Page 1

User's Guide
Page 2

Copyright © Acronis, Inc., 2000-2010. All rights reserved.
“Acronis” and “Acronis Secure Zone” are registered trademarks of Acronis, Inc.
"Acronis Compute with Confidence", “Acronis Startup Recovery Manager”, “Acronis Active Restore”
and the Acronis logo are trademarks of Acronis, Inc.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the
United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit
permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial
purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE
EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such thirdparties are detailed in the license.txt file located in the root installation directory. You can always find
the latest up-to-date list of the third party code and the associated license terms used with the
Software and/or Service at http://kb.acronis.com/content/7696.
Page 3

Table of conte nts
1 Introduction ..........................................................................................................................9
1.1 What is Acronis® True Image Home? ........................................................................................ 9
1.2 Acronis True Image Home basic concepts ...............................................................................10
1.3 New in Acronis True Image Home 2010 ..................................................................................12
1.4 System requirements and supported media ...........................................................................13
1.4.1 Minimum system requirements .................................................................................................................. 13
1.4.2 Supported operating systems ...................................................................................................................... 13
1.4.3 Supported file systems .................................................................................................................................. 13
1.4.4 Supported storage media ............................................................................................................................. 14
2 Acronis True Image Home installation and startup ................................................................ 15
2.1 Installing Acronis True Image Home ........................................................................................15
2.2 Extracting Acronis True Image Home ......................................................................................15
2.3 Running Acronis True Image Home .........................................................................................16
2.4 Upgrading Acronis True Image Home ......................................................................................16
2.5 Removing Acronis True Image Home ......................................................................................16
3 General information and proprietary Acronis technologies ................................................... 18
3.1 The difference between file archives and disk/partition images ............................................18
3.2 Full, incremental and differential backups ..............................................................................18
3.3 Backup file naming conventions ..............................................................................................19
3.4 Acronis Secure Zone™..............................................................................................................20
3.5 Acronis Startup Recovery Manager .........................................................................................21
3.5.1 How it works .................................................................................................................................................. 21
3.5.2 How to use ..................................................................................................................................................... 22
3.6 Viewing disk and partition information ...................................................................................22
3.7 What is Try&Decide™? ............................................................................................................22
3.8 Acronis DriveCleanser, File Shredder, and System Clean-up...................................................23
3.9 Support for Zip format .............................................................................................................23
3.10 Acronis Nonstop Backup ..........................................................................................................24
3.11 Booting from system image tib files ........................................................................................24
3.12 Acronis Universal Restore ........................................................................................................24
3.12.1 Purpose of Acronis Universal Restore ......................................................................................................... 24
3.12.2 General principles of Acronis Universal Restore ......................................................................................... 25
4 Preparing for disaster recovery ............................................................................................ 26
4.1 How to best prepare for a disaster ..........................................................................................26
4.1.1 Recommendations for testing that your backups can be used for recovery............................................ 26
4.1.2 Additional recommendations....................................................................................................................... 27
4.2 Testing bootable rescue media ...............................................................................................27
4.3 Creating a custom rescue CD ...................................................................................................30
Page 4

5 Getting to know Acronis True Image Home ........................................................................... 31
5.1 Program workspace .................................................................................................................31
5.2 Acronis One-click Backup .........................................................................................................32
5.3 Main screens ............................................................................................................................34
5.4 Options screen .........................................................................................................................36
6 Creating backup archives ..................................................................................................... 38
6.1 Preparing for your first backup ................................................................................................38
6.2 Deciding what data to back up ................................................................................................38
6.3 Some typical backup scenarios ................................................................................................39
6.3.1 Backing up a system partition ...................................................................................................................... 39
6.3.2 Backing up an entire system disk ................................................................................................................. 40
6.3.3 Backing up a data partition or disk .............................................................................................................. 42
6.3.4 Backing up files/folders ................................................................................................................................. 43
6.3.5 Backing up to a network share ..................................................................................................................... 44
7 Acronis Nonstop Backup ...................................................................................................... 46
7.1 What is Acronis Nonstop Backup .............................................................................................46
7.2 Enabling and setting up Acronis Nonstop Backup ...................................................................46
7.3 Using Acronis Nonstop Backup ................................................................................................48
7.4 Recovering partitions protected with Acronis Nonstop Backup .............................................49
7.5 Recovering files protected with Acronis Nonstop Backup ......................................................50
7.6 Managing Acronis Nonstop Backup storage ............................................................................52
8 Online backup ...................................................................................................................... 53
8.1 Creating an Online backup account .........................................................................................53
8.2 Backing up to Acronis Online Storage......................................................................................54
8.3 Recovering data from Online Storage .....................................................................................56
8.4 Managing Online Storage ........................................................................................................58
8.5 Setting online backup options .................................................................................................59
8.5.1 Connection attempts .................................................................................................................................... 59
8.5.2 Storage connection speed ............................................................................................................................ 60
8.5.3 Storage cleanup ............................................................................................................................................. 61
8.5.4 Proxy settings ................................................................................................................................................ 61
8.6 Recommendations on selecting data for storing online..........................................................62
9 Additional backup features .................................................................................................. 63
9.1 Making reserve copies of your backups ..................................................................................63
9.2 Archive to various places .........................................................................................................64
9.3 Backup Wizard – detailed information ....................................................................................67
9.3.1 Selecting what data to back up .................................................................................................................... 68
9.3.2 Selecting archive location ............................................................................................................................. 69
9.3.3 Scheduling ...................................................................................................................................................... 71
9.3.4 Backup method ............................................................................................................................................. 71
9.3.5 Selecting what to exclude ............................................................................................................................. 73
9.3.6 Selecting the backup options ....................................................................................................................... 74
9.3.7 Setting automatic consolidation .................................................................................................................. 74
9.3.8 Providing a comment .................................................................................................................................... 75
Page 5

9.3.9 The backup process ....................................................................................................................................... 76
9.4 Fine-tuning your backups ........................................................................................................76
9.4.1 Backup options .............................................................................................................................................. 76
9.4.2 Local storage settings .................................................................................................................................... 80
9.4.3 Creating a custom data category for backups ............................................................................................ 83
10 Data recovery with Acronis True Image Home ...................................................................... 84
10.1 Recovering your system partition ............................................................................................84
10.2 Recovering a disk backup to a different capacity hard disk ....................................................85
10.2.1 Recovering a disk without a hidden partition ............................................................................................. 86
10.2.2 Recovering a disk with a hidden partition ................................................................................................... 87
10.3 Recovering a data partition or disk ..........................................................................................89
10.4 Recovering files and folders .....................................................................................................90
10.4.1 Recovering files and folders from file archives ........................................................................................... 90
10.4.2 Recovering files and folders from image archives ...................................................................................... 91
11 Additional recovery information .......................................................................................... 93
11.1 Recovery Wizard - detailed information ..................................................................................93
11.1.1 Starting the Recovery Wizard ....................................................................................................................... 93
11.1.2 Archive selection ........................................................................................................................................... 93
11.1.3 Recovery method selection .......................................................................................................................... 94
11.1.4 Selecting a disk/partition to recover ............................................................................................................ 95
11.1.5 Selecting a target disk/partition ................................................................................................................... 96
11.1.6 Changing the recovered partition type ....................................................................................................... 97
11.1.7 Changing the recovered partition size and location ................................................................................... 97
11.1.8 Assigning a letter to the recovered partition .............................................................................................. 98
11.1.9 Setting recovery options ............................................................................................................................... 98
11.1.10 Executing recovery ........................................................................................................................................ 98
11.2 Setting default recovery options .............................................................................................99
11.2.1 File recovery options ..................................................................................................................................... 99
11.2.2 Overwrite file options ................................................................................................................................... 99
11.2.3 Pre/post commands .................................................................................................................................... 100
11.2.4 Recovery priority ......................................................................................................................................... 100
11.3 Detailed information on recovery operations involving dynamic/GPT disks and volumes...100
11.4 Using Acronis Universal Restore ............................................................................................101
12 Try&Decide ........................................................................................................................ 103
12.1 Using Try&Decide ..................................................................................................................106
12.1.1 Try&Decide options and notifications ....................................................................................................... 106
12.2 Try&Decide usage examples ..................................................................................................107
13 Scheduling tasks ................................................................................................................ 109
13.1 Creating scheduled tasks .......................................................................................................109
13.1.1 Setting up once only execution .................................................................................................................. 110
13.1.2 Setting up upon event execution ............................................................................................................... 111
13.1.3 Setting up periodical execution .................................................................................................................. 112
13.1.4 Setting up daily execution .......................................................................................................................... 112
13.1.5 Setting up weekly execution ...................................................................................................................... 113
13.1.6 Setting up monthly execution .................................................................................................................... 113
13.2 Importing scheduled tasks when upgrading ..........................................................................114
13.3 Managing scheduled tasks .....................................................................................................115
Page 6

13.4 Examples of backup scheduling scenarios .............................................................................115
13.4.1 Full backups with automatic deletion on quota violation ........................................................................ 115
13.4.2 Full backups with automatic deletion when backup storage is filled ...................................................... 116
13.4.3 Full backups to Acronis Secure Zone with automatic deletion ................................................................ 116
13.4.4 Full + incremental/differential backups with automatic rotation ........................................................... 117
14 Managing Acronis Secure Zone ........................................................................................... 119
14.1 Creating Acronis Secure Zone ................................................................................................119
14.2 Resizing Acronis Secure Zone ................................................................................................122
14.3 Changing password for Acronis Secure Zone ........................................................................122
14.4 Deleting Acronis Secure Zone ................................................................................................123
15 Creating bootable media .................................................................................................... 124
15.1 Creating Linux-based rescue media .......................................................................................124
15.2 Creating BartPE disc with Acronis True Image Home ............................................................126
15.3 Creating WinPE-based rescue media .....................................................................................128
15.3.1 Adding the Acronis Plug-in to WinPE 1.x ................................................................................................... 129
15.3.2 Adding the Acronis Plug-in to WinPE 2.x or 3.0 ........................................................................................ 130
16 Working with vhd files ....................................................................................................... 132
16.1 Converting tib images into vhd virtual disks and vice versa ..................................................132
16.1.1 Converting to Windows backup ................................................................................................................. 132
16.1.2 Converting to Acronis backup .................................................................................................................... 133
16.2 Recovery using vhd files created by Windows Backup ..........................................................134
16.3 Booting from a tib image of your Windows 7 system partition ............................................134
16.4 Acronis Boot Sequence Manager ..........................................................................................135
17 Exploring archives and mounting images ............................................................................ 137
17.1 Mounting an image ................................................................................................................137
17.2 Unmounting an image ...........................................................................................................140
18 Searching backup archives and their content ...................................................................... 141
18.1 Searching ...............................................................................................................................141
18.2 Windows Search and Google Desktop integration ................................................................142
18.2.1 Using Google Desktop with Acronis True Image Home ........................................................................... 143
18.2.2 Using Windows Search with Acronis True Image Home .......................................................................... 146
19 Other operations ............................................................................................................... 150
19.1 Validating backup archives ....................................................................................................150
19.2 Operation results notification ...............................................................................................151
19.2.1 E-mail notification ....................................................................................................................................... 152
19.2.2 WinPopup notification ................................................................................................................................ 153
19.3 Viewing Tasks and Logs..........................................................................................................153
19.4 Managing backup archives ....................................................................................................156
19.5 Consolidating backups ...........................................................................................................157
19.6 Removing backup archives ....................................................................................................160
19.7 Moving backup archives ........................................................................................................160
Page 7

20 Transferring the system to a new disk ................................................................................ 161
20.1 General information ..............................................................................................................161
20.2 Security ..................................................................................................................................161
20.3 Executing transfers ................................................................................................................162
20.3.1 Selecting Clone mode ................................................................................................................................. 162
20.3.2 Selecting source disk ................................................................................................................................... 163
20.3.3 Selecting destination disk ........................................................................................................................... 163
20.3.4 Partitioned destination disk ....................................................................................................................... 164
20.3.5 Selecting partition transfer method .......................................................................................................... 164
20.3.6 Cloning with manual partitioning............................................................................................................... 165
20.3.7 Cloning summary ........................................................................................................................................ 167
21 Adding a new hard disk ...................................................................................................... 168
21.1 Selecting a hard disk ..............................................................................................................168
21.2 Creating new partitions .........................................................................................................168
21.3 Disk add summary .................................................................................................................169
22 Security and Privacy Tools .................................................................................................. 171
22.1 Using File Shredder ................................................................................................................171
22.2 Acronis DriveCleanser ............................................................................................................172
22.3 Creating custom algorithms of data destruction ...................................................................175
22.4 System Clean-up ....................................................................................................................176
22.5 System Clean-up Wizard settings ..........................................................................................177
22.5.1 "Data Destruction Method" setting ........................................................................................................... 177
22.5.2 "Files" setting ............................................................................................................................................... 178
22.5.3 "Computers" setting ................................................................................................................................... 178
22.5.4 "Drive Free Space" setting .......................................................................................................................... 179
22.5.5 "Commands" setting ................................................................................................................................... 179
22.5.6 "Network Places Filter" setting .................................................................................................................. 180
22.6 Cleaning up separate system components ............................................................................180
23 Troubleshooting ................................................................................................................ 181
23.1 General ..................................................................................................................................181
23.2 Installation issues ...................................................................................................................181
23.3 Backup and validation issues .................................................................................................182
23.4 Recovery issues ......................................................................................................................184
23.5 Bootability after recovery issues ...........................................................................................184
23.6 Other issues ...........................................................................................................................185
24 Hard Disks and Boot Sequence ........................................................................................... 187
24.1 Arranging boot sequence in BIOS ..........................................................................................187
24.2 Installing hard disk drives in computers ................................................................................187
24.2.1 Installing an IDE hard disk drive, general scheme ..................................................................................... 187
24.2.2 Motherboard sockets, IDE cable, power cable ......................................................................................... 188
24.2.3 Configuring hard disk drives, jumpers ....................................................................................................... 189
24.2.4 Installing a SATA hard drive ........................................................................................................................ 190
24.2.5 Steps for installing a new internal SATA drive ........................................................................................... 190
24.3 Hard Disk Wiping methods ....................................................................................................191
Page 8

24.3.1 Functioning principles of Information wiping methods ........................................................................... 191
24.3.2 Information wiping methods used by Acronis .......................................................................................... 192
25 Startup Parameters ............................................................................................................ 193
25.1 Description .............................................................................................................................193
Page 9

1 Introduction
1.1 What is Acronis® True Image Home?
Acronis True Image Home is an integrated software suite that ensures security of all information on
your PC. It can back up the operating system, applications, settings and all of your data, while also
securely destroying any confidential data you no longer need. With this software, you can back up
selected files and folders, Windows applications' settings, settings and messages of Microsoft e-mail
clients — or even the entire disk drive or selected partitions. Acronis Online Backup will allow you to
store your most important files on a remote storage, so they will be protected even if your computer
gets stolen or your house burns down. Acronis Nonstop Backup continuously saves changes in your
system and files (as often as every five minutes) allowing you to rollback easily to any point in time if
the need arises.
Should your disk drive become damaged or your system attacked by a virus or malware, you can
recover the backed up data quickly and easily, eliminating hours or days of work trying to rebuild
your disk drive's data and applications from scratch.
Acronis True Image Home provides you with all the essential tools you need to recover your
computer system should a disaster occur, such as losing data, accidentally deleting critical files or
folders, or a complete hard disk crash. If failures occur that block access to information or affect
system operation, you will be able to recover the system and the lost data easily.
The unique technology developed by Acronis and implemented in Acronis True Image Home allows
you to perform exact, sector-by-sector disk backups, including all operating systems, applications and
configuration files, software updates, personal settings, and data.
Acronis True Image Home helps you protect your identity as well. Simply deleting old data will not
remove it permanently from your computer. Acronis True Image Home now includes Acronis
DriveCleanser that permanently destroys files and wipes personal information from partitions and/or
entire disks, as well as a wizard that cleans up your Windows system of all traces of user activity.
You can store backups on almost any PC storage device: internal or external hard drives, network
drives or a variety of IDE, SCSI, FireWire (IEEE-1394), USB and PC Card (formerly called PCMCIA)
removable media drives, as well as CD-R/RW, DVD-R/RW, DVD+R/RW, BD-R, BD-RE, magneto-optical,
Iomega Zip and Rev drives.
When performing scheduled backup tasks, Acronis True Image Home automatically selects a backup
mode (full, incremental, differential) in accordance with the backup policy set by the user.
If you are going to install a new hard disk drive, Acronis True Image Home will help you to transfer
information from the old one in minutes, including operating systems, applications, documents, and
personal settings. After migrating to the new hard disk you can destroy all confidential information
on the old one securely. This is the recommended procedure if you intend to donate, throw away, or
sell the old hard disk drive.
Wizards and a Windows Vista-style interface will make your work easier. Just perform a few simple
steps and let Acronis True Image Home take care of everything else! When a system problem occurs,
the software will get you up and running in no time.
9 Copyright © Acronis, Inc., 2000-2010
Page 10

1.2 Acronis True Image Home basic concepts
This section provides general information about basic concepts which could be useful for
understanding how the program works.
Backup
According to Wikipedia, "backup refers to making copies of data so that these additional copies may
be used to restore the original after a data loss event. Backups are useful primarily for two purposes.
The first is to restore a state following a disaster (called disaster recovery). The second is to restore
small numbers of files after they have been accidentally deleted or corrupted."
Acronis True Image Home provides for both purposes by creating disk (or partition) images and filelevel backups respectively. By default, Acronis True Image Home stores in an image only those hard
disk parts that contain data (for supported file systems). However, you may use an option that lets
you include in an image all of the sectors of a hard disk (so called sector-by-sector backup). When
you back up files and folders, only the data, along with the folder tree, is compressed and stored.
Disk cloning
This operation migrates/copies the entire contents of one disk drive to another (e.g., when installing
a larger disk) to get two identical drives with the same file structure. The "Disk Clone" tool effectively
copies all of the contents of one hard disk drive onto another hard disk drive. The operation allows
you to transfer all the information (including the operating system and installed programs) from one
hard disk drive to another without having to reinstall and reconfigure all of your software. If you
decide to use cloning, the best chance of success is to remove the existing drive from the computer
and install the new drive in its place. It should be connected in exactly the same way as the old drive.
Acronis True Image Home does not provide for cloning a single partition. You can clone only an entire
drive.
By the way, you can also transfer all the information from your hard disk drive to another one by
backing up the entire old hard disk and then recovering the backup to the new disk.
Backup archive components
Archive - Known as archive chain or archive group, it is the whole set of backup files managed by a
single backup task. The archive can consist of one or several slices.
Slice - It is a set of files created during each cycle of the task execution. The amount of slices created
is always equal to the amount of times the task is executed. A slice represents a point in time, to
which the system or data can be recovered.
Volume - It is a tib file associated with the slice. Usually there is only one volume per slice however,
each slice may consist of several volumes. If you have set archive splitting in the task options, the
resulting slice will be split into several files. In addition, Acronis True Image Home automatically splits
a slice into several files of 4GB each (except the last file) when you make a large backup to a FAT32
formatted hard disk. These files are the slice's volumes.
Snapshots
While creating disk images, Acronis True Image Home uses "snapshot" technology that allows
creating even system partition backups while running Windows with files open for reading and
writing without the necessity to reboot the computer. Once the program starts the partition backup
process, it temporarily freezes all the operations on the partition and creates its "snapshot".
10 Copyright © Acronis, Inc., 2000-2010
Page 11

Snapshot creation usually takes just several seconds. After that the operating system continues
working as the imaging process is under way and you will not notice anything unusual in the
operating system functionality.
In its turn, the Acronis driver continues working to keep the point-in-time view of the partition.
Whenever the driver sees a write operation directed at the partition, it checks whether these sectors
are already backed up and if they are not, the driver saves the data on the sectors to be overwritten
to a special buffer, then allows overwriting. The program backs up the sectors from the buffer, so
that all the partition sectors of the point-in-time when the snapshot was taken will be backed up
intact and an exact "image" of the partition will be created.
Backup file format
Acronis True Image Home saves backup data in the proprietary tib format using compression. This
provides for reducing the storage space requirements, as well as for backward compatibility with the
previous Acronis True Image Home version. While creating a tib file, the program calculates
checksum values for data blocks and adds these values to the data being backed up. These checksum
values allow verifying the backup data integrity. However, using the proprietary format means that
the data from such backups can be recovered only with the help of Acronis True Image Home itself –
either in Windows or in the recovery environment.
Backup archive validation
How can you be sure that you'll be able to recover your system if the need arises? The feature called
backup validation provides a high degree of such assurance. As was already said, the program adds
checksum values to the data blocks being backed up. During backup validation Acronis True Image
Home opens the backup file, re-calculates the checksum values and compares those values with the
stored ones. If all compared values match, the backup file is not corrupted and there is a high
probability that the backup can be successfully used for data recovery. It is highly recommended to
validate system partition backups after booting from the rescue media. For users of Windows 7
Enterprise and Windows 7 Ultimate Acronis True Image Home provides a unique way of ensuring
that you will be able to boot from the recovered system partition. The program allows booting from
a tib file containing the system partition image, though it first converts the tib file into a VHD used for
actual booting. So if you can boot from the converted vhd file, you will be able to boot after
recovering this backup to your disk.
Disaster recovery
Recovering from a disaster usually requires a rescue media, because such disaster often means that
your operating system does not boot either due to system data corruption (e.g. caused by a virus or
malware) or a hard disk failure. When the operating system fails to boot, you need some other
means of booting and using Acronis True Image Home to recover the system partition. So to be
better prepared for a disaster, you absolutely must have a rescue media. Owners of the boxed
product already have a bootable rescue CD. Other legal owners of the program can create a rescue
media using the tool called Media Builder.
To enable booting to the recovery environment, it is necessary to ensure that the BIOS boot
sequence includes the rescue media. See Arranging boot sequence in BIOS (p. 187).
Scheduling
For your backups to be really helpful, they must be as "up-to-date" as possible. This means that you
should run backup tasks on a regular basis, say once a day. Though creating a backup task in Acronis
True Image Home is quite easy, it would be very tedious remembering to do the same thing every
11 Copyright © Acronis, Inc., 2000-2010
Page 12
day. Well, with the scheduler you do not have to remember. You can schedule backups and forget
about them (at least while the backup disk has enough free space or until the need for recovery
arises).
The terms related to these concepts will be repeatedly used in the Acronis True Image Home
documentation, so understanding the above concepts may be helpful when using the program's
features.
1.3 New in Acronis True Image Home 2010
Acronis Nonstop Backup – Near-CDP (Continuous Data Protection) is now available to Acronis
True Image Home users. You will be able to revert your documents to previous states in time.
This may come in handy when you accidentally deleted an important document or made some
corrections that turned out to be wrong and you need to return the document to the state in
which it was, for example, two weeks ago. When you need to recover a file, a Windows Explorerlike browser with integrated search makes searching for a file you need to recover very easy. But
Acronis Nonstop Backup is much more than a versioning tool. It also provides for recovering your
system if you ever need that.
Online backup – you can make your critically important data much more secure by storing it off-
site. Because files are stored on a remote storage, they are protected even if your computer gets
stolen or your house burns down. So the risk of data loss as a result of fire, theft, or other natural
disasters is practically eliminated. And you can safely recover any corrupted, lost or deleted files
on your computer. Integrating Online backup into Acronis True Image Home provides a single
solution for all your data backup needs.
Acronis Online Backup might be unavailable in your region. To find more information, click here:
https://www.acronis.com/my/online-backup/
Powerful scheduler - The scheduler became more powerful and flexible. We expanded the set of
already existing scheduling options. The new scheduler allows you to specify the date when a
scheduled task should run for the first time. While scheduling a monthly task, you can use a
month calendar for specifying the date (e.g. 1st day of the month) or dates for running the task
(e.g. on 10th, 20th, Last day of the month). If you do not need to run a scheduled task for some
time, but intend to use it again in the future, you can disable the task for the time being and then
re-enable it when required. So it is not necessary to recreate the task from scratch. You can clone
a scheduled task and then introduce some minor changes into the duplicate. This may be useful
when creating several similar tasks. In combination with a selected backup method and
automatic consolidation rules, the scheduler allows implementing various backup strategies.
Selective validation – Earlier versions of Acronis True Image Home could validate only a whole
backup archive. Sometimes this may be inconvenient. Suppose, you have a full backup archive
with a size of 20GB and a longish chain of differential backups having sizes of several gigabytes
each and amounting to 100GB. In this case Acronis True Image Home validated the whole 120GB
archive and this could take quite a long time. Now the program will validate just a single selected
differential backup and the full one.
Support of dynamic/GPT disks (provided by separately purchased Acronis Plus Pack) –
operations with dynamic/GPT disks expand the range of hard drive configurations supported by
Acronis True Image Home. Dynamic disks offer greater flexibility for volume management and
may provide benefits in computers with more than one hard drive. GUID Partition Table (GPT) is
a new hard disk partitioning scheme providing advantages over the old MBR partitioning scheme.
It was introduced as a part of the Extensible Firmware Interface (EFI) initiative.
12 Copyright © Acronis, Inc., 2000-2010
Page 13

VHD format support – Virtual Hard Disk (VHD) is a file format containing the complete contents
and structure representing a hard disk drive. Furthermore, Windows Backup utility included into
Windows Vista (except Home editions) and Windows 7 operating systems now uses this format
for backing up an image of the system hard drive when users select the "Complete PC Backup"
option. Acronis True Image Home can convert vhd files into tib files and vice versa, recover
operating system from vhd files, and even boot from vhd images of Windows 7.
Booting from tib images containing Windows 7 – Users of the Windows 7 Enterprise and
Windows 7 Ultimate can boot from a tib image containing a backup of their system partition. This
will allow testing the bootability of the backed up system without actual recovery. If the
operating system boots from the tib file, then it will definitely boot after recovery from that tib
file. When you choose a tib file to boot from, Acronis True Image Home creates a temporary vhd
file by converting this tib file, so your hard disk must have enough free space for storing it. Then
the program adds a new item to the Windows boot loader list. When you select the tib file in the
boot loader list, your computer will actually boot from that temporary vhd file.
1.4 System requirements and supported media
1.4.1 Minimum system requirements
The hardware requirements of Acronis True Image Home correspond to the minimum requirements
for the operating system installed on the computer to be used for running Acronis True Image Home.
In addition Acronis True Image Home requires the following hardware:
CD-RW/DVD-RW drive for bootable media creation
Mouse or other pointing device (recommended).
Using Acronis Nonstop Backup requires at least 1 GB RAM.
Acronis True Image Home rescue media has the following hardware requirements:
256 MB RAM
Processor Pentium 1 GHz or faster
The recommended minimum screen resolution is 1152 x 864.
1.4.2 Supported ope r ating s yste ms
Acronis True Image Home has been tested on the following operating systems:
Windows XP SP3
Windows XP Professional x64 Edition SP2
Windows Vista SP2 (all editions)
Windows 7 (all editions)
Acronis True Image Home also enables creation of a bootable CD-R/DVD-R that can back up and
recover a disk/partition on a computer running any Intel- or AMD- based PC operating system,
including Linux®. The only exception is the Intel-based Apple Macintosh, which is currently not
supported in native mode.
1.4.3 Supported file systems
FAT16/32
13 Copyright © Acronis, Inc., 2000-2010
Page 14

NTFS
Ext2/Ext3 *
ReiserFS *
Linux SWAP *
If a file system is not supported or is corrupted, Acronis True Image Home can copy data using a
sector-by-sector approach.
* The Ext2/Ext3, ReiserFS, and Linux SWAP file systems are supported only for disk or partition backup/recovery
operations. You cannot use Acronis True Image Home for file-level operations with these file systems (file
backup, recovery, search, as well as image mounting and file recovering from images), as well as for backups to
disks or partitions with these file systems.
1.4.4 Supported st or age medi a
Hard disk drives*
Networked storage devices
FTP servers**
CD-R/RW, DVD-R/RW, DVD+R (including double-layer DVD+R), DVD+RW, DVD-RAM, BD-R, BD-
RE***
USB 1.0 / 2.0 /3.0, FireWire (IEEE-1394) and PC card storage devices
REV®, Jaz® and other removable media
* Acronis True Image Home does not support the following dynamic volume types: Mirrored and
RAID-5. There are some additional limitations on operations with dynamic and GPT disks:
To perform operations with dynamic and GPT disks, you need separately purchased Acronis
Plus Pack
Creation of Acronis Secure Zone is not supported.
Recovery of a dynamic volume as a dynamic volume with manual resizing is not supported
GPT disks can be recovered only "volume-to-volume" without the possibility of resizing
Try&Decide cannot be used for protecting dynamic and GPT disks
"Clone disk" operation is not supported for dynamic and GPT disks
** An FTP server must allow passive mode file transfers. Data recovery directly from an FTP server
requires the archive to consist of files of no more than 2GB each. It is recommended that you change
the source computer firewall settings to open Ports 20 and 21 for both TCP and UDP protocols and
disable the Routing and Remote Access Windows service.
*** Burned rewritable discs cannot be read in Linux without a kernel patch.
14 Copyright © Acronis, Inc., 2000-2010
Page 15
2 Acronis True Image Home installation and
startup
2.1 Installing Acronis True Image Home
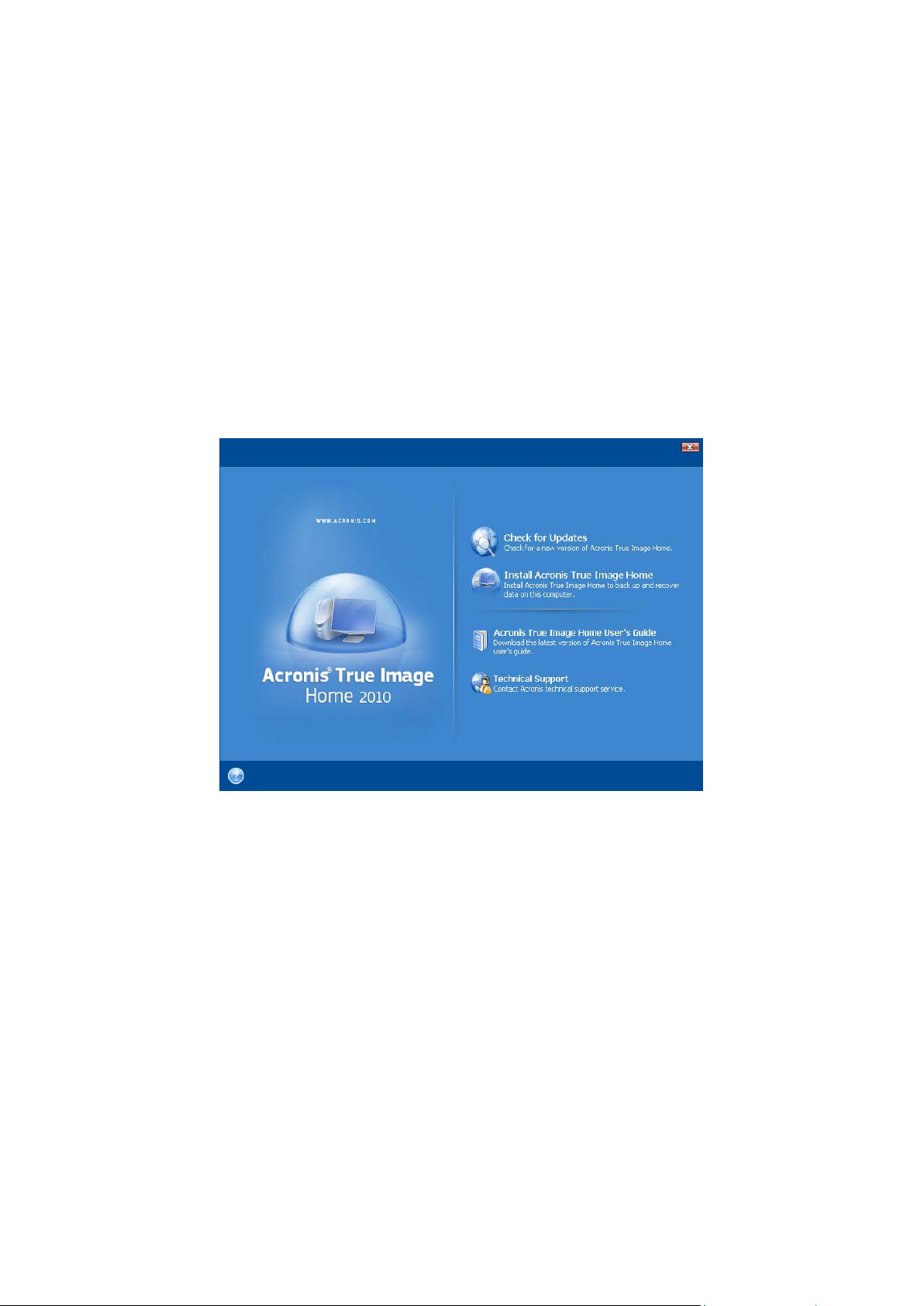
To install Acronis True Image Home:
Run the Acronis True Image Home setup file.
Before installation, you can check for a newer Acronis True Image Home build on the Acronis
Web site. If available, the newer version will be offered for installation.
In the Install Menu, select the program to install: Acronis True Image Home.
Follow the install wizard instructions on the screen.
Typical, Custom and Complete installation is available. Having pressed Custom, you can choose
not to install Rescue Media Builder.
With Rescue Media Builder you can create bootable rescue disks (see details in Creating
bootable media (p. 124)). You might not need this tool if you purchased a boxed product that
contains a bootable CD. Installing the Bootable Rescue Media Builder will allow you to create
bootable media or its ISO image at any time from the main program window or by running
Bootable Rescue Media Builder on its own.
When installed, Acronis True Image Home creates a new device in the Device Manager list (Control
Panel → System → Hardware → Device Manager → Acronis Devices → Acronis True Image Backup
Archive Explorer). Do not disable or uninstall this device, as it is necessary for connecting image
archives as virtual disks (see Exploring archives and mounting images (p. 137)).
2.2 Extracting Acronis True Image Home
When installing Acronis True Image Home, you can save the setup (.msi) file on a local or network
drive. This will help when modifying or recovering the existing component installation.
15 Copyright © Acronis, Inc., 2000-2010
Page 16

To save the setup file:
Run the Acronis True Image Home setup file.
In the Install Menu, right-click on the program name and select Extract.
Select a location for the setup file and click Save.
Recovering or updating the existing Acronis True Image Home installation with using the .msi file
must be done from the command line as follows:
1. Choose Start → Run
2. Type cmd.
3. When the command-line interpreter window opens, type the following command:
msiexec /i path_to_msi_file\msi_file_name.msi REINSTALL=ALL REINSTALLMODE=vomus
After the install wizard window opens, choose Typical, Custom or Complete installation for repairing
or changing the program's components.
2.3 Running Acronis True Image Home
You can run Acronis True Image Home in Windows by selecting Start → Programs → Acronis →
Acronis True Image Home → Acronis True Image Home or by clicking on the appropriate shortcut on
the desktop.
If your operating system does not load for some reason, you can run Acronis Startup Recovery
Manager. However, this must be activated prior to use; see Acronis Startup Recovery Manager (p.
21) to learn more about this procedure. To run the program, press F11 during bootup when you see a
corresponding message that tells you to press that key. Acronis True Image Home will be run in
standalone mode, allowing you to recover the damaged partitions.
If your disk data is totally corrupted and the operating system cannot boot (or if you have not
activated Acronis Startup Recovery Manager), load the standalone Acronis True Image Home version
from the bootable media, supplied with the retail box or created by you using Rescue Media Builder.
This boot disk will allow you to recover your disk from a previously created image.
2.4 Upgrading Acronis True Image Home
If you already have Acronis True Image Home installed, the new version will simply update it; there is
no need to remove the old version and reinstall the software.
Please keep in mind that the backups created by the later program version may be incompatible with
the previous program versions, so if you roll back Acronis True Image Home to an older version, you
likely will have to re-create the archives using the older version. We strongly recommend that you
create new bootable media after each Acronis True Image Home upgrade.
2.5 Removing Acronis True Image Home
Select Start → Settings → Control panel → Add or remove programs → <Acronis True Image
Home> → Remove. Then follow the instructions on the screen. You may have to reboot your
computer afterwards to complete the task.
16 Copyright © Acronis, Inc., 2000-2010
Page 17
If you use Windows Vista, select Start → Control panel → Programs and Features → <Acronis True
Image Home> → Remove. Then follow the instructions on the screen. You may have to reboot your
computer afterwards to complete the task.
If you have Acronis Secure Zone on your computer, remove it before removing the program itself because
removing Acronis True Image Home will not remove the zone.
17 Copyright © Acronis, Inc., 2000-2010
Page 18

3 General information and proprietary Acronis
technologies
3.1 The difference between file archives and disk/partition images
A backup archive is a file or a group of files (also called "backups" in this guide), that contains a copy
of selected file/folder data or a copy of all information stored on selected disks/partitions.
When you back up files and folders, only the data, along with the folder tree, is compressed and
stored.
Backing up disks and partitions is performed in a different way: Acronis True Image Home stores a
sector-by-sector snapshot of the disk, which includes the operating system, registry, drivers, software
applications and data files, as well as system areas hidden from the user. This procedure is called
"creating a disk image," and the resulting backup archive is often called a disk/partition image.
By default, Acronis True Image Home stores only those hard disk parts that contain data (for supported file
systems). Furthermore, it does not back up swap file information (pagefile.sys under Windows XP and later) and
hiberfil.sys (a file that keeps RAM contents when the computer goes into hibernation). This reduces image size
and speeds up image creation and recovery. However, you might use the Create an image using the sector-by-
sector approach option that lets you include all of the sectors of a hard disk in an image.
A partition image includes all files and folders. This includes all attributes (including hidden and system files),
boot record, and FAT (file allocation table); as well as files in the root directory and the zero track of the hard
disk with the master boot record (MBR).
A disk image includes images of all disk partitions as well as the zero track with the master boot record (MBR).
By default, files in all Acronis True Image Home archives have a ".tib" extension. Do not change this
file extension.
It is important to note that you can recover files and folders not only from file archives, but from
disk/partition images too. To do so, mount the image as a virtual disk (see Exploring archives and
mounting images (p. 137)) or start the image recovery and select Recover chosen files and folders.
3.2 Full, incremental and differential backups
Acronis True Image Home can create full, incremental and differential backups.
A full backup contains all data at the moment of backup creation. It forms a base for further
incremental or differential backup or is used as a standalone archive. A full backup has the shortest
recovery time compared to incremental or differential ones.
An incremental backup file only contains data changed since the last backup of any type (full,
incremental, or differential). Therefore, it is smaller and takes less time to create, but as it doesn't
contain all the data; all the previous backups and the initial full backup are required for recovery.
Unlike an incremental backup, when every backup procedure creates the next file in a "chain", a
differential backup creates an independent file, containing all changes since the last full backup.
18 Copyright © Acronis, Inc., 2000-2010
Page 19

Generally, a differential backup will be recovered faster than an incremental one, as it does not have
to process through a long chain of previous backups.
A standalone full backup might be an optimal solution if you often roll back the system to its initial
state or if you do not like to manage multiple files. If you are interested in saving only the last data
state to be able to recover it in case of system failure, consider the differential backup. It is
particularly effective if your data changes tend to be few compared to the full data volume.
The same is true for incremental backup. These are most useful when you need frequent backups
and the ability to roll back to a specific point in time. Having created a full backup once, if you then
create an incremental backup each day of a month, you will get the same result as if you created full
backups every day. Incremental images are considerably smaller than full or differential images.
Incremental or Differential?
The difference is typically that in an incremental backup, only the files changed or added since the
last time the backup ran are added to the archive. With a differential backup, all the files changed or
added since the initial full backup, are added to the archive. Thus, differential backups take longer to
run than incremental backups. When recovering from an incremental backup, the program must
copy the entire initial backup and then step through each of the previous backups to retrieve all the
updated files. A differential backup, on the other hand, can be recovered quicker because the
software must copy only the original backup and the most recent one.
An incremental or differential backup created after a disk is defragmented might be considerably
larger than usual. This is because the defragmentation program changes file locations on the disk and
the backups reflect these changes. Therefore, it is recommended that you re-create a full backup
after disk defragmentation.
3.3 Backup file naming conventions
Let's remember that Acronis True Image Home may split a full or incremental archive into volumes
either when a user sets the splitting option or when a large backup having a size bigger than 4GB is
saved to a FAT32 disk. See "Backup archive components" in Acronis True Image Home basic concepts
(p. 10).
Though users may assign any name to backups, many would still prefer using automatic naming and
the below information may come in handy when viewing the contents of a backup archive storage in
Windows Explorer and trying to figure out, e.g. which are full and which are incremental.
1) When you agree to use the One-Click Backup offered during the first start of the newly installed
program, the resultant backup file is named "SystemBackup_mm_dd_yyyy.tib", where mm_dd_yyyy
is the date of backup creation in the following format: month (one or two digits), day (one or two
digits), year (four digits).
When saved to a FAT32 disk, such backup may be split into volumes with the names
SystemBackup_mm_dd_yyyy1.tib, SystemBackup_mm_dd_yyyy2.tib,
SystemBackup_mm_dd_yyyy3.tib, etc.
As in this case the subsequent automatically scheduled backups will replace the previous one (once
every seven days by default) only after the next backup finishes (to keep the old backup in the event
of the current backup's failure), the backup filename(s) will be alternately named
SystemBackup_mm_dd_yyyy.tib and SystemBackup_mm_dd_yyyy(1).tib.
19 Copyright © Acronis, Inc., 2000-2010
Page 20

2) In some cases when you create a new full backup task at a new destination, the backup gets the
name "MyBackup_mm_dd_yyyy.tib".
If a backup is split (either automatically, e.g. due to the 4GB file size limit on FAT32 disks or when
configuring a backup task), the constituent backup files (volumes) are named as follows:
MyBackup_mm_dd_yyyy1.tib…MyBackup_mm_dd_yyyyN.tib, where N is the number of volumes
Subsequent incremental or differential backups to this full backup will get the names as follows –
MyBackup_mm_dd_yyyy2.tib, MyBackup_mm_dd_yyyy3.tib, etc. (if the full backup is not split) or
MyBackup_mm_dd_yyyyN+1.tib, MyBackup_mm_dd_yyyyN+2.tib, etc. For instance, if N=8,
incremental or differential backups will get the names MyBackup_mm_dd_yyyy9.tib,
MyBackup_mm_dd_yyyy10.tib, etc.
3) When you back up, for example, partitions C and D, the backup gets the name
"System_C_D_mm_dd_yyyy.tib".
4) When you perform file-level backups, they are named depending on the backup type:
My Data backup gets the following name: MyBackup_mm_dd_yyyy.tib;
System State backup gets the following name: System State_mm_dd_yyyy.tib;
My E-mail backup gets the following name: Email_mm_dd_yyyy.tib; and
My Application Settings backup gets the following name: Application Settings_mm_dd_yyyy.tib.
5) If you right-click on a folder in Windows Explorer and choose Back Up in the shortcut menu, the
backup file gets the name of the folder with appended date, e.g. My Documents_mm_dd_yyyy.tib.
If you right-click on a file in Windows Explorer and choose Back Up in the shortcut menu, the backup
file gets the name of the file with appended date, i.e. filename_mm_dd_yyyy.tib.
If you select in Windows Explorer several files in the same folder and then choose Back Up in the
shortcut menu, the backup file gets the name of the folder with appended date, e.g. My
Documents_mm_dd_yyyy.tib.
If you select in Windows Explorer two or more folders and then choose Back Up in the shortcut
menu, the backup file gets the name of the parent folder or disk letter (when you selected folders in
the root directory) with appended date, e.g. My Documents_mm_dd_yyyy.tib or C_mm_dd_yyyy.tib.
6) When you rename backups on the Data recovery and backup management screen, a backup is
renamed only in the program's metadata database; however, backup file names on the disk remain
unchanged.
3.4 Acronis Secure Zone™
The Acronis Secure Zone is a secure partition that enables keeping backup archives on a managed
machine disk space and therefore recovery of a disk to the same disk where the backup resides. In
the Acronis True Image Home wizards' windows, the zone is listed along with all locations available
for storing archives.
Certain Windows applications, such as Acronis disk management tools, can access the zone.
When you create Acronis Secure Zone, an icon appears under My Computer in the Other section.
Double-clicking on the Acronis Secure Zone icon opens the zone and you can view all the backup
archives it contains. You can also open the zone by right-clicking on its icon and choosing Open in the
20 Copyright © Acronis, Inc., 2000-2010
Page 21

shortcut menu. Double-clicking on an archive opens it and shows all backups (full, incremental,
differential) belonging to the archive. Right-clicking on a specific backup opens the shortcut menu
allowing to choose a desired operation – mount (for image archives), recover, validate, update,
remove the backup, and view the backup's details. If Acronis Secure Zone is password-protected, any
operation except viewing backup details will require entering the password. Double-clicking on a
backup will start the default operation (Mount for image backups and Recovery for data backups).
The shortcut menu that appears after right-clicking on the Acronis Secure Zone icon has two more
items – Create Shortcut (for placing it on the Desktop) and Explore for exploring the zone contents.
Choosing Explore opens Windows Explorer with Acronis Secure Zone selected on the directory tree
enabling you to explore the zone contents.
The Acronis Secure Zone is available as a location to store backup files as long as it has free space. If
there is not enough space, older backups will be deleted to create free space.
Acronis True Image Home uses the following approach to clean up Acronis Secure Zone:
If you are in the process of creating a backup and there is not enough free space in the zone to
create it, the program will display a dialog which warns you that the Acronis Secure Zone is full.
You can click Cancel to cancel the backup operation. In that case, you may want to increase the
size of the Acronis Secure Zone and then run the backup operation again. If you want to free up
some space in the zone, click OK and the oldest full backup of the type being created will be
deleted with all subsequent incremental/differential backups, then the backup operation will
recommence.
If deleting the oldest backup does not free up enough space, you will get the same warning
message again. You may delete the next oldest backup (if any) and repeat this until all the
previous backups are deleted.
If after deleting all the previous backups there is still not enough space for completing the
backup, you will get an error message and the backup will be canceled.
The program distinguishes only two types of backups in the zone: disk image backups and file-level
backups. My Data, System State, My E-mail, and My Application Settings backups are considered as
file-level type backups. For example, if you have an e-mail backup (My E-mail) in the zone and there
is not enough space for backing up a folder (My Data), the program will delete the e-mail backup to
free up space for the folder backup.
You can back up data automatically on a schedule (see Scheduling tasks (p. 109)). In order to not
worry about the zone becoming too full when Acronis True Image Home for Windows performs a
scheduled backup, it is recommended to select the When not enough space in ASZ, delete the oldest
archive box in the Backup options (Error handling) and the scheduled backup task options. However,
if you keep long chains of incremental backups, it will be good practice to periodically check the free
space in the zone.
For information on how to create, resize or delete Acronis Secure Zone using this wizard, see
Managing Acronis Secure Zone (p. 119).
3.5 Acronis Startup Recovery Manager
3.5.1 How it works
The Acronis Startup Recovery Manager lets you start Acronis True Image Home without loading the
operating system. With this feature, you can use Acronis True Image Home by itself to recover
21 Copyright © Acronis, Inc., 2000-2010
Page 22

damaged partitions, even if the operating system won't start up for some reason. As opposed to
booting from Acronis removable media, you will not need a separate media or network connection
to start Acronis True Image Home.
3.5.2 How to use
To be able to use Acronis Startup Recovery Manager at boot time, prepare as follows:
1. Install Acronis True Image Home.
2. Activate Acronis Startup Recovery Manager. To do so, click Activate Acronis Startup Recovery
Manager and follow the wizard's instructions.
When Acronis Startup Recovery Manager is activated, it overwrites the master boot record (MBR) with its own
boot code. If you have any third-party boot managers installed, you will have to reactivate them after activating
the Startup Recovery Manager. For Linux loaders (e.g. LiLo and GRUB), you might consider installing them to a
Linux root (or boot) partition boot record instead of MBR before activating Acronis Startup Recovery Manager.
If a failure occurs, turn on the computer and press F11 when you see the "Press F11 for Acronis
Startup Recovery Manager" message. This will start a standalone version of Acronis True Image
Home that differs only slightly from the complete version.
Be careful! Drive letters in standalone Acronis True Image Home might sometimes differ from the way Windows
identifies drives. For example, the D: drive identified in the standalone Acronis True Image Home might
correspond to the E: drive in Windows.
You won't be able to use the previously activated Acronis Startup Recovery Manager if the Try&Decide mode is
started.
3.6 Viewing disk and partition information
You can change the way data is represented in all schemes you see in various wizards.
The header may have up to three icons: Columns, Arrange Icons by and Disk properties, the latter
duplicated in the context menu opened by right-clicking objects.
To sort messages by a particular column, click the header (another click will switch the messages to
the opposite order) or the Arrange Icons by button and select the column.
To select which columns to view, right-click the headers line or left-click the Columns button. Then
flag the columns you want to display. When left-clicking the Columns button, you can also change
the display order of columns using the Move Up and Move Down buttons.
If you click the Disk properties button, you will see the selected partition or disk properties window.
This window contains two panels. The left panel contains the properties tree and the right describes
the selected property in detail. The disk information includes its physical parameters (connection
type, device type, size, etc.); partition information includes both physical (sectors, location, etc.), and
logical (file system, free space, assigned letter, etc.) parameters.
You can change the width of a column by dragging its borders with the mouse.
3.7 What is Try&Decide™?
The Acronis True Image Home Try&Decide feature allows you to perform potentially dangerous
operations such as software installation or opening e-mail attachments without putting your PC at
22 Copyright © Acronis, Inc., 2000-2010
Page 23

risk. It does this by creating essentially a controlled, secure, temporary workspace that is insulated
from the rest of your computer. If the system crashes or your computer stops responding during
these operations, you should revert the system to the previous state by discarding changes made in
the Try&Decide mode. If operations are successful, you have the choice of applying the changes to
the real system. (For more details see Try&Decide (p. 103))
3.8 Acronis DriveCleanser, File Shredder, and System Clean-up
Acronis True Image Home contains utilities for secure destruction of data on an entire hard disk
drive, individual partitions, as well as for erasing individual files and eliminating user system activity
traces. When replacing your old hard drive with a new, higher-capacity one, you may unwittingly
leave on the old disk lots of personal and confidential information that can be recovered, even if you
have reformatted it.
The Acronis DriveCleanser provides for the destruction of confidential information on hard disk
drives and/or partitions with the help of techniques that meet or exceed most national and state
standards. You can select an appropriate data destruction method depending on the importance of
your confidential information.
The File Shredder provides the same capabilities for individual files and folders.
Finally, the System Clean-up wizard ensures elimination of all your activity traces; while working with
a PC, you leave thousands of bytes of evidence showing your actions (records in various system files)
that you don’t even know about. This could include user names and passwords, as well as other
personal information that could be used to steal your identity if it fell into the wrong hands. This
utility wipes them completely from the disk drive.
3.9 Support for Zip format
Now you will be able to retrieve files from backups anywhere without using Acronis True Image
Home, if you choose the zip format instead of the tib format. You can back up files, for example, to a
USB stick and retrieve files from such archives on your notebook at home without installing Acronis
True Image Home, because the most widely used operating systems, namely Microsoft Windows and
Mac OS X have built-in support of the zip file format.
Please, be aware that built-in support of zip files in Windows does not cover operations with multivolume zip
archives, and zip archives exceeding 4GB in size or which contain files of more than 4GB each.
The Zip format is available when backing up files and/or folders as well as when making reserve
copies of your backups. Acronis True Image Home provides for the zip format most of the
functionality available for the tib format, except password protection and encryption – you can
schedule backups, validate zip backup archives, recover files and folders from zip archives, make
incremental and differential backups, and so on.
Acronis True Image Home can recover and validate only its own zip archives. If a zip archive was created by a
file archiver program, it cannot be recovered and validated by Acronis True Image Home.
23 Copyright © Acronis, Inc., 2000-2010
Page 24

3.10 Acronis Nonstop Backup
Acronis Nonstop Backup provides easy protection of your disks and files, and allows you to recover
both entire disks and individual files and even their versions from disaster. By default Nonstop
Backup will protect your system partition, though you can select other partitions and disks for
protection as well.
Once you start Acronis Nonstop Backup, it will perform an initial image backup of the partition(s)
selected for protection. Having finished this task, Acronis Nonstop Backup will save changes in your
system and files (including open ones) every five minutes, so you will be able to recover your system
to an exact state in time.
In general cases, states of the protected data will be backed up at 5-minute intervals for the last 24
hours.
Note, that if Acronis Nonstop Backup protects a non-system partition, and no changes have occurred
for 5 minutes since the last backup, the next scheduled backup will be skipped. Acronis Nonstop
Backup will wait for a significant data change and will create a new incremental backup only when
such change has been detected. In this case, the real time interval exceeds 5 minutes.
The older backups will be consolidated in such a way that Acronis True Image Home will keep daily
backups for the last 30 days and weekly backups until all Nonstop Backup data storage space is used.
3.11 Booting from system image tib files
Users of the Enterprise and Ultimate editions of Windows 7 can now test whether they will be able to
boot from the recovered system partition. Acronis True Image Home allows booting from a tib file
containing a system partition image. So if you are able to boot from such backup, you almost
certainly will be able to boot after an actual system recovery from that backup. When you choose a
tib file to boot from, Acronis True Image Home creates a temporary vhd file by converting this tib file,
so your hard disk must have enough free space for storing it. Then the program adds a new item to
the Windows boot loader list. When you select the tib file in the boot loader list, your computer will
actually boot from that temporary vhd file. After testing the bootability of the tib file, you can
remove the file from the boot loader list and delete the temporary vhd file, though you can keep it.
3.12 Acronis Universal Restore
3.12.1 Purpose of Acronis Universal Restore
Universal Restore is part of Acronis Plus Pack which is purchased separately, has its own license, and
is installed from its own setup file. You need to re-create bootable media to make the newly installed
Universal Restore add-on operational in the bootable recovery environment.
A system disk image can be restored easily on the hardware where it was created or to identical
hardware. However, if you change the motherboard or use another processor version — a likely
possibility in case of hardware failure — the recovered system could refuse to boot. An attempt to
transfer the system to a new, much more powerful computer will usually produce the same
unbootable result, because the new hardware is incompatible with the most critical drivers included
in the image.
Using Microsoft System Preparation Tool (Sysprep) does not solve this problem, because Sysprep
permits replacing drivers only for Plug-and-Play devices (sound cards, network adapters, video cards
24 Copyright © Acronis, Inc., 2000-2010
Page 25

etc.). As for system Hardware Abstraction Layer (HAL) and mass storage device drivers, they must be
identical on the source and the target computers (see Microsoft Knowledge Base, articles 302577
and 216915).
Acronis Universal Restore technology provides an efficient solution for hardware-independent
system restoration by replacing the crucial Hardware Abstraction Layer (HAL) and mass storage
device drivers.
Acronis Universal Restore is applicable for:
1. Instant recovery of a failed system on different hardware
2. Hardware-independent cloning of operating systems
3.12.1.1 Limitations in using Acronis Universal Restore
1. The system recovered by Acronis Universal Restore might not start if the partition structure in the
image or the target disk partitioning does not coincide with that of the source disk. As a result, the
loader restored from the image will point to the wrong partition and the system will not boot or will
malfunction.
This may occur if you:
back up only selected partitions but not the entire source disk
restore not the entire source disk, but only the selected partitions. In some cases, especially if
your system resides on a partition other than the first, this can confuse the loader and prevent
the restored system from startup.
To avoid the problem, we recommend that you back up and restore the entire system disk.
2. The Acronis Universal Restore option does not work if a computer is booted with Acronis Startup
Recovery Manager (using F11) or the backup image is located in Acronis Secure Zone. This is because
Acronis Startup Recovery Manager and Acronis Secure Zone are primarily meant for data recovery on
the same computer.
3.12.2 General principles of Acronis Universal Restore
1. Automatic selection of HAL and mass storage drivers
Acronis Universal Restore searches the Windows default driver storage folders (in the image being
restored) for HAL and mass storage device drivers and installs drivers that best fit the target
hardware. You can specify a custom driver repository (a folder or folders on a network drive or CD)
which will also be used to search for drivers. In addition, Acronis Universal Restore can search drivers
on removable media.
The Windows default driver storage folder is determined in the registry value "DevicePath", which can be found
in the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\DevicePath. This storage folder is
usually WINDOWS/inf.
2. Installing drivers for Plug-and-Play devices Acronis Universal Restore relies on the built-in Plug-
and-Play discovery and configuration process to handle hardware differences in devices that are not
critical for the system start, such as video, audio and USB. Windows takes control over this process
during the logon phase, and if some of the new hardware is not detected, you will have a chance to
install the drivers for it later manually.
25 Copyright © Acronis, Inc., 2000-2010
Page 26

4 Preparing for disaster recovery
4.1 How to best prepare for a disaster
Let us remind you of Murphy's Law: "Whatever can go wrong will go wrong" (and at the worst
possible time, in the worst possible way). And some people say that Murphy was an incurable
optimist. So be warned – your computer may crash and will eventually crash (and maybe just at the
worst possible moment). We may interpret Murphy's Law the other way around – it is vitally
important to consider all the possible things that can go wrong and act so as to prevent them. The
best way to counteract a possible disaster is by taking the necessary precautionary measures:
1) To be better prepared for a disaster, you need to make a full backup of your system disk (or at the
very least the partition containing Windows and your applications). To make this task easier, Acronis
has provided the One-Click Backup feature that allows you to back up the system partition and MBR
during the first start of the newly installed program. If you decide not to use the One-Click Backup,
e.g. because the external hard drive you plan to use for your backups has not been attached at that
time or because you plan to back up more than just the system partition, please, make such a backup
as soon as possible.
2) Whenever possible, you should store your system drive image on a hard drive other than your
primary hard disk C:, preferably on an external one. This gives an additional guarantee that you will
be able to recover your system if your primary hard disk drive fails. Furthermore, it is usually better
to keep your personal data separate from your operating system and applications, for example, on
disk D:. Such an arrangement speeds up the creation of your system and data disks (or partitions)
images and reduces the amount of information you will need to recover. This makes the backup file
of your system disk much smaller and recovery can be easier. In its turn, the smaller the backup file
size, the less chance of its corruption and the less time required for your system recovery.
3) If you store your data (documents, videos, photos, etc.) on a non-system disk, e.g. using the
arrangement described in item 2), it needs to be backed up too. You can either back up the folders
containing your data or create a data disk image. Remember that the imaging procedure is much
faster than copying files and could speed up the backup process significantly when it comes to
backing up large volumes of data. Incidentally, if the image file becomes corrupted for some reason,
it is sometimes possible to mount the image and save most files and folders by copying them from
the mounted image using Windows Explorer.
4) As recovery of your system from a disaster in most cases will be done after booting from the
rescue media, you must test the rescue media as described in the next section - Testing bootable
rescue media (p. 27).
4.1.1 Recommendations for testing that your backups can be
used for recovery
1) Even if you start recovery of the active partition in Windows, the program will reboot into the
Linux environment after the recovery process starts because Windows cannot be left running while
the recovery of its own partition is being carried out. So you will recover your active partition under
the recovery environment in all cases. If you have a spare hard drive, we strongly recommend you to
try a test recovery to this hard drive booting from the rescue media which uses Linux. If you do not
26 Copyright © Acronis, Inc., 2000-2010
Page 27

have a spare drive, please, at least validate the image in the recovery environment. A backup that
can be read during validation in Windows, may not always be readable under Linux environment.
When you use the Acronis True Image Home rescue media, the product creates disk drive letters that might
differ from the way Windows identifies drives. For example, the D: drive identified in the standalone Acronis
True Image Home might correspond to the E: drive in Windows. To be on the safe side, it is advisable to assign
unique names to all partitions on your hard drives. This will make finding the disk containing your backups
easier.
2) It may also be useful to complete all the steps in the Recovery Wizard right up to the Summary
screen, but not click the Proceed button. This will allow you to simulate the recovery process and to
make sure that Acronis True Image Home recognizes both the drive containing your backups and the
target drive. After completing all the Recovery Wizard's steps click Cancel on the Summary screen.
You may repeat this until you feel sure of your settings and choices.
3) Users of the Enterprise and Ultimate editions of Windows 7 now have a way of testing whether
they will be able to boot from the recovered system partition. Acronis True Image Home allows
booting from a tib file containing a system partition image (though it is converted into a VHD, which
is used for actual booting). So if you are able to boot from such backup, you almost certainly will be
able to boot after an actual recovery from that backup.
4.1.2 Additional recommendations
1) Many IT professionals recommend that you have at least two copies of your system backup (three
are even better). To be on the safe side, it is further recommended to keep one copy of a backup in a
different location from the other (preferably on other premises – for example, at work or at a friend's
home, if you use the backed up computer at home). One more argument in favor of several backups:
when starting recovery, Acronis True Image Home deletes the target partition (or disk), so when you
have just a single backup, the moment the system partition is deleted on the computer being
recovered you are at great risk - the only thing you have is the image being recovered and if it is
corrupted you are in big trouble.
2) It is better to format the hard drive used for storing your backups to the NTFS file system rather
than FAT32. This is due to the 4GB file size limit on FAT32 disks. So if your backup has a size of about
100GB, Acronis True Image Home will split it into 25 files. When there are several such full backups
on the hard disk, the number of files will multiply accordingly. This may be inconvenient if, for
example, you would like to move the backup to another location using Windows Explorer.
3) If you have only one computer at home, it is advisable to print some information that may be
helpful in recovering from a disaster, because you may not be able to use the Internet. Keep the
printed material in a safe place along with the rescue CD/DVD or another rescue media.
4.2 Testing bootable rescue media
To maximize the chances of your computer's recovery if need arises, you must test that your
computer can boot from the rescue media. In addition, you must make sure that the recovery media
contains all drivers required for operation of your mass storage devices and network adapter.
1) If you purchased a boxed version of the product that has a bootable CD, please, make sure that
your computer can boot from this CD. Though Acronis try to place drivers for the latest hardware on
the bootable CD, an almost infinite variety of hardware configurations exist, so we cannot give you a
one hundred percent guarantee of being able to boot from the rescue CD.
27 Copyright © Acronis, Inc., 2000-2010
Page 28

2) If you purchased the program after downloading it, you absolutely must create a bootable rescue
CD (or other rescue media, for example, a USB stick) following the recommendations given in the
User's Guide or program's Help and then make sure this rescue media is bootable on your computer.
You must configure your computer so as to enable booting from the rescue media and make your
rescue media device (CD-ROM/DVD-ROM drive or USB stick) the first boot device. See Arranging boot
sequence in BIOS (p. 187);
In case you have a rescue CD, press a key to start booting from the CD, as soon as you see the
prompt “Press any key to boot from CD”. If you fail to press a key within five seconds, you will need
to restart the computer. When using other rescue media, the procedure will be similar.
3) After the computer boots into the recovery environment, check that it detects all the hard drives
you have in your system, including external ones, if you use them for storing backups. Incidentally,
you must attach the external drive(s) before booting from the rescue media, otherwise the recovery
environment might not detect the drive(s).
4) If you store your backups on the network, you should also check that you can access the network
in the recovery environment. When booted from the rescue media, Acronis True Image Home might
not detect the network. If no computers are visible on the network, but the Computers near me icon
is found under My Computer, ensure that a DHCP server is running on your network. If you don't use
a DHCP server, specify network settings manually in the window available at Tools & Utilities →
Options → Network adapters.
If the Computers near me icon is not available under My Computer, there may be problems either
with your network card or with the card driver shipped with Acronis True Image.
Selecting video mode when booting from the rescue media
When booting from the rescue media the optimal video mode is selected automatically depending
on the specifications of your video card and monitor. However, sometimes the program can select
the wrong video mode, which is unsuitable for your hardware. In such case you can select a suitable
video mode as follows:
1. Start booting from the rescue media. When the boot menu appears, hover the mouse over
Acronis True Image Home (Full version) item and press the F11 key.
28 Copyright © Acronis, Inc., 2000-2010
Page 29
2. When the command line appears, type "vga=ask" (without quotes) and click OK.
3. Select Acronis True Image Home (Full version) in the boot menu to continue booting from the
rescue media. To see the available video modes, press the Enter key when the appropriate
message appears.
4. Choose a video mode you think best suitable for your monitor and type its number in the
command line. For instance, typing 338 selects video mode 1600x1200x16 (see the below figure).
Incidentally, when there is a digit or letter before a three-digit number, you can also select such
video mode by typing the corresponding single digit or letter ("v" in our instance).
5. Wait until Acronis True Image Home (Full version) starts and make sure that the quality of the
Welcome screen display on your monitor suits you.
29 Copyright © Acronis, Inc., 2000-2010
Page 30

To test another video mode, close Acronis True Image Home and repeat the above procedure.
After you find the optimal video mode for your hardware, you can create a new bootable rescue
media that will automatically select that video mode.
To do this, start Acronis Media Builder, select the required media components, and type the mode
number with the "0x" prefix (0x338 in our instance) in the command line at the "Bootable media
startup parameters" step, then create the media as usual.
4.3 Creating a custom rescue CD
In most cases you can use a standard rescue CD created with a help of Acronis Media Builder. For
more information see Creating bootable rescue media.
If the recovery environment cannot detect some of the hard disk drives or the network adapter,
usually there is a problem with the drivers. So when the standard rescue CD lacks some of your
hardware drivers, you need to create a custom one.
The Linux-based recovery environment used by Acronis does not provide the ability for users to add
new drivers. Because of this, you should request Acronis Customer Service Department to create a
custom rescue CD that will have all the drivers you need.
Before making a request, collect the information about your system. Select Generate System Report
in the Help menu. Acronis True Image Home will automatically collect the required information and
display a list of what is collected in the report. In the process of creating the report the program may
install some components required for collecting the necessary information. When the report is
complete, click Save As and select the desired folder or leave the default My Documents folder. The
program will archive the report into a zip file. Send the file to the Acronis Customer Service
Department. They will build an iso image of a custom rescue media compatible with your computer
hardware and send you an iso file. Burn this file to a CD/DVD using a program that can handle iso
files such as Nero. Incidentally, this report may also be useful when you request the Acronis
Customer Service Department to help you with a problem.
After burning your custom rescue CD, test it to make sure that your hard disk drives and network
adapter are now detected in the recovery environment.
30 Copyright © Acronis, Inc., 2000-2010
Page 31

5 Getting to know Acronis True Image Home
5.1 Program workspace
Starting Acronis True Image Home takes you to the Welcome screen. This screen provides quick
access to backup and recovery features, as well as highlights any issues with your system's
protection.
Your system is considered fully protected when it is backed up and a bootable rescue media is
created. If some of the aforementioned have not been done, Acronis True Image Home shows the
following links allowing to solve the protection issues: Back Up My System, Create Bootable Rescue
Media. After an issue is solved, the corresponding link disappears.
Clicking the items in the right pane takes you to the corresponding screen where you can either start
the backup or recovery task immediately or make further selections.
The My favorites area in the right pane lists the features you have used most often and provides
shortcuts to them in case you would like to use the features again. The Recent backups area lists the
backups you have recently run and allows you to update the backup archives with just one click.
You can easily access the Acronis True Image Home features through the so called sidebar occupying
the left side of the screen. Choosing an item on the sidebar takes you to a screen, where you can
access the corresponding features.
31 Copyright © Acronis, Inc., 2000-2010
Page 32

Acronis True Image Home uses wizards, which guide you through many operations. Like the main
program window, wizards also have the sidebar listing all the steps (both required and optional)
needed for completing the operation. For example, see the Backup Wizard screen shot below.
The completed steps are marked with green checkmarks. The green arrow shows the current step.
After you complete all the required steps and come to the Finish step, the program displays the
Summary screen. If you wish to omit the optional steps, read the summary of the operation to be
performed (to make sure that the default settings satisfy you) and then click Proceed to start the
task. Otherwise, click Options to go to the optional steps where you can change the default settings
for the current task.
Taskbar notification area icons
During most of the operations, special indicator icons appear in the Windows taskbar notification
area (the right portion of the status bar with the clock). If you mouse over the icon, you will see a
tool tip indicating the operation's progress or state. Right-clicking on the icon opens a shortcut menu
where you can change operation's status or cancel the operation if necessary. This icon doesn't
depend on the main program window being open. It is present for background execution of
scheduled tasks as well.
5.2 Acronis One-click Backup
The Acronis One-Click Backup tool allows you to begin protecting your computer as soon as you
install Acronis True Image Home. During installation the program creates Acronis One-Click Backup
shortcut on the desktop.
Double-clicking the shortcut starts the One-Click Backup tool, which automatically backs up your
system partition and the Master Boot Record (MBR) to a location it considers the optimum place for
backups. If there is no suitable location for the backup, the program displays an error message.
By the way, later you will be able to refresh the system partition backup by double-clicking the
shortcut again.
32 Copyright © Acronis, Inc., 2000-2010
Page 33
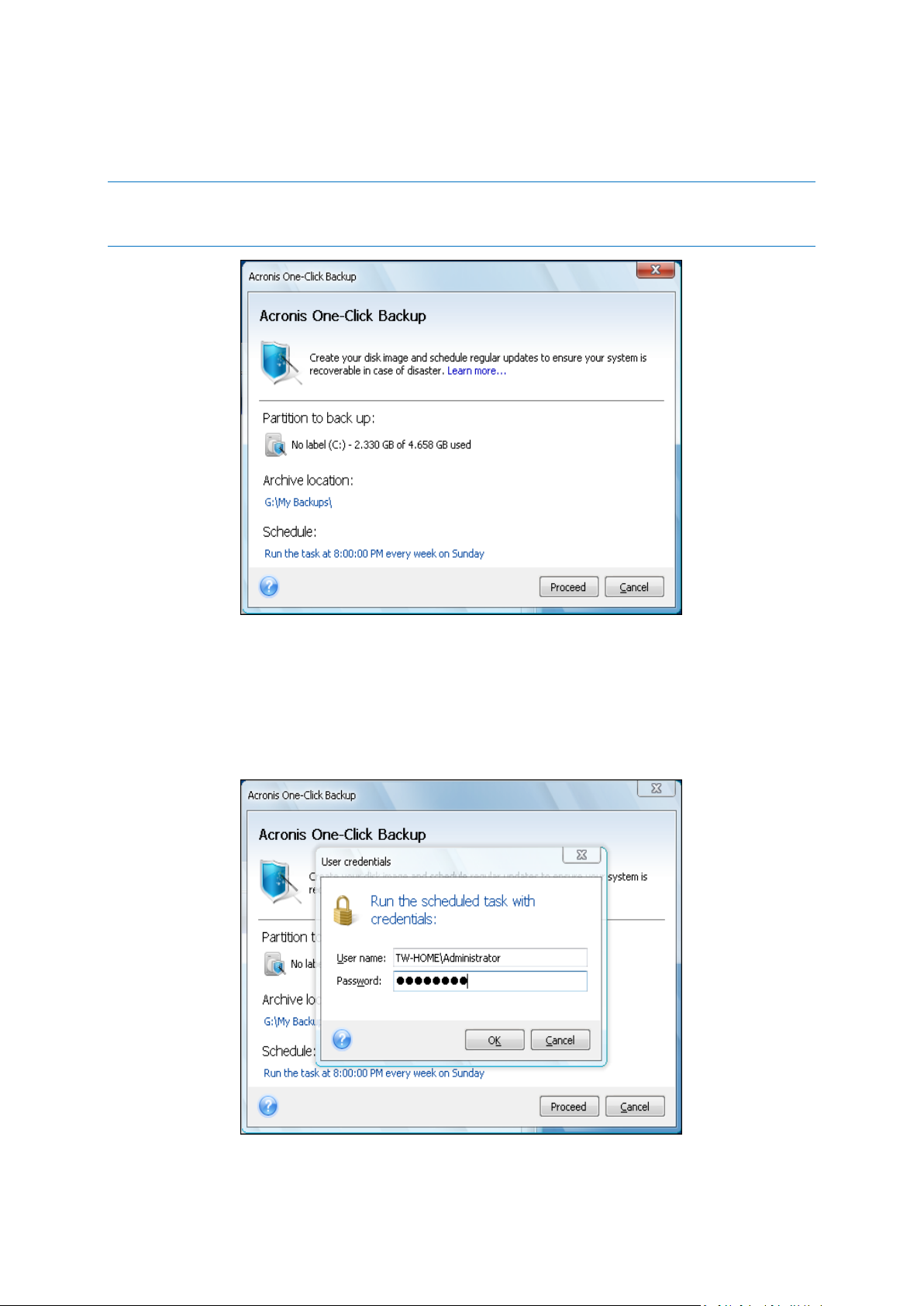
If you choose to not use the One-Click Backup shortcut, Acronis True Image Home will offer to
perform One-Click Backup during the first start after installation, as well as schedule subsequent full
backups – see the screen shot below.
The Acronis One-Click Backup tool performs only full backups of the system partition; scheduling an incremental
or differential backup is not possible. In addition, it does not support backup of drives protected by BitLocker
Drive Encryption in Windows Vista.
As we already mentioned, Acronis True Image Home offers the optimum place for backups.
If you would prefer another storage location, click the link with the default path to the location under
the Archive location: line and select the storage location most suitable for you.
Clicking Proceed will start the backup task. But before proceeding with the backup, the program will
ask you under whose user credentials the subsequent scheduled backups will run.
33 Copyright © Acronis, Inc., 2000-2010
Page 34

Clicking Cancel will cancel One-Click Backup. If you decide to use this feature later, select Tools &
Utilities on the sidebar and then choose One-Click Backup in the right pane of the screen.
In case the archive storage location is a USB flash drive, the backup will begin automatically when the
device is plugged in but only if a scheduled backup has been missed. The USB flash drive must be the
same as the one used for all previous backups; if you plug in another flash drive, the backup process
won't start.
The system will always keep the last backup archive. When a task for the current backup finishes, the
old backup is deleted – freeing up space for the next One-Click Backup.
If there is not enough free space on your PC, the program will notify you that it cannot back up your
system and will suggest that you specify a destination for backup yourself.
5.3 Main screens
And now let's get acquainted with some of the other screens you will use while working with Acronis
True Image Home.
To go to one more screen of interest, click Recovery on the sidebar.
The Data recovery and backup management screen gives detailed information on your backup
archives and provides for quickly performing operations on these archives – Recover, Validate, Move,
Remove, Consolidate, Update, Explore backup archives, as well as Mount, Convert image backups by
right-clicking on an archive and choosing the required operation. This starts the appropriate wizard
or performs the appropriate action.
In addition, this screen provides for recovery of your data from Nonstop Backup and Online Backup
storages by clicking the appropriate link.
34 Copyright © Acronis, Inc., 2000-2010
Page 35
Here you can also edit comments for backups, see detailed information on the backups, and assign
ratings to your backups. For instance, you may want to assign a high rating to an important backup. A
backup rating is indicated by the number of "stars" in the Rating column (more stars means a higher
rating). The default rating is three stars, but you can raise or lower it by clicking on the stars in the
column. The assigned backup ratings may be helpful, for example, when sometime later you will
need to consolidate the backups stored in an archive – it will be easier to choose which backups to
keep after consolidation. For more information on manual backup consolidation see Consolidating
backups (p. 157). In addition, these ratings might save you a lot of time you will otherwise spend on
exploring multiple files in your backup archives, trying to guess which of the outdated backups can be
deleted without losing important data.
Furthermore, this screen shows the results of searches for backup archives and their content. To
perform a search, enter a search string into the Search field at the top right of the Acronis True Image
Home window and then click the magnifying glass icon. For more information see Searching (p. 141).
Another useful screen shows the log of program operations and scheduled tasks. A calendar provides
quick access to the logs (for past dates) or tasks (for future dates). You just click on a desired date.
For more information see Viewing Tasks and Logs (p. 153).
We will not bore you with a description of other screens, because many of them are self-explanatory
and some are described in the appropriate chapters of this guide. In addition, you can always open
contextual help by clicking the corresponding button.
Incidentally, you can also select most of the features through the main program menu, which is
always at your disposal on the toolbar.
35 Copyright © Acronis, Inc., 2000-2010
Page 36

5.4 Options screen
Acronis True Image Home has options related to its appearance and various program functions. To
view or edit the default options, choose Tools & Utilities→ Options in the main program menu.
The Backup options item provides for making settings to be used by default in any backup task. You
can modify the settings depending on your backup needs. For detailed information on the backup
options and possible settings see Fine-tuning your backups (p. 76). In addition, you can change the
backup options while configuring a specific backup task. In such case the changed options will be
used only for this task.
Similarly, the Recovery options item provides for making settings to be used by default by any
recovery task. For detailed information on the recovery options and possible settings see Setting
default recovery options (p. 99). As with the backup options, you can change the recovery options for
a specific recovery task.
The Local storage settings item provides for making other settings related to the backup process, for
example, they may have a more or less noticeable effect on the backup process speed. For more
information see Fine-tuning your backups (p. 76).
The Search options allow you to enhance the Search function by integrating it with Windows Search
or Google Desktop search engines. If you have one of those search engines installed, you can include
tib files in their index files by selecting the appropriate box in the Desktop search options window.
For more information see Windows Search and Google Desktop integration (p. 142)
The Notifications options allow you to enable sending of notifications upon any backup/recovery
operation completion either by E-mail or through the Messenger (WinPopup) service. By default all
notifications are disabled. For more information see Operation results notification (p. 151).
The Appearance options allow modifying the appearance of the program's user interface by selecting
a font to be used on screens, in dialogs, etc. You can also modify a font to be used in the menu items.
To view the appearance of a concrete font, click the "..." button, select the font and have a look at
the sample text. If you are satisfied with the font's appearance, click OK, otherwise try another font
or click Cancel. In addition, the Appearance options let you filter all tasks created on your computer.
36 Copyright © Acronis, Inc., 2000-2010
Page 37

By default you see only your own tasks, but you have the option to view or manage tasks created by
other users. To do so, choose Filter and unselect the Show only tasks created by a current user box.
The Feedback option allows you to quit the Acronis Customer Experience Program, if you decided to
join it during Acronis True Image Home installation or join the program by selecting the Yes, I want
to participate in the program radio button. If you want to know more about the Customer
Experience Program, click the Learn more link.
If modifying the default options does not provide the desired results or if you just want to restore the
default options values set during Acronis True Image Home installation, click Reset all to default on
the toolbar. When you need to set the default values only for a selected option, click Reset the
current to default on the toolbar.
37 Copyright © Acronis, Inc., 2000-2010
Page 38

6 Creating backup archives
6.1 Preparing for your first backup
First of all you should decide where to store your backups. Acronis True Image Home supports quite
a lot of storage devices. For more information see Supported storage media (p. 14). Since hard disk
drives are now quite inexpensive, in most cases purchasing an external hard drive for storing your
backups will be an optimal solution. In addition to enhancing the security of your data – you can keep
it off-site (for example, at home if you back up your office computer and vice versa), many models
are hot-pluggable, so you can attach and detach the drive as required. You can choose various
interfaces – USB, FireWire, eSATA depending on the configuration of your computer ports and the
required data transfer rate. In many cases the best choice will be an external USB hard drive. If you
have a Gigabit Ethernet home network and a dedicated file server or NAS, for example, Buffalo
TeraStation 1.0 TB NAS Gigabit Ethernet Home Server, you can store backups on the file server or
NAS practically like onto an internal drive. Blank optical discs such as DVD-R, DVD+R are very cheap,
so they will be the lowest cost solution for backing up your data, though the slowest one, especially
when backing up directly to DVDs. Furthermore, if your backup consists of several DVDs, data
recovery from such backup will require a lot of disc swapping.
Due to the necessity of swapping discs, it is strongly recommended to avoid backing up to DVDs if the number of
discs is more than three.
If you decide to use an external hard drive, NAS, etc., you will need to check whether Acronis True
Image Home detects the selected backup storage.
Some external hard drives are sold preformatted FAT32. If so, it is better to convert the external hard
drive for backups from FAT32 into NTFS, because of the 4GB file size limit of the FAT32 system. Due
to this limitation, large backup files will automatically split into 4GB chunks, thus increasing the
chance that something will go wrong during data recovery.
If you plan to use an external USB hard drive with your desktop PC, connecting the drive to a rear
connector using a short cable will usually provide the most reliable operation, reducing the chance of
data transfer errors during backup/recovery.
6.2 Deciding what data to back up
As operating systems and application software become ever larger (for example, Windows Vista x64
requires 15GB of free space on a hard disk), usually it will take you several hours to reinstall your
operating system and application software from original CDs or DVDs on a new hard disk.
Furthermore, the practice of buying application software by downloading from the Internet is
becoming more and more popular. If you lose your registration information, for example, the
activation key and/or registration number, which are usually sent by software vendors by e-mail, you
may have problems with restoring your right to use the application. So making a backup of your
entire system disk (making a disk image) will save you a lot of valuable time in case of a disaster, as
well as safeguard you against other possible problems.
Backing up the entire system disk takes more disk space, but enables you to recover the system in
minutes in case of a system crash or hardware failure. Moreover, the imaging procedure is much
faster than copying files and could speed up the backup process significantly when it comes to
38 Copyright © Acronis, Inc., 2000-2010
Page 39

backing up large volumes of data (for details see The difference between file archives and
disk/partition images (p. 18)).
You might think it would take a while to make a copy of your entire hard disk, but the proprietary
technologies used in Acronis True Image Home ensure that image creation is quite fast. And the
program can also back up incrementally or differentially, so after the first time, updating your image
to reflect the current state of your hard disk requires only copying the files that are new or changed
and will take much less time. Because images can save you a lot of time when you need to recover
the operating system or data, it is recommended that you make them part of your backup strategy.
You should create images of your primary disk and any other partition you normally use. If you have
multiple partitions on a drive, it is advisable to include all of them in the image, because failure of the
hard drive in most cases will mean that all the partitions it contains also fail.
Although we strongly recommend you to create images of your hard disk on a regular basis, that is
just part of a reliable backup strategy.
Do you have bank records, family photos, videos, etc. you accumulated on your computer for several
years? Hardware and software can be replaced; your personal data cannot, because it is unique.
Though there may be some exceptions, the optimal backup strategy for most users consists of
creating both images and file-level backups.
After the initial full backup, file-level backups usually take comparatively little time to run, making it
easy to back up your data once (or even several times) a day. This ensures that your most recent
backup is never more than a day old. Because they also offer insurance against accidental deletion
(or change) and file damage, file-level backups are an essential part of a good backup strategy. But
file-level backups alone are not sufficient for two main reasons:
1) If your startup hard drive completely fails, you will not be able to do any work until you've
replaced it; and 2) Reinstalling an operating system and applications from their original CDs or DVDs
is a lengthy and tedious procedure that you could avoid with an image of your hard disk.
6.3 Some typical backup scenarios
Below are several scenarios of "classic" backups describing frequently used backup tasks. Depending
on your backup strategy, you may find some of them useful.
6.3.1 Backing up a system partition
It is recommended to back up the system partition when your C: disk consists of a single partition,
though in this case partition backup is equivalent to system disk backup. It is also makes sense to
back up the system partition if it contains all your applications and important data or if you do not
have enough free space for backing up the entire system disk. A system partition backup would be
most helpful when you need to recover the operating system corrupted by a virus, malware or, for
example, after Windows update installation. Recovery on a new hard disk drive is possible too,
though it may be a bit complicated in case you want to create more than one partition on the new
hard disk. Otherwise it is better to back up the entire system disk, especially if it has hidden recovery
or diagnostic partitions created by your computer's manufacturer. Furthermore, a system disk
backup is more convenient when recovering on a new disk. Backing up the system partition may also
be advisable when you like testing a lot of applications or games. Most applications cannot be
uninstalled without a trace, including Acronis True Image Home itself. You can make a basic system
partition backup containing your operating system and main applications like MS Office and Outlook.
39 Copyright © Acronis, Inc., 2000-2010
Page 40

Thereafter you will always be able to recover that basic system state after trying new programs – if
you don't like them or if something goes wrong.
The easiest way of backing up the system partition is using the One-Click Backup either during the
first start of Acronis True Image Home after installation or later. This tool is intended for backing up
only the system partition and MBR. Of course, you can use the Backup Wizard too, but here is the
procedure for using the One-Click Backup tool (not during the first start).
1. If you want to use your external drive for backing up the system partition, attach and power it on
before starting Acronis True Image Home.
Choose Tools & Utilities → One-Click Backup in the main program menu. Acronis True Image Home
will offer the destination for storing your backup (if you do not have the Acronis Secure Zone, the
destination will be the attached external hard drive). If you would prefer another backup destination,
click the link under the Archive location: line and select the storage location most suitable for you.
1. By default the One-Click Backup tool schedules subsequent full backups of your system partition
once every seven days, but you can change the interval between backups or cancel scheduling.
2. After you finish settings, click Protect to start the backup task.
It is recommended to validate the created backup by running a validation task either manually or on
schedule.
The Acronis One-Click Backup tool performs only full backups of the system partition; scheduling an incremental
or differential backup is not possible.
For those interested in how One-Click Backup tool selects a destination for backup, here is the
algorithm the program uses:
1) First of all the program estimates the space required for operation of the One-Click Backup tool.
2) If you have upgraded from a previous Acronis True Image Home version and already have Acronis
Secure Zone, the program will check its size and when the size is sufficient for backup, it will use
Acronis Secure Zone. In case the zone is too small for backing up the system partition, the program
will move to the next best option.
3) If there is an external hard drive with enough free space, your system partition backups will be
stored on that drive, as such backup place will provide better protection for your computer.
4) If the first two options are unavailable but you have at least two internal hard drives, the program
will back up to a non-system hard drive using a partition with the maximum free space.
5) If your computer has only one hard drive with several partitions (not counting hidden ones), then
the program will use a non-system partition with maximum free space.
6) Finally, if your computer has only one hard drive with a single partition (not counting hidden ones)
with enough free space, the program will suggest creating Acronis Secure Zone to use it for backup. If
you agree, the program will create the zone and use it for storing the backup.
If you start Acronis One-Click Backup the first time by double-clicking the appropriate shortcut, the program will
not suggest creating Acronis Secure Zone.
6.3.2 Backing up an entire system disk
When your backup storage device has enough free space, it is advisable to back up the entire system
disk. Such a backup is most suitable for recovering your system and applications both when you need
40 Copyright © Acronis, Inc., 2000-2010
Page 41

to recover them on the original hard disk drive or a new one, e.g. after your hard drive failed.
Incidentally, if your system disk contains several partitions, an entire disk backup also provides for
recovery of any individual partition.
Because system disk backups are the most important for disaster recovery, it is advisable to check
both the system disk and the hard disk to be used as the backup storage for errors with the help of
Microsoft's Chkdsk utility, which is part of Windows. The utility can repair errors and locate bad
sectors.
You can back up the system disk both in Windows and in the recovery environment. Before starting a
system disk backup in Windows it is advisable to close such applications as MS Outlook and DBMS
programs.
Though the program locks the system partition while making a so called "snapshot" (see Acronis True
Image Home basic concepts (p. 10)), some users still prefer backing up the system disk when
Windows is not running.
The subsequent description is made under the assumption that you boot from your bootable rescue
media and the program "sees" all your hard drives and other storage devices in the recovery
environment. See Testing bootable rescue media (p. 27).
Attach the external drive if it is to be used for backup storage and make sure that the drive is powered on. This
must be done before booting from Acronis rescue media.
1. Arrange the boot sequence in BIOS so as to make your rescue media device (CD, DVD or USB
stick) the first boot device. See Arranging boot sequence in BIOS (p. 187).
2. Boot from the rescue media and select Acronis True Image Home (Full version).
3. Click the My Disks link under Back Up on the Welcome screen.
4. Select the system disk as the source for backup by checking the appropriate disk box (this will
select all partitions on the disk, including the hidden ones).
5. Choose a target archive for the backup being configured – you can either add a new backup to an
existing archive or create a new one. Choose the backup location and assign a name to the
backup to be created. It is better to use meaningful names, e.g. Disk1_full.tib.
41 Copyright © Acronis, Inc., 2000-2010
Page 42

6. Carefully read the Summary of actions to be performed during backup and click Proceed if you
are satisfied with the backup task settings, otherwise click Options on the Summary screen to
change the settings.
7. Select a backup method. For a more detailed explanation of the methods see Full, incremental
and differential backups (p. 18). When performing backups in the recovery environment many
users prefer full backups, though you may choose another method depending on your needs.
8. Set the backup options. When backing up in the recovery environment you must set the options
manually for each backup task. You can encrypt the backup for data protection and select a
compression level (the program shows estimated backup sizes for each level). You can also
choose to validate the backup immediately after its creation, though it can be done later. In any
case validation of a system disk backup is best performed in the recovery environment, as you
will use the recovery environment when recovering the system partition or disk.
9. If you wish, provide comments to the backup. You will also be able to add comments later.
10. Click Proceed to start the backup.
It is extremely important to validate the system disk backup before trying to recover, because
Acronis True Image Home deletes the original partition(s) on the disk before starting recovery and if
it finds a problem with the backup file during recovery, you are left with nothing. It is even better to
try system disk recovery to a spare hard drive, if you have one.
6.3.3 Backing up a data partition or disk
Your personal data (MS Office documents, financial documents, pictures, music, videos, etc.) require
protection in no less degree than your operating system. Such data is better kept separately from
your operating system and applications on a dedicated partition or disk. This speeds up data partition
or disk image backup, as well as recovery. It is recommended to perform data disk backup in
Windows, because in most cases Windows drivers for storage devices operate better and faster than
the respective Linux drivers used in the recovery environment. In addition, recovery of data disks and
partitions usually occurs in Windows. Let's create a data disk backup task in Windows.
Attach the external drive if it is to be used as the backup destination and make sure that the drive is powered
on. This must be done before starting Acronis True Image Home.
1. Click the My Disks link under Back Up on the Welcome screen.
2. Select the box of your data partition or disk on the What to back up screen.
3. Choose a target archive for the backup task being configured – you can either add a new backup
to an existing archive or create a new one. Choose the backup location and assign a name to the
backup to be created. It is better to use meaningful names, e.g. Data_disk.tib. When you store
different backup archives in the same location, e.g. on an external drive, you may want to create
a new folder when creating a new backup archive. To do this, click Create new folder in the
toolbar, then assign a meaningful name to the folder.
4. Carefully read the Summary of actions to be performed during backup and click Proceed if you
are satisfied with the backup task settings, otherwise click Options on the Summary screen to
change the settings.
5. The first optional step offers to schedule the backup task. Scheduling together with a backup
method and automatic consolidation rules allows implementing a desired backup strategy. For
more information see Examples of backup scheduling scenarios (p. 115).
6. Choose a backup method. For a more detailed explanation of the methods see Full, incremental
and differential backups (p. 18). Let's reiterate that selection of the backup method may depend
on the desired backup strategy.
42 Copyright © Acronis, Inc., 2000-2010
Page 43

7. At the next step you may exclude certain files and folders from backup. For example, you
transferred some movies from your DVDs to the data disk. They occupy quite a lot of space and it
doesn't make sense to back them up because you have the DVDs.
8. Set the options for the backup task being created. For example, when your data disk contains
sensitive information, you may want to protect the information by encryption. You can also
choose to validate the backup right immediately after its creation, though it can be done later.
9. Set the automatic consolidation rules when required by the chosen automatic backup archive
management strategy. For more information see Setting automatic consolidation (p. 74).
10. If you wish, provide comments to the backup. You will also be able to add comments later.
11. Click Proceed when you are satisfied with the backup task settings.
If you have not included validation into the backup task settings, it is strongly recommended to
validate the backup later – by performing the validation task either manually or on schedule. You
should get into the habit of validating your backups.
6.3.4 Backing up files/folders
Though image backups of a data disk/partition contain all files and folders, there may be cases when
backing up an entire partition isn't efficient. Suppose you are working on an urgent project and make
changes only in the related files. Backing up the entire data partition with the project files will require
much more time and disk space, so backing up just the project files will be a more efficient solution.
For such situations Acronis True Image Home provides the My Data backup type.
Attach the external drive if it is to be used as the backup destination and make sure that the drive is powered
on. This must be done before starting Acronis True Image Home.
1. Start Acronis True Image Home and click the Files & Folders link under Back Up on the Welcome
screen.
2. Set a checkmark in the box of your project files folder (e.g. Myproject) on the What to back up
screen. The right side of the Files to back up pane will show the folder contents with all the
selected files and subfolders. There you can unselect the files you do not need to back up, if any.
3. Choose a target archive for the backup task being configured – in this case create a new one.
Choose the backup archive location and assign a name to the backup to be created. It is better to
use meaningful names, e.g. Project.tib. When you store different backup archives in the same
location, e.g. on an external drive, you may want to create a new folder when creating a new
backup archive. To do this, click Create new folder on the toolbar, then assign a meaningful
name to the folder.
4. As your project will take several days, it is reasonable to back up the project files at least once a
day by setting an appropriate schedule, so click Options at the Summary step to be able to create
a schedule.
5. Select the Daily scheduling option. If you think that your work results will be safer being backed
up more often, select Run the task every x hour(s) until the end of the day box and specify the
interval in hours. Your files can be open when backups are running, though it might be advisable
to close them when working with a database.
6. Choose a backup method. If you would like to save several versions of your project files, select
the Incremental method. Thus Acronis True Image Home will at first create a full backup, then
will supplement it with incremental backups till the project is finished. After finishing the project
you will be able to either delete the task or disable it until you need to run the task again.
7. The next step allows you to exclude from the backup temporary files created, e.g. by Microsoft
Word by providing appropriate criteria.
43 Copyright © Acronis, Inc., 2000-2010
Page 44

8. When the project files contain sensitive information, the backup options allow protecting your
backups with a password and encryption. In addition, you can set validation of backups
immediately after creation – this makes sense in case of frequent backups as it relieves you of
remembering to validate them later.
9. The next step allows setting automatic consolidation of the backup archive, for example, when
the "age" of backups exceeds the desired time period (30 days by default).
10. If you wish, provide comments to the backup. You will also be able to add comments later.
11. Click Proceed when you are satisfied with the backup task settings.
6.3.5 Backing up to a network share
With Acronis True Image Home you can back up your data to a network share. This may be desirable,
for example, when you have a file server and want to use it for backing up data from PCs in your
home network. Depending on your backup strategy, you may want to back up just files and folders or
entire disks. One more consideration is the data transfer rate provided by your network. For
example, a Gigabit Ethernet network has a bandwidth sufficient for all amounts of data to be backed
up. However backing up over Wi-Fi connection may be time-consuming when you need to back up a
hundred gigabytes.
Files and folders or data partitions can be backed up and recovered in Windows. If you plan to back
up your system disk or partition, please, make sure that the standalone version of Acronis True
Image Home can "see" the network share to be used for backups as system recovery will be done in
the recovery environment. After booting from the rescue media make sure that you can browse to
the share in the Backup wizard or Recovery wizard.
It may be advisable to first back up and recover some files to ensure that you can perform those
operations over the network. In addition, it is not recommended to map the drive containing the
network share. Specifying the UNC path makes it easier to establish network connection in most
cases.
Let's suppose you want to back up your system partition.
1. Start Acronis True Image Home and click the My Disks link under Back Up on the Welcome
screen.
2. Select the check box of your system partition on the Source selection screen.
3. When you are connecting to a networked computer, in most cases you will need to provide the
network credentials (user name and password) to access a network share. To do this, select the
Use NT authentication box and enter the user name and password into the appropriate fields.
Pressing the Test authentication and connection button allows testing the ability of the
computer to connect to the selected network share. If testing results in an error message, check
whether you provided the correct credentials and enter the right credentials for the network
share. When the Use NT authentication box is left unselected, the computer will try to log on to
the share with the credentials used for logging on to Windows. Having provided the required
information, click OK to continue. Choose a target archive for the backup task being configured –
you can either add a new backup to an existing archive or create a new one. It is better to use
meaningful names, e.g. Disk_C.tib.
4. Carefully read the Summary of actions to be performed during backup and click Proceed if you
are satisfied with the backup task settings, otherwise click Options on the Summary screen to
change the settings.
44 Copyright © Acronis, Inc., 2000-2010
Page 45

5. The first optional step offers to schedule the backup task. Scheduling together with a backup
method and automatic consolidation rules allows implementing a desired backup strategy. For
more information see Examples of backup scheduling scenarios (p. 115).
6. Choose a backup method. For a more detailed explanation of the methods see Full, incremental
and differential backups (p. 18). Let's reiterate that selection of the backup method may depend
on the desired backup strategy.
7. At the next step you may exclude certain files and folders from backup, e.g. temporary ones.
8. Set the options for the backup task being created. You can choose to validate the backup
immediately after its creation, though it can be done later.
9. Set the automatic consolidation rules when required by the chosen automatic backup archive
management strategy. For more information see Setting automatic consolidation (p. 74).
10. If you wish, provide comments to the backup. You will also be able to add comments later.
11. Click Proceed when you are satisfied with the backup task settings.
45 Copyright © Acronis, Inc., 2000-2010
Page 46

7 Acronis Nonstop Backup
7.1 What is Acronis Nonstop Backup
Acronis Nonstop Backup is a new Acronis True Image Home feature that provides convenient
protection of your disks and files, and allows you to recover from disaster both entire disks and
individual files and even their versions. By default Acronis Nonstop Backup will protect your system
partition, though you can select other partitions and disks to be protected too. Acronis True Image
Home will recommend you the disk (or partition) it considers the best location for storing the backup
data. The storage selection algorithm is similar to that used by the One-Click Backup feature, though
the Acronis Secure Zone cannot be used as the storage for Acronis Nonstop Backup.
Once you start Acronis Nonstop Backup, it will perform an initial image backup of the partition(s)
selected for protection. Having finished this task, Acronis Nonstop Backup will then save changes in
your system and files (including open ones) every five minutes, so you will be able to recover your
system to an exact state in time.
States of the protected partitions will be backed up at 5-minute intervals for the last 24 hours. The
older backups will be consolidated in such a way that Acronis True Image Home will keep daily
backups for the last 30 days and weekly backups until all Nonstop Backup storage space is used.
The consolidation will be performed every day between midnight and 01:00 AM. The first
consolidation will take place after the Nonstop Backup works not less than 24 hours. For example,
you have turned on the Nonstop Backup at 10:00 AM on September 12. In this case the first
consolidation will be performed between 00:00 and 01:00 AM on September 14. Then the program
will consolidate the data every day at the same time. If your computer is turned off between 00:00
and 01:00 AM, the consolidation will start when you turn the computer on. If you turn off the
Nonstop Backup for some time, the consolidation will start after you turn it on again.
You may think that at these backup rates the storage will fill in no time. Do not worry as Acronis True
Image Home will back up only so called "deltas". This means backing up not entire changed files, but
only differences between new and old versions. For example, if you use Microsoft Outlook or
Windows Mail, your pst file may be very large. Furthermore, it changes with each received or sent Email message. Backing up the entire pst file after each change would be a big waste for your storage
space, so Acronis backs up only its changed parts in addition to the initially backed up file.
The program checks partitions and files for changes every five minutes and creates a new time "slice"
only when it finds changes, so the intervals between "slices" can be more than five minutes. In
addition, if, for instance, you are working in Word and do not use the "Save" operation for an hour,
changes in the Word document will not be backed up every five minutes, because the program
checks file changes on the disk and not in the memory.
7.2 Enabling and setting up Acronis Nonstop Backup
You can make settings for Nonstop Backup and enable Nonstop Backup by selecting Backup →
Nonstop Backup on the sidebar and clicking the Nonstop Backup icon on the Acronis Nonstop
Backup screen. After analyzing your computer’s configuration Acronis True Image Home opens the
Nonstop Backup Options window. By default Acronis True Image Home selects your system partition
for Nonstop Backup and offers a storage it considers optimal for keeping Nonstop Backup data. Click
OK in the Nonstop Backup Options window to accept the default settings or change them according
46 Copyright © Acronis, Inc., 2000-2010
Page 47

to your preferences. Incidentally, you can also change the settings later. To do this, click the Settings
icon (the "cog-wheel") on the toolbar of the Time Explorer window when the Nonstop Backup tab is
selected.
Changing Acronis Nonstop Backup settings
The Nonstop Backup Options window allows you to change the settings of Acronis Nonstop Backup.
Protection management - select the partitions on your computer to be protected by Nonstop
Backup. To add a partition, select it on the right pane and click Protect on the toolbar. To remove
a partition from protected ones, select it and click Remove protection on the toolbar.
Removable storage devices cannot be protected by Acronis Nonstop backup.
Storage – select the storage for keeping Nonstop Backup data. Acronis True Image Home shows
here all hard disks and partitions available on your system dividing them into two categories:
acceptable and non-acceptable for creating a Nonstop Backup storage. The non-acceptable
category includes partitions that do not have enough free space for storing the backup data, as
well as partitions you want to protect by Nonstop Backup.
You can try to resolve the problems preventing a partition from becoming an acceptable one. For
instance, if the partition has a sufficient capacity for storing Nonstop Backup data you can try to
make it acceptable by cleaning up the occupied space. To do this, select the partition, click
Resolve on the toolbar, and then click Resolve the insufficient space issue. This will start
Microsoft’s Disk Cleanup utility which will offer various options for freeing up the disk space.
You cannot use mapped/network drives and Acronis Secure Zone as the storage for keeping Nonstop
Backup data.
Content exclusion - select the files and folders to be excluded from protection by Acronis
Nonstop Backup. By default, the program excludes files pagefile.sys and hiberfil.sys on the
system partition, as well as the default folders Windows uses for temporary files. You can
exclude other files and folders by selecting them (click Add folder or Add file on the toolbar and
select items to be excluded) or by creating masks for exclusion using the common Windows
wildcard characters (click Add mask and specify a mask. For instance, to exclude all files with
47 Copyright © Acronis, Inc., 2000-2010
Page 48

.bmp extension, type *.bmp.) You can also exclude files and folders by selecting them in
Windows Explorer and choosing Storages → Exclude from Nonstop Backup in the shortcut menu
that opens by right-clicking on the selected file or folder.
To change the default Nonstop Backup storage, click the Storage item in the Nonstop Backup
settings, select a new storage among acceptable ones and click Create Storage and Make Active on
the toolbar of the Nonstop Backup storage management window.
Having finished the settings, click OK and Acronis Nonstop Backup will start protection with the new
settings.
Acronis Nonstop Backup remains enabled after restarting Windows and even after switching the
computer off.
7.3 Using Acronis Nonstop Backup
Using Acronis Nonstop Backup is easy. After you start Nonstop Backup the program automatically
creates the initial image of the partitions you have selected for protection, and thereafter continues
to back up changes on those partitions until the Nonstop Backup Storage has free space.
Be aware that when all free space is used, Acronis Nonstop Backup does not delete the oldest data
automatically, but simply stops working and notifies you by displaying a balloon message in the
Windows taskbar notification area. In this case you will need either to clean up the obsolete data
manually to free up some space or select another location for Nonstop Backup Storage.
If you select a new location for storage, Acronis Nonstop Backup will create there a new initial image
of the partitions selected for protection, and then will operate like it has done with the previous
storage.
If you select a new storage while the old one is not yet filled up, you will be able to continue using
the old storage after some time. This may be useful when your old storage is an external hard disk
drive. You can disconnect it for a while, e.g. for safekeeping at a friend's house. When you decide to
48 Copyright © Acronis, Inc., 2000-2010
Page 49

use the storage again, attach the drive, select it on the Nonstop Backup storage management
window and make it the active storage.
After you activate the old storage, Acronis Nonstop Backup will consolidate the old backups
according to the algorithm it uses for consolidating backups and will then start to back up changes on
the selected partitions again.
When the need arises to recover some data, your actions will differ depending on what you want to
recover - partitions or files/folders.
A partition is recovered using the Recovery Wizard. If you need to recover a data partition, it is easier
to do in Windows. Recovery of the system partition is better to perform after booting from the
rescue media. For more information see Recovering partitions protected with Acronis Nonstop
Backup (p. 49). The Recovery Wizard allows you to recover files and folders as well, though in many
cases it is more convenient to recover files using Acronis Time Explorer. For more information see
Recovering files protected with Acronis Nonstop Backup (p. 50).
7.4 Recovering partitions protected with Acronis Nonstop Backup
You can recover partitions from Acronis Nonstop Backup Storage using the Recovery Wizard. Let's
first recover a data partition in Windows.
1. Start Acronis True Image Home.
2. Choose Recovery on the sidebar, then click the Disk backups tab on the right pane. Select the
backup archive from which you want to recover files at the Nonstop Backup Storages area. Rightclick on the backup and choose Recover in the shortcut menu to start the Recovery Wizard.
3. Select Recover whole disks and partitions on the Recovery method screen.
4. At the next step select the point in time at which the partition(s) to be recovered was in the
desired state. You can select a point in time for the files that changed within the last 24 hours
and a date for older backups. For backups that were made more than 30 days ago the program
will keep weekly backups highlighting the dates for which backed up data is kept. Having selected
the recovery point click Next.
5. The next steps of the Recovery Wizard are similar to those performed when recovering data
partitions or disks from a "classic" backup. For more information see Recovering a data partition
or disk (p. 89).
Depending on circumstances, recovery of the system partition may be performed both in Windows
and after booting from your rescue media (when Windows does not start). Recovery in Windows is
similar to recovery of a data partition, though it will require reboot. By the way, usually it is safer to
recover the system partition using the rescue media.
When using the rescue media, the recovery procedure is very similar to the procedure used for
recovering the system partition from a "classic" backup, except the Recovery point step that allows
selecting the point in time to which you recover the system partition. For more information see
Recovering your system partition (p. 84).
If you use as a Nonstop Backup Storage an external USB hard drive and after booting from the rescue media the
Disk backups tab does not show backups on that external hard drive in the Nonstop Backup Storages area, click
the Refresh backups button to find them.
Acronis True Image Home safe version does not support recovery from Nonstop Backup Storages.
49 Copyright © Acronis, Inc., 2000-2010
Page 50

7.5 Recovering files protected with Acronis Nonstop Backup
You can recover files from Acronis Nonstop Backup Storage using both the Recovery Wizard and
Acronis Time Explorer.
Recovering files using the Recovery Wizard
1. Choose Recovery on the sidebar, then click the Disk backups tab on the right pane.
2. Select the backup archive from which you want to recover files at the Nonstop Backup Storages
area. Right-click on the backup and choose Recover in the shortcut menu to start the Recovery
Wizard.
3. Select Recover chosen files and folders on the Recovery method screen.
4. At the next step select the point in time at which the files and folders to be recovered were in
desired states. You can select a point in time for the files that changed within the last 24 hours
and a date for older backups. For backups that were made more than 30 days ago the program
will keep weekly backups and will highlight the dates for which backed up data is kept. Having
selected the recovery point click Next.
5. The next steps of the Recovery Wizard are similar to those performed when recovering files and
folders from a "classic" backup. For more information see Recovering files and folders from
image archives (p. 91).
Recovering files using Acronis Time Explorer
Time Explorer provides more flexibility when you need to recover just a few files. It allows you to
view the number of versions of a file kept on the storage, select a specific version, open this version
in the associated application to make sure that the version contains the data you need and recover
just that version.
50 Copyright © Acronis, Inc., 2000-2010
Page 51

1. Choose Recovery on the sidebar, then click Recover data from nonstop backup on the right pane
to open Acronis Time Explorer.
2. Select the partition and then the folder that contains the files you want to recover on the
directory tree in the left pane. The right pane lists the files in that folder. Select the files to
recover. When selecting multiple files you can use the Ctrl and Shift keys like in Windows
Explorer. Having finished selection, right-click on the selected files and choose Recover in the
shortcut menu.
3. Acronis True Image Home opens the Browse for folder dialog. By default the original location
from which the files were backed up will be selected. If necessary, you can select another folder
or create a new folder for the files to be recovered to by clicking the Make New Folder button.
After selecting the folder click OK to proceed with recovery.
If you recover the files to the original folder and Acronis True Image Home finds a file there with the
same name, it will open a dialog window where you can choose what to do with the files: Recover
and replace the file on the disk, Do not recover (to keep the file on the disk), and Recover, but keep
both files (the recovered file will be renamed). If you want to use the choice for all files with identical
names, select the Apply to all files check box.
It is impossible to Recover and replace files on the disk which are being used or locked by the operating system
at the moment of recovery.
If you need to recover a specific version of a file, select the file either in Time Explorer or in Windows
Explorer, right-click and choose View Versions in the shortcut menu. This opens the File Versions
window. Select the required version by its backup time and click Recover on the toolbar. To choose
the right version, you can open the version in the associated application and view the file contents.
Select the file in the right pane and the backup times for all its versions kept on the Nonstop Backup
Storage will be shown in the bottom line of Time Explorer. Choose a version by its backup time, then
right-click on the file in the right pane and choose Open in the shortcut menu. Acronis True Image
51 Copyright © Acronis, Inc., 2000-2010
Page 52

Home will recover the file version to a temporary folder and then will open the file using the
associated application.
7.6 Managing Acronis Nonstop Backup storage
Inevitably the Acronis Nonstop Backup Storage becomes full after a period of time which depends on
the selected Nonstop Backup storage and the number and composition of partitions protected by
Acronis Nonstop Backup.
When your selected Acronis Nonstop Backup storage fills up, you can choose another storage
without losing the previously backed up data.
One more way of managing the Acronis Nonstop Backup storage is cleaning up the data you do not
need anymore. To clean up the storage, select Backup → Nonstop Backup on the sidebar and then
click the link to the active Nonstop Backup storage to the right of Storage for nonstop backups: on
the right pane. This will open the Nonstop Backup Options window. To clean up the active Nonstop
Backup storage, click the Storage item, select the active storage, and then click Clean up on the
toolbar.
Acronis True Image Home displays a window allowing you to select a period of time for deleting the
backups created during that period. Select the required period and click OK.
52 Copyright © Acronis, Inc., 2000-2010
Page 53

8 Online backup
Acronis Online Backup might be unavailable in your region. To find more information, click here:
https://www.acronis.com/my/online-backup/
The main reason for using Acronis Online Backup is that you will be able to keep your data secure by
storing off-site. Because your files are stored elsewhere, they are protected even if your computer
gets stolen or your house burns down. So the risk of data loss as a result of theft, fire, or other
natural disasters is practically eliminated. Online backup is basically a method of off-site data storage
whereby files and folders are regularly backed up on a remote storage. As a result, you can safely
recover any corrupted, lost or deleted files on your computer.
Of course, online backup is not without its shortcomings. If there is a problem with your Internet
connection, you could be left without access to your data for some time. And you won't be able to
boot up your computer from an online backup, so it is advisable to supplement online backup with
image backups to local hard disks.
The biggest drawback of online backup is speed. Even through a fast broadband connection, backing
up your data online will be much slower than backing up to a local hard drive. Depending on the
amount of data you want to store off-site, your first full online backup could last several hours,
though subsequent backups will take much less time, as you'll be backing up only new or changed
files.
If you decide to use encryption, the files will be encrypted before transmission over the Internet and
data will be stored on the Acronis Online Storage in encrypted form, so you can rest assured that
your private information is secure.
8.1 Creating an Online backup account
Performing backups to Acronis Online Storage requires subscription to the Online Backup service.
Select Back Up → Online Backup in the main program menu and then click the Subscribe to Online
Backup service link on the Online Backup Login window. This will open your web browser and take
you to the main Acronis Web site to continue registration.
If you already have an Acronis account, type the e-mail address and password for that account under
"Log in to Your Account" to the right. You will be taken to your account page where you will be able
to subscribe to the Online Backup Service.
If you do not have an Acronis account, fill in the appropriate fields, and the account will be created
for you. Provide your first and last names and e-mail address. You will be offered a country selected
on the basis of the IP address of your computer, though you can select another country, if you wish.
Then provide a password for your new account and confirm the password by retyping it once more in
the appropriate field. When you perform all actions necessary for account registration, please, wait
for an e-mail message that will confirm opening of the account.
To keep your personal data secure, choose a strong password for your online backups, guard it from getting into
the wrong hands, and change it from time to time.
After opening an Acronis Online Backup account, log in to your account page, subscribe to the Online
Backup service, and then wait for an e-mail message describing the details of your subscription plan
and expiration date. Now you can perform your first online backup.
53 Copyright © Acronis, Inc., 2000-2010
Page 54
8.2 Backing up to Acronis Online Storage
To perform an online backup, log on to your Online Backup service account by clicking Backup →
Online Backup on the sidebar and entering your e-mail address used for opening the account and the
password. In order to not enter the password during subsequent logons, you may want to select the
Remember the password check box. Make these settings and click Log In.
After the program connects to Acronis Online Backup Server, select a computer for connection to the
Online Storage. When logged on to the online backup service for the first time, register a computer
for work with Online Backup. To do this, click New computer, then type in the computer name.
If you want to use encryption for the data to be stored on the Online Storage, enter an encryption
key to be used for encrypting your data. Entering the encryption key automatically enables
encryption of all data stored on the Online Storage. The encryption key is similar to a password, but it
is used for unlocking access to your encrypted data. Acronis Online Backup uses the industrystandard AES-256 encryption algorithm. The data will be encrypted before transferring through the
Internet to the Online Storage and will be stored in encrypted form. You need to enter the
encryption key for the computer only once during its registration, though it will be required if you try
to recover files backed up from this computer when connected to the Online Storage from another
computer. Having made all the necessary settings, click Continue.
Until you log off, subsequent connections to the Online Storage from this computer will occur
automatically - you just need to select Online Backup.
If you already registered the computer, select it from the list of registered computers, then click
Continue. By default your current computer is selected for registration.
54 Copyright © Acronis, Inc., 2000-2010
Page 55

When the computer connects to the online storage, the Online storage screen with your storage
space quota appears.
If you have performed backup on this computer before, you will see how much Online storage space
is occupied by the backed up files and folders. The screen also shows the space occupied by the data
backed up from other computers (if any) and the remaining free space on the Online storage in
accordance with your quota.
When you are going to back up from the current computer for the first time (or need to change the
files and folders selected for online backup), click What to Back Up. This will open the What to Back
Up window with two tabs: Include and Exclude.
The Include tab displays your computer's file and folder tree. The area to the right of the tree shows
the contents of a selected folder. This tab allows you to select individual files and folders for backing
up, as well as data categories. For more information on categories see Selecting what data to back up
(p. 68). Furthermore, you can create a custom category by clicking Add new category. For more
information see Creating a custom data category for backups (p. 83). Select the files and folders that
need to be backed up.
The Exclude tab enables hidden and system files and folders to be excluded from online backup, as
well as files meeting the criteria you specify. Excluding unnecessary files may be useful for backups to
the Online storage as the data transfer rate and available space are limited.
You can also exclude/include files and folders by selecting them in Windows Explorer and choosing Storages →
Exclude from Online Backup (or Include in Online Backup ) in the shortcut menu that opens by right-clicking on
the selected file or folder. This shortcut is only available when you are logged on to the Online Backup service.
Having finished selecting files and folders for backing up to the Online storage and for excluding from
backup click OK. If you do not unselect the Run the updated online backup task now check box that
is selected by default, the online backup task will start immediately. Otherwise it will run according
to the schedule you set.
55 Copyright © Acronis, Inc., 2000-2010
Page 56

To schedule online backups, click the Edit schedule... link. For instance, you may want the backups to
be performed at night in order to not interfere with your web surfing. For more information see
Scheduling tasks (p. 109). When you finish scheduling and click OK, the schedule information will be
shown above the Edit schedule... link.
By default Acronis True Image Home schedules daily backups to the Online Storage with randomly selected
backup start time.
You can quickly start updating the files and folders backed up on the Online storage without creating
a backup schedule. To do so, click Update Backup Now. This may be useful when you want to back
up immediately some important changes to the files backed up on the Online Storage. Incidentally, if
the last scheduled online backup has failed, this link changes to Update Backup Now (Last backup
failed), allowing you to repeat the failed backup task right away. If you have suspended the previous
online backup for any reason, the link text will be as follows: Update Backup Now (Last backup
suspended).
8.3 Recovering data from Online Storage
Log on to your online backup account by clicking Backup → Online Backup on the sidebar and
entering your e-mail address used for opening the account and the password. After the program
connects to Acronis Online Backup Server, select a computer for registration on the Online Storage.
By default your current computer is selected for registration. Click the Continue button. The Online
storage screen opens with this computer selected. If you have data backed up from more than one
computer, you can select on this screen the computer from which to recover required files. Naturally,
you can only browse and recover the data backed up from other computers.
If you encrypted data on another computer, you will be asked to enter the encryption key for the
computer to get access to its data on the Online Storage.
1. Click Browse on the Online storage screen.
56 Copyright © Acronis, Inc., 2000-2010
Page 57

Acronis Time Explorer will be opened with the Online Storage tab selected.
2. This window also allows choosing the computer from which you backed up the files and folders
you need to recover. Select the computer by its name on the directory tree under Online Storage
in the left pane.
3. By default the state of the Online Storage after the latest backup is displayed, so the latest
versions of the files and folders will be recovered. If you need to recover earlier versions, select
the date and time on which you want to recover the state of the files and folders.
4. Select the folder containing the files you want to recover in the left pane. The right pane lists the
files in that folder. Select the files to recover. When selecting multiple files you can use the Ctrl
and Shift keys like in Windows Explorer. Having finished selection, click the Recover icon on the
toolbar.
5. Acronis True Image Home opens the Browse for folder dialog. By default the original location
from which the files were backed up will be selected. If necessary, you can select another folder
or create a new folder for the files to be recovered to by clicking the Make New Folder button.
After selecting the folder click OK.
If you recover the files to the original folder and Acronis True Image Home finds a file with the same
name there, it will open a dialog window where you can choose what to do with the file: Recover
and replace the file on the disk, Do not recover (to keep the file on the disk), and Recover, but keep
both files (the recovered file will be renamed). If you want to use the choice for all files with identical
names, select the Apply to all files check box.
It is impossible to Recover and replace files on the disk which are being used or locked by the operating system
at the moment of recovery.
If you need to recover a specific version of a file, select the file, right click and choose View Versions
in the shortcut menu. This opens the File Versions window. Select the required version by its backup
time and click Recover on the toolbar. You can also recover the version by dragging it into a selected
folder.
57 Copyright © Acronis, Inc., 2000-2010
Page 58

To choose the correct version, you can open the version in the associated application and view the
file contents. Select the file in the right pane and the bottom line of Time Explorer will show the
times of backing up all its versions kept on the Online Storage. Choose a version by its backup time,
then right-click on the file in the right pane and choose Open in the shortcut menu. Acronis True
Image Home will recover the file version to a temporary folder and then will open the file using the
associated application.
8.4 Managing Online Storage
As the available space on Acronis Online Storage is limited depending on the chosen backup plan,
you need to manage your Online Storage space by cleaning up the obsolete data. Cleanup can be
done in a variety of ways. The most "drastic" one is removing a computer registered on the Online
Storage, if you have registered more than one. Removing a computer results in deleting all data that
was backed up from that computer, so such an operation must be carried out with caution. To
remove a computer, select it on the Online storage screen by its name and click Remove
<Computer_name>, then click Yes in the confirmation window. After the deletion finishes, click
Refresh on the toolbar to refresh the storage state shown.
The Online backup options provide for automatic cleanup of the Online Storage. You can specify
deletion of files that have been kept on the storage longer than the specified number of months or
days. In addition, you can set the maximum number of file versions to be kept on the Online Storage.
You can accept the default settings for those options shown above the Change cleanup options...
link or set the values you need. To change the above options, click the link and set the desired values.
You can also manage Acronis Online Storage by deleting individual files or even some of their
versions.
1. Click Browse on the Online storage screen.
Acronis Time Explorer will be opened with the Online Storage tab selected.
58 Copyright © Acronis, Inc., 2000-2010
Page 59

2. Select the computer from which you backed up the files you need to manage by its name on the
directory tree under Online Storage in the left pane.
3. Select the folder containing the files you want to manage in the left pane. The right pane lists the
files in that folder.
4. If you want to delete some versions of a specific file, select the file and click View Versions on
the toolbar. This opens the File Versions window. Select the version you want to delete and click
Remove on the toolbar. When you want to delete several versions, use the Ctrl and Shift keys
like in Windows Explorer to select the versions for deletion and then click Remove on the
toolbar. Having finished removing the versions, click OK. To delete all versions of the file click
Remove All on the toolbar.
5. If you want to delete a file, select it in the right pane. When selecting multiple files for deletion
you can use the Ctrl and Shift keys like in Windows Explorer. Having finished selection, right-click
on the selection and choose Delete in the shortcut menu.
6. After you finish managing the Online Storage, close the Acronis Time Explorer window.
7. To see how much space you have freed up, click Refresh on the toolbar of the Storage state
screen and check the new value of free space.
8.5 Setting online backup options
You can set these options after logging on Acronis Online Backup and selecting a computer for use
with Online backup service. To do so, click Settings on the Storage state screen.
8.5.1 Connection attempts
This page allows you to optimize the settings Acronis True Image Home uses when establishing
connection to the Online Storage.
Here you can specify how many connection attempts will be made if the first attempt fails (the
default number is 10).
In addition you can specify a time interval between connection attempts (30 seconds by default).
59 Copyright © Acronis, Inc., 2000-2010
Page 60

8.5.2 Storage connection speed
One more option gives you the ability to "throttle" the bandwidth allocated for data transfer to the
Online Storage. Set the connection speed that will allow you to send e-mail or surf the Web without
annoying slowdowns while online backup is running. To do this, select the Limit transfer rate to:
check box and set the connection speed (8 Mbps by default).
To back up your data to the Online storage at the maximum speed your Internet connection can
provide, unselect the Limit transfer rate to: check box.
60 Copyright © Acronis, Inc., 2000-2010
Page 61

8.5.3 Storage cleanup
The Storage cleanup page is intended for setting the options that enable automatic cleanup of
obsolete file versions from the online storage to keep the storage from overfilling.
You can:
Delete versions that are older than the specified time period - 6 months by default.
Specify how many versions of your files must be kept on the Online Storage. This will allow you
to return to a previous file version if your changes in a file turn out to be erroneous. By default
Acronis True Image Home will keep 10 versions of your files, though you can specify any other
number.
8.5.4 Proxy settings
If your computer is connected to the Internet using a proxy server, enable use of the proxy server
and enter its settings.
Acronis Online Backup supports only http and https proxy servers.
In the Host name box, type the name or IP address of the proxy server, such as proxy.example.com
or 192.168.0.1.
In the Port box, type the proxy server's port, such as 8080.
In the User name and Password boxes, type the credentials you use for connecting to the proxy
server, if necessary.
To test the proxy server connection, click the Test button.
61 Copyright © Acronis, Inc., 2000-2010
Page 62

If you do not know your proxy server settings, contact your network administrator or Internet service
provider for assistance. Alternatively, you can take these settings from your browser's configuration.
8.6 Recommendations on selecting data for storing online
Because online backups are relatively slow, you should think over what data to back up. First of all
consider backing up your personal data that cannot be recovered if lost as a result of fire, computer
theft, etc. Before proceeding with a backup, estimate how long it will take to back up your data. For
instance, if your folders take up 10GB and your upload speed is 1000 Kbps (somewhat less than half a
gigabyte per hour), it should take more than 20 hours to perform your first full backup. So depending
on the speed of your Internet connection, you may want to back up just the most critical files.
62 Copyright © Acronis, Inc., 2000-2010
Page 63

9 Additional backup features
9.1 Making reserve copies of your backups
When you choose the My Data backup type for backing up selected files and folders, you can create
reserve copies of your backups and save them on the file system, a network drive, or a USB flash
drive.
In addition to enhancing the archive security with replication, this feature allows you to copy a set of
documents, for example, to a USB stick for working on them at home. So now you can perform a
normal backup and copy the same files to a USB stick or any local hard drive. You have the choice of
making a reserve copy in the form of regular files, a zip compressed file, or a tib file (optionally with
password protection and encryption). A password-protected reserve copy can be encrypted only if
you choose to encrypt the main backup and an encryption key of the same length will be used for
encrypting the reserve copy.
A reserve copy always contains all the files selected for backup, that is, when creating a reserve copy the
program always makes a full backup of the source data. You cannot make a reserve copy in the form of an
incremental or differential backup, even in tib format.
Also remember that you will pay for the enhanced convenience and increased security of your data
by the time required for performing the task, because normal backup and reserve copying are
performed one after another and not simultaneously.
And now let us consider a case when you may need to make a reserve copy of your backup.
Suppose you have worked hard on an urgent project all day and the deadline is tomorrow morning.
You decide to back up the results of the day's work in Acronis Secure Zone and make a reserve copy
of the project on a USB stick to finish the project at home. To make a reserve copy:
63 Copyright © Acronis, Inc., 2000-2010
Page 64

1. When you come to the Backup options step while configuring a My Data backup task in the
Backup Wizard (or select that step after completing all the required steps), choose Backup
reserve copy and then select the Create a reserve copy of my backups box (if it is not selected in
the default backup options).
2. Choose how to duplicate the project file(s) on the USB stick. If you need to save space, choose
duplicating as a zip file. Click on the Location link, select the drive letter of the USB stick and
create a folder for a reserve copy by clicking on the Create new folder icon.
3. Finish configuring your backup task as usual.
4. Click Proceed and do not forget to take the USB stick home.
Please be aware that built-in support of zip files in Windows does not cover operations with
multivolume zip archives, and zip archives exceeding 4GB in size or which contain files of more than 4
GB each. Also remember that CD/DVDs are not supported as locations for reserve copies created as
zip archives and flat files.
9.2 Archive to various places
Now Acronis True Image Home offers much greater flexibility. You can save full, incremental and
differential backups to different places including a network share, CD/DVD, USB stick, as well as any
local internal or external hard drive.
You cannot use Acronis Secure Zone as one of the places for storing a part of backups belonging to the same
backup "chain", because such backups may be automatically deleted during automatic backup archive
consolidation in Acronis Secure Zone. As a result, the backup chain will be corrupted. In addition, the Archive to
various places feature does not work with FTP servers.
64 Copyright © Acronis, Inc., 2000-2010
Page 65

One more useful aspect of this feature is its ability to split backups "on-the-fly". Suppose you perform
a backup to a hard disk and in the middle of the backup process Acronis True Image Home finds out
that the disk, to which you are backing up, does not have sufficient free space for completing the
backup. The program displays a message warning you that the disk is full.
To complete the backup, you may either try to free some space on the disk and click Retry or select
another storage device. To choose the latter option, click Browse in the information window. The
Browse for Location window appears.
The left pane shows the storage locations available on your computer. After you select a disk in the
left pane, the program shows the free space on that disk in the right pane. If the free space is enough
for completing the backup, assign a name for the file that will contain the remaining data being
backed up. You can either enter the name manually (for example, "Tail_end.tib") or use the file name
65 Copyright © Acronis, Inc., 2000-2010
Page 66
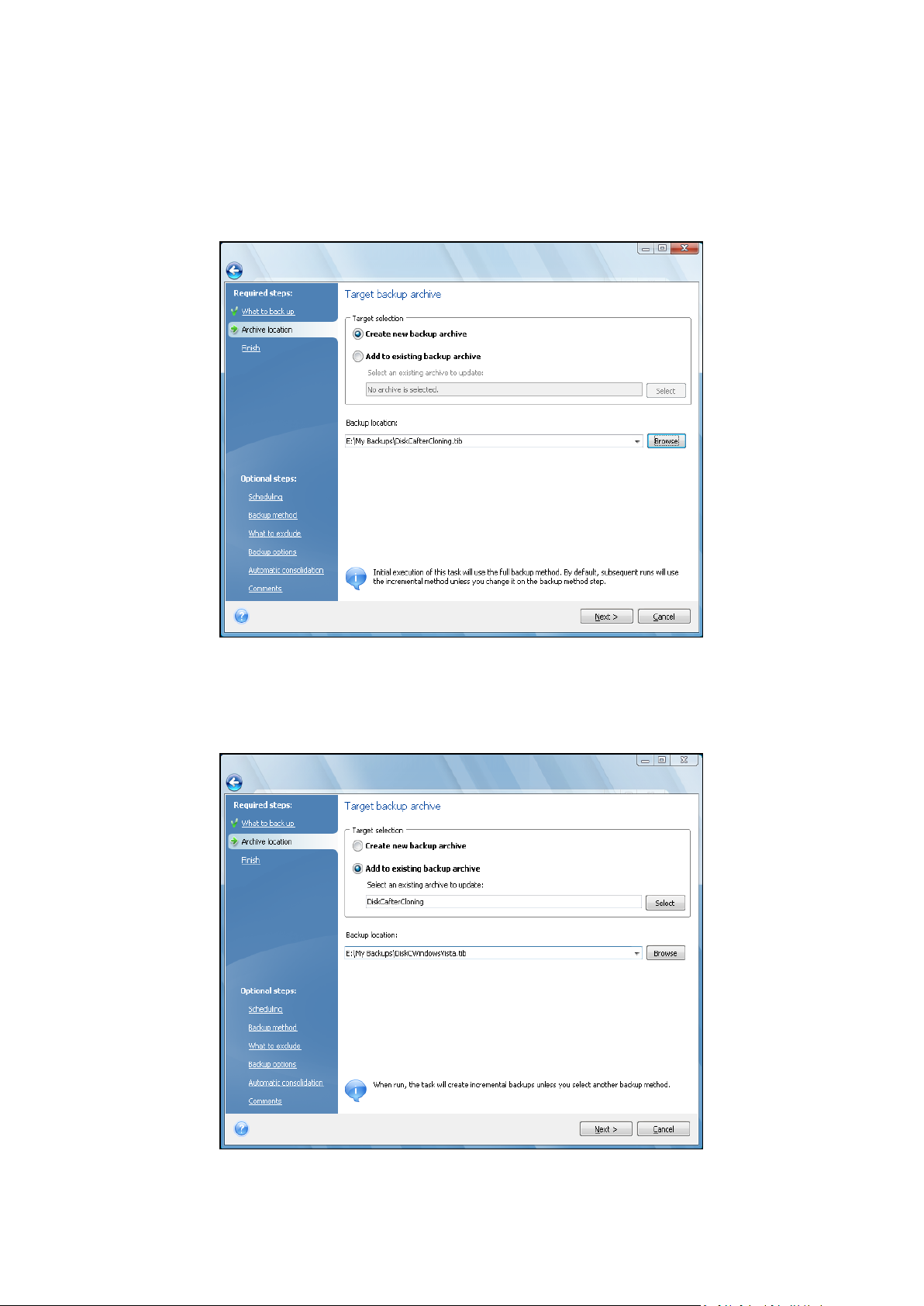
generator (a button to the right of the line). Then click OK and Acronis True Image Home will
complete the backup.
Acronis True Image Home permits to assign any backup archive whatever name you wish. Suppose
you bought a new hard disk drive and transferred to it the contents of the old one by cloning. You
decided to perform a full backup of the new system disk and named it "DiskCafterCloning".
After a while you chose to upgrade to Windows Vista. To be on the safe side, you made an
incremental backup before the upgrade and named it "DiskCBeforeUpgrading". Upon upgrading you
made sure that the new system and all your applications operate normally and made one more
incremental backup naming it "DiskCWindowsVista".
66 Copyright © Acronis, Inc., 2000-2010
Page 67

After working under Windows Vista for some time you decided that you would like to try Linux as
well. Before creating a partition for Linux you perform an incremental backup of the system disk and
name it "DiskCBeforePartitioning", and so on. As a result, if the need to recover arises, you will be
able to find at a glance a backup archive corresponding to the system disk state you want to recover.
As was already mentioned, you can save full and incremental or differential backups to different
locations. For example, you can save the initial full backup to an external USB hard drive, and then
burn the subsequent incremental backups (or differential backups that are an even better choice) to
CDs or DVDs. It is also possible to save such backups to a network share. If you have saved backups
belonging to the same backup "chain" to various places, Acronis True Image Home may prompt you
for the locations of previous backups during data recovery, in the case when the selected backup
archive does not contain the files you want to recover (or contains only a part of them).
9.3 Backup Wizard – detailed information
Here we give detailed information on all steps of the Backup Wizard. Let's go through all the steps:
1. Start Acronis True Image Home.
Click Backup on the sidebar, then select Disk and Partition Backup or File Backup in the right pane
depending on what you want to back up.
Backup Wizard allows you to perform the following backups:
Disk and Partition Backup (image backup of any set of disks/partitions)
My Data (file-level backup of any set of files, folders, or entire file categories)
System State (file-level backup of the boot files, registry, protected Windows files, and COM+ CLASS
registration database). Backing up the System state allows you to recover the system files, drivers,
etc., but not the data files and folders you use in your work. For more information on the System
State backup see Microsoft TechNet article Backing Up and Restoring Data.
67 Copyright © Acronis, Inc., 2000-2010
Page 68

My E-mail (file-level backup of Microsoft Outlook, Microsoft Outlook Express, and Windows Mail
settings and messages).
My Application Settings (file-level backup of Windows applications settings)
File-level backup operations are supported only for the FAT and NTFS file systems.
Selecting a backup type starts the Backup Wizard, which will guide you through the steps of creating
a backup task. Depending on the backup type chosen, the number of steps in the Backup Wizard may
change. For example, in case of backing up the System State, the program backs up predefined data
and requires the minimum number of settings for configuring a backup task.
After you finish configuring a backup task, it can be started immediately if you do not unselect the
Run task now box prior to clicking Proceed.
9.3.1 Selecting what data to back up
When the Backup Wizard screen appears, select what data to back up (in case of choosing the
System State, this step will be omitted).
Disk and Partition Backup - select the disks or partitions to back up. You can select a random set of
disks and partitions. The wizard's right pane shows the hard drives of your computer. Selecting a
hard drive results in selecting all partitions on that drive. If a hard drive has more than one partition,
you may want to select individual partitions for backing up. To do so, click on the Down arrow at the
right of the drive's line. Select the desired partition(s) in the displayed partition list. By default the
program copies only the hard disk sectors that contain data. However, sometimes it might be useful
to make a full sector-by-sector backup. For example, perhaps you deleted some files by mistake and
want to make a disk image before trying to undelete them because sometimes un-deleting may
create havoc in the file system. To make a sector-by-sector backup, select the Back up sector-by-
sector (requires more storage space) box. Please note that this mode increases processing time and
usually results in a larger image file because it copies both used and unused hard disk sectors. In
addition, when configuring a sector-by-sector backup of a complete hard disk you can include in the
backup unallocated space on the hard disk by selecting Back up unallocated space. Thus you will
include in the backup all physical sectors on the hard drive.
My Data - select the file category(ies) to back up: documents, finance, images, music, and video.
Each category represents all files of associated types found on the computer's hard drives.
Furthermore, you can add any number of custom categories containing files and folders. The new
categories will be saved and displayed along with the above. You can change contents of any custom
or default file category (edit the category) or delete it. The default file categories cannot be deleted.
For more information on custom categories see Creating a custom data category for backups (p. 83).
If you do not want to keep custom contents of the current backup by creating a data category, simply
select the files/folders from the tree. This set will be effective only for the current backup task. File
filtering can be applied to manually added folders in the optional What to exclude step.
My Application Settings - back up custom settings of Windows applications. This is a subset of filelevel backups that backs up predefined folders and requires minimum user selections. The program
displays a list of supported applications that have been found on the computer, sorted by categories.
You can select a random set of categories and applications.
It is important to note that the program backs up only your settings, and not the application executable files. If
an application seems to malfunction or ceases to run, reinstall it using the latest updates and then recover your
settings from the backup.
68 Copyright © Acronis, Inc., 2000-2010
Page 69

To select all the supported applications found on the computer for backing up, check the Installed
Applications box. For instant messenger applications, the program will back up both the settings and
history.
The list of supported applications will be expanded gradually. Updates will be available with new
program builds or via the Internet.
My E-mail - Acronis True Image Home offers a straightforward way to back up messages, accounts
and settings for Microsoft Outlook 2000, 2002, 2003, 2007, Microsoft Outlook Express, and Windows
Mail. E-mail backup is a subset of file-level backups that backs up predefined folders and requires
minimum user selections. However, if need be, you can select Microsoft Outlook components and
folders individually. The list of supported e-mail clients will be gradually built up. Updates will be
available with new program builds or via the Internet.
You can select the following items:
Messages contained in .PST/.DBX Database Files
E-mail accounts
For Microsoft Office Outlook 2000, 2002, 2003, 2007
Mail Folders
Calendar
Contacts
Tasks
Notes
Signatures
News Folders
User Settings
Address Book
For Microsoft Outlook Express
Mail Folders
Address Book (select Windows Address Book).
Acronis True Image Home provides backup of IMAP (Internet Messages Access Protocol) mail folders
for Microsoft Outlook. This means that you can back up folders stored on a mail server. For Microsoft
Outlook Express and Windows Mail only local e-mail folders backup is available.
Take note that Acronis True Image Home does not support Unicode characters in the items backed
up using My E-mail backup type.
9.3.2 Selecting archive location
Select the location for the backup archive and specify the archive name.
If you are going to create a new archive (i.e. perform a full backup), select Create new backup
archive and enter the path to the archive location and new archive file name in the Backup Location:
field below or click Browse, select the archive location on the directory tree and enter the new file
name in the File name line, or use the file name generator (a button to the right of the line).
69 Copyright © Acronis, Inc., 2000-2010
Page 70

When you have chosen the My Data backup type for backing up files and/or folders, you can select
the zip archive type. For more information see Support for Zip format (p. 23).
CD/DVD and the Acronis Secure Zone are not supported as locations for zip archives.
If you want to append an incremental or differential backup file to an existing archive, select Add to
existing backup archive and click the Select button to select the existing archive you are going to
update. If the archive already has incremental or differential backups, you can select any of the
target archive files. It doesn't matter which one you select, as the program recognizes them as a
single archive.
If you want to change the location of added backup files, browse for a new backup location after
clicking the Browse button, otherwise leave the location the same as that of the existing archive.
The "farther" you store the archive from the original folders, the safer it will be in case of disaster.
For example, saving the archive to another hard disk will protect your data if the primary disk is
damaged. Data saved to a network disk, an FTP server or removable media will survive even if all
your local hard disks are damaged. You can also use the Acronis Secure Zone for storing backups if
you are using the Windows version of the product. (see details in Acronis Secure Zone™ (p. 20)).
See notes and recommendations for supporting FTP servers in Supported storage media (p. 14).
After selecting the archive location and naming the backup archive to be created, you have
completed all the required steps for a backup task and this is confirmed by the fact that you come to
the Finish step with the Summary of the backup task being displayed on the right pane. All the
remaining steps are optional and in many cases you may omit them and just click Proceed. For
example, when you want to proceed with backup right away, you can omit the Scheduling step. If
you do not want to exclude any files from the backup, you can omit the What to exclude step. When
you want to use the default backup options, you can omit the Backup options step, and so on.
Now let's see what optional steps you can set up while configuring a backup task. Click the Options
button.
70 Copyright © Acronis, Inc., 2000-2010
Page 71

9.3.3 Scheduling
By default, the Do not schedule option is chosen so the task will run after completing the wizard and
clicking Proceed. However, you may wish to schedule the task being configured by choosing one of
the scheduling options.
For more information see Scheduling tasks (p. 109).
9.3.4 Backup method
Select whether you want to create a full, incremental or differential backup. If you have not backed
up the selected data yet, or the full archive is old and you want to create a new master backup file,
choose full backup. Otherwise it is recommended that you create an incremental or differential
backup (see Full, incremental and differential backups (p. 18)).
If you are adding a backup to the existing backup archive, the Full method will be unselectable.
You can set a backup policy for the backup task. Acronis True Image Home offers three types of
backup policies:
create full backups only
create full backups after a specified number of incremental backups
create full backups after a specified number of differential backups
When the first backup on a schedule is executed, Acronis True Image Home always creates a full
backup.
If you choose (1) by selecting the Full method, you can also choose what to do with the previous full
backup when creating a new one. By default Acronis True Image Home overwrites the previous full
backup, but you can choose to keep it by unselecting the A new full backup overwrites the previous
one box.
71 Copyright © Acronis, Inc., 2000-2010
Page 72

If you choose (2) or (3) by selecting the Create a new full backup after box, the next backups will be
incremental (or differential) until the specified number of incremental (differential) backups is
reached. After the selected number of incremental or differential backups is made, the next time a
new full backup and a set of subsequent incremental (differential) backups will be created; this
process will then continue until you decide to change it.
When the Delete previous backup archive box is selected, creation of a new full backup in
accordance with the specified backup policy results in deletion of the complete previous backup
chain – the previous full backup and its subsequent incremental (or differential) backups regardless
of the overall limitations you set on the archive at the Automatic consolidation step.
If you decide to keep old backups (by not selecting the Delete previous backup archive box) and
creation of a new full backup results in violation(s) of the limits set for automatic consolidation, the
program will use the following algorithm:
1. if the actual number of backups exceeds the maximum number of backups; the program
automatically consolidates the old full backup with the oldest incremental (differential) one to
correct this quota violation;
2. if after correcting the number of backups limit violation other quota violations remain; the
program consolidates the oldest backup to correct the storage period of old backups limit
violation (if possible - otherwise it deletes the old full backup);
3. if after correcting the storage period of old backups limit violation the archive size limit violation
remains; the program consolidates the old full backup with the oldest incremental (differential)
one, then will repeat consolidation (if necessary and possible);
4. if after consolidating all the previous backups the archive size quota violation remains; the old
backup archive will be deleted in order to correct the violation;
5. if the new full backup file size exceeds the archive size limit; the program will record a warning
into the log.
72 Copyright © Acronis, Inc., 2000-2010
Page 73

9.3.5 Selecting what to exclude
This step will be present only for the Disk and Partition Backup and My Data backup types. It enables
you to exclude unnecessary files from your backup in case you just want to exclude certain file types
without creating custom categories. You can exclude hidden or system files and folders, as well as
files matching the criteria you specify. You can add your own criteria by clicking Add. While adding
criteria, you can use the common Windows wildcard characters and type several criteria in the same
line separating them by semicolons. For example, to exclude all files with .gif and .bmp extensions,
you may type *.gif;*.bmp. One more thing – if, for example, you want to exclude all the files with the
name of test regardless of their extension, you should specify exclusion criteria such as test.*,
otherwise those files will not be excluded. You can also specify the path to a folder to be excluded,
for example, C:\Program Files\Common Files\. Note that the path must end with the "\" symbol,
otherwise the folder will not be excluded.
These filter settings will take effect for the current task. For information on how to set the default
filters that will be used each time you select folders to back up, see What to exclude (p. 76).
73 Copyright © Acronis, Inc., 2000-2010
Page 74

9.3.6 Selecting the backup options
Select the backup options (that is, backup file-splitting, compression level, password protection, etc.).
The settings of the options will be applied only to the current backup task.
Or, you can edit the default backup options and local storage settings if you want to save the current
settings for future tasks. For more information see Fine-tuning your backups (p. 76).
9.3.7 Setting automatic consolidation
Automatic consolidation of a backup archive is enabled by setting the overall limitations for the
archive. These limitations include:
a maximum number of backups
a maximum storage period for the archive files
74 Copyright © Acronis, Inc., 2000-2010
Page 75

a maximum archive size
By default there are no limits set and automatic consolidation is not performed. To enable automatic
consolidation, you must select at least one of the limits and either leave its default value or change it
according to your needs.
If limits are set, then after creating a backup the program checks the archive for quota violations,
such as exceeding a pre-set maximum number of gigabytes set aside for backups and, if any
limitation is exceeded, consolidates the oldest backups. For example, if you've pre-set your archive to
store 50GB of backup files and your backups reach 55GB, you have exceeded a quota and the system
will respond automatically based on rules that you've already set. This operation creates a temporary
file and thus requires disk space. Consider also that the quota must be violated so that the program
can detect the violation. Therefore, to be able to consolidate the files, the program needs some
space on the disk in excess of the archive quota. The extra amount of space can be estimated as the
size of the largest backup in the archive, though sometimes consolidation requires more space.
In case of setting a limit on the number of backups, the actual number of backups can exceed the
maximum number of backups by one. This enables the program to detect quota violation and start
consolidation. Similarly, if you pre-set a backup storage period, for example, 30 days, the program
will start consolidation when the oldest backup is stored for 31 days.
9.3.8 Providing a comment
Providing a comment for the archive can help identify the backup and prevent you from recovering
the wrong data. However, you can choose not to make any notes. The backup file size and creation
date are automatically appended, so you do not need to enter this information.
In addition, you can provide or edit a comment after the backup has been executed. This may be
helpful for adding comments to scheduled backups, which run unattended. To edit or add a
comment, go to the Data recovery and backup management screen by clicking Recovery on the
sidebar, choose the appropriate backup, right-click and select Edit comments in the shortcut menu.
75 Copyright © Acronis, Inc., 2000-2010
Page 76

9.3.9 The backup process
Clicking Proceed after completing all the optional steps you need for configuring the current backup
task will start the task execution if you have configured the task to be started manually, by choosing
the Do not schedule option at the Scheduling step, or having selected the Run task now box for a
scheduled task (to select the box, you should return to the Finish step). Otherwise the task will run
when the scheduled time comes.
The task progress will be shown in a special window. You can stop the procedure by clicking Cancel.
You can also close the progress window by clicking Hide. The backup creation will continue, but you
will be able to start another operation or close the main program window. In the latter case, the
program will continue working in the background and will automatically close once the backup
archive is ready. If you prepare some more backup operations, they will be queued after the current
one.
9.4 Fine-tuning your backups
You can fine-tune your backups to specific tasks. Such fine-tuning is made by configuring backup
options before starting a backup task.
You can set temporary backup options by changing the default backup options while creating a
backup task. If you would like to use the changed options for future tasks, make appropriate changes
in the default backup options after selecting Tools & Utilities → Options → Backup options.
Incidentally, you can always restore the default backup options to the values preset during
installation of Acronis True Image Home. To do this, click Reset all to default on the toolbar of the
Options window. To reset just a single backup option, select it on the left pane and click Reset the
current to default.
Clicking Reset all to default will reset all the default options (for backup/recovery, notifications, etc.) to their
preset values, so this button should be used with caution.
In addition, when backing up your data files, the program provides for creating custom data
categories for backup.
9.4.1 Backup options
9.4.1.1 What to exclude
By default, the program excludes files with the following extensions from backups: .~, .tmp, and .tib.
You can also set other default filters for file exclusion, for example, you may want hidden and system
files and folders not to be stored in the backup archives as well.
In addition, you can apply your own filters using the common Windows wildcard characters. For
example, to exclude all files with extension .exe, add *.exe mask. My???.exe will exclude all .exe files
with names consisting of five symbols and starting with "my".
This option affects real folders selected at My Data backup. If the name of a whole folder matches a
mask you set, this folder will be excluded with all its content. Backup of a file category uses file filters
preset at creation of the category. My Application Settings, System State or My E-mail backup
implies dedicated lists of files that must not be filtered.
76 Copyright © Acronis, Inc., 2000-2010
Page 77

9.4.1.2 Pre/post commands
You can specify commands or batch files to be executed automatically before and/or after the
backup procedure. For example, you may want to remove some temporary (.tmp) files from the disk
before starting backup or configure a third-party antivirus product to be used each time for scanning
the files to be backed up before the backup starts. Click Edit to open the Edit Command window
where you can easily input the command, its arguments and working directory or browse folders to
find a batch file.
Please do not try to execute interactive commands, i.e. commands that require user input (for
example, "pause"). These are not supported.
Unselecting the Do not perform operations until the command's execution is complete box,
selected by default, will permit the backup process to run concurrently with your command
execution.
If you want the backup to be performed even if your command fails, unselect the Abort the
operation if the user command fails box (selected by default).
You can test execution of the command you created by clicking Test command.
9.4.1.3 Compression level
The preset is Normal.
Let's consider such an example - you need to backup to a USB stick some files with a total size
comparable to or exceeding the USB stick's capacity and want to make sure that the stick
accommodates all the files. In this case use the Maximum compression for the files to be backed up.
However, you should take into account that the data compression ratio depends on the type of files
stored in the archive, for example, even the Maximum compression will not significantly reduce the
backup size if it contains files with already compressed data like .jpg, .pdf or .mp3. It does not make
any sense to select the Maximum compression for such files because in this case the backup
operation will take significantly longer and you will not get an appreciable reduction of backup size. If
you are not sure about the compression ratio of a file type, try to back up a couple of files and
compare the sizes of the original files and backup archive file. A couple of additional tips: generally,
you can use the Normal compression level, because in most cases it provides an optimal balance
between backup file size and backup duration. If you select None, the data will be copied without
any compression, which may significantly increase the backup file size, while making the fastest
backup.
9.4.1.4 Archive protection
The preset is no password.
Suppose you have some files with sensitive information, for example, your tax return, which you
need to back up. Acronis True Image Home can help you protect your sensitive information from
getting into the wrong hands. The simplest (and the least secure) way is protecting your backup with
a password. Let's remind you that to make a password more difficult to guess, it should consist of at
least eight symbols and contain both letters (upper and lower case, preferably) and numbers. If you
think that a password will not give you sufficient security, use encryption for your backup. Acronis
True Image Home allows encrypting backup files with the industry-standard AES cryptographic
algorithm. A 128-bit encryption key is sufficient for most applications. The longer the key, the more
secure your data. However, the 192 and 256-bit long keys significantly slow down the backup
77 Copyright © Acronis, Inc., 2000-2010
Page 78

process, though in the case being considered this will most likely not be an issue, because the files
will not be too large. The encryption settings are available only for password-protected archives.
If you try to recover data from a password-protected archive, or append an incremental/differential
backup to such an archive, Acronis True Image Home will ask for the password in a special window,
allowing access only to those who know the password.
9.4.1.5 Backup priority
The preset is Low.
The priority of any process running in a system determines the amount of CPU usage and system
resources allocated to that process. Decreasing the backup priority will free more resources for other
CPU tasks. Increasing the backup priority might speed up the backup process by taking resources
from the other currently running processes. The effect will depend on total CPU usage and other
factors.
9.4.1.6 File-level security settings
Preserve file security settings in archives
The preset is enabled.
By default, files and folders are saved in the archive with their original Windows security settings (i.e.
permissions for read, write, execute and so on for each user or user group, set in file Properties →
Security). If you recover a secured file/folder on a computer without the user specified in the
permissions, you may not be able to read or modify this file.
To eliminate this kind of problem, you can disable preserving file security settings in archives. Then
the recovered files/folders will always inherit the permissions from the folder to which they are
recovered (parent folder or disk, if recovered to the root).
Or, you can disable file security settings during recovery, even if they are available in the archive (see
Files recovery options (p. 99)). The result will be the same.
In archives, store encrypted files in a decrypted state
The preset is disabled.
If you do not use the encryption feature available in Windows XP and later operating systems, simply
ignore this option. (File/folder encryption is set in Properties → General → Advanced Attributes →
Encrypt contents to secure data).
Check the option if there are encrypted files in the backup and you want them to be accessed by any
user after recovery. Otherwise, only the user who encrypted the files/folders will be able to read
them. Decryption may also be useful if you are going to recover encrypted files on another computer.
These options relate only to file/folder backups. In addition, they are unavailable for zip backup
archives.
9.4.1.7 Error handling
Ignore bad sectors
The preset is disabled.
78 Copyright © Acronis, Inc., 2000-2010
Page 79

This option lets you run a backup even if there are bad sectors on the hard disk. Although most disks
do not have bad sectors, the possibility that they might occur increases during the course of the hard
disk's lifetime. If your hard drive has started making strange noises (for example, it starts making
quite loud clicking or grinding noises during operation), such noises may mean that the hard drive is
failing. When the hard drive completely fails, you can lose important data, so it is necessary to back
up the drive as soon as possible. There may be a problem though – the failing hard drive might
already have bad sectors. If the Ignore bad sectors box is left unselected, a backup task is aborted in
case of read and/or write errors that could occur on the bad sectors. Selecting this box lets you run a
backup even if there are bad sectors on the hard disk ensuring that you save as much information
from the hard drive as possible.
Do not show messages and dialogs while processing (silent mode)
The preset is disabled.
You can enable this setting to ignore errors during backup operations. This feature was mainly
designed for unattended backups when you cannot control the backup process. In this mode no
notifications will be displayed if errors occur during backup. Instead you can view the detailed log of
all operations after the task finishes by selecting Tasks and Log on the sidebar and then clicking the
Log tab. You may use this option when configuring a backup task to be run during the night.
When not enough space in ASZ, delete the oldest archive
The option can be set in the Windows version of Acronis True Image Home only; the preset is
enabled.
When this setting is disabled and there is not enough space in the Acronis Secure Zone for the
backup file being created, the program will display a dialog warning you that the zone is full and will
require your intervention. The backup is suspended until you take a required action and this makes
unattended backups impossible. The dialog opens even when the Do not show messages and dialogs
while processing (silent mode) setting is enabled. So it is advisable to select the When not enough
space in ASZ, delete the oldest archive box when planning unattended scheduled backups to the
Acronis Secure Zone.
9.4.1.8 Removable media set tin gs
Ask for first media while creating backup archives on removable media
The preset is enabled.
You can choose whether to display the Insert First Media prompt when backing up to removable
media. With the default setting, backing up to removable media may not be possible if the user is
away, because the program will wait for someone to press OK in the prompt box. Therefore, you
should disable the prompt when scheduling a backup to removable media. Then, if the removable
media is available (for example, CD-R/RW inserted) the task can run unattended.
Place Acronis One-Click Restore on media
The preset is disabled.
When backing up to removable media, you can make this media bootable and will not need a
separate rescue disk.
The Acronis One-Click Restore is a minimal addition to your backup media, allowing one-click data
recovery from an image archive stored on this media. This means that when booting from the media
79 Copyright © Acronis, Inc., 2000-2010
Page 80

you click "recover" all data will be recovered to its original place automatically. No options or
selections such as resizing partitions will be available.
The Acronis One-Click Restore can be added to the media only when creating a full backup of an entire hard
disk. It cannot be added when creating an incremental or differential backup, as well as backup of a partition. In
such case the Place Acronis One-Click Restore on media check box will not be present on the General tab of the
task's backup options even if the box is selected in the default backup options.
If you want more functionality during recovery, write a full standalone version of Acronis True Image
Home to the rescue media. As a result, you will be able to configure the recovery task using Recovery
Wizard.
By clicking the Advanced tab you can select Acronis True Image Home (Full version) and Acronis
System Report. In addition, Acronis True Image Home (Safe version) will be available for those who
purchased the boxed version of Acronis True Image Home and installed the appropriate add-on. If
you have other Acronis products installed on your computer, such as Acronis Disk Director Suite, the
bootable versions of these programs' components will be offered on this tab as well.
9.4.1.9 Timeout settings
Sometimes when the program performs an operation, an error message or a warning message may
interrupt the operation progress. To resume the operation, some additional information or a decision
is required from the user.
For example, such a situation may occur during a backup operation when the storage space in the
destination location becomes insufficient for completing the backup. The program will wait for your
decision on whether you want to cancel the backup, free some storage space or select another
destination for the backup.
Timeout settings allow you to specify the time interval the program should wait for your response.
Move the slider to the right to set the time interval (in minutes). Note that the Infinite setting is not
recommended. If the response is not received during the interval, the operation will be canceled.
9.4.2 Local storage settings
These settings also affect the backup process, for example, they may have a more or less noticeable
effect on the backup process speed. Their values also depend on the physical characteristics of the
local storage devices.
9.4.2.1 HDD writing speed
The preset is Maximum.
Backing up in the background to an internal hard disk (for example, to Acronis Secure Zone) may slow
other programs' performance because of the large amounts of data transferred to the disk. You can
limit the hard disk usage by Acronis True Image Home to a desired level. To set the desired HDD
writing speed for data being backed up, drag the slider or enter the writing speed in kilobytes per
second.
9.4.2.2 Network connect ion speed
The preset is Maximum.
80 Copyright © Acronis, Inc., 2000-2010
Page 81

If you frequently back up data to network drives, you may consider limiting the network bandwidth
used by Acronis True Image Home. To set the desired data transfer speed, drag the slider or enter
the bandwidth limit for transferring backup data in kilobytes per second.
9.4.2.3 Free space threshold
The preset is disabled.
You may want to be notified when the free space on the backup storage becomes less than the
specified value. To enable such notification, select the On insufficient free disk space box, then
specify the free space threshold value in the below fields.
When this option is enabled, Acronis True Image Home will monitor free space on your backup
storage. If after starting a backup task Acronis True Image Home finds out that the free space on the
selected backup archive location is already less than the specified value, the program will not begin
the actual backup process but will immediately inform you by displaying an appropriate message.
The message offers you three choices - to ignore it and proceed with the backup, to browse for
another location or to cancel the task. In case of choosing to cancel the backup you can either free
some space on the storage and restart the task or create a new task with another location for the
backup archive. If you choose Browse, select another storage, click OK and the backup file will be
created on that storage.
If the free space becomes less than the specified value while the backup task is being run, the
program will display the same message and you will have to make the same decisions. However, if
you choose to browse for another location, you will need to assign a name for the file that will
contain the remaining data being backed up (or you may accept the default name assigned by the
program).
Acronis True Image Home can monitor free space on the following storage devices:
Local hard drives
USB cards and drives
Networks shares (SMB/NFS)
This option cannot be enabled for FTP servers and CD/DVD drives.
The message will not be displayed if the "Do not show messages and dialogs while processing (silent
mode)" box is selected in the "Error handling" settings.
9.4.2.4 Archive splitting
Sizeable backups can be split into several files that together form the original backup. A backup file
can be split for burning to removable media or saving on an FTP server (data recovery directly from
an FTP server requires the archive to be split into files of no more than 2GB). A backup destined for
the Acronis Secure Zone cannot be split.
Suppose you have a full backup of your PC on an external hard disk, but want to make one more
backup copy of the system to keep it in a different location from the first one for added security.
However, you do not have one more external hard disk, and a USB stick would not accommodate
such a large backup. Using Acronis True Image Home you can make a reserve backup copy on blank
DVD-R/DVD+R discs, which are very cheap nowadays. The program can split large backups into
several files that together form the original backup. If you have enough space on your PC's hard disk,
you can first create a backup archive consisting of multiple files with a specified size on the hard disk
81 Copyright © Acronis, Inc., 2000-2010
Page 82

and burn the archive to DVD+R discs later on. To specify the split file size, select Fixed size mode for
Archive splitting and enter the desired file size or select it from the drop-down list.
If you do not have enough space to store the backup on your hard disk, select Automatic and create
the backup directly on DVD-R discs. Acronis True Image Home will split the backup archive
automatically and will ask you to insert a new disc when the previous one is full.
Creating backups directly on CD-R/RW or DVD+R/RW might take considerably more time than it
would on a hard disk.
9.4.2.5 Backup reserve c opy
The preset is disabled.
You may want Acronis True Image Home to make reserve copies of your backups in a certain location
each time when you choose the My Data backup type for backing up selected files and folders. To
enable creation of reserve copies, select the Create a reserve copy of my backups check box and
then choose the method for making reserve copies. You have three choices: duplicate the backups as
tib files, make reserve copies as zip archives, or simply copy the files and/or folders to a specified
location "as is".
To specify the location for storing reserve copies of your backups, click the Location link. Select a
location – a local hard disk, USB stick, or a network share. You can create a folder for reserve copies
by clicking the Create new folder icon. Reserve copies created as tib and zip files will be named
automatically as follows:
backupfilename_reserved_copy_mm-dd-yyyy hh-mm-ss AM.tib; or
backupfilename_reserved_copy_mm-dd-yyyy hh-mm-ss PM.zip,
where mm-dd-yyyy hh-mm-ss is the date and time of reserve copy creation in the following format:
month (one or two digits), day (one or two digits), year (four digits), hour (one or two digits), minute
(two digits), and second (two digits). AM or PM is a 12-hour period.
For example: MyBackup_reserved_copy_8-15-2008 9-37-42 PM.zip
If you choose reserve copies to be made in the form of flat files, those files will be placed into folders
which will be automatically created and named as follows: backupfilename_reserved_copy_mm-dd-
yyyy hh-mm-ss AM (or PM).
After you set the backup reserve copy settings, Acronis True Image Home will create reserve copies
each time you select the My Data backup type. If a reserve copy could not be made due to a lack of
free space in the selected location or due to disconnection of the selected storage device (e.g. a USB
stick), the program will write an error message to the event log.
9.4.2.6 Archive validation
Validate backup archive when it is created
The preset is disabled.
When enabled, the program will check the integrity of the just created or supplemented archive
immediately after backup. When setting up a backup of critical data or a disk/partition backup, we
strongly recommend you to enable the option to ensure that the backup can be used to recover lost
data.
82 Copyright © Acronis, Inc., 2000-2010
Page 83

9.4.3 Creating a custom data category f or backups
To add a custom data category, click Add New Category in the Files to back up screen of the Backup
Wizard, select the folder (data source) and provide a name for the category. You can include in the
category all files in the selected folder or apply filters to select the specific types of files that you wish
or do not wish to back up.
To set a filter, select its type: Back up files of the following types only or Back up files of all types in
the source except the following. Then click Add and select the desired file types in the window that
appears.
You can select file types as follows:
1. By name. Enter the file name in the upper Name field. You can use the common Windows
wildcard characters. For example, My???.exe will select all .exe files with names consisting of five
symbols and starting with "my".
2. By type. Select the desired file types in the list. You can also search the desired registered file
types by entering their extension or description in the Search field.
3. By extension. Click the Edit custom file types… link and enter the extensions (semicolon
separated) in the File extensions field.
If you do not want to keep custom contents of the current backup, simply select the files/folders
from the tree. This set will be effective only for the current backup task.
83 Copyright © Acronis, Inc., 2000-2010
Page 84

10 Data recovery with Acronis True Image Home
The ultimate purpose of data backup is recovery of the backed up data when the original is lost due
to hardware failure, fire, theft or just erroneous deletion of some important files.
There may be various reasons for recovering your system - from unstable operation after installing a
new application, driver or Windows update to complete failure of the system hard drive or
replacement of the old hard drive by a new larger one. In addition, it may be necessary to recover
either only the system partition or the entire system disk comprising several partitions including
hidden ones. Acronis True Image Home provides for all these cases, though details of recovery may
differ. In any case, it is better to perform system recovery when booting from the rescue media.
On the other hand, recovery of a data disk/partition or files and folders is usually performed in
Windows.
10.1 Recovering your system partition
Let's first consider the simplest case - recovery of the system partition to the original location on the
original hard disk drive.
As recovery of the system partition is one of the most important operations, it requires careful
preparation even when you just want to recover a previous "known good" Windows state. While
preparing for recovery you need to:
a) create and test Acronis bootable rescue media. For more information on testing media see Testing
bootable rescue media (p. 27);
b) boot from the rescue media and validate the backup you want to use for recovery. Such validation
is very important because Acronis True Image Home deletes the target partition (the system partition
in this case) when starting partition recovery, so you may find yourself without your system and
applications if the backup file is corrupted. In addition, there were reports from users that a backup
archive that has been successfully validated in Windows is declared corrupted when being validated
in the recovery environment. This may be due to the fact that Acronis True Image Home uses
different device drivers in Windows and the recovery environment.
c) assign unique names to the disks and partitions used on your computer. This is strongly
recommended because the drive lettering in Windows and in the recovery environment may differ. If
you have not done this before making the backup, you can assign names now. The names will help
you in finding the drive containing your backups as well as the target system partition.
d) optionally check the system hard drive for errors using Microsoft's Chkdsk utility, which is part of
Windows.
Assuming that you have carried out the above, let's proceed with recovery.
Attach the external drive if it contains the backup archive to be used for recovery and make sure that the drive is
powered on. This must be done before booting from Acronis rescue media.
1. Arrange the boot sequence in BIOS so as to make your rescue media device (CD, DVD or USB
stick) the first boot device. See Arranging boot sequence in BIOS (p. 187).
2. Boot from the rescue media and select Acronis True Image Home (Full version).
84 Copyright © Acronis, Inc., 2000-2010
Page 85

3. Select Recovery → Disk and Partition Recovery in the main menu and then choose the image
backup of your system partition (or entire system disk) that you want to use for recovery. Rightclick on the backup and choose Recover in the shortcut menu.
If the disks have different disk letters in Windows and the recovery environment, the program
will display the following error message: "Acronis True Image Home cannot detect volume N of
"Name" archive", where Name is the name of the required image backup archive and volume
number (N) may be different depending on the number of backups in the archive. Click Browse
and show the path to the archive.
4. Select Recover whole disks and partitions at the Recovery method step.
5. Select the system partition (usually C) on the What to recover screen. If the system partition has
a different letter, select the partition using the Flags column. It must have the Pri, Act flags. As
you are recovering the system partition to the original hard drive, there is no need to select the
"MBR and track 0" box.
6. At the "Settings of partition C" (or the letter of the system partition, if it is different) step check
the default settings and click Next if they are correct. Otherwise change the settings so as to suit
you before clicking Next.
7. Carefully read the summary of operations at the Finish step. If you have not resized the partition,
the sizes in the Deleting partition and Recovering partition items must match. If you do not want
to validate the backup, click Proceed, otherwise click Options and select the "Validate backup
archive before recovery" box before clicking Proceed.
8. When the operation finishes, exit the standalone version of Acronis True Image Home, remove
the rescue media and boot from the recovered system partition. After making sure that you
recovered Windows to the state you need, restore the original boot sequence.
10.2 Recovering a disk backup to a different capacity hard disk
Recovery of a disk backup containing several partitions to a hard disk that has a different capacity
using manual resizing of the partitions can be considered as one of the most complicated operations
in Acronis True Image Home. This is especially true when you have backed up the original hard disk
containing a hidden diagnostic or recovery partition.
Recovering a dual/multiboot system disk e.g. with Windows and some flavor of LINUX may be even
more fraught with difficulties. Quite often it requires some research on the appropriate forums
before attempting to perform a recovery so this section does not cover such case.
Make the preparations described at the beginning of the previous section Recovering your system
partition (p. 84). In case of upgrading the healthy system disk to a larger capacity new one, if you
have not assigned unique names to the partitions on the system disk before making a system disk
backup, it might make sense to assign such names and create a new backup of the entire disk. This
will allow identifying the partitions by their names and not by the letters which may differ when
booting from the rescue media. If you are recovering from a system disk drive failure, assign names
now anyway. The names will help you find the drive containing your backups, as well as the target
(new) drive.
The information on partition sizes, drive capacities, their manufacturers, and model numbers can
also help in correctly identifying the drives.
One more recommendation - it is highly recommended to install the new hard drive to the same
position in the computer and use the same cable and the same connector as for the original drive
85 Copyright © Acronis, Inc., 2000-2010
Page 86

(though this is not always possible, e.g. the old drive may be an IDE and the new drive may be a
SATA). In any case, install the new drive to where it will be used.
10.2.1 Recovering a disk without a hidden partition
At first let's consider recovery of a system disk containing two partitions (none of them hidden) using
a disk backup. In addition, we assume that the system disk does not contain a recovery partition
which may not be hidden. If the disk contains, for example, three partitions, the procedure will be
similar. We will describe recovery using the rescue media (as this approach usually gives the best
recovery results).
Attach the external drive if it contains the backup archive to be used for recovery and make sure that the drive is
powered on. This must be done before booting from Acronis rescue media.
1. Arrange the boot sequence in BIOS so as to make your rescue media device (CD, DVD or USB
stick) the first boot device. See Arranging boot sequence in BIOS (p. 187).
2. Boot from the rescue media and select Acronis True Image Home (Full version).
3. Select Recovery → Disk and Partition Recovery in the main menu, then choose the image
backup of your system disk that you want to use for recovery.
If the disks have different disk letters in Windows and the recovery environment, the program
will display the following error message: "Acronis True Image Home cannot detect volume N of
"Name" archive", where Name is the name of the required image backup archive and volume
number (N) may be different depending on the number of backups in the archive. Click Browse
and show the path to the archive.
4. Select Recover whole disks and partitions at the Recovery method step.
5. At the What to recover step select the boxes of the partitions to be recovered. Do not select the
MBR and Track 0 box, as this will result in selecting the entire disk for recovery. Recovering the
entire disk does not allow you to resize partitions manually. If necessary, you can recover the
MBR later. Select the partitions and click Next.
Selecting partitions leads to appearance of the relevant steps "Settings of partition ...". Take note
that these steps are in ascending partition drive letter order and that this order cannot be
changed. The order may differ from the physical order of the partitions on the hard disk. In the
case being considered (no hidden or recovery partitions), the physical order of the partitions on
the new disk does not have special importance as Acronis True Image Home automatically fixes
the appropriate Windows loader files.
Incidentally, this step allows you to find out whether the disk you are going to recover contains a
hidden partition. Hidden partitions do not have disk letters and they go first in the "Settings of
partition ..." steps. If you find a hidden partition, see Recovering a disk with a hidden partition (p.
87).
6. You can specify the following partition settings: location, type, and size. Most likely you will first
specify the settings of the system partition as it usually has the letter C. Because you are
recovering to the new disk, click New location. Select the destination disk by either its assigned
name or capacity.
If you have not assigned names to the disks and have any doubts when selecting the destination
disk, you may abort the recovery by clicking Cancel and try to identify the target disk by its model
number, interface, etc. To see this information, select Tools & Utilities → Add New Disk in the
main menu and the Disk selection screen will show the information. Use it for identifying the
destination disk number, then click Cancel, start the Recovery Wizard again, repeat the above
steps, and select the destination disk.
86 Copyright © Acronis, Inc., 2000-2010
Page 87

7. Clicking Accept will return you to the "Settings of partition ..." screen. Check the partition type
and change it, if necessary. You should remember that the system partition must be primary and
marked as active.
8. Proceed to specifying the partition size by clicking Change default in the Partition size area. By
default the partition will occupy the entire new disk. You can resize and relocate the partition by
dragging it or its borders with a mouse on the horizontal bar on the screen or by entering
corresponding values into the appropriate fields (Partition size, Free space before, Free space
after). While specifying the partition size remember that you need to leave as much unallocated
(free) space after the newly resized partition as will be needed for the second partition. Usually
the free space before partitions is equal to zero. Click Accept when the partition has the size you
have planned for it, then click Next.
9. Begin specifying the settings for the second partition. Click New location, then select unallocated
space on the destination disk that will receive the second partition. Click Accept, check the
partition type (change, if necessary) and then proceed to specifying the partition size which by
default is equal to the original size. Usually there is no free space after the last partition, so
allocate all the unallocated space to the second partition, click Accept and then click Next.
10. Carefully read the summary of operations to be performed. If you do not want to validate the
backup, click Proceed, otherwise click Options and select the "Validate backup archive before
recovery" box before clicking Proceed.
11. When the operation finishes, exit the standalone version of Acronis True Image Home.
Windows should not "see" both the new and old drive during the first boot after recovery. If you upgrade the old
drive to a larger capacity new one, disconnect the old drive before the first boot otherwise there may be
problems booting Windows.
Switch off the computer, if you need to disconnect the old drive, otherwise just reboot the computer
after removing the rescue media.
Boot the computer to Windows. It may report that new hardware (hard drive) is found and Windows
needs to reboot. After making sure that the system operates normally, restore the original boot
sequence.
10.2.2 Recovering a disk with a hidden partition
Recovering a backup of the system disk with a hidden partition (e.g. created by the PC manufacturer
for diagnostics or system recovery) to a different capacity hard drive, requires to take into account
some additional factors. First of all, for the best chance of success, it is necessary to keep on the new
drive the physical order of the partitions that exist on the old drive and place the hidden partition to
the same location - usually at the start or the end of the disk space. In addition, it is better to recover
the hidden partition without resizing to minimize the risk of possible problems.
So before proceeding with recovery, you need to know about all partitions existing on the system
disk, their sizes, and physical order. To see this information, start Acronis True Image Home and
choose Recovery → Disk and Partition Recovery in the main menu. Select a backup of your system
disk and click Details on the toolbar. Acronis True Image Home will display information about the
backed up disk, including a graphical view of all partitions the disk contains and their physical order
on the disk. If any partition display is too small for accommodating the relevant information, hover
the mouse pointer over the partition to see the information.
Assuming that you have got the information, let's proceed with recovery of a system disk using the
rescue media.
87 Copyright © Acronis, Inc., 2000-2010
Page 88

Attach the external drive if it contains the backup archive to be used for recovery and make sure that the drive is
powered on. This must be done before booting from Acronis rescue media.
1. Arrange the boot sequence in BIOS so as to make your rescue media device (CD, DVD or USB
stick) the first boot device. See Arranging boot sequence in BIOS (p. 187).
2. Boot from the rescue media and select Acronis True Image Home (Full version).
3. Select Recovery → Disk and Partition Recovery in the main menu and then choose the image
backup of your system disk that you want to use for recovery.
If the disks have different disk letters in Windows and the recovery environment, the program
will display the following error message: "Acronis True Image Home cannot detect volume N of
"Name" archive", where Name is the name of the required image backup archive and volume
number (N) may be different depending on the number of backups in the archive.
4. Select Recover whole disks and partitions at the Recovery method step.
5. At the What to recover step select the boxes of the partitions to be recovered. Do not select the
MBR and Track 0 box, as this will result in selecting the entire disk for recovery. Recovering the
entire disk does not allow you to resize partitions manually. You will recover the MBR later.
Select the partitions and click Next.
Selecting partitions leads to appearance of the relevant steps "Settings of partition ...". Take note
that these steps start with partitions without an assigned disk letter (as usually is the case with
hidden partitions), then go in ascending order of partition disk letters and this order cannot be
changed. The order may differ from the physical order of the partitions on the hard disk.
6. You can specify the following partition settings: location, type, and size. You will first specify the
settings of the hidden partition as it usually does not have a disk letter. Because you are
recovering to the new disk, click New location. Select the destination disk by either its assigned
name or capacity.
If you have not assigned names to the disks and have any doubts when selecting the destination
disk, you may abort the recovery by clicking Cancel and try to identify the target disk by its model
number, interface, etc. To see this information, select Tools & Utilities → Add New Disk in the
main menu and the Disk selection screen will show the information. Use it for identifying the
destination disk number, then click Cancel, start the Recovery Wizard again, repeat the above
actions, and select the destination disk.
7. Clicking Accept will return you to the "Settings of partition ..." screen. Check the partition type
and change it, if necessary.
8. Proceed to specifying the partition size by clicking Change default in the Partition size area. By
default the partition will occupy the entire new disk. You need to keep the hidden partition size
unchanged, as well as place it to the same location on the disk (at the start or the end of disk
space). To do this, resize and relocate the partition by dragging it or its borders with a mouse on
the horizontal bar on the screen or by entering corresponding values into the appropriate fields
(Partition size, Free space before, Free space after). Click Accept when the partition has the
required size and location and then click Next.
Specify the settings for the second partition which in this case is your system partition. Click New
location, then select unallocated space on the destination disk that will receive the partition.
Click Accept, check the partition type (change, if necessary). You should remember that the
system partition must be primary and marked as active. Specify the partition size which by
default equals the original size. Usually there is no free space after the partition, so allocate all
the unallocated space on the new disk to the second partition, click Accept and then click Next.
88 Copyright © Acronis, Inc., 2000 -2010
Page 89
9. Carefully read the summary of operations to be performed. If you do not want to validate the
backup, click Proceed, otherwise click Options and select the "Validate backup archive before
recovery" box before clicking Proceed.
10. When the operation finishes, proceed to MBR recovery. In this case you need to recover the MBR
as the PC manufacturer could change the generic Windows MBR or a sector on the track 0 to
provide access to the hidden partition.
11. Select the same backup once more, right-click and select Recover in the shortcut menu, choose
Recover whole disks and partitions at the Recovery method step and then select the MBR and
Track 0 box.
12. At the next step select the destination disk as the target for MBR recovery, click Next and then
Proceed. After MBR recovery is complete, exit the standalone version of Acronis True Image
Home.
Windows should not "see" both the new and old drive during the first boot after recovery. If you upgrade the old
drive to a larger capacity new one, disconnect the old drive before the first boot otherwise there may be
problems booting Windows.
Switch off the computer, if you need to disconnect the old drive, otherwise just reboot the computer
after removing the rescue media.
Boot the computer to Windows. It may report that new hardware (hard drive) is found and Windows
needs to reboot. After making sure that the system operates normally, restore the original boot
sequence.
10.3 Recovering a data partition or disk
As we already said, data partitions and disks are usually recovered in Windows because this allows
you to avoid such issues as the program not detecting your hard drives, changing disk letters, etc. To
reduce the risk of problems during recovery even more, validate the backup archive to be recovered
and check the destination disk for errors using chkdsk.
Attach the external drive if it contains the backup archive to be used for recovery and make sure that the drive is
powered on. This must be done before starting Acronis True Image Home.
1. Start Acronis True Image Home.
2. Select Recovery → Disk and Partition Recovery in the main menu, then choose the image
backup containing the data partition you want to recover.
3. Select Recover whole disks and partitions at the Recovery method step.
4. As you are going to recover a data partition, there is no need to select the "Recover MBR and
track 0" box at the What to recover step. Select just the data partition you want to recover.
5. The next step allows you to select settings for the partition to be recovered. When recovering the
partition to the original location, you only need to check the settings. If you want to recover the
partition to another location, select the new location and set the partition type you need (or
leave the default setting). When the new location is an existing partition, usually you may leave
its disk letter and size unchanged. When the new location is unallocated space e.g. after installing
a new hard drive you intend to use for your data, specify the size of the new partition and assign
a logical disk letter.
6. Carefully read the Summary. After making sure that you have made the correct settings, click
Proceed, if you do not need to change the default recovery options, otherwise click Options.
89 Copyright © Acronis, Inc., 2000-2010
Page 90

7. The Options step allows setting the recovery options, for example, to check the file system after
recovery. For more information about the recovery options see Setting default recovery options
(p. 99). After setting the recovery options click Proceed.
Recovering the entire data disk backup requires similar steps with few minor differences, for
example, there is no "Check file system after recovery" option. When recovering to the original hard
drive the steps of the Recovery Wizard are straightforward - just make sure that you select the disk
with the same number as the backed up disk, as the destination.
Recovering your data disk backup to a hard drive with a different capacity has some nuances
depending on its capacity and geometry (the number of heads and sectors per track). When
recovering to a smaller capacity hard drive, the partition(s) size will be proportionally reduced. When
recovering to a larger capacity hard drive, there are two cases: 1) if the hard drive has the same
geometry, the backed up disk will be recovered "as is" thus leaving unallocated space; and 2) if the
hard drive has different geometry, the partition(s) size will be proportionally enlarged.
10.4 Recovering files and folders
Depending on the backup types you have used, there may be several methods of recovering files and
folders. In most cases you recover files and folders in Windows. You can recover files and folders
from a file backup archive and from a disk/partition image as well. To recover files/folders from an
image, you can mount the image (see Mounting an image (p. 137)) and copy files/folders to a desired
location using Windows Explorer.
If you need to recover just a single file/folder or a few files, double-click on the required image
backup archive. Then drill-down to the folder containing the file(s) you need to recover, select the
file(s), right-click and choose Copy in the shortcut menu, open a folder for saving the files to be
recovered, right-click in the folder and choose Paste in the shortcut menu. You can also drag the files
from the backup archive into the destination folder. This method can also be used in case of My Data
type backup archives.
One more method of recovering files/folders from an image is described below. See Recovering files
and folders from image archives (p. 91).
10.4.1 Recovering files and folders from file archives
This section describes how to recover files and folders from a file backup archive.
1. Start the Recovery Wizard by selecting Recovery → File Recovery in the main program menu.
2. Select the archive.
Data recovery directly from an FTP server requires the archive to consist of files of no more than 2GB. If you
suspect that some of the files are larger, first copy the entire archive (along with the initial full backup) to a
local hard disk or a network share disk. See notes and recommendations for supporting FTP servers in
Supported storage media (p.
***
Please note that before recovering Microsoft Outlook mail messages, accounts, contacts, settings, etc. from
My E-mail backup on a new computer with a newly installed Microsoft Outlook, you should launch Outlook
at least once. If Microsoft Outlook is launched for the first time after recovering the E-mail information, it
may malfunction.
14).
If you use Microsoft Outlook Express and recover its mail folders, accounts, etc. from My E-mail backup on
another PC or after performing a so called "clean install" of Microsoft Windows, please, do not forget to
90 Copyright © Acronis, Inc., 2000-2010
Page 91
switch to your identity after recovery by selecting File → Switch Identity in Outlook Express and then
double-clicking on your identity in the list of the dialog box.
3. If you are going to recover files from an archive containing incremental backups, Acronis True
Image Home will enable selecting one of the successive incremental backups by its creation
date/time. Thus, you can roll back the files/folders state to a certain date.
To recover data from an incremental backup, you must have all the previous backup files and the initial full
backup. If any of the successive backups are missing, recovery is not possible.
To recover data from a differential backup, you must have the initial full backup as well.
4. Select a folder on your computer where you want to recover selected files/folders (a target
folder). You can recover data to its original location or choose a new one, if necessary. Choosing
a new location results in appearance of one more required step, namely, Destination.
When you choose a new location, by default the selected items will be recovered without
recovering the original, absolute path. You may also wish to recover the items with their entire
folder hierarchy. If this is the case, select Recover absolute path.
At the Destination step select a new location on the directory tree. You can create a new folder
for the files to be recovered to by clicking Create new folder.
5. At the What to recover step select the files and folders to recover. You can choose to recover all
data or browse the archive contents and select the desired folders or files. Clicking Next will
bring you to the Finish step. Click Proceed if you do not need to change the default recovery
options, otherwise click Options.
6. The first optional step allows you to keep useful data changes made since the selected backup
was created. Choose what to do if the program finds in the destination folder a file with the same
name as in the archive. By default, the program will overwrite existing files and folders, though
more recent files and folders are protected from overwriting. If necessary, you can protect the
system, hidden files and folders from being overwritten by selecting the appropriate check
boxes.
In addition, you can protect the files that meet the criteria you specify in this window from being
overwritten.
Unselecting the Overwrite existing files check box will give the files on the hard disk
unconditional priority over the archived files.
7. Select the options for the recovery process (that is, recovery process priority, file-level security
settings, etc.). The options you set on this page will be applied only to the current recovery task.
8. Up to this point, you can make changes in the created task by choosing the step you want to
change and editing its settings. Clicking Proceed will launch the task execution.
9. The task progress will be shown in a special window. You can stop the procedure by clicking
Cancel. Please keep in mind that the aborted procedure may still cause changes in the
destination folder.
10.4.2 Recovering files and folders from image archives
Image archives provide recovery of not only entire disks/partitions, but files/folders too.
1. Start the Recovery Wizard by selecting Recovery → Disk and Partition Recovery in the main
program menu.
2. Select the archive.
Data recovery directly from an FTP server requires the archive to consist of files of no more than 2GB. If you
suspect that some of the files are larger, first copy the entire archive (along with the initial full backup) to a
91 Copyright © Acronis, Inc., 2000-2010
Page 92

local hard disk or a network share disk. See notes and recommendations for supporting FTP servers in
Supported storage media (p. 14
).
3. If you are going to recover files from an archive containing incremental backups, Acronis True
Image Home will enable selecting one of the successive incremental backups by its creation
date/time. Thus, you can roll back the file/folder state to a certain date.
To recover data from an incremental backup, you must have all the previous backup files and the initial full
backup. If any of the successive backups are missing, recovery is not possible.
To recover data from a differential backup, you must have the initial full backup as well.
4. At the Recovery method step select Recover chosen files and folders.
5. Select where you want to recover the chosen files/folders. You can recover data to its original
location or choose a new one, if necessary.
When recovering files/folders under bootable rescue media, the Original location option is disabled,
because drive letters in standalone Acronis True Image Home might differ from the way Windows identifies
drives.
Choosing a new location results in appearance of one more required step, namely, Destination.
When you choose a new location, by default the selected items will be recovered without
recovering the original, absolute path. You may also wish to recover the items with their entire
folder hierarchy. If this is the case, select Recover absolute path.
At the Destination step select a new location on the directory tree. You can create a new folder
for the files to be recovered by clicking Create new folder.
6. Select the files and folders to recover. Make sure that you unselect all unnecessary folders.
Otherwise you will recover a lot of excess files.
7. The first optional step allows you to keep useful data changes made since the selected backup
was created. Choose what to do if the program finds a file in the destination folder with the same
name as in the archive. By default, the program will overwrite existing files and folders, though
more recent files and folders are protected from being overwritten. If necessary, you can protect
the system, hidden files and folders from being overwritten by selecting the appropriate check
boxes.
In addition, you can protect the files that meet the criteria you specify in this window from being
overwritten.
Unselecting the Overwrite existing files checkbox will give the files on the hard disk
unconditional priority over the archived files.
8. Select the options for the recovery process (that is, recovery process priority, file-level security
settings, etc.). The options you set on this page will be applied only to the current recovery task.
9. Up to this point, you can make changes in the created task by choosing the step you want to
change and editing its settings. Clicking Proceed will launch the task execution.
10. The task progress will be shown in a special window. You can stop the procedure by clicking
Cancel. Please keep in mind that the aborted procedure may still cause changes in the
destination folder(s).
92 Copyright © Acronis, Inc., 2000-2010
Page 93

11 Additional recovery information
11.1 Recovery Wizard - detailed information
The below description of the Recovery Wizard refers to recovering partitions/disks from image
backups. If you need to recover files and folders, see Recovering files and folders (p. 90).
11.1.1 Starting the Recovery Wizard
Start the Recovery Wizard by selecting Recovery → Disk and Partition Recovery in the main
program menu.
11.1.2 Archive selection
1. Select the archive. Acronis True Image Home will show the list of backup archives whose
locations it knows from the information stored in its database. If the program has not found the
backup you need (for example, when the backup was made in the recovery environment or by a
previous Acronis True Image Home version), you can find it manually by clicking Browse and then
selecting the backup location on the directory tree and choosing the backup in the right pane.
If the archive is located on removable media, e.g. CD, first insert the last CD and then insert disks in reverse
order when the Recovery Wizard prompts you.
***
Data recovery directly from an FTP server requires the archive to consist of files of no more than 2GB each.
If you suspect that some of the files are larger, first copy the entire archive (along with the initial full
backup) to a local hard disk or network share disk. See notes and recommendations for supporting FTP
servers in Supported storage media (p. 14).
***
93 Copyright © Acronis, Inc., 2000-2010
Page 94
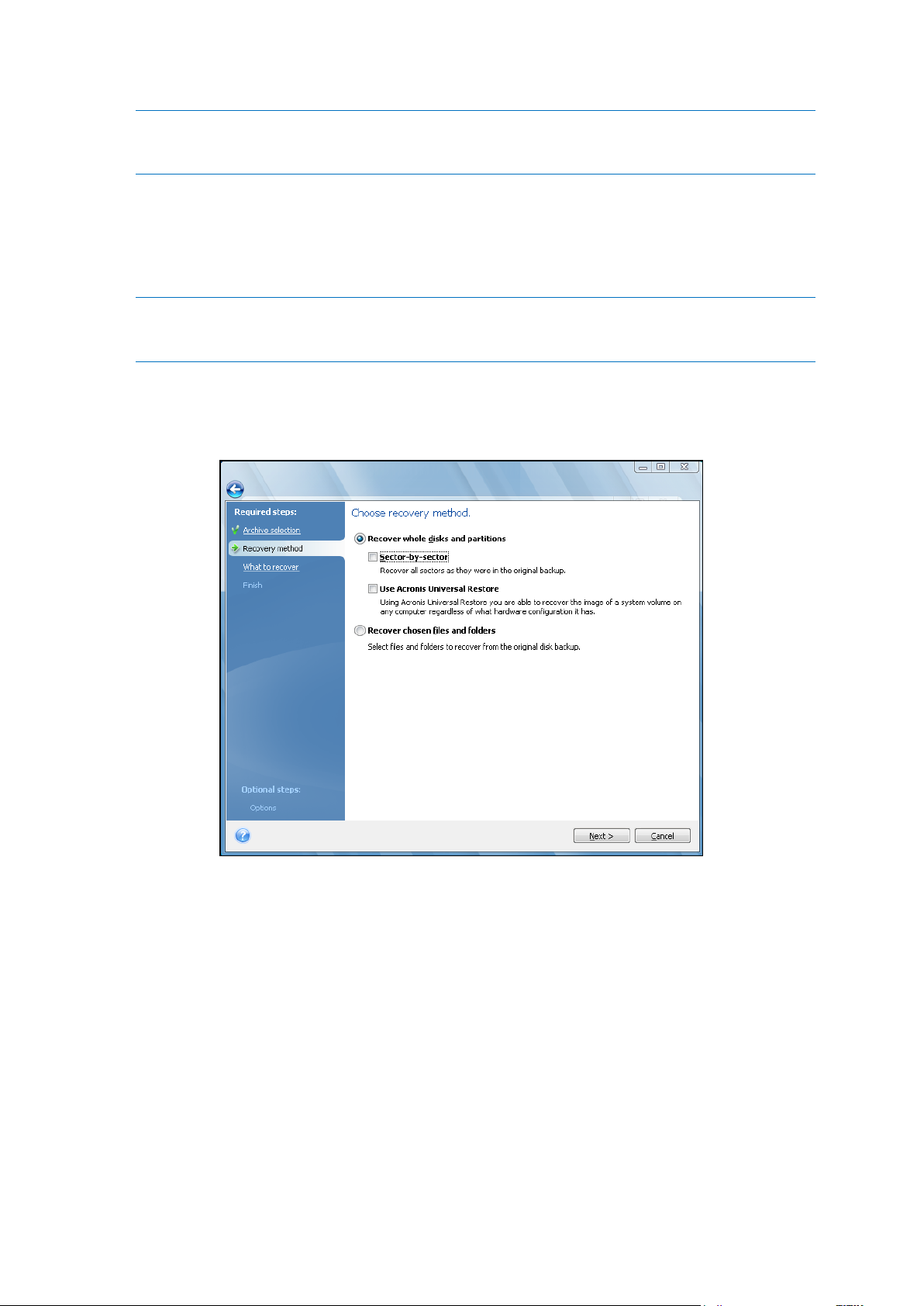
When recovering a backup of Windows Vista or Windows 7 system disk containing restore points, some of
your restore points (or all of them) may be missing if you boot from the recovered system disk and open the
System Restore tool.
If the archive is password-protected, Acronis True Image Home will ask for it. The partitions
layout and the Next button will be unavailable until you enter the correct password.
2. If you are going to recover data from an archive containing incremental backups, Acronis True
Image Home will enable selecting one of the successive incremental backups by its creation
date/time. Thus, you can roll back the disk/partition state to a certain date.
To recover data from an incremental backup, you must have all previous backup files and the initial full
backup. If any of the successive backups are missing, recovery is not possible. To recover data from a
differential backup, you must have the initial full backup as well.
11.1.3 Recovery method selection
Select what you want to recover:
Recover whole disks and partitions
Having chosen a disk and partition recovery type, you may need to select the following option.
Sector-by-sector
The program will recover both used and unused sectors of disks or partitions. This option will appear
only when you choose to recover a sector-by-sector backup.
Change size of disk or partition (for advanced users)
This box will appear only when you choose to recover a backup from CD/DVDs. By default the box is
unchecked and partition(s) will be recovered "as is". This allows you to reduce the amount of disc
swapping while recovering a partition when a backup archive spans several CD/DVDs. Selecting this
box when you need to resize a partition or disk greatly increases the amount of disc swapping, so we
recommend to copy all CD/DVDs to a folder on a hard disk and recover from this folder.
94 Copyright © Acronis, Inc., 2000-2010
Page 95

Use Acronis Universal Restore
Using Universal Restore (provided by separately purchased Acronis Plus Pack) allows recovering an
image of your system partition on a computer with dissimilar hardware.
Recover chosen files and folders
If you are not going to recover the system, but only want to repair damaged files, select Recover
chosen files and folders.
You can recover files from disk/partition images only if they have the FAT or NTFS file systems.
11.1.4 Selecting a disk/partition to recover
The selected archive file can contain images of several partitions or even disks. Select which
disk/partition to recover.
During a single session, you can recover several partitions or disks, one by one, by selecting one disk
and setting its parameters first and then repeating these actions for every partition or disk to be
recovered.
Disk and partition images contain a copy of track 0 along with the MBR (master boot record). It
appears in this window in a separate line. You can choose whether to recover the MBR and track 0 by
selecting the corresponding box. Recover the MBR if it is critical to your system booting.
When MBR recovery is chosen, the "Recover disk signature" box will appear in the bottom left corner
at the next step. Recovering disk signature may be desirable due to the following reasons:
1. Acronis True Image Home creates scheduled tasks using the signature of the source hard disk. If
you recover the same disk signature, you don't need to re-create or edit the tasks created
previously.
2. Some installed applications use disk signature for licensing and other purposes.
3. If you use Windows Restore Points, they will be lost when the disk signature is not recovered.
95 Copyright © Acronis, Inc., 2000-2010
Page 96

4. In addition, recovering disk signature allows to recover VSS snapshots used by Windows Vista
and Windows 7's "Previous Versions" feature.
If the box is unselected, Acronis True Image Home generates a new disk signature for the recovered
drive. This may be needed when you use an image backup not for disaster recovery but for cloning
your Windows Vista hard drive to another one. Trying to boot Windows after cloning with both
drives connected will result in a problem. During Windows booting, its loader checks the disk
signatures of all the connected drives, and if it finds two identical disk signatures, the loader changes
the signature of the second disk, which would be the clone disk. Once this happens, the clone disk
would not be able to boot up independently of the original disk, because the MountedDevices fields
in the clone's registry reference the disk signature of the original disk, which will not be available if
the original disk is disconnected.
11.1.5 Selecting a target disk/partition
1. Select a target disk or partition where you want to recover the selected image. You can recover
data to its initial location, to another disk/partition or to an unallocated space. The target
partition should be at least the same size as the uncompressed image data.
All the data stored on the target partition will be replaced by the image data, so be careful and watch for
non-backed-up data that you might need.
2. When recovering an entire disk, the program will analyze the target disk structure to see
whether the disk is free.
If there are partitions on the target disk, you will be prompted by the confirmation window stating
that the destination disk contains partitions, perhaps with useful data.
You will have to select between:
OK – all existing partitions will be deleted and all their data will be lost.
Cancel – no existing partition will be deleted, discontinuing the recovery operation. You will then
have to cancel the operation or select another disk.
96 Copyright © Acronis, Inc., 2000-2010
Page 97

Note that no real changes or data destruction will be performed at this time! For now, the program will just
map out the procedure. All changes will be implemented only when you click Proceed in the wizard's Summary
window.
11.1.6 Changing the recovered partition type
When recovering a partition, you can change its type, though it is not required in most cases.
To illustrate why you might need to do this, let's imagine that both the operating system and data
were stored on the same primary partition on a damaged disk.
If you are recovering a system partition to the new (or the same) disk and want to load the operating
system from it, you will select Active.
Acronis True Image Home automatically corrects boot information during recovery of the system
partition to make it bootable, even if it was not recovered to the original partition (or disk).
If you recover a system partition to another hard disk with its own partitions and OS, most likely you
will need only the data. In this case, you can recover the partition as Logical to access the data only.
By default, the original partition type is selected.
Selecting Active for a partition without an installed operating system could prevent your computer from
booting.
11.1.7 Changing the recovered partition size and location
You can resize and relocate a partition by dragging it or its borders with a mouse on the horizontal
bar on the screen or by entering corresponding values into the appropriate fields.
97 Copyright © Acronis, Inc., 2000-2010
Page 98

Using this feature, you can redistribute the disk space among partitions being recovered. In this case,
you will have to recover the partition to be reduced first.
These changes might be useful if you are going to copy your hard disk to a new high-capacity one by creating its
image and recovering it to a new disk with larger partitions.
11.1.8 Assigning a letter to the recovered partition
Acronis True Image Home will assign an unused letter to a recovered partition. You can select the
desired letter from a drop-down list or let the program assign a letter automatically by selecting the
Auto setting.
You should not assign letters to partitions inaccessible to Windows, such as to those other than FAT
and NTFS.
11.1.9 Setting recovery options
Clicking Options at the Finish step allows selecting the options for the recovery process (that is,
recovery process priority, etc.). The settings will be applied only to the current recovery task. Or, you
can edit the default options. See Setting default recovery options (p. 99) for more information.
11.1.10 Executing recovery
Up to this point, you can make changes in the created task by choosing the step you want to change
and editing its settings. If you click Cancel, no changes will be made to the disk(s). Clicking Proceed
will launch the task execution.
The task progress will be shown in a special window. You can stop the procedure by clicking Cancel.
However, it is critical to note that the target partition will be deleted and its space unallocated – the
98 Copyright © Acronis, Inc., 2000-2010
Page 99

same result you will get if the recovery is unsuccessful. To recover the "lost" partition, you will have
to recover it from the image again.
11.2 Setting default recovery options
To set the recovery options to be used by default during any data recovery, select Tools & Utilities →
Options → Recovery options. You can always restore the default recovery options to the values
preset during installation of Acronis True Image Home. To do this, click Reset the current to default
on the toolbar of the Options window. To reset just a single recovery option, select it on the left
pane and click Reset the current to default.
Clicking Reset all to default will reset all the default options (for backup/recovery, notifications, etc.) to their
preset values, so this button should be used with caution.
11.2.1 File recovery options
Recover files with their original security settings.
The preset is enabled.
If the file security settings were preserved during backup (see File-level security settings (p. 78)),
you can choose whether to restore them or let the files inherit the security settings of the folder
where they will be recovered.
This option is effective only when recovering files from file/folder archives.
Set current date and time for recovered files
The preset is disabled.
You can choose whether to recover the file date and time from the archive or assign the files the
current date and time. By default the file date and time from the archive will be assigned.
Validate backup archive before recovery
The preset is disabled.
Before data is recovered from the archive, Acronis True Image Home can check its integrity. If
you suspect that the archive might have been corrupted, enable this option.
Check the file system after recovery
The preset is disabled.
Having recovered a partition from an image, Acronis True Image Home can check the integrity of
the file system. To do so, enable this option.
Limitations on use of this option:
Check of the file system is available only when recovering partitions using FAT16/32 and NTFS file
systems.
The file system will not be checked if a reboot is required during recovery, for example, when
recovering the system partition to its original place.
11.2.2 Overwrite file options
This option is not applicable to recovery of disks and partitions from images.
By default, the program will overwrite existing files and folders, though more recent files and folders
are protected from overwriting.
99 Copyright © Acronis, Inc., 2000-2010
Page 100

You can set default filters for the specific types of files you wish to preserve during archive recovery.
For example, you may want hidden and system files and folders, newer files and folders, as well as
files matching selected criteria not to be overwritten by the archive files.
While specifying the criteria, you can use the common Windows wildcard characters. For example, to
preserve all files with extension .exe, add *.exe. My???.exe will preserve all .exe files with names
consisting of five symbols and starting with "my".
Unselecting the Overwrite existing files check box will give the files on the hard disk unconditional
priority over the archived files.
11.2.3 Pre/post commands
You can specify commands or batch files to be automatically executed before and after the recovery
procedure. Click Edit to open the Edit Command window where you can easily input the command,
its arguments and working directory or browse folders to find a batch file.
Please note that interactive commands, i.e. commands that require user input, are not supported.
Unselecting the Do not perform operations until the command's execution is complete box,
selected by default, will permit the recovery procedure to run concurrently with your command
execution.
If you want the recovery to be performed even if your command fails, uncheck the Abort the
operation if the user command fails box (checked by default).
You can test execution of the command you created by clicking the Test command button.
Please keep in mind that when recovering the system partition to the original place your post command will not
be executed because recovery of the system partition requires a reboot, resulting in loss of the command. Such
a command will also be lost if the program requests a reboot during any other recovery operation.
11.2.4 Recovery priority
The preset is Low.
The priority of any process running in a system determines the amount of CPU usage and system
resources allocated to that process. Decreasing the recovery priority will free more resources for
other CPU tasks. Raising recovery priority may speed up the recovery process as it takes resources
from other currently running processes. The effect will depend on total CPU usage and other factors.
11.3 Detailed information on recovery operations involving dynamic/GPT disks and volumes
The below information is intended for helping you with recovery operations involving dynamic/GPT
disks and volumes. There may be various situations, for example, where you may use both basic and
dynamic disks in your computer. Similarly, you may use disks with both MBR and GPT partition
schemes at the same time.
1) Acronis True Image Home supports recovery of dynamic volumes to the following locations on the
local hard drives:
to the original location (to the same dynamic volume)
100 Copyright © Acronis, Inc., 2000-2010
 Loading...
Loading...