Page 1

AirWave Wireless
Management Suite
Configuration Guide
Page 2

Copyright
© 2010 Aruba Networks, Inc. AirWave®, Aruba Networks®, Aruba Mobility Management System®, Bluescanner, For Wireless That
Works®, Mobile Edge Architecture®, People Move. Networks Must Follow®, RFProtect®, The All Wireless Workplace Is Now Open For
Business, Green Island, and The Mobile Edge Company® are trademarks of Aruba Networks, Inc. All rights reserved. All other
trademarks are the property of their respective owners.
While every effort has been made to ensure technical accuracy, information in this document is subject to change without notice and
does not represent a commitment on the part of AirWave Wireless.
AirWave Wireless is not connected, affiliated or related to Airwave O2 Limited in any manner.
Open Source Code
Certain Aruba products include Open Source software code developed by third parties, including software code subject to the GNU
General Public License (GPL), GNU Lesser General Public License (LGPL), or other Open Source Licenses. The Open Source code
used can be found at this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba Networks, Inc. switching platforms and software, by all individuals or corporations, to terminate other vendors' VPN
client devices constitutes complete acceptance of liability by that individual or corporation for this action and indemnifies, in full, Aruba
Networks, Inc. from any and all legal actions that might be taken against it with respect to infringement of copyright on behalf of those
vendors.
Warranty
This hardware product is protected by the standard Aruba warranty of one year parts/labor. For more information, refer to the
ARUBACARE SERVICE AND SUPPORT TERMS AND CONDITIONS. Altering this device (such as painting it) voids the warranty.
www.arubanetworks.com
1344 Crossman Avenue
Sunnyvale, California 94089
Phone: 408.227.4500
Fax 408.227.4550
AirWave Wireless Management Suite | Configuration Guide 0510802-01 | September 2010
Page 3

Contents
Preface.........................................................................................................................................7
Document Audience and Organization ........................................................................7
Related Documents ..................................................................................................... 7
Text Conventions .........................................................................................................8
Contacting AirWave Wireless and Aruba Networks.....................................................9
Chapter 1 Aruba Configuration in AWMS ...................................................................11
Introduction................................................................................................................11
Requirements, Restrictions, and AOS Support in AWMS .........................................12
Requirements.....................................................................................................................12
Restrictions........................................................................................................................12
AOS Support in AWMS......................................................................................................12
Overview of Aruba Configuration in AWMS...............................................................12
The Primary Pages of Aruba Configuration .......................................................................13
Device Setup > Aruba Configuration Page........................................................................13
Aruba AP Groups Section ..........................................................................................14
AP Overrides Section .................................................................................................15
WLANs Section...........................................................................................................16
Profiles Section...........................................................................................................16
Security Section..........................................................................................................17
Advanced Services Section........................................................................................ 18
Groups > Aruba Config Page.............................................................................................19
APs/Devices > List Page....................................................................................................19
APs/Devices > Manage Page ............................................................................................20
APs/Devices > Monitor Page.............................................................................................20
Groups > Basic Page.........................................................................................................21
Additional Concepts and Components of Aruba Configuration ................................21
Global Configuration and Scope .......................................................................................21
Embedded Profile Setup in Aruba Configuration...............................................................21
Controller Overrides...........................................................................................................22
Save, Save and Apply, and Revert Buttons.......................................................................23
Folders, Users, and Visibility..............................................................................................23
Additional Concepts and Benefits .....................................................................................23
Scheduling Configuration Changes............................................................................23
Auditing and Reviewing Configurations .....................................................................23
Licensing and Dependencies in Aruba Configuration ................................................24
Setting Up Initial Aruba Configuration .......................................................................24
Prerequisites...............................................................................................................24
Procedure ...................................................................................................................24
What Next? ........................................................................................................................30
Additional Capabilities of Aruba Configuration..................................................................31
Chapter 2 Using Aruba Configuration in Daily Operations........................................ 33
Introduction................................................................................................................33
General Aruba AP Groups Procedures and Guidelines .............................................34
General WLAN Procedures and Guidelines...............................................................37
AirWave Wireless Management Suite | Configuration Guide Contents | 3
Guidelines and Pages for Aruba AP Groups in Aruba Configuration ................................34
Selecting Aruba Controller Groups....................................................................................34
Configuring Aruba AP Groups ...........................................................................................34
What Next?.................................................................................................................36
Guidelines and Pages for WLANs in Aruba Configuration.................................................37
Configuring or Editing WLANs with Basic View.................................................................37
Configuring or Editing WLANs with Advanced View .........................................................38
Page 4

General Profiles Guidelines........................................................................................ 39
General Controller Procedures and Guidelines ......................................................... 40
Using Master, Standby Master, and Local Controllers in Aruba Configuration ................ 40
Pushing Device Configurations to Controllers................................................................... 40
Supporting APs with Aruba Configuration................................................................. 41
AP Overrides Guidelines.................................................................................................... 41
Configuring or Editing AP Overrides.................................................................................. 41
Changing Adaptive Radio Management (ARM) Settings................................................... 42
Changing SSID and Encryption Settings........................................................................... 43
Changing the Aruba AP Group for an AP Device.............................................................. 43
Using AWMS to Deploy Aruba APs for the First Time....................................................... 43
Using General AWMS Device Groups and Folders........................................................... 45
Visibility in Aruba Configuration................................................................................. 45
Visibility Overview.............................................................................................................. 45
Defining Visibility for Aruba Configuration ......................................................................... 46
Appendix A Aruba Configuration Reference ................................................................. 49
Introduction................................................................................................................ 49
Aruba AP Groups Pages and Field Descriptions ....................................................... 53
Aruba AP Groups............................................................................................................... 53
AP Overrides Pages and Field Descriptions.............................................................. 57
AP Overrides...................................................................................................................... 57
WLAN Pages and Field Descriptions......................................................................... 62
Overview of WLANs in Aruba Configuration...................................................................... 62
WLANs...............................................................................................................................62
WLANs > Basic..................................................................................................................63
WLANs > Advanced .......................................................................................................... 64
Profiles Pages and Field Descriptions ....................................................................... 68
Understanding Aruba Configuration Profiles..................................................................... 68
Profiles > AAA.................................................................................................................... 69
Profiles > AAA.................................................................................................................... 70
Profiles > AAA > Captive Portal Auth ................................................................................ 71
Modifying the Initial User Role.................................................................................... 73
Profiles > AAA > Mac Auth ................................................................................................ 73
Profiles > AAA > Stateful 802.1X Auth............................................................................... 75
Profiles > AAA > Wired Auth.............................................................................................. 76
Profiles > AAA > VPN Auth................................................................................................ 76
Profiles > AAA > Management Auth.................................................................................. 77
Profiles > AAA > 802.1x Auth ............................................................................................ 78
Profiles > AAA > Stateful NTLM Auth................................................................................ 83
Profiles > AAA > WISPr Auth............................................................................................. 84
Profiles > AP...................................................................................................................... 86
Profiles > AP > System...................................................................................................... 86
Profiles > AP > Regulatory Domain................................................................................... 91
Profiles > AP > AP Wired................................................................................................... 92
Profiles > AP > AP Ethernet Link ....................................................................................... 94
Profiles > AP > SNMP ....................................................................................................... 94
Profiles > AP > SNMP > SNMP User ................................................................................ 95
Aruba Controller Traps ......................................................................................................96
Access Point/Air Monitor Traps.................................................................................. 97
Profiles > IDS..................................................................................................................... 98
Profiles > IDS > General ..................................................................................................101
Profiles > IDS > Signature Matching ............................................................................... 102
Profiles > IDS > Signature Matching > Signatures..........................................................103
Profiles > IDS > Denial of Service.................................................................................... 103
Profiles > IDS > Denial of Service > Rate Threshold ....................................................... 106
Profiles > IDS > Impersonation........................................................................................ 108
Profiles > IDS > Unauthorized Device .............................................................................109
Profiles > Mesh................................................................................................................ 112
Profiles > Mesh > Radio .................................................................................................. 112
Profiles > Mesh > Radio > Mesh HT SSID ...................................................................... 114
4 |Contents AirWave Wireless Management Suite | Configuration Guide
Page 5

Profiles > Mesh > Cluster ................................................................................................116
Profiles > QoS..................................................................................................................117
Profiles > QoS > Traffic Management .............................................................................117
Profiles > QoS > VoIP Call Admission Control ................................................................118
Profiles > QoS > WMM Traffic Management...................................................................121
Profiles > RF ....................................................................................................................122
Profiles > RF > 802.11a/g Radio......................................................................................122
Profiles > RF > 802.11a/g Radio > ARM..........................................................................124
Profiles > RF > 802.11a/g Radio > High-Throughput (HT) Radio....................................128
Profiles > RF > Event Thresholds ....................................................................................129
Profiles > RF > Optimization............................................................................................130
Profiles > SSID.................................................................................................................132
Profiles > SSID > EDCA AP .............................................................................................134
Profiles > SSID > EDCA AP .............................................................................................138
Profiles > SSID > EDCA Station.......................................................................................140
Profiles > SSID > HT SSID...............................................................................................144
Profiles > SSID > 802.11K ...............................................................................................145
Security Pages and Field Descriptions ....................................................................147
Security > User Roles ......................................................................................................148
Security > User Roles > BW Contracts ...........................................................................150
Security > User Roles > VPN Dialers...............................................................................151
Security > Policies ...........................................................................................................153
Security > Policies > Destinations ...................................................................................154
Security > Policies > Services .........................................................................................155
Security > Server Groups ................................................................................................156
Server Groups Page Overview ................................................................................. 156
Supported Servers....................................................................................................156
Adding a New Server Group.....................................................................................157
Security > Server Groups > LDAP...................................................................................158
Security > Server Groups > RADIUS...............................................................................160
Security > Server Groups > TACACS..............................................................................160
Security > Server Groups > Internal ................................................................................161
Security > Server Groups > XML API ..............................................................................162
Security > Server Groups > RFC 3576............................................................................164
Security > Server Groups > Windows .............................................................................164
Security > TACACS Accounting ......................................................................................166
Security > Time Ranges...................................................................................................166
Security > User Rules ......................................................................................................167
Advanced Services Pages and Field Descriptions ..................................................168
Overview of IP Mobility Domains.....................................................................................168
Advanced Services > IP Mobility.....................................................................................170
Advanced Services > IP Mobility > Mobility Domain.......................................................173
Advanced Services > VPN Services................................................................................174
Advanced Services > VPN Services > IKE ......................................................................175
Advanced Services > VPN Services > L2TP....................................................................176
Advanced Services > VPN Services > PPTP...................................................................178
Advanced Services > VPN Services > IPSEC..................................................................179
Advanced Services > VPN Services > IPSEC > Dynamic Map.......................................180
Advanced Services > VPN Services > IPSEC > Dynamic Map > Transform Set ............ 181
Groups > Aruba Config Page and Section Information ...........................................182
Index...................................................................................................................................185
AirWave Wireless Management Suite | Configuration Guide Contents | 5
Page 6

6 |Contents AirWave Wireless Management Suite | Configuration Guide
Page 7
Preface
Document Audience and Organization
This configuration guide is intended for wireless network administrators and helpdesk personnel who
deploy ArubaOS (AOS) on the network and wish to manage it with the AirWave Wireless Management Suite
(AWMS). AWMS Versions 6.3 and later support Aruba Configuration. This document provides instructions
for using Aruba Configuration and contains the following chapters:
Table 1 Document Organization and Purposes
Chapter Description
Chapter 1, “Aruba Configuration in AWMS” Introduces the concepts, components, navigation, and initial
setup of Aruba Configuration.
Chapter 2, “Using Aruba Configuration in Daily
Operations”
Appendix A, “Aruba Configuration Reference” Provides an encyclopedic reference to the fields, settings, and
Provides a series of procedures for configuring, modifying, and
using Aruba Configuration once initial setup is complete. This
chapter is oriented around the most common tasks in Aruba
Configuration.
default values of all Aruba Configuration components, to include a
few additional procedures supporting more advanced
configurations.
Related Documents
The following documentation supports the AirWave Wireless Management Suite:
ArubaOS Documentation
z AOS User Guide
AirWave Wireless Management Suite / AirWave Management Platform
z Release Notes for the AirWave Wireless Management Suite
z AirWave Wireless Management Suite Knowledge Base
z AWMS Quick Start Guide
z AWMS User Guide
z Aruba Configuration Guide (this document)
z Supported APs/Devices
z Supported Firmware Versions
VisualRF
z Release Notes for the AirWave Wireless VisualRF Module
z Overview Page
z User Guide
AirWave Wireless Management Suite | Configuration Guide Preface | 7
Page 8
RAPIDS
z Overview Page
z AirWave Management Client User Guide
z Download AirWave Management Client
Best Practice Guides
z Aruba and AirWave Best Practices Guide
z Choosing the Right Server Hardware
z Helpdesk Guide: Troubleshooting WLAN Issues
z Converting Cisco IOS APs to LWAPP
Interfacing With AWMS
z AWMS Integration Matrix
z State and Statistical XML API Documentation
z Location XML API Documentation
NMS Integration
z See AMP Setup NMS
z Download AWMS Trap MIB
z AWMS/NMS Integration Guide
AMPWatch Widget
z AMPWatch is a widget for the Yahoo! Widget Engine
z Download AMPWatch
Text Conventions
The following conventions are used throughout this manual to emphasize important concepts:
Table 2 Text Conventions
Type Style Description
Italics This style is used to emphasize important terms and to mark the titles of books.
GUI components Bold, sans-serif font indicates that the AWMS GUI displays this item exactly as cited in
body text.
System items This fixed-width font depicts the following:
z Sample screen output
z System prompts
z Filenames, software devices, and specific commands when mentioned in the text
Commands In the command examples, this bold font depicts text that you must type exactly as
This document uses the following notice icons to emphasize advisories for certain actions, configurations,
or concepts:
8 | Preface AirWave Wireless Management Suite | AWMS Version 7.1
shown.
Page 9

NOTE
Indicates helpful suggestions, pertinent information, and important things to remember.
!
CAUTION
Indicates a risk of damage to your hardware or loss of data.
Contacting AirWave Wireless and Aruba Networks
Online Contact and Support
Main Website http://www.airwave.com
Email Contact
z AirWave Wireless Sales sales@airwave.com
z AirWave Wireless Technical Support support@airwave.com
z Aruba Networks general information info@arubanetworks.com
z Aruba Networks Sales sales@arubanetworks.com
z Aruba Networks Technical Support in the Americas
support@arubanetworks.com
and APAC
z Aruba Networks Technical Support in the EMEA emea_support@arubanetworks.com
z WSIRT Email—Please email details of any security
wsirt@arubanetworks.com
problem found in an AirWave or Aruba product.
Telephone Contact and Support
AirWave Wireless Corporate Headquarters +1 (408) 227-4500
FAX +1 (408) 227-4550
Support
z United States 800-WI-FI-LAN (800-943-4526)
z Universal Free Phone Service Number (UIFN):
Australia, Canada, China, France, Germany, Hong
Kong, Ireland, Israel, Japan, Korea, Singapore, South
Africa, Taiwan, and the UK.
z All Other Countries +1 (408) 754-1200
+800-4WIFI-LAN (+800-49434-526)
AirWave Wireless Management Suite |AWMS Version 7.1 Preface | 9
Page 10

10 | Preface AirWave Wireless Management Suite | AWMS Version 7.1
Page 11
Chapter 1
NOTE
Aruba Configuration in AWMS
Introduction
ArubaOS (AOS) is the operating system, software suite, and application engine that operates Aruba mobility
controllers and centralizes control over the entire mobile environment. The AOS Wizards, the AOS
command-line interface (CLI), and the AOS WebUI are the primary means by which to configure and deploy
AOS. For a complete description of AOS, refer to the ArubaOS User Guide for your release.
The Aruba Configuration feature in the AirWave Wireless Management Suite consolidates AOS
configuration and pushes global Aruba configurations from one utility. This chapter introduces the
components and initial setup of Aruba Configuration with the following topics:
Requirements, Restrictions, and AOS Support in AWMS
z Requirements
z Restrictions
z AOS Support in AWMS
Overview of Aruba Configuration in AWMS
z The Primary Pages of Aruba Configuration
z Device Setup > Aruba Configuration Page
Aruba AP Groups Section
AP Overrides Section
WLANs Section
Profiles Section
Security Section
Advanced Services Section
z Groups > Aruba Config Page
z APs/Devices > List Page
z APs/Devices > Manage Page
z APs/Devices > Monitor Page
z Groups > Basic Page
Additional Concepts and Components of Aruba Configuration
z Global Configuration and Scope
z Embedded Profile Setup in Aruba Configuration
z Controller Overrides
z Save, Save and Apply, and Revert Buttons
z Folders, Users, and Visibility
z Additional Concepts and Benefits
Setting Up Initial Aruba Configuration
AWMS supports Aruba AP Groups, and these are distinct and must not be confused with standard AWMS Device
Groups. This document provides information about the configuration and use of Aruba AP Groups, and describes
how Aruba AP Groups interoperate with standard AWMS Device Groups.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 11
Page 12
Requirements, Restrictions, and AOS Support in AWMS
NOTE
Requirements
Aruba Configuration has the following requirements in AWMS:
z AWMS 6.3 or a later AWMS version must be installed and operational on the network.
z Aruba Controllers on the network must have AOS installed and operational.
z Ensure you have Telnet/SSH credentials (configuration only) and the “enable” password (configuration
only). Without proper Telnet/SSH credentials a user is not able to fetch the running configuration, nor
acquire license and serial information from controllers.
Restrictions
Aruba Configuration has the following restrictions in AWMS:
z At the present time, Aruba Configuration in AWMS does not support every AOS Network component.
AWMS supports only
z Future versions of AWMS will support additional AOS features, to include Aruba AP Group and Profile
distribution from the Master Console.
AOS Support in AWMS
IP Mobility and VLANs in the Advanced Services section, for example.
Refer also to “Using AWMS to Deploy Aruba APs for the First Time” on page39.
AWMS users can choose between the existing template-based configuration and new GUI-based configuration
for Aruba devices on firmware 3.3.2.10 and greater. Upon upgrading to AWMS, groups with all devices in
monitor-only mode will automatically use the GUI-based configuration.
z Only global configuration is supported; AWMS can work in a master-local or an all-master configuration.
z Configuration changes are pushed to the controller via SSH with no reboot required.
z All settings for Profiles, Aruba AP Groups, Servers and Roles are supported, as is the AOS WLAN Wizard
(basic view). Controller IP addresses, VLANs and interfaces are not supported, nor are Advanced
Services with the exception of VPN and IP Mobility.
z AWMS now understands AOS license dependencies.
z You can provision thin APs from the AP/Devices > Manage page. You can move APs into Aruba AP
Groups
z You can configure AP names as AP Overrides on the Device Setup > Aruba Configuration page.
z Support for AOS GUI configuration via global groups and the AWMS Master Console will be added in a
from the Modify These Devices option on the APs/Devices > List page.
future release.
Changes to dependency between the AMP group and folders help customers who want to use the folder
structure to manage configuration; however, users are now be able to see (but not access) group and folder
paths for which they do not have permissions.
For more detailed information about this feature, as well as steps for transition from template-based
configuration to web-based configuration, refer to additional chapters in this user guide. For known issues
and details on the AOS version supported by each release, refer to the AWMS Release Notes.
Overview of Aruba Configuration in AWMS
This section describes the Device Setup > Aruba Configuration page and all additional pages in AWMS that
support Aruba Configuration.
12 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 13

The Primary Pages of Aruba Configuration
AWMS supports Aruba Configuration with the following pages:
z Device Setup > Aruba Configuration Page—deploys and maintains Aruba Configuration in AWMS. This
page supports several sections, as follows:
Aruba AP Groups Section
AP Overrides Section
WLANs Section
Profiles Section
Security Section
Advanced Services Section
z Groups > Aruba Config Page—manages Aruba AP group and other controller-wide settings defined on
the
Device Setup > Aruba Configuration page.
z APs/Devices > List Page—modifies or reboots all devices, including Aruba devices deployed with Aruba
Configuration.
z APs/Devices > Manage Page—supports device-level settings and changes in AWMS as a whole.
z APs/Devices > Monitor Page—supports device-level monitoring in AWMS as a whole.
z Groups > Basic Page—enables Aruba Configuration in the AWMS GUI and displays preferences for
Aruba and other devices.
Device Setup > Aruba Configuration Page
This page, shown in Figure 1, uses an expandable navigation pane to support Aruba AP Groups, AP
Overrides, WLANs, Profiles, Security, and Advanced Services.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 13
Page 14

Figure 1 Device Setup > Aruba Configuration Navigation Pane (Contracted and Expanded)
NOTE
Only Aruba AP Groups, AP Overrides, and WLANs contain custom-created items in the navigation pane.
The navigation pane can be used as follows:
z Any portion with a plus sign (+) expands with a click to display additional contents.
z Any portion of the navigation tree can be contracted by clicking the contract sign (-).
z You can display the Edit or Details page for any component with a single click.
Aruba AP Groups Section
An Aruba AP Group is a collection of configuration profiles that define specific settings on Aruba
controllers and the devices that they govern. An Aruba AP Group references multiple configuration profiles,
and in turn links to multiple WLANs.
Navigate to the
of this page.
14 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Device Setup > Aruba Configuration > Aruba AP Groups page. Figure 2 illustrates one example
Page 15
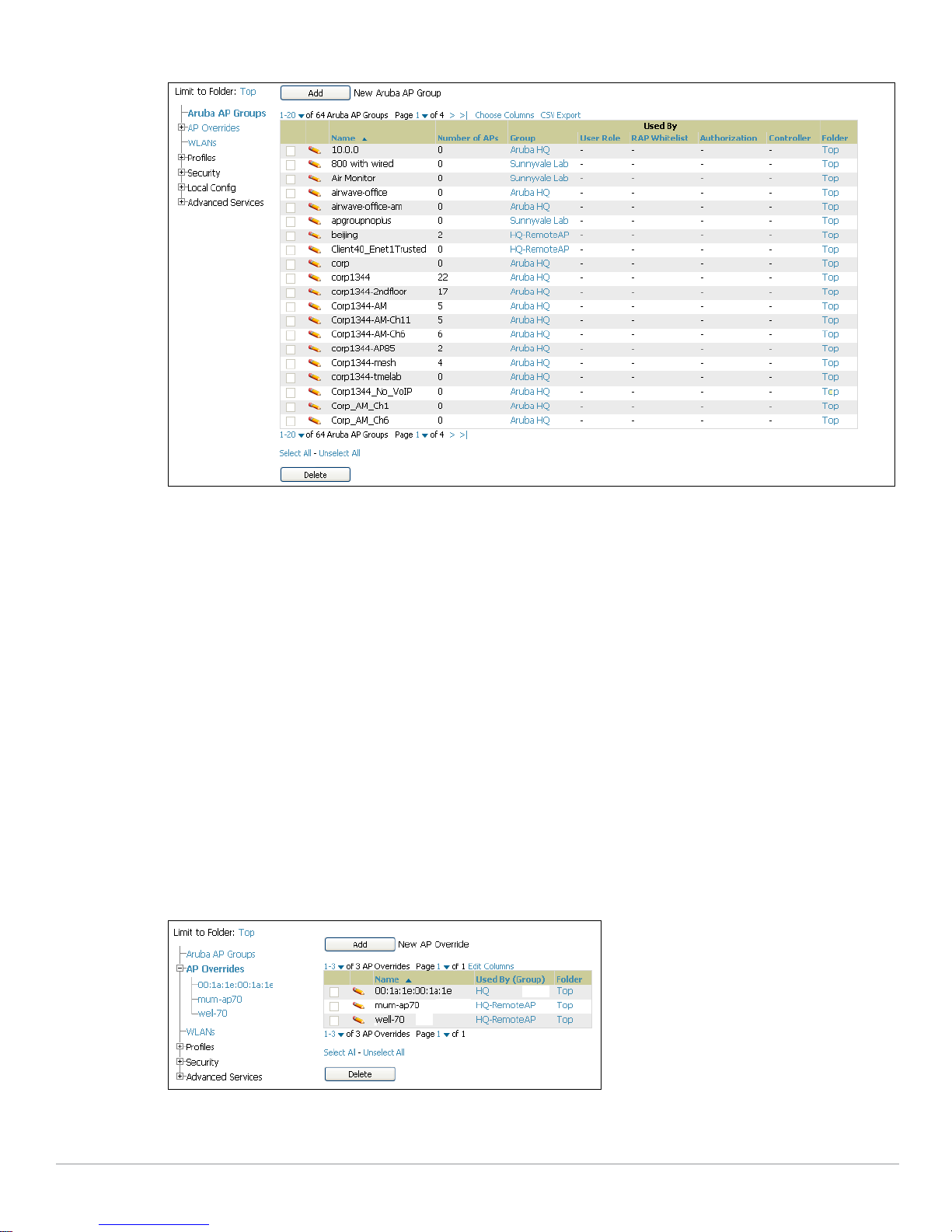
Figure 2 Device Setup > Aruba Configuration > Aruba AP Groups Navigation
Aruba AP Groups are not to be confused with conventional AWMS device groups. AWMS supports both
group types and both are viewable on the
Groups > List page when so configured.
Aruba AP Groups have the following characteristics:
z Aruba AP Groups are global, and any Aruba controller can support multiple Aruba AP Groups.
z Aruba AP Groups are assigned to folders, and folders define visibility. Using conventional AWMS folders
to define visibility, Aruba AP Groups can provide visibility to some or many components while blocking
visibility to other users for more sensitive components, such as SSIDs. Navigate to the
Users pages to
define folder visibility, and refer to “Visibility in Aruba Configuration” on page41.
z You can import a controller configuration file from ArubaOS for Aruba AP Group deployment in AWMS.
For additional information, refer to the following sections in this document:
z “Setting Up Initial Aruba Configuration” on page24
z “General Aruba AP Groups Procedures and Guidelines” on page30
AP Overrides Section
The second major component of Aruba Configuration is the AP Overrides page, appearing immediately
below
Aruba AP Groups in the Navigation Pane. Figure 3 illustrates this location and access:
Figure 3 Device Setup > Aruba Configuration > AP Overrides Navigation
AP Overrides operate as follows in Aruba Configuration:
z Custom-created AP Overrides appear in the Aruba Configuration navigation pane, as illustrated in Figure 3.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 15
Page 16
z Aruba controllers and AP devices operate in Aruba AP Groups that define shared parameters for all
devices in those groups. The
Device Setup > Aruba Configuration > Aruba AP Groups page displays all
current Aruba AP groups.
z AP Override allows you to change some parameters for any specific device without having to create an
Aruba AP group per AP.
z The name of any AP Override should be the same as the name of the device to which it applies.
This establishes the basis of all linking to that device.
z Once you have created an AP Override for a device in a group, you specify the WLANs to be included and
excluded.
z For additional information about how to configure and use AP Overrides, refer to these topics:
“AP Overrides Guidelines” on page37
“Configuring or Editing AP Overrides” on page37
“AP Overrides Pages and Field Descriptions” on page52
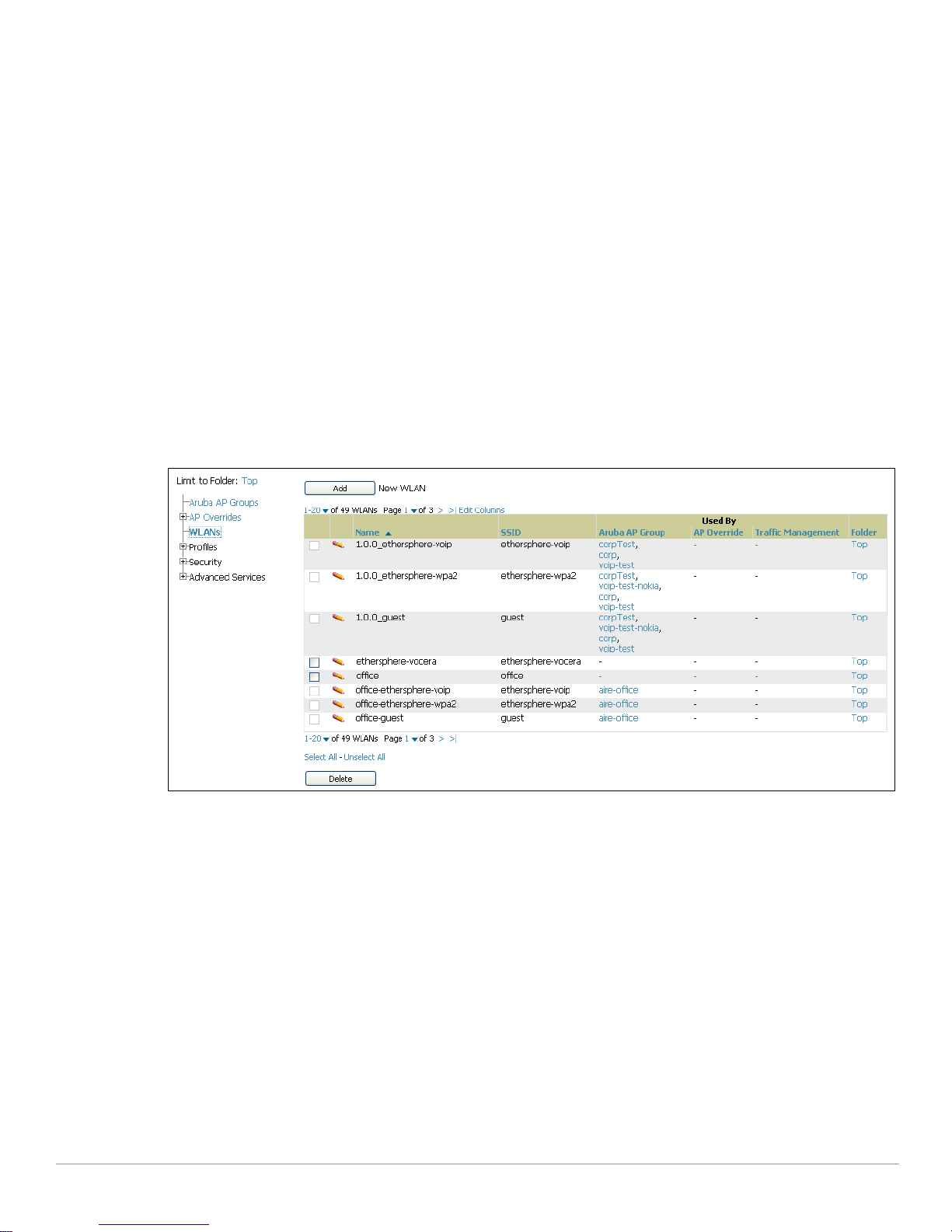
WLANs Section
Access WLANs with Device Setup > Aruba Configuration > WLANs, illustrated in Figure 4.
Figure 4 Device Setup > Aruba Configuration > WLANs Navigation
The following concepts govern the use of WLANs in Aruba Configuration:
z WLANs are the same as virtual AP configuration profiles.
z WLAN profiles contain several diverse settings to include SSIDs, referenced Aruba AP Groups, Traffic
Management
profiles, and device Folders.
This document describes WLAN configuration in the following section and chapter:
z “Setting Up Initial Aruba Configuration” on page24
z “General WLAN Procedures and Guidelines” on page33
z “WLAN Pages and Field Descriptions” on page56
Profiles Section
Profiles provide a way to organize and deploy groups of configurations for Aruba AP Groups, WLANs, and
other profiles. Profiles are assigned to folders; this establishes visibility to Aruba AP Groups and WLAN
settings. Access
16 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Profiles with Device Setup > Aruba Configuration > Profiles, illustrated in Figure 5.
Page 17

Figure 5 Device Setup > Aruba Configuration > Profiles Navigation
Profiles are organized by type in Aruba Configuration. Custom-named profiles do not appear in the
navigation pane as do custom-named Aruba AP Groups, WLANs, and AP Overrides.
For additional information about profile procedures and guidelines, refer to the following sections in this
document:
z “Setting Up Initial Aruba Configuration” on page24
z “General Profiles Guidelines” on page35
z “Profiles Pages and Field Descriptions” on page62
Security Section
The Security section displays, adds, edits, or deletes security profiles in multiple categories, to include user
roles, policies, rules, and servers such as RADIUS, TACACS+, and LDAP servers. Navigate to Security with
the
Device Setup > Aruba Configuration > Security path, illustrated in Figure 6.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 17
Page 18

Figure 6 Device Setup > Aruba Configuration > Security Navigation
The following general guidelines apply to
z Roles can have multiple policies; each policy can have numerous roles.
z Server groups are comprised of servers and rules. Security rules apply in Aruba
Security profiles in Aruba configuration:
Configuration in the same way as deployed in AOS.
For additional information about Security, refer to “Security Pages and Field
Descriptions” on page138.
Advanced Services Section
Navigate to Advanced Services with the Device Setup > Aruba Configuration > Advanced Services path. The
Advanced Services section includes IP Mobility and VPN Services. Figure 7 illustrates this navigation and
the components.
Figure 7 Device Setup > Aruba Configuration > Advanced Services Navigation
For additional information about IP Mobility and VPN Services, refer to “Advanced Services Pages and Field
Descriptions” on page157.
18 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 19
Groups > Aruba Config Page
This focused submenu page displays and edits all configured Aruba AP groups, with the following factors:
z Aruba AP Groups must be defined from the Device Setup > Aruba Configuration page before they are
visible on the
z Use this page to select the Aruba AP Groups that you push to controllers.
z Use this page to associate a standard device group to one or more Aruba AP Groups.
z From this page, you can select other profiles that are defined on the controller, like an internal server.
Figure 8 Groups > Aruba Config Page Illustration
Groups > Aruba Config page.
APs/Devices > List Page
This page supports devices in all of AWMS. This page supports controller reboot, controller re-provisioning,
and changing Aruba AP groups. Select
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 19
Modify Devices to configure thin AP settings.
Page 20
Figure 9 APs/Devices List Page Illustration (Partial Display)
APs/Devices > Manage Page
This page configures device-level settings, including Manage mode that enables pushing configurations to
controllers. For additional information, refer to “Pushing Device Configurations to Controllers” on page36.
Figure 10 APs/Devices > Manage Page Illustration (Partial Display)
APs/Devices > Monitor Page
Used in conjunction with the Manage page, the Monitor page enables review of device-level settings. This
page is large and often contains a great amount of information, to include the following sections:
z Status information
z User and Bandwidth flash graphs
z CPU Utilization and Memory Utilization flash graphs
z APs Managed by this Controller (when viewing a controller)
20 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 21

z Alert Summary
z Recent Events
z Audit Log
For additional information, refer to “Pushing Device Configurations to Controllers” on page36.
Groups > Basic Page
The Groups > Basic page deploys the following aspects of Aruba Configuration:
z This page contains a new Aruba GUI Config field. Use this page and field to make the Device Setup >
Aruba Config
z Use this page to control which device settings appear on the Groups pages.
z If you are using Aruba firmware prior to version 3.0, you should disable Aruba GUI configuration from
the
Groups > Basic page and use template-based configuration.
page visible. This page is enabled by default in AWMS.
Refer to Figure 14 for an illustration of this page.
Additional Concepts and Components of Aruba Configuration
Aruba Configuration emphasizes the following components and network management concepts:
z Global Configuration and Scope
z Embedded Profile Setup in Aruba Configuration
z Controller Overrides
z Save, Save and Apply, and Revert Buttons
z Folders, Users, and Visibility
z Additional Concepts and Benefits
Global Configuration and Scope
Aruba Configuration supports AOS as follows:
z AWMS supports global configuration from both a master-local controller deployment and an all-master
controller deployment:
In a master-local controller deployment, AOS is the agent that pushes global configurations from
master controllers to local controllers. AWMS supports this AOS functionality.
In an all-master-controller scenario, every master controller operates independent of other master
controllers. AWMS provides the ability to push configuration to all master controllers in this
scenario.
z AWMS Aruba Configuration supports AOS profiles, Aruba AP Profiles, Servers, and User Roles.
For additional information about these and additional functions, refer to “General Controller Procedures
and Guidelines” on page36.
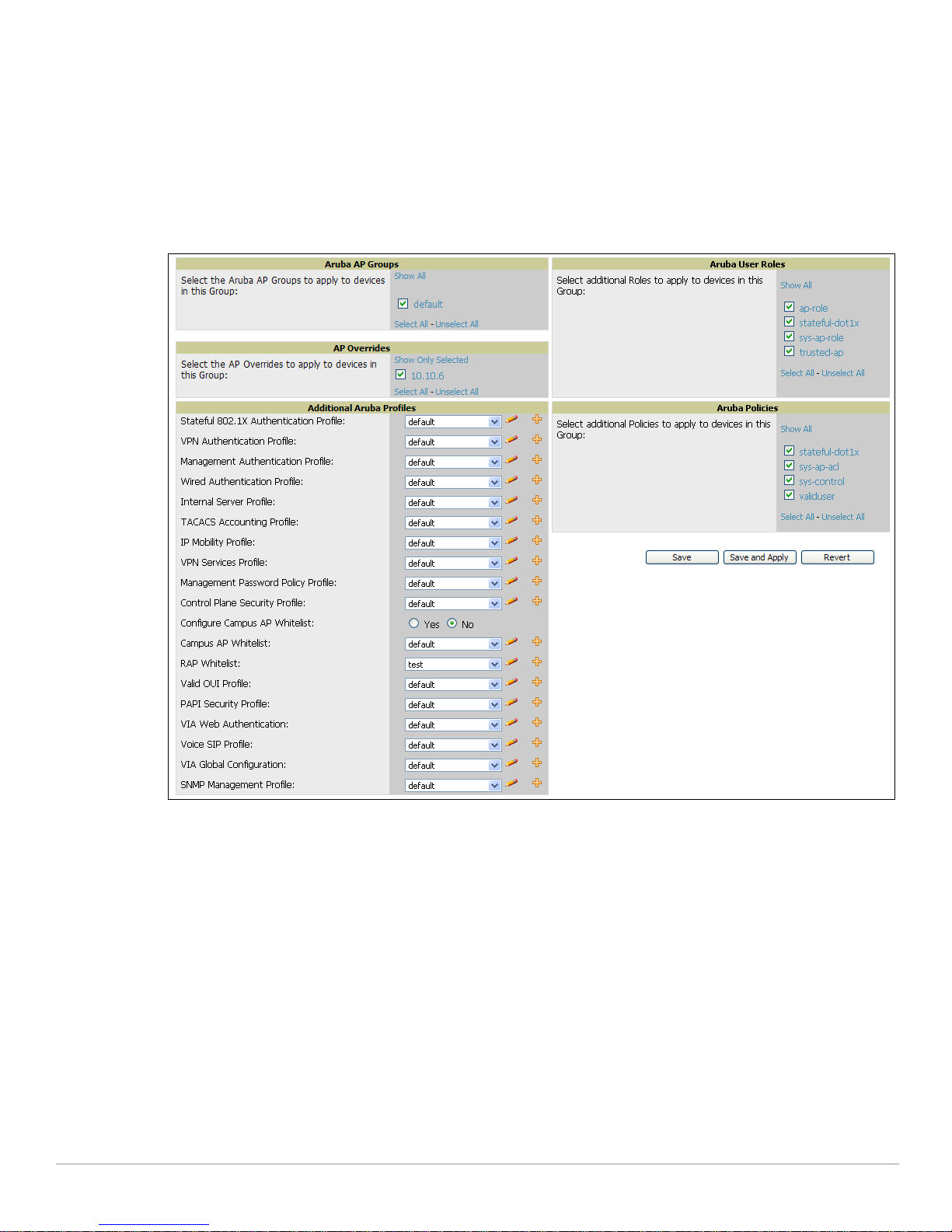
Embedded Profile Setup in Aruba Configuration
AWMS allows you to add or reconfigure many configuration profiles while guiding you through a larger
configuration sequence for an Aruba AP Group or WLAN. Consider the following example:
z When you create a new Aruba AP Group from the Device Setup > Aruba Configuration page, the
Referenced Profile section appears as shown in Figure 11:
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 21
Page 22

Figure 11 Embedded Profile Configuration for an Aruba AP Group
z Click the Add icon (the plus symbol) at right to add a referenced profile. Once you Save or Save and
Apply that profile, AWMS automatically returns you to the original Aruba AP Group configuration page.
z This embedded configuration is also supported on the Additional Aruba Profiles section of the
Groups > Aruba Config page.
Controller Overrides
You can create controller overrides for entire profiles or a specific profile setting per profile. This allows
you to avoid creating new profiles or Aruba AP Groups that differ by one more settings. Controller
overrides can be added from the controller's Manage page.
22 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 23

Figure 12 Overriding a Controller Profile
Save, Save and Apply, and Revert Buttons
Several Add or Detail pages in Aruba Configuration include the Save, Save and Apply, and Revert buttons.
These buttons function as follows:
z Save—This button saves a configuration but does not apply it, allowing you to return to complete or apply
the configuration at a later time. If you use this button, you may see the following alert on other Aruba
Configuration pages. You can apply the configuration when all changes are complete at a later time.
Figure 13 Unapplied Aruba Configuration Changes Message
z Save and Apply —This button saves and applies the configuration with reference to Manage and Monitor
modes. For example, you must click
devices immediately if the controller is in
Save and Apply for a configuration profile to propagate to all
Manage mode. If you have devices in Monitor mode, AWMS
compares the current device configuration with the new desired configuration. For additional
information and instructions about using
Manage and Monitor modes, refer to “Pushing Device
Configurations to Controllers” on page36.
z Revert—This button cancels out of a new configuration or reverts back to the last saved configuration.
Folders, Users, and Visibility
Access and edit folders and visibility using the Folder column on the Groups > Aruba Config page. Profiles
and Aruba AP Groups are assigned to folders. Folders allow you to set the visibility for controller
information, and to set read/write privileges as required.
z As one example, it may be necessary to provide AWMS users with RF radio parameters while restricting
access to SSID profiles.
Additional Concepts and Benefits
Scheduling Configuration Changes
You can schedule deployment of Aruba Configuration to minimize impact on network performance. For
example, configuration changes can be accumulated over time by using
Monitor mode, then pushing all configuration changes at one time by putting devices in Manage mode. Refer
to “Pushing Device Configurations to Controllers” on page36.
Save and Apply for devices in
AWMS pushes configuration settings that are defined in the GUI to the Aruba Controllers as a set of CLI
commands using Secure Shell (SSH). No controller reboot is required.
Auditing and Reviewing Configurations
AWMS supports auditing or reviewing in these ways.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 23
Page 24

1. You can review the AOS running configuration file. This is configuration information that AWMS reads
from the device. In template-based configuration, you can review the running configuration file when
working on a related template.
2. You can use the
3. Once you audit your controller, you can click
APs/Devices > Audit page for device-specific auditing.
Import from the APs/Devices > Audit page to reverse all of
the profiles on the controller.
Licensing and Dependencies in Aruba Configuration
You can review your current licensing status with the Licensing link on the APs/Devices > Monitor page.
AWMS requires that you have a policy enforcement firewall license always installed on all Aruba
controllers. If you push a policy to a controller without this license, a
and the controller will show as
Mismatched on AWMS pages that reflect device configuration status.
Good configuration will not result,
Aruba Configuration includes several settings or functions that are dependent on special licenses. The user
interface conveys that a special license is required for any such setting, function, or profile. AWMS does not
push such configurations when a license related to those configurations is unavailable. For details on the
licenses required by a specific version of ArubaOS, refer to the ArubaOS User Guide for that release.
Setting Up Initial Aruba Configuration
This section describes how to deploy an initial setup of Aruba Configuration in AWMS 6.4 or later versions.
Prerequisites
z Complete the AWMS upgrade to AWMS 6.4 or later. Refer to “Related Documents” on page7 for
installation or upgrade documents. Upon upgrade to AWMS Version 6.4 or later, Aruba Configuration is
enabled by default in groups with devices in monitor-only mode and AOS firmware of 3.3.2.10 or greater.
z Back up your ArubaOS controller configuration file. Information about backing AWMS is available in the
AWMS User Guide in the “Performing Daily Operations in AWMS” chapter.
Procedure
Perform the following steps to deploy Aruba Configuration when at least one Aruba AP Group currently
exists on at least one Aruba controller on the network:
1. On the
This configuration defines optional group display options. This step is not critical to setup, and default
settings will support groups appropriate for Aruba Configuration. One important setting on this page is
the
Groups > Basic page, enable device preferences for Aruba devices. Figure 14 illustrates this page.
Aruba GUI Config option. Ensure that setting is Yes, which is the default setting.
24 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 25
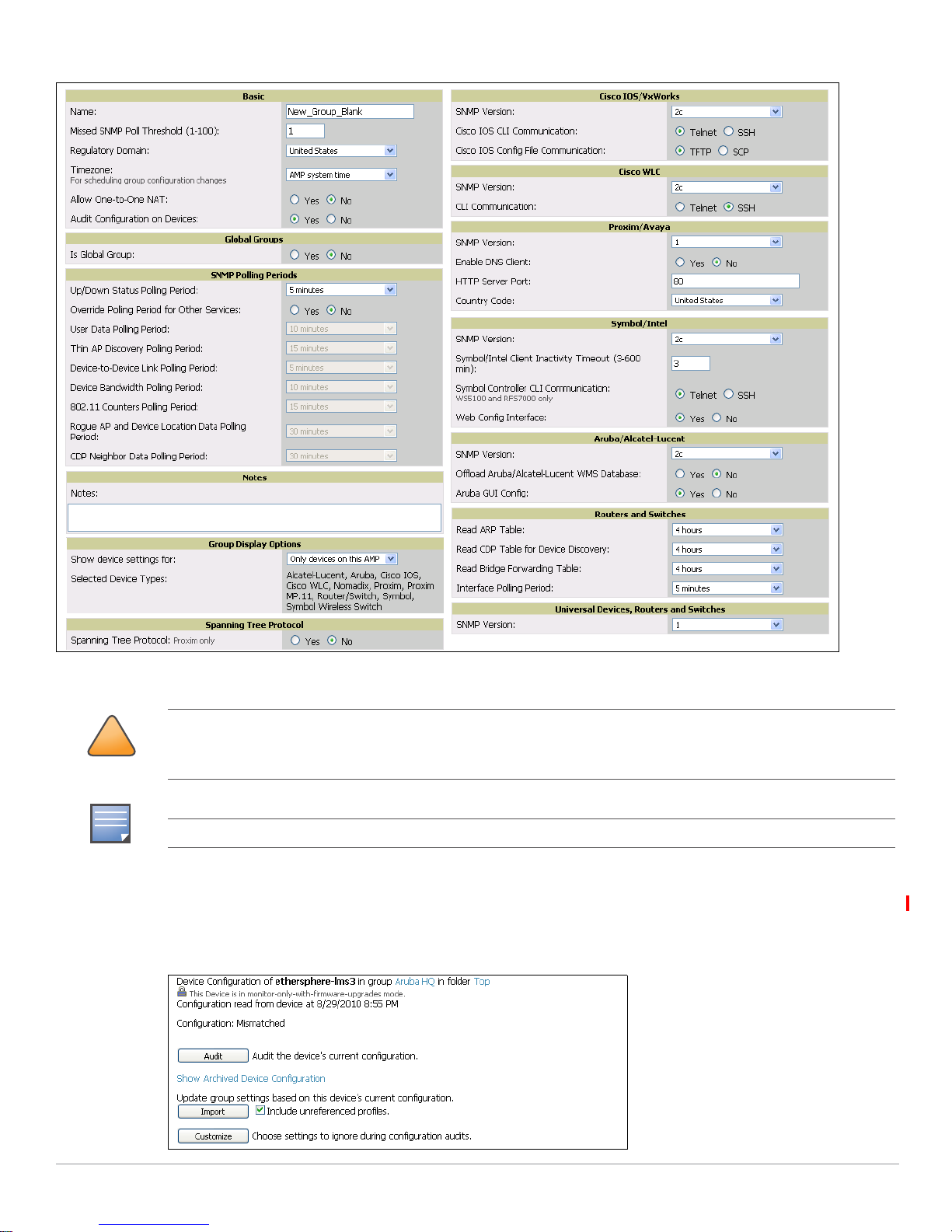
Figure 14 Groups > Basic Page Illustration (Partial Display)
!
CAUTION
NOTE
2. Authorize Aruba controllers into the AMP Group.
When authorizing the first controller onto a group, you must add the device in monitor-only mode. Otherwise,
AWMS removes the configuration of the controller before you have a chance to import the configuration, and this
would remove critical network configuration and status.
Aruba Configuration is enabled by default in AWMS.
3. Navigate to the
AP/s/Devices > Audit page for the first controller to prepare for importing an existing
Aruba controller configuration file. Figure 15 illustrates the information available on this page if the
device is mismatched.
Figure 15 APs/Devices > Audit Page Illustration
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 25
Page 26
If the page reports a device mismatch, the page will display an Import button that allows you to import
the Aruba controller settings from an Aruba Controller that has already been configured. To import the
complete configuration from the controller (including any unreferenced profiles) select the Include
unreferenced profiles checkbox. If you unselect the checkbox, AMP will delete the unreferenced
profiles/AP Groups on the controller when it imports that configuration.
Importing this configuration creates all the Profiles and Aruba AP Groups on the
Configuration
Aruba Config
page. This action also adds and selects the Aruba AP Groups that appear on the Groups >
page.
Device Setup > Aruba
The folder for all the Profiles and Aruba AP Groups is set to the top folder of the AWMS user who
imports the configuration. This folder is
Top in the case of managing administrators with read/write
privileges.
4. After configuration file import is complete, navigate to the
This page displays a list of APs authorized on the AMP that are using the Aruba AP Group.
The User Role is the Aruba User Role used in firewall settings. For additional information, refer to
Device Setup > Aruba Configuration page.
“Security > User Roles” on page139.
The Folder column cites the visibility level to devices in each Aruba AP Group. For additional
information, refer to “Visibility in Aruba Configuration” on page41.
5. Add or modify
a. Navigate to the
Aruba AP Groups as required.
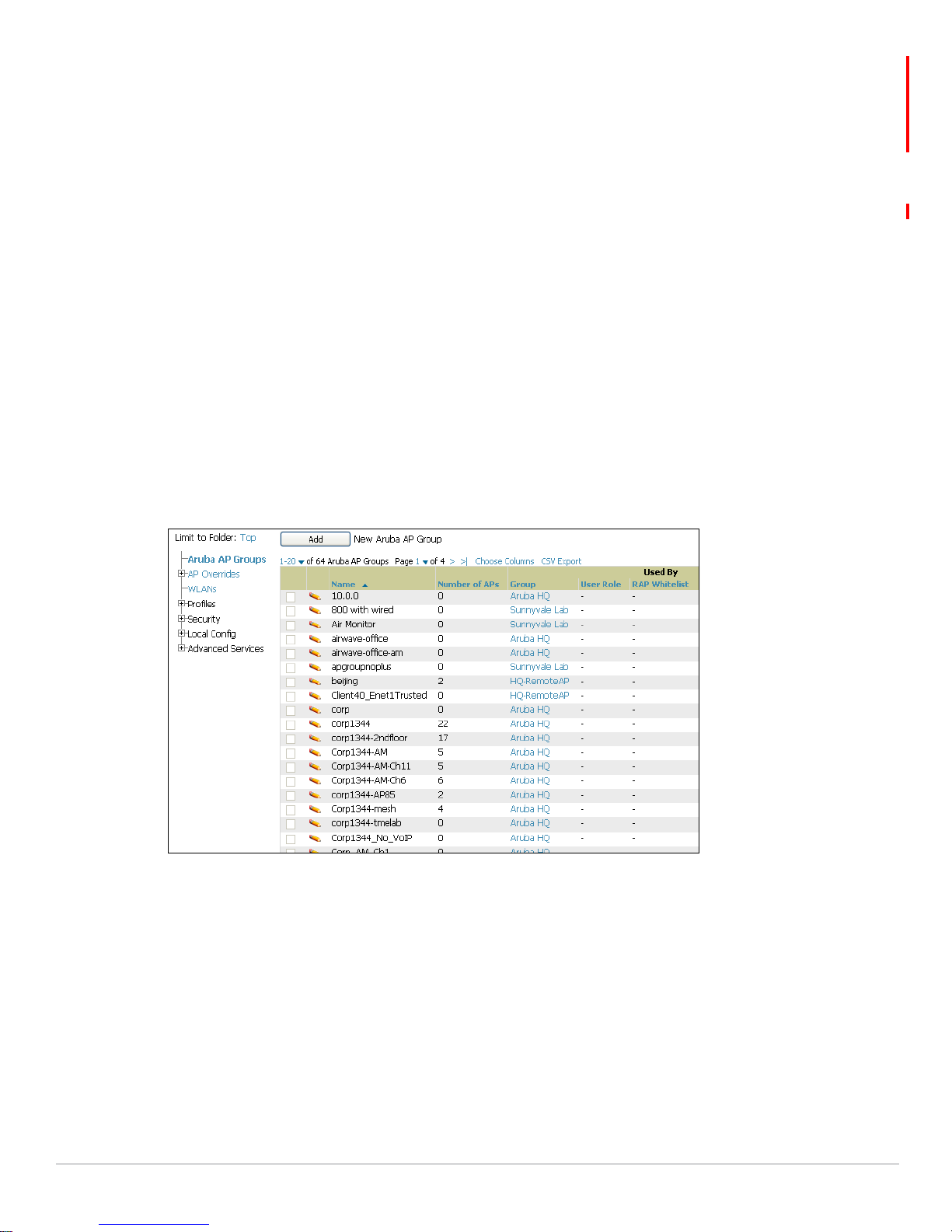
Device Setup > Aruba Configuration > Aruba AP Groups page, illustrated in Figure 16.
Figure 16 Device Setup > Aruba Configuration > Aruba AP Groups Page
a. Click
Add from the Aruba AP Groups page to create a new Aruba AP Group. To edit an Aruba AP
Group, click the pencil icon next to the group. The
appears. This page allows you to select the profiles to apply to the Aruba AP Group, and to select one
or more WLANs that support that Aruba AP Group. Figure 17 illustrates this page.
26 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Details page for the Aruba AP Group group
Page 27

Figure 17 Device Setup > Aruba Configuration > Aruba AP Groups > Add/Edit Details Page
The following section of this configuration guide provide additional information about configuring
Aruba AP Groups:
“General Aruba AP Groups Procedures and Guidelines” on page30
6. Add or edit WLANs in Aruba Configuration as required.
a. Navigate to
Device Setup > Aruba Configuration > WLANs page. This page can display all WLANs
currently configured, or can display only selected WLANs.
b. Click
Add to create a new WLAN, or click the pencil icon to edit an existing WLAN.
You can add or edit WLANs in one of two ways, as follows:
Basic—This display is essentially the same as the AOS Wizard View on the Aruba controller. This
page does not require in-depth knowledge of the profiles that define the Aruba AP Group.
Advanced—This display allows you to select individual profiles that define the WLAN and
associated Aruba AP Group. This page requires in-depth knowledge of all profiles and their
respective settings.
The following sections of this configuration guide provide additional information and illustrations for
configuring WLANs:
“General WLAN Procedures and Guidelines” on page33
“WLAN Pages and Field Descriptions” on page56
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 27
Page 28

7. Add or edit Aruba Configuration Profiles as required.
a. Navigate to
Device Setup > Aruba Configuration > Profiles section of the navigation pane.
b. You must select the type of profile to configure:
c. Click
Add from any of these specific profile pages to create a new profile, or click the pencil icon to
AAA, AP, Controller, IDS, Mesh, QoS, RF, or SSID.
edit an existing profile.
Most profiles in AWMS are similar to the
primary difference in AWMS is that
All Profiles display in the Aruba Controller WebUI. The
AAA and SSID profiles are not listed under the Wireless LAN
column as the controller.
d. Save changes to each element as you proceed through profile and WLAN configuration.
All other settings supported on Aruba controllers can be defined on the
Configuration
page. The following section in this document provides additional information about
Device Setup > Aruba
configuring profiles:
“General Profiles Guidelines” on page35
8. Provision multiple Aruba AP Groups on one or more controllers by putting the controllers into an AMP
group and configuring that group to use the selected Aruba AP Groups. Configure such Aruba AP
Groups settings on the
Group > Aruba Config page. The following section of this document provides
additional information:
“General Aruba AP Groups Procedures and Guidelines” on page30
9. As required, add or edit AP devices. The following section of this document has additional information:
“Supporting APs with Aruba Configuration” on page37
10. Each AP can be assigned to a single Aruba AP Group. Make sure to choose an AP Group that has been
configured on that controller using that controller's AMP Group. Use the
Devices
syslocation, and syscontact on the
field and the APs/Devices > Manage page. You can create or edit settings such as the AP name,
APs/Devices > Manage page. For additional information, refer to
APs/Devices > List, Modify
“Supporting APs with Aruba Configuration” on page37.
28 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 29
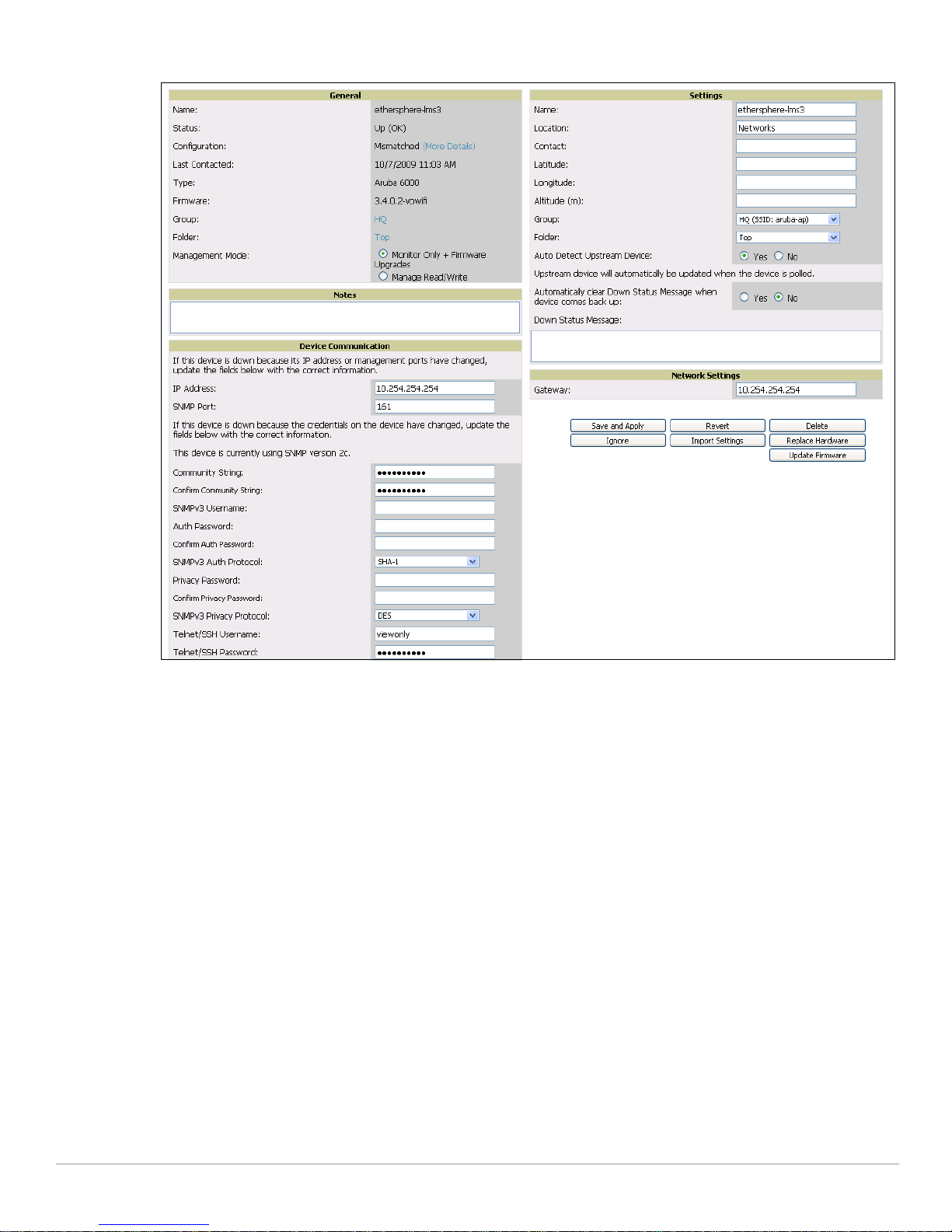
Figure 18 APs/Devices > Manage Page Illustration (Partial Display)
11. Navigate to the
APs/Devices > Audit page for the controller to view mismatched settings. This page
provides links to display additional and current configurations. You can display all mismatched devices
by navigating to the
APs/Devices > Mismatched page.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 29
Page 30
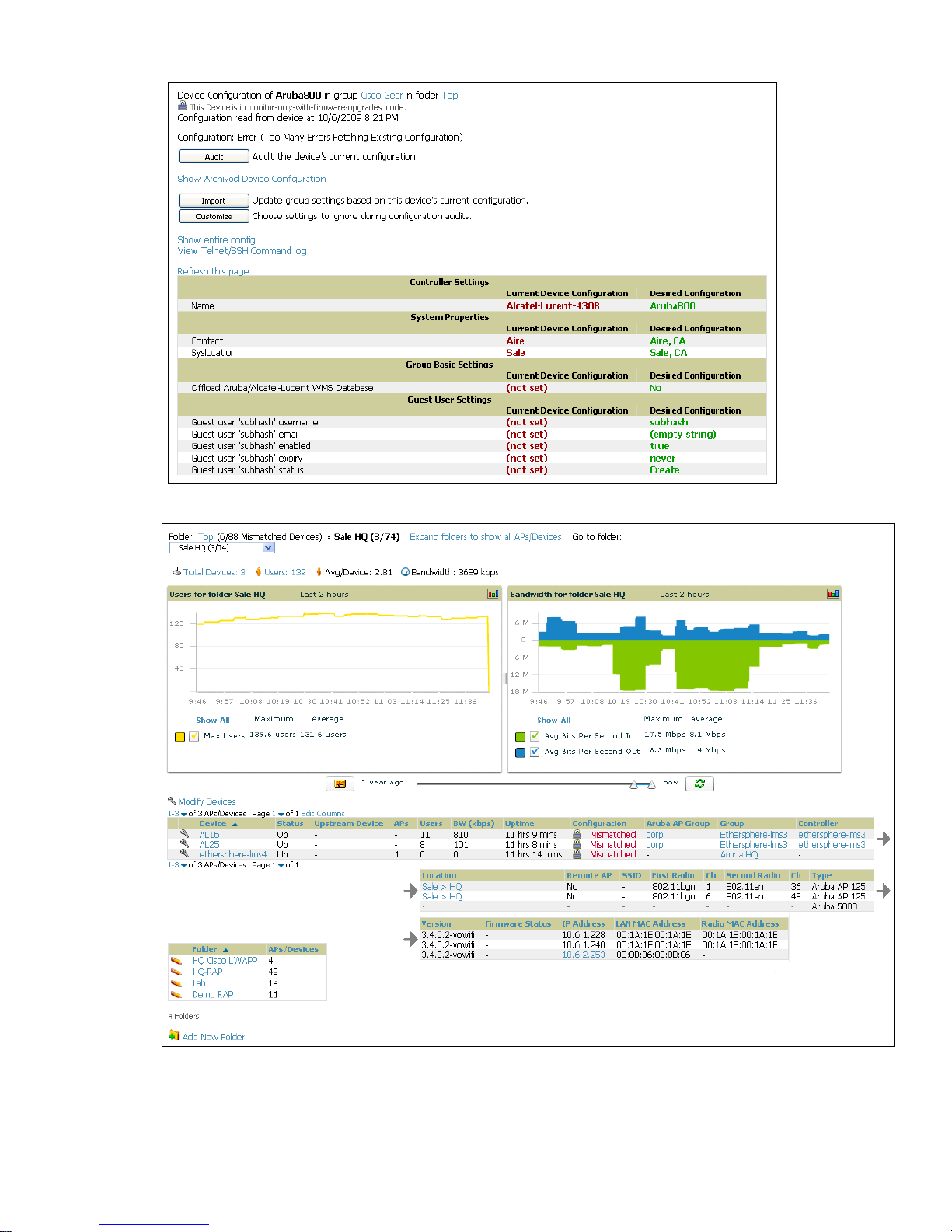
Figure 19 APs/Devices > Audit Page Illustration (Partial Display)
Figure 20 APs/Devices > Mismatched Page Illustration
What Next?
After initial AOS deployment with the Aruba Configuration feature, you can make many additional
configurations or continue with maintenance tasks, such as with the following examples:
30 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 31

z Once Aruba Configuration is deployed in AWMS, you can perform debugging with Telnet/SSH. Review
the
telnet_cmds file in the /var/log folder from the command line interface, or access this file from
the
System > Status page. Such configurations are supported on the Groups > Basic and Device Setup >
Communications
z To resolve communication issues, review the credentials on the AP Manage page.
z Mismatches can occur when importing profiles because AWMS deletes orphaned profiles, even if
pages of AWMS. Refer to the AWMS User Guide for additional information.
following a new import.
Additional Capabilities of Aruba Configuration
AWMS supports many additional AOS configurations and settings. Refer to these additional resources for
more information:
z AOS User Guide
z AWMS User Guide
z
AirWave and Aruba Best Practices Guide
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration in AWMS | 31
Page 32

32 | Aruba Configuration in AWMS AirWave Wireless Management Suite | Configuration Guide
Page 33

Chapter 2
NOTE
Using Aruba Configuration in
Daily Operations
Introduction
This chapter presents the more common tasks or concepts after initial setup of Aruba Configuration is
complete, as described in the section “Setting Up Initial Aruba Configuration” on page24. This chapter
emphasizes frequent procedures as follows:
General Aruba AP Groups Procedures and Guidelines
z Guidelines and Pages for Aruba AP Groups in Aruba Configuration
z Selecting Aruba Controller Groups
z Configuring Aruba AP Groups
General WLAN Procedures and Guidelines
z Guidelines and Pages for WLANs in Aruba Configuration
z Configuring or Editing WLANs with Basic View
z Configuring or Editing WLANs with Advanced View
General Controller Procedures and Guidelines
z Using Master, Standby Master, and Local Controllers in Aruba Configuration
z Pushing Device Configurations to Controllers
Supporting APs with Aruba Configuration
z AP Overrides Guidelines
z Configuring or Editing AP Overrides
z Changing the Aruba AP Group for an AP Device
z Changing Adaptive Radio Management (ARM) Settings
z Changing SSID and Encryption Settings
Visibility in Aruba Configuration
z Visibility Overview
z Defining Visibility for Aruba Configuration
Using AWMS to Deploy Aruba APs for the First Time
For a complete reference on all Aruba Configuration pages, field descriptions, and certain additional procedures
that are more specialized, refer to Appendix A, “Aruba Configuration Reference” on page49.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 33
Page 34

General Aruba AP Groups Procedures and Guidelines
Guidelines and Pages for Aruba AP Groups in Aruba Configuration
The fields and default settings for Aruba AP Groups are described in “Aruba AP Groups” on page53.
The following guidelines govern the configuration and use of Aruba AP Groups across AWMS:
z Aruba AP Groups function with standard AWMS groups that contain them. Add Aruba AP Groups to
standard AWMS groups. Additional procedures in this document explain their interoperability.
z APs can belong to a controller's AWMS group or to an AWMS group by themselves.
z All configurations of Aruba AP Groups must be pushed to Aruba controllers to become active on the
network.
z Additional dynamics between master, standby master, and local controllers still apply. In this case, refer
to “Using Master, Standby Master, and Local Controllers in Aruba Configuration” on page40.
The following pages in AWMS govern the configuration and use of Aruba AP Groups or standard device
groups across AWMS:
z The Device Setup > Aruba Configuration navigation pane displays standard AOS components and your
custom-configured Aruba AP Groups, WLANs, and AP Overrides.
z You define or modify Aruba AP Groups on the Device Setup > Aruba Configuration page. Click Aruba AP
Groups
z You select Aruba AP Groups to associate with AMP (AWMS) Groups with the Groups > Aruba Config page.
from the navigation pane.
z You modify devices in Aruba AP Groups with the APs/Devices > List page, clicking Modify These Devices.
This is the page at which you assign devices to a given group and Aruba AP Group.
Selecting Aruba Controller Groups
To select Aruba AP Groups, navigate to the Device Setup > Aruba AP Groups page. This page is central to
defining Aruba AP Groups, to viewing the AMP groups with which an Aruba AP Group is associated,
changing or deleting Aruba AP Groups, and assigning AP devices to an Aruba AP Group.
Configuring Aruba AP Groups
Perform the following steps to display, add, edit, or delete Aruba AP Groups in Aruba Configuration.
1. Browse to the
navigation pane on the left. The
Groups, as illustrated in Figure 21 and described in Table 3 of the Appendix.
Device Setup > Aruba Configuration page, and click the AP Groups heading in the
Groups Summary page appears and displays all current Aruba AP
34 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 35

Figure 21 Device Setup > Aruba Configuration > AP Groups Page Illustration
2. To add a new group, click the
To edit an existing group, click the
The
Group Details page appears with current or default configurations. Figure 22 illustrates the Details
Add AP Group button.
pencil icon next to the group name.
page for a new group to be defined. The settings on this page are described in Table 4 of the Appendix.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 35
Page 36

Figure 22 Device Setup > Aruba Configuration > Add/Edit Group Details Page Illustration
3. Click
Add or Save to finish creating or editing the Aruba AP Group. Click Cancel to back out of this
screen and to cancel the AP Group configurations.
4. New AP groups appear in the
clicking the group name takes you to the
AP Groups section of the Aruba Configuration navigation pane, and
Details page for that group.
5. When this and other procedures are completed, push the configuration to the Aruba controllers by
clicking
Save and Apply. The principles of Monitor and Manage mode still apply. For additional
information, refer to “Pushing Device Configurations to Controllers” on page40.
What Next?
Once Aruba AP groups are defined, ensure that all desired WLANs are referenced in Aruba AP Groups, as
required. Repeat the above procedure to revise WLANs as required. You can add or edit AP devices in Aruba
AP Groups, and you can configure AP Override settings that allow for custom AP configuration within the
larger group in which it operates.
36 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 37

General WLAN Procedures and Guidelines
Guidelines and Pages for WLANs in Aruba Configuration
z The Device Setup > Aruba Configuration navigation pane displays custom-configured WLANs and Aruba
AP Groups. You define or modify WLANs on the
from the navigation pane.
z You can create or edit any profile in an WLAN as you define or modify that WLAN. If you digress to
profile setup from a different page, AWMS returns you to your place on the
are done with profile setup.
z All configurations must be pushed to Aruba controllers to become active on the network.
Configuring or Editing WLANs with Basic View
Perform the following steps to create or configure a basic WLAN in Aruba Configuration.
Device Setup > Aruba Configuration page. Click WLANs
WLAN setup page once you
1. Navigate to the
Aruba Configuration > WLANs page. This page displays currently configured WLANs.
Figure 23 illustrates this page.
Figure 23 Device Setup > Aruba Configuration > WLANs Page Illustration
2. To add a new WLAN, click the
the WLAN name. Select
Add WLAN button. To edit an existing WLAN, click the pencil icon next to
Basic to define or modify the settings. Otherwise, refer to the “Configuring or
Editing WLANs with Advanced View” on page38 for additional information. Figure 27 illustrates the
Basic view. For a detailed explanation of all fields, refer to Table 8 in the Appendix.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 37
Page 38

Figure 24 Device Setup > WLANs > Add > Basic Page Illustration
3. Click
Add or Save. The added or edited WLAN appears on the WLANs page. You can now use this WLAN
with one or more Aruba AP Groups.
4. Repeat this procedure or continue to additional procedures to complete WLAN, Profile, Aruba AP Group
or other configurations.
5. Push the newly added or edited WLAN to the desired Aruba Controllers. Refer to “Pushing Device
Configurations to Controllers” on page40.
Configuring or Editing WLANs with Advanced View
1. Navigate to the Aruba Configuration > WLANs page. This page displays currently configured WLANs.
Figure 23 illustrates this page.
2. To add a new WLAN, click the
the WLAN name. Select
configuration. Figure 25 illustrates the
page, refer to Table 9 in the Appendix.
Add WLAN button. To edit an existing WLAN, click the pencil icon next to
Advanced to define or modify the settings that pertain to advanced WLAN
Advanced view. For complete description of all fields on this
38 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 39

Figure 25 Device Setup > Aruba Configuration > WLANs > Add > Advanced Page Illustration
3. Click
Add or Save. The added or edited WLAN appears on the WLANs page. You can now use this WLAN
with one or more Aruba AP Groups.
4. Repeat this procedure or continue to additional procedures to complete WLAN, Profile, Aruba AP Group
or other configurations.
5. Push the newly added or edited WLAN to the desired Aruba Controllers. For additional information,
refer to “Pushing Device Configurations to Controllers” on page40.
General Profiles Guidelines
AOS elements can be added or edited after an AOS configuration file is imported to AWMS and pushed to
controllers with the steps described in “Setting Up Initial Aruba Configuration” on page24.
Profiles in Aruba configuration entail the following concepts or dynamics:
z Profiles define nearly all parameters for Aruba AP Groups and WLANs, and Aruba Configuration
supports many diverse profile types.
z Some profiles provide the configurations for additional profiles that reference them. When this is the
case, this document describes the interrelationship of such profiles to each other.
z Profiles can be configured in standalone fashion using the procedures in this chapter, then applied
elsewhere as desired. Otherwise, you can define referenced profiles as you progress through Aruba AP
Group or WLAN setup. In the latter case, AWMS takes you to profile setup on separate pages, then
returns you to your place in Aruba AP Group or WLAN setup.
For complete Profiles inventory and field descriptions, refer to “Profiles Pages and Field Descriptions” on
page68.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 39
Page 40

General Controller Procedures and Guidelines
NOTE
Using Master, Standby Master, and Local Controllers in Aruba Configuration
AWMS implements the following general approaches in relation to controllers.
z Master Controller—This controller maintains and pushes all global configurations. AWMS pushes
configurations only to a master controller.
z Standby Controller—The master controller synchronizes with the standby master controller, which
remains ready to govern global configurations for all controllers should the active master controller fail.
z Local Controller—Master controllers push local configurations to local controllers. Local controllers
retain settings such as the interfaces and global VLANs.
AWMS is aware of differences in what is pushed to master controllers and local controllers, and
automatically pushes all configurations to the appropriate controllers. Thin AP provisioning is pushed to
the controller to which a thin AP is connected.
You can determine additional details about what is specific to each controller by reviewing information on
the
Groups > Aruba Config page, and the Groups > Monitor page for any specific AP that lists its master and
standby master controller.
Pushing Device Configurations to Controllers
When you add or edit device configurations, you can push device configurations to controllers as follows:
z Make device changes on the Device Setup > Aruba Configuration page and click Save and Apply.
z Make devices changes on the Groups > Aruba Config page and click Save and Apply.
A device must be in
If you click Save and Apply when a device is in Monitor mode, this initiates a verification process in which AWMS
advises you of the latest mismatches. Mismatches are viewable from the APs/Devices > Mismatched page.
Additional Audit and Group pages list mismatched status for devices.
Normally, devices are in
configuration changes in
general steps when implementing configuration changes for devices in
1. Make all device changes using the
page. Click Save and Apply as you complete device-level changes. This builds an inventory of
Config
Manage mode to push configurations in this way.
Monitor mode. It may be advisable in some circumstances to accumulate several
Monitor mode prior to pushing an entire set of changes to controllers. Follow these
Monitor mode:
Device Setup > Aruba Configuration page and the Groups > Aruba
pending configuration changes that have not been pushed to the controller and APs.
2. Review the entire set of newly mismatched devices on the
3. For each mismatched device, navigate to the
APs/Devices > Audit page to audit recent configuration
APs/Devices > Mismatched page.
changes as desired.
4. Once all mismatched device configurations are verified to be correct from the
use the
Modify Devices link on the Groups > Monitor page to place these devices into Management mode.
APs/Devices > Audit page,
This instructs AWMS to push the device configurations to the controller.
5. As desired, return devices to
Monitor mode until the next set of configuration changes is ready to push to
controllers.
40 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 41

Supporting APs with Aruba Configuration
AP Overrides Guidelines
The AP Override component of Aruba Configuration appears in the navigation pane of the Device Setup >
Aruba Configuration
z AP devices function within groups that define operational parameters for groups of APs. This is standard
across all of AWMS.
z AP Overrides allows you to change some parameters of any given AP without having to remove that AP
from the configuration group in which it operates.
z The name of any AP Override that you create should be the same as the name of the AP device to which
it applies. This establishes the basis of all linking to that AP device.
z Once you have created an AP Override, you select the WLANs in which it applies.
z Once you have created the AP Override, you can go one step further with the Exclude WLANs option of
AP Override, which allows you to exclude certain SSIDs from the AP override. For example, if you have a
set of WLANs with several SSIDs available, the
SSIDs to exclude from the
z You can also exclude mesh clusters from the AP Override.
page. This component operates with the following principles:
Exclude WLANs option allows you to specify which
AP Override.
In summary, the
APs that otherwise share parameters with other APs in a group.
AP Override feature prevents you from having to create a new AP group for customized
AP Override allows you to have less total AP
groups than you might otherwise require.
Configuring or Editing AP Overrides
Perform the following steps to create or edit AP Overrides.
1. Navigate to the
overrides. Figure 26 illustrates this page.
Figure 26 Device Setup > Aruba Configuration > AP Overrides Page Illustration
2. To add a new AP Override, click the
To edit an existing AP Override, click the
The details page appears. Figure 27 illustrates the
Aruba Configuration > AP Overrides page. This page displays currently configured AP
Add New AP Override button.
pencil icon next to the AP Override name.
AP Overrides detail view.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 41
Page 42

Figure 27 AP Overrides Add or Edit Page Illustration (Non-scrolling View)
For a description of all fields on this page, refer to Table 5 in the Appendix.
3. Click
Add or Save. The added or edited AP Override appears on the AP Overrides page.
4. Push the newly added or edited AP Override configuration to the desired Aruba Controllers. Refer to
“Pushing Device Configurations to Controllers” on page40.
5. Repeat this procedure or continue to additional procedures to complete WLAN, Profile, Aruba AP Group
or other configurations.
Changing Adaptive Radio Management (ARM) Settings
You can adjust ARM settings for the radios of a particular Aruba AP Group. To do so, refer to the following
topics that describe ARM in relation to Aruba AP groups and device-level radio settings:
z “Configuring Aruba AP Groups” on page34
z “Aruba AP Groups” on page53
z “Profiles > RF > 802.11a/g Radio > ARM” on page124
42 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 43

Changing SSID and Encryption Settings
You can adjust SSID and Encryption parameters for devices by adjusting the profiles that define these
settings, then applying those profiles to Aruba AP Groups and WLANs that support them. To do so, refer to
the following topics that describe relevant steps and configuration pages:
z “Configuring Aruba AP Groups” on page34
z “Guidelines and Pages for WLANs in Aruba Configuration” on page37
z “Profiles > SSID” on page132 and related profiles.
Changing the Aruba AP Group for an AP Device
You can change the Aruba AP Group to which an AP device is associated. Perform the following
steps to change the Aruba AP Group for an AP device:
1. As required, review the Aruba AP Groups currently configured in AWMS. Navigate to the
Aruba Configuration
page, and click Aruba AP Groups from the navigation pane. This page displays and
Device Setup >
allows editing for all Aruba AP Groups that are currently configured in AWMS.
2. Navigate to the
3. If necessary, add the device to AWMS using the
APs/Devices > List page to view all devices currently seen by AWMS.
APs/Devices > New page.
To discover additional devices, ensure that the controller is set to perform a thin AP poll period.
4. On the
Modify Devices to change more than one device, or click the Wrench icon associated with any specific
device to make changes. The
5. In the
APs/Devices > List page, you can specify the Group and Folder to which a device belongs. Click
APs/Devices > Manage page appears.
Settings section of the APs/Devices > Manage page, select the new Aruba AP Group to assign to
the device. Change or adjust any additional settings as desired.
6. Click
Save and Apply to retain these settings and to propagate them throughout AWMS, or click one of
the alternate buttons as follows for an alternative change:
Click Revert to cancel out of all changes on this page.
Click Delete to remove this device from AWMS.
Click Ignore to keep the device in AWMS but to ignore it.
Click Import Settings to define device settings from previously created configurations.
Click Replace Hardware to replace the AP device with a new AP device.
Click Update Firmware to update the Firmware that operates this device.
7. Push this configuration change to the AP controller that is to support this AP device. For additional
information, refer to “Pushing Device Configurations to Controllers” on page40.
Using AWMS to Deploy Aruba APs for the First Time
In addition to migrating Aruba access points (APs) from AOS-oriented administration to AWMS
administration, you can use AWMS to deploy Aruba APs for the first time without separate AOS
configuration. Be aware of the following dynamics in this scenario:
z AWMS can manage all wireless network management functions, to include:
the first-time provisioning of Aruba APs
managing Aruba controllers with AWMS
z In this scenario, when a new Aruba AP boots up, AWMS may discover the AP before you have a chance
to configure and launch it through AOS configuration on the Aruba controller. In this case, the AP
appears in AWMS with a device name based on the MAC address.
z When you provision the AP through the Aruba controller and then rename the AP, the new AP name is
not updated in AWMS.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 43
Page 44

One possible workaround to update an Aruba AP device name in AWMS would be as follows, and this is not
the most efficient approach:
1. Configure and deploy the AP from AOS (separate from AWMS).
2. Delete the AP from AWMS.
3. Have AWMS rediscover the device.
A more efficient and robust approach is to deploy Aruba APs in AWMS with the following steps:
1. Define communication settings for Aruba APs pending discovery. Use the
Device Setup > Communication
page. This assigns communication settings to multiple devices at the time of discovery, and prevents
having to define such settings manually for each device after discovery.
2. Discover new Aruba APs with AWMS. You can do so with the
3. Click
New Devices In the Status section at the top of any AWMS page, or navigate to the APs/Devices >
page, illustrated in Figure 28.
New
Device Setup > Discover page
Figure 28 APs/ Devices > New Page Illustration
4. Select (check) the box next to any AP you want to provision.
5. Rename all new APs. Type in the new device name in the
6. Scroll the bottom of the page and put APs in the appropriate AWMS group and folder. Set the devices to
Manage Read/Write mode.
7. Click
Add. Wait approximately five to 10 minutes. You can observe that the APs have been renamed not
only in AMP but also on the Aruba AP Group and Aruba controller with the
command.
8. To set the appropriate Aruba AP Group, select the
9. Click
Modify Devices under the User and Bandwidth flash graphics.
10. Select the APs you want to re-group.
11. In the field that states
and click
44 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Move.
Device column.
show ap database AOS
AP/Devices or Groups page and locate your APs.
Move to Aruba AP Group, below the list of the APs, select the appropriate group,
Page 45

NOTE
If the list of Aruba AP Groups are not there, ensure you either create these Aruba AP groups manually on the
NOTE
Device Setup > Aruba Configuration page, wherein you merely need the device names and not the settings, or
import the configuration from one of your controllers to learn the groups.
12. Wait another five to 10 minutes to observe the changes on AMP. The changes should be observable
within one or two minutes on the controller.
Using General AWMS Device Groups and Folders
AWMS only allows any given AP to belong to one AWMS device group at a time. Supporting one AP in two
or more AWMS device groups would create at least two possible issues, to include the following:
z Data collection for such an AP device would have two or more sources and two or more related
processes.
z A multi-group AP would be counted several times and that would change the value calculations for
AWMS graphs.
As a result, some users may wish to evaluate how they deploy the group or folder for any given AP.
Aruba APs can also belong to Aruba AP Groups, but each AP is still limited to one general AWMS device group.
You can organize and manage any group of APs by type and by location. Use groups and folders with either
of the following two approaches:
z Organize AP device groups by device type, and device folders by device location.
In this setup, similar devices are in the same device group, and operate from a similar configuration or
template. Once this is established, create and maintain device folders by location.
z Organize AP device groups by location, and device folders by type.
In this setup, you can organize all devices according to location in the device groups, but for viewing,
you organize the device hierarchy by folders and type.
Be aware of the following additional factors:
z Configuration audits are done at the AWMS group level.
z AWMS folders support multiple sublevels.
z Therefore, unless there is a compelling reason to use the folders-by-device-type approach, AirWave
generally recommends the first approach where you use groups for AP type and folders strictly for AP
location.
Visibility in Aruba Configuration
Visibility Overview
Aruba Configuration supports device configuration and user information in the following ways;
z user roles
z AP/Device access level
z folders.
These and additional factors for visibility are as follows:
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 45
Page 46

z Administrative and Management users in AWMS can view the Device Setup > Aruba Configuration page
and the
Administrative users are enabled to view all configurations.
Management users have access to all profiles and Aruba AP groups for their respective folders.
z The Device Setup > Aruba Configuration page has a limit to folder drop-down options for customers that
APs/Devices > Aruba Config pages.
manage different accounts and different types of users.
z Aruba Configuration entails specific user role and security profiles that define some components of
visibility, as follows:
z Security > User Roles
z Security > Policies
z AWMS continues to support the standard operation of folders, users, and user roles as described in the
AWMS User Guide.
Defining Visibility for Aruba Configuration
Perform these steps to define or adjust visibility for users to manage and support Aruba Configuration:
1. As required, create a new AWMS device folder with management access.
a. Navigate to the
supporting new folders is
b. Click the
APs/Device > List page, scroll to the bottom of the page. (An alternate page
Users > Connected page).
Add New Folder link. The Folder detail page appears, as illustrated in Figure 29:
Figure 29 APs/Devices > Add New Folder > Folders Page Illustration
c. Click
Add. The APs/Devices > List page reappears. You can view your new folder by selecting it from
the
Go to folder drop-down list at the top right of this page. Figure 30 illustrates an unpopulated
device page for an example folder.
Figure 30 APs/Devices > List Page With No Devices
2. Add Aruba controller devices to that folder as required. Use the
instructions available in the AWMS User Guide.
46 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Device Setup > Add page following
Page 47

3. As required, create or edit a user role that is to have rights and manage privileges required to support
their function in Aruba Configuration.
a. At least one user must have administrative privileges, but several additional users may be required,
with less rights and visibility, to support Aruba Configuration without access to the most sensitive
information, such as SSIDs or other security related data.
b. Navigate to the
appropriate rights, or click the
AMP Setup > Roles page, and click Add New Role to create a new role with
pencil (manage) icon next to an existing role to adjust rights as
required. The Role page appears, illustrated in Figure 31.
Figure 31 AMP Setup > Roles > Add/Edit Role Page Illustration
c. As per standard AWMS configuration, complete the settings on this page. The most important fields
with regard to Aruba Configuration, device visibility and user rights are as follows:
Type—Specify the type of user. Important consideration should be given to whether the user is an
administrative user with universal access, or an AP/Device manager to specialize in device
administration, or additional users with differing rights and access.
AP/Device Access Level—Define the access level that this user is to have in support of Aruba
controllers, devices, and general Aruba Configuration operations.
Top Folder—Specify the folder created earlier in this procedure, or specify the Top folder for an
administrative user.
d. Click
Add to complete the role creation, or click Save to retain changes to an existing role. The AMP
> Setup
page now displays the new or revised role.
4. As required, add or edit one or more users to manage and support Aruba Configuration. This step
creates or edits users to have rights appropriate to Aruba Configuration. This user inherits visibility to
Aruba controllers and Aruba Configuration data based on the role and device folder created earlier in
this procedure.
a. Navigate to the
AMP Setup > Users page.
b. Click
Add New User, or click the pencil (manage) icon next to an existing user to edit that user.
c. Select the user role created with the prior step, and complete the remainder of this page as per
standard AWMS configuration. Refer to the AWMS User Guide, as required.
5. Observe visibility created or edited with this procedure.
The user, role, and device folder created with this procedure are now available to configure, manage,
and support Aruba Configuration and associated devices according to the visibility defined in this
procedure. Any component of this setup can be adjusted or revised by referring to the steps and AWMS
pages in this procedure.
6. Add or discover devices for the device folder defined during step 1 of this procedure. Information about
devices is available in the AWMS User Guide.
7. Continue to other elements of Aruba Configuration, described in this document. Early emphasis entails
creation or editing of Aruba AP Groups and WLANs with which they are associated.
AirWave Wireless Management Suite | Configuration Guide Using Aruba Configuration in Daily Operations | 47
Page 48

48 | Using Aruba Configuration in Daily Operations AirWave Wireless Management Suite | Configuration Guide
Page 49

Appendix A
NOTE
Aruba Configuration
Reference
Introduction
This appendix describes the pages, field-level settings, and interdependencies of Aruba Configuration
profiles. Additional information is available as follows:
z Aruba Configuration components are summarized in “Additional Concepts and Components of Aruba
Configuration” on page21.
z For procedures that use several of these components, refer to earlier chapters in this document.
z For architectural information about ArubaOS (AOS), refer to the AOS User Guide.
The default values of profile parameters or functions may differ slightly between AOS releases.
Access all pages and field descriptions in this appendix from the
illustrated in Figure 32. The one exception is the additional
Device Setup > Aruba Configuration page,
Groups > Aruba Config page that you access
from the standard AWMS navigation menu.
Figure 32 Aruba Configuration Components
This appendix describes Aruba Configuration components with the following organization and topics:
Aruba AP Groups Pages and Field Descriptions
z Aruba AP Groups
AP Overrides Pages and Field Descriptions
z AP Overrides
WLAN Pages and Field Descriptions
z Overview of WLANs in Aruba Configuration
z WLANs
z WLANs > Basic
z WLANs > Advanced
Profiles Pages and Field Descriptions
z Understanding Aruba Configuration Profiles
z Profiles > AAA
Profiles > AAA > Captive Portal Auth
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 49
Page 50

Profiles > AAA > Mac Auth
Profiles > AAA > Stateful 802.1X Auth
Profiles > AAA > Wired Auth
Profiles > AAA > VPN Auth
Profiles > AAA > Management Auth
Profiles > AAA > 802.1x Auth
Profiles > AAA > Stateful NTLM Auth
Profiles > AAA > WISPr Auth
z Profiles > AP
Profiles > AP > System
Profiles > AP > Regulatory Domain
Profiles > AP > AP Wired
Profiles > AP > AP Ethernet Link
Profiles > AP > SNMP
Profiles > AP > SNMP > SNMP User
z Profiles > IDS
Profiles > IDS > General
Profiles > IDS > Signature Matching
Profiles > IDS > Signature Matching > Signatures
Profiles > IDS > Denial of Service
Profiles > IDS > Denial of Service > Rate Threshold
Profiles > IDS > Impersonation
Profiles > IDS > Unauthorized Device
z Profiles > Mesh
Profiles > Mesh > Radio
Profiles > Mesh > Radio > Mesh HT SSID
Profiles > Mesh > Cluster
z Profiles > QoS
Profiles > QoS > Traffic Management
Profiles > QoS > VoIP Call Admission Control
Profiles > QoS > WMM Traffic Management
z Profiles > RF
Profiles > RF > 802.11a/g Radio
Profiles > RF > 802.11a/g Radio > ARM
Profiles > RF > 802.11a/g Radio > High-Throughput (HT) Radio
Profiles > RF > Event Thresholds
Profiles > RF > Optimization
z Profiles > SSID
Profiles > SSID > EDCA AP
Profiles > SSID > EDCA Station
Profiles > SSID > HT SSID
Profiles > SSID > 802.11K
50 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 51

Security Pages and Field Descriptions
z Security > User Roles
Security > User Roles > BW Contracts
Security > User Roles > VPN Dialers
z Security > Policies
Security > Policies > Destinations
Security > Policies > Services
z Security > Server Groups
Security > Server Groups > LDAP
Security > Server Groups > RADIUS
Security > Server Groups > TACACS
Security > Server Groups > Internal
Security > Server Groups > XML API
Security > Server Groups > RFC 3576
Security > Server Groups > Windows
z Security > TACACS Accounting
z Security > Time Ranges
z Security > User Rules
Advanced Services Pages and Field Descriptions
z Advanced Services > IP Mobility
Advanced Services > IP Mobility > Mobility Domain
z Advanced Services > VPN Services
Advanced Services > VPN Services > IKE
Advanced Services > VPN Services > L2TP
Advanced Services > VPN Services > PPTP
Advanced Services > VPN Services > IPSEC
Advanced Services > VPN Services > IPSEC > Dynamic Map
Advanced Services > VPN Services > IPSEC > Dynamic Map > Transform Set
Groups > Aruba Config Page and Section Information
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 51
Page 52

Aruba AP Groups Pages and Field Descriptions
Aruba AP Groups appear at the top of the Aruba Configuration navigation pane. This section describes the
configuration pages and fields of Aruba AP Groups.
Aruba AP Groups
The Aruba AP Groups page displays all configured Aruba AP Groups and enables you to add or edit Aruba
AP Groups. For additional information about using this page, refer to “General Aruba AP Groups
Procedures and Guidelines” on page34. Figure 33 illustrates this page and location.
Figure 33 Aruba AP Groups Navigation and Page
The
Aruba AP Groups page displays the following information for every group currently configured:
Table 3 Device Setup > Aruba Configuration > Aruba AP Groups Page
Column Description
Name Displays the name of the Aruba AP Group. Click the pencil icon next to any group to edit.
(Used by)
Group
(Used by)
Number of AP
(Used By)
User Role
Folder Displays the folder that is associated with this Aruba AP Group, when defined.
Add to create a new Aruba AP Group, or click the pencil icon next to an existing Aruba AP Group to
Click
edit that group. The
Displays the AWMS device groups that define this Aruba AP Group. Click the name of any
group in this column to display the detailed Groups > Aruba Config page.
The device groups in this column receive the profile configurations from the associated
Aruba AP Group. Any Aruba AP Group profiles can define device groups.
Displays the number of APs in this Aruba AP Group. A detailed list of each AP by name can
be displayed by navigating to the Groups > List page and selecting that group.
Displays the user role or roles that support the respective Aruba AP Group, when defined.
A Top viewable folder for the role is able to view all devices and groups contained by the top
folder. The top folder and its subfolders must contain all of the devices in any of the groups it
can view.
Clicking any folder name takes you to the APs/Devices > List page for folder inventory and
configuration.
Add/Edit Aruba AP Group page contains the following fields, describes in Table 4.
52 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 53

Table 4 Device Setup > Aruba Configuration > Aruba AP Groups Details, Settings and Default Values
Field Default Description
General Settings
Folder Top Displays the folder with which the AP Group is associated. The drop-down menu displays all folders
available for association with the AP Group.
Folders provide a way to organize the visibility of device parameters that is separate from the
configuration groups of devices. Using folders, you can view basic statistics about device, and
define which users have visibility to which device parameters.
Name Default Enter the name of the AP Group.
WLANs
Add a new
N/A Click this link to create a new WLAN to support Aruba Configuration. Once created, that new WLAN
WLAN
Show only
N/A To set the WLANs that appear on this page, select (check) the desired WLANs, then click Show
selected
Select WLANs No WLANs
selected
by default
Referenced Profiles
802.11a Radio
5_am Defines AP radio settings for the 5 GHz frequency band, including the Adaptive Radio Management
Profile
802.11g Radio
2.4_am Defines AP radio settings for the 2.4 GHz frequency band, including the Adaptive Radio
Profile
will appear with others on this page.
Only Selected.
Displays the WLANs currently present in Aruba Configuration. You may select as few or as many
WLANS as desired for which this AP Group is active.
To configure additional WLANs that appear in this section, click Add a new WLAN or navigate to
the WLANs section of the Aruba Configuration tool.
(ARM) profile and the high-throughput (802.11n) radio profile.
Click the pencil icon next to this field to edit or create additional profile settings in the RF >
802.11a/g Radio page of Aruba Configuration. Click Save on this page to return to the Add AP
Group page.
Management (ARM) profile and the high-throughput (802.11n) radio profile. Each 802.11a and
802.11b radio profile includes a reference to an Adaptive Radio Management (ARM) profile.
If you would like the ARM feature to select dynamically the best channel and transmission power for
the radio, verify that the 802.11a/802.11g radio profile references an active and enabled ARM
profile. If you want to manually select a channel for each AP group, create separate 802.11a and
802.11g profiles for each AP group and assign a different transmission channel for each profile.
The drop-down menu displays these options:
z default
z nchannel too high
z nchannel too low
Click the pencil icon next to this field to edit profile settings in the RF > 802.11a/g Radio page of
Aruba Configuration. Click Save on this page to return to the Add AP Group page.
RF Optimization
Profile
default Enables or disables load balancing based on a user-defined number of clients or degree of AP
utilization on an AP. Use this profile to detect coverage holes, radio interference and STA
association failures and configure Received signal strength indication (RSSI) metrics.
Click the pencil icon next to this field to display the Profiles > RF section of Aruba Configuration,
and edit these settings as desired. Click Save on this page to return to the Add AP Group page.
Event
Thresholds
Profile
default Defines error event conditions, based on a customizable percentage of low-speed frames, non-
unicast frames, or fragmented, retry or error frames. The drop-down menu displays these options:
z default
z all additional RF profiles currently configured in Aruba Configuration
Click the pencil icon next to this field to display the Profiles > RF > Events Threshold section of
Aruba Configuration, and edit these settings as desired. Click Save on this page to return to the
Add AP Group page.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 53
Page 54

Table 4 Device Setup > Aruba Configuration > Aruba AP Groups Details, Settings and Default Values (Continued)
Field Default Description
Wired AP Profile default Controls whether 802.11 frames are tunneled to the controller using Generic Routing Encapsulation
(GRE) tunnels, bridged into the local Ethernet LAN (for remote APs), or a configured for combination
of the two (split-mode). This profile also configures the switching mode characteristics for the port,
and sets the port as either trusted or untrusted.
Click the pencil icon next to this field to display the Profiles > AP > Wired page of Aruba
Configuration, and adjust these settings as desired.
Click Save on this page to return to the Add AP Group page.
Ethernet
Interface 0 Link
Profile
default Sets the duplex mode and speed of AP’s Ethernet link for ethernet interface 0. The configurable
speed is dependent on the port type, and you can define a separate Ethernet Interface profile for
each Ethernet link.
Click the pencil icon next to this field to display the Profiles > AP > Ethernet Link details page of
Aruba Configuration, and adjust these settings as desired. Click Save on this page to return to the
Add AP Group page.
Ethernet
Interface 1 Link
Profile
default Sets the duplex mode and speed of AP’s Ethernet link for ethernet interface 1. The configurable
speed is dependent on the port type, and you can define a separate Ethernet Interface profile for
each Ethernet link.
Click the pencil icon next to this field to display the Profiles > AP > Ethernet Link details page of
Aruba Configuration, and adjust these settings as desired. Click Save on this page to return to the
Add AP Group page.
AP System
Profile
default Defines administrative options for the controller, including the IP addresses of the local, backup,
and master controllers, Real-time Locating Systems (RTLS) server values and the number of
consecutive missed heartbeats on a GRE tunnel before an AP reboots traps.
This field is a drop-down menu with the following options:
z Non-integer RTLS Server Station Message Frequency
z Too-high RTLS Server Port
z Too-low AeroScout RTLS Server Port
z Too-low RTLS Server Port
Click the pencil icon next to this field to display the Profiles > AP > System details page of Aruba
Configuration, and adjust these settings as desired. Click Save on this page to return to the Add
AP Group page.
Regulatory
Domain Profile
default Defines an AP’s country code and valid channels for both legacy and high-throughput 802.11a and
802.11b/g radios.
Click the pencil icon next to this field to display the Profiles > AP > Regulatory Domain page of
Aruba Configuration, and adjust these settings as desired. Click Save on this page to return to the
Add AP Group page.
SNMP Profile default Selects the SNMP profile to associate with this AP group. The drop-down menu lists all SNMP
profiles currently enabled in AWMS.
Click the pencil icon next to this field to display the Profiles > AP > SNMP page of Aruba
Configuration, and adjust these settings as desired.
Click Save on this page to return to the Add AP Group page.
VoIP Call
Admission
Control Profile
default Aruba’s Voice Call Admission Control limits the number of active voice calls per AP by load-
balancing or ignoring excess call requests. This profile enables active load balancing and call
admission controls, and sets limits for the numbers of simultaneous Session Initiated Protocol (SIP),
SpectraLink Voice Priority (SVP), Cisco Skinny Client Control Protocol (SCCP), Vocera or New
Office Environment (NOE) calls that can be handled by a single radio.
Click the pencil icon next to this field to display the Profiles > AP > Regulatory Domain page of
Aruba Configuration, and adjust these settings as desired. Click Save on this page to return to the
Add AP Group page.
802.11g Traffic
Management
Profile
default Specifies the minimum percentage of available bandwidth to be allocated to a specific SSID when
there is congestion on the wireless network, and sets the interval between bandwidth usage
reports. This setting pertains specifically to 802.11g.
54 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 55

Table 4 Device Setup > Aruba Configuration > Aruba AP Groups Details, Settings and Default Values (Continued)
Field Default Description
802.11a Traffic
Management
Profile
default Specifies the minimum percentage of available bandwidth to be allocated to a specific SSID when
there is congestion on the wireless network, and sets the interval between bandwidth usage
reports. This setting pertains specifically to 802.11a.
IDS Profile default Selects the IDS profile to be associated with the new AP Group. The drop-down menu contains
these options:
z ids-disabled
z ids-high-setting
z ids -low-setting
z ids-medium-setting
The IDS profiles configure the AP’s Intrusion Detection System features, which detect and disable
rogue APs and other devices that can potentially disrupt network operations. An AP is considered
to be a rogue AP if it is both unauthorized and plugged into the wired side of the network. An AP is
considered to be an interfering AP if it is seen in the RF environment but is not connected to the
wired network.
Click the pencil icon next to this field to display the Profiles > IDS page of Aruba Configuration, and
adjust these settings as desired. Click Save on this page to return to the Add AP Group page.
Mesh Radio
Profile
default Determines many of the settings used by mesh nodes to establish mesh links and the path to the
mesh portal, including the maximum number of children a mesh node can accept, and transmit
rates for the 802.11a and 802.11g radios.
Mesh Cluster Profiles
Add New Mesh
Cluster Profile
N/A Click to display a new Mesh Cluster Profile section to this page, as illustrated in Figure 36.
Figure 34 Add New Mesh Cluster Profile Illustration
This section has two fields, as follows:
z Mesh Cluster Profile—Drop-down menu displays all supported profiles. Select one from the
menu.
z Priority (1-16)—Type in the priority number for this profile. The priority may be any integer
between 1 to 16.
Complete these fields, click the Add button, and the profile displays as an option in the Mesh
Cluster Profile section, which may be selected for the AP Group to be added or edited.
Click Add to complete the creation or click Save to complete the editing of the Aruba AP Group. This group
now appears in the navigation pane of the Aruba Configuration page.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 55
Page 56

AP Overrides Pages and Field Descriptions
The AP Overrides component of Aruba Configuration allow you to define device-specific settings for an AP
device without having to remove that device from an existing Aruba AP Group or create a new Aruba AP
Group specifically for that device. The
with most settings in the Aruba AP Group in which it is managed.
AP Overrides
The AP Overrides page displays all AP overrides that are currently configured. These overrides also appear
in the navigation pane at left. The name of any override matches the AP device name.
AP Overrides page is for custom AP devices that otherwise comply
Figure 35
AP Overrides Page
Table 5 describes the fields on this page.
Table 5 AP Overrides Field Descriptions
Field Description
Name Displays the name of the AP Overrides profile. This name matches the name of the
specific AP device that it defines.
Used By (Group) Displays the name of and link to the Aruba AP Group in which this AP Override applies.
Additional details about the Aruba AP Group appear on the Groups > Aruba Config
page when you click the name of the group.
Folder Displays the folder associated with the AP Overrides profile. The folder establishes the
visibility of this profile to users.
Click
Add on the AP Overrides page to create a new AP Override, or click the pencil icon next to an existing
override to edit that override.Table 6 describes the fields on the
Table 6 Aruba Configuration > AP Overrides Add or Edit Page Fields
Field Default Description
Name Blank Name of the AP Override. Use the name of the AP device to which it
Folder Top Displays the folder with which the WLAN is associated. The drop-down
WLANs
WLANs N/A This section lists the WLANs currently defined in Aruba Configuration by
56 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
AP Overrides > Add/Edit Details page.
applies.
menu displays all folders available for association with the WLAN.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
default. You can display selected WLANs or all WLANs.
Select one or more WLANs for which AP Override is to apply.
Page 57

Table 6 Aruba Configuration > AP Overrides Add or Edit Page Fields
Field Default Description
Excluded WLANs
Excluded WLANs N/A This section displays WLANs currently defined in Aruba Configuration by
default. This section can display selected WLANs or all WLANs. Use this
section to specify which WLANs are not to support AP Override.
Referenced Profiles
802.11a Radio
Profile
5_am Defines AP radio settings for the 5 GHz frequency band, including the
Adaptive Radio Management (ARM) profile and the high-throughput
(802.11n) radio profile.
Click the pencil icon next to this field to edit or create additional profile
settings in the RF > 802.11a/g Radio page of Aruba Configuration. Click
Save on this page to return to the Add AP Group page.
For additional information, refer to “Profiles > RF > 802.11a/g Radio” on
page116.
802.11g Radio
Profile
2.4_am Defines AP radio settings for the 2.4 GHz frequency band, including the
Adaptive Radio Management (ARM) profile and the high-throughput
(802.11n) radio profile. Each 802.11a and 802.11b radio profile includes a
reference to an Adaptive Radio Management (ARM) profile.
If you would like the ARM feature to select dynamically the best channel
and transmission power for the radio, verify that the 802.11a/802.11g radio
profile references an active and enabled ARM profile. If you want to
manually select a channel for each AP group, create separate 802.11a and
802.11g profiles for each AP group and assign a different transmission
channel for each profile.
The drop-down menu displays these options:
z default
z nchannel too high
z nchannel too low
Click the pencil icon next to this field to edit or create additional profile
settings in the RF > 802.11a/g Radio page of Aruba Configuration. Click
Save on this page to return to the Add AP Group page.
For additional information, refer to “Profiles > RF > 802.11a/g Radio” on
page116.
RF Optimization
Profile
Event Thresholds
Profile
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 57
default Enables or disables load balancing based on a user-defined number of
clients or degree of AP utilization on an AP. Use this profile to detect
coverage holes, radio interference and STA association failures and
configure Received signal strength indication (RSSI) metrics.
Click the pencil icon next to this field to display the Profiles > RF section
of Aruba Configuration, and edit these settings as desired. Click Save on
this page to return to the Add AP Group page.
For additional information, refer to “Profiles > RF > 802.11a/g Radio” on
page116.
default Defines error event conditions, based on a customizable percentage of
low-speed frames, non-unicast frames, or fragmented, retry or error
frames. The drop-down menu displays these options:
z default
z all additional RF profiles currently configured in Aruba Configuration
Click the pencil icon next to this field to display the Profiles > RF >
Events Threshold section of Aruba Configuration, and edit these
settings as desired. Click Save on this page to return to the Add AP
Group page.
For additional information, refer to “Profiles > RF > Event Thresholds” on
page123.
Page 58

Table 6 Aruba Configuration > AP Overrides Add or Edit Page Fields
Field Default Description
Wired AP Profile default Controls whether 802.11 frames are tunneled to the controller using
Generic Routing Encapsulation (GRE) tunnels, bridged into the local
Ethernet LAN (for remote APs), or a configured for combination of the two
(split-mode). This profile also configures the switching mode
characteristics for the port, and sets the port as either trusted or untrusted.
Click the pencil icon next to this field to display the Profiles > AP > Wired
page of Aruba Configuration, and adjust these settings as desired.
Click Save on this page to return to the Add AP Group page.
For additional information, refer to “Profiles > AP > AP Wired” on page88.
Ethernet Interface 0
Link Profile
default Sets the duplex mode and speed of AP’s Ethernet link for ethernet
interface 0. The configurable speed is dependent on the port type, and you
can define a separate Ethernet Interface profile for each Ethernet link.
Click the pencil icon next to this field to display the Profiles > AP >
Ethernet Link details page of Aruba Configuration, and adjust these
settings as desired. Click Save on this page to return to the Add AP Group
page.
For additional information, refer to “Profiles > AP > AP Ethernet Link” on
page90.
Ethernet Interface 1
Link Profile
default Sets the duplex mode and speed of AP’s Ethernet link for ethernet
interface 1. The configurable speed is dependent on the port type, and you
can define a separate Ethernet Interface profile for each Ethernet link.
Click the pencil icon next to this field to display the Profiles > AP >
Ethernet Link details page of Aruba Configuration, and adjust these
settings as desired. Click Save on this page to return to the Add AP Group
page.
For additional information, refer to “Profiles > AP > AP Ethernet Link” on
page90.
AP System Profile default Defines administrative options for the controller, including the IP addresses
of the local, backup, and master controllers, Real-time Locating Systems
(RTLS) server values and the number of consecutive missed heartbeats on
a GRE tunnel before an AP reboots traps.
This field is a drop-down menu with the following options:
z Non-integer RTLS Server Station Message Frequency
z Too-high RTLS Server Port
z Too-low AeroScout RTLS Server Port
z Too-low RTLS Server Port
Click the pencil icon next to this field to display the Profiles > AP >
System details page of Aruba Configuration, and adjust these settings as
desired. Click Save on this page to return to the Add AP Group page.
For additional information, refer to “Profiles > AP > System” on page83.
Regulatory Domain
Profile
default Defines an AP’s country code and valid channels for both legacy and high-
throughput 802.11a and 802.11b/g radios.
Click the pencil icon next to this field to display the Profiles > AP >
Regulatory Domain page of Aruba Configuration, and adjust these
settings as desired. Click Save on this page to return to the Add AP Group
page.
For additional information, refer to “Profiles > AP > Regulatory Domain” on
page87.
58 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 59

Table 6 Aruba Configuration > AP Overrides Add or Edit Page Fields
Field Default Description
SNMP Profile default Selects the SNMP profile to associate with this AP group. The drop-down
menu lists all SNMP profiles currently enabled in AWMS.
Click the pencil icon next to this field to display the Profiles > AP > SNMP
page of Aruba Configuration, and adjust these settings as desired.
Click Save on this page to return to the Add AP Group page.
For additional information, refer to “Profiles > AP > SNMP” on page90.
VoIP Call
Admission Control
Profile
default Aruba’s Voice Call Admission Control limits the number of active voice
calls per AP by load-balancing or ignoring excess call requests. This
profile enables active load balancing and call admission controls, and sets
limits for the numbers of simultaneous Session Initiated Protocol (SIP),
SpectraLink Voice Priority (SVP), Cisco Skinny Client Control Protocol
(SCCP), Vocera or New Office Environment (NOE) calls that can be
handled by a single radio.
Click the pencil icon next to this field to display the Profiles > AP >
Regulatory Domain page of Aruba Configuration, and adjust these
settings as desired. Click Save on this page to return to the Add AP Group
page.
For additional information, refer to “Profiles > AP > SNMP” on page90.
802.11g Traffic
Management Profile
default Specifies the minimum percentage of available bandwidth to be allocated
to a specific SSID when there is congestion on the wireless network, and
sets the interval between bandwidth usage reports. This setting pertains
specifically to 802.11g.
For additional information, refer to “Profiles > QoS > Traffic Management”
on page112
802.11a Traffic
Management Profile
default Specifies the minimum percentage of available bandwidth to be allocated
to a specific SSID when there is congestion on the wireless network, and
sets the interval between bandwidth usage reports. This setting pertains
specifically to 802.11a.
For additional information, refer to “Profiles > QoS > Traffic Management”
on page112
IDS Profile default Selects the IDS profile to be associated with the new AP Group. The drop-
down menu contains these options:
z ids-disabled
z ids-high-setting
z ids -low-setting
z ids-medium-setting
The IDS profiles configure the AP’s Intrusion Detection System features,
which detect and disable rogue APs and other devices that can potentially
disrupt network operations. An AP is considered to be a rogue AP if it is
both unauthorized and plugged into the wired side of the network. An AP is
considered to be an interfering AP if it is seen in the RF environment but is
not connected to the wired network.
Click the pencil icon next to this field to display the Profiles > IDS page of
Aruba Configuration, and adjust these settings as desired. Click Save on
this page to return to the Add AP Group page.
For additional information, refer to “Profiles > IDS” on page94
Mesh Radio Profile default Determines many of the settings used by mesh nodes to establish mesh
links and the path to the mesh portal, including the maximum number of
children a mesh node can accept, and transmit rates for the 802.11a and
802.11g radios.
For additional information, refer to “Profiles > Mesh” on page107.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 59
Page 60

Table 6 Aruba Configuration > AP Overrides Add or Edit Page Fields
Field Default Description
Mesh Cluster Profiles
Add New Mesh
Cluster Profile
Excluded Mesh Cluster Profiles
Excluded Mesh
Cluster Profiles
The Add
Mesh Cluster
Profile section
is hidden by
default, until
the Add
button is
clicked.
Clicking this Add button displays a new Mesh Cluster Profile section to
this page, as illustrated in Figure 36.
Figure 36 Add New Mesh Cluster Profile Illustration
This section has two fields, as follows:
z Mesh Cluster Profile—Drop-down menu displays all supported
profiles. Select one from the menu.
z Priority (1-16)—Type in the priority number for this profile. The priority
may be any integer between 1 to 16.
Complete these fields, click the Add button, and the profile displays as an
option in the Mesh Cluster Profile section, which may be selected for the
AP Group to be added or edited.
For additional information about Mesh Cluster profiles, refer to these
sections:
z “Profiles > Mesh” on page107
z “Profiles > Mesh > Cluster” on page111.
If required, select one or more Mesh Cluster profiles from this field. This
field can display all Mesh Cluster profiles or can display only selected
Mesh Cluster profiles. For additional information about Mesh Cluster
profiles, refer to “Profiles > Mesh > Cluster” on page111.
Click Add to complete the creation of the new AP Overrides profile, or click Save to preserve changes to an
existing AO Overrides profile. The
AP Overrides page and the Aruba Configuration navigation pane display
the name of the AP Overrides profile.
WLAN Pages and Field Descriptions
Overview of WLANs in Aruba Configuration
You have a wide variety of options for authentication, encryption, access management, and user rights
when you configure a WLAN. However, you must configure the following basic elements:
z An SSID that uniquely identifies the WLAN
z Layer-2 authentication to protect against unauthorized access to the WLAN
z Layer-2 encryption to ensure the privacy and confidentiality of the data transmitted to and from the
network
z A user role and virtual local area network (VLAN) for the authenticated client
Refer to the AOS User Guide for additional information.
60 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 61

Use the following guidelines when configuring and using WLANs in Aruba Configuration:
z The Device Setup > Aruba Configuration navigation pane displays custom-configured WLANs and Aruba
AP Groups. All other components of the navigation pane are standard across all deployments of Aruba
Configuration.
z You define or modify WLANs on the Device Setup > Aruba Configuration page. Click WLANs from the
navigation pane.
z You can create or edit any profile in an WLAN as you define or modify that WLAN. If you digress to
profile setup from a different page, AWMS returns you to your place on the
WLAN setup page once you
are done with profile setup.
WLANs
The WLANs page displays all configured WLANs in Aruba Configuration and enables you to add or edit
WLANs. For additional information about using this page, refer to “General WLAN Procedures and
Guidelines” on page37. Figure 33 illustrates this page and location.
Figure 37 WLANs Navigation and Page
The
Aruba Configuration > WLANs page contains additional information as described in Table 7:
Table 7 Aruba Configuration > WLANs Page Field Descriptions
Field Description
Name Lists the name of the WLAN.
SSID Lists the SSID currently defined for the WLAN.
Aruba AP Group Lists the Aruba AP Group or Groups that use the associated WLAN.
AP Override Lists any AP Override configurations for specific APs on the WLAN and in the respective
Aruba AP Groups.
Traffic Management Lists Traffic Management profiles that are currently configured and deployed on the
Folder Lists the folder for the WLAN.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 61
WLAN.
Page 62

You can create new WLANs from this page by clicking the Add button. You can edit an existing WLAN by
clicking the pencil icon for that WLAN.
You have two pages by which to create or edit WLANs: the
Basic page and the Advanced page. The
remainder of this section describes these two pages.
WLANs > Basic
From the Aruba Configuration > WLANs page, click Add to create a new WLAN, or click the pencil icon to
edit an existing WLAN, then click
Table 8 describes the fields for this page.
Table 8 Aruba Configuration > WLANs > Basic Page Field Descriptions
Field Default Description
Name Blank Enter the name of the WLAN.
Folder Top Displays the folder with which the WLAN is associated. The drop-down
SSID N/A Select the SSID profile that defines encryption, EDCA or high-throughput
Basic. This page provides a streamlined way to create or edit a WLAN.
menu displays all folders available for association with the WLAN.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
SSID parameters. Access these SSID profiles by clicking Profiles > SSID
in the navigation pane at left. For additional information, refer to “Profiles >
SSID > EDCA AP” on page127.
Radio Type N/A Define whether the supported radio type on the WLAN is 802.11a,
Enable 802.11n Yes Define whether the WLAN is to support 802.11n.
VLAN 1 Select the VLAN ID number to be supported on this WLAN.
Intended Use Internal Define whether this WLAN is Internal to the enterprise or to support Guest
Encryption opensystem Select one or more encryption types, as desired, to be supported by this
Use Captive Portal No Select whether this WLAN will use captive portal authentication. Captive
Authenticated User
Role
Click
Add to create the WLAN, or click Save to finish reconfiguring an existing WLAN. The WLAN appears
on the
WLANs page in the Aruba Configuration navigation pane.
logon For the captive portal authentication profile, you specify the previously-
802.11g, or all.
users.
WLAN.
portal authentication directs clients to a special web page that typically
requires them to enter a username and password before accessing the
network. For additional information about this profile type, refer to “Profiles
> AAA > Captive Portal Auth” on page69.
created auth-guest user role as the default user role for authenticated
captive portal clients and the authentication server group (“Internal”). For
additional information, refer to “Security > User Roles” on page141.
The alternate way to create or edit WLANs is from the
“WLANs > Advanced” on page63.
62 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Advanced page. For additional information, refer to
Page 63

WLANs > Advanced
From the Aruba Configuration > WLANs page, click Add to create a new WLAN, or click the pencil icon to
edit an existing WLAN, then click Advanced. The Advanced page allows you to configure many more
sophisticated settings when creating or editing WLANs. Table 9 describes the fields for this page.
Table 9 Aruba Configuration > WLANs > Advanced Page Fields
Field Default Description
General Settings
Folder Top Displays the folder with which the WLAN is associated. The drop-down
menu displays all folders available for association with the WLAN.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Name of the WLAN.
Referenced Profiles
SSID Profile Select the SSID profile that defines encryption, EDCA or high-throughput
SSID parameters. Access these SSID profiles by clicking Profiles > SSID
in the navigation pane at left. For additional information, refer to “Profiles >
SSID > EDCA AP” on page127.
AAA Profile Select the AAA profile that defines RADIUS, TACACS+, or other AAA
server configurations for this WLAN. Access these SSID profiles by
clicking Profiles > AAA in the navigation pane at left. For additional
information, refer to “Profiles > AAA” on page67.
Other Settings
Virtual AP Enable Yes Enable this setting to allow virtual AP configurations to be deployed on this
WLAN.
This profile defines your WLAN by enabling or disabling the bandsteering,
fast roaming, and DoS prevention features. It defines radio band,
forwarding mode and blacklisting parameters, and includes references an
AAA Profile, an EDCA Parameters AP Profile and a High-throughput SSID
profile
Allowed Band all Select whether this WLAN is to support 802.11a, 802.11g, or both.
VLAN N/A Enter the VLAN or range of VLANs to be supported with this WLAN.
Forward Mode tunnel Define whether this WLAN is to support tunnel, bridge, or split-mode IP
forwarding.
Deny Time Range none Define the time range restrictions for the roles in this WLAN, if any.
Mobile IP Yes Enable or disable mobile IP functions. This setting specifies whether the
controller is the home agent for a client. When enabled, this setting detects
when a mobile client has moved to a foreign network and determines the
home agent for a roaming client.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 63
Page 64

Table 9 Aruba Configuration > WLANs > Advanced Page Fields (Continued)
Field Default Description
HA Discovery on
Association
No Enable or disable HA discovery on Association. In normal circumstances a
controller performs an HA discovery only when it is aware of the client’s IP
address which it learns through the ARP or any L3 packet from the client.
This limitation of learning the client’s IP and then performing the HA
discovery is not effective when the client performs an inter switch move
silently (does not send any data packet when in power save mode). This
behavior is commonly seen with various handheld devices, Wi-Fi phones,
etc. This delays HA discovery and eventually resulting in loss of
downstream traffic if any meant for the mobile client.
With HA discovery on association, a controller can perform a HA discovery
as soon as the client is associated. This feature can be enabled using the
ha-disc-on assoc parameter in the WLAN virtual <ap-profile>
command. By default, this feature is disabled. You can enable this on
virtual APs with devices in power-save mode and requiring mobility. This
option will also poll for all potential HAs.
DoS Prevention No Enable or disable DoS prevention functions, as defined in virtual AP
profiles.
Station Blacklisting Yes Enable or disable DoS prevention functions, as defined in virtual AP
profiles. The blacklisting option can be used to prevent access to clients
that are attempting to breach the security.
When a client is blacklisted in the Aruba system, the client is not allowed to
associate with any AP in the network for a specified amount of time. If a
client is connected to the network when it is blacklisted, a deauthentication message is sent to force the client to disconnect. While
blacklisted, the client cannot associate with another SSID in the network.
Blacklist Time 3600 If station blacklisting is enabled, specify the time in seconds for which
blacklisting is enabled. When a client is blacklisted in the Aruba system,
the client is not allowed to associate with any AP in the network for a
specified amount of time.
Authentication
Failure Blacklist
Time
3600 You can configure a maximum authentication failure threshold in seconds
for each of the following authentication methods:
z 802.1x
z MAC
z Captive portal
z VPN
When a client exceeds the configured threshold for one of the above
methods, the client is automatically
blacklisted by the controller, an event is logged, and an SNMP trap is sent.
By default, the maximum authentication failure threshold is set to 0 for the
above authentication methods, which means that there is no limit to the
number of times a client can attempt to authenticate.
With 802.1x authentication, you can also configure blacklisting of clients
who fail machine authentication.
NOTE: This requires that the External Services Interface (ESI) license be
installed in the controller.
NOTE: When clients are blacklisted because they exceed the
authentication failure threshold, they are blacklisted indefinitely by default.
You can configure the duration of the blacklisting;
Fast Roaming No Fast roaming is a component of virtual AP profiles in which client devices
are allowed to roam from one access point to another without requiring
reauthentication by the main RADIUS server.
Strict Compliance No Define whether clients should have strict adherence to settings on this
page for network access.
VLAN Mobility No Define whether clients in the WLAN and VLAN should have mobility or
64 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
roaming privileges.
Page 65
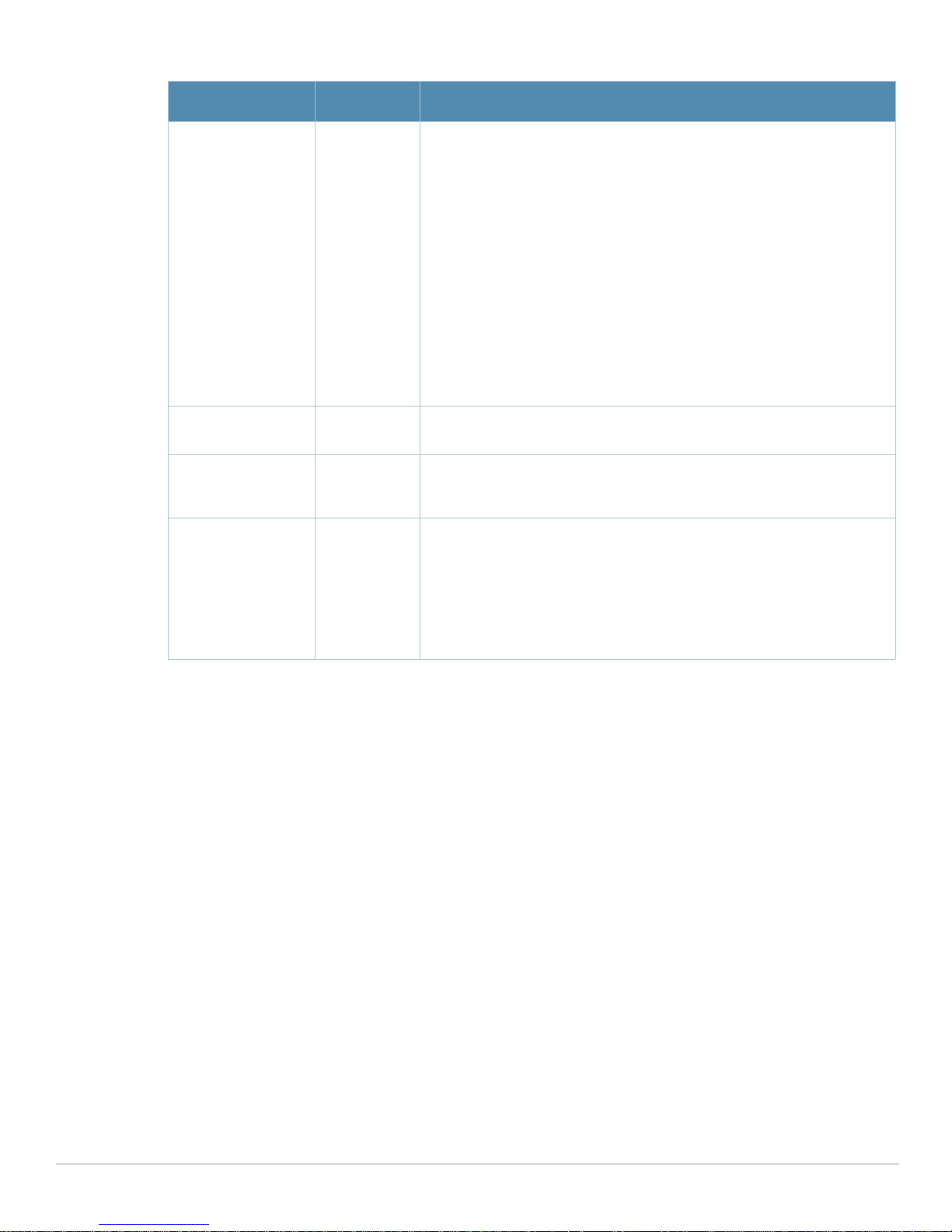
Table 9 Aruba Configuration > WLANs > Advanced Page Fields (Continued)
Field Default Description
Remote AP
Operation
standard Define the rights for remote APs in this WLAN. Options are as follows:
z standard
z persistent
z backup
z always
Remote APs connect to a controller using Layer-2 Tunneling Protocol and
Internet Protocol Security (L2TP/IPSec). AP control and 802.11 data traffic
are carried through this tunnel. Secure Remote Access Point Service
extends the corporate office to the remote site. Remote users can use the
same features as corporate office users. For example, voice over IP (VoIP)
applications can be extended to remote sites while the servers and the
PBX remain secure in the corporate office.
Secure Remote Access Point Service can also be used to secure control
traffic between an AP and the controller in a corporate environment. In this
case, both the AP and controller are in the company’s private address
space.
Drop Broadcast and
Multicast
Convert Broadcast
ARP Requests to
No Specify whether the WLAN should drop broadcast and multicast mesh
network advertising on the WLAN.
No Specify whether ARP table information should be distributed in broadcast
(default) or unicast fashion.
Unicast
Band Steering No Enable or disable band steering on the WLAN. Band steering reduces co-
channel interference and increases available bandwidth for dual-band
clients, because there are more channels on the 5GHz band than on the
2.4GHz band. Dual-band 802.11n-capable clients may see even greater
bandwidth improvements, because the band steering feature will
automatically select between 40MHz or 20MHz channels in 802.11n
networks. This feature is disabled by default, and must be enabled in a
Virtual AP profile.
Click Add to create the WLAN, or click Save to finish reconfiguring an existing WLAN. The WLAN appears
on the
WLANs page in the Aruba Configuration navigation pane.
The alternate way to create or edit WLANs is from the
Basic page.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 65
Page 66

Profiles Pages and Field Descriptions
Understanding Aruba Configuration Profiles
In ArubaOS, related configuration parameters are grouped into a profile that you can apply as needed to an
AP group or to individual APs. This section lists each category of AP profiles that you can configure and
then apply to an AP group or to an individual AP. Note that some profiles reference other profiles. For
example, a virtual AP profile references SSID and AAA profiles, while an AAA profile can reference an
802.1x authentication profile and server group.
You can apply the following types of profiles to an AP or AP group. See Figure 39. For additional details and
configuration instructions, continue to the related procedures in this section.
Perform the following initial steps to configure profiles.
1. Browse to the
pane on the left. Figure 38 illustrates general profile categories.
Figure 38 Profiles in the Aruba Configuration Navigation Pane
2. Expand the
illustrated in Figure 39.
Figure 39 Profile Navigation Pane of AWMS Aruba Configuration
Device Setup > Aruba Configuration page, and click the Profiles heading in the navigation
Profiles menu by clicking the plus sign (+) next to it. Several profile options appear, as
This document section describes the profiles and settings supported in Aruba Configuration.
66 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 67

Profiles > AAA
This profile type defines authentication settings for the WLAN users, including the role for unauthenticated
users, and the different roles that should be assigned to users authenticated via 802.1x, MAC or SIP
authentication. Perform these steps to determine the need for and to configure AAA profiles.
1. To view and configure AAA profiles, click the
AAA Profiles page appears and lists the current profiles. Figure 40 illustrates this page.
AAA profile heading in the navigation pane. The
Figure 40 AAA Profiles Page of Aruba Configuration
2. From the navigation pane, you can configure the following profile types:
AAA Profile—The AAA profile defines the authentication method and the default user role for
unauthenticated users. This profile type references additional profiles. Refer to “Profiles > AAA” on
page68.
Captive Portal Auth—Captive portal authentication directs clients to a special web page that
typically requires them to enter a username and password before accessing the network. This profile
defines login wait times and the URLs for login and welcome pages, and manages the default user
role for authenticated captive portal clients. You can also use this profile to set the maximum number
of authentication failures allowed per user before that user is blacklisted. This profile includes a
reference to an Server group profile. Refer to “Profiles > AAA > Captive Portal Auth” on page69.
MAC Auth—Defines parameters for MAC address authentication, including the case of MAC string
(upper- or lower-case), the format of the diameters in the string, and the maximum number of
authentication failures before a user is blacklisted. Refer to “Profiles > AAA > Mac Auth” on page71.
Stateful 802.11 Auth—Enables or disables 802.1x authentication for clients on non-Aruba APs, and
defines the default role for those users once they are authenticated. This profile also references a
server group to be used for authentication. Refer to “Profiles > AAA > Stateful 802.1X Auth” on
page72.
Wired Auth—This profile merely references an AAA profile to be used for wired authentication.
Refer to “Profiles > AAA > Wired Auth” on page73.
VPN Auth—Identifies the default role for authenticated VPN clients. This profile also references a
server group. Refer to “Profiles > AAA > VPN Auth” on page73.
Management Auth—Enables or disables management authentication, and identifies the default
role for authenticated management clients. This profile also references a server group. Refer to
“Profiles > AAA > Management Auth” on page74.
802.1x Auth—Manages settings for the 802.11k protocol. In a 802.1k network, if the AP with the
strongest signal is reaches its maximum capacity, clients may connect to an under utilized AP with a
weaker signal under utilized APs. Refer to “Profiles > AAA > 802.1x Auth” on page75.
Stateful NTLM Auth—Requires that you specify a server group which includes the servers
performing NTLM authentication, and a default role to be assigned to authenticated users. Refer to
“Profiles > AAA > Stateful NTLM Auth” on page80.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 67
Page 68

WISPr Auth—The Wireless Internet Service Provider roaming (WISPr) protocol allows users to
roam between service providers. A RADIUS server is used to authenticate subscriber credentials.
Refer to “Profiles > AAA > WISPr Auth” on page81.
Profiles > AAA
Perform these steps to configure a Captive Portal Authentication profile.
1. Click
2. Click the
Profiles > AAA in the Aruba Configuration Navigation pane.
Add button to create a new AAA profile, or click the pencil icon next to an existing profile to
edit that profile. The
Details page appears. Complete the settings as described in Table 11.
Table 10 Captive Portal Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the AAA profile.
Referenced Profiles
MAC Authentication
Profile
None Select a MAC Authentication profile to be referenced by the AAA profile
being configured. If necessary, click the pencil or add icon to add or edit a
MAC Authentication profile. Refer to “Profiles > AAA > Mac Auth” on
page 71 if required.
MAC Authentication
Server Group
802.1X Authentication
Profile
802.1X
Authentication
Server Group
RADIUS Accounting
Server Group
Other Settings
Initial Role ap-role Select the initial role to be referenced by the AAA profile being configured.
MAC Authentication
Default Role
default Select a MAC Authentication server group. You can add a new server
group by clicking the add icon or edit an existing server group by clicking
the pencil icon.
None Select the 802.1X Authentication Profile to be referenced by the AAA
profile being configured. You can add a new profile by clicking the add
icon or edit an existing profile by clicking the pencil icon. Refer to “Profiles
> AAA > 802.1x Auth” on page 75.
None Select the 802.1X Authentication server group. You can add a new server
group by clicking the add icon or edit an existing server group by clicking
the pencil icon.
None Select the RADIUS accounting server group to be referenced by the AAA
profile being configured. Click the add icon to create a new RADIUS server
group.
Add a new role by clicking the add icon, or edit an existing role by clicking
the pencil icon.
ap-role Select the MAC authentication default role to be referenced by the AAA
profile being configured. Add a new role by clicking the add icon, or edit an
existing role by clicking the pencil icon. This setting requires a policy
enforcement firewall license.
68 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 69

Table 10 Captive Portal Auth Profile Settings
Field Default Description
802.1X
Authentication
Default Role
User Derivation
Rules
Wired to Wireless
Roaming
SIP Authentication
Role
XML API Servers
XML API Servers N/A Select the XML API server to support the AAA profile being configured, if
ap-role Select the 802.1X authentication default role to be referenced by the AAA
profile being configured. Add a new role by clicking the add icon, or edit an
existing role by clicking the pencil icon. This setting requires a policy
enforcement firewall license.
None Select the user derivation rules to be referenced by the AAA profile being
configured. User derivation rules are executed before client authentication.
The user role can be derived from attributes from the client’s association
with an AP. You configure the user role to be derived by specifying
condition rules; when a condition is met, the specified user role is assigned
to the client. You can specify more than one condition rule; the order of
rules is important as the first matching condition is applied.
Add a new rule by clicking the add icon, or edit an existing rule by clicking
the pencil icon.
Yes Enable or disable support for roaming from wired to wireless networks.
None Select the role to function for SIP authentication. The controller supports
the stateful tracking of session initiation protocol (SIP) authentication
between a SIP client and a SIP registry server. Upon successful
registration, a user role is assigned to the SIP client. Click the add icon to
create a new role, or click the pencil icon to edit an existing role.
This setting requires a voice service license.
required. This section is blank if there are no XML API servers.
RFC 3576 Servers
RFC 3576 Servers N/A Select the RFC 3576 RADIUS server to support the AAA profile being
configured, if required. This section is blank if there are no such servers.
3. Click Add or Save. The added or edited AAA profile appears on the AAA Profiles page.
Profiles > AAA > Captive Portal Auth
In this section, you create an instance of the captive portal authentication profile and the AAA profile. For
the captive portal authentication profile, you specify the previously-created auth-guest user role as the
default user role for authenticated captive portal clients and the authentication server group (“Internal”).
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > Captive Portal Auth in the Aruba Configuration Navigation pane.
Add button to create a new Captive Portal Auth profile, or click the pencil icon next to an existing
profile to edit that profile. The
Table 11 Captive Portal Auth Profile Settings
Field Default Description
General Settings
Captive Portal Authentication profile.
Details page appears. Complete the settings as described in Table 11.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 69
Page 70

Table 11 Captive Portal Auth Profile Settings
Field Default Description
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters
that is separate from the configuration groups of devices. Using
folders, you can view basic statistics about device, and define which
users have visibility to which device parameters.
Name Blank Enter the name of the Captive Port Authentication profile.
Referenced Profiles
Server Group default Enter the name of the internal VPN authentication server group, or the
server group that performs 802.1x authentication.
Other Settings
Default Role default Role assigned to the Captive Portal user upon login. When both user
and guest logon are enabled, the default role applies to the user
logon; users logging in using the guest interface are assigned the
guest role. The Policy Enforcement Firewall license must be installed.
Redirect Pause
(0-60 sec)
10 Time, in seconds, that the system remains in the initial welcome page
before redirecting the user to the final web URL. If set to 0, the
welcome page displays until the user clicks on the indicated link.
User Login Yes Enables Captive Portal with authentication of user credentials.
Guest Login No Enables Captive Portal logon without authentication.
Logout Popup
Window
Yes Enables a pop-up window with the Logout link for the user to logout
after logon. If this is disabled, The user remains logged in until the
user timeout period has elapsed or the station reloads.
Use HTTP
Authentication
Logon Wait Minimum
Wait (1-10 sec)
No Use HTTP protocol on redirection to the Captive Portal page. If you
use this option, modify the captive portal policy to allow HTTP traffic.
5 Minimum time, in seconds, the user will have to wait for the logon
page to pop up if the CPU load is high. This works in conjunction with
the Logon wait CPU utilization threshold parameter.
Logon Wait
Maximum Wait
(0-10 sec)
Logon Wait CPU
Utilization Threshold
10 Maximum time, in seconds, the user will have to wait for the logon
page to pop up if the CPU load is high. This works in conjunction with
the Logon wait CPU utilization threshold parameter.
60 CPU utilization percentage above which the Logon wait interval is
applied when presenting the user with the logon page.
(0-100 sec)
Max Authentication
Failures
0 Maximum number of authentication failures before the user is
blacklisted.
Show FQDN No Allows the user to see and select the fully-qualified domain name
(FQDN) on the login page.
Use CHAP
(Non-standard)
Sygate-on-demand-
No Use CHAP protocol. You should not use this option unless instructed
to do so by an Aruba representative.
No Enables client remediation with Sygate-on-demand-agent (SODA).
agent
Login Page /auth/index.html URL of the page that appears for the user logon. This can be set to
Welcome Page /auth/
70 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
welcome.html
any URL.
URL of the page that appears after logon and before redirection to the
web URL. This can be set to any URL.
Page 71

Table 11 Captive Portal Auth Profile Settings
Field Default Description
Show Welcome Page Yes Enables the display of the welcome page. If this option is disabled,
Adding Switch IP
Address in
Redirection URL
No Select this option to send the controller’s IP address in the redirection
redirection to the web URL happens immediately after logon.
URL when external captive portal servers are used. An external
captive portal server can determine the controller from which a
request originated by parsing the ‘switchip’ variable in the URL.
3. Click Add or Save. The added or edited Captive Portal Auth profile appears on the AAA Profiles page.
Modifying the Initial User Role
The captive portal authentication profile specifies the captive portal login page and other configurable
parameters. The initial user role configuration must include the applicable captive portal authentication
profile instance. Therefore, you need to modify the guest-logon user role configuration to include the
guestnet captive portal authentication profile.
Profiles > AAA > Mac Auth
Before configuring MAC-based authentication, you must configure the following:
z The user role that will be assigned as the default role for the MAC-based authenticated clients. You
configure the default user role for MAC-based authentication in the AAA profile. If derivation rules exist
or if the client configuration in the internal database has a role assignment, these values take precedence
over the default user role.
z Authentication server group that the controller uses to validate the clients. The internal database can be
used to configure the clients for MAC-based authentication.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > Mac Auth in the Aruba Navigation pane.
Add button to create a new Mac Auth profile, or click the pencil icon next to an existing profile
to edit that profile. The
Details page appears. Complete the settings as described in Table 12:
Mac Auth profile.
Table 12 Aruba Configuration > Profiles > AAA > MAC Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters
that is separate from the configuration groups of devices. Using
folders, you can view basic statistics about device, and define
which users have visibility to which device parameters.
Name Blank Enter the name of the MAC Auth profile.
Other Settings
Delimiter none Delimiter used in the MAC string:
z colon specifies the format xx:xx:xx:xx:xx:xx
z dash specifies the format xx-xx-xx-xx-xx-xx
z none specifies the format xxxxxxxxxxxx
Case lower The case (upper or lower) used in the MAC string.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 71
Page 72

Table 12 Aruba Configuration > Profiles > AAA > MAC Auth Profile Settings
Field Default Description
Max Authentication
Failures (0-10)
0 Number of times a station can fail to authenticate before it is
blacklisted. A value of 0 disables blacklisting.
3. Click Add or Save. The added or edited Mac Auth profile appears on the AAA Profiles page, and on the
MAC Auth details page.
Profiles > AAA > Stateful 802.1X Auth
This profile type enables or disables 802.1x authentication for clients on non-Aruba APs, and defines the
default role for those users once they are authenticated. This profile also references a server group to be
used for authentication.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > Stateful 802.11 Auth in the Aruba Navigation pane.
Add button to create a new Stateful 802.11 Auth profile, or click the pencil icon next to an
existing profile to edit that profile. The
Table 13 Aruba Configuration > Profiles > AAA > Stateful 802.1X Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
Stateful 802.1X Auth profile.
Details page appears. Complete the settings described in Table 13:
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that
is separate from the configuration groups of devices. Using folders, you
can view basic statistics about device, and define which users have
visibility to which device parameters.
Name Blank Enter the name of the profile.
Referenced Profiles
Server Group N/A Select the AAA authentication server group. Click the pencil icon to edit
an existing server group or click the add icon to create a new server
group.
Other Settings
Default Role ap-role The user role to be associated with this authentication profile.
Timeout (1-20 sec) 10 Maximum time, in seconds, that the server waits before timing out the
request.
Enabled No When enabled with Ye s, activates the authentication server.
3. Click
Add or Save. The added or edited Stateful 802.11 Auth profile appears on the AAA Profiles page,
and on the
Stateful 802.11 Auth details page.
72 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 73

Profiles > AAA > Wired Auth
This profile type merely references an AAA profile to be used for wired authentication.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > Wired Auth in the Aruba Navigation pane.
Add button to create a new Wired Auth profile, or click the pencil icon next to an existing
profile to edit that profile. The
Wired Auth profile.
Details page appears. Complete the settings as described in Table 14:
Table 14 Aruba Configuration > Profiles > AAA > Wired Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the Wired Authentication profile.
Referenced Profiles
AAA None From the drop-down menu, select the AAA profile for wired authentication.
Click the pencil icon to edit an existing profile or click the add icon to
create a new profile.
3. Click
Add or Save. The added or edited Wired Auth profile appears on the AAA Profiles page, and on the
Wired Auth details page.
Profiles > AAA > VPN Auth
A VPN Authentication profile identifies the default role for authenticated VPN clients. This profile also
references a server group.
Before you enable VPN authentication, you must configure the authentication server(s) and server group
that the controller will use to validate the remote AP. When you provision the remote AP, you configure
IPSec settings for the AP, including the username and password. This username and password must be
validated by an authentication server before the remote AP is allowed to establish a VPN tunnel to the
controller. The authentication server can be any type of server supported by the controller, including the
controller’s internal database.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > VPN Auth in the Aruba Navigation pane.
Add button to create a new VPN Auth profile, or click the pencil icon next to an existing profile
to edit that profile. The
Details page appears. Complete the settings as described in Table 15:
VPN Auth profile.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 73
Page 74

Table 15 Aruba Configuration > Profiles > AAA > VPN Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Referenced Profiles
Server Group N/A Select the AAA authentication server group. Click the pencil icon to edit an
Other Settings
Default Role ap-role Select the role to be associated with this authentication profile.
Max Authentication
failures (0-10)
0 Enter the number of times a station can fail to authenticate before it is
existing server group or click the add icon to create a new server group.
blacklisted. A value of 0 disables blacklisting.
3. Click Add or Save. The added or edited VPN Auth profile appears on the AAA Profiles page, and on the
VPN Auth details page.
Profiles > AAA > Management Auth
Users who need to access the controller to monitor, manage, or configure the Aruba user-centric network
can be authenticated with RADIUS, TACACS+, or LDAP servers or the internal database.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AAA > Management Auth in the Aruba Navigation pane.
Add button to create a new Management Auth profile, or click the pencil icon next to an
existing profile to edit that profile. The
Table 16:
Management Auth profile.
Details page appears. Complete the settings as described in
Table 16 Aruba Configuration > Profiles > AAA > Management Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
Name Blank Enter the name of the profile.
74 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters
that is separate from the configuration groups of devices. Using
folders, you can view basic statistics about device, and define
which users have visibility to which device parameters.
Page 75

Table 16 Aruba Configuration > Profiles > AAA > Management Auth Profile Settings
Field Default Description
Referenced Profiles
Server Group N/A Select the AAA authentication server group. Click the pencil icon to
Other Settings
Default Role ap-role The role to be associated with this authentication profile.
Enable No When enabled with Ye s, this setting activates the authentication
edit an existing server group or click the add icon to create a new
server group.
server.
3. Click Add or Save. The added or edited Management Auth profile appears on the AAA Profiles page, and
on the
Management Auth details page.
Profiles > AAA > 802.1x Auth
802.1x authentication consists of three components:
z The supplicant, or client, is the device attempting to gain access to the network. You can configure the
Aruba user-centric network to support 802.1x authentication for wired users as well as wireless users.
z The authenticator is the gatekeeper to the network and permits or denies access to the supplicants. The
Aruba controller acts as the authenticator, relaying information between the authentication server and
supplicant. The EAP type must be consistent between the authentication server and supplicant and is
transparent to the controller.
z The authentication server provides a database of information required for authentication and informs
the authenticator to deny or permit access to the supplicant.
The 802.1x authentication server is typically an EAP-compliant Remote Access Dial-In User Service
(RADIUS) server which can authenticate either users (through passwords or certificates) or the client
computer.
An example of an 802.1x authentication server is the Internet Authentication Service (IAS) in Windows (see
http://technet2.microsoft.com/windowsserver/en/technologies/ias.mspx).
In Aruba user-centric networks, you can terminate the 802.1x authentication on the controller. The
controller passes user authentication to its internal database or to a “backend” non-802.1x server. This
feature, also called “AAA FastConnect,” is useful for deployments where an 802.1x EAP-compliant RADIUS
server is not available or required for authentication.
Perform these steps to configure an
1. Click
Profiles > AAA > 802.1x Auth in the Aruba Navigation pane. The details page summarizes the
802.1X Auth profile.
current profiles of this type.
2. Click the
profile to edit that profile. The
Add button to create a new 802.1x Auth profile, or click the pencil icon next to an existing
Details page appears. Complete the settings as described in Table 17:
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 75
Page 76

Table 17 Aruba Configuration > Profiles > AAA > 802.1x Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings
Max Authentication
Failures
Enforce Machine
Authentication
Machine
Authentication:
Default Machine
Role
Machine
Authentication
Cache Timeout
(1-1000 hrs)
0 Number of times a user can try to login with wrong credentials after which
the user will be blacklisted as a security threat.
Set to 0 to disable blacklisting, otherwise enter a non-zero integer to
blacklist the user after the specified number of failures.
This setting requires a wireless intrusion protection license.
No (For Windows environments only) Select this option to enforce machine
authentication before user authentication. If selected, either the Machine
Authentication Default Role or the User Authentication Default Role is
assigned to the user, depending on which authentication is successful.
This setting requires a policy enforcement firewall license.
ap-role Select the default role to be assigned to the user after completing machine
authentication.
24 When a Windows device boots, it logs onto the network domain using a
machine account. Within the domain, the device is authenticated before
computer group policies and software settings can be executed; this
process is known as machine authentication. Machine authentication
ensures that only authorized devices are allowed on the network.
You can configure 802.1x for both user and machine authentication (select
the Enforce Machine Authentication option described in Table 51 on page
272). This tightens the authentication process further since both the device
and user need to be authenticated.
Role Assignment with Machine Authentication Enabled
When you enable machine authentication, there are two additional roles
you can define in the 802.1x authentication profile:
z Machine authentication default machine role
z Machine authentication default user role
While you can select the same role for both options, you should define the
roles as per the polices that need to be enforced. Also, these roles can be
different from the 802.1x authentication default role configured in the AAA
profile.
With machine authentication enabled, the assigned role depends upon the
success or failure of the machine and user authentications. In certain
cases, the role that is ultimately assigned to a client can also depend upon
attributes returned by the authentication server or server derivation rules
configured on the controller.
This setting requires a policy enforcement firewall license.
Blacklist on
Machine
Authentication
Failure
76 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
No Define whether the user is blacklisted upon authentication failure.
This setting requires a policy enforcement firewall license.
Page 77

Table 17 Aruba Configuration > Profiles > AAA > 802.1x Auth Profile Settings (Continued)
Field Default Description
Machine
Authentication:
Default User Role
Interval Between
Identity Requests
(1-65535 sec)
Quiet Period after
Failed
Authentication
(1-65535 sec)
Reauthentication
Interval
(60-864000 sec
Use Server
Provided
Reauthentication
Interval
Multicast Key
Rotation
(60-864000 sec)
ap-role Select the default role to be assigned to the user after completing 802.1x
authentication.
This setting requires a policy enforcement firewall license.
30 Specify the interval in which identity requests are to be spaced between
each other.
30 Specify the amount of time in seconds in which failed authentication
denies access to a user, after failed authentication.
86,400
seconds
Select this option to force the client to do a 802.1x re-authentication after
the expiration of the default timer for re-authentication. The default value
of the timer (Reauthentication Interval) is 24 hours. If the user fails to reauthenticate with valid credentials, the state of the user is cleared.
If derivation rules are used to classify 802.1x-authenticated users, then the
Reauthentication timer per role overrides this setting.
No 802.1x re-authentication can be attempted after the expiration of the
default timer for re-authentication. Specify whether this is to be supported
from the authentication server.
No Define whether Multicast Key Rotation is enabled or disabled.
When enabled, unicast and multicast keys are updated after each
reauthorization. It is a best practice to configure the time intervals for
reauthentication, multicast key rotation, and unicast key rotation to be at
least 15 minutes.
Multicast Key
Rotation Time
Interval
(60-86400 sec)
Unicast Key
Rotation Time
Interval
(60-864000 sec)
Authentication
Server Retry
Interval
(5-65535 sec)
Authentication
Server Retry Count
(0-3)
Framed MTU
(500-1500)
Number of Times
ID-Requests are
Retried (1-10)
Maximum Number
of Reauthentication
Attempts (1-10)
1800 When enabled, unicast and multicast keys are updated after each
reauthorization. It is a best practice to configure the time intervals for
reauthentication, multicast key rotation, and unicast key rotation to be at
least 15 minutes. Make sure these intervals are mutually prime, and the
factor of the unicast key rotation interval and the multicast key rotation
900
interval is less than the reauthentication interval.
30 Specify the interface at which reauthentication is supported. The
supported range is from 1 to 6,535 seconds.
2 Define the number of times that failed authentication should be allowed to
retry authentication.
1100 Define the size, in bytes, for framed maximum transmission units.
3 Define the number of allowable times that failed ID requests are allowed to
retry the request.
3 Set the number of times that reauthentication is to be attempted if the first
authentication attempt fails.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 77
Page 78

Table 17 Aruba Configuration > Profiles > AAA > 802.1x Auth Profile Settings (Continued)
Field Default Description
Maximum Number
of Times Held State
Can Be Bypassed
(0-3)
Dynamic WEP Key
Message Retry
Count (1-3)
Dynamic WEP Key
Size (bits)
Interval Between
WPA/WPA2 Key
Messages
(10-5000 msec)
Display Between
EAP-Success and
WPA2 Unicast Key
Exchange
(0-2000 msec)
0 Define whether a held state can be bypassed, and the number of times this
is to be allowed.
1 Define the number of times that failed authentication with a WEP key
should be allowed to retry authentication. The range is from 0 to 3
attempts.
A primary means of cracking WEP keys is to capture 802.11 frames over
an extended period of time and searching for such weak implementations
that are still used by many legacy devices.
128 Specify the maximum size of the WEP key in bits. The options are 40 or
128.
1000 Specify the key message interval in milliseconds.
0 Full field name is Delay between EAP-Success and WPA2 Unicast Key
Exchange.
Define EAP for RADIUS server authentication.
802.1x uses the Extensible Authentication Protocol (EAP) to exchange
messages during the authentication process. The authentication protocols
that operate inside the 802.1x framework that are suitable for wireless
networks include EAP-Transport Layer Security (EAP-TLS), Protected EAP
(PEAP), and EAP-Tunneled TLS (EAP-TTLS). These protocols allow the
network to authenticate the client while also allowing the client to
authenticate the network.
Delay between
WPA/WPA2 Unicast
0 Specify the delay between processing these two key times during
authentication.
Key Exchange
(0-2000 msec)
WPA/WPA2 Key
Message Retry
3 Specify the number of times that WPA or WPA2 keys are allowed to retry.
The supported range is from 1 to 10.
Count (1-10)
Multicast Key
Rotation
Unicast Key
Rotation
No Enable or disable multicast key rotation, and define the related settings on
this page for multicast key rotation time and interval if this field is enabled.
No Enable or disable unicast key rotation, and define the related settings on
this page for unicast key rotation time and interval if t his field is enabled.
Reauthentication No Enable or disable reauthentication. Although reauthentication and rekey
timers are configurable on a per-SSID basis, an 802.1x transaction during
a call can affect voice quality. If a client is on a call, 802.1x reauthentication
and rekey are disabled by default until the call is completed. You disable or
re-enable the “voice aware” feature in the 802.1x authentication profile.
Opportunistic Key
Caching
Yes Enable or disable opportunistic key caching (also configured in the 802.1x
Authentication profile). This supports WPA2 clients.
Validate PMKID No Define whether PMKID authentication should be validated.
Use Session Key No Specify whether a client session should use a security key.
Use Static Key No The IEEE 802.1x authentication standard allows for the use of keys that are
dynamically generated on a per-client basis, or as a static key that is the
same on all devices in the network). Define whether to use a static key with
this setting.
78 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 79

Table 17 Aruba Configuration > Profiles > AAA > 802.1x Auth Profile Settings (Continued)
Field Default Description
xSec MTU
1300 bytes Define the maximum transmission unit size in bytes.
(1024 - 1500 Bytes)
Termination No Select this option to terminate 802.1x authentication on the controller.
Termination EAP-
No Specify if the EAP termination type is TLS.
Type TLS
Termination EAPType PEAP
0 Specify EAP-PEAP termination.
802.1x authentication based on PEAP with MS-CHAPv2 provides both
computer and user authentication. If a user attempts to log in without the
computer being authenticated first, the user is placed into a more limited
“guest” user role.
Windows domain credentials are used for computer authentication, and
the user’s Windows login and password are used for user authentication. A
single user sign-on facilitates both authentication to the wireless network
and access to the Windows server resources.
Termination Inner
EAP-Type
MSCHAPv2
No Enable or disable this setting. You can enable caching of user credentials
on the controller as a backup to an external authentication server. The
EAP-Microsoft Challenge Authentication Protocol version 2 (MS-CHAPv2),
described in RFC 2759, is widely supported by Microsoft clients.
Termination Inner
EAP-Type GTC
No Enable or disable GTC. EAP-Generic Token Card (GTC): Described in RFC
2284, this EAP method permits the transfer of unencrypted usernames
and passwords from client to server. The main uses for EAP-GTC are onetime token cards such as SecureID and the use of LDAP or RADIUS as the
user authentication server.
You can also enable caching of user credentials on the controller as a
backup to an external authentication server.
Token Caching Disabled Specify whether EAP token caching is enabled or disabled.
Token Caching
Period (1-240 hrs)
24 Specify token caching, in hours. The supported range is from 1 to 240
hours.
CA-Certificate N/A Type the CA certificate imported into the controller.
Server-Certificate N/A Specify a server certificate. The list of available certificates is taken from
the computer certificate store on which IAS is running. In this case, a selfsigned certificate was generated by the local certificate authority and
installed on the IAS system. On each wireless client device, the local
certificate authority is added as a trusted certificate authority, thus allowing
this certificate to be trusted.
TLS Guest Access No Specify if TLS authentication supports guest users.
User-level authentication is performed by an external RADIUS server using
PPP EAP-TLS. In this scenario, client and server certificates are mutually
authenticated during the EAP-TLS exchange. During the authentication,
the controller encapsulates EAP-TLS messages from the client into
RADIUS messages and forwards them to the server.
TLS Guest Role ap-role Specify the TLS authentication role that will support guests. This setting
requires a policy enforcement firewall license.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 79
Page 80

Table 17 Aruba Configuration > Profiles > AAA > 802.1x Auth Profile Settings (Continued)
Field Default Description
Ignore EAPOLSTART After
Authentication
Handle EAPOLLogoff
Ignore EAP ID
During Negotiation
WPA-FastHandover
Disable Rekey and
Reauthentication
for Clients on Call
No Enable or disable this setting.
EAP authentication starts with a EAPOL-start frame that is sent by the
wireless client to the AP. Upon reception of such a frame, the AP responds
back to the wireless client with an EAP-Identify-Request and also does
internal resource allocation. Attackers can use this vulnerability by sending
a lot of EAPOL-start frames to the Access point, either by spoofing the
MAC address or by emulating wireless clients. This forces the AP to
allocate increasing resource and eventually bringing it down. Enable this
setting to reduce the risk.
No Specify whether authentication should manage logoff activity.
No Specify whether EAP should be ignored during authentication.
No In the 802.1x Authentication profile, the WPA fast handover feature allows
certain WPA clients to use a pre-authorized PMK, significantly reducing
handover interruption. Check with the manufacturer of your handset to see
if this feature is supported. This feature is disabled by default.
No
Although reauthentication and rekey timers are configurable on a per-SSID
basis, an 802.1x transaction during a call can affect voice quality. If a client
is on a call, 802.1x reauthentication and rekey are disabled by default until
the call is completed. You disable or re-enable the “voice aware” feature in
the 802.1x authentication profile. This setting requires a voice service
license.
3. Click Add or Save. The added or edited 802.1x Auth profile appears on the AAA Profiles page, and on the
802.1x Auth details page.
Profiles > AAA > Stateful NTLM Auth
When the user logs off or shuts down the client machine, this profile allows the user to remain in the
authenticated role until the user ages out. Aging out means the user has sent no traffic for the amount of
time specified for the
The Stateful NT LAN Manager (NTLM) Authentication profile requires that you specify the following
components:
z a server group that includes the servers performing NTLM authentication
z a default role to be assigned to authenticated users.
The Wireless Internet Service Provider roaming (WISPr) protocol allows users to roam between service
providers. A RADIUS server is used to authenticate subscriber credentials.
For details on defining a Windows server used for NTLM authentication, refer to “Security > Server Groups
> Windows” on page156.
Perform these steps to configure a
1. Click
Profiles > AAA > Stateful NTLM Auth in the Aruba Navigation pane. The details page summarizes the
current profiles of this type.
2. Click the
Add button to create a new Stateful NTLM Auth profile, or click the pencil icon next to an existing
profile to edit that profile. The
Timeout parameter of this profile.
Stateful NTLM Auth profile.
Details page appears. Complete the settings as described in Table 18:
80 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 81

Table 18 Aruba Configuration > Profiles > AAA > Stateful NTLM Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings
Timeout 10 Set the aging out or timeout period, which is the amount of time for which
the user sends no traffic. The user’s role remains authenticated unless this
period of time is exceeded.
Server Group default Select a server from the drop-down menu. You can edit servers with the
Default Role guess Select a user role to associate with the user from the drop-down menu.
Pencil icon or add additional servers with the Add icon.
You can edit roles with the Pencil icon or add additional roles with the Add
icon.
3. Click Add or Save. The added or edited profile appears on the Stateful NTLM Auth page, and on the
details page.
Profiles > AAA > WISPr Auth
The Wireless Internet Service Provider roaming (WISPr) protocol allows users to roam between service
providers. A RADIUS server is used to authenticate subscriber credentials.
ArubaOS supports stateful 802.1x authentication, stateful NTLM authentication and authentication for
Wireless Internet Service Provider roaming (WISPr). Stateful authentication differs from 802.1x
authentication in that the controller does not manage the authentication process directly, but monitors the
authentication messages between a user and an external authentication server, and then assigns a role to
that user based upon the information in those authentication messages. WISPr authentication allows clients
to roam between hotspots using different ISPs.
Refer to the AOS User Guide for additional information about stateful NTLM and WISPr authentication.
Perform these steps to configure a
WISPr Auth profile.
1. Click
Profiles > AAA > WISPr Auth in the Aruba Navigation pane. The details page summarizes the current
profiles of this type.
2. Click the
Add button to create a new Stateful NTLM Auth profile, or click the pencil icon next to an existing
profile to edit that profile. The
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 81
Details page appears. Complete the settings as described in Table 18:
Page 82

Table 19 Aruba Configuration > Profiles > AAA > WISPr Auth Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings
Server Group default Select the AAA authentication server group. Click the pencil icon to edit an
existing server group or click the add icon to create a new server group.
Default Role guest Select the default role assigned to users that complete WISPr
authentication.
Logon Wait
Minimum Wait
Logon Wait
Maximum Wait
Logon Wait CPU
Utilization
Threshold
WISPr Location-ID
ISO Country Code
WISPr Location-ID
E.164 Area Code
WISPr Location-ID
SSID/zone
WISPr Operator
Name
WISPr Location
Name
5 Define the minimum wait time for additional logon attempts. If the
controller’s CPU utilization has surpassed the Logon Wait CPU utilization
threshold value, this wait parameter defines the minimum number of
seconds a user will have to wait prior to retrying a login attempt. The
supported range is 1 to 10 seconds.
10 Define the maximum wait time for additional logon attempts. If the
controller’s CPU utilization has surpassed the Login wait CPU utilization
threshold value, this wait parameter defines the maximum number of
seconds a user will have to wait prior to retrying a login attempt. The
supported range is form 1 to 10 seconds.
60 Set the percentage of CPU utilization at which the maximum and minimum
logon wait times are enforced. The supported range is from 1% to 100%.
N/A Enter the ISO Country Code section of the WISPr Location ID.
N/A Enter the E.164 Area Code section of the WISPr Location ID.
N/A Enter the SSID/Zone section of the WISPr Location ID.
N/A Enter a name identifying the hotspot operator.
N/A Enter a name identifying the hotspot location. If no name is defined, the
parameter will use the name of the AP to which the user has associated.
3. Click Add or Save. The added or edited profile appears on the Stateful NTLM Auth page, and on the
details page.
82 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 83

Profiles > AP
Display the currently configured AP profiles by navigating to Device Setup > Profiles > AP.
In AOS, related configuration parameters are grouped into a profile that you can apply as needed to an AP
group or to individual APs. This section lists each category of AP profiles that you can configure and apply
to an AP group or to an individual AP. Note that some profiles reference other profiles. For example, a
virtual AP profile references SSID and AAA profiles, while an AAA profile can reference an 802.1x
authentication profile and server group.You can apply the following types of profiles to an AP or AP group:
Perform these steps to configure AP profiles.
1. To view and configure AP profiles, click the
AP profile heading in the navigation pane.
Figure 41 AP Profiles in Aruba Configuration
2. From the navigation pane, you can configure the following profile types. The following AP profiles
configure AP operation parameters, regulatory domain, SNMP information, and more:
System—Defines administrative options for the controller, including the IP addresses of the local,
backup, and master controllers, Real-time Locating Systems (RTLS) server values and the number of
consecutive missed heartbeats on a GRE tunnel before an AP reboots traps. Refer to “Profiles > AP >
System” on page83
Regulatory domain—Defines an AP’s country code and valid channels for both legacy and high-
throughput 802.11a and 802.11b/g radios. Refer to “Profiles > AP > Regulatory Domain” on page87.
Wired—Controls whether 802.11 frames are tunneled to the controller using Generic Routing
Encapsulation (GRE) tunnels, bridged into the local Ethernet LAN (for remote APs), or a configured
for combination of the two (split-mode). This profile also configures the switching mode
characteristics for the port, and sets the port as either trusted or untrusted. Refer to “Profiles > AP >
AP Wired” on page88.
Ethernet Link—Sets the duplex mode and speed of AP’s Ethernet link. The configurable speed is
dependent on the port type, and you can define a separate Ethernet Interface profile for each
Ethernet link. Refer to “Profiles > AP > AP Ethernet Link” on page90.
SNMP—Defines and enables SNMP settings, to include community string and SNMP user profiles.
“Profiles > AP > SNMP” on page90.
SNMP User—Sets the SNMP user name and authentication profile to support more general SNMP
profiles. Refer to “Profiles > AP > SNMP > SNMP User” on page91.
Profiles > AP > System
Using DNS, the remote AP receives multiple IP addresses in response to a host name lookup. Known as the
backup controller list, remote APs go through this list to associate with a controller. If the primary
controller is unavailable or does not respond, the remote AP continues through the list until it finds an
available controller. This provides redundancy and failover protection.
If the remote AP loses connectivity on the IPSec tunnel to the controller, the remote AP establishes
connectivity with a backup controller from the list and automatically reboots. Network connectivity is lost
during this time. You can also configure a remote AP to revert back to the primary controller when it
becomes available.To complete this scenario, you must also configure the LMS IP address and the backup
LMS IP address.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 83
Page 84

Perform these steps to configure a System profile.
1. Click
Profiles > AP > System in the Aruba Navigation pane. This page summarizes the current profiles of
this type.
2. Click the
edit that profile. The
Add button to create a new System profile, or click the pencil icon next to an existing profile to
Details page appears. Complete the settings as described in Table 20:
Table 20 Aruba Configuration > Profiles > AP > System Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings
LMS IP N/A Enter an IP address.
For those APs that need to boot off the local controller, configure the LMS
IP address to point to the new local controller.
Backup LMS IP N/A Enter the IP address of the backup LMS controller.
LMS Preemption No The AP fallback feature allows an AP associated with the backup controller
LMS Hold-down
Period (1-3600 sec)
Master Controller IP
Address
LED Operating
Mode
RF Band g Indicates the band for mesh operation for multiband radios. Select a or g.
Double Encrypt No The double encryption feature applies only for traffic to and from a wireless
600 Enter the amount of time the remote AP must wait before moving back to
N/A Enter the IP address of the master controller.
normal Specify the LED operating mode for AP-12X controllers. Options are
(backup LMS) to fail back to the primary controller (primary LMS) if it
becomes available. Enable LMS preemption with this field.
the primary controller.
normal and off.
Important: If you create more than one mesh cluster profile for an AP or
AP group, each mesh cluster profile must use the same band.
client that is connected to a tunneled SSID. When this feature is enabled,
all traffic (which is already encrypted using Layer-2 encryption) is reencrypted in the IPSec tunnel. When this feature is disabled, the wireless
frame is only encapsulated inside the IPSec tunnel. All other types of data
traffic between the controller and the AP (wired traffic and traffic from a
split-tunneled SSID) are always encrypted in the IPSec tunnel.
Native VLAN ID
(0-4094)
SAP MTU N/A Specify the Service Access Point (SAP) maximum transmission unit (MTU)
84 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
1 Enter the ID of the native VLAN. The supported range is from 0 to 4094.
in bytes. The range is 1024 to 1578 bytes.
Page 85

Table 20 Aruba Configuration > Profiles > AP > System Profile Settings (Continued)
Field Default Description
Bootstrap
Threshold (1-65535)
8 Enter a threshold value from 0 to 65,535.
Adjust the bootstrap threshold to 30 if the network experiences packet
loss. This makes the AP recover more slowly in the event of a failure, but it
will be more tolerant to heartbeat packet loss.
Aruba recommends the default maximum request retries and bootstrap
threshold settings for most mesh networks; however, if you must keep
your mesh network alive, you can modify the settings as described in this
section. The modified settings are not applicable if mesh portals are
directly connected to the controller.
Request Retry
Interval
Maximum Request
Retries
10 Enter in seconds the amount of time for retries. The supported range is
from 1 to 65,535 seconds.
10 Maximum number of times to retry AP-generated requests. The default is
10 times. If you must modify this setting, Aruba recommends a value of
10,000. The range is from 1 to 65,535.
Keepalive Interval
60 Define the keepalive interval in a range of 30 to 65,535 seconds.
(30-65535)
Dump Server N/A Enter the IP address for the dump server.
Te ln e t No Enables Telnet in this system profile.
SNMP Sys-contact Enter an IP address to the value for SNMP sys_ contact, the SNMP system
Sys location.
RFprotect Server IP N/A Enter the IP address of the RFProtect server.
RFprotect Backup
Server IP
N/A Enter an IP address.
When an Aruba controller is present in an Aruba RFprotect system, an
Aruba AP that is acting as an RFprotect sensor can be configured and
managed from the controller. As a Managed Sensor, the Aruba AP is
managed by the controller but sends collected security data about the
wireless environment to an RFprotect Server.
Configure
No Enable this option if you wish to support an Aeroscout RTLS server.
Aeroscout RTLS
Server
Ortonics Walljack Yes Specify whether the Aruba controller uses an Ortonics walljack.
Ortronics® Wi-Jack™ and Wi-Jack Duo™ thin client access points are
centrally configured and managed by the Aruba Networks wireless
controllers to provide a high performance wireless network that integrates
seamlessly into the structured cabling infrastructure. When enabled, this
setting requires an Ortonics Access Point License.
Ortonics LED Off
Time-Out
Yes Enable the LED time-out function for Ortonics wall jacks when used. When
enabled, this setting requires an Ortonics Access Point License.
Ortonics Low Temp 100 Enter the low and high temperatures in Celsius for Ortonics wall jacks. The
range is from 0C to 255C degrees. When Ortonics is enabled, these
Ortonics High Temp 110
settings require an Ortonics Access Point License.
Configure RTLS
Server
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 85
No Enable this setting for Real-time Locating Systems (RTLS) server values
and the number of consecutive missed heartbeats on a GRE tunnel before
an AP reboots traps.
Page 86

Table 20 Aruba Configuration > Profiles > AP > System Profile Settings (Continued)
Field Default Description
Remote-AP DHCP
Server VLAN
(1-4094)
Remote-AP DHCP
Server ID
Remote-AP DHCP
Default Router
Remote-AP DHCP
DNS Server
Remote-AP DHCP
Pool Start
Remote-AP DHCP
Pool End
Remote-AP DHCP
Pool Netmask
Remote-AP DHCP
Lease Time
(0-30 days)
N/A Specify the VLAN to be associated with the remote-AP DHCP server. This
field requires a remote access points license, when used.
N/A Specify the IP address of the remote-AP DHCP server.
N/A Specify the IP address of the remote-AP DHCP default router. This field
requires a remote AP license. This field requires a remote access points
license, when used.
N/A Enter the IP address or addresses of one or more remote-AP DHCP DNS
servers.
N/A Specify the DHCP IP address pool. This configures the pool of IP
addresses from which the remote AP uses to assign IP addresses.
At the Remote-AP-DHCP Pool Start and End fields, enter the first and last
N/A
IP addresses of the pool. These fields require a remote access point
license, when used.
255.255.255.0 Enter the subnet mask. This field requires a remote access points license,
when used.
0 Specify the amount of time that the IP address of the DHCP server is valid.
The supported range is from 0 to 30 days. A value of 0 disables this
function. This field requires a remote access points license, when used.
Heartbeat DSCP
(0-63)
0 This setting defines DSCP for low-speed networks. The supported range is
from 0 to 63. To enable this function, enter a value greater than 0.
Session ACL none Select an access control list for user sessions. Options are as follows:
z none
z stateful-dot11x
z stateful kerbos
z valid user
Corporate DNS
N/A Enter the domain name service (DNS) domain or domains, one per line.
Domain
Image URL N/A If an AP developers license is active, enter the image URL in a range from
1 to 1024. This setting requires an AP Developer license, when used.
Maintenance Mode No You can configure APs to suppress traps and syslog messages related to
those APs. Known as AP maintenance mode, this setting in the AP system
profile is particularly useful when deploying, maintaining, or upgrading the
network. If enabled, APs stop flooding unnecessary traps and syslog
messages to network management systems or network operations centers
during a deployment or scheduled maintenance. The controller still
generates debug syslog messages if debug logging is enabled. After
completing the network maintenance, disable AP maintenance mode to
ensure all traps and syslog messages are sent. AP maintenance mode is
disabled by default.
3. Click Add or Save. The added or edited System profile appears on the System profiles list page.
86 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 87

Profiles > AP > Regulatory Domain
This profile type defines an AP’s country code and valid channels for both legacy and high-throughput
802.11a and 802.11b/g radios.
With the implementation of the high-throughput IEEE 802.11n draft standard, 40 MHz channels were added
in addition to the existing 20 MHz channel options. Available 20 MHz and 40 MHz channels are dependent
on the country code entered in the regulatory domain profile.
The following channel configurations are now available in ArubaOS:
z A 20 MHz channel assignment consists of a single 20 MHz channel assignment. This channel assignment
is valid for 802.11a/b/g and for 802.11n 20 MHz mode of operation.
z A 40 MHz channel assignment consists of two 20 MHz channels bonded together (a bonded pair). This
channel assignment is valid for 802.11n 40 MHz mode of operation and is most often utilized on the 5
GHz frequency band. If high-throughput is disabled, a 40 MHz channel assignment can be configured, but
only the primary channel assignment will be utilized. 20 MHz clients can also associate using this
configuration, but only the primary channel will be utilized.
A high-throughput (HT) AP can use a 40 MHz channel pair comprised of two adjacent 20 MHz channels
available in the regulatory domain profile for your country. When ARM is configured for a dual-band AP, it
will dynamically select the primary and secondary channels for these devices. It can, however, continue to
scan all changes in the a+b/g bands to calculate interference and detect rogue APs.
Perform these steps to configure a
1. Click
Profiles > AP > Regulatory Domain in the Aruba Navigation pane. This page summarizes the current
Regulatory Domain profile.
profiles of this type.
2. Click the
profile to edit that profile. The
Add button to create a new Regulatory Domain profile, or click the pencil icon next to an existing
Details page appears. Complete the settings as described in Table 21:
Table 21 Aruba Configuration > Profiles > AP > Regulatory Domain Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that
is separate from the configuration groups of devices. Using folders, you
can view basic statistics about device, and define which users have
visibility to which device parameters.
Name Blank Enter the name of the profile.
Other Settings
Country Code Designate the country with the 802.1X regulatory standard relevant to
Valid 802.11a
40MHz Channel
pairs
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 87
this WLAN.
N/A Select a 40MHz channel pair for 802.11a.
A high-throughput (HT) AP can use a 40 MHz channel pair comprised of
two adjacent 20 MHz channels available in the regulatory domain profile
for your country. When ARM is configured for a dual-band AP, it will
dynamically select the primary and secondary channels for these
devices. It can, however, continue to scan all changes in the a+b/g
bands to calculate interference and detect rogue APs.
Page 88

Table 21 Aruba Configuration > Profiles > AP > Regulatory Domain Profile Settings
Field Default Description
Valid 802.11g 40
MHz Channel Pairs
Valid 802.11a
40MHz Channels
Valid 802.11g 40
MHz Channels
N/A Select a 40MHz channel pair for 802.11ag
A high-throughput (HT) AP can use a 40 MHz channel pair comprised of
two adjacent 20 MHz channels available in the regulatory domain profile
for your country. When ARM is configured for a dual-band AP, it will
dynamically select the primary and secondary channels for these
devices. It can, however, continue to scan all changes in the a+b/g
bands to calculate interference and detect rogue APs.
N/A Specify the valid channels for 40MHz channel pairing in 802.11a.
N/A Specify the valid channels for 40MHz channel pairing in 802.11g.
3. Click Add or Save. The added or edited Regulatory Domain profile appears on the Regulatory Domain
Profiles
page.
Profiles > AP > AP Wired
The wired AP profile controls the configuration of the Ethernet port(s) on your AP. You can use the wired
AP profile to configure Ethernet ports for bridging or secure jack operation using the wired AP profile.
Perform these steps to configure a
1. Click
Profiles > AP > Wired in the Aruba Navigation pane. This page summarizes the current profiles of
this type.
2. Click the
edit that profile. The
Add button to create a new Wired profile, or click the pencil icon next to an existing profile to
Details page appears. Complete the settings as described in Table 22:
Wired AP profile.
Table 22 Aruba Configuration > Profiles > AP > Wired Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
Name Blank Enter the name of the profile.
Other Settings
Wired AP Enable No Designate whether Wired APs are to be enabled or disabled.
Forward Mode tunnel If Wired AP is enabled, designate whether forwarding is to be bridge-
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters
that is separate from the configuration groups of devices. Using
folders, you can view basic statistics about device, and define which
users have visibility to which device parameters.
based or tunnel-based.
88 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 89

Table 22 Aruba Configuration > Profiles > AP > Wired Profile Settings
Field Default Description
Switchport Mode Access Select access or trunk. These options only apply to bridge mode
configurations.
z Access mode forwards untagged packets received on the port to
the controller and they appear on the configured access mode
VLAN. Tagged packets are dropped. All packets received from the
controller and sent via this port are untagged. Define the access
mode VLAN in the Access mode VLAN field.
z Trunk mode contains a list of allowed VLANs. Any packet
received on the port that is tagged with an allowed VLAN is
forwarded to the controller. Untagged packets are forwarded to
the controller on the configured Native VLAN. Packets received
from the controller and sent out the port remain tagged unless the
tag value in the packet is the Native VLAN, in which case the tag is
removed. Define the Native VLAN in the Trunk mode native VLAN
field and the other allowed VLANs in the Trunk mode allowed
VLANs field.
Access Mode VLAN
(1-4096)
1 Access mode forwards untagged packets received on the port to the
controller and they appear on the configured access mode VLAN.
Tagged packets are dropped. All packets received from the controller
and sent via this port are untagged. Define the access mode VLAN in
the Access mode VLAN field. The VLAN range is from 1 to 4096.
Trunk Mode Native
VLAN (1-4096)
1 Trunk mode contains a list of allowed VLANs. Any packet received on
the port that is tagged with an allowed VLAN is forwarded to the
controller. Untagged packets are forwarded to the controller on the
configured Native VLAN. Packets received from the controller and
sent out the port remain tagged unless the tag value in the packet is
the Native VLAN, in which case the tag is removed. Define the Native
VLAN in the Trunk mode native VLAN field and the other allowed
VLANs in the Trunk mode allowed VLANs field.
Trunk Mode
Allowed VLANs
Define whether the trunk mode settings defined in additional fields of
this profile are to allow VLANs. The VLAN range is from 1 to 4094.
Enter a list or a range of numbers. The VLAN range is from 1 to 4096.
You can enter a range of numbers, specific numbers or a combination
of range and specific VLAN numbers, as desired.
Trusted No Use this option if the wired port is a trusted port.
Broadcast Yes Use this option if the wired port is a broadcast port.
3. Click Add or Save. The added or edited 802.1x Auth profile appears on the AAA Profiles page, and on the
802.1x Auth details page.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 89
Page 90

Profiles > AP > AP Ethernet Link
The configurable speed defined in this profile is dependent on the port type, and you can define a separate
Ethernet Interface profile for each Ethernet link.
Perform these steps to configure a
1. Click
2. Click the
Profiles > AP > Ethernet Link in the Aruba Navigation pane.
Add button to create a new System profile, or click the pencil icon next to an existing profile to
edit that profile. The
Details page appears. Complete the settings as described in Table 23:
Ethernet Link profile.
Table 23 Aruba Configuration > Profiles > AP > Ethernet Link Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings
Speed (Mbps) auto Designates the speed of the Ethernet link for this profile. Options are 10, 100,
or 1000 Mbits.
Duplex auto Defines this profile to support duplex Ethernet. Options are full, half, or auto.
3. Click
Add or Save. The added or edited Ethernet Link profile appears on the AAA Profiles page, and on
the
802.1x Auth details page.
Profiles > AP > SNMP
Aruba controllers and APs support versions 1, 2c, and 3 of Simple Network Management Protocol (SNMP)
for reporting purposes only. In other words, SNMP cannot be used for setting values in an Aruba system in
the current ArubaOS version. Perform these steps to configure a
1. Click
2. Click the
Profiles > AP > SNMP in the Aruba Navigation pane.
Add button to create a new SNMP profile, or click the pencil icon next to an existing profile to
edit that profile. The
Details page appears. Complete the settings as described in Table 24:
Table 24 Aruba Configuration > Profiles > AP > SNMP Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
SNMP profile.
Name Blank Enter the name of the profile.
90 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 91

Table 24 Aruba Configuration > Profiles > AP > SNMP Profile Settings
Field Default Description
Other Settings
SNMP Enable Yes Enable or disable SNMP in this profile.
Enter Community
String
Select SNMP User Profile
Select SNMP User
Profile
Text field allows you to type one or multiple SNMP community strings
applied to this profile.
If SNMP is enabled in this profile, and one or more profiles have been
configured, select the corresponding SNMP profile from this list.
3. Click Add or Save. The added or edited SNMP profile appears on the SNMP profiles page.
Profiles > AP > SNMP > SNMP User
Perform these steps to configure a SNMP profile.
1. Click
2. Click the
Table 25 Aruba Configuration > Profiles > AP > SNMP > SNMP User Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
Profiles > AP > SNMP > SNMP User in the Aruba Navigation pane.
Add button to create a new SNMP user, or click the pencil icon next to an existing user to edit
that user. The
Details page appears. Complete the settings as described in Table 24:
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that
is separate from the configuration groups of devices. Using folders, you
can view basic statistics about device, and define which users have
visibility to which device parameters.
Name Blank Name of the SNMP user profile. This is the name by which the SNMP
Other Settings
User Name Blank Actual name of the network user to be supported by this SNMP profile in
Authentication
Profile
3. Click
Add or Save. The added or edited SNMP user appears on the SNMP User page. This user can now
be referenced in SNMP profiles.
Refer to the following topics for additional information about SNMP profiles:
z “Aruba Controller Traps” on page92
z “Access Point/Air Monitor Traps” on page93
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 91
user is managed and accessed when cited by SNMP profiles
Aruba Configuration
none Select a protocol from the drop-down menu. Options are as follows:
z none—Uses no authentication type for the user being defined.
z md5—Sets the MD5 hashing algorithm for the user that hashes a
cleartext password.
z sha—Sets the SHA hashing algorithm for the user that hashes a
cleartext password.
Page 92

Aruba Controller Traps
Table 26 provides a list of key traps generated by the Aruba controller.
Table 26 Key SNMP Traps of the Aruba Controller
Trap Description Priority Level
Mobility controller IP
changed
Mobility controller role
changed
User entry created/
deleted/authenticated/deauthenticated/
authentication failed.
Authentication server
request timed out.
Authentication server
timed out
Authentication server up This trap indicates that an authentication server that was previously not responding
This indicates the controller IP has been changed. The controller IP is either the
loopback IP address or the IP address of the VLAN 1 interface (if no loopback IP
address is configured).
This indicates that the controller has transitioned from being a master controller to a
local controller or vice versa.
Each of these traps are triggered by an event related to a user event. The event can be
a new user entry being created in the user table, deletion of a user entry, a user getting
authenticated successfully, a user getting de-authenticated, or a failed authentication
attempt. Each of these traps will be generated by the controller on which the user
event occurs. In other words this is a local event to the controller where the user is
visible.
This trap indicates that a request to a authentication server did not receive a response
from the server within a specified amount of time and therefore the request timed out.
This usually indicates a connectivity problem from the Aruba controller to the
authentication server or some other problem related to the authentication server.
NOTE: Earlier versions of ArubaOS supported SNMP on individual APs. This feature is
not supported by this version of ArubaOS. This trap indicates that an authentication
server has been taken out of service. This is almost always same as
AuthServerReqTimedOut except when there is only one authentication server in
which case the server will never be taken out of service. In that case the
AuthServerReqTimedOut will continue to be raised but not then
AuthServerTimedOut.
has started responding to authentication requests. This will be triggered by a user
event that causes the controller to send an authentication request to the
authentication server.
Critical
Critical
Medium
High
High
Low.
Authentication user table
full
Authentication Bandwidth
contracts table full
Authentication ACL table
full
Power supply failure As the name indicates, this trap indicates the failure of one of the two possible power
Fan failure As the name indicates, this trap indicates a failure of the fan in the controller. Critical
Out of Range Voltage This trap indicates an out of range voltage being supplied to the controller. Critical
Out of Range temperature This trap indicates an out of range operating temperature being supplied to the
Line card inserted/
removed
Supervisor card inserted/
removed
Power supply missing This trap indicates that one of the power supplies is missing. Critical
This trap indicates that the authentication user table has reached its limit with the
number of user entries it can hold. This event is local to the controller that generates
the traps. The maximum number of user entries that can be present at the same time
in the user table is 4096.
This trap indicates that the maximum number of configured bandwidth contracts on
the controller has been exceeded. The threshold for this is 4096
This trap indicates that the maximum number of ACL entries in the ACL table has
been exceeded. The limit for this is 2048 entries on a controller.
supplies in the controller.
controller.
These traps indicate that a Line Card has been inserted or removed from the
controller.
These traps indicate that a Supervisor card has been inserted or removed from the
controller
Critical
High
High
Critical
Critical
Critical.
Critical
92 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 93

Access Point/Air Monitor Traps
Table 27 describes the key traps that can be generated by an Aruba access point or an air monitor:
Table 27 Key SNMP Traps from Aruba Access Points or Air Monitors
Trap Description Priority
Unsecure AP Detected This trap indicates that an air monitor has detected and classified an access point
as unsecure. It will indicate the location of the air monitor that has detected the
unsecure AP, the channel on which the AP was detected as well as the BSSID and
SSID of the detected AP.
Station impersonation This trap indicates an air monitor has detected a station impersonation event. The
trap will provide the location of the air monitor that has detected the event and the
MAC address of the station.
Reserved channel impersonation This trap indicates an access point is being detected is violating the reserved
channels. The location of the AP/AM that detects the event is provided in the trap.
In addition to this, the BSSID and SSID of the detected AP is also included.
Valid SSID violation This indicates a configuration in the configuration of the SSID of the AP. The AP
generates the trap and includes its BSSID, the configured SSID and the location of
the AP in the trap.
Channel misconfiguration This trap indicates an error in channel configuration of an AP. The AP generates the
trap and includes its BSSID, the configured SSID and the location of the AP in the
trap
OUI misconfiguration This trap indicates an error in the OUI configuration of an Access Point. The AP
generates the trap and includes its BSSID, the configured SSID and the location of
the AP in the trap
SSID misconfiguration This trap indicates an error in the SSID configuration of an Access Point. The AP
generates the trap and includes its BSSID, the configured SSID and the location of
the AP in the trap
Critical
Critical
High
High
High
High
High
Short Preamble misconfiguration This trap indicates an error in the Short Preamble configuration of an AP. The AP
generates the trap and includes its BSSID, the configured SSID and the location of
the AP in the trap. This check will be done only if the short-preamble option is
selected for the AP from the CLI or the WebUI. For a complete list of traps, refer to
the Aruba MIB Reference.
AM misconfiguration This trap indicates an error in the Short Preamble configuration of an AP. The AP
generates the trap and includes its BSSID, the configured SSID and the location of
the AP in the trap
Repeat WEP-IV violation This trap indicates that the AM has detected a valid station or a valid AP sending
consecutive frames that has the same IV (initialization vector). This usually means
that entity has a “flawed” WEP implementation and is therefore a potential security
risk.
Weak WEP-IV violation This trap indicates that the AM has detected a valid station or a valid AP sending
frames with an IV that is in the range of IV that are known to be cryptographically
weak and therefore are a potential security risk.
Adhoc networks detected This trap indicates that the AM has detected Adhoc networks High
Valid station policy violation This trap indicates that a valid station policy is being violated. High
AP interference This trap indicates that the indicated AM (identified by the BSSID/ SSID) is
detecting AP interference on the indicated channel.
High
High
High
High
Medium
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 93
Page 94

Table 27 Key SNMP Traps from Aruba Access Points or Air Monitors (Continued)
Trap Description Priority
Frame Retry rate exceeded This trap refers to the event when the percentage of received and transmitted
frames with the retry bit crosses the High watermark. This event can be triggered for
an AP, a station or a channel. The two values that should be configured related to
this event are Frame Retry Rate – High Watermark and Frame Retry Rate –Low
watermark. The High Watermark refers to the percentage threshold which if
surpassed triggers the event that causes the trap to be sent. The Low Watermark
refers to the percentage threshold such that if the retry rate reaches a value lower
than this value the event is reset. What this means is that the trap will be triggered
the first time the Frame Retry rate crosses the High Watermark and then will only be
triggered if the Frame Retry Rate goes under the Low Watermark and then crosses
the High Watermark again. This holds true for all the thresholds explained below as
well.
Frame Bandwidth rate exceeded This trap refers to the event of the bandwidth rate for a station exceeding a
configured threshold (High watermark). The terms High Watermark and Low
Watermark hold the same meaning as explained above.
Frame low speed rate exceeded This trap refers to the event when the percentage of received and transmitted
frames at low speed (less that 5.5Mbps for 802.11b and less that 24 Mbps for
802.11a) exceeds the configured High Watermark. The terms High Watermark and
Low Watermark hold the same meaning as explained above.
Profiles > IDS
The IDS profiles configure the AP’s Intrusion Detection System features, which detect and disable rogue
APs and other devices that can potentially disrupt network operations. An AP is considered to be a rogue
AP if it is both unauthorized and plugged into the wired side of the network. An AP is considered to be an
interfering AP if it is seen in the RF environment but is not connected to the wired network.
Medium
Medium
Medium
The top-level IDS profile, assigned to an Aruba AP group or AP name, references additional IDS profiles that
are also described in this section. ArubaOS includes predefined top-level IDS profiles that provide different
levels of sensitivity. The following are predefined IDS profiles:
z ids-disabled
z ids-high-setting
z ids-low-setting
z ids-medium-setting (the default setting)
You apply the top-level IDS profile to an AP group or specific AP.
To view IDS profiles, click
Profiles > IDS in the Aruba Configuration navigation pane.
Figure 42 IDS Profiles in Aruba Configuration
94 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 95

NOTE
A predefined IDS profile refers to specific instances of the other IDS profiles. You cannot create new instances of a
profile within a predefined IDS profile. You can modify parameters within the other IDS profiles.
IDS profiles reference other profiles. These additional profiles can be created before, during, or after the
configuration of the IDS profile.
Click the
that profile. The
Add button to create a new IDS profile, or click the pencil icon next to an existing profile to edit
Details page appears. Complete the settings as described in Table 29:
Table 28 Aruba Configuration > Profiles > IDS > General Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is associated.
The drop-down menu displays all folders available for association with the
profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Other Settings and AP SNMP User Profiles
IDS
Unauthorized
Device Profile
default Select the IDS Unauthorized Device Profile from the drop-down menu. This
profile is referenced by the overriding IDS profile currently being configured.
The drop-down menu contains any profiles that you have configured.
To create a new profile of this type, click the add icon. To edit an existing
profile, select that profile then click the pencil icon.
For additional information about configuring IDS Unauthorized Device Profiles,
refer to “Profiles > IDS > Unauthorized Device” on page 104.
IDS Signature
Matching Profile
IDS General
Profile
IDS
Impersonation
Profile
IDS DoS Profile default Select the IDS Impersonation Profile from the drop-down menu. The drop-
default Select the IDS Signature Matching Profile from the drop-down menu. The
drop-down menu lists all signature matching profiles that are currently
configured and available. To create a new profile of this type, click the add
icon. To edit an existing profile, select that profile then click the pencil icon.
For additional information about configuring IDS Unauthorized Device Profiles,
refer to “Profiles > IDS > Signature Matching” on page 97.
default Select the IDS General Profile from the drop-down menu. The drop-down
menu lists all General IDS profiles that are currently configured and available.
To create a new profile of this type, click the add icon. To edit an existing
profile, select that profile then click the pencil icon.
For additional information about configuring IDS Unauthorized Device Profiles,
refer to “Profiles > IDS > General” on page 96.
default Select the IDS Impersonation Profile from the drop-down menu. The drop-
down menu lists all such profiles that are currently configured and available.
To create a new profile of this type, click the add icon. To edit an existing
profile, select that profile then click the pencil icon.
For additional information about configuring IDS Impersonation Profiles, refer
to “Profiles > IDS > Impersonation” on page 103.
down menu lists all such profiles that are currently configured and available.
To create a new profile of this type, click the add icon. To edit an existing
profile, select that profile then click the pencil icon.
For additional information about configuring IDS Impersonation Profiles, refer
to “Profiles > IDS > Denial of Service” on page 98.
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 95
Page 96

4. Select the profile type to view or configure:
z General—Configures general AP attributes. Refer to “Profiles > IDS > General” on page96.
z Signature Matching—Configures signatures and signature matching for intrusion detection. Refer to
“Profiles > IDS > Signature Matching” on page97.
Signature—Defines a predefined signature. Refer to “Profiles > IDS > Signature Matching >
Signatures” on page98.
z Denial of Service—Configures traffic anomaly settings for Denial of Service (DoS) attacks. Refer to
“Profiles > IDS > Impersonation” on page103.
Rate Thresholds—Defines thresholds assigned to the different frame types for rate anomaly
checking. Refer to “Profiles > IDS > Denial of Service > Rate Threshold” on page101.
z Impersonation—Configures anomaly settings for impersonation attacks. Refer to “Profiles > IDS >
Impersonation” on page103.
z Unauthorized Device—Configures detection for unauthorized devices. Also configures rogue AP
detection and containment. Refer to “Profiles > IDS > Unauthorized Device” on page104.
5. Click
Add or Save. The added or edited IDS profile appears on the IDS profiles page.
Profiles > IDS > General
Perform these steps to configure a General IDS profile.
1. Click
Profiles > IDS > General in the Aruba Navigation pane. The list of current IDS profiles appears on
this page.
2. Click the
edit that profile. The
Add button to create a new General profile, or click the pencil icon next to an existing profile to
Details page appears. Complete the settings as described in Table 29:
Table 29 Aruba Configuration > Profiles > IDS > General Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
Name Blank Enter the name of the profile.
Other Settings and AP SNMP User Profiles
Stats Update Interval
(60-36000 sec)
60 Set the time interval, in seconds, for the AP to update the controller with
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
statistics.
NOTE: This setting takes effect only if the Aruba Mobility Manager
is configured. Otherwise, statistics update to the controller is
disabled.
AP Inactivity Timeout
(5-36000 sec)
STA Inactivity
Timeout
(30-36000 sec)
Min Potential AP
Beacon Rate
(0-100%)
96 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
5 Set the time, in seconds, after which an AP is aged out.
60 Set the time, in seconds, after which a STA is aged out.
25 Set the minimum beacon rate acceptable from a potential AP, in percentage
of the advertised beacon interval.
Page 97

Table 29 Aruba Configuration > Profiles > IDS > General Profile Settings
Field Default Description
Min Potential AP
Monitor Time
2 Set the minimum time, in seconds, a potential AP has to be up before it is
classified as a real AP.
(0-36000 sec)
Signature Quiet Time
(60-360000 sec)
Wireless
900 Set the time to wait, in seconds, after which the check can be resumed
when detecting a signature match.
Yes Enable or disable containment from the wireless side.
Containment
Debug Wireless
Containment
No Enable or disable debugging of containment from the wireless side.
Enabling this debug option causes containment to function improperly.
Wired Containment No Enable or disable containment from the wireless side.
3. Click Add or Save. The added or edited General profile appears on the IDS > General profiles page.
Profiles > IDS > Signature Matching
The IDS signature matching profile contains signatures for intrusion detection. This profile can include
predefined or custom signatures. Table 30 describes the predefined signatures that you can add to the profile.
Perform these steps to configure a
1. Click
2. Click the
Profiles > IDS > Signature Matching in the Aruba Navigation pane.
Add button to create a new Signature Matching profile, or click the pencil icon next to an existing
profile to edit that profile. The
Signature Matching profile.
Details page appears. Complete the settings as described in Table 30:
Table 30 Aruba Configuration > Profiles > IDS > Signature Matching Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that
is separate from the configuration groups of devices. Using folders, you
can view basic statistics about device, and define which users have
visibility to which device parameters.
Name Blank Enter the name of the profile.
Signature Profiles
Select Signature
Profiles
N/A Select from signature options as follows:
z AirJack
z ASLEAP
z Deauth-Broadcast
z Default
z Netstumbler Generic
z Netstrumbler Version 3.3.0x
z Null-Probe-Response
3. Click
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 97
Add or Save. The added or edited Signature Matching profile appears on the IDS > Signature
Matching
profiles page.
Page 98

Profiles > IDS > Signature Matching > Signatures
Perform these steps to create signatures for use with Signature Matching profiles.
1. Click
2. Click the
Profiles > IDS > Signature Matching > Signature in the Aruba Navigation pane.
Add button to create a new Signature, or click the pencil icon next to an existing profile to edit
that profile. The
Details page appears. Complete the settings as described in Table 31:
Table 31 Aruba Configuration > Profiles > IDS > Signature Creation Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the signature.
Add Click this button to add a new IDS signature. Complete the settings as
follows:
z Parameter, which can be one of the following:
bssid
dst-mac
frame-type
payload
seq-num
src-mac
z BSSID
Click Add when these signature settings are defined.
3. Click
Add on the Signature page. The added or edited Signature appears on the IDS > Signature Matching
> Signatures page.
Profiles > IDS > Denial of Service
This profile type defines traffic anomaly settings that detect and process denial-of-service attacks. This
profile type defines the parameters that are monitored and acted upon when detecting and blacklisting an
offending client from the Aruba system. When a client is blacklisted in the Aruba system, the client is not
allowed to associate with any AP in the network for a specified amount of time. If a client is connected to
the network when it is blacklisted, a de-authentication message is sent to force the client to disconnect.
While blacklisted, the client cannot associate with another SSID in the network.
Table 32 summarizes the predefined IDS Denial of Service profiles. These profiles are viewable with the
Profiles > IDS > Denial of Service path in the navigation pane.
98 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Page 99

Table 32 Predefined IDS DoS Profiles
Parameter ids-dosdisabled ids-dos-lowsetting ids-dosmedium-setting ids-dos-highsetting
Detect Disconnect Station
Attack
Disconnect STA Detection
Quiet Time
Spoofed Deauth Blacklist disabled disabled disabled disabled
Detect AP Flood Attack disabled disabled disabled disabled
AP Flood Threshold 50 50 50 50
AP Flood Increase Time 3 seconds 3 seconds 3 seconds 3 seconds
AP Flood Detection Quiet
Time
Detect EAP Rate Anomaly disabled disabled enabled enabled
EAP Rate Threshold 60 60 30 60
EAP Rate Time Interval 3 seconds 3 seconds 3 seconds 3 seconds
EAP Rate Quiet Time 900 seconds 900 seconds 900 seconds 900 seconds
Detect Rate Anomalies disabled disabled disabled enabled
Detect 802.11n 40 MHz
Intolerance Setting
disabled enabled enabled enabled
900 seconds 900 seconds 900 seconds 900 seconds
900 seconds 900 seconds 900 seconds 900 seconds
disabled enabled enabled enabled
Client 40 MHz Intolerance
Detection Quiet Time
Rate Thresholds for Assoc
Frames
Rate Thresholds for
Disassoc Frames
Rate Thresholds for
Deauth Frames
Rate Thresholds for Probe
Request Frames
Rate Thresholds for Probe
Response Frames
default default default default
900 seconds 900 seconds 900 seconds 900 seconds
default default default default
default default default default
default default default default
default probe-request-
response-thresholds
default proberequest-responsethresholds
probe-requestresponse-thresholds
probe-request-responsethresholds
probe-request-responsethresholds
Perform these steps to configure or edit an IDS Denial of Service profile, and to create or edit profiles that
are referenced by a DOC profile.
1. Click
2. Click the
Profiles > IDS > Denial of Service in the Aruba Navigation pane.
Add button to create a new Signature Matching profile, or click the pencil icon next to an existing
profile to edit that profile. The
Details page appears. Complete the settings as described in Table 33:
probe-requestresponse-thresholds
Rate Thresholds for Auth
Frames
AirWave Wireless Management Suite | Configuration Guide Aruba Configuration Reference | 99
Page 100

Table 33 Aruba Configuration > Profiles > IDS > Denial of Service Profile Settings
Field Default Description
General Settings
Folder Top Use this field to set and display the folder with which the profile is
associated. The drop-down menu displays all folders available for
association with the profile.
Folders provide a way to organize the visibility of device parameters that is
separate from the configuration groups of devices. Using folders, you can
view basic statistics about device, and define which users have visibility to
which device parameters.
Name Blank Enter the name of the profile.
Referenced Profiles
Rate Thresholds for
Assoc Frames
Rate Thresholds for
Disassoc Frames
Rate Thresholds for
Deauth Frames
Rate Thresholds for
Probe Request
Frames
Rate Thresholds for
Probe Response
Frames
Rate Thresholds for
Auth Frames
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for association
frames. The IDS rate threshold profile defines thresholds assigned to the
different frame types for rate anomaly checking.
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for
disassociation frames. The IDS rate threshold profile defines thresholds
assigned to the different frame types for rate anomaly checking.
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for deauthentication frames. The IDS rate threshold profile defines thresholds
assigned to the different frame types for rate anomaly checking.
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for probe
request frames. The IDS rate threshold profile defines thresholds assigned
to the different frame types for rate anomaly checking.
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for probe
response frames. The IDS rate threshold profile defines thresholds
assigned to the different frame types for rate anomaly checking.
default Select a profile from the drop-down menu, or click the edit (icon) or add
(icon) to edit or create a profile that sets the rate threshold for
authentication frames. The IDS rate threshold profile defines thresholds
assigned to the different frame types for rate anomaly checking.
Other Settings
Detect Disconnect
Station Attack
Disconnect STA
Detection Quiet
Time
Spoofed Deauth
Blacklist
Detect AP Flood
Attack
AP Flood Threshold 50 Sets the number of Fake AP beacons that must be received within the
100 | Aruba Configuration Reference AirWave Wireless Management Suite | Configuration Guide
Yes Enables or disables detection of station disconnection attacks.
900 After a station disconnection attack is detected, sets the time (in seconds)
that must elapse before another identical alarm can be generated.
No Enables or disables automatic client blacklisting of spoofed de-
authentication.
No Enables or disables the detection of flooding with fake AP beacons to
confuse legitimate users and to increase the amount of processing need
on client operating systems.
Flood Increase Time to trigger an alarm.
 Loading...
Loading...