Page 1

USER GUIDE
BarricadeTM N
150 Mbps 4-Port Wireless Broadband Router
SMCWBR14S-N4
Page 2

Barricade
TM
User Guide
SMCWBR14S-N4
20 Mason
Irvine, CA 92618
September 2009
Pub. # 149100000034W
E092009-CS-R01
Page 3

Information furnished by SMC Networks, Inc. (SMC) is believed to be accurate and reliable.
However, no responsibility is assumed by SMC for its use, nor for any infringements of patents or
other rights of third parties which may result from its use. No license is granted by implication or
otherwise under any patent or patent rights of SMC. SMC reserves the right to change specifications
at any time without notice.
Copyright © 2009 by
SMC Networks, Inc.
20 Mason
Irvine, CA 92618
All rights reserved
Trademarks:
SMC is a registered trademark; and Barricade, EZ Switch, TigerStack, TigerSwitch, and TigerAccess
are trademarks of SMC Networks, Inc. Other product and company names are trademarks or
registered trademarks of their respective holders.
Page 4

WARRANTY AND PRODUCT REGISTRATION
To register SMC products and to review the detailed warranty statement,
please refer to the Support Section of the SMC Website at http://
www.smc.com.
– 4 –
Page 5

COMPLIANCES
FEDERAL COMMUNICATION COMMISSION INTERFERENCE STATEMENT
This equipment has been tested and found to comply with the limits for a
Class B digital device, pursuant to Part 15 of the FCC Rules. These limits
are designed to provide reasonable protection against harmful interference
in a residential installation. This equipment generates, uses and can
radiate radio frequency energy and, if not installed and used in accordance
with the instructions, may cause harmful interference to radio
communications. This transmitter must not be co-located or operating in
conjunction with any other antenna or transmitter. However, there is no
guarantee that interference will not occur in a particular installation. If this
equipment does cause harmful interference to radio or television reception,
which can be determined by turning the equipment off and on, the user is
encouraged to try to correct the interference by one of the following
measures:
◆ Reorient or relocate the receiving antenna
◆ Increase the separation between the equipment and receiver
◆ Connect the equipment into an outlet on a circuit different from that to
which the receiver is connected
◆ Consult the dealer or an experienced radio/TV technician for help
This device complies with Part 15 of the FCC Rules. Operation is subject to
the following two conditions: (1) This device may not cause harmful
interference, and (2) this device must accept any interference received,
including interference that may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by the
party responsible for compliance could void the user's authority to operate
this equipment.
IEEE 802.11b or 802.11g operation of this product in the U.S.A. is
firmware-limited to channels 1 through 11.
IMPORTANT NOTE:
FCC RADIATION EXPOSURE STATEMENT
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment. This equipment should be installed and
operated with minimum distance 20 cm between the radiator and your
body.
– 5 –
Page 6

C
OMPLIANCES
IC STATEMENT
This Class B digital apparatus complies with Canadian ICES-003.
Operation is subject to the following two conditions: (1) this device may
not cause interference, and (2) this device must accept any interference,
including interference that may cause undesired operation of the device.
Cet appareil numérique de la classe B conforme á la norme NMB-003 du
Canada.
The device could automatically discontinue transmission in case of absence
of information to transmit, or operational failure. Note that this is not
intended to prohibit transmission of control or signaling information or the
use of repetitive codes where required by the technology.
IMPORTANT NOTE:
IC RADIATION EXPOSURE STATEMENT:
This equipment complies with IC RSS-102 radiation exposure limits set
forth for an uncontrolled environment. This equipment should be installed
and operated with minimum distance 20 cm between the radiator & your
body.
TAIWAN NCC
根據國家通信傳播委員會低功率電波輻射性電機管理辦法規定:
第十二條 經型式認證合格之低功率射頻電機,非經許可,公司、商號或使用者均不得擅自變更
頻率、加大功率或變更原設計之特性及功能。
第十四條 低功率射頻電機之使用不得影響飛航安全及干擾合法通信;經發現有干擾現象時,應
立即停用,並改善至無干擾時方得繼續使用。前項合法通信,指依電信法規定作業之無線電通
信。低功率射頻電機須忍受合法通信或工業、科學及醫療用電波輻射性電機設備之干擾。
EC CONFORMANCE DECLARATION
Marking by the above symbol indicates compliance with the Essential
Requirements of the R&TTE Directive of the European Union (1999/5/EC).
This equipment meets the following conformance standards:
◆ EN 60950-1 (IEC 60950-1) - Product Safety
◆ EN 55022/24 - ITE EMC
◆ EN 301 489-1-17 - RF EMC
◆ EN 300 328 - 802.11 b/g/n
– 6 –
Page 7

C
OMPLIANCES
This device is intended for use in the following European Community and
EFTA countries:
◆ Austria ◆ Belgium ◆ Bulgaria ◆ Cyprus ◆ Czech Republic
◆ Denmark ◆ Estonia ◆ Finland ◆ France ◆ Germany
◆ Greece ◆ Hungary ◆ Iceland ◆ Ireland ◆ Italy
◆ Latvia ◆ Lithuania ◆ Luxembourg ◆ Malta ◆ Netherlands
◆ Norway ◆ Poland ◆ Portugal ◆ Romania ◆ Slovakia
◆ Slovenia ◆ Spain ◆ Sweden ◆Switzerland ◆ United Kingdom
N
OTE
:
The user must use the configuration utility provided with this
product to ensure the channels of operation are in conformance with the
spectrum usage rules for European Community countries as described
below.
◆ This device will automatically limit the allowable channels determined
by the current country of operation. Incorrectly entering the country of
operation may result in illegal operation and may cause harmful
interference to other systems. The user is obligated to ensure the
device is operating according to the channel limitations, indoor/outdoor
restrictions and license requirements for each European Community
country as described in this document.
DECLARATION OF CONFORMITY IN LANGUAGES OF THE EUROPEAN
COMMUNITY
Czech
Česky
Estonian
Eesti
English Hereby, Manufacturer, declares that this Radio LAN device is in compliance with the
Finnish
Suomi
Dutch
Nederlands
French
Français
Swedish
Svenska
Danish
Dansk
Manufacturer tímto prohlašuje, že tento Radio LAN device je ve shodě se základními
požadavky a dalšími příslušnými ustanoveními směrnice 1999/5/ES.
Käesolevaga kinnitab Manufacturer seadme Radio LAN device vastavust direktiivi 1999/
5/EÜ põhinõuetele ja nimetatud direktiivist tulenevatele teistele asjakohastele sätetele.
essential requirements and other relevant provisions of Directive 1999/5/EC.
Valmistaja Manufacturer vakuuttaa täten että Radio LAN device tyyppinen laite on
direktiivin 1999/5/EY oleellisten vaatimusten ja sitä koskevien direktiivin muiden ehtojen
mukainen.
Hierbij verklaart Manufacturer dat het toestel Radio LAN device in overeenstemming is
met de essentiële eisen en de andere relevante bepalingen van richtlijn 1999/5/EG
Bij deze Manufacturer dat deze Radio LAN device voldoet aan de essentiële eisen en aan
de overige relevante bepalingen van Richtlijn 1999/5/EC.
Par la présente Manufacturer déclare que l'appareil Radio LAN device est conforme aux
exigences essentielles et aux autres dispositions pertinentes de la directive 1999/5/CE
Härmed intygar Manufacturer att denna Radio LAN device står I överensstämmelse med
de väsentliga egenskapskrav och övriga relevanta bestämmelser som framgår av direktiv
1999/5/EG.
Undertegnede Manufacturer erklærer herved, at følgende udstyr Radio LAN device
overholder de væsentlige krav og øvrige relevante krav i direktiv 1999/5/EF
– 7 –
Page 8

C
OMPLIANCES
German
Deutsch
Greek
Ελληνική
Hungarian
Magyar
Italian
Italiano
Latvian
Latviski
Lithuanian
Lietuvių
Maltese
Malti
Spanish
Español
Polish
Polski
Portuguese
Português
Slovak
Slovensky
Slovenian
Slovensko
Hiermit erklärt Manufacturer, dass sich dieser/diese/dieses Radio LAN device in
Übereinstimmung mit den grundlegenden Anforderungen und den anderen relevanten
Vorschriften der Richtlinie 1999/5/EG befindet". (BMWi)
Hiermit erklärt Manufacturer die Übereinstimmung des Gerätes Radio LAN device mit den
grundlegenden Anforderungen und den anderen relevanten Festlegungen der Richtlinie
1999/5/EG. (Wien)
με την παρουσα Manufacturer δηλωνει οτι radio LAN device συμμορφωνεται προσ τισ
ουσιωδεισ απαιτησεισ και τισ λοιπεσ σχετικεσ διαταξεισ τησ οδηγιασ 1999/5/εκ.
Alulírott, Manufacturer nyilatkozom, hogy a Radio LAN device megfelel a vonatkozó
alapvetõ követelményeknek és az 1999/5/EC irányelv egyéb elõírásainak.
Con la presente Manufacturer dichiara che questo Radio LAN device è conforme ai
requisiti essenziali ed alle altre disposizioni pertinenti stabilite dalla direttiva 1999/5/CE.
Ar šo Manufacturer deklarē, ka Radio LAN device atbilst Direktīvas 1999/5/EK būtiskajām
prasībām un citiem ar to saistītajiem noteikumiem.
Šiuo Manufacturer deklaruoja, kad šis Radio LAN device atitinka esminius reikalavimus ir
kitas 1999/5/EB Direktyvos nuostatas.
Hawnhekk, Manufacturer, jiddikjara li dan Radio LAN device jikkonforma mal-ħtiġijiet
essenzjali u ma provvedimenti oħrajn relevanti li hemm fid-Dirrettiva 1999/5/EC.
Por medio de la presente Manufacturer declara que el Radio LAN device cumple con los
requisitos esenciales y cualesquiera otras disposiciones aplicables o exigibles de la
Directiva 1999/5/CE
Niniejszym Manufacturer o
wymogami oraz pozostałymi stosownymi postanowieniami Dyrektywy 1999/5/EC.
Manufacturer declara que este Radio LAN device está conforme com os requisitos
essenciais e outras disposições da Directiva 1999/5/CE.
Manufacturer týmto vyhlasuje, že Radio LAN device spĺňa základné požiadavky a všetky
príslušné ustanovenia Smernice 1999/5/ES.
Manufacturer izjavlja, da je ta radio LAN device v skladu z bistvenimi zahtevami in ostalimi
relevantnimi določili direktive 1999/5/ES.
świadcza, że Radio LAN device jest zgodny z zasadniczymi
– 8 –
Page 9

C
OMPLIANCES
– 9 –
Page 10
ABOUT THIS GUIDE
PURPOSE This guide gives specific information on how to install the Wireless
Broadband Router and its physical and performance related characteristics.
It also gives information on how to operate and use the management
functions of the Wireless Broadband Router.
AUDIENCE This guide is for users with a basic working knowledge of computers. You
should be familiar with Windows operating system concepts.
CONVENTIONS The following conventions are used throughout this guide to show
information:
N
OTE
:
Emphasizes important information or calls your attention to related
features or instructions.
C
AUTION
damage the system or equipment.
W
ARNING
:
Alerts you to a potential hazard that could cause loss of data, or
:
Alerts you to a potential hazard that could cause personal injury.
RELATED PUBLICATIONS As part of the Wireless Broadband Router’s software, there is an online
web-based help that describes all management related features.
REVISION HISTORY This section summarizes the changes in each revision of this guide.
SEPTEMBER 2009 REVISION
This is the first revision of this guide.
– 10 –
Page 11

CONTENTS
WARRANTY AND PRODUCT REGISTRATION 4
C
OMPLIANCES 5
A
BOUT THIS GUIDE 10
C
ONTENTS 11
F
IGURES 16
T
ABLES 19
SECTION I GETTING STARTED 20
1INTRODUCTION 21
Key Hardware Features 21
Description of Capabilities 21
Applications 22
Package Contents 23
Hardware Description 23
LED Indicators 25
Ethernet WAN Port 26
Ethernet LAN Ports 26
Power Connector 26
Reset Button 27
WPS Button 27
2NETWORK PLANNING 29
Internet Gateway Router 29
LAN Access Point 30
Wireless Bridge 31
3INSTALLING THE GATEWAY ROUTER 33
System Requirements 33
– 11 –
Page 12

C
ONTENTS
Location Selection 33
Mounting on a Wall 34
Mounting on a Horizontal Surface 35
Gateway Mode Connections 35
Bridge Mode Connections 36
4INITIAL CONFIGURATION 38
ISP Settings 38
Connecting to the Login Page 38
Home Page and Main Menu 39
Common Web Page Buttons 40
Setup Wizard 40
Step 1 - Language Selection 40
Step 2 - SNTP Settings 41
Step 3 - WAN Settings - DHCP 42
Step 3 - WAN Settings - Static IP 43
Step 3 - WAN Settings - PPPoE 44
Step 3 - WAN Settings - PPTP 45
Step 4 - Wireless Security 46
Completion 47
SECTION II WEB CONFIGURATION 49
5OPERATION MODE 51
Logging In 52
Operation Mode 54
6INTERNET SETTINGS 55
WAN Setting 55
DHCP 55
Static IP 57
PPPoE 58
PPTP 59
LAN Setting 61
Advanced Routing 63
Advanced Routing Settings 63
Routing Table 64
– 12 –
Page 13

C
ONTENTS
Dynamic Route 65
7WIRELESS CONFIGURATION 67
Basic Settings 67
WLAN Security 69
Wired Equivalent Privacy (WEP) 70
WPA Pre-Shared Key 71
WPA Enterprise Mode 72
IEEE 802.1X and RADIUS 74
Advanced Settings 76
Wireless Network 76
HT Physical Mode Settings 77
Advanced Wireless 79
Wi-Fi Multimedia 81
Multicast-to-Unicast Converter 83
Wireless Distribution System (WDS) 84
Wi-Fi Protected Setup (WPS) 88
Station List 90
8FIREWALL CONFIGURATION 91
MAC/IP/Port Filtering 91
Current Filter Rules 93
Virtual Server Settings (Port Forwarding) 94
Current Virtual Servers in system 95
DMZ 95
System Security 96
Content Filtering 97
9ADMINISTRATION SETTINGS 99
System Management 100
Language Settings 100
Web Interface Settings 100
SNTP Settings 101
DDNS Settings 102
Upgrade Firmware 103
Configuration Settings 104
System Status 105
Statistics 107
– 13 –
Page 14

C
ONTENTS
System Log 108
SECTION III APPENDICES 110
ATROUBLESHOOTING 111
Diagnosing LED Indicators 111
If You Cannot Connect to the Internet 111
Before Contacting Technical Support 111
BHARDWARE SPECIFICATIONS 114
CC
ABLES AND PINOUTS 116
Twisted-Pair Cable Assignments 116
10/100BASE-TX Pin Assignments 117
Straight-Through Wiring 117
Crossover Wiring 118
DLICENSE INFORMATION 119
The GNU General Public License 119
GLOSSARY 123
– 14 –
Page 15

C
ONTENTS
– 15 –
Page 16

FIGURES
Figure 1: Top Panel 24
Figure 2: Rear Panel 25
Figure 3: LEDs 25
Figure 4: Operating as an Internet Gateway Router 30
Figure 5: Operating as an Access Point 31
Figure 6: Operating as a Wireless Bridge 31
Figure 7: Operating as a Wireless Repeater 32
Figure 8: Wall Mounting 34
Figure 9: Gateway Mode Connection 35
Figure 10: Bridge Mode Connection 36
Figure 11: Login Page 39
Figure 12: Home Page 39
Figure 13: Wizard Step 1 - Language Selection 40
Figure 14: Wizard Step 2 - Time and SNTP Settings 41
Figure 15: Wizard Step 3 - WAN Settings - DHCP 42
Figure 16: Wizard Step 3 - WAN Settings - Static IP 43
Figure 17: Wizard Step 3 - WAN Settings - PPPoE 44
Figure 18: Wizard Step 3 - WAN Settings - PPTP 45
Figure 19: Wizard Step 4 - Wireless Security 46
Figure 20: Logging On 52
Figure 21: Home Page 53
Figure 22: Operation Mode (Gateway) 54
Figure 23: DHCP Configuration 56
Figure 24: Static IP Configuration 57
Figure 25: PPPoE Configuration 58
Figure 26: PPTP Configuration 59
Figure 27: LAN Configuration 61
Figure 28: Advanced Routing (Gateway Mode) 63
Figure 29: Basic Settings 68
Figure 30: Security Mode Options 69
Figure 31: Security Mode - WEP 70
– 16 –
Page 17

F
IGURES
Figure 32: Security Mode - WPA-PSK 71
Figure 33: Security Mode - WPA 73
Figure 34: Security Mode - 802.1X 75
Figure 35: Advanced Settings — Wireless Network 76
Figure 36: HT Physical Mode Settings 77
Figure 37: Advanced Wireless Settings 79
Figure 38: Wi-Fi Multimedia Settings 81
Figure 39: WMM Configuration 82
Figure 40: Multicast-to-Unicast Converter 83
Figure 41: Manual WDS MAC Address Configuration 84
Figure 42: WDS Configuration Example 85
Figure 43: WDS Configuration 86
Figure 44: Enabling WPS 88
Figure 45: WPS Configuration 89
Figure 46: Station List 90
Figure 47: MAC/IP/Port Filtering 92
Figure 48: Virtual Server 94
Figure 49: DMZ 95
Figure 50: System Security 96
Figure 51: Content Filtering 97
Figure 52: System Management 100
Figure 53: SNTP Settings 101
Figure 54: DDNS Settings (Gateway Mode) 102
Figure 55: Upgrade Firmware 103
Figure 56: Configuration Settings 104
Figure 57: System Status (Gateway Mode) 105
Figure 58: Statistics 107
Figure 59: System Log 108
Figure 60: RJ-45 Connector 116
Figure 61: Straight-through Wiring 118
Figure 62: Crossover Wiring 118
– 17 –
Page 18

F
IGURES
– 18 –
Page 19

TABLES
Table 1: Key Hardware Features 21
Table 2: LED Behavior 26
Table 3: WMM Access Categories 81
Table 4: LED Indicators 111
Table 5: 10/100BASE-TX MDI and MDI-X Port Pinouts 117
– 19 –
Page 20

S
ECTION
GETTING STARTED
This section provides an overview of the Wireless Broadband Router, and
describes how to install and mount the unit. It also describes the basic
settings required to access the management interface and run the setup
Wizard.
This section includes these chapters:
◆ “Introduction” on page 21
◆ “Network Planning” on page 29
◆ “Initial Configuration” on page 38
I
◆ “Installing the Gateway Router” on page 33
– 20 –
Page 21

1 INTRODUCTION
The Barricade Wireless Broadband Router (SMCWBR14S-N4) supports
routing from an Internet Service Provider (ISP) connection (DSL or cable
modem) to a local network. It is simple to configure and can be up and
running in minutes.
KEY HARDWARE FEATURES
The following table describes the main hardware features of the Gateway
Router.
Table 1: Key Hardware Features
Feature Description
WAN Port One 100BASE-TX RJ-45 port for connecting to the Internet.
4 LAN Ports Four 100BASE-TX RJ-45 ports for local network connections.
WPS Button To set up a secure connection to a wireless device.
Reset Button For resetting the unit and restoring factory defaults.
LEDs Provides LED indicators for Power, WAN port, and LAN ports status.
Mounting Options Can be mounted on any horizontal surface such as a desktop or
DESCRIPTION OF CAPABILITIES
◆ Internet connection through an RJ-45 WAN port.
◆ Local network connection through four 10/100 Mbps Ethernet ports.
◆ DHCP for dynamic IP configuration.
◆ Firewall with Stateful Packet Inspection, client privileges, intrusion
detection, and NAT.
◆ NAT also enables multi-user Internet access via a single user account,
and virtual server functionality (providing protected access to Internet
services such as Web, FTP, e-mail, and Telnet).
shelf, or on a wall using two screws.
◆ VPN pass-through (PPTP).
◆ User-definable application sensing tunnel supports applications
requiring multiple connections.
– 21 –
Page 22

C
HAPTER
Description of Capabilities
1
| Introduction
APPLICATIONS Many advanced networking features are provided by the Barricade:
◆ Easy setup through a Web browser on any operating system that
supports TCP/IP.
◆ Compatible with all popular Internet applications.
In addition, the Gateway Router offers full network management
capabilities through an easy-to-configure web interface.
◆ Wired LAN — The Barricade provides connectivity to wired
10/100 Mbps devices, making it easy to create a network in small
offices or homes.
◆ Internet Access — This device supports Internet access through a
WAN connection. Since many DSL providers use PPPoE to establish
communications with end users, the Barricade includes built-in clients
for these protocols, eliminating the need to install these services on
your computer.
◆ Shared IP Address — The Barricade provides Internet access for up
to 253 users via a single shared IP address. Using only one ISP
account, multiple users on your network can browse the Web at the
same time.
◆ Virtual Server — If you have a fixed IP address, you can set the
Barricade to act as a virtual host for network address translation.
Remote users access various services at your site using a constant IP
address. Then, depending on the requested service (or port number),
the Barricade can route the request to the appropriate server (at
another internal IP address). This secures your network from direct
attack by hackers, and provides more flexible management by allowing
you to change internal IP addresses without affecting outside access to
your network.
◆ DMZ Host Support — Allows a networked computer to be fully
exposed to the Internet. This function is used when NAT and firewall
security prevent an Internet application from functioning correctly.
◆ Security — The Barricade supports security features that deny
Internet access to specified users, or filter all requests for specific
services the administrator does not want to serve. WPA (Wi-Fi
Protected Access) and MAC filtering provide security over the wireless
network.
◆ Virtual Private Network (VPN) — The Barricade supports one of the
most commonly used VPN protocols – PPTP. This protocol allows remote
users to establish a secure connection to their corporate network. If
your service provider supports VPNs, then these protocols can be used
to create an authenticated and encrypted tunnel for passing secure
data over the Internet (i.e., a traditionally shared data network). The
VPN protocols supported by the Barricade are briefly described below.
– 22 –
Page 23
PACKAGE CONTENTS
C
HAPTER
◆ Point-to-Point Tunneling Protocol — Provides a secure tunnel for
remote client access to a PPTP security gateway. PPTP includes
provisions for call origination and flow control required by ISPs.
The Barricade Wireless Broadband Router package includes:
◆ Barricade Wireless Broadband Router
◆ RJ-45 Category 5 network cable
◆ AC power adapter
◆ Quick Installation Guide
◆ EZ Installation & Documentation CD
1
| Introduction
Package Contents
Inform your dealer if there are any incorrect, missing or damaged parts. If
possible, retain the carton, including the original packing materials. Use
them again to repack the product in case there is a need to return it.
HARDWARE DESCRIPTION
The Barricade Wireless Broadband Router, from herein refered to as
Gateway Router, connects to the Internet using its RJ-45 WAN port. It
connects directly to your PC or to a local area network using its RJ-45 Fast
Ethernet LAN ports.
The Gateway Router includes an LED display on the front panel for system
power and port indications that simplifies installation and network
troubleshooting.
– 23 –
Page 24

C
LED Indicators
HAPTER
1
| Introduction
Hardware Description
Figure 1: Top Panel
– 24 –
Page 25
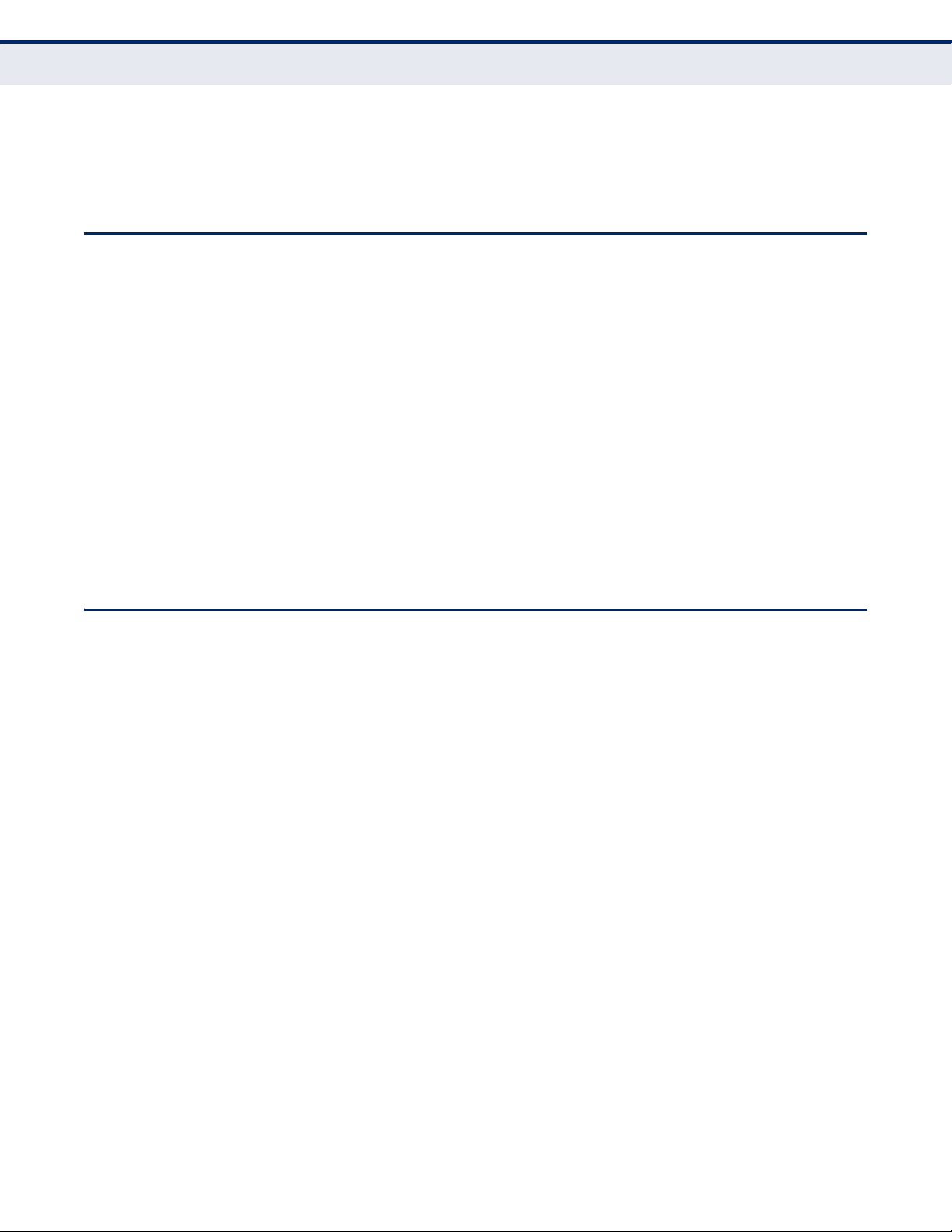
Figure 2: Rear Panel
RJ-45 WAN Port
RJ-45 LAN Ports
Reset Button
DC Power
Socket
WPS Button
LAN 1~4
WLAN
Power
WAN
WPS
C
HAPTER
1
| Introduction
Hardware Description
LED INDICATORS The Wireless Broadband Router includes seven status LED indicators, as
described in the following figure and table.
Figure 3: LEDs
– 25 –
Page 26
C
HAPTER
1
| Introduction
Hardware Description
Table 2: LED Behavior
LED Status Description
Power On Blue The unit is receiving power and is operating
Off There is no power currently being supplied to
WLAN On/Blinking Blue The 802.11n radio is enabled and
Off The 802.11n radio is disabled.
WPS Blinking WPS authentication is in progress.
Off WPS authentication is not in progress.
WAN On Blue The Ethernet WAN port is aquiring an IP
Blinking The Ethernet WAN port is connected and is
Off The Ethernet WAN port is disconnected or has
LAN1~LAN4 On Blue The Ethernet LAN port is connected to a PC or
Blinking The Ethernet port is connected and is
Off The Ethernet port is disconnected or has
normally.
the unit.
transmitting or receiving data through wireless
links.
address.
transmitting/receiving data.
malfunctioned.
server.
transmitting/receiving data.
malfunctioned.
ETHERNET WAN PORT A 100BASE-TX RJ-45 port that can be attached to an Internet access
device, such as a DSL or Cable modem.
ETHERNET LAN
P
ORTS
The Wireless Broadband Router has four 100BASE-TX RJ-45 ports that can
be attached directly to 10BASE-T/100BASE-TX LAN segments.
These port support automatic MDI/MDI-X operation, so you can use
straight-through cables for all network connections to PCs, switches, or
hubs.
POWER CONNECTOR The Wireless Broadband Router must be powered with its supplied power
adapter. Failure to do so results in voiding of any warrantly supplied with
the product. The power adapter automatically adjusts to any voltage
between 100~240 volts at 50 or 60 Hz, and supplies 5 volts DC power to
the unit. No voltage range settings are required.
– 26 –
Page 27

C
HAPTER
1
| Introduction
Hardware Description
RESET BUTTON This button is used to restore the factory default configuration. If you hold
down the button for 5 seconds or more, any configuration changes you
may have made are removed, and the factory default configuration is
restored to the Gateway Router.
WPS BUTTON Press to automatically configure the Wireless Broadband Router with other
WPS devices in the WLAN.
– 27 –
Page 28

C
HAPTER
1
| Introduction
Hardware Description
– 28 –
Page 29

2 NETWORK PLANNING
The Wireless Broadband Router is designed to be very flexible in its
deployment options. It can be used as an Internet gateway for a small
network, or as an access point to extend an existing wired network to
support wireless users. It also supports use as a wireless bridge to connect
up to four wired LANs.
This chapter explains some of the basic features of the Wireless Broadband
Router and shows some network topology examples in which the device is
implemented.
INTERNET GATEWAY ROUTER
The Wireless Broadband Router can connect directly to a cable or DSL
modem to provide an Internet connection for multiple users through a
single service provider account. Users connect to the Wireless Broadband
Router either through a wired connection to a LAN port, or though the
device’s own wireless network. The Wireless Broadband Router functions as
an Internet gateway when set to Gateway Mode.
An Internet gateway employs several functions that essentially create two
separate Internet Protocol (IP) subnetworks; a private internal network
with wired and wireless users, and a public external network that connects
to the Internet. Network traffic is forwarded, or routed, between the two
subnetworks.
– 29 –
Page 30

C
Wireless AP/Router
Server
(IP: 192.168.2.x)
Desktop PC
(IP: 192.168.2.x)
Cable/DSL
Modem
Internet
Service
Provider
Notebook PC
(IP: 192.168.2.x)
WAN (IP assigned from ISP)
LAN (IP: 192.168.2.x)
LAN Switch
HAPTER
2
| Network Planning
LAN Access Point
Figure 4: Operating as an Internet Gateway Router
LAN ACCESS POINT
The private local network, connected to the LAN port or wireless interface,
provides a Dynamic Host Configuration Protocol (DHCP) server for
allocating IP addresses to local PCs and wireless clients, and Network
Address Translation (NAT) for mapping the multiple "internal" IP addresses
to one "external" IP address.
The public external network, connected to the WAN port, supports DHCP
client, Point-to-Point Protocol over Ethernet (PPPoE) and static IP for
connection to an Internet service provider (ISP) through a cable or DSL
modem.
The Wireless Broadband Router can provide an access point service for an
existing wired LAN, creating a wireless extension to the local network. The
Wireless Broadband Router functions as purely an access point when set to
Bridge Mode. When used in this mode, there are no gateway functions
between the WAN port and the LAN and wireless interface.
A Wi-Fi wireless network is defined by its Service Set Identifier (SSID) or
network name. Wireless clients that want to connect to a network must set
their SSID to the same SSID of the network service.
– 30 –
Page 31

Figure 5: Operating as an Access Point
Server
(IP: 192.168.2.x)
Desktop PC
(IP: 192.168.2.x)
LAN Switch
Notebook PC
(IP: 192.168.2.x)
Wireless AP/Router
Desktop PCs
Desktop PCs
Cable/DSL
Modem
Gateway Router
(Bridge Mode)
WDS Link
Internet
Service
Provider
Gateway Router
(Gateway Mode)
C
HAPTER
2
| Network Planning
Wireless Bridge
WIRELESS BRIDGE
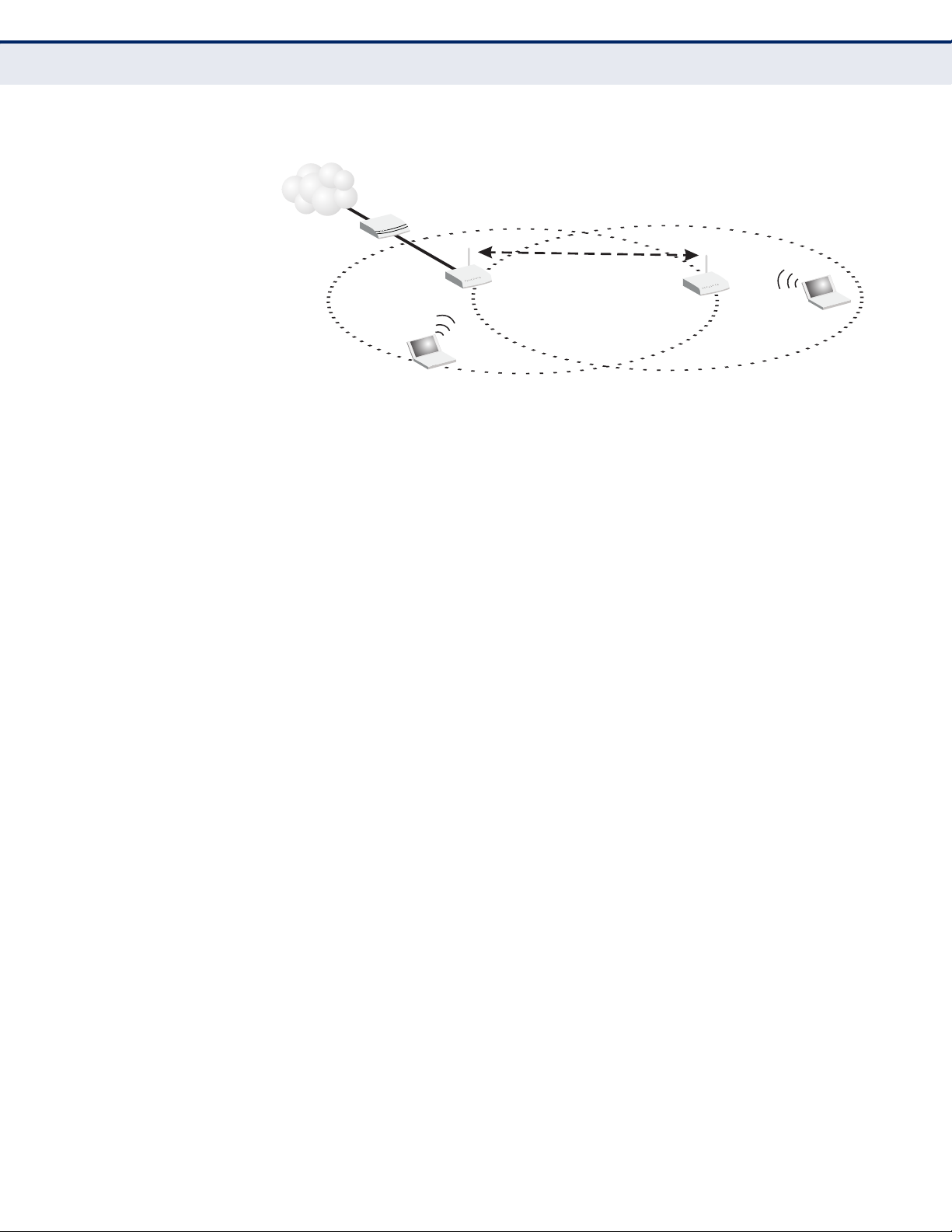
The IEEE 802.11 standard defines a Wireless Distribution System (WDS)
for bridge connections between access points. The Wireless Broadband
Router can use WDS to forward traffic on links between units.
Up to four WDS links can be specified for the Wireless Broadband Router.
The WDS feature enables two basic functions to be configured in the
wireless network. Either a repeater function that extends the range of the
wireless network, or a bridge function that connects a remote LAN segment
to an Internet connection.
Figure 6: Operating as a Wireless Bridge
– 31 –
Page 32
C
Cable/DSL
Modem
Gateway Router
(Bridge Mode)
WDS Link
Internet
Service
Provider
Notebook PC
Gateway Router
(Gateway Mode)
Notebook PC
HAPTER
2
| Network Planning
Wireless Bridge
Figure 7: Operating as a Wireless Repeater
– 32 –
Page 33

3 INSTALLING THE GATEWAY ROUTER
The Wireless Broadband Router has two basic operating modes that can be
set through the web-based management interface. For information on
setting the mode suitable for your network environment. See “Operation
Mode” on page 54.
◆ Gateway Mode — A gateway mode that connects a wired LAN and
wireless clients to an Internet access device, such as a cable or DSL
modem. This is the factory set default mode.
◆ Bridge Mode — An access point mode that extends a wired LAN to
wirelessclients.
In addition to these basic operating modes, the wireless interface supports
a Wireless Distribution System (WDS) link to another Wireless Broadband
Router. These advanced configurations are not described in this section.
See “Network Planning” on page 29 for more information.
In a basic configuration, how the Wireless Broadband Router is connected
depends on the operating mode. The sections in this chapter describe
connections for basic Gateway Mode and Bridge Mode operation.
SYSTEM REQUIREMENTS
You must meet the following minimum requirements:
◆ An Internet access device (DSL or Cable modem) with an Ethernet port
◆ An up-to-date web browser: Internet Explorer 6.0 or above or Mozilla
LOCATION SELECTION
The Wireless Broadband Router can be mounted on any horizontal surface,
or on a wall. The following sections describe the mounting options.
connection.
Firefox 2.0 or above.
– 33 –
Page 34

C
Mounting Slots
HAPTER
Mounting on a Wall
3
| Installing the Gateway Router
MOUNTING ON A WALL
The Wireless Broadband Router should be mounted only to a wall or wood
surface that is at least 1/2-inch plywood or its equivalent. To mount the
unit on a wall, always use its wall-mounting bracket. The unit must be
mounted with the RJ-45 cable connector oriented upwards to ensure
proper operation.
Figure 8: Wall Mounting
To mount on a wall, follow the instructions below.
1. Mark the position of the two screw holes on the wall. For concrete or
brick walls, you will need to drill holes and insert wall plugs for the
screws.
2. Insert the included screws into the holes, leaving about 0.08~0.12
inches (2-3 mm) clearance from the wall.
3. Line up the two mounting points on the unit with the screws in the wall,
then slide the unit down onto the screws until it is in a secured position.
– 34 –
Page 35

MOUNTING ON A HORIZONTAL SURFACE
4.
Set up wireless
devices
Notebook PC
3.
Connect AC power
adapter to
power source
2.
Connect LAN port
to PC
Cable/DSL Modem
1.
Connect WAN port to
cable/DSL modem
Internet
To keep the Wireless Broadband Router from sliding on the surface, the
Wireless Broadband Router has four rubber feet on the bottom of the unit.
It is recommended to select an uncluttered area on a sturdy surface, such
as a desktop or table. The unit can also be protected by securing all
attached cables to a table leg or other nearby fixed structure.
GATEWAY MODE CONNECTIONS
In its default Gateway Mode, the Wireless Broadband Router forwards
traffic between an Internet connected cable or ADSL modem, and wired or
wireless PCs or notebooks. The basic connections are illustrated in the
figure below.
Figure 9: Gateway Mode Connection
C
HAPTER
3
| Installing the Gateway Router
Mounting on a Horizontal Surface
To connect the Wireless Broadband Router in Gateway Mode for use as an
Internet gateway, follow these steps:
1. Connect an Ethernet cable from the Wireless Broadband Router’s WAN
2. Connect an Ethernet cable from the Wireless Broadband Router’s LAN
3. Power on the Wireless Broadband Router by connecting the AC power
port to your Internet connected cable or ADSL modem.
ports to your PCs. Alternatively, you can connect to a workgroup switch
to support more wired users. The Wireless Broadband Router can
support up to 253 wired and wireless users.
adapter and plugging it into a power source.
– 35 –
Page 36

C
4.
Set up wireless
devices
Notebook PC
2.
Connect AC power
adapter to
power source
3.
Connect LAN port
to PC
1.
Connect LAN and WAN
ports to an Ethernet LAN
switch or PCs
HAPTER
Bridge Mode Connections
3
| Installing the Gateway Router
C
AUTION
Broadband Router. Otherwise, the product may be damaged.
When you power on the Wireless Broadband Router, verify that the
Power LED turns on and that the other LED indicators start functioning
as described under see “LED Indicators” on page 25.
4. Set up wireless devices by pressing the WPS button on the Wireless
Broadband Router or by using the web interface. See “Initial
Configuration” on page 38 for more information on accessing the web
interface.
BRIDGE MODE CONNECTIONS
In Bridge Mode, the Wireless Broadband Router operates as a wireless
access point, extending a local wired network to associated wireless clients
(PCs or notebooks with wireless capability). From any nearby location, you
can then make a wireless connection to the Wireless Broadband Router and
access the wired network resources, including local servers and the
Internet.
:
Use ONLY the power adapter supplied with the Wireless
In Bridge Mode, the Wireless Broadband Router does not support gateway
functions on its WAN port. Both the LAN port and the WAN ports can be
connected to a local Ethernet LAN.
N
OTE
:
Bridge Mode is not the factory default mode and must be manually
set using the web management interface.
Figure 10: Bridge Mode Connection
To connect the Wireless Broadband Router for use as an access point,
follow these steps:
– 36 –
Page 37

C
HAPTER
3
| Installing the Gateway Router
Bridge Mode Connections
1. Using Ethernet cable connect the Wireless Broadband Router’s LAN and
WAN ports to PCs or a LAN switch.
2. Power on the Wireless Broadband Router by connecting the AC power
adapter and plugging it into a power source.
C
AUTION
:
Use ONLY the power adapter supplied with the Wireless
Broadband Router. Otherwise, the product may be damaged.
When you power on the Wireless Broadband Router, verify that the Power
LED turns on and that the other LED indicators start functioning as
described under “LED Indicators” on page 25.
3. Connect an Ethernet cable from the Wireless Broadband Router’s LAN
ports to your PCs. Alternatively, you can connect to a workgroup switch
to support more wired users. The Wireless Broadband Router can
support up to 253 wired and wireless users
4. Set up wireless devices by pressing the WPS button on the Wireless
Broadband Router or by using the web interface. See “Initial
Configuration” on page 38 for more information on accessing the web
interface.
– 37 –
Page 38

4 INITIAL CONFIGURATION
The Wireless Broadband Router offers a user-friendly web-based
management interface for the configuration of all the unit’s features. Any
PC directly attached to the unit can access the management interface using
a web browser, such as Internet Explorer (version 6.0 or above).
ISP SETTINGS
If you are not sure of your connection method, please contact your
Internet Service Provider. There are several connection types to choose
from: Static IP, DHCP (cable connection), PPPoE (DSL connection), and
PPTP.
N
OTE
:
If using the PPPoE option, you will need to remove or disable any
PPPoE client software on your computers.
CONNECTING TO THE LOGIN PAGE
It is recommended to make initial configuration changes by connecting a
PC directly to one of the Wireless Broadband Router’s LAN ports. The
Wireless Broadband Router has a default IP address of 192.168.2.1 and a
subnet mask of 255.255.255.0. You must set your PC IP address to be on
the same subnet as the Gateway Router (that is, the PC and Gateway
Router addresses must both start 192.168.2.x).
To access the Wireless Broadband Router’s management interface, follow
these steps:
1. Use your web browser to connect to the management interface using
the default IP address of 192.168.2.1.
2. Log into the interface by entering the default username “admin” and
password “smcadmin,” then click Login.
N
OTE
:
It is strongly recommended to change the default user name and
password the first time you access the web interface. For information on
changing user names and passwords, See “System Management” on
page 100.
– 38 –
Page 39

Figure 11: Login Page
C
HAPTER
4
| Initial Configuration
Home Page and Main Menu
HOME PAGE AND MAIN MENU
After logging in to the web interface, the Home page displays. The Home
page shows the main menu and the method to access the Setup Wizard.
Figure 12: Home Page
– 39 –
Page 40

C
HAPTER
Common Web Page Buttons
4
| Initial Configuration
COMMON WEB PAGE BUTTONS
The list below describes the common buttons found on most web
management pages:
◆ Apply – Applies the new parameters and saves them to memory. Also
displays a screen to inform you when it has taken affect. Clicking
‘Apply’ returns to the home page.
◆ Cancel – Cancels the newly entered settings and restores the previous
settings.
◆ Next – Proceeds to the next step.
◆ Back – Returns to the previous screen.
SETUP WIZARD
STEP 1 - LANGUAGE
SELECTION
The Wizard is designed to help you configure the basic settings required to
get the the Wireless Broadband Router up and running. There are only a
few basic steps you need to set up the the Wireless Broadband Router and
provide a connection.
Follow these steps:
Select between English or Traditional Chinese. Click Next to proceed to the
next step of the wizard.
Figure 13: Wizard Step 1 - Language Selection
The following items are displayed on the first page of the Setup Wizard:
◆ Select Language — Toggles between English or Traditional Chinese as
the interface language.
◆ Next — Proceeds to the next step.
– 40 –
Page 41

C
HAPTER
4
| Initial Configuration
Setup Wizard
STEP 2 - SNTP
SETTINGS
The Step 2 page of the Wizard configures time zone and SNTP settings.
Select a time zone according to where the device is operated. Click Next
after completing the setup.
Figure 14: Wizard Step 2 - Time and SNTP Settings
The following items are displayed on this page:
◆ Current Time — Receives a time and date stamp from an SNTP server.
◆ Time Zone — Select the time zone that is applicable to your region.
◆ SNTP Server — Enter the address of an SNTP server to receive time
updates.
◆ SNTP synchronization (hours) — Specify the interval between SNTP
server updates.
– 41 –
Page 42

C
HAPTER
Setup Wizard
4
| Initial Configuration
STEP 3 - WAN
SETTINGS - DHCP
The Step 3 page of the Wizard specifies the Internet connection
parameters for the Wireless Broadband Router’s WAN port. Click Next after
completing the setup.
By default, the access point WAN port is configured with DHCP enabled.
The options are Static IP, DHCP (cable modem), PPPoE (ADSL), and PPTP.
Each option changes the parameters that are displayed on the page.
Figure 15: Wizard Step 3 - WAN Settings - DHCP
The following items are displayed on this page:
◆ WAN Connection Type — Select the connection type for the WAN port
from the drop down list. (Default: DHCP)
◆ Hostname — Specifies the host name of the DHCP client.
(Default: SMCWBR14S-N4)
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server. A DNS maps numerical IP addresses to domain names and can
be used to identify network hosts by familiar names instead of the IP
addresses. To specify a DNS server, type the IP addresses in the text
field provided. Otherwise, leave the text field blank.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC, which is registered with the ISP. This setting allows
you to manually change the MAC address of the Wireless Broadband
Router's WAN interface to match the PC's MAC address provided to your
ISP for registration. You can enter the registered MAC address manually
by typing it in the boxes provided. Otherwise, connect only the PC with
the registered MAC address to the Wireless Broadband Router, then
click the “Clone your PC’s MAC Address”. (Default: Disabled)
– 42 –
Page 43

C
HAPTER
N
OTE
:
If you are unsure of the PC MAC address originally registered by
4
| Initial Configuration
Setup Wizard
your ISP, call your ISP and request to register a new MAC address for your
account. Register the default MAC address of the Wireless Broadband
Router.
STEP 3 - WAN
SETTINGS - STATIC IP
Configures a static IP for the WAN port.
Figure 16: Wizard Step 3 - WAN Settings - Static IP
The following items are displayed on this page:
◆ WAN Connection Type — Select the connection type for the WAN port
from the drop down list. (Default: DHCP)
◆ IP Address — The IP address of the Wireless Broadband Router. Valid
IP addresses consist of four decimal numbers, 0 to 255, separated by
periods.
◆ Subnet Mask — The mask that identifies the host address bits used for
routing to specific subnets.
◆ Default Gateway — The IP address of the gateway router for the
Wireless Broadband Router, which is used if the requested destination
address is not on the local subnet.
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server. A DNS maps numerical IP addresses to domain names and can
be used to identify network hosts by familiar names instead of the IP
addresses. To specify a DNS server, type the IP addresses in the text
field provided. Otherwise, leave the text field blank.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server.
– 43 –
Page 44

C
HAPTER
Setup Wizard
4
| Initial Configuration
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address. This setting allows you to manually change the MAC address
of the Wireless Broadband Router's WAN interface to match the PC's
MAC address provided to your ISP for registration. You can enter the
registered MAC address manually by typing it in the boxes provided.
Otherwise, connect only the PC with the registered MAC address to the
Wireless Broadband Router, then click the “Clone your PC’s MAC
Address” (Default: Disable)
STEP 3 - WAN
SETTINGS - PPPOE
Enable the Wireless Broadband Router IP address to be assigned
automatically from an Internet service provider (ISP) through an ADSL
modem using Point-to-Point Protocol over Ethernet (PPPoE).
Figure 17: Wizard Step 3 - WAN Settings - PPPoE
The following items are displayed on this page:
◆ User Name — Sets the PPPoE user name for the WAN port.
(Default: pppoe_user; Range: 1~32 characters)
◆ Password — Sets a PPPoE password for the WAN port.
(Default: pppoe_password; Range: 1~32 characters)
◆ Verify Password — Prompts you to re-enter your chosen password.
◆ Operation Mode — Enables and configures the keep alive time and
configures the on-demand idle time.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
provided. Otherwise, connect only the PC with the registered MAC
– 44 –
Page 45

C
HAPTER
4
| Initial Configuration
Setup Wizard
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
STEP 3 - WAN
S
ETTINGS - PPTP
Enables the Point-to-Point Tunneling Protocol (PPTP) for implementing
virtual private networks. The service is provided in many European
countries.
Figure 18: Wizard Step 3 - WAN Settings - PPTP
The following items are displayed on this page:
◆ Server IP — Sets the PPTP server IP Address. (Default: pptp_server)
◆ User Name — Sets the PPTP user name for the WAN port.
(Default: pptp_user; Range: 1~32 characters)
◆ Password — Sets a PPTP password for the WAN port. (Default:
pptp_password; Range: 1~32 characters)
◆ Verify Password — Prompts you to re-enter your chosen password.
◆ Address Mode — Sets a PPTP network mode. (Default: Static)
◆ IP Address — Sets the static IP address. (Default: 0.0.0.0, available
when PPTP Network Mode is set to static IP.)
◆ Subnet Mask — Sets the static IP subnet mask. (Default:
255.255.255.0, available when PPTP Network Mode is set to static IP.)
◆ Default Gateway — The IP address of a router that is used when the
requested destination IP address is not on the local subnet.
– 45 –
Page 46

C
HAPTER
Setup Wizard
4
| Initial Configuration
◆ Operation Mode — Enables and configures the keep alive time.
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server. A DNS maps numerical IP addresses to domain names and can
be used to identify network hosts by familiar names instead of the IP
addresses. To specify a DNS server, type the IP addresses in the text
field provided. Otherwise, leave the text field blank.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
provided. Otherwise, connect only the PC with the registered MAC
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
STEP 4 - WIRELESS
SECURITY
The Step 4 page of the Wizard configures the wireless network name and
security options.
Figure 19: Wizard Step 4 - Wireless Security
The following items are displayed on this page:
◆ Network Name (SSID) — The name of the wireless network service
provided by the Wireless Broadband Router. Clients that want to
connect to the network must set their SSID to the same as that of the
Wireless Broadband Router. (Default: “SMCWBR14S-N4_AP”; Range: 132 characters)
– 46 –
Page 47

C
HAPTER
4
| Initial Configuration
Setup Wizard
◆ Broadcast Network Name (SSID) — By default, the Wireless
Broadband Router always broadcasts the SSID in its beacon signal.
Disabling the SSID broadcast increases security of the network because
wireless clients need to already know the SSID before attempting to
connect. (Default: Enabled)
◆ AP Isolation — The Wireless Broadband Router will isolate
communincation between all clients in order to protect them. Normally
for users who are at hotspots. (Default: Disabled)
◆ BSSID — The identifier (MAC address) of the Wireless Broadband
Router in the Basic Service Set (BSS) network.
◆ Security Mode — Specifies the security mode for the SSID. Select the
security method and then configure the required parameters. For more
information, see “WLAN Security” on page 69. (Options: Disabled,
Open, Shared, WEP-AUTO, WPA-PSK, WPA2-PSK, WPA-PSK_WPA2-PSK,
WPA, WPA2, WPA1_WPA2, 802.1X; Default: Disabled)
N
OTE
:
To keep your wireless network protected and secure, you should
implement the highest security possible. For small networks, it is
recommended to select WPA2-PSK using AES encryption as the most
secure option. However, if you have older wireless devices in the network
that do not support AES encryption, select TKIP as the encryption
algorithm.
◆ Access Policy — The Wireless Broadband Router provides a MAC
address filtering facility. The access policy can be set to allow or reject
specific station MAC addresses. This feature can be used to connect
known wireless devices that may not be able to support the configured
security mode.
◆ Add a station MAC — Enter the MAC address of the station that you
want to filter. MAC addresses must be entered in the format
xx:xx:xx:xx:xx:xx.
COMPLETION After completion of the Wizard, the screen returns to the Home Page.
– 47 –
Page 48

C
HAPTER
4
Setup Wizard
| Initial Configuration
– 48 –
Page 49

S
ECTION
WEB CONFIGURATION
This section provides details on configuring the Wireless Broadband Router
using the web browser interface.
This section includes these chapters:
◆ “Operation Mode” on page 51
◆ “Internet Settings” on page 55
◆ “Wireless Configuration” on page 67
◆ “Firewall Configuration” on page 91
II
◆ “Administration Settings” on page 99
– 49 –
Page 50

S
ECTION
| Web Configuration
– 50 –
Page 51

5 OPERATION MODE
The Wireless Broadband Router offers a user-friendly web-based
management interface for the configuration of all the unit’s features. Any
PC directly attached to the unit can access the management interface using
a web browser, such as Internet Explorer (version 6.0 or above).
The following sections are contained in this chapter:
◆ “Logging In” on page 52
◆ “Operation Mode” on page 54
– 51 –
Page 52

C
HAPTER
Logging In
5
| Operation Mode
LOGGING IN
It is recommended to make initial configuration changes by connecting a
PC directly to one of the Wireless Broadband Router's LAN ports. The
Wireless Broadband Router has a default IP address of 192.168.2.1 and a
subnet mask of 255.255.255.0. If your PC is set to “Obtain an IP address
automatically” (that is, set as a DHCP client), you can connect immediately
to the web interface. Otherwise, you must set your PC IP address to be on
the same subnet as the Wireless Broadband Router (that is, the PC and
Wireless Broadband Router addresses must both start 192.168.2.x).
To access the configuration menu, follow these steps:
1. Use your web browser to connect to the management interface using
the default IP address of 192.168.2.1.
2. Log into the Wireless Broadband Router management interface by
entering the default user name “admin” and password “smcadmin,”
then click Login.
N
OTE
:
It is strongly recommended to change the default user name and
password the first time you access the web interface. For information on
changing user names and passwords, see “Administration Settings” on
page 99.
Figure 20: Logging On
– 52 –
Page 53
C
HAPTER
5
| Operation Mode
Logging In
The home page displays the main menu items at the top of the screen and
the Setup Wizard. See “Setup Wizard” on page 40.
Figure 21: Home Page
N
OTE
:
The displayed pages and settings may differ depending on whether
the unit is in Gateway or Bridge Mode. See “Operation Mode” on page 54.
– 53 –
Page 54

C
HAPTER
Operation Mode
5
| Operation Mode
OPERATION MODE
The Operation Mode Configuration page allows you to set up the mode
suitable for your network environment.
Figure 22: Operation Mode (Gateway)
◆ Bridge Mode — An access point mode that extends a wired LAN to
wireless clients.
◆ Gateway Mode — Normal gateway mode that connects a wired LAN
and wireless clients to an Internet access device, such as a cable or
DSL modem. This is the factory set default mode.
– 54 –
Page 55

6 INTERNET SETTINGS
The Internet Settings pages allow you to manage basic system
configuration settings. It includes the following sections:
◆ “WAN Setting” on page 55
■
“DHCP” on page 55
■
“Static IP” on page 57
■
“PPPoE” on page 58
■
“PPTP” on page 59
◆ “LAN Setting” on page 61
◆ “Advanced Routing” on page 63
WAN SETTING
N
OTE
:
In Bridge mode, the Wireless Broadband Router’s Internet Settings
options are significantly reduced, with only LAN Settings and the Client List
being available to the user.
The WAN Setting page specifies the Internet connection parameters. Click
on “Internet Settings” followed by “WAN”.
◆ WAN Connection Type — By default, the access point WAN port is
configured with DHCP enabled. After you have network access to the
access point, you can use the web browser interface to modify the
initial IP configuration, if needed. The options are Static IP, DHCP (cable
modem), PPPoE (ADSL), and PPTP. Each option changes the parameters
displayed below it. (Default: DHCP).
DHCP Enables Dynamic Host Configuration Protocol (DHCP) for the WAN port.
This setting allows the Wireless Broadband Router to automatically obtain
an IP address from a DHCP server normally operated by the Internet
Service Provider (ISP).
– 55 –
Page 56

C
HAPTER
WAN Setting
6
| Internet Settings
Figure 23: DHCP Configuration
The following items are displayed on this page:
◆ Hostname (Optional) — The hostname of the DHCP client.
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server. A DNS maps numerical IP addresses to domain names and can
be used to identify network hosts by familiar names instead of the IP
addresses. To specify a DNS server, type the IP addresses in the text
field provided. Otherwise, leave the text field blank.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
provided. Otherwise, connect only the PC with the registered MAC
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
N
OTE
:
If you are unsure of the PC MAC address originally registered by
your ISP, call your ISP and request to register a new MAC address for your
account. Register the default MAC address of the Wireless Broadband
Router.
– 56 –
Page 57

STATIC IP Configures a static IP for the WAN port.
Figure 24: Static IP Configuration
C
HAPTER
6
| Internet Settings
WAN Setting
◆ IP Address — The IP address of the Wireless Broadband Router. Valid
IP addresses consist of four decimal numbers, 0 to 255, separated by
periods.
◆ Subnet Mask — The mask that identifies the host address bits used for
routing to specific subnets.
◆ Default Gateway — The IP address of the gateway router for the
Wireless Broadband Router, which is used if the requested destination
address is not on the local subnet.
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server on the network. A DNS maps numerical IP addresses to domain
names and can be used to identify network hosts by familiar names
instead of the IP addresses. If you have one or more DNS servers
located on the local network, type the IP addresses in the text fields
provided. Otherwise, leave the addresses as all zeros (0.0.0.0).
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server on the network.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
– 57 –
Page 58

C
HAPTER
WAN Setting
6
| Internet Settings
provided. Otherwise, connect only the PC with the registered MAC
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
PPPOE Enables the Wireless Broadband Router IP address to be assigned
automatically from an Internet service provider (ISP) through an ADSL
modem using Point-to-Point Protocol over Ethernet (PPPoE).
Figure 25: PPPoE Configuration
◆ PPPoE User Name — Sets the PPPoE user name for the WAN port.
(Default: pppoe_user; Range: 1~32 characters)
◆ PPPoE Password — Sets a PPPoE password for the WAN port.
(Default: pppoe_password; Range: 1~32 characters)
◆ Verify Password — Prompts you to re-enter your chosen password.
◆ Operation Mode — Selects the operation mode as Keep Alive, On
Demand or Manual. (Default: Keep Alive)
■
Keep Alive Mode: The Wireless Broadband Router will periodically
check your Internet connection and automatically re-establish your
connection when disconnected. (Default: 60 seconds)
– 58 –
Page 59

C
HAPTER
■
On Demand Mode: The maximum length of inactive time the unit
6
| Internet Settings
WAN Setting
will stay connected to the DSL service provider before
disconnecting. (Default: 5 minutes)
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
provided. Otherwise, connect only the PC with the registered MAC
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
PPTP Enables the Point-to-Point Tunneling Protocol (PPTP) for implementing
virtual private networks. The service is provided in many European
countries.
Figure 26: PPTP Configuration
◆ Server IP — Sets a PPTP server IP Address. (Default: pptp_server)
◆ User Name — Sets the PPTP user name for the WAN port. (Default:
pptp_user; Range: 1~32 characters)
– 59 –
Page 60

C
HAPTER
WAN Setting
6
| Internet Settings
◆ Password — Sets a PPTP password for the WAN port. (Default:
pptp_password; Range: 1~32 characters)
◆ Verify Password — Prompts you to re-enter your chosen password.
◆ Address Mode — Sets a PPTP network mode. (Default: Static)
◆ IP Address — Sets the static IP address. (Default: 0.0.0.0, available
when PPTP Network Mode is set to static IP.)
◆ Subnet Mask — Sets the static IP subnet mask. (Default:
255.255.255.0, available when PPTP Network Mode is set to static IP.)
◆ Default Gateway — The IP address of the gateway router for the
Wireless Broadband Router, which is used if the requested destination
address is not on the local subnet.
◆ Operation Mode — Selects the operation mode as Keep Alive, or
Manual. (Default: Keep Alive)
■
Keep Alive Mode: The Wireless Broadband Router will periodically
check your Internet connection and automatically re-establish your
connection when disconnected. (Default: 60 seconds)
■
Manual Mode: The unit will remain connected to the Internet
without disconnecting.
◆ Primary DNS Server — The IP address of the Primary Domain Name
Server. A DNS maps numerical IP addresses to domain names and can
be used to identify network hosts by familiar names instead of the IP
addresses. To specify a DNS server, type the IP addresses in the text
field provided. Otherwise, leave the text field blank.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server.
◆ MAC Clone — Some ISPs limit Internet connections to a specified MAC
address of one PC. This setting allows you to manually change the MAC
address of the Wireless Broadband Router's WAN interface to match the
PC's MAC address provided to your ISP for registration. You can enter
the registered MAC address manually by typing it in the boxes
provided. Otherwise, connect only the PC with the registered MAC
address to the Wireless Broadband Router, then click the “Clone your
PC’s MAC Address” (Default: Disable)
– 60 –
Page 61

LAN SETTING
C
HAPTER
6
| Internet Settings
LAN Setting
The Wireless Broadband Router must have a valid IP address for
management using a web browser and to support other features. The unit
has a default IP address of 192.168.2.1. You can use this IP address or
assign another address that is compatible with your existing local network.
Click on “Internet Settings” followed by “LAN.”
Figure 27: LAN Configuration
◆ LAN IP Address — Valid IP addresses consist of four decimal
numbers, 0 to 255, separated by periods. The default setting is
192.168.2.1.
◆ Subnet Mask — Indicate the local subnet mask. (Default:
255.255.255.0.)
– 61 –
Page 62

C
HAPTER
LAN Setting
6
| Internet Settings
◆ MAC Address — The shared physical layer address for the Wireless
Broadband Router’s LAN ports.
◆ DHCP Server — Enable this feature to assign IP settings to wired and
wireless clients connected to the Gateway Router. The IP address,
subnet mask, default gateway, and Domain Name Server (DNS)
address are dynamically assigned to clients. (Options: Enable, Disable;
Default: Enable)
◆ Start/End IP Address — Specify the start and end IP addresses of a
range that the DHCP server can allocate to DHCP clients. Note that the
address pool range is always in the same subnet as the unit’s IP
setting. The maximum clients that the unit can support is 253.
◆ Primary DNS Server — The IP address of Domain Name Servers on
the network. A DNS maps numerical IP addresses to domain names
and can be used to identify network hosts by familiar names instead of
the IP addresses.
◆ Secondary DNS Server — The IP address of the Secondary Domain
Name Server on the network.
◆ Default Gateway — The default gateway is the IP address of the
router for the Wireless Broadband Router, which is used if the
requested destination address is not on the local subnet.
◆ Lease Time — Select a time limit for the use of an IP address from the
IP pool. When the time limit expires, the client has to request a new IP
address. The lease time is expressed in seconds. (Options: Forever, Two
weeks, One week, Two days, One day, Half day, Two hours, One hour,
Half hour; Default: One week)
◆ Statically Assigned — Up to three devices with specific MAC
addresses can be assigned static IP addresses. That is, the DHCP server
always assigns these devices the same IP addresses.
◆ LLTD — Link Layer Topology Discovery (LLTD) is a Microsoft proprietary
discovery protocol which can be used for both wired and wireless
networks. (Options: Disable/Enable, Default: Enable)
◆ IGMP Proxy — Enables IGMP proxy on the Wireless Broadband Router.
(Options: Disable/Enable, Default: Disable)
◆ UPNP — Allows the device to advertise its UPnP capabilities. (Default:
Enable)
◆ Router Advertisement — Enables the sending and receiving of
routing advertisements to discover the existence of neighboring
routers. (Options: Disable/Enable, Default: Disable)
◆ PPPoE Relay — When enabled, the Wireless Broadband Router will
forward PPPoE messages to clients. Clients are then able to connect to
the PPPoE service through the WAN port. (Options: Disable/Enable,
Default: Disable)
– 62 –
Page 63

ADVANCED ROUTING
C
HAPTER
◆ DNS Proxy — Enables DNS proxy on the LAN port. DNS Proxy receives
DNS queries from the local network and forwards them to an Internet
DNS server. (Default: Enable)
Routing setup allows a manual method to set up routing between
networks. The network administrator configures static routes by entering
routes directly into the routing table. Static routing has the advantage of
being predictable and easy to configure.
6
| Internet Settings
Advanced Routing
ADVANCED ROUTING
SETTINGS
This screen is used to manually configure static routes to other IP
networks, subnetworks, or hosts. Click “Internet Settings” followed by
“Advanced Routing”. (Maximum 32 entries are allowed.)
Figure 28: Advanced Routing (Gateway Mode)
– 63 –
Page 64

C
HAPTER
Advanced Routing
6
| Internet Settings
ROUTING TABLE This page displays the information necessary to forward a packet along the
◆ Destination — A destination network or specific host to which packets
can be routed.
◆ Type — Defines the type of destination. (Options: Host/Net, Default:
Host)
◆ Gateway — The IP address of the router at the next hop to which
matching frames are forwarded.
◆ Interface — The selected interface to which a static routing subnet is
to be applied.
◆ Comment — Enters a useful comment to help identify this route.
best path toward its destination. Each packet contains information about
its origin and destination. When a packet is received, a network device
examines the packet and matches it to the routing table entry providing
the best match for its destination. The table then provides the device with
instructions for sending the packet to the next hop on its route across the
network.
N
OTE
:
The Routing Table is only available when the Wireless Broadband
Router is set to Gateway Mode.
◆ Destination — Displays all destination networks or specific hosts to
which packets can be routed.
◆ Netmask — Displays the subnetwork associated with the destination.
◆ Gateway — Displays the IP address of the router at the next hop to
which matching frames are forwarded.
◆ Flags — Flags – Possible flags identify as below
■
0: reject route
■
1: route is up
■
3: route is up, use gateway
■
5: route is up, target is a host
■
7: route is up, use gateway, target is a host
◆ Metric — A number used to indicate the cost of the route so that the
best route, among potentially multiple routes to the same destination,
can be selected.
◆ Ref — Number of references to this route.
– 64 –
Page 65

C
HAPTER
6
| Internet Settings
Advanced Routing
◆ Use — Count of lookups for the route.
◆ Interface — Interface to which packets for this route will be sent.
◆ Comment — Displays a useful comment to identify the routing rules.
DYNAMIC ROUTE ◆ The Wireless Broadband Router supports RIP 1 and RIP 2 dynamic
routing protocol. Routing Information Protocol (RIP) is the most widely
used method for dynamically maintaining routing tables. RIP uses a
distance vector-based approach to routing. Routes are chosen to
minimize the distance vector, or hop count, which serves as a rough
estimate of transmission cost. Each router broadcasts its advertisement
every 30 seconds, together with any updates to its routing table. This
allows all routers on the network to build consistent tables of next hop
links which lead to relevant subnets.
◆ RIP — Enables or disable the RIP protocol for the WAN or LAN
interface. (Options: Disable/v1/v2, Default: Disable)
– 65 –
Page 66

C
HAPTER
6
| Internet Settings
Advanced Routing
– 66 –
Page 67

7 WIRELESS CONFIGURATION
The wireless settings section displays configuration settings for the access
point functionality of the Wireless Broadband Router. It includes the
following sections:
◆ “Basic Settings” on page 67
◆ “WLAN Security” on page 69
◆ “Advanced Settings” on page 76
◆ “Wireless Distribution System (WDS)” on page 84
◆ “Wi-Fi Protected Setup (WPS)” on page 88
◆ “Station List” on page 90
BASIC SETTINGS
The IEEE 802.11n interface includes configuration options for radio signal
characteristics and wireless security features.
The Wireless Broadband Router’s radio can operate in six modes, mixed
802.11b/g/n, mixed 802.11b/g, mixed 802.11g/n, 802.11n only, 802.11b
only, or 802.11g only. Note that 802.11g is backward compatible with
802.11b, and 802.11n is backward compatible with 802.11b/g at slower
data transmit rates.
N
OTE
:
The radio channel settings for the access point are limited by local
regulations, which determine the number of channels that are available.
The Basic Settings page allows you to configure the wireless network name
(Service Set Identifier or SSID) and set the wireless security method.
Click on “Wireless Settings,” followed by “Basic.”
– 67 –
Page 68

C
HAPTER
Basic Settings
7
| Wireless Configuration
Figure 29: Basic Settings
The following items are displayed on this page:
◆ Network Name (SSID) — The name of the wireless network service
provided by the Wireless Broadband Router. Clients that want to
connect to the network must set their SSID to the same as that of the
Wireless Broadband Router. (Default: “SMCWBR14S-N4_AP”; Range: 132 characters)
◆ Broadcast Network Name (SSID) — By default, the Wireless
Broadband Router always broadcasts the SSID in its beacon signal.
Disabling the SSID broadcast increases security of the network because
wireless clients need to already know the SSID before attempting to
connect. (Default: Enabled)
◆ AP Isolation — The Wireless Broadband Router will isolate
communincation between all clients in order to protect them. Normally
for users who are at hotspots. (Default: Disabled)
◆ BSSID — The identifier (MAC address) of the Wireless Broadband
Router in the Basic Service Set (BSS) network.
◆ Security Mode — The wireless network authentication and encryption
method. For a complete description, see “WLAN Security” on page 69.
(Default: Disabled)
– 68 –
Page 69

WLAN SECURITY
C
HAPTER
7
| Wireless Configuration
WLAN Security
◆ Access Policy — The Wireless Broadband Router provides a MAC
address filtering facility. The access policy can be set to allow or reject
specific station MAC addresses. This feature can be used to connect
known wireless devices that may not be able to support the configured
security mode.
◆ Add a station MAC — Enter the MAC address of the station that you
want to filter. MAC addresses must be entered in the format
xx:xx:xx:xx:xx:xx.
The Wireless Broadband Router’s wireless interface is configured by default
as an “open system,” which broadcasts a beacon signal including the
configured SSID. Wireless clients with a configured SSID of “ANY” can read
the SSID from the beacon, and automatically set their SSID to allow
immediate connection to the wireless network.
To implement wireless network security, you have to employ one or both of
the following functions:
◆ Authentication — It must be verified that clients attempting to
connect to the network are authorized users.
◆ Traffic Encryption — Data passing between the unit and clients must
be protected from interception and eavesdropping.
The Wireless Broadband Router supports supports ten different security
mechanisms that provide various levels of authentication and encryption
depending on the requirements of the network.
Click on “Wireless Settings,” followed by “Basic”.
Figure 30: Security Mode Options
The supported security mechanisms and their configuration parameters are
described in the following sections:
◆ OPEN, SHARED, WEP-AUTO — See “Wired Equivalent Privacy (WEP)”
on page 70
– 69 –
Page 70

C
HAPTER
WLAN Security
7
| Wireless Configuration
◆ WPA-PSK, WPA2-PSK, WPA-PSK_WPA2-PSK — See “WPA Pre-
Shared Key” on page 71
◆ WPA, WPA2, WPA1_WPA2 — See “WPA Enterprise Mode” on
page 72
◆ 802.1X — See “IEEE 802.1X and RADIUS” on page 74
WIRED EQUIVALENT
PRIVACY (WEP)
WEP provides a basic level of security, preventing unauthorized access to
the network, and encrypting data transmitted between wireless clients and
an access point. WEP uses static shared keys (fixed-length hexadecimal or
alphanumeric strings) that are manually distributed to all clients that want
to use the network.
When you select to use WEP, be sure to define at least one static WEP key
for user authentication or data encryption. Also, be sure that the WEP
shared keys are the same for each client in the wireless network.
Figure 31: Security Mode - WEP
Security Mode — Configures the WEP security mode used by clients.
When using WEP, be sure to define at least one static WEP key for the
Wireless Broadband Router and all its clients. (Default: Disable)
◆ OPEN — Open-system authentication accepts any client attempting to
connect the Wireless Broadband Router without verifying its identity. In
this mode the default data encryption type is “WEP.”
◆ SHARED — The shared-key security uses a WEP key to authenticate
clients connecting to the network and for data encryption.
◆ WEP-AUTO — Allows wireless clients to connect to the network using
Open-WEP (uses WEP for encryption only) or Shared-WEP (uses WEP
for authentication and encryption).
◆ Encrypt Type — Selects WEP for data encryption (OPEN mode only).
– 70 –
Page 71

C
HAPTER
7
| Wireless Configuration
WLAN Security
◆ Default Key — Selects the WEP key number to use for authentication
or data encryption. If wireless clients have all four WEP keys configured
to the same values, you can change the encryption key to any of the
settings without having to update the client keys. (Default: 1;
Range: 1~4)
◆ WEP Keys 1 ~ 4 — Sets WEP key values. The user must first select
ASCII or hexadecimal keys. Each WEP key has an index number. Enter
key values that match the key type and length settings. Enter 5
alphanumeric characters or 10 hexadecimal digits for 64-bit keys, or
enter 13 alphanumeric characters or 26 hexadecimal digits for 128-bit
keys. (Default: Hex, no preset value)
WPA PRE-SHARED
KEY
Wi-Fi Protected Access (WPA) was introduced as an interim solution for the
vulnerability of WEP pending the adoption of a more robust wireless
security standard. WPA2 includes the complete wireless security standard,
but also offers backward compatibility with WPA. Both WPA and WPA2
provide an “enterprise” and “personal” mode of operation.
For small home or office networks, WPA and WPA2 provide a simple
“personal” operating mode that uses just a pre-shared key for network
access. The WPA Pre-Shared Key (WPA-PSK) mode uses a common
password phrase for user authentication that is manually entered on the
access point and all wireless clients. Data encryption keys are
automatically generated by the access point and distributed to all clients
connected to the network.
Figure 32: Security Mode - WPA-PSK
Security Mode — Configures the WPA-PSK and WPA2-PSK security modes
used by clients. When using WPA-PSK or WPA2-PSK, be sure to define the
shared key for the Wireless Broadband Router and all its clients.
(Default: Disable)
◆ WPA-PSK — Clients using WPA with a Pre-shared Key are accepted for
authentication. The default data encryption type for WPA is TKIP.
◆ WPA2-PSK — Clients using WPA2 with a Pre-shared Key are accepted
for authentication. The default data encryption type for WPA is AES.
◆ WPA-PSK_WPA2-PSK — Clients using WPA or WPA2 with a Pre-
shared Key are accepted for authentication. The default data encryption
type is TKIP/AES.
– 71 –
Page 72

C
HAPTER
WLAN Security
7
| Wireless Configuration
◆ WPA Algorithms — Selects the data encryption type to use. (Default
is determined by the Security Mode selected.)
■
TKIP — Uses Temporal Key Integrity Protocol (TKIP) keys for
encryption. WPA specifies TKIP as the data encryption method to
replace WEP. TKIP avoids the problems of WEP static keys by
dynamically changing data encryption keys.
■
AES — Uses Advanced Encryption Standard (AES) keys for
encryption. WPA2 uses AES Counter-Mode encryption with Cipher
Block Chaining Message Authentication Code (CBC-MAC) for
message integrity. The AES Counter-Mode/CBCMAC Protocol (AESCCMP) provides extremely robust data confidentiality using a 128bit key. Use of AES-CCMP encryption is specified as a standard
requirement for WPA2. Before implementing WPA2 in the network,
be sure client devices are upgraded to WPA2-compliant hardware.
■
TKIP/AES — Uses either TKIP or AES keys for encryption. WPA and
WPA2 mixed modes allow both WPA and WPA2 clients to associate
to a common SSID. In mixed mode, the unicast encryption type
(TKIP or AES) is negotiated for each client.
WPA ENTERPRISE
MODE
◆ Pass Phrase — The WPA Preshared Key can be input as an ASCII
string (an easy-to-remember form of letters and numbers that can
include spaces) or Hexadecimal format. (Range: 8~63 ASCII
characters, or exactly 64 Hexadecimal digits)
◆ Key Renewal Interval — Sets the time period for automatically
changing data encryption keys and redistributing them to all connected
clients. (Default: 3600 seconds)
Wi-Fi Protected Access (WPA) was introduced as an interim solution for the
vulnerability of WEP pending the adoption of a more robust wireless
security standard. WPA2 includes the complete wireless security standard,
but also offers backward compatibility with WPA. Both WPA and WPA2
provide an “enterprise” and “personal” mode of operation.
For enterprise deployment, WPA and WPA2 use IEEE 802.1X for user
authentication and require a RADIUS authentication server to be
configured on the wired network. Data encryption keys are automatically
generated and distributed to all clients connected to the network.
– 72 –
Page 73

Figure 33: Security Mode - WPA
C
HAPTER
7
| Wireless Configuration
WLAN Security
Security Mode — Configures the WPA and WPA2 security modes used by
clients. When using WPA or WPA2, be sure there is a RADIUS server in the
connected wired network, and that the RADIUS settings are configured.
See “IEEE 802.1X and RADIUS” on page 74 for more information.
(Default: Disable)
◆ WPA — Clients using WPA with an 802.1X authentication method are
accepted for authentication. The default data encryption type for WPA
is TKIP.
◆ WPA2 — Clients using WPA2 with an 802.1X authentication method
are accepted for authentication. The default data encryption type for
WPA is AES.
◆ WPA1_WPA2 — Clients using WPA or WPA2 with an 802.1X
authentication method are accepted for authentication. The default
data encryption type is TKIP/AES.
◆ WPA Algorithms — Selects the data encryption type to use. (Default
is determined by the Security Mode selected.)
■
TKIP — Uses Temporal Key Integrity Protocol (TKIP) keys for
encryption. WPA specifies TKIP as the data encryption method to
replace WEP. TKIP avoids the problems of WEP static keys by
dynamically changing data encryption keys.
■
AES — Uses Advanced Encryption Standard (AES) keys for
encryption. WPA2 uses AES Counter-Mode encryption with Cipher
Block Chaining Message Authentication Code (CBC-MAC) for
message integrity. The AES Counter-Mode/CBCMAC Protocol (AESCCMP) provides extremely robust data confidentiality using a 128-
– 73 –
Page 74

C
HAPTER
WLAN Security
7
| Wireless Configuration
bit key. Use of AES-CCMP encryption is specified as a standard
requirement for WPA2. Before implementing WPA2 in the network,
be sure client devices are upgraded to WPA2-compliant hardware.
■
TKIP/AES — Uses either TKIP or AES keys for encryption. WPA and
WPA2 mixed modes allow both WPA and WPA2 clients to associate
to a common SSID. In mixed mode, the unicast encryption type
(TKIP or AES) is negotiated for each client.
◆ Key Renewal Interval — Sets the time period for automatically
changing data encryption keys and redistributing them to all connected
clients. (Default: 3600 seconds)
◆ PMK Cache Period — WPA2 provides fast roaming for authenticated
clients by retaining keys and other security information in a cache, so
that if a client roams away from an access point and then returns
reauthentication is not required. This parameter sets the time for
deleting the cached WPA2 Pairwise Master Key (PMK) security
information. (Default: 10 minutes)
IEEE 802.1X AND
RADIUS
◆ Pre-Authentication — When using WPA2, pre-authentication can be
enabled that allows clients to roam to another access point and be
quickly associated without performing full 802.1X authentication.
(Default: Disabled)
IEEE 802.1X is a standard framework for network access control that uses
a central RADIUS server for user authentication. This control feature
prevents unauthorized access to the network by requiring an 802.1X client
application to submit user credentials for authentication. The 802.1X
standard uses the Extensible Authentication Protocol (EAP) to pass user
credentials (either digital certificates, user names and passwords, or other)
from the client to the RADIUS server. Client authentication is then verified
on the RADIUS server before the client can access the network.
Remote Authentication Dial-in User Service (RADIUS) is an authentication
protocol that uses software running on a central server to control access to
RADIUS-aware devices on the network. An authentication server contains a
database of user credentials for each user that requires access to the
network.
The WPA and WPA2 enterprise security modes use 802.1X as the method
of user authentication. IEEE 802.1X can also be enabled on its own as a
security mode for user authentication. When 802.1X is used, a RADIUS
server must be configured and be available on the connected wired
network.
N
OTE
:
This guide assumes that you have already configured RADIUS
server(s) to support the access point. Configuration of RADIUS server
software is beyond the scope of this guide, refer to the documentation
provided with the RADIUS server software.
– 74 –
Page 75

C
HAPTER
Figure 34: Security Mode - 802.1X
7
| Wireless Configuration
WLAN Security
Security Mode — Configures the 802.1X security mode used by clients.
When using 802.1X, either with WPA/WPA2 or on its own, be sure there is
a configured RADIUS server in the connected wired network.
(Default: Disable)
802.1X WEP: Selects WEP keys for data encryption. When enabled, WEP
encryption keys are automatically generated by the RADIUS server and
distributed to all connected clients. (Default: Disabled)
RADIUS Server — Configures RADIUS server settings.
◆ IP Address — Specifies the IP address of the RADIUS server.
◆ Port — The User Datagram Protocol (UDP) port number used by the
RADIUS server for authentication messages. (Range: 1024-65535;
Default: 1812)
◆ Shared Secret — A shared text string used to encrypt messages
between the access point and the RADIUS server. Be sure that the
same text string is specified on the RADIUS server. Do not use blank
spaces in the string. (Maximum length: 20 characters)
◆ Session Timeout — Number of seconds the access point waits for a
reply from the RADIUS server before resending a request. (Range: 160 seconds; Default: 0)
◆ Idle Timeout — Sets the maximum time (in seconds) of client
inactivity before a session is terminated.
– 75 –
Page 76

C
HAPTER
Advanced Settings
7
| Wireless Configuration
ADVANCED SETTINGS
The Advanced Settings page includes additional parameters concerning the
wireless network, including HT Physical Mode, and Wi-Fi Multimedia
settings.
N
OTE
:
There are several variables to consider when selecting a radio mode
that make it fully functional. Simply selecting the mode you want is not
enough to ensure full compatibility for that mode. Information on these
variables may be found in the HT Physcial Mode Setting section.
WIRELESS NETWORK The Wireless Network section on the Wireless Settings Advanced page
includes basic radio parameters such as the working mode and operating
channel.
Figure 35: Advanced Settings — Wireless Network
The following items are displayed in this section on this page:
◆ Wireless On/Off — Enables or Disable the radio. (Default: Enable)
◆ Network Mode — Defines the radio operating mode. (Default: 11g/n
Mixed)
■
11b/g mixed: Both 802.11b and 802.11g clients can communicate
with the Wireless Broadband Router (up to 108 Mbps), but data
transmission rates may be slowed to compensate for 802.11b
clients. Any 802.11n clients will also be able to communicate with
the Wireless Broadband Router, but they will be limited to 802.11g
protocols and data transmission rates.
■
11b only: All 802.11b, 802.11g, and 802.11n clients will be able to
communicate with the Wireless Broadband Router, but the 802.11g
and 802.11n clients will be limited to 802.11b protocols and data
transmission rates (up to 11 Mbps).
– 76 –
Page 77

C
HAPTER
■
11g only: Both 802.11g and 802.11n clients will be able to
7
| Wireless Configuration
Advanced Settings
communicate with the Wireless Broadband Router, but the 802.11n
clients will be limited to 802.11g protocols and data transmission
rates (up to 54 Mbps). Any 802.11b clients will not be able to
communicate with the Wireless Broadband Router.
■
11n only: Only 802.11n clients will be able to communicate with
the Wireless Broadband Router (up to 150 Mbps).
■
11g/n mixed: Both 802.11g and 802.11n clients can communicate
with the Wireless Broadband Router (up to 150 Mbps), but data
transmission rates may be slowed to compensate for 802.11g
clients.
■
11b/g/n Mixed: All 802.11b/g/n clients can communicate with the
Wireless Broadband Router (up to 150 Mbps), but data transmission
rates may be slowed to compensate for 802.11b/g clients.
◆ Frequency (Channel) — The radio channel that the Wireless
Broadband Router uses to communicate with wireless clients. When
multiple access points are deployed in the same area, set the channel
on neighboring access points at least five channels apart to avoid
interference with each other. For example, you can deploy up to three
access points in the same area using channels 1, 6, 11. Note that
wireless clients automatically set the channel to the same as that used
by the Wireless Broadband Router to which it is linked. Selecting Auto
Select enables the Wireless Broadband Router to automatically select
an unoccupied radio channel. (Default: AutoSelect)
HT PHYSICAL MODE
SETTINGS
The HT Physical Mode section on the Wireless Settings Advanced page
includes additional parameters for 802.11n operation.
Figure 36: HT Physical Mode Settings
– 77 –
Page 78

C
HAPTER
Advanced Settings
7
| Wireless Configuration
The following items are displayed in this section on this page:
◆ HT Channel Bandwidth — The Wireless Broadband Router provides a
channel bandwidth of 40 MHz by default giving an 802.11g connection
speed of 108 Mbps (sometimes referred to as Turbo Mode) and a
802.11n connection speed of up to 150 Mbps. Setting the HT Channel
Bandwidth to 20 MHz slows connection speed for 802.11g and 802.11n
to 54 Mbps and 74 Mbps respectively and ensures backward compliance
for slower 802.11b devices. (Default: 20MHz)
◆ Guard Interval — The guard interval between symbols helps receivers
overcome the effects of multipath delays. When you add a guard time,
the back portion of useful signal time is copied and appended to the
front. (Default: Auto)
◆ MCS — The Modulation and Coding Scheme (MCS) is a value that
determines the modulation, coding and number of spatial channels.
(Options: value [range] = 0~7 (1 Tx Stream), 8~15 (2 TxStream), 32
and auto (33). Default: auto)
◆ Reverse Direction Grant (RDG) — When Reverse Direction Grant is
enabled, the Wireless Broadband Router can reduce the transmitted
data packet collision by using the reverse direction protocol. During
TXOP (Transmission Opportunity) period, the receiver could use
remaining transmission time to transmit data to a sender. The RDG
improves transmission performance and scalability in a wireless
environment.
◆ Extension Channel — When 20/40MHz channel bandwidth has been
set, the extension channel option will be enabled. The extension
channel will allow you to get extra bandwidth. (Options: 2417MHz/
Channel 2, 2457MHz/Channel 10. Default: AutoSelect.)
◆ Aggregate MSDU (A-MSDU) — This option enables Mac Service Data
Unit (MSDU) aggregation. (Default: Disable)
◆ Auto Block ACK — Select to block ACK (Acknowledge Number) or not
during data transferring.
◆ Decline BA Request — Select to reject peer BA-Request or not.
– 78 –
Page 79

C
HAPTER
7
| Wireless Configuration
Advanced Settings
ADVANCED WIRELESS The Advanced Wireless section on the Wireless Settings Advanced page
includes additional radio parameters.
Figure 37: Advanced Wireless Settings
The following items are displayed in this section on this page:
◆ BG Protection Mode — Enables a backward compatible protection
mechanism for 802.11b clients. There are three modes: (Default: Auto)
■
Auto — The unit enables its protection mechanism for 802.11b
clients when they are detected in the network. When 802.11b
clients are not detected, the protection mechanism is disabled.
■
On — Forces the unit to always use protection for 802.11b clients,
whether they are detected in the network or not. Note that enabling
b/g Protection can slow throughput for 802.11g/n clients by as
much as 50%.
■
Off — Forces the unit to never use protection for 802.11b clients.
This prevents 802.11b clients from connecting to the network.
◆ Beacon Interval — The rate at which beacon signals are transmitted
from the access point. The beacon signals allow wireless clients to
maintain contact with the access point. They may also carry powermanagement information. (Range: 20-999 TUs; Default: 100 TUs)
◆ Data Beacon Rate (DTIM) — The rate at which stations in sleep
mode must wake up to receive broadcast/multicast transmissions.
Known also as the Delivery Traffic Indication Map (DTIM) interval, it
indicates how often the MAC layer forwards broadcast/multicast traffic,
which is necessary to wake up stations that are using Power Save
mode. The default value of one beacon indicates that the access point
will save all broadcast/multicast frames for the Basic Service Set (BSS)
– 79 –
Page 80

C
HAPTER
Advanced Settings
7
| Wireless Configuration
and forward them after every beacon. Using smaller DTIM intervals
delivers broadcast/multicast frames in a more timely manner, causing
stations in Power Save mode to wake up more often and drain power
faster. Using higher DTIM values reduces the power used by stations in
Power Save mode, but delays the transmission of broadcast/multicast
frames. (Range: 1-255 beacons; Default: 1 beacon)
◆ Fragmentation Threshold – Configures the minimum packet size that
can be fragmented when passing through the access point.
Fragmentation of the PDUs (Package Data Unit) can increase the
reliability of transmissions because it increases the probability of a
successful transmission due to smaller frame size. If there is significant
interference present, or collisions due to high network utilization, try
setting the fragment size to send smaller fragments. This will speed up
the retransmission of smaller frames. However, it is more efficient to
set the fragment size larger if very little or no interference is present
because it requires overhead to send multiple frames. (Range: 2562346 bytes; Default: 2346 bytes)
◆ RTS Threshold — Sets the packet size threshold at which a Request to
Send (RTS) signal must be sent to a receiving station prior to the
sending station starting communications. The access point sends RTS
frames to a receiving station to negotiate the sending of a data frame.
After receiving an RTS frame, the station sends a CTS (clear to send)
frame to notify the sending station that it can start sending data.
If the RTS threshold is set to 0, the access point always sends RTS
signals. If set to 2347, the access point never sends RTS signals. If set
to any other value, and the packet size equals or exceeds the RTS
threshold, the RTS/CTS (Request to Send / Clear to Send) mechanism
will be enabled.
The access points contending for the medium may not be aware of each
other. The RTS/CTS mechanism can solve this “Hidden Node Problem.”
(Range: 1-2347 bytes: Default: 2347 bytes)
◆ Short Preamble — Sets the length of the signal preamble that is used
at the start of a data transmission. Use a short preamble (96
microseconds) to increase data throughput when it is supported by all
connected 802.11g clients. Use a long preamble (192 microseconds) to
ensure all 802.11b clients can connect to the network.
(Default: Disabled)
◆ Short Slot — Sets the basic unit of time the access point uses for
calculating waiting times before data is transmitted. A short slot time
(9 microseconds) can increase data throughput on the access point, but
requires that all clients can support a short slot time (that is, 802.11gcompliant clients must support a short slot time). A long slot time
(20 microseconds) is required if the access point has to support
802.11b clients. (Default: Enabled)
◆ TX Burst — A performance enhancement that transmits a number of
data packets at the same time when the feature is supported by
compatible clients. (Default: Enabled)
– 80 –
Page 81

C
HAPTER
7
| Wireless Configuration
Advanced Settings
◆ Packet Aggregate — A performance enhancement that combines data
packets together when the feature is supported by compatible clients.
(Default: Enabled)
WI-FI MULTIMEDIA The Wireless Broadband Router implements Quality of Service (QoS) using
the Wi-Fi Multimedia (WMM) standard. Using WMM, the access point is able
to prioritize traffic and optimize performance when multiple applications
compete for wireless network bandwidth at the same time. WMM employs
techniques that are a subset of the developing IEEE 802.11e QoS standard
and it enables access points to interoperate with both WMM-enabled clients
and other devices that may lack any WMM functionality.
WMM defines four access categories (ACs): voice, video, best effort, and
background. These categories correspond to traffic priority levels and are
mapped to IEEE 802.1D priority tags (see Tab l e 3 ). The direct mapping of
the four ACs to 802.1D priorities is specifically intended to facilitate
interoperability with other wired network QoS policies. While the four ACs
are specified for specific types of traffic, WMM allows the priority levels to
be configured to match any network-wide QoS policy. WMM also specifies a
protocol that access points can use to communicate the configured traffic
priority levels to QoS-enabled wireless clients.
Table 3: WMM Access Categories
Access
Category
AC_VO (AC3) Voice Highest priority, minimum delay. Time-sensitive
AC_VI (AC2) Video High priority, minimum delay. Time-sensitive
AC_BE (AC0) Best Effort Normal priority, medium delay and throughput.
AC_BK (AC1) Background Lowest priority. Data with no delay or
WMM
Designation
Description 802.1D
data such as VoIP (Voice over IP) calls.
data such as streaming video.
Data only affected by long delays. Data from
applications or devices that lack QoS
capabilities.
throughput requirements, such as bulk data
transfers.
Tags
7, 6
5, 4
0, 3
2, 1
The Wi-Fi Multimedia section on the Wireless Settings Advanced page
allows you to enable WMM and set detailed QoS parameters.
Figure 38: Wi-Fi Multimedia Settings
– 81 –
Page 82

C
HAPTER
Advanced Settings
7
| Wireless Configuration
The following items are displayed in this section on this page:
◆ WMM — Sets the WMM operational mode on the access point. When
enabled, the QoS capabilities are advertised to WMM-enabled clients in
the network. WMM must be supported on any device trying to
associated with the access point. Devices that do not support this
feature will not be allowed to associate with the access point.
(Default: Enabled)
◆ APSD — When WMM is enabled, Automatic Power Save Delivery
(APSD) can also be enabled. APSD is an efficient power management
method that enables client devices sending WMM packets to enter a
low-power sleep state between receiving and transmitting data.
(Default: Disabled)
◆ WMM Parameters — Click the WMM Configuration button to set
detailed WMM parameters.
Figure 39: WMM Configuration
The following items are displayed in the WMM Configuration window:
◆ AIFSN (Arbitration Inter-Frame Space) — The minimum amount of
wait time before the next data transmission attempt. Specify the AIFS
value in the range 0-15 microseconds.
◆ CWMin (Minimum Contention Window) — The initial upper limit of the
random backoff wait time before wireless medium access can be
attempted. The initial wait time is a random value between zero and
– 82 –
Page 83

C
HAPTER
7
| Wireless Configuration
Advanced Settings
the CWMin value. Specify the CWMin value in the range 0-15
microseconds. Note that the CWMin value must be equal or less than
the CWMax value.
◆ CWMax (Maximum Contention Window) — The maximum upper limit
of the random backoff wait time before wireless medium access can be
attempted. The contention window is doubled after each detected
collision up to the CWMax value. Specify the CWMax value in the range
0-15 microseconds. Note that the CWMax value must be greater or
equal to the CWMin value.
◆ Txop (Transmit Opportunity Limit) — The maximum time an AC
transmit queue has access to the wireless medium. When an AC queue
is granted a transmit opportunity, it can transmit data for a time up to
the TxOpLimit. This data bursting greatly improves the efficiency for
high data-rate traffic. Specify a value in the range 0-65535
microseconds.
◆ ACM — The admission control mode for the access category. When
enabled, clients are blocked from using the access category.
(Default: Disabled)
MULTICAST-TO-
UNICAST CONVERTER
◆ AckPolicy — By default, all wireless data transmissions require the
sender to wait for an acknowledgement from the receiver. WMM allows
the acknowledgement wait time to be turned off for each Access
Category (AC) 0-3. Although this increases data throughput, it can also
result in a high number of errors when traffic levels are heavy.
(Default: Acknowledge)
The Multicast-to-Unicast Converter section on the Wireless Settings
Advanced page allows you to enable multicast traffic conversion.
Converting multicast traffic to unicast before sending to wireless clients
allows a longer DTIM (Data Beacon Rate) interval to be set. A longer DTIM
interval prevents clients in power-save mode having to activate their radios
to receive the multicast data, which saves battery life.
Figure 40: Multicast-to-Unicast Converter
The following items are displayed in this section on this page:
◆ Multicast-to-Unicast — Enables multicast traffic streams to be
converted to unicast traffic before delivery to wireless clients.
(Default: Disabled)
– 83 –
Page 84

C
Internet
Service
Provider
MAC: 00-22-2D-62-EA-11
WDS MAC List:
00-22-2D-62-EA-22
00-22-2D-62-EA-33
00-22-2D-62-EA-44
MAC: 00-22-2D-62-EA-22
WDS MAC List:
00-22-2D-62-EA-11
Cable/DSL
Modem
WDS Link
MAC: 00-22-2D-62-EA-33
WDS MAC List:
00-22-2D-62-EA-11
MAC: 00-22-2D-62-EA-44
WDS MAC List:
00-22-2D-62-EA-11
WDS Link
WDS Link
HAPTER
7
| Wireless Configuration
Wireless Distribution System (WDS)
WIRELESS DISTRIBUTION SYSTEM (WDS)
The radio interface can be configured to operate in a mode that allows it to
forward traffic directly to other Wireless Gateway Router units. This feature
can be used to extend the range of the wireless network to reach remote
clients, or to link disconnected network segments to an Internet
connection.
To set up links between units, you must configure the Wireless Distribution
System (WDS) forwarding table by specifying the wireless MAC address of
all units to which you want to forward traffic.
N
OTE
:
All units in a WDS wireless network must be configured with the
same SSID and use the same radio channel. Also each WDS link must be
configured with the same encryption key on both units in the link.
Up to four WDS links can be specified for each unit in the WDS network.
The following figures illustrate an example WDS network. Figure 41 shows
the manual set up of MAC addresses for units in the WDS network.
Figure 42 shows the basic configuration required on each unit in the WDS
network.
Figure 41: Manual WDS MAC Address Configuration
– 84 –
Page 85

C
Internet
Service
Provider
Operation Mode: Gateway
DHCP Server: Enable
LAN IP Address: 192.168.2.1
WDS Mode: Bridge
Operation Mode: Bridge
WDS Mode: Repeater
DHCP Server: Disable
LAN IP Address: 192.168.2.2
Cable/DSL
Modem
WDS Link
Operation Mode: Bridge
WDS Mode: Lazy
DHCP Server: Disable
LAN IP Address: 192.168.2.3
Operation Mode: Gateway
WDS Mode: Lazy
DHCP Server: Disable
LAN IP Address: 192.168.2.4
WDS Link
WDS Link
HAPTER
7
| Wireless Configuration
Wireless Distribution System (WDS)
Figure 42: WDS Configuration Example
A WDS link between two units can be configured in any of the following
Operation Mode combinations:
1. Both units in a link are configured as Gateway Mode.
2. One unit in a link is configured in Gateway Mode and the other in Bridge
Mode.
3. Both units in a link are configured as Bridge Mode.
When two or more units in the WDS network are set to Gateway Mode, be
sure to check these settings:
◆ Be sure each unit is configured with a different LAN IP address.
◆ Be sure that only one unit has an Internet access on its WAN port.
◆ Be sure the DHCP server is enabled only on one unit. When one unit is
providing Internet access, enable the DHCP server on that unit.
N
OTE
:
When using WDS Lazy mode in the network, at least one unit must
be set to Bridge or Repeater mode.
– 85 –
Page 86

C
HAPTER
Wireless Distribution System (WDS)
7
| Wireless Configuration
Figure 43: WDS Configuration
The WDS settings configure WDS related parameters. Up to four MAC
addresses can be specified for each unit in the WDS network. WDS links
may either be manually configured (Bridge and Repeater modes) or autodiscovered (Lazy mode).
– 86 –
Page 87

C
HAPTER
Wireless Distribution System (WDS)
7
| Wireless Configuration
◆ WDS Mode — Selects the WDS mode of the SSID. (Options: Disable,
Lazy, Bridge, Repeater. Default: Disable)
■
Disable: WDS is disabled.
■
Lazy: Operates in an automatic mode that detects and learns WDS
peer addresses from received WDS packets, without the need to
configure a WDS MAC list entry. This feature allows the Wireless
Broadband Router to associate with other Wireless Broadband
Routers in the network and use their WDS MAC list. Lazy mode
requires one other Wireless Broadband Router within the wireless
network that is configured in Bridge or Repeater mode, and has a
configured MAC address list.
■
Bridge: Operates as a standard bridge that forwards traffic
between WDS links (links that connect to other units in Repeater or
Lazy mode). The MAC addresses of WDS peers must be configured
on the Wireless Broadband Router.
■
Repeater: Operates as a wireless repeater, extending the range for
remote wireless clients and connecting them to an AP connected to
the wired network. The MAC addresses of WDS peers must be
configured on the Wireless Broadband Router.
◆ Physical — The radio media coding used on all WDS links. CCK
corresponds to 11b, OFDM corresponds to 11g, and HTMIX corresponds
to 11n.
◆ Encryption Type — The data encryption used on the WDS link. Be
sure that both ends of a WDS link are configured with the same
encryption type and key. (Options: None, WEP, TKIP, AES.
Default: None)
◆ Encryption Key — The encryption key for the WDS link. The key type
and length varies depending on the encryption type selected. For WEP,
enter 5 alphanumeric characters or 10 hexadecimal digits for 64-bit
keys, or 13 alphanumeric characters or 26 hexadecimal digits for 128bit keys. For TKIP or AES, enter a password key phrase of between 8 to
63 ASCII characters, which can include spaces, or specify exactly 64
hexadecimal digits.
◆ AP MAC Address — The MAC address of the other Wireless Broadband
Router in the WDS link.
– 87 –
Page 88

C
HAPTER
Wi-Fi Protected Setup (WPS)
7
| Wireless Configuration
WI-FI PROTECTED SETUP (WPS)
Wi-Fi Protected Setup (WPS) is designed to ease installation and activation
of security features in wireless networks. WPS has two basic modes of
operation, Push-button Configuration (PBC) and Personal Identification
Number (PIN). The WPS PIN setup is optional to the PBC setup and
provides more security. The WPS button on the Wireless Broadband Router
can be pressed at any time to allow a single device to easily join the
network.
The WPS Settings page includes configuration options for setting WPS
device PIN codes and activating the virtual WPS button.
Click on “Wireless Settings,” followed by “WPS”.
Figure 44: Enabling WPS
◆ WPS — Enables WPS, locks security settings, and refreshes WPS
configuration information. (Default: Enabled)
– 88 –
Page 89

Figure 45: WPS Configuration
C
HAPTER
7
| Wireless Configuration
Wi-Fi Protected Setup (WPS)
WPS Summary — Provides detailed WPS statistical information.
◆ WPS Current Status — Displays if there is currently any WPS traffic
connecting to the Wireless Broadband Router. (Options: Start WSC
Process; Idle)
◆ WPS Configured — States if WPS for wireless clients has been
configured for this device.
◆ WPS SSID — The service set identifier for the unit.
◆ WPS Auth Mode — The method of authentication used.
◆ WPS Encryp Type — The encryption type used for the unit.
◆ WPS Default Key Index — Displays the WEP default key (1~4).
◆ WPS Key (ASCII) — Displays the WPS security key (ASCII) which can
be used to ensure the security of the wireless network.
◆ AP PIN — Displays the PIN Code for the Wireless Broadband Router.
The default is exclusive for each unit. (Default: 64824901)
◆ Reset OOB — Resets the WPS settings to factory default values.
– 89 –
Page 90

C
HAPTER
Station List
7
| Wireless Configuration
WPS Config — Configures WPS settings for the Wireless Broadband
Router.
◆ WPS Mode — Selects between methods of broadcasting the WPS
beacon to network clients wanting to join the network:
■
■
PIN: The Wireless Broadband Router, along with other WPS
devices, such as notebook PCs, cameras, or phones, all come with
their own eight-digit PIN code. When one device, the WPS enrollee,
sends a PIN code to the Wireless Broadband Router, it becomes the
WPS registrar. After configuring PIN-Code information you must
press “Apply” to send the beacon, after which you have up to two
minutes to activate WPS on devices that need to join the network.
PBC: This has the same effect as pressing the physical WPS button
that is located on the front of the Wireless Broadband Router. After
checking this option and clicking “Apply” you have up to two
minutes to activate WPS on devices that need to join the network.
STATION LIST
Displays the station information which associated to this Wireless
Broadband Router.
Figure 46: Station List
– 90 –
Page 91

8 FIREWALL CONFIGURATION
The Wireless Broadband Router provides extensive firewall protection by
restricting connection parameters to limit the risk of intrusion and
defending against a wide array of common hacker attacks.
Firewall Configuration contains the following sections:
◆ “MAC/IP/Port Filtering” on page 91
◆ “Virtual Server Settings (Port Forwarding)” on page 94
◆ “DMZ” on page 95
◆ “System Security” on page 96
◆ “Content Filtering” on page 97
MAC/IP/PORT FILTERING
MAC/IP/Port filtering restricts connection parameters to limit the risk of
intrusion and defends against a wide array of common hacker attacks.
MAC/IP/Port filtering allows the unit to permit, deny or proxy traffic
through its MAC addresses, IP addresses and ports.
The Wireless Broadband Router allows you define a sequential list of permit
or deny filtering rules (up to 32). This device tests ingress packets against
the filter rules one by one. A packet will be accepted as soon as it matches
a permit rule, or dropped as soon as it matches a deny rule. If no rules
match, the packet is either accepted or dropped depending on the default
policy setting.
– 91 –
Page 92

C
HAPTER
MAC/IP/Port Filtering
8
| Firewall Configuration
Figure 47: MAC/IP/Port Filtering
◆ MAC/IP/Port Filtering — Enables or disables MAC/IP/Port Filtering.
(Default: Disable)
◆ Default Policy — When MAC/IP/Port Filtering is enabled, the default
policy will be enabled. If you set the default policy to “Dropped”, all
incoming packets that don’t match the rules will be dropped. If the
policy is set to "Accepted," all incoming packets that don't match the
rules are accepted. (Default: Dropped)
◆ MAC Address — Specifies the MAC address to block or allow traffic
from.
◆ Destination IP Address — Specifies the destination IP address to
block or allow traffic from.
– 92 –
Page 93

C
HAPTER
8
| Firewall Configuration
MAC/IP/Port Filtering
◆ Source IP Address — Specifies the source IP address to block or allow
traffic from.
◆ Protocol — Specifies the destination port type, TCP, UDP or ICMP.
(Default: None).
◆ Destination Port Range — Specifies the range of destination port to
block traffic from the specified LAN IP address from reaching.
◆ Source Port Range — Specifies the range of source port to block
traffic from the specified LAN IP address from reaching.
◆ Action — Specifies if traffic should be accepted or dropped. (Default:
Accept)
◆ Comment — Enter a useful comment to help identify the filtering rules.
CURRENT FILTER
RULES
The Current Filter Table displays the configured IP addresses and ports that
are permitted or denied access to and from the ADSL/Router.
◆ Select — Selects a table entry.
◆ MAC Address — Displays a MAC address to filter.
◆ Destination IP Address — Displays the destination IP address.
◆ Source IP Address — Displays the source IP address.
◆ Protocol — Displays the destination port type.
◆ Destination Port Range — Displays the destination port range.
◆ Source Port Range — Displays the source port range.
◆ Action — Displays if the specified traffic is accepted or dropped.
◆ Comment — Displays a useful comment to identify the routing rules.
– 93 –
Page 94

C
HAPTER
Virtual Server Settings (Port Forwarding)
8
| Firewall Configuration
VIRTUAL SERVER SETTINGS (PORT FORWARDING)
Virtual Server (sometimes referred to as Port Forwarding) is the act of
forwarding a network port from one network node to another. This
technique can allow an external user to reach a port on a private IP
address (inside a LAN) from the outside through a NAT-enabled router.
(Maximum 32 entries are allowed.)
Figure 48: Virtual Server
◆ Virtual Server Settings — Selects between enabling or disabling port
forwarding the virtual server. (Default: Disable)
◆ IP Address — Specifies the IP address on the local network to allow
external access.
◆ Port Range — Specifies the port range through which traffic is
forwarded.
◆ Protocol — Specifies a protocol to use for port forwarding, either TCP,
UDP or TCP&UDP.
◆ Comment — Enter a useful comment to help identify the forwarded
port service on the network.
– 94 –
Page 95

C
HAPTER
8
| Firewall Configuration
DMZ
CURRENT VIRTUAL
SERVERS IN SYSTEM
DMZ
The Current Port Forwarding Table displays the entries that are allowed to
forward packets through the Wireless Broadband Router’s firewall.
◆ No. — The table entry number.
◆ IP Address — Displays an IP address on the local network to allow
external access to.
◆ Port Mapping — Displays the port the server is mapped.
◆ Protocol — Displays the protocol used for forwarding of this port.
◆ Comment — Displays a useful comment to identify the nature of the
port to be forwarded.
Enables a specified host PC on the local network to access the Internet
without any firewall protection. Some Internet applications, such as
interactive games or video conferencing, may not function properly behind
the Wireless Broadband Router's firewall. By specifying a Demilitarized
Zone (DMZ) host, the PC's TCP ports are completely exposed to the
Internet, allowing open two-way communication. The host PC should be
assigned a static IP address (which is mapped to its MAC address) and this
must be configured as the DMZ IP address.
Figure 49: DMZ
◆ DMZ Settings — Sets the DMZ status. (Default: Disable)
◆ DMZ IP Address — Specifies an IP address on the local network
allowed unblocked access to the WAN.
– 95 –
Page 96

C
HAPTER
System Security
8
| Firewall Configuration
SYSTEM SECURITY
The Wireless Broadband Router includes the facility to manage it from a
remote location. The unit can also be sent a ping message from a remote
location.
Figure 50: System Security
◆ Remote Management — Denies or allows management access to the
Gateway Router through the WAN interface. (Default: Deny)
◆ Ping from WAN Filter — When enabled, the Gateway Router does not
respond to ping packets received on the WAN port. (Default: Disable)
◆ Stateful Packet Inspection (SPI) — The Stateful Packet Inspection
(SPI) firewall protects your network and computers against attacks and
intrusions. A stateful packet firewall looks at packet contents to check if
the traffic may involve some type of security risk. (Default: Disable)
– 96 –
Page 97

CONTENT FILTERING
C
HAPTER
8
| Firewall Configuration
Content Filtering
The Wireless Broadband Router provides a variety of options for blocking
Internet access based on content, URL and host name.
Figure 51: Content Filtering
Web URL Filter Settings — By filtering inbound Uniform Resource
Locators (URLs) the risk of compromising the network can be reduced.
URLs are commonly used to point to websites. By specifying a URL or a
keyword contained in a URL traffic from that site may be blocked.
◆ Current URL Filters — Displays current URL filter.
◆ Add a URL Filter — Adds a URL filter to the settings. For example,
myhost.example.com.
Web Host Filter Settings — The Wireless Broadband Router allows
Internet content access to be restricted based on web address keywords
and web domains. A domain name is the name of a particular web site. For
example, for the address www.FUNGAMES.com, the domain name is
FUNGAMES.com. Enter the Keyword then click “Add”.
◆ Current Host Filters — Displays current Host filter.
– 97 –
Page 98

C
HAPTER
Content Filtering
8
| Firewall Configuration
◆ Add a Host Filter — Enters the keyword for a host filtering.
– 98 –
Page 99

9 ADMINISTRATION SETTINGS
The Wireless Broadband Router’s Administration Settings menu provides
the same configuration options in both Gateway and Bridge Mode. These
settings allow you to configure a management access password, set the
system time, upgrade the system software, display the system status and
statistics.
Administration Settings contains the following sections:
◆ “System Management” on page 100
◆ “SNTP Settings” on page 101
◆ “DDNS Settings” on page 102
◆ “Upgrade Firmware” on page 103
◆ “Configuration Settings” on page 104
◆ “System Status” on page 105
◆ “Statistics” on page 107
◆ “System Log” on page 108
– 99 –
Page 100

C
HAPTER
System Management
9
| Administration Settings
SYSTEM MANAGEMENT
The System Management commands allow you to change the language
settings displayed in the interface, and change the user name and
password.
Figure 52: System Management
LANGUAGE SETTINGS You can change the language displayed in web interface. Chooses the
appropriate language of your choice from the drop-down list, then click
“Apply”. (Options: English, Traditional Chinese. Default: English)
WEB INTERFACE
SETTINGS
To protect access to the management interface, you need to configure a
new Administrator’s user name and password as soon as possible. If a new
user name and password are not configured, then anyone having access to
the Wireless Broadband Router may be able to compromise the unit's
security by entering the default values.
◆ User Name — The name of the user. The default name for access to
the unit is “admin”. (Length: 3-16 characters, case sensitive)
◆ Password — The password for management access. The default
password preset for access to the unit is “smcadmin” (Length: 3-16
characters, case sensitive)
◆ Confirm Password — Prompts you to enter the password again for
verification.
– 100 –
 Loading...
Loading...