Page 1
Wireless
Broadband
Router
Model #: MI424WR
Firmware Version: 4.0.16.1.44.28
User Manual
Ver 2.0
Solutions for the Digital Life
™
Page 2

Table of Contents
1 Introduction 1
Package Contents 1
Minimum System Requirements 2
Features 2
Getting to Know the Router 4
2 Connecting the Router 9
Setting Up the Router 9
Computer Network Configuration 14
Home Page 16
3 Configuring My Network Settings 19
Accessing My Network 19
Using My Network 20
4 Creating a Wireless Network 27
Overview 27
Wireless Network Connection 28
Configuring a Wireless Windows XP Client 35
Connecting a Wireless Windows XP Client 37
5 Using Network Connections 41
Network (Home/Office) 42
Ethernet Connection 48
Coax Connection 51
Broadband Ethernet Connection 54
Coax Broadband Connection 60
WAN PPPoE/WAN PPPoE 2 65
6 Configuring the Router’s Security 71
General 73
Access Control 75
Port Forwarding 78
DMZ (Demilitarized Zone) Host 80
Port Triggering 81
Remote Administration 82
Website Blocking 84
Static NAT 86
Advanced Filtering 87
Security Log 90
7 Using Parental Controls 99
Activating Parental Controls 99
Creating a Filtering Policy 100
Advanced Options 104
Statistics 105
i
Page 3

Actiontec Wireless Broadband Router User Manual
8 Using Advanced Settings 107
About 109
Configuration File 109
Restart 110
Restoring Default Settings 110
Diagnostics 111
MAC Cloning 112
System Settings 113
Universal Plug and Play (UPnP) 118
Firmware Upgrade 119
Scheduler Rules 122
Date and Time 124
RADIUS (Client) 125
Users 125
ARP (Address Resolution Protocol) Table 127
Routing 127
Network Objects 129
Firmware Restore 131
Dynamic DNS 131
IP Address Distribution 133
DNS Server 137
Remote Administration 139
Protocols 140
9 Monitoring the Router 143
Monitoring Connections 143
Traffic Monitoring 144
System Log 145
Router Status 145
10 Troubleshooting 147
A Quality Of Service 151
Traffic Priority 151
Traffic Shaping 155
B Specifications 165
General 165
Wireless Operating Range 166
LED Indicators 166
Environmental 166
Notices 167
Regulatory Compliance Notices 167
Modifications 167
ii
ii
Page 4

Introduction
1
Thank you for purchasing the Actiontec Wireless Broadband Router. The Wireless
Broadband Router supports Multimedia over Coax Alliance (MoCA), a new net-
working standard that allows digital entertainment and information to be transmitted and distributed to multiple devices over coaxial cables. The Router also supports Ethernet and Wi-Fi networking, making it the most versatile router available.
If you want to take your home or office networking to the next level, the Actiontec
Wireless Broadband Router is sure to be one of the keys to your success.
Package Contents
s Actiontec Wireless Broadband Router
s Black Power cord
s Yellow cable (Ethernet, 6 ft.)
s White cable (Ethernet, 10 ft.)
s Quick Start Guide
s Installation Guide
s Wireless Networking Guide
s User Manual CD
1
Page 5
Actiontec Wireless Broadband Router User Manual
3
Chapter 1 Introduction
s Wall-mount template
s Vertical stand
s Warranty
Minimum System Requirements
s Computer with Ethernet capability
s Microsoft Windows 98SE, Me, 2000, or XP; Mac OS 9 or greater; Linux/
BSD, Unix
s Internet Explorer 5.0 or higher; Netscape Navigator 7.0 or higher
s TCP/IP network protocol installed on each computer
Features
s Supports multiple networking standards, including:
WAN - Ethernet and MoCA interfaces
LAN - 802.11g, 802.11b, Ethernet, and MoCA
s Integrated wired networking with 4-port 10/100 Mbps Ethernet switch
and MoCA
s Integrated wireless networking with 802.11g access point featuring:
802.11g enabled to support speeds up to 54 Mbps wirelessly
802.11b backward compatible, communicating with 802.11b wireless
products at speeds up to 11 Mbps
s Enterprise-level security, including :
Fully customizable firewall with Stateful Packet Inspection
Content filtering with URL-keyword based filtering, parental control,
customizable filtering policies per computer, and E-mail notification
Denial of service protection against IP spoofing attacks, intrusion and
scanning attacks, IP fragment overlap, ping of death, and fragmentation
attacks
Event logging
2
Page 6
Chapter 1 Introduction
Intrusion detection
MAC address filtering
NAT
DMZ hosting
Access control
Advanced wireless protection featuring WPA, WEP 64/128 bit encryp-
tion, 802.1x authentication, and MAC address filtering
ICSA certified
s Other Features
DHCP server option
DHCP server/PPPoE server auto-detection
DNS server
LAN IP and WAN IP address selection
MAC address cloning
Port forwarding
PPPoE support
QoS support (end to end layer 2/3) featuring Diffserv, 802.1p/q prioritization, configurable upstream/downstream traffic shaping, random early
detection and pass-through of WAN-side DSCPs, PHBs, and queuing to
LAN-side devices
Remote management and secured remote management using HTTPS
Reverse NAT
Static NAT
Static routing
Time zone support
VLAN multicast support
VPN IPSec (VPN passthrough only)
3
Page 7
Actiontec Wireless Broadband Router User Manual
5
Chapter 1 Introduction
1
2
3
4
MI424WR
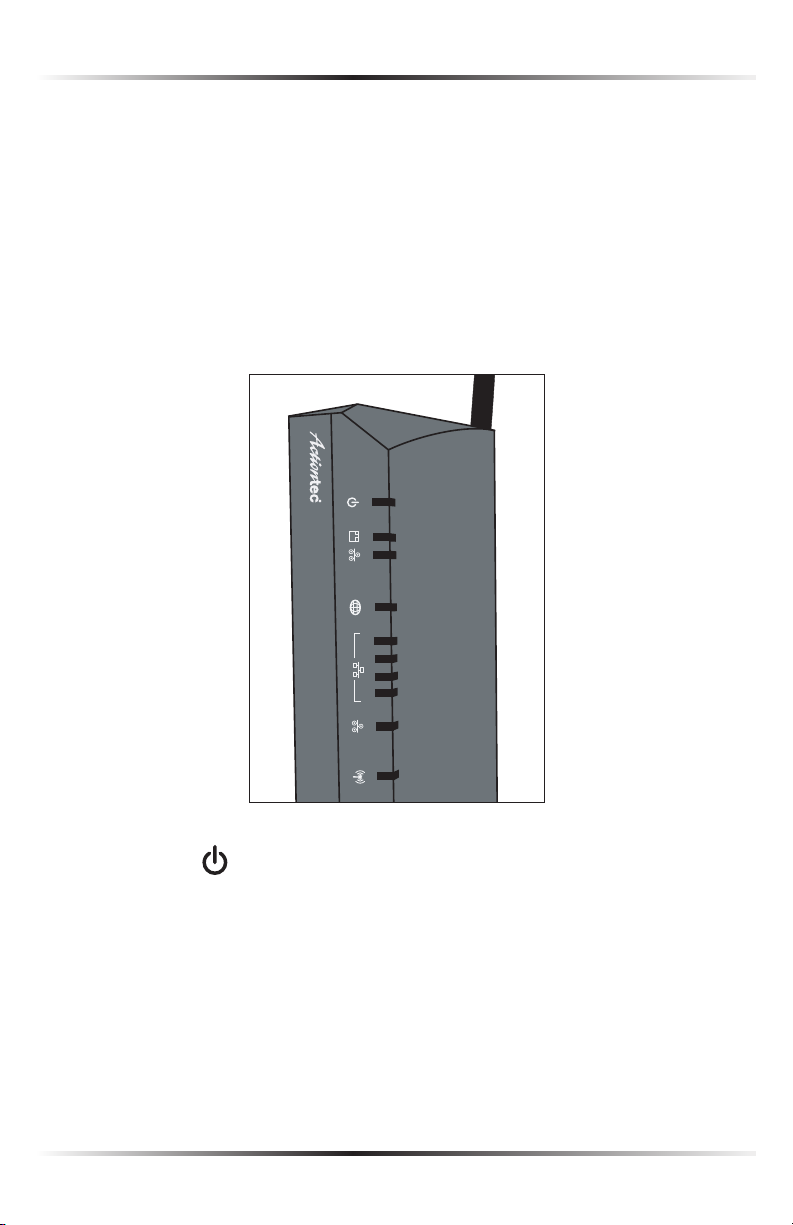
Getting to Know the Router
This section contains a quick description of the Router’s lights (LEDs), ports, etc.
The Router features several indicator lights on its front panel, and a series of ports
and switches on its rear panel.
Front Panel
The front panel of the Router features ten indicator lights: Power, Ethernet WAN,
Coax WAN, Internet, Ethernet LAN (4), Coax LAN, and Wireless.
Power Light
The Power light displays the Router’s current status. If the Power light glows
steadily green, the Router is receiving power and fully operational. When the
Power light flashes rapidly, the Router is initializing. If the Power light is not illuminated or glows red when the Power cord is plugged in and the Power switch is
turned on, the Router has suffered a critical error and technical support should
be contacted.
4
Page 8

Chapter 1 Introduction
Ethernet WAN Light
The Ethernet WAN light illuminates when the Router is connected to the
Internet via Ethernet. If flashing, data traffic is passing across the port.
Coax WAN Light
The Coax WAN light glows steadily or flashes when the Router is connected to
the Internet via coaxial cable.
Internet Light
When the Internet light glows steadily green, the Router is connected to the ISP
(Internet Service Provider). If it glows amber, there is a physical connection to
the ONT (Optical Network Terminator), but authentication has not taken place
(i.e., no IP address is present).
Ethernet LAN Lights (1, 2, 3, 4)
The Ethernet LAN lights illuminate when the Router is connected to a local
network via one or more of its Ethernet ports. If flashing, data traffic is passing
across the port(s).
Coax LAN Light
The Coax LAN light glows steadily or flashes when the Router is connected to a
local network via its Coax port.
Wireless Light
The Wireless light illuminates when the Router is connected wirelessly. If flashing, data traffic is passing across the wireless connection.
5
Page 9

Actiontec Wireless Broadband Router User Manual
7
Chapter 1 Introduction
1
Reset
2
3
4
1
00
1
00
Coax
ResetReset
On/Of
f
5VDC 3A
100
1
00
1
0
1
0
10
10
Rear Panel
The rear panel of the Router features seven ports (Coax, Ethernet WAN, Ethernet
LAN [4], and Power), as well as a Reset button and Power switch.
Coax Port
The Coax port connects the Router to the ISP or other devices using a coaxial
cable.
Reset Button
To restore the Router’s factory default settings, press and hold the Reset button
for approximately ten seconds. The reset process will start about ten seconds
after releasing the button. When the Router resets, all the lights on the front
panel turn off, and then the lights start flashing. The Router has completed its
reset process when the Power light glows steadily green.
Caution: Do not unplug the Power cord from the Router dur-
M
ing the reset process. Doing so may result in the loss of the
Router’s configuration information. If this occurs, reset the
Router again.
6
Page 10

Chapter 1 Introduction
Ethernet WAN Port
The Ethernet WAN port connects the Router to the ISP using an Ethernet cable.
Ethernet LAN Ports (4)
The Ethernet LAN ports connect devices to the Router via Ethernet cables to cre-
ate a local area network (LAN). The Ethernet LAN ports are 10/100 Mbps auto-
sensing ports, and either a straight-through or crossover Ethernet cable can be
used when connecting to the ports.
Power Switch
The Power switch powers the Router on and off.
Power Port
The Power port connects the Router to an electrical wall outlet via the
Power cord.
Caution: Do not unplug the Power cord from the Router dur-
M
ing the reset process. Doing so may result in the loss of the
Router’s configuration information. If this occurs, reset the
Router again.
7
Page 11

Actiontec Wireless Broadband Router User Manual
This page left intentionally blank.
8
Page 12

Connecting the Router
Connecting a computer or local network to the Wireless Broadband Router is a
simple procedure, varying slightly depending on the computer’s operating system,
and designed to seamlessly integrate the Router with the computer or local network. Moreover, zero-configuration is attained when taking advantage of Universal
Plug-and-Play support in Windows XP.
The Windows default network settings dictate that in most cases, the setup procedure described in the “Computer Network Configuration” will be unnecessary.
For example, the default DHCP setting in Windows 2000 is “client,” requiring no
further modification.
However, Actiontec advises following the setup procedure described below to verify all
communication parameters are valid and the physical cable connections are correct.
Setting Up the Router
There are three parts to setting up the Router: Connecting the Cables, Configuring
the Router, and Connecting Other Computers/Set Top Boxes.
Connecting the Cables
Note: If a different router was being used, disconnect it. Remove
☞
all router components, including power supplies and cables,
since they will not work with the Wireless Broadband Router.
2
1. Get the Router and black Power cord from the box.
2. Plug the black Power cord in the black port on the back of the Router and
then into a power outlet.
3. Turn the Router on.
4. Make sure the Power light on the front of the Router is glows steadily green.
5. Plug the yellow Ethernet cable from the box into one of the four yellow
Ethernet ports on the back of the Router.
9
Page 13
Actiontec Wireless Broadband Router User Manual
11
Chapter 2 Connecting the Router
6. Make sure the computer is powered on, then plug the other end of the yellow
Ethernet cable into an Ethernet port on the computer.
7. Make sure at least one of the Ethernet LAN lights on the front of the Router
glows steadily green. This may take a few moments.
8. The phone company previously installed a high-speed wall jack somewhere in
the house. Locate it and note its type (Ethernet or coaxial). If Ethernet, follow
steps 8a and 9a. If coaxial, follow steps 8b and 9b. Then, continue to step 10.
a) If connecting via Ethernet, get the white Ethernet cable from the box and
plug one end in the white port on the back of the Router.
b) If connecting via coaxial cable, get a coaxial cable and connect one end to
the red Coax port on the back of the Router.
9. a) If connecting via Ethernet, plug the other end of the white Ethernet cable
into the high-speed Ethernet jack.
b) If connecting via coaxial cable, connect the other end of the coaxial cable
to a coax jack.
10. Make sure the Ethernet WAN light (if connecting via Ethernet) or Coax WAN
light (if connecting via coaxial cable) on the front of the Router glows steadily
green. If connecting via coaxial cable, this may take a few minutes.
Note: If the Ethernet WAN light or Coax WAN light does not
☞
illuminate, make sure the cable (Ethernet or coaxial) is connected properly at both ends.
Configuring the Router
1. Open a web browser on the computer connected to the Router. In the
“Address” text box, type:
http://192.168.1.1
then press Enter on the keyboard.
10
Page 14
Chapter 2 Connecting the Router
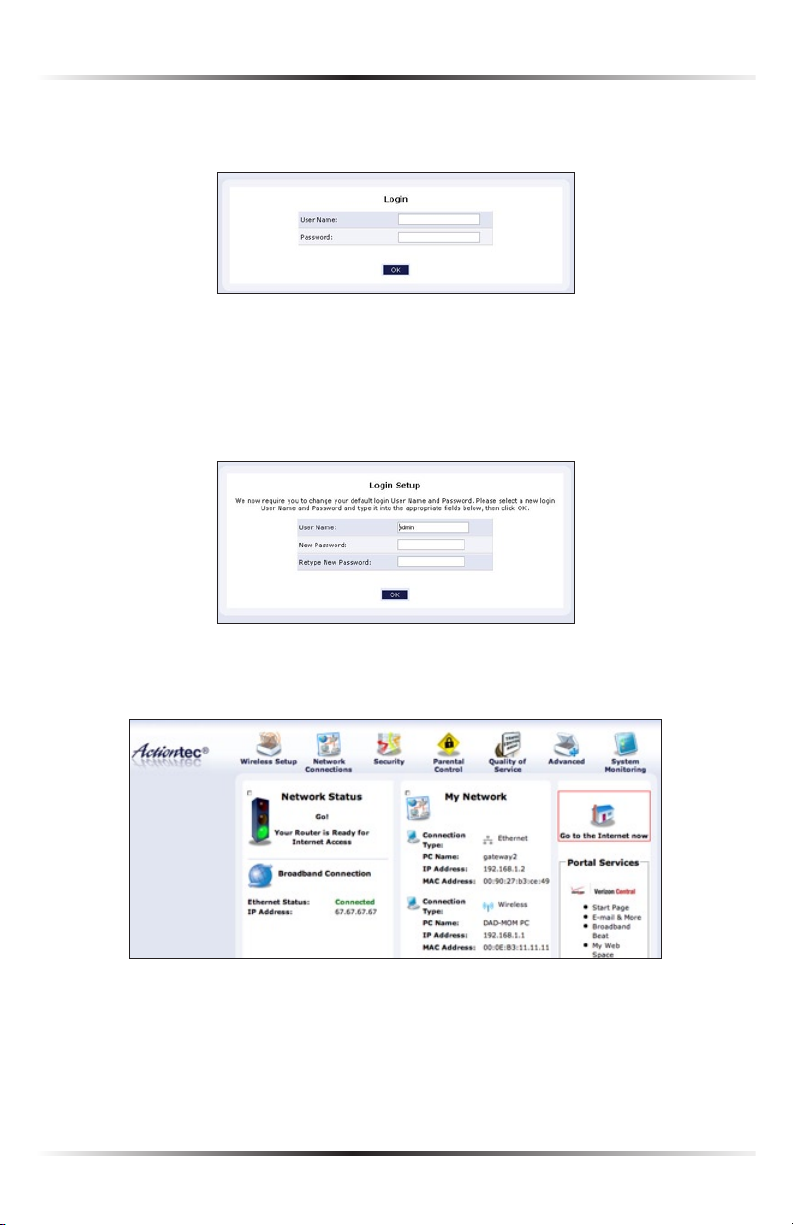
2. The “Login” screen appears. Enter the default user name (admin) and pass-
word (password) in the appropriate text boxes, then click OK.
3. The “Login Setup” screen appears. Select a new user name and password and
enter them in the appropriate text boxes (the password must be entered twice,
for validation purposes). Write the new user name and password down on a
piece of paper and keep it in a safe place, since they will be needed to access
the Router’s MegaControl Panel™ in the future.
4. The “Home” screen of the MegaControl Panel appears. Make sure the green
light is displayed in the “Network Status” section of the screen.
5. Make sure the “Ethernet Status” or “Coax Status” in the “Broadband
Connection” section displays “Connected,” as shown in the figure above.
11
Page 15
Actiontec Wireless Broadband Router User Manual
13
Chapter 2 Connecting the Router
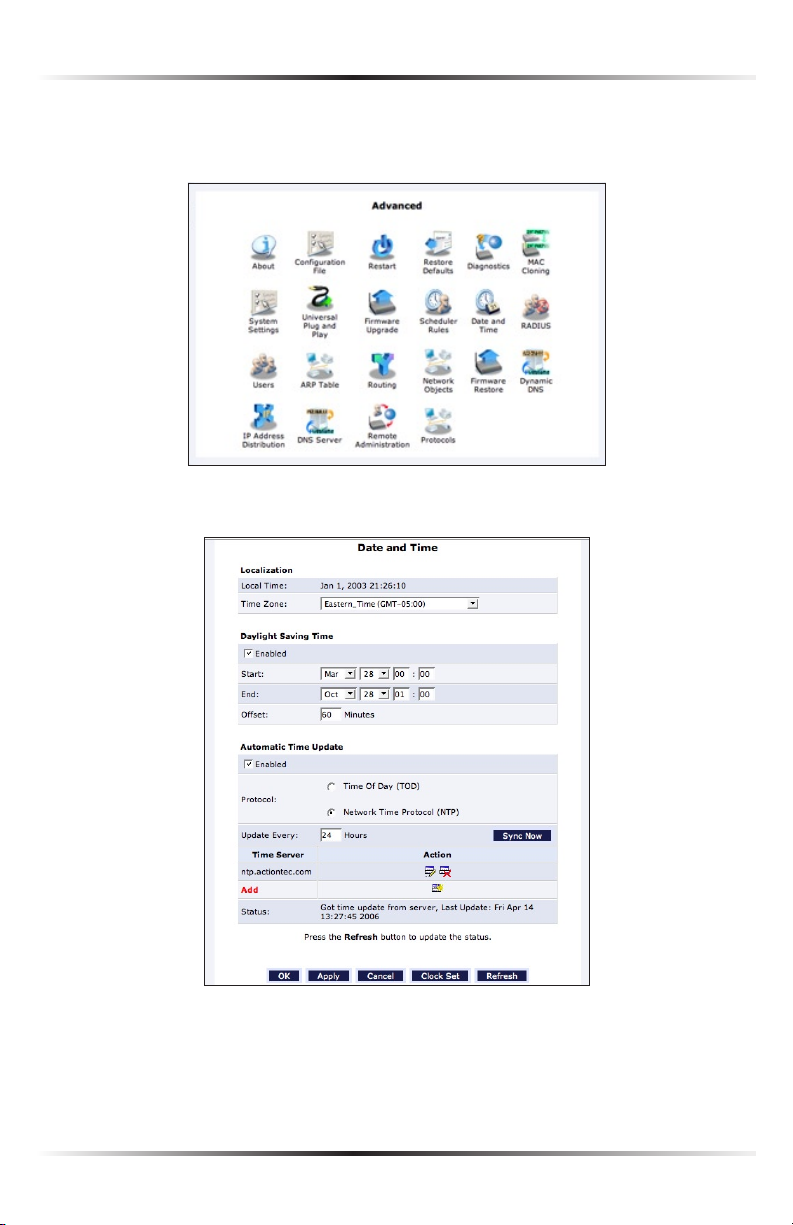
6. Click Advanced at the top of the Home screen. The “Advanced” screen
appears.
7. Click Date and Time. The “Date and Time” screen appears.
8. In the “Localization” section of the screen, select the correct time zone from
the “Time Zone” drop-down list, then click OK at the bottom of the screen.
The Router is now configured.
12
Page 16

Chapter 2 Connecting the Router
Connecting Other Computers/Set Top Boxes
The Router can connect to other computers or set top boxes in three ways: via
Ethernet, via wireless connection, or via coaxial cable.
Ethernet
1. Get an Ethernet cable and plug one end into one of the open yellow
Ethernet ports on the back of the Router.
2. Plug the other end of the Ethernet cable into an Ethernet port on the computer.
3. Make sure the corresponding Ethernet LAN light on the front of the Router
glows steadily green.
4. Repeat these steps for each computer to be connected to the Router
via Ethernet.
Wireless
1. Make sure each computer to be connected wirelessly has built-in wireless or
an attached wireless adapter.
2. Make sure the computer uses the same ESSID and WEP key as the Router by
launching the computer’s wireless application
3. Enter the ESSID and WEP key found on the sticker on the bottom of the
Router in the computer’s wireless settings and click Save. Make sure to configure the computer to use 64/40-bit WEP encryption.
4. Make sure the changes were implemented by surfing the Internet from
the computer.
5. Repeat these steps for every other computer to be connected to the
Router wirelessly.
Coaxial
1. Make sure all set top boxes are turned off.
2. Disconnect any adapter currently connected to the coaxial jack in the room
where the Router is.
13
Page 17

Actiontec Wireless Broadband Router User Manual
15
Chapter 2 Connecting the Router
3. Connect one end of the coaxial cable to the coaxial wall jack, and the other
end to the red Coax port on the back of the Router.
4. Power up the set top box.
5. Make sure the Coax LAN light on the front of the Router glows steadily
green. This may take a few minutes. When it does, the set top box is connected to the Router.
Computer Network Conguration
Each network interface on the computer should either be configured with a statically defined IP address and DNS address, or instructed to automatically obtain an
IP address using the Network DHCP server. The Router is set up, by default, with
an active DHCP server, and Actiontec recommends leaving this setting as is.
Configuring a Computer to Use Dynamic IP Addressing
To configure a computer to use dynamic IP addressing:
Windows XP
1. Select Network Connections in the Control Panel.
2. Right-click Ethernet Local Area Connection, then click Properties.
3. In the “General” tab, select Internet Protocol (TCP/IP), then click
Properties.
4. The “Internet Protocol (TCP/IP) Properties” window appears.
5. Click the “Obtain an IP address automatically” radio button.
6. Click the “Obtain DNS server address automatically” radio button.
7. Click OK to save the settings.
14
Page 18

Chapter 2 Connecting the Router
Windows 2000/98/Me
1. Select Network and Dialing Connections in the Control Panel.
2. Right-click on the Ethernet connection’s icon, then click Properties.
3. Select Internet Protocol (TCP/IP) component, then click Properties.
4. The “Internet Protocol (TCP/IP) Properties” window appears.
5. Click the “Obtain an IP address automatically” radio button.
6. Click the “Obtain DNS server address automatically” radio button.
Windows NT
1. Click Network in the Control Panel. The “Network” window appears.
2. In the “Protocol” tab, select Internet Protocol (TCP/IP) then click
Properties.
3. In the “IP Address” tab, click the “Obtain an IP address automatically” radio
button.
4. In the “DNS” tab, verify no DNS server is defined in the “DNS Service Search
Order” text box and no suffix is defined in the “Domain Suffix Search
Order” text box.
Linux
1. Login into the system as a super-user, by entering “su” at the prompt.
2. Type “ifconfig” to display the network devices and allocated IPs.
3. Type “pump -i <dev>,” where <dev> is the network device name.
4. Type “ifconfig” again to view the newly allocated IP address.
5. Make sure no firewall is active on device <dev>.
15
Page 19
Actiontec Wireless Broadband Router User Manual
17
Chapter 2 Connecting the Router
Home Page
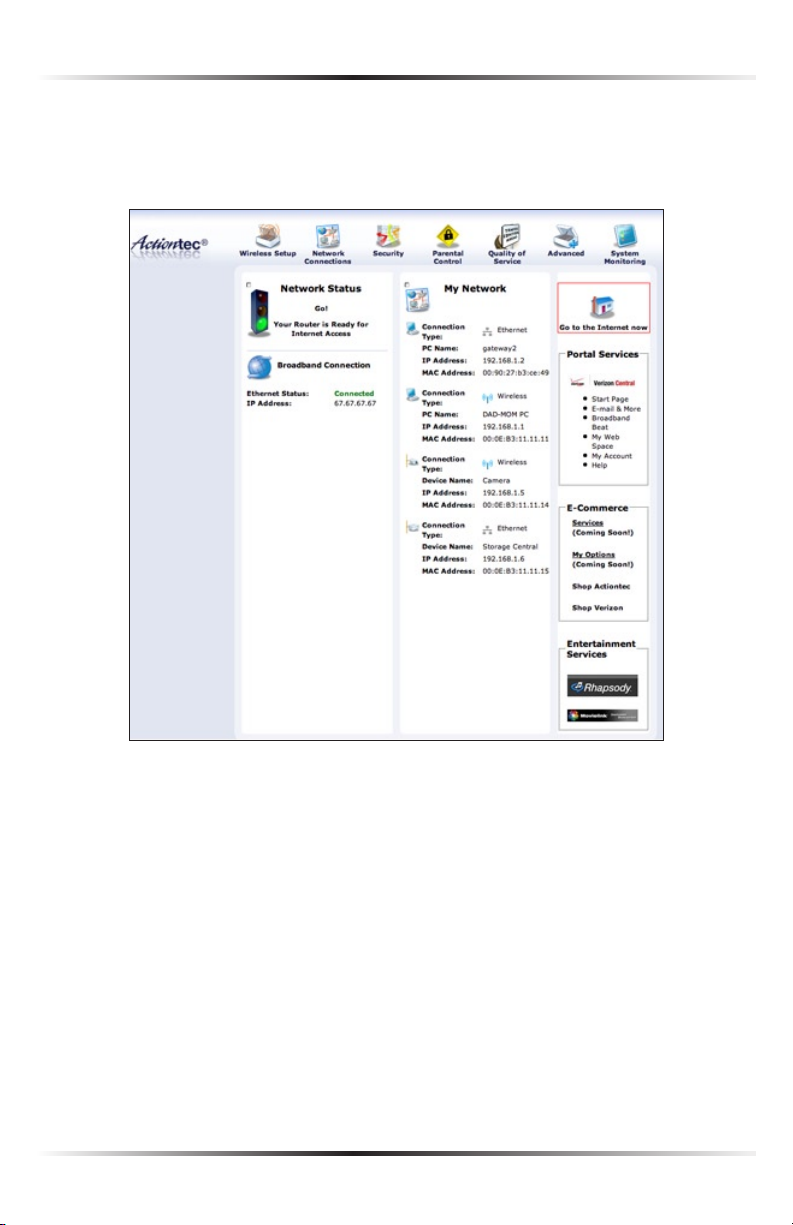
After logging into the Router’s MegaControl Panel (see “Configuring the Router” at
the beginning of this chapter), the “Home” screen appears.
The Home screen has a “Main Menu” that occupies the top of the screen. Below
that, the screen is divided into three columns: “Network Status,” “My Network,” and
“Entertainment/General Information.” A brief description of each continues below.
Main Menu
The “Main Menu” contains links to all of the configuration options of the Router:
Wireless Setup (explained in chapter 4 of this manual), Network Connections
(chapter 5), Security (chapter 6), Parental Control (chapter 7), Quality of
Service (appendix A), Advanced (chapter 8), and System Monitoring (chapter 9).
16
Page 20

Chapter 2 Connecting the Router
Network Status
This section displays the status of the Router’s network and Internet connection.
A green light signifies the Router is connected; a yellow light means the Router is
attempting to connect; and a red light signifies the Router’s connection is down.
Broadband Connection
The “Broadband Connection” section of Network Status displays the state of the
Router’s broadband connection (“Connected” or “Disconnected”) for the two
connection options (“Coax Status” and “Ethernet Status”).
My Network
The “My Network” section of the Home screen displays the connection type, name,
IP address, and MAC (Media Access Control) address of all devices connected to
the Router’s network. The icon associated with the device will be displayed normally (signifying an active device) or shaded (signifying the device has not been
active for at least 60 seconds). The user can also configure the basic settings of each
device by clicking on its icon. These settings are described in more detail in chapter
3, “Configuring My Network Settings.”
Entertainment/General Information
This section contains links to various Verizon Web sites, and other informational
links. Clicking on the flashing icon above “Go to Internet Now” connects the user
to the home page configured on the user’s web browser.
17
Page 21

Actiontec Wireless Broadband Router User Manual
This page left intentionally blank.
18
Page 22
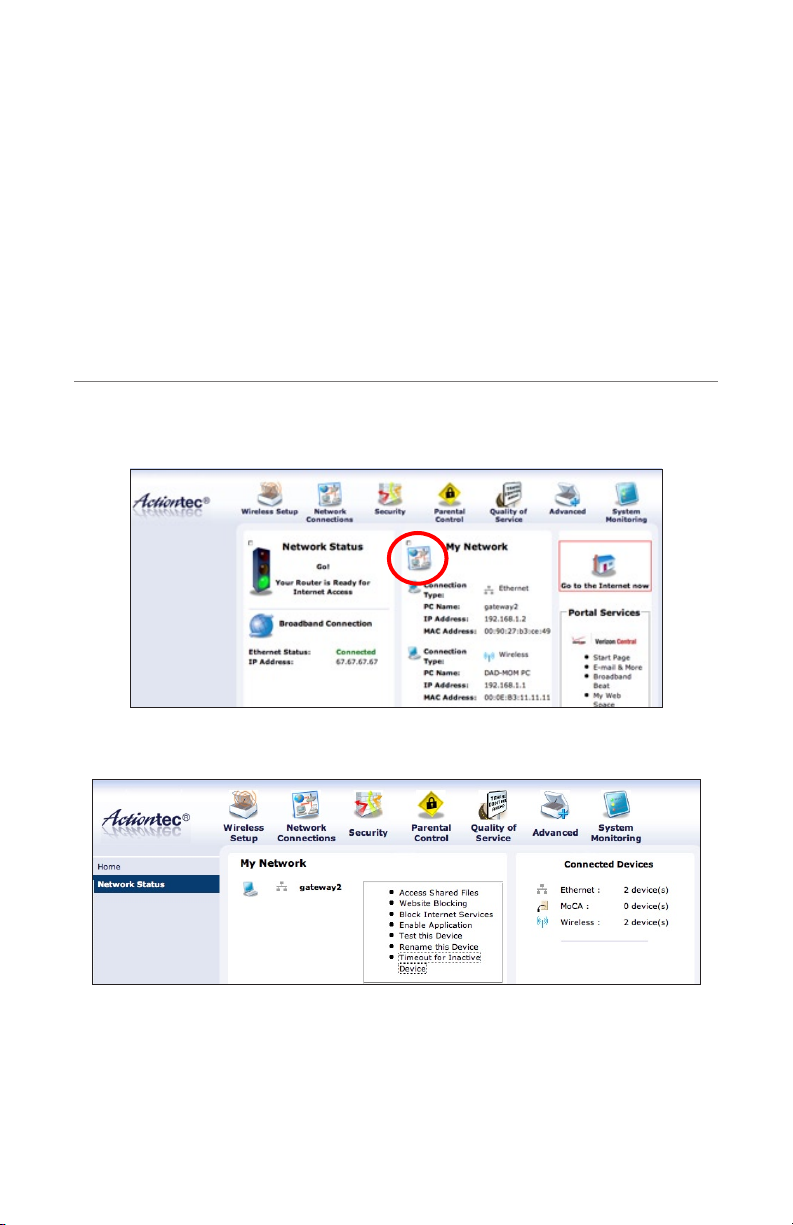
Configuring My Network Settings
Once the Wireless Broadband Router is physically connected and the MegaControl
Panel’s Home screen is displayed in a web browser, a list of the devices connected
to the Router’s network appears in the “My Network” section of the screen. From
here, some basic network settings can be configured.
Accessing My Network
To access My Network, click on the “My Network” icon:
The “My Network” screen appears:
3
On the far right side of the screen, in the “Connected Devices” section, is list of the
devices currently connected to the network, listed by connection type and number.
The center of the screen contains the “My Network” section, which displays each
device connected to the network, and a series of configuration settings.
19
Page 23

Actiontec Wireless Broadband Router User Manual
21
Chapter 3 Configuring My Network Settings
Using My Network
Various settings can be accessed for a particular device, as follows.
Access Device
For devices that can be accessed (such as Internet cameras and networked hard
drives), locate it in the My Network column, then click Access Devices to use the
device over the network.
Access Shared Folders
To access the shared folders on a particular device, locate the device in the My
Network column, then click Access Shared Folders. A list of shared folders
appears on the screen.
Website Blocking
Website blocking is used to prevent a device on the network from accessing particular websites on the Internet. To set up website blocking on a networked device,
locate the device in the My Network column, then click Website Blocking. The
“Blocked Website” screen appears.
1. Enter the website address (IP or URL) to block on the network (all pages
within the website will also be blocked). If the website address has multiple IP
addresses, the Router will resolve all additional addresses and automatically
add them to the restrictions table.
2. To apply website blocking to a single computer or group of computers on the
network, select them from the “Networked Computer/Device” drop-down list.
20
Page 24

Chapter 3 Configuring My Network Settings
3. If website blocking needs to be active all the time, select “Always” from the
“When should this rule occur?” drop-down list. If the rule will only be active at
certain times select “Specify Schedule” and click Add. Then, add a schedule rule
(for more details about schedule rules, see the “Advanced Settings” chapter of
this manual).
Note: Make sure the Router’s date and time settings for your
☞
time zone are set correctly.
4. Click OK to add the website to the table. The previous screen appears while
the Router attempts to find the site. “Resolving...” appears in the “Status” column while the site is being located.
5. If the site is successfully located, “Resolved” appears in the Status column. If
not, “Hostname Resolution Failed” appears. Click Refresh to update the status
if necessary. If the Router fails to locate the website, do the following:
• Use a web browser to verify the website is available. If it is, the website
address was entered incorrectly. See “Modifying a Website Address,” below.
• If the website is not available, return to the Website Blocking screen at a
later time and click Resolve Now to verify the website can be found and
blocked by the Router.
Block Internet Services
Internet services blocking is used to prevent a device on the network from accessing particular services on the Internet, such as receiving E-mail or downloading
from FTP sites. To set up Internet services blocking on a networked device, locate
the device in the My Network column, then click Block Internet Services. The
“Add Access Control Rule” screen appears.
1. If this access control rule applies to all networked devices, select “Any” from
the “Networked Computer/Device” list box. If this rule applies to certain
devices only, select “Specify Address” and click Add. Then, add a network
object (for more details about adding network objects, see the “Advanced
Settings” chapter of this manual).
21
Page 25

Actiontec Wireless Broadband Router User Manual
23
Chapter 3 Configuring My Network Settings
2. Select the Internet protocol to be blocked from the “Protocol” drop-down list.
3. If this rule will be active all the time, select “Always” from the “When should this
rule occur?” drop-down list. If the rule will only be active at certain times select
“Specify Schedule” and click Add. Then, add a schedule rule (for more details
about schedule rules, see the “Advanced Settings” chapter of this manual).
Note: Make sure the Router’s date and time settings for your
☞
time zone are set correctly.
4. Click OK to save the changes. The Access Control screen will display a sum-
mary of the access control rule.
Note: To block a service that is not included in the list select
☞
“Specify Protocol” from the Protocol drop-down menu. The
“Edit Service” screen appears. Define the service, then click OK.
The service will then be automatically added to the top section
of the “Add Access Control Rule” screen, and will be selectable.
The user may disable an access control and the service made available without
having to remove the service from the Access Control table. This may be useful to
make the service available only temporarily, with the expectation that the restriction will be reinstated later.
• To temporarily disable an access control clear the check box next to the service name.
• To reinstate the restriction at a later time select the check box next to the
service name.
• To remove an access restriction from the Access Control table click the
Remove button for the service. The service will be removed from the Access
Control table.
Note: When Web Filtering is enabled, HTTP services cannot be
☞
22
Page 26
Chapter 3 Configuring My Network Settings
blocked by access control.
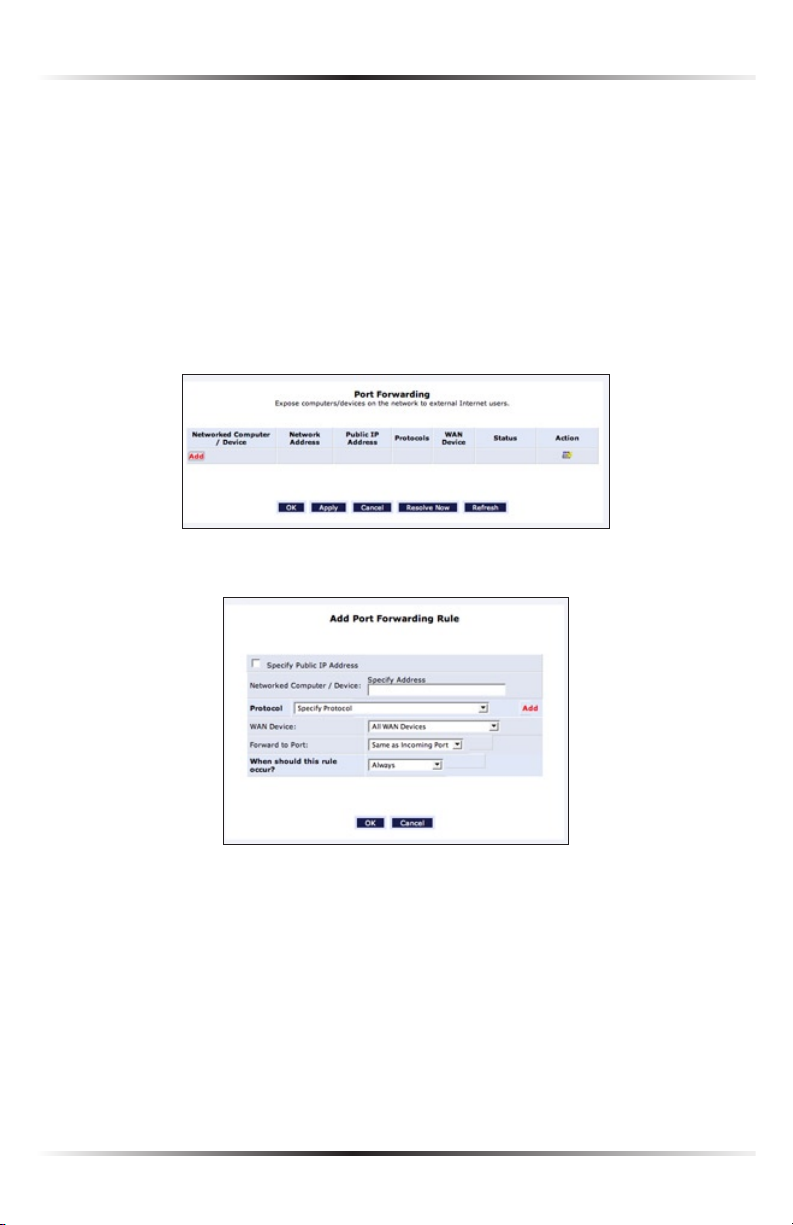
Enable Application
Activating “Enable Application” (also known as port forwarding) allows the network to be exposed to the Internet in certain limited and controlled ways, enabling
some applications to work from the local network (game, voice, and chat applications, for example), as well as allowing Internet access to servers in the network. To
set this up on a networked device, locate the device in the My Network column,
then click Enable Applications. The “Port Forwarding” screen appears.
1. Click Add. The “Add Port Forwarding Rule” screen appears.
2. Enter the local IP address or the host name of the computer providing the ser-
vice in the “Networked Computer/Device” text box. Note that only one local
network computer can be assigned to provide a specific service or application.
3. Select the Internet protocol to be provided from the “Protocol” drop-down
list.
4. To select a port to forward communications to (this is optional), select
“Specify” from the “Forward to Port” drop-down list, then, in the text box
23
Page 27

Actiontec Wireless Broadband Router User Manual
25
Chapter 3 Configuring My Network Settings
that appears, enter the port number. If no port is identified, select “Same as
Incoming Port.”
5. If this port will be active all the time, select “Always” from the “When should this
rule occur?” drop-down list. If the rule will only be active at certain times select
“Specify Schedule” and click Add. Then, add a schedule rule (for more details
about schedule rules, see the “Advanced Settings” chapter of this manual).
6. Click OK to save the changes.
Note: Some applications, such as FTP, TFTP, PPTP, and H323,
☞
require the support of special specific Application Level Gateway
(ALG) modules to work inside the local network. Data packets
associated with these applications contain information that allows
them to be routed correctly. An ALG is needed to handle these
packets and ensure they reach their intended destinations. The
Router is equipped with a robust list of ALG modules, enabling
maximum functionality in the local network.
The ALG is automatically assigned based on the destination port.
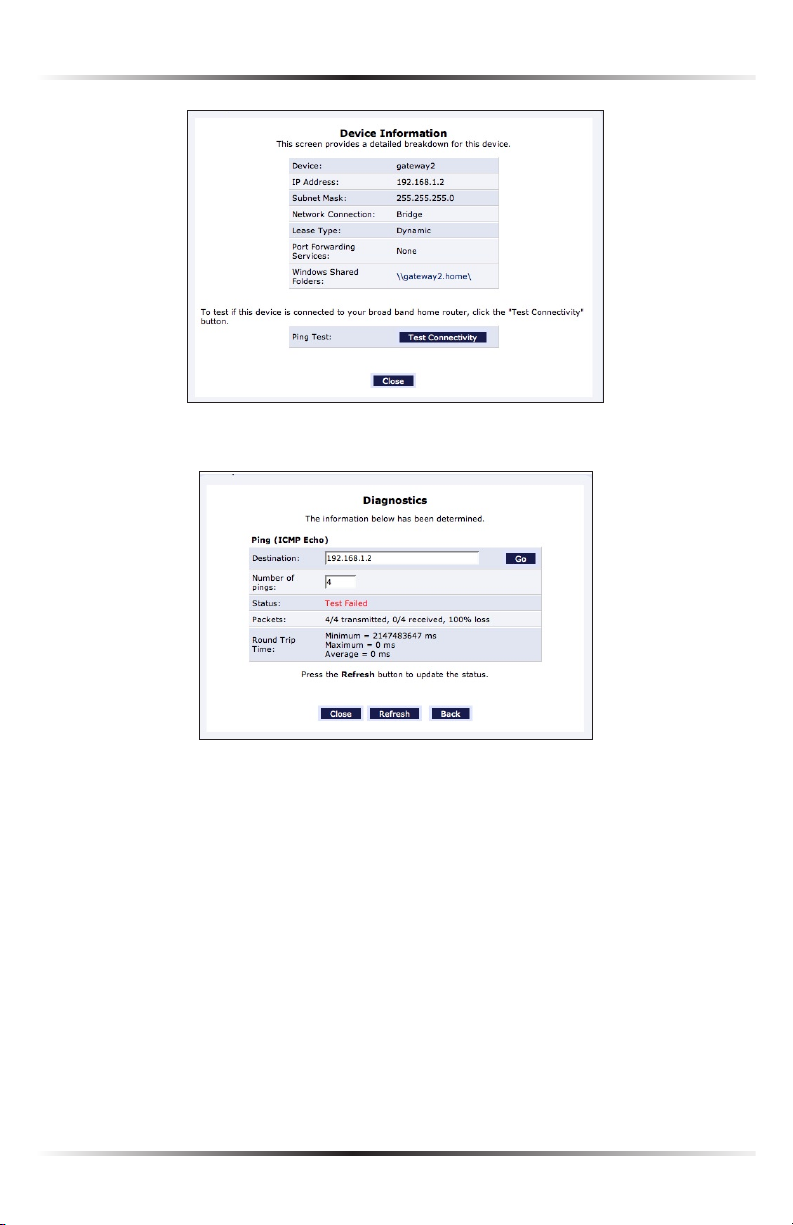
Test This Device
Selecting “Test This Device” generates a new screen that displays information
about the device, and also allows the user to test the connectivity of the device. To
test a networked device, locate the device in the My Network column, then click
Test This Device. The “Device Information” screen appears.
24
Page 28
Chapter 3 Configuring My Network Settings
1. Click Test Connectivity. The “Diagnostics” screen appears.
2. Click Go. The Router runs a ping test, and the results are displayed in the
Diagnostics screen.
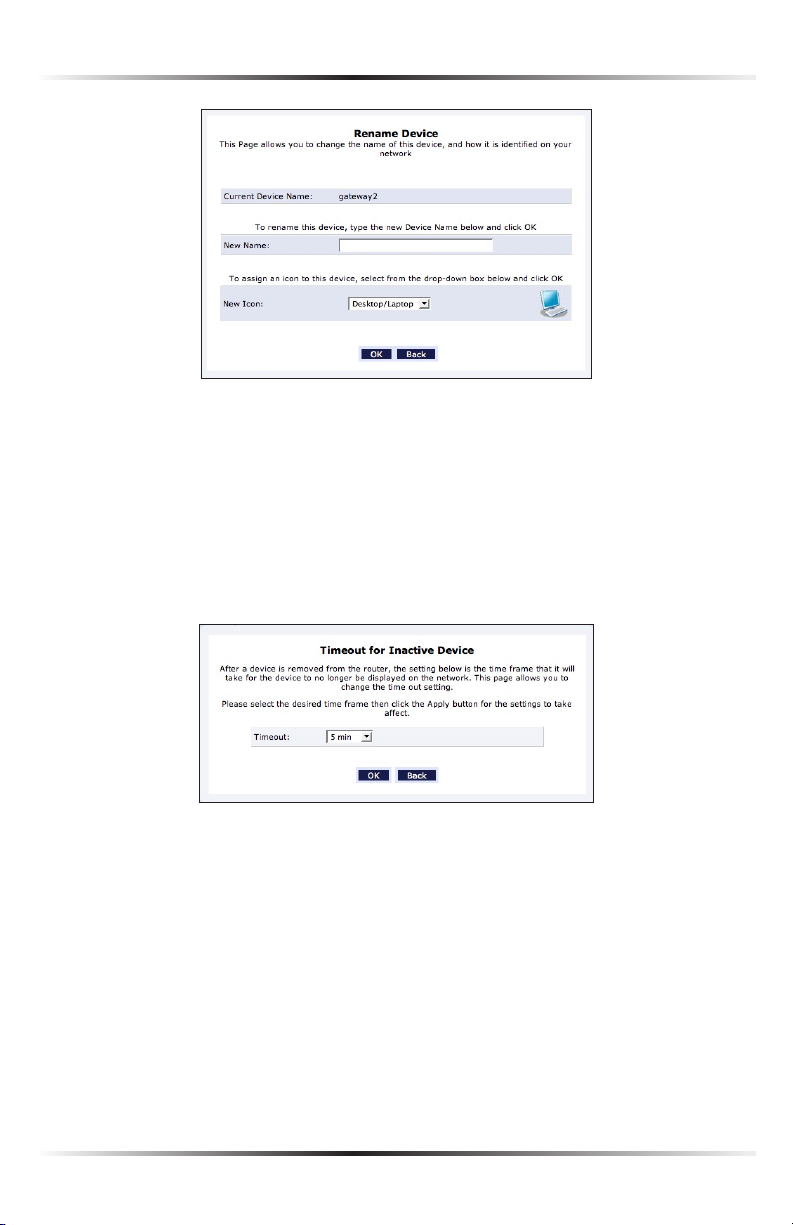
Rename This Device
To rename a networked device, locate the device in the My Network column, then
click Rename This Device. The “Rename Device” screen appears.
25
Page 29
Actiontec Wireless Broadband Router User Manual
Enter the new name of the device in the “New Name” text box and, if needed, select
a new icon for the device from the “New Icon” drop-down list.
Timeout for Inactive Device
The amount of time a device continues to be displayed on the network after it has
been disconnected is configured in the “Timeout for Inactive Device” screen. To
display the screen, click Timeout for Inactive Device.
Select the timeout period from the “Timeout” drop-down list. After the device has
been disconnected for this amount of time, it will no longer be displayed in the
“My Network” column.
26
Page 30

Creating a Wireless Network
This chapter explains how to create a wireless network using the Wireless
Broadband Router, including accessing and configuring wireless security options.
Overview
The Wireless Broadband Router provides the user with wireless connectivity over
the 802.11b and g standards (the most common wireless standards). 802.11b has
a maximum data rate of 11 Mbps, while 802.11g has a maximum data rate of 54
Mbps. Both operate in the 2.4 GHz range.
The Router’s wireless feature is turned on, with wireless security activated, by default.
The level of security is 64/40-bit WEP, with a unique WEP key already entered.
Note: The default WEP key is displayed on a sticker located on
☞
the bottom of the Router.
The Router integrates multiple layers of security. These include the IEEE 802.1x
port-based authentication protocol, RADIUS client, EAP-MD5, EAP-TLS, EAP-TTLS,
EAP-PEAP, Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA) and
firewall and VPN applications.
4
27
Page 31

Actiontec Wireless Broadband Router User Manual
29
Chapter 4 Creating a Wireless Network
Wireless Network Connection
As soon as the Router is turned on, wireless networking is available. This section
explains the wireless networking screens in the Router’s MegaControl Panel.
Wireless Setup
Clicking on the “Wireless Setup” icon at the top of the Home screen generates the
“Wireless Setup” screen. This screen displays various wireless connection properties.
Enable Wireless
Click in this check box to toggle the Router’s wireless operation on and off. The
Router ships with its wireless capabilities activated.
Status
Displays the status of the Router’s wireless connection.
SSID
The SSID (Service Set Identifier) is the network name shared among all devices
on a particular wireless network. The SSID must be identical for all devices on
the wireless network. It is case-sensitive and must not exceed 32 characters.
Make sure the SSID is the same for all devices to be connected to the wireless
network. The Router comes from the factory with an SSID already entered, but it
can be changed here. The default SSID can also be found on a sticker on the bottom of the Router.
28
Page 32

Chapter 4 Creating a Wireless Network
SSID Broadcast
Select this check box to enable SSID broadcast. If activated, the SSID of the
Router’s wireless network is broadcast wirelessly. To deactivate, click in the check
box to make the check mark disappear.
802.11 Mode
Select the wireless communication standard compatible with the devices to be
connected on the wireless network from the drop-down list. Options include
802.11b, 802.11g, or Mixed (allows both 802.11b- and 802.11g-equipped wire-
less devices to join the network).
Channel
Select the appropriate channel from the drop-down list. All devices on the wireless network must be on the same channel in order to function correctly.
Encryption
This text box displays the current encryption key for the Router’s wireless network security configuration. The default setting is 64/40-bit encryption with
a 10 character hexadecimal key, and is also shown on a sticker on the bottom
of the Router. For more information about wireless network security, see the
“Wireless Security” section in this chapter.
29
Page 33

Actiontec Wireless Broadband Router User Manual
31
Chapter 4 Creating a Wireless Network
Configure Wireless Access Point
Click Advanced at the bottom-right of the Wireless Setup screen to generate the
“Configure Wireless Access Point” screen. The top half of the screen is shown in
the figure, below:
General
This section displays general communication parameters of the Router’s wireless
connection. Actiontec recommends not changing the default values in this section unless the user is familiar with these networking concepts.
Status Displays the status of the wireless connection.
When should this rule occur? Displays the time during which the rule is active. To
configure schedule rules, see chapter 9, “Advanced Settings.”
Network Select the type of connection being configured from this drop-down
list (options: LAN, WAN, or DMZ). LAN stands for local area network, which
is another name for the home or office network. WAN stands for wide area net-
work, and, in this case, describes the Internet.
Connection Type Displays the type of connection.
30
Page 34

Chapter 4 Creating a Wireless Network
Physical Address Displays the physical address of the network card used for the
network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size per-
mitted for Internet transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the MTU according to the DHCP
connection, and “Manual,” which allows the user to set the MTU.
Wireless Access Point
This section of the Configure Wireless Access Point screen displays various settings of the Router’s wireless connection.
SSID The SSID (Service Set Identifier) is the network name shared among all
devices on a particular wireless network. The SSID must be identical for all
devices on the wireless network. It is case-sensitive and must not exceed 32 characters. Make sure the SSID is the same for all devices to be connected to the wire-
less network. The Router comes from the factory with an SSID already entered,
but it can be changed here. The default SSID can also be found on a sticker on
the bottom of the Router.
SSID Broadcast Select this check box to enable SSID broadcast. If activated, the
SSID of the Router’s wireless network is broadcast wirelessly. To deactivate, click
in the check box to make the check mark disappear.
802.11 Mode Select the wireless communication standard compatible with
the devices to be connected on the wireless network from the drop-down list.
Options include 802.11b, 802.11g, or Mixed (allows both 802.11b and 802.11gequipped wireless devices to join the network).
Channel Select the appropriate channel from the drop-down list. All devices on
the wireless network must be on the same channel in order to function correctly.
Network Authentication Select the appropriate network authentication level from
the drop-down list. Options include Open System Authentication, Shared Key
Authentication, or Both.
MAC Filtering Mode Select the appropriate MAC filtering mode from the drop-
down list. Options include Disable, Allow, or Deny. If Allow is selected, click
New MAC Address, and, in the screen that appears, enter the MAC address of
the device to be allowed on the wireless network. If Deny is selected, click New
MAC Address, and, in the screen that appears, enter the MAC address of the
device to be denied access to the wireless network. If Disable is selected, MAC
filtering is deactivated.
31
Page 35

Actiontec Wireless Broadband Router User Manual
33
Chapter 4 Creating a Wireless Network
Advanced Wireless Options
The bottom of the Configure Wireless Access Point screen comprises “Advanced
Wireless Options.” Only experienced network technicians should make any
changes to these settings.
Transmission Rate Select the wireless transmission rate from the drop-down list,
or select “Auto” to have the Router automatically select the best transmission
rate. This setting adjusts the bit rate of the Router’s wireless transmissions.
CTS Protection Mode Activating CTS (Clear to Send) Protection Mode allows
mixed 802.11b/g networks to operate at maximum efficiency. Select “Auto” from
the drop-down list to activate. Select “None” to deactivate .
Beacon Interval Beacons are transmitted by the Router to help identify wireless
networks. If beacons are transmitted too infrequently, networks may become
hard to reach; if too frequently, they become a resource waste. Enter the desired
beacon interval value (in milliseconds) in this text box.
DTIM Interval Enter the DTIM (Delivery Traffic Indication Message) interval
value (in milliseconds) in this text box. A DTIM is a countdown mechanism for
the Router, informing wireless network clients of the next window for listening
to broadcast and multicast messages.
Fragmentation Threshold Setting the correct fragmentation threshold can
increase the reliability of frame transmissions on the wireless network. Enter the
fragmentation threshold in this text box.
32
Page 36

Chapter 4 Creating a Wireless Network
RTS Threshold Enter the RTS (Request to Send) threshold in this text box. This
setting controls what size data packet the low level RF protocol issues to an
RTS packet.
Wireless Security
Set the type of wireless security for the Router’s wireless network in this section
of the screen. Make sure the “Enabled” check box is activated, then select the
type of security needed from the “Stations Security Type” drop-down list. The
Router comes from the factory with 802.1x WEP (Wired Equivalent Privacy)
enabled (see the sticker on the bottom of the Router for default SSID and
security keys).
WPA If WPA (Wi-Fi Protected Access) was chosen:
1. Verify the authentication method selected is “Pre-Shared Key.”
2. Enter a phrase of at least eight characters in the “Pre-Shared Key” text box.
Verify that “ASCII” is selected in the associated drop-down list.
3. Select the proper encryption algorithm (TKIP or AES).
4. Click in the “Group Key Update Interval” check box to activate the group
key update interval, and set the interval time in the text box to the right.
5. Click OK at the bottom of the screen to save changes.
33
Page 37

Actiontec Wireless Broadband Router User Manual
35
Chapter 4 Creating a Wireless Network
802.1X WEP If 802.1X WEP (Wired Equivalent Privacy) was chosen, no other set-
tings need to be changed.
802.1x WEP is a robust security protocol that uses port control with dynamically
changing encryption keys automatically updated over the network. 802.11x WEP
uses a RADIUS (Remote Authentication Dial-in Service) server for authentication
purposes. This server must be physically connected to the Router. Also, the user
must enable the RADIUS client embedded in the Router (to do this, see chapter 9,
“Advanced Settings”).
Non-802.1X WEP If Non-802.1X WEP was chosen:
1. Activate WEP key 1 by clicking in the circle next to “1” on the left side.
2. Select the length of key 1 by selecting “64/40 bit” or “128/104 bit” from the
appropriate drop-down list in the “Key Length” column.
3. Select the type of key from the appropriate drop-down list in the “Entry
Method” column. If “Hex” is selected, the key must be made up of hexadecimal digits. If “ASCII” is selected, the key can be made up of any characters.
34
Page 38

Chapter 4 Creating a Wireless Network
4. Enter the key in the appropriate text box in the “Encryption Key” column.
If 64/40 bit was chosen in step 2, enter 10 characters. If 128/104 bit was chosen, enter 24 characters. Depending on what option was selected in step 3,
enter hexadecimal or ASCII characters.
5. Click OK to save changes.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the wireless
connection. Actiontec recommends leaving this option deactivated.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the Router via the wireless
connection.
Configuring a Wireless Windows XP Client
If the computer has wireless capabilities and is running Windows XP, it will auto-
matically recognize this and create a wireless connection. View this connection
under Windows’ “Network Connections.”
Note: The following description and images are in accordance
☞
with Microsoft Windows XP, Version 2002, running Service Pack 2.
If running another operating system, see the documentation that
came with the wireless adapter being used.
1. Click Network Connections in the Control Panel. The “Network
Connections” window appears.
35
Page 39

Actiontec Wireless Broadband Router User Manual
37
Chapter 4 Creating a Wireless Network
2. Double-click the wireless connection icon. The “Wireless Network
Connection” screen appears, displaying all available wireless networks in the
vicinity. If the Router is connected and active, the Router’s wireless connection
is displayed. Note that the connection’s status is “Not connected” and defined
as “Unsecured wireless network” in the figure below.
3. Click the connection once to mark it, then click Connect at the bottom of the
screen. After the connection is established, its status will change to “Connected.”
An icon appears in the notification area, announcing the successful initiation
of the wireless connection.
4. Test the connection by disabling all other connections in the Network
Connections window and browsing the Internet.
The Router’s wireless network can now be accessed from the configured computer. However, any other user with a wireless-equipped device can also access the
wireless network. To prevent this, secure the wireless network, as explained in the
“Wireless Security” section of this chapter.
36
Page 40

Chapter 4 Creating a Wireless Network
Connecting a Wireless Windows XP Client
This section assumes the Router is set up with WPA security.
1. Click Network Connections in the Control Panel. The “Network
Connections” window appears.
2. Double-click the wireless connection icon. The “Wireless Network
Connection” screen appears, displaying the Router’s wireless connection. Note
that the connection is defined as “Security-enabled wireless network (WPA).”
37
Page 41

Actiontec Wireless Broadband Router User Manual
39
Chapter 4 Creating a Wireless Network
3. Click the connection once to mark it, then click Connect at the bottom of
the screen. The following login window appears, asking for a “Network Key,”
which is the pre-shared key used when configuring the Router’s WPA security
(see the “WPA” section in this chapter).
4. Enter the pre-shared key in both text boxes and click Connect. After the con-
nection is established, its status will change to “Connected,” as shown below.
An icon appears in the notification area, announcing the successful initiation
of the wireless connection.
5. Test the connection by disabling all other connections in the Network
Connections window and surfing the Internet.
If the login window shown in step 3 does not appear and the connection attempt
fails, configure the connection manually:
1. Click the connection once to mark it and then click Change Advanced
Settings in the “Related Tasks” box on the left part of the window.
38
Page 42

Chapter 4 Creating a Wireless Network
2. The “Wireless Network Connection Properties” window appears. Select
Wireless Networks.
3. Click the connection to highlight it, then click Properties. The connection’s
“Properties Window” appears.
4. From the “Network Authentication” drop-down list, select WPA-PSK.
5. From the “Data Encryption” drop-down list, select TKIP.
39
Page 43

Actiontec Wireless Broadband Router User Manual
6. Enter the pre-shared key in both the “Network key” and the “Confirm net-
work key” text boxes.
7. Click OK, then OK again.
8. When attempting to connect to the wireless network, the login window
appears, pre-populated with the pre-shared key. Press Connect to connect.
Since the network is now secured, only users who know the pre-shared key will be
able to connect. The WPA security protocol is similar to securing network access
using a password.
40
Page 44

Using Network Connections
The Wireless Broadband Router supports various local area network (LAN) and wide
area network (WAN, on Internet) connections via Ethernet or coaxial cables. Network
connections is used to configure the various parameters of the Router’s network and
Internet connections, and create new connections.
Caution: The settings covered in this chapter should be config-
M
ured by experienced network technicians only.
To access the Router’s network connections, click Network Connections at the top
of the Home screen. The “Network Connections” screen appears.
5
Click Advanced to expand the screen and display all connection entries.
41
Page 45

Actiontec Wireless Broadband Router User Manual
43
Chapter 5 Using Network Connections
To select a connection, click on its name. The rest of this chapter describes the different network connections available on the Router, as well as the connection types
that can be created.
Network (Home/Office)
Select Network (Home/Office) in the Network Connections screen to generate
the “Network (Home/Office) Properties” screen. This screen displays a list of the
local network’s properties. The only modifications that can be made from this
screen are disabling the connection (by clicking Disable) or renaming the connection (by entering a new name in the “Rule Name” text box).
Note: When a network is disabled, its formerly underlying
☞
devices will not be able to get the DHCP address from the net-
work interface to which they were connected.
The Network (Home/Office) connection is used to combine several network
devices under one virtual network. For example, a home/office network can be
created for Ethernet and other network devices.
42
Page 46

Chapter 5 Using Network Connections
Configuring the Home/Office Network
Click Settings in the “Network (Home/Office) Properties” screen to generate the
“Configure Network (Home/Office)” screen.
General
The top part of the Configure Network (Home/Office) screen displays general
communication parameters. Actiontec recommends not changing the default
values in this section unless familiar with networking concepts.
Status Displays the connection status of the network.
When should this rule occur? Displays when the rule is active. To schedule rules,
see the “Advanced Settings” chapter.
Network Select the type of connection being configured from the drop-down list
(options: Broadband Connection, Network [Home/Office], or DMZ).
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for the
network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size per-
mitted for Internet transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the MTU according to the DHCP
connection, and “Manual,” which allows the MTU to be set manually.
43
Page 47

Actiontec Wireless Broadband Router User Manual
45
Chapter 5 Using Network Connections
Internet Protocol
This section has three options: No IP Address, Obtain an IP Address
Automatically, and Use the Following IP Address.
No IP Address Select this option if the connection will have no IP address. This is
useful if the connection operates under a bridge.
Obtain an IP Address Automatically Select this option if the network connection
is required by the ISP to obtain an IP address automatically. The server assigning
the IP address also assigns a subnet mask address, which can be overridden by
entering another subnet mask address.
Use the Following IP Address Select this option if the network connection uses a
permanent (static) IP address, then the IP address and subnet mask address.
Bridge
The “Bridge” section of the Configure Network (Home/Office) screen is used to
specify which networks can join the network bridge.
Note: When a network is disabled, its formerly underlying
☞
devices inherit the network’s DHCP settings. For example, the
removal of a network configured as DHCP client automatically
configures the devices formerly constituting the network as
DHCP clients, with the exact DHCP client configuration.
Click in the check box next to the particular network to specify it. Make sure
there are no loops in the network configuration, and apply these settings in case
the network consists of multiple switches, or other bridges apart from those created by the Router.
Status The “Status” column displays the connection status of a particular device.
44
Page 48

Chapter 5 Using Network Connections
STP Click in the device’s “STP” check box to enable Spanning Tree Protocol on
the device. This protocol provides path redundancy while preventing undesirable loops in the network.
Action The “Action” column contains an icon that, when clicked, generates the
configuration screen of the particular device.
DNS Server
Domain Name System (DNS) is the method by which website or domain names
are translated into IP addresses. Specify such an address manually, according to
the information provided by the ISP.
To manually configure DNS server addresses, select Use the Following DNS
Server Addresses. Specify up to two different DNS server addresses, one pri-
mary, the other secondary.
IP Address Distribution
The “IP Address Distribution” section of the Configure Network (Home/Office)
screen is used to configure the Router’s Dynamic Host Configuration Protocol
(DHCP) server parameters. DHCP automatically assigns IP addresses to net-
work devices. If enabled, make sure to configure the network devices as “DHCP
Clients.” There are three options in this section: Disabled, DHCP Server, and
DHCP Relay.
Disabled Select this option if statically assigning IP addresses to the network
devices.
DHCP Server To set up the network bridge to function as a DHCP server:
1. Select DHCP Server.
2. Enter the IP address at which the Router starts issuing addresses in the
“Start IP Address” text boxes. Since the Router’s default IP address is
192.168.1.1, the Start IP Address must be 192.168.1.2.
3. Enter the end of the IP address range used to automatically issue IP address-
es in the “End IP Address” text boxes.
45
Page 49

Actiontec Wireless Broadband Router User Manual
47
Chapter 5 Using Network Connections
4. Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet
mask determines which portion of a destination LAN IP address is the network portion, and which portion is the host portion.
5. If Windows Internet Naming Service (WINS) is being used, enter the WINS
server address in the “WINS Server” text boxes.
6. Enter the amount of time a network device will be allowed to connect to
the Router with its currently issued dynamic IP address in the “Lease Time
in Minutes” text box. Just before the time is up, the device’s user will need to
make a request to extend the lease or get a new IP address.
7. Click in the “Provide Host Name If Not Specified by Client” check box to
have the Router automatically assign network devices with a host name, in
case a host name is not provided by the user.
DHCP Relay Select this option to have the Router function as a DHCP relay, and
enter the IP address in the screen that appears.
IP Address Distribution According to DHCP Option 60
DHCP Option 60 is used to preset a general name for a product or product fam-
ily, as well as set a specific IP range and priority level. In this way, one device and
its traffic can be given higher priority over another device.
Note: To use this feature, the device must output a vendor class
☞
ID for option 60 to assign it traffic prirority.
46
Page 50

Chapter 5 Using Network Connections
To add a new product or product family, click New IP Range. This generates the
“DHCP Server Pool Settings” screen. Enter the vendor class identifier (provided by
the manufacturer of the product), IP range, and priority level in the appropriate
text boxes.
Routing
The Router can be configured to use static or dynamic routing. Dynamic routing automatically adjusts how packets travel on the network, while static routing
specifies a fixed routing path to neighboring destinations.
There are two options in the “Routing” section of the Configure Network
(Home/Office) screen: Basic or Advanced.
Basic Select this option for basic routing operation.
Advanced To set up the Router’s network bridge for advanced routing:
1. Select Advanced from the “Routing” drop-down menu.
2. Enter a device metric in the “Device Metric” text box. The device metric is
a value used by the Router to determine whether one route is superior to
another, considering parameters such as bandwidth and delay time.
3. Click in the “Default Route” check box to define this device as a the
default route.
4. Click in the “Multicast - IGMP Proxy Internal” check box to activate
multicasting.
47
Page 51

Actiontec Wireless Broadband Router User Manual
49
Chapter 5 Using Network Connections
Routing Table
Clicking New Route generates the “New Route” window, where a new route can
be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the LAN
Bridge connection. Actiontec does NOT recommend activating this feature.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the Router via the
Network (Home/Office) connection.
Ethernet Connection
An Ethernet connection connects computers to the Router using Ethernet cables,
either directly or via network hubs and switches. Click Ethernet in the Network
Connections screen (if needed, click Advanced at the bottom of the screen to reveal
the “Ethernet” link below “Network [Home/Office]”) to generate the “Ethernet
Properties” screen. This screen displays a list of the connection’s properties. The
only modifications that can be made from this screen are disabling the connection
(by clicking Disable) or renaming the connection (by entering a new name in the
“Rule Name” text box).
Note: If disabling the connection, the Router must be rebooted
☞
for the change to take effect.
48
Page 52

Chapter 5 Using Network Connections
Configuring the Ethernet Connection
Click Settings at the bottom-right of the Ethernet Properties screen to generate
the “Configure Ethernet” screen.
General
The top part of the Configure Ethernet screen displays general communication
parameters. Actiontec recommends not changing the default values in this section
unless familiar with networking concepts.
Status Displays the connection status of the Ethernet switch.
When should this rule occur? Displays when the rule is active. To schedule rules,
see the “Advanced Settings” chapter.
Network Select the type of connection being configured from the drop-down list
(Network [Home/Office], Broadband Connection, or DMZ).
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for
the network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size per-
mitted for Internet transmission. “Automatic” sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the MTU according to the DHCP
connection, and “Manual,” which allows the MTU to be set manually.
49
Page 53

Actiontec Wireless Broadband Router User Manual
51
Chapter 5 Using Network Connections
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the Ethernet
connection. Actiontec does NOT recommend activating this feature.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the Router via the
Ethernet connection.
4 Ports Ethernet Switch
This section displays the connection status of the Router’s four Ethernet ports.
Clicking on a connection’s “Action” icon (in the column on the right) generates
the “Port VLANs” screen, where ingress and egress policies can be edited.
50
Page 54

Chapter 5 Using Network Connections
Coax Connection
A Coax connection connects devices (such as set-top boxes) to the Router using
a coaxial cable. Click Coax in the Network Connections screen (if needed, click
Advanced at the bottom of the screen to reveal the “Coax” link below “Network
[Home/Office]”) to generate the “Coax Properties” screen. This screen displays a list
of the connection’s properties. The only modifications that can be made from this
screen are disabling the connection (by clicking Disable) or renaming the connection (by entering a new name in the “Name” text box).
Note: If disabling the connection, the Router must be rebooted
☞
for the change to take effect.
51
Page 55

Actiontec Wireless Broadband Router User Manual
53
Chapter 5 Using Network Connections
Configure Coax
Click Settings at the bottom-right of the Coax Properties screen generates the
“Configure Coax” screen.
General
The top part of the Configure Coax screen displays general communication
parameters. Actiontec recommends not changing the default values in this section unless familiar with networking concepts.
Status Displays the status of the coax connection.
When should this rule occur? Displays when the rule is active. To schedule rules,
see the “Advanced Settings” chapter
Network Displays the type of network.
Connection Type Displays the type of connection.
Physical Address Displays the physical address of the network card used for the
network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size
permitted for Internet transmission. “Automatic” sets the MTU at 1500. Other
choices include “Automatic by DHCP,” which sets the MTU according to the
DHCP connection, and “Manual,” which allows the MTU to be set manually.
52
Page 56

Chapter 5 Using Network Connections
Coax Link
Set up the coax link options in this section of the Configure Coax screen.
Options include Channel, Privacy, and Password.
Channel Select the Channel from the drop-down list (select from 1-6, or
“Automatic”).
Privacy Toggle “Privacy” by clicking in the “Enabled” check box. If Privacy is
activated, all devices connected via coaxial cable must use the same password.
Actiontec recommends leaving the Privacy option deactivated.
Password Enter the Coax Link password in this text box.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the Coax Link
Ethernet connection. Actiontec does NOT recommend activating this feature.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen,
where additional IP addresses can be created to access the Router via the Coax
Link Ethernet connection.
53
Page 57

Actiontec Wireless Broadband Router User Manual
55
Chapter 5 Using Network Connections
Broadband Ethernet Connection
A Broadband Ethernet connection connects the Router to the Internet using an
Ethernet cable. Click Broadband Connection (Ethernet) from the Network
Connections screen to generate the “Broadband Connection (Ethernet) Properties”
screen. This screen displays a list of the connection’s properties. The only modifications that can be made from this screen are disabling the connection (by clicking
Disable) or renaming the connection (by entering a new name in the “Rule Name”
text box).
Note: If disabling the connection, the Router must be rebooted
☞
for the change to take effect.
54
Page 58

Chapter 5 Using Network Connections
Configuring the Broadband Ethernet Connection
Click Settings at the bottom-right of the Broadband Connection (Ethernet) Properties
window to generate the “Configure Broadband Connection (Ethernet)” screen.
General
The top part of the screen displays general communication parameters. Actiontec
recommends not changing the default values in this section unless familiar with
networking concepts.
Status Displays the status of the Ethernet connection (“Down,” “Connected,” etc.)
Schedule Displays when the rule is active. To configure rules, see the “Advanced
Settings” chapter.
Network Select the type of connection being configured from the drop-down list
(options: Network (Home/Office), Broadband Connection, or DMZ).
Connection Type Displays the type of connection. Since this is an Ethernet
Connection, “Ethernet” is displayed.
Physical Address Displays the physical address of the network card used for the
network.
55
Page 59

Actiontec Wireless Broadband Router User Manual
57
Chapter 5 Using Network Connections
MTU MTU (Maximum Transmission Unit) specifies the largest packet size per-
mitted for Internet transmission. “Automatic, sets the MTU at 1500. Other choices include “Automatic by DHCP,” which sets the MTU according to the DHCP
connection, and “Manual,” which allows the MTU to be set manually.
Internet Protocol
This section includes three options: No IP Address, Obtain an IP Address
Automatically, and Use the Following IP Address.
No IP Address Select this option if the connection has no IP address. This is use-
ful if the connection is operating under a bridge.
Obtain an IP Address Automatically Select this option if the ISP requires the con-
nection to obtain an IP address automatically. The server assigning the IP address
also assigns a subnet mask address, which can be overridden by clicking in the
“Override Subnet Mask” check box and entering another subnet mask address.
Additionally, the DHCP lease can be renewed and/or released by clicking on the
appropriate “DHCP Lease” button.
Use the Following IP Address Select this option if the connection uses a permanent (static) IP address. The ISP should provide this address, along with a subnet
mask address, default gateway address, and, optionally, primary and secondary
DNS server addresses.
DNS Server
The Domain Name System (DNS) is the method by which website or domain
names are translated into IP addresses. This connection can be configured to
automatically obtain a DNS server address, or such an address can be specified
manually, according to the information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select
Obtain DNS Server Address Automatically from the “DNS Server” drop-down
list. To manually configure DNS server addresses, select Use the Following DNS
Server Addresses. Specify up to two different DNS server addresses, one pri-
mary, the other secondary.
56
Page 60

Chapter 5 Using Network Connections
IP Address Distribution
The “IP Address Distribution” section of the Configure Broadband Connection
(Ethernet) screen is used to configure the Router’s Dynamic Host Configuration
Protocol (DHCP) server parameters. DHCP automatically assigns IP addresses
to network devices. If enabled, make sure to configure the network devices
as “DHCP Clients.” There are three options in this section: Disabled, DHCP
Server, and DHCP Relay.
Caution: Actiontec strongly recommends leaving this setting
M
at “Disabled.”
Disabled Select this option if statically assigning IP addresses to the network
devices.
DHCP Server To set up the Router to function as a DHCP server:
1. Select DHCP Server.
2. Enter the IP address at which the Router starts issuing addresses in the
“Start IP Address” text boxes. Since the Router’s default IP address is
192.168.1.1, the Start IP Address must be 192.168.1.2 or higher.
3. Enter the end of the IP address range used to automatically issue IP address-
es in the “End IP Address” text boxes.
4. Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet
mask determines which portion of a destination LAN IP address is the network portion, and which portion is the host portion.
5. If a Windows Internet Naming Service (WINS) is being used, enter the
WINS server address in the “WINS Server” text boxes.
6. Enter the amount of time a network device will be allowed to connect to
the Router with its currently issued dynamic IP address in the “Lease Time
in Minutes” text box. Just before the time is up, the device’s user will need to
make a request to extend the lease or get a new IP address.
7. Click in the “Provide Host Name If Not Specified by Client” check box to
have the Router automatically assign network devices with a host name, in
case a host name is not provided by the user.
DHCP Relay Select this option to have the Router function as a DHCP relay, and
enter the IP address in the screen that appears.
57
Page 61

Actiontec Wireless Broadband Router User Manual
59
Chapter 5 Using Network Connections
IP Address Distribution According to DHCP Option 60
DHCP Option 60 is used to preset a general name for a product or product fam-
ily, as well as set a specific IP range and priority level. In this way, one device and
its traffic can be given higher priority over another device.
Note: To use this feature, the device must output a vendor class
☞
ID for option 60 to assign it traffic prirority.
To add a new product or product family, click New IP Range. This generates the
“DHCP Server Pool Settings” screen. Set the device name, IP range, and priority level
in the appropriate text boxes.
Routing
The Router can be configured to use static or dynamic routing. Dynamic routing automatically adjusts how packets travel on the network, while static routing
specifies a fixed routing path to neighboring destinations.
There are two options in the “Routing” section of the “Configure WAN Coax
Link Ethernet” screen: Basic or Advanced.
Basic Select this option for basic routing operation.
Advanced To set up the Router’s Broadband Ethernet connection for advanced
routing:
1. Select Advanced from the Routing drop-down menu.
2. Enter a device metric in the “Device Metric” text box. The device metric is
a value used by the Router to determine whether one route is superior to
another, considering parameters such as bandwidth and delay time.
58
Page 62

Chapter 5 Using Network Connections
3. Click in the “Default Route” check box to define this device as a the default
route.
4. Click in the “Multicast - IGMP Proxy Internal” check box to activate multi-
casting.
Routing Table
Clicking New Route generates the “New Route” window, where a new route can
be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the connection.
Additional IP Addresses
Clicking New IP Address generates the “Additional IP Address Settings” screen, where
additional IP addresses can be created to access the Router via the connection.
59
Page 63

Actiontec Wireless Broadband Router User Manual
61
Chapter 5 Using Network Connections
Coax Broadband Connection
A Coax Broadband connection connects the Router to the Internet using a coaxial
cable. Click Broadband Connection (Coax) in the Network Connections screen
to generate the “Broadband Connection (Coax) Properties” screen. This screen displays a list of the connection’s properties. The only modifications that can be made
from this screen are disabling the connection (by clicking Disable) or renaming
the connection (by entering a new name in the “Name” text box).
Note: If disabling the connection, the Router must be rebooted
☞
for the change to take effect.
60
Page 64

Chapter 5 Using Network Connections
Configuring the Coax Broadband Connection
Click Settings at the bottom of the Broadband Connection (Coax) Properties
screen to generate the “Configure Broadband Connection (Coax)” screen.
General
The top part of the screen displays general communication parameters.
Actiontec recommends not changing the default values in this section unless
familiar with networking concepts.
Status Displays the status of the connection (“Down,” “Connected,” etc.).
When should this rule occur? Displays when the rule is active. To schedule rules,
see the “Advanced Settings” chapter.
Network Displays the type of network to which the link is connected. Since this
is a broadband connection (connected to the Internet), “Broadband Connection
is displayed.
Connection Type Displays the type of connection. Since this is a coaxial connection, “Coax” is displayed.
61
Page 65

Actiontec Wireless Broadband Router User Manual
63
Chapter 5 Using Network Connections
Physical Address Displays the physical address of the network card used for the
network.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size
permitted for Internet transmission. “Automatic” sets the MTU at 1500. Other
choices include “Automatic by DHCP,” which sets the MTU according to the
DHCP connection, and “Manual,” which allows the MTU to be set manually.
Coax Link
Configure the coax link connection in this section of the screen.
Privacy Toggle “Privacy” by clicking in the “Enabled” check box. If Privacy is
activated, all devices connected via coaxial cable must use the same password.
Actiontec recommends leaving the Privacy option deactivated.
Password Enter the Coax Link password here.
Internet Protocol
This section includes three options: No IP Address, Obtain an IP Address
Automatically, and Use the Following IP Address.
No IP Address Select this option if the connection has no IP address. This is use-
ful when the connection is operating under a bridge.
Obtain an IP Address Automatically Select if the ISP requires the connection to
obtain an IP address automatically. The server assigning the IP address also
assigns a subnet mask address, which can be overridden by clicking in the
“Override Subnet Mask” check box and entering another subnet mask address.
Use the Following IP Address Select if the WAN connection is configured using a
permanent (static) IP address. The ISP should provide this address, along with a
subnet mask address, default gateway address, and, optionally, primary and secondary DNS server addresses.
62
Page 66

Chapter 5 Using Network Connections
DNS Server
Domain Name System (DNS) is the method by which website or domain names
are translated into IP addresses. The connection can be set to automatically
obtain a DNS server address, or an address can be set manually, according to
information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select
Obtain DNS Server Address Automatically from the “DNS Server” drop-down
list. To manually configure DNS server addresses, select Use the Following DNS
Server Addresses. Specify up to two different DNS server addresses, one pri-
mary, the other secondary.
IP Address Distribution
The “IP Address Distribution” section of the Configure Broadband Connection
(Coax) screen allows the user to configure the Router’s Dynamic Host
Configuration Protocol (DHCP) server parameters. The DHCP automatically
assigns IP addresses to network devices. If enabled, make sure to configure the
network devices as “DHCP Clients.” There are three options in this section:
Disabled, DHCP Server, and DHCP Relay.
Caution: Actiontec strongly recommends leaving this setting
M
at “Disabled.”
Disabled Select this option if statically assigning IP addresses to the network
devices.
DHCP Server To set up the WAN Coax Link Ethernet connection to function as a
DHCP server:
1. Select DHCP Server.
2. Enter the IP address at which the Router starts issuing addresses in the
“Start IP Address” text boxes. Since the Router’s default IP address is
192.168.1.1, the Start IP Address must be 192.168.1.2.
3. Enter the end of the IP address range used to automatically issue IP address-
es in the “End IP Address” text boxes.
4. Enter the subnet mask address in the “Subnet Mask” text boxes. The subnet
mask determines which portion of a destination LAN IP address is the network portion, and which portion is the host portion.
63
Page 67

Actiontec Wireless Broadband Router User Manual
65
Chapter 5 Using Network Connections
5. If a Windows Internet Naming Service (WINS) is being used, enter the
WINS server address in the “WINS Server” text boxes.
6. Enter the amount of time a network device will be allowed to connect to
the Router with its currently issued dynamic IP address in the “Lease Time
in Minutes” text box. Just before the time is up, the device’s user will need to
make a request to extend the lease or get a new IP address.
7. Click in the “Provide Host Name If Not Specified by Client” check box to
have the Router automatically assign network devices with a host name, in
case a host name is not provided by the user.
DHCP Relay Select this option to have the Router function as a DHCP relay, and
enter the IP address in the screen that appears.
Routing
The Router can be configured to use dynamic routing. Dynamic routing automatically adjusts how packets travel on the network There are two options in the
“Routing” section of the Configure Broadband Connection (Coax) screen: Basic
or Advanced.
Warning: Do not use static routing unless instructed to do so
M
by Verizon.
Basic Select this option for basic routing operation.
Advanced To set up the Router’s Coax broadband connection for advanced rout-
ing:
1. Select Advanced from the Routing drop-down list.
2. Enter a device metric in the “Device Metric” text box. The device metric is
a value used by the Router to determine whether one route is superior to
another, considering parameters such as bandwidth and delay time.
3. Click in the “Default Route” check box to define this device as the
default route.
4. Click in the “Multicast - IGMP Proxy Internal” check box to activate
multicasting.
64
Page 68

Chapter 5 Using Network Connections
Routing Table
Click New Route to generate the “New Route” window, where a new route can
be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the connection.
Actiontec does NOT recommend activating this feature.
Additional IP Addresses
Click New IP Address to generate the “Additional IP Address Settings” screen, where
additional IP addresses can be created to access the Router via the connection.
WAN PPPoE/WAN PPPoE 2
WAN Point-to-Point Protocol over Ethernet (PPPoE) relies on two widely accepted
standards: Point-to-Point Protocol and Ethernet. PPPoE enables Ethernet net-
worked computers to exchange information with computers on the Internet. PPPoE
supports the protocol layers and authentication widely used in PPP and enables
a point-to-point connection to be established in the normally multipoint architecture of Ethernet. A discovery process in PPPoE determines the Ethernet MAC
address of the remote device in order to establish a session.
Click WAN PPPoE in the Network Connections screen to generate the “WAN
PPPoE Properties” screen. This screen displays a list of the connection’s proper-
ties. The only modifications that can be made from this screen are disabling the
connection (by clicking Disable) or renaming the connection (by entering a new
name in the “Name” text box).
65
Page 69

Actiontec Wireless Broadband Router User Manual
67
Chapter 5 Using Network Connections
Configuring the WAN PPPoE Connection
Click Settings in the WAN PPPoE Properties screen to generate the “Configure
WAN PPPoE” screen.
General
The top part of the Configure WAN PPPoE screen displays general communica-
tion parameters. Actiontec recommends not changing the default values in this
section unless familiar with networking concepts.
Status Displays the connection status of the WAN PPPoE connection. (“Down,”
“Disabled,” “Connected,” etc.)
66
Page 70

Chapter 5 Using Network Connections
When should this rule occur? Displays when the rule is active. To schedule rules,
see “Advanced Settings” chapter.
Network Select the type of connection being configured from the drop-down list
(Broadband Connection, Network (Home/Office), or DMZ).
Connection Type Displays the type of connection. Since this is PPPoE connection,
“PPPoE” is displayed.
MTU MTU (Maximum Transmission Unit) specifies the largest packet size
permitted for Internet transmission. “Automatic, sets the MTU at 1492. Other
choices include “Automatic,” which sets the MTU according to the connection to
the ISP, and “Manual,” which allows the MTU to be set manually.
Underlying Connection Specify the underlying connection above which the protocol initiates from the drop-down list, which displays all possible underlying devices.
PPP Configuration
Point-to-Point Protocol (PPP) is the most popular method for transporting
packets between the user and the ISP.
Service Name Specify the networking peer’s service name, if provided by the ISP,
in this text box.
On-Demand To use PPP on demand to initiate the point-to-point protocol session
only when packets are actually sent over the Internet, click in this check box. This
option should be active on a limited basis
Idle Time Before Hanging Up Enter the amount of idle time, in minutes, before the
PPP session automatically ends .
Time Between Reconnect Attempts In this text box, specify the duration between
PPP reconnect attempts, as provided by the ISP.
67
Page 71

Actiontec Wireless Broadband Router User Manual
69
Chapter 5 Using Network Connections
PPP Authentication
Point-to-Point Protocol (PPP) currently supports four authentication protocols: Password Authentication Protocol (PAP), Challenge Handshake
Authentication Protocol (CHAP), and Microsoft CHAP versions 1 and 2.
Select the authentication protocols the Router may use when negotiating with a
PPTP server in this section. Select all the protocols if no information is available
about the server’s authentication methods. Note that encryption is performed
only if Microsoft CHAP, Microsoft CHAP version 2, or both are selected.
Warning: The PPP Authentication settings should not be
M
changed unless instructed to do so by Verizon.
Login User Name Enter the user name (provided by the ISP) in this text box.
Login Password Enter the password (provided by the ISP) in this text box.
Support Unencrypted Password (PAP) Password Authentication Protocol (PAP)
is a simple, plain-text authentication scheme. The user name and password are
requested by the networking peer in plain-text. PAP, however, is not a secure
authentication protocol. Man-in-the-middle attacks can easily determine the
remote access client’s password. PAP offers no protection against replay attacks,
remote client impersonation, or remote server impersonation.
Support Challenge Handshake Authentication (CHAP) Click in this check box to
activate CHAP, a challenge-response authentication protocol that uses MD5 to
hash the response to a challenge. CHAP protects against replay attacks by using
an arbitrary challenge string per authentication attempt.
Support Microsoft CHAP Click in this check box if communicating with a peer
that uses Microsoft CHAP authentication protocol.
Support Microsoft CHAP Version 2 Select this check box if communicating with a
peer that uses Microsoft CHAP Version 2 authentication protocol.
PPP Compression
The PPP Compression Control Protocol (CCP) is responsible for configuring,
enabling, and disabling data compression algorithms on both ends of the pointto-point link. It is also used to signal a failure of the compression/ decompression mechanism in a reliable manner.
68
Page 72

Chapter 5 Using Network Connections
For each compression algorithm (BSD and Deflate), select one of the following
from the drop-down list:
Reject Selecting this option rejects PPP connections with peers that use the com-
pression algorithm. If Reject is activated, throughput may diminish.
Allow Selecting this option allows PPP connections with peers that use the com-
pression algorithm.
Require Selecting this option insures a connection with a peer using the compression algorithm.
Internet Protocol
Select one of the following Internet Protocol options from the “Internet
Protocol” drop-down list:
Obtain an IP Address Automatically This option is selected by default. Change only
if required by the ISP. The server that assigns the Router with an IP address also
assigns a subnet mask. Override the dynamically assigned subnet mask by selecting
the “Override Subnet Mask” and entering a different subnet mask.
Use the Following IP Address Select this option to configure the Router to use a
permanent (static) IP address. The ISP should provide this address.
DNS Server
The Domain Name System (DNS) is the method by which website or domain
names are translated into IP addresses. The Router can be configured to automatically obtain a DNS server address, or the address can be entered manually,
according to the information provided by the ISP.
To configure the connection to automatically obtain a DNS server address, select
Obtain DNS Server Address Automatically from the “DNS Server” drop-down
list. To manually configure DNS server addresses, select Use the Following DNS
Server Addresses from the “DNS Server” drop-down list. Up to two different
DNS server addresses can be entered (Primary and Secondary).
69
Page 73

Actiontec Wireless Broadband Router User Manual
Routing
Select Advanced or Basic from the “Routing” drop-down list. If Advanced is
selected, additional options appear, as listed below.
Routing Mode Select one of the following Routing modes:
• Route - Select this option to cause the Router to act as a router between
two networks.
• NAT - Select this option to activate Network Address Translation (NAT),
which translates IP addresses to a valid, public address on the Internet. NAT
adds security, since the IP addresses of the devices on the network are not
transmitted over the Internet. In addition, NAT allows many addresses to
exist behind a single valid address. Use the NAT routing mode only if the
local network consists of a single device, or collisions may occur if more than
one device attempts to communicate using the same port.
• NAPT - Select this option to activate NAPT (Network Address and Port
Translation), which refers to network address translation involving the
mapping of port numbers and allows multiple machines to share a single IP
address. Use NAPT if the local network contains multiple devices, a topol-
ogy that necessitates port translation in addition to address translation.
Device Metric The device metric is a value used by the Router to determine
whether one route is superior to another, considering parameters such as bandwidth, delay, and more.
Default Route Click in this check box to define the connection as a the default
route.
Multicast - IGMP Proxy Default Click in this check box to enable the Router to
issue IGMP (Internet Group Management Protocol) host messages on behalf of
hosts the Router discovers through standard IGMP interfaces. IGMP proxy enables
the routing of multicast packets according to the IGMP requests of local network
devices asking to join multicast groups.
Routing Table
Clicking New Route generates the “New Route” window, where a new route can
be configured.
Internet Connection Firewall
Click in the “Enabled” check box to activate the Router’s firewall on the WAN
PPPoE connection.
70
Page 74

Configuring the Router’s Security
The Wireless Broadband Router’s security suite includes comprehensive and robust
security services: Stateful Packet Inspection, a firewall, user authentication protocols, and password protection mechanisms. These features allow users to connect
their computers to the Internet and be protected from the security threats.
The Router’s firewall is the cornerstone of the Router’s security suite. It has been
exclusively tailored to the needs of the residential/office user and is pre-configured
to provide optimum security.
6
The firewall provides both the security and flexibility home and office users seek. It
provides a managed, professional level of network security while enabling the safe
use of interactive applications, such as Internet gaming and video-conferencing.
Additional features, including surfing restrictions and access control, can also be
configured locally through the Router’s MegaControl Panel, or remotely by a
service provider.
The firewall also supports advanced filtering, designed to allow comprehensive
control over the firewall’s behavior. Specific input and output rules can be defined,
the order of logically similar sets of rules can be controlled, and distinctions
between rules that apply to Internet and local network devices can be made.
71
Page 75

Actiontec Wireless Broadband Router User Manual
73
Chapter 6 Configuring the Router’s Security
This chapter covers these Security features:
• General - select the security level for the firewall.
• Access Control - restrict access from the local network to the Internet.
• Port Forwarding - enable access from the Internet to specified services
provided by computers on the local network.
• DMZ Host - configure a network host to receive all traffic arriving at the
Router which does not belong to a known session.
• Port Triggering - define port triggering entries to dynamically open the
firewall for some protocols or ports.
• Remote Administration - enable remote configuration of the Router from
any Internet-accessible computer.
• Website Blocking - block network access to a certain hosts or websites on
the Internet.
• Static NAT - allow multiple static NAT IP addresses to be designated to
devices on the network.
• Advanced Filtering - control the firewall’s settings and rules.
• Security Log - view and configure the security log.
72
Page 76

Chapter 6 Configuring the Router’s Security
General
The “General” screen is used to configure the Router’s basic security settings.
The firewall regulates the flow of data between the local network and the Internet.
Both incoming and outgoing data are inspected and then either accepted (allowed
to pass through the Router) or rejected (barred from passing through the Router)
according to a flexible and configurable set of rules. These rules are designed to
prevent unwanted intrusions from the outside, while allowing local network users
access to required Internet services.
The firewall rules specify what types of services available on the Internet can be
accessed from the local network and what types of services available in the local
network can be accessed from the Internet. Each request for a service the firewall
receives, whether originating in the Internet or from a computer in the local network, is checked against the firewall rules to determine whether the request should
be allowed to pass through the firewall. If the request is permitted to pass, all subsequent data associated with this request (a “session”) will also be allowed to pass,
regardless of its direction.
For example, when accessing a website on the Internet, a request is sent out to the
Internet for this site. When the request reaches the Router, the firewall identifies
the request type and origin (HTTP and a specific computer in the local network, in
this case). Unless the Router is configured to block requests of this type from this
computer, the firewall allows this request to pass out onto the Internet. When the
website is returned from the web server, the firewall will associate it with this session and allow it to pass, regardless of whether HTTP access from the Internet to
the local network is blocked or permitted.
73
Page 77

Actiontec Wireless Broadband Router User Manual
75
Chapter 6 Configuring the Router’s Security
Note that is it is the origin of the request, not subsequent responses to this request,
which determines whether a session can be established or not.
The Router features three pre-defined security levels: Minimum, Typical, and
Maximum. The table below summarizes the behavior of the Router for each of the
three security levels.
Requests from the Internet
Security Level
Maximum
Security
Typical Security
Minimum
Security
These services include Telnet, FTP, HTTP, HTTPS, DNS, IMAP, POP3 and SMTP.
Note: Some applications (such as some Internet messengers and
☞
Peer-To-Peer client applications) tend to use these ports if they
cannot connect with their own default ports. When applying
this behavior, these applications will not be blocked outbound,
even at the Maximum Security level.
(incoming traffic)
Blocked - No access to local
network from Internet,
except as configured in the
Port Forwarding, DMZ host,
and Remote Access screens.
Blocked - No access to local
network from Internet,
except as configured in the
Port Forwarding, DMZ host,
and Remote Access screens.
Unrestricted - Permits full
access from Internet to local
network; all connection
attempts permitted.
Requests from the local
network (outgoing traffic)
Limited - Only commonly
used services, such as web
browsing and E-mail, are
permitted.
Unrestricted - All services
are permitted, except as
configured in the Access
Control screen.
Unrestricted - All services
are permitted, except as
configured in the Access
Control screen.
To configure the Router’s security settings:
1. From the General screen, select a security level by clicking the appropriate radio
button. Using the Minimum Security setting may expose the local network to
significant security risks, and thus should only be used for short periods of time.
74
Page 78

Chapter 6 Configuring the Router’s Security
2. Check the “Block IP Fragments” box to protect the local network from a com-
mon type of hacker attack that uses fragmented data packets to sabotage the
network. Note that VPN over IPSec and some UDP-based services make legiti-
mate use of IP fragments. IP fragments must be allowed to pass into the local
network to use these services.
3. Click OK to save changes.
Access Control
Access control is used to block specific computers within the local network (or even
the whole network) from accessing certain services on the Internet. For example,
one computer can be prohibited from surfing the Internet, another computer from
transferring files using FTP, and the whole network from receiving incoming E-mail.
Access control defines restrictions on the types of requests that can pass from the
local network out to the Internet, and thus may block traffic flowing in both directions. In the E-mail example given above, computers in the local network can be
prevented from receiving E-mail by blocking their outgoing requests to POP3 serv-
ers on the Internet.
Access control also incorporates a list of preset services in the form of applications
and common port settings.
75
Page 79

Actiontec Wireless Broadband Router User Manual
77
Chapter 6 Configuring the Router’s Security
Allow or Restrict Services
To view and allow/restrict these services:
1. Select Access Control from the left side of any Security screen. The “Access
Control” screen appears.
Note: The “Allowed” section is only visible when the firewall is
☞
set to “Maximum.”
2. Click Add. The “Add Access Control Rule” screen appears.
Note: To block a service, click Add in the “Blocked” section of
☞
the Access Control screen. To allow outgoing traffic, click Add
in the “Allowed” section of the screen.
76
Page 80

Chapter 6 Configuring the Router’s Security
3. If this access control rule applies to all networked devices, select “Any” from
the “Networked Computer/Device” list box. If this rule applies to certain
devices only, select “Specify Address” and click Add. Then, add a network
object (for more details about adding network objects, see the “Advanced
Settings” chapter of this manual).
4. Select the Internet protocol to be allowed or blocked from the “Protocol”
drop-down list.
5. If the rule will be active all the time, select Always from the “When should this
rule occur?” drop-down list. If the rule will only be active at certain times, select
Specify Schedule and click Add. Then, add a schedule rule (for more details
about schedule rules, see the “Advanced Settings” chapter of this manual).
6. Click OK to save the changes. The Access Control screen will display a sum-
mary of the new access control rule.
Note: To block a service not included in the list, select Specify
☞
Protocol from the Protocol drop-down menu. The “Edit
Service” screen appears. Define the service, then click OK. The
service will then be automatically added to the top section of the
“Add Access Control Rule” screen, and will be selectable.
An access control can be disabled and the service made available without having
to remove the service from the Access Control table. This may be useful to make
the service available temporarily, with the expectation that the restriction will be
reinstated later.
• To temporarily disable an access control, clear the check box next to the service name.
• To reinstate the restriction at a later time, select the check box next to the
service name.
• To remove an access restriction from the Access Control table, click Remove
for the service. The service will be removed from the Access Control table.
77
Page 81

Actiontec Wireless Broadband Router User Manual
79
Chapter 6 Configuring the Router’s Security
Port Forwarding
In its default state, the Router blocks all external users from connecting to or
communicating with the network, making it safe from hackers who may try to
intrude on the network and damage it. However, the network can be exposed to
the Internet in certain limited and controlled ways to enable some applications to
work from the local network (game, voice, and chat applications, for example) and
to enable Internet access to servers in the network. Port forwarding (sometimes
referred to as “local servers”) supports both of these functions.
To grant Internet users access to servers inside the local network, each service provided, as well as the computer providing it, must be identified. To do this:
1. Select Port Forwarding from the left side of any Security screen. The “Port
Forwarding” screen appears.
2. Click Add. The “Add Port Forwarding Rule” screen appears.
3. Enter the local IP address or the host name of the computer providing the
service in the “Networked Computer/Device” text box, or select them from the
drop-down list. Note that only one local network computer can be assigned to
provide a specific service or application.
78
Page 82

Chapter 6 Configuring the Router’s Security
4. Select the Internet protocol to be provided from the “Protocol” drop-down
list. To see all options, select All Services.
5. Select a WAN connection type from the “WAN Connection Type” drop-down
list. Actiontec recommends selecting All Broadband Devices.
6. To select a port to forward communications to (this is optional), select Specify
from the “Forward to Port” drop-down list, then, in the text box that appears,
enter the port number. If no port is identified, select Same as Incoming Port.
7. If this port will be active all the time, select Always from the “When should this
rule occur?” drop-down list. If the rule will only be active at certain times, select
Specify Schedule and click Add. Then, add a schedule rule (for more details
about schedule rules, see the “Advanced Settings” chapter of this manual).
8. Click OK to save the changes.
Note: Some applications, such as FTP, TFTP, PPTP, and H323,
☞
require the support of special specific Application Level Gateway
(ALG) modules in order to work inside the local network. Data
packets associated with these applications contain information that
allows them to be routed correctly. An ALG is needed to handle
these packets and ensure that they reach their intended destinations. The Router is equipped with a robust list of ALG modules in
order to enable maximum functionality in the local network. The
ALG is automatically assigned based on the destination port.
How many computers can use a service or play a game simultaneously? Well, the
answer may be a bit confusing. All the computers on the network can behave as
clients and use a specific service simultaneously. Being a client means the computer within the network initiates the connection; for example, a computer on the
network can open an FTP connection with an FTP server on the Internet. But only
one computer on the network can operate as a server and respond to requests from
computers on the Internet (outside the local network).
79
Page 83

Actiontec Wireless Broadband Router User Manual
81
Chapter 6 Configuring the Router’s Security
DMZ (Demilitarized Zone) Host
The DMZ host feature allows one device on the network to operate outside the
firewall. Designate a DMZ host:
• To use an Internet service, such as an online game or video-conferencing
program, not present in the Port Forwarding list and for which no port
range information is available.
• To expose one computer to all services without restriction or security.
Warning: A DMZ host is not protected by the firewall and may be
M
vulnerable to attack. Designating a DMZ host may also put other
computers in the local network at risk. When designating a DMZ
host, consider the security implications and protect it if necessary.
To designate a local computer as a DMZ host:
1. Select DMZ Host from the left side of any Security screen. The “DMZ Host”
screen appears.
2. Click in the “DMZ Host IP Address” check box, then enter the IP address of the
computer to be designated as a DMZ host. Note that only one network computer can be a DMZ host at any time.
3. Click OK.
Click in the “DMZ Host IP Address” check box again to disable the DMZ host.
80
Page 84

Chapter 6 Configuring the Router’s Security
Port Triggering
Port triggering can be used for dynamic port forwarding configuration. By setting
port triggering rules, inbound traffic is allowed to arrive at a specific network host
using ports different than those used for the outbound traffic. The outbound traffic
triggers which ports inbound traffic is directed.
For example, a gaming server is accessed using UDP protocol on port 2222. The
gaming server responds by connecting the user using UDP on port 3333 when
starting gaming sessions. In this case, port triggering must be used, since it conflicts
with the following default firewall settings:
• The firewall blocks inbound traffic by default.
• The server replies to the Router’s IP, and the connection is not sent back to
the host, since it is not part of a session.
To resolve the conflict, a port triggering entry must be defined, which allows
inbound traffic on UDP port 3333, only after a network host generated traffic to
UDP port 2222. This results in accepting the inbound traffic from the gaming serv-
er, and sending it back to the network host which originated the outgoing traffic to
UDP port 2222.
To use port triggering:
1. Select Port Triggering from the left side of any Security screen. The “Port
Triggering” screen appears.
2. Select either “Specify Protocol” or “Show All Services” from the drop-down list
next to “Add.”
81
Page 85

Actiontec Wireless Broadband Router User Manual
83
Chapter 6 Configuring the Router’s Security
3. Click Add. An “Edit Service” screen appears.
3. Specify the port triggering entries by clicking New Trigger Ports and New
Opened Ports and entering the protocol and protocol number in the succeeding screens. For example, to set up port triggering for the scenario laid
out on the previous page, the service ports would be set to UDP and 2222,
while the opened ports would be set to UDP and 3333.
Remote Administration
The Router can be accessed and controlled not only from within the local network,
but also from the Internet using remote adminstration.
To access, select Remote Administration from the left side of any Security screen.
The “Remote Administration” screen appears.
82
Page 86

Chapter 6 Configuring the Router’s Security
Telnet
Telnet is used to create a command-line session and gain access to all system settings and parameters using a text-based terminal. Select the Telnet port to be used
by clicking in the appropriate check box, then click OK.
MegaControl Panel
MegaControl Panel is used to obtain access to the Router’s MegaControl Panel and
gain access to all settings and parameters,using a web browser. Both secure (HTTPS)
and non-secure (HTTP) access is available. Select the port to be used by clicking in
the appropriate text box, then click OK.
Note: Telnet and MegaControl Panel remote administration
☞
access may be used to modify or disable firewall settings. Local
IP addresses and other settings can also be changed, making
it difficult or impossible to access the Router from the local
network. Therefore, remote adminstration access to Telnet or
MegaControl Panel services should be activated only when
absolutely necessary.
Diagnostic Tools
Diagnostic Tools are used for troubleshooting and remote system management by a
user or the ISP.
Note: Encrypted remote administration is performed using a
☞
secure SSL connection, and requires an SSL certificate. When
accessing the Router for the first time using encrypted remote
administration, a warning appears regarding certificate authentication because the Router’s SSL certificate is self-generated. When
encountering this message under these circumstances, ignore it
and continue. Even though this message appears, the self-generated certificate is safe, and provides a secure SSL connection.
83
Page 87

Actiontec Wireless Broadband Router User Manual
85
Chapter 6 Configuring the Router’s Security
Website Blocking
The Router can be configured to block specific websites, preventing access to them
from computers on the local network. Restrictions can also be applied to a comprehensive, automatically updated table of sites to which access is not recommended. To view the table of websites currently being blocked, select Website Blocking
in any Security screen. To activate website blocking, click in the “Enable Website
Blocking” check box.
To add a new website to the table:
1. Click Add. The “Blocked Website” screen appears.
2. Enter the website’s address (IP or URL). All pages within the website will also be
blocked. If the website address has multiple IP addresses, the Router will resolve
all additional addresses and automatically add them to the restrictions table.
3. To apply website blocking to a single computer or group of computers on the
network, select them from the “Networked Computer/Device” drop-down list.
84
Page 88

Chapter 6 Configuring the Router’s Security
4. If website blocking needs to be active all the time, select Always from the “When
should this rule occur?” drop-down list. If the rule will only be active at certain
times, select Specify Schedule and click Add. Then, add a schedule rule (for more
details about schedule rules, see the “Advanced Settings” chapter of this manual).
Note: Make sure the Router’s date and time are set correctly for
☞
the local time zone.
5. Click OK to add the website to the table. The previous screen appears while the
Router attempts to find the site. “Resolving...” appears in the “Status” column
while the website is being located.
6. If the site is successfully located, “Resolved” appears in the Status column. If
not, “Hostname Resolution Failed” appears. Click Refresh to update the status,
if necessary. If the Router fails to locate the website, do the following:
• Use a web browser to verify the website is available. If it is, the website
address was entered incorrectly. See “Modifying a Website Address,” below.
• If the website is not available, return to the Website Blocking screen at a
later time and click Resolve Now to verify the website can be found and is
blocked by the Router.
Modifying a Website Address
To modify a website address currently in the table:
1. Click the appropriate icon in the “Action” column. The “Blocked Website”
screen appears.
2. Modify the website address, group, and schedule as necessary. Omit the
“http://” at the beginning and the “/” at the end of the address.
3. Click OK to save changes.
85
Page 89

Actiontec Wireless Broadband Router User Manual
87
Chapter 6 Configuring the Router’s Security
Static NAT
Note: A block of static IP addresses must be purchased from the
☞
ISP to configure this feature.
This option allows multiple static NAT IP addresses to be designated to devices on
the network. Static NAT IP addresses allow devices behind a firewall and configured
with private IP addresses appear to have public IP addresses on the Internet. This
allows an internal host, such as a web server, to have an unregistered (private) IP
address and still be reachable over the Internet. To do this:
1. Select Static NAT from any Security screen. The “Static NAT” screen appears.
2. Click Add. The “Add Static NAT” screen appears.
3. Enter the name of the computer to be used as the local host, or, to enter a
specific IP address, select Specify Address from the “Networked Computer/
Device” drop-down list and enter the IP address in the box on the right.
4. Enter a public IP address from the block of assigned public IP address
(received from the ISP) in the “Public IP Address” text box.
5. Select a connection from the “WAN Connection Type” drop-down list.
86
Page 90

Chapter 6 Configuring the Router’s Security
6. Select the protocol that needs to be accessible from the public IP address by
clicking in the check box next to “Enable Port Forwarding for Static NAT,” then
selecting a protocol from the drop-down menu. Click OK, and OK again.
Repeat these steps to add more static IP addresses from the network.
Advanced Filtering
Advanced filtering is designed to allow comprehensive control over the firewall’s
behavior. Specific input and output rules can be defined, the order of logically
similar sets of rules controlled, and distinctions made between rules that apply to
Internet and local network devices.
To access, select Advanced Filtering from any Security screen. The “Advanced
Filtering” screen appears.
87
Page 91

Actiontec Wireless Broadband Router User Manual
89
Chapter 6 Configuring the Router’s Security
Two sets of rules can be configured: input rules and output rules. Each set of rules
comprises three subsets: initial rules, network devices rules, and final rules. These
subsets determine the sequence by which the rules will be applied. Following is a
description of the set ordering for inbound and outbound packets.
Inbound Packets - Input Rule Sets
• Initial rules
• All rules defined for the network device on which the packet is
• Local servers rules from the local server tab in the security screen
• Rules to accept all the packets on a device in case the firewall check
box “Internet Connection Firewall” in the connection settings screen is
unchecked
• Remote administration rules from the remote administration tab
• DMZ host rules from the DMZ tab
• Final rules
Outbound Packets - Output Rules Sets
• Initial rules
• All rules defined for the network device on which the packet is
• Rules to accept all the packets on a device in case the firewall check
box “Internet Connection Firewall” in the connection settings screen is
unchecked
• IP/hostname filtering rules and access control rules from the tabs in the
security screen
• Final rules
There are numerous rules automatically inserted by the firewall in order to provide
improved security and block harmful attacks.
88
Page 92

Chapter 6 Configuring the Router’s Security
To configure advanced filtering rules, click Add next to the rule title. The “Add
Advanced Filter” screen appears.
To add an advanced filtering rule, define the following rule parameters:
Matching
To apply a firewall rule, a match must be made between IP addresses or ranges
and ports. Use the “Source Address” and “Destination Address” drop-down lists to
define the coupling of source and destination traffic. Port matching will be defined
when selecting protocols. For example, if the FTP protocol is selected, port 21 will be
checked for matching traffic flow between the defined source and destination IPs.
Operation
This is where the action the rule will take is defined. Select one of the following
radio buttons:
• Drop - Deny access to packets that match the source and destination IP
addresses and protocol ports defined in “Matching.”
• Reject - Deny access to packets that match the source and destination IP
addresses and protocol ports defined in upper section of the screen, and
send an ICMP error or a TCP reset to the origination peer.
89
Page 93

Actiontec Wireless Broadband Router User Manual
91
Chapter 6 Configuring the Router’s Security
• Accept - Allow access to packets that match the source and destination IP
addresses and protocol ports defined in upper section of the screen. The
data transfer session will be handled using Stateful Packet Inspection (SPI).
• Accept Packet - Allow access to packets that match the source and destination IP addresses and protocol ports defined in upper section of the
screen. The data transfer session will not be handled using Stateful Packet
Inspection (SPI), so other packets that match this rule will not be automati-
cally allowed access. This setting is useful when creating rules that allow
broadcasting.
Logging
Click in this check box to add entries relating to this rule to the security log.
Scheduler (When should this rule occur?)
If advanced filtering needs to be active all the time, select “Always” from the “When
should this rule occur?” drop-down list. If the rule will only be active at certain times
select Specify Schedule and click Add. Then, add a schedule rule (for more details
about schedule rules, see the “Advanced Settings” chapter of this manual)
Security Log
The security log displays a list of firewall-related events, including attempts to
establish inbound and outbound connections, attempts to authenticate at an
administrative interface (MegaControl Panel or Telnet terminal), firewall configuration, and system start-up.
To access the security log, select Security Log from any Security screen. The
“Security Log” screen appears.
90
Page 94

Chapter 6 Configuring the Router’s Security
Time
The time (based on the Router’s date and time settings) the event occurred.
Event
There are five kinds of events listed in the system log:
• Inbound Traffic - a result of an incoming packet
• Outbound Traffic - a result of an outgoing packet.
• Firewall Setup - configuration message
• WBM Login - a user logged in to WBM
• CLI Login - a user logged in to the command line interface via Telnet
Event-Type
Displays a textual description of the event.
Details
The “Details” column displays more information about the packet or the event,
such as protocol, IP addresses, ports, etc. The following are the available event types
that can be recorded in the security log:
• Firewall internal - from the firewall internal mechanism, in case this eventtype is recorded, an accompanying explanation will be added.
• Firewall status changed - the firewall changed status from up to down or
the vice versa, as specified in the event type description.
• STP packet - an STP (Spanning Tree Protocol) packet has been accepted/
rejected.
• Illegal packet options - the options field in the packet’s header is either illegal or forbidden.
• Fragmented packet - a fragment has been rejected.
• WinNuke protection - a WinNuke attack has been blocked.
91
Page 95

Actiontec Wireless Broadband Router User Manual
93
Chapter 6 Configuring the Router’s Security
• ICMP replay - an ICMP (Internet Control Message Protocol) replay message
has been blocked.
• ICMP redirect protection - an ICMP redirected message has been blocked.
• Packet invalid in connection - an invalid connection packet has been
blocked.
• ICMP protection - a broadcast ICMP message has been blocked.
• Broadcast/Multicast protection - a packet with a broadcast/multicast
source IP has been blocked.
• Spoofing protection - a packet from the Internet with a source IP belonging the local network has been blocked.
• DMZ network packet - a packet from a demilitarized zone network has
been blocked.
• Trusted device - a packet from a trusted device has been accepted.
• Default policy - a packet has been accepted/blocked according to the
default policy.
• Remote administration - a packet designated for the Router management
has been accepted/blocked.
• Access control - a packet has been accepted/blocked because of an access
control rule.
• Parental control - a packet has been blocked because of parental control.
• NAT out failed - NAT failed for this packet.
• DHCP request - the Router sent a DHCP request (depends on the distribu-
tion)
• DHCP response - the Router received a DHCP response (depends on the
distribution)
• DHCP relay agent - a DHCP relay packet has been received (depends on the
distribution)
• IGMP packet - an IGMP packet has been accepted.
• Multicast IGMP connection - a multicast packet has been accepted.
92
Page 96

Chapter 6 Configuring the Router’s Security
• PPTP connection - a packet inquiring whether the Router is ready to
receive a PPTP connection has been accepted.
• AUTH:113 request - an outbound packet for AUTH protocol has been
accepted (for maximum security level).
• IPV6 over IPV4 - an IPv6 over IPv4 packet has been accepted.
• ARP - an ARP packet has been accepted.
• PPP Discover - a PPP discover packet has been accepted.
• PPP Session - a PPP session packet has been accepted.
• 802.1Q - a 802.1Q (VLAN) packet has been accepted.
• Outbound Auth1X - an outbound Auth1X packet has been accepted.
• IP Version 6 - an IPv6 packet has been accepted.
• Router initiated traffic - all traffic the Router initiates is recorded.
• Maximum security enabled service - a packet has been accepted because it
belongs to a permitted service in the maximum security level.
• SynCookies Protection - a SynCookies packet has been blocked.
• ICMP Flood Protection - a packet has been blocked, stopping an ICMP
flood.
• UDP Flood Protection - a packet has been blocked, stopping a UDP flood.
• Service - a packet has been accepted because of a certain service, as specified
in the event type.
• Advanced Filter Rule - a packet has been accepted/blocked because of an
advanced filter rule.
• Fragmented packet, header too small - a packet has been blocked because,
after defragmentation, the header was too small.
• Fragmented packet, header too big - a packet has been blocked because,
after defragmentation, the header was too big.
• Fragmented packet, bad align - a packet has been blocked because, after
defragmentation, the packet was badly aligned.
93
Page 97

Actiontec Wireless Broadband Router User Manual
95
Chapter 6 Configuring the Router’s Security
• Fragmented packet, packet too big - a packet has been blocked because,
after defragmentation, the packet was too big.
• Fragmented packet, packet exceeds - a packet has been blocked because,
after defragmentation, the packet exceeded.
• Fragmented packet, no memory - a fragmented packet has been blocked
because there is no memory for fragments.
• Fragmented packet, overlapped - a packet has been blocked because, after
defragmentation, there were overlapping fragments.
• Defragmentation failed - the fragment has been stored in memory and
blocked until all fragments have arrived and defragmentation can be performed.
• Connection opened - debug message regarding connection.
• Wildcard connection opened - debug message regarding connection.
• Wildcard connection hooked - debug message regarding connection.
• Connection closed - debug message regarding connection.
• Echo/Chargen/Quote/Snork protection - a packet has been blocked due
to Echo/Chargen/Quote/Snork protection.
• First packet in connection is not a SYN packet - a packet has been
blocked due to a TCP connection that started without a SYN packet.
• Error : No memory - a new connection has not been established because
of lack of memory.
• NAT Error : connection pool is full. No connection created -a connec-
tion has not been created because the connection pool is full.
• NAT Error: No free NAT IP - no free NAT IP, so NAT has failed.
• NAT Error: Conflict Mapping already exists - a conflict occurred because
the NAT mapping already exists, so NAT failed.
• Malformed packet: Failed parsing - a packet has been blocked because it
is malformed.
• Passive attack on ftp-server: Client attempted to open Server ports - a
packet has been blocked.
94
Page 98

Chapter 6 Configuring the Router’s Security
• FTP port request to 3rd party is forbidden (Possible bounce attack) - a
packet has been blocked.
• Firewall Rules were changed - the firewall rule set has been modified.
• User authentication - a message arrived during login time, including both
successful and failed authentication.
Security Log Settings
To view or change the security log settings:
1. Click Settings in the Security Log screen. The “Security Log Settings” screen
appears.
2. Select the type of activities that will generate a log message:
• Accepted Incoming Connections - activating this check box generates a
log message for each successful attempt to establish an inbound connection
to the local network.
• Accepted Outgoing Connections - activating this check box generates a
log message for each successful attempt to establish an outgoing connection
to the public network.
95
Page 99

Actiontec Wireless Broadband Router User Manual
97
Chapter 6 Configuring the Router’s Security
3. Select the type of blocked events to be listed in the log:
• All Blocked Connection Attempts - activating this check box generates
log messages for all blocked events.
• Other Blocked Events - if “All Blocked Connection Attempts” is unchecked, select specific blocked events from this list to generate log messages.
4. Click in the “Remote Administration Attempts” check box to write a log mes-
sage for each remote-administration connection attempt, whether successful
or not.
5. Click in the “Connection States” check box to track connection handling by
the firewall and Application Level Gateways (ALGs).
6. Click OK to save changes.
96
Page 100

Chapter 6 Configuring the Router’s Security
97
 Loading...
Loading...