Page 1

Acronis® Backup & Recovery ™ 10
Advanced Workstation
Update 3
User's Guide
Page 2

Copyright © Acronis, Inc., 2000-2010. All rights reserved.
“Acronis” and “Acronis Secure Zone” are registered trademarks of Acronis, Inc.
"Acronis Compute with Confidence", “Acronis Startup Recovery Manager”, “Acronis Active Restore”
and the Acronis logo are trademarks of Acronis, Inc.
Linux is a registered trademark of Linus Torvalds.
VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the
United States and/or other jurisdictions.
Windows and MS-DOS are registered trademarks of Microsoft Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Distribution of substantively modified versions of this document is prohibited without the explicit
permission of the copyright holder.
Distribution of this work or derivative work in any standard (paper) book form for commercial
purposes is prohibited unless prior permission is obtained from the copyright holder.
DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE
EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
Third party code may be provided with the Software and/or Service. The license terms for such thirdparties are detailed in the license.txt file located in the root installation directory. You can always find
the latest up-to-date list of the third party code and the associated license terms used with the
Software and/or Service at http://kb.acronis.com/content/7696
Page 3

Table of contents
1 Introducing Acronis® Backup & Recovery™ 10 ......................................................................... 8
1.1 Acronis Backup & Recovery 10 overview .................................................................................. 8
1.2 Getting started ........................................................................................................................... 9
1.2.1 Using the management console ................................................................................................................11
1.3 Acronis Backup & Recovery 10 components ...........................................................................17
1.3.1 Agent for Windows .....................................................................................................................................18
1.3.2 Components for centralized management ...............................................................................................19
1.3.3 Management Console ................................................................................................................................21
1.3.4 Bootable Media Builder .............................................................................................................................21
1.3.5 Acronis WOL Proxy .....................................................................................................................................22
1.4 Supported file systems ............................................................................................................22
1.5 Supported operating systems ..................................................................................................23
1.6 System requirements ...............................................................................................................24
1.7 Technical Support ....................................................................................................................25
2 Understanding Acronis Backup & Recovery 10 ....................................................................... 26
2.1 Basic concepts ..........................................................................................................................26
2.2 Full, incremental and differential backups ..............................................................................30
2.3 User privileges on a managed machine ...................................................................................32
2.4 Owners and credentials ...........................................................................................................32
2.5 GFS backup scheme .................................................................................................................33
2.6 Tower of Hanoi backup scheme ..............................................................................................37
2.7 Retention rules ........................................................................................................................39
2.8 Backing up dynamic volumes (Windows) ................................................................................42
2.9 Tape support ............................................................................................................................44
2.9.1 Tape compatibility table .............................................................................................................................44
2.9.2 Using a single tape drive .............................................................................................................................45
2.10 Support for SNMP ....................................................................................................................46
2.11 Proprietary Acronis technologies ............................................................................................47
2.11.1 Acronis Secure Zone ...................................................................................................................................47
2.11.2 Acronis Startup Recovery Manager ...........................................................................................................48
2.11.3 Universal Restore (Acronis Backup & Recovery 10 Universal Restore) ....................................................49
2.11.4 Acronis Active Restore ...............................................................................................................................50
2.12 Understanding centralized management ................................................................................52
2.12.1 Basic concepts ............................................................................................................................................52
2.12.2 Setting up centralized data protection in a heterogeneous network ......................................................53
2.12.3 Grouping the registered machines ............................................................................................................57
2.12.4 Policies on machines and groups ...............................................................................................................57
2.12.5 Backup policy's state and statuses .............................................................................................................61
2.12.6 Deduplication .............................................................................................................................................64
2.12.7 Privileges for centralized management .....................................................................................................69
2.12.8 Communication between Acronis Backup & Recovery 10 components ..................................................73
3 Options .................................................................................................................................. 80
3.1 Console options .......................................................................................................................80
Page 4

3.1.1 Startup page ...............................................................................................................................................80
3.1.2 Pop-up messages ........................................................................................................................................80
3.1.3 Time-based alerts .......................................................................................................................................81
3.1.4 Number of tasks .........................................................................................................................................81
3.1.5 Fonts ...........................................................................................................................................................81
3.2 Management server options ...................................................................................................82
3.2.1 Logging level ...............................................................................................................................................82
3.2.2 Log cleanup rules ........................................................................................................................................82
3.2.3 Event tracing ...............................................................................................................................................83
3.2.4 Domain access credentials .........................................................................................................................84
3.2.5 Acronis WOL Proxy .....................................................................................................................................84
3.2.6 VM protection options ...............................................................................................................................84
3.2.7 Online backup proxy ...................................................................................................................................85
3.3 Machine options ......................................................................................................................86
3.3.1 Machine management ...............................................................................................................................86
3.3.2 Event tracing ...............................................................................................................................................87
3.3.3 Log cleanup rules ........................................................................................................................................89
3.3.4 Online backup proxy ...................................................................................................................................89
3.3.5 Customer Experience Program ..................................................................................................................89
3.4 Default backup and recovery options ......................................................................................90
3.4.1 Default backup options ..............................................................................................................................90
3.4.2 Default recovery options ......................................................................................................................... 112
4 Vaults .................................................................................................................................. 121
4.1 Centralized vaults ................................................................................................................. 122
4.1.1 Working with the "Centralized vault" view ............................................................................................ 123
4.1.2 Actions on centralized vaults .................................................................................................................. 124
4.1.3 Tape libraries ........................................................................................................................................... 129
4.2 Personal vaults ...................................................................................................................... 152
4.2.1 Working with the "Personal vault" view ................................................................................................. 153
4.2.2 Actions on personal vaults ...................................................................................................................... 154
4.3 Common operations ............................................................................................................. 155
4.3.1 Operations with archives stored in a vault ............................................................................................. 155
4.3.2 Operations with backups ........................................................................................................................ 156
4.3.3 Deleting archives and backups ................................................................................................................ 157
4.3.4 Filtering and sorting archives .................................................................................................................. 158
5 Scheduling ........................................................................................................................... 159
5.1 Daily schedule ....................................................................................................................... 160
5.2 Weekly schedule ................................................................................................................... 162
5.3 Monthly schedule ................................................................................................................. 164
5.4 Advanced scheduling settings .............................................................................................. 166
5.5 At Windows Event Log event ................................................................................................ 168
5.6 When an ADRM alert is received .......................................................................................... 170
5.7 Conditions ............................................................................................................................. 170
5.7.1 User is idle ................................................................................................................................................ 171
5.7.2 Location's host is available ...................................................................................................................... 171
5.7.3 Fits time interval ...................................................................................................................................... 172
5.7.4 User logged off ........................................................................................................................................ 172
5.7.5 Time since last backup ............................................................................................................................ 173
Page 5

6 Direct management ............................................................................................................. 174
6.1 Administering a managed machine ...................................................................................... 174
6.1.1 Dashboard ............................................................................................................................................... 174
6.1.2 Backup plans and tasks ........................................................................................................................... 176
6.1.3 Log ............................................................................................................................................................ 187
6.2 Creating a backup plan ......................................................................................................... 189
6.2.1 Why is the program asking for the password? ....................................................................................... 192
6.2.2 Backup plan's credentials ........................................................................................................................ 192
6.2.3 Source type .............................................................................................................................................. 192
6.2.4 Items to back up ...................................................................................................................................... 193
6.2.5 Access credentials for source .................................................................................................................. 194
6.2.6 Exclusions ................................................................................................................................................. 195
6.2.7 Archive ..................................................................................................................................................... 196
6.2.8 Simplified naming of backup files ........................................................................................................... 197
6.2.9 Access credentials for archive location ................................................................................................... 201
6.2.10 Backup schemes ...................................................................................................................................... 202
6.2.11 Archive validation .................................................................................................................................... 212
6.2.12 Setting up regular conversion to a virtual machine ............................................................................... 212
6.3 Recovering data .................................................................................................................... 213
6.3.1 Task credentials ....................................................................................................................................... 216
6.3.2 Archive selection ..................................................................................................................................... 216
6.3.3 Data type.................................................................................................................................................. 217
6.3.4 Content selection .................................................................................................................................... 217
6.3.5 Access credentials for location ................................................................................................................ 218
6.3.6 Destination selection ............................................................................................................................... 219
6.3.7 Access credentials for destination .......................................................................................................... 226
6.3.8 When to recover ...................................................................................................................................... 226
6.3.9 Universal Restore .................................................................................................................................... 226
6.3.10 How to convert a disk backup to a virtual machine ............................................................................... 228
6.3.11 Bootability troubleshooting .................................................................................................................... 229
6.3.12 Recovering the storage node .................................................................................................................. 232
6.4 Validating vaults, archives and backups ............................................................................... 233
6.4.1 Task credentials ....................................................................................................................................... 234
6.4.2 Archive selection ..................................................................................................................................... 234
6.4.3 Backup selection ...................................................................................................................................... 235
6.4.4 Location selection .................................................................................................................................... 236
6.4.5 Access credentials for source .................................................................................................................. 236
6.4.6 When to validate ..................................................................................................................................... 237
6.5 Mounting an image ............................................................................................................... 237
6.5.1 Archive selection ..................................................................................................................................... 238
6.5.2 Backup selection ...................................................................................................................................... 239
6.5.3 Access credentials ................................................................................................................................... 239
6.5.4 Volume selection ..................................................................................................................................... 239
6.6 Managing mounted images .................................................................................................. 240
6.7 Exporting archives and backups ........................................................................................... 240
6.7.1 Task credentials ....................................................................................................................................... 243
6.7.2 Archive selection ..................................................................................................................................... 243
6.7.3 Backup selection ...................................................................................................................................... 244
6.7.4 Access credentials for source .................................................................................................................. 244
6.7.5 Location selection .................................................................................................................................... 245
6.7.6 Access credentials for destination .......................................................................................................... 246
6.8 Acronis Secure Zone ............................................................................................................. 247
6.8.1 Creating Acronis Secure Zone ................................................................................................................. 247
Page 6

6.8.2 Managing Acronis Secure Zone ............................................................................................................... 249
6.9 Acronis Startup Recovery Manager ...................................................................................... 250
6.10 Bootable media ..................................................................................................................... 251
6.10.1 How to create bootable media ............................................................................................................... 252
6.10.2 Connecting to a machine booted from media ....................................................................................... 260
6.10.3 Working under bootable media .............................................................................................................. 260
6.10.4 List of commands and utilities available in Linux-based bootable media ............................................. 262
6.10.5 Recovering MD devices and logical volumes .......................................................................................... 263
6.10.6 Acronis PXE Server ................................................................................................................................... 267
6.11 Disk management ................................................................................................................. 268
6.11.1 Basic precautions ..................................................................................................................................... 269
6.11.2 Running Acronis Disk Director Lite .......................................................................................................... 269
6.11.3 Choosing the operating system for disk management .......................................................................... 270
6.11.4 "Disk management" view ........................................................................................................................ 270
6.11.5 Disk operations ........................................................................................................................................ 271
6.11.6 Volume operations .................................................................................................................................. 277
6.11.7 Pending operations ................................................................................................................................. 283
6.12 Collecting system information .............................................................................................. 284
7 Centralized management ..................................................................................................... 285
7.1 Administering Acronis Backup & Recovery 10 Management Server .................................... 285
7.1.1 Dashboard ............................................................................................................................................... 285
7.1.2 Backup policies ........................................................................................................................................ 287
7.1.3 Physical machines .................................................................................................................................... 292
7.1.4 Virtual machines ...................................................................................................................................... 309
7.1.5 Storage nodes .......................................................................................................................................... 314
7.1.6 Tasks ......................................................................................................................................................... 318
7.1.7 Log ............................................................................................................................................................ 320
7.1.8 Reporting ................................................................................................................................................. 324
7.2 Configuring Acronis Backup & Recovery 10 components .................................................... 329
7.2.1 Parameters set through administrative template .................................................................................. 330
7.2.2 Parameters set through GUI ................................................................................................................... 344
7.2.3 Parameters set through Windows registry ............................................................................................ 345
7.3 Creating a backup policy ....................................................................................................... 346
7.3.1 Policy credentials ..................................................................................................................................... 348
7.3.2 Items to back up ...................................................................................................................................... 349
7.3.3 Access credentials for source .................................................................................................................. 354
7.3.4 Exclusions ................................................................................................................................................. 354
7.3.5 Archive ..................................................................................................................................................... 355
7.3.6 Access credentials for location ................................................................................................................ 357
7.3.7 Backup scheme selection ........................................................................................................................ 357
7.3.8 Archive validation .................................................................................................................................... 367
8 Online backup ..................................................................................................................... 367
8.1 Introduction to Acronis Backup & Recovery 10 Online ........................................................ 368
8.1.1 What is Acronis Backup & Recovery 10 Online? .................................................................................... 368
8.1.2 What data can I back up and recover? ................................................................................................... 368
8.1.3 How long will my backups be kept in the online storage? ..................................................................... 369
8.1.4 How to secure my data? ......................................................................................................................... 369
8.1.5 How to back up virtual machines to the online storage? ...................................................................... 369
8.1.6 Backup and recovery FAQ ....................................................................................................................... 370
8.1.7 Initial Seeding FAQ ................................................................................................................................... 371
8.1.8 Large Scale Recovery FAQ ....................................................................................................................... 376
8.1.9 Subscription lifecycle FAQ ....................................................................................................................... 378
Page 7

8.2 Where do I start? .................................................................................................................. 380
8.3 Choosing a subscription ........................................................................................................ 380
8.4 Activating online backup subscriptions ................................................................................ 381
8.4.1 Activating subscriptions .......................................................................................................................... 381
8.4.2 Reassigning an activated subscription .................................................................................................... 382
8.5 Configuring proxy settings .................................................................................................... 383
8.6 Limitations of the online storage .......................................................................................... 384
8.7 Terminology reference ......................................................................................................... 385
9 Glossary ............................................................................................................................... 387
Page 8

1 Int roduci ng Acroni s® Backup & Recovery™ 10
1.1 Acronis Bac kup & Recovery 10 overview
Based on Acronis’ patented disk imaging and bare metal restore technologies, Acronis Backup &
Recovery 10 succeeds Acronis True Image Echo as the next generation disaster recovery solution.
Acronis Backup & Recovery 10 Advanced Workstation inherits the benefits of the Acronis True
Image Echo product family:
Backup of an entire disk or volume, including the operating system, all applications, and data
Bare metal recovery to any hardware
File and folder backup and recovery
Scalability from a single machine to an enterprise
Centralized management for distributed workstations
Dedicated servers for storage resource optimization.
Acronis Backup & Recovery 10 Advanced Workstation offers new benefits that help organizations
meet challenging Recovery Time Objectives while reducing both capital expense and software
maintenance costs.
Leveraging existing IT infrastructure
Data deduplication to reduce storage consumption and network bandwidth utilization
Flexible deduplication mechanism allowing deduplication of backup data both at the source
and at the storage
Improved support for robotic tape libraries
Backward compatibility and an easy upgrade from Acronis True Image Echo
Highly automated data protection
All-round planning of data protection (backup, retention and validation of backups) within a
backup policy
Built-in Tower of Hanoi and Grandfather-Father-Son backup schemes with customizable
parameters
A variety of events and conditions can be chosen to trigger a backup
Policy-based centralized management
Applying backup policies to groups of machines
Static and dynamic machine grouping
Easy work with virtual environments
Conversion of a backup to a fully configured VMware, Microsoft, Parallels, or Citrix virtual
machine
Redesigned GUI
Dashboard for quick operational decision making
Overview of all configured and running operations with color-coding for successful and failed
operations
Enterprise level of security
Controlling user rights to perform operations and access backups
8 Copyright © Acronis, Inc., 2000-2010
Page 9

Running services with minimal user rights
Restricted remote access to a backup agent
Secure communication between the product components
Using third-party certificates for authentication of the components
Data encryption options for both data transmission and storage
Backup of remote machines to a centralized storage node behind firewalls.
1.2 Getting started
Direct management
1. Install Acronis Backup & Recovery 10 Management Console and Acronis Backup & Recovery 10
Agent.
2. Start the console.
Windows
Start the console by selecting it from the start menu.
3. Connect the console to the machine where the agent is installed.
Where to go from here
For what to do next see "Basic concepts (p. 26)".
For understanding of the GUI elements see "Using the management console (p. 11)".
Centralized management
We recommend that you first try to manage the single machine using direct management as
described above.
To start with centralized management:
1. Install Acronis Backup & Recovery 10 Management Server (p. 19).
2. Install Acronis Backup & Recovery 10 Agents on the machines that need data protection. When
installing the agents, register each of the machines on the management server. To do so, enter
the server's IP or name and the centralized administrator's credentials in one of the installation
wizard's windows.
3. Install Acronis Backup & Recovery 10 Management Console (p. 21) on the machine from which
you prefer to operate. We recommend that you use the console that installs on Windows if you
have a choice between Windows and Linux console distributions. Install Acronis Bootable Media
Builder.
4. Start the console. Create the bootable media.
5. Connect the console to the management server.
The simplified way of centralized management
Backup
Using the Back up control, select the machine which you want to back up and then create a backup
plan (p. 389) on the machine. You can create backup plans on multiple machines in turn.
Recovery
Using the Recover control, select the machine where the data recovery is required and create a
recovery task on the machine. You can create recovery tasks on multiple machines in turn.
9 Copyright © Acronis, Inc., 2000-2010
Page 10

To recover the entire machine or the operating system that fails to start, use the bootable media (p.
390). You cannot control operations under bootable media using the management server, but you
can disconnect the console from the server and connect it to the machine booted from the media.
Managing plans and tasks
To manage the plans and tasks existing on the registered machines, select Machines > All machines
in the Navigation tree and then select each machine in turn. The Information pane below shows the
state and the details of plans and tasks existing on each machine and enables you to start, stop, edit,
and delete the plans and tasks.
You can also use the Tasks view that displays all tasks existing on the registered machines. The tasks
can be filtered by machines, backup plans and other parameters. Refer to the context help for
details.
Viewing log
To view the centralized log, collected from the registered machines, select Log in the Navigation
tree. The log entries can be filtered by machines, backup plans and other parameters. Refer to the
context help for details.
Creating centralized vaults
If you opt for storing all backup archives in a single or a few networked locations, create centralized
vaults in these locations. After a vault is created, you can view and administer its content by selecting
Vaults > Centralized > 'Vault name' in the Navigation tree. The shortcut to the vault will be deployed
to all the registered machines. The vault can be specified as a backup destination in any backup plan
created by you or by the registered machines' users.
The advanced way of centralized management
To make the best use of the centralized management capabilities offered by Acronis Backup &
Recovery 10, you can opt for:
Using deduplication
1. Install Acronis Backup & Recovery 10 Storage Node (p. 20) and add it to the management
server.
2. Create the deduplicating managed vault on the storage node.
3. Install the Acronis Deduplication add-on to the agent on all machines that will back up to the
deduplicating vault.
4. Ensure that the backup plans you create use the managed vault as destination for the backup
archives.
Creating a backup policy rather than backup plans
Set up a centralized backup policy and apply it to the All machines group. This way you will deploy
backup plans on each machine with a single action. Select Actions > Create backup policy from the
top menu and then refer to the context help.
Grouping the machines registered on the management server
Group the registered machines by appropriate parameters, create several policies and apply each
policy to the appropriate group of machines. For more information please refer to "Grouping the
registered machines (p. 57)".
The comprehensive example of advanced centralized management is provided in the "Setting up
centralized data protection in a heterogeneous network (p. 53)" section.
10 Copyright © Acronis, Inc., 2000-2010
Page 11
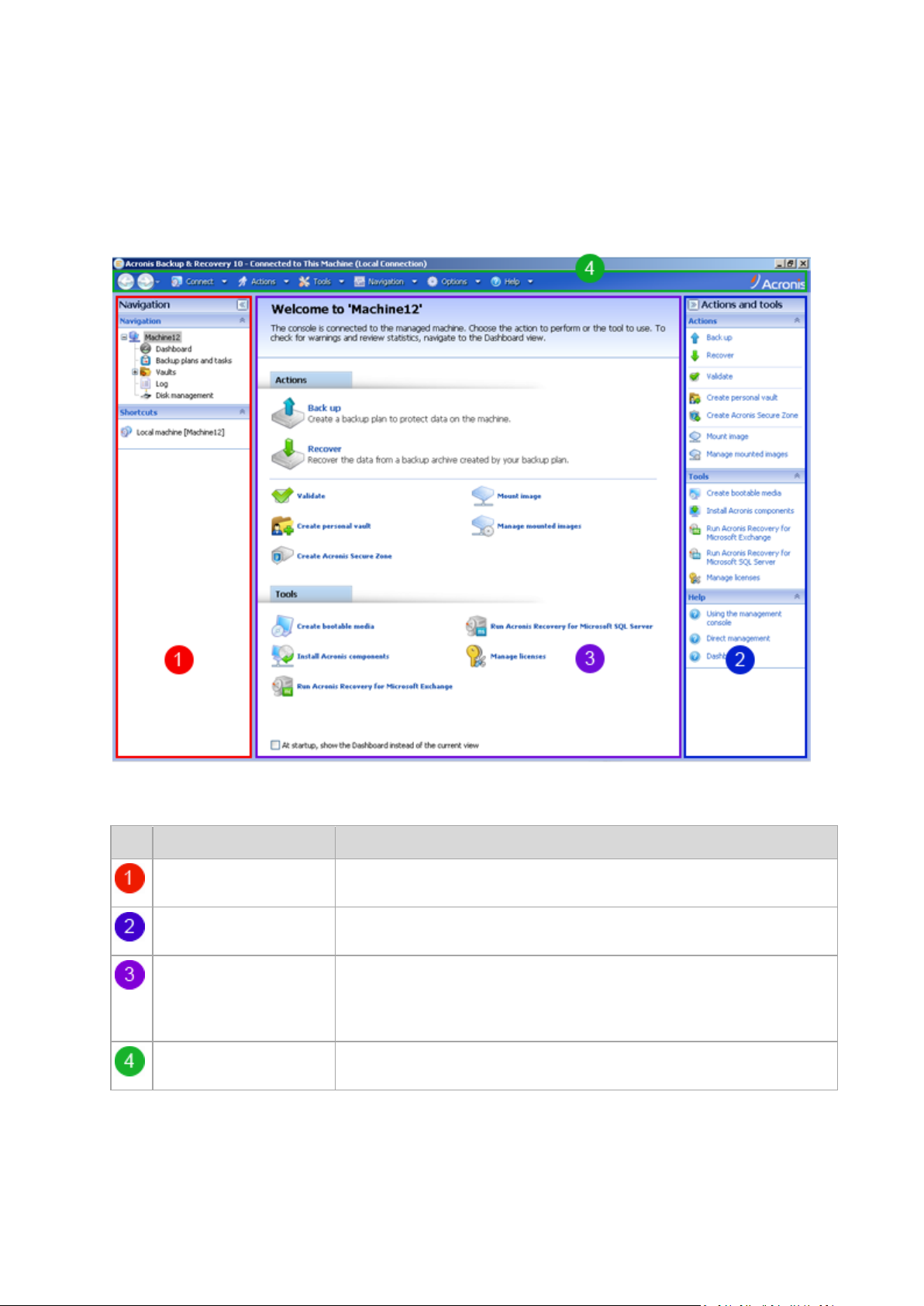
1.2.1 Using the management console
As soon as the console connects to a managed machine (p. 396) or to a management server (p. 397),
the respective items appear across the console's workspace (in the menu, in the main area with the
Welcome screen, the Navigation pane, the Actions and tools pane) enabling you to perform agentspecific or server-specific operations.
Acronis Backup & Recovery 10 Management Console - Welcome screen
Key elements of the console workspace
Name Description
Navigation pane Contains the Navigation tree and the Shortcuts bar and lets you navigate to
Actions and tools pane Contains bars with a set of actions that can be performed and tools (see the
Main area The main place of working, where you create, edit and manage backup plans,
Menu bar Appears across the top of the program window and lets you perform all the
1024x768 or higher display resolution is required for comfortable work with the management
console.
11 Copyright © Acronis, Inc., 2000-2010
the different views (see the Navigation pane (p. 12) section.)
Actions and Tools pane (p. 13) section).
policies, tasks and perform other operations. Displays the different views and
action pages (p. 15) depending on items selected in the menu, Navigation
tree, or on the Actions and Tools pane.
operations, available on both panes. Menu items change dynamically.
Page 12

1.2.1.1 "Navigation" pane
The navigation pane includes the Navigation tree and the Shortcuts bar.
Navigation tree
The Navigation tree enables you to navigate across the program views. Views depend on whether
the console is connected to a managed machine or to the management server.
Views for a managed machine
When the console is connected to a managed machine, the following views are available in the
navigation tree.
[Machine name]. Root of the tree also called a Welcome view. Displays the name of the
machine the console is currently connected to. Use this view for quick access to the main
operations, available on the managed machine.
Dashboard. Use this view to estimate at a glance whether the data is successfully
protected on the managed machine.
Backup plans and tasks. Use this view to manage backup plans and tasks on the managed
machine: run, edit, stop and delete plans and tasks, view their states and statuses, monitor
plans.
Vaults. Use this view to manage personal vaults and archives stored in there, add new
vaults, rename and delete the existing ones, validate vaults, explore backup content, mount
backups as virtual drives, etc.
Log. Use this view to examine information on operations performed by the program on
the managed machine.
Disk management. Use this view to perform operations on the machine's hard disk drives.
Views for a management server
When the console is connected to a management server, the following views are available in the
navigation tree.
[Management server name]. Root of the tree also called a Welcome view. Displays the name
of the management server the console is currently connected to. Use this view for quick access
to the main operations, available on the management server.
Dashboard. Use this view to estimate at a glance whether the data is successfully
protected on the machines registered on the management server.
Backup policies. Use this view to manage backup policies existing on the management
server.
Physical machines. Use this view to manage machines registered on the management
server.
Vaults. Use this view to manage centralized vaults and archives stored in there: create
new managed and unmanaged vaults, rename and delete the existing ones.
Storage nodes. Use this view to manage storage nodes. Add a storage node to be able to
create centralized vaults that will be managed by the node.
Tasks. Use this view to manage tasks, run, edit, stop and delete tasks, monitor their
states, examine task history.
12 Copyright © Acronis, Inc., 2000-2010
Page 13
Log. Use this view to examine the history of centralized management operations, such as
creating a managed entities group, applying a policy, managing a centralized vault; as well as
the history of operations logged in the local logs of the registered machines and the storage
nodes.
Shortcuts bar
The Shortcuts bar appears under the navigation tree. It offers you an easy and convenient way of
connection to the machines in demand by adding them as shortcuts.
To add a shortcut to a machine
1. Connect the console to a managed machine.
2. In the navigation tree, right-click the machine's name (a root element of the navigation tree), and
then select Create shortcut.
If the console and agent are installed on the same machine, the shortcut to this machine will be
added to the shortcuts bar automatically as Local machine [Machine name].
If the console has ever been connected to Acronis Management Server, the shortcut is added
automatically as AMS [Machine name].
1.2.1.2 "Actions and tools" pane
The Actions and tools pane enables you to easily and efficiently work with Acronis Backup &
Recovery 10. The pane's bars provide quick access to program's operations and tools. All items of the
Actions and tools bar are duplicated in the program menu.
Bars
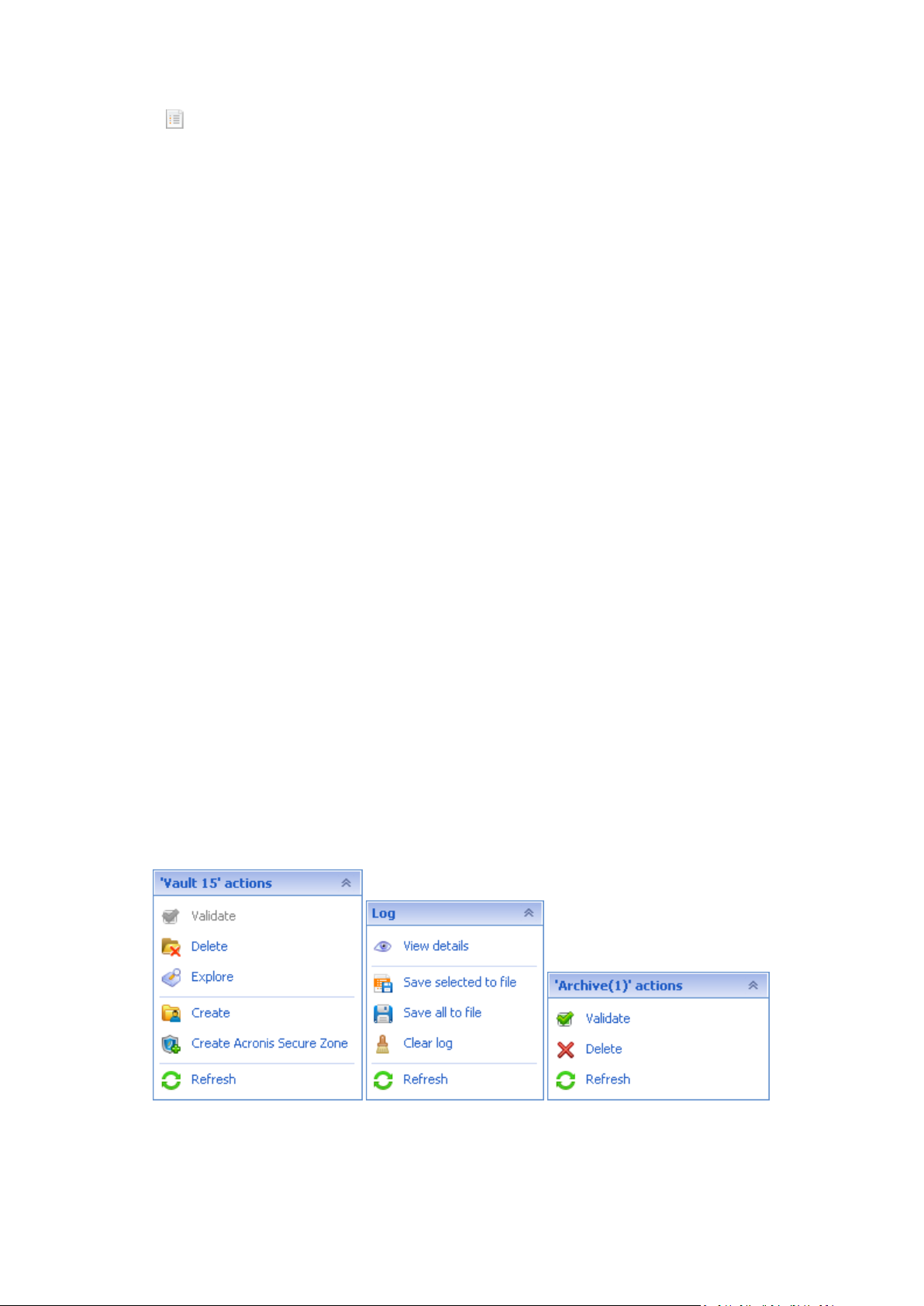
'[Item's name]' actions
Contains a set of actions that can be performed on the items selected in any of the navigation views.
Clicking the action opens the respective action page (p. 16). Items of different navigation views have
their own set of actions. The bar's name changes in accordance with the item you select. For
example, if you select the backup plan named System backup in the Backup plans and tasks view, the
actions bar will be named as 'System backup' actions and will have the set of actions typical to
backup plans.
All actions can also be accessed in the respective menu items. A menu item appears on the menu bar
when you select an item in any of the navigation views.
Examples of "'Item name' actions" bars
13 Copyright © Acronis, Inc., 2000-2010
Page 14
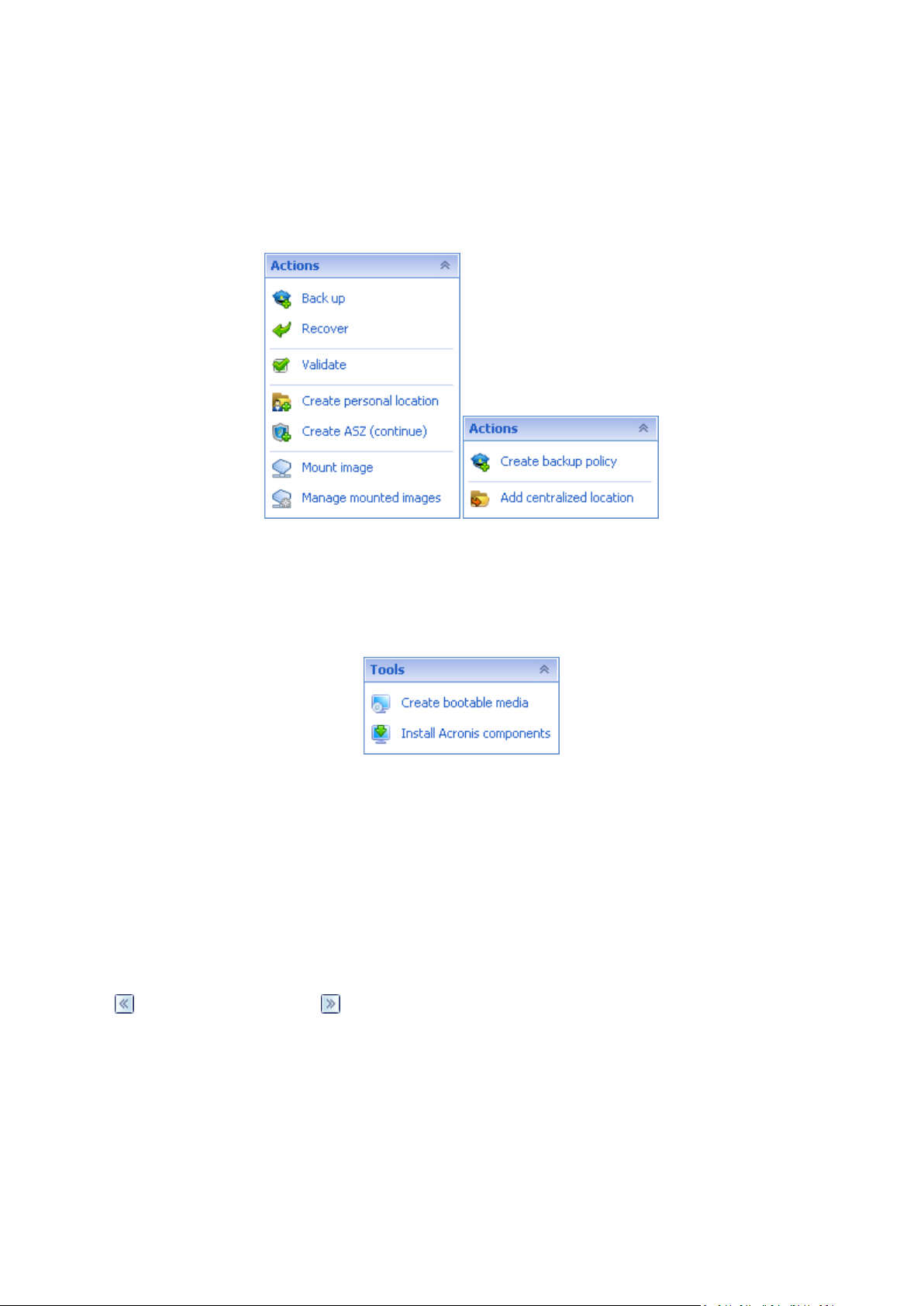
Actions
Contains a list of common operations that can be performed on a managed machine or on a
management server. Always the same for all views. Clicking the operation opens the respective
action page (see the Action pages (p. 16) section.)
All the actions can also be accessed in the Actions menu.
"Actions" bar on a managed machine and on a management server
Tools
Contains a list of the Acronis tools. Always the same across all the program views.
All the tools can also be accessed in the Tools menu.
"Tools" bar
Help
Contains a list of help topics. Different views and action pages of Acronis Backup & Recovery 10
provided with lists of specific help topics.
1.2.1.3 Operations with panes
How to expand/minimize panes
By default, the Navigation pane appears expanded and the Actions and Tools - minimized. You might
need to minimize the pane in order to free some additional workspace. To do this, click the chevron
- for the Navigation pane; - for the Actions and tools pane). The pane will be minimized and
(
the chevron changes its direction. Click the chevron once again to expand the pane.
How to change the panes' borders
1. Point to the pane's border.
2. When the pointer becomes a double-headed arrow, drag the pointer to move the border.
14 Copyright © Acronis, Inc., 2000-2010
Page 15
The management console "remembers" the way the panes' borders are set. When you run the
management console next time, all the panes' borders will have the same position that was set
previously.
1.2.1.4 Main area, views and action pages
The main area is a basic place where you work with the console. Here you create, edit and manage
backup plans, policies, tasks and perform other operations. The main area displays different views
and action pages according the items you select in the menu, Navigation tree, or on the Actions and
Tools pane.
Views
A view appears on the main area when clicking any item in the Navigation tree in the Navigation
pane (p. 12).
"Tasks" view
Common way of working with views
Generally, every view contains a table of items, a table toolbar with buttons, and the Information
panel.
Use filtering and sorting capabilities to search the table for the item in question
In the table, select the desired item
In the Information panel (collapsed by default), view the item's details
Perform actions on the selected item. There are several ways of performing the same action on
selected items:
By clicking the buttons on the table toolbar;
15 Copyright © Acronis, Inc., 2000-2010
Page 16
By clicking in the items in the [Item's name] Actions bar (on the Actions and Tools pane);
By selecting the items in the Actions menu;
By right-clicking the item and selecting the operation in the context menu.
Action pages
An action page appears in the main area when clicking any action item in the Actions menu, or in the
Actions bar on the Actions and tools pane. It contains steps you need to perform in order to create
and launch any task, or a backup plan, or backup policy.
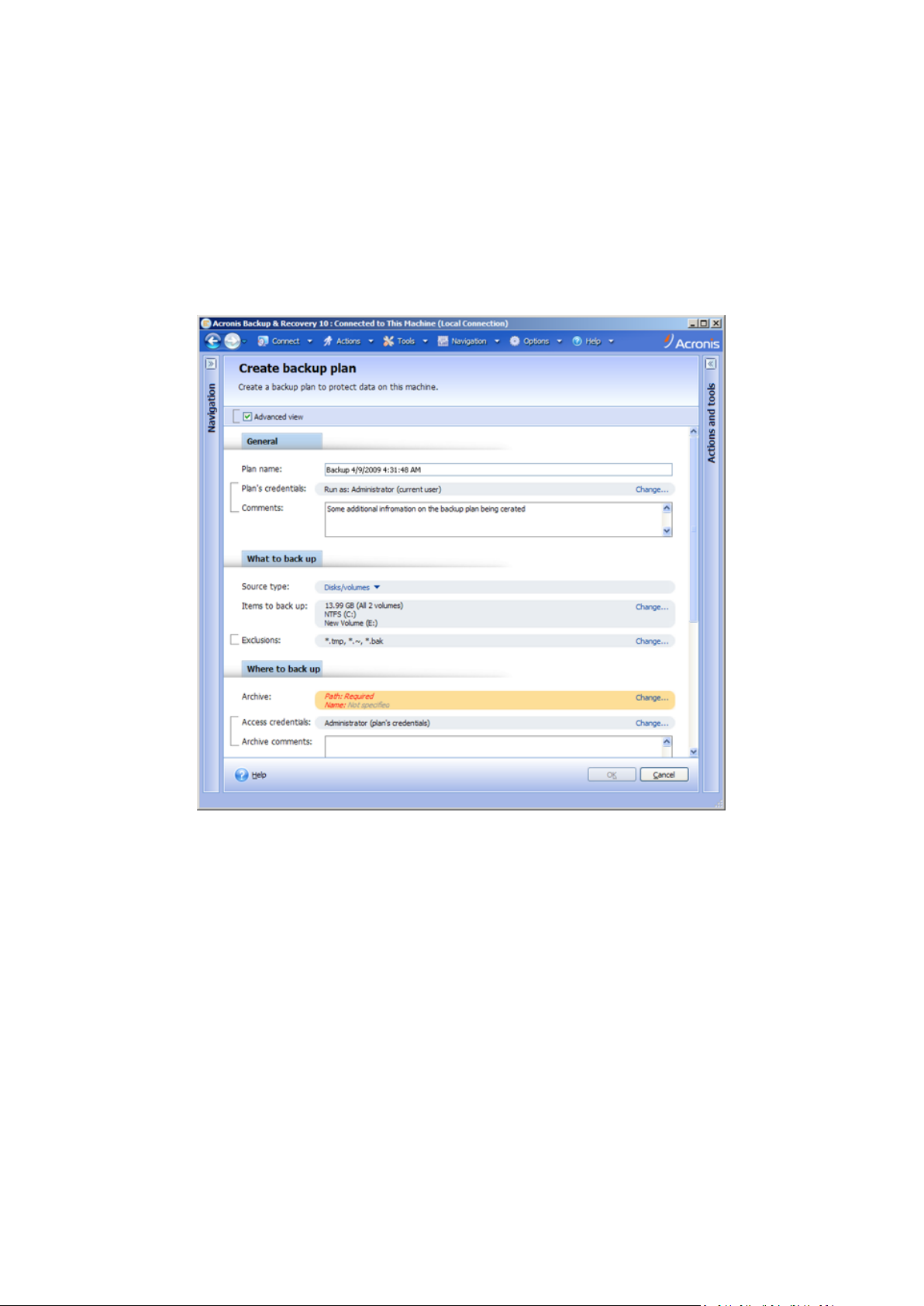
Action page - Create backup plan
Using controls and specifying settings
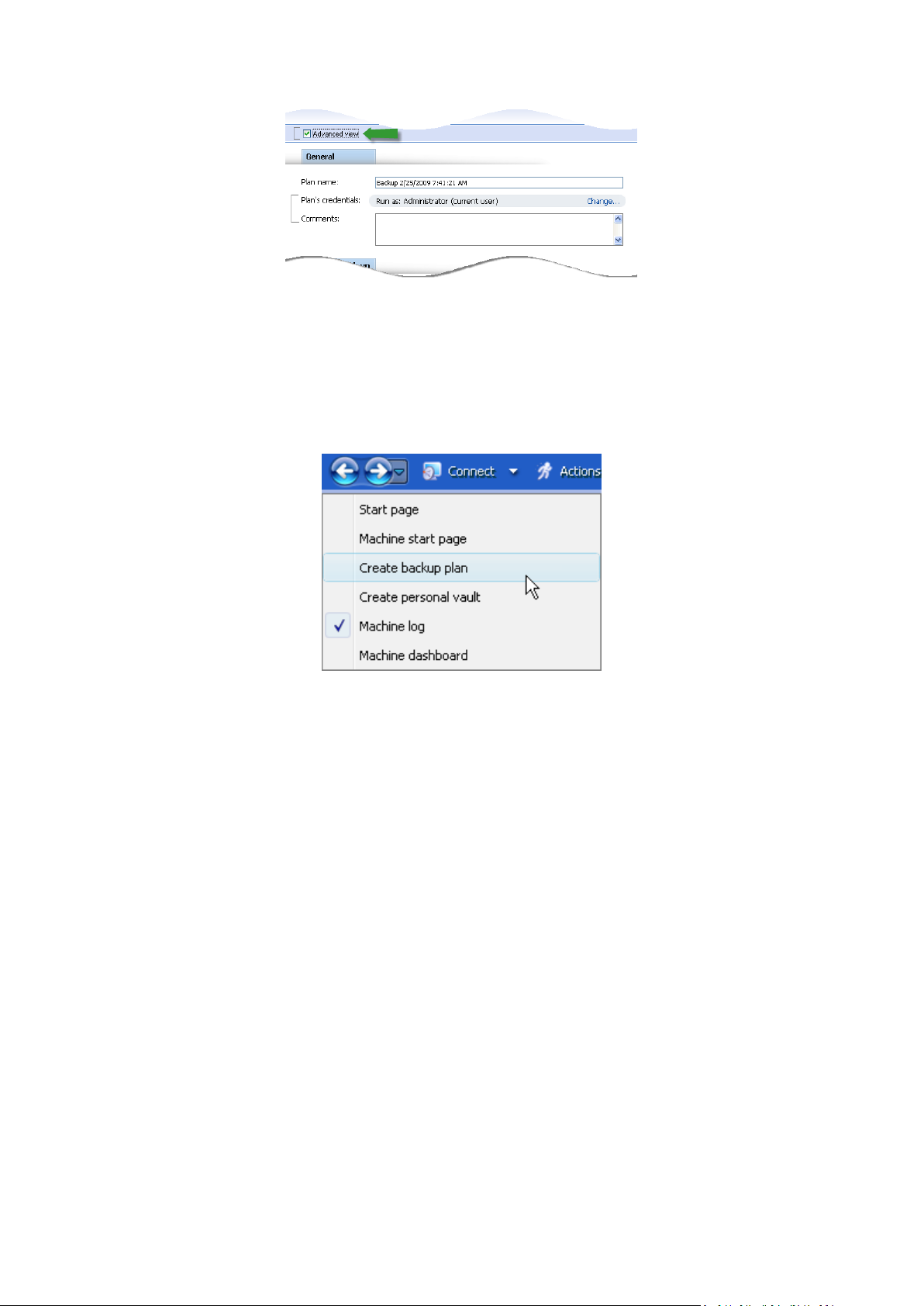
The action pages offer two ways of representation: basic and advanced. The basic representation
hides such fields as credentials, comments, etc. When the advanced representation is enabled, all
the available fields are displayed. You can switch between the views by selecting the Advanced view
check box at the top of the action page.
Most settings are configured by clicking the respective Change… links to the right. Others are
selected from the drop-down list, or typed manually in the page's fields.
16 Copyright © Acronis, Inc., 2000-2010
Page 17
Action page - Controls
Acronis Backup & Recovery 10 remembers the changes you made on the action pages. For example,
if you started to create a backup plan, and then for any reason switched to another view without
accomplishing the plan creation, you can click the Back navigation button on the menu. Or, if you
have passed several steps forward, click the Down arrow and select the page where you started the
plan creation from the list. Thus, you can perform the remaining steps and accomplish the backup
plan creation.
Navigation buttons
1.3 Acronis Bac kup & Recovery 10 c omponents
This section contains a full list of Acronis Backup & Recovery 10 components with a brief description
of their functionality.
Acronis Backup & Recovery 10 includes the following main types of components.
Components for a managed machine (agents)
These are applications that perform data backup, recovery and other operations on the machines
managed with Acronis Backup & Recovery 10. Agents require a license to perform operations on
each managed machine. Agents have multiple features, or add-ons, that enable additional
functionality and so might require additional licenses.
Components for centralized management
These components, delivered with the advanced editions, provide the centralized management
capability. Usage of these components is not licensed.
Console
The console provides Graphical User Interface and remote connection to the agents and other
Acronis Backup & Recovery 10 components. Usage of the console is not licensed.
17 Copyright © Acronis, Inc., 2000-2010
Page 18

Bootable media builder
With bootable media builder, you can create bootable media in order to use the agents and other
rescue utilities in a rescue environment. Availability of the agent add-ons in a rescue environment
depends on whether an add-on is installed on the machine where the media builder is working.
1.3.1 Agent for Windows
This agent enables disk-level and file-level data protection under Windows.
Disk backup
Disk-level data protection is based on backing up either a disk or a volume file system as a whole,
along with all the information necessary for the operating system to boot; or all the disk sectors using
the sector-by-sector approach (raw mode). A backup that contains a copy of a disk or a volume in a
packaged form is called a disk (volume) backup or a disk (volume) image. It is possible to recover
disks or volumes as a whole from such backup, as well as individual folders or files.
File backup
File-level data protection is based on backing up files and folders residing on the machine where the
agent is installed or on a network share. Files can be recovered to their original location or to another
place. It is possible to recover all files and folders that were backed up or select which of them to
recover.
Other operations
Conversion to a virtual machine
Rather than converting a disk backup to a virtual disk file, which requires additional operations to
bring the virtual disk into use, Agent for Windows performs the conversion by recovering a disk
backup to a new virtual machine of any of the following types: VMware Workstation, Microsoft
Virtual PC, Parallels Workstation or Citrix XenServer Open Virtual Appliance (OVA). Files of the fully
configured and operational machine will be placed in the folder you select. You can start the machine
using the respective virtualization software or prepare the machine files for further usage.
Disk management
Agent for Windows includes Acronis Disk Director Lite - a handy disk management utility. Disk
management operations, such as cloning disks; converting disks; creating, formatting and deleting
volumes; changing a disk partitioning style between MBR and GPT or changing a disk label, can be
performed either in the operating system or using bootable media.
1.3.1.1 Universal Restore
The Universal Restore add-on enables you to use the restore to dissimilar hardware functionality on
the machine where the agent is installed, and create bootable media with this functionality.
Universal Restore handles differences in devices that are critical for Windows start-up, such as
storage controllers, motherboard or chipset.
1.3.1.2 Deduplication
This add-on enables the agent to back up data to deduplicating vaults managed by Acronis Backup &
Recovery 10 Storage Node.
18 Copyright © Acronis, Inc., 2000-2010
Page 19

1.3.2 Components for centralized management
This section lists the components included in the Acronis Backup & Recovery 10 editions that provide
the centralized management capability. Besides these components, Acronis Backup & Recovery 10
Agents have to be installed on all machines that need data protection.
1.3.2.1 Management Server
Acronis Backup & Recovery 10 Management Server is the central server that drives data protection
within the enterprise network. The management server provides the administrator with:
a single entry point to the Acronis Backup & Recovery 10 infrastructure
an easy way to protect data on numerous machines (p. 396) using backup policies (p. 389) and
grouping
enterprise-wide monitoring and reporting functionality
the ability to create centralized vaults (p. 391) for storing enterprise backup archives (p. 388)
the ability to manage storage nodes (p. 398).
If there are multiple management servers on the network, they operate independently, manage
different machines and use different centralized vaults for storing archives.
The management server's databases
The management server uses three Microsoft SQL databases:
The configuration database that stores the list of registered machines and other configuration
information, including backup policies created by the administrator.
The synchronization database used for synchronization of the management server with
registered machines and storage nodes. This is a database with rapidly changing operational
data.
The reporting database that stores the centralized log. This database may grow large. Its size
depends on the logging level you set.
The configuration and synchronization databases should reside on the same Microsoft SQL Server
(called an operational server) preferably installed on the same machine as the management server.
The reporting database can be configured on the same or different SQL server.
When installing a management server, you can select for both operational and reporting servers
what server to use. The following options are available:
1. Microsoft SQL Server 2005 Express that comes with the installation package and installs on the
same machine. In this case, an SQL server instance with three databases will be created on the
machine.
2. Microsoft SQL Server 2008 (any edition) previously installed on any machine.
3. Microsoft SQL Server 2005 (any edition) previously installed on any machine.
VMware vCenter integration
This feature provides the capability to view virtual machines managed by a VMware vCenter Server
in the management server GUI, view the backup status of these machines in the vCenter, and
automatically register virtual machines created by Acronis Backup & Recovery 10 in the vCenter.
Integration is available in all Acronis Backup & Recovery 10 advanced editions; a license for Virtual
Edition is not required. No software installation is required on the vCenter Server.
19 Copyright © Acronis, Inc., 2000-2010
Page 20

This feature also enables automatic deployment and configuration of Agent for ESX/ESXi to any
ESX/ESXi server, that is not necessarily managed by the vCenter.
1.3.2.2 Storage Node
Acronis Backup & Recovery 10 Storage Node is a server aimed to optimize usage of various resources
(such as the corporate storage capacity, the network bandwidth, or the managed machines' CPU
load) required for the enterprise data protection. This goal is achieved through organizing and
managing the locations that serve as dedicated storages of the enterprise backup archives (managed
vaults).
The storage nodes enable creating highly scalable and flexible, in terms of the hardware support,
storage infrastructure. Up to 20 storage nodes can be set up, each being able to manage up to 20
vaults. The administrator controls the storage nodes centrally from the Acronis Backup & Recovery
10 Management Server (p. 397). Direct console connection to a storage node is not possible.
Setting up the storage infrastructure
Install the storage nodes, add them to the management server (the procedure is similar to the
managed machine registration (p. 398)) and create centralized vaults (p. 391). When creating a
centralized vault, specify the path to the vault, the storage node that will manage the vault, and the
management operations to be performed on the vault.
A managed vault can be organized:
on the hard drives local to the storage node
on a network share
on a Storage Area Network (SAN)
on a Network Attached Storage (NAS)
on a tape library locally attached to the storage node.
The management operations are as follows.
Storage node-side cleanup and validation
Archives, stored in unmanaged vaults, are maintained by the agents (p. 388) that create the archives.
This means that each agent not only backs up data to the archive, but also executes service tasks that
apply to the archive, the retention rules and validation rules specified by the backup plan (p. 389). To
relieve the managed machines of unnecessary CPU load, execution of the service tasks can be
delegated to the storage node. Since the tasks' schedule exists on the machine the agent resides on,
and therefore uses that machine’s time and events, the agent has to initiate the storage node-side
cleanup (p. 399) and the storage node-side validation (p. 399) according to the schedule. To do so,
the agent must be online. Further processing is performed by the storage node.
This functionality cannot be disabled in a managed vault. The next two operations are optional.
Deduplication
A managed vault can be configured as a deduplicating vault. This means that identical data will be
backed up to this vault only once to minimize the network usage during backup and storage space
taken by the archives. For more information, please see the "Deduplication (p. 64)" section in the
User Guide.
20 Copyright © Acronis, Inc., 2000-2010
Page 21

Encryption
A managed vault can be configured so that anything written to it is encrypted and anything read
from it is decrypted transparently by the storage node, using a vault-specific encryption key stored
on the node server. In case the storage medium is stolen or accessed by an unauthorized person, the
malefactor will not be able to decrypt the vault contents without access to this specific storage node.
If the archive is already encrypted by the agent, the storage node-side encryption is applied over the
encryption performed by the agent.
1.3.2.3 PXE Server
Acronis PXE Server allows for booting machines into Acronis bootable components through the
network.
The network booting:
Eliminates the need to have a technician onsite to install the bootable media (p. 390) into the
system that has to be booted
During group operations, reduces the time required for booting multiple machines as compared
to using physical bootable media.
1.3.2.4 License Server
The server enables you to manage licenses of Acronis products and install the components that
require licenses.
For more information about Acronis License Server please see "Using Acronis License Server".
1.3.3 Management Console
Acronis Backup & Recovery 10 Management Console is an administrative tool for remote or local
access to Acronis Backup & Recovery 10 agents, and in the product editions that include the
centralized management capability, to the Acronis Backup & Recovery 10 Management Server.
The console has two distributions for installation on Windows and installation on Linux. While both
distributions enable connection to any Acronis Backup & Recovery 10 agent and Acronis Backup &
Recovery 10 Management Server, we recommend that you use the console for Windows if you have
a choice between the two. The console that installs on Linux has limited functionality:
remote installation of Acronis Backup & Recovery 10 components is not available
the Active Directory-related features, such as browsing the AD, are not available.
1.3.4 Bootable Media Builder
Acronis Bootable Media Builder is a dedicated tool for creating bootable media (p. 390). The media
builder that installs on Windows can create bootable media based on either Windows Preinstallation
Environment, or Linux kernel.
The Universal Restore (p. 18) add-on enables you to create bootable media with the restore to
dissimilar hardware functionality. Universal Restore handles differences in devices that are critical for
Windows start-up, such as storage controllers, motherboard or chipset.
21 Copyright © Acronis, Inc., 2000-2010
Page 22

The Deduplication (p. 18) add-on enables you to create bootable media with the back up to a
deduplicating vault functionality.
1.3.5 Acronis WOL Proxy
This option works in combination with the Use Wake-On-LAN (p. 166) advanced scheduling setting.
Use this option if the management server has to wake up for backup machines located in another
subnet.
When the scheduled operation is about to start, the management server sends out magic packets to
wake up the appropriate machines. (A magic packet is a packet that contains 16 contiguous copies of
the receiving NIC's MAC address). The Acronis WOL Proxy, installed in the other subnet, transfers the
packets to machines located in that subnet.
The preset is: Disabled.
To bring this option into use:
1. Install Acronis WOL Proxy on any server in the subnet where the machines to be woken are
located. The server has to provide continuous services availability. With multiple subnets, install
Acronis WOL Proxy in every subnet where you need to use the Wake-On-LAN functionality.
2. Enable Acronis WOL Proxy in the Management server options as follows:
a. Select the Use the following proxies check box.
b. Click Add, and then enter the name or IP address of the machine where the Acronis WOL
Proxy is installed. Provide access credentials for the machine.
c. Repeat this step if there are several Acronis WOL Proxies.
3. When scheduling a backup policy, enable the Use Wake-On-LAN setting.
You also have the ability to delete proxies from the list. Please keep in mind that any change to this
option affects the entire management server. If you delete a proxy from the list, the Wake-On-LAN
functionality in the corresponding subnet will be disabled for all policies, including the policies
already applied.
1.4 Supported file s ystems
Acronis Backup & Recovery 10 can back up and recover the following file systems with the following
limitations:
FAT16/32
NTFS
Ext2/Ext3/Ext4
ReiserFS3 - particular files cannot be recovered from disk backups located on Acronis Backup &
Recovery 10 Storage Node
ReiserFS4 - volume recovery without the volume resize capability; particular files cannot be
recovered from disk backups located on Acronis Backup & Recovery 10 Storage Node
XFS - volume recovery without the volume resize capability; particular files cannot be recovered
from disk backups located on Acronis Backup & Recovery 10 Storage Node
JFS - particular files cannot be recovered from disk backups located on Acronis Backup &
Recovery 10 Storage Node
Linux SWAP
22 Copyright © Acronis, Inc., 2000-2010
Page 23

Acronis Backup & Recovery 10 can back up and recover corrupted or non-supported file systems
using the sector-by-sector approach.
1.5 Supported operating sy stems
Acronis License Server
Windows XP Professional SP2+ (x86, x64)
Windows 2000 – all editions except for the Datacenter edition
Windows Server 2003/2003 R2 - the Standard, Enterprise, Small Business Server editions (x86,
x64)
Windows Vista - all editions except for Vista Home Basic and Vista Home Premium (x86, x64)
Windows 7 - all editions except for the Starter and Home editions (x86, x64)
Windows Server 2008 - the Standard, Enterprise, Small Business Server, Foundation editions
(x86, x64)
Windows Server 2008 R2 - the Standard, Enterprise, Small Business Server, Datacenter,
Foundation editions
Windows MultiPoint Server 2010
Acronis Backup & Recovery 10 Management Console
Windows XP Professional SP2+ (x86, x64)
Windows 2000 – all editions except for the Datacenter edition
Windows Server 2003/2003 R2 - the Standard, Enterprise, Small Business Server editions (x86,
x64)
Windows Vista - all editions (x86, x64)
Windows 7 - all editions (x86, x64)
Windows Server 2008 - the Standard, Enterprise, Small Business Server, Foundation editions
(x86, x64)
Windows Server 2008 R2 - the Standard, Enterprise, Small Business Server, Datacenter,
Foundation editions
Windows MultiPoint Server 2010
Acronis Backup & Recovery 10 Management Server and Acronis Backup & Recovery
10 Storage Node
Windows XP Professional SP2+ (x86, x64)
Windows 2000 – all editions except for the Datacenter edition
Windows Server 2003/2003 R2 - the Standard, Enterprise, Small Business Server editions (x86,
x64)
Windows Vista - all editions except for Vista Home Basic and Vista Home Premium (x86, x64)
Windows 7* - all editions except for the Starter and Home editions (x86, x64)
Windows Server 2008 - the Standard, Enterprise, Small Business Server, Foundation editions
(x86, x64)
Windows Server 2008 R2* - the Standard, Enterprise, Small Business Server, Datacenter,
Foundation editions
Windows MultiPoint Server 2010*
23 Copyright © Acronis, Inc., 2000-2010
Page 24
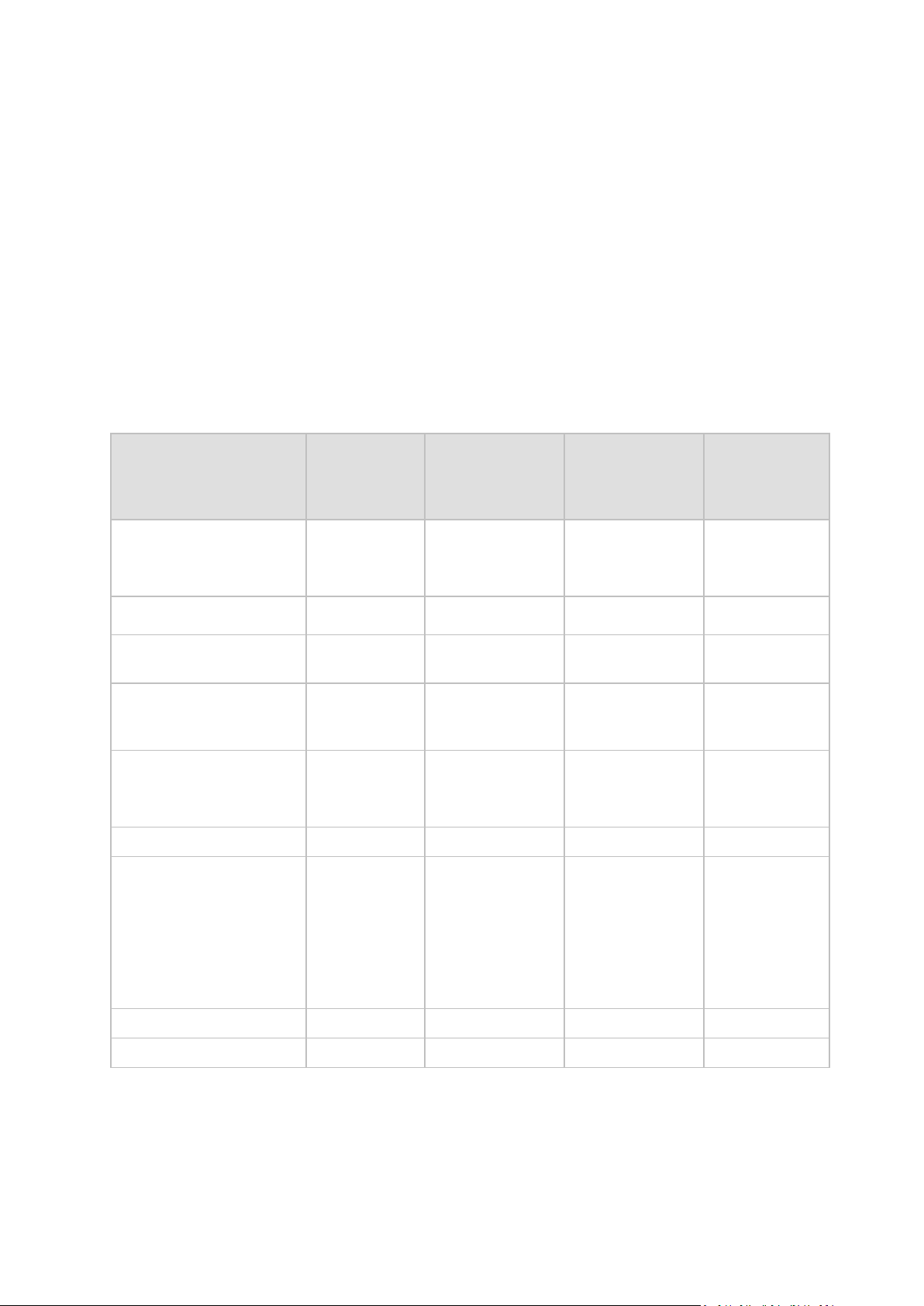
* Acronis Backup & Recovery 10 Storage Node handles tape libraries and autoloaders by using
Removable Storage Management (RSM). Since Windows 7, Windows Server 2008 R2 and
Windows MultiPoint Server 2010 do not support RSM, a storage node installed in these
operating systems does not support tape libraries and autoloaders.
Acronis Backup & Recovery 10 Agent for Windows
Windows 2000 Professional SP4
Windows XP Professional SP2+ (x86, x64)
Windows Vista - all editions except for Vista Home Basic and Vista Home Premium (x86, x64)
Windows 7 - all editions except for the Starter and Home editions (x86, x64)
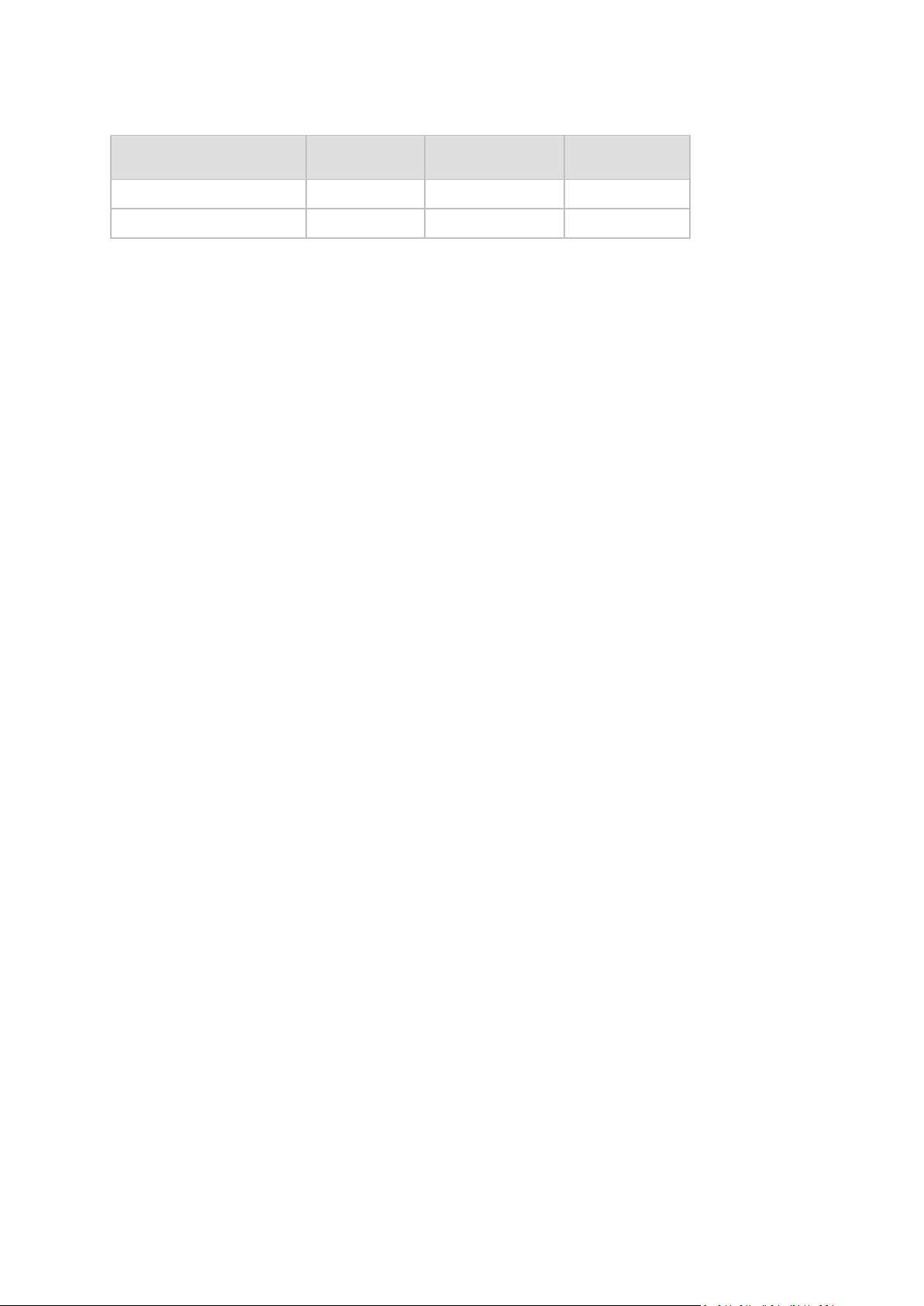
1.6 System requ irements
The components installed in Windows
Component Memory (above
the OS and
running
applications)
Disk space required
during installation or
update
Disk space occupied
by the component(s)
Additional
Complete installation 300 MB 2.7 GB 1.7 GB
including SQL
Express Server
Agent for Windows 120 MB 700 MB 260 MB
Bootable Media Builder 80 MB 700 MB 300 MB CD-RW or DVD-
Management Console 30 MB 950 MB 450 MB Screen resolution
Management Server 40 MB 250 MB
400 MB for SQL
Express Server
Wake-on-LAN Proxy Negligible 30 MB 5 MB
Storage Node 100 MB 150 MB 150 MB
250 MB
400 MB for SQL
Express Server
When using a tape
library, space
required for tapes
database: approx.
1 MB per 10
archives
RW drive
1024*768 pixels
or higher
Recommended
hardware:
4 GB RAM
High speed
storage such as
hardware RAID
License Server Negligible 25 MB 25 MB
PXE Server 5 MB 80 MB 15 MB
Network interface card or virtual network adapter is a common requirement for all the components.
24 Copyright © Acronis, Inc., 2000-2010
Page 25
Bootable media
Media type Memory ISO image size Additional
Based on Windows PE 512 MB 300 MB
Linux-based 256 MB 130 MB
1.7 Technical Support
Maintenance and Support Program
If you need assistance with your Acronis product, please go to http://www.acronis.eu/support/
Product Updates
You can download the latest updates for all your registered Acronis software products from our
website at any time after logging into your Account (https://www.acronis.eu/my) and registering the
product. See Registering Acronis Products at the Website (http://kb.acronis.com/content/4834) and
Acronis Website User Guide (http://kb.acronis.com/content/8128).
25 Copyright © Acronis, Inc., 2000-2010
Page 26

2 Understanding Acronis Backup & Reco ve ry 10
This section attempts to give its readers a clear understanding of the product so that they can use
the product in various circumstances without step-by-step instructions.
2.1 Basic concepts
Please familiarize yourself with the basic notions used in the Acronis Backup & Recovery 10 graphical
user interface and documentation. Advanced users are welcome to use this section as a step-by-step
quick start guide. The details can be found in the context help.
Backup under operating system
1. To protect data on a machine, install Acronis Backup & Recovery 10 agent (p. 388) on the
machine which becomes a managed machine (p. 396) from this point on.
2. To be able to manage the machine using Graphical User Interface, install Acronis Backup &
Recovery 10 Management Console (p. 392) on the same machine or any machine from which you
prefer to operate. If you have the standalone product edition, skip this step since in your case the
console installs with the agent.
3. Run the console. To be able to recover the machine's operating system if the system fails to start,
create bootable media (p. 390).
4. Connect the console to the managed machine.
5. Create a backup plan (p. 389).
To do so, you have to specify, at the very least, the data to be protected and the location where
the backup archive (p. 388) will be stored. This will create a minimal backup plan consisting of
one task (p. 399) that will create a full backup (p. 388) of your data every time the task is
manually started. A complex backup plan might consist of multiple tasks which run on schedule;
create full, incremental or differential backups (p. 30); perform archive maintenance operations
such as backup validation (p. 400) or deleting outdated backups (archive cleanup (p. 391)). You
can customize backup operations using various backup options, such as pre/post backup
commands, network bandwidth throttling, error handling or notification options.
6. Use the Backup plans and tasks page to view information about your backup plans and tasks and
monitor their execution. Use the Log page to browse the operations log.
7. The location where you store backup archives is called a vault (p. 400). Navigate to the Vaults
page to view information about your vaults. Navigate further to the specific vault to view
archives and backups and perform manual operations with them (mounting, validating, deleting,
viewing contents). You can also select a backup to recover data from it.
26 Copyright © Acronis, Inc., 2000-2010
Page 27
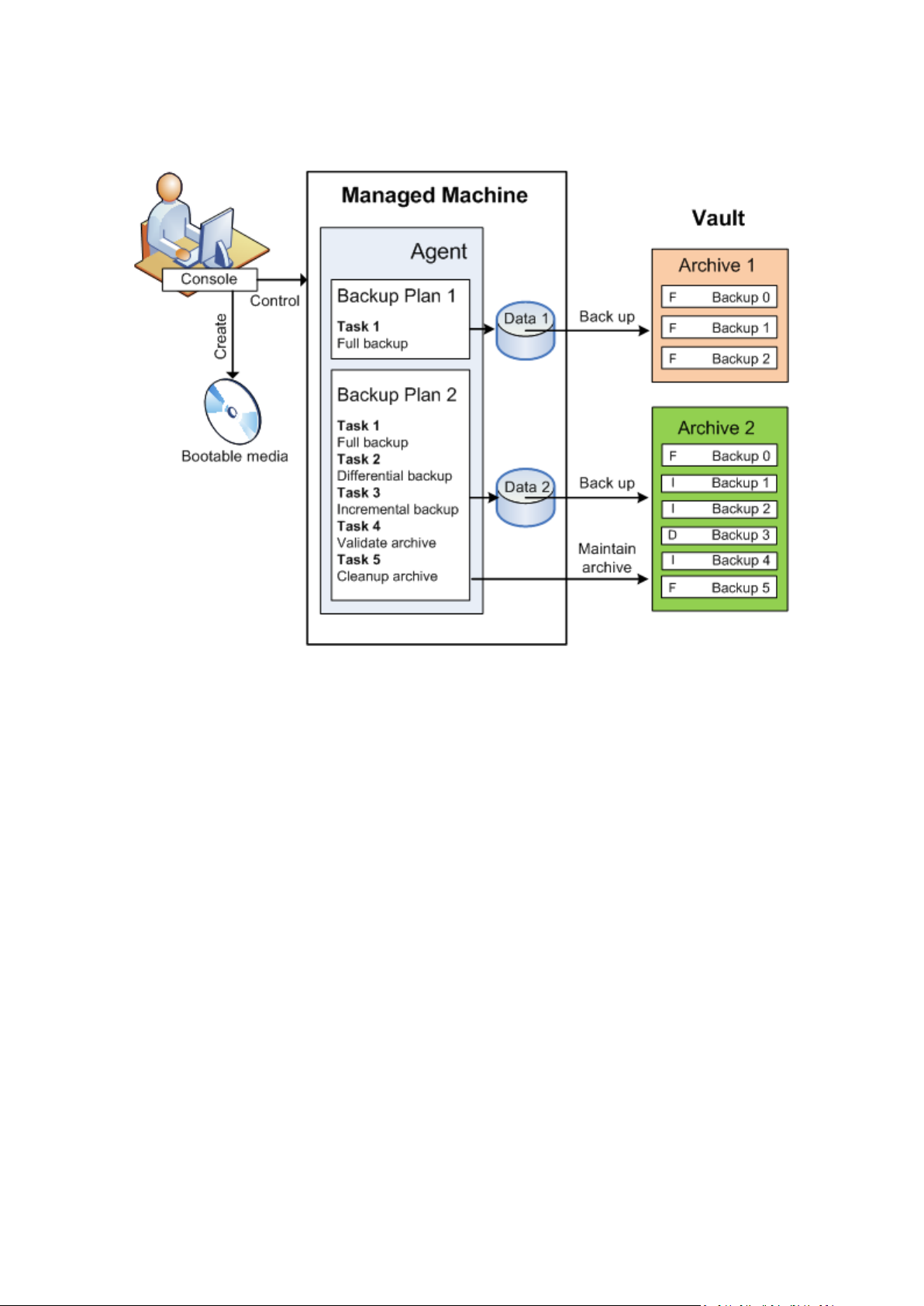
The following diagram illustrates the notions discussed above. For more definitions please refer to
the Glossary.
27 Copyright © Acronis, Inc., 2000-2010
Page 28
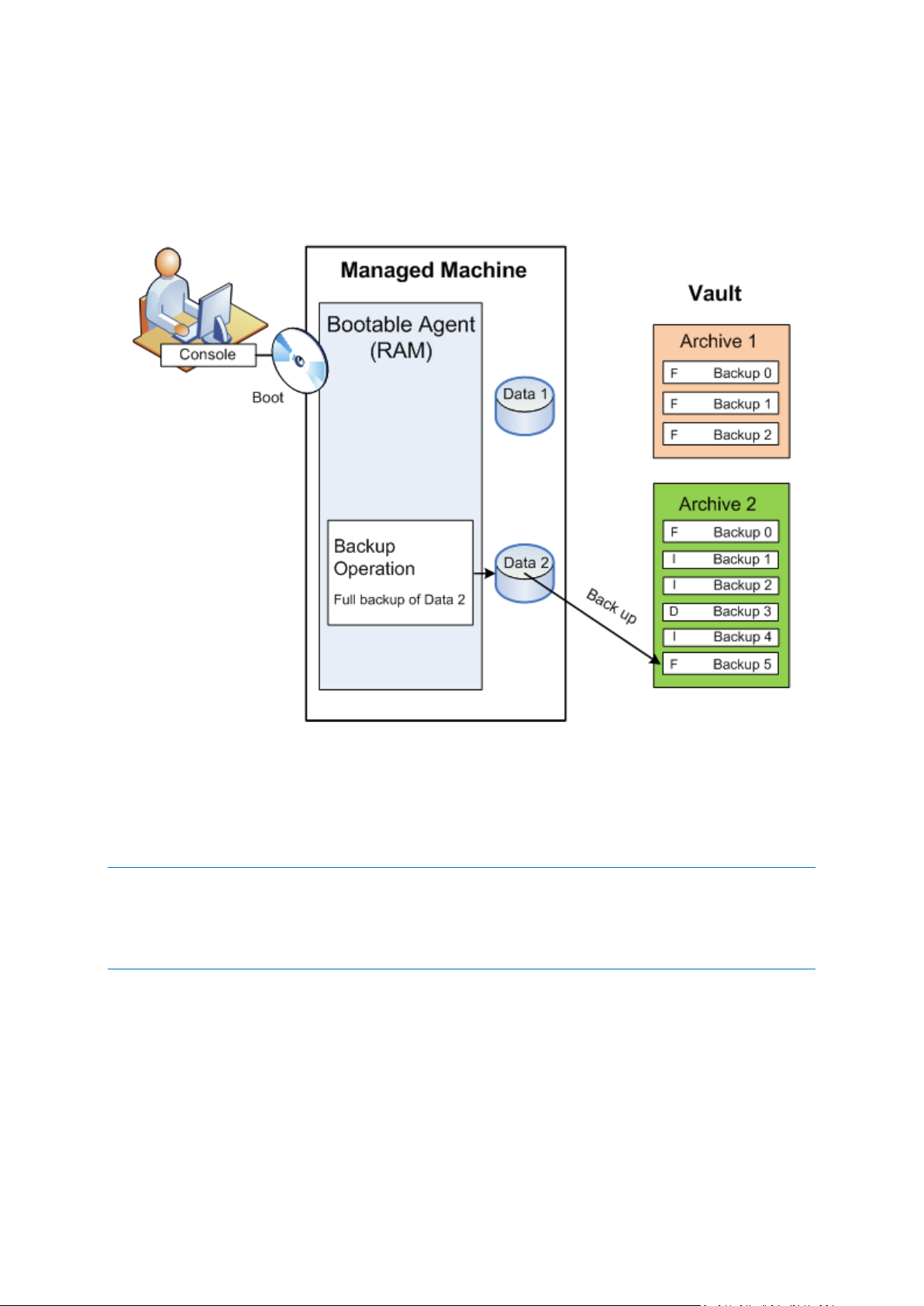
Backup using bootable media
You can boot the machine using the bootable media, configure the backup operation in the same
way as a simple backup plan and execute the operation. This will help you extract files and logical
volumes from a system that failed to boot, take an image of the offline system or back up sector-bysector an unsupported file system.
Recovery under operating system
When it comes to data recovery, you create a recovery task on the managed machine. You specify
the vault, then select the archive and then select the backup referring to the date and time of the
backup creation, or more precisely, to the time when the creation has started. In most cases, the
data will be reverted to that moment.
Examples of exceptions to this rule:
Recovering a database from a backup that contains the transaction log (a single backup provides multiple
recovery points and so you can make additional selections).
Recovering multiple files from a file backup taken without snapshot (each file will be reverted to the moment
when it was actually copied to the backup).
You also specify the destination where to recover the data. You can customize the recovery
operation using recovery options, such as pre/post recovery commands, error handling or
notification options.
28 Copyright © Acronis, Inc., 2000-2010
Page 29
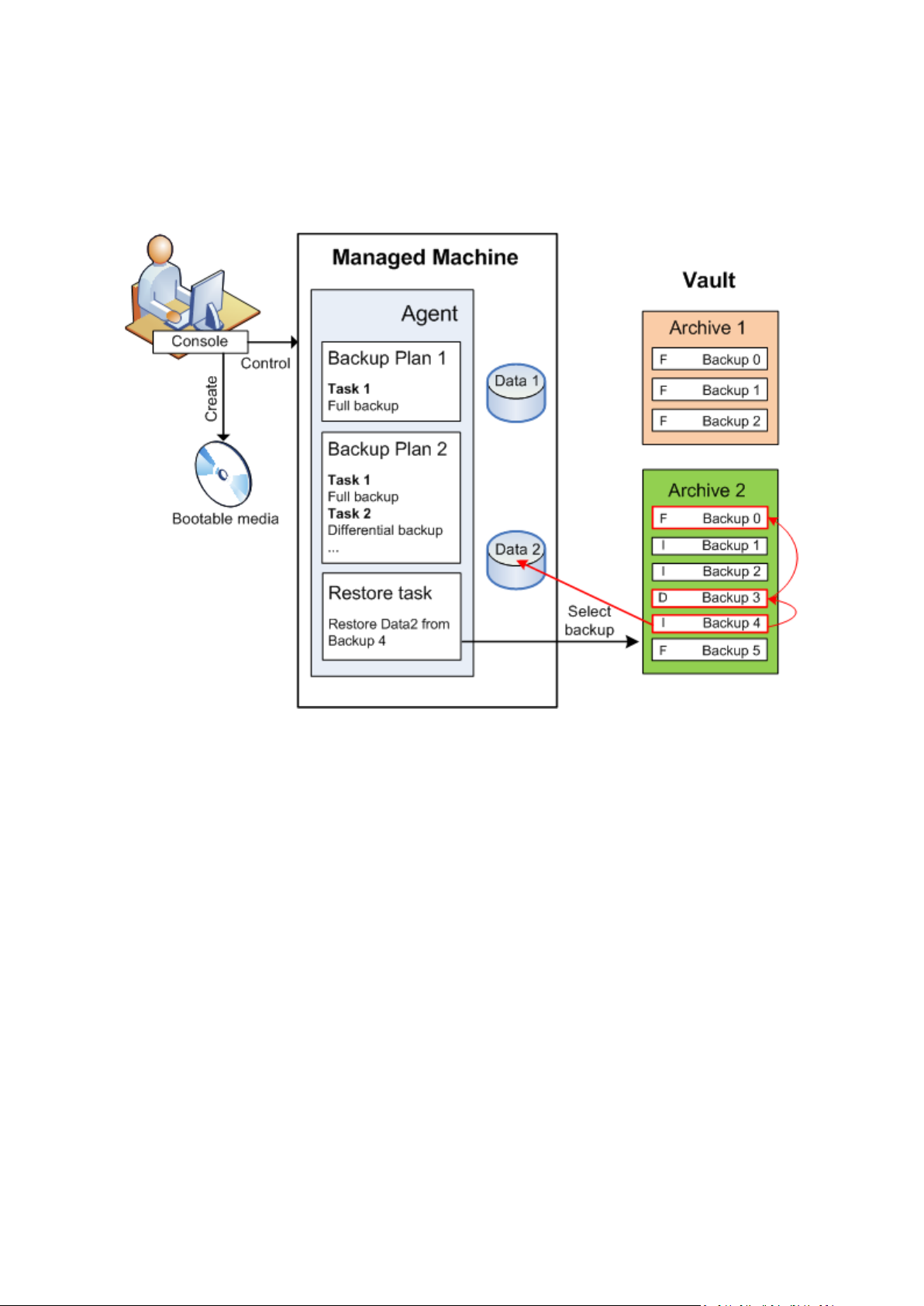
The following diagram illustrates data recovery under the operating system (online). No backup can
proceed on the machine while the recovery operation is taking place. If required, you can connect
the console to another machine and configure a recovery operation on that machine. This ability
(remote parallel recovery) first appeared in Acronis Backup & Recovery 10; the previous Acronis
products do not provide it.
Recovery using bootable media
Recovery over a volume locked by the operating system, such as the volume where the operating
system resides, requires a reboot to the bootable environment which is a part of the agent. After the
recovery is completed, the recovered operating system goes online automatically.
29 Copyright © Acronis, Inc., 2000-2010
Page 30
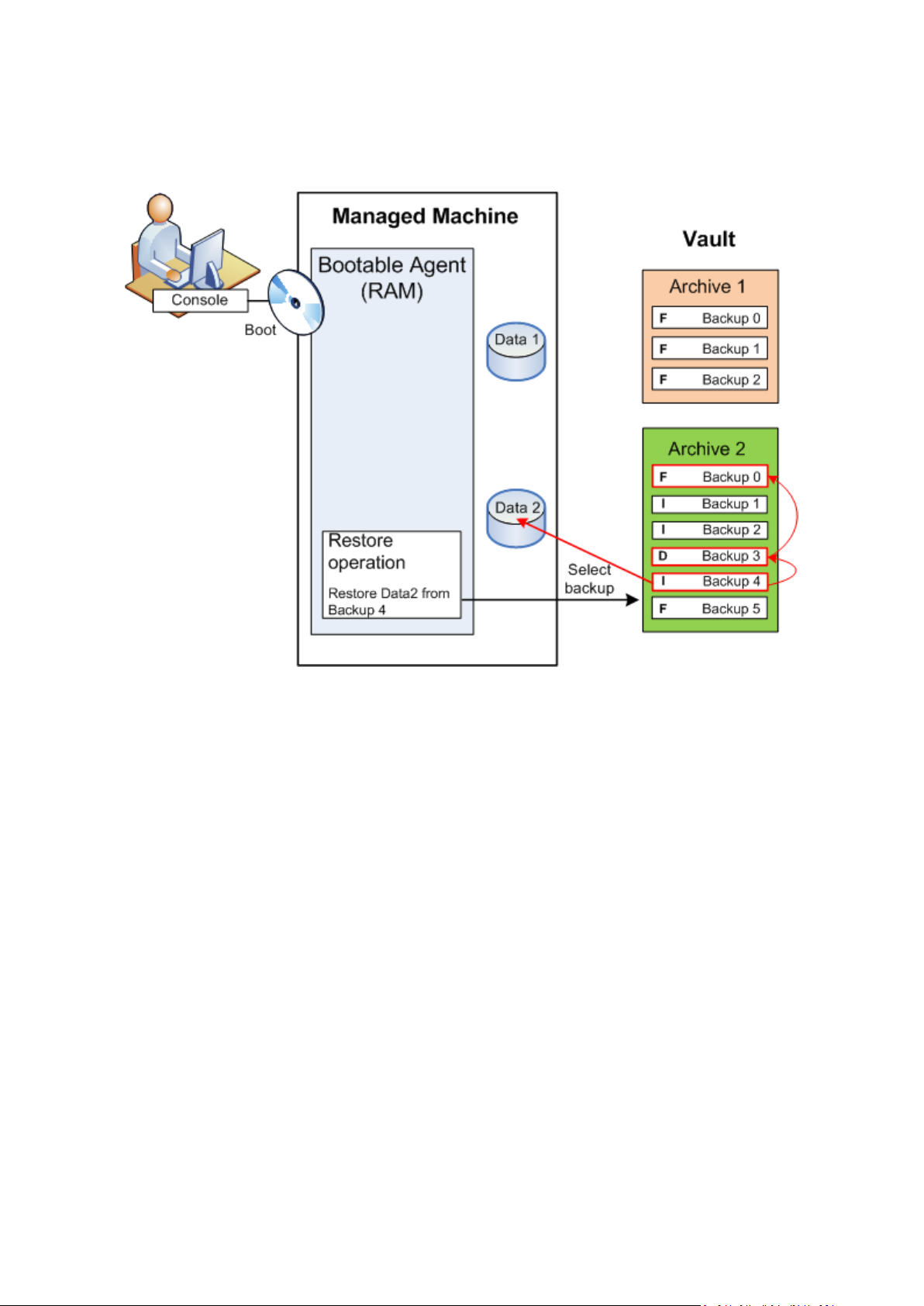
If the machine fails to boot or you need to recover data to bare metal, you boot the machine using
the bootable media and configure the recovery operation in the same way as the recovery task. The
following diagram illustrates the recovery using the bootable media.
2.2 Full, incremental and differential backups
Acronis Backup & Recovery 10 provides the capability to use popular backup schemes, such as
Grandfather-Father-Son and Tower of Hanoi, as well as to create custom backup schemes. All backup
schemes are based on full, incremental and differential backup methods. The term "scheme" in fact
denotes the algorithm of applying these methods plus the algorithm of the archive cleanup.
Comparing backup methods with each other does not make much sense because the methods work
as a team in a backup scheme. Each method should play its specific role according to its advantages.
A competent backup scheme will benefit from the advantages of all backup methods and lessen the
influence of all the methods’ shortcomings. For example, weekly differential backup facilitates
archive cleanup because it can be easily deleted along with the weekly set of daily incremental
backups depending on it.
Backing up with the full, incremental or differential backup method results in a backup (p. 388) of the
corresponding type.
Full backup
A full backup stores all data selected for backup. A full backup underlies any archive and forms the
base for incremental and differential backups. An archive can contain multiple full backups or consist
of only full backups. A full backup is self-sufficient - you do not need access to any other backup to
recover data from a full backup.
30 Copyright © Acronis, Inc., 2000-2010
Page 31

It is widely accepted that a full backup is the slowest to do but the fastest to restore. With Acronis
technologies, recovery from an incremental backup may be not slower than recovery from a full one.
A full backup is most useful when:
you need to roll back the system to its initial state
this initial state does not change often, so there is no need for regular backup.
Example: An Internet cafe, school or university lab where the administrator often undoes changes
made by the students or guests but rarely updates the reference backup (in fact, after installing
software updates only). The backup time is not crucial in this case and the recovery time will be
minimal when recovering the systems from the full backup. The administrator can have several
copies of the full backup for additional reliability.
Incremental backup
An incremental backup stores changes to the data against the latest backup. You need access to
other backups from the same archive to recover data from an incremental backup.
An incremental backup is most useful when:
you need the possibility to roll back to any one of multiple saved states
the data changes tend to be small as compared to the total data size.
It is widely accepted that incremental backups are less reliable than full ones because if one backup
in the "chain" is corrupted, the next ones can no longer be used. However, storing multiple full
backups is not an option when you need multiple prior versions of your data, because reliability of an
oversized archive is even more questionable.
Example: Backing up a database transaction log.
Differential backup
A differential backup stores changes to the data against the latest full backup. You need access to
the corresponding full backup to recover the data from a differential backup. A differential backup is
most useful when:
you are interested in saving only the most recent data state
the data changes tend to be small as compared to the total data size.
The typical conclusion is: "differential backups take longer to do and are faster to restore, while
incremental ones are quicker to do and take longer to restore." In fact, there is no physical difference
between an incremental backup appended to a full backup and a differential backup appended to
the same full backup at the same point of time. The above mentioned difference implies creating a
differential backup after (or instead of) creating multiple incremental backups.
An incremental or differential backup created after disk defragmentation might be considerably larger than
usual because defragmentation changes file locations on the disk and the backup reflects these changes. It is
recommended that you re-create a full backup after disk defragmentation.
The following table summarizes the advantages and shortcomings of each backup type as they
appear based on common knowledge. In real life, these parameters depend on numerous factors
such as the amount, speed and pattern of data changes; the nature of the data, the physical
specifications of the devices, the backup/recovery options you set, to name a few. Practice is the
best guide to selecting the optimal backup scheme.
Parameter Full backup Differential backup Incremental backup
31 Copyright © Acronis, Inc., 2000-2010
Page 32

Maximal
Medium
Minimal
Storage space
Creation time
Recovery time
Maximal Medium Minimal
Minimal Medium Maximal
2.3 User priv ileges on a m anaged mach ine
When managing a machine running Windows, the scope of a user's management rights depends on
the user's privileges on the machine.
Regular users
A regular user, such as a member of the Users group, has the following management rights:
Perform file-level backup and recovery of the files that the user has permissions to access—but
without using a file-level backup snapshot.
Create backup plans and tasks and manage them.
View—but not manage—backup plans and tasks created by other users.
View the local event log.
Administrative users
A user who has administrative privileges on the machine, such as a member of the Administrators or
Backup Operators group, additionally has the following management rights:
Back up and recover the entire machine or any data on the machine, with or without using a disk
snapshot.
Members of the Administrators group also can:
View and manage backup plans and tasks owned by any user on the machine.
2.4 Owners and credentials
This section explains the concept of owner and the meaning of a backup plan's (or task's) credentials.
Plan (task) owner
A local backup plan owner is the user who created or last modified the plan.
A centralized backup plan owner is the management server administrator who created or last
modified the centralized policy that spawned the plan.
Tasks, belonging to a backup plan, either local or centralized, are owned by the backup plan owner.
Tasks that do not belong to a backup plan, such as the recovery task, are owned by the user who has
created or last modified the task.
Managing a plan (task) owned by another user
Having Administrator privileges on the machine, a user can modify tasks and local backup plans
owned by any user registered in the operating system.
When a user opens a plan or task for editing, which is owned by another user, all passwords set in
the task are cleared. This prevents the "modify settings, leave passwords" trick. The program displays
32 Copyright © Acronis, Inc., 2000-2010
Page 33

a warning each time you are trying to edit a plan (task) last modified by another user. On seeing the
warning, you have two options:
Click Cancel and create your own plan or task. The original task will remain intact.
Continue editing. You will have to enter all credentials required for the plan or task execution.
Archive owner
An archive owner is the user who saved the archive to the destination. To be more precise, this is the
user whose account was specified when creating the backup plan in the Where to back up step. By
default, the plan's credentials are used.
Plan's credentials and task credentials
Any task running on a machine runs on behalf of a user. When creating a plan or a task, you have the
option to explicitly specify an account under which the plan or the task will run. Your choice depends
on whether the plan or task is intended for manual start or for executing on schedule.
Manual start
You can skip the Plan's (Task) credentials step. Every time you start the task, the task will run under
the credentials with which you are currently logged on. Any person that has administrative privileges
on the machine can also start the task. The task will run under this person's credentials.
The task will always run under the same credentials, regardless of the user who actually starts the
task, if you specify the task credentials explicitly. To do so, on the plan (task) creation page:
1. Select the Advanced view check box.
2. Select General -> Plan's (Task) credentials -> Change.
3. Enter the credentials under which the plan (task) will run.
Scheduled or postponed start
The plan (task) credentials are mandatory. If you skip the credentials step, you will be asked for
credentials after finishing the plan (task) creation.
Why does the program compel me to specify credentials?
A scheduled or postponed task has to run anyway, regardless if any user is logged on or not (for
example, the system is at the Windows "Welcome" screen) or a user other than the task owner is
logged on. It is sufficient that the machine be on (that is, not in standby or hibernate) at the
scheduled task start time. That's why the Acronis scheduler needs the explicitly specified credentials
to be able to start the task.
2.5 GFS backup scheme
This section covers implementation of the Grandfather-Father-Son (GFS) backup scheme in Acronis
Backup & Recovery 10.
With this backup scheme you are not allowed to back up more often than once a day. The scheme
enables you to mark out the daily, weekly and monthly cycles in your daily backup schedule and set
the retention periods for the daily, monthly and weekly backups. The daily backups are referred to as
“sons”; weekly backups are referred to as “fathers”; the longest lived monthly backups are called
“grandfathers”.
33 Copyright © Acronis, Inc., 2000-2010
Page 34

GFS as a tape rotation scheme
GFS was initially created and is often referred to as a tape rotation scheme. Tape rotation schemes,
as such, do not provide automation. They just determine:
how many tapes you need to enable recovery with the desired resolution (time interval between
recovery points) and roll-back period
which tapes you should overwrite with the forthcoming backup.
Tape rotation schemes enable you to get by with the minimal number of cartridges and not to be
buried in used tapes. A lot of Internet sources describe varieties of the GFS tape rotation scheme.
You are free to use any of the varieties when backing up to a locally attached tape device.
GFS by Acronis
With Acronis Backup & Recovery 10, you can easily set up a backup plan that will regularly back up
data and clean up the resulting archive according to the GFS scheme.
Create the backup plan as usual. For the backup destination, choose any storage device where
automatic cleanup can be performed, such as an HDD-based storage device or robotic tape library.
(Since the space freed on the tape after cleanup cannot be reused until all the tape becomes free,
take into account additional considerations when using GFS on a tape library (p. 139).)
The following is an explanation of the settings that are specific for the GFS backup scheme.
GFS-related settings of the backup plan
Start backup at:
Back up on:
This step creates the total backup schedule, that is, defines all the days you need to back up on.
Assume you select backing up at 8:00 PM on workdays. Here is the total schedule you have
defined.
“B” stands for “backup”.
The total schedule.
Schedule: Workdays at 8:00 PM
Weekly/Monthly
This step forms the daily, weekly and monthly cycles in the schedule.
Select a day of the week from the days selected in the previous step. Each 1st, 2nd and 3rd
backup created on this day of the week will be considered as a weekly backup. Each 4th backup
created on this day of the week will be considered as a monthly backup. Backups created on the
other days will be considered as daily backups.
Assume you select Friday for Weekly/Monthly backup. Here is the total schedule marked out
according to the selection.
“D” stands for the backup that is considered Daily. “W” stands for the backup that is considered
Weekly. “M” stands for the backup that is considered Monthly.
34 Copyright © Acronis, Inc., 2000-2010
Page 35
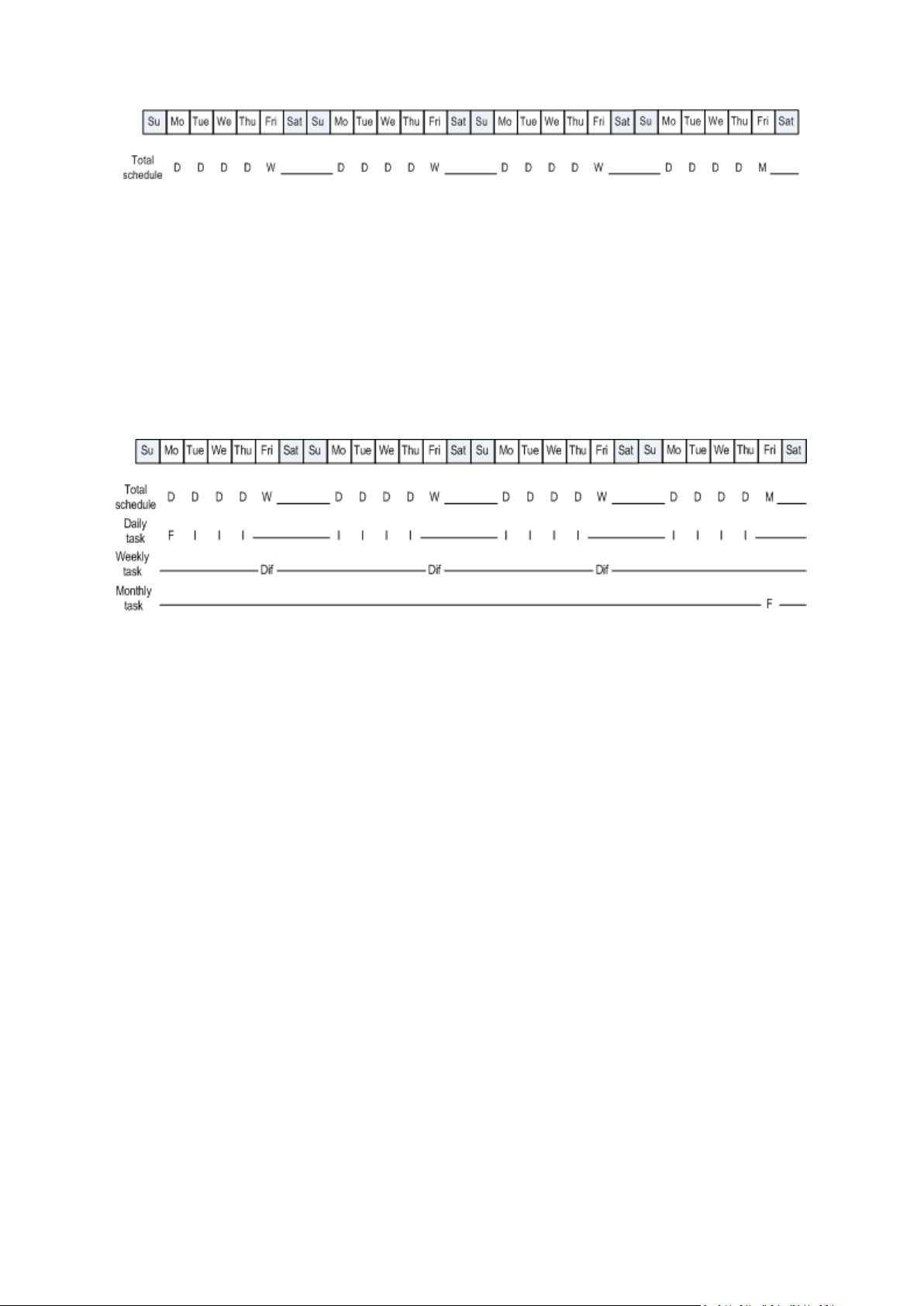
The schedule marked out according to the GFS scheme.
Schedule: Workdays at 8:00 PM
Weekly/Monthly: Friday
Acronis uses incremental and differential backups that help save storage space and optimize the
cleanup so that consolidation is not needed. In terms of backup methods, weekly backup is
differential (Dif), monthly backup is full (F) and daily backup is incremental (I). The first backup is
always full.
The Weekly/Monthly parameter splits the total schedule into daily, weekly and monthly
schedules.
Assume you select Friday for Weekly/Monthly backup. Here is the real schedule of the backup
tasks that will be created.
Backup tasks created according to the GFS scheme by Acronis Backup & Recovery 10.
Schedule: Workdays at 8:00 PM
Weekly/Monthly: Friday
Keep backups: Daily
This step defines the retention rule for daily backups. The cleanup task will run after each daily
backup and delete all daily backups that are older than you specify.
Keep backups: Weekly
This step defines the retention rule for weekly backups. The cleanup task will run after each
weekly backup and delete all weekly backups that are older than you specify. The weekly
backups' retention period cannot be less than the daily backups' retention period. It is usually set
several times longer.
Keep backups: Monthly
This step defines the retention rule for monthly backups. The cleanup task will run after each
monthly backup and delete all monthly backups that are older than you specify. The monthly
backups’ retention period cannot be less than the weekly backups’ retention period. It is usually
set several times longer. You have the option to keep the monthly backups indefinitely.
The resulting archive: ideal
Assume you select to keep daily backups for 7 days, weekly backups for 2 weeks and monthly
backups for 6 months. Here is how your archive would appear after the backup plan is launched if all
the backups were full and so could be deleted as soon as the scheme requires.
The left column shows days of the week. For each day of the week, the content of the archive after
the regular backup and the subsequent cleanup is shown.
35 Copyright © Acronis, Inc., 2000-2010
Page 36

“D” stands for the backup that is considered Daily. “W” stands for the backup that is considered
Weekly. “M” stands for the backup that is considered Monthly.
An ideal archive created according to the GFS scheme.
Schedule: Workdays at 8:00 PM
Weekly/Monthly: Friday
Keep daily backups: 7 days
Keep weekly backups: 2 weeks
Keep monthly backups: 6 months
Starting from the third week, weekly backups will be regularly deleted. After 6 months, monthly
backups will start to be deleted. The diagram for weekly and monthly backups will look similar to the
week-based timescale.
The resulting archive: real
In reality, the archive content will somewhat differ from the ideal scheme.
When using the incremental and differential backup methods, you cannot delete a backup as soon as
the scheme requires if later backups are based on this backup. Regular consolidation is unacceptable
because it takes too much system resources. The program has to wait until the scheme requires the
deletion of all the dependent backups and then deletes the entire chain.
Here is how the first month of your backup plan will appear in real life. “F” stands for full backup.
“Dif” stands for differential backup. “I” stands for incremental backup.
36 Copyright © Acronis, Inc., 2000-2010
Page 37

The backups that outlive their nominal lifetime because of dependencies are marked pink. The initial
full backup will be deleted as soon as all differential and incremental backups based on this backup
are deleted.
An archive created according to the GFS scheme by Acronis Backup & Recovery 10.
Schedule: Workdays at 8:00 PM
Weekly/Monthly: Friday
Keep daily backups: 7 days
Keep weekly backups: 2 weeks
Keep monthly backups: 6 months
2.6 Tower of Hanoi backup scheme
The need to have frequent backups always conflicts with the cost of keeping such backups for a long
time. The Tower of Hanoi (ToH) backup scheme is a useful compromise.
Tower of Hanoi overview
The Tower of Hanoi scheme is based on a mathematical puzzle of the same name. In the puzzle a
series of rings are stacked in size order, the largest on the bottom, on one of three pegs. The goal is
to move the ring series to the third peg. You are only allowed to move one ring at a time, and are
prohibited from placing a larger ring above a smaller ring. The solution is to shift the first ring every
other move (moves 1, 3, 5, 7, 9, 11...), the second ring at intervals of four moves (moves 2, 6, 10...),
the third ring at intervals of eight moves (moves 4, 12...), and so on.
37 Copyright © Acronis, Inc., 2000-2010
Page 38

For example, if there are five rings labeled A, B, C, D, and E in the puzzle, the solution gives the
following order of moves:
The Tower of Hanoi backup scheme is based on the same patterns. It operates with Sessions instead
of Moves and with Backup levels instead of Rings. Commonly an N-level scheme pattern contains (Nth power of two) sessions.
So, the five-level Tower of Hanoi backup scheme cycles the pattern that consists of 16 sessions
(moves from 1 to 16 in the above figure).
The table shows the pattern for the five-level backup scheme. The pattern consists of 16 sessions.
The Tower of Hanoi backup scheme implies keeping only one backup per level. All the outdated
backups have to be deleted. So the scheme allows for efficient data storage: more backups
accumulate toward the present time. Having four backups, you can recover data as of today,
yesterday, half a week ago, or a week ago. For the five-level scheme you can also recover data
backed up two weeks ago. So every additional backup level doubles the maximal roll-back period for
your data.
Tower of Hanoi by Acronis
The Tower of Hanoi backup scheme is generally too complex to mentally calculate the next media to
be used. But Acronis Backup & Recovery 10 provides you with automation of the scheme usage. You
can set up the backup scheme while creating a backup plan.
Acronis implementation for the scheme has the following features:
up to 16 backup levels
incremental backups on first level (A) - to gain time and storage savings for the most frequent
backup operations; but data recovery from such backups takes longer because it generally
requires access to three backups
full backups on the last level (E for five-level pattern) - the rarest backups in the scheme, take
more time and occupy more space in storage
differential backups on all intermediate levels (B, C and D for five-level pattern)
38 Copyright © Acronis, Inc., 2000-2010
Page 39
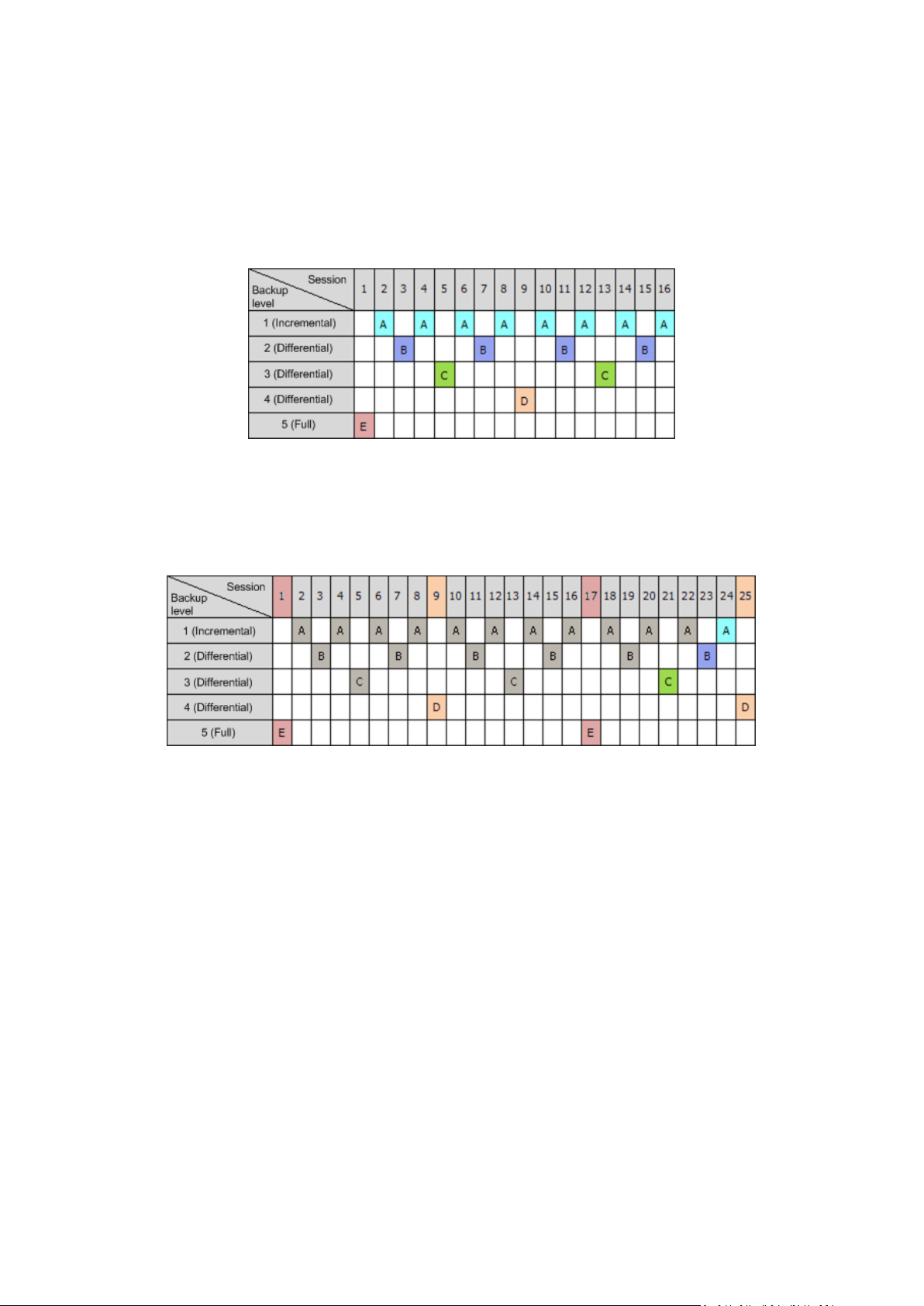
the pattern starts with a full backup since the very first backup cannot be incremental
the scheme forces every backup level to keep only the most recent backup, other backups from
the level have to be deleted; however backup deletion is postponed in cases where the backup is
a base for another incremental or differential one
an old backup on a level is kept until a new backup has been successfully created on the level.
The table shows the pattern for the five-level backup scheme. The pattern consists of 16 sessions.
As a result of using incremental and differential backups the situation may arise when an old backup
deletion must be postponed as it still is a base for other backups. The table below indicates the case
when deletion of full backup (E) created at session 1 is postponed at session 17 until session 25
because the differential backup (D) created at session 9 is still actual. In the table all cells with
deleted backups are grayed out:
Differential backup (D) created at session 9 will be deleted at session 25 after creation of a new
differential backup is completed. This way, a backup archive created in accordance with the Tower of
Hanoi scheme by Acronis sometimes includes up to two additional backups over the classical
implementation of the scheme.
For information about using Tower of Hanoi for tape libraries, see Using the Tower of Hanoi tape
rotation scheme (p. 146).
2.7 Retention rules
The backups produced by a backup plan make an archive. The two retention rules described in this
section enable you to limit the archive size and set the lifetime (retention period) of the backups.
The retention rules are effective if the archive contains more than one backup. This means that the
last backup in the archive will be kept, even if a retention rule violation is detected. Please do not try
to delete the only backup you have by applying the retention rules before backup. This will not work.
Use the alternative setting Clean up archive > When there is insufficient space while backing up (p.
208) if you accept the risk of losing the last backup.
39 Copyright © Acronis, Inc., 2000-2010
Page 40

1. Delete backups older than
This is a time interval counted back from the moment when the retention rules are applied. Every
time a retention rule is applied, the program calculates the date and time in the past corresponding
to this interval and deletes all backups created before that moment. None of the backups created
after this moment will be deleted.
2. Keep the archive size within
This is the maximum size of the archive. Every time a retention rule is applied, the program compares
the actual archive size with the value you set and deletes the oldest backups to keep the archive size
within this value. The diagram below shows the archive content before and after the deletion.
There is a certain risk that all but one backup will be deleted if the maximum archive size is set
improperly (too small) or a regular backup turns out to be too large. To protect the recent backups
from deletion, select the Never delete backups younger than check box and specify the maximum
age of backups that must be retained. The diagram below illustrates the resulting rule.
40 Copyright © Acronis, Inc., 2000-2010
Page 41

Combination of rules 1 and 2
You can limit both the backups’ lifetime and the archive size. The diagram below illustrates the
resulting rule.
Example
Delete backups older than = 3 Months
Keep the archive size within = 200GB
Never delete backups younger than = 10 Days
Every time the retention rules are applied, the program will delete all backups created more than
3 months (or more exactly, 90 days) ago.
If after the deletion the archive size is more than 200GB, and the oldest backup is older than 10
days, the program will delete that backup.
Then, if necessary, the next old backup will be deleted, until the archive size decreases to the
preset limit or the oldest backup age reaches 10 days.
Deleting backups with dependencies
Both retention rules presume deleting some backups while retaining the others. What if the archive
contains incremental and differential backups that depend on each other and on the full backups
they are based on? You cannot, say, delete an outdated full backup and keep its incremental
“children”.
When deletion of a backup affects other backups, one of the following rules is applied:
Retain the backup until all dependent backups become subject to deletion
The outdated backup will be kept until all backups that depend on it also become outdated. Then
all the chain will be deleted at once during the regular cleanup. This mode helps to avoid the
potentially time-consuming consolidation but requires extra space for storing backups whose
deletion is postponed. The archive size and/or the backup age can exceed the values you specify.
Consolidate the backup
The program will consolidate the backup that is subject to deletion with the next dependent
backup. For example, the retention rules require to delete a full backup but retain the next
incremental one. The backups will be combined into a single full backup which will be dated the
incremental backup date. When an incremental or differential backup from the middle of the
chain is deleted, the resulting backup type will be incremental.
This mode ensures that after each cleanup the archive size and the backups’ age are within the
bounds you specify. The consolidation, however, may take a lot of time and system resources.
And you still need some extra space in the vault for temporary files created during consolidation.
What you need to know about consolidation
41 Copyright © Acronis, Inc., 2000-2010
Page 42

Please be aware that consolidation is just a method of deletion but not an alternative to deletion.
The resulting backup will not contain data that was present in the deleted backup and was
absent from the retained incremental or differential backup.
Backups resulting from consolidation always have maximum compression. This means that all
backups in an archive may acquire the maximum compression as a result of repeated cleanup
with consolidation.
Best practices
Maintain the balance between the storage device capacity, the restrictive parameters you set and
the cleanup frequency. The retention rules logic assumes that the storage device capacity is much
more than the average backup size and the maximum archive size does not come close to the
physical storage capacity, but leaves a reasonable reserve. Due to this, exceeding the archive size
that may occur between the cleanup task runs will not be critical for the business process. The rarer
the cleanup runs, the more space you need to store backups that outlive their lifetime.
The Vaults (p. 121) page provides you with information about free space available in each vault.
Check this page from time to time. If the free space (which in fact is the storage device free space)
approaches zero, you might need to toughen the restrictions for some or all archives residing in this
vault.
2.8 Backing up dynamic volumes (Windows)
This section explains in brief how to back up and recover dynamic volumes (p. 395) using Acronis
Backup & Recovery 10. Basic disks that use the GUID Partition Table (GPT) are also discussed.
Dynamic volume is a volume located on dynamic disks (p. 394), or more exactly, on a disk group (p.
393). Acronis Backup & Recovery 10 supports the following dynamic volume types/RAID levels:
simple/spanned
striped (RAID 0)
mirrored (RAID 1)
a mirror of stripes (RAID 0+1)
RAID 5.
Acronis Backup & Recovery 10 can back up and recover dynamic volumes and, with minor limitations,
basic GPT volumes.
Backing up dynamic volumes
Dynamic and basic GPT volumes are backed up in the same way as basic MBR volumes. When
creating a backup plan through the GUI, all types of volumes are available for selection as Items to
back up. When using the command line, specify the dynamic and GPT volumes with the DYN prefix.
Command line examples
trueimagecmd /create /partition:DYN1,DYN2 /asz
This will back up DYN1 and DYN2 volumes to the Acronis Secure Zone.
trueimagecmd /create /harddisk:DYN /asz
This will back up all dynamic volumes in the system to the Acronis Secure Zone.
The boot code on basic GPT volumes is not backed up or recovered.
42 Copyright © Acronis, Inc., 2000-2010
Page 43

Recovering dynamic volumes
A dynamic volume can be recovered
over any type of existing volume
to unallocated space of a disk group
to unallocated space of a basic disk.
Recovery over an existing volume
When a dynamic volume is recovered over an existing volume, either basic or dynamic, the target
volume’s data is overwritten with the backup content. The type of target volume (basic,
simple/spanned, striped, mirrored, RAID 0+1, RAID 5) will not change. The target volume size has
to be enough to accommodate the backup content.
Recovery to disk group unallocated space
When a dynamic volume is recovered to disk group unallocated space, both the type and the
content of the resulting volume are recovered. The unallocated space size has to be enough to
accommodate the backup content. The way unallocated space is distributed among the disks is
also important.
Example
Striped volumes consume equal portions of space on each disk.
Assume you are going to recover a 30GB striped volume to a disk group consisting of two
disks. Each disk has volumes and a certain amount of unallocated space. The total size of
unallocated space is 40GB. The recovery will always result in a striped volume if the
unallocated space is distributed evenly among the disks (20GB and 20GB).
If one of the disks has 10GB and the other has 30GB of unallocated space, then the recovery
result depends on the size of the data being recovered.
If the data size is less than 20GB, then one disk can hold, say, 10GB; the other will hold the
remaining 10GB. This way, a striped volume will be created on both disks and 20GB on the
second disk will remain unallocated.
If the data size is more than 20GB, the data cannot be distributed evenly between the two
disks, but can fit into a single simple volume. A simple volume accommodating all the data
will be created on the second disk. The first disk will remain untouched.
Backed up (source):
Recovered to: Dynamic volume Basic MBR volume Basic GPT volume
Dynamic volume
Unallocated space (disk group)
Basic MBR volume
Basic GPT volume
Unallocated space (basic MBR disk)
43 Copyright © Acronis, Inc., 2000-2010
Dynamic volume
Type as of the
target
Dynamic volume
Type as of the
source
Basic MBR volume Basic MBR volume Basic MBR volume
Basic GPT volume Basic GPT volume Basic GPT volume
Basic MBR volume Basic MBR volume Basic MBR volume
Dynamic volume
Type as of the
target
Dynamic volume
Simple
Dynamic volume
Type as of the
target
N/A
Page 44

Basic GPT volume
Basic GPT volume
Basic GPT volume
ABR10
+ + +
+
Unallocated space (basic GPT disk)
Moving and resizing volumes during recovery
You can resize the resulting basic volume, both MBR and GPT, during recovery, or change the
volume's location on the disk. A resulting dynamic volume cannot be moved or resized.
Preparing disk groups and volumes
Before recovering dynamic volumes to bare metal you should create a disk group on the target
hardware.
You also might need to create or increase unallocated space on an existing disk group. This can be
done by deleting volumes or converting basic disks to dynamic.
You might want to change the target volume type (basic, simple/spanned, striped, mirrored, RAID
0+1, RAID 5). This can be done by deleting the target volume and creating a new volume on the
resulting unallocated space.
Acronis Backup & Recovery 10 includes a handy disk management utility which enables you to
perform the above operations both under the operating system and on bare metal. To find out more
about Acronis Disk Director Lite, see the Disk management (p. 268) section.
2.9 Tape support
Acronis Backup & Recovery 10 supports tape libraries, autoloaders, SCSI and USB tape drives as
storage devices. A tape device can be locally attached to a managed machine (in this case, the
Acronis Backup & Recovery 10 Agent writes and reads the tapes) or accessed through the Acronis
Backup & Recovery 10 Storage Node (p. 20). Storage nodes ensure fully automatic operation of tape
libraries and autoloaders (p. 129).
Backup archives created using different ways of access to tape have different formats. A tape written
by a storage node cannot be read by an agent.
Linux-based and PE-based bootable media allow for backup and recovery using both local access and
access through the storage node. Backups created using the bootable media can be recovered with
the Acronis Backup & Recovery 10 Agent running in the operating system.
2.9.1 Tape compatibility table
The following table summarizes the readability of tapes written by Acronis True Image Echo and
Acronis True Image 9.1 product families in Acronis Backup & Recovery 10. The table also illustrates
the compatibility of tapes written by various components of Acronis Backup & Recovery 10.
Tape written on
a locally
attached tape
Bootable Media ATIE 9.1 + + + +
ATIE 9.5 + + + +
ATIE 9.7 + + + +
...is readable on a tape device attached to a machine
with...
ABR10
Bootable
Media
ABR10
Agent for
Windows
ABR10
Agent for
Linux
ABR10
Storage
Node
44 Copyright © Acronis, Inc., 2000-2010
Page 45

device (tape
Agent for
ATIE 9.1
+ + +
+
drive or tape
library) by...
Tape written on
a tape device
through...
Windows
Agent for Linux ATIE 9.1 + + + +
Backup Server ATIE 9.1 + + + +
Storage Node ABR10 - - - +
ATIE 9.5 - - - +
ATIE 9.7 - - - +
ABR10 + + + +
ATIE 9.5 + + + +
ATIE 9.7 + + + +
ABR10 + + + +
ATIE 9.5 - - - +
ATIE 9.7 - - - +
2.9.2 Using a single tape drive
A tape drive that is locally attached to a managed machine can be used by local backup plans as a
storage device. The functionality of a locally attached autoloader or tape library is limited to the
ordinary tape drive. This means that the program can only work with the currently mounted tape and
you have to mount tapes manually.
Backup to a locally attached tape device
When creating a backup plan, you are able to select the locally attached tape device as the backup
destination. An archive name is not needed when backing up to a tape.
An archive can span multiple tapes but can contain only one full backup and an unlimited number of
incremental backups. Every time you create a full backup, you start with a new tape and create a
new archive. As soon as the tape is full, a dialog window with a request to insert a new tape will
appear.
The content of a non-empty tape will be overwritten on prompt. You have an option to disable
prompts, see Additional settings (p. 110).
Workaround
In case you want to keep more than one archive on the tape, for example, back up volume C and
volume D separately, choose incremental backup mode instead of a full backup when you create
an initial backup of the second volume. In other situations, incremental backup is used for
appending changes to the previously created archive.
You might experience short pauses that are required to rewind the tape. Low-quality or old tape, as
well as dirt on the magnetic head, might lead to pauses that can last up to several minutes.
Limitations
1. Multiple full backups within one archive are not supported.
2. Individual files cannot be recovered from a disk backup.
3. Backups cannot be deleted from a tape either manually or automatically during cleanup.
Retention rules and backup schemes that use automatic cleanup (GFS, Tower of Hanoi) are
disabled in the GUI when backing up to a locally attached tape.
4. Personal vaults cannot be created on tape devices.
5. Because the presence of an operating system cannot be detected in a backup located on a tape,
Acronis Universal Restore (p. 399) is proposed at every disk or volume recovery, even when
recovering a Linux or non-system Windows volume.
45 Copyright © Acronis, Inc., 2000-2010
Page 46

6. Acronis Active Restore (p. 387) is not available when recovering from a tape.
Recovery from a locally attached tape device
Before creating a recovery task, insert or mount the tape containing the backup you need to recover.
When creating a recovery task, select the tape device from the list of available locations and then
select the backup. After recovery is started, you will be prompted for other tapes if the tapes are
needed for recovery.
2.10 Support for SNMP
SNMP objects
Acronis Backup & Recovery 10 provides the following Simple Network Management Protocol (SNMP)
objects to SNMP management applications:
Type of event
Object identifier (OID): 1.3.6.1.4.1.24769.100.200.1.0
Syntax: OctetString
The value may be "Information", "Warning", 'Error" and "Unknown". "Unknown" is sent only in
the test message.
Text description of the event
Object identifier (OID): 1.3.6.1.4.1.24769.100.200.2.0
Syntax: OctetString
The value contains the text description of the event (it looks identical to messages published by
Acronis Backup & Recovery 10 in its log).
Example of varbind values:
1.3.6.1.4.1.24769.100.200.1.0:Information
1.3.6.1.4.1.24769.100.200.2.0:I0064000B
Supported operations
Acronis Backup & Recovery 10 supports only TRAP operations. It is not possible to manage Acronis
Backup & Recovery 10 using GET- and SET- requests. This means that you need to use an SNMP Trap
receiver to receive TRAP-messages.
About the management information base (MIB)
The MIB file acronis-abr.mib is located in the Acronis Backup & Recovery 10 installation directory. By
default: %ProgramFiles%\Acronis\BackupAndRecovery in Windows and
/usr/lib/Acronis/BackupAndRecovery in Linux.
This file can be read by a MIB browser or a simple text editor such as Notepad or vi.
About the test message
When configuring SNMP notifications, you can send a test message to check if your settings are
correct.
The parameters of the test message are as follows:
Type of event
46 Copyright © Acronis, Inc., 2000-2010
Page 47

OID: 1.3.6.1.4.1.24769.100.200.1.0
Value: "Unknown"
Text description of the event
OID: 1.3.6.1.4.1.24769.100.200.2.0
Value: "?00000000"
2.11 Proprietary Acronis technologies
This section describes the proprietary technologies inherited by Acronis Backup & Recovery 10 from
Acronis True Image Echo and Acronis True Image 9.1 product families.
2.11.1 Acronis Secure Z one
Acronis Secure Zone is a secure partition that enables keeping backup archives on a managed
machine disk space and therefore recovery of a disk to the same disk where the backup resides.
Certain Windows applications, such as Acronis disk management tools, can access the zone.
Should the disk experience a physical failure, the zone and the archives located there will be lost.
That's why Acronis Secure Zone should not be the only location where a backup is stored. In
enterprise environments, Acronis Secure Zone can be thought of as an intermediate location used for
backup when an ordinary location is temporarily unavailable or connected through a slow or busy
channel.
Advantages
Acronis Secure Zone:
Enables recovery of a disk to the same disk where the disk's backup resides.
Offers a cost-effective and handy method for protecting data from software malfunction, virus
attack, operator error.
Being an internal archive storage, eliminates the need for a separate media or network
connection to back up or recover the data. This is especially useful for mobile users.
Can serve as a primary destination when using dual destination (p. 107) backup.
Limitations
The zone cannot be organized on a dynamic disk or a disk using the GPT partitioning style.
Backup to Acronis Secure Zone is not possible when working under bootable media or Acronis
Startup Recovery Manager.
Managing the Acronis Secure Zone
Acronis Secure Zone is considered as a personal vault (p. 400). Once created on a managed machine,
the zone is always present in the list of Personal vaults. Centralized backup plans (p. 391) can use
Acronis Secure Zone as well as local plans (p. 396).
If you have used Acronis Secure Zone before, please note a radical change in the zone functionality.
The zone does not perform automatic cleanup, that is, deleting old archives, anymore. Use backup
schemes with automatic cleanup to back up to the zone, or delete outdated backups manually using
the archive management functionality.
With the new Acronis Secure Zone behavior, you obtain the ability to:
47 Copyright © Acronis, Inc., 2000-2010
Page 48

list archives located in the zone and backups contained in each archive
examine a backup's content
mount a disk backup to copy files from the backup to a physical disk
safely delete archives and backups from the archives.
For more information about operations available in Acronis Secure Zone, see the Personal vaults (p.
152) section.
Upgrade from Acronis True Image Echo
When upgrading from Acronis True Image Echo to Acronis Backup & Recovery 10, Acronis Secure
Zone will keep the archives created with Echo. The zone will appear in the list of personal vaults and
the old archives will be available for recovery.
2.11.2 Acronis Startup R ecovery Mana ger
A modification of the bootable agent (p. 390) can be placed on a system disk and configured to start
at boot time when F11 is pressed. This eliminates the need for rescue media or network connection
to start the bootable rescue utility. This feature has the trade name "Acronis Startup Recovery
Manager".
Acronis Startup Recovery Manager is especially useful for mobile users. If a failure occurs, the user
reboots the machine, hits F11 on prompt "Press F11 for Acronis Startup Recovery Manager…" and
performs data recovery in the same way as with ordinary bootable media. The user can also back up
using Acronis Startup Recovery Manager, while on the move.
On machines with the GRUB boot loader installed, the user selects the Acronis Startup Recovery
Manager from the boot menu instead of pressing F11.
Activation and deactivation of the Acronis Startup Recovery Manager
The operation that enables using Acronis Startup Recovery Manager is called "activation". To activate
Acronis Startup Recovery Manager, select Actions > Activate Acronis Startup Recovery Manager
from the program menu.
You can activate or deactivate the Acronis Startup Recovery Manager at any time from the Tools
menu. The deactivation will disable the boot time prompt "Press F11 for Acronis Startup Recovery
Manager…" (or removes the corresponding entry from GRUB's boot menu). This means you will need
bootable media in case the system fails to boot.
Limitation
Acronis Startup Recovery Manager requires re-activation of third-party loaders after activation.
Upgrade from Acronis True Image Echo
After upgrade from Acronis True Image Echo to Acronis Backup & Recovery 10, Acronis Startup
Recovery Manager appears as deactivated regardless of its status before the upgrade. You can
activate Acronis Startup Recovery Manager again at any time.
48 Copyright © Acronis, Inc., 2000-2010
Page 49

2.11.3 Universal R estore (Acronis Backup & R ecov ery 10 Universal
Restore)
Acronis Backup & Recovery 10 Universal Restore is the Acronis proprietary technology that helps
recover and boot up Windows on dissimilar hardware or a virtual machine. The Universal Restore
handles differences in devices that are critical for the operating system start-up, such as storage
controllers, motherboard or chipset.
Acronis Backup & Recovery 10 Universal Restore purpose
A system can be easily recovered from a disk backup (image) onto the same system or to identical
hardware. However, if you change a motherboard or use another processor version—a likely
possibility in case of hardware failure—the recovered system could be unbootable. An attempt to
transfer the system to a new, much more powerful computer will usually produce the same
unbootable result because the new hardware is incompatible with the most critical drivers included
in the image.
Using Microsoft System Preparation Tool (Sysprep) does not solve this problem, because Sysprep
permits installing drivers only for Plug and Play devices (sound cards, network adapters, video cards
etc.). As for system Hardware Abstraction Layer (HAL) and mass storage device drivers, they must be
identical on the source and the target computers (see Microsoft Knowledge Base, articles 302577
and 216915).
The Universal Restore technology provides an efficient solution for hardware-independent system
recovery by replacing the crucial Hardware Abstraction Layer (HAL) and mass storage device drivers.
Universal Restore is applicable for:
1. Instant recovery of a failed system on different hardware.
2. Hardware-independent cloning and deployment of operating systems.
3. Physical-to-physical, physical-to-virtual and virtual-to-physical machine migration.
The Universal Restore principles
1. Automatic HAL and mass storage driver selection.
Universal Restore searches for drivers in the network folders you specify, on removable media
and in the default driver storage folders of the system being recovered. Universal Restore
analyzes the compatibility level of all found drivers and installs HAL and mass storage drivers that
better fit the target hardware. Drivers for network adapters are also searched and passed to the
operating system which installs them automatically when first started.
The Windows default driver storage folder is determined in the registry value DevicePath, which can be
found in the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion. This
storage folder is usually WINDOWS/inf.
2. Manual selection of the mass storage device driver.
If the target hardware has a specific mass storage controller (such as a SCSI, RAID, or Fibre
Channel adapter) for the hard disk, you can install the appropriate driver manually, bypassing the
automatic driver search-and-install procedure.
3. Installing drivers for Plug and Play devices.
Universal Restore relies on the built-in Plug and Play discovery and configuration process to
handle hardware differences in devices that are not critical for the system start, such as video,
audio and USB. Windows takes control over this process during the logon phase, and if some of
the new hardware is not detected, you will have a chance to install drivers for it later manually.
49 Copyright © Acronis, Inc., 2000-2010
Page 50

Universal Restore and Microsoft Sysprep
Universal Restore is not a system preparation tool. You can apply it to any Windows image created
by Acronis products, including images of systems prepared with Microsoft System Preparation Tool
(Sysprep). The following is an example of using both tools on the same system.
Universal Restore does not strip the security identifier (SID) and user profile settings in order to run
the system immediately after recovery without re-joining the domain or re-mapping network user
profiles. If you are going to change the above settings on a recovered system, you can prepare the
system with Sysprep, image it and recover, if need be, using the Universal Restore.
Limitations
Universal Restore is not available:
when a computer is booted with Acronis Startup Recovery Manager (using F11) or
the backup image is located in the Acronis Secure Zone or
when using Acronis Active Restore,
because these features are primarily meant for instant data recovery on the same machine.
Universal Restore is not available when recovering Linux.
Getting Universal Restore
Universal Restore comes free with Acronis Backup & Recovery 10 Advanced Server SBS Edition and
Acronis Backup & Recovery 10 Advanced Server Virtual Edition.
Universal Restore for the other product editions is purchased separately, has its own license, and is
installed as a separate feature from the setup file. You need to re-create bootable media to make the
newly installed add-on operational in the bootable environment.
2.11.4 Acronis Active Restor e
Active Restore is the Acronis proprietary technology that brings a system online immediately after
the system recovery is started.
Customers familiar with Acronis Recovery for Microsoft Exchange can note that this product uses
Active Restore to achieve immediate availability of an Exchange information store after starting the
recovery. While based on the same technology, recovery of the Information Store proceeds in quite a
different way than the operating system recovery described in this section.
Supported operating systems
Acronis Active Restore is available when recovering Windows starting from Windows 2000.
Limitation
The only supported archive location is a local drive, or more precisely, any device available through
the machine’s BIOS. This may be Acronis Secure Zone, a USB hard drive, a flash drive or any internal
hard drive.
50 Copyright © Acronis, Inc., 2000-2010
Page 51

How it works
When configuring a recovery operation, you select disks or volumes to recover from a backup.
Acronis Backup & Recovery 10 scans the selected disks or volumes in the backup. If this scan finds a
supported operating system, the Acronis Active Restore option becomes available.
If you do not enable the option, the system recovery will proceed in the usual way and the machine
will become operational after the recovery is completed.
If you enable the option, the sequence of actions will be set as follows.
Once the system recovery is started, the operating system boots from the backup. The machine
becomes operational and ready to provide necessary services. The data required to serve incoming
requests is recovered with the highest priority; everything else is recovered in the background.
Because serving requests is performed simultaneously with recovery, the system operation can slow
down even if recovery priority in the recovery options is set to Low. This way, the system downtime
is reduced to a minimum at the cost of a temporary performance downgrade.
Usage scenarios
1. The system uptime is one of the efficiency criteria.
Examples: Client-oriented online services, Web-retailers, polling stations.
2. The system/storage space ratio is heavily biased toward storage.
Some machines are being used as storage facilities, where the operating system claims a small
space segment and all other disk space is committed to storage, such as movies, sounds or other
multimedia files. Some of these storage volumes can be extremely large as compared to the
system and so practically all the recovery time will be dedicated to recovering the files, which
might be used much later on, if in any near future at all.
If you opt for Acronis Active Restore, the system will be operational in a short time. Users will be
able to open the necessary files from the storage and use them while the rest of the files, which
are not immediately necessary, are being recovered in the background.
Examples: movie collection storage, music collection storage, multimedia storage.
How to use
1. Back up the system disk or volume to a location accessible through the system’s BIOS. This may
be Acronis Secure Zone, a USB hard drive, a flash drive or any internal hard drive.
If your operating system and its loader reside on different volumes, always include both volumes in the
backup. The volumes must also be recovered together; otherwise there is a high risk that the operating
system will not start.
2. Create bootable media.
3. If a system failure occurs, boot the machine using the bootable media. Start the console and
connect to the bootable agent.
4. Configure the system recovery: select the system disk or volume and select the Use Acronis
Active Restore check box.
Acronis Active Restore will choose for the boot-up and subsequent recovery the first operating system
found during the backup scan. Do not try to recover more than one operating system using Active Restore if
you want the result to be predictable. When recovering a multi-boot system, choose only one system
volume and boot volume at a time.
51 Copyright © Acronis, Inc., 2000-2010
Page 52

5. Once the system recovery is started, the operating system boots from the backup. The Acronis
Active Restore icon appears in the system tray. The machine becomes operational and ready to
provide necessary services. The immediate user sees the drive tree and icons and can open files
or launch applications even though they were not yet recovered.
The Acronis Active Restore drivers intercept system queries and set the immediate priority for
recovery of the files that are necessary to serve the incoming requests. While this on-the-fly
recovery proceeds, the continuing recovery process is transferred to the background.
Please do not shut down or reboot the machine until the recovery is completed. If you switch off the
machine, all the changes made to the system since the last boot up would be lost. The system will not be
recovered, not even partially. The only possible solution in this case will be to restart the recovery process
from a bootable media.
6. The background recovery continues until all the selected volumes are recovered, the log entry is
made and the Acronis Active Restore icon disappears from the system tray.
2.12 Understanding centralized management
This section contains an overview of centralized data protection with Acronis Backup & Recovery 10.
Please be sure you have an understanding of how data is protected on a single machine (p. 26)
before reading this section.
2.12.1 Basic concepts
Applying backup policies and tracking their execution
To protect data on a single machine, you install on the machine an agent (p. 388) or multiple agents
for various data types you want to protect. You connect the console to the machine and create a
backup plan (p. 389) or multiple backup plans.
What if you have to manage hundreds of machines? It takes time to create a backup plan on each
machine, while the plans may be quite similar – you need to back up, say, the system drive and the
users' documents. Tracking the plans' execution on each machine separately is also time-consuming.
To be able to propagate the management operations to multiple machines, you install Acronis
Backup & Recovery 10 Management Server (p. 397) and register (p. 398) the machines on the server.
After that you can create groups of machines and thus manage multiple machines as a whole. You
can protect all of them or your selection by setting up a common backup plan, which is called a
backup policy (p. 389).
Once you apply the policy to a group of machines, the management server deploys the policy to each
of the machines. On each machine the agents find the items to back up and create corresponding
centralized backup plans (p. 391). You will be able to monitor the policies’ statuses on a single screen
and navigate, if required, to each machine, plan or task to see their status and log entries. The
management server also enables you to monitor and manage the agent's locally originated activities.
Since you connect the console to the management server rather than to each machine and perform
all management operations through the central management unit, this way of management is called
centralized management (p. 391).
Centralized management does not rule out the direct management (p. 392) of each machine. You can
connect the console to each machine and perform any direct management operation. However,
centralized backup plans can be managed through the management server only, since a well-thought
out policy functions automatically and rarely requires human intervention.
52 Copyright © Acronis, Inc., 2000-2010
Page 53

Using the management server, you can create one or more centralized archive storages (centralized
vaults (p. 391)), which will be shared by the registered machines. A centralized vault can be used by
any backup policy as well as by any backup plan created on the registered machines using direct
management.
Organizing a managed archive storage
What should the capacity of your centralized vault be? What if transferring sizeable backups to the
vault will cause network congestion? Does backup of an online production server affect the server
performance? To ensure that the centralized backup will not slow down business processes in your
company and to minimize the resources required for the data protection, you install Acronis Backup
& Recovery 10 Storage Node (p. 398) and configure it to manage a centralized vault or multiple
centralized vaults. Such vaults are called managed vaults (p. 396).
The storage node helps the agent deduplicate (p. 392) backups before transferring them to managed
vaults and deduplicates the backups already saved in the vaults. Deduplication results in reducing
backup traffic and saving storage space. The storage node also undertakes operations with archives
(such as validation and cleanup), which otherwise are performed by the agent, and thus relieves the
managed machines from unnecessary computing load. Last but not least, Acronis Backup & Recovery
10 Storage Node enables using a tape library as a centralized vault for storing backup archives.
More than one storage node, each managing a number of vaults, can be set up and controlled
centrally from the Acronis Backup & Recovery 10 Management Server.
For more detailed information about storage nodes please refer to Acronis Backup & Recovery 10
Storage Node (p. 20).
2.12.2 Setting up centralized data protection in a heterogeneous
network
Assume that the network infrastructure includes servers (1, 2, 9) and workstations (3, 5-8) running
Windows and Linux. You also have a VMware ESX server (4) that hosts two guest systems.
53 Copyright © Acronis, Inc., 2000-2010
Page 54
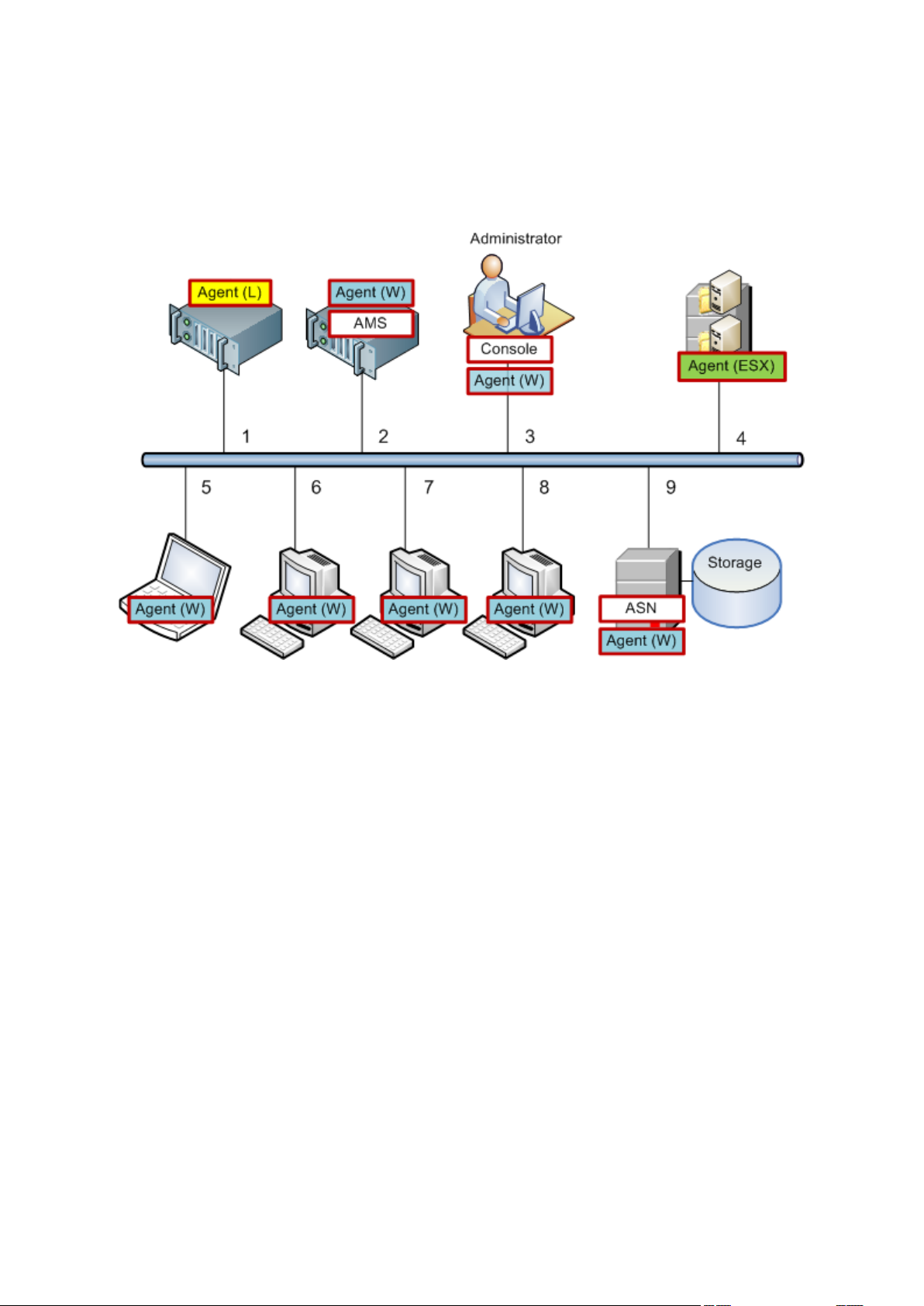
You have to protect each server as a whole, the users' data on the workstations, and the virtual
machines. You want to be able to track the health of the data protection, be sure that the backup
archives do not store duplicated information and that the obsolete backups are deleted from the
storage in a timely manner. These goals can be achieved by regular backup of the desired data items
to a centralized vault with deduplication.
Setting up the Acronis infrastructure
1. Install Acronis Backup & Recovery 10 Management Console [Console] on the machine which you
prefer to operate from (3). The console enables you to access and manage other Acronis
components through Graphical User Interface.
2. Install Acronis Backup & Recovery 10 Management Server [AMS] on one of the Windows servers
(2). The management server is your single entry point to the Acronis infrastructure.
3. Install Acronis Backup & Recovery 10 Agent on each of the machines to back up the machine's
disks, volumes or files.
Agent (W) - Agent for Windows
Agent (L) - Agent for Linux.
When installing the agents, register each of the machines on the management server. To do so,
enter the server's name or IP address and the server's administrator credentials in the
appropriate window of the installation wizard. Or, alternatively, add the machines to the
management server later using their names or IP addresses.
4. Install Acronis Backup & Recovery 10 Agent for ESX/ESXi [Agent (ESX)] on the ESX server (4) to
back up the virtual machines from the host. The agent is delivered as a virtual appliance.
5. Install Acronis Backup & Recovery 10 Storage Node [ASN] on one of the Windows servers (9). The
storage node enables you to organize the infrastructure for storing backup archives and to use
the deduplication functionality. The node can be installed together with the management server
if the host is capable enough.
54 Copyright © Acronis, Inc., 2000-2010
Page 55

When installing the storage node, register it on the management server in the same way as you
register the agents.
Installation tips
Both AMS and ASN can be installed on a workstation operating system as well.
There can be multiple storage nodes on the network. Each of the nodes can manage up to 20
local or remote vaults.
Multiple Acronis Backup & Recovery 10 components can be installed on a machine with a single
installation procedure.
In an Active Directory domain, you can deploy the components using the Group Policy.
Setting up the storage node
Before using the storage node, make sure that all users that will back up to the node's vaults have
Windows accounts on the node.
If the node is included in an Active Directory domain, all the domain users will be able to back up
to the node; and all the domain administrators will become node administrators.
In a workgroup, create a local user account for each user that will back up to the node. Members
of the Administrators group become node administrators. You can add more accounts later as
required.
1. Run the console, connect to the management server.
2. Create a managed vault as described in Operations with centralized vaults (p. 124). Enable
deduplication when creating a managed vault.
Setting up groups and policies
The detailed explanation of when and why you need to organize groups of machines can be found in
the Grouping the registered machines (p. 57) section. Here are some scenarios supported by the
aforementioned Acronis Backup & Recovery 10 implementation.
2.12.2.1 Protecting the servers
You will most likely create individual backup plans on each of the servers depending on their roles.
But it is necessary to perform a full backup of the entire server at least once. You might want to back
up the server during a maintenance window or backup window, after installing or updating software,
before relocation, etc. In our example, there is no need to back up entire servers on a regular basis.
You can manually delete old backups since they are not numerous.
1. Create a policy that backs up [All Volumes] to the managed vault on the storage node. Choose
Back up later, manual start and Full backup type.
2. Create a static group named, say, S_1. Add all the servers to this group. (A storage node can be
added in case the managed vault is not on the local node's drives. Otherwise the archive storage
will be backed up to itself).
3. Apply the policy to the S_1 group. Make sure that the policy has been successfully deployed to
each of the servers. The policy deployment state has to change from Deploying to Deployed and
its status has to be OK. To see the resulting backup plans on each of the servers:
a. navigate to the All machines group or the S_1 group
b. select the server
c. select the Backup plans and tasks tab on the Information pane.
55 Copyright © Acronis, Inc., 2000-2010
Page 56

When you need and have the opportunity to back up any of the servers, navigate to the backup plan
as described above, select the plan and run it.
2.12.2.2 Protecting the work stations
Here is how to set up the most popular schedule: weekly full backup and daily incremental backup of
users' default document folders. In addition, we will retain only backups from the last 7 days.
1. Create a policy that backs up [All Profiles Folder] to the managed vault on the storage node. This
will back up the folder where user profiles are located (for example, C:\Documents and Settings
in Windows XP). Choose the Custom backup scheme.
a. Schedule full backup as follows: Weekly, Every 1 week on: Sunday, Execute the task once at
12:00:00 AM. Advanced settings: Wake-on-LAN: On. You may also want to distribute the
backup start time within the time window to optimize the network usage and the storage
node CPU load.
b. Schedule incremental backup as follows: Weekly, Every 1 week on: Workdays, Execute the
task once at 08:00:00 PM. Also set the advanced settings as required.
c. Set up the retention rules as follows: Delete backups older than: 7 days. When deleting a
backup that has dependencies: Consolidate the backups. Leave the default settings for the
remaining retention rules. In Apply retention rules, set After backup.
2. Create a dynamic group named, say, W_1. Specify %Windows%XP% and %Windows%Vista% as
the criteria. This way, any workstation that will be registered on the management server later,
will be added to this group and protected by the same policy.
3. Apply the policy to the W_1 group. Make sure that the policy has been successfully deployed to
each of the workstations. The policy deployment state has to change from Deploying to
Deployed and its status has to be OK. To see the resulting backup plans on each of the
workstations:
a. navigate to the All machines group or the W_1 group
b. select the workstation
c. select the Backup plans and tasks tab on the Information pane.
You can also see the resulting tasks, created on the workstations, in the Tasks view.
4. Use the Dashboard or the Tasks view to track the daily activities related to the policy. Once you
ascertain that all tasks run as specified, you can only check the policy status in the Backup
policies view.
To protect data on a daily basis, you can also use the GFS or Tower of Hanoi backup schemes.
2.12.2.3 Protecting the vir tual ma chin es
Acronis Backup & Recovery 10 Agent for ESX/ESXi provides the flexibility to protect virtual machines
in multiple ways:
Connect the console to the virtual appliance (Agent for ESX/ESXi) and create a backup plan that
will back up all or some of the virtual machines.
Connect the console to the virtual appliance (Agent for ESX/ESXi) and create an individual backup
plan for each machine. The plan will back up the volumes you specify.
Register the virtual appliance (Agent for ESX/ESXi) on the management server. All virtual
machines, except for the virtual appliance, will appear in the All virtual machines group. You can
group these machines and apply any policy that backs up disks or volumes to them.
56 Copyright © Acronis, Inc., 2000-2010
Page 57

Install Agent for Windows or Agent for Linux on each virtual machine. Register the machines on
the management server. The machines will be considered as physical machines. You can apply a
backup policy to these machines or create a backup plan on each machine separately. If any of
the machines meets membership criteria set for a dynamic group of physical machines, the
machine will be protected by the policy applied to this group.
Advanced product editions other than Virtual Edition (Acronis Backup & Recovery 10 Advanced
Server, Advanced Server SBS Edition and Advanced Workstation) allow using only the last of the
above methods.
2.12.3 Grouping the registered machines
As soon as a machine is registered (p. 398) on the management server, the machine appears in the
All machines built-in group (p. 390). By applying a backup policy to this group, you protect all the
registered machines. The thing is that a single policy may not be satisfactory because of the different
roles of the machines. The backed up data is specific for each department; some data has to be
backed up frequently, other - twice a year; so you may want to create various policies applicable to
different sets of machines. In this case consider creating custom groups.
2.12.4 Policies on machines and groups
This section helps you understand the automatic deployment and revoking policies performed by the
management server when a policy or a number of policies are applied to machines and nested
groups of machines in various combinations; when a policy is revoked from machines and groups;
when a machine or a group is moved from one group to another.
Operations with groups to which backup policies are applied will result in changing the policies on
the member machines. On any hierarchy change, that is, when moving, removing, creating groups;
adding machines to static groups; or when machines enter a group based on dynamic criteria, a huge
number of inheritance changes may occur. Please familiarize yourself with this section to be sure
that your actions yield the desired result and to understand the result of the automated Acronis
Backup & Recovery 10 Management Server operations.
What is applying, deploying and revoking?
Applying a policy establishes the correspondence between the policy and one or more machines.
This process takes place inside the management server's database and does not take much time.
Deploying a policy transfers the established correspondence to the machines. Physically, a bundle of
tasks is created on each machine according to the configuration provided by the policy.
Revoking a policy is the reverse action to the aggregate of applying and deploying. Revoking removes
the correspondence between the policy and one or more machines and then removes the tasks from
the machines.
If a machine is not available or not reachable at the moment, the change will be propagated on the
machine when it becomes available. This means that deploying a policy to multiple machines is not a
momentary action. The same is true for revoking. These two processes may be durable and so the
management server tracks and displays personal statuses for each machine that it works with, as
well as the policy's cumulative status.
57 Copyright © Acronis, Inc., 2000-2010
Page 58

2.12.4.1 A poli cy o n a ma chi ne or a gr oup
In the diagrams below, each numbered scheme illustrates the result of the respectively numbered
action.
The container stands for a group; the colored circle stands for a machine with applied policy; the dark
colored circle stands for a machine with two applications of the same policy; the white circle stands
for a machine to which no policy is applied.
Policy on a machine
1. A policy can be applied to a machine.
2. A policy can be revoked from a machine.
Policy on a group
1. A policy can be applied to a group.
2. A policy can be revoked from a group.
3. A policy applied to a group cannot be revoked from a machine.
4. To revoke the policy from the machine, remove the machine from the group.
The same policy on a group and on a machine
1. The same policy can be applied to a group and to a machine. Nothing changes on the machine at
the second application of the same policy, but the server remembers that the policy has been
applied twice.
2. A policy, revoked from the group, remains on the machine.
3. A policy, revoked from the machine, remains on the group and therefore on the machine.
4. To completely revoke the policy from the machine, revoke it from both the group and the
machine.
2.12.4.2 Operations with a machine
This section is a simplified illustration of what happens with the policies on a machine when the
machine is moved, copied, or deleted from a group.
58 Copyright © Acronis, Inc., 2000-2010
Page 59

In the diagram below, the container stands for a group; the one-color circle stands for a machine
with one applied policy; the two-color circle stands for a machine with two applied policies; the
white circle stands for a machine with no policy applied.
1. Here is the initial state: two custom groups contain different machines. A policy is applied to one
group; another policy is applied to another group. The next schemes illustrate results of the specified
actions.
2. Move to another group: Machine #3 is moved from one group to another. The "orange" policy is
revoked; the "blue" policy is applied to the machine.
3. Add to another group: Machine #3 is added to another group. It becomes a member of both
groups. The "blue" policy is applied, but the "orange" policy remains on the machine.
4. Remove from the group: Machine #3 is removed from the group. The "orange" policy is revoked
from the machine. The machine remains in the All machines group.
2.12.4.3 Inheri tance of poli cies
Policy inheritance can be easily understood if we assume that a machine can be a member of only
one group besides the All machines group. Let's start from this simplified approach.
59 Copyright © Acronis, Inc., 2000-2010
Page 60

In the diagram below, the container stands for a group; the two-color circle stands for a machine
with two applied policies; the three-color circle stands for a machine with three applied policies and
so on.
Besides the All machines group, we have
the custom G1 group in the root and the
custom G2 group, which is G1's child.
The "green" policy, applied to the All
machines group, is inherited by all
machines.
The "orange" policy, applied to G1, is
inherited by the G1 members and all its
child groups, both immediate and indirect.
The "blue" policy, applied to G2, is
inherited only by the G2 members since
G2 does not have child groups.
The "violet" policy is applied straight to
machine #4. It will exist on machine #4
irrespectively of this machine's
membership in any group.
Let's assume we create the G3 group in
the root. If no policies are applied to the
group, all its members are supposed to be
"green". But if we add, say, the #1
machine to G3, the machine will bear both
"orange" and "green" policies, in spite of
the fact that G3 has nothing to do with the
"orange" policy.
That's why it is difficult to track the
policies' inheritance from the top of the
hierarchy if the same machine is included
in multiple groups.
In real life, it's much easier to view the inheritance from the machine's side. To do so, navigate to any
group that contains the machine, select the machine and then select the Backup policies tab on the
Information pane. The Inheritance column shows whether a policy is inherited or applied directly to
the machine. Click Explore inheritance to view the inheritance order of the policy. In our example,
the policy names, the Inheritance column and the inheritance order will be as follows:
For machine Name of the policy Inheritance Inheritance order
#1 or #2 or #3 "green"
Inherited
All machines -> #1 or #2 or #3
"orange"
60 Copyright © Acronis, Inc., 2000-2010
Inherited
G1 -> #1 or #2 or #3
Page 61

#4 "green"
"orange"
"blue"
"violet"
#5 or #6 "green"
"orange"
"blue"
Inherited
Inherited
Inherited
Applied directly
Inherited
Inherited
Inherited
All machines -> #4
G1 -> G2 -> #4
G2 -> #4
All machines -> #5 or #6
G1 -> G2 -> #5 or #6
G2 -> #5 or #6
2.12.5 Backup policy's state and statuses
Centralized management presumes that the administrator can monitor the health of the entire
product infrastructure using a few easily understandable parameters. The state and status of a
backup policy are included in such parameters. Issues, if any, arise from the very bottom of the
infrastructure (tasks on managed machines) to the cumulative policy status. The administrator
checks the status at a glance. If the status is not OK, the administrator can navigate down to the issue
details in a few clicks.
This section helps you understand the policies' states and statuses displayed by the management
server.
2.12.5.1 Policy dep loymen t s tate on a machin e
To see this parameter, select any group, containing the machine, in the tree, then select the
machine, and then select the Backup policies tab on the Information pane.
Once you apply a policy to a machine or a group of machines, the server deploys the policy to the
machines. On each of the machines, the agent creates a backup plan. While the policy is transferred
to the machine and the backup plan is being created, the policy's deployment state on the machine is
Deploying.
Once the backup plan is successfully created, the policy state on the machine becomes Deployed.
You may need to modify the policy for some reason. Once you confirm the changes, the
management server updates the policy on all machines the policy was deployed to. While the
changes are transferred to the machine and the agent updates the backup plan, the policy state on
the machine is Updating. Once the policy is updated, its state becomes Deployed again. This state
means that the policy is functioning and no changes are currently being made to it.
A policy that was modified while being deployed remains in the Deploying state. The management
server just starts to deploy the modified policy from the beginning.
You may need to revoke the policy from the machine or from the group the machine is included in.
Once you confirm the changes, the management server revokes the policy from the machine. While
the changes are transferred to the machine and the agent deletes the backup plan from it, the policy
state on the machine is Revoking.
You may change grouping conditions or the machine may change its properties so that the machine
leaves one group and is included into another. This may result in revoking one policy and deploying
61 Copyright © Acronis, Inc., 2000-2010
Page 62
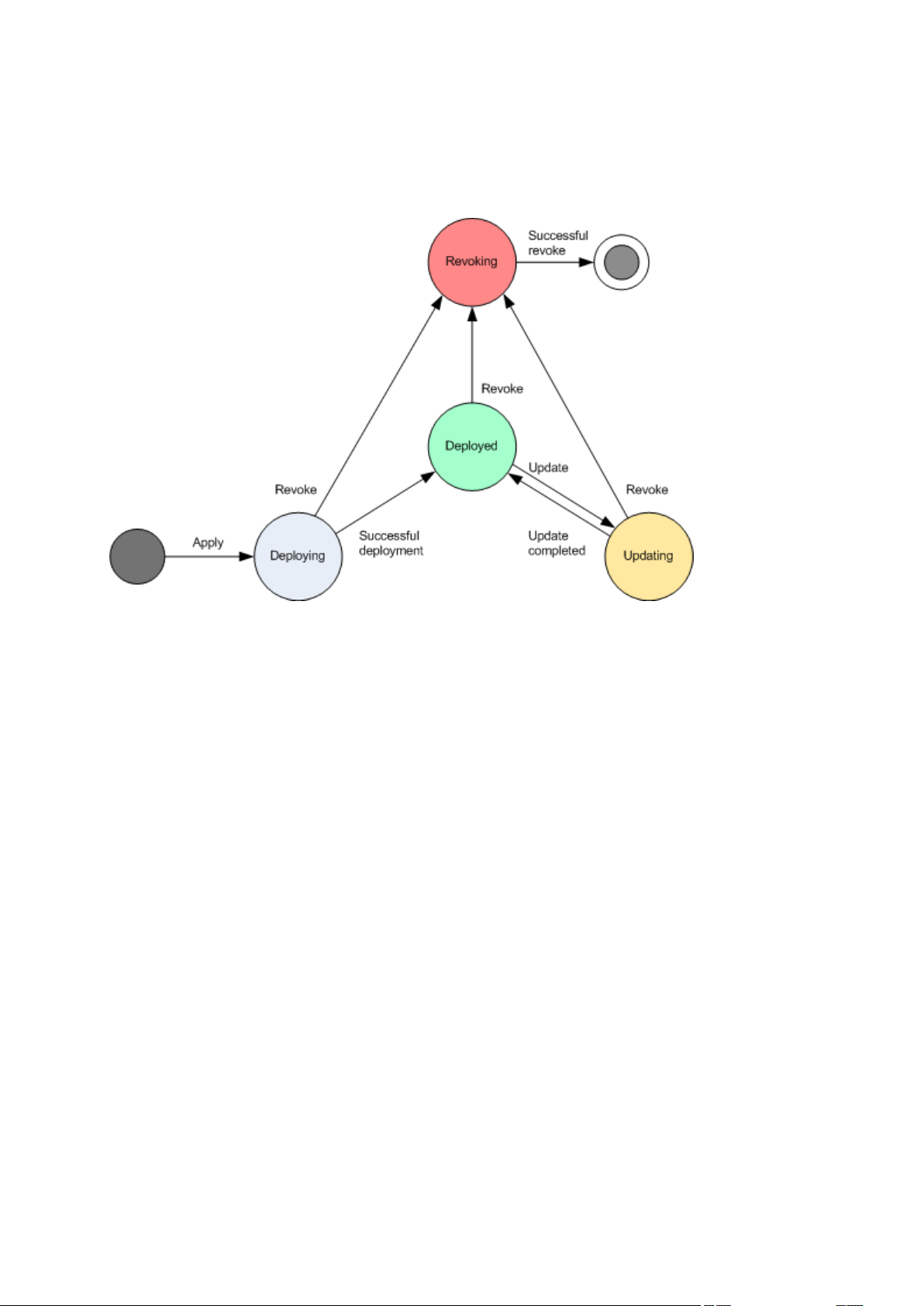
another policy. In this case, the first policy's state on the machine will be Revoking and the second
policy's state will be Deploying. The policies can appear in the GUI simultaneously or one after
another.
Backup policy state diagram
2.12.5.2 Policy status on a machine
To see this parameter, select any group of machines in the tree, then select the machine, and then
select the Backup policies tab on the Information pane.
In each of the states, the backup policy can have one of the following statuses: Error; Warning; OK.
While the policy is in the Deployed state, its status reflects how successfully the policy is executed.
While the policy is in any other state, its status reflects how successfully the policy is being modified.
Policy status when data to back up is not found on a machine
A backup policy can be applied to a machine that does not have data meeting the selection rules (p.
398). No error or warning will be logged during the policy deployment because it is assumed that the
data may appear in the future. A backup plan is created as usual and the policy state is changed to
Deployed.
If no data to back up is found at the time when the backup task starts, the task will fail and the policy
status will turn to Error. If at least one of the data items is found, the backup task will succeed with a
warning. The policy status will change accordingly.
The backup tasks will start on schedule as specified by the policy and produce a similar result until all
data items appear on the machine or the policy is edited to exclude the non-existent data items.
Examples
Assume, the selection rule states that the policy has to back up volumes D: and F:. The policy is
applied to both Linux and Windows machines. Once the first backup is started, the policy gets the
Error status on the Linux machines and on the Windows machines that do not have such volumes.
62 Copyright © Acronis, Inc., 2000-2010
Page 63

The policy gets the Warning status on Windows machines that have either a D: or F: volume, unless
an event that will result in an error occurs.
The policy that has to back up the [System] and the /dev/sda1 volumes, will get the Warning status
on the Windows machines (since /dev/sda is not found) and on the Linux machines that have the
/dev/sda1 volume (since the [System] volume is not found). The policy will get the Error status on
Linux machines that do not have a SCSI device.
The following table provides details.
State Status Description
Deploying Error The deployment log has errors, for example, disk space runs out
Warning The deployment log has warnings: the machine went offline during the
deployment; cannot connect for N days…
OK The deployment log does not have errors and warnings
Deployed Error The status of the corresponding backup plan is Error
Warning The status of the corresponding backup plan is Warning
OK The status of the corresponding backup plan is OK
Updating Error The updating log has errors: cannot delete the locked task, the Acronis
service is stopped…
Warning The updating log has warnings
OK The updating log does not have errors and warnings
Revoking Error The revoking log has errors
Warning The revoking log has warnings
OK The revoking log does not have errors and warnings
In addition to the deployment state and status as related to a specific machine, the backup policy has
the deployment state and status on a group of machines and the cumulative deployment state and
status of the policy.
2.12.5.3 Policy dep loymen t s tate on a group
To see this parameter, select Machines in the tree, then select the group, and then select the Backup
policies tab on the Information pane.
This state is defined as a combination of deployment states of the policy on the machines included in
the group and its child groups.
For example, you applied the policy to the group consisting of machines A and B. While the
deployment takes place on both machines, the policy's state on the group will be "Deploying". If the
deployment completes on one of the machines while it continues on the other, the state will be
"Deploying, Deployed". When the deployment completes on both machines, the state will be
"Deployed".
2.12.5.4 Policy status on a group
To see this parameter, select Machines in the tree, then select the group, and then select the Backup
policies tab on the Information pane.
63 Copyright © Acronis, Inc., 2000-2010
Page 64

This status is defined as the most severe status of the policy on the machines included in the group
and its child groups. If the policy is currently not applied to any machine, its status is "OK".
2.12.5.5 Cumulative state and status of a policy
In addition to the deployment state and status as related to a specific machine or group, the backup
policy has a cumulative deployment state and a cumulative status.
The cumulative state of a backup policy
To see this parameter, select Backup policies in the tree. The Deployment state column displays the
cumulative deployment state for each policy.
This state is defined as a combination of deployment states of the policy on all machines the policy is
applied to (directly or through inheritance). If the policy is currently not applied to any machine, it
does not have a deployment state and the column shows "Not applied".
For example, you applied the policy to machine A. The policy was successfully deployed. Then you
modify the policy and immediately apply it to the group consisting of machines B and C. The policy
has to be updated on A and deployed to B and C. While the processes take place, the policy's
cumulative state may look like "Updating, Deploying", then change to "Updating, Deployed" or
"Deployed, Deploying" and will normally end up with "Deployed".
The cumulative status of a backup policy
To see this parameter, select Backup policies in the tree. The Status column displays the cumulative
status for each policy.
This status is defined as the most severe status of the policy on all machines the policy is applied to.
If the policy is not applied to any machine, its status is "OK".
2.12.6 Deduplication
This section describes deduplication, a mechanism designed to eliminate data repetition by storing
identical data in archives only once.
2.12.6.1 Overview
Deduplication is the process of minimizing storage space taken by the data by detecting data
repetition and storing the identical data only once.
For example, if a managed vault where deduplication is enabled contains two copies of the same
file—whether in the same archive or in different archives—the file is stored only once, and a link to
that file is stored instead of the second file.
Deduplication may also reduce network load: if, during a backup, a file or a disk block is found to be a
duplicate of an already stored one, its content is not transferred over the network.
Deduplication is performed on disk blocks (block-level deduplication) and on files (file-level
deduplication), for disk-level and file-level backups respectively.
In Acronis Backup & Recovery 10, deduplication consists of two steps:
Deduplication at source
64 Copyright © Acronis, Inc., 2000-2010
Page 65

Performed on a managed machine during backup. Acronis Backup & Recovery 10 Agent uses the
storage node to determine what data can be deduplicated, and does not transfer the data whose
duplicates are already present in the vault.
Deduplication at target
Performed in the vault after a backup is completed. The storage node analyses the vault's
archives and deduplicates data in the vault.
When creating a backup plan, you have the option to turn off deduplication at source for that plan.
This may lead to faster backups but a greater load on the network and storage node.
Deduplicating vault
A managed centralized vault where deduplication is enabled is called a deduplicating vault. When
you create a managed centralized vault, you can specify whether to enable deduplication in it. A
deduplicating vault cannot be created on a tape device.
Deduplication database
Acronis Backup & Recovery 10 Storage Node managing a deduplicating vault, maintains the
deduplication database, which contains the hash values of all items stored in the vault—except for
those that cannot be deduplicated, such as encrypted files.
The deduplication database is stored in the folder which is specified by the Database path in the
Create centralized vault view when creating the vault. Deduplication database can be created in a
local folder only.
The size of the deduplication database is about one percent of the total size of archives in the vault.
In other words, each terabyte of new (non-duplicate) data adds about 10 GB to the database.
In case the database is corrupted or the storage node is lost, while the vault retains archives and the
service folder containing metadata, the new storage node rescans the vault and re-creates the
database.
2.12.6.2 How deduplication works
Deduplication at source
When performing a backup to a deduplicating vault, Acronis Backup & Recovery 10 Agent reads
items being backed up—disk blocks for disk backup or files for file backup—and calculates a
fingerprint of each block. Such a fingerprint, often called a hash value, uniquely represents the item's
content within the vault.
Before sending the item to the vault, the agent queries the deduplication database to determine
whether the item's hash value is the same as that of an already stored item.
If so, the agent sends only the item's hash value; otherwise, it sends the item itself.
Some items, such as encrypted files or disk blocks of a non-standard size, cannot be deduplicated,
and the agent always transfers such items to the vault without calculating their hash values. For
more information about restrictions of file-level and disk-level deduplication, see Deduplication
restrictions (p. 68).
65 Copyright © Acronis, Inc., 2000-2010
Page 66

Deduplication at target
After backup to a deduplicating vault is completed, the storage node runs the indexing task to
deduplicate data in the vault as follows:
1. It moves the items (disk blocks or files) from the archives to a special file within the vault, storing
duplicate items there only once. This file is called the deduplication data store. If there are both
disk-level and file-level backups in the vault, there are two separate data stores for them. Items
that cannot be deduplicated remain in the archives.
2. In the archives, it replaces the moved items with the corresponding references to them.
As a result, the vault contains a number of unique, deduplicated items, with each item having one or
more references to it from the vault's archives.
The indexing task may take considerable time to complete. You can see this task's state in the Tasks
view on the management server.
Compacting
After one or more backups or archives have been deleted from the vault—either manually or during
cleanup—the vault may contain items which are no longer referred to from any archive. Such items
are deleted by the compacting task, which is a scheduled task performed by the storage node.
By default, the compacting task runs every Sunday night at 03:00. You can re-schedule the task as
described in Actions on storage nodes (p. 315), under "Change the compacting task schedule". You
can also manually start or stop the task from the Tasks view.
Because deletion of unused items is resource-consuming, the compacting task performs it only when
a sufficient amount of data to delete has accumulated. The threshold is determined by the
Compacting Trigger Threshold (p. 331) configuration parameter.
2.12.6.3 When deduplication is most effective
The following are cases when deduplication produces the maximum effect:
When backing up in the full backup mode similar data from different sources. Such is the case
when you back up operating systems and applications deployed from a single source over the
network.
When performing incremental backups of similar data from different sources, provided that the
changes to the data are also similar. Such is the case when you deploy updates to these systems
and apply the incremental backup. Again, it is recommended that you first back up one machine
and then the others, all at once or one by one.
When performing incremental backups of data that does not change itself, but changes its
location. Such is the case when multiple pieces of data circulate over the network or within one
system. Each time a piece of data moves, it is included in the incremental backup which becomes
sizeable while it does not contain new data. Deduplication helps to solve the problem: each time
an item appears in a new place, a reference to the item is saved instead of the item itself.
Deduplication and incremental backups
In case of random changes to the data, de-duplication at incremental backup will not produce much
effect because:
The deduplicated items that have not changed are not included in the incremental backup.
66 Copyright © Acronis, Inc., 2000-2010
Page 67

The deduplicated items that have changed are not identical anymore and therefore will not be
deduplicated.
2.12.6.4 Deduplication best practices
Follow these recommendations when using deduplication:
When creating a deduplicating vault, place the vault and its deduplication database on different
disks. This will make deduplication faster, because deduplication involves extensive simultaneous
use of both the vault and the database.
Indexing of a backup requires that the vault have free space with a minimum size of 1.1
multiplied by the size of the archive the backup belongs to. If there is not enough free space in
the vault, the indexing task will fail and start again after 5–10 minutes, on the assumption that
some space has been freed up as a result of cleanup or of other indexing tasks. The more free
space there is in the vault, the faster your archives will reduce to the minimum possible size.
When backing up multiple systems with similar content, back up one of the similar systems first,
so that Acronis Backup & Recovery 10 Storage Node indexes all the system's files as potential
deduplication items. This will lead to faster backup processes and less network traffic (because of
effective deduplication at source), regardless of whether the backups are performed
simultaneously or not.
Before starting the subsequent backups, make sure that the indexing task has finished
deduplication of the first backup and is now idle. You can view the state of the indexing task in
the list of tasks on Acronis Backup & Recovery 10 Management Server.
2.12.6.5 Deduplication ratio
The deduplication ratio shows the size of archives in a deduplicating vault in relation to the size they
would occupy in a non-deduplicating vault.
For example, suppose that you are backing up two files with identical content from two machines. If
the size of each file is one gigabyte, then the size of the backups in a non-deduplicating vault will be
approximately 2 GB, but this size will be just about 1 GB in a deduplicating vault. This gives a
deduplication ratio of 2:1, or 50%.
Conversely, if the two files had different content, the backup sizes in non-deduplicating and
duplicating vaults would be the same (2 GB), and the deduplication ratio would be 1:1, or 100%.
What ratio to expect
Although, in some situations, the deduplication ratio may be very high (in the previous example,
increasing the number of machines would lead to ratios of 3:1, 4:1, etc.), a reasonable expectation
for a typical environment is a ratio between 1.2:1 and 1.6:1.
As a more realistic example, suppose that you are performing a file-level or disk-level backup of two
machines with similar disks. On each machine, the files common to all the machines occupy 50% of
disk space (say, 1 GB); the files that are specific to each machine occupy the other 50% (another
1 GB).
In a deduplicating vault, the size of the first machine's backup in this case will be 2 GB, and that of
the second machine will be 1 GB. In a non-deduplicating vault, the backups would occupy 4 GB in
total. As a result, the deduplication ratio is 4:3, or about 1.33:1.
67 Copyright © Acronis, Inc., 2000-2010
Page 68

Similarly, in case of three machines, the ratio becomes 1.5:1; for four machines, it is 1.6:1. It
approaches 2:1 as more such machines are backed up to the same vault. This means that you can
buy, say, a 10-TB storage device instead of a 20-TB one.
The actual amount of capacity reduction is influenced by numerous factors such as the type of data
that is being backed up, the frequency of the backup, and the backups' retention period.
2.12.6.6 Deduplication restrictions
Block-level deduplication restrictions
During a disk backup to an archive in a deduplicating vault, deduplication of a volume's disk blocks is
not performed in the following cases:
If the volume is a compressed volume
If the volume's allocation unit size—also known as cluster size or block size—is not divisible by
4 KB
Tip: The allocation unit size on most NTFS and ext3 volumes is 4 KB and so allows for block-level
deduplication. Other examples of allocation unit sizes allowing for block-level deduplication include 8 KB,
16 KB, and 64 KB.
If you protected the archive with a password
Tip: If you want to protect the data in the archive while still allowing it to be deduplicated, leave the archive
non-password-protected and encrypt the deduplicating vault itself with a password, which you can do
when creating the vault.
Disk blocks that were not deduplicated are stored in the archive as they would be in a nondeduplicating vault.
File-level deduplication restrictions
During a file backup to an archive in a deduplicating vault, deduplication of a file is not performed in
the following cases:
If the file is encrypted and the In archives, store encrypted files in decrypted state check box in
the backup options is cleared (it is cleared by default)
If the file is less than 4 KB in size
If you protected the archive with a password
Files that were not deduplicated are stored in the archive as they would be in a non-deduplicating
vault.
Deduplication and NTFS data streams
In the NTFS file system, a file may have one or more additional sets of data associated with it—often
called alternate data streams.
When such file is backed up, so are all its alternate data streams. However, these streams are never
deduplicated—even when the file itself is.
68 Copyright © Acronis, Inc., 2000-2010
Page 69

2.12.7 Privileges for centralized management
This section describes the users' privileges that are required to manage a machine locally and
remotely, to manage a machine registered on Acronis Backup & Recovery 10 Management Server,
and to access and manage Acronis Backup & Recovery 10 Storage Node.
2.12.7.1 Types of co nnecti on to a man aged machi ne
There are two types of connection to a managed machine: local connection and remote connection.
Local connection
The local connection is established between Acronis Backup & Recovery 10 Management Console on
a machine and Acronis Backup & Recovery 10 Agent on the same machine.
To establish a local connection
On the toolbar, click Connect, then point to New connection, and then click This machine.
Remote connection
A remote connection is established between Acronis Backup & Recovery 10 Management Console on
one machine and Acronis Backup & Recovery 10 Agent on another machine.
You might need to specify logon credentials to establish a remote connection.
To establish a remote connection
1. On the toolbar, click Connect, then point to New connection, and then click Manage a remote
machine.
2. In Machine, type or select the name or IP address of the remote machine to which you want to
connect; or click Browse to select the machine from the list.
3. To specify credentials for connection, click Options and then type the user name and password in
the User name and Password boxes respectively. In Windows, if you leave the User name box
empty, the credentials under which the console is running will be used.
4. To save the password for the specified user name, select the Save password check box; the
password will be saved in a secure storage on the machine where the console is running.
2.12.7.2 Privileges for local connection
Local connection on a machine running Windows can be established by any user who has the "Log on
locally" user right on the machine.
2.12.7.3 Privil eges for r emote con nection in Win dows
To establish a remote connection to a machine running Windows, the user must be a member of the
Acronis Remote Users security group on that machine.
After remote connection is established, the user has management rights on the remote machine as
described in User rights on a managed machine (p. 32).
Note: On a remote machine running Windows Vista with enabled User Account Control (UAC)—and which is not
part of a domain—only the built-in Administrator user can back up data and perform disk management
operations. To overcome the restriction, include the machine into a domain or disable UAC on the machine (by
default, UAC is enabled). The same applies to machines running Windows Server 2008 and Windows 7.
69 Copyright © Acronis, Inc., 2000-2010
Page 70

For information about Acronis security groups and their default members, see Acronis security
groups (p. 70).
2.12.7.4 Acronis security groups
On a machine running Windows, Acronis security groups determine who can manage the machine
remotely and act as Acronis Backup & Recovery 10 Management Server administrator.
These groups are created when Acronis Backup & Recovery 10 Agents or Acronis Backup & Recovery
10 Management Server are being installed. During installation, you can specify what users to include
in each group.
Acronis Backup & Recovery 10 Agents
When Acronis Backup & Recovery 10 Agent for Windows is being installed on a machine, the Acronis
Remote Users group is created (or updated).
A user who is a member of this group can manage the machine remotely by using Acronis Backup &
Recovery 10 Management Console, according to the management rights described in Users'
privileges on a managed machine (p. 32).
By default, this group includes all members of the Administrators group.
Acronis Backup & Recovery 10 Management Server
When Acronis Backup & Recovery 10 Management Server is being installed on a machine, two
groups are created (or updated):
Acronis Centralized Admins
A user who is a member of this group is a management server administrator. Management
server administrators can connect to the management server by using Acronis Backup &
Recovery 10 Management Console; they have the same management rights on the registered
machines as users with administrative privileges on those machines—regardless of the contents
of Acronis security groups there.
To be able to connect to the management server remotely, an administrator of the management
server must also be a member of the Acronis Remote Users group.
No user—even a member of the Administrators group—can be an administrator of the
management server without being a member of the Acronis Centralized Admins group.
By default, this group includes all members of the Administrators group.
Acronis Remote Users
A user who is a member of this group can connect to the management server remotely by using
Acronis Backup & Recovery 10 Management Console—provided that the user is also a member
of the Acronis Centralized Admins group.
By default, this group includes all members of the Administrators group.
On a domain controller
If a machine is a domain controller in an Active Directory domain, the names and default contents of
Acronis security groups are different:
Instead of Acronis Remote Users and Acronis Centralized Admins, the groups are named
DCNAME $ Acronis Remote Users and DCNAME $ Acronis Centralized Admins respectively; here,
70 Copyright © Acronis, Inc., 2000-2010
Page 71

DCNAME stands for the NetBIOS name of the domain controller. Each dollar sign is surrounded
by a single space on either side.
Instead of explicitly including the names of all members of the Administrators group, the
Administrators group itself is included.
Tip: To ensure proper group names, you should install Acronis components in a domain controller after you have
set up the domain controller itself. If the components were installed before you set up the domain controller,
create the groups DCNAME $ Acronis Remote Users and DCNAME $ Acronis Centralized Admins manually, and
then include the members of Acronis Remote Users and Acronis Centralized Admins in the newly created groups.
2.12.7.5 User privileges on a st orage node
The scope of a user's privileges on Acronis Backup & Recovery 10 Storage Node depends on the
user's rights on the machine where the storage node is installed.
A regular user, such as a member of the Users group on the storage node, can:
Create archives in any centralized vault managed by the storage node
View and manage archives owned by the user
A user who is a member of the Administrators group on the storage node can additionally:
View and manage any archive in any centralized vault managed by the storage node
Create centralized vaults to be managed by the storage node—provided that the user is also an
Acronis Backup & Recovery 10 Management Server administrator
Re-schedule the compacting task, as described in Operations with storage nodes (p. 315), under
"Change the compacting task schedule"
Users with these additional privileges are also called storage node administrators.
Recommendations on user accounts
To allow users to access the centralized vaults managed by a storage node, you must ensure that
those users have a right to access the storage node from the network.
If both the users' machines and the machine with the storage node are in one Active Directory
domain, you probably do not need to perform any further steps: all users are typically members of
the Domain Users group and so can access the storage node.
Otherwise, you need to create user accounts on the machine where the storage node is installed. We
recommend creating a separate user account for each user who will access the storage node, so that
the users are able to access only the archives they own.
When creating the accounts, follow these guidelines:
For users whom you want to act as storage node administrators, add their accounts to the
Administrators group.
For other users, add their user accounts to the Users group.
Additional right of machine administrators
A user who is a member of the Administrators group on a machine can view and manage any
archives created from that machine in a managed vault—regardless of the type of that user's account
on the storage node.
Example
71 Copyright © Acronis, Inc., 2000-2010
Page 72

Suppose that two users on a machine, UserA and UserB, perform backups from this machine to a
centralized vault managed by a storage node. On the storage node, let these users have regular (nonadministrative) accounts UserA_SN and UserB_SN, respectively.
Normally, UserA can access only the archives created by UserA (and owned by UserA_SN), and UserB
can access only the archives created by UserB (and owned by UserB_SN).
However, if UserA is a member of the Administrators group on the machine, this user can
additionally access the archives created from this machine by UserB—even though UserA's account
on the storage node is a regular one.
2.12.7.6 Management server administrator right s
Normally, the Acronis Backup & Recovery 10 Management Server administrator operates on a
registered machine on behalf of the Acronis Managed Machine Service (also known as the Acronis
service) on that machine and has the same privileges as the service has.
Alternatively, when creating a backup policy, the management server administrator has the option to
explicitly specify a user account under which the centralized backup plans will run on the registered
machines. In this case, the user account must exist on all the machines to which the centralized
policy will be deployed. This is not always efficient.
To be a management server administrator, the user must be a member of the Acronis Centralized
Admins group on the machine where the management server is installed.
2.12.7.7 Rights for A cronis services
The Acronis Backup & Recovery 10 Agent for Windows, Acronis Backup & Recovery 10 Management
Server, and Acronis Backup & Recovery 10 Storage Node components run as services. When installing
any of these components, you need to specify the account under which the component's service will
run.
For each service, you can either create a dedicated user account (recommended in most cases) or
specify an existing account of a local or domain user—for example: .\LocalUser or
DomainName\DomainUser.
If you choose to create dedicated user accounts for the services, the setup program will create the
following user accounts:
For the Acronis Backup & Recovery 10 Agent for Windows service, Acronis Agent User
For the Acronis Backup & Recovery 10 Management Server service, AMS User
For the Acronis Backup & Recovery 10 Storage Node service, ASN User
The newly created accounts are given the following privileges:
All three accounts are assigned the Log on as a service user right.
The Acronis Agent User user account is assigned the Adjust memory quotas for a process and
Replace a process level token user rights.
The Acronis Agent User and ASN User user accounts are included in the Backup Operators group.
The AMS User user account is included in the Acronis Centralized Admins group.
The setup program will assign the above listed user rights to any existing account you specify for a
corresponding service.
72 Copyright © Acronis, Inc., 2000-2010
Page 73

If you choose to specify an existing user account for the agent service or the storage node service,
make sure that this account is a member of the Backup Operators group, before proceeding with the
installation.
If you choose to specify an existing user account for the management server service, this account will
be added to the Acronis Centralized Admins group automatically.
If the machine is part of an Active Directory domain, make sure that the domain's security policies do
not prevent the accounts described in this section (whether existing or newly created) from having
the above listed user rights.
Important: After the installation, do not specify a different user account for a component's service. Otherwise,
the component may stop working.
The newly created user accounts are also granted access to the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Acronis (called Acronis registry key) with the following rights:
Query Value, Set Value, Create Subkey, Enumerate Subkeys, Notify, Delete, and Read Control.
In addition, there are two Acronis services which run under a system account:
The Acronis Scheduler2 Service provides scheduling for Acronis components' tasks. It runs under
the Local System account and cannot run under a different account.
The Acronis Remote Agent Service provides connectivity among Acronis components. It runs
under the Network Service account and cannot run under a different account.
2.12.8 Communication between Acronis Backup & Reco very 10
components
This section describes how Acronis Backup & Recovery 10 components communicate with each other
using secure authentication and encryption.
This section also provides information on configuring communication settings, selecting a network
port for communication, and managing security certificates.
2.12.8.1 Secure co mmuni cation
Acronis Backup & Recovery 10 provides the capability to secure the data transferred between its
components within a local area network and through a perimeter network (also known as
demilitarized zone, DMZ).
There are two mechanisms which ensure secure communication between Acronis Backup &
Recovery 10 components:
Secure authentication provides secure transfer of certificates needed to establish a connection,
by using the Secure Sockets Layer (SSL) protocol.
Encrypted communication provides secure transfer of information between any two
components—for example, between Acronis Backup & Recovery 10 Agent and Acronis Backup &
Recovery 10 Storage Node—by encrypting the data being transferred.
For instructions on how to set up secure authentication and data encryption settings, see Configuring
communication options (p. 74).
For instructions on how to manage SSL certificates used for secure authentication, see SSL
certificates (p. 77).
73 Copyright © Acronis, Inc., 2000-2010
Page 74

Note: The components of earlier Acronis products, including those of the Acronis True Image Echo family,
cannot connect to the Acronis Backup & Recovery 10 components, regardless of the secure authentication and
data encryption settings.
2.12.8.2 Client and server applications
There are two stakeholders of the secure communication process:
Client application, or client, is an application that tries to establish connection.
Server application, or server, is an application to which the client tries to connect.
For example, if Acronis Backup & Recovery 10 Management Console is connecting to Acronis Backup
& Recovery 10 Agent on a remote machine, the former is the client and the latter is the server.
An Acronis component can act as a client application, a server application, or both, as shown in the
following table.
Component name Can be
client
Acronis Backup & Recovery 10
Management Console
Acronis Backup & Recovery 10 Agent Yes Yes
Acronis Backup & Recovery 10
Management Server
Acronis Backup & Recovery 10 Storage
Node
Acronis PXE Server No Yes
Acronis Backup & Recovery 10
Bootable Agent
Yes No
Yes Yes
Yes Yes
Yes Yes
Can be
server
2.12.8.3 Configuring communication s ettings
You can configure communication settings, such as whether to encrypt transferred data, for Acronis
Backup & Recovery 10 components installed on one or more machines, by using Acronis
Administrative Template. For information on how to load the Administrative Template, see How to
load Acronis Administrative Template (p. 330).
When applied to a single machine, the Administrative Template defines the communication settings
for all the components on the machine; when applied to a domain or an organizational unit, it
defines the communication settings for all the components on the machines in that domain or
organizational unit.
To configure communication settings
1. Click Start, then click Run, and then type gpedit.msc
2. In the Group Policy console, expand Computer Configuration, then expand Administrative
Templates, and then click Acronis.
3. In the Acronis pane to the right, double-click a communication option that you want to configure.
The Administrative Template contains the following options (each option is explained later in this
topic):
74 Copyright © Acronis, Inc., 2000-2010
Page 75

Remote Agent ports
Client Encryption options
Server Encryption options
4. For the new communication settings to take effect, restart all running Acronis components—
preferably, by restarting Windows. If restart is not possible, make sure you do the following:
If Acronis Backup & Recovery 10 Management Console is running, close it and start it again.
If other Acronis components, such as Acronis Backup & Recovery 10 Agent for Windows or
Acronis Backup & Recovery 10 Management Server are running, restart their correspondent
services from the Services snap-in in Windows.
Remote Agent ports
Specifies the port that the component will use for incoming and outgoing communication with other
Acronis components.
Select one of the following:
Not configured
The component will use the default TCP port number 9876.
Enabled
The component will use the specified port; type the port number in the Server TCP Port box.
Disabled
The same as Not configured.
For details about the network port and instructions on how to specify it in Linux and a bootable
environment, see Network port configuration (p. 77).
Client Encryption options
Specifies whether to encrypt the transferred data when the component acts as a client application,
and whether to trust self-signed SSL certificates.
Select one of the following:
Not configured
The component will use the default settings, which is to use encryption if possible and to trust
self-signed SSL certificates (see the following option).
Enabled
Encryption is enabled. In Encryption, select one of the following:
Enabled
Data transfer will be encrypted if encryption is enabled on the server application, otherwise
it will be unencrypted.
Disabled
Encryption is disabled; any connection to a server application which requires encryption will
not be established.
Required
Data transfer will be performed only if encryption is enabled on the server application (see
"Server Encryption options"); it will be encrypted.
75 Copyright © Acronis, Inc., 2000-2010
Page 76

Authentication parameters
Selecting the Trust self-signed certificates check box allows the client to connect to the server
applications that use self-signed SSL certificates such as certificates created during the
installation of Acronis Backup & Recovery 10 components—see SSL certificates (p. 77).
You should keep this check box selected, unless you have a Public Key Infrastructure (PKI) in your
environment.
In Use Agent Certificate Authentication, select one of the following:
Do not use
The use of SSL certificates is disabled. Any connection to a server application which requires
the use of SSL certificates will not be established.
Use if possible
The use of SSL certificates is enabled. The client will use SSL certificates if their use is enabled
on the server application, and will not use them otherwise.
Always use
The use of SSL certificates is enabled. The connection will be established only if the use of SSL
certificates is enabled on the server application.
Disabled
The same as Not configured.
Server Encryption options
Specifies whether to encrypt the transferred data when the component acts as a server application.
Select one of the following:
Not configured
The component will use the default setting, which is to use encryption if possible (see the
following option).
Enabled
Encryption is enabled. In Encryption, select one of the following:
Enabled
Data transfer will be encrypted if encryption is enabled on the client application, otherwise it
will be unencrypted.
Disabled
Encryption is disabled; any connection to a client application which requires encryption will
not be established.
Required
Data transfer will be performed only if encryption is enabled on the client application (see
"Client Encryption options"); it will be encrypted.
Authentication parameters
In Use Agent Certificate Authentication, select one of the following:
Do not use
The use of SSL certificates is disabled. Any connection to a client application which requires
the use of SSL certificates will not be established.
Use if possible
76 Copyright © Acronis, Inc., 2000-2010
Page 77
The use of SSL certificates is enabled. The server will use SSL certificates if their use is
enabled on the client application, and will not use them otherwise.
Always use
The use of SSL certificates is enabled. The connection will be established only if the use of SSL
certificates is enabled on the client application.
Disabled
The same as Not configured.
2.12.8.4 Network port configuration
Acronis Backup & Recovery 10 components use the 9876/TCP network communication port by
default. The server listens to this port for incoming connection. This port is also used as default by
the Acronis client. During component installation you might be asked to confirm the port opening or
to open the port manually, in case you are using a firewall other than Windows Firewall.
After installation, you can change the ports at any time to match your preferable values or for the
purpose of security. This operation requires the restart of Acronis Remote Agent (in Windows) or the
Acronis_agent (in Linux) service.
After the port is changed on the server side, connect to the server using the <Server-IP>:<port> or
the <Server-hostname>:<port> URL notation.
Note: If you use network address translation (NAT), you can also configure the port by setting up port mapping.
Configuring the port in the operating system
Windows
To be able to change the ports' numbers, load and configure the Administrative Template, provided
by Acronis, as described in Configuring communication settings (p. 74), under "Remote Agent ports".
Linux
Specify the port in the /etc/Acronis/Policies/Agent.config file. Restart the Acronis_agent daemon.
Configuring the port in a bootable environment
While creating Acronis bootable media, you have the option to pre-configure the network port that
will be used by the Acronis Backup & Recovery 10 Bootable Agent. The choice is available between:
The default port (9876)
The currently used port
New port (enter the port number)
If a port has not been pre-configured, the agent uses the default port number.
2.12.8.5 SSL certificates
Acronis Backup & Recovery 10 components use Secure Sockets Layer (SSL) certificates for secure
authentication.
SSL certificates for the components can be one of the two types:
77 Copyright © Acronis, Inc., 2000-2010
Page 78

Self-signed certificates, such as certificates automatically generated during the installation of an
Acronis component.
Non-self-signed certificates, such as certificates issued by a third-party Certificate Authority
(CA)—for example, by a public CA such as VeriSign
®
or Thawte™—or by your organization's CA.
Certificate path
All Acronis components installed on a machine, when acting as a server application, use an SSL
certificate called the server certificate.
In Windows, the certificate path and the server certificate's file name are specified in the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Acronis\Encryption\Server. The default path is
%SystemDrive%\Program Files\Common Files\Acronis\Agent.
To ensure reliability, the certificate is stored in Windows Certificate Store at the following location:
Certificates (Local Computer)\Acronis Trusted Certificates Cache.
For self-signed certificates, the certificate thumbprint (also known as fingerprint or hash) is used for
future host identification: if a client has previously connected to a server by using a self-signed
certificate and tries to establish connection again, the server checks whether the certificate's
thumbprint is the same as the one used before.
In case the list of certificates for the local machine is not displayed in the Certificates console, you
can use the following procedure.
To open the list of a machine's certificates
1. Click Start, then click Run, and then type: mmc
2. In the console, on the File menu, click Add/Remove Snap-in.
3. In the Add/Remove Snap-in dialog box, click Add.
4. In the Add Standalone Snap-in dialog box, double-click Certificates.
5. Click Computer account, and then click Next.
6. Click Local computer, and then click Finish.
Tip: Alternatively, you can manage the list of certificates of a remote machine. To do this, click Another
computer and then type the remote machine's name.
7. Click Close to close the Add Standalone Snap-in dialog box, and then click OK to close the
Add/Remove Snap-in dialog box.
Self-signed certificates
On machines running Windows, if the certificate location contains no server certificate, a self-signed
server certificate is automatically generated and installed during the installation of any Acronis
component except Acronis Backup & Recovery 10 Management Console.
If the machine is renamed after its self-signed certificate was generated, the certificate cannot be
used and you will need to generate a new one.
To generate a new self-signed certificate
1. Log on as a member of the Administrators group.
2. In the Start menu, click Run, and then type: cmd
3. Run the following command (note quotation marks):
"%CommonProgramFiles%\Acronis\Utils\acroniscert" --reinstall
78 Copyright © Acronis, Inc., 2000-2010
Page 79

4. Restart Windows, or restart the running Acronis services.
Non-self-signed certificates
You have the option to use trusted third-party certificates or certificates created by your
organization's CA as an alternative to self-signed certificates, by using Acronis Certificate Commandline Utility.
To install a third-party certificate
1. Click Start, then click Run, and then type: certmgr.msc
2. In the Certificates console, double-click the name of the certificate that you want to install.
3. In the Details tab, in the list of fields, click Thumbprint.
4. Select and copy the field's value, called a certificate thumbprint—a string such as 20 99 00 b6 3d
95 57 28 14 0c d1 36 22 d8 c6 87 a4 eb 00 85
5. In the Start menu, click Run, and then type the following in the Open box:
"%CommonProgramFiles%\Acronis\Utils\acroniscert.exe" --install
"20 99 00 b6 3d 95 57 28 14 0c d1 36 22 d8 c6 87 a4 eb 00 85"
(Note quotation marks; substitute the sample thumbprint shown here with that of your
certificate.)
79 Copyright © Acronis, Inc., 2000-2010
Page 80

3 Options
This section covers Acronis Backup & Recovery 10 options that can be configured using Graphical
User Interface. The content of this section is applicable to both stand-alone and advanced editions of
Acronis Backup & Recovery 10.
3.1 Console options
The console options define the way information is represented in the Graphical User Interface of
Acronis Backup & Recovery 10.
To access the console options, select Options > Console options from the top menu.
3.1.1 Startup page
This option defines whether to show the Welcome screen or the Dashboard upon connection of the
console to a managed machine or to the management server.
The preset is: the Welcome screen.
To make a selection, select or clear the check box for Show the Dashboard view upon connection of
the console to a machine.
This option can also be set on the Welcome screen. If you select the check box for At startup, show
the Dashboard instead of the current view on the Welcome screen, the setting mentioned above
will be updated accordingly.
3.1.2 Pop-up messages
About tasks that need interaction
This option is effective when the console is connected to a managed machine or to the management
server.
The option defines whether to display the pop-up window when one or more tasks require user
interaction. This window enables you to specify your decision, such as to confirm reboot or to retry
after freeing-up the disk space, on all the tasks in the same place. Until at least one task requires
interaction, you can open this window at any time from the managed machine's Dashboard.
Alternatively, you can review the task execution states in the Tasks view and specify your decision on
each task in the Information pane.
The preset is: Enabled.
To make a selection, select or clear the Pop up the "Tasks Need Interaction" window check box.
About the task execution results
This option is effective only when the console is connected to a managed machine.
The option defines whether to display the pop-up messages about task run results: successful
completion, failure or success with warnings. When displaying of pop-up messages is disabled, you
can review the task execution states and results in the Tasks view.
80 Copyright © Acronis, Inc., 2000-2010
Page 81

The preset is: Enabled for all results.
To make a setting for each result (successful completion, failure or success with warnings)
individually, select or clear the respective check box.
3.1.3 Time-based alerts
Last backup
This option is effective when the console is connected to a managed machine (p. 396) or to the
management server (p. 397).
The option defines whether to alert if no backup was performed on a given machine for a period of
time. You can configure the time period that is considered critical for your business.
The preset is: alert if the last successful backup on a machine was completed more than 5 days ago.
The alert is displayed in the Alerts section of the Dashboard. When the console is connected to the
management server, this setting will also control the color scheme of the Last backup column's value
for each machine.
Last connection
This option is effective when the console is connected to the management server or to a registered
machine (p. 398).
The option defines whether to alert if no connection was established between a registered machine
and the management server for a period of time so indicating that the machine might not be
centrally managed (for instance in the case of network connection failure to that machine). You can
configure the length of time that is considered critical.
The preset is: alert if the machine's last connection to the management server was more than 5 days
ago.
The alert is displayed in the Alerts section of the Dashboard. When the console is connected to the
management server, this setting will also control the color scheme of the Last connect column's
value for each machine.
3.1.4 Number of tasks
This option is effective only when the console is connected to the management server.
The option defines how many tasks will be displayed at a time in the Tasks view. You can also use
filters available in the Tasks view to limit the number of displayed tasks.
The preset is: 400. The adjustment range is: 20 to 500.
To make a selection, choose the desired value from the Number of tasks drop-down menu.
3.1.5 Fonts
This option is effective when the console is connected to a managed machine or to the management
server.
81 Copyright © Acronis, Inc., 2000-2010
Page 82

The option defines the fonts to be used in the Graphical User Interface of Acronis Backup & Recovery
10. The Menu setting affects the drop-down and context menus. The Application setting affects the
other GUI elements.
The preset is: System Default font for both the menus and the application interface items.
To make a selection, choose the font from the respective combo-box and set the font's properties.
You can preview the font's appearance by clicking the button to the right.
3.2 Management server options
The management server options enable you to adjust the behavior of the Acronis Backup & Recovery
10 Management Server.
To access the management server options, connect the console to the management server and then
select Options > Management server options from the top menu.
3.2.1 Logging level
This option defines whether the management server has to collect log events from the registered
machines to the centralized log that is stored in a dedicated database and is available in the Log view.
You can set the option for all the events at once or select the event types to be collected. If you
completely disable collection of the log events, the centralized log will contain only the management
server's own log.
The preset is: Collect logs for All events.
Use the Types of events to log combo-box to specify the types of events that will be collected:
All events - all events (information, warnings and errors) occurred on all the machines registered
on the management server will be recorded to the centralized log
Errors and warnings - warnings and errors will be recorded to the centralized log
Errors only - only errors will be recorded to the centralized log.
To disable collection of the log events, clear the Collect logs check box.
3.2.2 Log cleanup rules
This option specifies how to clean up the centralized event log stored in the management server's
reporting database.
This option defines the maximum size of the reporting database.
The preset is: Maximum log size: 1 GB. On cleanup, keep 95% of the maximum log size.
When the option is enabled, the program compares the actual log size with the maximum size after
every 100 log entries. Once the maximum log size is exceeded, the program deletes the oldest log
entries. You can select the amount of log entries to retain. The default 95% setting will keep most of
the log. With the minimum 1% setting, the log will be nearly cleared.
Even if you remove the log size limit, logging events to an SQL Server Express database will stop after the log
size reaches 4 GB, because SQL Express Edition has the 4 GB per database limit. Set the maximum log size to
approximately 3.8 GB if you want to use the maximum capacity of the SQL Express database.
82 Copyright © Acronis, Inc., 2000-2010
Page 83

This parameter can also be set by using Acronis Administrative Template (p. 333).
3.2.3 Event tracing
You can configure the management server to log events in the Application Event Log of Windows,
besides the management server's own log.
You can configure the management server to send Simple Network Management Protocol (SNMP)
objects to a specified SNMP manager.
3.2.3.1 Windows event log
This option defines whether the management server has to record its own log events in the
Application Event Log of Windows (to see this log, run eventvwr.exe or select Control Panel >
Administrative tools > Event Viewer). You can filter the events to be recorded.
The preset is: Disabled.
To enable this option, select the Log events check box.
Use the Types of events to log check box to filter the events to be logged in the Application
Event Log of Windows:
All events - all events (information, warnings and errors)
Errors and warnings
Errors only.
To disable this option, clear the Log events check box.
3.2.3.2 SNMP notifications
This option defines whether the management server has to send its own log events to the specified
Simple Network Management Protocol (SNMP) managers. You can choose the types of events to be
sent.
For detailed information about using SNMP with Acronis Backup & Recovery 10, please see "Support
for SNMP (p. 46)".
The preset is: Disabled.
To set up sending SNMP messages
1. Select the Send messages to SNMP server check box.
2. Specify the appropriate options as follows:
Types of events to send – choose the types of events: All events, Errors and warnings, or
Errors only.
Server name/IP – type the name or IP address of the host running the SNMP management
application, the messages will be sent to.
Community – type the name of the SNMP community to which both the host running SNMP
management application and the sending machine belong. The typical community is "public".
Click Send test message to check if the settings are correct.
To disable sending SNMP messages, clear the Send messages to SNMP server check box.
The messages are sent over UDP.
83 Copyright © Acronis, Inc., 2000-2010
Page 84

3.2.4 Domain access credentials
This option determines the user name and password that the management server will use to access
the domain.
The preset is: No credentials
The management server needs domain access credentials when working with a dynamic group that is
based on the Organizational unit criterion (p. 307). When you are creating such group and no
credentials are given by this option, the program will ask you for credentials and save them in this
option.
It is sufficient to specify the credentials of a user who is a member of the Domain Users group on the
domain.
3.2.5 Acronis WOL Proxy
This option works in combination with the Use Wake-On-LAN (p. 166) advanced scheduling setting.
Use this option if the management server has to wake up for backup machines located in another
subnet.
When the scheduled operation is about to start, the management server sends out magic packets to
wake up the appropriate machines. (A magic packet is a packet that contains 16 contiguous copies of
the receiving NIC's MAC address). The Acronis WOL Proxy, installed in the other subnet, transfers the
packets to machines located in that subnet.
The preset is: Disabled.
To bring this option into use:
1. Install Acronis WOL Proxy on any server in the subnet where the machines to be woken are
located. The server has to provide continuous services availability. With multiple subnets, install
Acronis WOL Proxy in every subnet where you need to use the Wake-On-LAN functionality.
2. Enable Acronis WOL Proxy in the Management server options as follows:
a. Select the Use the following proxies check box.
b. Click Add, and then enter the name or IP address of the machine where the Acronis WOL
Proxy is installed. Provide access credentials for the machine.
c. Repeat this step if there are several Acronis WOL Proxies.
3. When scheduling a backup policy, enable the Use Wake-On-LAN setting.
You also have the ability to delete proxies from the list. Please keep in mind that any change to this
option affects the entire management server. If you delete a proxy from the list, the Wake-On-LAN
functionality in the corresponding subnet will be disabled for all policies, including the policies
already applied.
3.2.6 VM protection options
These options define the management server behavior as related to backup and recovery of virtual
machines hosted on virtualization servers.
84 Copyright © Acronis, Inc., 2000-2010
Page 85

3.2.6.1 VMware vCenter integration
This option defines whether to show virtual machines managed by a VMware vCenter Server in the
management server and show the backup status of these machines in the vCenter.
Integration is available in all Acronis Backup & Recovery 10 advanced editions; a license for Virtual
Edition is not required. No software installation is required on the vCenter Server.
On the management server side
When integration is enabled, the vCenter's VMs and Templates inventory view appears in the
management server's GUI under Navigation > Virtual machines.
From the management server's standpoint, this is a dynamic group of virtual machines. The group
name matches the vCenter Server name or IP address, whatever was specified when configuring
integration. The group content is synchronized with the vCenter Server and cannot be changed on
the management server side. In case of an occasional inconsistency, right click the group and select
Refresh.
The virtual machines managed by the vCenter Server also appear in the All virtual machines group.
You can view virtual machine properties and power state; create groups of virtual machines and add
virtual machines to existing groups.
Backup and recovery of a virtual machine is not possible, unless Acronis Backup & Recovery 10 Agent
for ESX/ESXi is deployed (p. 312) to the virtual machine's host. Such machines appear as not
manageable (grayed out).
Once the agent is deployed to an ESX/ESXi host (this requires a license for Acronis Backup & Recovery
10 Advanced Server Virtual Edition), the virtual machines from this host are ready for applying a
backup policy or individual backup. Such machines appear as manageable.
If Agent for Windows or Agent for Linux is installed in a guest system, but there is no Agent for ESX/ESXi on its
host, the virtual machine appears as not manageable under Virtual machines. Such machine has to be
managed as a physical one.
On the vCenter Server side
When integration is enabled, the vCenter Server will store and show information about when and
how successful each virtual machine was backed up. The same information is displayed in the Status
and the Last backup columns on the management server.
Backup status - the most severe status of all backup plans and backup policies on the machine. For
more information, see "Backup plan statuses (p. 177)" and "Policy status on a machine (p. 62)".
Last backup - how much time has passed since the last successful backup.
You can see this information in the virtual machine summary (Summary > Annotations) or on the
Virtual Machines tab for every host, datacenter, folder or entire vCenter Server (for example, View >
Inventory > Hosts and Clusters > select host > Virtual Machines).
3.2.7 Online backup proxy
This option is effective only for connection to Acronis Online Backup Storage over the Internet.
This option defines whether the management server will connect to the Internet through a proxy
server.
85 Copyright © Acronis, Inc., 2000-2010
Page 86

Note: Acronis Backup & Recovery 10 Online supports only HTTP and HTTPS proxy servers.
Proxy settings for the agent and the management server are configured separately, even if both are
installed on the same machine.
To set up proxy server settings
1. Select the Use a proxy server check box.
2. In Address, specify the network name or IP address of the proxy server—for example:
proxy.example.com or 192.168.0.1
3. In Port, specify the port number of the proxy server—for example: 80
4. If the proxy server requires authentication, specify the credentials in User name and Password.
5. To test the proxy server settings, click Test connection.
3.3 Machine options
The machine options define the general behavior of all Acronis Backup & Recovery 10 agents
operating on the managed machine, and so the options are considered machine-specific.
To access the machine options, connect the console to the managed machine and then select
Options > Machine options from the top menu.
3.3.1 Machine management
This option defines whether the machine has to be managed centrally by the Acronis Backup &
Recovery 10 Management Server.
To be able to use this option, you must be logged on as a member of the Administrators group on
the machine.
You have the opportunity to register the machine on the management server when installing an
Acronis Backup & Recovery 10 agent. If the machine is not registered, selecting Centralized
management here will initiate the registration (p. 398). Or you can add the machine to the
management server on the server side. Any of the three registration methods require the server
administrator privileges.
Selecting Stand-alone management on a registered machine will result in the machine stopping
communication with the server. On the management server, the machine appears as Withdrawn.
The management server administrator can delete the machine from the server or register the
machine once again.
The preset is: Stand-alone management.
To set up centralized management on the machine:
1. Select Centralized management.
2. Specify the Management Server IP/Name.
3. Specify the user name and password of the management server administrator on prompt.
4. In the Machine's registration address, select how the machine will be registered on the
management server: by its name (recommended) or by its IP address.
5. Click OK and the machine will be registered on the management server.
To disable centralized management, select Stand-alone management.
86 Copyright © Acronis, Inc., 2000-2010
Page 87

3.3.2 Event tracing
It is possible to duplicate log events generated by the agent(s), operating on the managed machine,
in the Application Event Log of Windows; or send the events to the specified SNMP managers. If you
do not modify the event tracing options anywhere except for here, your settings will be effective for
each local backup plan and each task created on the machine.
You can override the settings set here, exclusively for the events occurred during backup or during
recovery (see Default backup and recovery options (p. 90).) In this case, the settings set here will be
effective for operations other than backup and recovery, such as archive validation or cleanup.
You can further override the settings set in the default backup and recovery options, when creating a
backup plan or a recovery task. The settings you obtain in this case will be plan-specific or taskspecific.
3.3.2.1 Windows event log
This option is effective only in Windows operating systems.
This option is not available when operating under the bootable media.
This option defines whether the agent(s) operating on the managed machine have to log events in
the Application Event Log of Windows (to see this log, run eventvwr.exe or select Control Panel >
Administrative tools > Event Viewer). You can filter the events to be logged.
You can override the settings set here, exclusively for the events that occur during backup or during
recovery, in the Default backup and recovery options (p. 90). In this case, the settings set here will be
effective for operations other than backup and recovery, such as archive validation or cleanup.
You can further override the settings set in the default backup and recovery options, when creating a
backup plan or a recovery task. The settings you obtain in this case will be plan-specific or taskspecific.
The preset is: Disabled.
To enable this option, select the Log events check box.
Use the Types of events to log check box to filter the events to be logged in the Application
Event Log of Windows:
All events - all events (information, warnings and errors)
Errors and warnings
Errors only.
To disable this option, clear the Log events check box.
3.3.2.2 SNMP notifications
This option is effective for both Windows and Linux operating systems.
This option is not available when operating under the bootable media.
The option defines whether the agent(s) operating on the managed machine have to send the log
events to the specified Simple Network Management Protocol (SNMP) managers. You can choose the
types of events to be sent.
87 Copyright © Acronis, Inc., 2000-2010
Page 88

You can override the settings set here, exclusively for the events that occur during backup or during
recovery, in the Default backup and recovery options (p. 90). In this case, the settings set here will be
effective for operations other than backup and recovery, such as archive validation or cleanup.
You can further override the settings set in the default backup and recovery options, when creating a
backup plan or a recovery task. The settings you obtain in this case will be plan-specific or taskspecific.
For detailed information about using SNMP with Acronis Backup & Recovery 10, please see "Support
for SNMP (p. 46)".
The preset is: Disabled.
To set up sending SNMP messages
1. Select the Send messages to SNMP server check box.
2. Specify the appropriate options as follows:
Types of events to send – choose the types of events: All events, Errors and warnings, or
Errors only.
Server name/IP – type the name or IP address of the host running the SNMP management
application, the messages will be sent to.
Community – type the name of the SNMP community to which both the host running SNMP
management application and the sending machine belong. The typical community is "public".
Click Send test message to check if the settings are correct.
To disable sending SNMP messages, clear the Send messages to SNMP server check box.
The messages are sent over UDP.
The next section contains additional information about Setting up SNMP services on the receiving
machine (p. 88).
3.3.2.3 Setting up SNMP services on the receiving machine
Windows
To install the SNMP service on a machine running Windows:
1. Start > Control Panel > Add or Remove Programs > Add/Remove Windows Components.
2. Select Management and Monitoring Tools.
3. Click Details.
4. Select the Simple Network Management Protocol check box.
5. Click OK.
You might be asked for lmmib2.dll that can be found on the installation disc of your operating
system.
Linux
To receive SNMP messages on a machine running Linux, the net-snmp (for RHEL and SUSE) or the
snmpd (for Debian) package has to be installed.
SNMP can be configured using the snmpconf command. The default configuration files are located in
the /etc/snmp directory:
88 Copyright © Acronis, Inc., 2000-2010
Page 89

/etc/snmp/snmpd.conf - configuration file for the Net-SNMP SNMP agent
/etc/snmp/snmptrapd.conf - configuration file for the Net-SNMP trap daemon.
3.3.3 Log cleanup rules
This option specifies how to clean up the Acronis Backup & Recovery 10 agent log.
This option defines the maximum size of the agent log folder (in Windows XP/2003 Server,
%ALLUSERSPROFILE%\Application Data\Acronis\BackupAndRecovery\MMS\LogEvents).
The preset is: Maximum log size: 1 GB. On cleanup, keep 95% of the maximum log size.
When the option is enabled, the program compares the actual log size with the maximum size after
every 100 log entries. Once the maximum log size is exceeded, the program deletes the oldest log
entries. You can select the amount of log entries to retain. The default 95% setting will keep most of
the log. With the minimum 1% setting, the log will be nearly cleared.
This parameter can also be set by using Acronis Administrative Template (p. 338).
3.3.4 Online backup proxy
This option is effective only for backup to and recovery from Acronis Online Backup Storage over the
Internet.
This option defines whether the Acronis agent will connect to the Internet through a proxy server.
Note: Acronis Backup & Recovery 10 Online supports only HTTP and HTTPS proxy servers.
To set up proxy server settings
1. Select the Use a proxy server check box.
2. In Address, specify the network name or IP address of the proxy server—for example:
proxy.example.com or 192.168.0.1
3. In Port, specify the port number of the proxy server—for example: 80
4. If the proxy server requires authentication, specify the credentials in User name and Password.
5. To test the proxy server settings, click Test connection.
If you do not know the proxy server settings, contact your network administrator or Internet service
provider for assistance.
Alternatively, you can try to take these settings from your Web browser’s configuration. This is how
to find them in three popular browsers.
Microsoft Internet Explorer. On the Tools menu, click Internet Options. On the Connections tab,
click LAN settings.
Mozilla Firefox. On the Tools menu, click Options and then click Advanced. On the Network tab,
under Connection, click Settings.
Google Chrome. In Options, click Under the Hood. Under Network, click Change proxy settings.
3.3.5 Customer Experience Program
This option defines whether the machine will participate in the Acronis Customer Experience
Program (ACEP).
89 Copyright © Acronis, Inc., 2000-2010
Page 90

If you choose Yes, I want to participate in the ACEP, information about the hardware configuration,
the most and least used features and about any problems will be automatically collected from the
machine and sent to Acronis on a regular basis. The end results are intended to provide software
improvements and enhanced functionality to better meet the needs of Acronis customers.
Acronis does not collect any personal data. To learn more about the ACEP, read the terms of
participation on the Acronis Web site or in the product GUI.
Initially the option is configured during the Acronis Backup & Recovery 10 agent installation. This
setting can be changed at any time using the product GUI (Options > Machine options > Customer
Experience Program). The option can also be configured using the Group Policy infrastructure (p.
341). A setting defined by a Group Policy cannot be changed using the product GUI unless the Group
Policy is disabled on the machine.
3.4 Default backup and recovery options
3.4.1 Default backup options
Each Acronis agent has its own default backup options. Once an agent is installed, the default options
have pre-defined values, which are referred to as presets in the documentation. When creating a
backup plan, you can either use a default option, or override the default option with the custom
value that will be specific for this plan only.
You can also customize a default option itself by changing its value against the pre-defined one. The
new value will be used by default in all backup plans you will create later on this machine.
To view and change the default backup options, connect the console to the managed machine and
then select Options > Default backup and recovery options > Default backup options from the top
menu.
Availability of the backup options
The set of available backup options depends on:
The environment the agent operates in (Windows, bootable media)
The type of the data being backed up (disk, file)
The backup destination (networked location or local disk)
The backup scheme (Back up now or using the scheduler)
The following table summarizes the availability of the backup options.
Agent for Windows Bootable media
(Linux-based or PE-based)
Disk backup File backup Disk backup File backup
Archive protection (p. 92)
(password + encryption)
Source files exclusion (p. 93)
Pre/Post backup commands
90 Copyright © Acronis, Inc., 2000-2010
+ + + +
+ + + +
+ + PE only PE only
Page 91

(p. 94)
Pre/Post data capture
commands (p. 96)
Multi-volume snapshot (p. 98)
File-level backup snapshot (p.
97)
Use VSS (p. 98)
Compression level (p. 99)
Backup performance:
Backup priority (p. 100)
HDD writing speed (p. 100)
Network connection speed (p.
101)
Fast incremental/differential
backup (p. 104)
Backup splitting (p. 104)
File-level security (p. 105):
+ + - -
+ + - -
- + - -
+ + - -
+ + + +
+ + - -
Dest: HDD Dest: HDD Dest: HDD Dest: HDD
Dest:
network
share
Dest:
network
share
Dest:
network
share
Dest:
network
share
+ - + -
+ + + +
Preserve files’ security
settings in archives
In archives, store encrypted
files in decrypted state
Media components (p. 105)
Error handling (p. 106):
Do not show messages and
dialogs while processing
(silent mode)
Re-attempt if an error occurs
Ignore bad sectors
Dual destination (p. 107)
Task start conditions (p. 107)
Task failure handling (p. 108)
Tape support (p. 109)
Additional settings (p. 110):
- + - -
- + - -
Dest:
removable
media
Dest:
removable
media
- -
+ + + +
+ + + +
+ + + +
Dest: local Dest: local - -
+ + - -
+ + - -
Dest:
managed
vault on a
tape library
Dest:
managed
vault on a
tape library
Dest:
managed
vault on a
tape library
Dest:
managed
vault on a
tape library
91 Copyright © Acronis, Inc., 2000-2010
Page 92

Dest: Tape
Dest: Tape
Dest: Tape
Dest: Tape
+ + -
-
Overwrite data on a tape
without prompting for user
confirmation
Dismount media after backup
has finished
Ask for the first media while
backing up to removable
media
Reset archive bit
Dest:
removable
media
Dest:
removable
media
- + - +
Dest:
removable
media
Dest:
removable
media
Dest:
removable
media
Dest:
removable
media
Dest:
removable
media
Dest:
removable
media
Restart the machine
automatically after backup is
finished
Deduplicate backup only after
transferring it to the vault
Use FTP in Active mode
Notifications:
E-mail (p. 101)
Win Pop-up (p. 102)
Event tracing:
Windows events log (p. 103)
SNMP (p. 103)
- - + +
Dest: dedup.
vault
Dest: FTP
server
+ + - -
+ + - -
+ + - -
Dest: dedup.
vault
Dest: FTP
server
Dest: dedup.
vault
Dest: FTP
server
Dest: dedup.
vault
Dest: FTP
server
3.4.1.1 Archive protection
This option is effective for Windows and Linux operating systems and bootable media.
This option is effective for both disk-level and file-level backup.
The preset is: Disabled.
To protect the archive from unauthorized access
1. Select the Set password for the archive check box.
2. In the Enter the password field, type a password.
3. In the Confirm the password field, re-type the password.
4. Select one of the following:
Do not encrypt – the archive will be protected with the password only
AES 128 – the archive will be encrypted using the Advanced Encryption Standard (AES)
algorithm with a 128-bit key
AES 192 – the archive will be encrypted using the AES algorithm with a 192-bit key
AES 256 – the archive will be encrypted using the AES algorithm with a 256-bit key.
5. Click OK.
92 Copyright © Acronis, Inc., 2000-2010
Page 93

The AES cryptographic algorithm operates in the Cipher-block chaining (CBC) mode and uses a
randomly generated key with a user-defined size of 128, 192 or 256 bits. The larger the key size, the
longer it will take for the program to encrypt the archive and the more secure your data will be.
The encryption key is then encrypted with AES-256 using a SHA-256 hash of the password as a key.
The password itself is not stored anywhere on the disk or in the backup file; the password hash is
used for verification purposes. With this two-level security, the backup data is protected from any
unauthorized access, but recovering a lost password is not possible.
3.4.1.2 Source files exclusion
This option is effective for Windows and Linux operating systems and bootable media.
This option is effective for disk-level backup of NTFS and FAT file systems only. This option is effective
for file-level backup of all supported file systems.
The option defines which files and folders to skip during the backup process and thus exclude from
the list of backed-up items.
The preset is: Exclude files matching the following criteria: *.tmp, *.~, *.bak.
To specify which files and folders to exclude:
Set up any of the following parameters:
Exclude all hidden files and folders
This option is effective only for file systems that are supported by Windows. Select this check box
to skip files and folders with the Hidden attribute. If a folder is Hidden, all of its contents —
including files that are not Hidden — will be excluded.
Exclude all system files and folders
This option is effective only for file systems that are supported by Windows. Select this check box
to skip files and folders with the System attribute. If a folder is System, all of its contents —
including files that are not System — will be excluded.
You can view file or folder attributes in the file/folder properties or by using the attrib command. For more
information, refer to the Help and Support Center in Windows.
Exclude files matching the following criteria
Select this check box to skip files and folders whose names match any of the criteria — called file
masks — in the list; use the Add, Edit, Remove and Remove All buttons to create the list of file
masks.
You can use one or more wildcard characters * and ? in a file mask:
The asterisk (*) substitutes for zero or more characters in a file name; for example, the file mask
Doc*.txt yields files such as Doc.txt and Document.txt
The question mark (?) substitutes for exactly one character in a file name; for example, the file
mask Doc?.txt yields files such as Doc1.txt and Docs.txt — but not the files Doc.txt or Doc11.txt
To exclude a folder specified by a path containing the drive letter, add a backslash (\) to the folder
name in the criterion; for example: C:\Finance\
Exclusion examples
Criterion Example Description
93 Copyright © Acronis, Inc., 2000-2010
Page 94

Windows and Linux
By name F.log
F
By mask (*) *.log
F*
By mask (?) F???.log
By file path C:\Finance\F.log
By folder path C:\Finance\F\ Excludes the folder C:\Finance\F (be sure to specify the
By file path /home/user/Finance/F.log Excludes the file named "F.log" located in the folder
By folder path /home/user/Finance/ Excludes the folder /home/user/Finance
The above settings are not effective for the files or folders that were explicitly selected for backup. For example,
assume that you selected the folder MyFolder and the file MyFile.tmp outside that folder, and selected to skip
all .tmp files. In this case, all .tmp files in the folder MyFolder will be skipped during the backup process, but the
file MyFile.tmp will not be skipped.
Excludes all files named "F.log"
Excludes all folders named "F"
Excludes all files with the .log extension
Excludes all files and folders with names starting with "F"
(such as folders F, F1 and files F.log, F1.log)
Excludes all .log files with names consisting of four
symbols and starting with "F"
Windows
Excludes the file named "F.log" located in the folder
C:\Finance
full path starting from the disk letter)
Linux
/home/user/Finance
3.4.1.3 Pre/Post commands
This option is effective for Windows and Linux operating systems and PE-based bootable media.
The option enables you to define the commands to be automatically executed before and after the
backup procedure.
The following scheme illustrates when pre/post commands are executed.
Pre-backup
command
Examples of how you can use the pre/post commands:
delete some temporary files from the disk before starting backup
configure a third-party antivirus product to be started each time before the backup starts
copy an archive to another location after the backup ends.
The program does not support interactive commands, i.e. commands that require user input (for
example, "pause").
To specify pre/post commands
1. Enable pre/post commands execution by checking the following options:
Execute before the backup
Execute after the backup
Backup Post-backup
command
94 Copyright © Acronis, Inc., 2000-2010
Page 95

Selected
Selected
Cleared
Cleared
2. Do any of the following:
Click Edit to specify a new command or a batch file
Select the existing command or the batch file from the drop-down list
3. Click OK.
Pre-backup command
To specify a command/batch file to be executed before the backup process starts
1. In the Command field, type a command or browse to a batch file. The program does not support
interactive commands, i.e. commands that require user input (for example, "pause".)
2. In the Working directory field, specify a path to a directory where the command/batch file will
be executed.
3. In the Arguments field specify the command’s execution arguments, if required.
4. Depending on the result you want to obtain, select the appropriate options as described in the
table below.
5. Click Test command to check if the command is correct.
Check box Selection
Fail the task if the command
execution fails
Selected Cleared
Selected Cleared
Do not back up until the
command execution is
complete
Result
Preset
Perform the backup
only after the
command is
successfully
executed. Fail the
task if the command
execution fails.
Perform the
backup after the
command is
executed despite
execution failure
or success.
N/A Perform the backup
concurrently with
the command
execution and
irrespective of the
command execution
result.
Post-backup command
To specify a command/executable file to be executed after the backup is completed
1. In the Command field, type a command or browse to a batch file.
2. In the Working directory field, specify a path to a directory where the command/batch file will
be executed.
3. In the Arguments field, specify the command execution arguments, if required.
4. If successful execution of the command is critical for your backup strategy, select the Fail the
task if the command execution fails check box. In case the command execution fails, the
program will remove the resulting TIB file and temporary files if possible, and the task will fail.
When the check box is not selected, the command execution result does not affect the task
execution failure or success. You can track the command execution result by exploring the log or
the errors and warnings displayed on the Dashboard.
95 Copyright © Acronis, Inc., 2000-2010
Page 96

5. Click Test Command to check if the command is correct.
3.4.1.4 Pre/Post data capture commands
This option is effective for both Windows and Linux operating systems.
The option enables you to define the commands to be automatically executed before and after data
capture (that is, taking the data snapshot) performed by Acronis Backup & Recovery 10 at the
beginning of the backup procedure.
The following scheme illustrates when the pre/post data capture commands are executed.
Pre-backup
command
<------------------------------ Backup ---------------------------->
Pre-data
capture
command
Data
capture
Post-data
capture
command
If the Volume Shadow Copy Service (p. 98) option is enabled, the commands' execution and the
Microsoft VSS actions will be sequenced as follows:
"Before data capture” commands -> VSS Suspend -> Data capture -> VSS Resume -> "After data
capture" commands.
Using the pre/post data capture commands, you can suspend and resume a database or application
that is not compatible with VSS. As opposed to the Pre/Post commands (p. 94), the pre/post data
capture commands will be executed before and after the data capture process, which takes seconds,
while the entire backup procedure may take much longer, depending on the amount of data to be
backed up. Therefore, the database or application idle time will be minimal.
Post-backup
command
To specify pre/post data capture commands
1. Enable pre/post data capture commands execution by checking the following options:
Execute before the data capture
Execute after the data capture
2. Do any of the following:
Click Edit to specify a new command or a batch file
Select the existing command or the batch file from the drop-down list
3. Click OK.
Pre-data capture command
To specify a command/batch file to be executed before data capture
1. In the Command field, type a command or browse to a batch file. The program does not support
interactive commands, i.e. commands that require user input (for example, "pause".)
2. In the Working directory field, specify a path to a directory where the command/batch file will
be executed.
3. In the Arguments field specify the command’s execution arguments, if required.
4. Depending on the result you want to obtain, select the appropriate options as described in the
table below.
5. Click Test command to check if the command is correct.
Check box Selection
Fail the backup task if the
Selected Cleared
Selected Cleared
96 Copyright © Acronis, Inc., 2000-2010
Page 97

command execution fails
Do not perform the data
capture until the command
execution is complete
Preset
Perform the data
capture only after the
command is
successfully executed.
Fail the task if the
command execution
fails.
Selected Selected
Result
Perform the data
capture after the
command is
executed despite
execution failure
or success.
Cleared Cleared
N/A Perform the data
capture concurrently
with the command
and irrespective of
the command
execution result.
Post-data capture command
To specify a command/batch file to be executed after data capture
1. In the Command field, type a command or browse to a batch file. The program does not support
interactive commands, i.e. commands that require user input (for example, "pause".)
2. In the Working directory field, specify a path to a directory where the command/batch file will
be executed.
3. In the Arguments field specify the command’s execution arguments, if required.
4. Depending on the result you want to obtain, select the appropriate options as described in the
table below.
5. Click Test command to check if the command is correct.
Check box Selection
Fail the task if the command
execution fails
Do not back up until the
command execution is
complete
Selected Cleared
Selected Selected
Selected Cleared
Cleared Cleared
Result
Preset
Continue the backup
only after the
command is
successfully
executed. Delete the
TIB file and
temporary files and
fail the task if the
command execution
fails.
Continue the
backup after the
command is
executed despite
command
execution failure
or success.
N/A Continue the
backup concurrently
with the command
execution and
irrespective of the
command execution
result.
3.4.1.5 File-level backup snapshot
This option is effective only for file-level backup in Windows and Linux operating systems.
97 Copyright © Acronis, Inc., 2000-2010
Page 98

This option defines whether to back up files one by one or by taking an instant data snapshot.
Note: Files that are stored on network shares are always backed up one by one.
The preset is: Create snapshot if it is possible.
Select one of the following:
Always create a snapshot
The snapshot enables backing up of all files including files opened for exclusive access. The files
will be backed up at the same point in time. Choose this setting only if these factors are critical,
that is, backing up files without a snapshot does not make sense. To use a snapshot, the backup
plan has to run under the account with the Administrator or Backup Operator privileges. If a
snapshot cannot be taken, the backup will fail.
Create a snapshot if it is possible
Back up files directly if taking a snapshot is not possible.
Do not create a snapshot
Always back up files directly. Administrator or Backup Operator privileges are not required.
Trying to back up files that are opened for exclusive access will result in a read error. Files in the
backup may be not time-consistent.
3.4.1.6 Multi-volume snapshot
This option is effective only for Windows operating systems.
This option applies to disk-level backup. This option also applies to file-level backup when the filelevel backup is performed by taking a snapshot. (The File-level backup snapshot (p. 97) option
determines whether a snapshot will be taken during file-level backup).
The option determines whether to take snapshots of multiple volumes at the same time or one by
one.
The preset is: Enable.
When this option is set to Enable, snapshots of all volumes being backed up will be created
simultaneously. Use this option to create a time-consistent backup of data spanned across multiple
volumes, for instance for an Oracle database.
When this option is set to Disable, the volumes' snapshots will be taken one after the other. As a
result, if the data spans across several volumes, the resulting backup may be not consistent.
3.4.1.7 Volume Shadow Copy Service
This option is effective only for Windows operating systems.
The option defines whether a Volume Shadow Copy Service (VSS) provider—either Acronis VSS or
Microsoft VSS—has to notify VSS-aware applications that the backup is about to start. This ensures
the consistent state of all data used by the applications, in particular, completion of all database
transactions, at the moment of taking the data snapshot by Acronis Backup & Recovery 10. Data
consistency, in turn, ensures that the application will be recovered in the correct state and become
operational immediately after recovery.
The preset is: Create snapshots using VSS
98 Copyright © Acronis, Inc., 2000-2010
Page 99

Acronis Backup & Recovery 10 will select the VSS provider automatically based on the operating
system running on the machine and whether the machine is a member of an Active Directory
domain.
Create snapshots without using VSS
Choose this option if your database is incompatible with VSS. The data snapshot will be taken by
Acronis Backup & Recovery 10. Backup process is fastest, but data consistency of the applications
whose transactions are not completed at the time of taking a snapshot cannot be guaranteed. You
may use Pre/Post data capture commands (p. 96) to indicate which commands should be performed
before and after taking the snapshot, to ensure that the data is being backed up in a consistent state.
For instance, specify pre-data capture commands that will suspend the database and flush all caches
to ensure that all transactions are completed; and specify post-data capture commands that will
resume the database operations after the snapshot is taken.
Volume shadow copy writers
Before backing up the data of VSS-aware applications, make sure that the volume shadow copy
writers for those applications are turned on, by examining the list of writers that are present in the
operating system. To view this list, run the following command:
vssadmin list writers
Note: In Microsoft Windows Small Business Server 2003, the writer for Microsoft Exchange Server 2003 is
turned off by default. For instructions on how to turn it on, see the corresponding Microsoft Help and Support
http://support.microsoft.com/kb/838183/en.
article
3.4.1.8 Compression level
This option is effective for Windows and Linux operating systems and bootable media.
The option defines the level of compression applied to the data being backed up.
The preset is: Normal.
The optimal data compression level depends on the type of data being backed up. For example, even
maximum compression will not significantly reduce the archive size if the archive contains essentially
compressed files, such as .jpg, .pdf or .mp3. However, formats such as .doc or .xls will be compressed
well.
To specify the compression level
Select one of the following:
None – the data will be copied as is, without any compression. The resulting backup size will be
maximal.
Normal – recommended in most cases.
High – the resulting backup size will typically be less than for the Normal level.
Maximum – the data will be compressed as much as possible. The backup duration will be
maximal. You may want to select maximum compression when backing up to removable media
to reduce the number of blank disks required.
99 Copyright © Acronis, Inc., 2000-2010
 Loading...
Loading...