Page 1

User Guide
Omada Gigabit VPN Router
© 2021 TP-Link REV1.0.1 1910012985
Page 2

CONTENTS
About This Guide
Intended Readers ................................................................................................................................................................1
Conventions ...........................................................................................................................................................................1
More Information .................................................................................................................................................................1
Accessing the Router
Determine the Management Method ........................................................................................................................... 3
Web Interface Access ........................................................................................................................................................4
Viewing Status Information
System Status ....................................................................................................................................................................... 7
Traffic Statistics .................................................................................................................................................................. 8
Viewing the Interface Statistics .........................................................................................................................................................8
Viewing the IP Statistics .........................................................................................................................................................................9
Configuring Network
Overview .............................................................................................................................................................................. 12
Supported Features ..............................................................................................................................................................................12
WAN Configuration .......................................................................................................................................................... 13
Configuring the Number of WAN Ports ......................................................................................................................................13
Configuring the WAN Connection ................................................................................................................................................13
LAN Configuration ............................................................................................................................................................ 23
Configuring the IP Address of the LAN Port ............................................................................................................................23
Configuring the DHCP Server ..........................................................................................................................................................24
Viewing the DHCP Client List ...........................................................................................................................................................26
MAC Configuration ........................................................................................................................................................... 28
Configuring MAC Address ................................................................................................................................................................28
Switch Configuration ....................................................................................................................................................... 30
Viewing the Statistics (only for certain devices) ....................................................................................................................30
Configuring Port Mirror ........................................................................................................................................................................31
Configuring Rate Control (only for certain devices) ............................................................................................................32
Configuring Port Config ......................................................................................................................................................................33
Viewing Port Status ...............................................................................................................................................................................34
VLAN Configuration ......................................................................................................................................................... 35
Page 3

Creating a VLAN ......................................................................................................................................................................................35
Configuring the PVID of a Port ........................................................................................................................................................36
Configuring Preferences
Overview .............................................................................................................................................................................. 39
IP Group Configuration .................................................................................................................................................. 40
Adding IP Address Entries .................................................................................................................................................................40
Grouping IP Address Entries ............................................................................................................................................................41
Time Range Configuration ............................................................................................................................................. 42
VPN IP Pool Configuration ............................................................................................................................................. 44
Service Type Configuration .......................................................................................................................................... 45
Configuring Transmission
Transmission ...................................................................................................................................................................... 49
Overview ......................................................................................................................................................................................................49
Supported Features ..............................................................................................................................................................................49
NAT Configurations.......................................................................................................................................................... 51
Configuring the One-to-One NAT .................................................................................................................................................51
Configuring the Virtual Servers .......................................................................................................................................................52
Configuring the Port Triggering ......................................................................................................................................................53
Configuring the NAT-DMZ .................................................................................................................................................................54
Configuring the ALG .............................................................................................................................................................................54
Bandwidth Control Configuration ............................................................................................................................... 56
Session Limit Configurations ....................................................................................................................................... 58
Configuring Session Limit ..................................................................................................................................................................58
Viewing the Session Limit Information .......................................................................................................................................59
Load Balancing Configurations ................................................................................................................................... 60
Configuring the Load Balancing .....................................................................................................................................................60
Configuring the Link Backup ............................................................................................................................................................61
Configuring the Online Detection ..................................................................................................................................................62
Routing Configurations ................................................................................................................................................... 63
Configuring the Static Routing ........................................................................................................................................................63
Configuring the Policy Routing .......................................................................................................................................................64
Viewing the Routing Table .................................................................................................................................................................65
Configuration Examples ................................................................................................................................................. 66
Example for Configuring NAT ..........................................................................................................................................................66
Network Requirements ..........................................................................................................................................................66
Page 4

Network Topology ....................................................................................................................................................................66
Configuration Scheme ...........................................................................................................................................................66
Configuration Procedure ......................................................................................................................................................67
Example for Configuring Load Balancing ..................................................................................................................................68
Network Requirements ..........................................................................................................................................................68
Network Topology ....................................................................................................................................................................69
Configuration Scheme ...........................................................................................................................................................69
Configuration Procedure ......................................................................................................................................................69
Example for Configuring Virtual Server ......................................................................................................................................70
Network Requirements ..........................................................................................................................................................70
Network Topology ....................................................................................................................................................................70
Configuration Scheme ...........................................................................................................................................................70
Configuration Procedure ......................................................................................................................................................70
Example for Configuring Policy Routing ....................................................................................................................................71
Network Requirements ..........................................................................................................................................................71
Network Topology ....................................................................................................................................................................72
Configuration Scheme ...........................................................................................................................................................72
Configuration Procedure ......................................................................................................................................................72
Configuring Firewall
Firewall .................................................................................................................................................................................. 76
Overview ......................................................................................................................................................................................................76
Supported Features ..............................................................................................................................................................................76
Firewall Configuration ..................................................................................................................................................... 78
Anti ARP Spoofing ..................................................................................................................................................................................78
Adding IP-MAC Binding Entries ........................................................................................................................................78
Enable Anti ARP Spoofing ....................................................................................................................................................81
Configuring Attack Defense .............................................................................................................................................................83
Configuring Access Control .............................................................................................................................................................85
Configuration Examples ................................................................................................................................................. 87
Example for Anti ARP Spoofing ......................................................................................................................................................87
Network Requirements ..........................................................................................................................................................87
Configuration Scheme ...........................................................................................................................................................87
Configuration Procedure ......................................................................................................................................................88
Example for Access Control ............................................................................................................................................................90
Network Requirements ..........................................................................................................................................................90
Configuration Scheme ...........................................................................................................................................................91
Page 5

Configuration Procedure ......................................................................................................................................................91
Configuring Behavior Control
Behavior Control ............................................................................................................................................................... 97
Overview ......................................................................................................................................................................................................97
Supported Features ..............................................................................................................................................................................97
Behavior Control Configuration .................................................................................................................................. 98
Configuring Web Filtering ..................................................................................................................................................................98
Configure Web Group Filtering ..........................................................................................................................................98
Configuring URL Filtering ...................................................................................................................................................101
Configuring Web Security ...............................................................................................................................................................103
Configuration Examples ...............................................................................................................................................105
Example for Access Control .........................................................................................................................................................105
Network Requirements .......................................................................................................................................................105
Configuration Scheme ........................................................................................................................................................105
Configuration Procedure ...................................................................................................................................................106
Example for Web Security ..............................................................................................................................................................109
Network Requirements .......................................................................................................................................................109
Configuration Scheme ........................................................................................................................................................109
Configuration Procedure ...................................................................................................................................................109
Configuring VPN
VPN .......................................................................................................................................................................................112
Overview ...................................................................................................................................................................................................112
Supported Features ...........................................................................................................................................................................113
IPSec VPN Configuration .............................................................................................................................................116
Configuring the IPSec Policy.........................................................................................................................................................116
Configuring the Basic Parameters ...............................................................................................................................116
Configuring the Advanced Parameters .....................................................................................................................118
Verifying the Connectivity of the IPSec VPN tunnel ........................................................................................................120
L2TP Configuration ........................................................................................................................................................122
Configuring the VPN IP Pool ..........................................................................................................................................................122
Configuring L2TP Globally ..............................................................................................................................................................123
Configuring the L2TP Server ........................................................................................................................................................123
Configuring the L2TP Client ..........................................................................................................................................................124
(Optional) Configuring the L2TP Users ....................................................................................................................................126
Verifying the Connectivity of L2TP VPN Tunnel .................................................................................................................127
Page 6

PPTP Configuration ........................................................................................................................................................128
Configuring the VPN IP Pool ..........................................................................................................................................................128
Configuring PPTP Globally .............................................................................................................................................................129
Configuring the PPTP Server ........................................................................................................................................................129
Configuring the PPTP Client ..........................................................................................................................................................130
(Optional) Configuring the PPTP Users ...................................................................................................................................131
Verifying the Connectivity of PPTP VPN Tunnel ................................................................................................................132
Configuration Examples ...............................................................................................................................................134
Example for Configuring IPSec VPN .........................................................................................................................................134
Network Requirements .......................................................................................................................................................134
Network Topology .................................................................................................................................................................134
Configuration Scheme ........................................................................................................................................................134
Configuration Procedure ...................................................................................................................................................135
Example for Configuring L2TP VPN ..........................................................................................................................................138
Network Requirements .......................................................................................................................................................138
Configuration Scheme ........................................................................................................................................................139
Configuration Procedure ...................................................................................................................................................139
Example for Configuring PPTP VPN ..........................................................................................................................................141
Network Requirements .......................................................................................................................................................141
Configuration Scheme ........................................................................................................................................................141
Configuration Procedure ...................................................................................................................................................141
Configuring Authentication
Overview ............................................................................................................................................................................145
Typical Topology .................................................................................................................................................................................145
Portal Authentication Process .....................................................................................................................................................146
Supported Features ...........................................................................................................................................................................146
Supported Web Server .......................................................................................................................................................147
Supported Authentication Server.................................................................................................................................147
Guest Resources....................................................................................................................................................................147
Local Authentication Configuration .........................................................................................................................148
Configuring the Authentication Page .......................................................................................................................................148
Configuring the Local User Account ........................................................................................................................................151
Configuring the Local User Account ...........................................................................................................................151
(Optional) Configuring the Backup of Local Users ..............................................................................................154
Radius Authentication Configuration ......................................................................................................................155
Configuring Radius Authentication ............................................................................................................................................155
Page 7

Onekey Online Configuration .....................................................................................................................................158
Configuring the Authentication Page .......................................................................................................................................158
Guest Resources Configuration ................................................................................................................................160
Configuring the Five Tuple Type .................................................................................................................................................160
Configuring the URL Type...............................................................................................................................................................162
Viewing the Authentication Status ...........................................................................................................................164
Configuration Example .................................................................................................................................................165
Network Requirements .....................................................................................................................................................................165
Configuration Scheme .....................................................................................................................................................................165
Configuration Procedures ..............................................................................................................................................................166
Configuring the Authentication Page .........................................................................................................................166
Configuring Authentication Accounts for the Guests .......................................................................................167
Managing Services
Services ..............................................................................................................................................................................169
Overview ...................................................................................................................................................................................................169
Support Features .................................................................................................................................................................................169
Dynamic DNS Configurations ....................................................................................................................................170
Configure and View Peanuthull DDNS .....................................................................................................................................170
Configure and View Comexe DDNS .........................................................................................................................................171
Configure and View DynDNS ........................................................................................................................................................172
Configure and View NO-IP DDNS ...............................................................................................................................................174
UPnP Configuration .......................................................................................................................................................176
Configuration Example for Dynamic DNS..............................................................................................................177
Network Requirement .......................................................................................................................................................................177
Configuration Scheme .....................................................................................................................................................................177
Configuration Procedure .................................................................................................................................................................177
Specifying the IP Address of the Host .......................................................................................................................177
Configuring the DDNS function .....................................................................................................................................177
System Tools
System Tools ....................................................................................................................................................................180
Overview ...................................................................................................................................................................................................180
Support Features .................................................................................................................................................................................180
Admin Setup .....................................................................................................................................................................181
Admin Setup ...........................................................................................................................................................................................181
Remote Management .......................................................................................................................................................................182
Page 8

System Setting .....................................................................................................................................................................................182
Controller Settings .........................................................................................................................................................184
Enable Cloud-Based Controller Management ....................................................................................................................184
Configure Controller Inform URL ................................................................................................................................................185
Management .....................................................................................................................................................................186
Factory Default Restore ...................................................................................................................................................................186
Backup & Restore ................................................................................................................................................................................186
Reboot .......................................................................................................................................................................................................187
Firmware Upgrade ...............................................................................................................................................................................187
SNMP ...................................................................................................................................................................................188
Diagnostics .......................................................................................................................................................................189
Diagnostics .............................................................................................................................................................................................189
Configuring Ping .....................................................................................................................................................................189
Configuring Traceroute ......................................................................................................................................................190
Remote Assistance ............................................................................................................................................................................191
Time Settings ...................................................................................................................................................................192
Setting the System Time .................................................................................................................................................................192
Getting time from the Internet Automatically .........................................................................................................192
Setting the System Time Manually...............................................................................................................................193
Setting the Daylight Saving Time................................................................................................................................................193
Predefined Mode ....................................................................................................................................................................193
Recurring Mode ......................................................................................................................................................................194
Date Mode .................................................................................................................................................................................195
System Log .......................................................................................................................................................................196
Page 9

About This Guide Intended Readers
About This Guide
This User Guide provides information for managing Omada Gigabit VPN Router. Please
read this guide carefully before operation.
Intended Readers
This Guide is intended for network managers familiar with IT concepts and network
terminologies.
Conventions
When using this guide, notice that features available in SafeStream series products may
vary by model and software version. Availability of SafeStream series products may also
vary by region or ISP. All images, steps, and descriptions in this guide are only examples
and may not reflect your actual experience.
Some models featured in this guide may be unavailable in your country or region. For local
sales information, visit https://www.tp-link.com.
The information in this document is subject to change without notice. Every effort has
been made in the preparation of this document to ensure accuracy of the contents, but
all statements, information, and recommendations in this document do not constitute
the warranty of any kind, express or implied. Users must take full responsibility for their
application of any products.
In this Guide, the following conventions are used:
■ The symbol
you make better use of your device.
■ Menu Name > Submenu Name > Tab page indicates the menu structure. Status >
Traffic Statistics > Interface Statistics means the Interface Statistics page under the
Traffic Statistics menu option that is located under the Status menu.
■ Bold font indicates a button, toolbar icon, menu or menu item.
stands for Note. Notes contain suggestions or references that helps
More Information
■ The latest software and documentations can be found at Download Center at
https://www.tp-link.com/support.
■ The Installation Guide (IG) can be found where you find this guide or inside the package
of the router.
■ Specifications can be found on the product page at https://www.tp-link.com.
■ To ask questions, find answers, and communicate with TP-Link users or engineers,
please visit https://community.tp-link.com to join TP-Link Community.
■ Our Technical Support contact information can be found at the Contact Technical
Support page at https://www.tp-link.com/support.
User Guide
1
Page 10

Part 1
Accessing the Router
CHAPTERS
1. Determine the Management Method
2. Web Interface Access
Page 11
Accessing the Router Determine the Management Method
1
Determine the Management Method
Before building your network, choose a proper method to manage your router based on
your actual network situation. The router supports two configuration options: Standalone
Mode or Controller Mode.
■ Controller Mode
If you want to configure and manage a large-scale network centrally, which consists
of mass devices such as access points, switches, and gateways, Controller Mode is
recommended. In Controller Mode, the router can be centrally configured and monitored
via Omada SDN Controller.
To prepare the router for Omada SDN Controller Management, refer to Controller
Settings. For detailed instructions about the network topology in such situations
and how to use Omada SDN Controller, refer to the User Guide of Omada SDN
Controller. The guide can be found on the download center of our official website:
https://www.tp-link.com/support/download/.
■ Standalone Mode
If you have a relatively small-sized network and only one or just a small number of devices
need to be managed, Standalone Mode is recommended. In Standalone Mode, you can
access and manage the router using the GUI (Graphical User Interface, also called web
interface in this text). The router uses two built-in web servers, HTTP server and HTTPS
server, for user authentication.
This User Guide introduces how to configure and monitor the router in Standalone Mode.
Note:
The GUI is inaccessible while the router is managed by a controller. To turn the router back to Standalone
Mode and access its GUI, you can forget the router on the controller or reset the router.
User Guide
3
Page 12
Accessing the Router Web Interface Access
2
Web Interface Access
The following example shows how to log in via the web browser.
1) Connect a PC to a LAN port of the router with an RJ45 port properly. If your computer is
configured with a fixed IP address, change it to “Obtain an IP address automatically“.
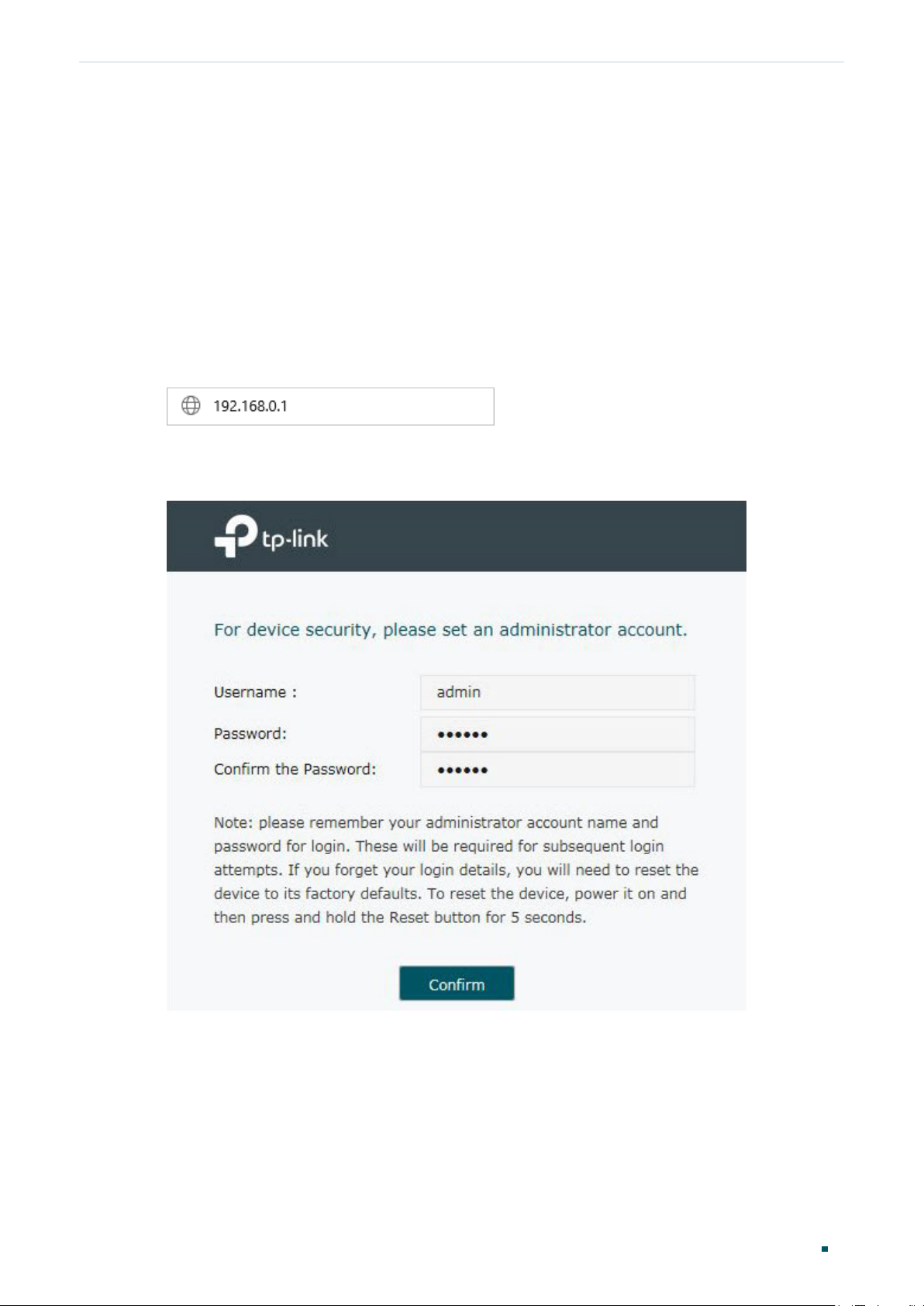
2) Open a web browser and type the default management address http://192.168.0.1 in
the address field of the browser, then press the Enter key.
Figure 2-1 Enter the router's IP Address In the Browser
3) Create a username and a password for subsequent login attempts.
Figure 2-2 Create a Username and a Password
User Guide 4
Page 13
Accessing the Router Web Interface Access
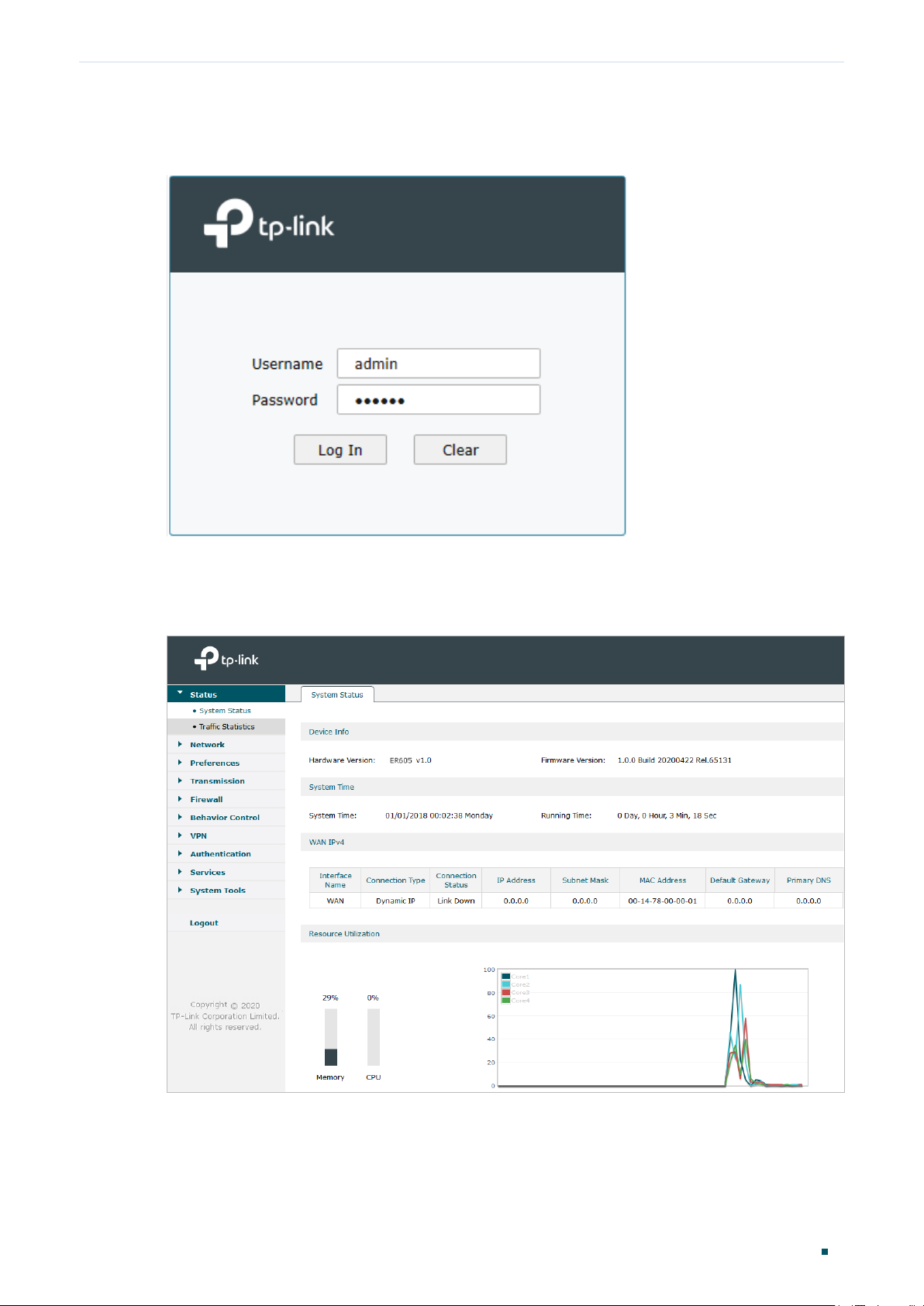
4) Use the username and password set above to log in to the webpage.
Figure 2-3 Login Authentication
5) After a successful login, the main page will appear as shown below, and you can
configure the function by clicking the setup menu on the left side of the screen.
Figure 2-4 Web Interface
User Guide
5
Page 14

Part 2
Viewing Status Information
CHAPTERS
1. System Status
2. Traffic Statistics
Page 15
Viewing Status Information System Status
1
System Status
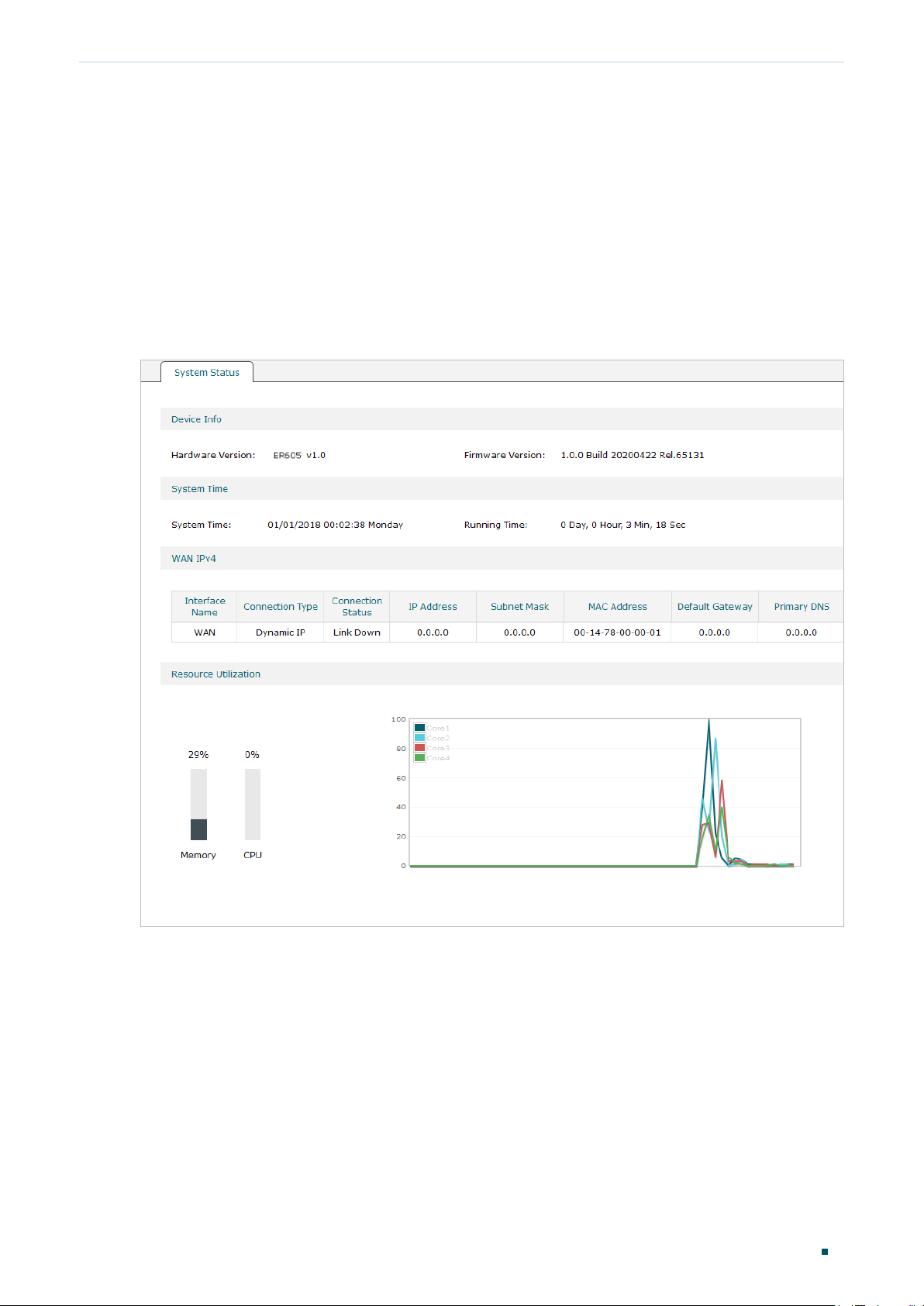
The System Status page displays the basic system information (like the hardware version,
firmware version and system time) and the running information (like the WAN interface
status, memory utilization and CPU utilization).
Choose the menu Status > System Status > System Status to load the following page.
Figure 1-1 System Status
User Guide
7
Page 16
Viewing Status Information Traffic Statistics
2
Traffic Statistics
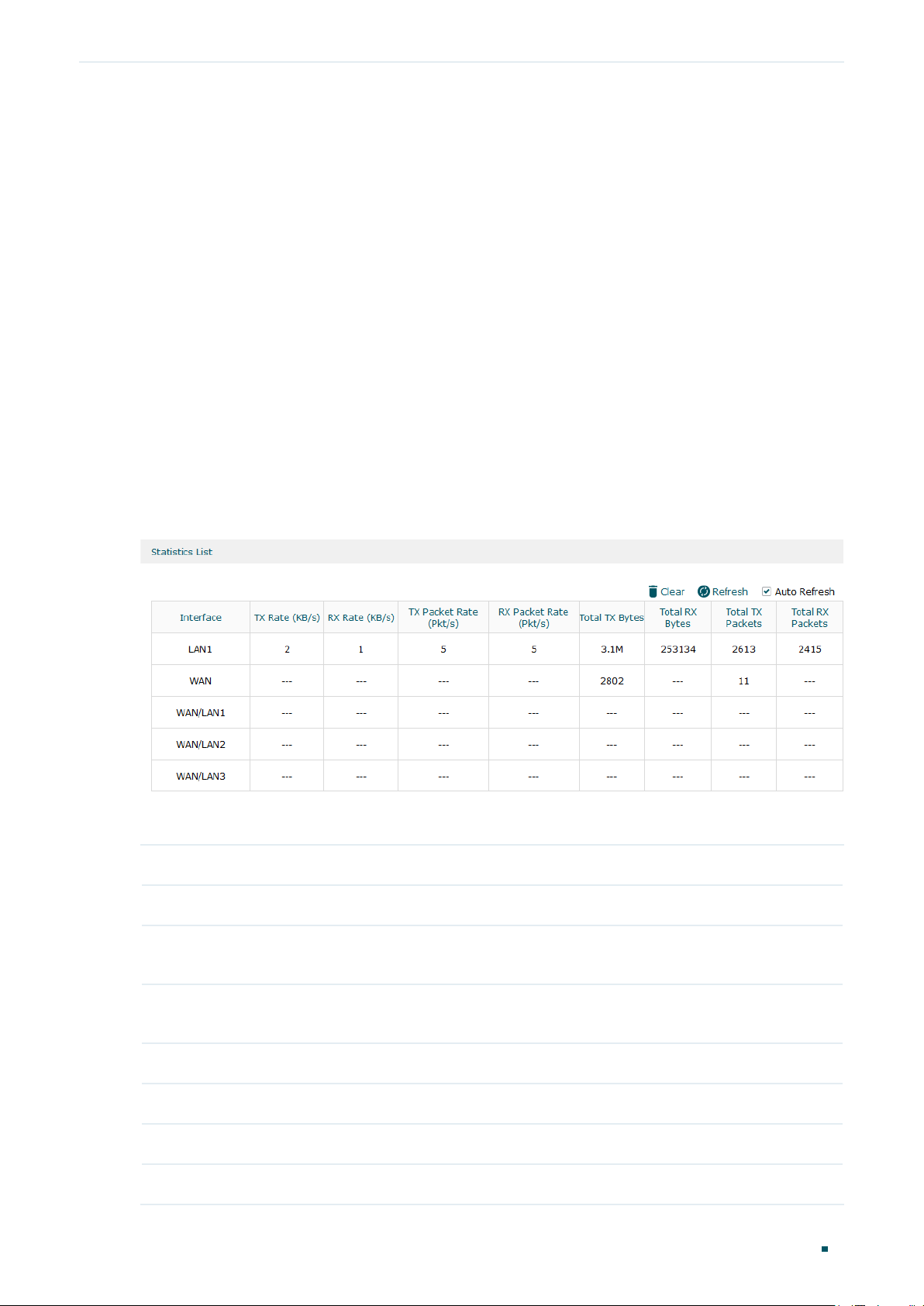
Traffic Statistics displays detailed information relating to the data traffic of interfaces and
IP addresses. You can monitor the traffic and locate faults according to this information.
With the Traffic Statistics function, you can:
■ View the traffic statistics on each interface.
■ Specify an IP address range, and view the traffic statistics of the IP addresses in this
range.
2.1 Viewing the Interface Statistics
Choose the menu Status > Traffic Statistics > Interface Statistics to load the following page.
Figure 2-1 Interface Statistics
View the detailed traffic information of each interface in the statistics list.
TX Rate (KB/s) Displays the rate for transmitting data in kilobytes per second.
RX Rate (KB/s) Displays the rate for receiving data in kilobytes per second.
TX Packet Rate
(Pkt/s)
RX Packet Rate
(Pkt/s)
Total TX Bytes Displays the bytes of packets transmitted on the interface.
Total RX Bytes Displays the bytes of packets received on the interface.
Total TX Packets Displays the number of packets transmitted on the interface.
Total RX Packets Displays the number of packets received on the interface.
Displays the rate for transmitting data in packets per second.
Displays the rate for receiving data in packets per second.
User Guide 8
Page 17
Viewing Status Information Traffic Statistics
You can enable Auto Refresh or click Refresh to get the latest statistics information, or
click Clear to clear the current statistics information.
2.2 Viewing the IP Statistics
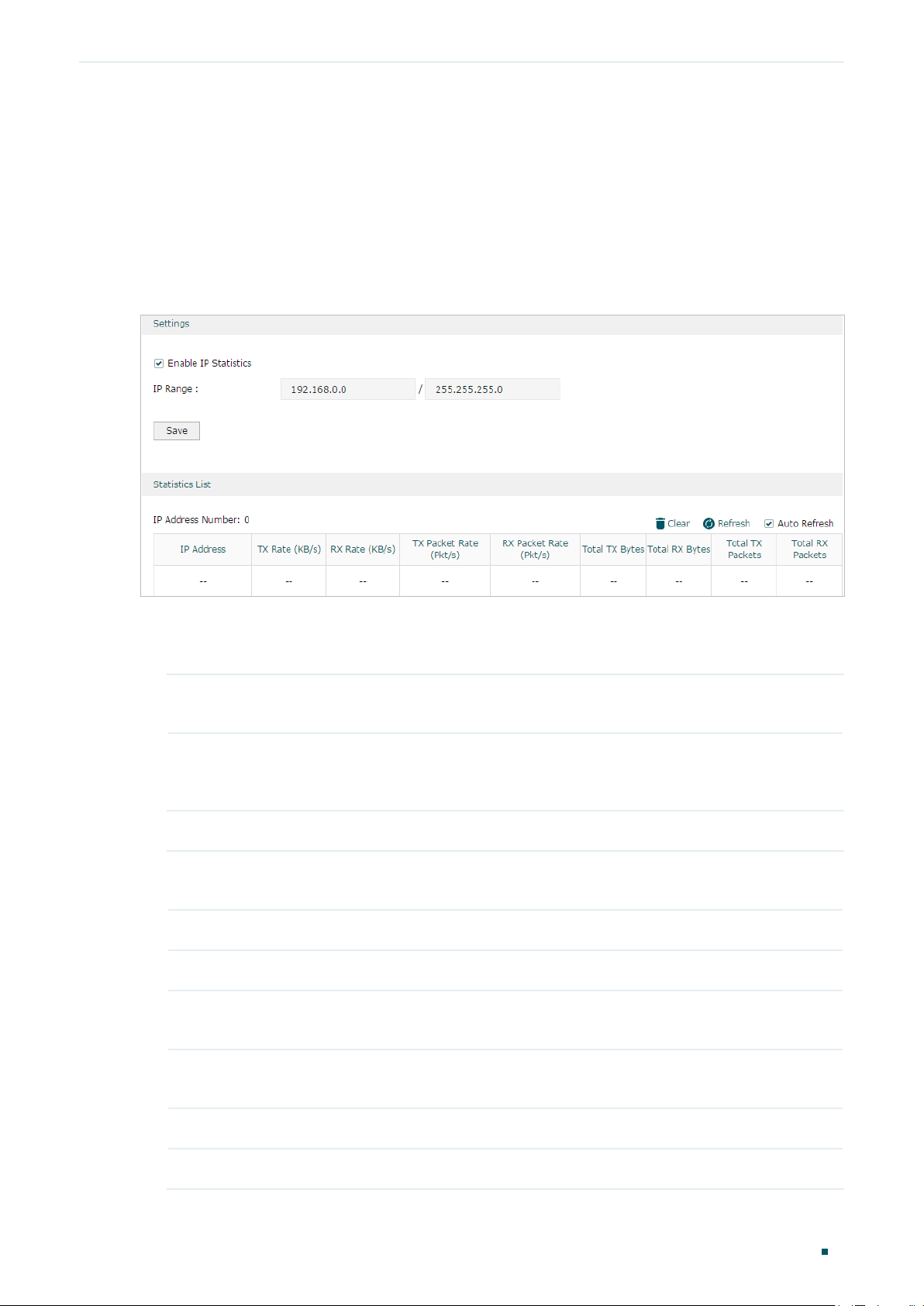
Choose the menu Status > Traffic Statistics > IP Statistics to load the following page.
Figure 2-2 IP Statistics
Follow these steps to view the traffic statistics of the specific IP addresses:
1) In the Settings section, enable IP Statistics and specify an IP range to monitor.
Enable IP
Statistics
IP Range Specify an IP range. The gateway will monitor the packets whose source
Check the box to enable IP Statistics.
IP addresses or destination IP addresses are in this range, and display the
statistics information in Statistics List.
2) In the Statistics List section, view the detailed traffic information of the IP addresses.
IP Address
Number
TX Rate (KB/s) Displays the rate for transmitting data in kilobytes per second.
RX Rate (KB/s) Displays the rate for receiving data in kilobytes per second.
TX Packet Rate
(Pkt/s)
RX Packet Rate
(Pkt/s)
Displays the number of active users whose IP address is in the specified IP
range.
Displays the rate for transmitting data in packets per second.
Displays the rate for receiving data in packets per second.
Total TX Bytes Displays the bytes of packets transmitted by the user who owns the IP address.
Total RX Bytes Displays the bytes of packets received by the user who owns the IP address.
User Guide
9
Page 18
Viewing Status Information Traffic Statistics
Total TX Packets Displays the number of packets transmitted by the user who owns the IP
address.
Total RX Packets Displays the number of packets received by the user who owns the IP address.
You can enable Auto Refresh or click Refresh to get the latest statistics information, or
click Clear to clear the current statistics information.
User Guide 10
Page 19

Part 3
Configuring Network
CHAPTERS
1. Overview
2. WAN Conguration
3. LAN Conguration
4. MAC Conguration
5. Switch Conguration
6. VLAN Conguration
Page 20

Configuring Network Overview
1
Overview
The Network module provides basic router functions, including WAN connection, DHCP
service, VLAN and more.
1.1 Supported Features
WAN
You can configure up to four WAN ports for your network. Each WAN port has its own
internet connection, providing link backup and load balancing.
LAN
For LAN configuration, you can configure the LAN IP address and DHCP (Dynamic Host
Configuration Protocol) server. With its DHCP server enabled, the router can automatically
assign IP addresses to hosts in the LAN.
MAC
You can change the default MAC address of the WAN port or LAN port according to your
needs.
Switch
The router supports some basic switch port management functions, like Port Mirror, Rate
Control, Flow Control and Port Negotiation, to help you monitor the traffic and manage the
network effectively.
VLAN
The router supports 802.1Q VLAN, which can divide the LAN into multiple VLANs, helping
manage the network more effectively.
User Guide 12
Page 21
Configuring Network WAN Configuration
2
WAN Configuration
You can configure multiple WAN ports for your network. Each WAN port can have its own
WAN connection, providing link backup and load balancing.
To complete WAN configuration, follow these steps:
1) Configure the number of WAN ports.
2) Configure the WAN connection.
2.1 Configuring the Number of WAN Ports
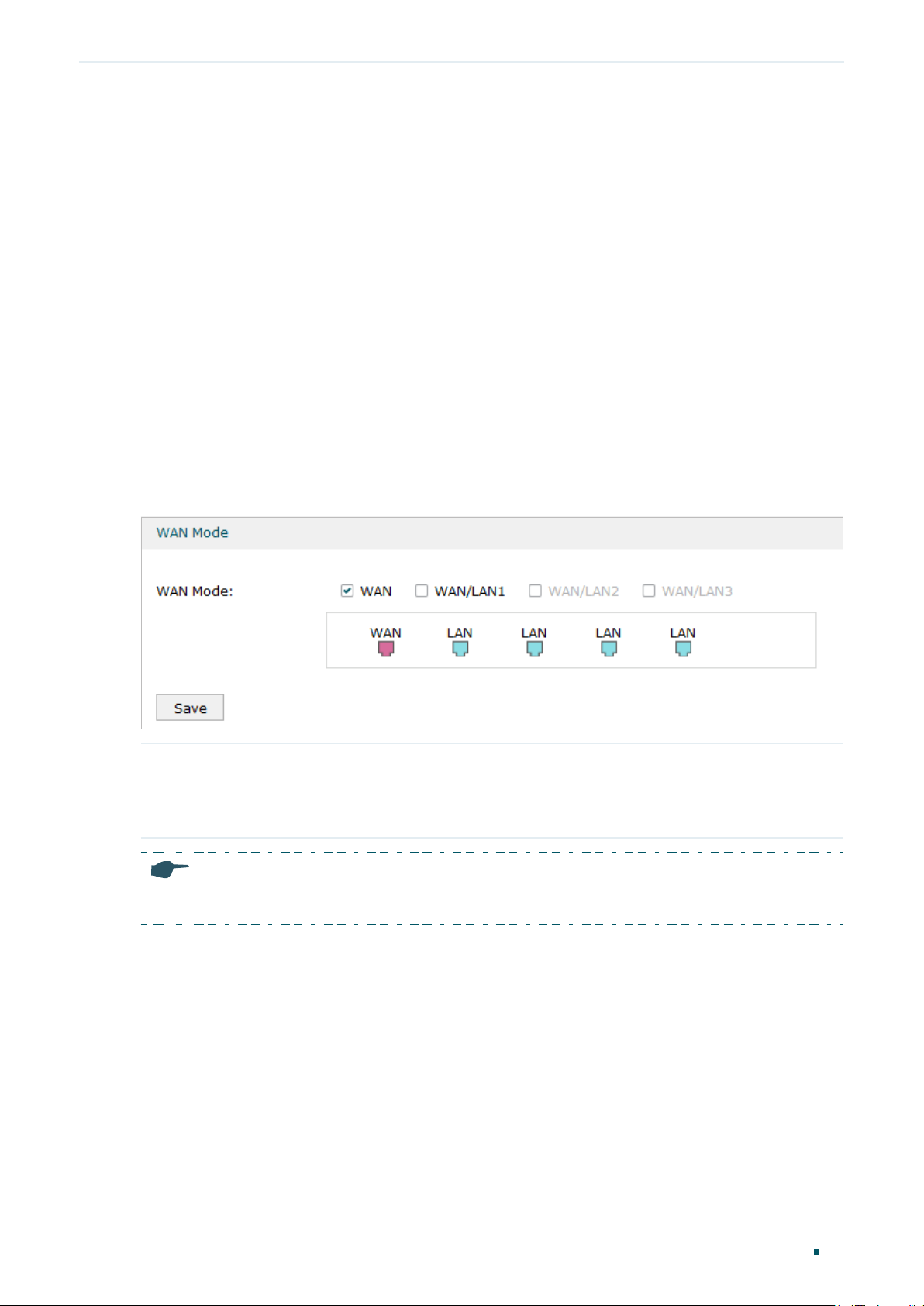
Choose the menu Network > WAN > WAN Mode to load the following page.
Figure 2-1 Configuring the WAN Mode
WAN Mode Click the check box to enable the port as a WAN port. To configure multiple WAN
ports, enable the ports one by one.
For certain devices, you can configure one SFP port as the WAN port.
Note:
The router will reboot after switching the WAN mode.
2.2 Configuring the WAN Connection
The router supports five connection types: Static IP, Dynamic IP, PPPoE, L2TP, PPTP, you
can choose one according to the service provided by your ISP.
Static IP: If your ISP provides you with a fixed IP address and the corresponding
parameters, choose Static IP.
Dynamic IP: If your ISP automatically assigns the IP address and the corresponding
parameters, choose Dynamic IP.
User Guide
13
Page 22
Configuring Network WAN Configuration
PPPoE: If your ISP provides you with a PPPoE account, choose PPPoE.
L2TP: If your ISP provides you with an L2TP account, choose L2TP.
PPTP: If your ISP provides you with a PPTP account, choose PPTP.
Note:
The number of configurable WAN ports is decided by WAN Mode. To configure Wan Mode, refer to
Configuring the Number of WAN Ports.
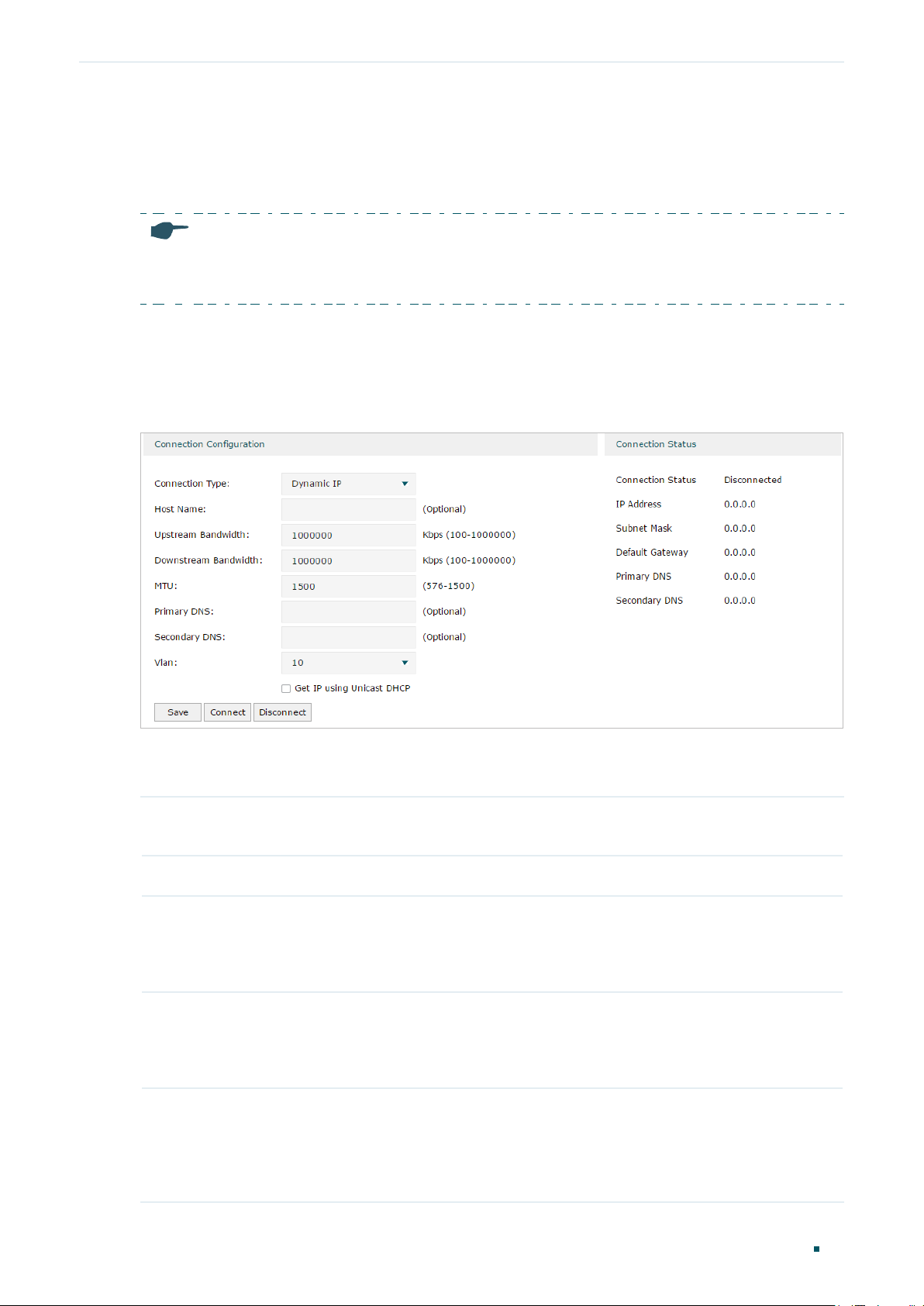
■ Configuring the Dynamic IP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-2 Configuring the Dynamic IP
In the Connection Configuration section, select the connection type as Dynamic IP. Enter
the corresponding parameters and click Save.
Connection Type Choose the connection type as Dynamic IP if your ISP automatically assigns the IP
address.
Host Name (Optional) Enter a name for the router. It is null by default.
Upstream
Bandwidth
Downstream
Bandwidth
MTU Specify the MTU (Maximum Transmission Unit) of the WAN port.
Specify the upstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
MTU is the maximum data unit transmitted in the physical network. When Dynamic
IP is selected, MTU can be set in the range of 576-1500 bytes. The default value is
1500.
User Guide 14
Page 23
Configuring Network WAN Configuration
Primary/
Secondary DNS
VLAN Add the WAN port to a VLAN. Generally, you don’t need to manually configure it
Get IP using
Unicast DHCP
Connect/
Disconnect
(Optional) Enter the IP address of the DNS server provided by your ISP.
unless required by your ISP.
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create
the corresponding VLAN first and configure its egress rule as TAG, then manually
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN.
The broadcasting requirement may not be supported by a few ISPs. Select this
option if you can not get the IP address from your ISP even with a normal network
connection. This option is not required generally.
Click the button to active/terminate the connection.
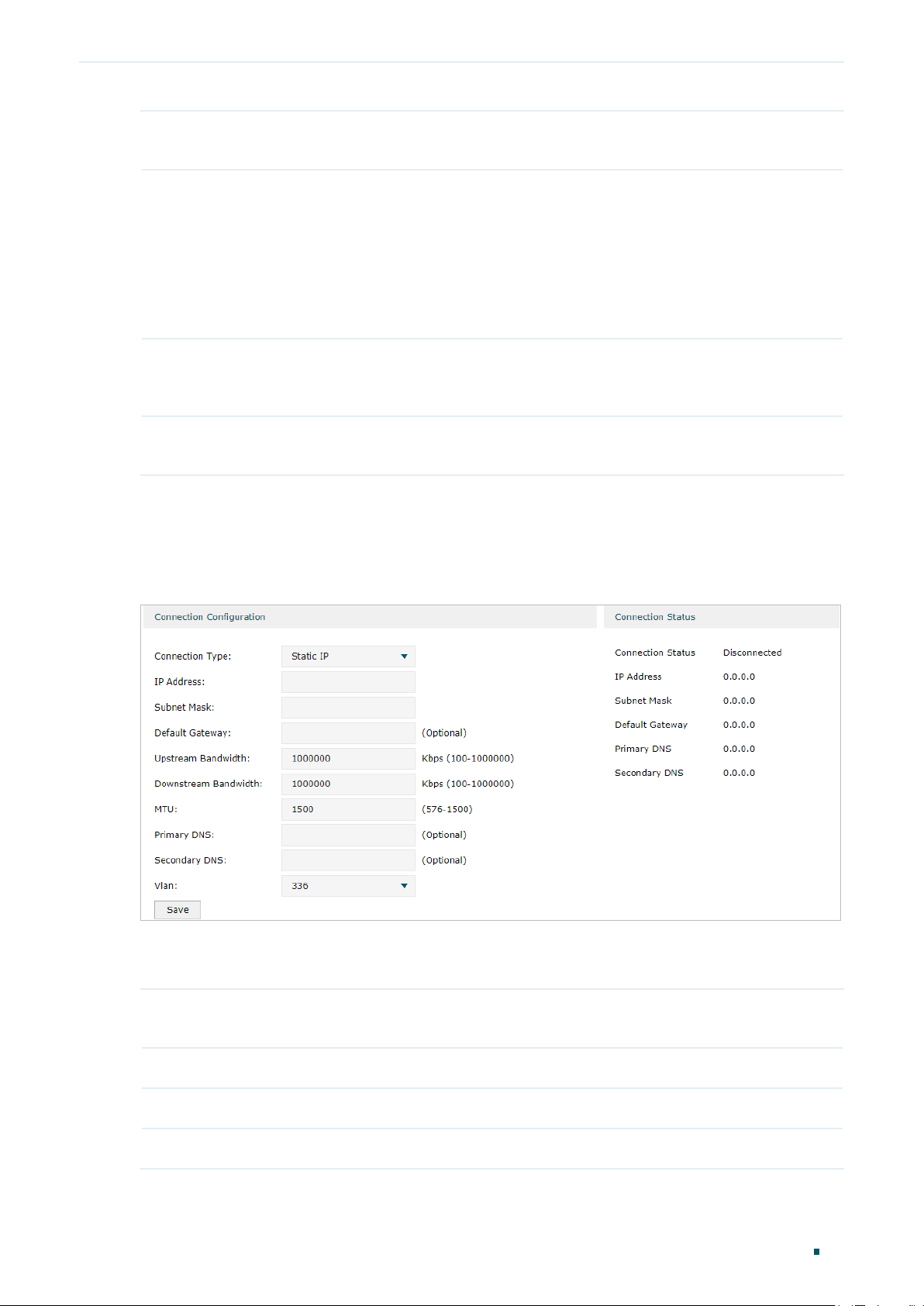
■ Configuring the Static IP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-3 Configuring the Static IP
In Connection Configuration section, select the connection type as Static IP. Enter the
corresponding parameters and click Save.
Connection Type Choose the connection type as Static IP if your ISP has offered you a fixed IP
address.
IP Address Enter the IP address provided by your ISP.
Subnet Mask Enter the subnet mask provided by your ISP.
Default Gateway Enter the default gateway provided by your ISP.
User Guide
15
Page 24
Configuring Network WAN Configuration
Upstream
Bandwidth
Downstream
Bandwidth
MTU Specify the MTU (Maximum Transmission Unit) of the WAN port.
Primary/
Secondary DNS
VLAN Add the WAN port to a VLAN. Generally, you don’t need to manually configure it
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
MTU is the maximum data unit transmitted in the physical network. When Static IP is
selected, MTU can be set in the range of 576-1500 bytes. The default value is 1500.
(Optional) Enter the IP address of the DNS server provided by your ISP.
unless required by your ISP.
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create
the corresponding VLAN first and configure its egress rule as TAG, then manually
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN.
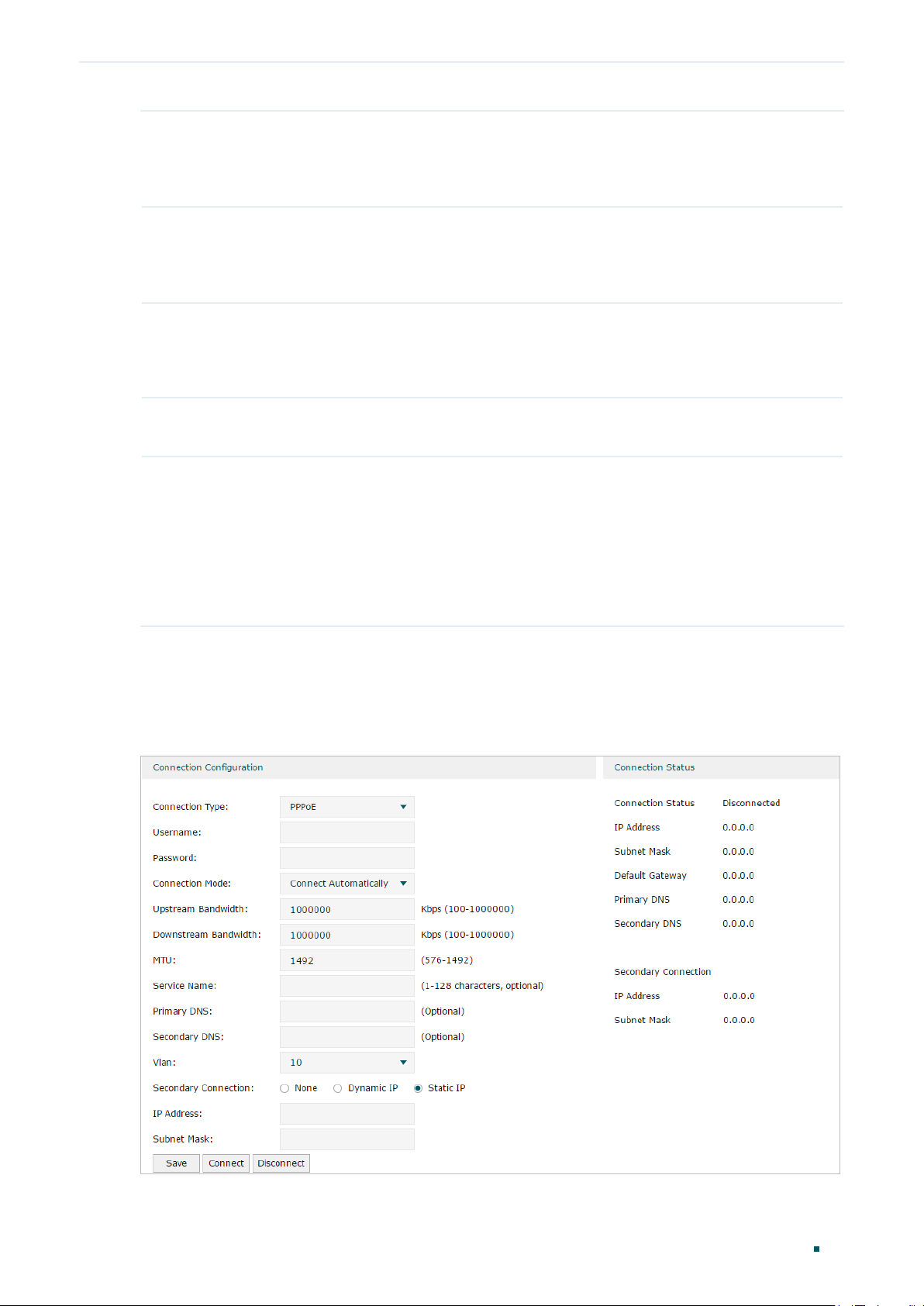
■ Configuring the PPPoE
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-4 Configuring the PPPoE
User Guide 16
Page 25
Configuring Network WAN Configuration
In the Connection Configuration section, select the connection type as PPPoE. Enter the
corresponding parameters and click Save.
Connection Type Choose the connection type as PPPoE if your ISP provides you with a PPPoE
account.
Username Enter the PPPoE username provided by your ISP.
Password Enter the PPPoE password provided by your ISP.
Connection
Mode
Time Choose the effective time range when the Connection Mode is chosen as Time-
Upstream
Bandwidth
Downstream
Bandwidth
Choose the connection mode, including Connect Automatically, Connect Manually
and Time-Based.
Connect Automatically: The router will activate the connection automatically when
the router reboots or the connection is down.
Connect Manually: You can manually activate or terminate the connection.
Time-Based: During the specified period, the router will automatically activate the
connection.
Based. To create the time range, go to Preferences > Time Range > Time Range.
Specify the upstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
MTU Specify the MTU (Maximum Transmission Unit) of the WAN port.
MTU is the maximum data unit transmitted in the physical network. When PPPoE is
selected, MTU can be set in the range of 576-1492 bytes. The default value is 1492.
Service Name (Optional) Enter the service name. This parameter is not required unless provided by
your ISP. It is null by default.
Primary/
Secondary DNS
VLAN Add the WAN port to a VLAN. Generally, you don’t need to manually configure it
(Optional) Enter the IP address of the DNS server provided by your ISP.
unless required by your ISP.
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create
the corresponding VLAN first and configure its egress rule as TAG, then manually
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN.
User Guide
17
Page 26
Configuring Network WAN Configuration
Secondary
Connection
Connect/
Disconnect
Secondary connection is required by some ISPs. Select the connection type required
by your ISP.
None: Select this if the secondary connection is not required by your ISP.
Dynamic IP: Select this if your ISP automatically assigns the IP address and subnet
mask for the secondary connection.
Static IP: Select this if your ISP provides you with a fixed IP address and subnet mask
for the secondary connection.
Click the button to active/terminate the connection.
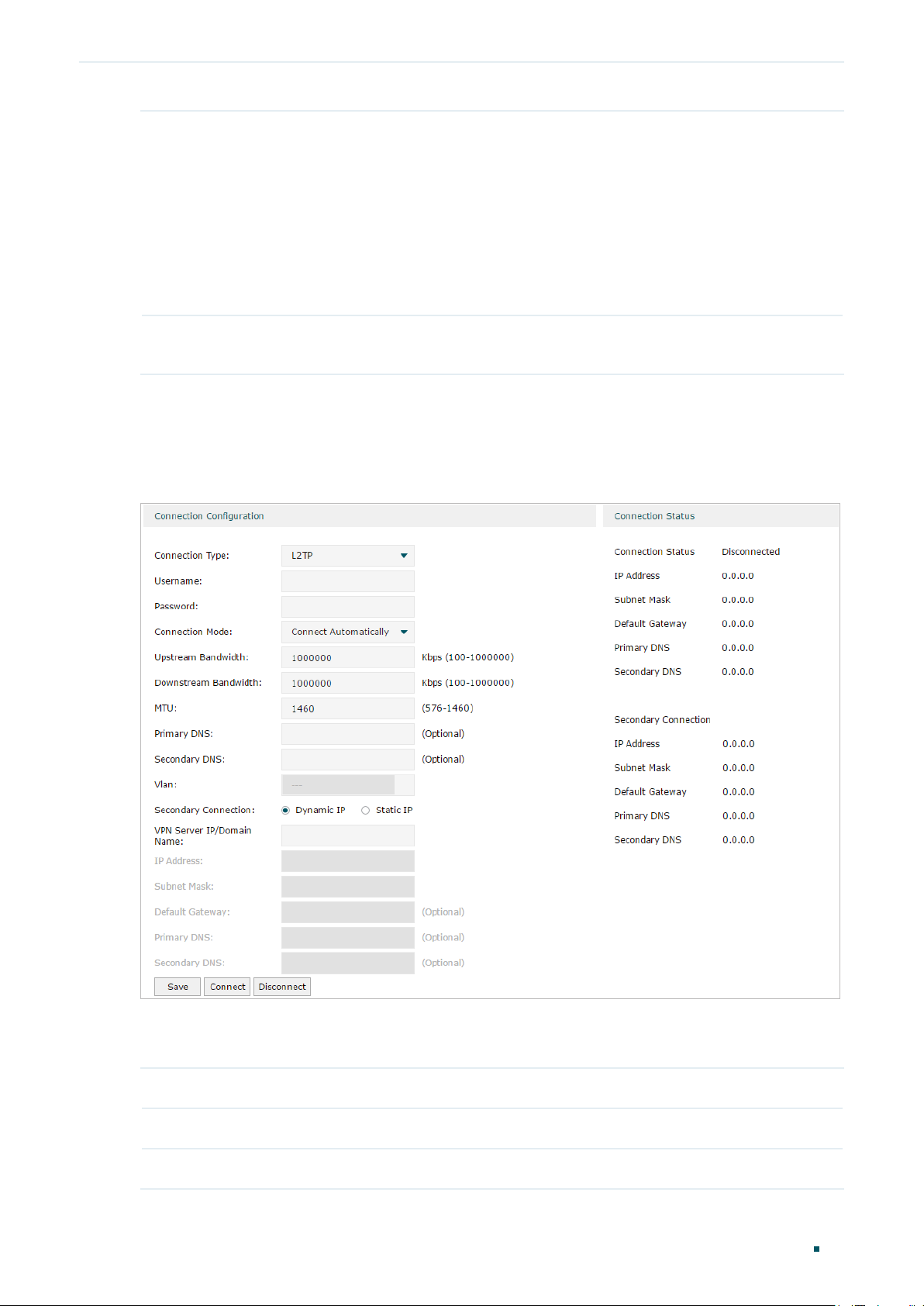
■ Configuring the L2TP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-5 Configuring the L2TP
In the Connection Configuration section, select the connection type as L2TP. Enter the
corresponding parameters and click Save.
Connection Type Choose the connection type as L2TP if your ISP provides you with an L2TP account.
Username Enter the L2TP username provided by your ISP.
Password Enter the L2TP password provided by your ISP.
User Guide 18
Page 27
Configuring Network WAN Configuration
Connection
Mode
Time Choose the effective time range when the Connection Mode is chosen as Time-
Upstream
Bandwidth
Downstream
Bandwidth
Choose the connection mode, including Connect Automatically, Connect Manually
and Time-Based.
Connect Automatically: The router will activate the connection automatically when
the router reboots or the connection is down.
Connect Manually: You can manually activate or terminate the connection.
Time-Based: During the specified period, the router will automatically activate the
connection.
Based. To create the time range, go to Preferences > Time Range > Time Range.
Specify the upstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
MTU Specify the MTU (Maximum Transmission Unit) of the WAN port.
MTU is the maximum data unit transmitted in the physical network. When L2TP is
selected, MTU can be set in the range of 576-1460 bytes. The default value is 1460.
Primary/
Secondary DNS
VLAN Add the WAN port to a VLAN. Generally, you don’t need to manually configure it
Secondary
Connection
(Optional) Enter the IP address of the DNS server provided by your ISP.
unless required by your ISP.
By default, the WAN port is automatically assigned to a VLAN, and the egress rule of
the VLAN is UNTAG, so the packets are transmitted by the WAN port without VLAN
tags. If you want the WAN port to transmit packets with VLAN tag, you need to create
the corresponding VLAN first and configure its egress rule as TAG, then manually
add the WAN port to that VLAN. To create VLANs, go to Network > VLAN > VLAN.
Select the secondary connection type provided by your ISP. If you select the
secondary connection type as Static IP, you need to configure IP Address, Subnet
Mask, Default Gateway, Primary/Second DNS.
The secondary connection is required for L2TP connection. The router will get
some necessary information after the secondary connection succeeded. These
information will be used in the L2TP connection process.
VPN Server/
Domain Name
IP Address Enter the IP address provided by your ISP for the secondary connection.
Subnet Mask Enter the subnet mask provided by your ISP for the secondary connection.
Enter the VPN Server/Domain Name provided by your ISP.
User Guide
19
Page 28
Configuring Network WAN Configuration
Default Gateway Enter the default gateway provided by your ISP for the secondary connection.
Primary/
Secondary DNS
Connect/
Disconnect
Enter the primary/secondary DNS provided by your ISP for the secondary
connection.
Click the button to active/terminate the connection.
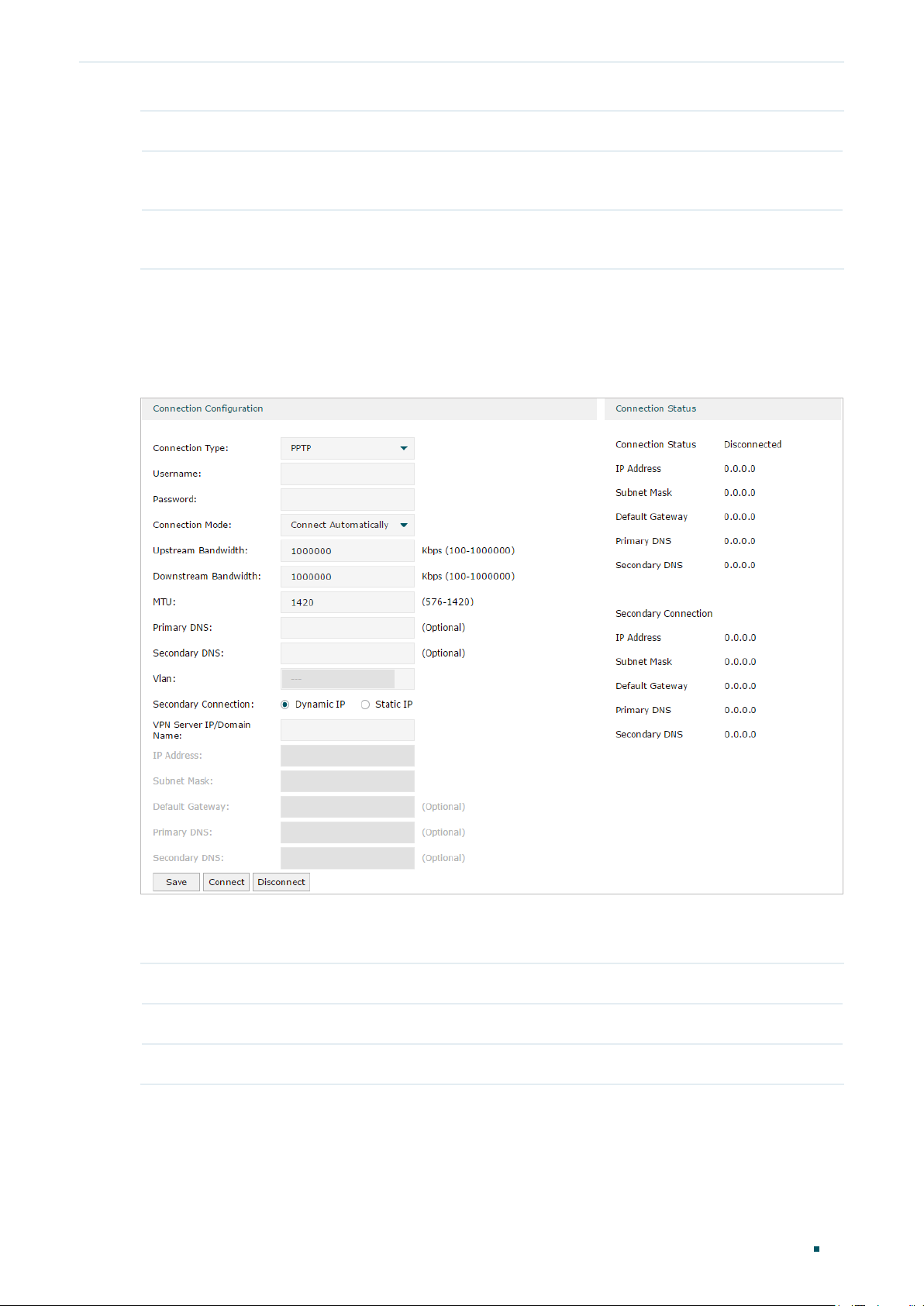
■ Configuring the PPTP
Choose the menu Network > WAN > WAN to load the following page.
Figure 2-6 Configuring the PPTP
In Connection Configuration section, select the connection type as PPTP. Enter the
corresponding parameters and click Save.
Connection Type Choose the connection type as PPTP if your ISP provides you with a PPTP account.
Username Enter the PPTP username provided by your ISP.
Password Enter the PPTP password provided by your ISP.
User Guide 20
Page 29
Configuring Network WAN Configuration
Connection
Mode
Time Choose the effective time range when the Connection Mode is chosen as Time-
Upstream
Bandwidth
Downstream
Bandwidth
Choose the connection mode, including Connect Automatically, Connect Manually
and Time-Based.
Connect Automatically: The router will activate the connection automatically when
the router reboots or the connection is down.
Connect Manually: You can manually activate or terminate the connection.
Time-Based: During the specified period, the router will automatically activate the
connection.
Based. To create the time range, go to Preferences > Time Range > Time Range.
Specify the upstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Upstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
Specify the downstream bandwidth of the WAN port. The value configured here is the
upper limit of the “Maximum Downstream Bandwidth” on Transmission > Bandwidth
Control > Bandwidth Control page, to make “Bandwidth Control” take effect, please
ensure this parameter is set correctly.
MTU Specify the MTU (Maximum Transmission Unit) of the WAN port.
MTU is the maximum data unit transmitted in the physical network. When PPTP is
selected, MTU can be set in the range of 576-1420 bytes. The default value is 1420.
Primary/
Secondary DNS
VLAN Add the WAN port to a VLAN. Generally, you don’t need to manually configure it
Secondary
Connection
(Optional) Enter the IP address of the DNS server provided by your ISP.
unless required by your ISP.
By default, the WAN port is automatically assigned to a VLAN by default, and the
egress rule of the VLAN is UNTAG, so the packets are transmitted by the WAN port
without VLAN tags. If you want the WAN port to transmit packets with VLAN tag, you
need to create the corresponding VLAN first and configure its egress rule as TAG,
then manually add the WAN port to that VLAN. To create VLANs, go to Network >
VLAN > VLAN.
Select the secondary connection type provided by your ISP. If you select the
secondary connection type as Static IP, you need to configure IP Address, Subnet
Mask, Default Gateway, Primary/Second DNS.
The secondary connection is required for PPTP connection. The router will get
some necessary information after the secondary connection succeeded. These
information will be used in the PPTP connection process.
VPN Server/
Domain Name
IP Address Enter the IP address provided by your ISP for the secondary connection.
Subnet Mask Enter the subnet mask provided by your ISP for the secondary connection.
Enter the VPN Server/Domain Name provided by your ISP.
User Guide
21
Page 30
Configuring Network WAN Configuration
Default Gateway Enter the default gateway provided by your ISP for the secondary connection.
Primary/
Secondary DNS
Connect/
Disconnect
Enter the primary/secondary DNS provided by your ISP for the secondary
connection.
Click the button to active/terminate the connection.
User Guide 22
Page 31

Configuring Network LAN Configuration
3
LAN Configuration
The LAN port is used to connect to the LAN clients, and works as the default gateway
for these clients. You can configure the DHCP server for the LAN clients, and clients will
automatically be assigned to IP addresses if the method of obtaining IP addresses is set as
“Obtain IP address automatically”.
For LAN configuration, you can:
■ Configure the IP address of the LAN port.
■ Configure the DHCP server.
3.1 Configuring the IP Address of the LAN Port
Choose the menu Network > LAN > LAN to load the following page.
Figure 3-1 Configuring the LAN IP Address
Enter the IP address of the LAN port, and click Save.
IP Address Enter the IP address of the LAN port.
This IP address is the default gateway of the LAN clients, and the IP addresses of all
the LAN clients should be in the same subnet with this LAN IP address.
Subnet Mask Enter the subnet mask of the LAN port.
User Guide
23
Page 32

Configuring Network LAN Configuration
Vlan Specify the VLAN of the LAN port, only the clients in the specified VLAN can access
and manage the router.
IGMP Proxy Check the box to enable IGMP Proxy.
IGMP Proxy sends IGMP querier packets to the LAN ports to detect if there is any
multicast member connected to the LAN ports.
IGMP Version Choose the IGMP version as V2 or V3. The default is IGMP V2.
Note:
Changing the IP address of LAN port will automatically redirect the browser to the new
•
management page. If the redirecting failed, please try to reconnect your PC to the router to
automatically get a new IP address, or configure a proper static IP address manually.
Changing the IP address of the LAN port may affect some related functions, like the IP pool of
•
the DHCP server.
3.2 Configuring the DHCP Server
You can configure an IP address pool for the DHCP server to assign IP addresses. When
clients send requests to the DHCP server, the server will automatically assign IP addresses
and the corresponding parameters to the clients. Moreover, if you want to reserve an IP
address for a certain client, you can use Address Reservation to bind the IP address with
the client’s MAC address, and the bound IP address will always be assigned to that client.
■ Configuring the DHCP Server
Choose the menu Network > LAN > DHCP Server to load the following page.
User Guide 24
Page 33

Configuring Network LAN Configuration
Figure 3-2 Configuring the DHCP Server
Configure the parameters of the DHCP server, then click Save.
Starting/Ending
IP Address
Lease Time Specify the lease time for DHCP clients.
Default Gateway (Optional) It is recommended to enter the IP address of the LAN port.
Default Domain (Optional) Enter the domain name of your network.
Primary/
Secondary DNS
Enter the starting IP address and ending IP address of the DHCP server’s IP pool. The
IP pool defines the IP range that can be assigned to the clients in the LAN.
Note: The starting IP address and ending IP address should be in the same subnet
with the IP address of the LAN port.
Lease time defines how long the clients can use the IP address assigned by the DHCP
server. Generally, the client will automatically request the DHCP server for extending
the lease time before the lease expired. If the request failed, the client will have to stop
using that IP address when the lease finally expired, and try to get a new IP address
from the other DHCP servers.
(Optional) Enter the DNS server address provided by your ISP. If you are not clear,
please consult your ISP.
User Guide
25
Page 34

Configuring Network LAN Configuration
Option 60 (Optional) Specify the option 60 for device identification. Mostly it is used under the
scenario where the clients apply for different IP addresses from different servers
according to the needs. By default, it is TP-LINK.
If a client requests option 60, the server will respond a packet containing the option
60 configured here. And then the client will compare the received option 60 with its
own. If they are the same, the client will accept the IP address assigned by the server,
otherwise the assigned IP address will not be accepted.
Option 138 (Optional) Specify the option 138, which can be configured as the management IP
address of an Omada controller. If the APs in the local network request this option,
the server will respond a packet containing this option to inform the APs of the
controller’s IP address.
Status Check the box to enable the DHCP server.
■ Configuring the Address Reservation
Choose the menu Network > LAN > Address Reservation and click Add to load the
following page.
Figure 3-3 Configuring the Address Reservation
Enter the MAC address of the client and the IP address to be reserved, then click OK.
MAC Address Enter the MAC address of the client.
IP Address Enter the IP address to be reserved.
Description (Optional) Enter a brief description for the entry. Up to 32 characters can be entered.
Export to IPMAC Binding
Status Check the box to enable this entry.
(Optional) Check the box to export this binding entry to IP-MAC Binding List on
Firewall > Anti ARP Spoofing > IP-MAC Binding page.
3.3 Viewing the DHCP Client List
Choose the menu Network > LAN > DHCP Client List to load the following page.
User Guide 26
Page 35

Configuring Network LAN Configuration
Figure 3-4 Viewing the DHCP Client List
Here you can view the DHCP client list.
Client Name Displays the name of the client.
MAC Address Displays the MAC address of the client.
Assigned IP
Address
Lease Time Displays the remaining lease time of the assigned IP address. After the lease expires,
Displays the IP address assigned to the client.
the IP address will be re-assigned.
User Guide
27
Page 36

Configuring Network MAC Configuration
4
MAC Configuration
Generally, the MAC address does not need to be changed. However, in some particular
situations, you may need to change the MAC address of the WAN port or LAN port.
■ Configure the MAC Address of the WAN port
In the condition that your ISP has bound the account to the MAC address of the dial-up
device, if you want to replace the dial-up device with this router, you can just set the MAC
address of this router’s WAN port as the same as that of the previous dial-up device for a
normal internet connection.
■ Configure the MAC Address of the LAN port
In a complex network where all the devices are ARP bound, if you want to replace the
current router with this router, you can just set the MAC address of this router’s LAN port
as the same as that of the previous router, which can avoid all the devices under this
network node to update their ARP binding tables.
4.1 Configuring MAC Address
Choose the menu Network > MAC > MAC to load the following page.
Figure 4-1 Configuring MAC Address
Configure the MAC address of the WAN port or LAN port according to your need, then click
Save.
Interface Name Displays the WAN port and LAN port.
Current MAC
Address
Configure the MAC address of the WAN port or LAN port.
User Guide 28
Page 37

Configuring Network MAC Configuration
MAC Clone Restore Factory MAC: Click this button to restore the MAC address to the factory
default value.
Clone Current PC’s MAC: Click this button to clone the MAC address of the PC you
are currently using to configure the router. It’s only available for the WAN ports.
Note:
To avoid a MAC address conflict in the LAN, it is not permitted to set the MAC address of the router’s
LAN port as the MAC address of the current management PC.
User Guide
29
Page 38

Configuring Network Switch Configuration
5
Switch Configuration
The router provides some basic switch port management function, including Statistics,
Port Mirror, Rate Control, Port Config and Port Status. Statistics and Rate Control are
available only for certain devices.
5.1 Viewing the Statistics (only for certain devices)
Choose the menu Network > Switch > Statistics to load the following page.
Figure 5-1 Viewing the Statistics
Statistics displays the detailed traffic information of each port, which allows you to monitor
the traffic and locate faults promptly.
Unicast Displays the number of normal unicast packets received or transmitted on the port.
Broadcast Displays the number of normal broadcast packets received or transmitted on the port.
Pause Displays the number of flow control frames received or transmitted on the port.
Multicast Displays the number of normal multicast packets received or transmitted on the port.
User Guide 30
Page 39

Configuring Network Switch Configuration
Total Displays the total bytes of the received or transmitted packets (including error
frames).
Undersize Displays the number of received packets which have a length less than 64 bytes
(including error frames).
Normal Displays the number of received packets which have length between 64 bytes and the
maximum frame length (including error frames).
Oversize Displays the number of received packets that have a length greater than the maximum
frame length (including error frames).
Note:
Error Frame: The frames that have a false checksum.
Maximum frame length: The maximum frame length supported by the router. For untagged frames,
it’s 1518 bytes long; for tagged packets, it’s 1522 bytes long.
5.2 Configuring Port Mirror
Port Mirror function allows the router to forward packet copies of the monitored port(s) to
a specific monitoring port. Then you can analyze the copied packets to monitor network
traffic and troubleshoot network problems.
Choose the menu Network > Switch > Mirror to load the following page.
Figure 5-2 Configuring Port Mirror
Follow these steps to configure Port Mirror:
1) In Settings section, enable Port Mirror function, and choose the mirror mode.
User Guide
31
Page 40

Configuring Network Switch Configuration
Enable Port
Mirror
Mirror Mode Choose the mirror mode which includes Ingress, Egress and Ingress and Egress.
Check the box to enable Port Mirror function.
Ingress: The packets received by the mirrored port will be copied to the mirroring
port.
Egress: The packets sent by the mirrored port will be copied to the mirroring port.
Ingress and Egress: Both the incoming and outgoing packets through the
mirrored port will be copied to the mirroring port.
2) In the Monitor List section, set the mirroring port and the mirrored port(s), then click
Save.
Mirroring Port The packets through the mirrored port will be copied to this port.
Usually, the mirroring port is connected to a data diagnose device, which is used
to analyze the mirrored packets for monitoring and troubleshooting the network.
Mirrored Port The packets through this port will be copied to the mirroring port.
Usually, the mirrored ports are the ports to be monitored.
5.3 Configuring Rate Control (only for certain devices)
Rate Control enables you to control the traffic rate for the specific packets on each port to
manage your network.
Choose the menu Network > Switch > Rate Control to load the following page.
Figure 5-3 Configuring Rate Control
Choose the port and configure the ingress frames or egress frames limitation, then click
Save.
Ingress Limit Check the box to enable the Ingress Limit feature.
User Guide 32
Page 41

Configuring Network Switch Configuration
Ingress Frame
Type
Ingress Rate
(Mbps)
Egress Limit Check the box to enable Egress Limit feature.
Egress Rate
(Mbps)
Specify the ingress frame type to be limited. It is All Frames by default.
All Frames: The ingress rate of all frames is limited.
Broadcast: The ingress rate of broadcast frames is limited.
Specify the limit rate for the ingress packets.
Specify the limit rate for the egress packets.
5.4 Configuring Port Config
You can configure the flow control and negotiation mode for the port.
Choose the menu Network > Switch > Port Config to load the following page.
Figure 5-4 Configuring Flow Control and Negotiation
Configure the flow control and negotiation mode for a port.
Flow Control Check the box to enable the flow control function.
Flow Control is the process of managing the data transmission of the sender to avoid
the receiver getting overloaded.
User Guide
33
Page 42

Configuring Network Switch Configuration
Negotiation
Mode
Select the negotiation mode for the port. You can set the mode as Auto, or manually
set the speed and duplex mode for the port. It is recommended to configure both
devices of a link to work in Auto-Negotiation mode or manually configure them to work
in the same speed and duplex mode.
If the two devices at both sides work in Auto mode, they will advertise their speed and
duplex abilities to each other, and negotiate the optimal speed and duplex mode.
If the local device works in Auto mode while the peer device does not, the local device
will automatically detect and match the speed with the peer device. The local device
will work in half-duplex mode, no matter what duplex mode the peer device is in.
5.5 Viewing Port Status
Choose the menu Network > Switch > Port Status to load the following page.
Figure 5-5 Viewing Port Status
Status Displays the port status.
Link Down: The port is not connected.
Link Up: The port is working normally.
Speed (Mbps) Displays the port speed.
Duplex Mode Displays the duplex mode of the port.
Flow Control Displays if the Flow Control is enabled.
User Guide 34
Page 43

Configuring Network VLAN Configuration
6
VLAN Configuration
The router supports 802.1Q VLAN, which can divide a LAN into multiple logical LANs.
Each logical LAN is a VLAN. Hosts in the same VLAN can communicate with each other.
However, hosts in different VLANs cannot communicate directly. Therefore, broadcast
packets can be limited to within the VLAN.
6.1 Creating a VLAN
Choose the menu Network > VLAN > VLAN and click Add to load the following page.
Figure 6-1 Creating a VLAN
Create a VLAN and add the port(s) to the VLAN, then click OK.
VLAN ID Enter a VLAN ID. The value ranges from 1 to 4094.
Name Specify the name of the VLAN for easy identification.
Ports Check the box to select the port and specify the port type in the specified VLAN. The
port can be divided into two types: TAG or UNTAG.
TAG: The egress rule of the packets transmitted by the port is Tagged.
UNTAG: The egress rule of the packets transmitted by the port is Untagged.
Description (Optional) Enter a brief description for easy management and searching.
User Guide
35
Page 44

Configuring Network VLAN Configuration
Viewing the VLANs
Choose the menu Network > VLAN > VLAN to load the following page.
Figure 6-2 Viewing the VLAN
In the VLAN list you can view all the VLANs existing in the router.
VLAN ID Displays the VLAN ID.
Name Displays the VLAN name.
Ports Displays the ports which belongs to the corresponding VLAN.
Description Displays the description of the VLAN.
Note:
The VLAN list contains all the VLANs existing in the router. Some of them are manually created by
the user, and can be edited or deleted. Some are automatically created and referenced by the router
for some special scenarios like management VLAN, and you cannot edit or delete these VLANs.
6.2 Configuring the PVID of a Port
Choose the menu Network > VLAN > Port to load the following page.
User Guide 36
Page 45

Configuring Network VLAN Configuration
Figure 6-3 Configuring the PVID
Configure the PVID of the port, then click Save.
Port Displays the port.
PVID
VLAN Displays the VLAN(s) the port belongs to.
Specify the PVID for the port.
port.
VID indicates the default VLAN for the corresponding
P
User Guide
37
Page 46

Part 4
Configuring Preferences
CHAPTERS
1. Overview
2. IP Group Configuration
3. Time Range Configuration
4. VPN IP Pool Configuration
5. Service Type Configuration
Page 47

Configuring Preferences Overview
1
Overview
You can preset certain preferences, such as IP groups, time ranges, IP Pools and
service types. These preferences will appear as options for you to choose when you are
configuring the corresponding parameters for some functions. For example, the IP groups
configured here will appear as options when you are configuring the effective IP addresses
for functions like Bandwidth Control, Session Limit , Policy Routing and so on.
Once you configure a preference here, it can be applied to multiple functions, saving time
during the configuration. For example, after configuring a time range in the Preferences
> Time Range > Time Range page, you can use this time range as the effective time of
Bandwidth Control rules, Link Backup rules, Policy Routing rules, and so on.
User Guide
39
Page 48

Configuring Preferences IP Group Configuration
2
IP Group Configuration
IP groups configured here can be used as effective IP addresses for multiple functions like
Bandwidth Control, Session Limit , Policy Routing and so on.
To complete IP Group configuration, follow these steps:
1) Add IP address entries.
2) Add IP address entries to an IP group.
2.1 Adding IP Address Entries
Choose the menu Preferences > IP Group > IP Address and click Add to load the following
page.
Figure 2-1 Add an IP Address Entry
Follow these steps to add an IP address entry:
1) Enter a name and specify the IP address range.
Name Enter a name for the IP address entry. Only letters, digits or underscores are
allowed.
IP Address Type Choose a type and enter the IP address in the corresponding format. Two types
are provided:
IP Address Range: Specify a starting IP address and an ending IP address.
IP Address/Mask: Specify a network address and the subnet mask.
Description (Optional) Enter an brief description of this IP address entry to make identifying it
easier.
2) Click OK.
User Guide 40
Page 49

Configuring Preferences IP Group Configuration
2.2 Grouping IP Address Entries
Choose the menu Preferences > IP Group > IP Group and click Add to load the following
page.
Figure 2-2 Create an IP Group
Follow these steps to create an IP group and add IP address entries to the group:
1) Specify a name and configure the range to add an IP address range.
Group Name Enter a name for the IP group. Only letters, digits or underscores are allowed.
Address Name Select the IP address entries as the members of the group from the drop-down
list. It is multi-optional.
If no IP address entries are selected, the rule that references this IP group will
have no effect on any IP addresses.
Description (Optional) Enter an brief description of this IP group to make identifying it easier.
2) Click OK.
You can also choose an existing IP group and click
to add or remove the IP address
members.
Note:
An IP group that is being referenced by a rule cannot be deleted.
User Guide
41
Page 50

Configuring Preferences Time Range Configuration
3
Time Range Configuration
Time range configuration allows you to define time ranges by specifying the period in a day
and days in a week. The time range configured here can be used as the effective time for
multiple functions like Bandwidth Control, Link Backup, Policy Routing and so on.
Choose the menu Preferences > Time Range > Time Range and click Add to load the
following page.
Figure 3-1 Add a Time Range Entry
Follow these steps to add a time range entry:
1) Enter a name for the time range entry.
Time Range
Name
2) Choose a mode to set the time range. Two modes are provided: Working Calendar and
Manually.
■ Working Calendar
Working Calendar mode allows you to set the time range on a calendar. In this mode,
the effective time can be accurate to the hour.
Choose Working Calendar mode and click
Enter a name for the time range entry. Only letters, digits or underscores are
allowed.
to load the following page.
User Guide 42
Page 51

Configuring Preferences Time Range Configuration
Figure 3-2 Working Calendar Mode
Select the time slices and click OK to set the time range. You can click the time slices,
or alternatively drag the areas to select or deselect the time slices.
■ Manually
Manually mode allows you to enter the time range and select the effective days in a
week manually. In this mode, effective time can be accurate to the minute.
Choose Manually mode to load the following page.
Figure 3-3 Manually Mode
Week Select the effective days in a week.
Time Range
Enter a start and end time. If the effective time is discontinuous, click
another time range.
to add
3) (Optional) Enter an brief description of this time range to make identifying it easier.
4) Click OK.
Note:
A time range entry that is being referenced by a rule cannot be deleted.
User Guide
43
Page 52

Configuring Preferences VPN IP Pool Configuration
4
VPN IP Pool Configuration
The VPN IP pools configured here can be used as the VPN IP address pools when
configuring L2TP VPN and PPTP VPN.
Choose the menu Preferences > VPN IP Pool > VPN IP Pool and click Add to load the
following page.
Figure 4-1 Add an IP Pool Entry
Follow these steps to add an IP Pool:
1) Enter a name and specify the starting and ending IP address of the IP Pool.
IP Pool Name Enter a name for the IP Pool. Only letters, digits or underscores are allowed.
Starting IP Address/
Ending IP Address
2) Click OK.
Note:
An IP pool entry that is being referenced by a rule cannot be deleted.
Specify the starting and ending IP address. The range of the IP pool cannot
overlap with the existing IP pools.
User Guide 44
Page 53

Configuring Preferences Service Type Configuration
5
Service Type Configuration
The service type entries configured here can be used as part of the matching conditions
when configuring the Access Control rules in Firewall.
Choose the menu Preferences > Service Type > Service Type to load the following page.
Figure 5-1 Service Type List
The entries in gray are system predefined service types. You can add other entries if your
service type is not in the list.
User Guide
45
Page 54

Configuring Preferences Service Type Configuration
Click Add to load the following page.
Figure 5-2 Add a Service Type Entry
Follow these steps to add a service type entry:
1) Enter a name for the service type.
Service Type Name Enter a name for the service type. Only letters, digits or underscores are
allowed.
2) Select the protocol for the service type. The predefined protocols include TCP, UDP,
TCP/UDP and ICMP. For other protocols, select the option Other.
When TCP, UDP, or TCP/UDP is selected, the following page will appear.
Figure 5-3 TCP/UDP Protocol
Source Port Range/
Destination Port Range
Specify range of the source port and destination port of the TCP or UDP
packets. Packets whose source port and destination port are both in the
range are considered as the target packets.
When ICMP is selected, the following page will appear.
Figure 5-4 ICMP Protocol
Type/Code Specify the type and code of the ICMP packets. ICMP packets with both
the type and code fields matched are considered as the target packets.
User Guide 46
Page 55

Configuring Preferences Service Type Configuration
When Other is selected, the following page will appear.
Figure 5-5 Other Protocols
Protocol Number Specify the protocol number of the packets. Packets with the protocol
number field matched are considered as the target packets.
3) (Optional) Enter a brief description of this service type to make identifying it easier.
4) Click OK.
Note:
A service type entry that is being referenced by a rule cannot be deleted.
User Guide
47
Page 56

Part 5
Configuring Transmission
CHAPTERS
1. Transmission
2. NAT Configurations
3. Bandwidth Control Configuration
4. Session Limit Configurations
5. Load Balancing Configurations
6. Routing Configurations
7. Configuration Examples
Page 57

Configuring Transmission Transmission
1
Transmission
1.1 Overview
Transmission function provides multiple traffic control measures for the network. You can
configure the transmission function according to your actual needs.
1.2 Supported Features
The transmission module includes NAT, Bandwidth Control, Session Limit, Load Balancing
and Routing.
NAT
NAT (Network Address Translation) is the translation between private IP and public IP.
NAT provides a way to allow multiple private hosts to access the public network using one
public IP at the same time, which alleviates the shortage of IP addresses. Furthermore, NAT
strengthens the LAN (Local Area Network) security since the address of LAN host never
appears on the internet. The router supports following NAT features:
■ One-to-One NAT
One-to-One NAT creates a relationship between a private IP address and a public IP
address. A device with a private IP address can be accessed through the corresponding
valid public IP address.
■ Virtual Servers
When you build up a server in the local network and want to share it on the internet, Virtual
Servers can realize the service and provide it to the internet users. At the same time
Virtual Servers can keep the local network safe as other services are still invisible from the
internet.
■ Port Triggering
Port Triggering is a feature used to dynamically forward traffic on a certain port to a
specific server on the local network. When a host in the local network initiates a connection
to the triggering port, all the external ports will be opened for subsequent connections. The
router can record the IP address of the host, when the data from the internet returns to the
external ports, the router can forward them to the corresponding host. Port Triggering is
mainly applied to online games, VoIPs, video players and so on.
■ NAT-DMZ
User Guide
49
Page 58

Configuring Transmission Transmission
When a PC is set to be a DMZ (Demilitarized Zone) host in the local network, it is totally
exposed to the internet, which can realize the unlimited bidirectional communication
between internal hosts and external hosts. The DMZ host becomes a virtual server with
all ports opened. When you are not clear about which ports to open in some special
applications, such as IP camera and database software, you can set the PC to be a DMZ
host.
■ ALG
Some special protocols such as FTP, H.323, SIP, IPSec and PPTP will work properly only
when ALG (Application Layer Gateway) service is enabled.
Bandwidth Control
You can control the bandwidth by configuring bandwidth control rules for limiting various
data flows. In this way, the network bandwidth can be reasonably distributed and utilized.
Session Limit
The amount of TCP and UDP sessions supported by the router is finite. If some local hosts
transmit too many TCP and UDP sessions to the public network, the communication quality
of the other local hosts will be affected, thus it is necessary to limit the sessions of those
hosts.
Load Balancing
You can configure the traffic sharing mode of the WAN ports to optimize the resource
utilization.
Routing
You can configure policy routing rules and static routing.
Policy routing provides a more accurate way to control the routing based on the policy
defined by the network administrator.
Static routing is a form of routing that is configured manually by adding non-aging entries
into a routing table. The manually-configured routing information guides the router in
forwarding data packets to the specific destination.
User Guide 50
Page 59

Configuring Transmission NAT Configurations
2
NAT Configurations
With NAT configurations, you can:
■ Configure the One-to-One NAT.
■ Configure the Virtual Servers.
■ Configure the Port Triggering.
■ Configure the NAT-DMZ.
■ Configure the ALG.
2.1 Configuring the One-to-One NAT
Choose the menu Transmission > NAT > One-to-One NAT and click Add to load the
following page.
Figure 2-1 Configuring the One-to-One NAT
Follow these steps to configure the One-to-One NAT:
1) Specify the name of the One-to-One NAT rule and configure other related parameters.
Interface Specify the effective interface for the rule. If you choose multiple ports, the entry
will be applied to all selected ports simultaneously.
Original IP Specify the original IP address for the rule. The original IP address cannot be the
broadcast address, network address or IP address of the interface.
User Guide
51
Page 60

Configuring Transmission NAT Configurations
Translated IP Specify the translated IP address for the rule. The translated IP address cannot be
the broadcast address, network address or IP address of the interface.
DMZ Forwarding Check the box to enable DMZ Forwarding. The packets transmitted to the
translated IP address will be forwarded to the host of original IP address if DMZ
Forwarding is enabled.
Description Give a description for the rule entry to facilitate your management.
Status Check the box to enable the rule.
2) Click OK.
Note:
One-to-One NAT takes effect only when the connection type of WAN is Static IP.
2.2 Configuring the Virtual Servers
Choose the menu Transmission > NAT > Virtual Servers and click Add to load the
following page.
Figure 2-2 Configuring the Virtual Servers
Follow these steps to configure the Virtual Servers:
1) Specify the name of the Virtual Server rule and configure other related parameters.
Interface Specify the effective interface for the rule. If you choose multiple ports, the entry
will be applied to all selected ports simultaneously.
External Port Enter the service port or port range the router provided for accessing external
network. The ports or port ranges cannot overlap with those of other virtual
server rules.
Internal Port Specify the service port or port range of the LAN host as virtual server.
User Guide 52
Page 61

Configuring Transmission NAT Configurations
Internal Server
IP
Protocol Specify the protocol used for the entry.
Status Check the box to enable the rule.
Enter the IP address of the specified internal server for the entry. All the requests
from the internet to the specified LAN port will be redirected to this host.
2) Click OK.
2.3 Configuring the Port Triggering
Choose the menu Transmission > NAT > Port Triggering and click Add to load the
following page.
Figure 2-3 Configuring the Port Triggering
Follow these steps to configure the Port Triggering:
1) Specify the name of the Port Triggering rule and configure other related parameters.
Interface Specify the effective interface for the rule. If you choose multiple ports, the entry
will be applied to all selected ports simultaneously.
Trigger Port Enter the trigger port or port range. Each entry supports at most 5 groups of
trigger ports. For example, you can enter 1-2, 3-4, 5-6, 7-8, 8-9. Note that the
ports or port ranges cannot overlap with those of other port triggering rules.
Trigger Protocol Specify the trigger protocol for the trigger port.
Incoming Port Enter the incoming port or port range. Each entry supports at most 5 groups of
incoming ports. For example, you can enter 1-2, 3-4, 5-6, 7-8, 8-9. Note that the
ports or port ranges cannot overlap with those of other port triggering rules.
Incoming
Protocol
Specify the incoming protocol for the incoming port.
User Guide
53
Page 62

Configuring Transmission NAT Configurations
Status Check the box to enable the rule.
2) Click OK.
2.4 Configuring the NAT-DMZ
Choose the menu Transmission > NAT > NAT-DMZ and click Add to load the following
page.
Figure 2-4 Configuring the NAT-DMZ
Follow these steps to configure the NAT-DMZ:
1) Specify the name of the NAT-DMZ rule and configure other related parameters.
Interface Specify the effective interface for the rule. If you choose multiple ports, the entry
will be applied to all selected ports simultaneously.
Host IP Address Specify the host IP address for NAT-DMZ.
Status Check the box to enable the rule.
2) Click OK.
2.5 Configuring the ALG
Choose the menu Transmission > NAT > ALG to load the following page.
User Guide 54
Page 63

Configuring Transmission NAT Configurations
Figure 2-5 Configuring the ALG
Enable related ALG according to your needs and click Save.
User Guide
55
Page 64

Configuring Transmission Bandwidth Control Configuration
3
Bandwidth Control Configuration
Bandwidth Control functions to control the bandwidth by configuring rules for limiting
various data flows. In this way, the network bandwidth can be reasonably distributed and
utilized.
Choose the menu Transmission> Bandwidth Control to load the following page.
Figure 3-1 Configuring the Bandwidth Control
Follow these steps to configure the Bandwidth Control rule:
1) In the Bandwidth Control Config Section, enable Bandwidth Control function globally.
Enable
Bandwidth
Control
Enable
Bandwidth
Control
2) In the Bandwidth Control Rule List section, click Add to load the following page.
Check the box to enable Bandwidth Control globally.
With “Enable Bandwidth Control” selected, you can specify a percentage, and the
Bandwidth Control will take effect only when the bandwidth usage reaches the
percentage you specified.
User Guide 56
Page 65

Configuring Transmission Bandwidth Control Configuration
Figure 3-2 Add Bandwidth Control rules
Specify the name of the Bandwidth Control rule and configure other related parameters.
Then click OK.
Direction Specify the data stream direction for the rule.
Group Specify the address group for the rule to define the controlled users. The IP group
referenced here can be created on the Preferences > IP Group > IP Group page.
Maximum
Upstream
Bandwidth
Maximum
Downstream
Bandwidth
Mode Specify the bandwidth control mode for the address group.
Specify the Maximum Upstream Bandwidth in Kbps for the rule.
Specify the Maximum Downstream Bandwidth in Kbps for the rule.
Individual means the bandwidth of each user is equal to the current bandwidth of
this entry.
Shared means the total bandwidth of all controlled IP addresses is equal to the
current bandwidth of this entry.
Effective Time Specify the time for the rule to take effect. Any means it always takes effect. The
time range referenced here can be created on the Preference > Time Range >
Time Range page.
Description Enter a brief description for the rule.
ID Append the rule to the right position to give a priority for the rule.
Status Check the box to enable the rule.
User Guide
57
Page 66

Configuring Transmission Session Limit Configurations
4
Session Limit Configurations
To complete Session Limit configuration, follow these steps:
1) Configure session limit.
2) View the session limit information.
4.1 Configuring Session Limit
Choose the menu Transmission> Session Limit > Session Limit to load the following
page.
Figure 4-1 Configuring the Session Limit
Follow these steps to configure the Session Limit rule:
1) In the General Section, enable Session Limit function globally.
2) In the Session Limit Rule List section, click Add to load the following page.
Figure 4-2 Add Session Limit rules
Specify the name of the Session Limit rule and configure other related parameters.
Then click OK.
User Guide 58
Page 67

Configuring Transmission Session Limit Configurations
Group Specify the address group to which the rule will be applied. The IP group
referenced here can be created on the Preferences > IP Group > IP Group page.
Max Sessions Specify the max sessions for the controlled users.
Status Check the box to enable the rule.
4.2 Viewing the Session Limit Information
Choose the menu Transmission> Session Limit > Session Monitor to load the following
page.
Figure 4-3 Viewing the Session Limit Information
View the Session Limit information of hosts configured with Session Limit. Click the
Refresh button to get the latest information.
User Guide
59
Page 68

Configuring Transmission Load Balancing Configurations
5
Load Balancing Configurations
With load balancing configurations, you can:
■ Configure the load balancing
■ Configure the link backup
■ Configure the online detection
5.1 Configuring the Load Balancing
Choose the menu Transmission > Load Balancing > Basic Settings to load the following
page.
Figure 5-1 Configuring the Load Balancing
Follow these steps to configure the load balancing:
1) In the General Section, enable load balancing function globally and click Save.
2) In the Basic Settings section, select the appropriate method for load balancing and
click Save.
Enable Application
Optimized Routing
Enable Bandwidth Based
Balance Routing on port(s)
With Application Optimized Routing enabled, the router will consider
the source IP address and destination IP address (or destination port)
of the packets as a whole and record the WAN port they pass through.
Then the packets with the same source IP address and destination IP
address (or destination port) will be forwarded to the recorded WAN
port. This feature ensures that multi-connected applications work
properly.
Select the WAN port from the drop-down list to enable Bandwidth
Based Balance Routing.
User Guide 60
Page 69

Configuring Transmission Load Balancing Configurations
5.2 Configuring the Link Backup
With Link Backup function, the router will switch all the new sessions from dropped lines
automatically to another to keep an always on-line network.
Choose the menu Transmission > Load Balancing > Link Backup and click Add to load
the following page.
Figure 5-2 Configuring the Link Backup Rule
Configure the following parameters on this page and click OK.
Primary WAN Specify the primary WAN port. You can choose one primary WAN port, or choose
multiple primary WAN ports to perform load balance.
Backup WAN Specify the backup WAN port to back up the traffic for the primary WAN port under
the specified condition.
Mode Specify the mode as Timing or Failover.
Timing: Link Backup will be enabled if the specified effective time is reached. All the
traffic on the primary WAN will switch to the backup WAN at the beginning of the
effective time; the traffic on the backup WAN will switch to the primary WAN at the
ending of the effective time.
Failover(Enable backup link when any primary WANs fails): Link Backup will be
enabled when any primary WANs fails.
Failover(Enable backup link when all primary WANs fail): Link Backup will be
enabled only when all primary WANs fail.
Effective Time Specify the time for the rule to take effect. “Any” means it takes effect at any time. The
time range referenced here can be created on the Preference > Time Range > Time
Range page.
Status Check the box to enable the rule.
User Guide
61
Page 70

Configuring Transmission Load Balancing Configurations
5.3 Configuring the Online Detection
With Online Detection function, you can detect the online status of the WAN port.
Choose the menu Transmission > Load Balancing > Online Detection and click
the following page.
Figure 5-3 Configuring the Online Detection
Configure the following parameters on this page and click OK.
Port Displays the name of WAN Port.
to load
Mode Select the online detection mode.
Auto: In Auto Mode, the DNS server of the WAN port will be selected as the destination
for DNS Lookup to detect whether the WAN is online.
Manual: In Manual Mode, you can configure the destination IP address for PING and
DNS Lookup manually to detect whether the WAN is online.
Always Online: In Always Online Mode, the status of the port will always be online.
Ping With “Manual Mode” selected, specify the destination IP for Ping. The corresponding
port will ping the IP address to detect whether the WAN port is online. 0.0.0.0 means
Ping detection is disabled.
DNS Lookup With “Manual Mode” selected, specify the IP address of DNS server. The
corresponding port will perform the DNS lookup using default domain name to detect
whether the WAN port is online. 0.0.0.0 means DNS Lookup is disabled.
User Guide 62
Page 71

Configuring Transmission Routing Configurations
6
Routing Configurations
With routing configurations, you can:
■ Configure the static routing
■ Configure the policy routing rule
■ View the routing table
6.1 Configuring the Static Routing
Choose the menu Transmission> Routing > Static Route and click Add to load the
following page.
Figure 6-1 Configuring the Static Routing
Specify the name of the static route entry and configure other related parameters. Then
click OK.
Destination IP Specify the destination IP address the route leads to.
Subnet Mask Specify the subnet mask of the destination network.
Next Hop Specify the IP address to which the packet should be sent next.
Interface Specify the physical network interface through which this route is accessible.
Metric Define the priority of the route. A smaller value means a higher priority. The default
value is 0. It is recommended to keep the default value.
User Guide
63
Page 72

Configuring Transmission Routing Configurations
Description Enter a brief description for the rule.
Status Check the box to enable the rule.
6.2 Configuring the Policy Routing
Choose the menu Transmission > Routing > Policy Routing and click Add to load the
following page.
Figure 6-2 Configuring the Policy Routing
Specify the name of the policy routing entry and configure other related parameters. Then
click OK.
Service Type Specify the service type for the rule.
Source IP Enter the source IP range for the rule. 0.0.0.0 - 0.0.0.0 means any IP is acceptable.
Destination IP Enter the destination IP range for the rule. 0.0.0.0 - 0.0.0.0 means any IP is acceptable.
WAN Specify the outcoming port for the rule. If you choose multiple ports, the entry will be
applied to all selected ports simultaneously.
Effective Time Specify the effective time for the rule.
User Guide 64
Page 73

Configuring Transmission Routing Configurations
Mode Specify the policy routing mode for the rule.
Priority: In Priority Mode, the rule depends on the online detection result. If any WAN
port that you specify is online, the rule will take effect. If all the WAN ports that you
specify are offline, the rule will not take effect.
Only: In Only Mode, the rule always takes effect regardless of the WAN port status or
online detection result.
Description Enter a brief description for the rule.
Status Check the box to enable the rule.
6.3 Viewing the Routing Table
Choose the menu Transmission> Routing > Routing Table to load the following page.
Figure 6-3 Routing Table
The Routing Table shows the information of the current route entries.
Destination IP Displays the destination IP address the route leads to.
Subnet Mask Displays the subnet mask of the destination network.
Next Hop Displays the gateway IP address to which the packet should be sent next.
Interface Displays the physical network interface through which this route is accessible.
Metric Displays the metric to reach the destination IP address.
User Guide
65
Page 74

Configuring Transmission Configuration Examples
7
Configuration Examples
7.1 Example for Configuring NAT
7.1.1 Network Requirements
A company has two departments: Market Department and RD department. Each
department is assigned to an individual subnet. The company has the following
requirements:
1) The two departments need to access the internet via the same router.
2) The company has a web server which needs to be accessed by the users on the
internet.
7.1.2 Network Topology
Figure 7-1 Network Topology
Web Server
192.168.0.20
RD Department
172.16.10.0/24
L3 Switch
Market Department
172.16.20.0/24
7.1.3 Configuration Scheme
To meet the first requirement, configure static routing on the gateway to make sure
the router know where to deliver the packets to IP addresses in different subnets
(172.16.10.0/24, 172.16.20.0/24).
To meet the second requirement, add One-to-One NAT entry for the Web Server on the
router, thus the web server with a private IP address can be accessed at a corresponding
LAN
Gateway
192.168.0.10
WAN1
123.1.1.3
Internet
User Guide 66
Page 75

Configuring Transmission Configuration Examples
valid public IP address. Note that One-to-One NAT take effects only when the connection
type of WAN port is Static IP.
7.1.4 Configuration Procedure
Follow the steps below to configure NAT on the router:
■ Configuring the static routing
1) Choose the menu Transmission > Routing > Static Route to load the configuration
page, and click Add.
2) Add static routes for the two departments respectively: Specify the entry name as RD/
Market, enter 172.16.10.0/172.16.20.0 as the destination IP, and specify the VLAN 1
interface IP of L3 switch as next hop, then choose the interface as WAN1. Keep Status
of this entry as Enable. Click OK.
Figure 7-2 Configuring the Static Routing for RD Department
Figure 7-3 Configuring the Static Routing for Market Department
■ Configuring the One-to-One NAT
1) Choose the menu Transmission > NAT > One-to-One NAT to load the configuration
page, and click Add.
User Guide
67
Page 76

Configuring Transmission Configuration Examples
2) Add a One-to-One NAT entry for the web server: Specify the entry name as web,
choose the interface as WAN1, and enter the orignal IP as 192.168.0.20, the translated
IP as 123.1.1.3. Enable DMZ Forwarding, then keep Status of this entry as Enable. Click
OK.
Figure 7-4 Adding a Multi-Nets Entry for RD Department
7.2 Example for Configuring Load Balancing
7.2.1 Network Requirements
To make good use of bandwidth, the network administrator decides to bind two WAN links
using load balancing.
User Guide 68
Page 77

Configuring Transmission Configuration Examples
7.2.2 Network Topology
Figure 7-5 Network Topology
Internet
WAN1
PPPoE 8Mbps
7.2.3 Configuration Scheme
To meet the requirement, configure WAN parameters on the router in order that the
two WAN links can work properly and have access to the internet, then configure load
balancing on the router to aggregate two WAN links.
7.2.4 Configuration Procedure
Internet
Gateway
WAN2
Dynamic IP 12Mbps
PC
Follow the steps below to configure load balancing on the router:
■ Configuring the WAN parameters
For WAN1 port, configure the connection type as PPPoE, and specify Upstream and
Downstream bandwidth for this link based on your ADSL bandwidth (You could consult
your internet Service Provider for the bandwidth information).
For WAN2 port, configure the connection type as Dynamic IP, and specify Upstream
and Downstream bandwidth for this link according to data that ISP provides.
Make sure two WAN links can work properly and have access to the internet.
■ Configuring the Load Balancing
Choose the menu Transmission> Load Balancing > Basic Settings to load the
configuration page. Enable Load Balancing globally, and click Save. Enable Application
Optimized Routing, and enable Bandwidth Based Balancing Routing on WAN1 port and
WAN2 port. Click Save.
User Guide
69
Page 78

Configuring Transmission Configuration Examples
Figure 7-6 Configuring the Load Balancing
7.3 Example for Configuring Virtual Server
7.3.1 Network Requirements
The network administrator builds up a FTP server on the local network and wants to share it
on the internet.
7.3.2 Network Topology
Figure 7-7 Network Topology
LAN
FTP Server
IP:192.168.0.100
Gateway
7.3.3 Configuration Scheme
In this scenario, both virtual server and DMZ host can be configured to meet the
requirement. Here we take configuring Virtual Server as an example, owing to that for a
DMZ host all ports are open which may result in unsafety. Configure the FTP server as a
virtual server on the router so that the FTP server can be accessed by the internet user.
WAN1
Internet
PC
7.3.4 Configuration Procedure
Follow the steps below to configure virtual server on the router:
1) Choose the menu Transmission > NAT > Virtual Servers to load the configuration
page, and click Add.
User Guide 70
Page 79

Configuring Transmission Configuration Examples
2) Specify the entry name as ftp, choose the interface as WAN1, and specify the internal/
external port as 21, enter the IP address of FTP server (192.168.0.100) as the internal
server IP. Select the protocol as All, then keep Status of this entry as Enable. Click OK.
Figure 7-8 Configuring the Virtual Server
7.4 Example for Configuring Policy Routing
7.4.1 Network Requirements
The network administrator has a router with 3 computers (192.168.0.2-192.168.0.4)
connected to the LAN side, all computers are routed to internet by WAN1 port and WAN2
port, the requirements are as follows:
■ WAN2 link is used to backup WAN1 link to keep an always on-line network.
■ The two computers with IP addresses 192.168.0.2 and 192.168.0.3 are required to use
WAN1 for web surfing, WAN2 for other internet activities.
User Guide
71
Page 80

Configuring Transmission Configuration Examples
7.4.1 Network Topology
Figure 7-9 Network Topology
Internet
WAN1
PC
192.168.0.2
192.168.0.3
PC
Internet
WAN2
Gateway
PC
192.168.0.4
7.4.2 Configuration Scheme
To meet the first requirement, configure link backup on the router. To meet the second
requirement, configure policy routing rules for two computers which use 192.168.0.2 and
192.168.0.3. Note that link backup rule has a higher priority than policy routing rule.
7.4.3 Configuration Procedure
Follow the steps below to configure link backup and policy routing on the router:
■ Configuring the Link Backup
1) Choose the menu Transmission > Load Balancing > Link Backup to load the
configuration page, and click Add.
2) Specify the primary WAN as WAN1, the backup WAN as WAN2 and the mode as
Failover (Enable backup link when any primary WAN fails), so that the backup WAN
will be enabled when the primary WAN failed. Keep Status of this entry as Enable. Click
OK.
User Guide 72
Page 81

Configuring Transmission Configuration Examples
Figure 7-10 Configuring the Link Backup
■ Configuring the Policy Routing Rules
1) Choose the menu Preferences > IP Group > IP Address to load the configuration page,
and click Add. Specify the IP address name as tp, the IP address type as IP Address
Range (192.168.0.2-192.168.0.3). Click OK.
Figure 7-11 Configuring the IP Address
2) Choose the menu Preferences > IP Group > IP Address to load the configuration
page and click Add. Specify the IP group name as group1, the IP address name as tp to
reference the IP address you have created. Click OK.
Figure 7-12 Configuring the IP Group
3) Choose the menu Transmission > Routing > Policy routing to load the configuration
page, and click Add.
User Guide
73
Page 82

Configuring Transmission Configuration Examples
Specify the policy routing rule name as policy1, the service type as HTTP, the source IP
as group1, the destination IP as IPGROUP_ANY which means no limit. Choose WAN1,
and keep Status of this entry as Enable. Click OK.
Figure 7-13 Configuring the Policy Routing Rule 1
Specify the policy routing rule name as policy2, the service type as ALL, the source IP
as group1, the destination IP as IPGROUP_ANY which means no limit. Choose WAN2,
and keep Status of this entry as Enable. Click OK.
Figure 7-14 Configuring the Policy Routing Rule 2
User Guide 74
Page 83

Part 6
Configuring Firewall
CHAPTERS
1. Firewall
2. Firewall Configuration
3. Configuration Examples
Page 84

Configuring Firewall Firewall
1
Firewall
1.1 Overview
Firewall is used to enhance the network security. It can prevent external network threats
from spreading to the internal network, protect the internal hosts from ARP attacks, and
control the internal users’ access to the external network.
1.2 Supported Features
The Firewall module supports four functions: Anti ARP Spoofing, Attack Defense, and
Access Control.
Anti ARP Spoofing
ARP (Address Resolution Protocol) is used to map IP addresses to the corresponding MAC
addresses so that packets can be delivered to their destinations. However, since ARP is
implemented with the premise that all the hosts and routers are trusted, there are high
security risks on real, complex networks. If attackers send ARP spoofing packets with false
IP address-to-MAC address mapping entries, the device will update the ARP table based
on the false ARP packets and record wrong mapping entries, which results in a breakdown
of normal communication.
Anti ARP Spoofing can protect the network from ARP spoofing attacks. It works based on
the IP-MAC Binding entries. These entries record the correct one-to-one relationships
between IP addresses and MAC addresses. When receiving an ARP packet, the router
checks whether it matches any of the IP-MAC Binding entries. If not, the router will ignore
the ARP packets. In this way, the router maintains the correct ARP table.
In addition, the router provides the following two sub functions:
■ Permitting the packets matching the IP-MAC Binding entries only and discarding other
packets.
■ Sending GARP packets to the hosts when it detects ARP attacks. The GARP packets
can inform hosts of the correct ARP table, preventing their ARP tables from being
falsified by ARP spoofing packets.
Attack Defense
Attacks on a network device can cause device or network paralysis. With the Attack
Defense feature, the router can identify and discard various attack packets which are sent
to the CPU, and limit the packet receiving rate. In this way, the router can protect itself and
the connected network against malicious attacks.
User Guide 76
Page 85

Configuring Firewall Firewall
The router provides two types of Attack Defense: Flood Defense and Packet Anomaly
Defense. Flood Defense limits the receiving rate of the specific types of packets, and
Packet Anomaly Defense discards the illegal packets directly.
Access Control
Access Control can filter the packets passing through the router based on the Access
Control rules. An Access Control rule includes a filter policy and some conditions, such as
service type, receiving interface and effective time. The router will apply the filter policy to
the packets matching these conditions, and thus to limit network traffic, manage network
access behaviors and more.
Access Control can prevent various network attacks, such as attacks on TCP (Transmission
Control Protocol) and ICMP (Internet Control Message Protocol) packets, and can also
manage network access behaviors, such as controlling access to the internet.
User Guide
77
Page 86

Configuring Firewall Firewall Configuration
2
Firewall Configuration
In Firewall module, you can configure the following features:
■ Anti ARP Spoofing
■ Attack Defense
■ Access Control
2.1 Anti ARP Spoofing
To complete Anti ARP Spoofing configuration, there are two steps. First, add IP-MAC
Binding entries to the IP-MAC Binding List. Then enable Anti ARP Spoofing for these
entries.
Note:
In case Anti ARP Spoofing causes access problems to the currently connected devices, we
recommend that you add and verify the IP-MAC Binding entries first before enabling Anti ARP
Spoofing.
2.1.1 Adding IP-MAC Binding Entries
You can add IP-MAC Binding entries in two ways: manually and via ARP scanning.
■ Adding IP-MAC Binding Entries Manually
You can manually bind the IP address, MAC address and interface together on the
condition that you have got the related information of the hosts on the network.
■ Adding IP-MAC Binding Entries via ARP Scanning
With ARP Scanning, the router sends the ARP request packets with the specific IP field to
the hosts. Upon receiving the ARP reply packet, the router can get the IP address, MAC
address and connected interface of the host.
The following sections introduce these two methods in detail.
User Guide 78
Page 87

Configuring Firewall Firewall Configuration
Adding IP-MAC Binding Entries Manually
Before adding entries manually, get the IP addresses and MAC addresses of the hosts on
the network and make sure of their accuracy.
Choose the menu Firewall > Anti ARP Spoofing > IP-MAC Binding to load the following
page.
Figure 2-1 IP-MAC Binding Page
Follow the steps below to add IP-MAC Binding entries manually. The entries will take effect
on the LAN interface.
1) In the IP-MAC Binding List section, click Add to load the following page.
Figure 2-2 Add IP-MAC Binding Entries Manually
2) Configure the following parameters on this page.
IP Address Enter an IP address to be bound.
MAC Address Enter a MAC address to be bound.
User Guide
79
Page 88

Configuring Firewall Firewall Configuration
Description Give a description for identification.
Status Enable this entry. Only when the status is Enable will this entry be effective.
3) Click OK and the added entry will be displayed in the list.
Adding IP-MAC Binding Entries via ARP Scanning
If you want to get the IP addresses and MAC addresses of the hosts quickly, you can use
ARP Scanning to facilitate your operation.
Note:
Before using this feature, make sure that your network is safe and the hosts are not suffering from
ARP attacks at present; otherwise, you may obtain incorrect IP-MAC Binding entries. If your network
is being attacked, it’s recommended to bind the entries manually.
Choose the menu Firewall > Anti ARP Spoofing > ARP Scanning to load the following
page.
Figure 2-3 Add IP-MAC Binding Etries via ARP Scanning
Follow the steps below to add IP-MAC Binding entries via ARP Scanning.
1) Click Scan and the following window will pop up.
Figure 2-4 ARP Scanning Process
2) Wait for a moment without any operation. The scanning result will be displayed in the
following table. Click
or select multiple entries and click
to export the corresponding entry to the IP-MAC Binding table,
to export the entries to the IP-MAC Binding
table in batch.
User Guide 80
Page 89

Configuring Firewall Firewall Configuration
Figure 2-5 ARP Scanning Result
Also, you can go to Firewall > Anti ARP Spoofing > ARP List to view and bind the ARP
Scanning entries. The ARP Scanning list displays all the historical scanned entries.
Click
to export the corresponding entry to the IP-MAC Binding table, or select multiple entries
and click
Figure 2-6 ARP List
to export the entries to the IP-MAC Binding table in batch.
2.1.2 Enable Anti ARP Spoofing
Choose the menu Firewall > Anti ARP Spoofing > IP-MAC Binding to load the following
page.
Figure 2-7 IP-MAC Binding-General Config
Follow the steps below to configure Anti ARP Spoofing rule:
User Guide
81
Page 90

Configuring Firewall Firewall Configuration
1) In the General section, enable ARP Spoofing Defense globally. With this option enabled,
the router can protect its ARP table from being falsified by ARP spoofing packets.
2) Choose whether to enable the two sub functions.
Permit the packets matching
the IP-MAC Binding entries only
Send GARP packets when ARP
attack is detected
Interval If the Send GARP packets when ARP attack is detected is
With this option enabled, when receiving a packet, the router
will check whether the IP address, MAC address and receiving
interface match any of the IP-MAC Binding entries. Only the
matched packets will be forwarded.
With this option enabled, the router will send GARP packets to the
hosts if it detects ARP spoofing packets on the network. The GARP
packets will inform the hosts of the correct ARP information, which
is used to replace the wrong ARP information in the hosts.
enabled, configure the time interval for sending GARP packets. The
valid values are from 1 to 10000 milliseconds.
3) Click Save.
Note:
Before enabling “Permit the packets matching the IP-MAC Binding entries only”, you should make
sure that your management host is in the IP-MAC Binding list. Otherwise, you cannot log in to the Web
management page of the router. If this happens, restore your router to factory defaults and then log in
using the default login credentials.
User Guide 82
Page 91

Configuring Firewall Firewall Configuration
2.2 Configuring Attack Defense
Choose the menu Firewall > Attack Defense > Attack Defense to load the following page.
Figure 2-8 Attack Defense
Follow the steps below to configure Attack Defense.
1) In the Flood Defense section, check the box and configure the corresponding
parameters to enable your desired feature. By default, all the options are disabled. For
details, refer to the following table:
Multi-connections TCP
SYN Flood
Multi-connections UDP
Flood
Multi-connections
ICMP Flood
With this feature enabled, the router will filter the subsequent TCP SYN
packets if the number of this kind of packets reaches the specified
threshold. The valid threshold ranges from 100 to 99999.
With this feature enabled, the router will filter the subsequent UDP packets
if the number of this kind of packets reaches the specified threshold. The
valid threshold ranges from 100 to 99999.
With this feature enabled, the router will filter the subsequent ICMP
packets if the number of this kind of packets reaches the specified
threshold. The valid threshold ranges from 100 to 99999.
User Guide
83
Page 92

Configuring Firewall Firewall Configuration
Stationary source TCP
SYN Flood
Stationary source UDP
Flood
Stationary source ICMP
Flood
With this feature enabled, the router will filter the subsequent stationary
source TCP SYN packets if the number of this kind of packets reaches the
specified threshold. The valid threshold ranges from 100 to 99999.
With this feature enabled, the router will filter the subsequent stationary
source UDP SYN packets if the number of this kind of packets reaches the
specified threshold. The valid threshold ranges from 100 to 99999.
With this feature enabled, the router will filter the subsequent stationary
source ICMP SYN packets if the number of this kind of packets reaches
the specified threshold. The valid threshold ranges from 100 to 99999.
2) In the Packet Anomaly Defense section, directly check the box to enable your desired
feature. By default, all the options are enabled. For details, refer to the following table:
Block TCP Scan (Stealth
FIN/Xmas/Null)
Block Ping of Death With this option enabled, the router will block Ping of Death attack. Ping of
Block Large Ping With this option enabled, the router will block Large Ping attacks. Large
With this option enabled, the router will filter the TCP scan packets of
Stealth FIN, Xmas and Null.
Death attack means that the attacker sends abnormal ping packets larger
than 65535 bytes to cause system crash on the target computer.
Ping attack means that the attacker sends multiple ping packets larger
than 1500 bytes to cause the system crash on the target computer.
Block Ping from WAN With this option enabled, the router will block the ICMP request from WAN.
Block WinNuke attack With this option enabled, the router will block WinNuke attacks. WinNuke
attack refers to a remote denial-of-service attack (DoS) that affects some
Windows operating systems, such as the Windows 95 and Windows N. The
attacker sends a string of OOB (Out of Band) data to the target computer
on TCP port 137, 138 or 139, causing system crash or Blue Screen of
Death.
Block TCP packets with
SYN and FIN Bits set
Block TCP packets with
FIN Bit set but no ACK
Bit set
Block packets with
specified IP options
With this option enabled, the router will filter the TCP packets with both
SYN Bit and FIN Bit set.
With this option enabled, the router will filter the TCP packets with FIN Bit
set but without ACK Bit set.
With this option enabled, the router will filter the packets with specified IP
options. You can choose the options according to your needs.
3) Click Save to save the settings.
User Guide 84
Page 93

Configuring Firewall Firewall Configuration
2.3 Configuring Access Control
Choose the menu Firewall > Access Control > Access Control and click Add to load the
following page.
Figure 2-9 Access Control
This table displays the Access Control entries. Follow the steps below to add a new Access
Control entry.
1) Click Add and the following page will appear.
Figure 2-10 Access Control
2) Configure the required parameters and click OK:
Name Specify a name for the rule. It can be 50 characters at most. The name of
each entry cannot be repeated.
Policy Select whether to block or allow the packets matching the rule to access the
network.
Service Type Select the effective service for the rule. The service referenced here can be
created on the Preferences > Service Type page.
Interface Select the effective interface for the rule.
User Guide
85
Page 94

Configuring Firewall Firewall Configuration
Source Select an IP group to specify the source address range for the rule. The IP
group referenced here can be created on the Preferences > IP Group page.
Destination Select an IP group to specify the destination address range for the rule. The
IP group referenced here can be created on the Preferences > IP Group
page.
Effective Time Select the effective time for the rule. The effective time referenced here can
be created on the Preferences > Time Range page.
ID Specify a rule ID. A smaller ID means a higher priority. This value is optional,
and the newly added rule without this value configured will get the largest ID
among all rules, which means the newly added rule has the lowest priority.
User Guide 86
Page 95

Configuring Firewall Configuration Examples
3
Configuration Examples
3.1 Example for Anti ARP Spoofing
3.1.1 Network Requirements
In the diagram below, several hosts are connected to the network via a layer 2 switch, and
the router is the gateway of this network. Since there exists the possibility that the attacker
will launch a series of ARP attacks, it is required to configure the router to protect itself and
the terminal hosts from the ARP attacks.
Figure 3-1 Network Topology
Internet
WAN
Router
Layer 2 Switch
Host A
192.168.0.10
00-19-56-8A-4C-71
Host B
192.168.0.20
00-19-56-82-3B-70
3.1.2 Configuration Scheme
The attacker can launch three types of ARP attacks: cheating router, imitating gateway and
cheating terminal hosts. The following section introduces the three ARP attacks and the
corresponding solutions.
LAN
192.168.0.1
Attacker
Host C
192.168.0.30
00-19-56-8D-22-75
■ Cheating Gateway
Cheating gateway attack is aimed at the router.
User Guide
87
Page 96

Configuring Firewall Configuration Examples
The attacker pretends to be legal terminal hosts and sends fake ARP packets to the router,
cheating the router into recording wrong ARP maps of the hosts. As a result, packets from
the gateway cannot be correctly sent to the hosts. To protect the router from this kind of
attack, you can configure Anti ARP Spoofing on the router.
■ Imitating Gateway and Cheating Hosts
These two attacks are aimed at the terminal hosts.
Imitating Gateway means that the attacker imitates the gateway and sends fake ARP
packets to the hosts. As a result, the hosts record wrong ARP map of the gateway and
cannot send packets to the router correctly.
Cheating Hosts means that the attacker pretends to be a legal host and sends fake ARP
packets to other hosts. As a result, the cheated hosts record an incorrect ARP map of the
legal host and cannot send packets to legal host correctly.
To protect the hosts from the attacks above, it is recommend to take both of the
precautions below.
» Configure the firewall feature on the hosts.
» Configure the router to send GARP packets to the hosts when the router detects ARP
attacks. The GARP packets will inform the hosts of the correct ARP maps, and the
wrong ARP maps in the hosts will be replaced by the correct ones.
In conclusion, to protect the network from ARP attacks, we should make sure both the
router and the hosts are configured with the relevant ARP defense features. Here we
introduce how to configure Anti ARP Spoofing on the router. There are mainly three steps:
1) Get the IP and MAC addresses of the legal hosts and bind them to the IP-MAC Binding
list.
2) Enable Anti ARP Spoofing.
3) Configure the router to send GARP packets when ARP attacks are detected.
3.1.3 Configuration Procedure
Follow the steps below to configure Anti ARP Spoofing on the router:
1) Choose the menu Firewall > Anti ARP Spoofing > IP-MAC Binding to load the following
page. In the IP-MAC Binding List section, click Add.
User Guide 88
Page 97

Configuring Firewall Configuration Examples
Figure 3-2 Anti ARP Spoofing Page
2) The following page will appear. Enter the IP address and MAC address of Host A, give a
description “Host A” for this entry. Keep Status of this entry as “Enable”. Click OK.
Figure 3-3 Add IP-MAC Binding Entry
3) Add the IP-MAC Binding entries for Host B and Host C as introduced above, and verify
your configurations.
Figure 3-4 Verify IP-MAC Binding Entires
4) In the General section on the same page, check the boxes to enable ARP Spoofing
Defense and Send GARP packets when ARP attack is detected, and keep the interval
as 1000 milliseconds. Click Save.
User Guide
89
Page 98

Configuring Firewall Configuration Examples
Figure 3-5 Configure Anti ARP Spoofing
3.2 Example for Access Control
3.2.1 Network Requirements
In the diagram below, the R&D and some other departments are connected to a layer 2
switch and access the internet via the router. To limit the acts of the R&D department users,
such as sending emails with the exterior mailbox, it is required that the R&D users can only
visit websites via HTTP and HTTPs on the internet at any time. For other departments, there
is no limitation.
Figure 3-1 Network Topology
Internet
WAN
1.1.1.2
Router
LAN
192.168.0.1/24
Layer 2 Switch
192.168.0.10/24-192.168.0.120/24
R&D Department
Other Departments
User Guide 90
Page 99

Configuring Firewall Configuration Examples
3.2.2 Configuration Scheme
To meet these requirements, we can configure Access Control rules on the router to filter
the specific types of packets from R&D department: only the HTTP and HTTPs packets
are allowed to be sent to the internet, and other types of packets are not allowed. The
configuration overview is as follows:
1) Add an IP group for the R&D department in the Preferences module.
2) By default, the HTTP service type already exists, and you need to add HTTPs to the
Service Type list in the Preferences module.
3) Create two rules to allow the HTTP and HTTPs packets from the R&D department to be
sent to the WAN.
4) Since visiting the internet needs DNS service, add a rule to allow the DNS packets to be
sent to the WAN. DNS service is already in the Service Type list by default.
5) Create a rule to block all packets from the R&D department to the WAN. This rule should
have the lowest priority among all the rules.
3.2.3 Configuration Procedure
Follow the steps below to complete the configuration:
1) Choose the menu Preferences > IP Group > IP Address to load the configuration page,
and click Add. Specify a name RD, select IP Address Range and enter the IP address
range of the R&D department. Click OK.
Figure 3-2 Configure IP Address Range
2) Choose the menu Preferences > IP Group > IP Group to load the configuration page,
and click Add. Specify a group name “RD_Dept”, select the preset address range "RD”
and click OK.
User Guide
91
Page 100

Configuring Firewall Configuration Examples
Figure 3-3 Configure IP Group
3) Choose the menu Preferences > Service Type > Service Type to load the
configuration page, and click Add. Specify the service type name as “HTTPS”, select
the protocol as “TCP”, specify the source port range as “0-65535” and destination port
range as “443-443”, and click OK.
Figure 3-4 Configure HTTPS Service Type
4) Choose the menu Firewall > Access Control > Access Control to load the
configuration page, and click Add. Specify a name for this rule. Select “Allow” as the rule
policy, “HTTP” as the service type, “LAN” as the effective interface, “RD_Dept” as the
source IP group, “IPGROUP_ANY” as the destination IP group, and “Any” as the effective
time. Click OK.
This rule means that all the HTTP packets from the R&D department are allowed to be
transmitted from LAN to the internet at any time.
User Guide 92
 Loading...
Loading...