ZyXEL USG20W-VPN Users Manual

CHAPTER 24
USG SecuExtender (Windows)
The USG automatically loads the USG SecuExtender for Windows client program to your computer
after a successful login to an SSL VPN tunnel with network extension support enabled.
Note: For information on using the USG SecuExtender for Mac client program, please see
its User’s Guide at the download library on the ZyXEL website.
The USG SecuExtender (Windows) lets you:
• Access servers, remote desktops and manage files as if you were on the local network.
• Use applications like e-mail, file transfer, and remote desktop programs directly without using a
browser. For example, you can use Outlook for e-mail instead of the USG’s web-based e-mail.
• Use applications, even proprietary applications, for which the USG does not offer SSL application
objects.
The applications must be installed on your computer. For example, to use the VNC remote desktop
program, you must have the VNC client installed on your computer.
24.1 The USG SecuExtender Icon
The USG SecuExtender icon color indicates the SSL VPN tunnel’s connection status.
Figure 271 USG SecuExtender Icon
• Green: the SSL VPN tunnel is connected. You can connect to the SSL application and network
resources. You can also use another application to access resources behind the USG.
• Gray: the SSL VPN tunnel’s connection is suspended. This means the SSL VPN tunnel is
connected, but the USG SecuExtender will not send any traffic through it until you right-click the
icon and resume the connection.
• Red: the SSL VPN tunnel is not connected. You cannot connect to the SSL application and
network resources.
24.2 Status
Right-click the USG SecuExtender icon in the system tray and select Status to open the Status
screen. Use this screen to view the USG SecuExtender’s connection status and activity statistics.
USG20(W)-VPN Series User’s Guide
391

Chapter 24 USG SecuExtender (Windows)
Figure 272 USG SecuExtender Status
The following table describes the labels in this screen.
Table 149 USG SecuExtender Status
LABEL DESCRIPTION
Connection Status
SecuExtender IP
Address
DNS Server 1/2 These are the IP addresses of the DNS server and backup DNS server for the SSL VPN
WINS Server 1/2 These are the IP addresses of the WINS (Windows Internet Naming Service) and backup
Network 1~8 These are the networks (including netmask) that you can access through the SSL VPN
Activity
Connected Time This is how long the computer has been connected to the SSL VPN tunnel.
Tra n s mitted This is how many bytes and packets the computer has sent through the SSL VPN
Received This is how many bytes and packets the computer has received through the SSL VPN
This is the IP address the USG assigned to this remote user computer for an SSL VPN
connection.
connection.
DNS (Domain Name System) maps a domain name to its corresponding IP address and
vice versa. The DNS server is extremely important because without it, you must know
the IP address of a computer before you can access it. Your computer uses the DNS
server specified here to resolve domain names for resources you access through the SSL
VPN connection.
WINS servers for the SSL VPN connection. The WINS server keeps a mapping table of
the computer names on your network and the IP addresses that they are currently using.
connection.
connection.
connection.
24.3 View Log
If you have problems with the USG SecuExtender, customer support may request you to provide
information from the log. Right-click the USG SecuExtender icon in the system tray and select Log
to open a notepad file of the USG SecuExtender’s log.
USG20(W)-VPN Series User’s Guide
392

Chapter 24 USG SecuExtender (Windows)
Figure 273 USG SecuExtender Log Example
##################################################################################
##############
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Build Datetime: Feb 24 2009/
10:25:07
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DEBUG] rasphone.pbk: C:\Documents and
Settings\11746\rasphone.pbk
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DEBUG] SecuExtender.log:
C:\Documents and Settings\11746\SecuExtender.log
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Check Parameters
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Connect to 172.23.31.19:443/
10444
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Parameter is OK
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Checking System status...
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Checking service (first) ...
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] SecuExtender Helper is running
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] System is OK
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DEBUG] Connect to 2887196435/443
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] Handshake LoopCounter: 0
[ 2009/03/12 13:35:50 ][SecuExtender Agent][DETAIL] 611 bytes of handshake data
received
24.4 Suspend and Resume the Connection
When the USG SecuExtender icon in the system tray is green, you can right-click the icon and
select Suspend Connection to keep the SSL VPN tunnel connected but not send any traffic
through it until you right-click the icon and resume the connection.
24.5 Stop the Connection
Right-click the icon and select Stop Connection to disconnect the SSL VPN tunnel.
24.6 Uninstalling the USG SecuExtender
Do the following if you need to remove the USG SecuExtender.
1 Click start > All Programs > ZyXEL > USG SecuExtender > Uninstall ZyWALL
SecuExtender.
2 In the confirmation screen, click Yes.
USG20(W)-VPN Series User’s Guide
393
Chapter 24 USG SecuExtender (Windows)
Figure 274 Uninstalling the USG SecuExtender Confirmation
3 Windows uninstalls the USG SecuExtender.
Figure 275 USG SecuExtender Uninstallation
USG20(W)-VPN Series User’s Guide
394
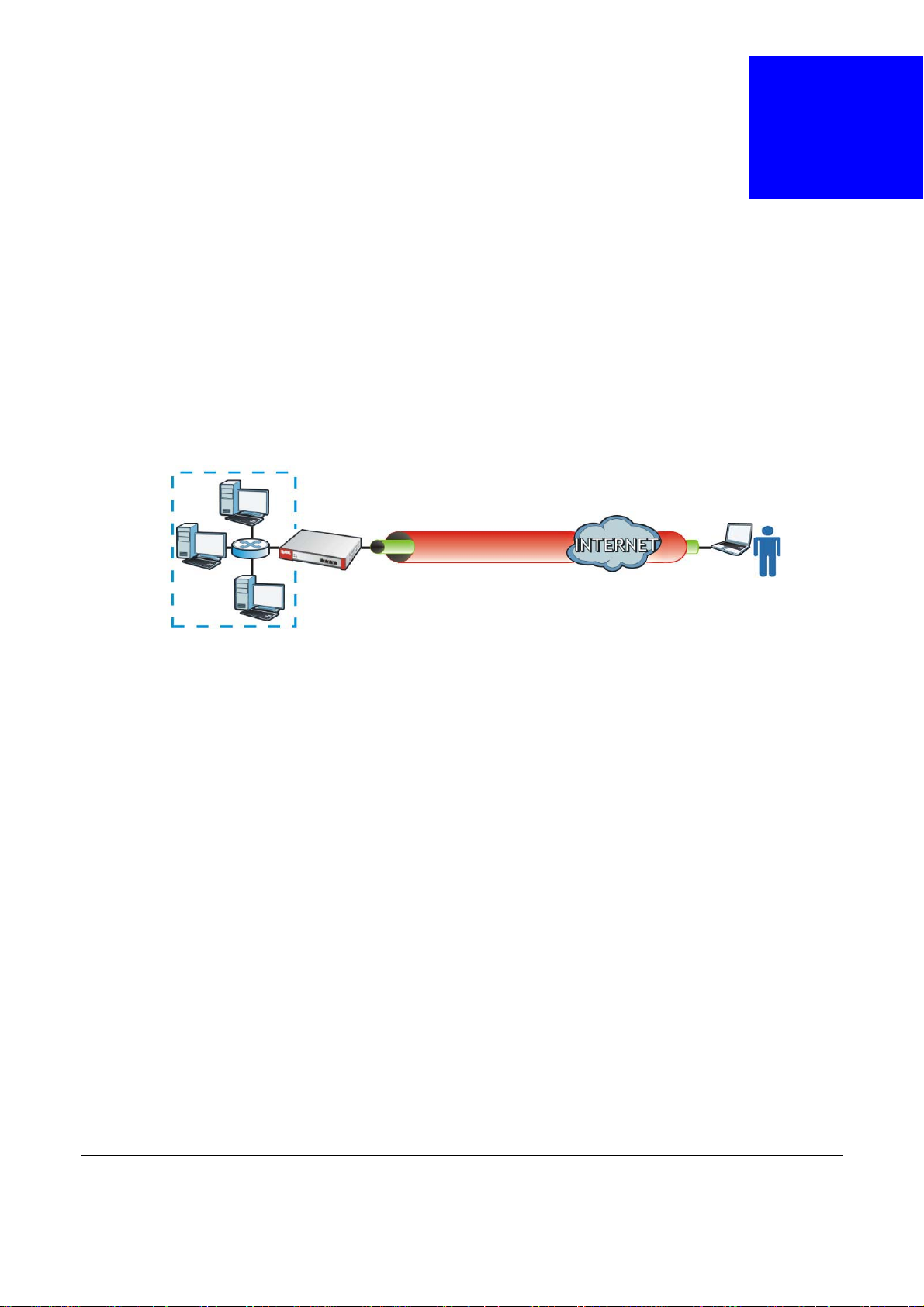
25.1 Overview
L2TP VPN uses the L2TP and IPSec client software included in remote users’ Android, iOS, Windows
or Mac OS X operating systems for secure connections to the network behind the USG. The remote
users do not need their own IPSec gateways or third-party VPN client software.
Figure 276 L2TP VPN Overview
CHAPTER 25
L2TP VPN
25.1.1 What You Can Do in this Chapter
•Use the L2TP VPN screen (see Section 25.2 on page 396) to configure the USG’s L2TP VPN
settings.
•Use the VPN Setup Wizard screen in Quick Setup (Chapter 4 on page 49) to configure the
USG’s L2TP VPN settings.
25.1.2 What You Need to Know
The Layer 2 Tunneling Protocol (L2TP) works at layer 2 (the data link layer) to tunnel network traffic
between two peers over another network (like the Internet). In L2TP VPN, an IPSec VPN tunnel is
established first and then an L2TP tunnel is built inside it. See Chapter 21 on page 332 for
information on IPSec VPN.
IPSec Configuration Required for L2TP VPN
You must configure an IPSec VPN connection prior to proper L2TP VPN usage (see Chapter 25 on
page 395 for details). The IPSec VPN connection must:
• Be enabled.
• Use transport mode.
•Use Pre-Shared Key authentication.
• Use a VPN gateway with the Secure Gateway set to 0.0.0.0 if you need to allow L2TP VPN
clients to connect from more than one IP address.
USG20(W)-VPN Series User’s Guide
395
Chapter 25 L2TP VPN
LAN_SUBNET
L2TP_POOL
Using the Quick Setup VPN Setup Wizard
The VPN Setup Wizard is an easy and convenient way to configure the L2TP VPN settings. Click
Configuration > Quick Setup > VPN Setup > VPN Settings for L2TP VPN Settings to get
started.
Policy Route
The Policy Route for return traffic (from LAN to L2TP clients) is automatically created when USG
adds a new L2TP connection, allowing users access the resources on a network without additional
configuration. However, if some of the traffic from the L2TP clients needs to go to the Internet, you
will need to create a policy route to send that traffic from the L2TP tunnels out through a WAN
trunk. This task can be easily performed by clicking the Allow L2TP traffic through WAN checkbox at
Quick Setup > VPN Setup > Allow L2TP traffic through WAN.
Figure 277 Policy Route for L2TP VPN
25.2 L2TP VPN Screen
Click Configuration > VPN > L2TP VPN to open the following screen. Use this screen to configure
the USG’s L2TP VPN settings.
Note: Disconnect any existing L2TP VPN sessions before modifying L2TP VPN settings.
The remote users must make any needed matching configuration changes and reestablish the sessions using the new settings.
Click on the icons to go to the OneSecurity.com website where there is guidance on configuration
walkthroughs, troubleshooting, and other information.
USG20(W)-VPN Series User’s Guide
396
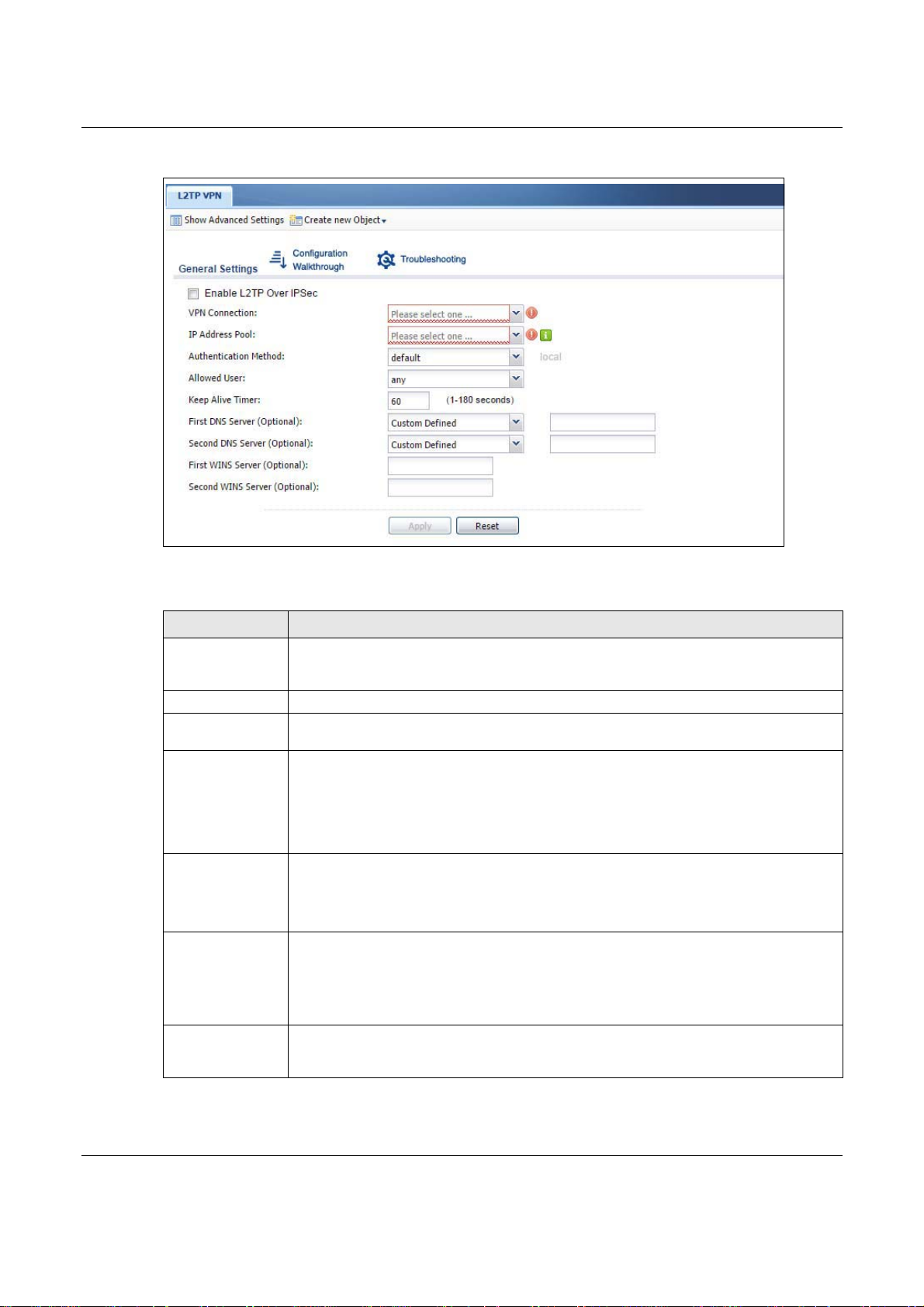
Chapter 25 L2TP VPN
Figure 278 Configuration > VPN > L2TP VPN
The following table describes the fields in this screen.
Table 150 Configuration > VPN > L2TP VPN
LABEL DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Create new Object Use to configure any new settings objects that you need to use in this screen.
Enable L2TP Over
IPSec
VPN Connection Select the IPSec VPN connection the USG uses for L2TP VPN. All of the configured VPN
Click this button to display a greater or lesser number of configuration fields.
Use this field to turn the USG’s L2TP VPN function on or off.
connections display here, but the one you use must meet the requirements listed in IPSec
Configur
ation Required for L2TP VPN on page 395.
Note: Modifying this VPN connection (or the VPN gateway that it uses) disconnects any
existing L2TP VPN sessions.
IP Address Pool Select the pool of IP addresses that the USG uses to assign to the L2TP VPN clients. Use
Authentication
Method
Authentication
Server Certificate
Create new Object if you need to configure a new pool of IP addresses.
This should not conflict with any WAN, LAN, DMZ or WLAN subnet even if they are not in
use.
Select how the USG authenticates a remote user before allowing access to the L2TP VPN
tunnel.
The authentication method has the USG check a user’s user name and password against
the USG’s local database, a remote LDAP, RADIUS, a Active Directory server, or more
than one of these.
Select the certificate to use to identify the USG for L2TP VPN connections. You must have
certificates already configured in the My Certificates screen. The certificate is used with
the EAP, PEAP, and MSCHAPv2 authentication protocols.
USG20(W)-VPN Series User’s Guide
397
Chapter 25 L2TP VPN
Table 150 Configuration > VPN > L2TP VPN (continued)
LABEL DESCRIPTION
Allowed User The remote user must log into the USG to use the L2TP VPN tunnel.
Select a user or user group that can use the L2TP VPN tunnel. Use Create new Object if
you need to configure a new user account. Otherwise, select any to allow any user with a
valid account and password on the USG to log in.
Keep Alive Timer The USG sends a Hello message after waiting this long without receiving any traffic from
First DNS Server,
Second DNS
Server
First WINS Server,
Second WINS
Server
Apply Click Apply to save your changes in the USG.
Reset Click Reset to return the screen to its last-saved settings.
the remote user. The USG disconnects the VPN tunnel if the remote user does not
respond.
Specify the IP addresses of DNS servers to assign to the remote users. You can specify
these IP addresses two ways.
Custom Defined - enter a static IP address.
From ISP - use the IP address of a DNS server that another interface received from its
DHCP server.
The WINS (Windows Internet Naming Service) server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Type the IP addresses of up to two WINS servers to assign to the remote users. You can
specify these IP addresses two ways.
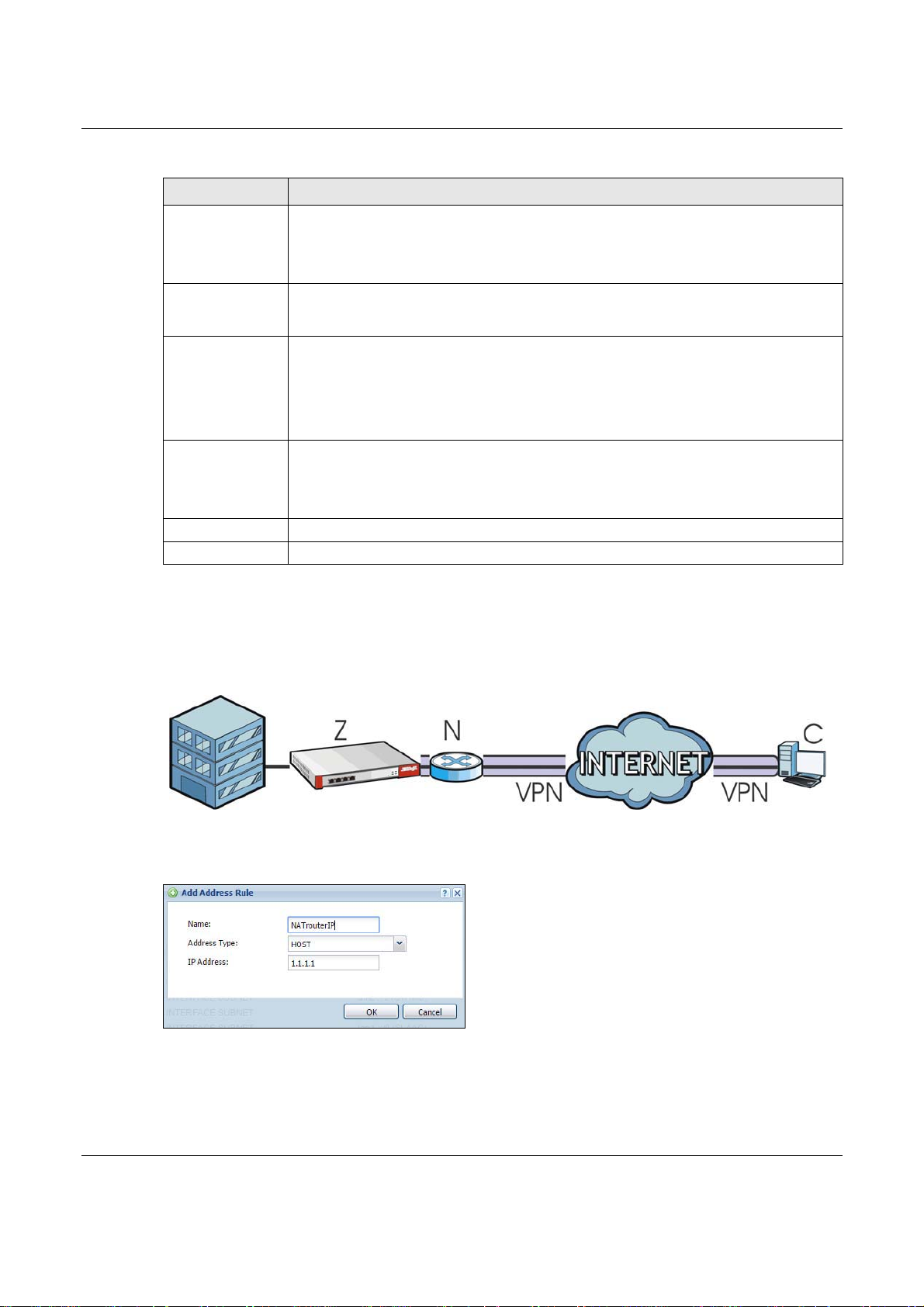
25.2.1 Example: L2TP and USG Behind a NAT Router
If the USG (Z) is behind a NAT router (N), then do the following for remote clients (C) to access the
network behind the USG (Z) using L2TP over IPv4.
1 Create an address object in Configuration > Object > Address for the WAN IP address of the
NAT router.
2 Go to Configuration > VPN > IPSec VPN > VPN Connection and click Add for IPv4
Configuration to create a new VPN connection.
3 Select Remote Access (Server Role) as the VPN scenario for the remote client.
USG20(W)-VPN Series User’s Guide
398
Chapter 25 L2TP VPN
4 Select the NAT router WAN IP address object as the Local Policy.
5 Go to Configuration > VPN > L2TP VPN and select the VPN Connection just configured.
USG20(W)-VPN Series User’s Guide
399

CHAPTER 26
BWM (Bandwidth Management)
26.1 Overview
Bandwidth management provides a convenient way to manage the use of various services on the
network. It manages general protocols (for example, HTTP and FTP) and applies traffic prioritization
to enhance the performance of delay-sensitive applications like voice and video.
26.1.1 What You Can Do in this Chapter
Use the BWM screens (see Section 26.2 on page 404) to control bandwidth for services passing
through the USG, and to identify the conditions that define the bandwidth control.
26.1.2 What You Need to Know
When you allow a service, you can restrict the bandwidth it uses. It controls TCP and UDP traffic.
Use policy routes to manage other types of traffic (like ICMP).
Note: Bandwidth management in policy routes has priority over TCP and UDP traffic
policies.
If you want to use a service, make sure both the security policy allow the service’s packets to go
through the USG.
Note: The USG checks security policies before it checks bandwidth management rules for
traffic going through the USG.
Bandwidth management examines every TCP and UDP connection passing through the USG. Then,
you can specify, by port, whether or not the USG continues to route the connection.
BWM Type
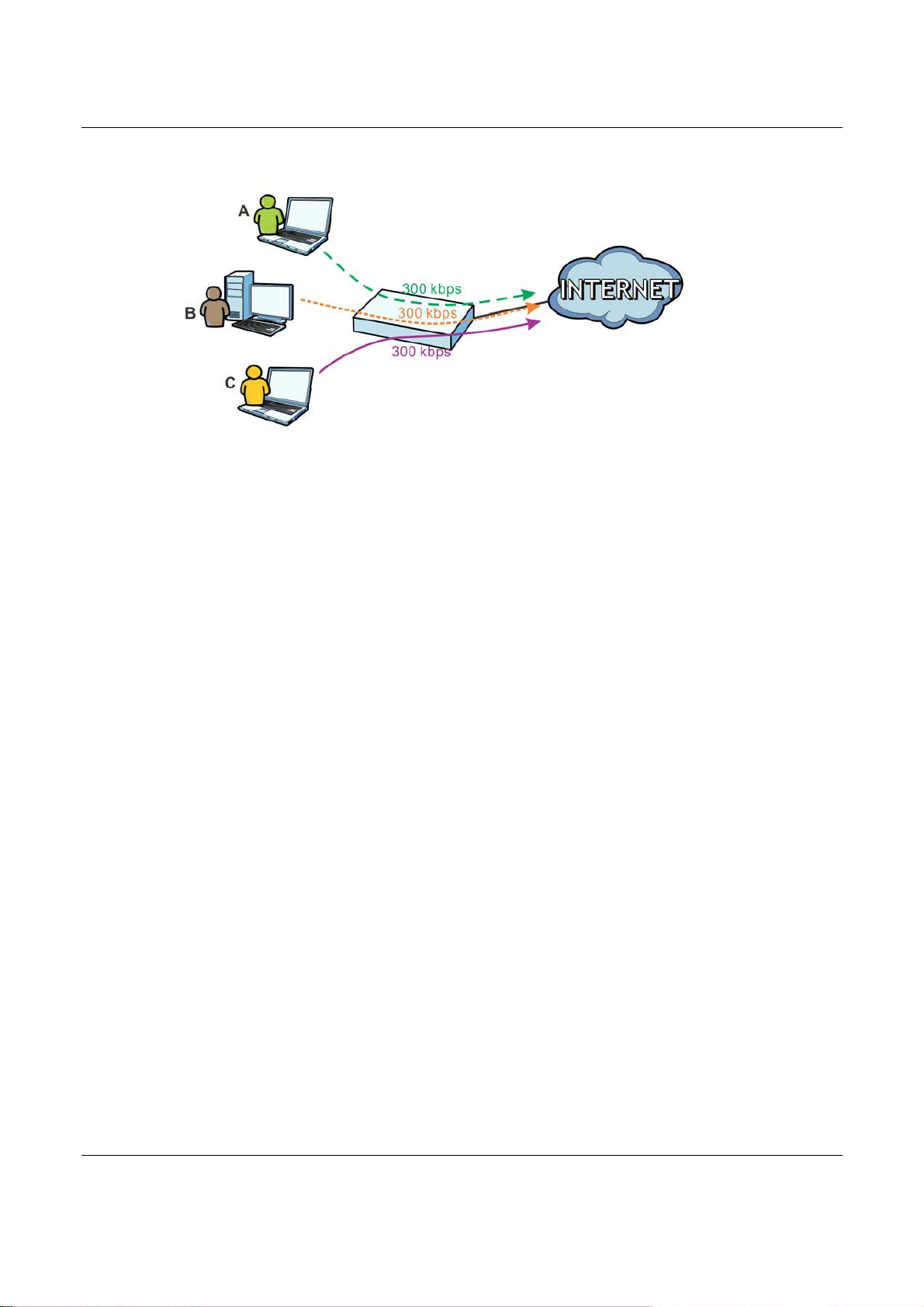
The USG supports three types of bandwidth management: Shared, Per user and Per-Source-IP.
The Shared BWM type is selected by default in a bandwidth management rule. All matched taffic
shares the bandwidth configured in the rule.
If the BWM type is set to Per user in a rule, each user that matches the rule can use up to the
configured bandwidth by his/her own.
Select the Per-Source-IP type when you want to set the maximum bandwidth for traffic from an
individual source IP address.
In the following example, you configure a Per user bandwidth management rule for radius-users to
limit outgoing traffic to 300 kbs. Then all radius-users (A, B and C) can send 300 kbps of traffic.
USG20(W)-VPN Series User’s Guide
400
Chapter 26 BWM (Bandwidth Management)
DiffServ and DSCP Marking
QoS is used to prioritize source-to-destination traffic flows. All packets in the same flow are given
the same priority. CoS (class of service) is a way of managing traffic in a network by grouping
similar types of traffic together and treating each type as a class. You can use CoS to give different
priorities to different packet types.
DiffServ (Differentiated Services) is a class of service (CoS) model that marks packets so that they
receive specific per-hop treatment at DiffServ-compliant network devices along the route based on
the application types and traffic flow. Packets are marked with DiffServ Code Points (DSCPs)
indicating the level of service desired. This allows the intermediary DiffServ-compliant network
devices to handle the packets differently depending on the code points without the need to
negotiate paths or remember state information for every flow. In addition, applications do not have
to request a particular service or give advanced notice of where the traffic is going.
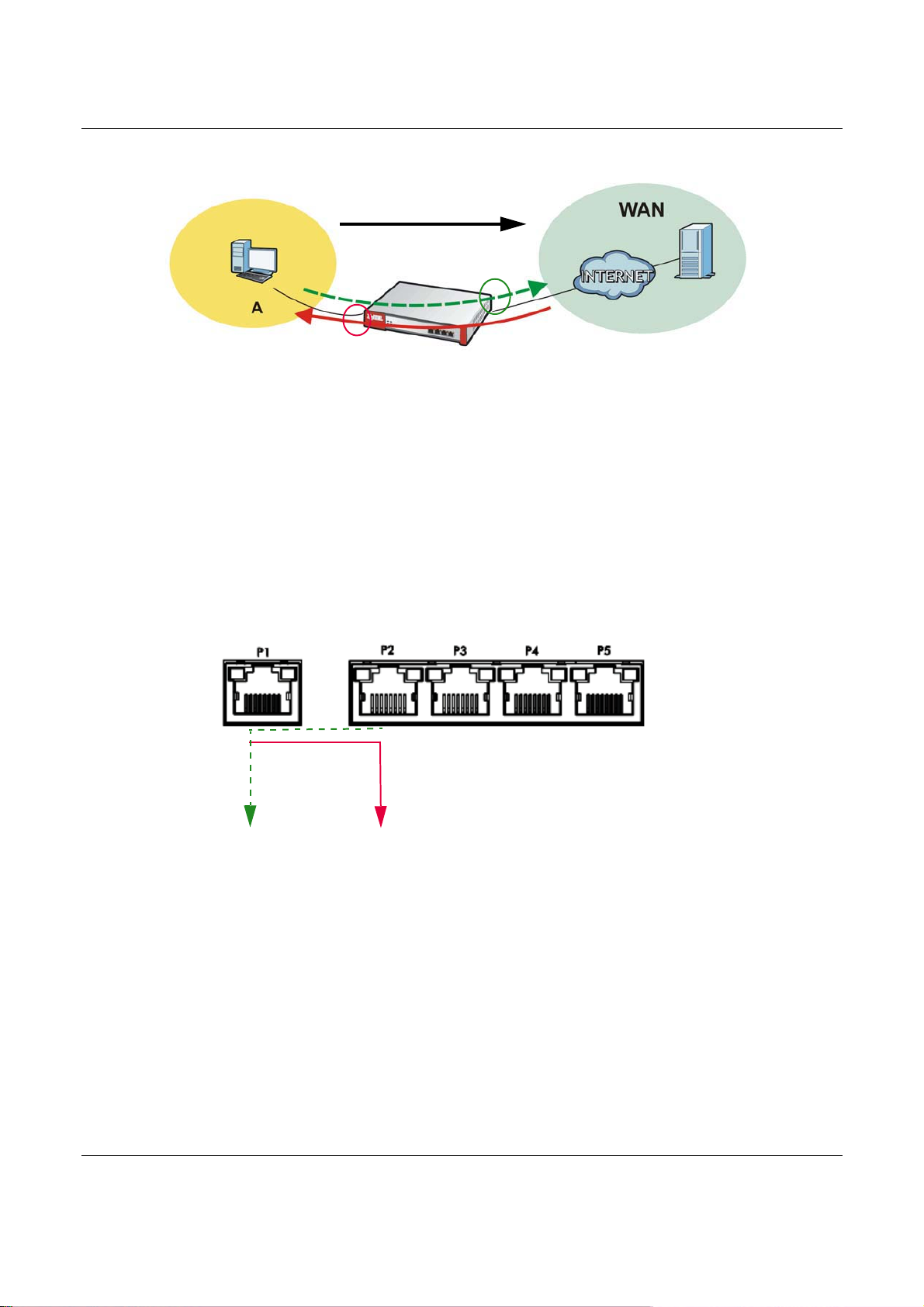
Connection and Packet Directions
Bandwidth management looks at the connection direction, that is, from which interface the
connection was initiated and to which interface the connection is going.
A connection has outbound and inbound packet flows. The USG controls the bandwidth of traffic of
each flow as it is going out through an interface or VPN tunnel.
• The outbound traffic flows from the connection initiator to the connection responder.
• The inbound traffic flows from the connection responder to the connection initiator.
For example, a LAN1 to WAN connection is initiated from LAN1 and goes to the WAN.
• Outbound traffic goes from a LAN1 device to a WAN device. Bandwidth management is applied
before sending the packets out a WAN interface on the USG.
• Inbound traffic comes back from the WAN device to the LAN1 device. Bandwidth management is
applied before sending the traffic out a LAN1 interface.
USG20(W)-VPN Series User’s Guide
401
Chapter 26 BWM (Bandwidth Management)
Connection
BWM
BWM
Outbound
Inbound
LAN1
Figure 279 LAN1 to WAN Connection and Packet Directions
Outbound and Inbound Bandwidth Limits
You can limit an application’s outbound or inbound bandwidth. This limit keeps the traffic from using
up too much of the out-going interface’s bandwidth. This way you can make sure there is bandwidth
for other applications. When you apply a bandwidth limit to outbound or inbound traffic, each
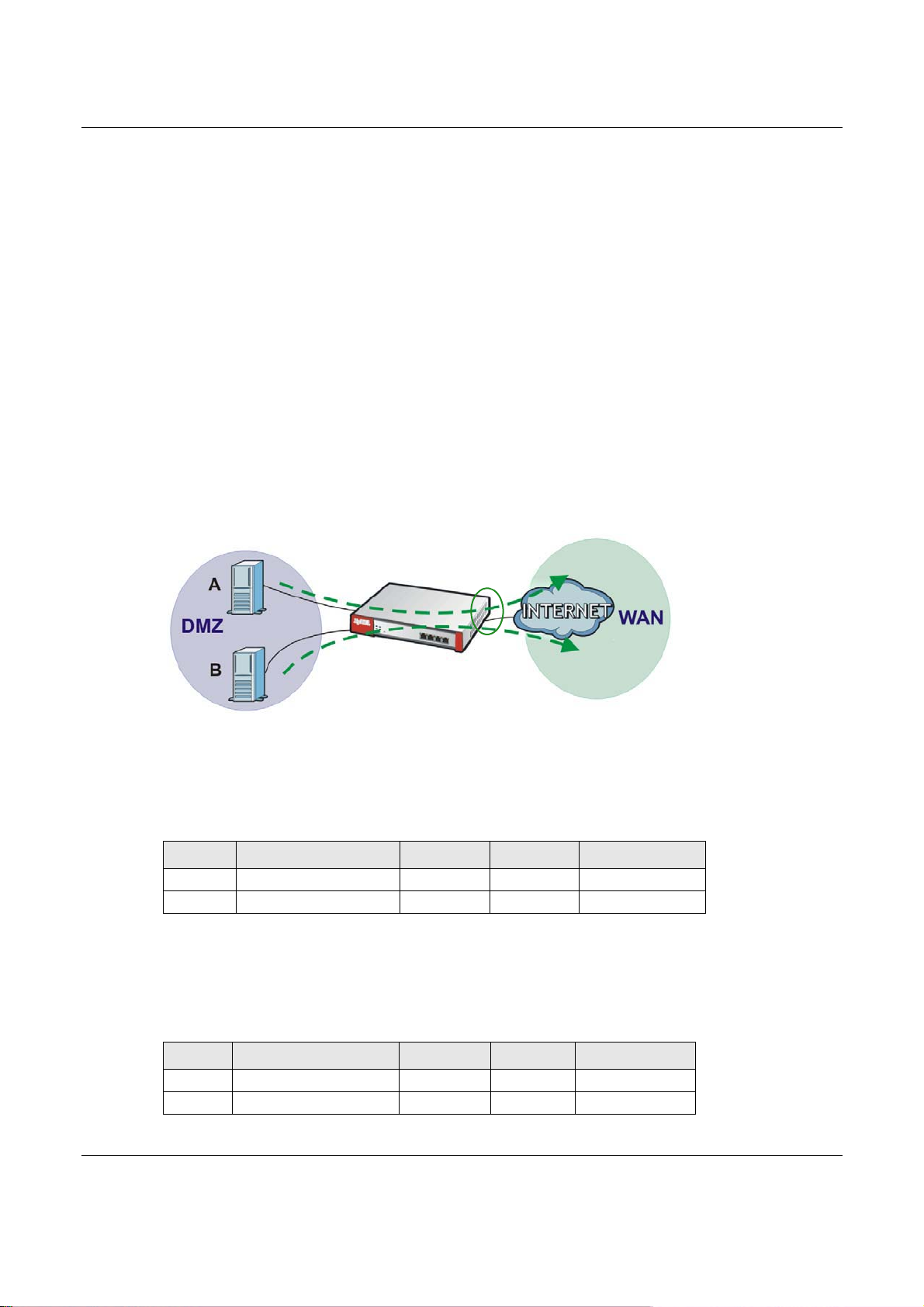
member of the out-going zone can send up to the limit. Take a LAN1 to WAN policy for example.
• Outbound traffic is limited to 200 kbps. The connection initiator is on the LAN1 so outbound
means the traffic traveling from the LAN1 to the WAN. Each of the WAN zone’s two interfaces can
send the limit of 200 kbps of traffic.
• Inbound traffic is limited to 500 kbs. The connection initiator is on the LAN1 so inbound means
the traffic traveling from the WAN to the LAN1.
Figure 280 LAN1 to WAN, Outbound 200 kbps, Inbound 500 kbps
Outbound
200 kbps
Inbound
500 kbps
Bandwidth Management Priority
• The USG gives bandwidth to higher-priority traffic first, until it reaches its configured bandwidth
rate.
• Then lower-priority traffic gets bandwidth.
• The USG uses a fairness-based (round-robin) scheduler to divide bandwidth among traffic flows
with the same priority.
• The USG automatically treats traffic with bandwidth management disabled as priority 7 (the
lowest priority).
USG20(W)-VPN Series User’s Guide
402
Chapter 26 BWM (Bandwidth Management)
1000 kbps
1000 kbps
BWM
1000 kbps
Maximize Bandwidth Usage
Maximize bandwidth usage allows applications with maximize bandwidth usage enabled to “borrow”
any unused bandwidth on the out-going interface.
After each application gets its configured bandwidth rate, the USG uses the fairness- based
scheduler to divide any unused bandwidth on the out-going interface amongst applications that
need more bandwidth and have maximize bandwidth usage enabled.
Unused bandwidth is divided equally. Higher priority traffic does not get a larger portion of the
unused bandwidth.
Bandwidth Management Behavior
The following sections show how bandwidth management behaves with various settings. For
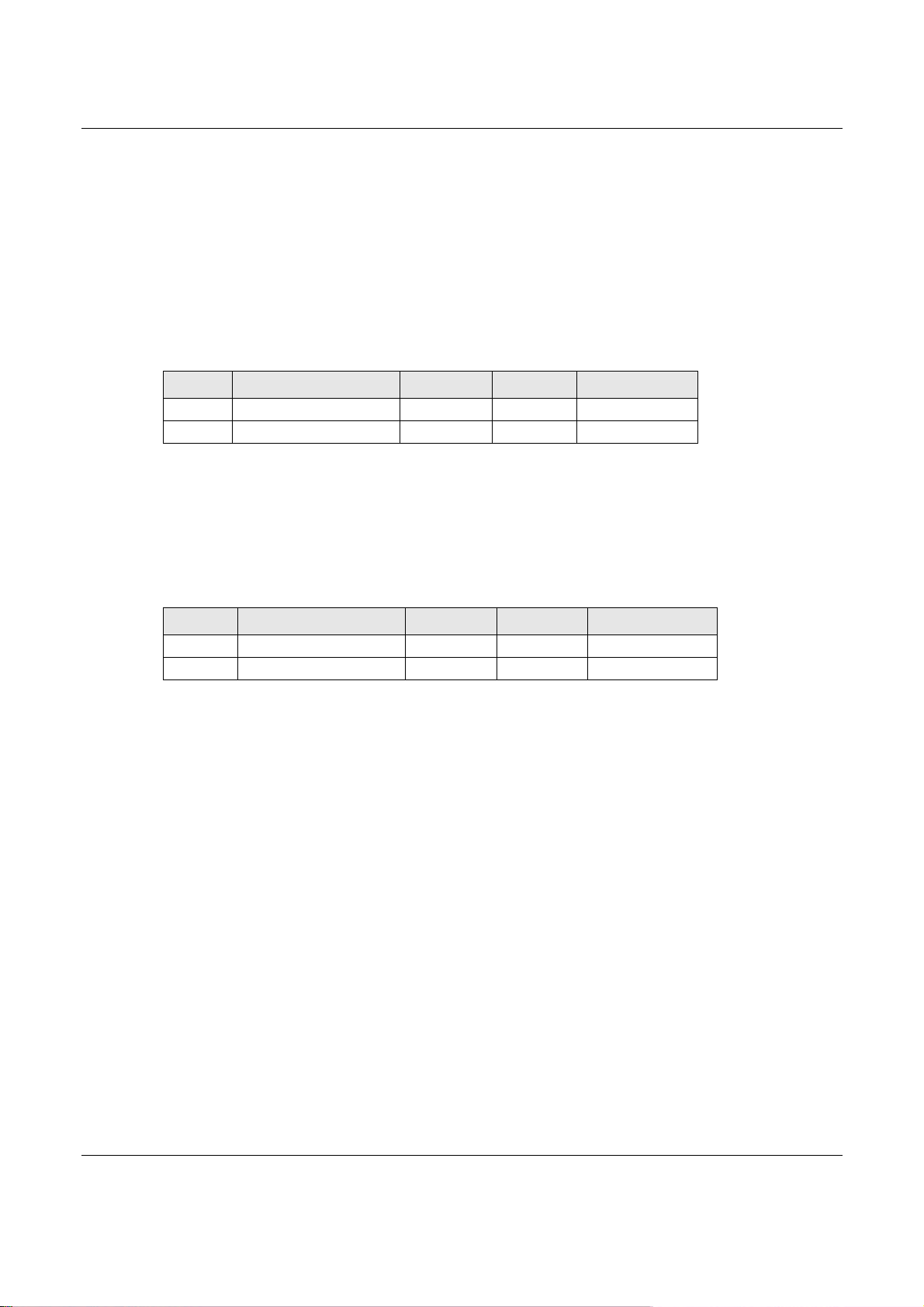
example, you configure DMZ to WAN policies for FTP servers A and B. Each server tries to send
1000 kbps, but the WAN is set to a maximum outgoing speed of 1000 kbps. You configure policy A
for server A’s traffic and policy B for server B’s traffic.
Figure 281 Bandwidth Management Behavior
Configured Rate Effect
In the following table the configured rates total less than the available bandwidth and maximize
bandwidth usage is disabled, both servers get their configured rate.
Table 151 Configured Rate Effect
POLICY CONFIGURED RATE MAX. B. U. PRIORITY ACTUAL RATE
A 300 kbps No 1 300 kbps
B 200 kbps No 1 200 kbps
Priority Effect
Here the configured rates total more than the available bandwidth. Because server A has higher
priority, it gets up to it’s configured rate (800 kbps), leaving only 200 kbps for server B.
Table 152 Priority Effect
POLICY CONFIGURED RATE MAX. B. U. PRIORITY ACTUAL RATE
A 800 kbps Yes 1 800 kbps
B 1000 kbps Yes 2 200 kbps
USG20(W)-VPN Series User’s Guide
403
Chapter 26 BWM (Bandwidth Management)
Maximize Bandwidth Usage Effect
With maximize bandwidth usage enabled, after each server gets its configured rate, the rest of the
available bandwidth is divided equally between the two. So server A gets its configured rate of 300
kbps and server B gets its configured rate of 200 kbps. Then the USG divides the remaining
bandwidth (1000 - 500 = 500) equally between the two (500 / 2 = 250 kbps for each). The priority
has no effect on how much of the unused bandwidth each server gets.
So server A gets its configured rate of 300 kbps plus 250 kbps for a total of 550 kbps. Server B
gets its configured rate of 200 kbps plus 250 kbps for a total of 450 kbps.
Table 153 Maximize Bandwidth Usage Effect
POLICY CONFIGURED RATE MAX. B. U. PRIORITY ACTUAL RATE
A 300 kbps Yes 1 550 kbps
B 200 kbps Yes 2 450 kbps
Priority and Over Allotment of Bandwidth Effect
Server A has a configured rate that equals the total amount of available bandwidth and a higher
priority. You should regard extreme over allotment of traffic with different priorities (as shown here)
as a configuration error. Even though the USG still attempts to let all traffic get through and not be
lost, regardless of its priority, server B gets almost no bandwidth with this configuration.
Table 154 Priority and Over Allotment of Bandwidth Effect
POLICY CONFIGURED RATE MAX. B. U. PRIORITY ACTUAL RATE
A 1000 kbps Yes 1 999 kbps
B 1000 kbps Yes 2 1 kbps
26.2 The Bandwidth Management Screen
The Bandwidth management screens control the bandwidth allocation for TCP and UDP traffic. You
can use source interface, destination interface, destination port, schedule, user, source, destination
information, DSCP code and service type as criteria to create a sequence of specific conditions,
similar to the sequence of rules used by firewalls, to specify how the USG handles the DSCP value
and allocate bandwidth for the matching packets.
Click Configuration > BWM to open the following screen. This screen allows you to enable/disable
bandwidth management and add, edit, and remove user-defined bandwidth management policies.
The default bandwidth management policy is the one with the priority of “default”. It is the last
policy the USG checks if traffic does not match any other bandwidth management policies you have
configured. You cannot remove, activate, deactivate or move the default bandwidth management
policy.
USG20(W)-VPN Series User’s Guide
404

Chapter 26 BWM (Bandwidth Management)
Figure 282 Configuration > Bandwidth Management
The following table describes the labels in this screen. See Section 26.2.1 on page 406 for
more
information as well.
Table 155 Configuration > Bandwidth Management
LABEL DESCRIPTION
Enable BWM Select this check box to activate management bandwidth.
Add Click this to create a new entry. Select an entry and click Add to create a new entry
Edit Select an entry and click this to be able to modify it.
Remove Select an entry and click this to delete it.
Activate To turn on an entry, select it and click Activate.
Inactivate To turn off an entry, select it and click Inactivate.
Move To change an entry’s position in the numbered list, select it and click Move to display
Status The activate (light bulb) icon is lit when the entry is active and dimmed when the
Priority This field displays a sequential value for each bandwidth management policy and it is
Description This field displays additional information about this policy.
BWM Type This field displays the below types of BWM:
User This is the type of user account to which the policy applies. If any displays, the policy
Schedule This is the schedule that defines when the policy applies. none means the policy
Incoming Interface This is the source interface of the traffic to which this policy applies.
Outgoing Interface This is the destination interface of the traffic to which this policy applies.
Source This is the source address or address group for whom this policy applies. If any
Destination This is the destination address or address group for whom this policy applies. If any
after the selected entry.
a field to type a number for where you want to put that entry and press [ENTER] to
move the entry to the number that you typed.
entry is inactive. The status icon is not available for the default bandwidth
management policy.
not associated with a specific setting.
This field displays default for the default bandwidth management policy.
• Shared, when the policy is set for all matched traffic
• Per User, when the policy is set for an individual user or a user group
• Per-Source-IP, when the policy is set for a source IP
applies to all user accounts.
always applies.
displays, the policy is effective for every source.
displays, the policy is effective for every destination.
USG20(W)-VPN Series User’s Guide
405
Chapter 26 BWM (Bandwidth Management)
Table 155 Configuration > Bandwidth Management
LABEL DESCRIPTION
DSCP Code These are the DSCP code point values of incoming and outgoing packets to which this
Service Type App and the service name displays if you selected Application Object for the
BWM In/Pri/Out/Pri This field shows the amount of bandwidth the traffic can use.
DSCP Marking This is how the USG handles the DSCP value of the incoming and outgoing packets
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
policy applies. The lower the number the higher the priority with the exception of 0
which is usually given only best-effort treatment.
any means all DSCP value or no DSCP marker.
default means traffic with a DSCP value of 0. This is usually best effort traffic
The “af” options stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences.
service type. An Application Object is a pre-defined service.
Obj and the service name displays if you selected Service Object for the service
type. A Service Object is a customized pre-defined service or another service.
Mouse over the service object name to view the corresponding IP protocol number.
In - This is how much inbound bandwidth, in kilobits per second, this policy allows
the matching traffic to use. Inbound refers to the traffic the USG sends to a
connection’s initiator. If no displays here, this policy does not apply bandwidth
management for the inbound traffic.
Out - This is how much outgoing bandwidth, in kilobits per second, this policy allows
the matching traffic to use. Outbound refers to the traffic the USG sends out from a
connection’s initiator. If no displays here, this policy does not apply bandwidth
management for the outbound traffic.
Pri - This is the priority for the incoming (the first Pri value) or outgoing (the second
Pri value) traffic that matches this policy. The smaller the number, the higher the
priority. Traffic with a higher priority is given bandwidth before traffic with a lower
priority. The USG ignores this number if the incoming and outgoing limits are both
set to 0. In this case the traffic is automatically treated as being set to the lowest
priority (7) regardless of this field’s configuration.
that match this policy.
In - Inbound, the traffic the USG sends to a connection’s initiator.
Out - Outbound, the traffic the USG sends out from a connection’s initiator.
If this field displays a DSCP value, the USG applies that DSCP value to the route’s
outgoing packets.
preserve means the USG does not modify the DSCP value of the route’s outgoing
packets.
default means the USG sets the DSCP value of the route’s outgoing packets to 0.
The “af” choices stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences.
26.2.1 The Bandwidth Management Add/Edit Screen
The Configuration > Bandwidth Management Add/Edit screen allows you to create a new
condition or edit an existing one.
USG20(W)-VPN Series User’s Guide
406
Chapter 26 BWM (Bandwidth Management)
802.1P Marking
Use 802.1P to prioritize outgoing traffic from a VLAN interface. The Priority Code is a 3-bit field
within a 802.1Q VLAN tag that’s used to prioritize associated outgoing VLAN traffic. "0" is the lowest
priority level and "7" is the highest.
Table 156 Single Tagged 802.1Q Frame Format
DA SA TPID Priority VID Len/Etype Data FCS IEEE 802.1Q
Table 157 802.1Q Frame
DA Destination Address Priority 802.1p Priority
SA Source Address Len/Etype Length and type of Ethernet frame
TPID Tag Protocol IDentifier Data Frame data
VID VLAN ID FCS Frame Check Sequence
The following table is a guide to types of traffic for the priority code.
Table 158 Priority Code and Types of Traffic
PRIORITY TRAFFIC TYPES
0 (lowest) Background
1 Best Effort
2 Excellent Effort
3 Critical Applications
4 Video, less than 100 ms latency and jitter
5 Voice, less than 10 ms latency and jitter
6 Internetwork Control
7 (highest) Network Control
customer
tagged frame
To access this screen, go to the Configuration > Bandwidth Management screen (see Section
26.2 on
page 404), and click either the Add icon or an Edit icon.
Figure 283 Configuration > Bandwidth Management > Edit (For the Default Policy)
USG20(W)-VPN Series User’s Guide
407
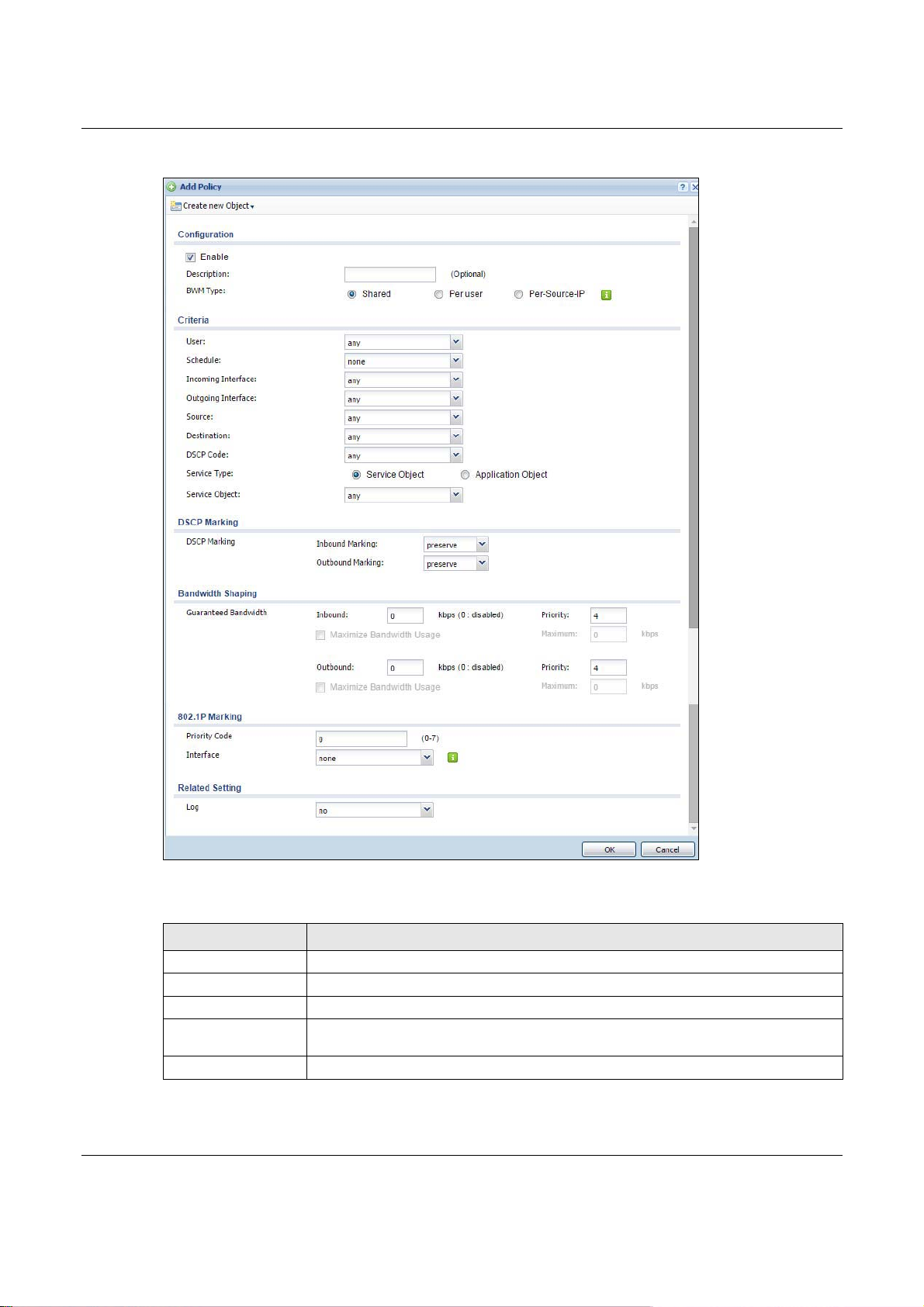
Chapter 26 BWM (Bandwidth Management)
Figure 284 Configuration > Bandwidth Management > Add/Edit
The following table describes the labels in this screen.
Table 159 Configuration > Bandwidth Management > Add/Edit
LABEL DESCRIPTION
Create new Object Use to configure any new settings objects that you need to use in this screen.
Configuration
Enable Select this check box to turn on this policy.
Description Enter a description of this policy. It is not used elsewhere. You can use alphanumeric
Criteria Use this section to configure the conditions of traffic to which this policy applies.
and ()+/:=?!*#@$_%- characters, and it can be up to 60 characters long.
USG20(W)-VPN Series User’s Guide
408
Chapter 26 BWM (Bandwidth Management)
Table 159 Configuration > Bandwidth Management > Add/Edit
LABEL DESCRIPTION
BWM Type This field displays the below types of BWM rule:
• Shared, when the policy is set for all users
• Per User, when the policy is set for an individual user or a user group
• Per Source IP, when the policy is set for a source IP
User Select a user name or user group to which to apply the policy. Use Create new
Schedule Select a schedule that defines when the policy applies or select Create Object to
Incoming Interface Select the source interface of the traffic to which this policy applies.
Outgoing Interface Select the destination interface of the traffic to which this policy applies.
Source Select a source address or address group for whom this policy applies. Use Create
Destination Select a destination address or address group for whom this policy applies. Use
DSCP Code Select a DSCP code point value of incoming packets to which this policy
User-Defined
DSCP Code
Service Type Select Service Object if you want a specific service (defined in a service object) to
Service Object This field is available if you selected Service Object as the service type.
DSCP Marking Set how the USG handles the DSCP value of the incoming and outgoing packets that
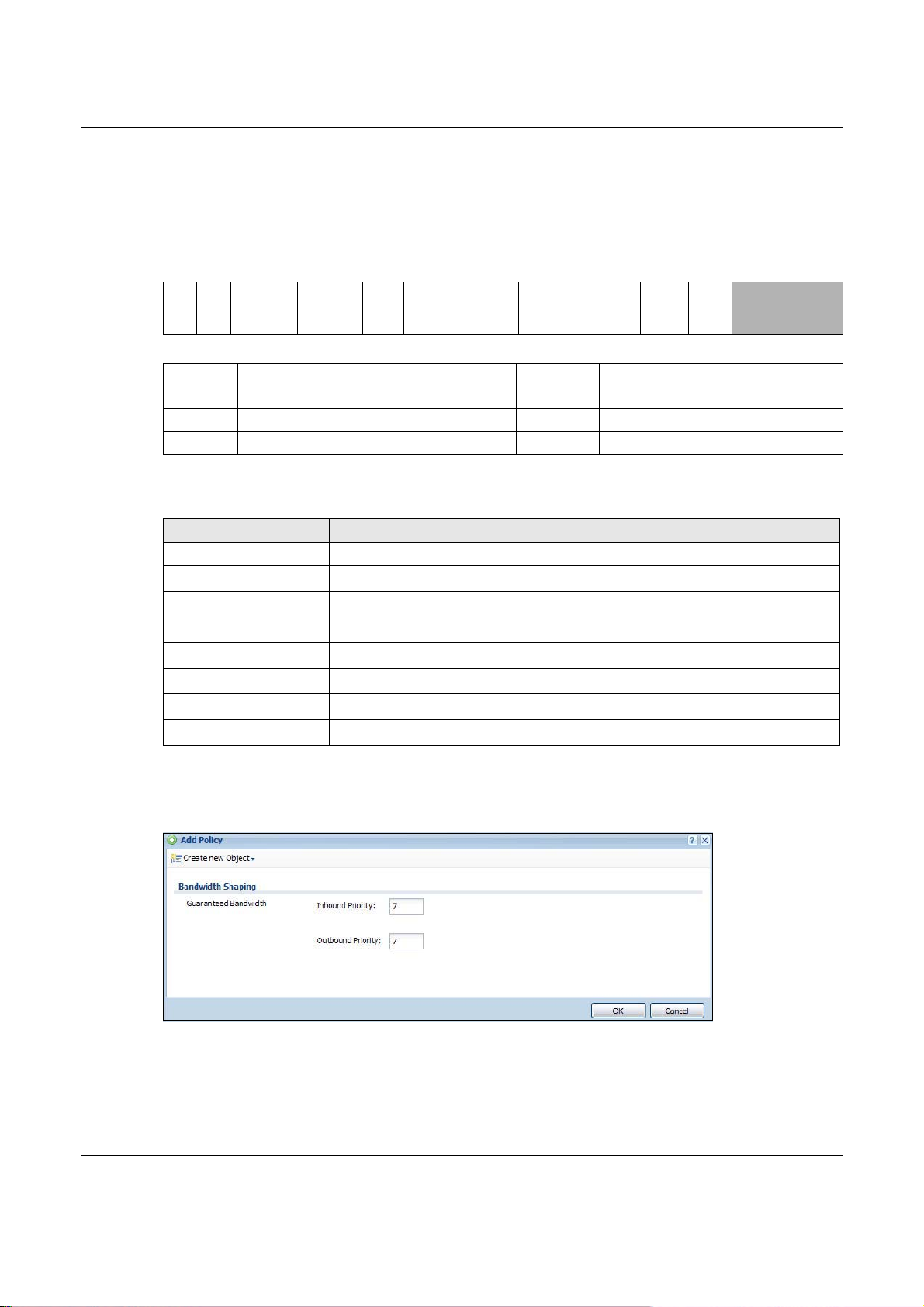
Bandwidth Shaping Configure these fields to set the amount of bandwidth the matching traffic can use.
Object if you need to configure a new user account. Select any to apply the policy for
every user.
configure a new one. Otherwise, select none to make the policy always effective.
new Object if you need to configure a new one. Select any if the policy is effective for
every source.
Create new Object if you need to configure a new one. Select any if the policy is
effective for every destination.
route applies or select User Defined to specify another DSCP code point. The lower
the number the higher the priority with the exception of 0 which is usually given only
best-effort treatment.
any means all DSCP value or no DSCP marker.
default means traffic with a DSCP value of 0. This is usually best effort traffic
The “af” choices stand for Assured Forwarding. The number following the “af”
identifies one of four classes and one of three drop preferences.
Use this field to specify a custom DSCP code point.
which the policy applies.
Select a service or service group to identify the type of traffic to which this policy
applies. any means all services.
match this policy. Inbound refers to the traffic the USG sends to a connection’s
initiator. Outbound refers to the traffic the USG sends out from a connection’s initiator.
Select one of the pre-defined DSCP values to apply or select User Defined to specify
another DSCP value. The “af” choices stand for Assured Forwarding. The number
following the “af” identifies one of four classes and one of three drop preferences.
Select preserve to have the USG keep the packets’ original DSCP value.
Select default to have the USG set the DSCP value of the packets to 0.
USG20(W)-VPN Series User’s Guide
409
Chapter 26 BWM (Bandwidth Management)
Table 159 Configuration > Bandwidth Management > Add/Edit
LABEL DESCRIPTION
Inbound kbps Type how much inbound bandwidth, in kilobits per second, this policy allows the traffic
Outbound kbps Type how much outbound bandwidth, in kilobits per second, this policy allows the
Priority This field displays when the inbound or outbound bandwidth management is not set to
Maximize
Bandwidth Usage
Maximum If you did not enable Maximize Bandwidth Usage, then type the maximium unused
802.1P Marking Use 802.1P to prioritize outgoing traffic from a VLAN interface.
Priority Code This is a 3-bit field within a 802.1Q VLAN tag that’s used to prioritize associated
Interface Choose a VLAN interface to which to apply the priority level for matching frames.
Related Setting
Log Select whether to have the USG generate a log (log), log and alert (log alert) or
OK Click OK to save your changes back to the USG.
Cancel Click Cancel to exit this screen without saving your changes.
to use. Inbound refers to the traffic the USG sends to a connection’s initiator.
If you enter 0 here, this policy does not apply bandwidth management for the
matching traffic that the USG sends to the initiator. Traffic with bandwidth
management disabled (inbound and outbound are both set to 0) is automatically
treated as the lowest priority (7).
If the sum of the bandwidths for routes using the same next hop is higher than the
actual transmission speed, lower priority traffic may not be sent if higher priority
traffic uses all of the actual bandwidth.
traffic to use. Outbound refers to the traffic the USG sends out from a connection’s
initiator.
If you enter 0 here, this policy does not apply bandwidth management for the
matching traffic that the USG sends out from the initiator. Traffic with bandwidth
management disabled (inbound and outbound are both set to 0) is automatically
treated as the lowest priority (7).
If the sum of the bandwidths for routes using the same next hop is higher than the
actual transmission speed, lower priority traffic may not be sent if higher priority
traffic uses all of the actual bandwidth.
0. Enter a number between 1 and 7 to set the priority for traffic that matches this
policy. The smaller the number, the higher the priority.
Traffic with a higher priority is given bandwidth before traffic with a lower priority.
The USG uses a fairness-based (round-robin) scheduler to divide bandwidth between
traffic flows with the same priority.
The number in this field is ignored if the incoming and outgoing limits are both set to
0. In this case the traffic is automatically treated as being set to the lowest priority (7)
regardless of this field’s configuration.
This field displays when the inbound or outbound bandwidth management is not set to
0 and the BWM Type is set to Shared. Enable maximize bandwidth usage to let the
traffic matching this policy “borrow” all unused bandwidth on the out-going interface.
After each application or type of traffic gets its configured bandwidth rate, the USG
uses the fairness-based scheduler to divide any unused bandwidth on the out-going
interface among applications and traffic types that need more bandwidth and have
maximize bandwidth usage enabled.
bandwidth that traffic matching this policy is allowed to “borrow” on the out-going
interface (in Kbps), here.
outgoing VLAN traffic. "0" is the lowest priority level and "7" is the highest. See Tab le
58 on page 407. The setting configured here overwrites existing priority settings.
1
neither (no) when any traffic matches this policy.
USG20(W)-VPN Series User’s Guide
410
Chapter 26 BWM (Bandwidth Management)
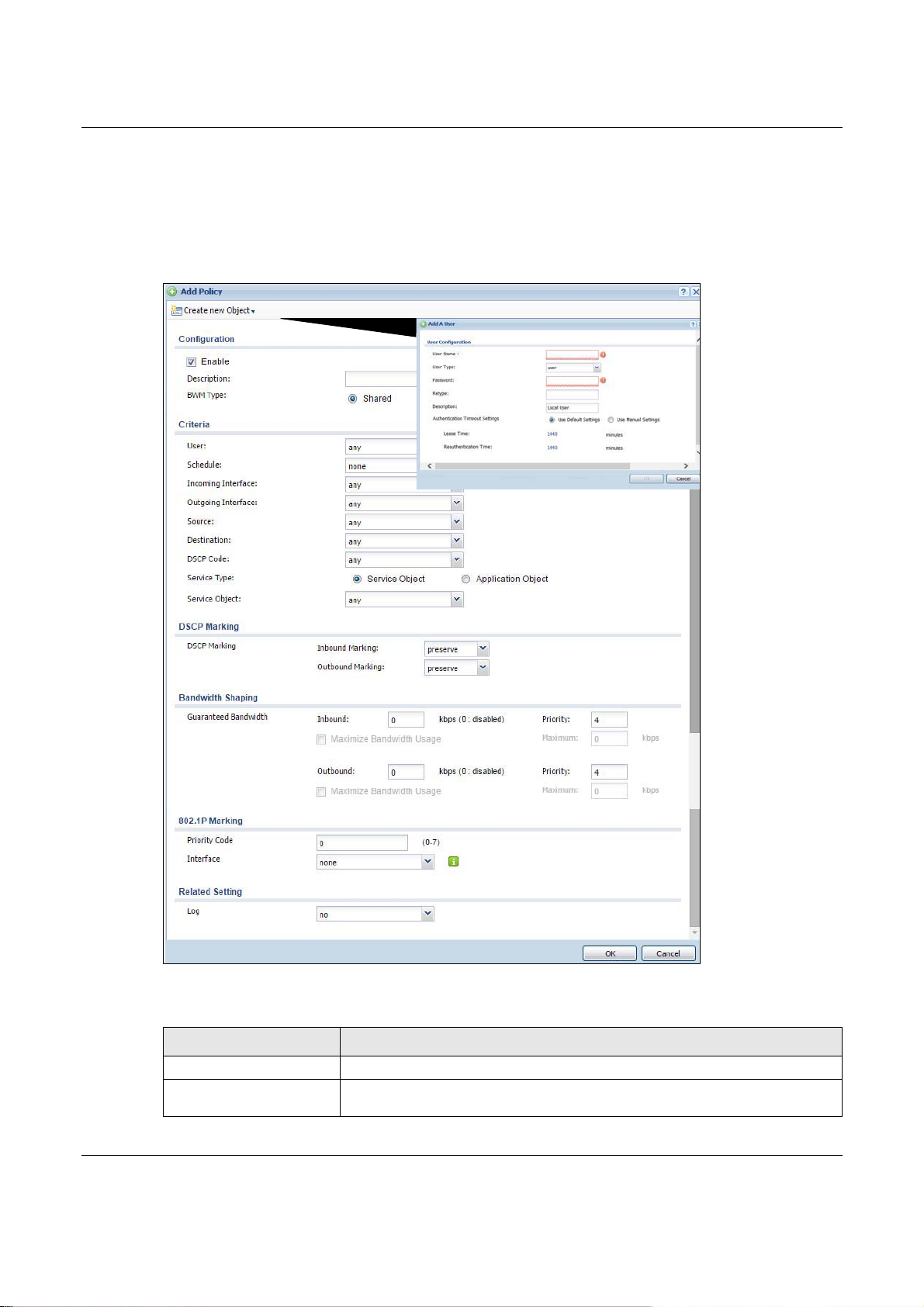
26.2.1.1 Adding Objects for the BWM Policy
Objects are parameters to which the Policy rules are built upon. There are three kinds of objects
you can add/edit for the BWM policy, they are User, Schedule and Address objects. Click
Configuration > BWM > Add > Create New Object > Add User to see the following screen.
Figure 285 Configuration >BWM > Create New Object > Add User
The following table describes the fields in the above screen.
Table 160 Configuration > BWM > Create New Object > Add User
LABEL DESCRIPTION
User Name Type a user or user group object name of the rule.
User Type Select a user type from the drop down menu. The user types are Admin, Limited
admin, User, Guest, Ext-user, Ext-group-user.
USG20(W)-VPN Series User’s Guide
411
Chapter 26 BWM (Bandwidth Management)
Table 160 Configuration > BWM > Create New Object > Add User
LABEL DESCRIPTION
Password Type a password for the user object. The password can consist of alphanumeric
Retype Retype the password to confirm.
Description Enter a description for this user object. It is not used elsewhere. You can use
Authentication Timeout
Settings
Lease Time This shows the Lease Time setting for the user, by default it is 1,440 minutes.
Reauthentication Time This shows the Reauthentication Time for the user, by default it is 1,440
OK Click OK to save the setting.
Cancel Click Cancel to abandon this screen.
characters, the underscore, and some punctuation marks (+-/*= :; .! @$&%#~
‘ \ () ), and it can be up to eight characters long.
alphanumeric and ()+/:=?!*#@$_%- characters, and it can be up to 60
characters long.
Choose either Use Default setting option, which shows the default Lease Time
of 1,440 minutes and Reauthentication Time of 1,440 minutes or you can enter
them manually by choosing Use Manual Settings option.
minutes.
USG20(W)-VPN Series User’s Guide
412
Chapter 26 BWM (Bandwidth Management)
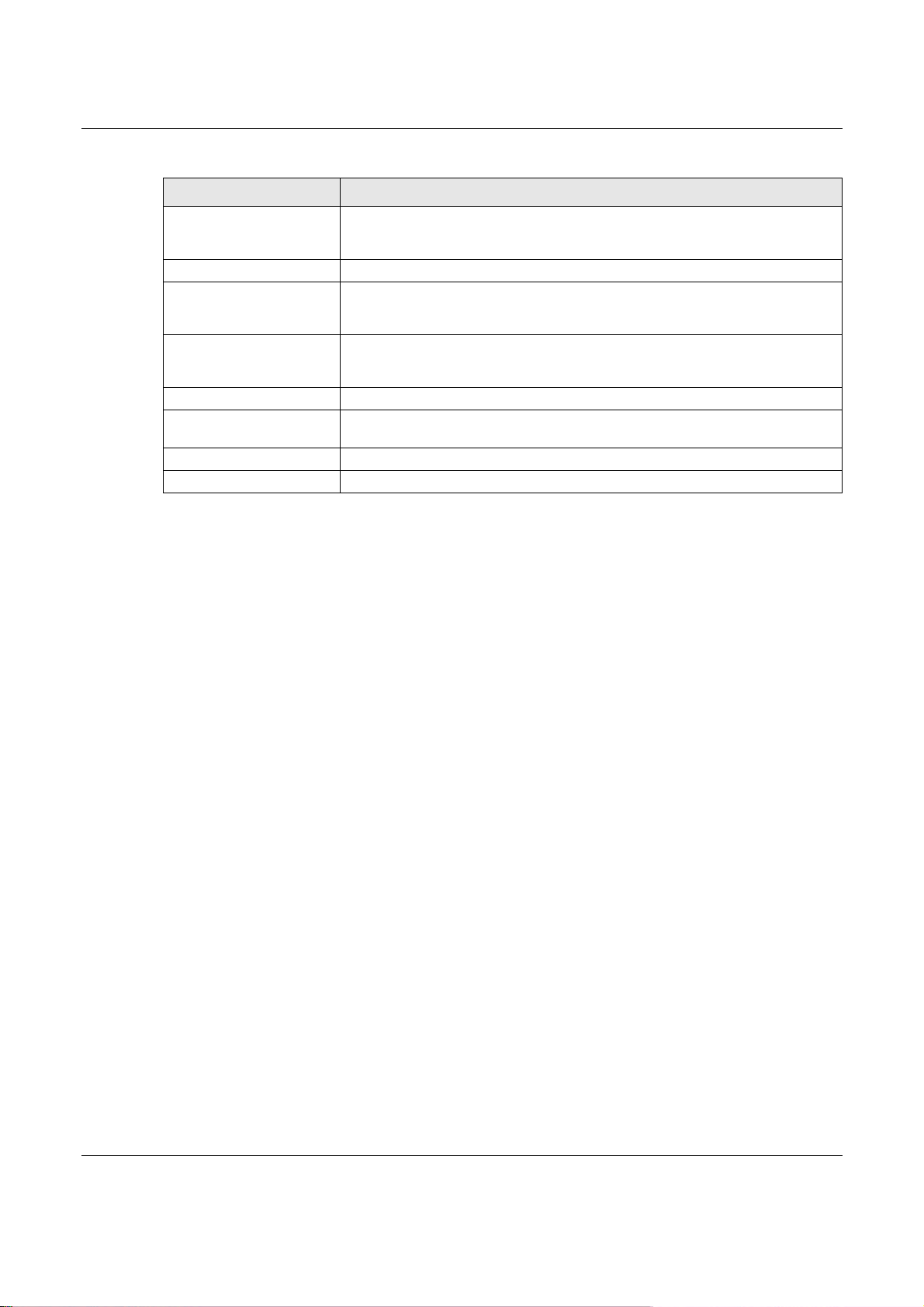
Figure 286 Configuration > BWM > Create New Object > Add Schedule
The following table describes the fields in the above screen.
Table 161 Configuration > BWM > Create New Object > Add Schedule
LABEL DESCRIPTION
Name Enter a name for the schedule object of the rule.
Type Select an option from the drop down menu for the schedule object. It will show
Start Date Click the icon menu on the right to choose a Start Date for the schedule object.
Start Time Click the icon menu on the right to choose a Start Time for the schedule object.
Stop Date Click the icon menu on the right to choose a Stop Date for schedule object.
Stop Time Click the icon menu on the right to choose a Stop Time for the schedule object.
One Time or Recurring.
USG20(W)-VPN Series User’s Guide
413
Chapter 26 BWM (Bandwidth Management)
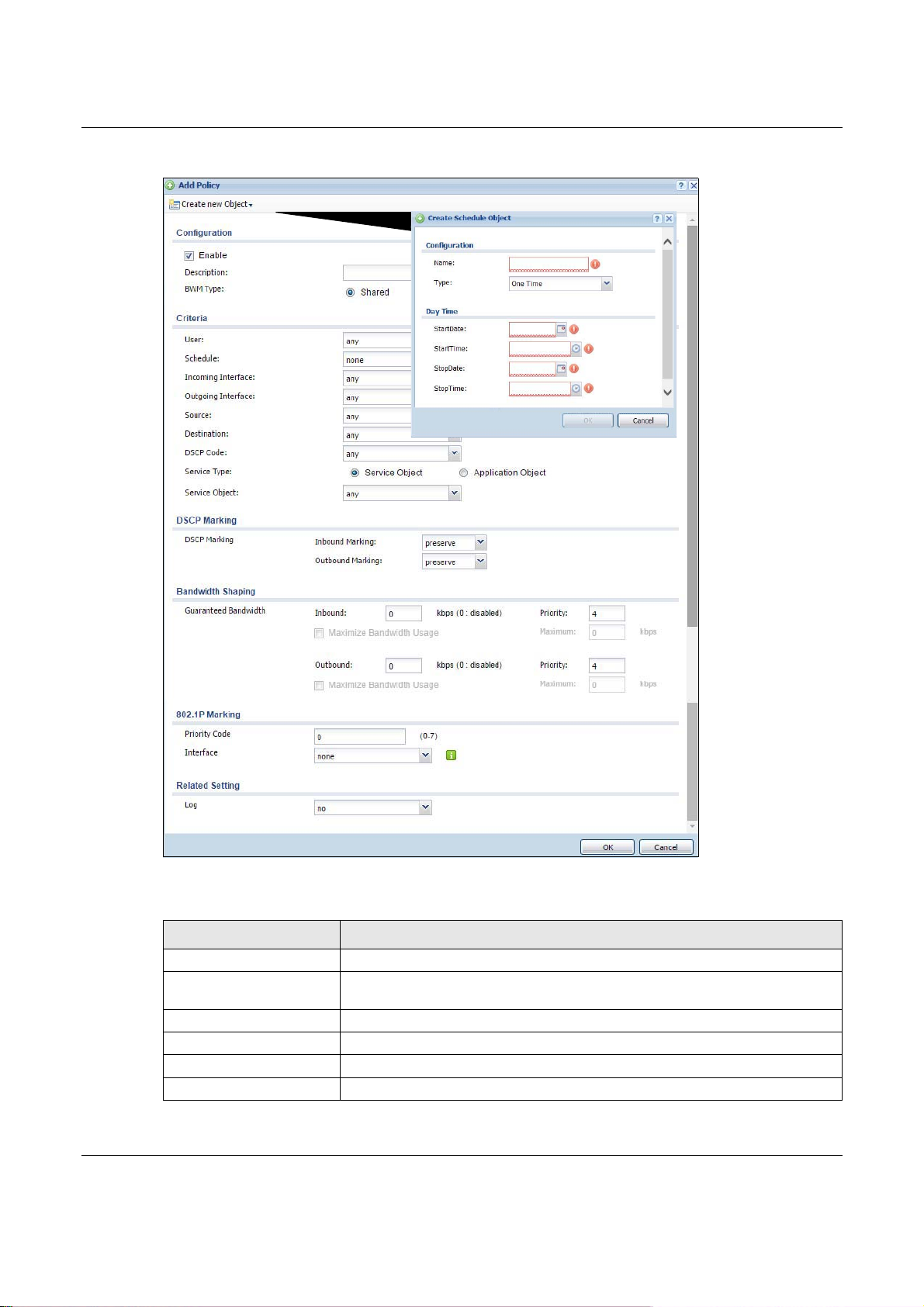
Figure 287 Configuration > BWM > Create New Object > Add Address
The following table describes the fields in the above screen.
Table 162 Configuration > BWM > Create New Object > Add Address
LABEL DESCRIPTION
Name Enter a name for the Address object of the rule.
Address Type Select an Address Type from the drop down menu on the right. The Address
IP Address Enter an IP address for the Address object.
OK Click OK to save the setting.
Cancel Click Cancel to abandon the setting.
Types are Host, Range, Subnet, Interface IP, Interface Subnet, and Interface
Gateway.
USG20(W)-VPN Series User’s Guide
414

CHAPTER 27
27.1 Overview
Use the content filtering feature to control access to specific web sites or web content.
27.1.1 What You Can Do in this Chapter
•Use the Filter Profile screens (Section Figure 289 on page 420) to set up content filtering
profiles.
•Use the Trusted Web Sites screens (Section 27.4 on page 430) to create a common list of good
(allowed) web site addresses.
•Use the Forbidden Web Sites screens (Section 27.5 on page 431) to create a common list of
bad (blocked) web site addresses.
Content Filtering
27.1.2 What You Need to Know
Content Filtering
Content filtering allows you to block certain web features, such as cookies, and/or block access to
specific web sites. It can also block access to specific categories of web site content. You can create
different content filter policies for different addresses, schedules, users or groups and content filter
profiles. For example, you can configure one policy that blocks John Doe’s access to arts and
entertainment web pages during the workday and another policy that lets him access them after
work.
Content Filtering Policies
A content filtering policy allows you to do the following.
• Use schedule objects to define when to apply a content filter profile.
• Use address and/or user/group objects to define to whose web access to apply the content filter
profile.
• Apply a content filter profile that you have custom-tailored.
Content Filtering Profiles
A content filtering profile conveniently stores your custom settings for the following features.
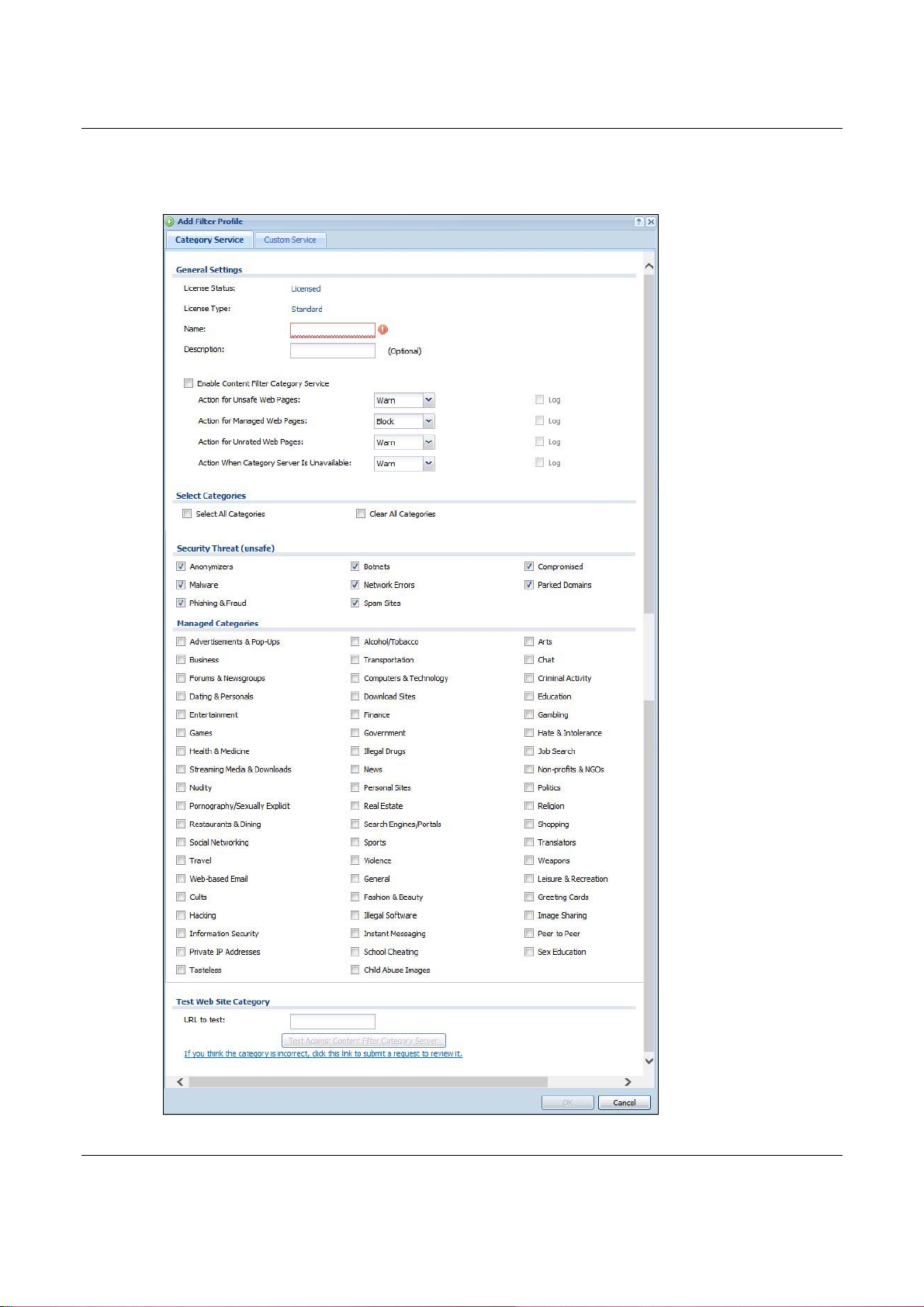
• Category-based Blocking
The USG can block access to particular categories of web site content, such as pornography or
racial intolerance.
USG20(W)-VPN Series User’s Guide
415

Chapter 27 Content Filtering
• Restrict Web Features
The USG can disable web proxies and block web features such as ActiveX controls, Java applets
and cookies.
• Customize Web Site Access
You can specify URLs to which the USG blocks access. You can alternatively block access to all
URLs except ones that you specify. You can also have the USG block access to URLs that contain
particular keywords.
Content Filtering Configuration Guidelines
When the USG receives an HTTP request, the content filter searches for a policy that matches the
source address and time (schedule). The content filter checks the policies in order (based on the
policy numbers). When a matching policy is found, the content filter allows or blocks the request
depending on the settings of the filtering profile specified by the policy. Some requests may not
match any policy. The USG allows the request if the default policy is not set to block. The USG
blocks the request if the default policy is set to block.
External Web Filtering Service
When you register for and enable the external web filtering service, your USG accesses an external
database that has millions of web sites categorized based on content. You can have the USG block,
block and/or log access to web sites based on these categories.
Keyword Blocking URL Checking
The USG checks the URL’s domain name (or IP address) and file path separately when performing
keyword blocking.
The URL’s domain name or IP address is the characters that come before the first slash in the URL.
For example, with the URL www.zyxel.com.tw/news/pressroom.php
www.zyxel.com.tw
The file path is the characters that come after the first slash in the URL. For example, with the URL
www.zyxel.com.tw/news/pressroom.php
Since the USG checks the URL’s domain name (or IP address) and file path separately, it will not
find items that go across the two. For example, with the URL www.zyxel.com.tw/news/
pressroom.php, the USG would find “tw” in the domain name (www.zyxel.com.tw). It would also
find “news” in the file path (news/pressroom.php
.
Finding Out More
•See Section 27.6 on page 432 for content filtering background/technical information.
27.1.3 Before You Begin
• You must configure an address object, a schedule object and a filtering profile before you can set
up a content security policy.
• You must have Content Filtering license in order to use the function.subscribe to use the external
database content filtering (see the Licensing > Registration screens).
, the domain name is
, the file path is news/pressroom.php.
) but it would not find “tw/news”.
USG20(W)-VPN Series User’s Guide
416
Chapter 27 Content Filtering
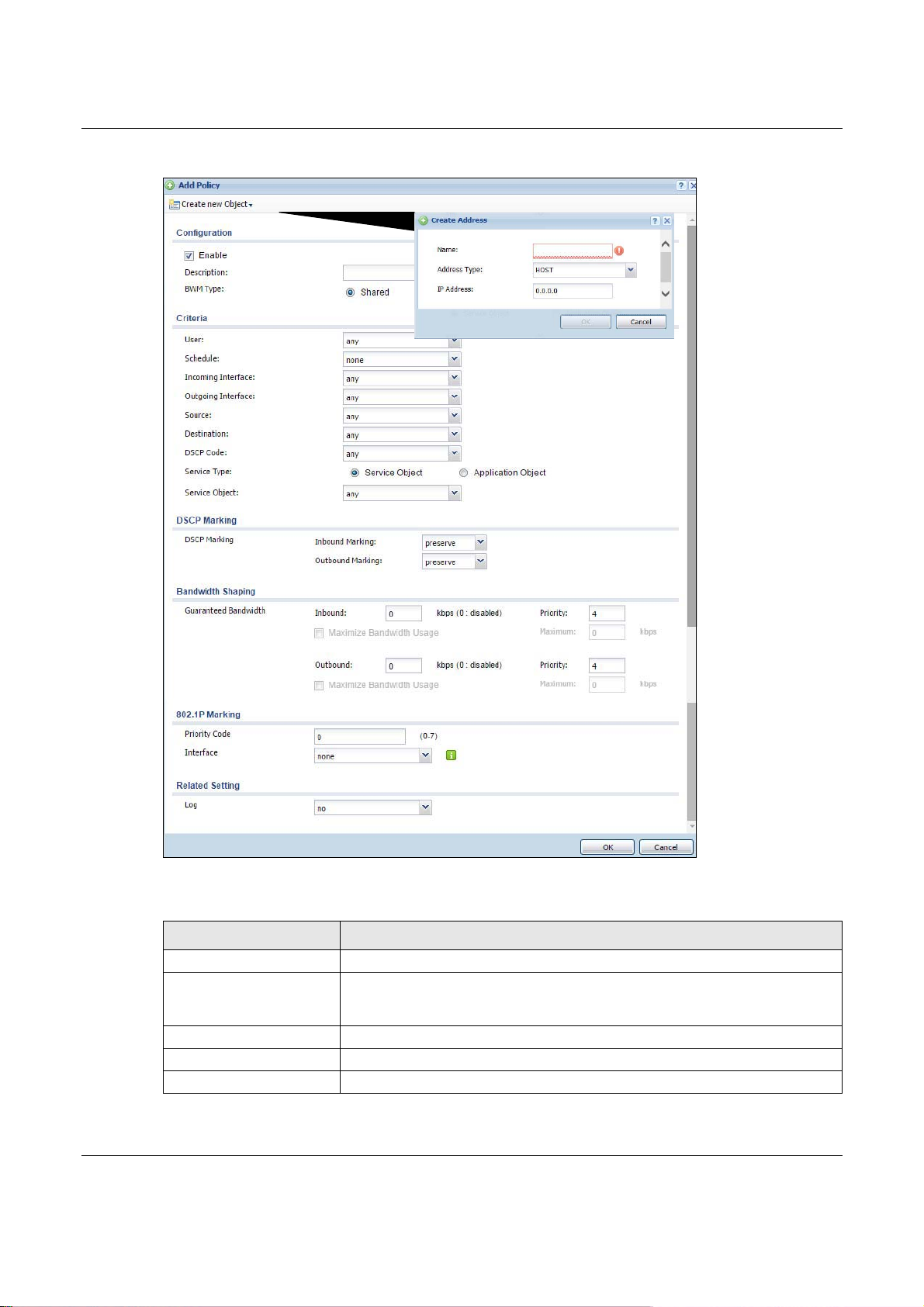
27.2 Content Filter Profile Screen
Click Configuration > UTM Profile> Content Filter > Profile to open the Content Filter
Profile screen. Use this screen to enable content filtering, view and order your list of content filter
policies, create a denial of access message or specify a redirect URL and check your external web
filtering service registration status.
Click on the icons to go to the OneSecurity.com website where there is guidance on configuration
walkthroughs, troubleshooting and other information.
Figure 288 Configuration > UTM Profile > Content Filter > Profile
The following table describes the labels in this screen.
Table 163 Configuration > UTM Profile > Content Filter > Profile
LABEL DESCRIPTION
General Settings
Enable Content Filter
Report Service
Report Server Click this link to choose where your USG is registered: myZyXEL.com or
Content Filter Category
Service Timeout
Select this check box to have the USG collect category-based content filtering
statistics.
myZyXEL.com 2.0. Choose myZyXEL.com 2.0 for a model in this series.
Specify the allowable time period in seconds for accessing the external web
filtering service’s server.
USG20(W)-VPN Series User’s Guide
417
Chapter 27 Content Filtering
Table 163 Configuration > UTM Profile > Content Filter > Profile (continued)
LABEL DESCRIPTION
Denied Access Message Enter a message to be displayed when content filter blocks access to a web page.
Redirect URL Enter the URL of the web page to which you want to send users when their web
Profile Management
Add Click Add to create a new content filter rule.
Edit Click Edit to make changes to a content filter rule.
Remove Click Remove the delete a content filter rule.
Object Reference Select an entry and click Object References to open a screen that shows which
# This column lists the index numbers of the content filter profile.
Name This column lists the names of the content filter profile rule.
Description This column lists the description of the content filter profile rule.
Reference This displays the number of times an Object Reference is used in a rule.
License Status This read-only field displays the status of your content-filtering database service
License Type This read-only field displays what kind of service registration you have for the
Expiration Date This field displays the date your service license expires.
Register Now This link appears if you have not registered for the service or the service has
Apply Click Apply to save your changes back to the USG.
Reset Click Reset to return the screen to its last-saved settings.
Use up to 127 characters (0-9a-zA-Z;/?:@&=+$\.-_!~*'()%,”). For example,
“Access to this web page is not allowed. Please contact the network
administrator”.
It is also possible to leave this field blank if you have a URL specified in the
Redirect URL field. In this case if the content filter blocks access to a web page,
the USG just opens the web page you specified without showing a denied access
message.
access is blocked by content filter. The web page you specify here opens in a new
frame below the denied access message.
Use “http://” or “https://” followed by up to 262 characters (0-9a-zA-Z;/
?:@&=+$\.-_!~*'()%). For example, http://192.168.1.17/blocked access.
settings use the entry. Click Refresh to update information on this screen.
registration.
Not Licensed displays if you have not successfully registered and activated the
service.
Expired displays if your subscription to the service has expired.
Licensed displays if you have successfully registered the USG and activated the
service.
You can view content filter reports after you register the USG and activate the
subscription service in the Registration screen.
content-filtering database.
None displays if you have not successfully registered and activated the service.
Standard displays if you have successfully registered the USG and activated the
service.
Trial displays if you have successfully registered the USG and activated the trial
service subscription.
expired. Click this link to go to the screen where you can register for the service.
USG20(W)-VPN Series User’s Guide
418

Chapter 27 Content Filtering
27.3 Content Filter Profile Add or Edit Screen
Click Configuration > UTM > Content Filter > Profile > Add or Edit to open the Add Filter
Profile screen. Configure Category Service and Custom Service tabs.
USG20(W)-VPN Series User’s Guide
419
Chapter 27 Content Filtering
27.3.1 Content Filter Add Profile Category Service
Figure 289 Content Filter > Profile > Add Filter Profile > Category Service
USG20(W)-VPN Series User’s Guide
420
 Loading...
Loading...