Grandstream GVC32XX User Manual

Grandstream Networks, Inc.
GVC32XX Series
Video Conference System for Android
TM
Security Guide

P a g e | 1
GVC32xx Security Guide
Table of Contents
OVERVIEW ..................................................................................................................... 3
WEB UI/SSH ACCESS ................................................................................................... 4
GVC32xx Web UI Access ..................................................................................................................... 4
Web UI Access Protocols ..................................................................................................................... 4
User Login ............................................................................................................................................ 4
User Management Levels .................................................................................................................... 5
SSH Access .......................................................................................................................................... 6
DEVICE CONTROL SECURITY ..................................................................................... 7
Screen lock ........................................................................................................................................... 7
Permission to install apps from unknown sources ............................................................................... 7
GUI Config Tool Settings ...................................................................................................................... 7
SECURITY FOR SIP ACCOUNTS AND CALLS ............................................................ 8
Protocols and Ports .............................................................................................................................. 8
Anonymous/Unsolicited Calls Protection ........................................................................................... 10
SRTP .................................................................................................................................................. 11
NETWORK SECURITY ................................................................................................. 12
VPN .................................................................................................................................................... 12
802.1X ................................................................................................................................................ 12
Bluetooth ............................................................................................................................................ 13
SECURITY FOR GVC32XX SERVICES ....................................................................... 14
Provisioning via Configuration File ..................................................................................................... 14
Firmware Upgrading ........................................................................................................................... 16
TR-069 ................................................................................................................................................ 17
ADB Service ....................................................................................................................................... 18
LDAP .................................................................................................................................................. 18
Syslog ................................................................................................................................................. 19
SECURITY GUIDELINES FOR GVC32XX DEPLOYMENT.......................................... 20

P a g e | 2
GVC32xx Security Guide
Table of Figures
Figure 1: Web UI Access Settings................................................................................................................. 4
Figure 2: GVC32xx Web UI Login ................................................................................................................. 5
Figure 3: GVC32xx Admin Password Change .............................................................................................. 5
Figure 4: SSH Access on GVC32xx .............................................................................................................. 6
Figure 5: Cust File Provision Page ............................................................................................................... 7
Figure 6: Configure TLS as SIP Transport .................................................................................................... 8
Figure 7: SIP TLS Settings on GVC32xx ...................................................................................................... 8
Figure 8: Additional SIP TLS Settings ........................................................................................................... 9
Figure 9: Settings to Block Unwanted Calls ................................................................................................ 10
Figure 10: SRTP Settings ........................................................................................................................... 11
Figure 11: GVC32xx VPN profile configuration ........................................................................................... 12
Figure 12: 802.1X Settings.......................................................................................................................... 13
Figure 13: 802.1X for GVC32xx Deployment.............................................................................................. 13
Figure 15: GVC32xx Config File Provisioning............................................................................................. 14
Figure 16: Validate Certification Chain ........................................................................................................ 15
Figure 17: Certificate Management ............................................................................................................. 15
Figure 18: Firmware Upgrade Configuration............................................................................................... 16
Figure 19: Validate Certification Chain ........................................................................................................ 16
Figure 20: Certification Management .......................................................................................................... 17
Figure 21: TR-069 Connection Settings Page ............................................................................................ 17
Figure 23: Enabling Developer Mode ......................................................................................................... 18
Figure 24: GVC32xx LDAP Settings ........................................................................................................... 18
Figure 25: Syslog Protocol .......................................................................................................................... 19

P a g e | 3
GVC32xx Security Guide
OVERVIEW
This document presents a summary of security measures, factors, and configurations that users are
recommended to consider when configuring and deploying the GVC32xx.
Note: We recommend using the latest firmware for latest security patches.
The following sections are covered in this document:
• Web UI/SSH Access
Web UI access is protected by username/password and login timeout. Two-level user management is
configurable. SSH access is supported for mainly troubleshooting purpose and it’s recommended to disable
it in normal usage.
• Device Control Security
The GVC32xx has multiple ways to limit the use for network settings, apps, and other settings if not
necessary for the end user.
• Security for SIP Account and Calls
The SIP account uses specific port for signaling and media stream transmission. It also offers configurable
options to block anonymous calls and unsolicited calls.
• Network Security
The GVC32xx supports VPN, 802.1X, Bluetooth for network access. VPN secures remote connection and
802.1X provides network access control. it’s recommended to turn Bluetooth off if not used.
• Security for GVC32XX Services
GVC32xx supports service such as HTTP/HTTPS/TFTP provisioning, TR-069, LDAP, as well as allows
ADB and FTP access. For provisioning, we recommend using HTTPS with username/password and using
password-protected XML file. For services such as ADB, we recommend disabling them if not used to avoid
potential port exposure
• Deployment Guidelines for GVC32XX
This section introduces protocols and ports used on GVC32xx and recommendations for routers/firewall
settings.
This document is subject to change without notice.
Reproduction or transmittal of the entire or any part, in any form or by any means, electronic or print, for
any purpose without the express written permission of Grandstream Networks, Inc. is not permitted.
P a g e | 4
GVC32xx Security Guide
WEB UI/SSH ACCESS
GVC32xx Web UI Access
The GVC32xx embedded web server responds to HTTP/HTTPS GET/POST requests. Embedded HTML
pages allow users to configure the device through a web browser such as Microsoft IE, Mozilla Firefox,
Google Chrome and etc. With this, administrators can access and configure all available GVC32xx
information and settings. It is critical to understand the security risks involved when placing the GVC32xx
phone on public networks and it’s recommended not to do so.
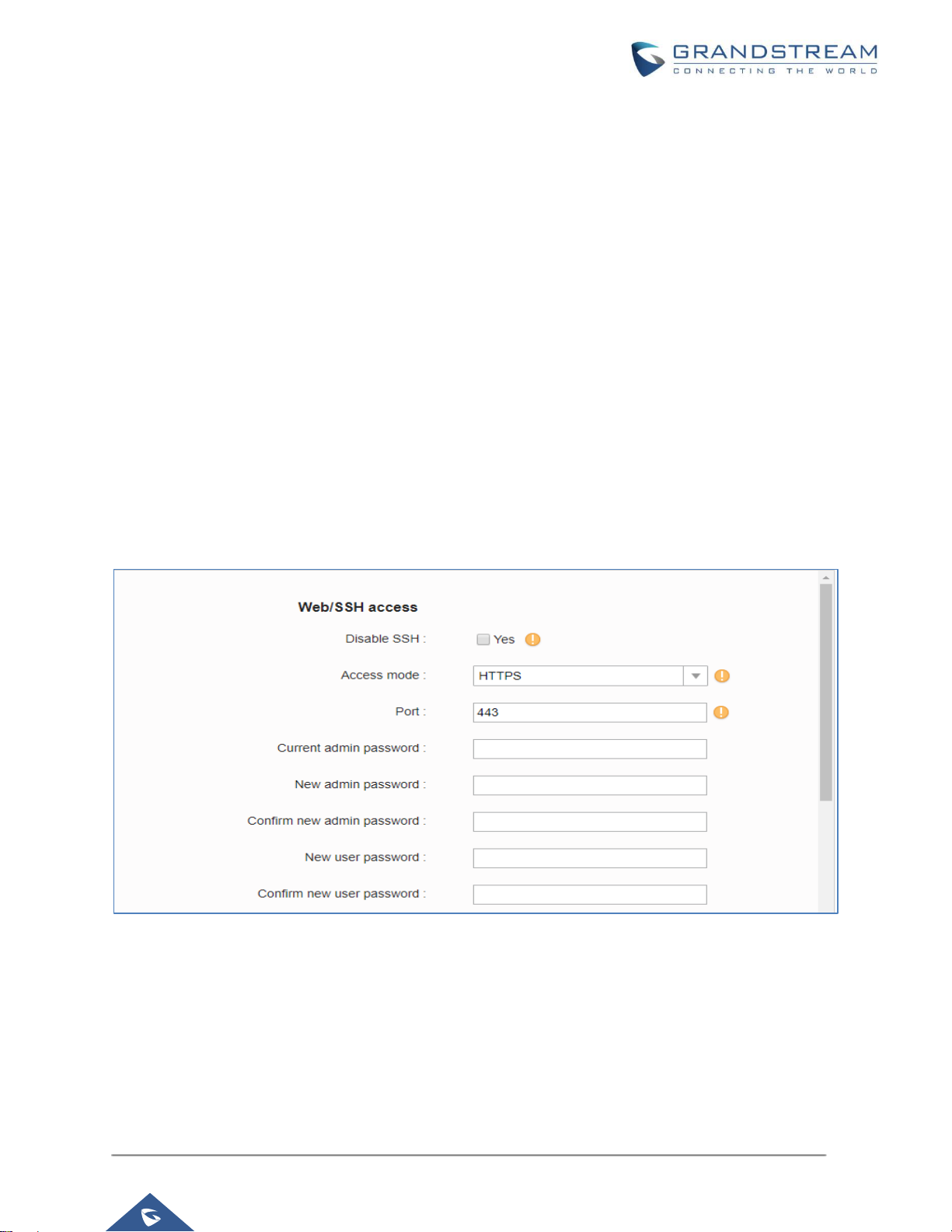
Web UI Access Protocols
HTTP and HTTPS are supported to access the GVC32xx web UI and can be configured under web UI →
Settings → Security Settings → Web/SSH Access. To secure transactions and prevent unauthorized access,
it is highly recommended to:
1. Use HTTPS instead of HTTP.
2. Avoid using well known port numbers such as 80 and 443.
Figure 1: Web UI Access Settings
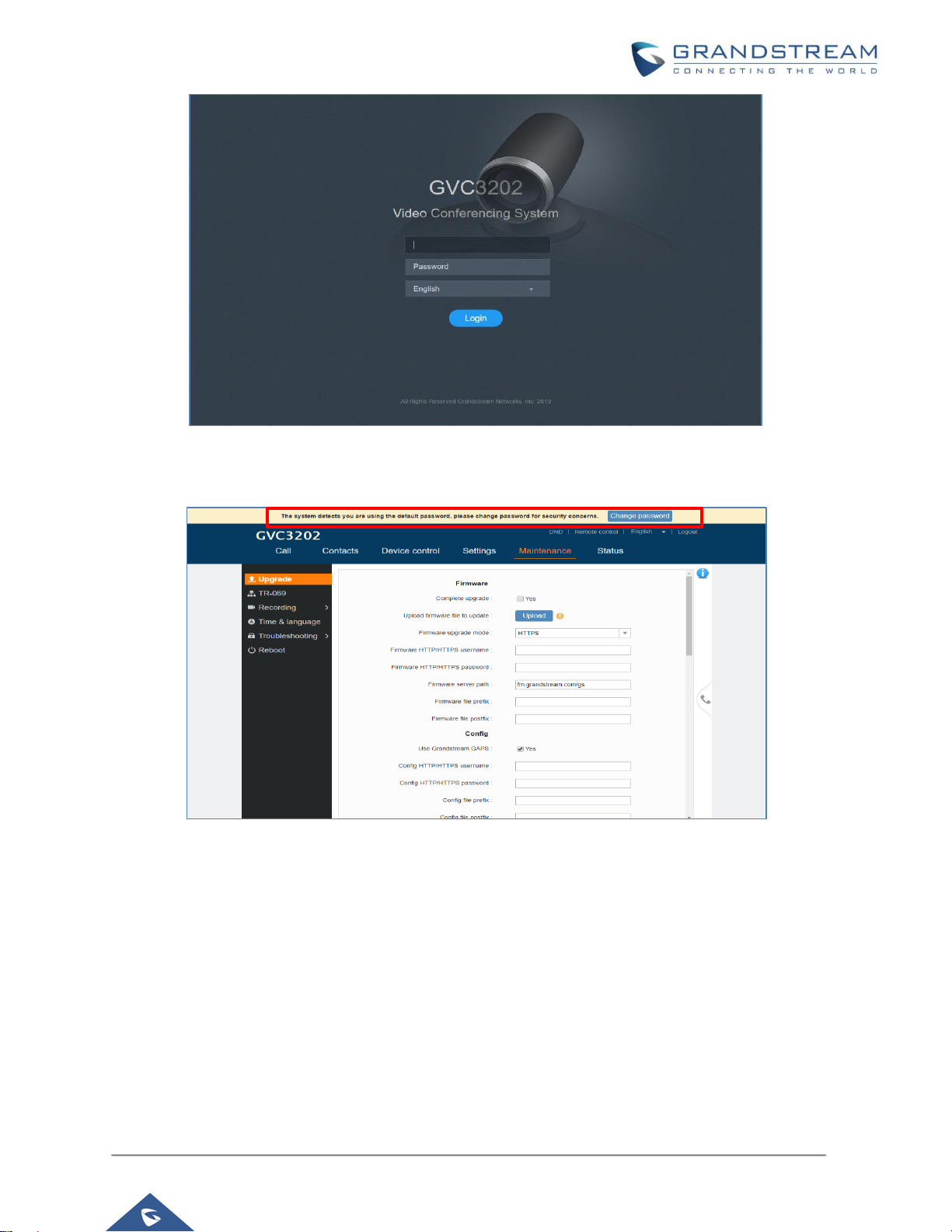
User Login
Username and password are required to log in the GVC32XX web UI.
P a g e | 5
GVC32xx Security Guide
Figure 2: GVC32xx Web UI Login
After logging in, the system will detect that the default password is used and requires users to change it.
Figure 3: GVC32xx Admin Password Change
Users can press on Change Password to change the password for default user "admin", or navigate to
Settings → Security Settings-> Web/SSH access and change the Admin/User password. The password
length must be between 6 and 32 characters. Strong password with a combination of numbers, uppercase
letters, lowercase letters, and special characters is always recommended for security purpose.
User Management Levels
Two user privilege levels are currently supported:
• Admin
• User
P a g e | 6
GVC32xx Security Guide
Admin login has access to all of the GVC32xx’s web UI pages and can execute all available operations.
User login has limited access to the web UI pages. With user login, the user is allowed to access and
configure the following settings:
• Call
• Contacts
• Device Control
• Status
• Settings: Network Settings, Peripheral, security settings
• Maintenance: Recording, Time & Language, Troubleshooting.
It is recommended to keep admin login with administrator only. And end user should be provided with user-
level login only, if web UI access is needed.
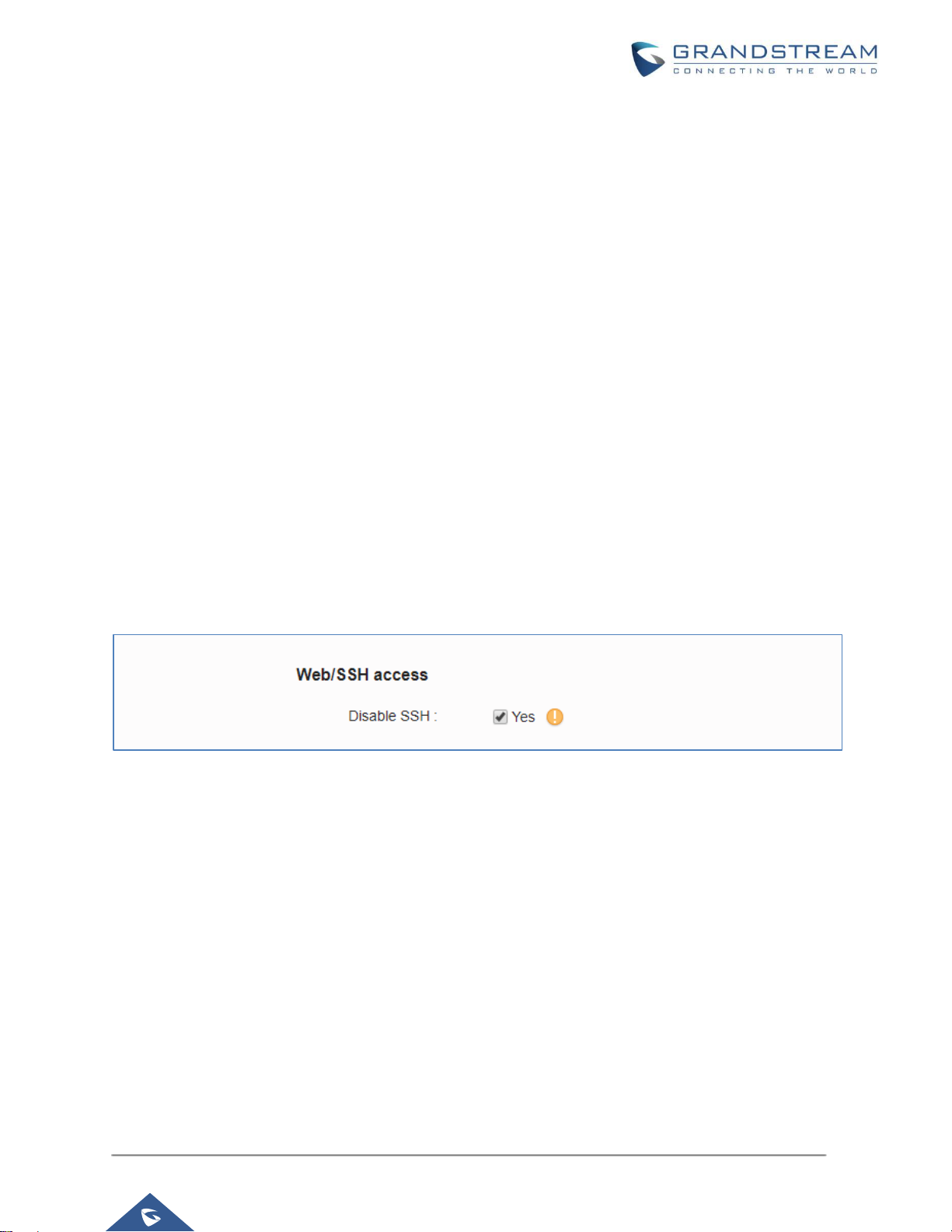
SSH Access
The GVC32xx allows access via SSH for advanced troubleshooting purpose. This is usually not needed
unless the administrator or Grandstream support needs it for troubleshooting purpose. SSH access on
GVC32XX is enabled by default and uses port number 22. It’s recommended to disable it for daily normal
usage from web UI → Settings → Security settings → Web/SSH access → Disable SSH, changing this
setting will require reboot to take effect.
Figure 4: SSH Access on GVC32xx
 Loading...
Loading...