Page 1

Wireless N USB Adapter
Page 2

User Manual
2007 © All rights reserved. Version 1.0
No part of this document may be reproduced, republished, or retransmitted in any form or by any means
whatsoever, whether electronically or mechanically, including, but not limited to, by way of photocopying,
recording, information recording, or through retrieval systems without the express written permission. We
reserve the right to revise this document at any time without the obligation to notify any person and/or
entity. All other company or product names mentioned are used for identification purposes only and may
be trademarks of their respective owners.
LIMITATION OF LIABILITY AND DAMAGES
THE PRODUCT AND THE SOFTWARES WITHIN ARE PROVIDED "AS IS," BASIS. THE MANUFACTURER AND
MANUFACTURER’S RESELLERS (COLLECTIVELY REFERRED TO AS “THE SELLERS”) DISCLAIM ALL WARRANTIES,
EXPRESS, IMPLIED OR STATUTORY, INCLUDING WITHOUT LIMITATION THE IMPLIED WARRANTIES OF NONINFRINGEMENT, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE, OR ANY WARRANTIES ARISING
FROM COURSE OF DEALING, COURSE OF PERFORMANCE, OR USAGE OF TRADE. IN NO EVENT WILL THE SELLERS
BE LIABLE FOR DAMAGES OR LOSS, INCLUDING BUT NOT LIMITED TO DIRECT, INDIRECT, SPECIAL WILLFUL,
PUNITIVE, INCIDENTAL, EXEMPLARY, OR CONSEQUENTIAL, DAMAGES, DAMAGES FOR LOSS OF BUSINESS
PROFITS, OR DAMAGES FOR LOSS OF BUSINESS OF ANY CUSTOMER OR ANY THIRD PARTY ARISING OUT OF THE
USE OR THE INABILITY TO USE THE PRODUCT OR THE SOFTWARES, INCLUDING BUT NOT LIMITED TO THOSE
RESULTING FROM DEFECTS IN THE PRODUCT OR SOFTWARE OR DOCUMENTATION, OR LOSS OR INACCURACY OF
DATA OF ANY KIND, WHETHER BASED ON CONTRACT, TORT OR ANY OTHER LEGAL THEORY, EVEN IF THE PARTIES
HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THE ENTIRE RISK AS TO THE RESULTS AND
PERFORMANCE OF THE PRODUCT OR ITS SOFTWARE IS ASSUMED BY CUSTOMER. BECAUSE SOME STATES DO NOT
ALLOW THE EXCLUSION OR LIMITATION OF LIABILITY FOR DAMAGES, THE ABOVE LIMITATION MAY NOT APPLY
TO THE PARTIES. IN NO EVENT WILL THE SELLERS’ TOTAL CUMULATIVE LIABILITY OF EACH AND EVERY KIND IN
RELATION TO THE PRODUCT OR ITS SOFTWARE EXCEED THE AMOUNT PAID BY CUSTOMER FOR THE PRODUCT.
Page 2 of 29
Page 3

User Manual
Contents
About the Product ...................................................................................................... 4
System Requirements .................................................................................4
LED Indicators .............................................................................................. 5
Getting Started........................................................................................................... 5
Check Package Contents.............................................................................. 6
Using the USB Extension ..........................................................................................6
Remove or Disable Conflicts ........................................................................6
Internet Sharing, Proxy, and Security Applications.................................................7
Configuring Internet Properties ...............................................................................7
Removing Temporary Internet Files ........................................................................7
Installation.................................................................................................................8
For Windows Vista ....................................................................................... 8
For Windows XP/2000................................................................................. 9
Driver Only Installation...........................................................................................10
About WL950USB Utility ...........................................................................................11
Configuration Tab..................................................................................................... 11
Advanced Configuration ............................................................................ 13
Security Enable (Privacy Configuration) .................................................... 14
Wireless LAN Security Overview ............................................................................16
Site Survey Tab......................................................................................................... 27
About Tab.................................................................................................................28
Page 3 of 29
Page 4

User Manual
About the Product
WL950USB provides wireless connectivity to desktop and notebook computers. The
device performs the function of a radio broadcaster and receiver to communicate with a
wireless network. This gives the computer connected with WL950USB the capability to
communicate with other devices and use the Internet service available in the wireless
network.
WL950USB is capable of connecting with wireless networks that utilize the Wireless N
protocol. Wireless N broadcasts data at a speed of up to 270 Megabits per second
(Mbps). This device also supports connection to other wireless network standards like
Wireless G or Wireless B. WL950USB is easy to setup - install the necessary driver
software, connect it to an available USB slot, and then connect to a wireless network. The
device comes with a Windows-based software called WL950USB Utility that can be used
to connect to wireless networks and create profiles which remembers the configuration
details for a wireless network.
Note: Wireless connection speed is not correlated to Internet access speed. Internet
access speed from popular broadband DSL or cable Internet services normally
provides up to 3 Mbps connection, which can be easily handled even by the slower
Wireless B protocol.
System Requirements
Your computer should meet these minimum requirements:
Windows® 2000, XP (32 and 64 bit), or Vista (32 bit)
32MB RAM
5MB available hard disk space
A free USB Port
CD-ROM drive
A wireless network with an active Internet connection
Page 4 of 29
Page 5
User Manual
LED Indicators
The LED lights up when the device is connected to a wireless network. The LED flickers
when the device is scanning for all available networks or transmitting/receiving data.
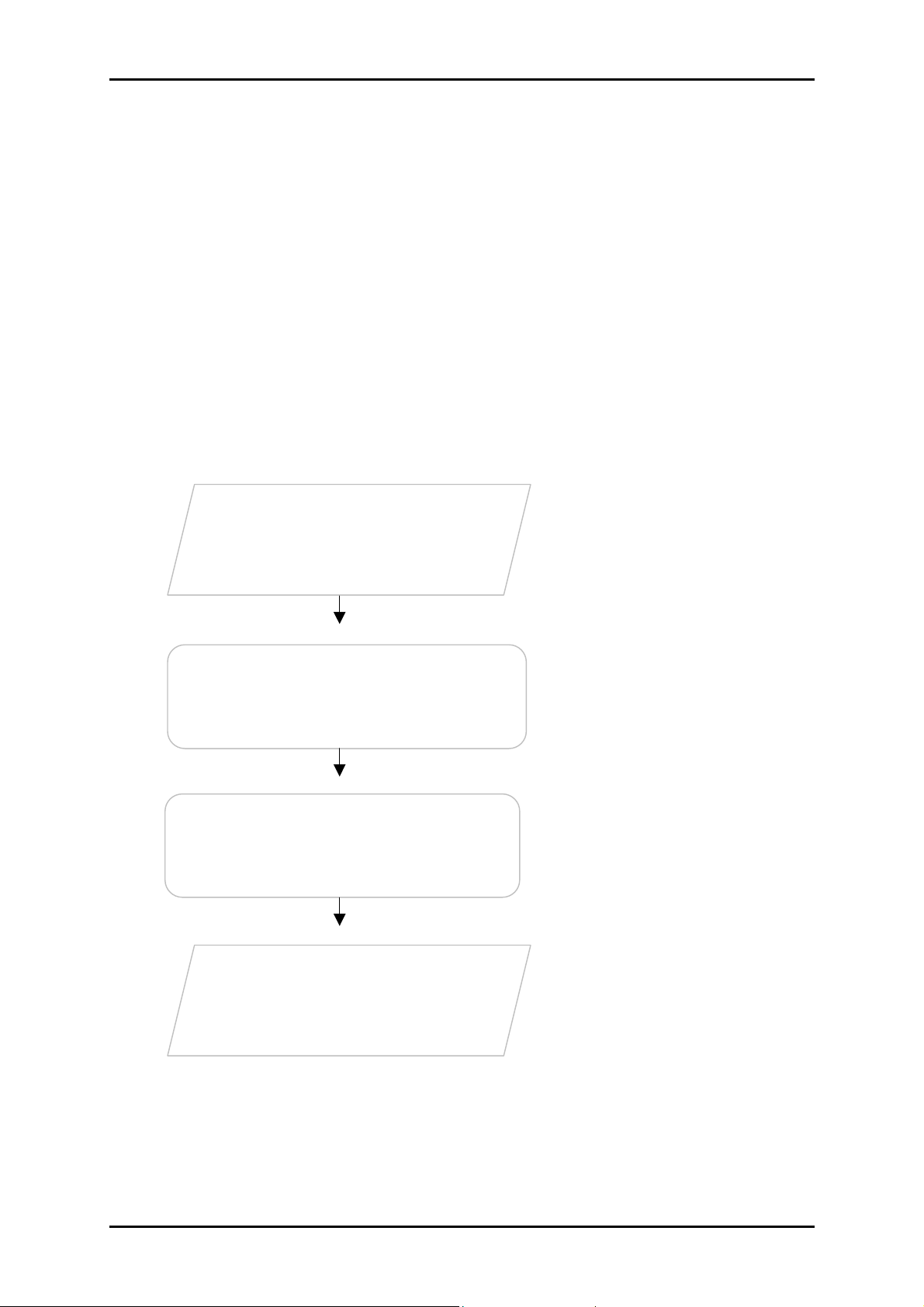
Getting Started
Setting up the device is easy. The flowchart below provides an outline of the steps
needed to complete the installation. Brief descriptions appear beside each step. Detailed
instructions are provided in the subsequent pages.
The package includes the Wireless
Check Package
Contents
N USB Adapter, Easy Start Guide,
Resource CD and USB Extension.
Check proxy application, TCP/IP
Remove/Disable
Conflicts
Install the Device
Settings, Internet Properties, and
remove temporary Internet files.
Install the device and then connect
to a wireless network.
Ready to Use
Page 5 of 29
Page 6

User Manual
Check Package Contents
Make sure that you have the following items. If any of the items is damaged or missing,
please contact your dealer immediately.
WL950USB Utility USB 2.0 Adaptor
Easy Start Guide
Resource CD – contains WL950 Utility installer, Easy Start Guide, and User Manual
USB Extension
Using the USB Extension
The USB Extension helps you place the device to a more prominent location and to
achieve a better reception of the wireless network. It is most useful for desktop
computers with USB 2.0 ports placed behind the computer casing. USB ports placed in the
front of the computer are usually the slower USB 1.0 variant.
To use the USB Extension, connect one end to a USB 2.0 port in your computer, and then
attach the WL950USB at the other end.
Remove or Disable Conflicts
To make sure the device installation moves on smoothly, you need to remove or disable
conflicts that may interfere the installation. Probable conflicts may include:
Internet sharing applications
Proxy software
Security software
Internet properties
Temporary Internet files
Page 6 of 29
Page 7

User Manual
Internet Sharing, Proxy, and Security Applications
Internet sharing, proxy software, and firewall applications may interfere with the
installation. These should be removed or disabled before start the installation.
If you have any of the following or similar applications installed on your computer,
remove or disable them according to the manufacturer’s instructions.
Internet Sharing Applications Proxy Software Security Software
Microsoft Internet Sharing WinGate Symantec
WinProxy Zone Alarm
Configuring Internet Properties
To set the Internet Properties:
1. Click the Start button, and then click Run. This opens the Run dialog box.
2. Type control inetcpl.cpl, and then click OK. This opens Internet Properties.
3. Click Connections tab.
4. In Dial-up and Virtual Private Network settings, check Never dial a connection.
5. To close Internet Properties, click OK.
Removing Temporary Internet Files
Temporary Internet files are files from Web sites that are stored in your computer. Delete
these files to clean the cache and remove footprints left by the Web pages you visited.
To remove temporary Internet files:
1. Click the Start button, and then click Run. This opens the Run dialog box.
2. Type control, and then click OK. This opens Control Panel.
3. Double-click Internet Options. This opens Internet Options.
4. In the Temporary Internet Files pane, click Delete Cookies.
5. Click Delete Files.
6. To close Internet Properties, click OK.
Page 7 of 29
Page 8

User Manual
Installation
Here are the instructions on how to install the driver software and connect to the
wireless network.
For Windows Vista
Note: Do not connect the device until the Utility is not completely installed.
To install the driver software:
1. Insert the Resource CD to the CD-ROM. This opens the WL950USB Utility Setup. If
the Utility does not open automatically, click the Start button, and then click Run.
Enter d:\setup.exe, where d is the CD-ROM drive.
2. Click Next to proceed.
3. Click Next to install the driver software files.
4. Click Next to accept the default file location.
5. Click Next to use the default program folder.
6. Click Next to add shortcuts on the desktop and the Startup Menu.
7. Select Install this driver software anyway.
8. To complete the installation, click Finish.
9. Connect the device to an available USB port. Your computer will detect the device.
To connect to a wireless network:
1. When you complete the installation, a new icon appears in the System tray - .
Double-click this icon to open WL950USB Utility.
2. Click Site Survey.
3. Select an ESSID and then click Join. The Privacy Configuration dialog box opens
when a network key is required from the selected ESSID. Enter the Network key,
Page 8 of 29
Page 9

confirm the Network key, and then click OK. The System tray icon changes to any
of the following:
• - You have a good or excellent connection to a wireless network
• - You have a usable but weak connection to a wireless network
• - Searching or not connected to a wireless network
For Windows XP/2000
Note: Do not connect the device until the Utility is not completely installed.
User Manual
To install the driver software:
1. Insert the Resource CD to the CD-ROM. This opens the WL950USB Utility Setup. If
the Utility does not open automatically, click the Start button, and then click Run.
Enter d:\setup.exe, where d is the CD-ROM drive.
2. Click Next to proceed.
3. Click Next to install the driver files.
4. Click Next to accept the default file location.
5. Click Next to use the default program folder.
6. Click Next to add shortcuts to the desktop and the Startup Menu.
7. To complete the installation, click Finish.
8. Connect WL950USB to an available USB port. This opens the Found New Hardware
Wizard.
9. Select No, not this time, and then click Next.
10. Select Install the software automatically (Recommended), and then click Next.
11. Click Continue Anyway when the Hardware Installation dialog box appears.
12. To close Found New Hardware Wizard, click Finish.
Page 9 of 29
Page 10

User Manual
To connect to a wireless network:
1. When you complete the installation, a new icon appears in the System tray - .
Double-click this icon to open WL950USB Utility.
2. Click Site Survey.
3. Select an ESSID and then click Join. The Privacy Configuration dialog box opens
when a Network key is required from the selected ESSID. Enter the Network key,
confirm the Network key, and then click OK. The System tray icon changes to
either of the following:
• - You have a good or excellent connection to a wireless network
• - You have usable but weak connection to a wireless network
• - Searching or not connected to a wireless network
Driver Only Installation
To install only the driver files in Windows XP:
1. Connect the device to an available USB port. This opens the Found New Hardware
Wizard.
2. Select No, not this time, and click Next.
3. Select Install from a list of specific location (Advanced), and then click Next.
4. Insert the Resource CD into your CD-ROM drive, select Search removable media
(floppy, CD-ROM…), and then click Next.
5. To complete the installation, click Finish.
Page 10 of 29
Page 11

User Manual
About WL950USB Utility
WL950USB Utility is a software application used in tandem with the device to connect to
a wireless network and to configure the device settings. WL950USB Utility can be
installed on computers running Windows 2000, XP, or Vista.
To connect to a wireless network:
1. Connect Wireless N USB adapter to a USB port.
2. When your device is detected, a new icon appears in the System tray
Double-click this icon to open WL950USB Utility.
.
Configuration Tab
The Configuration Tab provides all basic and advanced configuration settings for the
wireless network connection.
Configuration Tab
Page 11 of 29
Page 12

User Manual
Profile A Profile is a name identifier to wireless network connections that have been saved. Profiles are
created to relieve your from reentering the wireless network settings every time you want to connect to a
wireless network.
Configuration
SSID Represents the name of the wireless network. An SSID is case sensitive and can have a
maximum of 32 characters without spaces.
Network Type WL950USB supports two network types:
• Infrastructure Used for connecting to a wireless network
• Adhoc used for setting up a group of wireless stations for file and printer sharing
Ad-Hoc Channel Allows you to specify 1-13 channels to be used for an Ad hoc network
Transmit Rate Default Transmit Rate value is Auto. This setting allows your device to automatically
switch the data transmission rate based on the conditions available in your environment. When
the quality drops below a certain level, the WL950USB will automatically switch to a lower data
rate. Otherwise, when the quality improves, the Wireless USB Adapter will gradually increase the
data rate until it has reached the highest available transmit rate.
Status Provides a general overview of the connection quality.
Status parameters include:
• State Displays the Network Type, wireless network name (ESSID), and MAC address of the
access point. When operating in Ad-Hoc mode, State displays the virtual MAC address
used by computers participating in the Ad-Hoc network.
• Current Channel Displays the channel used.
• Current Tx Rate Displays the highest transmit rate of the wireless network.
• Throughput Displays the short term transmit and receive throughput in bytes/second.
• Link Quality Displays the link quality. There are 5 states of link quality:
o 100%~80% Excellent link quality
o 80%~60% Good link quality
o 60%~40% Fair link quality
o Below 40% Poor or no connection
• Signal Strength Displays the signal strength measurement. There are 5 states of signal
strength:
o 100%~80% Excellent signal strength
o 80%~60% Good signal strength
Page 12 of 29
o 60%~40% Fair signal strength.
o Below 40% Poor or no signal strength
• Rescan Click to perform a new scan of all available wireless networks.
Page 13

User Manual
Advanced Configuration
The Utility provides advanced configuration options that allow you specify the wireless
protocol to be used, enable power saving mode, enable RTS Threshold, and
Fragmentation Threshold.
Note: Advanced configuration is only enabled for Windows 2000 and XP.
Advanced Configuration options include:
Wireless Mode Allows you to specify the wireless protocol
Power Save Designed to conserve computer battery life. When Power Save is enabled, your Wireless USB
Adapter will go into sleep mode to minimize power consumption. When power saving mode is enabled,
the Access Points you use need to support power saving mode as well so that the communication can be
established.
RTS Threshold Prevent the
the packet size. The RTS mechanism will be activated if the data size exceeds the value you set. It is highly
recommended that you set the value ranging from 0 to 1500. This is disabled by default. Enabling RTS
Threshold would cause redundant network overhead that could negatively affect the throughput
performance instead of providing a remedy.
Fragmentation Threshold Used for improving the efficiency during high traffic. It chunks down large pieces
of data into smaller packets which are more manageable during transmission.
Hidden Node
problem. If the Hidden Node problem is an issue, please specify
Page 13 of 29
Page 14

User Manual
Security Enable (Privacy Configuration)
Security is applied to wireless networks to ensure integrity and limit unauthorized access
within the network. To open Security Enable (Privacy Configuration), check Security
Enable, and then click Config. This opens Privacy Configuration which has the Security and
Certification tabs.
When security is enabled, transmitted data is encrypted. It scrambles all data packets
transmitted among the wireless stations to keep network communications private. These
wireless stations must use the same security settings for data to be encrypted and
decrypted.
Page 14 of 29
Page 15

Note: All the security settings you provide must be similar to the security settings
defined from the wireless access point.
Privacy
Authentication Mode Authentication modes include:
• Open, Shared, WPA-PSK, WPA, WPA2-PSK, and WPA2
Encryption Mode Encryption modes include:
• WEP, AES, and TKIP
IEEE 802.1X Authentication
Enable IEEE 802.1X authentication for the network Select to allow you to use
User Manual
certificates instead of password keys to authenticate your application into the
wireless network
EAP Type EAP Types include:
• PEAP (MS-CHAPV2 and GTC), TLS, TTLS (PAP, CHAP, MS-CHAP, MS-CHAPV2),
and SIM
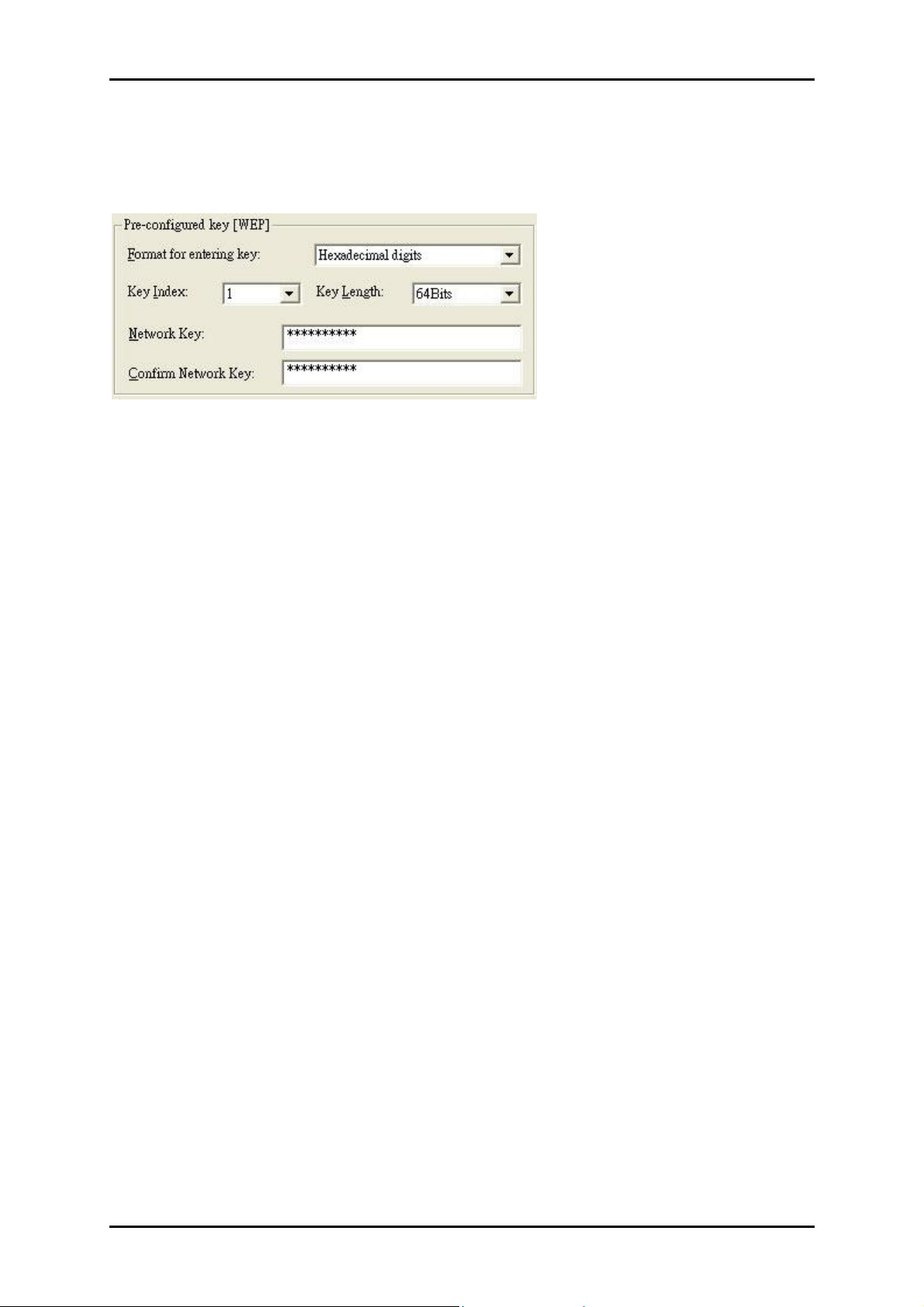
Preconfigured key
Format for entering key
• ASCII characters or Hexadecimal digits
Key Index 1-4 Allows you to specify which of the four keys will be used as the
default key
Key Length Determines the length of the network key
• 64Bits or 128Bits
Network Key A string of characters used to function as a password to connect to
the network. Parameters may vary depending on the encryption mode, format
and length used.
Confirm new key Requires you to retype the network key to confirm its value
Page 15 of 29
Page 16

User Manual
Wireless LAN Security Overview
Wireless LAN security is vital to your network to protect wireless communications against
hacker entering your system and prevent unauthorized wireless station from accessing
data transmitted over the network; the WL950USB Utility offers a sophisticated security
algorithm. If you do not enable any wireless security on your wireless network, it will be
accessible to any wireless networking device within the coverage area.
Data Encryption with WEP
WL950USB allows you to configure up to four 64-bit or 128-bit WEP keys. However, only
one key is used as the default key at any one time. The Key index field allows you
specify which of the four keys you use to transmit data on your wireless LAN. You can
change the default key by clicking on the up or down arrow and make sure the default
Page 16 of 29
Page 17
User Manual
key is set up exactly the same on the Wireless LAN stations as they are on the wireless
Access Points.
For 64bit encryption you may choose:
• Alphanumeric: entering
5 characters
(case sensitive) ranging from “a-z”, “A-Z”
and “0-9” (e.g. MyKey).
• Hexadecimal: entering
10 hexadecimal digits
in the range of “A-F”, “a-f” and “0-
9” (e.g. 11AA22BB33).
For 128bit encryption you may choose:
• Alphanumeric: entering
13 characters
(case sensitive) ranging from “a-z”, “A-Z”
and “0-9” (e.g. MyKey12345678).
• Hexadecimal: entering 26
hexadecimal digits
in the range of “A-F”, “a-f” and “0-
9” (e.g. 00112233445566778899AABBCC).
EAP Authentication
EAP (Extensible Authentication Protocol) is an authentication protocol which runs on the
top of IEEE 802.1x transport mechanism in order to support multiple types of user
authentication. By using EAP to interact with an EAP-compatible RADIUS server, an access
point helps a wireless station and a RADIUS server perform authentication.
The type of authentication you use depends on the RADIUS server and an intermediary
AP that supports IEEE 802.1X. You must first have a wired connection to the network and
obtain the certificate from a certificate authority (CA). A certificate can be used to
authenticate users and a CA issues certificates and guarantees the identity of each
certificate owner.
Page 17 of 29
Page 18

User Manual
WPA (2)
Wi-Fi Protected Access (WPA) is a subset of the IEEE 802.11i standard. WPA2 is a wireless
security standard that defines stronger encryption, authentication and key management
than WPA.
WPA: Allows you to gain access to a more secured wireless network that requires mutual
authentication between client and access point with a Radius authentication server or
other authentication server on the network. WPA uses 802.1X and Extensible
Authentication Protocol (EAP) for authentication. WPA offers Enterprise and individual
needs to meet the different market segments. This product supports various EAP types
(TLS and PEAP), which require different credential authentication. In order to access the
wireless network, you must select EAP type your service provider supplied in the section
of IEEE802.11X Authentication. Choose WPA2 if needed from Authentication Mode.
Page 18 of 29
Page 19

User Manual
WPA-PSK: WPA offers a Personal mode of operation. In the Personal mode of operation, a
pre-shared key is used for authentication. WPA-PSK allows you to gain access to a
secured wireless network that the station and the access point use the same pre-shared
key to authenticate. You must type a mixture of numbers and letters in the Pre-shared
key section of this menu. You may input either 8-63 ASCII characters or 64 HEX
characters. Choose WPA-PSK if needed from Authentication Mode.
Page 19 of 29
Page 20

User Manual
WPA2: WPA2 provides a stronger encryption mechanism than WPA. WPA2 is the second
generation of WPA security, providing personal and enterprise users with a high level of
assurance that only authorized users can access to their wireless network. There is no
difference between WPA and WPA2. The only difference is that WPA2 provides a stronger
data encryption via the AES, contrast to WPA, which uses Temporal Key Integrity Protocol
(TKIP). Choose WPA2 if needed from Authentication Mode.
Page 20 of 29
Page 21

User Manual
WPA2-PSK: Like WPA, WPA2-Personal offers authentication via a pre-shared key. Pre-
shared key is usually used for Personal authentication. Personal mode requires only an
access point and client on the network. Similarly, you need to type a mixture of numbers
and letters in the Pre-shared key section of this menu. You may input either 8-63 ASCII
characters or 64 HEX characters. Choose WPA2-PSK if needed from Authentication Mode.
Page 21 of 29
Page 22

User Manual
Encryption Mode
WPA improves data encryption by using Temporal Key Integrity Protocol (TKIP), Message
Integrity Check (MIC) and IEEE 802.1X. WPA2 use Advanced Encryption Standard (AES) in
the Counter mode with Cipher block chaining Message authentication code Protocol
(CCMP) to offer stronger encryption than TKIP.
The encryption mechanism used for WPA(2) and WPA(2)-PSK are the same. The only
difference between them is that WPA(2)-PSK uses a simple common password, instead
of user specific credentials. The common password approach makes WPA(2)-PSK
susceptible to brute-force password-guessing attacks but it’s still an improvement over
WEP as it employs a consistent, single, alphanumeric password to derive a PMK which is
used to generate unique temporal encryption keys.
Page 22 of 29
Page 23

User Manual
IEEE 802.1X Authentication
WPA and WPA2 apply IEEE 802.1X and Extensible Authentication Protocol (EAP) to
authenticate wireless stations using an external RADIUS database. WPA2 reduces the
number of key exchange messages from six to four (CCMP 4 way handshake) and
shortens the time required to connect to a network. Other WPA2 authentication features
that are different from WPA include key caching and pre-authentication.
After you select the EAP type, you need to click Certification Tab to make advanced
setting. The following describes configuration of each available EAP type.
TLS: Clicking the Certification tab for TLS shows the following menu.
TLS requires the entry of Certificate Information and Login Information for mutual
authentication. This utility will auto-detect the Certificate Information for you to configure
TLS easily. You only need to enter the Login Name in the Login information filed to
authenticate. If you desire to use the Server Certificate manually, you can click the check
box next to “Verify Server Certificate” and choose the usable selection in the User
Certificate field using drop-down menu.
User Certificated: select one of user certificates you have enrolled.
Page 23 of 29
Page 24

User Manual
TLS is used to create a secure tunnel through which authentication and encryption keys
can be passed and require server and client side keys. To save the information you
entered in the appropriate field, click the OK button. Otherwise, click the Cancel button to
close the menu. If you want to return to select other EAP type, click the Security tab.
PEAP: Clicking the Certification tab for PEAP displays the following menu.
PEAP requires the use of Certificate Information and User Information. This utility will
automatically identify Certificate Information and Login Information for users to configure
PEAP easily. You only need to enter User Name and Password in the User information
filed to authenticate. If you click the “Verify Server Certificate” check box, you are able to
choose one of User Certificate from the drop-down menu. Furthermore, you need to input
User Name and Password in the User Name.
To save the information you entered in the appropriate field, click the OK button.
Otherwise, click the Cancel button to close the menu. If you want to return to select other
EAP type, click the Security tab.
Page 24 of 29
Page 25

LEAP: Clicking the Certification tab for LEAP shows the following menu.
User Manual
LEAP requires the mutual authentication between station and access points. You must
present a User Name and Password in the User Information field that will be verified by
LEAP-capable server. This mutual authentication ensures that only authorized users are
allowed access to the network.
Page 25 of 29
Page 26

User Manual
Authentication Type
The IEEE 802.11b/g standard describes a simple authentication method between the
wireless stations and AP. Two authentication types are defined: Open system mode and a
Shared key mode.
• Open system mode is implemented for ease-of-use and when security is not an
issue. It requires NO authentication, since it allows any device to join a network
without performing any security check. The wireless station and the AP do not
share a secret key. Thus the wireless stations can associate with any AP and listen
to any data transmitted plaintext.
• Shared key mode involves a shared secret key to authenticate the wireless station
to the AP. It requires that the station and the access point use the same WEP key
to authenticate. This basically means that WEP must be enabled and configured
on both the AP and the other wireless stations with a same key. Shows as below:
Page 26 of 29
Page 27

User Manual
Site Survey Tab
Site Survey displays the available wireless networks you can connect to. To connect to a
wireless network, select the ESSID and then click the Join. Click Rescan to rescan the
network.
Site Survey displays the following information:
• ESSID Displays the available wireless networks
• BSSID Displays the MAC Address of the wireless access point
• Channel Displays the Channel number used by the wireless device
• Network Type Displays the network type of the wireless device (Infrastructure or
Ad Hoc)
• Security Displays the status of wireless security. When Activated, it will display
WEP, WPA, WPA-PSK, or WPA2, WPA2-PSK. If security is deactivated, it will be
blank.
• Signal Displays the signal strength of the wireless network.
• Support Rates Displays the supported data rate.
Page 27 of 29
Page 28

User Manual
About Tab
The About tab displays the version of the Configuration Utility, Network Driver, Network
Firmware, the device MAC Address, and Frequency Domain.
Page 28 of 29
Page 29

User Manual
Safety Warnings
For your safety, be sure to read and follow all warning notices and instructions.
Do not open the device. Opening or removing the device can expose you to
dangerous voltage points or other risks. Only qualified service personnel can
service the device. Please contact your vendor for further information.
Do not use your device during a thunderstorm. There may be a risk of electric
shock brought about by lightning.
Do not expose your device to dust or corrosive liquids.
Do not use this product near water sources.
Do not obstruct the ventilation slots.
Page 29 of 29
 Loading...
Loading...