Sonicwall SONICOS 5.8 Netflow reporting

NetFlow Reporting
Document Scope
Rapid growth of IP networks has created interest in new business applications and services. These new
services have resulted in increases in demand for network bandwidth, performance, and predictable quality
of service as well as VoIP, multimedia and security oriented network services. Simultaneously, the need has
emerged for measurement technology to support this growth by efficiently providing the information
required to record network and application resource utilization. NetFlow provides solutions for each of
these challenges.
This SonicOS 5.8.0 feature module guide provides an overview of NetFlow benefits and includes technical
overview of features, details about the NetFlow cache, export formats and NetFlow operation. This docu
ment also provides configuration and troubleshoot procedures and examples.
This document contains the following sections:
• “NetFlow Reporting Overview” section on page 1
• “Administrator Prerequisites” section on page 4
• “Configuring NetFlow Reporting Task List” section on page 5
• “User Configuration Tasks” section on page 12
• “Appendix” section on page 19
-
NetFlow Reporting Overview
This section provides an introduction to the NetFlow Reporting feature. After reading the NetFlow
Reporting Overview section, you will be able to start configuring your SonicWALL security appliance
network interface to enable NetFlow services. This section contains the following subsections:
• “NetFlow Benefits” section on page 2
• “What Is A Flow?” section on page 2
• “NetFlow Export Version Formats” section on page 3
• “NetFlow Export Packet Header Format” section on page 3
• “Supported Interfaces, Encapsulations and Protocols” section on page 3
• “NetFlow Collectors” section on page 4
• “Supported Platforms” section on page 4
• “Supported Standards” section on page 4
SonicOS 5.8 NetFlow Reporting Feature Guide
1

NetFlow Reporting Overview
NetFlow Benefits
NetFlow traditionally enables several key customer applications including:
• Network Monitoring—NetFlow data enables extensive near real time network monitoring capabilities.
Flow-based analysis techniques may be utilized to visualize traffic patterns associated with individual
routers and switches as well as on a network-wide basis (providing aggregate traffic or application based
views) to provide proactive problem detection, efficient troubleshooting, and rapid problem resolution.
• Application Monitoring and Profiling—NetFlow data enables network managers to gain a detailed,
time-based, view of application usage over the network. This information is used to plan, understand
new services, and allocate network and application resources (e.g. Web server sizing and VoIP
deployment) to responsively meet customer demands.
• User Monitoring and Profiling—NetFlow data enables network engineers to gain detailed
understanding of customer/user utilization of network and application resources. This information may
then be utilized to efficiently plan and allocate access, backbone and application resources as well as to
detect and resolve potential security and policy violations.
• Network Planning—NetFlow can be used to capture data over a long period of time producing the
opportunity to track and anticipate network growth and plan upgrades to increase the number of
routing devices, ports, or higher- bandwidth interfaces. NetFlow services data optimizes network
planning including peering, backbone upgrade planning, and routing policy planning. NetFlow helps to
minimize the total cost of network operations while maximizing network performance, capacity, and
reliability. NetFlow detects unwanted WAN traffic, validates bandwidth and Quality of Service (QOS)
and allows the analysis of new network applications. NetFlow will give you valuable information to
reduce the cost of operating your network.
• Security Analysis—NetFlow identifies and classifies DDOS attacks, viruses and worms in real-time.
Changes in network behavior indicate anomalies that are clearly demonstrated in NetFlow data. The
data is also a valuable forensic tool to understand and replay the history of security incidents.
NetFlow has two key components: (1) the NetFlow cache or data source which stores IP Flow information
and (2) the NetFlow export or transport mechanism that sends NetFlow data to a network management
collector for data reporting.
What Is A Flow?
A flow is identified as a unidirectional stream of packets between a given source and destination—both
defined by a network-layer IP address and transport-layer source and destination port numbers. Specifically,
a flow is identified as the combination of the following seven key fields:
• Source IP address
• Destination IP address
• Source port number
• Destination port number
• Layer 3 protocol type
• Input logical interface (ifIndex)
These seven key fields define a unique flow. If a flow has one different field than another flow, then it is
considered a new flow. A flow contains other accounting fields (such as the AS number in the NetFlow
export Version 5 flow format) that depend on the version record format that you configure for export.
Flows are processed in a NetFlow cache.
2

NetFlow Export Version Formats
The NetFlow Export datagram consists of a header and a sequence of flow records. The header contains
information such as sequence number, record count and sysuptime. The flow record contains flow
information, for example IP addresses, ports, and routing information. For more information, see
“Appendix” section on page 19
The Version 5 format is an enhancement that adds Border Gateway Protocol (BGP) autonomous system
information and flow sequence numbers. The distinguishing feature of the NetFlow Version 9 format is that
it is template based. Templates provide an extensible design to the record format, a feature that should allow
future enhancements to NetFlow services without requiring concurrent changes to the basic flow-record
format.
Using templates with NetFlow Version 9 provides several key benefits:
• Almost any information can be exported from a router or switch including layer 2 through 7
information, routing information, IPv6, IPv4, multicast and MPLS information. This new information
will allow new applications for flow data and new views of network behavior.
• Third-party business partners who produce applications that provide collector or display services for
NetFlow will not be required to recompile their applications each time a new NetFlow export field is
added. Instead, they may be able to use an external data file that documents the known template
formats.
• New features can be added to NetFlow more quickly, without breaking current implementations.
• NetFlow is "future-proofed" against new or developing protocols, because the Version 9 format can be
adapted to provide support for them and other non-Flow based data measurements.
NetFlow Reporting Overview
NetFlow Export Packet Header Format
In these versions, the datagram consists of a header and one or more flow records. The first field of the
header contains the version number of the export datagram. Typically, a receiving application that accepts
any of the format versions allocates a buffer large enough for the largest possible datagram from any of the
format versions and then uses the header to determine how to interpret the datagram. The second field in
the header contains the number of records in the datagram (indicating the number of expired flows
represented by this datagram) and is used to index through the records. Datagram headers for NetFlow
Export versions 5 and 9 also include a "sequence number" field used by NetFlow data consuming
applications to check for lost datagrams.
Supported Interfaces, Encapsulations and Protocols
NetFlow supports IPv4 (and IPv4-encapsulated) routed traffic over a wide range of interface types and
encapsulations. This includes Frame Relay, Asynchronous Transfer Mode, Inter-Switch Link, 802.1q,
Multi-link Point to Point Protocol, General Routing Encapsulation, Layer 2 Tunneling Protocol,
Multi-protocol Label Switching VPNs, and IP Sec Tunnels.
NetFlow is supported per interface.
NetFlow support for multicast exists on all SonicWALL platforms.
NetFlow supports IPv6 environments in the release of SonicOS 5.8 and up.
SonicOS 5.8 NetFlow Reporting Feature Guide
3

Administrator Prerequisites
NetFlow Collectors
SonicWALL NetFlow collector provides fast, scalable, and economical data collection from multiple
NetFlow Export-enabled devices. The collector consumes flow datagrams from multiple NetFlow
Export-enabled devices and performs data volume reduction through selective filtering and aggregation,
performs bi-directional flow analysis and flow de-duplication.
Supported Platforms
This feature is supported only on the SonicOS 5.8 release. The SonicOS 5.8 release supports the following
platforms:
• TZ series
• NSA series
Supported Standards
SonicOS 5.8 NetFlow Reporting is supported on the following NetFlow Export Formats:
• NetFlow Version 5
• NetFlow Version 9
• IPFIX (NetFlow Version 10)
• IPFIX with extensions
Administrator Prerequisites
NetFlow Activation and Deployment Information
SonicWALL recommends careful planning of NetFlow deployment with NetFlow services activated on
strategically located edge/aggregation routers which capture the data required for planning, monitoring and
accounting applications. Key deployment considerations include the following:
• Understanding your application-driven data collection requirements: accounting applications may only
require originating and terminating router flow information whereas monitoring applications may
require a more comprehensive (data intensive) end-to-end view
• Understanding the impact of network topology and routing policy on flow collection strategy: for
example, avoid collecting duplicate flows by activating NetFlow on key aggregation routers where
traffic originates or terminates and not on backbone routers or intermediate routers which would
provide duplicate views of the same flow information
• NetFlow can be implemented in the SonicOS management interface to understand the number of flow
in the network and the impact on the router. NetFlow export can then be setup at a later date to
complete the NetFlow deployment.
NetFlow is in general an ingress measurement technology which should be deployed on appropriate
interfaces on edge/aggregation or WAN access routers to gain a comprehensive view of originating and
terminating traffic to meet customer needs for accounting, monitoring or network planning data. The key
mechanism for enhancing NetFlow data volume manageability is careful planning of NetFlow deployment.
NetFlow can be deployed incrementally (i.e. interface by interface) and strategically (i.e. on well chosen
routers) —instead of widespread deployment of NetFlow on every router in the network.
4

Configuring NetFlow Reporting Task List
Configuring NetFlow Reporting Task List
The Log > Flow Reporting screen allows you to view statistics based on Flow Reporting and Internal
Reporting. From this screen, you can also configure settings for internal and external flow reporting and
external flow reporting.
Flow Reporting Statistics
The Flow Reporting Statistics apply to all external flows. This section shows reports of the flows that are
sent to the server, not collected, dropped, stored in and removed from the memory, reported and non
reported to the server. This section also includes the number of NetFlow/IPFIX templates sent and general
static flows reported.
NetFlow/IPFIX Packets Sent Total number of IPFIX/NetFlow packets sent to
the external collector.
Data Flows Enqueued Total number of connection related flows that is
collected so far.
Data Flows Dequeued Total number of connection related flows that have
been reported either to internal collectors or
external collectors.
Data Flows Dropped Total number of collected connection related flows
that failed to get reported.
Data Flows Skipped Reporting Total number of connection related flows that
skipped reporting. This can happen when running
in periodic mode where collected flows are more
than configured value for reporting.
General Flows Enqueued Total number of all non-connection related flows
that have been collected.
General Flows Dequeued Total number of all non-connection related flows
that have been reported either to external collectors
or internal collectors.
General Flows Dropped Total number of all non-connection related flows
dropped due to too many requests.
SonicOS 5.8 NetFlow Reporting Feature Guide
5
Configuring NetFlow Reporting Task List
NetFlow/IPFIX Templates Sent Total number of templates that has been reported
General Static Flows Reported Total number of static non-connection related
App Flow Reporting Statistics
The App Flow Reporting Statistics apply to all internal flows. Similar to the Flow Reporting Statistics, this
section shows reports of the flows that are sent to the server, not collected, dropped, stored in and removed
from the memory, reported and non reported to the server. This section also includes the number of static
flows removed from the queue, internal errors, and the total number of flows within the internal database.
Data Flows Enqueued Total number of connection related flows that have
Data Flows Dequeued Total number of connection related flows that have
Data Flows Dropped Total number of collected connection related flows
Data Flows Skipped Reporting Total number of connection related flows that
General Flows Enqueued Total number of all non-connection related flows in
General Flows Dequeued Total number of all non-connection related flows in
General Flows Dropped Total number of all non-connection related flows
General Static Flows Dequeued Total number of non-connection related static
App Flow Collector Errors Total number of internal database errors.
Total Flows in DB Total number of connection related flows in DB.
to the external collector.
flows that have been reported. This includes lists of
applications/viruses/spyware/intrusions/table-ma
p/column-map/location map.
been queued to internal collector.
been successfully inserted into the database.
that failed to get inserted into the database due to
high connection rate.
skipped reporting.
DB queue.
DB queue.
failed to get inserted due to high rate.
flows that have been successfully inserted into the
DB.
6
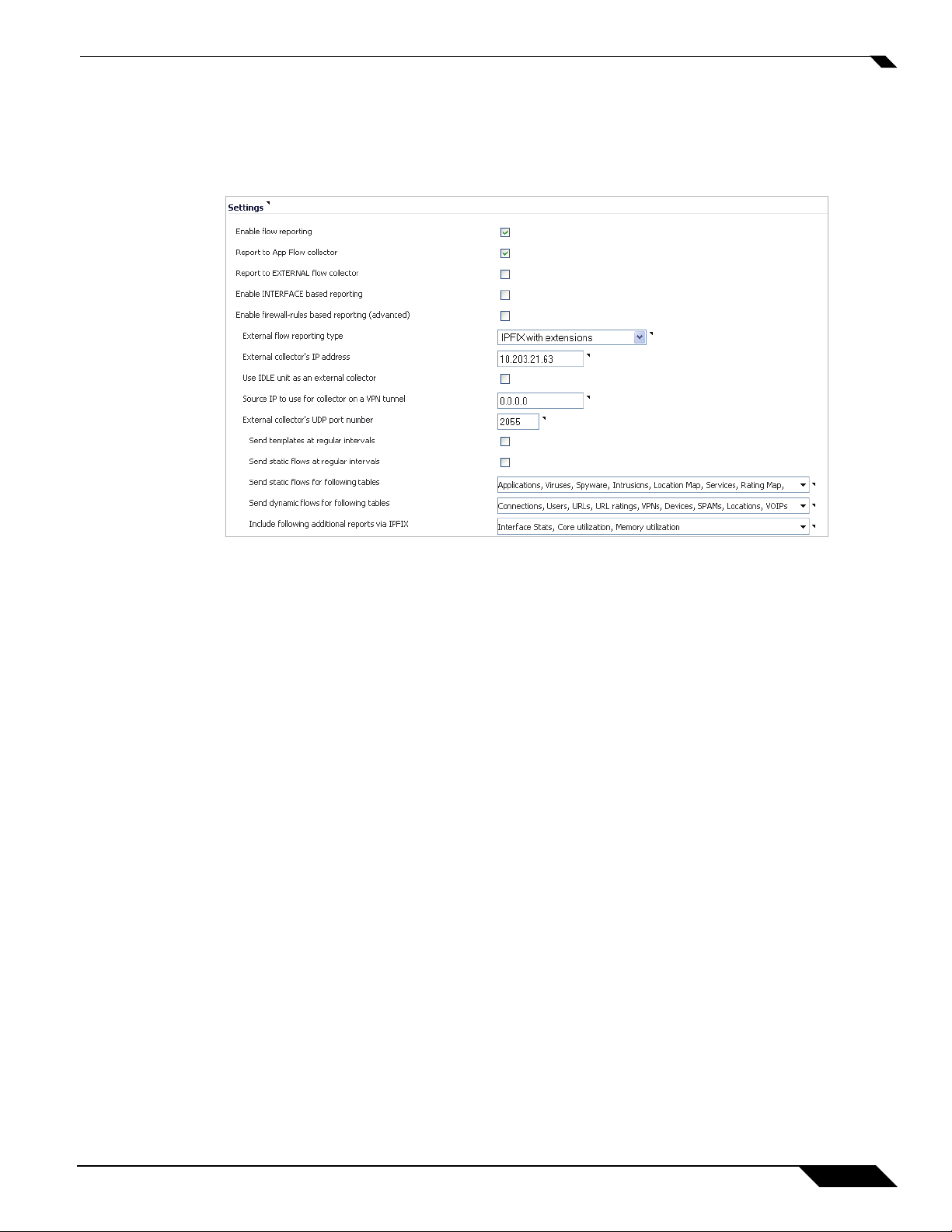
Settings
Configuring NetFlow Reporting Task List
The Settings section has configurable options for internal flow reporting, external flow reporting, and the
IPFIX collector. You can also configure the settings for what is reported to an external controller.
• Enable Flow Reporting—This is a global checkbox that enables or disables the complete flow
reporting feature. Selecting this checkbox enables flow reporting, which you can view on the Dashboard
screen. When this is disabled, both internal and external flow reporting are also disabled.
• Report to App Flow Collector—Selecting this checkbox enables the specified flows to be reported to
a flow collector within the SonicWALL appliance. Note that this option is enabled by default and used
for visualization. If disabled, the Flow Monitor and Real Time Monitor on the Dashboard will not
display any flows. You may leave this option disabled if you choose to rely only on external reporting,
rather than SonicWALL visualization.
SonicOS 5.8 NetFlow Reporting Feature Guide
7

Configuring NetFlow Reporting Task List
• Report to EXTERNAL flow collector—Selecting this checkbox enables the specified flows to be
reported to an external flow collector. Some options include another SonicWALL appliance configured
as a collector, a SonicWALL Linux collector, or a third party collector. Note that not all collectors will
work with all modes of flow reporting.
• Enable INTERFACE Based Reporting—Selecting this checkbox enables flow reporting based on
the initiator or responder interface. This provides a way to control what flows are reported externally
or internally. If enabled, the flows are verified against the per interface flow reporting configuration,
located in the Network>Interface screen. If an interface has its flow reporting disabled, then flows
associated with that interface are skipped.
• Enable Firewall-Rules Based Reporting—Selecting this checkbox enables flow reporting based on
already existing firewall rules. This is similar to interface-based reporting; the only difference is instead
of checking per interface settings, the per firewall rule is selected. Every firewall rule has a checkbox to
enable flow reporting. If a flow matching a firewall rule is to be reported, this enabled checkbox will
force to verify if firewall rules have flow reporting enabled or not. This is an additional way to control
which flows need to be reported. Note that this option is applicable to both internal and external flow
reporting.
–
External Flow Reporting Type—If the “Report to EXTERNAL Flow Collector” option is
selected, you must specify the flow reporting type from the provided list in the dropdown menu:
NetFlow version-5, NetFlow version-9, IPFIX, or IPFIX with extensions. If the reporting type is
set to Netflow versions 5, 9, or IPFIX, then any third-party collector can be used to show flows
reported from the device. It uses standard data types as defined in IETF. If the reporting type is
set to IPFIX with extensions, then the collectors that are SonicWALL flow aware can only be used.
The following are recommended options for collectors:
• A second SonicWALL appliance, acting as an external collector
• An external Linux collector running the SonicWALL provided package
8
