Page 1

Site Recovery Manager Administration
vCenter Site Recovery Manager 5.5
This document supports the version of each product listed and
supports all subsequent versions until the document is
replaced by a new edition. To check for more recent editions
of this document, see http://www.vmware.com/support/pubs.
EN-001112-00
Page 2

Site Recovery Manager Administration
You can find the most up-to-date technical documentation on the VMware Web site at:
http://www.vmware.com/support/
The VMware Web site also provides the latest product updates.
If you have comments about this documentation, submit your feedback to:
docfeedback@vmware.com
Copyright © 2008–2013 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. VMware products are covered by one or more patents listed at
http://www.vmware.com/go/patents.
VMware is a registered trademark or trademark of VMware, Inc. in the United States and other jurisdictions. All other marks
and names mentioned herein may be trademarks of their respective companies.
VMware, Inc.
3401 Hillview Ave.
Palo Alto, CA 94304
www.vmware.com
2 VMware, Inc.
Page 3

Contents
About VMware vCenter Site Recovery Manager Administration 7
SRM Privileges, Roles, and Permissions 9
1
How SRM Handles Permissions 10
SRM and the vCenter Server Administrator Role 10
SRM and vSphere Replication Roles 11
Managing Permissions in a Shared Recovery Site Configuration 11
Assign SRM Roles and Permissions 13
SRM Roles Reference 14
vSphere Replication Roles Reference 17
Replicating Virtual Machines 21
2
How the Recovery Point Objective Affects Replication Scheduling 21
Replicating a Virtual Machine and Enabling Multiple Point in Time Instances 22
Configure Replication for a Single Virtual Machine 22
Configure Replication for Multiple Virtual Machines 24
Replicate Virtual Machines By Using Replication Seeds 25
Reconfigure Replications 26
Stop Replicating a Virtual Machine 27
Creating Protection Groups 29
3
About Array-Based Protection Groups and Datastore Groups 29
How SRM Computes Datastore Groups 30
Create Array-Based Protection Groups 31
Edit Array-Based Protection Groups 32
Create vSphere Replication Protection Groups 32
Edit vSphere Replication Protection Groups 33
Apply Inventory Mappings to All Members of a Protection Group 33
VMware, Inc.
Creating, Testing, and Running Recovery Plans 35
4
Testing a Recovery Plan 36
Test Networks and Datacenter Networks 37
Performing a Planned Migration or Disaster Recovery By Running a Recovery Plan 37
Running a Recovery with Forced Recovery 38
Differences Between Testing and Running a Recovery Plan 38
How SRM Interacts with DPM and DRS During Recovery 39
How SRM Interacts with Storage DRS or Storage vMotion 39
Using SRM with Array-Based Replication on Sites with Storage DRS or Storage vMotion 39
Using SRM with vSphere Replication on Sites with Storage DRS or Storage vMotion 40
How SRM Interacts with vSphere High Availability 41
Protecting Microsoft Cluster Server and Fault Tolerant Virtual Machines 41
3
Page 4

Site Recovery Manager Administration
Create, Test, and Run a Recovery Plan 42
Create a Recovery Plan 43
Edit a Recovery Plan 43
Suspend Virtual Machines When a Recovery Plan Runs 44
Test a Recovery Plan 44
Clean Up After Testing a Recovery Plan 45
Run a Recovery Plan 45
Recover a Point-in-Time Snapshot of a Virtual Machine 46
Export Recovery Plan Steps 47
View and Export Recovery Plan History 47
Cancel a Test or Recovery 48
Delete a Recovery Plan 48
Reprotecting Virtual Machines After a Recovery 49
5
How SRM Performs Reprotect 50
Preconditions for Performing Reprotect 51
Reprotect Virtual Machines 51
Reprotect States 52
Restoring the Pre-Recovery Site Configuration By Performing Failback 53
6
Perform a Failback 54
Customizing a Recovery Plan 57
7
Recovery Plan Steps 57
Specify the Recovery Priority of a Virtual Machine 58
Creating Custom Recovery Steps 58
Types of Custom Recovery Steps 59
How SRM Handles Custom Recovery Steps 60
Create Top-Level Command Steps 60
Create Top-Level Message Prompt Steps 61
Create Command Steps for Individual Virtual Machines 61
Create Message Prompt Steps for Individual Virtual Machines 62
Guidelines for Writing Command Steps 62
Environment Variables for Command Steps 62
Customize the Recovery of an Individual Virtual Machine 63
Customizing IP Properties for Virtual Machines 65
8
Customize IP Properties For an Individual Virtual Machine 66
Report IP Address Mappings for Recovery Plans 67
Customizing IP Properties for Multiple Virtual Machines 67
Syntax of the DR IP Customizer Tool 68
Structure of the DR IP Customizer CSV File 69
Modifying the DR IP Customizer CSV File 72
Run DR IP Customizer to Customize IP Properties for Multiple Virtual Machines 77
Advanced SRM Configuration 79
9
Configure Protection for a Virtual Machine or Template 79
Configure Resource Mappings for a Virtual Machine 80
4 VMware, Inc.
Page 5

Specify a Nonreplicated Datastore for Swap Files 80
Recovering Virtual Machines Across Multiple Hosts on the Recovery Site 81
Resize Virtual Machine Disk Files During Replication Using Replication Seeds 82
Resize Virtual Machine Disk Files During Replication Without Using Replication Seeds 82
Reconfigure SRM Settings 82
Change Local Site Settings 83
Change Logging Settings 83
Change Recovery Settings 85
Change Remote Site Settings 86
Change the Timeout for the Creation of Placeholder Virtual Machines 86
Change Storage Settings 86
Change Storage Provider Settings 87
Change vSphere Replication Settings 88
Modify Settings to Run Large SRM Environments 89
Contents
Troubleshooting SRM Administration 93
10
Limitations to Protection and Recovery of Virtual Machines 93
vSphere Replication Limitations 96
SRM Events and Alarms 96
How SRM Monitors Connections Between Sites 96
Configure SRM Alarms 97
SRM Events Reference 97
vSphere Replication Events and Alarms 106
Configure vSphere Replication Alarms 106
List of vSphere Replication Events 106
Collecting SRM Log Files 109
Collect SRM Log Files By Using the SRM Interface 109
Collect SRM Log Files Manually 110
Access the vSphere Replication Logs 112
Manually Access the vSphere Replication Logs 112
Resolve SRM Operational Issues 113
SRM Doubles the Number of Backslashes in the Command Line When Running Callouts 113
Powering on Many Virtual Machines Simultaneously on the Recovery Site Can Lead to Errors 114
LVM.enableResignature=1 Remains Set After a SRM Test Failover 114
Adding Virtual Machines to a Protection Group Fails with an Unresolved Devices Error 115
Configuring Protection fails with Placeholder Creation Error 115
Planned Migration Fails Because Host is in an Incorrect State 116
Recovery Fails with a Timeout Error During Network Customization for Some Virtual
Machines 116
Recovery Fails with Unavailable Host and Datastore Error 117
Reprotect Fails with a vSphere Replication Timeout Error 117
Recovery Plan Times Out While Waiting for VMware Tools 117
Reprotect Fails After Restarting vCenter Server 118
Rescanning Datastores Fails Because Storage Devices are Not Ready 118
Scalability Problems when Replicating Many Virtual Machines with a Short RPO to a Shared
VMFS Datastore on ESXi Server 5.0 119
Application Quiescing Changes to File System Quiescing During vMotion to an Older Host 120
Reconfigure Replication on Virtual Machines with No Datastore Mapping 120
Configuring Replication Fails for Virtual Machines with Two Disks on Different Datastores 121
VMware, Inc. 5
Page 6

Site Recovery Manager Administration
vSphere Replication RPO Violations 121
vSphere Replication Does Not Start After Moving the Host 122
Unexpected vSphere Replication Failure Results in a Generic Error 122
Generating Support Bundles Disrupts vSphere Replication Recovery 123
Recovery Plan Times Out While Waiting for VMware Tools 123
Index 125
6 VMware, Inc.
Page 7

About VMware vCenter Site Recovery Manager Administration
VMware vCenter Site Recovery Manager (SRM) is an extension to VMware vCenter Server that delivers a
business continuity and disaster recovery solution that helps you plan, test, and run the recovery of
vCenter Server virtual machines. SRM can discover and manage replicated datastores, and automate
migration of inventory from one vCenter Server instance to another.
Intended Audience
This book is intended for SRM administrators who are familiar with vSphere and its replication
technologies, such as host-based replication and replicated datastores. This solution serves the needs of
administrators who want to configure protection for their vSphere inventory. It might also be appropriate
for users who need to add virtual machines to a protected inventory or to verify that an existing inventory is
properly configured for use with SRM.
VMware, Inc.
7
Page 8

Site Recovery Manager Administration
8 VMware, Inc.
Page 9

SRM Privileges, Roles, and
Permissions 1
SRM provides disaster recovery by performing operations for users. These operations involve managing
objects, such as recovery plans or protection groups, and performing operations, such as replicating or
powering off virtual machines. SRM uses roles and permissions so that only users with the correct roles and
permissions can perform operations.
SRM adds several roles to vCenter Server, each of which includes privileges to complete SRM and
vCenter Server tasks. You assign roles to users to permit them to complete tasks in SRM.
Privilege
Role
Permission
For information about the roles that SRM adds to vCenter Server and the privileges that users require to
complete tasks, see “SRM Roles Reference,” on page 14.
How SRM Handles Permissions on page 10
n
SRM determines whether a user has permission to perform an operation, such as configuring
protection or running the individual steps in a recovery plan. This permission check ensures the
correct authentication of the user, but it does not represent the security context in which the operation
is performed.
SRM and the vCenter Server Administrator Role on page 10
n
If a user or user group has the vCenter Server administrator role on a vCenter Server instance when
you install SRM, that user or user group obtains all SRM privileges.
The right to perform an action, for example to create a recovery plan or to
modify a protection group.
A collection of privileges. Default roles provide the privileges that certain
users require to perform a set of SRM tasks, for example users who manage
protection groups or perform recoveries. A user can have at most one role on
an object, but roles can be combined if the user belongs to multiple groups
that all have roles on the object.
A role granted to a particular user or user group on a specific object. A user
or user group is also known as a principal. A permission is a combination of
a role, an object, and a principal. For example, a permission is the privilege to
modify a specific protection group.
VMware, Inc.
SRM and vSphere Replication Roles on page 11
n
When you install vSphere Replication with SRM, the vCenter Server administrator role inherits all of
the SRM and vSphere Replication privileges.
Managing Permissions in a Shared Recovery Site Configuration on page 11
n
You can configure SRM to use with a shared recovery site. The vCenter Server administrator on the
shared recovery site must manage permissions so that each customer has sufficient privileges to
configure and use SRM, but no customer has access to resources that belong to another customer.
9
Page 10

Site Recovery Manager Administration
Assign SRM Roles and Permissions on page 13
n
During installation, SRM administrator rights are assigned to the vCenter Server administrator role. At
this time, only vCenter Server administrators can log in to SRM, unless they explicitly grant access to
other users.
SRM Roles Reference on page 14
n
SRM includes a set of roles. Each role includes a set of privileges, which allow users with those roles to
complete different actions.
How SRM Handles Permissions
SRM determines whether a user has permission to perform an operation, such as configuring protection or
running the individual steps in a recovery plan. This permission check ensures the correct authentication of
the user, but it does not represent the security context in which the operation is performed.
SRM performs operations in the security context of the user ID that is used to connect the sites, or in the
context of the ID under which the SRM service is running, for example, the local system ID.
After SRM verifies that a user has the appropriate permissions on the target vSphere resources, SRM
performs operations on behalf of users by using the vSphere administrator role.
For configuration operations, SRM validates user permissions when the user requests the operation.
Operations other than configuration operations require two phases of validation.
1 During configuration, SRM verifies that the user configuring the system has the correct permissions to
complete the configuration on the vCenter Server object. For example, a user must have permission to
protect a virtual machine and use resources on a secondary vCenter Server that the recovered virtual
machine uses.
2 The user performing the configuration must have the correct permissions to complete the task that they
are configuring. For example, a user must have permissions to run a recovery plan. SRM then
completes the task on behalf of the user as a vCenter Server administrator.
As a result, a user who completes a particular task, such as a recovery, does not necessarily require
permissions to act on vSphere resources. The role authorizes the action, but the action is performed by SRM
acting as an administrator. SRM performs the operations by using the administrator credentials that you
provide when you connect the protected and recovery sites.
SRM maintains a database of permissions for internal SRM objects that uses a model similar to the one the
vCenter Server uses. SRM verifies its own SRM privileges even on vCenter Server objects. For example, SRM
checks for the Resource.Recovery Use permission on the target datastore rather than checking multiple lowlevel permissions, such as Allocate space.
SRM and the vCenter Server Administrator Role
If a user or user group has the vCenter Server administrator role on a vCenter Server instance when you
install SRM, that user or user group obtains all SRM privileges.
SRM does not perform verification of roles or permissions after installation. If you assign the vCenter Server
administrator role to users or user groups after you install SRM, you must manually assign the SRM roles to
those users.
You can assign SRM roles to users or user groups that do not have the vCenter Server administrator role. In
this case, those users have permission to perform SRM operations, but they do not have permission to
perform all vCenter Server operations.
10 VMware, Inc.
Page 11
Chapter 1 SRM Privileges, Roles, and Permissions
SRM and vSphere Replication Roles
When you install vSphere Replication with SRM, the vCenter Server administrator role inherits all of the
SRM and vSphere Replication privileges.
If you manually assign an SRM role to a user or user group, or if you assign an SRM role to a user or user
group that is not a vCenter Server administrator, these users do not obtain vSphere Replication privileges.
The SRM roles do not include the privileges of the vSphere Replication roles. For example, the SRM
Recovery Administrator role includes the privilege to run recovery plans, including recovery plans that
contain vSphere Replication protection groups, but it does not include the privilege to configure
vSphere Replication on a virtual machine. The separation of the SRM and vSphere Replication roles allows
you to distribute responsibilities between different users. For example, one user with the VRM
administrator role is responsible for configuring vSphere Replication on virtual machines, and another user
with the SRM Recovery Administrator role is responsible for running recoveries.
In some cases, a user who is not vCenter Server administrator might require the privileges to perform both
SRM and vSphere Replication operations. To assign a combination of SRM and vSphere Replication roles to
a single user, you can add the user to two user groups.
Example: Assign SRM and vSphere Replication Roles to a User
By creating two user groups, you can grant to a user the privileges of both an SRM role and a
vSphere Replication role, without that user being a vCenter Server administrator.
1 Create two user groups.
2 Assign an SRM role to one user group, for example SRM administrator.
3 Assign a vSphere Replication role to the other user group, for example VRM administrator.
4 Add the user to both user groups.
The user has all the privileges of the SRM administrator role and of the VRM administrator role.
Managing Permissions in a Shared Recovery Site Configuration
You can configure SRM to use with a shared recovery site. The vCenter Server administrator on the shared
recovery site must manage permissions so that each customer has sufficient privileges to configure and use
SRM, but no customer has access to resources that belong to another customer.
In the context of a shared recovery site, a customer is the owner of a pair of SRM Server instances.
Customers with adequate permissions must be able to access the shared recovery site to create, test, and run
the recovery plans for their own protected site. The vCenter Server administrator at the shared recovery site
must create a separate user group for each customer. No customer's user accounts can be a member of the
vCenter Server Administrators group. The only supported configuration for a shared recovery site is for one
organization to manage all of the protected sites and the recovery site.
CAUTION Certain SRM roles allow users to run commands on SRM Server, so you should assign these roles
to trusted administrator-level users only. See “SRM Roles Reference,” on page 14 for the list of SRM roles
that run commands on SRM Server.
On a shared recovery site, multiple customers share a single vCenter Server instance. In some cases,
multiple customers can share a single ESXi host on the recovery site. You can map the resources on the
protected sites to shared resources on the shared recovery site. You might share resources on the recovery
site if you do not need to keep all of the customers' virtual machines separate, for example if all of the
customers belong to the same organization.
VMware, Inc. 11
Page 12

Site Recovery Manager Administration
You can also create isolated resources on the shared recovery site and map the resources on the protected
sites to their own dedicated resources on the shared recovery site. You might use this configuration if you
must keep all of the customers' virtual machines separate from each other, for example if all of the
customers belong to different organizations.
Guidelines for Sharing Customer Resources
Follow these guidelines when you configure permissions for sharing customer resources on the shared
recovery site:
All customers must have read access to all folders of the vCenter Server on the shared recovery site.
n
Do not give a customer the permission to rename, move, or delete the datacenter or host.
n
Do not give a customer the permission to create virtual machines outside of the customer’s dedicated
n
folders and resource pools.
Do not allow a customer to change roles or assign permissions for objects that are not dedicated to the
n
customer’s own use.
To prevent unwanted propagation of permissions across different organizations’ resources, do not
n
propagate permissions on the root folder, datacenters, and hosts of the vCenter Server on the shared
recovery site.
Guidelines for Isolating Customer Resources
Follow these guidelines when you configure permissions for isolating customer resources on the shared
recovery site:
Assign to each customer a separate virtual machine folder in the vCenter Server inventory.
n
Set permissions on this folder to prevent any other customer from placing their virtual machines in
n
it. For example, set the Administrator role and activate the propagate option for a customer on that
customer's folder. This configuration prevents duplicate name errors that might otherwise occur if
multiple customers protect virtual machines that have identical names.
Place all of the customer's placeholder virtual machines in this folder, so that they can inherit its
n
permissions.
Do not assign permissions to access this folder to other customers.
n
Assign dedicated resource pools, datastores, and networks to each customer, and configure the
n
permissions in the same way as for folders.
Viewing Tasks and Events in a Shared Recovery Site Configuration
In the Recent Tasks panel of the vSphere Client, users who have permissions to view an object can see tasks
that other users start on that object. All customers can see all of the tasks that other users perform on a
shared resource. For example, all users can see the tasks that run on a shared host, datacenter, or the
vCenter Server root folder.
Events that all of the instances of SRM Server generate on a shared recovery site have identical permissions.
All users who can see events from one instance of SRM Server can see events from all SRM Server instances
that are running on the shared recovery site.
12 VMware, Inc.
Page 13

Assign SRM Roles and Permissions
During installation, SRM administrator rights are assigned to the vCenter Server administrator role. At this
time, only vCenter Server administrators can log in to SRM, unless they explicitly grant access to other
users.
To allow other users to access SRM, vCenter Server administrators must grant them permissions in the SRM
interface. Permission assignments apply on a per-site basis. You must add corresponding permissions on
both sites.
SRM requires permissions on vCenter Server objects as well as on SRM objects. To configure permissions on
the remote vCenter Server installation, start another instance of the vSphere Client. You can change SRM
permissions from the same interface on both sites after you connect the protected and recovery sites.
SRM augments vCenter Server roles and permissions with additional permissions that allow detailed
control over SRM specific tasks and operations. For information about the permissions that each SRM role
includes, see “SRM Roles Reference,” on page 14.
Procedure
1 Click Sites in the SRM interface, and select the site on which to assign permissions.
2 Click the Permissions tab.
Chapter 1 SRM Privileges, Roles, and Permissions
3 Right-click anywhere in the panel for either the local or remote sites and select Add Permission.
4 Click Add.
5 Identify a user or group for the role.
a From the Domain drop-down menu, select the domain that contains the user or group.
b Enter a user or user group name in the Search text box or select a name from the Name list.
c Click Add and click OK.
6 Select a role from the Assigned Role drop-down menu to assign to the user or user group that you
selected.
The Assigned Role drop-down menu includes all of the roles that vCenter Server and its plug-ins make
available. SRM adds several roles to vCenter Server.
Option Action
Allow a user or user group to
perform all SRM configuration and
administration operations.
Allow a user or user group to
manage and modify protection
groups and to configure protection
on virtual machines.
Allow a user or user group to
perform recoveries and test
recoveries.
Allow a user or user group to
create, modify, and test recovery
plans.
Allow a user or user group to test
recovery plans.
Assign the SRM Administrator role.
Assign the SRM Protection Groups Administrator role.
Assign the SRM Recovery Administrator role.
Assign the SRM Recovery Plans Administrator role.
Assign the SRM Recovery Test Administrator role.
When you select a role, the hierarchical list displays the privileges that the role includes. Click a
privilege in the hierarchical list to see a description of that privilege. You cannot modify the list of
privileges that each role includes.
VMware, Inc. 13
Page 14

Site Recovery Manager Administration
7 Select Propagate to Child Objects to apply the selected role to all of the child objects of the inventory
objects that this role can affect.
For example, if a role contains privileges to modify folders, selecting this option extends the privileges
to all the virtual machines in a folder. You might deselect this option to create a more complex
hierarchy of permissions. For example, deselect this option to override the permissions that are
propagated from the root of a certain node from the hierarchy tree, but without overriding the
permissions of the child objects of that node.
8 Click OK to assign the role and its associated privileges to the user or user group.
9 Repeat Step 1 through Step 8 to assign roles and privileges to the users or user groups on the other SRM
site.
You assigned a given SRM role to a user or user group. This user or user group has privileges to perform the
actions that the role defines on the objects on the SRM site that you configured.
Example: Combining SRM Roles
You can assign only one role to a user or user group. If a user who is not a vCenter Server administrator
requires the privileges of more than one SRM role, you can create multiple user groups. For example, a user
might require the privileges to manage recovery plans and to run recovery plans.
1 Create two user groups.
2 Assign the SRM Recovery Plans Administrator role to one group.
3 Assign the SRM Recovery Administrator role to the other group.
4 Add the user to both user groups.
By being a member of groups that have both the SRM Recovery Plans Administrator and the SRM Recovery
Administrator roles, the user can manage recovery plans and run recoveries.
SRM Roles Reference
SRM includes a set of roles. Each role includes a set of privileges, which allow users with those roles to
complete different actions.
Roles can have overlapping sets of privileges and actions. For example, the SRM Administrator role and the
SRM Protection Groups Administrator have the Create privilege for protection groups. With this privilege,
the user can complete one aspect of the set of tasks that make up the management of protection groups.
Assign roles to users on SRM objects consistently on both sites, so that protected and recovery objects have
identical permissions.
All users must have at least the System.Read privilege on the root folders of vCenter Server and the SRM
root nodes on both sites.
14 VMware, Inc.
Page 15
Table 1‑1. SRM Roles
Role Actions that this Role Permits
SRM Administrator The SRM Administrator grants
permission to perform all SRM
configuration and administration
operations.
Configure advanced settings.
n
Configure connections.
n
Configure inventory
n
preferences.
Configure placeholder
n
datastores.
Configure array managers.
n
Manage protection groups.
n
Manage recovery plans.
n
Perform reprotect operations.
n
Configure protection on
n
virtual machines.
Edit protection groups.
n
Remove protection groups.
n
Users with this role cannot run
recoveries. Only users with the
SRM Recovery Administrator
role can perform recoveries.
Chapter 1 SRM Privileges, Roles, and Permissions
Privileges that this
Role Includes
Site Recovery
Manager.Advanced
Settings.Modify
Site Recovery
Manager.Array
Manager.Configure
Site Recovery
Manager.Diagnostics.Ex
port
Site Recovery
Manager.Inventory
Preferences.Modify
Site Recovery
Manager.Placeholder
Datastores.Configure
Site Recovery
Manager.DiagnosticsEx
port
Site Recovery
Manager.Protection
Group.Assign to Plan
Site Recovery
Manager.Protection
Group.Create
Site Recovery
Manager.Protection
Group.Modify
Site Recovery
Manager.Protection
Group.Remove
Site Recovery
Manager.Protection
Group.Remove from
Plan
Site Recovery
Manager.Recovery
History .View Deleted
Plans
Site Recovery
Manager.Recovery
Plan.Configure
Site Recovery
Manager.Recovery
Plan.Create
Site Recovery
Manager.Recovery
Plan.Modify
Site Recovery
Manager.Recovery
Plan.Remove
Site Recovery
Manager.Recovery
Plan.Reprotect
Site Recovery
Manager.Recovery
Plan.Test
Objects in vCenter Server
Inventory that this Role Can
Access
Virtual machines
n
Datastores
n
vCenter Server folders
n
Resource pools
n
SRM service instances
n
Networks
n
SRM folders
n
Protection groups
n
Recovery plans
n
Array managers
n
VMware, Inc. 15
Page 16

Site Recovery Manager Administration
Table 1‑1. SRM Roles (Continued)
Role Actions that this Role Permits
SRM Protection
Groups
Administrator
SRM Recovery
Administrator
The SRM Protection Groups
Administrator role allows users
to manage protection groups.
Create protection groups.
n
Modify protection groups.
n
Add virtual machines to
n
protection groups.
Delete protection groups.
n
Configure protection on
n
virtual machines.
Remove protection from
n
virtual machines.
Users with this role cannot
perform or test recoveries or
create or modify recovery plans.
The SRM Recovery Administrator
role allows users to perform
recoveries and reprotect
operations.
Remove protection groups
n
from recovery plans.
Test recovery plans.
n
Run recovery plans.
n
Run reprotect operations.
n
Configure custom command
n
steps on virtual machines.
View deleted recovery plans.
n
Edit virtual machine recovery
n
properties.
Users with this role cannot
configure protection on virtual
machines, or create or modify
recovery plans.
Privileges that this
Role Includes
Site Recovery
Manager.Remote
Site.Modify
Datastore.Replication.P
rotect
Datastore.Replication.U
nprotect
Resource.Recovery Use
Virtual Machine. SRM
Protection.Protect
Virtual Machine. SRM
Protection.Stop
Site Recovery
Manager.Protection
Group.Create
Site Recovery
Manager.Protection
Group.Modify
Site Recovery
Manager.Protection
Group.Remove
Datastore.Replication.P
rotect
Datastore.Replication.U
nprotect
Resource.Recovery Use
Virtual Machine. SRM
Protection.Protect
Virtual Machine. SRM
Protection.Stop
Site Recovery
Manager.Protection
Group.Remove from
plan
Site Recovery
Manager.Recovery
Plan.Modify
Site Recovery
Manager.Recovery
Plan.Test
Site Recovery
Manager.Recovery
Plan.Recovery
Site Recovery
Manager.Recovery
Plan.Reprotect
Site Recovery
Manager.Recovery
Plan.Configure
commands
Site Recovery
Manager.Recovery
History.View deleted
plans
Objects in vCenter Server
Inventory that this Role Can
Access
SRM folders
n
Protection groups
n
Protection groups
n
Recovery plans
n
SRM service instances
n
16 VMware, Inc.
Page 17

Table 1‑1. SRM Roles (Continued)
Role Actions that this Role Permits
SRM Recovery Plans
Administrator
SRM Test
Administrator
The SRM Recovery Plans
Administrator role allows users
to create and test recovery plans.
Add protection groups to
n
recovery plans.
Remove protection groups
n
from recovery plans.
Configure custom command
n
steps on virtual machines.
Create recovery plans.
n
Test recovery plans.
n
Cancel recovery plan tests.
n
Edit virtual machine recovery
n
properties.
Users with this role cannot
configure protection on virtual
machines, or perform recoveries
or reprotect operations.
The SRM Test Administrator role
only allows users to test recovery
plans.
Test recovery plans.
n
Cancel recovery plan tests.
n
Edit virtual machine recovery
n
properties.
Users with this role cannot
configure protection on virtual
machines, create protection
groups or recovery plans, or
perform recoveries or reprotect
operations.
Chapter 1 SRM Privileges, Roles, and Permissions
Privileges that this
Role Includes
Site Recovery
Manager.Protection
Group.Assign to plan
Site Recovery
Manager.Protection
Group.Remove from
plan
Site Recovery
Manager.Recovery
Plan.Configure
Commands
Site Recovery
Manager.Recovery
Plan.Create
Site Recovery
Manager.Recovery
Plan.Modify
Site Recovery
Manager.Recovery
Plan.Remove
Site Recovery
Manager.Recovery
Plan.Test
Resource.Recovery Use
Site Recovery
Manager.Recovery
Plan.Modify
Site Recovery
Manager.Recovery
Plan.Test
Objects in vCenter Server
Inventory that this Role Can
Access
Protection groups
n
Recovery plans
n
vCenter Server folders
n
Datastores
n
Resource pools
n
Networks
n
Recovery plans
vSphere Replication Roles Reference
vSphere Replication includes a set of roles. Each role includes a set of privileges, which enable users with
those roles to complete different actions.
NOTE When assigning permissions with no propagation, make sure that you have at least Read-only
permission on all parent objects.
VMware, Inc. 17
Page 18

Site Recovery Manager Administration
Table 1‑2. vSphere Replication Roles
Role Actions that this Role Permits Privileges that this Role Includes
VRM
replication
viewer
VRM virtual
machine
replication
user
n
n
n
n
n
n
Requires a corresponding user
with the same role on the target
site and additionally
vSphere Replication target
datastore user role on the target
datacenter, or datastore folder
or each target datastore.
View replications.
Cannot change replication
parameters.
View replications.
Manage datastores.
Configure and unconfigure
replications.
Manage and monitor
replications.
VRM remote.View VR
VRM remote.View VRM
VRM datastore mapper.View
Host.vSphere Replication.Manage
replication
Virtual machine.vSphere
Replication.Monitor replication
Datastore.Browse Datastore
VRM remote.View VR
VRM remote.View VRM
VRM datastore mapper.Manage
VRM datastore mapper.View
Host.vSphere Replication.Manage
replication
Virtual machine.vSphere
Replication.Configure replication
Virtual machine.vSphere
Replication.Manage replication
Virtual machine.vSphere
Replication.Monitor replication
Objects in vCenter Server
Inventory that this Role Can
Access
vCenter Server root folder
with propagation, at source
site (outgoing replications)
and target site (incoming
replications).
Alternatively, vCenter Server
root folder without
propagation on both sites and
virtual machine without
propagation on the source
site.
vCenter Server root folder
with propagation on both
sites.
Alternatively, vCenter Server
root folder without
propagation on both sites,
virtual machine without
propagation on the source
site, source datastores without
propagation on the source
site.
18 VMware, Inc.
Page 19

Chapter 1 SRM Privileges, Roles, and Permissions
Table 1‑2. vSphere Replication Roles (Continued)
Role Actions that this Role Permits Privileges that this Role Includes
VRM
administrator
VRM
diagnostics
Incorporates all
vSphere Replication privileges.
Generate, retrieve, and delete
log bundles.
VRM remote.Manage VR
VRM remote.View VR
VRM remote.Manage VRM
VRM remote.View VRM
VRM datastore mapper.Manage
VRM datastore mapper.View
VRM diagnostics .Manage
VRM session .Terminate
Datastore.Browse datastore
Datastore.Low level file
operations
Host.vSphere Replication.Manage
replication
Resource.Assign virtual machine
to resource pool
Virtual
machine.Configuration.Add
existing disk
Virtual
machine.Configuration.Add or
remove device
Virtual machine.Interaction.Power
On
Virtual
machine.Interaction.Device
connection
Virtual
machine.Inventory.Register
Virtual machine.vSphere
Replication.Configure replication
Virtual machine.vSphere
Replication.Manage replication
Virtual machine.vSphere
Replication.Monitor replication
VRM remote.View VR
VRM remote.View VRM
VRM diagnostics .Manage
Objects in vCenter Server
Inventory that this Role Can
Access
vCenter Server root folder
with propagation on both
sites.
Alternatively, vCenter Server
root folder without
propagation on both sites,
virtual machine without
propagation on the source
site, target datastore, target
virtual machine folder with
propagation on the target site,
target host or cluster with
propagation on the target site.
vCenter Server root folder on
both sites.
VMware, Inc. 19
Page 20

Site Recovery Manager Administration
Table 1‑2. vSphere Replication Roles (Continued)
Role Actions that this Role Permits Privileges that this Role Includes
VRM target
datastore user
VRM virtual
machine
recovery user
Configure and reconfigure
replications.
Used on target site in
combination with the VRM
virtual machine replication user
role on both sites.
Recover virtual machines. Datastore.Browse datastore
Datastore.Browse datastore
Datastore.Low level file
operations
Datastore.Low level file
operations
Host.vSphere Replication.Manage
replication
Virtual
machine.Configuration.Add
existing disk
Virtual
machine.Configuration.Add or
remove device
Virtual machine.Interaction.Power
On
Virtual
machine.Interaction.Device
connection
Virtual
machine.Inventory.Register
Resource.Assign virtual machine
to resource pool
Objects in vCenter Server
Inventory that this Role Can
Access
Datastore objects on target
site, or datastore folder with
propagation at target site, or
target datacenter with
propagation.
Secondary vCenter Server root
folder with propagation.
Alternatively, secondary
vCenter Server root folder
without propagation, target
datastore without
propagation, target virtual
machine folder with
propagation, target host or
cluster with propagation.
20 VMware, Inc.
Page 21

Replicating Virtual Machines 2
Before you create protection groups, you must configure replication on the virtual machines to protect.
You can replicate virtual machines by using either array-based replication, vSphere Replication, or a
combination of both.
This information concerns replication using vSphere Replication. To configure array-based replication on
virtual machines, consult the documentation from your storage array manager (SRA) vendor.
This chapter includes the following topics:
“How the Recovery Point Objective Affects Replication Scheduling,” on page 21
n
“Replicating a Virtual Machine and Enabling Multiple Point in Time Instances,” on page 22
n
“Configure Replication for a Single Virtual Machine,” on page 22
n
“Configure Replication for Multiple Virtual Machines,” on page 24
n
“Replicate Virtual Machines By Using Replication Seeds,” on page 25
n
“Reconfigure Replications,” on page 26
n
“Stop Replicating a Virtual Machine,” on page 27
n
How the Recovery Point Objective Affects Replication Scheduling
The Recovery Point Objective (RPO) value you set during replication configuration affects replication
scheduling.
If you set an RPO of x minutes, the latest available replication instance can never reflect a state that is older
than x minutes. A replication instance reflects the state of a virtual machine at the time the replication starts.
You set the RPO during replication configuration to 15 minutes. If the replication starts at 12:00 and it takes
five minutes to transfer to the target site, the instance becomes available on the target site at 12:05, but it
reflects the state of the virtual machine at 12:00. The next replication can start no later than 12:10. This
replication instance is then available at 12:15 when the first replication instance that started at 12:00 expires.
If you set the RPO to 15 minutes and the replication takes 7.5 minutes to transfer an instance,
vSphere Replication transfers an instance all the time. If the replication takes more than 7.5 minutes, the
replication encounters periodic RPO violations. For example, if the replication starts at 12:00 and takes 10
minutes to transfer an instance, the replication finishes at 12:10. You can start another replication
immediately, but it finishes at 12:20. During the time interval 12:15-12:20, an RPO violation occurs because
the latest available instance started at 12:00 and is too old.
VMware, Inc.
21
Page 22
vSphere Web Client
VR Appliance
t1
VM
VM VM VM
t3t2
vSphere Web Client
VR Appliance
VM
Replication
Source Site
Target Site
t0
Site Recovery Manager Administration
The replication scheduler tries to satisfy these constraints by overlapping replications to optimize
bandwidth use and might start replications for some virtual machines earlier than expected.
To determine the replication transfer time, the replication scheduler uses the duration of the last few
instances to estimate the next one.
Replicating a Virtual Machine and Enabling Multiple Point in Time Instances
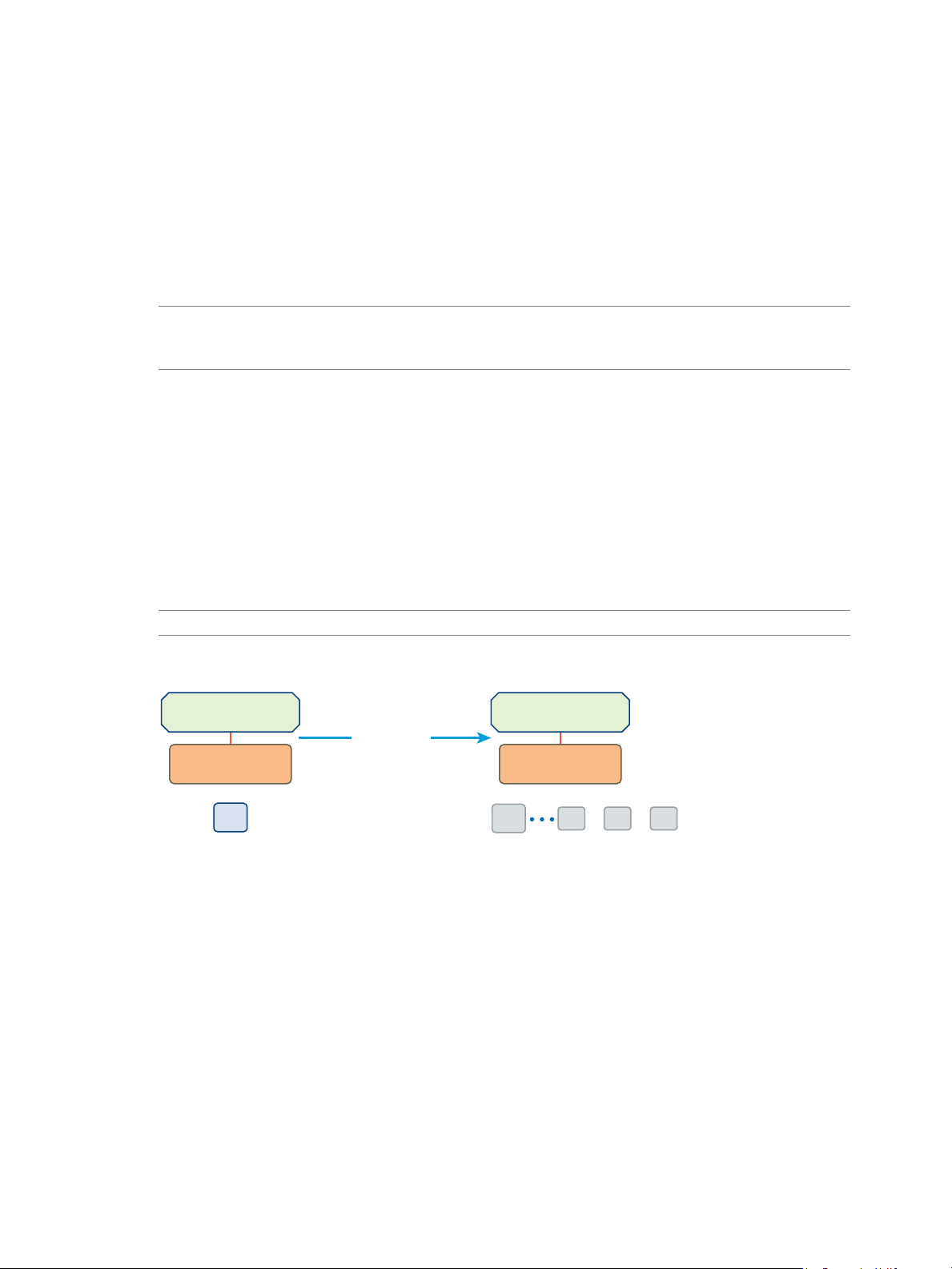
You can recover virtual machines at specific points in time (PIT) such as the last known consistent state.
NOTE You cannot use the SRM interface to configure replication that uses point in time (PIT) snapshots. To
enable PIT snapshots, configure replication of a virtual machine by using the vSphere Web Client. See
Configure Replication for a Single Virtual Machine in vSphere Replication Administration.
When you configure replication of a virtual machine, you can enable multiple point in time (PIT) instances
in the recovery settings in the Configure Replication wizard. vSphere Replication retains instances of the
virtual machine on the target site based on the number of retention policy that you specify.
vSphere Replication supports maximum of 24 instances. After you recover a virtual machine, you can revert
it to a specific snapshot.
During replication, vSphere Replication replicates all aspects of the virtual machine to the target site,
including any potential viruses and corrupted applications. If a virtual machine suffers from a virus or
corruption and you have configured vSphere Replication to keep PIT snapshots, you can recover the virtual
machine and then revert it to a snapshot of the virtual machine in its uncorrupted state.
You can also use the PIT instances to recover the last known good state of a database.
NOTE vSphere Replication does not replicate virtual machine snapshots.
Figure 2‑1. Recovering a Virtual Machine at Points in Time (PIT)
SRM only recovers the most recent PIT snapshot during a recovery. To recover older snapshots, you must
enable the vrReplication > preserveMpitImagesAsSnapshots option in Advanced Settings in the SRM
interface. See “Change vSphere Replication Settings,” on page 88.
To recover a virtual machine from an older PIT snapshot, you must manually revert the virtual machine to
that snapshot after the recovery. See “Recover a Point-in-Time Snapshot of a Virtual Machine,” on page 46.
Configure Replication for a Single Virtual Machine
vSphere Replication can protect individual virtual machines and their virtual disks by replicating them to
another location.
22 VMware, Inc.
When you configure replication, you set a recovery point objective (RPO) to determine the period of time
between replications. For example, an RPO of 1 hour seeks to ensure that a virtual machine loses no more
than 1 hour of data during the recovery. For smaller RPOs, less data is lost in a recovery, but more network
bandwidth is consumed keeping the replica up to date.
Page 23

Chapter 2 Replicating Virtual Machines
Every time that a virtual machine reaches its RPO target, vSphere Replication records approximately 3800
bytes of data in the vCenter Server events database. If you set a low RPO period, this can quickly create a
large volume of data in the database. To avoid creating large volumes of data in the vCenter Server events
database, limit the number of days that vCenter Server retains event data. See Configure Database Retention
Policy in the vCenter Server and Host Management Guide. Alternatively, set a higher RPO value.
NOTE You cannot use the SRM interface to configure replication that uses point in time (PIT) snapshots. To
enable PIT snapshots, configure replication of a virtual machine by using the vSphere Web Client. See
Configure Replication for a Single Virtual Machine in vSphere Replication Administration.
To recover a virtual machine from an older PIT snapshot, you must manually revert the virtual machine to
that snapshot after the recovery. See “Recover a Point-in-Time Snapshot of a Virtual Machine,” on page 46.
vSphere Replication guarantees crash consistency amongst all the disks that belong to a virtual machine. If
you use VSS quiescing, you might obtain a higher level of consistency. The available quiescing types are
determined by the virtual machine's operating system. See Compatibility Matrixes for vSphere Replication
5.5 for Microsoft Volume Shadow Copy Service (VSS) quiescing support for Windows virtual machines.
You can configure virtual machines to replicate to a Virtual SAN datastore on the target site. See Using
vSphere Replication with Virtual SAN in Site Recovery Manager Installation and Configuration for the
limitations when using vSphere Replication with Virtual SAN.
NOTE vSphere 5.5 includes Virtual SAN as an experimental feature. You can perform testing with Virtual
SAN, but it is not supported for use in a production environment. See the release notes for this release for
information about how to enable Virtual SAN.
Prerequisites
Verify that you have deployed and connected vSphere Replication appliances and SRM Server instances at
each site.
Procedure
1 On the vSphere Client Home page, click VMs and Templates.
2 Browse the inventory to find the single virtual machine to replicate using vSphere Replication.
3 Right-click the virtual machine and select vSphere Replication.
4 Use the RPO slider or enter a value to configure the maximum amount of data that can be lost in the
case of a site failure.
The available RPO range is from 15 minutes to 24 hours.
5 Select a Guest OS Quiescing configuration, if applicable to the source virtual machine operating system.
6 If no target file location is specified or to override the default determined by the datastore mappings,
click Browse to select a target location for the virtual machine.
Option Description
Place virtual machine in a datastore
directly
Place virtual machine in a specific
folder in a datastore
Select a datastore and click OK.
Select Specify datastore folder, click Browse to locate the folder, then
double-click the desired folder.
VMware, Inc. 23
Page 24

Site Recovery Manager Administration
7 Select a replication destination for each media device for the virtual machine.
The next pages are created dynamically depending on the media devices installed on the virtual
machine. They might include multiple virtual drives, all of which you can configure individually.
Configurable settings include whether the virtual drive is replicated, the virtual drive's replication
destination, and information about how the replicated virtual drive is configured. If the disk is to be
replicated, select a replication destination for the disk before proceeding.
8 Accept the automatic assignment of a vSphere Replication server or select a particular server on the
target site.
9 Review the settings and click Finish to establish replication.
Configure Replication for Multiple Virtual Machines
You can configure replication for multiple virtual machines using the multi-VM configure replication
wizard.
When you configure replication, you set a recovery point objective (RPO) to determine the period of time
between replications. For example, an RPO of 1 hour seeks to ensure that a virtual machine loses no more
than 1 hour of data during the recovery. For smaller RPOs, less data is lost in a recovery, but more network
bandwidth is consumed keeping the replica up to date.
Every time that a virtual machine reaches its RPO target, vSphere Replication records approximately 3800
bytes of data in the vCenter Server events database. If you set a low RPO period, this can quickly create a
large volume of data in the database. To avoid creating large volumes of data in the vCenter Server events
database, limit the number of days that vCenter Server retains event data. See Configure Database Retention
Policy in the vCenter Server and Host Management Guide. Alternatively, set a higher RPO value.
NOTE You cannot use the SRM interface to configure replications that use point in time (PIT) snapshots. To
enable PIT snapshots, configure replication of virtual machines by using the vSphere Web Client. See
Configure Replication for Multiple Virtual Machines in vSphere Replication Administration.
To recover a virtual machine from an older PIT snapshot, you must manually revert the virtual machine to
that snapshot after the recovery. See “Recover a Point-in-Time Snapshot of a Virtual Machine,” on page 46.
vSphere Replication guarantees crash consistency amongst all the disks that belong to a virtual machine. If
you use VSS quiescing, you might obtain a higher level of consistency. The available quiescing types are
determined by the virtual machine's operating system. See Compatibility Matrixes for vSphere Replication
5.5 for Microsoft Volume Shadow Copy Service (VSS) quiescing support for Windows virtual machines.
You can configure virtual machines to replicate to a Virtual SAN datastore on the target site. See Using
vSphere Replication with Virtual SAN in Site Recovery Manager Installation and Configuration for the
limitations when using vSphere Replication with Virtual SAN.
NOTE vSphere 5.5 includes Virtual SAN as an experimental feature. You can perform testing with Virtual
SAN, but it is not supported for use in a production environment. See the release notes for this release for
information about how to enable Virtual SAN.
Prerequisites
To replicate virtual machines using vSphere Replication, you must deploy the vSphere Replication
appliance at the source and target sites. You must power on the virtual machines to begin replication.
Before you replicate multiple machines, configure datastore mappings in the SRM user interface. You
configure the mappings so that information is available to SRM regarding the target datastore destinations
for replication.
Procedure
1 On the vSphere Web Client Home page, click VMs and Templates.
24 VMware, Inc.
Page 25

Chapter 2 Replicating Virtual Machines
2 Select a folder or datacenter in the left pane and click the Virtual Machines tab.
3 Select the virtual machines to replicate using the Ctrl or Shift keys.
4 Right-click the virtual machines and select vSphere Replication.
5 Use the RPO slider or enter a value to configure the maximum amount of data that can be lost in the
case of a site failure.
The available RPO range is from 15 minutes to 24 hours.
6 Select a Guest OS Quiescing configuration, if applicable to the source virtual machine operating system.
7 (Optional) Choose whether to enable Initial copies of .vmdk files have been placed on the target
datastore.
Select this option if you have physically copied VMDK files to the target site for use as replication seeds.
SRM uses datastore mappings and source virtual machine information to find and use initial copies.
SRM shows progress and status as it searches for initial copies. You can stop the search process or start
it again.
8 Accept the automatic assignment of a vSphere Replication server or select a particular server on the
target site.
9 Review the settings and click Finish to establish replication.
10 Select the vSphere Replication view in the SRM interface.
11 Select the remote vSphere Replication site and click the Virtual Machines tab.
If you have configured the datastore mappings for vSphere Replication, the virtual machines
synchronize with the target site.
What to do next
If you did not configure the datastore mappings for vSphere Replication before configuring replication, the
virtual machines appear in red with the status Datastore mappings were not configured. Reconfigure
vSphere Replication on the virtual machines manually.
Replicate Virtual Machines By Using Replication Seeds
You can make the initial replication of VDMK files more efficient by physically moving files onto a storage
device. vSphere Replication uses the physically moved files as replication seeds.
You might need to use replication seeds if it is not practical to copy the files over the network because the
amount of data is too large, the bandwidth available is too small, or some combination of the two.
When replicating virtual machines, ensure that virtual machines are replicated to subdirectories in
datastores. Copied disks work if the transfer method preserves the identity information stored in the VMDK
file.
Prerequisites
You deployed the vSphere Replication appliance at both sites.
n
You paired the SRM Server instances at each site, and you paired the vSphere Replication appliances.
n
Power off the source virtual machine before downloading the VMDK files to use as seeds for the
n
replication. Replication begins when the virtual machine is powered on.
Procedure
1 Use the vSphere Client to connect to a vCenter Server that can manage the virtual machines to be
physically moved.
2 Click Datastores.
VMware, Inc. 25
Page 26

Site Recovery Manager Administration
3 In the left pane, browse to the datastore that contains the files for the virtual machine, select the
datastore, and in the right pane, click Browse this datastore.
4 Select the folders for all virtual machines to be physically moved, right-click the selection, and click
Download.
5 Select a destination to which to copy the files and click OK.
6 Click Yes.
7 After the download finishes, transfer the files to a location on the paired site to upload them.
8 On the vSphere Client Home page at the paired site, click Datastores.
9 In the left pane, browse to the datastore to contain the files for the virtual machine, select the datastore,
and in the right pane, click Browse this datastore.
10 Select the folder to contain the copies of the virtual machines, right-click the selection, and click Upload
Folder.
11 Select the folder containing the virtual machines, and click OK.
12 On the protected site, right-click the virtual machine to replicate and select vSphere Replication.
13 Set the recovery point objective and target file location as normal and click Next.
14 Click Browse in the Target Disk File Location panel.
15 Select the target datastore, select the Specify datastore folder check box, and click Browse.
16 Select the target datastore and click Open.
17 Select the datastore folder that contains the seed files, change the file type to All Files, select the VMDK
file to use as a replication seed, and click OK.
18 Click Yes to confirm that you want to use this file as an initial copy.
19 Follow the prompts to select a vSphere Replication server and click Finish to complete the
configuration.
Reconfigure Replications
You can reconfigure the replication to enable or disable a virtual machine disk file for replication, modify
replication options, such as RPO or the quiescing method. You can also specify a different target datastore
for replica configuration and disk files and move the virtual machine to a different vSphere Replication
server.
Prerequisites
You configured vSphere Replication on one or more virtual machines.
Procedure
1 Select the vSphere Replication view of the SRM interface.
2 Select a vSphere Replication server and click the Virtual Machines tab.
3 Select a virtual machine or use the Ctrl or Shift keys to select multiple virtual machines, right-click and
select Configure Replication.
4 (Optional) Use the RPO slider or enter a value to reconfigure the maximum amount of data that can be
lost in the case of a site failure.
The available RPO range is from 15 minutes to 24 hours.
5 (Optional) Change the Guest OS Quiescing configuration, if applicable to the virtual machine guest
operating system
26 VMware, Inc.
Page 27

6 (Optional) Change the target location for the virtual machine files.
Option Description
Reconfigure replication of a single
virtual machine
Reconfigure replication of multiple
virtual machines
Click Browse to change the target location for the virtual machine files.
Select Initial copies of .vmdk files have been placed on the target
datastore if you have copied replication seeds to a new target datastore.
7 (Optional) Change the replication destination for each media device for the virtual machine.
The next pages are created dynamically depending on the media devices installed on the virtual
machine. They might include multiple virtual drives, all of which you can configure individually.
Configurable settings include whether the virtual drive is replicated, the virtual drive's replication
destination, and information about how the replicated virtual drive is configured. If the disk is to be
replicated, select a replication destination for the disk before proceeding.
8 (Optional) Select a different vSphere Replication server to manage the replication of this virtual
machine.
9 Review the settings and click Finish to establish replication.
Stop Replicating a Virtual Machine
Chapter 2 Replicating Virtual Machines
If you do not need to replicate a virtual machine, you can stop the replication of that virtual machine.
Stopping replication of a virtual machine does not remove it from any protection groups of which it is a
member.
Prerequisites
You have configured vSphere Replication on a virtual machine that you no longer need to protect.
Procedure
1 Select the vSphere Replication view of the SRM interface.
2 Select a vSphere Replication server and click the Virtual Machines tab.
3 Select a virtual machine and click Remove Replication.
4 Click Yes to confirm that you want to stop replicating this virtual machine.
5 Select the Protection Groups view of the SRM interface.
6 Select the protection group of which the virtual machine is a member, and click the Virtual Machines
tab.
7 Select the virtual machine on which you stopped replication and click Remove Protection.
8 Click Yes to confirm that you want to stop protecting this virtual machine.
The virtual machine does not replicate to the target site.
The virtual machine is no longer included in a protection group.
VMware, Inc. 27
Page 28

Site Recovery Manager Administration
28 VMware, Inc.
Page 29

Creating Protection Groups 3
After you configure a replication solution, you can create protection groups. A protection group is a
collection of virtual machines and templates that you protect together by using SRM.
You include one or more protection groups in each recovery plan. A recovery plan specifies how SRM
recovers the virtual machines in the protection groups that it contains.
You must configure the virtual machines in a protection group so that SRM can add them to the
vCenter Server inventory at the recovery site.
You configure virtual machines and create protection groups differently depending on whether you use
array-based replication or vSphere Replication. You cannot create protection groups that combine virtual
machines for which you configured array-based replication with virtual machines for which you configured
vSphere Replication. However, you can include array-based protection groups and vSphere Replication
protection groups in the same recovery plan.
About Array-Based Protection Groups and Datastore Groups on page 29
n
When you create a protection group for array-based replication, you specify array information and
then SRM computes the set of virtual machines into a datastore group. Datastore groups contain all
the files of the protected virtual machines.
Create vSphere Replication Protection Groups on page 32
n
You can create protection groups that contain virtual machines that vSphere Replication protects.
Apply Inventory Mappings to All Members of a Protection Group on page 33
n
If you add virtual machines to a protection group, or if virtual machines lose their protection, you can
configure protection for all unconfigured virtual machines by using the existing inventory mappings,
in one step.
About Array-Based Protection Groups and Datastore Groups
When you create a protection group for array-based replication, you specify array information and then
SRM computes the set of virtual machines into a datastore group. Datastore groups contain all the files of
the protected virtual machines.
You can add virtual machines to a protection group by creating them on one of the datastores that belong to
the datastore groups that SRM associates with the protection group. You can also add virtual machines to
the protection group by using Storage vMotion to move their storage to one of the datastores in the
datastore group. You can remove a member from a protection group by moving the virtual machine's files
to another datastore.
If you disable protection on a virtual machine, you must move the files of that virtual machine to an
unprotected datastore. If you leave the files of an unprotected virtual machine in a protected datastore,
recovery fails for all the virtual machines in that datastore.
VMware, Inc.
29
Page 30

Site Recovery Manager Administration
To configure array-based replication, you must assign each virtual machine to a resource pool, folder, and
network that exist at the recovery site. You can specify defaults for these assignments by selecting inventory
mappings. SRM applies inventory mappings when you create the protection group. If you do not specify
inventory mappings, you must configure them individually for each member of the protection group. SRM
does not protect virtual machines that you did not configure or that you incorrectly configured for
replication, even if they reside on a protected datastore.
If your storage array supports consistency groups, SRM is compatible with vSphere Storage DRS and
vSphere Storage vMotion. You can use Storage DRS and Storage vMotion to move virtual machine files
within a consistency group that SRM protects. If your storage array does not support consistency groups,
you cannot use Storage DRS and Storage vMotion in combination with SRM.
How SRM Computes Datastore Groups on page 30
n
SRM determines the composition of a datastore group by the set of virtual machines that have files on
the datastores in the group, and by the devices on which those datastores are stored.
Create Array-Based Protection Groups on page 31
n
You create array-based protection groups to enable the protection of virtual machines in datastore
groups that you configure to use array-based replication.
Edit Array-Based Protection Groups on page 32
n
You can change the name and description of an array-based protection group and add or remove
datastore groups that are part of the protection group.
How SRM Computes Datastore Groups
SRM determines the composition of a datastore group by the set of virtual machines that have files on the
datastores in the group, and by the devices on which those datastores are stored.
When you use array-based replication, each storage array supports a set of replicated datastores. On storage
area network (SAN) arrays that use connection protocols such as Fibre Channel and iSCSI, these datastores
are called logical storage units (LUN) and are composed of one or more physical datastores. On network file
system (NFS) arrays, the replicated datastores are typically referred to as volumes. In every pair of
replicated storage devices, one datastore is the replication source and the other is the replication target. Data
written to the source datastore is replicated to the target datastore on a schedule controlled by the
replication software of the array. When you configure SRM to work with an SRA, the replication source is at
the protected site and the replication target is at the recovery site.
A datastore provides storage for virtual machine files. By hiding the details of physical storage devices,
datastores simplify the allocation of storage capacity and provide a uniform model for meeting the storage
needs of virtual machines. Because any datastore can span multiple devices, SRM must ensure that all
devices backing the datastore are replicated before it can protect the virtual machines that use that datastore.
SRM must ensure that all datastores containing protected virtual machine files are replicated. During a
recovery or test, SRM must handle all such datastores together.
To achieve this goal, SRM aggregates datastores into datastore groups to accommodate virtual machines
that span multiple datastores. SRM regularly checks that datastore groups contain all necessary datastores
to provide protection for the appropriate virtual machines. When necessary, SRM recalculates datastore
groups. For example, this can occur when you add new devices to a virtual machine, and you store those
devices on a datastore that was not previously a part of the datastore group.
A datastore group consists of the smallest set of datastores required to ensure that if any of a virtual
machine's files is stored on a datastore in the group, all of the virtual machine's files are stored on datastores
that are part of the same group. For example, if a virtual machine has disks on two different datastores, then
SRM combines both datastores into a datastore group. SRM also combines devices into datastore groups
according to set criteria.
A virtual machine has files on two different datastores.
n
30 VMware, Inc.
Page 31

Chapter 3 Creating Protection Groups
Two virtual machines share a raw disk mapping (RDM) device on a SAN array, as in the case of a
n
Microsoft cluster server (MSCS) cluster.
Two datastores span extents corresponding to different partitions of the same device.
n
A single datastore spans two extents corresponding to partitions of two different devices. The two
n
extents must be in a single consistency group and the SRA must report consistency group information
from the array in the device discovery stage. Otherwise, the creation of protection groups based on this
datastore is not possible even though the SRA reports that the extents that make up this datastore are
replicated.
Multiple datastores belong to a consistency group. A consistency group is a collection of replicated
n
datastores where every state of the target set of datastores existed at a specific time as the state of the
source set of datastores. Informally, the datastores are replicated together such that when recovery
happens using those datastores, software accessing the targets does not see the data in a state that the
software is not prepared to deal with.
Protecting Virtual Machines on VMFS Datastores that Span Multiple LUNs or
Extents
Not all SRAs report consistency group information from the storage array, because not all storage arrays
support consistency groups. If an SRA reports consistency group information from the array following a
datastore discovery command, the LUNs that constitute a multi-extent VMFS datastore must be in the same
storage array consistency group. If the array does not support consistency groups and the SRA does not
report any consistency group information, SRM cannot protect virtual machines located on on the multiextent datastore.
Create Array-Based Protection Groups
You create array-based protection groups to enable the protection of virtual machines in datastore groups
that you configure to use array-based replication.
SRM computes the datastore groups when you configure the array pair or when you refresh the list of
devices.
After you create a protection group, SRM creates placeholder virtual machines and applies inventory
mappings for each virtual machine in the group. If SRM cannot map a virtual machine to a folder, network,
and resource pool on the recovery site, SRM sets the virtual machine in the Mapping Missing status, and
does not create a placeholder for it.
You can organize protection groups in folders. Different views in the Recovery interface display the names
of the protection groups, but they do not display the folder names. If you have two protection groups with
the same name in different folders, it might be difficult to tell them apart in some views in the Recovery
interface. Consequently, ensure that protection group names are unique across all folders. In environments
in which not all users have view privileges for all folders, to be sure of the uniqueness of protection group
names, do not place protection groups in folders.
When you create protection groups, wait to ensure that the operations finish as expected. Make sure that
SRM creates the protection group and that the protection of the virtual machines in the group is successful.
Procedure
1 Click Protection Groups in the SRM interface, and click Create Protection Group.
2 On the Select a Site and Protection Group Type page, select which site to protect and select Array Based
Replication.
3 Select an array pair, and click Next.
VMware, Inc. 31
Page 32

Site Recovery Manager Administration
4 Select a datastore group from the list, and click Next.
When you select a datastore group, the virtual machines in that datastore group appear in the Virtual
Machines on the Selected Datastore Group pane, and are marked for inclusion in the protection group
after you create the protection group.
5 Type a name and optional description for the protection group, and click Next.
6 Click Finish to create the protection group and begin the protection of the specified virtual machines.
You can monitor the progress of the tasks to create the protection group and protect the virtual
machines in the Recent Tasks panel of the vSphere Client.
What to do next
Create a recovery plan with which to associate your protection groups. See “Create a Recovery Plan,” on
page 43.
Edit Array-Based Protection Groups
You can change the name and description of an array-based protection group and add or remove datastore
groups that are part of the protection group.
Procedure
1 Click Protection Groups, right-click an array-based protection group and select Edit Protection Group.
2 Click Next.
3 Add or remove datastore groups in the protection group and click Next.
4 Edit the name or description of the protection group and click Next.
5 Click Finish.
Create vSphere Replication Protection Groups
You can create protection groups that contain virtual machines that vSphere Replication protects.
You can organize protection groups in folders. Different views in the Recovery interface display the names
of the protection groups, but they do not display the folder names. If you have two protection groups with
the same name in different folders, it might be difficult to tell them apart in some views in the Recovery
interface. Consequently, ensure that protection group names are unique across all folders. In environments
in which not all users have view privileges for all folders, to be sure of the uniqueness of protection group
names, do not place protection groups in folders.
When you create a vSphere Replication protection group, you can add to the protection group any virtual
machines that you configured for vSphere Replication.
Prerequisites
Use the vSphere Client to configure vSphere Replication for virtual machines. See “Configure Replication
for a Single Virtual Machine,” on page 22 or “Configure Replication for Multiple Virtual Machines,” on
page 24.
Procedure
1 Click Protection Groups in the SRM interface and click Create Protection Group.
2 Select the site to be the protected site, select vSphere Replication, and click Next.
3 Select virtual machines from the list and click Next.
Only virtual machines that you configured for vSphere Replication and that are not already in a
protection group appear in the list.
32 VMware, Inc.
Page 33

Chapter 3 Creating Protection Groups
4 Type a name and optional description for the protection group, and click Next.
5 Click Finish to create the protection group.
What to do next
Create a recovery plan with which to associate your protection groups. See “Create a Recovery Plan,” on
page 43.
Edit vSphere Replication Protection Groups
You can edit a vSphere Replication protection group to change its name and to add or remove virtual
machines to the group.
Procedure
1 Click Protection Groups in the left pane and right-click a vSphere Replication protection group.
2 Select Edit Protection Group and click Next.
You cannot change the Protected Site or Protection Group Type settings.
3 Add virtual machines to the protection group and click Next.
4 Edit the name or description of the protection group and click Next.
5 Click Finish.
6 (Optional) To remove a virtual machine from a vSphere Replication protection group, click the Virtual
Machines tab, select a virtual machine and click Remove Protection.
Apply Inventory Mappings to All Members of a Protection Group
If you add virtual machines to a protection group, or if virtual machines lose their protection, you can
configure protection for all unconfigured virtual machines by using the existing inventory mappings, in one
step.
Procedure
1 Click Protection Groups in the left pane, select a protection group, and click the Virtual Machines tab.
2 Click Configure All.
At least one virtual machine in the protection group must be in the Not Configured state for the
Configure All button to be activated.
VMware, Inc. 33
Page 34

Site Recovery Manager Administration
34 VMware, Inc.
Page 35

Creating, Testing, and Running
Recovery Plans 4
After you configure SRM at the protected and recovery sites, you can create, test, and run a recovery plan.
A recovery plan is like an automated run book. It controls every step of the recovery process, including the
order in which SRM powers on and powers off virtual machines, the network addresses that recovered
virtual machines use, and so on. Recovery plans are flexible and customizable.
A recovery plan includes one or more protection groups. You can include a protection group in more than
one recovery plan. For example, you can create one recovery plan to handle a planned migration of services
from the protected site to the recovery site, and another plan to handle an unplanned event such as a power
failure or natural disaster. Having these different recovery plans allows you to decide how to perform
recovery.
Testing a recovery plan runs the plan without affecting services at the protected or recovery sites, apart from
suspending non-critical virtual machines on the recovery site if you configure the recovery plan to do so.
You can perform planned migrations from the protected site to the recovery site or disaster recoveries by
running a recovery plan.
You can run only one recovery plan at a time to recover a particular protection group. If you simultaneously
test or run multiple recovery plans that specify the same protection group, only one recovery plan can
operate on the protection group. Other running recovery plans that specify the same protection group
report warnings for that protection group and the virtual machines it contains. The warnings explain that
the virtual machines were recovered, but do not report other protection groups that the other recovery plans
cover.
VMware, Inc.
Testing a Recovery Plan on page 36
n
When you create or modify a recovery plan, test it before you try to use it for planned migration or for
disaster recovery.
Performing a Planned Migration or Disaster Recovery By Running a Recovery Plan on page 37
n
You can run a recovery plan under planned circumstances to migrate virtual machines from the
protected site to the recovery site. You can also run a recovery plan under unplanned circumstances if
the protected site suffers an unforeseen event that might result in data loss.
Differences Between Testing and Running a Recovery Plan on page 38
n
Testing a recovery plan has no lasting effects on either the protected site or the recovery site, but
running a recovery plan has significant effects on both sites.
How SRM Interacts with DPM and DRS During Recovery on page 39
n
Distributed Power Management (DPM) and Distributed Resource Scheduler (DRS) are not mandatory,
but SRM supports both services and enabling them provides certain benefits when you use SRM.
How SRM Interacts with Storage DRS or Storage vMotion on page 39
n
You can use SRM when protecting virtual machines on sites that are configured for Storage DRS or
Storage vMotion if you follow certain guidelines.
35
Page 36

Site Recovery Manager Administration
How SRM Interacts with vSphere High Availability on page 41
n
You can use SRM to protect virtual machines on which vSphere High Availability (HA) is enabled.
Protecting Microsoft Cluster Server and Fault Tolerant Virtual Machines on page 41
n
You can use SRM to protect Microsoft Cluster Server (MSCS) and fault tolerant virtual machines, with
certain limitations.
Create, Test, and Run a Recovery Plan on page 42
n
You perform several sets of tasks to create, test, and run a recovery plan.
Export Recovery Plan Steps on page 47
n
You can export the steps of a recovery plan in various formats for future reference, or to keep a hard
copy backup of your plans.
View and Export Recovery Plan History on page 47
n
You can view and export reports about each run of a recovery plan, test of a recovery plan, or test
cleanup.
Cancel a Test or Recovery on page 48
n
You can cancel a recovery plan test at any time during its run. You can cancel a planned migration or
disaster recovery at certain times during its run.
Delete a Recovery Plan on page 48
n
You can delete a recovery plan if you do not need it.
Testing a Recovery Plan
When you create or modify a recovery plan, test it before you try to use it for planned migration or for
disaster recovery.
By testing a recovery plan, you ensure that the virtual machines that the plan protects recover correctly to
the recovery site. If you do not test recovery plans, an actual disaster recovery situation might not recover all
virtual machines, resulting in data loss.
Testing a recovery plan exercises nearly every aspect of a recovery plan, although SRM makes several
concessions to avoid disrupting ongoing operations on the protected and recovery sites. Recovery plans that
suspend local virtual machines do so for tests as well as for actual recoveries. With this exception, running a
test recovery does not disrupt replication or ongoing activities at either site.
If you use vSphere Replication, when you test a recovery plan, the virtual machine on the protected site can
still synchronize with the replica virtual machine disk files on the recovery site. The vSphere Replication
server creates redo logs on the virtual machine disk files on the recovery site, so that synchronization can
continue normally. When you perform cleanup after running a test, The vSphere Replication server removes
the redo logs from the disks on the recovery site.
You can run test recoveries as often as necessary. You can cancel a recovery plan test at any time.
Permission to test a recovery plan does not include permission to run a recovery plan. Permission to run a
recovery plan does not include permission to test a recovery plan. You must assign each permission
separately. See “Assign SRM Roles and Permissions,” on page 13.
36 VMware, Inc.
Page 37

Chapter 4 Creating, Testing, and Running Recovery Plans
Test Networks and Datacenter Networks
When you test a recovery plan, SRM can create a test network that it uses to connect recovered virtual
machines. Creating a test network allows the test to run without potentially disrupting virtual machines in
the production environment.
The test network is managed by its own virtual switch, and in most cases recovered virtual machines can
use the network without having to change network properties such as IP address, gateway, and so on. You
use the test network by selecting Auto when you configure the network settings when you run a test.
A datacenter network is a network that typically supports existing virtual machines at the recovery site. To
use it, recovered virtual machines must conform to its network address availability rules. These virtual
machines must use a network address that the network's switch can serve and route, must use the correct
gateway and DNS host, and so on. Recovered virtual machines that use DHCP can connect to this network
without additional customization. Other virtual machines require IP customization and additional recovery
plan steps to apply the customization.
You must recover any virtual machines that must interact with each other to the same test network. For
example, if a Web server accesses information on a database, those Web server and database virtual
machines should recover together to the same network.
Performing a Planned Migration or Disaster Recovery By Running a Recovery Plan
You can run a recovery plan under planned circumstances to migrate virtual machines from the protected
site to the recovery site. You can also run a recovery plan under unplanned circumstances if the protected
site suffers an unforeseen event that might result in data loss.
During a planned migration, SRM synchronizes the virtual machines on the recovery site with the virtual
machines on the protected site, then stops replication. SRM attempts to replicate all virtual machines and
gracefully shut down the protected machines. If errors occur during a planned migration, the plan stops so
that you can resolve the errors and rerun the plan. You can reprotect the virtual machines after the recovery.
During disaster recoveries, SRM restores virtual machines on the recovery site to their most recent available
state, according to the recovery point objective (RPO). When you run a recovery plan to perform a disaster
recovery, SRM attempts to shut down the virtual machines on the protected site. If SRM cannot shut down
the virtual machines, SRM still starts the copies at the recovery site, and automatic reprotect might not be
possible.
If SRM detects that a datastore on the protected site is in the all paths down (APD) state and is preventing a
virtual machine from shutting down, SRM waits for a period before attempting to shut down the virtual
machine again. The APD state is usually transient, so by waiting for a datastore in the APD state to come
back online, SRM can gracefully shut down the protected virtual machines on that datastore.
SRM uses VMware Tools heartbeat to discover when a virtual machine is running on the recovery site. In
this way, SRM can ensure that all virtual machines are running on the recovery site. For this reason, install
VMware Tools on protected virtual machines. If you do not or cannot install VMware Tools on the protected
virtual machines, you must configure SRM not to wait for VMware Tools to start in the recovered virtual
machines and to skip the guest operating system shutdown step. See “Change Recovery Settings,” on
page 85.
After SRM completes the final replication, SRM makes changes at both sites that require significant time and
effort to reverse. Because of this time and effort, you must assign the privilege to test a recovery plan and
the privilege to run a recovery plan separately.
VMware, Inc. 37
Page 38

Site Recovery Manager Administration
Running a Recovery with Forced Recovery
If the protected site is offline and SRM cannot perform its usual tasks, you can run the recovery with the
forced recovery option. Forced recovery starts the virtual machines on the recovery site without performing
any operations on the protected site.
Forced recovery is for use in cases where storage arrays fail at the protected site and, as a result, protected
virtual machines are unmanageable and cannot be shut down, powered off, or unregistered. In such a case,
the system state cannot be changed for extended periods. To resolve this situation, you can force recovery.
Forcing recovery does not complete the process of shutting down the virtual machines at the protected site.
As a result, a split-brain scenario occurs, but the recovery might complete more quickly.
CAUTION Only use forced recovery in cases where the recovery time objective (RTO) is severely affected by
a lack of connectivity to the protection site.
Running forced recovery with array-based replication can affect the mirroring between the protected and
the recovery storage arrays. After you run forced recovery, you must check that mirroring is set up correctly
between the protected array and the recovery array before you can perform further replication operations. If
mirroring is not set up correctly, you must repair the mirroring by using the storage array software.
When you enable forced recovery, any outstanding changes on the protection site are not replicated to the
recovery site before the sequence begins. Replication of the changes occurs according to the recovery point
objective (RPO) period of the storage array. If a new virtual machine or template is added on the protection
site and recovery is initiated before the storage RPO period has elapsed, the new virtual machine or
template does not appear on the replicated datastore and is lost. To avoid losing the new virtual machine or
template, wait until the end of the RPO period before running the recovery plan with forced recovery.
After the forced recovery completes and you have verified the mirroring of the storage arrays, you can
resolve the issue that necessitated the forced recovery. After you resolve the underlying issue, run planned
migration on the recovery plan again, resolve any problems that occur, and rerun the plan until it finishes
successfully. Running the recovery plan again does not affect the recovered virtual machines at the recovery
site.
Differences Between Testing and Running a Recovery Plan
Testing a recovery plan has no lasting effects on either the protected site or the recovery site, but running a
recovery plan has significant effects on both sites.
You need different privileges when testing and running a recovery plan.
Table 4‑1. How Testing a Recovery Plan Differs from Running a Recovery Plan
Area of Difference Test a Recovery Plan Run a Recovery Plan
Required privileges Requires Site Recovery
Manager.Recovery Plans.Test
permission.
Effect on virtual machines at
protected site
Effect on virtual machines at
recovery site
None SRM shuts down virtual machines in
SRM suspends local virtual machines
if the recovery plan requires this.
SRM restarts suspended virtual
machines after cleaning up the test.
Requires Site Recovery
Manager.Recovery Plans.Recovery.
reverse priority order.
SRM suspends local virtual machines if
the recovery plan requires this.
38 VMware, Inc.
Page 39

Chapter 4 Creating, Testing, and Running Recovery Plans
Table 4‑1. How Testing a Recovery Plan Differs from Running a Recovery Plan (Continued)
Area of Difference Test a Recovery Plan Run a Recovery Plan
Effect on replication SRM creates temporary snapshots of
replicated storage at the recovery
site. For array-based replication,
SRM rescans the arrays to discover
them.
Network If you explicitly assign test networks,
SRM connects recovered virtual
machines to a test network. If virtual
machine network assignment is
Auto, SRM assigns virtual machines
to temporary networks that are not
connected to any physical network.
Interruption of recovery plan You can cancel a test at any time. You can cancel the recovery in some cases.
During a planned migration, SRM
synchronizes replicated datastores, then
stops replication, then makes the target
devices at the recovery site writable.
During a disaster recovery, SRM attempts
the same steps , but if they do not succeed,
SRM ignores the errors.
SRM connects recovered virtual machines
to a datacenter network.
How SRM Interacts with DPM and DRS During Recovery
Distributed Power Management (DPM) and Distributed Resource Scheduler (DRS) are not mandatory, but
SRM supports both services and enabling them provides certain benefits when you use SRM.
DPM is a VMware feature that manages power consumption by ESX hosts. DRS is a VMware facility that
manages the assignment of virtual machines to ESX hosts.
SRM temporarily disables DPM for the cluster and ensures that all hosts in it are powered on before
recovery begins. After the recovery or test is complete, SRM reenables DPM for the cluster. The hosts in it
are left in the running state so that DPM can power them down as needed. SRM registers virtual machines
across the available ESX hosts in a round-robin order, to distribute the potential load as evenly as possible.
SRM always uses DRS placement to balance the load intelligently across hosts before it powers on recovered
virtual machines on the recovery site, even if DRS is disabled on the cluster. If DRS is enabled and in fully
automatic mode, DRS might move other virtual machines to further balance the load across the cluster while
SRM is powering on the recovered virtual machines. DRS continues to balance all virtual machines across
the cluster after SRM has powered on the recovered virtual machines.
How SRM Interacts with Storage DRS or Storage vMotion
You can use SRM when protecting virtual machines on sites that are configured for Storage DRS or Storage
vMotion if you follow certain guidelines.
The behavior of Storage DRS or Storage vMotion depends on whether you use SRM with array-based
replication or with vSphere Replication.
Using SRM with Array-Based Replication on Sites with Storage DRS or Storage vMotion
You must follow the guidelines if you use array-based replication to protect virtual machines on sites that
use Storage DRS or Storage vMotion.
If your storage array supports consistency groups, SRM is compatible with vSphere Storage DRS and
n
vSphere Storage vMotion. You can use Storage DRS and Storage vMotion to move virtual machine files
within a consistency group that SRM protects. If your storage array does not support consistency
groups, you cannot use Storage DRS and Storage vMotion in combination with SRM.
VMware, Inc. 39
Page 40

Site Recovery Manager Administration
If you enable Storage DRS on the protection site, a datastore cluster must contain one and only one
n
consistency group. Do not include any datastore that does not belong to the consistency group in the
cluster. Placing multiple consistency groups into the same cluster might result in virtual machines being
lost during a recovery. This guideline also applies on the recovery site if Storage DRS is enabled on the
recovery site.
Do not use Storage DRS or Storage vMotion to move virtual machines regularly. Do not accept
n
recommendations to manually move virtual machines regularly. You can move virtual machines
occasionally, but excessive movement of virtual machines can cause problems. Moving virtual
machines requires the array to replicate virtual machines over the network, which takes time and
consumes bandwidth. When Storage DRS or Storage vMotion moves virtual machines, you might
encounter problems during a recovery:
If Storage DRS or Storage vMotion moves a virtual machine to a different consistency group within
n
the same protection group, there is a short period between SRM propagating the new location of
the virtual machine to the recovery site and the array replicating the changes to the recovery site. In
addition, there is another period during which the arrays replicate the source and target
consistency groups to a consistent state on the recovery site. While the array is propagating all of
the changes to the recovery site, disaster recovery of this virtual machine might fail.
If Storage DRS or Storage vMotion moves a virtual machine to a different protection group, SRM
n
generates a protection error for this virtual machine. You must unconfigure protection of the
virtual machine in the old protection group and configure protection of the virtual machine in the
new protection group. Until you configure protection in the new protection group, planned
migration or disaster recovery of this virtual machine fails.
Adding a disk to a protected virtual machine results in the same problems as for moving an entire
n
virtual machine. SRM does not prevent you from doing this, but if a virtual machine contains a nonreplicated disk and you do not exclude the disk from protection, powering on the virtual machine fails
after the move.
Moving a protected disk to a different consistency group results in the same problems as for moving an
n
entire virtual machine. These problems occur if you move a disk to a different consistency group within
the same protection group or if you move it into a different protection group. SRM does not prevent
you from doing this, but if a disk has moved to a different consistency group, powering on the virtual
machine fails after the move.
Using SRM with vSphere Replication on Sites with Storage DRS or Storage vMotion
You must follow the guidelines if you use vSphere Replication to protect virtual machines on sites that use
Storage DRS or Storage vMotion.
vSphere Replication is compatible with vSphere Storage vMotion and vSphere Storage DRS on the
n
protected site. You can use Storage vMotion and Storage DRS to move the disk files of a virtual machine
that vSphere Replication protects, with no impact on replication.
vSphere Replication is compatible with Storage vMotion and saves the state of a disk or virtual machine
n
when the home directory of a disk or virtual machine moves. Replication of the disk or virtual machine
continues normally after the move.
A full sync causes Storage DRS to trigger Storage vMotion only if you set the Storage DRS rules to be
n
very aggressive, or if a large number of virtual machines perform a full sync at the same time. The
default I/O latency threshold for Storage DRS is 15ms. By default, Storage DRS performs loading
balancing operations every 8 hours. Storage DRS also waits until it has collected sufficient statistics
about the I/O load before it generates Storage vMotion recommendations. Consequently, a full sync
only affects Storage DRS recommendations if the full sync lasts for a long time and if, during that time,
the additional I/O that the full sync generates causes the latency to exceed the I/O latency threshold.
40 VMware, Inc.
Page 41

Chapter 4 Creating, Testing, and Running Recovery Plans
How SRM Interacts with vSphere High Availability
You can use SRM to protect virtual machines on which vSphere High Availability (HA) is enabled.
HA protects virtual machines from ESXi host failures by restarting virtual machines from hosts that fail on
new hosts within the same site. SRM protects virtual machines against full site failures by restarting the
virtual machines at the recovery site. The key difference between HA and SRM is that HA operates on
individual virtual machines and restarts the virtual machines automatically. SRM operates at the recovery
plan level and requires a user to initiate a recovery manually.
To transfer the HA settings for a virtual machine onto the recovery site, you must set the HA settings on the
placeholder virtual machine before performing recovery, at any time after you have configured the
protection of the virtual machine.
You can replicate HA virtual machines by using array-based replication or vSphere Replication. If HA
restarts a protected virtual on another host on the protected site, vSphere Replication will perform a full
sync after the virtual machine restarts.
SRM does not require HA as a prerequisite for protecting virtual machines. Similarly, HA does not require
SRM.
Protecting Microsoft Cluster Server and Fault Tolerant Virtual Machines
You can use SRM to protect Microsoft Cluster Server (MSCS) and fault tolerant virtual machines, with
certain limitations.
To use SRM to protect MSCS and fault tolerant virtual machines, you might need to change your
environment.
General Limitations to Protecting MSCS and Fault Tolerant Virtual Machines
Protecting MSCS and fault tolerant virtual machines is subject to the following limitations.
You can use array-based replication only to protect MSCS virtual machines. Protecting MSCS virtual
n
machines with vSphere Replication is not supported.
Reprotect of MSCS or fault tolerant virtual machines requires VMware High Availability (HA) and
n
VMware Distributed Resource Scheduler (DRS). When you move MSCS or fault tolerant virtual
machines across their primary and secondary sites during reprotect, you must enable HA and DRS, and
set the affinity and antiaffinity rules as appropriate. See “DRS Requirements for Protection of MSCS
Virtual Machines,” on page 42.
vSphere does not support vSphere vMotion for MSCS virtual machines.
n
ESXi Host Requirements for Protection of MSCS Virtual Machines
To protect MSCS or fault tolerant virtual machines, the ESXi host machines on which the virtual machines
run must meet certain criteria.
You must run a fault tolerant virtual machine and its shadow on two separate ESXi Server instances.
n
VMware, Inc. 41
Page 42

Site Recovery Manager Administration
You can run a cluster of MSCS virtual machines in the following possible configurations.
n
Cluster-in-a-box
The MSCS virtual machines in the cluster run on a single ESXi Server.
You can have a maximum of five MSCS nodes on one ESXi Server.
Cluster-across-boxes
You can spread the MSCS cluster across a maximum of five ESXi Server
instances. You can protect only one virtual machine node of any MSCS
cluster on a single ESXi Server instance. You can have multiple MSCS
node virtual machines running on an ESXi host, as long as they do not
participate in the same MSCS cluster. This configuration requires shared
storage on a Fibre Channel SAN for the quorum disk.
DRS Requirements for Protection of MSCS Virtual Machines
To use DRS on sites that contain MSCS virtual machines, you must configure the DRS rules to allow SRM to
protect the virtual machines. By following the guidelines, you can protect MSCS virtual machines on sites
that run DRS if the placeholder virtual machines are in either a cluster-across-boxes MSCS deployment or in
a cluster-in-a-box MSCS deployment.
Because vSphere does not support vSphere vMotion for MSCS virtual machines, you must set the VM to
n
Host DRS rule so that DRS does not perform vMotion on MSCS nodes. Set the VM to Host rule for the
virtual machines on the protected site and for the shadow virtual machines on the recovery site.
Set the DRS rules on the virtual machines on the protected site before you configure MSCS in the guest
n
operating systems. Set the DRS rules immediately after you deploy, configure, or power on the virtual
machines.
Set the DRS rules on the virtual machines on the recovery site immediately after you create a protection
n
group of MSCS nodes, as soon as the placeholder virtual machines appear on the recovery site.
DRS rules that you set on the protected site are not transferred to the recovery site after a recovery. For
n
this reason, you must set the DRS rules on the placeholder virtual machines on the recovery site.
Do not run a test recovery or a real recovery before you set the DRS rules on the recovery site.
n
If you do not follow the guidelines on either the protected site or on the recovery site, vSphere vMotion
might move MSCS virtual machines to a configuration that SRM does not support.
In a cluster-in-a-box deployment on either the protected or recovery site, vSphere vMotion might move
n
MSCS virtual machines to different ESXi hosts.
In a cluster-in-a-box deployment on either the protected or recovery site, vSphere vMotion might move
n
some or all of the MSCS virtual machines to a single ESXi host.
Create, Test, and Run a Recovery Plan
You perform several sets of tasks to create, test, and run a recovery plan.
Procedure
1 Create a Recovery Plan on page 43
You create a recovery plan to establish how SRM recovers virtual machines.
2 Edit a Recovery Plan on page 43
You can edit a recovery plan to change the properties that you specified when you created it. You can
edit recovery plans from the protected site or from the recovery site.
3 Suspend Virtual Machines When a Recovery Plan Runs on page 44
SRM can suspend virtual machines on the recovery site during a recovery and a test recovery.
42 VMware, Inc.
Page 43

Chapter 4 Creating, Testing, and Running Recovery Plans
4 Test a Recovery Plan on page 44
When you test a recovery plan, SRM runs the recovery plan on a test network and a temporary
snapshot of replicated data at the recovery site. SRM does not disrupt operations at the protected site.
5 Clean Up After Testing a Recovery Plan on page 45
After you test a recovery plan, you can return the recovery plan to the Ready state by running a
cleanup operation.
6 Run a Recovery Plan on page 45
When you run a recovery plan, SRM migrates all virtual machines in the recovery plan to the recovery
site. SRM attempts to shut down the corresponding virtual machines on the protected site.
7 Recover a Point-in-Time Snapshot of a Virtual Machine on page 46
With vSphere Replication, you can retain point-in-time snapshots of a virtual machine. You can
configure SRM to recover a number of point-in-time snapshots of a virtual machine when you run a
recovery plan.
Create a Recovery Plan
You create a recovery plan to establish how SRM recovers virtual machines.
During tests, isolate the virtual machines that SRM recovers. If SRM brings duplicate machines on line and
they begin to interact with unprotected virtual machines in your production network, errors can occur.
Procedure
1 Click Recovery Plans, click the Summary tab, and click Create Recovery Plan.
2 Select the recovery site.
3 Select one or more protection groups for the plan to recover, and click Next.
4 Select a recovery site network to which recovered virtual machines connect during recovery plan tests,
and click Next.
You can isolate virtual machine SRM restorations during test recoveries by selecting Auto, which is an
isolated network, or by selecting a manually created network that is not connected to other networks.
5 Type a name for the plan in the Recovery Plan Name text box, add an optional description, and click
Next.
6 Review the summary information and click Finish to create the recovery plan.
You can monitor the creation of the plan in the Recent Tasks view.
Edit a Recovery Plan
You can edit a recovery plan to change the properties that you specified when you created it. You can edit
recovery plans from the protected site or from the recovery site.
Procedure
1 Click Recovery Plans, right-click a recovery plan, and select Edit Recovery Plan.
2 Click Next.
You cannot change the recovery site.
3 Select one or more protection groups for the plan to recover, and click Next.
4 Select a recovery site network to which recovered virtual machines connect during recovery plan tests,
and click Next.
5 Change the name of the plan in the Recovery Plan Name text box and add an optional description.
VMware, Inc. 43
Page 44

Site Recovery Manager Administration
6 Click Next.
7 Review the summary information and click Finish to make the specified changes to the recovery plan.
You can monitor the update of the plan in the Recent Tasks view.
Suspend Virtual Machines When a Recovery Plan Runs
SRM can suspend virtual machines on the recovery site during a recovery and a test recovery.
Suspending virtual machines on the recovery site is useful in active-active datacenter environments and
where non-critical workloads run on recovery sites. By suspending any virtual machines that host noncritical workloads on the recovery site, SRM frees capacity for the recovered virtual machines.
You can only add virtual machines to suspend at the recovery site. To suspend virtual machines at both the
protected and recovery sites, you must perform a recovery and then reverse protection by performing a
reprotect operation before you can add virtual machines to suspend at the original protected site. If you
configure virtual machines to suspend at both sites, the plan starts virtual machines at one site and suspends
them at the other with each recovery that you run.
Procedure
1 On the recovery site, click Recovery Plans in the left pane and select the recovery plan to edit.
2 Click the Recovery Steps tab and click Add Non-Critical VM.
3 Expand the hierarchical list to select virtual machines on the recovery site to suspend during a recovery.
4 Click OK.
SRM suspends the virtual machines on the recovery site when the recovery plan runs.
Test a Recovery Plan
When you test a recovery plan, SRM runs the recovery plan on a test network and a temporary snapshot of
replicated data at the recovery site. SRM does not disrupt operations at the protected site.
Testing a recovery plan runs all the steps in the plan with the exception of powering down virtual machines
at the protected site and forcing devices at the recovery site to assume mastership of replicated data. If the
plan requires the suspension of local virtual machines at the recovery site, SRM suspends those virtual
machines during the test. Running a test of a recovery plan makes no other changes to the production
environment at either site.
Procedure
1 Click Recovery Plans in the SRM interface.
2 Select the recovery plan to test, and click Test.
3 (Optional) Select Replicate recent changes to recovery site.
Selecting this option ensures that the recovery site has the latest copy of protected virtual machines, but
the synchronization might take more time.
4 Click Next.
5 Review the test information and click Start.
44 VMware, Inc.
Page 45

Chapter 4 Creating, Testing, and Running Recovery Plans
6 Click the Recovery Steps tab to monitor the progress of the test and respond to messages.
The Recovery Steps tab displays the progress of individual steps. The Summary tab reports the
progress of the overall plan.
NOTE SRM initiates recovery steps in the prescribed order, with one exception. It does not wait for the
Prepare Storage step to finish for all protection groups before continuing to the next steps.
What to do next
Run a cleanup operation after the recovery plan test finishes to restore the recovery plan to its original state
from before the test.
Clean Up After Testing a Recovery Plan
After you test a recovery plan, you can return the recovery plan to the Ready state by running a cleanup
operation.
SRM performs several cleanup operations after a test.
Powers off the recovered virtual machines.
n
Replaces recovered virtual machines with placeholders, preserving their identity and configuration
n
information.
Cleans up replicated storage snapshots that the recovered virtual machines used during the test.
n
Prerequisites
Verify that you tested a recovery plan.
Procedure
1 Click Recovery Plans in the SRM interface, select the recovery plan that you tested, and click Cleanup.
2 Review the cleanup information and click Next.
3 Click Start.
4 After the cleanup finishes, if it reports errors, run the cleanup again, selecting the Force Cleanup
option.
The Force Cleanup option forces the removal of virtual machines, ignoring any errors, and returns the
plan to the Ready state. If necessary, run cleanup several times with the Force Cleanup option, until the
cleanup succeeds.
Run a Recovery Plan
When you run a recovery plan, SRM migrates all virtual machines in the recovery plan to the recovery site.
SRM attempts to shut down the corresponding virtual machines on the protected site.
CAUTION A recovery plan makes significant alterations in the configurations of the protected and recovery
sites and it stops replication. Do not run any recovery plan that you have not tested. In the case of arraybased replication, recovered virtual machines and services might need to be supported at the recovery site
for a period of time. Reversing these changes might cost significant time and effort and can result in
prolonged service downtime.
Prerequisites
To use forced recovery, you must first enable this function. You enable forced recovery by enabling the
recovery.forceRecovery setting as described in “Change Recovery Settings,” on page 85.
VMware, Inc. 45
Page 46

Site Recovery Manager Administration
Procedure
1 Click Recovery Plans in the left pane, select the recovery plan to run, and click Recovery.
2 Review the information in the confirmation prompt, and select I understand that this process will
permanently alter the virtual machines and infrastructure of both the protected and recovery
datacenters.
3 Select the type of recovery to run.
Option Description
Planned Migration
Disaster Recovery
4 (Optional) Select the Forced Recovery - recovery site operations only check box.
This option is available if you selected Disaster Recovery and you enabled the forced recovery function.
5 Click Next.
6 Review the recovery information and click Start.
Recovers virtual machines to the recovery site when both sites are running.
If errors occur on the protected site during a planned migration, the
planned migration operation fails.
Recovers virtual machines to the recovery site if the protected site
experiences a problem. If errors occur on the protected site during a
disaster recovery, the disaster recovery continues and does not fail.
7 Click the Recovery Steps tab.
The Recovery Steps tab displays the progress of individual steps. The Recent Tasks area reports the
progress of the overall plan.
Recover a Point-in-Time Snapshot of a Virtual Machine
With vSphere Replication, you can retain point-in-time snapshots of a virtual machine. You can configure
SRM to recover a number of point-in-time snapshots of a virtual machine when you run a recovery plan.
You configure the retention of point-in-time snapshots when you configure vSphere Replication on a virtual
machine. For more information about point-in-time snapshots, see “Replicating a Virtual Machine and
Enabling Multiple Point in Time Instances,” on page 22.
NOTE You cannot use the SRM interface to configure replication that uses point in time (PIT) snapshots. To
enable PIT snapshots, configure replication of a virtual machine by using the vSphere Web Client. See
Configure Replication for a Single Virtual Machine in vSphere Replication Administration.
SRM only recovers the most recent PIT snapshot during a recovery. To recover older snapshots, you must
enable the vrReplication > preserveMpitImagesAsSnapshots option in Advanced Settings in the SRM
interface. See “Change vSphere Replication Settings,” on page 88.
Point-in-time recovery is not available with array-based replication.
Procedure
1 Configure SRM to retain older point-in-time snapshots by setting the vrReplication >
preserveMpitImagesAsSnapshots option.
2 Use the vSphere Web Client to configure replication of a virtual machine, selecting the option to retain a
number of point-in-time snapshots.
3 In the SRM interface, add the virtual machine to a vSphere Replication protection group.
4 Include the vSphere Replication protection group in a recovery plan.
46 VMware, Inc.
Page 47

5 Run the recovery plan.
When the recovery plan is finished, the virtual machine is recovered to the recovery site, with the
number of point-in-time snapshots that you configured.
6 In the VMs and Templates view, right-click the recovered virtual machine and select Snapshot >
Snapshot Manager.
7 Select one of the point-in-time snapshots of this virtual machine and click Go to.
The recovered virtual machine reverts to the point-in-time snapshot that you selected.
Export Recovery Plan Steps
You can export the steps of a recovery plan in various formats for future reference, or to keep a hard copy
backup of your plans.
You cannot export the recovery plan steps while a test recovery or a real recovery is in progress.
Prerequisites
Verify that you have a recovery plan.
Procedure
1 Click Recovery Plans in the SRM interface, select a recovery plan, and click the Recovery Steps tab.
Chapter 4 Creating, Testing, and Running Recovery Plans
2 Click Export Steps.
You can save the recovery plan steps as a MS Word, Excel, HTML, CSV, or XML document.
View and Export Recovery Plan History
You can view and export reports about each run of a recovery plan, test of a recovery plan, or test cleanup.
Recovery plan histories provide information about each run, test, or cleanup of a recovery plan. The history
contains information about the result and the start and end times for the whole plan and for each step in the
plan. You cannot export the recovery plan history while a test recovery, real recovery, or test cleanup is in
progress.
Prerequisites
You ran or tested a recovery plan, or cleaned up after a test.
Procedure
1 Click Recovery Plans in the SRM interface, select a recovery plan, and click the History tab.
2 (Optional) Click View for a recovery plan run, test, or cleanup operation.
The history opens in a browser.
3 (Optional) Click Export for a recovery plan run, test, or cleanup operation.
You can save the recovery plan history as a MS Word, Excel, HTML, CSV, or XML document.
VMware, Inc. 47
Page 48

Site Recovery Manager Administration
Cancel a Test or Recovery
You can cancel a recovery plan test at any time during its run. You can cancel a planned migration or
disaster recovery at certain times during its run.
When you cancel a test or recovery, SRM does not start steps, and uses certain rules to stop steps that are in
progress.
Steps that cannot be stopped, such as powering on or waiting for a heartbeat, run to completion before
n
the cancellation finishes.
Steps that add or remove storage devices are undone by cleanup operations if you cancel.
n
The time it takes to cancel a test or recovery depends on the type and number of steps that are currently in
progress.
Procedure
To cancel a test or recovery, click Cancel on the recovery plan toolbar.
u
Delete a Recovery Plan
You can delete a recovery plan if you do not need it.
Deleting a recovery plan does not delete the history of the plan, which you can still view in the All Recovery
Plans > All History tab.
Procedure
1 Click Recovery Plans and select the recovery plan to delete.
2 (Optional) Click the History tab and click Export List to download the history of the plan.
3 Right-click the recovery plan to delete, and select Delete Recovery Plan.
48 VMware, Inc.
Page 49

Reprotecting Virtual Machines After a
Recovery 5
After a recovery, the recovery site becomes the new protected site, but it is not protected yet. If the original
protected site is operational, you can reverse the direction of protection to use the original protected site as a
new recovery site to protect the new protected site.
Manually reestablishing protection in the opposite direction by recreating all protection groups and
recovery plans is time consuming and prone to errors. SRM provides the reprotect function, which is an
automated way to reverse protection.
After SRM performs a recovery, the protected virtual machines start up on the recovery site. Because the
former protected site might be offline, these virtual machines are not protected. By running reprotect when
the protected site comes back online, you reverse the direction of replication to protect the recovered virtual
machines on the recovery site back to the original protected site.
Reprotect uses the protection information that you established before a recovery to reverse the direction of
protection. You can complete the reprotect process only after a recovery finishes. If the recovery finishes
with errors, you must fix all errors and rerun the recovery, repeating this process until no errors occur.
You can conduct tests after a reprotect operation completes, to confirm that the new configuration of the
protected and recovery sites is valid.
You can perform reprotect on protection groups that contain virtual machines that are configured for both
array-based replication and for vSphere Replication.
Example: Performing a Reprotect Operation
Site A is the protected site and site B is the recovery site. If site A goes offline, SRM recovers the protected
virtual machines to site B. After the recovery, the protected virtual machines from site A start up on site B
without protection.
When site A comes back online, you can run a reprotect operation to protect the recovered virtual machines
on site B. Site B becomes the protected site, and site A becomes the recovery site. SRM reverses the direction
of replication from site B to site A.
VMware, Inc.
49
Page 50

appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
Site A
Protection
group
Replica
virtual
machines
power off
Site B
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
Direction of replication is reversed after a planned migration
Recovery site becomes
protected site
Protected site
becomes recovery
Site Recovery Manager Administration
Figure 5‑1. SRM Reprotect Process
How SRM Performs Reprotect on page 50
n
The reprotect process involves two stages. SRM reverses the direction of protection, then forces a
synchronization of the storage from the new protected site to the new recovery site.
Preconditions for Performing Reprotect on page 51
n
You can perform reprotect only if you meet certain preconditions.
Reprotect Virtual Machines on page 51
n
Reprotect results in the reconfiguration of SRM protection groups and recovery plans to work in the
opposite direction. With reprotect, you can recover virtual machines back to the original site after a
recovery.
How SRM Performs Reprotect
50 VMware, Inc.
Reprotect States on page 52
n
The reprotect process passes through several states that you can observe in the recovery plan in the
SRM plug-in in the vSphere Client.
The reprotect process involves two stages. SRM reverses the direction of protection, then forces a
synchronization of the storage from the new protected site to the new recovery site.
When you initiate the reprotect process, SRM instructs the underlying storage arrays or vSphere Replication
to reverse the direction of replication. After reversing the replication, SRM creates placeholder virtual
machines at the new recovery site, which was the original protected site before the reprotect.
When creating placeholder virtual machines on the new protected site, SRM uses the location of the original
protected virtual machine to determine where to create the placeholder virtual machine. SRM uses the
identity of the original protected virtual machine to create the placeholder and any subsequent recovered
virtual machines. If the original protected virtual machines are no longer available, SRM uses the inventory
mappings from the original recovery site to the original protected site to determine the resource pools and
folders for the placeholder virtual machines. You must configure inventory mappings on both sites before
running reprotect, or reprotect might fail.
When performing reprotect with array-based replication, SRM places the files for the placeholder virtual
machines in the placeholder datastore for the original protected site, not in the datastore that held the
original protected virtual machines.
Forcing synchronization of data from the new protection site to the new recovery site ensures that the
recovery site has a current copy of the protected virtual machines running at the protection site. Forcing this
synchronization ensures that recovery is possible immediately after the reprotect finishes.
When performing reprotect with vSphere Replication, SRM uses the original VMDK files as initial copies
during synchronization. The full synchronization that appears in the recovery steps mostly performs
checksums, and only a small amount of data is transferred through the network.
Page 51

Preconditions for Performing Reprotect
You can perform reprotect only if you meet certain preconditions.
You can perform reprotect on protection groups that contain virtual machines that are configured for both
array-based replication and for vSphere Replication.
Before you can run reprotect, you must satisfy the preconditions.
1 Run a planned migration and make sure that all steps of the recovery plan finish successfully. If errors
occur during the recovery, resolve the problems that caused the errors and rerun the recovery. When
you rerun a recovery, operations that succeeded previously are skipped. For example, successfully
recovered virtual machines are not recovered again and continue running without interruption.
2 The original protected site must be available. The vCenter Server instances, ESXi Servers, SRM Server
instances, and corresponding databases must all be recoverable.
3 If you performed a disaster recovery operation, you must perform a planned migration when both sites
are running again. If errors occur during the attempted planned migration, you must resolve the errors
and rerun the planned migration until it succeeds.
Reprotect is not available under certain circumstances.
Recovery plans cannot finish without errors. For reprotect to be available, all steps of the recovery plan
n
must finish successfully.
Chapter 5 Reprotecting Virtual Machines After a Recovery
You cannot restore the original site, for example if a physical catastrophe destroys the original site. To
n
unpair and recreate the pairing of protected and recovery sites, both sites must be available. If you
cannot restore the original protected site, you must reinstall SRM on the protected and recovery sites.
Reprotect Virtual Machines
Reprotect results in the reconfiguration of SRM protection groups and recovery plans to work in the
opposite direction. With reprotect, you can recover virtual machines back to the original site after a
recovery.
Prerequisites
See “Preconditions for Performing Reprotect,” on page 51.
Procedure
1 Click Recovery Plans in the SRM interface, select a recovery plan, and click Reprotect.
2 Select the check box to confirm that you understand that the reprotect operation is irreversible.
3 Review the reprotect information and click Start.
4 Click the Recovery Steps tab to monitor the progress of the reprotect operation.
Certain steps do not apply to all virtual machines. For example, virtual machines that you configured
for array-based replication appear under Configure Storage to Reverse Direction > Protection Group >
Configure VR Replication, even though this step does not perform any actions on them. These virtual
machines are marked Not Applicable when the step runs.
SRM reverses the recovery site and protected sites. SRM creates placeholder copies of virtual machines from
the new protected site at the new recovery site.
VMware, Inc. 51
Page 52

Site Recovery Manager Administration
Reprotect States
The reprotect process passes through several states that you can observe in the recovery plan in the SRM
plug-in in the vSphere Client.
If reprotect fails, or succeeds partially, you can perform remedial actions to complete the reprotect.
Table 5‑1. Reprotect States
State Description Remedial Action
Reprotect In Progress SRM is running reprotect. None
Partial Reprotect Occurs if multiple recovery
Incomplete Reprotect Occurs because of failures
Reprotect Interrupted Occurs if one of the SRM
plans share the same protection
groups and reprotect succeeds
for some groups in some plans,
but not for others.
during reprotect. For example,
this state might occur because
of a failure to synchronize
storage or a failure to create
placeholder virtual machines.
Servers stops unexpectedly
during the reprotect process.
Run reprotect again on the partially reprotected
plans.
If a reprotect operation fails to synchronize
n
storage, make sure that sites are connected,
review the reprotect progress in the vSphere
Client , and start the reprotect task again. If
reprotect still won't complete, run the
reprotect task with the Force Cleanup option.
If SRM fails to create placeholder virtual
n
machines, recoveries are still possible. Review
the reprotect steps in the vSphere Client,
resolve any open issues, and start the reprotect
task again.
Ensure that both SRM Servers are running and
start the reprotect task again.
52 VMware, Inc.
Page 53

Restoring the Pre-Recovery Site
Configuration By Performing
Failback 6
To restore the original configuration of the protected and recovery sites after a recovery, you can perform a
sequence of optional procedures known as failback.
After a planned migration or a disaster recovery, the former recovery site becomes the protected site.
Immediately after the recovery, the new protected site has no recovery site to which to recover. If you run
reprotect, the new protected site is protected by the original protection site, reversing the original direction
of protection. See Chapter 5, “Reprotecting Virtual Machines After a Recovery,” on page 49 for information
about reprotect.
To restore the configuration of the protected and recovery sites to their inital configuration before the
recovery, you perform failback.
To perform failback, you run a sequence of reprotect and planned migration operations.
1 Perform a reprotect. The recovery site becomes the protected site. The former protected site becomes the
recovery site.
2 Perform a planned migration to shut down the virtual machines on the protected site and start up the
virtual machines on the recovery site. To avoid interruptions in virtual machine availability, you might
want to run a test before you complete the planned migration. If the test identifies errors, you can
resolve them before you perform the planned migration.
3 Perform a second reprotect, to revert the protected and recovery sites to their original configuration
before the recovery.
You can configure and run a failback when you are ready to restore services to the original protected site,
after you have brought it back online after an incident.
Example: Performing a Failback Operation
Site A is the protected site and B is the recovery site. A recovery occurs, migrating the virtual machines from
site A to site B. To restore site A as the protected site, you perform a failback.
Perform a reprotect. Site B, the former recovery site, becomes the protected site. SRM uses the
n
protection information to establish the protection of site B. Site A becomes the recovery site.
Perform a planned migration to recover the protected virtual machines on site B to site A.
n
Perform a second reprotect. Site A becomes the protected site and site B becomes the recovery site.
n
VMware, Inc.
53
Page 54

Replica
virtual
machines
power off
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
1. Planned Migration
Site A
Protected
virtual
machines
power off
Replica
virtual
machines
power on
Virtual machines replicate from site A to site B
Site B
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
Site A Site B
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
2. Reprotect–Recovery site becomes protected site
Direction of replication is reversed
Protected
virtual
machines
power on
Protected
virtual
machines
power on
Recovery site becomes
protected site
Protected site becomes
recovery site
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
Site A
Protected
virtual
machines
power off
Replica
virtual
machines
power on
Site B
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
3. Planned Migration
Migrate virtual machines from protected to recovery site
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
Site A
Replica
virtual
machines
power off
Protection and recovery sites and direction of replication
are restored to pre-migration condition
Site B
appsOSapps
OS
appsOSapps
OS
appsOSapps
OS
4. Reprotect again– original protected and
recovery site configuration restored
Site Recovery Manager Administration
Figure 6‑1. SRM Failback Process
Perform a Failback
After SRM performs a recovery, you can perform a failback to restore the original configuration of the
protected and recovery sites.
To aid comprehension, the original protected site from before a recovery is site A. The original recovery site
is site B. After a recovery from site A to site B, the recovered virtual machines are running on site B without
54 VMware, Inc.
protection.
Prerequisites
Verify that the following conditions are in place.
You have performed a recovery, either as part of a planned migration or as part of a disaster recovery.
n
The original protected site, site A, is running.
n
If you performed a disaster recovery, you must perform a planned migration recovery when the hosts
n
and datastores on the protected site, site A, are running again.
You did not run reprotect since the recovery.
n
Procedure
1 Click Recovery Plans in the SRM interface, select a recovery plan, and click Reprotect.
2 Select the check box to confirm that you understand that the reprotect operation is irreversible.
3 Review the reprotect information and click Start.
4 Monitor the reprotect operation on the Recovery Steps tab until it finishes.
Page 55

Chapter 6 Restoring the Pre-Recovery Site Configuration By Performing Failback
5 (Optional) If necessary, rerun reprotect until it finishes without errors.
At the end of the reprotect operation, SRM has reversed replication, so that the original recovery site,
site B, is now the protected site.
6 (Optional) Click Test and follow the prompts to test the recovery plan.
Testing the recovery plan verifies that the recovery plan works after the reprotect operation.
7 Click Recovery to run the recovery plan as a planned migration.
8 Review the information in the confirmation prompt, and select I understand that this process will
permanently alter the virtual machines and infrastructure of both the protected and recovery
datacenters.
9 Select Planned Migration, click Next, and click Start.
10 Monitor the planned migration operation on the Recovery Steps tab until it finishes.
The planned migration shuts down the virtual machines on the new protected site, site B, and starts up
the virtual machines on the new recovery site, site A. If necessary, rerun the planned migration until it
finishes without errors.
When the planned migration completes, the virtual machines are running on the original protected site,
site A, but the virtual machines are not protected. The virtual machines on the original recovery site,
site B, are powered off.
11 Click Reprotect and follow the instructions of the wizard to perform a second reprotect operation.
Running reprotect again reestablishes protection in the original direction from before the recovery.
You restored the protected and recovery sites to their original configuration before the recovery. The
protected site is site A, and the recovery site is site B.
VMware, Inc. 55
Page 56

Site Recovery Manager Administration
56 VMware, Inc.
Page 57

Customizing a Recovery Plan 7
You can customize a recovery plan to run commands, display messages that require a response when the
plan runs, and change the recovery priority of protected virtual machines.
A simple recovery plan, that specifies only a test network to which the recovered virtual machines connect
and response times that the test should expect, can provide an effective way to test an SRM configuration.
Most recovery plans require configuration for use in production. For example, a recovery plan for an
emergency at the protected site might be different from a recovery plan for the planned migration of
services from one site to another.
NOTE A recovery plan always reflects the current state of the protection groups that it recovers. If any
members of a protection group show a status other than OK, you must correct the problems before you can
make any changes to the recovery plan.
Recovery Plan Steps on page 57
n
A recovery plan runs a series of steps that must be performed in a specific order. You cannot change
the order or purpose of the steps, but you can insert your own steps that display messages and run
commands.
Specify the Recovery Priority of a Virtual Machine on page 58
n
By default, SRM sets all virtual machines in a new recovery plan to recovery priority level 3. You can
increase or decrease the recovery priority of a virtual machine.
Creating Custom Recovery Steps on page 58
n
You can create custom recovery steps that run commands or present messages to the user during a
recovery.
Customize the Recovery of an Individual Virtual Machine on page 63
n
You can configure a virtual machine in a recovery plan to use a prescribed customization specification,
or to run message or command steps when it is recovered.
Recovery Plan Steps
A recovery plan runs a series of steps that must be performed in a specific order. You cannot change the
order or purpose of the steps, but you can insert your own steps that display messages and run commands.
SRM runs different recovery plan steps in different ways.
Some steps run during all recoveries.
n
Some steps run only during test recoveries.
n
VMware, Inc.
57
Page 58

Site Recovery Manager Administration
Some steps are always skipped during test recoveries.
n
Understanding recovery steps, their order, and the context in which they run is important when you
customize a recovery plan.
Recovery Order
When you run a recovery plan, it starts by powering off the virtual machines at the protected site. SRM
powers off virtual machines according to the priority that you set, with high-priority machines powering off
last. SRM omits this step when you test a recovery plan.
SRM powers on groups of virtual machines on the recovery site according to the priority that you set. Before
a priority group starts, all of the virtual machines in the next-higher priority group must recover or fail to
recover. If dependencies exist between virtual machines in the same priority group, SRM first powers on the
virtual machines on which other virtual machines depend. If SRM can meet the virtual machine
dependencies, SRM attempts to power on as many virtual machines in parallel as vCenter Server supports.
Recovery Plan Timeouts and Pauses
Several types of timeouts can occur during the running of recovery plan steps. Timeouts cause the plan to
pause for a specified interval to allow the step time to finish.
Message steps force the plan to pause until the user acknowledges the message. Before you add a message
step to a recovery plan, make sure that it is necessary. Before you test or run a recovery plan that contains
message steps, make sure that a user can monitor the progress of the plan and respond to the messages as
needed.
Specify the Recovery Priority of a Virtual Machine
By default, SRM sets all virtual machines in a new recovery plan to recovery priority level 3. You can
increase or decrease the recovery priority of a virtual machine.
If you change the priority of a virtual machine, SRM applies the new priority to all recovery plans that
contain this virtual machine.
SRM starts virtual machines on the recovery site according to the priority that you set. SRM starts priority 1
virtual machines first, then priority 2 virtual machines second, and so on. SRM uses VMware Tools
heartbeat to discover when a virtual machine is running on the recovery site. In this way, SRM can ensure
that all virtual machines of a given priority are running before it starts the virtual machines of the next
priority. For this reason, you must install VMware Tools on protected virtual machines.
Procedure
1 Click Recovery Plans in the left pane, select a recovery plan, and click the Virtual Machines tab or the
Recovery Steps tab.
2 Right-click a virtual machine and select Priority.
3 Select a new priority for the virtual machine.
The highest priority is 1. The lowest priority is 5.
4 Click Yes to confirm the change of priority.
Creating Custom Recovery Steps
You can create custom recovery steps that run commands or present messages to the user during a recovery.
SRM can run custom steps either on the SRM Server or in a virtual machine that is part of the recovery plan.
58 VMware, Inc.
Page 59

Chapter 7 Customizing a Recovery Plan
During reprotect, SRM preserves all custom recovery steps in the recovery plan. If you perform a recovery
or test after a reprotect, custom recovery steps are run on the new recovery site, which was the original
protected site.
After reprotect, you can usually use custom recovery steps that show messages directly without
modifications. You might need to modify some custom recovery steps after a reprotect, if these steps run
commands that contain site-specific information, such as network configurations.
Types of Custom Recovery Steps on page 59
n
You can create different types of custom recovery steps to include in recovery plans.
How SRM Handles Custom Recovery Steps on page 60
n
SRM handles custom recovery steps differently based on the type of recovery step.
Create Top-Level Command Steps on page 60
n
You can add top-level commands anywhere in the recovery plan.
Create Top-Level Message Prompt Steps on page 61
n
You can add top-level message prompts anywhere in the recovery plan.
Create Command Steps for Individual Virtual Machines on page 61
n
You can configure custom recovery steps to perform tasks for a virtual machine before and after SRM
powers them on.
Create Message Prompt Steps for Individual Virtual Machines on page 62
n
You can configure custom recovery steps to prompt users to perform tasks for a virtual machine
before and after the virtual machine powers on.
Guidelines for Writing Command Steps on page 62
n
All batch files or commands for custom recovery steps that you add to a recovery plan must meet
certain requirements.
Environment Variables for Command Steps on page 62
n
SRM makes environment variables available that you can use in commands for custom recovery steps.
Types of Custom Recovery Steps
You can create different types of custom recovery steps to include in recovery plans.
Custom recovery steps are either command recovery steps or message prompt steps.
Command Recovery Steps
Command recovery steps run commands that you write. Command recovery steps run in their own
processes. Command recovery steps contain either top-level commands or per-virtual machine commands.
Top-Level Commands
Per-Virtual Machine
Commands
Run on the SRM Server. For example, you might use these commands to
power on physical devices or to redirect network traffic.
SRM associates per-virtual machine commands with newly recovered virtual
machines during the recovery process. You can use these commands to
complete configuration tasks after powering on a virtual machine. You can
run the commands either before or after powering on a virtual machine.
Commands that you configure to run after the virtual machine is powered on
can run either on the SRM Server or in the newly recovered virtual machine.
VMware, Inc. 59
Page 60

Site Recovery Manager Administration
Message Prompt Recovery Steps
Present a message in the SRM user interface during the recovery. You can use this message to pause the
recovery and provide information to the user running the recovery plan. For example, the message can
instruct users to perform a manual recovery task or to verify steps. The only action users can take in direct
response to a prompt is to click OK, which dismisses the message and allows the recovery to continue.
How SRM Handles Custom Recovery Steps
SRM handles custom recovery steps differently based on the type of recovery step.
SRM attempts to complete all custom recovery steps, but some command recovery steps might fail to finish.
Command Recovery Steps
By default, SRM waits for 5 minutes for command recovery steps to finish. You can configure the timeout
for each command. If a command finishes within this timeout period, the next recovery step in the recovery
plan runs. How SRM handles failures of custom commands depends on the type of command.
Type of Command Description
Top-level
commands
Per-virtual machine
commands
If a recovery step fails, SRM logs the failure and shows a warning on the Recovery Steps tab.
Subsequent custom recovery steps continue to run.
Run in batches either before or after a virtual machine powers on. If a command fails, the
remaining per-virtual machine commands in the batch do not run. For example, if you run five
commands for before power on and five commands for after power on, and the third command in
the batch before power on fails, the remaining two commands for before power on do not run.
SRM does not power on the virtual machine and does run commands for after power on.
Message Prompt Recovery Steps
Custom recovery steps that issue a message prompt cannot fail. The recovery plan pauses until the user
dismisses the prompt by clicking OK.
Create Top-Level Command Steps
You can add top-level commands anywhere in the recovery plan.
Prerequisites
You have a recovery plan to which to add custom steps.
Procedure
1 Click Recovery Plans in the SRM interface, and select a recovery plan.
2 Click the Recovery Steps tab.
3 Right-click a step before or after which to add a custom step, and select Add Step.
4 Select Command on SRM Server.
5 In the Name text box, type a name for the step.
6 In the Content text box, type the commands for the step to run.
7 (Optional) Modify the Timeout setting.
8 Select where in the sequence of steps to insert the new step.
Before selected step
n
After selected step
n
60 VMware, Inc.
Page 61

9 Click OK to add the step to the recovery plan.
Create Top-Level Message Prompt Steps
You can add top-level message prompts anywhere in the recovery plan.
Prerequisites
You have a recovery plan to which to add custom steps.
Procedure
1 Click Recovery Plans in the SRM interface, and select a recovery plan.
2 Click the Recovery Steps tab.
3 Right-click a step before or after which to add a custom step, and select Add Step.
4 Select Prompt.
5 In the Name text box, type a name for the step.
6 In the Content text box, type the prompt message.
7 Select where in the sequence of steps to insert the new step.
Before selected step
n
Chapter 7 Customizing a Recovery Plan
After selected step
n
8 Click OK to add the step to the recovery plan.
Create Command Steps for Individual Virtual Machines
You can configure custom recovery steps to perform tasks for a virtual machine before and after SRM
powers them on.
SRM associates command steps with a protected or recovered virtual machine in the same way as
customization information. If different recovery plans contain the same virtual machine, the commands and
prompts are the same.
Prerequisites
You have a recovery plan to which to add custom steps.
Procedure
1 Click Recovery Plans in the SRM interface, and select a recovery plan.
2 Click the Virtual Machines tab.
3 Right-click a virtual machine and click Configure.
4 Select Pre-Power On Steps or Post Power On Steps in the left pane, and click Add.
5 Select Command on SRM Server or Command on Recovered VM.
6 In the Name text box, type a name for the step.
7 In the Content text box, type the commands for the step to run.
8 (Optional) Modify the Timeout setting.
9 Click OK to add the step to the recovery plan.
10 Click OK to reconfigure the virtual machine to run the command before or after it powers on.
VMware, Inc. 61
Page 62

Site Recovery Manager Administration
Create Message Prompt Steps for Individual Virtual Machines
You can configure custom recovery steps to prompt users to perform tasks for a virtual machine before and
after the virtual machine powers on.
SRM associates message prompt steps with a protected virtual machine in the same way as customization
information. If different recovery plans contain the same virtual machine, the commands and prompts are
the same.
Prerequisites
You have a recovery plan to which to add custom steps.
Procedure
1 Click Recovery Plans in the SRM interface, and select a recovery plan.
2 Click the Virtual Machines tab.
3 Right-click a virtual machine and click Configure.
4 Select Pre-Power On Steps or Post Power On Steps in the left pane, and click Add.
5 Select Prompt.
6 In the Name text box, type a name for the step.
7 In the Content text box, type the prompt message.
8 Click OK to add the step to the recovery plan.
9 Click OK to reconfigure the virtual machine to prompt the user with a message before or after it powers
on.
Guidelines for Writing Command Steps
All batch files or commands for custom recovery steps that you add to a recovery plan must meet certain
requirements.
When you create a command step to add to a recovery plan, make sure that it takes into account the
environment in which it must run. Errors in a command step affect the integrity of a recovery plan. Test the
command on the recovery site SRM Server before you add it to the plan.
You must start the Windows command shell using its full path on the local host. For example, to run a
n
script located in c:\alarmscript.bat, use the following command line:
c:\windows\system32\cmd.exe /c c:\alarmscript.bat
You must install batch files and commands on the SRM Server at the recovery site.
n
Batch files and commands must finish within 300 seconds. Otherwise, the recovery plan terminates
n
with an error. To change this limit, see “Change Recovery Settings,” on page 85.
Batch files or commands that produce output that contains characters with ASCII values greater than
n
127 must use UTF-8 encoding. SRM records only the final 4KB of script output in log files and in the
recovery history. Scripts that produce more output should redirect the output to a file rather than
sending it to the standard output to be logged.
Environment Variables for Command Steps
SRM makes environment variables available that you can use in commands for custom recovery steps.
Command steps run with the identity of the LocalSystem account on the SRM Server host at the recovery
site. When a command step runs, SRM makes environment variables available for it to use.
62 VMware, Inc.
Page 63

Chapter 7 Customizing a Recovery Plan
Table 7‑1. Environment Variables Available to All Command Steps
Name Value Example
VMware_RecoveryName Name of the recovery plan that is
running.
VMware_RecoveryMode Recovery mode. Test or recovery
VMware_VC_Host Host name of the vCenter Server at
the recovery site.
VMware_VC_Port Network port used to contact
vCenter Server.
Plan A
vc_hostname.example.com
443
SRM makes additional environment variables available for per-virtual machine command steps that run
either on SRM Server or on the recovered virtual machine.
Table 7‑2. Environment Variables Available to Per-Virtual Machine Command Steps
Name Value Example
VMware_VM_Uuid UUID used by vCenter to uniquely identify
this virtual machine.
VMware_VM_Name Name of this virtual machine, as set at the
protected site.
VMware_VM_Ref Managed object ID of the virtual machine. vm-1199
VMware_VM_GuestName Name of the guest OS as defined by the VIM
API.
VMware_VM_GuestIp IP address of the virtual machine, if known. 192.168.0.103
VMware_VM_Path Path to this VMDK of this virtual machine.
4212145a-eeae-a02c-e525-ebba70b0d4f3
My New Virtual Machine
otherGuest
[datastore-123] jquser-vm2/jquservm2.vmdk
Customize the Recovery of an Individual Virtual Machine
You can configure a virtual machine in a recovery plan to use a prescribed customization specification, or to
run message or command steps when it is recovered.
Message and command steps added to the recovery steps for a virtual machine operate like message and
command steps added to a recovery plan. See “Guidelines for Writing Command Steps,” on page 62.
Procedure
1 Connect the vSphere Client to the vCenter Server instance on the recovery site.
2 In the SRM interface, click Recovery Plans in the left pane, and click the plan to customize.
3 Click the Recovery Steps tab or the Virtual Machines tab.
4 Right-click a virtual machine in the list, and click Configure.
5 Click IP Settings.
You can also type a description of the specification you apply. Only the IP properties from the selected
specification are applied. If you used the dr-ip-customizer.exe command to customize virtual
machines in the recovery plan, you do not need to specify that customization here.
6 Select the appropriate entry to add a message or command step that runs before the machine is
powered on.
7 Select the appropriate entry to add a message or command step that runs after the machine is powered
on.
VMware, Inc. 63
Page 64

Site Recovery Manager Administration
The customizations that you specify become associated with the protected virtual machine. As a result, the
settings are shared between all recovery plans that apply to this virtual machine.
NOTE If you remove the protection of a virtual machine, all recovery customizations are lost.
64 VMware, Inc.
Page 65

Customizing IP Properties for Virtual
Machines 8
You can customize IP settings for virtual machines for the protected site and the recovery site. Customizing
the IP properties of a virtual machine overrides the default IP settings when the recovered virtual machine
starts at the destination site.
If you do not customize the IP properties of a virtual machine, SRM uses the IP settings for the recovery site
during a recovery or a test from the protection site to the recovery site. SRM uses the IP settings for the
protection site after reprotect during the recovery or a test from the original recovery site to the original
protection site.
SRM supports different types of IP customization.
Use IPv4 and IPv6 addresses.
n
Configure different IP customizations for each site.
n
Use DHCP, Static IPv4, or Static IPv6 addresses.
n
Customize addresses of Windows and Linux virtual machines.
n
Customize multiple NICs for each virtual machine.
n
See the Compatibility Matrix for vCenter Site Recovery Manager 5.5 for the list of guest operating systems
for which SRM supports IP customization.
You associate customization settings with protected virtual machines. As a result, if the same protected
virtual machine is a part of multiple recovery plans, then all recovery plans use a single copy of the
customization settings. You configure IP customization as part of the process of configuring the recovery
properties of a virtual machine. If you do not customize a NIC on one site, the NIC uses the IP settings from
the other site.
You can apply IP customizations to individual or to multiple virtual machines.
If you configure IP customization on virtual machines, SRM adds recovery steps to those virtual machines.
Guest OS Startup
Customize IP
Guest OS Shutdown
The Guest Startup process happens in parallel for all virtual machines for
which you configure IP customization.
SRM pushes the IP customizations to the virtual machine.
SRM shuts down the virtual machine and reboots it to ensure that the
changes take effect and that the guest operating system services apply them
when the virtual machine restarts.
VMware, Inc. 65
Page 66

Site Recovery Manager Administration
After the IP customization process finishes, virtual machines power on according to the priority groups and
any dependencies that you set. The power on process happens immediately before the Wait for VMTools
process for each virtual machine.
NOTE To customize the IP properties of a virtual machine, you must install VMware Tools or the VMware
Operating System Specific Packages (OSP) on the virtual machine. See
http://www.vmware.com/download/packages.html.
Customize IP Properties For an Individual Virtual Machine on page 66
n
You can customize IP settings for individual virtual machines for both the protected site and the
recovery site.
Report IP Address Mappings for Recovery Plans on page 67
n
The IP address map reporter generates an XML document describing the IP properties of protected
virtual machines and their placeholders, grouped by site and recovery plan. This information can help
you understand the network requirements of a recovery plan.
Customizing IP Properties for Multiple Virtual Machines on page 67
n
Manually configuring IP settings for many virtual machines at a recovery site can be time consuming
and can lead to errors in configuration. To facilitate the configuration process for multiple virtual
machines, SRM includes the DR IP Customizer tool.
Customize IP Properties For an Individual Virtual Machine
You can customize IP settings for individual virtual machines for both the protected site and the recovery
site.
Procedure
1 Click Recovery Plans, and click the plan that you want to customize.
2 Click the Virtual Machines tab, right-click a virtual machine, and select Configure.
3 Select the NIC for which you will modify IP Settings.
4 To customize settings, enable the Customize IP settings during recovery option.
5 Click Configure Protection or Configure Recovery, depending on which set of IP settings you want to
configure.
6 Click the General tab to configure settings.
a Choose the type of addressing to be used.
Available options include DHCP, static IPv4, or static IPv6.
b For static addresses, enter an IP address, subnet information, and gateway server addresses.
Alternately, if the virtual machine is powered on and has VMware Tools installed, you can click
Update to import current settings configured on the virtual machine.
7 Click the DNS tab to configure DNS settings.
a Choose how DNS servers are found.
You can use DHCP to find DNS servers or you can specify primary and alternate DNS servers.
b Enter a DNS suffix and click Add or select an existing DNS suffix and click Remove, Move Up, or
Move Down.
8 Click the WINS tab to enter primary and secondary WINS addresses.
The WINS tab is available only when configuring DHCP or IPv4 addresses for Windows virtual
machines.
66 VMware, Inc.
Page 67

Chapter 8 Customizing IP Properties for Virtual Machines
9 Repeat Step 5 through Step 8 to configure recovery or protection settings, if required.
For example, if you configured IP settings for the protected site, you might want to configure settings
for the recovery site.
10 Repeat the configuration process for other NICs, as required, beginning by choosing another NIC as
described in Step 3.
Report IP Address Mappings for Recovery Plans
The IP address map reporter generates an XML document describing the IP properties of protected virtual
machines and their placeholders, grouped by site and recovery plan. This information can help you
understand the network requirements of a recovery plan.
Because the IP address mapping reporter must connect to both sites, you can run the command at either site.
You are prompted to supply the vCenter login credentials for each site when the command runs.
Procedure
1 Open a command shell on the SRM Server host at either the protected or recovery site.
2 Change to the C:\Program Files\VMware\VMware vCenter Site Recovery Manager\bin directory.
3 Run the dr-ip-reporter.exe command, as shown in this example.
dr-ip-reporter.exe --cfg ..\config\vmware-dr.xml --out c:\tmp\report.xml
To restrict the list of networks to just the ones required by a specific recovery plan, include the -plan
option on the command line, as shown in this example.
dr-ip-reporter.exe --cfg ..\config\vmware-dr.xml --out c:\tmp\report.xml -plan Plan-B
NOTE The command normally asks you to verify the thumbprints presented by the certificates at each
site. You can suppress the verification request by including the -I option.
Customizing IP Properties for Multiple Virtual Machines
Manually configuring IP settings for many virtual machines at a recovery site can be time consuming and
can lead to errors in configuration. To facilitate the configuration process for multiple virtual machines, SRM
includes the DR IP Customizer tool.
You use the DR IP Customizer tool to apply customized networking settings to virtual machines when they
start on the recovery site. You provide the customized settings to the DR IP Customizer tool in a commaseparated value (CSV) file.
Rather than manually creating a CSV file, you can use the DR IP Customizer tool to export a CSV file that
contains information about the networking configurations of the protected virtual machines. You can use
this file as a template for the CSV file to apply on the recovery site by customizing the values in the file.
1 Run DR IP Customizer to generate a CSV file that contains the networking information for the
protected virtual machines.
2 Modify the generated CSV file with networking information that is relevant to the recovery site.
3 Run DR IP Customizer again to apply the CSV with the modified networking configurations to apply
when the virtual machines start up on the recovery site.
You can run the DR IP Customizer tool on either the protected site or on the recovery site. Virtual machine
IDs for protected virtual machines are different at each site, so whichever site you use when you run the DR
IP Customizer tool to generate the CSV file, you must use the same site when you run DR IP Customizer
again to apply the settings.
VMware, Inc. 67
Page 68

Site Recovery Manager Administration
You can customize the IP settings for the protected and the recovery sites so that SRM uses the correct
configurations during reprotect operations.
See the Compatibility Matrix for vCenter Site Recovery Manager 5.5 for the list of guest operating systems
for which SRM supports IP customization.
Syntax of the DR IP Customizer Tool on page 68
n
The DR IP Customizer tool includes options that you can use to gather networking information about
the virtual machines that SRM protects. You can also use the options to apply customizations to
virtual machines when they start up on the recovery site.
Structure of the DR IP Customizer CSV File on page 69
n
The DR IP Customizer comma-separated value (CSV) file consists of a header row that defines the
meaning of each column in the file, and one or more rows for each placeholder virtual machine in a
recovery plan.
Modifying the DR IP Customizer CSV File on page 72
n
You modify the DR IP Customizer comma-separated value (CSV) file to apply customized networking
settings to virtual machines when they start on the recovery site.
Run DR IP Customizer to Customize IP Properties for Multiple Virtual Machines on page 77
n
You can use the DR IP Customizer tool to customize the IP properties for multiple virtual machines
that SRM protects.
Syntax of the DR IP Customizer Tool
The DR IP Customizer tool includes options that you can use to gather networking information about the
virtual machines that SRM protects. You can also use the options to apply customizations to virtual
machines when they start up on the recovery site.
You find the dr-ip-customizer.exe executable file in C:\Program Files\VMware\VMware vCenter Site
Recovery Manager\bin on the SRM Server host machine. When you run dr-ip-customizer.exe, you specify
different options depending on whether you are generating or applying a comma-separated value (CSV)
file.
dr-ip-customizer.exe
--cfg SRM Server configuration XML
--cmd apply/drop/generate
[--csv Name of existing CSV File]
[--out Name of new CSV file to generate]
[--vc vCenter Server address]
[--ignore-thumbprint]
[--extra-dns-columns]
[--verbose]
You can run the DR IP Customizer tool on either the protected site or on the recovery site. Virtual machine
IDs for protected virtual machines are different at each site, so whichever site you use when you run the DR
IP Customizer tool to generate the CSV file, you must use the same site when you run DR IP Customizer
again to apply the settings.
Some of the options that the DR IP Customizer tool provides are mandatory, others are optional.
Table 8‑1. DR IP Customizer Options
Option Description Mandatory
-h [ --help ]
--cfg arg
68 VMware, Inc.
Displays usage information about
dr-ip-customizer.exe.
Path to the XML configuration file of
the SRM Server, vmware-dr.xml file.
No
Yes
Page 69

Chapter 8 Customizing IP Properties for Virtual Machines
Table 8‑1. DR IP Customizer Options (Continued)
Option Description Mandatory
--cmd arg
--csv arg
-o [ --out ] arg
--vc arg
-i [ --ignore-thumbprint ]
-e [ --extra-dns-columns ]
-v [ --verbose ]
You specify different commands to
run DR IP Customizer in different
modes.
n
The apply command applies the
network customization settings
from an existing CSV file to the
recovery plans on the
SRM Server instances.
n
The generate command
generates a basic CSV file for all
virtual machines that SRM
protects for a vCenter Server
instance.
n
The drop command removes the
recovery settings from virtual
machines specified by the input
CSV file.
Always provide the same
vCenter Server instance for the apply
and drop commands as the one that
you used to generate the CSV file.
Path to the CSV file to use as input.
Name of the new CSV output file that
the generate command creates. If
you provide the name of an existing
CSV file, the generate command
overwrites its current contents.
vCenter Server host name. Virtual
machine IDs for the protected virtual
machines are different at each site.
Use the same vCenter Server instance
when you generate the CSV file and
when you apply it.
Ignore the vCenter Server
thumbprint confirmation prompt.
Obsolete. No
Enable verbose output. You can
include a --verbose option on any
dr-ip-customizer.exe command
line to log additional diagnostic
messages.
Yes
Yes, when running the apply and
drop commands.
Yes, when you run the generate
command.
Yes
No
No
Structure of the DR IP Customizer CSV File
The DR IP Customizer comma-separated value (CSV) file consists of a header row that defines the meaning
of each column in the file, and one or more rows for each placeholder virtual machine in a recovery plan.
Configuring IP settings for both sites is optional. You can provide settings for only the protected site, or
settings for only the recovery site, or settings for both sites. You can configure each site to use a different set
of network adapters in a completely different way.
Certain fields in the CSV file must be completed for every row. Other fields can be left blank if no
customized setting is required.
VMware, Inc. 69
Page 70

Site Recovery Manager Administration
Table 8‑2. Columns of the DR IP Customizer CSV File
Column Description Customization Rules
VM ID Unique identifier that DR IP
VM Name The human-readable name of the
vCenter Server Address of a vCenter Server instance
Adapter ID ID of the adapter to customize.
DNS Domain DNS domain for this adapter. Customizable. Can be left blank.
Net BIOS Select whether to activate NetBIOS
Primary WINS DR IP Customizer validates that
Customizer uses to collect
information from multiple rows for
application to a single virtual
machine. This ID is internal to DR IP
Customizer and is not the same as
the virtual machine ID that
vCenter Server uses.
virtual machine as it appears in the
vCenter Server inventory.
on either the protected site or the
recovery site. You set the IP settings
for a virtual machine on each site in
the vCenter Server column.
Adapter ID 0 sets global settings on
all adapters for a virtual machine.
Setting values on Adapter ID 1, 2, 3,
and so on, configures settings for
specific NICs on a virtual machine.
on this adapter.
WINS settings are applied only to
Windows virtual machines, but it
does not validate NetBIOS settings.
Not customizable. Cannot be blank.
Not customizable. Cannot be blank.
Not customizable. Cannot be blank.
This column can contain both
vCenter Server instances. Each
vCenter Server instance requires its
own row. You can configure one set of
IP settings to use on one site and
another set of IP settings to use on the
other site. You can also provide IP
settings to be used on both sites, for
reprotect operations.
Customizable. Cannot be left blank.
The only fields that you can modify for
a row in which the Adapter ID is 0 are
DNS Server(s) and DNS Suffix(es).
These values, if specified, are inherited
by all other adapters in use by that VM
ID.
You can include multiple DNS servers
on multiple lines in the CSV file. For
example, if you require two global
DNS hosts, you include two lines for
Adapter ID 0.
One line that contains all the
n
virtual machine information plus
one DNS host.
One line that contains only the
n
second DNS host.
To add another DNS server to a
specific adapter, add the DNS server to
the appropriate Adapter line. For
example, add the DNS server to
Adapter ID 1.
If you do enter a value, it must be in
the format example.company.com.
Customizable. Can be left blank.
If not left empty, this column must
contain one of the following strings:
disableNetBIOS, enableNetBIOS, or
enableNetBIOSViaDhcp.
Customizable. Can be left blank.
70 VMware, Inc.
Page 71

Chapter 8 Customizing IP Properties for Virtual Machines
Table 8‑2. Columns of the DR IP Customizer CSV File (Continued)
Column Description Customization Rules
Secondary WINS DR IP Customizer validates that
WINS settings are applied only to
Windows virtual machines, but it
does not validate NetBIOS settings.
IP Address IPv4 address for this virtual machine. Customizable. Cannot be blank.
Subnet Mask Subnet mask for this virtual machine. Customizable. Can be left blank.
Gateway(s) IPv4 gateway or gateways for this
virtual machine.
IPv6 Address IPv6 address for this virtual machine. Customizable. Can be left blank if you
IPv6 Subnet Prefix length Ipv6 subnet prefix length to use. Customizable. Can be left blank.
IPv6 Gateway(s) IPv4 gateway or gateways for this
adapter.
DNS Server(s) Address of the DNS server or servers. Customizable. Can be left blank.
DNS Suffix(es) Suffix or suffixes for DNS servers. Customizable. Can be left blank.
Customizable. Can be left blank.
Virtual machines can have multiple
virtual network adapters. You can
configure each virtual network adapter
with one static IPv4 address or one
static IPv6 address. For example, if you
set a static address for IPv4, you must
set the IPv6 address to DHCP.
Customizable. Can be left blank.
do not use IPv6.
Virtual machines can have multiple
virtual network adapters. You can
configure each virtual network adapter
with one static IPv4 address or one
static IPv6 address. For example, if you
set a static address for IPv6, you must
set the IPv4 address to DHCP.
If you run SRM Server on Windows
Server 2003 and you customize IPv6
addresses for a virtual machine, you
must enable IPv6 on the SRM Server
instances. SRM performs validation of
IP addresses during customization,
which requires IPv6 to be enabled on
the SRM Server if you are customizing
IPv6 addresses. Later versions of
Windows Server have IPv6 enabled by
default.
Customizable. Can be left blank.
If you enter this setting in an Adapter
ID 0 row, it is treated as a global
setting. On Windows virtual machines,
this setting applies for each adapter if
you set it in the Adapter ID rows other
than Adapter ID 0.
On Linux virtual machines, this is
always a global setting for all adapters.
This column can contain one or more
IPv4 or IPv6 DNS servers for each
NIC.
These are global settings for all
adapters on both Windows and Linux
virtual machines.
VMware, Inc. 71
Page 72

Site Recovery Manager Administration
Modifying the DR IP Customizer CSV File
You modify the DR IP Customizer comma-separated value (CSV) file to apply customized networking
settings to virtual machines when they start on the recovery site.
One challenge of representing virtual machine network configurations in a CSV file is that virtual machine
configurations include hierarchical information. For example, a single virtual machine might contain
multiple adapters, and each adapter might have multiple listings for elements such as gateways. The CSV
format does not provide a system for hierarchical representations. As a result, each row in the CSV file that
the DR IP Customizer generates might provide some or all of the information for a specific virtual machine.
For a virtual machine with a simple network configuration, all the information can be included in a single
row. In the case of a more complicated virtual machine, multiple rows might be required. Virtual machines
with multiple network cards or multiple gateways require multiple rows. Each row in the CSV file includes
identification information that describes to which virtual machine and adapter the information applies.
Information is aggregated to be applied to the appropriate virtual machine.
Follow these guidelines when you modify the DR IP Customizer CSV file.
Omit values if a setting is not required.
n
Use the minimum number of rows possible for each adapter.
n
Do not use commas in any field.
n
Specify Adapter ID settings as needed. DR IP Customizer applies settings that you specify on Adapter
n
ID 0 to all NICs. To apply settings to individual NICs, specify the values in the Adapter ID 1, 2, ..., n
fields.
To specify more than one value for a column, create an additional row for that adapter and include the
n
value in the column in that row. To ensure that the additional row is associated with the intended
virtual machine, copy the VM ID, VM Name, vCenter Server, and Adapter ID column values.
To specify multiple IP addresses for a network adapter or to specify multiple DNS server addresses,
n
add a new row for each address. Copy the VM ID, VM Name, and Adapter ID values to each row.
Examples of DR IP Customizer CSV Files
You obtain a CSV file that contains the networking information for the protected virtual machines on the
vCenter Server by running dr-ip-customizer.exe with the --cmd generate command. You edit the CSV file
to customize the IP settings of the protected virtual machines.
You can download a bundle of the example CSV files that this section describes.
Example: A Generated DR IP Customizer CSV File
For a simple setup with only two protected virtual machines, the generated CSV file might contain only the
virtual machine ID, the virtual machine name, the names of the vCenter Server instances on both sites, and a
single adapter.
VM ID,VM Name,vCenter Server,Adapter ID,DNS Domain,Net BIOS,
Primary WINS,Secondary WINS,IP Address,Subnet Mask,Gateway(s),
IPv6 Address,IPv6 Subnet Prefix length,IPv6 Gateway(s),
DNS Server(s),DNS Suffix(es)
protected-vm-10301,vm-3-win,vcenter-server-site-B,0,,,,,,,,,,,,
protected-vm-10301,vm-3-win,vcenter-server-site-A,0,,,,,,,,,,,,
protected-vm-20175,vm-1-linux,vcenter-server-site-B,0,,,,,,,,,,,,
protected-vm-20175,vm-1-linux,vcenter-server-site-A,0,,,,,,,,,,,,
72 VMware, Inc.
Page 73

Chapter 8 Customizing IP Properties for Virtual Machines
This generated CSV file shows two virtual machines, vm-3-win and vm-1-linux. The virtual machines are
present on the protected site and on the recovery site, vcenter-server-site-B, and vcenter-server-site-A. DR IP
Customizer generates an entry for each virtual machine and each site with Adapter ID 0. You can add
additional lines to customize each NIC, once you are aware of how many NICs are on each virtual machine.
Example: Setting Static IPv4 Addresses
You can modify the generated CSV file to assign two network adapters with static IPv4 addresses to one of
the virtual machines, vm-3-win, on the protected site and the recovery site.
For readability, the example CSV file in the following table omits empty columns. The DNS Domain,
NetBIOS, IPv6 Address, IPv6 Subnet Prefix length, and IPv6 Gateway(s) columns are all omitted.
Table 8‑3. Setting Static IPv4 Addresses in a Modified CSV File
VM IDVMName
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
vm-3win
vm-3win
vm-3win
vm-3win
vCent
er
Server
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-A
vcenter
serversite-A
vcenter
serversite-A
vcenter
serversite-A
Adapt
er ID
0 example.c
0 eng.exam
1 2.2.3.4 2.2.3.5 192.168.1
2 2.2.3.4 2.2.3.5 192.168.1
0 1.1.0.1 example.c
0 1.1.0.2 eng.exam
1 192.168.0
2 1.2.3.4 1.2.3.5 192.168.0
Primar
y
WINS
Secon
dary
WINSIPAddress
.21
.22
.21
.22
Subnet
Mask
255.255.2
55.0
255.255.2
55.0
255.255.2
55.0
255.255.2
55.0
DNS
Gatewa
y(s)
192.168.1.11.1.1.1
192.168.1.11.1.1.2
192.168.0
.1
192.168.0
.1
Server(s)DNS
Suffix(es)
om
ple.com
om
ple.com
The information in this CSV file applies different static IPv4 settings to vm-3-win on the protected site and
on the recovery site.
On the vcenter-server-site-B site:
n
Sets the DNS suffixes example.com and eng.example.com for all NICs for this virtual machine.
n
Adds a NIC, Adapter ID 1, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, a static
n
IPv4 address 192.168.1.21, and DNS server 1.1.1.1.
VMware, Inc. 73
Page 74

Site Recovery Manager Administration
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, a static
n
IPv4 address 192.168.1.22, and DNS server 1.1.1.2.
On the vcenter-server-site-A site:
n
Sets the DNS suffixes example.com and eng.example.com for all NICs for this virtual machine.
n
Sets the DNS servers 1.1.0.1 and 1.1.0.2 for all NICs for this virtual machine.
n
Adds a NIC, Adapter ID 1, with a static IPv4 address 192.168.0.21.
n
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 1.2.3.4 and 1.2.3.5 and a
n
static IPv4 address 192.168.0.22.
Example: Setting Static and DHCP IPv4 Addresses
You can modify the generated CSV file to assign multiple NICs to one of the virtual machines, vm-3-win,
that use a combination of static and DHCP IPv4 addresses. The settings can be different on the protected site
and the recovery site.
For readability, the example CSV file in the following table omits empty columns. The DNS Domain,
NetBIOS, IPv6 Address, IPv6 Subnet Prefix length, and IPv6 Gateway(s) columns are all omitted.
Table 8‑4. Setting Static and DHCP IPv4 Addresses in a Modified CSV File
VM IDVMName
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
protecte
dvm-1030
1
vm-3win
vm-3win
vm-3win
vm-3win
vCent
er
Server
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-B
vcenter
serversite-A
vcenter
serversite-A
vcenter
serversite-A
vcenter
serversite-A
Primar
Adapt
er ID
0 example.c
0 eng.exam
1 2.2.3.4 2.2.3.5 dhcp 1.1.1.1
2 2.2.3.4 2.2.3.5 192.168.1
0 1.1.0.1 example.c
0 1.1.0.2 eng.exam
1 dhcp
2 1.2.3.4 1.2.3.5 192.168.0
y
WINS
Secon
dary
WINSIPAddress
.22
.22
Subnet
Mask
255.255.2
55.0
255.255.2
55.0
DNS
Gatewa
y(s)
192.168.1.11.1.1.2
192.168.0
.1
Server(s)DNS
Suffix(es)
om
ple.com
om
ple.com
74 VMware, Inc.
Page 75

Chapter 8 Customizing IP Properties for Virtual Machines
The information in this CSV file applies different static and dynamic IPv4 settings to vm-3-win on the
protected site and on the recovery site.
On site vcenter-server-site-B:
n
Sets the DNS suffixes example.com and eng.example.com for all NICs for this virtual machine.
n
Adds a NIC, Adapter ID 1, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, that uses
n
DHCP to obtain an IP address and sets the static DNS server 1.1.1.1.
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, with a
n
static IPv4 address 192.168.1.22 and DNS server 1.1.1.2.
On site vcenter-server-site-A:
n
Sets the DNS suffixes to example.com and eng.example.com for all NICs for this virtual machine.
n
Sets the DNS servers 1.1.0.1 and 1.1.0.2 for all NICs for this virtual machine.
n
Adds a NIC, Adapter ID 1, that uses DHCP to obtain an IPv4 address and the globally assigned
n
DNS server information.
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 1.2.3.4 and 1.2.3.5, and a
n
static IPv4 address 192.168.0.22.
Example: Setting Static and DHCP IPv4 and IPv6 Addresses
You can modify the generated CSV file to assign multiple NICs to vm-3-win, one of the virtual machines.
The NICs can use a combination of static and DHCP IPv4 and IPv6 addresses. The settings can be different
on both the protected site and the recovery site.
For readability, the example CSV file in the following table omits empty columns. The DNS Domain and
NetBIOS columns are omitted.
Table 8‑5. Setting Static and DHCP IPv4 and IPv6 Addresses in a Modified CSV File
IPv6
VM ID
protec
tedvm-10
301
protec
tedvm-10
301
protec
tedvm-10
301
VM
Nam
e
vm3win
vm3win
Sec
vCe
nter
Serv
er
vcen
terserv
ersiteB
vcen
terserv
ersiteB
vcen
terserv
ersiteB
Prim
ond
Ada
ary
ary
IP
pter
WIN
WIN
Addr
ID
S
S
ess
0 exampl
0 eng.exa
1 2.2.3.42.2.3.5192.16
8.1.21
Subn
et
Mask
255.25
5.255.
0
Gate
way(s
)
192.16
8.1.1
IPv6
Addr
ess
dhcp 1.1.1.1
Subn
et
Prefix
lengt
h
IPv6
Gate
way(s
)
DNS
Serve
r(s)
DNS
Suffix(
es)
e.com
mple.co
m
VMware, Inc. 75
Page 76

Site Recovery Manager Administration
Table 8‑5. Setting Static and DHCP IPv4 and IPv6 Addresses in a Modified CSV File (Continued)
vCe
VM
nter
Nam
Serv
VM ID
protec
tedvm-10
301
protec
tedvm-10
301
protec
tedvm-10
301
protec
tedvm-10
301
protec
tedvm-10
301
protec
tedvm-10
301
e
vm3win
vm3win
er
vcen
terserv
ersiteB
vcen
terserv
ersiteA
vcen
terserv
ersiteA
vcen
terserv
ersiteA
vcen
terserv
ersiteA
vcen
terserv
ersiteA
IPv6
Sec
Prim
ond
Ada
ary
ary
IP
pter
WIN
WIN
Addr
ID
S
S
ess
2 2.2.3.42.2.3.5dhcp ::ffff:
0 exampl
0 eng.exa
1 dhcp ::ffff:
1 ::ffff:
2 1.2.3.41.2.3.5192.16
8.0.22
Subn
et
Mask
255.25
5.255.
0
Gate
way(s
)
192.16
8.0.1
IPv6
Addr
ess
192.16
8.1.22
192.16
8.0.22
Subn
et
Prefix
lengt
h
32 ::ffff:
32 ::ffff:
IPv6
Gate
way(s
)
192.16
8.1.1
192.16
8.0.1
DNS
Serve
r(s)
1.1.1.2
::ffff:
192.16
8.0.25
0
192.16
8.0.25
1
1.1.1.1
DNS
Suffix(
es)
e.com
mple.co
m
The information in this CSV file applies different IP settings to vm-3-win on the protected site and on the
recovery site.
On site vcenter-server-site-B:
n
Sets the DNS suffixes example.com and eng.example.com for all NICs for this virtual machine.
n
Adds a NIC, Adapter ID 1, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, that sets a
n
static IPv4 address 192.168.1.21, uses DHCP to obtain an IPv6 address, and uses DNS server 1.1.1.1.
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 2.2.3.4 and 2.2.3.5, that uses
n
DHCP to obtain an IPv4 address, sets a static IPv6 address ::ffff:192.168.1.22, and uses DNS server
1.1.1.2.
On site vcenter-server-site-A:
n
Sets the DNS suffixes to example.com and eng.example.com for all NICs for this virtual machine.
n
76 VMware, Inc.
Page 77

Chapter 8 Customizing IP Properties for Virtual Machines
Adds a NIC, Adapter ID 1, that uses DHCP to obtain an IPv4 address and sets a static IPv6
n
address ::ffff:192.168.1.22. Adapter ID 1 uses static IPv6 DNS servers ::ffff:192.168.0.250 and ::ffff:
192.168.0.251.
Adds a NIC, Adapter ID 2, with primary and secondary WINS servers 1.2.3.4 and 1.2.3.5, a static
n
IPv4 address 192.168.0.22, and DNS server 1.1.1.1. By leaving the IPv6 column blank, Adapter ID 2
uses DHCP for IPv6 addresses.
Run DR IP Customizer to Customize IP Properties for Multiple Virtual Machines
You can use the DR IP Customizer tool to customize the IP properties for multiple virtual machines that
SRM protects.
Prerequisites
Use the DR IP Customizer tool on a computer with access to vCenter Server instances in your environment.
Procedure
1 Open a command shell on the SRM Server host.
2 Change directory to C:\Program Files\VMware\VMware vCenter Site Recovery Manager\bin.
3 Run the dr-ip-customizer.exe command to generate a comma-separated value (CSV) file that contains
information about the protected virtual machines.
dr-ip-customizer.exe --cfg ..\config\vmware-dr.xml --cmd generate --out
"C:\MassIPCustCSVs\MassIPCust-generate-output.csv" --vc vc04.eng.example.com
This example points dr-ip-customizer.exe to the vmware-dr.xml file of the SRM Server and generates
the file MassIPCust-generate-output.csv for the vCenter Server instance vc04.eng.example.com.
4 (Optional) Check the vCenter Server thumbprint and type y to confirm that you trust this
vCenter Server instance.
If you specified the --ignore-thumbprint option, you are not prompted to check the thumbprint.
5 Enter the login credentials for the vCenter Server instance.
You might be prompted again to confirm that you trust this vCenter Server instance.
6 Edit the generated CSV file to customize the IP properties for the virtual machines in the recovery plan.
You can use a spread sheet application to edit the CSV file. Save the modified CSV file under a new
name.
7 Run dr-ip-customizer.exe to apply the customized IP properties from the modified CSV file.
You can run the DR IP Customizer tool on either the protected site or on the recovery site. Virtual
machine IDs for protected virtual machines are different at each site, so whichever site you use when
you run the DR IP Customizer tool to generate the CSV file, you must use the same site when you run
DR IP Customizer again to apply the settings.
dr-ip-customizer.exe --cfg ..\config\vmware-dr.xml --cmd apply --csv
"C:\MassIPCustCSVs\MassIPCust-ipv6.csv" --vc vc04.eng.example.com
This example points dr-ip-customizer.exe to the vmware-dr.xml file of the SRM Server and applies the
customizations in the file MassIPCustCSVs\MassIPCust-ipv6.csv to the vCenter Server instance
vc04.eng.example.com.
The specified customizations are applied to all of the virtual machines named in the CSV file during a
recovery. You do not need to manually configure IP settings for these machines when you edit their
recovery plan properties.
VMware, Inc. 77
Page 78

Site Recovery Manager Administration
78 VMware, Inc.
Page 79

Advanced SRM Configuration 9
The SRM default configuration enables some simple recovery scenarios. Advanced users can customize
SRM to support a broader range of site recovery requirements.
This chapter includes the following topics:
“Configure Protection for a Virtual Machine or Template,” on page 79
n
“Configure Resource Mappings for a Virtual Machine,” on page 80
n
“Specify a Nonreplicated Datastore for Swap Files,” on page 80
n
“Recovering Virtual Machines Across Multiple Hosts on the Recovery Site,” on page 81
n
“Resize Virtual Machine Disk Files During Replication Using Replication Seeds,” on page 82
n
“Resize Virtual Machine Disk Files During Replication Without Using Replication Seeds,” on
n
page 82
“Reconfigure SRM Settings,” on page 82
n
Configure Protection for a Virtual Machine or Template
You can edit the protection properties of any virtual machine or template in a protection group. You can
change the resource mappings, attached storage devices and their datastores, and other properties that
control the configuration with which SRM recovers the virtual machine.
VMware, Inc.
You must configure protection for virtual machines that have a status of Not Configured or Mapping
Missing.
If you are using array-based replication, editing the properties of a virtual machine to add or change storage
devices, such as hard disks or DVD drives, can affect the protection of that machine if the device that you
add is stored on a datastore that is not replicated, or that is protected by a different protection group.
If the new device is created on a replicated datastore that is not part of any protection group, the
n
datastore is added to the virtual machine's protected datastore group and the protection of the virtual
machine is unaffected.
If the new device is created on a replicated datastore that is protected by a different protection group,
n
this invalidates the protection of the virtual machine.
If the new device is created on a nonreplicated datastore, this invalidates the protection of the virtual
n
machine.
If you use Storage vMotion to move a virtual machine to a nonreplicated datastore, or to a replicated
n
datastore on an array that SRM has not been configured to manage (through an SRA), this invalidates
the protection of the virtual machine. You can use Storage vMotion to move a virtual machine to
datastore that is part of another protection group.
79
Page 80

Site Recovery Manager Administration
Procedure
1 Click Protection Groups in the SRM interface and select the protection group that includes the virtual
machine to configure.
2 On the Virtual Machines tab, right-click a virtual machine and select Configure Protection.
3 In the Virtual Machine Properties window, review and configure properties as needed.
a Click Folder to specify an alternate destination folder.
b Click Recovery Pool to specify an alternate resource pool in which to place the recovered virtual
machine.
c If configuring protection for a template, click Recovery Host to specify an alternate host to which
to recover the virtual machine.
This step only applies to templates.
d Click Network to specify an alternate recovery network to which to restore the virtual machine.
4 Click OK to apply the new configuration to the selected virtual machine.
Configure Resource Mappings for a Virtual Machine
If you have not specified inventory mappings for your site, you must configure resource mappings for
individual virtual machines. You can configure resource mappings only if site-wide inventory mappings
have not been established.
If inventory mappings have been established for a site, you cannot override them by configuring the
protection of individual virtual machines. If you need to override inventory mappings for a few members of
a protection group, use the vSphere Client to connect to the recovery site and edit the settings of the
placeholders or move them to a different folder or resource pool.
Procedure
1 Click Protection Groups, and navigate to the protection group that includes the virtual machine that
you want to configure.
2 On the Virtual Machines page, right-click a virtual machine and click Configure Protection.
If you established inventory mappings, they are applied.
3 Configure mappings as needed.
For most virtual machines, you can change the Folder and Compute Resource mappings. For more
information, see “Configure Protection for a Virtual Machine or Template,” on page 79.
Specify a Nonreplicated Datastore for Swap Files
Every virtual machine requires a swap file. By default, vCenter Server creates swap files in the same
datastore as the other virtual machine files. To prevent SRM from replicating swap files you can configure
virtual machines to create them in a nonreplicated datastore.
CAUTION Under normal circumstances, you should keep the swap files in the same datastore as the other
virtual machine files. However, you might need to prevent replication of swap files to avoid excessive
consumption of network bandwidth. Also, some storage vendors recommend that you do not replicate
swap files. Only prevent replication of swap files if it is absolutely necessary.
If you are using a nonreplicated datastore for swap files, you must create a nonreplicated datastore for all
protected clusters at both the protected and recovery sites. The nonreplicated datastore must be visible to all
hosts in the cluster, otherwise vMotion will not work.
80 VMware, Inc.
Page 81

Chapter 9 Advanced SRM Configuration
Procedure
1 In the vSphere Client, right-click an ESXi cluster and click Edit Settings.
2 In the Settings page for the cluster, click Swapfile Location, select Store the swapfile in the datastore
specified by the host, and click OK.
3 For each host in the cluster, select a nonreplicated datastore.
a Select a host and click the Configuration tab.
b In the Software panel, click Virtual Machine Swapfile Location, and click Edit at the top right of
the main panel.
c On the Virtual Machine Swapfile Location page, select a nonreplicated datastore and click OK.
4 For standalone hosts that are not part of a cluster, select the host and click the Configuration tab.
5 In the Software panel, click Virtual Machine Swapfile Location, and click Edit at the top right of the
main panel.
6 Select Store the swapfile in a swapfile datastore selected below, select the datastore, and click OK.
7 Power off and power on all of the virtual machines in the cluster.
Resetting the guest operating system is not sufficient. The change of swapfile location takes effect after
you power off then power on the virtual machines.
8 Browse the datastore that you selected for swapfiles and verify that VSWP files are present for the
virtual machines in the cluster.
Recovering Virtual Machines Across Multiple Hosts on the Recovery Site
You can create recovery plans that recover virtual machines across multiple recovery site hosts in a
quarantined test network.
With SRM, the vSwitches can be DVS based and span hosts. If you accept the default test network
configured as Auto, then virtual machines that are recovered across hosts are placed in their own test
network. Each test switch is isolated between hosts. As a result, virtual machines in the same plan are
isolated when the recovery finishes. To allow the virtual machines to communicate, establish and select DVS
switches or VLANs. With an isolated VLAN that connects all hosts to each other but not to a production
network, you can more realistically test a recovery. To achieve connectivity among recovery hosts, but
maintain isolation from the production network, follow these recommendations:
Create DVS switches that are connected to an isolated VLAN that is private. Such a VLAN allows hosts
n
and virtual machines to be connected, but to be isolated from production virtual machines. Use a
naming convention that clearly designates that the DVS is for testing use, and select this DVS in the
recovery plan test network column in the recovery plan editor.
Create test VLANs on a physical network, providing no route back to the protected site. Trunk test
n
VLANs to recovery site vSphere clusters and create virtual switches for test VLAN IDs. Use a clear
naming convention to identify that these switches are for testing. Select these switches from the test
recovery network column in the recovery plan editor.
VMware, Inc. 81
Page 82

Site Recovery Manager Administration
Resize Virtual Machine Disk Files During Replication Using Replication Seeds
vSphere Replication prevents you from resizing the virtual machine disk file during replication. If you used
replication seeds for the target disk, you can resize the disk manually.
Procedure
1 Unconfigure replication on the virtual machine.
2 Resize the disk on the source site.
3 Resize the target disk that is left over after you unconfigure replication.
4 Reconfigure replication on the virtual machine.
Resize Virtual Machine Disk Files During Replication Without Using Replication Seeds
vSphere Replication prevents you from resizing the virtual machine disk file during replication. If you did
not use replication seeds during configuration of the target disk, vSphere Replication deletes the target disk
when you stop the replication.
To resize a virtual machine disk if you did not initially use replication seeds, you must perform a test
recovery, clone the recovered virtual machine, and reconfigure the disk manually using replication seeds.
Procedure
1 Run a test recovery for the virtual machine.
2 Clone the recovered virtual machine on the same datastore where the replication occurs after you
reconfigure the replication.
3 Revert the test recovery.
4 Unconfigure the replication.
5 Resize the disk on the source site.
6 Resize the disk on the cloned virtual machine on the target site.
7 Unregister the cloned virtual machine on the target site, but do not delete the disks.
8 Enable replication by using the disks of the cloned virtual machine as seeds.
Reconfigure SRM Settings
Using the Advanced Settings, you can view or change many custom settings for the SRM service. Advanced
Settings provide a way for a user with adequate privileges to change default values that affect the operation
of various SRM features.
SRM applies the advanced settings to the virtual machines that you protect on a given site, and not to
recovery plans. SRM applies advanced settings to a virtual machine at the moment that you configure
protection on that virtual machine. If you change any of the advanced settings after you have configured the
protection of a virtual machine, the new settings do not apply to that virtual machine. Modifications to
advanced settings apply only to virtual machines that you protect after you changed the settings. This is by
design, because if SRM were to apply changed advanced settings to virtual machines on which you have
already configured protection, this could lead to unwanted changes in the protection of those virtual
machines.
82 VMware, Inc.
Page 83

Chapter 9 Advanced SRM Configuration
To apply changes that you make to advanced settings to virtual machines that you have already protected,
you must reconfigure protection for those virtual machines individually. You can also remove the protection
from the virtual machine by removing it from a protection group, and then reconfigure protection by
adding it back in the protection group.
Change Local Site Settings
SRM monitors consumption of resources on the SRM Server host, and it raises an alarm if a resource
threshold is reached. You can change the thresholds and the way that SRM raises the alarms.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click localSiteStatus.
3 Change the settings as needed.
Option Action
Change the interval at which SRM
checks the CPU usage, disk space,
and free memory at the local site
Change the name of the local site
Change the timeout during which
SRM waits between raising alarms
about CPU usage, disk space, and
free memory at the local site
Change the percentage of CPU
usage that causes SRM to raise a
high CPU usage event
Change the percentage of free disk
space that causes SRM to raise a
low disk space event
Change the amount of free memory
that causes SRM to raise a low
memory event
4 Click OK to save your changes.
Type a new value in the localSiteStatus.checkInterval text box.
Type a new value in the localSiteStatus.displayName text box.
Type a new value in the localSiteStatus.eventFrequency text box.
Type a new value in the localSiteStatus.maxCpuUsage text box.
Type a new value in the localSiteStatus.minDiskSpace text box.
Type a new value in the localSiteStatus.minMemory text box.
Change Logging Settings
You can change the levels of logging that SRM provides for the SRM Server components.
SRM Server operates log rotation. When you restart SRM Server, or when a log file becomes large,
SRM Server creates a new log file and writes subsequent log messages to the new log file. When SRM Server
creates new log files, it compresses the old log files to save space.
You might reduce the logging levels for some SRM Server components because log files become too large
too quickly. You might increase logging levels for certain components to help diagnose problems. The list of
available logging levels is the same for all SRM Server components.
none
quiet
panic
VMware, Inc. 83
Turns off logging.
Records minimal log entries.
Records only panic log entries. Panic messages occur in cases of complete
failure.
Page 84

Site Recovery Manager Administration
error
Records panic and error log entries. Error messages occur in cases of
problems that might or might not result in a failure.
warning
Records panic, error, and warning log entries. Warning messages occur for
behavior that is undesirable but that might be part of the expected course of
operation.
info
Records panic, error, warning, and information log entries. Information
messages provide information about normal operation.
verbose
Records panic, error, warning, information, and verbose log entries. Verbose
messages provide more detailed information than information messages.
trivia
Records panic, error, warning, information, verbose, and trivia log entries.
Trivia messages provide all available information. This level of logging is
useful for debugging but it can produce so much data that it might affect
performance.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click logManager.
3 Modify the logging settings.
By default, all components record verbose level logs, unless stated otherwise in the description of the
logging level.
Option Description
Set logging level for all components
that do not have an entry in
logManager
Set logging level for the external
API module
Set logging level for
vSphere Replication
Set logging level for the IP
Customizer tool
Set logging level for inventory
mapping
Set logging level for licensing
issues
Set logging level for persistence
issues
Set logging level for recovery
operations
Set logging level for recovery
configuration operations
Set logging level for array-based
replication operations
Set logging level for authorization
issues between SRM Server and
vCenter Server
Set logging level for session
management
Select a logging level from the logManager.Default drop-down menu.
Select a logging level from the logManager.ExternalAPI drop-down menu.
Select a logging level from the logManager.HbrProvider drop-down
menu.
Select a logging level from the logManager.IPCustomizer drop-down
menu.
Select a logging level from the logManager.InventoryMapper drop-down
menu.
Select a logging level from the logManager.Licensing drop-down menu.
Select a logging level from the logManager.Persistence drop-down menu.
Select a logging level from the logManager.Recovery drop-down menu.
By default, recovery logging is set to trivia.
Select a logging level from the logManager.RecoveryConfig drop-down
menu.
Select a logging level from the logManager.Replication drop-down menu.
Select a logging level from the logManager.ServerAuthorization dropdown menu.
Select a logging level from the logManager.SessionManager drop-down
menu.
84 VMware, Inc.
Page 85

Chapter 9 Advanced SRM Configuration
Option Description
Set logging level for the SOAP Web
Services adapter
Set logging level for storage issues
Set logging level for messages from
the array-based storage provider
Select a logging level from the logManager.SoapAdapter drop-down
menu. Due to the levels of traffic that the SOAP adapter generates, setting
the logging level to trivia might affect performance. By default, SOAP
adapter logging is set to info.
Select a logging level from the logManager.Storage drop-down menu.
Select a logging level from the logManager.StorageProvider drop-down
menu.
4 Click OK to save your changes.
The new logging levels apply as soon as you click OK. You do not need to restart the SRM service. If
you restart SRM Server, logging remains set to the level that you choose.
Change Recovery Settings
You can adjust default values for timeouts that occur when you test or run a recovery plan. You might
adjust default values if tasks fail to finish because of timeouts.
Several types of timeouts can occur when recovery plan steps run. These timeouts cause the plan to pause
for a specified interval to give the step time to finish.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click recovery.
3 Modify the recovery site settings.
Option Action
Change the IP customization
timeout
Change the default priority for
recovering a virtual machine
Enable or disable forced recovery
Change the timeout for hosts in a
cluster to power on
Change the timeout for guest OS to
power off
Change the delay after powering on
a virtual machine before starting
dependent tasks
Change the timeout to wait for
VMware Tools when powering on
virtual machines
Enable or disable skipping the
shutdown of the guest OS
Type a new value in the recovery.customizationTimeout text box.
Type a new value in the recovery.defaultPriority text box.
Select or deselect the recovery.forceRecovery check box. You should only
activate forced recovery in cases where a lack of connectivity to the
protected site severely affects RTO.
Type a new value in the recovery.hostPowerOnTimeout text box.
Type a new value in the recovery.powerOffTimeout text box. The new
time-out value applies to power-off tasks for virtual machines at the
recovery site.
Type a new value in the recovery.powerOnDelay text box. The new value
applies to power-on tasks for virtual machines at the recovery site.
Type a new value in the recovery.powerOnTimeout text box. The new
power-on value applies to power-on tasks for virtual machines at the
recovery site. If protected virtual machines do not have VMware Tools
installed, set this value to 0.
Select or deselect the recovery.skipGuestShutdown check box. If
protected virtual machines do not have VMware Tools installed and the
guest shutdown timeout is not set to 0, you must select this option. If you
do not select this option and VMware Tools is not installed, a recovery
cannot progress past the step Shutdown VMs at the recovery site.
4 Click OK to save your changes.
VMware, Inc. 85
Page 86

Site Recovery Manager Administration
Change Remote Site Settings
You can modify the default values that the SRM Server at the protected site uses to determine whether the
SRM Server at the remote site is available.
SRM monitors the connection between the protected site and the recovery site and raises alarms if the
connection breaks. You can change the criteria that cause SRM to raise a connection event and change the
way that SRM raises alarms.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click remoteSiteStatus.
3 Modify the settings.
Option Action
Change the number of remote site
status checks (pings) to try before
declaring the check a failure
Change the number of failed pings
before raising a site down event
Change the interval at which SRM
checks whether the SRM Server at
the remote site is available
4 Click OK to save your changes.
Type a new value in the remoteSiteStatus.pingFailedDelay text box.
Type a new value in the remoteSiteStatus.panicDelay text box.
Type a new value in the remoteSiteStatus.pingInterval text box.
Change the Timeout for the Creation of Placeholder Virtual Machines
You can adjust replication settings to modify how long SRM waits for the creation of virtual machine
placeholders to finish.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click replication.
3 Change the replication.placeholderVmCreationTimeout setting to modify the number of seconds to
wait when creating a placeholder virtual machine.
4 Click OK to save your changes.
Change Storage Settings
You can adjust the settings of your storage array, to modify how SRM and vCenter Server communicate
with the storage replication adapter (SRA).
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click storage.
86 VMware, Inc.
Page 87

3 Modify the storage settings.
Option Action
Change SRA update timeout
Change the maximum number of
concurrent SRA operations
Change the minimum amount of
time in seconds between datastore
group computations
Change the interval between status
updates for ongoing data
synchronization operations
Change the interval between
storage array discovery checks
Change the maximum amount of
time permitted for data
synchronization operations to
complete
4 Click OK to save your changes.
Change Storage Provider Settings
Chapter 9 Advanced SRM Configuration
Type a new value in the storage.commandTimeout text box.
Type a new value in the storage.maxConcurrentCommandCnt text box.
Type a new value in the storage.minDsGroupComputationInterval text
box.
Type a new value in the storage.querySyncStatusPollingInterval text box.
Type a new value in the storage.storagePingInterval text box.
Type a new value in the storage.syncTimeout text box.
For array-based replication, the SAN provider is the interface between SRM and your storage replication
adapter (SRA). Some SRAs require you to change default SAN provider values. You can change the default
timeout values and other behaviors of the SRM SAN provider.
You can change settings for resignaturing, fixing datastore names, host rescan counts, and timeouts. For
more information about these values, see the SRA documentation from your array vendor.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click storageProvider.
3 Modify the SAN provider settings.
Option Action
Make SRM attempt to detach and
reattach LUNs with duplicate
volumes
Set the LVM.EnableResignature
flag on ESXi hosts during test and
recovery
Force removal, upon successful
completion of a recovery, of the
snap-xx prefix applied to recovered
datastore names
Select the storageProvider.autoDetachLUNsWithDuplicateVolume check
box.
In the storageProvider.autoResignatureMode text box, type 0 to disable, 1
to enable, or 2 to ignore the flag. The default setting is 0. If you set this flag
to 1, SRM resignatures all known VMFS snapshot volumes, including any
volumes that SRM does not manage. If you leave the flag set to 0, SRM
only resignatures the VMFS snapshot volumes that it manages.
Select the storageProvider.fixRecoveredDatastoreNames check box.
VMware, Inc. 87
Page 88

Site Recovery Manager Administration
Option Action
Delay host scans during testing and
recovery
Repeat host scans during testing
and recovery
Change the interval that SRM waits
for each HBA rescan to complete
Set the number of times that SRM
attempts to resignature a VMFS
volume
Set a timeout for resignaturing a
VMFS volume
Search for VMX files in recovered
datastores to identify virtual
machines that Storage vMotion has
moved before or during a test or a
recovery
Identify VMX file paths that SRM
should not consider as potential
VMX file candidates after Storage
vMotion
4 Click OK to save your changes.
SRAs can send responses to SRM before a promoted storage device on the
recovery site is available to the ESXi hosts. When SRM receives a response
from an SRA, it rescans the storage devices. If the storage devices are not
fully available yet, ESXi Server does not detect them and SRM does not
find the replicated devices when it rescans. Datastores are not created and
recovered virtual machines cannot be found.
To delay the start of storage rescans until they are available on the ESXi
hosts, type a new value in the storageProvider.hostRescanDelaySec text
box.
Only change this value if you experience problems with unavailable
datastores.
Type a new value in the storageProvider.hostRescanRepeatCnt text box.
Some storage arrays require more than one rescan, for example to discover
the snapshots of failed-over LUNs.
In previous releases, you might have used the
storageProvider.hostRescanRepeatCnt parameter to introduce a
delay in recoveries. Use the storageProvider.hostRescanDelaySec
parameter instead.
Type a new value in the storageProvider.hostRescanTimeoutSec text box.
Type a new value in the storageProvider.resignatureFailureRetryCount
text box.
Type a new value in the storageProvider.resignatureTimeoutSec text box.
If you change the storageProvider.hostRescanTimeoutSec setting,
increase the storageProvider.resignatureTimeoutSec setting to the same
timeout that you use for storageProvider.hostRescanTimeoutSec.
The option is selected by default. Deselect the
storageProvider.storageVmotionVmxSearch check box to disable this
option.
Some arrays create VMX file paths that the
storageProvider.storageVmotionVmxSearch search algorithm should
ignore. Type a comma-separated list of strings in the
storageProvider.storageVmotionVmxFilePathsToSkip text box to identify
VMX file paths to ignore after Storage vMotion. SRM does not consider
VMX file paths that contain one or more of these strings as potential
candidate VMX files after Storage vMotion.
Change vSphere Replication Settings
You can adjust global settings to change how SRM interacts with vSphere Replication.
Procedure
1 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
2 Click vrReplication.
88 VMware, Inc.
Page 89

3 Modify the vSphere Replication settings.
Option Description
Allow vSphere Replication to
recover virtual machines that are
included in SRM recovery plans
independently of SRM
Keep older multiple point in time
(PIT) snapshots during recovery
Change the timeout period for
reverse replication during reprotect
operations
Change the timeout period for
vSphere Replication
synchronization operations
Change the default RPO setting for
replications
If you configure vSphere Replication on a virtual machine and include the
virtual machine in an SRM recovery plan, you cannot recover the virtual
machine by using vSphere Replication independently of SRM. To allow
vSphere Replication to recover virtual machines independently of SRM,
select the allowOtherSolutionTagInRecovery check box.
If you configure vSphere Replication to take PIT snapshots of protected
virtual machines, SRM only recovers the most recent snapshot when you
perform a recovery. To recover older PIT snapshots during recovery, select
the preserveMpitImagesAsSnapshots check box.
Type a new value in the reverseReplicationTimeout text box. Change this
value if you experience timeout errors when vSphere Replication reverses
replication during reprotect operations.
Type a new value in the synchronizationTimeout text box. Change this
value if you experience timeout errors when vSphere Replication
synchronizes virtual machines on the recovery site.
Type a new value in the vrReplication.timeDefault text box. The default
value is 240 minutes (4 hours). This value is selected when you configure
replications, but you can specify a different RPO in the Configure
Replication wizard when you configure replication for an individual
virtual machine or for a group of virtual machines.
4 Click OK to save your changes.
Chapter 9 Advanced SRM Configuration
Modify Settings to Run Large SRM Environments
If you use SRM to test or recover a large number of virtual machines, you might need to modify the default
SRM settings to achieve the best possible recovery times in your environment or to avoid timeouts.
In large environments, SRM might simultaneously power on or power off large numbers of virtual
machines. Simultaneously powering on or powering off large numbers of virtual machines can create a
heavy load on the virtual infrastructure, which might lead to timeouts. You can modify certain SRM settings
to avoid timeouts, either by limiting the number of power on or power off operations that SRM performs
concurrently, or by increasing the timeout periods.
The limits that you set on power on or power off operations depend on how many concurrent power on or
power off operations your infrastructure can handle.
You modify certain options in the Advanced Settings menus in the vSphere Client or in the SRM client
plug-in. To modify other settings, you edit the vmware-dr.xml configuration file on the SRM Server. Always
modify settings by using the client menus when an option exists. If you modify settings, you must make the
same modifications on the SRM Server and vCenter Server instances on both the protected and recovery
sites.
For descriptions of the settings that you can change, see “Settings for Large SRM Environments,” on
page 90.
Procedure
1 Right-click a cluster in the vCenter Server Inventory and select Edit Settings > vSphere DRS >
Advanced Options.
VMware, Inc. 89
Page 90

Site Recovery Manager Administration
2 Set the srmMaxBootShutdownOps setting.
Option Description
Option text box
Value text box
3 Click OK to save your changes.
4 Log into the SRM Server host.
5 Open the vmware-dr.xml file in a text editor.
You find the vmware-dr.xml file in the C:\Program Files\VMware\VMware vCenter Site Recovery
Manager\config folder.
6 Change the defaultMaxBootAndShutdownOpsPerCluster and defaultMaxBootAndShutdownOpsPerHost
settings in the vmware-dr.xml file:
<config>
...
<defaultMaxBootAndShutdownOpsPerCluster>24</defaultMaxBootAndShutdownOpsPerCluster>
<defaultMaxBootAndShutdownOpsPerHost>4</defaultMaxBootAndShutdownOpsPerHost>
...
</config>
Type srmMaxBootShutdownOps.
Type the maximum number of boot shutdown operations, for example 32.
7 Restart the SRM Server to apply the new settings.
8 Click Sites in the SRM interface, right-click the site on which to change settings, and select Advanced
Settings.
9 Select vrReplication and increase the synchronizationTimeout setting.
For example, increase the synchronizationTimeout value to 7200 seconds.
10 Select storage and increase the commandTimeout setting.
For example, increase the commandTimeout value to 3600 seconds.
11 Click OK to save your changes.
Settings for Large SRM Environments
To protect a large number of virtual machines, you can modify the default SRM settings to achieve the best
possible recovery times in your environment or to avoid timeouts.
You modify certain options in the Advanced Settings menus in the vSphere Client or in the SRM client
plug-in. To modify other settings, you edit the vmware-dr.xml configuration file on the SRM Server. Always
modify settings by using the client menus when an option exists. If you modify settings, you must make the
same modifications on the SRM Server and vCenter Server instances on both the protected and recovery
sites.
To modify the settings, see “Modify Settings to Run Large SRM Environments,” on page 89.
90 VMware, Inc.
Page 91

Chapter 9 Advanced SRM Configuration
Table 9‑1. Settings that Modify the Number of Simultaneous Power On or Power Off Operations
Option Description
srmMaxBootShutdownOps Specifies the maximum number of concurrent power-on
operations for any given cluster. Guest shutdowns, but not
forced power offs, are throttled according to this value.
Guest shutdowns occur during primary site shutdowns
(planned failover) and IP customization workflows.
Modify this option per cluster in the vSphere Client by
right-clicking a cluster and selecting Edit Settings >
vSphere DRS > Advanced Options. This setting overrides
the defaultMaxBootAndShutdownOpsPerCluster value
that you can set in the vmware-dr.xml file. You can set a
global value
defaultMaxBootAndShutdownOpsPerCluster in the
vmware-dr.xml file, and then set different
srmMaxBootShutdownOps values for individual clusters
in the vSphere Client. By default, throttling is turned off.
defaultMaxBootAndShutdownOpsPerCluster Specifies the maximum number of concurrent power-on
operations for all clusters that SRM protects. Guest
shutdowns, but not forced power offs, are throttled
according to this value. Guest shutdowns occur during
primary site shutdowns (planned failover) and IP
customization workflows. You modify this setting in the
vmware-dr.xml file. The srmMaxBootShutdownOps
value that you can set in the vSphere Client overrides the
defaultMaxBootAndShutdownOpsPerCluster value. You
can set a global value
defaultMaxBootAndShutdownOpsPerCluster in the
vmware-dr.xml file, and then set different
srmMaxBootShutdownOps values for individual clusters
in the vSphere Client. By default, throttling is turned off.
defaultMaxBootAndShutdownOpsPerHost Specifies the maximum number of concurrent power-on
operations on any standalone host. You can only set the
option in the vmware-dr.xml file. By default, throttling is
turned off.
Table 9‑2. Settings that Modify Timeout Periods
Option Description
synchronizationTimeout SRM enforces a timeout to complete an online or offline
synchronization for virtual machines replicated by
vSphere Replication during a test or failover. If a
synchronization does not finish within the given timeout,
for example, because of a slow network or a large virtual
machine, SRM reports a failure during a test or failover.
Modify this option in Advanced Settings > vrReplication
in the SRM client plug-in. The default value is 60 minutes.
commandTimeout The timeout for running SRA commands in ABR-related
workflows. In some cases, such as surfacing LUNs and
snapshots, some arrays take longer than the default time to
respond. Modify this option in Advanced Settings >
storage in the SRM client plug-in. The default value is 5
minutes.
VMware, Inc. 91
Page 92

Site Recovery Manager Administration
92 VMware, Inc.
Page 93

Troubleshooting SRM Administration 10
To help identify the cause of any problems you encounter during the day-to-day running of SRM, you might
need to collect SRM Server or client log files to review or send to VMware Support.
Errors that you encounter during SRM operations appear in error dialog boxes or appear in the Recent
Tasks window. Most errors also generate an entry in an SRM log file. Check the recent tasks and log files for
the recovery site and the protected site.
When searching for the cause of a problem, also check the VMware knowledge base at
http://kb.vmware.com.
This chapter includes the following topics:
“Limitations to Protection and Recovery of Virtual Machines,” on page 93
n
“SRM Events and Alarms,” on page 96
n
“vSphere Replication Events and Alarms,” on page 106
n
“Collecting SRM Log Files,” on page 109
n
“Access the vSphere Replication Logs,” on page 112
n
“Resolve SRM Operational Issues,” on page 113
n
Limitations to Protection and Recovery of Virtual Machines
The protection and recovery by SRM of virtual machines is subject to limitations.
Protection and Recovery of Suspended Virtual Machines
When you suspend a virtual machine, vSphere creates and saves its memory state. When the virtual
machine resumes, vSphere restores the saved memory state to allow the virtual machine to continue without
any disruption to the applications and guest operating systems that it is running.
Protection and Recovery of Virtual Machines with Snapshots
Array-based replication supports the protection and recovery of virtual machines with snapshots, but with
limitations.
You can specify a custom location for storing snapshot delta files by setting the workingDir parameter in
VMX files. SRM does not support the use of the workingDir parameter.
Limitations also apply if you are running versions of ESX or ESXi Server older than version 4.1.
If the virtual machine has multiple VMDK disk files, all the disk files must be contained in the same
n
folder as the VMX file itself.
VMware, Inc.
93
Page 94

Site Recovery Manager Administration
If a virtual machine is attached to a Raw Disk Mapping (RDM) disk device, you must store the mapping
n
file in the same folder as the VMX file. RDM snapshots are only available if you create the RDM
mapping using Virtual Compatibility Mode.
If you are running a ESX or ESXi Server 4.1 or later, these limitations do not apply.
vSphere Replication supports the protection of virtual machines with snapshots, but you can only recover
the latest snapshot. vSphere Replication erases the snapshot information in the recovered virtual machine,
so snapshots are no longer available after recovery.
Protection and Recovery of Virtual Machines with Memory State Snapshots
When protecting virtual machines with memory state snapshots, the ESXi hosts at the protection and
recovery sites must have compatible CPUs, as defined in the VMware knowledge base articles VMotion
CPU Compatibility Requirements for Intel Processors and VMotion CPU Compatibility Requirements for
AMD Processors. The hosts must also have the same BIOS features enabled. If the BIOS configurations of the
servers do not match, they show a compatibility error message even if they are otherwise identical. The two
most common features to check are Non-Execute Memory Protection (NX / XD) and Virtualization
Technology (VT / AMD-V).
Protection and Recovery of Linked Clone Virtual Machines
vSphere Replication does not support the protection and recovery of virtual machines that are linked clones.
Array-based replication supports the protection and recovery of virtual machines that are linked clones if all
the nodes in the snapshot tree are replicated.
Protection and Recovery of Virtual Machines with Reservations, Affinity Rules,
or Limits
When SRM recovers a virtual machine to the recovery site, it does not preserve any reservations, affinity
rules, or limits that you have placed on the virtual machine. SRM does not preserve reservations, affinity
rules, and limits on the recovery site because the recovery site might have different resource requirements to
the protected site.
You can set reservations, affinity rules, and limits for recovered virtual machines by configuring
reservations and limits on the resource pools on the recovery site and setting up the resource pool mapping
accordingly. Alternatively, you can set reservations, affinity rules, or limits manually on the placeholder
virtual machines on the recovery site.
Protection and Recovery of Virtual Machines Attached to RDM Disk Devices
The protection and recovery of virtual machines that are attached to a raw disk mapping (RDM) disk device
is subject to different support depending on whether you use array-based replication or
vSphere Replication.
Array-based replication supports RDM devices in physical mode and in virtual mode.
n
vSphere Replication supports RDM devices in virtual mode only, for both the source and target device.
n
Planned Migration of Virtual Machines on Datastores that Use SIOC
You cannot use SRM to perform a planned migration of virtual machines on datastores that have storage I/O
control (SIOC) enabled. Datastores with SIOC enabled cannot be unmounted, so cannot be part of a planned
migration. You must disable SIOC on datastores included in a recovery plan before running a planned
migration.
94 VMware, Inc.
Page 95

Chapter 10 Troubleshooting SRM Administration
Disaster Recovery and Reprotect of Virtual Machines on Datastores that Use
SIOC
If you run a recovery with SIOC enabled, the recovery will succeed with errors. After the recovery, you
must manually disable SIOC on the protected site and run a planned migration recovery again. You cannot
run reprotect until you have successfully run a planned migration.
Protection and Recovery of Virtual Machines with Components on Multiple
Arrays
Array-based replication in SRM depends on the concept of an array pair. SRM defines groups of datastores
that it recovers as units. As a consequence, limitations apply to how you can store the components of virutal
machines that you protect using array-based replication.
SRM does not support storing virtual machine components on multiple arrays on the protected site that
n
replicate to a single array on the recovery site.
SRM does not support storing virtual machine components on multiple arrays on the protected site that
n
replicate to mulitple arrays on the recovery site, if the virtual machine components span both arrrays.
If you replicate virtual machine components from multiple arrays to a single array or to a span of arrays on
the recovery site, the VMX configurations of the UUID of the datastores on the protected site do not match
the configurations on the recovery site.
The location of the VMX file of a virtual machine determines which array pair a virtual machine belongs to.
A virtual machine cannot belong to two array pairs, so if it has more than one disk and if one of those disks
is in an array that is not part of the array pair to which the virtual machine belongs, SRM cannot protect the
whole virtual machine. SRM handles the disk that is not on the same array pair as the virtual machine as a
non-replicated device.
As a consequence, store all the virtual disks, swap files, RDM devices, and the working directory for the
virtual machine on LUNs in the same array so that SRM can protect all the components of the virtual
machine.
Protection and Recovery of Active Directory Domain Controllers
Do not use SRM to protect Active Directory domain controllers. Active Directory provides its own
replication technology and restore mode. Use the Active Directory replication technology and restore mode
technologies to handle disaster recovery situations.
Using SRM with Admission Control Clusters
You can use Admission Control on a cluster to reserve resources on the recovery site. However, using
Admission Control can affect disaster recovery by preventing SRM from powering on virtual machines
when running a recovery plan. Admission Control can prevent virtual machines from powering on if
powering them on would violate the relevant Admission Control constraints.
You can add a command step to a recovery plan to run a PowerCLI script that disables Admission Control
during the recovery. See “Creating Custom Recovery Steps,” on page 58 for information about creating
command steps.
1 Create a pre-power on command step in the recovery plan that runs a PowerCLI script to disable
Admission Control.
Get-Cluster cluster_name | Set-Cluster -HAAdmissionControlEnabled:$false
VMware, Inc. 95
Page 96

Site Recovery Manager Administration
2 Create a post-power on command step in the recovery plan to reenable Admission Control after the
virtual machine powers on.
Get-Cluster cluster_name | Set-Cluster -HAAdmissionControlEnabled:$true
If you disable Admission Control during recovery, you must manually reenable Admission Control after
you perform cleanup following a test recovery. Disabling Admission Control might affect the ability of High
Availability to restart virtual machines on the recovery site. Do not disable Admission Control for
prolonged periods.
vSphere Replication Limitations
vSphere Replication is subject to some limitations when replicating virtual machines.
Replicating Large Volumes
vSphere Replication can replicate virtual machines greater than 2TB with the following limitations:
If you move a virtual machine with replicated disks over 2032GB back to a machine on an older release,
n
vSphere Replication cannot replicate or power on the virtual machine.
Full sync of very large disks can take days.
n
vSphere Replication must track changed blocks and consumes more memory on larger disks.
n
vSphere Replication tracks larger blocks on disks over 2TB. Replication performance on a disk over 2TB
n
might be different on a disk over 2TB for the same workload depending on how much of the disk goes
over the network for a particular set of changed blocks.
Replication might consume more or less bandwidth depending on the workload and how it changes
n
blocks on the disk during the RPO interval.
Shared Disk Support
vSphere Replication cannot replicate virtual machines that share vmdk files in this release.
SRM Events and Alarms
SRM supports event logging. Each event includes a corresponding alarm that SRM can trigger if the event
occurs. This provides a way to track the health of your system and to resolve potential issues before they
affect the protection that SRM provides.
How SRM Monitors Connections Between Sites
SRM monitors the connection between the protected and recovery sites and logs events if the remote site
stops responding.
When SRM establishes the connection between two paired SRM Server instances, the SRM Server that
initiated the connection sends a RemoteSiteUpEvent.
If SRM detects that a monitored connection has broken, it starts periodic connection checks by sending a
ping request to the remote site. SRM monitors the connection checks and logs events.
SRM sends pings at regular intervals. You can configure this interval by setting the
n
remoteSiteStatus.pingInterval value. The default is five minutes.
The connection monitor skips a number of failed pings. You can configure this number by setting the
n
remoteSiteStatus.pingFailedDelay value.
When the number of skipped failed pings exceeds the value of the remoteSiteStatus.pingFailedDelay
n
setting, SRM sends a RemoteSitePingFailedEvent event.
96 VMware, Inc.
Page 97

Chapter 10 Troubleshooting SRM Administration
When the number of skipped failed pings exceeds a higher limit SRM sends a RemoteSiteDownEvent
n
event for every failed ping and stops sending RemoteSitePingFailedEvent events. You can configure
this higher limit of failed pings by setting the remoteSiteStatus.panicDelay setting.
SRM continues to send RemoteSiteDownEvent events until the connection is reestablished.
n
Configure SRM Alarms
SRM adds alarms to the alarms that vCenter Server supports. You can configure SRM alarms to send an
email notification, send an SNMP trap, or to run a script on the vCenter Server host.
The Alarms tab in the SRM interface lists all of the SRM alarms. You can edit the settings for each alarm to
specify the action for SRM to take when an event triggers the alarm. By default, none of the SRM alarms act
until you configure the alarm.
Prerequisites
For alarms to send email notifications, you must configure the Mail settings in the vCenter Server Settings
menu.
Procedure
1 In the left pane, click Sites, and select a site.
2 Click the Alarms tab to display the list of SRM alarms.
3 Right-click an alarm and click Edit Settings.
4 Click the Actions tab.
5 Click Add to add an action to perform when this alarm is triggered.
6 Select an action from the drop-down list.
Option Description
Send Email
Send SNMP Trap
Run Script
The default action. Type an email address in the Value text box.
Type the name of an SNMP trap in the Value text box.
Type the path to the script to run in the Value text box.
7 Click the General tab.
8 Select the Enable this alarm check box to enable the action for this alarm.
SRM Events Reference
SRM monitors different types of events.
Site Status Events
Site status events provide information about the status of the protected and recovery sites and the
connection between them.
Table 10‑1. Site Status Events
Event Key Event Description Cause
UnknownStatusEvent
RemoteSiteDownEvent
RemoteSitePingFailedEvent
Unknown Status SRM Server status is not available
Remote Site Down SRM Server has lost its connection
with the remote SRM Server.
Remote Site Ping Failed Failures at the remote site or network
connectivity problems.
VMware, Inc. 97
Page 98

Site Recovery Manager Administration
Table 10‑1. Site Status Events (Continued)
Event Key Event Description Cause
RemoteSiteCreatedEvent
RemoteSiteUpEvent
RemoteSiteDeletedEvent
Protection Group Events
Protection Group events provide information about actions and status related to protection groups.
These events have three categories:
Protection Group Replication Informational Events
n
Protection Group Replication Warning Events
n
Protection Group Replication Error Events
n
Table 10‑2. Protection Group Replication Informational Events
Event Key Event Description Cause
ProtectionGroup > CreatedEvent Created protection group. Posted on both vCenter Servers in the
ProtectionGroup > RemovedEvent Removed protection group. Posted on both vCenter Servers in the
ProtectionGroup >
ReconfiguredEvent
ProtectedVmCreatedEvent Virtual machine in group is
ProtectedVmRemovedEvent Virtual machine in group is no longer
ProtectedVmReconfiguredProtection
SettingsEvent
ProtectedVmReconfiguredRecoveryL
ocationSettingsEvent
Remote Site Created Remote site is created.
Remote Site Up SRM Server re-establishes its
connection with the remote
SRM Server.
Remote Site Deleted Remote SRM site has been deleted.
completion of the Commit phase of
creating a protection group.
completion of the Commit phase of
removing a protection group.
Reconfigured protection group. Posted on both vCenter Servers in the
completion of the Commit phase of
reconfiguring a protection group.
Posted on both vCenter Servers in the
configured for protection.
configured for protection.
Reconfigured protection settings for
virtual machine.
Reconfigured recovery location
settings for virtual machine.
completion of the Commit phase of the
protection of a virtual machine.
Posted on both vCenter Servers in the
completion of the Commit phase of
unprotecting a virtual machine.
Posted on both vCenter Servers in the
completion of the Commit phase of
reconfiguring virtual machine
protection settings.
Posted on the protected site vCenter
Server only on the successful
completion of reconfiguring the
recovery location settings for a
protected virtual machine.
98 VMware, Inc.
Page 99

Chapter 10 Troubleshooting SRM Administration
Table 10‑2. Protection Group Replication Informational Events (Continued)
Event Key Event Description Cause
PlaceholderVmCreatedEvent The placeholder virtual machine was
created in the VMware vCenter
Server inventory.
PlaceholderVmCreatedFromOldProd
uctionVmEvent
The placeholder virtual machine was
created in the VMware vCenter
Server inventory using the identity of
the old protected virtual machine.
Posted on the Recovery site vCenter
Server only when we create the
placeholder virtual machine as a result
of protection, repair.
Posted on the Recovery site vCenter
Server only when we create the
placeholder virtual machine as a result
of swapping for the old protected
virtual machine during or after
reprotect.
Table 10‑3. Protection Group Replication Warning Events
Event Key Event Description Cause
VmNotFullyProtectedEvent Virtual machine in group: One or
more devices need to be configured
for protection.
PlaceholderVmUnexpectedlyDeleted
Event
Virtual machine in group: The
placeholder virtual machine was
removed from the VMware vCenter
Server inventory.
Posted on the protected site vCenter
Server only upon device handling
updating the recovery location settings
with a non-empty unresolvedDevices
set. This can be triggered by changes to
the protected virtual machine or
during reprotect of a virtual machine.
Posted on the Recovery site vCenter
Server only when we detect that the
placeholder virtual machine was
unexpectedly deleted or removed from
the vCenter inventory.
Table 10‑4. Protection Group Replication Error Events
Event Key Event Description Cause
ProductionVmDeletedEvent Virtual machine in group: The
protected virtual machine has been
removed from the virtual
machineware vCenter Server
inventory.
ProductionVmInvalidEvent Virtual machine in group: Cannot
resolve the file locations of the
protected virtual machine for
replication.
Posted when we detect that the
protected virtual machine’s protected
virtual machine has been deleted or
removed from the vCenter inventory.
Posted whenever we handle device or
recovery location changes but notice
that the provider cannot find the
protected virtual machine files in order
to replicate them.
VMware, Inc. 99
Page 100

Site Recovery Manager Administration
Recovery Events
Recovery events provide information about actions and status related to the SRM recovery processes.
Table 10‑5. Recovery Events
Event Key Event Description Cause
RecoveryVmBegin
RecoveryVmEnd
RecoveryPlanCreate
RecoveryPlanDestroy
RecoveryPlanEdit
RecoveryPlanExecuteTestBegin
RecoveryPlanExecuteTestEnd
RecoveryPlanExecuteCleanupBegin
RecoveryPlanExecuteCleanupEnd
RecoveryPlanExecuteBegin
RecoveryPlanExecuteEnd
RecoveryPlanExecuteReprotectBeg
in
RecoveryPlanExecuteReprotectEnd
RecoveryPlanPromptDisplay
RecoveryPlanPromptResponse
Recovery Plan has begun recovering
the specified virtual machine.
Recovery Plan has completed
recovering the virtual machine.
Recovery Plan has been created. Signaled when a new plan is created or
Recovery Plan has been destroyed. Signaled when a plan has been deleted
Recovery Plan was changed. Signaled when an existing plan is
Recovery Plan has begun a test. Signaled on the recovery site when a
Recovery Plan has completed a test. Signaled on the recovery site when a
Recovery Plan has begun a test
cleanup.
Recovery Plan has completed a test
cleanup.
Recovery Plan has begun a recovery. Signaled on the recovery site when a
Recovery Plan has completed a
recovery.
Recovery Plan has begun a reprotect
operation.
Recovery Plan has completed a
reprotect operation.
Recovery Plan is displaying a prompt
and is waiting for user input.
Recovery Plan has received an
answer to its prompt.
Signaled when the recovery virtual
machine was successfully created. If
some error occurred before the virtual
machine ID is known the event is not
fired.
Signaled after the last post-power on
script has completed, or after a
recovery-stopping error has occurred
for the virtual machine.
cloned. It will be sent to each
vCenter Server instance where the
plan is hosted.
from the site. Note that on the site
where the plan has been requested to
deleted there can be a significant
delay, while it waits for the plan to be
deleted at the other site. It will be sent
to each vCenter Server instance where
the plan is hosted.
edited.
recovery test is initiated.
recovery test has completed. If an error
occurred it is available as described.
Signaled on the recovery site when a
test cleanup is initiated.
Signaled on the recovery site when a
test cleanup has completed. If an error
occurred it is available as described.
recovery is initiated.
Signaled on the recovery site when a
recovery has completed. If an error
occurred it is available as described.
Signaled on the recovery site when a
reprotect is initiated.
Signaled on the recovery site when a
reprotect has completed. If an error
occurred it is available as described.
Signaled on the recovery site when a
prompt step is encountered. The key is
a unique identifier for the prompt.
Signaled on the recovery site when a
prompt step is closed.
100 VMware, Inc.
 Loading...
Loading...