Sonicwall SONICOS 5.7 ANTI-SPOOF Manual

MAC-IP Anti-Spoof
Document Scope
This document describes the MAC-IP Anti-Spoof feature available in SonicOS 5.6, and its functionality in
helping to prevent various attacks against a network.
This document contains the following sections:
• “Feature Overview” section on page 1
• “Using MAC-IP Anti-Spoof” section on page 3
• “Glossary” section on page 9
Feature Overview
This section provides an introduction to the MAC-IP Anti-Spoof feature and contains the following
subsections:
• “What Is MAC-IP Anti-Spoof?” section on page 1
• “Benefits” section on page 2
• “How Does MAC-IP Anti-Spoof Work?” section on page 2
• “Platforms” section on page 2
What Is MAC-IP Anti-Spoof?
MAC and IP address-based attacks are increasingly common in today’ s network security environment. These
types of attacks often target a Local Area Network (LAN) and can originate from either outside or inside a
network. In fact, anywhere internal LANs are somewhat exposed, as in conference rooms, schools, or
libraries, could provide an opening for these types of attacks. These attacks also g o by various names:
man-in-the-middle attacks, ARP poisoning, and SPIT ONLY.
MAC-IP Anti-Spoof prevents against ARP-based attacks such as poisoning or spoofing and also provides
MAC-IP address-based ingress admission control. The MAC-IP Anti-Spoof feature also lowers the risk of
these attacks by providing administrators with different ways to control access to a network, and by
eliminating spoofing attacks at OSI Layer 2/3.
SonicOS 5.6 - MAC-IP Anti-Spoof
1

Feature Overview
Benefits
• Provides administrators with more dynamic control over which devices gain access to a network.
• Provides OSI Layer 2 and Layer 3 admission control, along with Layer 2 (MAC) based anti-spoof, or
ARP guard.
• A dedicated MAC-IP Anti-Spoof cache that maintains lists of both “authorized” and “blacklisted”
devices.
How Does MAC-IP Anti-Spoof Work?
The effectiveness of the MAC-IP Anti-Spoof feature focuses on two areas. The first is admission control
which allows administrators the ability to select which devices gain access to the network. The second area
is the elimination of spoofing attacks, such as denial-of-service attacks, at Layer 2. To achieve these goals,
two caches of information must be built: the MAC-IP Anti-Spoof Cache, and the ARP Cache.
The MAC-IP Anti-Spoof cache validates incoming packets and deter mines whether they are to be allowed
inside the network. An incoming packet’s source MAC and IP addresses are looked up in this cache. If they
are found, the packet is allowed through. The MAC-IP Anti-Spoof cache is built through one or more of
the following sub-systems:
• DHCP Server-based leases (SonicWALL’s - DHCP Server)
• DHCP relay-based leases (SonicWALL’s - IP Helper)
• Static ARP entries
Platforms
• User created static entries
The ARP Cache is built through the following subsystems:
• ARP packets; both ARP requests and responses
• Static ARP entries from user-created entries
• MAC-IP Anti-Spoof Cache
The MAC-IP Anti-Spoof subsystem achieves egress control by locking t he AR P c ach e, s o e g r es s p acke ts
(packets exiting the network) are not spoofed by a bad device or by unwanted ARP packets. This prevents
a firewall from routing a packet to the unintended device, based on mapping. This also prevents
man-in-the-middle attacks by refreshing a client’s own MAC address inside its ARP cache.
The MAC-IP Anti-Spoof feature is available in SonicOS Enhanced 5.6.
2
SonicOS 5.6 - MAC-IP Anti-Spoof
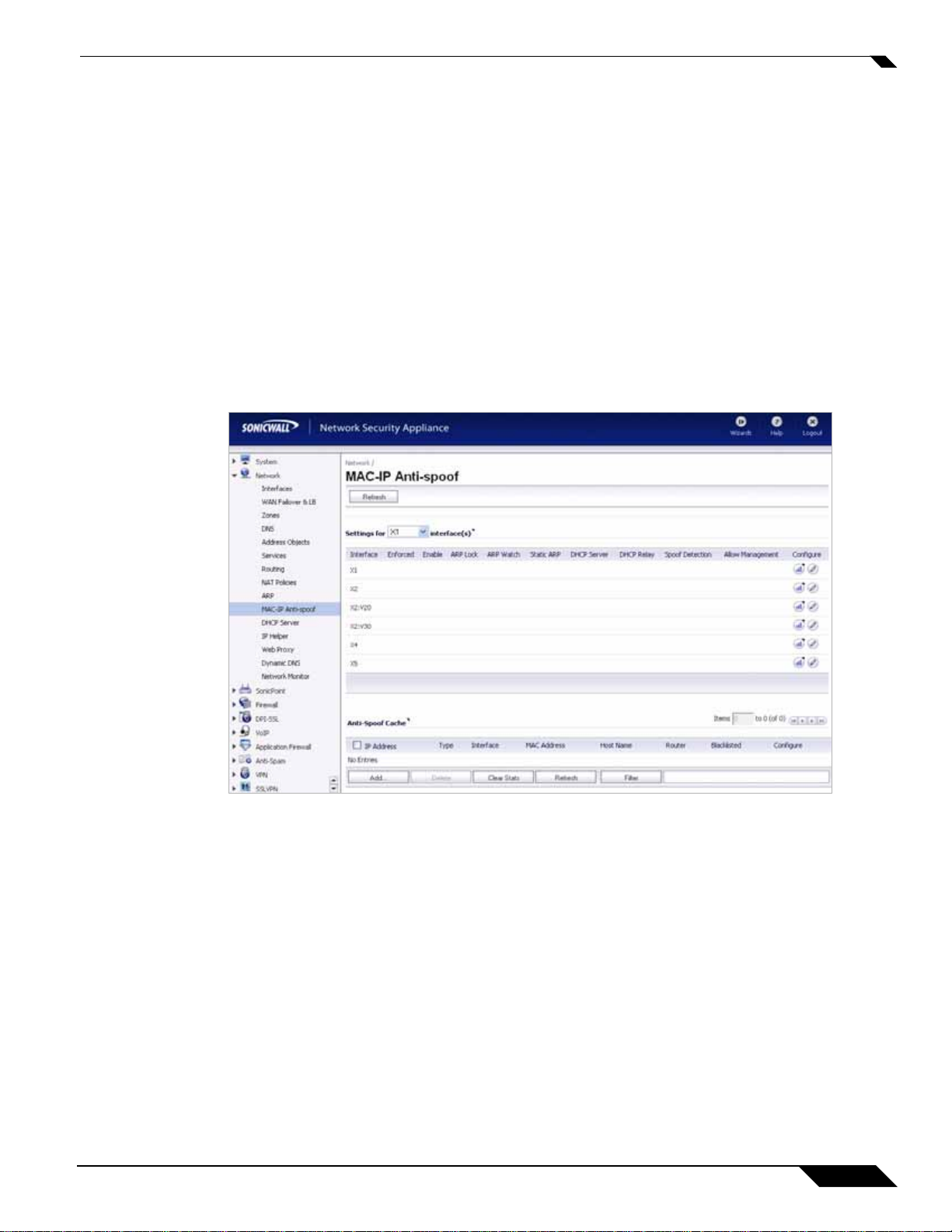
Using MAC-IP Anti-Spoof
This section contains the following subsections:
• “Interface Settings” section on page 3
• “Anti-Spoof Cache” section on page 5
• “Spoof Detect List” section on page 7
• “Extension to IP Helper” section on page 9
Interface Settings
To edit MAC-IP Anti-Spoof settings within the Network Security Appliance management interface, go to
Network > MAC-IP Anti-spoof.
Using MAC-IP Anti-Spoof
SonicOS 5.6 - MAC-IP Anti-Spoof
3
 Loading...
Loading...