Page 1

vCloud Suite Architecture Overview and
Use Cases
vCloud Suite 5.8
This document supports the version of each product listed and
supports all subsequent versions until the document is
replaced by a new edition. To check for more recent editions
of this document, see http://www.vmware.com/support/pubs.
EN-001564-00
Page 2

vCloud Suite Architecture Overview and Use Cases
You can find the most up-to-date technical documentation on the VMware Web site at:
http://www.vmware.com/support/
The VMware Web site also provides the latest product updates.
If you have comments about this documentation, submit your feedback to:
docfeedback@vmware.com
Copyright © 2014 VMware, Inc. All rights reserved. Copyright and trademark information.
VMware, Inc.
3401 Hillview Ave.
Palo Alto, CA 94304
www.vmware.com
2 VMware, Inc.
Page 3

Contents
About this book 5
Introduction to vCloud Suite 7
1
List of vCloud Suite Components 7
Architecture Overview 11
2
Conceptual Design of a vCloud Suite Environment 13
vCloud Suite Components in the Management Cluster 15
Software-Defined Data Center Core Infrastructure 16
Delivering an Infrastructure Service 22
Delivering Platform as a Service 25
Deploying vCloud Suite 27
3
Install vCloud Suite Components 27
Update vCloud Suite Components 29
External Dependencies for Deploying vCloud Suite 30
System Requirements of vCloud Suite Components 31
Security Considerations 31
Licensing 41
vCloud Suite Use Cases 51
4
Disaster Recovery to Cloud 51
Infrastructure Provisioning 57
Index 63
VMware, Inc. 3
Page 4

vCloud Suite Architecture Overview and Use Cases
4 VMware, Inc.
Page 5

About this book
The vCloud Suite Architecture Overview and Use Cases publication provides information about the design and
capabilities of cloud environments based on VMware vCloud® Suite.
vCloud Suite is a collection of interoperable VMware products. vCloud Suite Architecture Overview and Use
Cases provides a listing of components, high-level design guidelines for vCloud Suite deployment and
operation, as well as example use cases.
The provided architecture overview is based on concepts from the practical approach used by the VMware
Professional Services organization.
vCloud Suite Architecture Overview does not include detailed installation and configuration instructions for
individual components. You can find that information in the dedicated documentation sets for individual
VMware products.
Intended Audience
This information is intended for IT professionals and business decision makers with prior knowledge of
virtualization and data center operations, who want to understand the capabilities of vCloud Suite and learn
about recommended deployment models and example use cases.
VMware Technical Publications Glossary
VMware Technical Publications provides a glossary of terms that might be unfamiliar to you. For definitions
of terms as they are used in VMware technical documentation, go to
http://www.vmware.com/support/pubs.
VMware, Inc.
5
Page 6

vCloud Suite Architecture Overview and Use Cases
6 VMware, Inc.
Page 7

Introduction to vCloud Suite 1
vCloud Suite lets you build and operate software-defined data centers based on vSphere. vCloud Suite
contains components that must be integrated to deliver IT as a service.
You download, install, and configure vCloud Suite components separately. When deployed and configured,
the interoperable components enable the software-defined data center (SDDC), where resources are
virtualized and available as a service. Control of the data center is fully automated by software, and
hardware configuration is maintained through software systems. vCloud Suite makes it possible for
workloads to run in private, public, or hybrid clouds.
Individual products in vCloud Suite are delivered as either installation packages for Windows or Linuxbased virtual appliances that you can deploy on ESXi hosts.
You can extend your vCloud Suite by using VMware vCloud Air as a second site in your datacenter
environment. Use vCloud Suite together with with the vCloud Air to satisfy business needs such as business
continuity and burst capacity.
vCloud Suite can serve the needs of different organizations, from SMBs to large enterprises and
organizations in the public sector.
List of vCloud Suite Components
A vCloud Suite edition contains individual products with different versions. To ensure interoperability, you
should verify that the components of your vCloud Suite environment are the correct versions.
vCenter Server is required for building the core inrastructure of the software-defined data center.
Table 1‑1. Components of vCloud Suite 5.8 and their versions
Product name Version Description
ESXi 5.5 Update 2 Provides bare-metal virtualization of
servers so you can consolidate your
applications on less hardware.
vCenter Server 5.5 Update 2 Provides a centralized platform for
managing vSphere environments.
vCenter Orchestrator 5.5.2 Provides the capability to create
workflows that automate activities
such as provisioning virtual machine,
performing scheduled maintenance,
initiating backups, and many others.
vCenter Update Manager 5.5 Update 2 Provides centralized, automated patch
and version management for vSphere
and offers support for ESXi hosts,
virtual machines, and virtual
appliances.
VMware, Inc. 7
Page 8

vCloud Suite Architecture Overview and Use Cases
Table 1‑1. Components of vCloud Suite 5.8 and their versions (Continued)
Product name Version Description
vCloud Networking and Security 5.5.3 Provides a security suite for vSphere.
vCloud Director 5.5.2 Provides the ability to build secure,
vCloud Automation Center 6.1 Provides functionality for deploying
vCloud Automation Center
Application Service
vCenter Operations Manager 5.8.3 Provides comprehensive visibility and
vCenter Configuration Manager 5.7.2 Provides automation of configuration
vCenter Hyperic 5.8.2 Provides monitoring of operating
vCenter Infrastructure Navigator 5.8.2 Provides automated discovery of
vSphere Replication 5.8 Provides replication, at the individual
vCenter Site Recovery Manager 5.8 Provides disaster recovery capability
vSphere Data Protection 5.8 Provides advanced data protection
vCloud Networking and Security
(formerly vShield) is a critical security
component for protecting virtualized
datacenters from attacks and misuse to
help you achieve your compliancemandated goals.
multi-tenant clouds by pooling virtual
infrastructure resources into virtual
datacenters.
and provisioning of business-relevant
cloud services across private and
public clouds, physical infrastructure,
hypervisors, and public cloud
providers.
vCloud Automation Center Enterprise
includes
vCloud Automation Center
Application Service.
6.1 Provides automated application
provisioning in the cloud including
deploying and configuring the
application's components and
dependent middleware platform
services on infrastructure clouds.
insights into the performance, capacity
and health of your infrastructure.
and compliance management across
your virtual, physical and cloud
environments, assessing them for
operational and security compliance.
systems, middleware and applications
running in physical, virtual, and cloud
environments.
application services, visualizes
relationships, and maps dependencies
of applications on virtualized
compute, storage and network
resources.
virtual machine disk level, between
datastores hosted on any storage.
that lets you perform automated
orchestration and nondisruptive
testing for virtualized applications.
with backup and recovery to disk via
VMware vSphere with Operations
Management Data Protection features.
8 VMware, Inc.
Page 9

Chapter 1 Introduction to vCloud Suite
Table 1‑1. Components of vCloud Suite 5.8 and their versions (Continued)
Product name Version Description
vSphere Big Data Extensions 2.0 Simplifies running Big Data workloads
on the vSphere platform.
vSphere App HA 1.1 Provides high availability for the
applications that are running on the
virtual machines in your environment.
vCenter Support Assistant 5.5.1.1 Provides proactive support, by
collecting support bundles on a
regular basis.
VMware, Inc. 9
Page 10

vCloud Suite Architecture Overview and Use Cases
10 VMware, Inc.
Page 11

Architecture Overview 2
To enable the full set of vCloud Suite features, you must perform a series of installation and configuration
operations. The software-defined data center provides different types of capabilities, with more complex
features building on top of underlying infrastructure.
Delivering the full operational capabilities of vCloud Suite to your organization or clients is a structured
process. In a large organization, it might involve cycles of assessment, design, deployment, knowledge
transfer, and solution validation. Depending on your organization, you should plan for an extended process
that involves different roles.
Not every environment needs the full scope of vCloud Suite capabilities at a given time. Start by deploying
the datacenter core infrastructure, because it enables you to add capabilities as your organization requires
them. Each of the software-defined data center layers might require you to plan and perform a separate
deployment process.
VMware, Inc.
11
Page 12

Self-service application
development
Application blueprinting
Application deployment
standardization
Infrastructure Service
Self-service user portal
Low administration
overhead
Management
Monitoring with performance
and capacity
Orchestration
Virtualization of physical compute, storage, and network assets
Catalogs and
standard templates
Software-defined Data Center Core Infrastructure
Application Platform Service
vCloud Suite Architecture Overview and Use Cases
Figure 2‑1. Layers of the Software-Defined Data Center
SDDC Core
Infrastructure
Infrastructure Service
Application Platform
Service
You can enhance your vCloud Suite environment by integrating additional products and services by
VMware, in order to enable capabilities such as disaster recovery to cloud, software-defined storage, and
software-defined networking. For information about implementing failover protection for virtual machines
in vCloud Air, see “Disaster Recovery to Cloud,” on page 51.
The basis of the vCloud Suite deployment is the resource abstraction layer.
By using VMware software, you can virtualize compute, network, and
storage resources in your data center and abstract them from the underlying
hardware. ESXi and vCenter Server enable you to establish a robust
virtualized environment into which all other solutions integrate. The
resource abstraction layer provides the foundation for the integration of
orchestration and monitoring solutions by VMware. Additional processes
and technologies build on top of the infrastructure to enable infrastructure as
a service and platform as a service.
Infrastructure services introduce fast, self-service provisioning of virtual
machines to physical, virtualized, or hybrid clouds. The IaaS layer is
represented mainly by vCloud Automation Center, which provides service
provisioning, catalog management, policy based management ,and
authorization.
The application platform service enables end-to-end deployment and
configuration of applications, along with their dependencies, to a target
deployment infrastructure.
12 VMware, Inc.
Page 13

Chapter 2 Architecture Overview
Conceptual Design of a vCloud Suite Environment on page 13
n
To start deploying vCloud Suite, you need a small number of physical hosts. Distribute your hosts into
three types of clusters, in order to establish the foundation of a deployment that can later scale to tens
of thousands of VMs.
vCloud Suite Components in the Management Cluster on page 15
n
The number of vCloud Suite components in the management cluster increases as you add capabilities.
A management cluster can contain a minimal set of products, and you expand it as needed.
Software-Defined Data Center Core Infrastructure on page 16
n
The core of vCloud Suite environments consists of vSphere and the associated monitoring and
orchestration products, such asvCenter Operations Manager and vCenter Orchestrator.
Delivering an Infrastructure Service on page 22
n
The ability to deliver infrastructure as a service represents the technological and organizational
transformation from traditional data center operations to cloud. The infrastructure service lets you
model and provision VMs and services across private, public, or hybrid cloud infrastructure.
Delivering Platform as a Service on page 25
n
Platform-as-a-Service (PaaS) lets you model and provision applications across private, public, and
hybrid cloud infrastructures.
Conceptual Design of a vCloud Suite Environment
To start deploying vCloud Suite, you need a small number of physical hosts. Distribute your hosts into three
types of clusters, in order to establish the foundation of a deployment that can later scale to tens of
thousands of VMs.
Management, Edge, and payload clusters run the entire vCloud Suite infrastructure, in addition to customer
workloads.
Deploying and leveraging vCloud Suite is a process that involves both technological transformation and
operational transformation. As new technologies are deployed in the data center, your organization must
also implement appropriate processes and assign the necessary roles.
In the diagram below, technological capabilities in color appear over organizational constructs in grayscale.
VMware, Inc. 13
Page 14
Organization
Operations
Provider
IT Business
Control
Service
Control
Operations
Control
Infrastructure
Control
Orchestration
Virtualization Management
Management cluster
Edge cluster Payload cluster
● Start with three hosts
● Start with three hosts
● Start with three hosts
● Start with two clusters
Load balancer
Tenant
Portal
IaaS, PaaS, ITaaS Engine
Portal
Performance
and
capacity
management
vCloud Suite Architecture Overview and Use Cases
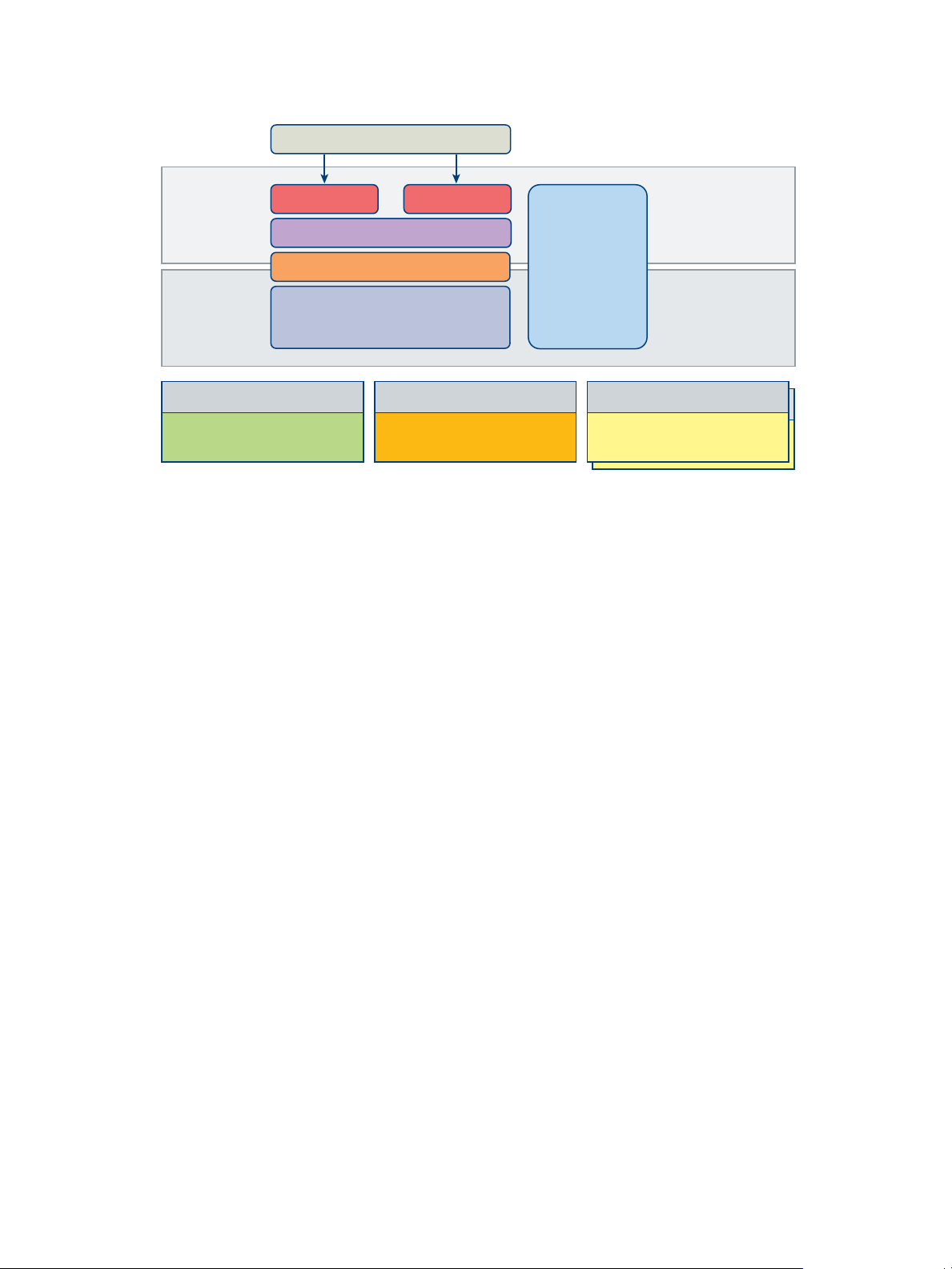
Figure 2‑2. Conceptual Design of a vCloud Suite environment
Management cluster
Edge cluster
Payload cluster
The hosts in the management cluster run all management components
required to support the software-defined data center. A single management
cluster is required within a physical location. ESXi hosts running in the
management cluster can be manually installed and configured to boot using
local hard drives.
A management cluster provides resource isolation. Production applications,
test applications, and other types of applications cannot use the cluster
resources reserved for management, monitoring, and infrastructure services.
Resource isolation helps management and infrastructure services to operate
at their best possible performance level. A separate cluster can satisfy an
organization's policy to have physical isolation between management and
production hardware.
The Edge cluster supports network devices that provide interconnectivity
between environments. It provides protected capacity by which internal data
center networks connect via gateways to external networks. Networking
edge services and network traffic management take place in the cluster. All
external facing network connectivity terminates in this cluster.
The ESXi hosts in the edge cluster are managed by a dedicated
vCenter Server instance paired with VMware vCloud Networking and
Security. Payload clusters that require access to external networks are
managed by the same vCenter Server instance. As the platform scales, you
should deploy additional Edge clusters to service specific groups of payload
clusters.
This specialized cluster will likely be small and can be made up of older, less
capable server systems when compared to the management and payload
clusters.
The payload cluster supports the delivery of all consumer workloads. The
cluster remains empty until a consumer of the environment begins to
populate it with virtual machines. You can scale up by adding more payload
clusters.
14 VMware, Inc.
Page 15
You can create new edge and payload clusters, scale up, or scale out, as the data center grows in size.
NOTE You can choose to combine the management and Edge clusters into a single entity. However, the
model with three types of clusters provides the best basis for scaling your environment.
vCloud Suite Components in the Management Cluster
The number of vCloud Suite components in the management cluster increases as you add capabilities. A
management cluster can contain a minimal set of products, and you expand it as needed.
Typically, you deploy more vCloud Suite components in the management cluster than you do in other types
of clusters.
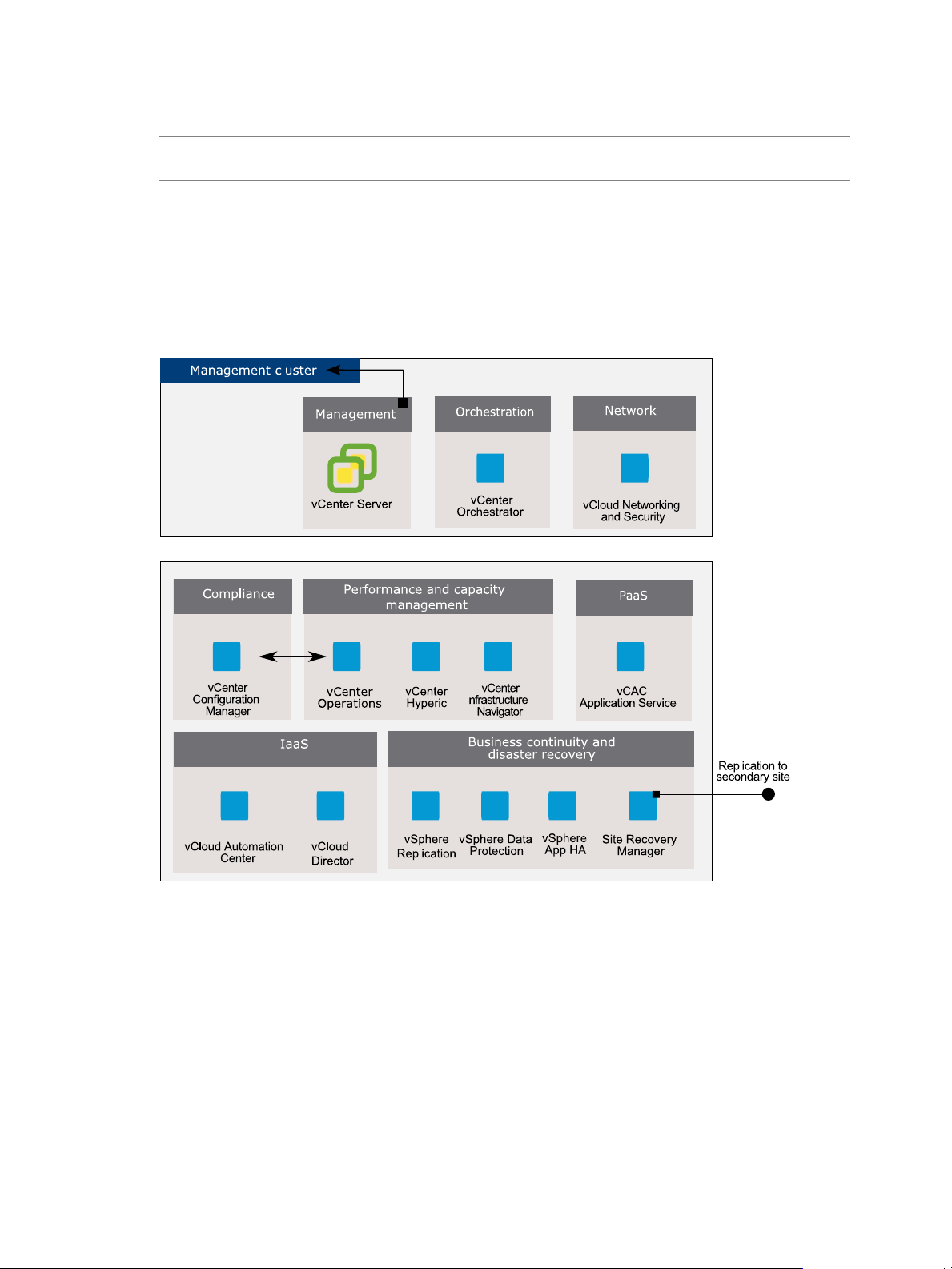
Figure 2‑3. VMware products in the management cluster
Chapter 2 Architecture Overview
Minimal set of
components
Extended set of
components
VMware, Inc. 15
An example set of VMware products required for the management cluster
always includes a vCenter Server instance. vCenter Orchestrator is a
vCloud Suite component that you should deploy at early stage, in order to
prepare the environment for IaaS and PaaS capabilities.
As the complexity of the environment increases, you install and configure
additional products. vCenter Operations Manager and related products
provide advanced monitoring features. vCloud Automation Center is the key
element of your IaaS solution. A vCenter Site Recovery Manager instance
provides replication to a secondary site.
Page 16

Virtualization
Orchestration Monitoring
SDDC
Infrastructure
Ready
vCloud Suite Architecture Overview and Use Cases
Software-Defined Data Center Core Infrastructure
The core of vCloud Suite environments consists of vSphere and the associated monitoring and orchestration
products, such asvCenter Operations Manager and vCenter Orchestrator.
The software-defined data center infrastructure layer includes the core virtualization, monitoring, and
orchestration sub-layers. The infrastructure enables consolidation and pooling of physical resources, in
addition to providing orchestration and monitoring capabilities, while reducing the costs associated with
operating an on-premise data center.
Once the SDDC infrastructure is in place, you can extend it to provide Infrastructure as a Service (IaaS) and
Platform as a Service (PaaS) offerings to consumers of IT resources inside or outside the organization. IaaS
and PaaS complete the SDDC platform, and provide further opportunities for extending capabilities. With
IaaS and PaaS, you increase the agility of IT and developer operations.
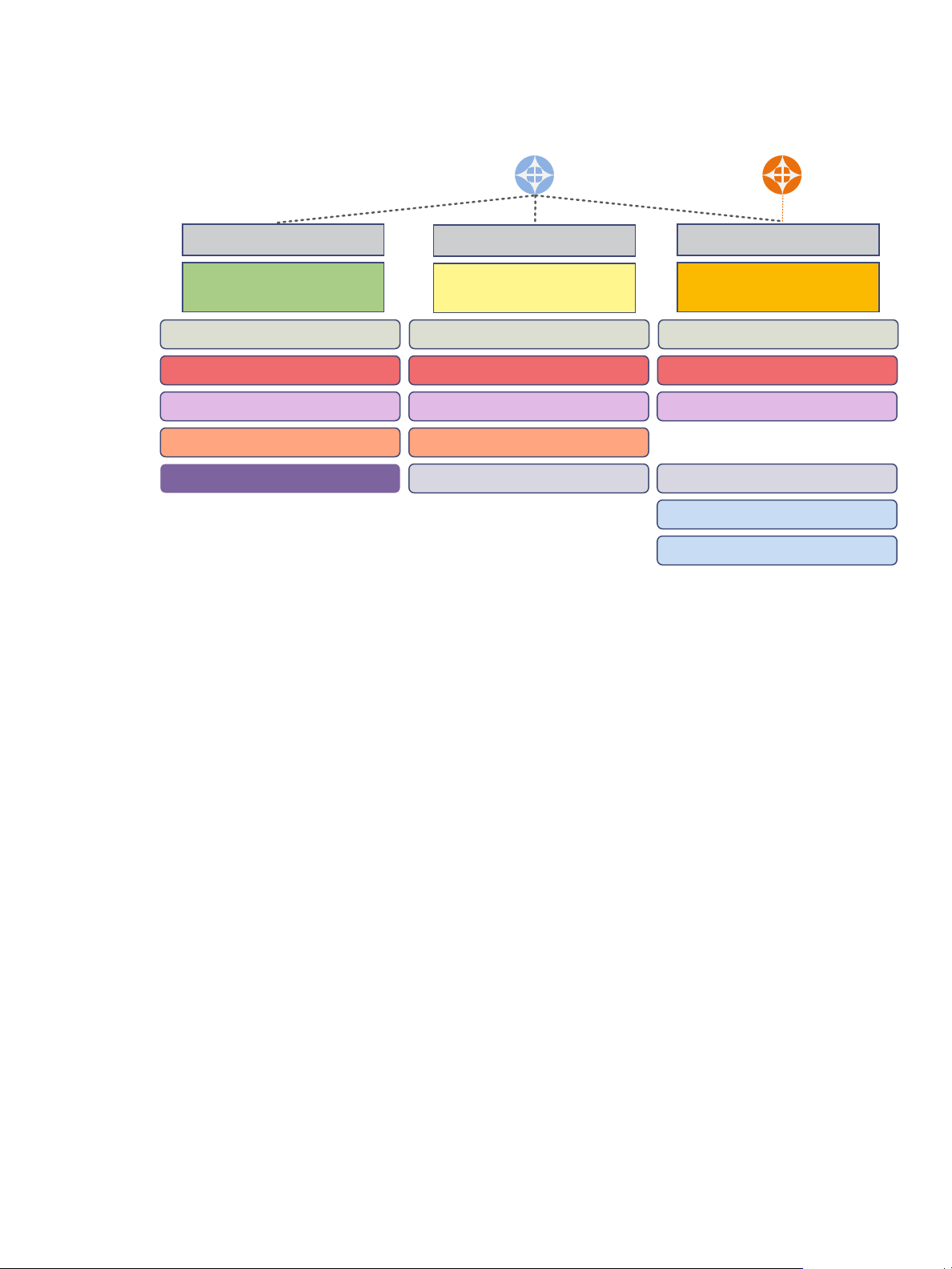
Figure 2‑4. The stages of building the software-defined data center infrastructure
Virtualization and Management as an Element of vCloud Suite Infrastructure on page 16
n
VMware products provide the virtualization and management capabilities required for the
vCloud Suite foundation. You should consider the design choices that are available to you.
Monitoring as an Element of vCloud Suite Core Infrastructure on page 19
n
Monitoring is a required element of a software-defined data center. The monitoring element provides
capabilities for performance and capacity management of related infrastructure components,
including requirements, specifications, management, and their relationships.
Orchestration as an Element of vCloud Suite Core Infrastructure on page 21
n
The software-defined data center requires orchestration capability. In vCloud Suite, you can use
vCenter Orchestrator to orchestrate processes by using workflows.
Virtualization and Management as an Element of vCloud Suite Infrastructure
VMware products provide the virtualization and management capabilities required for the vCloud Suite
foundation. You should consider the design choices that are available to you.
Virtualization and management components are the core of the software-defined data center. For
organizations of all sizes, they reduce costs and increase agility. Establishing a robust foundation for your
datacenter requires you to install and configure vCenter Server and ESXi, as well as supporting components.
ESXi and vCenter Server Design Considerations on page 17
n
Design decisions for the virtualization component of the software-defined data center must address
the deployment and support specifics of ESXi and vCenter Server.
Network Design Considerations on page 17
n
As virtualization and cloud computing become more popular in the data center, a shift in the
traditional three-tier networking model is taking place. The traditional core-aggregate-access model is
being replaced by the leaf and spine design.
Shared Storage Design Considerations on page 18
n
A proper storage design provides the basis for a virtual data center that performs well.
16 VMware, Inc.
Page 17

Chapter 2 Architecture Overview
ESXi and vCenter Server Design Considerations
Design decisions for the virtualization component of the software-defined data center must address the
deployment and support specifics of ESXi and vCenter Server.
Consider the following design decisions when planning the deployment of ESXi hosts.
ESXi
Use a tool such as VMware Capacity Planner to analyze the the performance and use of existing servers.
n
Use supported server platforms that are listed in the VMware Compatibility Guide at
n
http://www.vmware.com/resources/compatibility.
Verify that your servers meet the minimum required system requirements for running ESXi.
n
To eliminate variability and achieve a manageable and supportable infrastructure, standardize the
n
physical configuration of the ESXi hosts.
You can deploy ESXi hosts either manually or by using VMware Auto Deploy. One valid approach is to
n
deploy the management cluster manually, and implement Auto Deploy as your environment grows.
vCenter Server
You can deploy vCenter Server as a Linux-based virtual appliance or in a 64-bit Windows virtual
n
machine.
NOTE vCenter Server on Windows scales up to support up to 10,000 powered-on virtual machines. The
vCenter Server Virtual Appliance is an alternative choice that comes pre-configured and enables faster
deployment method along with reduced Microsoft licensing costs. When using an external Oracle
database, the vCenter Server Virtual Appliance can support a maxium of 3,000 virtual machines.
Provide sufficient virtual system resources for vCenter Server.
n
Deploy the vSphere Web Client and the vSphere Client for user interfaces to the environment. Deploy
n
the VMware vSphere Command-Line Interface, VMware vSphere PowerCLI, or VMware vSphere
Management Assistant for command-line and scripting management.
Network Design Considerations
As virtualization and cloud computing become more popular in the data center, a shift in the traditional
three-tier networking model is taking place. The traditional core-aggregate-access model is being replaced
by the leaf and spine design.
The network must be designed to meet the diverse needs of many different entities in an organization.
n
These entities include applications, services, storage, administrators, and users.
The network design should improve availability. Availability is typically achieved by providing
n
network redundancy
The network design should provide an acceptable level of security. Security can be achieved through
n
controlled access where required and isolation where necessary.
Simplify the network architecture by using a leaf and spine design.
n
Configure common port group names across hosts to support virtual machine migration and failover.
n
Separate the network for key services from one another to achieve greater security and better
n
performance.
Network isolation is often recommended as a best practice in the data center. In a vCloud Suite
environment, you might have several key VLANs, spanning two or more physical clusters.
VMware, Inc. 17
Page 18
Management cluster
Edge cluster
Payload cluster
VLAN ESXi/DHCP Helper
VLAN IP Storage
VLAN vMotion
VLAN Fault Tolerance
VLAN Management Server
VLAN Fault Tolerance
VLAN Transport/VXLAN VLAN Transport/VXLAN
VLAN Internet
VLAN DMZ
VLAN vMotion VLAN vMotion
VLAN IP Storage VLAN IP Storage
VLAN ESXi/DHCP Helper VLAN ESXi/DHCP Helper
Internet/DMZ
Sample ESXi host Sample ESXi host Sample ESXi host
vCloud Suite Architecture Overview and Use Cases
Figure 2‑5. Network isolation in the software-defined data center
ESXi/DHCP Helper
The helper network is used for PXE booting ESXi images by using Auto
Deploy.
IP Storage
Network storage traffic over Ethernet should be isolated for performance
and security reasons.
vMotion
vMotion traffic is not encrypted by default. Isolate the vMotion traffic to
increase security while migrating the state of virtual machines and the
contents of virtual disks between hosts.
Fault Tolerance
Management Server
Shared Storage Design Considerations
FT logging traffic should use a dedicated VLAN.
Management traffic between vCenter Server and ESXi hosts.
A proper storage design provides the basis for a virtual data center that performs well.
The storage design must be optimized to meet the diverse needs of applications, services,
n
administrators, and users.
Tiers of storage have different performance, capacity, and availability characteristics.
n
Designing different storage tiers is cost efficient, given that not every application requires expensive,
n
high-performance, highly available storage.
n
Fibre Channel, NFS, and iSCSI are mature and viable options to support virtual machine needs.
18 VMware, Inc.
Page 19

Chapter 2 Architecture Overview
Monitoring as an Element of vCloud Suite Core Infrastructure
Monitoring is a required element of a software-defined data center. The monitoring element provides
capabilities for performance and capacity management of related infrastructure components, including
requirements, specifications, management, and their relationships.
VMware monitoring components in vCenter Operations Manager Suite include the following products:
Table 2‑1. Monitoring products in vCloud Suite
Monitoring component Description
vCenter Operations Manager Provides comprehensive visibility and insights into the
performance, capacity and health of your infrastructure.
vCenter Infrastructure Navigator Automatically discovers application services, visualizes
relationships and maps dependencies of applications on
virtualized compute, storage and network resources.
vCenter Hyperic Monitors application health and is fundamental to the
operation of VMware AppHA.
A subset of the products can be deployed without damaging the integrity of the solution.
vCenter Operations Manager is distributed as virtual appliance that you can deploy on ESXi hosts. You
need to configure the virtual appliance and register it with a vCenter Server system. For an in-depth
discussion of vCenter Operations Manager and related products, see
https://www.vmware.com/support/pubs/vmware-vcops-suite-pubs.html.
VMware, Inc. 19
Page 20
vCenter
vCenter Operations vApp
UI VM
Admin
WebApp
Custom
WebApp
vSphere
WebApp
Capacity Analytics
Postgres
DB
Postgres
DB
FSDB
DB
ActiveMQ
Collector
Analytics VM
Performa nce Analytics
VPN
Hyperic
Log Insight
Network
Complia nce
Storage
Adapters enabled
Management Cluster
Edge Cluster
Payload Clusters
vCenter
vCenter Adapter
vCloud Suite Architecture Overview and Use Cases
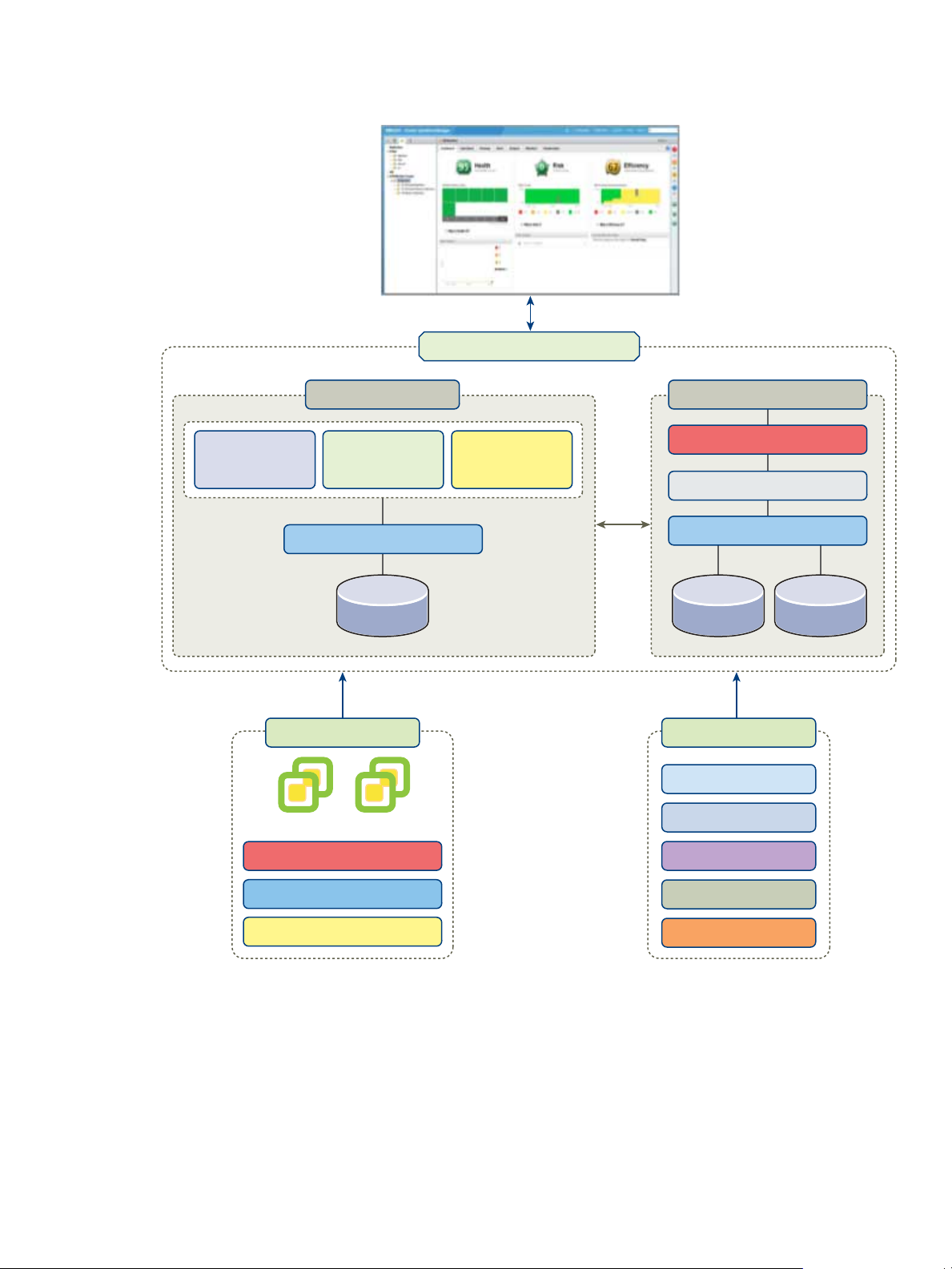
Figure 2‑6. Monitoring with vCenter Operations Manager
The vCenter Operations Manager vApp contains two virtual machines. One of the virtual machines runs the
analytics engine, and the other runs the user interface component. Plug-ins enable you to add additional
functionality, according to the needs of your environment. You can use and configure vCenter Operations
Manager by using the Web-based interface.
20 VMware, Inc.
Page 21
vCenter Orchestrator
configuration
vCenter Orchestrator
design
vCO plug-ins
Embedded
database
Authentication
AD, LDAP or SSO
vCenter Server
Multi Node
AD
vCenter Orchestrator Appliance
Plug-ins enabled
Chapter 2 Architecture Overview
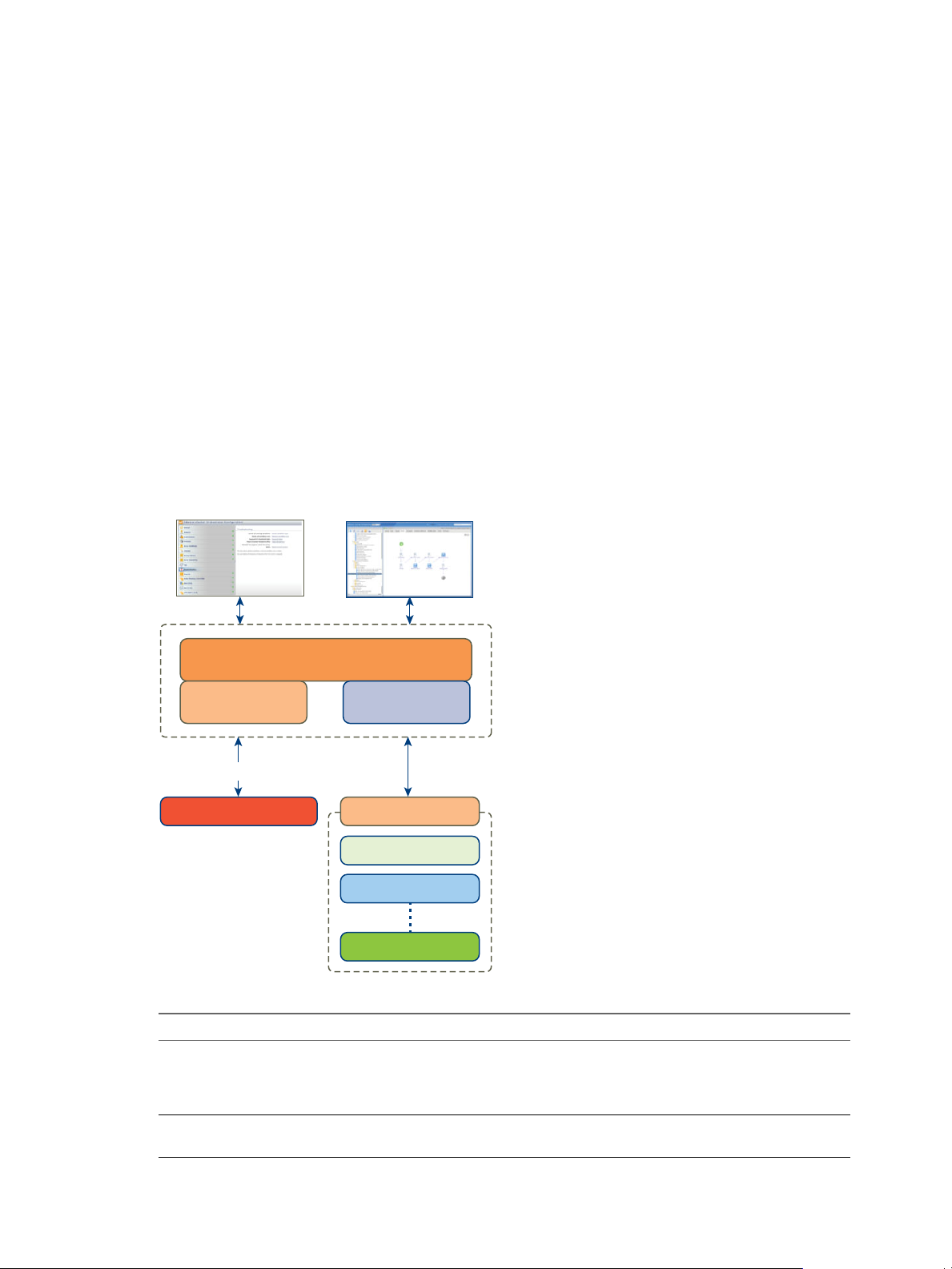
Orchestration as an Element of vCloud Suite Core Infrastructure
The software-defined data center requires orchestration capability. In vCloud Suite, you can use vCenter
Orchestrator to orchestrate processes by using workflows.
The orchestration layer of the software-defined data center provides the ability to build macro-like
workflows that automate manual processes and is instrumental when delivering repeatable operations.
Traditionally, orchestration is implemented when the Infrastructure Service and Platform Application
Service layers of the SDDC solution are being considered. In the IaaS layer, vCloud Automation Center can
trigger vCenter Orchestrator workflows, and you can publish workflows in your service catalog.
Establishing the orchestration engine early in the process benefits all levels of customer maturity and
provides a foundation that the rest of the solution builds on. You should deploy one vCenter Orchestrator
instance for each vCenter Server system in your environment.
The main elements of the orchestration layer are:
vCenter Orchestrator
n
vCenter Orchestrator plug-ins
n
Figure 2‑7. Design of the orchestration layer
VMware, Inc. 21
Table 2‑2. Components of vCloud Suite orchestration
Component Description
vCenter Orchestrator Appliance You can deploy vCenter Orchestrator as a virtual
Authentication Authentication can be provided by Active Directory or
appliance. The vCenter Orchestrator Appliance, running in
stand-alone mode (not HA) is the recommended approach
for deployment.
vCenter Single Sign-on.
Page 22

vCloud Suite Architecture Overview and Use Cases
Table 2‑2. Components of vCloud Suite orchestration (Continued)
Component Description
vCenter Orchestrator configuration interface The Web-based interface where you configure the
vCenter Orchestrator designer interface The Web-based interface where your create and customize
vCenter Server plug-in An Orchestrator plug-in that lets you manage multiple
Multi Node plug-in An Orchestrator plug-in that provides remote vCO
Delivering an Infrastructure Service
The ability to deliver infrastructure as a service represents the technological and organizational
transformation from traditional data center operations to cloud. The infrastructure service lets you model
and provision VMs and services across private, public, or hybrid cloud infrastructure.
In the software-defined data center, provider groups or organizations can isolate and abstract resources in
the form of infrastructure and application services, and make them available to tenant groups or
organizations.
appliance database, SSL certificate, license, and so on.
workflows.
vCenter Server instances. The vCenter Server plug-in
provides a library of standard workflows that automate
vCenter Server operations.
management and remote workflow execution.
The Infrastructure Service layer delivers a self-service user portal that lowers administrative overhead
through the use of policies to provision infrastructure services. Policies allow administrators to control the
consumption of services in a granular and flexible fashion. The portal also provides robust approval
capabilities.
The core of the IaaS layer is the vCloud Automation Center virtual appliance that you must deploy on an
ESXi host and configure.
You can build the infrastructure service core by using the following components:
Table 2‑3. Infrastructure service components
Infrastructure service section Design components
vCloud Automation Center virtual appliance
vCloud Automation Center IaaS
Distributed execution vCloud Automation Center distributed execution
Integration vCloud Automation Center Agent machines
Cost management IT Business Management
vCloud Automation Center Portal Web/App server
n
vCloud Automation Center vPostgreSQL database
n
vCloud Automation Center IaaS Web server
n
vCloud Automation Center IaaS Manager services
n
managers:
Orchestrator
n
Workers
n
22 VMware, Inc.
Page 23

Table 2‑3. Infrastructure service components (Continued)
Self-Service
Portal
Infrastructure
Components
Services and
Tenants
Cost
Management
Infrastructure
Service Ready
Infrastructure service section Design components
Provisioning infrastructure
Supporting infrastructure
vSphere environment
n
vCloud Director environment
n
vCenter Orchestrator environment
n
Other supported physical, virtual, or cloud
n
environment
Microsoft SQL database environment
n
vPostgresSQL database environment (if not embedded
n
in the virtual appliance)
LDAP or Active Directory environment
n
SMTP and email environment
n
The stages of deploying an infrastructure service are illustrated in the graphic below.
Figure 2‑8. IaaS components
Chapter 2 Architecture Overview
For an in-depth discussion of key IaaS concepts, see the vCloud Automation Center documentation.
Self-service portal
vCloud Automation Center provides a secure portal where authorized
administrators, developers or business users can request new IT services.
Infrastructure
Components
Services and Tenants
vCloud Automation Center requires you to configure vSphere endpoints,
Fabric groups, and blueprints.
The service catalog provides a unified self-service portal for consuming IT
services. Users can browse the catalog to request items they need, track their
requests, and manage their provisioned items.
Cost Management
Understanding and controlling costs is an important SDDC feature. Cost
management capability is solutions that integrate with vCloud Automation
Center, such as VMware ITBM.
VMware, Inc. 23
Page 24
Private Network
External Network
Resource Providers
Fabric Groups Fabric Groups
Developers Group
Production Groups Validation Groups
Marketing Groups
Resources on demand Resources on demand
apps
OS
DB
OS
vSE
vSE
DB
OS
apps
OS
DB
OS
apps
OS
Tenant 1
apps
OS
DB
OS
vSE
DB
OS
apps
OS
DB
OS
apps
OS
Tenant 2
Private Network
Private Network
Internet
Corporate
External Network
vSphere Resources
vCloud Resources
External Resources
vCloud Suite Architecture Overview and Use Cases
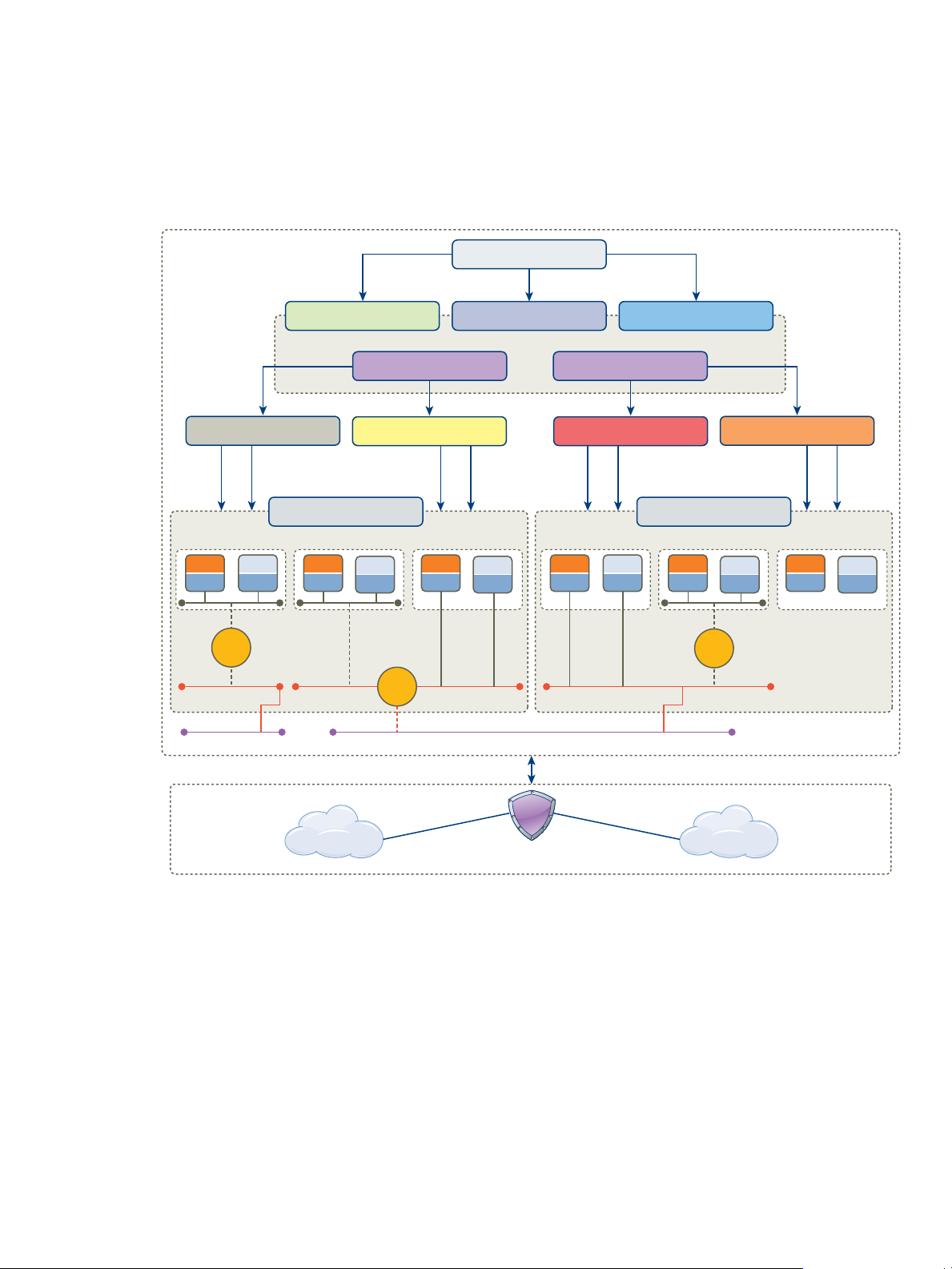
Conceptual Design of an IaaS Environment
In a vCloud Suite environment that is configured to deliver infrastructure as a service, tenants have access to
compute, network, and storage resources that have been preconfigured for them by the provider.
Figure 2‑9. Conceptual diagram of an IaaS environment
Resource providers
Providers are groups in the organization that configure and support the
underlying virtual infrastructure.
Fabric Groups
Fabric groups organize virtualization compute resources and cloud
endpoints by type and intent. An IaaS administrator also assigns one or more
fabric administrators to manage the resources in the fabric group.
Business Groups
Create business groups to associate a set of services and resources to a set of
users, often corresponding to a line of business, department, or other
organizational unit. Users must belong to a business group to request
machines.
24 VMware, Inc.
Page 25

Chapter 2 Architecture Overview
Tenants
The networks in the example diagram are routed by using vShield Edge instances, which in turn connect to
internal and external networks.
Tenant can represent business units in a company that subscribe to cloud
services from a service provider. Each tenant has its own dedicated
configuration. Some system-level configuration is shared across tenants.
Delivering Platform as a Service
Platform-as-a-Service (PaaS) lets you model and provision applications across private, public, and hybrid
cloud infrastructures.
PaaS is a type of cloud computing service that provides a computing platform and a solution stack as a
service. Along with Software-as-a-Service (SaaS) and Infrastructure-as-Service (IaaS), PaaS is a service model
of cloud computing that lets you create an application (or service) using tools and libraries supplied by the
provider. You control software deployment and configuration settings. The provider provides the networks,
servers, storage, and other services required to host your application.
Automate Application Provisioning
A key aspect of PaaS is the ability to automate the provisioning of applications. VMware vCloud
Automation Center is a model-based application provisioning solution that simplifies creating and
standardizing application deployment topologies on cloud infrastructures. Application architects use the
drag-and-drop interface to create application deployment topologies called application blueprints. These
application blueprints define the structure of the application, enable the use of standardized application
infrastructure components, and include installation dependencies and default configurations for custom and
packaged enterprise applications. You can use the prepopulated and extensible catalog of standard logical
templates, application infrastructure service, components, and scripts to model an application blueprint.
These blueprints standardize the structure of the application, including software components,
dependencies, and configurations, for repeated deployments. Application blueprints are logical deployment
topologies that are portable across VMware-based IaaS clouds such as vCloud Director and vCloud
Automation Center, and across public clouds such as Amazon EC2.
Using vCloud Automation Center, you "declare" the application and service structure with the assumption
that the underlying cloud infrastructure will deliver the necessary compute, network and storage
requirements. Once built you can deploy the blueprints on any VMware vSphere-based private or public
cloud, delivering on the cloud promise of choice. This application provisioning model frees developers and
application administrators from dealing with infrastructure, OS, and middleware configuration issues, and
allows you to focus on delivering business value with your applications.
Enterprise users can standardize, deploy, configure, update, and scale complex applications in dynamic
cloud environments. These applications can range from simple Web applications to complex custom
applications and packaged applications. With its catalog of standard components, or services, vCloud
Application Director automates and manages the update life cycle of deployments for multi-tier enterprise
applications in hybrid cloud environments.
Monitor Application Performance
Monitoring provides capabilities for performance management related to applications.
Pre-built Application Components
VMware Cloud Management Marketplace provides blueprints, services, scripts and plugins that you can
download and use to more rapidly develop your own application services. The pre-built components are
provided by leading middleware, networking, security and application vendors using highly reusable and
flexible configurations that you can insert into any multi-tier application-provisioning plan.
VMware, Inc. 25
Page 26

vCloud Suite Architecture Overview and Use Cases
26 VMware, Inc.
Page 27

Deploying vCloud Suite 3
To leverage the capabilities of vCloud Suite, you must install its components separately and ensure that the
required prerequisites and configuration requirements are met.
This book provides high-level design recommendations and deployment sequences. For installation
instructions and in-depth discussions of individual vCloud Suite components, see the documentation for
those products.
This chapter includes the following topics:
“Install vCloud Suite Components,” on page 27
n
“Update vCloud Suite Components,” on page 29
n
“External Dependencies for Deploying vCloud Suite,” on page 30
n
“System Requirements of vCloud Suite Components,” on page 31
n
“Security Considerations,” on page 31
n
“Licensing,” on page 41
n
Install vCloud Suite Components
VMware, Inc.
Follow the recommended sequence of installation to build a stable and scalable vCloud Suite environment.
The recommended installation sequence has been verified for a greenfiled virtual environment.
NOTE If you want to use vCenter Operations Manager to monitor applications, you must install
vCenter Infrastructure Navigator first. If you want to use vSphere App HA, you must install
vCenter Hyperic first.
You download and install vCloud Suite components separately. Depending on the type of cluster that you
are building, you might need to omit some components from the installation sequence.
Prerequisites
Verify that you have system resources that are sufficient for the deployment of vCloud Suite components.
Verify that your environment meets the requirements for external dependencies. See “External
Dependencies for Deploying vCloud Suite,” on page 30.
Verify that you have a valid vCloud Suite license. See “Licensing,” on page 41.
27
Page 28

vCloud Suite Architecture Overview and Use Cases
Procedure
1 Install ESXi.
If you install vCenter Server on a physical machine, you can install vCenter Server first.
See Installing ESXi.
2 Install vCenter Server.
See Installing vCenter Server.
3 Install vCloud Networking and Security.
See vShield Installation and Upgrade Guide.
4 Install the following suite components:
Product Installation instructions
vCenter Orchestrator Installing Orchestrator
vCloud Automation Center Installing vCloud Automation Center
vCenter Operations Manager Deployment and Configuration Guide
vCloud Director Installation and Upgrade Guide
5 Install the following suite components:
Product Installation instructions
vCloud Automation Center Application Service Installing vCloud Application Director
vCenter Hyperic vCenter Hyperic Installation and Configuration
6 Install the following suite components:
Product Installation instructions
vCenter Site Recovery Manager Installing SRM
vSphere Replication Installing vSphere Replication
vCenter Infrastructure Navigator Installation and Configuration Guide
vSphere Data Protection Administration Guide
vSphere Big Data Extensions Installing Big Data Extensions
vCenter Configuration Manager Installation Guide
7 Install the following suite components:
Product Installation instructions
vShield Edge vShield Installation and Upgrade Guide
vShield App vShield Installation and Upgrade Guide
vShield Endpoint vShield Installation and Upgrade Guide
vCenter Update Manager Installing Update Manager
28 VMware, Inc.
Page 29

Update vCloud Suite Components
Updating vCloud Suite components to newer versions requires you to perform separate update procedures.
Follow the recommended update order to ensure that vCloud Suite updates complete without problems.
You should perform the update operations according to the recommeded sequence. Some of the products in
the sequence are bundled in groups. You can install the products that belong to a specific group in any
order.
Prerequisites
Verify that you have the required installation or upgrade packages.
n
Verify that you have administrator privileges for all systems.
n
Procedure
1 Upgrade vCloud Automation Center.
See Upgrading to vCloud Automation Center 6.1.
2 Update the following components:
Product Update documentation
vCloud Automation Center Application Service Upgrade Guide
vCenter Configuration Manager Installation Guide
vCloud Director Upgrading vCloud Director
Chapter 3 Deploying vCloud Suite
You can migrate data from Application Director to a
fresh installation of
vCloud Automation Center Application Service.
3 Update vCloud Networking and Security.
See vShield Installation and Upgrade Guide.
4 Update vCenter Server.
See Upgrading vCenter Server.
5 Update vCenter Orchestrator.
Installing and Upgrading Orchestrator.
6 Update the following components:
Product Update documentation
vCenter Site Recovery Manager Upgrading SRM
vSphere Replication Upgrading vSphere Replication
vCenter Operations Manager Deployment and Configuration Guide
vSphere Data Protection Administration Guide
vCenter Infrastructure Navigator Installation and Configuration Guide
vCenter Hyperic vCenter Hyperic Installation and Configuration
vSphere Big Data Extensions Upgrading Big Data Extensions
VMware, Inc. 29
Page 30

vCloud Suite Architecture Overview and Use Cases
7 Update ESXi.
See Upgrading Your Hosts.
You should update VMware tools on your VMs after the ESXi update.
8 Update the following components:
Product Installation instructions
vShield Edge vShield Installation and Upgrade Guide
vShield App vShield Installation and Upgrade Guide
vShield Endpoint vShield Installation and Upgrade Guide
You have updated vCloud Suite components.
External Dependencies for Deploying vCloud Suite
External dependencies address other systems or technologies that depend on or might be affected by the
vCloud Suite infrastructure.
Table 3‑1. External Dependencies in vCloud Suite
Component Description
Active Directory Active Directory is required to implement and operate the
vCloud Suite infrastructure.
DNS DNS must be configured for connectivity between
vCenter Server, Active Directory, ESXi hosts, and virtual
machines.
DHCP/TFP PXE boot is required for vSphere Auto Deploy
functionality.
64-bit Windows OS Some vCloud Suite components can be installed on
Windows Server 2008 and later. vCloud Director requires
RHEL or CentOS Linux.
Microsoft SQL or Oracle database vCloud Suite components can work with embedded or
external databases, depending on the product and your
environment.
Network infrastructure Network infrastructure with 1Gbps or 10Gbps switches.
Depending on the needs of your environment, higher
throughput is recommended.
Storage Area Network Stability and performance of the SAN affects the virtual
machines.
Time synchronization Accurate time keeping and time synchronization is critical
for a healthy vSphere infrastructure. All components,
including ESXi hosts, vCenter Server, the SAN, physical
network infrastructure, and virtual machine guest
operating systems must have accurate time keeping. This is
especially critical for virtual machines protected by FT.
Staff Properly trained IT staff is critical for the correct
implementation, operation, support, and enhancement of
your environment.
Policies and procedures The policies and procedures governing the use of
information technology must be revised to properly
incorporate the unique properties and capabilities of
virtualization and cloud operations.
30 VMware, Inc.
Page 31

System Requirements of vCloud Suite Components
The software and hardware requirement for vCloud Suite depend on the set of components that you have
deployed. Information for each product or feature is available in the individual product documentation sets.
Documentation resources
Table 3‑2. List of system requirements documentation for vCloud Suite 5.8 components
Product System requirements documentation
vSphere System Requirements
vCenter Orchestrator Orchestrator System Requirements
vCenter Update Manager System Requirements
vCloud Networking and Security vShield Installation and Upgrade Guide
vCloud Automation Center Preparing for Installation
vCloud Automation Center Application Service System Requirements
vCenter Operations Manager Deployment and Configuration Guide
vCenter Configuration Manager Installation Guide
vCenter Hyperic Supported Configurations and System Requirements
vCenter Infrastructure Navigator Installing vCenter Infrastructure Navigator
vCloud Director Hardware and Software Requirements
vSphere Replication Installing vSphere Replication
vCenter Site Recovery Manager SRM System Requirements
Chapter 3 Deploying vCloud Suite
Security Considerations
The vSphere platform is an inherently secure environment from a technical standpoint, with a minimal
hypervisor footprint, APIs for monitoring that eliminate the need for third-party software on the host,
secure syslog activity, Active Directory integration, and more. There are however several guidelines for
securing a vSphere implementation. See the vSphere hardening guide for detailed configurations.
For a detailed discussion of security considerations for the SDDC core layer, see vSphere Security.
Security and Virtual Machines on page 32
n
Virtual machines are the containers in which applications and guest operating systems run. By design,
all VMware virtual machines are isolated from one another. This isolation enables multiple virtual
machines to run securely while sharing hardware and provides both their ability to access hardware
and their uninterrupted performance.
Security and Virtual Networks on page 34
n
If an ESXi host is accessed through vCenter Server, it is typical to protect vCenter Server using a
firewall. This firewall provides basic protection for the network.
Securing Virtual Machines with VLANs on page 34
n
The network can be one of the most vulnerable parts of any system. The virtual machine network
requires as much protection as its physical counterpart. Virtual Machine network security can be
enhanced in several ways, including through the use of virtual local area networks (VLANS).
VMware, Inc. 31
Page 32

vCloud Suite Architecture Overview and Use Cases
Securing Standard Switch Ports on page 36
n
As with physical network adapters, a virtual network adapter can send frames that appear to be from
a different machine or impersonate another machine so that it can receive network frames intended for
that machine. Also, like physical network adapters, a virtual network adapter can be configured so
that it receives frames targeted for other machines.
Securing iSCSI Storage on page 37
n
The storage configured for a host might include one or more storage area networks (SANs) that use
iSCSI. When iSCSI is configured on a host, several measures can be taken to minimize security risks.
Securing ESXi and the ESX Management Interfaces on page 38
n
Security of the ESXi management interface is critical to protect against unauthorized intrusion and
misuse. If a host is compromised in certain ways, the virtual machines it interacts with might also be
compromised. To minimize the risk of an attack through the management interface, ESXi is protected
with a firewall.
Securing vCenter Server Systems on page 39
n
Securing vCenter Server includes ensuring security of the host where vCenter Server is running,
following best practices for assigning privileges and roles, and verifying the integrity of the clients that
connect to vCenter Server.
Encryption and Security Certificates on page 39
n
ESXi and vCenter Server support standard X.509 version 3 (X.509v3) certificates to encrypt session
information sent over Secure Socket Layer (SSL) protocol connections between components. If SSL is
enabled, data is private, protected, and cannot be modified in transit without detection.
vCenter Single Sign-On on page 39
n
vCenter Single Sign-On is a component of the management infrastructure that provides the capability
to manage the environment with Active Directory credentials.
Security and Virtual Machines
Virtual machines are the containers in which applications and guest operating systems run. By design, all
VMware virtual machines are isolated from one another. This isolation enables multiple virtual machines to
run securely while sharing hardware and provides both their ability to access hardware and their
uninterrupted performance.
Even a user with system administrator privileges on a virtual machine's guest operating system cannot
breach this layer of isolation to access another virtual machine without privileges explicitly granted by the
ESXi system administrator. As a result of virtual machine isolation, if a guest operating system running in a
virtual machine fails, other virtual machines on the same host continue to run. The guest operating system
failure has no effect on:
The ability of users to access the other virtual machines.
n
The ability of the operational virtual machines to access the resources they need.
n
The performance of the other virtual machines.
n
Each virtual machine is isolated from other virtual machines running on the same hardware. Although
virtual machines share physical resources such as CPU, memory, and I/O devices, a guest operating system
on an individual virtual machine cannot detect any device other than the virtual devices made available to
it.
32 VMware, Inc.
Page 33
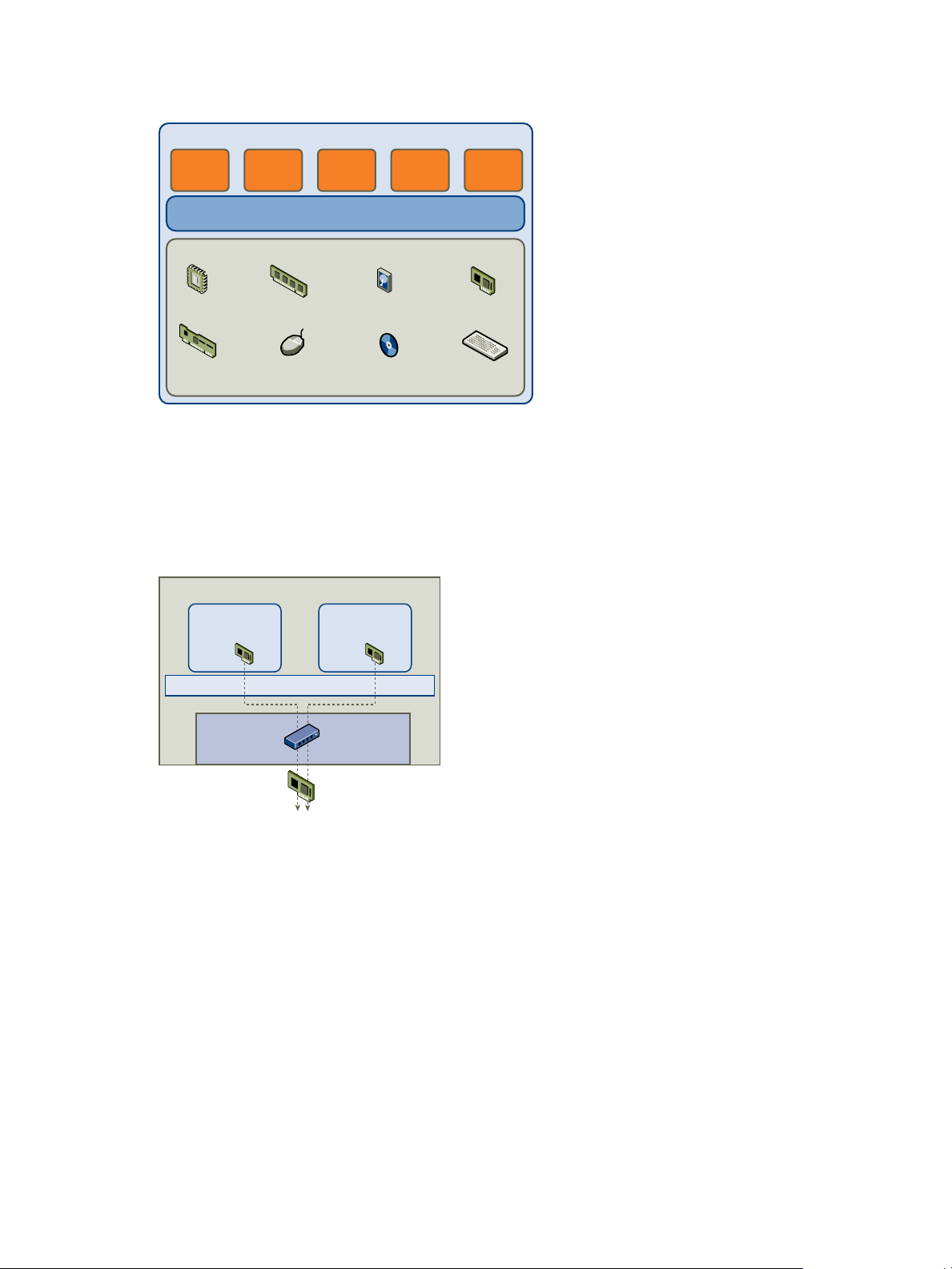
CPU memory disk network and
video cards
SCSI
controller
mouse CD/DVD keyboard
Virtual Machine
Operating System
Virtual Machine Resources
app app app app app
Hardware Network Adapter
links virtual machines to
the physical network
Physical Network
virtual
network
adapter
ESXi
Virtual Machine
virtual
network
adapter
Virtual Machine
VMkernel
Virtual
Networking
Layer
Virtual Switch
links virtual
machines together
Chapter 3 Deploying vCloud Suite
Figure 3‑1. Virtual Machine Isolation
Because the VMkernel mediates the physical resources and all physical hardware access takes place through
the VMkernel, virtual machines cannot circumvent this level of isolation.
Just as a physical machine communicates with other machines in a network through a network card, a
virtual machine communicates with other virtual machines running in the same host through a virtual
switch. Further, a virtual machine communicates with the physical network, including virtual machines on
other ESXi hosts, through a physical network adapter.
Figure 3‑2. Virtual Networking Through Virtual Switches
These characteristics apply to virtual machine isolation in a network context:
If a virtual machine does not share a virtual switch with any other virtual machine, it is completely
n
isolated from virtual networks within the host
If no physical network adapter is configured for a virtual machine, the virtual machine is completely
n
isolated from any physical networks.
If the same safeguards are used (firewalls, antivirus software, and so forth) to protect a virtual machine
n
from the network as if it were a physical machine, the virtual machine is as secure as the physical
machine.
Virtual machines can be further protected by setting up resource reservations and limits on the host. For
example, through the detailed resource controls available in ESXi, a virtual machine can be configured so
that it always receives at least 10 percent of the host's CPU resources, but never more than 20 percent.
VMware, Inc. 33
Page 34

vCloud Suite Architecture Overview and Use Cases
Resource reservations and limits protect virtual machines from performance degradation that would result
if another virtual machine consumed excessive shared hardware resources. For example, if one of the virtual
machines on a host is incapacitated by a denial-of-service (DoS) attack, a resource limit on that machine
prevents the attack from taking up so much of the hardware resources that the other virtual machines are
also affected. Similarly, a resource reservation on each of the virtual machines provides that, in the event of
high resource demands by the virtual machine targeted by the DoS attack, all the other virtual machines still
have enough resources to operate.
By default, ESXi imposes a form of resource reservation by applying a distribution algorithm that divides
the available host resources equally among the virtual machines while keeping a certain percentage of
resources for use by other system components. This default behavior provides a degree of natural protection
from DoS and distributed denial-of-service (DDoS) attacks. Specific resource reservations and limits are set
on an individual basis to customize the default behavior so that the distribution is not equal across the
virtual machine configuration
Security and Virtual Networks
If an ESXi host is accessed through vCenter Server, it is typical to protect vCenter Server using a firewall.
This firewall provides basic protection for the network.
A firewall might lie between the clients and vCenter Server. Alternatively, vCenter Server and the clients
can be behind the firewall, depending on deployment. The main point is to provide a firewall at what is
considered to be an entry point for the system.
Networks configured with vCenter Server can receive communications through the vSphere Client or thirdparty network management clients that use the SDK to interface with the host. During normal operation,
vCenter Server listens for data from its managed hosts and clients on designated ports. vCenter Server also
assumes that its managed hosts listen for data from vCenter Server on designated ports. If a firewall is
present between any of these elements, it needs to be confirmed that the firewall has open ports to support
data transfer.
Firewalls might also be included at a variety of other access points in the network, depending on how the
network is planned to be used and the level of security various devices require. Select the locations for
firewalls based on the security risks that have been identified for network configuration. The following is a
list of firewall locations common to ESXi implementations.
Securing Virtual Machines with VLANs
The network can be one of the most vulnerable parts of any system. The virtual machine network requires
as much protection as its physical counterpart. Virtual Machine network security can be enhanced in several
ways, including through the use of virtual local area networks (VLANS).
If the virtual machine network is connected to a physical network, it can be subject to breaches to the same
degree that a network made up of physical machines is. Even if the virtual machine network is isolated from
any physical network, virtual machines in the network can be subject to attacks from other virtual machines
in the network. The requirements for securing virtual machines are often the same as those for physical
machines.
Virtual machines are isolated from each other. One virtual machine cannot read or write another virtual
machine's memory, access its data, use its applications, and so forth. However, within the network, any
virtual machine or group of virtual machines can still be the target of unauthorized access from other virtual
machines and might require further protection by external means.
Adding firewall protection to the virtual network by installing and configuring host-based firewalls on
n
some or all of its virtual machines.
34 VMware, Inc.
Page 35

Chapter 3 Deploying vCloud Suite
For efficiency, private virtual machine Ethernet networks or virtual networks can be configured. With
n
virtual networks, a host-based firewall is installed on a virtual machine at the head of the virtual
network. This serves as a protective buffer between the physical network adapter and the remaining
virtual machines in the virtual network.
Installing a host-based firewall on virtual machines at the head of virtual networks is a good security
n
practice. However, because host-based firewalls can slow performance, it's important to balance
security needs against performance before deciding to install host-based firewalls on virtual machines
elsewhere in the virtual network.
Keeping different virtual machine zones within a host on different network segments. If virtual
n
machine zones on their own network segments are isolated, the risks of data leakage from one virtual
machine zone to the next is minimized. Segmentation prevents various threats, including Address
Resolution Protocol (ARP) spoofing, in which an attacker manipulates the ARP table to remap MAC
and IP addresses, thereby gaining access to network traffic to and from a host. Attackers use ARP
spoofing to generate Man in the Middle attacks, DoS attacks, hijack the target system, and otherwise
disrupt the virtual network.
Planning segmentation carefully lowers the chances of packet transmissions between virtual machine
n
zones, which prevents sniffing attacks that require sending network traffic to the victim. Also, an
attacker cannot use an insecure service in one virtual machine zone to access other virtual machine
zones in the host. Segmentation can be implemented by using either of two approaches, each of which
has different benefits.
Use separate physical network adapters for virtual machine zones so that the zones are isolated.
n
Maintaining separate physical network adapters for virtual machine zones is probably the most
secure method and is less prone to misconfiguration after the initial segment creation.
Set up virtual local area networks (VLANs) to help safeguard the network. Because VLANs
n
provide almost all of the security benefits inherent in implementing physically separate networks
without the hardware overhead, they offer a viable solution that can save the cost of deploying and
maintaining additional devices, cabling, and so forth.
This level of security can be implemented in different ways.
VLANs are an IEEE standard networking scheme with specific tagging methods that allow routing of
packets to only those ports that are part of the VLAN. When properly configured, VLANs provide a
dependable means to protect a set of virtual machines from accidental or malicious intrusions.
VLANs let you segment a physical network so that two machines in the network are unable to transmit
packets back and forth unless they are part of the same VLAN. For example, accounting records and
transactions are among a company’s most sensitive internal information. In a company whose sales,
shipping, and accounting employees all use virtual machines in the same physical network, you might
protect the virtual machines for the accounting department by setting up VLANs.
VMware, Inc. 35
Page 36
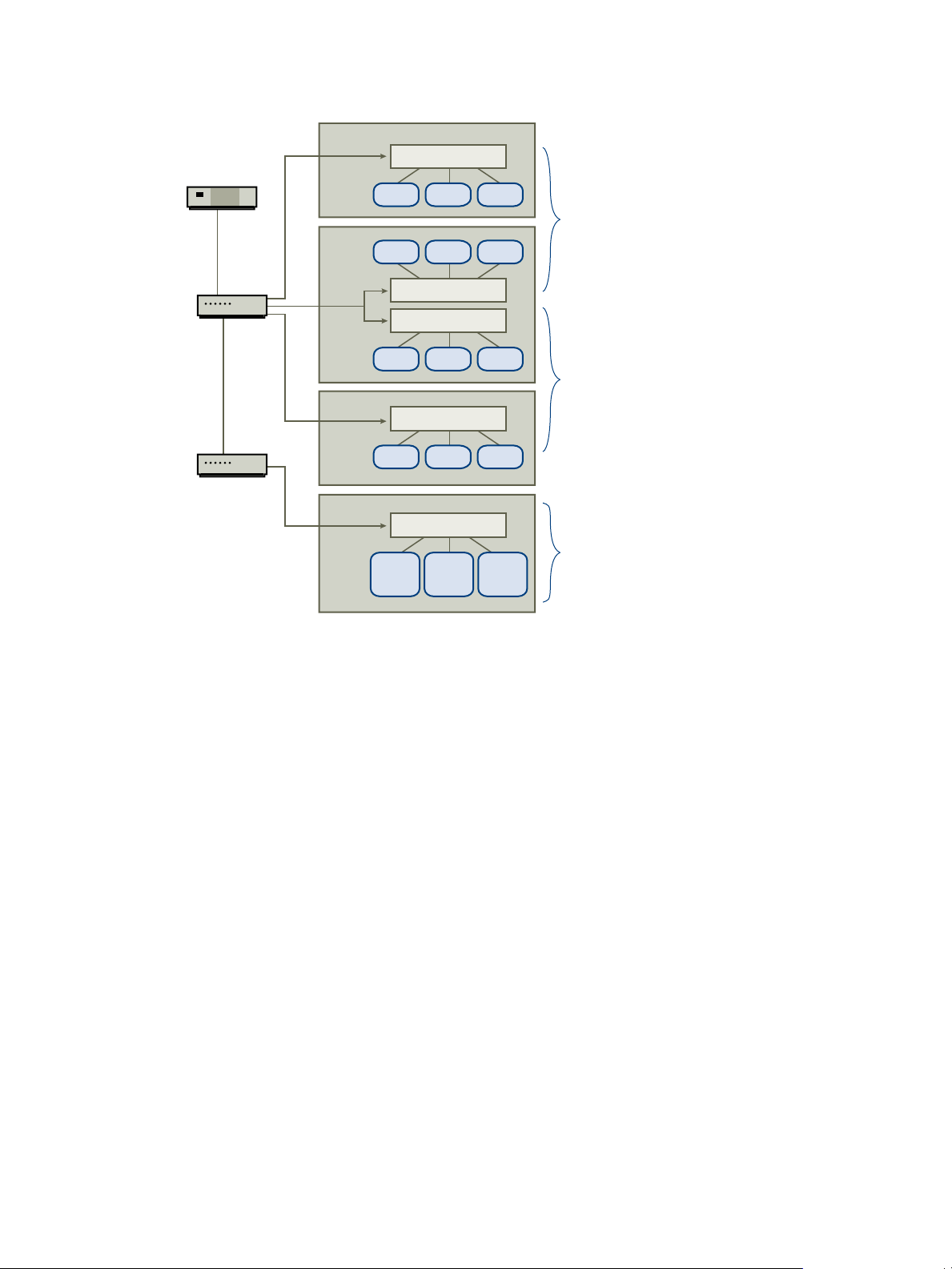
VM3 VM4
Standard Switch
VM5
Standard Switch
VM6 VM7 VM8
Standard Switch
VM0 VM1 VM2
Standard Switch
VM9 VM10 VM11
VM12
VLAN
B
VM13
VLAN
A
VM14
VLAN
B
Standard Switch
Router
Host 1
Host 3
Host 4
Host 2
Switch 1
Switch 2
Multiple VLANs
on the same
virtual switch
Broadcast
Domains A and B
VLAN A
Broadcast
Domain A
VLAN B
Broadcast
Domain B
vCloud Suite Architecture Overview and Use Cases
Figure 3‑3. Sample VLAN Layout
In this configuration, all employees in the accounting department use virtual machines in VLAN A and the
employees in sales use virtual machines in VLAN B.
The router forwards packets containing accounting data to the switches. These packets are tagged for
distribution to VLAN A only. Therefore, the data is confined to Broadcast Domain A and cannot be routed
to Broadcast Domain B unless the router is configured to do so.
This VLAN configuration prevents the sales force from intercepting packets destined for the accounting
department. It also prevents the accounting department from receiving packets intended for the sales group.
The virtual machines serviced by a single virtual switch can be in different VLANs.
Securing Standard Switch Ports
As with physical network adapters, a virtual network adapter can send frames that appear to be from a
different machine or impersonate another machine so that it can receive network frames intended for that
machine. Also, like physical network adapters, a virtual network adapter can be configured so that it
receives frames targeted for other machines.
When a standard switch is created, port groups are added to impose a policy configuration for the virtual
machines and storage systems attached to the switch. Virtual ports are created through the vSphere Web
Client or the vSphere Client.
As part of adding a port or standard port group to a standard switch, the vSphere Client configures a
security profile for the port. This security profile can be used so that the host prevents the guest operating
systems for its virtual machines from impersonating other machines on the network. This security feature is
implemented so that the guest operating system responsible for the impersonation does not detect that the
impersonation was prevented.
36 VMware, Inc.
Page 37

Chapter 3 Deploying vCloud Suite
The security profile determines how strongly the protection is enforced against impersonation and
interception attacks on virtual machines. To correctly use the settings in the security profile, one must
understand the basics of how virtual network adapters control transmissions and how attacks are staged at
this level.
Each virtual network adapter has its own MAC address assigned when the adapter is created. This address
is called the initial MAC address. Although the initial MAC address can be reconfigured from outside the
guest operating system, it cannot be changed by the guest operating system. In addition, each adapter has
an effective MAC address that filters out incoming network traffic with a destination MAC address different
from the effective MAC address. The guest operating system is responsible for setting the effective MAC
address and typically matches the effective MAC address to the initial MAC address.
When sending packets, an operating system typically places its own network adapter's effective MAC
address in the source MAC address field of the Ethernet frame. It also places the MAC address for the
receiving network adapter in the destination MAC address field. The receiving adapter accepts packets only
when the destination MAC address in the packet matches its own effective MAC address.
Upon creation, a network adapter's effective MAC address and initial MAC address are the same. The
virtual machine's operating system can alter the effective MAC address to another value at any time. If an
operating system changes the effective MAC address, its network adapter receives network traffic destined
for the new MAC address. The operating system can send frames with an impersonated source MAC
address at any time. This means an operating system can stage malicious attacks on the devices in a network
by impersonating a network adapter that the receiving network authorizes.
Standard switch security profiles can be used on hosts to protect against this type of attack by setting three
options. If any default settings for a port are changed, the security profile must be modified by editing
standard switch settings in the vSphere Client.
Securing iSCSI Storage
The storage configured for a host might include one or more storage area networks (SANs) that use iSCSI.
When iSCSI is configured on a host, several measures can be taken to minimize security risks.
The storage configured for a host might include one or more storage area networks (SANs) that use iSCSI.
When iSCSI is configured on a host, several measures can be taken to minimize security risks.
iSCSI is a means of accessing SCSI devices and exchanging data records by using TCP/IP over a network
port rather than through a direct connection to a SCSI device. In iSCSI transactions, blocks of raw SCSI data
are encapsulated in iSCSI records and transmitted to the requesting device or user.
One means of securing iSCSI devices from unwanted intrusion is to require that the host, or initiator, be
authenticated by the iSCSI device, or target, whenever the host attempts to access data on the target LUN.
The goal of authentication is to prove that the initiator has the right to access a target, a right granted when
authentication is configured. ESXi does not support Kerberos, Secure Remote Protocol (SRP), or public-key
authentication methods for iSCSI. Additionally, it does not support IPsec authentication and encryption.
Use the vSphere Client or the vSphere Web Client to determine whether authentication is being performed
and to configure the authentication method.
iSCSI SANs enable the efficient use of existing Ethernet infrastructures to provide hosts access to storage
resources that they can dynamically share. iSCSI SANs provide an economical storage solution for
environments that rely on a common storage pool to serve numerous users. As with any networked system,
iSCSI SANs can be subject to security breaches.
VMware, Inc. 37
Page 38

vCloud Suite Architecture Overview and Use Cases
Securing ESXi and the ESX Management Interfaces
Security of the ESXi management interface is critical to protect against unauthorized intrusion and misuse. If
a host is compromised in certain ways, the virtual machines it interacts with might also be compromised. To
minimize the risk of an attack through the management interface, ESXi is protected with a firewall.
To protect the host against unauthorized intrusion and misuse, VMware imposes constraints on several
parameters, settings, and activities. Constraints can be relaxed to meet configuration needs, but if done so,
measures have to be taken to protect the network as a whole and the devices connected to the host.
Consider the following recommendations when evaluating host security and administration.
To improve security, restrict user access to the management interface and enforce access security
n
policies like setting up password restrictions.
The ESXi Shell has privileged access to certain parts of the host. Therefore, provide only trusted users
n
with ESXi Shell login access.
When possible, run only the essential processes, services, and agents such as virus checkers, and virtual
n
machine backups.
When possible, use the vSphere Web Client or a third-party network management tool to administer
n
ESXi Server hosts instead of working though the command-line interface as the root user. The usage of
the vSphere Client enables limitations to the accounts with access to the ESXi Shell and one can safely
delegate responsibilities and set up roles that prevent administrators and users from using capabilities
they do not need.
The host runs a variety of third-party packages to support management interfaces or tasks that an operator
must perform. VMware does not support upgrading these packages from anything other than a VMware
source. If a download or patch is used from another source, management interface security or functions
might be compromised. Regularly check third-party vendor sites and the VMware knowledge base for
security alerts.
In addition to implementing the firewall, risks to the hosts are mitigated using other methods.
By default, all ports not specifically required for management access to the host are closed. Ports must
n
be specifically opened if additional services are required.
By default, weak ciphers are disabled and all communications from clients are secured by SSL. The
n
exact algorithms used for securing the channel depend on the SSL handshake. Default certificates
created on ESXi use SHA-1 with RSA encryption as the signature algorithm.
VMware monitors all security alerts that could affect ESXi security and, if needed, issues a security
n
patch.
Insecure services such as FTP and Telnet are not installed, and the ports for these services are closed by
n
default. Because more secure services such as SSH and SFTP are easily available, always avoid using
these insecure services in favor of their safer alternatives. If insecure services must be used sufficient
protection for the host must be implemented, specific ports must be opened to support these services.
To increase the security of the ESXi Server hosts, they can be put in lockdown mode. When lockdown mode
is enabled, no users other than vpxuser have authentication permissions, nor can they perform operations
against the host directly. Lockdown mode forces all operations to be performed through vCenter Server.
When a host is in lockdown mode, vSphere CLI commands cannot be executed from an administration
server, from a script, or from VMware vSphere Management Assistant against the host. External software or
management tools might not be able to retrieve or modify information from the ESXi host.
38 VMware, Inc.
Page 39

Chapter 3 Deploying vCloud Suite
Securing vCenter Server Systems
Securing vCenter Server includes ensuring security of the host where vCenter Server is running, following
best practices for assigning privileges and roles, and verifying the integrity of the clients that connect to
vCenter Server.
Strictly control vCenter Server administrator privileges to increase security for the system, as follows:
Full administrative rights to vCenter Server should be removed from the local Windows administrator
n
account and granted to a special-purpose local vCenter Server administrator account. Grant full
vSphere administrative rights only to those administrators who are required to have it. Do not grant
this privilege to any group whose membership is not strictly controlled.
Avoid allowing users to log in directly to the vCenter Server system. Allow only those users who have
n
legitimate tasks to perform to log into the system and confirm that these events are audited.
Install vCenter Server using a service account instead of a Windows account. A service account or a
n
Windows account can be used to run vCenter Server. Using a service account allows to enable
Windows authentication for SQL Server, which provides more security. The service account must be an
administrator on the local machine.
Check for privilege reassignment when restarting vCenter Server. If the user or user group that is
n
assigned the Administrator role on the root folder of the server cannot be verified as a valid user or
group, the Administrator privileges are removed and assigned to the local Windows Administrators
group.
Grant minimal privileges to the vCenter Server database user. The database user requires only certain
privileges specific to database access. In addition, some privileges are required only for installation and
upgrade. These can be removed after the product is installed or upgraded.
Encryption and Security Certificates
ESXi and vCenter Server support standard X.509 version 3 (X.509v3) certificates to encrypt session
information sent over Secure Socket Layer (SSL) protocol connections between components. If SSL is
enabled, data is private, protected, and cannot be modified in transit without detection.
Certificate checking is enabled by default and SSL certificates are used to encrypt network traffic. However,
ESXi and vCenter Server use automatically generated certificates that are created as part of the installation
process and stored on the server system. These certificates are unique and make it possible to begin using
the server, but they are not verifiable and are not signed by a trusted, well-known certificate authority (CA).
These default certificates are vulnerable to possible man-in-the-middle attacks. To receive the full benefit of
certificate checking, particularly if encrypted remote connections are to be used externally, install new
certificates that are signed by a valid internal certificate authority or acquire a certificate from a trusted
security authority.
The SSL Certificate Automation Tool is a command-line utility that automates the Self- or CA-signed
certificate renewal process for vSphere 5.5. See VMware KB 2057340.
vCenter Single Sign-On
vCenter Single Sign-On is a component of the management infrastructure that provides the capability to
manage the environment with Active Directory credentials.
In product versions earlier than vCenter Server 5.1, when users connect to vCenter Server, they were
authenticated when vCenter Server validated their credentials against an Active Directory domain or the list
of local operating system users. In vCenter Server 5.5, users authenticate through vCenter Single Sign On.
VMware, Inc. 39
Page 40

vCloud Suite Architecture Overview and Use Cases
ESXi 5.5 is not integrated with vCenter Single Sign-On, and ESXi users cannot be created with the vSphere
Web Client. ESXi users must be created and administered with the vSphere Client. vCenter Server is not
aware of users that are local to ESXi. In addition, ESXi is not aware of vCenter Server users. However, Single
Sign-On can be configured to use an Active Directory domain as an identity source and the ESXi host can be
configured to point to the same Active Directory domain to obtain user and group information. This action
allows the same set of users to be available to the host and to vCenter Server.
In vCenter Single Sign-On 5.5, the way that vCenter Single Sign-On is deployed and the type of user who
installs vCenter Single Sign-On no longer affects which administrator user accounts have privileges on the
Single Sign-On server and on vCenter Server. During the vCenter Server installation process, certain users
are granted privileges to log in to vCenter Server and certain users are granted privileges to manage vCenter
Single Sign-On. The vCenter Server administrator might not be the same user as the vCenter Single Sign-On
administrator. This means that when a user logs in to the vSphere Web Client as the default Single Sign-On
administrator (administrator@vsphere.local), they might not see any vCenter Server systems in the
inventory. The inventory appears to be empty because the only see the systems upon which they have
privileges in the vSphere Web Client.
This also means that when an operator logs in to the vSphere Web Client as the default vCenter Server
administrator, they might not see the vCenter Single Sign-On configuration tool. The configuration tool is
not present because only the default vCenter Single Sign-On Administrator (administrator@vsphere.lcoal) is
allowed to view and manage vCenter Single Sign-On after installation. The Single Sign-On administrator
can create additional administrator users if necessary.
A conflict might occur if Local OS users cannot be seen or if there is a multiple site or node configuration
issue. In that case, the identity source must be configured, or SSO must be used with vsphere.local domain
authentication.
After SSO is installed (no matter the configuration), validate the identity sources which are configured so
that they are both present and accurate to the way that authentication should proceed. Note that there is
only one default domain in Single Sign-On 5.5, and as a result choose the most frequently logged into
domain as the default domain.
Single Sign-On provides several different deployment methods to best suit your environment.
Basic deployment
A single standalone instance of vCenter Single Sign-On supports the
connectivity of identity sources and is installed on the same host as vCenter
Server. This type of deployment meets the requirements of most users.
Multiple instances in the
same location
Multiple vCenter Single Sign-On nodes are installed at a local site and
configured for high availability. In vSphere 5.5, vCenter Single Sign-On has
its own Directory Service that automatically replicates information to other
vCenter Single Sign-On nodes in the environment.
Multiple instances in
different locations
vCenter Single Sign-On nodes are installed at geographically separate sites.
Each site has one or more vCenter Single Sign-On installations and data is
replicated between sites. Multi-site deployment is required if configuring
Linked Mode vCenter Server instances across sites.
The following vCloud Suite components support vCenter Single Sign-On:
vCenter Server
n
vCenter Orchestrator
n
vCloud Automation Center
n
vCloud Director
n
vCloud Networking and Security
n
vSphere Big Data Extensions
n
40 VMware, Inc.
Page 41

Licensing
The components of a vCloud Suite edition are activated by using a single licence. You can perform the
activation of all components by using the vSphere Web Client or the licensing interfaces of individual
products.
vCloud Suite Licensing Model
VMware vCloud Suite 5.8 combines multiple components into a single product to cover the complete set of
cloud infrastructure capabilities. When used together, the vCloud Suite components provide virtualization,
software-defined data center services, policy-based provisioning, disaster recovery, application
management, and operations management.
A vCloud Suite 5.8 edition combines components such as vSphere Enterprise Plus, vCloud Director,
vCloud Networking and Security, and others, under a single license. vCloud Suite editions are licensed on a
per-processor basis. Many of the vCloud Suite components are also available as standalone products
licensed on a per-virtual machine basis. However, when these components are obtained through the
vCloud Suite, they are licensed on a per-processor basis.
The components from a vCloud Suite edition are activated with a single license key. For example, if you
have a license key for vCloud Suite 5.8 Standard, you can use the same key to activate vSphere Enterprise
Plus, vCloud Director, vCloud Networking and Security, and so on.
Chapter 3 Deploying vCloud Suite
All virtual machines running on a processor licensed with a vCloud Suite edition can use all components
included in that vCloud Suite edition. To run virtual machines on processors that are not licensed for
vCloud Suite, you need individual licenses for the products that you want to use.
vCloud Suite Licenseable Components
The different vCloud Suite 5.8 editions include different sets of components. You must assign the
vCloud Suite license to all components in your vCloud Suite edition.
The following vCloud Suite components correspond to vCloud Suite 5.8 Enterprise edition.
Table 3‑3. vCloud Suite 5.8 components that require a license
Components Description
VMware vSphere Provides virtualization technology to serve as the platform
for cloud infrastructure.
VMware vCloud® Director Provides the ability to build secure, multi-tenant clouds by
pooling virtual infrastructure resources into virtual
datacenters.
VMware vCloud Networking and Security Provides a security suite for VMware vSphere.
vCloud Networking and Security (formerly vShield) is a
critical security component for protecting virtualized
datacenters from attacks and misuse to help you achieve
your compliance-mandated goals.
VMware vCenter Operations Management Suite Automates operations management and provides
integrated performance, capacity, and configuration
management for virtualized and cloud infrastructure.
VMware, Inc. 41
Page 42

vCloud Suite Architecture Overview and Use Cases
Table 3‑3. vCloud Suite 5.8 components that require a license (Continued)
Components Description
VMware vCenter Site Recovery Manager Provides business continuity and disaster recovery
VMware vCloud Automation Center Provides functionality for deploying and provisioning of
Distributing the Processor Capacity of a vCloud Suite License
Each vCloud Suite license has a certain processor capacity that you can use to license multiple physical
processors on ESXi hosts where you run the vCloud Suite components. When you assign a vCloud Suite
license key to a host, the amount of processor capacity that is consumed is equal to the number of physical
processors on the host.
capabilities that help you plan, test, and perform recovery
of virtual machines between one site (the protected site)
and another site (the recovery site).
business-relevant cloud services across private and public
clouds, physical infrastructure, hypervisors, and public
cloud providers.
vCloud Automation Center Enterprise includes
vCloud Automation Center Application Service that
automates application provisioning in the cloud including
deploying and configuring the application's components
and dependent middleware platform services on
infrastructure clouds.
To license physical processor that run vCloud Suite components, you need to assign the ESXi hosts a
vCloud Suite license key with processor capacity that is sufficient to license all physical processors on the
host.
For example, to run vCloud Suite on two ESXi 5.x hosts that have four processors each, you need to assign
the hosts a vCloud Suite license key with a minimum capacity of eight processors.
You can assign and reassign the processor capacity of a vCloud Suite license key to any combination of ESXi
hosts. For example, suppose that you purchase a vCloud Suite license key for 10 processors. You can assign
the license key to any of the following combinations of hosts.
Five 2-processor hosts.
n
Three 2-processor hosts and one 4-processor host.
n
Two 4-processor hosts and one 2-processor host.
n
One 8-processor host and one 2-processor host.
n
Dual-core and quad-core processors, such as Intel processors that combine two or four independent
processors on a single chip, count as one processor.
Activating vCloud Suite Components in the vSphere Web Client
You must assign the vCloud Suite license key to all suite components. For components that integrate with
the vSphere Web Client, you can use the license management option in the client.
NOTE The vCloud Suite 5.8 license is compatible with vCenter Server 5.1 and 5.5.
Add the vCloud Suite License in the vSphere Web Client
To assign the vCloud Suite license key to the suite components, you must add the key to the license
inventory of vCenter Server.
Prerequisites
Required privilege: Global.Licenses
42 VMware, Inc.
Page 43

Chapter 3 Deploying vCloud Suite
Procedure
1 From the vSphere Web Client navigator home, select Administration, and under Licensing select
Licenses .
2 On the License Keys tab, click Add License Keys .
3 Type the vCloud Suite license key and click Next.
You can copy and paste the license key from My VMware.
4 Click Finish.
What to do next
Assign the vCloud Suite license key to the suite components that integrate with the vSphere Web Client.
Assign the vCloud Suite License to vSphere in the vSphere Web Client
You must assign the vCloud Suite license key to the ESXi hosts that run the vCloud Suite components. You
can assign the license key by using the license management option in the vSphere Web Client.
Prerequisites
Verify that the vCloud Suite license key is added in the inventory of vCenter Server. See “Add the
n
vCloud Suite License in the vSphere Web Client,” on page 42
Required privilege: Global.Licenses
n
Procedure
1 From the vSphere Web Client navigator home, select Administration, and under Licensing select
Licenses .
2 On the Hosts tab, select the ESXi hosts that run the vCloud Suite components and click Assign License
Key.
To select multiple hosts, use Shift+click.
3 Select the vCloud Suite license key and click OK.
The ESXi hosts are licensed for vCloud Suite.
Activating vCloud Suite Components in the vSphere Client
You must assign the vCloud Suite license to all suite components to unlock the vCloud Suite capabilities.
For components that integrate with the vSphere Client, you can use the license management option in the
client.
NOTE The vCloud Suite 5.8 license is compatible with vCenter Server 5.1 and 5.5.
Add the vCloud Suite License by Using the vSphere Client
To assign the vCloud Suite license key to the suite components, you must add the key to the license
inventory of vCenter Server.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Procedure
1 In the vSphere Client, select Home > Administration > Licensing.
VMware, Inc. 43
Page 44

vCloud Suite Architecture Overview and Use Cases
2 Select Manage vSphere Licenses.
3 In the Add License Keys page, type or paste the vCloud Suite license key, and type an optional label for
the key.
4 Click Add License Keys.
5 Review the details for the license key, click Next on the remaining pages of the wizard, and click Finish.
The vCloud Suite license key is added to the license inventory of vCenter Server.
What to do next
Assign the vCloud Suite license key to vSphere, vCenter Operations Management Suite,
vCenter Site Recovery Manager, and vCloud Networking and Security.
Assign the vCloud Suite License to vSphere in the vSphere Client
You must assign the vCloud Suite license key to the ESXi hosts that run the components of vCloud Suite.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, select Home > Administration > Licensing.
2 Select Manage vSphere Licenses.
3 Click Next.
4 On the Assign Licenses page, select ESX.
5 Select the ESXi hosts that run the vCloud Suite components.
6 From the Product pane, select the vCloud Suite license key.
7 On the Remove License Keys page, click Next.
8 Click Finish to save your changes.
Assign the vCloud Suite License to vCenter Operations Management Suite in the vSphere Client
Assign the vCloud Suite license key to the components of vCenter Operations Management Suite to use
them as part of vCloud Suite.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, select Home > Administration > Licensing.
2 Select Manage vSphere Licenses.
44 VMware, Inc.
Page 45

Chapter 3 Deploying vCloud Suite
3 Click Next.
4 On the Assign Licenses page, select Solutions.
5 Select the components of vCenter Operations Management Suite that you want to run as part of
vCloud Suite.
6 From the Product pane, select the vCloud Suite license key.
7 On the Remove License Keys page, click Next.
8 Click Finish to save your changes.
Assign the vCloud Suite License to vCloud Networking and Security in the vSphere Client
Assign the vCloud Suite license key to vCloud Networking and Security to use it as part of the suite.
NOTE vCloud Networking and Security components appear under vShield in the vSphere Client.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, select Home > Administration > Licensing.
2 Select Manage vSphere Licenses.
3 Click Next.
4 On the Assign Licenses page, select Solutions.
5 Select vCloud Networking and Security (vShield) .
6 From the Product pane, select the vCloud Suite license key.
7 On the Remove License Keys page, click Next.
8 Click Finish to save your changes.
Assign the vCloud Suite License Key to vCenter Site Recovery Manager
Assign the vCloud Suite license key to vCenter Site Recovery Manager to use it as part of the suite.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, select Home > Administration > Licensing.
2 Select Manage vSphere Licenses.
3 Click Next.
VMware, Inc. 45
Page 46

vCloud Suite Architecture Overview and Use Cases
4 On the Assign Licenses page, select Solutions.
5 Select vCenter Site Recovery Manager.
6 From the Product pane, select the vCloud Suite license key.
7 On the Remove License Keys page, click Next.
8 Click Finish to save your changes.
Activating vCloud Suite Components by Using Their Own Licensing Interfaces
You must assign the vCloud Suite license to all suite components. vCloud Director,
vCloud Automation Center, and vCloud Automation Center Application Service provide their own
licensing interfaces for license assignments.
NOTE The vCloud Suite 5.8 license is compatible with vCenter Server 5.1 and 5.5.
Assigning the vCloud Suite License to vCloud Automation Center Application Service
You can assign the vCloud Suite license key to vCloud Automation Center Application Service to enable full
functionality.
If vCloud Automation Center Application Service is already installed and running and has another license
key assigned, reinstall the product and assign it the vCloud Suite license key.
The license key unlocks the vCloud Automation Center Application Service for Release Automation edition,
which includes the basic features, updating a deployed application, and deploying applications to the
Amazon EC2 environment capabilities.
Assign the vCloud Suite License to vCloud Director
To use vCloud Director as part of the vCloud Suite, you must assign vCloud Director the vCloud Suite
license key.
You can assign the vCloud Suite license key to vCloud Director while installing the component, or you can
assign the license key to an already running instance of vCloud Director.
Prerequisites
You must be logged in to vCloud Director as an administrator.
Procedure
1 On the home page of the vCloud Director Web console, select Administration.
2 Under System Settings, select License.
3 In the Serial number text box, type or copy and paste the vCloud Suite license key.
4 Click Apply.
vCloud Director is licensed for vCloud Suite. The Licensed VM count field does not display any number of
virtual machines, as vCloud Suite license is per-processor.
Assign the vCloud Suite License to vCloud Automation Center 6.0
To use vCloud Automation Center 6.0 as part of vCloud Suite, you must assign it the vCloud Suite license.
To enable the full functionality of vCloud Automation Center, you must assign the license in both the
vCloud Automation Center Appliance and in Infrastructure as a Service.
46 VMware, Inc.
Page 47

Chapter 3 Deploying vCloud Suite
Procedure
1 Assign the License Key in the vCloud Automation Center Appliance on page 47
You must assign the license key in the vCloud Automation Center Appliance to activate the product.
2 Assign the License Key for Infrastructure as a Service on page 47
You must assign the license key for Infrastructure as a Service to enable IaaS capabilities. Without a
license, you cannot configure infrastructure endpoints or other features.
Assign the License Key in the vCloud Automation Center Appliance
You must assign the license key in the vCloud Automation Center Appliance to activate the product.
Procedure
1 Navigate to the vCloud Automation Center Appliance management console by using its fully qualified
domain name (https://vcac-va-hostname.domain.name:5480/).
2 Log in with user name root and the password you specified when deploying the
vCloud Automation Center Appliance.
3 Select vCAC Settings > Licensing.
4 In the New License Key text box, type or copy and paste the vCloud Suite license key.
5 Click Submit Key.
Assign the License Key for Infrastructure as a Service
You must assign the license key for Infrastructure as a Service to enable IaaS capabilities. Without a license,
you cannot configure infrastructure endpoints or other features.
Prerequisites
You must assign the license key in the vCloud Automation Center Appliance before you can access the
Infrastructure-as-a-Service administration console. See “Assign the License Key in the vCloud Automation
Center Appliance,” on page 47.
Procedure
1 Log in to the vCloud Automation Center console as an IaaS administrator.
2 Select Infrastructure > Administration > Licensing.
3 Click Add License.
The Add License dialog box appears.
4 In the License key text box, type or copy and paste the vCloud Suite license key.
5 Click OK.
6 (Optional) Repeat this procedure to enter additional license keys, for example, if you have standalone
vCloud Automation Center license keys in addition to vCloud Suite license keys.
If you add both a vCloud Suite license key and a standalone vCloud Automation Center license key in
IaaS, a message appears that you have overlapping licenses, but it is not an error. You can proceed with
adding the license.
The following restrictions apply when assigning multiple licenses to vCloud Automation Center.
Only one vCloud Suite license can be active. If you have an existing license and enter a new license
n
key, it replaces the previous license.
Only one vCloud Automation Center Advanced Edition or Enterprise Edition license can be active.
n
If you have an existing license and enter a new license key, it replaces the previous license.
VMware, Inc. 47
Page 48

vCloud Suite Architecture Overview and Use Cases
When replacing a vCloud Suite or standalone vCloud Automation Center license, the new license
n
must be of the same level or higher. For example, a license for vCloud Automation Center
Advanced Edition can only be replaced by another license for vCloud Automation Center
Advanced Edition or Enterprise Edition. A license for vCloud Automation Center Enterprise
Edition can only be replaced by another license for vCloud Automation Center Enterprise Edition.
A vCloud Automation Center Desktop license can be used in combination with any vCloud Suite
n
or standalone vCloud Automation Center license.
After you add a license to IaaS, you cannot remove it.
Monitoring License Usage for vCloud Suite
You can monitor the license usage and the available license capacity for all assigned vCloud Suite licenses
by using the license reporting function in vCenter Server.
You can use the license reporting function in vCenter Server to perform the following tasks:
View statistics for the license usage and capacity of vCloud Suite filtered by a vCenter Server system
n
and time period.
Export license usage reports in CSV files for further analysis and processing.
n
View the License Usage for vCloud Suite in the vSphere Client
To make sure that the license usage for vCloud Suite meets the compliance criteria for the product, you can
regularly track the CPU usage for the assigned vCloud Suite licenses.
vCenter Server takes snapshots of the license usage every hour. A license usage snapshot contains data
about the current license assignments and usage. The usage information in the license reporting interface
contains aggregated statistics from snapshots that are taken in the period that you select.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, navigate to Home > Administration > Licensing and select the Reporting tab.
2 From the vCenter Server drop-down list, select a vCenter Server system.
Leave the default All vCenter Server instances selection.
3 From the Time period drop-down menu, select a preconfigured or a custom time period for which you
want to aggregate license usage data.
For a custom time period, you must specify the start and end dates, and click Recalculate .
4 From the Products Chart pane, select a vCloud Suite product.
Details about the license usage for vCloud Suite for the selected time period appear in the Product Details
pane. The license usage is calculated as the average daily high water mark for the selected period.
48 VMware, Inc.
Page 49

Chapter 3 Deploying vCloud Suite
View the License Usage for vCloud Suite in the vSphere Web Client
You can use the license reporting function in the vSphere Web Client to track the license usage for
vCloud Suite.
vCenter Server takes snapshots of the license usage every hour. A license usage snapshot contains data
about the current license assignments and usage. The usage information in the license reporting interface
contains aggregated statistics from snapshots that are taken in the period that you select.
Prerequisites
Required privilege: Global.Licenses
Procedure
1 From the vSphere Web Client navigator home, select Administration, and under Licensing select
License Reports.
2 From the vCenter Server drop-down list, select a vCenter Server system.
3 (Optional) To aggregate license usage data for a vCenter Server system that is part of a Linked Mode
group, select Show data only for the selected vCenter Server.
4 From the Time period drop-down menu, select a preconfigured or a custom time period for which you
want to aggregate license usage data.
For a custom time period, you must specify the start and end dates, and click Recalculate .
5 From the Products Chart pane, select a vCloud Suite product.
Details about the license usage for vCloud Suite for the selected time period appear in the Product Details
pane. The license usage is calculated as the average daily high water mark for the selected period.
Export a License Usage Report for vCloud Suite
You can export a report of the license usage for vCloud Suite for a time period and vCenter Server system.
The report is exported in a CSV file that you can later open with third-party applications.
The license usage data in an exported report contains the license usage snapshots that vCenter Server
collects every hour.
NOTE A tamper-detection feature in vCenter Server protects the license usage information. If the licensing
data in the vCenter Server database has been edited, you cannot export a license usage report.
Prerequisites
Required privilege: Global.Licenses
n
Verify that the vSphere Client is connected to the vCenter Server system.
n
Verify that the vCloud Suite license key is added in the repository of vCenter Server. See “Add the
n
vCloud Suite License by Using the vSphere Client,” on page 43
Procedure
1 In the vSphere Client, navigate to Home > Administration > Licensing and select the Reporting tab.
2 Click Export.
3 From the vCenter Server drop-down list, select the vCenter Server system for which you want to export
a license usage report.
Leave the default All vCenter Server instances selection.
VMware, Inc. 49
Page 50

vCloud Suite Architecture Overview and Use Cases
4 From the Time period drop-down menu, select a preconfigured or a custom time period.
5 Click Export.
6 Save the report on your local system.
Export a License Usage Report for vCloud Suite in the vSphere Web Client
In the vSphere Web Client, you can export a report of the license usage for vCloud Suite for a time period
and vCenter Server system. The report is exported in a CSV file that you can later open with third-party
applications.
The license usage data in an exported report contains the license usage snapshots that vCenter Server
collects every hour.
NOTE A tamper-detection feature in vCenter Server protects the license usage information. If the licensing
data in the vCenter Server database has been edited, you cannot export a license usage report.
Prerequisites
Required privilege: Global.Licenses
Procedure
1 From the vSphere Web Client navigator home, select Administration, and under Licensing select
License Reports.
2 Click Export.
3 From the vCenter Server drop-down list, select the vCenter Server system for which you want to export
a license usage report.
If you select a vCenter Server system that is part of a Linked Mode group, the report contains license
use data for the entire group.
4 (Optional) To export data for a vCenter Server system that is part of a Linked Mode group, select
Export license data only for the selected vCenter Server instance.
5 From the Time period drop-down menu, select a preconfigured or a custom time period.
6 Click Export.
7 Save the report on your local system.
50 VMware, Inc.
Page 51

vCloud Suite Use Cases 4
Scenarios in this chapter instruct you how to achieve realistic user goals by using vCloud Suite.
This chapter includes the following topics:
“Disaster Recovery to Cloud,” on page 51
n
“Infrastructure Provisioning,” on page 57
n
Disaster Recovery to Cloud
As a system administrator, you can configure cloud failover for virtual machines, so that you can guarantee
that important workloads keep running even when your on-site data center experiences problems. You can
combine the VM replication functionality provided by the vSphere Replication virtual appliance with the
VMware vCloud Air service to achieve business continuity goals without the need for a second data center
or additional equipment .
In your on-premise data center, the vSphere Replication virtual appliance lets you select the virtual
machines that you want to replicate to a remote site over the Internet. The vCloud Air service can serve as a
remote site for your virtual machines, ensuring that failover happens in a predictable and verifiable manner.
When the protected virtual machines go offline at the primary site, you can power on their copies in the
cloud.
VMware, Inc.
Disaster Recovery to Cloud subscriptions do not include service integration with shared and dedicated
provisioning in vCloud Air.
The following VMware products are used in the scenario:
Table 4‑1. vCloud Suite Components Required for Disaster Recovery to Cloud
vCloud Suite component Description
ESXi 5.5 Update 2 The VMware hypervisor that lets you run a virtualized
environment.
vCenter Server 5.5 Update 2 Provides management capabilities in a browser-based
interface, as well as integration points for other vCloud
Suite components.
vSphere Replication 5.8 vSphere Replication is an extension to vCenter Server that
provides hypervisor-based virtual machine replication and
recovery.
vCloud Suite components that enable you to perform recovery to cloud can coexist with other solutions of
compatible version. See “List of vCloud Suite Components,” on page 7.
NOTE You cannot use vSphere Replication to protect virtual machines that are protected by using Site
Recovery Manager.
51
Page 52

vCloud Suite Architecture Overview and Use Cases
The following example objects are used in the scenario:
Table 4‑2. Sample Environment Details
Object Description
ACME Corp VM 1 A Linux virtual machine that runs one of your mission
ACME Corp VM 2 A Windows virtual machine that runs another of your
critical applications .
mission-critical applications.
52 VMware, Inc.
Page 53
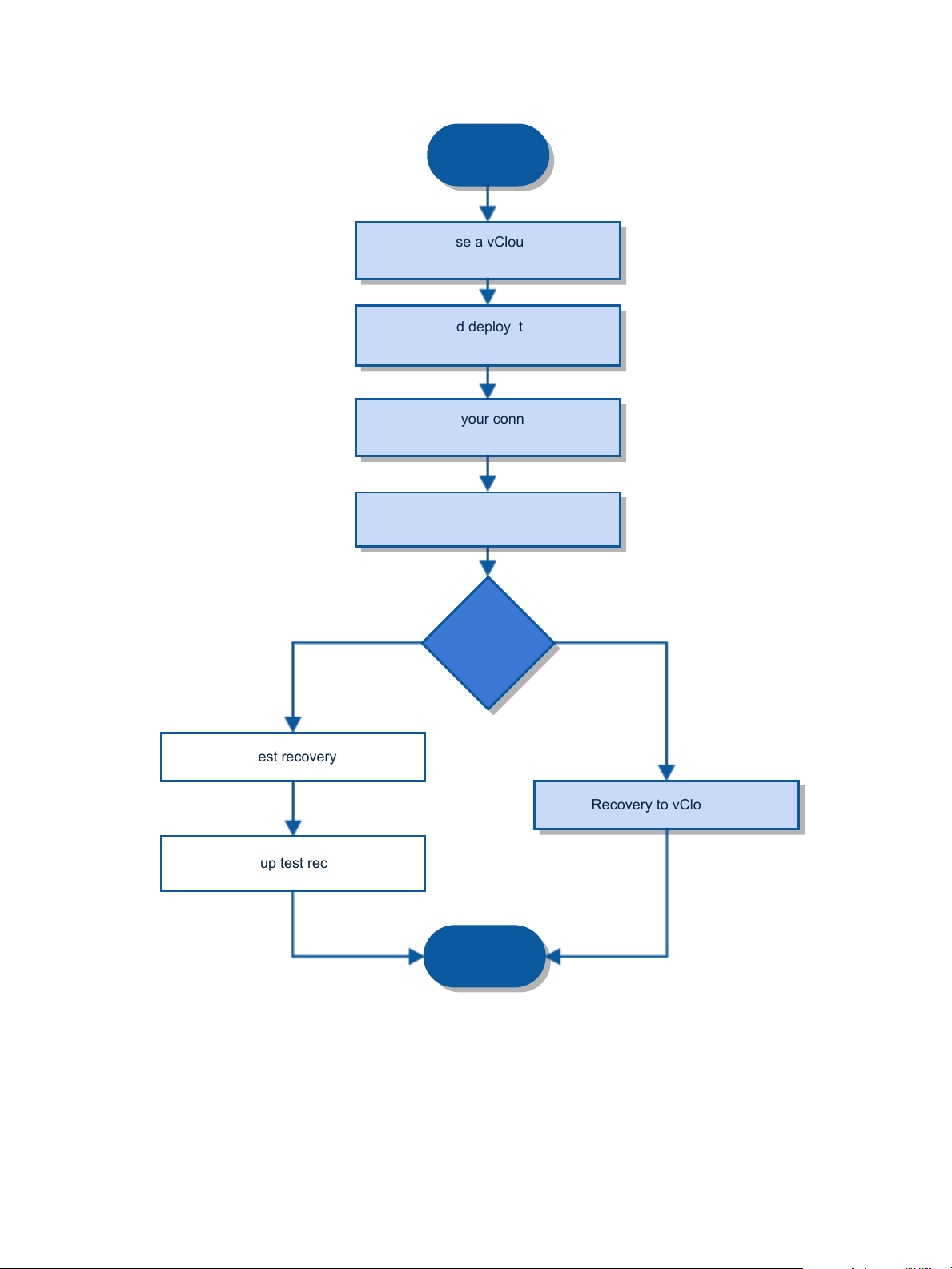
Figure 4‑1. Disaster recovery to cloud workflow
Start
Purchase a vCloud Air –
DR to Cloud subscription.
Download and deploy the vSphere
Replication 5.8 appliance
Configure your connection to
vCloud Air
Clean up test recovery
Test recovery
Select type of
recovery
Replicate virtual machines
Recovery to vCloud Air
End
Test Failover
Chapter 4 vCloud Suite Use Cases
To verify your setup, you can perform test recoveries before an actual recovery is required. Test recoveries
are not enabled by default. You need to file a service request to make the test functionality available.
By using vCloud Connector, you can copy virtual machines from vCloud Air to your on-premise data
center.
Prerequisites
VMware, Inc. 53
Verify that your virtual machines are running in a vSphere environment.
n
Page 54

vCloud Suite Architecture Overview and Use Cases
Verify that you have sufficient privileges to perform administrative operations in the vSphere Web
n
Client.
Verify that you have valid licenses for all products in your environment.
n
Verify that you have vCloud Air credentials for the Disaster Recovery to Cloud service.
n
Procedure
1 Download and Deploy the vSphere Replication Virtual Appliance on page 54
To start preparing your vCloud Sutite environment for DR2C, you must install and configure
vSphere Replication. vSphere Replication is distributed as an OVF virtual appliance.
2 Configure Network Connection to vCloud Air on page 55
You have deployed the vSphere Replication appliance in your on-premise environment. The next step
of preparing your environment for DR2C is to set up a connection to vCloud Air.
3 Replicate Virtual Machines to the Cloud on page 56
In the vSphere Web Client, you can select your mission-critical virtual machines for replication to
vCloud Air.
4 Recover a Virtual Machine in the Cloud on page 56
By using the Web interface of vCloud Air, you can recover the virtual machines that you replicated.
Recovering a virtual machine shuts down the virtual machine at your source site (if possible) and
recovers it in the cloud. During recovery, all replication activity is stopped.
Download and Deploy the vSphere Replication Virtual Appliance
To start preparing your vCloud Sutite environment for DR2C, you must install and configure
vSphere Replication. vSphere Replication is distributed as an OVF virtual appliance.
You can use vSphere Replication with the vCenter Server Appliance or with a vCenter Server installation on
Windows.
Prerequisites
Verify that you have a valid vSphere Replication license.
n
Verify that you have valid credentials for accessing the vCloud Air service.
n
Verify that you have the vSphere Client Integration Plug-in installed.
n
Procedure
1 Visit the VMware corporate Web site or MyVMware to download the vSphere Replication virtual
appliance.
You should save the template file to the local machine on which you use the vSphere Web Client.
2 Log in to the vSphere Web Client.
3 Select vCenter > Hosts and Clusters.
4 Right-click the host on which you want to deploy the appliance, and select Deploy OVF template.
5 Select Local File and browse to the vSphere Replication template file on your local machine.
The default name of the file is vSphere_Replication_OVF10.ovf.
6 Complete the template deployment wizard.
7 Log out of the vSphere Web Client, close the browser, and then log back in.
vSphere Replication is present on the Home tab of the vSphere Web Client.
54 VMware, Inc.
Page 55

Chapter 4 vCloud Suite Use Cases
What to do next
Configure the connection to vCloud Air.
Configure Network Connection to vCloud Air
You have deployed the vSphere Replication appliance in your on-premise environment. The next step of
preparing your environment for DR2C is to set up a connection to vCloud Air.
vSphere Replication replicates the virtual machines from your on-premise data center to vCloud Air by
using a secure connection over the Internet.
When you subscribe to the DR2C service, VMware creates two default networks for the service, an isolated
network and an external routed network. The gateway for the routed network has a public IP address on its
outside interface so that the routed networkon the inside interface is accessible through the Intranet. You
can use these networks for your virtual machines protected by the DR2C service.
When you configure VMs for disaster recovery in vSphere Replication by using the Connect to a cloud
provider wizard, you specify which networks to use for the Test network and the Recovery network. The
network choices that appear in the wizard are the networks configured for vCloud Air.
Procedure
1 In the vSphere Web Client, on the vSphere Replication tab under Manage, click the cloud connection
icon .
The Connect to a Cloud Provider wizard opens.
2 On the Connection settings page, type the cloud provider address, the organization name, and
credentials to authenticate with the cloud.
By default, vSphere Replication uses these credentials to establish a user session to the cloud and for
system monitoring purposes. The login credential are in the message that you received with your
vCloud Air account. The cloud provider address for vCloud Air has the format
https://unique_identifier.vchs.vmware.com.
3 Click Next.
The Connect to a Cloud Provider wizard displays a list of virtual data centers to which you can connect.
A virtual data center that is configured for disaster recovery is created for you in vCloud Air.
4 Select a virtual data center as a target for the connection and click Next.
5 Review your settings and click Finish.
When you add a new connection to the cloud, at first its status appears as Missing network settings
status.
6
On the vSphere Replication tab under Manage, click the target network settings icon .
7 From the drop-down menus, select a recovery network and a test network, and click Next.
The drop-down menus display only the networks that are configured for vCloud Air.
8 On the Ready to complete page, review your settings and click Finish.
When you test a replication or perform a recovery operation, vCloud Air attaches the virtual machine to
the test or recovery network respectively.
What to do next
Select the virtual machines to be replicated to vCloud Air.
VMware, Inc. 55
Page 56

vCloud Suite Architecture Overview and Use Cases
Replicate Virtual Machines to the Cloud
In the vSphere Web Client, you can select your mission-critical virtual machines for replication to vCloud
Air.
When you configure replication, you set a recovery point objective (RPO) to determine the period of time
between replication operations. For example, an RPO of 1 hour aims to ensure that a virtual machine loses
no more than 1 hour of data during the recovery.
Procedure
1 On the vSphere Web Client Home page, click vSphere Replication.
2 Select the vCenter Server instance that manages your virtual machines, and in the left pane, double-
click Virtual Machines.
3 Select the virtual machines ACME Corp VM 1 and ACME Corp VM 2 to replicate.
You can select multiple inventory objects by using the Ctrl or Shift keys.
4 Right-click the virtual machines and select All vSphere Replication Actions > Configure replication.
The Configure Replication wizard opens, and Disaster Recovery to Cloud validates the virtual
machines that can be configured for replication.
5 Verify the validation results and click Next.
6 Select Replicate to a cloud provider and click Next.
7 Select a target virtual data center in the vCloud Air site that you configured in the previous task, and
click Next.
8 On the Target location page, select where to store replication data.
9 (Optional) On the Replication options page, select the quiescing method for the guest operating system
of the source virtual machine and click Next.
10 On the Recovery settings page, use the RPO slider or the time spinners to set the longest period for
which data loss is acceptable in the case of a site failure, and click Next.
The available RPO range is from 15 minutes to 24 hours.
11 Click Finish.
For each source virtual machine that is configured successfully, a replication task appears on the vSphere
Replication tab under Monitor. When you configure replication by using vSphere Replication at your
source site, the disaster recovery service creates placeholder virtual machines in vCloud Air that represent
the virtual machines at your source site.
What to do next
Log in to the vCloud Air Web console and recover the virtual machines.
Recover a Virtual Machine in the Cloud
By using the Web interface of vCloud Air, you can recover the virtual machines that you replicated.
Recovering a virtual machine shuts down the virtual machine at your source site (if possible) and recovers it
in the cloud. During recovery, all replication activity is stopped.
You can recover a virtual machine by using vCloud Air when your source site is no longer accessible. You
might be able to begin a recovery from your source site by using your local vSphere Web Client; for
example, if you have sufficient warning of an outage and still have access to your local vSphere Web Client
so that you can run a planned migration.
56 VMware, Inc.
Page 57

Chapter 4 vCloud Suite Use Cases
In a production environment, you should verify that you tested the recovery before recovering the virtual
machine to the cloud.
Procedure
1 Log in to the vCloud Air Web console.
2 On the Dashboard tab, click the virtual data center that is enabled for disaster recovery.
3 Click the Virtual Machine tab.
The table of virtual machines appears.
4 Select the virtual machines ACME Corp VM 1 and ACME Corp VM 2 to recover.
5 From the menu, click Recovery.
The confirmation dialog box appears.
6 Click Continue.
Recovering the virtual machine has the following result:
In the Virtual Machine tab, the Recovery Status changes from Placeholder or Test to Recovered.
n
Connects the virtual machine to the production network.
n
Powers on the virtual machine in the cloud.
n
After you recover a virtual machine to the cloud, it has the same capabilities that the virtual machine had at
the source site. You can access and operate your virtual machine recovered to the cloud for the time periods
listed in the vCloud Air documentation.
Infrastructure Provisioning
As a tenant administrator in ACME Corporation, you use the infrastructure service to deploy, configure,
and manage workloads, so that you can quickly address the IT needs of your organization.
You can use the vCloud Automation Center portal to provision workloads to a vSphere environment.
VMware, Inc. 57
Page 58

Start
Request VM from blueprint
Approval and provisioning to
vSphere
Manage and customize VM
Retire VM
End
Manage workload snapshots
vCloud Suite Architecture Overview and Use Cases
Figure 4‑2. Workload Provisioning Workflow
Table 4‑3. Environment Details
vCloud Suite component Description
vSphere endpoint vCloud Automation Center can deploy workloads to a
vSphere blueprint The Inventory Manager blueprint exists in your catalog. The
Configured service with a catalog A service exists with the name Development Infrastructure.
A functional IaaS environment is based on several components.
vSphere environment that administrators configured for
use in ACME Corp. A fabric group and a network
reservation are configured for the vSphere environment.
You can configure other types of endpoints, for example
vCloud Air or AWS.
virtual machine runs an application that is used in ACME
Corp. The prefix that is configured for the workload is
InventoryMgr-.
58 VMware, Inc.
Page 59

Chapter 4 vCloud Suite Use Cases
Table 4‑4. vCloud Suite Components Required for the Infrastructure Service
vCloud Suite component Description
ESXi VMware bare-metal hypervisor that lets you run a
virtualized environment.
vCenter Server Provides management capabilities in a browser-based
interface, and integration points for other vCloud Suite
components.
vCenter Orchestrator Enables you to create workflows that automate activities in
the data center.
vCloud Automation Center Provides a secure portal where authorized administrators,
developers, or business users can request new IT services.
vCloud Director vCloud Director lets you provision services as virtual data
centers with virtualized compute, networking, storage, and
security.
vCloud Networking and Security Enables consumption of networks that
vCloud Networking and Security Manager manages.
Prerequisites
Verify that the following conditions are met.
You have the required components in your environment.
n
You have a configured vSphere instance to serve as an vCloud Automation Center endpoint.
n
You have set a reservation policy.
n
You have created blueprints based on vSphere snapshots.
n
Procedure
1 Request a Virtual Machine Workload on page 60
A new instance of a virtual machine that runs an inventory management application is required at
ACME Corp. As an administrator for the tenant group that is responsible for inventory management,
you can use the vCloud Suite Infrastructure as a Service capability to deploy and manage the
workload.
2 Provision the Workload on page 61
After you request the workload, you can provision the workload when you receive an approval.
3 Customize the Virtual Machine on page 61
You requested and provisioned the virtual machine. You can customize the virtual machine to
increase or decrease the amount of memory, the number of CPUs, and so on.
4 Manage Workload Snapshots on page 62
You deployed and configured the workload. You can create snapshots of your running workloads
from the self-service portal.
5 Retire the Virtual Machine on page 62
The final stage in the lifecycle of a workload is the retirement operation. Alternatively, the tenant
administrator can send a reclamation request to the owners of machines.
VMware, Inc. 59
Page 60

vCloud Suite Architecture Overview and Use Cases
Request a Virtual Machine Workload
A new instance of a virtual machine that runs an inventory management application is required at ACME
Corp. As an administrator for the tenant group that is responsible for inventory management, you can use
the vCloud Suite Infrastructure as a Service capability to deploy and manage the workload.
In this scenario, the infrastructure service is preconfigured for your organization.
Procedure
1 Open a Web browser and log in to the vCloud Automation Center portal.
2 Select Infrastructure > Blueprints > Blueprints.
3 Review the configuration of the Warehouse Manager blueprint.
When deployed, the vSphere blueprint uses the reservation policy vSphere and the machine prefix is
WarehouseMgr-.
4 In the vCloud Automation Center portal, click Catalog.
All services are listed.
5 Select a service in the catalog.
All catalog items appear that are linked to the Development Infrastructure service and that are available
for the user.
Select the Development Infrastructure service.
6 Click an item to view details.
The Catalog Item Details page shows information regarding the item, including the type and available
configurations.
#Machines
n
Lease duration
n
#CPUs
n
Memory (MB)
n
Storage (GB)
n
Description
n
Reason for request
n
All modifications change the daily and lease costs.
When you are finished reviewing the settings, click Submit , and click OK.
7 Click Request.
What to do next
Wait for an approval from the assigned role, and provision your workload.
60 VMware, Inc.
Page 61

Chapter 4 vCloud Suite Use Cases
Provision the Workload
After you request the workload, you can provision the workload when you receive an approval.
Procedure
1 In the vCloud Automation Center portal, click Request to monitor status.
The workload request changes status several times during deployment. When it is finished, the request
shows the status Successful.
Workloads in the portal can be associated with third-party CMDB systems so that other roles in the
company can approve the request before the workloads deploy. The request is coming from
vCloud Automation Center through vCenter Orchestrator. Administrators can customize the details
that are sent from vCloud Automation Center.
2 Click Items and click InventoryMgr-000 to review workloads requests.
The virtual machine is now deployed.
What to do next
You received an approval and succesfully provisioned the workload. You can customize the virtual machine
to adjust the amount of memory or other characteristics, so that the virtual machine performs better.
Customize the Virtual Machine
You requested and provisioned the virtual machine. You can customize the virtual machine to increase or
decrease the amount of memory, the number of CPUs, and so on.
You perform the customization in the vCloud Automation Center portal. You cannot add more to the
system than the amount permitted by the reservation policy for your organization.
Procedure
1 Review the VM configuration in the VM console.
a Click Connect Using VMRC to launch a remote connection to this virtual machine.
To log in, you need valid credentials for the virtual machine.
2 Click Close.
3 Reconfigure the workload.
a Next to InventoryMgr-000, click the right arrow and select Edit.
b Increase the assigned memory.
On the Execution tab, the default action is to immediately run the request and to shut down the
virtual machine before reconfiguration.
c Click Submit to begin the reconfiguration task, and click OK.
4 Verify that memory is increased.
When the status changes to On, click the VM and note the increased amount of memory.
What to do next
After you have customized the virtual machines to meet your requirements, you can snapshot the virtual
machine to preserve your changes.
VMware, Inc. 61
Page 62

vCloud Suite Architecture Overview and Use Cases
Manage Workload Snapshots
You deployed and configured the workload. You can create snapshots of your running workloads from the
self-service portal.
Procedure
1 In the vCloud Automation Center portal, click Items and click Machines.
2 Click InventoryMgr-000 and click Snapshots.
3 Click New Snapshot.
4 Click Snapshot the machine's memory and click OK.
5 Wait for the snapshot creation to complete, and click Close.
You can view and delete existing snapshots on the Snapshots tab of the virtual machine.
What to do next
When you have performed the required task by using the provisioned virtual machine, you can archive it.
Retire the Virtual Machine
The final stage in the lifecycle of a workload is the retirement operation. Alternatively, the tenant
administrator can send a reclamation request to the owners of machines.
If a blueprint does not specify a lease period, machines are provisioned from that blueprint with no
expiration date. If a blueprint specifies a single value for lease duration, machines are provisioned from that
blueprint with an expiration date based on the blueprint lease duration.
Procedure
1 In the vCloud Automation Center portal, click Machines.
2 ClickInventoryMgr-000.
3 Click Destroy and confirm the operation.
You requested, provisioned, customized, and retired a workload.
62 VMware, Inc.
Page 63

Index
A
activate vCloud Suite components 44
add the vCloud Suite license 42
assign license 46
assign license key 44
assign licenses 42
assign vCloud Suite license
vCenter Operations Management Suite 44
vCenter Site Recovery Manager 45
assign vCloud Suite License, vCloud Networking
and Security 45
B
business continuity 51, 56
C
common services 39
conceptual design 13
D
Deployment 27
design considerations 17
disaster recovery to cloud
configure network connection 55
deploy vSphere Replication 54
DR2C 51, 56
E
encryption and security certificates 39
ESXi and the ESX Management Interfaces 38
external dependencies 30
G
glossary 5
I
IaaS
customize VM 61
provision VM 60
provision workload 61
retire VM 62
take VM snapshot 62
intended audience 5
introduction 7
iSCSI storage 37
iSCSI storage security 37
isolation, virtual machines 32
L
license, usage 49
license capacity, processor 42
license key
add 43
assign 43, 46
license usage
CPU usage 48
export report 49, 50
monitor 48
license assignment 46
licensing, vCloud Suite 42
logical design 15
M
Monitoring 19
N
network 17
networks, security 34
O
Orchestration layer 21
P
PaaS 25
platform-as-a-service 25
R
recover VMs 56
replicate VMs to cloud 56
resource limits and guarantees, security 32
S
scenarios 51
SDDC Infrastructure 16
SDDC model 11
security
resource guarantees and limits 32
virtual machines 32
virtual machines with VLANs 34
security considerations 31
shared storage 18
standard switch ports 36
VMware, Inc.
63
Page 64

vCloud Suite Architecture Overview and Use Cases
system requirements 31
V
vCenter Server and security 39
vCenter Server systems 39
vCenter Single Sign-On 39
vCloud Suite
components 41
licensing 41, 42
vSphere Web Client 42
vCloud Suite components
activate 43, 44, 46, 47
add license key 43
assign license 43, 44, 46
custom licensing interface 46
license management function 43, 44
license vCloud Director 46
vCloud Automation Center 46, 47
vCloud Suite installation 27
vCloud Suite license, adding 42
vCloud Suite update 29
virtual machines
resource reservations and limits 32
security 32
virtual network, security 34
virtual networks 34
virtualization and management in SDDC 16
VLANs, security 34
64 VMware, Inc.
 Loading...
Loading...