Page 1

TL-ER5120
Gigabit Load Balance Broadband Router
REV2.0.0
1910010931
Page 2
COPYRIGHT & TRADEMARKS
Specifications are subject to change without notice. is a registered trademark of
TP-LINK TECHNOLOGIES CO., LTD. Other brands and product names are trademarks of their
respective holders.
No part of the specifications may be reproduced in any form or by any means or used to make any
derivative such as translation, transformation, or adaptation without permission from TP-LINK
TECHNOLOGIES CO., LTD. Copyright © 2013 TP-LINK TECHNOLOGIES CO., LTD. All rights
reserved.
http://www.tp-link.com
FCC STATEMENT
This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference when the equipment is operated in a commercial environment. This
equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in
accordance with the instruction manual, may cause harmful interference to radio communications.
Operation of this equipment in a residential area is likely to cause harmful interference in which case
the user will be required to correct the interference at his own expense.
This device complies with part 15 of the FCC Rules. Operation is subject to the following two
conditions:
1) This device may not cause harmful interference.
2) This device must accept any interference received, including interference that may cause
undesired operation.
Any changes or modifications not expressly approved by the party responsible for compliance could
void the user’s authority to operate the equipment.
CE Mark Warning
This is a class A product. In a domestic environment, this product may cause radio interference, in
which case the user may be required to take adequate measures.
-I-
Page 3
Продукт сертифіковано згідно с правилами системи УкрСЕПРО на відповідність вимогам
нормативних документів та вимогам, що передбачені чинними законодавчими актами України.
Safety Information
z When product has power button, the power button is one of the way to shut off the product; When
there is no power button, the only way to completely shut off power is to disconnect the product or
the power adapter from the power source.
z Don’t disassemble the product, or make repairs yourself. You run the risk of electric shock and
voiding the limited warranty. If you need service, please contact us.
z Avoid water and wet locations.
安全諮詢及注意事項
●請使用原裝電源供應器或只能按照本產品注明的電源類型使用本產品。
●清潔本產品之前請先拔掉電源線。請勿使用液體、噴霧清潔劑或濕布進行清潔。
●注意防潮,請勿將水或其他液體潑灑到本產品上。
●插槽與開口供通風使用,以確保本產品的操作可靠並防止過熱,請勿堵塞或覆蓋開口。
●請勿將本產品置放於靠近熱源的地方。除非有正常的通風,否則不可放在密閉位置中。
●請不要私自打開機殼,不要嘗試自行維修本產品,請由授權的專業人士進行此項工作。
此為甲類資訊技術設備,于居住環境中使用時,可能會造成射頻擾動,在此種情況下,使用者會被要求
採取某些適當的對策。
This product can be used in the following countries:
AT BG BY CA CZ DE DK EE
ES FI FR GB GR HU IE IT
LT LV MT NL NO PL PT RO
RU SE SK TR UA
-II-
Page 4

CONTENTS
Package Contents..................................................................................................................1
Chapter 1 About this Guide
1.1 Intended Readers ..................................................................................................................2
1.2 Conventions ...........................................................................................................................2
1.3 Overview of this Guide...........................................................................................................2
Chapter 2 Introduction
2.1 Overview of the Router ..........................................................................................................4
2.2 Features.................................................................................................................................5
2.3 Appearance............................................................................................................................6
2.3.1 Front Panel ................................................................................................................6
2.3.2 Rear Panel.................................................................................................................7
Chapter 3 Configuration
3.1 Network..................................................................................................................................8
...................................................................................................2
..........................................................................................................4
........................................................................................................8
3.1.1 Status.........................................................................................................................8
3.1.2 System Mode.............................................................................................................9
3.1.3 WAN ........................................................................................................................ 11
3.1.4 LAN..........................................................................................................................29
3.1.5 DMZ.........................................................................................................................33
3.1.6 MAC Address...........................................................................................................34
3.1.7 Switch ......................................................................................................................36
3.2 User Group ..........................................................................................................................42
3.2.1 Group.......................................................................................................................43
3.2.2 User .........................................................................................................................43
3.2.3 View.........................................................................................................................44
3.3 Advanced .............................................................................................................................45
3.3.1 NAT..........................................................................................................................45
3.3.2 Traffic Control ..........................................................................................................54
-III-
Page 5

3.3.3 Session Limit ...........................................................................................................58
3.3.4 Load Balance...........................................................................................................59
3.3.5 Routing ....................................................................................................................64
3.4 Firewall.................................................................................................................................70
3.4.1 Anti ARP Spoofing ...................................................................................................70
3.4.2 Attack Defense ........................................................................................................73
3.4.3 MAC Filtering ...........................................................................................................75
3.4.4 Access Control.........................................................................................................76
3.4.5 App Control..............................................................................................................82
3.5 Services ...............................................................................................................................84
3.5.1 PPPoE Server..........................................................................................................84
3.5.2 E-Bulletin .................................................................................................................90
3.5.3 Dynamic DNS ..........................................................................................................91
3.5.4 UPnP .......................................................................................................................97
3.6 Maintenance ........................................................................................................................99
3.6.1 Admin Setup ............................................................................................................99
3.6.2 Management..........................................................................................................102
3.6.3 Statistics.................................................................................................................104
3.6.4 Diagnostics ............................................................................................................106
3.6.5
Time.......................................................................................................................108
3.6.6 Logs....................................................................................................................... 110
Chapter 4 Application
4.1 Network Requirements.......................................................................................................112
........................................................................................................112
4.2 Configurations....................................................................................................................112
4.2.1 Internet Setting ......................................................................................................112
4.2.2 Network Management............................................................................................ 115
4.2.3 Network Security.................................................................................................... 119
Chapter 5 CLI….
................................................................................................................125
-IV-
Page 6

5.1 Configuration......................................................................................................................125
5.2 Interface Mode ...................................................................................................................128
5.3 Online Help ........................................................................................................................129
5.4 Command Introduction.......................................................................................................131
5.4.1 ip............................................................................................................................131
5.4.2 ip-mac....................................................................................................................131
5.4.3 sys .........................................................................................................................132
5.4.4 user........................................................................................................................133
5.4.5 history ....................................................................................................................134
5.4.6 exit .........................................................................................................................135
Appendix A Hardware Specifications
Appendix B FAQ
Appendix C Glossary
.........................................................................................................137
..................................................................................................139
...........................................................................136
-V-
Page 7
Package Contents
The following items should be found in your box:
¾ One TL-ER5120 Router
¾ One Power Cord
¾ One Console Cable
¾ Two mounting brackets and other fittings
¾ Quick Installation Guide
¾ Resource CD
Note:
Make sure that the package contains the above items. If any of the listed items are damaged or
missing, please contact with your distributor.
-1-
Page 8

Chapter 1 About this Guide
This User Guide contains information for setup and management of TL-ER5120 router. Please read
this guide carefully before operation.
1.1 Intended Readers
This Guide is intended for Network Engineer and Network Administrator.
1.2 Conventions
In this Guide the following conventions are used:
¾ The router or TL-ER5120 mentioned in this Guide stands for TL-ER5120 Gigabit Load Balance
Broadband Router without any explanation.
¾ Menu Name→Submenu Name→Tab page indicates the menu structure. Advanced→NAT
→Basic NAT means the Basic NAT page under the NAT menu option that is located under the
Advanced menu.
¾ Bold font indicates a toolbar icon, menu or menu item.
¾ <Font> indicate a button.
Symbols in this Guide:
Symbol Description
Ignoring this type of note might result in a malfunction or damage to the
Note:
Tips:
device.
This format indicates important information that helps you make better use of
your device.
1.3 Overview of this Guide
Chapter 1 About This Guide Introduces the guide structure and conventions.
Chapter 2 Introduction Introduces the features and appearance of TL-ER5120 router.
Chapter 3 Configurations Introduces how to configure the router via Web management page.
Chapter 4 Application Introduces the practical application of the router on the enterprise
network.
Chapter5 CLI Introduces how to log in and set up the router using CLI commands by
console port.
-2-
Page 9

Appendix A Hardware
Lists the hardware specifications of this router.
Specifications
Appendix B FAQ Provides the possible solutions to the problems that may occur during
the installation and operation of the router.
Appendix C Glossary Lists the glossary used in this guide.
-3-
Page 10

Chapter 2 Introduction
Thanks for choosing the Gigabit Load Balance Broadband Router TL-ER5120.
2.1 Overview of the Router
The Gigabit Load Balance Broadband Router TL-ER5120 from TP-LINK possesses excellent data
processing capability and multiple powerful functions including Load Balance, Access Control,
Bandwidth Control, Session Limit, IM/P2P Blocking, PPPoE Server and so on, which consumedly
meet the needs of small and medium enterprise, hotels and communities with volumes of users
demanding a efficient and easy-to-manage network with high security.
z Powerful Data Processing Capability
+ Built-in MIPS64 network processor and 128MB DDRII high-speed RAM allows the stability and
reliability for operation.
z Online Behavior Management
+ Complete Functions of Access Rules can allow managers to select the network service levels to
block or allow applications of FTP downloading, Email, Web browsing and so on.
+ Deploying One-Click restricting of IM/P2P applications to save time & energy while reserving
exceptional groups for certain users.
+ Supporting URL Filtering to prevent potential hazards from visiting the malicious Web sites.
z Powerful Firewall
+ Supporting One-Click IP-MAC Binding to avoid ARP spoofing and guarantee a network without
stagnation.
+ Featured Attack Defense to protect the network from a variety of flood attack and packet
anomaly attack.
+ Possessing MAC Filtering function to block the access of illegal hosts.
z Flexible Traffic Control
+ Featured Bandwidth Control with flexible bandwidth management to automatically control the
bandwidth of the host in bi-direction to avoid bandwidth over occupation, as well as optimize
bandwidth usage.
+ Supporting Session Limit to avoid the complaint of a few people to force whole sessions.
z Multi-WAN Ports
+ Providing three adjustable 10/100/1000M WAN/LAN ports for users to configure the amount of
WAN ports based on need and connect multiple Internet lines for bandwidth expansion.
+ Supporting multiple Load Balance modes, including Bandwidth Based Balance Routing,
Application Optimized Routing, and Policy Routing to optimize bandwidth usage.
-4-
Page 11

+ Featured Link Backup to switch all the new sessions from dropped line automatically to another
for keeping an always on-line network.
z Easy-to-use
+ Providing easy-to-use GUI with clear configuration steps and detailed help information for the
users to configure the router simply.
+ Helping administrators to monitor the whole network status and take actions to malfunctions
according to the recorded log information.
+ Supporting remote management to manage the router from remote places.
2.2 Features
Hardware
¾ 1 fixed gigabit WAN port (port 1), 3 adjustable gigabit WAN/LAN ports, 1 LAN/DMZ port (port 5)
and 1 Console port
¾ Built-in high-quality power supply with non-fun system design for quietness
¾ Possesses standard-sized, 19-inch outfit for standard rack
¾ Supports Professional 4kV common mode
¾ Complies with IEEE 802.3, IEEE 802.3u, IEEE 802.3ab standards
¾ Supports TCP/IP, DHCP, ICMP, NAT, NAPT protocols
¾ Supports PPPoE, SNTP, HTTP, DDNS, UPnP, NTP protocols
Basic Functions
¾ Supports Static IP, Dynamic IP, PPPoE/Russian PPPoE, L2TP/Russian L2TP, PPTP/Russian
PPTP, Dual Access, BigPond Internet connections
¾ Supports Virtual Server, Port Triggering, ALG, Static Route and RIP v1/v2
¾ Built-in Switch supporting Port Mirror, Port VLAN, Rate Control and so on
¾ Supports to change the MAC address of LAN, WAN, DMZ port
¾ Supports Logs, Statistics, Time setting
¾ Supports Remote and Web management
lightning protection
¾ Supports Diagnostic (Ping/Tracert) and Online Detection
Traffic Control
¾ Supports Bandwidth Control
¾ Supports Session Limit
Security
¾ Built-in firewall supporting URL/MAC Filtering
-5-
Page 12

¾ Supports Access Control
¾ Supports Attack Defense
¾ Supports IP-MAC Binding
¾ Supports GARP (Gratuitous ARP)
¾ Deploys One-Click restricting of IM/P2P applications
2.3 Appearance
2.3.1 Front Panel
The front panel of TL-ER5120 is shown as the following figure.
z
LEDs
LED Status Indication
On The router is powered on
PWR
Off The router is powered off or power supply is abnormal
Flashing The router works properly
SYS
On/Off The router works improperly
On There is a device linked to the corresponding port
Link/Act
Speed
Off There is no device linked to the corresponding port
Flashing The corresponding port is transmitting or receiving data
On (Green) The linked device is running at 1000Mbps
On (Yellow) The linked device is running at 100Mbps
WAN
DMZ
Off
On The port is working in WAN mode
Off The port is working in LAN mode
On The port is working in DMZ mode
Off The port is working in LAN mode
There is no device linked to the corresponding port or the
linked device is running at 10Mbps
-6-
Page 13

z
Interface Description
Interface Port Description
WAN 1~4
The WAN port is for connecting the router to a DSL/Cable
modem or Ethernet by the RJ45 cable
LAN 2~5
The LAN port is for connecting the router to the local PCs or
switches by the RJ45 cable
DMZ 5 The DMZ port is for connecting the router to the servers
Console /
z
Reset button
The Console port is for connecting with the serial port of a
computer or terminal to monitor and configure the router
Use the button to restore the router to the factory defaults. With the router powered on, use a pin to
press and hold the Reset button (about 4~5 seconds). After the SYS LED goes out, release the Reset
button. If the SYS LED is flashing with a high frequency about two or three seconds, it means the router
is restored successfully.
2.3.2 Rear Panel
The rear panel of TL-ER5120 is shown as the following figure.
z
Power Socket
Connect the female connector of the power cord to this power socket, and the male connector to the AC
power outlet. Please make sure the voltage of the power supply meets the requirement of the input voltage
(100-240V~ 50/60Hz).
z
Grounding Terminal
The router already comes with lightning protection mechanism. You can also ground the router through
the PE (Protecting Earth) cable of AC cord or with Ground Cable.
Note:
Please use only the power cord provided with this router.
-7-
Page 14
Chapter 3 Configuration
3.1 Network
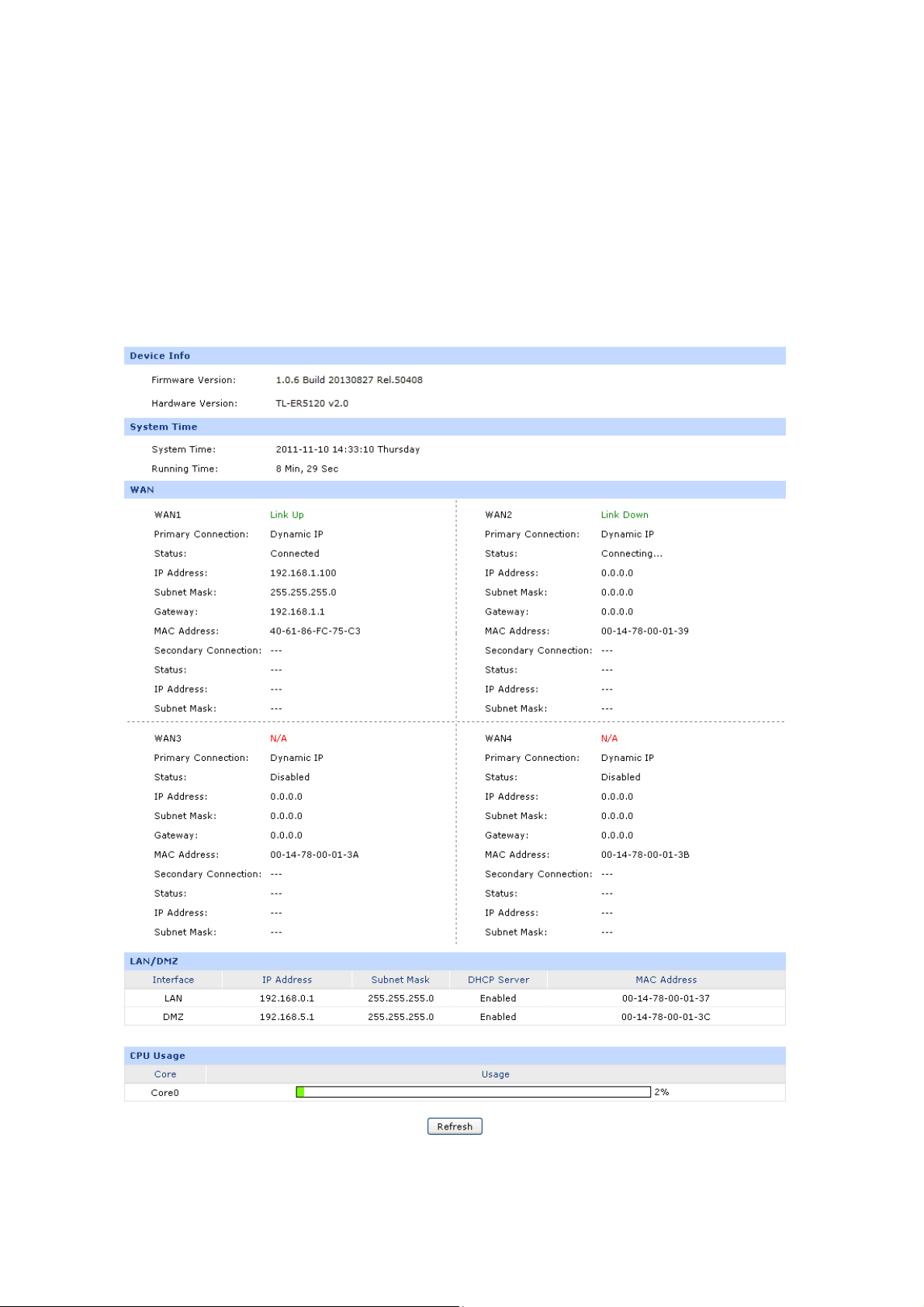
3.1.1 Status
The Status page shows the system information, the port connection status and other information
related to this router.
Choose the menu Network→Status to load the following page.
Figure 3-1 Status
-8-
Page 15
3.1.2 System Mode
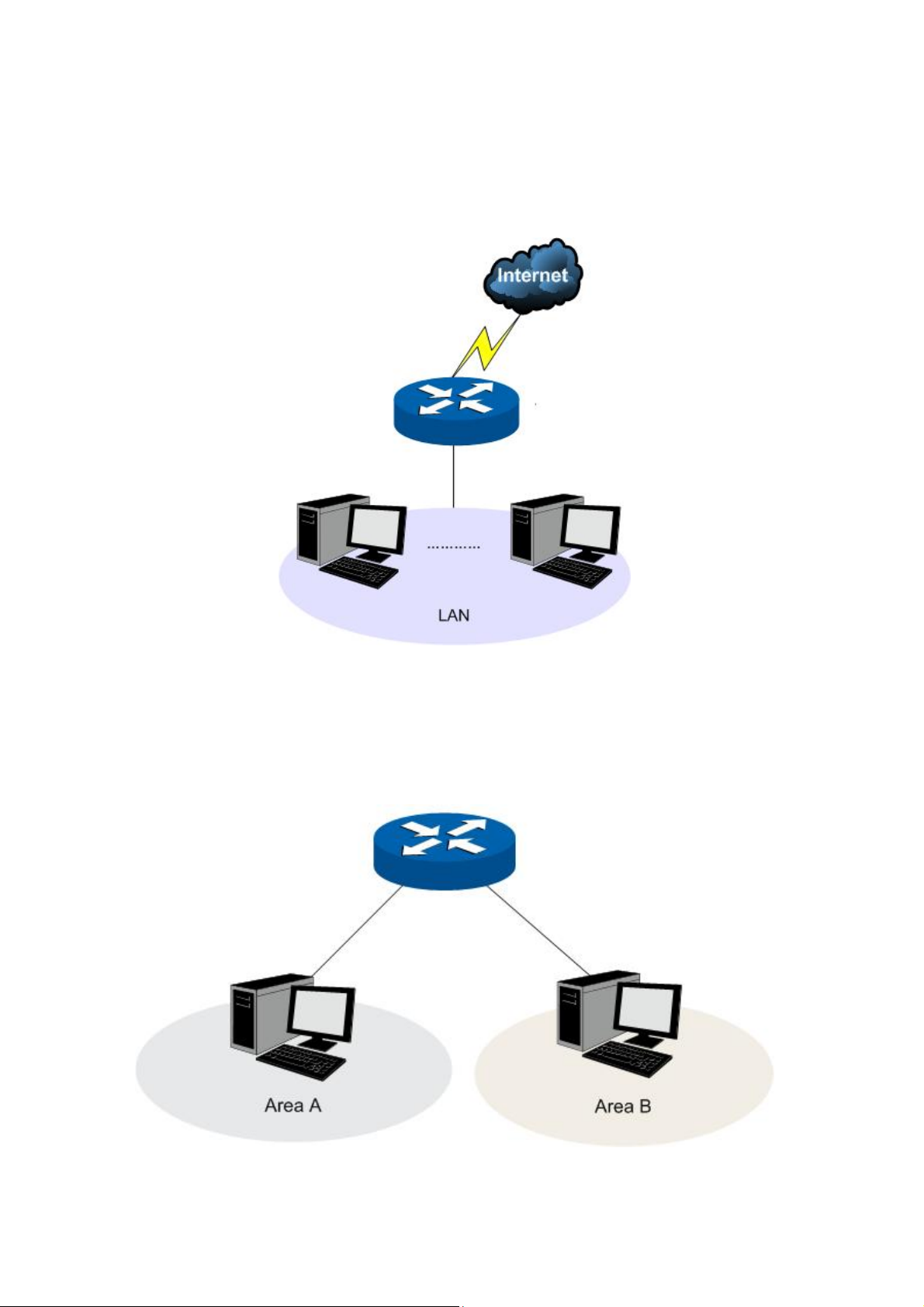
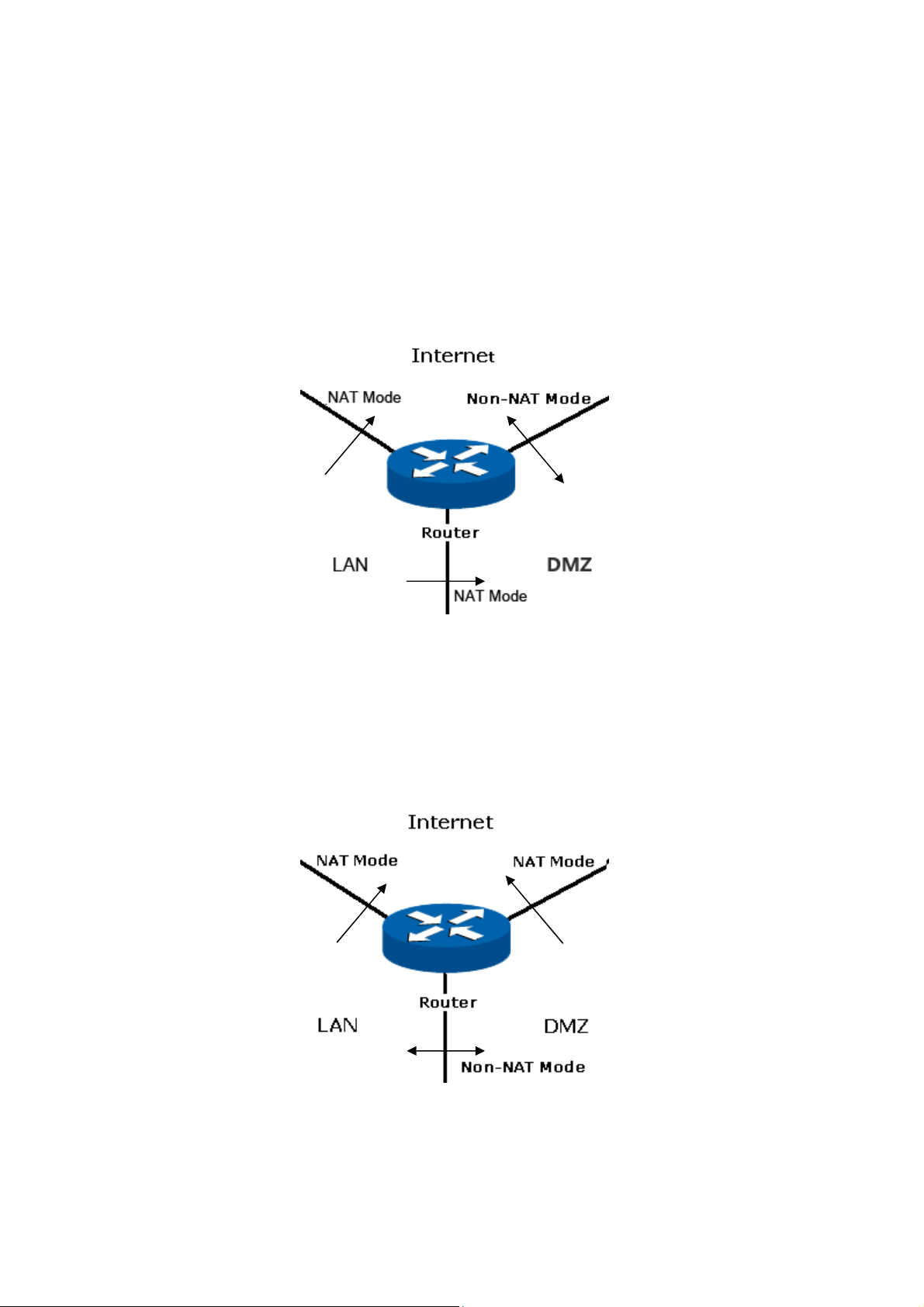
The TL-ER5120 router can work in three modes: NAT, Non-NAT and Classic.
If your router is hosting your local network’s connection to the Internet with a network topology as the
Figure 3-2 shows, you can set it to NAT mode.
Figure 3-2 Network Topology - NAT Mode
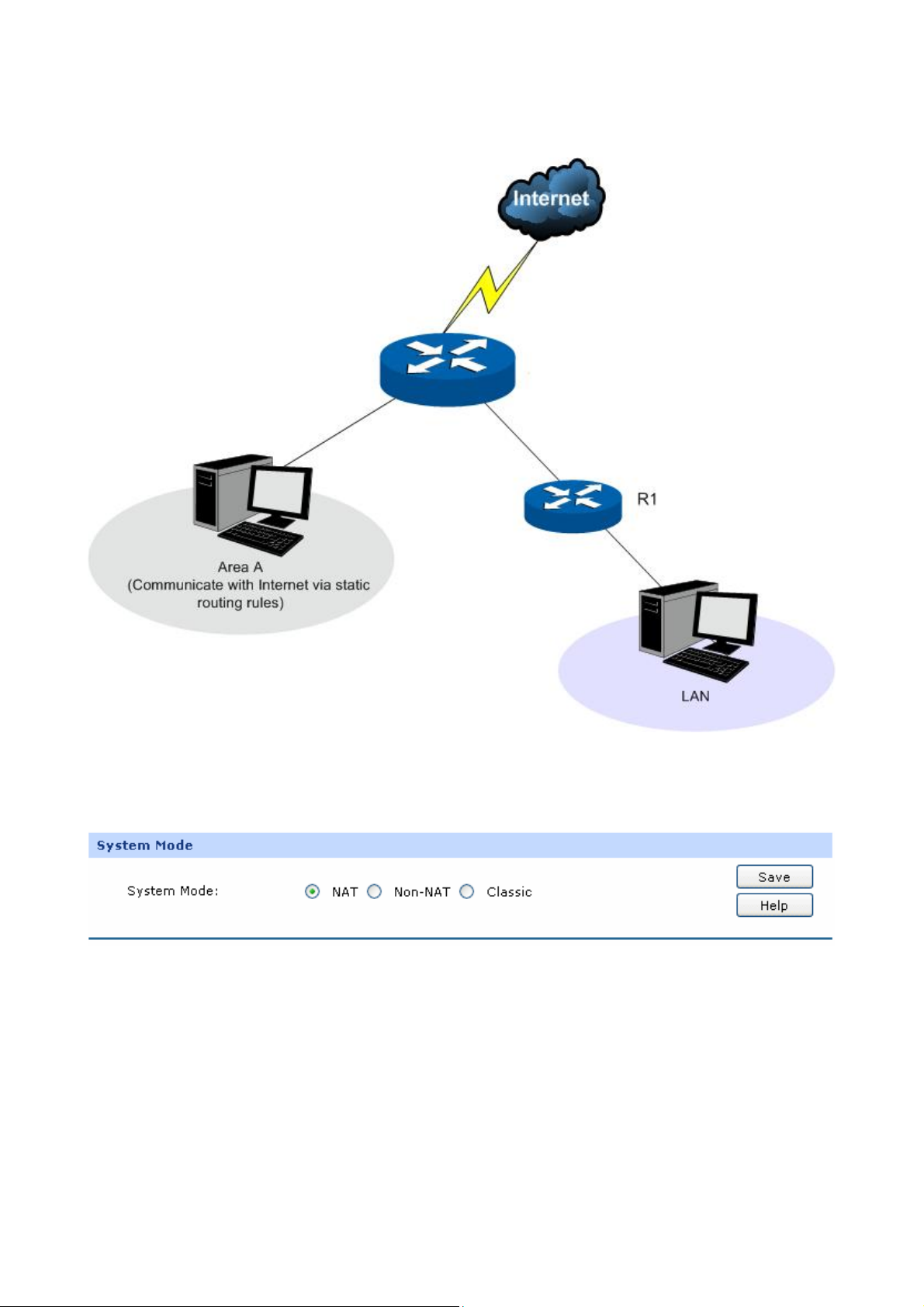
If your router is connecting the two networks of different areas in a large network environment with a
network topology as the Figure 3-3 shows, and forwards the packets between these two networks by
the Routing rules, you can set it to Non-NAT mode.
Figure 3-3 Network Topology – Non-NAT Mode
-9-
Page 16
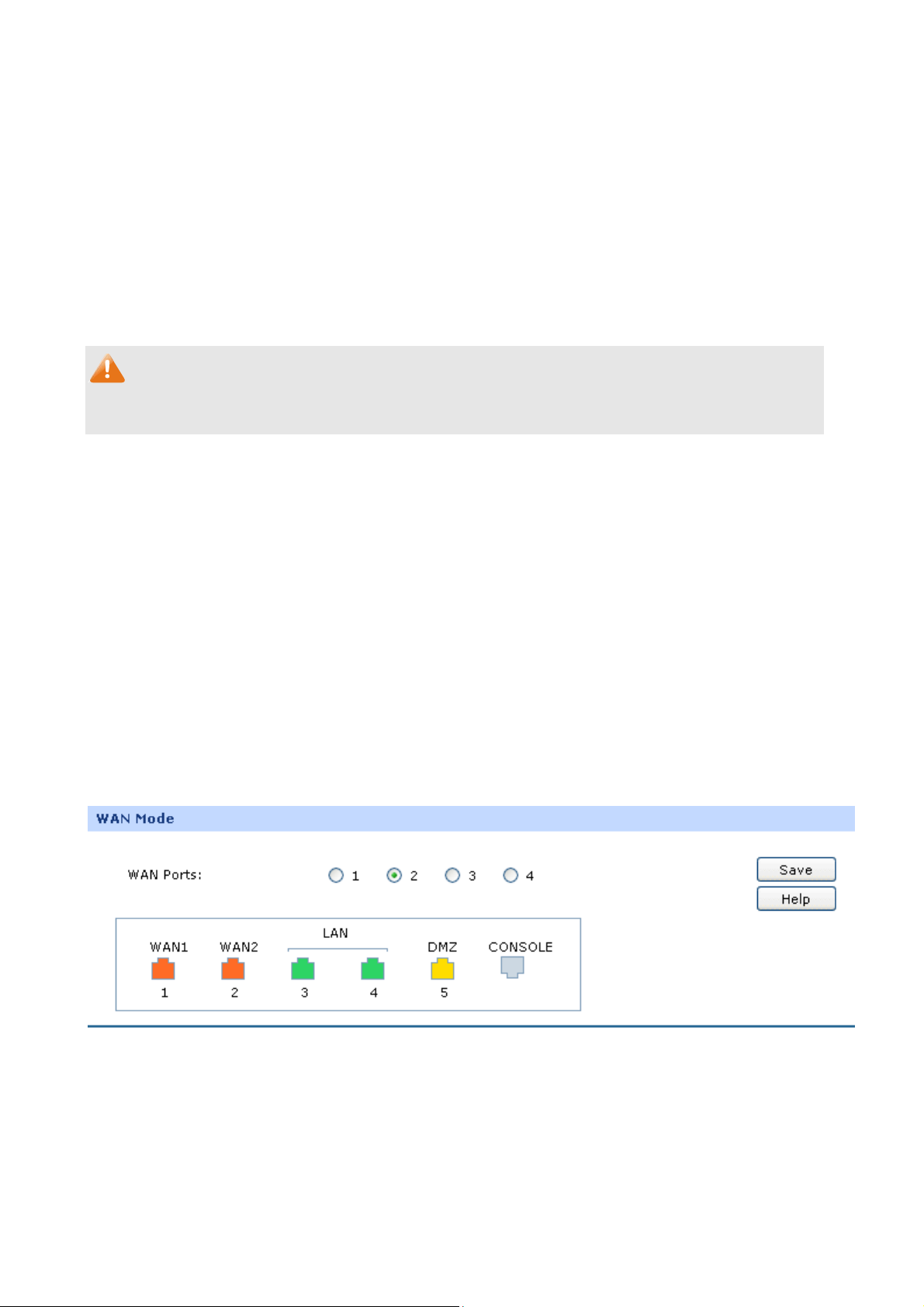
If your router is connected in a combined network topology as the Figure 3-4 shows, you can set it to
Classic Mode.
Figure 3-4 Network Topology – Classic Mode
Choose the menu Network→System Mode to load the following page.
Figure 3-5 System Mode
You can select a System Mode for your router according to your network need.
z NAT Mode
NAT (Network Address Translation) mode allows the router to translate private IP addresses within
internal networks to public IP addresses for traffic transport over external networks, such as the
Internet. Incoming traffic is translated back for delivery within the internal network. However, the router
will drop all the packets whose source IP addresses are in different subnet of LAN port. For example: If
the LAN port of the router is set to 192.168.0.1 for IP address and 255.255.255.0 for the Subnet Mask,
-10-
Page 17
then the subnet of LAN port is 192.168.0.0/24. The packet with 192.168.0.123 as its source IP address
can be transported by NAT, whereas the packet with 20.31.76.80 as its source IP address will be
dropped.
z Non-NAT Mode
In this mode, the router functions as the traditional Gateway and forwards the packets via routing
protocol. The Hosts in different subnets can communicate with one another via the routing rules
whereas no NAT is employed. For example: If the DMZ port of the router is in WAN mode, the Hosts in
the subnet of DMZ port can access the servers in Internet only when the Static router rules permit.
Note:
In Non-NAT mode, all the NAT forwarding rules will be disabled.
z Classic Mode
It's the combined mode of NAT mode and Non-NAT mode. In Classic mode, the router will first
transport the packets which are compliant with NAT forwarding rules and then match the other packets
to the static routing rules. The matched packets will be transmitted based on the static routing rules
and the unmatched ones will be dropped. In this way, the router can implement NAT for the packets
without blocking the packets in the different subnet of the ports.
3.1.3 WAN
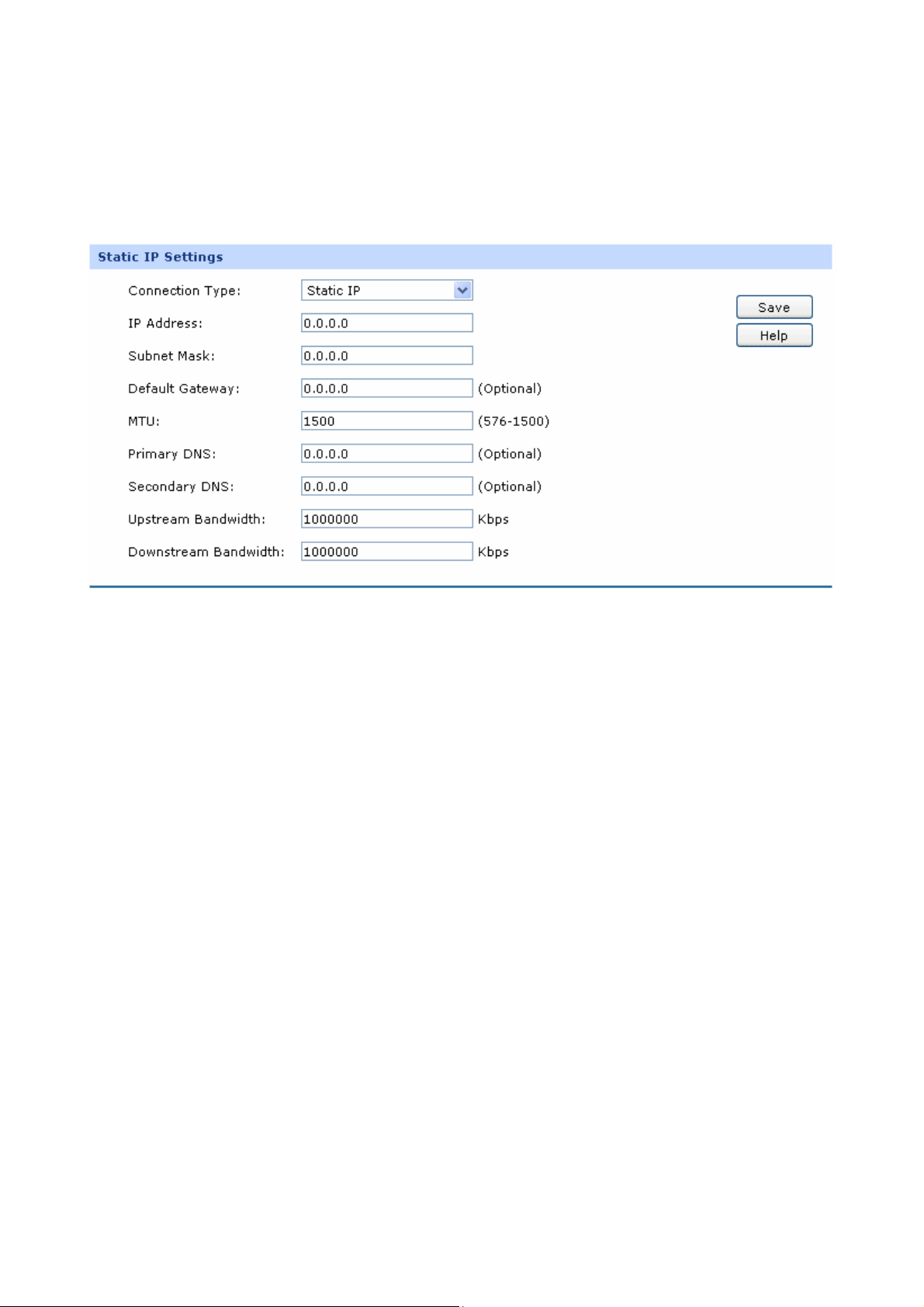
3.1.3.1 WAN Mode
TL-ER5120 provides four available WAN ports. You can set the number of WAN ports on this page.
Choose the menu Network→WAN→WAN Mode to load the following page.
Figure 3-6 WAN Mode
-11-
Page 18

¾ WAN Mode
WAN Ports:
Note:
● By default, TL-ER5120 is set to work in the mode of dual WAN ports.
● Any change to the number of WAN ports may lead to a loss of current configurations. Please be
sure to backup your configurations in advance.
● The DMZ port will not be available if four WAN ports are enabled.
Select the total number of WAN ports you prefer to use.
And the router will adjust the physical ports accordingly,
which can be illustrated on the following port sketch.
3.1.3.2 WAN1
TL-ER5120 provides the following six Internet connection types: Static IP, Dynamic IP, PPPoE/Russian
PPPoE, L2TP/Russian L2TP, PPTP/Russian PPTP and BigPond. To configure the WAN, please first
select the type of Internet connection provided by your ISP (Internet Service Provider).
Tips:
● It’s allowed to set the IP addresses of multiple WAN ports within the same subnet. However, to
guarantee a normal communication, make sure that the WAN ports can access the same network,
such as Internet or a local area network.
● The amount of tab pages for WAN port varies with the number of the WAN ports. For the
configurations of the other WAN ports, please refer to the instructions of WAN1.
-12-
Page 19
Choose the menu Network→WAN→WAN1 to load the configuration page.
1) Static IP
If a static IP address has been provided by your ISP, please choose the Static IP connection type to
configure the parameters for WAN port manually.
Figure 3-7 WAN – Static IP
The following items are displayed on this screen:
¾ Static IP
Connection Type:
Select Static IP if your ISP has assigned a static IP address for your
computer.
IP Address:
Enter the IP address assigned by your ISP. If you are not clear,
please consult your ISP.
Subnet Mask:
Default Gateway:
Enter the Subnet Mask assigned by your ISP.
Optional. Enter the Gateway assigned by your ISP.
MTU:
MTU (Maximum Transmission Unit) is the maximum data unit
transmitted by the physical network. It can be set in the range of
576-1500. The default MTU is 1500. It is recommended to keep the
default value if no other MTU value is provided by your ISP.
-13-
Page 20
Primary DNS:
Enter the IP address of your ISP’s Primary DNS (Domain Name
Server). If you are not clear, please consult your ISP. It’s not allowed
to access the Internet via domain name if the Primary DNS field is
blank.
Secondary DNS:
Upstream Bandwidth:
Downstream
Optional. If a Secondary DNS Server address is available, enter it.
Specify the bandwidth for transmitting packets on the port.
Specify the bandwidth for receiving packets on the port.
Bandwidth:
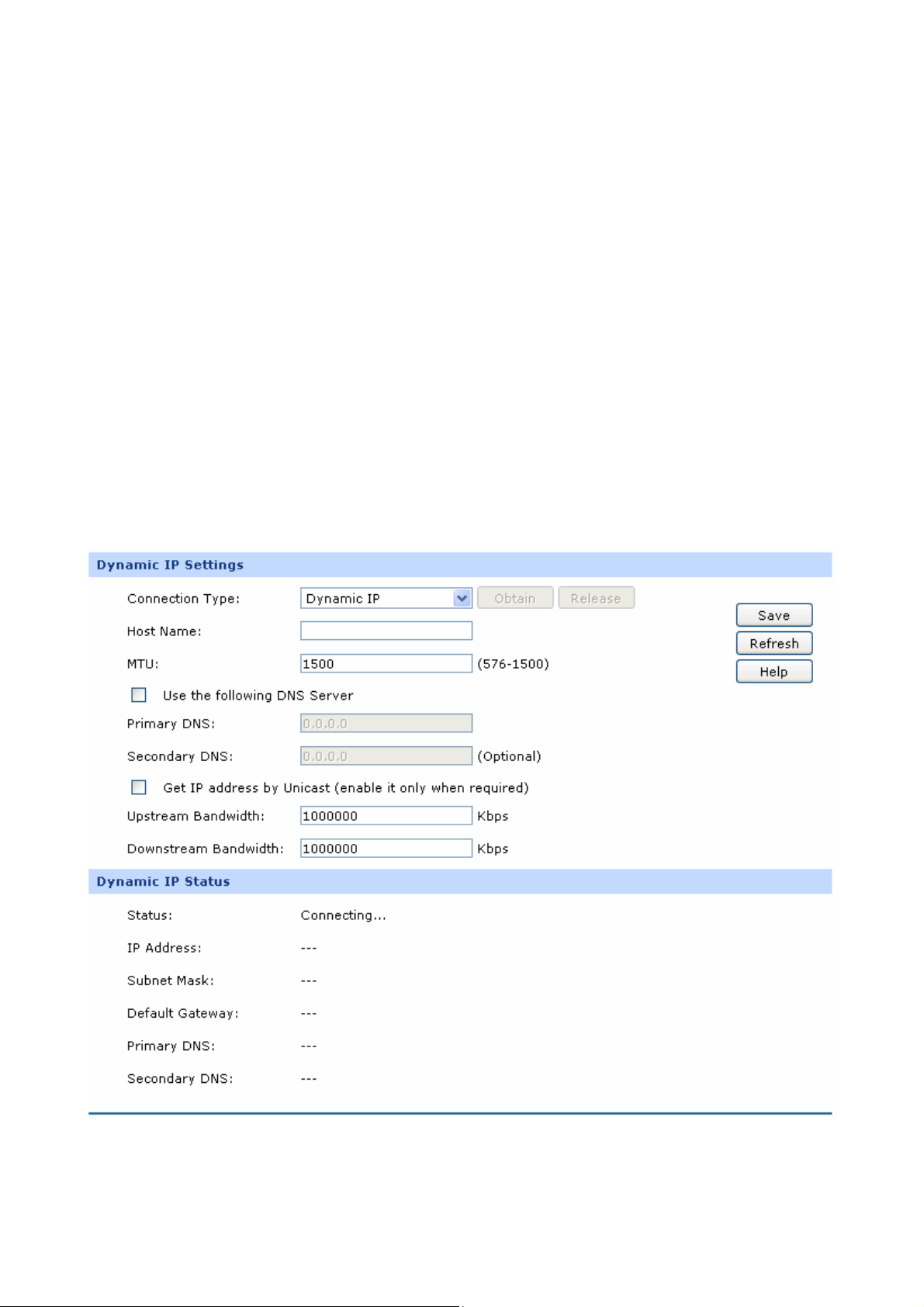
2) Dynamic IP
If your ISP (Internet Service Provider) assigns the IP address automatically, please choose the
Dynamic IP connection type to obtain the parameters for WAN port automatically.
Figure 3-8 WAN – Dynamic IP
-14-
Page 21

The following items are displayed on this screen:
¾ Dynamic IP
Connection Type:
Host Name:
MTU:
Get IP Address by
Unicast:
Select Dynamic IP if your ISP assigns the IP address automatically.
Click <Obtain> to get the IP address from your ISP’s server. Click
<Release> to release the current IP address of WAN port.
Optional. This field allows you to give a name for the router. It's
blank by default.
MTU (Maximum Transmission Unit) is the maximum data unit
transmitted by the physical network. It can be set in the range of
576-1500. The default MTU is 1500. It is recommended to keep the
default value if no other MTU value is provided by your ISP.
The broadcast requirement may not be supported by a few ISPs.
Select this option if you can not get the IP address from your ISP
even with a normal network connection. This option is not required
generally.
Use the following DNS
Server:
Primary DNS:
Secondary DNS:
Upstream Bandwidth:
Downstream
Bandwidth:
Select this option to enter the DNS (Domain Name Server) address
manually.
Enter the IP address of your ISP’s Primary DNS (Domain Name
Server). If you are not clear, please consult your ISP.
Optional. If a Secondary DNS Server address is available, enter it.
Specify the bandwidth for transmitting packets on the port.
Specify the bandwidth for receiving packets on the port.
-15-
Page 22

¾ Dynamic IP Status
Status:
IP Address:
Subnet Mask:
Displays the status of obtaining an IP address from your ISP.
z “Disabled” indicates that the Dynamic IP connection type is not
applied.
z “Connecting” indicates that the router is obtaining the IP
parameters from your ISP.
z “Connected” indicates that the router has successfully obtained
the IP parameters from your ISP.
z “Disconnected” indicates that the IP address has been
manually released or the request of the router gets no
response from your ISP. Please check your network connection
and consult your ISP if this problem remains.
Displays the IP address assigned by your ISP.
Displays the Subnet Mask assigned by your ISP.
Gateway Address:
Primary DNS:
Secondary DNS:
Displays the Gateway Address assigned by your ISP.
Displays the IP address of your ISP’s Primary DNS.
Displays the IP address of your ISP’s Secondary DNS.
-16-
Page 23
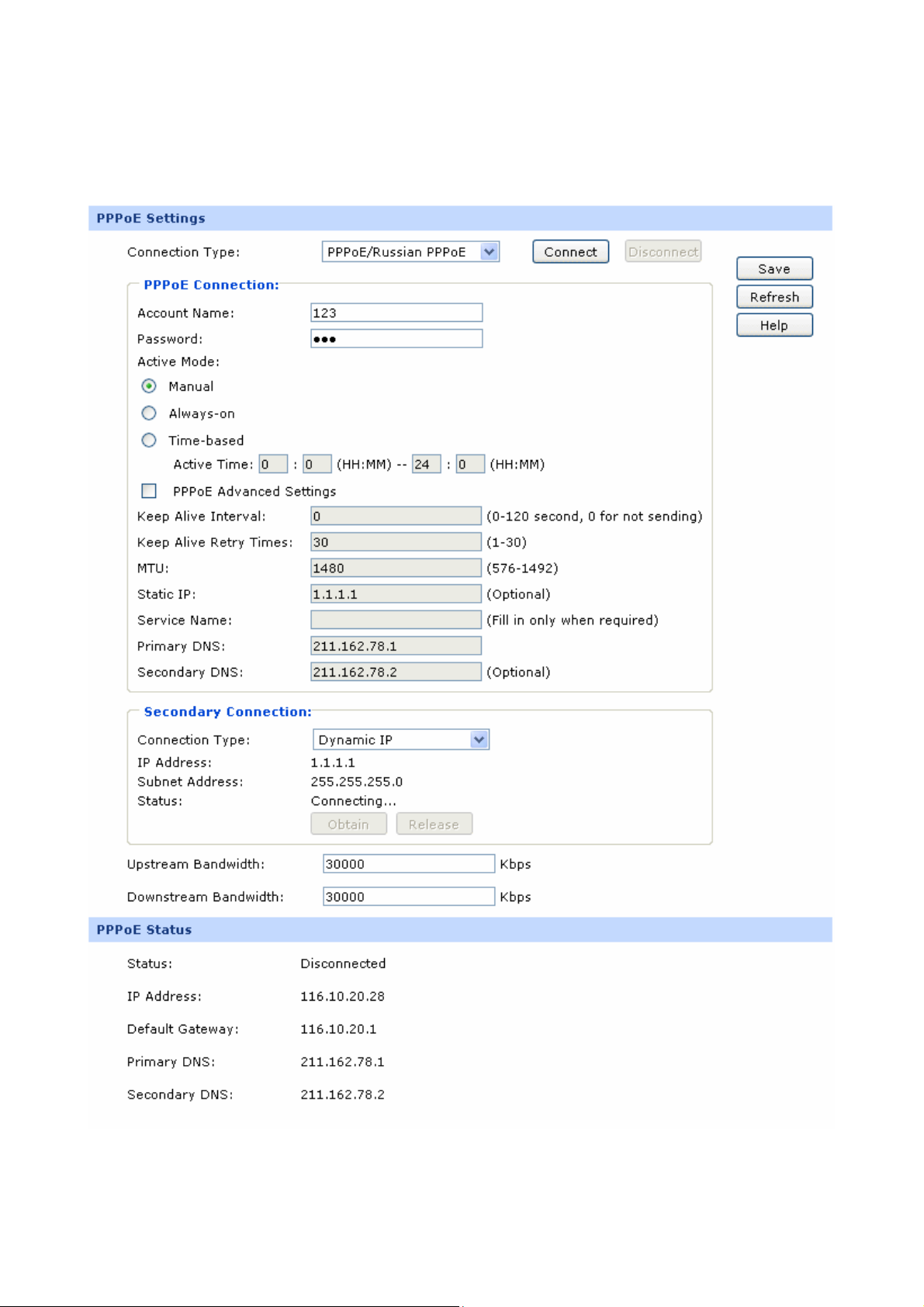
3) PPPoE
If your ISP (Internet Service Provider) has provided the account information for the PPPoE connection,
please choose the PPPoE/Russian PPPoE connection type (Used mainly for DSL Internet service).
Figure 3-9 WAN - PPPoE
The following items are displayed on this screen:
-17-
Page 24

¾ PPPoE Settings
Connection Type:
Account Name:
Password:
Active Mode:
Select PPPoE/Russian PPPoE if your ISP provides xDSL Virtual
Dial-up connection. Click <Connect> to dial-up to the Internet and
obtain the IP address. Click <Disconnect> to disconnect the Internet
connection and release the current IP address.
Enter the Account Name provided by your ISP. If you are not clear,
please consult your ISP.
Enter the Password provided by your ISP.
You can select the proper Active mode according to your need.
z Manual: Select this option to manually activate or terminate the
Internet connection by the <Connect> or <Disconnect> button.
It’s optimum for the dial-up connection charged on time.
z Always-on: Select this option to keep the connection always
on. The connection can be re-established automatically when it
PPPoE Advanced
Settings:
Keep Alive:
MTU:
is down.
z Time-based: Select this option to keep the connection on
during the Active time you set.
Check here to enable PPPoE advanced settings.
Once PPPoE is connected, the router will send keep-alive packets
every "Keep Alive Interval" sec and "Keep Alive Retry Times" to
make sure the connection is still alive. If the router does not get the
response from ISP after sending keep-alive packets, then the router
will terminate the connection.
MTU (Maximum Transmission Unit) is the maximum data unit
transmitted by the physical network. It can be set in the range of
576-1492. The default MTU is 1480. It is recommended to keep the
ISP Address:
default value if no other MTU value is provided by your ISP.
Optional. Enter the ISP address provided by your ISP. It's null by
default.
-18-
Page 25

Service Name:
Primary DNS:
Secondary DNS:
Secondary Connection:
Connection Type:
IP Address:
Optional. Enter the Service Name provided by your ISP. It's null by
default.
Enter the IP address of your ISP’s Primary DNS.
Optional. Enter the IP address of your ISP’s Secondary DNS.
Here allows you to configure the secondary connection. Dynamic IP
and Static IP connection types are provided.
Select the secondary connection type. Options include Disable,
Dynamic IP and Static IP.
If Static IP is selected, configure the IP address of WAN port. If
Dynamic IP is selected, the obtained IP address of WAN port is
displayed.
Subnet Address:
Status:
Upstream Bandwidth:
Downstream Bandwidth:
If Static IP is selected, configure the subnet address of WAN port. If
Dynamic IP is selected, the obtained subnet address of WAN port is
displayed.
Displays the status of secondary connection.
Specify the bandwidth for transmitting packets on the port.
Specify the bandwidth for receiving packets on the port.
-19-
Page 26

¾ PPPoE Status
Status:
IP Address:
Displays the status of PPPoE connection.
z “Disabled” indicates that the PPPoE connection type is
not applied.
z “Connecting” indicates that the router is obtaining the IP
parameters from your ISP.
z “Connected” indicates that the router has successfully
obtained the IP parameters from your ISP.
z “Disconnected” indicates that the connection has been
manually terminated or the request of the router has no
response from your ISP. Please ensure that your settings
are correct and your network is connected well. Consult
your ISP if this problem remains.
Displays the IP address assigned by your ISP.
Gateway Address:
Primary DNS:
Secondary DNS:
Displays the Gateway Address assigned by your ISP.
Displays the IP address of your ISP’s Primary DNS.
Displays the IP address of your ISP’s Secondary DNS.
-20-
Page 27
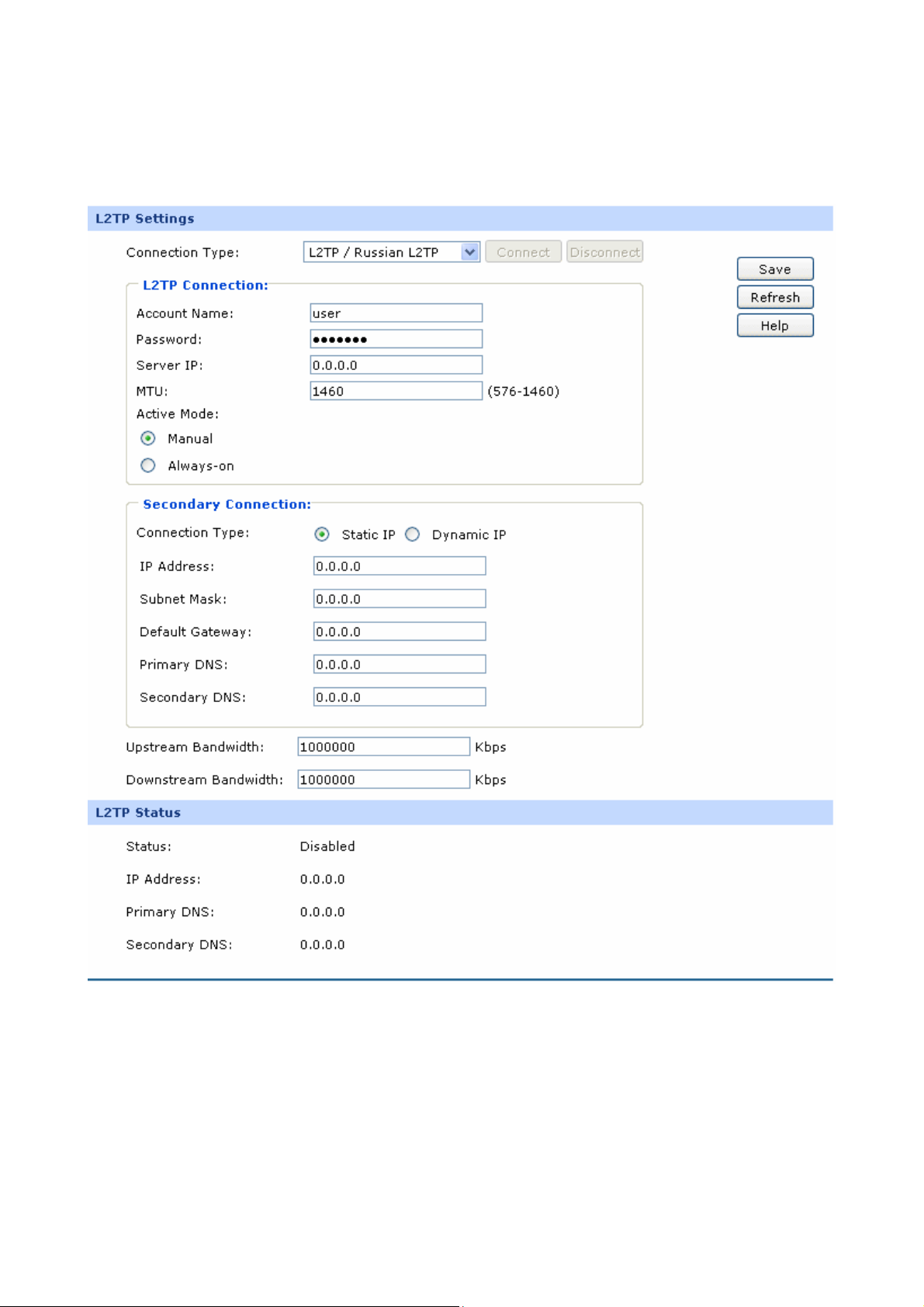
4) L2TP
If your ISP (Internet Service Provider) has provided the account information for the L2TP connection,
please choose the L2TP/Russian L2TP connection type.
Figure 3-10 WAN - L2TP
-21-
Page 28

The following items are displayed on this screen:
¾ L2TP Settings
Connection Type:
Account Name:
Password:
Server IP:
MTU:
Select L2TP/Russian L2TP if your ISP provides a L2TP
connection. Click <Connect> to dial-up to the Internet and
obtain the IP address. Click <Disconnect> to disconnect the
Internet connection and release the current IP address.
Enter the Account Name provided by your ISP. If you are not
clear, please consult your ISP.
Enter the Password provided by your ISP.
Enter the Server IP provided by your ISP.
MTU (Maximum Transmission Unit) is the maximum data unit
transmitted by the physical network. It can be set in the
range of 576-1460. The default MTU is 1460. It is
recommended to keep the default value if no other MTU
value is provided by your ISP.
Active Mode:
Secondary Connection:
Connection Type:
You can select the proper Active Mode according to your
need.
z Manual: Select this option to manually activate or
terminate the Internet connection by the <Connect> or
<Disconnect> button. It is optimum for the dial-up
connection charged on time.
z Always-on: Select this option to keep the connection
always on. The connection can be re-established
automatically when it is down.
Here allows you to configure the secondary connection.
Dynamic IP and Static IP connection types are provided.
Select the secondary connection type. Options include
Disable, Dynamic IP and Static IP.
-22-
Page 29

IP Address:
Subnet Mask:
Default Gateway:
Primary DNS/Secondary DNS:
Upstream
If Static IP is selected, configure the IP address of WAN port.
If Dynamic IP is selected, the IP address of WAN port
obtained is displayed.
If Static IP is selected, configure the subnet mask of WAN
port. If Dynamic IP is select, the subnet mask of WAN port
obtained is displayed.
If Static IP is selected, configure the default gateway. If
Dynamic IP is selected, the obtained default gateway is
displayed.
If Static IP is selected, configure the DNS. If Dynamic IP is
selected, the obtained DNS is displayed.
Specify the bandwidth for transmitting packets on the port.
Bandwidth:
Downstream Bandwidth:
¾ L2TP Status
Status:
Specify the bandwidth for receiving packets on the port.
Displays the status of L2TP connection.
z “Disabled” indicates that the L2TP connection type is
not applied.
z “Connecting” indicates that the router is obtaining the IP
parameters from your ISP.
z “Connected” indicates that the router has successfully
obtained the IP parameters from your ISP.
z “Disconnected” indicates that the connection has been
manually terminated or the request of the router has no
IP Address:
response from your ISP. Please ensure that your
settings are correct and your network is connected well.
Consult your ISP if this problem remains.
Displays the IP address assigned by your ISP.
-23-
Page 30
Primary DNS:
Secondary DNS:
Displays the IP address of your ISP’s Primary DNS.
Displays the IP address of your ISP’s Secondary DNS.
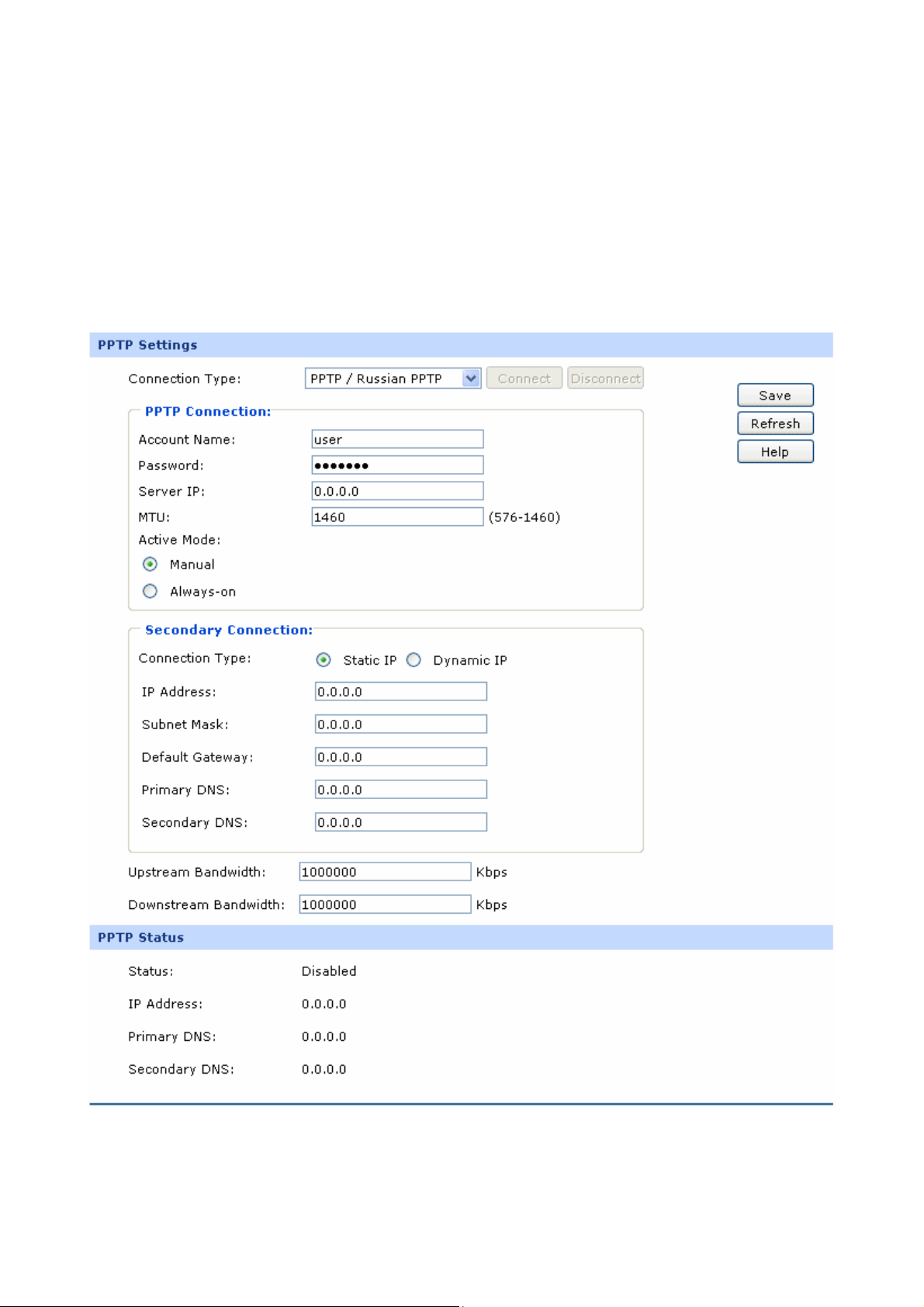
5) PPTP
If your ISP (Internet Service Provider) has provided the account information for the PPTP connection,
please choose the PPTP/Russian PPTP connection type.
Figure 3-11 WAN - PPTP
The following items are displayed on this screen:
-24-
Page 31

¾ PPTP Settings
Connection Type:
Account Name:
Password:
Server IP:
MTU:
Select PPTP/Russian PPTP if your ISP provides a PPTP
connection. Click <Connect> to dial-up to the Internet and
obtain the IP address. Click <Disconnect> to disconnect the
Internet connection and release the current IP address.
Enter the Account Name provided by your ISP. If you are not
clear, please consult your ISP.
Enter the Password provided by your ISP.
Enter the Server IP provided by your ISP.
MTU (Maximum Transmission Unit) is the maximum data
unit transmitted by the physical network. It can be set in the
range of 576-1460. The default MTU is 1460. It is
recommended to keep the default value if no other MTU
value is provided by your ISP.
Active Mode:
SecondaryConnections:
Connection Type:
You can select the proper Active mode according to your
need.
z Manual: Select this option to manually activate or
terminate the Internet connection by the <Connect> or
<Disconnect> button. It’s optimum for the dial-up
connection charged on time.
z Always-on: Select this option to keep the connection
always on. The connection can be re-established
automatically when it is down.
Here allows you to configure the secondary connection.
Dynamic IP and Static IP connection types are provided.
Select the secondary connection type. Options include
Disable, Dynamic IP and Static IP.
IP Address:
If Static IP is selected, configure the IP address of WAN port.
If Dynamic IP is selected, the IP address of WAN port
obtained is displayed.
-25-
Page 32

Subnet Mask:
Default Gateway:
Primary DNS/Secondary DNS:
Upstream Bandwidth:
Downstream Bandwidth:
¾ PPTP Status
If Static IP is selected, configure the subnet mask of WAN
port. If Dynamic IP is select, the subnet mask of WAN port
obtained is displayed.
If Static IP is selected, configure the default gateway. If
Dynamic IP is selected, the obtained default gateway is
displayed.
If Static IP is selected, configure the DNS. If Dynamic IP is
selected, the obtained DNS is displayed.
Specify the bandwidth for transmitting packets on the port.
Specify the bandwidth for receiving packets on the port.
Status:
IP Address:
Displays the status of PPTP connection.
z “Disabled” indicates that the PPTP connection type is
not applied.
z “Connecting” indicates that the router is obtaining the
IP parameters from your ISP.
z “Connected” indicates that the router has successfully
obtained the IP parameters from your ISP.
z “Disconnected” indicates that the connection has been
manually terminated or the request of the router has no
response from your ISP. Please ensure that your
settings are correct and your network is connected
well. Consult your ISP if this problem remains.
Displays the IP address assigned by your ISP.
Primary DNS:
Secondary DNS:
Displays the IP address of your ISP’s Primary DNS.
Displays the IP address of your ISP’s Secondary DNS.
-26-
Page 33

6) BigPond
If your ISP (Internet Service Provider) has provided the account information for the BigPond
connection, please choose the BigPond connection type.
Figure 3-12 WAN – Bigpond
The following items are displayed on this screen:
¾ BigPond Settings
Connection Type:
Select BigPond if your ISP provides a BigPond connection. Click
<Connect> to dial-up to the Internet and obtain the IP address. Click
<Disconnect> to disconnect the Internet connection and release the
current IP address.
Account Name:
Enter the Account Name provided by your ISP. If you are not clear,
please consult your ISP.
-27-
Page 34

Password:
Auth Server:
Auth Domain:
Auth Mode:
Enter the Password provided by your ISP. If you are not clear, please
consult your ISP.
Enter the address of authentication server. It can be IP address or
server name.
Enter the domain name of authentication server. It's only required when
the address of Auth Server is a server name.
You can select the proper Active mode according to your need.
z Manual: Select this option to manually activate or terminate the
Internet connection by the <Connect> or <Disconnect> button. It’s
optimum for the dial-up connection charged on time.
z Always-on: Select this option to keep the connection always on.
The connection can be re-established automatically when it is
down.
MTU:
Upstream/Downstream
Bandwidth:
¾ BigPond Status
Status:
MTU (Maximum Transmission Unit) is the maximum data unit
transmitted by the physical network. It can be set in the range of
576-1500. The default MTU is 1500.
Specify the Upstream/Downstream Bandwidth for the port. To make
"Load Balance" and "Bandwidth Control" take effect, please set these
parameters correctly.
Displays the status of BigPond connection.
z “Disabled” indicates that the BigPond connection type is not
applied.
z “Connecting” indicates that the router is obtaining the IP
parameters from your ISP.
z “Connected” indicates that the router has successfully obtained
the IP parameters from your ISP.
z “Disconnected” indicates that the connection has been
manually terminated or the request of the router has no
response from your ISP. Please ensure that your settings are
-28-
Page 35

correct and your network is connected well. Consult your ISP if
this problem remains.
IP Address:
Subnet Mask:
Default Gateway:
Note:
To ensure the BigPond connection re-established normally, please restart the connection at least 5
seconds after the connection is off.
Displays the IP address assigned by your ISP.
Displays the Subnet Mask assigned by your ISP.
Displays the IP address of the default gateway assigned by your
ISP.
3.1.4 LAN
3.1.4.1 LAN
On this page, you can configure the parameters for LAN port of this router.
Choose the menu Network→LAN→LAN to load the following page.
Figure 3-13 LAN
The following items are displayed on this screen:
¾ LAN
IP Address:
Subnet Mask:
Enter the LAN IP address of the router. 192.168.0.1 is
the default IP address. The Hosts in LAN can access
the router via this IP address. It can be changed
according to your network.
Enter the Subnet Mask. The default subnet mask is
255.255.255.0.
-29-
Page 36

Note:
If the LAN IP address is changed, you must use the new IP address to log into the router. To guarantee
a normal communication, be sure to set the Gateway address and the Subnet Mask of the Hosts on
the LAN to the new LAN IP address and the Subnet Mask of the router.
3.1.4.2 DHCP
The router with its DHCP (Dynamic Host Configuration Protocol) server enabled can automatically
assign an IP address to the computers in the LAN.
Choose the menu Network→LAN→DHCP to load the following page.
Figure 3-14 DHCP Settings
The following items are displayed on this screen:
¾ DHCP Settings
DHCP Server:
Start IP Address:
End IP Address:
Enable or disable the DHCP server on your router. To enable the
router to assign the TCP/IP parameters to the computers in the LAN
automatically, please select Enable.
Enter the Start IP address to define a range for the DHCP server to
assign dynamic IP addresses. This address should be in the same IP
address subnet with the router’s LAN IP address. The default address
is 192.168.0.2.
Enter the End IP address to define a range for the DHCP server to
assign dynamic IP addresses. This address should be in the same IP
address subnet with the router’s LAN IP address. The default address
is 192.168.0.254.
-30-
Page 37

Lease Time:
Default Gateway:
Default Domain:
Primary DNS:
Secondary DNS:
3.1.4.3 DHCP Client
Specify the length of time the DHCP server will reserve the IP address
for each computer. After the IP address expired, the client will be
automatically assigned a new one.
Optional. Enter the Gateway address to be assigned. It is
recommended to enter the IP address of the LAN port of the router.
Optional. Enter the domain name of your network.
Optional. Enter the Primary DNS server address provided by your
ISP. It is recommended to enter the IP address of the LAN port of the
router.
Optional. If a Secondary DNS Server address is available, enter it.
On this page, you can view the information about all the DHCP clients connected to the router.
Choose the menu Network→LAN→DHCP Client to load the following page.
Figure 3-15 DHCP Client
You can view the information of the DHCP clients in this table. Click the Refresh button for the updated
information.
3.1.4.4 DHCP Reservation
DHCP Reservation feature allows you to reserve an IP address for the specified MAC address. The
client with this MAC address will always get the same IP address each time when it accesses the
DHCP server.
Choose the menu Network→LAN→DHCP Reservation to load the following page.
-31-
Page 38

Figure 3-16 DHCP Reservation
The following items are displayed on this screen:
¾ DHCP Reservation
MAC Address:
Enter the MAC address of the computer for which you want to reserve
the IP address.
IP Address:
Description:
Enter the reserved IP address.
Optional. Enter a description for the entry. Up to 28 characters can be
entered.
Status:
Activate or Inactivate the corresponding entry.
¾ List of Reserved Address
In this table, you can view the information of the entries and edit them by the Action buttons. Up
to 512 DHCP static address entries can be supported for LAN and DMZ separately by this
router.
The first entry in Figure 3-16 indicates: The IP address 192.168.0.101 is reserved for the
computer with the MAC address 00-19-66-83-53-CF, and this entry is activated.
Note:
It's recommended that users first bind the IP address and the MAC address in 3.4.1.1 IP-MAC Binding,
then import the entries from the IP-MAC binding table to the List of Reserved Address in buck by
clicking <Import> button in Figure 3-16 DHCP Reservation.
-32-
Page 39
3.1.5 DMZ
DMZ (Demilitarized Zone) is a network which has fewer default firewall restrictions than the LAN does.
TL-ER5120 provides a DMZ port to allow all the local hosts connected to this port to be exposed to the
Internet for some special-purpose services, such as such as Internet gaming and video-conferencing.
The DMZ physical port can work in Public mode and Private mode.
In Public mode, the DMZ port allows the Hosts in DMZ to directly communicate with Internet via routing
mode using public IP address. However, the Hosts in DMZ cannot access LAN.
Figure 3-17 DMZ – Public Mode
In Private mode, the DMZ port allows the Hosts in DMZ to access Internet via NAT mode which
translates private IP addresses within DMZ to public IP addresses for transport over Internet. The
Hosts in DMZ can directly communicate with LAN using the private IP addresses within the different
subnet of LAN.
Figure 3-18 DMZ – Private Mode
3.1.5.1 DMZ
This page allows you to configure the DMZ port of TL-ER5120.
-33-
Page 40

Choose the menu Network→DMZ→DMZ to load the following page.
Figure 3-19 DMZ
The following items are displayed on this screen:
¾ DMZ
Status:
Mode:
IP Address:
Subnet Mask:
Tips:
The DHCP service, DHCP Client and DHCP Reservation functions are available when the DMZ port is
enabled. For the configuration instructions, please refer to section 3.1.4.1 to.3.1.4.4.
Note:
Activate or inactivate this entry. The DMZ port functions as a normal
LAN port when it’s disabled.
Select the mode for DMZ port to control the connection way among
DMZ, LAN and Internet. Options include: Public and Private.
Enter the IP address of DMZ port.
Enter the Subnet Mask of DMZ port.
When the DMZ port is enabled in Public Mode, please do not enable the DHCP service of DMZ port if
your ISP provides a single public IP address. Otherwise, the Hosts in DMZ will be unable to access
Internet normally. If an IP address range is provided by your ISP, please configure the DHCP pool
based on the IP address range.
3.1.6 MAC Address
The MAC (Media Access Control) address, as the unique identifier of the router in network, does not
need to be changed commonly.
-34-
Page 41

Set the MAC Address for LAN port:
In a complex network topology with all the ARP bound devices, if you want to change to use
TL-ER5120 instead of the current router in a network node, you can just set the MAC address of
TL-ER5120 ‘s LAN port the same to the MAC address of the previous router, which can avoid all the
devices under this network node to update their ARP binding tables.
Set the MAC Address for WAN port:
In the condition that your ISP has bound the account and the MAC address of the dial-up device, if you
want to change the dial-up device to be TL-ER5120, you can just set the MAC address of
TL-ER5120’s WAN port the same to the MAC address of the previous dial-up device for a normal
Internet connection.
Set the MAC Address for DMZ port:
The application of MAC address for DMZ port is similar to that for LAN port.
Choose the menu Network→MAC Address→MAC Address to load the following page.
Figure 3-20 MAC Address
The following items are displayed on this screen:
¾ MAC Address
Port:
Current MAC Address:
Displays the port type of the router.
Displays the current MAC address of the port.
-35-
Page 42

MAC Clone:
Note:
To avoid a conflict of MAC address on the LAN, it’s not allowed to set the MAC address of the router’s
LAN port to the MAC address of the current management PC.
It’s only available for WAN port. Click the <Restore Factory MAC>
button to restore the MAC address to the factory default value or
click the <Clone Current PC’s MAC> button to clone the MAC
address of the PC you are currently using to configure the router.
Then click <Save> to apply.
3.1.7 Switch
Some basic switch port management functions are provided by TL-ER5120, which facilitates you to
monitor the traffic and manage the network effectively.
3.1.7.1 Statistics
Statistics screen displays the detailed traffic information of each port, which allows you to monitor the
traffic and locate faults promptly.
Choose the menu Network→Switch→Statistics to load the following page.
Figure 3-21 Statistics
-36-
Page 43

The following items are displayed on this screen:
¾ Statistics
Unicast:
Broadcast:
Pause:
Multicast:
Undersize:
Normal:
Displays the number of normal unicast packets received or transmitted
on the port.
Displays the number of normal broadcast packets received or
transmitted on the port.
Displays the number of flow control frames received or transmitted on
the port.
Displays the number of normal multicast packets received or transmitted
on the port.
Displays the number of the received frames (including error frames) that
are less than 64 bytes long.
Displays the number of the received packets (including error frames) that
are between 64 bytes and the maximum frame length. The maximum
untagged frame this router can support is 1518 bytes long and the
maximum tagged frame is 1522 bytes long.
Oversize:
Total (Bytes):
Check the box and click the <Clear> button to clear the traffic statistics of the corresponding port.
Click the <Clear All> button to clear all the traffic statistics.
Displays the number of the received packets (including error frames) that
are longer than the maximum frame.
Displays the total number of the received or transmitted packets
(including error frames).
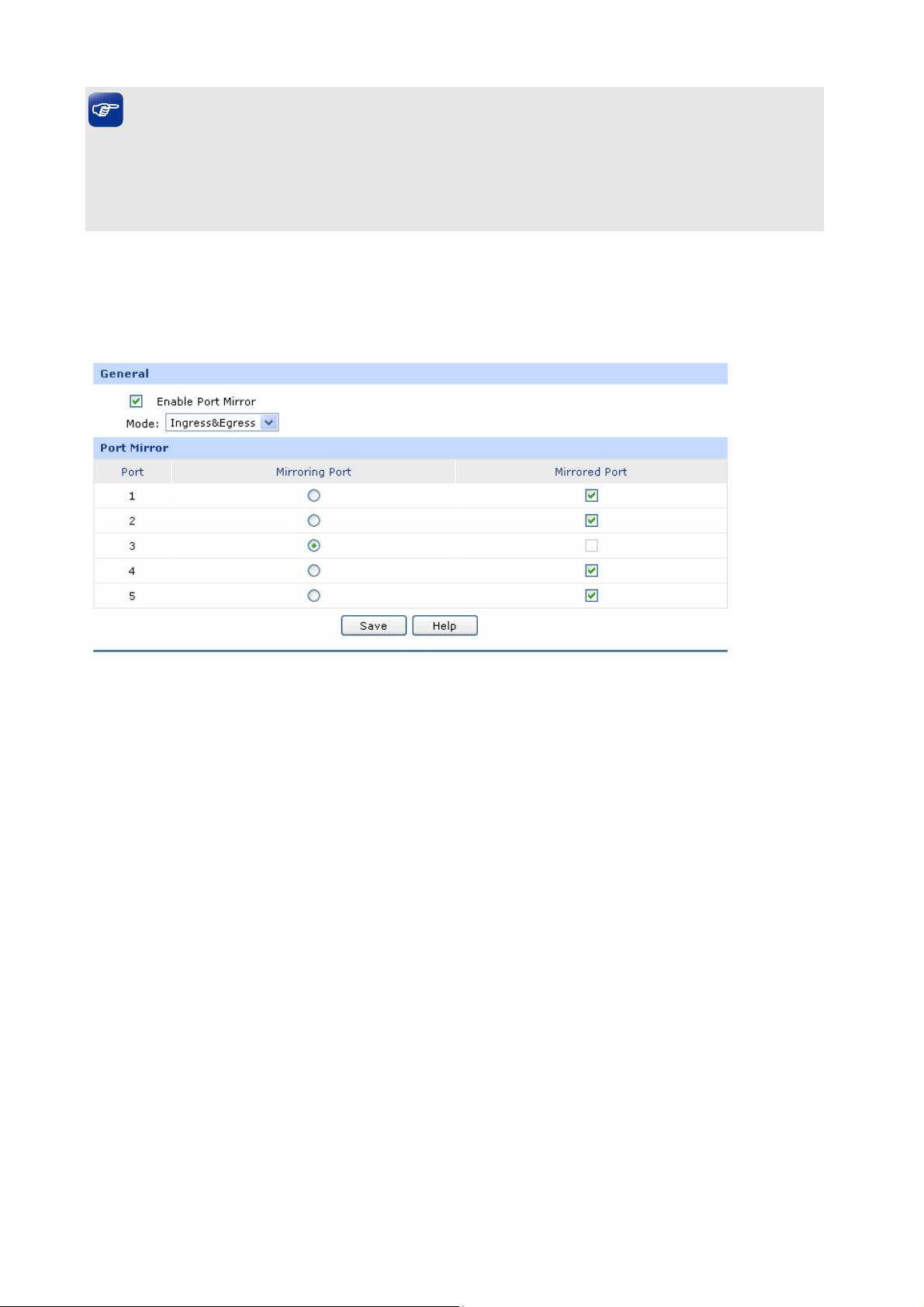
3.1.7.2 Port Mirror
Port Mirror, the packets obtaining technology, functions to forward copies of packets from one/multiple
ports (mirrored port) to a specific port (mirroring port). Usually, the mirroring port is connected to a data
diagnose device, which is used to analyze the mirrored packets for monitoring and troubleshooting the
network.
Choose the menu Network→Switch→Port Mirror to load the following page.
-37-
Page 44

Figure 3-22 Port Mirror
The following items are displayed on this screen:
¾ General
Enable Port Mirror:
Mode:
¾ Port Mirror
Check the box to enable the Port Mirror function. If unchecked, it will be
disabled.
Select the mode for the port mirror function. Options include:
z Ingress: When this mode is selected, only the incoming packets
sent by the mirrored port will be copied to the mirroring port.
z Egress: When this mode is selected, only the outgoing packets sent
by the mirrored port will be copied to the mirroring port.
z Ingress&Egress: When this mode is selected, both the incoming
and outgoing packets through the mirrored port will be copied to the
mirroring port.
Mirroring Port:
Select the Mirroring Port to which the traffic is copied. Only one port can
be selected as the mirroring port.
Mirrored Port:
Select the Mirrored Port from which the traffic is mirrored. One or multiple
ports can be selected as the mirrored ports.
The entry in Figure 3-22 indicates: The outgoing packets sent by port 1, port 2, port 3 and port 5
(mirrored ports) will be copied to port 4 (mirroring port).
-38-
Page 45
Tips:
If both the mirrored port and the mirroring port are the LAN ports, these two LAN ports should be in the
same Port VLAN. For example, if port 3 (the mirroring port) and port 4 (the mirrored port) are the LAN
ports, the Port Mirror function can take effect only when port 3 and port 4 are in the same Port VLAN.
Application Example:
To monitor all the traffic and analyze the network abnormity for an enterprise’s network, please set the
Port Mirror function as below:
1) Check the box before Enable Port Mirror to enable the Port Mirror function and select the
Ingress & Egress mode.
2) Select Port 3 to be the Mirroring Port to monitor all the packets of the other ports.
3) Select all the other ports to be the Mirrored Ports.
4) Click the <Save> button to apply.
3.1.7.3 Rate Control
On this page, you can control the traffic rate for the specific packets on each port so as to manage your
network flow.
Choose the menu Network→Switch→Rate Control to load the following page.
-39-
Page 46

Figure 3-23 Rate Control
The following items are displayed on this screen:
¾ Rate Control
Port:
Ingress Limit:
Ingress Mode:
Ingress Rate:
Egress Limit:
Egress Rate:
Displays the port number.
Specify whether to enable the Ingress Limit feature.
Select the Ingress Mode for each port. Options include:
z All Frames: Select this option to limit all the frames.
z Broadcast&Multicast: Select this option to limit
broadcast frame and multicast frame.
z Broadcast: Select this option to limit the broadcast
frame
Specify the limit rate for the ingress packets.
Specify whether to enable Egress Limit feature.
Specify the limit rate for the egress packets.
The first entry in Figure 3-23 indicates: The Ingress and Egress Limits are enabled for port 1. The
Ingress mode is Flood while the Ingress and Egress Rates are 1Mbps. That is, the receiving rate for
the ingress packets of Flood mode will not exceed 1Mbps, and the transmitting rate for all the egress
packets will not exceed 1Mbps.
3.1.7.4 Port Config
On this page, you can configure the basic parameters for the ports.
Choose the menu Network→Switch→Port Config to load the following page.
-40-
Page 47

Figure 3-24 Port Config
The following items are displayed on this screen:
¾ Port Config
Status:
Flow Control:
Negotiation Mode:
All Ports:
Specify whether to enable the port. The packets can be transported via
this port after being enabled.
Allows you to enable/disable the Flow Control function.
Select the Negotiation Mode for the port.
Allows you to configure the parameters for all the ports at one time.
3.1.7.5 Port Status
On this page, you can view the current status of each port.
Choose the menu Network→Switch→Port Status to load the following page.
Figure 3-25 Port Status
-41-
Page 48

3.1.7.6 Port VLAN
A VLAN (Virtual Local Area Network) is a network topology configured according to a logical scheme
rather than the physical layout, which allows you to divide the physical LAN into multiple logical LANs
so as to control the communication among the ports
The VLAN function can prevent the broadcast storm in LANs and enhance the network security. By
creating VLANs in a physical LAN, you can divide the LAN into multiple logical LANs, each of which
has a broadcast domain of its own. Hosts in the same VLAN communicate with one another as if they
are in a LAN. However, hosts in different VLANs cannot communicate with one another directly.
Therefore, broadcast packets are limited in a VLAN.
TL-ER5120 provides the Port VLAN function, which allows you to create multiple logical VLANs for the
LAN ports based on their port numbers.
Choose the menu Network→Switch→Port VLAN to load the following page.
.
Figure 3-26 Port VLAN
The following items are displayed on this screen:
¾ Port VLAN
Network:
VLAN:
Tips:
● The Port VLAN can only be created among the LAN ports.
● The change of DMZ status will affect the configurations of Port VLAN. You're recommended to
check or reconfigure the Port VLAN if the status of DMZ is changed.
Displays the current logical network of the physical port.
Select the desired VLAN for the port.
3.2 User Group
The User Group function is used to group different users for unified management, so that you can
perform other applications such as Bandwidth Control, Session Limit, and Access Control etc. on per
group.
-42-
Page 49

3.2.1 Group
On this page you can define the group for management.
Choose the menu User Group→Group to load the following page.
3-27 Group Configuration
Figure
The following items are displayed on this screen:
¾ Group Config
Group Name:
Description:
¾ List of Group
Specify a unique name for the group.
Give a description for the group. It's optional.
In this table, you can view the information of the Groups and edit them by the Action buttons.
3.2.2 User
On this page, you can configure the User for the group.
Choose the menu User Group→User to load the following page.
Figure 3-28 User Configuration
-43-
Page 50
The following items are displayed on this screen:
¾ User Config
User Name:
IP Address:
Specify a unique name for the user.
Enter the IP Address of the user. It cannot be the network address or
broadcast address of the port.
Description:
¾ List of User
Give a description to the user for identification. It's optional.
In this table, you can view the information of the Users and edit them by the Action buttons.
3.2.3 View
On this page, you can configure the User View or Group View.
Choose the menu User Group→View to load the following page.
Figure 3-29 View Configuration
The following items are displayed on this screen:
-44-
Page 51

¾ View Config
View:
User Name:
Available Group:
Selected Group:
Group Name:
Group Structure:
Available Member:
Select the desired view for configuration.
Select the name of the desired User.
Displays the Groups that the User can join.
Displays the Groups to which this User belongs.
Select the name of the desired Group.
Click this button to view the tree structure of this group. All the members of
this group will be displayed, including Users and sub-Groups. The Group
Names are displayed in bold.
Displays the Users and the Groups which can be added into this group.
Selected Member:
Displays the members of this group, including Users and Groups.
3.3 Advanced
3.3.1 NAT
NAT (Network Address Translation) is the translation between private IP and public IP, which allows
private network users to visit the public network using private IP addresses.
With the explosion of the Internet, the number of available IP addresses is not enough. NAT provides a
way to allow multiple private hosts to access the public network with one public IP at the same time,
which alleviates the shortage of IP addresses. Furthermore, NAT strengthens the LAN (Local Area
Network) security of the network since the address of LAN host never appears on the Internet.
3.3.1.1 NAT Setup
On this page, you can set up the NAT function.
Choose the menu Advanced→NAT→NAT Setup to load the following page.
-45-
Page 52

Figure 3-30 NAT Setup
The following items are displayed on this screen:
¾ NAPT
Source Port Range:
Enter the source port range between 2049 and 65000, the span of which
must be not less than 100.
¾ NAT-DMZ
NAT-DMZ:
Enable or disable NAT-DMZ. NAT DMZ is a special service of NAT
application, which can be considered as a default forwarding rule. When
NAT DMZ (Pseudo DMZ) is enabled, all the data initiated by external
network falling short of the current connections or forwarding rules will be
forwarded to the preset NAT DMZ host.
Host IP Address:
Enter the IP address of the host specified as NAT DMZ server.
3.3.1.2 One-to-One NAT
On this page, you can configure the One-to-One NAT.
Choose the menu Advanced→NAT→One-to-One NAT to load the following page.
-46-
Page 53

Figure 3-31 NAT Setup
The following items are displayed on this screen:
¾ One-to-One NAT
Mapping IP Address:
Interface:
DMZ Forwarding:
Description:
Status:
¾ List of Rules
Enter the Original IP Address in the first checkbox and Translated
IP Address in the second checkbox. TL-ER5120 allows mapping from LAN
port to WAN port and DMZ in LAN Mode.
Select an interface for forwarding data packets.
Enable or disable DMZ Forwarding. The packets transmitted to the
Translated IP Address will be forwarded to the host of Original IP if DMZ
Forwarding is enabled.
Give a description for the entry.
Activate or inactivate the entry.
In this table, you can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-31 indicates: The IP address of host1 in local network is 192.168.0.128 and
the WAN IP address after NAT mapping is specified to be 222.135.48.128. The data packets are
transmitted from WAN1 port. DMZ Forwarding and this entry are both activated.
Note:
One-to-One NAT entries take effect only when the Connection Type of WAN is Static IP. Changing the
Connection type from Static IP to other ones will make the entries attached to the interface disabled.
-47-
Page 54

3.3.1.3 Multi-Nets NAT
Multi-Nets NAT functions to allow the IP under LAN or DMZ port within multiple subnets to access the
Internet via NAT.
Choose the menu Advanced→NAT→Multi-Nets NAT to load the following page.
Figure 3-32 Multi-Nets NAT
The following items are displayed on this screen:
¾ Multi-Nets NAT
Subnet/Mask:
Interface:
Description:
Status:
¾ list of Rules
You can view the information of the entries and edit them by the Action buttons.
Enter the subnet/mask to make the address range for the entry.
Select the interface for the entry. You can select LAN or DMZ port.
Give a description for the entry.
Activate or inactivate the entry.
The first entry in Figure 3-32 indicates that: This is a Multi-Nets NAT entry named tplink1. The subnet
under the LAN port of the router is 192.168.2.0/24 and this entry is activated. After the corresponding
Static Route entry is set, the hosts within this subnet can access the Internet through the router via
NAT.
-48-
Page 55

Note:
● Multi-Nets NAT entry takes effect only when cooperating with the corresponding Static Route
entries.
● The DMZ port will display in the drop-down list only when the DMZ port is enabled.
● For detailed setting of subnet mask, please refer to the Appendix B FAQ
Application Example:
Network Requirements
The LAN subnet of TL-ER5120 is 192.168.0.0 /24, the subnet of VLAN2 under a three layer switch is
192.168.2.0 /24, while the subnet of VLAN3 is 192.168.3.0 /24. The IP of VLAN for cascading the
switch to the router is 192.168.0.2. Now the hosts within VLAN2 and VLAN3 desire to access the
Internet.
The network topology is shown as the following:
-49-
Page 56

Configuration procedure
1. Establish the Multi-Nets NAT entries with Subnet/Mask of VLAN2 and VLAN3.
The configured entries are as follows:
2. Then set the corresponding Static Route entry, enter the IP address of the interface connecting
the router and the three layer switch into the Next Hop field.
Choose the menu Advanced→Routing→Static Route to load the following page.
The set Static Route entry is as follows:
-50-
Page 57

3.3.1.4 Virtual Server
Virtual server can be used for setting up public services in your private network, such as DNS, Email
and FTP. Virtual server can define a service port. All the service requests to this port will be transmitted
to the LAN server appointed by the router via IP address.
Choose the menu Advanced→NAT→Virtual Server to load the following page.
Figure 3-33 Virtual Server
The following items are displayed on this screen:
¾ Virtual Server
Name:
External Port:
Internal Port:
Protocol:
Enter a name for Virtual Server entries. Up to 28 characters can be
entered.
Enter the service port or port range provided by router for accessing
external network. All requests from Internet to this service port or port
range will be redirected to the specified server in local network.
Specify the service port of the LAN host as virtual server.
Specify the protocol used for the entry.
Internal Server IP:
Enter the IP address of the specified internal server for the entry. All
the requests from the Internet to the specified LAN port will be
redirected to this host.
-51-
Page 58

Status:
Note:
● The External port and Internal Port should be set in the range of 1-65535.
● The external ports of different entries should be different, whereas the internal ports can be the
same.
¾ List of Rules
In this table, you can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-33 indicates: This is a Virtual Server entry named host1, all the TCP data
packets from Internet to port 65534-65535 of the router will be redirected to the port 65534-65535 of
the LAN host with IP address of 192.168.0.103, and this entry is activated.
Activate or inactivate the entry.
3.3.1.5 Port Triggering
Some applications require multiple connections, like Internet games, video conferencing, Internet
calling, P2P download and so on. Port Triggering is used for those applications requiring multiple
connections.
When an application initiates a connection to the trigger port, all the ports corresponding to the
incoming port will open for follow-up connections.
Choose the menu Advanced→NAT→Port Triggering to load the following page.
Figure 3-34 Port Triggering
The following items are displayed on this screen:
-52-
Page 59

¾ Port Triggering
Name:
Trigger Port:
Trigger Protocol:
Incoming Port:
Incoming Protocol:
Status:
Enter a name for Port Triggering entries. Up to 28 characters can be
entered.
Enter the trigger port number or range of port numbers. Only when the
trigger port initiates connection will all the corresponding incoming
ports open and provide service for the applications, otherwise the
incoming ports will not open.
Select the protocol used for trigger port.
Enter the incoming port number or range of port numbers. The
incoming port will open for follow-up connection after the trigger port
initiates connection.
Select the protocol used for incoming port.
Activate or inactivate the entry.
Note:
● The Trigger Port and Incoming Port should be set in the range of 1-65535. The Incoming Port can
be set in a continuous range such as 8690-8696.
● The router supports up to 16 Port Triggering entries. Each entry supports at most 5 groups of
trigger ports and overlapping between the ports is not allowed.
● Each entry supports at most 5 groups of incoming ports and the sum of incoming ports you set for
each entry should not be more than 100.
¾ List of Rules
In this table, you can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-34 indicates that: This is a Port Triggering entry named host1, When the LAN
host initiates a TCP request via port of 5354, the incoming port 5355 will open for TCP and UDP
protocol. This entry is activated.
3.3.1.6 ALG
Some special protocols such as FTP, H.323, SIP, IPsec and PPTP will work properly only when ALG
(Application Layer Gateway) service is enabled.
-53-
Page 60

Choose the menu Advanced→NAT→ALG to load the following page.
Figure 3-35 ALG
The following items are displayed on this screen:
¾ ALG
FTP ALG:
H.323 ALG:
SIP ALG:
IPsec ALG:
PPTP ALG:
Enable or disable FTP ALG. The default setting is enabled. It is
recommended to keep the default setting if no special
requirement.
Enable or disable H.323 ALG. The default setting is enabled.
H.323 is used for various applications such as NetMeeting and
VoIP.
Enable or disable SIP ALG. The default setting is enabled. It is
recommended to keep the default setting if no special
requirement.
Enable or disable IPsec ALG. The default setting is enabled. It is
recommended to keep default if no special requirement.
Enable or disable PPTP ALG. The default setting is enabled. It is
recommended to keep default if no special requirement.
3.3.2 Traffic Control
Traffic Control functions to control the bandwidth by configuring rules for limiting various data flows. In
this way, the network bandwidth can be reasonably distributed and utilized.
3.3.2.1 Setup
Choose the menu Advanced→Traffic Control→Setup to load the following page.
-54-
Page 61

Figure 3-36 Configuration
The following items are displayed on this screen:
¾ General
Disable Bandwidth
Select this option to disable Bandwidth Control.
Control:
Enable Bandwidth
Select this option to enable Bandwidth Control all the time.
Control all the time:
Enable Bandwidth
Control When:
With this option selected, the Bandwidth Control will take effect when the
bandwidth usage reaches the specified value.
¾ Default Limit
Limited Bandwidth:
Default Limit applies only for users that are not constrained by Bandwidth
Control Rules. These users share certain bandwidth with upper limit
configured here. Value 0 means all the remained bandwidth is available to
use.
-55-
Page 62
¾ Interface Bandwidth
Interface:
Upstream
Bandwidth:
Downstream
Bandwidth:
Note:
● The Upstream/Downstream Bandwidth of WAN port you set must not be more than the bandwidth
provided by ISP. Otherwise the Traffic Control will be invalid.
● If there are data flowing into the router from interface A and out from interface B while the
downstream bandwidth of A is different from the upstream bandwidth of B, then the smaller one
should be considered as the effective bandwidth, and vise versa.
Displays the current enabled WAN port(s). The Total bandwidth is equal to
the sum of bandwidth of the enabled WAN ports.
Displays the bandwidth of each WAN port for transmitting data. The
Upstream Bandwidth of WAN port can be configured on WAN page.
Displays the bandwidth of each WAN port for receiving data. The
Downstream Bandwidth of WAN port can be configured on WAN page.
● Click the <View IP Traffic Statistics> button to jump to IP Traffic Statistics page.
3.3.2.2 Bandwidth Control
On this page, you can configure the Bandwidth Control function.
Choose the menu Advanced→Traffic Control→Bandwidth Control to load the following page.
Figure 3-37 Bandwidth Control
The following items are displayed on this screen:
-56-
Page 63

¾ Bandwidth Control Rule
Direction:
Group:
Mode:
Guaranteed
Bandwidth (Up):
Limited Bandwidth
Select the data stream direction for the entry. The direction of arrowhead
indicates the data stream direction The DMZ port displays in the
drop-down list only when the DMZ port is enabled. WAN-ALL means all
WAN ports through which the data flow might pass. Individual WAN port
cannot be selected after WAN-ALL rules are added.
Select the group to define the controlled users.
Individual: The bandwidth of each user equals to the current bandwidth
of this entry.
Shared: The total bandwidth of all controlled IP addresses equals to the
current bandwidth of this entry.
Specify the Guaranteed Upstream Bandwidth for this entry.
Specify the Limited Upstream Bandwidth for this entry.
(Up):
Guaranteed
Specify the Guaranteed Downstream Bandwidth for this entry.
Bandwidth (Down):
Limited Bandwidth
Specify the Limited Downstream Bandwidth for this entry.
(Down):
Effective Time:
Description:
Status:
Specify the time for the entry to take effect.
Give a description for the entry.
Activate or inactivate the entry.
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-37 indicates: The users within group “sales” share the bandwidth and the
Downstream/Upstream Guaranteed Bandwidth is 5000kbps, while the Downstream/Upstream Limited
bandwidth is 10000kbps. This entry takes effect at 8 a.m. to 10 p.m. from Monday to Friday.
-57-
Page 64

Note:
● The premise for single rule taking effect is that the bandwidth of the interface for this rule is
sufficient and not used up.
● It is impossible to satisfy all the guaranteed bandwidth if the total guaranteed bandwidth specified
by all Bandwidth Control rules for certain interface exceeds the physical bandwidth of this
interface.
● When DMZ port is disabled, it is only allowed deleting operation to the related rules.
3.3.3 Session Limit
The amount of TCP and UDP sessions supported by the router is finite. If there are some local hosts
transmitting too many TCP and UDP sessions to the public network, the communication quality of the
other local hosts will be affected, thus it is necessary to limit the sessions of those hosts.
3.3.3.1 Session Limit
On this page, you can configure the session limit to specified PCs.
Choose the menu Advanced→Session Limit→Session Limit to load the following page.
Figure 3-38 Session Limit
The following items are displayed on this screen:
¾ General
Enable Session
Limit:
Check here to enable Session Limit, otherwise all the Session Limit
entries will be disabled.
-58-
Page 65

¾ Session Limit
Group:
Max. Sessions:
Description:
Status:
¾ List of Session Limit
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-38 indicates: The amount of maximum sessions for the hosts within group1
is 100 and this entry is enabled.
Session List
On this page, you can view the Session Limit information of hosts configured with Session Limit.
Select a group to define the controlled user.
Enter the max. Sessions for the users.
Give a description for the entry.
Activate or inactivate the entry.
Choose the menu Advanced→Session Limit→Session List to load the following page.
Figure 3-39 Session List
In this table, you can view the session limit information of users configured with Session Limit. Click
the <Refresh> button to get the latest information.
3.3.4 Load Balance
On this part, you can configure how the traffic load is shared by the WAN ports to optimize the
resource utilization.
3.3.4.1 Configuration
Choose the menu Advanced→Load Balance→Configuration to load the following page.
-59-
Page 66

Figure 3-40 Configuration
With the box before Enable Application Optimized Routing checked, the router will consider the
source IP address and destination IP address of the packets as a whole and record the WAN port they
pass through. And then the packets with the same source IP address and destination IP address or
destination port will be forwarded to the recorded WAN port. This feature is to ensure the
multi-connected applications to work properly.
Check the box before Enable Bandwidth Based Balance Routing and select the WAN port below,
Load Balance of the specified WAN port will be enabled automatically if no routing rules are set.
Then click the <Save> button to apply the settings.
Note:
The WAN ports not connecting to the Internet will not apply Intelligent Balance, please do not select
them.
3.3.4.2 Policy Routing
Policy Routing provides a more accurate way to control the routing based on the policy defined by the
network administrator.
Choose the menu Advanced→Load Balance→Policy Routing to load the following page.
Figure 3-41 Policy Routing
-60-
Page 67

The following items are displayed on this screen:
¾ General
Protocol:
Source IP:
Destination IP:
Source Port:
Destination Port:
Select the protocol for the entry in the drop-down list. If the protocol you
want to set is not in the list, you can add it to the list on 3.3.4.4 Protocol
page.
Enter the source IP range for the entry. 0.0.0.0 - 0.0.0.0 means any IP is
acceptable.
Enter the destination IP range for the entry. 0.0.0.0 - 0.0.0.0 means any
IP is acceptable.
Enter the source Port range for the entry, which is effective only when the
protocol is TCP, UDP or TCP/UDP. The default value is 1 – 65535, which
means any port is acceptable.
Enter the destination port range for the entry, which is effective only when
the protocol is TCP, UDP or TCP/UDP. The default value is 1 – 65535,
which means any port is acceptable.
WAN :
Effective Time:
Status:
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-41 indicates: All the packets with Source IP between 192.168.0.100 and
192.168.0.199 and Destination IP between 116.10.20.28 and 116.10.20.29 will be forwarded from
WAN1 port, regardless of the port and protocol. This entry is activated d and will take effect at 8 am to
10 pm from Monday to Friday.
Select the WAN port for transmitting packets.
Specify the time for the entry to take effect.
Activate or inactivate the entry.
3.3.4.3 Link Backup
With Link Backup function, the router will switch all the new sessions from dropped line automatically
to another to keep an always on-line network.
-61-
Page 68

On this page, you can configure the Link Backup function based on actual need to reduce the traffic
burden of WAN port and improve the network efficiency.
Choose the menu Advanced→Load Balance→Link Backup to load the following page.
Figure 3-42 Link Backup
The following items are displayed on this screen:
¾ General
WAN Ports:
Displays all the WAN ports in use. You can drag the light-blue WAN button to
primary and backup WAN list. The color of WAN button changing to gray
indicates that the WAN port is already in the primary and backup WAN list.
WAN Config:
The WAN port in the secondary WAN list will share the traffic for the WAN in
the primary WAN list under the specified condition. The primary WAN list can
contain one or more WAN ports, while the backup WAN list contains only one
WAN port.
Mode:
You can select Timing or Failover.
-62-
Page 69

Timing:
Failover:
Backup
Effective Time:
Status: Activate or inactivate the entry.
Link Backup will be enabled if the specified effective time is reached. All the
traffic on the primary WAN will switch to the backup WAN at the beginning of
the effective time; the traffic on the backup WAN will switch to the primary
WAN at the ending of the effective time.
Specify the premise for Failover Mode. The backup WAN port will be enabled
only when the premise is met.
Specify the backup effective time if Timing Mode has been selected. Then the
backup WAN port will be enabled, while the primary WAN port is disabled in
the specified time period. When the start time you enter is not earlier than the
end time, the default effective time is from the start time of the day to the end
time of the next day.
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-42 indicates: WAN1 is the primary port and WAN2 is the backup port. WAN2
will be enabled while WAN1 is failed. This entry is enabled.
Note:
The same WAN port cannot be added to the primary and secondary WAN lists at the same time, and
one WAN port should be added to only one list.
3.3.4.4 Protocol
On this page, you can specify the protocol for routing rules conveniently. A protocol constitutes of the
name and number. The router predefines three commonly used protocols such as TCP, UDP and
TCP/UDP. Moreover, you can also add new protocols as your wish.
Choose the menu Advanced→Load Balance→Protocol to load the following page.
-63-
Page 70
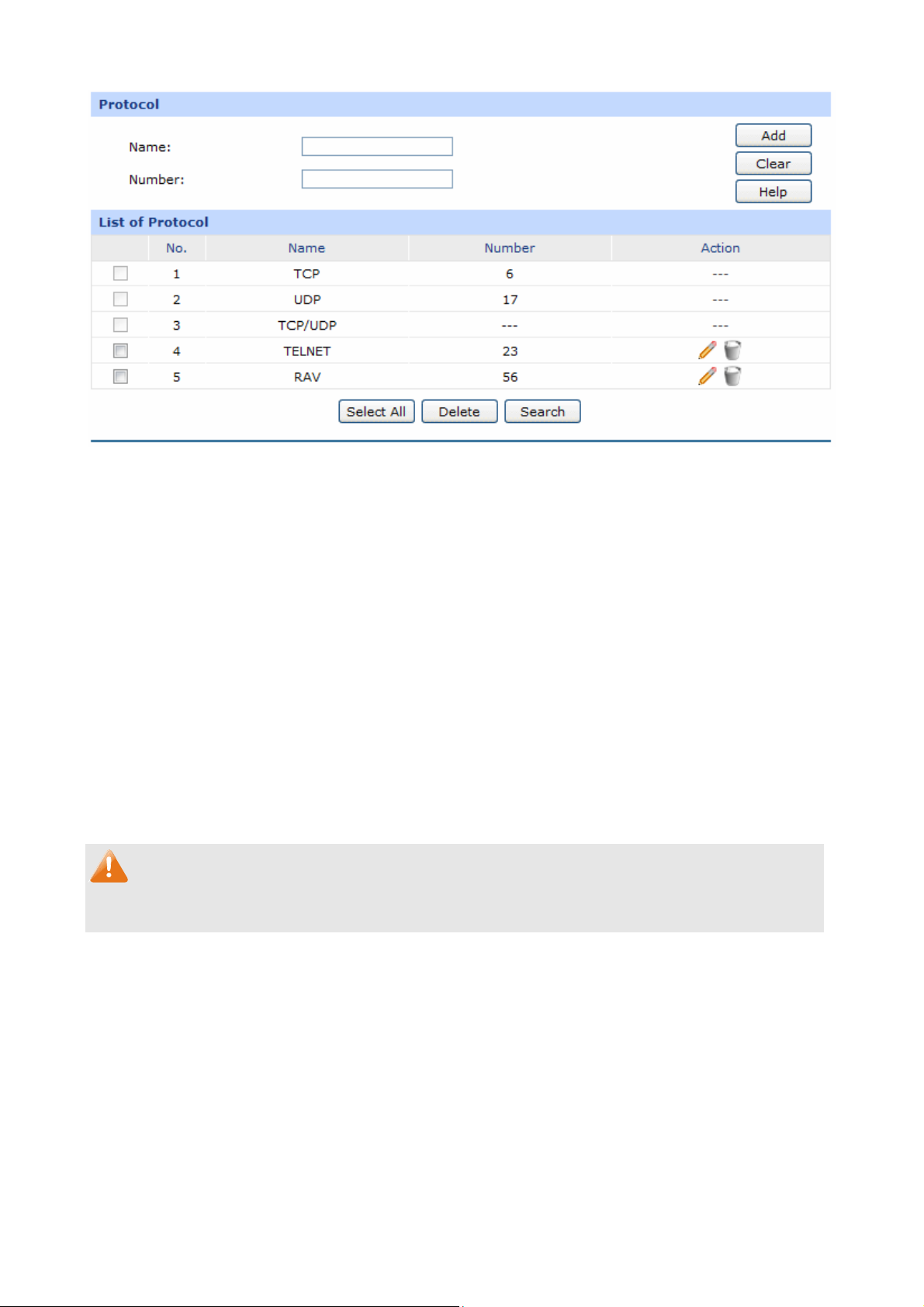
Figure 3-43 Protocol
The following items are displayed on this screen:
¾ Protocol
Name:
Number:
¾ List of Protocol
You can view the information of the entries and edit them by the Action buttons.
Note:
The system predefined protocols cannot be configured.
Enter a name to indicate a protocol. The name will display in the
drop-down list of Protocol on Access Rule page.
Enter the Number of the protocol in the range of 0-255.
3.3.5 Routing
3.3.5.1 Static Route
Routing is the process of selecting optimized paths in a network along which to send network traffic.
Static Route is a kind of special routing configured by the administrator, which is simple, efficient, and
reliable.
Commonly used in small-sized network with fixed topology, Static Route does not change along with
the network topology automatically. The administrator should modify the static route information
manually as long as the network topology or link status is changed.
-64-
Page 71
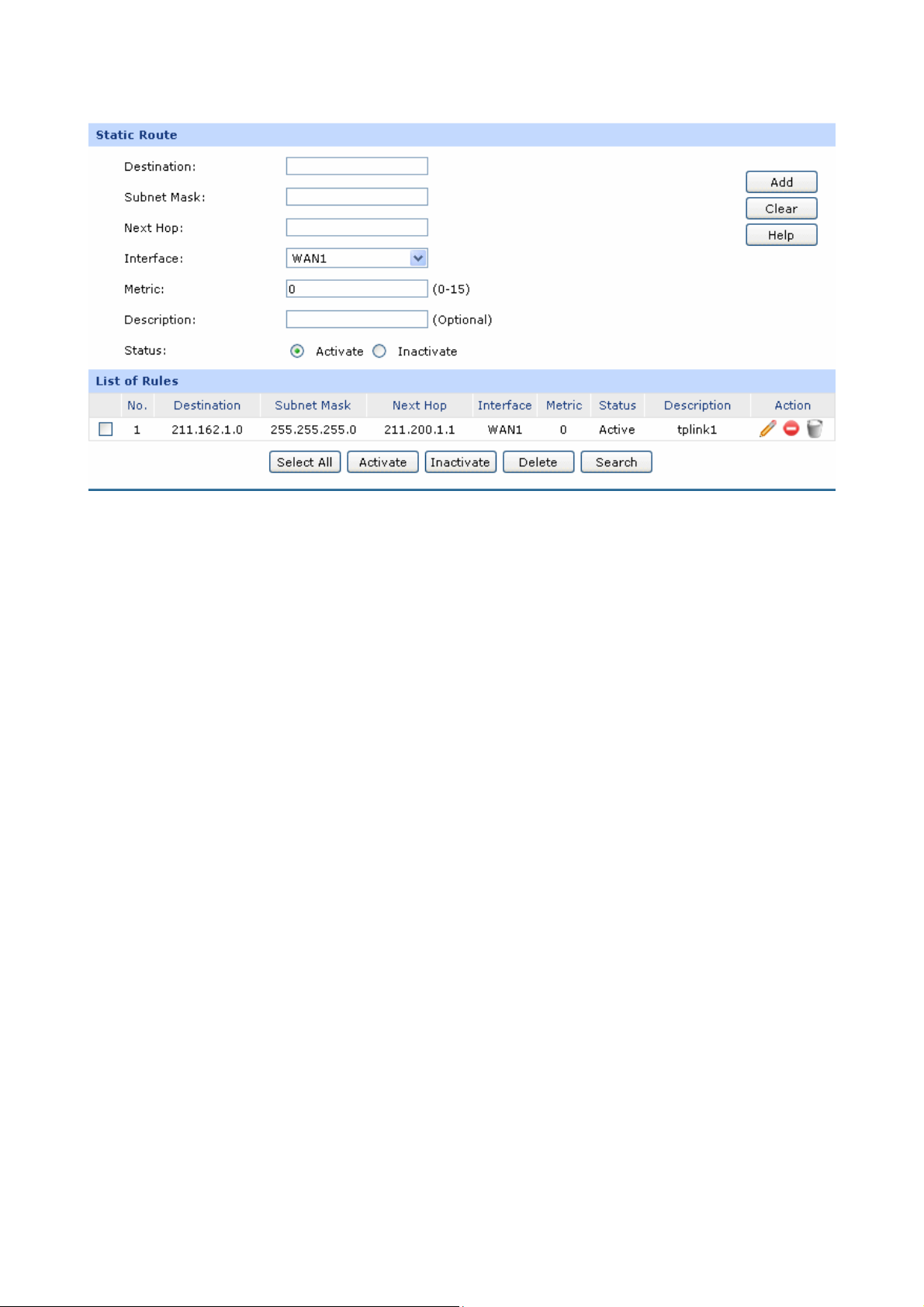
Choose the menu Advanced→Routing→Static Route to load the following page.
Figure 3-44 Static Route
The following items are displayed on this screen:
¾ Static Route
Destination:
Subnet Mask:
Next Hop:
Interface:
Enter the destination host the route leads to.
Enter the Subnet Mask of the destination network.
Enter the gateway IP address to which the packet should be sent next.
Select the physical network interface, through which this route is
accessible.
Metric:
Defines the priority of the route. The smaller the value is, the higher the
priority is. The default value is 0. Keep the default value if unnecessary.
Description:
Status:
Give a description for the entry.
Activate or inactivate the entry.
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
-65-
Page 72

The first entry in Figure 3-44 indicates: If there are packets being sent to a device with IP address of
211.162.1.0 and subnet mask of 255.255.255.0, the router will forward the packets from WAN1 port to
the next hop of 211.200.1.1.
Application Example
Network Requirements
LAN1 is under the router and it uses network segment 192.168.0.0 /24. LAN2 and LAN3 are under a
layer 3 switch and they use network segments 192.168.2.0 /24 and 192.168.3.0 /24 respectively. The IP
address of the cascading LAN port between the layer 3 switch and the router is 192.168.0.2. Now the
hosts within LAN1 desire to access the hosts within LAN2 and LAN3.
The network topology is shown as the following:
Configuration procedure
1. On the Static Route page, add a static routing rule for LAN2 with destination address 192.168.2.0
(LAN2’s IP address) and next hop address 192.168.0.2 (IP address of the cascading LAN port) as
shown in the following figure. Then click the <Add> button.
-66-
Page 73

2. Add a static routing rule for LAN3 by referring to step 2.
The static routing rules are shown in the following figure.
3.3.5.2 RIP
RIP (Routing Information Protocol) is a dynamic route protocol using distance vector algorithm to select
the optimal path. With features of easy configuration, management and implementation, it is widely used
in small and medium-sized networks such as the campus network.
The distance of RIP refers to the hop counts that a data packet passes through before reaching its
destination, the value range of which is 1–15. It means the destination cannot be reached if the value is
more than 15. Optimal path indicates the path with the fewest hop counts. RIP exchanges the route
information every 30 seconds by broadcasting UDP packets. If one router has not sent route information
in 180 seconds, the RIP of the other routers would set the distance to this router into infinity and delete
the corresponding information from route table.
RIP develops from initial RIPv1 to RIPv2 gradually. Compared with RIPv1, RIPv2 supports VLSM
(Variable Length Subnet Mask), simple plain text authentication, MD5 cryptograph authentication, CIDR
(Classless Inter-Domain Routing) and multicast.
TL-ER5120 supports both RIPv1 version and RIPv2 version, thus you can configure the RIP version
based on the actual need to improve the network performance.
Choose the menu Advanced→Routing→RIP to load the following page.
-67-
Page 74

Figure 3-45 RIP
The following items are displayed on this screen:
¾ General
Interface:
Displays the interfaces which has been physically connected or assigned
static IP.
Status:
RIP Version:
Password
Authentication:
Enable or disable RIP protocol.
Select RIPv1 or RIPv2. RIPv2 supports multicast and broadcast.
If RIPv2 is enabled, set the Password Authentication according to the actual
network situation, and the password should not be more than 15 characters.
All Interfaces:
Here you can operate all the interfaces in bulk. All the interfaces will not apply
RIP if “Disable” option for All Interfaces is selected.
¾ List of RIP
After RIP is enabled, the information of RIP forwarding the packets received by the router will be
displayed in the list.
The first entry in Figure 3-45 indicates: when receiving packets with destination IP is 116.10.20.28, the
router will select WAN1 which is in the same network with the destination IP as next hop and forward
-68-
Page 75

data via this port. The IP address of next hop is 116.10.1.254 and the hop count is 1. The effective
time of this entry is 1 second.
Note:
● RIP function cannot be set if the router is in NAT Mode. To set RIP function, please change the
System Mode to Routing or Full Mode.
● The RIP function of WAN port takes effects only when the Connection Type of this WAN port is
Static IP.
3.3.5.3 Route Table
This page displays the information of the system route table.
Choose the menu Advanced→Routing→Route Table to load the following page.
Figure 3-46 RIP
The following items are displayed on this screen:
¾ Route Table
Destination:
Gateway:
Flags:
Logical Interface:
Physical
Interface:
The Destination of route entry.
The Gateway of route entry.
The Flags of route entry. The Flags describe certain characteristics of the
route.
The logical interface of route entry.
The physical interface of route entry.
-69-
Page 76
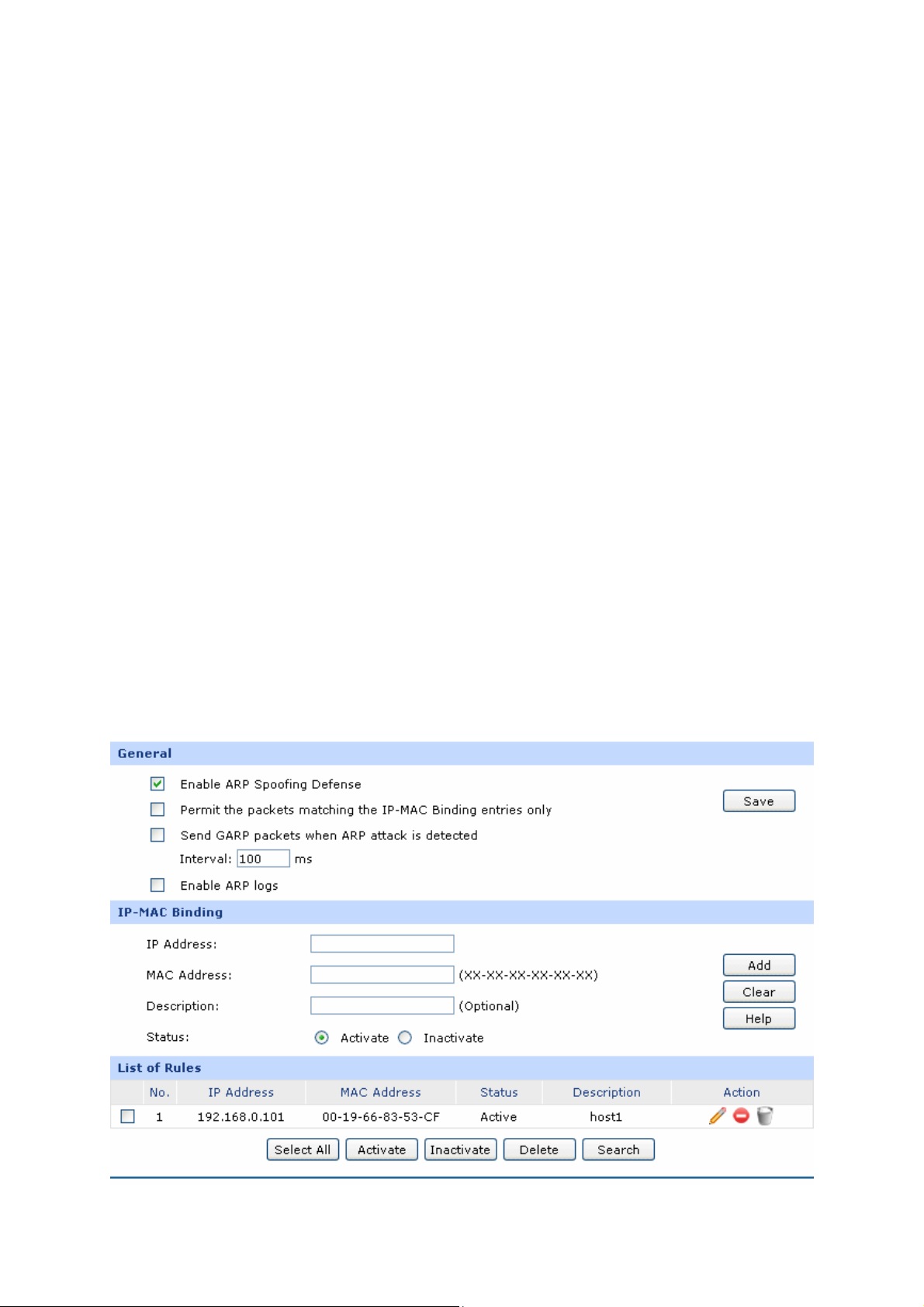
Metric
The Metric of route entry.
3.4 Firewall
3.4.1 Anti ARP Spoofing
ARP (Address Resolution Protocol) is used to analyze and map IP addresses to the corresponding
MAC addresses so that packets can be delivered to their destinations correctly.
ARP functions to translate the IP address into the corresponding MAC address and maintain an ARP
Table, where the latest used IP address-to-MAC address mapping entries are stored. ARP protocol
can facilitate the Hosts in the same network segment to communicate with one another or access to
external network via Gateway. However, since ARP protocol is implemented with the premise that all
the Hosts and Gateways are trusted, there are high security risks during ARP Implementation
Procedure in the actual complex network.
The attacker may send the ARP spoofing packets with false IP address-to-MAC address mapping
entries, and then the device will automatically update the ARP table after receiving wrong ARP
packets, which results in a breakdown of the normal communication. Thus, ARP defense technology is
generated to prevent the network from this kind of attack.
3.4.1.1 IP-MAC Binding
IP-MAC Binding functions to bind the IP address, MAC address of the host together and only allows the
Hosts matching the bound entries to access the network.
Choose the menu Firewall→Anti ARP Spoofing→IP-MAC Binding to load the following page.
Figure 3-47 IP-MAC Binding
-70-
Page 77

The following items are displayed on this screen:
¾ General
It is recommended to check all the options. You should import the IP and MAC address of the host to
List of IP-MAC Binding and enable the corresponding entry before enabling “Permit the packets
matching the IP-MAC Binding entries only”.
When suffered ARP attack, the correct ARP information will be sent to the device suffering attack
initiatively by GARP (Gratuitous ARP) packets, thus the error ARP information of the device will be
replaced. You can set the packets sending rate in the Interval field.
Check the box before Enable ARP Logs, and the router will send ARP logs to the specified server.
The IP address of server is the Server IP set on 3.6.6 Logs.
¾ IP-MAC Binding
IP Address:
MAC Address:
Description:
Status:
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-47 indicates: The IP address of 192.168.1.101 and MAC address of
00-19-66-83-53-CF have been bound and this entry is activated.
Note:
If all the entries in the binding list are disabled and “Permit the packets of IP-MAC Binding entries only”
Enter the IP Address to be bound.
Enter the MAC Address corresponding to the IP Address.
Give a description for the entry.
Activate or inactivate the entry.
option is selected and saved, the WEB management page of the router cannot be login. At the
moment, you should restore the router to factory default and login again.
3.4.1.2 ARP Scanning
ARP Scanning feature enables the router to scan the IP address and corresponding MAC address and
display them on the List of Scanning Result.
Choose the menu Firewall→Anti ARP Spoofing→ARP Scanning to load the following page.
-71-
Page 78

Figure 3-48 ARP Scanning
Enter the start and the end IP addresses in the Scanning IP Range field. Then click the <Scan> button,
the router will scan all the active hosts within the scanning range and display the result in the list.
The entries displayed on the List of Scanning Result do not mean the IP and MAC addresses are
already bound. The current status for the entry will display in the “Status” field.
--- Indicates that the IP and MAC address of this entry is not bound and may be
replaced by error ARP information.
To bind the entries in the list, check these entries and click the <Import> button, then the settings will
take effect if the entries do not conflict with the existed entries.
Note:
Indicates that this entry is imported to the list on IP-MAC Binding page, but not
effective yet.
Indicates that the IP and MAC address of this entry is already bound.
If the local hosts suffered from ARP attack, you cannot add IP-MAC Binding entries on this page.
Please add entries manually on 3.4.1.1 IP-MAC Binding.
3.4.1.3 ARP List
On this page, the IP-MAC information of the hosts which communicated with the router recently will be
saved in the ARP list.
Choose the menu Firewall→Anti ARP Spoofing→ARP List to load the following page.
-72-
Page 79

Figure 3-49 ARP List
The configurations for the entries is the same as the configuration of List of Scanning Result on 3.4.1.2
ARP Scanning page.
The unbound IP-MAC information will be replaced by new IP-MAC information or be automatically
removed from the list if it has not been communicated with others for a long time. This period is
regarded as the aging time of the ARP information.
3.4.2 Attack Defense
With Attack Defense function enabled, the router can distinguish the malicious packets and prevent
the port scanning from external network, so as to guarantee the network security.
Choose the menu Firewall→Attack Defense→Attack Defense to load the following page.
-73-
Page 80

Figure 3-50 Attack Defense
The following items are displayed on this screen:
¾ General
Flood Defense:
Flood attack is a kind of commonly used DoS (Denial of Service),
which including TCP SYN, UDP, ICMP and so on. It is
recommended to check all the Flood Defense options and specify
the corresponding thresholds. Keep the default settings if you are
not sure.
-74-
Page 81

Packet Anomaly
Defense:
Enable Attack
Defense Logs:
Packet Anomaly refers to the abnormal packets. It is
recommended to select all the Packet Anomaly Defense options.
With this box checked, the router will record the defense logs.
3.4.3 MAC Filtering
On this page, you can control the access to the Internet of local host by specifying their MAC
addresses.
Choose the menu Firewall→MAC Filtering→MAC Filtering to load the following page.
Figure 3-51 MAC Filtering
The following items are displayed on this screen:
¾ General
To control the access to Internet for hosts in you private network, it is recommended to check the
box before Enable MAC Filtering and select a filtering mode according to actual situation.
¾ MAC Filtering
MAC Address:
Description:
Enter the MAC Address to be filtered.
Give a description for the entry.
-75-
Page 82

¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
3.4.4 Access Control
3.4.4.1 URL Filtering
URL (Uniform Resource Locator) specifies where an identified resource is available and the
mechanism for retrieving it. URL Filter functions to filter the Internet URL address, so as to provide a
convenient way for controlling the access to Internet from LAN hosts.
Choose the menu Firewall→Access Control→URL Filtering to load the following page.
Figure 3-52 URL Filtering
The following items are displayed on this screen:
¾ General
To control the access to Internet for hosts in your private network, you are recommended to
check the box before Enable URL Filtering and select a filtering rule based on the actual
situation.
¾ URL Filtering Rule
Object:
Select the range in which the URL Filtering takes effect:
z Group: URL Filtering will take effect to all the users in group.
z ANY: URL Filtering will take effect to all the users.
-76-
Page 83

Mode:
Select the mode for URL Filtering. “Keywords’’ indicates that all
the URL addresses including the specified keywords will be
filtered. “URL Path” indicates that the URL address will be filtered
only when it exactly matches the specified URL.
Effective Time:
Description:
Specify the time for the entry to take effect.
Give a description for the entry.
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
Application Example:
Network Requirements:
Prevent the local hosts from accessing Internet website www.aabbcc.com anytime and downloading
the files with suffix of “exe” at 8:00-20:00 from Monday to Friday.
Configuration Procedure:
Select Keywords mode and type ”exe“ in the field, select URL mode and type “www.aabbcc.com” as
the following figure shows, then specify the effective time and click the <Add> button to make the
setting take effect.
-77-
Page 84

3.4.4.2 Web Filtering
On this page, you can filter the desired web components.
Choose the menu Firewall→Access Control→Web Filtering to load the following page.
Figure 3-53 Web Filtering
Check the box before Enable Web Filtering and select the web components to be filtered.
3.4.4.3 Access Rules
Choose the menu Firewall→Access Control→Access Rules to load the following page.
Figure 3-54 Access Rule
The following items are displayed on this screen:
-78-
Page 85

¾ Access Rules
Policy:
Service:
Interface:
Select a policy for the entry:
z Block: When this option is selected, the packets obeyed the rule
will not be allowed to pass through the router.
z Allow: When this option is selected, the packets obeyed the rule
will be allowed to pass through the router.
Select the service for the entry. Only the service belonging to the
specified service type is limited by the entry. For example, if you
select “Block” for Policy and only FTP for Service, the packets of other
service types can still pass through the router. You can add new
service types on 3.4.4.4 Service.
Select interface for the entry. The entry will take effect when the
interface to which the data is flowing is selected. WAN, LAN or DMZ
refers to all the WAN, LAN or DMZ interfaces.
Source:
Destination:
Select the Source IP Range for the entries, including the following
three ways:
z IP/MASK: Enter an IP address or subnet mask. ("0.0.0.0/32"
means any IP).
z Group: Select a predefined group of users. You can set the group
on3.2.1 Group.
z ANY: means for any users.
Select the Destination IP Range for the entries, including the following
two ways:
z IP/MASK: Enter an IP address or subnet mask. ("0.0.0.0/32"
means any IP is acceptable).
z ANY: means for any users.
Effective Time:
Description:
Specify the time for the entry to take effect.
Give a description for the entry.
-79-
Page 86

Priority:
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons. The smaller the value
is, the higher the priority is.
The first entry in Figure 3-54 indicates: The TELNET packets transmitted from the hosts within the
network of 192.168.0.0/24 will be not allowed to pass through the router at 8:00-20:00 from Tuesday to
Saturday.
Note:
● For the users in the private network and not being set access rule, the default Policy is Allow.
● To specify all IP addresses, type “0.0.0.0 / 32” in the Policy field.
Select this option to specify the priority for the added entries. The
latest enabled entry will be displayed at the end of the list by default.
● For detailed setting of subnet mask, please refer to Appendix B FAQ.
3.4.4.4 Service
The Service function allows you to specify the protocol and port number to be filtered for Firewall
function conveniently. Protocol name and port range constitute a service type. The router predefines
three commonly used services such as HTTP, FTP and TELNET and you can also add customized
services if needed.
Choose the menu Firewall→Access Control→Service to load the following page.
-80-
Page 87

Figure 3-55 Service
The following items are displayed on this screen:
¾ Service
Name:
Enter a name for the service. The name should not be more than 28
characters. The name will display in the drop-down list of Protocol on
Access Rule page.
Protocol:
Select the protocol for the service. The system predefined protocols
include TCP, UDP and TCP/UDP.
Dest. Port:
Enter the start and end ports to make a destination port range for the
service. The start port number cannot be greater than the end port
number.
¾ List of Service
You can view the information of the entries and edit them by the Action buttons.
Note:
The service types predefined by the system cannot be modified.
-81-
Page 88

3.4.5 App Control
3.4.5.1 Control Rules
On this page, you can enable the Application Rules function.
Choose the menu Firewall→App Control→Control Rules to load the following page.
Figure 3-56 Application Rules
The following items are displayed on this screen:
¾ General
Check the box before Enable Application Control to make the Application Control function
take effect. The specified application used by the specified local users will be not allowed to
access the Internet if the Application Control entry is enabled.
¾ Control Rules
Object:
Group:
Specify the object for the entry. You can select “Group” to limit the
predefined group, or select “ANY” to limit all the users.
If select “Group” as object, you can select the group in the drop-down list.
To establish new group, please refer to 3.2.1 Group.
-82-
Page 89

Application:
Effective Time:
Description:
Status:
¾ List of Rules
You can view the information of the entries and edit them by the Action buttons.
The first entry in Figure 3-56 indicates: The group1 is applied with Application Rules. You can click
<View> to view the limited applications in the popup checkbox. The effective time of this entry is
Click the <Application List> button to select applications from the popup
checkbox. The applications include IM, Web IM, SNS, P2P, Media, Basic
and Proxy. The default setting is to limit all the applications in the
application list except for Basic and Proxy.
Specify the time for the entry to take effect.
Give a description for the entry.
Activate or inactivate the entry.
7:00-9:00 on Monday, Tuesday, Friday, Saturday and Sunday. This entry is enabled.
Note:
To set the group and group members, please refer to 3.2.1 Group.
3.4.5.2 Database
On this page, you can upgrade the application database.
Choose the menu Firewall→App Control→Database to load the following page.
Figure 3-57 Database
The database refers to all the applications in the application list on the Application Rules page, you can
download the latest database from http://www.tp-link.com
file, and then click the <Upgrade> button to upgrade the database.
-83-
, Click the <Browse> button and select the
Page 90

3.5 Services
3.5.1 PPPoE Server
The router can be configured as a PPPoE server to specify account and IP address to users in LAN and
thus you can control the dial-up of users for a high efficiency in network management.
The PPPoE configuration can be implemented on General, IP Address Pool, Account, Exceptional
IP and List of Account pages.
3.5.1.1 General
On this page, you can configure PPPoE function globally.
Choose the menu Services→PPPoE Server→General to load the following page.
Figure 3-58 General
The following items are displayed on this screen:
¾ General
PPPoE Server:
Dial-up Access Only:
PPPoE User Isolation:
Specify whether to enable the PPPoE Server function.
Specify whether to enable the Dial-up Access Only function. If
enabled, only the Dial-in Users and the user with Exceptional IP can
access the Internet.
Specify whether to allow the Dial-in Users to communicate with one
another.
-84-
Page 91

Primary/Secondary
DNS:
Max Sessions:
Max Echo-Requests:
Idle Timeout:
Authentication:
Enter the Primary/Secondary DNS server address. The default is
0.0.0.0.
Specify the maximum number of the sessions for PPPoE server. The
default is 256.
Specify the maximum number of Echo-Requests sent by the server to
wait for response. The default is 10. The link will be dropped when the
number of the unacknowledged LCP echo requests reaches your
specified Max Echo-Requests.
Enter the maximum idle time. The session will be terminated after it
has been inactive for this specified period. It can be 0-10080 minutes.
If you want your Internet connection to remain on at all times, enter 0
in the Idle Timeout field. The default value is 30.
Select the Authentication type. It can be Local authentication and
Auth Protocol:
Radius Server:
Remote authentication. Select Local authentication for authentication
in PPPoE server and select Remote authentication for authentication
in the remote server.
Select at least one authentication protocol for Local Authentication.
z PAP, transferring username and password in plain text in the
network, is used in a less secured network.
z CHAP is more secured for it adopts three handshakes and does
not transfer password in plain text.
z MS-CHAP, put forward by Microsoft, adopts a different encryption
algorithm of CHAP.
z MS-CHAP v2 with a higher security is an improved version of
MS-CHAP.
It is available when Remote Authentication is selected. RADIUS
(Remote Authentication Dial In User Service) provides an
authentication for dial-up users. Enter the Radius Server address for
Remote authentication.
Shared Key:
Enter the Shared Key for Remote authentication. It should be the
same to the shared key of the Radius Server.
3.5.1.2 IP Address Pool
On this page, you can define or edit the IP Address Pool.
Choose the menu Services→PPPoE Server→IP Address Pool to load the following page.
-85-
Page 92
Figure 3-59 IP Address Pool
The following items are displayed on this screen:
¾ IP Address Pool
Pool Name:
Specify a unique name to the IP Address Pool for identification and
management purposes.
IP Address Range:
Specify the start and the end IP address for IP Pool. The start IP address
should not exceed the end address and the IP address ranges must not
overlap.
¾ List of IP Pool
In this table, you can view the information of IP Address Pools and edit them by the Action buttons.
3.5.1.3 Account
On this page, you can configure the PPPoE account.
Choose the menu Services→PPPoE Server→Account to load the following page.
-86-
Page 93

Figure 3-60 Account
The following items are displayed on this screen:
¾ Account
Account Name:
Enter the account name. This name should not be the same with the
one in L2TP/PPTP connection settings.
Password:
IP Address Assigned
Mode:
Enter the password.
Select the IP Address Assigned Mode for IP assignment.
z Static: Select this option to assign a static IP address to the client.
z Dynamic: Select this option to assign available IP addresses to the
client automatically.
Static IP Address:
It's available on Static mode. Enter a static IP address for the client.
IP Address Pool:
Max Sessions:
Expiration Date:
It's available on Dynamic mode. Select an IP Address Pool to make a
range to assign dynamic IPs.
Specify the maximum number of sessions for the client. The default
value is 1.
Specify the Expiration Date of the account. The default is 2099-1-1.
-87-
Page 94

Description:
Status:
MAC Binding:
MAC Address:
Enter the description for management and search purposes. Up to 28
characters can be entered.
Activate or inactivate the entry.
Select a MAC Binding type from the pull-down list. Options include:
z Disable: Select this option to disable the MAC Binding function.
z Manual: Select this option to bind the account to a MAC address
manually. Only from the Host with this MAC address can the
account log on to the server.
z Automatical: Select this option to bind the account to the MAC
address of its first login automatically. Only from the Host with this
MAC address can the account log on to the server.
It is available when Manually is selected. Enter the MAC address of the
Host to bind with the account.
Session Timeout:
Enter a time after which the connection will be dropped. To keep the
connection always on, enter 0 in the Session Timeout field. The default
is 48. If Enable Advanced Account Features is not selected, the
Session Timeout value is 0 by default.
¾ List of Account
In this table, you can view the information of accounts and edit them by the Action buttons.
3.5.1.4 Exceptional IP
When the Dial-up Access Only function is enabled, only the Dial-in Users and the user with
Exceptional IP can access the Internet. On this page, you can specify the Exceptional IP.
Choose the menu Services→PPPoE Server→Exceptional IP to load the following page.
-88-
Page 95

Figure 3-61 Exceptional IP
The following items are displayed on this screen:
¾ Exceptional IP
IP Address Range:
Specify the start and the end IP address to make an exceptional IP address
range. This range should be in the same IP range with LAN port or DMZ
port of the router. The start IP address should not exceed the end address
and the IP address ranges must not overlap.
Description:
Status:
¾ List of Account
Give a description to the exceptional IP address range for identification.
Activate or inactivate the entry.
In this table, you can view the information of Exceptional IPs and edit them by the Action buttons.
3.5.1.5 List of Account
On this page, you can view the detailed information of all accounts you have established.
Choose the menu Services→PPPoE Server→List of Account to load the following page.
Figure 3-62 List of Account
Figure 3-62 displays the connection information of PPPoE users. Click
Click the <Disconnect All> button to disconnect all accounts.
-89-
to disconnect the account.
Page 96

3.5.2 E-Bulletin
With E-Bulletin function, bulletin information can be released to the specified users. On this page you
can edit the bulletin content and specify the receiving user group.
Choose the menu Services→E-Bulletin to load the following page.
Figure 3-63 E-Bulletin
The following items are displayed on this screen:
¾ General
Enable E-Bulletin:
Interval:
Specify whether to enable electronic bulletin function.
Specify the interval to release the bulletin.
-90-
Page 97

Enable Logs:
¾ E-Bulletin
Title:
Content:
Object:
Specify whether to log the E-Bulletin.
Enter a title for the bulletin.
Enter the content of the bulletin.
Select the object of this bulletin. Options include:
z ANY: The bulletin will be released to all the users and the PCs on the
LAN.
z Group: The bulletin will be released to the users in the selected group.
You can click < > button to add a group to the selected group
and click <
> to remove a group from the selected group.
Group is created on User Group→Group page.
Effective Time:
Specify the effective time for the bulletin. Only one bulletin can be set for
the object at the same time.
Publisher:
Description:
Status:
¾ List of E-Bulletin
Enter the name of the bulletin's publisher.
Enter the description for the bulletin.
Activate or inactivate the entry.
In this table, you can view the existing bulletins and edit them by the Action button.
The No.1 entry in Figure 3-63 indicates: this bulletin is released by the administrator, and it is
released to the Group1 from 8am to 20pm on Thursday and Friday every a bulletin interval. (the
interval in the figure is 30 min). This entry is enabled.
Tips:
For the configuration for groups and users, please refer to the User Group section.
3.5.3 Dynamic DNS
DDNS (Dynamic DNS) service allows you to assign a fixed domain name to a dynamic WAN IP
address, which enables the Internet hosts to access the router or the hosts in LAN using the domain
names.
-91-
Page 98

As many ISPs use DHCP to assign public IP addresses in WAN, the public IP address assigned to the
client is unfixed. In this way, it’s very difficult for other clients to get the latest IP address of this client
for access.
DDNS (Dynamic DNS) server provides a fixed domain name for DDNS client and maps its latest IP
address to this domain name. When DDNS server works, DDNS client informs the DDNS server of the
latest IP address, the server will update the mappings between the domain name and IP address in
DNS database. Therefore, the users can use the same domain name to access the DDNS client even
if the IP address of the DDNS client has changed. DDNS is usually used for the Internet users to
access the private website and FTP server, both of which are established based on Web server.
The router, as a DDNS client, cannot provide DDNS service. Prior to using this function, be sure you
have registered on the official websites of DDNS service providers for username, password and
domain name. TL-ER5120 router offers PeanutHull DDNS client, Dyndns DDNS client, NO-IP DDNS
client and Comexe DDNS client.
The Dynamic DNS can be implemented on DynDNS DDNS, No-IP DDNS, Peanuthull DDNS and
Comexe DDNS pages.
3.5.3.1 DynDNS
On this page, you can configure DynDNS client.
Choose the menu Services→Dynamic DNS→DynDNS to load the following page.
Figure 3-64 DynDNS DDNS
The following items are displayed on this screen:
-92-
Page 99

¾ Dyndns DDNS
Account Name:
Password:
Domain Name:
DDNS Service:
WAN Port:
DDNS Status:
Enter the Account Name of your DDNS account. If you have not registered,
click <Go to register> to go to the website of Dyndns for register.
Enter the password of your DDNS account.
Enter the Domain Name that you registered with your DDNS service
provider.
Activate or inactivate DDNS service here.
Displays the WAN port for which Dyndns DDNS is selected.
Displays the current status of DDNS service
z Offline: DDNS service is disabled.
z Connecting: client is connecting to the server.
z Online: DDNS works normally.
z Authorization fails: The Account Name or Password is incorrect.
Please check and enter it again.
¾ List of DynDNS Account
In this table, you can view the existing DDNS entries or edit them by the Action button.
3.5.3.2 No-IP
On this page you can configure NO-IP DDNS client.
Choose the menu Services→Dynamic DNS→No-IP to load the following page.
-93-
Page 100
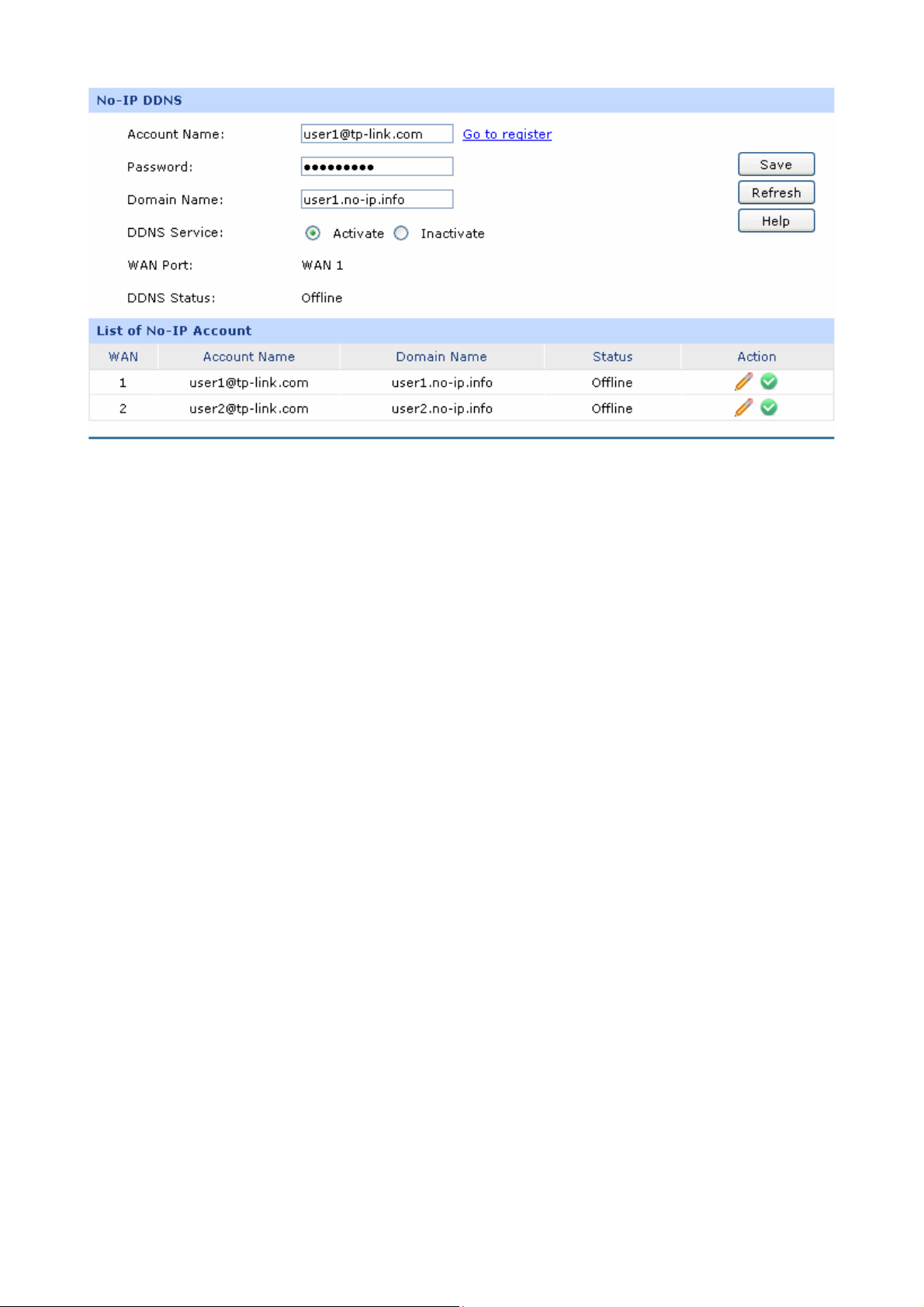
Figure 3-65 NO-IP DDNS
The following items are displayed on this screen:
¾ No-IP DDNS
Account Name:
Password:
Domain Name:
DDNS Service:
WAN Port:
DDNS Status:
Enter the Account Name of your DDNS account. If you have not registered,
click <Go to register> to go to the website of No-IP for register.
Enter the password of your DDNS account.
Enter the Domain Name that you registered with your DDNS service
provider.
Activate or inactivate DDNS service here.
Displays the WAN port for which No-IP DDNS is selected.
Displays the current status of DDNS service
z Offline: DDNS service is disabled.
z Connecting: client is connecting to the server.
z Online: DDNS works normally.
z Authorization fails: The Account Name or Password is incorrect.
Please check and enter it again.
¾ List of No-IP Account
In this table, you can view the existing DDNS entries or edit them by the Action button.
-94-
 Loading...
Loading...