Page 1

Active System Manager
Version 7.5 Quick Installation Guide
Page 2

Notes, Cautions, and Warnings
NOTE: A NOTE indicates important information that helps you make better use of your computer.
CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you
how to avoid the problem.
WARNING: A WARNING indicates a potential for property damage, personal injury, or death.
Copyright © 2014 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. Dell™ and the Dell logo are trademarks of Dell Inc. in the United States and/or other
jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies.
2014 - 04
Rev. A02
Page 3

Contents
1 Overview......................................................................................................................5
About this Document............................................................................................................................5
What is New in this Release.................................................................................................................. 5
Accessing Online Help.......................................................................................................................... 5
Other Documents You May Need........................................................................................................ 6
Licensing................................................................................................................................................6
Virtual Appliance Requirements............................................................................................................6
Software Requirements.........................................................................................................................6
Supported Resources............................................................................................................................ 7
Supported Dell PowerEdge Chassis ...............................................................................................7
Supported PowerEdge Servers and Firmware Matrix.....................................................................7
Supported Cisco UCS Servers and Firmware Matrix...................................................................... 7
Supported Storage and Firmware Matrix........................................................................................8
Supported Networks and Firmware Matrix.....................................................................................8
Supported Adapters and Firmware Matrix......................................................................................9
2 Installation and Quick Start..................................................................................11
Information Prerequisites.................................................................................................................... 11
Installing Active System Manger..........................................................................................................11
Deployment Prerequisites .............................................................................................................11
System Center Virtual Machine Manager (SCVMM) Prerequisites............................................... 13
Deploying Active System Manager from VMware vSphere Client...............................................14
Deploying Active System Manager using SCVMM........................................................................15
Deploying Active System Manager on Hyper-V host...................................................................16
3 Configuring the Active System Manager Virtual Appliance.........................19
Changing Dell Administrator Password..............................................................................................19
Configuring Static IP Address in the Virtual Appliance...................................................................... 19
Configuring ASM Virtual Appliance as PXE Boot Responder............................................................ 20
Configure DHCP on Windows 2012 DHCP Server......................................................................20
Configure DHCP on Windows 2008 DHCP Server......................................................................21
Configuring DHCP for Linux.........................................................................................................23
Deploying WinPE on the Virtual Appliance........................................................................................26
Create a repository with Windows installation media on ASM Appliance.................................. 26
Creating WinPE Image and Updating Install Media for Windows 2012 and Windows 2012
R2................................................................................................................................................... 27
Copying WinPE and Install Media to ASM Repository and Updating Permissions..................... 28
Updating default-unattended.xml.erb and wim_boot.erb files for Windows 2012 R2..............28
Page 4

Updating Unattended Installation for Windows 2012 Version other than Windows 2012
Standard.........................................................................................................................................29
Updating Unattended Installation for Windows Hyper-V for Versions other than Windows
2012 R2 Datacenter.......................................................................................................................29
Importing Linux ISOs on the Virtual Appliance for Operating System Deployment........................30
4 Completing Initial Configuration.......................................................................33
Page 5

1
Overview
Active System Manager (ASM) is Dell’s unified management product that provides a comprehensive
infrastructure and workload automation solution for IT administrators and teams. ASM simplifies and
automates the management of heterogeneous environments, enabling IT to respond more rapidly to
dynamic business needs.
IT organizations today are often burdened by complex data centers that contain a mix of technologies
from different vendors and cumbersome operational tasks for delivering services while managing the
underlying infrastructure. These tasks are typically performed through multiple management consoles for
different physical and virtual resources, which can dramatically slow down service deployment.
The new Active System Manager 7.5 features an enhanced user interface that provides an intuitive, endto-end infrastructure and workload automation experience through a unified console. This speeds up
workload delivery and streamlines infrastructure management, enabling IT organizations to accelerate
service delivery and time to value for customers.
About this Document
This document version is updated for Active System Manager, version 7.5.2.
What is New in this Release
This release of Active System Manager supports:
• Support for Microsoft System Center Virtual Machine Manager (SCVMM), including SCVMM discovery,
Hyper-V deployment, and cluster creation
• Ability to provision multiple EqualLogic Storage components in a template for Hyper-V only
• IP and IQN authentication on EqualLogic Storage
• Static IP addressing for public and private networks Hyper-V only
Accessing Online Help
Active System Manger (ASM) online help system provides context-sensitive help available from every page
in the ASM user interface.
After you log in to ASM user interface, you can access the online help in any of the following ways:
• To open context-sensitive online help for the active page, click ?, and then click Help.
• To open context-sensitive online help for a dialog box, click ? in the dialog box.
5
Page 6

Additionally, in the online help, use the Enter search items option in the Table of Contents to search for a
specific topic or keyword.
Other Documents You May Need
In addition to this guide, the following documents available on the Dell Support website at dell.com/
support/manuals provide additional information about the Active System Manager (ASM).
On the Manuals page, in the Select a product section, click Software & Security → Enterprise System
Management
• Dell Active System Manager version 7.5 User’s Guide
• Dell Active System Manager version 7.5.2 Release Notes
→ Active System Manager → Dell Active System Manager 7.5.
Licensing
Active System Manager (ASM) licensing is based on the total number of managed resources, except for
VMware vCenter and Windows SCVMM instances. In ASM 7.5 release, standard is the only valid license
type supported.
The standard license is a full-access license type.
You will receive an email from customer service with instructions on how to download the license file to
a local network share.
If you are using ASM for the first time, you must upload the license file through the Initial Setup wizard.
You can then upload and activate subsequent licenses on the Virtual Appliance Management page under
Settings. After uploading an initial license, subsequent uploads replaces the existing license.
Virtual Appliance Requirements
Active System Manager runs as a virtual appliance on a Dell server configured with the following
hardware and software:
• Two virtual CPUs
• 8.0 GB RAM
• Hypervisor - vSphere Client (5.1 or 5.5) with ESXi (5.1 or 5.5) or Windows 2012 running Hyper-V
Software Requirements
To display Active System Manager (ASM) correctly, a system must have a minimum 1024 x 768 screen
resolution and a Web browser that meets minimum requirements based on the operating system.
Operating System Internet Explorer Mozilla Firefox Google Chrome
Windows Server 2012 Version 9 and Later Version 26 and Later Version 32 and Later
Windows Server 2012 R2Version 9 and Later Version 26 and Later Version 32 and Later
6
Page 7
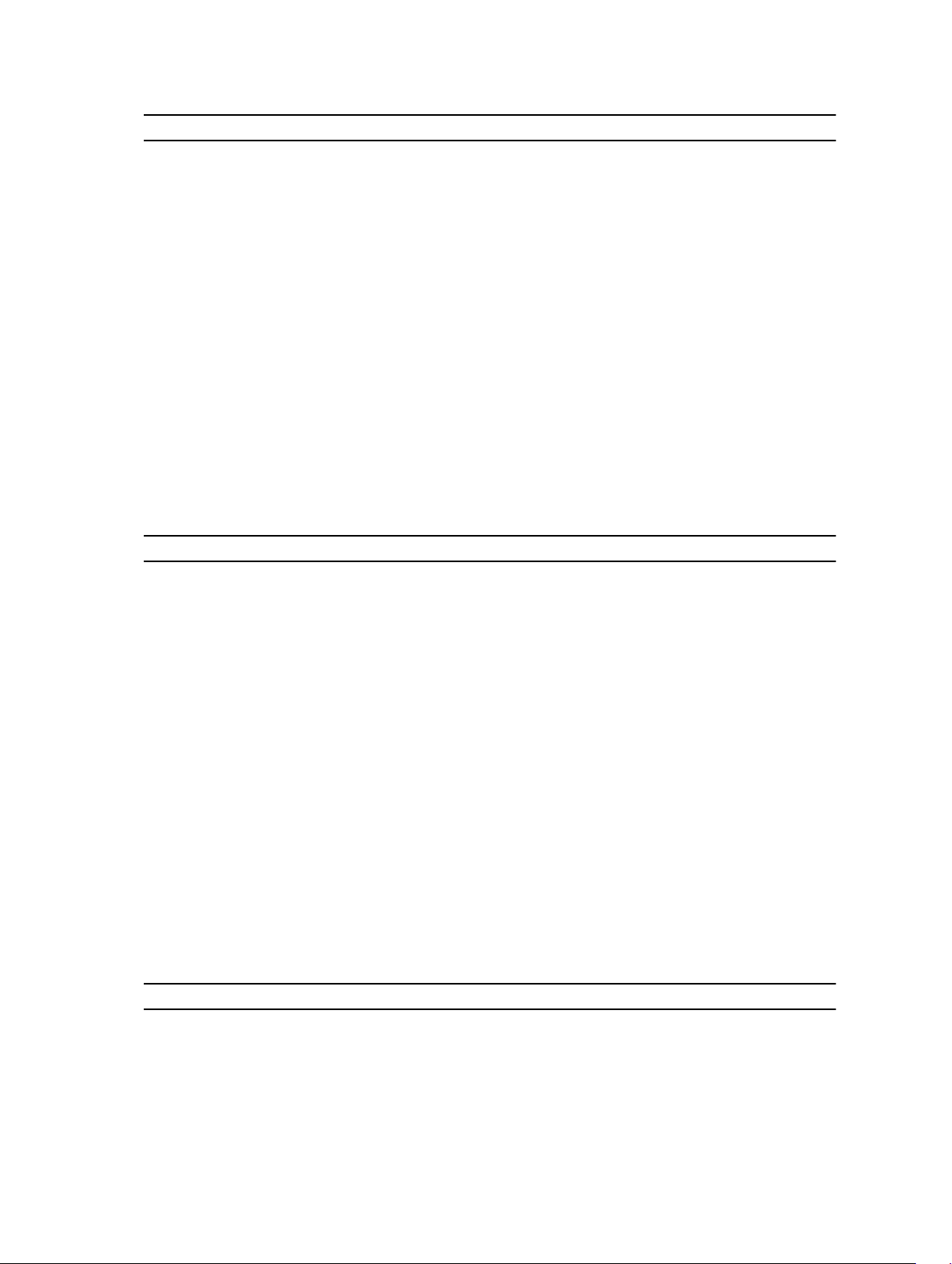
Operating System Internet Explorer Mozilla Firefox Google Chrome
Windows 7 Version 9 and Later Version 26 and Later Version 32 and Later
Red Hat Enterprise
Linux 6.5
Cent OS 6.5 Not Supported Version 26 and Later Version 32 and Later
Not Supported Version 26 and Later Version 32 and Later
Supported Resources
This section provides information about the resources supported by Active System Manager (ASM). The
information has been segmented based on the resource types.
Supported Dell PowerEdge Chassis
PowerEdge M1000e, version CMC 4.5
Supported PowerEdge Servers and Firmware Matrix
The following table provides information about the supported servers.
Resource BIOS iDRAC LC
Dell PowerEdge M420 2.0.23 1.51.51 1.3
Dell PowerEdge M520 2.0.23 1.51.51 1.3
Dell PowerEdge M620 2.1.6 1.51.51 1.3
Dell PowerEdge M820 1.7.3 1.51.51 1.3
Dell PowerEdge R420 2.0.22 1.51.51 1.3
Dell PowerEdge R520 2.0.22 1.51.51 1.3
Dell PowerEdge R620 2.1.3 1.51.51 1.3
Dell PowerEdge R720 2.1.3 1.51.51 1.3
Dell PowerEdge R720XD 2.1.3 1.51.51 1.3
Dell PowerEdge R820 1.7.2 1.51.51 1.3
Supported Cisco UCS Servers and Firmware Matrix
Resource Firmware Supported
Cisco UCS B200 M1 2.1(3b)
Cisco UCS B200 M2 2.1(3b)
7
Page 8
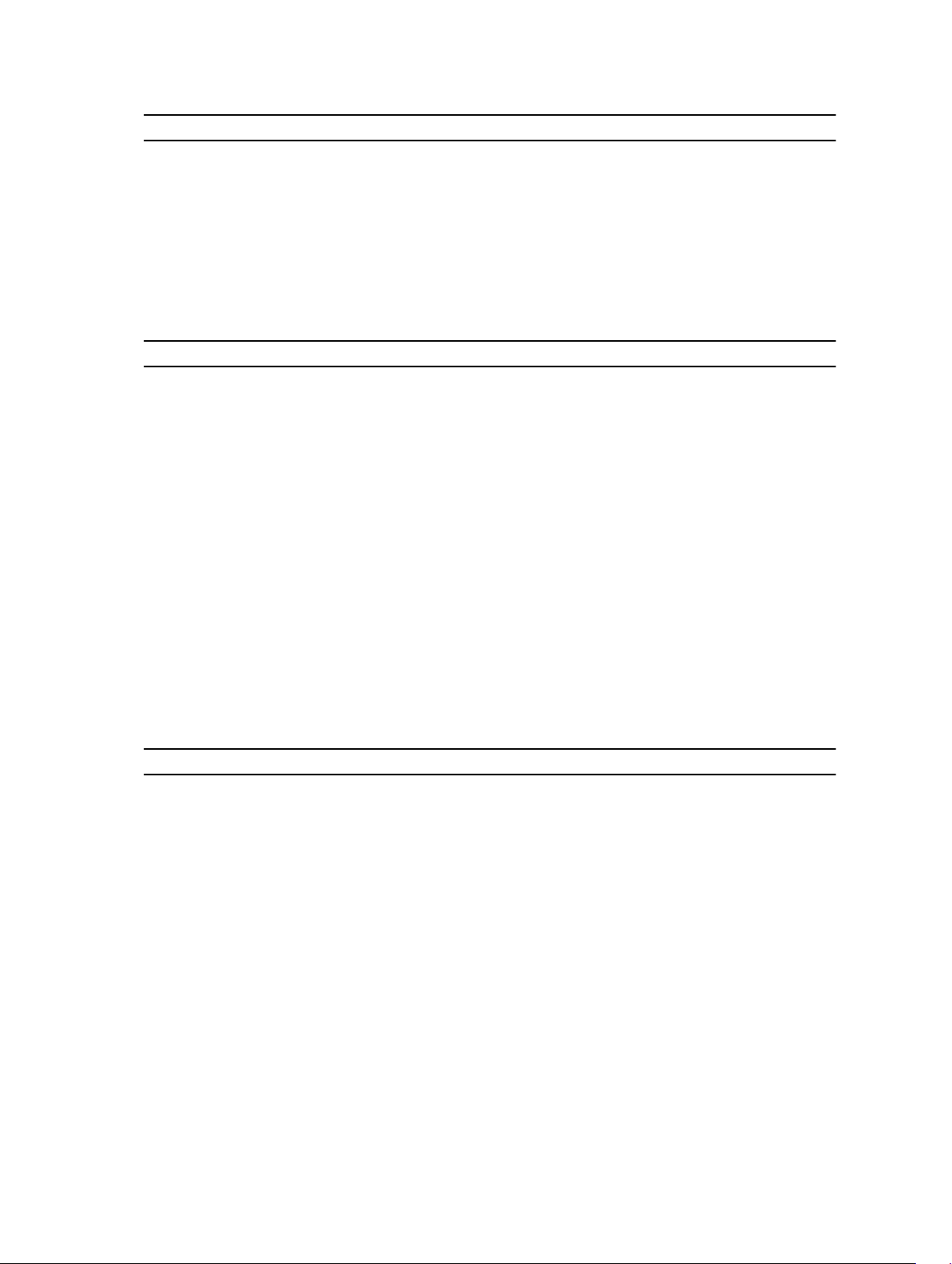
Resource Firmware Supported
Cisco UCS B230 M2 2.1(3b)
Cisco UCS B250 M1 2.1(3b)
Cisco UCS B200 M3 2.1(3b)
Supported Storage and Firmware Matrix
The following table provides information about the supported storage resources.
Resources Firmware Supported
Dell PS4100 7.0
Dell PS6100 7.0
Dell PS6110 7.0
Dell PS6210 7.0
Dell SC8000
Dell SC200
Dell SC220
*
Indicates that the resource is supported only in ASM 7.5.1 and later versions.(Only for ESXi)
*
*
*
6.3
6.3
6.3
Supported Networks and Firmware Matrix
The following table provides information about the supported Networks.
Resource Firmware Supported
Dell Networking PCT 7024 5.1.2.3
Dell Networking S4810 9.3.0.0
Dell Networking S5000 9.3.0.0
Dell Networking S6000 9.3.0.0
Dell PowerEdge M I/O Aggregator switch 9.2.0.0
Dell Networking MXL 10/40GbE blade switch 9.2.0.0
Cisco Nexus 5548 6.0(2)N2(3)
Dell Networking 8/4Gbps FC SAN Module
*
v7.2.0.a
8
Page 9

Resource Firmware Supported
Brocade M5424
*
v7.2.0.a
Brocade 6510
*
Indicates that the resource is supported only in ASM 7.5.1 and later versions. (Only for ESXi)
*
v7.2.0.a
Supported Adapters and Firmware Matrix
The following table provides information about the supported adapters.
Resource Firmware Supported
Broadcom 5719 Quad-Port 1GbE Network
Daughter Card
Broadcom 57810 -k Dul-Port 10Gb Mezzanine 7.8
Broadcom 57810 Dual-Port 10GbE Network
Daughter Card
Broadcom 5719 Quad-Port 1Gb Network Interface
Card
Broadcom 5719 Quad-Port 1GbE Network
Daughter Card
Broadcom 57840-k Quad-Port 10GbE Mezzanine 7.8
7.8
7.8
7.8
7.8
Broadcom 57840 Quad-Port 10Gb Converged
7.8
Network Adapter
QLE 2562 8Gb FC
QME 2572 8Gb FC
QLE 2662 16Gb FC
QME 2662 16Gb FC
*
Indicates that the resource is supported only in ASM 7.5.1 and later versions. (Only for ESXi)
*
*
*
*
03.20.06
03.20.06
03.10.07
03.10.07
9
Page 10

10
Page 11

2
Installation and Quick Start
The following sections provide installation and quick start information, including step-by-step
instructions for deploying and configuring Active System Manager (ASM) in VMware vSphere Client or
SCVMM. Only one instance of ASM should be installed within a network environment. Exceeding this limit
can cause conflicts in device communication.
Information Prerequisites
Before you begin the installation process:
• Gather TCP/IP address information to assign to the virtual appliance.
• If you want to deploy the ASM virual appliance on VMware vCenter, make sure that VMware vCenter
Server and VMware vSphere Client are currently running.
• If you want to deploy the ASM virual appliance on Windows Hyper-V, make sure SCVMM Instance is
up and running and Hyper-V host on which ASM virtual appliance deployed is already installed on
SCVMM.
• Download the ASM appliance file, which contains either the virtual appliance .ovf file for (VMware) or
the virtual appliance virtual hard drive .vhd (Hyper-V).
• Determine the host on which the ASM virtual appliance will be installed. You can use any host
managed by VMware vCenter or Hyper-V manager that has network connectivity with your out-ofband (OOB), management, and potentially iSCSI networks. This is required for discovery to complete
successfully.
CAUTION: The ASM virtual appliance functions as a regular virtual machine. Therefore, any
interruptions or shut downs affects the overall functionality.
Installing Active System Manger
Before you begin, make sure that systems are connected and VMware vCenter Server, VMware vSphere
Client, and SCVMM are running.
Deployment Prerequisites
Specification Prerequisite
Connection Requirements
• The virtual appliance is able to communicate
with the out-of-band management network
and any other networks from which you want
to discover the resources.
• The virtual appliance is able to communicate
with the PXE network in which the appliance is
11
Page 12

Specification Prerequisite
deployed. It is recommended to configure the
virtual appliance directly on the PXE network,
and not on the external network.
• The virtual appliance is able to communicate
with the hypervisor management network.
• The DHCP server is fully functional with
appropriate PXE settings to PXE boot images
from ASM in your deployment network.
Firmware and BIOS Requirements Make sure all the resources are configured with the
firmware versions listed in the section Supported
Resources
PowerEdge M1000e Chassis, blade server, and IO
aggregators
Dell PowerEdge Hypervisor Servers Server iDRAC is configured and has the out-of-
Dell PowerEdge Servers
• Chassis Management Controller (CMC) for
M1000e chassis is configured and has the
management IP address and login credentials
assigned.
• Server iDRAC and IOA is configured and has the
management IP address and login credentials
assigned using CMC management interface.
band IP address and login credentials.
• Dell PowerEdge Servers are configured and
have the management IP address and login
credentials assigned.
NOTE: The user name (root) and password
required.
• If you deploy ESXi to the SD card, the SD card
must already be enabled as a device in the BIOS
boot order.
• If you deploy Windows to the local Hard Disk
Drive, the Hard Disk Drive must already be
enabled as a device in the boot order.
• If you deploy ESXi to the SD card and your
server has redundant SD cards then “Internal SD
Card Redundancy” should be set to “Mirror”.
• For Microsoft Hyper-V provisioning, only fabric
A is supported. Make sure B and C fabric
Network adapters are disabled in the BIOS.
Dell PowerConnect 7024 switches
12
• The management IP address is configured for
the switches.
• ASM creates the virtual machine (VM) traffic
VLANs dynamically.
• Users have access to the switches with enable
passwords.
• Switches have SSH connectivity enabled.
Page 13

Specification Prerequisite
Dell Force10 S4810 switches (Top-of-Rack [ToR])
• The management IP address is configured for
the ToR switches.
• Any VLAN which is dynamically provisioned by
ASM must exist on the ToR switch.
• Server facing ports must be in hybrid mode.
• Server facing ports must be in switchport
mode.
• Server facing ports must be configured for
spanning tree portfast.
• ASM creates the virtual machine (VM) traffic
VLANs dynamically.
Dell 8 | 4 I/O modules
EqualLogic Storage Array
Compellent Storage Array .
VMware vCenter 5.1 or 5.5
• The management IP address is configured for
the Brocade switches.
• The management and group IP addresses are
configured for Storage Array.
• All storage array members are added to the
group.
NOTE: The Equallogic management
interface must be configured to enable
dedicated management network.
• EqualLogic array must have a SNMP community
name set to "public".
• The management IP address is configured for
Storage Array
• All storage array members are added to the
group.
• VMware vCenter 5.1 or 5.5 is configured and
accessible through the management and
hypervisor management network.
• Appropriate licenses are deployed on the
VMware vCenter.
System Center Virtual Machine Manager (SCVMM)
PXE Setup
• See System Center Virtual Machine Manager
(SCVMM) Prerequisites.
• The details of PXE setup is described in the
Configuring ASM Virtual Appliance as PXE Boot
Responder section.
System Center Virtual Machine Manager (SCVMM) Prerequisites
Active System Manager (ASM) manages resource on Microsoft System Center Virtual Machine Manager
through Windows Remote Management (WinRM). Windows RM must be enabled on the SCVMM server.
13
Page 14

ASM requires Windows RM to utilize default port and basic authentication. To enable these settings, on
the SCVMM server, open a Windows PowerShell interface with administrator permissions and run the
following commands:
winrm set winrm/config/client/auth '@{Basic="true"}'
winrm set winrm/config/service/auth '@{Basic="true"}'
winrm set winrm/config/service '@{AllowUnencrypted="true"}'
The default amount of memory allocated for WinRM processes is limited to 150 MB. To avoid out of
memory errors, increase the memory size to 1024:
winrm set winrm/config/winrs '@{MaxMemoryPerShellMB="1024"}'
NOTE: There is a known issue with WMF 3.0. The MaxMemoryPerShellMB configuration may be
ignored. For more information, see KB2842230. The fix for Windows 8/Windows 2012 x64 (non R2)
is available at the following link. The fix is not necessary for Windows 2012 R2.
Make sure SCVMM has time synchronized with a time server. If SCVMM time is off from deployed HyperV hosts then you may not be able to add hosts and create clusters in SCVMM.
Deploying Active System Manager from VMware vSphere Client
1. Extract the .zip file to a location accessible by VMware vSphere Client. It is recommended to use a
local drive or CD/DVD, because installing from a network location can take up to 30 minutes.
2. In vSphere Client, select File → Deploy OVF Template. The Deploy OVF Template wizard displays.
3. On the Source page, click Browse, and then select the OVF package. Click Next to continue.
4. On the OVF Template Details page, review the information that is displayed. Click Next to continue.
5. On the Name and Location page, enter a name with up to 80 characters and then, select an
Inventory Location where the template will be stored. Click Next to continue.
6. On the End User License Agreement page, read the license agreement and click Accept. Click Next
to continue.
7. Depending on the vCenter configuration, one of the following options display:
• If resource pools are configured — On the Resource Pool page, select the pool of virtual servers
on which you want to deploy the appliance virtual machine.
• If resource pools are NOT configured — On the Hosts/Clusters page, select the host or cluster
on which you want to deploy the appliance virtual machine.
Click Next to continue.
8. If there is more than one datastore available on the host, the Datastore page displays. Select the
location to store virtual machine (VM) files, and then click Next to continue.
9. On the Disk Format page, choose one of the following options:
• To allocate storage space to virtual machines as it is needed, click thin provisioned format.
• To pre-allocate physical storage space to virtual machines at the time a disk is created, click thick
provisioned format.
Click Next to continue.
10. On the Ready to Complete page, review the options you selected on previous pages and click Finish
to run the deployment job. A completion status window displays where you can track job progress.
14
Page 15

Deploying Active System Manager using SCVMM
To deploy Active System Manager (ASM) using SCVMM:
1. Extract the .zip file for the ASM build to a local folder on your SCVMM appliance
<ASM_INSTALLER_ROOT_DIR>.
2. To add ASM to the Library of Physical Library Objects in SCVMM, do the following:
a. In the left pane, click Library.
b. In the Home tab, click Import Physical Resource.
c. Click the Add Resource button. Browse to the location of the ASM .vhd file:
<ASM_INSTALLER_ROOT_DIR>\Virtual Hard Disks\Dell-ActiveSystemManager-7.5.2-.vhd
d. Under the Select library server and destination for imported resources section, click the
Browse button. Select the destination folder in which the ASM install VHD is located (for
example, My_SCVMM -> MSCVMMLibrary -> VHDs), and then click OK.
e. Click the Import button.
15
Page 16

3. To deploy the ASM virtual appliance:
a. In the left pane, click VMs and Services.
b. Click the Create Virtual Machine button.
c. Select Use an existing virtual machine, VM template, or virtual hard disk, and then click the
Browse button
d. From the list of sources, select VHD -> Dell-ActiveSystemManager-7.5.2- <bulid>.vhd, and then
click OK.
e. Click Next.
f. In the Virtual machine name text box, type the virtual machine name for your appliance, and
then click Next.
g. On the Configure Hardware page, do the following:
1. In the Compatibility section, set Cloud Capability Profile to Hyper-V.
2. In the Processors section, change the processor value to 2, and then in the Memory
section, change the memory value to 8 GB.
3. In the Network Adapter 1 section, assign the adapter to your PXE VM Network.
4. Click Next.
h. On the Select Destination page, select the destination host group that contains the Hyper-V
server where you want to deploy ASM VM. Click Next.
i. On the Select Host page, select the host on which you want to deploy ASM, and then click
Next.
j. On the Configuration Settings page, make the changes for your environment, if required.
k. On the Select networks page, select your PXE network and configure it appropriately.
l. On the Add Properties page, set to Always turn on the Virtual Machine and the OS as CentOS
Linux (64 bit), and then click Next.
m. Review the summary, select the Start Virtual machine after deploying it option, and then click
the Create button.
Deploying Active System Manager on Hyper-V host
To deploy ASM on Hyper-V host:
1. Open Hyper-V Manager in the Windows 2012 host. The Windows 2012 host should be displayed
under Hyper-V Manager.
2. Select the host and select Action → Import Virtual Machine.
3. Select the folder containing the ASM virtual appliance including snapshots, virtual hard disks, virtual
machines, and import files. Click Next.
4. On the Select Virtual Machine page, select the virtual machine to import (there is only one option
available), and then click Next.
5. On the Choose Import Type page, select Copy the virtual machine, and then click Next.
6. On the Choose Destination page, retain the default values or select the location of the virtual
machine, snapshot, and smart paging, and click Next.
7. On the Choose Storage Folders page, retain the default values or click Browse and select the
location of virtual hard disks, and then click Next.
8. On the Summary page, review the options you selected on earlier pages, and then click Finish to
deploy the ASM virtual appliance on the Hyper-V host.
16
Page 17

9. After the ASM virtual appliance is deployed, right-click the ASM virtual appliance, and then click
Settings.
10. In the Settings wizard, to enable the virtual switch, select VM-Bus Network Adapter. Optionally,
provide a VLAN ID, if the host is tagged on a particular network, and then click OK.
11. Select the ASM virtual appliance, and then click Start under Actions.
17
Page 18

18
Page 19

3
Configuring the Active System Manager Virtual Appliance
You must configure the following settings in the virtual appliance console before you start using Active
System Manager (ASM):
• Change Dell administrator password. For more detailed information, see Changing Delladmin
Password
• Configure static IP Address in the virtual appliance. For detailed information, see Configuring Static IP
Address in the Virtual Appliance
• Configure ASM Virtual Appliance as PXE boot responder. For detailed information, see Configuring
ASM Virtual Appliance as PXE Boot Responder
• Import Windows ISO on the virtual appliance. For detailed information, see Importing Windows ISO
on Virtual Appliance
• Deploy the WinPE image file to the virtual appliance. For detailed information, see Deploying WinPE
on the Virtual Appliance
Changing Dell Administrator Password
To change “delladmin” password:
1. You must use the SSH protocol to connect to ASM virtual appliance IP.
2. Log in to the console with the user name delladmin and password delladmin and press Enter.
3. At the command line interface, run the command passwd. Follow the prompts to update the
password.
4. To log in using the new password, at the command line interface, enter the old credentials and the
new password.
Configuring Static IP Address in the Virtual Appliance
1. In VMware Sphere, click the Console tab to open the console of the virtual appliance.
2. Log in to the console with the user name delladmin, enter current delladmin password, and then
press Enter.
NOTE: The default password for delladmin account is delladmin.
3. At the command line interface, run the command sudo su - and then enter the current delladmin
password.
4. In the Properties dialog box, click Network Configuration.
5. In the Network Connections dialog box, click Wired → Auto eth0, and then click Edit.
6. In the Editing Auto eth0 dialog box, click IPv4 Settings tab.
7. Select Manual from the Method drop-down list.
19
Page 20

8. In the Addresses table, type the static IP address, subnet mask, gateway, and then click Add.
9. Click Apply to set the static IP address of the appliance.
10. For Hyper-V only, reboot ASM virtual appliance.
Configuring ASM Virtual Appliance as PXE Boot Responder
Active System Manager (ASM) requires both PXE and DHCP network services to function. The ASM virtual
appliance contains a PXE service that is used to register resources with ASM so that workloads can be
deployed. The ASM virtual appliance must be deployed directly on the network configured for the PXE
service.
The PXE service requires a DHCP server configured to provide boot server (TFTP PXE server) information
and specific start-up file information. The ASM PXE implementation uses the iPXE specification so that the
configuration details include instructions to allow legacy PXE servers and resources to boot properly to
this iPXE implementation.
This section provides information about configuring DHCP on the following servers. The information
includes only the basic configuration options and declarations required for an iPXE environment. These
details should be used as a cumulative addition to the settings currently used in your DHCP
implementation (if you already have a DHCP environment).
• Microsoft Windows 2012 Server. See Configure DHCP on Windows 2012 DHCP Server
• Microsoft Windows 2008 Server R2. See Configure DHCP on Windows 2008 DHCP Server
• Linux DHCPd (ISC DHCP). See Configuring DHCP for Linux
Configure DHCP on Windows 2012 DHCP Server
To configure the DHCP on Windows 2012 DHCP Server, perform the following tasks:
1. Create DHCP User Class
2. Create DHCP Policy
3. Create Boot File scope option
For additional information, see http://ipxe.org/howto/msdhcp
Create the DHCP User Class
You must create the user class for the DHCP server before creating the DHCP Policy.
1. Open the Windows 2012 DHCP Server DHCP Manager.
2. In the console tree, navigate to IPv4. Right click IPv4, and then click Define User Classes from the
drop-down menu.
3. In the DHCP User Classes dialog box, click Add.
4. In the New Class dialog box, enter the following information and click OK to create a user class.
a. In the Display Name box, enter iPXE
b. In the Description box, enter iPXE Clients
c. In the data pane, under ASCII, enter iPXE
20
Page 21

5. Click Close.
Create the DHCP Policy
1. Open the Windows 2012 DHCP Server DHCP Manager.
2. In the console tree, expand the scope that will service your ASM PXE network. Right click Policies
and select New Policy.
The DHCP Policy Configuration Wizard is displayed.
3. Next to Policy Name, type iPXE and enter the description as iPXE Client. Click Next.
4. On the Configure Conditions for the policy page, click Add.
5. In the Add/Edit Condition dialog box, perform the following actions, and then click OK.
• Select User Class from the Criteria list.
• Select iPXE from the list of Values and click Add.
6. On the Configure Conditions for the policy page, select the AND operator and click Next.
7. On the Configure settings for the policy page, select the AND operator and click Next.
• If you want to use only the portion of the DHCP scope for PXE, click Yes, and then enter the IP
address range to limit the policy.
• If you do not want to use the portion of the DHCP scope for PXE, click No.
8. For PXE service to function properly, under Available Options, select 067 Bootfile Name, and enter
the string value as bootstrap.ipxe.
9. Click Next, and then click Finish.
Create the Boot File Scope Option
1. Open the Windows 2012 DHCP Server DHCP Manager.
2. In the console tree, expand the scope that will service your ASM PXE network. Right click Scope
Options
3. In the right pane, enter the following information:
• Click 066 Boot Server Host Name and enter the IP address or DNS name of the ASM server in the
• For PXE service to function properly, click 067 Bootfile Name and enter undionly.kpxe in the
4. In the right pane, based on your network settings, configure the following:
• 003 Router (default gateway that is on the PXE network)
• 006 Name Server (DNS server IP address)
and select Configure Options.
Value column.
Value column.
Configure DHCP on Windows 2008 DHCP Server
To configure the DHCP on Windows 2008 DHCP Server, perform the following tasks:
1. Create DHCP User Class
2. Create DHCP Policy
3. Create Boot File Scope Option
For additional information, see http://ipxe.org/howto/msdhcp
21
Page 22

Create the DHCP User Class
You must create the user class for the DHCP server before creating the DHCP Policy.
1. Open the Windows 2008 DHCP Server DHCP manager.
2. In the console tree, navigate to IPv4. Right click IPv4, and then click Define User Classes from the
drop-down menu.
3. In the DHCP User Class dialog box, click Add to create a new user class.
4. In the New Class dialog box, enter the following information and click OK to create a user class.
a. In the Display Name box, enter iPXE.
b. In the Description box, enter iPXE Clients.
c. In the data pane, under ASCII, enter iPXE.
5. Click Close.
Create the DHCP Policy
Use the new User Class to create a DHCP policy scope option.
1. Open the Windows 2008 DHCP Server DHCP manager.
2. Add a scope option to the DHCP scope that will service the ASM PXE environment.
3. In the Scope Options dialog box, click the Advanced tab, select 067 Bootfile Name check box, and
in the String value box, enter bootstrap.ipxe .
NOTE: For PXE service to function properly, you must enter bootstrap.ipxe for the 067 Bootfile
Name.
4. Select DHCP Standard Options from the Vendor class drop-down list.
5. Select iPXEclass from the User Class drop-down list.
6. Click OK to save the scope option.
The policy is created by utilizing the new User Class with a scope option.
Create the Boot File Scope Option
The Boot File option is created for the DHCP scope that services your ASM PXE.
1. Open the Windows 2008 DHCP Server DHCP Manager.
2. In the console tree, expand the scope that will service your ASM PXE network. Right click Scope
Options and select Configure Options.
3. In the right pane, enter the following information:
• Click 066 Boot Server Host Name and enter the IP address or DNS name of the ASM server in the
Value column.
• For PXE service to function properly, click 067 Bootfile Name and enter undionly.kpxe in the
Value column.
4. Additionally, in the right pane, based on you network settings, configure the following:
• 003 Router (default gateway that is on the PXE network)
• 006 Name Server (DNS server IP address)
22
Page 23

Configuring DHCP for Linux
You can manage the configuration of the Linux DHCPD service by editing the dhcpd.conf configuration
file. The dhcpd.conf is located at /etc/dhcp directory of most Linux distributions. If the DHCP is not
installed on your Linux server, install the Network Infrastructure Server or similar services.
Before you start editing the dhcpd.conf file, it is recommended to back up the file. After you install the
appropriate network services, you must configure the dhcpd.conf file before you start the DHCPD
service.
The DHCP configuration must include the following options:
• next-server <IP address>
Indicates the IP address of the PXE server. That is, the IP address of the ASM appliance vNIC that exists
on the PXE network.
• filename "bootstrap.ipxe"
NOTE: For PXE service to function properly, you must specify bootstrap.ipxe for the file name.
The PXE service uses iPXE service. You must use two different bootstrap files for the PXE environment,
one for the initial PXE boot, which starts up the system to the final iPXE boot file.
To run this operation, add the following code to the dhcpd.conf file:
if exists user-class and option user-class = "iPXE" {
filename "bootstrap.ipxe";
} else {
filename "undionly.kpxe";
}
Secondly, add the following code to the subnet declaration within your dhcpd.conf file. This code
instructs a legacy PXE server to boot to a legacy boot file, and then directs to the iPXE boot file. For more
details, see the Sample DHCP Configuration
The configuration file must contain the following information:
# dhcpd.conf
# Sample configuration file for ISC dhcpd
next-server 192.168.123.21;# IP address of ASM Server
default-lease-time 6000;
max-lease-time 7200;
authoritative;
log-facility local7;
subnet 192.168.123.0 netmask 255.255.255.0 {
range 192.168.123.24 192.168.123.29;
option subnet-mask 255.255.255.0;
option routers 192.168.123.1;
if exists user-class and option user-class = "iPXE" {
filename "bootstrap.ipxe";
} else {
filename "undionly.kpxe";
}
}
23
Page 24

After you modify the dhcpd.conf file based on your environment, you need to start or restart your
DHCPD service. For more information, see http://ipxe.org/howto/dhcpd
Sample DHCP Configuration
# dhcpd.conf
#
# Sample configuration file for ISC dhcpd
#
#option definitions common to all supported networks...
#option domain-name "example.org";
#option domain-name-servers 192.168.203.46;
#filename "pxelinux.0";
next-server 192.168.123.21;# IP address of ASM Server
default-lease-time 6000;
max-lease-time 7200;
# Use this to enble / disable dynamic dns updates globally.
#ddns-update-style none;
# If this DHCP server is the official DHCP server for the local
# network, the authoritative directive should be uncommented.
authoritative;
# Use this to send dhcp log messages to a different log file (you also
have to hack syslog.conf to complete the redirection.
log-facility local7;
# No service will be given on this subnet, but declaring it helps the
# DHCP server to understand the network topology.
#subnet 192.168.123.0 netmask 255.255.255.0 {
#}
# This is a very basic subnet declaration.
subnet 192.168.123.0 netmask 255.255.255.0 {
range 192.168.123.24 192.168.123.29;
option subnet-mask 255.255.255.0;
option routers 192.168.123.1;
if exists user-class and option user-class = "iPXE" {
filename "bootstrap.ipxe";
} else {
filename "undionly.kpxe";
}
}
# This declaration allows BOOTP clients to get dynamic addresses,
# which we don't really recommend.
24
Page 25

#subnet 10.254.239.32 netmask 255.255.255.224 {
#range dynamic-bootp 10.254.239.40 10.254.239.60;
#option broadcast-address 10.254.239.31;
#option routers rtr-239-32-1.example.org;
#}
#A slightly different configuration for an internal subnet.
#subnet 10.5.5.0 netmask 255.255.255.224 {
#range 10.5.5.26 10.5.5.30;
#option domain-name-servers ns1.internal.example.org;
#option domain-name "internal.example.org";
#option routers 10.5.5.1;
#option broadcast-address 10.5.5.31;
#default-lease-time 600;
#max-lease-time 7200;
#}
# Hosts which require special configuration options can be listed in
# host statements. If no address is specified, the address will be
# allocated dynamically (if possible), but the host-specific information
# will still come from the host declaration.
#host passacaglia {
# hardware ethernet 0:0:c0:5d:bd:95;
# filename "vmunix.passacaglia";
# server-name "toccata.fugue.com";
#}
# Fixed IP addresses can also be specified for hosts. These addresses
# should not also be listed as being available for dynamic assignment.
# Hosts for which fixed IP addresses have been specified can boot using
# BOOTP or DHCP. Hosts for which no fixed address is specified can only
# be booted with DHCP, unless there is an address range on the subnet
# to which a BOOTP client is connected which has the dynamic-bootp flag
# set.
#host fantasia {
# hardware ethernet 08:00:07:26:c0:a5;
# fixed-address fantasia.fugue.com
#}
# You can declare a class of clients and then do address allocation
# based on that. The example below shows a case where all clients
# in a certain class get addresses on the 10.17.224/24 subnet, and all
# other clients get addresses on the 10.0.29/24 subnet.
#class "foo" {
# match if substring (option vendor-class-identifier, 0, 4) = "SUNW";
#}
#shared-network 224-29 {
#subnet 10.17.224.0 netmask 255.255.255.0 {
#option routers rtr-224.example.org;
# }
# subnet 10.0.29.0 netmask 255.255.255.0 {
# option routers rtr-29.example.org;
# }
25
Page 26

# pool {
# allow members of "foo";
# range 10.17.224.10 10.17.224.250;
# }
# pool {
# deny members of "foo";
# range 10.0.29.10 10.0.29.230;
# }
#}
Deploying WinPE on the Virtual Appliance
You need to perform the following configuration tasks before using ASM to deploy Windows OS.
NOTE: You should use Microsoft ADK 8.1 or ADK 8.0 installed in the default location..
1. Create a Windows repository with Windows installation media on ASM appliance. For more
information, see Create a repository with Windows installation media on ASM Appliance
2. Create a WinPE image to support Windows 2012 or Windows 2012 R2 deployment for bare metal or
a VMware virtual machine, and update install media for Windows 2012 or Windows 2012 R2 to
include drivers and necessary updates to support ASM. For more information, see Creating WinPE
Image and Update Install Media for Windows 2012 and Windows 2012 R2
3. Copy WinPE and install media to the ASM repository and update permissions for all files in the
repository. For more information, see Copy WinPE and install media back to the ASM repository and
update permissions
4. (Windows 2012 R2) Update default-unattended.xml.erb and wim_boot.erb files on ASM virtual
appliance. For more information, see Updating default unattended.xml.erb and wim_boot.erb files
5. (Optional) Update unattended installation for Windows 2012 version other than Windows 2012
standard. For more information, see Updating unattended Installation For Windows 2012 Version
other than Windows 2012 Standard
Create a repository with Windows installation media on ASM Appliance
1. Log in to the virtual appliance with the user name delladmin.
2. Copy the Windows.iso file to the directory /var/lib/razor/repo-store/
3. Using a text editor, create a /tmp/windows_repo.json file with the following content:
{
"name": "<your windows repo name>",
"iso-url": "file:///var/lib/razor/repo-store/<windows ISO name>.iso"
}
4. To register the .iso file, run the following command. At command line interface, you have to enter
your delladmin password .
"sudo razor create-repo --json /tmp/windows_repo.json"
5. To verify whether or not the repository is created, run the following command:
"sudo razor repos"
6. Run the following commands to extract the .iso file from the directory /var/lib/razor/repo-store to
the directory /var/lib/razor/repo-store/win2012. Make sure that your Windows .iso file is available in
“repo-store” directory where you run the following commands.
"sudo mount -o loop /var/lib/razor/repo-store/<windows_ISO_name>.iso /mnt"
"sudo rsync -av /mnt/ /var/lib/razor/repo-store/<your Windows repo name>"
"sudo umount /mnt"
26
Page 27

7. Update permissions for the directory, by running the command:
"sudo find <your Windows repo name> -print0 | sudo xargs -0 chown
razor:razor"
Creating WinPE Image and Updating Install Media for Windows 2012 and Windows 2012 R2
To create WinPE Image and update Install Media for Windows 2012 and Windows 2012 R2:
1. Log in to the ASM virtual appliance and copy the scripts build-razor-winpe.ps1 and razor-client.ps1
from the /opt/razor-server/build-winpe directory to a folder created in the ADK machine. For
example, ADK machine directory may be c:\buildpe.
2. In the razor-client.ps1 file, replace ${server} with the IP address of your ASM virtual appliance in
the following code:
$baseurl = http://${server}:8080/svc
After completing this task, the following line is displayed.
$baseurl = http://192.168.0.17:8080/svc
You should have Windows Assessment and Deployment toolkit that contains the Windows PE
environment used to automate the Windows installer installed in the DEFAULT location on a
Windows machine. Licensing for Windows PE requires that you build your own customized WinPE
WIM image containing the required scripts.
NOTE:
• If you want deploy Windows to VMWare VMs, the WinPE drivers for the VMXNET3 virtual
network adapter from VMWare is also required. The instructions for obtaining a VMXNET3
driver from VMWare are listed below.
• While deploying Windows to an m420 server, drivers for Broadcom network adapters must
be added to the image as they are not included in Windows. The instructions for including
these drivers are listed below.
The install scripts require the default location for the ADK. This package is obtained from
Microsoft.
3. Copy the build-razor-winpe.ps1 and razor-client.ps1 scripts created to a directory on your machine
with ADK 8.0 or 8.1 installed in the default location as described in step 1.
4. Obtain a copy of the Broadcom Drivers for an m420 server from dell.com and install the driver
package on a Windows 2012 or 2012 R2 machine. Locate the Windows install drivers on the
filesystem and copy them to the Drivers folder created in the step 3. These drivers typically start with
"b57".
5. Obtain a copy of the VMware Windows drivers for the VMXNET 3 adapter from VMware. To obtain
the VMware Windows drivers:
a. Install VMware tools on a running Windows 2012 or Windows 2012 R2 and on the virtual
machine.
b. Go to the C:\Program Files\Common Files\VMware\Drivers directory.
c. Copy the contents in the Drivers folder to the directory that contains your WinPE build scripts.
6. Copy the files boot.wim and install.wim from the ASM virtual appliance to the directory on your ADK
machine. The boot.wim and install.wim files can be found in the /var/lib/razor/repo-store/<your
Windows repo>/SOURCES directory.
7. Using a command line tool for Powershell, go to the directory containing your build scripts, Drivers
folder, and boot.wim and install.wim files. This directory should contain these files only.
27
Page 28

8. To run the build script, run the command:
powershell -executionpolicy bypass -noninteractive -file build-razorwinpe.ps1
NOTE: This step takes some time to complete. After completion, it creates a directory with the
name razor-winpe under the current working directory. The final custom WinPE image,
bootmgr.exe (for Windows 2012 R2 repositories), boot.wim, and install.wim are copied to this
directory.
Copying WinPE and Install Media to ASM Repository and Updating Permissions
To copy WinPE and install media to ASM repository and update permissions for all files in the repository:
1. Copy the new boot.wim and install.wim files to ASM virtual appliance under /var/lib/razor/repo-
store/<your 2012 repo>/SOURCES
2. Make sure you update the permissions on the boot.wim and install.wim files on ASM virtual
appliance. Therefore you can run the files. To perform this task, run the following commands:
"sudo chmod 755 /var/lib/razor/repo-store/<your windows repo>/sources/
boot.wim"
"sudo chmod 755 /var/lib/razor/repo-store/<your windows repo>/sources/
install.wim"
3. Rename the new WinPE image file that you have created in the earlier section to razor-winpe.wim,
and then copy the file to the root of your Windows repository created using the steps described in
the section Create a repository with Windows installation media on ASM appliance.
4. If you are deploying Windows 2012 R2, you should also copy the latest bootmgr.exe file to the root
of your Windows repository created using the steps described in the section
Windows installation media on ASM appliance. This file is available in the output directory when you
create your customized WinPE image as specified in the earlier section.
5. Make sure that the right privileges are granted to the repository files.
"sudo chmod 755 /var/lib/razor/repo-store/<your windows repo>/bootmgr.exe"
"sudo chmod 755 /var/lib/razor/repo-store/<your windows repo>/razorwinpe.wim"
"sudo find <your windows repo> -print0 | sudo xargs -0 chown razor:razor"
“sudo setsebool -P samba_export_all_ro 1”
Create a repository with
Updating default-unattended.xml.erb and wim_boot.erb files for Windows 2012 R2
You must update the default-unattended.xml.erb and wim_boot.erb files on the ASM virtual appliance for
Windows 2012 R2.
To update default-unattended.xml.erb and wim_boot.erb files on ASM virtual appliance:
1. Using a text editor with sudo permissions, open the default-unattended.xml.erb file available in the
following directory /opt/razor-server/installers/windows/8-pro/. Use sudo and enter the delladmin
password.
2. Enter the Windows product key where the product key is saved in the default-unattended.xml.erb
file.
NOTE: To obtain Windows license keys, contact your vendor.
3. To deploy Windows 2012 R2, you must also update the Windows Image Type in the default-
unattended.xml.erb
2012 Version other than Windows 2012 Standard.
28
file. For more information, see Updating Unattended Installation For Windows
Page 29

4. Go to the /opt/razor-server/installers/windows/ folder on your ASM virtual appliance, and using sudo
and a text editor open the wim_boot.erb file.
5. Replace the two instances of bootmgr with bootmgr.exe and save the file.
Updating Unattended Installation for Windows 2012 Version other than Windows 2012 Standard
Windows 2012 operating system deployments other than Windows 2012 Standard require modifications
to the
default-unattended.xml.erb file. The current default-unattended.xml.erb file that supports
unattended Windows installs defaults to deployment of Windows 2012 Standard. If another version of
Windows 2012 is required, the appropriate string must be modified in the default-unattended.xml.erb file.
To modify the string in the default-unattended.xml.erb file based on the operating system:
1. On the ASM virtual appliance, navigate to the default-unattended.xml.erb in the /opt/razor-server/
installers/windows/8-pro directory.
2. Open the default-unattended.xml.erb file with a text editor. Use sudo to make sure that you have
permissions to edit this file. This requires delladmin password.
3. Enter the correct string required for the Windows image.
Examples of the strings for Windows 2012 are:
• Windows Server 2012 SERVERDATACENTER,
• Windows Server 2012 SERVERDATACENTERCORE,
• Windows Server 2012 SERVERSTANDARD,
• Windows Server 2012 SERVERSTANDARDCORE.
Examples of the strings for Windows 2012 R2 are:
• Windows Server 2012 R2 SERVERDATACENTER
• Windows Server 2012 R2 SERVERDATACENTERCORE
• Windows Server 2012 R2 SERVERSTANDARD
• Windows Server 2012 R2 SERVERSTANDARDCORE
NOTE: For more information about modifying Windows unattended files, see Microsoft
documentation.
Updating Unattended Installation for Windows Hyper-V for Versions other than Windows 2012 R2 Datacenter
Windows Hyper-V 2012 operating system deployments other than Windows 2012 R2 server datacenter
require modifications to the default hyper-v-unattended.xml.erb file. The current default hyper-vunattended.xml.erb file supports unattended Hyper-V installations which is default for Windows 2012 R2
server datacenter. If another version of Windows is required for Hyper-V, the appropriate string must be
modified in the default
To modify the string in the default hyper-v-unattended.xml.erb file based on the operating system:
1. On the ASM virtual appliance, locate the default hyper-v-unattended.xml.erb file in the /opt/razor-
server/installers/windows/8-pro directory.
2. Open the default hyper-v-unattended.xml.erb file with a text editor. Use sudo to make sure that you
have permissions to edit this file. This requires delladmin password.
hyper-v-unattended.xml.erb file.
29
Page 30

3. Enter the correct string required for the Windows image.
Examples of the strings for Windows 2012 are:
• Windows Server 2012 SERVERDATACENTER,
• Windows Server 2012 SERVERDATACENTERCORE,
• Windows Server 2012 SERVERSTANDARD,
• Windows Server 2012 SERVERSTANDARDCORE.
Examples of the strings for Windows 2012 R2 are:
• Windows Server 2012 R2 SERVERDATACENTER
• Windows Server 2012 R2 SERVERDATACENTERCORE
• Windows Server 2012 R2 SERVERSTANDARD
• Windows Server 2012 R2 SERVERSTANDARDCORE
NOTE: For more information about modifying Windows unattended files, see Microsoft
documentation.
Importing Linux ISOs on the Virtual Appliance for Operating System Deployment
The following steps provide instructions to import Red Hat Enterprise Linux 6.5 ISO on the ASM virtual
appliance for Operating System Deployment.
1. Log in to virtual appliance with the user name delladmin.
2. Copy the ISO file to the directory /var/lib/razor/repo-store/.
3. To create a Red Hat Enterprise Linux 6.5 repository, create a /tmp/rhel65_repo.json file with the
following content:
{
“name”: “<your rhel repo name>”,
“iso-url”: file:///var/lib/razor/repo-store/<Red Hat ISO name>.iso
}
4. To register the .iso file, run the following command using the content file created in step 3. The
example here uses the
sudo razor create-repo --json /tmp/rhel65_repo.json
5. To verify whether or not the repository is created, run:
sudo razor repos
6. Change directory to /var/lib/razor/repo-store/rhel65 directory. If the operating system files are
already available, continue to Step 7. Otherwise, run the following commands to extract the .iso file
from the directory /var/lib/razor/repo-store to the directory /var/lib/razor/repo-store/rhel65. Make
sure that the Linux .iso file is available in “repo-store” directory where you run the following
commands.
“sudo mount -o loop /var/lib/razor/repo-store/<RHEL ISO NAME>.iso /mnt”
“sudo rsync -av /mnt/* /var/lib/razor/rep-store/<your rhel repo name>”
rhel65_repo.json file created in the earlier step.
“sudo umount /mnt”
30
Page 31

7. Make sure that the correct privileges are granted to the repository files.
“sudo find <your rhel repo name> -print0 | sudo xargs -0 sudo chown
razor:razor”
8. Active System Manager uses a default kickstart file to automate the installation of Linux. If you want
to customize while installing the operating system, you can customize the kickstart file template
“kickstart.erb” used to automate the installation.
Use the sudo command to edit the kickstart.erb file available in the following directory /opt/razorserver/installers/redhat
information about editing kickstart files for Linux install automation, refer to Linux documentation.
NOTE: Currently, only one kickstart version is supported for Linux. Changes here affects both
CentOS and Red Hat OS installations.
, and then enter the necessary customizations for the install. For more
31
Page 32

32
Page 33

4
Completing Initial Configuration
Log in to Active System Manager using the appliance IP address after completing the steps in this guide,
After logging into ASM, you need complete the basic configuration setup in the Initial Setup wizard. For
more information about completing the initial setup see the Active System Manger Version 7.5 User’s
Guide.
33
 Loading...
Loading...