Sonicwall SONICOS 5.6 DPI-SSL

DPI-SSL
Document Scope
This document describes the DPI-SSL feature available in SonicOS 5.6. This document contains the
following sections:
• “DPI-SSL Overview” section on page 1
• “Using DPI-SSL” section on page 2
DPI-SSL Overview
Deep Packet Inspection of Secure Socket Layer (DPI-SSL) extends SonicWALL’s Deep Packet Inspection
technology to allow for the inspection of encrypted HTTPS traffic and other SSL-based traffic. The SSL
traffic is decrypted transparently, scanned for threats and then re-encrypted and sent along to its destination
if no threats or vulnerabilities are found. DPI-SSL provides additional security, application control, and data
leakage prevention for analyzing encrypted HTTPS and other SSL-based traffic.
The following security services and features are capable of utilizing DPI-SSL:
• Gateway Anti-Virus
• Gateway Anti-Spyware
• Intrusion Prevention
• Content Filtering
• Application Firewall
• Packet Capture
• Packet Mirror
DPI-SSL has two main deployment scenarios:
• Client DPI-SSL: Used to inspect HTTPS traffic when clients on the SonicWALL security appliance’s
LAN access content located on the WAN.
• Server DPI-SSL: Used to inspect HTTPS traffic when remote clients connect over the WAN to access
content located on the SonicWALL security appliance’s LAN.
SonicOS 5.6 - DPI-SSL
1

Using DPI-SSL
Platforms
The DPI-SSL feature is available in SonicOS Enhanced 5.6. The following table shows which platforms
support DPI-SSL and the maximum number of concurrent connections on which the appliance can perform
DPI-SSL inspection.
Hardware Model Max Concurrent DPI-SSL inspected connections
NSA 3500 250
NSA 4500 350
NSA 5000 1000
NSA E5500 2000
NSA E6500 3000
NSA E7500 8000
Using DPI-SSL
DPI-SSL has two main deployment scenarios:
• Client DPI-SSL: Used to inspect HTTPS traffic when clients on the SonicWALL security appliance’s
LAN access content located on the WAN.
• Server DPI-SSL: Used to inspect HTTPS traffic when remote clients connect over the WAN to access
content located on the SonicWALL security appliance’s LAN.
This section contains the following subsections:
• “Client DPI-SSL” on page 2
• “Server DPI-SSL” on page 6
Client DPI-SSL
The Client DPI-SSL deployment scenario typically is used to inspect HTTPS traffic when clients on the
LAN browse content located on the WAN. In the Client DPI-SSL scenario, the SonicWALL UTM appliance
typically does not own the certificates and private keys for the content it is inspecting. After the appliance
performs DPI-SSL inspection, it re-writes the certificate sent by the remote server and signs this newly
generated certificate with the certificate specified in the Client DPI-SSL configuration. By default, this is
the SonicWALL certificate authority (CA) certificate, or a different certificate can be specified. Users should
be instructed to add the certificate to their browser’s trusted list to avoid certificate trust errors.
The following sections describe how to configure Client DPI-SSL:
• “Configuring General Client DPI-SSL Settings” on page 3
• “Configuring the Inclusion/Exclusion List” on page 3
• “Selecting the Re-Signing Certificate Authority” on page 4
• “Content Filtering” on page 5
2
SonicOS 5.6 - DPI-SSL
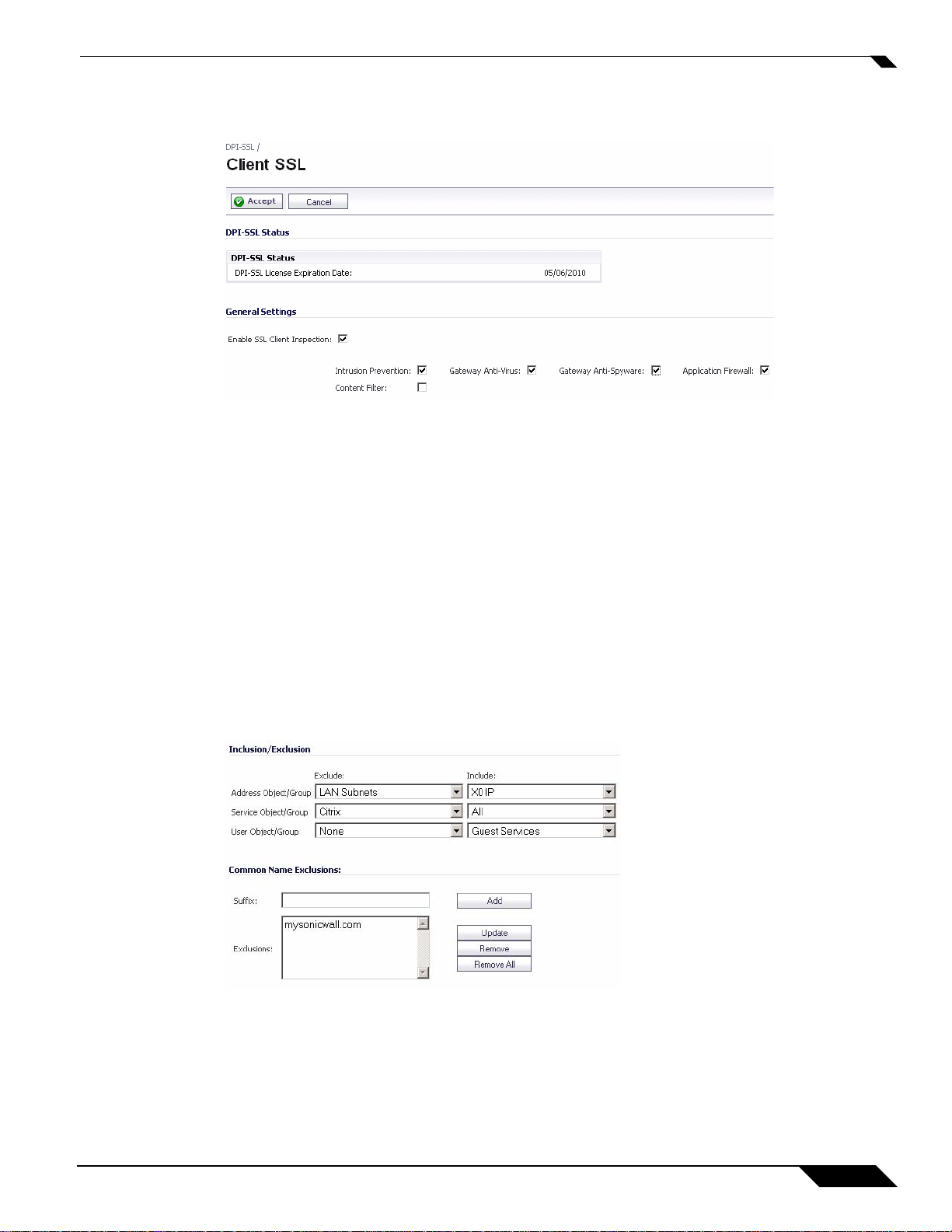
Configuring General Client DPI-SSL Settings
To enable Client DPI-SSL inspection, perform the following steps:
1. Navigate to the DPI-SSL > Client SSL page.
2. Select the Enable SSL Inspection checkbox.
3. Select which of the following services to perform inspection with: Intrusion Prevent, Gateway
Anti-Virus, Gateway Anti-Spyware, Application Firewall, and Content Filter.
4. Click Accept.
Using DPI-SSL
Configuring the Inclusion/Exclusion List
By default, the DPI-SSL applies to all traffic on the appliance when it is enabled. You can configure an
Inclusion/Exclusion list to customize which traffic DPI-SSL inspection will apply to. The
Inclusion/Exclusion list provides the ability to specify certain objects, groups, or hostnames. In
deployments that are processing a large amount of traffic, it can be useful to exclude trusted sources in order
to reduce the CPU impact of DPI-SSL and to prevent the appliance from reaching the maximum number
of concurrent DPI-SSL inspected connections.
The Inclusion/Exclusion section of the Client SSL page contains four options for specifying the
inclusion list:
• On the Address Object/Group line, select an address object or group from the Exclude pulldown
menu to exempt it from DPI-SSL inspection.
• On the Service Object/Group line, select a service object or group from the Exclude pulldown menu
to exempt it from DPI-SSL inspection.
SonicOS 5.6 - DPI-SSL
3
 Loading...
Loading...