Page 1

Xerox® Workplace Cloud
5.6.1
Security Guide
Page 2

© 2021 Xerox® Corporation. All rights reserved. Xerox®, AltaLink®, ConnectKey®, Global Print
Driver®, and VersaLink® are trademarks of Xerox® Corporation in the United States and/or other
countries. BR32181
Apache OpenOffice™ is a trademark of the Apache Software Foundation in the United States and/or
other countries.
®
Apple
and Mac® are trademarks of Apple, Inc. registered in the United States and/or other
countries.
Chrome™ is a trademark of Google Inc.
Firefox
Intel
IOS
®
is a registered trademark of Mozilla Corporation.
®
Core™ is a trademark of the Intel Corporation in the United States and/or other countries.
®
is a trademark or registered trademark of Cisco in the United States and other countries and
is used under license.
Microsoft®, SQL Server®, Microsoft®.NET, Windows®, Windows Server®, Windows 8®, Office®,
®
Excel
and Internet Explorer® are either registered trademarks or trademarks of Microsoft
Corporation in the United States and/or other countries.
Xerox® PDF Reader Powered by Foxit Software Company (http://www.foxitsoftware.com).
This product includes software developed by Aspose (http://www.aspose.com).
Other company trademarks are also acknowledged.
Document Version: 1.0 (March 2021). BR32181
Copyright protection claimed includes all forms and matters of copyrightable material and
information now allowed by statutory or judicial law or hereinafter granted including without
limitation, material generated from the software programs which are displayed on the screen, such
as icons, screen displays, looks, etc.
Changes are periodically made to this document. Changes, technical inaccuracies, and
typographic errors will be corrected in subsequent editions.
Page 3
Conventions in this Document
Throughout this document, you will find tags that will indicate when the content is unique to a
specific solution of the platform. These tags will include:
[PMM] Content applies only to Print Management and Mobility
[FM] Content applies only to Fleet Management
These tags will typically be found on section titles; however, they may be found at other points in
the documentation.
NOTE: Any section not showing a tag should be assumed to follow the tags of any higher-level
sections. If there are no tags on the section or on the higher-level sections then the section applies
to all solutions.
For example, if you are implementing just Fleet Management, you will want to read sections tagged
[FM] and all untagged sections (but you can skip the [PMM] tagged sections)
Xerox® Workplace Cloud 5.6.1 – Security Guide i
Page 4
Table of Contents
1. Introduction ....................................................................................................................................... 6
Purpose ............................................................................................................................................... 6
Target Audience .................................................................................................................................. 6
Disclaimer ........................................................................................................................................... 6
2. Product Description .......................................................................................................................... 7
Overview ............................................................................................................................................. 7
Printing and Print Management .......................................................................................................... 7
Submission Methods ....................................................................................................................... 7
Release Methods ............................................................................................................................ 7
Combined Submission/Release Methods ....................................................................................... 7
Printer Authentication Methods ....................................................................................................... 8
Xerox® @PrintByXerox................................................................................................................... 8
Xerox® Workplace Cloud Printing and Print Management ........................................................... 10
Xerox® Workplace Cloud (Agentless) [PMM] ............................................................................... 11
Description of System Components [PMM] .................................................................................. 11
Xerox® Workplace Cloud Fleet Management (with an Agent) [FM] .............................................. 13
Xerox® Workplace Cloud Fleet Management (Agentless) [FM] .................................................... 14
Description of System Components [FM] ..................................................................................... 14
3. System Architecture ....................................................................................................................... 16
Xerox® Workplace Cloud ................................................................................................................... 16
Xerox® Workplace Cloud Volatile Memory .................................................................................... 16
Xerox® Workplace Cloud Non-Volatile Memory ............................................................................ 16
Workplace Cloud Agent .................................................................................................................... 17
Workplace Cloud Agent Volatile Memory ..................................................................................... 17
Workplace Cloud Agent Non-Volatile Memory .............................................................................. 17
Desktop Print Client [PMM] ............................................................................................................... 18
Desktop Print Client Volatile Memory ........................................................................................... 18
Desktop Print Client Non-Volatile Memory .................................................................................... 18
Xerox® Workplace App [PMM] .......................................................................................................... 19
Workplace App Volatile Memory ................................................................................................... 19
Workplace App Non-Volatile Memory ........................................................................................... 19
Open-Source Components ............................................................................................................... 19
Xerox® Workplace Cloud 5.6.1 – Security Guide ii
Page 5

4. System Interaction .......................................................................................................................... 20
System Components ......................................................................................................................... 20
Xerox® Workplace App [PMM] ...................................................................................................... 20
Xerox® Workplace Cloud ............................................................................................................... 20
LDAP/ADS Server ......................................................................................................................... 25
Azure AD ....................................................................................................................................... 25
OKTA ............................................................................................................................................. 27
Third Party Public Print Provider [PMM] ....................................................................................... 29
Workplace Cloud Agent ................................................................................................................ 30
Server Based Print Queues .......................................................................................................... 31
Printer ............................................................................................................................................ 32
Xerox® @PrintByXerox App [PMM] .............................................................................................. 33
Customer Email Server ................................................................................................................. 33
User Workstation (Workplace Cloud Client) [PMM] ...................................................................... 33
Microsoft Office 365 – Email Service ............................................................................................ 36
Network Appliance [PMM] ............................................................................................................. 36
Xerox® Services Manager ............................................................................................................. 36
Content Delivery Network (CDN) [PMM] ....................................................................................... 36
App in the Gallery [PMM] .............................................................................................................. 37
App Server [PMM] ......................................................................................................................... 37
Xerox® Device Agent [FM] ............................................................................................................ 37
Xerox Auto Update Service [FM]................................................................................................... 37
System Component Interfaces .......................................................................................................... 38
Communication between the Workplace App and Workplace Cloud [PMM] ................................ 38
Communication between the Workplace App and the Customer Email Server [PMM] ................ 38
Communication between the Customer Email Server and Workplace Cloud .............................. 38
Communication between Workplace Cloud and the Workplace Cloud Agent .............................. 38
Communication between the Workplace Cloud Agent and the Printer ......................................... 39
Communication between the Workplace Cloud Agent and a Third-Party Print Queue [PMM] ..... 40
Communication between the Workplace Cloud Client and Workplace Cloud [PMM] ................... 40
Communication between the Workplace Cloud Client and the Printer [PMM] ............................. 42
Communication between the Workplace Cloud Client and the Azure IoT Hub [PMM] ................. 42
Communication between the Workplace Cloud Agent and the Customer ADS (LDAP) Server ... 42
Communication between Workplace Cloud and Xerox® Services Manager................................. 42
Communication between LPR or Shared Windows Print (SMB) Clients and the Workplace Cloud
Agent [PMM].................................................................................................................................. 43
Xerox® Workplace Cloud 5.6.1 – Security Guide iii
Page 6

Communication between the App from the Gallery, the App Server, and Workplace Cloud [PMM]
...................................................................................................................................................... 43
Communication between Workplace Cloud and the Printer ......................................................... 43
Communication between the Printer and the IoT Hub .................................................................. 44
Communication between the Xerox® Device Agent and Workplace Cloud [FM] .......................... 44
Communication between the Xerox® Device Agent and the Xerox Auto Update Service [FM] .... 44
5. Logical Access, Network Protocol Information ........................................................................... 45
Protocols and Ports ........................................................................................................................... 45
Xerox® Workplace App Ports [PMM] ............................................................................................. 45
Workplace Cloud Agent Ports ....................................................................................................... 45
Xerox® @PrintByXerox App Ports [PMM] .................................................................................... 46
Printer Ports .................................................................................................................................. 47
Workplace Cloud Client Ports [PMM] ............................................................................................ 48
Network Appliance Ports [PMM] ................................................................................................... 48
Xerox® Device Agent Ports [FM] ................................................................................................... 49
Firewall Rules .................................................................................................................................... 49
Port Diagrams ................................................................................................................................... 50
Print Management Port Diagram [PMM] ....................................................................................... 50
Fleet Management Port Diagram [FM] .......................................................................................... 52
6. System Access ................................................................................................................................ 54
User Accounts ................................................................................................................................... 54
Web Portal ........................................................................................................................................ 54
Workplace Cloud Agent .................................................................................................................... 54
Xerox® Workplace App [PMM] .......................................................................................................... 55
Workplace Cloud Client for Windows and Mac [PMM] ..................................................................... 55
Printer ................................................................................................................................................ 56
Xerox® @PrintByXerox App [PMM].................................................................................................. 56
Content Delivery Network (CDN) [PMM] ........................................................................................... 57
7. Additional Security Items ............................................................................................................... 59
Xerox® Workplace Cloud Endpoint Table ......................................................................................... 59
Cloud Endpoints ............................................................................................................................ 59
Cloud Endpoint Descriptions ......................................................................................................... 60
Certificate Validation ......................................................................................................................... 62
Connection Details ........................................................................................................................ 62
Auto Release Using Network Appliance Workflow [PMM] ................................................................ 63
Xerox® Workplace Cloud 5.6.1 – Security Guide iv
Page 7

Models ........................................................................................................................................... 63
Audit Log ........................................................................................................................................... 63
Azure Data Centers ........................................................................................................................... 64
Usage Tracking and Reporting [PMM] .............................................................................................. 64
Single Sign-On [PMM] ....................................................................................................................... 65
User Import via CSV File................................................................................................................... 66
Packet Inspection .............................................................................................................................. 66
File Encryption using Keys [PMM] ................................................................................................... 66
Content Security [PMM] ................................................................................................................... 67
Microsoft Azure Universal Print [PMM] ............................................................................................ 68
8. Additional Information and Resources ......................................................................................... 70
Security @ Xerox® ............................................................................................................................ 70
Responses to Known Vulnerabilities ................................................................................................. 70
Additional Resources ........................................................................................................................ 70
Xerox® Workplace Cloud 5.6.1 – Security Guide v
Page 8

1. Introduction
Xerox® Workplace Cloud (WC) is a workflow solution that connects a corporation mobile workforce
to new productive ways of printer management, printing, and controlling user access to Xerox®
Multifunction Printers (MFP). Customers can manage the configuration of their printers and ensure
settings are consistent across their fleet of devices. Printing is easy and convenient from any
mobile device without needing standard drivers and cables. This solution also supports Desktop
Printing, allowing printing to a common queue with the ability to release jobs to any printer. This
reduces waste from uncollected jobs and provides security for sensitive information, since jobs are
only printed when the user is standing at the printer.
WC provides a Single Sign-On (SSO) infrastructure. Apps in the Xerox App Gallery which have
been modified to support this new infrastructure may use WC as a storage vault for user login
information (e.g., credentials or tokens). After logging into WC, a user may select an SSO enabled
Gallery App, which queries WC to obtain the user’s login information for that app. If available (and
valid – e.g., not expired), the app uses that information to log the user into the Gallery App without
the need to provide additional login credentials.
Purpose
The purpose of the Security Guide is to disclose information for Xerox® Workplace Cloud with
respect to application security. Application security, in this context, is defined as how data is stored
and transmitted, how the product behaves in a networked environment, and how the product may
be accessed, both locally and remotely. This document describes design, functions, and features of
the Xerox® Workplace Cloud relative to Information Assurance (IA) and the protection of customer
sensitive information. Please note that the customer is responsible for the security of their network
and the Xerox® Workplace Cloud does not establish security for any network environment.
This document does not provide tutorial level information about security, connectivity or Xerox®
Workplace Suite features and functions. This information is readily available elsewhere. We
assume that the reader has a working knowledge of these types of topics.
Target Audience
The target audience for this document is Xerox field personnel and customers concerned with IT
security. It is assumed that the reader is familiar with the solution; as such, some user actions are
not described in detail.
Disclaimer
The content of this document is provided for information purposes only. Performance of the
products referenced herein is exclusively subject to the applicable Xerox Corporation terms and
conditions of sale and/or lease. Nothing stated in this document constitutes the establishment of
any additional agreement or binding obligations between Xerox Corporation and any third party.
Xerox® Workplace Cloud 5.6.1 – Security Guide 6
Page 9

2. Product Description
Overview
Workplace Cloud supports two different cloud solutions:
1. Printing and Print Management – Includes mobile and desktop printing, printer authentication / access
and reporting.
2. Fleet Management – Which includes the ability to configure and manage settings on a set of devices.
Printing and Print Management
This workflow can be limited to just mobile printing, or it can be extended to include desktop printing,
printer authentication (such as badge access) and advanced reporting.
The workflow of mobile printing is quite simple. A user using a mobile device such as a smart phone,
tablet, or laptop sends a document to the Workplace Cloud. Depending on the submission method, the
job is either printed without any further user action or the user manually releases the job to print.
For desktop printing, the user installs the Workplace Cloud Client. The client will help with printer install
and also manages communication with the Workplace Cloud solution. With this service in place, users
can submit pull-print jobs as well as direct print jobs.
Workplace Cloud provides a Single Sign-On (SSO) infrastructure. The Apps in the Xerox App Gallery,
which were modified to support this new infrastructure, can use Workplace Cloud as a storage vault for
user login information. User login information can be user credentials or tokens. After logging into the
Workplace Cloud, a user can select an SSO enabled Gallery App, which queries Workplace Cloud to
obtain the login information of the user for that app. If the login information is available and valid, the app
uses that information to log in the user into the Gallery App without the need to provide additional login
credentials.
There are several methods for a user to submit or release a job to print. The Submission method is
technically decoupled from the release method. However, certain submission/release pairs make more
sense than other pairs.
S U B M I S S IO N M E TH O D S
Email
Workplace App
Desktop Print Client (upload)
RE L E AS E M E T H O D S
Printing device UI (using EIP)
Workplace App
Auto Release using Authentication
Auto Release using Network Appliance
CO M B I N E D S UB M I S S IO N / R E LE A SE ME T H O DS
Note: Job will print without any explicit user action after submission.
Xerox® Workplace Cloud 5.6.1 – Security Guide 7
Page 10

Email
Workplace App
Web Portal (Web browser interface to Workplace Cloud)
Desktop Print Client (upload and print)
Desktop Print Client (direct print)
P R I N TE R A U TH E NT I C A T IO N M E TH O DS
Card Access (Proximity Cards, Magnetic Stripe Cards, NFC on Android)
Alternate Login (Cloud Authentication, LDAP or PIN) [Note: OKTA and Azure AD do not support
this method]
Mobile Phone Unlock (using the Xerox® Workplace App for iOS or Android: NFC, QR Code, or
Manual Code Entry)
The common link between all submission and release methods is the Xerox® Workplace Cloud.
Documents are stored in the cloud until they are deleted or until an administrative timeout has passed.
With release 5.6, Xerox® Workplace Cloud added the ability to support an Agentless method of Printer
Authentication. This feature makes use of the Azure IoT Hub capability to provide this functionality and
is supported by Xerox AltaLink devices (A special firmware release is required).
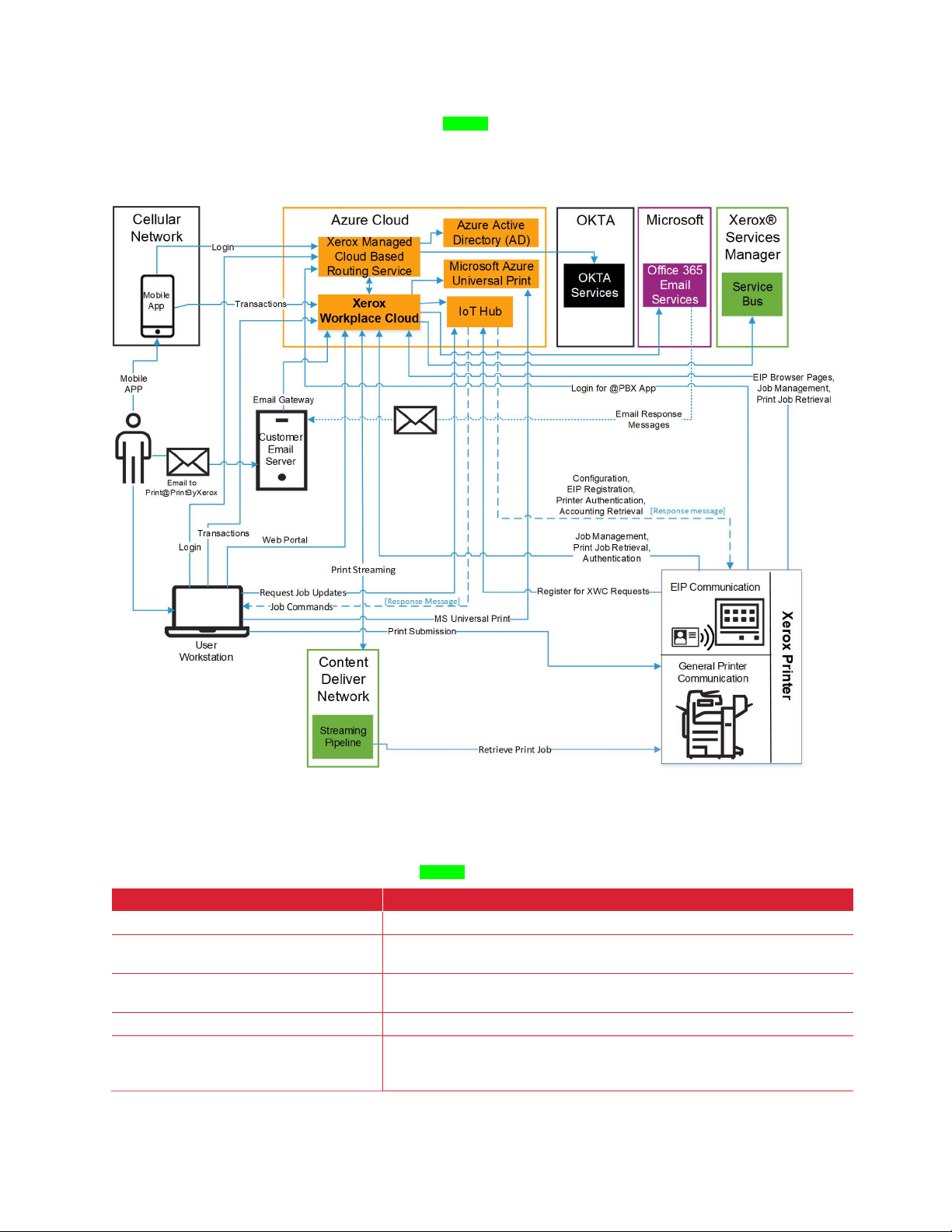
X E R O X® @P R I N T BY X ER O X
The Xerox® @PrintByXerox App, available using the Xerox App Gallery and included as an “In-Box” App
on some devices is designed to give customers an introduction to the Workplace Cloud system. Users are
able to submit jobs using Email, by sending them to print@printbyxerox.com, and then release them
using the Xerox® @PrintByXerox App. Below is a diagram outlining the different components used as
part of this workflow.
Xerox® Workplace Cloud 5.6.1 – Security Guide 8
Page 11
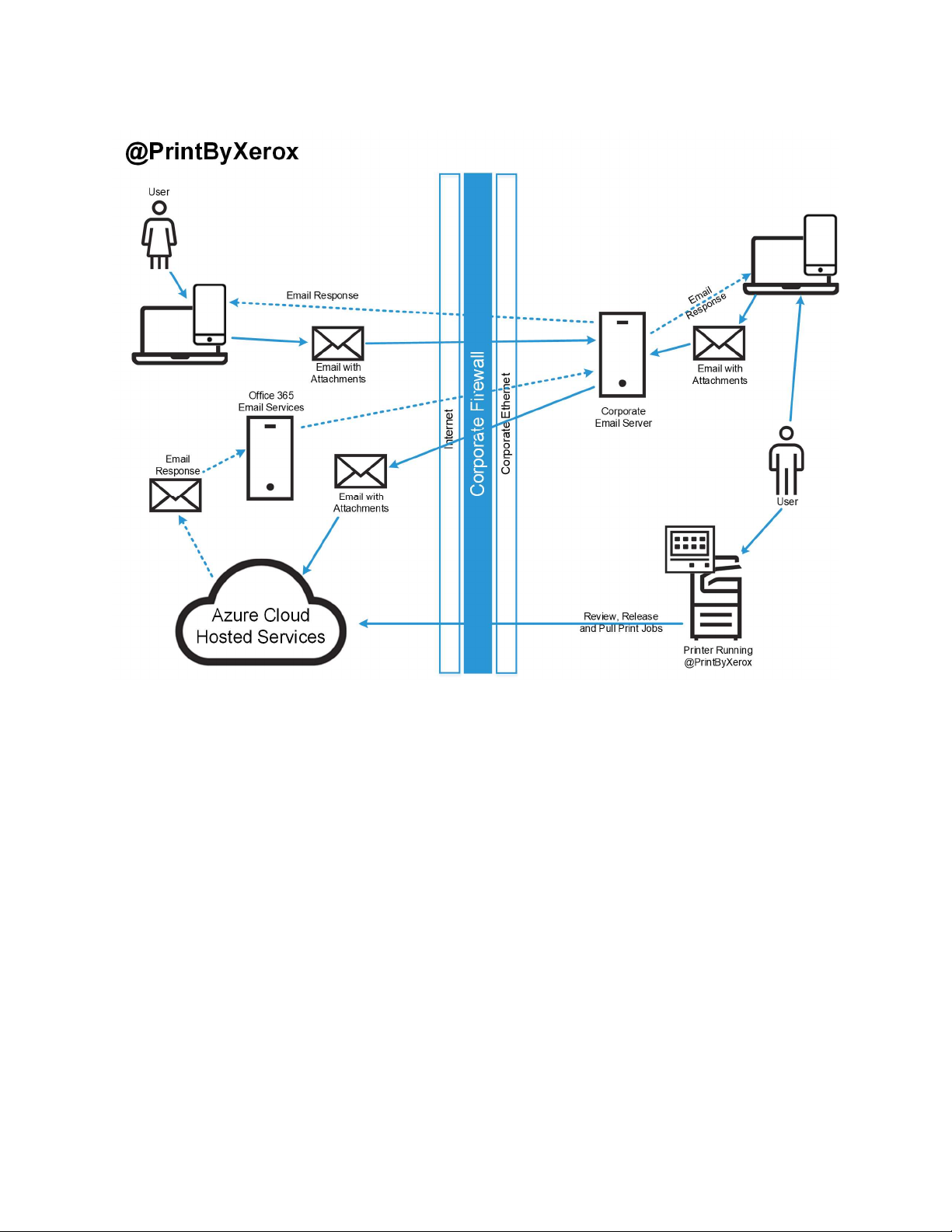
Figure 2–1: @PrintByXerox
Xerox® Workplace Cloud 5.6.1 – Security Guide 9
Page 12
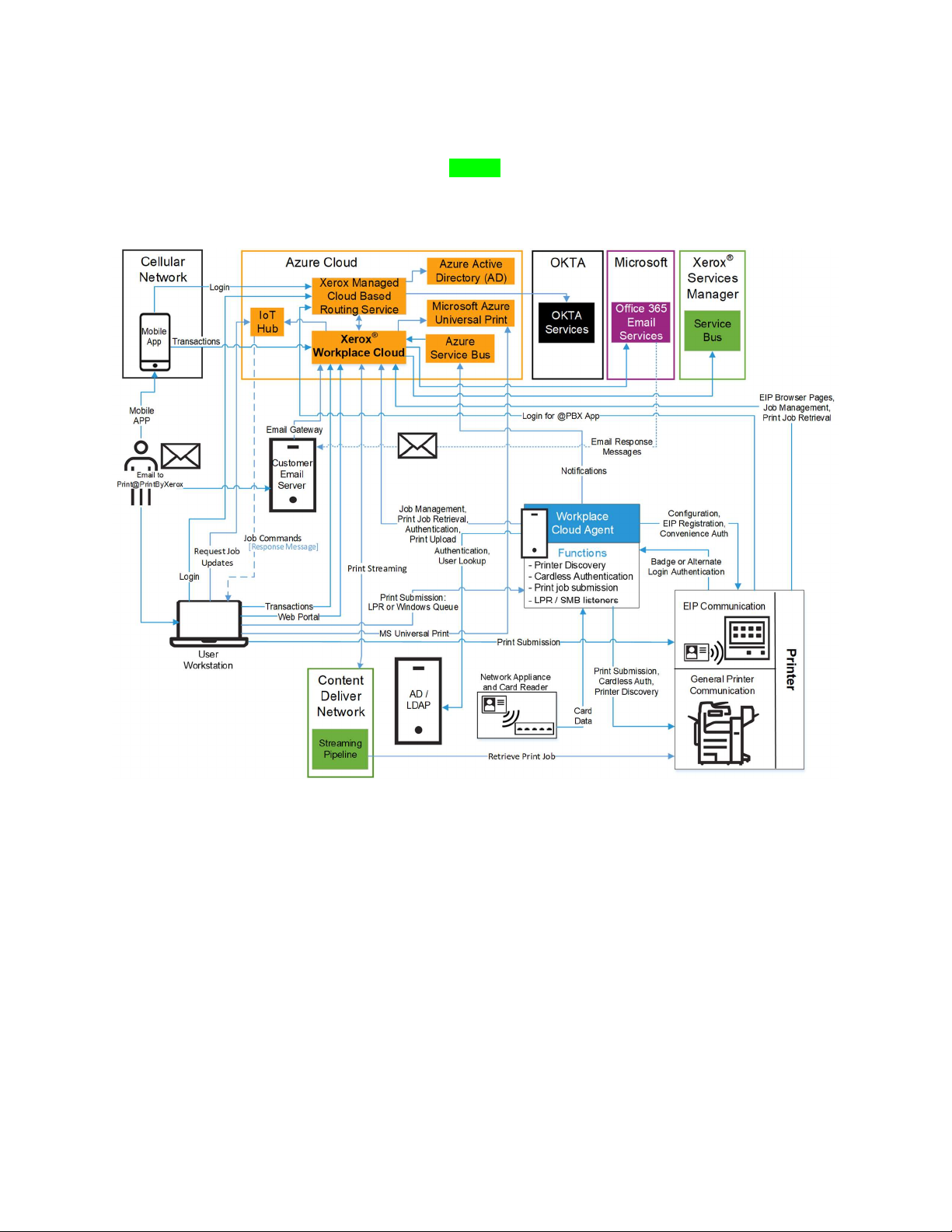
X E R O X® WO R KP L A C E C L OU D P R I N T IN G A N D P RI N T M A N AG E M EN T
Xerox® Workplace Cloud (with an Agent) [PMM]
The following diagram shows the system components used for the full Xerox® Workplace Cloud
for Printing and Print Management solution using an Agent.
Figure 2–2: Xerox® Workplace Cloud with an Agent
Xerox® Workplace Cloud 5.6.1 – Security Guide 10
Page 13
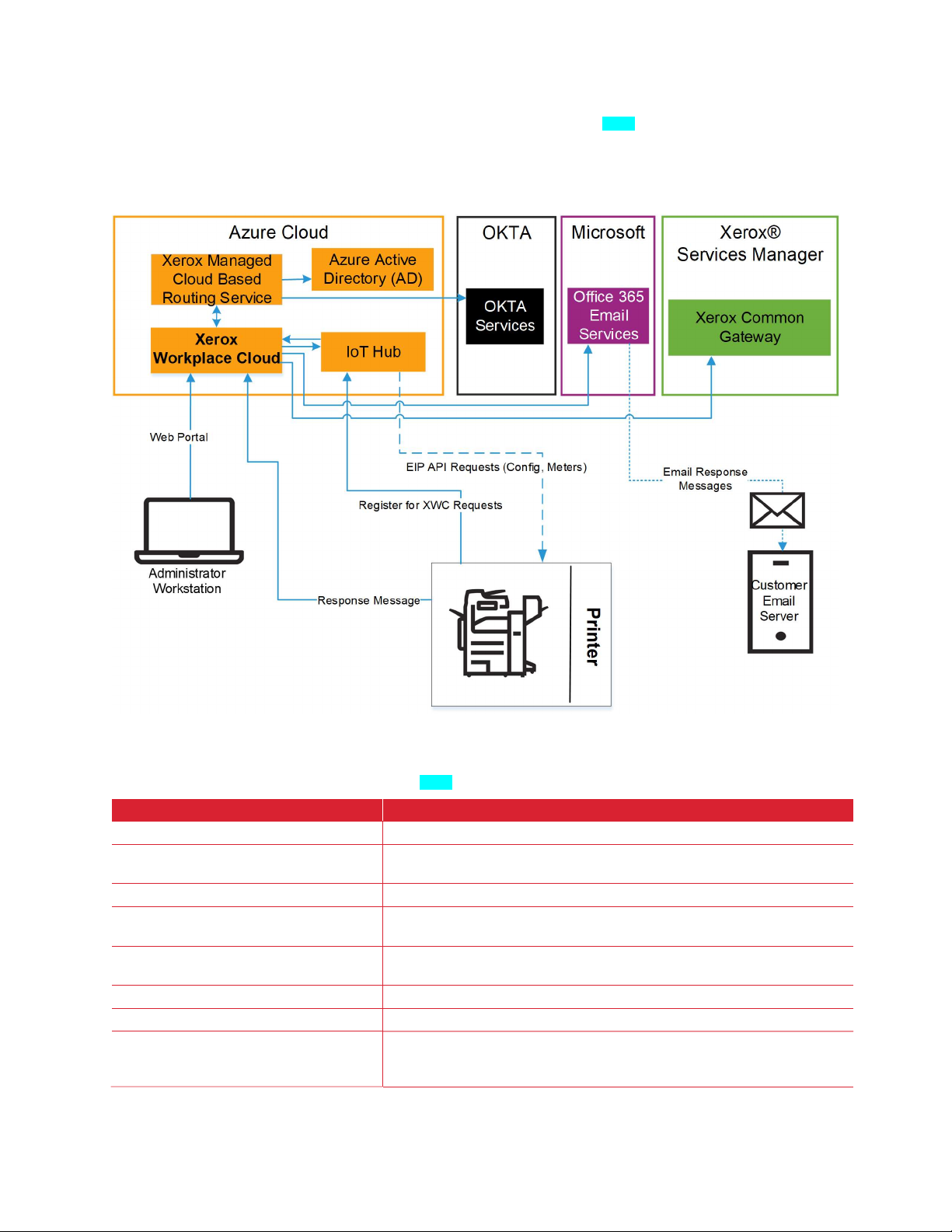
X E R O X® WO R KP L A C E C L OU D ( A G E N TL E S S ) [ P M M ]
The following diagram shows the system components used for the full Xerox® Workplace Cloud (Printing
and Print Management) without an Agent.
Figure 2–3: Xerox® Workplace Cloud Agentless
DE S C RI P T I O N O F S Y S T E M C O MP O N E N T S [P M M]
Component Description
User A user of the Xerox® Workplace Cloud.
Xerox® Workplace App Mobile application for iOS, Android, and Chrome that allows the user to
find printers and upload / send print jobs to Workplace Cloud.
Xerox® Workplace Cloud The Azure hosted cloud service that provides the Workplace Cloud
functionality.
Customer ADS/LDAP Server Used for user authentication.
Azure AD [Optional] May be used for user authentication. Microsoft’s Azure AD
may in turn forward authentication requests to the customer’s hosted
AD system.
Xerox® Workplace Cloud 5.6.1 – Security Guide 11
Page 14
Component Description
Azure IoT Hub [Optional] Is used for the desktop client “Local Print Optimization” feature
and for Agentless Authentication.
OKTA [Optional] May be used for user authentication.
Third-Party Public Print Provider Allows print jobs to be submitted to Third-Party Providers.
Workplace Cloud Agent On-premise application that runs on customer provided hardware, which
supports Printer Discovery, Print transmission, Convenience
Authentication and Network Accounting. Also provides LPR and
Windows printer listening ports for systems that do not support a desktop
client (e.g. Linux).
Server Based Print Queues Allows print jobs to be forwarded to other 3rd Party Solutions for added
job tracking, accounting, and so on.
Printer Any printing device (Xerox or Non-Xerox) that is enabled to support
Workplace Cloud.
Customer Email Server The Customer Email Server is used to get print jobs to the
Workplace Cloud.
User Workstation User’s system on which the Workplace Cloud Client can be installed,
which allows print jobs to be submitted to Workplace Cloud Printers from
a PC or Mac. Also supports the Home Worker Print Tracker feature
which monitors a user’s print history, even when printing to printers not
enabled in Workplace Cloud.
Microsoft Office 365 Email Service Used to send email responses back to users of Workplace Cloud.
Network Appliance External hardware device that supports card-based document release at
Non-Xerox or Non-EIP Devices.
Xerox® Services Manager External Xerox application used in managed service accounts.
Content Delivery Network (CDN) Enabled high-bandwidth print job streaming from Azure to local printers
in the customer environment.
App from Gallery An App found in the Xerox App Gallery that is modified to support SSO.
App Server A backend system that handles the browser-based calls and processing
needed by the App. Maintains knowledge and information about the
SSO server.
Microsoft Azure Universal Print Microsoft’s Universal Print infrastructure hosted in Azure.
Xerox® Workplace Cloud 5.6.1 – Security Guide 12
Page 15
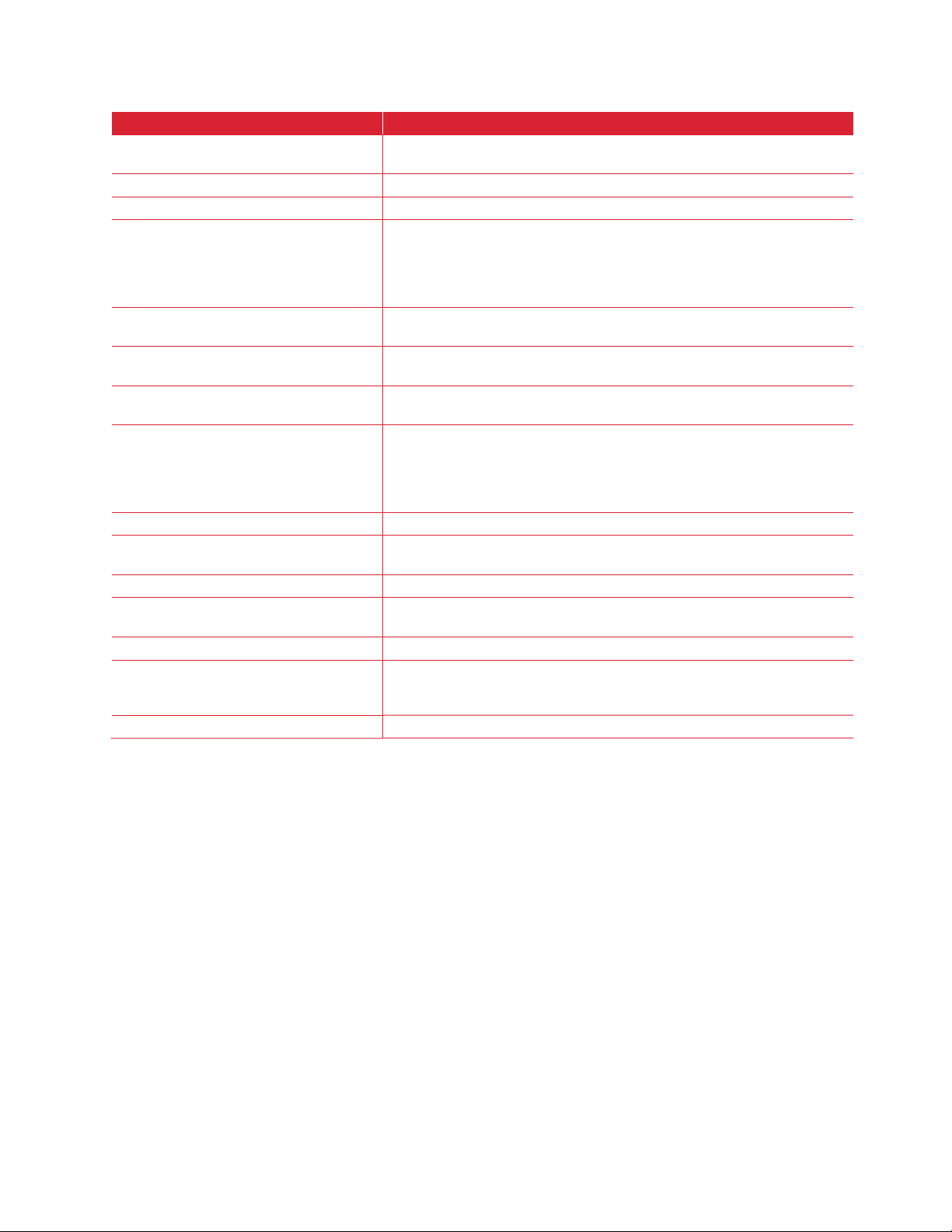
Fleet Management
The Fleet Management functionality allows the administrator to define configuration sets, push these to a
printer and monitor the configuration of devices to ensure settings do not change. Different configurations
can be defined for different sets of printers. Customers that use the Fleet Management feature can link
their account to Xerox® Services Manager. This allows the same set of devices being monitored using
Xerox® Device Agent(s) to also be managed using Workplace Cloud Fleet Management.
X E R O X® W O R KP L AC E C L OU D F L E E T M AN A G E M E N T ( W I TH A N AG E NT ) [ F M ]
The following diagram shows the system components used for the Xerox® Workplace Cloud Fleet
Management only functionality using an Agent.
Figure 2–4: Xerox® Workplace Cloud Fleet Management – With an Agent
Xerox® Workplace Cloud 5.6.1 – Security Guide 13
Page 16
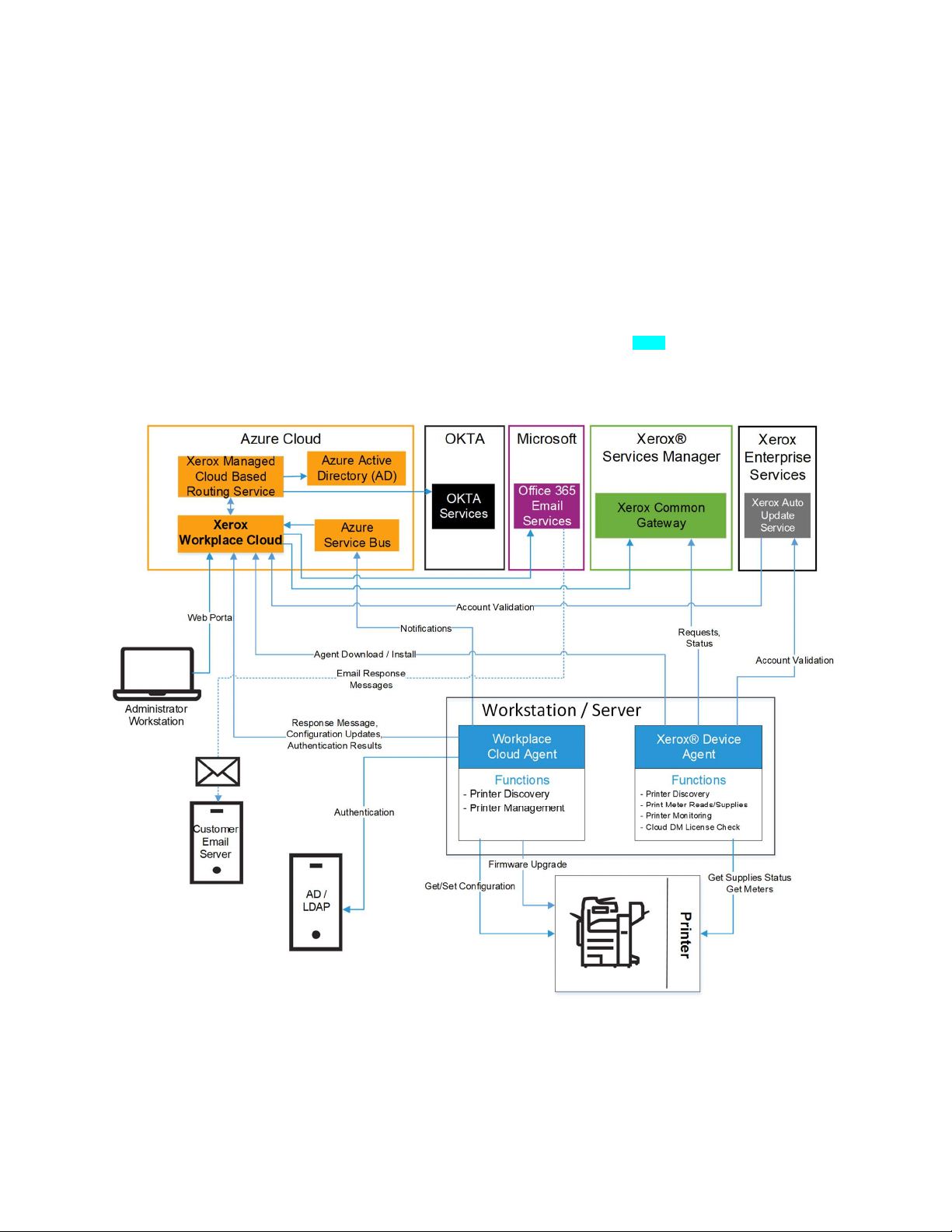
X E R O X® W O R KP L AC E C L OU D F L E E T M AN A G E M E N T ( A G EN T LE S S ) [F M ]
The following diagram shows the system components used for the Xerox® Workplace Cloud Fleet
Management only functionality without an Agent.
Figure 2–5: Xerox® Workplace Cloud Fleet Management – Agentless
DE S C RI P T I O N O F S Y S T E M C O MP O N E N T S [F M ]
Component Description
User A user of the Xerox® Workplace Cloud.
Xerox® Workplace Cloud
Azure IoT Hub Is used for Fleet Management requests sent to the Agent.
Workplace Cloud Agent On-premise application that runs on customer provided hardware, which
Printer Any printing device (Xerox or Non-Xerox) that is enabled to support
Microsoft Office 365 Email Service Used to send email responses back to users of Workplace Cloud.
Xerox® Services Manager External Xerox application used in managed service accounts.
Xerox® Device Agent External Xerox application for device monitoring that has been extended
Xerox® Workplace Cloud 5.6.1 – Security Guide 14
The Azure hosted cloud service that provides the Workplace Cloud
functionality.
supports Printer Discovery, and Fleet Management.
Workplace Cloud.
to support the installation of the WC Agent for managed print service
environments using Xerox® Services Manager.
Page 17

Component Description
Xerox Auto Update Service External Xerox application hosted by Xerox (internet accessible). Used
to update the Device Agent.
Xerox® Workplace Cloud 5.6.1 – Security Guide 15
Page 18
3. System Architecture
Xerox® Workplace Cloud
The Xerox® Workplace Cloud consists of number of different services that run as an Azure role
(Web Role or Worker Role). The type of role used depends upon the function of the service. If the
service is interfacing externally using some type of API or interface, it’s typically a Web Role and if
the service performs internal processing, then it’s typically a Worker Role. Each role runs on its
own Azure VM instance, and the number of such instances will vary based on the system load.
Each service is assigned a fixed size set of RAM and HDD for the given VM, which varies based on
the service and its needs.
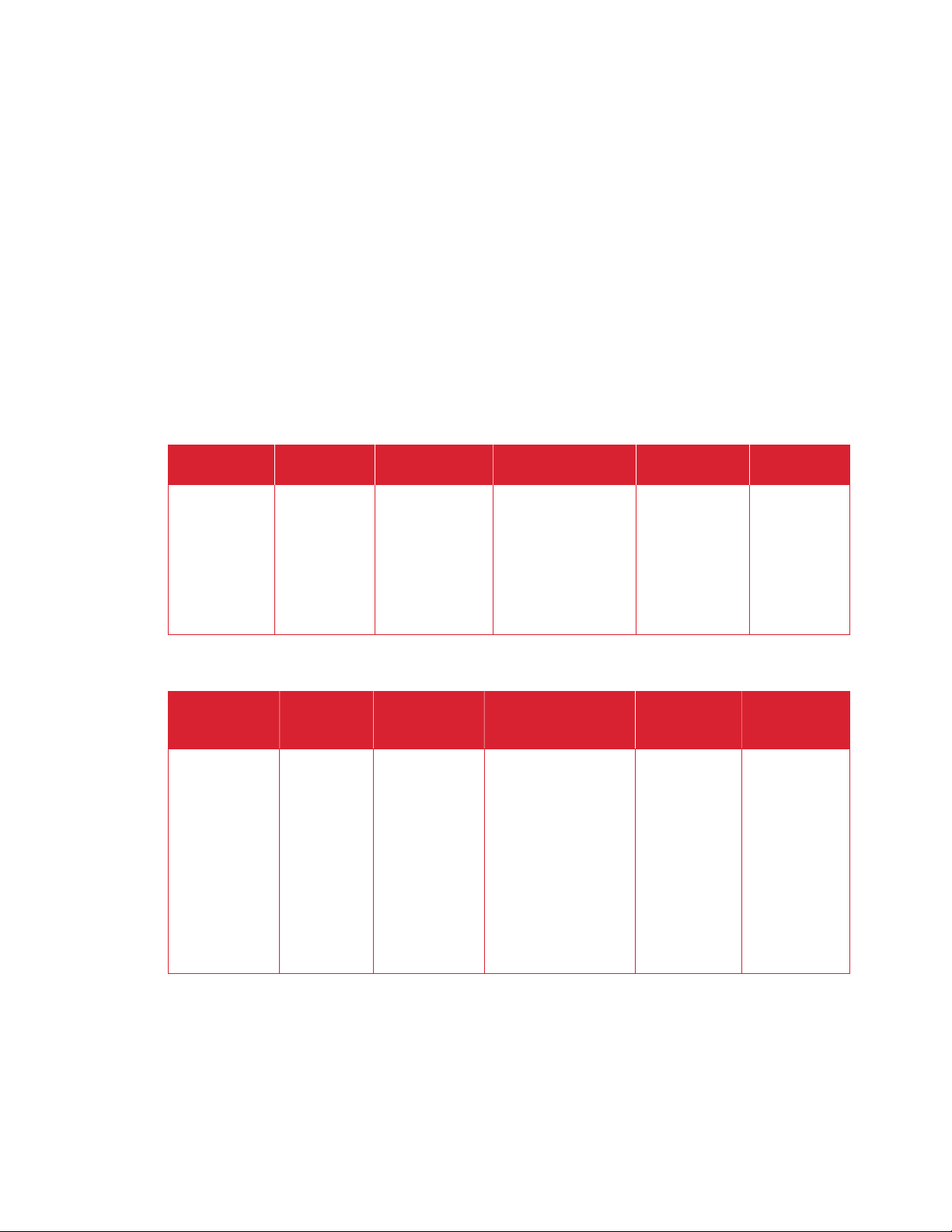
X E R O X® W O R KP L AC E C L OU D V O L A T IL E M E M O R Y
Type (SRAM,
DRAM, etc.)
Azure
storage –
System
Memory
Size User Modifiable
(Y/N)
Varies
N Executable code,
Based on
Service
Function or Use Contains
temporary storage
for messages
processing
related data,
variables, state
information, and
so on.
X E R O X® W O R KP L AC E C L OU D N O N - V O L A T I L E M EM O R Y
Type (Flash,
EEPROM,
etc.)
HDD Varies
Size User
Modifiable
(Y/N)
N Storage of
Based on
Service
Function or Use Contains
binaries, libraries,
graphic images,
HTML pages,
JavaScript pages,
certs,
configuration, logs,
user documents,
print drivers,
installers,
templates, job
metadata
Process to
Customer Data
Clear:
Y Power Off
or Exit of
the Service
Process to
Customer
Data
Clear:
Y Requires
removal of
Xerox roles
Xerox® Workplace Cloud 5.6.1 – Security Guide 16
Page 19
Workplace Cloud Agent
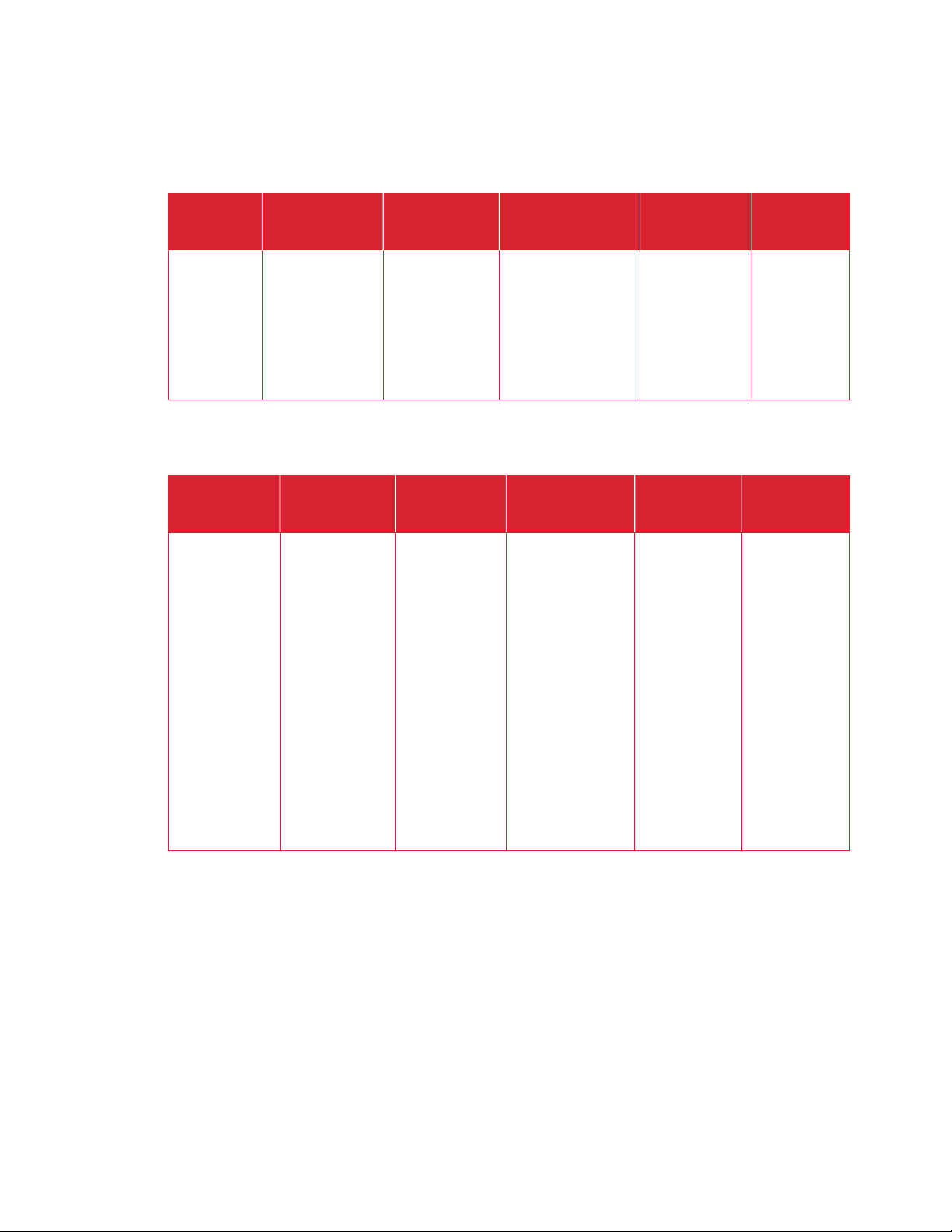
WO R K P L A CE CL O UD AG E NT V O L A T I L E M E M O R Y
Type
(SRAM,
DRAM, etc.)
RAM Customer
Size User Modifiable
(Y/N)
N Executable code,
Provided
Function or Use Contains
temporary
storage for
processing
related data,
variables, state
information, and
so on.
WO R K P L A CE CL O UD AG E NT N O N - V O L A T IL E M E M O RY
Type (Flash,
EEPROM,
etc.)
HDD Customer
Size User
Modifiable
(Y/N)
N Storage of
Provided
Function or Use Contains
binaries,
libraries, logs,
printer
information
Process to
Customer Data
Clear:
Y Power Off
or Exit of
the Service
Process to
Customer
Data
Clear:
N Removal /
Un-install of
the Agent.
Data may be
manually
deleted by
users with
access rights
to the PC on
which the
Agent is
running.
Periodic
removal of
some data
based on
time.
Xerox® Workplace Cloud 5.6.1 – Security Guide 17
Page 20

Desktop Print Client [PMM]
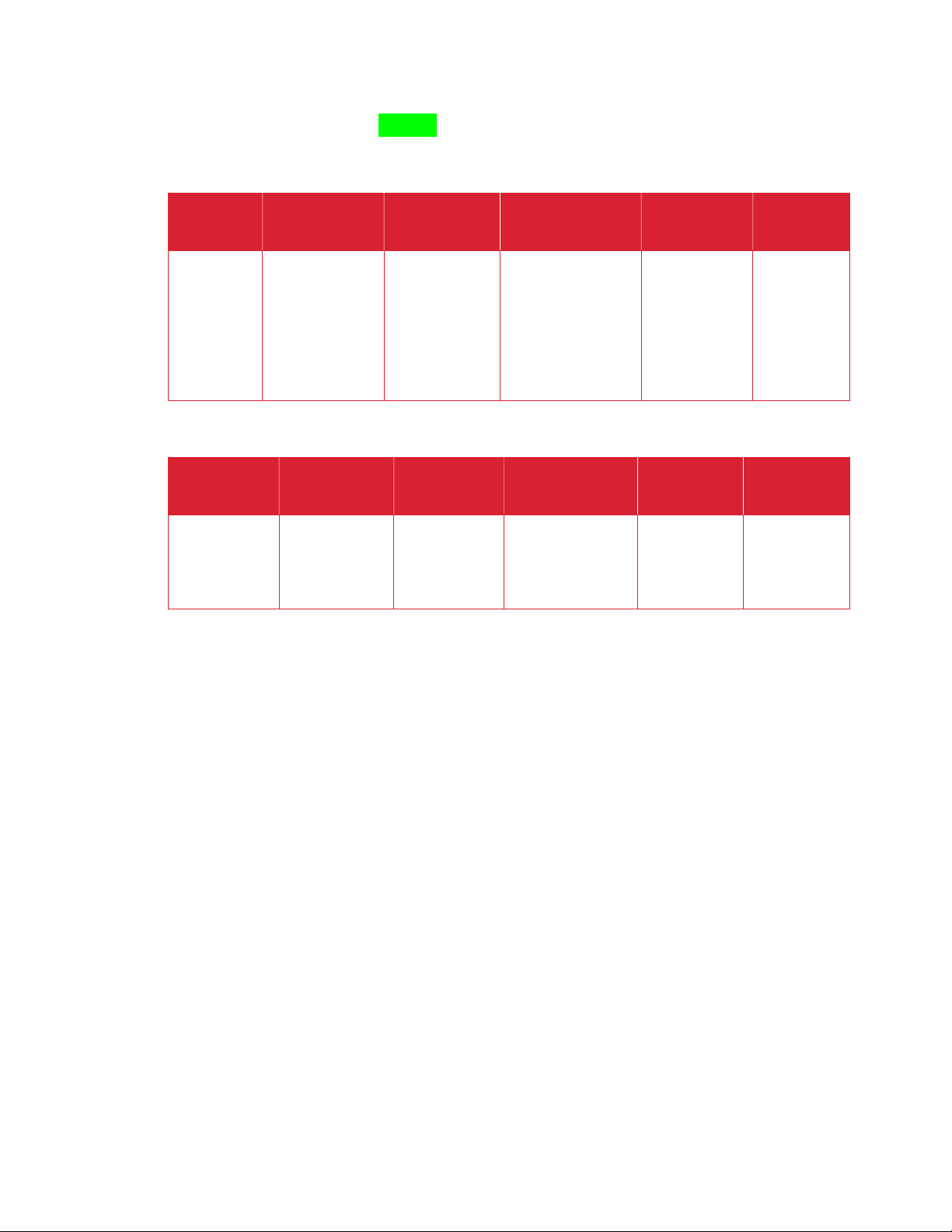
DE S K TO P P R I N T C L I E N T V O L AT I LE ME M OR Y
Type
(SRAM,
DRAM, etc.)
RAM Customer
Size User Modifiable
(Y/N)
N Executable code,
Provided
Function or Use Contains
temporary
storage for
processing
related data,
variables, state
information, and
so on.
DE S K TO P P R I N T C L I E N T N O N - V O L A T I L E M E MO R Y
Type (Flash,
EEPROM,
etc.)
HDD Customer
Size User
Modifiable
(Y/N)
N Storage of
Provided
Function or Use Contains
binaries,
libraries, logs,
printer
information
Process to
Customer Data
Clear:
Y Power Off
or Exit of
the Service
Process to
Customer
Data
Clear:
N Removal /
Un-install of
the Agent.
Data may be
manually
deleted by
users with
access rights
to the PC on
which the
Agent is
running.
Periodic
removal of
some data
based on
time.
Xerox® Workplace Cloud 5.6.1 – Security Guide 18
Page 21
Xerox® Workplace App [PMM]
WO R K P L A CE AP P V O LA T IL E M E M O RY
Type
(SRAM,
DRAM, etc.)
RAM Customer
Size User Modifiable
(Y/N)
N Executable code,
Provided
WO R K P L A CE AP P N O N- V OL A T I L E M E M O R Y
Type (Flash,
EEPROM,
etc.)
ROM Customer
Size User
Modifiable
(Y/N)
N Storage of
Provided
Function or Use Contains
Customer Data
Y Power Off
temporary
storage for
processing
related data,
variables, state
information, and
so on.
Function or Use Contains
Customer
Data
Y Removal /
binaries,
libraries, printer
information, print
job data
Process to
Clear:
Process to
Clear:
Un-install of
the App.
Open-Source Components
Xerox® Workplace Cloud uses Open-Source software modules in its different components, such as
the Cloud hosted Workplace Cloud, the Desktop Client, and so on. An up-to-date bill of materials
for this solution is available upon request from Xerox.
Xerox® Workplace Cloud 5.6.1 – Security Guide 19
Page 22

4. System Interaction
System Components
X E R O X® W O R KP L AC E A P P [P M M ]
The Xerox® Workplace App is the main user interface to the Xerox® Workplace Cloud.
The application requires users to authenticate with the Workplace Cloud before using the
application. When authenticated, the user’s credentials and authentication token are stored in the
application until they log out. For more information about authentication and communicationsrelated security information, refer to Communication between the Workplace App and Workplace
Cloud.
The Xerox® Workplace App does not provide the capability to remotely wipe the mobile device.
It is ultimately the responsibility of the user to secure their mobile device. Users can enable device
level passwords and manage physical access to the device. If the mobile device is lost or stolen,
the user can access the webpage to change their password making the device unable to access
the Workplace Cloud solution.
X E R O X® W O R KP L AC E C L OU D
The Workplace Cloud runs in the Microsoft® Windows Azure Platform and utilizes the SQL Azure
Database for storage. There are a number of considerations for security based on this architecture
as follows:
Windows Azure Platform specific security information
SQL Azure Database specific security information
Workplace Cloud specific security
Workplace Cloud Printer Client Application specific security
Workplace Cloud Client
Workplace Cloud Web Portal
Workplace Cloud Email Service
Each consideration is covered below.
Windows Azure Platform Specific
The Windows Azure Platform operates in the Microsoft® Global Foundation Services (GFS)
infrastructure, portions of which are ISO27001-certified.
Windows Azure Security Highlights:
Built-in Identity Management for administrator access
Dedicated hardware firewall
Stateful packet inspection technology employed
Application-layer firewalls
Hypervisor firewalls
Host-based firewalls
SSL termination / load balancing / application layer content switching
Each deployed hosted service is segmented in its own VLAN, preventing compromised
node access
Xerox® Workplace Cloud 5.6.1 – Security Guide 20
Page 23

Go to the following Microsoft website for more information:
Windows Azure Security Overview:
https://docs.microsoft.com/en-us/azure/security/
Microsoft Azure Trust Center:
https://www.microsoft.com/en-us/trustcenter/cloudservices/azure
SQL Azure Database Specific
The application data is stored in a SQL Azure database. This database contains information about
the printers, print queues, jobs and so on. The SSO Vault data is also stored in the SQL Azure
Database and entries are encrypted using AES. The entire SQL database is then encrypted using
Microsoft Azure Transparent encryption.
SQL Azure is protected by two levels of security. In addition to username and password to access
the database, Microsoft protects access to SQL Azure databases by allowing configuration of a
whitelist of IP Addresses that can connect to the database.
Only internal Xerox IP Addresses have been configured on the whitelist for this database. Only
authorized Xerox personnel have access to this data.
Passwords, Printer MAC Addresses and Printer Serial Numbers are stored in an encrypted format
in the database.
Xerox® Workplace Cloud Specific
Original documents and printable documents are stored within Azure Storage. Both the original and
printable documents are stored in an encrypted format. Files are encrypted using an AES
encryption method. A symmetric key is generated to encrypt the file, and then the key is
asymmetrically encrypted using a public certificate. Files uploaded from the Desktop Client are
always encrypted using this method. File received from the Workplace App, Web Portal or via
Email are encrypted upon receipt before being stored in the Cloud. More details on File Encryption
can be found in the section titled “Additional Security Items”.
Access to these documents is only available to the following:
The owner of the documents using the Xerox® Workplace App for preview.
The owner of the documents using the Xerox® Workplace App or the Xerox® Workplace Cloud
Printer Client Application for Print Release.
Authorized Xerox personnel who are responsible for deployment and maintenance of the
system. Since the documents are encrypted even the authorized personnel cannot open the
document to view its contents.
Each document printed follows a document retention policy which is applied to the document at the
time of printing. The document retention policy is either immediate, 1 day or 7 days. If set to
immediate, the document is deleted immediately after printing. If the document retention policy is
set to 1 or 7 days, then after printing, the document is removed after the number of configured
days. Therefore, documents are stored in the system for a maximum of 7 days.
Accounting information may be stored within Azure Storage. It is stored in an encrypted format.
Accounting information that can be saved is:
Default accounting information to be used when printing Welcome Pages to printers and print
queues that require accounting information. If the administrator chooses to enter this
information, it will be saved within Azure.
User accounting information that is entered by the user when they print a job to a printer is
identified with having Xerox Network Accounting or Xerox Standard Accounting, or a print
Xerox® Workplace Cloud 5.6.1 – Security Guide 21
Page 24

queue that is set with server-based accounting. The administrator can configure the software to
allow user accounting data to be saved. The default is to not save user accounting data.
All communications to and from the Workplace Cloud are over HTTPS using TLS (SSLv2 and v3
are not used). Documents are transmitted securely always and are protected by TLS security
during upload and download.
Files encrypted using the Workplace Cloud default public certificate will be decrypted when they
are retrieved by either the Agent or by the Printer if it using the EIP Pull Print API. The actual
decryption is done by the Workplace Cloud backend system on the print file as it is streamed by the
receiving endpoint. The actual decrypted file will never reside on any physical storage media in the
cloud.
Files encrypted using a customer provided public certificate will always remain in an encrypted
format when in the Cloud, including during upload and download. They can only be decrypted by
the Agent that has the matching private certificate in its Windows certificate store. If you have a
Xerox® AltaLink product (C80xx / B80xx) running release 103.xxx.020.23120 or later, the printer
itself supports the ability to decrypt these print jobs without needing to be routed to the Agent. Both
the private certificate and the CA root used to sign it must be installed on the printer in order to use
the native decryption feature.
Certificates used for encryption/decryption of documents are stored in the Windows Azure
Certificate store as per Microsoft guidelines. This is a highly secure area protected by Microsoft.
Account administrators can only upload certificates to this store. Downloads are not allowed. Only
applications running within the same Windows Azure subscription can access the certificate.
Xerox® Workplace Cloud Printer Client Application Specific [PMM]
When accessing the Xerox® Workplace Cloud Printer Client Application, webpages (HTML,
JavaScript, icons, and so on.) are served up by the Workplace Cloud. This pathway includes the
ability to provide login credentials to view and manage a user’s list of jobs, including print job
deletion or print initiation. This pathway also includes the ability for a Workplace Cloud
Admin/System Administrator to manage some of the settings of the printer, including: Printer
Enablement, Public Print Enablement, Site and Friendly Name.
All communications between the Xerox® Workplace Cloud Printer Client Application and the
Workplace Cloud are over HTTPS using TLS. Certificates used for this communication path are
stored in the Windows Azure Certificate store as per Microsoft guidelines.
Xerox® Workplace Cloud Virtual Machines
Xerox will monitor vendor security bulletins and products update announcements, and assess what
actions are required on the Azure virtual machines. These bulletins and announcements can come
from Microsoft and other external vendors, as well as internal partners supplying components used
in the product system. Xerox will update the virtual machines to maintain the health and integrity of
the product system.
As anti-virus definition files are released more frequently than application and operating system
patches, these updates will occur on a more frequent basis. Virtual machines are configured to
perform full scans weekly, and update the anti-virus definition files before the full scan.
Xerox® Workplace Cloud Web Portal User Access
All user web pages are accessed using HTTPS over TLS from a browser.
Xerox® Workplace Cloud 5.6.1 – Security Guide 22
Page 25

Workplace Cloud customer account users must authenticate with the Workplace Cloud to access
the Web Portal. Once authenticated the user can view or use:
The Print tab, allowing access to all printers enabled by the customer account administrator
inclusive of printer name, printer location, and the printer’s direct email submission
email address.
Only jobs submitted by the user inclusive of document names, date of completion, and printer
name of printer used to print the job.
The user’s profile – allowing them to view their email address, LDAP Username and Domain if
applicable, User Groups to which they are a member, their badge/card number, their company
code, user preferences (notifications, retention policy and print preferences). If SSO is
enabled, the user can view which the Apps that they have stored login information, as well as
having the ability to clear their stored SSO data.
Note: User Access does not apply when using the Fleet Management license, as only
administrators would access the system in this scenario.
Xerox® Workplace Cloud 5.6.1 – Security Guide 23
Page 26

Xerox® Workplace Cloud Web Portal Administrator Access
All administrator web pages are accessed using HTTPS over TLS from a browser.
Workplace Cloud customer account administrators have to authenticate with the Workplace Cloud
to access the administrator user web pages. When authenticated, the administrator user can view
everything that users can in addition to the following:
1. Users associated with their customer account using a listing that includes email addresses and
the user’s authentication / access card / badge number.
2. All jobs processed for the account inclusive of document names, date of completion, email
address of user that submitted the document, and printer name of printer used to print the job.
This includes documents submitted by users who are not members of the customer account,
but have seen and printed to one of the account printers.
3. Licensing information that includes license activation keys and associated serial numbers. After
a license is installed for a customer account, the license activation keys and associated serial
numbers cannot be reused to install in other customer accounts.
4. IP addresses for all printers discovered by the customer account’s Workplace Cloud Agents.
For each printer, the administrator can view and manage the enablement for Workplace Cloud,
as well as the enablement for Convenience Authentication and if the printer has the Workplace
Cloud Printer Client Application installed.
5. The addresses of sites where printers are located.
6. For the Fleet Management workflow, the administrator can view and manage the configuration
profiles, configuration policies and compliance reports for their printers.
Xerox® Workplace Cloud Agents that have been created and registered with the customer account.
This includes the agents Activation Codes which are tied to the customer account and cannot be
used to register an Agent in another customer account. This information is displayed for the
customer account administrators only. It is the responsibility of the administrator in sharing
Activation Codes with others.
Xerox® Workplace Cloud – Email Service
The Workplace Cloud hosts its own Email SMTP service in Azure. This is used to receive all
incoming email transmissions. Email receipt is accepted using SMTP port 25. No credentials are
needed to send email to this server. Support for encryption is available using the STARTTLS
mechanism.
Xerox® Workplace Cloud – Single Sign-on [PMM]
The Workplace Cloud solution provides the SSO functionality that can be called or accessed from
supported Apps in the Xerox App Gallery. The server acts as the network interface accepting and
responding to requests to store or retrieve authentication information, as well as the keeper of that
information. All SSO related information is stored in the SQL database used by Workplace Cloud.
Sensitive information such as the actual stored authentication data, the private key used to decrypt
the SSO requests sent by an App, and the public key used to validate signed requests from an App
are all stored in encrypted format within the SQL Azure database. In addition, the entire SQL
Azure database itself is encrypted using Microsoft Azure Transparent Encryption.
Xerox® Workplace Cloud 5.6.1 – Security Guide 24
Page 27

LD A P /A DS S ER V ER
The LDAP/ADS Server is part of the customer’s network and is not a deliverable of Workplace
Cloud. Therefore, the security and maintenance of the LDAP/ADS Server is outside of the
responsibility of Workplace Cloud.
When Company Authentication Type is enabled for LDAP Authentication, or Convenience
Authentication is configured for LDAP when using Alternate Login or Auto Enrollment of Cards,
Workplace Cloud will verify user credentials against Active Directory. The workplace credentials
consist of Domain Name, Domain Username and Domain Password. The communication path
uses either LDAP (Port 389) or LDAP over SSL (Port 636). Once a user is verified, the following
LDAP fields will be retrieved and written to the Workplace Cloud user record:
Email Address: mail
Username: sAMAccountName
Department: department
Groups: memberof
By default, the Workplace Cloud runs in automatic configuration mode, where the Workplace Cloud
Agent retrieves and stores a list of available active directory domains based on the context of the
logged in user on the Agent computer. Standard LDAP/AD fields are used to retrieve information
about the user. The administrator has the option to enable a manual LDAP configuration mode,
allowing them to control which LDAP domains will be used for authentication as well as configuring
which LDAP fields will be read and used to populate the user fields in Workplace Cloud user
record. Besides the normal fields of Email Address, Username, Department and Groups, the
administrator can also define a field to retrieve the Primary PIN of the user (Access Card Number).
The manual LDAP configuration mode also supports the ability to store LDAP system credentials
for each LDAP server. These are stored in the SQL Azure database, and the password is
encrypted. The system credentials allow the solution to support card on-boarding, by looking up
unknown card access numbers in LDAP and importing a matching user into Workplace Cloud. The
credentials also support the ability to validate that a user attempting to log into a printer through an
access card is still a user in the LDAP/AD system, and is not deleted.
AZ U R E AD
The Microsoft Azure AD system is part of the Microsoft Azure backend system and is not a
deliverable of Workplace Cloud. However, it is possible to configure Workplace Cloud to use Azure
AD as a user authentication mechanism. This is a company-specific setting, and when enabled
applies to all interfaces of Workplace Cloud that require authentication credentials.
When using Azure AD, the user will supply their email address, which is then used to look up which
account they are in and which authentication mechanism to use for that account. If using Azure AD,
the authentication mechanism with Azure uses OAUTH. This is an open standard, commonly used
on the Internet to delegate authorization decisions across a network of web enabled applications.
When using OAUTH, the Workplace Cloud system will turn control for user validation over to Azure
AD. The user will actually authenticate with the Azure AD site and then delegate permission to use
the Workplace Cloud solution. When using OAUTH, Workplace Cloud solution never sees the
user’s password. What is returned to the Workplace Cloud solution is the result of the
authentication request as well as an Azure Authentication Token and Refresh Token. Workplace
Cloud will validate the Azure authentication token authenticity. The Azure AD Graph API is used to
retrieve the following fields for the user: ‘mail’, ‘userPrincipalName’ & ‘department’. The mail and
userPrincipalName fields are used to validate that the original email address passed into the
Workplace Cloud system matches at least one of those fields in the user’s basic profile. After the
authentication token is validated, the Workplace Cloud solution will grant the user a Workplace
Xerox® Workplace Cloud 5.6.1 – Security Guide 25
Page 28

Cloud authentication token. The expiration time of the Workplace Cloud authentication token
matches that of the Azure Authentication token.
The Workplace Cloud solution will store both the WC authentication token and Azure refresh token
on the specific device and interface to which the user logged in. In this case either:
The Xerox® Workplace App on the users’ mobile device
On the PC or Mac running the desktop Client
Note: Users can also log in to Workplace Cloud using the Web Portal (browser), the Agent, and the
Printer Client (Xerox® @PrintByXerox App), however, the Workplace Cloud Authentication Token
and Azure Refresh Token are never stored in these scenarios.
If a user tries to access the given interface above and the Workplace Cloud authentication token
has expired, then the system will attempt to re-authenticate with Azure using the Azure refresh
token (assuming it has not expired). If successful, this results in a new Azure authentication token
and refresh token, which is then used to generate a new Workplace Cloud authentication token.
The default Azure authentication token lifetime is 2 hours and the default Azure refresh token
lifetime is 2 weeks. These can of course be modified through Azure by the customer, but this is
outside the scope of Workplace Cloud. The relevant point here is that the authentication token
lifetime is very short, and therefore the Xerox authentication token lifetime is short. This forces the
Workplace Cloud interfaces to frequently revalidate that the user is still in valid within the Azure AD
system before updating the Workplace Cloud authentication token.
All Azure AD communication between the give Workplace Cloud interface (Web Portal, Workplace
Cloud Mobile App, Desktop Client, or Xerox® @PrintByXerox App) is done using HTTPS over port
443.
[The Azure AD alternate login feature has been deprecated. This section is left in place for legacy
customers that may still be using this feature.] There is a login scenario for Workplace Cloud using
Azure AD that does NOT use OAUTH. This case is where the printer authentication is being used,
and the user manually enters user credentials using the Alternate Login feature or when trying to
auto-register a card. In this scenario, the Xerox printer does not have the ability to display a
browser-based screen allowing the OAUTH login page to be shown. Because of this device side
limitation, the printer will use native screens to prompt for the Azure AD username and password.
This information is passed from the printer, to the Agent, to the Workplace Cloud and finally to
Azure for validation and authentication. The same validation is done on the returned Azure Access
Token as is done in the OAUTH scenario. The user data is always encrypted using HTTPS along
each path, and is never stored on any of the devices. When logging in using this method, no tokens
are ever stored. The user session will end at the printer when the user logs out or a system timeout
occurs.
For those customers that have enabled the auto-registration process, the Workplace Cloud will use
an email-based user validation process to register an unknown card. When a user scans an
unknown card number, the solution will ask the user to supply their email address. An email will be
sent to the user with a link. If the user selects the link, they will be taken to a login page where they
must login to Azure AD using an OAUTH login page. If they successfully log in, their badge will be
associated with their user account in Workplace Cloud.
Xerox® Workplace Cloud 5.6.1 – Security Guide 26
Page 29

O K T A
OKTA is an external identity management system and is not a deliverable of Workplace Cloud. It is
possible to configure Workplace Cloud to use OKTA as a user authentication mechanism. This is a
company-specific setting, and when enabled, applies to all interfaces of Workplace Cloud that
require authentication credentials.
OKTA Setup
OKTA authentication can be enabled from the Company Profile page. To use OKTA with
Workplace Cloud, the administrator will need to log into the OKTA web interface and add the
Workplace Cloud application. There is a Wizard interface for Workplace Cloud that will step the
administrator through this process.
Step 1: The administrator must set the Server Issuer URI:
e.g., https://{oktadomain}/oauth2/{authorizationserverid}
This value can be found on the OKTA web interface. In addition to the URI, the Workplace Cloud
will require the following scopes, which should be listed under the OKTA authorization server:
OpenID (Default = No; Metadata Publish = Yes)
Profile (Default = No; Metadata Publish = Yes)
Offline Access (Default = No; Metadata Publish = Yes)
Step 2: Create a ‘Web Application’ within OKTA. Follow the instructions as outline in the Web
Portal of Workplace Cloud.
Step 3: Create a ‘Native Application within OKTA’. Follow the instructions as outline in the Web
Portal of Workplace Cloud.
Step 4: Create a ‘Single Page Application within OKTA’. Follow the instructions as outline in the
Web Portal of Workplace Cloud.
OKTA User Login
When using OKTA, the user will supply their email address to Workplace Cloud, which is then used
to look up the account to which they belong as well as the authentication mechanism used by that
account. If using OKTA, the authentication mechanism relies upon OAUTH when entering
credentials. This is an open standard, commonly used on the Internet to delegate authorization
decisions across a network of web enabled applications. When using OAUTH, the Workplace
Cloud system will turn control for user validation over to OKTA. The user will actually authenticate
with the OKTA site. When using OAUTH, Workplace Cloud solution never sees the user’s
password. What is returned to the Workplace Cloud solution is the result of the authentication
request as well as an OKTA Authentication Token and Refresh Token. Workplace Cloud will
validate the OKTA authentication token authenticity. The user must log into OKTA using the same
email as supplied to Workplace Cloud. After the authentication token is validated, the Workplace
Cloud solution will grant the user a Workplace Cloud authentication token. The expiration time of
the Workplace Cloud authentication token matches that of the OKTA Authentication token.
The Workplace Cloud solution will store both the Workplace Cloud authentication token and OKTA
refresh token on the specific device and interface to which the user logged in. In this case either:
The Xerox® Workplace App on the users’ mobile device
On the PC or Mac running the Workplace Cloud Client
Xerox® Workplace Cloud 5.6.1 – Security Guide 27
Page 30

Note: Users can also log in to Workplace Cloud using the Web Portal (browser), the Agent and the
Xerox® @PrintByXerox EIP App, however, the Workplace Cloud Authentication Token and OKTA
Refresh Token are never stored in these scenarios.
If a user tries to access the given interface above and the Workplace Cloud authentication token
has expired, then the system will attempt to re-authenticate with OKTA using the OKTA refresh
token (assuming it has not expired). If successful, this results in a new OKTA authentication token
and refresh token, which is then used to generate a new Workplace Cloud authentication token.
The OKTA authentication token lifetime and the refresh token lifetime comes from OKTA, and is
not something that is set or defined by Workplace Cloud. In general, the authentication token
lifetime is very short, and therefore the Xerox authentication token lifetime is short. This forces the
Workplace Cloud interfaces to frequently re-validate that the user is still in valid within OKTA before
updating the Workplace Cloud authentication token.
All OKTA communication between the given Workplace Cloud interface (Web Portal, Workplace
Cloud Mobile App, Desktop Client, or Xerox® @PrintByXerox App) is done using HTTPS over port
443.
In order to support badge/card auto-registration, the Workplace Cloud will use an email-based user
validation process to register an unknown card. When a user scans an unknown card number, the
solution will ask the user to supply their email address. An email will be sent to the user with a link.
If the user selects the link, they will be taken to a login page where they must login to OKTA using
an OAUTH login page. If they successfully log in, their badge will be associated with their user
account in Workplace Cloud.
Xerox® Workplace Cloud 5.6.1 – Security Guide 28
Page 31

T H I R D P A R T Y P U B L I C PR I N T P R O V I D E R [ P M M ]
This diagram shows the flow between Workplace Cloud components and a third-party public print
provider. All communication is over HTTPS using TLS.
Workplace Cloud, when configured to do so, offers the capability to a user of printing to a thirdparty public print provider from the Xerox® Workplace App. These third-party networks provide
access to printers at hotels, airport lounges, and other public locations.
When printing to a third-party public print provider, the user is alerted that they are sending their
document outside of the Workplace Cloud. Each document printed to a third-party public print
provider is stored within Azure Storage. It follows a 7-day document retention policy, which is
applied to the document at the time of printing. The original document is stored within Azure
Storage in an encrypted format.
Access to these documents is only available to the following:
The owner of the documents using the Xerox® Workplace App for preview.
Authorized Xerox personnel responsible for deployment and maintenance of the system.
Since the documents are encrypted, even the authorized personnel cannot open the
document to view its contents.
Original documents printed to a third-party print provider are delivered to the Public Print Service,
which is co-located with the Workplace Cloud in Microsoft® Windows Azure.
Original documents are transmitted from the Public Print Service to the third-party public print
provider in a secure manner. All communications to and from the Workplace Cloud and Public Print
Xerox® Workplace Cloud 5.6.1 – Security Guide 29
Page 32

Service are over HTTPS using TLS. Documents are always transmitted securely and are protected
by TLS security during transmission to the third-party public print provider.
The third-party public print provider may respond with a release code or other information the user
would need to retrieve their printed output. It is delivered securely over HTTPS. This information is
available using the Xerox® Workplace App only by the user who printed the document.
Xerox maintains the security and integrity of the document up until the point that it is transmitted to
the third party. Xerox cannot assume responsibility for the security of any content of the document
that is transferred.
WO R K P L A CE CL O UD AG E NT
The Workplace Cloud Agent has multiple functions based on the licensing and configuration of the
account:
Print Management (Mobile Printing, Desktop Printing, Printer Authentication, Accounting):
1. The Agent is responsible for discovering printers within the customer’s network, determining
the printer capabilities, and relaying that information to the Workplace Cloud.
2. The Agent is responsible for routing print jobs to target printers and print queues. If the
customer is using the File Encryption feature with their own public and private keys using
certificates, the Agent will decrypt the job after retrieving from Workplace Cloud and then send
it to the printer via the configured print protocol for that device.
3. The Agent is responsible for performing printer configuration. This includes the following
feature areas:
Convenience Authentication – The agent will make SNMP queries and modifications to the
following device settings: enable/disable for Convenience Authentication/Xerox® Secure
Access, Blocking Screen strings, Alternate Login, and Service Locking.
Workplace Cloud Printer Client Application – The agent will register the Workplace Cloud
Printer Client Application on the printer.
4. The Agent will implement the EIP Convenience Authentication API, acting as the authentication
server, which allows users to authenticate their identity and unlock the printer.
5. The Agent is responsible for domain authentication lookups of users.
6. The Agent will listen for Network Appliance card data, and will release any pending jobs to the
associated printer.
7. The Agent can optionally cancel jobs that have been sent to a device and not yet printed when
a user logs out of the printer or their session ends.
8. The Agent can support both an LPR and a Windows Shared Network (SMB) printer listening
port to accept jobs from platforms not supported via the desktop client (Windows and Mac). In
particular the primary client would be Linux, both other platforms could leverage this capability
as well.
Fleet Management:
The Agent is responsible for executing configuration policies on enabled printers. This
includes querying the printer configuration based on the associated configuration profiles for
various settings and if needed modifying the configuration to match the policy. It also includes
checking firmware levels and applying necessary upgrades to the devices.
The Agent performs device monitoring and alerting, such as when consumable like paper are
needed.
The Agent is installed on a PC. The installing user must have administrator privileges since the
Agent software is installed as a Windows service. The Agent cannot be connected to the
Workplace Cloud unless the Workplace Cloud is configured to accept the Agent.
Xerox® Workplace Cloud 5.6.1 – Security Guide 30
Page 33

The Agent user interface is available to all users who can log on to the agent PC. It displays the
printers discovered by the agent and print queues served by the agent. It allows only the proxy
server address for that agent to be changed. It does not present any user or customer specific
information.
If the Agent Proxy setting is configured by a user, the Agent will in turn set the system level proxy
of the PC on which the Agent is running. The system level proxy settings would then be usable by
other applications running on the same PC.
A local database is maintained on the Agent PC. This database stores printer discovery settings
and printer information for each printer discovered, and print queue information as entered by the
administrator. Access to the database is restricted to user’s who have permission to log into the
agent PC.
The Agent installs by default in the following location:
Program Files(x86) > XEROX > Xerox Workplace Cloud Agent
Access to this folder and sub-folders is limited to users logged on to the agent PC. It contains the
agent executable file, its database, and language libraries.
Agents may be set to upgrade automatically when a new version of the agent software is available.
Agents connect to the Workplace Cloud and, if a newer version is available, it is automatically
downloaded over HTTPS using TLS and installed. The administrator can disable this feature as
needed.
Threats include physical damage to the system, attacks over the network, as well as damage
caused by viruses. The goal is to minimize the security risks as much as possible, and have
policies in place to detect and reduce the negative impact of a security incident. Examples of things
that can be done to reduce risks include proper use of logins and passwords, restricting network
access, applying security-related operating system updates, and the use of virus detection
software.
The customer is ultimately responsible for securing their environment to meet their specific security
needs. Depending on the customer needs, the customer can increase security by installing a
firewall, and/or physically securing the hardware to a limited access area. The customer,
depending on their needs, should use tools to monitor and log physical and network access to the
Agent hardware and software to determine if and when a security incident has occurred. The
customer should also back-up their data to ensure that it may be recovered in case of deletion or
corruption.
For more information about authentication and communications-related security information, refer
to Communication between Workplace Cloud and the Workplace Cloud Agent, Communication
between the Workplace Cloud Agent and the Printer, or Communication between LPR Clients and
the Workplace Cloud Agent.
For details regarding File Encryption using Keys, refer to the section titled “Additional Security
Items”.
S E R V ER BA S ED P R I NT Q U E UE S
For a server that hosts third-party print queues used by Workplace Cloud, nothing special is
required. To minimize security risks, leverage any security features of print control software.
Incorporate standard security measures, apply security-related operating system updates, use antivirus software and add hard disk encryption.
The customer is ultimately responsible for securing their environment to meet their specific security
needs. Depending on the customer needs, the customer can increase security by installing a
Xerox® Workplace Cloud 5.6.1 – Security Guide 31
Page 34

firewall, and/or physically securing the hardware to a limited access area. The customer should
back up their data to ensure that it may be recovered if deletion or corruption occurs.
P R I N TE R
Xerox printers have various security features that can be employed to increase security. Availability
of these features will vary depending on model. It is the customer’s responsibility to understand and
implement appropriate controls for printer behavior.
Secure Print allows you to control the print timing of your documents. When using Secure Print
during print job submission, users enter a passcode, and then must enter the same passcode to
retrieve the job at the printer.
Users may choose to use Secure Print with Secure Print enabled printers, or the administrator may
configure their Workplace Cloud account to require that Secure Print be used for all jobs sent using
Workplace Cloud to that printer.
Secure Print passcodes are never stored on the mobile App or in the Workplace Cloud. They are
transferred securely over TLS. Passcodes are never stored externally to the job on the printer.
Passcodes are numeric and conform to the requirements of the printer model. Auto-generated
passcodes are a minimum of 6 digits for all printers whose maximum is at least 6 digits.
For information on the security of a job while it is stored on the printer, refer to your printer
documentation.
Additional security can be enforced at the printer if the printer is EIP Capable and/or supports the
EIP Convenience Authentication API. For those printers which support this capability, the
Workplace Cloud provides the capability to lock the printer’s local user interface, and require the
user to authenticate themselves at the printer in order to gain access to any of the
services/features of the printer. More details on printer authentication can be found in the “System
Access” section of this document.
In conjunction with authentication feature, Workplace Cloud supports a feature called AutoRelease. This feature is disabled by default, but may be enabled by the Administrator for the given
account. Upon successfully completing the authentication step at a printer, if the Auto-Release
feature is enabled, any print jobs uploaded to the Cloud system will automatically be released and
printed at the device.
Other examples of printer security features are as follows:
Image Overwrite electronically shreds information stored on the hard drive of devices as part of
routine job processing.
Data Encryption uses state-of-the-art encryption technology on data stored within the device as
well as for data in motion in and out of the device.
Certificate Validation forces the printer to validate all certificates used for HTTPS
communication to ensure that they originate from a trusted certificate authority.
For more information about the above examples as well as for other printer security-related
technologies, refer to
http://www.xerox.com/information-security/product-security
The Workplace Cloud supports printers from various manufacturers. It is the customer’s
responsibility to understand the security features of any non-Xerox printers configured for use in
the system.
Xerox® Workplace Cloud 5.6.1 – Security Guide 32
Page 35

X E R O X® @P R I N T BY X ER O X AP P [P M M]
Devices which are EIP capable have the ability to support the Xerox® @PrintByXerox App. This
EIP app allows users to log into their account, view and manage their print jobs. There are two
methods of adding / using Xerox® @PrintByXerox:
1. Xerox® ConnectKey® 2.0i, Xerox® AltaLink®, and Xerox® VersaLink® Products – Support the
Xerox® @PrintByXerox App. This form of App is installed by the customer, typically a system
administrator using the Xerox App Gallery, or it may come pre-installed (as an in-box app).
2. Workplace Cloud Agent – The Workplace Cloud Agent installs the Xerox® @PrintByXerox App
directly on the printer based on configuration settings made using the Xerox® Workplace Cloud
Web Portal.
There are 3 modes of execution for the Xerox® @PrintByXerox App. The first of which is the
unlicensed mode. This mode is only supported with the ConnectKey App, and the user is limited to
the basic workflow of email submission and EIP print release. When using this mode, there is no
Agent installed on the customer’s network. Print jobs are retrieved from the Workplace Cloud by
the printer using HTTPS over TLS with port 443.
The second mode of execution for the Xerox® @PrintByXerox App is a licensed mode, without an
Agent. This mode is only supported with the ConnectKey App. In this mode, the user has access to
most of the features of Workplace Cloud, including use of the Workplace App. Print jobs are
retrieved from the Workplace Cloud by the printer using HTTPS over TLS with port 443.
The third mode of execution for the Xerox® @PrintByXerox App is the traditional Workplace Cloud
environment, with a license and one or more Agents. The Agent will install EIP in this mode, using
the EIP Registration API, which is done using HTTP/HTTPS. Print jobs are received using the
Agent using LPR (port 515) or Raw IP (port 9100).
CU S T OM E R E MA I L S ER V ER
The Customer Email Server is used to get print jobs to the Workplace Cloud. It acts as a mail relay
system to route jobs to the mail service hosted in Azure. The setup, maintenance, and security of
the customer email server is outside the scope of Workplace Cloud.
US E R W O R K S T A T IO N ( WO R K P L A CE C L O UD CL I E N T ) [ P M M ]
Users may install the Workplace Cloud Client on their Windows PC or Apple Mac. This application
will install the administrator defined default print queues on the user’s workstation. If using a PC,
the client will install either the Xerox® Global Print Driver® (GPD) or an administrator uploaded
custom driver for any Workplace Cloud enabled printers, as well as install and start a background
service and a sys tray utility. If the Home Worker Print Tracker feature is enabled, the Workplace
Cloud Client will install a print tracker v3 port monitor to all printers on the user’s local workstation
that are using v3 print drivers and which are not a Workplace Cloud enabled printer. The port
monitor is actually hidden (not visible in the Windows Printer Properties port page), and acts like
shim, allowing the solution to intercept the job and collect information such as username, job name,
print attributes like number of pages or color and if enabled it will also prompt for accounting
information. This allows tracking of print jobs to printers not enabled in Workplace Cloud. The
primary intent of this feature is to track print use on company owned workstation, even if the user is
print to devices that are outside of the normal solution workflows. The supported printer port types
include:
Standard TCPIP Port
Local Port
USB Port
Xerox® Workplace Cloud 5.6.1 – Security Guide 33
Page 36

WSD Port
The background service is used to monitor for new job submissions using the installed Workplace
Cloud Client and send these up to the cloud server. All communication between the Workplace
Cloud Client and the Workplace Cloud hosted in Azure is done using HTTPS over port 443.
If the user workstation is configured to use a proxy server, the Workplace Cloud Client will use the
configured proxy setting when communicating with the Workplace Cloud. This includes the ability to
use proxy authentication if enabled in the system-wide proxy settings.
The Workplace Cloud Client can be downloaded and installed by the user using the Web Portal, or
it may be pushed by the IT department of the customer to the end user. If installed using the Web
Portal, Workplace Cloud will create an install package for the printer or print queue based on the
authentication token for the user who is logged in. This means the login token will be included in
the installer. If the install package is pushed by the IT department of the customer, then no token is
included.
To use the Desktop Client, users must provide their credentials. When validated, authentication for
the user is maintained on the workstation for future use. The expiration period of the authentication
token is configurable by the cloud account administrator, with a range of 1-365 days. When the
authentication token expires, the user will be re-prompted to supply their credentials.
The Workplace Cloud Client makes use of the following locations to store user-based information:
C:\Users\<USERNAME>\AppData\Local\Xerox\XMPC – This area is used to temporarily
store jobs submitted to XWC that are being processed (e.g. job metadata collection) prior to
notifying the cloud backend of the new job. This is also where locally stored follow-you jobs
are retained while waiting for release at a printer and where jobs are temporarily stored during
in order to be parsed if the Content Security feature is enabled.
C:\Users\<USERNAME>\AppData\Roaming\Xerox\XMPC – Contains data related to the
specific user that should be persistent across reboots. This would include items such as the
user’s current access token, client configuration, account information and cached printer
information for fallback printing.
Linked Company
By default, users are able to log in and out of the client using any registered cloud user account.
This includes logging in with accounts from different Workplace Cloud companies. If the
administrator for a Cloud company would like to restrict the client installed on a given workstation to
only be used by users in that same company, they may supply a configuration option when
installing the client on the user’s workstation. It is assumed that the Desktop Client is being
installed via an IT push mechanism such as SCCM. As part of that managed installation, the
appropriate configuration file can be included with the client installation package. Details on how to
link a client can be found in the administration guide.
Print Job Path (for Workplace Cloud Printers)
When using the Desktop Client to submit jobs to a pull-print queue (where jobs are held for later
release), the administrator can configure where the job will be stored while it is waiting for the user
to release it. This feature is called “Local Print Optimization”. By default, this is set to “Enabled with
Cloud Backup”, meaning that the desktop client will store a local copy of the job and send a backup
to the cloud service. The administrator can also define a maximum file size to be uploaded to the
cloud when using this option. If the file exceeds the configured maximum, it will not be sent to the
cloud. Administrators may also provide an optional flag in the local configuration of the client which
will allows them to override the account Local Print Optimization feature on a workstation-byworkstation basis. This gives the customer the flexibility to establish a company default for the
Xerox® Workplace Cloud 5.6.1 – Security Guide 34
Page 37

majority of users, while using a different setting for a select few (e.g. a small branch office). To
modify the configuration file, the user must have administrator rights on the workstation.
When jobs are released, the solution will attempt to send the local copy of the job to the printer first.
If there is a connection issue from the local workstation to the printer, the cloud copy of the job will
be sent to the printer. The desktop client will clean-up the local copy of the job the next time it
synchronizes with the cloud backend. The administrator can also configure this setting such that
jobs are never stored locally and are always sent to the cloud, or they can configure it such that
jobs are only stored locally and never sent to the cloud. Locally stored jobs are saved on the hard
drive of the user’s workstation, at the following location:
C:\Users\<USERNAME>\AppData\Local\Xerox\XMPC\VirtualPrint\RetainedJobs
The job will be removed either after printing or based on configured retention settings.
Print Job Encryption
The Desktop Client always encrypts print jobs that are uploaded to the Cloud. By default, the file is
encrypted using a key from a public cert that is generated by Workplace Cloud. This is a common
certificate across all tenants of the solution. If the customer prefers, they can upload their own
certificate, which will be retrieved by the client application during it’s normal 24 configuration synch.
The client will use the key from the public certificate, either the customer uploaded version (if
available) or the default Workplace Cloud certificate, to encrypt the job before it is uploaded to
Workplace Cloud. For additional details on File Encryption using Keys, please refer to the section
titled “Additional Security Items”.
Failover Support
In order to improve the user experience of the Workplace Cloud Client for scenarios where the
solution is not able to communicate with the cloud backend system (such as networking issues or
the service is temporarily down), a special offline printing mode is supported. In cases where the
cloud backend system is not available, the user will be notified of the connection issue when they
attempt to print. They will be given the option to continue to print and wait for the connection to be
restored so the job can be processed, or they will be offered the option to print the job immediately
to one of up to 10 different devices. The set of available devices is based on the user’s favorite
printers from the Workplace App as well as recently used printers. The Workplace Cloud system
will maintain this list of devices and the Desktop Client will periodically retrieve it and store it locally
at:
C:\Users\<USERNAME>\AppData\Roaming\Xerox\XMPC\VirtualPrint\
This file includes information like the name of the printer, IP Address, MAC Address, Manufacturer,
Model, Site, Printer Language, User’s Email Address, Printing Port Numbers and the Device ID of
the printer. If a user opts to print to one of the available printers using the offline mode, the Desktop
Client will send the job directly to the printer using the configured print protocol (LPR, RawIP,
IPP/S) and will maintain some metadata about the job so that it can update the print history after
connection to the cloud is re-established.
The auto-detected offline printing mode is only supported for a maximum of 24 hours. After that
time, users will no longer be able to print using the offline method. Jobs will be held until the client
is able to establish connection with the Workplace Cloud. This is designed prevent unauthorized
printing for an extended period without validation that the user still exists in the backend system.
The system administrator should address any connectivity issues within that 24-hour period.
Customers have the option to enable the ability for the desktop client to periodically check for an
enforced offline mode based on querying DNS for a specific entry. Details on this capability are
documented in the administration guide.
Xerox® Workplace Cloud 5.6.1 – Security Guide 35
Page 38

M I C RO S O F T O F F I C E 3 65 – E M A I L S ER V I C E
Email responses sent to the end user are handled by Office 365. This service is hosted by
Microsoft using an Office 365 email account. Login access to this Workplace Cloud email account
is limited to a few key Xerox personal on the Workplace Cloud team. Email transmission is done
using Exchange Web Services over port 443 (HTTPS).
NE T W O R K A P PL I AN C E [ P M M ]
The network appliance, sometimes referred to as an ID Controller, is an external hardware device
that supports the ability to plug in a USB keyboard mode card reader and transfer card information
to a configured application. In this case, the Network Appliance is configured to send card data to
the Agent.
The network appliance and the Agent communicate using raw TCP sockets with proprietary data
exchange based on the manufacturer of the appliance.
Elatec: The Elatec TCP Conv and TCP Conv2/Conv3 use ports 7778 and 7777 respectively. The
card data is sent in plain text.
RF Ideas: The RF Ideas Ethernet 241 uses port 2001. By default, the card data is not encrypted,
but the option to use encryption is available.
X E R O X® S E R V I C E S M A N A G E R
Xerox® Workplace Cloud can be configured to connect to Xerox® Services Manager (SM) in order
to perform the following actions:
Export Job Data (Page count, Plex, and so on.)
Import Printers, Sites, and Printer/Site Mappings
Each of these methods of synchronizing with SM has its own configuration as well as specific
limitations on the system as a whole. Connectivity to SM is achieved using a special connection
URL and creating a new account that is linked to SM. The Administrator will need to select an SM
Account at the time the Workplace Cloud account is created. If the SM account is portioned by
chargeback code, the Administrator will additionally need to provide the SM Chargeback Code to
use. The Importing of Printers and Sites requires the SA to configure an SM Username and
Password. The SM user must have Account Entity View and CustomerChargebackEntry Entity
View permissions to be successful.
All communication between SM and Workplace Cloud will be over HTTPS (port 443).
CO N T EN T D E L I V E R Y N E T W O R K (C DN ) [P M M]
Microsoft Azure supports the use of CDN as a mechanism to improve the distribution of data,
enabling fast and localized downloads. Microsoft partners with different CDN providers, which
have many geographically distributed servers with high-speed connections to Azure. Xerox makes
use of the Akamai as a provider of CDN functionality in partnership with Microsoft Azure. When
print ready jobs are made available for release at a printer, and that printer supports the EIP Pull
Print API (e.g., ConnectKey, AltaLink and VersaLink devices), the @PBX app and the Agent can
tell the printer to retrieve the print job from the Cloud (pulling the job down to the printer over
HTTPS on port 443 and submitting it to print). The CDN endpoint is also supported by the Agent
and Agent retrieved jobs. This print retrieval supports the CDN path to stream the job data from
Azure blob storage in the Workplace Cloud through the Akamai CDN edge server that is closest to
the printer and then down to the printer. Caching is disabled on the Akamai edge servers,
however, while transitioning from the Azure<->Akamai SSL connection to the Akamai<->Customer
Xerox® Workplace Cloud 5.6.1 – Security Guide 36
Page 39

SSL connection, the content needs to be decrypted and re-encrypted in memory due to the
different certificates involved in the transfer. Customers who may be concerned with this data
transfer can use the enhanced encryption feature under policies to ensure desktop jobs remain
encrypted throughout the transfer or leave the feature disabled.
All communication between the printer and the CDN will be over HTTPS (port 443).
AP P IN T H E G A L L E R Y [ P M M ]
This item refers to an App in the Xerox® App Gallery that is modified to use the Single Sign-On
feature provided by Workplace Cloud and is running on the EIP browser of the printer. The App is
expected to retrieve configuration from the printer and pass this back to the App Server so that it
can determine if the SSO feature is supported by the Workplace Cloud solution. The App and EIP
browser act as an intermediary between the App Server and the Workplace Cloud Solution. All
communication between the App, the App Server and the Workplace Cloud uses TLS.
Note: The App is not written by or controlled by the Workplace Cloud solution. It is an external
component to the system that is making use of functionality provided by the Workplace Cloud.
AP P SE R V E R [ P M M ]
The server hosting the functionality supplied by an App in the Gallery. This can be a Xerox hosted
server or a 3rd party server, depending upon who created the App. The App Server never directly
communicates with the Workplace Cloud. All communication is funneled through the instance of
the App running on a printer and the EIP browser of that device. Communication between the App
Server and the App uses TLS.
Note: The App is not written by or controlled by the Workplace Cloud solution. It is an external
component to the system that is making use of functionality provided by the Workplace Cloud.
X E R O X® D E V IC E A G EN T [ F M]
The Xerox® Device Agent is not part of the Workplace Cloud solution. It’s an application designed
for managed print environments that wish to collect printer information such as configuration and
meters and report them to Xerox® Services Manager (SM). The Device Agent has been modified
to support easy installation of the Xerox® Workplace Cloud Agent. The Device Agent includes a
small background service which will query the Workplace Cloud backend system to see if the
Device Agent’s associated SM account has been linked to a Workplace Cloud account. If the
Workplace Cloud account exists and is linked to SM, the service will pull over and install the
Workplace Cloud Agent on the same workstation / server, and will register it to use the linked
WC/SM account. Communication between the Device Agent and the Workplace Cloud backend is
via HTTPS (port 443).
Full details on the Device Agent and all of this features and functionality are not included in this
document. Please refer to the Security & Evaluation Guide for the Xerox® Device Agent.
X E R O X AU T O U P D A T E S E R V I C E [ F M ]
The Xerox Auto Update Service is not part of the Workplace Cloud solution. It’s a service hosted
by Xerox on the internet that is used by the Device Agent for doing upgrades of the Device Agent.
This service has been extended to support a specific request by the Device Agent to check if its
associated SM account has been linked to a Workplace Cloud account. If the account is not linked,
the Device Agent will not communicate with Workplace Cloud.
Xerox® Workplace Cloud 5.6.1 – Security Guide 37
Page 40

System Component Interfaces
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE A PP AN D W O RK P L A C E C L O U D [ P M M ]
The Xerox® Workplace App uses the HTTPS over TLS protocol for all communication with the
Xerox® Workplace Cloud. It establishes an HTTPS secure connection with the Workplace Cloud
relying on the mobile device operating system to validate the security certificate as part of
establishing the TLS connection. The security certificate is issued by Comodo (a trusted certificate
authority) and ensures that the application has been verified and validated.
The Xerox® Workplace App requires users to authenticate before using any of its features. Basic
authentication is performed with the Xerox® Workplace App providing username and password
information over the HTTPS protocol, using TLS.
After authentication is complete, data is passed between the Xerox® Workplace App and the
Workplace Cloud to enable the features of the service within the Xerox® Workplace App. This
includes all data for previewing and printing jobs, location of printers, and user location data as
determined by the mobile device. Users are only able to access documents they submitted and
printers to which they have been granted access.
Users should consult their network provider on best practices for securing their cellular
(3G/4G/LTE) communications on their mobile devices.
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE A PP AN D T H E C U S T OM E R E MA I L S ER V E R
[P M M ]
Emails submitted to the Xerox® Workplace Cloud by a user’s mobile device or computer will use
the security mechanism defined by the user’s email client. User documents are the primary data
transmitted using email to the Workplace Cloud. It is the user’s responsibility to ensure that
appropriate email security controls are in place.
CO M M UN I CA T I O N B E TW E EN TH E C U ST O M E R E M A I L S E RV E R A N D W O R K P L AC E C L O U D
Emails are processed and consumed immediately upon receipt by the Xerox® Workplace Cloud.
Emails are not stored in any repository or inbox.
CO M M UN I CA T I O N B E TW E EN WO R K P L AC E CL O U D A N D T HE WO R KP L A C E C L OU D A G EN T
The Xerox® Workplace Cloud Agent uses the HTTPS protocol over TLS for all communication with
the Workplace Cloud. It establishes an HTTPS over TLS secure connection with the Workplace
Cloud relying on the PC’s operating system to validate the security certificate as part of
establishing the TLS connection.
After successful installation of the Agent software, it will attempt to register itself with the Workplace
Cloud. The Agent’s registration process provides the Workplace Cloud with the Agents account
administrator credentials, the Agent Activation Code, and a machine hash code. The Workplace
Cloud returns an Agent registration identifier to complete the registration process. The Workplace
Cloud account’s administrator credentials are only held in memory during the registration process
and removed when the registration process is complete.
After successful registration of the Agent, requests or notifications from Workplace Cloud to the
Agent to perform certain functions are sent as response messages via the Azure Service Bus
(used for both the Print Management and Fleet Management workflows) as well as via the Azure
IoT Hub interface (used for Fleet Management). Upon receiving notification of a new action, the
Agent will call back to Workplace Cloud for the details of the request.
Xerox® Workplace Cloud 5.6.1 – Security Guide 38
Page 41

Requests might include discovering a printer, getting the current configuration of the printer, or
modifying settings, sending a print job, performing an authentication request or retrieving
accounting data from the printer.
Print job data is transmitted between the Workplace Cloud and the Agent in the form of print ready
files. This data may exist in memory on the agent PC while it is being spooled to the printer. In
addition, data about printers discovered and printer capabilities is transmitted. If the CDN feature is
enabled, the Agent will retrieve print jobs that are ready to be sent to a printer using the Akamai
endpoints. This helps speed up the download of large print jobs.
If the Convenience Authentication feature is enabled, the Agent will facilitate communications
acting as a middleman between the printer and the Workplace Cloud, receiving authentication
requests from either entity and converting them to the appropriate response and passing that onto
the recipient. All such communication is done using HTTPS.
As part of the Convenience Authentication feature, the Agent will support a failover mode for cardbased authentication. The Agent will create an SQL CE database on the hard drive of the machine
on which it is running. The database is password protected using a password that is generated by
the Workplace Cloud backend system. This password is shared across all Agents for any one
account, but is unique across all accounts. Once per day, the Agent will retrieve from Workplace
Cloud, the list of users for the account, and will store this in the local SQL CE database. The
information stored for each user consists of:
Email Address
Network User Name
User ID (GUID) – This is just an internal identifier
Card Number
NFC Number(s) – Android phone identifiers when used with the Elatec TWN 4 reader
Legacy Card Number – For customers using Xerox® Secure Access readers.
When a user tries to authenticate with a printer, the authentication request is transmitted to the
Agent. If the Agent is not able to communicate with the Workplace Cloud, it will fall back to using its
local database of users. If the user is logging on with a card (or an Android Phone using the TWN 4
reader), the Agent will look up the card or NFC number and if found will allow the user to log in to
the printer. Note that the auto-release jobs feature is not available in this fallback authentication
mode. In addition, the Alternate Login feature and the Xerox® @PrintByXerox App will not be
available in this scenario. The intent of this feature is to allow users to access other services on the
printer, such as Copy, Scan, Fax, even if the cloud backend cannot be reached.
The auto-failover authentication mode is only supported for a maximum of 24 hours. After that time,
users will no longer be able to authenticate with the printer. This mode is designed to prevent
unauthorized access to the device for an extended period without validation that the user still exists
in the backend system. The system administrator should address any connectivity issues within
that 24-hour period.
For scenarios where the XWC backend may be partially up, but not responding correctly, the
administrator has the option to manually enable or force the agent into failover authentication
mode. This can be done on the UI of the Agent itself. The resulting behavior would mimic that of
auto failover method, however, there would be no 24-hour timeout period.
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D A GE N T A ND T H E P R IN T ER
The Xerox® Workplace Cloud Agent uses SNMPv1/v2 or SNMPv3 to discover printers and printer
capabilities. For SNMP v1/v2, customers can configure the community name strings for the agent
Xerox® Workplace Cloud 5.6.1 – Security Guide 39
Page 42

to use if they have configured their printers to use non-default values. For SNMPv3, customers can
configure a user name for the administrator account, an encryption mechanism and passwords for
authentication and privacy. These same settings must be configured on the printers in order to use
SNMPv3.
For newer Xerox devices that support the EIP Pull Print API, and which have access to the internet,
the Agent will direct the printer (via the Pull Print API) to retrieve print jobs directly from the cloud.
Otherwise, the Agent will route print jobs to the target printer using either Raw Port 9100, LPR/LPD
Port 515 or IPP over SSL on Port 443. The LPR and RawIP ports are both configurable.
Customers can further secure the print path by enabling IPsec between their Agent PC and their
printers provided the printers support IPsec. When configuring IPsec, ensure that the
communication between the Agent and Workplace Cloud does not employ IPsec.
When a printer is enabled, the Agent may register the Workplace Cloud Printer Client Application,
or it may enable the Convenience Authentication feature based on the printer configuration settings
supplied by the administrator. The Xerox® @PrintByXerox App will be registered using the EIP
Registration API, which requires the printer’s administrator credentials. The Convenience
Authentication feature enablement and configuration is done using SNMP using the SET
Community string for SNMPv1/v2 or the SNMPv3 administrator account and passwords along with
the administrator credentials for the printer.
If the Convenience Authentication feature is enabled, the Agent will play a role in authenticating a
user at the printer. The Agent will facilitate communications between the printer and the Workplace
Cloud, receiving authentication requests from either entity and converting them to the appropriate
response and passing that onto the recipient. All such communication is done using HTTPS.
In conjunction with the Convenience Authentication feature, Workplace Cloud supports an optional
security mode that will cancel any pending jobs released to the printer which have not yet
completed printing. The assumption being that if the user session has ended, then the user is
likely not at the printer. The feature is off by default, but when enabled, includes a configurable
time period after logout or session termination is detected before any unfinished jobs will be
cancelled. The time period is 30 to 3600 seconds. To use this capability, the Local Print
Optimization setting must be disabled. This feature is only supported for desktop follow-you jobs
submitted using a custom driver, and released using the Xerox® @PrintByXerox App to a
VersaLink or AltaLink printer
The Agent may be enabled to support iOS Native printing. When enabled, devices running iOS
may locate and send print jobs directly to the Agent. This is done using the IPP protocol using port
631. For further details on this capability, refer to the Workplace Cloud Administrator Guide.
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D A GE N T A ND A T HI R D- P A R T Y P RI N T
Q U E U E [ PM M ]
Customers identify their print queues to the Agent by providing information on the server, port and
queue name.
The Agent will route print jobs to the print queue using LPR/LPD Port 515. This port is configurable.
Customers can further secure the print path by enabling IPsec between the Agent PC and the
server hosting the third-party queue. When configuring IPsec, ensure that the communication
between the Agent and Workplace Cloud does not employ IPsec.
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D C LI E NT A N D W O RK P LA C E C L O U D
[P M M ]
When a user sends a job to a Xerox® Workplace Cloud enabled printer using the Desktop Client,
the file is converted to Postscript and stored temporarily on the hard disk of the workstation.
Xerox® Workplace Cloud 5.6.1 – Security Guide 40
Page 43

Similarly, if the Home Worker Print Tracker feature is enabled, the port monitor will intercept the job
and store it temporarily on the hard disk of the workstation. The location of the stored files is
dependent upon the user:
C:\Users\<USERNAME>\AppData\Local\Xerox\XMPC\VirtualPrint\Jobs
The Workplace Cloud Client runs in the background and monitors this folder for any new files.
When one is detected, it then processes that job based on the type of printer: Workplace Cloud or
Home Worker Print Tracker. For a Workplace Cloud enable printer, the job will be processed
based on the configured “Local Print Optimization” feature, either storing locally, or uploading to
cloud or both. For uploads to the cloud, the file is sent to Workplace Cloud using HTTPS (TLS)
over port 443. For locally stored jobs, the file is moved to:
C:\Users\<USERNAME>\AppData\Local\Xerox\XMPC\VirtualPrint\RetainedJobs
For a Home Worker Print Tracker job, the client will parse the job to determine the following set of
information:
Email Address of the user logged into the Workplace Cloud Client.
Job Name
Submission Time
Printer Name
Number of Copies
Simplex or Duplex
Number of Color Pages
Number of Black & White Pages
[OPTIONAL] Accounting Data (User ID / Account ID)
Network User Name of the person logged onto the workstation (Domain\Username or
Device\Username)
[OPTIONAL] Matching Content Security Strings
This information will be uploaded to the Workplace Cloud and included in the Reporting data
accessible by the account administrator.
After upload to cloud and/or transfer to the “RetainedJobs” directory, any temporary files are
deleted from the hard disk.
The Workplace Cloud Client will also periodically retrieve a list of the 10 most recently used/favorite
printers for the user and will store this on the hard drive of the workstation on which the client is
running. This information is used for print failover if the cloud service is not available. The Client will
also maintain job history information for any jobs printed using the failover method and will report
this back to the Workplace Cloud solution when connection is re-established.
The Workplace Cloud Client will report a small set of information to the Workplace Cloud. This
information is used for customer support as well as for planning purposes for future changes to the
client functionality and supported operating systems. The set of information includes:
Client ID
Client Version
Operating System Version
.NET Version
Email address of last logged in user
Account ID of last logged in user
IoT Hub Device ID
Last Communication Date
Xerox® Workplace Cloud 5.6.1 – Security Guide 41
Page 44

CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D C LI E NT A N D T H E P RI N T E R [ P MM ]
If a workstation running the Desktop Client and the Printer to which a job is to be released is on the
same network, the Desktop Client will send the job directly to the printer. This process avoids the
need to send the job to the Workplace Cloud. The Desktop Client detects that the printer is on the
same network when sending the print job. The print job itself will be sent using Raw IP (Port 9100),
LPR (Port 515) or IPP over TLS (Port 443) to the printer based on the printer configuration. If the
Desktop Client is running in failover printing mode, jobs will be transferred to the printer directly
using the configured print protocol for that device (Raw IP, LPR or IPP/S).
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D C LI E NT A N D T H E A Z U R E I OT H U B
[P M M ]
In order to support the “Local Print Optimization” feature, where jobs are stored locally, the Desktop
Client makes use of Microsoft’s Azure IoT Hub. This allows the Desktop Client to receive
notifications about stored jobs, such as releasing the job or deleting the job. The Desktop Client
opens a connection to the IoT Hub, which allows the Workplace Cloud solution to send commands
through the IoT Hub and back down to the client in response. The result is an open connection
between the Desktop Client and the Azure IoT Hub. All communication is done using AMQP over
Web Sockets using port 443. This connection is outbound from the client to the Azure IoT Hub,
which allows responses to be sent back through this connection. User workstations should allow
outbound traffic over port 443, which is typically allowed in most environments. If your environment
is very restrictive to HTTPS traffic, you may need to review the setup of workstations, proxies and
internet firewalls.
CO M M UN I CA T I O N B E TW E EN TH E W OR K P L A CE C LO U D A GE N T A ND T H E C U ST O M E R A D S
(L D A P) SE R VE R
When Company Authentication Type is enabled for LDAP Authentication, Workplace Cloud will
verify user credentials against Active Directory. The workplace credentials consist of Domain
Name, Domain Username and Domain Password.
Workplace Credentials are not stored on the Agent computer or in the Cloud database. The Agent
will query Active Directory for available domains.
In order to communicate with Active Directory, Workplace Cloud uses the Active Directory Services
Interfaces (ADSI) technology that is available in all Windows Operating Systems supported by
Workplace Cloud. The communication with the Active Directory servers occurs using the standard
LDAP port 389 or using LDAP over SSL with port 636. Communication is secured using SASL bind
usually using the GSSAPI mechanism.
If LDAP is configured for manual configuration mode, then Workplace Cloud supports the ability to
store LDAP system credentials for each LDAP server. These are stored in the SQL Azure
database, and the password is encrypted. The system credentials allow the solution to support
card on-boarding, by looking up unknown card access numbers in LDAP and importing a matching
user into Workplace Cloud. The credentials also support the ability to validate that a user
attempting to log into a printer through an access card is still a user in the LDAP/AD system and
has not been deleted.
CO M M UN I CA T I O N B E TW E EN WO R K P L AC E CL O U D A N D X E R O X® S E R V I C E S M A N A G E R
All communication between Xerox® Services Manager and Xerox® Workplace Cloud will be over
HTTPS (port 443).
Xerox® Workplace Cloud 5.6.1 – Security Guide 42
Page 45

CO M M UN I CA T I O N B E TW E EN LP R O R S H AR E D W IN D O W S P R I N T ( S MB ) C L I E N TS A N D T HE
WO R K P L A CE CL O UD AG E NT [ P M M]
The Agent supports the ability to enable both an LPR listening port and a Network Shared Printer
(SMB) port, which can accept incoming print jobs from LPR Clients and SMB based Clients (e.g.
Linux) that may not support the ability to print to the shared network pull queues used by Microsoft
Windows workstations. This feature might be used by Linux workstations or possibly even
mainframes. By default, this interface uses LPR over port 515, but the port is configurable and
SMB over port 445. [Note: jobs submitted to the Agent via LPR or a Shared Windows Queue are
never stored locally on the Agent. They are always uploaded to the Workplace Cloud. This
applies to both follow-you jobs as well as LPR “direct” jobs (where the queue name in the LPR
protocol matches the IP Address or Friendly name of a printer enabled in XWC). The Local Print
Optimization feature does NOT apply to jobs received by the Agent over LPR or a Shared Windows
Network Printer.]
CO M M UN I CA T I O N B E TW E EN TH E A P P F R O M T HE GA L L E R Y , T HE AP P S E R V E R , AN D
WO R K P L A CE CL O UD [P M M]
All SSO related communication requests to get or set a user’s authentication data uses TLS.
Sensitive information in all communications is also encrypted at the message or data item level in
addition to the encryption of the data stream itself using TLS. Message level encryption uses
shared keys pairs (a public and private key) for exchange of data between Workplace Cloud and
the App Server. Data is both encrypted and signed to ensure authenticity and privacy. Encryption is
done using an RSA algorithm with key size of 10240. Additional details on SSO can be found in
Chapter 7 Single Sign-On of this document.
CO M M UN I CA T I O N B E TW E EN WO R K P L AC E CL O U D A N D T HE PR I NT E R
@PrintByXerox App [PMM]
For Xerox devices that support the EIP browser and EIP Apps, the Xerox® @PrintByXerox App will
pull page content to be displayed in the browser of the printer UI panel from Workplace Cloud.
This includes all page content, authentication, available jobs, job selection and job status. All
communication is via HTTPS over Port 443.
Printing [PMM]
For newer Xerox devices that support the EIP Pull Print API (ConnectKey, AltaLink & VersaLink),
the printer can be directed to retrieve print jobs directly from the cloud (either from Azure blob
storage or if CDN is enabled, then through an Akamai edge server). Job release from the Xerox®
@PrintByXerox App always uses this method to get print jobs to devices which support this API. It
is also possible to enable the Agent to support this print path (again for printers supporting this
API). The Agent would direct the printer to pull the print job instead of routing the job through an
Agent and then to the printer. This will decrease network load as well as load on the Agent itself.
Establish IoT Hub Connection
Agentless Authentication and/or Device Management is supported primarily via the Azure IoT Hub.
The establishment of the IoT Hub connection requires the printer to call the Workplace Cloud
backend in Azure to get the IoT Hub connection string. This connection string is specific for each
device based on printer unique information. The printer must pass this information to WC using a
proprietary API, which is protected via certificate validation. This call is over HTTPS using port
443.
Agentless Authentication [PMM]
In regards to Agentless Authentication, the EIP Convenience Authentication API requires the
printer to make some of the authentication API requests directly from the Printer to the Workplace
Cloud backend system hosted in Azure. These calls are initiated from the printer (e.g. initiate a
Xerox® Workplace Cloud 5.6.1 – Security Guide 43
Page 46

new session as a result of a card swipe or selecting the Alternate Login button). This
communication path uses HTTPS over port 443.
EIP Response Messages
Response messages to EIP API requests coming through the IoT Hub are sent directly from the
printer to Workplace Cloud via web service APIs. These message use HTTPS over port 443.
CO M M UN I CA T I O N B E TW E EN TH E P RI N T ER A N D T H E I O T H U B
After the printer receives the IoT Hub connection string for Workplace Cloud, the printer directly
calls the Azure IoT Hub APIs to create an IoT Hub connection. This call is over AMPQ using port
5671 (with HTTPS over 443 as a fallback). The IoT Hub channel is an out-bound connection from
the printer to the IoT Hub, which then allows responses (new requests) to be send back down
through this channel. These are response messages from a networking perspective, not new
inbound connections. The WC will use this connection path to the printer for authentication,
configuration, accounting and device management in an Agentless environment.
CO M M UN I CA T I O N B E TW E EN TH E X E R O X® D E V IC E A G E N T A N D W OR K P L A CE CL O U D [ F M ]
The Device Agent includes a small background service which will query the Auto Update Service to
see if the Device Agent’s associated SM account has been linked to a Workplace Cloud account. If
the account exists and is linked, the service will pull over and install the Workplace Cloud Agent on
the same workstation / server, and will register it to use the linked WC/SM account.
Communication between the Device Agent and the Workplace Cloud backend is via HTTPS (port
443).
CO M M UN I CA T I O N B E TW E EN TH E X E R O X® D E V IC E A G E N T A N D T HE X E R O X AU T O U P D A T E
S E R V IC E [ FM ]
The Device Agent includes a small background service which will query the Auto Update Service
hosted by Xerox to see if the Device Agent’s associated SM account has been linked to a
Workplace Cloud account. If the account is linked, then the Device Manager will then call the
Workplace Cloud to download the Cloud Agent installer. Communication between the Device
Agent and the Auto Update Service is via HTTPS (port 443).
Xerox® Workplace Cloud 5.6.1 – Security Guide 44
Page 47

5. Logical Access, Network Protocol Information
TLS
TLS
TLS
Protocols and Ports
The following table lists the standard default ports used by the Workplace Cloud solution. Some
port numbers are configurable on the printer, such as the Raw IP printing port. Other port numbers
are non-configurable and cannot be changed.
X E R O X® W O R KP L AC E A P P P O R T S [ P M M ]
Protocol Transport
and Port
Value
HTTPS
TCP 443 Authentication, Job
using
TLS
Use Option Component Direction
/ Printer Listing,
Nonconfigurable
App to WS
Service
Initiate Print
Conversion
HTTPS
using
IPP TCP 631 iOS Native Print
HTTPS
using
WO R K P L A CE CL O UD AG E NT P O RT S
Protocol Transport
HTTPS
using
TLS
TCP 443 Authentication Non-
configurable
Non-
Submission
TCP 443 Authentication (for
Chrome SSO)
Use Option Component Direction
and Port
Value
configurable
Nonconfigurable
TCP 443 Retrieval of configuration,
sending printer info, retrieval
of print jobs or firmware
Nonconfigurable
App to Azure
AD or OKTA
App to Agent Out
App to
Google
Agent to
Workplace
Cloud
releases, authentication,
print job upload for LPR/SMB
listener ports.
Raw IP TCP
9100
HTTPS TCP 443 Azure Service Bus (with
[PMM] Print Submission
[FM] Firmware Update
application-level encryption)
Configurable Agent to
Printer
Nonconfigurable
Agent to
Workplace
Cloud
LPR TCP 515 [PMM] Print Submission Configurable Agent to
Printer or
to Print
Queue
HTTPS
using
TCP 443 [PMM] Retrieval of print job
from CDN
Nonconfigurable
Agent to
CDN
(Akamai)
Out
Out
Out
Out
Out
Out
Out
Out
Xerox® Workplace Cloud 5.6.1 – Security Guide 45
Page 48

IPP over
SSL
TLS
TLS
TLS
Sockets
TCP 443 [PMM] Print Submission Non-
configurable
LDAP TCP 389 [PMM] Authentication Non-
configurable
LDAP
over SSL
HTTPS
using
TLS
TCP 636 [PMM] Authentication Non-
configurable
TCP 443 [PMM] Printer Authentication,
EIP Registration, Accounting
Non-
configurable
Data Configuration and
Retrieval, Pull Print Request,
Job Management
HTTPS
using
TCP 443 [PMM] Printer Authentication Non-
configurable
Agent to
Printer
Agent to
ADS
Server
Agent to
ADS
Server
Agent to
Printer
Printer to
Agent
Out
Out
Out
Out
In
HTTPS
TCP 443
using
SNMP UDP 161
LPR TCP 515
Windows
TCP 445
Shared
Printer
(SMB)
HTTPS
TCP 443
using
AMQP
TCP 443
Web
[PMM] Authentication
Printer Discovery, Configuration
[PMM] Incoming Print Queue –
Receive prints from LPR Clients
[PMM] Incoming Print Queue –
Receive prints from SMB Clients
Note: there may be additional
ports needed for MS Printing.
Refer to:
https://docs.microsoft.com/enus/troubleshoot/windowsserver/networking/serviceoverview-and-network-portrequirements
[PMM] Single Sign-On Requests
/ Responses
[FM] Azure IoT Hub connection
for Fleet Management requests
Non-
configurable
Agent to
Azure AD
or OKTA
Nonconfigurable
Agent to
Printer
Configurable LPR Client
to Agent
Configurable SMB Client
to Agent
Nonconfigurable
Nonconfigurable
Printer
Agent
Agent to
Azure IoT
Hub
Out
Out
In
In
In/Out
Out
X E R O X® @P R I N T BY X ER O X AP P PO RT S [ P M M ]
Protocol Transport
and Port
Value
HTTPS
TCP 443 Retrieval of EIP
using
TLS
Use Option Component Direction
Browser pages for
display on the UI.
Nonconfigurable
@PBX to
Workplace
Cloud
Out
Authentication, Job
Listing, Initiate Print
Conversion
Xerox® Workplace Cloud 5.6.1 – Security Guide 46
Page 49

HTTPS
TLS
TLS
SSL
fallback)
TCP 443 Authentication Non-
using
HTTPS
TCP 443 QR Code icon
using
P R I N TE R P O R T S
retrieval
configurable
Nonconfigurable
@PBX to
Azure AD or
OKTA
@PBX to
Azure Blob
Storage
Out
Out
Protocol Transport
and Port
Value
Use Option Component Direction
SNMP UDP 161 Printer Discovery,
Configuration
LPR TCP 515 [PMM] Incoming
Print Queue –
Receive prints
from LPR Clients
Raw IP TCP 9100 [PMM] Print
Submission
IPP over
TCP 443 [PMM] Print
Submission
HTTPS
using TLS
TCP 443 EIP Registration,
Initiate Pull Print,
Configuration, Job
Management
HTTPS
using TLS
TCP 443 Pull Print
Request, (Azure)
IoT Hub
Connection
Request and
Response
Messages to
requests sent
over the IoT Hub
HTTPS
using TLS
HTTPS
using TLS
TCP 443 [PMM] Pull Print
Request to CDN
TCP 443
[PMM] Printer
Authentication
(Agent)
Nonconfigurable
Cloud Agent
to Printer
Configurable LPR Client to
Cloud Agent
Configurable Cloud Agent
to Printer
Nonconfigurable
Nonconfigurable
Nonconfigurable
Cloud Agent
to Printer
Cloud Agent
to Printer
Printer to
Workplace
Cloud
Nonconfigurable
Printer to
CDN
(Akamai)
Nonconfigurable
Printer
to/from Cloud
Agent
In
In
In
In
In
Out
Out
In/Out
AMQP
(with
HTTPS
using TLS
TCP 5671
(TCP 443
fallback)
Azure IoT Hub
connection for
Agentless
requests.
Nonconfigurable
Printer to
Azure IoT
Hub
Out
as a
SNMP UDP 161
Xerox® Workplace Cloud 5.6.1 – Security Guide 47
[FM] Printer
Discovery, Meter
Reads, Monitoring
Nonconfigurable
Device Agent
to Printer
In
Page 50
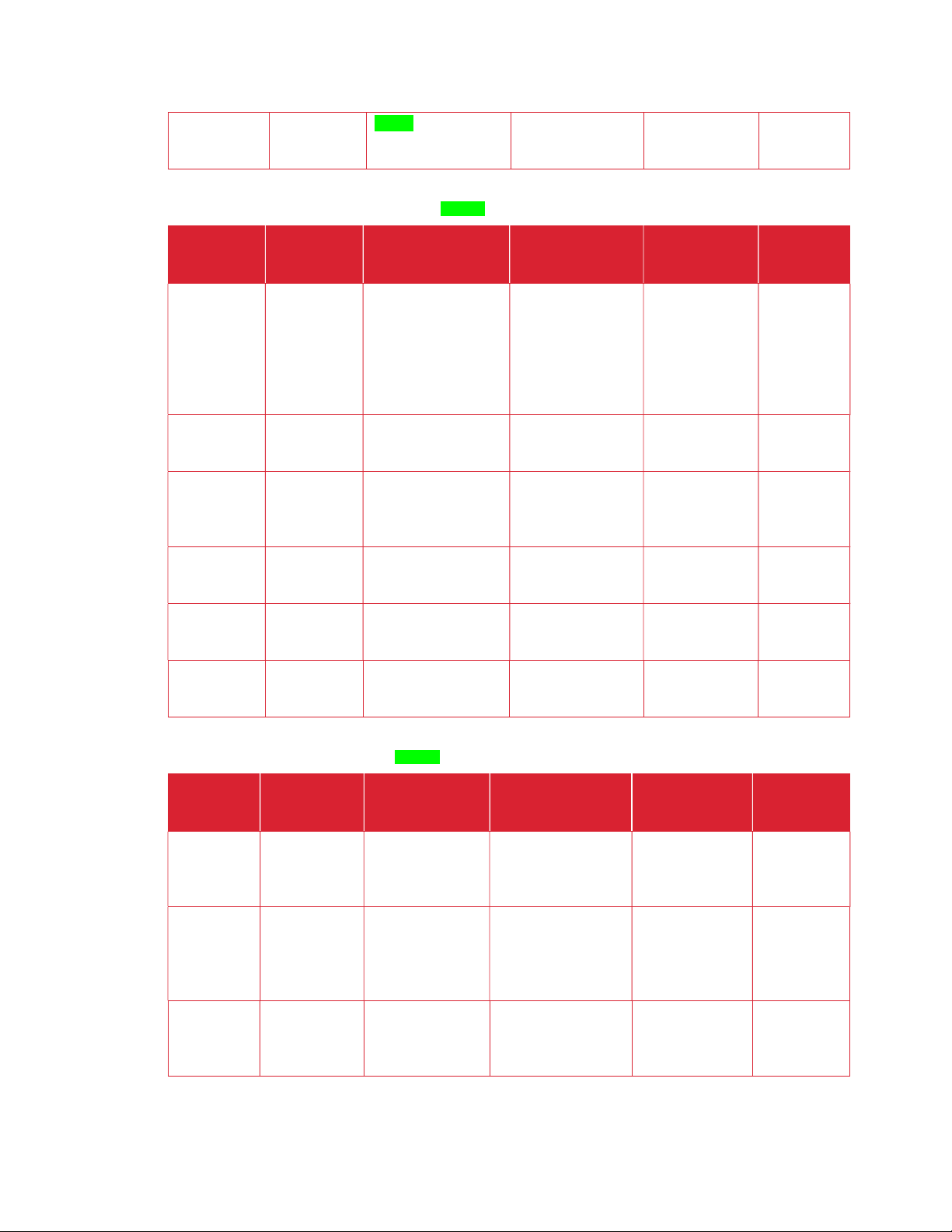
HTTPS
using TLS
WO R K P L A CE CL O UD CL I EN T P O R T S [ P MM ]
TCP 443
[PPM] Single SignOn for Gallery Apps
Nonconfigurable
Print to
Workplace
Cloud portal
Out
Protocol Transport
and Port
Value
HTTPS
TCP 443 Printer
using TLS
Use Option Component Direction
Configuration,
Driver Download,
Nonconfigurable
Client to
Workplace
Cloud
Print Submission,
Home Worker
Print Tracker job
details
HTTPS
using TLS
TCP 443 Authentication Non-
configurable
Client to
Azure AD or
OKTA
AMQP
Web
Sockets
TCP 443 Print job release
notification
Nonconfigurable
Client
(Windows
PC) to Azure
IoT Hub
LPR TCP 515 Print Submission Configurable Client
(Windows
PC) to Printer
Raw IP TCP 9100 Print Submission Configurable Client
(Windows
PC) to Printer
IPP over
SSL
TCP 443 Print Submission Non-
configurable
Client
(Windows
PC) to Printer
Out
Out
Out
Out
Out
Out
NE T W O R K A P PL I AN C E P OR T S [ P M M ]
Protocol Transport
and Port
Value
Raw TCP 7778 Receive Card
Use Option Component Direction
Swipe Data
from Elatec
Configurable Network
Appliance to
Agent
Out
TCPConv
Raw TCP 7777 Receive Card
Swipe Data
from Elatec
Configurable Network
Appliance to
Agent
Out
TCPConv2 /
Conv3
Raw TCP 2001 Receive Card
Swipe Data
from RFIdeas
Configurable Network
Appliance to
Agent
Out
Ethernet 241
Xerox® Workplace Cloud 5.6.1 – Security Guide 48
Page 51

X E R O X® D E V IC E A G EN T P O R T S [ F M ]
TLS
HTTPS
Protocol Transport
and Port
Value
HTTPS
TCP 443 Agent Installer
using
Use Option Component Direction
Download
SNMP UDP 161 Printer Discovery,
Meter Reads,
Monitoring
HTTPS
using
TLS
TCP 443 Command
Requests, Printer
Configuration and
Monitoring
Information,
Configuration,
Status
HTTPS
TCP 443 Account Validation Non-
using
TLS
Nonconfigurable
Nonconfigurable
Nonconfigurable
configurable
Device Agent
to Workplace
Cloud
Device Agent
to Printer
Device Agent
to Services
Manager
Device Agent
to Xerox Auto
Update
Service
Out
Out
Out
Out
Firewall Rules
The following table lists the standard firewall rules used by the Workplace Cloud solution. It is
expected that the administrator will modify the firewall rules of the PC running the Agent if these
features are being used at the customer site.
Protocol Default Use Port
Value
TCP 443 Authentication In
Raw TCP 7778 Receive Card Swipe Data from
Raw TCP 7777 Receive Card Swipe Data from
Raw TCP 2001 Receive Card Swipe Data from
Use Direction
In
Elatec TCP Conv
In
Elatec TCP Conv2 / Conv3
In
RFIdeas Ethernet 241
Xerox® Workplace Cloud 5.6.1 – Security Guide 49
Page 52

Port Diagrams
The following diagram gives a pictorial representation of the components and ports being used to
facilitate communication.
P R I N T M A N A G E M EN T P O R T D I A G R A M [P M M ]
Print Management Port Diagram (with an Agent)
Xerox® Workplace Cloud 5.6.1 – Security Guide 50
Page 53

Print Management Port Diagram (Agentless)
Xerox® Workplace Cloud 5.6.1 – Security Guide 51
Page 54

FL E E T MA N A G E M E N T P OR T D I A G R A M [ F M ]
Fleet Management Port Diagram (with an Agent)
Xerox® Workplace Cloud 5.6.1 – Security Guide 52
Page 55

Fleet Management Port Diagram (Agentless)
Xerox® Workplace Cloud 5.6.1 – Security Guide 53
Page 56

6. System Access
User Accounts
Xerox® Workplace Cloud is a multi-tenant solution based on a set of registered companies. Each
company is assigned a unique company code. This code is used to link a user to one of these
registered companies. Users of Workplace Cloud can only be actively linked (often referred to as
“homed”) to one company. As part of the initial user account creation, they can supply the
company code to ensure they are homed to the correct company. It is also possible (upon request)
to associated an email domain or list of domains to a registered company, so that user’s onboarding for the first time will not need to provide a company code and will automatically get homed
to the correct company. As part of the user account creation, the user will need to authenticate via
the configured mechanism of the home company (Cloud Authentication, LDAP, Azure AD or
OKTA).
Workplace Cloud does allow users to change their home account using the Web Portal or the
Workplace App. The login interface provides an option to change companies, and when selected,
prompts the user to supply the company code of the new company that they wish to be associated
with. When a user changes companies (re-homes their account), any jobs they had previously
upload to the system (which are based on the user being homed to the old company) will be
deleted and no longer available to be released.
Web Portal
When accessing the Xerox® Workplace Cloud directly (using the Web Portal for either general user
access or administrative access), the user will connect to:
https://xwc.services.xerox.com/Login
Users will need to provide their email address. Workplace Cloud will look up the user’s email
address to determine the company account to which they are homed, and then based on that
company’s authentication configuration, they will be prompted to enter either their Workplace Cloud
password, their company LDAP credentials (DOMAIN\USERNAME and PASSWORD), their OKTA
credentials, or their Azure AD credentials. When using LDAP, the Domain will be used to route the
LDAP requests to the correct Agent, which will then communicate with the ADS/LDAP server.
Credentials (either the Workplace Cloud Password, the LDAP credentials, or the Azure credentials)
are never saved in the browser. In addition, the user’s browser session will timeout after 20
minutes of inactivity.
Workplace Cloud Agent
When the Agent is initially installed, the company’s Xerox® Workplace Cloud administrator must
provide their credentials (Workplace Cloud, LDAP, OKTA or Azure AD) and Company Code so that
the App can communicate with the Workplace Cloud and register the Agent with their account.
Subsequent communication to Workplace Cloud will use computed access credentials for the
Agent based on the hardware of the workstation on which the Agent is running. The Administrator
credentials are not stored or used after the initial registration occurs.
Xerox® Workplace Cloud 5.6.1 – Security Guide 54
Page 57

Xerox® Workplace App [PMM]
When accessing the Xerox® Workplace App, users will need to provide their email address. Xerox®
Workplace Cloud will look up the user’s email address to determine the company account to which
they are homed, and then based on that company’s authentication configuration, they will be
prompted to enter their Workplace Cloud password, their company LDAP credentials
(DOMAIN\USERNAME and PASSWORD), their OKTA credentials, or their Azure AD credentials.
When using LDAP, the Domain will be used to route the LDAP requests to the correct Agent, which
then will communicate with the ADS/LDAP server.
The results of successfully authenticating with Workplace Cloud is an access token. The token is
stored on the phone and used for subsequent communication with Workplace Cloud. The lifetime
of the access token is 1-365 days based on the configuration set by the company account
administrator. Prior to the token expiring, the phone will obtain a new token, which requires the use
of the user’s login credentials. So, the Workplace App will store the user’s access credentials on
the phone in encrypted format in order to support renewing the access token. For Android devices,
the credentials are encrypted and saved to internal storage of mobile device and this is only
accessible by the Workplace App. For iOS devices, the credentials are saved in a keychain which
is encrypted and only accessible by the Workplace App. The OS of the mobile device will delete
any saved data including the credentials when the application gets un-installed.
There is a version of the Workplace App that supports Google Chromebooks as well as an
extension to the Google Chrome browser. When run in these environments, the Workplace App will
support authentication using the Cloud solution supported mechanisms, as well as supporting
“single sign-on” using your Google credentials to validate the user in place of manually entering
credentials.
For Chrome using one of the supported authentication mechanisms for Workplace Cloud, the
access token will only be stored in memory. Once the token expires, the user will be required to reauthenticate with Workplace Cloud.
In the case of Chrome using the Single Sign-On (SSO) feature, when a user attempts to log in, the
app will pre-populate the email field with the logged-on user’s email address. When this is
submitted to the server, the app will also include the Google authentication token of the logged-on
user as well as the AppID of the Workplace App. The Workplace Cloud backend system will
validate the email, token and AppID with Google using HTTPS over port 443. If these are valid, the
user is considered authenticated. The Workplace Cloud then creates a Mobile Print access token
and returns that to the Workplace App on Chrome. The user then remains logged in to the App until
the access token expires. At this time, the app will attempt to repeat the process.
Workplace Cloud Client for Windows and Mac [PMM]
When installing the Workplace Cloud Client, users will need to provide their email address. Xerox®
Workplace Cloud will look up the user’s email address to determine the company account to which
they are homed, and then based on that company’s authentication configuration, they will be
prompted to enter their Workplace Cloud password, their company LDAP credentials
(DOMAIN\USERNAME and PASSWORD), their OKTA credentials, or their Azure AD credentials.
When using LDAP, the Domain will be used to route the LDAP requests to the correct Agent, which
then will communicate with the ADS/LDAP server using LDAP (Port 389) or LDAP over SSL (Port
636).
The results of successfully authenticating with Workplace Cloud is an access token. The token is
stored on the user’s workstation and used for subsequent communication with Workplace Cloud.
The token is encrypted using AES before being stored on the local workstation. The lifetime of the
Xerox® Workplace Cloud 5.6.1 – Security Guide 55
Page 58

access token is 1 to 365 days based on the configuration set by the company account
administrator. Once the access token is expired, the user will be prompted to re-supply their
authentication credentials, after which a new access token will be created. For Azure AD or OKTA,
the lifetime of the Workplace Cloud access token matches that of the Azure AD or OKTA access
token lifetime. When this expires, Workplace Cloud will attempt to use the Azure AD or OKTA
refresh token to obtain a new Azure AD or OKTA access and refresh token, which then will
generate a new Workplace Cloud access token.
Printer
Additional security can be enforced at the printer if the printer is EIP Capable and/or supports the
EIP Convenience Authentication API. For those printers which support this capability, the
Workplace Cloud provides the capability to lock the printer’s local user interface, and require the
user to authenticate themselves at the printer in order to gain access to any of the
services/features of the printer. There are three ways in which a user can authenticate:
1. The user may supply their Workplace Cloud user credentials (user name/password, LDAP, or
Azure AD credentials (deprecated) depending upon the Company/Account configuration) at the
printer, or if the PIN Authentication feature is enabled, they can enter a PIN to login to the
printer. [Note: OKTA as well as new accounts using Azure AD do not support this
authentication workflow].
2. The user can identify themselves using their access card (for example, employee badge).
3. The user can use the Xerox® Workplace App with its “Unlock Printer” feature. The supported
methods of unlocking the printer include:
NFC – Use your Android device or iPhone 7 or newer with iOS 11.
QR Code – Scan the QR code found on the Welcome Sheet or for some printers on the
authentication blocking screen.
Manual Code Entry - Enter the 4-character code found on the local user interface of the
machine into the Workplace App.
Any of these methods will identify the printer in the App and the user can confirm that they
wish to unlock the device.
In each of the above scenarios, upon supplying valid credentials or making the unlock request, the
printer will remove the blocking screen and the user will have access to the services / features of
the printer. If the printer is an EIP capable device and the Workplace Cloud Print Client Application
is installed, then the user may select the App and view their list of jobs without providing additional
login credentials for the app.
Workplace Cloud supports a special administrator logon capability for Printer Authentication.
Enabling this setting allows a user to log into the printer control panel via the Alternate Login
feature and access administrator functions of the printer. To use this feature, the user must enter
the user name of “admin” on the first Alternate Login screen, and then enter the password
configured by the WC administrator. The password is common across all devices which have
been enabled for printer authentication by Workplace Cloud. This feature is disabled by default.
Xerox® @PrintByXerox App [PMM]
To access the Xerox® @PrintByXerox App, users will either need to log in to the printer using the
Convenience Authentication feature, or they will need to log in to the @PBX App itself. User will
start by providing their email address. Xerox® Workplace Cloud will look up the user’s email
address to determine the company account to which they are homed, and then based on that
company’s authentication configuration, they will be prompted to enter their Workplace Cloud
Xerox® Workplace Cloud 5.6.1 – Security Guide 56
Page 59

password, their company LDAP credentials (DOMAIN\USERNAME and PASSWORD), their OKTA
credentials, or their Azure AD credentials. When using LDAP, the Domain will be used to route the
LDAP requests to the correct Agent, which then will communicate with the ADS/LDAP server.
The Xerox® @PrintByXerox App will never save the user’s credentials. Users can log out of the
@PBX App manually, by selecting the “Exit” button in the App, or by navigating out of the App
(such as selecting the All Services, Machine Status, or Job Status buttons on the UI panel). The UI
itself has a built-in inactivity timer that will log the user out if the user is not interacting with the UI.
The inactivity period is configurable by the device administrator. In addition to the device timer, the
@PBX App itself has its own 5-minute timer. The @PBX App timeout will log the user out of the
App after 5 minutes of use, unless they dismiss warning pop-up, which restarts the 5-minute timer.
The Workplace Cloud solution supports the ability for the administrator to define or configure a
delegate or set of delegates for any given user. This allows a user that has been granted
delegation rights to release or delete that users’ jobs when accessing the @PrintByXerox App.
[When an administrator grants delegation rights, both the delegate and main user are sent an email
notifying them of this configuration change]. Upon entry to the @PrintByXerox App, the user
(delegate) can then view their own print jobs, but they have the ability to switch to viewing the jobs
of a user for which they are a delegate. This is a one-way access switch within the app. Once the
delegate switches from viewing their jobs to that of the other user, then cannot switch back and
they cannot switch to viewing the jobs of another user. They must log out and re-logon if they wish
to view their own jobs or those of another user. When a delegate releases a job of another user,
that job will be tracked as if the original user released the job in the job history and reporting data.
An email notification will be sent to the original job owner, notifying them that a delegate printed
their job.
Content Delivery Network (CDN) [PMM]
Microsoft Azure supports the use of CDN as a mechanism to improve the distribution of data,
enabling fast and localized downloads. Microsoft partners with different CDN providers, which
have many geographically distributed servers with high-speed connections to Azure. Xerox makes
use of Akamai as a provider of CDN functionality in partnership with Microsoft Azure. When print
ready jobs are made available for release at a printer, and either that printer supports the EIP Pull
Print API (e.g., ConnectKey, AltaLink and VersaLink devices), or the job is being downloaded by
the Agent, then @PBX app and the Agent can tell the printer to retrieve the print job from the Cloud
(pulling the job down to the printer over HTTPS on port 443 and submitting it to print), or the Agent
will download the job directly via CDN and submit it to the printer using the configure print protocol.
This print retrieval supports the CDN path to stream the job data from Azure blob storage in the
Workplace Cloud through the Akamai CDN edge server that is closest to the printer/agent and then
down to the printer or agent. The path between Azure blob storage and the CDN edge server is
essentially a super highway to quickly get the data from one of the Azure sites used by Workplace
Cloud (US or UK) to the CDN endpoint. The data is then pulled down to the printer/agent from the
CDN edge server, which is physically close to the printer, minimizing the network path that the data
needs to travel. The print job data is never stored in the CDN endpoint. Caching is disabled on
the Akamai edge servers, however, while transitioning from the Azure<->Akamai SSL connection
to the Akamai<->Customer SSL connection, the content needs to be decrypted and re-encrypted in
memory due to the different certificates involved in the transfer. Customers who may be concerned
with this data transfer can use the enhanced encryption feature under policies to ensure desktop
jobs remain encrypted throughout the transfer or leave the feature disabled.
The CDN feature is optional for Workplace Cloud accounts. The feature is disabled by default for
new Workplace Cloud accounts. For the Agent to directly download jobs via CDN, it must be at
version 5.5 or later. To configure CDN support, the administrator must go to the: Account >
Xerox® Workplace Cloud 5.6.1 – Security Guide 57
Page 60

Settings > Performance page and modify the ‘Enable CDN’ checkbox. The URLs that need to be
accessed by the printer are shown below:
https://xwcsvccdn.services.xerox.com
The above URL is actually a DNS CNAME for:
https://xwcsvccdn.azureedge.net
Printers must have access to the internet (either directly or via a proxy) in order to take advantage
of this feature.
The size of a print job has implications for whether or not CDN is used. For small files, the job will
just be pulled directly from Azure Blob storage and CDN will not be used. There is some overhead
to setting up the CDN that makes it inefficient to use for smaller jobs. Logic is built into Workplace
Cloud to only use the CDN pathway when it makes sense.
The print ready files stored in Azure Blob storage are encrypted using a unique (per job) symmetric
key and initialization vector. The files are decrypted by the Workplace Cloud as they are
downloaded. [Note: if the customer is using their own certificates with keys for encryption, please
see the section titled “File Encryption using Customer Keys”]. The lifetime of the print ready files
stored in Azure Blob storage is dependent upon the company’s retention period for downloaded
jobs: Immediate, 1 day or 7 days. An unprinted job would be removed from Azure Blob storage
after 7 days.
The access token for the print ready file URL which is created and given to the @PBX App or the
Agent to make a pull print request has a very short lifetime (15 minutes) and is a single use token
(meaning you can’t download the file from the same URL more than once). If there is no request to
retrieve the job during the token lifetime, the URL will expire and no longer be valid. This is done to
ensure that there is only a small window of availability to retrieve the file.
For those customers that are concerned about regionalization and keeping user data (in this case
the print job data) within a given region (e.g., GDPR concerns), the Akamai platform relies upon
many edge servers distributed throughout the world. When a printer or agent attempts to retrieve a
job from Azure blob storage, which in turn makes use of the CDN platform, the URL of the job will
consist of a base FQDN that is the same for each of the 3 primary Azure data centers used to
perform document conversion:
xwcsvccdn.services.xerox.com
When the printer/agent attempts to resolve that URL, which contains the above FQDN value, the
printer’s local DNS server will get routed to an Akamai DNS server. Akamai’s DNS server system
will attempt to locate the closest edge server to the requestor (the printer). The printer or agent’s
DNS server is used as a proxy for the actual location of the printer/agent.
Xerox® Workplace Cloud 5.6.1 – Security Guide 58
Page 61

7. Additional Security Items
Xerox® Workplace Cloud Endpoint Table
The following endpoints, provided FQDN format, are accessed by various components of the
Xerox® Workplace Cloud solution that reside inside a customer’s network. The customer must
ensure that these components have access to the Internet, and in particular these specific
endpoints, in order for this solution to work properly. All endpoints are accessed using HTTPS with
TLS (port 443).
CL O U D E ND P O I NT S
Component Product Ref# Endpoint FQDN
Xerox® Workplace
Cloud Agent
[PMM]
[FM]
1
https://xwc.services.xerox.com
[PMM]Xerox®
Workplace Cloud
Printer Client
Application – Xerox®
@PrintByXerox and
Xerox EIP Printer
[PMM]
[FM]
[PMM]
[FM]
[PMM]
[PMM]
[PMM]
[FM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[FM]
2
5
9
10
11
12
1
3
2
4
4
9
10
11
13
https://xmpcws.services.xerox.com
*.servicebus.windows.net
(Azure AD only) https://login.microsoftonline.com
(OKTA only) customer defined URL
[OPTIONAL] https://xwcsvccdn.services.xerox.com
(Fleet Management) https://clouddm.azure-devices.net
https://xwc.services.xerox.com
https://xmpceip.services.xerox.com
https://xmpcws.services.xerox.com
https://xcpproduction.blob.core.windows.net
https://xpmmsuks.blob.core.windows.net
(Azure AD only) https://login.microsoftonline.com
(OKTA only) customer defined URL
[OPTIONAL] https:// xwcsvccdn.services.xerox.com
[OPTIONAL] https://wdm.services.xerox.com
[PMM]
[FM]
[PMM]Xerox®
Workplace
Application – Mobile
App
Xerox® Workplace Cloud 5.6.1 – Security Guide 59
[PMM]
[PMM]
[PMM]
[PMM]
14
[OPTIONAL] https://clouddm.azure-devices.net
6
2
7
9
https://xccsts.services.xerox.com
https://xmpcws.services.xerox.com
https://publicprintapi.services.xerox.com
(Azure AD only) https://login.microsoftonline.com
Page 62

[PMM] 10 (OKTA only) customer defined URL
Xerox® Workplace
Cloud Web Portal –
Customer Web
Pages
[PMM]Xerox®
Workplace Cloud
Client
[FM]Xerox® Device
Agent
[PMM]
[FM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[PMM]
[FM]
[FM]
1
9
10
6
2
1
8
8
8
9
10
1
2
https://xwc.services.xerox.com
(Azure AD only) https://login.microsoftonline.com
(OKTA only) customer defined URL
https://xccsts.services.xerox.com
https://xmpcws.services.xerox.com
https://xwc.services.xerox.com
https://virtualprintiothub.azure-devices.net
https://virtualprintiothubukw.azure-devices.net
https://virtualprintiothubus.azure-devices.net
(Azure AD only) https://login.microsoftonline.com
(OKTA only) customer defined URL
https://xwc.services.xerox.com
https://xmpcws.services.xerox.com
CL O U D E ND P O I NT DE S C R I P T I O N S
Ref# Endpoint FQDN Description
1 https://xwc.services.xerox.com [PMM Hosts the web portal interface used
by administrators and users for
configuration and web submission of print
jobs. Used for SSO.
2
https://xmpcws.services.xerox.com
Hosts the web service endpoint allowing
print job submission and management as
well as retrieving and setting configuration
data for an account.
3
https://xmpceip.services.xerox.com
[PMM] Web server used to host the
Xerox® @PrintByXerox browser pages
available on EIP printers.
4
5
https://xcpproduction.blob.core.windows.net
https://xpmmsuks.blob.core.windows.net
*.servicebus.windows.net
[PMM] Location of the QR Code displayed
on the authentication blocking screen if this
feature is enabled.
Azure service bus endpoints used by the
Agent to connect to the Azure service bus
gateway.
6
https://xccsts.services.xerox.com
The Xerox routing service used during
login. Maps the user’s email to their home
company and the configured authentication
mechanism for that account. Performs
authentication if Cloud or routes to an
external authentication mechanism (LDAP,
OKTA or Azure AD). Grants access token.
7
https://publicprintapi.services.xerox.com
[PMM] Used for printing to third party
providers if enabled in the company
account.
Xerox® Workplace Cloud 5.6.1 – Security Guide 60
Page 63

8
9
https://virtualprintiothub.azure-devices.net
https://virtualprintiothubukw.azure-devices.net
https://virtualprintiothubus.azure-devices.net
(Azure AD only) https://login.microsoftonline.com
Azure IoT Hub for print job release
notifications to the Workplace Client when
jobs are stored locally as a result of the
Local Print Optimization feature.
Azure AD login for authentication of users.
10
11
12
13
14
(OKTA only) customer defined URL
[OPTIONAL] https://xwcsvccdn.services.xerox.com
(Fleet Management) https://clouddm.azuredevices.net
(Agentless only) https://wdm.services.xerox.com
(Agentless only) https://clouddm.azure-devices.net
OKTA login for authentication of users.
[PMM] High speed Content Delivery
Network endpoints hosted by Akamai.
Used for print job retrieval by the printer
when using the Xerox® @PrintByXerox
App, or when the Agent retrieves jobs to be
pushed to a printer.
Azure IoT Hub for fleet management
notifications to the Workplace Cloud Agent
for printer configuration and monitoring.
Request Azure IoT Hub connection details
to be used for establishing an IoT Hub
connection to be used for Agentless
Authentication and Device Management.
Return EIP response messages for
requests that come through the IoT Hub.
Azure IoT Hub connection endpoint for
Agentless Authentication, Print Release
and Device Management commands.
Xerox® Workplace Cloud 5.6.1 – Security Guide 61
Page 64

Certificate Validation
Xerox® Workplace Cloud is a cloud hosted service, available to anyone that has Internet access.
To ensure that users are connecting to a known trusted entity, the cloud hosted service in Azure
uses a digital certificate created by a well-known and trusted certificate authority.
CO N NE C T IO N D E T A I LS
Following, are details on the different access methods users have available to them when
connecting to the Xerox® Workplace Cloud as related to certificate validation.
Web Portal
Well-known browsers which are up to date (version and security patches) such as Internet
Explorer, Chrome, Firefox, Edge, include the public keys for most of the well-known certificate
authorities (CA) used on the Internet. This includes the CA used to generate the Xerox® Workplace
Cloud root certificate. As such, these browsers will test and validate the Workplace Cloud server
certificate when a connection is made to the Workplace Cloud Web Portal. No special setup or
configuration is needed from the user to take advantage of this capability.
Workplace App [PMM]
Similar to the browser on a PC, Android, iOS and Chrome include the public keys for most of the
well-known certificate authorities used on the Internet. These public keys are available to
applications running on the mobile phone. The Xerox® Workplace App is designed such that it
always validates the server certificate for all communication with the Xerox® Workplace Cloud. If
this validation fails, the Workplace App will prevent any further communication with Workplace
Cloud and therefore prevent the user from using the App.
Xerox® @PrintByXerox App [PMM]
Most of the newer Xerox devices that support EIP have the capability to perform certificate
validation. By default, these devices have validation turned off. It is recommended that the user
enable this capability on the printer. If the Xerox® @PrintByXerox App has been loaded using the
Xerox App Gallery or App Studio, or the App is pre-installed on the MFP, then the public root
certificate is included with App and will be used when validation is enabled. If the Xerox®
@PrintByXerox App has been loaded using the Agent, then no public root certificate will be
programmatically pushed to the printer. The user will need to obtain the public root cert for the
following site:
https://xwc.services.xerox.com/Login
When the cert is available, it will need to be imported into the trusted root certs of each printer
where the Xerox® @PrintByXerox App is installed.
Note: Not all Xerox capable EIP printers support certificate validation.
Xerox® Workplace Cloud 5.6.1 – Security Guide 62
Page 65

Auto Release Using Network Appliance Workflow [PMM]
Held print jobs are released automatically when the user scans a card at a mapped network
appliance associated with the printer.
Network appliances are small network boxes that attach to the network and permit Xerox®
Workplace Cloud to control the release of user documents to printers that do not support the use of
Xerox® Secure Access / Convenience Authentication. A network appliance is configured on the
network by the administrator, the appliance is associated with the particular printer in the
Workplace Cloud Admin Web Portal, and the user can release their jobs at the printer by swiping
their card using the card reader associated with the printer. One network appliance is required for
each printer.
M O D E LS
Three network appliance models are supported by Xerox® Workplace Cloud: RF Ideas
1. Ethernet 241
2. Elatec TCP Conv2 / Conv3
3. Elatec TCP Conv
Each of these models is available by default on the Web Portal administration site at
Account > Settings > Network Appliances > Models. If any or all of these models are not going to
be part of your site installation, they can be disabled to turn the listeners off on the server.
The listeners use these default ports:
RF Ideas Ethernet 241 - 2001
Elatec TCP Conv2 / Conv3 - 7777
Elatec TCP Conv - 7778
The default ports can be changed by the administrator if the network appliances on your system
have been configured to use a different port. Any firewall on the Agent must be configured to allow
communication through the port(s).
By default, the network appliances support communication using non-encrypted channels.
Therefore, card data is sent in plain text format when transmitting the card data from the network
appliance to the Agent. The RF Ideas Ethernet 241 is the only network appliance that supports
encryption, using SSL, of the communication path.
Note: The Ethernet 241 supports SSLv3. It does not support TLS1.x.
Audit Log
The Xerox® Workplace Cloud will maintain a history of the users that have logged in Workplace
Cloud using any of the interfaces: Workplace App, Web Portal, Xerox® @PrintByXerox, or
Convenience Authentication. Entries are maintained for a period of 1 year. Entries older than that
are purged from the log.
Xerox® Workplace Cloud 5.6.1 – Security Guide 63
Page 66

Azure Data Centers
The Xerox® Workplace Cloud is hosted in the cloud using Microsoft Azure, which is a public cloud
computing platform. The Workplace Cloud solution uses four different Azure data centers:
South Central US – located in Texas
UK South – located in London
UK West – located in Cardiff
West Europe – Netherlands (Amsterdam)
All User and Account information is stored in both the UK South and UK West data centers. The
data is replicated across both sites to support failover scenarios. Print job data is stored in either
the US or UK centers based on geo-location. Job reporting information (detailed job history and job
accounting information) is stored in the West Europe center. Within the UK data centers, there is
full active redundancy for services and the database. A US data center failure will fail over to the
UK data centers. A UK West data center failure will automatically fail over to the UK South data
center. A UK South data center failure may cause temporary loss of service globally depending on
the type of failure encountered and the time associated with the full switch over to the UK West
site. Due to the centralized nature of the User and Account database being in the UK and because
of EU Privacy policies, the UK sites will never failover to the US. Job History (Reporting) data is
stored in the West Europe site using the Azure Data Lakes capability for large data storage.
Usage Tracking and Reporting [PMM]
The Xerox® Workplace Cloud supports the ability to collect network accounting information from
Xerox devices that support this feature. This includes job information for Copy, Scan and Fax jobs
as well as Print jobs. For printers that don’t support Xerox Network Accounting, the Workplace
Cloud will supplement print job data that it collects (includes print jobs sent to Workplace Cloud
enabled printers as well as print jobs submitted to a Home Worker Print Tracker supported printer)
with that retrieved from Xerox Network Accounting. This is an optional feature that is disabled by
default and must be enabled globally to make it available on a printer-by-printer basis. Usage
tracking data collected by Workplace Cloud is stored in Azure SQL in the UK Azure sites. The
Analytics feature in Workplace Cloud accesses the Azure SQL to generate tables and graphs. If
the administrator of a company wishes to have the ability to export the raw reporting data to a CSV
file, or to use the reporting dashboards, then they must separately enable this export capability
using the Web Portal. When this export capability is enabled, data will periodically be copied from
the reporting data in Azure SQL, analyzed (to collect dashboard information) and stored in Azure
using their Data Lakes storage mechanism. The copied reporting data is stored in Microsoft’s
Azure Data Center located in Amsterdam (West Europe). Customers that do not wish to have job
reporting information stored in the Data Lakes location can turn off the export option.
Xerox® Workplace Cloud 5.6.1 – Security Guide 64
Page 67

Single Sign-On [PMM]
The SSO capability is designed with a focus on security of the Gallery App authentication data
(credentials, token, and so on). Below is a highlight of the main security points of this solution:
All communication is over HTTPS.
The Workplace Cloud validates the certificate of the App Server vault. The certificate must be
from a well-known and trusted provider.
The SSO authentication data for a given user and app is given to the Workplace Cloud in an
encrypted format. The Workplace Cloud can never view the authentication data.
Note: It is the responsibility of the App from the Gallery and/or its backend server to encrypt the
authentication data before sending it to Workplace Cloud for storage.
Exchange of sensitive information between Workplace Cloud and the App/App Server uses
public key cryptography with asymmetric keys. Each side (Workplace Cloud and App Server)
has its own public and private keys, and shares the public key with the opposite side, but keep
its private key hidden. Data is encrypted by the public key and then sent to the owner of the
private key to decrypt it.
All message exchanges related to authentication data include digital signatures, so that the
receiver can always validate that the request is coming from a trusted entity.
Messages containing authentication data include 3 levels of encryption:
1. The channel is encrypted via HTTPS.
2. Message content is encrypted using public key cryptography with asymmetric keys. An
RSA algorithm is used for encryption with a key size maximum of 16384.
3. Authentication data is encrypted by the Gallery App or its backend server prior to storing it
with Workplace Cloud. The format and encryption method used are up to the Gallery APP
vault.
Data sent from one entity to the other is always encrypted using the public key of the receiver. As
an example, let’s assume the App/Gallery App Server would like to store new authentication data in
Workplace Cloud. The steps to manage the encryption of this data are as follows:
1. The Gallery App Server constructs the appropriate message data to be sent to Workplace
Cloud, and then encrypts that data using the public key of Workplace Cloud.
2. That data is then signed by the App Server using its own private key.
3. When this data is received by Workplace Cloud, it validates the signature using the public key
of the Gallery App Server.
4. The message is then decrypted by Workplace Cloud using its private key.
A similar exchange takes place when sending the response message from the SSO vault to the
Gallery App Server.
Xerox® Workplace Cloud 5.6.1 – Security Guide 65
Page 68

User Import via CSV File
Xerox® Workplace Cloud supports the ability for an administrator to import a list of users into their
cloud company account, thereby avoiding the user from having to on-board themselves to the
company. The primary focus of this feature is allowing both the creation of the user and the
assignment of a PIN or Badge / Card number to the user. The PIN assignment is particularly
import for customers with a large number of users that do not have access cards or badges, and
want a single factor form of authentication at the printer to release jobs.
The import feature is constrained such that only user’s with pre-staged email domains for that
company will be allowed to be created and linked to the account. For example, if Company XYZ
owns the email domain of “@xyz.com”, they can request the Workplace Cloud team to link that
email domain to their company account. This process is carried out off-line and is performed by
Xerox® Workplace Cloud personnel. If the administrator attempts to import a user with an email
domain that has not been linked to their company (e.g., @gmail.com), that user will be ignored by
the system.
The set of support fields that may be imported into the user database of Workplace Cloud are:
Email
Last Name
First Name
Middle Name
Group [Note: Groups must exist prior to import]
Department
Username (e.g. DOMAIN\USERNAME for LDAP)
PIN (Card Number)
[Note: PINs are not auto-created by Workplace Cloud. The administrator must pre-define the PINs
and ensure they are unique].
The results of importing a list of users will be emailed to the administrator that requested the import
as well as the contact person for the company account.
Packet Inspection
Xerox® Workplace Cloud makes use of both the Azure Service Bus and Azure IoT Hub
mechanisms for the Workplace Cloud Agent and Workplace Cloud Client to receive response
messages from the cloud hosted solution. These interfaces make use of certificate validation.
These Azure communication mechanisms in conjunction with the Workplace Cloud Agent and
Client prevent the use of packet inspection being used to view the contents of the messages being
exchanged over these interfaces. Web inspection utilities that attempt to analyze data going into or
out of their company will cause Xerox® Workplace Cloud to fail for the Azure Service Bus and
Azure IoT Hub communication pathways.
File Encryption using Keys [PMM]
Xerox® Workplace Cloud will always store both original documents and print ready documents in
an encrypted format when in the cloud. Files are encrypted using an AES encryption method. A
symmetric key is generated to encrypt the file, and then the key itself is asymmetrically encrypted
using a public certificate. The point at which a document is encrypted depends upon the
submission method:
Xerox® Workplace Cloud 5.6.1 – Security Guide 66
Page 69

Desktop Client – (Requires Windows® Client version 5.5 or newer and Mac client 1.2 or
newer) Files uploaded from the Desktop Client are always encrypted before being uploaded to
the cloud using this method.
Workplace App – A file uploaded from the Workplace App will be encrypted upon receipt by
Workplace Cloud before being stored.
Web Portal – A file received from the Web Portal will be encrypted upon receipt before being
stored in the Cloud.
Email - A file received from email will be encrypted upon receipt before being stored in the
Cloud.
For the Desktop Client submission path, the administrator has the option to create and use a pair of
x509 certificates, one which contains a public key and the other which contains a private key, that
will be used for the encryption and decryption. The customer uploads the public certificate to
Workplace Cloud, and this is then pushed to all of the XWC Clients. Files encrypted using a
customer provided public certificate will always remain in an encrypted format when in the Cloud,
including during upload and download.
Jobs received from the Workplace App, Web Portal and through email will be encrypted upon
receipt of the file into the Workplace Cloud solution before being stored to Azure blob storage.
Files encrypted using the Workplace Cloud default public certificate will be decrypted when they
are retrieved by either the Agent or by the Printer if it using the EIP Pull Print API. The actual
decryption is done by the Workplace Cloud backend system as it is streamed by the receiving
endpoint. The actual decrypted file will never reside on any physical storage media in the cloud.
If the customer is using their own x509 certificate pair for desktop jobs, then the customer will
install the private cert (used to decrypt the print jobs) on each XWC Agent deployed at the
customer site. If the customer has AltaLink devices that natively support decryption, then the
private certificate as well as the root CA (Certificate Authority) used to sign the private certificate
can be installed on each AltaLink device. All desktop jobs that have been encrypted with a private
key, upon release, will be routed to the Agent, or in the case of the AltaLink, they may directly be
pulled down from the cloud to the printer. This includes print jobs released by the Xerox®
@PrintByXerox App. The XWC Agent must pull the job down in its encrypted format, and then the
Agent will decrypt it and sent it to the printer. [Note: Use of customer installed certificates with keys
is only supported by Agents with a version of 5.5 or newer and with desktop clients with a version
of 5.5 or newer for Windows® and 1.2 or newer for Mac®]. Files encrypted using a customer
provided public certificate will always remain in an encrypted format when in the Cloud, including
during upload and download. They can only be decrypted by the Agent that has the matching
private certificate in its Windows certificate store. For AltaLink devices with the appropriate release
and installed certificates, the printer will decrypt and spool the job directly. Files encrypted using a
customer provided public certificate will always remain in an encrypted format when in the Cloud,
including during upload and download. They can only be decrypted by the Agent that has the
matching private certificate in its Windows® certificate store, or by an appropriately configured
printer that has the matching private certificate as well as the root CA certificate used to sign the
private certificate. The print will validate the chain of trust between the private certificate and the
root CA certificate. If the chain of trust cannot be made, the print will delete the encrypted print job
and nothing will be printed.
Content Security [PMM]
The Content Security Workflow allows an administrator to create a Content Profile, whereby they
define a set of search strings which are used to track documents processed by Workplace Cloud.
The solution will then process each job (limited to desktop jobs submitted with the Windows
desktop client application). The client application will parse submitted jobs.
Xerox® Workplace Cloud 5.6.1 – Security Guide 67
Page 70

Logging the matching strings in the Job History.
Emailing (notifying) a list of recipients with details on the job (e.g., who printed it, name of the
job, the device it was printed to, the time and date it was printed).
Microsoft Azure Universal Print [PMM]
Workplace Cloud can be integrated with Microsoft Azure Universal Print. This feature allows a
cloud company to create a single pull print queue in the Microsoft Azure Universal Print resource.
Once created in the Azure tenant, the print queue can be authorized and shared out to all the users
of the organization like any other Microsoft Universal Print Printer. This will allow Windows 10
Azure AD joined devices to add the printer and submit content to the queue, which in turn will
cause the jobs to be pulled into the Workplace Cloud solution for later release to a printer. Details
on setup of this feature can be found in the administration guide.
The Microsoft Azure Universal Print integration with Workplace Cloud requires the customer to
create a new application in their Azure AD Tenant that is accessible by Workplace Cloud. The
application must have the following Permissions listed below. Note that two of the below items
indicate “Delegated” permissions. It is vital that the administrator configuring Microsoft Universal
Print in the Workplace Cloud web portal have those permissions in their Azure AD tenant or the
registration process will fail.
API Permissions Type Description
Microsoft Graph Users.Read Delegated Sign in and read user profile
Universal Print Printers.Create Delegated Create (register) new printers
Universal Print Printers.Read Application Read printers
Universal Print PrintProperties.ReadWrite Application Read and write the properties and
attributes of printers
Universal Print PrinteJob.Read Application Read the metadata and payload of
users’ print jobs
Universal Print PrinteJob.ReadWriteBasic Application Read and write the metadata of
users’ print jobs
In order for Workplace Cloud to access the created web application in the customer’s tenant, the
customer must create a client secret under Certificates & Secrets for the new application. In
Workplace Cloud, the cloud company administrator must then supply the following information for
the app:
Tenant ID (from the Azure AD Tenant Overview)
Application ID (from the Web Application created for Workplace Cloud)
Client Secret (which was created as noted above)
As part of the registration process allowing Workplace Cloud to retrieve jobs submitted to the Azure
tenant’s Universal Print queue, the customer must also configure where the submitted jobs will be
stored once retrieve by Workplace Cloud. The locations correspond to the Azure sites used in the
deployment of Xerox® Workplace Cloud:
UK South
South Central US
Xerox® Workplace Cloud 5.6.1 – Security Guide 68
Page 71

The normal retention settings for the customer company account will apply to the Universal Print
jobs once retrieved by Workplace Cloud.
For more information on Microsoft Universal Print please see the latest documentation from
Microsoft here.
Xerox® Workplace Cloud 5.6.1 – Security Guide 69
Page 72

8. Additional Information and Resources
Security @ Xerox®
Xerox maintains an evergreen public web page that contains the latest security information
pertaining to its products. Please see https://www.xerox.com/security.
Responses to Known Vulnerabilities
Xerox has created a document which details the Xerox Vulnerability Management and Disclosure
Policy used in discovery and remediation of vulnerabilities in Xerox software and hardware. It can
be downloaded from this page: https://www.xerox.com/information-security/information-security-
articles-whitepapers/enus.html.
Additional Resources
Below are additional resources.
Security Resource URL
Frequently Asked Security Questions https://www.xerox.com/en-us/information-
security/frequently-asked-questions
Common Criteria Certified Products https://security.business.xerox.com/en-
us/documents/common-criteria/
Current Software Release Quick Lookup
Table
Bulletins, Advisories,
and Security Updates
Security News Archive https://security.business.xerox.com/en-us/news/
https://www.xerox.com/security
https://www.xerox.com/security
Xerox® Workplace Cloud 5.6.1 – Security Guide 70
 Loading...
Loading...