Sonicwall SONICOS 5.6 Single Sign-On

Single Sign-On in SonicOS Enhanced 5.6
Document Scope
This document describes how to install and configure the Single Sign-On feature in the SonicOS Enhanced
5.6 release.
This document contains the following sections:
• “Single Sign-On Overview” section on page 1
• “Installing the SonicWALL SSO Agent” section on page 11
• “Installing the SonicWALL Terminal Services Agent” section on page 16
• “Configuring the SonicWALL SSO Agent” section on pag e 18
• “Configuring the SonicWALL Terminal Services Agent” section on page 25
• “Using NDConnector with SonicWALL SSO” section on page 27
• “Configuring Your SonicWALL Security Appliance” section on page 32
• “Glossary” section on page 61
Single Sign-On Overview
This section provides an introduction to the SonicWALL Single Sign-On feature. This section contains the
following subsections:
• “What Is Single Sign-On?” section on page 1
• “Benefits of SonicWALL SSO” section on page 3
• “Platforms and Suppor ted Standards” section on pag e 3
• “How Does Single Sign-On Work?” section on page 5
• “How Does SonicWALL SSO Agent Work?” section on page 6
• “How Does SonicWALL Terminal Services Agent Work?” section on page 9
What Is Single Sign-On?
Single Sign-On (SSO) is a transparent user authentication mechanism that provides privileged access to
multiple network resources with a single login to the domain from a workstation or through a Windows
Terminal Services or Citrix server. SonicWALL security appliances provide SSO functionality using the
SonicW ALL Single Sign-On Agent (SSO Agent) and SonicW ALL Terminal Services Agent (TSA) to identify
Single Sign-On in SonicOS Enhanced 5.6
1
Single Sign-On Overview
user activity. The SonicWALL Single Sign-On Agent (SSO Agent) identifies users based on workstation IP
address. The SonicWALL TSA identifies users through a combination of server IP address, user name, and
domain.
SonicWALL SSO is configured in the Users > Settings page of the SonicOS management interface. SSO
is separate from the Authentication method for login settings, which can be used at the same time for
authentication of VPN/L2TP client users or administrative users.
SonicWALL SSO Agent and TSA use a protocol compatible with SonicWALL ADConnector and
NDConnector, and automatically determine when a user has logged out to prevent unauthorized access.
Based on data from SonicWALL SSO Agent or TSA, the SonicWALL security appliance queries LDAP or
the local database to determine group membership. Memberships are optionally check ed by firew all policies
to control who is given access, and can be used in selecting policies for Content Filtering and Application
Firewall to control what they are allowed to access. User names learned via SSO are reported in logs of
traffic and events from the users. The configured inacti vity timer applies with SSO but the session limit does
not, though users who are logged out are automatically and transparently logg ed back in when they send
further traffic.
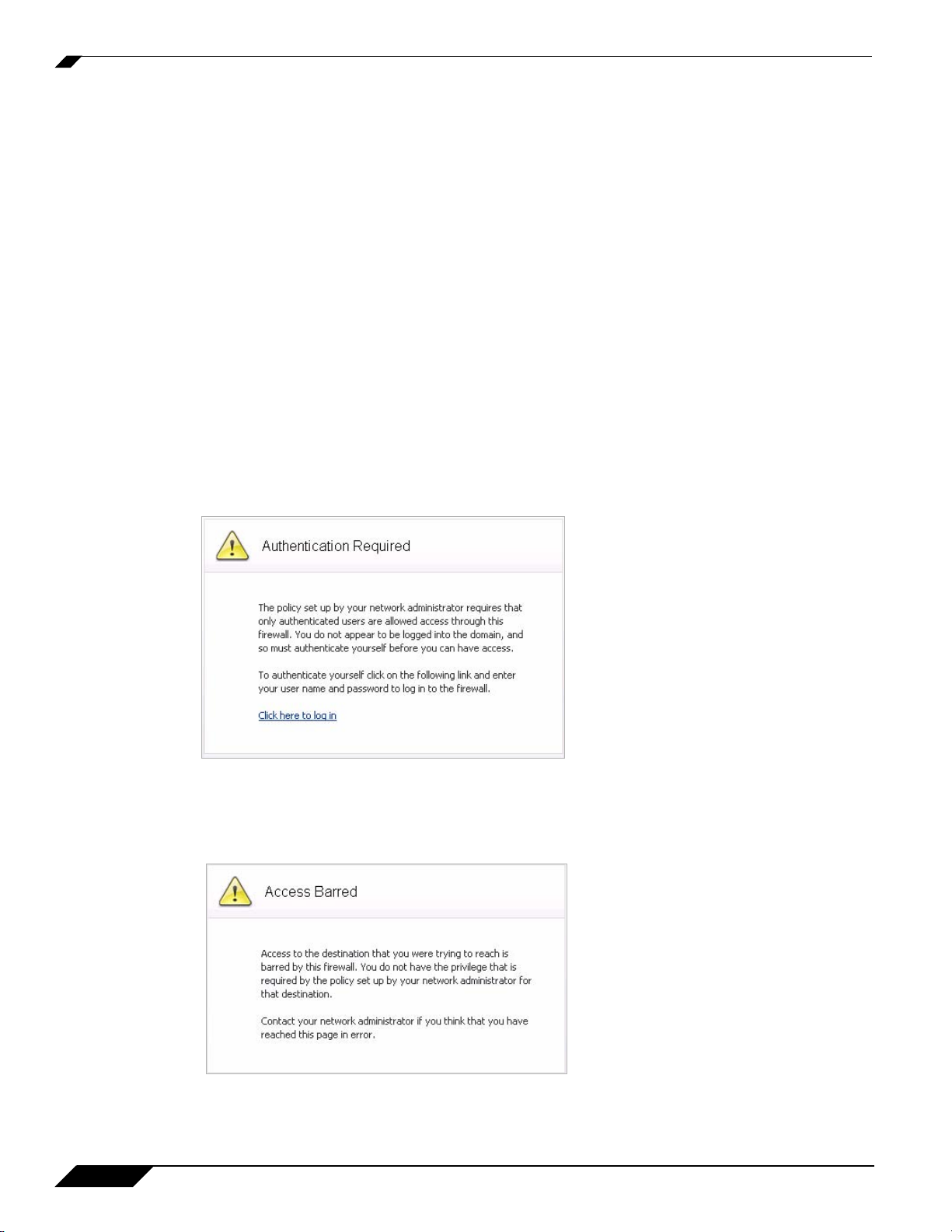
Users logged into a workstation or Terminal Services/Citrix server directly, but not logged into the domain
will not be authenticated by default (although they can optionally be authenticated for limited access). For
users that are not authenticated by SonicWALL SSO, the following screen will display, indicating that a
manual login will be required for further authentication.
Figure 1 Authentication Required
Users that are identified but lack the group memberships required by the configured policy rules are
redirected to the Access Barred page.
Figure 2 Access Barred
2
Single Sign-On in SonicOS Enhanced 5.6

Benefits of SonicWALL SSO
SonicW ALL SSO is a reliable and time-saving feature that utilizes a single login to provide access to multiple
network resources based on administrator-configured group memberships and policy matching.
SonicWALL SSO is transparent to end users and requires minimal administrator configuration.
By automatically determining when users have logged in or out based on workstation IP address traffic, or,
for Terminal Services or Citrix, traffic from a particular user at the ser ver IP address, SonicWALL SSO is
secure and hands-free. SSO authentication is designed to operate wi th any external agent that can return the
identity of a user at a workstation or Terminal Services/Citrix server IP address using a SonicWALL
ADConnector-compatible protocol.
SonicWALL SSO works for any service on the SonicWALL security appliances that uses user-level
authentication, including Content Filtering Service (CFS), Firewall Access Rules, group membership and
inheritance, and security services (IPS, GAV, SPY and Application Firewall) inclusion/exclusion lists.
Other benefits of SonicWALL SSO include:
• Ease of use — Users only need to sign in once to gain automatic access to multiple resources.
• Improved user experience — Windows domain credentials can be used to authenticate a user for any
traffic type without logging in using a Web browser.
• Transparency to users — Users are not required to re-enter user nam e and passw ord for authe ntication.
• Secure communication — Shared key encryption for data transmission protection.
• SonicWALL SSO Agent an be installed on any Windows server on the LAN, and TSA can be installed
on any terminal ser ver.
• Multiple SSO Agents — Up to 8 agents are supported to provide capacity for large installations.
Single Sign-On Overview
• Multiple TSAs — Multiple terminal services agents (one per ter minal server) are supported. The
number depends on the SonicWALL UTM appliance model and ranges from 4 to 256.
• Login mechanism works with any protocol, not just HTTP.
Platforms and Supported Standards
SonicWALL SSO is available on SonicWALL NSA Series appliances runnin g SonicOS Enhanced 5.0 or
higher, and SonicWALL PRO security appliances running SonicOS Enha nced 4.0 or higher. The
SonicWALL SSO Agent is compatible with all versions of SonicOS Enhanced that support SonicWALL
SSO. The SonicWALL TSA is supported on SonicOS Enhanced 5.6 and higher, running on SonicWALL
NSA Series and TZ 210 Series appliances.
The SonicWALL SSO feature supports LDAP and local database protocols. SonicWALL SSO supports
SonicWALL Directory Connector. SonicWALL SSO can also interwork with ADConnector in an
installation that includes a SonicWALL CSM, but Directory Connector is recommended. Fo r all featu res of
SonicWALL SSO and the SSO Agent to work properly, SonicOS Enhanced 5.5 or higher should be used
with Directory Connector 3.1.7 or higher. To use SonicWALL SSO with Windows Terminal Serv ices or
Citrix, SonicOS Enhanced 5.6 or higher is required, and SonicWALL TSA must be installed on the server.
SonicWALL SSO on SonicOS Enhanced 5.5 and higher is compatible with SonicWALL NDConnector for
interoperability with Novell users. NDConnector is also available as part of Directory Connector.
To use SonicWALL SSO, it is required that the SonicWALL SSO Agent be installed on a server within your
Windows domain that can reach clients and can be reached from the appliance, either directly or through a
VPN path, and/or SonicWALL TSA be installed on any terminal servers in the domain.
Single Sign-On in SonicOS Enhanced 5.6
3

Single Sign-On Overview
SSO Agent Supported Platforms
The following requirements must be met in order to run the SonicWALL SSO Agent:
• UDP port 2258 (by default) must be open; the firewall uses UDP port 2258 b y default to communic ate
with SonicWALL SSO Agent; if a custom port is configured instead of 2258, then this requirement
applies to the custom port
• Windows Server, with latest service pack:
–
Windows Server 2008, 32-bit and 64-bit
–
Windows Server 2003, 32-bit and 64-bit
–
Windows 2000 Server, 32-bit and 64-bit
• .NET Framework:
–
.NET Framework 3.5
–
.NET Framework 3.0
–
.NET Framework 2.0
• Net API or WMI
Note The following Microsoft Windows operating systems and service packs are not supported as
platforms on which SonicWALL SSO Agent can be installed:
– Windows 7 – All versions
– Windows Vista – All versions
– Windows XP – All versions
– Windows 2000 – All non-server versions
Note Mac and Linux PCs do not support the Windows networking requests that are used by the
SonicWALL SSO Agent, and hence do not work with SonicWALL SSO. Mac and Linux users
can still get access, but will need to log in to do so. They can be redirected to the login
prompt if policy rules are set to require authentication. For more information, see
“Accommodating Mac and Linux Users” on page 55.
TSA Supported Platforms
The following requirements must be met in order to run the SonicWALL TSA:
• UDP port 2259 (by default) must be open on all terminal servers on which TSA is installed; the firewall
uses UDP port 2259 by default to communicate with SonicWALL TSA; if a custom por t is configured
instead of 2259, then this requirement applies to the custom por t
• Windows Server, with latest service pack:
–
Windows Server 2008, 32-bit and 64-bit
–
Windows Server 2003, 32-bit and 64-bit
• Windows Terminal Services or the following Citrix version installed on the Windows Server system(s):
–
Citrix XenApp 5.0
4
Single Sign-On in SonicOS Enhanced 5.6

How Does Single Sign-On Work?
SonicWALL SSO requires minimal administrator configuration and is transparent to the user.
For users on individual workstations, the SSO Agent handles the authentication requests from the
SonicWALL UTM appliance. There are six steps involved in SonicWALL SSO authentication, as illustrated
in Figure 3.
Figure 3 SonicWALL Single Sign-On Process Using the SSO Agent
User Login Authorization
Single Sign-On Overview
user workstation
1
User attempts to
1
send traffic through
SonicWALL UTM
appliance.
SonicWALL UTM appliance
2
user’s IP address to the
are saved.
The SSO agent
3
name of the user
the workstation.
Internet Access and Polling
user workstation
SonicWALL UTM appliance
Network Security Appliance
2
Network Security Appliance
6
E7500
5
E7500
Internet
Sonic-
allows the user
Internet
6
The SonicWALL UTM appliance
polls the SSO agent to make
sure the same user is still logged
on
(polling time can be configured in
the GUI).
SSO agent
LDAP server
The SonicWALL SSO authentication process is initiated when user traffic passes through a SonicWALL
security appliance, for example, when a user accesses the Internet. The sent packets are temporaril y block ed
and saved while the SonicWALL security appliance sends a “User Name” request and workstation IP address
to the authorization agent running the SSO Agent.
The authorization agent running the SSO Ag ent provides the SonicWALL security appliance with the
username currently log ged into the workstation. A User IP Table entry is created for the logged in user,
similarly to RADIUS and LDAP.
Single Sign-On in SonicOS Enhanced 5.6
5

Single Sign-On Overview
For users logged in from a Terminal Services or Citrix server, the SonicWALL TSA takes the place of the
SSO Agent in the authentication process. The process is differe nt in several ways:
• The TSA runs on the same ser ver that the user is logg ed into, and includes the user name and domain
• Users are identified by a user number as well as the IP address (for non-Terminal Services users, there
• The TSA sends a close notification to the UTM when the user logs out, so no polling occurs.
Once a user has been identified, the SonicW ALL security appliance queries LD AP or a local database (based
on administrator configuration) to find user group memberships, match the memberships against policy, and
grant or restrict access to the user accordingly . Upon successful completion of the login sequence, the saved
packets are sent on. If pack ets are r ecei v ed from the same source address before the sequence is completed,
only the most recent packet will be saved.
User names are returned from the authorization agent running the SSO Ag ent in the format
<domain>/<user-name>. For locally configured user groups, the user name can be configured to be the
full name returned from the authorization agent r unning the SSO Ag ent (configuring the names in the
SonicWALL security appliance local user database to match) or a simple user name with the domain
component stripped off (default).
For the LD AP protocol, the <domai n>/<user-name> format is conv erted to an LD AP distinguished name
by creating an LDAP search for an object of class “domain” with a “dc” (domain component) attribute that
matches the domain name. If one is found, then its distinguished name will be used as the direc tory sub-tree
to search for the user’s object. For example, if the user name is returned as “SV/bob” then a search for an
object with “objectClass=domain” and “dc=SV” will be performed. If that retur ns an object with
distinguished name “dc=sv,dc=us,dc=sonicwall,dc=com,” then a search under that directory sub-tree will
be created for (in the Active Directory case) an object with “objectClass=user” and
“sAMAccountName=bob”. If no domain object is found, then the search for the user object will be made
from the top of the directory tree.
Once a domain object has been found, the information is saved to avoid searching for the same object. If
an attempt to locate a user in a saved domain fails, the sav ed domain information will be deleted and another
search for the domain object will be made.
along with the server IP address in the i nitial notifica tion to the SonicWALL UTM appliance.
is only one user at any IP address and so no user number is used). A non-zero user number is displayed
in the SonicOS management interface usi ng the format "x.x.x.x user n", where x.x.x.x is the server IP
address and n is the user number.
User logout is handled slightly differently by SonicWALL SSO using the SSO Agent as compared to SSO
with the TSA. The SonicWALL security appliance polls the authorization agent running the SSO Agent at
a configurable rate to determine when a user has logg ed out. Upon user log out, the authentication ag ent
running the SSO Agent sends a User Logg ed Out response to the SonicWALL security appliance,
confirming that the user has been logged out and terminating the SSO session. Rather than being polled by
the SonicWALL UTM appliance, the TSA itself monitors the Terminal Services / Citrix server for logout
events and notifies the SonicWALL UTM appliance as they occur, terminating the SSO session. For both
agents, configurable inactivity timers can be set, and for the SSO Agent the user name request polling rate
can be configured (set a short poll time for quick detection of logouts, or a longer polling time for less
overhead on the system).
How Does SonicWALL SSO Agent Work?
The SonicWALL SSO Agent can be installed on any workstation with a Windows domain that can
communicate with clients and the SonicWALL security appliance directly using the IP address or using a
path, such as VPN. For installation instructions for the SonicWALL SSO Agent, refer to the “Installing the
SonicWALL SSO Agent” section on page 11.
6
Single Sign-On in SonicOS Enhanced 5.6

Single Sign-On Overview
Multiple SSO agents are supported to accommodate large installations with thousands of users. You can
configure up to eight SSO agents, each running on a dedicated, high-performance PC in your network. Note
that one SSO agent on a fast PC can support up to 2500 users.
The SonicWALL SSO Agent only communicates with clients and the SonicWALL security appliance.
SonicWALL SSO Agent uses a shared key for encryption of messages between the SSO Agent and the
SonicWALL security appliance.
Note The shared key is generated in the SSO Agent and the key entered in the SonicWALL
security appliance during SSO configuration must match the SSO Agent-generated key
exactly.
Figure 4 SonicWALL SSO Agent Process
SonicWALL SSO with SSO Agent
SonicWALL UTM Appliance
Network Security Appliance
E7500
2
Internet
5
1
4
SSO Agent
default port 2258
SSO Agent is installed on any
server with LAN access*
3
A client logs into the network and attempts to access the Internet or other network resources.
1
The SSO module on the SonicWALL UTM appliance queries the SonicWALL SSO Agent (default
2
port 2258) for the client ID.
Steps
The SonicWALL SSO Agent forwards the request to the
3
client and the client responds with its client ID.
Client ID information is passed back from the SonicWALL
4
SSO Agent to the SonicWALL UTM appliance.
Based on the client ID, the SonicWALL UTM appliance
5
checks with the LDAP server to determine group membership and permissions.
2 3 4
Communication in these steps
(between the SSO Agent and
client / firewall) is encrypted
using a shared key which is
generated by the SSO Agent.
The SonicW ALL security appliance queries the SonicW ALL SSO Agent over the default port 2258. The SSO
Agent then communicates between the client and the SonicWALL security appliance to deter mine the
client’s user ID. The SonicWALL SSO Agent is polled, at a rate that is configurable by the administrator, by
the SonicWALL security appliance to continually confirm a user’s login status.
Single Sign-On in SonicOS Enhanced 5.6
7

Single Sign-On Overview
Logging
The SonicWALL SSO Agent sends log event messages to the Windows Event Log based on
administrator-selected logging levels.
The SonicWALL security appliance also logs SSO Agent-specific events in its event log. The following is a
list of SSO Agent-specific log event messages from the SonicWALL security appliance:
• User login denied - not allowed by policy rule – The user has been identified and does not belong
to any user groups allowed by the policy blocking the user’s traffic.
• User login denied - not found locally – The user has not been found locally, and Allow only users
listed locally is selected in the SonicWALL security appliance.
• User login denied - SSO Agent agent timeout – Attempts to contact the SonicWALL SSO Agent
have timed out.
• User login denied - SSO Agent configuration error – The SSO Agent is not properly configured to
allow access for this user.
• User login denied - SSO Agent communication problem – There is a problem communicating with
the workstation running the SonicWALL SSO Agent.
• User login denied - SSO Agent agent name resolution failed – The SonicWALL SSO Agent is
unable to resolve the user name.
• SSO Agent retur ned use r name too long – T he user name is too long.
• SSO Agent retur ned domain name too long – T he domain name is to o long.
Note The notes field of log messages specific to the SSO Agent will contain the text
<domain/user-name>, authentication by SSO Agent.
8
Single Sign-On in SonicOS Enhanced 5.6

Single Sign-On Overview
How Does SonicWALL Terminal Services Agent Work?
The SonicWALL TSA can be installed on any Windows Server machine with Terminal Services or Citrix
installed. The server must belong to a Windows domain that can communicate with the SonicW ALL se curity
appliance directly using the IP address or using a path, such as VPN.
SonicWALL SSO with Terminal Services Agent
SonicWALL UTM Appliance
Network Security Appliance
3
4
Internet
2
5
LDAP
Server
7
1
6
A client logs into the network via the Terminal Services or Citrix server and attempts to access the
1
Internet or other network resources for the first time.
The TSA on the Terminal Services or Citrix server notifies the SonicWALL UTM of the user’s name,
2
domain, the session ID, the connection IP address, port, and protocol. The UTM sends a reply.
The SonicWALL UTM queries the LDAP server or the local database for the user’s group member-
3
ships.
The SonicWALL UTM checks the groups against Firewall,
4
CFS, and App FW policies, and grants access accordingly,
allocates a user number for the user on the terminal server,
and logs the user in.
The user closes the Internet connection and the TSA
5
notifies the UTM of the close.
The user opens further connections, and steps (2) and (5),
6
but not (3) and (4), are repeated for each connection.
When the user logs out of the terminal server, the TSA
7
notifies the SonicWALL UTM of the logout and the user is
logged out on the UTM.
Steps
Communication in these steps
is encrypted when the user
name and domain are included,
using a shared key which is
generated by the TSA.
2 3
For installation instructions for the SonicWALL TSA, refer to the “Installing the SonicWALL Terminal
Services Agent” section on page 16.
See the following sections for information about the SonicWALL TSA:
• “Multiple TSA Support” on page 10
• “Encryption of TSA Messages and Use of Session IDs” on pag e 10
• “Connections to Local Subnets” on page 10
• “Non-Domain User Traffic from the Terminal Server” on page 10
• “Non-User Traffic from the Terminal Ser ver” on page 11
Single Sign-On in SonicOS Enhanced 5.6
9

Single Sign-On Overview
Multiple TSA Support
T o accommodate large installations with thousands of users , SonicWALL UTM appliances are configurable
for operation with multiple terminal services agents (one per ter minal server). The number of agents
supported depends on the model, as shown in Ta ble 1.
Table 1 Multiple TSA Support per Model
SonicWALL UTM Model TS Agents Supported
NSA E7500 256
NSA E6500 128
NSA E5500 64
NSA 5000 32
NSA 4500 16
NSA 3500 16
NSA 2400 8
NSA 240 4
TZ 210 Series 4
TZ 200 Series Not supported
TZ 100 Series Not supported
For all SonicWALL UTM models, a maximum of 32 IP addresses is supported per terminal server.
Encryption of TSA Messages and Use of Session IDs
SonicW ALL TSA uses a shared key for encryption of messages between the TSA and the SonicWALL UTM
appliance when the user name and domain are contained in the message. The first open notification for a
user is always encrypted, because the TSA includes the user name and domain.
Note The shared key is created in the TSA, and the key entered in the SonicWALL UTM appliance
during SSO configuration must match the TSA key exactly.
The TSA includes a user session ID in all notifications rather than includ ing the user name and domain every
time. This is efficient, secure, and allows the TSA to re-synchronize with Terminal Services users after the
agent restarts.
Connections to Local Subnets
The TSA dynamically learns network topology based on information returned from the appliance and, once
learned, it will not send notifications to the appliance for subsequent user connections that do not go
through the appliance. As there is no mechanism for the TSA to “unlearn” these local destinations , the TSA
should be restarted if a subnet is moved between interfaces on the appliance.
Non-Domain User Traffic from the Terminal Server
The SonicWALL UTM appliance has the Allow limited access for non-domain users setting for
optionally giving limited access to non-domain users (users logged into their local machine and not into the
domain), and this works for terminal services users as it does for other SSO users.
10
Single Sign-On in SonicOS Enhanced 5.6

Non-User Traffic from the Terminal Server
Non-user connections are opened from the Terminal Ser ver for Windows updates and anti-virus updates.
The TSA can identify a connection from a logged-in service as being a non-user connection , and indicates
this in the notification to the appliance.
T o control handling of these non-user connections, an Allow Terminal Server non-user traffic to bypass
user authentication in access rules checkbox is available in the TSA configuration on the appliance.
When selected, these connections are allowed. If this c heckbox is not selected, then the services are treated
as local users and can be given access by selecting the Allow limited access for non-domain users setting
and creating user accounts on the appliance with the corresponding ser vi ce names.
Installing the SonicWALL SSO Agent
Install the SonicWALL SSO Agent on at least one, and up to eight, servers on your network within the
Windows domain that have access to the Active Directory server using VPN or IP. The SonicWALL SSO
Agent must have access to your SonicWALL UTM security appliance.
SonicWALL SSO Agent is available as part of SonicWALL Directory Services Connector 3.1.1 or higher,
which you can download without charge from MySonicWALL. For best results, download the most recent
version. To install the SonicWALL SSO Agent, perform the following steps:
Installing the SonicWALL SSO Agent
Step 1 Download one of the following installation programs, depending on your computer:
–
SonicWALL Director y Connector (32-bit) 3 .1.x.exe
–
SonicWALL Director y Connector (64-bit) 3 .1.x.exe
You can find these on http://www.mysonicwall.com under Directory Ser vices Con nector.
Step 2 Double-click the installation program to begin installation. If prompted, install the Microsoft .NET
framework.
Step 3 On the Welcome page, click Next to continue.
Step 4 The License Agreement displays. Select I accept the terms in the license agreement and click Next to
continue.
Single Sign-On in SonicOS Enhanced 5.6
11

Installing the SonicWALL SSO Agent
Step 5 On the Customer Information page, enter your name in the User Name field and your organization name
in the Organization field. Select to install the application for Anyone who uses this computer (all users)
or Only for me. Click Next to continue.
Step 6 Select the destination folder. To use the default folder, C:\Program Files\SonicWALL\DCON , click Next.
To specify a custom location, click Change, select the folder, and click Next.
Step 7 On the Custom Setup page, the installation icon is displayed by default next to the
SonicWALL SSO Agent feature.
Optionally, you can select SonicWALL NDC to enable SonicWALL SSO to work with Novell users if this
server has network access to the eDirectory server. For information about installing SonicWALL NDC, see
“Installing NDConnector for Use with a SonicWALL UTM” on page 28.
Optionally , you can also select SonicWALL ADC if this server belongs to an Active Directory domain, and
will be used to communicate with a SonicWALL CSM appliance. For more information, see the SonicOS CF
2.6 Administrator’s Guide, available on
http://www.sonicwall.com/us/Support.html
12
Single Sign-On in SonicOS Enhanced 5.6

Installing the SonicWALL SSO Agent
Click Next.
Step 8 On the Ready to Install the Program page, click Install to install the SonicWALL SSO Ag ent.
Single Sign-On in SonicOS Enhanced 5.6
13
Installing the SonicWALL SSO Agent
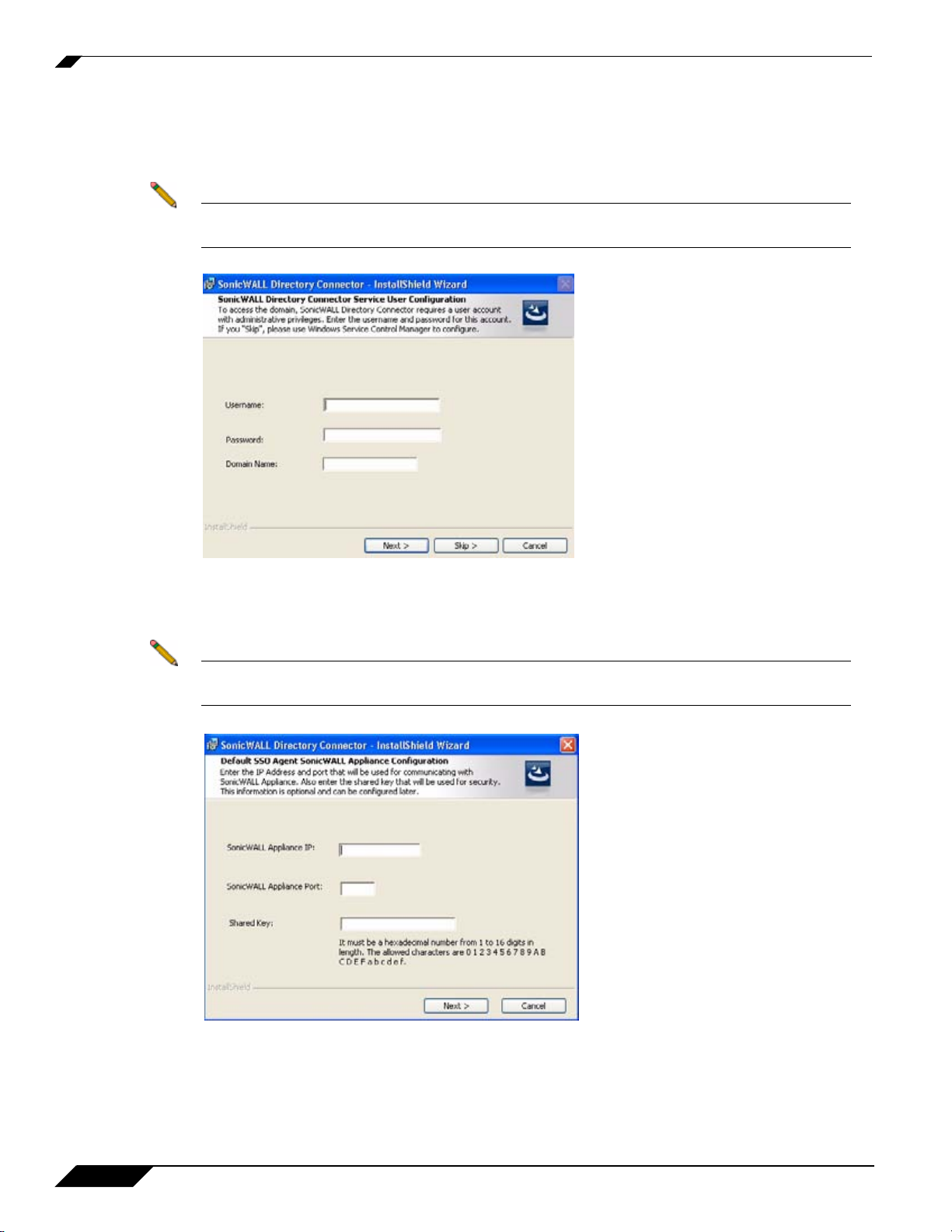
Step 9 To configure a common service account that the SonicWALL SSO Agent will use to log into a specified
Windows domain, enter the username of an account with administrative privileges in the Username field,
the password for the account in the Password field, and the domain name of the account in the Domain
Name field. Click Next.
Note This section can be configured at a later time. To skip this step and configure it later,
click Skip.
Step 10 Enter the IP address of your SonicWALL security appliance in the SonicWALL Appliance IP field. Type
the port number for the same appliance in the SonicWALL Appliance Port field. Enter a shared key (a
hexadecimal number from 1 to 16 digits in length) in the Shared Key field. Click Next to continue.
Note This information can be configured at a later time. To skip this step and configure it later,
leave the fields blank and click Next.
14
Single Sign-On in SonicOS Enhanced 5.6

Installing the SonicWALL SSO Agent
Step 11 If you selected either SonicWALL ADC or SonicWALL NDC in addition to SonicWALL SSO Agent in
the Custom Setup screen (Step 7), the Default CSM Appliance Configuration screen is displayed next. Enter
the IP address and port number for your SonicWALL CSM appliance and enter the 16 digit shared key for
communicating securely with the SonicWALL CSM, and then click Next.
Step 12 Wait while the SonicWALL SSO Agent installs. The progress bar indicates the status.
Step 13 When installation is complete, optionally select the Launch SonicWALL Directory Connector checkbox
to launch the SonicWALL Directory Connector Configurator, and then click Finish. If you selected the
Launch SonicWALL Directory Connector checkbox, the SonicWALL Directory Connector Configurator
will display.
Single Sign-On in SonicOS Enhanced 5.6
15

Installing the SonicWALL Terminal Services Agent
Installing the SonicWALL Terminal Services Agent
Install the SonicW ALL TSA on one or more terminal servers on your network within the Windows domain.
The SonicWALL TSA must have access to your SonicWALL UTM security appliance, and the appliance
must have access to the TSA. If you have a software firewall running on the ter min al server, you may need
to open up the UDP port number for incoming messages from the appliance.
SonicW ALL TSA is a v ailable for do wnload without charge from MySonicWALL. To install the SonicWALL
TSA, perform the following steps:
Step 1 On a Windows T erminal Server system, download one of the following installation programs, depending on
your computer:
–
SonicWALL TSAInstaller32.msi (32 bit, version 3.0.28.1001 or higher)
–
SonicWALL TSAInstaller64.msi (64 bit, version 3.0.28.1001 or higher)
You can find these on http://www.mysonicwall.com.
Step 2 Double-click the installation program to begin installation.
Step 3 On the Welcome page, click Next to continue.
Step 4 The License Agreement displays. Select I agree and click Next to continue.
Step 5 On the Select Installation Folder window, select the destination folder. To use the default folder,
C:\Program Files\SonicWALL\SonicWALL Terminal Services Agent\, click Next. To specify a custom
location, click Browse, select the folder, and click Next.
16
Single Sign-On in SonicOS Enhanced 5.6

Installing the SonicWALL Terminal Services Agent
Step 6 On the Confirm Installation window, click Next to start the installation.
Step 7 Wait while the SonicWALL Terminal Services Agent installs. The progress bar indicates the status.
Step 8 When installation is complete, click Close to exit the installer.
Step 9 You must restart your system before starting the SonicWALL Terminal Ser vices Ag ent. To restart
immediately, click Yes in the dialog box. To restart later, click No.
Single Sign-On in SonicOS Enhanced 5.6
17
Configuring the SonicWALL SSO Agent
Configuring the SonicWALL SSO Agent
The SonicWALL SSO Agent communicates with workstations using NetAPI or WMI, which both provide
information about users that are log g ed into a workstation, including domain users, local users, and
Windows services. WMI is pre-installed on Windows Server 2008, Windows Server 2003, Windows XP
Windows ME, and Windows 2000. For other Windows versions, visit www.microsoft.com to download
WMI. Verify that WMI or NetAPI is installed prior to configuring the SonicWALL SSO Agent.
The .NET Framework 2.0 must installed prior to configuring the SonicWALL SSO Agent. The .NET
Framework can be downloaded from Microsoft at www.microsoft.com.
See the following sections:
• “Configuring Communication Properties” on page 18
• “Adding a SonicWALL Security Appliance” on page 22
• “Editing Appliances in SonicWALL SSO Agent” on page 24
• “Deleting Appliances in SonicWALL SSO Agent” on pag e 24
• “Modifying Services in SonicWALL SSO Agent” on page 24
Configuring Communication Properties
1
,
To configure the communication properties of the SonicWALL SSO Agent, perfor m the following tasks:
Step 1 Launch the SonicWALL Configuration Tool by double-clicking the desktop shortcut or by navigating to
Start > All Programs > SonicWALL > Sonic WALL Directory Connector > SonicWALL
Configuration Tool.
18
1. Windows XP with Service Pack 2 has a limitation that can affect the SonicWALL SSO Agent, and so
is not recommended.
Single Sign-On in SonicOS Enhanced 5.6
Configuring the SonicWALL SSO Agent
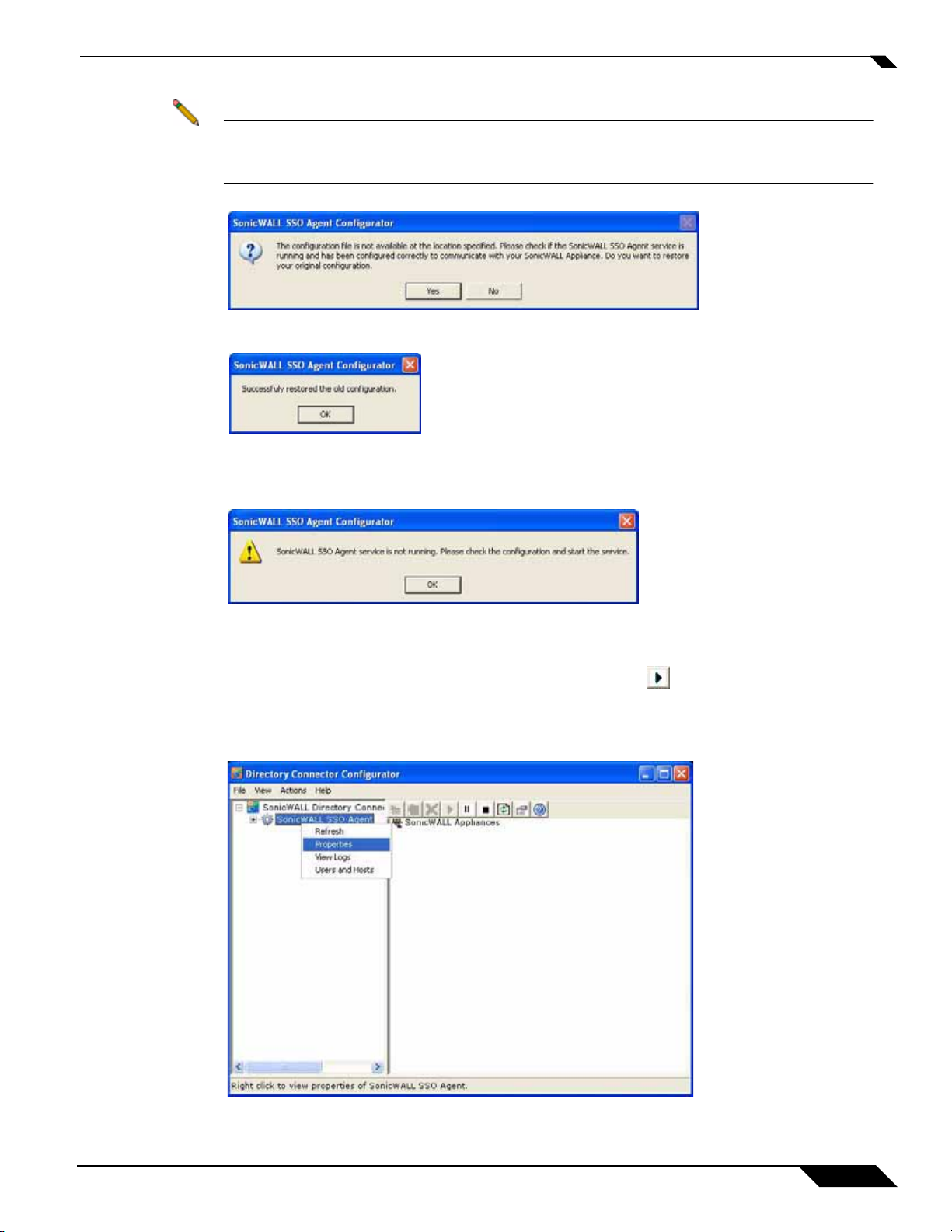
Note If the IP address for a default SonicWALL security appliance was not configured, or if it was
configured incorrectly, a pop up will display. Click Yes to use the default IP address
(192.168.168.168) or click No to use the current configuration.
If you clicked Yes, the message Successfully restore d the old configuration will dis play. Click OK.
If you clicked No, or if you clicked Yes but the default configuration is incorrect, the message SonicWALL
SSO Agent service is not running. Please check the configuration and start the service. will display.
Click OK.
If the message SonicWALL SSO Agent ser vice is not running. Please check the configuration and
start the service displays, the SSO Agent service will be disabled by default. To enable the service, expand
the SonicW ALL Directory Connector Configuration T ool in the left navigation panel by clicking the + icon,
highlight the SonicWALL SSO Agent underneath it, and click the button.
Step 2 In the left-hand navigation panel, expand the SonicWALL Directory Connector Configuration Tool by
clicking the + icon. Right click the SonicWALL SSO Agent and select Properties.
Single Sign-On in SonicOS Enhanced 5.6
19
