Page 1

Cisco Small Business
SG200 Series 8-port Smart Switch
ADMINISTRATION
GUIDE
Page 2
Contents
Chapter 1: Getting Started 8
Starting the Web-Based Switch Configuration Utility 8
Launching the Utility 9
Logging In 9
Logging Out 10
Quick Start Device Configuration 10
Window Navigation 11
Application Header 11
Other Resources 12
Navigation Window 13
Management Buttons 13
Chapter 2: Viewing Statistics 16
System Summary 16
Displaying the System Summary 16
Configuring System Settings 19
Interface Statistics 20
Etherlike Statistics 21
802.1X EAP Statistics 22
IPv6 DHCP Statistics 23
RADIUS Statistics 24
Statistics 25
Logs 26
RAM Memory Log 27
Flash Memory Log 28
Chapter 3: Administration 30
Configuring System Settings 31
Management Interface 32
Configuring an IPv4 Management Interface 32
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 2
Page 3
Contents
Configuring an IPv6 Management Interface 34
Adding IPv6 Addresses 34
IPv6 Default Router Table 35
Viewing and Adding IPv6 Neighbors 35
Managing User Accounts 36
Adding a User 37
Changing a User Password 38
Deleting a User 38
Enabling Management Services 38
Configuring the Idle Session Timeout 39
Login Sessions 39
Login History 40
Time Settings 40
Setting System Time 40
Configuring the SNTP Setting 42
Configuring SNTP Authentication 46
System Logs 47
Configuring Log Settings 47
Configuring Remote Log Servers 49
File Management 50
Upgrading and Backing Up Firmware and Language Files 51
Downloading and Backing Up the Configuration and Log Files 53
Downloading a Configuration File to Restore Settings 53
Backing Up the Configuration File and Logs 54
Delete Configuration 56
Copying and Saving Configuration Files 56
DHCP Auto Configuration 57
Overview 57
DHCP Server Message Details 58
Alternate TFTP Server and File Name 59
Configuration File Download Details 59
Setting DHCP Auto Configuration 61
Firmware Recovery Over HTTP 63
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 3
Page 4
Contents
Rebooting the Switch 65
Pinging Hosts 65
Configuring Control Packet Forwarding 66
Diagnostics 67
Testing Copper Ports 67
Configuring Port Mirroring 68
CPU/Memory Utilization 70
Enabling Bonjour 71
LLDP-MED 72
Configuring Global LLDP-MED Properties 72
Configuring LLDP-MED on a Port 73
LLDP-MED Port Status Details 75
LLDP-MED Neighbor Information 77
Configuring DHCP Client Vendor Options 79
Chapter 4: Port Management 80
Configuring Port Settings 80
Link Aggregation 81
Configuring LAGs 82
Configuring LAG Settings 83
Configuring LACP Settings 84
Configuring PoE 85
Configuring PoE Properties 85
Configuring PoE Port Settings 86
Green Ethernet 89
Configuring Green Ethernet Properties 89
Configuring Green Ethernet Port Settings 90
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 4
Page 5
Contents
Chapter 5: VLAN Management 93
Creating VLANs 94
Configuring VLAN Interface Settings 94
Changing the Interface VLAN Mode 97
Configuring VLAN Membership 98
Configuring Port to VLAN 99
Configuring Port VLAN Membership 100
Setting the Default VLAN 101
Voice and Media 102
Displaying and Adding Telephony OUI 103
Configuring OUI Based Voice and Media 103
Configuring SIP/H323 Based Voice and Media 104
Media VLAN 105
Auto VoIP Sessions 107
Chapter 6: Spanning Tree 108
Overview of Spanning Tree 108
Configuring STP Status & Global Settings 109
Configuring Global and Bridge Settings 109
Configuring STP Interface Settings 111
RSTP Interface Settings 113
Chapter 7: MAC Address Tables 115
Configuring Static MAC Addresses 115
Configuring the Aging Time for Dynamic Addresses 117
Dynamic MAC Addresses 117
Chapter 8: Multicast 119
Multicast Properties 120
Configuring a Multicast Forwarding Mode on all VLANs 120
Configuring Multicast Properties on an Individual VLAN 121
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 5
Page 6

Contents
Configuring MAC Group Addresses 121
Viewing the MAC Group Address Table 122
Adding a Static MAC Group Address Table Entry 122
Configuring MAC Address Group Port Membership 123
Configuring IGMP Snooping 123
Configuring MLD Snooping 125
Configuring IGMP Multicast Router Interfaces 127
Configuring MLD Multicast Router Interfaces 128
Chapter 9: IP Configuration 129
ARP Table 129
Domain Name System 129
Configuring DNS Servers 130
Configuring Global DNS Settings 130
Adding DNS Servers 131
Hostname Mapping 131
Configuring Static DNS Mappings 131
Viewing and Deleting Dynamic DNS Entries 132
Chapter 10: Security 133
RADIUS 133
Configuring Global RADIUS Settings 134
Adding a RADIUS Server 134
Password Strength 136
Management Access Profile Rules 137
Configuring an Access Profile and Rules 137
Modifying and Deleting Access Profiles and Rules 139
Authentication Methods 140
Storm Control 141
Port Security 142
Enabling Port Security 142
Viewing and Configuring Secure MAC Addresses 144
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 6
Page 7
Contents
802.1X 144
Defining 802.1X Properties 145
Modifying Port PAE Capabilities 146
Configuring Port Authentication 147
Configuring Supplicant Port Authentication 149
Displaying Authenticated Hosts 150
Chapter 11: Quality of Service 151
QoS Properties 152
Defining Queues 153
Queue Configuration Recommendations 154
Configuring Queues 154
Mapping CoS/802.1p Priorities to Queues 155
Mapping IP Precedence to Queues 156
Mapping DSCP Values to Queues 157
Defining Rate Limit Profiles 158
Applying Rate Limit Profiles to Interfaces 159
Traffic Shaping 160
Cisco Small Business SG200 Series 8-port Smart Switch Administration Guide 7
Page 8

Getting Started
This chapter provides an introduction to the web-based switch configuration
utility, and includes the following topics:
• Starting the Web-Based Switch Configuration Utility
• Quick Start Device Configuration
• Window Navigation
2
Starting the Web-Based Switch Configuration Utility
This section describes how to navigate the web-based switch configuration utility.
Browsers have the following restrictions:
• If you are using Internet Explorer 8, open a browser window and configure
the following settings:
Click To ol s > Internet Options and then select the Security tab. Select
Local Intranet and click Sites. Click Advanced and then click Add. Add the
intranet address of the switch (http://<ip-address>) to the local intranet
zone. The IP address can also be specified as the subnet IP address, so that
all addresses in the subnet are added to the local intranet zone.
• If you are using Internet Explorer 6, you cannot directly use an IPv6 address
to access the switch. You can, however, use the Domain Name System
(DNS) server to create a domain name that contains the IPv6 address, and
then use that domain name in the address bar in place of the IPv6 address.
• If you have multiple IPv6 interfaces on your management station, use the
IPv6 global address instead of IPv6 link local address to access the switch
from your browser.
• Screen resolutions at 800x600 or lower in Internet Explorer browsers and
Firefox 3.6 are not supported by the web-based switch configuration utility.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 8
Page 9
Getting Started
Starting the Web-Based Switch Configuration Utility
Launching the Utility
To open the web-based switch configuration utility:
STEP 1 Open a web browser.
STEP 2 Enter the IP address of the switch that you are configuring in the address bar on
the browser, and then press Enter. The Login page opens.
NOTE When logging in by using HTTP or HTML, if you are provided an option to choose
from more than one network port, select the lowest number port.
Logging In
2
To log in to the web-based switch configuration utility:
STEP 1 Enter the username and password. The factory default user name is cisco and the
default password is cisco.
Note: When the switch boots with the factory default configuration, the web-
based switch configuration utility appears in the default language. After you log in,
you can download additional languages by using the Upgrade/Backup Firmware/
Language page.
STEP 2 If this is the first time that you logged on with the default user name (cisco) and the
default password (cisco) or your password has expired, the Change Admin
Password page opens. Enter the new password, confirm it, click Apply, and then
click Close. The new password is saved. (The characters ', ", %, and ? are not
supported.)
STEP 3 Click Login.
When the login attempt is successful, the Getting Started page opens.
If you entered an incorrect user name or password, an error message is displayed
and the Login page remains displayed on the screen.
Select Don’t show this page on startup to prevent the Getting Started page from
being displayed each time that you logon to the system. If you select this option,
the System Summary page is opened instead of the Getting Started page.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 9
Page 10

Getting Started
!
Quick Start Device Configuration
Logging Out
By default, the application automatically logs you out after 10 minutes of inactivity.
See Configuring the Idle Session Timeout for instructions on changing the
default timeout period.
To log out at any time, click Logout in the top right corner of any page.
CAUTION Unless the Running Configuration is copied to the Startup Configuration file type,
all changes made since the last time the file type was saved are lost if the switch is
rebooted. We recommend that you save the Running Configuration to the Startup
Configuration file type before logging off to preserve any changes you made
during this session.
A red X icon displayed to the left of the Save button indicates that Running
Configuration changes have been made that have not yet been saved to the Startup
Configuration file type.
2
When you click Save, the page displays (see Downloading and Backing Up the
Configuration and Log Files). Save the Running Configuration by copying it to the
Startup Configuration file type. After this save, the red X icon and the Save button
no longer display.
Quick Start Device Configuration
To simplify device configuration through quick navigation, the Getting Started
page provides links to the most commonly-used pages.
Links on the Getting Started Page
Category Link Name (on the Page) Linked Page
Initial Setup Change Device IP Address IPv4 Interface
Create VLAN Create VLAN
Configure Port Settings Port Settings
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 10
Page 11

Getting Started
Window Navigation
2
Links on the Getting Started Page (Continued)
Category Link Name (on the Page) Linked Page
Device
Status
Quick
Access
Window Navigation
System Summary System Summary
Port Statistics Interface
RMON Statistics RMON Statistics
View Log RAM Memory
Change Device Password User Accounts
Upgrade Device Software Upgrade/Backup Firmware/
Language
Backup Device
Configuration
Configure QoS QoS Properties
Configure Port Mirroring Port Mirroring
Download/Backup Configuration/
Log
This section describes the features of the web-based switch configuration utility.
Application Header
The Application Header is displayed on every page. It provides the following
buttons:
Buttons
Button Name Description
The Syslog Alert Status button (red circle with an X) is
displayed when a new Syslog message, above the critical
severity level, is logged. Click to open the Status and
Statistics > View Log > RAM Memory Log page. After
you access this page, the Syslog Alert Status button is no
longer displayed.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 11
Page 12

Getting Started
Window Navigation
2
Buttons (Continued)
Button Name Description
A red X icon, displayed to the left of the Save button,
indicates that configuration changes have been made and
have not yet been saved to the Startup Configuration file.
When you click this button, the Download/Backup
Configuration/Log page displays. Save the Running
Configuration by copying it to the Startup Configuration
file type. After this save, the red X icon and the Save button
are no longer displayed. When the switch is rebooted, it
copies the Startup Configuration file type to the Running
Configuration and sets the switch parameters according to
the data in the Running Configuration.
User The name of the user logged on to the switch. The default
user name is cisco.
Language Menu Select a language or load a new language file into the
device. If the language required is displayed in the menu,
select it. If not, select Download Language. For more
information about adding a new language, refer to the
Upgrade/Backup Firmware/Language page.
Log Out Click to log out of the web-based switch configuration
utility.
About Click to display the switch type and switch version
number.
Help Click to display the online help.
Other Resources
You can use the following links on the Getting Started page for additional
information and assistance with using your switch:
• Support—Displays the support web page for Cisco Small Business
Managed Switches.
• Forums—Displays the web page for the Cisco Small Business Support
Community.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 12
Page 13
Getting Started
Window Navigation
2
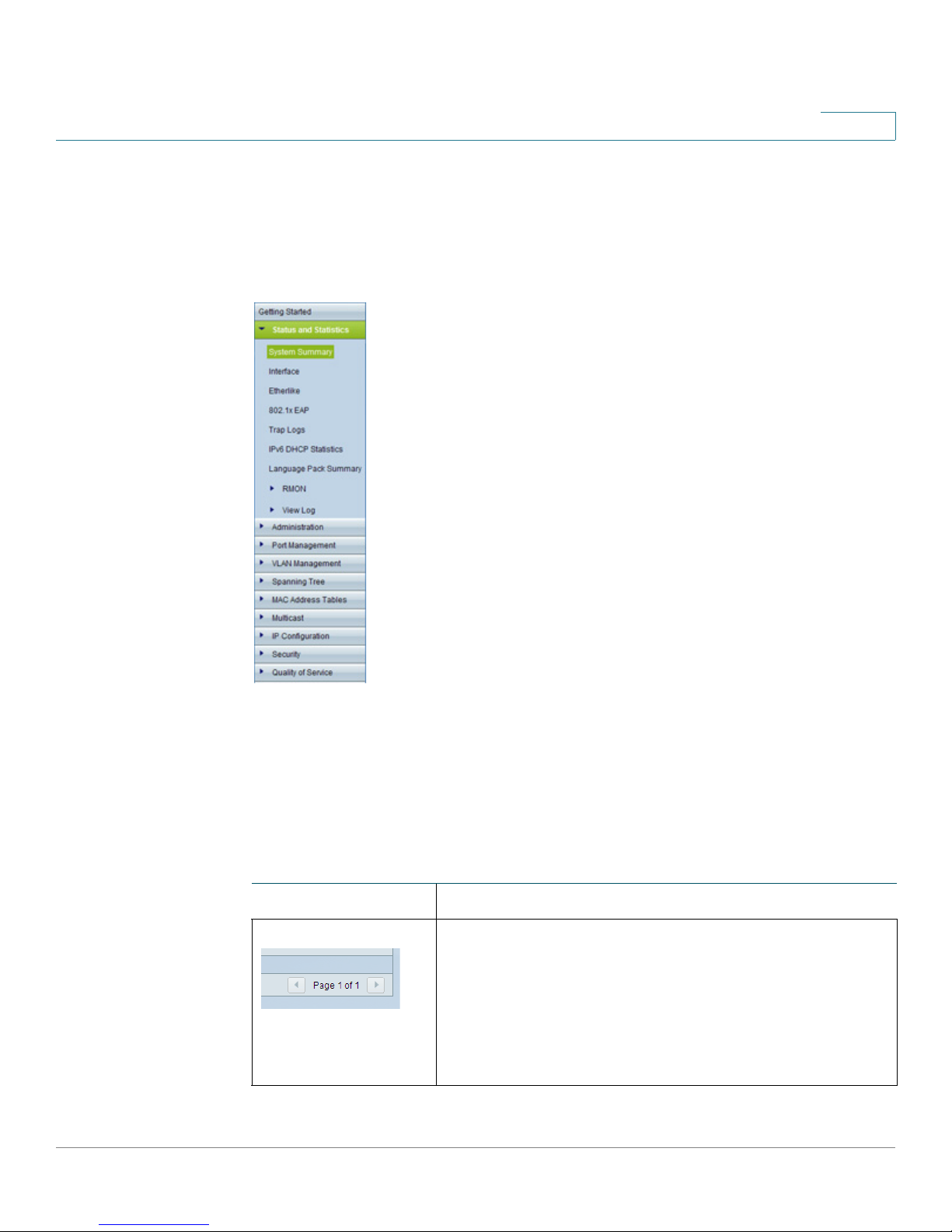
Navigation Window
A navigation window is located on the left side of each page. Click a top-level
category to display links to related pages. Links that are preceded by an arrow are
subcategories that expand to display the related page links.
Management Buttons
The following table describes the commonly-used buttons that appear on various
pages in the system.
Management Buttons
Button Name Description
Depending on the number of pages and the currently
displayed page, use these features to navigate through
the pages of the table. Click |< to go to the first page,
click < to go to the previous page, click > to go to the
next page, and click >| to go to the last page. Use the
Page <number> of <number> drop-down list to choose
a particular page.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 13
Page 14

Getting Started
Window Navigation
2
Management Buttons (Continued)
Button Name Description
Select the number of table entries to display on each
page.
Indicates a mandatory field.
Add Click to display the related Add page and add an entry
to a table. Enter the information and click Apply. Click
Close to return to the main page.
Note: Your changes are applied to the running
configuration only. If the switch is rebooted, the running
configuration is lost. To save your changes to the startup
configuration, click Save. For more information, see
Copying and Saving Configuration Files.
Apply Click to apply the changes that you entered on the
selected page.
Note: Your changes are applied to the running
configuration only. If the switch is rebooted, the running
configuration is lost. To save your changes to the startup
configuration, click Save. For more information, see
Copying and Saving Configuration Files.
Cancel Click to “undo” the changes that you made on the page
and to reset the values to the previously applied entries.
Clear All Interfaces
Counters
Clear Interface
Counters
Clear Logs Click to clear the log files.
Clear Table Click to clear the table entries.
Close Click to return to the main page. If there are changes that
Click to clear the statistic counters for all interfaces.
Click to clear the statistic counters for the selected
interface.
were not applied to the Running Configuration, a
message is displayed.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 14
Page 15

Getting Started
Window Navigation
2
Management Buttons (Continued)
Button Name Description
Copy Settings A table typically contains one or more entries containing
configuration settings. Instead of modifying each entry
individually, it is possible to modify one entry and then
copy it to multiple entries, as described below:
• Select the entry to be copied. Click Copy
Settings.
• Enter the destination entry numbers.
• Click Apply to save the changes to the Running
Configuration.
• Click Close to return to the main page.
Delete Select the entry in the table to be deleted and click
Delete. The entry is deleted.
Details Click to display details associated with the entry
selected on the main page.
Edit Select an entry and click Edit to open it for editing. The
Edit page opens, and the entry can be modified.
• Click Apply to save the changes to the Running
Configuration. (Note that there is no message to
confirm that the parameters have been saved to
the Running Configuration. This is normal
behavior.)
• Click Close to return to the main page.
Te st Click Te s t to perform related tests.
Clear Filter Click Clear Filter to redisplay data on a page with the
default criteria.
Go Click Go to filter the data displaying on a page using the
selected criteria.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 15
Page 16

Getting Started
Window Navigation
2
Management Buttons (Continued)
Button Name Description
Sort buttons If the This table is sortable message appears below a
table, each column heading is a sort button. Click a
column heading to sort the records in ascending order,
based on the contents of the selected column. After the
sort is applied, an arrow appears in the column heading.
You can click this arrow to reverse the sort order.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 16
Page 17

Viewing Statistics
This chapter describes how to display switch statistics.
It contains the following topics.
• System Summary
• Interface Statistics
• Etherlike Statistics
3
• 802.1X EAP Statistics
• IPv6 DHCP Statistics
• Statistics
• Logs
System Summary
The System Summary page displays basic information such as the hardware
model description, software version, langauge packs, and system up time.
Displaying the System Summary
To view system information, click Status and Statistics > System Summary in the
navigation window. Or, click System Summary under Device Status on the
Getting Started page.
The System Summary page displays the following information:
• System Description—A description of the system.
• System Location—Physical location of the switch. Click Edit to display the
System Settings page and enter this value.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 17
Page 18

Viewing Statistics
System Summary
3
• System Contact—Name of a contact person. Click Edit to display the
System Settings page and enter this value.
• Hostname—Name of the switch. Click Edit to display the System Settings
page and enter this value. The default hostname is the word switch
followed by the last three octets of the base MAC address. For example, a
switch with a MAC address of 010203040506 has the default hostname
switch040506 (the six furthest right hexadecimal digits).
• System Uptime—Time that has elapsed since the last reboot.
• Current Time—Current system time.
• Base MAC Address—Switch MAC address.
Hardware and Firmware Version Information
The following hardware and software information displays for the switch:
• Serial Number—Serial number of the switch.
• PID VID—Part number and version ID.
• Maximum Available Power (W)—(PoE switches only) Maximum available
power that can be delivered by the PoE ports.
• Firmware Version—Firmware version number of the active image.
• Firmware MD5 Checksum—MD5 checksum of the active image.
• Boot Version—Version of the boot code.
• Boot MD5 Checksum—MD5 checksum of the boot code.
In additional, the graphic view of the switch enables you to view settings for each
switch port. To view to display the Port Settings page, click the port.
TCP and UDP Services
This table lists the information for each service that uses TCP or UDP:
• Service Name—The commonly–used name of the service, if available, such
as HTTP.
• Type—The transport protocol used for this service (TCP or UDP).
• Port—The Internet Assigned Numbers Authority (IANA) port number for the
service.
• IP Address—The IP address, if any, of a remote device that is connected to
this service on the switch.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 18
Page 19
Viewing Statistics
System Summary
3
• Remote Port—The IANA port number of any remote device communicating
with this service.
• State—The state of the service. For UDP, only connections in the Active state
display in the table. In the Active state, a connection is established between
the switch and a client or server. The TCP states are:
- Listen—The service is listening for connection requests.
- Active—A connection session is established and packets are being
transmitted and received.
- Established—A connection session is established between the switch
and a server or client, depending on each device’s role with respect to
this protocol.
Language Pack Table
This table displays information about the languages available on the switch. A
language can be selected by the administrator when logging into the configuration
utility.
English is the default language and it is built into the software. You can use the
Upgrade/Backup Firmware/Language page to download additional language
packs. Language files are available from the Cisco firmware download page.
The Language Pack Table displays the following information for each available
language:
• Language—Language name.
• Locale—Internet Engineering Task Force (IETF) locale code that identifies
the language and the country or region.
• Version—Language file version.
• MD5 Checksum—128-bit hash code used to check file integrity.
• File Type—Indicates one of the following values:
- Built-In—Default language provided within the software and therefore
cannot be downloaded as a separate file.
- External—A language file that has been downloaded to the switch and
• File Size—The file size in KB.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 19
can be selected at login.
Page 20

Viewing Statistics
System Summary
STEP 1 Click Status and Statistics > System Summary. The System Settings page
STEP 2 Click Edit to modify the following settings:
3
• Default—Displays Yes to indicate that the web-based switch configuration
utility login page will display in this language whenever the switch is
rebooted.
• Status—Displays Active or Inactive. At log-in, the user can choose a
language. The selected language is the Active language.
Configuring System Settings
To configure the system settings:
opens.
• System Location—Enter the location where the switch is physically located.
• System Contact—Enter the name of a contact person.
• Hostname—Enter the hostname. Use only letters, digits, and hyphens. Host
names cannot begin or end with a hyphen. No other symbols, punctuation
characters, or blank spaces are permitted (as specified in RFC1033,
RFC1034, and RFC1035). The default hostname is the word switch followed
by the first three bytes of the base MAC address. For example, a switch with
a MAC address of 010203040506 has the default hostname switch010203.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 20
Page 21
Viewing Statistics
Interface Statistics
Interface Statistics
Use the Interface page to display statistics for received and transmitted packets.
To display this page, click Status and Statistics > Interface in the navigation
window, or click Port Statistics under Device Status on the Getting Started
page.
Select the interface (Port or LAG) for which you want to display statistics, then
select a refresh rate for the statistics. The following information displays for the
selected interface:
• Tot al By te s (O ct et s) —Total number of octets transmitted or received on the
• Unicast Packets—Total number of unicast packets transmitted or received
3
selected interface since the switch was last refreshed.
on the selected interface since the switch was last refreshed.
• Multicast Packets—Total number of multicast packets transmitted or
received on the selected interface since the switch was last refreshed.
• Broadcast Packets—Total number of broadcast packets transmitted or
received on the selected interface since the switch was last refreshed.
• Packets with Errors—Total number of packets with errors received on the
selected interface since the switch was last refreshed.
• STP BPDUs—Total number of Spanning Tree Protocol (STP) Bridge Protocol
Data Units (BPDUs) transmitted or received on the selected interface since
the switch was last refreshed.
• RSTP BPDUs—Total number of Rapid Spanning Tree Protocol BPDUs
transmitted or received on the selected interface since the switch was last
refreshed.
To clear statistics counters:
• Click Clear Interface Counters to reset all counters to 0 for the selected
interface.
• Click Clear All Interface Counters to reset all counters to 0 for all
interfaces.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 21
Page 22
Viewing Statistics
Etherlike Statistics
Etherlike Statistics
The system collects and reports statistics on ports and LAGs in accordance with
RFC2665.
To display this page, click Status and Statistics > Etherlike in the navigation
window.
Select the interface (Port or LAG) for which you want to display statistics, then
select a refresh rate for the statistics. These statistics are cumulative since the last
time the page was refreshed. The following information displays for the selected
interface:
• Frame Check Sequence (FCS) Errors—FCS errors received.
• Single Collision Frames—Signal collision frame errors received.
3
• Late Collisions—Late collision frames received.
• Excessive Collisions—Excessive collision frames received.
• Multiple Collisions—Multiple collision frames received.
• Oversize Packets—Packets received that were longer than 1518 octets
(excluding framing bits and including FCS octets) and were otherwise wellformed.
• Internal MAC Receive Errors—Internal MAC errors received on the LAG or
interface.
• Alignment Errors—Packets received with alignment errors
• Pause Frames Received—Pause frames received on the LAG or interface.
• Pause Frames Transmitted—Pause frames transmitted from the LAG or
interface.
To clear statistics counters:
• Click Clear Interface Counters to reset all counters to 0 for the selected
interface.
• Click Clear All Interface Counters to reset all counters to 0 for all
interfaces.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 22
Page 23
Viewing Statistics
802.1X EAP Statistics
802.1X EAP Statistics
The switch ports can be configured to use the IEEE 802.1X Extensible
Authentication Protocol (EAP) to control network access (see 802.1X). You can use
the 802.1X EAP page to display information about EAP packets received on a port.
To display the 802.1X EAP page, click Status and Statistics > 802.1X EAP in the
navigation window.
STEP 1 Select the Port for which you want to display statistics.
STEP 2 Select a Refresh Rate for the statistics. These statistics are cumulative since the
last time the page was refreshed.
The following information displays for the selected interface:
3
• EAPOL Frames Received—Valid Extensible Authentication Protocol over
LAN (EAPOL) frames received on the port.
• EAPOL Frames Transmitted—EAPOL frames transmitted through the port.
• EAPOL Start Frames Received—EAPOL Start frames received on the port.
• EAPOL Logoff Frames Received—EAPOL Logoff frames received on the
port.
• Invalid EAPOL Frames Received—Unrecognized EAPOL frames received
on this port.
• EAP Length Error Frames Received—EAPOL frames with an invalid packet
body length received on this port.
To clear statistics counters:
• Click Clear Interface Counters to reset all counters to 0 for the selected
interface.
• Click Clear All Interface Counters to reset all counters to 0 for all
interfaces.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 23
Page 24
Viewing Statistics
IPv6 DHCP Statistics
IPv6 DHCP Statistics
The switch can be configured to allow management over an IPv6 interface, and to
receive its management IPv6 address through the Dynamic Host Configuration
Protocol (DHCPv6). See Management Interface for information on configuring
IPv6 and DHCP on the management interface. You can use the IPv6 DHCP
Statistics page to display information on transmitted and received DHCPv6
packets.
To display this page, click Status and Statistics > IPv6 DHCP Statistics in the
navigation window.
Select a refresh rate for the page. The page displays the following statistics, which
are cumulative since the last time the page refreshed.
• DHCPv6 Advertisement Packets Received
3
• DHCPv6 Reply Packets Received
• Received DHCPv6 Advertisement Packets Discarded
• Received DHCPv6 Reply Packets Discarded
• DHCPv6 Malformed Packets Received
• Total DHCPv6 Packets Received
• DHCPv6 Solicit Packets Transmitted
• DHCPv6 Request Packets Transmitted
• DHCPv6 Renew Packets Transmitted
• DHCPv6 Rebind Packets Transmitted
• DHCPv6 Release Packets Transmitted
• Total DHCPv6 Packets Transmitted
Click Clear Counters to reset all counters to 0.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 24
Page 25
Viewing Statistics
RADIUS Statistics
RADIUS Statistics
The switch can be configured to communicate with a RADIUS server for user
authentication. To display the RADIUS Statistics page, click
Status and Statistics > RADIUS Statistics in the navigation window.
Select a RADIUS server from the list and select a refresh rate for the page. The
page displays the following statistics, which are cumulative since the last time the
page refreshed.
• Access Requests—The number of Authentication-Request packets
• Access Retransmissions—Number of Authentication-Request packets
• Access Accepts—Number of Authentication-Request packets accepted
3
transmitted to the RADIUS server.
retransmitted to the RADIUS server.
by the RADIUS server.
• Access Rejects—Number of Authentication-Request packets rejected by
the RADIUS server.
• Access Challenges—Number of Access-Challenge packets sent by the
RADIUS server to the switch.
• Malformed Access Responses—Number of reply packets from the
RADIUS server that were malformed.
• Bad Authenticators—Number of Authentication-Request packets that
contained invalid Message Authenticator attributes.
• Pending Requests—Number of Authentication-Request packets that were
sent to the server and have not been replied to.
• Timeouts—Number of Authentication-Request packets that were timed out
due to no response from the server.
• Unknown Types—Number of RADIUS packets of unknown type that were
received by the switch.
• Packets Dropped—Number of RADIUS packets dropped by the switch.
Click Clear All Statistics to reset all counters to 0.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 25
Page 26
Viewing Statistics
Statistics
Statistics
STEP 1 Click Status and Statistics > RMON > Statistics in the navigation window.
STEP 2 Select the port or LAG for which you want to display statistics.
STEP 3 Select a refresh rate for the page.
3
The RMON Statistics page displays detailed information regarding packet sizes
and information regarding physical layer errors. The information shown is
according to the RMON standard.
To view statistics:
The following information displays for the selected interface:
• Bytes Received—Octets received on the interface since the switch was last
refreshed. This number includes bad packets and FCS octets, but excludes
framing bits.
• Drop Events—Number of times that packets have been dropped on the
interface since the switch was last refreshed.
• Packets Received—Packets received on the interface, including bad
packets, multicast and broadcast packets, since the switch was last
refreshed.
• Broadcast Packets Received—Good broadcast packets received on the
interface since the switch was last refreshed. This number does not include
multicast packets.
• Multicast Packets Received—Good multicast packets received on the
interface since the switch was last refreshed.
• CRC & Align Errors—CRC and Align errors that have occurred on the
interface since the switch was last refreshed.
• Undersize Packets—Undersized packets (less than 64 octets) received on
the interface since the switch was last refreshed.
• Oversize Packets—Oversized packets (over 1518 octets) received on the
interface since the switch was last refreshed.
• Fragments—Fragments (packets with less than 64 octets, excluding
framing bits, but including frame check sequence octets) received on the
interface since the switch was last refreshed.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 26
Page 27
Viewing Statistics
Logs
3
• Jabbers—Packets received that were more than 1518 octets long and had
an FCS error during the sampling session.
• Collisions—Collisions received on the interface since the switch was last
refreshed.
• Frames of 64 Bytes—64-byte frames received on the interface since the
switch was last refreshed.
• Frames of 65 to 127 Bytes—65-byte to 127-byte frames received on the
interface since the switch was last refreshed.
• Frames of 128 to 255 Bytes—128-byte to 255-byte frames received on the
interface since the switch was last refreshed.
• Frames of 256 to 511 Bytes—256-byte to 511-byte frames received on the
interface since the switch was last refreshed.
Logs
• Frames of 512 to 1023 Bytes—512-byte to 1023-byte frames received on
the interface since the switch was last refreshed.
• Frames of 1024 to 1518 Bytes—1024-byte to 1518-byte frames received
on the interface since the switch was last refreshed.
The switch generates messages to identify the state of the system and to assist in
diagnosing issues that arise during switch operation. Messages might be
generated in response to events, faults, or errors occurring on the platform and to
changes in configuration.
Logs of these messages are stored in RAM and flash memory. Entries in the flash
log—unlike those in RAM—are stored across platform reboots.
To access the log menu items, click Status and Statistics > View Log in the
navigation window. The log menu includes the following pages:
• RAM Memory Log
• Flash Memory Log
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 27
Page 28
Viewing Statistics
Logs
3
RAM Memory Log
Use the RAM Memory page to view information about specific RAM (cache) log
entries, including the time the log was entered, the log severity, and a description
of the log.
To display this page, click Status and Statistics > View Log > RAM Memory in the
navigation window.
NOTE This page might take up to 45 seconds to display when the table contains the
maximum number of entries.
The RAM Memory Log Table contains the following fields:
• Log Index—Numeric ID for the log entry.
• Log Time—Time at which the log was entered in the Log RAM Table.
• Severity—The log severity can be one of the following:
- Emergency (0)—System is unusable.
- Alert (1)—Action must be taken immediately.
- Critical (2)—Critical conditions.
- Error (3)—Error conditions.
- Warning (4)—Warning conditions.
- Notice (5)—Normal but significant conditions.
- Informational (6)—Informational messages.
- Debug (7)—Provides detailed information about an event.
You can use the Log Set tings page to select the severity levels that are
recorded in the log.
• Component - The software component or service that produced the log
entry.
• Description—The log description.
You can click Clear Logs to remove all log entries from RAM.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 28
Page 29
Viewing Statistics
Logs
STEP 1 Click Status and Statistics > View Log > Flash Memory in the navigation window.
STEP 2 Select a log type from the list:
3
Flash Memory Log
The Log File contains information about specific log entries, including the time the
log was entered, the log severity, and a description of the log. Several log types
are supported, and the system stores up to three versions of each type.
To v ie w a F l a sh lo g :
• Default—Entries from the startup and operational logs.
• Startup—Log entries created during system restarts.
• Operational—Log entries created during system operation.
STEP 3 Select a log version to display.
The Version 1 log is the current or most recently created log file, the Version 2 log
is the next most recent, and the Version 3 log is the oldest. When a new log of the
specified type is created, the Version 3 log is deleted and the Version 1 and
Version 2 logs are renamed to Version 2 and Version 3, respectively.
When a different version and log is selected, the new log automatically displays in
the Flash Memory Log Table. When the table contains the maximum number of
entries, this page might take up to 45 seconds to display.
The Flash Memory Log Table contains the following fields:
• Log Index—Numeric ID for the log entry.
• Log Time—Time that the log was created in the Flash Memory Table.
• Severity—The log severity can be one of the following:
- Alert (1)—Action must be taken immediately.
- Critical (2)—Critical conditions.
- Error (3)—Error conditions.
- Warning (4)—Warning conditions.
- Notice (5)—Normal but significant conditions.
- Informational (6)—Informational messages.
- Debug (7)—Provides detailed information about an event.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 29
Page 30
Viewing Statistics
Logs
3
You can use the Log Set tings page to select the severity levels that are
recorded in the log.
• Component—Software component that produced the log entry.
• Description—The log description.
NOTE You can click Clear Logs to remove all log entries from flash memory. You can click
Backup Logs to open the Download/Backup Configuration/Log page, where you
can use TFTP or HTTP to back up the log files to a TFTP server or network location.
For more information, see Backing Up the Configuration File and Logs.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 30
Page 31

Administration
This chapter describes how to configure global system settings and perform
diagnostics.
It contains the following topics.
• Configuring System Settings
• Management Interface
4
• Managing User Accounts
• Enabling Management Services
• Configuring the Idle Session Timeout
• Login Sessions
• Login History
• Time Settings
• System Logs
• File Management
• Rebooting the Switch
• Pinging Hosts
• Configuring Control Packet Forwarding
• Diagnostics
• Enabling Bonjour
• LLDP-MED
• Configuring DHCP Client Vendor Options
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 31
Page 32

Administration
Configuring System Settings
Configuring System Settings
The System Settings page enables you to configure information that identifies the
switch within the network.
To configure system settings:
STEP 1 Click Administration > System Settings in the navigation window.
The System Description is hard-coded in the firmware.
STEP 2 Enter the parameters:
• System Location—Description of the physical location of the switch. (The
characters ', ", %, and ? are not supported.)
• System Contact—Contact person for the switch.
4
• Hostname—Administratively-assigned name for this managed node. By
convention, this is the fully-qualified domain name of the node. The default
hostname is switch concatenated with the last 6 hex digits of the MAC
address of the switch. Hostname labels contain only letters, digits and
hyphens. Hostname labels cannot begin or end with a hyphen. No other
symbols, punctuation characters, or blank spaces are permitted.
STEP 3 Click Apply. The changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 32
Page 33

Administration
Management Interface
Management Interface
Switch management interface enables access to the web-based switch
configuration utility from a management station on the network. The switch
supports configuration of a management VLAN that segregates the management
traffic from other traffic on the switch.
The management interface can be configured with an IPv4 address or with an IPv6
address. The addresses can be configured statically or they can be obtained
through DHCP/BOOTP servers.
See the following topics for more information on the configuration pages available
in the Administration > Management Interface menu:
• Configuring an IPv4 Management Interface
• Configuring an IPv6 Management Interface
4
• Viewing and Adding IPv6 Neighbors
Configuring an IPv4 Management Interface
You can use the IPv4 Interface page to configure the management VLAN and IPv4
address.
To configure the IPv4 management interface:
STEP 1 Click Administration > Management Interface > IPv4 Interface in the navigation
window.
STEP 2 Select a management VLAN from the list.
A port must be a member of the management VLAN to gain access to the webbased switch configuration utility. By default, VLAN 1 is configured as the
management VLAN and all switch ports are configured as members of VLAN 1.
At least one port must be a member of the management VLAN. The Member
Ports list displays all current members of the selected management VLAN.
Note that when you change the management VLAN, you must reassign any
members of the previous management VLAN to the new VLAN to continue their
management access.
STEP 3 Select one of the following options for the IP Address Type:
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 33
Page 34

Administration
!
Management Interface
4
• DHCP—The management interface obtains its IPv4 address from a DHCP
server.
• BOOTP—The management interface obtains its IPv4 address from a BOOTP
server.
• Static—The management interface IPv4 address assigned in the IP
Address field.
By default, DHCP is enabled and the switch requests an IP address from a
DHCP server. If it is unable to get the IP address from a server, the switch falls
back to the factory default static IP address. The System LED flashes
continuously in this situation. The switch will keep trying to get its IP address
from a DHCP server. The factory default static IP address is 192.168.1.254/
24, with default gateway192.168.1.1.
If the IP Address Type is set to Static, specify the following:
- IP Address—Enter an IPv4 address.
- Mask—Enter a 32-bit network mask (for example, 255.255.255.0).
Or select Prefix Length and specify the number of bits (0–32) that make
up the network prefix (for example, 24).
- Default Gateway—Select User Defined and specify the default
gateway IP address for management packets.
Or select None to prevent management packets from being transmitted
outside the subnet.
• Operational Default Gateway—The current default gateway in use.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
CAUTION Changing the management IP address and IP Address Type terminates the current
management session. Changing the Management VLAN and its port memberships
might disrupt your communication with the switch and thus terminate the current
management session.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 34
Page 35

Administration
Management Interface
STEP 1 Click Administration > Management Interface > IPv6 Interface in the navigation
STEP 2 Configure the following settings:
4
Configuring an IPv6 Management Interface
Use the IPv6 Interface page to enable access to the web-based switch
configuration utility over IPv6. You can configure the switch to dynamically learn its
IPv6 addresses and you can configure IPv6 addresses statically.
To enable IPv6 management access:
window.
• IPv6 Mode—Select to enable IPv6 management access.
• IPv6 Address Auto Configuration—Select to enable the switch to auto-
configure its link-local address(es) in EUI-64 format, using the MAC address
of the port(s) for the link-local part of the address. The switch listens to router
advertisements to detect and autoconfigure the global part of the address.
• DHCPv6—Select to enable the switch to obtain its IPv6 address(es) from a
DHCPv6 server.
• IPv6 Gateway—Enter the link local address of the IPv6 router where the
switch should send IPv6 packets destined for a device outside the subnet.
STEP 3 Click Apply. Your changes are saved to the Running Configuration. You can click
Cancel to clear the changes.
Adding IPv6 Addresses
The IPv6 Address table lists static addresses currently configured on the switch. It
contains the following fields:
• IPv6 Address—IPv6 address in IPv6 global address format.
• DAD Status—The Duplicate Address Direction status. When you configure
an IPv6 address on the switch, before the switch actually assigns the
address, it performs neighbor discovery to detect if that address is already
in use on the network.
- If the address is already in use, its DAD status is True, and the address is
not usable for management access.
- If the address is found to be unique, its DAD status is False, and the
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 35
address can be used for management access.
Page 36

Administration
Management Interface
STEP 1 Click Add.
STEP 2 Enter an IPv6 address followed by a slash (/) and the prefix length.
STEP 3 Select EUI-64 if the address conforms to the EUI-64 format, whereby the first
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
4
You can configure multiple IPv6 addresses. Each address should have a different
prefix so that the switch can be managed from stations on different subnets. When
a route to one subnet fails, the switch can be managed from another subnet.
To add a static IPv6 address:
three to five octets are the Organizationally Unique Identifier (OUI) and the
remaining octets are a unique assigned address.
IPv6 Default Router Table
When IPv6 management is enabled, the switch uses the IPv6 neighbor discovery
process to identify the default router for communicating with devices outside the
local IPv6 subnet. The default router in IPv6 networks is similar in function to the
default router in IPv4 networks.
The IPv6 Default Router table lists the default router IP address for each IPv6
management address. A default router address consists of the link-local address
of the IPv6 interface on the subnet.
Viewing and Adding IPv6 Neighbors
When IPv6 management is enabled, the switch identifies IPv6-enabled devices on
attached links. The switch supports the discovery of up to 1,000 dynamic IPv6
neighbors and supports the static configuration of IPv6 neighbors.
The IPv6 Neighbors page lists dynamically discovered and statically configured
neighbors, and enables adding static hosts.
To view the IPv6 neighbor Table, click Administration > Management Interface >
IPv6 Neighbors in the navigation window.
The IPv6 Neighbor Table displays the following fields for each dynamic entry:
• IPv6 Address—IPv6 address of neighbor.
• MAC Address—MAC address of the neighbor.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 36
Page 37

Administration
Managing User Accounts
4
• State—State of the neighbor. The following are the states for dynamic
entries:
- Reachable—Confirmation was received within a preconfigured interval
that the forward path to the neighbor is functioning properly. While in the
Reachable state, the device takes no special action as packets are sent.
- Delay—More time has elapsed than a preconfigured interval since the
last confirmation was received that the forward path was functioning
properly.
• Age Updated—The time in seconds that has elapsed since an entry was
added to the cache.
• Type—Neighbor discovery cache information entry type (static or
dynamic).
You can click Clear Dynamic Neighbors to clear the table.
Adding Static IPv6 Neighbors
The switch supports up to 16 static IPv6 neighbor entries. To add a static
neighbor:
STEP 1 Click Add.
STEP 2 Enter an IPv6 global address (not including a prefix length).
STEP 3 Enter the MAC address of the neighbor.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Managing User Accounts
One management user is configured on the switch by default:
• User Name: cisco
• Password: cisco
You can use the User Accounts page configure up to five additional users and to
change a user password.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 37
Page 38

Administration
Managing User Accounts
STEP 1 Click Administration > User Accounts in the navigation window.
STEP 2 Click Add.
STEP 3 Enter a user name between 1 to 32 alphanumeric characters. Only numbers 0-9
STEP 4 Enter a password between 1 and 64 characters (depending upon the Password
4
Adding a User
To add a new user:
The User Account Table displays the currently configured users.
and letters a-z (upper or lower) are allowed for user names. Creating a username
default is not allowed.
Strength setting) and confirm the password. (The characters ', ", %, and ? are not
supported.)
As you enter a password, the number and color of vertical bars changes to
indicate the password strength, as follows:
• Red—The password fails to meet the minimum complexity requirements.
The text Below Minimum displays to the right of the meter.
• Orange—The password meets the minimum complexity requirements but
the password strength is weak. The text Weak displays to the right of the
meter.
• Green—The password is strong. The text Strong displays to the right of the
meter.
The Apply button will not be available until the strength meter is orange and the
password is confirmed.
When adding a user, you can temporarily disable the password strength check
feature to allow configuring a password that does not meet the strength check
criteria. Click Disable Password Strength Enforcement and then click OK when
the warning displays.
To disable the password strength check feature for all users, or to configure its
characteristics, use the Password Strength page.
STEP 5 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 38
Page 39

Administration
Enabling Management Services
Changing a User Password
To change a user password:
STEP 1 Click Administration > User Accounts in the navigation window.
STEP 2 Select the user to configure and click Edit.
STEP 3 Enter a password between 1 and 64 characters (depending upon the Password
Strength setting) and confirm the password. (The characters ', ", %, and ? are not
supported.)
As you enter a password, the number and color of vertical bars changes to
indicate the strength of your password. Red bars indicate a weaker password.
Orange bars indicate a stronger password, and green bars indicate the strongest
password level.
4
When changing a password, you can temporarily disable the password strength
check feature to allow configuring a password that does not meet the strength
check criteria. Click Disable Password Strength Enforcement and then click OK
when the warning displays.
To disable the password strength check feature for all users, or to configure its
characteristics, use the Password Strength page.
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Deleting a User
You can delete all users except the default user, typically the cisco user ID.
To delete a user, select the user name in the User Accounts Table and click Delete.
Enabling Management Services
Use the Management Services Page to configure the TCP port number for HTTP
connections to the web-based switch configuration utility.
The default port number for HTTP connections is the well-known IANA port
number 80. To configure a different HTTP port number:
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 39
Page 40

Administration
Configuring the Idle Session Timeout
STEP 1 Click Administration > Mgmt Services in the navigation window.
STEP 2 Enter the logical port number to use, from 1025 to 65535. The default is port 80.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
Configuring the Idle Session Timeout
The software automatically logs users off the management interface when there is
no activity for a specified period of time. The user must reauthenticate after a
timeout.
You can use the Idle Session Timeout page to configure the timeout period. To
display this page, click Administration > Idle Session Timeout in the navigation
window.
4
Login Sessions
The inactivity timeout for HTTP sessions can be from 1 to 60 minutes.The default
value is 10 minutes.
If you change the value, click Apply to save your change to the Running
Configuration.
The Login Sessions page displays active management login sessions. To display
this page, click Administration > Login Sessions in the navigation window.
The page lists the following information for each user currently logged in:
• ID—A system-generated ID for the login session.
• User Name—Name that the user used to log in.
• Connection From—IP address of the host.
• Idle Time—Time that has elapsed since the last activity from this user.
• Session Time—Amount of time that has elapsed since this user logged in.
• Session Type—Protocol in use for the management session (HTTP).
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 40
Page 41

Administration
Login History
Login History
4
You can use the Login History page to display data on previous logins to the
management software. To display this page, click Administration > Login History
in the navigation window.
This page displays the following fields:
• Login Time—Date and time the user logged in.
• User Name—Name that the user used to log in.
• Protocol—Protocol the user is using to the configuration software, which
can be HTTP, Telnet, Serial, SSH, or SNMP.
• Location—IP address of the host.
Time Settings
A system clock is used to provide a network-synchronized time-stamping service
for switch software events such as message logs. You can configure the system
clock manually or configure the switch as a Simple Network Time Protocol (SNTP)
client that obtains the clock data from a server.
See the following topics for information on the configuration pages available in the
Administration > Time Settings menu:
• Setting System Time
• Configuring the SNTP Setting
• Configuring SNTP Authentication
Setting System Time
Use the System Time page to set the system time manually or to configure the
system to acquire its time settings from an SNTP server. To display this page, click
Administration > Time Settings > System Time in the navigation window.
By default, the time is configured locally on the switch.
NOTE The actual system time, date, time zone information, and daylight savings time
status appears at the bottom of the page.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 41
Page 42

Administration
Time S et ting s
4
Specifying Clock Settings Locally
To configure the time settings locally:
STEP 1 On the System Time page, select Use Local Settings.
STEP 2 Select Timezone Source - DHCP if you want to have the switch to acquire its
timezone from a DHCP server.
STEP 3 Select Set Date/Time from Computer to have the switch retrieve the time
settings from the computer you are using to access the switch.
Or clear this field and configure the following time settings:
• Date—Enter the date in mm/dd/yyyy format, such as 01/01/2010 for
January 1, 2010.
• Local Time—Enter the current time in HH:mm:ss format, such as 22:00:00 for
10 p.m. (The hint text displays HH if the time is based on a 24-hour clock or
hh if the time is in 12-hour clock format.)
• GMT Time Zone Offset—Select the number of hours and minutes
difference between the local time zone and Greenwich Mean Time (GMT).
STEP 4 In the Time Zone Acronym field, specify an optional acronym up to four characters
to identify the configured settings. This field is for reference only. (The characters ',
", %, and ? are not supported.)
STEP 5 Select Daylight Saving to configure Daylight Savings Time (DST) settings, if
applicable to your time zone. When selected, configure the following fields:
• USA/European/Other—Select USA or European to have the DST offset
confi gured to the va lues use d in t hos e lo catio ns . Or s ele ct Other to configure
the settings manually. When configuring manually, you can configure the
settings for the upcoming DST period only, or you can configure recurring
settings.
• DST Time Zone Acronym—Specify an optional acronym up to four
characters to identify the configured settings. This field is for reference only.
(The characters ', ", %, and ? are not supported.)
• Daylight Savings Offset—Specify the number of minutes to move the clock
forward when DST begins.
• From/ To—Specify the date and time when DST starts and ends.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 42
Page 43

Administration
Time S et ting s
4
• Recurring—Select to specify recurring DST periods by selecting the day of
the week and number of weeks into the year when DST begins and ends
each year.
STEP 6 Click Apply. Your changes are saved to the Running Configuration.
Configuring the Switch as an SNTP Client
You can also configure the switch to acquire time from an SNTP server by
configuring the switch SNTP Settings.
To configure the switch to acquire time settings from an SNTP server:
STEP 1 On the System Time page, select Use SNTP Server.
STEP 2 Configure the SNTP client operation mode of the switch:
• Unicast—Configures the switch to send unicast SNTP requests to
configured unicast SNTP servers only. You must add at least one unicast
SNTP server to enable this feature.
• Broadcast—Configures the switch to get its time settings from SNTP
messages broadcast from SNTP servers.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
STEP 4 Use the Configuring the SNTP Setting and Configuring SNTP Authentication to
configure additional SNTP settings, such as polling intervals, unicast server
addresses, and authentication information the switch needs to access SNTP
servers.
Configuring the SNTP Setting
The switch supports the Simple Network Time Protocol (SNTP). SNTP ensures
accurate network device time synchronization up to the millisecond. Time
synchronization is performed by a network SNTP server. The switch operates as
an SNTP client only and cannot provide time services to other systems.
To display the SNTP Setting page, click Administration > Time Settings >
SNTP Setting in the navigation window.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 43
Page 44

Administration
Time S et ting s
4
Configuring the SNTP Setting
STEP 1 Ensure that the Use SNTP Server option is selected on the System Time page and
that the Unicast or Broadcast mode is selected as required.
STEP 2 On the SNTP Setting page, configure the following:
• Client Port—The logical port number to use for the SNTP client on the
switch. The default is the well-known IANA port number for this service, 123.
• Unicast Poll Interval—The relative rate at which the switch sends
synchronization messages to the SNTP server. This field is editable only
when SNTP Unicast reception is selected. Enter a value from 3 to 16. The
actual interval, in seconds, is the specified value to the power of 2; for
example, if you enter 4, the poll interval is 16 seconds.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
Viewing Active Server Properties and Global Parameters
The SNTP Setting page displays the following properties for the SNTP server, if
any, from which the switch most recently acquired its time settings. This page also
displays global (nonconfigurable) parameters.
Active Server:
• Server Host Address—IP address of the SNTP server.
• Server Type—IP protocol version the server uses (IPv4 or IPv6).
• Server Stratum—Hierarchical level of the SNTP server that identifies its
distance from a reference clock.
• Server Reference Id—32-bit code that identifies the reference clock that
this server uses.
• Server Mode—Mode in which the server is operating:
- Unicast—The SNTP server listens to unicast requests from SNTP
clients.
- Broadcast—The SNTP server sends broadcast messages periodically
to SNTP clients.
- Reserved—No reply has been received from an SNTP Server. When a
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 44
response is received from a server, it is overwritten with one of the valid
states (Broadcast or Unicast)
Page 45

Administration
Time S et ting s
4
Global Parameters:
• SNTP Client Version—The highest SNTP protocol version supported by the
switch.
• Last Update Time—The time of receipt of the most recent SNTP update.
• Last Unicast Attempt Time—The time of the most recent attempt by the
switch to synchronize with an SNTP unicast server.
• Client Mode—The configured SNTP client mode (Unicast or Broadcast).
See the Setting System Time to configure this mode.
• Server Maximum Entries—Maximum number of servers that you can
configure on the switch.
• Server Current Entries—Number of SNTP servers currently configured on
the system, as listed in the Unicast SNTP Servers Table.
• Broadcast Count—Number of SNTP broadcast packets that the switch has
received from SNTP servers.
Adding and Modifying SNTP Servers
The Unicast SNTP Servers Table displays the following information for each SNTP
server that you configure:
• SNTP Server—IP address or hostname of the SNTP server.
• Authentication Key ID—Encryption key required to communicate with the
SNTP server.
• Last Attempt Time—The time of the most recent attempt by the switch to
synchronize with an SNTP unicast server.
• Status—Operating status of the SNTP server. Possible values are:
- Success—Client could get the time from this server.
- Request timed-out—Client request timed out.
- Bad Date Encoded—A bad date format was received from server.
- Version Not Supported—Server does not support the SNTP version
configured on the switch.
- Server Unsynchronized—Switch time is not synchronized with the
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 45
server.
Page 46

Administration
Time S et ting s
4
- Server Kiss of Death—SNTP server has replied with a kiss of death
packet, instructing the switch to stop sending requests to the server, due
to traffic spikes or other error conditions.
- Other—The status could not be determined.
• Last Response—Time of the last response from the SNTP server.
• Version—SNTP protocol version the server uses.
• Port—Protocol port number (123 is a well-known port number for SNTP).
• Polling Mode—Whether the switch is configured to send SNTP requests to
this server (Enabled or Disabled).
• Tot al Un i ca s t R eq u es t s—The total number of synchronization requests the
switch has made to the unicast server.
To edit the settings for a server, check the box to select it, and then click Edit. To
remove a server, check the box to select it, and then click Delete. To add a new
server, click Add, and then enter the settings, as described below.
To add an SNTP server:
STEP 1 Click Add.
STEP 2 Enter the parameters:
• SNTP Server—Enter an IPv4 address or a domain name. To use a domain
name, ensure that the DNS service is enabled on the switch (see Domain
Name System).
• Authentication Key—Select Enable if authentication is needed when
communicating with the SNTP server.
• Authentication Key ID—If authentication is used, select the Authentication
Key ID from the list. See Configuring SNTP Authentication for information
on configuring authentication keys.
• Polling Mode—Select Enable to allow the switch to send requests to this
server.
• Port—Specify the UDP port number to be specified in the SNTP message
headers. By default, the port number is the well-known IANA value of 123.
• Version—Specify the highest SNTP version (1–4) that the server supports.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 46
Page 47

Administration
Time S et ting s
4
STEP 3 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Configuring SNTP Authentication
Use the SNTP Authentication page to configure encryption keys, which contain
the identifying information that the switch uses to authenticate to STNP servers.
You also use this page to enable the SNTP authentication service.
When you define SNTP servers that the switch can use, you specify whether a
server uses authentication and which authentication key it uses.
NOTE You must configure at least one trusted authentication key before you enable SNTP
authentication. Otherwise, the Failed to enable SNTP Authentication
message displays.
To configure an authentication key and enable this service:
STEP 1 Click Administration > Time Settings > SNTP Authentication in the navigation
window.
The SNTP Authentication Table displays each currently configured authentication
key and whether the key is currently enabled for use as a trusted key.
STEP 2 Select Enable to require the switch to authenticate to an SNTP server before
synchronizing its time.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
STEP 4 In the SNTP Authentication Table, click Add to add a key to the list.
STEP 5 Enter the parameters:
• Authentication Key ID—The key number. When you define an SNTP server
on the system, you specify which key it uses for authentication.
• Authentication Key—The value of the key. The value is the cryptographic
key that is used to encrypt and decrypt SNTP messages to and from the
server.
• Trusted Key—Indicates whether this key is a trusted key. Only trusted keys
are available for use. At least one trusted key must be configured to enable
the SNTP authentication service.
Keys are used with unicast SNTP servers only. A key is used to authenticate
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 47
Page 48

Administration
System Logs
STEP 6 Click Apply and then click Close. Your changes are saved to the Running
System Logs
4
an SNTP server only when the key is enabled as trusted. A keys that is
configured on the switch but specified as untrusted will not be used. An
administrator can add an untrusted key to have it available for use at another
time.
Configuration.
The switch generates messages in response to events, faults, errors, changes in
the configuration, and other occurrences. These messages are stored locally in
the system memory and are forwarded to one or more centralized points of
collection for monitoring or long-term archiving.
See the following topics for more information on the configuration pages available
in the Administration > System Log menu:
• Configuring Log Settings
• Configuring Remote Log Servers
Configuring Log Settings
Use the Log Settings page to enable logs globally, and to define which event
types are logged into temporary memory (RAM) and persistent memory (flash).
Log messages in flash memory are retained across a reboot. When the log is full,
the oldest events are automatically deleted and replaced with the new entries.
To configure log settings:
STEP 1 Click Administration > System Log > Log Settings in the navigation window.
STEP 2 Enable the types of logging to be performed on the system:
• Log Aggregation—When enabled, this feature combines multiple logs of the
same type into a single log message. If two or more identical log messages
are received consecutively within a configured time interval, then these
messages are aggregated into a single log message.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 48
Page 49

Administration
System Logs
4
• Log Aggregation Interval—If Log Aggregation is enabled, specify the
interval in seconds. Consecutive messages that are received within this
interval will be aggregated into a single log message. The range is 15
seconds to 120 seconds.
• RAM Memory Logging—Select to enable logging in RAM.
• Flash Memory Logging—Select to enable logging in flash memory.
• Flash Log Size—Enter the maximum number of log messages to store in the
flash memory log.
STEP 3 Enable the event severity levels to be logged for each log type. The severity levels
are listed from the highest to the lowest severity, as follows:
• Emergency—System is not usable.
• Alert—Action is needed.
• Critical—System is in a critical condition.
• Error—System is in error condition.
• Warning—System warning has occurred.
• Notice—System is functioning properly, but a system notice has occurred.
• Informational—Device information.
• Debug—Provides detailed information about an event.
NOTE: When you select a severity level, any events of that level or higher are
automatically selected for logging.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 49
Page 50

Administration
System Logs
4
Configuring Remote Log Servers
You can define one or more remote log servers that the switch sends Syslog
messages to. Use the Remote Log Servers page to define log servers and to set
the severity level of the log events to be sent to the server.
To enable Syslog operation and configure a remote log servers:
STEP 1 Click Administration > Remote Log Servers in the navigation window.
STEP 2 For the Syslog Logging mode, click Enable, and then configure the following
settings:
• Facility—Select a value from the list that identifies the classification of
syslog messages from this switch. The meaning of these values (Local 0
through Local 7) is determined by the network administrator.
• Local Port—Specify the IANA port number for the switch. The default is the
well-known port number for the Syslog protocol, 514.
STEP 3 In the Remote Log Server Table, click Add.
STEP 4 Enter the parameters:
• Log Server—IPv4 address or hostname of the server to send logs to.
• UDP Port—The logical UDP port number the remote server uses for the
Syslog protocol. The default value is the well-known IANA Syslog port
number, 514.
• Minimum Severity—Only items that meet or exceed this severity level are
sent to the remote server. See Configuring Log Settings for a description of
the severity levels.
STEP 5 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 50
Page 51

Administration
File Management
File Management
You can use the file management features to upgrade or backup the firmware,
update the language files, save configuration changes, copy configuration files
within the switch, and set up autoconfiguration feature.
NOTE When any download or upload to or from the switch is in progress, all management
access to the switch is blocked until the transfer is complete to protect the switch
from any unknown changes.
NOTE When logging in by using HTTP/HTML, and you can choose from more than one
network port, you should the lowest number port.
See the following topics for more information on the configuration pages available
in the File Management menu:
4
• Upgrading and Backing Up Firmware and Language Files
• Downloading and Backing Up the Configuration and Log Files
• Delete Configuration
• Copying and Saving Configuration Files
• DHCP Auto Configuration
• Firmware Recovery Over HTTP
Files and File Types
The following types of configuration and operational files are found on the switch:
• Running Configuration—Parameters that are currently used by the switch
to operate. It is the only file type that is modified by you when the parameter
values are changed by using one of the configuration interfaces, and must be
manually saved to another file type, such as the Startup Configuration, to be
preserved after a reboot.
If the switch is rebooted, the Running Configuration is lost. When the switch
is rebooted, the Startup Configuration stored in the Flash is copied to the
Running Configuration stored in RAM.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 51
Page 52

Administration
File Management
4
• Startup Configuration—The parameter values that were saved by you by
copying another configuration (usually the Running Configuration) to the
Startup Configuration.
The Startup Configuration is retained in Flash and is preserved any time the
switch is rebooted. When it is rebooted, the Startup Configuration is copied
to RAM and identified as the Running Configuration.
• Backup Configuration—A manual copy of the parameter definitions for
protection against system shutdown or for the maintenance of a specific
operating state. You can copy the Mirror Configuration, Startup
Configuration, or Running Configuration to a Backup Configuration file. The
Backup Configuration exists in Flash and is preserved if the device is
rebooted.
• Mirror Configuration—A copy of the Startup Configuration, created by the
switch after:
- The switch has been operating continuously for 24 hours.
- Configuration changes have been made to the Running Configuration in
the previous 24 hours, but have not been saved.
Only the switch can copy the Startup Configuration to the Mirror
Configuration. However, you can copy from the Mirror Configuration to other
file types or to another device.
• Firmware—The operating system. More commonly referred to as the
image.
• Boot Code—Controls the basic system startup and launches the firmware
image.
• Language File—The dictionary that allows the windows to be displayed in
the selected language.
• Flash Log—SYSLOG messages stored in Flash memory.
Upgrading and Backing Up Firmware and Language Files
You can use the Upgrade/Backup Firmware/Language page to:
• Upgrade the firmware by downloading a new image from a server.
• Upgrade the boot code by downloading a new boot file from a server.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 52
Page 53

Administration
File Management
4
• Update the language files by downloading a new file from a server.
Language files determine the language options for the web-based switch
configuration utility. You can select the display language when you log in.
• Back up the firmware image to a server.
English is always the default language.
NOTE You can also back up or restore the configuration files. See Downloading and
Backing Up the Configuration and Log Files for more information.
To upgrade or backup the firmware or to update the boot code or language file:
STEP 1 Click Administration > File Management > Upgrade/Backup Firmware/
Language in the navigation window.
STEP 2 Enter the parameters:
• Transfer Method—Select the protocol to be used for the file transfer (TFTP
or HTTP), which corresponds to the type of server you are downloading to
or uploading from.
• Save Action—Select Upgrade to download a file to the switch, or select
Backup to copy a file from the switch to the server.
• File Type—Select the type of file to upgrade or back up (you can back up
only the firmware image):
- Firmware Image—Software that controls all switch features and
interfaces.
- Boot Code—Software that controls the initial system bootup.
- Language Pack—The files that enable the system interface to display
the language specified by the user on the login page.
• TFTP Server (TFTP only)—Specify the IPv4 or IPv6 address of the TFTP
server.
• Source File Name—For upgrades via TFTP, enter the filename, including the
path. For upgrades via HTTP, browse and select the file from your computer.
• Destination File Name—For backups via TFTP, enter the filename, including
the path. This field does not appear for backups via HTTP.
STEP 3 Click Apply to begin the upgrade or backup. A progress bar indicates the status of
the file transfer. A typical image transfer might take 5-6 minutes to complete.
STEP 4 Reboot the switch to use the new configuration or firmware.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 53
Page 54

Administration
File Management
4
WARNING Ensure that power to the switch remains uninterrupted while downloading an image
or a boot code file to the switch. If a power failure occurs while downloading a file,
the file contents in persistent memory are lost.
If a power outage occurs during boot code file download, the switch will not be
able to boot. Contact the Cisco Small Business Support Center for assistance.
If a power outage occurs during image download, the image will not load, but the
boot loader will continue to be operational. See Firmware Recovery Over HTTP
for instructions on downloading a working image.
Downloading and Backing Up the Configuration and Log Files
You can use the Download/Backup Configuration/Log page to download a saved
configuration file to the switch to restore previously saved settings, or back up the
current configuration file to a network location. You also can use these pages to
back up log files.
• Downloading a Configuration File to Restore Settings
• Backing Up the Configuration File and Logs
Downloading a Configuration File to Restore Settings
To download a configuration file to the switch to restore a previously backed-up
file:
STEP 1 Click Administration > File Management > Download/Backup Configuration/
Log in the navigation window.
STEP 2 Select the Transfer Method (HTTP or TFTP).
STEP 3 For the Save Action, select Upgrade to download the file that you will specify
below.
STEP 4 Enter the following parameters:
• TFTP Server (TFTP only)—Specify the IPv4 or IPv6 address of the TFTP
server. Or specify the server name if DNS is enabled in the IP configuration
(see Domain Name System).
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 54
Page 55

Administration
!
File Management
4
• Source File Name—For TFTP, specify the filename, including the path. For
HTTP, browse to select the file from your computer.
• Destination File Type—Select one of the following options:
- Startup Configuration—If the specified configuration file is valid, then it
will replace the current Startup Configuration file. It will be the active
configuration file when you reboot.
- Backup Configuration—The specified file will replace the current
backup configuration file.
STEP 5 Click Apply to begin the upgrade. A progress bar indicates the status of the
upgrade.
CAUTION Ensure that power to the switch remains uninterrupted while the configuration file
is downloading to the switch. If a power failure occurs while downloading the
configuration file, the file is lost and the process must be restarted.
Backing Up the Configuration File and Logs
To back up the configuration file or log:
STEP 1 Click Administration > File Management > Download/Backup Configuration/
Log in the navigation window.
STEP 2 Select the Transfer Method (HTTP or TFTP).
STEP 3 For the Save Action, select Backup.
STEP 4 Enter the parameters:
• TFTP Server (TFTP only)—Specify the IP address of the TFTP server. Or
specify the server’s domain name if DNS is enabled in the IP configuration
(see Domain Name System).
• Destination File Name (TFTP only)—Specify a name for the saved file,
including the path on the TFTP server.
• Source File Type—Select the configuration file type:
- Running Configuration—The current configuration, including any
changes applied in the current management session.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 55
Page 56

Administration
File Management
4
- Startup Configuration—The configuration file saved to flash memory.
This file does not include any configuration changes applied in RAM but
not yet saved to the switch.
- Backup Configuration—An additional configuration file saved on the
switch for use as a backup. The administrator can copy the Backup
Configuration file to the Startup Configuration file type, then reboot the
switch to use the Backup Configuration file.
- Mirror Configuration—If the Running Configuration is not modified for at
least 24 hours, it is automatically saved to a Mirror Configuration file type,
and a log message with severity alert is generated to indicate that a new
mirror file is available. This feature allows the administrator to view the
previous version of the configuration before it is saved to the Startup
Configuration file type or to copy the Mirror Configuration file type to
another configuration file type. If the switch is rebooted, the Mirror
Configuration is reset to the factory default parameters.
- Flash Log—Log of events saved to flash memory.
- Operational Log—Log of events in RAM that are not saved to the Startup
Log.
- Startup Log—The first 32 messages logged when the switch is booted.
Subsequent messages are logged into the Operational Log. The Startup
Log is not aged out; it retains the messages until the switch is rebooted.
STEP 5 Click Apply.
For HTTP backups, you are prompted to browse to a location to save the file. A
progress bar indicates the status of the file transfer.
Delete Configuration
The Delete Configuration page enables you to delete the Startup configuration or
the Backup configuration. If you delete both the startup and the backup
configuration files, when the switch reboots it will use the default configuration file.
To delete the Startup or Backup Configuration file:
STEP 1 Click Administration > File Management > Delete Configuration in the navigation
window.
STEP 2 Select the Startup Configuration or Backup Configuration file type.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 56
Page 57

Administration
File Management
4
STEP 3 Click Apply.
Copying and Saving Configuration Files
The Copy/Save Configuration page enables you to copy files within the file
system. For example, you can copy the Backup Configuration file to the Startup
Configuration file so that it will be used the next time you boot up the switch.
To copy a file to the Startup or Backup Configuration file:
STEP 1 Click Administration > File Management > Copy/Save Configuration in the
navigation window.
STEP 2 Select the Source File Name:
• Running Configuration—Current configuration, including any changes
applied in the current management session.
• Startup Configuration—Configuration file type used when the switch last
booted. This does not include any configuration changes applied but not yet
saved to the switch.
• Backup Configuration—Backup configuration file type saved on the switch.
• Mirror Configuration—If the Running Configuration is not modified for at
least 24 hours, it is automatically saved to the Mirror Configuration file type,
and a log message with severity level Alert is generated to indicate that a
new Mirror Configuration file is available. The Mirror Configuration file can be
used when the switch has problems booting with the Startup or Backup
Configuration file types. In such cases, the administrator can copy the Mirror
Configuration to either the Startup or Backup Configuration file type and
reboot.
STEP 3 For the Destination File Name, select the file type to be overwritten with the file
you are copying:
• Startup Configuration—Configuration file type used when the switch last
booted. This does not include any configuration changes applied but not yet
saved to the switch.
• Backup Configuration—Backup configuration file type saved on the switch.
STEP 4 Click Apply to begin the copy process.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 57
Page 58

Administration
File Management
4
When complete, a window displays the message, Copy Operation Successful.
DHCP Auto Configuration
The switch supports Auto Configuration through DHCP to facilitate configuration
deployment and upgrades. This feature enables the configuration of a switch
automatically when no configuration file is found in device storage during the boot
process or when a newer configuration file is available for download.
NOTE The Auto Configuration feature depends upon the proper configuration of other
devices in the network, including a DHCP or BOOTP server, a TFTP server, and if
necessary, a DNS server.
Overview
During startup, the switch attempts communication with a DCHP server to obtain
its IP address and other information. If Auto Configuration is enabled, the switch
might also download a startup configuration file, depending on the TFTP server
and startup configuration file name it receives from the DHCP server. Auto
Configuration is enabled by default.
DHCP Auto Configuration initiates when the switch is rebooted with Auto
Configuration enabled, and any of the following conditions occur:
1. Information on the TFTP server and Startup Configuration is received from the
DHCP server, and Auto Configuration has not previously downloaded the
configuration file.
2. Information on the TFTP server and Startup Configuration is received from the
DHCP server, and the configuration file name differs from the file name
advertised in a previous DHCP message.
3. The Startup Configuration file is not present and no information on the TFTP
server or Startup Configuration is received from the DHCP server.
When conditions 1 and 2 occur, the switch saves the file to flash memory. Upon
subsequent startups, it compares the stored file name to the name specified in
option 66/67 in the current DHCP message. If they differ, the new file is
downloaded and written to flash memory.
NOTE When the system boots up for the first time, the switch does not have a specific
name for the configuration file received from the DHCP server, as it has not
downloaded a Startup Configuration file yet. If these options are received in the
DHCP message, then that file name is saved and the download process begins.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 58
Page 59

Administration
File Management
4
When option 3 occurs, the switch looks for the TFTP server and Startup
Configuration file as described in Default Network Configuration File.
DHCP Server Message Details
Any of the following fields might be returned by a BOOTP or DHCP server and
processed by the switch:
• The name of the configuration file (bootfile or option 67) to be downloaded
from the TFTP server.
• The identification of the TFTP server from which to obtain the bootfile.
The TFTP server IP address can be deduced from the multiple sources in a
DHCP reply. The switch makes its selection based on the following criteria,
from the highest priority to the lowest:
1. The sname field in a DHCP or BOOTP reply.
2. The TFTP server name (option 66) field in a DHCP reply.
3. The TFTP server address (option 150) field in a DHCP reply.
4. The siaddr field of a DHCP or BOOTP reply.
If only the sname or option 66 values are returned to the switch, a DNS
server is needed to resolve the IP address of the TFTP server. After an IP
address is assigned to the switch, if a hostname is not already assigned,
Auto Configuration sends a DNS request for the corresponding hostname.
Alternate TFTP Server and File Name
On the DHCP Auto Configuration page, you can configure an alternate TFTP
server and configure file name to be used when the server or file name provided
by the DHCP server cannot be located. The following procedure is followed:
1. The switch sends unicast messages to the TFTP server identified through
DHCP, if provided.
2. If the DHCP information is not provided or the server or file name cannot be
found, then the server uses the alternate information, if configured.
3. If the alternate information is not configured or the server or file name cannot be
found, then the switch sends broadcast messages to the TFTP server identified
through DHCP.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 59
Page 60

Administration
File Management
4
Configuration File Download Details
The switch will attempt to download a host-specific configuration file first. If not
possible, it will download configuration file <hostname>.cfg if Default Network
Configuration Mode is enabled.
Host-specific Configuration File
The switch attempts to download the host specific configuration file whose name
is specified as the bootfile name in the reply from a DHCP/BOOTP server, or is
configured as the Backup Configuration File for DHCP Auto Configuration. The
switch makes three unicast TFTP requests for the specified bootfile. If the unicast
attempts fail, or if a TFTP server address was not provided, the switch makes
three broadcast requests to any available TFTP server for the specified bootfile.
When the switch gets the configuration file, the configuration is validated for
errors. If the validation is successful, the switch copies the configuration to the
Startup Configuration file type, stores the configuration file name in non-volatile
memory, and reboots the unit.
NOTE The switch requires the bootfile name to be *.cfg.
Default Network Configuration File
If Default Network Configuration Mode is enabled, the switch will download the
configuration file <hostname>.cfg when any one of the following conditions
occurs:
• A host specific configuration file is not specified or configured.
• A host specific configuration file does not exist on the TFTP server.
• A failure occurs during the download.
To resolve the hostname in the configuration file, the switch first downloads
fp-net.cfg from the TFTP server. The fp-net.cfg file is referred as the default
network configuration file and contains one or more IP-address-to-host-name
mappings. The switch determines the hostname from the mappings with its IP
address. If there is no mapping, the switch uses reverse DNS lookup to discover
the hostname.
The following is a sample fp-net.cfg file.
config
...
ip host switch_to_setup 192.168.1.10
ip host another_switch 192.168.1.11
... <other hostname definitions>
exit
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 60
Page 61

Administration
File Management
4
When a hostname has been determined, the switch issues a TFTP request for a file
named "<hostname>.cfg", where <hostname> is the first eight characters of the
switch hostname.
The switch uses the IP address to do a DNS reverse name lookup. For example, if
the switch IP address is 192.168.1.10, the hostname becomes switch_t.cfg (the
first eight characters in the example above).
The default switch name is derived as switch+last 6 digits of hex address. The
mapping file should have the hostnames such as ip host switchD99FA5
192.168.1.10. Then, the hostname learned for the <hostname.cfg> is
switchD9.cfg for the switch having the IP address 192.168.1.10.
If the switch is unable to map its IP address to a hostname, Auto Configuration
sends TFTP requests for the default configuration file host.cfg.
When the switch gets the default configuration file, the configuration is validated
for errors. If the validation is successful, then the switch copies the configuration to
the Startup Configuration file type and reboots. In this case, the default
configuration file name is not stored in the non-volatile memory.
NOTE If the switch is unable to get the valid configuration file, then the process described
above is repeated every 20 minutes until the switch gets a valid configuration file.
The administrator can create a Startup Configuration file by manually saving the
Running Configuration. The administrator can also disable Auto Configuration if
desired.
The following table summarizes the configuration files that can be downloaded,
and the order in which they are sought.
Order
Sought
1 <bootfile>.cfg Host-specific configuration file,
2 fp-net.cfg Default network configuration file No
3 <hostname>.cfg Host-specific configuration file,
4 host.cfg Default configuration file Yes
File Name Description Final File
Sought
Ye s
ending in a *.cfg file extension
associated with hostname
1
Ye s
1. This file name might be learned through DHCP or manually configured, as described in
Alternate TFTP Server and File Name.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 61
Page 62

Administration
File Management
4
An operator can terminate Auto Configuration at any time prior to the downloading
of the file. This should be done when the switch is disconnected from the network,
or if the required configuration files have not been set up on TFTP servers.
When a configuration file is successfully downloaded and saved to the Startup
Configuration file type, the switch logs a message with severity level Alert prior to
rebooting.
Setting DHCP Auto Configuration
You can use the DHCP Auto Configuration page to enable and disable the feature,
configure TFTP server and file name settings, and view status information.
When DHCP Auto Configuration is enabled, it will be in the Waiting for boot
options state, until it receives the notification from the DHCP client. The DHCP
client triggers the Auto Install process when it receives the IP address from the
DHCP server, after which the status changes to Processing DHCP/BOOTP
options, checking preconditions.
The following additional messages might display:
• Waiting for boot options
• Processing DHCP/BOOTP options, checking preconditions
• Downloading tftp://<tftp address>/<filename>
• Applying downloaded configuration
• Waiting for restart timeout
• Saving the downloaded configuration
• Stopped
• AutoInstall is completed.
• AutoInstall process is terminated:File <filename> validation failed.
• AutoInstall process is terminated:Failed to save the downloaded
configuration file<bootfile> to start-up config.
• AutoInstall process is terminated:Startup config is created manually.
• AutoInstall process is terminated :Boot file matched with the last
downloaded file.
• AutoInstall process is terminated:Failed to resolve the boot file name.
To configure DHCP Auto Configuration:
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 62
Page 63

Administration
File Management
4
STEP 1 Click Administration > File Management > DHCP Auto Configuration in the
navigation window.
STEP 2 Enter the parameters:
• Auto Configuration Via DHCP—Select Enable to enable this feature on the
switch.
• Default Network Config Mode—Select Enable to have the switch
download a default configuration file named fp-net.cfg when no hostspecific file is found on the switch. See Default Network Configuration File
for details.
• Alternate TFTP Server—Specify the IP address of a TFTP server to serve
as a backup. An alternate TFTP server is used when unicast requests to the
TFTP server specified in option 66 fails three times. (The length of the string
cannot exceed 96 characters.)
• Alternate Configuration File—Specify an alternate configuration file name
to serve as a backup. If no startup configuration file identified in DHCP option
67, or if the specified file cannot be found on the TFTP server, Auto
Configuration looks for the alternate file name. (The length of the string
cannot exceed 32 characters.)
• Last Auto Configuration File Name—The configuration file name used the
last time the Auto Configuration process executed. If a different file name is
identified through DHCP, the file download process will begin.
• Current Status—The status of the Auto Configuration process. Possible
values are AutoInstall Complete or In Progress.
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 63
Page 64

Administration
File Management
4
Firmware Recovery Over HTTP
The switch has a firmware recovery feature that enables the restoration of a valid
image on the switch after a failed download. If the power goes down during an
image download, the switch might not be able to boot. In this event, although the
image is not usable, the boot loader file that loads the firmware image from Flash
memory to RAM should continue to be functional. An HTTP server is embedded in
the boot loader file, enabling the administrator to connect to the switch over a
switch port and use a web browser to download and install a new firmware image.
The switch enters the HTTP firmware recovery mode when the switch is booted
and the boot loader cannot find a valid image in flash memory. In this mode, the
boot loader sets the switch’s internal network port to the following static IP
address:
• IP Address: 192.168.1.254
• Network Mask: 255.255.255.0
• Default Gateway: 192.168.1.1
An HTTP server starts and listens for client connections on port 80.
To use this feature to download a new firmware image:
STEP 1 Directly connect a management PC to any switch port.
STEP 2 Configure the IP address and mask on the management PC to be in the same
subnet as the switch.
NOTE: You can access the system across a network if the default gateway IP
address is 192.168.1.1.
STEP 3 Open a web browser and enter the IP address of the switch in the address bar
(192.168.1.254).
NOTE: The HTTP firmware recovery features supports the following browsers:
• Firefox 3.0 and later versions
• Internet Explorer 6 and later versions
A Firmware Recovery page displays. No authentication is required.
The web page displays the PIC VID (product ID and vendor ID), serial number, and
MAC Address of the switch.
STEP 4 Select Browse and select a valid firmware image to download.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 64
Page 65

Administration
Rebooting the Switch
4
A progress bar appears while the file is downloading.
The file selected by administrator is downloaded to RAM and is validated for
following conditions:
• The CRC of the file is good.
• The STK file is built for this platform.
• The STK file size is within the partition limits (4.5 MB is reserved for this file).
If these conditions are met, the file is written to Flash memory and the system is
rebooted using the new firmware.
If any of these checks fail, the image is not written to Flash memory and the
recovery process is stopped. You can restart the recovery process with a correct
image file.
If the transfer is aborted because the browser window is refreshed or closed, the
session is cleared and the session times out immediately. If the transfer is aborted
because the network is unreachable, the session times out after 45 seconds. After
the session times out, you can begin the recovery process again.
Rebooting the Switch
Use the Reboot page reboot the switch. To reboot the switch:
STEP 1 Click Administration > Reboot in the navigation window.
STEP 2 Select one of the following options:
• Reboot—Reboots the switch using the latest save configuration.
• Reboot to Factory Default—Reboots the switch using with the factory
default configuration file. Any customized settings are lost.
A window appears to enable you to confirm or cancel the reboot. The current
management session might be terminated.
STEP 3 Confirm or cancel the reboot.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 65
Page 66

Administration
Pinging Hosts
Pinging Hosts
STEP 1 Click Administration > Ping in the navigation window.
STEP 2 Select IPv4 or IPv6 as the Address Type.
STEP 3 For an IPv4 address, enter the following parameters:
4
Use the Ping page to send a Ping request from the switch to a specified IP
address. You can use this feature to check whether the switch can communicate
with a particular network host.
To ping a network host:
• IP Address/Hostname—Enter the IP address or the hostname of the station
you want the switch to ping.
• Count—Specify the number of pings to send.
• Interval—Specify the number of seconds between pings sent.
• Datagram Size—Specify the data size of the ping packet to send.
For an IPv6 address, enter the following parameters:
• Ping Type—Select Global to ping an address outside the local subnet.
Select Link Local to ping an address on the local subnet.
• IPv6 Address/Hostname—(Global addresses only) Enter the 128-bit global
address.
• IPv6 Link-Local Address—(Link-local addresses only) Enter the link local
address if the address is on the same subnet as the switch.
• Datagram Size—Specify the data size of the ping packet to send (between
48 and 2048 bytes).
STEP 4 Click Apply to send the ping. You can view the status in the Ping window.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 66
Page 67

Administration
Configuring Control Packet Forwarding
Configuring Control Packet Forwarding
You can use the Control Packet Forwarding page to configure how the switch
handles packets of the following protocol types:
• CDP-The Cisco Discovery Protocol (CDP), which is supported on many
types of Cisco networking equipment. CDP enables directly connected
devices to share information such as their IP addresses, capabilities, and
software versions. Although the switch does not itself support CDP, by
default it forwards CDP packets on behalf of connected devices within a
VLAN.
• Dot1X-The IEEE 802.1X protocol defines how Extensible Authentication
Protocol (EAP) packets are encapsulated over a LAN. Dot1X provides a way
to authenticate users and allow or deny them access to services made
available by switch ports. See 802.1X for information on configuring the
Dot1X feature on the switch.
4
• LLDP-Network devices use the Link Layer Discovery Protocol to advertise
their capabilities to other devices. See LLDP-MED for information on
configuring the LLDP feature on the switch.
To configure control packet forwarding:
STEP 1 Click Administration > Control Packet Forwarding in the navigation window.
STEP 2 Select the protocol you want to configure (CDP, LLDP, or DOT1x).
STEP 3 Select the action that a port will take when received packets of the specified type:
• Drop—All packets of the selected type are dropped.
• Forward—All packets of the selected type are forwarded within the
specified VLAN.
• Te rm i nat e—The packet is accepted and processed on the switch. This
option is not available for CDP packets.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 67
Page 68

Administration
Diagnostics
Diagnostics
4
You can use the diagnostics pages to perform virtual cable tests for copper and
fiber optics cables, set up a diagnostic monitor for a port or VLAN, and to view
CPU utilization data.
See the following topics for more information on the configuration pages available
in the Administration > Diagnostics menu:
• Testing Copper Ports
• Configuring Port Mirroring
• CPU/Memory Utilization
Testing Copper Ports
Use the Copper Ports page to perform tests on copper cables. These physical
layer diagnostics can be used to help determine where in the cable a break might
exist.
The Copper Ports Table lists each port and the following data, which it learned
through the most recent test (default data appears if the port has not been tested):
• Test Result—Results of the most recent cable test. Possible values are:
- Normal—Cable is working correctly.
- Open—Cable is disconnected or the connector is faulty.
- Short—Cable has an electrical short.
- Untested—No test has been performed.
- Cable status test failed—Cable status could not be determined by the
test. The cable might be working.
• Distance to Fault—Distance in meters from the port where the cable error,
if any, was detected in the most recent cable test.
• Last Update—Last time the port was tested.
• Cable Length—Length of the cable in meters.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 68
Page 69

Administration
Diagnostics
4
To initiate a copper port test:
STEP 1 Click Administration > Diagnostics > Copper Ports in the navigation window.
STEP 2 Select a port and click Te s t .
If the port has an active link while a cable test is run, the link might go down for the
duration of the test. It might take several seconds to run the test. When complete, a
window appears with the test results.
Configuring Port Mirroring
Use the port mirroring feature to send network traffic on a port copied to another
port for analysis by a network analyzer.
A mirroring session consists of a destination probe port and at least one source
port. A mirror copy of the traffic on the source port(s) being probed are
transmitted from the source port to the destination probe port. A network analyzer
can be connected to a destination probe port to analyze network traffic.
A port configured as a destination probe port acts as a mirroring port as long as
the session is operationally active. When the session is not active, the port
transmits and receives traffic based on the other configuration parameters.
NOTE When a port is configured as a probe port, the switch does not forward or receive
any traffic or respond to a ping.
To display the Port Mirroring page, click Administration > Diagnostics > Port
Mirroring in the navigation window.
Four mirroring sessions are available for configuration and are disabled by default.
The Port Mirroring Session Table displays the following fields for each session:
• Session ID—A monitoring session ID number.
• Admin Mode—Indicates whether the port mirroring session is enabled or
disabled.
• Destination Interface— To enable this feature, select it and choose the
port to where the traffic on the source port is mirrored to the destination
probe port.
• Source Interface—List of the source interfaces selected to participate in
this mirroring session.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 69
Page 70

Administration
!
Diagnostics
4
The Port Mirroring Source Interface Table lists the source interfaces assigned to
each session. You can select Filter and select a Session ID to display data for only
one session.
To set up port mirroring, you first assign source interfaces to a session. Then, you
define a destination port and enable the session.
To configure a mirroring session:
STEP 1 In the Port Mirroring Source Interface Table, click Add.
STEP 2 Select a Session ID.
STEP 3 Select the Source Interface and the type of traffic to be mirrored.
STEP 4 By using the Type radio button, specify the direction of the traffic at the source
interface that is to be monitored:
• Rx Only—Incoming traffic
• Tx Only—Outgoing traffic
• Tx and Rx—Both incoming and outgoing traffic
STEP 5 Click Apply. Your changes are saved to the Running Configuration.
You can repeat the process to assign multiple Source Interfaces to the same
session. However, a source interface can be used in only one active session at a
time.
STEP 6 In the Port Mirroring Session Table, select the session to activate and click Edit.
STEP 7 For the Admin Mode, select Enable.
STEP 8 For the Destination Interface, select Enable and select a Destination Interface to
mirror the data.
STEP 9 Select Reset Session to clear any configuration applied to that session.
CAUTION When a port is configured as a destination probe port, the switch does not forward
or receive any traffic on that port and it does not respond to any pings received on
that port. All the previous configuration parameters on that port are cleared and the
port must be reconfigured when mirroring is removed from the port configuration.
STEP 10 Click Apply and then click Close. The probe session begins.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 70
Page 71

Administration
Diagnostics
4
NOTE To end a probe session, select the session in the Port Mirroring Session Table and
click Edit. Clear the Admin Mode checkbox, click Apply, and then click Close.
CPU/Memory Utilization
Use the CPU/Memory Utilization page to monitor CPU and memory usage. To
display this page, click Administration > Diagnostics > CPU/Memory Utilization
in the navigation window.
The page displays the following data:
• Refresh Rate—Specify that the page refresh with the latest data every 15,
30, or 60 seconds, or leave the default as No Refresh.
• CPU Utilization Report—The utilization percentage for 5 second, 1 minute,
and 5 minute intervals.
• Memory Utilization Report—The following data is reported:
- Allocated Memory—Amount of memory available to the operating
system (OS).
- Free Memory—Amount of memory available to the OS that is currently
free.
- Tot a l M em o r y—Total system memory, which includes the Allocated
Memory, plus free memory, plus memory reserved for use by code and
data sections of the software image.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 71
Page 72

Administration
Enabling Bonjour
Enabling Bonjour
Bonjour enables the switch and its services to be discovered by using multicast
DNS (mDNS). Bonjour advertises switch services to the network and answers
queries for service types it supports, simplifying network configuration in small
business environments.
The switch advertises the following service types:
When a Bonjour-enabled switch is attached to a network, any Bonjour client can
discover and get access to the management interface without prior configuration.
4
• Cisco-specific device description (csco-sb)—This service enables clients
to discover Cisco switches and other products deployed in small business
networks.
• Management user interfaces—This service identifies the management
interfaces available on the switch (HTTP).
A system administrator can use an installed Internet Explorer plug-in to discover
the switch. The web-based switch configuration utility shows up as a tab in the
browser.
Bonjour works in both IPv4 and IPv6 networks.
To enable the switch to be discovered through Bonjour:
STEP 1 Click Administration > Discovery - Bonjour in the navigation window.
STEP 2 Select Enable.
STEP 3 Click Apply.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 72
Page 73

Administration
LLDP-MED
LLDP-MED
4
The IEEE 802.1AB standard, Link Layer Discovery Protocol (LLDP), describes a
method by which stations residing on a LAN advertise identification information,
capabilities, and physical descriptions. The information is exchanged in LLDP data
units (LLDPDUs) which comprise type-length-value (TLV) structures. Various TLVs
might be included in LLDPDUs, depending on the information that the
administrator configures the port to advertise.
Information learned through LLDPDUs is stored in MIBs, and the information might
be accessible by a network management system (NMS) such as SNMP. This
framework is extensible and allows advanced utilization in areas such as VoIP
networks.
NOTE LLDPDUs only communicate information; they do not automatically configure the
switch.
The switch supports the LLDP Media Endpoint Discovery (LLDP-MED) extensions
to the LLDP protocol. LLDP-MED enables auto-discovery of LAN policies, device
location, and other device characteristics, and automates management of Powerover-Ethernet (PoE) endpoints.
See the following topics for more information on the configuration pages available
in the Administration > Discovery - LLDP menu:
• Configuring Global LLDP-MED Properties
• Configuring LLDP-MED on a Port
• LLDP-MED Port Status Details
• LLDP-MED Neighbor Information
Configuring Global LLDP-MED Properties
Use the LLDP MED Properties page to specify global parameters for this feature.
To configure global LLDP-MED properties:
STEP 1 Click Administration > Discovery - LLDP-MED > Properties in the navigation
window.
STEP 2 For Asset ID, enter the asset ID for the switch, advertised in Inventory TLVs.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 73
Page 74

Administration
LLDP-MED
4
STEP 3 Specify the Location Parameters to identify the physical location of the switch for
emergency calls:
• Subtype—Select one of the following options to configure how the switch
location is identified in TLVs:
- Coordinate Based—Switch location is identified using GPS coordinates
in hexadecimal format.
- Civic Address—Switch location is identified using a geographic
description of the location, such as city, street name, and building name.
The characters ', ", %, and ? are not supported.
- ELIN—Switch location is identified using the Emergency Location
Identification Number (ELIN) of the switch.
• Coordinates—Switch GPS coordinates in hexadecimal format.
• ELIN Address—The ELIN number.
• Country—Country where the city is located.
• City—City where the street is located.
• Street—Street where the building is located.
• Building—Building in which the switch is located.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Configuring LLDP-MED on a Port
The LLDP for Media Endpoint Devices (LLDP-MED) protocol provides extensions
to the LLDP standard for network configuration and policy, device location, Powerover-Ethernet management, and inventory management.
Use the LLDP MED Port Settings page to view and configure LLDP-MED
operation on ports.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 74
Page 75

Administration
LLDP-MED
4
To configure these settings on a port:
STEP 1 Click Administration > Discovery - LLDP-MED > LLDP MED Port Settings in the
navigation window.
Each entry in the LLDP MED Port Settings Table displays the LLDP-MED
configuration for a port.
STEP 2 Select a port to configure and click Edit.
STEP 3 Specify the following for the selected port:
• LLDP MED Status—Select to enabled LLDP-MED operation on the port.
• Configuration Notification—Select to enable the switch to send
notifications when there are topology changes on the network.
STEP 4 Select the Available TLVs that you want the port to include in LLDP
advertisements:
• Network Policy—VLAN ID, the 802.1p class-of-service value, and the
Differentiated Services Code Point (DSCP) value. This information is used to
implement the Voice VLAN feature (see Voice and Media).
• Location—Hexadecimal GPS location coordinates for the switch.
• PSE—Indicates whether the port advertises itself as Power Sourcing
Equipment capable of providing power to a connected Power-over Ethernet
device. This option appears only on SG200-08p devices.
• PD—Indicates whether the port advertises itself as a Powered Device,
capable of receiving Power-over-Ethernet. This option can be selected only
for port g1 of SG200-08 devices.
• Inventory—Hardware and software version information.
• System Capabilities—Identifies the basic functionality of the switch such as
bridging.
STEP 5 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
NOTE You can click Configure Network Policy to display the Media VLAN page. (You can
also click VLAN Management > Voice and Media > Media VLAN in the navigation
window.) This page enables you to assign LLDP-MED applications to VLANs and
configure priority settings for associated traffic.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 75
Page 76

Administration
LLDP-MED
4
LLDP-MED Port Status Details
The LLDP MED Port Status Details page displays the LLDP-MED configuration for
all ports on which the feature is enabled. To display this page, click
Administration > Discovery - LLDP-MED > LLDP MED Port Status Details in the
navigation window.
Select a port from the Port list. The Network Policies Table shows the fields for
each service or policy advertised through LLDP:
• Media Policy Application Type—Type of service, such as Voice,
associated with the LLDP network policy.
• VLAN ID—VLAN ID associated with the network policy.
• Priority—802.1p class-of-service value associated with the network policy.
• DSCP—DSCP value for the network policy.
• Tagged—Network policy is defined for tagged VLANs.
The following switch parameters are advertised in Inventory TLVs.
• Hardware Revision—Switch hardware revision ID.
• Firmware Revision—Switch firmware revision number.
• Software Revision—Switch software revision number.
• Serial Number—Switch serial number.
• Manufacturer Name—Switch manufacturer name.
• Model Name—Switch model name.
• Asset ID—LLDP-MED asset ID for the switch.
The following switch parameters are advertised in system TLVs.
• Chassis ID—The hardware address of the switch.
• Chassis ID Subtype—The type of hardware address.
• System Description—A preconfigured system description.
• System Name—The user-configured hostname (see the System Settings
page).
• Management Address SubType—The protocol version for the
management IP address.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 76
Page 77

Administration
LLDP-MED
4
• Management Address—The management port IP address (see the IPv4
Interface page or the IPv6 Interface page).
• Port ID SubType—The type of the port identifier.
• Port ID—The port identifier.
• Port Description—The port description.
• System Capabilities Enabled—The capabilities that are enabled on the
switch.
• System Capabilities Supported—The capabilities that are currently
advertised as supported by the switch.
The following switch parameters are advertised in location TLVs.
• Subtype—The supported type of location information (civic, ELIN, or
coordinate-based).
• Coordinates—Switch GPS coordinates in hexadecimal format, if
coordinate-based location information type is used.
• ELIN Address—The ELIN number, if this location information type is used.
• Country—Country where the city is located, if the civic location information
type is used.
• City—City where the street is located, if the civic location information type
is used.
• Street—Street where the building is located, if the civic location information
type is used.
• Building—Building in which the switch is located, if the civic location
information type is used.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 77
Page 78

Administration
LLDP-MED
4
LLDP-MED Neighbor Information
The Neighbor Information page displays information received from other LLDPMED-capable devices in the network. To display this page, click Administration >
Discovery - LLDP-MED > Neighbor Information in the navigation window.
The Neighbor Information Table displays the following fields for each LLDP
neighbor device for which an advertisement has been received:
• Local Port—Port number on the local device on which the LLDP
advertisement was received.
• Remote ID—Physical address of the port on the neighboring device.
• Device Class—Advertised class of the remote device.
You can select an entry and click Details to display additional information from the
LLDP-MED advertisement from the neighbor.
The Neighbor Information—Details page displays the following information:
MED Capabilities:
• Capabilities Supported—Advertised capabilities of the device.
• Capabilities Enabled—Advertised capabilities that are enabled on the
device.
• Device Class—Advertised class of the remote device.
Network Policies:
• Media Policy Application Type—Type of service, such as voice, associated
with the LLDP network policy.
• VLAN ID—VLAN ID associated with the network policy.
• Priority—802.1p class-of-service value associated with the network policy.
• DSCP—DSCP value for the network policy.
• Unknown—Neither the 802.1p value nor the DSCP value is configured for
this Network Policy.
• Tagged—network policy is defined for tagged VLANs.
Inventory:
• Hardware Revision—Switch hardware revision ID.
• Firmware Revision—Switch firmware revision number.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 78
Page 79

Administration
LLDP-MED
4
• Software Revision—Switch software revision number.
• Manufacturer Name—Switch manufacturer name.
• Model Name—Switch model name.
• Asset ID—LLDP-MED asset ID for the switch.
Location:
• Subtype—Select one of the following options to configure how the switch
location is identified in TLVs:
- Coordinate Based—Switch location is identified by using GPS
coordinates in hexadecimal format.
- Civic Address—Switch location is identified by using a geographic
description of the location, such as city, street name, and building name.
(The characters ', ", %, and ? are not supported.)
- ELIN—Switch location is identified by using the Emergency Location
Identification Number of the switch.
• Location Information—Switch location information, in the format specified
by the Subtype field.
Extended PoE:
• PoE Device Type—If PoE functionality is advertised, this field indicates
whether the device is a Powered Device (PD) or Power Sourcing Equipment
(PSE).
Extended PoE PD:
If the device is powered by PoE, the following properties can be advertised:
• PoE Power Value—Power in watts requested by the device.
• PoE Power Source—Indicates how the powered device receives power:
- Primary—A power supply is connected directly to the device.
- Backup—The device receives power from a PoE power sourcing
equipment.
• PoE Power Priority—Displays High, Low, or Critical to indicate how the
port is prioritized when there is less PoE power to deliver than requested by
all powered devices.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 79
Page 80

Administration
Configuring DHCP Client Vendor Options
Configuring DHCP Client Vendor Options
You can configure the DHCP client functionality on the switch to include vendor
information in its DHCP requests (DHCP option 60). A DHCP server might use
vendor information to differentiate between clients based on the identified
hardware type or functionality.
To configure DHCP vendor option string:
STEP 1 Click Administration > DHCP Options in the navigation window.
In addition to the vendor option and string, the page displays the format that the
switch uses when obtaining its timezone information from a DHCP server and
indicates whether such information has been received. To configure the switch to
acquire its timezone from DHCP, see Time Settings.
4
STEP 2 Select Enable for the Vendor Option.
STEP 3 Enter a value in the Vendor Option String text box.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 80
Page 81

Port Management
This chapter describes how to configure switch port settings, combine ports into
link aggregation groups, and configure port power features.
The following topics are included:
• Configuring Port Settings
• Link Aggregation
5
• Configuring PoE
• Green Ethernet
Configuring Port Settings
The Port Settings page enables you to administratively enable and disable ports
and to configure autonegotiation of port speed and duplex mode. You can also use
this page to configure flow control on the port.
To configure port settings:
STEP 1 Click Port Management > Port Settings in the navigation window.
STEP 2 Select the interface to configure, and then click Edit.
STEP 3 Specify the following for the selected port:
• Administrative Status—Select Up to enable the port or Down to disable it.
• Auto Negotiation—Select Enable to allow the switch autonegotiate the port
speed and duplex mode with the connected device. If Autonegotiation is
enabled, the Administrative Port Speed and Duplex Mode fields are not
editable.
• Administrative Port Speed—If Auto Negotiation is disabled, select whether
the port is capable of 10 Mbit/s or 100 Mbit/s operation.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 81
Page 82

Port Management
Link Aggregation
5
• Administrative Duplex Mode—If Auto Negotiation is disabled, select Half
for half-duplex or Full for full-duplex operation.
• Admin Advertisement—If Autonegotiation is enabled, select the highest
port speed and duplex setting that you want the port to negotiate. If you
select Max Capacity, the port autonegotiates up to the highest port speed
and duplex setting supported by hardware.
• Flow Control—Select to enable IEEE 802.3x flow control. Flow control helps
to prevent data loss when the port cannot keep up with the amount of frames
being switched. When enabled, the switch can send a PAUSE frame to stop
traffic on a port if the amount of memory used by packets on the port
exceeds a preconfigured threshold. The paused port does not forward
packets for the period of time specified in the PAUSE frame. When the
PAUSE frame time elapses or the utilization returns to a specified low
threshold, the switch enables the port to again transmit frames.
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Link Aggregation
Link Aggregation allows one or more full-duplex Ethernet links to be aggregated
together to form a Link Aggregation Group (LAG). The switch treats the LAG as if it
is a single physical port, with improved fault tolerance and load- sharing capability.
A LAG interface can be either static or dynamic:
• Member in LAG—Indicates whether the port is a member of a Link
Aggregation Group. See Link Aggregation for information on configuring
LAGs.
• MTU—Specify the maximum transmission unit size in bytes. The default
MTU is 1518 and the range is between 1518 and 9216 bytes.
• Static LAG—Ports are assigned to a LAG directly by the administrator. The
ports remain dedicated LAG members until configured otherwise.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 82
Page 83

Port Management
Link Aggregation
5
• Dynamic LAG—A dynamic LAG is configured with one or more candidate
ports. The LAG is formed by exchanging Link Aggregation Control Protocol
Data Units with the remote device connecting to the candidate ports. When
formed, the LAG might include only a subset of the eligible ports,
depending on the port number limitations for LAGs and other factors.
Candidate ports that are not selected as active member ports of a LAG are
standby ports. A standby port can be selected as an active member when
an active port in the same LAG fails.
The following topics provide additional information on the configuration pages
available in the Port Management > Link Aggregation menu:
• Configuring LAGs
• Configuring LAG Settings
• Configuring LACP Settings
Configuring LAGs
The switch supports up to 4 LAGs, with 8 ports per LAG. Use the LAG
Management page to assign ports to LAGs and LACPs.
To display this page, click Port Management > Link Aggregation > LAG
Management in the navigation window.
Four dynamic LAGs are preconfigured by default named ch1 through ch4. They
have no port members and are disabled.
You can add or remove ports to or from a LAG without disrupting traffic on the
LAG.
LAGs can be assigned membership in VLANs; however, individual ports lose their
individual VLAN memberships when they become LAG members. When a port is
removed from a LAG, it rejoins the VLANs that it previously belong to as specified
in the startup configuration.
To configure a LAG:
STEP 1 Select a LAG to configure, and then click Edit.
STEP 2 Specify the following for the selected LAG:
• LAG Name—Enter up to 15 alphanumeric characters to identify the LAG.
• Type—Select Static to manually assign ports to the LAG. Select Dynamic to
enable the ports to exchange LACPDUs to dynamically form the LAG.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 83
Page 84

Port Management
Link Aggregation
STEP 3 Click Apply and then click Close. Your changes are saved to the Running
5
• Port List/LAG Member—To add or remove ports from a static LAG, select
each port and click the left or right arrow to move it between the Port and
LAG Member lists.
Configuration.
Configuring LAG Settings
You can use the LAG Settings page to administratively enable or disable a LAG
and configure load balancing settings.
To configure LAG settings:
STEP 1 Click Port Management > Link Aggregation > LAG Settings in the navigation
window.
The LAG Settings Table lists each available LAG.
STEP 2 Select a LAG to configure, and then click Edit.
STEP 3 Specify the following for the selected LAG:
• Administrative Status—Select Up or Down to administratively enable or
disable the LAG. When a LAG is disabled, its member ports operate as
standalone physical ports.
• Load Balance Algorithm—Select one of the options to enable the switch to
load-balance outgoing packets among member ports of a LAG. The switch
selects one of the links in the channel for transmitting specific packets. The
switch prioritizes each criteria for load balancing in the order listed in the
option. The options are:
- Src/Dest MAC, VLAN, EType, incoming port—Source and destination
MAC addresses, the VLAN membership, the Ethertype field, and the port
on which the packet was received.
- Src/Dest IP and TCP/UDP Port Fields—Src IP—Source and destination
IP address and the TCP or UDP port number in the IP packet.
If the IP packet option is selected, non-IP packets received on the port are
balanced using the Src and Dest MAC address.
• MTU—Specify the maximum transmission unit size in bytes. The default
MTU is 1518 and the range is between 1518 and 9216 bytes.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 84
Page 85

Port Management
Link Aggregation
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
STEP 1 Click Port Management > Link Aggregation > LACP in the navigation window.
5
Configuration.
Configuring LACP Settings
The switch uses the Link Aggregation Control Protocol (LACP) to automate the
formation of dynamic LAGs. LACP-enabled ports send protocol data units
(LACPDUs) to detect each other on a network and negotiate a LAG.
Use the LACP page to view and configure protocol operation.
To configure LACP settings on individual ports:
The LACP Interface Table displays the local (actor) and remote (partner) LACP
configuration for each port on the switch. The LACP actor settings include a the
System Priority for the switch and Admin Key that uniquely identifies the port in
LACP messages. These values are not configurable.
STEP 2 Select the port to configure and click Edit.
STEP 3 Configure the following settings for the selected port:
• Mode—Check the box to enable LACP on the port.
• Actor Timeout—Information from the actor is no longer valid after the
timeout period elapses.
- Short—Short LACP timeout is 3 times the short periodic timer to
transmit LACP packets. The default Short LACP timeout is 3 seconds.
- Long—Long LACP timeout is 3 times the long periodic timer to transmit
LACP packets. The default Long LACP timeout is 90 seconds.
• Partner Timeout—Information from the partner is no longer valid after the
timeout period elapses.
- Short—Short LACP timeout is 3 times the short periodic timer to
transmit LACP packets. The default Short LACP timeout is 3 seconds.
- Long—Long LACP timeout is 3 times the long periodic timer to transmit
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 85
LACP packets. The default Long LACP timeout is 90 seconds.
Page 86

Port Management
Configuring PoE
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Configuring PoE
On the SG200-08P, ports 1–4 can operate as a Power-over-Ethernet (PoE) PoE
Power Sourcing Equipment (PSE). A PSE can provide power to connected PoE
Powered Devices (PDs).
On SG200-08P switches, see the following topics for information on the
configuration pages available in the Port Management > PoE menu:
5
• Configuring PoE Properties
• Configuring PoE Port Settings
NOTE These configuration pages do not display on switches that do not support PSE
functionality.
Configuring PoE Properties
You can use the Properties page to configure whether the switch generates trap
messages under certain conditions and to view current power settings.
To configure PoE properties:
STEP 1 Click Port Management > PoE > Properties in the navigating window.
STEP 2 Set the following parameters:
• Power Trap Threshold—Specify a percentage of total available system
power. When the requested power on PoE ports exceeds the threshold, a
trap is generated to the log.
• Power Management Mode—Select how the switch prioritizes the power
that it provides to multiple ports:
- Static with Port Priority—Static with priority power management. This
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 86
algorithm pre-allocates power based on the configured power limit and
the priority of the port.
Page 87

Port Management
Configuring PoE
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
5
- Dynamic with Port Priority—Dynamic with priority power
management. This algorithm supplies power to devices as long as the
consumption is within the configured limit and priority. There is no preallocation of power.
In both modes, a port with a higher port priority is given preference when the
switch supplies power to multiple ports. If two or more port priorities are
equal, the port with the lower port number is given preference.
• Reset Mode—Select Enable to enable the switch initialize all PoE ports state
machines.
NOTE This page displays the following data for PoE power on the switch:
• Power: The current power status. If On, the switch is currently providing
power through PoE to a connected device. If Off, the switch is not providing
power through PoE to any connected devices.
• Maximum Available Power—The total power in watts that the switch is
capable of making available to all PoE-capable ports.
• Threshold Power—The cutoff power value above which no additional PDs
are powered. This threshold is calculated based on the Power Trap
Threshold setting.
• Allocated Power—The total power in watts that the switch is actually
providing to PoE ports.
Configuring PoE Port Settings
You can use the Port Settings page to view and configure settings for ports acting
as PSEs.
To configure PoE settings for a port:
STEP 1 Click Port Management > PoE > Port Settings in the navigation window.
The PoE Setting Table displays which ports are enabled for PoE operation, their
priority, power allocation in milliwatts, and other settings for each port.
STEP 2 Select the port to configure and click Edit.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 87
Page 88

Port Management
Configuring PoE
STEP 3 Configure the following settings:
5
• PoE—Check the Enable box to configure the port as a PSE.
• Power Priority Level—Select Critical, High, or Low to configure the port
priority level, for the delivery of power to an attached device.
The switch might not be able to supply power to all connected devices that
request it. The port priority determines which ports supply power when
adequate power capacity is not available for all enabled ports. For ports that
have the same priority level, the lower-numbered port has higher priority. For
a system delivering peak power to a certain number of devices, if a new
device is attached on a high-priority port, power is shut down to a device on
a low-priority port, and the new device is powered up.
• Power Limit Type— Select one of the following methods to limit the power
that the switch provides to a connected device.
- Dot3AF—The maximum power that can be delivered by the port is
limited by the detected IEEE 802.3af class.
- User-defined—The maximum power that can be delivered by the port
is specified by the user. If you select this option, specify a value in the
Power Allocation field.
- LLDP-MED—The maximum power that can be delivered by the port is
limited by the value in LLDP-MED TLVs received from a port device. The
value specified by the device should be in the range of 3-16.2 watts. If it
is not in this range, then the default value of 16.2 watts is used.
Note: If the selected Power Limit Type is LLDP-MED, then the priority
setting from the remote device is not honored; instead the switch uses
the Power Priority Level setting configured for the port.
- Dot3AF and LLDP-MED—The maximum power that can be delivered
by the port is limited by the value in LLDP-MED TLVs received from a
port device. The value specified by the device should be in the range of
3-16.2 watts. If it is not in this range, then the maximum power is limited
by the IEEE 802.3AF class.
- User-Defined and LLDP-MED—The maximum power that can be
delivered by the port is limited by the value in LLDP-MED TLVs received
from a port device. The value specified by the device should be in the
range of 3-16.2 watts. If it is not in this range, then the maximum power is
limited by the value that you specify in the Power Allocation field.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 88
Page 89

Port Management
Configuring PoE
5
• Power Allocation—If you configured a user-defined option for Power Limit
Type, enter the power in milliwatts to be allocated to the port, between 3000
to 16200 milliwatts.
• Detection Type—Select one of the following methods to detect PoE-
powered devices connected to the ports.
- Legacy Only—Only capacitive signature devices are detected.
- 802.3af 4point Only—Only resistive signature devices are detected
with the first algorithm.
- 802.3af 4point and Legacy—Both capacitive and resistive signature
devices are detected by using the second algorithm.
- 802.3af 2point Only—Only resistive signature devices are detected
with the first algorithm.
- 802.3af 2point and Legacy—Both capacitive and resistive signature
devices are detected using the first algorithm.
• Reset Mode—Select Enable to enable the switch initialize the ports PoE
state machines.
The following statistics also appear:
• Power Consumption—Actual power consumption on the port.
• Overload Counter—Total number of power overload occurrences.
• Short Counter—Total number of power short condition (electrical shorts) on
a port.
• Denied Counter—Number of times the powered device was denied power.
• Absent Counter—Number of times the power supply was stopped to the
powered device because the powered device was no longer detected.
• Invalid Signature Counter—Number of times an invalid signature was
received. Signatures are the means by which the powered device identifies
itself to the PSE. A signature is generated during powered device detection,
classification, or maintenance.
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 89
Page 90

Port Management
Green Ethernet
Green Ethernet
5
On each gigabit Ethernet copper port the switch provides a Green Ethernet power
saving feature called Energy Detect Mode. It reduces chip power by forcing a port
PHY into a low-power mode when the signal from a copper link partner is not
present. (PHY is an abbreviation for the physical layer of the OSI model.)
When the Energy Detect is enabled and energy on the line is lost, the switch
automatically enters the low-power mode. It resumes normal operation when
energy is detected. When the port PHY is in low-power mode, the PHY wakes up
after a period of time, and sends link pulses to monitor for energy from the link
partner. If energy is detected while the port is in wake-up mode, the switch returns
the port to normal operation. When the wake-up period expires, the port returns to
low-power mode.
When Short Reach Auto is enabled, a cable test is performed when a link comes
up. If the length of the cable is less than 10 meters, the PHY can be put into lowpower mode so that only enough power is used to support a short cable. When
the link goes down, low-power mode is disabled.
The switch also supports Short Reach Force, where the port is administratively
forced into low-power mode.
Wnen enabled, the Green Ethernet features function whether the port has
autonegotiation enabled or disabled.
Configuring Green Ethernet Properties
Use the Green Ethernet Properties page to enable Green Ethernet functionality
globally. The global settings are applied to all ports.
NOTE You can override the global settings by configuring these features on individual
ports (see Configuring Green Ethernet Port Settings); however, changes that you
subsequently make to the global settings override any individual port configuration.
To configure global Green Ethernet properties:
STEP 1 Click Port Management > Green Ethernet > Properties in the navigation window.
By default, Energy Detect mode and Short Reach Auto mode are enabled globally
and on all ports.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 90
Page 91

Port Management
Green Ethernet
STEP 2 Configure the settings:
STEP 3 Click Apply. Your changes are saved to the Running Configuration.
5
• Energy Detect—Select Enable to enable the Energy Detect mode on the
switch. The switch automatically enters the low-power mode when energy
on the line is lost, and it resumes normal operation when energy is detected.
• Short Reach Auto—Select Enable to perform a cable test when the link
comes up on a Green Ethernet port. If a short cable is detected, the port is
put into low-power mode. When the link goes down, low-power mode is
disabled.
• Short Reach Force—Select Enable to administratively force all ports into
low-power mode by default. This setting can be overridden for individual
ports (see Configuring Green Ethernet Port Settings).
Configuring Green Ethernet Port Settings
Use the Green Ethernet Settings page to view and configure the Green Ethernet
settings on individual ports.
NOTE Green Ethernet port settings are overridden if the global settings are subsequently
changed (see Configuring Green Ethernet Properties).
To configure Green Ethernet port settings:
STEP 1 Click Port Management > Green Ethernet > Port Settings in the navigation
window.
The Green Ethernet Settings Table page displays the following information for
each port:
Energy Detect fields:
• Admin—Indicates whether Energy Detect is enabled on the port.
• Operational—Indicates whether Energy Detect mode is currently
operational (“Enabled”) on the port.
• Reason—Indicates why the operational status is enabled or disabled. The
following reason can display when the Energy Detect operational status is
Enabled.
- No Energy Detected—No energy is detected on the link.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 91
Page 92

Port Management
Green Ethernet
5
The following reasons might display when the Energy Detect operational
status is Disabled:
- Fiber—The administrative status might be active, but the port is
functioning in fiber mode. (Green Ethernet functionality applies only to
copper ports.)
- Link up—There is activity on the link.
- Admin Down—Energy detect mode is administratively disabled.
Short Reach fields:
• Auto—Indicates whether Short Reach mode is enabled administratively on
the port.
• Force—Indicates whether Short Reach Force mode is enabled on the port.
• Operational—Indicates whether Short Reach mode is operational (enabled)
on the port.
• Reason—Indicates why the Short Reach operational status is active or
inactive. The following reason might display when the Short Reach
operational status is enabled.
- Short Cable—The port has been detected as having Short Reach cables.
- Forced—Short Reach mode has been administratively forced on the
port.
The following reasons might display when the Short Reach operational
status is Disabled.
- Long Cable—The cable is greater than 10m.
- Link Down—The link is down.
- Fiber—Port is operating in fiber mode and is not eligible for Green
Ethernet operation.
- Admin Down—Short Reach is administratively disabled.
- Not at GIG speed—Port is not operating at 1G speed and therefore is
ineligible for Green Ethernet operation.
- Cable length Unknown—Cable length could not be determined.
STEP 2 Select the port to configure and click Edit.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 92
Page 93

Port Management
Green Ethernet
STEP 3 Configure the following settings:
STEP 4 Click Apply to save any changes to the Running Configuration.
5
• Energy Detect—Select to administratively enable Energy Detect on the
port.
• Short Reach Auto—Select to enable Short Reach mode on the port.
• Short Reach Force—Select to enable Force Reach mode on the port.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 93
Page 94

VLAN Management
This chapter describes how to configure virtual LANs.
It includes the following topics:
• Creating VLANs
• Configuring VLAN Interface Settings
• Configuring VLAN Membership
6
• Configuring Port VLAN Membership
• Setting the Default VLAN
• Media VLAN
• Voice and Media
Virtual LAN (VLAN) on a Layer 2 switch offers some of the benefits of both
bridging and routing. Like a bridge, a VLAN switch forwards traffic based on the
Layer 2 header which is fast. Like a router, it partitions the network into logical
segments, providing better administration, security, and management of multicast
traffic.
A VLAN is a set of end stations and the switch ports that connect them. You might
have many reasons for the logical division, such as department or project
membership. The only requirement is that the end station and the port to which it is
connected both belong to the same VLAN(s).
Each VLAN in a network has an associated VLAN ID, which appears in the IEEE
802.1Q tag, also known as VLAN tag, in the Layer 2 header of packets transmitted
on a VLAN. If an end station omits the tag, or the VLAN portion of the tag, the first
switch port to receive the packet either rejects it or inserts a tag matching its
default VLAN ID. A port can handle traffic for more than one VLAN, but it can only
support the Port VLAN ID (PVID).
The switch is pre-configured with VLAN ID 1 as the Default VLAN. All ports are
members of this VLAN, and use its VLAN ID (1) as their PVID.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 94
Page 95

VLAN Management
Creating VLANs
Creating VLANs
The Create VLAN page enables you to define and configure VLANs on the
network. To display this page VLAN Management > Create VLAN in the
navigation window.
The VLAN Table displays the VLAN ID, name, if one exists, and type for the preconfigured VLAN (VLAN ID 1) and any VLANs that you add. One port must be
configured as the Default VLAN. The type for all other ports is Static. The switch is
pre-configured with VLAN ID 1 as the Default VLAN. All ports are members of this
VLAN, and use its VLAN ID (1) as their PVID.
If you create additional VLANs, you can configure one of them as the Default VLAN.
(See Setting the Default VLAN.) The configured Default VLAN cannot be deleted.
A Static VLAN can be deleted. However, VLAN ID 1 cannot be deleted, even if it is
configured as a Static VLAN.
6
You can create up to 16 VLANs, and assign VLAN IDs up to 4094. To create a new
VLAN or a range of VLANs:
STEP 1 Click Add.
STEP 2 Select VLAN and enter a VLAN ID.
Or, create a range of VLANs by selecting Range and specifying the beginning and
ending VLAN IDs in the range.
STEP 3 If you are creating a single VLAN, you can enter an optional VLAN name for easy
reference.
STEP 4 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Configuring VLAN Interface Settings
You can use the Interface Settings page to view and configure port VLAN tagging
capabilities. To display this page click VLAN Management > Interface Settings in
the navigation window.
The Interface Setting Table shows the VLAN configuration for each port. To display
the VLAN configuration on link aggregation groups, select LAG from the Interface
Typ e l i st .
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 95
Page 96

VLAN Management
Configuring VLAN Interface Settings
To configure VLAN interface settings:
STEP 1 Select the port or LAG to configure and click Edit.
STEP 2 Configure the following settings for the selected port or LAG:
• Interface VLAN Mode—Select the port type (with respect to VLAN
6
membership and tagging). The port VLAN ID (PVID) indicates the default
VLAN that the interface is a member of. Set the PVID for a General port to any
valid VLAN ID on the switch. Set the PVID for an Access port to the Access
VLAN ID. Set the PVID for a Trunk port to the configured Native VLAN ID.
- General—The port can be a member of one or more tagged or untagged
VLANs. This mode allows the full capabilities specified in the IEEE 802.1Q
specification, “VLAN Tagging.” If you selected General, set the PVID equal
to the VLAN ID where a port is an untagged member.
- Access—The port can accept only untagged frames. An access port can
be a member of only one VLAN and it uses the VLAN ID as its port VLAN
ID (PVID). Access ports are typically used to connect hosts, which
become members of the VLAN by virtue of being physically connected
to the port. If you selected Access, the access port can be a member of
only one VLAN, called the access VLAN. Set the Access VLAN to the
PVID for the access port.
- Trunk—The port can be assigned to only one untagged VLAN, the native
VLAN, and can be assigned to any number of tagged VLANs (or none).
Trunk ports carry traffic for multiple VLANs from the switch to other
network devices, such as an upstream router or an edge switch.
• PVID—(General ports only) The port VLAN ID indicates the default VLAN
that the interface is a member of. Set the PVID equal to a VLAN ID where the
port is an untagged member. (For Access ports, the PVID is automatically set
to the Access VLAN ID. For Trunk ports, the PVID is set to the configured
Native VLAN ID or, if None is configured, to the default VLAN ID.)
• Native VLAN—(Trunk ports only) The native VLAN identifies the one
untagged VLAN membership for a trunk port. Select one of the following:
- None—The port has no untagged VLAN membership. The PVID for the
port is set to the default VLAN ID.
- Default—The Native VLAN equals the default VLAN. The PVID for the
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 96
port is also set to the default VLAN ID.
Page 97

VLAN Management
Configuring VLAN Interface Settings
• Access VLAN—(Access por ts only) An access por t can be a member of set
• Frame Type—Specifies the frame type accepted on the port:
6
- User defined—The VLAN ID you specify is used as the untagged VLAN
membership for the Trunk port. The PVID for the port is also set to the
specified VLAN ID.
only to the Access VLAN ID.
- Admit Untagged Only—Only untagged frames are accepted on the port.
Tagged frames are discarded.
- Admit Tagged Only—Only tagged frames are accepted on the port.
Untagged frames are discarded.
- Admit All—Both tagged and untagged frames are accepted on the port.
An access port can admit untagged frames only. A trunk port can be a
member of at most one untagged VLAN and one or more tagged VLANs. If a
trunk port is member of both untagged and tagged VLANs, it admits all frame
types. If the trunk port is member of tagged VLANs only, it admits tagged
frames only.
• Ingress Filtering—Select to enable ingress filtering on the port. When
ingress filtering is enabled, the switch accepts frames only from the VLANs
of which it is a member. It discards frames received from other VLANs. All
ports in access or trunk mode will always have their Ingress Filtering
enabled. Disabling and enabling Ingress Filtering is only available on ports
set to General Mode.
• VLAN Priority—The default 802.1p priority value for the port. The value will
be applied to the incoming packets based on the QoS trust mode configured
at the port and the types of the packets. See QoS Properties for information
and instructions on configuring the port trust mode.
STEP 3 Click Apply and then click Close. Your changes are saved to the Running
Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 97
Page 98

VLAN Management
Configuring VLAN Interface Settings
Changing the Interface VLAN Mode
When the interface VLAN mode of a port is changed, the switch automatically
handles the affected VLAN membership configuration, as follows:
Changing from Access Port to Trunk Port
The VLAN configuration remains unchanged. The Access port VLAN becomes the
native VLAN for the Trunk port. The port must follow the restrictions for Trunk
ports.
Changing from Trunk Port to Access Port
If the original trunk port has an untagged VLAN member on the port, the port is
removed from all its VLANs except the untagged VLAN on the port. The PVID is set
to the untagged VLAN ID.
If the original Trunk port does not have an untagged VLAN member on the port, the
port is removed from all its VLANs and becomes a member of the default VLAN. Its
PVID is set to the default VLAN ID and the port is set to admit only untagged or
priority-tagged packets. The port is untagged for the default VLAN.
6
Changing from Access Port to General Port
The VLAN configuration remains unchanged except that the port can now admit all
frames. As a General port, it can be a tagged or an untagged member of any
VLAN.
Changing from General Port to Access Port
If the General port has no untagged VLAN membership that provides the PVID for
the port, when the port is changed to an Access port it is removed from all the
General port's VLANs and becomes an untagged member of the default VLAN.
The Access port PVID is set to the default VLAN.
The Access port admits only untagged or priority-tagged packets.
Changing from Trunk Port to General Port
The VLAN configuration remains unchanged. As a General port, the port can be a
tagged or an untagged member of any VLAN.
Changing from General Port to Trunk Port
The VLAN configuration remains unchanged. The PVID of the General port is used
to configure the native VLAN of the Trunk port. The port must follow the
restrictions of the Trunk port.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 98
Page 99

VLAN Management
Configuring VLAN Membership
For example, assume a General port is an untagged member of VLANs 1, 10, and
20, and the port’s PVID is 1.
When the port is changed to a Trunk port, VLAN 1 becomes the native VLAN. The
Trunk port remains a member of VLANs 10 and 20, but now with tagging enabled.
Deleting a VLAN
When a VLAN is deleted, the following actions occur:
6
• If the deleted VLAN was a Trunk port’s native VLAN, the trunk port’s native
VLAN and PVID are changed to the default VLAN.
• If an Access port was a member of the deleted VLAN, the Access port
becomes a member of the default VLAN and its PVID is changed to the
default VLAN.
• If a General port was configured to use the VLAN ID as its PVID, the General
port’s PVID is changed to the default VLAN ID. No other VLAN memberships
are changed.
Configuring VLAN Membership
You can use these pages to view and configure VLAN memberships:
• The Port to VLAN page enables you to select a VLAN and configure its
member ports. See Configuring Port to VLAN.
• The Port VLAN Membership page enables you to select a port and
configure it as a member of one or more VLANs. See Configuring Port
VLAN Membership.
By default, all ports are members of VLAN 1. You can change the VLAN
membership of any port. VLAN memberships can be configured as tagged or
untagged.
• If the switch receives an untagged frame from a VLAN, the switch will insert
a VLAN tag before forwarding the frame to the egress ports that are
configured as tagged members of the VLAN.
• If the switch receives an untagged frame from a VLAN, the switch will
forward the frame as is to egress ports that are configured as untagged
members of the VLAN.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 99
Page 100

VLAN Management
Configuring VLAN Membership
Configuring Port to VLAN
To use the Port to VLAN page to assign ports to VLANs.
STEP 1 Click VLAN Management > Port to VLAN in the navigation window.
For the selected VLAN ID and port/LAG, this page displays the administrative
configuration of the interface port mode (access, trunk, and general), membership,
tagging option, and PVID of every port with respect to the VLAN. (See Configuring
VLAN Interface Settings for instructions on configuring this setting.)
6
• If the switch receives an tagged frame from a VLAN, the switch will remove
the VLAN tag before forwarding the frame to the egress ports that are
configured as untagged members of the VLAN.
• If the switch receives an tagged frame from a VLAN, the switch will forward
the frame as is to egress ports that are configured as tagged members of
the VLAN.
STEP 2 Select the VLAN ID to configure and use the Interface Type list to display either
ports or LAGs.
STEP 3 For each interface, configure the following parameters:
• Member—Check this box if a port is to be member of the VLAN. Uncheck
this box if a port is not to be member of the VLAN. A port is not member of
the VLAN by default.
• Tagged—Select Tagged if all the packets of the VLAN egress to the port are
to be tagged. Otherwise, select Untagged. A trunk port is tagged by default.
This option is only relevant if the port is a member of the VLAN.
• Untagged—Select Untagged if the packets from the VLAN egress to the
port are to be untagged. Otherwise, select Tagged. An access port is always
untagged. An general port is untagged by default. This option is relevant only
if the port is a member of the VLAN.
• PVID—Check this box if a port is to use the selected VLAN ID as its port
VLAN ID (PVID). Otherwise, uncheck this box. If PVID is selected for an
access or trunk port, the port must be an untagged member of the VLAN.
Untagged packets received from the port will be assigned to the
corresponding VLAN.
STEP 4 Click Apply. Your changes are saved to the Running Configuration.
Cisco Small Business SG200 Series 8-port Smart Switches Administration Guide 100
 Loading...
Loading...