Dell AppDefense on VxRail Installation Manual

Install and Config Guide
Installing and Configuring VMware
AppDefense on VxRail
Abstract
This document describes the procedure used for installing VMware
AppDefense on a VxRail cluster and for protecting the VxRail Manager
virtual machine.
January 2021
Revisions
Date
Description
May 2019
Initial release
Revisions
The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this
publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose.
Use, copying, and distribution of any software described in this publication requires an applicable software license.
Copyright © 2019-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. or its
subsidiaries. Other trademarks may be trademarks of their respective owners. [1/6/2021]
2 Installing and Configuring VMware AppDefense on VxRail Manager

Table of contents
Table of contents
Revisions............................................................................................................................................................................. 2
Table of contents ................................................................................................................................................................ 3
1 AppDefense Installation ............................................................................................................................................... 4
1.1 Enable Platinum License .................................................................................................................................... 4
1.1.1 Install AppDefense Plug-in ................................................................................................................................. 4
1.1.2 Register the AppDefense Appliance with vCenter Server .................................................................................. 5
1.1.3 Enable AppDefense Service (SaaS Connectivity Mode) ................................................................................... 6
1.2 Install the Host Module ....................................................................................................................................... 8
1.3 Install the Guest Module ..................................................................................................................................... 8
1.3.1 Linux Guest Prerequisites .................................................................................................................................. 8
1.3.2 Install Guest Module on Linux System Using Local Download .......................................................................... 9
1.3.3 For SLES systems: ............................................................................................................................................. 9
1.4 After Installation ................................................................................................................................................ 12
2 Using AppDefense Manager ...................................................................................................................................... 15
2.1.1 Creating a scope............................................................................................................................................... 15
2.1.2 Review of state in AppDefense Manager (Cloud) ............................................................................................ 16
2.1.3 Switching from Discovery to Protection Mode .................................................................................................. 18
2.1.4 AppDefense Informational screenshots ........................................................................................................... 20
2.2 VxRail Manager issues when in protection mode ............................................................................................ 22
2.2.1 Adding node: Attestation Alarm ........................................................................................................................ 22
2.2.2 Adding Node – raised AppDefense Events ...................................................................................................... 23
2.2.3 Re-adding a node ............................................................................................................................................. 28
2.2.4 Post-Add Node ................................................................................................................................................. 29
2.2.5 LCM: Upgrading VxRail .................................................................................................................................... 31
3 Installing and Configuring VMware AppDefense on VxRail Manager

1 AppDefense Installation
Installation is straightforward, as described in the VMware guide, Installing AppDefense with AppDefense
Plug-In. The main steps are:
1. Enable the Platinum license.
2. Install the AppDefense plug-in.
3. Install the host module on the cluster host.
4. Install the Guest module on the VMs that you want to protect.
1.1 Enable Platinum license
1. In vCenter, navigate to: Home > Administration > Licenses.
2. Click: +Add New Licenses.
3. Add license.
4. Set Name: VMware vSphere 6 for Platinum with AppDefense Plugin
5. Navigate to: Licenses > Assets > Hosts.
6. Select all hosts on the VxRail cluster.
7. Click: Assign License and select Platinum from the list. Click OK.
1.1.1 Install AppDefense plug-in
Refer to the VMware guide here.
1. Download the AppDefense OVA.
2. Install the AppDefense appliance by installing the OVA template in vCenter, and use the following
settings:
• VM Name: AppDefense-Appliance
• Location: <VxRail-Datacenter name>
• Compute Resource: <VxRail cluster name>
• Storage: VxRail vSAN Datastore, policy: VXRAIL-SYSTEM-STORAGE-PROFILE
• Network: Management Network
• Customize template:
i. Initial root, admin pwds
ii. Default GW
iii. Domain name
iv. Domain search path
v. DNS
vi. IP
vii. Netmask
The following figure shows how the Deploy OVF template screen should look:
4 Installing and Configuring VMware AppDefense on VxRail Manager
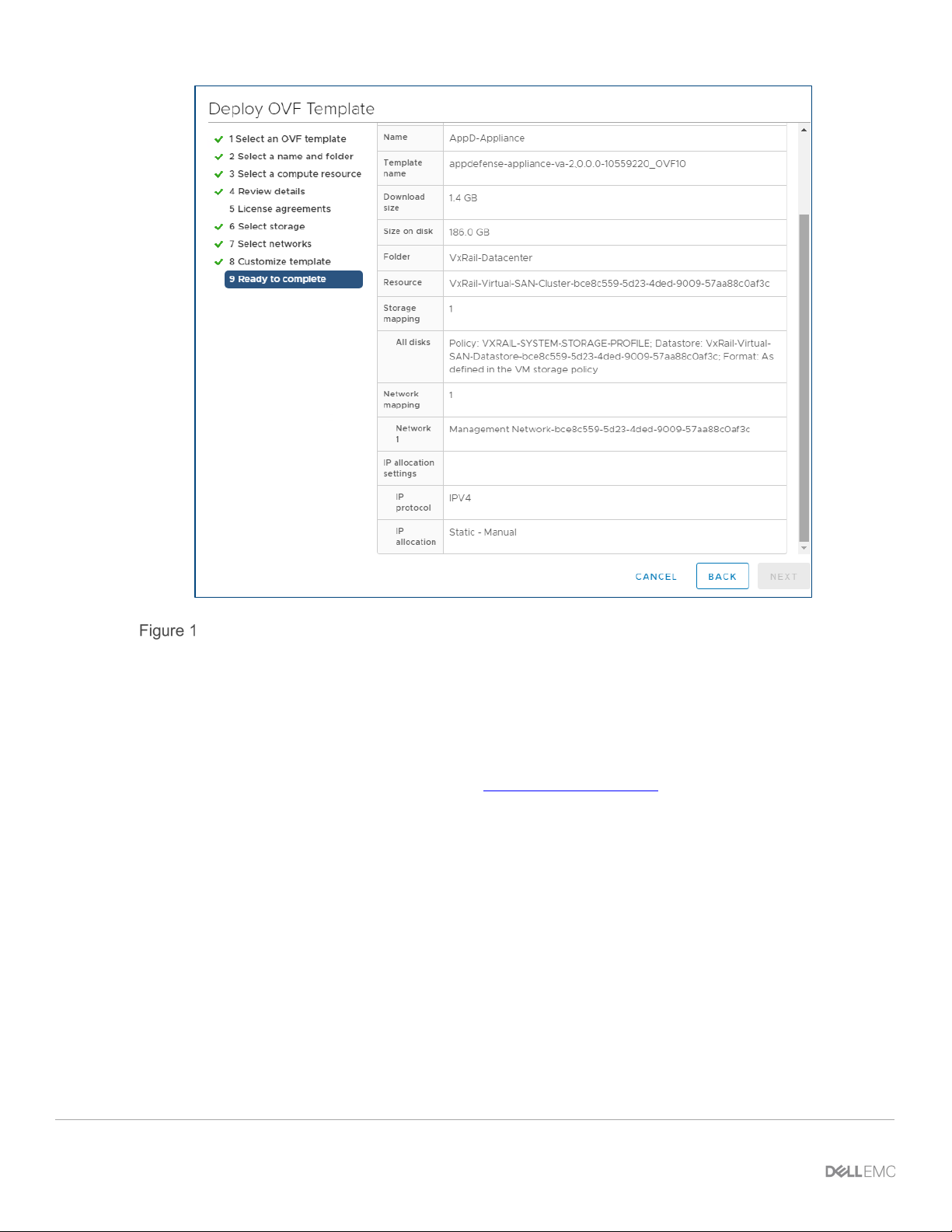
OVF template
• Click Finish. vCenter imports the OVF and displays the AppDefense appliance VM in the VxRail
cluster.
• Log out of vCenter and log back in. Notice the AppDefense icon is now part of the Home menu in
vCenter.
1.1.2 Register the AppDefense appliance with vCenter Server
1. Browse to the AppDefense appliance at https://<AppDefense-IP>.
2. Go to the Configuration > Registration tab.
3. Leave Connectivity Mode set to Online for the moment.
4. Under the SSO lookup configuration, enter the PSC hostname and provide its credentials.
5. Select the vCenter server from the dropdown list and register it.
The following figure shows how the AppDefense Manager registration screen should look:
5 Installing and Configuring VMware AppDefense on VxRail Manager
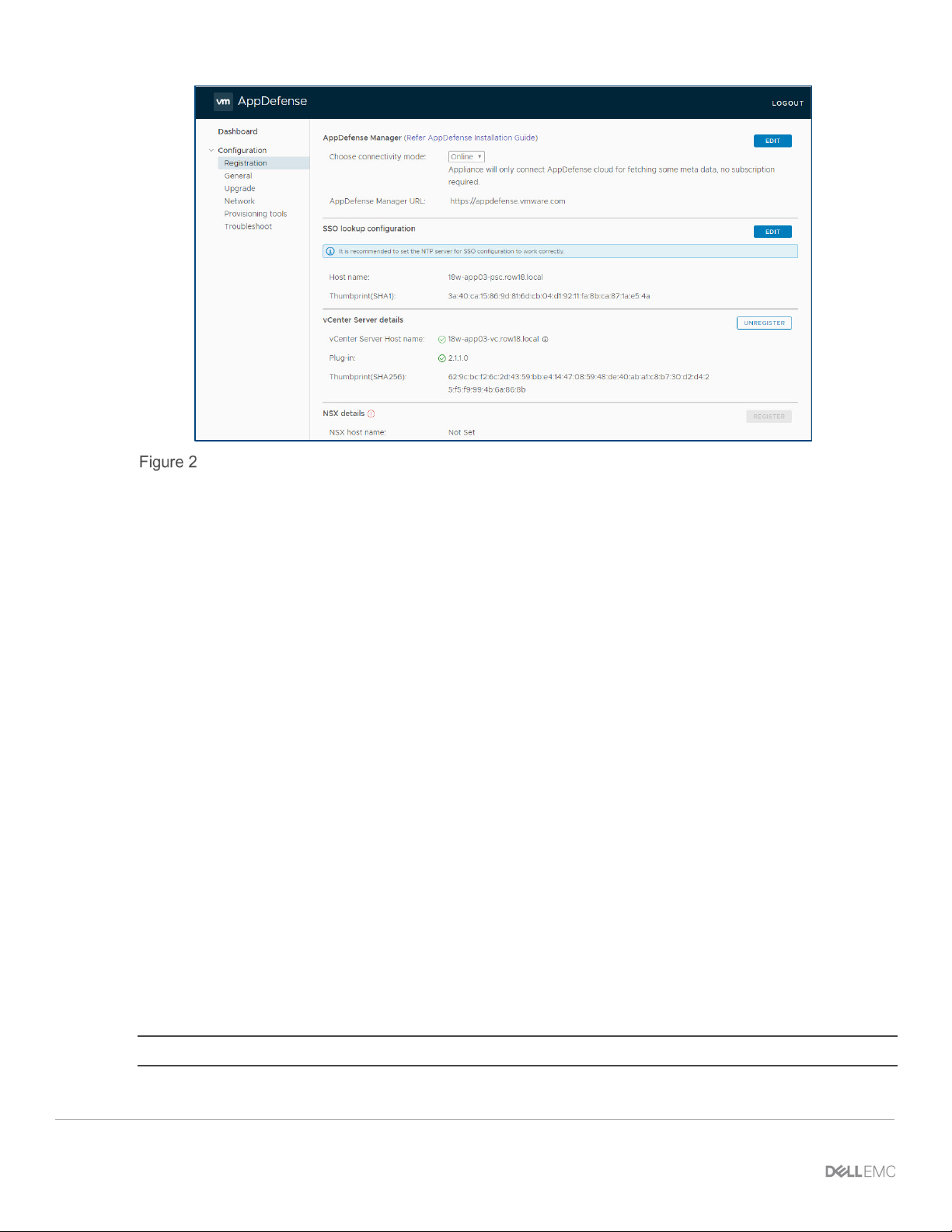
AppDefense Manager Registration
1.1.3 Enable AppDefense service (SaaS connectivity mode)
You can enable the AppDefense service when you register the AppDefense appliance with vCenter server.
Switching the AppDefense appliance connectivity to SaaS enables the AppDefense appliance to
communicate with the AppDefense service, enabling the complete solution.
1.1.3.1 Prerequisites
• You have installed the AppDefense appliance.
• The AppDefense appliance VM is powered-on.
• You have provisioned the AppDefense appliance as described in the following steps.
1. Log in to AppDefense Manager.
2. Navigate to the settings icon > Appliance > Provision New Appliance page. The New appliance
window opens.
3. Create an appliance by entering the appliance name.
The appliance name is an identifier and does not need to match the actual VM name within the
vCenter Server, but the best practice is to match the names. For example, AppDefense appliance.
4. Click Provision.
5. The New Appliance Created window displays the URL for the manager in the region, UUID, and
appliance API key. Keep this window open until the appliance configuration is done, or make a note
of the information which will be used in SaaS configuration.
1.1.3.2 Procedure
1. Open a web browser and navigate to the AppDefense appliance GUI at https://<appliance
ip address>. The Select a Certificate window opens.
2. Log in to the AppDefense appliance using either the admin credentials or using the certificate.
• If you want to log in to the AppDefense appliance using the admin credentials, click Cancel. Use
the admin credentials that you added while installing the AppDefense appliance OVA file.
Important: Do not click OK to accept the certificate.
6 Installing and Configuring VMware AppDefense on VxRail Manager
• If you want to log in to the AppDefense appliance using a self-signed or CA certificate, follow the
procedure described in the VMware Log In to AppDefense Appliance with Certificate
topic.
The AppDefense dashboard opens as the default home page.
3. Go to the Configuration > Registration tab.
4. In the AppDefense Manager section, click Edit, change connectivity mode to SAAS, and
configure the following values (noted during the appliance creation process in section 1.1.3.1):
• AppDefense Manager URL
• Manager UUID
• Manager API key
5. Click Save.
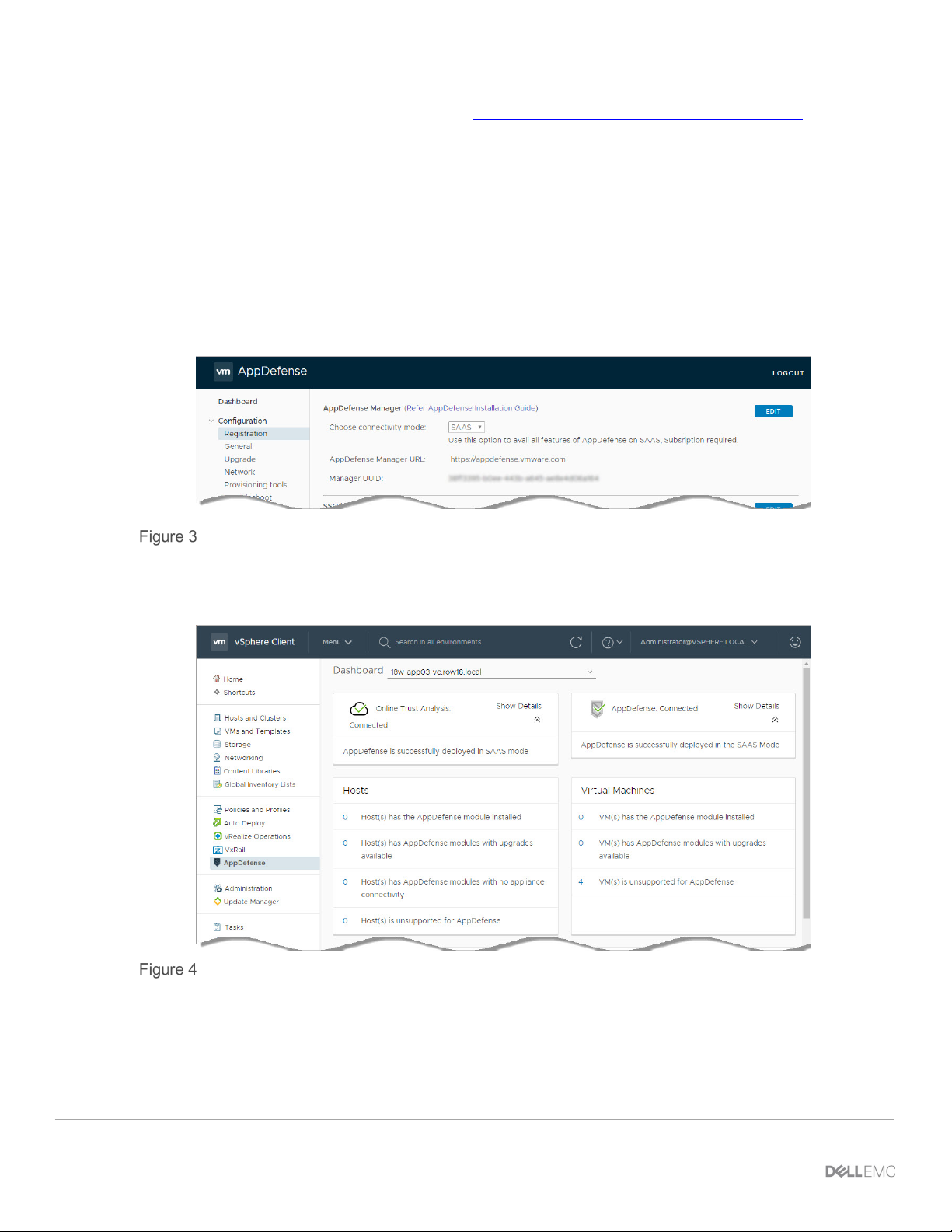
The AppDefense Manager pane in the Registration screen of the AppDefense appliance should now
reflect the new SAAS connectivity mode as shown in the following figure:
AppDefense Manager pane
Having registered the required information in the AppDefense appliance, we can now see the
AppDefense plug-in showing the AppDefense dashboard in vSphere Client as shown in the following
figure:
Vsphere Client – AppDefense dashboard
Notice the connectivity mode is now SAAS and no hosts or virtual machines have the AppDefense
module installed yet.
7 Installing and Configuring VMware AppDefense on VxRail Manager
1.2 Install the host module
After you have installed and registered the plug-in, you are ready to install the AppDefense host module on
your ESXi hosts. As the VMware manual
time, or you can install it individually on each host.
The easiest way is to install it on all hosts, with a single click from the Cluster > Configuration, and click
Enable AppDefense For All Hosts.
1.3 Install the guest module
The installation of the AppDefense guest module includes the AppDefense package, Guest Introspection
package, and the netfilter dependencies. The guest module must be installed on all workload VMs that you
want to protect.
LIMITATIONS:
• AppDefense does not work with virtual machines that have Fault Tolerance enabled. This
limitation applies to both Linux and Windows guest virtual machines.
• Monitoring vCenter, PSC’s and AppDefense itself is currently not supported.
page shows, you can install it on all hosts in a cluster at the same
NOTE: If a resource allocation such as CPU or memory is changed at any time, you must reboot the guest
VM.
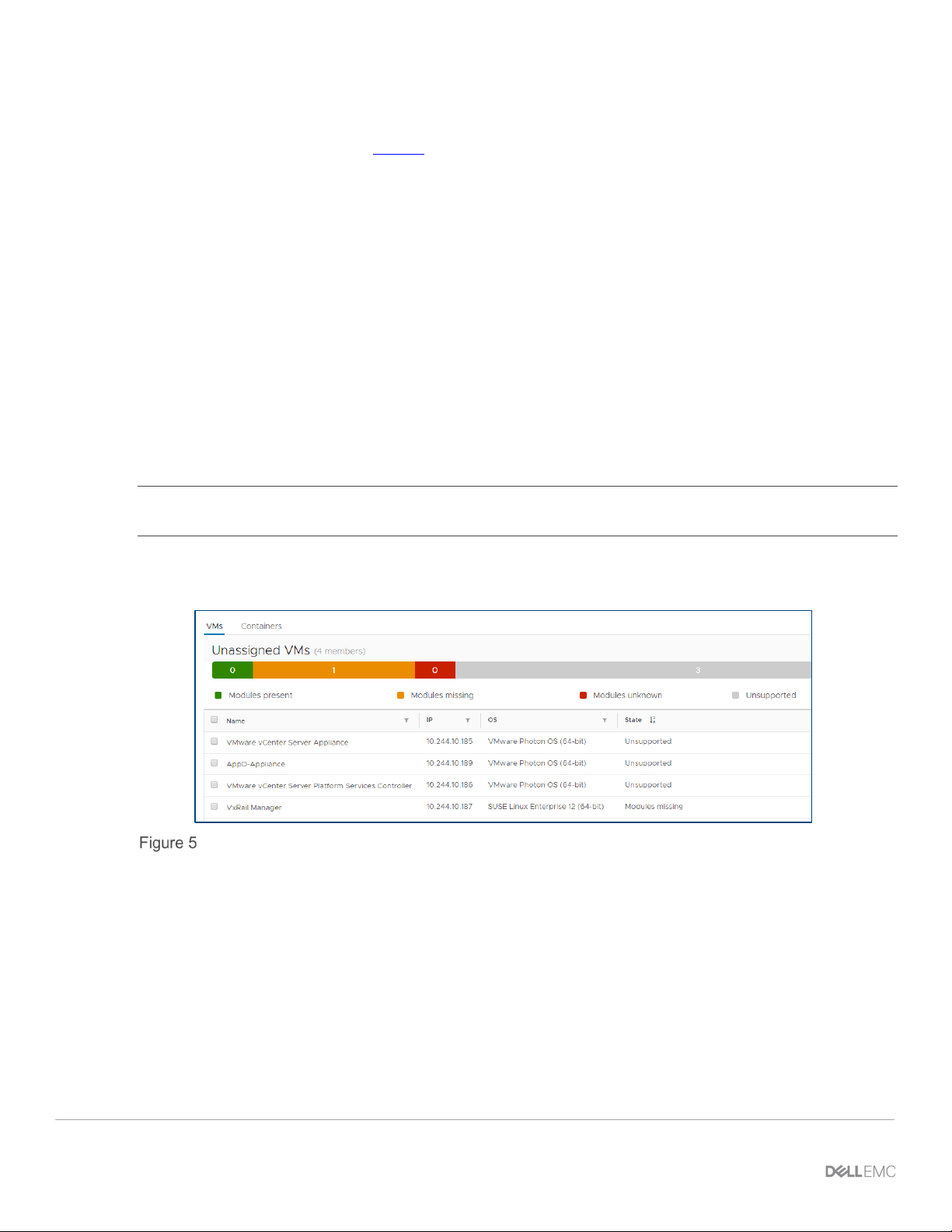
In the following screenshot, taken from AppDefense Manager, the only VMs in our cluster are the vCSA, PSC,
VxRail Manager and AppDefense appliance.
Unassigned VMs
1.3.1 Linux guest prerequisites
Ensure that the guest virtual machine (VM) complies with the following prerequisites:
• ESXi 6.5 U1 or later is installed.
The VxRail Manager VM runs on the cluster hosts, which run VMware ESXi 6.7.0.
• A supported version of Linux is installed.
The VxRail Manager VM running SLES 12.2.
• iptables package of 1.4.11 version or later is installed.
Iptables version is: v1.4.21
8 Installing and Configuring VMware AppDefense on VxRail Manager

• Verify glib 2 is installed on the Linux VM.
The following glib packages are already installed:
1.3.2 Install guest module on Linux system using local download
VMware manual page here.
This is a common step for any Linux distribution. Download and import the complete VMware package using
the given URLs. Use the following commands to unpack the required tar files:
18w-app03-vxm:~ # cd /AppDefense/LinuxGuestModule
18w-app03-vxm:~/AppDefense/LinuxGuestModule # ls -l
total 2676
-rw-r--r-- 1 root root 696320 Oct 20 19:33 AppDefense.tar
-rw-r--r-- 1 root root 522240 Oct 20 19:33 guest-introspection-for-vmware-nsx.tar
-rw-r--r-- 1 root root 1495040 Oct 20 19:33 guest-introspection-os-bundle.tar
18w-app03-vxm:~/AppDefense/LinuxGuestModule # for f in *.tar;do tar -xf $f; done
18w-app03-vxm:~/AppDefense/LinuxGuestModule # ls -l
total 2676
drwxr-xr-x 6 361763 201 4096 Oct 20 18:44 AppDefense
-rw-r--r-- 1 root root 696320 Oct 20 19:33 AppDefense.tar
drwxr-xr-x 4 361763 201 4096 Oct 20 18:44 guest-introspection-for-vmware-nsx
-rw-r--r-- 1 root root 522240 Oct 20 19:33 guest-introspection-for-vmware-nsx.tar
drwxr-xr-x 6 361763 201 4096 Oct 20 18:44 guest-introspection-os-bundle
-rw-r--r-- 1 root root 1495040 Oct 20 19:33 guest-introspection-os-bundle.tar
1.3.3 For SLES systems:
1. Get the public key and import into rpm:
18w-app03-vxm:~ # cd /root/AppDefense/LinuxGuestModule/AppDefense/key
18w-app03-vxm:~/AppDefense/LinuxGuestModule/AppDefense/key # rpm --import VMWARE-APPDEFENSEPACKAGING-GPG-RSA-KEY.pub
2. Add the following repositories:
18w-app03-vxm:~/AppDefense # zypper ar "file:/root/AppDefense/LinuxGuestModule/AppDefense/latest" AppDefense
Adding repository 'AppDefense'
...............................................................................................................
................................[done]
Repository 'AppDefense' successfully added
URI : file:/root/AppDefense/LinuxGuestModule/AppDefense/latest
Enabled : Yes
GPG Check : Yes
Autorefresh : No
Priority : 99 (default priority)
Repository priorities are without effect. All enabled repositories share the same priority.
18w-app03-vxm:~/AppDefense # zypper ar "file:/root/AppDefense/LinuxGuestModule/guest-introspection-for-vmwarensx/latest/sles/x86_64/" guest-introspection-for-vmware-nsx
Adding repository 'guest-introspection-for-vmware-nsx'
...............................................................................................................
........[done]
Repository 'guest-introspection-for-vmware-nsx' successfully added
URI : file:/root/AppDefense/LinuxGuestModule/guest-introspection-for-vmware-nsx/latest/sles/x86_64/
Enabled : Yes
GPG Check : Yes
Autorefresh : No
Priority : 99 (default priority)
Repository priorities are without effect. All enabled repositories share the same priority.
9 Installing and Configuring VMware AppDefense on VxRail Manager

3. For SLES 11.4, 12.2, or 12.3: To install a dependent component, run the following command to add
the extra repository:
18w-app03-vxm:~/AppDefense # zypper ar "file:/root/AppDefense/LinuxGuestModule/guest-introspection-
os-bundle/sles/12.2/" gios
Adding repository 'gios'
...............................................................................................................
......................................[done]
Repository 'gios' successfully added
URI : file:/root/AppDefense/LinuxGuestModule/guest-introspection-os-bundle/sles/12.2/
Enabled : Yes
GPG Check : Yes
Autorefresh : No
Priority : 99 (default priority)
Repository priorities are without effect. All enabled repositories share the same priority.
4. Install the AppDefense Guest Module package.
Note: There is a pre-existing SLES repo defined, which points to a remote IP location. This causes a timeout
and prevents using the AppDefense repos that have just been added, resulting in a failure to install.
The repository that you must remove is a default SLES repository and can be identified as follows:
To identify the repositories that are currently defined in zipper:
18w-app03-vxm:~/AppDefense # zypper lr
Repository priorities are without effect. All enabled repositories share the same priority.
# | Alias | Name | Enabled | GPG Check | Refresh
--+------------------------------------+------------------------------------+---------+-----------+--------
1 | SLES12-SP2-12.2-0 | SLES12-SP2-12.2-0 | Yes | (r ) Yes | Yes
2 | AppDefense | AppDefense | Yes | ( p) Yes | No
3 | gios | gios | Yes | ( p) Yes | No
4 | guest-introspection-for-vmware-nsx | guest-introspection-for-vmware-nsx | Yes | ( p) Yes | No
18w-app03-vxm:~/AppDefense # ls -l /etc/zypp/repos.d/
total 16
-rw-r--r-- 1 root root 147 Nov 30 12:56 SLES12-SP2-12.2-0.repo
-rw-r--r-- 1 root root 112 Feb 5 09:28 AppDefense.repo
-rw-r--r-- 1 root root 129 Feb 5 09:28 gios.repo
-rw-r--r-- 1 root root 173 Feb 5 09:28 guest-introspection-for-vmware-nsx.repo
The pre-existing SLES repository is currently enabled:
18w-app03-vxm:~/AppDefense # more /etc/zypp/repos.d/SLES12-SP2-12.2-0.repo
::::::::::::::
/etc/zypp/repos.d/SLES12-SP2-12.2-0.repo
::::::::::::::
[SLES12-SP2-12.2-0]
name=SLES12-SP2-12.2-0
enabled=1
autorefresh=1
baseurl=http://<baseurlIP>/build/.0/repo/iso
path=/
type=yast2
keeppackages=0
With all repos having equal priority and the SLES repo being repo #1, it will use that repo first. For now,
disabling that repo should resolve the installation issue. In the SLES repository file, change the value
for enabled from 1 to 0:
::::::::::::::
/etc/zypp/repos.d/SLES12-SP2-12.2-0.repo
::::::::::::::
[SLES12-SP2-12.2-0]
name=SLES12-SP2-12.2-0
enabled=0 # DISABLED BY CHANGING THIS FROM 1 to 0
10 Installing and Configuring VMware AppDefense on VxRail Manager
 Loading...
Loading...