setting; see Power on page 7-13. For more information about Hand Held Products
Li-ion batteries, see Battery Power on page 3-10.
To Power a Terminal and Charge its Main Battery
1. Install the battery pack in the terminal; see Install the Main Battery Pack on page 2-5.
1. Connect the HomeBase to the power supply provided by Hand Held Products.
2. Slide the terminal into the terminal well until the Dock LED lights green to indicate that the terminal is properly seated.
3. The battery pack begins charging.
Charging a Spare Battery in the Auxiliary Battery Well
The auxiliary battery well (Auxiliary Battery Well, page 13-3) located on the back of the HomeBase charges a spare battery
independently of the terminal well. The Aux Battery LED on the front panel indicates the status of the battery in this well. Charge
time is less than four hours.
Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim. Rev (c) 4/11/05 13 - 5

1. Insert the end of the battery without the locking tab into the bottom of the auxiliary well opening.
2. Snap the battery into place with a hinging motion. The Aux Battery LED lights orange.
3. Use the AUX Battery LED to monitor charging progress.
Communications
There are two types of communication: USB and RS-232.
USB The HomeBase also supports USB communications via the USB port located on the back. The
RS-232 The HomeBase supports RS-232 communications via the RS-232 Communications Port located on
Note: The HomeBase should have only one type of interface cable connected at a time, either USB or RS-232. You must be
using ActiveSync, version 3.7 or higher.
Required Equipment
• HomeBase powered by a power cable and power adapter cable from Hand Held Products
•USB Cable
•Serial Cable
• ActiveSync v3.7 or higher
•Windows
Note: The HomeBase does not support Windows
®
98 Second Edition*, Windows® Me, Windows® 2000, or Windows® XP computer.
support USB
HomeBase acts as a USB device by interfacing the USB signals of the Dolphin to the USB of the host
computer. Using a standard USB cable, the HomeBase’s USB interface allows the Dolphin terminal
to communicate with a personal computer or to be networked through a USB hub.
the back of the device. This port enables the Dolphin terminal to communicate to a personal
computer, modem, or any RS-232 device using a standard serial cable and communications
software.
NT® when using a USB connection.
.
*Windows® 98 second edition provides full USB support.
This is because Windows
NT
does not
Setting Up the HomeBase for USB Communication
The Dolphin terminal is defaulted to support USB communications out of the box.
To Install the HomeBase Using USB
1. Plug in the power supply and connect it to the back of the HomeBase.
2. Plug the USB cable into the back of the HomeBase.
3. At this point, the hardware is installed and operating. You may need to reboot your PC to complete the installation process.
Setting up the Terminal for ActiveSync Communications
1. On the terminal, tap Start > ActiveSync > Tools > Options. Activesync opens displaying the PC tab.
2. In the Use this PC drop-down list, select the name of the host PC.
13 - 6 Dolphin® 7900 Series Mobile Computer User’s Guide-Prelim.
Rev (c) 4/11/05
 Loading...
Loading...