
Vodafone MachineLink
IPSec Configuration Guide

IPSec Configuration Guide – Vodafone MachineLink
2 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Document history
This guide covers the following products:
Vodafone MachineLink 3G (NWL-10)
Vodafone MachineLink 3G Plus (NWL-12)
Vodafone MachineLink 4G (NWL-22)
Ver.
Document description
Date
v. 1.0
Initial document release.
March 2013
v. 2.0
Revised content based on current firmware.
September 2016
Table i - Document revision history
Note – Before performing the instructions in this guide, please ensure that you have the latest firmware version installed on your router.
Visit http://vodafone.netcommwireless.com to download the latest firmware.
Note – The functions described in this document require that the router is assigned with a publicly routable IP address.
Please ensure that your mobile carrier has provided you with a publicly routable IP address before performing the instructions in this
document.
Copyright
Copyright© 2016 NetComm Wireless Limited. All rights reserved.
Copyright© 2016 Vodafone Group Plc. All rights reserved.
The information contained herein is proprietary to NetComm Wireless and Vodafone. No part of this document may be
translated, transcribed, reproduced, in any form, or by any means without prior written consent of NetComm Wireless
and Vodafone.
Trademarks and registered trademarks are the property of NetComm Wireless Limited or Vodafone Group or their
respective owners. Specifications are subject to change without notice. Images shown may vary slightly from the actual
product.
Note – This document is subject to change without notice.
IPSec Configuration Guide – Vodafone MachineLink
3 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Contents
Introduction ..................................................................................................................................................................................................................................... 4
Concepts and Basics ..................................................................................................................................................................................................................... 5
Site-to-site IPsec VPN pre-conditions .................................................................................................................................................................................................................................... 5
IKE Phase 1 and Phase 2 .............................................................................................................................................................................................................................................................. 6
IPsec VPN Web Interface ............................................................................................................................................................................................................. 8
Dead Peer Detection (DPD) mechanism .............................................................................................................................................................................................................................. 9
RSA Key mode .................................................................................................................................................................................................................................................................................. 9
Digital Certificate mode ............................................................................................................................................................................................................................................................ 10
IPsec VPN Configuration Examples .................................................................................................................................................................................... 11
IPsec VPN Tunnel (Cisco router/Pre-shared key mode) ............................................................................................................................................................................................ 11
IPSec VPN configuration .......................................................................................................................................................................................................................................................................................................... 12
Verify IPSec VPN connection status ................................................................................................................................................................................................................................................................................... 14
IPsec VPN Tunnel (Pre-shared Key mode) ....................................................................................................................................................................................................................... 14
IPsec VPN configuration for local router ........................................................................................................................................................................................................................................................................... 16
IPsec VPN configuration for remote router...................................................................................................................................................................................................................................................................... 17
Verify IPSec VPN connection status ................................................................................................................................................................................................................................................................................... 18
IPsec VPN tunnel (RSA Key mode) ....................................................................................................................................................................................................................................... 18
IPsec VPN RSA configuration for local router ................................................................................................................................................................................................................................................................. 21
IPsec VPN RSA configuration for remote router ............................................................................................................................................................................................................................................................ 22
Verify IPsec VPN connection status .................................................................................................................................................................................................................................................................................... 23
IPsec VPN Tunnel (Digital Certificate mode) ................................................................................................................................................................................................................... 24
IPsec VPN Digital Certificate configuration for local router ...................................................................................................................................................................................................................................... 26
IPsec VPN Digital Certificate configuration for remote router ................................................................................................................................................................................................................................. 27
Verify IPSec VPN connection status ................................................................................................................................................................................................................................................................................... 28
Notation
The following symbols are used in this user guide:
The following note requires attention.
The following note provides a warning.
The following note provides useful information.

IPSec Configuration Guide – Vodafone MachineLink
4 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Introduction
A VPN (Virtual private network) is a secure connection between two or more endpoints. It can also be seen as an
extension to a private network.
There are two key types of VPN scenarios:
Site-to-site VPN
Remote Access VPN
In a site-to-site VPN, data is encrypted from one VPN gateway to the other, providing a secure link between two sites
over an insecure third party network like the Internet.
In a remote access VPN scenario, a secure connection is made from an individual computer to a VPN gateway. This
enables users to access their e-mail, files and other resources at work from wherever they may be, providing they have
an Internet connection.
The Vodafone MachineLink router supports three types of Virtual Private Network (VPN) technologies:
Point-to-Point Tunnelling Protocol (PPTP) VPN
OpenVPN
Internet Protocol Security (IPsec) VPN
Point-to-Point Tunnelling Protocol (PPTP) VPN
PPTP works on a client server model. The Vodafone MachineLink router has a built-in PPTP client. Further details on how
to set up a PPTP VPN tunnel connection is described in a separate document.
OpenVPN
OpenVPN is an open source virtual private network (VPN) program for creating point-to-point or server-to-multi-client
encrypted tunnels between host computers. The Vodafone MachineLink router supports three different OpenVPN
modes:
OpenVPN Server
OpenVPN Client
OpenVPN Peer-to-Peer VPN connection.
Further details on how to set up an OpenVPN tunnel connection is described in a separate document.

IPSec Configuration Guide – Vodafone MachineLink
5 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Internet Protocol Security (IPsec) VPN
IPSec operates on Layer 3 and as such can protect higher layer protocols.
IPSec is used for both Site-to-site VPN and Remote Access VPN.
The Vodafone MachineLink router supports IPsec end points and can be configured with Site-to-site VPN tunnels with
other MachineLink routers or third party VPN routers.
Further configuration instructions for IPsec VPN tunnels on the M2M Series Router are provided in this document.
Concepts and Basics
Site-to-site IPsec VPN pre-conditions
When setting up a Site to Site VPN with IPsec, firstly check the following pre-conditions.
Make sure that there is connectivity between the two end points/VPN routers before you configure an IPsec VPN
tunnel between them.
For example, you may do a simple ‘Ping’ test between the two VPN end points/Routers to verify connectivity.
When a firewall or filtering router exists between IPSec peers, it must be configured to forward IPSec traffic on
UDP source and destination port 500, IP protocol 50 (Encryption Service Payload: ESP), or IP protocol 51
(Authentication Header: AH). If you are using IPSec NAT-T, the firewall or filtering router must also be configured
to forward IPSec traffic on UDP source and destination port 4500.
If there is no firewall or filtering router between the IPsec end points, the MachineLink router will automatically
create internal firewall rules to allow VPN tunnel connections to be established once an IPsec VPN is configured
on the management interface. This behaviour will occur regardless of whether the firewall setting is ‘Enabled’
under the web management interface > system > administration page.
The next step is to select an authentication method for use on the VPN Tunnel. This defines what authentication key
mode that you are going to use, either:
Pre-shared key
RSA key
Install a digital certificate

IPSec Configuration Guide – Vodafone MachineLink
6 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Please note that both VPN routers must use the same type of credentials (either both using pre-shared keys or both using digital certificates).
If pre-shared keys are used, then both routers’ keys would have to match each other.
In general, the pre−shared key method is the simplest to configure. Digital certificates require more complex configuration however they
provide a more scalable solution, better suited for enterprise use.
IKE Phase 1 and Phase 2
IPsec VPN's are configured and processed in two phases, Phase 1 and 2. They are also called the Internet Key Exchange
(IKE) phase 1 and IKE phase 2. In the Vodafone MachineLink router VPN web-based graphical user interface, the IKE
phase 2 parameters are named IPsec parameters.
IKE phase 1 focuses on establishing authentication and a secure tunnel for IKE phase 2 (IPsec tunnel) exchange. There
are two modes in IKE phase 1: the main mode or aggressive mode. The Main mode is more secure, but slower than the
aggressive mode. In Main mode, peers exchange identities with encryption whereas in aggressive mode, peers
exchange identities without encryption.
IKE phase 1 requires the following elements to be configured. Attributes of the points 2-6 below must match on both
VPN peers/routers before establishing an IKE phase 1 connection.
Remote peer IP or hostname
Key distribution method and authentication method: Pre-shared Key, RSA Key or Digital Certificates. If you use a
digital certificate you could generate all the required files using OpenSSL, an open source Certificate Authority
(CA).
Encryption Algorithm for confidentiality: DES, 3DES or AES, AES 128, 192, 256 bit key strength. AES is the
strongest protocol.
Hashing Algorithm for Data Integrity and authentication: SHA1 or MD5. SHA1 is the stronger authentication
algorithm.
Diffie−Hellman Group Level: This is a method of the establishment of a shared key over an insecure medium.
DH1, 2, 5, 14, 15, 16, 17 and 18 are available on the Vodafone MachineLink router.
IKE Security Association (SA) Lifetime in seconds: As a general rule, a shorter lifetime provides more secure IKE
negotiations. In the MachineLink router series routers, it is named the IKE rekey interval time in seconds.
IKE Phase 2 (IPsec) focuses on establishing secure IPsec tunnel for data transfer. IKE Phase 2 or IPsec requires the
following elements.
Transform set
This includes the encapsulation negotiation protocol to be used, either selecting Authentication Header (AH) or
Encryption Security Payload (ESP). The Authentication Header only provides authentication and data integrity.
The Encryption Security Payload provides authentication, data integrity and encryption. If you select ESP, you

IPSec Configuration Guide – Vodafone MachineLink
7 of 28
September 2016 v2.0
vodafone.netcommwireless.com
need to specify authentication (SHA1 or MD5) and encryption (DES, 3DES or AES 128, 192, or 256-bit key
strength). The transform set is used to transfer the clear text data to cipher text going across the IPsec tunnel.
Attributes in the transform set on both VPN routers and SA life time are required to be matched across both ends
of the tunnel.
Peer information
The IP address of the VPN routers.
Interesting traffic designation
Defines what traffic is to be sent encrypted to the remote VPN router and what traffic is expected to be encrypted
from the remote VPN router and vice versa. This is to specify what traffic will go across the VPN. An IP address,
Network address, or IP address range needs to be specified.
IPsec SA life time
The IPSec Security Association lifetime in the MachineLink router VPN configuration page is named the ‘SA Life’
Time.
There is another optional security parameter to the IPsec phase, which basically performs a Diffie-Hellman exchange of
the key when requesting a new IPsec SA. It is called Perfect Forward Secrecy (PFS). It ensures that a given IPsec SA key
was not derived from any other secret. If PFS is not enabled, someone can potentially break the IKE SA secret key, copy
all the IPsec protected data, and then use knowledge of the IKE SA secret in order to compromise the IPsec SAs setup
by this IKE SA. With PFS, breaking IKE does not give an attacker immediate access to IPsec. The attacker needs to break
each IPsec SA individually.
Note that these are the general steps in configuring your IPsec VPN router, and when you configure the peer VPN router, remember to
configure it with the exact same settings as you configured your local router or else the VPN tunnel will not form successfully.
IPSec Configuration Guide – Vodafone MachineLink
8 of 28
September 2016 v2.0
vodafone.netcommwireless.com
IPsec VPN Web Interface
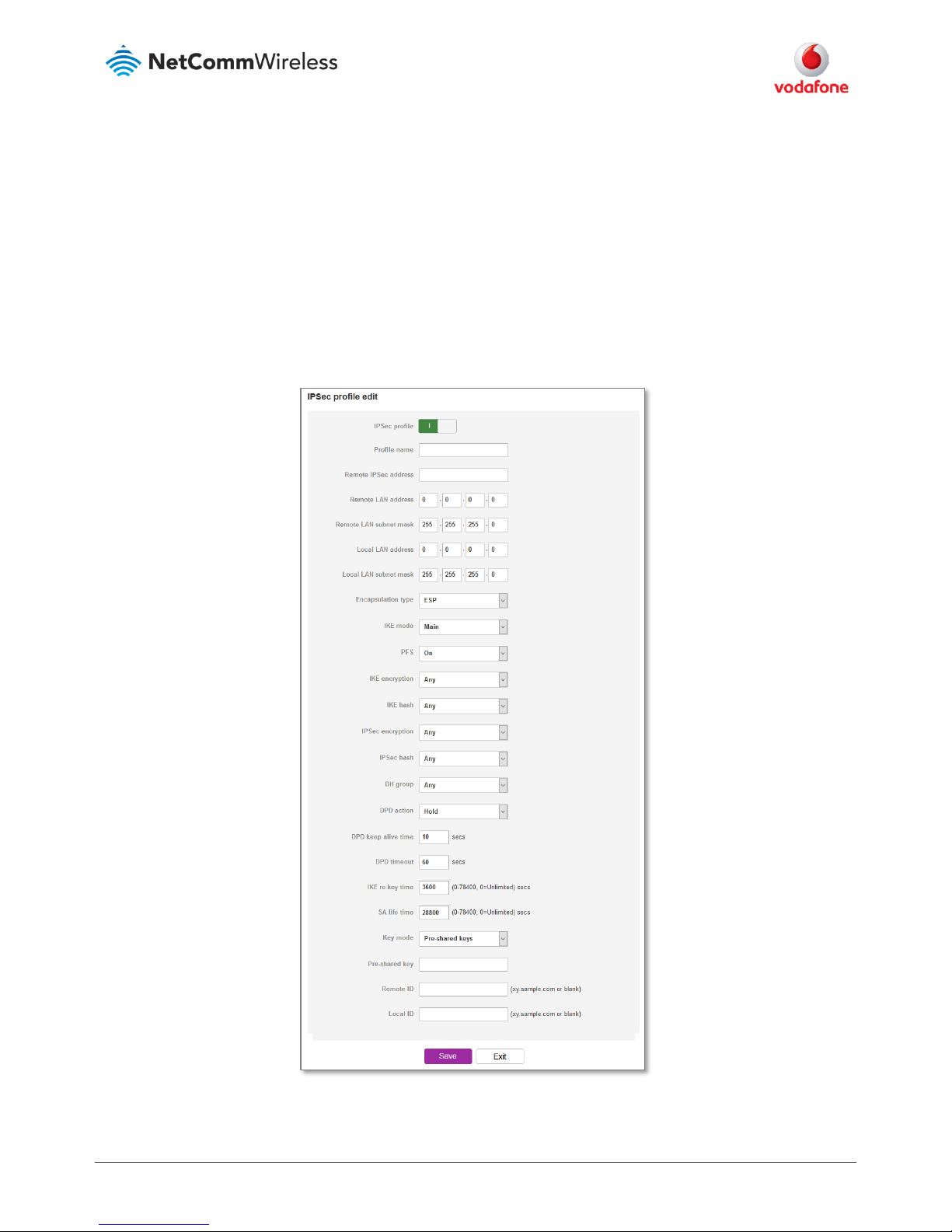
On the Vodafone MachineLink router, both the IKE phase 1 and phase 2 parameters are shown in one single
configuration page (Figure 1). Open the IPSec configuration page by clicking the Networking toolbar item, then open
the VPN menu item on the left and select IPSec.
The IPSEC tunnel list page appears, click the +Add button to open a new IPSec profile configuration edit page.
Figure 1 - IPSec Configuration Page of Web User Interface

IPSec Configuration Guide – Vodafone MachineLink
9 of 28
September 2016 v2.0
vodafone.netcommwireless.com
Dead Peer Detection (DPD) mechanism
The Vodafone MachineLink router supports Dead Peer Detection: A Traffic-Based method of detecting dead IKE peers.
DPD works using a keepalive system, when a tunnel is idle. Both sides attempt to exchange “hello” messages until the
DPD timeout value has elapsed. If there still hasn't been any traffic received, the peer is declared to be dead, and the
Security Association (SA) deleted, and related route removed from the table.
There are four DPD Action options:
None - the DPD mechanism is disabled. This is the default setting
Clear
Hold
Restart
The DPD Action parameter determines what the router does when a peer is determined to be dead. If set to "hold", the
router will place the entire tunnel into a “hold” status, and wait for the peer to return. If set to "clear" it will remove the
connection entirely. Lastly, Restart will recreate the tunnel after the dead peer is detected once again.
It is recommended that "Hold" be used for statically defined tunnels, and "Clear" be used for roadwarrior tunnels. Use
“Restart” if you want the tunnel connection to restart after dead peer detected.
There are two timer options:
DPD Keep Alive Time
DPD Timeout
Thus, the mechanism works as follows:
During idle periods, the router sends R_U_THERE packets every DPD_Keep_Alive_Time seconds.
If the tunnel is idle and the router havn’t received an R_U_THERE_ACK from our peer in DPD_Timeout seconds, the
router declares the peer dead, and clears the Security Association (SA). Hence the entire tunnel is removed. Note that
both sides must have either DPD Keep Alive Time or DPD Time out set for DPD to be proposed or accepted.
If one directive is set but not the other, the defaults are used (DPD Keep Alive Time=30, DPD Time Out =120).
RSA Key mode
RSA is an acronym composed of the first letter of each of its inventors' last names (Ronald Rivest, Adi Shamir, and
Leonard Adleman).
The RSA algorithm is a public-key cryptosystem that offers both encryption and digital signatures authentication. The
Vodafone MachineLink router has a built-in RSA key generator. The RSA public key of your router can be genreated by
 Loading...
Loading...