Dell W-IAP175P, W-IAP175AC User Manual

Dell Networking W-Series
Instant 6.4.0.2-4.1
Syslog Messages
Reference Guide

Copyright
© 2014 Aruba Networks, Inc. Aruba Networks trademarks include , Aruba Networks
Networks
®
, the registered Aruba the Mobile Edge Company logo, and Aruba Mobility Management System®. Dell™, the
®
, Aruba Wireless
DELL™ logo, and PowerConnect™ are trademarks of Dell Inc.
All rights reserved. Specifications in this manual are subject to change without notice.
Originated in the USA. All other trademarks are the property of their respective owners.
Open Source Code
Certain Aruba products include Open Source software code developed by third parties, including software code subject to
the GNU General Public License (GPL), GNU Lesser General Public License (LGPL), or other Open Source Licenses.
Includes software from Litech Systems Design. The IF-MAP client library copyright 2011 Infoblox, Inc. All rights reserved.
This product includes software developed by Lars Fenneberg, et al. The Open Source code used can be found at this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba Networks, Inc. switching platforms and software, by all individuals or corporations, to terminate other
vendors’ VPN client devices constitutes complete acceptance of liability by that individual or corporation for this action and
indemnifies, in full, Aruba Networks, Inc. from any and all legal actions that might be taken against it with respect to
infringement of copyright on behalf of those vendors.
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide 0511593-01 | June 2014

Contents
About this Guide ...................................................................................... 5
Document Organization......................................................................................... 5
Format of Messages..............................................................................................5
Severity Levels ................................................................................................6
Message Process Generation ............................................................................... 6
Syslog Server.........................................................................................................7
Filtering Syslogs ....................................................................................................7
Driver Log Messages.............................................................................................7
Related Documents ............................................................................................... 8
Contacting Support ...............................................................................................8
Security Messages .................................................................................. 9
Critical Messages .................................................................................................. 9
Error Messages....................................................................................................10
Warning Messages ..............................................................................................22
Notice Messages ................................................................................................. 22
Information Messages .........................................................................................23
Debug Messages................................................................................................. 25
System Messages.................................................................................. 27
Emergency Messages ......................................................................................... 27
Alert Messages .................................................................................................... 27
Critical Messages ................................................................................................ 28
Error Messages....................................................................................................28
Warning Messages ..............................................................................................36
Notice Messages ................................................................................................. 43
Information Messages .........................................................................................47
Debug Messages................................................................................................. 53
User Messages ...................................................................................... 61
Error Messages....................................................................................................61
Warning Messages ..............................................................................................64
Notice Messages ................................................................................................. 67
Information Messages .........................................................................................71
Debug Messages ................................................................................................ 73
Wireless Messages................................................................................ 87
Error Messages....................................................................................................87
Warning Messages ..............................................................................................87
Notice Messages ................................................................................................. 92
Information Messages .........................................................................................93
Debug Messages................................................................................................. 93
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide | 3

ARM Messages ...................................................................................... 95
Error Messages....................................................................................................95
Warning Messages ..............................................................................................95
Debug Messages................................................................................................. 95
4 | Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

About this Guide
This document covers syslog messages included in Dell Networking W-Series Instant 6.4.0.2-4.1 release.
In this edition, message definition, recommended action and in some cases the cause that generated he syslog
message are included. Syslog messages were prioritized for definition; this edition includes definitions for
approximately 70% of Instant syslog messages. For those messages yet to be defined, the phrase “No description
available” appears.
Document Organization
This document contains the complete listings of all syslog messages generated by Instant. Each chapter lists
the syslogs for a single category as follows:
Security
System
User
Wireless
ARM
Each chapter contains the severity level syslog messages in table format (see Table 1for the complete list of
severity levels). The syslog messages are the actual text displayed by Instant when encountering the syslog,
and some further descriptive text, giving more information about the syslog. The entry may also include
recommended action when this syslog is encountered.
Format of Messages
Take the following message as an example:
Jan 23 16:26:51 2013 sapd[148]: <404003> <WARN> |AP 00:0b:86:cb:85:db@10.34.84.14 sapd|
AM 00:0b:86:38:5d:b0: Interfering AP detected with SSID 06B408550367 and BSSID
00:12:0e:44:d4:2c
In this case, the message elements are:
<date and time stamp> = Jan 23 16:26:51 2013
<error location>: = sapd[148]:
<error number> = <404003> (a unique number within the set of messages generated by Dell
Networking W-Series Instant)
<severity> = <WARN> (Warning severity level)
|<process>| = |AP 00:0b:86:cb:85:db@10.34.84.14 sapd| (the Access Point Media Access
Control (MAC) device address, along with the IP address)
message text = the remaining part of the message.
The message text portion is frequently constructed from information returned with the syslog. For example,
the message text for the syslog above is constructed as:
(the specific module location where this syslog was generated)
AM <BSSID>: Interfering AP detected with SSID <SSID> and BSSID <BSSID>
Where:
<BSSID> = 00:0b:86:38:5d:b0
<SSID> = 06B408550367
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide About this Guide | 5

<BSSID> = 00:12:0e:44:d4:2c
These substitutions generate message text as follows:
AM 00:0b:86:38:5d:b0: Interfering AP detected with SSID 06B408550367 and BSSID
00:12:0e:44:d4:2c
In the following chapters, messages are defined in generic terms with variables shown to indicate where
substitutions of actual data will occur.
Severity Levels
The severity levels defined for syslogs are outlined in Table 1, which orders the severity from most to least
severe. Note that the syslog messages with the lowest severity level, “Debug”, is listed in this manual. Also,
note that the severity level string (such as EMERG, or CRIT), as well as the numeric value associated with
that particular severity, is listed in the tables.
Table 1 Message Severity Levels
Level Val ue Meaning
Emergency <EMERG> 0 Panic condition that occurs when the system becomes unusable.
Alert <ALERT> 1 Any condition requiring immediate attention and correction.
Critical <CRIT> 2 Any critical conditions such as a hard drive error.
Error <ERR> 3 Error condition.
Warning <WARNING> 4 Warning message.
Notification <NOTICE> 5 Significant event of a non-critical and normal nature.
Informational <INFO> 6 Message of general interest to system users.
Debug <DEBUG> 7 Message containing information useful for debugging.
Message Process Generation
The process that generates syslog messages is detailed in Table 2.
Table 2 Process Generating Syslog Messages
Process Description Categories used by this component
ecurity, user
802.1X Network Access Control authentication
am Logging for AirMonitor security, system, wireless
meshd Logging for Mesh daemon system
s
radius Logging for RADIUS authentication security, system, user
sapd
stm Logging for Station Management system, user, wireless
vc Logging for Virtual Controller system
6 | About this Guide Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Logging for Access Point Manager (AP) system
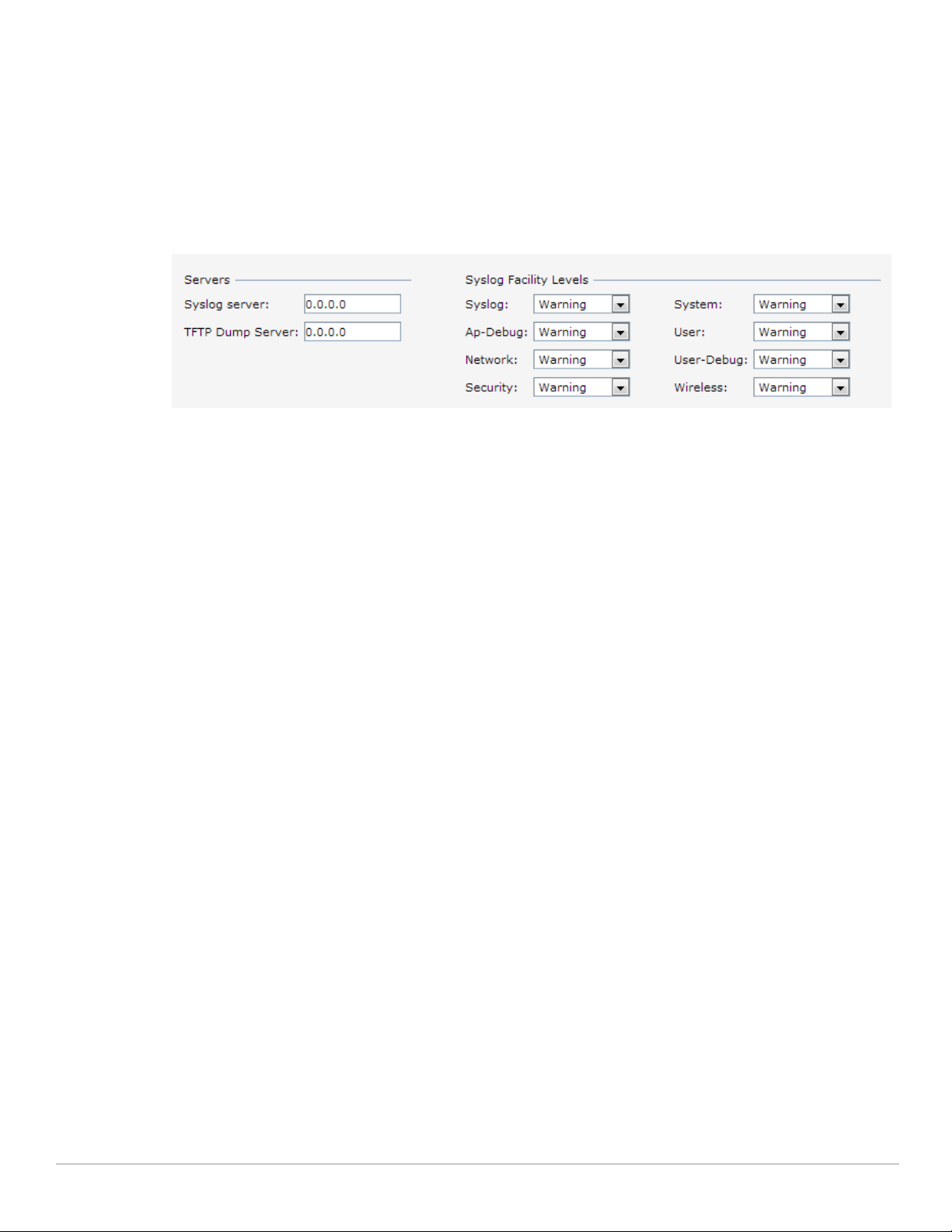
Syslog Server
To specify a Syslog Server for sending syslog messages to the external servers, navigate to System > Show
advanced options > Monitoring in the UI and update the following fields.
Syslog server— Enter the IP address of the server to send system logs.
Syslog level— For a global level configuration, select one of the logging levels from the standard list of
syslog levels. The default value is Notice.
Figure 1 Configuring Syslog Server Settings
You can also configure Syslog server details and logging levels by using the command-line Interface (CLI).
To configure a Syslog server:
(Instant Access Point)(config)# syslog-server <IP-address>
To configure logging levels:
(Instant Access Point)(config)# syslog-level <level>{apdebug|network|security|system|user|user-debug|wireless}
Filtering Syslogs
Searching through the logs for specific events, error categories, or other information, is often quite useful.
In addition, long term storage of data required for audits and other business requirements involving
information kept in the system logs is important. The capabilities required for handling logs should include
the following:
Efficient log management
Sophisticated analysis capabilities
Consistent report generation
Scalability
Security
Analyzing system logs, and extracting relevant information from them, requires an efficient pattern
matching engine, where the desired patterns can be created with standard pattern matching commands,
such as a regular expression engine.
Driver Log Messages
Some driver log messages such as LIKELY Tx Radio/Antenna Issues - Probe Failure(96%) Total
1252 Failed 1206 are generated when there are TX Radio and Antenna Issues. The IAP uses a timer to
monitor TX probe response each hour. If more than 95% failed, this log is triggered. For example, Probe
Failure (98%) Total 1126 Failed 1104 means that within the measured timeframe (1 hour) hour, the IAP
tried to send 1126 Probe responses, but failed to receive an answer 1104 times.
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide About this Guide | 7
Related Documents
In addition to this document, the Dell Networking W-Series Instant product documentation includes the
following:
Dell Networking W-Series Instant Access Point Installation Guides
Dell Networking W-Series Instant 6.4.0.2-4.1 Quick Start Guide
Dell Networking W-Series Instant 6.4.0.2-4.1 User Guide
Dell Networking W-Series Instant 6.4.0.2-4.1 Command Line Reference Guide
Dell Networking W-Series Instant 6.4.0.2-4.1 MIB Reference Guide
Dell Networking W-Series Instant 6.4.0.2-4.1 Release Notes
Contacting Dell
Table 3 Contact Information
Web Site Support
Main Website dell.com
Contact Information dell.com/contactdell
Support Website dell.com/support
Documentation Website dell.com/support/manuals
8 | About this Guide Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

Chapter 1
Security Messages
Critical Messages
Table 5 Security Critical Messages
Message ID Message and Description
132002 Enabling dot1x termination for AP [mac:%m] [auth_profile:%s] before cert download.
Description: Termination is being enabled before certificate is downloaded.
132014 “AP [bssid:%m] [apname:%s] Incomplete AP configuration. Check if WEP Key, WEP
Transmit Key or WPA Passphrase is not configured.
Description: AP’s configuration is not complete. Either WEP key/WEP Transmit Key/
WPA Passphrase is not configured.
132135 Failed to create SSL_CTX.
Description: System failed to create SSL Context.
132136 Loading Certificate from [fname:%s] failed
Description: Failed to load the Certificate for 802.1x termination.
132137 Private key does not match cert
Description: Private key is not found in the certificate
132138 Failed to alloc BIO in.
Description: Failed to allocate BIO structure.
132139 Failed to alloc BIO out.
Description: Failed to allocate BIO out structure.
132140 Failed to set the cipher - ssl3_get_cipher_by_char.
Description: Failed to set the cipher using ssl3_get_cipher_by_char.
132141 Failed to create buf - BUF_MEM_new.
Description: Failed to create a buffer using BUF_MEM_new.
132142 ssl3_output_cert_chain returned error.
Description: Failed to output the certificate chain.
132143 Failed to download MODEXP for dot1x-termination.
Description: Failed to download MODEXP to datapath for 802.1x termination.
132144 Failed to download the cert for dot1x-termination.
Description: Failed to download the server certificate for dot1x termination.
132145 BIO_read failed len [ln:%d].
Description: BIO read failed.
132146 ssl_get_server_send_cert faileds
Description: sl_get_server_send_cert failed
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 9

Error Messages
Table 6 Security Error Messages
Message ID Message and Description
121000 Failed to calculate the HMAC-MD5 digest
Description: Controller failed to calculate the HMAC-MD5 digest for RADIUS packet
due to an internal error.
Recommended Action: If the problem persists, contact Dell support provider.
121001 Error [errno:%d],[errstr:%s] receiving packet [packet_len:%d], fd=[fd:%d]
Description: A socket error occurred while receiving RADIUS server response
Recommended Action: If the problem persists, contact your support provider.
121002 An error occurred while receiving RADIUS server response
Description: An error occurred while receiving RADIUS server response
Recommended Action: If the problem persists, contact your support provider.
121003 Discarding unknown response from server
Description: RADIUS Server has returned a response that does not match the request
or the packet could be corrupt
Recommended Action: Validate RADIUS server configuration. If the problem persists,
contact your support provider.
121005 An error occurred while receiving RADIUS server response on port 3799 (RFC 3576)
Description: An error occurred while receiving RADIUS server response on port 3799
(RFC 3576)
Recommended Action: If the problem persists, contact your support provider.
121008 RADIUS: Error [errno:%d],[errstr:%s] creating client socket
Description: Internal error occurred while initiating connection with the RADIUS server
Recommended Action: If the problem persists, contact your support provider.
121009 RADIUS: Error [errno:%d],[errstr:%s] in bind.
Description: Internal error occurred while connecting with the RADIUS server.
Recommended Action: If the problem persists, contact your support provider.
121010 Error [errno:%d],[errstr:%s] sending [data_len:%d] bytes on radius socket [sockfd:%d]
Description: Internal error occurred while sending data to the RADIUS server.
Recommended Action: If the problem persists, contact your support provider.
121011 Received RADIUS server response with invalid length [len:%d].
Description: The expected length of a RADIUS server response packet is between 20
and 4096 bytes.
Recommended Action: Check the length of response packet from the RADIUS server.
121012 Not enough buffer space to verify RADIUS server response packet with length
[totallen:%d].
Description: The internal buffer is not big enough for the RADIUS response packet and
RADIUS secret.
Recommended Action: Check the length of the RADIUS response packet from the
RADIUS server and the length of RADIUS secret.
121013 Received non-matching ID in RADIUS server response [id:%d], expecting [seq_nbr:%d].
Description: Received a response from the RADIUS server, but the sequence number
doesn’t match the request.
Recommended Action: Check the RADIUS server is configured properly.
10 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

Table 6 Security Error Messages (Continued)
Message ID Message and Description
121014 Received invalid reply digest from RADIUS server.
Description: The reply digest received from the RADIUS server doesn’t match the
calculated digest.
Recommended Action: Check the RADIUS server is configured properly and verify
shared secret configuration on the controller matches that on the RADIUS server.
121016 RADIUS server [server:%s],[fqdn:%s][ipaddr:%s] is out of sequence.
Description: The PENDING request buffer to RADIUS server is already full (256).
Response from RADIUS server seems to be slower than the rate at which the users are
coming in.
Recommended Action: Check the RADIUS server is configured properly and the
connectivity between the controller and RADIUS server is good.
121018 Unknown RADIUS attribute ID [attrid:%d] in [func:%s]
Description: The RADIUS attribute is not known.
Recommended Action: Use the show aaa radius-attributes command to check if the
attribute ID is supported.
121019 Received attribute with invalid length [attrlen:%d] in [func:%s]
Description: Received RADIUS attribute with invalid length, while extracting the
attribute-value pairs
Recommended Action: Check the RADIUS server is configured properly and the
connectivity between controller and RADIUS server is good.
121021 RADIUS attribute [name:%s] has unknown type [type:%d] in [func:%s]
Description: Received unknown RADIUS attribute type, while extracting the attributevalue pairs.
Recommended Action: Please check the supported RADIUS attribute type.
121022 Unknown RADIUS attribute name [name:%s] in [func:%s]
Description: Received unknown RADIUS attribute name, while extracting the attributevalue pairs
Recommended Action: Please use the show aaa radius-attributes command to check
if the attribute name is supported.
121023 Unknown RADIUS attribute [attr_value:%s] in [func:%s]
Description: Controller received an unknown RADIUS attribute while extracting the
attribute-value pairs from Radius server response.
Recommended Action: Please use the show aaa radius-attributes command to check
if the attribute value is supported.
121025 Value pair is NULL or empty attribute [id:%d] in [func:%s].
Description: Internal error occurred while converting the attribute-value pairs received
in RADIUS response to strings.
Recommended Action: If the problem persists, contact your support provider.
121029 RADIUS: Error [errno:%d], [errstr:%s] creating rfc3576 socket.
Description: Internal error occurred while initiating connection with RADIUS server.
Recommended Action: Please contact Dell technical support if this problem persists.
121030 RADIUS: Error [errno:%d], [errstr:%s] in rfc3576 bind.
Description: Error occurred while connecting to RADIUS server.
Recommended Action: IPlease contact Dell technical support if this problem persists.
121033 “rc_pack_list: Attribute list exceeds 8192 bytes, dropping request.
Description: rc_pack_list: Attribute list exceeds 8192 bytes, dropping request
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 11

Table 6 Security Error Messages (Continued)
Message ID Message and Description
121036 RADIUS: Error [errno:%d],[errstr:%s] setting client socket options.
Description: Internal error occurred while setting connection options with the RADIUS
server.
Recommended Action: Contact Dell technical support if this problem persists.
121047 Failed to add user Port ID in the Radius Accounting Pkt [pkt:%s].
Description: This shows an internal debug message
121048 Unknown result type [resultType:%d].
Description: This shows an internal debug message
121049 Failed to add user Port ID in the Radius Accounting Start Pkt [portStr:%s].
Description: This shows an internal debug message
132003 xSec vlan not configured for [port:%s]
Description: xSec vlan is not configured for the specified port.
Recommended Action: Configure VLAN that supports XSEC on specified port..
132004 Unknown AP [mac:%m] [bssid:%m] [menc:%s] [vlan:%d].
Description: Authentication process has detected an unknown AP.
Recommended Action: Execute the show ap database command to determine if
system is aware of the Access Point. Power-cycle the unknown AP.
132005 AP [mac:%m] [apname:%s] is not enabled.
Description: Specified AP is not enabled.
Recommended Action: Configure AP with a valid virtual-AP or wired profile..
132006 Station Add failed [mac:%m] [bssid:%m] [apname:%s] [uenc:%s] [menc:%s]
Description: Station failed to complete the security association with authentication
process.
Recommended Action: Confirm that the SSID that the supplicant is associating to is
configured to support 802.1X authentication and is configured correctly..
132008 Station delete failed, does not exists in the station table.
Description: Failed to clear the station from the AP’s station table.
Recommended Action: Station does not exist in authentication process tables.
Confirm by running the show station command.
132009 Station’s dot1x context not initialized [name:%s] [mac:%m] [bssid:%m]
Description: Station’s internal context is not completely initialized.
Recommended Action: Internal error. Clear the station by running the aaa user delete
command and reconnect.
132013 AP [bssid:%m] [apname:%s] Configuration not complete, No Transmit WEP Key set
Description: AP’s configuration is not complete. Check if the WEP transmit key is set
Recommended Action: Check of the WEP transmit key is set in the ssid-profile
132015 Failed to Deauthenticate the station [mac:%m] [name:%s]
Description: Failed to deauthenticate the specified station
Recommended Action: Internal error. Clear the station and reconnect.
12 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Table 6 Security Error Messages (Continued)
Message ID Message and Description
132016 Local Database Server not available to cache the machine auth for user [name:%s]
132017 Failed to update Machine Auth status to local DB for Station [mac:%m] [name:%s]
132018 Station [mac:%m] [bssid:%m] was deleted before the response from the local database
[mac:%m]
Description: Internal server is not available for caching the machine authentication for
the specified User.
Recommended Action: Run the aaa test-server pap internal command to verify
connectivity to the local database server. If unavailability of local database server
persists and controller is a local-controller, verify connectivity to master-controller. If all
else fails, restart the udbserver process on the master-controller by executing the
process restart udbserver command and restart the AUTH process on the localcontroller by executing the process restart auth command.
Description: Failed to update the Machine authentication Status for the specified User
because udbserver process is not responding.
Recommended Action: Run the aaa test-server pap internal command to verify
connectivity to the local database server. If unavailability of local database server
persists and controller is a local-controller, verify connectivity to master-controller. If all
else fails, restart the udbserver process on the master-controller by executing the
process restart udbserver and restart the AUTH process on the local-controller by
executing process restart auth.
server
Description: Station was deleted before receiving response from the Internal Server
due to high latency between local-controller’s AUTH process and master-controller’s
UDBSERVER process.
Recommended Action: Diagnose external IP-latency issues between mastercontroller and local-controller and have the client re-attempt their authenticationrequest.
132023 802.1x authentication is disabled in profile [prof:%s] Station [mac:%m] [bssid:%m]
Description: 802.1x authentication is disabled for the specified profile.
Recommended Action: Configure the specified aaa-profile to enable 802.1x
authentication.
132024 Station [mac:%m] pre-authenticating with Unknown AP [bssid:%m] vlan [vl:%d]
Description: Station is trying to pre-authenticate with an AP that is not registered. This
log-message is generated when we detect a race-condition between STM, SOS and
AUTH. AUTH is receiving EAP packets from SOS before it received the New-AP
message from STM. Execute show ap database to determine if STM is aware of the
AP. If not, try rebooting the AP by executing apboot or powercycling the AP. If
symptoms persist, then AUTH is either not receiving or not processing New-AP
messages from STM. If all else fails, restart the AUTH process by executing process
restart auth or reload the controller.
132025 Station [mac:%m] [bssid:%m] is not enabled for pre-auth.
Description: Preauthentication is always disabled
132026 Station [mac:%m] [bssid:%m] trying to pre-authenticate with AP that does not have
WPA2 enabled
Description: Station trying to preauhenticate with AP that is not WPA2 enabled.
Configure the ssid-profile to enable WPA2 and reload the AP.
132027 Station [mac:%m] associating to Unknown AP [bssid:%m] [menc:%d] [vl:%d]
Description: Station is trying to associate with AP that is not registered. This logmessage is generated when we detect a race-condition between STM, SOS and AUTH.
AUTH is receiving EAP packets from SOS before it received the New-AP message from
STM. If not, try rebooting the AP by executing apboot or powercycling the AP. If
symptoms persist, then AUTH is either not receiving or not processing New-AP
messages from STM. If all else fails, restart the AUTH process by executing process
restart auth or reload the controller.
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 13

Table 6 Security Error Messages (Continued)
Message ID Message and Description
132029 Station [mac:%m] [bssid:%m] sent Unsupported EAPOL Type [type:%d]
Description: Station sent an unsupported EAPOL packet.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If the problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132030 Dropping EAPOL packet sent by Station [mac:%m] [bssid:%m]
Description: Dropping the EAPOL packet sent by the specified station.
Recommended Action: Check preceding log-messages to determine the reason the
EAPOL packet is being dropped.
132032 Invalid length in the [msg:%s] from Station [mac:%m] [bssid:%m] [len:%d]
Description: Station sent the specified packet with invalid length.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132033 Invalid WPA Key Description Version [ver:%d] Station [mac:%m]
Description: Station sent a WPA key message with invalid version.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132035 Invalid WPA2 Key Description Version [ver:%d] Station [mac:%m]
Description: Station sent a WPA key message with invalid version.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132036 Station [mac:%m] [bssid:%m] sent Unknown EAP-Request [eaptype:%d]
Description: Station send an EAP packet that is invalid.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132037 Station [mac:%m] [bssid:%m] sent username greater than [MAX_USERNAME_SIZE:%d]
Description: The user name sent by the station is larger than the maximum size
supported.
Recommended Action: Configure station to use a shorter username and attempt
authentication again.
132038 Station [mac:%m] [bssid:%m] sent Unsupported EAP type [eaptype:%d]]
Description: Station sent an EAP packet that is not supported.
Recommended Action: Ensure the station is configured correctly to perform an EAP
authentication method that is supported by the controller. Ensure that the aa a-profile
associated with the authentication request matches the authentication-method the
client is sending to authenticate. If problem persists, check for packet-corruption by
capturing sniffer-traces between client, AP and controller.
132039 Station [mac:%m] [bssid:%m] sent Unsupported EAP Code [eapcode:%d]
Description: Station send an EAP packet with unknown EAP code. Ensure the station
is configured correctly to perform an EAP authentication method that is supported by
the Dell controller. Ensure that the aaa-profile associated with the authentication request
matches the authentication-method the client is sending to authenticate. If problem
persists, check for packet-corruption by capturing sniffer-traces between client, AP and
controller.
14 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Table 6 Security Error Messages (Continued)
Message ID Message and Description
132040 Station [mac:%m] [bssid:%m] sent Unsupported MD5 EAP type [eaptype:%d].
Description: Station sent an EAP packet that is not supported. Ensure the station is
configured correctly to perform an EAP authentication method that is supported by the
Dell controller. Ensure that the aaa-profile associated with the authentication request
matches the authentication-method the client is sending to authenticate. If problem
persists, check for packet-corruption by capturing sniffer-traces between client, AP and
controller.
132042 Sending empty username for user [mac:%m] - WPS is not enabled on AP [bssid:%m]
[apname:%s]
Description: Station sent no user name in the EAP Identity Request message.Ensure
the station is configured correctly to perform EAP authentication. If problem persists,
check for packet-corruption by capturing sniffer-traces between client, AP and
controller.
132045 Error remove stateful dot1x ACL
Description: Failed to remove the Acts configured for stateful dot1x authentication
from the stateful_role or logon_role.
Cause: This is because the stateful-dot1x ACL is not associated with the stateful_role
or logon_role.
Recommended Action: Since we are disabiling stateful-dot1x anyway, no further
action is required.
132049 “Received Invalid digest from Server [srvip:%p], AP [ip:%p]
Description: Received radius packet with invalid digest during stateful dot1x
authentication.
Cause: This error suggests a possible man-in-the-middle attack.
Recommended Action: Contact your administrator to check status of your Radius
server. Radius packet will be dropped.
132050 “No Stateful configuration found that could verify the stateful response. [nasip:%p],
132051 Failed to validate stateful radius response [nasip:%p] [srvip:%p] station [mac:%m]
132053 Dropping the radius packet for Station [mac:%m] [bssid:%m] doing 802.1x
132055 “[__FUNCTION__:%s]: missing configuration for dot1x profile \””[prof:%s]\””
[srvip:%p]
Description: No server config entry was found for verifying the stateful dot1x response.
Recommended Action: Verify that the Radius server in question is configured in the
applicable server-group on the controller.
Description: Stateful dot1x authentication failed because validation failed.
Recommended Action: Refer to previous log-message. If CONFIG_NOTFOUND, verify
that the Radius server in question is configured in the applicable server-group on the
controller. Otherwise, this may be a potential man-in-the-middle attack.Contact your
administrator to validate the status of your Radius sever.”
Description: Radius packet for the specified station is dropped.
Cause: Either the station has disconnected, has already authenticated or it is busy.
Recommended Action: If reauthentication is required, the station will request
authentication again.
Description: Specified Dot1x profile is not configured or has been deleted.
Recommended Action: Validate that the controller configuration contains the specified
dot1x profile.
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 15

Table 6 Security Error Messages (Continued)
Message ID Message and Description
132056 “[__FUNCTION__:%s]: missing server-group configuration for dot1x in aaa-profile
132057 Failed to send the radius request for Station [mac:%m] [bssid:%m]
132059 Multicast Key type of the AP [bssid:%m] [apname:%s] is not static-wep or dynamic-wep
132060 Unknown Multicast Key-type [menc:%d] for AP [mac:%m] [apname:%s]
132061 AP [bssid:%m] [apname:%s] configured with aaa profile [prof:%s] does not have an
\””[prof:%s]\”” for Station [mac:%m] [bssid:%m]
Description: Specified server group for dot1x authentication in the aaa profile is not
configured or has been deleted.
Recommended Action: Validate that the controller configuration contains the specified
server-group profile.
Description: Radius request for specified station is being dropped due to lack of
system resources.
Recommended Action: Free up system memory and other resources by throttling
user-authentication requests.
Description: Multicast key type is not static wep or dynamic wep for the specified AP.
Recommended Action: Confirm that the specified ssid-profile is configured for WEP
Description: The multicast key type for the specified AP is not known.
Recommended Action: Validate the SSID-profile associated with the AP and reboot
the AP.
associated dot1x profile
Description: No dot1x profile is configured for the specified aaa profile.
Recommended Action: Configure a dot1x profile in the specified aaa profile.
132062 Wrong slot configured for AP [bssid:%m] [apname:%s]
Description: Invalid key slot configured for the specified AP. This should never happen.
Recommended Action: If this happens, an internal error has occurred. Reboot your
controller.
132063 WPA Preshared Key not configured for AP [mac:%m]
Description: WPA Preshared Key is not configured for the specified AP.
Recommended Action: Configure a WPA Preshared Key for this AP.
132064 WPA Passphrase not configured for AP [bssid:%m] [apname:%s]
Description: WPA passphrase not configured for the specified AP.
Recommended Action: Configure a WPA Passphrase for this AP.
132065 AP [mac:%m] [apname:%s] configured with invalid static-wep key length [slot:%d]
[size:%d]
Description: AP is configured with invalid Static WEP key length. The valid key length is
40bits or 128bits.
Recommended Action: Configure the AP with either a 40bit or 128bit key.
132069 No Radius server configuration with [srvip:%p] available for creating Stateful AP
Configuration entry
Description: While automatically creating stateful dot1x configuration entry the radius
server specified was not found.
Recommended Action: Configure the specified radius server configuration and try
again.
132073 Wrong WPA OUI Element [oui:%d] from Station [mac:%m] [bssid:%m] [apname:%s]
Description: Station sent WPA key message with invalid OUI element.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
16 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Table 6 Security Error Messages (Continued)
Message ID Message and Description
132074 Version [stver:%d] does not match [apver:%d] in the [msg:%s] IE Elements from Station
132075 Multicast cipher from Station [mac:%m] [stmc:%X] does not match with AP [bssid:%m]
132076 Station [mac:%m] [bssid:%m] [apname:%s] sent invalid number of unicast ciphers
132077 Station’s [mac:%m] [stuc:%X] and AP’s [bssid:%m] [apuc:%X] [apname:%s] unicast
132078 Station [mac:%m] [bssid:%m] [apname:%s] sent invalid number of key management
[mac:%m] [bssid:%m] [apname:%s]
Description: Station sent WPA key message with invalid Version.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
[apmc:%X] [apname:%s]
Description: Mismatch in the multicast ciphers specified by the station and AP.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
[uc:%d]
Description: Station sent invalid number of unicast cipher in the WPA IE element.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
cipher suites does not match
Description: Mismatch in the unicast cipher specified by the station and the AP
suite [km:%d]
Description: Station sent invalid number of key management suite in the WPA IE
element
132079 Station’s [mac:%m] [stkm:%X] and AP’s [bssid:%m] [apkm:%X] [apname:%s] key
management suites does not match
Description: Mismatch in the key management suite specified by the station and the
AP
132080 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the multicast cipher and the
configured multicast cipher [mc:%X] did not match the default cipher TKIP
Description: Station did not specify any multicast cipher and the multicast cipher
specified by the is not TKIP
132081 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the unicast cipher and the
132082 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the key management
132083 [Num:%d] TKIP Michael MIC failure was detected
132084 Two TKIP Michael MIC Failures were detected within [last_scan_time:%d] seconds.AP
configured unicast cipher [mc:%X] did not match the default cipher TKIP
Description: Station did not specify any unicast cipher and the multicast cipher
specified by the AP is not TKIP
selector and the configured key management [km:%X] did not match the default -
802.1x
Description: Station did not specify any key management selector and the configured
key management on the AP is not 802.1x
Description: Specified number of TKIP MIC failure was detected
will be shutdown for next 60 seconds
Description: Two MIC failures was received from the station within 60 secs.
Recommended Action: The AP must be shutdown for 60 secs
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 17

Table 6 Security Error Messages (Continued)
Message ID Message and Description
132085 Maximum number of %s Key exchanges attempted for station [name:%s] [mac:%m]
132088 “Invalid WPA [ver:%d] Key message from Station [mac:%m] [bssid:%m] [apname:%s],
132089 “Invalid WPA [ver:%d] Key message from Station [mac:%m] [bssid:%m]
132090 Received TKIP Michael MIC Failure Report from the Station [mac:%m] [bssid:%m]
132091 Wrong key type [kt:%d] in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
132092 Request bit set in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
132093 [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s] did not match the replay
[bssid:%m] [apname:%s]
Description: Maximum number of key exchanges was attempted for the station
reason:ACK bit set
Description: WPA key message with ACK bit set was received from the station. This is
invalid
[apname:%s],reason: Error flag without Request bit set
Description: WPA key message with error flag without request bit set was received
from the station. This is invalid
[apname:%s]
Description: Specified Station sent TKIP MIC failure report
Description: Station sent wrong key type in the WPA key message
Description: Station sent WPA key message with request bit set
counter [stcnt1:%d][stcnt2:%d] vs [apcnt1:%d][apcnt2:%d]
Description: Station and AP’s replay counter does not match. The WPA key message
from the station has to be dropped
132099 [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s] has invalid datalen [ln:%d]
!= 0]
Description: Station sent WPA key message with invalid key length
132104 Invalid character in the passphrase [ch:%c]
Description: Invalid characters in the WPA passphrase
132105 Invalid password len [ln:%d]
Description: Invalid WPA passphrase length
132106 Invalid ssid len [ln:%d]
Description: Invalid SSID length
132113 Station’s [mac:%m] [strsn:%X] and AP’s [bssid:%m] [aprsn:%X] [apname:%s] RSN
Capability does not match
Description: Station and AP’s RSN capability does not match
132114 Failed to add xSec station [mac:%m] to AP [bssid:%m]
Description: Failed to add xSec station to AP’s station table
132147 Invalid length [ln:%d] during inner EAP handling
Description: Station sent invalid length in the inner eap
132149 MAC User Table Lookup Failed mac=[mac:%m] bssid=[bssid:%m]
Description: Specified MAC is missing in the MAC User Table while trying to process
the dot1x packet.
18 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

Table 6 Security Error Messages (Continued)
Message ID Message and Description
132150 Station [mac:%m] [bssid:%m] does not have 802.1x context
Description: Station [mac:%m] [bssid:%m] does not have 802.1x context.
132152 802.1x termination is disabled user [mac:%m], profile [dot1x_auth_profile:%s]
Description: 802.1x termination is disabled for the specified profile.
132155 Station [mac:%m] [bssid:%m] sent inner EAP type [eaptype:%d] that is not supported
Description: Station sent inner eap type that is not supported.
132156 Station [mac:%m] [bssid:%m] sent inner EAP Start
Description: Station sent inner EAP start packet. This is invalid.
132157 Station [mac:%m] [bssid:%m] sent inner EAP packet with more-fragments bit set
Description: Station sent inner EAP packet with more fragment bit set. This is invalid.
132158 Station [mac:%m] [bssid:%m] sent invalid EAP flag
Description: Station sent invalid flag in the inner EAP packet.
132159 Station[mac:%m] [bssid:%m] sent invalid inner EAP Packet [eaplen:%d]
Description: Station sent invalid len in the inner EAP packet.
132161 Station [mac:%m] [bssid:%m] sent Invalid TLS Record Layer Type [tlsrectype:%d]
Description: Station sent invalid TLS record layer type.
132162 Station [mac:%m] [bssid:%m] sent with unsupported TLS client version [ver:%X]
Description: Station sent unsupported TLS client version.
132165 Station[mac:%m] [bssid:%m] sent invalid MAC in the TLS Record layer
Description: Station send invalid MAC in the TLS record layer.
132166 Station[mac:%m] [bssid:%m] sent more than one TLS Application Data Record Layer
Description: Station send more than one TLS application data record layer.
132167 Verification of TLS Record Layer from Station [mac:%m] [bssid:%m] failed
Description: Verification of the TLS record layer from the station failed.
132171 “Received EAP-NAK from Station [mac:%m] [bssid:%m], Station is configured with
[eaptype:%s]
Description: Station sent inner eap-nak.
132177 Station [mac:%m] [bssid:%m] sent client finish is that is not 3DES encrypted
Description: Station send client finish that is not 3DES encrypted. This is not
supported
132179 Failed to decrypt the client finish message from Station [mac:%m] [bssid:%m]
Description: Station sent the client finish message that failed to decrypt
132180 Station [mac:%m] [bssid:%m] sent Unknown SSL type in the client finish header
[type:%d]
Description: Station sent unknown SSL type in the client finish header
132182 Verify data sent by the Station [mac:%m] [bssid:%m] is not valid
Description: Verify data sent by the specified station in not valid
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 19

Table 6 Security Error Messages (Continued)
Message ID Message and Description
132185 Failed to send the server finish for Station [mac:%m] [bssid:%m]
Description: Failed to send server finish for the specified station
132188 No user-name found in the inner EAP id response from Station [mac:%m] [bssid:%m]
Description: Station did not send any user name in the inner EAP id response
132195 Invalid EAP code [code:%d] in the EAP-TLV/Phase2 response from Station [mac:%m]
[bssid:%m]
Description: Station sent invalid EAP code in the TLV response
132196 Invalid EAP TLV-Type [tlv_type:%d] in the EAP-TLV/Phase2 response from Station
132197 “Maximum number of retries was attempted for station [name:%s] [mac:%m]
132198 Failed to load the CA List File [file:%s]
132199 Failed to set up SSL buffers
132200 Received TLS Client Finish but the client certificate [mac:%m][bssid:%m] is not verified
132201 Failed to cache EAP-GTC authentication info of Station [name:%s] [mac:%m]
132203 “Station [mac:%m][bssid:%m] sent a EAP-NAK, requesting unsupported inner-eap-type
[mac:%m] [bssid:%m]
Description: Station sent invalid TLV type
[bssid:%m], deauthenticating the station
Description: Maximum number of retries was attempted for station to complete the
authentication phase.
Recommended Action: Deauthenticating the station
Description: Failed to load the specified CA List File for 802.1x termination
Description: Failed to set up SSL buffers
Description: Received TLS Client Finish but the client certificate is not verified
[bssid:%m] in the Local Database Server
Description: Failed to cache EAP-GTC authentication information of the station in the
Internal server
[type:%d]
Description: Unsupported inner-eaptype requested by station
132204 Inner eapid mismatched [id1:%d]:[id2:%d] for station [mac:%m] [bssid:%m]
Description: Mismatch between the eapid station sent and what was expected
132205 Invalid inner-eaptype configured [eaptype:%d]
Description: Configured eaptype is not supported
132206 Multiple user name attributes in response packet.
Description: The RADIUS response packet is invalid because it contains multiple user
name attributes
132207 RADIUS reject for station [name:%s] [mac:%m] from server [server:%s].
Description: Radius packet for the specified station was rejected by the server.
132208 Station setup failed [mac:%m] [bssid:%m] [apname:%s] [uenc:%s] [menc:%s]
Description: Station failed to start the security association
20 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Table 6 Security Error Messages (Continued)
Message ID Message and Description
132209 No unicast ciphers supported by AP [bssid:%m] [apname:%s]
Description: No unicast ciphers supported by AP with WPA2 opcode
132210 “Error in cb msg processing, message to
132211 Station [mac:%m] [bssid:%m] sent a cert from which we couldn’t extract the public key
132212 Station [mac:%m] [bssid:%m] certificate signature verification failed.
132217 Failed to convert cert into DER format before sending to certmgr.
132221 Invalid EAP type [eaptype:%d] received for station[mac:%m][bssid:%m] configured in
132222 Received EAP packet on the wrong BSSID for station [mac:%m][bssid:%m]
132224 Station [mac:%m] [bssid:%m] sent Unsupported EAP code [eapcode:%d]]
[ip:%s]:[port:%d]([app_name:%s]),[msg_code:%d], Msglen [len:%d], and Msgtype
[msg_type:%d] failed with Errno [errno:%d], Errstr [errstr:%s] “
Description: Error occurred during key propagation for a client in split/bridge/d-tunnel
mode for DWEP/AES/TKIP encryption.
Recommended Action: The msg is corrupted, retry the authentication to resolve the
issue.
Description: Station sent a cert from which we couldn’t extract the public key
Description: Station sent a cert, but the certificate signature verification failed.
Description: Failed to convert cert into DER format before sending to certmgr.
termination mode
Description: Received invalid EAP type for station that is configured in termination
mode
Description: Received EAP packet on the wrong BSSID.
Description: Station sent an EAP packet that is not supported. Ensure the station is
configured correctly to perform an EAP authentication method that is supported by the
Dell controller.
Recommended Action: Ensure that the aaa-profile associated with the authentication
request matches the authentication-method the client is sending to authenticate. If
problem persists, check for packet-corruption by capturing sniffer-traces between
client, AP and controller.
132225 MAC Authentication was not done for station [mac:%m] [bssid:%m]
Description: MAC Authentication was not done for the specific station
132226 MAC Authentication was not successful and l2-fail-thru is not enabled for station
[mac:%m] [bssid:%m]
Description: MAC Authentication was not successful and l2 fail thru knob was not
enabled for the specific station
132229 Failed to publish PMK Cache to GSM channel for Station [mac:%m] [bssid:%m]
Description: Failed to publish PMK Cache to GSM channel for the specified station
132230 Failed to publish Key Cache to GSM channel for Station [mac:%m]
Description: Failed to publish Key Cache to GSM channel for the specified station
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 21

Warning Messages
Table 7 Security Warning Messages
Message ID Message and Description
106010 “AM [bssid:%s]: Containment enabled on Suspect Rogue AP: BSSID [ap_bssid_str:%s],
121004 RADIUS server [name:%s]-[fqdn:%s]-[ipaddr:%s]-[sin_port:%u] timeout for
121006 RADIUS server [name:%s]-[fqdn:%s]-[ipaddr:%s]-[sin_port:%u] timeout for
121007 RADIUS (RFC 3576): Ignoring request from client [srv_ipaddr:%s] port([srv_port:%d])
132058 Vendor Id [vid:%d] not supported
SSID [ssid:%s], Conf-Level [conf_level:%d] “
Description: Containment has been enabled for a suspected rogue AP because the
confidence level for that AP equals or exceeds the configured value for that setting
client=[cbuf:%s] auth method [server:%s].
Description: RADIUS Server is unreachable. The server could be down or there is
connectivity problem.
Recommended Action: Check RADIUS server connectivity
client=[cbuf:%s] auth method [server:%s].
Description: RADIUS Server is unreachable. The server could be down or there is
connectivity problem.
Recommended Action: Check RADIUS server connectivity .
with unknown code [code:%d].
Description: A request was received on RADIUS port 3799 (RFC 3576) with unknown
code.
Recommended Action: Check RADIUS server and RFC 3799 client configuration.
Description: Vendor ID in the radius response is not supported. Radius packet will be
dropped.
132094 MIC failed in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
Description: Station sent an WPA key message whose MIC verification failed
Notice Messages
Table 8 Security Notice Messages
Message ID Message and Description
106000 AM [bssid:%s]: Potentially rogue AP detected BSSID [bssid_str:%s] SSID [ssid:%s]
MATCH MAC [mac:%s]
Description: An AP has been detected with conditions that may cause it to be
classified as a rogue (unsecure) or suspected rogue
106001 AM [bssid:%s]: Potentially rogue AP detected BSSID [bssid_str:%s] SSID [ssid:%s]
Description: An AP has been detected with conditions that may cause it to be
classified as a rogue (unsecure) or suspected rogue
106005 AM: Wireless containment: Sending type [subtype:%s] to AP [bssid:%s] from STA
[mac:%s] channel [channel:%d]
Description: No description available.
106006 AM: Wireless containment: Sending type [subtype:%s] from AP [bssid:%s] to STA
[mac:%s] channel [channel:%d]
Description: No description available.
22 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
Table 8 Security Notice Messages
Message ID Message and Description
106012 AM: Wireless tarpit containment: Sending Probe-Response with fake channel from AP
106013 AM: Wireless tarpit containment: Sending Probe-Response with fake BSSID for frame
106014 AM: Wireless tarpit containment: Sending Auth reply for frame from AP [bssid:%m] to
106015 AM: Wireless tarpit containment: Sending Assoc-Response for frame from AP
106016 AM: Wireless tarpit containment: Client [mac:%m] is in tarpit for fake BSSID [bssid:%s]
106017 AM: Wireless tarpit containment: Client [mac:%m] is in tarpit for fake channel
[bssid:%m] to STA [mac:%m] on channel [channel:%d] with fake_channel [fc:%d]
Description: No description available.
from AP [bssid:%m] to STA [mac:%m] on channel [channel:%d] with fake_bssid
[fbssid:%m]
Description: No description available.
STA [mac:%m] on channel [channel:%d] with algorithm [alg:%d] transaction [xn:%d]
seq [seq:%d]
Description: No description available.
[bssid:%m] to STA [mac:%m] on channel [channel:%d] with aid [aid:%d] seq [seq:%d]
Description: No description available.
on channel [channel:%d]
Description: No description available.
[channel:%d] for BSSID [bssid:%m]
Description: No description available.
121015 “Purge Request: [packet_id:%d], [srv_ipaddr:%s], [fd:%d], [timer_id:%d]”
Description: A new config was received (write memory on master), hence purging all
the pending radius requests.
121017 Unknown vendor or attribute ID [vendor:%d]/[attrid:%d] in [func:%s].
Description: The RADIUS vendor or the attribute ID is not known.
Recommended Action: Use show aaa radius-attributes command to check if the
vendor or attribute ID is supported.
121032 “Purge Request: [packet_id:%d], [srv_ipaddr:%s], [fd:%d], [timer_id:%d]”
Description: Radius Client IP change, hence purging all the pending radius requests
Information Messages
Table 9 Security Information Messages
Message ID Message and Description
106009 AM: Wired Containment: MAC:[mac_addr:%s] IP:[ip:%s]
Description: No description available.
106011 AM: Wired Containment Tagged: MAC:[mac_addr:%s] IP:[ip:%s] VLAN:[vlanid:%d] GW-
MAC:[gw_mac:%s] GW-IP:[gw_ip:%s]
Description: No description available.
121034 RADIUS attribute not sent: [attribute:%s]
Description: Controller has a reference to a RADIUS attribute that will be dropped.
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 23

Table 9 Security Information Messages
Message ID Message and Description
121035 RADIUS type not sent: [type:%s]
Description: Controller has a reference to a RADIUS type that will be dropped.
132000 xSec is enabled wired usersx
Description: Sec is enabled for wired users
132001 xSec is disabled for wired usersx
Description: Sec is disabled for wired users
132019 Station [name:%s] [mac:%m] was Machine authenticated
Description: Station successfully authenticated the machine account
132020 Station [name:%s] [mac:%m] failed Machine authentication update role [rl:%s]
Description: Station failed to authenticate the machine account
132021 Station [mac:%m] [bssid:%m] entered Held state
Description: Authenticator is in the held state for the specified station. In this state no
response from the station is accepted till the end of quiet period. This is done to avoid
DOS attacks.
132028 Dropping EAPOL request from Station [mac:%m] reason:AP [bssid:%m] [apname:%s]
only is configured for Static-WEP
Description: Station is trying to send EAP packets to AP that is only configured with
Static-WEP.
Recommended Action: Either configure your client to support static-WEP
authentication or configure the ssid-profile on the controller to support an 802.1x
authentication method.
132044 Enabled Stateful Radius“
Description: Stateful Dot1x is enabled. Controller will start monitoring EAPOL frames
to track authentication status.
132048 Disabled Stateful Radius“Stateful Dot1x is disabled.
Description: Controller will stop monitoring EAPOL frames to track authentication
status.
132066 Station[mac:%m] [bssid:%m] [apname:%s] [vl:%d] [gretype:%d] VLAN has been
132067 Cleaning up the Stateful AP Configuration
132068 Removing all the Stateful config entries.
132070 Removing trusted AP [mac:%m]
132071 Added trusted AP [mac:%m]
updated
Description: Station VLAN has been changed.
Cause: This is because of VLAN derivation rules
Description: Clear all the stateful dot1x configuration entries
Description: Remove all stateful dot1 configuration entries.
Description: Remove the Trusted AP with the specified MAC address.
Description: Add the trusted AP with the specified MAC address.
132086 “WPA [ver:%d] Key exchange failed to complete, de-authenticating the station
24 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide
[mac:%m] associated with AP [bssid:%m] [apname:%s] “
Description: WPA key exchange failed to complete, deauthenticating the station
Table 9 Security Information Messages
Message ID Message and Description
132131 FIPS mode is enabled.
Description: FIPS mode is enabled.
132132 FIPS mode is disabled
Description: FIPS mode is disabled.
132133 WPA Countermeasure is enabled
Description: WPA Countermeasure is enabled
132134 WPA Countermeasure is disabled
Description: WPA Countermeasure is disabled
132202 Successfully downloaded the certs [rootcert:%s] [servercert:%s] for EAP termination
Description: Successfully downloaded the certificates for EAP termination
132218 Skipping certificate common name check for username=[user:%s] MAC=[mac:%s]
Description: Based on configuration settings, the check for the certificate common
name against a AAA server was skipped.
132219 MAC=[mac:%s] Local User DB lookup result for Machine auth=[r3:%s] Role=[r4:%s]
Description: Local user database lookup result for Machine authentication status.
Debug Messages
Table 10 Security Debug Messages
Message ID Message and Description
121031 \[[file:%s]:[line:%d]] [message:%s]
Description: aaa module’s debug message
121037 [func:%s]: sta_add_rad_class_attr failed.
Description: This shows an internal debug message
121038 Save Class in station for MAC [mac:%s].
Description: This shows an internal debug message
121039 [func:%s]: sta_update_last_authserver failed.
Description: This shows an internal debug message
121040 [func:%s]: last_authserver [authserver:%s].
Description: This shows an internal debug message
121041 User [user:%s] MAC=[mac:%s] not found.
Description: This shows an internal debug message
121042 [func:%s]: Server FQDN is '[server:%s]', IP Address is '[ipaddr:%s]'.
Description: This shows an internal debug message
121043 [func:%s]: Server FQDN '[fqdn:%s]' not found in hash.
Description: This shows an internal debug message
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide Security Messages | 25

Table 10 Security Debug Messages
Message ID Message and Description
121044 Radius authenticate user ([user:%s]) PAP query using server [server:%s].
Description: This shows an internal debug message
121045 [func:%s]: sta_update_last_srv_grp failed.
Description: This shows an internal debug message
121046 [func:%s]: last_srv_grp [last_srv_grp:%s].
Description: This shows an internal debug message
121050 [msg:%s]
Description: This is an internal RADIUS debug log
132007 Clearing Station state on AP [bssid:%m]
Description: Station is forced to be cleared from the AP’s stations table
132022 Station [mac:%m] [bssid:%m] sent 802.1x packet before association/l2 miss - dropping
packet
Description: Received an EAP packet from the station before receiving an association/
l2 miss message.
Cause: This log-message is generated when we detect a race-condition between STM,
SOS and AUTH. AUTH is receiving association-request messages from STM before it
received the L2-Miss message from SOS.
Recommended Action: If symptoms persist, then AUTH is either not receiving or not
processing L2-Miss messages from SOS. Restart the AUTH process by executing
“”process restart auth”” or reload the controller.
132047 Disabling Stateful 802.1x - removing all Stateful Config entries
Description: Removing all the stateful dot1x config entries that was created
132213 Failed to perform revocation check for client cert
Description: Auth failed to contact certmgr to perform revocation check for client cert
132214 Client certificate for mac [mac:%m] and bssid [bssid:%m] has been revoked
Description: Client certificate has been revoked
132215 Client certificate for mac [mac:%m] and bssid [bssid:%m] has NOT been revoked
Description: Client certificate has not been revoked
132216 Revocation check request for mac [mac:%m] and bssid [bssid:%m] sent to certmgr
Description: Auth sent a revocation check request to certmgr process
132220 Debug Log
Description: Debug Log
132223 EAP-ID mismatched [id1:%d]:[id2:%d] for station [mac:%m] [bssid:%m]
Description: Mismatch between the eapid station sent and what was expected.
132227 EAPOL-Logoff ignored for station [mac:%m] [bssid:%m]
Description: EAPOL-Logff ignored for the specific station.
132228 Station [mac:%m] got stm-msg with bssid = [bssid:%m] while sap-bssid =
[sapbssid:%m]
Description: Should not delete the specified station for this station down.
26 | Security Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

Emergency Messages
Table 11 System Emergency Messages
Message ID Message and Description
330203 MESHD process initialization failed.
Cause: MESHD process initialization failed possibly because the mesh-node is not
correctly provisioned.
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
330204 MESHD process exiting. No MESH role was specified.
Cause: No MESH role was specified.
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
Chapter 2
System Messages
330205 MESHD process exiting. No MESH cluster profile was specified.
Cause: No MESH cluster
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
341008 [msg:%s]
Description: No description available.
profile was specified.
Alert Messages
Table 12 System Alert Messages
Message ID Message and Description
341007 [msg:%s]
Description: No description available.
341091 [func:%s]: [line:%d]: out of memory.
Description: The AP is upgrading image from awc.
341276 Could not program ACL = [acl:%d] to datapath.
Description: Datapath ACL programming failed.
341286 Could not download the required file, reason [reason:%s].
Description: Could not download the required file
341287 Managed mode: Could not apply the config fetched from server [reason:%s], error code
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide System Messages | 27
[error_code:%d].
Description: Could not apply the configuration fetched from server.

Critical Messages
Table 13 Critical System Messages
Message ID Message and Description
341006 [msg:%s]
Description: No description available.
341275 VPN tunnel switch to [tunnel:%s], reason:[reason:%s].
Description: VPN tunnel switch.
341279 Description: Managed mode: Could not download the configuration from the server.
Recommended Action: Could not download the configuration from the server.
Error Messages
Table 14 Error System Messages
Message ID Message and Description
304000 Unexpected stm (Station management) runtime error at [func:%s], [line:%d].
Description: Unexpected condition occurred in the station manager (stm).
Recommended Action: Contact your support provider
304001 Unexpected stm (Station management) runtime error at [func:%s], [line:%d], [data:%s].
Description: Unexpected condition occurred in the station manager (stm).
Recommended Action: Contact your support provider
304035 PAPI_Send failed: [error:%d]; from [sport:%d] to [toaddr:%p]:[toport:%d] len [len:%d]
304039 VPOOL: Maximum capacity ([count:%d]) reached for Vlan Pool hash table
304040 VPOOL: Vlan Pool hash table ([vap:%s]) collision at [entry:%d]. Not handled!
304041 VPOOL: Error allocating VLAN from Virtual AP pool [name:%s]
304045 Connection to User DB failed
304046 Creation of Client Blacklist tables in User DB failed
304047 SQL Command [command:%s] failed on User DB. Reason: [reason:%s]
type [type:%d].
Description: Inter-process communication message failed to reach the target.
Recommended Action: Contact your support provider
Recommended Action: Contact your support provider
Recommended Action: Contact your support provider
Description: The application was not able to connect to the user database.
Description: The application was not able to create the Client Blacklist tables in the
user database.
Description: This log indicates that an SQL command failed when it was executed on
the user database.
304049 Update to client blacklist database table failed.
Description: This log indicates that an update to the client blacklist database table
failed.
28 | System Messages Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide

Table 14 Error System Messages (Continued)
Message ID Message and Description
304054 Client blacklist is full and caused an entry to not be added. Limit: [limit: %d].
Description: This log indicates that the client blacklist table is full and an entry that
would have been added could not be added.
304055 Contact Dell tech-support.“Unexpected stm (Station management) runtime error at
304058 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]; opcode [opcode:%d] action
304060 [func:%s], [line:%d]: Sibyte reply truncated; opcode [opcode:%d] action [action:%d]
304062 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]
304063 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]
304064 PAPI_Send failed, [func:%s], [line:%d]: [error:%s], dstport [dst:%d], msgcode [code:%d]
304065 PAPI_Send failed, [func:%s], [line:%d]: [error:%s], dstport [dst:%d]
304067 PAPI_Send failed: [func:%s], [line:%d]: [error:%s]; from [sport:%d] to
[func:%s], [line:%d], [data:%s]
Description: Unexpected condition occurred in the station manager (stm)
[action:%d]
Description: Inter-process communication message failed to reach datapath.
Description: Datapath reply to PAPI message sent is truncated.
Description: Inter-process communication message failed to reach auth manager.
Description: Inter-process communication message failed to reach air monitor.
Description: Inter-process communication message failed to reach destination.
Description: Inter-process communication message failed to reach destination.
[toaddr:%p]:[toport:%d] len [len:%d] type [type:%d]
Description: Inter-process communication message failed to reach the target.
311013 Image upgrade failed; details follow.
Description: The AP was unable to upgrade its image. Message 311014 will
follow with details about the error.
311014 [line:%s]
Description: This message presents detailed information about an AP image
upgrade error.
311016 Unable to create domain list file
Description: Internal error occured while accessing domain lists file.
311017 Error occured while resolving IP’s for domains
Description: Internal error occured while resolving the domain names
Recommended Action: Contact your support provider
311018 Unable to read domain results file
Description: Internal error occured while processing the domain results file
Recommended Action: Contact your support provider
311019 Unable to generate certificate signing request (CSR). AP will reboot.
Description: The access point was unable to generate a certificate signing
request (CSR).
Recommended Action: Contact your support provider
Dell Networking W-Series Instant 6.4.0.2-4.1 | Syslog Messages Reference Guide System Messages | 29
 Loading...
Loading...