
Prestige 794M
SHDSL 4-Port Internet Security Gateway
User’s Guide
Version 1.00
10/2005
Edition 1

Prestige 794M User’s Guide
Copyright
Copyright © 2005 by ZyXEL Communications Corporation.
The contents of this publication may not be reproduced in any part or as a whole, transcribed,
stored in a retrieval system, translated into any language, or transmitted in any form or by any
means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or
otherwise, without the prior written permission of ZyXEL Communications Corporation.
Published by ZyXEL Communications Corporation. All rights reserved.
Disclaimer
ZyXEL does not assume any liability arising out of the application or use of any products, or
software described herein. Neither does it convey any license under its patent rights nor the
patent rights of others. ZyXEL further reserves the right to make changes in any products
described herein without notice. This publication is subject to change without notice.
Trademarks
ZyNOS (ZyXEL Network Operating System) is a registered trademark of ZyXEL
Communications, Inc. Other trademarks mentioned in this publication are used for
identification purposes only and may be properties of their respective owners.
Copyright 2
Prestige 794M User’s Guide
Federal Communications
Commission (FCC) Interference
Statement
This device complies with Part 15 of FCC rules. Operation is subject to the following two
conditions:
• This device may not cause harmful interference.
• This device must accept any interference received, including interference that may cause
undesired operations.
This equipment has been tested and found to comply with the limits for a Class B digital
device pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable
protection against harmful interference in a commercial environment. This equipment
generates, uses, and can radiate radio frequency energy, and if not installed and used in
accordance with the instructions, may cause harmful interference to radio communications.
If this equipment does cause harmful interference to radio/television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the
interference by one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and the receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver
is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Notice 1
Changes or modifications not expressly approved by the party responsible for compliance
could void the user's authority to operate the equipment.
Certifications
1 Go to www.zyxel.com.
2 Select your product from the drop-down list box on the
ZyXEL home page to go to that product's page.
3 Select the certification you wish to view from this page.
3 Federal Communications Commission (FCC) Interference Statement

Prestige 794M User’s Guide
Safety Warnings
For your safety, be sure to read and follow all warning notices and instructions.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel can
service the device. Please contact your vendor for further information.
• Connect the power cord to the right supply voltage (110V AC in North America or 230V
AC in Europe).
• Place connecting cables carefully so that no one will step on them or stumble over them.
Do NOT allow anything to rest on the power cord and do NOT locate the product where
anyone can walk on the power cord.
• If you wall mount your device, make sure that no electrical, gas or water pipes will be
damaged.
• Do NOT install nor use your device during a thunderstorm. There may be a remote risk of
electric shock from lightning.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Make sure to connect the cables to the correct ports.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
• Do NOT store things on the device.
• Connect ONLY suitable accessories to the device.
Safety Warnings 4

Prestige 794M User’s Guide
ZyXEL warrants to the original end user (purchaser) that this product is free from any defects
in materials or workmanship for a period of up to two years from the date of purchase. During
the warranty period, and upon proof of purchase, should the product have indications of failure
due to faulty workmanship and/or materials, ZyXEL will, at its discretion, repair or replace the
defective products or components without charge for either parts or labor, and to whatever
extent it shall deem necessary to restore the product or components to proper operating
condition. Any replacement will consist of a new or re-manufactured functionally equivalent
product of equal value, and will be solely at the discretion of ZyXEL. This warranty shall not
apply if the product is modified, misused, tampered with, damaged by an act of God, or
subjected to abnormal working conditions.
Note
Repair or replacement, as provided under this warranty, is the exclusive remedy of the
purchaser. This warranty is in lieu of all other warranties, express or implied, including any
implied warranty of merchantability or fitness for a particular use or purpose. ZyXEL shall in
no event be held liable for indirect or consequential damages of any kind of character to the
purchaser.
ZyXEL Limited Warranty
To obtain the services of this warranty, contact ZyXEL's Service Center for your Return
Material Authorization number (RMA). Products must be returned Postage Prepaid. It is
recommended that the unit be insured when shipped. Any returned products without proof of
purchase or those with an out-dated warranty will be repaired or replaced (at the discretion of
ZyXEL) and the customer will be billed for parts and labor. All repaired or replaced products
will be shipped by ZyXEL to the corresponding return address, Postage Paid. This warranty
gives you specific legal rights, and you may also have other rights that vary from country to
country.
Safety Warnings
1 To reduce the risk of fire, use only No. 26 AWG or larger telephone wire.
2 Do not use this product near water, for example, in a wet basement or near a swimming
pool.
3 Avoid using this product during an electrical storm. There may be a remote risk of
electric shock from lightening.
5 ZyXEL Limited Warranty
Prestige 794M User’s Guide
Customer Support
Please have the following information ready when you contact customer support.
• Product model and serial number.
• Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
METHOD
LOCATION
CORPORATE
HEADQUARTERS
(WORLDWIDE)
CZECH REPUBLIC
DENMARK
FINLAND
FRANCE
GERMANY
HUNGARY
KAZAKHSTAN
NORTH AMERICA
NORWAY
SUPPORT E-MAIL TELEPHONE
SALES E-MAIL FAX FTP SITE
support@zyxel.com.tw +886-3-578-3942 www.zyxel.com
sales@zyxel.com.tw +886-3-578-2439 ftp.zyxel.com
info@cz.zyxel.com +420-241-091-350 www.zyxel.cz ZyXEL Communications
info@cz.zyxel.com +420-241-091-359
support@zyxel.dk +45-39-55-07-00 www.zyxel.dk ZyXEL Communications A/S
sales@zyxel.dk +45-39-55-07-07
support@zyxel.fi +358-9-4780-8411 www.zyxel.fi ZyXEL Communications Oy
sales@zyxel.fi +358-9-4780 8448
info@zyxel.fr +33-4-72-52-97-97 www.zyxel.fr ZyXEL France
+33-4-72-52-19-20
support@zyxel.de +49-2405-6909-0 www.zyxel.de ZyXEL Deutschland GmbH.
sales@zyxel.de +49-2405-6909-99
support@zyxel.hu +36-1-3361649 www.zyxel.hu ZyXEL Hungary
info@zyxel.hu +36-1-3259100
http://zyxel.kz/support +7-3272-590-698 www.zyxel.kz ZyXEL Kazakhstan
sales@zyxel.kz +7-3272-590-689
support@zyxel.com 1-800-255-4101
+1-714-632-0882
sales@zyxel.com +1-714-632-0858 ftp.us.zyxel.com
support@zyxel.no +47-22-80-61-80 www.zyxel.no ZyXEL Communications A/S
sales@zyxel.no +47-22-80-61-81
A
WEB SITE
www.europe.zyxel.com
ftp.europe.zyxel.com
www.us.zyxel.com ZyXEL Communications Inc.
REGULAR MAIL
ZyXEL Communications Corp.
6 Innovation Road II
Science Park
Hsinchu 300
Ta iw a n
Czech s.r.o.
Modranská 621
143 01 Praha 4 - Modrany
Ceská Republika
Columbusvej
2860 Soeborg
Denmark
Malminkaari 10
00700 Helsinki
Finland
1 rue des Vergers
Bat. 1 / C
69760 Limonest
France
Adenauerstr. 20/A2 D-52146
Wuerselen
Germany
48, Zoldlomb Str.
H-1025, Budapest
Hungary
43, Dostyk ave.,Office 414
Dostyk Business Centre
050010, Almaty
Republic of Kazakhstan
1130 N. Miller St.
Anaheim
CA 92806-2001
U.S.A.
Nils Hansens vei 13
0667 Oslo
Norway
Customer Support 6
Prestige 794M User’s Guide
METHOD
LOCATION
POLAND
RUSSIA
SPAIN
SWEDEN
UKRAINE
UNITED KINGDOM
a. “+” is the (prefix) number you enter to make an international telephone call.
SUPPORT E-MAIL TELEPHONE
SALES E-MAIL FAX FTP SITE
info@pl.zyxel.com +48-22-5286603 www.pl.zyxel.com ZyXEL Communications
+48-22-5206701
http://zyxel.ru/support +7-095-542-89-29 www.zyxel.ru ZyXEL Russia
sales@zyxel.ru +7-095-542-89-25
support@zyxel.es +34-902-195-420 www.zyxel.es ZyXEL Communications
sales@zyxel.es +34-913-005-345
support@zyxel.se +46-31-744-7700 www.zyxel.se ZyXEL Communications A/S
sales@zyxel.se +46-31-744-7701
support@ua.zyxel.com +380-44-247-69-78 www.ua.zyxel.com ZyXEL Ukraine
sales@ua.zyxel.com +380-44-494-49-32
support@zyxel.co.uk +44-1344 303044
08707 555779 (UK only)
sales@zyxel.co.uk +44-1344 303034 ftp.zyxel.co.uk
A
WEB SITE
REGULAR MAIL
ul.Emilli Plater 53
00-113 Warszawa
Poland
Ostrovityanova 37a Str.
Moscow, 117279
Russia
Alejandro Villegas 33
1º, 28043 Madrid
Spain
Sjöporten 4, 41764 Göteborg
Sweden
13, Pimonenko Str.
Kiev, 04050
Ukraine
www.zyxel.co.uk ZyXEL Communications UK
Ltd.,11 The Courtyard,
Eastern Road, Bracknell,
Berkshire, RG12 2XB,
United Kingdom (UK)
7 Customer Support

Prestige 794M User’s Guide
Table of Contents
Copyright ..................................................................................................................2
Federal Communications Commission (FCC) Interference Statement ............... 3
Safety Warnings ....................................................................................................... 4
ZyXEL Limited Warranty.......................................................................................... 5
Customer Support.................................................................................................... 6
Table of Contents ..................................................................................................... 8
List of Figures ........................................................................................................ 14
List of Tables .......................................................................................................... 16
Preface ....................................................................................................................18
Chapter 1
Introduction ...........................................................................................................20
1.1 About Your Prestige ..........................................................................................20
1.2 Features ............................................................................................................20
1.3 Applications .......................................................................................................22
1.3.1 Internet Access .........................................................................................22
1.3.2 Firewall for Secure Broadband Internet Access .......................................23
1.3.3 VPN Application ........................................................................................23
1.3.4 LAN-to-LAN Application ............................................................................23
1.4 Hardware Connection ........................................................................................24
1.4.1 Front Panel .............................................................................................24
1.5 Rear Panel ........................................................................................................25
Chapter 2
The Web Configurator ........................................................................................... 26
2.1 Overview ............................................................................................................26
2.2 Accessing the Web Configurator .......................................................................26
2.3 Resetting the Prestige .......................................................................................27
2.3.1 Procedure To Use The Reset Button ........................................................27
2.4 Navigating the Web Configurator .......................................................................27
2.4.1 The Status Screen ...................................................................................27
2.5 System Status ...................................................................................................28
2.6 ARP Table .........................................................................................................29
Table of Contents 8

Prestige 794M User’s Guide
2.6.1 How ARP Works .....................................................................................29
2.7 Routing Table ...................................................................................................30
2.7.1 PPTP Status ...........................................................................................31
2.7.2 IPSec Status ...........................................................................................31
2.7.3 L2TP Status ............................................................................................32
2.7.4 Email Status ............................................................................................33
2.7.5 Event Log ................................................................................................33
2.7.6 Error Log .................................................................................................34
2.7.7 NAT Sessions .........................................................................................35
2.8 Internet Access Quick Start Setup ...................................................................35
2.8.1 Auto Scan ...............................................................................................37
Chapter 3
LAN .........................................................................................................................38
3.1 Overview ............................................................................................................38
3.2 LAN TCP/IP ........................................................................................................38
3.2.1 Factory LAN Defaults ...............................................................................38
3.2.2 IP Address and Subnet Mask ...................................................................38
3.2.3 RIP ............................................................................................................39
3.3 The Ethernet Screen ..........................................................................................39
3.4 Ethernet Client Filter .........................................................................................40
3.4.1 Ethernet Client Filter Candidates .............................................................41
3.5 Port Setting .......................................................................................................42
3.6 DHCP .................................................................................................................43
3.6.1 IP Pool Setup ............................................................................................43
3.6.2 DNS Servers .............................................................................................43
3.6.3 DHCP Setup .............................................................................................43
3.6.4 DHCP Relay Agent ...................................................................................46
3.6.3.1 Disable DHCP ................................................................................44
3.6.3.2 DHCP Server Setup ........................................................................44
Chapter 4
WAN......................................................................................................................... 48
4.1 Overview ............................................................................................................48
4.1.1 Encapsulation Types .................................................................................48
4.1.1.1 RFC 1483 .......................................................................................48
4.1.1.2 PPPoE .............................................................................................48
4.1.1.3 PPPoA .............................................................................................49
4.1.1.4 IPoA ................................................................................................49
4.2 ISP .....................................................................................................................49
4.2.1 Edit Settings .............................................................................................50
4.2.1.1 Advanced PPP Options ...................................................................51
4.2.2 Change Connection Type .........................................................................53
9 Table of Contents

Prestige 794M User’s Guide
4.3 DNS ...................................................................................................................54
4.4 SHDSL Parameters ............................................................................................55
Chapter 5
System .................................................................................................................... 58
5.1 Overview ............................................................................................................58
5.2 Time Zone ..........................................................................................................58
5.3 Remote Access ..................................................................................................59
5.4 Firmware Upgrade ............................................................................................60
5.5 Backup/Restore ................................................................................................60
5.6 Restart Router ....................................................................................................61
5.7 User Management ..............................................................................................62
5.7.1 Create a New User Account .....................................................................62
Chapter 6
Firewall....................................................................................................................64
6.1 Overview ...........................................................................................................64
6.2 Types of Firewalls ..............................................................................................64
6.2.1 Packet Filtering Firewalls ..........................................................................64
6.2.2 Application-level Firewalls ........................................................................64
6.2.3 Stateful Inspection Firewalls .....................................................................65
6.3 General Settings ................................................................................................66
6.4 Packet Filter .......................................................................................................67
6.4.1 Add a New TCP/UDP Packet Filter ..........................................................69
6.4.2 Add a New Raw Packet Filter ...................................................................70
6.5 Intrusion Detection .............................................................................................71
6.6 URL Filter ...........................................................................................................73
6.6.1 Keywords Filtering ...................................................................................74
6.6.2 Domain Filtering .......................................................................................75
6.7 Firewall Log .......................................................................................................76
Chapter 7
VPN..........................................................................................................................78
7.1 Overview ............................................................................................................78
7.2 PPTP ..................................................................................................................78
7.2.1 PPTP Summary .......................................................................................78
7.2.2 Creating a PPTP VPN Rule ......................................................................79
7.2.2.1 Remote Access Connection ..........................................................79
7.2.2.2 LAN to LAN Connection .................................................................81
7.3 IPSec ..................................................................................................................83
7.3.1 AH (Authentication Header) .....................................................................83
7.3.2 ESP (Encapsulating Security Payload) ....................................................83
7.3.3 Perfect Forward Secrecy (PFS) ...............................................................84
Table of Contents 10

Prestige 794M User’s Guide
7.3.4 Pre-Shared Key ........................................................................................84
7.3.5 IPSec VPN Summary ..............................................................................84
7.3.6 IPSec VPN Configuration ........................................................................85
7.4 L2TP ..................................................................................................................87
7.4.1 Creating a New L2TP Rule .......................................................................88
7.5 VPN Example ....................................................................................................93
7.5.1 Example: Remote PPTP VPN Dial-in Connection ....................................93
7.5.2 Example: Remote PPTP VPN Dial-out Connection ..................................94
Chapter 8
QoS (Quality of Service) ........................................................................................ 96
8.1 Overview ............................................................................................................96
8.1.1 Prioritization .............................................................................................96
8.2 IP Throttling ......................................................................................................98
8.3 QoS Example ...................................................................................................100
8.3.1 Example Prioritization with QoS ............................................................100
8.3.2 Rate Limiting with IP Throttling Example ...............................................101
8.4 Time Schedule ................................................................................................101
8.4.1 Configuring a Time Schedule .................................................................102
7.4.1.1 Remote Access L2TP Connection .................................................88
7.4.1.2 LAN to LAN L2TP Connection .......................................................90
Chapter 9
Static Route ..........................................................................................................104
9.1 Overview .........................................................................................................104
9.2 Configuration ....................................................................................................104
Chapter 10
Dynamic DNS........................................................................................................ 106
10.1 Overview ........................................................................................................106
10.1.1 Configuration ........................................................................................106
Chapter 11
Check Emails........................................................................................................108
11.1 Overview ........................................................................................................108
11.2 Configuring .....................................................................................................108
Chapter 12
Device Management............................................................................................. 110
12.1 Overview .......................................................................................................110
12.1.1 Universal Plug and Play (UPnP) ...........................................................110
12.1.1.1 How do I know if I'm using UPnP? .............................................. 110
12.1.1.2 Cautions with UPnP .................................................................... 110
11 Table of Contents

Prestige 794M User’s Guide
12.1.2 SNMP .................................................................................................. 110
12.1.2.1 SNMPv3 ..................................................................................... 111
12.1.2.2 SNMP Traps and MIBs .............................................................. 112
12.2 The Device Management Screen ................................................................... 112
12.3 IGMP ............................................................................................................. 115
Index...................................................................................................................... 116
Table of Contents 12

Prestige 794M User’s Guide
13 Table of Contents

Prestige 794M User’s Guide
List of Figures
Figure 1 Application: Internet Access .................................................................... 22
Figure 2 Application: Firewall ................................................................................ 23
Figure 3 Application: VPN ..................................................................................... 23
Figure 4 Application: LAN-to-LAN ......................................................................... 24
Figure 5 Front Panel: LEDs ................................................................................... 24
Figure 6 Rear Panel ............................................................................................. 25
Figure 7 Web Configurator: Login ......................................................................... 26
Figure 8 Web Configurator: Status ....................................................................... 27
Figure 9 Status: ARP Table ................................................................................... 29
Figure 10 Status: Routing Table ............................................................................ 30
Figure 11 Status: PPTP Status .............................................................................. 31
Figure 12 Status: IPSec Status ............................................................................. 31
Figure 13 Status: L2TP Status .............................................................................. 32
Figure 14 Status: Email Status ............................................................................. 33
Figure 15 Event Log .............................................................................................. 34
Figure 16 Status: Error Log ................................................................................... 34
Figure 17 Status: NAT Session ............................................................................. 35
Figure 18 Quick Start ............................................................................................ 36
Figure 19 Quick Start: Auto Scan ......................................................................... 37
Figure 20 LAN: Ethernet ....................................................................................... 40
Figure 21 LAN: Ethernet Client Filter .................................................................... 41
Figure 22 LAN: Ethernet Client Filter: Active PC in LAN ....................................... 41
Figure 23 LAN: Port Setting .................................................................................. 42
Figure 24 LAN: DHCP Server ............................................................................... 44
Figure 25 LAN: DHCP Server: Disable ................................................................. 44
Figure 26 LAN: DHCP Server: DHCP ................................................................... 45
Figure 27 LAN: DHCP Server: DHCP: Fixed Host ................................................ 46
Figure 28 LAN: DHCP Server: DHCP Relay Agent .............................................. 47
Figure 29 WAN: ISP .............................................................................................. 49
Figure 30 WAN: ISP: Edit ..................................................................................... 50
Figure 31 WAN: Edit: Advanced PPP Options ...................................................... 52
Figure 32 ISP: Change Connection Type .............................................................. 53
Figure 33 ISP: Change Connection Type Settings (RFC 1483 Routed) ............... 54
Figure 34 DNS ...................................................................................................... 55
Figure 35 SHDSL ................................................................................................... 55
Figure 36 System: Time Zone ............................................................................... 58
Figure 37 System: Remote Access ...................................................................... 59
Figure 38 System: Firmware Upgrade .................................................................. 60
List of Figures 14

Prestige 794M User’s Guide
Figure 39 System: Firmware Upgrade: Progress .................................................. 60
Figure 40 System: Firmware Upgrade: Device Configuration Option ................... 60
Figure 41 System: Configuration Backup/Restore ................................................ 61
Figure 42 System: Restart .................................................................................... 61
Figure 43 System: User Management .................................................................. 62
Figure 44 System: User Management: Edit Account ............................................ 63
Figure 45 Firewall: General Settings ..................................................................... 66
Figure 46 Firewall: Packet Filter ............................................................................ 68
Figure 47 Firewall: Packet Filters: Add TCP/UDP Filter ........................................ 69
Figure 48 Firewall: Packet Filters: Add Raw Filter ................................................ 70
Figure 49 Firewall: Intrusion Detection .................................................................. 72
Figure 50 Firewall: URL Filter ............................................................................... 74
Figure 51 Firewall: URL Filter: Keywords Filtering ................................................ 75
Figure 52 Firewall: URL Filter: Domains Filtering ................................................. 75
Figure 53 Firewall: Firewall Logs .......................................................................... 76
Figure 54 VPN: PPTP ........................................................................................... 78
Figure 55 VPN: PPTP ........................................................................................... 79
Figure 56 VPN: PPTP: Remote Access ............................................................... 79
Figure 57 VPN: PPTP: LAN to LAN Connection .................................................. 81
Figure 58 IPSec Summary ................................................................................... 84
Figure 59 IPSec: Create ........................................................................................ 85
Figure 60 VPN: L2TP ............................................................................................ 87
Figure 61 VPN: L2TP: Create ............................................................................... 88
Figure 62 L2TP: Remote Access Connection ....................................................... 88
Figure 63 L2TP: LAN to LAN Connection ............................................................. 91
Figure 64 Remote PPTP VPN Dial-in Network Example ...................................... 93
Figure 65 Remote PPTP VPN Dial-In Configuration Example .............................. 94
Figure 66 PPTP: Remote VPN Dial-out Access .................................................... 94
Figure 67 PPTP VPN Example: Configuration for the Office ................................ 95
Figure 68 QoS: Prioritization ................................................................................. 97
Figure 69 QoS: Outbound IP Throttling ................................................................. 99
Figure 70 QoS Network Example .......................................................................... 100
Figure 71 QoS: Prioritization Example .................................................................. 100
Figure 72 Rating Limiting with IP Throttling Example ........................................... 101
Figure 73 Configuration: Time Schedule ............................................................... 102
Figure 74 Configuration: Time Schedule: Edit ........................................................ 102
Figure 75 Static Route: Network Example ] ........................................................... 104
Figure 76 Advanced: Static Route ......................................................................... 104
Figure 77 Advanced: Dynamic DNS .................................................................... 106
Figure 78 Advanced: Check Emails ....................................................................... 108
Figure 79 SNMP Management Model ................................................................... 111
Figure 80 Advanced: Device Management ........................................................... 113
Figure 81 Advanced: IGMP ................................................................................... 115
15 List of Figures

Prestige 794M User’s Guide
List of Tables
Table 1 Front Panel: LEDs .................................................................................... 24
Table 2 Rear Panel ................................................................................................ 25
Table 3 Status ........................................................................................................ 28
Table 4 Status: ARP Table ..................................................................................... 30
Table 5 Status: Routing Table ................................................................................ 30
Table 6 Status: PPTP Status ................................................................................. 31
Table 7 Status: IPSec Status ................................................................................. 32
Table 8 Status: L2TP Status .................................................................................. 32
Table 9 Status: Email Status .................................................................................. 33
Table 10 Status: Error Log ..................................................................................... 34
Table 11 Status: NAT Session ............................................................................... 35
Table 12 Quick Start .............................................................................................. 36
Table 13 LAN: Ethernet ......................................................................................... 40
Table 14 LAN: Ethernet Client Filter ...................................................................... 41
Table 15 LAN: Ethernet Client Filter: Active PC in LAN ........................................ 42
Table 16 LAN: Port Setting .................................................................................... 42
Table 17 LAN: DHCP Server ................................................................................. 44
Table 18 LAN: DHCP Server: DHCP ..................................................................... 45
Table 19 LAN: DHCP Server: DHCP: Fixed Host ................................................. 46
Table 20 LAN: DHCP Server: DHCP Relay Agent ................................................ 47
Table 21 WAN: ISP ................................................................................................ 49
Table 22 WAN: ISP: Edit (PPPoE) ........................................................................ 50
Table 23 WAN: Edit: Advanced PPP Options ........................................................ 52
Table 24 DNS ........................................................................................................ 55
Table 25 SHDSL .................................................................................................... 56
Table 26 System: Time Zone ................................................................................. 59
Table 27 System: User Management .................................................................... 62
Table 28 System: User Management: Edit Account .............................................. 63
Table 29 Firewall: General Settings ...................................................................... 66
Table 30 Pre-defined Port Filter ............................................................................ 67
Table 31 Firewall: Packet Filter ............................................................................. 68
Table 32 Firewall: Packet Filters: Add TCP/UDP Filter ......................................... 69
Table 33 Firewall: Packet Filters: Add Raw Filter .................................................. 70
Table 34 IDS: Detectable Attacks ........................................................................ 71
Table 35 Firewall: Intrusion Detection ................................................................... 73
Table 36 Firewall: URL Filter ................................................................................. 74
Table 37 Firewall: URL Filter: Keywords Filtering ................................................. 75
Table 38 Firewall: URL Filter: Domains Filtering ................................................... 76
List of Tables 16

Prestige 794M User’s Guide
Table 39 Firewall: Firewall Logs ............................................................................ 76
Table 40 VPN: PPTP ............................................................................................. 79
Table 41 VPN: PPTP: Remote Access .................................................................. 80
Table 42 VPN PPTP: LAN to LAN Connection ...................................................... 81
Table 43 ESP and AH ........................................................................................... 83
Table 44 VPN Rules (IKE): Add Policy .................................................................. 85
Table 45 VPN: PPTP ............................................................................................. 87
Table 46 VPN: L2TP: Create: Remote Access Connection .................................. 89
Table 47 VPN: L2TP: Create: LAN to LAN ............................................................ 91
Table 48 Remote PPTP VPN Dial-In Configuration Example ................................ 94
Table 49 Remote PPTP VPN Dial-In Configuration Example ................................ 95
Table 50 QoS: Prioritization ................................................................................... 97
Table 51 DSCP Mapping ....................................................................................... 98
Table 52 QoS: Outbound/Inbound IP Throttling .................................................... 99
Table 53 Rate Limiting with IP Throttling Example ................................................ 101
Table 54 Configuration: Time Schedule ................................................................ 102
Table 55 Configuration: Time Schedule: Edit ........................................................ 103
Table 56 Advanced: Static Route .......................................................................... 105
Table 57 Advanced: Dynamic DNS ....................................................................... 107
Table 58 Advanced: Check Emails ........................................................................ 108
Table 59 MIBs and Attributes ................................................................................ 112
Table 60 Advanced: Device Management ............................................................. 113
Table 61 Advanced: IGMP .................................................................................... 115
17 List of Tables

Prestige 794M User’s Guide
Preface
Congratulations on your purchase of the Prestige 794M.
Note: Register your product online to receive e-mail notices of firmware upgrades and
information at
North American products.
Your Prestige is easy to install and configure.
About This User's Guide
This manual is designed to guide you through the configuration of your Prestige for its various
applications using the web-based configurator.
Related Documentation
• Supporting Disk
www.zyxel.com for global products, or at www.us.zyxel.com for
Refer to the included CD for support documents.
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away. They
contain connection information and instructions on getting started.
• ZyXEL Glossary and Web Site
Please refer to www.zyxel.com for an online glossary of networking terms and additional
support documentation.
User Guide Feedback
Help us help you. E-mail all User Guide-related comments, questions or suggestions for
improvement to techwriters@zyxel.com.tw or send regular mail to The Technical Writing
Team, ZyXEL Communications Corp., 6 Innovation Road II, Science-Based Industrial Park,
Hsinchu, 300, Taiwan. Thank you!
Syntax Conventions
• “Enter” means for you to type one or more characters. “Select” or “Choose” means for
you to use one predefined choices.
• The SMT menu titles and labels are in Bold Times New Roman font. Predefined field
choices are in Bold Arial font. Command and arrow keys are enclosed in square
brackets. [ENTER] means the Enter, or carriage return key; [ESC] means the Escape key
and [SPACE BAR] means the Space Bar.
• Mouse action sequences are denoted using a comma. For example, “click the Apple icon,
Control Panels and then Modem” means first click the Apple icon, then point your
mouse pointer to Control Panels and then click Modem.
Preface 18

Prestige 794M User’s Guide
• For brevity’s sake, we will use “e.g.,” as a shorthand for “for instance”, and “i.e.,” for
“that is” or “in other words” throughout this manual.
• The Prestige 794M may be referred to as “the Prestige” in this user’s guide.
Graphics Icons Key
Prestige Computer Notebook computer
Server DSLAM Firewall
Telephone Switch Router
Wireless Signal
19 Preface

1.1 About Your Prestige
Your Prestige integrates high-speed 10/100Mbps auto-negotiating LAN interface(s) and a
high-speed SHDSL port into a single package. The Prestige is ideal for high-speed Internet
browsing and making LAN-to-LAN connections to remote networks. The Prestige is also an
SHDSL router.
By integrating SHDSL and NAT, the Prestige provides ease of installation and Internet access.
The Prestige is also a complete security solution with a robust firewall and content filtering.
Prestige 794M User’s Guide
CHAPTER 1
Introduction
1.2 Features
The following sections describe the features of the Prestige.
Multi-Mode Standard
Your Prestige supports symmetric data rates of up to 4.6Mbps. It also supports rate
management that allows subscribers to select a speed to fit their needs and budgets. The
Prestige uses the ITU standard PAM16 Line Code, complies with G.991.2 and G.994.1
standards.
10/100M Auto-negotiating Ethernet/Fast Ethernet Interface(s)
This auto-negotiation feature allows the Prestige to detect the speed of incoming transmissions
and adjust appropriately without manual intervention. It allows data transfer of either 10 Mbps
or 100 Mbps in either half-duplex or full-duplex mode depending on your Ethernet network.
4-Port Switch
A combination of switch and router makes your Prestige a cost-effective and viable network
solution. You can connect up to four computers to the Prestige without the cost of a hub. Use a
hub to add more than four computers to your LAN.
Encapsulation
The Prestige supports PPPoA (RFC 2364 - PPP over ATM Adaptation Layer 5), RFC 1483
encapsulation over ATM, MAC encapsulated routing (ENET encapsulation), IPoA
(RFC1577) as well as PPP over Ethernet (RFC 2516).
Chapter 1 Introduction 20

Prestige 794M User’s Guide
Multiplexing
The Prestige supports VC-based and LLC-based multiplexing.
Full Network Management
The embedded web configurator is an all-platform web-based utility that allows you to easily
access the Prestige’s management settings. Most functions of the Prestige are also
configurable via the CLI (Command Line Interface) over a telnet/console connection.
Universal Plug and Play (UPnP)
Using the standard TCP/IP protocol, the Prestige and other UPnP enabled devices can
dynamically join a network, obtain an IP address and convey its capabilities to other devices
on the network.
Network Address Translation (NAT)
Network Address Translation (NAT) allows the translation of an Internet protocol address
used within one network (for example a private IP address used in a local network) to a
different IP address known within
the Internet).
another network (for example a public IP address used on
Firewall
The Prestige is a stateful inspection firewall with DoS (Denial of Service) protection. By
default, when the firewall is activated, all incoming traffic from the WAN to the LAN is
blocked unless it is initiated from the LAN. The Prestige firewall supports TCP/UDP
inspection, DoS detection and prevention, real time alerts, reports and logs.
Content Filtering
The Prestige can block web features such as ActiveX controls, Java applets and cookies, as
well as disable web proxies. The Prestige can block or allow access to web sites that you
specify. The Prestige can also block access to web sites containing keywords that you specify.
You can define time periods and days during which content filtering is enabled and include or
exclude a range of users on the LAN from content filtering.
Packet Filtering
The packet filtering mechanism blocks unwanted traffic from entering/leaving your network.
Dynamic DNS (DDNS)
With Dynamic DNS support, you can have a static hostname alias for a dynamic IP address,
allowing the host to be more easily accessible from various locations on the Internet. You must
register for this service with a Dynamic DNS service provider.
21 Chapter 1 Introduction
Prestige 794M User’s Guide
VPN
Establish a Virtual Private Network (VPN) to connect with business partners and branch
offices using data encryption and the Internet to provide secure communications without the
expense of leased site-to-site lines. The Prestige VPN is based on the IPSec standard and is
fully interoperable with other IPSec-based VPN products.
DHCP (Dynamic Host Configuration Protocol)
DHCP (Dynamic Host Configuration Protocol) allows the individual client computers to
obtain the TCP/IP configuration at start-up from a centralized DHCP server. The Prestige has
built-in DHCP server capability, disabled by default, which means it can assign IP addresses,
an IP default gateway and DNS servers to all systems that support the DHCP client.
SNMP
SNMP (Simple Network Management Protocol) is a protocol used for exchanging
management information between network devices. SNMP is a member of the TCP/IP
protocol suite. Your Prestige supports SNMP agent functionality, which allows a manager
station to manage and monitor the Prestige through the network.
Firmware Upgradeable
The firmware of the Prestige can be upgraded via the web configurator.
1.3 Applications
Here are some examples of what you can do with your Prestige.
1.3.1 Internet Access
The Prestige is the ideal high-speed Internet access solution. Your Prestige supports the TCP/
IP protocol, which the Internet uses exclusively. It is compatible with all major DSL DSLAM
(Digital Subscriber Line Access Multiplexer) providers. A DSLAM is a rack of DSL line cards
with data multiplexed into a backbone network interface/connection (for example, T1, OC3,
DS3, ATM or Frame Relay). Think of it as the equivalent of a modem rack for SHDSL.
Figure 1 Application: Internet Access
Chapter 1 Introduction 22
Prestige 794M User’s Guide
1.3.2 Firewall for Secure Broadband Internet Access
The Prestige provides protection from attacks by Internet hackers. By default, the firewall
blocks all incoming traffic from the WAN. The firewall supports TCP/UDP inspection and
DoS (Denial of Services) detection and prevention, as well as real time alerts, reports and logs.
Figure 2 Application: Firewall
1.3.3 VPN Application
The Prestige’s VPN feature makes it an ideal cost-effective way to connect branch offices and
business partners over the Internet without the need (and expense) for leased lines between
sites. VPN ensures the privacy and integrity of your data transmissions.
Figure 3 Application: VPN
1.3.4 LAN-to-LAN Application
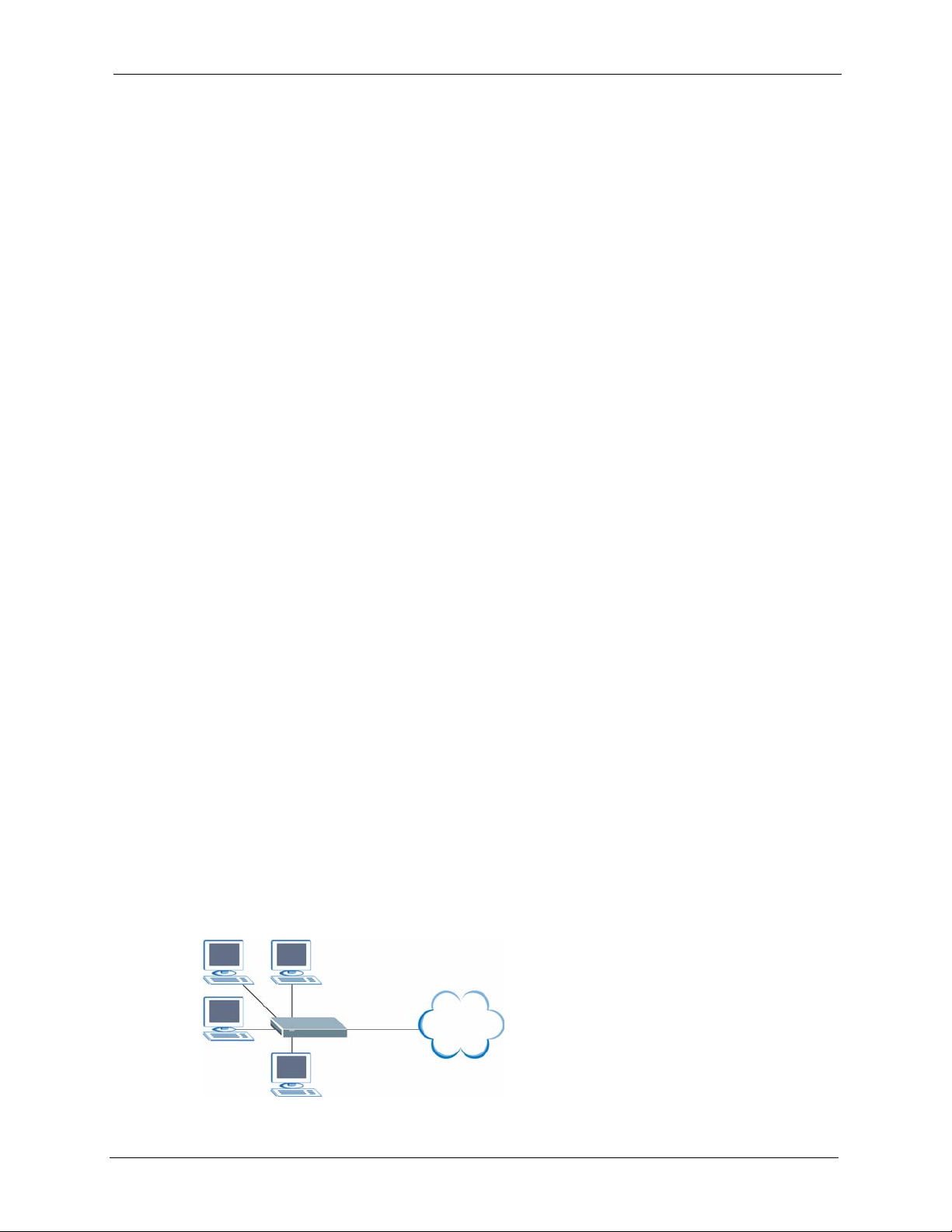
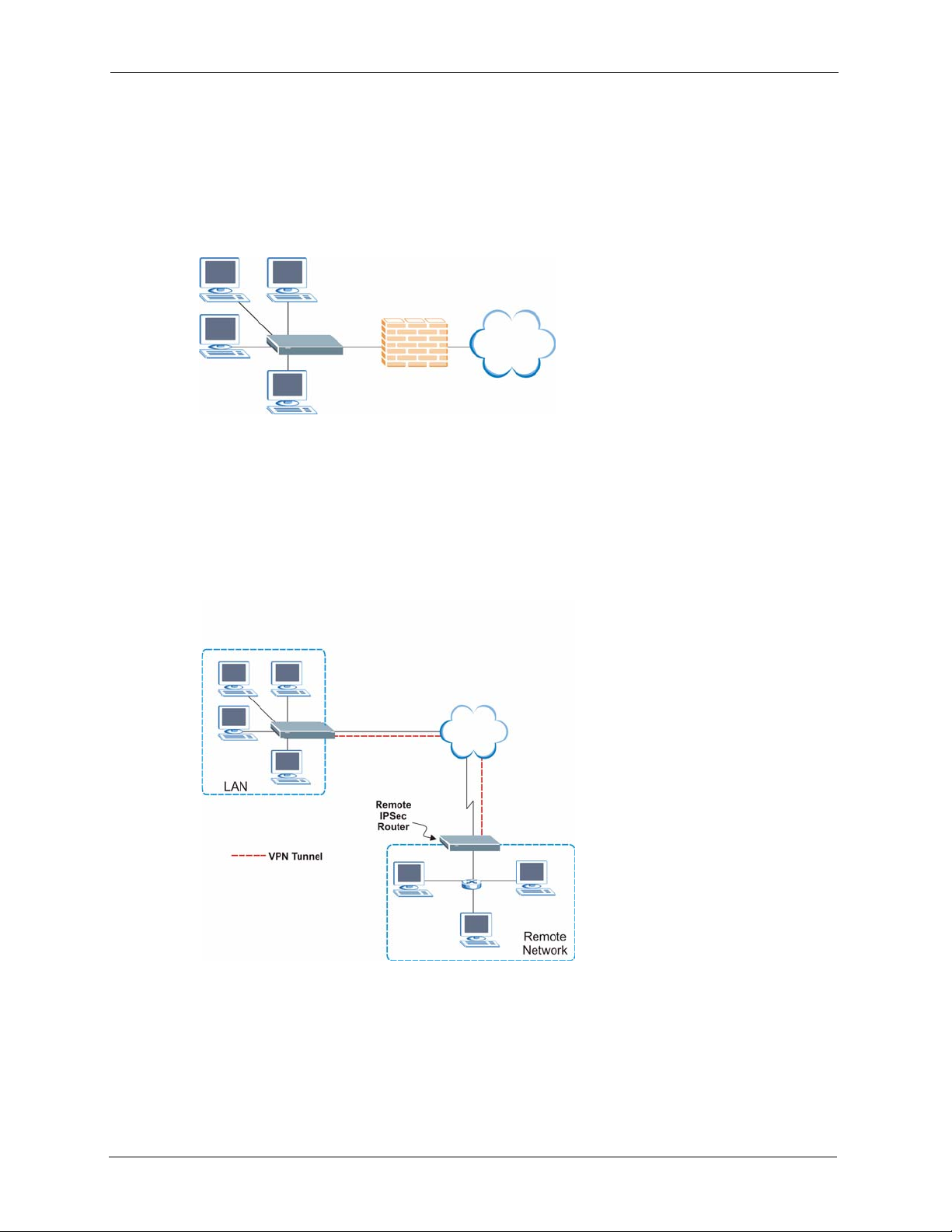
You can use the Prestige to connect two geographically dispersed networks over the SHDSL
line. A typical LAN-to-LAN application for your Prestige is shown as follows.
23 Chapter 1 Introduction
Figure 4 Application: LAN-to-LAN
1.4 Hardware Connection
Refer to the Quick Start Guide for more information on hardware connection and initial setup
using the Quick Start screen.
1.4.1 Front Panel
Prestige 794M User’s Guide
The following figure shows the front panel LEDs.
Figure 5 Front Panel: LEDs
The following table describes the LEDs.
Table 1 Front Panel: LEDs
LED COLOR STATUS DESCRIPTION
PWR Green On The Prestige is turned on.
Off The Prestige is turned off.
SYS Green On The Prestige is ready and working properly.
Flashing The Prestige is starting up or rebooting.
Off The Prestige is not ready.
Chapter 1 Introduction 24
Prestige 794M User’s Guide
Table 1 Front Panel: LEDs (continued)
LED COLOR STATUS DESCRIPTION
LAN 1..4 Orange On The Prestige has a successful 10Mbps Ethernet connection.
Green On The Prestige has a successful 100Mbps Ethernet connection.
LINE 1, 2 Green On The Prestige has a successful SHDSL link.
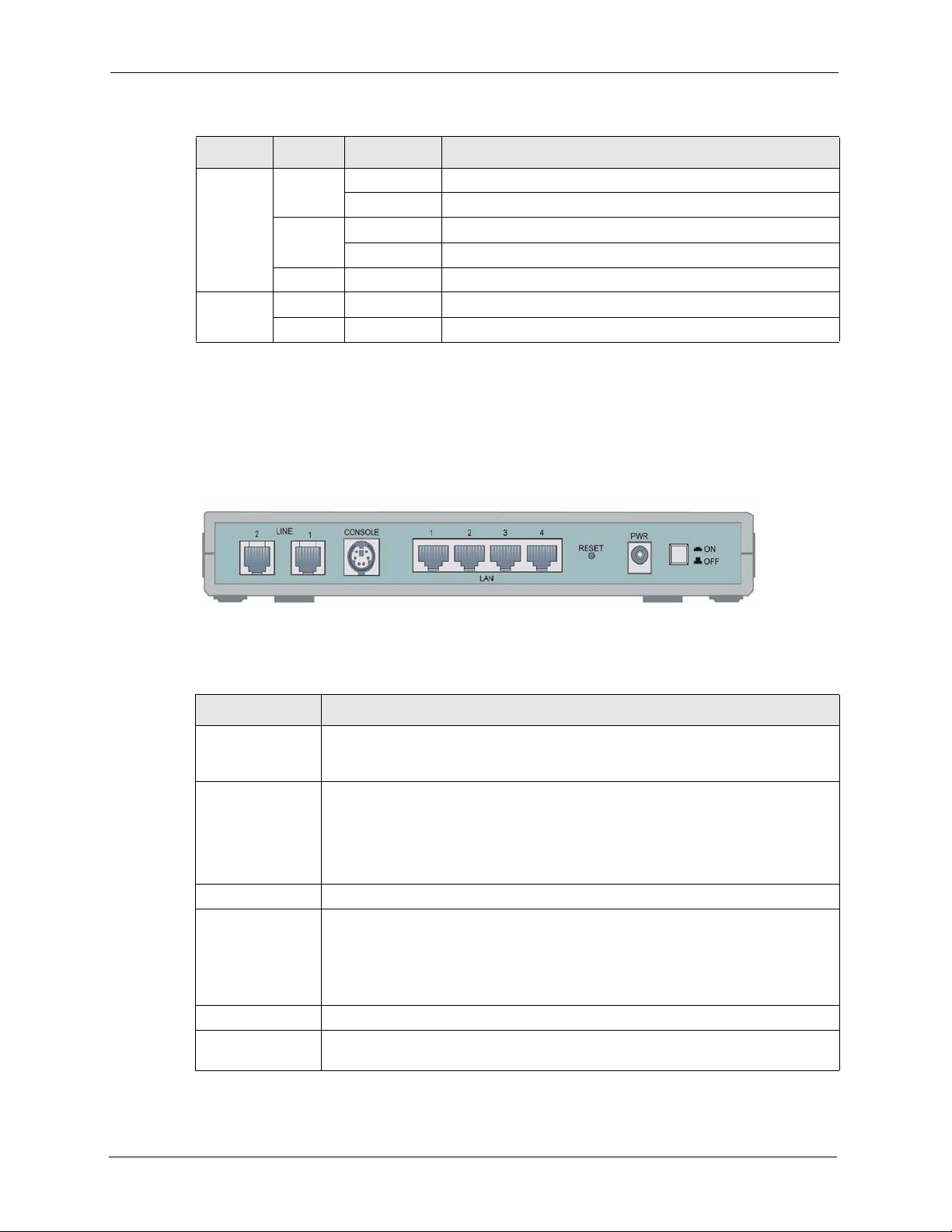
1.5 Rear Panel
The following figure shows the rear panel of the Prestige.
Figure 6 Rear Panel
Flashing The 10M LAN is sending or receiving packets.
Flashing The 100M LAN is sending or receiving packets.
Off The LAN is not connected.
Off The SHDSL link is down or not connected.
The following table describes the ports.
Table 2 Rear Panel
LABEL DESCRIPTION
LAN 1..4
(RJ-45 connector)
CONSOLE Only connect this port if you want to configure the Prestige via console port.
LINE 1..2 Connect to a telephone jack using the included telephone cable.
RESET You only need to use this button if you’ve forgotten the Prestige’s password. It
PWR Connect to a power source using only the included power adaptor for your region.
Power Switch After you’ve made the connections and connect the power adaptor to a power
Connect a computer to this port with an Ethernet cable. This port is autonegotiating (can connect at 10 or 100Mbps) and auto-crossover (automatically
adjust to straight-through or crossover Ethernet cable).
Connect one end of the console cable to the console port of the Prestige and the
other end to a serial port (COM1, COM2 or other COM port) on your computer.
Your computer should have a terminal emulation communications program (such
as HyperTerminal) set to VT100 terminal emulation, no parity, 8 data bits, 1 stop
bit, no flow control and 9600 bps port speed.
returns the Prestige to the factory defaults.
Press this button is for less than three seconds to restart the Prestige.
Press this button in for more than six seconds to reset the Prestige to the factory
default settings.
supply, push in the power button to turn on the Prestige.
25 Chapter 1 Introduction
This chapter introduces the web configurator and describes the Quick Start screen.
2.1 Overview
The embedded web configurator (eWC) allows you to manage the Prestige from anywhere
through a browser such as Microsoft Internet Explorer or Netscape Navigator. Use Internet
Explorer 6.0 and later or Netscape Navigator 7.0 and later versions with JavaScript enabled. It
is recommended that you set your screen resolution to 1024 by 768 pixels. The screens you see
in the web configurator may vary somewhat from the ones shown in this document due to
differences between individual firmware versions.
Prestige 794M User’s Guide
CHAPTER 2
The Web Configurator
2.2 Accessing the Web Configurator
1 Make sure your Prestige hardware is properly connected and prepare your computer/
computer network to connect to the Prestige (refer to the Quick Start Guide).
2 Make sure the IP addresses of your computer and the Prestige are in the same range.
Refer to the appendix on setting up your computer IP address for more information.
3 Launch your web browser and type "192.168.1.1" as the URL.
4 Enter the username (“admin” is the default) and the password (“1234” is the default).
5 Click OK to log in.
Figure 7 Web Configurator: Login
6 You should now see the HOME screen.
Note: The management session automatically times out when the time period expires
(default 180 seconds or 3 minutes). Simply log back into the Prestige if this
happens to you. You can change this timeout in the Device Management
screen (see
Chapter 2 The Web Configurator 26
Section 12.2 on page 112).
Prestige 794M User’s Guide
2.3 Resetting the Prestige
If you forget your password or cannot access the web configurator, you will need to reload the
factory-default configuration file or use the RESET button on the Prestige. Uploading this
configuration file replaces the current configuration file with the factory-default configuration
file. This means that you will lose all configurations that you had previously and the password
will be reset to 1234, also.
2.3.1 Procedure To Use The Reset Button
1 Make sure the PWR LED is on before you begin this procedure.
2 Press the RESET button for more than six seconds, and then release it. If the SYS LED
begins to blink, the defaults have been restored and the Prestige restarts.
2.4 Navigating the Web Configurator
The following summarizes how to navigate the web configurator from the HOME screen.
2.4.1 The Status Screen
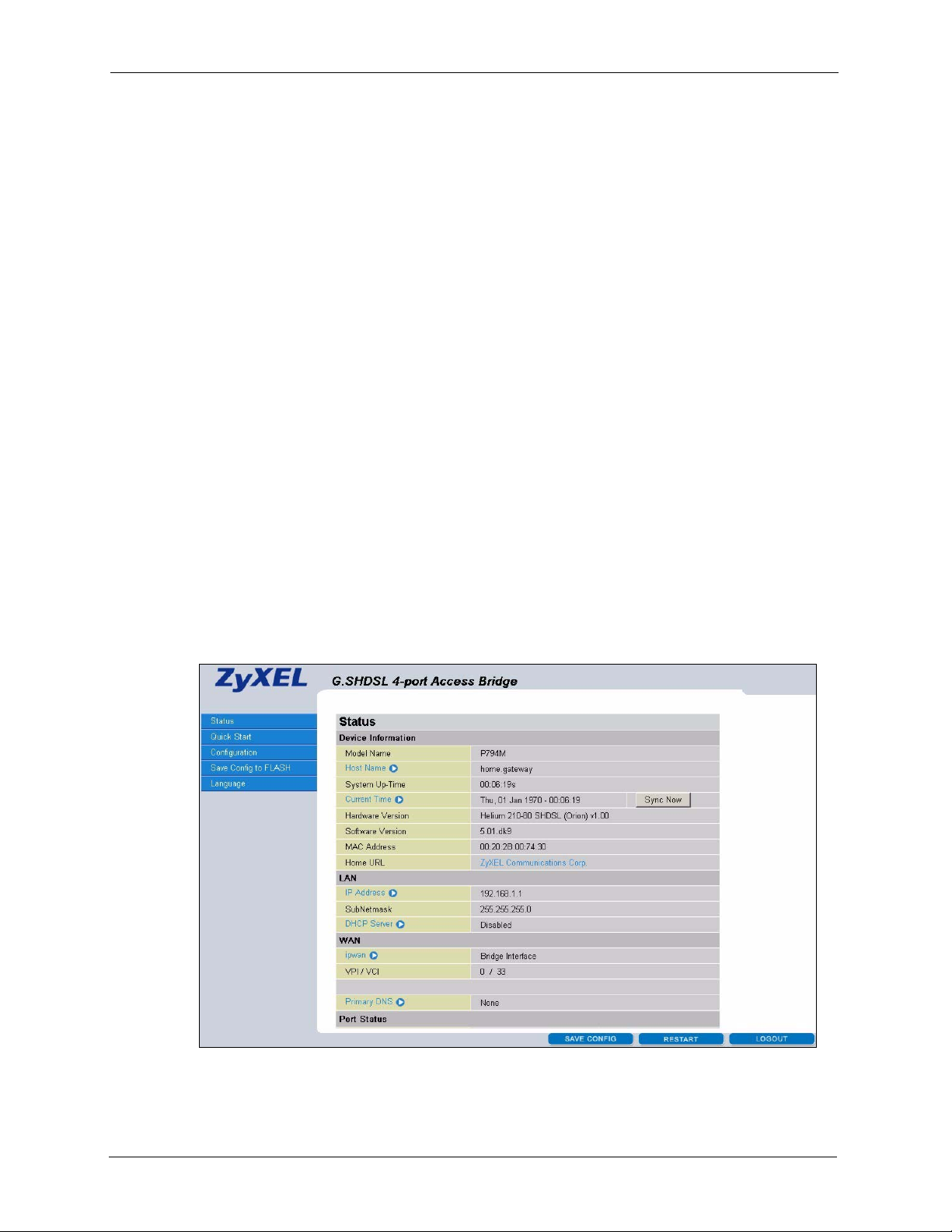
The following screen shows the Status screen. This is the first screen that displays every time
you access the web configurator.
Figure 8 Web Configurator: Status
• Click the links in the navigation panel to configure the Prestige features.
• Click the SAVE CONFIG button to save the current settings to the Prestige.
27 Chapter 2 The Web Configurator
• Click the RESTART button to reboot the Prestige.
• Click the LOGOUT button at any time to exit the web configurator.
2.5 System Status
Display the Status screen (see Figure 8 on page 27) to view general system information. The
following table describes the labels in this screen.
Table 3 Status
LABEL DESCRIPTION
Device Information
Model Name This field displays the model number of your Prestige.
Host Name This field displays the host name of the Prestige for identification purposes. Click
System Up-Time This field displays the time (in the format of hh:mm:ss) since the Prestige was last
Current TIme This field displays the system time. Click this label to display the Time Zone
Hardware Version This is the hardware version associated with your Prestige.
Software Version This is the firmware version the Prestige is currently using.
MAC Address This is the MAC (Media Access Control) or Ethernet address unique to your
Home URL Click this link to go to the ZyXEL company web site.
LAN
IP Address This is the IP address (in dotted decimal notation) on the LAN. Click the label to
Subnet Mask This is the subnet mask (in dotted decimal notation) on the LAN.
DHCP Server This field displays the LAN DNCP server status. Click the label to display the
WAN
ipwan This field displays the type of WAN interface. Click this label to display the WAN
VPI/VCI This field displays the VCI (Virtual Circuit Identifier) and VPI (Virtual Path Identifier)
Primary DNS This field displays the primary DNS server IP address (in dotted decimal notation).
Port Status
Port This field displays interface name (Ethernet or SHDSL). Click a label to display the
Connected This field displays a check to indicate that a port is up. Otherwise a cross is
Stat istics
Prestige 794M User’s Guide
this label to display the Host Name screen.
restarted.
screen.
Click Sync Now to synchronize the system time to the time server specified in the
Time Zone screen.
Prestige.
display the Ethernet screen.
DHCP Server screen.
Connection screen.
numbers.
Click this label to display the DNS screen.
Port Setting or the SHDSL screen.
displayed.
Chapter 2 The Web Configurator 28
Prestige 794M User’s Guide
Table 3 Status (continued)
LABEL DESCRIPTION
RFC1483 WAN
Link
Ethernet This field displays the number of packets received/transmitted. Click this label to
SAVE CONFIG Click SAVE CONFIG to save the changes.
RESTART Click RESTART to reboot the device. All unsaved changes will be lost.
LOGOUT Click LOGOUT to exit from the web configurator. All unsaved changes will be lost.
This field displays the VCI and VPI number and the number of packets received/
transmitted. Click this label to display detailed information.
display detailed information.
2.6 ARP Table
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP
address) to a physical machine address, also known as a Media Access Control (MAC)
address, on the local area network. An IP (version 4) address is 32 bits long. In an Ethernet
LAN, MAC addresses are 48 bits long. The ARP table maintains an association between each
MAC address and its corresponding IP address.
2.6.1 How ARP Works
When an incoming packet destined for a host device on a local area network arrives at the
device, the device's ARP program looks in the ARP table and, if it finds the address, sends it to
the device. If no entry is found for the IP address, ARP broadcasts the request to all the devices
on the LAN. The device fills in its own MAC and IP address in the sender address fields, and
puts the known IP address of the target in the target IP address field. In addition, the device
puts all ones in the target MAC field (FF.FF.FF.FF.FF.FF is the Ethernet broadcast address).
The replying device (which is either the IP address of the device being sought or the router that
knows the way) replaces the broadcast address with the target's MAC address, swaps the
sender and target pairs, and unicasts the answer directly back to the requesting machine. ARP
updates the ARP table for future reference and then sends the packet to the MAC address that
replied.
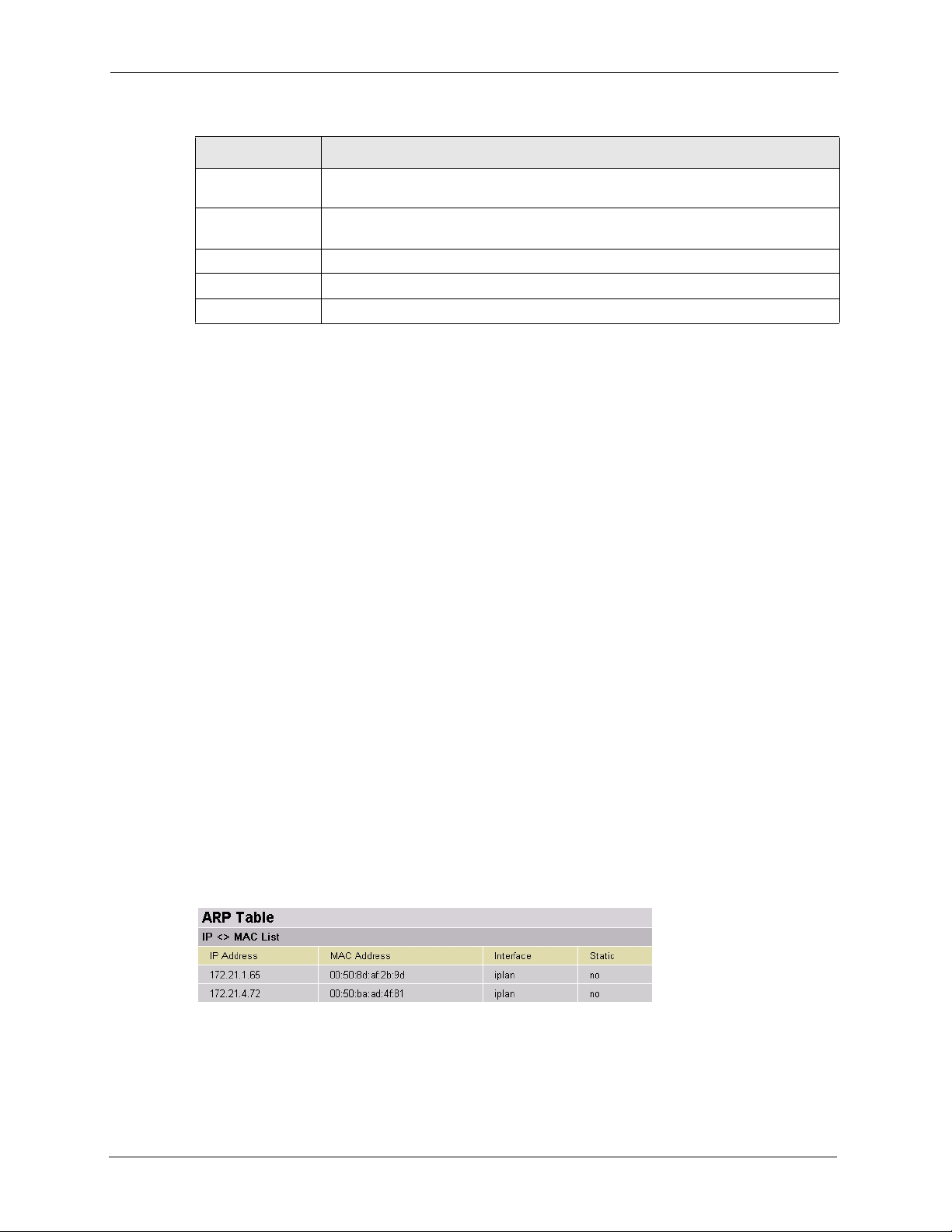
To view the ARP table, click Status and ARP Table in the navigation panel.
Figure 9 Status: ARP Table
29 Chapter 2 The Web Configurator
The following table describes the labels in this screen.
Table 4 Status: ARP Table
LABEL DESCRIPTION
IP Address This is the learned IP address of a device connected to a switch port with
MAC Address This is the MAC address of the device with corresponding IP address above.
Interface This is the interface name on the Prestige to which a device is connected.
Stat ic This shows whether the MAC address is dynamic (learned by the Prestige) or
2.7 Routing Table
The routing table contains the route information to the network(s) that the Prestige can reach.
The Prestige automatically updates the routing table with the RIP information received from
other Ethernet devices.
Prestige 794M User’s Guide
corresponding MAC address below.
static (manually entered).
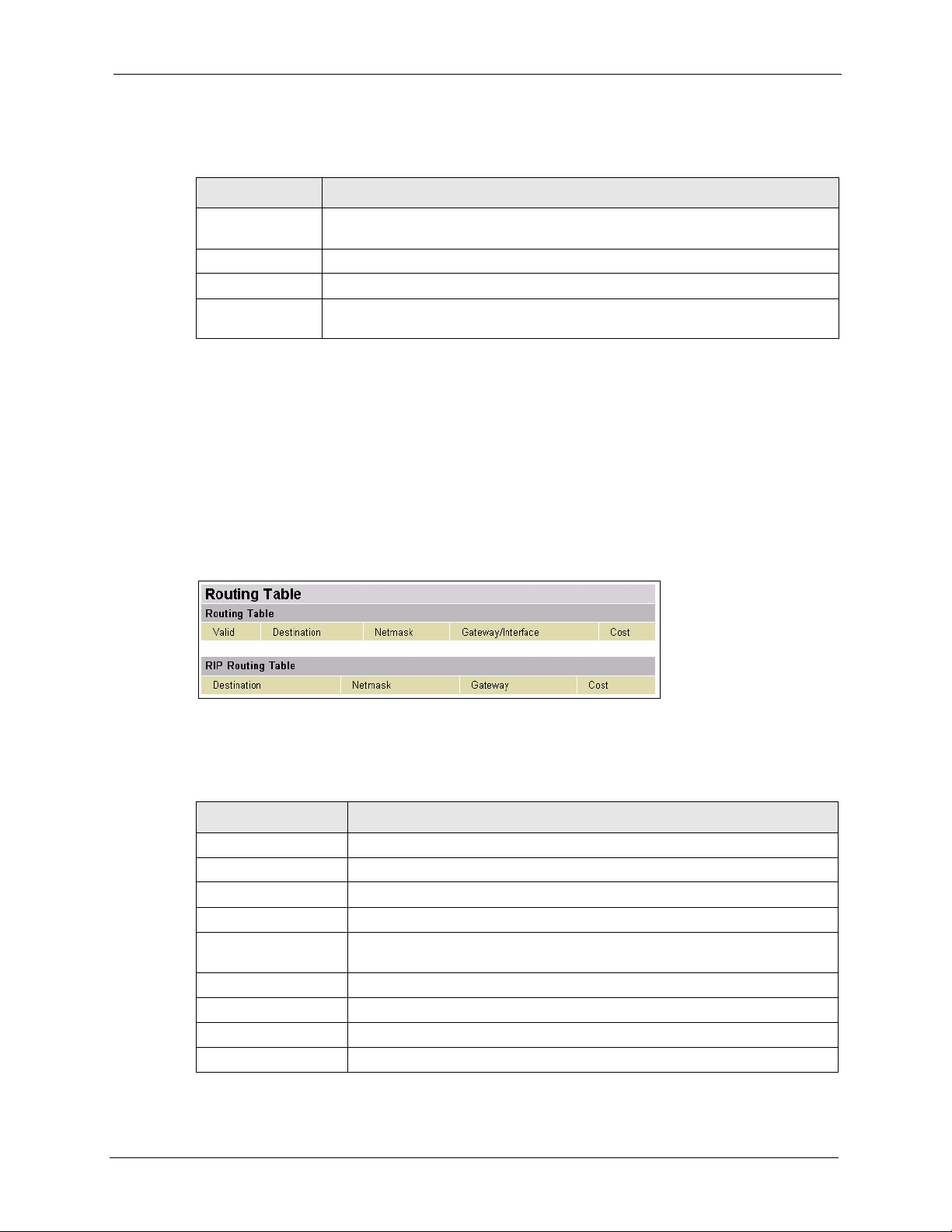
Click Status and Routing Ta ble in the navigation panel to display the Routing Table screen.
Figure 10 Status: Routing Table
The following table describes the labels in this screen.
Table 5 Status: Routing Table
LABEL DESCRIPTION
Routing Table
Valid This field indicates whether a routing status is successful.
Destination This field displays the IP address of a destination network.
Netmask This field displays the subnet mask of a destination network.
Gateway/Interface This field displays the IP address of a gateway or the interface name on the
Prestige this route uses.
Cost This field displays the cost (or hope count) for this route.
RIP Routing Table
Destination This field displays the IP address of a destination network.
Netmask This field displays the subnet mask of a destination network.
Chapter 2 The Web Configurator 30

Prestige 794M User’s Guide
Table 5 Status: Routing Table (continued)
LABEL DESCRIPTION
Gateway This field displays the IP address of a gateway that this route uses.
Cost This field displays the cost (or hope count) for this route.
2.7.1 PPTP Status
Use the PPTP Status screen to view PPTP VPN connection information. Click Status and
PPTP Status in the navigation panel to display the screen as shown next.
Figure 11 Status: PPTP Status
The following table describes the labels in this screen.
Table 6 Status: PPTP Status
LABEL DESCRIPTION
Name This field displays the name of the VPN rule used for this connection.
Type This field displays the type of VPN connection (dial-in or dial-out).
Enable This field indicates whether the VPN rule is currently enabled.
Active This field indicates whether the VPN rule is activated.
Tunnel Connected This field indicates whether the VPN tunnel is up.
Call Connected If the Call for this VPN entry is currently connected.
Encryption This field displays the encryption type for this VPN connection.
2.7.2 IPSec Status
Use the IPSec Status screen to view IPSec VPN connection information. Click Status and
IPSec Status in the navigation panel to display the screen as shown next.
Figure 12 Status: IPSec Status
31 Chapter 2 The Web Configurator

The following table describes the labels in this screen.
Table 7 Status: IPSec Status
LABEL DESCRIPTION
Name This field displays the name of the VPN rule used for this connection.
Active This field indicates whether the VPN rule is activated.
Connection State This field displays the connection status (Connected or Disconnected).
Stat istics This field displays the number of packets sent using this VPN connection.
Local Subnet This field displays the IP address and/or subnet mask of the local network behind
Remote Subnet This field displays the subnet mask of the local network behind the remote IPSec
Remote Gateway This field displays the IP address of the remote IPsec router.
SA This field displays the number of Security Association (SA) for this VPN
2.7.3 L2TP Status
Prestige 794M User’s Guide
the Prestige.
router.
connection.
Use the L2TP Status screen to view L2TP VPN connection information. Click Status and
L2TP Status in the navigation panel to display the screen as shown next.
Figure 13 Status: L2TP Status
The following table describes the labels in this screen.
Table 8 Status: L2TP Status
LABEL DESCRIPTION
Name This field displays the name of the VPN rule used for this connection.
Type This field displays the type of VPN connection (dial-in or dial-out).
Enable This field indicates whether the VPN rule is currently enabled.
Active This field indicates whether the VPN rule is activated.
Tunnel Connected This field indicates whether the VPN tunnel is up.
Call Connected If the Call for this VPN entry is currently connected.
Encryption This field displays the encryption type for this VPN connection.
Chapter 2 The Web Configurator 32

Prestige 794M User’s Guide
2.7.4 Email Status
The Email Status screen shows the current E-mail account information (that you configured
in the Check Email screen). You can also check your Email account status in this screen.
Click Status and Email Status in the navigation panel.
Figure 14 Status: Email Status
The following table describes the labels in this screen.
Table 9 Status: Email Status
LABEL DESCRIPTION
Email Account
Account Name This field displays the E-mail account user name.
POP3 Mail Server This field displays the IP address or domain name of a POP3 mail server.
Email Status This field displays the status of this mail account.
Reset Status This button is available when you enable this E-mail account.
Check Now This button is available when you enable this E-mail account.
2.7.5 Event Log
Use the Event Log screen to view system logs (such as when an SHDSL connection is up).
Click Status and Event Log in the navigation panel to display the screen as shown next.
Note: To display and log firewall events, enable firewall event logging in the Firewall
Log screen.
Click Reset Status to reset the status.
Click Check Now to check for any new mail(s) on the mail server.
Note: You need to use an E-mail program (such as Microsoft
Outlook or Netscape Composer) to retrieve and view Emails.
33 Chapter 2 The Web Configurator

Figure 15 Event Log
Click Refresh to update the event log entries. Click Clear to delete all event log entries from
the text box.
2.7.6 Error Log
Prestige 794M User’s Guide
Use the Error Log screen to view errors (such as VPN configuration errors).
Note: This screen automatically displays when you click Apply and there is an error
in the configuration screen. If this happens, simply check the error message
here and try configuring the screen again.
Click Status and Error Log in the navigation panel to display the screen as shown next.
Figure 16 Status: Error Log
The following table describes the labels in this screen.
Table 10 Status: Error Log
LABEL DESCRIPTION
When This field displays the time (in seconds since the Prestige was last restarted) the error
occurred.
Process This field displays the name of the application process (or system job) that creates this error.
Error Log This field displays detailed error message.
Chapter 2 The Web Configurator 34

Prestige 794M User’s Guide
2.7.7 NAT Sessions
ClicK Status and NAT Sessions in the navigation panel to display current NAT sessions.
Figure 17 Status: NAT Session
The following table describes the fields in the text box.
Table 11 Status: NAT Session
LABEL DESCRIPTION
Prot. This field displays the protocol name (such as TCP, UDP or ICMP) of the NAT
session.
Local IP This field displays the local IP address of the NAT session.
Port local/public This field displays the local-to-public port translation.
Remote IP This field displays the public IP address used for this NAT session.
Port This field displays the port number used to connect to the local port.
Idle This field displays the time (in seconds) this NAT session is not being used.
TCP This field displays the number of TCP NAT sessions.
UDP This field displays the number of UDP NAT sessions.
Others This field displays the number of NAT sessions that are not of either TCP or UDP
type.
To ta l This field displays the total number of NAT sessions.
Refresh Click Refresh to update the NAT session information.
2.8 Internet Access Quick Start Setup
This section shows you how to configure the Prestige for Internet access using the Quick
Start screen.
Note: You must already have an Internet access account and obtained the
connection information from an ISP Internet Service Provider).
35 Chapter 2 The Web Configurator

Prestige 794M User’s Guide
Click Quick Start in the navigation panel to display the screen as shown.
Figure 18 Quick Start
The following table describes the labels in this screen.
Table 12 Quick Start
LABEL DESCRIPTION
Connection
Encapsulation Select the connection type from the drop-down list.
Click Auto Scan to have the Prestige automatically detect and select the
connection type. Refer to
VCI Enter the VCI number.
VPI Enter the VPI number.
NAT Select Enable to allow more than one computer behind the Prestige to access the
Internet.
Select Disable to allow only one user to access the Internet or if computer(s)
behind the Prestige is provided with a public IP address(es).
Optional Settings
IP Address Enter the IP address (in dotted decimal notation) If you are provided with a static
public IP address.
Otherwise, enter 0.0.0.0 if your ISP provides you with a dynamic IP address.
Subnet Mask Enter the subnet mask (in dotted decimal notation) associated with the static IP
address above.
Default Gateway Enter the IP address of the default gateway.
DNS
Primary/
Secondary DNS
PPP Set the fields below if you select PPPoA or PPPoE in the Encapsulation field.
If provided by your ISP, enter the IP address(es) of the DNS server(s).
above.
Section 2.8.1 on page 37 for more information.
Chapter 2 The Web Configurator 36

Prestige 794M User’s Guide
Table 12 Quick Start (continued)
LABEL DESCRIPTION
Username Enter the Internet access account username.
Password Enter the password associated with the username above.
Apply Click Apply to save the changes.
Cancel Click Cancel to start configuring this screen again.
2.8.1 Auto Scan
Use the Auto Scan screen to set the Prestige to automatically detect the Internet connection
type.
Follow the steps below to allow the Prestige to automatically detect the Internet connection
settings.
1 Click Auto Scan in the Quick Start screen to display the screen as shown next.
Figure 19 Quick Start: Auto Scan
2 If provided, enter the IP addresses of the DSLAM device or a gateway.
3 Click Start to begin the scanning process.
4 When the auto scan is complete and successful, a screen displays. Select your option from
the list and click Apply. Otherwise, click Cancel and return to the Quick Start screen
and configure the Internet access settings manually.
37 Chapter 2 The Web Configurator

This chapter describes how to configure LAN settings.
3.1 Overview
Local Area Network (LAN) is a shared communication system to which many computers are
attached. The LAN screens can help you configure a LAN DHCP server and manage IP
addresses.
3.2 LAN TCP/IP
Prestige 794M User’s Guide
CHAPTER 3
LAN
The Prestige has built-in DHCP server capability that assigns IP addresses and DNS servers to
systems that support DHCP client capability.
3.2.1 Factory LAN Defaults
The LAN parameters of the Prestige are preset in the factory with the following values:
• IP address of 192.168.1.1 with subnet mask of 255.255.255.0 (24 bits).
• DHCP server is disabled.
These parameters should work for the majority of installations. If your ISP gives you explicit
DNS server address(es), read the embedded web configurator help regarding what fields need
to be configured.
3.2.2 IP Address and Subnet Mask
Similar to the way houses on a street share a common street name, so too do computers on a
LAN share one common network number.
Where you obtain your network number depends on your particular situation. If the ISP or
your network administrator assigns you a block of registered IP addresses, follow their
instructions in selecting the IP addresses and the subnet mask.
If the ISP did not explicitly give you an IP network number, then most likely you have a single
user account and the ISP will assign you a dynamic IP address when the connection is
established. If this is the case, it is recommended that you select a network number from
192.168.0.0 to 192.168.255.0 and you must enable the Network Address Translation (NAT)
feature of the Prestige. The Internet Assigned Number Authority (IANA) reserved this block
Chapter 3 LAN 38

Prestige 794M User’s Guide
of addresses specifically for private use; please do not use any other number unless you are
told otherwise. Let's say you select 192.168.1.0 as the network number; which covers 254
individual addresses, from 192.168.1.1 to 192.168.1.254 (zero and 255 are reserved). In other
words, the first three numbers specify the network number while the last number identifies an
individual computer on that network.
Once you have decided on the network number, pick an IP address that is easy to remember,
for instance, 192.168.1.1, for your Prestige, but make sure that no other device on your
network is using that IP address.
The subnet mask specifies the network number portion of an IP address. Your Prestige will
compute the subnet mask automatically based on the IP address that you entered. You don't
need to change the subnet mask computed by the Prestige unless you are instructed to do
otherwise.
3.2.3 RIP
RIP (Routing Information Protocol, RFC 1058 and RFC 1389) allows a router to exchange
routing information with other routers. By default, the Prestige sends and receives RIP
packets.
RIP version controls the format and the broadcasting method of the RIP packets that the
Prestige sends (it recognizes both formats when receiving). The follow lists the RIP versions
that your Prestige supports:
• RIP v1 is universally supported (and is probably adequate for most networks, unless you
have an unusual network topology).
• RIP v2 carries more information.
• RIP v2 Multicast sends routing data in RIP-2 format using multicasting. Multicasting
can reduce the load on non-router machines since they generally do not listen to the RIP
multicast address and so will not receive the RIP packets. However, if one router uses
multicasting, then all routers on your network must use multicasting, also.
3.3 The Ethernet Screen
To set the LAN TCP/IP settings, click Configuration, LAN and Ethernet in the navigation
panel to display the screen as shown next.
39 Chapter 3 LAN

Prestige 794M User’s Guide
Figure 20 LAN: Ethernet
The following table describes the labels in this screen.
Table 13 LAN: Ethernet
LABEL DESCRIPTION
Primary IP Address
IP Address Type the IP address of your Prestige in dotted decimal notation. 192.168.1.1 is the
factory default.
IP Subnet Mask The subnet mask specifies the network number portion of an IP address. Your
RIP The RIP field controls the format and the broadcasting method of the RIP packets
Secondary IP Address
You can assign a different IP address (in the same subnet as the primary IP address) to the LAN
interface.
IP Address Type the secondary IP address of your Prestige in dotted decimal notation.
Prestige automatically calculate the subnet mask based on the IP address that you
assign. Unless you are implementing subnetting, use the subnet mask computed
by the Prestige.
that the Prestige sends (it recognizes both formats when receiving).
Select RIP v1 if you are unsure what RIP version other Ethernet device(s)
supports. RIP v1 is universally supported.
Select RIP v2 to send detailed routing data.
Select RIP v2 Multicast to set the Prestige to send routing data in RIP-2 format
using multicasting.
Note: Make sure this IP address is in the same subnet as the
primary IP address above.
Apply Click Apply to save your changes back to the Prestige.
3.4 Ethernet Client Filter
Use the Ethernet Client Filter screen to set the Prestige to allow or block specified Ethernet
devices from accessing the LAN.
Click LAN and Ethernet Client Filter in the navigation panel to display the configuration
screen.
Chapter 3 LAN 40

Prestige 794M User’s Guide
Figure 21 LAN: Ethernet Client Filter
The following table describes the labels in this screen.
Table 14 LAN: Ethernet Client Filter
LABEL DESCRIPTION
Ethernet Client
Filter
MAC Address List Specify the computer(s) which you want to allow or deny network access. Enter
Apply Click Apply to save the settings.
Select Disable to deactivate this feature. This allows any computer to access the
network through the Prestige.
Select Allowed to set the Prestige to permit the specified computers to access the
network.
Select Blocked to set the Prestige to deny the specified computers from
accessing the network.
the MAC address of a computer in hexadecimal notation.
Click Candidates to add one or more MAC addresses of the devices that are
currently connected to the Prestige.
3.4.1 Ethernet Client Filter Candidates
You can display a list of MAC address of the devices that are currently connected to the
Prestige. You can use the Active PC in LAN screen to add the selected MAC address(es) to the
Ethernet Client Filter screen.
In the Ethernet Client Filter screen, click Candidates to display the screen.
Figure 22 LAN: Ethernet Client Filter: Active PC in LAN
41 Chapter 3 LAN

The following table describes the labels in this screen.
Table 15 LAN: Ethernet Client Filter: Active PC in LAN
LABEL DESCRIPTION
IP Address This field displays the IP address of an Ethernet device connected to the Prestige.
MAC Address This field displays the MAC address associated with the IP address in the IP
Add Click Add to add the select entry(ies) in the Ethernet Client Filter screen.
3.5 Port Setting
Use the Port Setting screen to configure the LAN port settings on the Prestige. Click
Configuration, LAN and Port Setting to display the screen as shown next.
Figure 23 LAN: Port Setting
Prestige 794M User’s Guide
Address field.
The following table describes the labels in this screen.
Table 16 LAN: Port Setting
LABEL DESCRIPTION
Port 1 .. 4
Connection
Type
IPv4 TOS
Priority Control
Select the speed and the duplex mode of the Ethernet connection on this port.
Choices are Auto, 10Mfalfduplex, 10Mfullduplex, 100Mhalfduplex and
100Mfullduplex.
Selecting Auto (auto-negotiation) allows one port to negotiate with a peer port
automatically to obtain the connection speed and duplex mode that both ends support.
When auto-negotiation is turned on, a port on the Prestige negotiates with the peer
automatically to determine the connection speed and duplex mode. If the peer port
does not support auto-negotiation or turns off this feature, the Prestige determines the
connection speed by detecting the signal on the cable and using half duplex mode.
When the Prestige’s auto-negotiation is turned off, a port uses the pre-configured
speed and duplex mode when making a connection, thus requiring you to make sure
that the settings of the peer port are the same in order to connect.
Select Enable to set the Prestige to send traffic based on the priority level.
Select Disable to set the Prestige to treat all traffic equally.
Chapter 3 LAN 42

Prestige 794M User’s Guide
Table 16 LAN: Port Setting (continued)
LABEL DESCRIPTION
Set High
Priority TOS
Apply Click Apply to save your changes.
3.6 DHCP
DHCP (Dynamic Host Configuration Protocol, RFC 2131 and RFC 2132) allows individual
clients to obtain TCP/IP configuration at start-up from a server. You can configure the Prestige
as a DHCP server or disable it. When configured as a server, the Prestige provides the TCP/IP
configuration for the clients. If DHCP service is disabled, you must have another DHCP server
on your LAN, or else the computer must be manually configured.
3.6.1 IP Pool Setup
When you set the Prestige as a DHCP server, you can use the default DHCP client IP address
pool setting. The default address pool has 20 IP addresses starting from 192.168.1.2 to
192.168.1.21. This configuration leaves the other IP addresses for other server computers, for
instance, servers for mail, FTP, TFTP, web, etc., that you may have.
This field is applicable when you enable TOS priority control.
IEEE 802.1p defines up to 8 separate traffic types by inserting a tag into a MAC-layer
frame that contains bits to define class of service. Frames without an explicit priority
tag are given the default priority of the ingress (incoming) port.
Select the high priority level(s). The Prestige will first send packets with matching
priority level(s).
3.6.2 DNS Servers
There are two places where you can configure DNS setup on the Prestige.
1 Use the WAN DNS screen to configure the Prestige to use a DNS server to resolve
domain names for Prestige system features like VPN, DDNS and the time server.
2 Use the LAN DHCP Server screen to configure the DNS server information that the
Prestige sends to the DHCP client devices on the LAN.
3.6.3 DHCP Setup
To configure DHCP settings on the LAN, click Configuration, LAN and DHCP Server to
display the screen as shown.
43 Chapter 3 LAN

Figure 24 LAN: DHCP Server
The following table describes the labels in this screen.
Table 17 LAN: DHCP Server
LABEL DESCRIPTION
Configuration
DHCP Server
Mode
Next Click Next to continue.
Select Disable to disable DHCP on the LAN.
Select DHCP Server to set the Prestige as a DHCP server.
Select DHCP Relay Agent to set the Prestige to act as a DHCP relay agent.
Prestige 794M User’s Guide
3.6.3.1 Disable DHCP
Follow the steps below to disable DHCP server/relay on the LAN.
1 In the DHCP Server screen (see Figure 24 on page 44), select Disable and click Next.
2 A screen displays as shown next. Click Apply.
Figure 25 LAN: DHCP Server: Disable
3.6.3.2 DHCP Server Setup
To set the Prestige as a DHCP server, select DHCP Server and click Next in the DHCP
Server screen. A screen displays as shown next.
Chapter 3 LAN 44

Prestige 794M User’s Guide
Figure 26 LAN: DHCP Server: DHCP
The follow table describes the labels in this screen.
Table 18 LAN: DHCP Server: DHCP
LABEL DESCRIPTION
DHCP Server
Allow Bootp Select Enable to allow BootP (Bootstrap Protocol) clients. Otherwise, select
Disable.
Allow Unknown
Clients
Use Default
Range
Starting IP
Address
Ending IP
Address
Default Lease
Time
Maximum Lease
Time
Use Router as
DNS Server
Primary/
Secondary DNS
Server
Use Router as
Default Gateway
Apply Click Apply to save your changes back to the Prestige.
Select Enable to assign network settings (such as IP address) to any client
computer.
Select Disable to assign network settings (such as IP address) to the client(s) you
specify in the Fixed Host screen.
Select this check box to use the default client IP address pool.
The default address pool has 20 IP addresses starting from 192.168.1.2 to
192.168.1.21.
This field specifies the first of the contiguous addresses in the IP address pool.
This field specifies the last of the contiguous addresses in the IP address pool.
Specify the default time (in seconds) a client is allowed to use the assigned IP
address.
Specify the maximum time (in seconds) a client is allowed to use the assigned IP
address.
Select this check box to use the Prestige as the default DNS server. The Prestige
performs the domain name lookup and forwards the mapping information to the
requesting client.
This field is applicable when the Use Router as DNS Server check box is not
selected.
Enter the IP address of the DNS server in dotted decimal notation.
Select this check box to use the Prestige as a default gateway for the client
computer(s) on the LAN.
45 Chapter 3 LAN

Table 18 LAN: DHCP Server: DHCP (continued)
LABEL DESCRIPTION
Reset Click Reset to start configuring this screen again.
Fixed Host Click Fixed Host to display a screen where you can assign a static LAN IP address
3.6.3.2.1 Fixed Host
You can set the Prestige to assign one IP address on the LAN to a specific computer based on
the MAC address. In the DHCP screen (see
display the screen as shown next.
Figure 27 LAN: DHCP Server: DHCP: Fixed Host
Prestige 794M User’s Guide
to the specified device MAC address.
Figure 26 on page 45), click Fixed Host to
The following table describes the labels in this screen.
Table 19 LAN: DHCP Server: DHCP: Fixed Host
LABEL DESCRIPTION
Name Enter a descriptive name for identification purposes.
IP Address Type the IP address that you want to assign to the computer on your LAN.
Alternatively, click the right mouse button to copy and/or paste the IP address.
MAC Address Type the MAC address of a computer on your LAN.
Maximum
Lease Time
Specify the maximum time (in seconds) the client is allowed to use the assigned IP
address.
Note: If you do not specify the lease time here, the Prestige uses the
global lease time setting in the DHCP screen (see
page 45).
Apply Click Apply to save your changes back to the Prestige.
3.6.4 DHCP Relay Agent
If there is an Ethernet device that performs the DHCP server function for your network, then
you can configure the Prestige as a DHCP relay agent. When the switch receives a request
from a computer on your network, it contacts the Ethernet device (the DHCP server) for the
necessary IP information, and then relays the assigned information back to the computer.
Figure 26 on
Chapter 3 LAN 46

Prestige 794M User’s Guide
In the main DHCP Server screen, select DHCP Relay and click Next to display the
configuration screen.
Figure 28 LAN: DHCP Server: DHCP Relay Agent
The following table describes the labels in this screen.
Table 20 LAN: DHCP Server: DHCP Relay Agent
LABEL DESCRIPTION
DHCP Server IP
Address
Apply Click Apply to save the settings and return to the previous screen.
Enter the IP address of the DHCP server on the LAN.
47 Chapter 3 LAN

This chapter describes how to configure WAN settings.
4.1 Overview
A WAN (Wide Area Network) is an outside connection to another network or the Internet. Use
the WAN screens to change your Prestige's WAN settings, click Configuration and WAN in
the navigation panel.
4.1.1 Encapsulation Types
This section describes the various encapsulation (Internet connection) types the Prestige
offers.
Prestige 794M User’s Guide
CHAPTER 4
WAN
4.1.1.1 RFC 1483
RFC 1483 describes two methods for Multiprotocol Encapsulation over ATM Adaptation
Layer 5 (AAL5). The first method allows multiplexing of multiple protocols over a single
ATM virtual circuit (LLC-based multiplexing) and the second method assumes that each
protocol is carried over a separate ATM virtual circuit (VC-based multiplexing). Please refer
to the RFC for more detailed information.
In addition, the Prestige supports two RFC 1483 methods; routed or bridged. In RFC 1483
Bridged, the Prestige sends the packets based on the MAC address information. That is, the
Prestige bridges the packets. In RFC 1483 Routed, the Prestige sends the packets based on the
IP address. That is, the Prestige routes the packets. Refer to the RFC for more information.
4.1.1.2 PPPoE
The Prestige supports PPPoE (Point-to-Point Protocol over Ethernet). PPPoE is an IETF Draft
standard (RFC 2516) specifying how a computer interacts with a broadband modem (DSL,
cable, wireless, etc.) connection. PPPoE is for a dial-up connection using PPPoE. For the
service provider, PPPoE offers an access and authentication method that works with existing
access control systems (for example RADIUS). PPPoE provides a login and authentication
method that the existing Microsoft Dial-Up Networking software can activate, nd therefore
requires no new learning or procedures for Windows users. One of the benefits of PPPoE is the
ability to let you access one of multiple network services, a function known as dynamic
service selection. This enables the service provider to easily create and offer new IP services
for individuals.
Chapter 4 WAN 48

Prestige 794M User’s Guide
Operationally, PPPoE saves significant effort for both you and the ISP or carrier, as it requires
no specific configuration of the broadband modem at the customer site. By implementing
PPPoE directly on the Prestige (rather than individual computers), the computers on the LAN
do not need PPPoE software installed, since the Prestige does that part of the task.
Furthermore, with NAT, all of the LAN computers will have access.
4.1.1.3 PPPoA
PPPoA stands for Point to Point Protocol over ATM Adaptation Layer 5 (AAL5). A PPPoA
connection functions like a dial-up Internet connection. The Prestige encapsulates the PPP
session based on RFC1483 and sends it through an ATM PVC (Permanent Virtual Circuit) to
the Internet Service Provider’s (ISP) DSLAM (digital access multiplexer). Please refer to RFC
2364 for more information on PPPoA. Refer to RFC 1661 for more information on PPP.
4.1.1.4 IPoA
With IPoA (IP over ATM), the Prestige attempts to map the IP subnet onto the ATM network.
4.2 ISP
Use the ISP screens to configure the Prestige for Internet access. The screen differs by the
encapsulation.
Figure 29 WAN: ISP
The following table describes the labels in this screen.
Table 21 WAN: ISP
LABEL DESCRIPTION
Name This field displays the descriptive name of this Internet access setting for
identification purposes.
Encapsulation This field displays the connection type.
Creator This field indicates how this Internet access setting is created.
VPI This field displays the VPI (Virtual Path Identifier) number.
VCI This field displays the VCI (Virtual Circuit Identifier) number.
Edit Click Edit to change the Internet access settings. The configuration screen varies
depending on the encapsulation (or connection type).
Change Click Change to select a different encapsulation and change the settings.
49 Chapter 4 WAN

4.2.1 Edit Settings
Click Edit in the main ISP screen to modify the settings. The configuration screen varies
depending on the encapsulation type.
Figure 30 WAN: ISP: Edit
Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 22 WAN: ISP: Edit (PPPoE)
LABEL DESCRIPTION
Description This read-only field displays the encapsulation type.
VPI The valid range for the VPI is 0 to 255. Enter the VPI assigned to you.
VCI The valid range for the VCI is 32 to 65535 (0 to 31 is reserved for local
management of ATM traffic). Enter the VCI assigned to you.
ATM Class Select CBR (Continuous Bit Rate) to specify fixed (always-on) bandwidth for voice
Encapsulation
Method
Ether Filter Type Specify what kind of Ethernet packets the Prestige allows through the WAN
or data traffic.
Select UBR (Unspecified Bit Rate) for applications that are non-time sensitive,
such as e-mail.
Select UBRPlus for non-real-time applications (such as e-mail). However,
UBRPlus guarantees service at least the MCR (Maximum Cell Rate).
Select VBR (Variable Bit Rate) for bursty traffic and bandwidth sharing with other
applications. Select VBR-rt (Variable Bit Rate - Real Time) for bursty traffic that is
intolerable of delays.
This information is provided by your ISP. Select the encapsulation method your
ISP uses.
connection.
Select All to allow all Ethernet packet types.
Select Ip to allow only IP or ARP related Ethernet packets to pass through.
Select Pppoe to allow only PPPoE Ethernet packets to pass through.
Chapter 4 WAN 50

Prestige 794M User’s Guide
Table 22 WAN: ISP: Edit (PPPoE) (continued)
LABEL DESCRIPTION
Spanning Bridge
Interface
NAT Select Enable to activate NAT (Network Address Translation) to allow more than
Username This field is applicable for PPPoA or PPPoE only.
Password This field is applicable for PPPoA or PPPoE only.
Service Name This field is applicable for PPPoE only.
IP Address This field is applicable for PPPoA and PPPoE only.
Authentication
Protocol
Connection Select Always On when you want your connection up all the time. The Prestige
Idle Timeout Specify an idle time-out (in minutes) when you select Connect on Demand in the
RIP The RIP field controls the format and the broadcasting method of the RIP packets
MTU Specify the MTU (Maximum Transmission Unit) in this field.
Apply Click Apply to save the settings and return to the main ISP screen.
Advanced Options Click Advanced Options to configure advanced PPPoE settings.
Select Enable to activate spanning tree feature on the WAN interface.
Select Disable to deactivate this feature.
one computer to access the Internet through the Prestige.
Otherwise, select Disable. In this case, only one computer can access the Internet
from the LAN.
Enter the user name exactly as your ISP assigned. If assigned a name in the form
user@domain where domain identifies a service name, then enter both
components exactly as given.
Enter the password associated with the user name above.
Type the name of your PPPoE service here.
Enter a static public IP address (in dotted decimal notation) provided by your ISP.
Leave this field as 0.0.0.0 to set the Prestige to obtain an IP address (and other
TCP/IP information) from the ISP every time.
Select an authentication type your ISP uses. Choices are CHAP and PAP.
Select None if no authentication is required.
will try to bring up the connection automatically if it is disconnected.
Select Connect on Demand when you don't want the connection up all the time
and specify an idle time-out in the Idle Timeout field.
Connection field.
The default setting is 0, which means the Internet session will not timeout.
that the Prestige sends (it recognizes both formats when receiving).
Select RIP v1 if you are unsure what RIP version other Ethernet device(s)
supports. RIP v1 is universally supported.
Select RIP v2 to send detailed routing data.
Select RIP v2 Multicast to set the Prestige to send routing data in RIP-2 format
using multicasting.
Refer to Section 3.2.2 on page 38 for more information.
4.2.1.1 Advanced PPP Options
For PPPoA or PPPoE connection type, you can configure advanced PPP settings in the
Advanced Options screen.
In the WAN Connection screen, click Advanced Options to display the screen shown next.
51 Chapter 4 WAN

Figure 31 WAN: Edit: Advanced PPP Options
The following table describes the labels in his screen.
Prestige 794M User’s Guide
Table 23 WAN: Edit: Advanced PPP Options
LABEL DESCRIPTION
LLC Header Specify an encapsulation mode in this field. Select true for LLC or false for VC.
Create Route Specify whether the Prestige is to add a route after IPCP (Internet Protocol Control
Specific Route Specify whether the route created (after a successful PPP connection) is a default
Subnet Mask Specify the subnet mask for PPP connection. If you enter 0.0.0.0, the Prestige
Route Mask Specify the subnet mask the route (after a successful PPP connection) uses. If you
MRU This field is optional. Enter the MRU (Maximum Receive Unit) if your ISP provides
Discover Primary/
Secondary DNS
Give DNS to Relay Enable this feature to set the Prestige to provide DNS server information to DNS
Give DNS to Client Enable this feature to set Prestige to provide DNS server information to a remote
Protocol) negotiation is completed.
Select true to add a route to direct packets to the remote end of the PPP link.
Otherwise, select false to disable auto-route creation.
or specific route.
Select true to set the created route for packets between the Prestige and the
remote network. The address of this subnet is obtained during the connection
negotiation.
Select false to set the route as a default route for all packets.
calculates the subnet mask from the IP address obtained during connection
negotiation.
enter 0.0.0.0, the subnet mask is determined by the IP address of the remote end.
The IP address is obtained during connection negotiation.
the information. The MRU is automatically obtained during the LCP protocol stage.
Enable this feature to allow the Prestige to automatically obtain the DNS server IP
address(es) from the ISP. Otherwise, select false.
request from a local computer.
PPP peer device.
Chapter 4 WAN 52

Prestige 794M User’s Guide
Table 23 WAN: Edit: Advanced PPP Options (continued)
LABEL DESCRIPTION
Give DNS to
DHCP Server.
Discover Primary/
Secondary NBNS.
Discover Subnet
Mask
Give Subnet Mask
to DHCP Server
Apply Click Apply to save the changes.
Reset Click Reset to start configuring this screen again.
Enable this feature to set the Prestige to provide DNS server information to a
DHCP server.
Enable this feature to set the Prestige to request NBNS (NetBIOS Name Server)
server information from the remote PPP peer device.
An NBNS server (also known as a WINS server) maps a NetBIOS name to an IP
address.
Enable this feature to set the Prestige to use the subnet mask obtained after the
Internet connection is established.
Enable this feature to set the Prestige to provide the subnet mask information to
the DHCP server. The subnet mask is obtained during the connection negotiation.
4.2.2 Change Connection Type
Follow the steps below to change your Internet connection type and settings.
1 Click Change in the main ISP screen (see Figure 29 on page 49).
2 A screen displays as shown. Select the connection type your ISP uses and click Next.
Click Quick Start to configure the line settings in the Quick Start screen (refer to
Section 2.7.4 on page 33 for more information).
Figure 32 ISP: Change Connection Type
3 A configuration screen displays. This screen varies depending on the connection type you
select. Refer to
Section 4.2 on page 49 for more information.
53 Chapter 4 WAN

Prestige 794M User’s Guide
Figure 33 ISP: Change Connection Type Settings (RFC 1483 Routed)
4 Click Apply to save the changes and return to the main ISP screen.
4.3 DNS
Use DNS (Domain Name System) to map a domain name to its corresponding IP address and
vice versa, for instance, the IP address of www.zyxel.com is 204.217.0.2. The DNS server is
extremely important because without it, you must know the IP address of a computer before
you can access it.
The Prestige can get the DNS server addresses in the following ways.
Use the DNS screen to specify the DNS server IP address(es) provided by your ISP.
1 The ISP tells you the DNS server addresses, usually in the form of an information sheet,
when you sign up. If your ISP gives you DNS server addresses, manually enter them in
the DNS server fields.
2 If your ISP dynamically assigns the DNS server IP addresses (along with the Prestige’s
WAN IP address), set the DNS server fields to get the DNS server address from the ISP.
3 You can manually enter the IP addresses of other DNS servers. These servers can be
public or private. A DNS server could even be behind a remote IPSec router.
Chapter 4 WAN 54

Prestige 794M User’s Guide
Figure 34 DNS
The following table describes the labels in this screen.
Table 24 DNS
LABEL DESCRIPTION
Primary/
Secondary DNS
Apply Click Apply to save the settings.
Cancel Click Cancel to discard all changes.
Enter the DNS server IP address(es) in dotted decimal notation. For example,
192.168.1.1.
4.4 SHDSL Parameters
Use the SHDSL screen to configure advanced SHDSL settings. Click Configuration, WA N
and SHDSL in the navigation panel to display the screen as shown next.
Figure 35 SHDSL
The following table describes the labels in this screen.
55 Chapter 4 WAN

Prestige 794M User’s Guide
Table 25 SHDSL
LABEL DESCRIPTION
4 Wire Connection Select Enable to activate 4-wire connection. The 4-wire mode is described in ITU-
T G.991.2. 4-wire mode can increase the reach of a particular data rate without
having to regenerate the signal. It can also give increased bandwidth for LAN-toLAN applications.
Otherwise, select Disable.
Mode Select CPE (Customer Premises Equipment) if the Prestige is connected to the
ISP. This is the default setting.
To connect the Prestige to another SHDSL router, select CO (Central Office) here
and set the remote SHDSL router to CPE mode. Or vise versa if you select CPE
on the Prestige.
Annex Type Select a DSL operating mode.
Annex_A (default) is mostly used in North America, whereas Annex_B is more
widespread in Europe.
Annex_A_B, Annex_A_B_ANFP (Access Network Frequency Plan) and
Annex_B_ANFP are automatically selected when the DSL line is in training state.
These options are not available in CO mode.
Note: For LAN-LAN connection, make sure the annex type is the
same on Prestige and the remote SHDSL router.
Bit Rate Mode Specify the bit rate. Choices are fixed or adaptive.
Fix Bit Rate This field is applicable when you select Fixed in the Bit Rate Mode field.
Select a fixed transfer rate for the DSL line from the drop-down list box.
Activate Line Select false to disable SHDSL connection.
Select true to enable SHDSL connection.
Note: After you change the SHDSL line settings here, you must
disable and enable the SHDSL line again to make the
changes take effect.
DSP
FirmwareVersion
Connected This field displays current SHDSL connection status.
Stat e This field displays current SHDSL connection state.
Bit Rate This field displays the connection speed.
Apply Click Apply to save the changes.
Cancel Click Cancel to discard all changes.
This read-only field displays the SHDSL line code firmware version.
Chapter 4 WAN 56

Prestige 794M User’s Guide
57 Chapter 4 WAN

This chapter describes the System screens.
5.1 Overview
Use the System screens to configure the time server and user account settings, upgrade
firmware and backup/restore configuration on the Prestige.
5.2 Time Zone
To change your Prestige’s time and date, click Configuration, System and Time Server in
the navigation panel. The screen appears as shown. Use this screen to configure the Prestige’s
time based on your local time zone.
Prestige 794M User’s Guide
CHAPTER 5
System
The world map and the v indicator shows the current time zone you select.
Figure 36 System: Time Zone
The following table describes the labels in this screen.
Chapter 5 System 58

Prestige 794M User’s Guide
Table 26 System: Time Zone
LABEL DESCRIPTION
Time Zone Select Enable to use the time zone settings to set your Prestige system time.
Time Zone List Specify the order of the Local Time Zone list is to be displayed.
Local Time Zone
(GMT Time)
SNTP Server IP
Address
Daylight Saving This field is available when you select By City in the Time Zone List field.
Resync Period Specify the time period (in minutes) the Prestige waits before updating the system
Apply Click Apply to save the settings.
Cancel Click Cancel to discard all changes.
Select Disable to deactivate this feature.
Select By City to display the list alphabetically based on the cities for each time
zone.
Select By Time Different to display the list in ascending order.
Select a time zone from the drop-down list box.
Note that world map indicates the current time zone you select.
Enter the IP address or URL of your time server. Check with your ISP/network
administrator if you are unsure of this information.
Daylight saving is a period from late spring to early fall when many countries set
their clocks ahead of normal local time by one hour to give more daytime light in
the evening.
Select Automatic if you use daylight savings time.
time with the time server specified.
5.3 Remote Access
Use the Remote Access screen to the session time limit a user is allowed to remotely access
the Prestige for management. After the time period is reached, the Prestige automatically
disconnects a management session. In this case, you need to log in again with the login
username and password.
Click Configuration, System and Remote Access to display the screen as shown.
Figure 37 System: Remote Access
Enter a time period (in minutes) in the Allow Access field. Enter a time period of 0 to not time
out a management session. Then click Enable.
59 Chapter 5 System

5.4 Firmware Upgrade
Find firmware at www.zyxel.com in a file that (usually) uses the system model name with a
“.bin” extension, e.g., "prestige.bin". The upload process may take up to two minutes. After a
successful upload, the system will reboot.
1 Click Configuration, System and Firmware Upgrade in the navigation panel to display
the screen as shown.
Figure 38 System: Firmware Upgrade
2 Click Browse... to find the firmware file you want to upload. Remember that you must
decompress compressed (.zip) files before you can upload them.
3 Click Upload to begin the upload process. A screen displays showing the firmware
upgrade progress.
Prestige 794M User’s Guide
Note: Do NOT turn off the Prestige while firmware upload is in progress!
Figure 39 System: Firmware Upgrade: Progress
4 After the Prestige successfully upgrades the firmware, a screen displays. Select Current
Settings to keep current Prestige settings. Select Factory Default Settings to reset the
Prestige to the factory defaults.
Figure 40 System: Firmware Upgrade: Device Configuration Option
5 Click Restart to reboot the Prestige. Wait for about one minute before accessing the
Prestige again.
5.5 Backup/Restore
Use the Backup/Restore screen for configuration file maintenance. Click Configuration,
System and Backup/Restore in the navigation panel.
Chapter 5 System 60

Prestige 794M User’s Guide
Figure 41 System: Configuration Backup/Restore
Backup configuration allows you to back up (or save) the Prestige’s current configuration to a
file on your computer. Once your Prestige is configured and functioning properly, it is highly
recommended that you back up your configuration file before making configuration changes.
The backup configuration file will be useful in case you need to return to your previous
settings.
Click Backup to save the Prestige’s current configuration to your computer.
Restore configuration allows you to upload a new or previously saved configuration file from
your computer to your Prestige.
Click Browse... to find the file you want to upload. Click Restore to begin the upload process.
Note: Restore only the configuration file that you have previously backed up using the
Backup/Restore screen.
Do NOT manually edit the configuration file.
5.6 Restart Router
The Restart Router screen allows you to reboot the Prestige without turning the power off.
Click Configuration, System and Restart in the navigation panel to display the screen as
shown below.
Figure 42 System: Restart
In the Restart Router with field, select Current Settings and click Restart to reboot the
Prestige with the current settings.
61 Chapter 5 System

Note: All unsaved configuration settings will be lost.
Select Factory Default Settings and click Restart to reboot and reset the Prestige to the
factory default.
Note: All custom settings will be lost.
5.7 User Management
Use the User Management screen to maintain login accounts.
Figure 43 System: User Management
Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 27 System: User Management
LABEL DESCRIPTION
Valid This field indicates whether the account is activated (true) or not (false).
User This field displays the account username.
Comment This field displays additional information about the login account.
Edit Click Edit to change the settings of a login account. Refer to Table 28 on page 63 for field
Delete Click Delete to remove an account from the table.
descriptions.
Note: You cannot delete the account with the “admin” username.
Create Click Create to add a new login account.
5.7.1 Create a New User Account
To add a new user account, click Create in the User Management screen. A screen displays
as shown.
Chapter 5 System 62

Prestige 794M User’s Guide
Figure 44 System: User Management: Edit Account
The following table describes the labels in this screen.
Table 28 System: User Management: Edit Account
LABEL DESCRIPTION
Username Enter an account username.
Password Enter a password associated to the username above.
Confirm Enter the password again for confirmation.
Val id Select true to activate this account. Otherwise, select false to disable it.
Comment Enter additional information about this account.
Create Click Create to add this new account and return to the main User Management
Reset Click Reset to start configuring this screen again.
screen.
63 Chapter 5 System

This chapter gives some background information on firewalls.
6.1 Overview
Originally, the term firewall referred to a construction technique designed to prevent the
spread of fire from one room to another. The networking term firewall is a system or group of
systems that enforces an access-control policy between two networks. It may also be defined
as a mechanism used to protect a trusted network from an untrusted network. Of course,
firewalls cannot solve every security problem. A firewall is one of the mechanisms used to
establish a network security perimeter in support of a network security policy. It should never
be the only mechanism or method employed. For a firewall to guard effectively, you must
design and deploy it appropriately. This requires integrating the firewall into a broad
information-security policy. In addition, specific policies must be implemented within the
firewall itself.
Prestige 794M User’s Guide
CHAPTER 6
Firewall
6.2 Types of Firewalls
There are three main types of firewalls:
1 Packet Filtering Firewalls
2 Application-level Firewalls
3 Stateful Inspection Firewalls
6.2.1 Packet Filtering Firewalls
Packet filtering firewalls restrict access based on the source/destination computer network
address of a packet and the type of application.
6.2.2 Application-level Firewalls
Application-level firewalls restrict access by serving as proxies for external servers. Since they
use programs written for specific Internet services, such as HTTP, FTP and telnet, they can
evaluate network packets for valid application-specific data. Application-level gateways have
a number of general advantages over the default mode of permitting application traffic directly
to internal hosts:
Chapter 6 Firewall 64

Prestige 794M User’s Guide
1 Information hiding prevents the names of internal systems from being made known via
DNS to outside systems, since the application gateway is the only host whose name must
be made known to outside systems.
2 Robust authentication and logging pre-authenticates application traffic before it reaches
internal hosts and causes it to be logged more effectively than if it were logged with
standard host logging. Filtering rules at the packet filtering router can be less complex
than they would be if the router needed to filter application traffic and direct it to a
number of specific systems. The router need only allow application traffic destined for
the application gateway and reject the rest.
6.2.3 Stateful Inspection Firewalls
Stateful inspection firewalls restrict access by screening data packets against defined access
rules. They make access control decisions based on IP address and protocol. They also
"inspect" the session data to assure the integrity of the connection and to adapt to dynamic
protocols. These firewalls generally provide the best speed and transparency; however, they
may lack the granular application level access control or caching that some proxies support.
Firewalls, of one type or another, have become an integral part of standard security solutions
for enterprises.
Your Prestige includes a full SPI (Stateful Packet Inspection) firewall for controlling Internet
access from your LAN, as well as helping to prevent attacks from hackers. In addition to this,
when using NAT (Network Address Translation), the Prestige acts as a “natural” Internet
firewall, as all computers on your LAN will use private IP addresses that cannot be directly
accessed from the Internet.
The following lists the different security features on the Prestige:
• Firewall: This prevents access from outside your network. The router provides three
levels of security support:
• NAT: This masks the IP addresses of the computers on the LAN invisible to the WAN.
This makes it much more difficult for a hacker to target a machine on your network.
• Firewall Security and Policy (General Settings): Inbound direction of packet filter
rules to block unauthorized computers or applications access to your local network from
the Internet.
• Intrusion Detection: Enable this feature to detect, prevent and log malicious attacks.
• Access Control: Prevents specified local computers from accessing your local network:
• Firewall Security and Policy (General Settings): Outbound direction of packet filter
rules to block unauthorized computers or applications access from the Internet.
• MAC Filter rules: To prevent unauthorized computers from accessing the network
through the Prestige.
• URL Filter: To block computers on your local network from accessing specific web
sites.
65 Chapter 6 Firewall

6.3 General Settings
Enable the firewall in the General Settings screen. Click Configuration, Firewall and
General Settings in the navigation panel to display the screen as shown.
Figure 45 Firewall: General Settings
Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 29 Firewall: General Settings
LABEL DESCRIPTION
Security Select Enable to activate firewall on the Prestige.
Select Disable to deactivate firewall on the Prestige.
Policy The options are applicable when you select Enable in the Security field.
Select All blocked/User-defined to block all out-going (LAN to Internet) and
incoming packets (Internet to LAN) based on the firewall filters you configure. By
default, there is no custom filters.
Select High security level, Medium security level (default) or Low security
level to block packets based on the pre-defined firewall filters. Refer to
on page 67 for more information.
Block WAN
Request
Apply Click Apply to save the settings.
Select Enable to set the Prestige not to respond to any incoming Ping requests.
Select Disable to deactivate this feature. THe Prestige will respond to all Ping
requests.
Table 30
Chapter 6 Firewall 66

Prestige 794M User’s Guide
The following table lists inbound (Internet to LAN) and outbound (LAN to Internet) traffic
that is allowed or not allowed for the pre-defined port filters. The Prestige uses the pre-defined
port filters when you select a security level in the General Settings screen.
Table 30 Pre-defined Port Filter
PORT
APPLICATION PROTOCOL
HTTP(80) TCP(6) 80 80 NO YES NO YES NO YES
DNS (53) UDP(17) 53 53 NO YES NO YES YES YES
DNS (53) TCP(6) 53 53 NO YES NO YES YES YES
FTP(21) TCP(6) 21 21 NO NO NO YES NO YES
Telnet(23) TCP(6) 23 23 NO NO NO YES NO YES
SMTP(25) TCP(6) 25 25 NO YES NO YES NO YES
POP3(110) TCP(6) 11 0 11 0 NO YES NO YES NO YES
NEWS(119) TCP(6) 119 11 9 NO NO NO YES NO YES
RealAudio
(7070)
PING ICMP(1) N/A N/A NO YES NO YES NO YES
UDP(17) 7070 7070 NO NO YES YES YES YES
NUMBER
START END INBOUND OUTBOUND INBOUND OUTBOUND INBOUND OUTBOUND
FIREWALL
HIGH MEDIUM LOW
H.323(1720) TCP(6) 1720 1720 NO NO NO YES YES YES
T.120(1503) TCP(6) 1503 1503 NO NO NO YES YES YES
SSH(22) TCP(6) 22 22 NO NO NO YES YES YES
NTP(123) UDP(17) 123 123 NO YES NO YES NO YES
HTTPS(443) TCP(6) 443 443 NO NO NO YES NO YES
ICQ (5190) TCP(6) 5190 5190 NO NO NO NO YES YES
6.4 Packet Filter
The packet filters are applicable when the firewall is enabled in the General Settings screen.
Use the Packet Filter screen to configure port and address filters. Click Configuration,
Firewall and Packet Filters.
67 Chapter 6 Firewall

Prestige 794M User’s Guide
The Prestige comes with pre-configured packet filters as shown in the screen. These filters are
for the Policy security levels in the Firewall: General Settings screen (refer to
Section 6.3 on
page 66). You can modify or delete the pre-configured packet filters.
Figure 46 Firewall: Packet Filter
The following table describes the labels in this screen.
Table 31 Firewall: Packet Filter
LABEL DESCRIPTION
Add TCP/UDP
Filter
Add Raw IP Filter Click Add Raw IP Filter to configure a new IP packet filter.
Chapter 6 Firewall 68
Click Add TCP/UDP Filter to configure a new TCP/UFDP packet filter.

Prestige 794M User’s Guide
Table 31 Firewall: Packet Filter (continued)
LABEL DESCRIPTION
Packet Filter Rules
Rule Name This field displays the descriptive name for a rule.
Time Schedule This field displays the time when this rule is active.
Source IP/
Netmask
Destination IP/
Netmask
Protocol This field displays the protocol name.
Source Port This field displays the source port number or port number range.
Destination Port This field displays the destination port number or port number range.
Inbound This field displays whether the incoming packets are forwarded (Allow) or dropped
Outbound This field displays whether the outgoing packets are forwarded (Allow) or dropped
Edit Click Edit to modify the settings of the selected filter.
Delete Click Delete to remove the selected filter.
This field displays the source IP address and subnet mask.
This field displays the destination IP address and subnet mask
(Block).
(Block).
6.4.1 Add a New TCP/UDP Packet Filter
To add a new TCP/UDP packet filter, click Add TCP/UDP Filter in the Packet FIlter screen.
Figure 47 Firewall: Packet Filters: Add TCP/UDP Filter
The following table describes the labels in this screen.
Table 32 Firewall: Packet Filters: Add TCP/UDP Filter
LABEL DESCRIPTION
Rule Name Enter a descriptive name for identification purposes.
Time Schedule Specify the time in which this filter is active. Select Always On to activate the rule
all the time. Otherwise select a time you configure in the Time Schedule screen.
69 Chapter 6 Firewall

Table 32 Firewall: Packet Filters: Add TCP/UDP Filter (continued)
LABEL DESCRIPTION
Prestige 794M User’s Guide
Source IP
Address(es)
Destination IP
Address(es)
Type Select the packet type to filter. Choices are TCP and UDP.
Source Port Specify the source port or a range of source port numbers in the fields provided.
Destination Port Specify the destination port or a range of destination port numbers in the fields
Inbound/Outbound Specify whether to deny (Block) or allow (Allow) incoming (from the Internet) or
Apply Click Apply to save the settings and return to the main Packet Filter screen.
Return Click Return to discard all changes and go back to the main Packet Filter screen.
Enter the start source IP address in dotted decimal notation. For example,
192.168.1.10.
In the Netmask field, enter the source subnet mask address in dotted decimal
notation. For example, 255.255.255.0.
Enter the end source IP address in dotted decimal notation. Enter the same source
IP address here if you want to filter packets to or from an IP address. For example,
192.168.1.10.
In the Netmask field, enter the destination subnet mask in dotted decimal notation.
For example, 255.255.255.0.
provided.
out-going (to the Internet) traffic.
6.4.2 Add a New Raw Packet Filter
To add a new raw packet filter, click Add Raw Filter in the Packet Filters screen.
Figure 48 Firewall: Packet Filters: Add Raw Filter
The following table describes the labels in this screen.
Table 33 Firewall: Packet Filters: Add Raw Filter
LABEL DESCRIPTION
Rule Name Enter a descriptive name for identification purposes.
Time Schedule Specify the time in which this filter is active. Select Always On to activate the rule
all the time. Otherwise select a time you configure in the Time Schedule screen.
Protocol Number Enter a protocol number.
Inbound/Outbound Specify whether to deny (Block) or allow (Allow) incoming (from the Internet) or
out-going (to the Internet) traffic.
Chapter 6 Firewall 70

Prestige 794M User’s Guide
Table 33 Firewall: Packet Filters: Add Raw Filter (continued)
LABEL DESCRIPTION
Apply Click Apply to save the settings and return to the main Packet Filter screen.
Return Click Return to discard all changes and go back to the main Packet Filter screen.
6.5 Intrusion Detection
The Prestige’s Intrusion Detection System (IDS) is used to detect hacker attacks and intrusion
attempts from the Internet. When you enable IDS on the Prestige, inbound packets are filtered
and blocked depending on whether they are detected as possible hacker attacks, intrusion
attempts or other connections that the router determines to be suspicious.
If the Prestige detects a possible attack, the source IP or destination IP address will be added to
the Blacklist. Any further attempts using this IP address will be blocked for the time period
specified in the Block Duration field. The default setting for this function is false (disabled).
Some attack types are denied immediately without using the Blacklist function, such as Land
attack and Echo/CharGen scan.
The following table lists the types of attacks that the IDS is able to detect and the actions
performed.
Table 34 IDS: Detectable Attacks
NAME PARAMETER BLACKLIST
Ascend Kill Ascend Kill data Source IP DoS Yes Yes
WinNuke TCP
Port 135, 137~139,
Flag: URG
Smurf ICMP type 8
Des IP is broadcast
Land attack SrcIP = DstIP Yes Ye s
Echo/
CharGen
Scan
Echo Scan UDP Dst Port =
CharGen
Scan
X’mas Tree
Scan
IMAP
SYN/FIN
Scan
UDP Echo Port and
CharGen Port
Echo(7)
UDP Dst Port =
CharGen(19)
TCP Flag: X’mas Source IP Scan Ye s Yes
TCP Flag: SYN/FIN
DstPort: IMAP(143)
SrcPort: 0 or 65535
Source IP DoS Yes Yes
Destination IPVictim Protection Ye s Yes
Source IP Scan Yes Ye s
Source IP Scan Yes Ye s
Source IP Scan Yes Ye s
TYPE OF BLOCK
DURATION
DROP PACKET LOG
Yes Ye s
71 Chapter 6 Firewall

Table 34 IDS: Detectable Attacks (continued)
Prestige 794M User’s Guide
NAME PARAMETER BLACKLIST
SYN/FIN/
RST/ACK
Scan
Net Bus
Scan
Back Orifice
Scan
SYN Flood Max TCP Open
ICMP Flood Max ICMP Count
ICMP Echo Max PING Count
TCP,
No Existing session
And Scan Hosts more
than five.
TCP
No Existing session
DstPort = Net Bus
12345,12346, 3456
UDP, DstPort =
Orifice Port (31337)
Handshaking Count
(Default 100 c/sec)
(Default 100 c/sec)
(Default 15 c/sec)
Source IP Scan Yes Yes
Source IP Scan Yes Yes
Source IP Scan Yes Yes
TYPE OF BLOCK
DURATION
DROP PACKET LOG
Yes
Yes
Yes
Click Configuration, Firewall and Intrusion Detection in the navigation panel to display the
screen as shown.
Note: The Intrusion Detection screen is available when you enable the firewall
feature on the Prestige.
Figure 49 Firewall: Intrusion Detection
Chapter 6 Firewall 72

Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 35 Firewall: Intrusion Detection
LABEL DESCRIPTION
Intrusion Detection Select Enable to activate this feature.
Victim Protection
Block Duration
Scan Attack Block
Duration
DoS Attack Block
Duration
Max TCP Open
Handshaking
Count
Max PING Count This is the rate of ICMP echo (or Ping) requests that the Prestige receives per
Max ICMP Count This is the rate of ICMP packets that the Prestige receives per second. If the
Apply Click Apply to save the settings.
Clear Blacklist Click Clear Blacklist to reset the blacklist.
Select Disable to deactivate this feature.
Specify the time period (in seconds) the Prestige blocks any Smurf attacks when
detected.
Specify the time period (in seconds) the Prestige blocks hosts that attempt a
possible Scan attack. Scan attack types include X’mas scan, IMAP SYN/FIN scan
and similar attempts.
Specify the time period (in seconds) the Prestige blocks hosts that attempt a
possible Denial of Service (DoS) attack.
Possible DoS attacks this attempts to block include Ascend Kill and WinNuke.
This is the rate of new TCP handshake open sessions that causes the firewall to
determine that this is a SYN Flood attack. The Prestige then starts to delete new
sessions.
second. If the current rate is above this number, the firewall decides that this is an
ICMP Echo Storm attack.
current rate is above this number, the firewall decides that this is an ICMP Flood
attack.
Note: For SYN Flood, ICMP Echo Storm and ICMP flood attacks, the Prestige logs
the event in the Event Log screen. The Prestige cannot prevent such attacks
from occurring.
6.6 URL Filter
URL (Uniform Resource Locator) filtering allows you to create and enforce Internet access
policies tailored to your needs. URL filtering gives you the ability to block web sites that
contain key words (that you specify) in the web address (such as www.xxx.com). You can set
a schedule for when the Prestige performs content filtering.
Note: URL filter blocks web browser (HTTP) connection attempts using port 80 only.
Click Configuration, Firewall and URL Filter in the navigation panel to display the screen
as shown next.
73 Chapter 6 Firewall

Prestige 794M User’s Guide
Figure 50 Firewall: URL Filter
The following table describes the labels in this screen.
Table 36 Firewall: URL Filter
LABEL DESCRIPTION
URL Filter Select Enable to activate this feature.
Select Disable to deactivate this feature.
Block Mode Select Always Block to apply the filter(s) at all times.
Select Block From and specify the time period the Prestige applies the filter(s).
Keywords Filtering Select Enable to set the Prestige to block access to web address containing the
specified keyword(s). Click Details to configure the keywords.
Domain Filtering Select Disable all WEB traffic except for Trusted Domains to set the Prestige to
allow access to the specified web sites whose address contains trusted keywords
or domains you configure in the Keyword Filer and Domain Filter screens.
Restrict URL
Features
Apply Click Apply to save the settings.
Cancel Click Cancel to discard all changes.
Select Block Java Applet to prevent Java applet applications from running.
Select Block surfing by IP address to set the Prestige to disallow Internet access
based on a device’s IP address.
6.6.1 Keywords Filtering
Use the Keywords Filtering screen to specify the keywords in the URL. For example, if you
specify the keyword "xxx", the Prestige blocks all sites containing this keyword including the
URL http://www.website.com/xxx.html.
In the URL Filter screen, select Enable for Keywords Filtering and click Details to display
the screen as shown next.
Chapter 6 Firewall 74

Prestige 794M User’s Guide
Figure 51 Firewall: URL Filter: Keywords Filtering
The following table describes the labels in this screen.
Table 37 Firewall: URL Filter: Keywords Filtering
LABEL DESCRIPTION
Create
Keyword Enter a keyword in this field.
Apply Click Apply to add the keyword to the table below.
Block WEB URLs
which contain
these keywords
Name This field displays the name of the filter rule.
Keyword This field displays the keyword you created.
Delete Click Delete to remove the select keyword from this table.
This read-only table lists the keywords in the web site address to which the
Prestige blocks access.
6.6.2 Domain Filtering
Use the Domains Filtering screen to specify the URL domain. For example, if you specify the
domain “www.xxx.com”, the Prestige blocks access to the sites in this domain, including
“www.xxx”.
In the URL Filter screen, select Enable for Domains Filtering and click Details to display
the screen as shown next.
Figure 52 Firewall: URL Filter: Domains Filtering
75 Chapter 6 Firewall

Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 38 Firewall: URL Filter: Domains Filtering
LABEL DESCRIPTION
Domain Name
Domain Name Enter a domain name in this field.
Type Specify whether to allow access (Trusted Domain) or deny access (Forbidden
Domain) from the drop-down list box.
Apply Click Apply to add the keyword to the table below.
Trusted Domain This read-only table lists the domains to which the Prestige allows access.
Name This field displays the name of the filter rule.
Domain This field displays the specified domain.
Forbidden Domain This read-only table lists the domains to which the Prestige blocks access.
Name This field displays the name of the filter rule.
Domain This field displays the specified domain.
Delete Click Delete to remove the select keyword from this table.
6.7 Firewall Log
Use the Firewall Log screen to set the Prestige to log firewall events (such as when an attack
is detected). View the event logs in the Event Log screen.
Click Configuration, Firewall and Firewall Log in the navigation panel to display the screen
as shown.
Figure 53 Firewall: Firewall Logs
The following table describes the labels in this screen.
Table 39 Firewall: Firewall Logs
LABEL DESCRIPTION
Filtering Log Select Enable to log filtering events.
Select Disable not to log filtering events.
Chapter 6 Firewall 76

Prestige 794M User’s Guide
Table 39 Firewall: Firewall Logs (continued)
LABEL DESCRIPTION
Intrusion Log Select Enable to log intrusion detections.
URL Blocking Log Select Enable to log URL blocking events.
Select Disable not to log intrusion detections.
Select Disable not to log URL blocking events.
77 Chapter 6 Firewall

This chapter shows you how to configure the Prestige for VPN connection.
7.1 Overview
A VPN (Virtual Private Network) provides secure communications between sites without the
expense of leased site-to-site lines. A secure VPN is a combination of tunneling, encryption,
authentication, access control and auditing technologies/services used to transport traffic over
the Internet or any insecure network that uses the TCP/IP protocol suite for communication.
Your Prestige supports three main types of VPN (Virtual Private Network): PPTP, IPSec and
L2TP.
Prestige 794M User’s Guide
CHAPTER 7
VPN
7.2 PPTP
Point-to-Point Tunneling Protocol (PPTP) is a network protocol that enables secure transfer of
data from a remote client to a private server, creating a Virtual Private Network (VPN) using
TCP/IP-based networks.
PPTP supports on-demand, multi-protocol and virtual private networking over public
networks, such as the Internet. You can set the Prestige to initiate a VPN connection or accept
connection requests from a VPN client.
7.2.1 PPTP Summary
To view PPTP VPN rule summary, click VPN and PPTP in the navigation panel to display the
main PPTP screen.
Figure 54 VPN: PPTP
Chapter 7 VPN 78

Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 40 VPN: PPTP
LABEL DESCRIPTION
Enable Select this option to activate this VPN rule.
Disable Select this option to deactivate this VPN rule.
Name This field displays the descriptive name for the VPN rule.
Type This field displays whether the Prestige acts as a client (Dialout) or server (Dialin)
Status This field displays whether the VPN rule is in use or not.
Edit Click Edit to modify the settings of the selected rule.
Create Click Create to add a new VPN rule.
Apply Click Apply to save the changes.
for the VPN rule.
7.2.2 Creating a PPTP VPN Rule
To configure a PPTP VPN rule, click Create in the summary screen to display the screen as
shown.
Figure 55 VPN: PPTP
In the Connection Type field, select Remote Access or LAN to LAN and click Next to
display the configuration screen.
7.2.2.1 Remote Access Connection
Use PPTP Remote Access Connection screen to configure the Prestige to set up PPTP
connection to a remote VPN device.
Figure 56 VPN: PPTP: Remote Access
79 Chapter 7 VPN

Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 41 VPN: PPTP: Remote Access
LABEL DESCRIPTION
Connection Name Enter a descriptive name for identification purposes.
Type Select Dial Out if you want your Prestige to operate as a client (connecting to a
remote VPN device).
Select Dial In to allow computers to establish a VPN connection to the Prestige.
Server IP
Address (or
Domain
Name)
Private IP
Address
Assigned to
Dialin User
Username If you select Dial Out in the Ty pe field, enter the username provided.
Password Enter the password associated with the username above.
PPP
Authentication
Type
Data Encryption You can set the Prestige to encrypt data sent over the VPN connection using
Key Length Specify the key length for data encryption. Choices are Auto, 40 bits and 128
This field is applicable when you select Dial Out in the Type field
Enter the IP address or the domain name of the remote VPN device.
This field is applicable when you select Dial In in the Type field.
Enter the IP address (in dotted decimal notation) to assign to the remote VPN
client that initiates the VPN connection. For example, 192.168.1.10.
If you select Dial In in the Typ e field, enter a username to be used when
establishing a VPN connection.
Specify the authentication type to use when accepting or establishing a VPN
connection. Choices are PAP (Password Authentication Protocol) and CHAP
(Challenge Handshake Authentication Protocol). The default is CHAP.
When you select PAP, password is sent unencrypted. While CHAP provides better
security by encrypting the password before transmission and reauthenticates the
VPN client to protect against identity theft.
MPPE (Microsoft Point to Point Encryption).
Select Auto to set the Prestige to automatically detect whether the remote VPN
device uses data encryption.
Select Enable to activate data encryption on the Prestige. Make sure the remote
VPN device also has data encryption activated with the same encryption settings
as the Prestige.
Select Disable to deactivate data encryption on the Prestige. You cannot establish
a VPN connection if data encryption in enabled on the remote VPN device.
bits.
Select Auto to set the Prestige to automatically detect the key length used by the
remote VPN device.
Otherwise select 40 bits or 128 bits (for stronger encryption) to set the key length
manually.
Note: Make sure the key length is the same on the Prestige and the
remote VPN device.
Mode Specify the encryption mode. Choices are Stateful and Stateless.
Select Stateful to use a different encryption key after 256 packets of data
transmitted.
Select Stateless to use a different encryption key for each packet.
Chapter 7 VPN 80

Prestige 794M User’s Guide
Table 41 VPN: PPTP: Remote Access (continued)
LABEL DESCRIPTION
Idle Time Specify the time interval in minutes (where there is no traffic between the Prestige
and the computer) that can elapse before the Prestige automatically disconnects
the connection.
Enter 0 to allow connection up all the time.
Apply Click Apply to save the changes.
7.2.2.2 LAN to LAN Connection
Use the PPTP LAN to LAN screen to configure the Prestige to accept connection requests
from a VPN client.
Figure 57 VPN: PPTP: LAN to LAN Connection
The following table describes the labels in this screen.
Table 42 VPN PPTP: LAN to LAN Connection
LABEL DESCRIPTION
Connection Name Enter a descriptive name for identification purposes.
Type Select Dial Out if you want your Prestige to operate as a client (connecting to a
remote VPN device).
Select Dial In to allow computers to establish a VPN connection to the Prestige.
When configuring your Prestige as a client, enter the remote Server IP Address
(or Hostname) you wish to connection to.
When configuring your router as a server, enter the Private IP Address Assigned
to Dial in User address.
Server IP
Address (or
Domain
Name)
Private IP
Address
Assigned to
Dialin User
This field is applicable when you select Dial Out in the Type field
Enter the IP address or the domain name of the remote VPN device.
This field is applicable when you select Dial In in the Type field.
Enter the IP address (in dotted decimal notation) to assign to the remote VPN
client that initiates the VPN connection. For example, 192.168.1.10.
81 Chapter 7 VPN

Prestige 794M User’s Guide
Table 42 VPN PPTP: LAN to LAN Connection (continued)
LABEL DESCRIPTION
Netmask This field is applicable when you select Dial In in the Type field.
Enter the subnet mask (in dotted decimal) notation to assign to the remote VPN
client that initiates this VPN connection. For example, 255.255.255.0.
Peer Network IP Enter the IP address (in dotted decimal notation) of the remote network. For
example, 192.168.1.1.
Username If you select Dial Out in the Ty pe field, enter the username provided.
If you select Dial In in the Typ e field, enter a username to be used when
establishing a VPN connection.
Password Enter the password associated with the username above.
PPP
Authentication
Type
Data Encryption You can set the Prestige to encrypt data sent over the VPN connection using
Key Length Specify the key length for data encryption. Choices are Auto, 40 bits and 128
Specify the authentication type to use when accepting or establishing a VPN
connection. Choices are PAP (Password Authentication Protocol) and CHAP
(Challenge Handshake Authentication Protocol). The default is CHAP.
When you select PAP, password is sent unencrypted. While CHAP provides better
security by encrypting the password before transmission and reauthenticates the
VPN client to protect against identity theft.
MPPE (Microsoft Point to Point Encryption).
Select Auto to set the Prestige to automatically detect whether the remote VPN
device uses data encryption.
Select Enable to activate data encryption on the Prestige. Make sure the remote
VPN device also has data encryption activated with the same encryption settings
as the Prestige.
Select Disable to deactivate data encryption on the Prestige. You cannot establish
a VPN connection if data encryption in enabled on the remote VPN device.
bits.
Select Auto to set the Prestige to automatically detect the key length used by the
remote VPN device.
Otherwise select 40 bits or 128 bits (for stronger encryption) to set the key length
manually.
Note: Make sure the key length is the same on the Prestige and the
remote VPN device.
Mode Specify the encryption mode. Choices are Stateful and Stateless.
Select Stateful to use a different encryption key after 256 packets of data
transmitted.
Select Stateless to use a different encryption key for each packet.
Idle Time Specify the time interval in minutes (where there is no traffic between the Prestige
and the computer) that can elapse before the Prestige automatically disconnects
the connection.
Enter 0 to allow connection up all the time.
Apply Click Apply to save the changes.
Chapter 7 VPN 82

Prestige 794M User’s Guide
7.3 IPSec
Internet Protocol Security (IPSec) is a standards-based VPN that offers flexible solutions for
secure data communications across a public network like the Internet. IPSec is built around a
number of standardized cryptographic techniques to provide confidentiality, data integrity and
authentication at the IP layer.
7.3.1 AH (Authentication Header)
AH protocol (RFC 2402) was designed for integrity, authentication, sequence integrity (replay
resistance), and non-repudiation but not for confidentiality, for which the ESP was designed.
In applications where confidentiality is not required or not sanctioned by government
encryption restrictions, an AH can be employed to ensure integrity. This type of
implementation does not protect the information from dissemination but will allow for
verification of the integrity of the information and authentication of the originator.
7.3.2 ESP (Encapsulating Security Payload)
The ESP protocol (RFC 2406) provides encryption as well as the services offered by AH. ESP
authenticating properties are limited compared to the AH due to the non-inclusion of the IP
header information during the authentication process. However, ESP is sufficient if only the
upper layer protocols need to be authenticated.
An added feature of the ESP is payload padding, which further protects communications by
concealing the size of the packet being transmitted.
Table 43 ESP and AH
ESP AH
Encryption DES (default)
Data Encryption Standard (DES) is a
widely used method of data encryption
using a secret key. DES applies a 56-bit
key to each 64-bit block of data.
3DES
Triple DES (3DES) is a variant of DES,
which iterates three times with three
separate keys (3 x 56 = 168 bits),
effectively doubling the strength of DES.
AES
Advanced Encryption Standard is a
newer method of data encryption that
also uses a secret key. Various secret
key lengths (128, 192 and 256 bits) are
implemented. AES is faster than 3DES.
Select NULL to set up a phase 2 tunnel
without encryption.
83 Chapter 7 VPN

Table 43 ESP and AH (continued)
ESP AH
Authentication None (default)
No authentication
MD5
MD5 (Message Digest 5) produces a
128-bit digest to authenticate packet
data.
SHA1
SHA1 (Secure Hash Algorithm) produces
a 160-bit digest to authenticate packet
data.
Select MD5 for minimal security and SHA1 for maximum security.
7.3.3 Perfect Forward Secrecy (PFS)
Enabling PFS means that the key is transient. The key is thrown away and replaced by a brand
new key using a new Diffie-Hellman exchange for each new IPSec SA setup. With PFS
enabled, if one key is compromised, previous and subsequent keys are not compromised,
because subsequent keys are not derived from previous keys. The (time-consuming) DiffieHellman exchange is the trade-off for this extra security.
Prestige 794M User’s Guide
MD5 (default)
MD5 (Message Digest 5) produces a
128-bit digest to authenticate packet
data.
SHA1
SHA1 (Secure Hash Algorithm) produces
a 160-bit digest to authenticate packet
data.
This may be unnecessary for data that does not require such security, so PFS is disabled
(None) by default in the Prestige. Disabling PFS means new authentication and encryption
keys are derived from the same root secret (which may have security implications in the long
run) but allows faster SA setup (by bypassing the Diffie-Hellman key exchange).
7.3.4 Pre-Shared Key
A pre-shared key identifies a communicating party during a phase 1 IKE negotiation. It is
called pre-shared because you have to share it with another party before you can communicate
with them over a secure connection.
7.3.5 IPSec VPN Summary
To configure a IPSec VPN rule, click VPN and IPSec in the navigation panel to display the
main IPSec screen. Click Create to configure a new IPSec VPN connection.
Figure 58 IPSec Summary
Chapter 7 VPN 84

Prestige 794M User’s Guide
7.3.6 IPSec VPN Configuration
To configure an IPSec VPN connection, click Create in the main IPSec screen.
Figure 59 IPSec: Create
The following table describes the labels in this screen.
Table 44 VPN Rules (IKE): Add Policy
LABEL DESCRIPTION
Connection Name Enter a descriptive name for identification purposes.
Local Configure the fields to allow one or more than one computer on the LAN to use a
VPN connection.
Single Address Select Single Address to allow one VPN client with the specified IP address to
use the VPN connection.
Enter a single IP address in the IP Address field.
Subnet Select Subnet Address to allow more than one computer in the specified
subnet to use the VPN connection.
Enter the IP address and subnet mask in the IP Address and Netmask fields
respectively.
IP Range Select IP Range to allow more than one computer in the specified IP address
range to use the VPN connection.
Enter the starting and ending IP addresses in the IP Address and End IP fields
respectively.
Remote Configure the fields to allow one or more than one computer on the remote
network to use a VPN connection.
Secure Gateway
Address (or
Hostname)
Type the WAN IP address or hostname of the remote IPSec router with which
you're making the VPN connection.
85 Chapter 7 VPN

Prestige 794M User’s Guide
Table 44 VPN Rules (IKE): Add Policy (continued)
LABEL DESCRIPTION
Single Address Select Single Address to allow one VPN client with the specified IP address to
use the VPN connection.
Enter a single IP address in the IP Address field.
Subnet Select Subnet Address to allow more than one computer in the specified
subnet to use the VPN connection.
Enter the IP address and subnet mask in the IP Address and Netmask fields
respectively.
IP Range Select IP Range to allow more than one computer in the specified IP address
range to use the VPN connection.
Enter the starting and ending IP addresses in the IP Address and End IP fields
respectively.
Proposal
ESP Select ESP to provide basic authentication and data encryption for the VPN
connection.
Authentication Specify the method to authenticate data packet in this field. Choices are None,
Encryption Specify the method to encrypt data packet in this field. Choices are NULL, DES,
AH Select AH to authenticate and ensure the integrity of data packets.
Authentication Specify the method to authenticate data packet in this field. Choices are MD5
Perfect Forward
Secret
MD5 and SHA1.
Select None to disable authentication.
Select MD5 (Message Digest 5) for minimal security and SHA1 (Secure Hash
Algorithm) for maximum security.
3DES, AES128, AES 192 and AES 256.
When DES is used for data communications, both sender and receiver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key.
Triple DES (3DES) is a variation on DES that uses a 168-bit key. As a result,
3DES is more secure than DES. It also requires more processing power,
resulting in increased latency and decreased throughput.
For this implementation, select AES 128, AES 192 or AES 256 that uses
different encryption key lengths. AES is faster than 3DES. S
elect NULL to set up a tunnel without encryption. When you select NULL, you
do not enter an encryption key.
and SHA1.
Select MD5 (Message Digest 5) for minimal security and SHA1 (Secure Hash
Algorithm) for maximum security.
Perfect Forward Secret (PFS) is disabled (None) by default in phase 2 IPSec
SA setup. This allows faster IPSec setup, but is not so secure.
Specify an MODP (Modular Exponentiation Groups) mode from the drop-down
list box. Choices are MODP 768-bit (Group 1), MODP 1024-bit (Group 2) and
MODP 1536-bit (Group 5). The larger the random number bits, the higher the
security ut slower.
Chapter 7 VPN 86

Prestige 794M User’s Guide
Table 44 VPN Rules (IKE): Add Policy (continued)
LABEL DESCRIPTION
Pre-Shared Key Enter your pre-shared key in this field. A pre-shared key identifies a
Apply Click Apply to save the changes.
Cancel Click Cancel to discard all changes and return to the main VPN screen.
communicating party during a phase 1 IKE negotiation. It is called "pre-shared"
because you have to share it with another party before you can communicate
with them over a secure connection.
Type from 8 to 31 case-sensitive ASCII characters or from 16 to 62 hexadecimal
("0-9", "A-F") characters. You must precede a hexadecimal key with a "0x (zero
x), which is not counted as part of the 16 to 62 character range for the key. For
example, in "0x0123456789ABCDEF", 0x denotes that the key is hexadecimal
and 0123456789ABCDEF is the key itself.
Note: Both ends of the VPN tunnel must use the same pre-
shared key.
You will receive a PYLD_MALFORMED (payload malformed) packet if the same
pre-shared key is not used on both ends.
7.4 L2TP
L2TP (Layer 2 Tunneling Protocol) is another tunneling protocol to support VPN. L2TP
allows a PPP session to travel through the Internet and a user to access a corporate network.
Click VPN and L2TP to display the summary screen.
Figure 60 VPN: L2TP
The following table describes the labels in this screen.
Table 45 VPN: PPTP
LABEL DESCRIPTION
Enable Select this option to activate this VPN rule.
Disable Select this option to deactivate this VPN rule.
Name This field displays the descriptive name for the VPN rule.
Type This field displays whether the Prestige acts as a client (Dialout) or server (Dialin)
for the VPN rule.
87 Chapter 7 VPN

Table 45 VPN: PPTP (continued)
LABEL DESCRIPTION
Status This field displays whether the VPN rule is in use or not.
Edit Click Edit to modify the settings of the selected rule.
Create Click Create to add a new VPN rule.
Apply Click Apply to save the changes.
Delete Click Delete to remove the selected VPN rule.
7.4.1 Creating a New L2TP Rule
Click Create to configure a new VPN connection. There are two types of L2TP VPN
supported, Remote Access and LAN-to-LAN. Select a connection type and click Next.
Figure 61 VPN: L2TP: Create
Prestige 794M User’s Guide
7.4.1.1 Remote Access L2TP Connection
Use the L2TP Remote Access Connection screen to create an L2TP VPN rule for accessing a
remote network.
Figure 62 L2TP: Remote Access Connection
Chapter 7 VPN 88

Prestige 794M User’s Guide
The following table describes the labels in this screen.
Table 46 VPN: L2TP: Create: Remote Access Connection
LABEL DESCRIPTION
Connection Name Enter a descriptive name for identification purposes.
Type Select Dial Out to set the Prestige to act as a client (connecting to a remote
Server IP Address (or
Domain Name)
Private IP Address
Assigned to Dial in
User
Username If you select Dial Out in the Type field, enter the username provided.
Password Enter the password associated with the username above.
Authentication Type Specify the authentication type to use when accepting or establishing a VPN
Idle Time Specify the time interval in minutes (where there is no traffic between the
Active as default route Select this option to set this VPN connection as a default route.
IPSec Select this option to enable IPSec security for your LT2P VPN connection.
Authentication Specify the method to authenticate data packet in this field. Choices are
Encryption Specify the method to encrypt data packet in this field. Choices are NULL,
VPN server).
Select Dial In to set the Prestige to act as a VPN server.
This field is applicable when you select Dial Out in the Type field
Enter the IP address or the domain name of the remote VPN device.
This field is applicable when you select Dial In in the Type field.
Enter the IP address (in dotted decimal notation) to assign to the remote VPN
client that initiates the VPN connection. For example, 192.168.1.10.
If you select Dial In in the Typ e field, enter a username to be used when
establishing a VPN connection.
connection. Choices are PAP (Password Authentication Protocol) and CHAP
(Challenge Handshake Authentication Protocol). The default is CHAP.
When you select PAP, password is sent unencrypted. While CHAP provides
better security by encrypting the password before transmission and
reauthenticates the VPN client to protect against identity theft.
Prestige and the computer) that can elapse before the Prestige automatically
disconnects the connection.
Enter 0 to allow connection up all the time.
None, MD5 and SHA1.
Select None to disable authentication.
Select MD5 (Message Digest 5) for minimal security and SHA1 (Secure Hash
Algorithm) for maximum security.
DES, 3DES, AES128, AES 192 and AES 256.
When DES is used for data communications, both sender and receiver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key.
Triple DES (3DES) is a variation on DES that uses a 168-bit key. As a result,
3DES is more secure than DES. It also requires more processing power,
resulting in increased latency and decreased throughput.
For this implementation, select AES 128, AES 192 or AES 256 that uses
different encryption key lengths. AES is faster than 3DES.
elect NULL to set up a tunnel without encryption. When you select NULL, you
do not enter an encryption key.
89 Chapter 7 VPN

Prestige 794M User’s Guide
Table 46 VPN: L2TP: Create: Remote Access Connection (continued)
LABEL DESCRIPTION
Encryption Select the encryption method from the pull-down menu. There are four
options, DES, 3DES, AES and NONE. NONE means it is a tunnel only with no
encryption. 3DES and AES are more powerful but increase latency.
• DES stands for Data Encryption Standard, it uses 56 bits as an encryption
method.
•3DES stands for Triple Data Encryption Standard, it uses 168 (56*3) bits
as an encryption method.
• AES stands for Advanced Encryption Standards, it uses 128 bits as an
encryption method.
Perfect Forward
Secrecy
Pre-shared Key Enter your pre-shared key in this field. A pre-shared key identifies a
Perfect Forward Secret (PFS) is disabled (None) by default in phase 2 IPSec
SA setup. This allows faster IPSec setup, but is not so secure.
Specify an MODP (Modular Exponentiation Groups) mode from the dropdown list box. Choices are MODP 768-bit (Group 1), MODP 1024-bit (Group
2) and MODP 1536-bit (Group 5). The larger the random number bits, the
higher the security ut slower.
communicating party during a phase 1 IKE negotiation. It is called "preshared" because you have to share it with another party before you can
communicate with them over a secure connection.
Type from 8 to 31 case-sensitive ASCII characters or from 16 to 62
hexadecimal ("0-9", "A-F") characters. You must precede a hexadecimal key
with a "0x (zero x), which is not counted as part of the 16 to 62 character
range for the key. For example, in "0x0123456789ABCDEF", 0x denotes that
the key is hexadecimal and 0123456789ABCDEF is the key itself.
Note: Both ends of the VPN tunnel must use the same pre-
shared key.
You will receive a PYLD_MALFORMED (payload malformed) packet if the
same pre-shared key is not used on both ends.
Remote Host Name This optional field is applicable when you select Dial Out in the Type field
above.
Enter the host name of the remote VPN device. The name must match to
establish a VPN connection.
Local Host Name This field is optional.
Enter the host name of the Prestige.
Tunnel Authentication Select this option to set the Prestige to authenticate both the remote L2TP
client and host. The remote L2TP client and host must also support this
feature.
Secret This field is applicable when you select Tunnel Authentication above.
Enter the authentication key up to 16 alphanumerical characters.
Apply Click Apply after changing settings.
7.4.1.2 LAN to LAN L2TP Connection
Use the L2TP LAN to LAN screen to create an L2TP VPN rule to connect to another VPN
device on the LAN.
Chapter 7 VPN 90

Prestige 794M User’s Guide
Figure 63 L2TP: LAN to LAN Connection
The following table describes the labels in this screen.
Table 47 VPN: L2TP: Create: LAN to LAN
LABEL DESCRIPTION
Connection Name Enter a descriptive name for identification purposes.
Type Select Dial Out to set the Prestige to act as a client (connecting to a remote
VPN server).
Select Dial In to set the Prestige to act as a VPN server.
Server IP Address (or
Domain Name)
Private IP Address
Assigned to Dial in
User
Username If you select Dial Out in the Type field, enter the username provided.
Password Enter the password associated with the username above.
Authentication Type Specify the authentication type to use when accepting or establishing a VPN
Idle Time Specify the time interval in minutes (where there is no traffic between the
This field is applicable when you select Dial Out in the Type field
Enter the IP address or the domain name of the remote VPN device.
This field is applicable when you select Dial In in the Type field.
Enter the IP address (in dotted decimal notation) to assign to the remote VPN
client that initiates the VPN connection. For example, 192.168.1.10.
If you select Dial In in the Typ e field, enter a username to be used when
establishing a VPN connection.
connection. Choices are PAP (Password Authentication Protocol) and CHAP
(Challenge Handshake Authentication Protocol). The default is CHAP.
When you select PAP, password is sent unencrypted. While CHAP provides
better security by encrypting the password before transmission and
reauthenticates the VPN client to protect against identity theft.
Prestige and the computer) that can elapse before the Prestige automatically
disconnects the connection.
Enter 0 to allow connection up all the time.
91 Chapter 7 VPN

Prestige 794M User’s Guide
Table 47 VPN: L2TP: Create: LAN to LAN (continued)
LABEL DESCRIPTION
Active as default route Select this option to set this VPN connection as a default route.
IPSec Select this option to enable IPSec security for your LT2P VPN connection.
Authentication Specify the method to authenticate data packet in this field. Choices are
Encryption Specify the method to encrypt data packet in this field. Choices are NULL,
Encryption Select the encryption method from the pull-down menu. There are four
Perfect Forward
Secrecy
Pre-shared Key Enter your pre-shared key in this field. A pre-shared key identifies a
None, MD5 and SHA1.
Select None to disable authentication.
Select MD5 (Message Digest 5) for minimal security and SHA1 (Secure Hash
Algorithm) for maximum security.
DES, 3DES, AES128, AES 192 and AES 256.
When DES is used for data communications, both sender and receiver must
know the same secret key, which can be used to encrypt and decrypt the
message or to generate and verify a message authentication code. The DES
encryption algorithm uses a 56-bit key.
Triple DES (3DES) is a variation on DES that uses a 168-bit key. As a result,
3DES is more secure than DES. It also requires more processing power,
resulting in increased latency and decreased throughput.
For this implementation, select AES 128, AES 192 or AES 256 that uses
different encryption key lengths. AES is faster than 3DES.
elect NULL to set up a tunnel without encryption. When you select NULL, you
do not enter an encryption key.
options, DES, 3DES, AES and NONE. NONE means it is a tunnel only with no
encryption. 3DES and AES are more powerful but increase latency.
• DES stands for Data Encryption Standard, it uses 56 bits as an encryption
method.
•3DES stands for Triple Data Encryption Standard, it uses 168 (56*3) bits
as an encryption method.
• AES stands for Advanced Encryption Standards, it uses 128 bits as an
encryption method.
Perfect Forward Secret (PFS) is disabled (None) by default in phase 2 IPSec
SA setup. This allows faster IPSec setup, but is not so secure.
Specify an MODP (Modular Exponentiation Groups) mode from the dropdown list box. Choices are MODP 768-bit (Group 1), MODP 1024-bit (Group
2) and MODP 1536-bit (Group 5). The larger the random number bits, the
higher the security ut slower.
communicating party during a phase 1 IKE negotiation. It is called "preshared" because you have to share it with another party before you can
communicate with them over a secure connection.
Type from 8 to 31 case-sensitive ASCII characters or from 16 to 62
hexadecimal ("0-9", "A-F") characters. You must precede a hexadecimal key
with a "0x (zero x), which is not counted as part of the 16 to 62 character
range for the key. For example, in "0x0123456789ABCDEF", 0x denotes that
the key is hexadecimal and 0123456789ABCDEF is the key itself.
Note: Both ends of the VPN tunnel must use the same pre-
shared key.
You will receive a PYLD_MALFORMED (payload malformed) packet if the
same pre-shared key is not used on both ends.
Chapter 7 VPN 92

Prestige 794M User’s Guide
Table 47 VPN: L2TP: Create: LAN to LAN (continued)
LABEL DESCRIPTION
Remote Host Name This optional field is applicable when you select Dial Out in the Type field
Local Host Name This field is optional.
Tunnel Authentication Select this option to set the Prestige to authenticate both the remote L2TP
Secret This field is applicable when you select Tunnel Authentication above.
Apply Click Apply after changing settings.
7.5 VPN Example
above.
Enter the host name of the remote VPN device. The name must match to
establish a VPN connection.
Enter the host name of the Prestige.
client and host. The remote L2TP client and host must also support this
feature.
Enter the authentication key up to 16 alphanumerical characters.
This section shows some VPN configuration examples.
7.5.1 Example: Remote PPTP VPN Dial-in Connection
The following network example shows a remote VPN client connecting to the LAN behind the
Prestige from the Internet.
Figure 64 Remote PPTP VPN Dial-in Network Example
Create a PPTP dial in VPN connection for this network example. The Prestige assigns an IP
address of 192.168.1.200 to the remote VPN client when the VPN connection is established.
93 Chapter 7 VPN

Prestige 794M User’s Guide
Figure 65 Remote PPTP VPN Dial-In Configuration Example
1
2
3
4
The following table describes the configuration steps.
Table 48 Remote PPTP VPN Dial-In Configuration Example
STEP FIELD SETTING DESCRIPTION
1 Connection Name Example This name is for identification purposes only.
2 Dial in Select this field to allow a remote VPN client to
establish a VPN connection to the Prestige.
Private IP Address
Assigned to Dialing
User
3 Username test Specify the user name and password the remote VPN
Password test
4 Auth.Type Chap(Auto) In this network example, the default authentication and
Data Encryption Auto
Key Length Auto
Mode stateful
Idle Time 0 A value of 0 means the connection is always on.
192.168.1.200 The Prestige assigns this IP address to the remote
VPN client after the VPN connection is established.
client must supply to establish a VPN connection.
encryption settings are used.
7.5.2 Example: Remote PPTP VPN Dial-out Connection
The following figure depicts a VPN network example where a computer on the LAN behind
the Prestige can establish a VPN connection to the public file server.
Figure 66 PPTP: Remote VPN Dial-out Access
Chapter 7 VPN 94

Prestige 794M User’s Guide
On the Prestige, create a dial-out PPTP VPN rule to allow a computer on the LAN to access
the public file server securely.
Figure 67 PPTP VPN Example: Configuration for the Office
The following table describes the configuration steps.
Table 49 Remote PPTP VPN Dial-In Configuration Example
1
2
3
4
STEP FIELD SETTING DESCRIPTION
1 Connection Name Example This name is for identification purposes only.
2 Dial out Select this field to allow a VPN client behind the
Server IP Address
(or Hostname)
3 Username test Specify the user name and password a VPN client
Password test
4 Auth.Type Chap(Auto) In this network example, the default authentication
Data Encryption Auto
Key Length Auto
Mode stateful
Idle Time 0 A value of 0 means the connection is always on.
myfileserver.com This is the domain name for the file server on the
Prestige to establish a VPN connection to a remote
network.
Internet. You may also enter the IP address.
must supply to establish a VPN connection.
and encryption settings are used.
Note: Both the local and remote networks MUST in different subnets with LAN to LAN
application.
95 Chapter 7 VPN

This chapter shows you how to configure QoS on the Prestige.
8.1 Overview
QoS function helps you to control your network traffic for each application from LAN to
WAN (Internet). It facilitates you to control the different quality and speed of throughput for
each application when the system is running with full loading of upstream.
You can find two items under the QoS section: Prioritization and IP Throttling (bandwidth
management).
Prestige 794M User’s Guide
CHAPTER 8
QoS (Quality of Service)
8.1.1 Prioritization
The Prestige provides three priority settings:
•High
• Normal (This is the default for the traffic type(s) that does not match any rules.)
•Low
Click Configuration, QoS and Prioritization in the navigation panel to display the screen as
shown.
Chapter 8 QoS (Quality of Service) 96

Prestige 794M User’s Guide
Figure 68 QoS: Prioritization
The following table describes the labels in this screen.
Table 50 QoS: Prioritization
LABEL DESCRIPTION
Application Enter a descriptive name for identification purposes.
Time Schedule Specify when this rule is active. Select Always On to activate the rule all the time.
Otherwise, select a schedule (that you configure in the Time Schedule screen).
Priority Select a priority level. Choices are High and Low.
Protocol Select a protocol type from the drop-down list box. Choices are any, tcp, udp,
icmp and gre.
Source Port Enter the source port number from which traffic travels.
Destination Port Enter the destination port number to which traffic travels.
Source IP Address
Range
Destination IP
address Range
You can set the Prestige to prioritize traffic from specified source IP address(es).
Specify one or a range of source IP address(es). Leave the fields as 0.0.0.0 to
prioritize packets from any source IP address.
You can set the Prestige to prioritize traffic to specified destination IP address(es).
Specify one or a range of destination IP address(es). Leave the fields as 0.0.0.0 to
prioritize packets from any destination IP address.
97 Chapter 8 QoS (Quality of Service)

Prestige 794M User’s Guide
Table 50 QoS: Prioritization (continued)
LABEL DESCRIPTION
DSCP Marking DiffServ Code Point (DSCP) marking allows the classification of traffic based on
the DSCP value.
Select Disabled to deactivate DSCP marking or select a marking scheme. Refer to
Table 51 on page 98 for the mapping table.
Apply Click Apply to save the settings.
The following is a mapping table between the Prestige DSCP marking scheme and the
standard DSCP value.
Table 51 DSCP Mapping
PRESTIGE SETTING STANDARD DSCP MARKING
Disabled None
Best Effort Best Effort (000000)
Premium Express Forwarding (101110)
Gold Service (L) Class 1, Gold (001010)
Gold Service (M) Class 1, Silver (001100)
Gold Service (H) Class 1, Bronze (001110)
Silver Service (L) Class 2, Gold (010010)
Silver Service (M) Class 2, Silver (010100)
Silver Service (H) Class 2, Bronze (010110)
Bronze Service (L) Class 3, Gold (011010)
Bronze Service (M) Class 3, Silver (011100)
Bronze Service (H) Class 3 , Br onz e (0 11110)
8.2 IP Throttling
IP Throttling (or bandwidth management) helps you make sure that the Prestige forwards
certain types of traffic (especially real-time applications) with minimum delay.
Use the Outbound IP Throttling screen to limit rates on traffic from the LAN to the WAN
interface on the Prestige.
Use the Inbound IP Throttling screen to limit rates on traffic from the WAN to the LAN
interface on the Prestige.
Chapter 8 QoS (Quality of Service) 98

Prestige 794M User’s Guide
Figure 69 QoS: Outbound IP Throttling
The following table describes the labels in this screen.
Table 52 QoS: Outbound/Inbound IP Throttling
LABEL DESCRIPTION
Application Enter a descriptive name for identification purposes.
Time Schedule Specify when this rule is active. Select Always On to activate the rule all the
time. Otherwise, select a schedule (that you configure in the Time Schedule
screen).
Protocol Select a protocol type from the drop-down list box. Choices are any, tcp, udp,
icmp and gre.
Source Port Enter the source port number from which traffic travels.
Destination Port Enter the destination port number to which traffic travels.
Source IP Address
Range
Destination IP
address Range
You can set the Prestige to prioritize traffic from specified source IP
address(es).
Specify one or a range of source IP address(es). Leave the fields as 0.0.0.0 to
prioritize packets from any source IP address.
You can set the Prestige to prioritize traffic to specified destination IP
address(es).
Specify one or a range of destination IP address(es). Leave the fields as
0.0.0.0 to prioritize packets from any destination IP address.
99 Chapter 8 QoS (Quality of Service)

Table 52 QoS: Outbound/Inbound IP Throttling (continued)
LABEL DESCRIPTION
Upstream Rate Limit Specify an outgoing bandwidth limit on the WAN port to assign for this rule.
Apply Click Apply to save the settings.
8.3 QoS Example
The following figure shows a network example where you want to limit the rates on different
traffic types. The total upstream rate and the downstream rate of the Prestige are 928kbps and
8Mbps respectively.
Figure 70 QoS Network Example
Prestige 794M User’s Guide
Enter a number that is a multiple of 32.
8.3.1 Example Prioritization with QoS
You can use the Prioritization screen to prioritize time-sensitive applications (like VoIP). Set
a high priority level for VoIP traffic to improve service quality and prevent other applications
from using most of the bandwidth. In the example figure, computer B is a restricted user
whose traffic has the lowest priority on the network.
Figure 71 QoS: Prioritization Example
Chapter 8 QoS (Quality of Service) 100
 Loading...
Loading...