Page 1
VIVOTEK ST3402
User’s Manual
0
Page 2

105BContents
Chapter 1 Installation.................................................................................................1-3
1.1 System Hardware Requirements...............................................................1-3
1.1.1 Recommended minimum system hardware requirements...............1-3
1.1.2 Suggestions......................................................................................1-4
1.2 Software Installation.................................................................................1-7
1.3 First Start up............................................................................................1-12
Chapter 2 Launcher .................................................................................................2-14
2.1 Security for Launcher .............................................................................2-14
2.2 User Interface..........................................................................................2-15
Chapter 3 Monitor ...................................................................................................3-21
3.1 Features of Monitor Tool........................................................................3-21
3.1.1 Traditional Surveillance Features ..................................................3-21
3.1.2 Special Features .............................................................................3-21
3.2 Application Layout and Functionalities..................................................3-22
3.3 Logging In...............................................................................................3-24
3.3.1 The Privilege of Each Group .........................................................3-24
3.4 Camera Configurations...........................................................................3-25
3.4.1 The Layout of the Configuration ...................................................3-26
3.4.2 Local Settings.................................................................................3-26
3.4.3 Alert Settings and Recording Settings...........................................3-29
3.4.4 Changing the Camera Order in the List.........................................3-30
3.4.5 Saving the Changes........................................................................3-31
3.5 Global Settings........................................................................................3-31
3.6 Display & UI Settings.............................................................................3-35
3.7 Using Monitor Tool.................................................................................3-39
3.7.1 Connection of the Video Server / Network Camera Series............3-39
3.7.2 The Layout.....................................................................................3-46
3.7.3 Backup ...........................................................................................3-53
3.7.4 About..............................................................................................3-54
3.7.5 Miscellaneous Functions................................................................3-54
3.7.6 Common Control Functions...........................................................3-56
3.7.7
UMultiple FocusU ...............................................................................3-57
3.7.8 Status Bar.......................................................................................3-57
Chapter 4 Scheduling...............................................................................................4-58
4.1 Invoke Scheduling Tool..........................................................................4-59
1
Page 3

4.1.1 Starting the Scheduling tool...........................................................4-59
4.2 The Layout and Functionalities ..............................................................4-59
4.2.1 Introduction....................................................................................4-59
4.2.2 The Functionalities of Configuration Components........................4-61
4.2.3 The Schedule Scheme operations ..................................................4-61
4.3 Primary Schedule....................................................................................4-62
4.3.1 Schedule with Time Lines..............................................................4-62
4.3.2 Schedule with Time Picker ............................................................4-63
4.3.3 Schedule in event mode.................................................................4-65
4.3.4 Schedule in Continuous mode .......................................................4-65
4.4 Secondary Schedule................................................................................4-66
4.4.1 Schedule modes .............................................................................4-66
Chapter 5 Playback..................................................................................................5-67
5.1 Features of Playback...............................................................................5-67
5.2 Logging In...............................................................................................5-68
5.3 Layout.....................................................................................................5-69
5.3.1 Main Areas.....................................................................................5-69
5.3.2 Indicators........................................................................................5-72
5.3.3 Pull Bar ..........................................................................................5-72
5.4 Settings....................................................................................................5-72
5.5 Normal (Single Frame) Mode.................................................................5-75
5.5.1 Histogram Area..............................................................................5-76
5.6 Preview (Multiple Frame) Mode ............................................................5-77
5.6.1 Histogram Area..............................................................................5-78
5.6.2 Histogram Legend..........................................................................5-79
5.7 Using Tools.............................................................................................5-79
5.7.1 Selector Tools.................................................................................5-79
5.7.2 Play Control ...................................................................................5-81
5.7.3 Display Adjustment Toolbox .........................................................5-83
5.7.4 Searching Range Adjustment Toolbox...........................................5-84
5.7.5 Toolbox..........................................................................................5-85
5.7.6 System Control Toolbox................................................................5-86
2
Page 4
Chapter 1 0BInstallation
1.1 5BSystem Hardware Requirement s
Before installing the application software, make sure your system has the following
recommended minimum hardware requirements.
1.1.1 28BRecommended minimum system hardware
requirements
The system requirement recommended for this application is as follows.
OS: MS Windows 2000/XP/98SE/Me
CPU: Intel 2.0 GHz Pentium IV or above and AMD Athlon or above
SDRAM: 512 MB SDRAM or above for 16 channels
256 MB SDRAM for 9 channels
Hard disk: 40 GB
Display Chip: nVidia, GeForce series with 32 MB Display memory
ATI Radeon series with 32 MB Display memory
Table 1-1 Recommended System Ha rdware Requirements
The following notes should help you with the proper installation of the software on to
the recommended hardware system.
This application software only supports Intel Pentium IV series or above and AMD
Athlon or above CPUs.
It is also recommended to run this application software on Win2000 OS to avoid any
functional limitation.
Make sure all Power Management and Screen Saver functions are turned off to avoid
system hang-ups.
1-3
Page 5
1.1.2 29BSuggestions
The following suggestions will help you to run our software faster and smooth. All
suggestions are optional.
1. Maximum supported hard disk space -
200GB is the maximum tested supported hard disk space. Performance can’t be
guaranteed if the recording hard disk space is greater than 200GB.
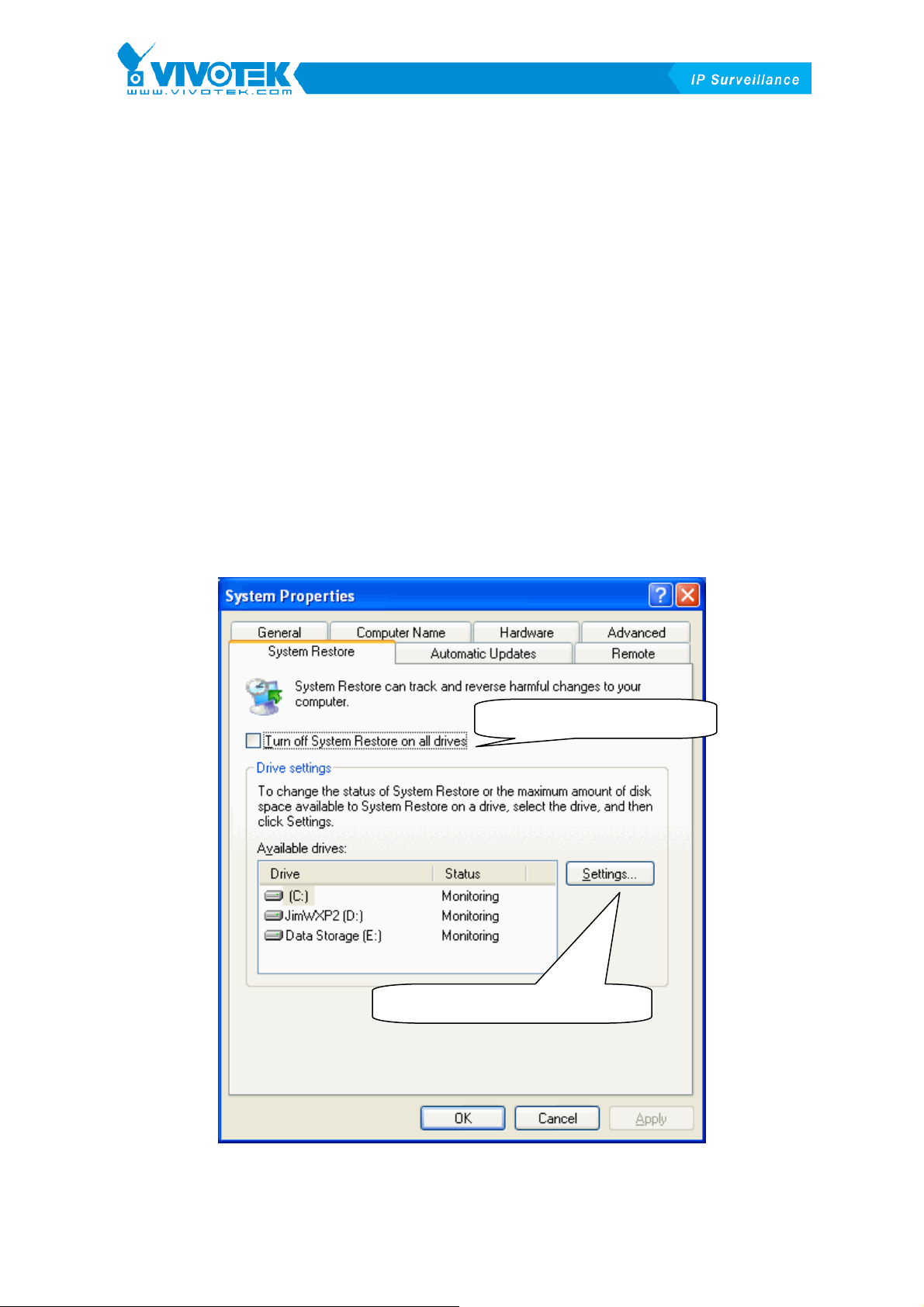
2. In Window XP system, close system restore -
In Window XP, system restore will help you to back to the previous restore point
that recorded a snapshot of your computer. But when system restore is turned on,
the disk I/O would be much worse. This means the recording of our application
would be affected dramatically. So we recommend turning off the system restore
for the application’s recording disk. You can disable system restore in System
Properties page (Start \ Control Panel \ System \ System Restore).
Click to disable system restore
Disable system restore of specify disk
Figure 1-1 System Restore
1-4
Page 6
As shown in XFigure 1-1X, you can disable system restore of all disk or specified
t
disk.
3. Exclude file protectation for specified files in AntiVirus -
The following XTable 1-2X represents the specified files that should be excluded in
AntiVirus to accelerate our application.
Suggest to Exclude
DBS, DES, DIA, DSK, DSS
HGD, WAP, BCK
Table 1-2 Specified Files to Exclude
There are two ways to exclude file protection of above files from AntiVirus:
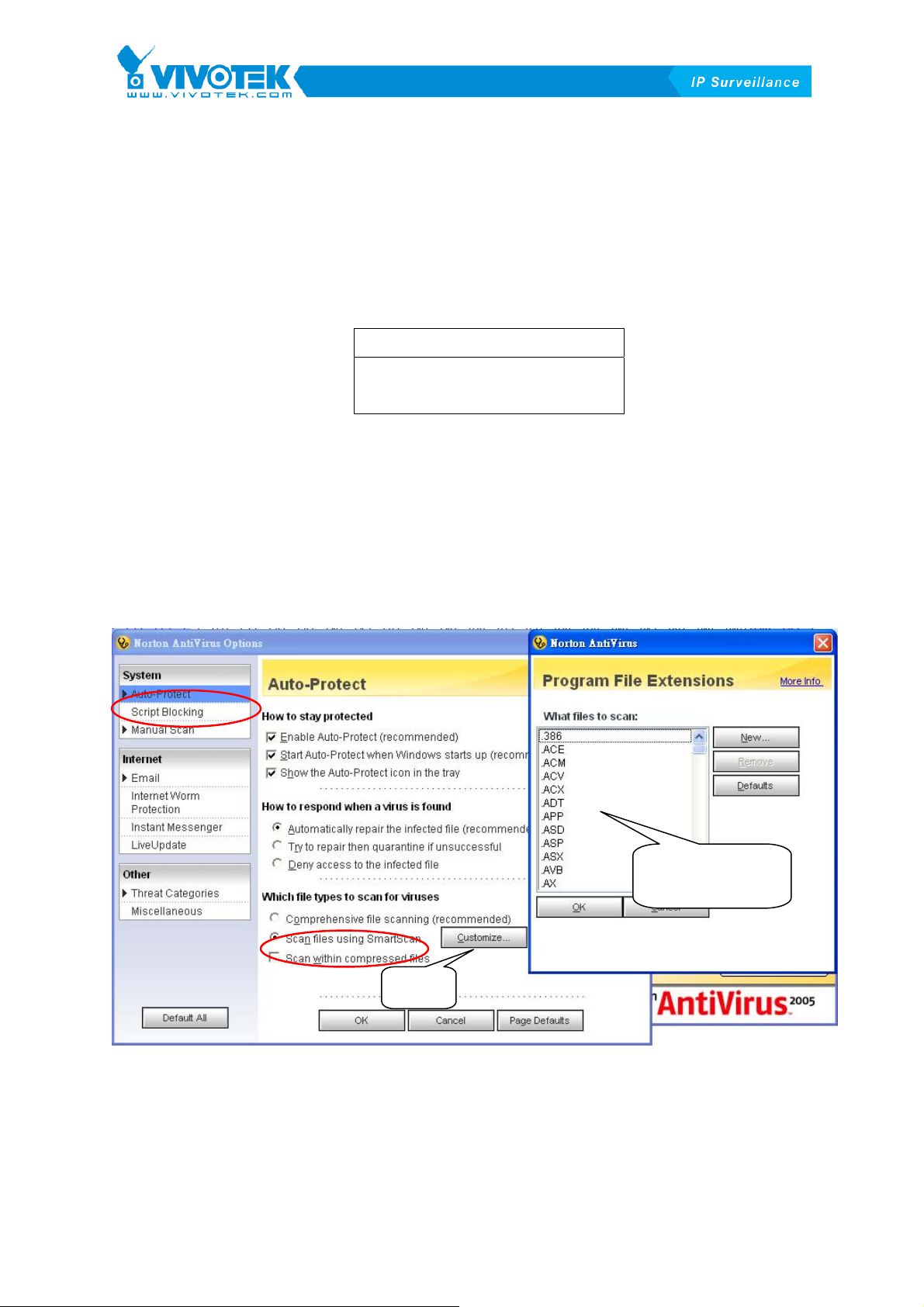
Method One:
Find “Option \ Auto-Protect \ Scan files using SmartScan \ Customize” and
ensure above files don’t exist on the list. The following
XFigure 1-2X shows the
location of the list.
Ensure specified
files don’t exis
Click
Figure 1-2 The File List in AntiVirus
Method Two:
Find “Option \ Auto-Protect \ Exclusions” and ensure all above specified files are
added on the list. The following XFigure 1-3X shows the list.
1-5
Page 7
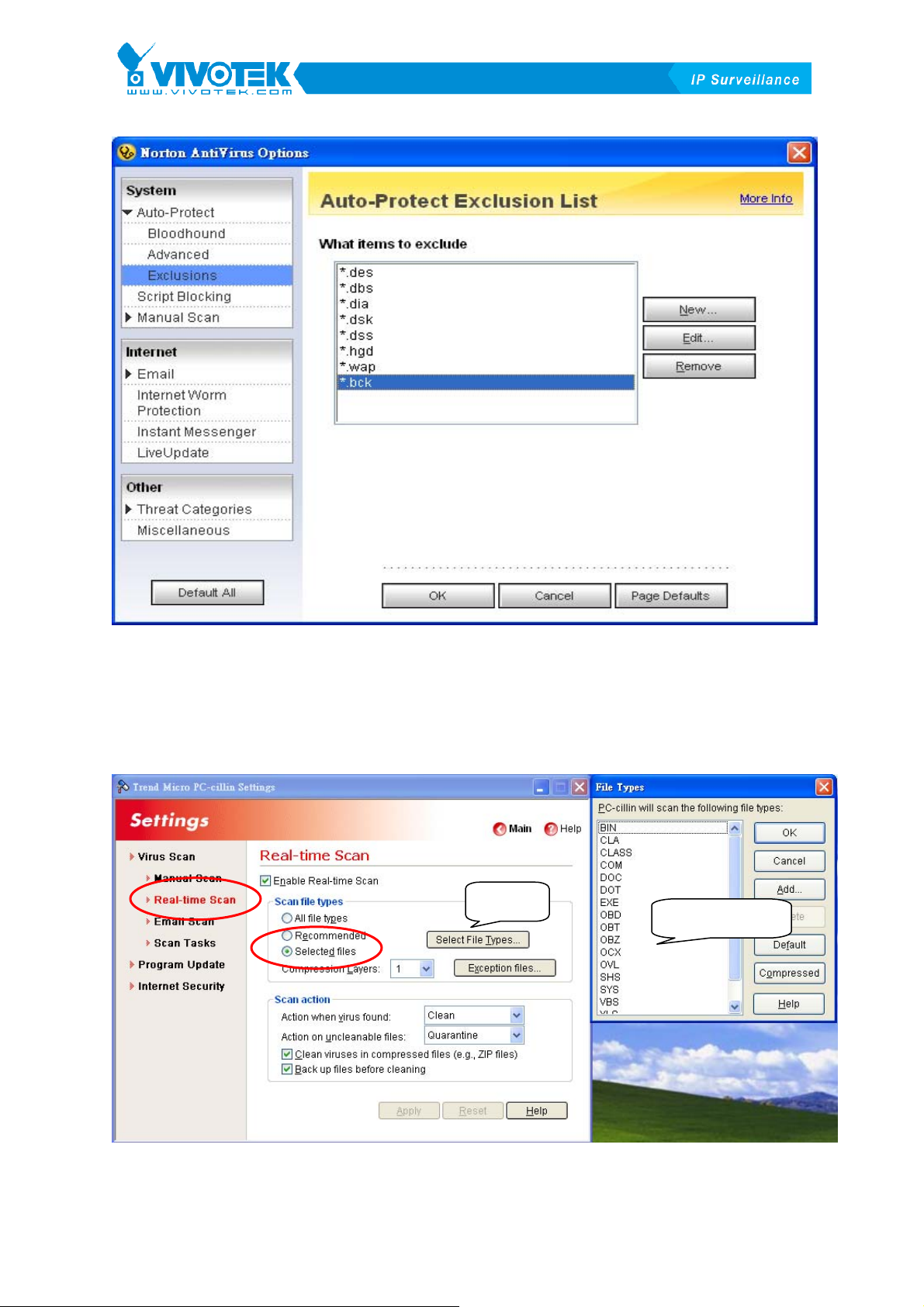
Figure 1-3 Auto-Protect Exclusion List
4. Exclude file protectation for specified files in PC-cillin -
As shown in XFigure 1-4X, find “Settings \ Real-time scan \ Selected files \ Select File
Types” and ensure the files described in table 1-1 do not exist in the list.
Click
Files list
Figure 1-4 The File List in PC-cillin
1-6
Page 8

NOTE: If the above settings cannot help you to improve performance, try to use disk
defragmenter “Start \ All Programs \ Accessories \ System Tools \ Disk Defragmenter”
to reconfigure your hard disk may help your computer more efficient.
1.2 6BSoftware Installation
The following are steps for the software installation.
STEP 1: Put the Installation disk into the CD-ROM drive, and installation should start
automatically. If installation does not start, click on “Start” on the lower left corner of
your screen and open “My Computer” and double click on the CD-ROM icon. The IP
surveillance Recorder Installation Window will appear as XFigure 1-5X in below.
Figure 1-5 ST3402 Smart VS-IP Recorder Installation Window
STEP 2: There are links on this page, including Quick Guide, User’s Manual, Release
Note, and Install Software DVR. Click on “Install Software DVR” to launch the
intallation shield. The InstallShield Wizard will come on and
XFigure 1-6X will appear.
1-7
Page 9
Figure 1-6 Welcome page for the VIVOTEK ST3402
STEP 3: If you click on “Next” and XFigure 1-7X appears, it means you have inst alled a
previous version of the recording software (the previous version is the video-only
version, which means it would not get the audio stream from servers). If you want to
keep the previous version, choose the second option. If you are new to the Smart
VS-IP recorder software, this window will not appear; skip on over to Step 4.
Figure 1-7 Video only version detected
STEP 4: Click on “Next”and the “User information” window will appear as in XFigure
1-8X. This window prompts you to enter a username, company name. Click on “Next”
1-8
Page 10
to continue.
Figure 1-8 User information for Smart VS-IP Recorder
STEP 5: Set up the administrator’s password by entering a password and confirm the
password as shown in XFigure 1-9X. Click on “Next” to continue.
Figure 1-9 Confirm Password
1-9
Page 11
STEP 6: Select the installation directory for this application software and click on
“Next”, as shown in XFigure 1-10X. You can also change the installation directory from
the Default directory by clicking on “Browse…”
Figure 1-10 Destination Location for Installation
STEP 7: Select a program folder to install the application software into and then click
on “Next”, as shown in XFigure 1-11 X.
Figure 1-11 Select Program Folder
1-10
Page 12
STEP 8: Af ter checking all the set up information shown in XFigure 1-12X, click on “Next”
to start file movement and registries update.
Figure 1-12 Check Setup Information
STEP 9: Click on “Finish”, as shown in XFigure 1-13X, to finish installation. This
completes the program installation.
Figure 1-13 Finish the Installation
1-11
Page 13
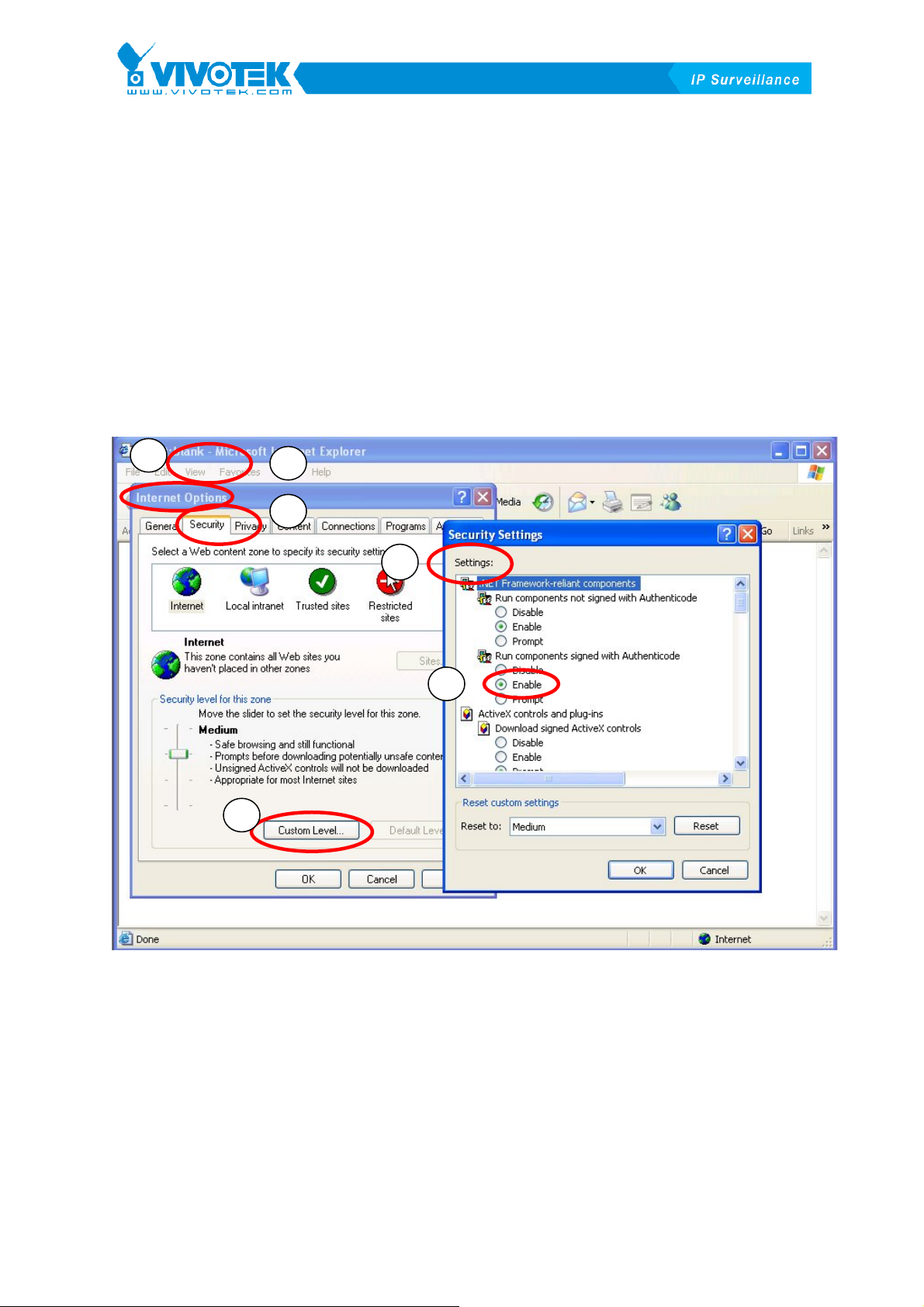
1.3 7BFirst Start up
After installation, one of the IE settings needs to be changed before you can start
running the Monitor program. Enable the mechanism for submitting non-encrypted
data in the path “Start->Settings->control Panel->Internet Options->Security->Custom
Level…\Setting:” You can also find the path from the IE browser, as it is depicted in
the following. You can follow the instructions to complete this setting, as shown in
XFigure 1-14X.
2
1
3
5
6
4
Figure 1-14 Enable Submitting Non-encrypted Form Data
Upon completion of the settings, you can start to invoke the Monitor program.
1-12
Page 14

Chapter 2 1BLauncher
1BLauncher is a controller program that allows starting the recording procedure before
the user logs in and the program will run as a service procedure after Window starts
up automatically. LauncherUI is the program that provides a uer interface to allow the
user to invoke Monitor or Playback quickly. In the following we refer to Launcher for
both Launcher and LauncherUI.
2.1 8BSecurity for Launcher
Starting Launcher does not require passing the username/password check. Once
invoked, Launcher can run automatically. Howe ver, if the user clicks on the Launcher
icon in the system tray, the program will pop up a username/password dialog. This
happens if this is a first time menu pop up, or when LauncherUI was locked. If the
user fails to pass the authentication check, no menu will appear.
There are three kinds of group: root, power user and general user. After passing
identification and authentication, functions will be enabled according to the login
user’s group. For more detail about user’s group, please refer to section 2.2 User
Inferface. The user can lock the Launcher as a security measure. When the Launcher
is locked, it turns back to the Start-up state. The user needs to pass identification and
authentication again to get to the popup menu.
ATTENTION: Only the login user or users of root group can unlock the program when
the program is locked. Refer to X2.2X XUser InterfaceX to obtain more detail about the
privilege of user’s group.
Below is the login window:
2-13
Page 15
Figure 2-1 Login Dialog
When the Launcher is locked, the unlock window is as follows:
Figure 2-2 Unlock Dialog
The input area of the dialog will be grayed (disabled) for 60 seconds after three failure
attempts.
2.2 9BUser Interface
This is the user interface for Launcher:
Figure 2-3 Popup Menu
The main user interface for Launcher is an icon on the system tray. The popup menu
2-14
Page 16
is displayed by clicking on the right or left buttons on the mouse. The menu items are
listed below:
1. Lock Launcher – When this item is selected, Launcher will enter Lock mode. In
Lock mode, whenever the user wants to invoke the menu, a dialog asking for
username and password appears. The interface for this dialog is covered in the
previous section.
2. Tools – This contains utilities; currently only change password and user
management are implemented.
I. Change password:
The tool can be used to change the password of the login user. Below is the
change password screen:
Figure 2-4 Change Password Dialog
II. User management:
XFigure 2-5X shows the tool of user management. The tool can be used to add,
modify or delete user. The maximum available user is 30 and the number of
available user will be shown in “Resource” field. As shown in XFigure 2-6X,
when you want to add a new user, you should specify user name, password
and user’s group for the user. You can modify user’s status in Modify Status
window.
ATTENTION: The tool can only be invoked by users of root group. The default root
(root / admin) cannot be removed and the user could remove the other users of root
group
2-15
Page 17
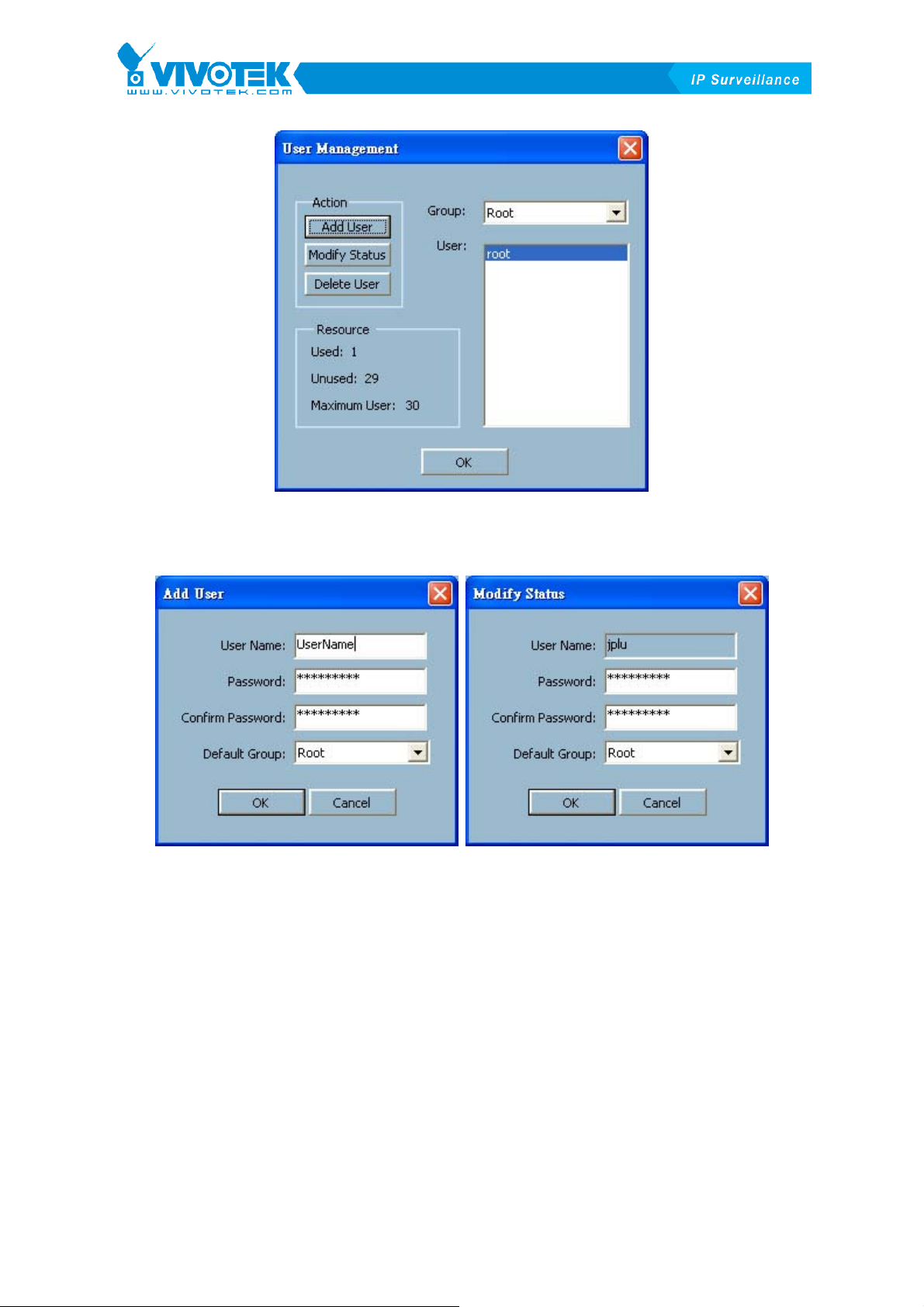
Figure 2-5 User Management Window
Figure 2-6 Add and Modify User Windows
Functionalities may be disabled according to the login user’s group. The following
XTable 2-1X represents the privilege of each group in Lanuncher.
2-16
Page 18
Item Root Power User General
User
Monitor Start Up
ˇ
Mode
User Management ˇ
Playback ˇ ˇ
Change Password ˇ ˇ ˇ
Exit ˇ ˇ ˇ
Lock / Unlock ˇ ˇ ˇ
Logout ˇ ˇ ˇ
Table 2-1 The Privilege in Launcher
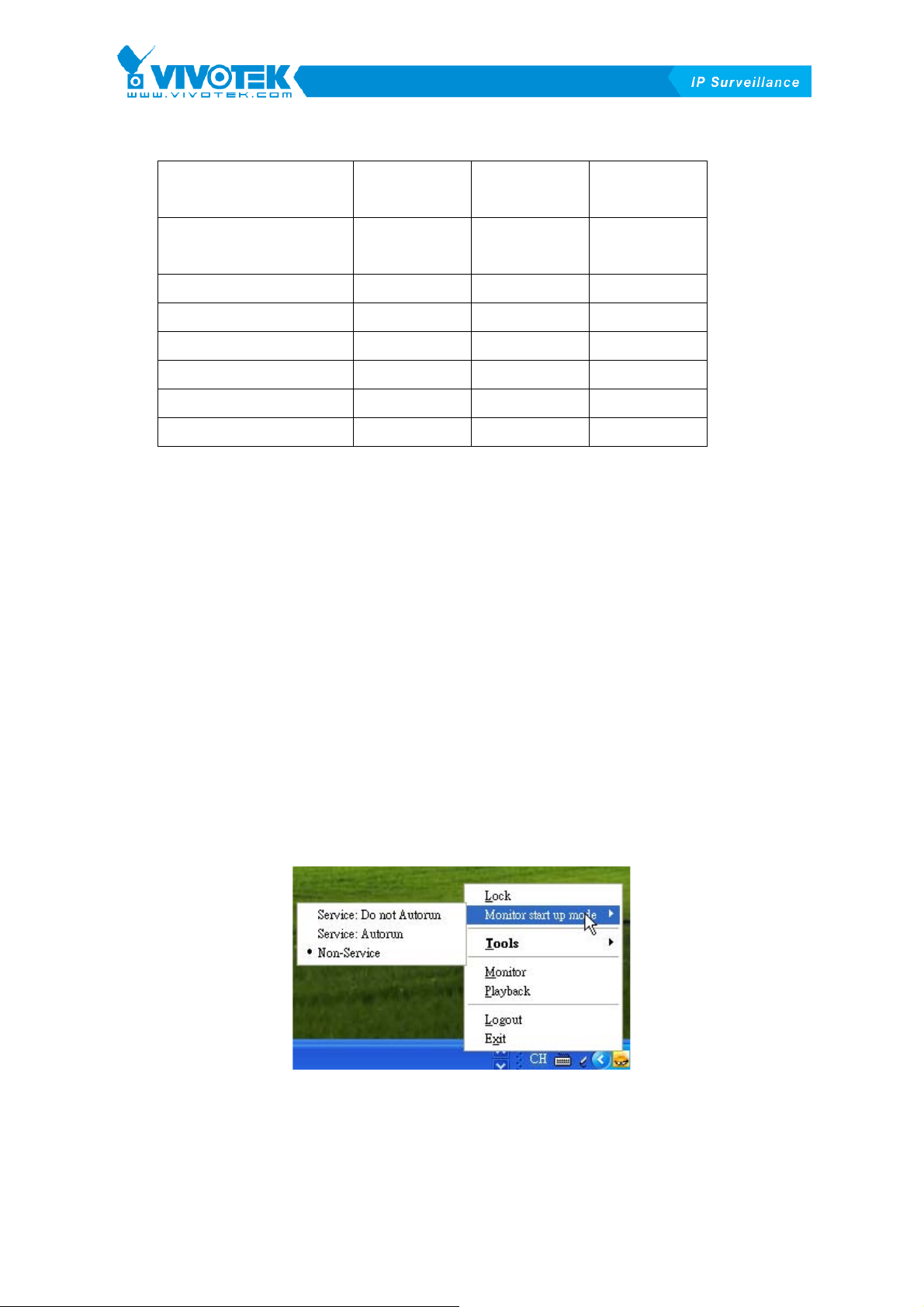
3. Monitor start up mode – The option decides the program type of Monitor that is
described in section 3 after Window boot up. There are three kinds of types:
Service: Do not Autorun – The Monitor will be run as a service but it will not be
invoked automatically after Window boot up. Manual startup is needed.
Service: Autorun – The Monitor will be run as a service procedure and it will be
invoked after Window boot up automatically without login. Recording procedure
will be also invoked if proper schedule is configured. More detail about scheduler
in Monitor, refer section 4.
Non-Service – The Monitor will be run as a normal procedure (non-service). User
can invoke Monitor by using the interface provided by Launcher.
Figure 2-7 Monitor Start Up Mode
NOTE: When Monitor runs as service procedure, it will work in background after
2-17
Page 19

closing (click on the close button in Monitor). It means that the recording procedure
will be continued and user does not need to worry about missing media data that you
like to record.
As the following XFigure 2-8X, a useful hint can help user to monitor the state of
running channel, monitoring channel and recording channel. Move cursor on
Launcher icon on system tray and the hint will pop up automatically.
Figure 2-8 The Hint of State
Running – The number of current running channel(s) in Monitor. Regardless of
schedule, all connected channel will be counted.
Monitoring – The number of the channel that is running with schedule. If the
connected channel without schedule, the channel will not be counted. XFigure 2-9X
and XFigure 2-10X show Launcher icon when the number is equal to zero and not 0
respectively.
Figure 2-9 Launcher Icon with Zero Monitoring Channel
Figure 2-10 Launcher Icon with Non-Zero Monitoring Channel
Recording – The number of the channel that is recording now. The following
XFigure 2-11X shows Launcher icon when recording procedure is running.
Figure 2-11 Launcher Icon with Recording
4. Monitor – This starts up the Monitor. If the Monitor is already running, move the
focus to it.
5. Playback – This starts up Playback. If Playback is already running, move the
focus to it.
2-18
Page 20

6. Exit – This ends Launcher. If the user chooses this option, a message box will
pop up to confirm whether the user really wants to exit. It warns the user that
exiting Launcher will also close Monitor and Playback.
2-19
Page 21

Chapter 3 2BMonitor
3.1 10BFeatures of Monitor Tool
In this section, we will depict all features of the Monitor tool in this software.
3.1.1 30BTraditional Surveillance Features
The traditional surveillance features include the following
9 Real-time monitor
9 PTZ control
9 Recording
3.1.2 31BSpecial Features
In our digital surveillance system, we support not only the features listed above but
also the following features, making the system more powerful and convenient to use.
9 Simultaneous real-time monitoring and audio and video recording
9 High quality video, up to full-screen display
9 High compression ratio
9 Maximum support of 16 cameras with different monitor layouts
9 Smart playback
9 Triggered event browsing with 9 preview video windows
9 Fast database searching
9 Auto alarm in different ways
9 Account-password protection
9 Different recording modes: Event-driven, Scheduled and Manual recording for
each camera
9 Intelligent database index modes: indexing by sharp time tag, time interval,
motion-detected events and digital-input events.
9 Just-in-time snapshot
9 AVI export
9 Motion detection with 3 alert windows for each camera
3-20
Page 22
3.2 11BApplication Layout and
Functionalities
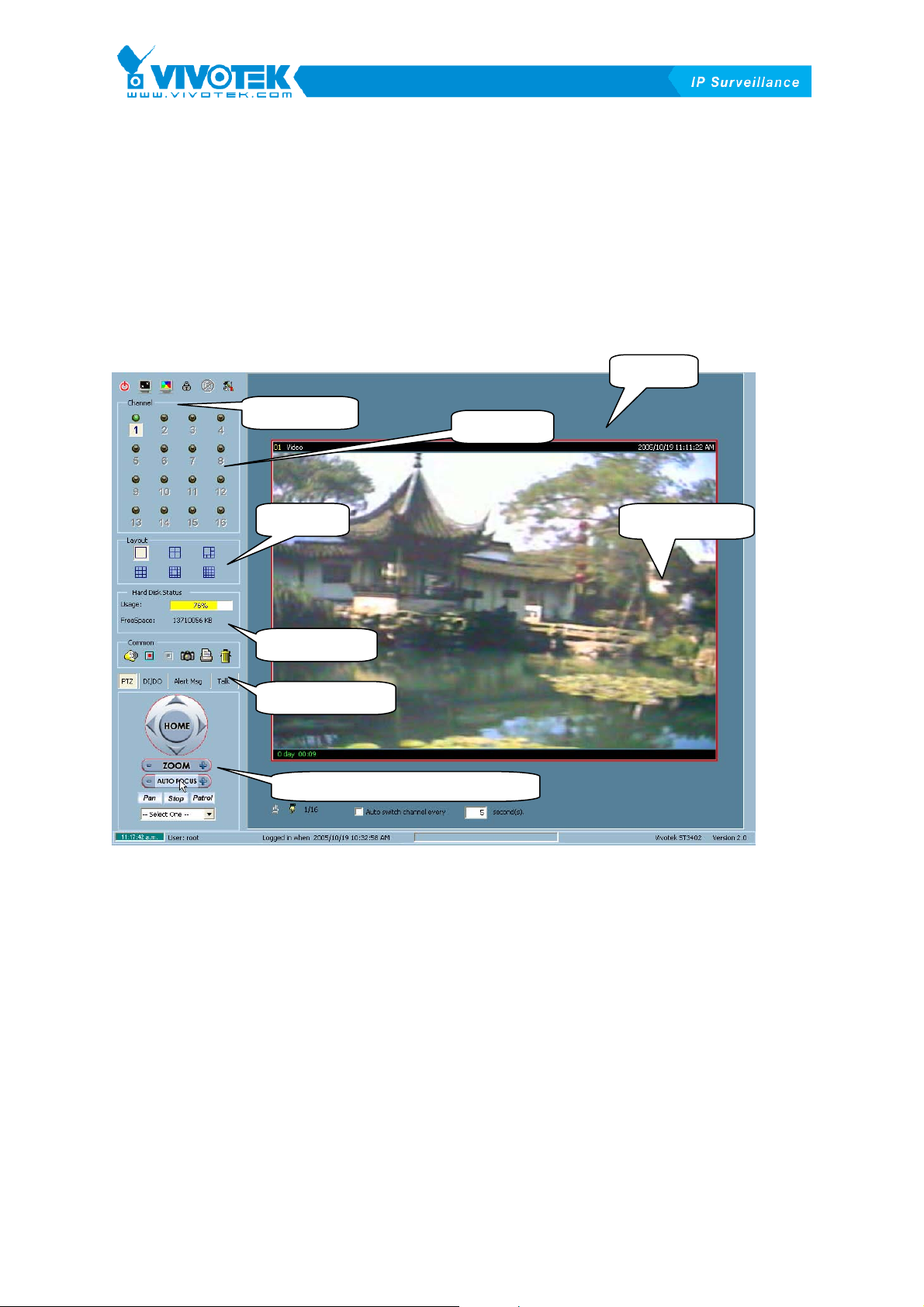
This section demonstrates a global view of the Monitor tool, as shown in XFigure 3-1X.
Components of the Monitor tool in details are shown in the following sections.
Misc. functions
Channel area
Layout area
Hard disk status
Common controls
PTZ, DI/DO, Alert message and Talk
Video area
Display frame
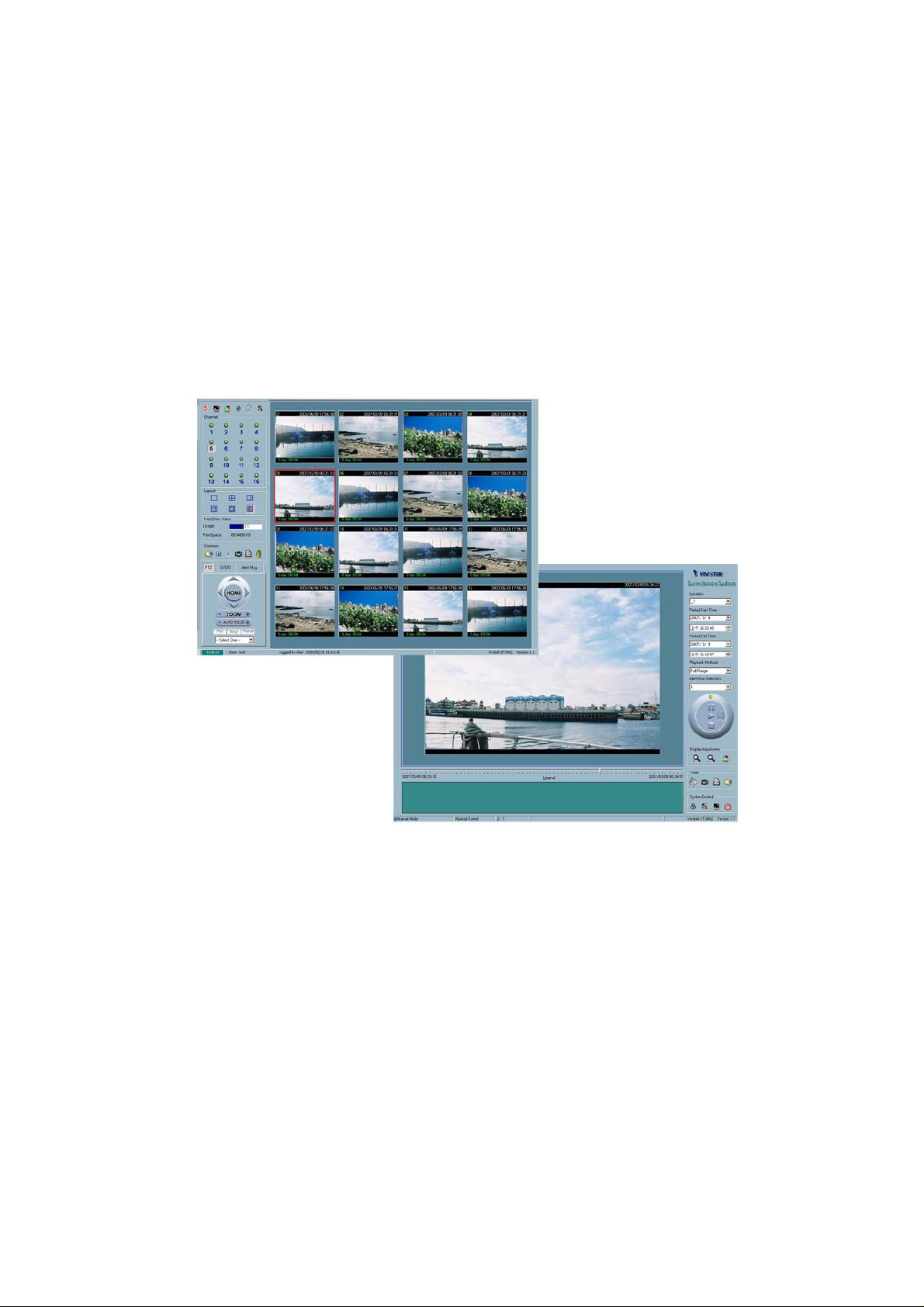
Figure 3-1 Overview of the Monitor Tool
There are several parts in the monitor tool:
9 Miscellaneous functions:
These include application exit, minimization, full-screen display, lock, stop alert,
and configuration menu for camera configurations, global settings, display and UI
settings, scheduler settings, video/audio database backup, and the user
information of this application software. The operation tips are provided on-line
when you move the mouse cursor over each item.
9 Channel area
This area displays the status of each channel. The information indicates the
3-21
Page 23

status of connection, recording, selection, and alert-event triggered.
9 Video area
In this area, you can see the video of the selected channel in the display frame.
The number of display frames in the video area depends on the layout chosen by
the user. You can also do some convenient controls for the video display in it.
9 Layout area
You can change different monitoring layouts in this area. There are six kinds of
layouts the user can choose from: 1, 4, 6, 9, 13, or 16 video display frames in the
video area.
9 Hard disk status
In this area, you can get the status of the hard disk that the media datamedia
database resides in. This reminds you to arrange for available storage size of the
recorded media database. If the path set for recording is no longer valid or does
not exist any more, the free space will show “Invalid Path” to remind you to update
the setting.
9 Common control area
This area includes volume controller, manual recording, video printing, and
snapshot, as well as a trash can to remove any video from display frames.
9 PTZ control
In this area you can do PTZ control, auto pan, auto patrol, and preset location
control of the selected channel. The camera must be a remote Visual Server /
Network Camera series product that supports PTZ functions.
9 DI/DO control
This tool receives digital input signal and sends digital output signal to the remote
Video Server/ Network Camera series product associated with the dedicated
channel.
9 Alert Message
This tool allows the display of the latest alert messages received from the remote
Video Server / Network Camera series product associated with the selected
channel.
3-22
Page 24

9 Talk
If the connected Video Server / Network Camera series product supports
two-way audio feature, the tool can be used to talk with remote side by using
additional device, such as mircophone.
3.3 12BLogging In
The authentication mechanism is implemented in Launcher. If user has already
passed the authentication in Launcher, Monitor can be invoked without further
authentication. If not, the Authentication of Launcher will be popped up and user must
pass it to get Monitor shows up. There are three privileges in the user-protection
system: the root, the power user and the general user.
3.3.1 32BThe Privilege of Each Group
In the Monitor tool system, root privilege includes the right to access Video Server /
Network Camera series products as well as changing local settings. However, this
root privilege is not the same as that of the root privilege of the Video Server /
Network Camera series product. You can change the settings of each selected Video
Server / Network Camera in the remote site only if you have the root privilege of the
remote Video Server / Network Camera series product.
The following XTable 3-1X shows the privilege and limitation of each group in Monitor:
3-23
Page 25

Item Root Power User General User
Backup
Camera configuration
Display & UI settings
Global settings
ˇ
ˇ
ˇ
ˇ
Record ˇ
Schedule
ˇ
DI/DO control ˇ ˇ
PTZ contrl ˇ ˇ
Change layout
Lock
Printer
Snapshot
Stop alert
Table 3-1 The Privilege of Each Group in Monitor
ˇ ˇ ˇ
ˇ ˇ ˇ
ˇ ˇ ˇ
ˇ ˇ ˇ
ˇ ˇ ˇ
Again, if you need to change the settings of remote Video Server / Network Camera
series products, you must have the root user password for each of the products.
3.4 13BCamera Configurations
When you log in for the first time, you need to configure this application software to
connect to the remote Video Server / Network Camera series products in
“Configuration Menu \ Camera Configuration”, as shown in XFigure 3-2X. You must have
the root (administrator) privilege in order to run the configuration.
Figure 3-2 Camera Configuration
ATTENTION: Once you click on “Configuration Menu\Camera Configuration” for
3-24
Page 26
setting each camera, a warning window will pop up to warn you that all recording
processes will be stopped.
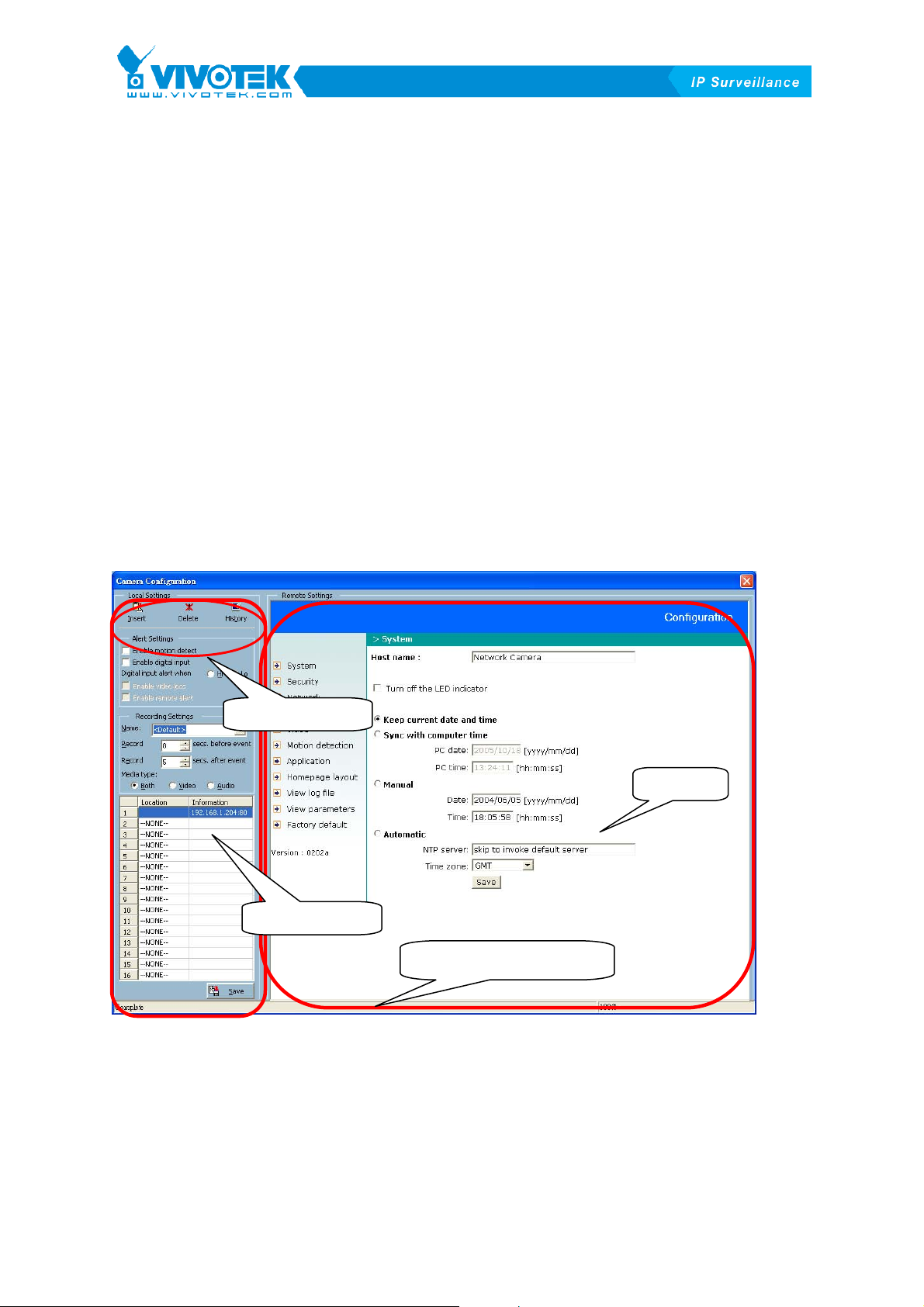
3.4.1 33BThe Layout of the Configuration
In this section, we discuss the local settings of the connection and the functional
configurations of each camera. If you are interested in the remote settings for each
camera, you can refer to each Video Server / Network Camera series product’ s user’s
manual that was shipped with the hardware. The following XFigure 3-3X shows layout of
Camera Configuration window.
NOTE: As for the location of the selected camera, you need to make sure the location
string does not include prohibited characters such as “"\ / : * ? " < > |”. Otherwise, the
“wrong” location string will cause the application program to malfunction. You can
change the location string in “Video->Text on Video” of the remote setting webpage.
Local settings
Setup page
Camera selections
Remote setting webpage
Figure 3-3 Layouts of Camera Configurations
B
3-25
Page 27
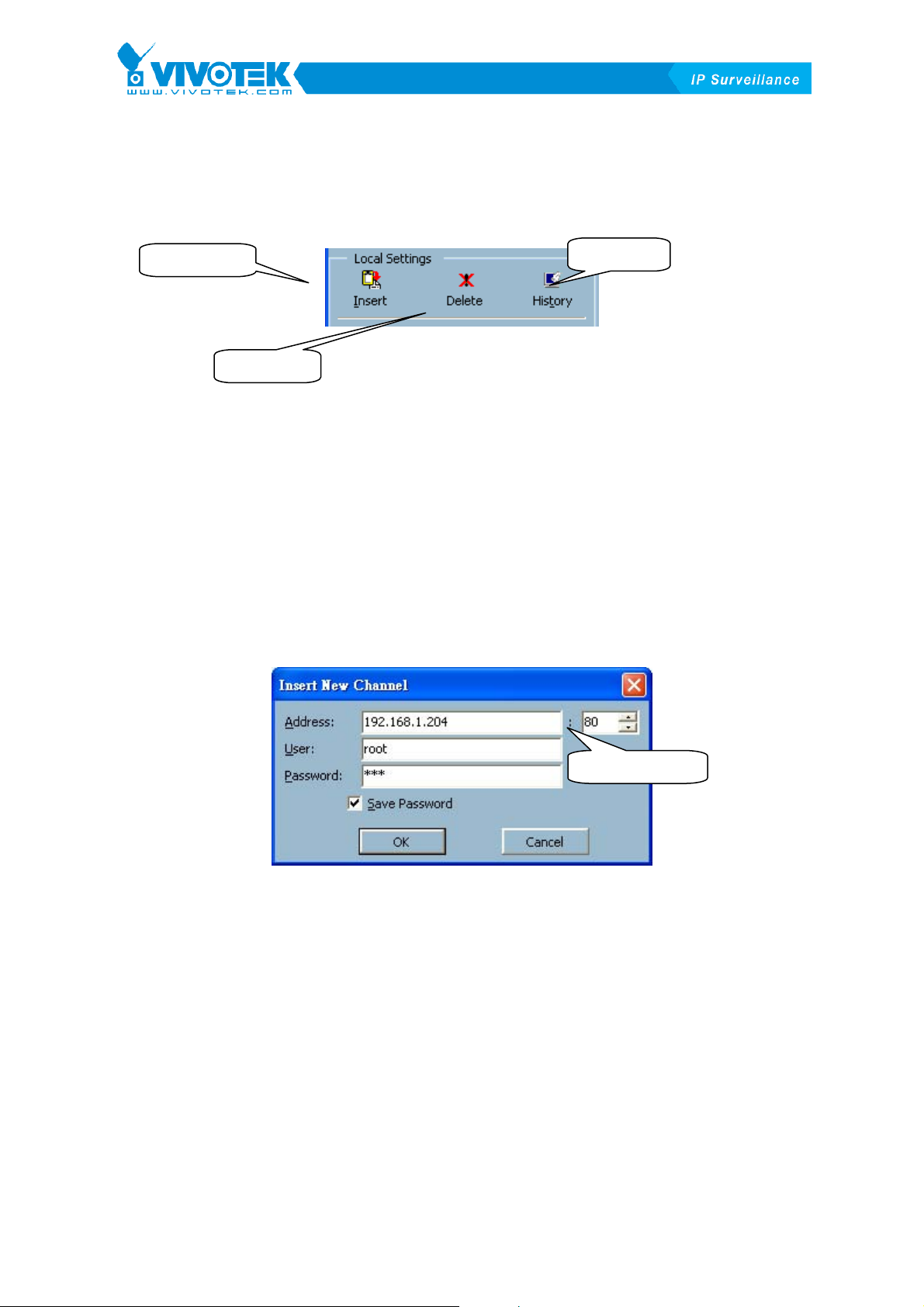
3.4.2 Local Settings
In the local settings, as shown in XFigure 3-4X, there are three main functions:
Insert camera
Delete camera
Figure 3-4 Local Settings
Insert – This allows the user to insert a remote Video Server / Network Camera
series product to the camera list. Click on the “Insert” button, an “Insert New Channel”
History
dialog will pop up, as shown inXFigure 3-5X. Specify the IP address, port and root
password of the remote Video Server / Network Camera series product, and click on
the “Ok” button to close the dialog. The system will try to connect to the selected
camera. If the connection is successful, the camera will be inserted to the list.
IP address and port
Figure 3-5 Insert New Channel Dialog
Delete – This removes the selected Video Server / Network Camera series product
from the camera list. You should select a camera as shown in XFigure 3-6X to remove.
3-26
Page 28

The selected camera will be deleted.
Figure 3-6 Delete a camera to the list
History – Clicking on the “History” button pops up a camera history list that shows the
latest cameras that has been inserted into the camera list. The list could contain up to
16 entries. When you click on one of the cameras in the history list, the camera will be
inserted into the camera list. The history list is shown in
XFigure 3-7X.
Historical camera list
Figure 3-7 Popup historical camera list
.
3-27
Page 29

3.4.3 35BAlert Settings and Recording Settings
Figure 3-8 Alert Settings and Recording Settings
Alert Settings:
These settings guide this program how to handle motion detection, digital input alerts,
video loss and remote alert.
9 Enable motion detect -
With this checkbox checked, the program will trigger the alert sound (specified in
“3.5 XGlobal SettingsX \ Alert Sound”) if motion is detected for the specified channel.
9 Enable digital input -
This function is similar with that of “Enable Motion Detect”. Selecting this option
will activate the alert sound when the digital input of the remote Video Server /
Network Camera series product is triggered.
9 Digital input alert -
This option allows for defining the triggering criterion of the digital input of the
remote Video Server / Network Camera series product. It can either be high-level
triggered or low-level triggered.
-
9 Enable video loss
Enable this option will trigger alert when video loss. The video loss will occur
when Video Server is connected and do not connect to any proper camera.
9 Enable remote alert
-
3-28
Page 30

Alert sound will be played on remote side if the option is enabled, alert sound has
been configured and the one of the above three alerts (motion/digital/video loss)
triggered.
NOTE: Above items may be disabled when the connected server doesn’t support the
features.
Recording Settings:
9 Name -
If you want to specify your own location name, specify it in this field. Otherwise,
leave this field with the default value “<Default>”. You will get a default location
name which concatenates the string in the server’s “Text on video” field with an
underline and the channel index.
9 Record # secs. before event -
Once the event recording is activated (using HSchedulingH) for channels, you can
use this setting to regulate the time for the recording of the triggered event. The
recording will start at the set time before the alert event starts.
9 Record # secs. after event -
This set how long the recording will last after the alert event triggered.
9 Media Type -
You can use this to specify which media type you want to record, Video, Audio, or
both. In some case that the connection contains only media data, the recorded
data will contains only media data though the choosen recording media type is
both. Similarly , if the choosen type is audio, and the connection has not audio data,
nothing will be recorded.
3.4.4 36BChanging the Camera Order in the List
You can use “drag and drop” in the grid area of the camera list to change the
sequence of the connected Video Server / Network Camera series products, as
shown in XFigure 3-9X. This is helpful when you want to rearrange the cameras’ order.
3-29
Page 31

Step 1: Step 2:
Press left mouse button at the gray
index field.
Move mouse to where you want to move and then release the
mouse button. Then Video 1 will be moved to the 10th row .
Figure 3-9 Change the Sequence of the Connected Camera
3.4.5 37BSaving the Changes
Once you have clicked on the “Save” button in the bottom left corner of this window,
the changes for all camera configurations will be saved and validated immediately in
this IP surveillance system.
NOTE: If you try to change the remote settings of any Video Server / Network Camera
series product in the web page (right part of this window), you will need to apply the
“SAVE” button in each corresponding page in order to save the settings to the remote
servers. There are different “SAVE” buttons for changing the settings of the local IP
surveillance system and that of the remote Video Server / Network Camera series
product.
3.5 14BGlobal Settings
After completing the connection for each remote Video Server / Network Camera
series product, you will need to configure the global settings for all the connected
servers. These include the media datamedia database directory, the usage of the
hard disk, internet settings and backup status information.
3-30
Page 32

Figure 3-10 Global Settings
You can activate the global setting window from “Configuration Menu \ Global
Settings...” as shown in XFigure 3-10X.
ATTENTION: A warning window will pop up to alert you that all recording processes
will be stopped when activating the global setting window.
Backup status
information
Figure 3-11 Global Settings Window
Directory Settings:
3-31
Page 33

9 Snapshot directory -
This is the directory for storing the snapshots in *.bmp format from channels as
shown in XFigure 3-11X.
9 Recording directory -
This is the directory for storing the recorded media data from remote channels.
9 Scheduler directory -
This is the directory for storing the default and user-customized plots for the
recording schedule of each channel.
Record Diskspace Usage Settings:
9 Cycle Recording -
When this setting is turned on, the media database system will overwrite the
oldest data if the usage of the current database has reached its storage limitation.
In other words, it will record media data circularly . If this setting is not selected, i.e.
unchecked, a warning message will pop up when it is approaching the limitation.
After that, it stops recording when the limitation of the hard disk usage is reached.
9 Reserved space -
This indicates the size of the hard disk to be reserved on the recording disk. If the
recording data exceeds this limitation, the new in-coming media data will replace
the oldest data if “Cycle Recording” was selected. Pre-buffer mechanism will take
some space if some channel is already configured but not recording.
Internet Settings:
You can set the proxy server and the IP filter by clicking on the “Internet Settings”
button. This setting is helpful for connecting Video Server / Network Camera series
product in the Intranet while the proxy server is in use at the same time.
You can enable or disable the usage of the proxy server by the check box shown
inXFigure 3-12X. If you enable both the proxy server and IP restriction, the listed IP
addresses will not be applied to the proxy server. Often, the listed IP address will be
the one assigned to the Visual Server / Network Camera series product in the
Intranet.
3-32
Page 34

Check here to enable IP filter
Enter IP address here to add
IP address list
Check here to enable proxy server
Set the port
Add an IP address to list
Delete an IP Address from list
Figure 3-12 Internet Proxy Settings
Backup Settings:
In this setting, you can select the directory, maybe a remote hard disk, for the media
database backup; as well as the backup size of your backup media.
Backup Location Select:
This window provides the settings for backup and the deletion of media datamedia
database. You can select the check box to direct which channels need to be backed
up. You can also click the “Delete” button on the right to delete the media datamedia
database corresponding to the selected channel. Several kinds of backup status
information will be shown for each channel. Normally the status shows the time of the
last backup, which indicates the time you last backed up to the dedicated media. “No
Data” means that there is no media data recorded for this channel. “All Backup”
means all the data in this location have been backed up. “First Backup” means there
are media data recorded for this location and there has not been any backup
operation prior. Please refer to Section X3.7.3X for the activation of backup operations.
Network Account:
As shown in
XFigure 3-13X, if you want to set the record path to the network drives, you
should enable the option “Account to Access Network Drive”, and give the local user’s
name, password and network domain (or Host Name / IP). To backup data to network
driver, you also need to setup the account.
3-33
Page 35

Figure 3-13 Network Accou nt Drive settings
NOTE: The network account must be able to login the machine that runs the
application (ST3402) and also the machine that provides the network drive. You can
also specify the Host Name or IP to enable network account settings.
3.6 15BDisplay & UI Settings
Options of video display and alert settings can be modify in Display & UI Settings
dialog. Recording and monitoring can be continued when you open this dialog. You
can activate the Display & UI setting dialog from “Configuration Menu \ Display & UI
Settings...” as shown in XFigure 3-14X.
Figure 3-14 Display & UI Settings
3-34
Page 36

Figure 3-15 Display & UI Settings Window
Local Alert Settings:
You can load custom *.wav file for the sound of alert triggering. You can also listen to
the sample of the chosen sound file by clicking on the “Play” button (the button with
black right arrow).
Remote Alert Settings:
As local alert settings, you can load *.wav file for the sound of alert triggering and the
sound will be played on the remote side.
NOTE: If user doesn’t enable alert settings that described in section 3.4.3, alert sound
can’t be play when proper event occurs. Remember to enable alert settings which you
like to.
Snapshot Format:
There are two kinds of snapshot format (.jpg and .bmp) that can be selected by user.
Modulation Mode:
You must select the input signal format (NTSC, PAL or CMOS) to display the original
resolution of video stream from the remote Video Server / Network Camera series
product.
3-35
Page 37

NOTE: You must select the input signal format according to the camera type or CCD
module type that is connected to the remote Video Server / Network Camera series
product, regardless of the power line connected is 50 or 60 Hz.
Display Options:
In the video displaying frame of each channel, there are two status bars associated
with it. On the upper side, the status contains “Camera location” and “the time of the
remote site”. On the lower side, the status includes “Connection time” and “Recording
time”. As shown in XFigure 3-16X, all can be enabled or disabled individually. The “Apply
to full screen mode” can also be turned on. Once it has been selected, the status bar
in each channel will show the date, location, connection and recording time in both
displaying frame mode and full screen mode.
Location (channel number + Text on Video)
Connection Ti me (Day:Hour:M in)
Remote Time (according to time format)
Recording Time (Day:Hour:Min)
Figure 3-16 St atus on the Displaying Frame
Miscellaneous:
9 Click on image to enable PTZ -
Enable this option can let you control PTZ by clicking on displaying frame. If this
option is enabled, the cursor icon will be changed when cursor moving into a
displaying frame which associates with a PTZ-enabled Video Server / Network
Camera series product, as shown in XFigure 3-17X. You can move camera to any
point you want by clicking on displaying frame.
3-36
Page 38

Figure 3-17 Cursor change to click on image mode
9 Enable PTZ hot key -
When the option is enabled, user can control PTZ camera by using keyboard.
The following table represents functionality of each hot key:
9 Hot Key 9 Functionality
9 NUMPAD_0 9 AutoFocus
9 NUMPAD_1 9 Focus -
9 NUMPAD_2 9 Down
9 NUMPAD_3 9 Focus +
9 NUMPAD_4 9 Left
9 NUMPAD_5 9 Home
9 NUMPAD_6 9 Right
9 NUMPAD_7 9 Zoom -
9 NUMPAD_8 9 Up
9 NUMPAD_9 9 Zoom +
9 NUMPAD_DIVIDE 9 Pan
9 NUMPAD_MULTIPLY 9 Stop
9 NUMPAD_SUBTRACT 9 Patrol
9 Apply to new device -
Table 3-2 PTZ Hot Key
After reconnected to Network Camera or video server, if Monitor found that the
server type changes, for example, the original camera is with a built-in PT len, but
the connected device is a video server. This setting tells the Monitor to a ccept the
new device and use the previous setting values (such as schedule and recording
media type, …ect) For more detail, please refer to section 3.7.1.
3-37
Page 39

3.7 16BUsing Monitor Tool
This section depicts methods of manipulating the Monitor tool.
3.7.1 38BConnection of the Video Server / Network
Camera Series
Channel:
Once you have connected a Video Server / Network Camera series product, you can drag and drop
the camera to the video area. As for the channel area shown in
camera for the channel, the color of the channel number will be gray. Once you have set up the camera
in the channel, the color of the channel number will be blue. This also means that this channel is
associated with the remote Video Server / Network Camera series produ ct. You can then click, drag,
and drop the camera to the video area to monitor the remote video, and apply other features, if your
privileges allow.
XFigure 3-18X, if you have not set up the
Connected and monitoring
Configured channel
Selected channel
Not connected (no video)
Recording
Not configured channel
Trashcan
Figure 3-18 Channel Area
3-38
Page 40

There is a unique light signal associated with each channel number. It indicates the
status of the dedicated channel, as listed below.
9 Off (Black)
The channel is not connected with any remote Video Server / Network Camera
series product.
9 Green
The green light means the Video Server / Network Camera series product
associated with this channel number is connected, and the video is being
monitored in the video area.
9 Orange
The orange light indicates the video from this channel is recording into the media
database. In this mode, you do not need to click, drag, and drop the channel to the
video area. This means the application software supports real-time recording with
and without real-time monitoring for the dedicated channel.
9 Red
The red light indicates the connection to server has been unexpectedly
disconnected and Monitor is trying to reconnect to the server. There are several
cases that will cause server is disconnected:
Authentication Fail–
Suppose user changes server from model A to model B by himself without using
Camera Configuration tool which described in section 3.4. If the login passwords
are different between those two models, the hint of “Authentication Fail” will be
popped up as shown in
XFigure 3-19X:
Figure 3-19 The Hhint of Authentication Fail
As shown in XFigure 3-20X, within such case, user can invoke authentication
window by clicking corresponding channel number and re-input correct password
to reconnect to server. XFigure 3-21X shows the authentication window.
3-39
Page 41

Click to invoke
authentication window
Figure 3-20 Invoke Authen tication Window
Re-input correct
password to reconnect.
Press button to reconnect.
Figure 3-21 Authentication Window
NOTE: The hint will also be popped up when user changes login password in IE.
Incorrect Settings–
If the option of “Apply to new device” doesn’t be enabled, the hint of “Incorrect
Settings” will be popped up when the settings (model A) that were configured in
Camera Configuration window (section 3.4) are different with the connecting
server (model B). The following XFigure 3-22X shows the hint of “Incorrect
Settings”:
Figure 3-22 The Hint of Incorrect Settings
In this case, user can enable the option of “Apply to new device” and the
application will reconnect to server automatically.
Unknown Type–
3-40
Page 42

If the connecting device is not supported Video Server / Network Camera series
product (such as PC or another network device), the hint of “Unknown Type” will
be popped up. Please check what device is assigned the specified IP address
and change to supported Video Server / Network Camera series product. The
hint is shown in XFigure 3-23X.
Figure 3-23 The Hint of Unknown Type
ATTENTION: The above three cases will occur if those two models A and B are set as
the same IP address. Otherwise, the hint of “Disconnect” will be displayed.
9 Blink
If the motion detection mechanism is set in the remote Video Server / Network
Camera series product, the light corresponding to the channel will blink if a motion
event is detected.
If you do not want to monitor one video, you can click, drag, and drop the video (in the
video area) to the trashcan in the common control area of the Monitor tool. The
following shows the step-by-step procedure of “drag and drop”.
3.7.1.1 67BShow the video of the specific channel
This section depicts the method of showing the video of a specific channel in the
dedicated displaying frame in the video area.
Step 1: Move the mouse cursor to the channel number, as shown in XFigure 3-24X.
3-41
Page 43

Mouse cursor
Location hint
Display frame
Channel number
Figure 3-24 Mouse Cursor on the Channel Number
Step 2 : Press and hold down the left mouse button and drag the mouse cursor to the
displaying frame in the video area, as shown in XFigure 3-25X. Note that the cursor will
be changed according to the area indicating whether the selection can be dropped
there.
Droppable area
Not droppable area
Figure 3-25 Drag the Channel to the Displaying Frame
Step 3 : Move the mouse cursor to the area in which the selection can be dropped (in
3-42
Page 44

this case, it should be the video area), and then release the mouse button. In each
layout, each channel is corresponding to one and only one displaying frame in the
video area, as shown in XFigure 3-26X. Therefore, the drag and drop from the channel
number to the displaying frame can be treated as “exchange of channels in the
displaying frames”. That means whatever video is on the newly selected channel will
replace the one on the current display frame. You can apply this criterion to exchange
the channels in different displaying frames. Let us assume the video of Channel 1 is
shown at display Frame X and the video of Channel 2 is shown at display Frame Y.
The channels associated with the dedicated display frames will be switched when you
drag and drop the video from display Frame X to display Frame Y and vice versa.
Also, you can move the channel from its original display frame to a vacant display
frame. All these functions can be performed by a single mouse operation “drag and
drop”. This makes it very convenient to customize the video display layout for
monitoring.
NOTE: Monitor will automatically associate newly added channel to empty frame of
each layout. So you will find that the channel is automaticaly shown in layout after
closing Camera Configuration dialog. But if you have manually changed the
association in one layout, the automation for that layout would be disabled. There is no
way to re-enable the automation.
3-43
Page 45

Cursor changed, video shown.
Empty video box
Figure 3-26 Showing Video on the Displaying Frame
3.7.1.2 68BClose the channel in displaying frame
This section discusses how to close the video change in the display frame.
Step 1 : Move the mouse cursor to the display frame associated with the channel you
want to close.
Step 2 : The cursor will turn into a hand-shaped icon when it is moved to the display
frame. Press and hold with the left mouse button.
Step 3 : Move the cursor and drag it to the trashcan in the common control panel of
the Monitor tool.
Step 4: The cursor shape will change to an arrow-shape icon over the trashcan.
Release the left mouse button. The video in the corresponding display frame will
disappear. These operations are shown in XFigure 3-27X.
3-44
Page 46

Press and hold mouse button here.
Move mouse cursor here, and then
release mouse button here.
Figure 3-27 Close the Channel
NOTE: Even the channel is closed for current layout. The network connection is still
connected. The reason to keep the connection is that if the connection is closed, it is
not possible for Monitor to judge if any event is triggered.
3.7.2 39BThe Layout
There are six kinds of layouts shown in XFigure 3-28X for displaying frames in the
Monitor tool. You can select one of them by clicking on the left mouse button over the
layout icon you want. In each layout, you can select, drag, and drop the “channel
number” to any display frame in the video area. The video from the remote site will be
shown. Following the procedures described in Section X3.7.1.1X, you can add the video
of the channel to the display frame of the selected layout in the video area one by one.
After that, you can also exchange video between different display frames by the same
select, drag, and drop method.
3-45
Page 47

1 camera layout
4 cameras layout
6 cameras layout
Figure 3-28 Layout of the Monitor tool
9 cameras layout
Whether you choose the one-camera layout or the four-camera layout, the “Page up”
13 cameras layout
16 cameras layout
and “Page down” buttons will be shown in the bottom-left corner of the video area.
You can use these two buttons to switch the pages, as shown in XFigure 3-29X. Use the
“Page Up” and “Page Down” key in keyboard could also swith the page. Page can be
switched automatically if “Auto switch channel” is enabled. You can specify interval
time and page will be swiched based upon the time.
Switch between cameras
Enable Auto-Switch
Auto-Switch interval (sec.)
Figure 3-29 Four-camera Layout
NOTE: Auto-switch function will skip the page that doesn’t contain any channel.
When you want to view one individual camera from the multi-camera layout shown in
3-46
Page 48

XFigure 3-30X, double-click on the display frame associated with the dedicated channel
in the video area. You will see the size of the display frame is the same as the
one-camera layout. As shown in XFigure 3-31X, clicking on the “Back” button in the
upper-left corner of the video area will switch to the previous selected multi-camera
layout.
The position for each channel in any layout will be kept for the next time when the
layout is selected again for monitoring.
Double click on the video to switch to double size video
Figure 3-30 Double-clicking on the Displaying frame
3-47
Page 49

Back to previous layout
Figure 3-31 Single View Mode When in Multi-camera Layout
Input/Output Control Tools
PTZ Control
Digital Input /
Digital Output
Talk Control
Alert Message
Figure 3-32 Input/Output Control Tool
This application software provides another three tools, shown in XFigure 3-32X, in the
bottom-left corner, for controlling the remote Video Server / Network Camera series
product of the associated channel. You can click on the dedicated buttons to switch to
different control tools that include PTZ (Pan/Tilt/Zoom) control, DI/DO (Digital Input /
3-48
Page 50

Digital Output) control, Alert Message receiver and Talk control.
3.7.2.1 69BPTZ Control
The PTZ (Pan / Tilt / Zoom) tool is shown in XFigure 3-33X. If the remote Video Server/
Network Camera series product associated with the selected channel is connected
with a PTZ enabled camera, this PTZ control tool will be activated. You can do PTZ
operations, as well as going to the preset location set by the previously user-defined
position. Auto-pan and auto-patrol are enabled when the selected channel is
associated with PT Network Camera series product. You can also apply PTZ control
to several cameras simultaneously. See Section X3.7.7X.
Tilt up
Return to Home
Pan left
Auto focus
Focus near
Auto pan
Go to the preset location
Pan right
Tilt down
Zoom in
Focus far
Auto patrol
Stop Auto pan or
Figure 3-33 PTZ Control
3.7.2.2 70BDI/DO Control
After clicking on the “DI/DO” button, shown in XFigure 3-34X, the control page will be
switched to the DI/DO control tool. Only users of root group and power user group
can access the DI/DO control of the remote Video Server / Network Camera series
product. In this application software, the color of the channel number indicates the
status of the DI (Digital Input) of the channel. You can click on the “Switch button” to
change the HI/LOW state of the DO (Digital Output). These features allow you to
monitor the remote sensor input from DI and also trigger the remote by the DO switch.
3-49
Page 51

Digital input is low
Set digital output to HIGH
Digital input is high
Set digital output to LOW
No Connection
Figure 3-34 DI/DO Control
The color of the DI status is depicted as follows:
9 OFF
When the color of the channel number is gray, that means this channel is not
connected to any remote Video Server / Network Camera series product.
9 Red
The channel number turns red indicating the DI of the remote Video Server /
Network Camera series product associated with the selected channel is in high
level.
9 Blue
The channel number turns blue if the DI of the remote Video Server / Network
Camera series product associated with the selected channel is in low level.
3.7.2.3 71BAlert Message
3-50
Page 52

Figure 3-35 Alert Message
If you select the check box for “Enable Motion Detect”, “Enable Digital Input” or
“Enable Video loss” in the path “Configuration Menu \ Camera Configurations \ Alert
Settings”, the alert message will show in the window as shown in; refer to “Alert
Settings” in Section X3.4.3X. An alert message appears in this window when an alert is
triggered by user defined motion detection or a digital input level change. You can
also use the scroll bar of this box to check on the alert event’s history.
The message format is described as follows:
“time”=>”alert type” #”channel number”(“win1”,”win2”,”win3”)
The message “02:41:00=>MO #1(0,1,1)” means that this was a motion detection alert
occurred at 02:41:00 AM in Motion Window 2 and Motion Window 3.
The message “14:41:56=>DI #1” means there was an alert triggered by the first DI at
02:41:56 PM.
The message format of video loss is as follows:
“time”=>video loss”#”channel number
For example, “07:20:03=>Video Loss#5” means that a video loss alert occurred at
07:20:03 AM in channel 5.
3.7.2.4 72BTalk Control
Talk Control is shown as follows:
3-51
Page 53

Talking
Talk available
Talk unavailable
No connection
Talk volume setting
Figure 3-36 Talk Control
9 Talk Available
When the connected Video Server / Network Camera series product supports the
feature of 2-way audio, talk with remote side is available. User can click the
button to establish talk channel. When the channel is established, the state will
enter to talking and user can talk with remote side by microphone.
9 Talk Unavailable
Talk may be unavailable if the connected Video Server / Network Camera series
product doesn’t support 2-way audio feature.
9 Talking
The state means that the channel is talking with remote side now. You can adjust
volume by using Volume Setting tool or stop talk by click the button.
9 Talk Volume Setting
User can adjust the volume of talk by using this tool. Click the button and the
Volume window will be invoked.
NOTE: Remote alert will also occupy talk channel. Only one talk channel can be
established at the same time for a server. You can establish maximum 16 talk
channels with different servers simultaneously. If the talk channel has benn
established with specified server, a warning message will be pop up and the talk
channel can’t be established success.
3-52
Page 54

3.7.3 40BBackup
Figure 3-37 the Process of Backup Operation
“Backup” allow you to copy the recorded media data to another media according to
the location and the size you have selected. You can refer to Section X3.5X
“Configuration Menu \ Global Settings \ Backup Settings” for more details on backup
settings. From the backed up media data in the media, you can duplicate the
backup-data to any removable device, such as CD-ROM, ZIP disk, DVD-RAM, or
tape, manually.
After backup settings have been configured, you can activate the backup operation
by clicking on “Configuration Menu \ Backup”, as shown in XFigure 3-37X. Once the
backup process is started, and, while in progress, you are prohibited to configure the
remote Visual Server / Network Camera series product, or change any local settings.
You can cancel the backup process by simply clicking on the “Configuration Menu \
Cancel Backup” option and choose the status of the progress. A message box pops
up to indicate backup is complete.
3.7.4 41BAbout
Clicking on the menu “Configuration Menu \ About…” as shown in XFigure 3-38X, pops
up a dialog box with information including product name, version, user information
and serial number.
Figure 3-38 About
3-53
Page 55

k
Quit
Full Screen
2B
Minimize
Loc
Figure 3-39 Miscellaneous functions
Configuration Menu
Stop Alert Sound
3.7.5 Miscellaneous Functions
This section describes other miscellaneous functions represented by small icons in
this application software, as shown in XFigure 3-39X. These functions can be applied
regardless of which is the currently focused channel. These functions are each
described below.
Quit
Clicking on this button closes this application software with the latest saved settings.
Minimization
Clicking on this button minimizes the Monitor application.
Full Screen
Clicking on this button enlarges the selected channel to a full-screen display. To
switch back to the original layout, press on the “ESC” key at the top-left corner of the
keyboard, or double click on the mouse cursor on screen.
Lock
Click on this button to lock this program. When in lock mode, the main window will be
hidden and the lock dialog will appear. To return to the main window, you need to
re-enter the root’s password or the password of the user who locked application.
3-54
Page 56

Stop Alert Sound
Whenever an alert is triggered, an alarm will sound if it was set up. You can click this
button to stop the alarm. It will also switch the I/O Control Tool to the Alert Message
Tool, as depicted in Section X3.7.2.3X, and automatically shows the alert messages.
Configuration Menu
This menu includes Camera Configuration, Global Settings, Scheduler, Backup, and
About options.
3-55
Page 57

3.7.6 43BCommon Control Functions
Volume
Stop Record
Trashcan
Record
Figure 3-40 Common Control Functions
Printer
Snapshot
This section describes other Common control functions, respresented by small icons,
as shown in XFigure 3-40X. These functions can only be applied to the focused
channels. These functions are each described below.
Volume
Clicking on this button to adjust the audio volume when monitoring provided the
camera supports audio.
Record
By clicking on this button, you can manually activate video recording on the selected
channel.
Stop record
This allows you to manually stop the video recording on the selected channel;
whether the recording was event-driven or by scheduled triggering, or manually
activated.
Printer
You can print all views currently shown in the view window.
Snapshot
This function is to take a snapshot of the selected channels in the current layout, and
save the pictures as bitmap files to the hard disk. You can pre-set the directory in
which these bitmap files are stored in “Configuration menu \ Global Settings”. Please
3-56
Page 58

refer to Section X3.5X for details.
Trashcan
You can drap and drop the channel to the Trashcan. This does not close the video
connection with the remote Video Server / Network Camera series product. But the
display for the channel in current layout will be removed.
You can apply Volume, Record, Stop record, Printer, and Snapshot to several
cameras simultaneously. See Section 3.7.7.
3.7.7 44BMultiple Focus
Some functions can be applied to more than one camera simultaneously. These
functions include PTZ controls, Volume control, Record, Stop Record, Printer, and
Snapshot. First, set multiple focuses to the cameras you want to control, and then do
operations such as PTZ controls, Record, etc. The way to focus more than one
camera at a time is to press CTRL and click on display frames in the view window.
You can only set multiple focuses to the cameras on the same layout page, and only
select them from the view window, not from the channel panel.
3.7.8 45BStatus Bar
Local time
Status message bar
Current login user
Login time
Figure 3-41 Status Bar
9 Local time -shows the current time of the local site.
Software name
Software version
9 Current login user - shows the current login user’s name.
9 Login time - shows the time when user logged in.
9 Status message bar - shows messages on some background operations,
such as repairing database or locations.
9 Software name - shows the software name of this application.
9 Software version - shows the software version of this application.
3-57
Page 59

Chapter 4 3BScheduling
The Scheduling tool helps the user to schedule the time to record the media stream of
the selected channels from the remote Video Server / Network Camera series
product. With both the graphic user interface and time period selection options, you
can easily schedule each channel.
The main features of the Scheduling tool are depicted as follows:
User-friendly graphic interface for schedule editing
Flexible schedule scheme suitable for most applications need
Individual schedule for each channel
Automatic period recording
4.1 17BInvoke Scheduling Tool
This section describes how to invoke the Scheduling tool.
4.1.1 46BStarting the Scheduling tool
Figure 4-1 Open Scheduler Tool
Before starting the Scheduling tool, click on the “Configuration Menu \ Scheduler…”
as shown in XFigure 4-1X, there must be at least one camera on the camera list.
Otherwise, the Scheduling tool cannot be invoked. You will need to specify the
database directory of the schedule schemes and the video stream in the path
“Configuration Menu \ Global Settings \ Directory Settings”. Refer to Section X3.5X for
more detailed information. After all of the above are set, you can click on
“Configuration Menu \ Scheduler…” to invoke the Scheduling tool.
4-58
Page 60

4.2 18BThe Layout and Functionalities
In this section, the layout and the functionalities of the Scheduling tool are depicted in
detail.
4.2.1 47BIntroduction
XFigure 4-2X shows the layout of the Scheduling tool’s components.
1
2
3
4
Figure 4-2 Overview of the Scheduling Tool
The layout is roughly divided into 4 parts:
Channel Selection Area:
It provides the IP addresses and location information of the connected channel. You
can select one channel in this area and start to edit a dedicated schedule scheme for
it.
Primary Sschedule:
4-59
Page 61

It consists of day time-line, week time-line, begin time selector, end time selector, and
event mode settings.
Secondary Schedule:
It consists of event mode settings.
Operation Buttons:
It contains operation buttons for the user to fine tune the edited schedule-scheme of
the selected channel, and close the Scheduling tool window.
These four parts will later be described in detail.
4.2.2 48BThe Functionalities of Configuration
Components
IP address
Location
Channel
Figure 4-3 Channel Selector
The channel selector shown in XFigure 4-3X is typical for a dedicated channel. When
you click on the row to select the channel, the scheduling tool will load the dedicated
schedule scheme associated with the selected channel automatically. If the remote
Video Server / Network Camera series product has been properly configured, the IP
address and location of the selected channel will be shown. Please note that when
you switch between channels in this selector, any editing and changes in the
schedule scheme will be saved temporarily in system memory. To save the settings
permanenty, please click on the “Save” button.
4-60
Page 62

4.2.3 49BThe Schedule Scheme operations
There are six related buttons, “Load…”, “Undo”, “Clear”, “Save”, “Save as…” and
“Close” for handling the scheduling schemes. These are shown in XFigure 4-4X.
Figure 4-4 Operations for the Schedule Scheme Manipulation
Load…
This button is used for loading other pre-edited schedule schemes from the specified
directory. Note that you will need to save the current-edited settings before applying
this function. Otherwise, any editing changes will be lost.
Undo
This button is used for undoing all plotting markers for this schedule scheme from the
last save.
Clear
This button is used for clearing all plotting markers in the current-editing schedule
scheme of the selected channel.
Save
This button is used for saving the editing changes for the current schedule scheme.
Save as…
This button is used for saving the current-edited schedule scheme to another file
name instead of the default name.
Close
This button is used for closing the scheduling. Any unsaved setting will be lost.
4.3 19BPrimary Schedule
4.3.1 50BSchedule with Time Lines
There are two time-lines of different scales: hour unit time-line and week unit time-line.
4-61
Page 63

You can make your own schedule scheme by plotting markers in all time-lines. These
two time lines are associated with each other. That is, if you make changes in one
time-line, the corresponding changes will be applied, in scale, to the other time-lines
in the same schedule scheme.
4.3.1.1 73BWeek Time-Line
XFigure 4-5X shows the Week time-line. It includes the time-line, scheduling information,
and the selected day of the week.
Selected day
Figure 4-5 Week Time-line
4.3.1.2 74BMarking/Unmarking the Recoding Time
Click
Figure 4-6 One-click on Week Time-line
Result in hour time-line
The corresponding changes for the markers on the week time-line will be
automatically added to the hour time-line, as shown in XFigure 4-6X. You can also mark
and unmark the plotted bar by using the left and right mouse buttons.
NOTE: Time hint will be popped up when mouse cursor enters the hour time-line.
4.3.1.3 75BHour Time-Line
XFigure 4-7X shows Hour time-line. It includes the time-line, scheduling information.
Figure 4-7 Hour time-line
NOTE: If you want to inquire about the scheduling information on Hour time-line, you
can double-click the marked-rectangle. Start time and end time will be displayed on
4-62
Page 64

the time picker that will be described in section 4.3.2 automatically.
4.3.1.4 76BMarking/Unmarking the Recording Time
You only need one click on the left mouse button to mark the time on this time-line.
The operating method for the hour time-line is the same as that of the week time-lines.
Please refer to Section X4.3.1.1X for details.
4.3.2 51BSchedule with Time Picker
4.3.2.1 77BBegin and End Time
Hour picker
Minute picker
Day picker
Figure 4-8 Begin Time and End Time Selectors
There are three controlling units in both “Begin Time” and “End Time” selectors, as
shown in XFigure 4-8X. The first part of each of these two selectors is the Day Picker.
You can select the day of the week with it and set the beginning time and the ending
time for the recording interval.
The second and third units are the Hour Picker and the Minute Picker. You can
change the hour and minute settings for the beginning and ending time with them.
NOTE: Normally, the time set in “Begin time” must be earlier than that in “End time”.
But if this is not the case, it means the time is over two days.
4.3.2.2 78BAdd and Erase Buttons
After you have selected the time period with the “Begin time” and “End time” pickers,
you can apply the period picker, shown in XFigure 4-9X and set the type of time interval
that associates with the beginning and end time. After having the settings in “Begin
Time”, “End Time” and “Period Picker” done, click on the “Apply” button to confirm the
settings. Click on the “Erase” button to clear all scheduling information just entered.
All newly entered scheduling time interval information will take effect only after the
“Apply” button has been clicked.
4-63
Page 65

Period picker
Apply
Erase
Figure 4-9 Period Picker, Apply button and Erase button
4-64
Page 66

4.3.3 52BSchedule in event mode
You can select to record in Event mode or Continuous mode by the Schedule mode
selector as shown in XFigure 4-10X. There are two types of event recording, please refer
to Section X4.3.3.1X and Section X4.3.3.2X for more information.
Figure 4-10 Schedule Mode Selector
4.3.3.1 79BMotion detection
Figure 4-11 Motion Detection Selector
XFigure 4-11X shows the window selection you want to record when motion detection is
triggered.
4.3.3.2 80BDigital input
Figure 4-12 Digital Input Selector
XFigure 4-12X shows the four digital input conditions. Select the triggering condition that
you would like to start recording.
high : Event will be triggered when the digital input is high.
low : Event will be triggered when the digital input is low.
rising : Event will be triggered if the digital input changes from low to high.
falling : Event will be triggered if the digital input changes from high to low.
4.3.4 53BSchedule in Continuous mode
XFigure 4-13X shows that if you have selected the Continuous mode then it will record
4-65
Page 67

continuously according to the schedule set up by the user.
4.4 20BSecondary Schedule
Secondary schedule is the time that is outside the Primary schedule.
4.4.1 54BSchedule modes
Figure 4-13 Secondary Schedule Mode Selector
As shown in XFigure 4-13X, there are three selections in the Secondary schedule mode
selector: Disable, Event mode, and Continuous mode. You can disable the
Secondary schedule, choose the Event mode or choose the Continuous mode. The
two modes are the same as those in the Primary schedule. Please refer to Section
X4.3.3X and Section X4.3.4X.
4-66
Page 68

Chapter 5 4BPlayback
5.1 21BFeatures of Playback
The Playback program of this application software is a very powerful yet convenient
and user-friendly tool the user can use in browsing the recorded media datamedia
database. It has two display modes (normal display mode and event preview mode)
and three playback methods (full range, time period, and events preview). There are
several main tools consisting of special features in this Playback tool. These tools are
depicted as follow.
Powerful play control tools:
Play
Stop
Pause
Step forward
Fast play (from x1 to x16)
Slow play (from /1 to /16)
Convenient display adjustment tools:
Zoom in (from 1:1 to 2.25:1)
Zoom out (from 1:1 to 1:2)
Full screen
Flexible searching range adjustment tools:
User input (from full range to 1 second)
Zoom in (from full range to 10 seconds)
Zoom out (up to full range)
Page searching
Full range
Various tools:
AVI file transducer
5-67
Page 69

BMP file snapshot
Output to printer directly
Volume control
System control tools:
Lock Program
System settings
Minimize
Miscellaneous tools:
Location selector
Alert window selector
5.2 22BLogging In
The authentication mechanism is implemented in Launcher. If the user has passed
authentication in Launcher, Playback can be invoked without further authentication.
Otherwise, Authentication diglog of Launcher will pop up and the user must pass
authentication in order to use Playback.
NOTE: Playback can be invoked by user of root group or power user group. More
detail about user’s group, please refer to section 2.2.
5-68
Page 70

5.3 23BLayout
Display Area
Area Selection Indicator
Control Area
Pull Bar
Histogram Area
Status Area
Figure 5-1 Playback Main Window
Once you have successfully logged in to the Playback system, the main window
appears at the top of the screen and the display resolution will be changed to
1024x768 automatically, if the current resolution is less. As shown in XFigure 5-1X, there
are four main areas in this window: Display area, Histogram area, Control area, and
Status area. There are also three visual indicators of the controls: Area Selection
Indictor, Frame Selection Indictor, and Pull Bar. These features provide for powerful
search for specific video recorded in the surveillance database.
5.3.1 55BMain Areas
5.3.1.1 81BDisplay Area
As shown in XFigure 5-2X, the Display Area can show the surveillance database of each
camera in three ways: by events triggered, by alert, or by time. You can change video
5-69
Page 71

size by using the Display Adjustment Tool and choose playback method by using the
Play Control Tool.
Playback method
Display adjustment tool
Figure 5-2 Display By T ime (Normal Display Mode)
As shown in XFigure 5-3X, there are three kinds of information (loaction name, remote
time and original recording size) that are displayed on the upper and lower bars
respectively. When the display size is equal to the original recording size, the color of
the original recording size will be changed to green, otherwise red. User can modify
the display size in “Display Adjustment“(section 5.7.3) and “System Control” (section
5.4).
Location
Remote time
Green when display size is
Original recording size
equal to the original size
Figure 5-3 Video Information
5-70
Page 72

5.3.1.2 82BHistogram Area
The Histogram is an interactive control. In the control, you can display events’ time
domain location and the percentage of motion. You can also select a group of events
or a specific period, from the Histogram Area.
5.3.1.3 83BControl Area
The Control Area contains most of the control selections and toolboxes you need to
browse the database, except Page Control. The Page Control Tool is located on the
bottom-right corner of the Display Area when the program is operating in the event
preview mode (as shown in XFigure 5-4X). The control tools include: Location Selector,
Period Selector, Playback Method Selector, Jog Dial, Display adjustment, Searching
Range Adjustment, Exporting, and System Control. Details are discussed in Section
X5.7X ”XUsing ToolsX”.
Frame Selection Indicator
Page Control
Figure 5-4 Display By Events (Event Display Mode)
5.3.1.4 84BStatus Area
The Status Area is located at the bottom of the main window. It shows all program
status information, including display mode, display size, display speed, exporting file
5-71
Page 73

format, and exporting file name.
5.3.2 56BIndicators
5.3.2.1 85BArea Selection Indicator
As shown in XFigure 5-1X, the Display Area is surrounded by a blue rectangle. This is
the Area Selection Indicator. This can be set to indicate either the Display Area or the
Histogram Area. Move your mouse cursor to the area you want to select. When you
have selected the Display Area, the Display Adjustment Tool will appear in the control
area. If you have selected the Histogram Area, the Display Adjustment Tool will
disappear and the Searching Range Adjustment Tool will be shown in the same place
of the control area.
5.3.2.2 86BFrame Selection Indicator
The Frame Selection Indicator only appears when you change the display mode to
event preview mode (as shown in XFigure 5-4X). It is a red rectangle surrounding to one
of the nine event preview frames. Once a frame has been selected, you can control
the playing status using the jog dial in the control area.
5.3.3 57BPull Bar
The Pull Bar is a fast, flexible control for seeking specific data in the selected time
period. In the total length of time in that period, you can click, or pull on the indicator
on the Pull Bar to pin point a start time you wish to see. The video display will start
playing the video sequence from that point on. If the replay is paused, the display
area will show the point you have selected. Note that Pull Bar will only function under
normal display mode.
5.4 24BSettings
Click on the “Settings” button shown in XFigure 5-5X in the system control tool, and the
setting dialog will appear on the screen as shown in XFigure 5-6X.
5-72
Page 74

Lock Windows
Settings
Minimize
Exit
Figure 5-5 System Control Tool
Database location
The most important item in the settings dialog is the database path setting. You must
set it to the directory that contains the surveillance database to make the program to
work properly.
AVI files lo cation
This sets the storing directory when you export AVI files. The exported AVI files will be
stored in a sub-directory under the directory you have chosen here.
Snapshot files location
It sets the directory when you use the snapshot to export bitmap files. These exported
bitmap files will be stored in a sub-directory under the directory you have chosen
here.
5-73
Page 75

Figure 5-6 Settings Dialog
AVI Compression Mode
We use only 24 bits color depth to export the AVI file in this mode. In the AVI
compression mode selection, you can select one of the compression methods (both
video and audio) that your computer supports to export the AVI file. The compression
methods may be different from computer to computer due to different compression
methods in different computer installations.
Modulation Mode
The modulation mode decides the on-screen video size. It depends on how the video
sequence was recorded in the monitor program. If you have selected the wrong
modulation mode, the displayed video will be distorted. To correct this, open the
Settings dialog and change into the correct mode.
5-74
Page 76

Control Panel Position
This provides a convenient way to change the position of the control area, either to to
the left or right side of the main window, according to your preference.
Time Format
There are two kinds of time format (12-hour / 24-hour) that can be selected by user to
determine the time format in the upper status bar of display area.
Snapshot Format
Two formats (.jpg and .bmp) can be selected by user to determine the file format of
snapshot.
5.5 25BNormal (Single Frame) Mode
There are several methods you can enter into the normal display mode with only one
displaying frame:
(1) Change the database path from one to another in the settings dialog of “System
Control” tool
(2) Change the location from one to another by using the selector location in the
control area.
(3) Change the playback method selector to “Full Range”.
(4) Change the playback method selector to “Time Period”.
5-75
Page 77

Period Start Ti me Label
Histogram Area
Period End Time Label
Figure 5-7 Normal Display Mode
Under the Normal display (single frame) mode, you can use all the tools the Playback
program provides except the Page control. In this mode, the two labels under the Pull
Bar show the individual starting and ending time of the interval (as shown in XFigure
5-7X).
5.5.1 58BHistogram Area
Dark Region
Inverted Region
Figure 5-8 Histogram Area in Normal Display Mode
The Histogram Area in the Normal display (single frame) mode only indicates the
events’ occurred time and the percent age of motion detection as red bars. If you want
to access the histogram area, you must change the Area Selection Indicator to the
Histogram Area. You can mark one time interval you want to see with a color-inverted
region by dragging your mouse cursor as you hold down the left mouse button (as
shown in X Figure 5-8X). As you release the left button, the color-inverted region will
replace the original time range as the new period the program displays. If you click on
the left button without holding down and dragging it, the command will be the same as
5-76
Page 78

clicking on the Pull Bar in the same x-axis position. That means the Playback system
will be shifted to the appointed time and shows the video in the displaying frame. The
dark regions in the histogram area means there is no media data existed in these
intervals. If you click on these regions, a warning message will pop up.
5.6 26BPreview (Multiple Frame) Mode
You can enter the event Preview mode only if you have changed the playback method
selector to “Events Preview”. This can help you to identify the objects that triggered
the events, not only by the time information and the alert percentage in the histogram
area but also by playing the real video preview. This allows you to easily distinguish
between different alert situations. Under the Event Preview mode, the Pull Bar,
“Transducer” button in the exporting toolbox, and the Display Adjustment Toolbox are
disabled. The two labels under the Pull Bar show both the number of displayed
events and the total event count. There are nine frames in the display area that we
call one “page”. Each of the nine frames on each page displays a different video
sequence event. Each event displayed will be of at least 10 seconds in length. You
can use the “Page Up” and “Page Down” button in Page Control to browse the events
in the selected period, up to nine events per page. There is also page status informing
you the current page number and the total page count (as shown in XFigure 5-9X).
5-77
Page 79

Page Status
Displayed Event Number
Histogram Area
Total Event Count
Page Up
Page Down
Figure 5-9 Preview Mode
5.6.1 59BHistogram Area
The Histogram Area in the event Preview mode shows the event occuring time and
the percentage of the detected motion with red bars. It also indicates the current
displayed events with green bars and the selected event with blue bars. If you want to
access the Histogram Area, you must change the area selection indicator to the
Histogram Area. You can then mark a color-inverted region over it by holding down
the left mouse button and drag the cursor to the desired area (as shown in XFigure
5-10X).
Inverted Region
Selected event
Dark Region
Figure 5-10 Histogram Area in Preview Mode
Displaying events
As you release the left mouse button, the color-inverted region will be enlarged to fill
the entire histogram area. This color-inverted region will become the new period the
program is going to display. If you click on the left mouse button without holding down
and dragging it, the display area will show the event page closest to the point you
5-78
Page 80

have selected. The dark regions means there is no video sequence existed in these
intervals. If you click on these regions, a warning dialog will pop up.
5.6.2 60BHistogram Legend
Figure 5-11 Legend of the Histogram
XFigure 5-11X shows the legends corresponding to the colors represented in the
histogram. You can call up this diagram by clicking on the Legend button.
5.7 27BUsing Tools
This section discusses the method of how to use the tools in the control area, as
shown in XFigure 5-1X.
5.7.1 61BSelector Tools
XFigure 5-12X shows the Selector tools. These are: Location Selector , Period Start Time
Selector for the selection of the beginning time, Period End Time Selector for the
selection of the ending time, Playback Method Selector, and Alert Area Selector.
5-79
Page 81

Figure 5-12 Selector Tools
5.7.1.1 87BLocation Selector
The Location Selector lets you select the camera you want to view from (refer to
XFigure 5-12X). The location information is the same as the location name associated
with the dedicated channel in the Monitor program. If there are more than one time
segments in the same location, another dialog will appear (as shown in XFigure 5-13X).
You must select an interval in that dialog. If your selection is cor rect, the Playback
program will automatically switch to that location and start to display.
Figure 5-13 Time Interval Selection Dialog
5.7.1.2 88BPeriod Selector
Period Selector provides you a precise way to choose the start time and the end time
of a new period. The end time should be larger than the start time. After you have
given the correct start and end times, clicking on the “Play” button in the Jog Dial. The
system will display the new period in the display area and change the period start and
the end time labels. The Pull Bar and Histogram Area will be changed, too. If the
selected period is not present in the database, the data in the period selector will be
changed back to the previously correct start and end times and a warning message
5-80
Page 82

will be shown.
5.7.1.3 89BPlayback Method Selector
Full Range
If you select this method, the database will be displayed from the beginning to the end
of this location. Any change in the period selector will have no effect unless you
change this selector to “Time Period”.
Time Period
If you change the playback method to “Time Period”, you can modify the start and end
times in the period selector. When you click on the “Play” button in the Jog Dial, the
period you have selected will be displayed.
Events Preview
This method changes the display mode from the Normal display mode to the Event
Preview mode or vice versa.
The program will save the previous start and end time settings in “Time Period” mode.
Therefore, if you want to change the Period Selector to see in another period, you
must first use the Playback Method Selector to change to the mode you want to use.
Otherwise, the Period Selector will revert back to the previous period when you last
changed the playback method.
5.7.1.4 90BAlert Area Selector
In the Preview mode, the Playback program only shows one type of the alert events
each time. If you want to see the other type of events, you must use the Alert Area
Selector to change to other event type. In the Normal display mode, the alert type that
the Alert Area Selector indicates will be highlighted with a red rectangle. The Alert
Area Selector will be changed to alert window 1 by default settings when you change
the location selector.
5.7.2 62BPlay Control
For Play Control, we used a jog dial, as shown in XFigure 5-14X, to make it easier to
control video sequence display. Except for the “Play” button, all other buttons can
control the displaying frame in the Normal display mode and the selected displaying
frame in the event Preview mode.
5-81
Page 83

Speed Indicator
Play from beginning
Pause/Resume
Step Forward
Stop
Figure 5-14 Jog Dial
Play from Beginning
The “Play” button we support here is an intelligent user-interface. The functionality of
this button can vary to fit different circumstances. In the Normal display mode, click on
the “Play” button restarts the displaying video sequence. In the Preview mode, if you
do not change the data of the period selector, clicking on this button restarts the
selected displaying frame. If the data of the period selector has been changed,
clicking on the “Play” button restarts all frames to display the first nine events in the
new period.
Stop
When you want to stop displaying the video sequence, you can click on the “Stop”
button. Note that once you had pressed the “Stop” button, the start point will be reset
to the beginning of the present period.
Pause/Resume
The “Pause” button provides you a way to pause video sequence display. When the
displaying video is paused, clicking on the “Pause” button again will resume video
display.
Step Forward
This button is valid only when the displaying video sequence is paused. Each time the
“Step Forward” button is clicked, it will display the next frame in that period
Fast Play and Slow Play
We support up to a maximum of x16 fast forward play and a minimum of 1/16 slow
forward play. This function provides you with more flexibility in browsing through the
surveillance database. If you want to change the playing speed, you only need to
move the speed indicator. To increase playing speed, move the indicator in the
5-82
Page 84

clockwise direction. To decrease playing speed, move it in the counterclockwise
direction. Current speed you are set at will be shown in the second column of the
status area.
NOTE: You can press Ctrl key and the corresponding button introduced above
simultaneously to stop/pause/resume/play all events in event preview mode.
5.7.3 63BDisplay Adjustment T oolbox
When you move the mouse cursor over to the displaying area, the display adjustment
toolbox will appear. Using the display adjustment toolbox, you can change the
displaying video sequence to the size you want to see in the Normal display mode.
Move the area selection indicator to the display area. XFigure 5-15X shows the display
adjustment toolbox and its own three elements, i.e. “Zoom In”, “Zoom Out”, and “Full
Screen”.
Figure 5-15 Display Adjustment Toolbox
5.7.3.1 91BZoom In
Each time you click on the “Zoom In” button the image size in the display area
will be magnified 12.5 percent of the original size. Due to the limitation of the
display area size, the maximum zoom in size we support here is 792 x 540 for NTSC
modulation mode, 660 x 540 for PAL modulation mode and 720 x 540 for CMOS
modulation. If you want to see the image in more details, you can use the Full Screen
function we support in the same toolbox.
5.7.3.2 92BZoom Out
Each time you click on the “Zoom Out” button, the image size in the display
area will be minified 12.5 percent to the original size. In order to completely
show the location and time, the minimum zoom out ratio is limited to 0.5:1.
5-83
B
Page 85

5.7.3.3 Full Screen
When you click on the “Full Screen” button, the video sequence will be
enlarged to fill up the entire screen instantly. You can double-click on the
mouse button in any area on the screen, or press the “ESC” key to return to the
original state.
5.7.4 64BSearching Range Adjustment Toolbox
When you move the mouse cursor over to the Histogram Area, the Searching Range
Adjustment Toolbox will appear in the same position as that of the Display Adjustment
Toolbox. The Searching Range Adjustment Toolbox provides you a faster way to
change the range of the displayed time period. By using this toolbox, you can browse
the database of one location from any 10-second interval of the entire range. XFigure
5-16X shows the searching range adjustment toolbox composed of its own three
elements, i.e. “Zoom In”, “Zoom Out”, and “Full Range”.
Figure 5-16 Searching Range Adjustment Toolbox
5.7.4.1 94BZoom In
Each time you click on the “Zoom In” button in the Searching Range
Adjustment Toolbox, the displayed time period will be half of the original time
period until the period is equal to 10 seconds, the minimum. You can see the new
interval in more details. The scale of Pull Bar and Histogram Area will change, as well
as that of the period start and end time. The Period Selector will show the new start
and end time. The Display Area will restart to display the new period from the newly
defined start time.
5.7.4.2 95BZoom Out
Each time you click on the “Zoom Out” button in the Searching Range
Adjustment Toolbox, the displayed time period will be doubled, unless the
start time or end time exceeds the location time-boundary. The scale of the Pull Bars
and Histogram Area will also be changed. The Period Selector will show the new start
and end time. And the Display Area will restart to display the new period from the
5-84
Page 86

newly defined start time.
5.7.4.3 96BFull Range
Clicking on the “Full Range” button would yield the same effect as you would
in the Playback Method.
5.7.5 65BToolbox
In our playback program, you can check the database and you can export the
database to other media. Using the toolbox, you can export the database into other
more portable formats, such as AVI file, bitmap file, or paper (hard-copy). You can
also use Windows media player or other programs to browse the exporting data.
Under Normal display mode, you can use all the exporting tools. Under Preview mode,
only snapshot and print can be used. XFigure 5-17X shows the elements of the toolbox.
Figure 5-17 Toolbox
5.7.5.1 97BTransducer
Using the Transducer tool, you can transpose the displaying video sequence
to AVI file. Click on the “Transducer” button and the conversion procedure will
start. The speed of exporting data depends on the speed of the computer’s processor .
During any time of the exporting interval, you can click on the “Transducer” button
again to stop the procedure in process. You will get an AVI file from the start time to
the time you click on the “Transducer” button. The exported AVI filename will be
generated automatically and listed in the fourth column of the status area. If you want
to change the AVI file output directory, you can go to the Settings window as we have
described in Section
X5.4X. To get a better quality of exporting AVI file, it is suggested to
set the video format to normal size (please refer to Section X3.4X “XCamera
Configurations
X”).
5.7.5.2 98BSnapshot
image shown in the display area. In the Preview mode, it is the image that you
Each time you click on the “Snapshot” button you can make the program
export a bitmap file. In the Normal display mode, the exporting bitmap is the
5-85
Page 87

selected through the frame selection indicator. The size of the bitmap will be the same
as the source image you have selected. The exported bitmap filename will be
generated automatically and be listed in the fourth column of the status area. If you
want to change the bitmap file output directory, you can go to the Settings window as
we have described in Section X5.4X under “XSettingsX”.
5.7.5.3 99BPrint
When you click on the “Print” button, a printing dialog will appear. After you
have made your selection and send it to the printer, the images in the display
area will be printed out. The printing functionality is designed based on the idea,
“what you see is what you get”. Therefore, the output data will be the same as
whatever you see in the display area.
5.7.5.4 100BVolume
When you click on the “V olume” button, a volume control dialog (X Figure 5-18X)
will appear. After you have made your selection, it will change the volume to
the value you have selected. You can also check the mute checkbox to silent the
system.
Figure 5-18 Volume Control Dialog
5.7.6 66BSystem Control Toolbox
The System Control Toolbox provides you some basic operations for the Playback
program. XFigure 5-19X shows the elements of the System Control Toolbox, i.e. “Lock
Program”, “Settings”, “Minimize”, and “Exit”.
Figure 5-19 System Control Toolbox
5-86
Page 88

5.7.6.1 101BLock Program
If you are to be away from your computer, for security concerns, we suggest
you lock the Playback program. You can simply click on the “Lock Window”
button to lock the main window. Once this is invoked, the main window will be hidden
and the login dialog will appear (as shown in XFigure 2-2X). To return to the main
window, you need to re-enter the root’s password or the password of the user who
locked the application.
5.7.6.2 102BSettings
The Settings dialog pops up when you click on the “Settings” button. For more
information about setting this program, please refer to Section X5.4X “XSettingsX”.
5.7.6.3 103BMinimize
The Playback program will be minimized as you click on the “Minimize” button.
You can invoke Playback again by clicking on the playback window on the
task bar or choose Playback from the Launcher.
5.7.6.4 104BExit
The Playback program will close as you click on the “Exit” button. If the AVI
exporting procedure is running, this procedure will be stopped first.
5-87
 Loading...
Loading...