
ZyWALL USG
ZLD 2.21 Support Notes
Revision 1.00
August, 2010
Written by CSO

ZyXEL – ZyWALL USG Support Notes
2
Table of Contents
Scenario 1 — Connecting your USG to the Internet ................................................................................................................................................................................... 4
1.1 Application Scenario ....................................................................................................................................................................................................................... 4
1.2 Configuration Guide ....................................................................................................................................................................................................................... 5
Scenario 2 — WAN Load Balancing and Customized Usage of WAN Connection for Specific Traffic .................................................................................................... 12
2.1 WAN Load Balancing..................................................................................................................................................................................................................... 12
2.1.1 Load Balancing Algorithm ......................................................................................................................................................................................................... 12
2.2 Customized Usage of WAN Connection for Specific Traffic Type............................................................................................................................................... 14
2.3 Application Scenario ..................................................................................................................................................................................................................... 15
2.4 Configuration Guide ..................................................................................................................................................................................................................... 16
Scenario 3 — How to configure NAT if you have Internet-facing public servers .................................................................................................................................... 22
3.1 Application Scenario ..................................................................................................................................................................................................................... 22
3.2 Configuration Guide ..................................................................................................................................................................................................................... 23
Scenario 4 — Secure site-to-site connections using IPSec VPN ............................................................................................................................................................... 27
4.1 Application Scenario ..................................................................................................................................................................................................................... 27
4.2 Configuration Guide ..................................................................................................................................................................................................................... 28
Scenario 5 — Secure client-to-site connections using IPSec VPN ............................................................................................................................................................ 35
5.1 Application Scenario ..................................................................................................................................................................................................................... 35
5.2 Configuration Guide ..................................................................................................................................................................................................................... 36
Scenario 6 — Deploying SSL VPN for Tele-workers to Access Company Resources ............................................................................................................................... 45
6.1 Application Scenario ..................................................................................................................................................................................................................... 45
6.2 Configuration Guide ..................................................................................................................................................................................................................... 46
Scenario 7 — Reserving Highest Bandwidth Management Priority for VoIP Traffic ............................................................................................................................... 55
7.1 Application Scenario ..................................................................................................................................................................................................................... 55
7.2 Configuration Guide ..................................................................................................................................................................................................................... 56
Step4. Create a bandwidth management rule and configure .......................................................................................................................................................... 60
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL USG Support Notes
3
Scenario 8 — Reserving Highest Bandwidth Management Priority for a Superior User and Control Session per Host ...................................................................... 61
8.1 Application Scenario ..................................................................................................................................................................................................................... 61
8.2 Configuration Guide ..................................................................................................................................................................................................................... 62
Scenario 9 — Using ZyWALL to Control Popular P2P Applications .......................................................................................................................................................... 71
9.1 Application Scenario ..................................................................................................................................................................................................................... 71
9.2 Configuration Guide ..................................................................................................................................................................................................................... 72
Scenario 10 — Deploying Content Filtering to Manage Employee Browsing Behavior ......................................................................................................................... 77
10.1 Introduction to ZSB (ZyXEL Safe Browsing) ............................................................................................................................................................................... 78
10.2 Application Scenario ................................................................................................................................................................................................................... 78
10.3 Configuration Guide ................................................................................................................................................................................................................... 79
Scenario 11 — Quick Setup for Allowing WLAN Users to Access LAN Services ...................................................................................................................................... 86
11.1 Application Scenario ................................................................................................................................................................................................................... 86
11.2 Configuration Guide ................................................................................................................................................................................................................... 87
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
4
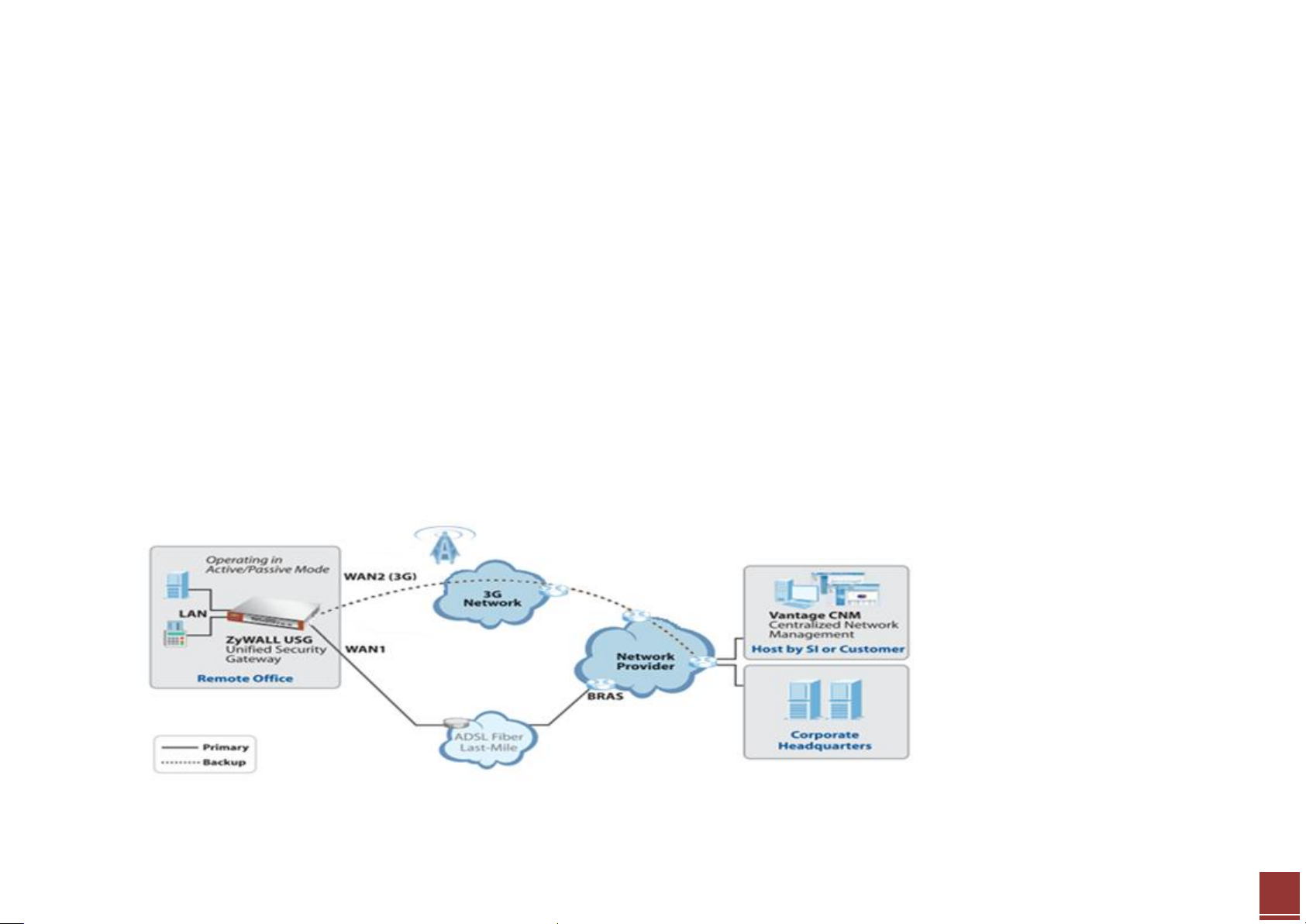
Scenario 1 — Connecting your USG to the Internet
1.1 Application Scenario
A WAN (Wide Area Network) connection is an outside connection to another network or the Internet. It connects your private network such as LAN (Local
Area Network) and other networks, so that a computer in one location can communicate with computers in other locations.
The USG has a multiple WAN feature which enables you to link your network with up to two ISPs or other networks via Ethernet, PPPoE or 3G connections.
User can either use trunks for WAN traffic load balancing to increase overall network throughput (“active-active” load sharing mode) or as a backup to
enhance network reliability (“active-passive” failover mode).
Load balancing will be described further in Scenario 2. In the figure below we first show the scenario for non-stop Internet access with the PPPoE as primary
WAN and 3G backup through USB. This means that the USG will normally use the PPPoE interface for Internet access, and it will only resort to the 3G interface
when the PPPoE interface’s connection fails.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
5
USG-50:
- WAN1_PPP: PPP over Ethernet
- Cellular1: 3G
ZyWALL-5 UTM:
- WAN1: PPP over Ethernet
- WAN2: 3G
ZLD configuration
ZyNOS configuration
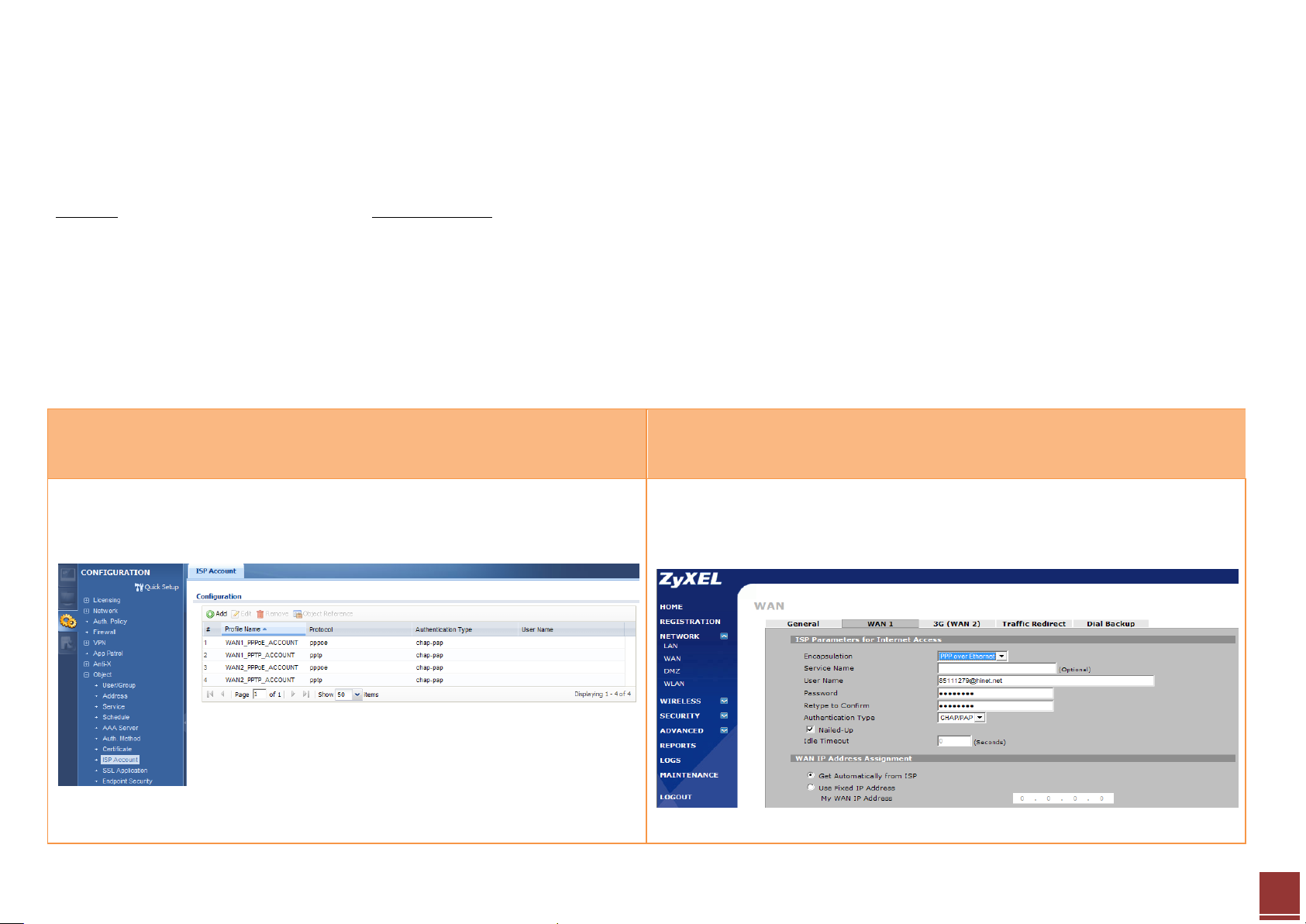
Step 1. Click CONFIGURATION > Object > ISP Account to create an ISP
account first.
Step 1. Click Network > WAN > WAN1 to open the configuration screen.
1.2 Configuration Guide
Network Conditions:
Goal to achieve:
Use the PPPoE interface as device’s primary WAN connection and switch to the 3G interface automatically when the PPPoE interface’s connection fails.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
6
Step 2. Fill in the PPPoE user name and password.
Step 3. Click CONFIGURATION > Network > Interface > PPP to open the
configuration page. User can click the system default rule and edit it.
Step 2. Fill in the PPPoE parameters:
- Select PPP over Ethernet encapsulation mode
- User name
- Password
Step 3. Click the Apply button to save and apply the setting.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
7
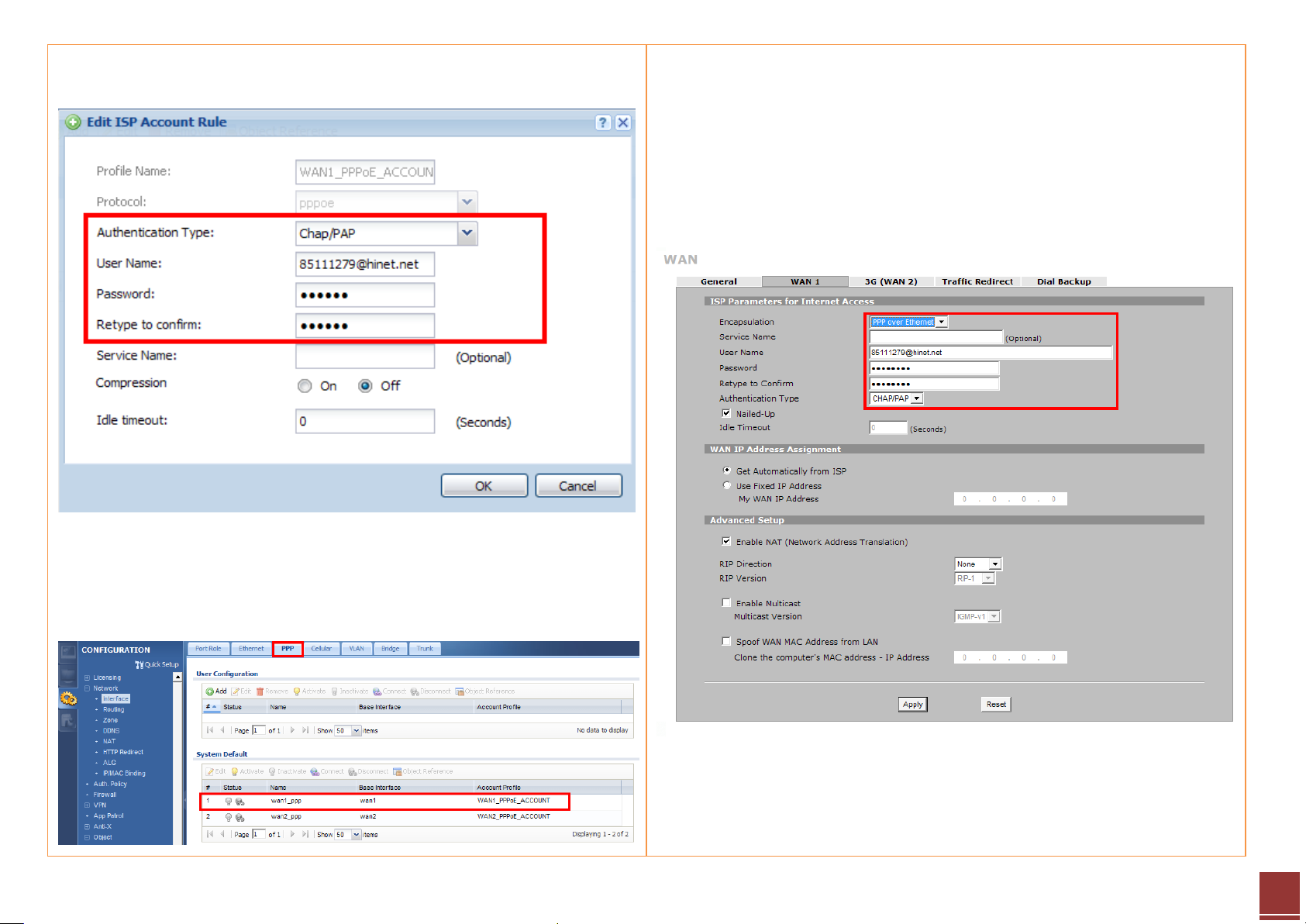
Step 4. Enable the interface and select the pre-configured ISP account to
activate the PPPoE rule.
Step 5. When the configuration is done, click the Connect button to enable
the PPPoE link. Once the connection is established, the connected icon will
be displayed in front of the rule.
Step 4. Check the connection status on the dashboard.
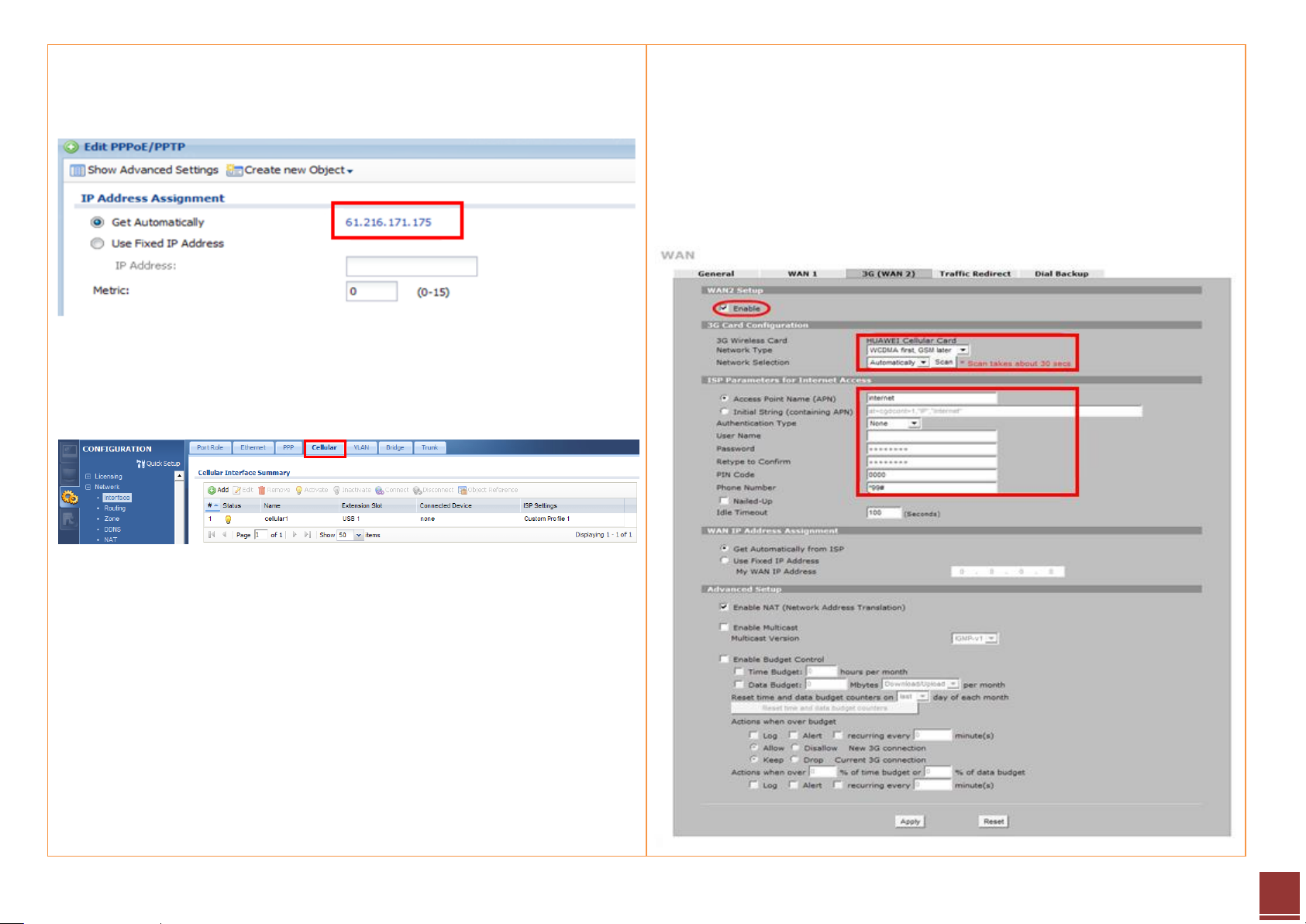
Step 5. Click Network > WAN > 3G (WAN2) to open the configuration screen.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
8
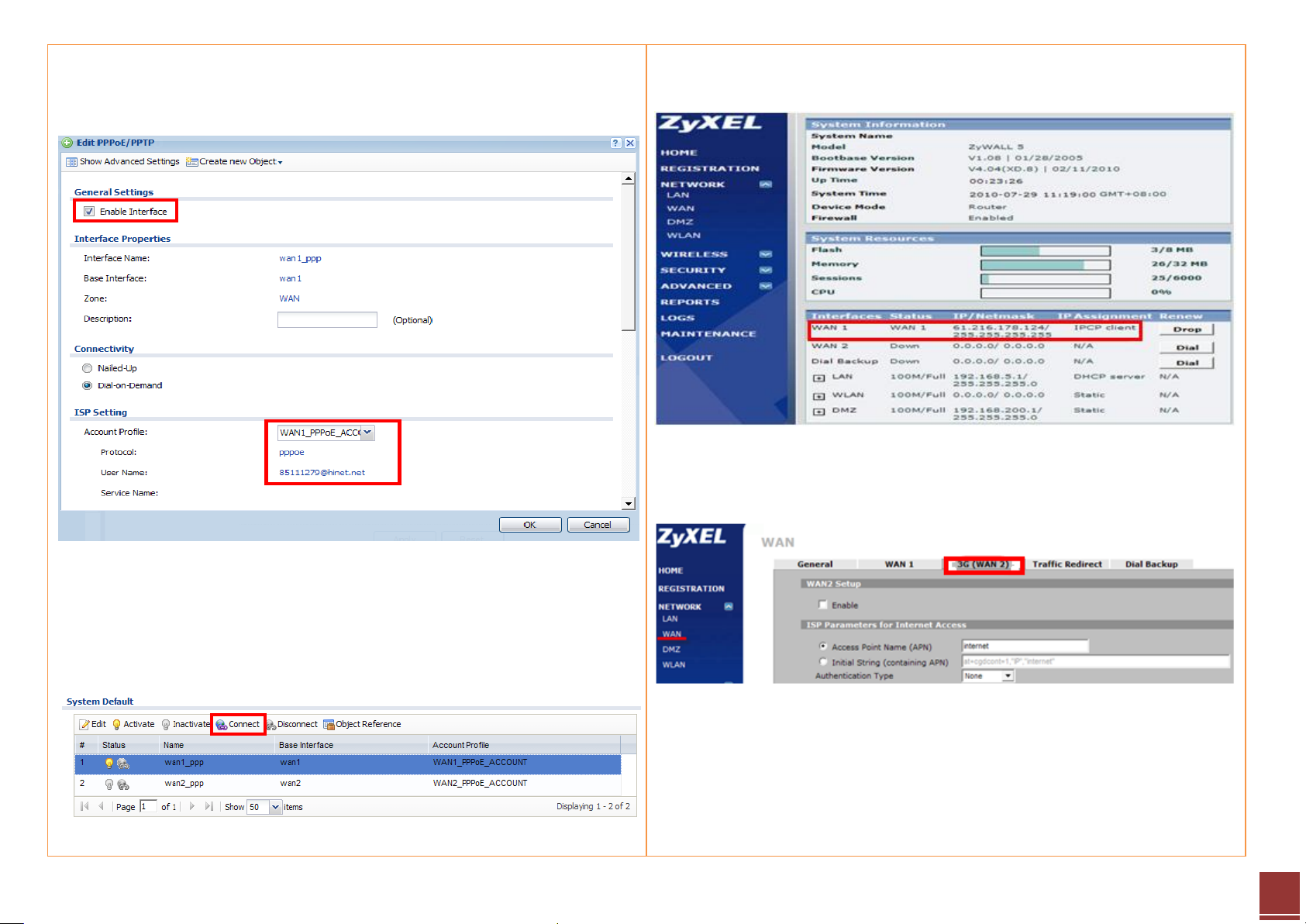
Step 6. To check the PPPoE IP address, click the PPPoE rule and check the IP
address part for the information.
Step 7. Click CONFIGURATION > Network > Interface > Cellular to open the
configuration page.
Step 6. Fill in the 3G connection parameters:
- The card information will be detected by device automatically
- Internet Access setting
Access Point Name (APN)
PIN code
Phone number (enter *99# if not sure what number to fill in)
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
9
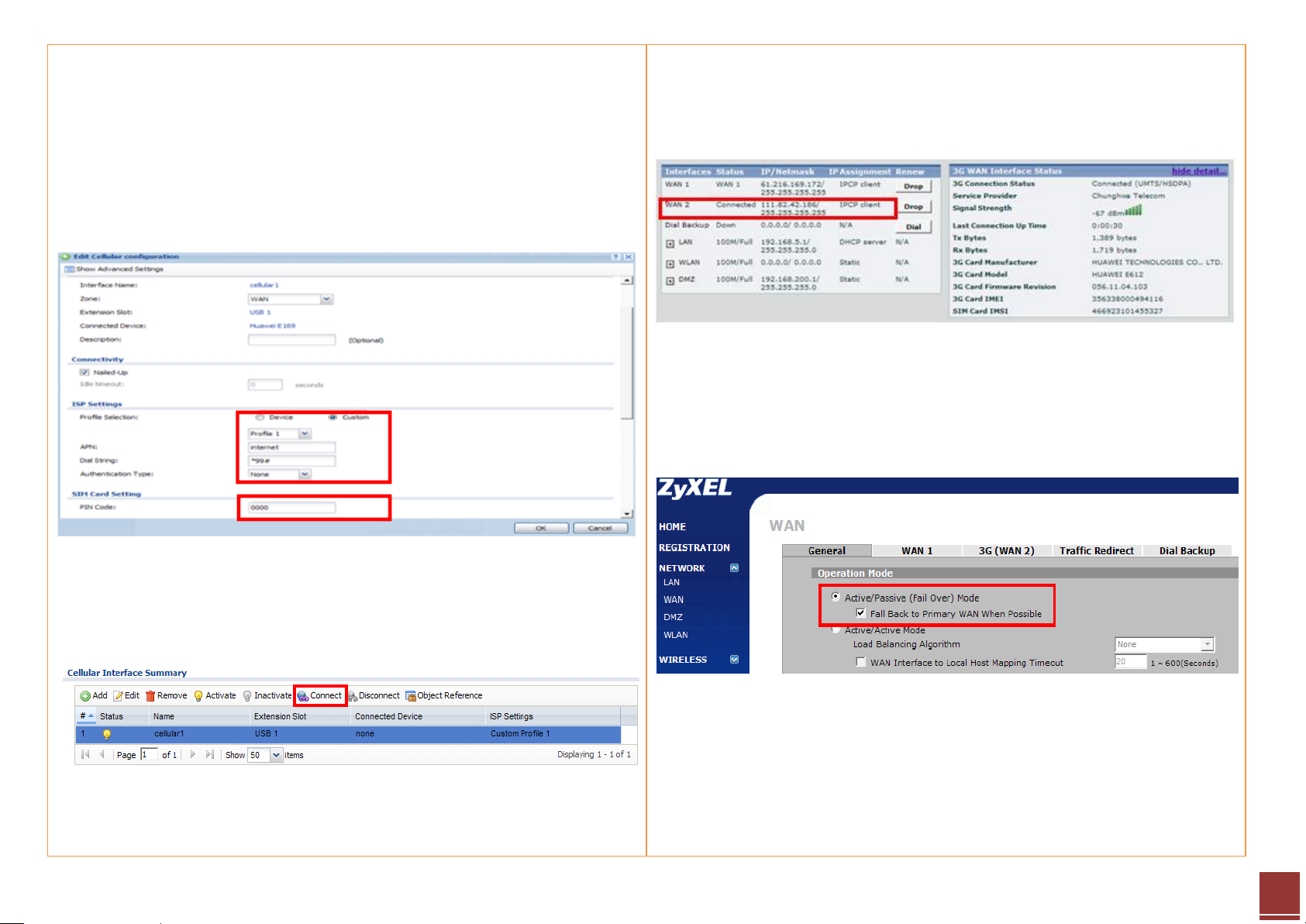
Step 8. Fill in the 3G connection parameters:
- The card information will be detected by device automatically
- ISP Settings
APN name
Dial String
- PIN code
Step 9. After the configuration is done, click Activate to enable the rule. And
then click Connect button to enable the 3G connection.
Step 7. Go to the dashboard and click the Dial button to trigger the rule. User
can check the 3G WAN interface status to get the 3G modem detail
information.
Step 8. Now the both PPPoE and 3G connection are UP. Click on Network >
WAN > General page to select the Active/Passive Mode to achieve the
backup mechanism.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
10
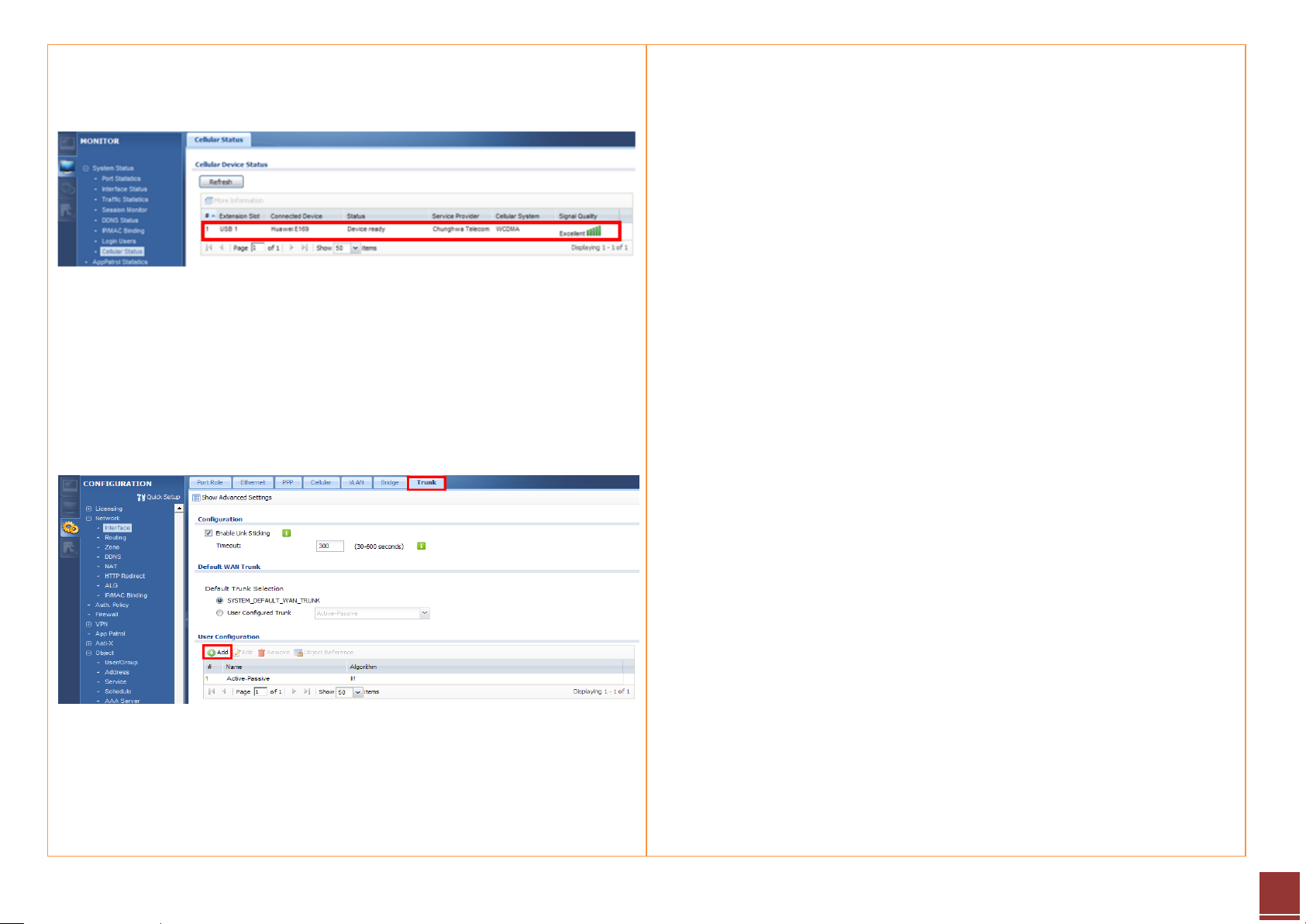
Step 10. User can check the 3G connection status on MONITOR > System
Status > Cellular Status screen.
Step 11. Now both the PPPoE and 3G connection are UP. Click on
CONFIGURATION > Network > Interface > Trunk to open the configuration
screen.
Step 12. Click the Add button to add a User Configuration rule.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
11
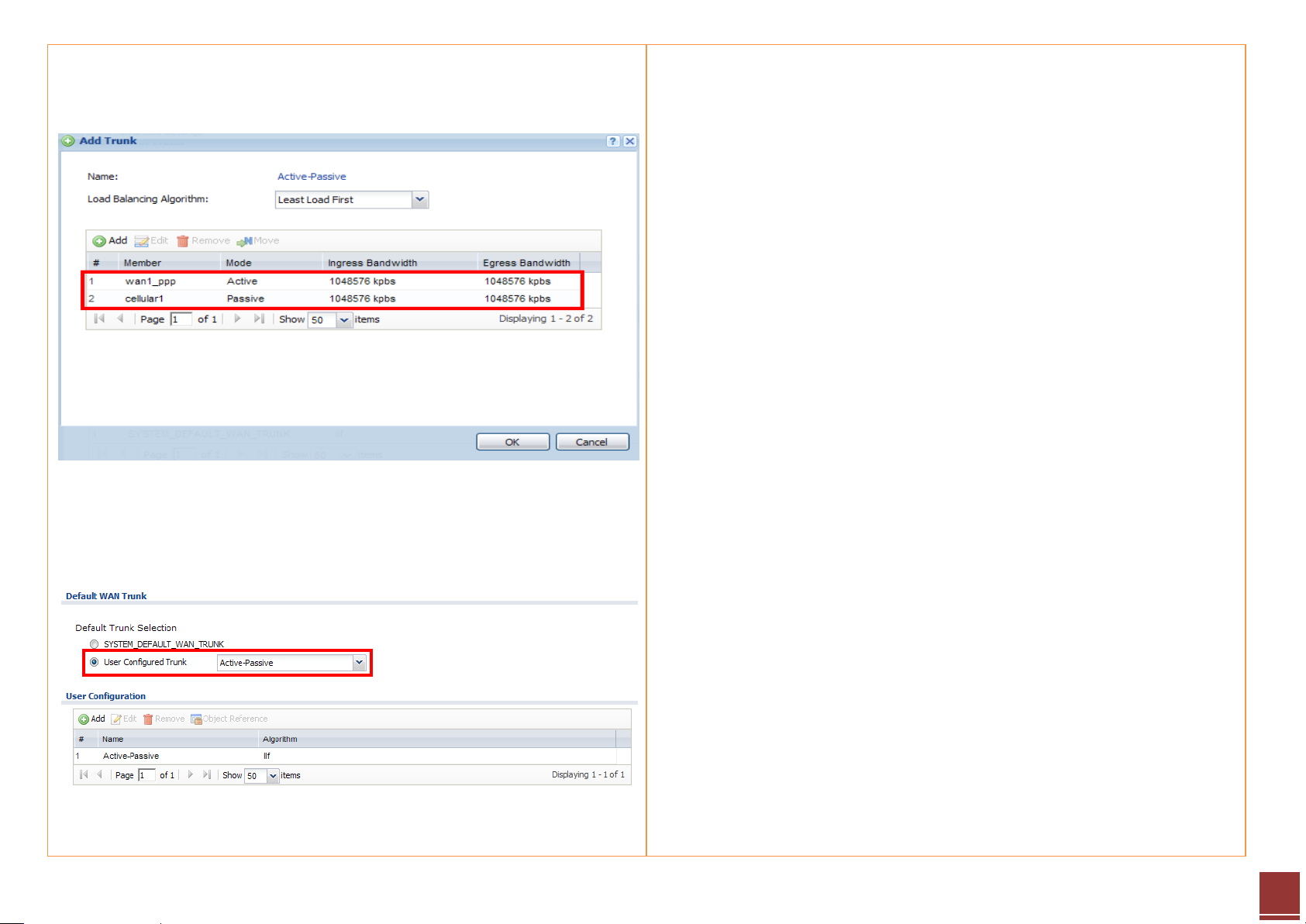
Step 13. Configure the trunk name and add the two interfaces: PPPoE for
Active and 3G for Passive mode.
Step 14. Select the User Configured Trunk rule as the default WAN trunk.
Then it will work using PPPoE as primary and 3G as a backup connection.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.

ZyXEL – ZyWALL USG Support Notes
12
Scenario 2 — WAN Load Balancing and Customized Usage of WAN Connection for Specific
Traffic
2.1 WAN Load Balancing
As an enterprise network gateway, the USG ZyWALL often has more than one WAN connection to share the company network traffic load. Without WAN load
balancing, a single WAN connection may get too congested, causing the Internet traffic to become slow or even get lost.
USG ZyWALL provides network administrators with flexible ways of implementing WAN load balancing according to their demands. The outbound traffic is
shared among multiple internet connections. Therefore, Internet traffic can get passed through the USG ZyWALL smoothly, improving your service quality and
ensuring the Internet connections get effectively utilized.
2.1.1 Load Balancing Algorithm
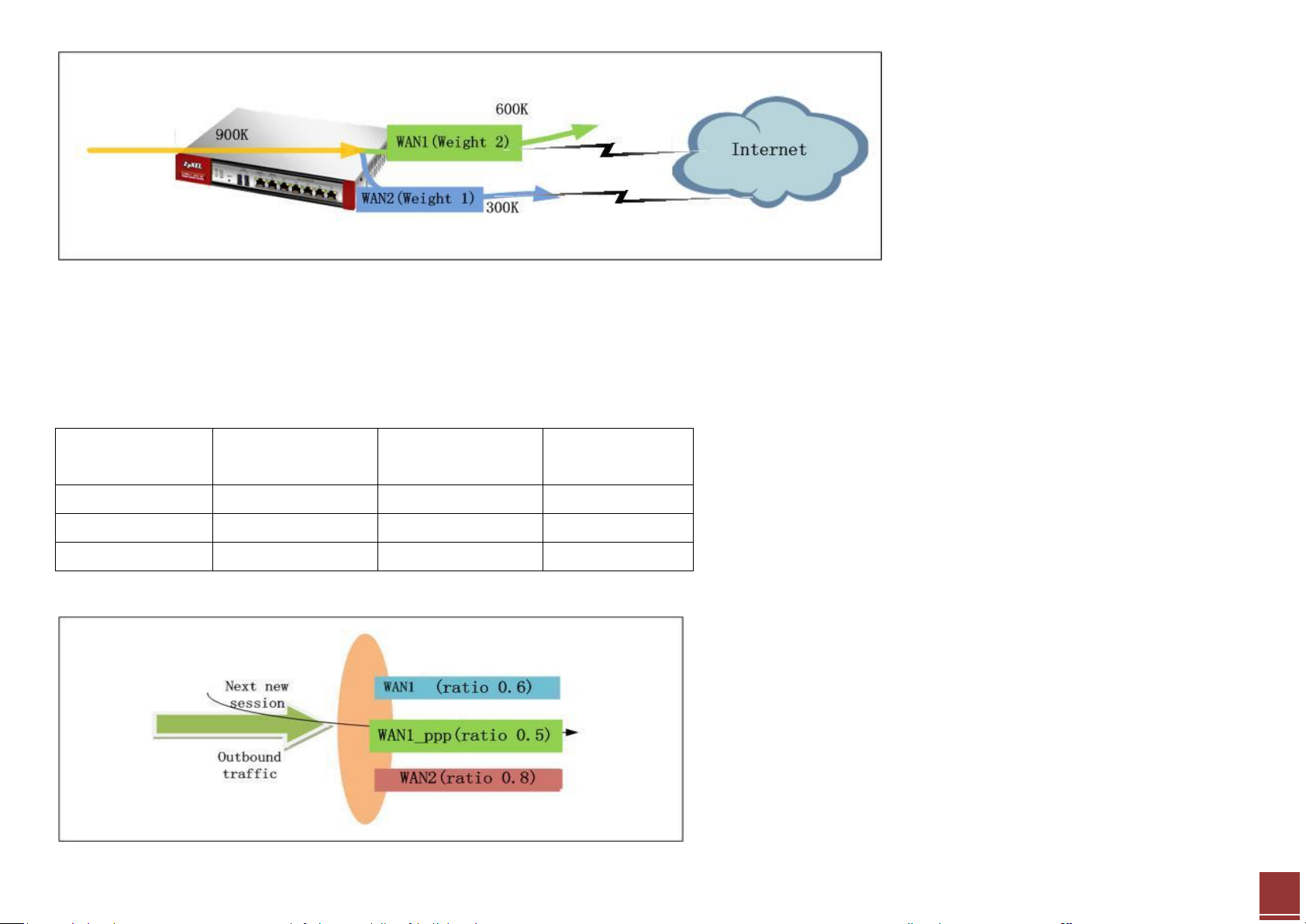
WRR — Weighted Round Robin
We can assign different weights to different internet connections according to their bandwidth. The outbound traffic sessions will be sent out among the
multiple WAN connections in turn; sessions will be assigned to different connections according to their proportional weights. Take the following for example:
WAN1 bandwidth: 1 Mbps.
WAN2 bandwidth: 512 Kbps.
Since WAN1 has a bandwidth about twice that of WAN2, we can assign the weights to WAN1 and WAN2 as follows:
WAN1 Weight: 2
WAN2 Weight: 1
The outbound traffic sessions will be assigned to WAN1 and WAN2 according to their proportional weights. E.g., when there’s total outbound traffic of 900K,
600K will be sent out over WAN1 and 300K will be sent out over WAN2.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
13
Interface
Available
Bandwidth
Current measured
Traffic
Utilization
Ratio
WAN1
1M
600K
0.6
WAN1_ppp
512K
256K
0.5
WAN2
2M
1.6M
0.8
LLF — Least Load First
When choosing LLF as the load balancing algorithm, the USG will calculate each WAN interface’s current outbound traffic utilization against the interface’s
available bandwidth. Then it will use each interface’s traffic utilization ratio as the index to decide via which WAN interface it will send the next new session.
The interface with the least outbound traffic utilization ratio will be used to send the next new session.
Take the following for example:
The next outbound new session will be sent over WAN1_ppp.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
14
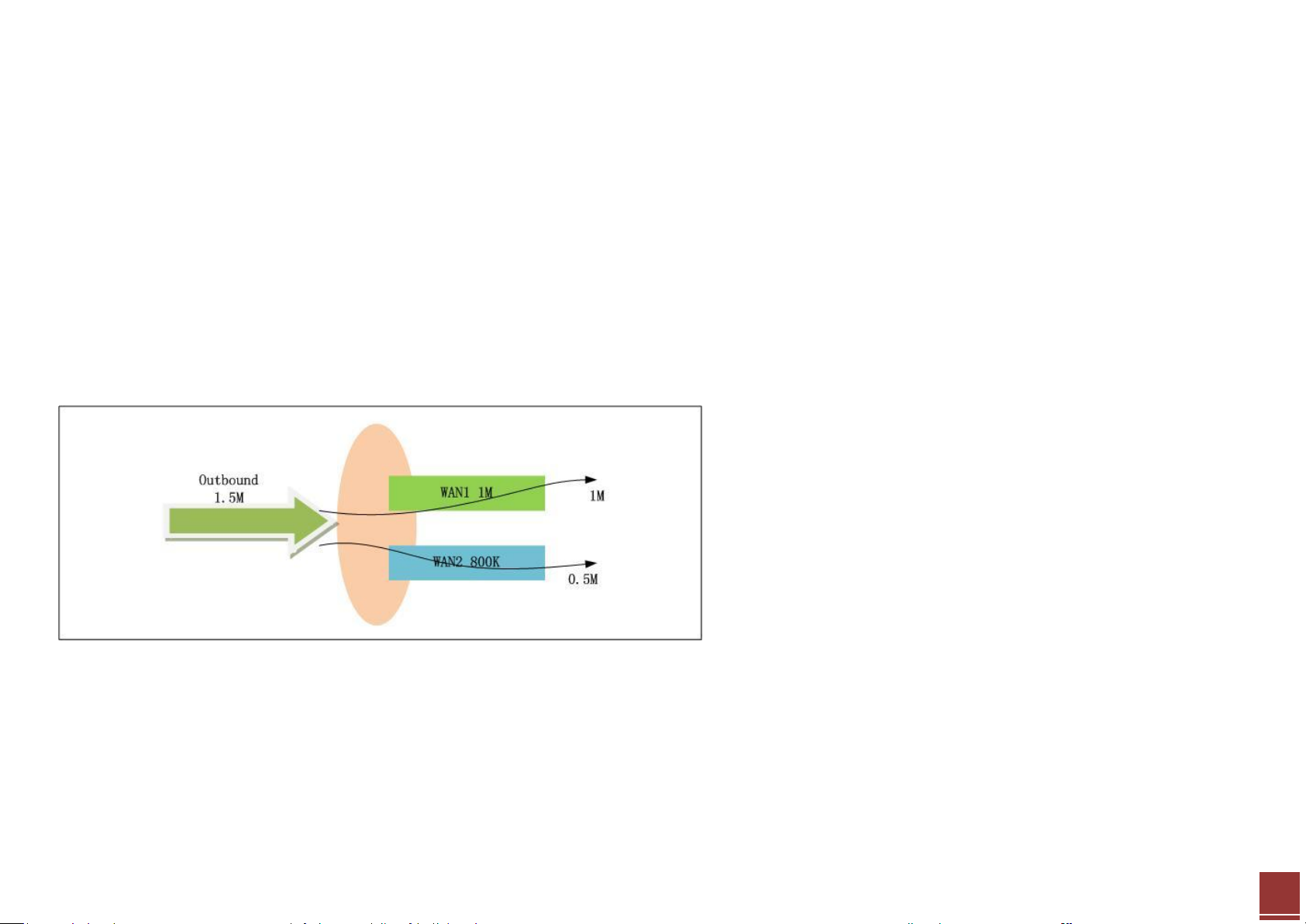
Spill-over
When choosing the Spill-over load balancing algorithm, the USG will send outbound traffic to the first interface member in the WAN trunk until its ma ximum
allowable bandwidth is reached. Then the USG will send the excess outbound traffic to the second interface member in the WAN trunk.
This algorithm is used when the first WAN connection is free or has a lower billing rate than the second WAN connection. The company can use this load
balancing algorithm to reduce Internet fees while avoiding congestion on the first WAN connection.
See the example below:
WAN1 (free connection) bandwidth: 1M
WAN2 (billing connection) bandwidth: 800K
Total outbound traffic is 1.5M. The traffic distribution among the two connections:
WAN1: 1M
WAN2: 0.5M
2.2 Customized Usage of WAN Connection for Specific Traffic Type
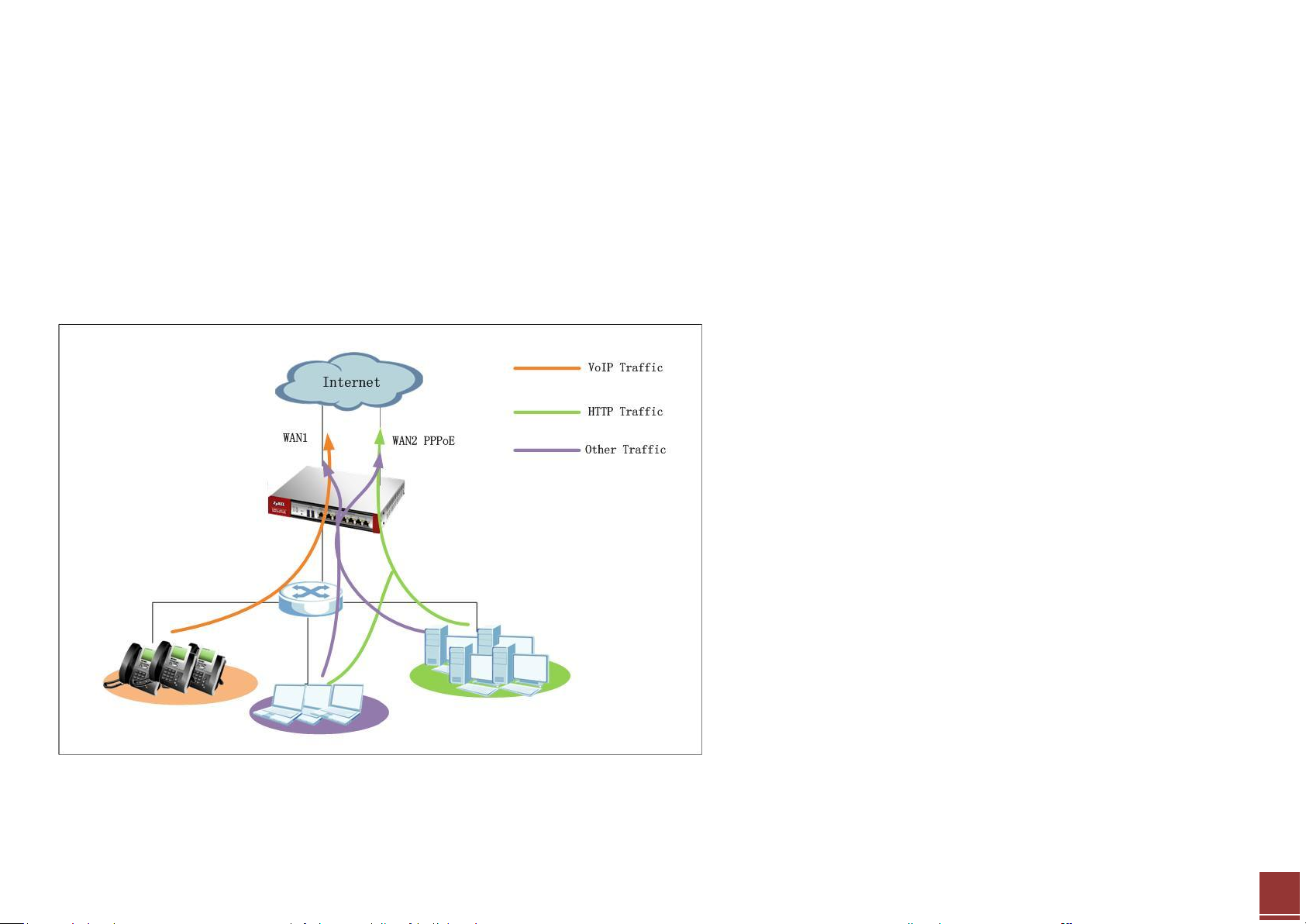
In some cases, the network administrator may prefer to send out some specific type of traffic over a specific WAN connection. For example, the ISP for WAN1
connection is also the company’s ITSP (VoIP provider). Therefore, network administrator can set the gateway to send VoIP traffic out over WAN1.
Both ZyNOS ZyWALL and USG ZyWALL can achieve this application by Policy Route.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
15
2.3 Application Scenario
The company has two WAN connections for sharing outbound internet traffic. WAN1 uses static IP, and WAN2 uses a PPPoE connection. Since WAN1 ISP is
also the company’s VoIP provider, the network administrator wants VoIP traffic primarily sent out over WAN1. In case WAN1 is down, the VoIP traffic can still
go out over WAN2 PPPoE connection. Network administrator also wants HTTP traffic sent over WAN2 PPPoE connection primarily. In case WAN2 PPPoE is
down, LAN users can still surf internet over WAN1. For all other types of traffic, administrator needs the two WAN connections to share the outbound traffic
load, performing load balancing.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
16
- LAN subnet: 192.168.1.0/24
- WAN1 IP: 200.0.0.1
- WAN2 PPPoE IP: Dynamic
- WAN1 download bandwidth: 2M
- WAN2 download bandwidth: 2M
ZLD configuration
ZyNOS configuration
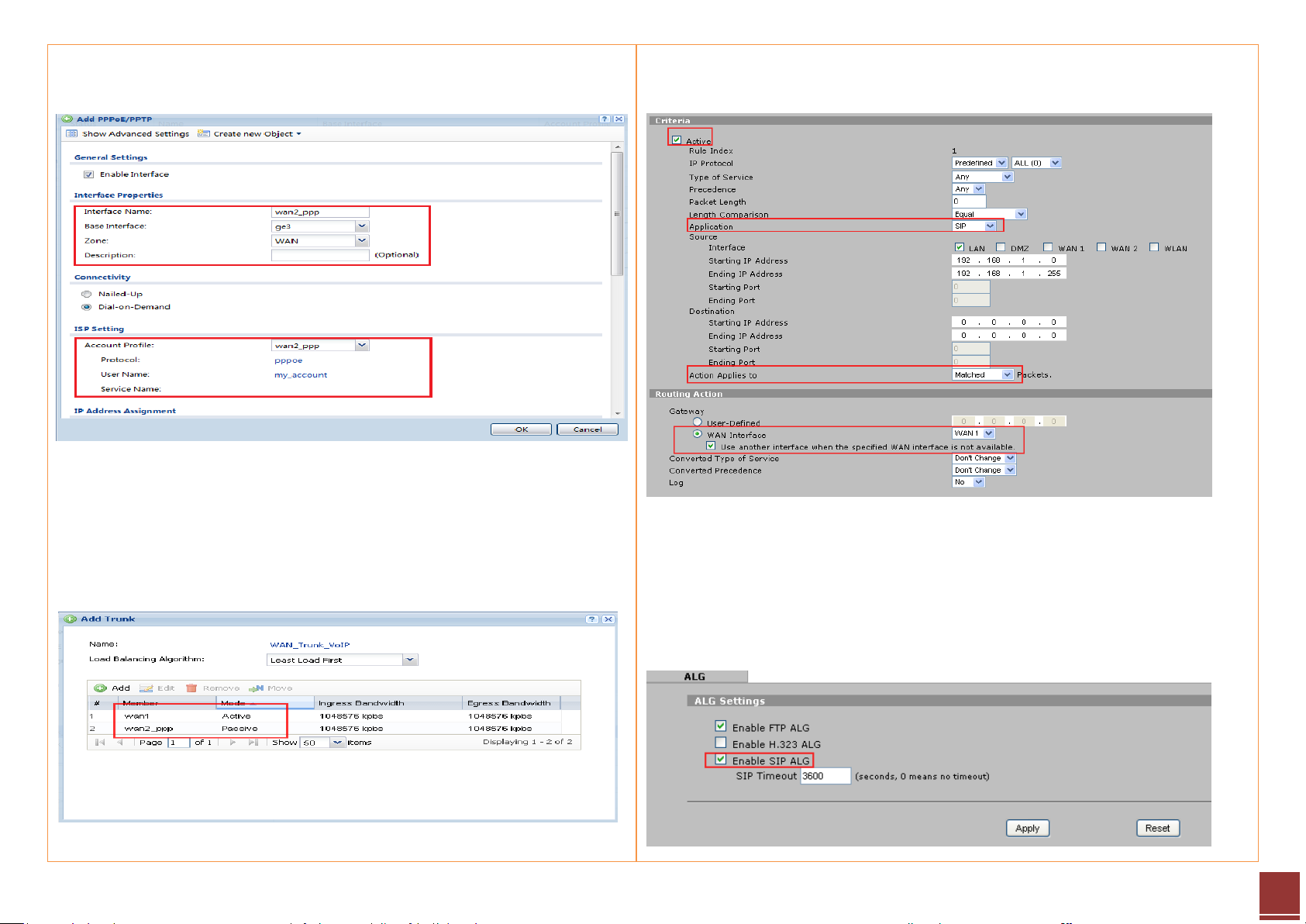
Step 1. Configure a PPPoE account on WAN2 interface.
a. Go to CONFIGURATION > Object > ISP Account, add a PPPoE account:
Step 1. Go to Advanced > Policy Route, add policy route to route VoIP traffic out
primarily from WAN1, and WAN2 as backup.
Criteria:
Application: SIP
Source: Choose LAN interface. Address range: 192.168.1.0~192.168.1.255
Destination: Any.
Action Applies to: Matched packets.
Routing Action:
2.4 Configuration Guide
Network Conditions:
Goals to achieve:
1) VoIP traffic goes out primarily through WAN1. In case WAN1 is down, it will go out via WAN2 PPPoE connection.
2) HTTP traffic goes out primarily through WAN2 PPPoE connection. In case WAN2 PPPoE is down, it will go out via WAN1.
3) All other traffic goes out via WAN trunk performing Load Balancing with Least Load Balancing algorithm.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
17
b. Go to CONFIGURATION > Network > Interface > PPP, add a new PPP
interface which is based on WAN 2(ge3) interface:
Step 2. Go to CONFIGURATION > Network > Interface > Trunk. Add WAN
Trunks.
a. Add WAN trunk for VoIP traffic — Set WAN1 as Active mode, while
setting WAN2_ppp as Passive mode.
Choose WAN interface WAN1, and enable Use another interface when the
specified WAN interface is not available.
Please enable SIP ALG to let this policy route apply to all VoIP traffic including
both SIP signaling and RTP (voice data).
Go to Advanced > ALG, enable SIP ALG.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
18
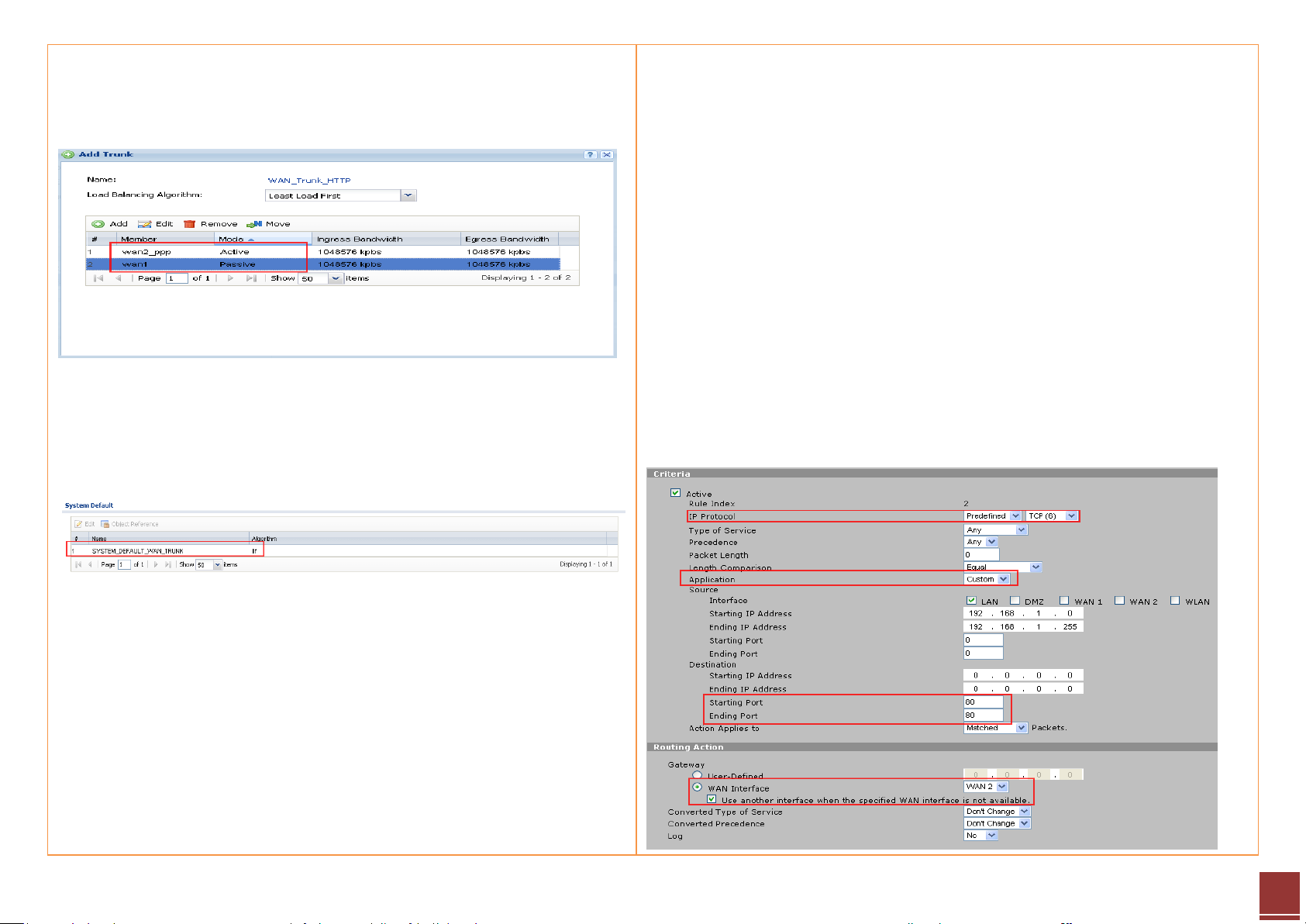
b. Add WAN trunk for HTTP traffic — Set WAN2_ppp as Active mode,
while setting WAN1 as Passive mode.
c. Use SYSTEM_DEFAULT_WAN_TRUNK to do load balancing for all other
traffic.
Step 2. Go to Advanced > Policy Route, add a policy route to route HTTP traffic
out primarily through WAN2, leaving WAN1 as backup.
Criteria:
IP Protocol: TCP (6)
Application: Custom
Source IP: Choose interface LAN. Address range: 192.168.1.0~192.168.1.255
Source port: Any
Destination IP: Any
Destination Port: 80
Action Applies to: Matched packets.
Routing Action:
Choose WAN interface WAN2, and enable Use another interface when the
specified WAN interface is not available.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
19
Step 3. Go to CONFIGURATION > Network > Routing > Policy Route, add
policy routes for VoIP traffic and HTTP traffic.
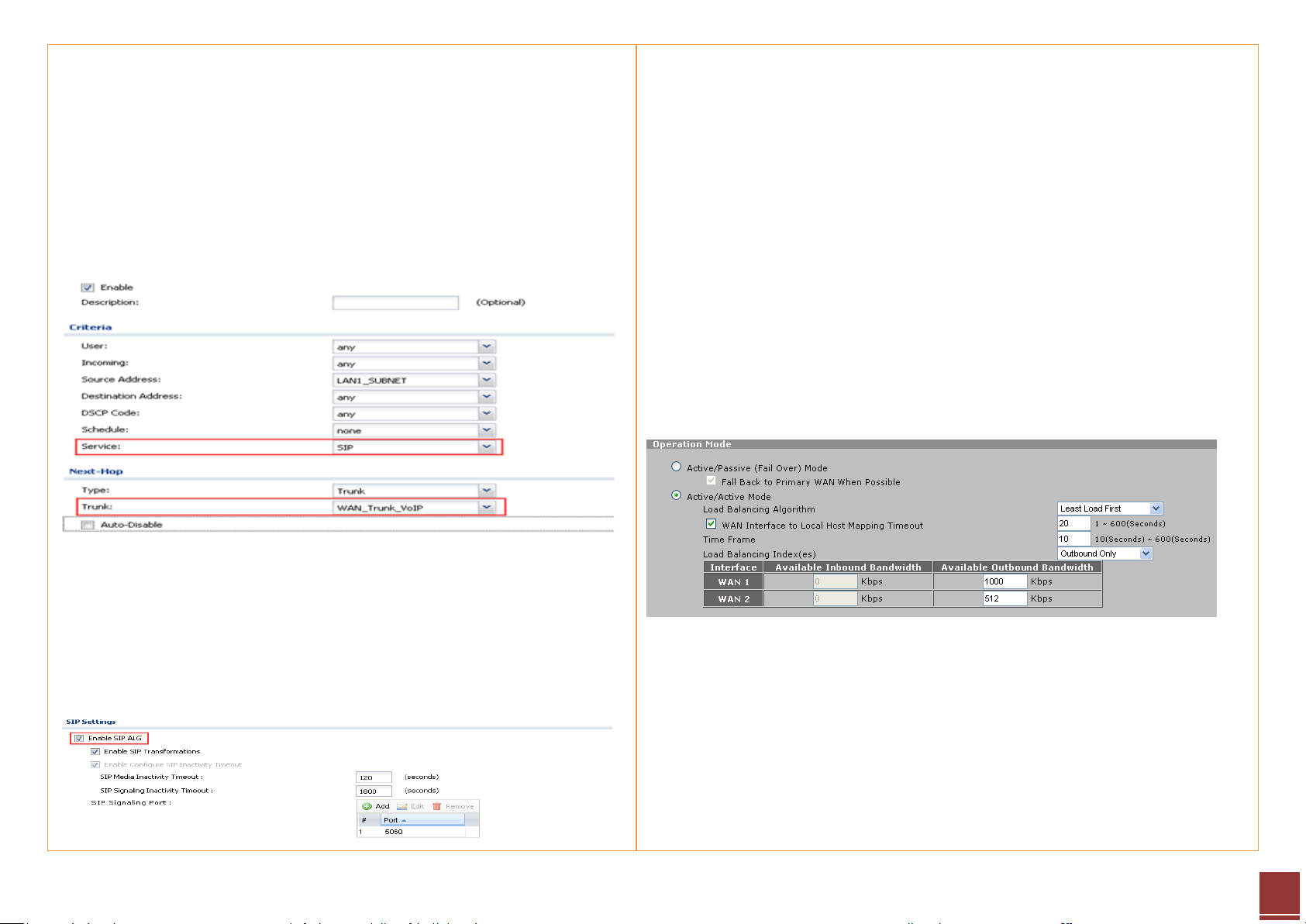
a. Add a policy route for VoIP traffic:
Source: LAN1_subnet
Destination: Any
Service: SIP
Next Hop: select the newly created WAN trunk WAN_Trunk_VoIP
Please note that to make sure this policy route applies to all VoIP traffic,
including both the SIP signaling and RTP (voice data), we need to enable SIP
ALG. Go to Configuration > Network > ALG, enable SIP ALG.
Step 3. For all other traffic, we use the two WAN connections to perform load
balancing. Go to Network > WAN > General.
Choose Active/Active Mode.
Set the Load Balancing Algorithm to Least Load First.
To avoid the situation where traffic from the same LAN host may be sent over
different WAN interfaces, which may cause servers to refuse the connection due
to a different source IP, we enable and set “WAN Interface to Local Host
Mapping Timeout” to a specific time period.
For Load Balancing Index (es), we choose Outbound Only.
Set the available outbound bandwidth for the two WAN connections according
to the bandwidth obtained from each ISP.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
20
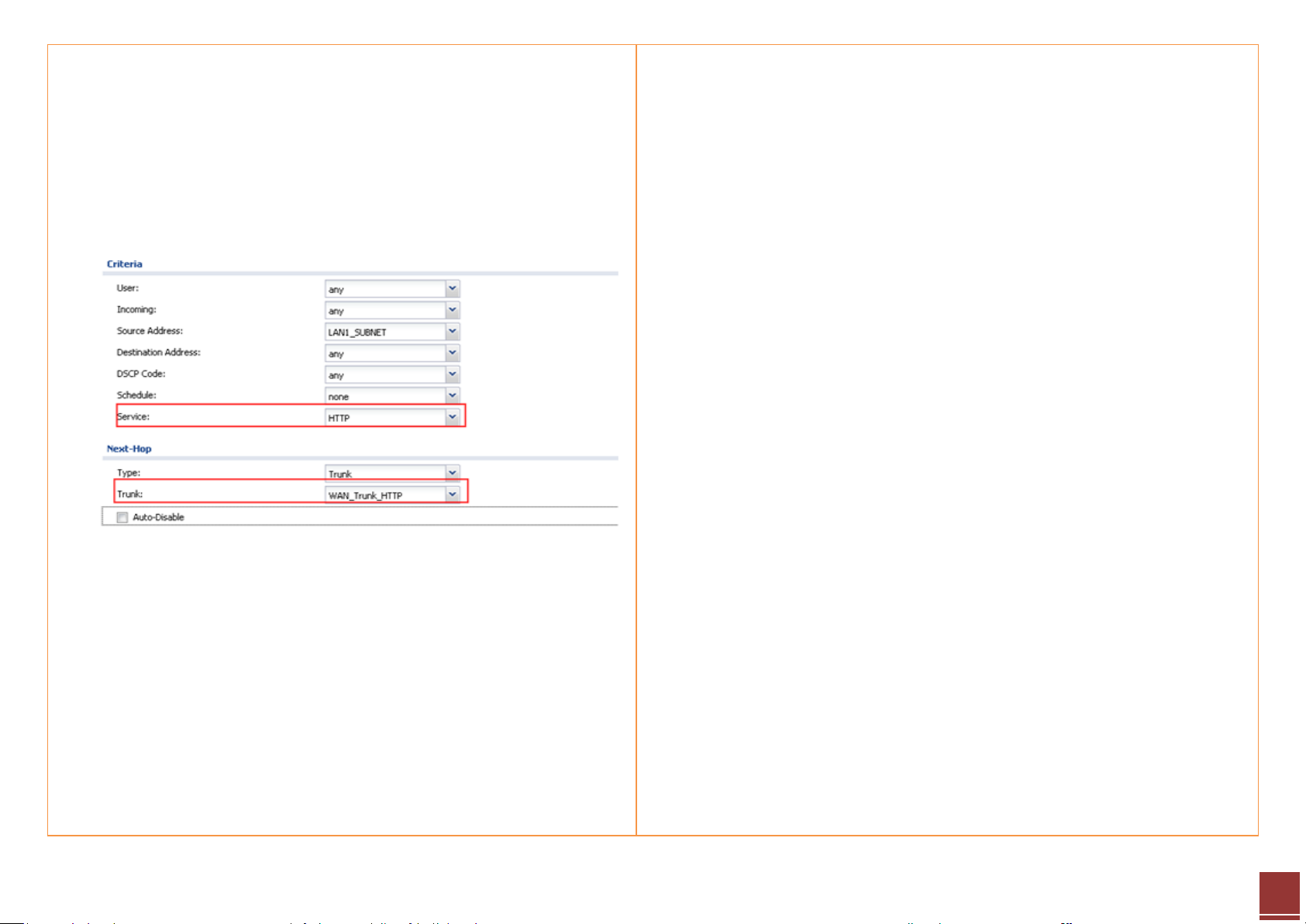
b. Add a policy route for HTTP traffic:
Source: LAN1_subnet
Destination: Any
Service: HTTP
Next Hop: Select the newly created WAN trunk WAN_Trunk_HTTP.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
21
c. For all other traffic, use SYSTEM_DEFAULT_WAN_TRUNK to do load
balancing.
Go to Configuration > Network > Interface > Trunk. Click Show
Advanced Settings.
Make sure Default SNAT is enabled. Select
SYSTEM_DEFAULT_WAN_TRUNK in Default Trunk Selection.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
22
Scenario 3 — How to configure NAT if you have Internet-facing public servers
3.1 Application Scenario
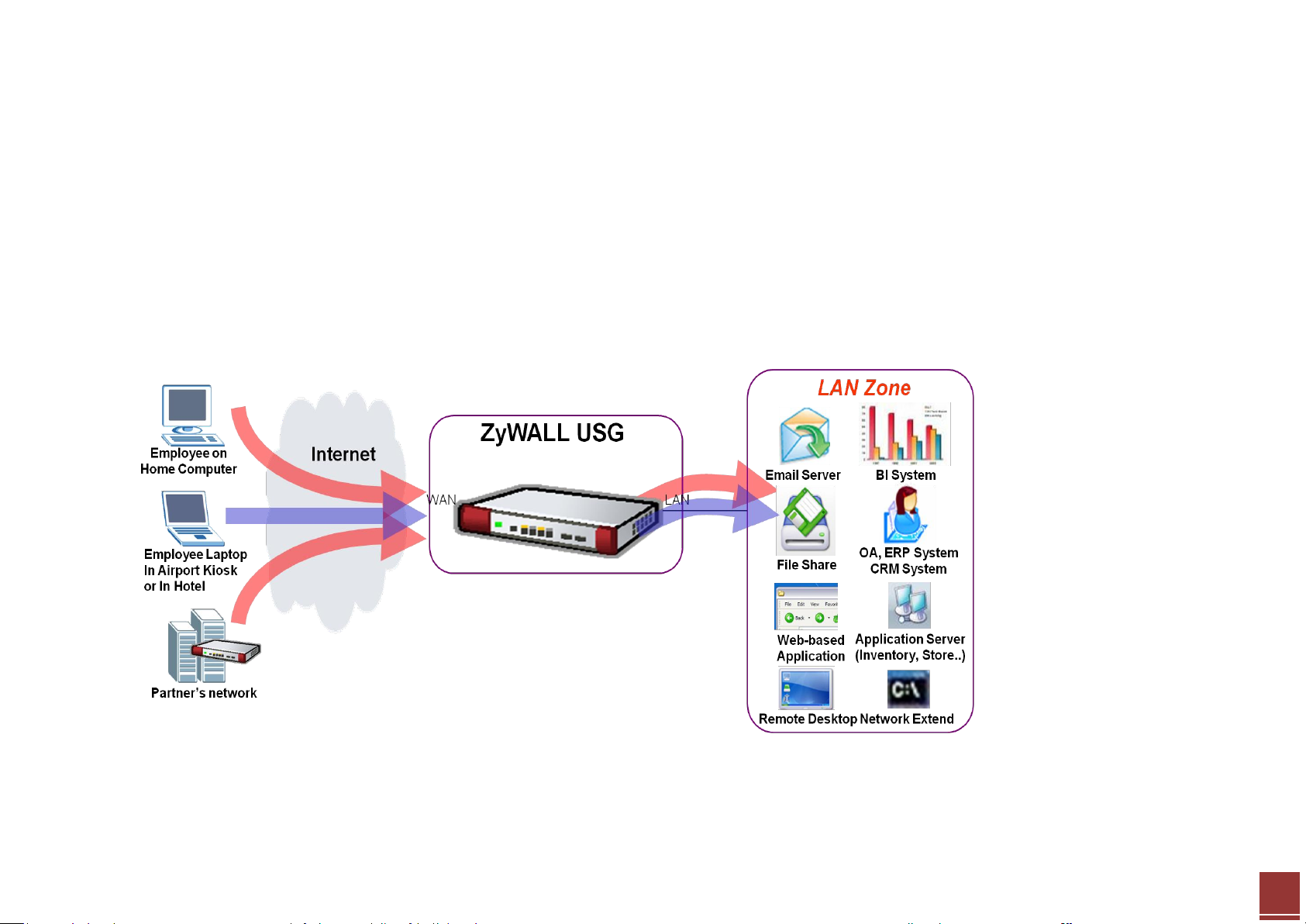
It is a common practice to place company servers behind the USG’s protection; while at the same time letting WAN side clients/servers access the intranet
servers. To give an example, the company may have an internal FTP server, which needs to be accessible from the Internet as well. To fulfill this requirement,
user can configure a NAT mapping rule to forward the traffic from Internet side to intranet side. This feature can not only ensure service availability but also
helps avoid exposing the server’s real IP address to be attacked.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
23
3.2 Configuration Guide
USG-50:
- WAN IP: 59.124.163.152
- FTP server IP:192.168.50.33
ZyWALL-5 UTM:
- WAN IP: 10.59.1.50
- FTP server IP: 192.168.5.33
ZLD configuration
ZyNOS configuration
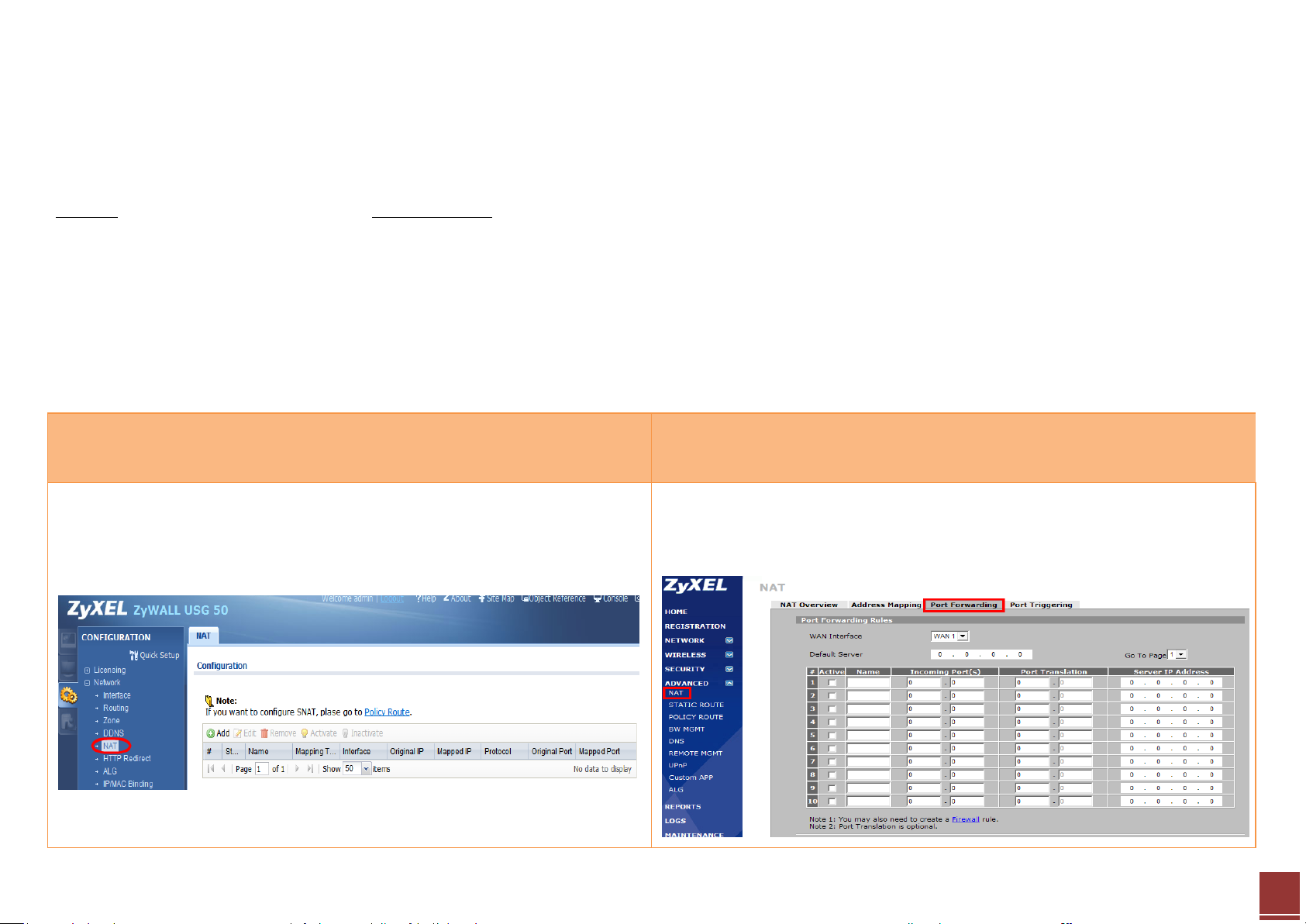
Step 1. Click CONFIGURATION > Network > NAT to open the configuration
screen.
Step 1. Click ADVANCED > NAT > Port Forwarding to open the configuration
screen.
Network Conditions:
Goal to achieve:
User Tom can access the internal FTP server by accessing the Internet-facing WAN IP address.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
24
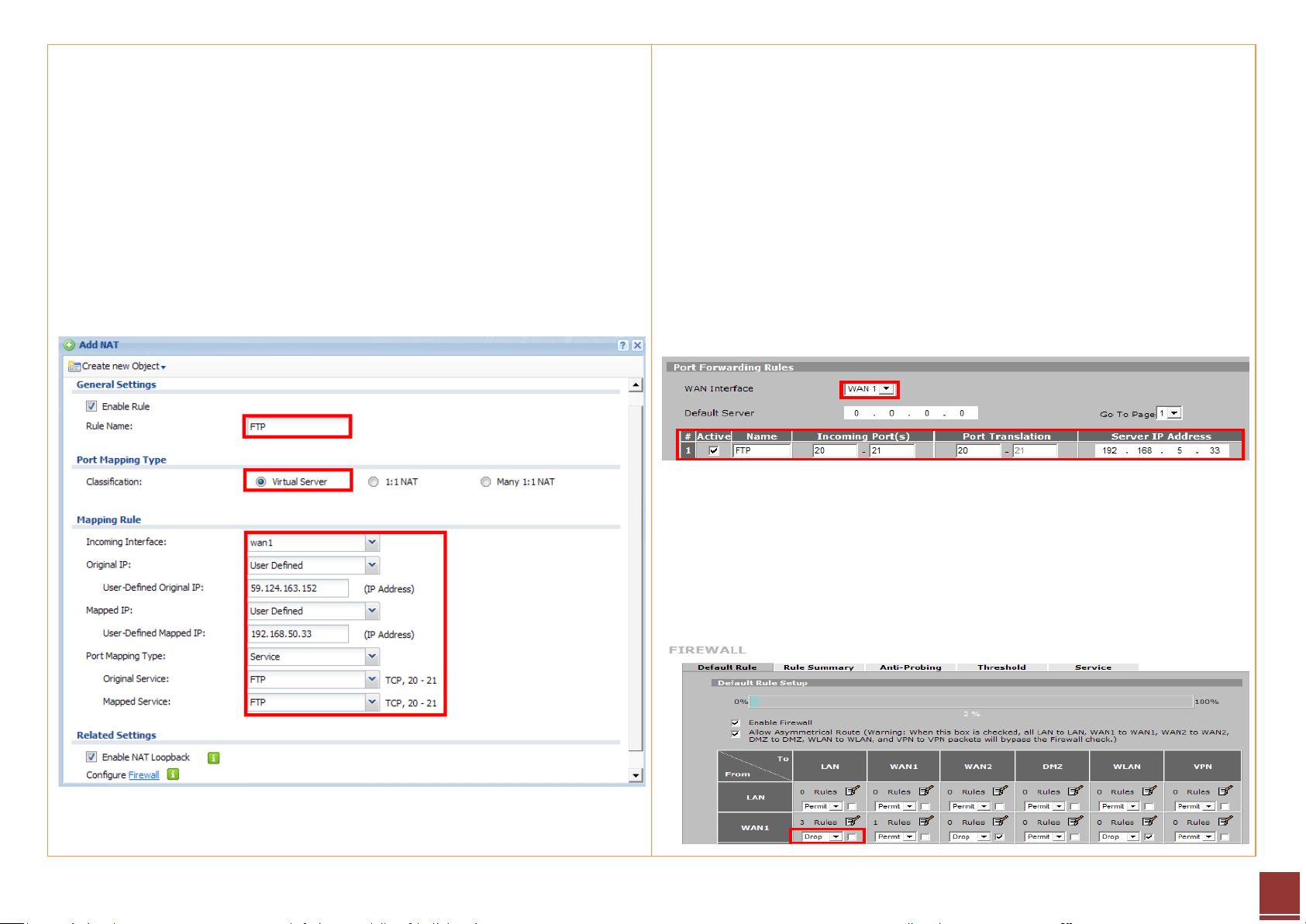
Step 2. Click the Add button to create a mapping rule.
Step 3. In this page user needs to configure:
- Rule’s name
- Select Virtual Server type to let USG-50 do packet forwarding
- Fill in the Original IP (WAN IP) address
- Fill in the Mapped IP (Internal FTP server IP) address
- Select the service to be mapped (FTP); the ports will be selected
automatically
Step 2. Configure the mapping rule. User needs to select the WAN interface
for the incoming access, choosing the WAN IP for users to access.
Step 3. Then configure the incoming ports, translation ports and the internal
FTP server IP address.
In this case, when the user accesses the WAN IP address with the port 20/21,
the ZyWALL-5 UTM will forward the request to the FTP server, 192.168.5.33,
with the port 20/21. Thus, user can access the internal FTP server without
problem.
Step 4. The port forwarding rule enables delivery of the access request from
WAN to the internal network, but the user still needs to configure access
privileges by adjusting the firewall rule. By default all WAN to LAN access is
dropped.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
25
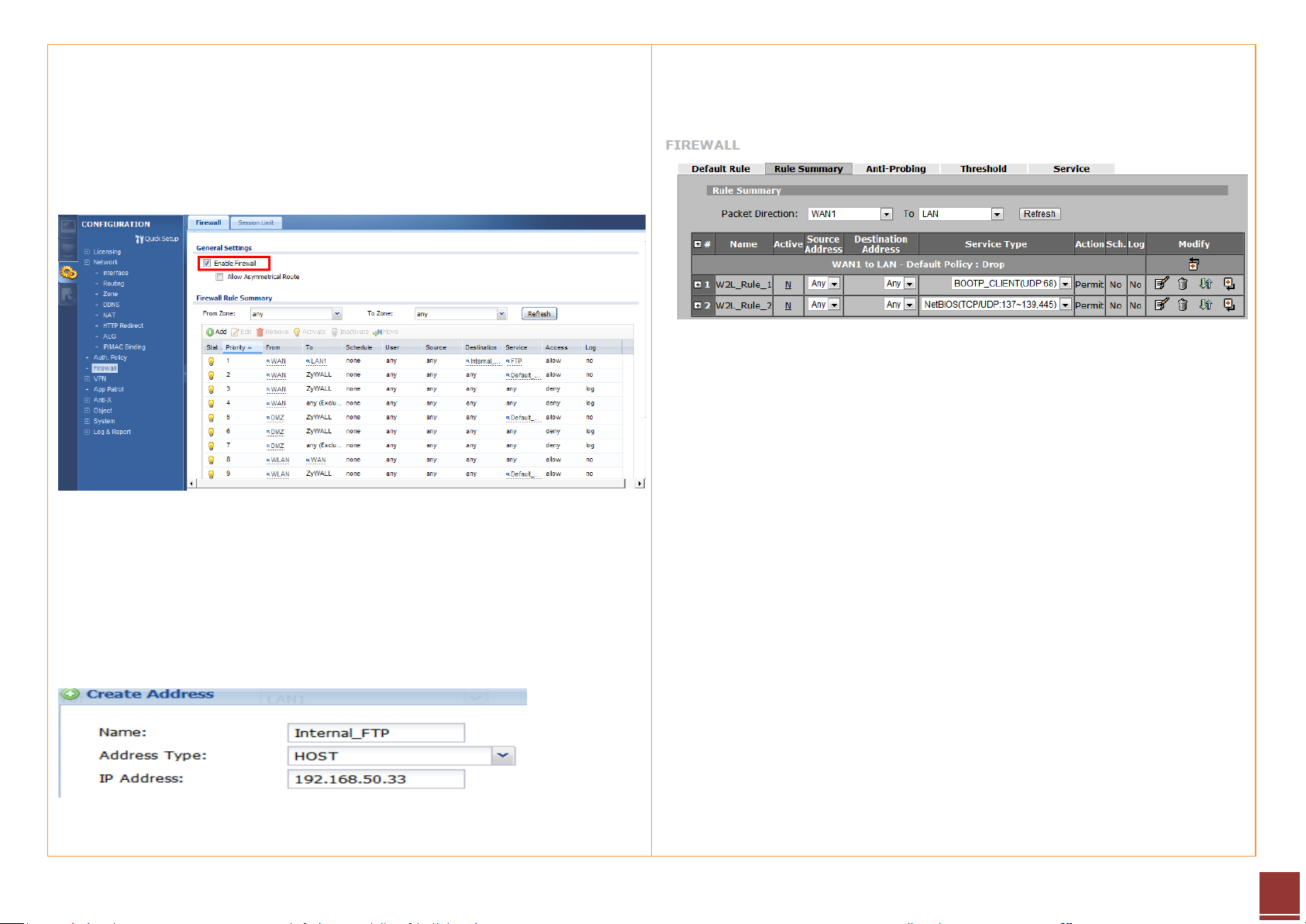
Step 4. Click CONFIGURATION > Network > Firewall to open the firewall
configuration screen.
Here assume the user already assigned the WAN interface to WAN zone and
LAN interface to LAN1 zone.
Step 5. Click the Add button to create a firewall rule to enable the FTP service
to pass from WAN to LAN1.
Step 6. User can create an address object for the internal FTP server for
further configuration usage. Click Create new Object for this function.
Step 5. Click Rule Summary to customize the setup. The default is to drop all
packets.
Step 6. Configure the firewall rule to enable the FTP service to pass from
WAN1 to LAN.
- Source IP address is not specific
- Destination IP address is the FTP server’s address
- Select FTP service (with port 20/21) to be enabled
- Select the Permit action for matched packets
After this configuration, user can access the FTP server from WAN side.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
26
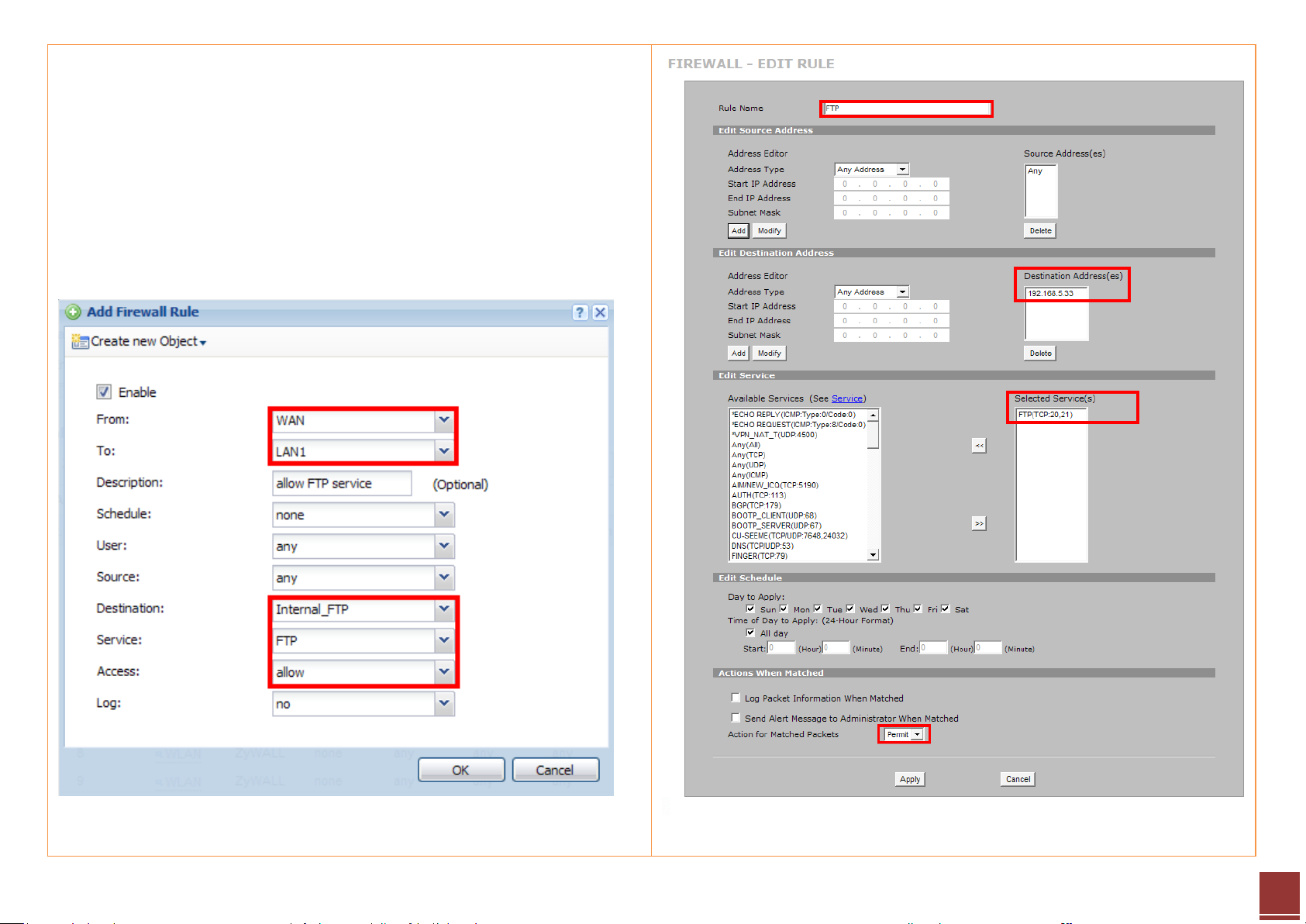
Step 7. Configure the rule to:
- Allow access from WAN to LAN1
- Source IP address is not specific
- Destination IP address is the FTP server’s address
- Select FTP service (with port 20/21) to be enabled
- Select the allow action for matched packets
After this configuration, user can access the FTP server from WAN side.
ZyXEL – ZyWALL USG Support Notes
All contents copyright (c) 2010 ZyXEL Communications Corporation.
ZyXEL – ZyWALL USG Support Notes
27
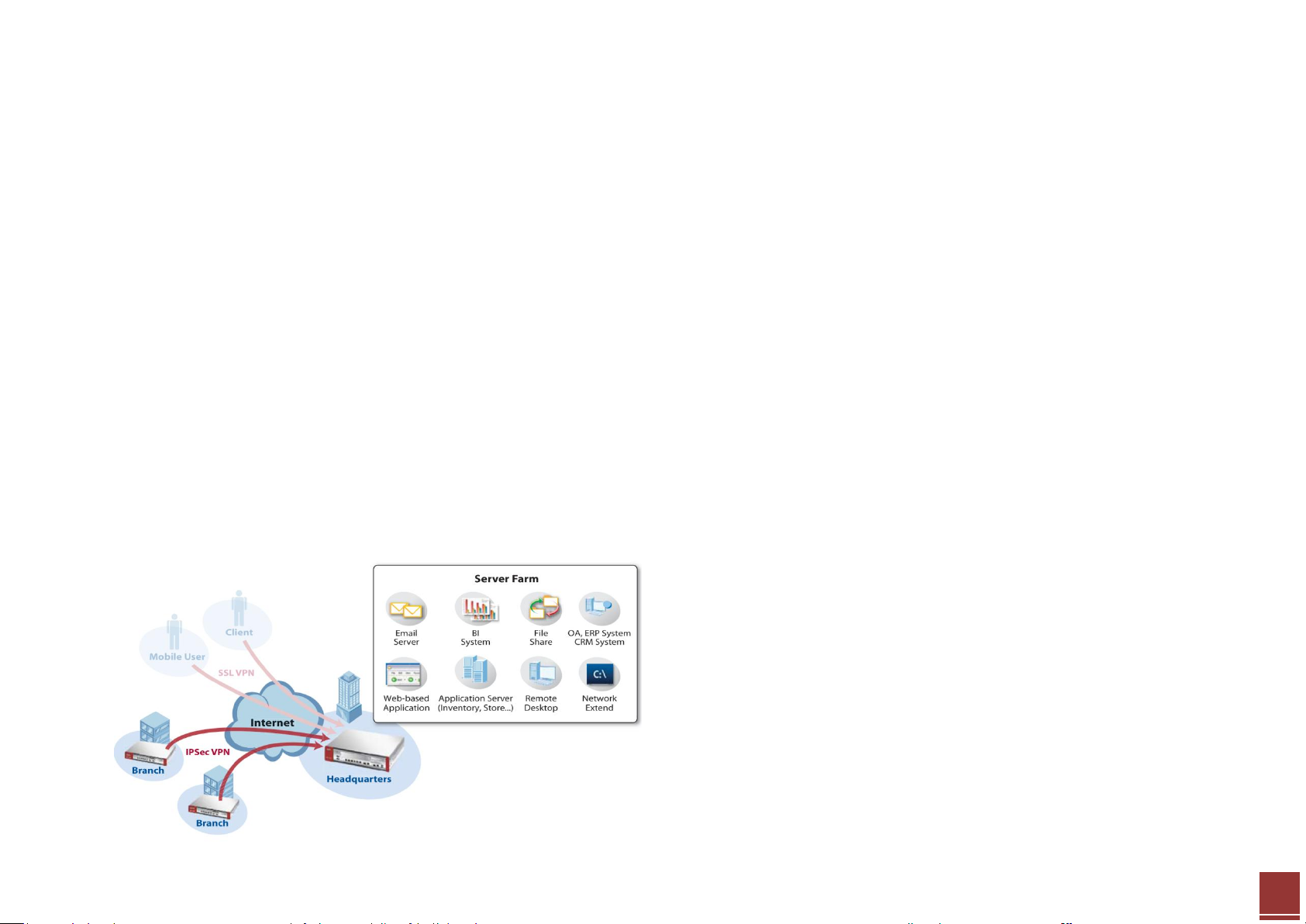
Scenario 4 — Secure site-to-site connections using IPSec VPN
4.1 Application Scenario
A virtual private network (VPN) provides secure communications between sites without the expense of leased site-to-site lines. A secure VPN is a combination
of tunneling, encryption, authentication, access control and auditing. It is used to transport traffic over the Internet or any insecure network that uses TCP/IP
for communication.
Internet Protocol Security (IPSec) offers standards-based VPN solutions that enable flexible scenarios for secure data communications across a public network
like the Internet. An IPSec VPN tunnel is usually established in two phases. Each phase establishes a security association (SA), a contract indicating what
security parameters the ZyWALL and the remote IPSec router will use. The first phase establishes an Internet Key Exchange (IKE) SA between the ZyWALL and
a remote IPSec router. The second phase uses the IKE SA to securely establish an IPSec SA through which the ZyWALL and remote I PSec router can send data
between computers on the local network and remote network.
The USG can provide secure site-to-site access between remote locations and corporate resources through the Internet. Using IPSec VPN, companies can
secure connections to branch offices, partners and headquarters as the illustration below.
All contents copyright (c) 2010 ZyXEL Communications Corporation.
 Loading...
Loading...