Page 1

CLI Manual
Product Model :
Modular Layer 3 Chassis Ethernet Switch
Release 3
TM
DES-6500
Page 2

Table of Contents
Introduction ............................................................................................................................................ 1
Using the Console CLI ............................................................................................................................. 4
Command Syntax.................................................................................................................................... 8
Basic Switch Commands ....................................................................................................................... 10
Switch Port Commands ......................................................................................................................... 25
Port Security Commands....................................................................................................................... 28
Network Management (SNMP) Commands ............................................................................................. 31
Switch Utility Commands...................................................................................................................... 52
Network Monitoring Commands ............................................................................................................ 58
Multiple Spanning Tree Protocol (MSTP) Commands ............................................................................. 75
Forwarding Database Commands.......................................................................................................... 89
Broadcast Storm Control Commands .................................................................................................... 97
QoS Commands .................................................................................................................................. 102
Port Mirroring Commands ................................................................................................................... 114
VLAN Commands ................................................................................................................................ 118
Link Aggregation Commands............................................................................................................... 127
IP Commands (Including Multiple IP interfaces per VLAN)................................................................... 134
IGMP Commands (Including IGMP v3)................................................................................................. 139
IGMP Snooping Commands................................................................................................................. 143
Access Authentication Control Commands .......................................................................................... 152
SSH Commands .................................................................................................................................. 176
SSL Commands................................................................................................................................... 184
802.1X Commands ............................................................................................................................. 190
Access Control List (ACL) Commands (Including CPU)......................................................................... 209
Safeguard Engine Commands ............................................................................................................. 235
Traffic Segmentation Commands......................................................................................................... 238
D-Link Single IP Management Commands........................................................................................... 240
Time and SNTP Commands ................................................................................................................. 251
ARP Commands .................................................................................................................................. 257
VRRP Commands ................................................................................................................................ 261
Routing Table Commands ................................................................................................................... 268
Route Redistribution Commands ........................................................................................................ 271
DHCP Relay Commands ...................................................................................................................... 277
DNS Relay Commands ........................................................................................................................ 283
RIP Commands ................................................................................................................................... 287
Page 3

DVMRP Commands............................................................................................................................. 290
PIM Commands................................................................................................................................... 295
IP Multicasting Commands ................................................................................................................. 299
MD5 Configuration Commands ........................................................................................................... 301
OSPF Configuration Commands .......................................................................................................... 303
Jumbo Frame Commands ................................................................................................................... 323
Command History List ........................................................................................................................ 325
Technical Specifications ...................................................................................................................... 328
Page 4

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
1
INTRODUCTION
The xStack DES-6500 layer 3 modular chassis Ethernet switch is a member of the D-Link xStack family. Ranging from
10/100Mbps edge switches to core gigabit switches, the xStack switch family has been future-proof designed to provide a
stacking architecture with fault tolerance, flexibility, port density, robust security and maximum throughput with a user-friendly
management interface for the networking professional.
The Switch can be managed through the Switch’s serial port, Telnet, or the Web-based management agent. The Command Line
Interface (CLI) can be used to configure and manage the Switch via the serial port or Telnet interfaces.
This manual provides a reference for all of the commands contained in the CLI. Configuration and management of the switch
via the Web-based management agent is discussed in the User’s Guide.
Accessing the Switch via the Serial Port
The Switch’s serial port’s default settings are as follows:
• 115200 baud
• no parity
• 8 data bits
• 1 stop bit
A computer running a terminal emulation program capable of emulating a VT-100 terminal and a serial port configured as
above is then connected to the Switch’s serial port via an RS-232 DB-9 cable.
With the serial port properly connected to a management computer, the following screen should be visible. If this screen does
not appear, try pressing Ctrl+r to refresh the console screen.
Figure 1-1. Initial CLI screen
1
Page 5

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
There is no initial username or password. Just press the Enter key twice to display the CLI input cursor − DES-6500:4#. This is
the command line where all commands are input.
Setting the Switch’s IP Address
Each switch must be assigned its own IP Address, which is used for communication with an SNMP network manager or other
TCP/IP application (for example BOOTP, TFTP). The Switch’s default IP address is 10.90.90.90. You can change the default
switch IP address to meet the specification of your networking address scheme.
The Switch is also assigned a unique MAC address by the factory. This MAC address cannot be changed, and can be found on
the initial boot console screen – shown below.
Figure 1-2. Boot Screen
The Switch’s MAC address can also be found in the Web management program on the Switch Information (Basic Settings)
window on the Configuration menu.
The IP address for the Switch must be set before it can be managed with the Web-based manager. The Switch IP address can be
automatically set using BOOTP or DHCP protocols, in which case the actual address assigned to the Switch must be known.
The IP address may be set using the Command Line Interface (CLI) over the console serial port as follows:
1. Starting at the command line prompt, enter the commands config ipif System ipaddress
xxx.xxx.xxx.xxx/yyy.yyy.yyy.yyy. Where the x’s represent the IP address to be assigned to the IP interface named
System and the y’s represent the corresponding subnet mask.
2. Alternatively, you can enter config ipif System ipaddress xxx.xxx.xxx.xxx/z. Where the x’s represent the IP address
to be assigned to the IP interface named System and the z represents the corresponding number of subnets in CIDR
notation.
The IP interface named System on the Switch can be assigned an IP address and subnet mask which can then be used to connect
a management station to the Switch’s Telnet or Web-based management agent.
2
Page 6
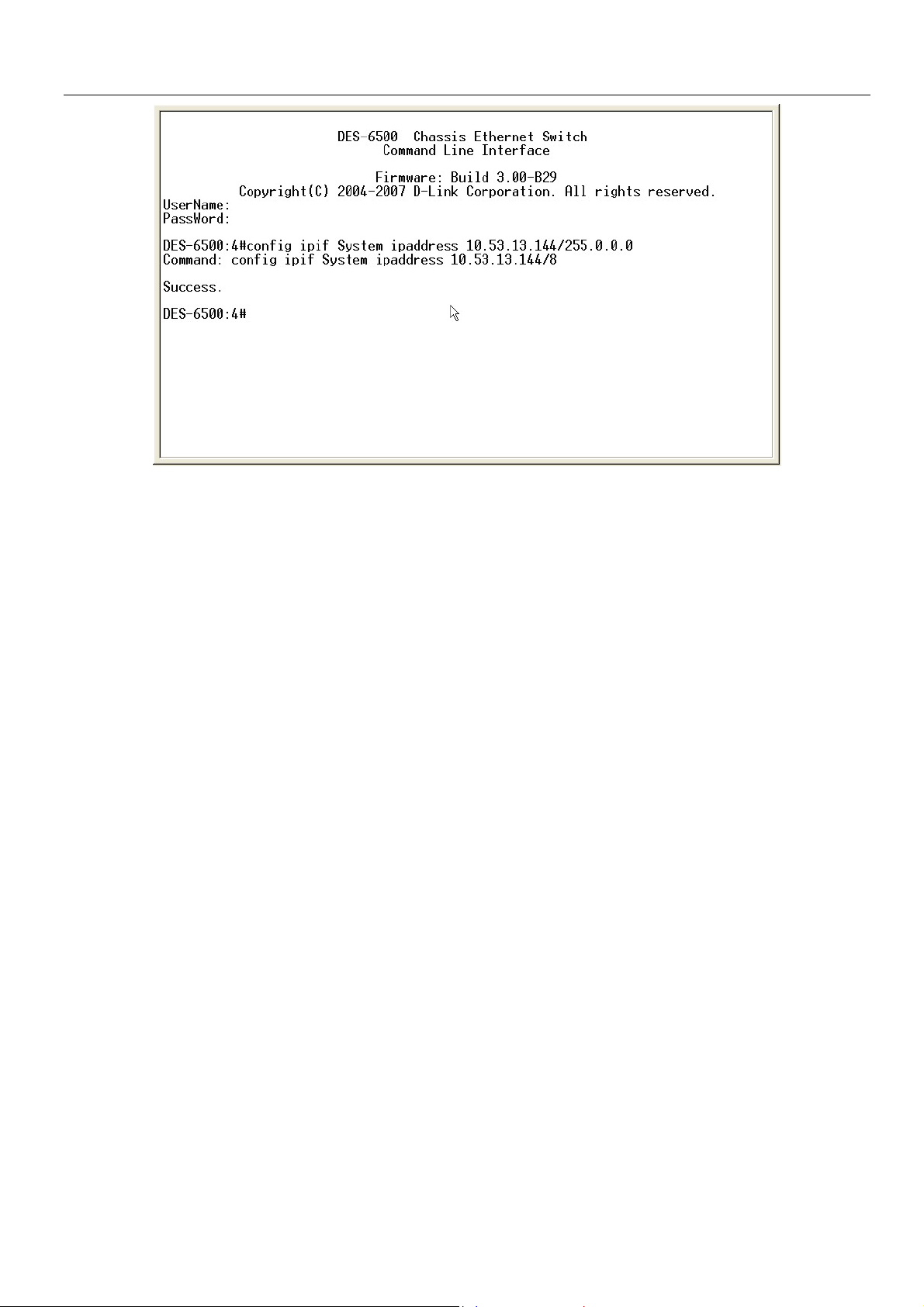
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Figure 1-3. Assigning an IP Address
In the above example, the Switch was assigned an IP address of 10.53.13.144 with a subnet mask of 255.0.0.0. The system
message Success indicates that the command was executed successfully. The Switch can now be configured and managed via
Telnet and the CLI or via the Web-based management agent using the above IP address to connect to the Switch.
3
Page 7

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
2
USING THE CONSOLE CLI
The XStack DES-6500 supports a console management interface that allows the user to connect to the Switch’s management
agent via a serial port and a terminal or a computer running a terminal emulation program. The console can also be used over the
network using the TCP/IP Telnet protocol. The console program can be used to configure the Switch to use an SNMP-based
network management software over the network.
This chapter describes how to use the console interface to access the Switch, change its settings, and monitor its operation.
Note: Switch configuration settings are saved to non-volatile RAM using
the save command. The current configuration will then be retained in the
Switch’s NV-RAM, and reloaded when the Switch is rebooted. If the
Switch is rebooted without using the save command, the last configuration
saved to NV-RAM will be loaded.
Connecting to the Switch
The console interface is used by connecting the Switch to a VT100-compatible terminal or a computer running an ordinary
terminal emulator program (e.g., the HyperTerminal program included with the Windows operating system) using an RS-232C
serial cable. Your terminal parameters will need to be set to:
• VT-100 compatible
• 115200 baud
• 8 data bits
• No parity
• One stop bit
• No flow control
You can also access the same functions over a Telnet interface. Once you have set an IP address for your Switch, you can use a
Telnet program (in VT-100 compatible terminal mode) to access and control the Switch. All of the screens are identical,
whether accessed from the console port or from a Telnet interface.
After the Switch reboots and you have logged in, the console looks like this:
4
Page 8

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Figure 2-1. Initial Console Screen
Commands are entered at the command prompts, DES-6500:4#.
There are a number of helpful features included in the CLI. Entering the ? command will display a list of all of the top-level
commands.
Figure 2-2. The ? Command
When entering a command without its required parameters, the CLI will prompt you with a Next possible completions:
message.
5
Page 9

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Figure 2-3. Example Command Parameter Help
In this case, the command config account was entered with the parameter <username>. The CLI will then prompt to enter the
<username> with the message, Next possible completions:. Every command in the CLI has this feature, and complex
commands have several layers of parameter prompting.
In addition, after typing any given command plus one space, you can see all of the next possible sub-commands, in sequential
order, by repeatedly pressing the Tab key.
To re-enter the previous command at the command prompt, press the up arrow cursor key. The previous command will appear at
the command prompt.
Figure 2-4. Using the Up Arrow to Re-enter a Command
In the above example, the command config account was entered without the required parameter <username>, the CLI returned
the Next possible completions: <username> prompt. The up arrow cursor control key was pressed to re-enter the previous
command (config account) at the command prompt. Now the appropriate User name can be entered and the config account
command re-executed.
All commands in the CLI function in this way. In addition, the syntax of the help prompts are the same as presented in this
manual − angle brackets < > indicate a numerical value or character string, braces { } indicate optional parameters or a choice of
parameters, and brackets [ ] indicate required parameters.
6
Page 10

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
If a command is entered that is unrecognized by the CLI, the top-level commands will be displayed under the Available
commands: prompt.
Figure 2-5. The Available Commands Prompt
The top-level commands consist of commands such as show or config. Most of these commands require one or more parameters
to narrow the top-level command. This is equivalent to show what? or config what? Where the what? is the next parameter.
For example, if you enter the show command with no additional parameters, the CLI will then display all of the possible next
parameters.
Figure 2-6. Next possible completions: Show Command
In the above example, all of the possible next parameters for the show command are displayed. At the next command prompt,
the up arrow was used to re-enter the show command, followed by the account parameter. The CLI then displays the user
accounts configured on the Switch.
7
Page 11

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
3
COMMAND SYNTAX
The following symbols are used to describe how command entries are made and values and arguments are specified in this
manual. The online help contained in the CLI and available through the console interface uses the same syntax.
Note: All commands are case-sensitive. Be sure to disable Caps Lock or
any other unwanted function that changes text case.
<angle brackets>
Purpose Encloses a variable or value that must be specified.
Syntax
Description In the above syntax example, the user must supply an IP
Example Command
create ipif <ipif_name> <network_address> <vlan_name 32>
{secondary | state [enabled | disabled]}
interface name in the <ipif_name> space, a VLAN name in the
<vlan_name 32> space, and the network address in the
<network_address> space. Do not type the angle brackets.
create ipif Engineering 10.24.22.5/255.0.0.0 Design
[square brackets]
Purpose Encloses a required value or set of required arguments. One
value or argument can be specified.
Syntax
Description
Example Command
create account [admin | user] <username 15>
In the above syntax example, you must specify either an admin
or a user level account to be created. Do not type the square
brackets.
create account admin
| vertical bar
Purpose Separates two or more mutually exclusive items in a list, one of
which must be entered.
Syntax
Description
Example Command
create account [admin | user] <username 15>
In the above syntax example, you must specify either admin, or
user. Do not type the vertical bar.
show snmp community
8
Page 12

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
{braces}
Purpose Encloses an optional value or set of optional arguments.
Syntax
Description In the above syntax example, you have the option to specify
Example command
reset {[config | system]}
config or system. It is not necessary to specify either optional
value, however the effect of the system reset is dependent on
which, if any, value is specified. Therefore, with this example
there are three possible outcomes of performing a system
reset. See the following chapter, Basic Commands for more
details about the reset command.
reset config
Line Editing Key Usage
Delete Deletes the character under the cursor and then shifts the
remaining characters in the line to the left.
Backspace Deletes the character to the left of the cursor and shifts the
remaining characters in the line to the left.
Left Arrow Moves the cursor to the left.
Right Arrow Moves the cursor to the right.
Up Arrow Repeat the previously entered command. Each time the up
arrow is pressed, the command previous to that displayed
appears. This way it is possible to review the command history
for the current session. Use the down arrow to progress
sequentially forward through the command history list.
Down Arrow The down arrow will display the next command in the command
history entered in the current session. This displays each
command sequentially as it was entered. Use the up arrow to
review previous commands.
Tab Shifts the cursor to the next field to the left.
Multiple Page Display Control Keys
Space Displays the next page.
CTRL+c Stops the display of remaining pages when multiple pages are to
be displayed.
ESC Stops the display of remaining pages when multiple pages are to
be displayed.
n Displays the next page.
p Displays the previous page.
q Stops the display of remaining pages when multiple pages are to
be displayed.
r Refreshes the pages currently displayed.
a Displays the remaining pages without pausing between pages.
Enter Displays the next line or table entry.
9
Page 13
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
4
BASIC SWITCH COMMANDS
The basic switch commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in the
following table.
Command Parameters
create account [admin | user] <username 15>
config account <username 15>
show account
delete account <username 15>
show config [current_config | config_in_NVRAM]
show session
show switch
show device status
show serial_port
config serial_port {auto_logout [never | 2_minutes | 5_minutes | 10_minutes |
15_minutes]}
enable clipaging
disable clipaging
enable telnet <tcp_port_number 1-65535>
disable telnet
enable web <tcp_port_number 1-65535>
disable web
save
reboot
reset {[config | system]}
login
logout
config
command_prompt
config
greeting_message
[<string 16> | username | default]
{default}
show
greeting_message
Each command is listed, in detail, in the following sections.
10
Page 14

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create account
Purpose Used to create user accounts.
Syntax
Description
Parameters admin <username> - Entering this parameter will give the
Restrictions Only Administrator-level users can issue this command.
Example usage:
To create an administrator-level user account with the username “dlink”.
create [admin | user] <username 15>
The create account command is used to create user accounts
that consist of a username of 1 to 15 characters and a password
of 0 to 15 characters. Up to 8 user accounts can be created.
specified user administrative-level privileges over configuring
functions of the Switch. This user may perform any function listed
in this manual. A username of up to 15 characters must be
created with this command to identify the admin user.
user <username> - Entering this parameter will give the specified
user user-level privileges over configuring functions of the Switch.
User-level privileges limit the execution of many commands listed
in this manual. A username of up to 15 characters must be
created with this command to identify the user.
Usernames can be between 1 and 15 characters.
Passwords can be between 0 and 15 characters.
DES-6500:4#create account admin dlink
Command: create account admin dlink
Enter a case-sensitive new password:****
Enter the new password again for confirmation:****
Success.
DES-6500:4#
config account
Purpose Used to configure user accounts
Syntax
Description
Parameters <username>- Enter the username of the account to be configured.
Restrictions Only Administrator-level users can issue this command.
config account <username>
The config account command configures a user account that
has been created using the create account command.
Usernames can be between 1 and 15 characters.
Example usage:
To configure the user password of “dlink” account:
Passwords can be between 0 and 15 characters.
11
Page 15
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config account dlink
Command: config account dlink
Enter a old password:****
Enter a case-sensitive new password:****
Enter the new password again for confirmation:****
Success.
DES-6500:4#
show account
Purpose Used to display user accounts.
Syntax
Description Displays all user accounts created on the Switch. Up to 8 user
Parameters None.
Restrictions None.
Example usage:
To display the accounts that have been created:
show account
accounts can exist on the Switch at one time.
DES-6500:4#show account
Command: show account
Current Accounts:
Username Access Level
--------------- -----------dlink Admin
DES-6500:4#
delete account
Purpose Used to delete an existing user account.
Syntax
Description
Parameters <username>- Enter the username of the account to be deleted.
Restrictions Only Administrator-level users can issue this command.
Example usage:
To delete the admin account “System”:
delete account <username>
The delete account command deletes a user account that has
been created using the create account command.
12
Page 16
Example usage:
To delete the user account “System2”:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#delete account System
Command: delete account System
Are you sure to delete the last administrator account?(y/n)y
Success.
DES-6500:4#
DES-6500:4#delete account System2
Command: delete account System2
Success.
DES-6500:4#
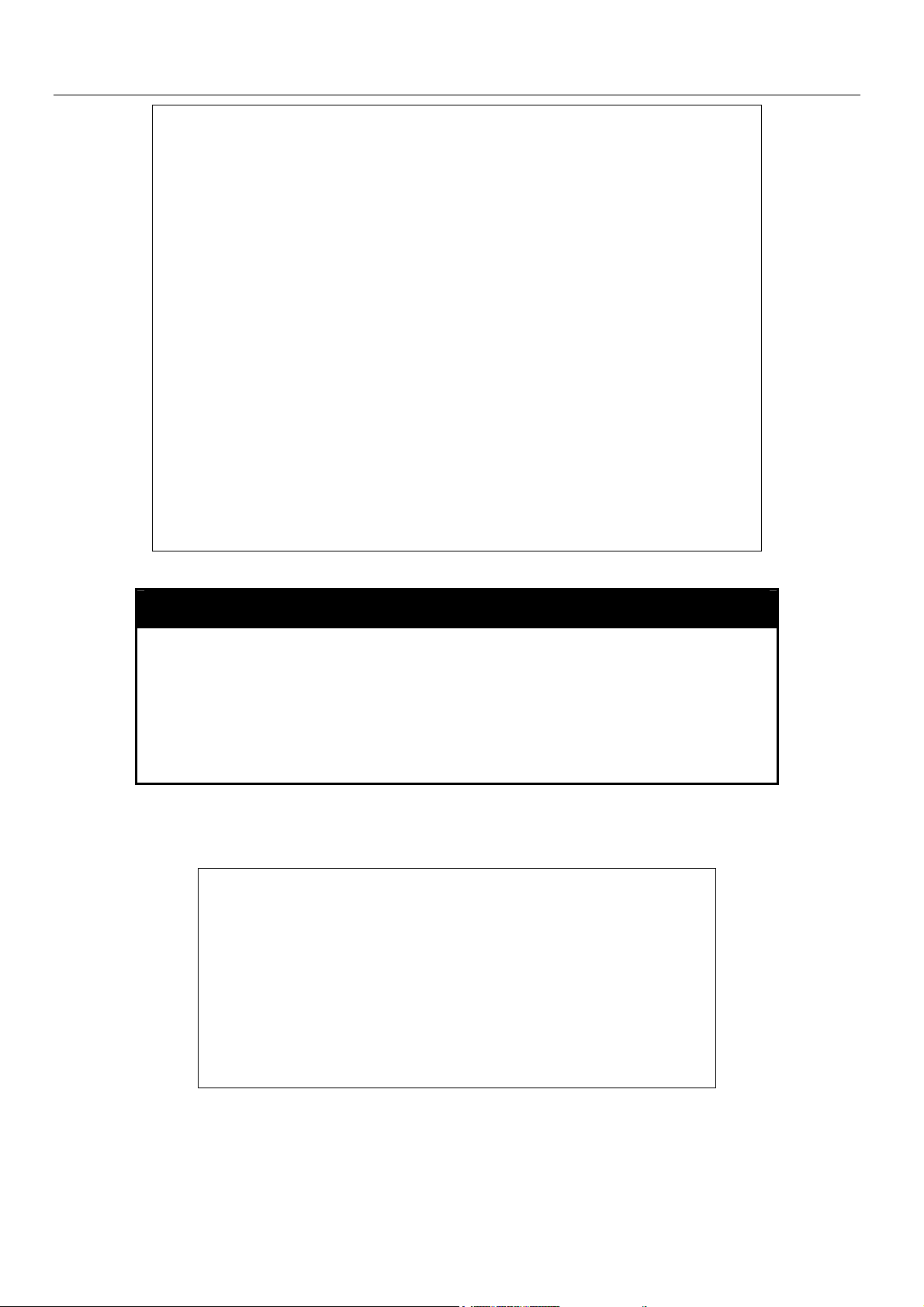
show config
Purpose Used to display a list of configuration commands entered into the
Switch.
Syntax
Description This command displays a list of configuration commands entered
Parameters current_config – Entering this parameter will display configurations
Restrictions None.
Example usage:
To view configurations entered on the Switch that were saved to NVRAM:
show config [current_config | config_in_NVRAM]
into the Switch.
entered without being saved to NVRAM.
config_in_NVRAM - Entering this parameter will display
configurations entered and saved to NVRAM.
13
Page 17
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Command: show config config_in_NVRAM
#-----------------------------------------------------------------------------------------------------# DES-6500 Configuration
#
# Firmware: Build 3.00-B29
# Copyright(C) 2004-2007 D-Link Corporation. All rights reserved.
#------------------------------------------------------------------------------------------------------
# BASIC
config serial_port baud_rate 115200 auto_logout never
enable telnet 23
enable web 80
enable clipaging
# STORM
config traffic control 1:1-1:26 broadcast disable multicast disable dlf disable
threshold 128
config traffic control 2:1-2:24 broadcast disable multicast disable dlf disable
show session
Purpose Used to display a list of currently logged-in users.
Syntax
Description This command displays a list of all the users that are logged-in at
Parameters None.
Restrictions None.
Example usage:
To display the way that the users logged in:
CTRL+C ESC q Quit SPACE n Next Page ENTER Next Entry a All
show session
the time the command is issued.
DES-6500:4#show session
Command: show session
ID Live Time From Level Name
-- --------- -------------- ----- --------------*8 03:36:27 Serial Port 4 Anonymous
Total Entries: 1
CTRL+C ESC q Quit SPACE n Next Page ENTER Next Entry a All
14
Page 18
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
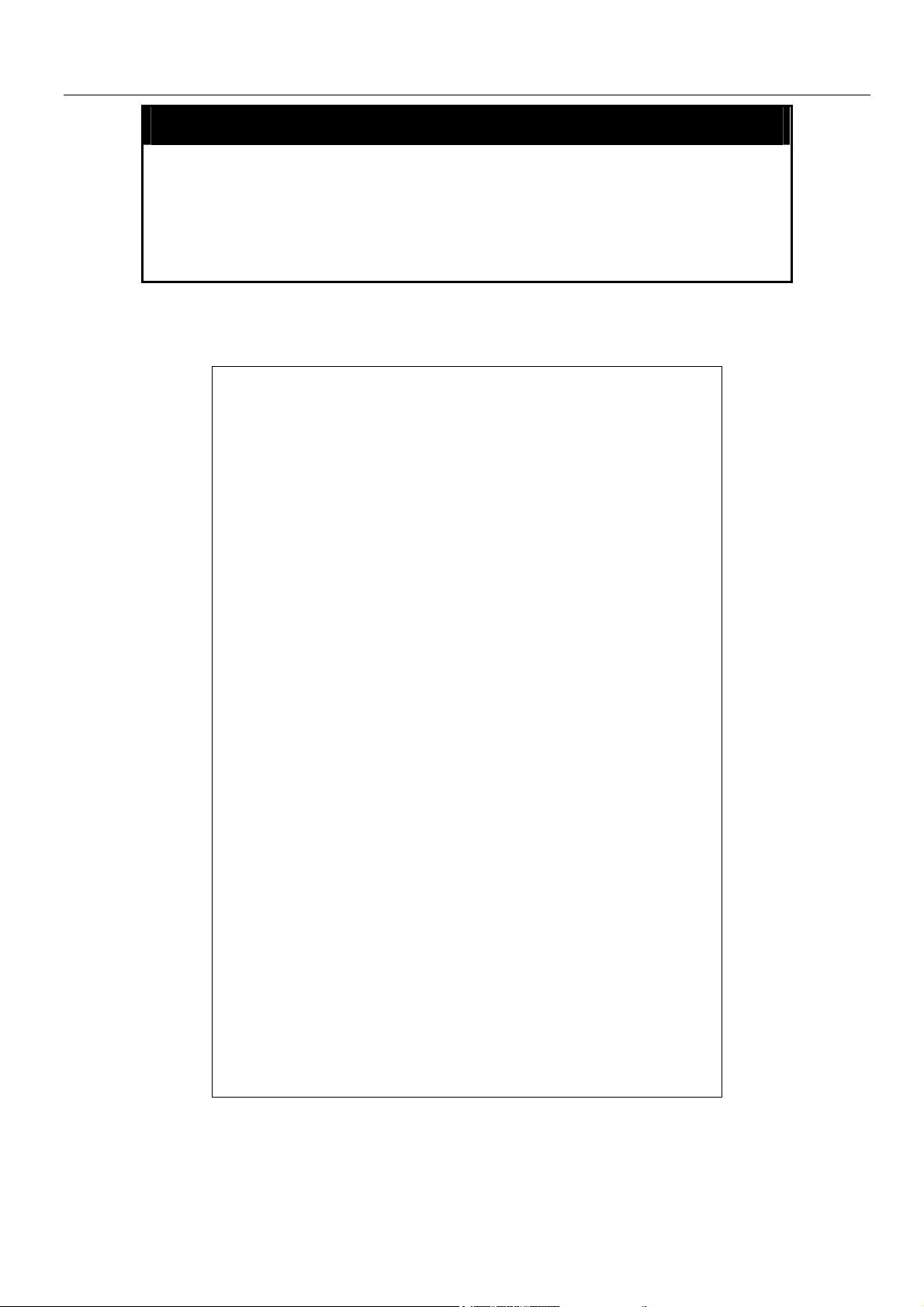
show switch
Purpose Used to display information about the Switch.
Syntax
Description This command displays information about the Switch.
Parameters None.
Restrictions None.
Example usage:
To display the Switch information:
show switch
DES-6500:4#show switch
Command: show switch
Device Type : DES-6500 Chassis Ethernet Switch
Unit ID : 1
MAC Address : DA-10-21-00-00-01
IP Address : 10.41.44.22 (Manual)
VLAN Name : default
Subnet Mask : 255.0.0.0
Default Gateway : 0.0.0.0
Boot PROM Version : Build 00170B20
Firmware Version : Build 2.00-B29
Hardware Version : 2A1
Device S/N :
System Name : DES-6500_#3
System Location : 7th_flr_east_cabinet
System Contact : Julius_Erving_212-555-6666
Spanning Tree : Disabled
GVRP : Disabled
IGMP Snooping : Disabled
802.1X : Disabled
Jumbo Frame : Off
Clipaging : Enabled
Port Mirror : Disabled
SNTP : Disabled
DHCP Relay : Disabled
DNSR Status : Disabled
VRRP : Disabled
DVMRP : Disabled
PIM-DM : Disabled
RIP : Disabled
OSPF : Disabled
TELNET : Enabled (TCP 23)
WEB : Enabled (TCP 80)
RMON : Enabled
HOL Prevention State : Enabled
Syslog Global State : Disabled
DES-6500:4#
15
Page 19
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
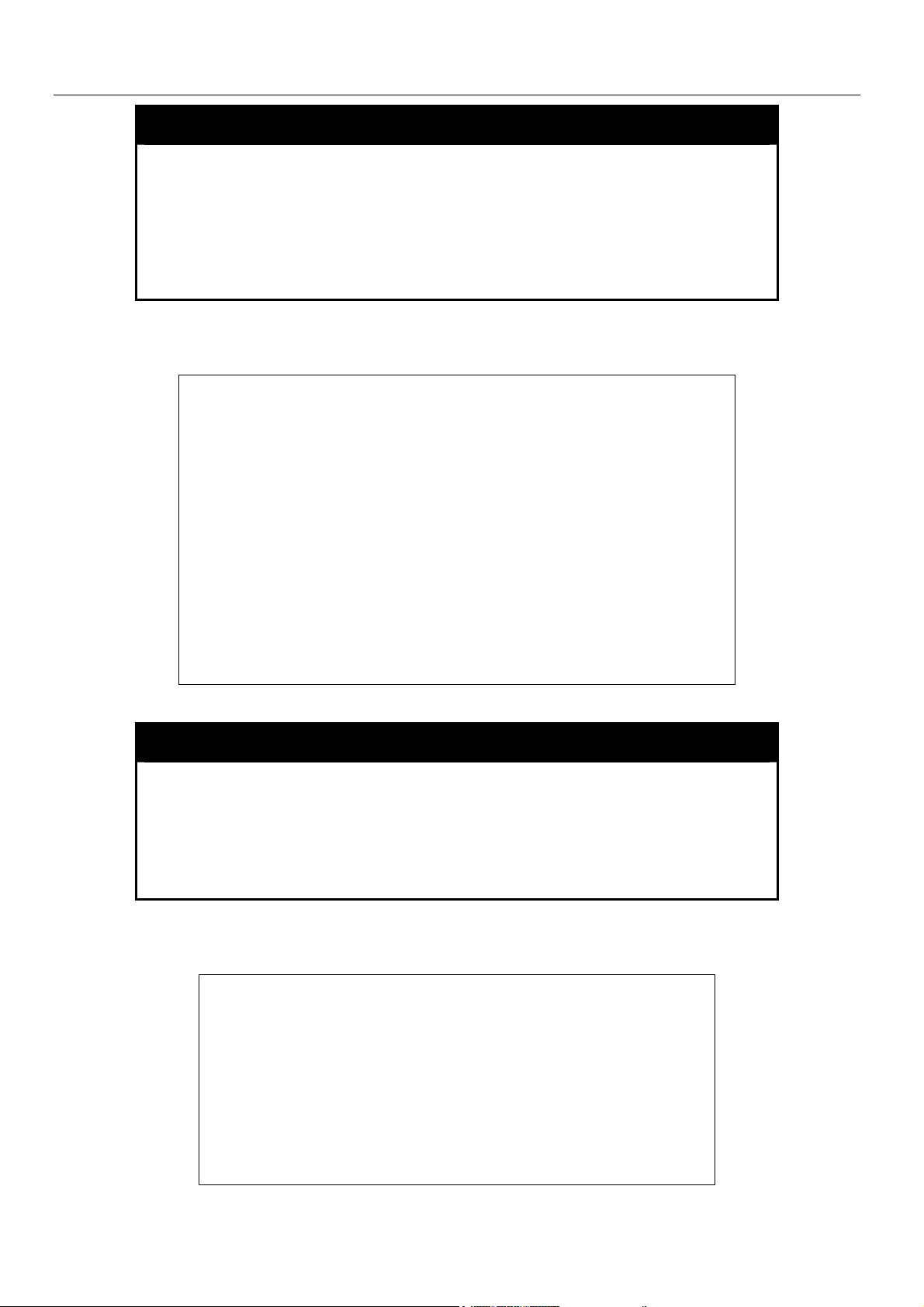
show device_status
Purpose Used to display the current status of the hardware of the Switch.
Syntax
Description This command displays the current status of the Switch’s physical
Parameters None.
Restrictions None.
Example usage:
To show the current hardware status of the Switch:
show device_status
elements.
DES-6500:4#show device_status
Command: show device_status
RPS1 Status:
Output voltage: Normal
FAN1: Normal
FAN2: Normal
RPS2 Status:
Not Exist
System FAN1: Normal
System FAN2: Normal
System FAN3: Normal
System FAN4: Normal
DES-6500:4#
show serial_port
Purpose Used to display the current serial port settings.
Syntax
Description This command displays the current serial port settings.
Parameters None.
Restrictions None.
Example usage:
To display the serial port settings:
show serial_port
DES-6500:4#show serial_port
Command: show serial_port
Baud Rate : 115200
Data Bits : 8
Parity Bits : None
Stop Bits : 1
Auto-Logout : 10 mins
DES-6500:4#
16
Page 20
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
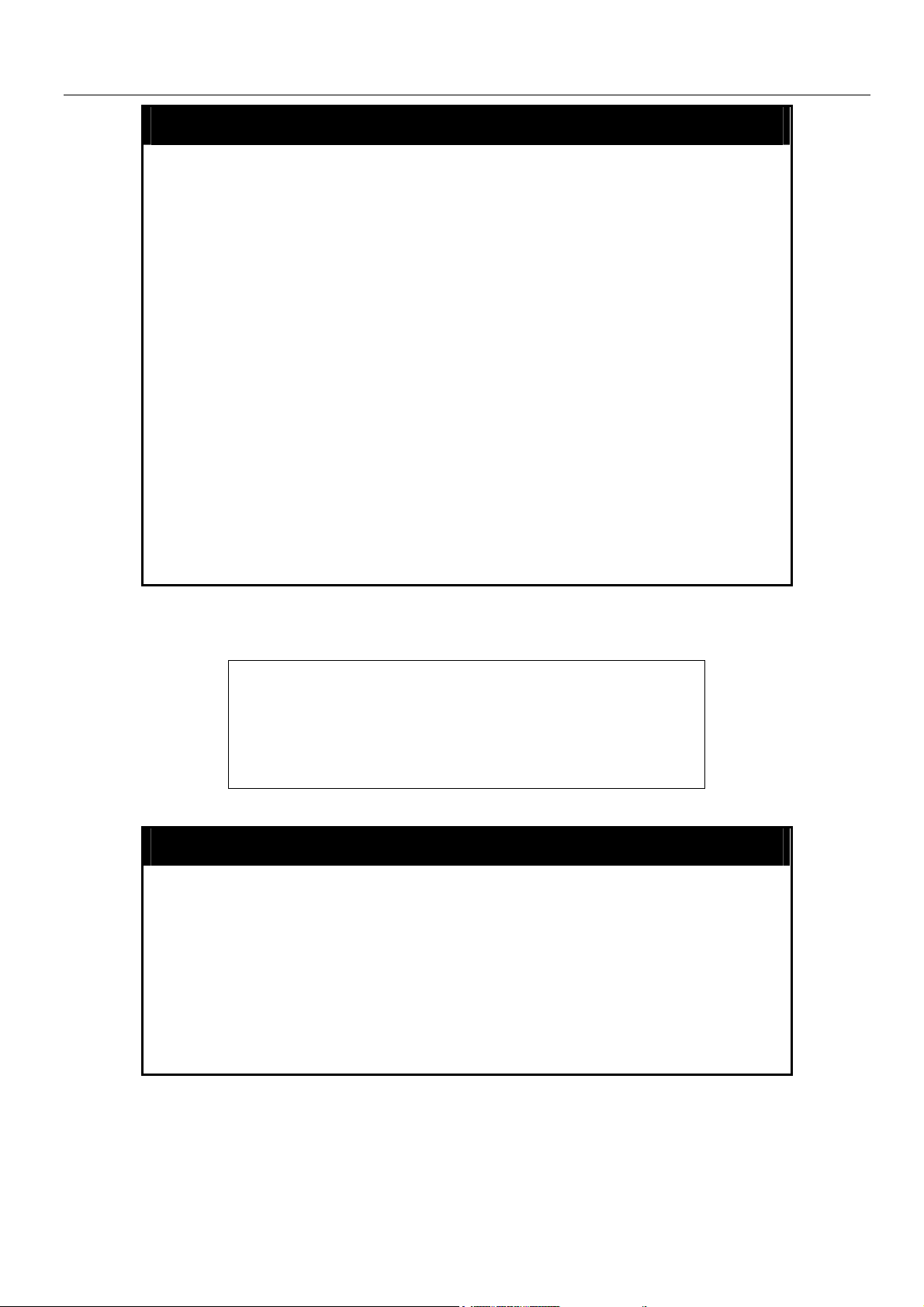
config serial_port
Purpose Used to configure the serial port.
Syntax
Description This command is used to configure the serial port’s baud rate
Parameters auto_logout – The user may select a time period from the
Restrictions Only administrator-level users can issue this command.
Example usage:
config serial_port {auto_logout [never | 2_minutes |
5_minutes | 10_minutes | 15_minutes]}
and auto logout settings.
following list which the Switch will automatically log out of the
serial port.
• never − No time limit on the length of time the console can
be open with no user input.
• 2_minutes − The console will log out the current user if
there is no user input for 2 minutes.
• 5_minutes − The console will log out the current user if
there is no user input for 5 minutes.
• 10_minutes − The console will log out the current user if
there is no user input for 10 minutes.
• 15_minutes − The console will log out the current user if
there is no user input for 15 minutes.
To configure baud rate:
DES-6500:4#config serial_port baud_rate 115200
Command: config serial_port baud_rate 115200
Success.
DES-6500:4#
enable clipaging
Purpose Used to pause the scrolling of the console screen when the show
command displays more than one page.
Syntax
Description This command is used when issuing the show command which
Parameters None.
Restrictions Only administrator-level users can issue this command.
enable clipaging
causes the console screen to rapidly scroll through several
pages. This command will cause the console to pause at the end
of each page. The default setting is enable.
Example usage:
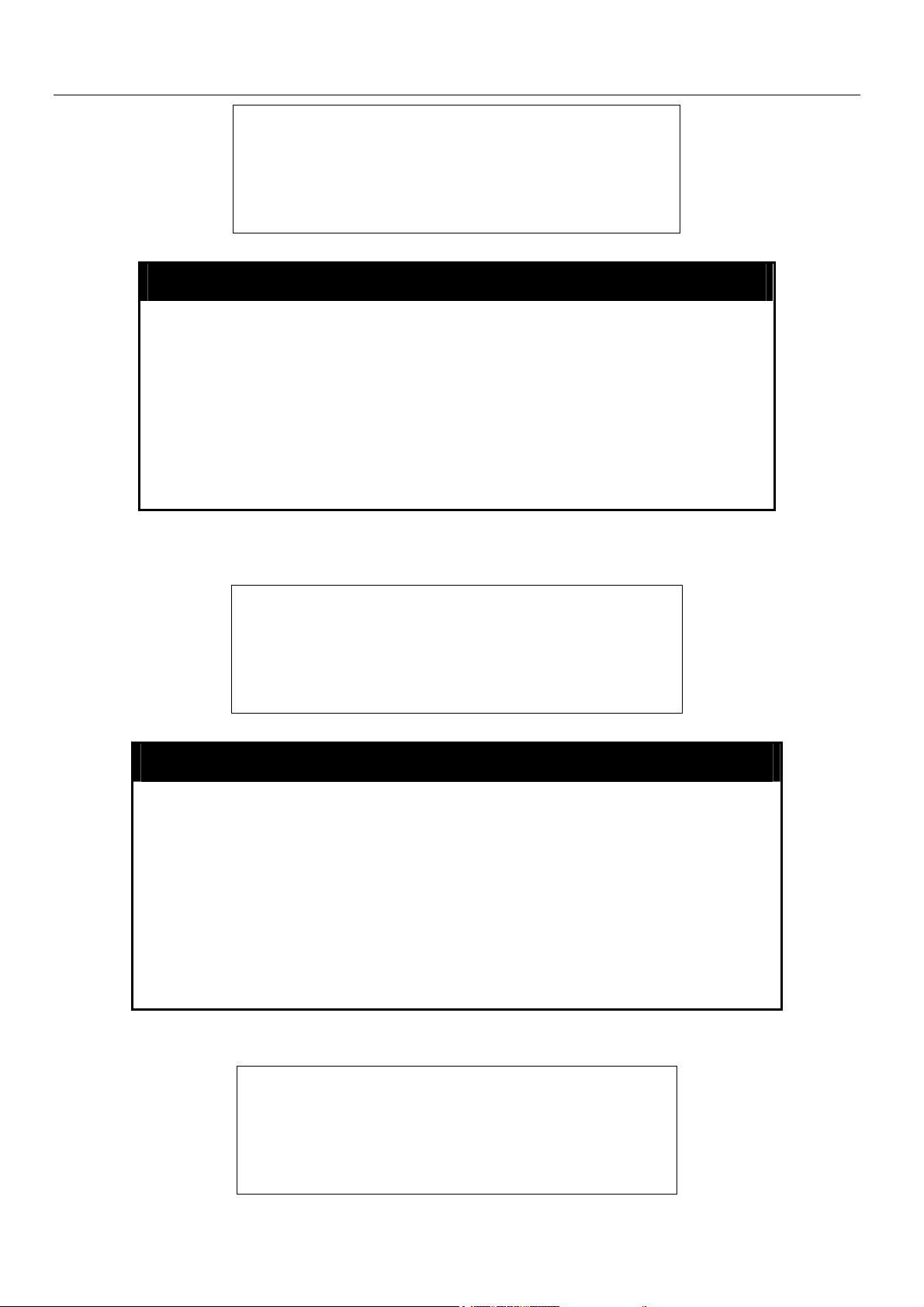
To enable pausing of the screen display when the command output reaches the end of the page:
17
Page 21
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#enable clipaging
Command: enable clipaging
Success.
DES-6500:4#
disable clipaging
Purpose Used to disable the pausing of the console screen scrolling at
the end of each page when the show command displays more
than one screen of information.
Example usage:
To disable pausing of the screen display when show command output reaches the end of the page:
enable telnet
Purpose Used to enable communication with and management of the
Syntax
Description This command is used to disable the pausing of the console
Parameters None.
Restrictions Only administrator-level users can issue this command.
DES-6500:4#disable clipaging
Command: disable clipaging
Success.
DES-6500:4#
disable clipaging
screen at the end of each page when the show command
would display more than one screen of information.
Switch using the Telnet protocol.
Syntax
Description This command is used to enable the Telnet protocol on the
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To enable Telnet and configure port number:
enable telnet <tcp_port_number 1-65535>
Switch. The user can specify the TCP or UDP port number the
Switch will use to listen for Telnet requests.
<tcp_port_number 1-65535>
ports are numbered between 1 and 65535. The “well-known”
TCP port for the Telnet protocol is 23.
DES-6500:4#enable telnet 23
Command: enable telnet 23
Success.
DES-6500:4#
18
−
The TCP port number. TCP
Page 22
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
disable telnet
Purpose Used to disable the Telnet protocol on the Switch.
Syntax
Description This command is used to disable the Telnet protocol on the
Parameters None.
Restrictions Only administrator-level users can issue this command.
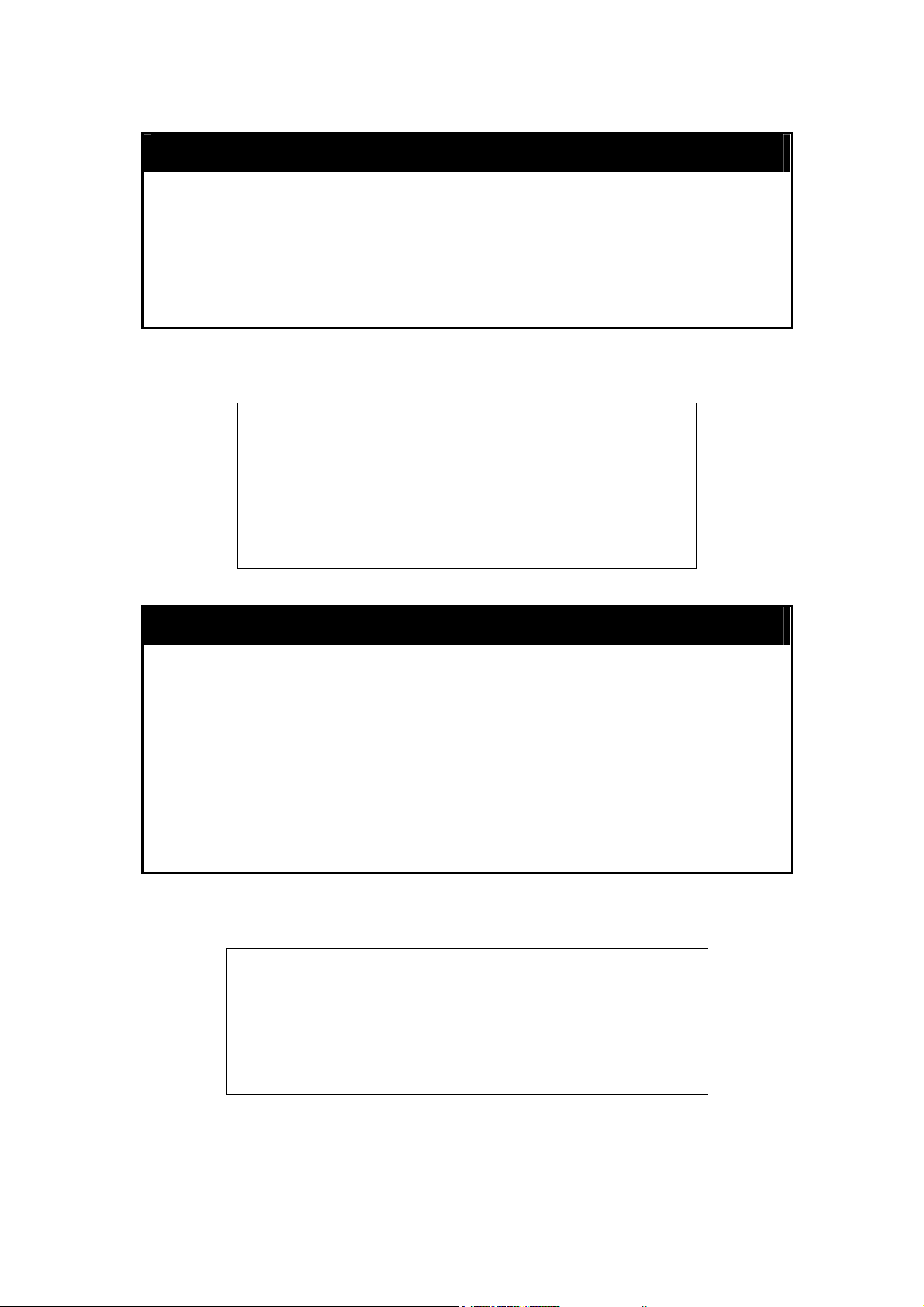
Example usage:
To disable the Telnet protocol on the Switch:
enable web
Purpose Used to enable the HTTP-based management software on the
disable telnet
Switch.
DES-6500:4#disable telnet
Command: disable telnet
Success.
DES-6500:4#
Switch.
Syntax
Description This command is used to enable the Web-based management
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To enable HTTP and configure port number:
enable web <tcp_port_number 1-65535>
software on the Switch. The user can specify the TCP port
number the Switch will use to listen for Telnet requests.
<tcp_port_number 1-65535> − The TCP port number. TCP ports
are numbered between 1 and 65535. The “well-known” port for
the Web-based management software is 80.
DES-6500:4#enable web 80
Command: enable web 80
Note: SSL will be disabled if web is enabled.
Success.
DES-6500:4#
19
Page 23
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
disable web
Purpose Used to disable the HTTP-based management software on the
Switch.
Syntax
Description This command disables the Web-based management software
Parameters None.
Restrictions Only administrator-level users can issue this command.
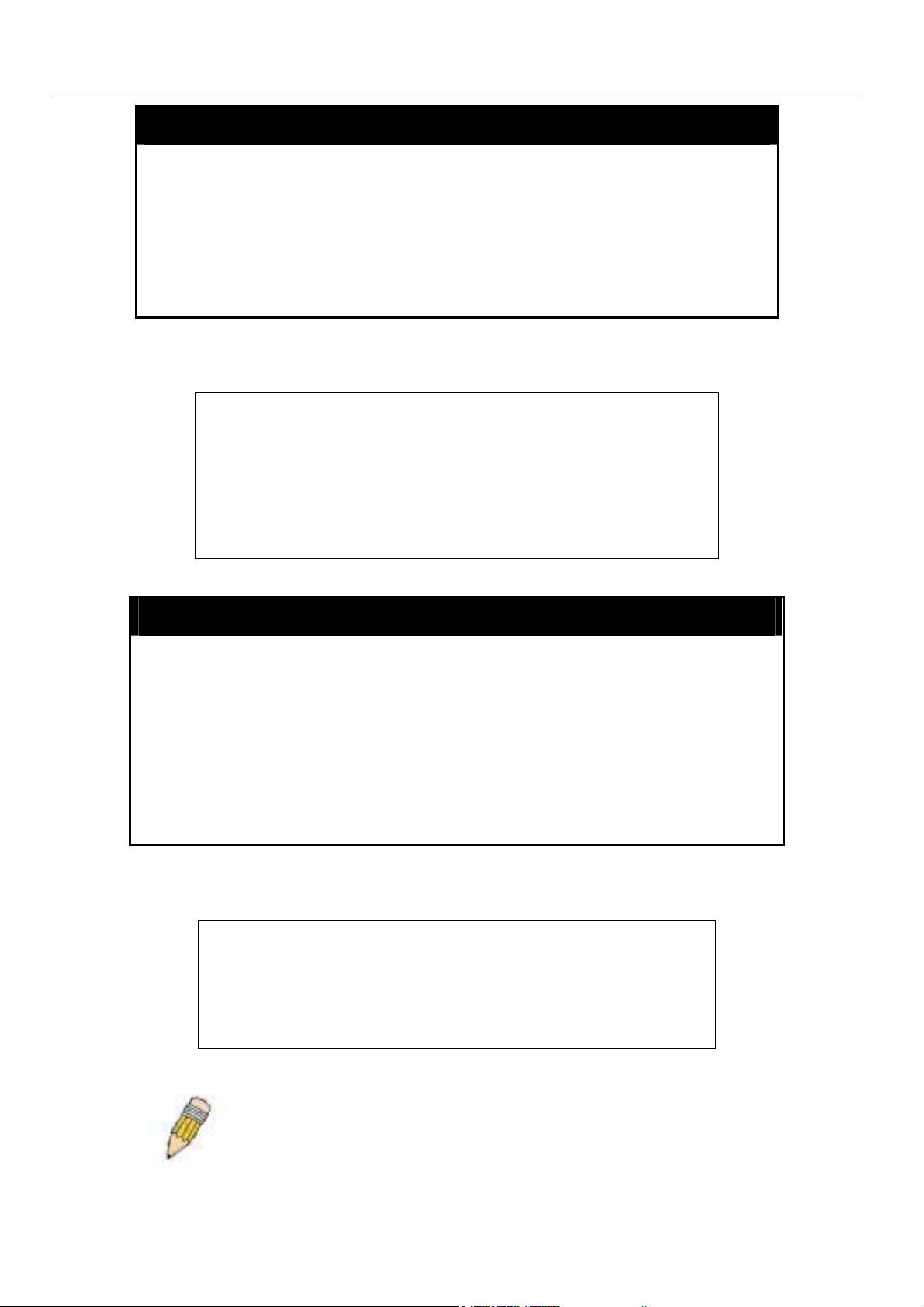
Example usage:
To disable HTTP:
save
Purpose Used to save changes in the Switch’s configuration to non-volatile
disable web
on the Switch.
DES-6500:4#disable web
Command: disable web
Success.
DES-6500:4#
RAM.
Syntax
Description This command is used to enter the current switch configuration into
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To save the Switch’s current configuration to non-volatile RAM:
save
non-volatile RAM. The saved switch configuration will be loaded into
the Switch’s memory each time the Switch is restarted.
Entering just the save command will save only the Switch configuration
to NV-Ram.
DES-6500:4#save
Command: save
Saving all configurations to NV-RAM… Done.
DES-6500:4#
NOTE: The DES-6500 does not support a change in box mode from Auto
to Static.
20
Page 24
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
reboot
Purpose Used to restart the Switch.
Syntax
Description This command is used to restart the Switch.
Parameters None.
Restrictions None.
Example usage:
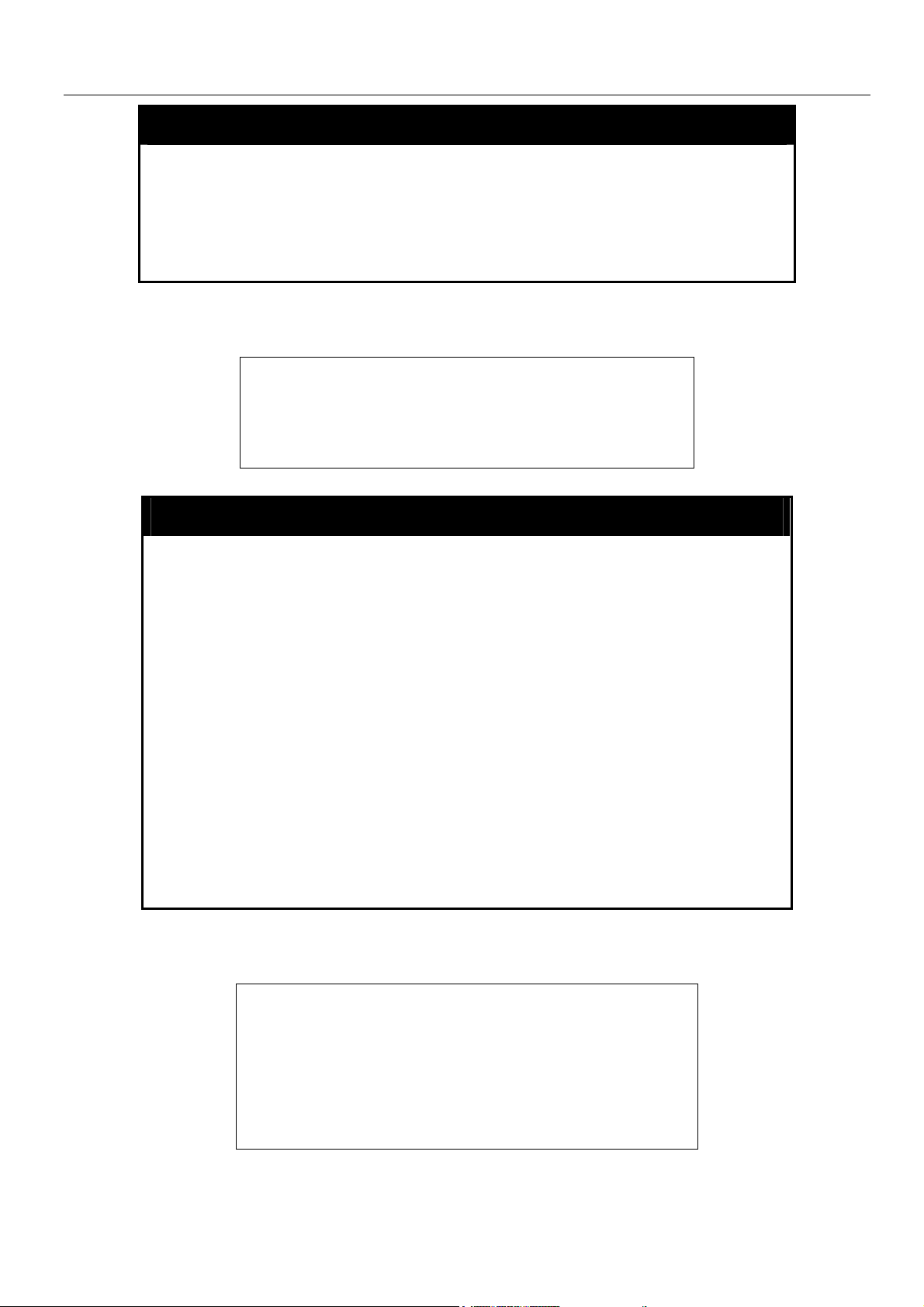
To restart the Switch:
DES-6500:4#reboot
Command: reboot
Are you sure want to proceed with the system reboot? (y/n)
Please wait, the Switch is rebooting...
reset
Purpose Used to reset the Switch to the factory default settings.
Syntax
Description This command is used to restore the Switch’s configuration to the
reboot
reset {[config | system]}
default settings assigned from the factory.
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To restore all of the Switch’s parameters to their default values:
DES-6500:4#reset config
Command: reset config
Success.
config − If the keyword ‘config’ is specified, all of the factory
default settings are restored on the Switch including the IP
address, user accounts, and the Switch history log. The Switch
will not save or reboot.
system − If the keyword ‘system’ is specified all of the factory
default settings are restored on the Switch. The Switch will save
and reboot after the settings are changed to default. Rebooting
will clear all entries in the Forwarding Data Base.
If no parameter is specified, the Switch’s current IP address, user
accounts, and the Switch history log are not changed. All other
parameters are restored to the factory default settings. The Switch
will not save or reboot.
DES-6500:4#
21
Page 25
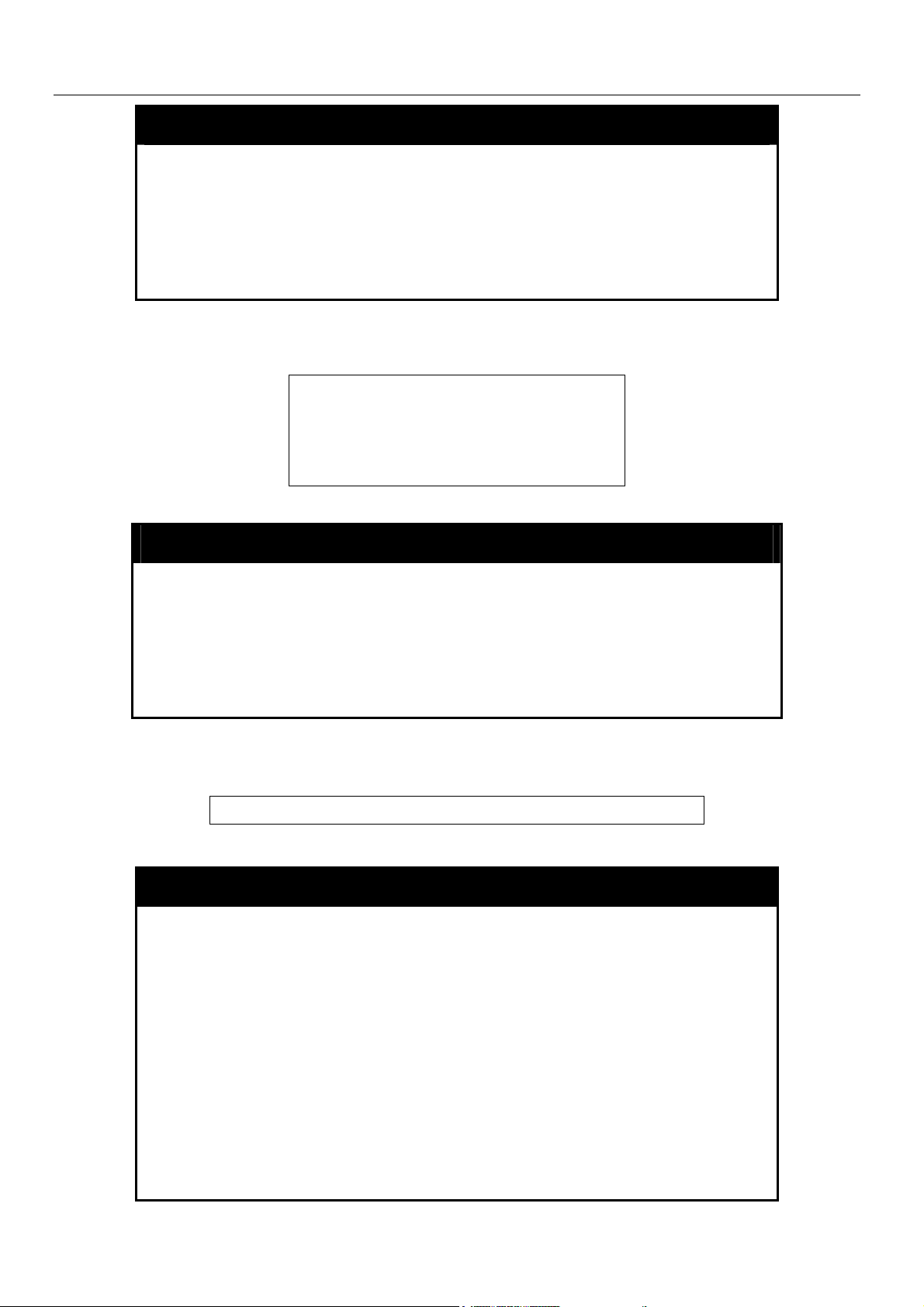
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
login
Purpose Used to log in a user to the Switch’s console.
Syntax
Description This command is used to initiate the login procedure. The user
Parameters None.
Restrictions None.
Example usage:
To initiate the login procedure:
logout
Purpose Used to log out a user from the Switch’s console.
Syntax
Description This command terminates the current user’s session on the
login
will be prompted for his Username and Password.
DES-6500:4#login
Command: login
UserName:
logout
Switch’s console.
Parameters None.
Restrictions None.
Example usage:
To terminate the current user’s console session:
config command_prompt
Purpose Used to configure the command prompt for the Command Line
Syntax
Description This command is used to configure the command prompt for the
DES-6500:4#logout
Interface.
config command_prompt [<string 16> | username | default]
CLI interface of the Switch. The current command prompt
consists of “product name + : + user level + product name” (ex.
DES-6500:4#). The user may replace all parts of the command
prompt, except the # by entering a string of 16 alphanumerical
characters with no spaces, or the user may enter the current
login username configured on the Switch.
Parameters <string 16> - Enter an alphanumeric string of no more than 16
characters to define the command prompt for the CLI interface.
username – Entering this parameter will replace the current CLI
command prompt with the login username configured on the
22
Page 26
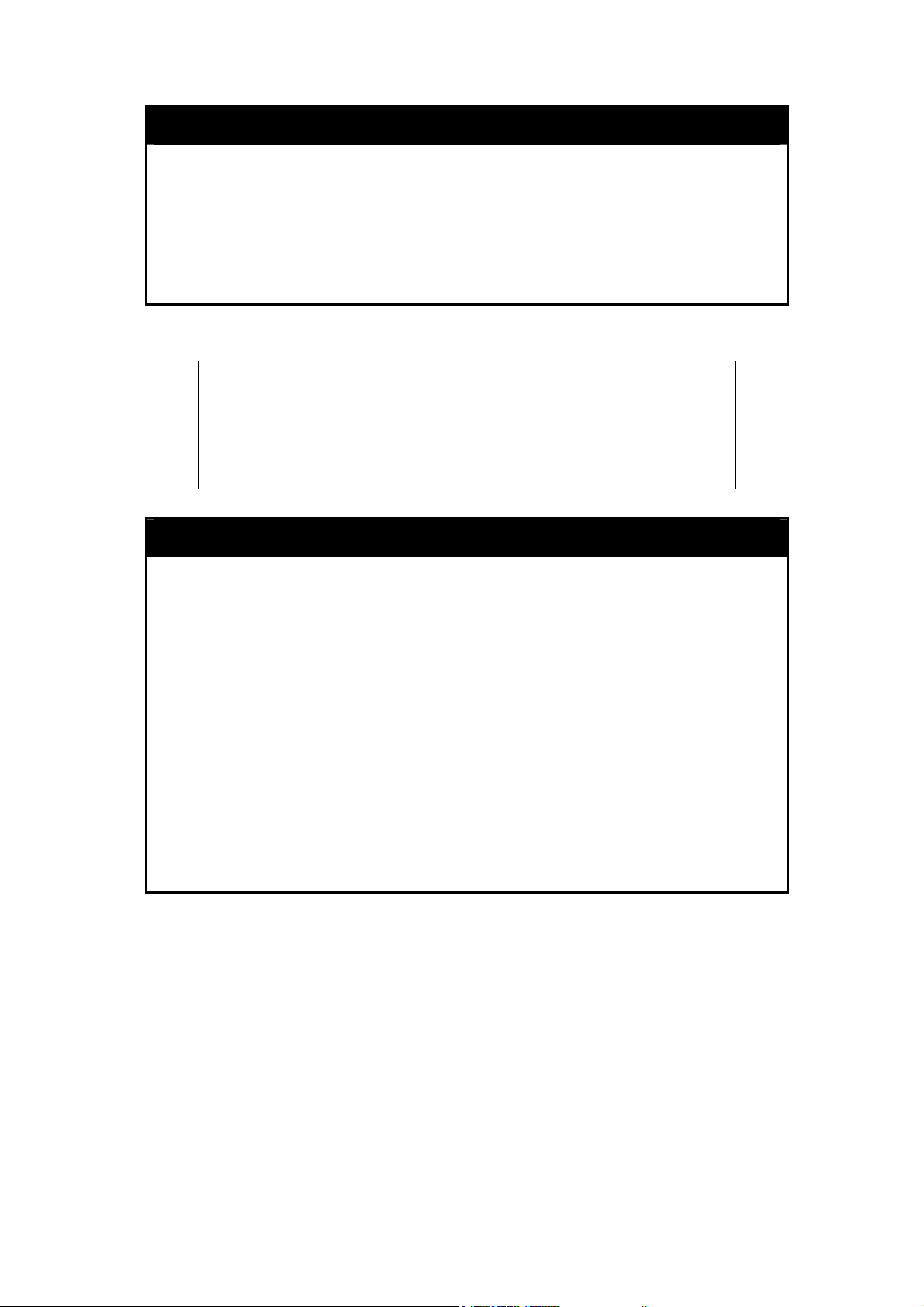
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config command_prompt
Switch.
default – Entering this parameter will return the command
prompt to its original factory default setting.
Restrictions
Example usage:
To configure the command prompt:
DES-6500:4#config command prompt Trinity
Command: config command prompt Trinity
Success.
Trinity#
The reset command will not alter the configured command
prompt, yet the reset system command will return the command
prompt to its original factory default setting.
Only administrator-level users can issue this command.
config greeting_message
Purpose Used to configure the greeting message or banner for the
opening screen of the Command Line Interface.
Syntax
Description This command is used to configure the greeting message or
config greeting_message {default}
login banner for the opening screen of the CLI.
Parameters default – Adding this parameter will return the greeting command
to its original factory default configuration.
Restrictions
Example usage:
To configure the greeting message:
The reset command will not alter the configured greeting
message, yet the reset system command will return the
greeting message to its original factory default setting.
The maximum character capacity for the greeting banned is 6
lines and 80 characters per line. Entering Ctrl+W will save the
current configured banner to the DRAM only. To enter it into the
FLASH memory, the user must enter the save command.
Only administrator-level users can issue this command.
23
Page 27
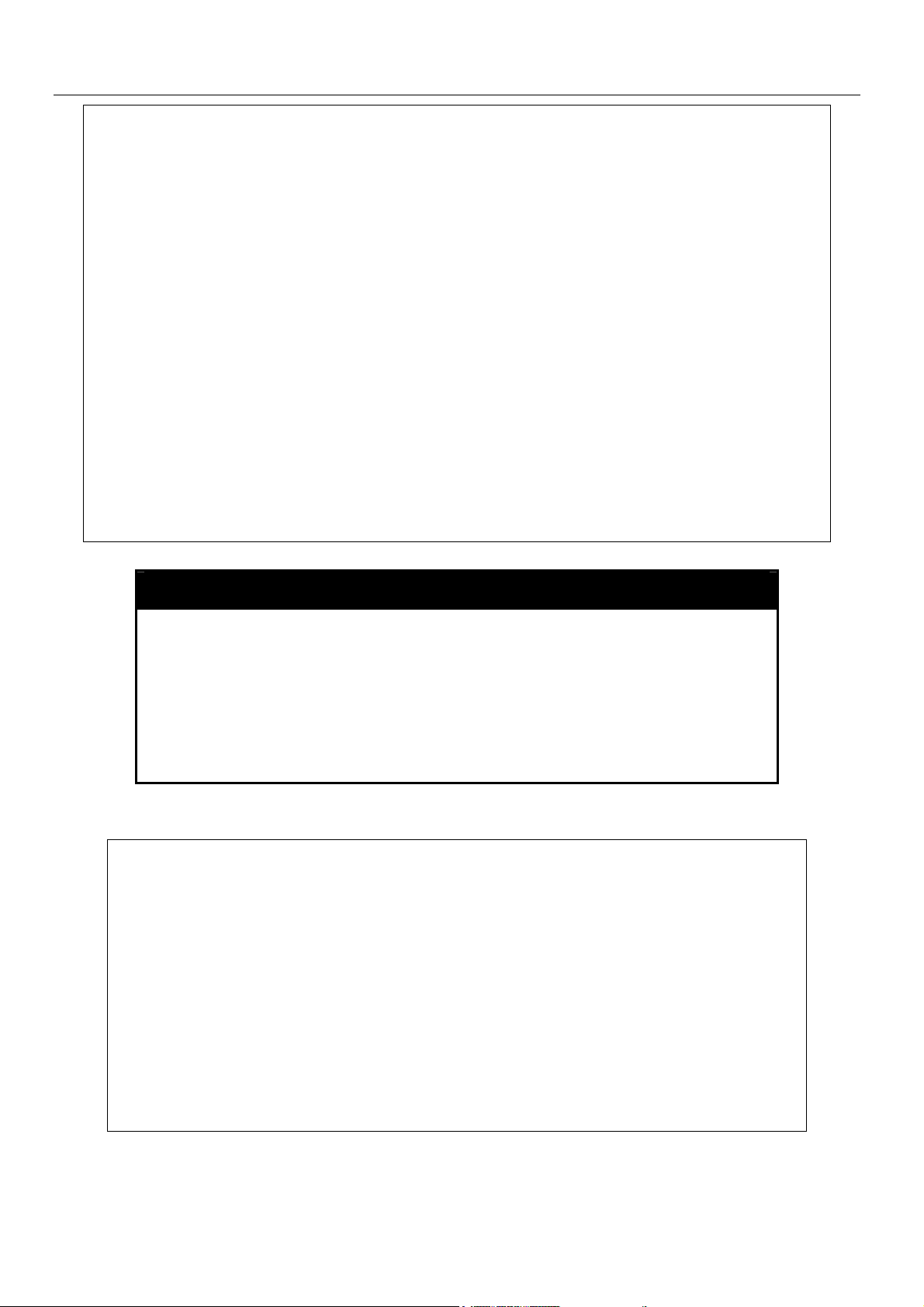
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config greeting_message
Command: config greeting_message
Greeting Messages Editor
===============================================================================
DES-6500 Chassis Ethernet Switch
Command Line Interface
Firmware: Build 3.00-B29
Copyright(C) 2004-2007 D-Link Corporation. All rights Reserved
===============================================================================
<Function Key> <Control Key>
Ctrl+C Quit without save left/right/
Ctrl+W Save and quit up/down Move cursor
Ctrl+D Delete line
Ctrl+X Erase all setting
Ctrl+L Reload original setting
------------------------------------------------------------------------------------------------------------------------------------------
Success.
DES-6500:4#
show greeting_message
Purpose Used to view the currently configured greeting message
configured on the Switch.
Syntax
Description This command is used to view the currently configured greeting
Parameters None.
Restrictions None.
Example usage:
To view the currently configured greeting message:
DES-6500:4#show greeting_message
Command: show greeting_message
=========================================================================
DES-6500 Chassis Ethernet Switch
Command Line Interface
Firmware: Build 3.00-B14
Copyright(C) 2004-2007 D-Link Corporation. All rights Reserved
=========================================================================
Success.
DES-6500:4#
show greeting_message
message on the Switch.
24
Page 28
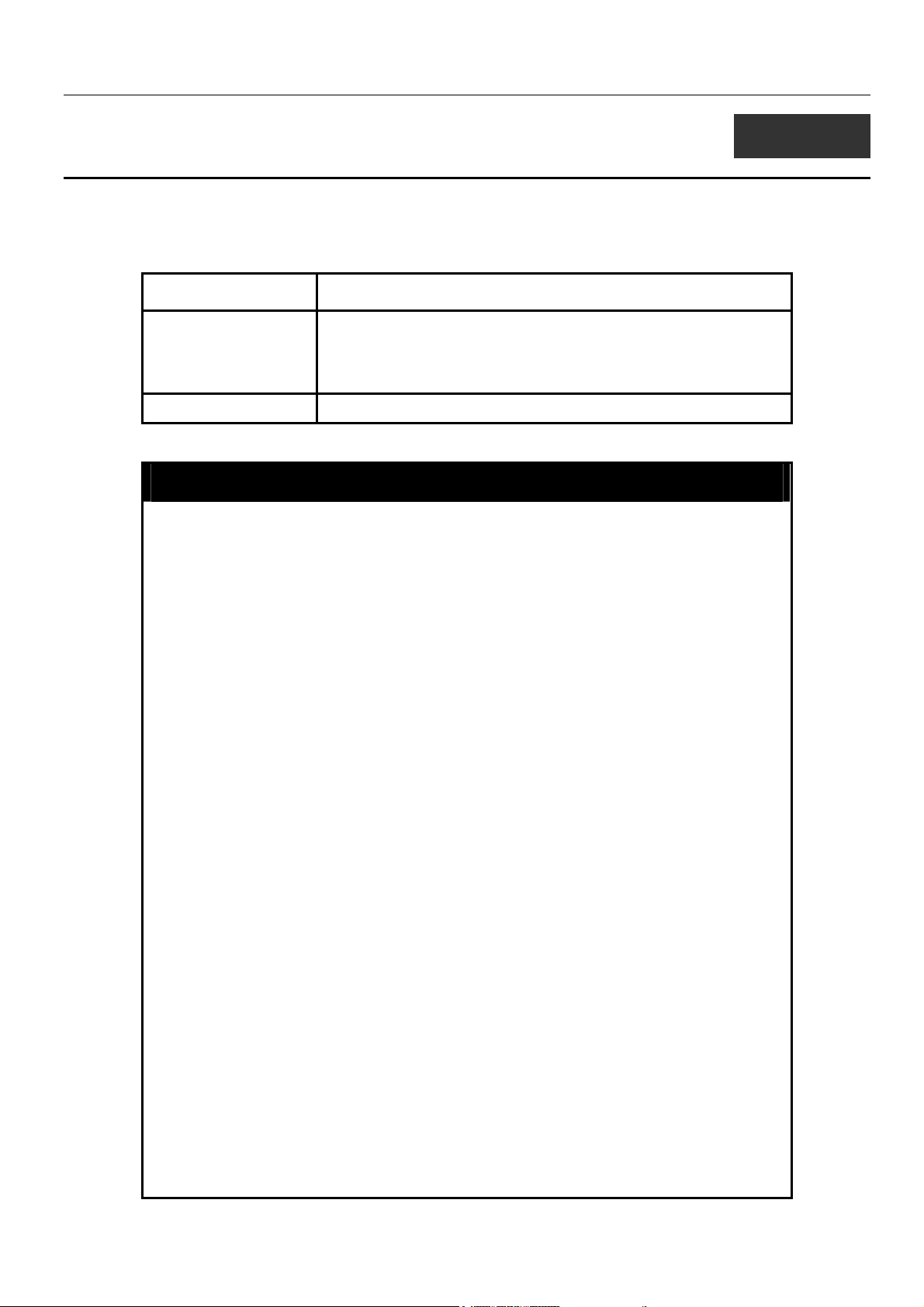
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
5
SWITCH PORT COMMANDS
The switch port commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in the
following table.
Command Parameters
config ports [<portlist> | all] {speed [auto | 10_half | 10_full | 100_half | 100_full
| 1000_full {[master | slave | None]} | flow_control [enabled |
disabled] | learning [enabled | disabled] state [enabled | disabled] |
description <desc 32> | clear]}
show ports {<portlist>} {description}
Each command is listed, in detail, in the following sections.
config ports
Purpose Used to configure the Switch’s Ethernet port settings.
Syntax
Description This command allows for the configuration of the Switch’s
Parameters
[<portlist> | all] {speed [auto | 10_half | 10_full | 100_half |
100_full | 1000_full {[master | slave | None]} | flow_control
[enabled | disabled] | learning [enabled | disabled] state
[enabled | disabled] | description <desc 32> | clear]}
Ethernet ports. Only the ports listed in the <portlist> will be
affected.
all − Configure all ports on the Switch.
<portlist> − Specifies a range of ports to be configured. The port
list is specified by listing the lowest switch number and the
beginning port number on that switch, separated by a colon. Then
the highest switch number, and the highest port number of the
range (also separated by a colon) are specified. The beginning
and end of the port list range are separated by a dash. For
example, 1:3 specifies switch number 1, port 3. 2:4 specifies
switch number 2, port 4. 1:3-2:4 specifies all of the ports between
switch 1, port 3 and switch 2, port 4 − in numerical order.
auto − Enables auto-negotiation for the specified range of ports.
[10 | 100 | 1000] − Configures the speed in Mbps for the specified
range of ports.
[half | full] − Configures the specified range of ports as either full-
or half-duplex.
[master | slave | None] – The master and slave parameters refer
to connections running a 1000BASE-T cable for connection
between the Switch port and other device capable of a gigabit
connection. The master setting will allow the port to advertise
capabilities related to duplex, speed and physical layer type. The
master setting will also determine the master and slave
relationship between the two connected physical layers. This
relationship is necessary for establishing the timing control
between the two physical layers. The timing control is set on a
master physical layer by a local source. The slave setting uses
loop timing, where the timing comes form a data stream received
25
Page 29

config ports
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure the speed of port 3 of unit 1 to be 10 Mbps, full duplex, learning and state enable:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
from the master. If one connection is set for 1000 master, the
other side of the connection must be set for 1000 slave. Any other
configuration will result in a link down status for both ports. None
denotes the Switch will serve no role for stacking.
flow_control [enabled | disabled] – Enable or disable flow control
for the specified ports.
learning [enabled| disabled] − Enables or disables the MAC
address learning on the specified range of ports.
state [enabled | disabled] − Enables or disables the specified
range of ports.
description <desc 32> - Enter an alphanumeric string of no more
than 32 characters to describe a selected port interface.
clear – Enter this command to clear the port description of the
selected port(s).
DES-6500:4#config ports 1:1-1:3 speed 10_full learning enabled state enabled
Command: config ports 1:1-1:3 speed 10_full learning enable stated enabled
Success.
DES-6500:4#
show ports
Purpose Used to display the current configuration of a range of ports.
Syntax
Description This command is used to display the current configuration of a
Parameters
show ports {<portlist>} {description}
range of ports.
{<portlist>} − Specifies a range of ports to be displayed. The port
list is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. Then the highest
slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 −
in numerical order.
Restrictions None.
Example usage:
To display the configuration of all ports on a standalone switch:
{description} – Adding this parameter to the command will allow
the user to view previously configured descriptions set on various
ports on the Switch.
26
Page 30
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show ports
Command: show ports
Port Port Settings Connection Address
State Speed/Duplex/FlowCtrl Speed/Duplex/FlowCtrl Learning
------ -------- --------------------- --------------------- -------1:1 Enabled Auto/Enabled Link Down Enabled
1:2 Enabled Auto/Enabled Link Down Enabled
1:3 Enabled Auto/Enabled Link Down Enabled
1:4 Enabled Auto/Enabled Link Down Enabled
1:5 Enabled Auto/Enabled Link Down Enabled
1:6 Enabled Auto/Enabled Link Down Enabled
1:7 Enabled Auto/Enabled Link Down Enabled
1:8 Enabled Auto/Enabled Link Down Enabled
1:9 Enabled Auto/Enabled Link Down Enabled
1:10 Enabled Auto/Enabled 100M/Full/802.3x Enabled
1:11 Enabled Auto/Enabled Link Down Enabled
1:12 Enabled Auto/Enabled Link Down Enabled
2:1 Enabled Auto/Disabled Link Down Enabled
2:2 Enabled Auto/Disabled Link Down Enabled
2:3 Enabled Auto/Disabled Link Down Enabled
2:4 Enabled Auto/Disabled Link Down Enabled
2:5 Enabled Auto/Disabled Link Down Enabled
2:6 Enabled Auto/Disabled Link Down Enabled
2:7 Enabled Auto/Disabled Link Down Enabled
2:8 Enabled Auto/Disabled Link Down Enabled
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
Example usage;
To display port descriptions:
DES-6500:4#show ports 1:1 description
Command: show ports 1:1 description
Port Port Settings Connection Address
State Speed/Duplex/FlowCtrl Speed/Duplex/FlowCtrl Learning
------ -------- --------------------- --------------------- -------1:1 Enabled Auto/Enabled Link Down Enabled
Description: Accounting
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
27
Page 31

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
6
PORT SECURITY COMMANDS
The port security commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in the
following table.
Command Parameters
config port_security ports [<portlist> | all] {admin_state [enabled | disabled] |
max_learning_addr <max_lock_no 0-64> |
lock_address_mode [Permanent | DeleteOnTimeout |
DeleteOnReset]}
show port_security {ports <portlist>}
delete
port_security_entry_vlan_name
Each command is listed, in detail, in the following sections.
<vlan_name 32> port <port> mac_address <macaddr>
config port_security ports
Purpose Used to configure port security settings.
Syntax
Description This command allows for the configuration of the port security
Parameters
[<portlist> | all] {admin_state [enabled | disabled] |
max_learning_addr <max_lock_no 0-64> |
lock_address_mode [Permanent | DeleteOnTimeout |
DeleteOnReset]}
feature. Only the ports listed in the <portlist> are effected.
<portlist> − Specifies a range of ports to be displayed. The port
list is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. Then the highest
slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 −
in numerical order.
all − Configure port security for all ports on the Switch.
admin_state [enabled | disabled] – Enable or disable port security
for the listed ports.
max_learning_addr <max_lock_no 0-64> - Use this to limit the
number of MAC addresses dynamically listed in the FDB for the
ports.
lock_address_mode [Permanent | DeleteOnTimeout |
DeleteOnReset] – Indicates the method of locking addresses. The
user has three choices:
Permanent – The locked addresses will not age out after
the aging timer expires.
DeleteOnTimeout – The locked addresses will age out
after the aging timer expires.
DeleteOnReset – The locked addresses will not age out
until the Switch has been reset.
Restrictions Only administrator-level users can issue this command.
28
Page 32

Example usage:
To configure the port security:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config port_security ports 5:1-5:5 admin_state enabled
max_learning_addr 5 lock_address_mode DeleteOnReset
Command: config port_security ports 5:1-5:5 admin_state enabled
max_learning_addr 5 lock_address_mode DeleteOnReset
Success
show port_security
Purpose Used to display the current port security configuration.
Syntax
Description This command is used to display port security information of the
Parameters
Restrictions None.
Example usage:
DES-6500:4#
show port_security {ports <portlist>}
Switch ports. The information displayed includes port security admin
state, maximum number of learning address and lock mode.
ports <portlist> − Specifies a range of ports to be displayed. The
port list is specified by listing the lowest slot number and the
beginning port number on that switch, separated by a colon. Then the
highest slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 − in
numerical order.
To display the port security configuration:
DES-6500:4#show port_security ports 1:1-1:10
Command: show port_security ports 1:1-1:10
Port# Admin State Max. Learning Addr. Lock Address Mode
---- ----------- ------------------- ----------------1:1 Disabled 1 DeleteOnReset
1:2 Disabled 1 DeleteOnReset
1:3 Disabled 1 DeleteOnReset
1:4 Disabled 1 DeleteOnReset
1:5 Disabled 1 DeleteOnReset
1:6 Disabled 1 DeleteOnReset
1:7 Enabled 10 DeleteOnReset
1:8 Disabled 1 DeleteOnReset
1:9 Disabled 1 DeleteOnReset
1:10 Disabled 1 DeleteOnReset
DES-6500:4#
29
Page 33

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
delete port_security_entry_vlan_name
Purpose Used to delete an entry from the Switch’s port security settings.
Syntax
Description This command is used to remove an entry from the port security
Parameters <vlan_name 32> - Enter the corresponding VLAN of the entry to
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete an entry from the port security list:
DES-6500:4#delete port_security_entry_vlan_name default port
1:1 mac_address 00-0C-6E-73-2B-C9
Command: delete port_security_entry_vlan_name default port
1:1 mac_address 00-0C-6E-73-2B-C9
delete
port_security_entry_vlan_name <vlan_name 32> port
<port> mac_address <macaddr>
entries learned by the Switch and entered into the forwarding
database.
delete.
port <port> - Enter the corresponding port of the entry to delete. The
port is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. For example, 1:3
specifies switch number 1, port 3. 2:4 specifies switch number 2,
port 4.
mac_address <macaddr> - Enter the corresponding MAC address of
the entry to delete.
Success
DES-6500:4#
30
Page 34

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
p
7
NETWORK MANAGEMENT (SNMP) COMMANDS
The network management commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in
the following table.
The xStack DES-6500 support the Simple Network Management Protocol (SNMP) versions 1, 2c, and 3. You can specify which
version of the SNMP you want to use to monitor and control the Switch. The three versions of SNMP vary in the level of
security provided between the management station and the network device. The following table lists the security features of the
three SNMP versions:
SNMP Version Authentication Method Description
v1 Community String
v2c Community String
v3 Username
v3 MD5 or SHA
v3 MD5 DES or SHA DES
Each command is listed, in detail, in the following sections.
Command Parameters
create snmp user create snmp user <SNMP_name 32> <groupname 32>
{encrypted [by_password auth [md5 <auth_password 8-16> | sha
<auth_password 8-20>] priv [none | des <priv_password 8-16>] |
by_key auth [md5 <auth_key 32-32> | sha <auth_key 40-40>]
priv [none | des <priv_key 32-32>]]}
delete snmp user <SNMP_name 32>
Community String is used for authentication − NoAuthNoPriv
Community String is used for authentication − NoAuthNoPriv
Username is used for authentication − NoAuthNoPriv
Authentication is based on the HMAC-MD5 or HMAC-SHA
algorithms − AuthNoPriv
Authentication is based on the HMAC-MD5 or HMAC-SHA
algorithms − AuthPriv.
DES 56-bit encryption is added based on the CBC-DES
(DES-56) standard
show snmp user
create snmp view <view_name 32> <oid> view_type [included | excluded]
delete snmp view <view_name 32> [all | oid]
show snmp view <view_name 32>
create snmp community <community_string 32> view <view_name 32> [read_only |
read_write]
delete snmp community <community_string 32>
show snmp community <community_string 32>
config snmp engineID <snmp_engineID>
show snmp engineID
create snmp group <groupname 32> {v1 | v2c | v3 [noauth_nopriv | auth_nopriv |
auth
riv]} {read view <view name 32> | write view
31
Page 35

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Command Parameters
<view_name 32> | notify_view <view_name 32>}
delete snmp group <groupname 32>
show snmp groups
create snmp host <ipaddr> {v1 |v2c | v3 [noauth_nopriv | auth_nopriv | auth_priv]}
<auth_string 32>
delete snmp host <ipaddr> <auth_string 32>
show snmp host <ipaddr>
create trusted_host <ipaddr>
delete trusted_host <ipaddr>
show trusted_host <ipaddr>
enable snmp traps
enable snmp
authenticate_traps
show snmp traps
disable snmp traps
disable snmp
authenticate_traps
config snmp system
contact
config snmp system
location
config snmp system
name
enable rmon
disable rmon
Each command is listed, in detail, in the following sections.
<sw_contact>
<sw_location>
<sw_name>
create snmp user
Purpose Used to create a new SNMP user and adds the user to an SNMP
group that is also created by this command.
Syntax
Description
create snmp user <SNMP_name 32> <groupname 32>
{encrypted [by_password auth [md5 <auth_password 8-16> |
sha <auth_password 8-20>] priv [none | des <priv_password 816>] | by_key auth [md5 <auth_key 32-32> | sha <auth_key 4040>] priv [none | des <priv_key 32-32>]]}
The create snmp user command creates a new SNMP user and
adds the user to an SNMP group that is also created by this
command. SNMP ensures:
Message integrity − Ensures that packets have not been tampered
with during transit.
Authentication − Determines if an SNMP message is from a valid
source.
32
Page 36

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create snmp user
Encryption − Scrambles the contents of messages to prevent it from
being viewed by an unauthorized source.
Parameters
<username 32> − An alphanumeric name of up to 32 characters
that will identify the new SNMP user.
<groupname 32> − An alphanumeric name of up to 32 characters
that will identify the SNMP group with which the new SNMP user
will be associated.
encrypted – Allows the user to choose a type of authorization for
authentication using SNMP. The user may choose:
•
by_password – Requires the SNMP user to enter a
password for authentication and privacy. The password is
defined by specifying the auth_password below. This
method is recommended.
•
by_key – Requires the SNMP user to enter a encryption
key for authentication and privacy. The key is defined by
specifying the key in hex form below. This method is not
recommended.
auth - The user may also choose the type of authentication
algorithms used to authenticate the snmp user. The choices are:
•
md5 − Specifies that the HMAC-MD5-96 authentication
level will be used. md5 may be utilized by entering one of
the following:
<auth password 8-16> - An alphanumeric sting of
between 8 and 16 characters that will be used to
authorize the agent to receive packets for the host.
<auth_key 32-32> - Enter an alphanumeric sting of
exactly 32 characters, in hex form, to define the key that
will be used to authorize the agent to receive packets for
the host.
−
•
priv – Adding the priv (privacy) parameter will allow for encryption in
addition to the authentication algorithm for higher security. The user
may choose:
•
Specifies that the HMAC-SHA-96 authentication
sha
level will be used.
<auth password 8-20> - An alphanumeric sting of
between 8 and 20 characters that will be used to
authorize the agent to receive packets for the host.
<auth_key 40-40> - Enter an alphanumeric sting of
exactly 40 characters, in hex form, to define the key that
will be used to authorize the agent to receive packets for
the host.
des – Adding this parameter will allow for a 56-bit
encryption to be added using the DES-56 standard using:
<priv_password 8-16> - An alphanumeric string of
between 8 and 16 characters that will be used to
encrypt the contents of messages the host sends to
33
Page 37

Example usage:
To create an SNMP user on the Switch:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create snmp user
the agent.
• <priv_key 32-32> - Enter an alphanumeric key string
of exactly 32 characters, in hex form, that will be
used to encrypt the contents of messages the host
sends to the agent.
none – Adding this parameter will add no encryption.
Restrictions Only administrator-level users can issue this command.
DES-6500:4#create snmp user dlink default encrypted
by_password auth md5 auth_password priv none
Command: create snmp user dlink default encrypted
by_password auth md5 auth_password priv none
Success.
delete snmp user
Purpose Used to remove an SNMP user from an SNMP group and also to
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete a previously entered SNMP user on the Switch:
DES-6500:4#
delete the associated SNMP group.
delete snmp user <SNMP_name 32>
The delete snmp user command removes an SNMP user from
its SNMP group and then deletes the associated SNMP group.
<SNMP_name 32> − An alphanumeric string of up to 32
characters that identifies the SNMP user that will be deleted.
DES-6500:4#delete snmp user dlink
Command: delete snmp user dlink
Success.
DES-6500:4#
show snmp user
34
Page 38

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show snmp user
Purpose Used to display information about each SNMP username in the
SNMP group username table.
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To display the SNMP users currently configured on the Switch:
create snmp view
show snmp user
The show snmp user command displays information about each
SNMP username in the SNMP group username table.
DES-6500:4#show snmp user
Command: show snmp user
Username Group Name VerAuthPriv
--------------- -------------------- -------------------- initial initial V3 None None
Total Entries: 1
DES-6500:4#
Purpose Used to assign views to community strings to limit which MIB
Syntax create snmp view <view_name 32> <oid> view_type [included |
Description The create snmp view command assigns views to community
Parameters <view_name 32> − An alphanumeric string of up to 32 characters
Restrictions Only administrator-level users can issue this command.
Example usage:
To create an SNMP view:
objects and SNMP manager can access.
excluded]
strings to limit which MIB objects an SNMP manager can access.
that identifies the SNMP view that will be created.
<oid> − The object ID that identifies an object tree (MIB tree) that
will be included or excluded from access by an SNMP manager.
included − Include this object in the list of objects that an SNMP
manager can access.
excluded − Exclude this object from the list of objects that an SNMP
manager can access.
35
Page 39

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#create snmp view dlinkview 1.3.6 view_type included
Command: create snmp view dlinkview 1.3.6 view_type included
Success.
DES-6500:4#
delete snmp view
Purpose Used to remove an SNMP view entry previously created on the
Switch.
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete a previously configured SNMP view from the Switch:
delete snmp view <view_name 32> [all | <oid>]
The delete snmp view command is used to remove an SNMP
view previously created on the Switch.
<view_name 32> − An alphanumeric string of up to 32 characters
that identifies the SNMP view to be deleted.
all − Specifies that all of the SNMP views on the Switch will be
deleted.
<oid> − The object ID that identifies an object tree (MIB tree) that
will be deleted from the Switch.
DES-6500:4#delete snmp view dlinkview all
Command: delete snmp view dlinkview all
Success.
show snmp view
Purpose Used to display an SNMP view previously created on the Switch.
Syntax
Description
Parameters
Restrictions None.
Example usage:
To display SNMP view configuration:
DES-6500:4#
show snmp view {<view_name 32>}
The show snmp view command displays an SNMP view
previously created on the Switch.
<view_name 32> − An alphanumeric string of up to 32 characters
that identifies the SNMP view that will be displayed.
DES-6500:4#show snmp view
36
Page 40

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Command: show snmp view
Vacm View Table Settings
View Name Subtree View Type
-------------------- ------------------------- --------- ReadView 1 Included
WriteView 1 Included
NotifyView 1.3.6 Included
restricted 1.3.6.1.2.1.1 Included
restricted 1.3.6.1.2.1.11 Included
restricted 1.3.6.1.6.3.10.2.1 Included
restricted 1.3.6.1.6.3.11.2.1 Included
restricted 1.3.6.1.6.3.15.1.1 Included
CommunityView 1 Included
CommunityView 1.3.6.1.6.3 Excluded
CommunityView 1.3.6.1.6.3.1 Included
Total Entries: 11
DES-6500:4#
create snmp community
Purpose Used to create an SNMP community string to define the relationship
between the SNMP manager and an agent. The community string acts
like a password to permit access to the agent on the Switch. One or
more of the following characteristics can be associated with the
community string:
An Access List of IP addresses of SNMP managers that are permitted to
use the community string to gain access to the Switch’s SNMP agent.
An MIB view that defines the subset of all MIB objects that will be
accessible to the SNMP community.
Read-write or read-only level permission for the MIB objects accessible
to the SNMP community.
Syntax
Description
Parameters
create snmp community <community_string 32> view <view_name
32> [read_only | read_write]
The create snmp community command is used to create an SNMP
community string and to assign access-limiting characteristics to this
community string.
<community_string 32> − An alphanumeric string of up to 32 characters
that is used to identify members of an SNMP community. This string is
used like a password to give remote SNMP managers access to MIB
objects in the Switch’s SNMP agent.
view <view_name 32> − An alphanumeric string of up to 32 characters
that is used to identify the group of MIB objects that a remote SNMP
manager is allowed to access on the Switch.
read_only − Specifies that SNMP community members using the
community string created with this command can only read the contents
of the MIBs on the Switch.
read_write − Specifies that SNMP community members using the
community string created with this command can read from and write to
the contents of the MIBs on the Switch.
Restrictions Only administrator-level users can issue this command.
37
Page 41

Example usage:
To create the SNMP community string “dlink:”
delete snmp community
Purpose Used to remove a specific SNMP community string from the
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#create snmp community dlink view ReadView read_write
Command: create snmp community dlink view ReadView read_write
Success.
DES-6500:4#
Switch.
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete the SNMP community string “dlink:”
show snmp community
delete snmp community <community_string 32>
The delete snmp community command is used to remove a
previously defined SNMP community string from the Switch.
<community_string 32> − An alphanumeric string of up to 32
characters that is used to identify members of an SNMP
community. This string is used like a password to give remote
SNMP managers access to MIB objects in the Switch’s SNMP
agent.
DES-6500:4#delete snmp community dlink
Command: delete snmp community dlink
Success.
DES-6500:4#
Purpose Used to display SNMP community strings configured on the
Switch.
Syntax
Description
Parameters
Restrictions None.
show snmp community {<community_string 32>}
The show snmp community command is used to display SNMP
community strings that are configured on the Switch.
<community_string 32> − An alphanumeric string of up to 32
characters that is used to identify members of an SNMP
community. This string is used like a password to give remote
SNMP managers access to MIB objects in the Switch’s SNMP
agent.
38
Page 42

Example usage:
To display the currently entered SNMP community strings:
config snmp engineID
Purpose Used to configure a name for the SNMP engine on the Switch.
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show snmp community
Command: show snmp community
SNMP Community Table
Community Name View Name Access Right
------------------------------ ------------------------------ -----------dlink ReadView read_write
private CommunityView read_write
public CommunityView read_only
Total Entries: 3
DES-6500:4#
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To give the SNMP agent on the Switch the name “0035636666”
show snmp engineID
config snmp engineID <snmp_engineID>
The config snmp engineID command configures a name for the
SNMP engine on the Switch.
<snmp_engineID> − An alphanumeric string that will be used to
identify the SNMP engine on the Switch.
DES-6500:4#config snmp engineID 0035636666
Command: config snmp engineID 0035636666
Success.
DES-6500:4#
Purpose Used to display the identification of the SNMP engine on the
Syntax
Description
Parameters None.
Restrictions None.
Example usage:
Switch.
show snmp engineID
The show snmp engineID command displays the identification of
the SNMP engine on the Switch.
39
Page 43

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
To display the current name of the SNMP engine on the Switch:
DES-6500:4#show snmp engineID
Command: show snmp engineID
SNMP Engine ID : 0035636666
DES-6500:4#
create snmp group
Purpose Used to create a new SNMP group, or a table that maps SNMP
users to SNMP views.
Syntax
Description
Parameters
create snmp group <groupname 32> [v1 | v2c | v3
[noauth_nopriv | auth_nopriv | auth_priv]] {read_view
<view_name 32> | write_view <view_name 32> | notify_view
<view_name 32>}
The create snmp group command creates a new SNMP group,
or a table that maps SNMP users to SNMP views.
<groupname 32> − An alphanumeric name of up to 32 characters
that will identify the SNMP group the new SNMP user will be
associated with.
v1 – Specifies that SNMP version 1 will be used. The Simple
Network Management Protocol (SNMP), version 1, is a network
management protocol that provides a means to monitor and
control network devices.
v2c – Specifies that SNMP version 2c will be used. The SNMP
v2c supports both centralized and distributed network
management strategies. It includes improvements in the Structure
of Management Information (SMI) and adds some security
features.
v3 – Specifies that the SNMP version 3 will be used. SNMP v3
provides secure access to devices through a combination of
authentication and encrypting packets over the network. SNMP v3
adds:
Message integrity − Ensures that packets have not been
tampered with during transit.
Authentication − Determines if an SNMP message is from
a valid source.
Encryption − Scrambles the contents of messages to
prevent it being viewed by an unauthorized source.
noauth_nopriv − Specifies that there will be no authorization and
no encryption of packets sent between the Switch and a remote
SNMP manager.
auth_nopriv − Specifies that authorization will be required, but
there will be no encryption of packets sent between the Switch
and a remote SNMP manager.
auth_priv − Specifies that authorization will be required, and that
packets sent between the Switch and a remote SNMP manger will
40
Page 44

create snmp group
Restrictions Only administrator-level users can issue this command.
Example usage:
To create an SNMP group named “sg1:”
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
be encrypted.
read_view – Specifies that the SNMP group being created can
request SNMP messages.
write_view – Specifies that the SNMP group being created has
write privileges.
<view_name 32> − An alphanumeric string of up to 32 characters
that is used to identify the group of MIB objects that a remote
SNMP manager is allowed to access on the Switch.
notify_view − Specifies that the SNMP group being created can
receive SNMP trap messages generated by the Switch’s SNMP
agent.
DES-6500:4#create snmp group sg1 v3 noauth_nopriv read_view v1
write_view v1 notify_view v1
Command: create snmp group sg1 v3 noauth_nopriv read_view v1
write_view v1 notify_view v1
Success.
DES-6500:4#
delete snmp group
Purpose Used to remove an SNMP group from the Switch.
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete the SNMP group named “sg1”.
delete snmp group <groupname 32>
The delete snmp group command is used to remove an SNMP
group from the Switch.
<groupname 32> − An alphanumeric name of up to 32 characters
that will identify the SNMP group to be deleted.
DES-6500:4#delete snmp group sg1
Command: delete snmp group sg1
Success.
DES-6500:4#
41
Page 45

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show snmp groups
Purpose Used to display the group-names of SNMP groups currently
configured on the Switch. The security model, level, and status of
each group are also displayed.
Syntax
Description
Parameters None.
Restrictions None.
Example usage:
To display the currently configured SNMP groups on the Switch:
show snmp groups
The show snmp groups command displays the group-names of
SNMP groups currently configured on the Switch. The security
model, level, and status of each group are also displayed.
DES-6500:4#show snmp groups
Command: show snmp groups
Vacm Access Table Settings
Group Name : Group3
ReadView Name : ReadView
WriteView Name : WriteView
Notify View Name : NotifyView
Security Model : SNMPv3
Security Level : NoAuthNoPriv
Group Name : Group4
ReadView Name : ReadView
WriteView Name : WriteView
Notify View Name : NotifyView
Security Model : SNMPv3
Security Level : authNoPriv
Group Name : Group5
ReadView Name : ReadView
WriteView Name : WriteView
Notify View Name : NotifyView
Security Model : SNMPv3
Security Level : authNoPriv
Group Name : Group6
ReadView Name : ReadView
WriteView Name : WriteView
Notify View Name : NotifyView
Security Model : SNMPv3
Security Level : authPriv
Group Name : Group7
ReadView Name : ReadView
WriteView Name : WriteView
Notify View Name : NotifyView
Security Model : SNMPv3
Security Level : authPriv
Group Name : initial
42
Page 46

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
ReadView Name : restricted
WriteView Name :
Notify View Name : restricted
Security Model : SNMPv3
Security Level : NoAuthNoPriv
Group Name : ReadGroup
ReadView Name : CommunityView
WriteView Name :
Notify View Name : CommunityView
Security Model : SNMPv1
Security Level : NoAuthNoPriv
Group Name : ReadGroup
ReadView Name : CommunityView
WriteView Name :
Notify View Name : CommunityView
Security Model : SNMPv2
Security Level : NoAuthNoPriv
Group Name : WriteGroup
ReadView Name : CommunityView
WriteView Name : CommunityView
Notify View Name : CommunityView
Security Model : SNMPv1
Security Level : NoAuthNoPriv
Group Name : WriteGroup
ReadView Name : CommunityView
WriteView Name : CommunityView
Notify View Name : CommunityView
Security Model : SNMPv2
Security Level : NoAuthNoPriv
Total Entries: 10
DES-6500:4#
create snmp host
Purpose Used to create a recipient of SNMP traps generated by the
Switch’s SNMP agent.
Syntax
Description
Parameters
create snmp host <ipaddr> [v1 | v2c | v3 [noauth_nopriv |
auth_nopriv | auth_priv]] <auth_string 32>
The create snmp host command creates a recipient of SNMP
traps generated by the Switch’s SNMP agent.
<ipaddr> − The IP address of the remote management station
that will serve as the SNMP host for the Switch.
v1 – Specifies that SNMP version 1 will be used. The Simple
Network Management Protocol (SNMP), version 1, is a network
management protocol that provides a means to monitor and
control network devices.
v2c – Specifies that SNMP version 2c will be used. The SNMP
v2c supports both centralized and distributed network
management strategies. It includes improvements in the Structure
43
Page 47

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create snmp host
of Management Information (SMI) and adds some security
features.
v3 – Specifies that the SNMP version 3 will be used. SNMP v3
provides secure access to devices through a combination of
authentication and encrypting packets over the network. SNMP
v3 adds:
noauth_nopriv − Specifies that there will be no authorization and
no encryption of packets sent between the Switch and a remote
SNMP manager.
auth_nopriv − Specifies that authorization will be required, but
there will be no encryption of packets sent between the Switch
and a remote SNMP manager.
Message integrity − Ensures that packets have not been
tampered with during transit.
Authentication − Determines if an SNMP message is from
a valid source.
Encryption − Scrambles the contents of messages to
prevent it being viewed by an unauthorized source.
Restrictions Only administrator-level users can issue this command.
Example usage:
To create an SNMP host to receive SNMP messages:
delete snmp host
Purpose Used to remove a recipient of SNMP traps generated by the
auth_priv − Specifies that authorization will be required, and that
packets sent between the Switch and a remote SNMP manger
will be encrypted.
<auth_sting 32> − An alphanumeric string used to authorize a
remote SNMP manager to access the Switch’s SNMP agent.
DES-6500:4#create snmp host 10.48.74.100 v3 auth_priv public
Command: create snmp host 10.48.74.100 v3 auth_priv public
Success.
DES-6500:4#
Switch’s SNMP agent.
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
delete snmp host <ipaddr> <auth_string 32>
The delete snmp host command deletes a recipient of SNMP
traps generated by the Switch’s SNMP agent.
<ipaddr> − The IP address of a remote SNMP manager that will
receive SNMP traps generated by the Switch’s SNMP agent.
<auth_sting 32> − The alphanumeric string created to authorize a
remote SNMP manager to access the Switch’s SNMP agent.
44
Page 48

Example usage:
To delete an SNMP host entry:
show snmp host
Purpose Used to display the recipient of SNMP traps generated by the
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#delete snmp host 10.48.74.100 public
Command: delete snmp host 10.48.74.100 public
Success.
DES-6500:4#
Switch’s SNMP agent.
Syntax
Description
Parameters
Restrictions None.
Example usage:
To display the currently configured SNMP hosts on the Switch:
show snmp host {<ipaddr>}
The show snmp host command is used to display the IP
addresses and configuration information of remote SNMP
managers that are designated as recipients of SNMP traps that
are generated by the Switch’s SNMP agent.
<ipaddr> − The IP address of a remote SNMP manager that will
receive SNMP traps generated by the Switch’s SNMP agent.
DES-6500:4#show snmp host
Command: show snmp host
SNMP Host Table
Host IP Address SNMP Version Community Name/SNMPv3 User Name
--------------- --------------------- ------------------------------
10.48.76.23 V2c private
10.48.74.100 V3 authpriv public
Total Entries: 2
DES-6500:4#
create trusted_host
Purpose Used to create the trusted host.
Syntax
Description
create trusted_host <ipaddr>
The create trusted_host command creates the trusted host.
The Switch allows specification up to four IP addresses that are
allowed to manage the Switch via in-band SNMP or TELNET
based management software. These IP addresses must be
members of the Management VLAN. If no IP addresses are
specified, then there is nothing to prevent any IP address from
accessing the Switch, provided the user knows the Username
and Password.
45
Page 49

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create trusted_host
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To create the trusted host:
show trusted_host
Purpose Used to display a list of trusted hosts entered on the Switch using
Syntax
Description This command is used to display a list of trusted hosts entered on
Parameters None.
<ipaddr> − The IP address of the trusted host.
DES-6500:4#create trusted_host 10.48.74.121
Command: create trusted_host 10.48.74.121
Success.
DES-6500:4#
the create trusted_host command above.
show trusted_host
the Switch using the create trusted_host command above.
Restrictions None.
Example Usage:
To display the list of trust hosts:
delete trusted_host
Purpose
DES-6500:4#show trusted_host
Command: show trusted_host
Management Stations
IP Address
--------------------
10.53.13.94
Total Entries: 1
DES-6500:4#
Used to delete a trusted host entry made using the create
trusted_host command above.
Syntax
Description This command is used to delete a trusted host entry made using
Parameters
Restrictions Only administrator-level users can issue this command.
delete trusted _host <ipaddr>
the create trusted_host command above.
<ipaddr> − The IP address of the trusted host.
46
Page 50

Example Usage:
To delete a trusted host with an IP address 10.48.74.121:
enable snmp traps
Purpose Used to enable SNMP trap support.
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#delete trusted_host 10.48.74.121
Command: delete trusted_host 10.48.74.121
Success.
DES-6500:4#
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To enable SNMP trap support on the Switch:
DES-6500:4#enable snmp traps
Command: enable snmp traps
Success.
DES-6500:4#
enable snmp traps
The enable snmp traps command is used to enable SNMP trap
support on the Switch.
enable snmp authenticate_traps
Purpose Used to enable SNMP authentication trap support.
Syntax
enable snmp authenticate_traps
Description This command is used to enable SNMP authentication trap
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example Usage:
To turn on SNMP authentication trap support:
support on the Switch.
DES-6500:4#enable snmp authenticate_traps
Command: enable snmp authenticate_traps
Success.
DES-6500:4#
47
Page 51

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show snmp traps
Purpose Used to show SNMP trap support on the Switch .
Syntax
Description This command is used to view the SNMP trap support status
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To view the current SNMP trap support:
DES-6500:4#show snmp traps
Command: show snmp traps
SNMP Traps : Enabled
Authenticate Traps : Enabled
DES-6500:4#
show snmp traps
currently configured on the Switch.
disable snmp traps
Purpose Used to disable SNMP trap support on the Switch.
Syntax
Description This command is used to disable SNMP trap support on the
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example Usage:
To prevent SNMP traps from being sent from the Switch:
disable snmp authenticate_traps
Purpose Used to disable SNMP authentication trap support.
Syntax
disable snmp traps
Switch.
DES-6500:4#disable snmp traps
Command: disable snmp traps
Success.
DES-6500:4#
disable snmp authenticate_traps
Description This command is used to disable SNMP authentication support on
the Switch.
Parameters None.
Restrictions Only administrator-level users can issue this command.
48
Page 52

Example Usage:
To disable the SNMP authentication trap support:
config snmp system_contact
Purpose Used to enter the name of a contact person who is responsible for
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#disable snmp authenticate_traps
Command: disable snmp authenticate_traps
Success.
DES-6500:4#
the Switch.
Syntax
Description
Parameters <sw_contact> - A maximum of 255 characters is allowed. A NULL
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure the Switch contact to “
DES-6500:4#config snmp system_contact MIS Department II
Command: config snmp system_contact MIS Department II
Success.
DES-6500:4#
config snmp system_contact {<sw_contact>}
The config snmp system_contact command is used to enter the
name and/or other information to identify a contact person who is
responsible for the Switch. A maximum of 255 character can be
used.
string is accepted if there is no contact.
MIS Department II
”:
config snmp system_location
Purpose Used to enter a description of the location of the Switch.
Syntax
Description
Parameters <sw_location> - A maximum of 255 characters is allowed. A NULL
Restrictions Only administrator-level users can issue this command.
Example usage:
config snmp system_location {<sw_location>}
The config snmp system_location command is used to enter a
description of the location of the Switch. A maximum of 255
characters can be used.
string is accepted if there is no location desired.
49
Page 53

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
To configure the Switch location for “
DES-6500:4#config snmp system_location HQ 5F
Command: config snmp system_location HQ 5F
Success.
DES-6500:4#
config snmp system_name
Purpose Used to configure the name for the Switch.
Syntax
Description
Parameters <sw_name> - A maximum of 255 characters is allowed. A NULL
Restrictions Only administrator-level users can issue this command.
config snmp system_name {<sw_name>}
The config snmp system_name command configures the name
of the Switch.
string is accepted if no name is desired.
HQ 5F
”:
Example usage:
To configure the Switch name for “
DES-6500:4#config snmp system_name DES-6500 Chassis Switch
Command: config snmp system_name DES-6500 Chassis Switch
Success.
DES-6500:4#
enable rmon
Purpose Used to enable RMON on the Switch.
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
enable rmon
This command is used, in conjunction with the disable rmon
command below, to enable and disable remote monitoring
(RMON) on the Switch.
DES-6500 Chassis Switch
”:
Example Usage:
To enable RMON:
50
Page 54

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#enable rmon
Command: enable rmon
Success.
DES-6500:4#
disable rmon
Purpose Used to disable RMON on the Switch.
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example Usage:
To disable RMON:
DES-6500:4#disable rmon
Command: disable rmon
Success.
DES-6500:4#
disable rmon
This command is used, in conjunction with the enable rmon
command above, to enable and disable remote monitoring
(RMON) on the Switch.
51
Page 55

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
8
SWITCH UTILITY COMMANDS
The switch utility commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in the
following table.
Command
download
upload
ping <ipaddr> {times <value 1-255>} {timeout <sec 1-99>}
traceroute <ipaddr> {ttl <value 1-60> | port <value 30000-64900> | timeout
enable autoconfig
disable autoconfig
show autoconfig
Each command is listed, in detail, in the following sections.
Parameters
[firmware_fromTFTP <ipaddr> <path_filename 64> unit
[all_line_card | cpu | <unitid 1-8>]} | cfg_fromTFTP <ipaddr>
<path_filename 64> {increment}
[cfg_toTFTP | log_toTFTP] <ipaddr> <path_filename 64>
<sec 1-65535> | probe <value <1-9>
download
Purpose Used to download and install new firmware or a switch
configuration file from a TFTP server or a CompactFlash memory
card.
Syntax
[firmware_fromTFTP <ipaddr> <path_filename 64> unit
[all_line_card | cpu | <unitid 1-8>]} | cfg_fromTFTP <ipaddr>
<path_filename 64> {increment}
Description This command is used to download a new firmware or a switch
configuration file from a TFTP server or a CompactFlash memory
card.
Parameters
firmware_fromTFTP − Download and install new firmware on the
Switch from a TFTP server.
<ipaddr> − The IP address of the TFTP server. The TFTP
server must be on the same IP subnet as the Switch.
<path_filename 64> − The DOS path and filename of the
firmware or switch configuration file on the TFTP server. For
example, C:\3226S.had.
unit [all_line_card | cpu | <unitid 1-8>] − all specifies all
installed modules except the CPU module, cpu specifies the
chassis’ CPU module and <unitid> is the unit ID of a specific
installed module that will receive the download.
cfg_fromTFTP - Download a switch configuration file from a TFTP
server.
<ipaddr> − The IP address of the TFTP server. The TFTP
server must be on the same IP subnet as the Switch.
<path_filename 64> − The DOS path and filename of the
firmware or switch configuration file on the TFTP server or
CompactFlash card. For example, C:\3226S.had.
52
Page 56

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
download
Restrictions The TFTP server must be on the same IP subnet as the Switch.
Only administrator-level users can issue this command.
Example usage:
To download a configuration file:
DES-6500:4#download cfg_to TFTP 10.48.74.121 c:\cfg\setting.txt
Command: download cfg_to TFTP 10.48.74.121 c:\cfg\setting.txt
Connecting to server................... Done.
Download configuration............. Done.
DES-6500:4#
increment − Allows the download of a partial switch
configuration file. This allows a file to be downloaded that will
change only the Switch parameters explicitly stated in the
configuration file. All other switch parameters will remain
unchanged.
Due to a backward compatability issue, when a user upgrades to R3 firmware (3.00-B29),
all settings previously configured for any ACL function (CPU ACL included) on the Switch
will be lost. We recommend that the user save a configuration file of current settings before
upgrading to R3 firmware.
upload
Purpose Used to upload the current switch settings or the switch history log
to a TFTP server or a CompactFlash memory card.
Syntax
Description This command is used to upload either the Switch’s current settings,
Parameters
upload [cfg_toTFTP | log_toTFTP] <ipaddr> <path_filename 64>
the Switch’s history log or firmware to a TFTP server or a
CompactFlash memory card.
cfg_toTFTP − Specifies that the Switch’s current settings will be
uploaded to the TFTP server.
log_toTFTP − Specifies that the Switch’s current log will be
uploaded to the TFTP server.
<ipaddr> − The IP address of the TFTP server. The TFTP
server must be on the same IP subnet as the Switch.
<path_filename 64> − Specifies the location of the Switch
configuration file on the TFTP server. This file will be replaced
by the uploaded file from the Switch.
Restrictions The TFTP server must be on the same IP subnet as the Switch.
Example usage:
To upload a configuration file:
Only administrator-level users can issue this command.
53
Page 57

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#upload cfg_toTFTP 10.48.74.121 c:\cfg\log.txt
Command: upload cfg_to TFTP 10.48.74.121 c:\cfg\log.txt
Connecting to server................... Done.
Upload configuration...................Done.
DES-6500:4#
ping
Purpose Used to test the connectivity between network devices.
Syntax
Description The ping command sends Internet Control Message Protocol
Parameters <ipaddr> - Specifies the IP address of the host.
Restrictions None.
Example usage:
To ping the IP address 10.48.74.121 four times:
DES-6500:4#ping 10.48.74.121 times 4
Command: ping 10.48.74.121
Reply from 10.48.74.121, time<10ms
Reply from 10.48.74.121, time<10ms
Reply from 10.48.74.121, time<10ms
Reply from 10.48.74.121, time<10ms
Ping statistics for 10.48.74.121
Packets: Sent =4, Received =4, Lost =0
DES-6500:4#
ping <ipaddr> {times <value 1-255>} {timeout <sec 1-99>}
(ICMP) echo messages to a remote IP address. The remote IP
address will then “echo” or return the message. This is used to
confirm connectivity between the Switch and the remote device.
times <value 1-255> - The number of individual ICMP echo
messages to be sent. The maximum value is 255. The default is 0.
timeout <sec 1-99> - Defines the time-out period while waiting for a
response from the remote device. A value of 1 to 99 seconds can
be specified. The default is 1 second.
Pinging an IP address without the times parameter will ping the
target device an infinite amount of times.
traceroute
Purpose Used to trace the routed path between the Switch and a destination
endstation.
Syntax
Description The traceroute command allows you to trace a route between the Switch
traceroute <ipaddr> {ttl <value 1-60> | port <value 30000-64900> |
timeout <sec 1-65535> | probe <value <1-9>}
and a give host on the network.
54
Page 58

traceroute
Parameters <ipaddr> - Specifies the IP address of the host.
Restrictions None.
Example usage:
To trace the routed path between the Switch and 10.48.74.121.
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
ttl <value 1-60> - The time to live value of the trace route request. This is
the maximum number of routers the traceroute command will cross while
seeking the network path between two devices.
port <value 30000-64900> - The port number. Must be above 1024.The
value range is from 30000 to 64900.
timeout <sec 1-65535> - Defines the time-out period while waiting for a
response from the remote device. The user may choose an entry
between 1 and 65535 seconds.
probe <value 1-9> - The probe value is the number of times the Switch
will send probe packets to the next hop on the intended traceroute path.
The default is 1.
DES-6500:4#traceroute 10.48.74.121
Command: traceroute 10.48.74.121
1 <10ms 10.254.254.251
2 <10ms 10.55.25.35
3 <10ms 10.22.35.1
DES-6500:4#
probe 3
probe 3
enable autoconfig
Purpose Used to activate the autoconfiguration function for the Switch. This will load a
previously saved configuration file for current use.
Syntax
Description When autoconfig is enabled on the Switch, the DHCP reply will contain a
Parameters None.
Restrictions When autoconfig is enabled, the Switch becomes a DHCP client automatically
enable autoconfig
configuration file and path name. It will then request the file from the TFTP
server specified in the reply. When autoconfig is enabled, the ipif settings will
automatically become DHCP client.
(same as: config ipif System dhcp). The DHCP server must have the TFTP
server IP address and configuration file name, and be configured to deliver
this information in the data field of the DHCP reply packet. The TFTP server
must be running and have the requested configuration file in its base directory
when the request is received from the Switch. Consult the DHCP server and
TFTP server software instructions for information on loading a configuration
file.
If the Switch is unable to complete the autoconfiguration process the
previously saved local configuration file present in Switch memory will be
loaded.
55
Page 59

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
NOTE: Dual-purpose (DHCP/TFTP) server utility software may require entry of the
configuration file name and path within the user interface. Alternatively, the DHCP
software may require creating a separate ext file with the configuration file name
and path in a specific directory on the server. Consult the documentation for the
DCHP server software if you are unsure.
When autoconfig is enabled and the Switch is rebooted, the normal login screen will appear for a few moments while the
autoconfig request (i.e. download configuration) is initiated. The console will then display the configuration parameters as they
are loaded from the configuration file specified in the DHCP or TFTP server. This is exactly the same as using a download
configuration command. After the entire Switch configuration is loaded, the Switch will automatically “logout” the server. The
configuration settings will be saved automatically and become the active configuration.
Upon booting up the autoconfig process is initiated, the console screen will appear similar to the example below. The
configuration settings will be loaded in normal order.
Example usage:
To enable autoconfiguration on the Switch:
DES-6500:4#enable autoconfig
Command: enable autoconfig
Success.
DES-6500:4#
DES-6500 Chassis Ethernet Switch
Command Line Interface
Firmware: Build 3.00-B29
Copyright(C) 2004-2007 D-Link Corporation. All rights reserved.
DES-6500:4#
DES-6500:4#
DES-6500:4#download configuration 10.41.44.44 c:\cfg\setting.txt
Command: download configuration 10.41.44.44 c:\cfg\setting.txt
Connecting to server................... Done.
Download configuration................. Done.
The very end of the autoconfig process including the logout appears like this:
DES-6500:4#disable authen_policy
Command: disable authen_policy
Success.
DES-6500:4#
DES-6500:4##------------------------------------------------------------------DES-6500:4## End of configuration file for DES-6500
DES-6500:4#
**********
* Logout *
**********
56
Page 60

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
disable autoconfig
Purpose Use this to deactivate autoconfiguration from DHCP.
Syntax
Description This instructs the Switch not to accept autoconfiguration instruction from
Parameters None.
Restrictions None.
Example usage:
To stop the autoconfiguration function:
DES-6500:4#disable autoconfig
Command: disable autoconfig
Success.
DES-6500:4#
disable autoconfig
the DHCP server. This does not change the IP settings of the Switch. The
ipif settings will continue as DHCP client until changed with the config ipif
command.
NOTE: With autoconfig enabled, the Switch ipif settings now define the
Switch as a DHCP client. Use the show switch command to display the
new IP settings status.
show autoconfig
Purpose Used to display the current autoconfig status of the Switch.
Syntax
Description This will list the current status of the autoconfiguration function.
Parameters None.
Restrictions None.
Example usage:
To show the autoconfig configuration set on the Switch:
DES-6500:4#show autoconfig
Command: show autoconfig
Autoconfig disabled.
Success.
DES-6500:4#
show autoconfig
57
Page 61

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
9
NETWORK MONITORING COMMANDS
The network monitoring commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in
the following table.
Command Parameters
show packet ports <portlist>
show error ports <portlist>
show utilization [ports | cpu]
show stack information
clear counters ports <portlist>
clear log
show log index <value_list>
enable syslog
disable syslog
show syslog
create syslog host [<index 1-4> | all] {severity [informational | warning | all] | facility
[local0 | local1 | local2 | local3 | local4 | local5 | local6 | local7] |
udp_port <udp_port_number> | ipaddress <ipaddr> | state
[enabled | disabled]}
config syslog host <index 1-4> {severity [informational | warning | all] | facility [local0
| local1 | local2 | local3 | local4 | local5 | local6 | local7] | udp_port
<udp_port_number> | ipaddress <ipaddr> | state [enabled |
disabled]}
config syslog host all {severity [informational | warning | all] | facility [local0 | local1 |
local2 | local3 | local4 | local5 | local6 | local7] | udp_port
<udp_port_number> | state [enabled | disabled]}
delete syslog host [<index 1-4> | all]
show syslog host [<index 1-4>]
config system_severity [trap | log | all] [critical | warning | information]
show system_severity
Each command is listed, in detail, in the following sections.
show packet ports
Purpose Used to display statistics about the packets sent and received by
the Switch.
Syntax
Description This command is used to display statistics about packets sent and
show packet ports <portlist>
received by ports specified in the port list. The results are
separated into three tables, labeled A, B, and C in the window
above. Table A is relevant to the size of the packets, Table B is
relevant to the type of packets and Table C is relevant to the type
of frame associated with these packets.
58
Page 62

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show packet ports
Parameters
Restrictions None.
Example usage:
To display the packets analysis for port 7 of module 2:
<portlist> − Specifies a range of ports to be displayed. The port list
is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. Then the highest
slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 −
in numerical order.
DES-6500:4#show packet port 2:7
Command: show packet port 2:7
Port number : 2:7
(A) (B)
Frame Size Frame Counts Frames/sec Frame Type Total Total/sec
------------ ------------ ---------- ---------- ------- --------64 3275 10 RX Bytes 408973 1657
65-127 755 10 RX Frames 4395 19
128-255 316 1
256-511 145 0 TX Bytes 7918 178
512-1023 15 0 TX Frames 111 2
1024-1518 0 0
(C)
Unicast RX 152 1
Multicast RX 557 2
Broadcast RX 3686 16
L3 Unicast RX 0 0
L3 Unicast TX 0 0
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
show error ports
Purpose Used to display the error statistics for a range of ports.
Syntax
Description This command will display all of the packet error statistics
Parameters
Restrictions None.
show error ports <portlist>
collected and logged by the Switch for a given port list.
<portlist> − Specifies a range of ports to be displayed. The port
list is specified by listing the lowest slot number and the
beginning port number on that slot, separated by a colon. Then
the highest slot number, and the highest port number of the
range (also separated by a colon) are specified. The beginning
and end of the port list range are separated by a dash. For
example, 1:3 specifies slot number 1, port 3. 2:4 specifies slot
number 2, port 4. 1:3-2:4 specifies all of the ports between slot 1,
port 3 and slot 2, port 4 − in numerical order.
59
Page 63

Example usage:
To display the errors of the port 3 of module 1:
show utilization
Purpose Used to display real-time port and cpu utilization statistics.
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show errors ports 1:3
Command: show errors ports 1:3
RX Frames TX Frames
--------------- ---------------CRC Error 19 Excessive Deferral 0
Undersize 0 CRC Error 0
Oversize 0 Late Collision 0
Fragment 0 Excessive Collision 0
Jabber 11 Single Collision 0
Drop Pkts 20837 Collision 0
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
Syntax
Description This command will display the real-time port and cpu utilization
Parameters cpu – Entering this parameter will display the current cpu
Restrictions None.
Example usage:
To display the current CPU utilization:
show utilization [ports | cpu]
statistics for the Switch.
utilization of the Switch, as a percentage.
ports – Entering this parameter will display the current utilization of
all ports on the Switch.
DES-6500:4#show utilization cpu
Command: show utilization cpu
CPU utilization :
------------------------------------------------------------------------------Five seconds - 15% One minute - 25% Five minutes - 14%
DES-6500:4#
To display the port utilization statistics:
60
Page 64

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show utilization ports
Command: show utilization ports
Port TX/sec RX/sec Util Port TX/sec RX/sec Util
---- ---------- ---------- ---- ---- ---------- ---------- --- 1:1 0 0 0 2:10 0 0 0
1:2 0 0 0 2:11 0 0 0
1:3 0 0 0 2:12 0 0 0
1:4 0 0 0 3:1 0 0 0
1:5 0 0 0 3:2 0 0 0
1:6 0 0 0 3:3 0 0 0
1:7 0 0 0 3:4 0 0 0
1:8 0 0 0 3:5 0 0 0
1:9 0 0 0 3:6 0 0 0
1:10 0 0 0 3:7 0 30 1
1:11 0 0 0 3:8 0 0 0
1:12 0 0 0 3:9 30 0 1
2:1 0 0 0 3:10 0 0 0
2:2 0 0 0 3:11 0 0 0
2:3 0 0 0 3:12 0 0 0
2:4 0 0 0 4:1 0 0 0
2:5 0 0 0 4:2 0 0 0
2:6 0 0 0 4:3 0 0 0
2:7 0 0 0 4:4 0 0 0
2:8 0 0 0 4:4 0 0 0
2:9 0 0 0 4:5 0 0 0
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
show stack_information
Purpose Used to display the stack information table.
Syntax
Description This command display stack information.
Parameters None.
Restrictions None.
Usage Example:
To display stack information:
show stack_information
61
Page 65

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show stack_information
Command: show stack_information
Box Prio- Prom Runtime H/W
ID Type Exist rity version version version
--- ----------- ----- ----- -------- -------- ------- 1 DES-6507 exist 16 2.00-B20 3.00-B29 1A1
2 USR-NOT-CFG no
3 USR-NOT-CFG no
4 USR-NOT-CFG no
5 USR-NOT-CFG no
6 USR-NOT-CFG no
7 USR-NOT-CFG no
8 USR-NOT-CFG no
-------------------------------------------------------------------------------------------------Topology :STAR
Current state :MASTER
Box Count :1
DES-6500:4#
clear counters
Purpose Used to clear the Switch’s statistics counters.
Syntax
Description This command will clear the counters used by the Switch to compile
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To clear the counters:
DES-6500:4#clear counters ports 2:7-2:9
Command: clear counters ports 2:7-2:9
Success.
DES-6500:4#
clear counters {ports <portlist>}
statistics.
ports <portlist> − Specifies a range of ports to be displayed. The
port list is specified by listing the lowest slot number and the
beginning port number on that slot, separated by a colon. Then the
highest slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 − in
numerical order.
62
Page 66

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
clear log
Purpose Used to clear the Switch’s history log.
Syntax
Description This command will clear the Switch’s history log.
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To clear the log information:
show log
Purpose Used to display the Switch history log.
clear log
DES-6500:4#clear log
Command: clear log
Success.
DES-6500:4#
Syntax
Description This command will display the contents of the Switch’s history log.
Parameters
Restrictions None.
Example usage:
To display the Switch history log:
show log {index <value_list>}
index <value_list> − Enter a value that corresponds to an entry
made in the log. Multiple entries may be made in the form of x-x
where x is the number of an entry in the log. The smallest number
(and therefore the earlier entry) will be first.
DES-6500:4#show log index 1-4
Command: show log index 1-4
Index Date Time Log Text
----- ---------- -------- ----------------------------------------------------4 2000-03-02 01:54:53 Port 1:13 link up, 100Mbps FULL duplex
3 2000-03-02 01:54:53 Spanning Tree Protocol is enabled
2 2000-03-02 01:54:53 Unit 1, System started up
1 2000-02-28 06:06:09 Spanning Tree Protocol is disabled
DES-6500:4#
63
Page 67

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
enable syslog
Purpose Used to enable the system log to be sent to a remote host.
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To the syslog function on the Switch:
disable syslog
Purpose Used to disable the system log function on the Switch.
enable syslog
The enable syslog command enables the system log to be sent
to a remote host.
DES-6500:4#enable syslog
Command: enable syslog
Success.
DES-6500:4#
Syntax
Description
Parameters None.
Restrictions Only administrator-level users can issue this command.
Example usage:
To disable the syslog function on the Switch:
disable syslog
The disable syslog command disables the system log function on
the Switch. After disabling, Syslog entries will no longer be sent to
a remote host.
DES-6500:4#disable syslog
Command: disable syslog
Success.
DES-6500:4#
64
Page 68

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show syslog
Purpose Used to display the syslog protocol status as enabled or disabled.
Syntax
Description
Parameters None.
Restrictions None.
Example usage:
To display the current status of the syslog function:
create syslog host
Purpose Used to create a new syslog host.
show syslog
The show syslog command displays the syslog status as
enabled or disabled.
DES-6500:4#show syslog
Command: show syslog
Syslog Global State: Enabled
DES-6500:4#
Syntax
Description
Parameters
create syslog host [<index 1-4>] {severity [informational | warning
| all] facility [local0 | local1 | local2 | local3 | local4 | local5 | local6
| local7] | udp_port <udp_port_number> | ipaddress <ipaddr> |
state [enabled | disabled]
The create syslog host command is used to create a new syslog host.
<index 1-4> − Specifies that the command will be applied to an index of
hosts. There are four available indexes, numbered 1 through 4.
severity − Severity level indicator, as shown below:
Bold font indicates that the corresponding severity level is currently
supported on the Switch.
Numerical Severity
Code
0 Emergency: system is unusable
1 Alert: action must be taken immediately
2 Critical: critical conditions
3 Error: error conditions
4 Warning: warning conditions
5 Notice: normal but significant condition
6 Informational: informational messages
7 Debug: debug-level messages
informational − Specifies that informational messages will be sent to the
remote host. This corresponds to number 6 from the list above.
warning − Specifies that warning messages will be sent to the remote
host. This corresponds to number 4 from the list above.
all
−
Specifies that all of the currently supported syslog messages that
are generated by the Switch will be sent to the remote host.
65
Page 69

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
create syslog host
facility − Some of the operating system daemons and processes have
been assigned Facility values. Processes and daemons that have not
been explicitly assigned a Facility may use any of the "local use"
facilities or they may use the "user-level" Facility. Those Facilities that
have been designated are shown in the following: Bold font indicates
the facility values that the Switch currently supports.
Numerical Facility
Code
0 kernel messages
1 user-level messages
2 mail system
3 system daemons
4 security/authorization messages
5 messages generated internally by syslog
6 line printer subsystem
7 network news subsystem
8 UUCP subsystem
9 clock daemon
10 security/authorization messages
11 FTP daemon
12 NTP subsystem
13 log audit
14 log alert
15 clock daemon
16 local use 0 (local0)
17 local use 1 (local1)
18 local use 2 (local2)
19 local use 3 (local3)
20 local use 4 (local4)
21 local use 5 (local5)
22 local use 6 (local6)
23 local use 7 (local7)
local0 − Specifies that local use 0 messages will be sent to the remote
host. This corresponds to number 16 from the list above.
local1 − Specifies that local use 1 messages will be sent to the remote
host. This corresponds to number 17 from the list above.
local2 − Specifies that local use 2 messages will be sent to the remote
host. This corresponds to number 18 from the list above.
local3 − Specifies that local use 3 messages will be sent to the remote
host. This corresponds to number 19 from the list above.
−
local4
host. This corresponds to number 20 from the list above.
local5 − Specifies that local use 5 messages will be sent to the remote
host. This corresponds to number 21 from the list above.
local6 − Specifies that local use 6 messages will be sent to the remote
host. This corresponds to number 22 from the list above.
local7 − Specifies that local use 7 messages will be sent to the remote
host. This corresponds to number 23 from the list above.
udp_port <udp_port_number> − Specifies the UDP port number that
the syslog protocol will use to send messages to the remote host.
ipaddress <ipaddr> − Specifies the IP address of the remote host
Specifies that local use 4 messages will be sent to the remote
66
Page 70

create syslog host
Restrictions Only administrator-level users can issue this command.
Example usage:
To create syslog host:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
where syslog messages will be sent.
state [enabled | disabled] − Allows the sending of syslog messages to
the remote host, specified above, to be enabled and disabled.
DES-6500:4#create syslog host 1 severity all facility local0 ipaddress
10.53.13.94 state enabled
Command: create syslog host 1 severity all facility local0 ipaddress
10.53.13.94 state enabled
Success.
DES-6500:4#
config syslog host
Purpose Used to configure the syslog protocol to send system log data to a
remote host.
Syntax
Description
Parameters
config syslog host <index 1-4> [severity [informational |
warning | all] | facility [local0 | local1 | local2 | local3 | local4 |
local5 | local6 | local7] | udp_port<udp_port_number> |
ipaddress <ipaddr> | state [enabled | disabled]]
The config syslog host command is used to configure the syslog
protocol to send system log information to a remote host.
<index 1-4> − Specifies that the command will be applied to an
index of hosts. There are four available indexes, numbered 1
through 4.
severity − Severity level indicator. These are described in the
following:
Bold font indicates that the corresponding severity level is
currently supported on the Switch.
Numerical Severity
Code
0 Emergency: system is unusable
1 Alert: action must be taken immediately
2 Critical: critical conditions
3 Error: error conditions
4 Warning: warning conditions
5 Notice: normal but significant condition
6 Informational: informational messages
7 Debug: debug-level messages
informational − Specifies that informational messages will be sent
to the remote host. This corresponds to number 6 from the list
above.
67
Page 71

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config syslog host
warning − Specifies that warning messages will be sent to the
remote host. This corresponds to number 4 from the list above.
all − Specifies that all of the currently supported syslog messages
that are generated by the Switch will be sent to the remote host.
facility − Some of the operating system daemons and processes
have been assigned Facility values. Processes and daemons that
have not been explicitly assigned a Facility may use any of the
"local use" facilities or they may use the "user-level" Facility.
Those Facilities that have been designated are shown in the
following: Bold font indicates the facility values the Switch
currently supports.
Numerical Facility
Code
0 kernel messages
1 user-level messages
2 mail system
3 system daemons
4 security/authorization messages
5 messages generated internally by syslog
6 line printer subsystem
7 network news subsystem
8 UUCP subsystem
9 clock daemon
10 security/authorization messages
11 FTP daemon
12 NTP subsystem
13 log audit
14 log alert
15 clock daemon
16 local use 0 (local0)
17 local use 1 (local1)
18 local use 2 (local2)
19 local use 3 (local3)
20 local use 4 (local4)
21 local use 5 (local5)
22 local use 6 (local6)
23 local use 7 (local7)
local0 − Specifies that local use 0 messages will be sent to the
remote host. This corresponds to number 16 from the list above.
local1 − Specifies that local use 1 messages will be sent to the
remote host. This corresponds to number 17 from the list above.
local2 − Specifies that local use 2 messages will be sent to the
remote host. This corresponds to number 18 from the list above.
local3 − Specifies that local use 3 messages will be sent to the
remote host. This corresponds to number 19 from the list above.
local4 − Specifies that local use 4 messages will be sent to the
remote host. This corresponds to number 20 from the list above.
local5 − Specifies that local use 5 messages will be sent to the
remote host. This corresponds to number 21 from the list above.
local6 − Specifies that local use 6 messages will be sent to the
remote host. This corresponds to number 22 from the list above.
local7 − Specifies that local use 7 messages will be sent to the
68
Page 72

config syslog host
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure a syslog host:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
remote host. This corresponds to number 23 from the list above.
udp_port <udp_port_number> − Specifies the UDP port number
that the syslog protocol will use to send messages to the remote
host.
ipaddress <ipaddr> − Specifies the IP address of the remote host
where syslog messages will be sent.
state [enabled | disabled] − Allows the sending of syslog
messages to the remote host, specified above, to be enabled and
disabled.
DES-6500:4#config syslog host 1 severity all
Command: config syslog host 1 severity all
Success.
DES-6500:4##config syslog host 1 facility local0
Command: config syslog host 1 facility local0
Success.
DES-6500:4# config syslog host 1 udp_port 6000
Command: config syslog host 1 udp_port 6000
Success.
DES-6500:4# config syslog host 1 ipaddress 10.44.67.8
Command: config syslog host 1 ipaddress 10.44.67.8
Success.
DES-6500:4# config syslog host 1 state enabled
Command: config syslog host 1 state enabled
Success.
DES-6500:4#
config syslog host all
Purpose Used to configure the syslog protocol to send system log data to a
remote host.
Syntax
Description
Parameters
config syslog host all [severity [informational | warning | all] |
facility [local0 | local1 | local2 | local3 | local4 | local5 | local6 |
local7] | udp_port <udp_port_number> | state [enabled |
disabled]]
The config syslog host all command is used to configure the
syslog protocol to send system log information to a remote host.
all − Specifies that the command will be applied to all hosts.
69
Page 73

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config syslog host all
severity − Severity level indicator, as described below:
Bold font indicates that the corresponding severity level is
currently supported on the Switch.
Numerical Severity
Code
0 Emergency: system is unusable
1 Alert: action must be taken immediately
2 Critical: critical conditions
3 Error: error conditions
4 Warning: warning conditions
5 Notice: normal but significant condition
6 Informational: informational messages
7 Debug: debug-level messages
informational − Specifies that informational messages will be sent
to the remote host. This corresponds to number 6 from the list
above.
warning − Specifies that warning messages will be sent to the
remote host. This corresponds to number 4 from the list above.
all − Specifies that all of the currently supported syslog messages
that are generated by the Switch will be sent to the remote host.
facility − Some of the operating system daemons and processes
have been assigned Facility values. Processes and daemons that
have not been explicitly assigned a Facility may use any of the
"local use" facilities or they may use the "user-level" Facility.
Those Facilities that have been designated are shown in the
following: Bold font indicates that the facility values the Switch
currently supports.
Numerical Facility
Code
0 kernel messages
1 user-level messages
2 mail system
3 system daemons
4 security/authorization messages
5 messages generated internally by syslog
6 line printer subsystem
7 network news subsystem
8 UUCP subsystem
9 clock daemon
10 security/authorization messages
11 FTP daemon
12 NTP subsystem
13 log audit
14 log alert
15 clock daemon
16 local use 0 (local0)
17 local use 1 (local1)
18 local use 2 (local2)
19 local use 3 (local3)
20 local use 4 (local4)
21 local use 5 (local5)
22 local use 6 (local6)
23 local use 7 (local7)
70
Page 74

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config syslog host all
local0 − Specifies that local use 0 messages will be sent to the
remote host. This corresponds to number 16 from the list above.
local1 − Specifies that local use 1 messages will be sent to the
remote host. This corresponds to number 17 from the list above.
local2 − Specifies that local use 2 messages will be sent to the
remote host. This corresponds to number 18 from the list above.
local3 − Specifies that local use 3 messages will be sent to the
remote host. This corresponds to number 19 from the list above.
local4 − Specifies that local use 4 messages will be sent to the
remote host. This corresponds to number 20 from the list above.
local5 − Specifies that local use 5 messages will be sent to the
remote host. This corresponds to number 21 from the list above.
local6 − Specifies that local use 6 messages will be sent to the
remote host. This corresponds to number 22 from the list above.
local7 − Specifies that local use 7 messages will be sent to the
remote host. This corresponds to number 23 from the list above.
udp_port <udp_port_number> − Specifies the UDP port number
that the syslog protocol will use to send messages to the remote
host.
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure all syslog hosts:
state [enabled | disabled] − Allows the sending of syslog
messages to the remote host, specified above, to be enabled and
disabled.
DES-6500:4#config syslog host all severity all
Command: config syslog host all severity all
Success.
DES-6500:4##config syslog host all facility local0
Command: config syslog host all facility local0
Success
DES-6500:4# config syslog host all udp_port 6000
Command: config syslog host all udp_port 6000
Success.
DES-6500:4# config syslog host all ipaddress 10.44.67.8
Command: config syslog host all ipaddress 10.44.67.8
Success.
DES-6500:4# config syslog host all state enabled
Command: config syslog host all state enabled
Success.
DES-6500:4#
71
Page 75

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
delete syslog host
Purpose Used to remove a syslog host, that has been previously
configured, from the Switch.
Syntax
Description
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete a previously configured syslog host:
show syslog host
delete syslog host [<index 1-4> | all]
The delete syslog host command is used to remove a syslog
host that has been previously configured from the Switch.
<index 1-4> − Specifies that the command will be applied to an
index of hosts. There are four available indexes, numbered 1
through 4.
all − Specifies that all syslog hosts will be deleted.
DES-6500:4#delete syslog host 4
Command: delete syslog host 4
Success.
DES-6500:4#
Purpose Used to display the syslog hosts currently configured on the
Syntax
Description
Parameters
Restrictions None.
Example usage:
To show syslog host information:
Switch.
show syslog host {<index 1-4>}
The show syslog host command is used to display the syslog
hosts that are currently configured on the Switch.
<index 1-4> − Specifies that the command will be applied to an
index of hosts. There are four available indexes, numbered 1
through 4.
DES-6500:4#show syslog host
Command: show syslog host
Syslog Global State: Disabled
Host Id Host IP Address Severity Facility UDP port Status
------- --------------- -------------- -------- -------- ------- 1 10.1.1.2 All Local0 514 Disabled
2 10.40.2.3 All Local0 514 Disabled
3 10.21.13.1 All Local0 514 Disabled
Total Entries : 3
DES-6500:4#
72
Page 76

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config system_severity
Purpose To configure when and where severity messages are to be
recorded.
Syntax
config system_severity [trap | log | all] [critical | warning |
information]
Description This command is used to configure the system severity levels on the
Switch. When an event occurs on the Switch, a message will be sent
to the SNMP agent (trap), the Switch’s log or both. Events occurring
on the Switch are separated into three main categories.
• Information – Events classified as information are basic events
occurring on the Switch that are not deemed as problematic,
such as enabling or disabling various functions on the Switch.
• Warning - Events classified as warning are problematic events
that are not critical to the overall function of the Switch but do
require attention, such as unsuccessful downloads or uploads
and failed logins.
• Critical – Events classified as critical are fatal exceptions
occurring on the Switch, such as hardware failures or spoofing
attacks.
Parameters Choose one of the following to identify where severity messages are
to be sent.
• trap – Entering this parameter will define which events
occurring on the Switch will be sent to a SNMP agent for
analysis.
• log – Entering this parameter will define which events
occurring on the Switch will be sent to the Switch’s log for
analysis.
• all – Entering this parameter will define which events occurring
Choose one of the following to identify what type of severity
warnings are to be sent to the destination entered above.
• critical – Entering this parameter along with the proper
• warning – Entering this parameter along with the proper
• information – Entering this parameter along with the proper
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure the system severity:
on the Switch will be sent to a SNMP agent and the Switch’s
log for analysis.
destination, stated above, will instruct the Switch to send only
critical events to the Switch’s log or SNMP agent.
destination, stated above, will instruct the Switch to send
critical and warning events to the Switch’s log or SNMP agent.
destination, stated above, will instruct the switch to send
informational, warning and critical events to the Switch’s log or
SNMP agent.
73
Page 77

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config system_severity trap critical
Command: config system_severity trap critical
Success.
DES-6500:4#
show system_severity
Purpose To display the current severity settings set on the Switch.
Example usage:
To view the system severity settings currently implemented on the Switch:
Syntax
Description This command is used to view the severity settings that have been
Parameters None.
Restrictions None.
DES-6500:4#show system_severity
Command: show system_severity
system_severity log : information
system_severity trap : critical
DES-6500:4#
show system_severity
implemented on the Switch using the config system_severity
command.
74
Page 78

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
10
MULTIPLE SPANNING TREE PROTOCOL (MSTP) COMMANDS
This switch supports three versions of the Spanning Tree Protocol; 802.1d STP, 802.1w Rapid STP and 802.1s MSTP. Multiple
Spanning Tree Protocol, or MSTP, is a standard defined by the IEEE community that allows multiple VLANs to be mapped to a
single spanning tree instance, which will provide multiple pathways across the network. Therefore, these MSTP configurations
will balance the traffic load, preventing wide scale disruptions when a single spanning tree instance fails. This will allow for
faster convergences of new topologies for the failed instance. Frames designated for these VLANs will be processed quickly
and completely throughout interconnected bridges utilizing either of the three spanning tree protocols (STP, RSTP or MSTP).
This protocol will also tag BPDU packets so receiving devices can distinguish spanning tree instances, spanning tree regions
and the VLANs associated with them. These instances will be classified by an instance_id. MSTP will connect multiple
spanning trees with a Common and Internal Spanning Tree (CIST). The CIST will automatically determine each MSTP region,
its maximum possible extent and will appear as one virtual bridge that runs a single spanning tree. Consequentially, frames
assigned to different VLANs will follow different data routes within administratively established regions on the network,
continuing to allow simple and full processing of frames, regardless of administrative errors in defining VLANs and their
respective spanning trees. Each switch utilizing the MSTP on a network will have a single MSTP configuration that will have
the following three attributes:
a) A configuration name defined by an alphanumeric string of up to 32 characters (defined in the config stp mst_config_id
command as name <string>).
b) A configuration revision number (named here as a revision_level) and;
c) A 4096 element table (defined here as a vid_range) which will associate each of the possible 4096 VLANs supported
by the Switch for a given instance.
To utilize the MSTP function on the Switch, three steps need to be taken:
a) The Switch must be set to the MSTP setting (config stp version)
b) The correct spanning tree priority for the MSTP instance must be entered (config stp priority).
c) VLANs that will be shared must be added to the MSTP Instance ID (config stp instance_id).
The Multiple Spanning Tree Protocol commands in the Command Line Interface (CLI) are listed (along with the appropriate
parameters) in the following table.
Command Parameters
enable stp
disable stp
config stp version [mstp | rstp | stp]
config stp {maxage <value 6-40> | maxhops <value 1-20> | hellotime <value
1-10> | forwarddelay <value 4-30>| txholdcount <value 1-10> |
fbpdu [enable | disable] | lbd [enable | disable] | lbd_recover_timer
[0 | <sec 60-1000000>]}
config stp ports <portlist> {externalCost [auto | <value 1-200000000>] | hellotime
<value 1-10> | migrate [yes | no] edge [true | false] | p2p [true |
false | auto ] | state [enable | disable] | lbd [enable | disable]}
create stp instance_id <value 1-15>
config stp instance _id <value 1-15> [add_vlan | remove_vlan] <vidlist>
delete stp instance_id <value 1-15>
75
Page 79

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Command Parameters
config stp priority <value 0-61440> instance_id <value 0-15>
config stp
mst_config_id
config stp mst_ports <portlist> instance_id <value 0-15> {internalCost [auto | value 1-
show stp
show stp ports {<portlist>}
show stp instance_id {<value 0-15>}
show stp mst_config id
Each command is listed, in detail, in the following sections.
{revision_level <int 0-65535> | name <string>}
200000000] | priority <value 0-240>}
enable stp
Purpose Used to globally enable STP on the Switch.
Syntax
Description This command allows the Spanning Tree Protocol to be globally
Parameters None.
Restrictions Only administrator-level users can issue this command.
enable stp
enabled on the Switch.
Example usage:
To enable STP, globally, on the Switch:
disable stp
Purpose Used to globally disable STP on the Switch.
Syntax
Description This command allows the Spanning Tree Protocol to be globally
Parameters None.
Restrictions Only administrator-level users can issue this command.
DES-6500:4#enable stp
Command: enable stp
Success.
DES-6500:4#
disable stp
disabled on the Switch.
Example usage:
To disable STP on the Switch:
76
Page 80

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#disable stp
Command: disable stp
Success.
DES-6500:4#
config stp version
Purpose Used to globally set the version of STP on the Switch.
Syntax
Description This command allows the user to choose the version of the
Parameters mstp – Selecting this parameter will set the Multiple Spanning
Restrictions Only administrator-level users can issue this command.
Example usage:
To set the Switch globally for the Multiple Spanning Tree Protocol (MSTP):
DES-6500:4#config stp version mstp
Command: config stp version mstp
Success.
DES-6500:4#
config stp version [mstp | rstp | stp]
spanning tree to be implemented on the Switch.
Tree Protocol (MSTP) globally on the Switch.
rstp - Selecting this parameter will set the Rapid Spanning Tree
Protocol (RSTP) globally on the Switch.
stp - Selecting this parameter will set the Spanning Tree Protocol
(STP) globally on the Switch.
config stp
Purpose Used to setup STP, RSTP and MSTP on the Switch.
Syntax
Description This command is used to setup the Spanning Tree Protocol (STP)
Parameters
config stp {maxage <value 6-40> | maxhops <value 1-20> |
hellotime <value 1-10> | forwarddelay <value 4-30>|
txholdcount <value 1-10> | fbpdu [enable | disable] | lbd
[enable | disable] | lbd_recover_timer [0 | <sec 60-1000000>]}
for the entire switch. All commands here will be implemented for
the STP version that is currently set on the Switch.
maxage <value 6-40> − This value may be set to ensure that old
information does not endlessly circulate through redundant paths
in the network, preventing the effective propagation of the new
information. Set by the Root Bridge, this value will aid in
determining that the Switch has spanning tree configuration
77
Page 81

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config stp
values consistent with other devices on the bridged LAN. If the
value ages out and a BPDU has still not been received from the
Root Bridge, the Switch will start sending its own BPDU to all
other switches for permission to become the Root Bridge. If it
turns out that your switch has the lowest Bridge Identifier, it will
become the Root Bridge. The user may choose a time between 6
and 40 seconds. The default value is 20.
maxhops <value 1-20> - The number of hops between devices in
a spanning tree region before the BPDU (bridge protocol data
unit) packet sent by the Switch will be discarded. Each switch on
the hop count will reduce the hop count by one until the value
reaches zero. The Switch will then discard the BDPU packet and
the information held for the port will age out. The user may set a
hop count from 1 to 20. The default is 20.
hellotime <value 1-10> − The user may set the time interval
between transmission of configuration messages by the root
device in STP, or by the designated router in RSTP, thus stating
that the Switch is still functioning. A time between 1 and 10
seconds may be chosen, with a default setting of 2 seconds.
In MSTP, the spanning tree is configured by port and
therefore, the hellotime must be set using the configure stp ports
command for switches utilizing the Multiple Spanning Tree
Protocol.
forwarddelay <value 4-30> − The maximum amount of time (in
seconds) that the root device will wait before changing states. The
user may choose a time between 4 and 30 seconds. The default is
15 seconds.
txholdcount <value 1-10> - The maximum number of BDPU Hello
packets transmitted per interval. Default value = 3.
fbpdu [enable | disable] − Allows the forwarding of STP BPDU
packets from other network devices when STP is disabled on the
Switch. The default is enable.
lbd [enable | disable] – Enabling this feature temporarily blocks
STP on the Switch when a BPDU packet has been looped back to
the Switch. When the Switch detects its own BPDU packet coming
back, it signifies a loop on the network. STP will automatically be
blocked and an alert will be sent to the administrator. The LBD
STP port will restart (change to discarding state) when the LBD
Recover Time times out. The default is enabled.
lbd_recover_timer [0 | <value 60-1000000>] - This field will set the
time the STP port will wait before recovering the STP state set. 0
will denote that the LBD will never time out or restart until the
administrator personally changes it. The user may also set a time
between 60 and 1000000 seconds. The default is 60 seconds.
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure STP with maxage 18 and maxhops of 15:
78
Page 82

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config stp maxage 18 maxhops 15
Command: config stp maxage 18 maxhops 15
Success.
DES-6500:4#
config stp ports
Purpose Used to setup STP on the port level.
Syntax
Description This command is used to create and configure STP for a group of
Parameters
config stp ports <portlist> {externalCost [auto | <value 1200000000>] | hellotime <value 1-10> | migrate [yes | no] edge
[true | false] | p2p [true | false | auto ] | state [enable | disable]
| lbd [enable | disable]}
ports.
<portlist> − Specifies a range of ports to be displayed. The port list
is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. Then the highest
slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3 specifies
slot number 1, port 3. 2:4 specifies slot number 2, port 4. 1:3-2:4
specifies all of the ports between slot 1, port 3 and slot 2, port 4 −
in numerical order.
externalCost − This defines a metric that indicates the relative cost
of forwarding packets to the specified port list. Port cost can be set
automatically or as a metric value. The default value is auto.
auto – Setting this parameter for the external cost will
automatically set the speed for forwarding packets to the
specified port(s) in the list for optimal efficiency. Default port
cost: 100Mbps port = 200000. Gigabit port = 20000.
<value 1-200000000> - Define a value between 1 and
200000000 to determine the external cost. The lower the
number, the greater the probability the port will be chosen to
forward packets.
hellotime <value 1-10> − The time interval between transmission
of configuration messages by the designated port, to other
devices on the bridged LAN, thus stating that the Switch is still
functioning. The user may choose a time between 1 and 10
seconds. The default is 2 seconds.
migrate [yes | no] – Setting this parameter as “yes” will set the
ports to send out BDPU packets to other bridges, requesting
information on their STP setting If the Switch is configured for
RSTP, the port will be capable to migrate from 802.1d STP to
802.1w RSTP. If the Switch is configured for MSTP, the port is
capable of migrating from 802.1d STP to 802.1s MSTP. RSTP
and MSTP can coexist with standard STP, however the benefits of
RSTP and MSTP are not realized on a port where an 802.1d
network connects to an 802.1w or 802.1s enabled network.
Migration should be set as yes on ports connected to network
79
Page 83

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config stp ports
stations or segments that are capable of being upgraded to
802.1w RSTP or 802.1s MSTP on all or some portion of the
segment.
edge [true | false] – true designates the port as an edge port.
Edge ports cannot create loops, however an edge port can lose
edge port status if a topology change creates a potential for a
loop. An edge port normally should not receive BPDU packets. If a
BPDU packet is received it automatically loses edge port status.
false indicates that the port does not have edge port status.
p2p [true | false | auto] – true indicates a point-to-point (P2P)
shared link. P2P ports are similar to edge ports however they are
restricted in that a P2P port must operate in full-duplex. Like edge
ports, P2P ports transition to a forwarding state rapidly thus
benefiting from RSTP. A p2p value of false indicates that the port
cannot have p2p status. auto allows the port to have p2p status
whenever possible and operate as if the p2p status were true. If
the port cannot maintain this status (for example if the port is
forced to half-duplex operation) the p2p status changes to operate
as if the p2p value were false. The default setting for this
parameter is auto.
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure STP with path cost 19, hellotime set to 5 seconds, migration enable, and state enable for ports 1-5 of
module 1.
create stp instance_id
state [enable | disable] − Allows STP to be enabled or disabled for
the ports specified in the port list. The default is enable.
lbd [enable | disable] - Used to enable or disable the loopback
detection function on the switch for the ports configured above in
the config stp command.
DES-6500:4#config stp ports 1:1-1:5 externalCost 19 hellotime 5
migrate yes state enable
Command: config stp ports 1:1-1:5 externalCost 19 hellotime 5
migrate yes state enable
Success.
DES-6500:4#
Purpose Used to create a STP instance ID for MSTP.
Syntax
Description This command allows the user to create a STP instance ID for the
Parameters <value 1-15> - Enter a value between 1 and 15 to identify the
Restrictions Only administrator-level users can issue this command.
create stp instance_id <value 1-15>
Multiple Spanning Tree Protocol. There are 16 STP instances on
the Switch (one internal CIST, unchangeable) and the user may
create up to 15 instance IDs for the Switch.
Spanning Tree instance on the Switch.
80
Page 84

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Example usage:
To create a spanning tree instance 2:
DES-6500:4#create stp instance_id 2
Command: create stp instance_id 2
Success.
DES-6500:4#
config stp instance_id
Purpose Used to add or delete an STP instance ID.
Syntax
Description This command is used to map VIDs (VLAN IDs) to previously
Parameters <value 1-15> - Enter a number between 1 and 15 to define the
config stp instance_id <value 1-15> [add_vlan | remove_vlan]
<vidlist>
configured STP instances on the Switch by creating an instance_id. A
STP instance may have multiple members with the same MSTP
configuration. There is no limit to the number of STP regions in a
network but each region only supports a maximum of 16 spanning tree
instances (one unchangeable default entry). VIDs can belong to only
one spanning tree instance at a time.
Note that switches in the same spanning tree region having the same
STP instance_id must be mapped identically, and have the same
configuration revision_level number and the same name.
instance_id. The Switch supports 16 STP regions with one
unchangeable default instance ID set as 0.
add_vlan – Along with the vid_range <vidlist> parameter, this
command will add VIDs to the previously configured STP
instance_id.
remove_vlan – Along with the vid_range <vidlist> parameter,
this command will remove VIDs to the previously configured STP
instance_id.
<vidlist> – Specify the VID range from configured VLANs set
on the Switch. Supported VIDs on the Switch range from ID
number 1 to 4094.
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure instance ID 2 to add VID 10:
DES-6500:4#config stp instance_id 2 add_vlan 10
Command : config stp instance_id 2 add_vlan 10
Success.
DES-6500:4#
Example usage:
To remove VID 10 from instance ID 2:
81
Page 85

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#config stp instance_id 2 remove_vlan 10
Command : config stp instance_id 2 remove_vlan 10
Success.
DES-6500:4#
delete stp instance_id
Purpose Used to delete a STP instance ID from the Switch.
Syntax
Description This command allows the user to delete a previously configured
Parameters <value 1-15> - Enter a value between 1 and 15 to identify the
Restrictions Only administrator-level users can issue this command.
Example usage:
To delete STP instance id 2 from the Switch.
DES-6500:4#delete stp instance_id 2
Command: delete stp instance_id 2
Success.
DES-6500:4#
delete stp instance_id <value 1-15>
STP instance ID from the Switch.
Spanning Tree instance on the Switch.
config stp priority
Purpose Used to update the STP instance configuration.
Syntax
config stp priority <value 0-61440> instance_id <value 0-15>
Description This command is used to update the STP instance configuration
settings on the Switch. The MSTP will utilize the priority in
selecting the root bridge, root port and designated port. Assigning
higher priorities to STP regions will instruct the Switch to give
precedence to the selected instance_id for forwarding packets.
The lower the priority value set, the higher the priority.
Parameters priority <value 0-61440> - Select a value between 0 and 61440 to
specify the priority for a specified instance ID for forwarding
packets. The lower the value, the higher the priority. This entry
must be divisible by 4096.
instance_id <value 0-15> - Enter the value corresponding to the
previously configured instance ID of which to set the priority value.
An instance id of 0 denotes the default instance_id (CIST)
internally set on the Switch.
Restrictions Only administrator-level users can issue this command.
82
Page 86

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Example usage:
To set the priority value for instance_id 2 as 4096:
DES-6500:4#config stp priority 4096 instance_id 2
Command : config stp priority 4096 instance_id 2
Success.
DES-6500:4#
config stp mst_config_id
Purpose Used to update the MSTP configuration identification.
Syntax
Description This command will uniquely identify the MSTP configuration
Parameters revision_level <int 0-65535>– Enter a number between 0 and
Restrictions Only administrator-level users can issue this command.
Example usage:
To configure the MSTP region of the Switch with revision_level 10 and the name “Trinity”:
DES-6500:4#config stp mst_config_id revision_level 10 name Trinity
Command : config stp mst_config_id revision_level 10 name Trinity
Success.
DES-6500:4#
config stp mst_config_id {revision_level <int 0-65535> | name
<string>
currently configured on the Switch. Information entered here will
be attached to BDPU packets as an identifier for the MSTP region
to which it belongs. Switches having the same revision_level and
name will be considered as part of the same MSTP region.
65535 to identify the MSTP region. This value, along with the
name will identify the MSTP region configured on the Switch. The
default setting is 0.
name <string> - Enter an alphanumeric string of up to 32
characters to uniquely identify the MSTP region on the Switch.
This name, along with the revision_level value will identify the
MSTP region configured on the Switch. If no name is entered, the
default name will be the MAC address of the device.
config stp mst_ports
Purpose Used to update the port configuration for a MSTP instance.
Syntax
Description This command will update the port configuration for a STP
config stp mst_ports <portlist> instance_id <value 0-15>
{internalCost [auto | <value 1-20000000>] `priority <value 0240>}
instance_id. If a loop occurs, the MSTP function will use the port
priority to select an interface to put into the forwarding state. Set a
83
Page 87

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config stp mst_ports
higher priority value for interfaces to be selected for forwarding
first. In instances where the priority value is identical, the MSTP
function will implement the lowest port number into the forwarding
state and other interfaces will be blocked. Remember that lower
priority values mean higher priorities for forwarding packets.
Parameters <portlist> - Specifies a port or range of ports to be configured. The
port list is specified by listing the lowest slot number and the
beginning port number on that slot, separated by a colon. Then
the highest slot number, and the highest port number of the range
(also separated by a colon) are specified. The beginning and end
of the port list range are separated by a dash. For example, 1:3
specifies slot number 1, port 3. 2:4 specifies slot number 2, port
4. 1:3-2:4 specifies all of the ports between slot 1, port 3 and slot
2, port 4 − in numerical order.
instance_id <value 0-15> - Enter a numerical value between 0 and
15 to identify the instance_id previously configured on the Switch.
An entry of 0 will denote the CIST (Common and Internal
Spanning Tree.
internalCost – This parameter is set to represent the relative cost
of forwarding packets to specified ports when an interface is
selected within a STP instance. The default setting is auto. There
are two options:
Restrictions Only administrator-level users can issue this command.
Example usage:
To designate ports 1 through 5 on module one, with instance ID 2, to have an auto internalCost and a priority of 16:
auto – Selecting this parameter for the internalCost will
set quickest route automatically and optimally for an
interface. The default value is derived from the media speed
of the interface.
value 1-2000000 – Selecting this parameter with a value
in the range of 1-2000000 will set the quickest route when a
loop occurs. A lower internalCost represents a quicker
transmission.
priority <value 0-240> - Enter a value between 0 and 240 to set
the priority for the port interface. A higher priority will designate the
interface to forward packets first. A lower number denotes a
higher priority.
DES-6500:4#config stp mst_config_id ports 1:1-1:5 instance_id 2
internalCost auto priority 16
Command : config stp mst_config_id ports 1:1-1:5 instance_id 2
internalCost auto priority 16
Success.
DES-6500:4#
84
Page 88

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show stp
Purpose Used to display the Switch’s current STP configuration.
Syntax
Description This command displays the Switch’s current STP configuration.
Parameters None.
Restrictions None.
Example usage:
To display the status of STP on the Switch:
Status 1: STP enabled with STP compatible version
show stp
DES-6500:4#show stp
Command: show stp
STP Status : Enabled
STP Version : STP Compatible
Max Age : 20
Hello Time : 2
Forward Delay : 15
Max Age : 20
TX Hold Count : 3
Forwarding BPDU : Enabled
Loopback Detection : Enabled
LBD Recover Time : 60
DES-6500:4#
Status 2 : STP enabled for RSTP
DES-6500:4#show stp
Command: show stp
STP Status : Enabled
STP Version : RSTP
Max Age : 20
Hello Time : 2
Forward Delay : 15
Max Age : 20
TX Hold Count : 3
Forwarding BPDU : Enabled
Loopback Detection : Enabled
LBD Recover Time : 60
DES-6500:4#
Status 3 : STP enabled for MSTP
DES-6500:4#show stp
Command: show stp
STP Status : Enabled
STP Version : MSTP
Max Age : 20
Forward Delay : 15
85
Page 89

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
Max Age : 20
TX Hold Count : 3
Forwarding BPDU : Enabled
Loopback Detection : Enabled
LBD Recover Time : 60
DES-6500:4#
show stp ports
Purpose Used to display the Switch’s current instance_id configuration.
Syntax
Description This command displays the STP Instance Settings and STP
Parameters
Restrictions None.
Example usage:
To show stp ports 1 through 9 on switch one:
DES-6500:4#show stp ports 1:1-1:9
Command: show stp ports 1:1-1:9
MSTP Port Information
---------------------Port Index : 1:1 , Hello Time: 2 /2 , Port STP enabled , LBD: No
External PathCost : Auto/200000 , Edge Port : No /No , P2P : Auto /Yes
Msti Designated Bridge Internal PathCost Prio Status Role
----- ------------------ ----------------- ---- ---------- ---------0 8000/0050BA7120D6 200000 128 Forwarding Root
1 8001/0053131A3324 200000 128 Forwarding Master
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
show stp ports <portlist>
Instance Operational Status currently implemented on the Switch.
<portlist> − Specifies a range of ports to be displayed. The port
list is specified by listing the lowest slot number and the beginning
port number on that slot, separated by a colon. Then the highest
slot number, and the highest port number of the range (also
separated by a colon) are specified. The beginning and end of the
port list range are separated by a dash. For example, 1:3
specifies slot number 1, port 3. 2:4 specifies slot number 2, port
4. 1:3-2:4 specifies all of the ports between slot 1, port 3 and slot
2, port 4 − in numerical order.
show stp instance_id
Purpose Used to display the Switch’s STP instance configuration
Syntax
Description This command displays the Switch’s current STP Instance
Parameters <value 0-15> - Enter a value defining the previously configured
show stp instance_id <value 0-15>
Settings and the STP Instance Operational Status.
instance_id on the Switch. An entry of 0 will display the STP
86
Page 90

show stp instance_id
Restrictions None.
Example usage:
To display the STP instance configuration for instance 0 (the internal CIST) on the Switch:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
configuration for the CIST internally set on the Switch.
DES-6500:4#show stp instance_id 0
Command: show stp instance_id 0
STP Instance Settings
-------------------------- Instance Type : CIST
Instance Status : Enabled
Instance Priority : 32768(bridge priority : 32768, sys ID ext : 0 )
STP Instance Operational Status
------------------------------- Designated Root Bridge : 32766/00-90-27-39-78-E2
External Root Cost : 200012
Regional Root Bridge : 32768/00-53-13-1A-33-24
Internal Root Cost : 0
Designated Bridge : 32768/00-50-BA-71-20-D6
Root Port : 1:1
Max Age : 20
Forward Delay : 15
Last Topology Change : 856
Topology Changes Count : 2987
CTRL+C ESC q Quit SPACE n Next Page p Previous Page r Refresh
show stp mst_config_id
Purpose Used to display the MSTP configuration identification.
Syntax
Description This command displays the Switch’s current MSTP configuration
Parameters None.
Restrictions None.
Example usage:
To show the MSTP configuration identification currently set on the Switch:
show stp mst_config_id
identification.
87
Page 91

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show stp mst_config_id
Command: show stp mst_config_id
Current MST Configuration Identification
----------------------------------------
Configuration Name : 00:53:13:1A:33:24 Revision Level :0
MSTI ID Vid list
------- ---------- CIST 2-4094
1 1
DES-6500:4#
88
Page 92

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
11
FORWARDING DATABASE COMMANDS
The forwarding database commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in
the following table.
Command Parameters
create fdb <vlan_name 32> <macaddr> port <port>
create multicast_fdb <vlan_name 32> <macaddr>
config multicast_fdb <vlan_name 32> <macaddr> [add | delete] <portlist>
delete multicast_fdb <vlan_name 32> <macaddr>
config fdb aging_time <sec 10-1000000>
delete fdb <vlan_name 32> <macaddr>
clear fdb [vlan <vlan_name 32> | port <port> | all]
show multicast_fdb {vlan <vlan_name 32> | mac_address <macaddr>}
show fdb {port <port> | vlan <vlan_name 32> | mac_address <macaddr> |
static | aging_time}
show ipfdb {<ipaddr>}
Each command is listed, in detail, in the following sections.
create fdb
Purpose Used to create a static entry to the unicast MAC address
forwarding table (database).
Syntax
Description This command will make an entry into the Switch’s unicast MAC
Parameters
create fdb <vlan_name 32> <macaddr> port <port>
address forwarding database.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that will be added to the
forwarding table.
port <port> − Enter the corresponding port of the entry to delete.
The port is specified by listing the lowest slot number and the
beginning port number on that slot, separated by a colon. For
example, 1:3 specifies slot number 1, port 3. 2:4 specifies switch
number 2, port 4.
Restrictions Only administrator-level users can issue this command.
Example usage:
To create a unicast MAC FDB entry:
89
Page 93

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#create fdb default 00-00-00-00-01-02 port 2:5
Command: create fdb default 00-00-00-00-01-02 port 2:5
Success.
DES-6500:4#
create multicast_fdb
Purpose Used to create a static entry to the multicast MAC address
forwarding table (database)
Syntax
Description This command will make an entry into the Switch’s multicast MAC
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To create multicast MAC forwarding:
create multicast_fdb <vlan_name 32> <macaddr>
address forwarding database.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that will be added to the
forwarding table.
DES-6500:4#create multicast_fdb default 01-00-00-00-00-01
Command: create multicast_fdb default 01-00-00-00-00-01
Success.
DES-6500:4#
config multicast_fdb
Purpose Used to configure the Switch’s multicast MAC address forwarding
database.
Syntax
Description This command configures the multicast MAC address forwarding
Parameters
config multicast_fdb <vlan_name 32> <macaddr> [add |
delete] <portlist>
table.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that will be configured in the
multicast forwarding table.
[add | delete] − Add will add ports to the forwarding table. Delete
will remove ports from the multicast forwarding table.
90
Page 94

config multicast_fdb
Restrictions Only administrator-level users can issue this command.
Example usage:
To add multicast MAC forwarding:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
<portlist> − Specifies a range of ports to be displayed the
beginning port number on that slot, separated by a colon.
Then the highest slot number, and the highest port number
of the range (also separated by a colon) are specified. The
beginning and end of the port list range are separated by a
dash. For example, 1:3 specifies slot number 1, port 3. 2:4
specifies slot number 2, port 4. 1:3-2:4 specifies all of the
ports between slot 1, port 3 and slot 2, port 4 − in numerical
order.
DES-6500:4#config multicast_fdb default 01-00-00-00-00-01 add 1:1-1:5
Command: config multicast_fdb default 01-00-00-00-00-01 add 1:1-1:5
Success.
delete multicast_fdb
Purpose Used to delete a static entry from the multicast MAC address
Syntax
Description This command will delete an entry from the Switch’s multicast
Parameters
Restrictions Only administrator-level users can issue this command.
Example usage:
To create multicast MAC forwarding:
DES-6500:4#
forwarding table (database)
delete multicast_fdb <vlan_name 32> <macaddr>
MAC address forwarding database.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that will be added to the
forwarding table.
DES-6500:4#delete multicast_fdb default 01-00-00-00-00-01
Command: delete multicast_fdb default 01-00-00-00-00-01
Success.
DES-6500:4#
91
Page 95

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
config fdb aging_time
Purpose Used to set the aging time of the forwarding database.
Syntax
Description The aging time affects the learning process of the Switch.
Parameters
Example usage:
To set the fdb aging time:
config fdb aging_time <sec 10-1000000>
Dynamic forwarding table entries, which are made up of the
source MAC addresses and their associated port numbers, are
deleted from the table if they are not accessed within the aging
time. The aging time can be from 10 to 1000000 seconds with a
default value of 300 seconds. A very long aging time can result in
dynamic forwarding table entries that are out-of-date or no longer
exist. This may cause incorrect packet forwarding decisions by the
Switch. If the aging time is too short however, many entries may
be aged out too soon. This will result in a high percentage of
received packets whose source addresses cannot be found in the
forwarding table, in which case the Switch will broadcast the
packet to all ports, negating many of the benefits of having a
switch.
<sec 10-1000000> − The aging time for the MAC address
forwarding database value. The value in seconds may be between
10 and 1000000 seconds. The default is 300 seconds.
Only administrator-level users can issue this command. Restrictions
DES-6500:4#config fdb aging_time 300
Command: config fdb aging_time 300
Success.
DES-6500:4#
delete fdb
Purpose Used to delete an entry to the Switch’s forwarding database.
Syntax
Description This command is used to delete a previous entry to the Switch’s
Parameters
Restrictions Only administrator-level users can issue this command.
delete fdb <vlan_name 32> <macaddr>
MAC address forwarding database.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that will be deleted from the
forwarding table.
Example usage:
To delete a permanent FDB entry:
92
Page 96

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#delete fdb default 00-00-00-00-01-02
Command: delete fdb default 00-00-00-00-01-02
Success.
DES-6500:4#
Example usage:
To delete a multicast fdb entry:
DES-6500:4#delete fdb default 01-00-00-00-01-02
Command: delete fdb default 01-00-00-00-01-02
Success.
DES-6500:4#
Example usage:
To clear all FDB dynamic entries:
clear fdb
Purpose Used to clear the Switch’s forwarding database of all
dynamically learned MAC addresses.
Syntax
Description This command is used to clear dynamically learned entries to
Parameters
Restrictions Only administrator-level users can issue this command.
DES-6500:4#clear fdb all
clear fdb [vlan <vlan_name 32> | port <port> | all]
the Switch’s forwarding database.
vlan <vlan_name 32> − The name of the VLAN on which the
MAC address resides.
port <port> − Enter the corresponding port of the entry to delete.
The port is specified by listing the lowest slot number and the
beginning port number on that slot, separated by a colon. For
example, 1:3 specifies slot number 1, port 3. 2:4 specifies slot
number 2, port 4.
all − Clears all dynamic entries to the Switch’s forwarding
database.
Command: clear fdb all
Success.
DES-6500:4#
93
Page 97

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
show multicast_fdb
Purpose Used to display the contents of the Switch’s multicast forwarding
database.
Syntax
Description This command is used to display the current contents of the
Parameters
Restrictions None.
Example usage:
To display multicast MAC address table:
show mulitcast_fdb [vlan <vlan_name 32> | mac_address
<macaddr>]
Switch’s multicast MAC address forwarding database.
vlan <vlan_name 32> − The name of the VLAN on which the
MAC address resides.
mac_address <macaddr> − The MAC address that is present in
the forwarding database table.
DES-6500:4#show multicast_fdb
Command: show multicast_fdb
VLAN Name : default
MAC Address : 01-00-5E-00-00-00
Egress Ports : 1:1-1:5,1:26,2:26
Mode : Static
Total Entries : 1
DES-6500:4#
show fdb
Purpose Used to display the current unicast MAC address forwarding
database.
Syntax
Description This command will display the current contents of the Switch’s
Parameters
Restrictions None.
show fdb {port <port> | vlan <vlan_name 32> | mac_address
<macaddr> | static | aging_time}
forwarding database.
port <port> − The port number corresponding to the MAC
destination address. Enter the corresponding port of the entry to
delete. The port is specified by listing the lowest slot number and
the beginning port number on that slot, separated by a colon. For
example, 1:3 specifies slot number 1, port 3. 2:4 specifies slot
number 2, port 4.
<vlan_name 32> − The name of the VLAN on which the MAC
address resides.
<macaddr> − The MAC address that is present in the forwarding
database table.
static − Displays the static MAC address entries.
aging_time − Displays the aging time for the MAC address
forwarding database.
94
Page 98

Example usage:
To display unicast MAC address table:
xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show fdb
Command: show fdb
Unicast MAC Address Aging Time = 300
VID VLAN Name MAC Address Port Type
---- ---------------- ----------------- ------ ----------------
1 default 00-00-39-34-66-9A 1:12 Dynamic
1 default 00-00-51-43-70-00 1:12 Dynamic
1 default 00-00-5E-00-01-01 1:12 Dynamic
1 default 00-00-74-60-72-2D 1:12 Dynamic
1 default 00-00-81-05-00-80 1:12 Dynamic
1 default 00-00-81-05-02-00 1:12 Dynamic
1 default 00-00-81-48-70-01 1:12 Dynamic
1 default 00-00-E2-4F-57-03 1:12 Dynamic
1 default 00-00-E2-61-53-18 1:12 Dynamic
1 default 00-00-E2-6B-BC-F6 1:12 Dynamic
1 default 00-00-E2-7F-6B-53 1:12 Dynamic
1 default 00-00-E2-82-7D-90 1:12 Dynamic
1 default 00-00-F8-7C-1C-29 1:12 Dynamic
1 default 00-01-02-03-04-00 CPU Self
1 default 00-01-02-03-04-05 1:12 Dynamic
1 default 00-01-30-10-2C-C7 1:12 Dynamic
1 default 00-01-30-FA-5F-00 1:12 Dynamic
1 default 00-02-3F-63-DD-68 1:12 Dynamic
CTRL+C ESC q Quit SPACE n Next Page ENTER Next Entry a All
show ipfdb
Purpose Used to display the current IP address forwarding database table.
Syntax
Description This command will display the current contents of the Switch’s IP
Parameters <ipaddr> - The user may enter an IP address to view the table by.
Restrictions None.
Example usage:
To view the IP forwarding database table:
show ipfdb <ipaddr>
forwarding database.
95
Page 99

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
DES-6500:4#show ipfdb
Command: show ipfdb
Interface IP Address Port Learned
------------ --------------- ------ -----------System 10.0.0.1 1:13 Dynamic
System 10.0.0.2 1:13 Dynamic
System 10.0.0.3 1:13 Dynamic
System 10.0.0.4 1:13 Dynamic
System 10.0.0.7 1:13 Dynamic
System 10.0.0.30 1:13 Dynamic
System 10.0.34.1 1:13 Dynamic
System 10.0.51.1 1:13 Dynamic
System 10.0.58.4 1:13 Dynamic
System 10.0.85.168 1:13 Dynamic
System 10.1.1.1 1:13 Dynamic
System 10.1.1.99 1:13 Dynamic
System 10.1.1.101 1:13 Dynamic
System 10.1.1.102 1:13 Dynamic
System 10.1.1.103 1:13 Dynamic
System 10.1.1.152 1:13 Dynamic
System 10.1.1.157 1:13 Dynamic
System 10.1.1.161 1:13 Dynamic
System 10.1.1.162 1:13 Dynamic
System 10.1.1.163 1:13 Dynamic
CTRL+C ESC q Quit SPACE n Next Page ENTER Next Entry a All
96
Page 100

xStack DES-6500 Modular Layer 3 Chassis Ethernet Switch CLI Manual
12
BROADCAST STORM CONTROL COMMANDS
On a computer network, packets such as Multicast packets and Broadcast packets continually flood the network as normal
procedure. At times, this traffic may increase do to a malicious endstation on the network or a malfunctioning device, such as a
faulty network card. Thus, switch throughput problems will arise and consequently affect the overall performance of the switch
network. To help rectify this packet storm, the Switch implements two methods to monitor and control the situation.
1. Hardware: The packet storm is monitored using the Switch’s hardware to determine if too many packets are
flooding the network, based on the threshold level provided by the user. Once a packet storm has been detected, the
Switch will drop packets coming into the Switch until the storm has subsided. This method can be utilized by
selecting the drop option of the Action field in the config traffic control command below.
2. Software: The device’s software will scan and monitor packets coming into the Switch by monitoring the Switch’s
chip counter. This method is only viable for Broadcast and Multicast storms because the chip only has counters for
these two types of packets. Once a storm has been detected (that is, once the packet threshold set below has been
exceeded), the Switch will shutdown the port to all incoming traffic with the exception of STP BPDU packets for a
time period, specified using the countdown field. If this field times out and the packet storm continues, the port will
be placed in a Shutdown Forever mode which will produce a warning message to be sent to the Trap Receiver. Once
in Shutdown Forever mode, the only method of recovering this port is to manually recoup it using the config traffic
control_recover setting seen in the command list below. To utilize the Software method of Storm Control, choose
the shutdown option of the action field in the config traffic control command below.
The broadcast storm control commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters)
in the following table.
Command Parameters
config traffic control [<portlist> | all] {broadcast [enabled | disabled] | multicast [enabled
| disabled] | dlf [enabled | disabled] | action [drop | shutdown] |
threshold <value 0-2047> | countdown [<value 0> | <value 5-30>] |
time_interval <value 5-10>}
config traffic
control_recover
config traffic trap [none | storm_occurred | storm_cleared | both]
show traffic control {<portlist>}
Each command is listed, in detail, in the following sections.
[<portlist> | all]
config traffic control
Purpose Used to configure broadcast/multicast/dlf packet storm control.
The software mechanism is provided to monitor the traffic rate in
addition to the hardware storm control mechanism previously
provided.
Syntax
config traffic control [<portlist> | all] {broadcast [enabled |
disabled] | multicast [enabled | disabled] | dlf [enabled |
disabled] | action [drop | shutdown] | threshold <value 02047> | countdown [<value 0> | <value 5-30>] | time_interval
<value 5-10>}
Description This command is used to configure broadcast/multicast/dlf storm
control. By adding the new software traffic control mechanism, the
user can now use both a hardware and software mechanism, the
97
 Loading...
Loading...