Dell PowerEdge M IO Aggregator, PowerEdge Web Server, PowerEdge XL 5133-4, PowerEdge M1000e, Force10 M I/O Aggregator Command Reference Manual
Page 1
Dell PowerEdge Configuration
Guide for the M I/O Aggregator
Publication Date: March 2013
Page 2

Notes, Cautions, and Warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to
avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
Information in this publication is subject to change without notice.
© 2012 Dell Force10. All rights reserved.
Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden.
Trademarks used in this text: Dell(TM), the Dell logo, Dell Boomi(TM), Dell Precision(TM) , OptiPlex(TM), Latitude(TM), PowerEdge(TM),
PowerVault(TM), PowerConnect(TM), OpenManage(TM), EqualLogic(TM), Compellent(TM), KACE(TM), FlexAddress(TM),
Force10(TM) and Vostro(TM) are trademarks of Dell Inc. Intel(R), Pentium(R), Xeon(R), Core(R) and Celeron(R) are registered trademarks
of Intel Corporation in the U.S. and other countries. AMD(R) is a registered trademark and AMD Opteron(TM), AMD Phenom(TM) and
AMD Sempron(TM) are trademarks of Advanced Micro Devices, Inc. Microsoft(R), Windows(R), Windows Server(R), Internet Explorer(R),
MS-DOS(R), Windows Vista(R) and Active Directory(R) are either trademarks or registered trademarks of Microsoft Corporation in the United
States and/or other countries. Red Hat(R) and Red Hat(R)Enterprise Linux(R) are registered trademarks of Red Hat, Inc. in the United States
and/or other countries. Novell(R) and SUSE(R) are registered trademarks of Novell Inc. in the United States and other countries. Oracle(R)
is a registered trademark of Oracle Corporation and/or its affiliates. Citrix(R), Xen(R), XenServer(R) and XenMotion(R) are either registered
trademarks or trademarks of Citrix Systems, Inc. in the United States and/or other countries. VMware(R), Virtual SMP(R), vMotion(R),
vCenter(R) and vSphere(R) are registered trademarks or trademarks of VMware, Inc. in the United States or other countries. IBM(R) is a
registered trademark of International Business Machines Corporation.
Other trademarks and trade names may be used in this publication to refer to either the entities claiming the marks and names or their products.
Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.
March 2013
Page 3

| iii
Page 4

www.dell.com | support.dell.com
iv |
Page 5

1 About this Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Objectives . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
Audience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Information Symbols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Related Documents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
2 Before You Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Default Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3
Other Auto-Configured Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4
DCB Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
FCoE Connectivity and FIP Snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
iSCSI Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
Link Aggregation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Link Tracking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Uplink LAG. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Server-Facing LAGs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
Stacking Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
Where to Go From Here . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
3 Configuration Fundamentals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Accessing the Command Line . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
CLI Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Navigating CLI Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
do Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
Undoing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .12
Obtaining Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13
Entering and Editing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Command History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Filtering show Command Outputs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Multiple Users in Configuration Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
4 Getting Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Front Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Port Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Server-Facing Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Uplink Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Stacking Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Port Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Console access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Serial Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
| v
Page 6

External Serial Port with a USB Connector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Boot Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Configure a Host Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
Access the System Remotely . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .28
Access the Aggregator Remotely . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Configure the Management Port IP Address . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Configure a Management Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
Configure a Username and Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
Configure the Enable Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30
Configuration File Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
Copy Files to and from the System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
www.dell.com | support.dell.com
File System Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
View the Command History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
Upgrading and Downgrading FTOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
Important Points to Remember . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Save the Running-Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
View Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
View Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
5 Aggregator Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
Log Messages in the Internal Buffer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39
Disabling System Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Send System Messages to a Syslog Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Using a Unix System as a Syslog Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Changing System Logging Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41
Displaying the Logging Buffer and Logging Configuration . . . . . . . . . . . . . . . . . . . . . . . .42
Configuring a UNIX Logging Facility Level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43
Enabling Time Stamps on Syslog Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .44
File Transfer Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .44
Configuration Task List for File Transfer Services . . . . . . . . . . . . . . . . . . . . . . . . . . .44
Enabling the FTP Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
Configuring the FTP Server Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
Terminal Lines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
Telnet to Another Network Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
Recovering from a Forgotten Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47
Recovering from a Forgotten Enable Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47
Recovering from a Failed Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
6 Data Center Bridging (DCB) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Ethernet Enhancements in Data Center Bridging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
Priority-Based Flow Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
Enhanced Transmission Selection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
vi |
Page 7

Data Center Bridging Exchange Protocol (DCBX) . . . . . . . . . . . . . . . . . . . . . . . . . .55
Data Center Bridging in a Traffic Flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .55
Data Center Bridging: Auto-DCB-Enable Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
When DCB is Disabled (Default) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
When DCB is Enabled . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
Lossless Traffic Handling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
Enabling DCB on Next Reload . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Enabling Auto-DCB-Enable Mode on Next Reload . . . . . . . . . . . . . . . . . . . . . . . . . .58
QoS dot1p Traffic Classification and Queue Assignment . . . . . . . . . . . . . . . . . . . . . . . .59
How Priority-Based Flow Control is Implemented . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
How Enhanced Transmission Selection is Implemented . . . . . . . . . . . . . . . . . . . . . . . . .61
ETS Operation with DCBX . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
Bandwidth Allocation for DCBX CIN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
DCB Policies in a Switch Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
DCBX Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
DCBX Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
DCBX Port Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
DCB Configuration Exchange . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65
Configuration Source Election . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Propagation of DCB Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Auto-Detection of the DCBX Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
DCBX Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .67
DCBX Prerequisites and Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .68
DCBX Error Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
An error in DCBX operation is displayed using the following syslog messages:.69
Debugging DCBX on an Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Verifying DCB Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .70
Example: PFC and ETS Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .79
Hierarchical Scheduling in ETS Output Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
7 Dynamic Host Configuration Protocol (DHCP) . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
DHCP Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83
DHCP Packet Format and Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .84
Assigning an IP Address Using DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .85
DHCP Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .86
Releasing and Renewing DHCP-based IP Addresses . . . . . . . . . . . . . . . . . . . . . . .87
Viewing DHCP Statistics and Lease Information . . . . . . . . . . . . . . . . . . . . . . . . . . .87
Debugging DHCP Client Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .88
How DHCP Client is Implemented . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .90
DHCP Client on a Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .91
DHCP Client on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
DHCP Client Operation with Stacking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
| vii
Page 8

8 FIP Snooping. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Fibre Channel over Ethernet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .93
Ensuring Robustness in a Converged Ethernet Network . . . . . . . . . . . . . . . . . . . . . . . .93
FIP Snooping on Ethernet Bridges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95
FIP Snooping in a Switch Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
How FIP Snooping is Implemented . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
FIP Snooping on VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
FC-MAP Value . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
Bridge-to-FCF Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
Impact on other Software Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
FIP Snooping Prerequisites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
www.dell.com | support.dell.com
FIP Snooping Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
Displaying FIP Snooping Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .100
FIP Snooping Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .107
Debugging FIP Snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .108
9 Internet Group Management Protocol (IGMP). . . . . . . . . . . . . . . . . . . . . . . . . . . 109
IGMP Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .109
IGMP Version 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .109
Joining a Multicast Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .110
Leaving a Multicast Group. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .110
IGMP Version 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Joining and Filtering Groups and Sources. . . . . . . . . . . . . . . . . . . . . . . . . . . . .112
Leaving and Staying in Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113
IGMP Snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .113
How IGMP Snooping is Implemented on an Aggregator . . . . . . . . . . . . . . . . . . . . .114
Disabling Multicast Flooding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .114
Displaying IGMP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .114
10 Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Basic Interface Configuration: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .117
Advanced Interface Configuration: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Interface Auto-Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Interface Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .118
Viewing Interface Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Disabling and Re-enabling a Physical Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .121
Layer 2 Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .122
Management Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .122
Accessing an Aggregator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .122
Configuring a Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .123
Configuring a Static Route for a Management Interface . . . . . . . . . . . . . . . . . . . . .125
VLAN Membership . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .126
viii |
Page 9

Default VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .126
Port-Based VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .127
VLANs and Port Tagging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .127
Configuring VLAN Membership . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .128
Displaying VLAN Membership . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .129
Adding an Interface to a Tagged VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .130
Port Channel Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .131
Port Channel Definition and Standards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .132
Port Channel Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .132
Port Channel Implementation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .132
1GbE and 10GbE Interfaces in Port Channels . . . . . . . . . . . . . . . . . . . . . . . . .133
Uplink Port Channel: VLAN Membership. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .133
Server-Facing Port Channel: VLAN Membership . . . . . . . . . . . . . . . . . . . . . . .133
Displaying Port Channel Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .134
Interface Range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Bulk Configuration Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Create a Single-Range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Create a Multiple-Range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Exclude a Smaller Port Range. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Overlap Port Ranges. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Commas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Monitor and Maintain Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Maintenance Using TDR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .139
Flow Control Using Ethernet Pause Frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .140
MTU Size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .141
Auto-Negotiation on Ethernet Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .142
Setting Speed and Duplex Mode of Ethernet Interfaces . . . . . . . . . . . . . . . . . .142
Setting Auto-Negotiation Options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .143
Viewing Interface Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .145
Displaying Non-Default Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .145
Clearing Interface Counters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .147
11 iSCSI Optimization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
iSCSI Optimization Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .149
Monitoring iSCSI Traffic Flows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .150
Information Monitored in iSCSI Traffic Flows . . . . . . . . . . . . . . . . . . . . . . . . . . . . .150
Detection and Autoconfiguration for Dell EqualLogic Arrays . . . . . . . . . . . . . . . . . .151
Detection and Port Configuration for Dell Compellent Arrays . . . . . . . . . . . . . . . . .151
iSCSI Optimization: Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
Default iSCSI Optimization Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
Displaying iSCSI Optimization Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .153
| ix
Page 10

12 Link Aggregation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
How the LACP is Implemented on an Aggregator . . . . . . . . . . . . . . . . . . . . . . . . . . . . .155
Uplink LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .155
Server-Facing LAGs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .156
LACP Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .156
Auto-Configured LACP Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .156
LACP Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .157
Verifying LACP Operation and LAG Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . .158
13 Layer 2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Managing the MAC Address Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .163
www.dell.com | support.dell.com
Clearing MAC Address Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .163
Displaying the MAC Address Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .164
Network Interface Controller (NIC) Teaming . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .164
MAC Address Station Move . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165
MAC Move Optimization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165
14 Link Layer Discovery Protocol (LLDP). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .167
Protocol Data Units . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .167
Optional TLVs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .168
Management TLVs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .168
Organizationally Specific TLVs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .169
IEEE Organizationally Specific TLVs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .169
TIA-1057 (LLDP-MED) Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .170
TIA Organizationally Specific TLVs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .171
LLDP-MED Capabilities TLV . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .172
LLDP-MED Network Policies TLV . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .173
Extended Power via MDI TLV . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .174
LLDP Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .175
Viewing the LLDP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .175
Viewing Information Advertised by Adjacent LLDP Agents . . . . . . . . . . . . . . . . . . . . . .176
Clearing LLDP Counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .178
Debugging LLDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .179
Relevant Management Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .180
15 Port Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Important Points to Remember . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .185
Port Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .186
Configuring Port Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .188
x |
Page 11

16 Simple Network Management Protocol (SNMP) . . . . . . . . . . . . . . . . . . . . . . . . . 191
Implementation Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .191
Configuring the Simple Network Management Protocol . . . . . . . . . . . . . . . . . . . . . . . .191
Important Point to Remember . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .191
Setting up SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .192
Creating a Community . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .192
Read Managed Object Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .192
Displaying the Ports in a VLAN Using SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .194
Fetching Dynamic MAC Entries Using SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .195
Deriving Interface Indices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .197
Monitor Port-channels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .199
Entity MIBS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .200
17 Stacking. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .203
Stacking Aggregators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .203
Stack Management Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .204
Stack Master Election . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .205
Failover Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .205
MAC Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .206
Stacking LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .206
Stacking VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .206
Stacking Port Numbers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .207
Configuring a Switch Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .207
Stacking Prerequisites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .208
Cabling Stacked Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .208
Cabling Restrictions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .208
Cabling Redundancy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .208
Cabling Procedure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .209
Accessing the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .209
Configuring and Bringing Up a Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .209
Adding a Stack Unit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .210
Resetting a Unit on a Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .211
Removing an Aggregator from a Stack and Restoring Quad Mode . . . . . . . . . . . .211
Verifying a Stack Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .212
Using LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .212
Using Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .212
Troubleshooting a Switch Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .215
Troubleshooting Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .215
Failure Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .217
Stack Member Fails. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .217
Unplugged Stacking Cable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .217
Master Switch Fails . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .218
| xi
Page 12

Stack-Link Flapping Error . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .218
Master Switch Recovers from Failure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .218
Stack Unit in Card-Problem State Due to Incorrect FTOS Version . . . . . . . . . .219
Stack Unit in Card-Problem State Due to Configuration Mismatch . . . . . . . . . .219
Upgrading a Switch Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .220
Upgrading a Single Stack Unit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .221
18 Broadcast Storm Control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
Displaying Broadcast-Storm Control Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .223
Disabling Broadcast Storm Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .223
www.dell.com | support.dell.com
19 System Time and Date . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Setting the Time for the Hardware Clock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .225
Setting the Time for the Software Clock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .226
Synchronizing the Hardware Clock Using the Software Clock . . . . . . . . . . . . . . . .226
Setting the Time Zone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .227
Setting Daylight Savings Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .228
Setting Daylight Saving Time Once. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .228
Setting Recurring Daylight Saving Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .229
20 Uplink Failure Detection (UFD) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Feature Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .231
How Uplink Failure Detection Works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .232
UFD and NIC Teaming . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .233
Important Points to Remember . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .234
Disabling Uplink Failure Detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .235
Configuring the Defer Timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .235
Displaying Uplink Failure Detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .236
Debugging UFD on an Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .239
21 Upgrade Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
22 Debugging and Diagnostics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Debugging Aggregator Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .244
All interfaces on the Aggregator are operationally down . . . . . . . . . . . . . . . . . . . . .244
Symptom: All Aggregator interfaces are down. . . . . . . . . . . . . . . . . . . . . . . . . .244
Resolution: Ensure that port channel 128 is up and that the Aggregator-facing port channel on
the top-of-rack switch is correctly configured. . . . . . . . . . . . . . . . . . . . . . . . . . .244
Steps to Take: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .244
Broadcast, unknown multicast, and DLF packets are switched at a very low rate .245
Symptom: Broadcast, unknown multicast, and DLF packets are switched at a very low rate.
245
xii |
Page 13

Resolution: Disable broadcast storm control globally on the Aggregator. . . . . .245
Steps to Take: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .245
Flooded packets on all VLANs are received on a server . . . . . . . . . . . . . . . . . . . .246
Symptom: All packets flooded on all VLANs on an Aggregator are received on a server , even if
the server is configured as a member of only a subset of VLANs. This behavior happens
because all Aggregator ports are, by default, members of all (4094) VLANs.. .246
Resolution: Configure a port that is connected to the server with restricted VLAN membership.
246
Steps to Take: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .246
Auto-configured VLANs do not exist on a stacked Aggregator . . . . . . . . . . . . . . . .247
Symptom: When an Aggregator is configured and used in a stack, traf fic does not flow and the
VLAN auto-configuration on all ports is lost. This behavior happens because an Aggregator in
stacking mode does not support auto-configured VLANs. Only VLANs that were previously
manually configured are retained on the master stack unit. . . . . . . . . . . . . . . .247
Resolution: You must manually configure VLAN membership on each stack-unit port.247
Steps to Take: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .247
Software show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .248
Offline Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .250
Important Points to Remember . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .250
Running Offline Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .250
Trace Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .251
Auto Save on Crash or Rollover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .251
Show Hardware Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .252
Environmental Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .253
Recognize an Over-Temperature Condition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .255
Troubleshoot an Over-Temperature Condition . . . . . . . . . . . . . . . . . . . . . . . . . . . .255
Recognize an Under-Voltage Condition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .256
Troubleshoot an Under-Voltage Condition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .256
Buffer Tuning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .257
Deciding to Tune Buffers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Buffer Tuning Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Using a Pre-Defined Buffer Profile. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .262
Sample Buffer Profile Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .263
Troubleshooting Packet Loss . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .263
Displaying Drop Counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .264
Dataplane Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .265
Displaying Stack Port Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .267
Displaying Stack Member Counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .267
Application Core Dumps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .268
Mini Core Dumps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .268
TCP Dumps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .270
23 Standards Compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
IEEE Compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .271
| xiii
Page 14

RFC and I-D Compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .272
General Internet Protocols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .272
General IPv4 Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .273
Network Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .274
MIB Location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .276
www.dell.com | support.dell.com
xiv |
Page 15

About this Guide
Objectives
This guide describes the supported protocols and software features, and provides configuration instructions
and examples, for the Dell Force10 M I/O Aggregator running FTOS version 8.3.17.4.
The M I/O Aggregator is installed in a Dell PowerEdge M1000e Enclosure. For information about how to
install and perform the initial switch configuration, refer to the Getting Started Guides on the Dell Support
website at http://support.dell.com/manuals.
Though this guide contains information about protocols, it is not intended to be a complete reference. This
guide is a reference for configuring protocols on Dell Force10 systems. For complete information about
protocols, refer to other documentation, including IETF requests for comment (RFCs). The instructions in
this guide cite relevant RFCs, and Standards Compliance contains a complete list of the supported RFCs
and management information base files (MIBs).
1
Note: You can perform some of the configuration tasks described in this document by using either the
FTOS command line or the Chassis Management Controller (CMC) graphical interface. Tasks supported
by the CMC interface are shown with the CMC icon:
Audience
This document is intended for system administrators who are responsible for configuring and maintaining
networks and assumes you are knowledgeable in Layer 2 and Layer 3 networking technologies.
About this Guide | 1
Page 16

Conventions
This document uses the following conventions to describe command syntax:
Convention Description
keyword
parameter
{X} Keywords and parameters within braces must be entered in the CLI.
[X] Keywords and parameters within brackets are optional.
www.dell.com | support.dell.com
x | y Keywords and parameters separated by bar require you to choose one.
Keywords are in bold and must be entered in the CLI as listed.
Parameters are in italics and require a number or word to be entered in the CLI.
Information Symbols
Table 1-1 describes symbols contained in this guide.
Table 1-1. Information Symbols
Symbol Meaning Description
FTOS Behavior This symbol informs you of an FTOS behavior. These behaviors are
Exception This symbol is a note associated with some other text on the page that is
inherent to the Dell Force10 system or FTOS feature and are
non-configurable.
marked with an asterisk.
Chassis Management
Controller (CMC)
user interface
Related Documents
For more information about the Dell Force10 MXL 10/40GbE Switch IO Module, refer to the following
documents:
• Dell Force10 FTOS Command Line Reference Guide for the M I/O Aggregator
• Dell PowerEdge M I/O Aggregator Getting Started Guide
• Release Notes for the M I/O Aggregator (FTOS version 8.3.17.4)
2 | About this Guide
This symbol indicates that you can also perform the specified
configuration task on an Aggregator by using the CMC graphical interface.
For information about how to access the CMC to configure an Aggregator,
refer to the Dell PowerEdge M1000e Enclosure Hardware Owner's
Manual or Dell Chassis Management Controller (CMC) User’s Guide on
the Dell Support website at http://support.dell.com/support/edocs/systems/
pem/en/index.htm.
Page 17

Before You Start
By following the instructions in the Dell PowerEdge M I/O Aggr egator Getting Started Guide
that is shipped with the product, you install the Aggregator in a Dell PowerEdge M1000e
Enclosure.
The Aggregator installs with zero-touch configuration. After you power it on, an Aggregator
boots up with default settings and auto-configures with software features enabled. This
chapter describes the default settings and software features that are automatically configured
at startup. Use the tasks described in the other chapters to reconfigure the Aggregator for
customized network operation.
Default Settings
The I/O Aggregator provides zero-touch configuration with the following default
configuration settings:
2
• Default user name (root)
• Password (calvin)
• VLAN (vlan1) and IP address for in-band management (DHCP-assigned)
• IP address for out-of-band (OOB) management (DHCP-assigned)
• Read-only SNMP community name (public)
• Broadcast storm control (enabled)
• Unregistered IGMP multicast packet flooding (enabled)
• IGMP snooping in all VLANs except the default VLAN (enabled)
• VLAN configuration (all ports belong to all VLANs)
You can change any of these default settings using the CLI. Refer to the appropriate chapter
for details
.
Note: You can also change many of the default settings using the chassis management
controller (CMC) interface. In this document, configuration tasks that you can perform from
the CMC interface are shown with a CMC icon:
For information about how to access the CMC to configure an Aggregator, refer to the Dell
PowerEdge M1000e Enclosure Hardware Owner's Manual or Dell Chassis Management
Controller (CMC) User’s Guide on the Dell Support website at http://support.dell.com/
support/edocs/systems/pem/en/index.htm.
Before Y ou Start | 3
Page 18

Other Auto-Configured Settings
After the Aggregator powers on, it auto-configures and is operational with software features
enabled, including:
• Ports: Ports are administratively up and auto-configured to operate as hybrid ports to
transmit tagged and untagged VLAN traffic.
Ports 1 to 32 are internal server-facing ports, which can operate in either 1GbE or 10GbE
mode. Ports 33 to 56 are external ports auto-configured to operate by default as follows:
— The base-module ports operate in standalone 4x10GbE mode. You can configure
these ports to operate in 40GbE stacking mode. When configured for stacking, the
40GbE base-module ports cannot be used for uplinks.
www.dell.com | support.dell.com
— Ports on the 2-Port 40-GbE QSFP+ module operate only in 4x10GbE mode. They
cannot be used for stacking.
— Ports on the 4-Port 10-GbE SFP+ and 4-Port 10GBASE-T modules operate only in
10GbE mode.
For more information on how ports are numbered, see Port Numbering.
• Link aggregation: All uplink ports are configured in a single LAG (LAG 128).
• VLANs: All ports are configured as members of all (4094) VLANs. All VLANs are up
and can send or receive layer 2 traffic. For more information, see VLAN Membership.
• Data Center Bridging Capability Exchange Protocol (DCBX): Server-facing ports
auto-configure in auto-downstream port roles; uplink ports auto-configure in
auto-upstream port roles.
• Fibre Channel over Ethernet (FCoE) connectivity and FCoE Initiation Protocol (FIP)
snooping: The uplink port channel (LAG 128) is enabled to operate in FCF port mode.
• Link Layer Discovery Protocol (LLDP): Enabled on all ports to advertise management
TLV and system name with neighboring devices.
• iSCSI optimization
• IGMP snooping
• Jumbo frames: Ports are set to a maximum MTU of 12,000 bytes by default.
• Link tracking: Uplink-state group 1 is automatically configured. In uplink state-group 1,
server-facing ports auto-configure as downstream interfaces; the uplink port-channel
(LAG 128) auto-configures as an upstream interface. Server-facing links are
auto-configured to be brought up only if the uplink port-channel is up.
• Stacking is not enabled by default and is supported in 40GbE mode only on the basemodule ports. To configure a switch stack, you must use the CLI. See Stacking for more
information.
4 | Before You Start
Page 19

DCB Support
DCB enhancements for data center networks are supported to eliminate packet loss and
provision links with required bandwidth.
The Aggregator provides zero-touch configuration for DCB. The Aggregator auto-configures
DCBX port roles as follows:
• Server-facing ports are configured as auto-downstream interfaces.
• Uplink ports are configured as auto-upstream interfaces.
In operation, DCBX auto-configures uplink ports to match the DCB configuration in the ToR
switches to which they connect.
The Aggregator supports DCB only in standalone mode; DCB is not supported in stacking
mode.
FCoE Connectivity and FIP Snooping
Many data centers use Fibre Channel (FC) in storage area networks (SANs). Fibre Channel
over Ethernet (FCoE) encapsulates Fibre Channel frames over Ethernet networks.
On an Aggregator, the internal ports support FCoE connectivity and connect to the converged
network adapter (CNA) in blade servers. FCoE allows Fibre Channel to use 10-Gigabit
Ethernet networks while preserving the Fibre Channel protocol.
The Aggregator also provides zero-touch configuration for FCoE configuration. The
Aggregator auto-configures to match the FCoE settings used in the ToR switches to which it
connects through its uplink ports.
FIP snooping is automatically configured on an Aggregator. The auto-configured port
channel (LAG 128) operates in FCoE forwarder (FCF) port mode.
iSCSI Operation
Support for iSCSI traffic is turned on by default when the Aggregator powers up. No
configuration is required.
When the Aggregator powers up, it monitors known TCP ports for iSCSI storage devices on
all interfaces. When a session is detected, an entry is created and monitored as long as the
session is active.
The Aggregator also detects iSCSI storage devices on all interfaces and auto-configures to
optimize performance. Performance optimization operations, such as Jumbo frame size
support, STP port-state fast, and disabling of storm control on interfaces connected to an
iSCSI storage device, are applied automatically.
CLI configuration is necessary only when the configuration includes iSCSI storage devices
that cannot be automatically detected and when non-default QoS handling is required.
Before Y ou Start | 5
Page 20

Link Aggregation
All uplink ports are configured in a single LAG (LAG 128). Server-facing ports are
auto-configured as part of link aggregation groups if the corresponding server is configured
for LACP-based NIC teaming. Static LAGs are not supported.
Tip: The recommended LACP timeout is long-timeout mode.
Link Tracking
By default, all server-facing ports are tracked by the operational status of the uplink LAG. If
the uplink LAG goes down, the Aggregator loses its connectivity and is no longer
www.dell.com | support.dell.com
operational; all server-facing ports are brought down.
Tip: If installed servers do not have connectivity to a ToR switch, check the Link Status LED
of uplink ports on the Aggregator. If all LEDs are on, check the LACP configuration on the
ToR switch that is connected to the Aggregator to ensure the LACP is correctly configured.
Note: Link tracking is also referred to as uplink failure detection (UFD).
VLANs
By default, all Aggregator ports belong to all 4094 VLANs and are members of untagged
VLAN 1. You can use the CLI or CMC interface to configure only the required VLANs on a
port.
When you configure VLANs on server-facing interfaces (ports 1 to 32), you can assign
VLANs to a port or a range of ports by entering the vlan tagged or vlan untagged commands
in interface configuration mode; for example:
FTOS(conf)# interface tengigabitethernet 0/2 - 4
FTOS(conf-if-range-te-0/2-4)# vlan tagged 5,7,10-12
FTOS(conf-if-range-te-0/2-4)# vlan untagged 3
Note: You can also use the CMC interface to configure VLANs.
Uplink LAG
The tagged VLAN membership of the uplink LAG is automatically configured based on the
VLAN configuration of all server-facing ports (ports 1 to 32).
The untagged VLAN used for the uplink LAG is always the default VLAN.
Server-Facing LAGs
The tagged VLAN membership of a server-facing LAG is automatically configured based on
the server-facing ports that are members of the LAG.
6 | Before You Start
Page 21

The untagged VLAN of a server-facing LAG is configured based on the untagged VLAN to
which the lowest numbered server-facing port in the LAG belongs.
Tip: Dell Force10 recommends that you configure the same VLAN membership on all LAG
member ports.
Stacking Mode
Stacking is supported only on the 40GbE ports on the base module. A single stack is limited
to two Aggregators in the same chassis. Up to three stacks are supported in an M1000e
chassis. To configure a switch stack, you must use the CLI. See Stacking for more
information.
When you configure an Aggregator to operate in stacking mode, VLANs are reconfigured as
follows:
• If an Aggregator port belonged to all 4094 VLANs in standalone mode (default), all
VLAN membership is removed and the port is assigned only to default VLAN 1. You
must configure additional VLAN membership as necessary.
• If you had manually configured an Aggregator port to belong to one or more VLANs
(non-default) in standalone mode, the VLAN configuration is retained in stacking mode
only on the master switch.
When you reconfigure an Aggregator from stacking to standalone mode, Aggregator ports
that you manually configured for VLAN membership in stacking mode retain their VLAN
configuration in standalone mode. To restore the default auto-VLAN mode of operation (in
which all ports are members of all 4094 VLANs) on a port, enter the auto vlan command; for
example:
FTOS(conf)# interface tengigabitethernet 0/2
FTOS(conf-if-te-0/2)# auto vlan
Where to Go From Here
You can customize the Aggregator for use in your data center network as necessary. To
perform additional switch configuration, do one of the following:
• For remote out-of-band management, enter the OOB management interface IP address
into a Telnet or SSH client and log in to the switch using the user ID and password to
access the CLI.
• For local management using the CLI, use the attached console connection.
• For remote in-band management from a network management station, enter the IP
address of the default VLAN and log in to the switch to access the CLI.
If you installed the Aggregator in a stack, you can configure additional settings for switch
stacking.
Before Y ou Start | 7
Page 22

In case of an FTOS upgrade, you can check to see that an Aggregator is running the latest
FTOS version by entering the show version command. To download an FTOS version, go to
http://support.dell.com.
Refer to the appropriate chapter for detailed information on how to reconfigure specific
software settings.
www.dell.com | support.dell.com
8 | Before You Start
Page 23
Configuration Fundamentals
The Dell Force10 operating software (FTOS) command line interface (CLI) is a text-based interface
through which you can configure interfaces and protocols. The CLI is structured in modes for security and
management purposes. Different sets of commands are available in each mode, and you can limit user
access to modes using privilege levels.
In FTOS, after you enable a command, it is entered into the running configuration file. You can view the
current configuration for the whole system or for a particular CLI mode. To save the current configuration,
copy the running configuration to another location. For more information, refer to Save the
Running-Configuration.
Note: You can use the chassis management controller (CMC) out-of-band management interface to
access and manage an Aggregator using the FT OS command-line interface. For information about how to
access the CMC to configure an Aggregator, refer to the Dell Chassis Management Controller (CMC)
User's Guide on the Dell Support website at http://support.dell.com/support/edocs/systems/pem/en/
index.htm.
3
Accessing the Command Line
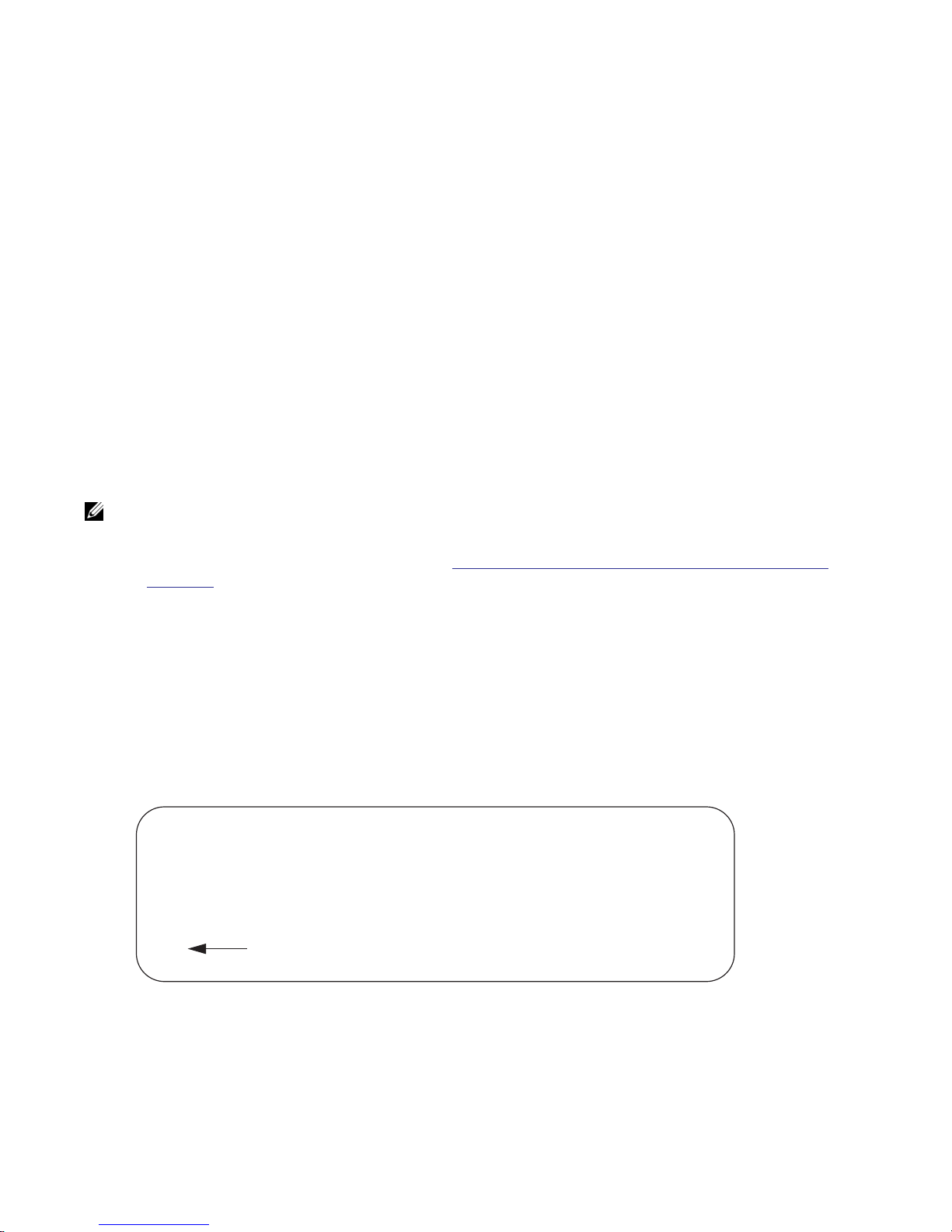
Access the command line through a serial console port or a Telnet session (Figure 3-1). When the system
successfully boots, enter the command line in EXEC mode.
Figure 3-1. Logging into the System using Telnet
telnet 172.31.1.53
Trying 172.31.1.53...
Connected to 172.31.1.53.
Escape character is '^]'.
Login: username
Password:
FTOS>
EXEC mode prompt
Configuration Fundamentals | 9
Page 24

CLI Modes
Different sets of commands are available in each mode. A command found in one mode cannot be
executed from another mode (with the exception of EXEC mode commands preceded by the command
for more information, refer to do Command and EXEC Privilege Mode commands).
The FTOS CLI is divided into three major mode levels:
• EXEC mode is the default mode and has a privilege level of 1, which is the most restricted level. Only
a limited selection of commands is available, notably the
system information.
• EXEC Privilege mode has commands to view configurations, clear counters, manage configuration
www.dell.com | support.dell.com
files, run diagnostics, and enable or disable debug operations. The privilege level is 15, which is
unrestricted. You can configure a password for this mode. For more information, refer to Configure the
Enable Password.
• CONFIGURATION mode allows you to configure security features, time settings, set logging and
simple network management protocol (SNMP) functions, and static address resolution protocol (ARP)
and MAC addresses on the system.
Beneath CONFIGURATION mode are sub-modes that apply to interfaces, protocols, and features.
Figure 3-2 shows this sub-mode command structure. When configuring the chassis for the first time, the
following two sub-CONFIGURATION modes are important:
do;
show commands, which allow you to view
• INTERFACE sub-mode is the mode in which you configure Layer 2 and Layer 3 protocols and IP
services specific to an interface. An interface can be physical (management interface, 10-Gigabit
Ethernet, or 40-Gigabit Ethernet) or logical (Loopback, Null, port channel, or VLAN).
• LINE sub-mode is the mode in which you configure the console and virtual terminal lines.
Note: At any time, entering a question mark (?) displays the available command options. For example,
when you are in CONFIGURATION mode, entering the question mark first lists all the available
commands, including the possible sub-modes.
Figure 3-2. FTOS CLI Modes Supported on the Aggregator
EXEC
EXEC Privilege
CONFIGURATION
INTERFACE
10 GIGABIT ETHERNET
INTERFACE RANGE
MANAGEMENT ETHERNET
LINE
CONSOLE
VIRTUAL TERMINAL
MONITOR SESSION
10 | Configuration Fundamentals
Page 25
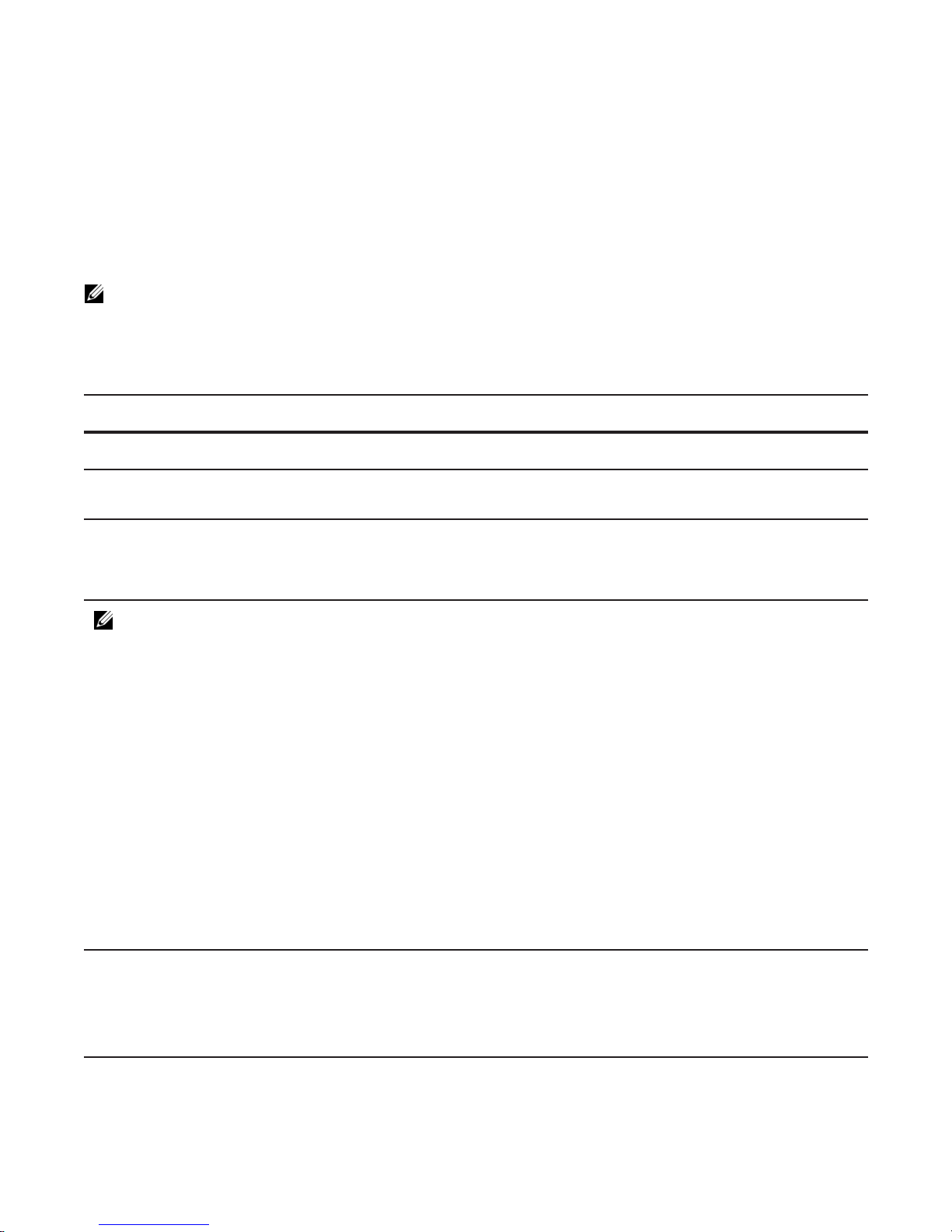
Navigating CLI Modes
The FTOS prompt changes to indicate the CLI mode. Table 3-1 lists the CLI mode, its prompt, and
information about how to access and exit this CLI mode. You must move linearly through the command
modes, with the exception of the
exit command moves you up one command mode level.
Note: Sub-CONFIGURATION modes all have the letters “conf” in the prompt with additional modifiers to
identify the mode and slot/port information. These are shown in Table 3-1.
Table 3-1. FTOS Command Modes
end command, which takes you directly to EXEC Privilege mode and the
CLI Command Mode Prompt
EXEC
EXEC Privilege
CONFIGURATION
FTOS>
FTOS# • From EXEC mode, enter the command enable.
FTOS(conf)# • From EXEC privilege mode, enter the command
Note: Access the following modes from CONFIGURATION mode:
10 Gigabit Ethernet
Interface
FTOS(conf-if-te-0/1)
INTERFACE modes
Interface Range
Management Ethernet
Interface
FTOS(conf-if-range)
FTOS(conf-if-ma-0/0)
Access Command
Access the router through the console or Telnet.
• From any other mode, enter the command end.
configure.
• From every mode except EXEC and EXEC
Privilege, enter the command exit.
#
#
#
interface
interface
interface
Monitor Session FTOS(conf-mon-sess) monitor session
IP COMMUNITY-LIST FTOS(conf-community-list)# ip community-list
CONSOLE FTOS(conf-line-console)#
LINE
VIRTUAL TERMINAL FTOS(conf-line-vty)#
line
line
Configuration Fundamentals | 11
Page 26

Figure 3-3 shows how to change the command mode from CONFIGURATION mode to INTERFACE
configuration mode.
Figure 3-3. Changing CLI Modes
FTOS(conf)# interface tengigabitethernet 1/2
FTOS(conf-if-te-1/2)#
do Command
New command prompt
www.dell.com | support.dell.com
Enter an EXEC mode or EXEC privilege mode command from any CONFIGURATION mode (such as
CONFIGURATION, INTERFACE, etc.) without returning to EXEC mode by preceding the EXEC mode
command with the command
Note: The following commands cannot be modified by the do command: enable, disable, exit, and configure.
Figure 3-4. Using the do Command
FTOS(conf)#do show system brief
Stack MAC : 00:01:e8:00:ab:03
-- Stack Info -Unit UnitType Status ReqTyp CurTyp Version Ports
----------------------------------------------------------------------------------- 0 Member not present
1 Management online I/O-Aggregator I/O-Aggregator 8-3-17-38 56
2 Member not present
3 Member not present
4 Member not present
5 Member not present
FTOS(conf)#
do. Figure 3-4 illustrates the do command.
“do” form of show command
Undoing Commands
When you enter a command, the command line is added to the running configuration file. Disable a
command and remove it from the running-config by entering the original command preceded by the
command
ip-address
Note: Use the help or ? command as described in Obtaining Help to help you construct the no form of a
command.
12 | Configuration Fundamentals
no. For example, to delete an ip address configured on an interface, use the no ip-address
command, as shown in Figure 3-5.
Page 27
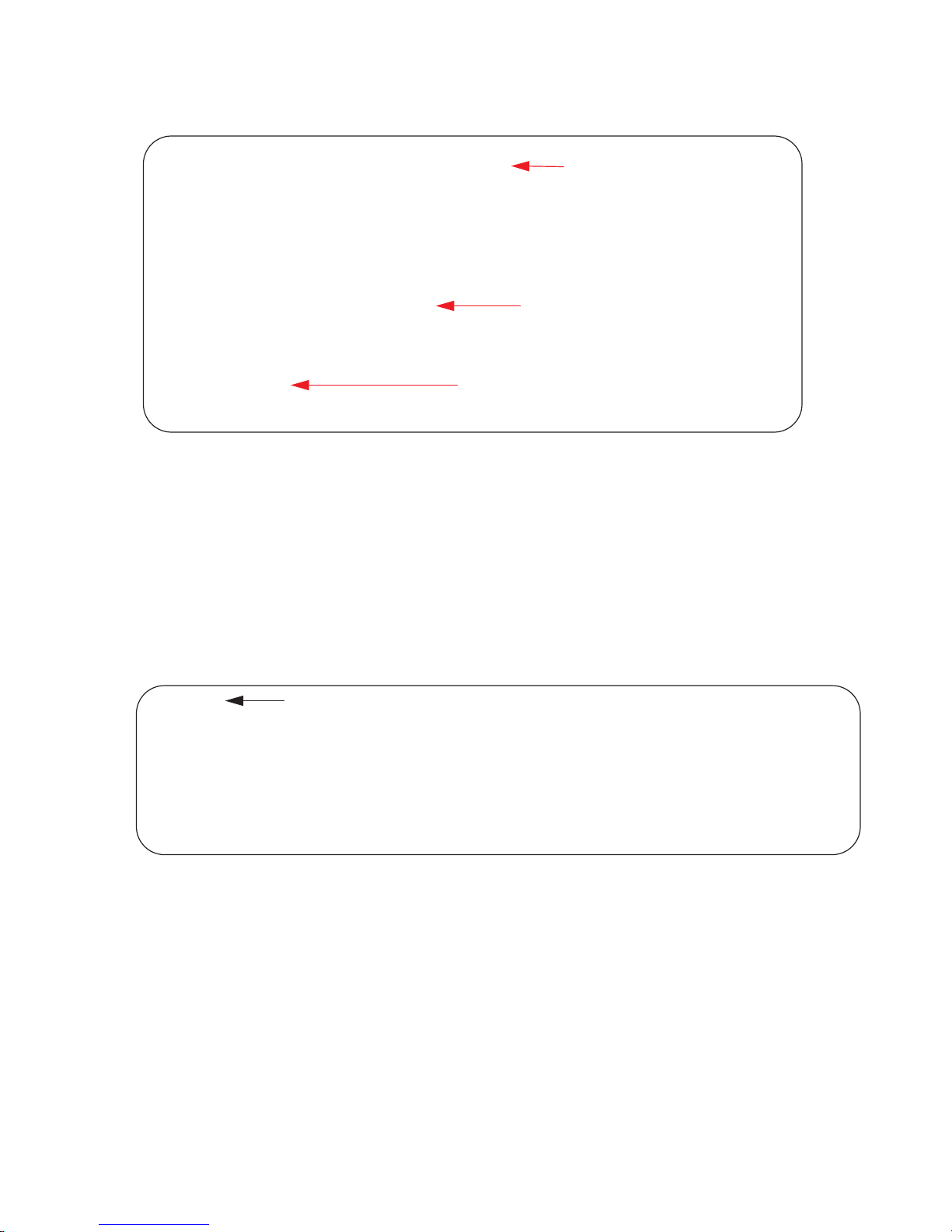
Figure 3-5. Undoing a command with the no Command
FTOS(conf)# interface managementethernet 0/0
FTOS(conf-if-ma-0/0)# ip address 192.168.5.6/16
FTOS(conf-if-ma-0/0)#
FTOS(conf-if-ma-0/0)#
FTOS(conf-if-ma-0/0)#show config
!
interface ManagementEthernet 0/0
ip address 192.168.5.6/16
no shutdown
FTOS(conf-if-ma-0/0)#
FTOS(conf-if-ma-0/0)# no ip address
FTOS(conf-if-ma-0/0)#
FTOS(conf-if-ma-0/0)# show config
!
interface ManagementEthernet 0/0
no ip address
no shutdown
FTOS(conf-if-ma-0/0)#
Obtaining Help
Obtain a list of keywords and a brief functional description of those keywords at any CLI mode using the ?
or
help commands:
Assign an IP address
Enter “no” form of IP address command
Verify that the IP address was removed
• Enter
? at the prompt or after a keyword to list the keywords available in the current mode.
•
? after a prompt lists all of the available keywords. The output of this command is the same for the
help command.
Figure 3-6. ? Command Example
FTOS#?
start Start Shell
capture Capture Packet
cd Change current directory
clear Reset functions
clock Manage the system clock
configure Configuring from terminal
copy Copy from one file to another
--More--
“?” at prompt for list of commands
• ? after a partial keyword lists all of the keywords that begin with the specified letters.
Configuration Fundamentals | 13
Page 28
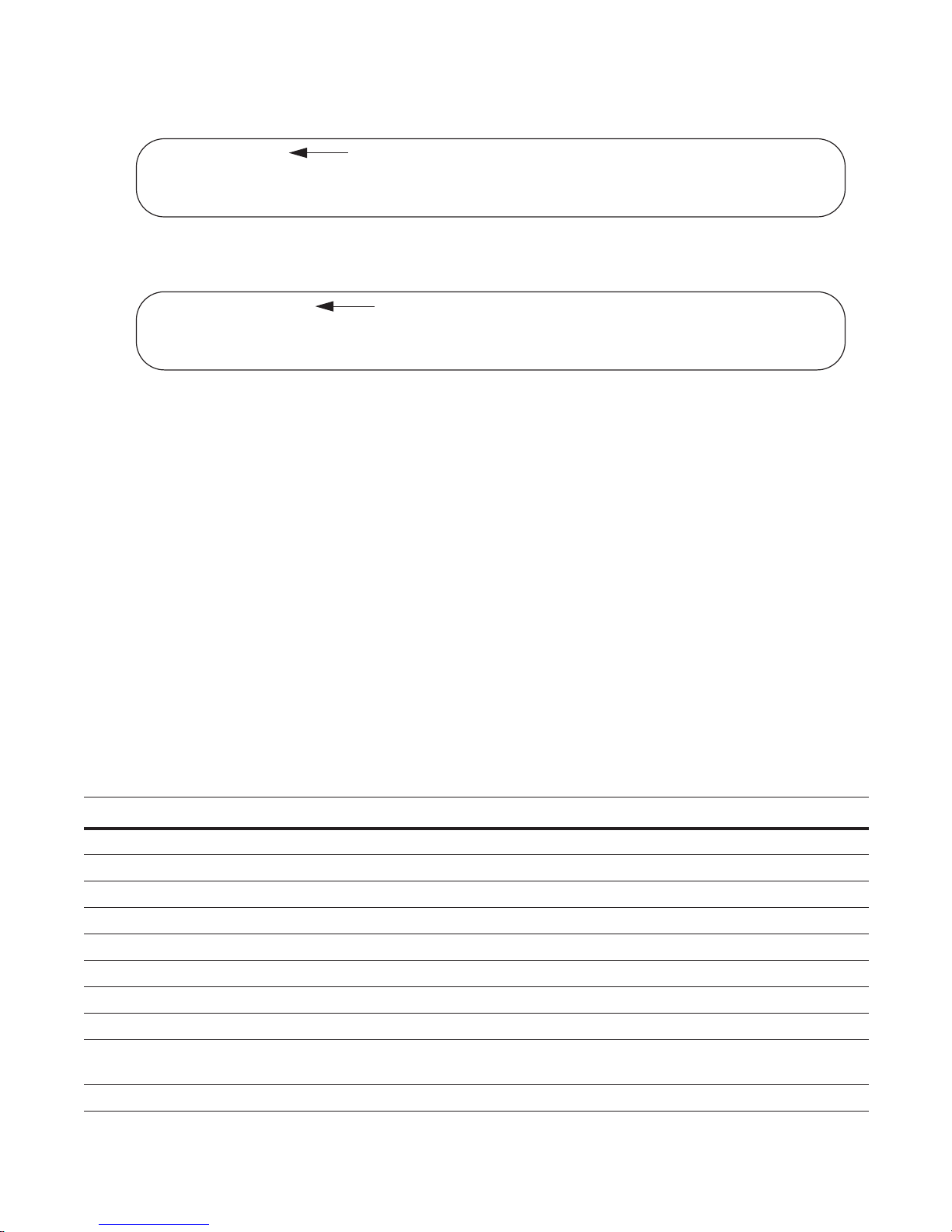
Figure 3-7. Keyword? Command Example
FTOS(conf)#cl?
clock
FTOS(conf)#cl
partial keyword plus “?” for matching keywords
• A keyword followed by [space]? lists all of the keywords that can follow the specified keyword.
Figure 3-8. Keyword ? Command Example
FTOS(conf)#clock ?
summer-time Configure summer (daylight savings) time
timezone Configure time zone
FTOS(conf)#clock
www.dell.com | support.dell.com
keyword plus “[space]?” for compatible keywords
Entering and Editing Commands
When entering commands:
• The CLI is not case sensitive.
• You can enter partial CLI keywords.
• You must enter the minimum number of letters to uniquely identify a command. For example,
cannot be entered as a partial keyword because both the clock and class-map commands begin with
the letters “cl.” You can, however, enter
begins with those three letters.
• The TAB key auto-completes keywords in commands.
• The UP and DOWN arrow keys display previously entered commands (refer to Command
History).
• The BACKSPACE and DELETE keys erase the previous letter.
• Key combinations are available to move quickly across the command line, refer to Table 3-2.
cl
clo as a partial keyword because only one command
Table 3-2. Short-Cut Keys and their Actions
Key Combination Action
CNTL-A Moves the cursor to the beginning of the command line.
CNTL-B Moves the cursor back one character.
CNTL-D Deletes the character at cursor.
CNTL-E Moves the cursor to the end of the line.
CNTL-F Moves the cursor forward one character.
CNTL-I Completes a keyword.
CNTL-K Deletes all characters from the cursor to the end of the command line.
CNTL-L Re-enters the previous command.
CNTL-N Return to more recent commands in the history buffer after recalling commands with CTRL-P or the
UP arrow key.
CNTL-P Recalls commands, beginning with the last command.
14 | Configuration Fundamentals
Page 29

Table 3-2. Short-Cut Keys and their Actions (continued)
Key Combination Action
CNTL-R Re-enters the previous command.
CNTL-U Deletes the line.
CNTL-W Deletes the previous word.
CNTL-X Deletes the line.
CNTL-Z Ends continuous scrolling of command outputs.
Esc B Moves the cursor back one word.
Esc
F Moves the cursor forward one word.
D Deletes all characters from the cursor to the end of the word.
Esc
Command History
FTOS maintains a history of previously-entered commands for each mode. For example:
• When you are in EXEC mode, the UP and DOWN arrow keys display the previously-entered EXEC
mode commands.
• When you are in CONFIGURATION mode, the UP or DOWN arrows keys recall the
previously-entered CONFIGURATION mode commands.
Filtering show Command Outputs
Filter the output of a show command to display specific information by adding | [except | find | grep | no-more
| save]
specified_text after the command. The variable specified_text is the text for which you are filtering and
it IS case sensitive unless you use the
The
grep command accepts an ignore-case sub-option that forces the search to be case-insensitive. For
example, the commands:
• show run | grep Ethernet returns a search result with instances containing a capitalized “Ethernet,” such
as interface TenGigabitEthernet 0/0.
•
show run | grep ethernet would not return that search result because it only searches for instances
containing a non-capitalized “ethernet.”
Executing the
show run | grep Ethernet ignore-case command would return instances containing both
“Ethernet” and “ethernet.”
•
grep displays only the lines containing specified text. Figure 3-9 shows this command used in
combination with the
do show stack-unit all stack-ports pfc details | grep 0 command.
ignore-case sub-option.
Configuration Fundamentals | 15
Page 30
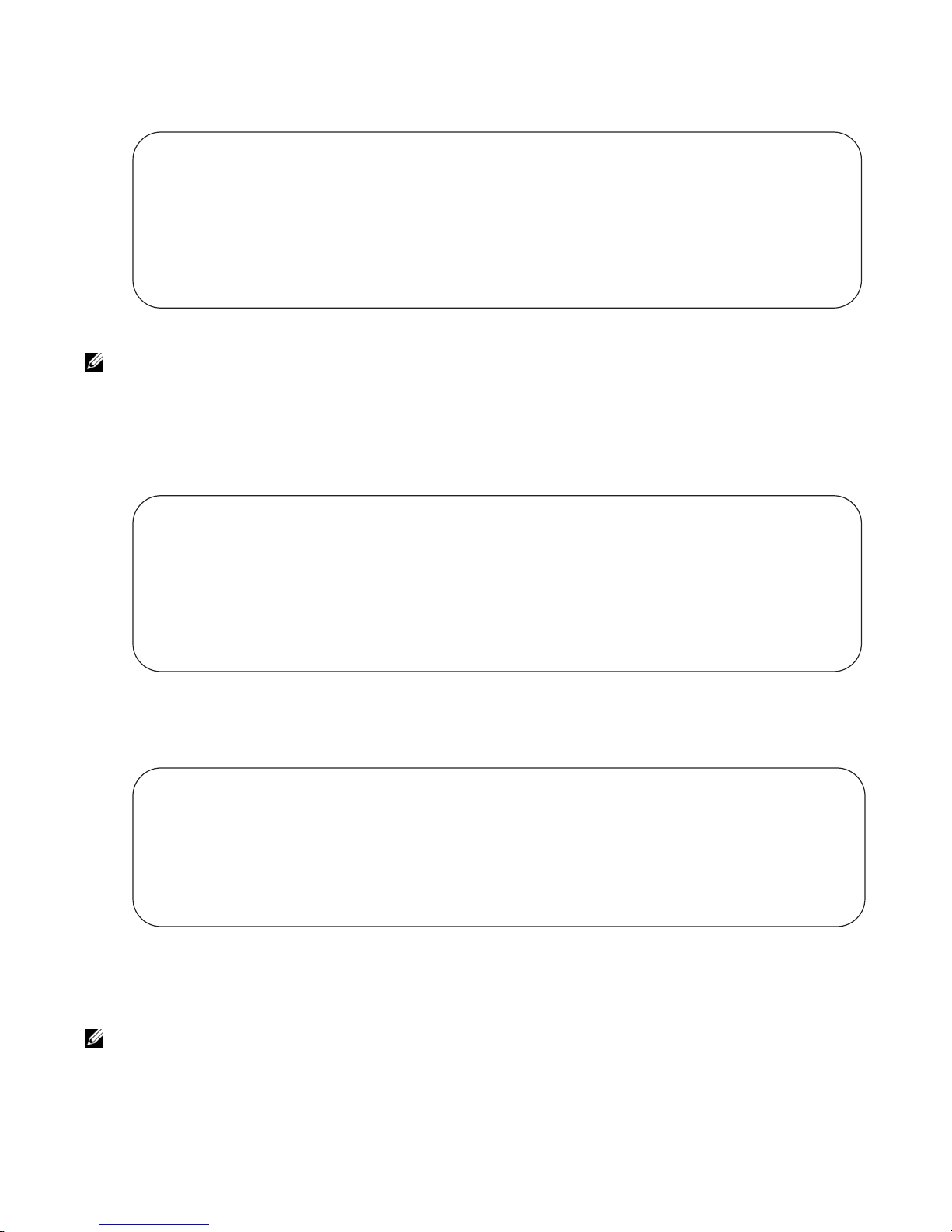
Figure 3-9. Filtering Command Outputs with the grep Command
FTOS(conf)#do show stack-unit all stack-ports all pfc details | grep 0
stack unit 0 stack-port all
0 Pause Tx pkts, 0 Pause Rx pkts
0 Pause Tx pkts, 0 Pause Rx pkts
0 Pause Tx pkts, 0 Pause Rx pkts
0 Pause Tx pkts, 0 Pause Rx pkts
0 Pause Tx pkts, 0 Pause Rx pkts
0 Pause Tx pkts, 0 Pause Rx pkts
Note: FTOS accepts a space or no space before and after the pipe. To filter on a phrase with spaces,
www.dell.com | support.dell.com
underscores, or ranges, enclose the phrase with double quotation marks.
• except displays text that does not match the specified text. Figure 3-10 shows this command used in
combination with the
Figure 3-10. Filtering Command Outputs with the except Command
FTOS(conf)#do show stack-unit all stack-ports all pfc details | except 0
Admin mode is On
Admin is enabled
Local is enabled
Link Delay 45556 pause quantum
do show stack-unit all stack-ports all pfc details | except 0 command.
stack unit 1 stack-port all
Admin mode is On
Admin is enabled
• find displays the output of the show command beginning from the first occurrence of specified text
Figure 3-11 shows this command.
Figure 3-11. Filtering Command Outputs with the find Command
FTOS(conf)#do show stack-unit all stack-ports all pfc details | find 0
stack unit 0 stack-port all
Admin mode is On
Admin is enabled
Local is enabled
Link Delay 45556 pause quantum
0 Pause Tx pkts, 0 Pause Rx pkts
stack unit 1 stack-port all
• no-more displays the output all at once rather than one screen at a time. This is similar to the terminal
length
command except that the no-more option affects the output of the specified command only.
•
save copies the output to a file for future reference.
Note: You can filter a single command output multiple times. The save option should be the last option
entered. For example:
FTOS# command | grep regular-expression | except regular-expression | grep
other-regular-expression | find regular-expression | save
16 | Configuration Fundamentals
Page 31

Multiple Users in Configuration Mode
FTOS notifies all users in the event that there are multiple users logged into CONFIGURATION mode. A
warning message indicates the username, type of connection (console or vty), and in the case of a vty
connection, the IP address of the terminal on which the connection was established. For example:
• On the system that telnets into the switch, Message 1 appears:
Message 1 Multiple Users in Configuration Mode Telnet Message
% Warning: The following users are currently configuring the system:
User "<username>" on line console0
• On the system that is connected over the console, Message 2 appears:
Message 2 Multiple Users in Configuration Mode Telnet Message
% Warning: User "<username>" on line vty0 "10.11.130.2" is in configuration mode
If either of these messages appear, Dell Force10 recommends coordinating with the users listed in the
message so that you do not unintentionally overwrite each other’s configuration changes.
Configuration Fundamentals | 17
Page 32

www.dell.com | support.dell.com
18 | Configuration Fundamentals
Page 33

Getting Started
This chapter contains the following major sections:
• Front Panel
• Port Numbering
• Console access
• Boot Process
• Configure a Host Name
• Configure a Host Name
• Access the System Remotely
• Configure the Enable Password
• Configuration File Management
• File System Management
• View the Command History
• Upgrading and Downgrading FTOS
4
When the boot process is complete, the console monitor displays the Dell Force10 operating software
(FTOS) banner and EXEC mode prompt (Figure 4-3).
For details about using the command line interface (CLI), refer to the Accessing the Command Line
section in the Configuration Fundamentals chapter.
Getting Started | 19
Page 34

Front Panel
Figure 4-1 shows the Aggregator front panel:
Figure 4-1. Front Panel of the M I/O Aggregator
www.dell.com | support.dell.com
Flex IO Module in
Top Expansion Slot
Flex IO Module in Bottom
Expansion Slot
USB Storage Port
40GbE QSFP+ Ports on
Base Module
Port Numbering
When installed in a PowerEdge M1000e Enclosure, Aggregator ports are numbered 1 to 56 and consist of
internal server-facing ports, uplink ports, and stacking ports (Figure 4-2).
Server-Facing Ports
Ports 1 to 32 are internal server-facing ports, which can operate in either 1GbE or 10GbE mode and
connect to servers installed in the M1000e chassis over the midplane.
USB Console Port
20 | Getting Started
Page 35

Uplink Ports
Ports 33 to 56 are external ports used for uplinks and numbered from the bottom to the top of the switch as
follows:
• The two base module ports operate by default in standalone 4x10GbE mode and are numbered 33 to 36
and 37 to 40.
• Ports on the 2-Port 40-GbE QSFP+ module operate only in 4x10GbE mode:
• In the bottom expansion slot, ports are numbered 41 to 44 and 45 to 48.
• In the top expansion slot, ports are numbered 49 to 52 and 53 to 56.
• Ports on the 4-Port 10-GbE SFP+ and 4-Port 10GBASE-T modules operate only in 10GbE mode:
• In the bottom expansion slot, ports are numbered 41 to 44.
• In the top expansion slot, ports are numbered 49 to 52.
Stacking Ports
Stacking is supported only on the ports on the base module. When you configure the Aggregator for
stacking, the base module ports operate in 40GbE mode and are numbered 33 and 37. When configured for
stacking, the 40GbE base-module ports cannot be used for uplinks.
Port Configuration
To configure a port, you must specify the slot (0-5; default: 0) and port number (1 to 56) in the interface
port-type slot/port command, where slot is the unit number of the Aggregator displayed in the show
system brief command; for example:
FTOS(conf)# interface tengigabitethernet 0/4
Getting Started | 21
Page 36

Figure 4-2. Port Numbering on an Aggregator
2-Port 40-GbE QSFP+ FlexIO
Module (4x10GbE mode):
Ports 53 to 56 (top port)
Ports 49 to 52 (bottom port)
2-Port 40-GbE QSFP+ FlexIO
Module (4x10GbE mode):
Ports 45 to 48 (top port)
Ports 41 to 44(bottom port)
www.dell.com | support.dell.com
4-Port 10-GbE SFP+ or
4-Port 10GBASE-T FlexIO Module:
Ports 49 to 52 (4x10GbE mode)
4-Port 10-GbE SFP+ or
4-Port 10GBASE-T FlexIO Module:
Ports 41 to 44 (4x10GbE mode)
40GbE QSFP+ Port 37 (stacking)
or
Ports 37 to 40 (4x10GbE mode)
40GbE QSFP+ Port 33 (stacking)
or
Ports 33 to 36 (4x10GbE mode)
Console access
The Aggregator has two management ports available for system access: a serial console port and an
out-of-bounds (OOB) port.
Serial Console
A universal serial bus (USB) (A-Type) connector is located on the front panel. The USB can be defined as
an External Serial Console (RS-232) port, and is labeled on the Aggregator. The USB is on the lower side
of an installed Aggregator, as you face the I/O side of the M1000e chassis (Figure 4-1). For the console
port piMnout, refer to Table 4-1.
To access the console port, follow these steps.
Step Task
1 Connect the USB connector to the front panel. Use the RS-232 Serial Line cable to connect the Aggregator
console port to a terminal server.
2 Connect the other end of the cable to the DTE terminal server.
22 | Getting Started
Page 37

Step Task (continued)
Note: Terminal settings on the console port cannot be changed in the software and are set as follows:
• 9600 baud rate
• No parity
• 8 data bits
• 1 stop bit
• No flow control
External Serial Port with a USB Connector
Table 4-1 lists the pin assignments.
Table 4-1. Pin Assignments
USB Pin Number Signal Name
Pin 1 RTS
Pin 2 RX
Pin 3 TX
Pin 4 CTS
Pin 5, 6 GND
RxD Chassis GND
Boot Process
After you follow the instructions in the Installation Procedur e in the Getting Started Guide, the Aggregator
boots up. The Aggregator with FTOS version 8.3.17.0 requires boot flash version 4.0.1.0 and boot selector
version 4.0.0.0. Figure 4-3 through Figure 4-7 show the completed boot process.
Getting Started | 23
Page 38

Figure 4-3. Completed Boot Process
syncing disks... done
unmounting file systems...
unmounting /f10/flash (/dev/ld0e)...
unmounting /usr (mfs:31)...
unmounting /lib (mfs:23)...
unmounting /f10 (mfs:20)...
unmounting /tmp (mfs:15)...
unmounting /kern (kernfs)...
unmounting / (/dev/md0a)... done
rebooting...
þ
NetLogic XLP Stage 1 Loader
Built by build at tools-sjc-01 on Fri Mar 16 9:03:43 2012
Navasota IOM Boot Selector Label 4.0.0.0bt
www.dell.com | support.dell.com
##############################################
# #
# x-loader: for Navasota board #
# #
##############################################
Nodes online: 1
GPIO 22 init'ed as an output
GPIO 23 init'ed as an output
I2C0 speed = 30 KHz, prescaler = 0x0377.
Initialized I2C0 Controller.
I2C1 speed = 100 KHz, prescaler = 0x0109.
Initialized I2C1 Controller.
DDR SPD: Node 0 Channel 0 Mem size = 2048 MB
DDR SPD: Node 0 DRAM frequency 666 MHz
DDR SPD: Node 0 CPU frequency 1200 MHz
RTT Norm:44
NBU0 DRAM BAR0 base: 00000000 limit: 0013f000 xlate: 00000001 node: 00000000 ( 0 MB -> 320 MB,
size: 320 MB)
NBU0 DRAM BAR1 base: 001d0000 limit: 0088f000 xlate: 00090001 node: 00000000 ( 464 MB -> 2192 MB,
size: 1728 MB)
Modifying Default Flash Address map..Done
Initialized e.MMC Host Controller
Detected SD Card
BLC is 1 (preset 10)
Hit any key to stop autoboot: 0
F10 Boot Image selection
Reading the Boot Block Info...Passed !!
Images are OK A:0x0 B:0x0
Boot Selector set to Bootflash Partition A image...
Verifying Copyright Information..success for Image - 0
Boot Selector: Booting Bootflash Partition A image...
Copying stage-2 loader from 0xb6120000 to 0x8c100000(size = 0x100000)
F10 Boot Image selection DONE.
## Starting application at 0x8C100000 ...
U-Boot 2010.03-rc1(Dell Force10)
Built by antonyr at login-sjc-05 on Wed May 2 0:57:04 2012
Navasota IOM Boot Label 4.0.1.0bt
DRAM: 2 GB
24 | Getting Started
Page 39

Figure 4-4. Completed Boot Process (Contd.)
##########################################
# #
# u-boot: for Navasota board #
# #
##########################################
Initialized CPLD on CS3
Detected [XLP308 (Lite) Rev A0]
CPLD reg 06 val 0xf7
This is a NAVASOTA ...
Initializing I2C0: speed = 30 KHz, prescaler = 0x0377 -- done.
Initializing I2C1: speed = 100 KHz, prescaler = 0x0109 -- done.
Initialized eMMC Host Controller
Detected SD Card
Now running in RAM - U-Boot [N64 ABI, Big-Endian] at: ffffffff8c100000
Flash: 256 MB
PCIE (B0:D01:F0) : Link up.
In: serial
Out: serial
Err: serial
Net: nae-0: PHY is Broadcom BCM54616S
--More--
RELEASE IMAGE HEADER DATA :
--------------------------
--More--
SOFTWARE IMAGE HEADER DATA :
----------------------------
--More-Starting Dell Force10 application
00:00:15: %STKUNIT0-M:CP %RAM-6-ELECTION_ROLE: Stack unit 0 is transitioning to Management unit.
00:00:16: %STKUNIT0-M:CP %CHMGR-5-STACKUNITDETECTED: Stack unit 0 present
00:00:18: %STKUNIT0-M:CP %CHMGR-5-CHECKIN: Checkin from Stack unit 0 (type I/O-Aggregator, 56 ports)
00:00:18: %I/O-Aggregator:0 %LCMGR-5-IOM_STATE: Switch status of stack-unit 0 is set to Good
00:00:18: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed uplink state group Admin state to up: Group 1
00:00:18: %STKUNIT0-M:CP %CHMGR-5-STACKUNITUP: Stack unit 0 is up
00:00:20: %STKUNIT0-M:CP %CHMGR-5-SYSTEM_READY: System ready
00:00:20: %STKUNIT0-M:CP %IFMGR-5-OSTATE_UP: Changed interface state to up: Ma 0/0
00:00:22: %I/O-Aggregator:0 %POLLMGR-2-MODULE_POWER_STATE: Module 0 in unit 0 changed to POWER GOOD
state
00:00:23: %STKUNIT0-M:CP %CHMGR-0-TEMP_STATUS_CHANGE: Unit 0 temperature state changed to 1.
00:00:24: %STKUNIT0-M:CP %RAM-5-STACK_STATE: Stack unit 0 is in Active State.
00:00:25: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_QSFP: Optics QSFP inserted in slot 0 port 33
00:00:25: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_QSFP: Optics QSFP inserted in slot 0 port 34
00:00:25: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_QSFP: Optics QSFP inserted in slot 0 port 35
00:00:26: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_QSFP: Optics QSFP inserted in slot 0 port 36
00:00:26: %STKUNIT0-M:CP %CHMGR-5-MODULE_INSERTED: SFP+ module has been inserted in stack-unit 0
optional slot 0
00:00:27: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_PLUS: Optics SFP+ inserted in slot 0 port 41
00:00:28: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_PLUS: Optics SFP+ inserted in slot 0 port 42
00:00:28: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_PLUS: Optics SFP+ inserted in slot 0 port 43
00:00:28: %I/O-Aggregator:0 %IFAGT-5-INSERT_OPTICS_PLUS: Optics SFP+ inserted in slot 0 port 44
Getting Started | 25
Page 40

Figure 4-5. Completed Boot Process (Contd.)
FTOS>00:00:30: %STKUNIT0-M:CP %IFMGR-5-IFM_ISCSI_ENABLE: iSCSI has been enabled causing flow control
to be enabled on all interfaces. EQL detection and enabling iscsi profile-compellent on an interface
may cause some automatic configurations to occur like jumbo frames on all ports and no storm control
on the port of detection
00:00:30: %STKUNIT0-M:CP %SEC-5-LOGIN_SUCCESS: Login successful for user on line console
00:00:31: %STKUNIT0-M:CP %SNMP-6-SNMP_WARM_START: Agent Initialized - SNMP WARM_START.
00:00:31: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Changed uplink state group state to down: Group 1
00:00:32: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/1
00:00:32: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/1
00:00:43: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/2
00:00:44: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/2
00:00:44: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/3
00:00:44: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/3
00:00:45: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/4
00:00:45: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/4
00:00:45: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/5
www.dell.com | support.dell.com
00:00:45: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/5
00:00:46: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/6
00:00:46: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/6
00:00:46: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/7
00:00:46: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/7
00:00:47: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/8
00:00:47: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/8
00:00:47: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/9
00:00:47: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/9
00:00:48: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/10
00:00:48: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/10
00:00:48: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/11
00:00:48: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/11
00:00:49: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/12
00:00:49: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/12
00:00:49: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/13
00:00:50: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/13
00:00:50: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/14
00:00:50: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/14
00:00:51: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/15
00:00:51: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/15
00:00:51: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/16
00:00:51: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/16
00:00:52: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/17
00:00:52: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/17
00:00:52: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/18
00:00:52: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/18
00:00:52 : IO-AGG [Active]: Informing IOM booted successfully to CMC : Passed
00:00:53: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/19
00:00:53: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/19
00:00:53: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/20
00:00:53: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/20
00:00:54: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/21
00:00:54: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/21
00:00:54: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/22
00:00:55: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/22
00:00:55: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/23
00:00:55: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/23
00:00:56: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/24
00:00:56: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/24
00:00:56: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/25
00:00:56: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/25
00:00:57: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/26
00:00:57: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/26
00:00:57: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/27
00:00:57: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/27
00:00:58: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/28
00:00:58: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/28
26 | Getting Started
Page 41

Figure 4-6. Completed Boot Process (Contd.)
00:00:59: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/29
00:00:59: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/30
00:00:59: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/30
00:01:00: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/31
00:01:00: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/31
00:01:00: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/32
00:01:00: %STKUNIT0-M:CP %IFMGR-5-OSTATE_DN: Downstream interface set to UFD error-disabled: Te 0/32
00:01:01: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/33
00:01:01: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/34
00:01:02: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/35
00:01:03: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides
theconfiguration of ETS Recommend TLV transmitstatus: Te 0/33
00:01:03: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/34
00:01:03: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/35
00:01:03: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/36
00:01:03: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/37
00:01:04: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/36
00:01:04: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/37
00:01:04: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/38
00:01:04: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/38
00:01:04: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/39
00:01:04: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/40
00:01:04: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/39
00:01:04: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/40
00:01:05: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/41
00:01:05: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/41
00:01:05: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/42
00:01:06: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/43
00:01:06: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/42
00:01:06: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/43
00:01:06: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/44
00:01:07: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/44
00:01:07: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/45
0:01:07: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/46
00:01:08: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/45
00:01:08: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/46
00:01:08: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/47
00:01:08: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/47
00:01:09: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/48
00:01:09: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/48
00:01:09: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/49
00:01:09: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/50
00:01:10: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/49
00:01:10: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/50
00:01:10: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/51
00:01:10: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/51
00:01:10: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/52
00:01:10: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/53
00:01:11: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/52
00:01:11: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/53
Getting Started | 27
Page 42

Figure 4-7. Completed Boot Process (Contd.)
00:01:11: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/54
00:01:11: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/54
00:01:11: %STKUNIT0-M:CP %IFMGR-5-ASTATE_UP: Changed interface Admin state to up: Te 0/54
00:01:11: %STKUNIT0-M:CP %DIFFSERV-4-DSM_DCBX_ETS_RECO_TX_OVERRIDE: Port Role Change overrides the
configuration of ETS Recommend TLV transmitstatus: Te 0/54
Configure a Host Name
The host name appears in the prompt. The default host name is FTOS.
www.dell.com | support.dell.com
• Host names must start with a letter and end with a letter or digit.
• Characters within the string can be letters, digits, and hyphens.
To configure a host name, follow this steps:
Step Task Command Syntax Command Mode
1 Create a new host name.
Figure 4-8 shows the
hostname command.
Figure 4-8. Configuring a Hostname
Default Hostname
FTOS(conf)#hostname R1
R1(conf)#
New Hostname
Access the System Remotely
You can configure the system to access it remotely by Telnet. The Aggregator has a dedicated management
port and a management routing table that is separate from the IP routing table.
hostname name
CONFIGURATION
28 | Getting Started
Page 43

Access the Aggregator Remotely
Configuring the Aggregator for Telnet access is a three-step process:
1. Configure an IP address for the management port. Refer to Configure the Management Port IP
Address.
2. Configure a management route with a default gateway. Refer to Configure a Management Route.
3. Configure a username and password. Refer to Configure a Username and Password.
Configure the Management Port IP Address
Assign IP addresses to the management ports in order to access the system remotely. To configure the
management port IP address, follow these steps:
Step Task Command Syntax Command Mode
1 Enter INTERFACE mode for the
Management port.
2
3
Assign an IP address to the
interface.
Enable the interface.
interface ManagementEthernet slot/port
• slot: 0
• port: 0
ip address ip-address/mask
• ip-address: an address in dotted-decimal format
(A.B.C.D).
• mask: a subnet mask in /prefix-length format (/
xx).
no shutdown
CONFIGURATION
INTERFACE
INTERFACE
You can also configure a management port to acquire its IP address dynamically from a DHCP server by
using the
Task Command Syntax Command Mode
Acquire an IP address from the DHCP
server.
ip address dhcp command:
ip address dhcp INTERFACE
Getting Started | 29
Page 44

Configure a Management Route
Define a path from the system to the network from which you are accessing the system remotely.
Management routes are separate from IP routes and are only used to manage the system through the
management port.
To configure a management route, follow this step:
Step Task Command Syntax Command Mode
Configure a management route to
1
the network from which you are
www.dell.com | support.dell.com
accessing the system.
Configure a Username and Password
Configure a system username and password to access the system remotely.
To configure a username and password, follow this step:
Step Task Command Syntax Command Mode
Configure a username and
1
password to access the system
remotely.
management route ip-address/mask gateway
• ip-address: the network address in
dotted-decimal format (A.B.C.D).
mask: a subnet mask in /prefix-length format (/
•
xx).
•
gateway: the next hop for network traffic
originating from the management port.
username username password [encryption-type]
password
encryption-type
password, is 0 by default, and is not required.
• 0 is for inputting the password in clear text.
• 7 is for inputting a password that is already
encrypted using a Type 7 hash. Obtaining the
encrypted password from the configuration of
another Dell Force10 system.
specifies how you are inputting the
CONFIGURATION
CONFIGURATION
Configure the Enable Password
Access EXEC Privilege mode using the enable command. EXEC Privilege mode is unrestricted by default.
Configure a password as a basic security measure. There are two types of
•
enable password stores the password in the running/startup configuration using a DES encryption
method.
•
enable secret is stored in the running/startup configuration in using a stronger , MD5 encryption method.
30 | Getting Started
enable passwords:
Page 45

Dell Force10 recommends using the enable secret password.
To configure an enable password:
Task Command Syntax Command Mode
Create a password to
access EXEC Privilege
mode.
enable [password | secret] [level level] [encryption-type] password
is the privilege level, is 15 by default, and is not required.
level
encryption-type specifies how you are inputting the password, is 0 by
default, and is not required.
• 0 is for inputting the password in clear text.
• 7 is for inputting a password that is already encrypted using a
DES hash. Obtain the encrypted password from the configuration
file of another Dell Force10 system. Can be used only for enable
password.
• 5 is for inputting a password that is already encrypted using an
MD5 hash. Obtain the encrypted password from the configuration
file of another Dell Force10 system. Can be used only for enable
secret password.
Configuration File Management
You can store on and access files from various storage media. Rename, delete, and copy files on the system
from EXEC Privilege mode.
Note: Using flash memory cards in the system that have not been approved by Dell Force10 can cause
unexpected system behavior, including a reboot.
CONFIGURATION
Copy Files to and from the System
The command syntax for copying files is similar to UNIX. The copy command uses the format copy
source-file-url destination-file-url.
Note: For a detailed description of the copy command, refer to the FTOS Command Reference Guide.
Getting Started | 31
Page 46

• To copy a local file to a remote system, combine the file-origin syntax for a local file location with the
file-destination syntax for a remote file location (Table 4-2).
• To copy a remote file to a Dell Force10 system, combine the
with the
Table 4-2. Forming a copy Command
Local File Location
Internal flash:
file-destination syntax for a local file location (Table 4-2).
source-file-url Syntax destination-file-url Syntax
file-origin syntax for a remote file location
flash
USB flash:
www.dell.com | support.dell.com
usbflash
copy flash://filename flash://filename
usbflash://filename usbflash://filename
Remote File Location
FTP server copy ftp://username:password@{hostip |
hostname}
/filepath/filename
TFTP server copy tftp://{hostip | hostname}/filepath/
filename
SCP server copy scp://username:password@{hostip |
hostname}
/filepath/filename
Important Points to Remember
• You may not copy a file from one remote system to another.
• You may not copy a file from one location to the same location.
• When copying to a server, you can only use a hostname if a DNS server is configured.
Figure 4-9 shows an example of using the
Figure 4-9. Copying a file to a Remote System
ftp://username:password@{hostip
filepath/filename
tftp://{hostip | hostname}/filepath/filename
scp://username:password@{hostip
filepath/filename
copy command to save a file to an FTP server.
| hostname}/
| hostname}/
Local Location
FTOS#copy flash://FTOS-EF-8.2.1.0.bin ftp://myusername:mypassword@10.10.10.10//FTOS/FTOS-EF-8.2.1.0
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
27952672 bytes successfully copied
32 | Getting Started
Remote Location
Page 47

Figure 4-10 shows an example of using the copy command to import a file to the Dell Force10 system from
an FTP server.
Figure 4-10. Copying a file from a Remote System
Remote Location
Local Location
FTOS#copy ftp://myusername:mypassword@10.10.10.10//FTOS/FTOS-EF-8.2.1.0.bin flash://
Destination file name [FTOS-EF-8.2.1.0.bin.bin]:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
26292881 bytes successfully copied
Save the Running-Configuration
The running-configuration contains the current system configuration. Dell Force10 recommends copying
your running-configuration to the startup-configuration. The system uses the startup-configuration during
boot-up to configure the system. The startup-configuration is stored in the internal flash on the IOM by
default, but you can save the startup-configuration to a USB flash device or on a remote server.
To save the running-configuration:
Task Command Syntax Command Mode
Save re-configured settings to the
write memory
CONFIGURATION
startup configuration.
Note: The following commands are the same format as those in Copy Files to and from the System on
page 31 but use the filenames startup-config and running-config. These commands assume that current
directory is the internal flash, which is the system default.
Task Command Syntax Command Mode
Save the running-configuration to:
the startup-configuration on the
internal flash
the usb flash on the IOM copy running-config usbflash://filename
an FTP server
a TFTP server copy running-config tftp://{hostip | hostname}/filepath/
copy running-config startup-config
copy running-config ftp://
username:password@{hostip
filename
filename
| hostname}/filepath/
EXEC Privilege
EXEC Privilege
EXEC Privilege
EXEC Privilege
Getting Started | 33
Page 48

Task Command Syntax Command Mode
an SCP server
Note: When copying to a server, you can only use a hostname if a DNS server is configured.
View Files
You can only view file information and content on local file systems.
www.dell.com | support.dell.com
To view a list of files on the internal or external Flash, follow this step:
Step Task Command Syntax Command Mode
1 View a list of files on:
the internal flash
the usbflash
The output of the command
modification for each file (Figure 4-11).
copy running-config scp://
username:password@{hostip
filename
dir flash:
dir usbflash:
dir also shows the read/write privileges, size (in bytes), and date of
| hostname}/filepath/
EXEC Privilege
EXEC Privilege
EXEC Privilege
Figure 4-11. Viewing a List of Files in the Internal Flash
FTOS#dir
Directory of flash:
1 drwx 4096 Jan 01 1980 00:00:00 +00:00 .
2 drwx 2048 Jul 24 2012 09:46:34 +00:00 ..
3 drwx 4096 Apr 03 2012 20:25:02 +00:00 TRACE_LOG_DIR
4 drwx 4096 Apr 03 2012 20:25:02 +00:00 CORE_DUMP_DIR
5 d--- 4096 Apr 03 2012 20:25:02 +00:00 ADMIN_DIR
6 -rwx 506724352 Apr 19 2012 23:32:02 +00:00 out3
7 -rwx 715651180 Apr 17 2012 23:17:30 +00:00 out1
8 -rwx 30670080 May 18 2012 04:42:06 +00:00 FTOS-nav_ascii.bin
9 -rwx 76 May 02 2012 05:37:42 +00:00 dhcpBindConflict
10 -rwx 1 Jul 06 2012 07:30:44 +00:00 testhttp
11 -rwx 56839 May 17 2012 01:05:24 +00:00 writefru
12 -rwx 150227 Jun 07 2012 16:57:24 +00:00 aaa
13 -rwx 150227 Jun 07 2012 17:31:52 +00:00 bbb
14 -rwx 561 Jun 26 2012 06:36:46 +00:00 jumpstartcfg
15 -rwx 149553 Jul 04 2012 04:27:48 +00:00 startup-config.bak
--More--
34 | Getting Started
Page 49

To view the contents of a file, follow this step:
Step Task Command Syntax Command Mode
1 View the:
contents of a file in the internal flash
contents of a file in the usb flash
running-configuration
startup-configuration
show file flash://filename
show file usbflash://filename
show running-config
show startup-config
EXEC Privilege
EXEC Privilege
EXEC Privilege
EXEC Privilege
View Configuration Files
Configuration files have three commented lines at the beginning of the file (Figure 4-12), to help you track
the last time any user made a change to the file, which user made the change(s), and when the file was last
saved to the startup-configuration.
In the running-configuration file, if there is a difference between the timestamp on the “Last configuration
change,” and “Startup-config last updated,” you have made changes that have not been saved and will not
be preserved upon a system reboot.
Figure 4-12. Tracking Changes with Configuration Comments
FTOS#show running-config
Current Configuration ...
! Version E8-3-17-38
! Last configuration change at Tue Jul 24 20:33:08 2012 by default
!
boot system stack-unit 1 primary tftp://10.11.9.21/dv-m1000e-2-b2
boot system stack-unit 1 default system: A:
boot system gateway 10.11.209.62
!
redundancy auto-synchronize full
!
service timestamps log datetime
!
hostname FTOS
!
--More--
Getting Started | 35
Page 50

File System Management
The Dell Force10 system can use the internal Flash, USB Flash, or remote devices to store files. The
system stores files on the internal Flash by default, but you can configure it to store files elsewhere.
To view file system information:
Task Command Syntax Command Mode
View information about each file system.
The output of the
www.dell.com | support.dell.com
memory, file structure, media type, and read/write privileges for each storage device in use.
show file-systems command (Figure 4-13) shows the total capacity, amount of free
Figure 4-13. show file-systems Command Example
FTOS#show file-systems
Size(b) Free(b) Feature Type Flags Prefixes
2143281152 836878336 FAT32 USERFLASH rw flash:
- - - network rw ftp:
- - - network rw tftp:
- - - network rw scp:
FTOS#
You can change the default file system so that file management commands apply to a particular device or
memory.
To change the default storage location:
Task Command Syntax Command Mode
show file-systems
EXEC Privilege
Change the default directory.
You can change the default storage location to the USB Flash (Figure 4-14). File management commands
then apply to the USB Flash rather than the internal Flash.
36 | Getting Started
cd directory
EXEC Privilege
Page 51

Figure 4-14. Alternative Storage Location
FTOS#cd usbflash:
FTOS#copy running-config test
!
3998 bytes successfully copied
FTOS#dir
Directory of usbflash:
1 drwx 4096 Jan 01 1980 00:00:00 +00:00 .
2 drwx 2048 May 02 2012 07:05:06 +00:00 ..
3 -rwx 1272 Apr 29 2011 16:15:14 +00:00 startup-config
4 -rwx 3998 May 11 2011 23:36:12 +00:00 test
View the Command History
The command-history trace feature captures all commands entered by all users of the system with a time
stamp and writes these messages to a dedicated trace log buffer. The system generates a trace message for
each executed command. No password information is saved to the file.
No File System Specified
File Saved to USB Flash
To view the command-history trace, use the
show command-history command (Figure 4-15).
Figure 4-15. show command-history Command Example
FTOS# show command-history
[5/18 21:58:32]: CMD-(TEL0):[enable]by admin from vty0 (10.11.68.5)
[5/18 21:58:48]: CMD-(TEL0):[configure]by admin from vty0 (10.11.68.5)
- Repeated 1 time.
[5/18 21:58:57]: CMD-(TEL0):[interface port-channel 1]by admin from vty0 (10.11.68.5)
[5/18 21:59:9]: CMD-(TEL0):[show config]by admin from vty0 (10.11.68.5)
[5/18 22:4:32]: CMD-(TEL0):[exit]by admin from vty0 (10.11.68.5)
[5/18 22:4:41]: CMD-(TEL0):[show interfaces port-channel brief]by admin from vty0
(10.11.68.5)
Upgrading and Downgrading FTOS
Note: To upgrade or downgrade FTOS, refer to the Release Notes for the FTOS version you want to load
on the Aggregator.
Getting Started | 37
Page 52

www.dell.com | support.dell.com
38 | Getting Started
Page 53

Aggregator Management
This chapter explains the different protocols or services used to manage an Aggregator including:
• Logging
• Disabling System Logging
• File Transfer Services
• Terminal Lines
• Telnet to Another Network Device
• Recovering from a Forgotten Password
• Recovering from a Forgotten Enable Password
• Recovering from a Failed Start
5
Logging
FTOS tracks changes in the system using event and error messages. By default, FTOS logs these messages
on:
• the internal buffer
• console and terminal lines
• any configured syslog servers
Log Messages in the Internal Buffer
All error messages, except those beginning with %BOOTUP (Message), are logged in the internal buffer.
Message 1 BootUp Events
%BOOTUP:RPM0:CP %PORTPIPE-INIT-SUCCESS: Portpipe 0 enabled
Aggregator Management | 39
Page 54

Disabling System Logging
By default, logging is enabled and log messages are sent to the logging buffer, all terminal lines, console,
and syslog servers.
To enable and disable system logging:
Task Command Syntax Command Mode
Disable all logging except on the console.
Disable logging to the logging buffer.
www.dell.com | support.dell.com
Disable logging to terminal lines.
Disable console logging.
Send System Messages to a Syslog Server
To send system messages to a syslog server:
Task Command Syntax Command Mode
Specify the server to which you want to send system
messages. You can configure up to eight syslog servers.
Using a Unix System as a Syslog Server
Configure a UNIX system as a syslog server by adding the following lines to /etc/syslog.conf on the Unix
system and assigning write permissions to the file.
no logging on
no logging buffer
no logging monitor
no logging console
logging {ip-address | hostname} CONFIGURATION
CONFIGURATION
CONFIGURATION
CONFIGURATION
CONFIGURATION
• on a 4.1 BSD UNIX system, add the line: local7.debugging /var/log/log7.log
• on a 5.7 SunOS UNIX system, add the line: local7.debugging /var/adm/ftos.log
In the lines above, local7 is the logging facility level and debugging is the severity level.
40 | Aggregator Management
Page 55

Changing System Logging Settings
You can change the default settings of the system logging by changing the severity level and the storage
location. The default is to log all messages up to debug level, that is, all system messages. By changing the
severity level in the logging commands, you control the number of system messages logged.
To change the severity level of messages logged to a syslog server, use any or all of the following
commands in CONFIGURATION mode:
Task Command Syntax Command Mode
Specify the minimum severity level for logging to the
logging buffer.
Specify the minimum severity level for logging to the
console.
Specify the minimum severity level for logging to
terminal lines.
Specifying the minimum severity level for logging to a
syslog server.
Specify the minimum severity level for logging to the
syslog history table.
Task Command Syntax Command Mode
Specify the size of the logging buffer.
Note: When you decrease the buffer size, FTOS deletes
all messages stored in the buffer. Increasing the buffer
size does not affect messages in the buffer.
Specify the number of messages that FTOS saves to its
logging history table.
logging buffered level CONFIGURATION
logging console level
logging monitor level
logging trap level
logging history level
logging buffered size CONFIGURATION
logging history size size
CONFIGURATION
CONFIGURATION
CONFIGURATION
CONFIGURATION
CONFIGURATION
To view the logging buffer and configuration, enter the
(Figure 5-1).
To view the logging configuration, enter the
(Figure 5-2).
show logging command in EXEC privilege mode
show running-config logging command in EXEC privilege mode
Aggregator Management | 41
Page 56

Displaying the Logging Buffer and Logging Configuration
T o display the current contents of the logging buf fer and the logging settings for the system, enter the show
logging
command in EXEC privilege mode (Figure 5-1).
Figure 5-1. show logging Command Example
FTOS#show logging
Syslog logging: enabled
Console logging: level debugging
Monitor logging: level debugging
Buffer logging: level debugging, 58 Messages Logged, Size (40960 bytes)
Trap logging: level informational
Logging to 172.31.1.4
www.dell.com | support.dell.com
Logging to 172.16.1.162
Logging to 133.33.33.4
Logging to 10.10.10.4
Logging to 10.1.2.4
May 20 20:00:10: %STKUNIT0-M:CP %SYS-5-CONFIG_I: Configured from vty0 ( 10.11.68
.5 )by admin
May 20 19:57:45: %STKUNIT0-M:CP %SEC-3-AUTHENTICATION_ENABLE_SUCCESS: Enable pas
sword authentication success on vty0 ( 10.11.68.5 )
May 20 19:57:40: %STKUNIT0-M:CP %SEC-5-LOGIN_SUCCESS: Login successful for user
admin on vty0 (10.11.68.5)
May 20 19:37:08: %STKUNIT0-M:CP %SEC-5-LOGOUT: Exec session is terminated for us
er admin on line vty0 (10.11.68.5)
May 20 18:59:36: %STKUNIT0-M:CP %SYS-5-CONFIG_I: Configured from vty0 ( 10.11.68
.5 )by admin
May 20 18:45:44: %STKUNIT0-M:CP %SEC-3-AUTHENTICATION_ENABLE_SUCCESS: Enable pas
sword authentication success on vty0 ( 10.11.68.5 )
May 20 18:45:39: %STKUNIT0-M:CP %SEC-5-LOGIN_SUCCESS: Login successful for user
admin on vty0 (10.11.68.5)
May 20 17:18:08: %STKUNIT0-M:CP %SEC-5-LOGOUT: Exec session is terminated for us
er admin on line vty0 (10.11.68.5)
May 20 16:42:40: %STKUNIT0-M:CP %SYS-5-CONFIG_I: Configured from vty0 ( 10.11.68
.5 )by admin
- repeated 2 times
May 20 16:37:41: %STKUNIT0-M:CP %SEC-3-AUTHENTICATION_ENABLE_SUCCESS: Enable pas
sword authentication success on vty0 ( 10.11.68.5 )
May 20 16:37:28: %STKUNIT0-M:CP %SEC-5-LOGIN_SUCCESS: Login successful for user
admin on vty0 (10.11.68.5)
May 20 16:37:17: %STKUNIT0-M:CP %SEC-5-LOGOUT: Exec session is terminated for us
er admin on line vty0 (10.11.68.5)
May 20 16:37:08: %STKUNIT0-M:CP %SEC-3-AUTHENTICATION_ENABLE_SUCCESS: Enable pas
sword authentication success on vty0 ( 10.11.68.5 )
sword authentication success on vty0 ( 10.11.68.5 )
--More--
To view any changes made, use the show running-config logging command (Figure 5-2) in the EXEC
privilege mode.
42 | Aggregator Management
Page 57

Configuring a UNIX Logging Facility Level
You can save system log messages with a UNIX system logging facility.
To configure a UNIX logging facility level, use the following command in CONFIGURATION mode:
Command Syntax Command Mode Purpose
logging facility [facility-type]
CONFIGURATION Specify one of the following parameters.
• auth (for authorization messages)
• cron (for system scheduler messages)
• daemon (for system daemons)
• kern (for kernel messages)
• local0 (for local use)
• local1 (for local use)
• local2 (for local use)
• local3 (for local use)
• local4 (for local use)
• local5 (for local use)
• local6 (for local use)
• local7 (for local use). This is the default.
• lpr (for line printer system messages)
• mail (for mail system messages)
• news (for USENET news messages)
• sys9 (system use)
• sys10 (system use)
• sys11 (system use)
• sys12 (system use)
• sys13 (system use)
• sys14 (system use)
• syslog (for syslog messages)
• user (for user programs)
• uucp (UNIX to UNIX copy protocol)
The default is local7.
To view non-default settings, use the
Figure 5-2. show running-config logging Command Example
FTOS#show running-config logging
!
service timestamps log datetime
!
logging 172.16.1.162
logging 10.10.10.4
logging 10.1.2.4
logging 172.31.1.4
logging 133.33.33.4
FTOS#
show running-config logging command (Figure 4-3) in EXEC mode.
Aggregator Management | 43
Page 58

Enabling Time Stamps on Syslog Messages
By default, syslog messages do not include a time/date stamp stating when the error or message was
created.
To have FTOS include a timestamp with the syslog message, use the following command syntax in
CONFIGURATION mode:
Command Syntax Command Mode Purpose
service timestamps [log | debug] [datetime
[localtime] [msec] [show-timezone] | uptime]
www.dell.com | support.dell.com
To view the configuration, enter the
To disable time stamping on syslog messages, enter the
File Transfer Services
With FTOS, you can configure the system to transfer files over the network using file transfer protocol
(FTP). One FTP application copies the system image files over an interface on to the system; however,
FTP is not supported on VLAN interfaces.
For more information about FTP, refer to RFC 959, File Transfer Protocol.
CONFIGURATION Add timestamp to syslog messages. Specify
the following optional parameters:
• datetime: You can add the keyword
localtime to include the localtime, msec,
and show-timezone. If you do not add the
keyword
• uptime. To view time since last boot.
If neither parameter is specified, FTOS
configures uptime.
show running-config logging command in EXEC privilege mode.
no service timestamps [log | debug] command.
localtime, the time is UTC.
Configuration Task List for File Transfer Services
The following list includes the configuration tasks for file transfer services:
• Enabling the FTP Server (mandatory)
• Configuring the FTP Server Parameters (optional)
For a complete listing of FTP related commands, refer to RFC 959, File Transfer Protocol.
44 | Aggregator Management
Page 59

Enabling the FTP Server
To enable the system as an FTP server, use the following command in CONFIGURATION mode:
Command Syntax Command Mode Purpose
ftp-server enable
To view the FTP configuration, enter the
CONFIGURATION Enable FTP on the system.
show running-config ftp command in EXEC privilege mode
(Figure 5-3).
Figure 5-3. show running-config ftp Command Example
FTOS#show running-config ftp
!
ftp-server enable
ftp-server username nairobi password 0 zanzibar
FTOS#
Configuring the FTP Server Parameters
After you enable the FTP server on the system, you can configure different parameters.
To configure FTP server parameters, use any or all of the following commands in CONFIGURATION
mode:
Command Syntax Command Mode Purpose
ftp-server topdir dir
ftp-server username username
password [encryption-type]
password
Note: You cannot use the change directory (cd) command until you configure ftp-server topdir.
To view the FTP configuration, enter the
CONFIGURATION Specify the directory for users using FTP to reach the
system.
The default is the internal flash directory.
CONFIGURATION Specify a user name for all FTP users and configure either
a plain text or encrypted password. Configure the
following optional and required parameters:
• username: Enter a text string
• encryption-type: Enter 0 for plain text or 7 for
encrypted text.
• password: Enter a text string.
show running-config ftp command in EXEC privilege mode.
Aggregator Management | 45
Page 60

Terminal Lines
You can access the system remotely and restrict access to the system by creating user profiles. The terminal
lines on the system provide different means of accessing the system. The virtual terminal lines (VTY)
connect you through Telnet to the system.
Telnet to Another Network Device
To telnet to another device (Figure 5-4):
www.dell.com | support.dell.com
Task Command Syntax Command Mode
T elnet to the stack-unit.You do not need to configure the management port
on the stack-unit to be able to telnet to it.
T elnet to a device with an IPv4 address. If you do not enter an IP address,
FTOS enters a Telnet dialog that prompts you for one.
• Enter an IPv4 address in dotted decimal format (A.B.C.D)
Figure 5-4. Telnet to Another Network Device
FTOS#telnet 10.11.206.66
Trying 10.11.206.66...
Connected to 10.11.206.66.
Exit character is '^]'.
cmc-9MZ0TS1.localdomain login: root
Password:
Welcome to the CMC firmware version 4.30.X03.201207271729
$
telnet-peer-stack-unit
telnet [ip-address]
EXEC Privilege
EXEC Privilege
46 | Aggregator Management
Page 61

Recovering from a Forgotten Password
If you configure authentication for the console and you exit out of EXEC mode or your console session
times out, you are prompted to re-enter the password.
If you forget your password, follow these steps:
Step Task Command Syntax Command Mode
1 Log onto the system using the console.
2 Power-cycle the Aggregator by using the CMC interface or removing it from the M1000e and re-inserting it in the
chassis.
3 During bootup, press any key during the second countdown to abort the boot process and access the uBoot
command-line interface. You are placed at the Boot User command prompt.
4 Set the system parameters to ignore
the startup configuration when the
system reloads.
5 Reload the system.
6 Copy startup-config.bak to the
running config.
7 Remove all authentication
parameters configured for the
console.
8 Save the running-config to the
startup-config.
Note: The startup configuration is ignored only the first time the Aggregator reloads. During subsequent
reloads, the startup configuration is loaded and its configured settings are applied.
ignore startup-config
reload
copy flash://startup-config.bak running-config
no authentication login
no password
copy running-config startup-config
Recovering from a Forgotten Enable Password
If you forget the enable password, follow these steps:
BOOT USER
BOOT USER
EXEC Privilege
LINE
EXEC Privilege
Step Task Command Syntax Command Mode
1 Log onto the system via console.
2 Power-cycle the Aggregator by using the CMC interface or removing it from the M1000e and re-inserting it in the
chassis.
3 During bootup, press any key during the second countdown to abort the boot process and access the uBoot
command-line interface. You are placed at the Boot User command prompt.
Aggregator Management | 47
Page 62

Step Task Command Syntax Command Mode
4 Set the system parameters to ignore
the enable password when the system
reloads.
5 Reload the system.
6 Configure a new enable password.
7 Configure a new enable password.
8 Save the running-config to the
startup-config.
www.dell.com | support.dell.com
Note: The enable password is ignored only the first time the Aggregator reloads. If you do not reconfigure
the enable password before the session times out, you will be placed in EXEC mode and prompted to
enter the enable password again.
Recovering from a Failed Start
An Aggregator that does not start correctly might be attempting to boot from a corrupted FTOS image or
from a mis-specified location. In that case, you can restart the system and interrupt the boot process to
point the system to another boot location.
ignore enable-password
reload
copy flash://startup-config.bak running-config
enable {secret | password)
copy running-config startup-config
BOOT USER
BOOT USER
EXEC Privilege
CONFIGURATION
EXEC Privilege
For more information about uBoot commands, refer to the Boot User chapter in the FTOS Command Line
Reference for the M IO Aggregator.
To recover from failed start, follow these steps:
Step Task Command Syntax Command Mode
1 Log onto the system via console.
2 Power-cycle the Aggregator by using the CMC interface or removing it from the M1000e and re-inserting it in the
chassis.
3 During bootup, press any key during the second countdown to abort the boot process and access the uBoot
command-line interface. You are placed at the Boot User command prompt.
4 Reconfigure the default image paths to
be used to load the primary FTOS
image when the system reloads.
5 Assign an IP address to the
management Ethernet interface.
6 Assign an IP address as the default
gateway for the system.
7 Reload the system.
boot change primary
interface management ethernet ip address
ip-address/mask
default-gateway ip-address
reload
BOOT USER
BOOT USER
BOOT USER
BOOT USER
48 | Aggregator Management
Page 63

Figure 5-5. Recovering from a Failed Start: Example
U-Boot 2010.03-rc1(Dell Force10)
Built by build at tools-sjc-01 on Thu May 31 23:53:38 2012
IOM Boot Label 4.0.1.0
DRAM: 2 GB
Initialized CPLD on CS3
Detected [XLP308 (Lite+) Rev A0]
Initializing I2C0: speed = 30 KHz, prescaler = 0x0377 -- done.
Initializing I2C1: speed = 100 KHz, prescaler = 0x0109 -- done.
Initialized eMMC Host Controller
Detected SD Card
Now running in RAM - U-Boot [N64 ABI, Big-Endian] at: ffffffff8c100000
Flash: 256 MB
PCIE (B0:D01:F0) : Link up.
PCIE (B0:D01:F1) : No Link.
In: serial
Out: serial
Err: serial
Net: nae-0: PHY is Broadcom BCM54616S
IOM MAC Addr: 00:1E:C9:F1:00:99
Hit any key to stop autoboot: 0
***** Welcome to Dell Force10 Boot Interface *****
Use "help" or "?" for more information.
BOOT_USER #
BOOT_USER # boot change primary
'-' = go to previous field; '.' = clear non-essential field
boot device : tftp
file name : IOA
Server IP address : 10.16.127.34
BOOT_USER #
BOOT_USER # interface management ethernet ip address 10.16.130.149/16
Management ethernet IP address: 10.16.130.149/16
BOOT_USER #
BOOT_USER # default-gateway 10.16.130.254
Gateway IP address 10.16.130.254
BOOT_USER #
BOOT_USER # reload
NetLogic XLP Stage 1 Loader
Built by build at tools-sjc-01 on Thu May 31 23:53:38 2012
IOM Boot Selector Label 4.0.0.0
Aggregator Management | 49
Page 64

www.dell.com | support.dell.com
50 | Aggregator Management
Page 65

Data Center Bridging (DCB)
On an Aggregator, data center bridging (DCB) features are auto-configured in standalone mode. You can
display information on DCB operation by using
Note: DCB features are not supported on an Aggregator in stacking mode.
This chapter describes the following data center bridging topics:
• Ethernet Enhancements in Data Center Bridging
• Data Center Bridging: Auto-DCB-Enable Mode
• QoS dot1p Traffic Classification and Queue Assignment
• How Priority-Based Flow Control is Implemented
• How Enhanced Transmission Selection is Implemented
• DCB Policies in a Switch Stack
• DCBX Operation
• Verifying DCB Configuration
• Example: PFC and ETS Operation
show commands.
6
Ethernet Enhancements in Data Center Bridging
Data center bridging (DCB) refers to a set of IEEE Ethernet enhancements that provide data centers with a
single, robust, converged network to support multiple traffic types, including local area network (LAN),
server, and storage traffic. Through network consolidation, DCB results in reduced operational cost,
simplified management, and easy scalability by avoiding the need to deploy separate application-specific
networks.
For example, instead of deploying an Ethernet network for LAN traffic, additional storage area networks
(SANs) to ensure lossless fibre-channel traffic, and a separate InfiniBand network for high-performance
inter-processor computing within server clusters, only one DCB-enabled network is required in a data
center. The Dell Force10 switches that support a unified fabric and consolidate multiple network
infrastructures use a single input/output (I/O) device called a converged network adapter (CNA).
A CNA is a computer input/output device that combines the functionality of a host bus adapter (HBA) with
a network interface controller (NIC). Multiple adapters on different devices for several traffic types are no
longer required.
Data Center Bridging (DCB) | 51
Page 66

Data center bridging satisfies the needs of the following types of data center traffic in a unified fabric:
• LAN traffic consists of a large number of flows that are generally insensitive to latency requirements,
while certain applications, such as streaming video, are more sensitive to latency . Ethernet functions as
a best-effort network that may drop packets in case of network congestion. IP networks rely on
transport protocols (for example, TCP) for reliable data transmission with the associated cost of greater
processing overhead and performance impact.
• Storage traffic based on Fibre Channel media uses the SCSI protocol for data transfer. This traffic
typically consists of large data packets with a payload of 2K bytes that cannot recover from frame loss.
To successfully transport storage traffic, data center Ethernet must provide no-drop service with
lossless links.
• Servers use InterProcess Communication (IPC) traffic within high-performance computing clusters to
www.dell.com | support.dell.com
share information. Server traffic is extremely sensitive to latency requirements.
To ensure lossless delivery and latency-sensitive scheduling of storage and service traffic and I/O
convergence of LAN, storage, and server traffic over a unified fabric, IEEE data center bridging adds the
following extensions to a classical Ethernet network:
• 802.1Qbb - Priority-based Flow Control (PFC)
• 802.1Qaz - Enhanced Transmission Selection (ETS)
• 802.1Qau - Congestion Notification
• Data Center Bridging Exchange (DCBX) protocol
Note: In FTOS version 8.3.17.x, only the PFC, ETS, and DCBX features are supported in data center
bridging.
Priority-Based Flow Control
In a data center network, priority-based flow control (PFC) manages large bursts of one traffic type in
multiprotocol links so that it does not affect other traffic types and no frames are lost due to congestion.
When PFC detects congestion on a queue for a specified priority, it sends a pause frame for the 802.1p
priority traffic to the transmitting device. In this way, PFC ensures that large amounts of queued LAN
traffic do not cause storage traffic to be dropped, and that storage traffic does not result in high latency for
high-performance computing (HPC) traffic between servers.
PFC enhances the existing 802.3x pause and 802.1p priority capabilities to enable flow control based on
802.1p priorities (classes of service). Instead of stopping all traffic on a link (as performed by the
traditional Ethernet pause mechanism), PFC pauses traffic on a link according to the 802.1p priority set on
a traffic type. You can create lossless flows for storage and server traffic while allowing for loss in case of
LAN traffic congestion on the same physical interface.
Figure 6-1 shows how PFC handles traffic congestion by pausing the transmission of incoming traffic with
dot1p priority 3.
52 | Data Center Bridging (DCB)
Page 67

Figure 6-1. Priority-Based Flow Control
PFC is implemented as follows in the Dell Force10 operating software (FTOS):
• PFC is supported on specified 802.1p priority traffic (dot1p 0 to 7) and is configured per interface.
However, only two lossless queues are supported on an interface: one for FCoE converged traffic and
one for SCSI storage traffic. You must configure the same lossless queues on all ports.
• PFC delay constraints place an upper limit on the transmit time of a queue after receiving a message to
pause a specified priority.
• By default, PFC is enabled on an interface with no dot1p priorities configured. You can configure the
PFC priorities if the switch negotiates with a remote peer using DCBX.
• During DCBX negotiation with a remote peer:
• If the negotiation succeeds and the port is in DCBX W illing mode to receive a peer configuration,
PFC parameters from the peer are used to configured PFC priorities on the port. If you enable the
link-level flow control mechanism on the interface, DCBX negotiation with a peer is not
performed.
• If the negotiation fails and PFC is enabled on the port, any user-configured PFC input policies are
applied. If no PFC input policy has been previously applied, the PFC default setting is used (no
priorities configured). If you do not enable PFC on an interface, you can enable the 802.3x
link-level pause function. By default, the link-level pause is disabled.
• PFC supports buffering to receive data that continues to arrive on an interface while the remote system
reacts to the PFC operation.
• PFC uses the DCB MIB IEEE802.1azd2.5 and the PFC MIB IEEE802.1bb-d2.2.
Enhanced Transmission Selection
Enhanced transmission selection (ETS) supports optimized bandwidth allocation between traffic types in
multiprotocol (Ethernet, FCoE, SCSI) links. ETS allows you to divide traffic according to its 802.1p
priority into different priority groups (traffic classes) and configure bandwidth allocation and queue
scheduling for each group to ensure that each traffic type is correctly scheduled and receives its required
bandwidth. For example, you can prioritize low-latency storage or server cluster traffic in a traffic class to
receive more bandwidth and restrict best-effort LAN traffic assigned to a different traffic class.
Data Center Bridging (DCB) | 53
Page 68

Although you can configure strict-priority queue scheduling for a priority group, ETS introduces flexibility
that allows the bandwidth allocated to each priority group to be dynamically managed according to the
amount of LAN, storage, and server traffic in a flow. Unused bandwidth in a priority-group is dynamically
allocated to other priority groups for which traffic is available to be scheduled. T raf fic is queued according
to its 802.1p priority assignment, while flexible bandwidth allocation and the configured queue-scheduling
for a priority group is supported.
Figure 6-2 shows how ETS allows you to allocate bandwidth when different traffic types are classed
according to 802.1p priority and mapped to priority groups.
Figure 6-2. Enhanced Transmission Selection
www.dell.com | support.dell.com
ETS uses the following traffic groupings to select multiprotocol traffic for transmission:
• Priority group: A group of 802.1p priorities used for bandwidth allocation and queue scheduling. All
802.1p priority traffic in a group should have the same traffic handling requirements for latency and
frame loss.
• Group ID: A 4-bit identifier assigned to each priority group. Valid values are from 0 to 7.
• Group bandwidth: Percentage of available bandwidth allocated to a priority group.
• Group transmission selection algorithm (TSA): Type of queue scheduling used by a priority group.
ETS is implemented as follows in FTOS:
• ETS supports groups of 802.1p priorities that have:
• PFC enabled or disabled
• No bandwidth limit or no ETS processing
• Bandwidth allocated by the ETS algorithm is made available after strict-priority groups are serviced. If
a priority group does not use its allocated bandwidth, the unused bandwidth is made available to other
priority groups.
• For ETS traffic selection, an algorithm is applied to priority groups using:
• Strict-priority shaping
• ETS shaping
Credit-based shaping is not supported.
• ETS uses the DCB MIB IEEE802.1azd2.5.
54 | Data Center Bridging (DCB)
Page 69

Data Center Bridging Exchange Protocol (DCBX)
The data center bridging exchange (DCBX) protocol is enabled by default on any switch on which PFC or
ETS are enabled. DCBX allows a switch to automatically discover DCB-enabled peers and exchange
configuration information. PFC and ETS use DCBX to exchange and negotiate parameters with peer
devices. DCBX capabilities include:
• Discovery of DCB capabilities on peer-device connections
• Determination of possible mismatch in DCB configuration on a peer link
• Configuration of a peer device over a DCB link
DCBX requires the link layer discovery protocol (LLDP) to provide the path to exchange DCB parameters
with peer devices. Exchanged parameters are sent in organizationally specific type, length, values (TLVs)
in LLDP data units. For more information, refer to the Link Layer Discovery Protocol (LLDP) chapter.
The following LLDP TLVs are supported for DCB parameter exchange:
• PFC parameters: PFC Configuration TLV and Application Priority Configuration TLV.
• ETS parameters: ETS Configuration TLV and ETS Recommendation TLV.
Data Center Bridging in a Traffic Flow
Figure 6-3 shows how DCB handles a traffic flow on an interface.
Figure 6-3. DCB PFC and ETS Traffic Handling
Ingress Traffic
Apply QoS traffic
classification using
dot1p priority and
map to queue
Egress Traffic
Map priority traffic
to ETS priority
groups
Apply ETS bandwidth
allocation and
scheduling to
priority-group traffic
Apply PFC no-drop handling
for lossless queues of
ingress priority traffic
Switching
Transmit ETS-handled
priority traffic
on egress queue
Data Center Bridging (DCB) | 55
Page 70

Data Center Bridging: Auto-DCB-Enable Mode
On an Aggregator in standalone mode, the default mode of operation for data center bridging on Ethernet
ports is auto-DCB-enable mode. In this mode, Aggregator ports detect whether peer devices support
converged enhanced Ethernet (CEE) or not, and enable DCBX and PFC or link-level flow control
accordingly:
• Interfaces come up with DCB disabled and link-level flow control enabled to control data transmission
between the Aggregator and other network devices (see Flow Control Using Ethernet Pause Frames).
When DCB is disabled on an interface, PFC, ETS, and DCBX are also disabled.
• When DCBX protocol packets are received, interfaces automatically enable DCB and disable
link-level flow control.
www.dell.com | support.dell.com
DCB is required for PFC, ETS, DCBX, and FCoE initialization protocol (FIP) snooping to operate.
Note: Normally, interfaces do not flap when DCB is automatically enabled.
DCB processes VLAN-tagged packets and dot1p priority values. Untagged packets are treated with a
dot1p priority of 0.
For DCB to operate effectively, ingress traffic is classified according to its dot1p priority so that it maps to
different data queues. The dot1p-queue assignments used on an Aggregator are shown in Table 6-1 in QoS
dot1p Traffic Classification and Queue Assignment.
When DCB is Disabled (Default)
By default, Aggregator interfaces operate with DCB disabled and link-level flow control enabled. When an
interface comes up, it is automatically configured with:
• Flow control enabled on input interfaces
• A DCB input policy with PFC disabled
• A DCB output policy with ETS disabled
Figure 6-4 shows a default interface configuration with DCB enabled and link-level flow control enabled.
When the first Aggregator interface with DCB disabled receives an LLDP packet with a DCBX TLV
advertisement, DCB is enabled on the interface and on all uplink interfaces.
56 | Data Center Bridging (DCB)
Page 71

Figure 6-4. show interfaces Command Example: DCB disabled and Flow Control enabled
FTOS#show interfaces tengigabitethernet 0/2
interface TenGigabitEthernet 0/2
mtu 12000
portmode hybrid
switchport
auto vlan
flowcontrol rx on tx off
dcb-policy input smux-dcb-in
dcb-policy output smux-dcb-out
!
protocol lldp
advertise management-tlv system-name
dcbx port-role auto-downstream
no shutdown
When DCB is Enabled
When a server-facing interface receives DCBX protocol packets, it automatically enables DCB and
disables link-level flow control. The DCB input and output policies and the flow control configuration are
removed as shown in Figure 6-5.
When no DCBX TLVs are received on a DCB-enabled interface for 180 seconds, DCB is automatically
disabled and flow control is re-enabled. When all 10GbE server-facing interfaces have DCB disabled,
DCB is also disabled on all 40GbE uplink interfaces.
Figure 6-5. show interfaces Command Example: DCB enabled and Flow Control disabled
FTOS#show interfaces tengigabitethernet 0/2
interface TenGigabitEthernet 0/2
mtu 12000
auto vlan
!
port-channel-protocol LACP
port-channel 1 mode active
!
protocol lldp
advertise management-tlv system-name
dcbx port-role auto-downstream
no shutdown
Lossless Traffic Handling
In auto-DCB-enable mode, Aggregator ports operate with the auto-detection of DCBX traffic. At any
moment, some ports may operate with link-level flow control while others operate with DCB-based PFC
enabled.
As a result, lossless traffic is ensured only if traffic ingresses on a PFC-enabled port and egresses on
another PFC-enabled port.
Lossless traffic is not guaranteed when it is transmitted on a PFC-enabled port and received on a link-level
flow control-enabled port, or transmitted on a link-level flow control-enabled port and received on a
PFC-enabled port.
Data Center Bridging (DCB) | 57
Page 72

Enabling DCB on Next Reload
To configure the Aggregator so that all interfaces come up with DCB enabled and flow control disabled,
use the
for DCB to be enabled on all interfaces. Internal PFC buffers are automatically configured.
Task Command Command Mode
dcb enable on-next-reload command. You must save the configuration change and reload the switch
Globally enable DCB on all interfaces
after next switch reload.
T o reconfigure the Aggregator so that all interfaces come up with DCB disabled and link-level flow control
www.dell.com | support.dell.com
enabled, use the no dcb enable on-next-reload command. You must save the configuration change and
reload the switch for DCB to be disabled on all interfaces. PFC buffer memory is automatically freed.
Enabling Auto-DCB-Enable Mode on Next Reload
To configure the Aggregator so that all interfaces come up in auto-DCB-enable mode with DCB disabled
and flow control enabled, use the
configuration change and reload the switch for auto-DCB-enable mode to be enabled on all interfaces.
Task Command Command Mode
Globally enable auto-detection of DCBX
and auto-enabling of DCB on all
interfaces after switch reload.
Figure 6-6. dcb enable auto-detect on-next-reload Command Example
FTOS#dcb enable auto-detect on-next-reload
dcb enable
on-next-reload
dcb enable aut-detect on-next-reload command. You must save the
dcb enable
auto-detect
on-next-reload
CONFIGURATION
CONFIGURATION
Aug 25 18:47:50: %STKUNIT0-M:CP %DIFFSERV-6-DCB_ENABLE_CFG_ON_RELOAD: Global DCB will be
enabled on subsequent reload, PFC buffers will be reserved for all pfc ports and max loss
less queues supported for each stack unit. For the pfc-buffering change to take effect,
please save the config and reload the system.
58 | Data Center Bridging (DCB)
Page 73

QoS dot1p Traffic Classification and Queue Assignment
DCB supports PFC, ETS, and DCBX to handle converged Ethernet traffic that is assigned to an egress
queue according to the following quality of service (QoS) methods:
• Honor dot1p: dot1p priorities in ingress traffic are used at the port or global switch level.
• Layer 2 class maps: dot1p priorities are used to classify traffic in a class map and apply a service
policy to an ingress port to map traffic to egress queues.
Important: of two
Note: Dell Force10 does not recommend mapping all ingress traffic to a single queue when using PFC
and ETS. Ingress traffic classification using the service-class dynamic dot1p command (honor dot1p) is
recommended on all DCB-enabled interfaces. If you use L2 class maps to map dot1p priority traffic to
egress queues, take into account the default dot1p-queue assignments in Table 6-1 and the maximum
number of two lossless queues supported on a port.
Although FTOS allows you to change the default dot1p priority-queue assignments, DCB policies applied
to an interface may become invalid if dot1p-queue mapping is reconfigured. If the configured DCB policy
remains valid, the change in the dot1p-queue assignment is allowed. For DCB ETS enabled interfaces,
traffic destined to queue that is not mapped to any dot1p priority will be dropped.
Table 6-1. dot1p Priority-Queue Assignment
dot1p Value in Incoming Frame Egress Queue Assignment
00
10
20
31
42
53
63
73
Data Center Bridging (DCB) | 59
Page 74

How Priority-Based Flow Control is Implemented
Priority-based flow control provides a flow control mechanism based on the 802.1p priorities in converged
Ethernet traffic received on an interface and is enabled by default. As an enhancement to the existing
Ethernet pause mechanism, PFC stops traffic transmission for specified priorities (CoS values) without
impacting other priority classes. Different traffic types are assigned to different priority classes.
When traffic congestion occurs, PFC sends a pause frame to a peer device with the CoS priority values of
the traffic that needs to be stopped. DCBX provides the link-level exchange of PFC parameters between
peer devices. PFC creates zero-loss links for SAN traffic that requires no-drop service, while at the same
time retaining packet-drop congestion management for LAN traffic.
www.dell.com | support.dell.com
PFC is implemented on an Aggregator as follows:
• If DCB is enabled, as soon as a DCB policy with PFC is applied on an interface, DCBX starts
exchanging information with PFC-enabled peers. The IEEE802.1Qbb, CEE and CIN versions of PFC
TLV are supported. DCBX also validates PFC configurations received in TLVs from peer devices.
• To achieve complete lossless handling of traffic, enable PFC operation
traffic and
• All 802.1p priorities are enabled for PFC. Queues to which PFC priority traffic is mapped are lossless
by default. Traffic may be interrupted due to an interface flap (going down and coming up).
• For PFC to be applied on an Aggregator port, the auto-configured priority traf fic must be supported by
a PFC peer (as detected by DCBX).
• A DCB input policy for PFC applied to an interface may become invalid if dot1p-queue mapping is
reconfigured (refer to Create Input Policy Maps). This situation occurs when the new dot1p-queue
assignment exceeds the maximum number (2) of lossless queues supported globally on the switch. In
this case, all PFC configurations received from PFC-enabled peers are removed and re-synchronized
with the peer devices.
• FTOS does not support MACsec Bypass Capability (MBC).
enabled on all DCB egress port traffic.
is enabled on ingress port
60 | Data Center Bridging (DCB)
Page 75

How Enhanced Transmission Selection is Implemented
Enhanced transmission selection (ETS) provides a way to optimize bandwidth allocation to outbound
802.1p classes of converged Ethernet traffic. Different traffic types have different service needs. Using
ETS, groups within an 802.1p priority class are auto-configured to provide different treatment for traffic
with different bandwidth, latency, and best-effort needs.
For example, storage traffic is sensitive to frame loss; interprocess communication (IPC) traffic is
latency-sensitive. ETS allows different traffic types to coexist without interruption in the same converged
link.
Note: The IEEE 802.1Qaz, CEE, and CIN versions of ETS are supported.
ETS is implemented on an Aggregator as follows:
• Traffic in priority groups is assigned to strict-queue or WERR scheduling in an ETS output policy and
is managed using the ETS bandwidth-assignment algorithm. FTOS de-qeues all frames of
strict-priority traffic before servicing any other queues. A queue with strict-priority traffic can starve
other queues in the same port.
• ETS-assigned bandwidth allocation and scheduling apply only to data queues, not to control queues.
• FTOS supports hierarchical scheduling on an interface. FTOS control traffic is redirected to control
queues as higher priority traffic with strict priority scheduling. After control queues drain out, the
remaining data traffic is scheduled to queues according to the bandwidth and scheduler configuration
in the ETS output policy . The available bandwidth calculated by the ETS algorithm is equal to the link
bandwidth after scheduling non-ETS higher-priority traffic.
• By default, equal bandwidth is assigned to each port queue and each dot1p priority in a priority group.
• By default, equal bandwidth is assigned to each priority group in the ETS output policy applied to an
egress port. The sum of auto-configured bandwidth allocation to dot1p priority traffic in all ETS
priority groups is 100%.
• dot1p priority traffic on the switch is scheduled according to the default dot1p-queue mapping. dot1p
priorities within the same queue should have the same traffic properties and scheduling method.
• A priority group consists of 802.1p priority values that are grouped together for similar bandwidth
allocation and scheduling, and that share the same latency and loss requirements. All 802.1p priorities
mapped to the same queue should be in the same priority group.
• By default:
— All 802.1p priorities are grouped in priority group 0.
— 100% of the port bandwidth is assigned to priority group 0. The complete bandwidth is
equally assigned to each priority class so that each class has 12 to 13%.
• The maximum number of priority groups supported in ETS output policies on an interface is equal
to the number of data queues (4) on the port. The 802.1p priorities in a priority group can map to
multiple queues.
• A DCB output policy is created to associate a priority group with an ETS output policy with
scheduling and bandwidth configuration, and applied on egress ports.
• The ETS configuration associated with 802.1p priority traffic in a DCB output policy is used in
DCBX negotiation with ETS peers.
Data Center Bridging (DCB) | 61
Page 76

• When an ETS output policy is applied to an interface, ETS-configured scheduling and bandwidth
allocation take precedence over any auto-configured settings in the QoS output policies.
• ETS is enabled by default with the default ETS configuration applied (all dot1p priorities in the
same group with equal bandwidth allocation).
ETS Operation with DCBX
In DCBX negotiation with peer ETS devices, ETS configuration is handled as follows:
• ETS TLVs are supported in DCBX versions CIN, CEE, and IEEE2.5.
• ETS operational parameters are determined by the DCBX port-role configurations.
www.dell.com | support.dell.com
• ETS configurations received from TLVs from a peer are validated.
• In case of a hardware limitation or TLV error:
• DCBX operation on an ETS port goes down.
• New ETS configurations are ignored and existing ETS configurations are reset to the previously
configured ETS output policy on the port or to the default ETS settings if no ETS output policy
was previously applied.
• ETS operates with legacy DCBX versions as follows:
• In the CEE version, the priority group/traffic class group (TCG) ID 15 represents a non-ETS
priority group. Any priority group configured with a scheduler type is treated as a strict-priority
group and is given the priority-group (TCG) ID 15.
• The CIN version supports two types of strict-priority scheduling:
— Group strict priority: Allows a single priority flow in a priority group to increase its
bandwidth usage to the bandwidth total of the priority group. A single flow in a group can
use all the bandwidth allocated to the group.
— Link strict priority: Allows a flow in any priority group to increase to the maximum link
bandwidth.
CIN supports only the default dot1p priority-queue assignment in a priority group.
Bandwidth Allocation for DCBX CIN
After an ETS output policy is applied to an interface, if the DCBX version used in your data center
network is CIN, a QoS output policy is automatically configured to overwrite the default CIN bandwidth
allocation. This default setting divides the bandwidth allocated to each port queue equally between the
dot1p priority traffic assigned to the queue.
62 | Data Center Bridging (DCB)
Page 77

DCB Policies in a Switch Stack
A DCB input policy with PFC and ETS configuration is applied to all stacked ports in a switch stack or on
a stacked switch.
DCBX Operation
The data center bridging exchange protocol (DCBX) is used by DCB devices to exchange configuration
information with directly connected peers using the link layer discovery protocol (LLDP) protocol. DCBX
can detect the misconfiguration of a peer DCB device, and optionally, configure peer DCB devices with
DCB feature settings to ensure consistent operation in a data center network.
DCBX is a prerequisite for using DCB features, such as priority-based flow control (PFC) and enhanced
traffic selection (ETS), to exchange link-level configurations in a converged Ethernet environment. DCBX
is also deployed in topologies that support lossless operation for FCoE or iSCSI traffic. In these scenarios,
all network devices are DCBX-enabled (DCBX is enabled end-to-end).
The following versions of DCBX are supported on an Aggregator: CIN, CEE, and IEEE2.5.
DCBX requires the LLDP to be enabled on all DCB devices.
DCBX Operation
DCBX performs the following operations:
• Discovers DCB configuration (such as PFC and ETS) in a peer device.
• Detects DCB misconfiguration in a peer device; that is, when DCB features are not compatibly
configured on a peer device and the local switch. Misconfiguration detection is feature-specific
because some DCB features support asymmetric configuration.
• Reconfigures a peer device with the DCB configuration from its configuration source if the peer
device is willing to accept configuration.
• Accepts the DCB configuration from a peer if a DCBX port is in “willing” mode to accept a peer’s
DCB settings and then internally propagates the received DCB configuration to its peer ports.
Data Center Bridging (DCB) | 63
Page 78

DCBX Port Roles
The following DCBX port roles are auto-configured on an Aggregator to propagate DCB configurations
learned from peer DCBX devices internally to other switch ports:
• Auto-upstream: The port advertises its own configuration to DCBX peers and receives its
configuration from DCBX peers (ToR or FCF device). The port also propagates its configuration to
other ports on the switch.
The first auto-upstream that is capable of receiving a peer configuration is elected as the configuration
source. The elected configuration source then internally propagates the configuration to auto-downstream ports. A port that receives an internally propagated configuration overwrites its local configuration with the new parameter values.
www.dell.com | support.dell.com
When an auto-upstream port (besides the configuration source) receives and overwrites its configuration with internally propagated information, one of the following actions is taken:
• If the peer configuration received is compatible with the internally propagated port configuration,
the link with the DCBX peer is enabled.
• If the received peer configuration is not compatible with the currently configured port
configuration, the link with the DCBX peer port is disabled and a syslog message for an
incompatible configuration is generated. The network administrator must then reconfigure the peer
device so that it advertises a compatible DCB configuration.
The configuration received from a DCBX peer or from an internally propagated configuration is not
stored in the switch’s running configuration.
On a DCBX port in an auto-upstream role, the PFC and application priority TLVs are enabled. ETS
recommend TLVs are disabled and ETS configuration TLVs are enabled.
• Auto-downstream - The port advertises its own configuration to DCBX peers but is not willing to
receive remote peer configuration. The port always accepts internally propagated configurations from
a configuration source. An auto-downstream port that receives an internally propagated configuration
overwrites its local configuration with the new parameter values.
When an auto-downstream port receives and overwrites its configuration with internally propagated
information, one of the following actions is taken:
• If the peer configuration received is compatible with the internally propagated port configuration,
the link with the DCBX peer is enabled.
• If the received peer configuration is not compatible with the currently configured port
configuration, the link with the DCBX peer port is disabled and a syslog message for an
incompatible configuration is generated. The network administrator must then reconfigure the peer
device so that it advertises a compatible DCB configuration.
The internally propagated configuration is not stored in the switch's running configuration.
On a DCBX port in an auto-downstream role, all PFC, application priority , ETS recommend, and ETS
configuration TLVs are enabled.
Default DCBX port role: Uplink ports are auto-configured in an auto-upstream role. Server-facing ports
are auto-configured in an auto-downstream role.
64 | Data Center Bridging (DCB)
Page 79

Note: On a DCBX port, application priority TLV advertisements are handled as follows:
- The application priority TLV is transmitted only if the priorities in the advertisement match the configured
PFC priorities on the port.
- On auto-upstream and auto-downstream ports:
- If a configuration source is elected, the ports send an application priority TLV based on the application
priority TLV received on the configuration-source port. When an application priority TLV is received on the
configuration-source port, the auto-upstream and auto-downstream ports use the internally propagated
PFC priorities to match against the received application priority. Otherwise, these ports use their locally
configured PFC priorities in application priority TLVs.
- If no configuration source is configured, auto-upstream and auto-downstream ports check to see that
the locally configured PFC priorities match the priorities in a received application priority TLV.
- On manual ports: An application priority TLV is advertised only if the priorities in the TLV match the PFC
priorities configured on the port.
DCB Configuration Exchange
On an Aggregator, the DCBX protocol supports the exchange and propagation of configuration
information for the following DCB features.
• Enhanced transmission selection (ETS)
• Priority-based flow control (PFC)
DCBX uses the following methods to exchange DCB configuration parameters:
• Asymmetric: DCB parameters are exchanged between a DCBX-enabled port and a peer port without
requiring that a peer port and the local port use the same configured values for the configurations to be
compatible. For example, ETS uses an asymmetric exchange of parameters between DCBX peers.
• Symmetric: DCB parameters are exchanged between a DCBX-enabled port and a peer port with the
requirement that each configured parameter value is the same for the configurations to be compatible.
For example, PFC uses an symmetric exchange of parameters between DCBX peers.
Data Center Bridging (DCB) | 65
Page 80

Configuration Source Election
When an auto-upstream or auto-downstream port receives a DCB configuration from a peer, the port first
checks to see if there is an active configuration source on the switch.
• If a configuration source already exists, the received peer configuration is checked against the local
port configuration. If the received configuration is compatible, the DCBX marks the port as
DCBX-enabled. If the configuration received from the peer is not compatible, a warning message is
logged and the DCBX frame error counter is incremented. Although DCBX is operationally disabled,
the port keeps the peer link up and continues to exchange DCBX packets. If a compatible peer
configuration is later received, DCBX is enabled on the port.
• If there is no configuration source, a port may elect itself as the configuration source. A port may
www.dell.com | support.dell.com
become the configuration source if the following conditions exist:
• No other port is the configuration source.
• The port role is auto-upstream.
• The port is enabled with link up and DCBX enabled.
• The port has performed a DCBX exchange with a DCBX peer.
• The switch is capable of supporting the received DCB configuration values through either a
symmetric or asymmetric parameter exchange.
A newly elected configuration source propagates configuration changes received from a peer to the other
auto-configuration ports. Ports receiving auto-configuration information from the configuration source
ignore their current settings and use the configuration source information.
Propagation of DCB Information
When an auto-upstream or auto-downstream port receives a DCB configuration from a peer, the port acts
as a DCBX client and checks if a DCBX configuration source exists on the switch.
• If a configuration source is found, the received configuration is checked against the currently
configured values that are internally propagated by the configuration source. If the local configuration
is compatible with the received configuration, the port is enabled for DCBX operation and
synchronization.
• If the configuration received from the peer is not compatible with the internally propagated
configuration used by the configuration source, the port is disabled as a client for DCBX operation and
synchronization and a syslog error message is generated. The port keeps the peer link up and continues
to exchange DCBX packets. If a compatible configuration is later received from the peer, the port is
enabled for DCBX operation.
Note: When a configuration source is elected, all auto-upstream ports other than the configuration source
are marked as willing disabled. The internally propagated DCB configuration is refreshed on all
auto-configuration ports and each port may begin configuration negotiation with a DCBX peer again.
66 | Data Center Bridging (DCB)
Page 81

Auto-Detection of the DCBX Version
The Aggregator operates in auto-detection mode so that a DCBX port automatically detects the DCBX
version on a peer port. Legacy CIN and CEE versions are supported in addition to the standard IEEE
version 2.5 DCBX.
A DCBX port detects a peer version after receiving a valid frame for that version. The local DCBX port
reconfigures to operate with the peer version and maintains the peer version on the link until one of the
following conditions occurs:
• The switch reboots.
• The link is reset (goes down and up).
• The peer times out.
• Multiple peers are detected on the link.
DCBX operations on a port are performed according to the auto-configured DCBX version, including fast
and slow transmit timers and message formats. If a DCBX frame with a different version is received, a
syslog message is generated and the peer version is recorded in the peer status table. If the frame cannot be
processed, it is discarded and the discard counter is incremented.
DCBX Example
Figure 6-7 shows how DCBX is used on an Aggregator installed in a PowerEdge M1000e chassis in which
servers are also installed.
• The external 40GbE ports on the base module (ports 33 and 37) of two switches are used for uplinks
configured as DCBX auto-upstream ports. The Aggregator is connected to third-party, top-of-rack
(ToR) switches through 40GbE uplinks. The ToR switches are part of a Fibre Channel storage
network.
• The internal ports (ports 1-32) connected to the 10GbE backplane are configured as auto-downstream
ports.
• On the Aggregator, PFC and ETS use DCBX to exchange link-level configuration with DCBX peer
devices.
Data Center Bridging (DCB) | 67
Page 82

Figure 6-7. DCBX Sample Topology
www.dell.com | support.dell.com
DCBX Prerequisites and Restrictions
• DCBX requires LLDP in both send (TX) and receive (RX) mode to be enabled on a port interface. If
multiple DCBX peer ports are detected on a local DCBX interface, LLDP is shut down.
• The CIN version of DCBX supports only PFC, ETS, and FCOE; it does not support iSCSI, backward
congestion management (BCN), logical link down (LLD), and network interface virtualization (NIV).
68 | Data Center Bridging (DCB)
Page 83

DCBX Error Messages
An error in DCBX operation is displayed using the following syslog messages:
LLDP_MULTIPLE_PEER_DETECTED: DCBX is operationally disabled after detecting more than one DCBX
peer on the port interface.
LLDP_PEER_AGE_OUT: DCBX is disabled as a result of LLDP timing out on a DCBX peer interface.
DSM_DCBX_PEER_VERSION_CONFLICT: A local port expected to receive the IEEE, CIN, or CEE version
in a DCBX TLV from a remote peer but received a different, conflicting DCBX version.
DSM_DCBX_PFC_PARAMETERS_MATCH and DSM_DCBX_PFC_PARAMETERS_MISMATCH: A local DCBX port received
a compatible (match) or incompatible (mismatch) PFC configuration from a peer.
DSM_DCBX_ETS_PARAMETERS_MATCH and DSM_DCBX_ETS_PARAMETERS_MISMATCH: A local DCBX port received
a compatible (match) or incompatible (mismatch) ETS configuration from a peer.
LLDP_UNRECOGNISED_DCBX_TLV_RECEIVED: A local DCBX port received an unrecognized DCBX TLV from
a peer.
Debugging DCBX on an Interface
To enabled DCBX debug traces for all or a specific control path, use the following command:
Task Command Command Mode
Enable DCBX debugging, where:
• all: Enables all DCBX debugging operations.
• auto-detect-timer: Enables traces for DCBX
debug dcbx {all | auto-detect-timer |
config-exchng | fail | mgmt |
resource | sem | tlv}
EXEC PRIVILEGE
auto-detect timers.
• config-exchng: Enables traces for DCBX
configuration exchanges.
• fail: Enables traces for DCBX failures.
• mgmt: Enables traces for DCBX management
frames.
• resource: Enables traces for DCBX system
resource frames.
• sem: Enables traces for the DCBX state
machine.
• tlv: Enables traces for DCBX TLVs.
Data Center Bridging (DCB) | 69
Page 84

Verifying DCB Configuration
Use the show commands in Table 6-2 to display DCB configurations and statistics.
Table 6-2. Displaying DCB Configurations
Command Output
show dcb [stack-unit unit-number] (Figure 6-8) Displays data center bridging status, number of PFC-enabled ports, and
number of PFC-enabled queues. On the master switch in a stack, you can
specify a stack-unit number. Valid values: 0 to 5.
show interface port-type slot/port pfc statistics
(Figure 6-9)
www.dell.com | support.dell.com
show interface port-type slot/port pfc {summary
| detail} (Figure 6-10)
show interface port-type slot/port ets {summary
| detail} (Figure 6-11 and Figure 6-12)
Figure 6-8. show dcb Command Example
Displays counters for the PFC frames received and transmitted (by dot1p
priority class) on an interface.
Displays the PFC configuration applied to ingress traffic on an interface,
including priorities and link delay.
T o clear PFC TLV counters on all ports or a specified port, use the clear pfc
counters {stack-unit
unit-number | tengigabitethernet slot/port} command.
Displays the ETS configuration applied to egress traffic on an interface,
including priority groups with priorities and bandwidth allocation.
To clear ETS TLV counters on all ports or a specified port, enter the clear
ets counters stack-unit
unit-number command.
FTOS# show dcb
stack-unit 0 port-set 0
DCB Status : Enabled
PFC Port Count : 56 (current), 56 (configured)
PFC Queue Count : 2 (current), 2 (configured)
Figure 6-9. show interface pfc statistics Command Example
FTOS#show interfaces tengigabitethernet 0/3 pfc statistics
Interface TenGigabitEthernet 0/3
Priority Rx XOFF Frames Rx Total Frames Tx Total Frames
------------------------------------------------------------------------------0 0 0 0
1 0 0 0
2 0 0 0
3 0 0 0
4 0 0 0
5 0 0 0
6 0 0 0
7 0 0 0
70 | Data Center Bridging (DCB)
Page 85

Figure 6-10. show interfaces pfc summary Command Example
FTOS# show interfaces tengigabitethernet 0/49 pfc summary
Interface TenGigabitEthernet 0/49
Admin mode is on
Admin is enabled
Remote is enabled, Priority list is 4
Remote Willing Status is enabled
Local is enabled
Oper status is Recommended
PFC DCBX Oper status is Up
State Machine Type is Feature
TLV Tx Status is enabled
PFC Link Delay 45556 pause quantams
Application Priority TLV Parameters :
------------------------------------- FCOE TLV Tx Status is disabled
ISCSI TLV Tx Status is disabled
Local FCOE PriorityMap is 0x8
Local ISCSI PriorityMap is 0x10
Remote FCOE PriorityMap is 0x8
Remote ISCSI PriorityMap is 0x8
FTOS# show interfaces tengigabitethernet 0/49 pfc detail
Interface TenGigabitEthernet 0/49
Admin mode is on
Admin is enabled
Remote is enabled
Remote Willing Status is enabled
Local is enabled
Oper status is recommended
PFC DCBX Oper status is Up
State Machine Type is Feature
TLV Tx Status is enabled
PFC Link Delay 45556 pause quanta
Application Priority TLV Parameters :
------------------------------------- FCOE TLV Tx Status is disabled
ISCSI TLV Tx Status is disabled
Local FCOE PriorityMap is 0x8
Local ISCSI PriorityMap is 0x10
Remote FCOE PriorityMap is 0x8
Remote ISCSI PriorityMap is 0x8
0 Input TLV pkts, 1 Output TLV pkts, 0 Error pkts, 0 Pause Tx pkts, 0 Pause Rx pkts
Table 6-3. show interface pfc summary Command Description
Field Description
Interface Interface type with stack-unit and port number.
Admin mode is on
Admin is enabled
PFC Admin mode is on or off with a list of the configured PFC priorities.
When PFC admin mode is on, PFC advertisements are enabled to be sent and
received from peers; received PFC configuration takes effect.
The admin operational status for a DCBX exchange of PFC configuration is
enabled or disabled.
Data Center Bridging (DCB) | 71
Page 86

Table 6-3. show interface pfc summary Command Description
Field Description
Remote is enabled, Priority list
Remote Willing Status is
enabled
Local is enabled DCBX operational status (enabled or disabled) with a list of the configured
Operational status (local port) Port state for current operational PFC configuration:
www.dell.com | support.dell.com
PFC DCBX Oper status Operational status for exchange of PFC configuration on local port: match
State Machine Type Type of state machine used for DCBX exchanges of PFC parameters:
TLV Tx Status Status of PFC TLV advertisements: enabled or disabled.
PFC Link Delay Link delay (in quanta) used to pause specified priority traffic.
Application Priority TLV:
FCOE TLV Tx Status
Operational status (enabled or disabled) of peer device for DCBX exchange of
PFC configuration with a list of the configured PFC priorities.
Willing status of peer device for DCBX exchange (Willing bit received in
PFC TLV): enabled or disabled.
PFC priorities.
Init: Local PFC configuration parameters were exchanged with peer.
Recommend: Remote PFC configuration parameters were received from peer.
Internally propagated: PFC configuration parameters were received from
configuration source.
(up) or mismatch (down).
Feature - for legacy DCBX versions; Symmetric - for an IEEE version.
Status of FCoE advertisements in application priority TLVs from local DCBX
port: enabled or disabled.
Application Priority TLV:
ISCSI TLV Tx Status
Application Priority TLV:
Local FCOE Priority Map
Application Priority TLV:
Local ISCSI Priority Map
Application Priority TLV:
Remote FCOE Priority Map
Application Priority TLV:
Remote ISCSI Priority Map
PFC TLV Statistics:
Input TLV pkts
PFC TLV Statistics:
Output TLV pkts
PFC TLV Statistics:
Error pkts
PFC TLV Statistics:
Pause Tx pkts
PFC TLV Statistics:
Pause Rx pkts
Status of ISCSI advertisements in application priority TLVs from local DCBX
port: enabled or disabled.
Priority bitmap used by local DCBX port in FCoE advertisements in
application priority TLVs.
Priority bitmap used by local DCBX port in ISCSI advertisements in
application priority TLVs.
Priority bitmap received from the remote DCBX port in FCoE advertisements
in application priority TLVs.
Priority bitmap received from the remote DCBX port in iSCSI advertisements
in application priority TLVs.
Number of PFC TLVs received.
Number of PFC TLVs transmitted.
Number of PFC error packets received.
Number of PFC pause frames transmitted.
Number of PFC pause frames received
72 | Data Center Bridging (DCB)
Page 87

Figure 6-11. show interface ets summary Command Example
FTOS(conf)# show interfaces tengigabitethernet 0/0 ets summary
Interface TenGigabitEthernet 0/0
Max Supported TC Groups is 4
Number of Traffic Classes is 8
Admin mode is on
Admin Parameters:
-----------------Admin is enabled
TC-grp Priority# Bandwidth TSA
0 0,1,2,3,4,5,6,7 100% ETS
1 0% ETS
2 0% ETS
3 0% ETS
4 0% ETS
5 0% ETS
6 0% ETS
7 0% ETS
Priority# Bandwidth TSA
0 13% ETS
1 13% ETS
2 13% ETS
3 13% ETS
4 12% ETS
5 12% ETS
6 12% ETS
7 12% ETS
Remote Parameters:
------------------Remote is disabled
Local Parameters:
-----------------Local is enabled
TC-grp Priority# Bandwidth TSA
0 0,1,2,3,4,5,6,7 100% ETS
1 0% ETS
2 0% ETS
3 0% ETS
4 0% ETS
5 0% ETS
6 0% ETS
7 0% ETS
Priority# Bandwidth TSA
0 13% ETS
1 13% ETS
2 13% ETS
3 13% ETS
4 12% ETS
5 12% ETS
6 12% ETS
7 12% ETS
Oper status is init
Conf TLV Tx Status is disabled
Traffic Class TLV Tx Status is disabled
Data Center Bridging (DCB) | 73
Page 88

Figure 6-12. show interface ets detail Command Example
FTOS# show interfaces tengigabitethernet 0/34 ets detail
Interface TenGigabitEthernet 0/34
Max Supported PG is 4
Number of Traffic Classes is 8
Admin mode is on
Admin Parameters :
-----------------Admin is enabled
PG-grp Priority# Bandwidth TSA
-----------------------------------------------0 0,1,2,3,4,5,6,7 100% ETS
1 - -
www.dell.com | support.dell.com
2 - 3 - 4 - 5 - 6 - 7 - -
Remote Parameters :
------------------Remote is disabled
Local Parameters :
-----------------Local is enabled
PG-grp Priority# Bandwidth TSA
-----------------------------------------------0 0,1,2,3,4,5,6,7 100% ETS
1 - 2 - 3 - 4 - 5 - 6 - 7 - -
Oper status is init
ETS DCBX Oper status is Down
State Machine Type is Asymmetric
Conf TLV Tx Status is enabled
Reco TLV Tx Status is enabled
0 Input Conf TLV Pkts, 0 Output Conf TLV Pkts, 0 Error Conf TLV Pkts
0 Input Reco TLV Pkts, 0 Output Reco TLV Pkts, 0 Error Reco TLV Pkts
Table 6-4. show interface ets detail Command Description
Field Description
Interface Interface type with stack-unit and port number.
Max Supported TC Group Maximum number of priority groups supported.
Number of Traffic Classes Number of 802.1p priorities currently configured.
74 | Data Center Bridging (DCB)
Page 89

Table 6-4. show interface ets detail Command Description
Field Description
Admin mode ETS mode: on or off.
When on, the scheduling and bandwidth allocation configured in an ETS
output policy or received in a DCBX TLV from a peer can take effect on an
interface.
Admin Parameters ETS configuration on local port, including priority groups, assigned dot1p
priorities, and bandwidth allocation.
Remote Parameters ETS configuration on remote peer port, including Admin mode (enabled if a
valid TLV was received or disabled), priority groups, assigned dot1p
priorities, and bandwidth allocation. If the ETS Admin mode is enabled on the
remote port for DCBX exchange, the Willing bit received in ETS TLVs from
the remote peer is included.
Local Parameters ETS configuration on local port, including Admin mode (enabled when a
valid TLV is received from a peer), priority groups, assigned dot1p priorities,
and bandwidth allocation.
Operational status (local port) Port state for current operational ETS configuration:
Init: Local ETS configuration parameters were exchanged with peer.
Recommend: Remote ETS configuration parameters were received from peer.
Internally propagated: ETS configuration parameters were received from
configuration source.
ETS DCBX Oper status Operational status of ETS configuration on local port: match or mismatch.
State Machine Type Type of state machine used for DCBX exchanges of ETS parameters:
Feature - for legacy DCBX versions; Asymmetric - for an IEEE version.
Conf TLV Tx Status Status of ETS Configuration TLV advertisements: enabled or disabled.
Reco TLV Tx Status Status of ETS Recommendation TLV advertisements: enabled or disabled.
Input Conf TLV pkts
Output Conf TLV pkts
Number of ETS Configuration TLVs received and transmitted, and number of
ETS Error Configuration TLVs received.
Error Conf TLV pkts
Input Reco TLV pkts
Output Reco TLV pkts
Number of ETS Recommendation TLVs received and transmitted, and
number of ETS Error Recommendation TLVs received.
Error Reco TLV pkts
Data Center Bridging (DCB) | 75
Page 90

Figure 6-13. show stack-unit all stack-ports all pfc details Command Example
FTOS# show stack-unit all stack-ports all pfc details
stack unit 0 stack-port all
Admin mode is On
Admin is enabled, Priority list is 4-5
Local is enabled, Priority list is 4-5
Link Delay 45556 pause quantum
0 Pause Tx pkts, 0 Pause Rx pkts
stack unit 1 stack-port all
Admin mode is On
Admin is enabled, Priority list is 4-5
Local is enabled, Priority list is 4-5
Link Delay 45556 pause quantum
0 Pause Tx pkts, 0 Pause Rx pkts
www.dell.com | support.dell.com
Figure 6-14. show stack-unit all stack-ports all ets details Command Example
FTOS# show stack-unit all stack-ports all ets details
Stack unit 0 stack port all
Max Supported TC Groups is 4
Number of Traffic Classes is 1
Admin mode is on
Admin Parameters:
-------------------Admin is enabled
TC-grp Priority# Bandwidth TSA
-----------------------------------------------0 0,1,2,3,4,5,6,7 100% ETS
1 - 2 - 3 - 4 - 5 - 6 - 7 - 8 - -
Stack unit 1 stack port all
Max Supported TC Groups is 4
Number of Traffic Classes is 1
Admin mode is on
Admin Parameters:
-------------------Admin is enabled
TC-grp Priority# Bandwidth TSA
-----------------------------------------------0 0,1,2,3,4,5,6,7 100% ETS
1 - 2 - 3 - 4 - 5 - 6 - 7 - 8 - -
76 | Data Center Bridging (DCB)
Page 91

Figure 6-15. show interface dcbx detail Command Example
FTOS# show interface tengigabitethernet 0/49 dcbx detail
FTOS# show interface te 0/49 dcbx detail
E-ETS Configuration TLV enabled e-ETS Configuration TLV disabled
R-ETS Recommendation TLV enabled r-ETS Recommendation TLV disabled
P-PFC Configuration TLV enabled p-PFC Configuration TLV disabled
F-Application priority for FCOE enabled f-Application Priority for FCOE disabled
I-Application priority for iSCSI enabled i-Application Priority for iSCSI disabled
------------------------------------------------------------------------------------------
Interface TenGigabitEthernet 0/49
Remote Mac Address 00:00:00:00:00:11
Port Role is Auto-Upstream
DCBX Operational Status is Enabled
Is Configuration Source? TRUE
Local DCBX Compatibility mode is CEE
Local DCBX Configured mode is CEE
Peer Operating version is CEE
Local DCBX TLVs Transmitted: ErPfi
Local DCBX Status
---------------- DCBX Operational Version is 0
DCBX Max Version Supported is 0
Sequence Number: 2
Acknowledgment Number: 2
Protocol State: In-Sync
Peer DCBX Status:
--------------- DCBX Operational Version is 0
DCBX Max Version Supported is 255
Sequence Number: 2
Acknowledgment Number: 2
Total DCBX Frames transmitted 27
Total DCBX Frames received 6
Total DCBX Frame errors 0
Total DCBX Frames unrecognized 0
Table 6-5. show interface dcbx detail Command Description
Field Description
Interface Interface type with chassis slot and port number.
Port-Role Configured DCBX port role: auto-upstream or auto-downstream.
DCBX Operational Status Operational status (enabled or disabled) used to elect a configuration source
and internally propagate a DCB configuration. The DCBX operational status
is the combination of PFC and ETS operational status.
Configuration Source Specifies whether the port serves as the DCBX configuration source on the
switch: true (yes) or false (no).
Local DCBX Compatibility
mode
DCBX version accepted in a DCB configuration as compatible. In
auto-detection mode, a port can only operate on a DCBX version supported on
the remote peer.
Data Center Bridging (DCB) | 77
Page 92

Table 6-5. show interface dcbx detail Command Description
Field Description
Local DCBX Configured mode DCBX version configured on the port: CEE, CIN, IEEE v2.5, or Auto (port
auto-configures to use the DCBX version received from a peer).
Peer Operating version DCBX version that the peer uses to exchange DCB parameters.
Local DCBX TLVs Transmitted Transmission status (enabled or disabled) of advertised DCB TLVs (see TLV
code at the top of the show command output).
Local DCBX Status:
DCBX Operational Version
www.dell.com | support.dell.com
Local DCBX Status:
DCBX Max Version Supported
Local DCBX Status:
Sequence Number
Local DCBX Status:
Acknowledgment Number
Local DCBX Status:
Protocol State
Peer DCBX Status:
DCBX Operational Version
Peer DCBX Status:
DCBX Max Version Supported
Peer DCBX Status:
Sequence Number
Peer DCBX Status:
Acknowledgment Number
Total DCBX Frames transmitted Number of DCBX frames sent from local port.
DCBX version advertised in Control TLVs.
Highest DCBX version supported in Control TLVs.
Sequence number transmitted in Control TLVs.
Acknowledgement number transmitted in Control TLVs
Current operational state of DCBX protocol: Waiting for ACK or IN-SYNC.
DCBX version advertised in Control TLVs received from peer device.
Highest DCBX version supported in Control TLVs received from peer device.
Sequence number transmitted in Control TLVs received from peer device.
Acknowledgement number transmitted in Control TLVs received from peer
device.
Total DCBX Frames received Number of DCBX frames received from remote peer port.
Total DCBX Frame errors Number of DCBX frames with errors received.
Total DCBX Frames
unrecognized
78 | Data Center Bridging (DCB)
Number of unrecognizable DCBX frames received.
Page 93

Example: PFC and ETS Operation
This section contains examples of DCB input and output policies applied on an interface.
In the example shown in Figure 6-16 for an Aggregator:
• Incoming SAN traffic is configured for priority-based flow control.
• Outbound LAN, IPC, and SAN traffic is mapped into three ETS priority groups and configured for
enhanced traffic selection (bandwidth allocation and scheduling).
• One lossless queue is used.
Figure 6-16. Example: PFC and ETS Applied to LAN, IPC, and SAN Priority Traffic
dot1p priority 3
SAN
priority 3
IPC
priority 4
dot1p priority
0, 1, 2, 4, 5
Converged LAN, SAN, and IPC traffic
dot1p priority 0-7
Data Center Bridging (DCB) | 79
Page 94

QoS T raffic Classification: On the Aggregator, the service-class dynamic dot1p command has been used in
Global Configuration mode to map ingress dot1p frames to the queues shown in Table 6-6. For more
information, refer to QoS dot1p Traffic Classification and Queue Assignment.
Table 6-6. Example: dot1p-Queue Assignment
dot1p Value in Incoming Frame Queue Assignment
00
10
20
www.dell.com | support.dell.com
31
42
53
63
73
Lossless SAN traffic with dot1p priority 3 is assigned to queue 1. Other traffic types are assigned the
802.1p priorities shown in Table 6-7 and the bandwidth allocations shown in Table 6-8.
Table 6-7. Example: dot1p-priority class group Assignment
dot1p Value in Incoming Frame Priority Group Assignment
0 LAN
1 LAN
2 LAN
3 SAN
4 IPC
5 LAN
6 LAN
7 LAN
80 | Data Center Bridging (DCB)
Page 95

Table 6-8. Example: priority group-bandwidth Assignment
Priority Group Bandwidth Assignment
IPC 5%
SAN 50%
LAN 45%
Hierarchical Scheduling in ETS Output Policies
On an Aggregator, ETS supports up to three levels of hierarchical scheduling. For example, ETS output
policies with the following configurations can be applied:
• Priority group 1 assigns traffic to one priority queue with 20% of the link bandwidth and strict-priority
scheduling.
• Priority group 2 assigns traffic to one priority queue with 30% of the link bandwidth.
• Priority group 3 assigns traffic to two priority queues with 50% of the link bandwidth and
strict-priority scheduling.
In this example, ETS bandwidth allocation and scheduler behavior is as follows:
• Unused bandwidth usage: Normally , if there is no traffic or unused bandwidth for a priority group, the
bandwidth allocated to the group is distributed to the other priority groups according to the bandwidth
percentage allocated to each group. However, when three priority groups with different bandwidth
allocations are used on an interface:
• If priority group 3 has free bandwidth, it is distributed as follows: 20% of the free bandwidth to
priority group 1 and 30% of the free bandwidth to priority group 2.
• If priority group 1 or 2 has free bandwidth, (20 + 30)% of the free bandwidth is distributed to
priority group 3. Priority groups 1 and 2 retain whatever free bandwidth remains up to the (20+
30)%.
• Strict-priority groups: If two priority groups have strict-priority scheduling, traffic assigned from the
priority group with the higher priority-queue number is scheduled first. However, when three priority
groups are used and two groups have strict-priority scheduling (such as groups 1 and 3 in the example),
the strict priority group whose traffic is mapped to one queue takes precedence over the strict priority
group whose traffic is mapped to two queues.
Therefore, in the example, scheduling traffic to priority group 1 (mapped to one strict-priority queue)
takes precedence over scheduling traffic to priority group 3 (mapped to two strict-priority queues).
Data Center Bridging (DCB) | 81
Page 96

www.dell.com | support.dell.com
82 | Data Center Bridging (DCB)
Page 97

Skippy812
7
Dynamic Host Configuration Protocol (DHCP)
The Aggregator is auto-configured to operate as a DHCP client. The DHCP server, DHCP relay agent, and
secure DHCP features are not supported.
DHCP Overview
Dynamic host configuration protocol (DHCP) is an application layer protocol that dynamically assigns IP
addresses and other configuration parameters to network end-stations (hosts) based on configuration
policies determined by network administrators. DHCP:
• relieves network administrators of manually configuring hosts, which can be a tedious and error-prone
process when hosts often join, leave, and change locations on the network.
• reclaims IP addresses that are no longer in use to prevent address exhaustion.
DHCP is based on a client-server model. A host discovers the DHCP server and requests an IP address, and
the server either leases or permanently assigns one. There are three types of devices that are involved in
DHCP negotiation:
• DHCP Server—a network device offering configuration parameters to the client.
• DHCP Client—a network device requesting configuration parameters from the server.
• Relay agent—an intermediary network device that passes DHCP messages between the client and
server when the server is not on the same subnet as the host.
Note: The DHCP server and relay agent features are not supported on an Aggregator.
Dynamic Host Configuration Protocol (DHCP) | 83
Page 98

DHCP Packet Format and Options
DHCP uses the user datagram protocol (UDP) as its transport protocol. The server listens on port 67 and
transmits to port 68; the client listens on port 68 and transmits to port 67. The configuration parameters are
carried as options in the DHCP packet in type, length, value (TLV) format; many options are specified in
RFC 2132. To limit the number parameters that servers must provide, hosts specify the parameters that
they require, and the server sends only those; some common options are given in Table 7-1.
Figure 7-1. DHCP Packet Format
htype
op
hlen
hops
xid
flags
secs
ciaddr
yiaddr
siaddr
giaddr
chaddr sname
options
file
www.dell.com | support.dell.com
Code
Length
Table 7-1. Common DHCP Options
Option Code Description
Subnet Mask 1 Specifies the clients subnet mask.
Router 3 Specifies the router IP addresses that may serve as the client’s default
gateway.
Domain Name Server 6 Specifies the DNS servers that are available to the client.
Domain Name 15 Specifies the domain name that client should use when resolving hostnames
via DNS.
IP Address Lease Time 51 Specifies the amount of time that the client is allowed to use an assigned IP
address.
DHCP Message Type 53 1: DHCPDISCOVER
2: DHCPOFFER
3: DHCPREQUEST
4: DHCPDECLINE
5: DHCPACK
6: DHCPNACK
7: DHCPRELEASE
8: DHCPINFORM
Parameter Request List 55 Clients use this option to tell the server which parameters it requires. It is a
series of octets where each octet is DHCP option code.
Renewal Time 58 Specifies the amount of time after the IP address is granted that the client
attempts to renew its lease with the original server.
Rebinding Time 59 Specifies the amount of time after the IP address is granted that the client
attempts to renew its lease with any server, if the original server does not
respond.
End 255 Signals the last option in the DHCP packet.
Value
84 | Dynamic Host Configuration Protocol (DHCP)
Page 99

Assigning an IP Address Using DHCP
er
When a client joins a network:
1. The client initially broadcasts a DHCPDISCOVER message on the subnet to discover available
DHCP servers. This message includes the parameters that the client requires and might include
suggested values for those parameters.
2. Servers unicast or broadcast a DHCPOFFER message in response to the DHCPDISCOVER that
offers to the client values for the requested parameters. Multiple servers might respond to a single
DHCPDISCOVER; the client might wait a period of time and then act on the most preferred offer.
3. The client broadcasts a DHCPREQUEST message in response to the offer, requesting the offered
values.
4. After receiving a DHCPREQUEST, the server binds the clients’ unique identifier (the hardware
address plus IP address) to the accepted configuration parameters and stores the data in a database
called a binding table. The server then broadcasts a DHCPACK message, which signals to the client
that it may begin using the assigned parameters.
There are additional messages that are used in case the DHCP negotiation deviates from the process
described above and shown in Figure 7-2.
• DHCPDECLINE—A client sends this message to the server in response to a DHCPACK if the
configuration parameters are unacceptable, for example, if the offered address is already in use. In this
case, the client starts the configuration process over by sending a DHCPDISCOVER.
• DHCPINFORM—A client uses this message to request configuration parameters when it assigned an
IP address manually rather than with DHCP. The server responds by unicast.
• DHCPNAK—A server sends this message to the client if it is not able to fulfill a DHCPREQUEST,
for example, if the requested address is already in use. In this case, the client starts the configuration
process over by sending a DHCPDISCOVER.
• DHCPRELEASE—A DHCP client sends this message when it is stopped forcefully to return its IP
address to the server.
Figure 7-2. Assigning Network Parameters using DHCP
Client
1. DHCPDISCOVER
3. DHCPREQUEST
Serv
2. DHCPOFFER
4. DHCPACK
Dynamic Host Configuration Protocol (DHCP) | 85
Page 100

FTOS Behavior: DHCP is implemented in FTOS based on RFC 2131 and 3046.
DHCP Client
An Aggregator is auto-configured to operate as a DHCP client. The DHCP client functionality is enabled
only on the default VLAN and the management interface.
A DHCP client is a network device that requests an IP address and configuration parameters from a DHCP
www.dell.com | support.dell.com
server. On an Aggregator, the DHCP client functionality is implemented as follows:
• The public out-of-band management (OOB) interface and default VLAN 1 are configured, by default,
as a DHCP client to acquire a dynamic IP address from a DHCP server.
You can override the DHCP-assigned address on the OOB management interface by manually config-
uring an IP address using the CLI or CMC interface. If no user-configured IP address exists for the
OOB interface exists and if the OOB IP address is not in the startup configuration, the Aggregator will
automatically obtain it using DHCP.
You can also manually configure an IP address for the VLAN 1 default management interface using
the CLI. If no user-configured IP address exists for the default VLAN management interface exists and
if the default VLAN IP address is not in the startup configuration, the Aggregator will automatically
obtain it using DHCP.
• The default VLAN 1 with all ports configured as members is the only L3 interface on the Aggregator.
When the default management VLAN has a DHCP-assigned address and you reconfigure the default
VLAN ID number, the Aggregator:
• Sends a DHCP release to the DHCP server to release the IP address.
• Sends a DHCP request to obtain a new IP address. The IP address assigned by the DHCP server is
used for the new default management VLAN.
86 | Dynamic Host Configuration Protocol (DHCP)
 Loading...
Loading...