Page 1

Cisco Unified IP Phone 7970G/7971G-GE
Administration Guide for Cisco Unified
Communications Manager 7.0
(SCCP
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
Fax: 408 527-0883
and SIP)
800 553-NETS (6387)
Text Part Number: OL-15299-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant
to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial
environment. This equipment generates, uses, and can radiate radio-frequency energy and, if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case users will be required
to correct the interference at their own expense.
The following information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it is not
installed in accordance with Cisco’s installation instructions, it may cause interference with radio and television reception. This equipment has been tested and found to
comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These specifications are designed to provide reasonable
protection against such interference in a residential installation. However, there is no guarantee that interference will not occur in a particular installation.
Modifying the equipment without Cisco’s written authorization may result in the equipment no longer complying with FCC requirements for Class A or Class B digital
devices. In that event, your right to use the equipment may be limited by FCC regulations, and you may be required to correct any interference to radio or television
communications at your own expense.
You can determine whether your equipment is causing interference by turning it off. If the interference stops, it was probably caused by the Cisco equipment or one of its
peripheral devices. If the equipment causes interference to radio or television reception, try to correct the interference by using one or more of the following measures:
• Turn the television or radio antenna until the interference stops.
• Move the equipment to one side or the other of the television or radio.
• Move the equipment farther away from the television or radio.
• Plug the equipment into an outlet that is on a different circuit from the television or radio. (That is, make certain the equipment and the television or radio are on circuits
controlled by different circuit breakers or fuses.)
Modifications to this product not authorized by Cisco Systems, Inc. could void the FCC approval and negate your authority to operate the product.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
CCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, the Cisco logo, DCE, and Welcome to the Human Network are trademarks; Changing the Way
We Work, Live, Play, and Learn is a service mark; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA,
CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo,
Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient,
IOS, iPhone, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study, IronPort, the IronPort logo, LightStream, Linksys, MediaTone, MeetingPlace, MGX,
Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The
Fastest Way to Increase Your Internet Quotient, TransPath, WebEx, and the WebEx logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United
States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (0805R)
The Java logo is a trademark or registered trademark of Sun Microsystems, Inc. in the U.S. or other countries.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
© 2008 Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
Preface xi
Overview xi
Audience xi
Organization xi
Related Documentation xii
Obtaining Documentation, Obtaining Support, and Security Guidelines xiii
Cisco Product Security Overview xiii
Document Conventions xiii
CHAPTER
1 An Overview of the Cisco Unified IP Phone 1-1
Understanding the Cisco Unified IP Phone 7970 Series 1-1
What Networking Protocols Are Used? 1-3
What Features are Supported on the Cisco Unified IP Phone 7970 Series? 1-7
Feature Overview 1-7
Configuring Telephony Features 1-8
Configuring Network Parameters Using the Cisco Unified IP Phone 1-8
Providing Users with Feature Information 1-8
Understanding Security Features for Cisco Unified IP Phones 1-8
Overview of Supported Security Features 1-10
Understanding Security Profiles 1-12
Identifying Authenticated, Encrypted, and Protected Phone Calls 1-13
Establishing and Identifying Secure Conference Calls 1-14
Establishing and Identifying Protected Calls 1-14
Call Security Interactions and Restrictions 1-15
Supporting 802.1X Authentication on Cisco Unified IP Phones 1-16
Overview 1-16
Required Network Components 1-16
Best Practices—Requirements and Recommendations 1-17
Security Restrictions 1-17
OL-15299-01
Overview of Configuring and Installing Cisco Unified IP Phones 1-18
Configuring Cisco Unified IP Phones in Cisco Unified Communications Manager 1-18
Checklist for Configuring the Cisco Unified IP Phone 7970 Series in
Cisco Unified Communications Manager 1-19
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
iii
Page 4

Contents
Installing Cisco Unified IP Phones 1-21
Checklist for Installing the Cisco Unified IP Phone 7970 Series 1-21
CHAPTER
2 Preparing to Install the Cisco Unified IP Phone on Your Network 2-1
Understanding Interactions with Other Cisco Unified IP Communications Products 2-2
Understanding How the Cisco Unified IP Phone Interacts with Cisco Unified Communications
Manager 2-2
Understanding How the Cisco Unified IP Phone Interacts with the VLAN 2-3
Providing Power to the Phone 2-3
Power Guidelines 2-4
Phone Power Consumption and Display Brightness 2-5
Power Outage 2-5
Obtaining Additional Information about Power 2-6
Understanding Phone Configuration Files 2-6
Understanding the Phone Startup Process 2-7
Adding Phones to the Cisco Unified Communications Manager Database 2-9
Adding Phones with Auto-Registration 2-10
Adding Phones with Auto-Registration and TAPS 2-11
Adding Phones with Cisco Unified Communications Manager Administration 2-12
Adding Phones with BAT 2-12
Using Cisco Unified IP Phones with Different Protocols 2-12
Converting a New Phone from SCCP to SIP 2-13
Converting an In-Use Phone from SCCP to SIP 2-13
Converting an In-Use Phone from SIP to SCCP 2-13
Deploying a Phone in an SCCP and SIP Environment 2-14
CHAPTER
iv
Determining the MAC Address of a Cisco Unified IP Phone 2-14
3 Setting Up the Cisco Unified IP Phone 3-1
Before You Begin 3-1
Network Requirements 3-1
Cisco Unified Communications Manager Configuration 3-2
Understanding the Cisco Unified IP Phone 7970 Series Components 3-2
Network and Access Ports 3-2
Handset 3-3
Speakerphone 3-3
Headset 3-3
Audio Quality Subjective to the User 3-4
Connecting a Headset 3-4
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 5

Disabling a Headset 3-4
Using External Devices 3-4
Installing the Cisco Unified IP Phone 3-5
Attaching the Cisco Unified IP Phone Expansion Module 7914 3-7
Adjusting the Placement of the Cisco Unified IP Phone 3-8
Adjusting Cisco Unified IP Phone Footstand and Phone Height 3-8
Securing the Phone with a Cable Lock 3-8
Mounting the Phone to the Wall 3-9
Verifying the Phone Startup Process 3-10
Configuring Startup Network Settings 3-11
Configuring Security on the Cisco Unified IP Phone 3-12
Contents
CHAPTER
4 Configuring Settings on the Cisco Unified IP Phone 4-1
Configuration Menus on the Cisco Unified IP Phone 7970 Series 4-1
Displaying a Configuration Menu 4-2
Unlocking and Locking Options 4-3
Editing Values 4-3
Overview of Options Configurable from a Phone 4-4
Network Configuration Menu 4-5
Device Configuration Menu 4-10
Unified CM Configuration 4-11
SIP Configuration Menu (SIP Phones Only) 4-12
SIP General Configuration Menu 4-13
Line Settings Menu (SIP Phones Only) 4-14
Call Preferences Menu (SIP Phones Only) 4-14
HTTP Configuration Menu 4-15
Locale Configuration Menu 4-16
NTP Configuration Menu (SIP Phones Only) 4-17
UI Configuration Menu 4-17
Media Configuration Menu 4-19
Power Save Configuration Menu 4-22
Ethernet Configuration Menu 4-23
Security Configuration Menu 4-23
QoS Configuration Menu 4-25
Network Configuration 4-25
OL-15299-01
Security Configuration Menu 4-29
CTL File Menu 4-30
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
v
Page 6

Contents
Trust List Menu 4-31
802.1X Authentication and Status 4-31
CHAPTER
CHAPTER
5 Configuring Features, Templates, Services, and Users 5-1
Telephony Features Available for the Phone 5-1
Configuring Corporate and Personal Directories 5-16
Configuring Corporate Directories 5-17
Configuring Personal Directory 5-17
Modifying Phone Button Templates 5-17
Modifying a Phone Button Template for Personal Address Book or Fast Dials 5-18
Configuring Softkey Templates 5-19
Setting Up Services 5-20
Adding Users to Cisco Unified Communications Manager 5-20
Managing the User Options Web Pages 5-21
Giving Users Access to the User Options Web Pages 5-21
Specifying Options that Appear on the User Options Web Pages 5-21
6 Customizing the Cisco Unified IP Phone 6-1
Customizing and Modifying Configuration Files 6-1
Creating Custom Phone Rings 6-2
Ringlist.xml File Format Requirements 6-2
PCM File Requirements for Custom Ring Types 6-3
Configuring a Custom Phone Ring 6-3
CHAPTER
vi
Creating Custom Background Images 6-3
List.xml File Format Requirements 6-4
PNG File Requirements for Custom Background Images 6-5
Configuring a Custom Background Image 6-5
Configuring Wideband Codec 6-6
Configuring the Idle Display 6-7
Automatically Disabling the Cisco Unified IP Phone Touchscreen 6-7
7 Viewing Model Information, Status, and Statistics on the Cisco Unified IP Phone 7-1
Model Information Screen 7-2
Status Menu 7-3
Status Messages Screen 7-3
Network Statistics Screen 7-9
Firmware Versions Screen 7-11
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 7

Expansion Module(s) Screen 7-12
Call Statistics Screen 7-13
Contents
CHAPTER
CHAPTER
8 Monitoring the Cisco Unified IP Phone Remotely 8-1
Accessing the Web Page for a Phone 8-1
Disabling and Enabling Web Page Access 8-3
Device Information 8-3
Network Configuration 8-4
Network Statistics 8-8
Device Logs 8-10
Streaming Statistics 8-10
9 Troubleshooting and Maintenance 9-1
Resolving Startup Problems 9-1
Symptom: The Cisco Unified IP Phone Does Not Go Through its Normal Startup Process 9-2
Symptom: The Cisco Unified IP Phone Does Not Register with Cisco Unified Communications
Manager 9-2
Identifying Error Messages 9-3
Checking Network Connectivity 9-3
Verifying TFTP Server Settings 9-3
Verifying IP Addressing and Routing 9-3
Verifying DNS Settings 9-4
Verifying Cisco Unified Communications Manager Settings 9-4
Cisco CallManager and TFTP Services Are Not Running 9-4
Creating a New Configuration File 9-5
Registering the Phone with Cisco Unified Communications Manager 9-5
Symptom: Cisco Unified IP Phone Unable to Obtain IP Address 9-6
OL-15299-01
Cisco Unified IP Phone Resets Unexpectedly 9-6
Verifying Physical Connection 9-6
Identifying Intermittent Network Outages 9-6
Verifying DHCP Settings 9-7
Checking Static IP Address Settings 9-7
Verifying Voice VLAN Configuration 9-7
Verifying that the Phones Have Not Been Intentionally Reset 9-7
Eliminating DNS or Other Connectivity Errors 9-7
Checking Power Connection 9-8
Troubleshooting Cisco Unified IP Phone Security 9-8
General Troubleshooting Tips 9-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
vii
Page 8

Contents
General Troubleshooting Tips for the Cisco Unified IP Phone Expansion Module 7914 9-12
Resetting or Restoring the Cisco Unified IP Phone 9-13
Performing a Basic Reset 9-13
Performing a Factory Reset 9-14
Using the Quality Report Tool 9-14
Monitoring the Voice Quality of Calls 9-15
Using Voice Quality Metrics 9-15
Troubleshooting Tips 9-16
Where to Go for More Troubleshooting Information 9-17
Cleaning the Cisco Unified IP Phone 9-17
APPENDIX
APPENDIX
APPENDIX
A Providing Information to Users Via a Website A-1
How Users Obtain Support for the Cisco Unified IP Phone A-1
Giving Users Access to the User Options Web Pages A-1
How Users Access the Online Help System on the Phone A-2
How Users Get Copies of Cisco Unified IP Phone Manuals A-2
Accessing Cisco 7900 Series Unified IP Phone eLearning Tutorials (SCCP Phones Only) A-2
How Users Subscribe to Services and Configure Phone Features A-3
How Users Access a Voice-Messaging System A-3
How Users Configure Personal Directory Entries A-4
Installing and Configuring the Cisco Unified IP Phone Address Book Synchronizer A-4
B Feature Support by Protocol for the Cisco Unified IP Phones 7970 Series B-1
C Supporting International Users C-1
Adding Language Overlays to Phone Buttons C-1
Installing the Cisco Unified Communications Manager Locale Installer C-1
Support for International Call Logging C-2
APPENDIX
APPENDIX
viii
D Technical Specifications D-1
Physical and Operating Environment Specifications D-1
Cable Specifications D-2
Network and Access Port Pinouts D-2
E Basic Phone Administration Steps E-1
Example User Information for these Procedures E-1
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 9

I
NDEX
Contents
Adding a User to Cisco Unified Communications Manager E-2
Adding a User From an External LDAP Directory E-2
Adding a User Directly to Cisco Unified Communications Manager E-2
Configuring the Phone E-3
Performing Final End User Configuration Steps E-7
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
ix
Page 10

Contents
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
x
OL-15299-01
Page 11

Overview
Preface
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications
Manager 7.0 provides the information you need to understand, install, configure, manage, and
troubleshoot the phones in the Cisco Unified IP Phone 7970 series on a Voice-over-IP (VoIP) network.
Because of the complexity of a Unified Communications network, this guide does not provide complete
and detailed information for procedures that you need to perform in Cisco Unified Communications
Manager (formerly Cisco Unified CallManager) or other network devices. See the “Related
Documentation” section on page xii for a list of related documentation.
Audience
Network engineers, system administrators, or telecom engineers should review this guide to learn the
steps required to properly set up the Cisco Unified IP Phone 7970 Series on the network.
The tasks described are administration-level tasks and are not intended for end-users of the phones.
Many of the tasks involve configuring network settings and affect the phone’s ability to function in the
network.
Because of the close interaction between the Cisco Unified IP Phone and
Cisco Unified Communications Manager, many of the tasks in this manual require familiarity with
Cisco Unified Communications Manager.
Organization
This manual is organized as follows:
Chapter 1, “An Overview of the Cisco Unified IP Phone” Provides a conceptual overview and description of the
Cisco Unified IP Phone
Chapter 2, “Preparing to Install the Cisco Unified IP Phone
on Your Network”
Chapter 3, “Setting Up the Cisco Unified IP Phone” Describes how to properly and safely install and configure the
Describes how the Cisco Unified IP Phone interacts with
other key IP telephony components, and provides an overview
of the tasks required prior to installation
Cisco Unified IP Phone on your network
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
xi
Page 12
Preface
Chapter 4, “Configuring Settings on the Cisco
Unified IP Phone”
Chapter 5, “Configuring Features, Templates, Services, and
Users”
Chapter 6, “Customizing the Cisco Unified IP Phone” Explains how to customize phone ring sounds, background
Chapter 7, “Viewing Model Information, Status, and
Statistics on the Cisco Unified IP Phone”
Chapter 8, “Monitoring the Cisco Unified IP Phone
Remotely”
Chapter 9, “Troubleshooting and Maintenance” Provides tips for troubleshooting the Cisco Unified IP Phone
Appendix A, “Providing Information to Users Via a Website” Provides suggestions for setting up a website for providing
Appendix B, “Feature Support by Protocol for the Cisco
Unified IP Phones 7970 Series”
Appendix C, “Supporting International Users” Provides information about setting up phones in non-English
Appendix D, “Technical Specifications” Provides technical specifications of the
Appendix E, “Basic Phone Administration Steps” Provides procedures for basic administration tasks such as
Describes how to configure network settings, verify status,
and make global changes to the Cisco Unified IP Phone
Provides an overview of procedures for configuring telephony
features, configuring directories, configuring phone button
and softkey templates, setting up services, and adding users to
Cisco Unified Communications Manager
images, and the phone idle display at your site
Explains how to view model information, status messages,
network statistics, and firmware information from
the Cisco Unified IP Phone
Describes the information that you can obtain from the
phone’s web page, and how to use this information to
remotely monitor the operation of a phone and to assist with
troubleshooting
users with important information about their Cisco Unified IP
Phones
Provides information about feature support for the Cisco
Unified IP Phone using the SCCP or SIP protocol
environments
Cisco Unified IP Phone
adding a user and phone to Cisco Unified Communications
Manager and then associating the user to the phone.
Related Documentation
For more information about Cisco Unified IP Phones or Cisco Unified Communications Manager, refer
to the following publications:
Cisco Unified IP Phone 7970 Series
These publications are available at the following URL:
http://www.cisco.com/en/US/products/hw/phones/ps379/tsd_products_support_series_home.html
• Cisco Unified IP Phone 7970 Series Phone Guide
• Cisco Unified IP Phone Features A–Z
• Cisco Unified IP Phone Expansion Module 7914 Phone Guide
• Installing the Wall Mount Kit for the Cisco Unified IP Phone
• Regulatory Compliance and Safety Information for the Cisco Unified IP Phones
• Open Source License Notices for the Cisco Unified IP Phones 7900 Series
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
xii
OL-15299-01
Page 13

Preface
Cisco Unified Communications Manager Administration
These publications are available at the following URL:
http://www.cisco.com/en/US/products/sw/voicesw/ps556/tsd_products_support_series_home.html
Cisco Unified Communications Manager Business Edition
These publications are available at the following URL:
http://www.cisco.com/en/US/products/ps7273/tsd_products_support_series_home.html
Obtaining Documentation, Obtaining Support, and Security
Guidelines
For information on obtaining documentation, obtaining support, providing documentation feedback,
security guidelines, and also recommended aliases and general Cisco documents, see the monthly What’s
New in Cisco Product Documentation, which also lists all new and revised Cisco technical
documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Cisco Product Security Overview
This product contains cryptographic features and is subject to United States and local country laws
governing import, export, transfer and use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption. Importers, exporters, distributors
and users are responsible for compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable to comply with U.S. and local
laws, return this product immediately.
Further information regarding U.S. export regulations may be found at
http://www.access.gpo.gov/bis/ear/ear_data.html.
Document Conventions
This document uses the following conventions:
Convention Description
boldface font Commands and keywords are in boldface.
italic font Arguments for which you supply values are in italics.
[ ] Elements in square brackets are optional.
{ x | y | z } Alternative keywords are grouped in braces and separated by vertical bars.
[ x | y | z ] Optional alternative keywords are grouped in brackets and separated by vertical bars.
string A nonquoted set of characters. Do not use quotation marks around the string or the string
will include the quotation marks.
screen font Terminal sessions and information the system displays are in screen font.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
xiii
Page 14

Preface
Convention Description
boldface screen font Information you must enter is in boldface screen font.
italic screen font Arguments for which you supply values are in italic screen font.
^ The symbol ^ represents the key labeled Control—for example, the key combination ^D in
a screen display means hold down the Control key while you press the D key.
< > Nonprinting characters, such as passwords are in angle brackets.
Note Means reader take note. Notes contain helpful suggestions or references to material not covered in the
publication.
Caution Means reader be careful. In this situation, you might do something that could result in equipment
damage or loss of data.
Warning
Means danger. You are in a situation that could cause bodily injury. Before you work on any
equipment, be aware of the hazards involved with electrical circuitry and be familiar with standard
practices for preventing accidents.
xiv
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 15

CHAP T ER
1
An Overview of the Cisco Unified IP Phone
The Cisco Unified IP Phone 7970 Series are full-featured telephones that provide voice communication
over an Internet Protocol (IP) network. They function much like digital business phones, allowing you
to place and receive phone calls and to access features such as mute, hold, transfer, speed dial, call
forward, and more. In addition, because Cisco Unified IP Phones are connected to your data network,
they offer enhanced IP telephony features, including access to network information and services, and
customizeable features and services. The phones also support security features that include file
authentication, device authentication, signaling encryption, and media encryption.
The Cisco Unified IP Phone 7970 Series provides a color touchscreen, support for up to eight line or
speed dial numbers, context-sensitive online help for buttons and features, and a variety of other
sophisticated functions.
The Cisco Unified IP Phone, like other network devices, must be configured and managed. These phones
encodes G.711a, G.711µ, G.722, G.729a, G.729ab, iLBC, and decode G.711a, G.711µ, G722, iLBC, and
G.729, G729a, G.729b, and G.729ab. These phones also support uncompressed wideband (16bits,
16kHz) audio.
This chapter includes the following topics:
• Understanding the Cisco Unified IP Phone 7970 Series, page 1-1
• What Networking Protocols Are Used?, page 1-3
• What Features are Supported on the Cisco Unified IP Phone 7970 Series?, page 1-7
• Understanding Security Features for Cisco Unified IP Phones, page 1-8
• Overview of Configuring and Installing Cisco Unified IP Phones, page 1-18
Caution Using a cell, mobile, or GSM phone, or two-way radio in close proximity to a Cisco Unified IP Phone
might cause interference. For more information, refer to the manufacturer documentation of the
interfering device.
Understanding the Cisco Unified IP Phone 7970 Series
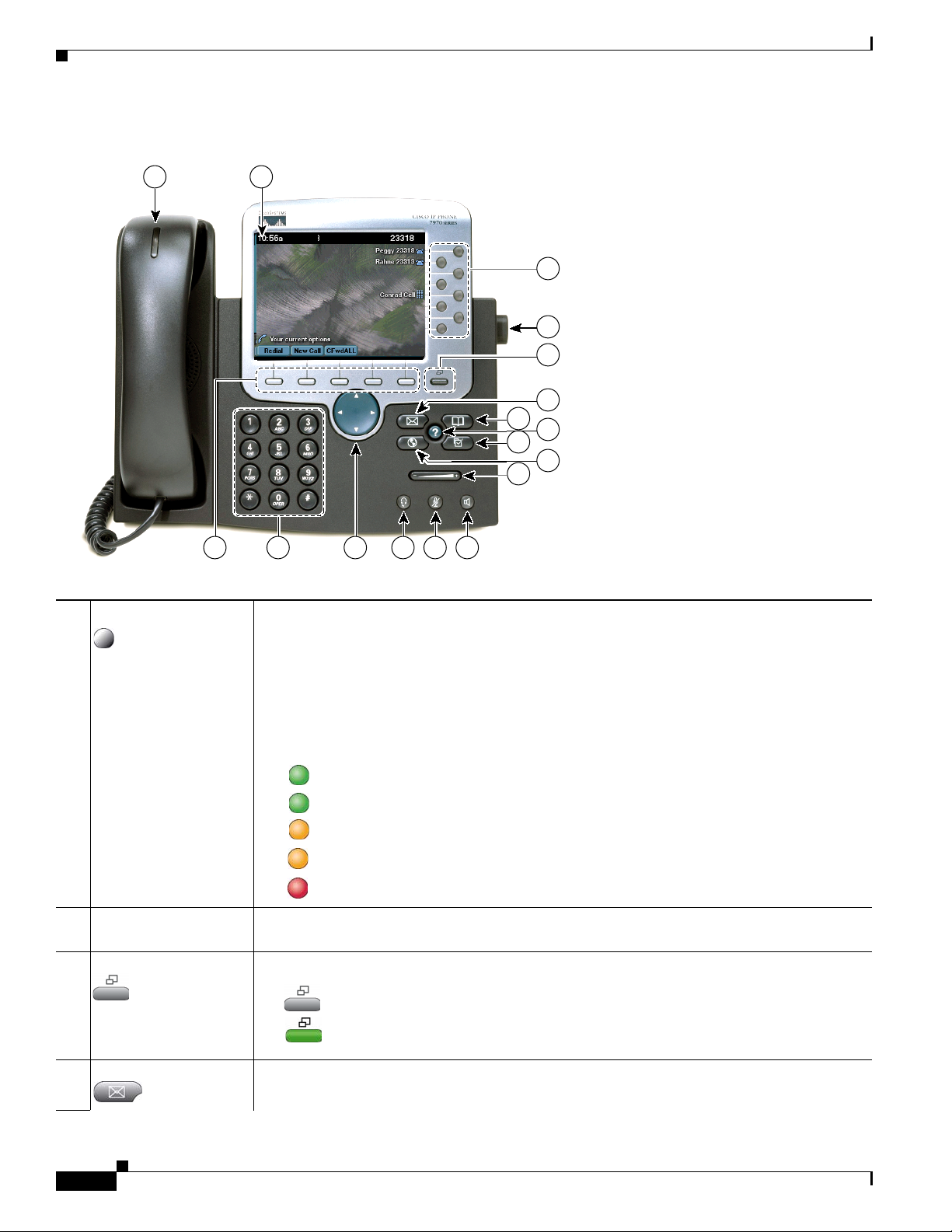
Figure 1-1 shows the main components of the Cisco Unified IP Phone 7970 Series.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-1
Page 16
Understanding the Cisco Unified IP Phone 7970 Series
Figure 1-1 Cisco Unified IP Phone
16 17
Chapter 1 An Overview of the Cisco Unified IP Phone
1
2
3
4
5
6
7
8
9
10
1112131415
186428
1 Programmable buttons Depending on configuration, programmable buttons provide access to:
• Phone lines (line buttons)
• Speed-dial numbers (speed-dial buttons, including the BLF speed-dial feature)
• Web-based services (for example, a Personal Address Book button)
• Phone features (for example, a Privacy button)
Buttons illuminate to indicate status:
Green, steady—Active call
Green, flashing—Held call
Amber, steady—Privacy in use
Amber, flashing—Incoming call
Red, steady—Remote line in use (shared line or BLF status)
2 Footstand adjustment
Allows you to adjust the angle of the phone base.
button
3 Display button Awakens the touchscreen from sleep mode or disables it for cleaning.
No color—Ready for input
Green flashing—Disabled
Green steady—Sleep mode
4 Messages button Auto-dials your voice message service (varies by service).
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-2
OL-15299-01
Page 17
Chapter 1 An Overview of the Cisco Unified IP Phone
What Networking Protocols Are Used?
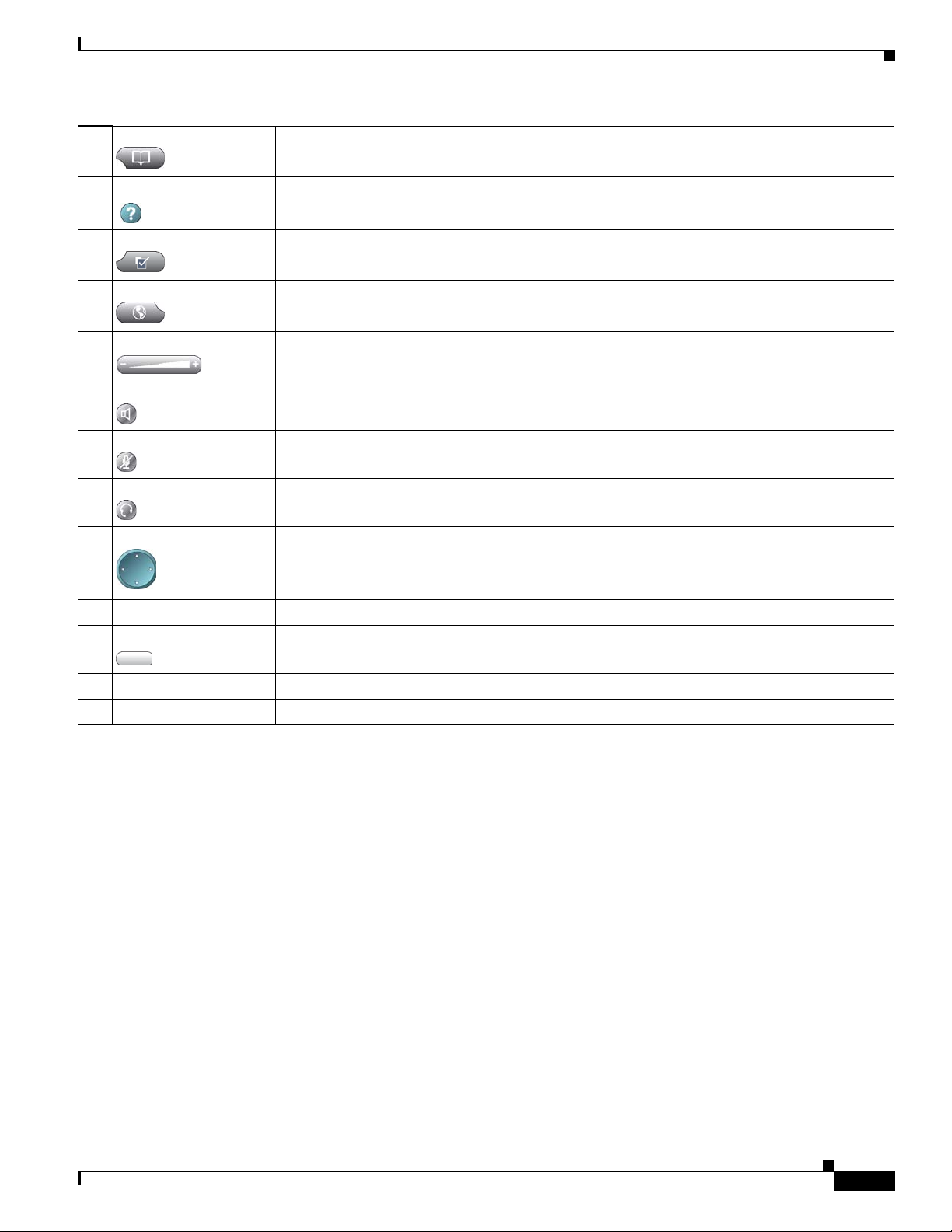
5 Directories button Opens/closes the Directories menu. Use it to access call logs and directories.
6 Help
7 Settings button Opens/closes the Settings menu. Use it to change touchscreen and ring settings.
8 Services button Opens/closes the Services menu.
9 Volume button Controls the handset, headset, and speakerphone volume (off-hook) and the ringer volume
10 Speaker button Toggles the speakerphone on or off.
11 Mute button Toggles the Mute feature on or off.
12 Headset button Toggles the headset on or off.
13 Navigation button Allows you to scroll through menus and highlight items. When the phone is on-hook, displays
14 Keypad Allows you to dial phone numbers, enter letters, and choose menu items.
15 Softkey buttons Each activates a softkey option (displayed on your touchscreen).
button Activates the Help menu.
(on-hook).
phone numbers from your Placed Calls log.
16 Handset light strip Indicates an incoming call or new voice message.
17 Touchscreen Shows phone features.
What Networking Protocols Are Used?
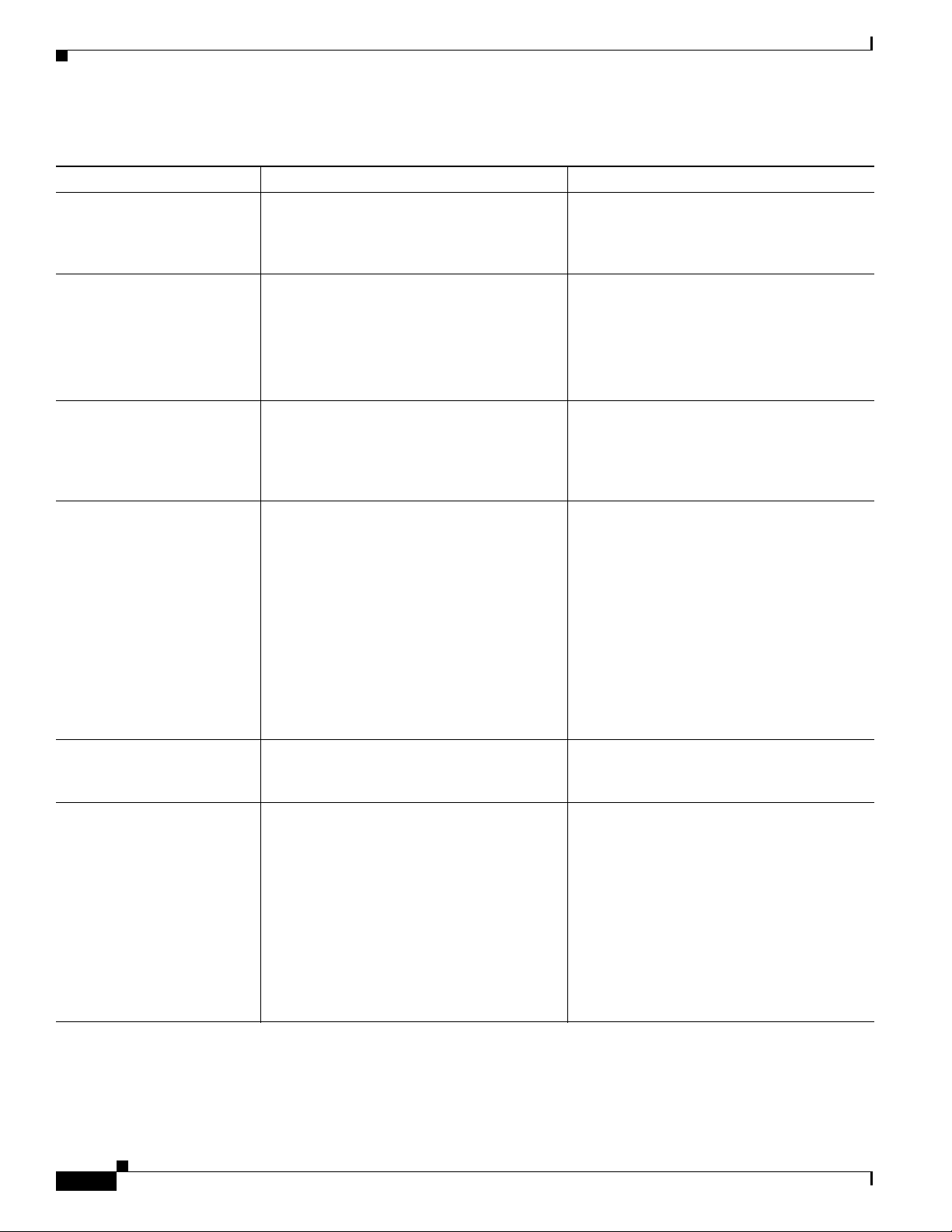
Cisco Unified IP Phones support several industry-standard and Cisco networking protocols required for
voice communication. Table 1 - 1 provides an overview of the networking protocols that the
Cisco Unified IP Phone 7970 Series supports.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-3
Page 18
Chapter 1 An Overview of the Cisco Unified IP Phone
What Networking Protocols Are Used?
Table 1-1 Supported Networking Protocols on the Cisco Unified IP Phone
Networking Protocol Purpose Usage Notes
Bootstrap Protocol (BootP) BootP enables a network device such as the
Cisco Unified IP Phone to discover certain
startup information, such as its IP address.
Cisco Discovery Protocol
(CDP)
CDP is a device-discovery protocol that runs
on all Cisco-manufactured equipment.
Using CDP, a device can advertise its
existence to other devices and receive
information about other devices in the
network.
Cisco Peer-to-Peer
Distribution Protocol
(CPPDP)
CPPDP is a Cisco proprietary protocol used to
form a-peer-to-peer hierarchy of devices.
CPPDP is also used to copy firmware or other
files from peer devices to neighboring
devices.
Dynamic Host Configuration
Protocol (DHCP)
DHCP dynamically allocates and assigns an
IP address to network devices.
DHCP enables you to connect an IP phone
into the network and have the phone become
operational without needing to manually
assign an IP address or configure additional
network parameters.
Hypertext Transfer Protocol
(HTTP)
HTTP is the standard way of transferring
information and moving documents across the
Internet and the web.
IEEE 802.1X The IEEE 802.1X standard defines a
client-server-based access control and
authentication protocol that restricts
unauthorized clients from connecting to a
LAN through publicly accessible ports.
Until the client is authenticated, 802.1X
access control allows only Extensible
Authentication Protocol over LAN (EAPOL)
traffic through the port to which the client is
connected. After authentication is successful,
normal traffic can pass through the port.
If you are using BootP to assign IP addresses
to the Cisco Unified IP Phone, the BOOTP
Server option shows “Yes” in the network
configuration settings on the phone.
The Cisco Unified IP Phone uses CDP to
communicate information such as auxiliary
VLAN ID, per port power management details,
and Quality of Service (QoS) configuration
information with the Cisco Catalyst switch.
CPPDP is used by the Peer Firmware Sharing
feature.
DHCP is enabled by default. If disabled, you
must manually configure the IP address,
subnet mask, gateway, and a TFTP server on
each phone locally.
Cisco recommends that you use DHCP
custom option 150. With this method, you
configure the TFTP server IP address as the
option value. For additional information
about DHCP configurations, refer to the
“Cisco TFTP” chapter in Cisco
Unified Communications Manager System
Guide.
Cisco Unified IP Phones use HTTP for the
XML services and for troubleshooting
purposes.
The Cisco Unified IP Phone implements the
IEEE 802.1X standard by providing support
for the EAP-MD5 option for 802.1X
authentication.
When 802.1X authentication is enabled on the
phone, you should disable the PC port and
voice VLAN. Refer to the “Supporting
802.1X Authentication on Cisco Unified IP
Phones” section on page 1-16 for additional
information.
1-4
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 19
Chapter 1 An Overview of the Cisco Unified IP Phone
What Networking Protocols Are Used?
Table 1-1 Supported Networking Protocols on the Cisco Unified IP Phone (continued)
Networking Protocol Purpose Usage Notes
Internet Protocol (IP) IP is a messaging protocol that addresses and
sends packets across the network.
To communicate using IP, network devices
must have an assigned IP address, subnet, and
gateway.
IP addresses, subnets, and gateways
identifications are automatically assigned if
you are using the Cisco Unified IP Phone
with Dynamic Host Configuration Protocol
(DHCP). If you are not using DHCP, you must
manually assign these properties to each
phone locally.
Link Layer Discovery
Protocol (LLDP)
Link Layer Discovery
Protocol-Media Endpoint
Devices (LLDP-MED)
Real-Time Control Protocol
(RTCP)
Real-Time Transport Protocol
(RTP)
LLDP is a standardized network discovery
protocol (similar to CDP) that is supported on
some Cisco and third-party devices.
LLDP-MED is an extension of the LLDP
standard developed for voice products.
RTCP works with Real-Time Transport
Protocol (RTP) to provide QoS data (such as
jitter, latency, and round trip delay) on RTP
streams.
RTP is a standard protocol for transporting
real-time data, such as interactive voice and
video, over data networks.
The Cisco Unified IP Phone supports LLDP
on the PC port.
The Cisco Unified IP Phone supports
LLDP-MED on the SW port to communicate
information such as:
• Voice VLAN configuration
• Device discovery
• Power management
• Inventory management
For more information about LLDP-MED
support, see the LLDP-MED and Cisco
Discovery Protocol white paper:
http://www.cisco.com/en/US/tech/tk652/tk70
1/technologies_white_paper0900aecd804cd4
6d.shtml
RTCP is disabled by default, but you can
enable it on a per-phone basis using Cisco
Unified Communications Manager. For more
information, see the “Network Configuration”
section on page 4-25.
Cisco Unified IP Phones use the RTP protocol
to send and receive real-time voice traffic
from other phones and gateways.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-5
Page 20
Chapter 1 An Overview of the Cisco Unified IP Phone
What Networking Protocols Are Used?
Table 1-1 Supported Networking Protocols on the Cisco Unified IP Phone (continued)
Networking Protocol Purpose Usage Notes
Session Initiation Protocol
(SIP)
SIP is the Internet Engineering Task Force
(IETF) standard for multimedia conferencing
over IP. SIP is an ASCII-based
application-layer control protocol (defined in
RFC 3261) that can be used to establish,
maintain, and terminate calls between two or
more endpoints.
Like other VoIP protocols, SIP is designed to
address the functions of signaling and session
management within a packet telephony
network. Signaling allows call information to
be carried across network boundaries. Session
management provides the ability to control
the attributes of an end-to-end call.
You can configure the Cisco Unified IP Phone
to use either SIP or Skinny Client Control
Protocol (SCCP).
Skinny Client Control
Protocol (SCCP)
Session Description Protocol
(SDP)
Transmission Control
Protocol (TCP)
Transport Layer Security
(TLS)
Trivial File Transfer Protocol
(TFTP)
User Datagram Protocol
(UDP)
SCCP includes a messaging set that allows
communications between call control servers
and endpoint clients such as IP Phones. SCCP
is proprietary to Cisco Systems.
SDP is the portion of the SIP protocol that
determines which parameters are available
during a connection between two endpoints.
Conferences are established using only the
SDP capabilities that are supported by all
endpoints in the conference.
TCP is a connection-oriented transport
protocol.
TLS is a standard protocol for securing and
authenticating communications.
TFTP allows you to transfer files over the
network.
On the Cisco Unified IP Phone, TFTP enables
you to obtain a configuration file specific to
the phone type.
UDP is a connectionless messaging protocol
for delivery of data packets.
Cisco Unified IP Phones use SCCP for call
control. You can configure the Cisco
Unified IP Phone to use either SCCP or
Session Initiation Protocol (SIP).
SDP capabilities, such as codec types, DTMF
detection, and comfort noise, are normally
configured on a global basis by Cisco Unified
Communications Manager or Media Gateway
in operation. Some SIP endpoints may allow
these parameters to be configured on the
endpoint itself.
Cisco Unified IP Phones use TCP to connect
to Cisco Unified Communications Manager
and to access XML services.
When security is implemented, Cisco
Unified IP Phones use the TLS protocol when
securely registering with Cisco
Unified Communications Manager.
TFTP requires a TFTP server in your network,
which can be automatically identified from
the DHCP server. If you want a phone to use
a TFTP server other than the one specified by
the DHCP server, you must manually assign
TFTP server from the Network Configuration
menu on the phone.
Cisco Unified IP Phones transmit and receive
RTP streams, which utilize UDP.
1-6
Related Topics
• Understanding Interactions with Other Cisco Unified IP Communications Products, page 2-2
• Understanding the Phone Startup Process, page 2-7
• Network Configuration Menu, page 4-5
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 21

Chapter 1 An Overview of the Cisco Unified IP Phone
What Features are Supported on the Cisco Unified IP Phone 7970 Series?
What Features are Supported on the Cisco
Unified
IP Phone 7970 Series?
The Cisco Unified IP Phone functions much like a digital business phone, allowing you to place and
receive telephone calls. In addition to traditional telephony features, the Cisco Unified IP Phone includes
features that enable you to administer and monitor the phone as a network device.
This section includes the following topics:
• Feature Overview, page 1-7
• Configuring Telephony Features, page 1-8
• Configuring Network Parameters Using the Cisco Unified IP Phone, page 1-8
• Providing Users with Feature Information, page 1-8
Feature Overview
Cisco Unified IP Phones provide traditional telephony functionality, such as call forwarding and
transferring, redialing, speed dialing, conference calling, and voice messaging system access.
Cisco Unified IP phones also provide a variety of other features. For an overview of the telephony
features that the Cisco Unified IP Phone supports, see the “Telephony Features Available for the Phone”
section on page 5-1.
As with other network devices, you must configure Cisco Unified IP Phones to prepare them to access
Cisco Unified Communications Manager and the rest of the IP network. By using DHCP, you have fewer
settings to configure on a phone, but if your network requires it, you can manually configure an IP
address, TFTP server, subnet information, etc. For instructions on configuring the network settings on
the Cisco Unified IP Phones, see Chapter 4, “Configuring Settings on the Cisco Unified IP Phone.”
The Cisco Unified IP Phone can interact with other services and devices on your IP network to provide
enhanced functionality. For example, you can integrate the Cisco Unified IP Phones with the corporate
Lightweight Directory Access Protocol 3 (LDAP3) standard directory to enable users to search for
co-workers contact information directly from their IP phones. You can also use XML to enable users to
access information such as weather, stocks, quote of the day, and other web-based information. For
information about configuring such services, see the “Configuring Corporate Directories” section on
page 5-17 and the “Setting Up Services” section on page 5-20.
Finally, because the Cisco Unified IP Phone is a network device, you can obtain detailed status
information from it directly. This information can assist you with troubleshooting any problems users
might encounter when using their IP phones. See Chapter 7, “Viewing Model Information, Status, and
Statistics on the Cisco Unified IP Phone,” for more information.
OL-15299-01
Related Topics
• Configuring Settings on the Cisco Unified IP Phone, page 4-1
• Configuring Features, Templates, Services, and Users, page 5-1
• Troubleshooting and Maintenance, page 9-1
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-7
Page 22

Understanding Security Features for Cisco Unified IP Phones
Configuring Telephony Features
You can modify certain settings for the Cisco Unified IP Phone from the Cisco Unified Communications
Manager Administration application. Use this web-based application to set up phone registration criteria
and calling search spaces, to configure corporate directories and services, and to modify phone button
templates, among other tasks. See the “Telephony Features Available for the Phone” section on page 5-1
and Cisco Unified Communications Manager Administration Guide for additional information.
For more information about the Cisco Unified Communications Manager Administration application,
refer to Cisco Unified Communications Manager documentation, including Cisco
Unified Communications Manager System Guide. You can also use the context-sensitive help available
within the application for guidance.
You can access the complete Cisco Unified Communications Manager documentation suite at this
location:
http://www.cisco.com/en/US/products/sw/voicesw/ps556/tsd_products_support_series_home.html
Related Topic
• Telephony Features Available for the Phone, page 5-1
Chapter 1 An Overview of the Cisco Unified IP Phone
Configuring Network Parameters Using the Cisco Unified IP Phone
You can configure parameters such as DHCP, TFTP, and IP settings on the phone itself. You can also
obtain statistics about a current call or firmware versions on the phone.
For more information about configuring features and viewing statistics from the phone, see Chapter 4,
“Configuring Settings on the Cisco Unified IP Phone,” and see Chapter 7, “Viewing Model Information,
Status, and Statistics on the Cisco Unified IP Phone.”
Providing Users with Feature Information
If you are a system administrator, you are likely the primary source of information for Cisco Unified IP
Phone users in your network or company. To ensure that you distribute the most current feature and
procedural information, familiarize yourself with Cisco Unified IP Phone documentation. Make sure to
visit the Cisco Unified IP Phone web site:
http://www.cisco.com/en/US/products/hw/phones/ps379/tsd_products_support_series_home.html
From this site, you can access various user guides, including wallet cards.
In addition to providing users with documentation, it is important to inform them about available
Cisco Unified IP Phone features—including features specific to your company or network—and about
how to access and customize those features, if appropriate.
For a summary of some of the key information that phone users need their system administrators to
provide, see Appendix A, “Providing Information to Users Via a Website.”
Understanding Security Features for Cisco Unified IP Phones
Implementing security in the Cisco Unified Communications Manager system prevents identity theft of
the phone and Cisco Unified Communications Manager server, prevents data tampering, and prevents
call signaling and media stream tampering.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-8
OL-15299-01
Page 23
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
To alleviate these threats, the Cisco Unified IP telephony network establishes and maintains
authenticated and encrypted communication streams between a phone and the server, digitally signs files
before they are transferred to a phone, and encrypts media streams and call signaling between
Cisco Unified IP phones.
The Cisco Unified IP Phones Series use the Phone Security Profile, which defines whether the device is
nonsecure, authenticated, or encrypted. For information on applying the security profile to the phone,
refer to Cisco Unified Communications Manager Security Guide.
If you configure security-related settings in Cisco Unified Communications Manager Administration,
the phone configuration file will contain sensitive information. To ensure the privacy of a configuration
file, you must configure it for encryption. For detailed information, refer to the “Configuring Encrypted
Phone Configuration Files” chapter in Cisco Unified Communications Manager Security Guide.
Table 1-2 shows where you can find additional information about security in this and other documents.
Table 1-2 Cisco Unified IP Phone and Cisco Unified Communications Manager Security Topics
Topic Reference
Detailed explanation of security, including set up,
configuration, and troubleshooting information for Cisco
Unified Communications Manager and Cisco Unified IP
Phones
Security features supported on the Cisco Unified IP Phone See the “Overview of Supported Security Features” section on
Restrictions regarding security features See the “Security Restrictions” section on page 1-17
Viewing a security profile name See the “Understanding Security Profiles” section on
Identifying phone calls for which security is implemented See the “Identifying Authenticated, Encrypted, and Protected
TLS connection See the “What Networking Protocols Are Used?” section on
Refer to Cisco Unified Communications Manager Security
Guide
page 1-10
page 1-12
Phone Calls” section on page 1-13
page 1-3
See the “Understanding Phone Configuration Files” section on
page 2-6
Security and the phone startup process See the “Understanding the Phone Startup Process” section on
page 2-7
Security and phone configuration files See the “Understanding Phone Configuration Files” section on
page 2-6
Changing the TFTP Server 1 or TFTP Server 2 option on the
phone when security is implemented
Understanding security icons in the Unified CM 1 through
See Table 4-2 in the “Network Configuration Menu” section
on page 4-5
See the “Unified CM Configuration” section on page 4-11
Unified CM 5 options in the Device Configuration Menu on
the phone
Items on the Security Configuration menu that you access
See the “Security Configuration Menu” section on page 4-23
from the Device Configuration menu on the phone
Items on the Security Configuration menu that you access
See the “Security Configuration Menu” section on page 4-29
from the Settings menu on the phone
Unlocking the CTL file See the “CTL File Menu” section on page 4-30
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
1-9
Page 24
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Table 1-2 Cisco Unified IP Phone and Cisco Unified Communications Manager Security Topics (continued)
Topic Reference
Disabling access to web pages for a phone See the “Disabling and Enabling Web Page Access” section on
page 8-3
Troubleshooting See the “Troubleshooting Cisco Unified IP Phone Security”
section on page 9-8
Refer to Cisco Unified Communications Manager Security
Guide, Troubleshooting chapter
Deleting the CTL file from the phone See the “Resetting or Restoring the Cisco Unified IP Phone”
section on page 9-13
Resetting or restoring the phone See the “Resetting or Restoring the Cisco Unified IP Phone”
section on page 9-13
802.1X Authentication for Cisco Unified IP Phones See these sections:
• “Supporting 802.1X Authentication on Cisco Unified IP
Phones” section on page 1-16
• “802.1X Authentication and Status” section on page 4-31
• “Troubleshooting Cisco Unified IP Phone Security”
Overview of Supported Security Features
Table 1-3 provides an overview of the security features that the Cisco Unified IP Phone 7970 Series
supports. For more information about these features and about Cisco Unified Communications Manager
and Cisco Unified IP Phone security, refer to Cisco Unified Communications Manager Security Guide.
For information about current security settings on a phone, look at the Security Configuration menus on
the phone (choose Settings > Security Configuration and choose Settings > Device Configuration >
Security Configuration). For more information, see Chapter 4, “Configuring Settings on the Cisco
Unified IP Phone.”
Note Most security features are available only if a certificate trust list (CTL) is installed on the phone. For
more information about the CTL, refer to “Configuring the Cisco CTL Client” chapter in the Cisco
Unified Communications Manager Security Guide.
section on page 9-8
1-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 25
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Table 1-3 Overview of Security Features
Feature Description
Image authentication Signed binary files (with the extension .sbn) prevent tampering with the firmware
image before it is loaded on a phone. Tampering with the image causes a phone to
fail the authentication process and reject the new image.
Customer-site certificate installation Each Cisco Unified IP Phone requires a unique certificate for device
authentication. Phones include a manufacturing installed certificate (MIC), but for
additional security, you can specify in Cisco Unified Communications Manager
Administration that a certificate be installed by using the CAPF (Certificate
Authority Proxy Function). Alternatively, you can install an LSC from the Security
Configuration menu on the phone. See the “Configuring Security on the Cisco
Unified IP Phone” section on page 3-12 for more information.
Device authentication Occurs between the Cisco Unified Communications Manager server and the phone
when each entity accepts the certificate of the other entity. Determines whether a
secure connection between the phone and a Cisco Unified Communications
Manager should occur, and, if necessary, creates a secure signaling path between
the entities using TLS protocol. Cisco Unified Communications Manager does not
register phones unless they can be authenticated by the
Cisco Unified Communications Manager.
File authentication Validates digitally signed files that the phone downloads. The phone validates the
signature to make sure that file tampering did not occur after the file creation. Files
that fail authentication are not written to Flash memory on the phone. The phone
rejects such files without further processing.
Signaling Authentication Uses the TLS protocol to validate that no tampering has occurred to signaling
packets during transmission.
Manufacturing installed certificate Each Cisco Unified IP Phone contains a unique manufacturing installed certificate
(MIC), which is used for device authentication. The MIC is a permanent unique
proof of identity for the phone, and allows Cisco Unified Communications
Manager to authenticate the phone.
Secure SRST reference
(SCCP phones only)
Media encryption Uses SRTP to ensure that the media streams between supported devices proves
Signaling encryption
(SCCP phones only)
CAPF (Certificate Authority Proxy
Function)
After you configure a SRST reference for security and then reset the dependent
devices in Cisco Unified Communications Manager Administration, the TFTP
server adds the SRST certificate to the phone cnf.xml file and sends the file to the
phone. A secure phone then uses a TLS connection to interact with the
SRST-enabled router.
secure and that only the intended device receives and reads the data. Includes
creating a media master key pair for the devices, delivering the keys to the devices,
and securing the delivery of the keys while the keys are in transport.
Ensures that all SCCP signaling messages that are sent between the device and the
Cisco Unified Communications Manager server are encrypted.
Implements parts of the certificate generation procedure that are too
processing-intensive for the phone, and it interacts with the phone for key
generation and certificate installation. The CAPF can be configured to request
certificates from customer-specified certificate authorities on behalf of the phone,
or it can be configured to generate certificates locally.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-11
Page 26
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Table 1-3 Overview of Security Features (continued)
Feature Description
Security profiles Defines whether the phone is nonsecure, authenticated, encrypted, or protected.
See the “Understanding Security Profiles” section on page 1-12 for more
information.
Encrypted configuration files Lets you ensure the privacy of phone configuration files.
Optional disabling of the web server
functionality for a phone
Phone hardening Additional security options, which you control from
802.1X Authentication The Cisco Unified IP Phone can use 802.1X authentication to request and gain
You can prevent access to a phone’s web page, which displays a variety of
operational statistics for the phone.
Cisco Unified Communications Manager Administration:
• Disabling PC port
• Disabling Gratuitous ARP (GARP)
• Disabling PC Voice VLAN access
• Disabling access to the Setting menus, or providing restricted access that
allows access to the User Preferences menu and saving volume changes only
• Disabling access to web pages for a phone.
Note You can view current settings for the PC Port Disabled, GARP Enabled,
and Voice VLAN enabled options by looking at the phone’s Security
Configuration menu. For more information, see the “Device Configuration
Menu” section on page 4-10.
access to the network. See the “Supporting 802.1X Authentication on Cisco
Unified IP Phones” section on page 1-16 for more information.
Related Topics
• Understanding Security Profiles, page 1-12
• Identifying Authenticated, Encrypted, and Protected Phone Calls, page 1-13
• Establishing and Identifying Secure Conference Calls, page 1-14
• Device Configuration Menu, page 4-10
• Supporting 802.1X Authentication on Cisco Unified IP Phones, page 1-16
• Security Restrictions, page 1-17
Understanding Security Profiles
Cisco Unified IP Phones that support Cisco Unified Communications Manager 7.0 or later use a security
profile, which defines whether the phone is nonsecure, authenticated, or encrypted. For information
about configuring the security profile and applying the profile to the phone, refer to Cisco Unified
Communications Manager Security Guide.
To view the security mode that is set for the phone, look at the Security Mode setting in the Security
Configuration menu. For more information, see the “Security Configuration Menu” section on
page 4-23.
1-12
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 27
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Related Topics
• Identifying Authenticated, Encrypted, and Protected Phone Calls, page 1-13
• Device Configuration Menu, page 4-10
• Security Restrictions, page 1-17
Identifying Authenticated, Encrypted, and Protected Phone Calls
When security is implemented for a phone, you can identify authenticated or encrypted phone calls by
icons on the screen that is on the phone.You can also determine if the connected phone is secure and
protected if a security tone plays at the beginning of the call.
In an authenticated call, all devices participating in the establishment of the call are authenticated by
Cisco Unified Communications Manager. When a call in progress is authenticated, the call progress icon
to the right of the call duration timer in the phone screen changes to this icon:
In an encrypted call, all devices participating in the establishment of the call are authenticated by the
Cisco Unified Communications Manager. In addition, call signaling and media streams are encrypted.
An encrypted call offers a high level of security, providing integrity and privacy to the call. When a call
in progress is being encrypted, the call progress icon to the right of the call duration timer in the phone
screen changes to this icon:
Note If the call is routed through non-IP call legs, for example, PSTN, the call may be nonsecure even though
it is encrypted within the IP network and has a lock icon associated with it.
In a protected call, a security tone plays at the beginning of a call to indicate that the other connected
phone is also receiving and transmitting encrypted audio. If your call is connected to a non-protected
phone, the security tone does not play.
Note Protected calling is supported for connections between two phones only. Some features, such as
conference calling, shared lines, Extension Mobility, and Join Across Lines are not available when
protected calling is configured. Protected calls are not authenticated.
Related Topic
• Understanding Security Features for Cisco Unified IP Phones, page 1-8
• Understanding Security Profiles, page 1-12
OL-15299-01
• Security Restrictions, page 1-17
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-13
Page 28
Understanding Security Features for Cisco Unified IP Phones
Establishing and Identifying Secure Conference Calls
You can initiate a secure conference call and monitor the security level of participants. A secure
conference call is established using this process:
1. A user initiates the conference from a secure phone (encrypted or authenticated security mode).
2. Cisco Unified Communications Manager assigns a secure conference bridge to the call.
3. As participants are added, Cisco Unified Communications Manager verifies the security mode of
each phone (encrypted or authenticated) and maintains the secure level for the conference.
4. The phone displays the security level of the conference call. A secure conference displays
(
encrypted) or (authenticated) icon to the right of “Conference” on the phone screen. If icon
displays, the conference is not secure.
Note There are interactions, restrictions, and limitations that affect the security level of the conference call
depending on the security mode of the participant’s phones and the availability of secure conference
bridges. See Tabl e 1 - 4 and Table 1- 5 for information about these interactions.
Chapter 1 An Overview of the Cisco Unified IP Phone
Establishing and Identifying Protected Calls
A protected call is established when your phone, and the phone on the other end, is configured for
protected calling. The other phone can be in the same Cisco Unified IP network, or on a network outside
the IP network. Protected calls can only be made between two phones. Conference calls and other
multiple-line calls are not supported.
A protected call is established using this process:
1. A user initiates the call from a protected phone (protected security mode).
2. The phone displays the icon (encrypted) on the phone screen. This icon indicates that the phone
is configured for secure (encrypted) calls, but this does not mean that the other connected phone is
also protected.
3. A security tone plays if the call is connected to another protected phone, indicating that both ends
of the conversation are encrypted and protected. If the call is connected to a non-protected phone,
then the secure tone is not played.
Note Protected calling is supported for conversations between two phones. Some features, such as conference
calling, shared lines, Extension Mobility, and Join Across Lines are not available when protected calling
is configured.
1-14
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 29
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Call Security Interactions and Restrictions
Cisco Unified Communications Manager checks the phone security status when conferences are
established and changes the security indication for the conference or blocks the completion of the call
to maintain integrity and also security in the system. Table 1-4 provides information about changes to
call security levels when using Barge.
Table 1-4 Call Security Interactions When Using Barge
Initiator’s Phone
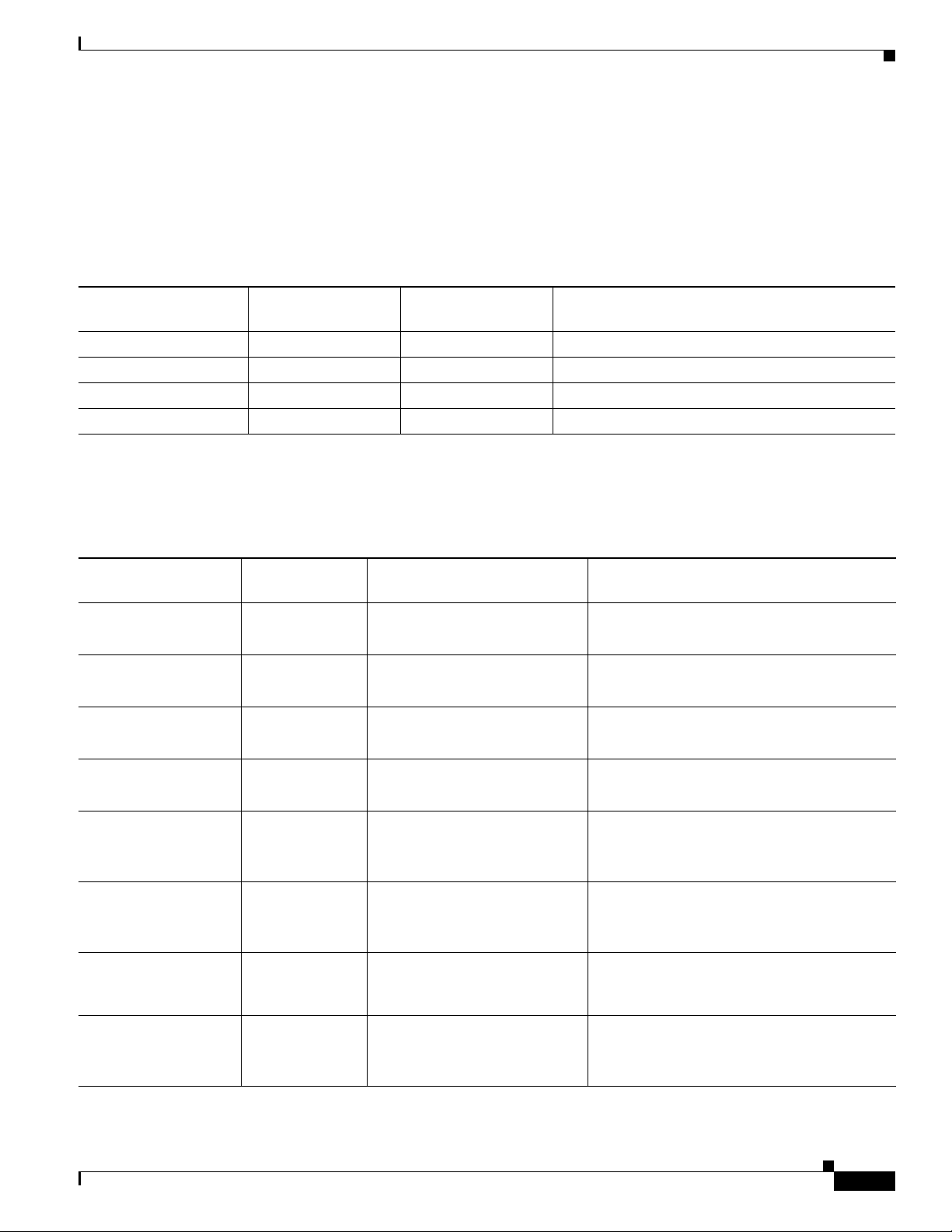
Security Level Feature Used Call Security Level Results of Action
Non-secure Barge Encrypted call Call barged and identified as non-secure call
Secure (encrypted) Barge Authenticated call Call barged and identified as authenticated call
Secure (authenticated) Barge Encrypted call Call barged and identified as authenticated call
Non-secure Barge Authenticated call Call barged and identified as non-secure call
Table 1-5 provides information about changes to conference security levels depending on the initiator’s
phone security level, the security levels of participants, and the availability of secure conference bridges.
Table 1-5 Security Restrictions with Conference Calls
Initiator’s Phone
Security Level Feature Used Security Level of Participants Results of Action
Non-secure Conference Encrypted or authenticated Non-secure conference bridge
Non-secure conference
Secure (encrypted or
authenticated)
Conference At least one member is
non-secure
Secure conference bridge
Non-secure conference
Secure (encrypted) Conference All participants are encrypted Secure conference bridge
Secure encrypted level conference
Secure (authenticated) Conference All participants are encrypted or
authenticated
Secure conference bridge
Secure authenticated level conference
Non-secure Conference Encrypted or authenticated Only secure conference bridge is available
and used
Non-secure conference
Secure (encrypted or
authenticated)
Conference Encrypted or authenticated Only non-secure conference bridge is
available and used
Non-secure conference
Secure (encrypted or
authenticated)
Conference Encrypted or secure Conference remains secure. When one
participant tries to hold the call with MOH,
the MOH does not play.
Secure (encrypted) Join Encrypted or authenticated Secure conference bridge
OL-15299-01
Conference remains secure (encrypted or
authenticated)
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-15
Page 30
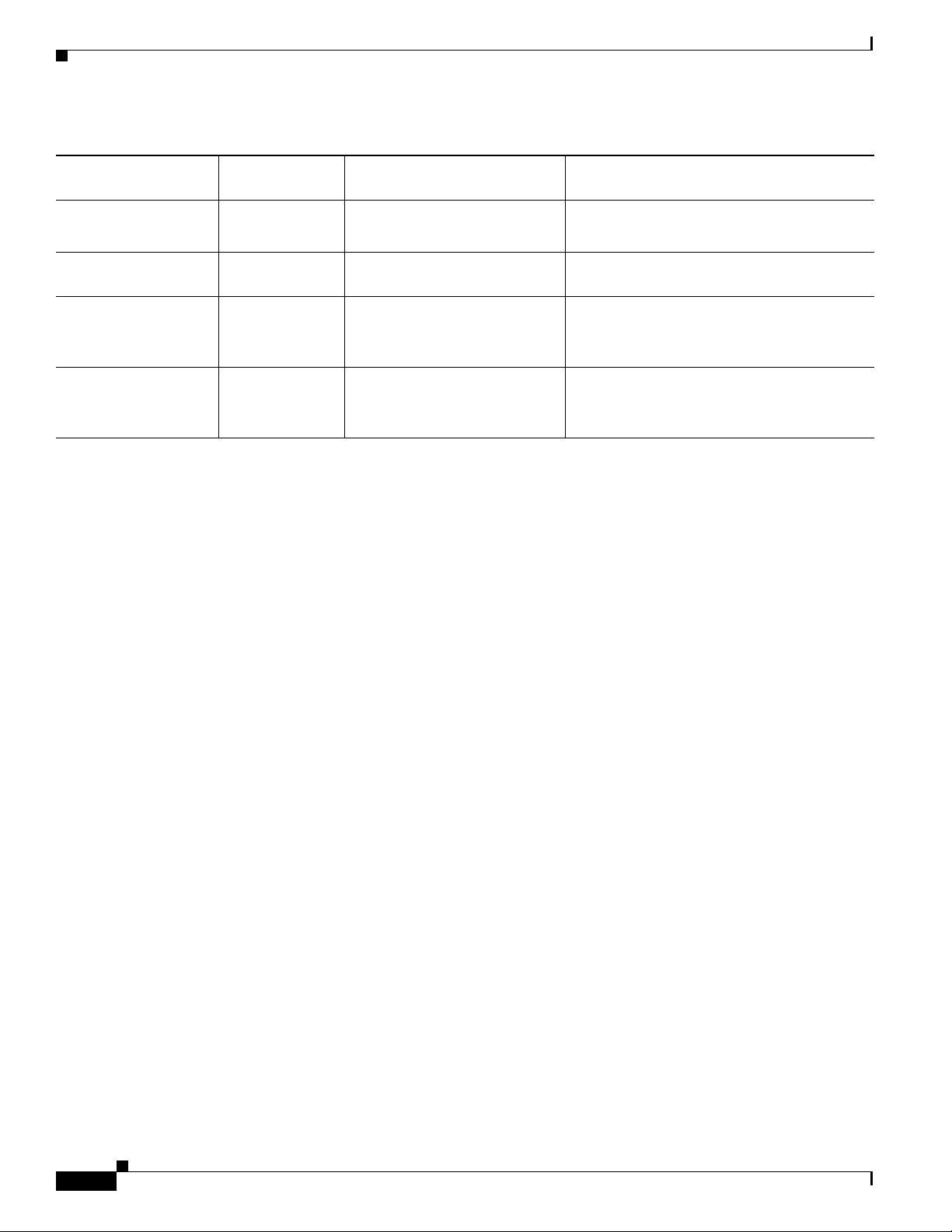
Chapter 1 An Overview of the Cisco Unified IP Phone
Understanding Security Features for Cisco Unified IP Phones
Table 1-5 Security Restrictions with Conference Calls (continued)
Initiator’s Phone
Security Level Feature Used Security Level of Participants Results of Action
Non-secure cBarge All participants are encrypted Secure conference bridge
Conference changes to non-secure
Non-secure MeetMe Minimum security level is
encrypted
Secure (encrypted) MeetMe Minimum security level is
authenticated
Secure (encrypted) MeetMe Minimum security level is
non-secure
Initiator receives message “Does not meet
Security Level”, call rejected.
Secure conference bridge
Conference accepts encrypted and
authenticated calls
Only secure conference bridge available and
used
Conference accepts all calls
Supporting 802.1X Authentication on Cisco Unified IP Phones
Overview
These sections provide information about 802.1X support on the Cisco Unified IP Phones:
• Overview, page 1-16
• Required Network Components, page 1-16
• Best Practices—Requirements and Recommendations, page 1-17
Cisco Unified IP phones and Cisco Catalyst switches have traditionally used Cisco Discovery Protocol
(CDP) to identify each other and to determine parameters such as VLAN allocation and inline power
requirements. However, CDP is not used to identify any locally attached PCs. Therefore, Cisco Unified
IP Phones provide an EAPOL pass-through mechanism, whereby a PC locally attached to the IP phone
may pass through EAPOL messages to the 802.1X authenticator in the LAN switch. This capability
prevents the IP phone from having to act as the authenticator, yet allows the LAN switch to authenticate
a data end point prior to accessing the network.
In conjunction with the EAPOL pass-through mechanism, Cisco Unified IP Phones provide a proxy
EAPOL-Logoff mechanism. If the locally attached PC is disconnected from the IP phone, the LAN
switch would not see the physical link fail, because the link between the LAN switch and the IP phone
is maintained. To avoid compromising network integrity, the IP phone sends an EAPOL-Logoff message
to the switch on behalf of the downstream PC, which triggers the LAN switch to clear the authentication
entry for the downstream PC.
The Cisco Unified IP phones contain an 802.1X supplicant in addition to the EAPOL pass-through
mechanism. This supplicant allows network administrators to control the connectivity of IP phones to
the LAN switch ports. The IP phone 802.1X supplicant implements the EAP-MD5 option for 802.1X
authentication.
Required Network Components
Support for 802.1X authentication on Cisco Unified IP Phones requires several components, including:
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-16
OL-15299-01
Page 31

Chapter 1 An Overview of the Cisco Unified IP Phone
• Cisco Unified IP Phone—The phone acts as the 802.1X supplicant, which initiates the request to
access the network.
• Cisco Secure Access Control Server (ACS) (or other third-party authentication server)—The
authentication server and the phone must both be configured with a shared secret that is used to
authenticate the phone.
• Cisco Catalyst Switch (or other third-party switch)—The switch must support 802.1X to act as the
authenticator and pass the messages between the phone and the authentication server. When the
exchange is completed, the switch grants or denies the phone access to the network.
Best Practices—Requirements and Recommendations
• Enable 802.1X Authentication—If you want to use the 802.1X standard to authenticate Cisco
Unified IP Phones, make sure that you have properly configured the other components before
enabling it on the phone. See the “802.1X Authentication and Status” section on page 4-31 for more
information.
• Configure PC Port—The 802.1X standard does not take into account the use of VLANs and thus
recommends that only a single device be authenticated to a specific switch port. However, some
switches (including Cisco Catalyst switches) support multi-domain authentication. The switch
configuration determines whether you can connect a PC to the phone PC port.
Understanding Security Features for Cisco Unified IP Phones
–
Enabled—If you are using a switch that supports multi-domain authentication, you can enable
the PC port and connect a PC to it. In this case, Cisco Unified IP Phones support proxy
EAPOL-Logoff to monitor the authentication exchanges between the switch and the attached
PC. For more information about IEEE 802.1X support on the Cisco Catalyst switches, refer to
the Cisco Catalyst switch configuration guides at:
http://www.cisco.com/en/US/products/hw/switches/ps708/tsd_products_support_series_home.
html
–
Disabled—If the switch does not support multiple 802.1X-compliant devices on the same port,
you should disable the PC Port when 802.1X authentication is enabled. See the “Security
Configuration Menu” section on page 4-23 for more information. If you do not disable this port
and subsequently attempt to attach a PC to it, the switch will deny network access to the phone
and the PC.
• Configure Voice VLAN—Because the 802.1X standard does not account for VLANs, you should
configure this setting based on the switch support.
–
Enabled—If you are using a switch that supports multi-domain authentication, you can continue
to use the voice VLAN.
–
Disabled—If the switch does not support multi-domain authentication, disable the Voice VLAN
and consider assigning the port to the native VLAN. See the “Security Configuration Menu”
section on page 4-23 for more information.
• Enter MD5 Shared Secret—If you disable 802.1X authentication or perform a factory reset on the
phone, the previously configured MD5 shared secret is deleted. See the “802.1X Authentication and
Status” section on page 4-31 for more information.
Security Restrictions
A user cannot barge into an encrypted call if the phone that is used to barge is not configured for
encryption. When barge fails in this case, a reorder tone (fast busy tone) plays on the phone on which
the user initiated the barge.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
1-17
Page 32

Chapter 1 An Overview of the Cisco Unified IP Phone
Overview of Configuring and Installing Cisco Unified IP Phones
If the initiator phone is configured for encryption, the barge initiator can barge into an authenticated or
nonsecure call from the encrypted phone. After the barge occurs, Cisco Unified Communications
Manager classifies the call as nonsecure.
If the initiator phone is configured for encryption, the barge initiator can barge into an encrypted call,
and the phone indicates that the call is encrypted.
A user can barge into an authenticated call, even if the phone that is used to barge is nonsecure. The
authentication icon continues to appear on the authenticated devices in the call, even if the initiator
phone does not support security.
Overview of Configuring and Installing Cisco Unified IP Phones
When deploying a new IP telephony system, system administrators and network administrators must
complete several initial configuration tasks to prepare the network for IP telephony service. For
information and a checklist for setting up and configuring a complete Cisco Unified IP telephony
network, refer to the “System Configuration Overview” chapter in Cisco Unified Communications
Manager System Guide.
After you have set up the IP telephony system and configured system-wide features in Cisco Unified
Communications Manager, you can add IP phones to the system.
The following topics provide an overview of procedures for adding Cisco Unified IP Phones to your
network:
• Configuring Cisco Unified IP Phones in Cisco Unified Communications Manager, page 1-18
• Installing Cisco Unified IP Phones, page 1-21
Configuring Cisco Unified IP Phones in Cisco Unified Communications Manager
To add phones to the Cisco Unified Communications Manager database, you can use:
• Auto-registration
• Cisco Unified Communications Manager Administration
• Bulk Administration Tool (BAT)
• BAT and the Tool for Auto-Registered Phones Support (TAPS)
For more information about these choices, see the “Adding Phones to the Cisco Unified Communications
Manager Database” section on page 2-9.
For general information about configuring phones in Cisco Unified Communications Manager, refer to
the “Cisco Unified IP Phone” chapter in Cisco Unified Communications Manager System Guide and to
the “Cisco Unified IP Phone Configuration” chapter in Cisco Unified Communications Manager
Administration Guide.
1-18
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 33

Chapter 1 An Overview of the Cisco Unified IP Phone
Overview of Configuring and Installing Cisco Unified IP Phones
Checklist for Configuring the Cisco Unified IP Phone 7970 Series in Cisco Unified Communications Manager
Table 1-6 provides an overview and checklist of configuration tasks for the Cisco Unified IP Phone 7970
Series in Cisco Unified Communications Manager Administration. The list presents a suggested order
to guide you through the phone configuration process. Some tasks are optional, depending on your
system and user needs. For detailed procedures and information, refer to the sources in the list.
Table 1-6 Checklist for Configuring the Cisco Unified IP Phone 7970 Series
Task Purpose For More Information
1. Gather the following information about the phone:
• Phone Model
• MAC address
• Physical location of the phone
• Name or user ID of phone user
• Device pool
• Partition, calling search space, and location information
• Number of lines and associated directory numbers
(DNs) to assign to the phone
Refer to Cisco Unified Communications Manager
System Guide, “Cisco Unified IP Phone” chapter.
See the “Telephony Features Available for the Phone”
section on page 5-1.
• Cisco Unified Communications Manager user to
associate with the phone
• Phone usage information that affects phone button
template, softkey template, phone features, IP Phone
services, or phone applications
Provides list of configuration requirements for setting up
phones.
Identifies preliminary configuration that you need to
perform before configuring individual phones, such as
phone button templates or softkey templates.
2. Customize phone button templates (if required).
Changes the number of line buttons, speed-dial buttons,
Service URL buttons or adds a Privacy button to meet user
needs.
3. Add and configure the phone by completing the required
fields in the Phone Configuration window. Required fields
are indicated by an asterisk (*) next to the field name; for
example, MAC address and device pool.
Adds the device with its default settings to the Cisco Unified
Communications Manager database.
Refer to Cisco Unified Communications Manager
Administration Guide, “Phone Button Template
Configuration” chapter.
See the“Modifying Phone Button Templates” section
on page 5-17.
Refer to Cisco Unified Communications Manager
Administration Guide, “Cisco Unified IP Phone
Configuration” chapter.
For information about Product Specific Configuration
fields, refer to “?” Button Help in the Phone
Configuration window.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-19
Page 34

Chapter 1 An Overview of the Cisco Unified IP Phone
Overview of Configuring and Installing Cisco Unified IP Phones
Table 1-6 Checklist for Configuring the Cisco Unified IP Phone 7970 Series (continued)
Task Purpose For More Information
4. Add and configure directory numbers (lines) on the phone by
completing the required fields in the Directory Number
Configuration window. Required fields are indicated by an
asterisk (*) next to the field name; for example, directory
number and presence group.
Adds primary and secondary directory numbers and features
associated with directory numbers to the phone.
5. Customize softkey templates.
Adds, deletes, or changes order of softkey features that
display on the user’s phone to meet feature usage needs.
6. Configure speed-dial buttons and assign speed-dial numbers
(optional).
Adds speed-dial buttons and numbers.
Note Users can change speed-dial settings on their phones
by using Cisco Unified CM User Options.
7. Configure Cisco Unified IP Phone services and assign
services (optional).
Provides IP Phone services.
Note Users can add or change services on their phones by
using the Cisco Unified CM User Options web pages.
Refer to Cisco Unified Communications Manager
Administration Guide, “Directory Number
Configuration” chapter, “Creating a Cisco Unity Voice
Mailbox” section.
See the “Telephony Features Available for the Phone”
section on page 5-1.
Refer to Cisco Unified Communications Manager
Administration Guide, “Softkey Template
Configuration” chapter.
See the “Configuring Softkey Templates” section on
page 5-19.
Refer to Cisco Unified Communications Manager
Administration Guide, “Cisco Unified IP Phone
Configuration” chapter, “Configuring Speed-Dial
Buttons” section.
Refer to Cisco Unified Communications Manager
Administration Guide, “Cisco Unified IP Phone
Services Configuration” chapter.
See the “Setting Up Services” section on page 5-20.
8. Assign services to phone buttons (optional).
Provides single button access to an IP phone service or URL.
9. Add user information by configuring required fields.
Required fields are indicated by an asterisk (*); for example,
User ID and last name.
Note Assign a password (for User Options web pages) and
PIN (for Extension Mobility and Personal Directory)
Adds user information to the global directory for Cisco
Unified Communications Manager.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-20
Refer to Cisco Unified Communications Manager
Administration Guide, “Cisco Unified IP Phone
Configuration” chapter, “Adding a Cisco
Unified IP Phone Service to a Phone Button” section.
Refer to Cisco Unified Communications Manager
Administration Guide, “End User Configuration”
chapter.
See the “Adding Users to Cisco
Unified Communications Manager” section on
page 5-20.
OL-15299-01
Page 35

Chapter 1 An Overview of the Cisco Unified IP Phone
Table 1-6 Checklist for Configuring the Cisco Unified IP Phone 7970 Series (continued)
Task Purpose For More Information
10. Associate a user to a user group.
Assigns users a common list of roles and permissions that
apply to all users in a user group. Administrators can manage
user groups, roles, and permissions to control the level of
access (and, therefore, the level of security) for system users.
11. Associate a user with a phone (optional).
Provides users with control over their phone such as
forwarding calls or adding speed-dial numbers or services.
Note Some phones, such as those in conference rooms, do
not have an associated user.
Refer to the Cisco Unified Communications Manager
Administration Guide:
• “End User Configuration” chapter, “End User
Configuration settings” section.
• “User Group Configuration” chapter, “Adding
Users to a User Group” section.
Refer to Cisco Unified Communications Manager
Administration Guide, “End User Configuration”
chapter, “Associating Devices to a User” section.
Installing Cisco Unified IP Phones
Installing Cisco Unified IP Phones
After you have added the phones to the Cisco Unified Communications Manager database, you can
complete the phone installation. You (or the phone users) can install the phone at the users’s location.
The Cisco Unified IP Phone Installation Guide, which is available on cisco.com, provides directions for
connecting the phone handset, cables, and other accessories.
Note Before you install a phone, even if it is new, upgrade the phone to the current firmware image. For
information about upgrading, refer to the Readme file for your phone, which is located at:
http://www.cisco.com/cgi-bin/tablebuild.pl/ip-7900ser
After the phone is connected to the network, the phone startup process begins and the phone registers
with Cisco Unified Communications Manager. To finish installing the phone, configure the network
settings on the phone depending on whether you enable or disable DHCP service.
If you used auto-registration, you need to update the specific configuration information for the phone
such as associating the phone with a user, changing the button table, or directory number.
Checklist for Installing the Cisco Unified IP Phone 7970 Series
Table 1-7 provides an overview and checklist of installation tasks for the Cisco Unified IP Phone 7970
Series. The list presents a suggested order to guide you through the phone installation. Some tasks are
optional, depending on your system and user needs. For detailed procedures and information, refer to
the sources in the list.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-21
Page 36

Chapter 1 An Overview of the Cisco Unified IP Phone
Installing Cisco Unified IP Phones
Table 1-7 Checklist for Installing the Cisco Unified IP Phone 7970 Series
Task Purpose For More Information
1. Choose the power source for the phone:
• Power over Ethernet (PoE)
• External power supply
Determines how the phone receives power.
2. Assemble the phone, adjust phone placement, and
connect the network cable.
Locates and installs the phone in the network.
3. Add a Cisco Unified IP Phone Expansion Module
7914 (optional).
Extends functionality to a Cisco Unified IP Phone by
adding 14 line appearances or speed dial numbers.
4. Monitor the phone startup process.
Verifies that phone is configured properly.
See the “Providing Power to the Phone” section on
page 2-3.
See the “Installing the Cisco Unified IP Phone” section
on page 3-5.
See the “Adjusting the Placement of the Cisco Unified IP
Phone” section on page 3-8.
See the “Attaching the Cisco Unified IP Phone
Expansion Module 7914” section on page 3-7.
See the “Verifying the Phone Startup Process” section on
page 3-10.
1-22
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 37

Chapter 1 An Overview of the Cisco Unified IP Phone
Table 1-7 Checklist for Installing the Cisco Unified IP Phone 7970 Series (continued)
Task Purpose For More Information
5. When you are configuring the network settings on the
phone, you can set up an IP address for the phone by
either using DHCP or manually entering an IP address.
Using DHCP—To enable DHCP and allow the DHCP
server to automatically assign an IP address to the
Cisco Unified IP Phone and direct the phone to a TFTP
server, choose Settings > Network Configuration>
IPv4 Configuration and:
• To enable DHCP, set DHCP Enabled to Yes .
DHCP is enabled by default.
• To use an alternate TFTP server, set Alternate
TFTP Server to Yes , and enter the IP address for
the TFTP Server.
Note Consult with the network administrator if you
need to assign an alternative TFTP server
instead of using the TFTP server assigned by
DHCP.
See the “Configuring Startup Network Settings” section
on page 3-11.
See the “Network Configuration Menu” section on
page 4-5.
Installing Cisco Unified IP Phones
Without DHCP—You must configure the IP address,
subnet mask, TFTP server, and default router locally
on the phone, choose Settings > Network
Configuration> IPv4 Configuration:
To disable DHCP and manually set an IP address:
a. To disable DHCP, set DHCP Enabled to No.
b. Enter the static IP address for phone.
c. Enter the subnet mask.
d. Enter the default router IP addresses.
e. Set Alternate TFTP Server to Yes , a n d enter the
IP address for TFTP Server 1.
You must also enter the domain name where the phone
resides by Choosing Settings > Network
Configuration.
6. Set up security on the phone.
Provides protection against data tampering threats and
identity theft of phones.
7. Make calls with the Cisco Unified IP Phone.
Verifies that the phone and features work correctly.
8. Provide information to end users about how to use
their phones and how to configure their phone options.
Ensures that users have adequate information to
successfully use their Cisco Unified IP Phones.
See the “Configuring Security on the Cisco Unified IP
Phone” section on page 3-12.
Refer to Cisco Unified IP Phone 7970 Series Guide.
See Appendix A, “Providing Information to Users Via a
Website.”
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
1-23
Page 38

Installing Cisco Unified IP Phones
Chapter 1 An Overview of the Cisco Unified IP Phone
1-24
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 39

CHAP T ER
2
Preparing to Install the Cisco Unified IP Phone on Your Network
Cisco Unified IP Phones enable you to communicate using voice over a data network. To provide this
capability, the IP Phones depend upon and interact with several other key Cisco Unified IP Telephony
and network components, including Cisco Unified Communications Manager, DNS and DHCP servers,
TFTP servers, media resources, Cisco prestandard PoE, and so on.
This chapter focuses on the interactions between the Cisco Unified IP Phone 7970 Series and
Cisco Unified Communications Manager, DNS and DHCP servers, TFTP servers, and switches. It also
describes options for powering phones.
For related information about voice and IP communications, refer to this URL:
http://www.cisco.com/en/US/products/sw/voicesw/index.html
This chapter provides an overview of the interaction between the Cisco Unified IP Phone 7970 Series
and other key components of the Voice over IP (VoIP) network. It includes these topics:
• Understanding Interactions with Other Cisco Unified IP Communications Products, page 2-2
• Providing Power to the Phone, page 2-3
• Understanding Phone Configuration Files, page 2-6
• Understanding the Phone Startup Process, page 2-7
• Adding Phones to the Cisco Unified Communications Manager Database, page 2-9
• Using Cisco Unified IP Phones with Different Protocols, page 2-12
• Determining the MAC Address of a Cisco Unified IP Phone, page 2-14
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-1
Page 40

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Understanding Interactions with Other Cisco Unified IP Communications Products
Understanding Interactions with Other Cisco
Unified
IP Communications Products
To function in the IP telephony network, the Cisco Unified IP Phone must be connected to a networking
device, such as a Cisco Catalyst switch. You must also register the Cisco Unified IP Phone with a
Cisco Unified Communications Manager system before sending and receiving calls.
This section includes these topics:
• Understanding How the Cisco Unified IP Phone Interacts with Cisco Unified Communications
Manager, page 2-2
• Understanding How the Cisco Unified IP Phone Interacts with the VLAN, page 2-3
Understanding How the Cisco Unified IP Phone Interacts with Cisco
Unified
Communications Manager
Cisco Unified Communications Manager is an open and industry-standard call processing system.
Cisco Unified Communications Manager software sets up and tears down calls between phones,
integrating traditional PBX functionality with the corporate IP network. Cisco Unified Communications
Manager manages the components of the IP telephony system—the phones, the access gateways, and the
resources necessary for features such as call conferencing and route planning. Cisco Unified
Communications Manager also provides:
• Firmware for phones
• Authentication and encryption (if configured for the telephony system)
• Configuration file and CTL file, via TFTP service
• Phone registration
• Call preservation, so that a media session continues if signaling is lost between the primary
Communications Manager and a phone
For information about configuring Cisco Unified Communications Manager to work with the IP devices
described in this chapter, refer to Cisco Unified Communications Manager Administration Guide, Cisco
Unified Communications Manager System Guide, and Cisco Unified Communications Manager Security
Guide.
For an overview of security functionality for the Cisco Unified IP Phone, see the “Understanding
Security Features for Cisco Unified IP Phones” section on page 1-8.
Note If the Cisco Unified IP Phone model that you want to configure does not appear in the Phone Type
drop-down list in Cisco Unified Communications Manager Administration, go to the following URL and
install the latest support patch for your version of Cisco Unified Communications Manager:
http://www.cisco.com/kobayashi/sw-center/sw-voice.shtml
Related Topic
• Telephony Features Available for the Phone, page 5-1
2-2
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 41

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Providing Power to the Phone
Understanding How the Cisco Unified IP Phone Interacts with the VLAN
The Cisco Unified IP Phone 7970 Series have an internal Ethernet switch, enabling forwarding of
packets to the phone, and to the access port and the network port on the back of the phone.
If a computer is connected to the access port, the computer and the phone share the same physical link
to the switch and share the same port on the switch. This shared physical link has the following
implications for the VLAN configuration on the network:
• The current VLANs might be configured on an IP subnet basis. However, additional IP address
might not be available to assign the phone to the same subnet as other devices connect to the same
port.
• Data traffic present on the data/native VLAN may reduce the quality of Voice-over-IP traffic.
• Network security may indicate a need to isolate the VLAN voice traffic from the VLAN data traffic.
You can resolve these issues by isolating the voice traffic onto a separate VLAN. The switch port that
the phone is connected to would be configured to have separate VLANs for carrying:
• Voice traffic to and from the IP phone (auxiliary VLAN, on the Cisco Catalyst 6000 series, for
example)
• Data traffic to and from the PC connected to the switch through the access port of the IP phone
(native VLAN)
Isolating the phones on a separate, auxiliary VLAN improves the quality of the voice traffic and allows
a large number of phones to be added to an existing network where there are not enough IP addresses
for each phone.
For more information, refer to the documentation included with a Cisco switch. You can also access
related documentation at this URL:
http://cisco.com/en/US/products/hw/switches/index.html
Related Topics
• Understanding the Phone Startup Process, page 2-7
• Network Configuration Menu, page 4-5
Providing Power to the Phone
Models in the Cisco Unified IP Phone 7970 Series can be powered with external power or with Power
over Ethernet (PoE). External power is provided through a separate power supply. PoE is provided by a
switch through the Ethernet cable attached to a phone.
Note When you install a phone that is powered with external power, connect the power supply to the phone
and to a power outlet before you connect the Ethernet cable to the phone. When you remove a phone that
is powered with external power, disconnect the Ethernet cable from the phone before you disconnect the
power supply.
OL-15299-01
The following sections provide more information about powering a phone:
• Power Guidelines, page 2-4
• Phone Power Consumption and Display Brightness, page 2-5
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-3
Page 42

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Providing Power to the Phone
• Power Outage, page 2-5
• Obtaining Additional Information about Power, page 2-6
Power Guidelines
Table 2-1 provides guidelines that apply to external power and to PoE power for phones the
Cisco Unified IP Phone 7970 Series.
Table 2-1 Guidelines for Powering the Cisco Unified IP Phone 7970 Series
Power Type Guidelines
External power— Provided
through the CP-PWR-CUBE-3
external power supply
External power—
Provided through the Cisco
Unified IP Phone Power Injector
PoE power—Provided by a
switch through the Ethernet
cable attached to the phone
The Cisco Unified IP Phone Series uses the CP-PWR-CUBE-3 power supply.
The Cisco Unified IP Phone Power Injector may be used with any Cisco Unified IP Phone.
Functioning as a midspan device, the injector delivers inline power to the attached phone.
The Cisco Unified IP Phone Power Injector is connected between a switch port and the IP
Phone, and supports a maximum cable length of 100m between the unpowered switch and
the IP Phone.
• The inline power patch panel WS-PWR-PANEL is not compatible with the Cisco
Unified IP Phone 7970 Series.
• To ensure uninterruptible operation of the phone, make sure that the switch has a
backup power supply.
• Make sure that the CatOS or IOS version running on your switch supports your
intended phone deployment. Refer to the documentation for your switch for operating
system version information.
2-4
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 43

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Phone Power Consumption and Display Brightness
The power consumed by a phone depends on its power configuration. See Table 2- 1 for a power
configuration overview. See Table 2-2 for the maximum power consumed by a phone for each
configuration option and the correlating phone screen brightness level.
Note Power consumption values shown in the table include power losses in the cable that connects the phone
to the switch.
Table 2-2 Power Consumption and Display Brightness for Power Configurations
Phone Model Power Configuration
Cisco Unified IP
Phone 7970G
Cisco Unified IP
Phone 7971G-GE
1. Starts at approximately 1/2 brightness, changes to full brightness when the phone negotiates additional power.
Cisco prestandard PoE from a switch that supports a maximum of 7
W power per port, with bidirectional power negotiation enabled
Cisco prestandard PoE from a Cisco Switch that supports 7 W or
15.4 W power per port, without bidirectional power negotiation
IEEE 802.3af Class 3 power from a Cisco switch, without
bidirectional power negotiation
IEEE 802.3af Class 3 power from a third-party switch 6.3 W Approx. 1/2
IEEE 802.3af Class 3 power from a Cisco switch, with bidirectional
power negotiation enabled
Cisco prestandard PoE from a Cisco Switch that supports 15.4 W
power per port, with bidirectional power negotiation enabled
External power — Full
IEEE 802.3af Class 3 power from a Cisco switch (with or without
bidirectional power negotiation enabled) or from a third-party
switch
External power — Full
Providing Power to the Phone
Max. Power
Consumed from a
Switch
6.3 W Approx. 1/2
6.3 W Approx. 1/2
6.3 W Approx. 1/2
10.25 W Full
10.25 W Full
15.4 W Near full
Phone Screen
Brightness
1
Note When a phone is powered with a method that does not support full brightness for the phone screen, the
Power Outage
OL-15299-01
phone Brightness control (Settings > User Preferences > Brightness) does not allow you to set the
brightness to the maximum value.
Your accessibility to emergency service through the phone is dependent on the phone being powered. If
there is an interruption in the power supply, Service and Emergency Calling Service dialing will not
function until power is restored. In the case of a power failure or disruption, you may need to reset or
reconfigure equipment before using the Service or Emergency Calling Service dialing.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-5
Page 44

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Understanding Phone Configuration Files
Obtaining Additional Information about Power
For related information about power, refer to the documents shown in Tab l e 2-3. These documents
provide information about these topics:
• Cisco switches that work with the Cisco Unified IP Phone 7970 Series
• The Cisco IOS releases that support bidirectional power negotiation
• Other requirements and restrictions regarding power
Table 2-3 Related Documentation for Power
Document Topics URL
Cisco Unified IP Phone
Power Injector
PoE Solutions http://www.cisco.com/en/US/netsol/
Cisco Catalyst Switches http://cisco.com/en/US/products/hw/switches/index.html
Integrated Service Routers http://www.cisco.com/en/US/products/hw/routers/index.html
Cisco IOS Software http://www.cisco.com/en/US/products/sw/iosswrel/products_ios_cisco_
http://www.cisco.com/en/US/products/hw/phones/ps379/prod_installati
on_guides_list.html
ns340/ns394/ns147/ns412/networking_solutions_package.html
ios_software_category_home.html
Understanding Phone Configuration Files
Configuration files for a phone are stored on the TFTP server and define parameters for connecting to
Cisco Unified Communications Manager. In general, any time you make a change in Cisco
Unified Communications Manager that requires the phone to be reset, a change is automatically made
to the phone’s configuration file.
Configuration files also contain information about which image load the phone should be running. If this
image load differs from the one that is currently loaded on a phone, the phone contacts the TFTP server
to request the required load files. (These files are digitally signed to ensure the authenticity of the file
source.)
In addition, if the device security mode in the configuration file is set to Authenticated and the CTL file
on the phone has a valid certificate for Cisco Unified Communications Manager, the phone establishes
a TLS connection to Cisco Unified Communications Manager. Otherwise, the phone establishes a TCP
connection. For SIP phones, a TLS connection requires that the transport protocol in the phone
configuration file be set to TLS, which corresponds to the transport type in the SIP Security Profile in
Cisco Unified Communications Manager.
Note If the device security mode in the configuration file is set to Authenticated or Encrypted, but the phone
has not received a CTL file, the phone continuously tries to obtain a CTL file so it can register securely.
If you configure security-related settings in Cisco Unified Communications Manager Administration,
the phone configuration file will contain sensitive information. To ensure the privacy of a configuration
file, you must configure it for encryption. For detailed information, refer to the “Configuring Encrypted
Phone Configuration Files” chapter in Cisco Unified Communications Manager Security Guide.
2-6
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 45

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
A phone accesses a default configuration file named XmlDefault.cnf.xml from the TFTP server when
these conditions exist:
• You have enabled auto-registration in Cisco Unified Communications Manager
• The phone has not been added to the Cisco Unified Communications Manager Database
• The phone is registering for the first time
If auto registration is not enabled and the phone has not been added to the Cisco
Unified Communications Manager database, the phone registration request will be rejected. In this case,
the phone resets and attempts to register repeatedly.
If the phone has registered before, the phone accesses the configuration file named
SEPmac_address.cnf.xml, where mac_address is the MAC address of the phone.
For SIP phones, the TFTP server generates these SIP configuration files:
• SIP IP Phone:
–
For unsigned and unencrypted files—SEP<mac>.cnf.xml
–
For signed files—SEP<mac>.cnf.xml.sgn
–
For signed and encrypted files—SEP<mac>.cnf.xml.enc.sgn
Understanding the Phone Startup Process
• Dial Plan—<dialplan>.xml
• Softkey Template—<softkey_template>.xml
The filenames are derived from the MAC Address and Description fields in the Phone Configuration
window of Cisco Unified Communications Manager Administration. The MAC address uniquely
identifies the phone. For more information refer to Cisco Unified Communications Manager
Administration Guide.
For more information about how the phone interacts with the TFTP server, refer to Cisco Unified
Communications Manager System Guide, “Cisco TFTP” chapter.
Understanding the Phone Startup Process
When connecting to the VoIP network, the Cisco Unified IP Phone goes through a standard startup
process, as described in Tabl e 2 -4. Depending on your specific network configuration, not all of these
process steps may occur on your Cisco Unified IP Phone.
Table 2-4 Cisco Unified IP Phone Startup Process
Task Purpose Related Topics
1. Obtaining Power from the Switch.
If a phone is not using external power, the switch provides
in-line power through the Ethernet cable that is attached to
the phone.
2. Loading the StoredPhone Image.
The Cisco Unified IP Phone has non-volatile flash memory
in which it stores firmware images and user-defined
preferences. At startup, the phone runs a bootstrap loader
that loads a phone image stored in flash memory. Using this
image, the phone initializes its software and hardware.
See the “Providing Power to the Phone” section on
page 2-3.
See the “Resolving Startup Problems” section on
page 9-1.
See the “Resolving Startup Problems” section on
page 9-1.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-7
Page 46

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Understanding the Phone Startup Process
Table 2-4 Cisco Unified IP Phone Startup Process (continued)
Task Purpose Related Topics
3. Configuring VLAN.
If the Cisco Unified IP Phone is connected to a Cisco
switch, the switch next informs the phone of the voice
VLAN defined on the switch port. The phone needs to
know its VLAN membership before it can proceed with the
Dynamic Host Configuration Protocol (DHCP) request for
an IP address.
4. Obtaining an IP Address.
If the Cisco Unified IP Phone is using DHCP to obtain an
IP address, the phone queries the DHCP server to obtain
one. If you are not using DHCP in your network, you must
assign static IP addresses to each phone locally.
5. Accessing a TFTP Server.
on to assigning an IP address, the DHCP server directs the
Cisco Unified IP Phone to a TFTP Server. If the phone has
a statically defined IP address, you must configure the
TFTP server locally on the phone; the phone then contacts
the TFTP server directly.
See the “Network Configuration Menu” section
on page 4-5.
See the “Resolving Startup Problems” section on
page 9-1.
See the “Network Configuration Menu” section
on page 4-5.
See the “Resolving Startup Problems” section on
page 9-1.
See the “Network Configuration Menu” section
on page 4-5.
See the “Resolving Startup Problems” section on
page 9-1.
Note You can also assign an alternative TFTP server to
use instead of the one assigned by DHCP.
6. Requesting the CTL file.
The TFTP server stores the certificate trust list (CTL) file.
This file contains a list of Cisco Unified Communications
Managers and TFTP servers that the phone is authorized to
connect to. It also contains the certificates necessary for
establishing a secure connection between the phone and
Cisco Unified Communications Manager.
Refer to Cisco Unified Communications Manager
Security Guide, “Configuring the Cisco CTL
Client” chapter.
2-8
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 47

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Adding Phones to the Cisco Unified Communications Manager Database
Table 2-4 Cisco Unified IP Phone Startup Process (continued)
Task Purpose Related Topics
7. Requesting the Configuration File.
The TFTP server has configuration files, which define
parameters for connecting to Cisco
Unified Communications Manager and other information
for the phone.
8. Contacting Cisco Unified Communications Manager.
The configuration file defines how the Cisco
Unified IP Phone communicates with Cisco
Unified Communications Manager and provides a phone
with its load ID. After obtaining the file from the TFTP
server, the phone attempts to make a connection to the
highest priority Cisco Unified Communications Manager
on the list. If security is implemented, the phone makes a
TLS connection. Otherwise, it makes a non-secure TCP
connection.
If the phone was manually added to the database, Cisco
Unified Communications Manager identifies the phone. If
the phone was not manually added to the database and
auto-registration is enabled in Cisco
Unified Communications Manager, the phone attempts to
auto-register itself in the Cisco Unified Communications
Manager database.
See the “Understanding Phone Configuration
Files” section on page 2-6.
See the “Resolving Startup Problems” section on
page 9-1.
See the “Resolving Startup Problems” section on
page 9-1.
Note Auto-registration is disabled when security is
enabled on Cisco Unified Communications
Manager. In this case, the phone must be manually
added to the Cisco Unified Communications
Manager database.
Adding Phones to the Cisco Unified Communications Manager
Database
Before installing the Cisco Unified IP phone, you must choose a method for adding phones to the
Cisco Unified Communications Manager database. These sections describe the methods:
• Adding Phones with Auto-Registration, page 2-10
• Adding Phones with Auto-Registration and TAPS, page 2-11
• Adding Phones with Cisco Unified Communications Manager Administration, page 2-12
• Adding Phones with BAT, page 2-12
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-9
Page 48

Adding Phones to the Cisco Unified Communications Manager Database
Table 2-5 provides an overview of these methods for adding phones to the
Cisco Unified Communications Manager database.
Table 2-5 Methods for Adding Phones to the Cisco Unified Communications Manager
Database
Requires MAC
Method
Address? Notes
Auto-registration No
Auto-registration with
No Requires auto-registration and the Bulk
TAPS
Using the Cisco Unified
Yes Requires phones to be added individually
Communications
Manager Administration
Using BAT Yes Can add groups of same model of phone.
Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
• Results in automatic assignment of directory
numbers.
• Not available when security or encryption is
enabled.
Administration Tool (BAT); updates the Cisco
Unified Communications Manager database with
the MAC address and DNs for the device when user
calls TAPS from the phone.
Can schedule when phones are added to the Cisco
Unified Communications Manager database.
Adding Phones with Auto-Registration
By enabling auto-registration before you begin installing phones, you can:
• Add phones without first gathering MAC addresses from the phones.
• Automatically add a Cisco Unified IP Phone to the Cisco Unified Communications Manager
database when you physically connect the phone to your IP telephony network. During
auto-registration, Cisco Unified Communications Manager assigns the next available sequential
directory number to the phone.
• Quickly enter phones into the Cisco Unified Communications Manager database and modify any
settings, such as the directory numbers, from Cisco Unified Communications Manager.
• Move auto-registered phones to new locations and assign them to different device pools without
affecting their directory numbers.
Note Cisco recommends you use auto-registration to add less than 100 phones to your network. To add more
than 100 phones to your network, use the Bulk Administration Tool (BAT). See the “Adding Phones with
BAT” section on page 2-12.
Auto-registration is disabled by default. In some cases, you might not want to use auto-registration; for
example, if you want to assign a specific directory number to the phone or if you plan to implement
authentication or encryption, as described in Cisco Unified Communications Manager Security Guide.
For information about enabling auto-registration, refer to “Enabling Auto-Registration” in the Cisco
Unified Communications Manager Administration Guide.
2-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 49

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Adding Phones to the Cisco Unified Communications Manager Database
Note When you configure the cluster for mixed mode through the Cisco CTL client, auto-registration is
automatically disabled. When you configure the cluster for non-secure mode through the Cisco CTL
client, auto-registration is automatically enabled.
Related Topics
• Adding Phones with Auto-Registration and TAPS, page 2-11
• Adding Phones with Cisco Unified Communications Manager Administration, page 2-12
• Adding Phones with BAT, page 2-12
Adding Phones with Auto-Registration and TAPS
You can add phones with auto-registration and TAPS, the Tool for Auto-Registered Phones Support,
without first gathering MAC addresses from phones.
TAPS works with the Bulk Administration Tool (BAT) to update a batch of phones that were already
added to the Cisco Unified Communications Manager database with dummy MAC addresses. Use TAPS
to update MAC addresses and download pre-defined configurations for phones.
Note Cisco recommends you use auto-registration and TAPS to add less than 100 phones to your network. To
add more than 100 phones to your network, use the Bulk Administration Tool (BAT). See the “Adding
Phones with BAT” section on page 2-12.
To implement TAPS, you or the end-user dial a TAPS directory number and follow voice prompts. When
the process is complete, the phone will have downloaded its directory number and other settings, and the
phone will be updated in Cisco Unified Communications Manager Administration with the correct MAC
address.
Auto-registration must be enabled in Cisco Unified Communications Manager Administration
(System > Cisco Unified CM) for TAPS to function.
Note When you configure the cluster for mixed mode through the Cisco CTL client, auto-registration is
automatically disabled. When you configure the cluster for non-secure mode through the Cisco CTL
client, auto-registration is automatically enabled.
Refer to Cisco Unified Communications Manager Bulk Administration Guide for detailed instructions
about BAT and about TAPS.
Related Topics
• Adding Phones with Auto-Registration, page 2-10
• Adding Phones with Cisco Unified Communications Manager Administration, page 2-12
• Adding Phones with BAT, page 2-12
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-11
Page 50

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Using Cisco Unified IP Phones with Different Protocols
Adding Phones with Cisco Unified Communications Manager Administration
You can add phones individually to the Cisco Unified Communications Manager database using
Cisco Unified Communications Manager Administration. To do so, you first need to obtain the MAC
address for each phone.
For information about determining a MAC address, see the “Determining the MAC Address of a Cisco
Unified IP Phone” section on page 2-14.
After you have collected MAC addresses, in Cisco Unified Communications Manager Administration,
choose Device > Phone and click Add New to begin.
For complete instructions and conceptual information about Cisco Unified Communications Manager,
refer to Cisco Unified Communications Manager Administration Guide and to Cisco Unified
Communications Manager System Guide.
Related Topics
• Adding Phones with Auto-Registration, page 2-10
• Adding Phones with Auto-Registration and TAPS, page 2-11
• Adding Phones with BAT, page 2-12
Adding Phones with BAT
Cisco Unified Communications Manager Bulk Administration Tool (BAT), a standard Cisco Unified
Communications Manager application, enables you to perform batch operations, which includes registration,
on multiple phones.
To add phones using BAT only (not in conjunction with TAPS), you first need to obtain the appropriate
MAC address for each phone.
For information about determining a MAC address, see the “Determining the MAC Address of a Cisco
Unified IP Phone” section on page 2-14.
For detailed instructions about using BAT, refer to Cisco Unified Communications Manager Bulk
Administration Guide.
Related Topics
• Adding Phones with Auto-Registration, page 2-10
• Adding Phones with Auto-Registration and TAPS, page 2-11
• Adding Phones with Cisco Unified Communications Manager Administration, page 2-12
Using Cisco Unified IP Phones with Different Protocols
The Cisco Unified IP Phone can operate with SCCP (Skinny Client Control Protocol) or SIP (Session
Initiation Protocol). You can convert a phone that is using one protocol for use with the other protocol.
This section includes these topics:
2-12
• Converting a New Phone from SCCP to SIP, page 2-13
• Converting an In-Use Phone from SCCP to SIP, page 2-13
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 51

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
• Converting an In-Use Phone from SIP to SCCP, page 2-13
• Deploying a Phone in an SCCP and SIP Environment, page 2-14
Converting a New Phone from SCCP to SIP
A new, unused phone is set for SCCP by default. To convert this phone to SIP, perform these steps:
Procedure
Step 1 Take one of these actions:
• To auto-register the phone, set the Auto Registration Phone Protocol parameter in Cisco Unified
Communications Manager Administration to SIP.
• To provision the phone using the Bulk Administration Tool (BAT), choose the appropriate phone
model and choose SIP from the BAT.
• To provision the phone manually, make the appropriate changes for SIP on the Phone configuration
window in Cisco Unified Communications Manager Administration.
Refer to Cisco Unified Communications Manager Administration Guide for detailed information about
Cisco Unified Communications Manager configuration. Refer to Cisco Unified Communications
Manager Bulk Administration Guide for detailed information about using the BAT.
Step 2 If you are not using DHCP in your network, configure the network parameters for the phone.
Using Cisco Unified IP Phones with Different Protocols
See the “Configuring Startup Network Settings” section on page 3-14.
Step 3 Save the configuration updates, reset the phone, and have the user power cycle the phone.
Converting an In-Use Phone from SCCP to SIP
You can use the Bulk Administration Tool (BAT) to convert a phone that is in use in your network from
SCCP to SIP. To access BAT from Cisco Unified Communications Manager Administration, choose
Bulk Administration > Phones > Migrate Phones > SCCP to SIP. For detailed information, refer to
Cisco Unified Communications Manager Bulk Administration Guide.
Converting an In-Use Phone from SIP to SCCP
To convert a phone that is in use in your network from SIP to SCCP, perform these steps. For more
information, Cisco Unified Communications Manager Administration Guide.
Tip Before deleting a SIP phone (that you want to convert to a SCCP phone) from the Cisco Unified
Communications Manager database, copy all of the phone configuration information, so when you add
the phone back to the database, you will have the configuration information readily available.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
2-13
Page 52

Chapter 2 Preparing to Install the Cisco Unified IP Phone on Your Network
Determining the MAC Address of a Cisco Unified IP Phone
Procedure
Step 1 In Cisco Unified Communications Manager Administration, delete the existing SIP phone from the
Cisco Unified Communications Manager database.
Step 2 In Cisco Unified Communications Manager Administration, create the phone as an SCCP phone.
Step 3 Power cycle the phone.
Deploying a Phone in an SCCP and SIP Environment
To deploy Cisco Unified IP Phones in an environment that includes SCCP and SIP and in which the
Cisco Unified Communications Manager Auto-Registration parameter is SCCP, perform these general
steps:
1. Set the Cisco Unified Communications Manager auto_registration_protocol parameter to SCCP.
From Cisco Unified Communications Manager Administration, choose System > Enterprise
Parameters.
2. Install the phones.
3. Change the Auto Registration Protocol enterprise parameter to SIP.
4. Auto-register the SIP phones.
Determining the MAC Address of a Cisco Unified IP Phone
Several of the procedures that are described in this manual require you to determine the MAC address
of a Cisco Unified IP Phone. You can determine the MAC address for a phone in any of these ways:
• From the phone, choose Settings > Network Configuration and look at the MAC Address field.
• Look at the MAC label on the back of the phone.
• Display the web page for the phone and click the Device Information hyperlink.
For information about accessing the web page, see the “Accessing the Web Page for a Phone” section
on page 8-1.
2-14
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 53

CHAP T ER
3
Setting Up the Cisco Unified IP Phone
This chapter includes the following topics, which help you install the Cisco Unified IP Phone 7970
Series on an IP telephony network:
• Before You Begin, page 3-1
• Understanding the Cisco Unified IP Phone 7970 Series Components, page 3-2
• Installing the Cisco Unified IP Phone, page 3-5
• Attaching the Cisco Unified IP Phone Expansion Module 7914, page 3-7
• Adjusting the Placement of the Cisco Unified IP Phone, page 3-8
• Verifying the Phone Startup Process, page 3-10
• Configuring Startup Network Settings, page 3-11
• Configuring Security on the Cisco Unified IP Phone, page 3-12
Note Before you install a Cisco Unified IP phone, you must decide how to configure the phone in your
network. Then you can install the phone and verify its functionality. For more information, see
Chapter 2, “Preparing to Install the Cisco Unified IP Phone on Your Network.”
Before You Begin
Before installing the Cisco Unified IP Phone, review the requirements in these sections:
• Network Requirements, page 3-1
• Cisco Unified Communications Manager Configuration, page 3-2
Network Requirements
For the Cisco Unified IP Phone 7970 Series to successfully operate as a Cisco Unified IP Phone endpoint
in your network, your network must meet these requirements:
• Working Voice over IP (VoIP) network:
–
VoIP configured on your Cisco routers and gateways
–
Cisco Unified Communications Manager Release 7.0 or higher installed in your network and
configured to handle call processing
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-1
Page 54

Chapter 3 Setting Up the Cisco Unified IP Phone
Understanding the Cisco Unified IP Phone 7970 Series Components
• IP network that supports DHCP or manual assignment of IP address, gateway, and subnet mask
Note The Cisco Unified IP Phone displays the date and time from Cisco Unified Communications Manager.
If the Cisco Unified Communications Manager server is located in a different time zone than the phones,
the phones will not display the correct local time.
Cisco Unified Communications Manager Configuration
The Cisco Unified IP Phone requires Cisco Unified Communications Manager to handle call
processing. Refer to Cisco Unified Communications Manager Administration Guide or to
context-sensitive help in the Cisco Unified Communications Manager application to ensure that
Cisco Unified Communications Manager is set up properly to manage the phone and to properly route
and process calls.
If you plan to use auto-registration, verify that it is enabled and properly configured in
Cisco Unified Communications Manager before connecting any Cisco Unified IP Phone to the network.
For information about enabling and configuring auto-registration, refer to Cisco
Unified Communications Manager Administration Guide. Also, see the “Adding Phones to the Cisco
Unified Communications Manager Database” section on page 2-9.
You must use Cisco Unified Communications Manager to configure and assign telephony features to the
Cisco Unified IP Phones. See the “Telephony Features Available for the Phone” section on page 5-1 for
details.
In Cisco Unified Communications Manager, you can add users to the database and associate them with
specific phones. In this way, users gain access to web pages that allow them to configure items such as
call forwarding, speed dialing, and voice messaging system options. See the “Adding Users to Cisco
Unified Communications Manager” section on page 5-20 for details.
Understanding the Cisco Unified IP Phone 7970 Series
Components
The Cisco Unified IP Phone 7970 Series includes these components on the phone or as accessories for
the phone:
• Network and Access Ports, page 3-2
• Handset, page 3-3
• Speakerphone, page 3-3
• Headset, page 3-3
Network and Access Ports
3-2
The back of the Cisco Unified IP Phone includes these ports:
• Network port—Labeled 10/100 SW on the Cisco Unified IP Phone 7970G and 10/100/1000 SW on
the Cisco Unified IP Phone 7971G-GE
• Access port—Labeled 10/100 PC on the Cisco Unified IP Phone 7970G and 10/100/1000 PC on the
Cisco Unified IP Phone 7971G-GE
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 55

Chapter 3 Setting Up the Cisco Unified IP Phone
Each port supports 10/100 or 10/100/1000 Mbps half- or full-duplex connections to external devices.
You can use either Category 3 or 5 cabling for 10-Mbps connections, but you must use Category 5 for
100 and 1000 Mbps connections.
Use the SW network port to connect the phone to the network. You must use a straight-through cable on
this port. The phone can also obtain inline power from a switch over this connection. See the “Providing
Power to the Phone” section on page 2-3 for details.
Use the PC access port to connect a network device, such as a computer, to the phone. You must use a
straight-through cable on this port.
Handset
The handset is designed especially for use with a Cisco Unified IP Phone. It includes a light strip that
indicates incoming calls and voice messages waiting.
To connect a handset to the Cisco Unified IP Phone, remove the hookswitch clip from the cradle area,
as shown in Figure 3-1. Then plug the cable into the handset and into the Handset port on the back of
the phone.
Understanding the Cisco Unified IP Phone 7970 Series Components
Speakerphone
Headset
Figure 3-1 Removing the Hookswitch Clip
185165
By default, the speakerphone is enabled on Cisco Unified IP Phone 7970 Series.
You can disable the speakerphone by using Cisco Unified Communications Manager Administration. To
do so, choose Device > Phone and locate the phone you want to modify. In the Phone Configuration for
the phone, check the Disable Speakerphone check box.
Although Cisco Systems performs internal testing of third-party headsets for use with the Cisco Unified
IP Phones, Cisco does not certify or support products from headset or handset vendors.
OL-15299-01
Cisco recommends the use of good quality external devices, for example, headsets that are screened
against unwanted radio frequency (RF) and audio frequency (AF) signals. Depending on the quality of
headsets and their proximity to other devices, such as mobile phones and two-way radios, some audio
noise or echo may still occur. An audible hum or buzz may be heard by either the remote party of by both
the remote party and the Cisco Unified IP Phone user. Humming or buzzing sounds can be caused by a
range of outside sources; for example, electric lights, electric motors, or large PC monitors. See Using
External Devices, page 3-4, for more information.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-3
Page 56

Understanding the Cisco Unified IP Phone 7970 Series Components
Note In some cases, hum may be reduced or eliminated by using a local power cube or power injector.
These environmental and hardware inconsistencies in the locations where Cisco Unified IP Phones are
deployed means that there is not a single headset solution that is optimal for all environments.
Cisco recommends that customers test headsets in their intended environment to determine performance
before making a purchasing decision and deploying en mass.
Note The Cisco Unified IP Phone 7970G/7971G-GE supports wideband headsets.
Audio Quality Subjective to the User
Beyond the physical, mechanical and technical performance, the audio portion of a headset must sound
good to the user and the party on the far end. Sound quality is subjective and Cisco cannot guarantee the
performance of any headsets or handsets. However, a variety headsets from leading headset
manufacturers have been reported to perform well with Cisco Unified IP Phones. See manufacturer’s
sites for details.
Chapter 3 Setting Up the Cisco Unified IP Phone
Connecting a Headset
To connect a headset to the Cisco Unified IP Phone, plug it into the Headset port on the back of the
phone. Press the Headset button on the phone to place and answer calls by using the headset.
You can use the headset with all of the features on the Cisco Unified IP Phone, including the Volume and
Mute buttons. Use these buttons to adjust the ear piece volume and to mute the speech path from the
headset microphone.
Disabling a Headset
You can disable the headset by using Cisco Unified Communications Manager Administration. If you do
so, you also will disable the speakerphone.
To disable the headset from Cisco Unified Communications Manager Administration, choose Device >
Phone and locate the phone that you want to modify. In the Phone Configuration for the phone, check
the Disable Speakerphone and Headset check box.
Using External Devices
The following information applies when you use external devices with the Cisco Unified IP Phone:
Cisco recommends the use of good quality external devices that are shielded (screened) against
unwanted radio frequency (RF) and audio frequency (AF) signals.
Depending on the quality of these devices and their proximity to other devices such as mobile phones or
two-way radios, some audio noise may still occur. In these cases, Cisco recommends that you take one
or more of the following actions:
• Move the external device away from the source of the RF or AF signals.
• Route the external device cables away from the source of the RF or AF signals.
3-4
• Use shielded cables for the external device, or use cables with a better shield and connector.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 57

Chapter 3 Setting Up the Cisco Unified IP Phone
• Shorten the length of the external device cable.
• Apply ferrites or other such devices on the cables for the external device.
Cisco cannot guarantee the performance of the system because Cisco has no control over the quality of
external devices, cables, and connectors. The system will perform adequately when suitable devices are
attached using good quality cables and connectors.
Caution In European Union countries, use only external headsets that are fully compliant with the EMC Directive
[89/336/EC].
Installing the Cisco Unified IP Phone
You must connect the Cisco Unified IP Phone to the network and to a power source before using it.
Table 3-1 describes the tasks. See Figure 3-2 for a graphical representation of the connections.
Note Before you install a phone, even if it is new, upgrade the phone to the current firmware image.
Before using external devices, read the “Using External Devices” section on page 3-4 for safety and
performance information.
Installing the Cisco Unified IP Phone
Before You Begin
Remove the hookswitch clip (see the “Handset” section on page 3-3) from the cradle area.
To install a Cisco Unified IP Phone, perform the following steps:
Table 3-1 Installing the Cisco Unified IP Phone 7970G-7971G-GE
Task Purpose Related Topics
1. Connect the handset to the Handset port. —
2. Connect a headset to the Headset port.
Optional. You can add a headset later if you do not connect
See the “Headset” section on page 3-3 for supported
headsets.
one now.
3. Connect the power supply to the Cisco DC Adapter
portOptional.
4. Connect a Category 3 or 5 straight-through Ethernet cable
from the switch to the 10/100 SW port (Cisco Unified IP
See the “Providing Power to the Phone” section on
page 2-3.
See the “Network and Access Ports” section on
page 3-2 for guidelines.
Phone 7970) or the 10/100/1000 SW port (Cisco Unified IP
Phone 7971G-GE).
Each Cisco Unified IP Phone ships with one Ethernet cable
in the box.
5. Connect a Category 3 or 5 straight-through Ethernet cable
from another network device, such as a desktop computer,
See the “Network and Access Ports” section on
page 3-2 for guidelines.
to the 10/100 PC port (Cisco Unified IP Phone 7970) or the
10/100/1000 PC port (Cisco Unified IP Phone 7971G-GE).
Optional. You can connect another network device later if
you do not connect one now.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-5
Page 58

Installing the Cisco Unified IP Phone
Figure 3-2 Cisco Unified IP Phone 7970 Series Rear Cable Connections
1
AUX
10/100/1000 SW 10/100/1000 PC
Chapter 3 Setting Up the Cisco Unified IP Phone
DC48V
3
2
5
4
6
7
130055
1 DC adapter port (DC48V) 5 Access port (1000 appears on the Cisco
Unified IP Phone 7971G-GE only)
2 Power supply with DC Connector 6 Handset port
3 Power cable with AC wall plug 7 Headset port
4 Network port (1000 appears on the Cisco
Unified IP Phone 7971G-GE only)
Related Topics
• Before You Begin, page 3-1
• Attaching the Cisco Unified IP Phone Expansion Module 7914
• Adjusting the Placement of the Cisco Unified IP Phone, page 3-8
3-6
• Configuring Startup Network Settings, page 3-11
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 59

Chapter 3 Setting Up the Cisco Unified IP Phone
Attaching the Cisco Unified IP Phone Expansion Module 7914
Attaching the Cisco Unified IP Phone Expansion Module 7914
The Cisco Unified IP Phone Expansion Module 7914 can be attached to Cisco Unified IP Phone 7970
Series to extend the number of line appearances or speed dial buttons. You can customize the button
templates for the Cisco Unified IP Phone Expansion Module 7914 to determine the number of line
appearances and speed dial buttons. See the “Modifying Phone Button Templates” section on page 5-17
for details.
You can attach a Cisco Unified IP Phone Expansion Module 7914 to a phone:
• When you initially add the phone to Cisco Unified Communications Manager by selecting
7914 14-Button Line Expansion Module in the Module 1 or Module 2 fields and selecting the
appropriate expansion module firmware. See Step 6 in the following procedure.
• After the phone is configured in Cisco Unified Communications Manager.
To configure the Cisco Unified IP Phone Expansion Module 7914 on a Cisco Unified IP Phone, follow
these steps:
Procedure
Step 1 Log in to Cisco Unified Communications Manager Administration.
Cisco Unified Communications Manager Administration displays.
Step 2 From the menu, choose Device > Phone.
The Find and List Phone window displays. You can search for one or more phones that you want to
configure for the Cisco Unified IP Phone Expansion Module 7914.
Step 3 Select and enter your search criteria and click Find.
The Find and List Phone window redisplays and shows a list of the phones that match your search
criteria.
Step 4 Click the IP Phone that you want to configure for the Cisco Unified IP Phone Expansion Module 7914.
The Phone configuration window displays.
Step 5 Scroll to the Phone Button and Expansion Module Template Information section.
Step 6 Add support for expansion modules:
• To add one expansion module, in the Module 1 field, choose 7914 14-Button Line Expansion
Module.
• To add a second expansion module, in the Module 2 field, choose 7914 14-Button Line Expansion
Module.
In the Firmware Load Information section, there are two fields for specifying the firmware load for
Modules 1 and 2. You can leave these fields blank to use the default firmware load.
Step 7 Scroll to the top of the page and click Update.
A message displays asking you to reset the phone for the changes to take effect. Click OK.
OL-15299-01
Step 8 Click Reset Phone for the changes to take effect.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-7
Page 60

Chapter 3 Setting Up the Cisco Unified IP Phone
Adjusting the Placement of the Cisco Unified IP Phone
Note Refer users to their User Options web pages so they can configure buttons and program buttons to access
phone services on the Cisco Unified IP Phone Expansion Module 7914. See the “How Users Subscribe
to Services and Configure Phone Features” section on page A-3 for more details.
Related Topics
• Before You Begin, page 3-1
• Adjusting the Placement of the Cisco Unified IP Phone, page 3-8
• Configuring Startup Network Settings, page 3-11
Adjusting the Placement of the Cisco Unified IP Phone
The Cisco Unified IP Phone includes an adjustable footstand. When placing the phone on a desktop
surface, you can adjust the tilt height to several different angles in 7.5 degree increments from flat to 60
degrees. You can also mount the phone to the wall by using the footstand or by using the optional locking
wall mount kit.
Adjusting Cisco Unified IP Phone Footstand and Phone Height
You can adjust the footstand adjustment plate on the Cisco Unified IP Phone to the height that provides
optimum viewing of the phone screen. See Figure 3-4 for more information.
Procedure
Step 1 Push in the footstand adjustment button.
Step 2 Adjust the footstand to the desired height.
Securing the Phone with a Cable Lock
You can secure the Cisco Unified IP Phone 7970G and 7971G-GE to a desktop by using a laptop cable
lock. The lock connects to the security slot on the back of the phone, and the cable can be secured to a
desktop.
The security slot can accommodate a lock up to 20 mm. Compatible laptop cable locks include the
Kensington laptop cable lock and laptop cable locks from other manufacturers that can fit into the
security slot on the back of the phone.
See Figure 3-3.
3-8
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 61

Chapter 3 Setting Up the Cisco Unified IP Phone
Figure 3-3 Connecting a Cable Lock to the Cisco Unified IP Phone 7970 Series
Adjusting the Placement of the Cisco Unified IP Phone
Mounting the Phone to the Wall
You can mount the Cisco Unified IP Phone on the wall by using the footstand as a mounting bracket or
you can use special brackets available in a Cisco Unified IP Phone wall mount kit. (Wall mount kits must
be ordered separately from the phones.) If you attach the phone to a wall by using the standard footstand
and not the wall mount kit, you need to supply the following tools and parts:
• Screwdriver
• Screws to secure the Cisco Unified IP phone to the wall
See Figure 3-4 for a graphical representation of the phone parts.
Before You Begin
To ensure that the handset attaches securely to a wall-mounted phone, remove the handset wall hook
from the handset rest, rotate the hook 180 degrees, and reinsert the hook. Turning the hook exposes a lip
on which the handset catches when the phone is vertical. For an illustrated procedure, refer to Installing
the Wall Mount Kit for the Cisco Unified IP Phone at:
http://www.cisco.com/en/US/products/hw/phones/ps379/prod_installation_guides_list.html
To mount the phone on the wall by using the standard footstand, follow these steps:
144477
OL-15299-01
Caution Use care not to damage wires or pipes located inside the wall when securing screws to wall studs.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-9
Page 62

Verifying the Phone Startup Process
Procedure
Step 1 Push in the footstand adjustment button.
Step 2 Adjust the footstand so it is flat against the back of the phone.
Step 3 Insert two screws into a wall stud, matching them to the two screw holes on the back of the footstand.
The keyholes fit standard phone jack mounts.
Step 4 Hang the phone on the wall.
Figure 3-4 Parts Used in Wall Mounting the Cisco Unified IP Phone
Chapter 3 Setting Up the Cisco Unified IP Phone
1 Footstand adjustment button—Raises and lowers adjustment plate
2 Wall mounting screw holes
3 Adjustment plate—Raises and lowers phone vertically
Verifying the Phone Startup Process
After the Cisco Unified IP Phone has power connected to it, the phone begins its startup process by
cycling through these steps.
1. These buttons flash on and off in sequence:
–
Headset. (Only if the handset is off-hook when the phone powers up. In this case, hang up the
handset within 3 seconds or the phone launches its secondary load instead of its primary load.)
–
Mute.
–
Speaker.
2. Some or all of the line keys flash orange.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-10
OL-15299-01
Page 63

Chapter 3 Setting Up the Cisco Unified IP Phone
Caution If the line keys flash red in sequence after flashing yellow, do not power down the phone until the
sequence of red flashes completes. This sequence can take several minutes to complete.
3. Some or all of the line keys flash green.
Normally, this sequence takes just a few seconds. However, if the phone flash memory is erased or
the phone load is corrupted, the sequence of green flashes will continue while the phone begins a
software update procedure. If the phone performs this procedure, the following buttons light to
indicate progress:
–
Headset—Phone is waiting for the network and completing CDP and DHCP configuration. (A
DHCP server must be available in your network.)
–
Mute—Phone is downloading images from the TFTP server.
–
Speaker—Phone is writing images to its flash memory.
4. The phone screen displays the Cisco Systems, Inc., logo screen.
5. These messages display as the phone starts:
–
Verifying load (if the phone load does not match the load on the TFTP server). If this message
displays, the phone start up again and repeats step 1 through step 4 above.
–
Configuring IP.
–
Updating CTL.
Configuring Startup Network Settings
–
Updating Locale.
–
Configuring Unified CM List.
–
Registering.
6. The main phone screen displays:
–
Current date and time
–
Primary directory number
–
Additional directory numbers and speed dial numbers, if configured
–
Softkeys
If the phone successfully passes through these stages, it has started up properly. If the phone does not
start up properly, see the “Resolving Startup Problems” section on page 9-1.
Configuring Startup Network Settings
If you are not using DHCP in your network, you must configure these network settings on the
Cisco Unified IP Phone after installing the phone on the network:
• IP address
• IP subnet information
• Default gateway IP address
• TFTP server IP address
OL-15299-01
You may also configure these optional settings as necessary:
• Domain name
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-11
Page 64

Chapter 3 Setting Up the Cisco Unified IP Phone
Configuring Security on the Cisco Unified IP Phone
• DNS server IP address
Collect this information and see the instructions in Chapter 4, “Configuring Settings on the Cisco
Unified IP Phone.”
Configuring Security on the Cisco Unified IP Phone
The security features protect against several threats, including threats to the identity of the phone and to
data. These features establish and maintain authenticated communication streams between the phone and
the Cisco Unified Communications Manager server, and digitally sign files before they are delivered.
For more information about the security features, see the “Understanding Security Features for Cisco
Unified IP Phones” section on page 1-8. Also, refer to Cisco Unified Communications Manager Security
Guide.
A Locally Significant Certificate (LSC) installs on phones after you perform the necessary tasks that are
associated with the Certificate Authority Proxy Function (CAPF). You can use
Cisco Unified Communications Manager Administration to configure an LSC, as described in
Cisco Unified Communications Manager Security Guide.
Alternatively, you can initiate the installation of an LSC from the Security Configuration menu on the
phone. This menu also lets you update or remove an LSC.
Before you begin, make sure that the appropriate Cisco Unified Communications Manager and the
CAPF security configurations are complete:
• The CTL file should have a CAPF certificate.
• The CAPF certificate must exist in the /usr/local/cm/.security/certs folder in every server in the
cluster.
• The CAPF is running and configured.
Refer to Cisco Unified Communications Manager Security Guide for more information.
To configure an LSC on the phone, perform the following procedure. Depending on how you have
configured the CAPF, this procedure installs an LSC, updates an existing LSC, or removes an existing
LSC.
Procedure
Step 1 Obtain the CAPF authentication code that was set when the CAPF was configured.
Step 2 From the phone, press the Settings > Security Configuration.
Note You can control access to the Settings Menu by using the Settings Access field in the
Cisco Unified Communications Manager Administration Phone Configuration window. For
more information, see Cisco Unified Communications Manager Administration Guide.
3-12
Step 3 Press **# to unlock settings on the Security Configuration menu. (See the “Unlocking and Locking
Options” section on page 4-3 for information about using locking and unlocking options.)
Note If a Settings Menu password has been provisioned, SIP phones present an “Enter password”
prompt after you enter **#.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 65

Chapter 3 Setting Up the Cisco Unified IP Phone
Step 4 Scroll to LSC and press the Update softkey.
The phone prompts for an authentication string.
Step 5 Enter the authentication code and press the Submit softkey.
The phone begins to install, update, or remove the LSC, depending on how the CAPF was configured.
During the procedure, a series of messages displays in the LSC option field in the Security Configuration
menu so you can monitor progress. When the procedure completes successfully, the phone will display
Installed or Not Installed.
The LSC install, update, or removal process can take a long time to complete. You can stop the process
at any time by pressing the Stop softkey from the Security Configuration menu. (Settings must be
unlocked before you can press this softkey.)
When the phone successfully completes the installation procedure, it displays “Success.” If the phone
displays, “Failure,” the authorization string may be incorrect or the phone may not be enabled for
upgrading. Refer to error messages generated by the CAPF and take appropriate actions.
You can verify that an LSC is installed on the phone by choosing Settings > Model Information and
ensuring that the LSC setting shows Installed.
Configuring Security on the Cisco Unified IP Phone
Related Topic
• Understanding Security Features for Cisco Unified IP Phones, page 1-8
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
3-13
Page 66

Configuring Security on the Cisco Unified IP Phone
Chapter 3 Setting Up the Cisco Unified IP Phone
3-14
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 67

CHAP T ER
4
Configuring Settings on the Cisco Unified IP Phone
The Cisco Unified IP Phone includes many configurable network and device settings that you may need
to modify before the phone is functional for your users. You can access these settings, and change many
of them, through menus on the phone.
This chapter includes the following topics:
• Configuration Menus on the Cisco Unified IP Phone 7970 Series, page 4-1
• Overview of Options Configurable from a Phone, page 4-4
• Network Configuration Menu, page 4-5
• Device Configuration Menu, page 4-10
• Security Configuration Menu, page 4-29
Configuration Menus on the Cisco Unified IP Phone 7970 Series
The Cisco Unified IP Phone includes the following configuration menus:
• Network Configuration menu—Provides options for viewing and making a variety of network
settings. For more information, see the “Network Configuration Menu” section on page 4-5.
• Device Configuration menu—Provides access to sub-menus from which you can view a variety of
non network-related settings. For more information, see the “Device Configuration Menu” section
on page 4-10.
• Security Configuration menu—Provides options for displaying and modifying security settings. For
more information, see the “Security Configuration Menu” section on page 4-29.
Before you can change option settings on the Network Configuration menu, you must unlock options for
editing. See the “Unlocking and Locking Options” section on page 4-3 for instructions.
For information about the keys you can use to edit or change option settings, see the “Editing Values”
section on page 4-3.
You can control whether a phone user has access to phone settings by using the Settings Access field in
Cisco Unified Communications Manager Administration Phone Configuration.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Unlocking and Locking Options, page 4-3
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-1
Page 68

Configuration Menus on the Cisco Unified IP Phone 7970 Series
• Editing Values, page 4-3
• Overview of Options Configurable from a Phone, page 4-4
• Network Configuration Menu, page 4-5
• Device Configuration Menu, page 4-10
• Security Configuration Menu, page 4-29
Displaying a Configuration Menu
To display a configuration menu, perform the following steps.
Note You can control whether a phone has access to the Settings menu or to options on this menu by using the
Settings Access field in the Cisco Unified Communications Manager Administration Phone
configuration window. The Settings Access field accepts these values:
• Enabled—Allows access to the Settings menu.
• Disabled—Prevents access to the Settings menu.
Chapter 4 Configuring Settings on the Cisco Unified IP Phone
• Restricted—Allows access to the User Preferences menu and allows volume changes to be saved.
Prevents access to other options on the Settings menu.
If you cannot access an option on the Settings menu, check the Settings Access field.
Procedure
Step 1 Press the Settings button to access the Settings menu.
Step 2 Perform one of these actions to display the desired menu:
• Use the Navigation button to select the desired menu and then press the Select softkey.
• Use the keypad on the phone to enter the number that corresponds to the menu.
Step 3 To display a submenu, repeat Step 2.
Step 4 To exit a menu, press the Exit softkey.
Related Topics
• Unlocking and Locking Options, page 4-3
• Editing Values, page 4-3
• Overview of Options Configurable from a Phone, page 4-4
4-2
• Network Configuration Menu, page 4-5
• Device Configuration Menu, page 4-10
• Security Configuration Menu, page 4-29
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 69

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Unlocking and Locking Options
Configuration options that can be changed from a phone are locked by default to prevent users from
making changes that could affect the operation of a phone. You must unlock these options before you
can change them.
When options are inaccessible for modification, a locked padlock icon appears on the configuration
menus. When options are unlocked and accessible for modification, an unlocked padlock icon
appears on these menus.
To unlock or lock options, press **#. This action either locks or unlocks the options, depending on the
previous state.
Note If a Settings Menu password has been provisioned, SIP phones present an “Enter password” prompt after
you enter **#.
Make sure to lock options after you have made your changes.
Caution Do not press **# to unlock options and then immediately press **# again to lock options. The phone
will interpret this sequence as **#**, which will reset the phone. To lock options after unlocking them,
wait at least 10 seconds before you press **# again.
Configuration Menus on the Cisco Unified IP Phone 7970 Series
Editing Values
Related Topics
• Displaying a Configuration Menu, page 4-2
• Editing Values, page 4-3
• Overview of Options Configurable from a Phone, page 4-4
• Network Configuration Menu, page 4-5
• Device Configuration Menu, page 4-10
When you edit the value of an option setting, follow these guidelines:
• Use the keys on the keypad to enter numbers and letters.
• To enter letters by using the keypad, use a corresponding number key. Press the key one or more
times to display a particular letter. For example, press the 2 key once for “a,” twice quickly for “b,”
and three times quickly for “c.” After you pause, the cursor automatically advances to allow you to
enter the next letter.
• To enter a period (for example, in an IP address), press the . (period) softkey or press * on the
keypad.
• Press the << softkey if you make a mistake. This softkey deletes the character to the left of the
cursor.
• Press the Cancel softkey before pressing the Save softkey to discard any changes that you have
made.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-3
Page 70

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Overview of Options Configurable from a Phone
Note The Cisco Unified IP Phone provides several methods you can use to reset or restore option settings, if
necessary. For more information, see the “Resetting or Restoring the Cisco Unified IP Phone” section
on page 9-13.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Unlocking and Locking Options, page 4-3
• Overview of Options Configurable from a Phone, page 4-4
• Network Configuration Menu, page 4-5
• Device Configuration Menu, page 4-10
• Security Configuration Menu, page 4-29
Overview of Options Configurable from a Phone
The settings that you can change on a phone fall into several categories, as shown in Tab l e 4 -1. For a
detailed explanation of each setting and instructions for changing them, see the “Network Configuration
Menu” section on page 4-5.
Note There are several options on various configuration menus that are for display only or that you can
configure from Cisco Unified Communications Manager. These options also are also described in this
chapter.
Table 4-1 Settings Configurable from the Phone
Category Description Network Configuration Menu Option
General Network Settings
VLAN settings Admin. VLAN ID allows you to change the administrative
VLAN used by the phone. PC VLAN allows the phone to
interoperate with third-party switches that do not support a
Admin. VLAN ID
PC VLAN
voice VLAN.
Port settings Allow you to set the speed and duplex of the network and
access ports.
IPv4 Network Settings
DHCP settings Dynamic Host Configuration Protocol (DHCP)
automatically assigns IP address to devices when you
connect them to the network. Cisco Unified IP Phones
SW Port Configuration
PC Port Configuration
DHCP
DHCP Address Released
enable DHCP by default.
4-4
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 71

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Network Configuration Menu
Table 4-1 Settings Configurable from the Phone (continued)
Category Description Network Configuration Menu Option
IP settings If you do not use DHCP in your network, you can make IP
settings manually.
TFTP settings If you do not use DHCP to direct the phone to a TFTP server,
you must manually assign a TFTP server. You can also
assign an alternative TFTP server to use instead of the one
assigned by DHCP.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Unlocking and Locking Options, page 4-3
• Editing Values, page 4-3
• Network Configuration Menu, page 4-5
Domain Name
IP Address
Subnet Mask
Default Router 1-5
DNS Server 1-5
TFTP Server 1
Alternate TFTP
TFTP Server 2
• Device Configuration Menu, page 4-10
Network Configuration Menu
The Network Configuration menu provides options for viewing and making a variety of network settings.
Table 4-2 and Tab l e 4- 3 describe these options and, where applicable, explains how to change them.
For information about how to access the Network Configuration menu, see the “Displaying a
Configuration Menu” section on page 4-2.
Note The phone also has a Network Configuration menu that you access directly from the Settings menu. For
information about the options on that menu, see the “Network Configuration” section on page 4-25.
Before you can change an option on this menu, you must unlock options as described in the “Unlocking
and Locking Options” section on page 4-3. The Edit, Yes , or No softkeys for changing network
configuration options appear only if options are unlocked.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-5
Page 72

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Network Configuration Menu
For information about the keys you can use to edit options, see the “Editing Values” section on page 4-3.
Table 4-2 Network Configuration Menu Options
Option Description To Change
IPv4 Configuration In the IPv4 Configuration menu, you can do the
following:
• Enable or disable the phone to use the IP address
that is assigned by the DHCP server.
• Manually set the IP Address, Subnet Mask,
Default Routers, DNS Server, and Alternate TFTP
servers.
For more information on the IPv4 address fields, refer
to Table 4-3.
IPv6 Configuration This menu setting is disabled in this release.
MAC Address Unique Media Access Control (MAC) address of the
phone.
Host Name Unique host name that the DHCP server assigned to
the phone.
Domain Name Name of the Domain Name System (DNS) domain in
which the phone resides.
Operational VLAN IDAuxiliary Virtual Local Area Network (VLAN)
configured on a Cisco Catalyst switch in which the
phone is a member.
If the phone has not received an auxiliary VLAN, this
option indicates the Administrative VLAN.
If neither the auxiliary VLAN nor the Administrative
VLAN are configured, this option is blank.
Admin. VLAN ID Auxiliary VLAN in which the phone is a member.
1. Unlock network configuration options.
2. Scroll to IPv4 Configuration and press the
Select softkey.
Display only—Cannot configure.
Display only—Cannot configure.
1. Unlock network configuration options.
2. Set the DHCP Enabled option to No.
3. Scroll to the Domain Name option, press
the Edit softkey, and then enter a new
domain name.
4. Press the Val id at e softkey and then press
the Save softkey.
The phone obtains its Operational VLAN ID
via Cisco Discovery Protocol (CDP) from the
switch to which the phone is attached. To
assign a VLAN ID manually, use the Admin
VLAN ID option.
1. Unlock network configuration options.
4-6
Used only if the phone does not receive an auxiliary
VLAN from the switch; otherwise it is ignored.
2. Scroll to the Admin. VLAN ID option,
press the Edit softkey, and then enter a
new Admin VLAN setting.
3. Press the Val id at e softkey and then press
the Save softkey.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 73

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-2 Network Configuration Menu Options (continued)
Option Description To Change
SW Port
Configuration
PC Port
Configuration
Speed and duplex of the network port (labeled 10/100
SW on the Cisco Unified IP Phone 7970, and
10/100/1000 SW on the Cisco
Unified IP Phone 7971G-GE). Valid values:
• Auto Negotiate
• 10 Half—10-BaseT/half duplex
• 10 Full—10-BaseT/full duplex
• 100 Half—100-BaseT/half duplex
• 100 Full—100-BaseT/full duplex
• 1000 Full—1000-BaseT/full duplex
If the phone is connected to a switch, configure the
port on the switch to the same speed/duplex as the
phone, or configure both to auto-negotiate.
If you change the setting of this option, you must
change the PC Port Configuration option to the same
setting.
Speed and duplex of the access port (labeled 10/100
PC on the Cisco Unified IP Phone 7970, and
10/100/1000 PC on the Cisco
Unified IP Phone 7971G-GE). Valid values:
• Auto Negotiate
• 10 Half—10-BaseT/half duplex
• 10 Full—10-BaseT/full duplex
• 100 Half—100-BaseT/half duplex
1. Unlock network configuration options.
2. Scroll to the SW Port Configuration
option and then press the Edit softkey.
3. Scroll to the setting that you want and then
press the Select softkey.
4. Press the Save softkey.
1. Unlock network configuration options.
2. Scroll to the PC Port Configuration option
and then press the Edit softkey.
3. Scroll to the setting that you want and then
press the Select softkey.
4. Press the Save softkey.
Network Configuration Menu
• 100 Full—100-BaseT/full duplex
• 1000 Full—1000-BaseT/full duplex
If the phone is connected to a switch, configure the
port on the switch to the same speed/duplex as the
phone, or configure both to auto-negotiate.
If you change the setting of this option, you must
change the SW Port Configuration option to the same
setting.
PC VLAN Allows the phone to interoperate with 3rd party
switches that do not support a voice VLAN. The
Admin VLAN ID option must be set before you can
change this option.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
1. Unlock network configuration options.
2. Make sure the Admin VLAN ID option is
set.
3. Scroll to the PC VLAN option, press the
Edit softkey, and then enter a new PC
VLAN setting.
4. Press the Val id at e softkey and then press
the Save softkey.
4-7
Page 74

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Network Configuration Menu
Table 4-3 IPv4 Configuration Menu Options
Option Description To Change
DHCP Server IP address of the Dynamic Host Configuration
Protocol (DHCP) server from which the phone
obtains its IP address.
IP Address Internet Protocol (IP) address of the phone.
If you assign an IP address with this option, you
must also assign a subnet mask and default router.
See the Subnet Mask and Default Router options
in this table.
Subnet Mask Subnet mask used by the phone.
Default Router 1
Default Router 2
Default router used by the phone (Default Router
1) and optional backup routers (Default Router
2–5).
Default Router 3
Default Router 4
Default Router 5
Display only—Cannot configure.
1. Unlock network configuration options.
2. Set the DHCP Enabled option to No.
3. Scroll to the IP Address option, press the Edit
softkey, and then enter a new IP Address.
4. Press the Val id at e softkey and then press the
Save softkey.
1. Unlock network configuration options.
2. Set the DHCP Enabled option to No.
3. Scroll to the Subnet Mask option, press the
Edit softkey, and then enter a new subnet mask.
4. Press the Val id at e softkey and then press the
Save softkey.
1. Unlock network configuration options.
2. Set the DHCP Enabled option to No.
3. Scroll to the appropriate Default Router option,
press the Edit softkey, and then enter a new
router IP address.
4. Press the Val id at e softkey.
5. Repeat Steps 3 and 4 as needed to assign
backup routers.
DNS Server 1
DNS Server 2
Primary Domain Name System (DNS) server
(DNS Server 1) and optional backup DNS servers
(DNS Server 2–5) used by the phone.
DNS Server 3
DNS Server 4
DNS Server 5
DHCP Indicates whether the phone has DHCP enabled or
disabled.
When DHCP is enabled, the DHCP server assigns
the phone an address. When DHCP is disabled, the
administrator must manually assign an IP address
to the phone.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-8
6. Press the Save softkey.
1. Unlock network configuration options.
2. Set the DHCP Enabled option to No.
3. Scroll to the appropriate DNS Server option,
press the Edit softkey, and then enter a new
DNS server IP address.
4. Press the Val id at e softkey.
5. Repeat Steps 3 and 4 as needed to assign
backup DNS servers.
6. Press the Save softkey.
1. Unlock network configuration options.
2. Scroll to the DHCP Enabled option and press
the No softkey to disable DHCP, or press the
Ye s softkey to enable DHCP.
3. Press the Save softkey.
OL-15299-01
Page 75

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-3 IPv4 Configuration Menu Options (continued)
Option Description To Change
DHCP Address
Released
Alternate TFTP Indicates whether the phone is using an alternative
TFTP Server 1 Primary Trivial File Transfer Protocol (TFTP)
Releases the IP address assigned by DHCP. 1. Unlock network configuration options.
2. Scroll to the DHCP Address Released option
and press the Yes softkey to release the IP
address assigned by DHCP, or press the No
softkey if you do not want to release this IP
address.
3. Press the Save softkey.
1. Unlock network configuration options.
TFTP server.
2. Scroll to the Alternate TFTP option and press
the Ye s softkey if the phone should use an
alternative TFTP server.
3. Press the Save softkey.
1. Unlock the CTL file if necessary (for example,
server used by the phone. If you are not using
DHCP in your network and you want to change
this server, you must use the TFTP Server 1
option.
If you set the Alternate TFTP option to yes, you
must enter a non-zero value for the TFTP Server 1
option.
If neither the primary TFTP server nor the backup
TFTP server is listed in the CTL file on the phone,
you must unlock the CTL file before you can save
changes to the TFTP Server 1 option. In this case,
if you are changing the administrative domain
of the phone).
2. If DHCP is enabled, set the Alternate TFTP
option to Ye s.
3. Scroll to the TFTP Server 1 option, press the
Edit softkey, and then enter a new TFTP server
IP address.
4. Press the Val id at e softkey, and then press the
Save softkey.
Note If you forgot to unlock the CTL file, you
the phone will delete the CTL file when you save
changes to the TFTP Server 1 option. A new CTL
file will be downloaded from the new TFTP Server
1 address.
For information about the CTL file, refer to Cisco
Unified Communications Manager Security
Guide. For information about unlocking the CTL
file, see the “Security Configuration Menu”
section on page 4-29.
Network Configuration Menu
can change the TFTP Server 1 address in
the CTL file, then erase the CTL file by
pressing the Erase softkey from the
Security Configuration menu. A new CTL
file will be downloaded from the new TFTP
Server 1 address.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-9
Page 76

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-3 IPv4 Configuration Menu Options (continued)
Option Description To Change
TFTP Server 2 Optional backup TFTP server that the phone uses
if the primary TFTP server is unavailable.
If neither the primary TFTP server nor the backup
TFTP server is listed in the CTL file on the phone,
you must unlock the CTL file before you can save
changes to the TFTP Server 2 option. In this case,
the phone will delete the CTL file when you save
changes to the TFTP Server 2 option. A new CTL
file will be downloaded from the new TFTP Server
2 address.
For information about the CTL file, refer to Cisco
Unified Communications Manager Security
Guide. For information about unlocking the CTL
file, see to the “Security Configuration Menu”
section on page 4-29.
BOOTP Server Indicates whether the phone obtains its
configuration from a Bootstrap Protocol (BootP)
server instead of from a DHCP server.
1. Unlock the CTL file, if necessary (for example,
if you are changing the administrative domain
of the phone).
2. Unlock network configuration options.
3. Enter an IP address for the TFTP Server 1
option.
4. Scroll to the TFTP Server 2 option, press the
Edit softkey, and then enter a new backup
TFTP server IP address.
5. Press the Val id at e softkey, and then press the
Save softkey.
Note If you forgot to unlock the CTL file, you
Display only—Cannot configure.
can change the TFTP Server 2 address in
the CTL file, then erase the CTL file by
pressing the Erase softkey from the
Security Configuration menu. A new CTL
file will be downloaded from the new TFTP
Server 2 address.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Unlocking and Locking Options, page 4-3
• Editing Values, page 4-3
• Overview of Options Configurable from a Phone, page 4-4
• Device Configuration Menu, page 4-10
Device Configuration Menu
The Device Configuration menu provides access to nine sub-menus from which you can view a variety
of settings that are specified in the configuration file for a phone. (The phone downloads the
configuration file from the TFTP server.) These sub-menus are:
• Unified CM Configuration, page 4-11
• SIP Configuration Menu (SIP Phones Only), page 4-12
• Call Preferences Menu (SIP Phones Only), page 4-14
• HTTP Configuration Menu, page 4-15
• Locale Configuration Menu, page 4-16
• UI Configuration Menu, page 4-17
4-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 77

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
• Media Configuration Menu, page 4-19
• Power Save Configuration Menu, page 4-22
• Ethernet Configuration Menu, page 4-23
• Security Configuration Menu, page 4-23
• QoS Configuration Menu, page 4-25
• Network Configuration, page 4-25
For instructions about how to access the Device Configuration menu and its sub-menus, see the
“Displaying a Configuration Menu” section on page 4-2.
Unified CM Configuration
The Unified CM Configuration contains the options Unified CM1, Unified CM 2, Unified CM3, Unified
CM4, and Unified CM5. These options show Cisco Unified Communications Manager servers that are
available for processing calls from the phone, in prioritized order. To change these options, use
Cisco Unified Communications Manager Administration, Cisco Unified CM Group Configuration.
For an available Cisco Unified Communications Manager server, an option on the Unified CM
Configuration will show the Cisco Unified Communications Manager server IP address or name and one
of the states shown in Table 4 - 4.
Device Configuration Menu
Table 4-4 Cisco Unified Communications Manager Server States
State Description
Active Cisco Unified Communications Manager server from which the
phone is currently receiving call-processing services
Standby Cisco Unified Communications Manager server to which the phone
switches if the current server becomes unavailable
Blank No current connection to this Cisco Unified Communications
Manager server
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-11
Page 78

Device Configuration Menu
An option may also display one of more of the designations or icons shown in Table 4 -5:
Table 4-5 Cisco Unified Communications Manager Server Designations
Designation Description
SRST Indicates a Survivable Remote Site Telephony router capable of
TFTP Indicates that the phone was unable to register with a Cisco Unified
(Authentication icon)
(Encryption icon)
Chapter 4 Configuring Settings on the Cisco Unified IP Phone
providing Cisco Unified Communications Manager functionality
with a limited feature set. This router assumes control of call
processing if all other Cisco Unified Communications Manager
servers become unreachable. The SRST Cisco
Unified Communications Manager always appears last in the list of
servers, even if it is active. For more information, refer to Cisco
Unified Communications Manager Administration Guide.
You configure an SRST router address in the
Cisco Unified Communications Manager Administration SRST
Reference Configuration window (choose System > SRST). You
configure an SRST reference in the Device Pool Configuration
window (choose System > Device Pool).
Communications Manager listed in its configuration file and that it
registered with the TFTP server instead.
Indicates that the connection to the Cisco Unified Communications
Manager is authenticated. For more information about authentication,
refer to Cisco Unified Communications Manager Security Guide.
Indicates that the connection to the Cisco Unified Communications
Manager is authenticated and encrypted. For more information about
authentication and encryption, refer to Cisco Unified
Communications Manager Security Guide.
The Encryption icon is also displayed when a Cisco Unified IP phone
is configured as protected. For more information about protected
calls, refer to Cisco Unified Communications Manager Security
Guide. Protected calls are not authenticated.
SIP Configuration Menu (SIP Phones Only)
The SIP Configuration menu is available on SIP phones. This menu contains these sub-menus:
• SIP General Configuration Menu, page 4-13
• Line Settings Menu (SIP Phones Only), page 4-14
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-12
OL-15299-01
Page 79

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
SIP General Configuration Menu
The SIP General Configuration menu displays information about the configurable SIP parameters on a
SIP phone. Table 4-6 describes the options in this menu.
Table 4-6 SIP General Configuration Menu Options
Option Description To Change
Preferred CODEC Displays the CODEC to use when a call is
initiated. This value will always be set to none.
Out of Band DTMF Displays the configuration of the out-of-band
signaling (for tone detection on the IP side of a
gateway). The Cisco Unified IP Phone (SIP)
supports out-of-band signaling by using the AVT
tone method. This value will always be set to avt.
Register with Proxy Displays if the phone must register with a proxy
server during initialization. This value will
always be set to Yes.
Register Expires Displays the amount of time, in seconds, after
which a registration request expires.
Phone Label Displays the text that is displayed on the top
right status line of the LCD on the phone. This
text is for end-user display only and has no effect
on caller identification or messaging. This value
will always be set to null.
Enable VAD Displays if voice activation detection (VAD) is
enabled. This value is set to No by default.
Start Media Port Displays the start Real-Time Transport Protocol
(RTP) range for media.
End Media Port Displays the end Real-Time Transport Protocol
(RTP) range for media.
NAT Enabled Displays if Network Address Translation (NAT)
is enabled. This value will always be set to false.
NAT Address Displays the WAN IP address of the NAT or
firewall server. This value will always be set to
null.
Call Statistics Displays if call statistics are enabled on the
phone.This value is set to No by default.
Display only—cannot configure.
Display only—cannot configure.
Display only—cannot configure.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
Display only—cannot configure.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
Display only—cannot configure.
Display only—cannot configure.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
Device Configuration Menu
OL-15299-01
Related Topics
• Displaying a Configuration Menu, page 4-2
• Device Configuration Menu, page 4-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-13
Page 80

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Line Settings Menu (SIP Phones Only)
The Line Settings menu displays information that relates to the configurable parameters for each of the
lines on a SIP phone. Tab l e 4-7 describes the options in this menu.
Table 4-7 Line Settings Menu Options
Option Description To Change
Name Displays the lines and the number used to
register each line.
Short Name Displays the short name configured for the line. Use Cisco Unified Communications Manager
Authentication Name Displays the name used by the phone for
authentication if a registration is challenged by
the call control server during initialization.
Display Name Displays the identification the phone uses for
display for caller identification purposes.
Proxy Address The value is left blank because it is not
applicable to SIP phones that are using Cisco
Unified Communications Manager.
Proxy Port The value is left blank because it is not
applicable to SIP phones that are using Cisco
Unified Communications Manager.
Shared Line Displays if the line is part of a shared line (Yes)
or not (No).
Use Cisco Unified Communications Manager
Administration to modify.
Administration to modify.
Use Cisco Unified Communications Manager
Administration to modify.
Use Cisco Unified Communications Manager
Administration to modify.
Display only—Cannot configure.
Display only—Cannot configure.
Display only—Cannot configure.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Device Configuration Menu, page 4-10
Call Preferences Menu (SIP Phones Only)
The Call Preferences menu displays settings that relate to the settings for the call preferences on a SIP
phone. Table 4 - 8 describes the options in this menu.
Table 4-8 Call Preferences Menu Options
Option Description To Change
Caller ID Blocking Indicates whether caller ID blocking is enabled
(Yes) or disabled (No) for the phone.
Anonymous Call Block Indicates whether anonymous call block is
enabled (Yes) or disabled (No) for the phone.
Call Waiting
Preferences
Displays a sub-menu that indicates whether call
waiting is enabled (Yes) or disabled (No) for
each line.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
From Cisco Unified Communications Manager
Administration, choose Call Routing >
Directory Number.
4-14
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 81

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-8 Call Preferences Menu Options (continued)
Option Description To Change
Call Hold Ringback Indicates whether the call hold ringback feature
is enabled (Yes) or disabled (No) for the phone.
Stutter Msg Waiting Indicates whether stutter message waiting is
enabled (Yes) or disabled (No) for the phone.
Call Logs BLF Enabled Indicates whether BLF for call logs is enabled
(Yes) or disabled (No) for the phone.
Auto Answer
Preferences
Displays a sub-menu that indicates whether auto
answer is enabled (Yes) or disabled (No) for the
each line.
Speed Dials Displays a sub-menu that displays the lines
available on the phone. Select a line to see the
speed dial label and number assigned to that
line.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
From Cisco Unified Communications Manager
Administration, choose Device >
Device Settings > SIP Profile.
Use Cisco Unified Communications Manager
Administration.
From Cisco Unified Communications Manager
Administration, choose Call Routing >
Directory Number.
From Cisco Unified Communications Manager
Administration, choose Device > Add a New
Speed Dial.
Device Configuration Menu
Related Topics
• Displaying a Configuration Menu, page 4-2
• Device Configuration Menu, page 4-10
HTTP Configuration Menu
The HTTP Configuration menu displays the URLs of servers from which the phone obtains a variety of
information. This menu also displays information about the idle display on the phone.
Table 4-9 describes the options on the HTTP Configuration menu.
Table 4-9 HTTP Configuration Menu Options
Option Description To Change
Directories URL URL of the server from which the phone obtains
directory information.
Services URL URL of the server from which the phone obtains
Cisco Unified IP Phone services.
Messages URL URL of the server from which the phone obtains
message services.
Information URL URL of the help text that appears on the phone. From Cisco Unified Communications Manager
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Use Cisco Unified Communications Manager
Administration to modify > Device > Phone >
Phone Configuration.
Administration, choose > Device > Phone >
Phone Configuration.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-15
Page 82

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-9 HTTP Configuration Menu Options (continued)
Option Description To Change
Authentication URL URL that the phone uses to validate requests
made to the phone web server.
Proxy Server URL URL of proxy server, which makes HTTP
requests to non-local host addresses on behalf of
the phone HTTP client and provides responses
from the non-local host to the phone HTTP
client.
Idle URL URL of an XML service that the phone displays
when the phone has not been used for the time
specified in the Idle URL Time option and no
menu is open. For example, you could use the
Idle URL option and the Idle URL Timer option
to display a stock quote or a calendar on the LCD
screen when the phone has not been used for 5
minutes.
Idle URL Time Number of seconds that the phone has not been
used and no menu is open before the XML
service specified in the Idle URL option is
activated.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Locale Configuration Menu
The Locale Configuration menu displays information about the user locale and the network locale used
by the phone. Table 4-10 describes the options on this menu.
Table 4-10 Locale Configuration Menu Options
Option Description To Change
User Locale User locale associated with the phone user. The
user locale identifies a set of detailed
information to support users, including
language, font, date and time formatting, and
alphanumeric keyboard text information.
User Locale Version Version of the user locale loaded on the phone. Display only—Cannot configure.
User Locale Char Set Character set that the phone uses for the user
locale.
Network Locale Network locale associated with the phone user.
The network locale identifies a set of detailed
information that supports the phone in a specific
location, including definitions of the tones and
cadences used by the phone.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Display only—Cannot configure.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
4-16
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 83

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-10 Locale Configuration Menu Options (continued)
Option Description To Change
Network Locale Version Version of the network locale loaded on the
phone.
NTP Configuration (SIP
phones only)
Provides access to the NTP Configuration Menu.
For more information, see the “NTP
Configuration Menu (SIP Phones Only)” section
on page 4-17
Display only—Cannot configure.
Display only—Cannot configure.
NTP Configuration Menu (SIP Phones Only)
The NTP Configuration menu displays information about the NTP server and mode configuration used
by SIP phones. Table 4-11 describes the options on this menu.
Table 4-11 NTP Configuration Menu Options
Option Description To Change
NTP Server 1 IP address of the primary NTP server. Display only—Cannot configure.
NTP Server 2 IP address of the secondary or backup NTP
server.
NTP Mode 1 Primary server mode. Supported modes are
Directed Broadcast and Unicast.
NTP Mode 2 Secondary server mode. Supported modes are
Directed Broadcast and Unicast.
Display only—Cannot configure.
Display only—Cannot configure.
Display only—Cannot configure.
UI Configuration Menu
The UI Configuration menu displays the status of various user interface features on the phone.
Table 4-12 describes the options on this menu.
Table 4-12 UI Configuration Menu Options
Option Description To Change
Auto Line Select Indicates whether the phone shifts the call focus
to incoming calls on all lines.
When this option is disabled, the phone only
shifts the call focus to incoming calls on the line
that is in use. When this option is enabled, the
phone shifts the call focus to the line with the
most recent incoming call.
Default: Disabled
BLF for Call Lists Indicates whether the Busy Lamp Field (BLF) is
enabled for call lists.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose System > Enterprise
Parameters.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-17
Page 84

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-12 UI Configuration Menu Options (continued)
Option Description To Change
Reverting Focus Priority Indicates whether the phone shifts the call focus
on the phone screen to an incoming call or a
reverting hold call. Settings include:
Lower—Focus priority given to incoming calls.
Higher—Focus priority given to reverting calls.
Even—Focus priority given to the first call.
Auto Call Select Indicates whether the phone automatically shifts
the call focus to an incoming call on the same
line when the user is already on a call.
When this option is enabled, the phone shifts the
call focus to the most recent incoming call.
When this option is disabled, all automatic focus
changes, including Auto Line Select, are
disabled regardless of their setting.
Default: Enabled
“more” Softkey Timer Indicates the number of seconds that additional
softkeys are displayed after the user presses
more. If this timer expires before the user
presses another softkey, the display reverts to the
initial softkeys.
From Cisco Unified Communications Manager
Administration, choose System > Device Pool.
See also: Hold Reversion.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone > Phone
Configuration.
Wideband Headset UI
Control
Range: 5 to 30; 0 represents an infinite timer.
Default: 5
Indicates whether the user can configure the
Wideband Headset option in the phone user
interface.
Va lu e s:
• Enabled—The user can configure the
Wideband Headset option in the Audio
Preferences menu on the phone (choose
> User Preferences > Audio
Preferences> Wideband Headset).
• Disabled—The value of the Wideband
Headset option in Cisco Unified
Communications Manager Administration
gets used (see Media Configuration Menu,
page 4-19
Default: Enabled
Use Cisco Unified Communications Manager
Administration > Device > Phone > Phone
Configuration.
4-18
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 85

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-12 UI Configuration Menu Options (continued)
Option Description To Change
Wideband Handset UI
Control
Indicates whether the user can configure the
Wideband Handset option in the phone user
interface.
Va lu e s:
• Enabled—The user can configure the
Wideband Handset option in the Audio
Preferences menu on the phone (choose
> User Preferences > Audio
Preferences> Wideband Handset).
• Disabled—The value of the Wideband
Handset option in Cisco Unified
Communications Manager Administration
gets used (see Media Configuration Menu,
page 4-19).
Default: Enabled
Personalization Indicates whether the phone has been enabled
for configuring custom ring tones and wallpaper
images.
Default: Enabled
Single Button Barge Indicates whether the Single Button Barge
feature is enabled for the phone.
Default: Disabled.
Use Cisco Unified Communications Manager
Administration > Device > Phone > Phone
Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Device Configuration Menu
Media Configuration Menu
The Media Configuration menu displays whether the headset, speakerphone, and video capability (SCCP
phones only) are enabled on the phone. This menu also displays options for recording tones that the
phone may play to indicate that a call may be recorded. Table 4-13 describes the options on this menu.
Table 4-13 Media Configuration Menu Options
Option Description To Change
Headset Enabled Indicates whether the Headset button is enabled
on the phone.
Speaker Enabled Indicates whether the speakerphone is enabled
on the phone.
Video Capability
Enabled
(SCCP phones only)
Indicates whether the phone can participate in
video calls when connected to an appropriately
equipped computer.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-19
Page 86

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-13 Media Configuration Menu Options (continued)
Option Description To Change
Recording Tone Indicates whether a recording tone (often
referred to as a beep tone) is enabled or disabled
for the phone. If the recording tone option is
enabled, the phone plays the beep tone in both
directions of every call, regardless of whether
the call actually gets recorded. The beep tone
first sounds when a call is answered.
You may want to notify your users if you enable
this option.
Default: Disabled
Related Parameters:
• Recording Tone Local Volume
• Recording Tone Remote Volume
• Recording Tone Duration
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Recording Tone Local
Vo l u m e
Recording Tone Remote
Vo l u m e
Other related parameters—Beep tone frequency
in hz, the length of the beep tone (called
duration), and how often the beep tone plays
(called interval)—are defined on a per-Network
Locale basis in the xml file that defines tones.
This xml file is usually named tones.xml or
g3-tones.xml.
Indicates the loudness setting for the beep tone
that is received by the party whose phone has the
Recording Tone option enabled.
This setting applies for each listening device
(handset, speakerphone, headset).
Range: 0 percent (no tone) to 100 percent (same
level as current volume setting on the phone).
Default: 100
See also: Recording Tone
Indicates the loudness setting for the beep tone
that the remote party receives. The remote party
is the party who is on a call with the party whose
phone has the Recording Tone option enabled.
Range: 0 percent to 100 percent. (0 percent is
–66 dBM and 100 percent is –3 dBM.)
Default: 84 percent (–10dBM)
See also: Recording Tone
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
4-20
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 87

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-13 Media Configuration Menu Options (continued)
Option Description To Change
Recording Tone
Duration
Indicates the length of time in milliseconds that
the beep tone plays.
If the value you configure here is less than one
third the interval, then this value overrides the
default provided by the Network Locale.
Range: 0 to 3000
Note For some Network Locales that use a
complex cadence, this setting applies
only to the first beep tone.
See also: Recording Tone
Wideband Headset Indicates whether wideband is enabled or
disabled for the headset.
Default: Disabled
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
• If Wideband Headset UI Control is enabled,
you or the user can use the phone and
choose >
User Preferences > Audio Preferences >
Wideband Headset.
Device Configuration Menu
Wideband Handset Indicates whether wideband is enabled or
disabled for the handset.
Default: “Use Phone Default” on Cisco Unified
Communications Manager Administration.
(This default means that the phone will be
enabled for a wideband handset only if the
phone was shipped with a wideband handset.)
• If Wideband Headset UI Control is disabled,
from Cisco Unified Communications
Manager Administration and choose Device
> Phone > Phone Configuration to set this
value.
Note If you allowed this option to be user
controllable (in the Wideband Headset
UI Control option), the user-configured
value takes precedence.
• If Wideband Handset UI Control is enabled,
you or the user can choose >
User Preferences >
Audio Preferences > Wideband Handset.
• If Wideband Handset UI Control is
disabled, use Cisco Unified
Communications Manager Administration
and choose Device > Phone > Phone
Configuration to set this value.
Note If you allowed this option
to be user controllable (in
the Wideband Handset UI
Control option), the
user-configured value
takes precedence.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-21
Page 88

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-13 Media Configuration Menu Options (continued)
Option Description To Change
Enterprise Advertise
G.722 Codec
Device Advertise G.722
Codec
Enables/disables Cisco Unified IP Phones to
advertise the G.722 codec to Cisco Unified
Communications Manager. If enabled (default),
and if each endpoint in the attempted call supports
G.722 in its capabilities set, Cisco Unified
Communications Manager will choose G.722
for the call.
Note When a phone is registered with a Cisco
Unified Communications Manager that
does not support this setting, the default
is “Disabled.”
Allows you to override the Enterprise Advertise
G.722 Codec on a per-phone basis.
The default is “Use System Default,” which
means the value configured for the Enterprise
Advertise G.722 Codec parameter gets used.
From Cisco Unified Communications Manager
Administration and choose System >
Enterprise Parameters.
From Cisco Unified Communications Manager
Administration and choose Device > Phone.
Power Save Configuration Menu
The Power Save Configuration menu displays the settings that control when the LCD screen on a phone
turns off to conserve power. Table 4-14 describes the options on this menu.
For detailed information about configuring these settings, see the “Automatically Disabling the Cisco
Unified IP Phone Touchscreen” section on page 6-7.
Table 4-14 Power Save Configuration Menu Options
Option Description To Change
Display On Time Time each day that the LCD screen turns on
automatically (except on the days specified in
the Days Display Not Active field).
Display On Duration Length of time that the LCD screen remains on
after turning on at the time shown in the Display
On Time option.
Display Idle Timeout Length of time that the phone is idle before the
display turns off. Applies only when the display
was off as scheduled and was turned on by an
end-user (by pressing a button on the phone,
touching the touchscreen, or lifting the handset).
Days Display Not
Active
Days that the display does not turn on
automatically at the time specified in the
Display On Time option.
Display On When
Incoming Call
Indicates whether the LCD screen automatically
illuminates when a call is received.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
4-22
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 89

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Ethernet Configuration Menu
The Ethernet Configuration menu includes the options that are described in Table 4-15.
Table 4-15 Ethernet Configuration Menu Option
Option Description To Change
Forwarding Delay Indicates whether the internal switch begins
forwarding packets between the PC port and
switched port on the phone when the phone
becomes active.
• When forwarding delay is set to disabled,
the internal switch begins forwarding
packets immediately.
• When forwarding delay is set to enabled, the
internal switch waits 8 seconds before
forwarding packets between the PC port and
the switch port.
From Cisco Unified Communications Manager
Administration, choose Device > Phone > Phone
Configuration.
Device Configuration Menu
Default is disabled.
Span to PC Port Indicates whether the phone will forward
packets transmitted and received on the network
port to the access port.
Enable this option if an application that requires
monitoring of the phone’s traffic is being run on
the access port. These applications include
monitoring and recording applications (common
in call center environments) and network packet
capture tools that are used for diagnostic
purposes.
Security Configuration Menu
The Security Configuration menu that you display from the Device Configuration menu displays settings
that relate to security for the phone.
Note The phone also has a Security Configuration menu that you access directly from the Settings menu. For
information about the security options on that menu, see the “Security Configuration Menu” section on
page 4-29.
From Cisco Unified Communications Manager
Administration, choose Device > Phone > Phone
Configuration.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-23
Page 90

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-16 describes the options on the Security Configuration menu.
Table 4-16 Security Configuration Menu Options
Option Description To Change
PC Port Disabled Indicates whether the access port on the phone is
enabled or disabled.
Note If disabled, video will not work on this
phone, even if video is enabled.
GARP Enabled Indicates whether the phone learns MAC
addresses from Gratuitous Address Resolution
Protocol (ARP) responses. Disabling the
phone’s ability to accept Gratuitous ARP will
prevent applications that use this mechanism to
monitor and record voice streams from working.
If voice monitoring is not desired, set this option
to No (disabled).
Voice VLAN Enabled Indicates whether the phone allows a device
attached to the access port to access the Voice
VLAN. Setting this option to No (disabled)
prevents the attached PC from sending and
receiving data on the Voice VLAN. This setting
also prevents the PC from receiving data sent
and received by the phone. Set this setting to Yes
(enabled) if an application that requires
monitoring of the phone’s traffic is running on
the PC. These applications include monitoring
and recording applications and network
monitoring software.
Web Access Enabled Indicates whether web access is enabled (Yes) or
disabled (No) for the phone.
Security Mode Displays the security mode that is set for the
phone.
Logging Display For use by the Cisco Technical Assistance Center (TAC), if necessary.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
Use Cisco Unified Communications Manager
Administration to modify.
4-24
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 91

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
QoS Configuration Menu
The QoS Configuration menu displays information that relates to quality of service (QoS) for the phone.
Table 4-17 describes the options on this menu.
Table 4-17 QoS Configuration Menu Options
Option Description To Change
DSCP For Call Control Differentiated Services Code Point (DSCP) IP
classification for call control signaling.
DSCP For Configuration DSCP IP classification for any phone
configuration transfer.
DSCP For Services DSCP IP classification for phone-based
services.
From Cisco Unified Communications Manager
Administration, choose System > Enterprise
Parameters.
From Cisco Unified Communications Manager
Administration, choose System > Enterprise
Parameters.
From Cisco Unified Communications Manager
Administration, choose System > Enterprise
Parameters.
Device Configuration Menu
Related Topics
• Displaying a Configuration Menu, page 4-2
• Network Configuration Menu, page 4-5
Network Configuration
The Network Configuration menu displays device-specific network configuration settings on the phone.
Table 4-18 describes the options in this menu.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-25
Page 92

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Note The phone also has a Network Configuration menu that you access directly from the Settings menu. For
information about the options on that menu, see the “Network Configuration Menu” section on page 4-5.
Table 4-18 Network Configuration Menu Options
Option Description To Change
Load Server Used to optimize installation time for phone firmware
upgrades and offload the WAN by storing images locally,
negating the need to traverse the WAN link for each phone's
upgrade.
You can set the Load Server to another TFTP server IP address
or name (other than the TFTP Server 1 or TFTP Server 2)
from which the phone firmware can be retrieved for phone
upgrades. When the Load Server option is set, the phone
contacts the designated server for the firmware upgrade.
Note The Load Server option allows you to specify an
alternate TFTP server for phone upgrades only. The
phone continues to use TFTP Server 1 or TFTP Server
2 to obtain configuration files. The Load Server option
does not provide management of the process and of
the files, such as file transfer, compression, or
deletion.
RTP Control Protocol Indicates whether the phone supports the Real-Time Control
Protocol (RTCP). Settings include:
• Enabled
• Disabled—default
If this feature is disabled, several call statistic values display
as 0. For additional information, see the following sections:
• Call Statistics Screen, page 7-13
From Cisco Unified
Communications Manager
Administration, choose Device >
Phone > Phone Configuration.
From Cisco Unified
Communications Manager
Administration, choose Device >
Phone > Phone Configuration.
4-26
• Streaming Statistics, page 8-10
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 93

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Table 4-18 Network Configuration Menu Options (continued)
Option Description To Change
Peer Firmware Sharing The Peer Firmware Sharing feature provides these advantages
in high speed campus LAN settings:
• Limits congestion on TFTP transfers to centralized TFTP
servers
• Eliminates the need to manually control firmware
upgrades
• Reduces phone downtime during upgrades when large
numbers of devices are reset simultaneously
Peer Firmware Sharing may also aid in firmware upgrades in
branch/remote office deployment scenarios over
bandwidth-limited WAN links.
When enabled, it allows the phone to discover like phones on
the subnet that are requesting the files that make up the
firmware image, and to automatically assemble transfer
hierarchies on a per-file basis. The individual files making up
the firmware image are retrieved from the TFTP server by
only the root phone in the hierarchy, and are then rapidly
transferred down the transfer hierarchy to the other phones on
the subnet using TCP connections
This menu option indicates whether the phone supports peer
to peer image distribution. Settings include:
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration.
Device Configuration Menu
• Enabled
• Disabled—default
Log Server Indicates the IP address and port of the remote logging
machine to which the phone sends log messages. These log
messages help in debugging the peer to peer image
distribution feature.
Note The remote logging setting does not affect the sharing
log messages sent to the phone log.
CDP: PC Port Indicates whether CDP is enabled on the PC port (default is
enabled).
Enable CDP on the PC port when Cisco VT
Advantage/Unified Video Advantage (CVTA) is connected to
the PC port. CVTA does not work without CDP interaction
with the phone.
Note When CDP is disabled in Cisco Unified
Communications Manager, a warning is displayed,
indicating that disabling CDP on the PC port prevents
CVTA from working.
The current PC and switch port CDP values are shown on the
Settings menu.
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration.
From Cisco Unified
Communications Manager
Administration, choose Device >
Phone.
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-27
Page 94

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Device Configuration Menu
Table 4-18 Network Configuration Menu Options (continued)
Option Description To Change
CDP: SW Port Indicates whether CDP is enabled on the switch port (default
is enabled).
• Enable CDP on the switch port for VLAN assignment for
the phone, power negotiation, QoS management, and
802.1x security.
• Enable CDP on the switch port when the phone is
connected to a Cisco switch.
Note When CDP is disabled in Cisco Unified
Communications Manager, a warning is presented,
indicating that CDP should be disabled on the switch
port only if the phone is connected to a non-Cisco
switch.
The current PC and switch port CDP values are shown on the
Settings menu.
LLDP: PC Port Enables and disables Link Layer Discovery Protocol (LLDP)
on the PC port. Use this setting to force the phone to use a
specific discovery protocol. Settings include:
• Enabled—default
• Disabled
LLDP-MED: SW Port Enables and disables Link Layer Discovery Protocol Media
Endpoint Discovery (LLDP-MED) on the switch port. Use
this setting to force the phone to use a specific discovery
protocol, which should match the protocol supported by the
switch. Settings include:
• Enabled—default
• Disabled
LLDP Power Priority Advertises the phone’s power priority to the switch, enabling
the switch to appropriately provide power to the phones.
Settings include:
• Unknown—default
• Low
From Cisco Unified
Communications Manager
Administration, choose Device >
Phone.
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration
• High
• Critical
LLDP Asset ID Identifies the asset ID assigned to the phone for inventory
management.
Related Topics
• Displaying a Configuration Menu, page 4-2
• Network Configuration Menu, page 4-5
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-28
From Cisco Unified
Communications Manager
Administration, choose
Device > Phone > Phone
Configuration
OL-15299-01
Page 95

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Security Configuration Menu
The Security Configuration that you access directly from the Settings menu provides information about
various security settings. It also provides access to the CTL File menu and the Trust List menu, if a CTL
file is installed on the phone.
For information about how to access the Security Configuration menu and its sub-menus, see the
“Displaying a Configuration Menu” section on page 4-2.
Note The phone also has a Security Configuration menu that you access from the Device menu. For
information about the security options on that menu, see the “Security Configuration Menu” section on
page 4-23.
Table 4-19 describes the options in the security configuration menu.
Table 4-19 Security Menu Settings
Option Description To Change
Web Access Enabled Indicates whether web access is enabled (Yes)
or disabled (No) for the phone.
Security Mode Displays the security mode that is set for the
phone.
MIC Indicates whether a manufacturing installed
certificate (used for the security features) is
installed on the phone (Yes) or is not installed
on the phone (No).
LSC Indicates whether a locally significant
certificate (used for the security features) is
installed on the phone (Yes) or is not installed
on the phone (No).
CTL File Displays the MD5 hash of the certificate trust
list (CTL) file that is installed in the phone. If
no CTL file is installed on the phone, this
field displays No. (If security is configured
for the phone, the CTL file installs
automatically when the phone reboots or
resets.
Trust List If a CTL file is installed on the phone,
provides access to the Trust List menu.
CAPF Server Displays the IP address and the port of the
CAPF server that the phone uses.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
From Cisco Unified Communications Manager
Administration, choose Device > Phone >
Phone Configuration.
For information about how to manage the MIC
for your phone, refer to the “Using the
Certificate Authority Proxy Function” chapter in
Cisco Unified Communications Manager
Security Guide.
For information about how to manage the LSC
for your phone, refer to the “Using the
Certificate Authority Proxy Function” chapter in
Cisco Unified Communications Manager
Security Guide.
For more information about this file, refer to the
“Configuring the Cisco CTL Client” section in
Cisco Unified Communications Manager
Security Guide.
If a CTL file is installed on the phone, also
provides access to the CTL File screen. For more
information, see the “CTL File Menu” section
on page 4-30.
For more information, see the “Trust List Menu”
section on page 4-31.
For more information about this server, refer to
the “Using the Certificate Authority Proxy
Function” section in Cisco
Unified Communications Manager Security
Guide.
Security Configuration Menu
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-29
Page 96

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Security Configuration Menu
Table 4-19 Security Menu Settings (continued)
Option Description To Change
802.1X Authentication Allows you to enable 802.1X authentication
for this phone.
802.1X Authentication
Status
Displays real-time status progress of the
802.1X authentication transaction.
See the “802.1X Authentication and Status”
section on page 4-31.
Display only—Cannot configure.
CTL File Menu
The CTL File screen includes the options that are described in Table 4-20.
If a CTL file is installed on the phone, you can access the CTL File menu by pressing the Settings button
and choosing Security Configuration > CTL File.
Table 4-20 CTL File Settings
Option Description To Change
CTL File Displays the MD5 hash of the certificate trust
list (CTL) file that is installed in the phone. If
security is configured for the phone, the CTL
file installs automatically when the phone
reboots or resets.
For more information about the CTL file, refer to
the “Configuring the Cisco CTL Client” section
in Cisco Unified Communications Manager
Security Guide.
• A locked padlock icon in this option
indicates that the CTL file is locked.
• An unlocked padlock icon indicates
that the CTL file is unlocked.
Unified CM/TFTP Server IP address of a Cisco Unified
Communications Manager and TFTP server
used by the phone. Also displays a certificate
icon if a certificate is installed for this
server.
If neither the primary TFTP (TFTP Server 1)
server nor the backup TFTP server (TFTP
Server 2) is listed in the CTL file, you must
unlock the CTL file before you can save
changes that you make to the TFTP Server 1
option or to the TFTP Server 2 option on the
Network Configuration menu.
CAPF Server IP address of the CAPF server used by the
phone. Also displays a certificate icon if a
certificate is installed for this server.
Unlocking the CTL File
To unlock the CTL file from the Security Configuration menu, follow these steps:
For information about changing these options,
see the “Network Configuration Menu” section
on page 4-5.
For more information about this server, refer to
the “Using the Certificate Authority Proxy
Function” section in Cisco
Unified Communications Manager Security
Guide.
4-30
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 97

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Procedure
Step 1 Press **# to unlock options on the CTL File menu.
If you decide not to continue, press **# again to lock options on this menu.
Step 2 Highlight the CTL option.
Step 3 Press the Unlock softkey to unlock the CTL file.
After you change and save the applicable TFTP server option, the CTL file will be locked automatically.
Note When you press the Unlock softkey, it changes to Lock. If you decide not to change the TFTP
server option, press the Lock softkey to lock the CTL file.
Trust List Menu
Security Configuration Menu
The Trust List menu displays information about all of the servers that the phone trusts and includes the
options that are described in Table 4-21.
If a CTL file is installed on the phone, you can access the Trust List menu by pressing the Settings button
and choosing Security Configuration > Trust List.
Table 4-21 Trust List Menu Settings
Option Description To Change
Unified CM/TFTP Server IP address of a Cisco Unified
Communications Manager and TFTP server
used by the phone. Also displays a certificate
icon if a certificate is installed for this
server.
CAPF Server IP address of the CAPF used by the phone.
Also displays a certificate icon if a
certificate is installed for this server.
SRST Router IP address of the trusted SRST router that is
available to the phone, if such a device has
been configured in Cisco Unified
Communications Manager Administration.
Also displays a certificate icon if a
certificate is installed for this server.
For more information about these settings, refer
to the “Configuring the Cisco CTL Client”
section in Cisco Unified Communications
Manager Security Guide.
For more information about these settings, refer
to the “Configuring the Cisco CTL Client”
section in Cisco Unified Communications
Manager Security Guide.
For more information about these settings, refer
to the “Configuring the Cisco CTL Client”
section in Cisco Unified Communications
Manager Security Guide.
802.1X Authentication and Status
The 802.1X Authentication and 802.1X Authentication Status menus allow you to enable 802.1X
authentication and monitor its progress. These options are described in Table 4-22 and Table 4-23.
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
4-31
Page 98

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
Security Configuration Menu
You can access the 802.1X Authentication settings by pressing the Settings button and choosing
Security Configuration > 802.1X Authentication. To exit this menu, press the Exit softkey.
Table 4-22 802.1X Authentication Settings
Option Description To Change
Device Authentication Determines whether 802.1X authentication is
enabled:
• Enabled—Phone uses 802.1X
authentication to request network access.
• Disabled—Default setting in which the
phone uses CDP to acquire VLAN and
network access.
EAP-MD5 Specifies a password for use with 802.1X
authentication using the following menu
options (described in the following rows):
• Device ID
1. Choose Settings > Security Configuration
> 802.1X Authentication > Device
Authentication.
2. Set the Device Authentication option to
Enabled or Disabled.
3. Press the Save softkey.
Choose Settings > Security Configuration >
802.1X Authentication > EAP-MD5.
• Shared Secret
• Realm
Device ID—Derivative of the phone’s model
number and unique MAC address displayed in
this format: CP-<model>-SEP-<MAC>
Shared Secret—Choose a password to use on
the phone and on the authentication server.
The password must be between 6 and 32
characters, consisting of any combination of
numbers or letters.
Note If you disable 802.1X authentication
or perform a factory reset of the
phone, the shared secret is deleted.
Realm—Indicates the user network domain,
always set as Network
Display only—Cannot configure.
1. Choose EAP-MD5 > Shared Secret.
2. Enter the shared secret.
3. Press Save.
See the “Troubleshooting Cisco Unified IP
Phone Security” section on page 9-8 for
assistance in recovering from a deleted shared
secret.
Display only—Cannot configure.
4-32
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
Page 99

Chapter 4 Configuring Settings on the Cisco Unified IP Phone
You can access the 802.1X Authentication Real-Time Status by pressing the Settings button and
choosing Security Configuration > 802.1X Authentication Status. To exit this menu, press the Exit
softkey.
Table 4-23 802.1X Authentication Real-Time Status
Option Description To Change
802.1X Authentication Status Real-time progress of the 802.1X authentication
status, displaying one of the following states:
• Disabled—802.1X is disabled and
transaction was not attempted
• Disconnected—Physical link is down or
disconnected
• Connecting—Trying to discover or acquire
the authenticator
• Acquired—Authenticator acquired,
awaiting authentication to begin
• Authenticating—Authentication in progress
• Authenticated—Authentication successful
or implicit authentication due to timeouts
Display only—Cannot configure.
Security Configuration Menu
• Held—Authentication failed, waiting before
next attempt (approximately 60 seconds)
OL-15299-01
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
4-33
Page 100

Security Configuration Menu
Chapter 4 Configuring Settings on the Cisco Unified IP Phone
4-34
Cisco Unified IP Phone 7970G/7971G-GE Administration Guide for Cisco Unified Communications Manager 7.0
OL-15299-01
 Loading...
Loading...