Page 1

WGSD-1022
8-Port 10/100Mbps
User's Manual
+ 2-Port Gigabit TP/SFP Combo
Managed Ethernet Switch
Page 2
Trademarks
Copyright © PLANET Technology Corp. 2007.
Contents subject to which revision without prior notice.
PLANET is a registered trademark of PLANET Technology Corp. All other trademarks belong to the ir
respective owners.
Disclaimer
PLANET Technology does not warrant that the hardware will work properly in all environments and
applications, and makes no warranty and representation, either implied or expressed, with respect to the
quality, performance, merchantability, or fitness for a particular purpose.
PLANET has made every effort to ensure that this User's Manual is accurate; PLANET disclaims liability
for any inaccuracies or omissions that may have occurred.
Information in this User's Manual is subject to change without notice and does not represent a
commitment on the part of PLANET. PLANET assumes no responsibility for any inaccuracies that may be
contained in this User's Manual. PLANET makes no commitment to update or keep current the
information in this User's Manual, and reserves the right to make improvements to this User's Manual
and/or to the products described in this User's Manual, at any time without notice.
If you find information in this manual that is incorrect, misleading, or incomplete, we would appreciate
your comments and suggestions.
FCC Warning
This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant
to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference when the equipment is operated in a commercial environment. This equipment generates,
uses, and can radiate radio frequency energy and, if not installed and used in accordance with the
Instruction manual, may cause harmful interference to radio communications. Operation of this
equipment in a residential area is likely to cause harmful interference in which case the us er will be
required to correct the interference at whose own expense.
CE Mark Warning
This is a Class A product. In a domestic environment, this product may cause radio interference, in which
case the user may be required to take adequate measures.
WEEE Warning
To avoid the potential effects on the environment and human health as a result of the
presence of hazardous substances in electrical and electronic equipment, end users
of electrical and electronic equipment should understand the meaning of the
crossed-out wheeled bin symbol. Do not dispose of WEEE as unsorted municipal
waste and have to collect such WEEE separately.
Page 3

Revision
PLANET 8-Port 10/100Mbps + 2 Gigabit TP/SFP combo Managed Ethernet Switch User's Manual
FOR MODEL: WGSD-1022
REVISION: 1.2 (November.2007)
Part No. 2081-A34030-002
Page 4

TABLE OF CONTENTS
1. INTRODUCTION ................................................................................................................................15
Packet Contents...............................................................................................................................15
How to Use This Manual..................................................................................................................15
Product Feature...............................................................................................................................16
Product Specification.......................................................................................................................17
2. INSTALLATION...................................................................................................................................19
2.1 Product Description....................................................................................................................19
2.1.1 Product Overview ............................................................................................................19
2.1.2 Switch Front Panel...........................................................................................................20
2.1.3 LED Indications................................................................................................................20
2.1.4 Switch Rear Panel...........................................................................................................20
2.2 Install the Switch........................................................................................................................21
2.2.1 Desktop Installation .........................................................................................................21
2.2.2 Rack Mounting.................................................................................................................22
2.2.3 Installing the SFP transceiver..........................................................................................23
3. CONFIGURATION..............................................................................................................................25
3.1 Management Access Overview..................................................................................................25
3.1.1 Administration Console ....................................................................................................26
3.1.2 Direct Access...................................................................................................................26
3.2 Web Management......................................................................................................................27
3.3 SNMP-Based Network Management .........................................................................................27
3.4 Protocols....................................................................................................................................27
3.4.1 Virtual Terminal Protocols ................................................................................................27
3.4.2 SNMP Protocol................................................................................................................28
3.4.3 Management Architecture................................................................................................28
4. Web Configuration ..............................................................................................................................29
4.1 Main Screen...............................................................................................................................31
4.2 System.......................................................................................................................................32
4.2.1 Information.......................................................................................................................32
4.2.2 IP Config..........................................................................................................................33
4.2.3 SNTP...............................................................................................................................34
4.3 Port Configuration......................................................................................................................37
4.3.1 Port Settings....................................................................................................................37
4.3.2 Link Aggregation..............................................................................................................41
4.3.3 LACP Config....................................................................................................................43
4.4 VLAN Configuration...................................................................................................................44
4.4.1 Create VLAN....................................................................................................................45
Page 5

4.4.2 Port Config.......................................................................................................................46
4.4.3 VLAN Group ....................................................................................................................47
4.4.4 GVRP Config...................................................................................................................48
4.5. Spanning Tree...........................................................................................................................50
4.5.1 STP Config ......................................................................................................................50
4.5.2 STP Port Config...............................................................................................................52
4.5.3 RSTP Port Config............................................................................................................54
4.5.4 MSTP Config ...................................................................................................................56
4.5.5 MSTP Instance Config.....................................................................................................57
4.5.6 MSTP Interface Settings..................................................................................................59
4.6 Multicast.....................................................................................................................................62
4.6.1 IGMP Snooping ...............................................................................................................62
4.6.2 Bridge Multicast...............................................................................................................63
4.7 QoS............................................................................................................................................66
4.7.1 Queue Scheduling ...........................................................................................................66
4.7.2 802.1p Settings................................................................................................................67
4.7.3 DSCP Settings.................................................................................................................69
4.7.4 Rate Limit ........................................................................................................................70
4.7.5 Port Qos ..........................................................................................................................71
4.7.6 Policy Qos........................................................................................................................72
4.8 Access Control...........................................................................................................................78
4.8.1 Layer3 Based ACL...........................................................................................................78
4.8.2 Layer2 Based ACL...........................................................................................................81
4.9 Security......................................................................................................................................83
4.9.1 ACL Binding.....................................................................................................................83
4.9.2 Radius Config..................................................................................................................84
4.9.3 TACACS+ Config.............................................................................................................86
4.9.4 802.1x settings.................................................................................................................88
4.9.5 Port Security....................................................................................................................89
4.9.6 Multiple Hosts..................................................................................................................91
4.9.7 Storm control....................................................................................................................92
4.10 SNMP ......................................................................................................................................93
4.10.1 Parameters....................................................................................................................93
4.10.2 Group Profile..................................................................................................................95
4.10.3 Group Membership........................................................................................................96
4.10.4 Communities..................................................................................................................98
4.10.5 Notification Recipient...................................................................................................100
4.11 Manage..................................................................................................................................102
Page 6

4.11.1 User Authentication......................................................................................................103
4.11.2 Dynamic Address.........................................................................................................104
4.11.3 Mirroring.......................................................................................................................105
4.11.4 Firmware Upgrade .......................................................................................................106
4.11.5 Save Configuration ......................................................................................................108
4.11.6 Warm Startup ............................................................................................................... 110
4.11.7 Factory Default............................................................................................................. 111
4.12 Statistics.................................................................................................................................112
4.12.1 RMON Statistic............................................................................................................112
4.12.2 EAP Statistic................................................................................................................ 114
4.12.3 GVRP Statistics...........................................................................................................115
5. COMMAND STRUCTURE................................................................................................................ 117
5.1 Connect to PC’s RS-232 serial port.........................................................................................117
5.2 Using the CLI...........................................................................................................................118
5.2.1 CLI Command Modes.................................................................................................... 118
5.2.2 Starting the CLI..............................................................................................................121
5.2.3 Editing Features.............................................................................................................122
5.3 AAA Commands.......................................................................................................................125
5.3.1 aaa authentication login.................................................................................................125
5.3.2 aaa authentication enable..............................................................................................126
5.3.3 login authentication........................................................................................................128
5.3.4 enable authentication.....................................................................................................128
5.3.5 ip http authentication......................................................................................................129
5.3.6 ip https authentication....................................................................................................130
5.3.7 show authentication methods ........................................................................................131
5.3.8 password .......................................................................................................................132
5.3.9 enable password............................................................................................................132
5.3.10 username .....................................................................................................................133
5.3.11 show users accounts....................................................................................................134
5.4 Address Table Commands.......................................................................................................134
5.4.1 bridge address...............................................................................................................134
5.4.2 bridge multicast filtering.................................................................................................135
5.4.3 bridge multicast address................................................................................................136
5.4.4 bridge multicast forbidden address................................................................................137
5.4.5 bridge multicast forward-unregistered............................................................................138
5.4.6 bridge multicast forbidden forward-unregistered............................................................139
5.4.7 bridge multicast forward-all............................................................................................140
5.4.8 bridge multicast forbidden forward-all............................................................................140
Page 7

5.4.9 bridge aging-time...........................................................................................................141
5.4.10 clear bridge..................................................................................................................142
5.4.11 port security .................................................................................................................143
5.4.12 port security routed secure-address ............................................................................143
5.4.13 show bridge address-table...........................................................................................144
5.4.14 show bridge address-table static .................................................................................145
5.4.15 show bridge address-table count.................................................................................146
5.4.16 show bridge multicast address-table............................................................................146
5.4.17 show bridge multicast filtering......................................................................................148
5.4.18 show ports security......................................................................................................148
5.5 Clock Commands.....................................................................................................................149
5.5.1 clock set.........................................................................................................................149
5.5.2 clock source...................................................................................................................150
5.5.3 clock timezone...............................................................................................................151
5.5.4 clock summer-time.........................................................................................................151
5.5.5 sntp authentication-key..................................................................................................153
5.5.6 sntp authenticate ...........................................................................................................154
5.5.7 sntp trusted-key.............................................................................................................154
5.5.8 sntp client poll timer.......................................................................................................155
5.5.9 sntp broadcast client enable..........................................................................................156
5.5.10 sntp anycast client enable ...........................................................................................156
5.5.11 sntp client enable (interface)........................................................................................157
5.5.12 sntp unicast client enable ............................................................................................158
5.5.13 sntp unicast client poll..................................................................................................158
5.5.14 sntp server...................................................................................................................159
5.5.15 show clock...................................................................................................................160
5.5.16 show sntp configuration...............................................................................................161
5.5.17 show sntp status..........................................................................................................162
5.6 Configuration and Image Files.................................................................................................163
5.6.1 copy...............................................................................................................................163
5.6.2 show startup-config........................................................................................................167
5.7 Ethernet Configuration Commands..........................................................................................168
5.7.1 interface ethernet...........................................................................................................168
5.7.2 interface range ethernet.................................................................................................168
5.7.3 shutdown .......................................................................................................................169
5.7.4 description .....................................................................................................................170
5.7.5 speed.............................................................................................................................170
5.7.6 duplex............................................................................................................................171
Page 8

5.7.7 negotiation.....................................................................................................................172
5.7.8 flowcontrol......................................................................................................................172
5.7.9 mdix...............................................................................................................................173
5.7.10 back-pressure..............................................................................................................174
5.7.11 port jumbo-frame..........................................................................................................175
5.7.12 clear counters..............................................................................................................175
5.7.13 set interface active.......................................................................................................176
5.7.14 show interfaces configuration ......................................................................................176
5.7.15 show interfaces status .................................................................................................178
5.7.16 show interfaces description..........................................................................................179
5.7.17 show interfaces counters.............................................................................................180
5.7.18 show ports jumbo-frame ..............................................................................................183
5.7.19 port storm-control broadcast enable............................................................................183
5.7.20 port storm-control broadcast rate.................................................................................184
5.7.21 show ports storm-control..............................................................................................185
5.8 GVRP Commands ...................................................................................................................185
5.8.1 gvrp enable (global).......................................................................................................185
5.8.2 gvrp enable (interface)...................................................................................................186
5.8.3 garp timer ......................................................................................................................187
5.8.4 gvrp vlan-creation-forbid................................................................................................188
5.8.5 gvrp registration-forbid...................................................................................................188
5.8.6 clear gvrp statistics........................................................................................................189
5.8.7 show gvrp configuration.................................................................................................190
5.8.8 show gvrp statistics........................................................................................................191
5.8.9 show gvrp error-statistics...............................................................................................192
5.9 IGMP Snooping Commands ....................................................................................................193
5.9.1 ip igmp snooping (Global)..............................................................................................193
5.9.2 ip igmp snooping (Interface) ..........................................................................................193
5.9.3 ip igmp snooping mrouter ..............................................................................................194
5.9.4 ip igmp snooping host-time-out......................................................................................195
5.9.5 ip igmp snooping mrouter-time-out ................................................................................195
5.9.6 ip igmp snooping leave-time-out....................................................................................196
5.9.7 show ip igmp snooping mrouter.....................................................................................197
5.9.8 show ip igmp snooping interface....................................................................................197
5.9.9 show ip igmp snooping groups ......................................................................................198
5.10 IP Addressing Commands .....................................................................................................199
5.10.1 ip address....................................................................................................................199
5.10.2 ip address dhcp ...........................................................................................................200
Page 9

5.10.3 ip default-gateway........................................................................................................201
5.10.4 show ip interface..........................................................................................................202
5.10.5 arp ...............................................................................................................................202
5.10.6 arp timeout...................................................................................................................203
5.10.7 clear arp-cache............................................................................................................204
5.10.8 show arp......................................................................................................................204
5.11 LACP Commands ..................................................................................................................205
5.11.1 lacp system-priority......................................................................................................205
5.11.2 lacp port-priority ...........................................................................................................205
5.11.3 lacp timeout..................................................................................................................206
5.11.4 show lacp ethernet.......................................................................................................207
5.11.5 show lacp port-channel................................................................................................207
5.12 Line Commands.....................................................................................................................209
5.12.1 line............................................................................................................................... 209
5.12.2 speed...........................................................................................................................209
5.12.3 exec-timeout................................................................................................................210
5.12.4 show line...................................................................................................................... 211
5.13 Management ACL Commands...............................................................................................212
5.13.1 management access-list..............................................................................................212
5.13.2 permit (management) ..................................................................................................213
5.13.3 deny (management).....................................................................................................214
5.13.4 management access-class ..........................................................................................215
5.13.5 show management access-list.....................................................................................215
5.13.6 show management access-class.................................................................................216
5.14 PHY Diagnostics Commands.................................................................................................217
5.14.1 test copper-port tdr ......................................................................................................217
5.14.2 show copper-ports tdr..................................................................................................217
5.14.3 show copper-ports cable-length...................................................................................218
5.14.4 show fiber-ports optical-transceiver .............................................................................219
5.15 Port Channel Commands.......................................................................................................221
5.15.1 interface port-channel..................................................................................................221
5.15.2 interface range port-channel........................................................................................221
5.15.3 channel-group..............................................................................................................222
5.15.4 show interfaces port-channel.......................................................................................223
5.16 Port Monitor Commands........................................................................................................224
5.16.1 port monitor..................................................................................................................224
5.16.2 show ports monitor ......................................................................................................225
5.17 QoS Commands ....................................................................................................................226
Page 10

5.17.1 qos...............................................................................................................................226
5.17.2 show qos......................................................................................................................226
5.17.3 wrr-queue cos-map......................................................................................................227
5.17.4 wrr-queue bandwidth...................................................................................................228
5.17.5 priority-queue out num-of-queues................................................................................229
5.17.6 show qos interface.......................................................................................................230
5.17.7 qos map dscp-queue ...................................................................................................233
5.17.8 qos trust (Global).........................................................................................................233
5.17.9 qos trust (Interface)......................................................................................................234
5.17.10 qos cos ......................................................................................................................235
5.17.11 qos cos override.........................................................................................................236
5.17.12 show qos map............................................................................................................236
5.18 Radius Commands ................................................................................................................238
5.18.1 radius-server host........................................................................................................238
5.18.2 radius-server key.........................................................................................................239
5.18.3 radius-server retransmit...............................................................................................240
5.18.4 radius-server source-ip................................................................................................240
5.18.5 radius-server timeout...................................................................................................241
5.18.6 radius-server deadtime................................................................................................242
5.18.7 show radius-servers.....................................................................................................242
5.19 RMON Commands.................................................................................................................243
5.19.1 show rmon statistics.....................................................................................................243
5.19.2 rmon collection history.................................................................................................245
5.19.3 show rmon collection history........................................................................................246
5.19.4 show rmon history........................................................................................................247
5.19.5 rmon alarm...................................................................................................................250
5.19.6 show rmon alarm-table ................................................................................................252
5.19.7 show rmon alarm.........................................................................................................253
5.19.8 rmon event...................................................................................................................255
5.19.9 show rmon events........................................................................................................255
5.19.10 show rmon log ...........................................................................................................257
5.19.11 rmon table-size...........................................................................................................258
5.20 SNMP Commands.................................................................................................................258
5.20.1 snmp-server community ..............................................................................................258
5.20.2 snmp-server contact ....................................................................................................260
5.20.3 snmp-server location ...................................................................................................260
5.20.4 snmp-server enable traps............................................................................................261
5.20.5 snmp-server trap authentication ..................................................................................262
Page 11

5.20.6 snmp-server host.........................................................................................................262
5.20.7 snmp-server set...........................................................................................................263
5.20.8 show snmp...................................................................................................................264
5.21 Spanning-Tree Commands....................................................................................................266
5.21.1 spanning-tree...............................................................................................................266
5.21.2 spanning-tree mode.....................................................................................................266
5.21.3 spanning-tree forward-time..........................................................................................267
5.21.4 spanning-tree hello-time ..............................................................................................267
5.21.5 spanning-tree max-age................................................................................................268
5.21.6 spanning-tree priority...................................................................................................269
5.21.7 spanning-tree disable ..................................................................................................269
5.21.8 spanning-tree cost .......................................................................................................270
5.21.9 spanning-tree port-priority............................................................................................271
5.21.10 spanning-tree portfast................................................................................................271
5.21.11 spanning-tree link-type...............................................................................................272
5.21.12 spanning-tree pathcost method .................................................................................273
5.21.13 spanning-tree bpdu....................................................................................................273
5.21.14 clear spanning-tree detected-protocols......................................................................274
5.21.15 show spanning-tree ...................................................................................................275
5.22 SSH and SLOGIN Commands...............................................................................................277
5.22.1 ip ssh port....................................................................................................................277
5.22.2 ip ssh server ................................................................................................................277
5.22.3 crypto key generate dsa ..............................................................................................278
5.22.4 crypto key generate rsa ...............................................................................................279
5.22.5 ip ssh pubkey-auth.......................................................................................................279
5.22.6 crypto key pubkey-chain ssh........................................................................................280
5.22.7 user-key.......................................................................................................................280
5.22.8 key-string.....................................................................................................................281
5.22.9 show ip ssh..................................................................................................................282
5.22.10 show crypto key mypubkey........................................................................................283
5.22.11 show crypto key pubkey-chain ssh ............................................................................284
5.23 System Management.............................................................................................................285
5.23.1 ping..............................................................................................................................285
5.23.2 traceroute.....................................................................................................................286
5.23.3 telnet............................................................................................................................288
5.23.4 resume.........................................................................................................................291
5.23.5 reload...........................................................................................................................292
5.23.6 hostname.....................................................................................................................292
Page 12

5.23.7 show users...................................................................................................................293
5.23.8 show sessions .............................................................................................................294
5.23.9 show system................................................................................................................294
5.23.10 show version..............................................................................................................296
5.24 Syslog Commands.................................................................................................................296
5.24.1 logging on....................................................................................................................296
5.24.2 logging.........................................................................................................................297
5.24.3 logging console............................................................................................................298
5.24.4 logging buffered...........................................................................................................299
5.24.5 logging buffered size....................................................................................................299
5.24.6 clear logging ................................................................................................................300
5.24.7 logging file....................................................................................................................300
5.24.8 clear logging file...........................................................................................................301
5.24.9 show logging................................................................................................................302
5.24.10 show logging file ........................................................................................................303
5.24.11 show syslog-servers...................................................................................................304
5.25 TACACS Commands.............................................................................................................305
5.25.1 tacacs-server host .......................................................................................................305
5.25.2 tacacs-server key.........................................................................................................306
5.25.3 tacacs-server timeout...................................................................................................307
5.25.4 tacacs-server source-ip................................................................................................307
5.25.5 show tacacs.................................................................................................................308
5.26 User Interface Commands.....................................................................................................309
5.26.1 enable..........................................................................................................................309
5.26.2 disable .........................................................................................................................310
5.26.3 configure......................................................................................................................310
5.26.4 login.............................................................................................................................311
5.26.5 exit(configuration) ........................................................................................................312
5.26.6 exit(EXEC)...................................................................................................................312
5.26.7 end...............................................................................................................................313
5.26.8 help..............................................................................................................................313
5.26.9 history..........................................................................................................................314
5.26.10 history size.................................................................................................................314
5.26.11show history................................................................................................................315
5.26.12 show privilege............................................................................................................315
5.27 VLAN Commands..................................................................................................................316
5.27.1 vlan database ..............................................................................................................316
5.27.2 vlan..............................................................................................................................317
Page 13

5.27.3 default-vlan disable......................................................................................................317
5.27.4 interface vlan ...............................................................................................................318
5.27.5 interface range vlan .....................................................................................................319
5.27.6 name............................................................................................................................319
5.27.7 switchport mode...........................................................................................................320
5.27.8 switchport access vlan.................................................................................................321
5.27.9 switchport trunk allowed vlan.......................................................................................321
5.27.10 switchport trunk native vlan........................................................................................322
5.27.11 switchport general allowed vlan .................................................................................323
5.27.12 switchport general pvid..............................................................................................324
5.27.13 switchport general ingress-filtering disable................................................................324
5.27.14 switchport general acceptable-frame-type taggedonly...............................................325
5.27.15 switchport forbidden vlan...........................................................................................326
5.27.16 map protocol protocols-group ....................................................................................326
5.27.17 switchport general map protocols-group vlan ............................................................327
5.27.18 ip internal-usage-vlan ................................................................................................328
5.27.19 show vlan...................................................................................................................329
5.27.20 show vlan internal usage ...........................................................................................329
5.27.21 show interfaces switchport.........................................................................................330
5.28 Web Server Commands.........................................................................................................331
5.28.1 ip http server................................................................................................................331
5.28.2 ip http port....................................................................................................................332
5.28.3 ip https server..............................................................................................................332
5.28.4 ip https port..................................................................................................................333
5.28.5 crypto certificate generate ...........................................................................................334
5.28.6 show ip http..................................................................................................................334
5.28.7 show ip https................................................................................................................335
5.29 802.1x Commands.................................................................................................................335
5.29.1 aaa authentication dot1x..............................................................................................335
5.29.2 dot1x system-auth-control............................................................................................336
5.29.3 dot1x port-control.........................................................................................................337
5.29.4 dot1x re-authentication ................................................................................................338
5.29.5 dot1x timeout re-authperiod.........................................................................................338
5.29.6 dot1x re-authenticate...................................................................................................339
5.29.7 dot1x timeout quiet-period ...........................................................................................340
5.29.8 dot1x timeout tx-period ................................................................................................340
5.29.9 dot1x max-req..............................................................................................................341
5.29.10 dot1x timeout supp-timeout........................................................................................342
Page 14

5.29.11 dot1x timeout server-timeout......................................................................................342
5.29.12 show dot1x.................................................................................................................343
5.29.13 show dot1x users.......................................................................................................345
5.29.14 show dot1x statistics..................................................................................................346
5.29.15 dot1x auth-not-req .....................................................................................................348
5.29.16 dot1x multiple-hosts...................................................................................................348
5.29.17 dot1x single-host-violation .........................................................................................349
5.29.18 show dot1x advanced................................................................................................350
TROUBLE SHOOTING.........................................................................................................................352
APPENDEX A.......................................................................................................................................353
A.1 Switch's RJ-45 Pin Assignments .............................................................................................353
A.2 RJ-45 cable pin assignment ....................................................................................................354
A.3 Available Modules....................................................................................................................355
Page 15

Packet Contents
Check the contents of your package for following parts:
• Managed Fast Ethernet Switch x1
• CD-ROM user's manual x1
• Quick install ation guide x1
• 19" rack mounting kit x1
• AC adapter x1
• RS-232 console x 1
• Rubber feet x 4
1. INTRODUCTION
If any of these are missing or damaged, please contact your dealer immediately, if possible, retain the
carton including the original packing material, and use them against to repack the product in case there is
a need to return it to us for repair.
How to Use This Manual
This User Manual is structured as follows:
• Section 2, Installation
The section explains the functions of the Switch and how to physically install the Switch.
• Section 3, Configuration
The section contains the information about the software function of the Switch.
• Section 4, Switch Operation
The section contains specifications of the Switch.
• Appendex A
The section contains cable information of the Switch.
In the following section, terms "Switch" with upper case denotes the WGSD-1022 Managed Ethernet
switch. Terms with lower case "switch" means other Ethernet switch devices.
Page 16

Product Feature
Generic Features
Comply with the IEEE 802.3, IEEE 802.3u, IEEE 802.3ab, IEEE 802.3z Gigabit Ethernet
standard
8-Port 10/100Mbps TP interfaces with auto-negotiation.
2 10/100/1000Mbps TP ports and 2 SFP shared combo interfaces
Supports auto-negotiation and Half-Duplex / Full-Duplex modes for all 10Base-T/100Base-TX
and 1000Base-T ports.
Auto-MDI/MDI-X detection on each RJ-45 port
Prevents packet loss with back pressure (Half-Duplex) and IEEE 802.3x PAUSE frame flow
control (Full-Duplex)
High performance Store and Forward architecture, broadcast storm control, runt/CRC filtering
eliminates erroneous packets to optimize the network bandwidth
8K MAC address table, automatic source address learning and ageing
1Mbit embedded memory for packet buffers
Layer-2 Switching
Supports IEEE 802.1Q Tagged based VLAN
GVRP protocol for VLAN Management
Support up to 4 Trunk groups, each trunk for up to maximum 4 port with 800Mbps
bandwidth( Full Duplex Mode)
Support IGMP Snooping
IEEE 802.1d, IEEE 802.1w, classic Spanning Tree Algorithm or Rapid Spanning Tree support
Supports the IEEE 802.1s specification for multiple spanning trees on a single port (spanning
tree per VLAN).
Port Mirroring to monitor the incoming or outgoing traffic on a particular port
Quality of Service
4 priority queues on all switch ports.
Support for strict priority and weighted round robin (WRR) CoS policies
Support QoS and bandwidth control on each port
Traffic-policing policies on the switch port
Security
802.1x Port-Based Authentication
L2-L4 ACL to management the per-flow traffic
Port Security to limit the number of clients to access network
Management
WEB-Based, Telnet, Console Command Line management
Console interface for Switch basic management and setup
Page 17
Access through SNMPv1,v2c and v3 security set and get requests.
Four groups (history, statistics, alarms, and events) of embedded remote monitoring (RMON)
agents for network monitoring and traffic analysis
Built-in Trivial File Transfer Protocol (TFTP) client
Virtual Cable Test (VCT) technology provides the mechanism to detect and report potential
cabling issues, such as cable opens, cable shorts, etc. on Copper Links
EMI standards comply with FCC, CE class A,WEEE RoHS
Product Specification
Product
Hardware Specification
Ports
Gigabit ports
Switch Processing
Scheme
Switch fabric
Throughput
Address Table
Share data Buffer
Flow Control
Dimension (W x D x H)
Weight
Power Requirement
WGSD-1022
8-Port 10/100Mbps + 2 Gigabit TP / SFP combo Managed Ethernet Switch
8 10/ 100Base-TX RJ-45 Auto-MDI/MDI-X ports
2 share 10/100/1000Base-T / SFP combo interfaces
Store-and-Forward
5.6Gbps / Non-Blocking
4.17Mpps / Wire-Speed
8K entries
1 Mbit
Back pressure for Half-Duplex, IEEE 802.3x Pause Frame for Full-Duplex
267 x 170 x 45 mm, 1U height
1.2 KG
100~240V AC, 50-60, Auto-sensing
Power Consumption
Management Interface
Smart function
System Configuration
Port configuration
Port Status
VLAN
Port trunking
QoS
13.2 Watts / 45 BTU
Console. Telnet, SSH, Web, SSL, SNMP
Console / Web / telnet interfaces
Port disable/enable. Auto-negotiation 10/100Mbps full and half duplex mode
selection. Flow control Disable / Enable. Bandwidth control on each port.
Display each port’s speed duplex mode, link status, Flow control status. Auto
negotiation status, trunk status.
IEEE 802.1Q Tagged Based VLAN ,up to 255 VLAN groups
Support 4 groups of 4-Port trunk support
Traffic classification based on Port Number, 802.1p pri ority, DS/TOS field in
Page 18
IP Packet
IGMP Snooping
Standards Conformance
Regulation Compliance
Standards Compliance
Environment
Regulation Compliance
Operating Temperature
Allow to disable or enable.
FCC Part 15 Class A, CE
IEEE 802.3 10BASE-T
IEEE 802.3u 100BASE-TX/100BASE-FX
IEEE 802.3z Gigabit SX/LX
IEEE 802.3ab Gigabit 1000T
IEEE 802.3x Flow Control and Back pressure
IEEE 802.3ad Port trunk with LACP
IEEE 802.1d Spanning tree protocol
IIEEE 802.1w Rapid spanning tree protocol
IEEE 802.1p Class of service
IEEE 802.1Q VLAN Tagging
FCC Part 15 Class A, CE
0℃~50℃,
Storage Temperature
Operating Humidity
Storage Humidity
-40℃~70℃,
5% to 90%, relative humidity, non-condensing
5% to 90%, relative humidity, non-condensing
Page 19

2. INSTALLATION
This section describes the functionalities of the Switch's components and guides how to install it on the
desktop or shelf. Basic knowledge of networking is assumed. Please read this chapter completely before
continuing.
2.1 Product Description
The PLANET WGSD-1022 is a 8-Port 10/100Mbps with 2 shared SFP/copper GbE interfaces Gigabit
Ethernet Switch. It boasts a high performance switch architecture that is capable of providing
non-blocking switch fabric and wire-speed throu ghput as high as 5.6Gbps. Its two built-in GbE uplink
ports also offer incredible extensibility, flexibility and connectivity to the Core switch or Servers.
2.1.1 Product Overview
PLANET WGSD-1022 is loaded with powerful traffic management and QoS features to enhance services
offered by telcos. It provides 4 priority queues per port for different types of traffics, allowing
administrators to set policies for classified filtering and rule-based rate limitation. The WGSD-1022
prioritizes applications with WFQ (Weighted Fair Queuing) scheduling algorithm to allocate more
bandwidth to key traffics such as voice transmission, empowering the enterprise to take full advantages
of the limited network resources and guarantee the best performance.
PLANET WGSD-1022 offers comprehensive Access Control List (ACL) for enforcing security to the edge.
Its protection mechanisms comprised of port-based 802.1x user and device authentication. The
administrators can now construct highly secured corporate networks with time and effort considerably
less then before.
With its built-in web-based management, the PLANET WGSD-1022 offers an easy-to-use,
platform-independent management and configuration facility. The PLANET WGSD-1022 supports
standard Simple Network Management Protocol (SNMP) and can be manage d via any standard-based
management software. For text-based management, the WGSD-1022 can also be accessed via Telnet
and the console port. For secure remote management, the WGSD-1022 support SSL and SSH
connection which encrypt the packet content at each session.
Page 20
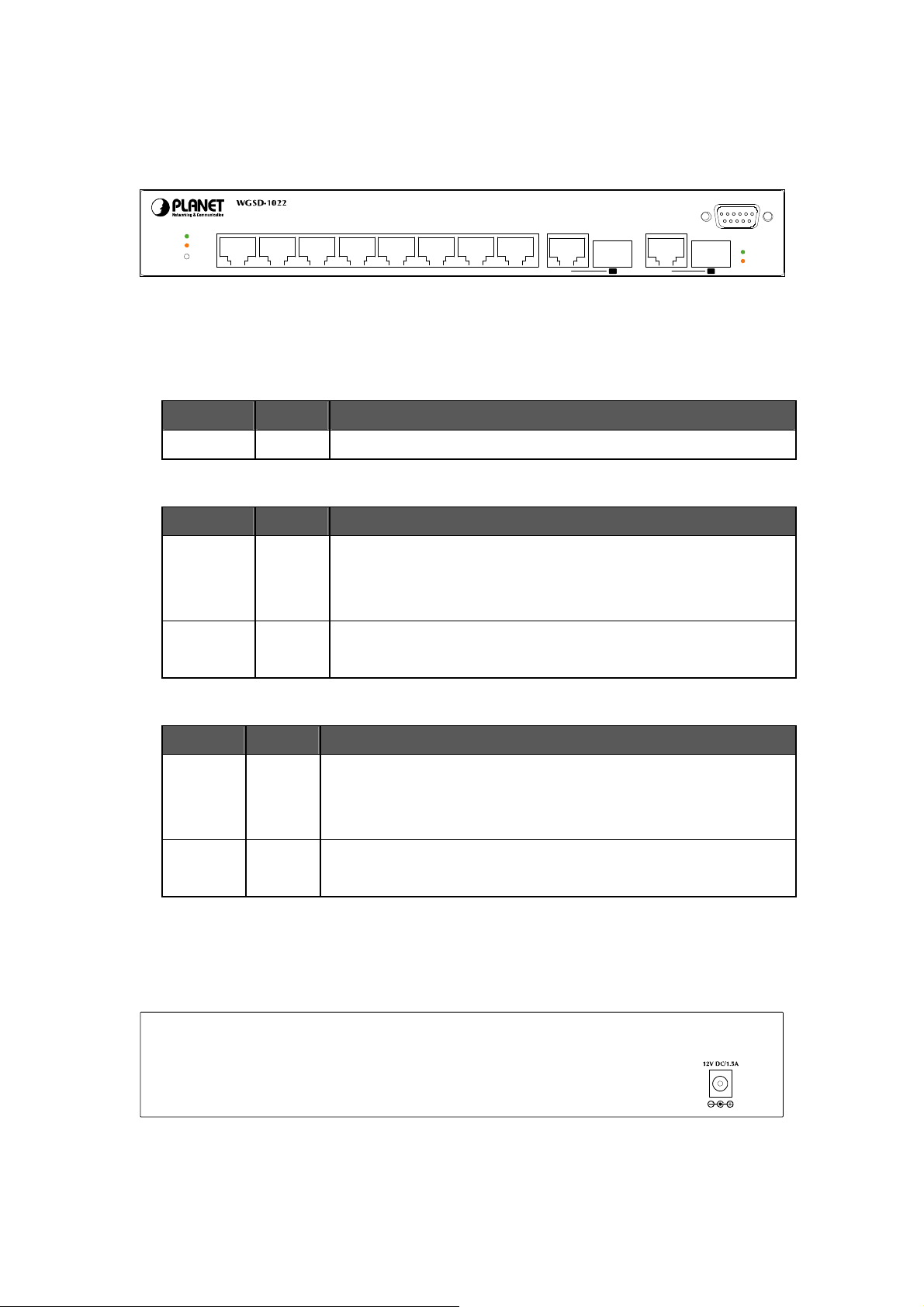
2.1.2 Switch Front Panel
Figure 2-1 shows the front panel of the Switch.
LNK/ACT
100
PWR
13574268910
Figure 2-1 WGSD-1022 front panel.
2.1.3 LED Indications
System
LED Color Function
PWR
Per 10/100Mbps port
LED Color Function
LNK/ACT
100
Green
Green
Orange
Lights to indicate that the Switch has power.
Lights to indicate the link through that port is successfully established.
Blink: indicate that the Switch is actively sending or receiving data over
that port.
Lights to indicate the port is running in 100Mbps speed.
Off: indicate that the port is operating at 10Mbps.
Intelligent 8-Port 10/100Mbps+2 Gigabit Ethernet Switch
G1 G2
mini-GBIC
910
mini-GBIC
38400, N, 8, 1
G1/G2
LNK/ACT
1000
Per 10/100/1000Base-T port /SFP interfaces
LED Color Function
Lights to indicate the link through that port is successfully established.
LNK/ACT
Green
Blink: indicate that the Switch is actively sending or receiving data over that
port.
Lights to indicate the port is running in 1000Mbps speed.
1000
Orange
Off: indicate that the port is operating at 10Mbps or 100Mbps.
2.1.4 Switch Rear Panel
Figure 2-2 shows the rear panel of the Switch
Figure 2-2 WGSD-1022 rear panel.
Page 21

Power Notice:
1. The device is a power-required device, it means, it will not work till it is powered. If your
networks should active all the time, please consider using UPS (Uninterrupted Power Supply)
for your device. It will prevent you from network data loss or network downtime.
2. In some area, installing a surge suppression device may also help to protect your switch from
being damaged by unregulated surge or current to the Switch or the power adapter.
2.2 Install the Switch
This section describes how to install the Ethernet Switch and make connections to it. Please read the
following topics and perform the procedures in the order being presented.
2.2.1 Desktop Installation
To install the Switch on desktop or shelf, please follows these steps:
Step1: Attach the rubber feet to the recessed areas on the bottom of the Switch.
Step2: Place the Switch on the desktop or the shelf near an AC power source.
Step3: Keep enough ventilation space between the Switch and the surrounding objects.
When choosing a location, please keep in mind the environmental restrictions
#Note:
Step4: Connect the Switch to network devices.
A. Connect one end of a standard network cable to the 10/100 RJ-45 ports or Gigabit RJ-45 / SFP
mini-GBIC slot on the front of the Switch
B. Connect the other end of the cable to the network devices such as printer servers, workstations
or routers…etc.
#Note:
Step5: Supply power to the Switch.
A. Connect one end of the power cable to the Switch.
B. Connect the power plug of the power cable to a standard wall outlet.
When the Switch receives power, the Power LED should remain solid Green.
discussed in Chapter 1, Section 4, and Specification.
Connection to the Switch requires UTP Category 5 network cabling with RJ-45 tips.
For more information, please see the Cabling Specification in Appendix A.
Page 22
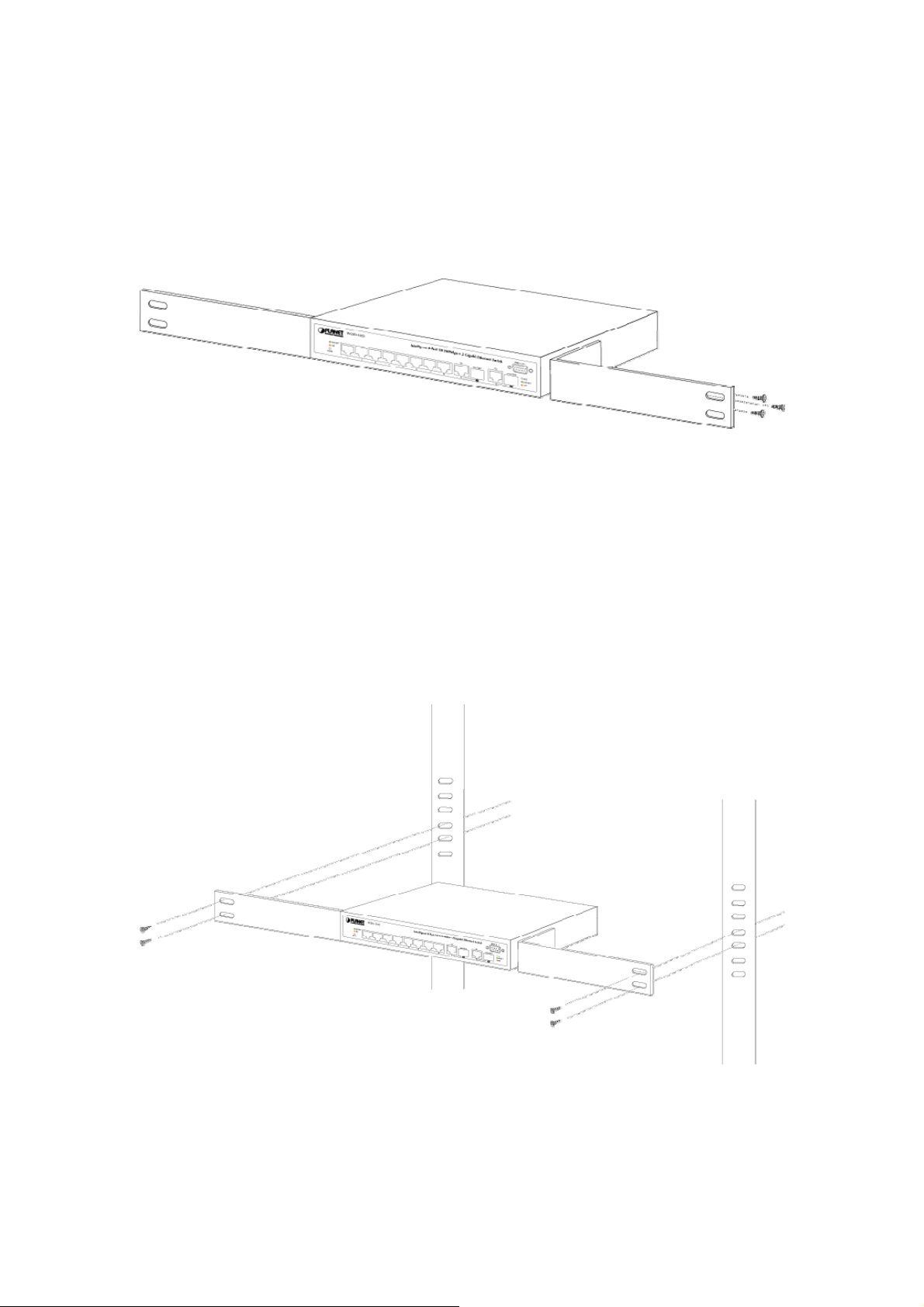
2.2.2 Rack Mounting
To install the Switch in a 19-inch standard rack, please follows the instructions described below.
Step1: Place the Switch on a hard flat surface, with the front panel positioned towards the front side.
Step2: Attach the rack-mount bracket to each side of the Switch with supplied screws attached to the
package. Figure 2-5 shows how to attach brackets to one side of the Switch.
Figure 2-5 Attach brackets to the Switch.
Caution:
You must use the screws supplied with the mounting brackets. Damage caused to the parts by
using incorrect screws would invalidate the warranty.
Step3: Secure the brackets tightly.
Step4: Follow the same steps to attach the second bracket to the opposite side.
Step5: After the brackets are attached to the Switch, use suitable screws to securely attach the brackets
to the rack, as shown in Figure 2-6
Figure 2-6 Mounting the Switch in a Rack
Step6: Proceeds with the steps 4 and steps 5 of session 2.2.1 Desktop Installation to connect the
network cabling and supply power to the Switch.
Page 23

2.2.3 Installing the SFP transceiver
The sections describe how to insert an SFP transceiver into an SFP slot.
The SFP transceivers are hot-plug e and hot-swappable. You can plug-in and out the transceiver to/from
any SFP port without having to power down the Switch. As the Figure 2-7 appears.
Figure 2-7 Plug-in the SFP transceiver
Approved PLANET SFP Transceivers
PLANET WGSD-1022 support both single mode and multi mode SFP transceiver. The following list of
approved PLANET SFP transceivers is correct at the time of publication:
■MGB-SX SFP (1000BASE-SX SFP transceiver )
■MGB-LX SFP (1000BASE-LX SFP transceiver )
It recommends using PLANET SFPs on the Switch. If you insert a SFP transceiver
#Note:
Before connect the other switches, workstation or Media Converter.
1. Make sure both side of the SFP transfer are with the same media type, for example: 1000Base-SX to
1000Base-SX, 1000Bas-LX to 1000Base-LX.
2. Check the fiber-optic cable type match the SFP transfer model.
¾ To connect to 1000Base-SX SFP transfer, use the multi-mode fiber cable- with one side must
be male duplex LC connector type.
that is not supported, the Switch will not recognize it.
¾ To connect to 1000Base-LX SFP transfer, use the single-mode fiber cable-with one side
must be male duplex LC connector type.
Page 24

Connect the fiber cable
1. Attach the duplex LC connector on the network cable into the SFP transceiver.
2. Connect the other end of the cable to a device – switches with SFP installed, fiber NIC on a
workstation or a Media Converter..
3. Check the LNK/ACT LED of the SFP slot on the front of the Switch. Ensure that the SFP transceiver
is operating correctly.
4. Check the Link mode of the SFP port if the link failed. Co works with some fiber-NICs or Media
Converters, set the Link mode to “1000 Force” is needed.
Page 25

3. CONFIGURATION
This chapter explains the methods that you can use to configure management access to the S witch. It
describes the types of management applications and the communication and management protocols that
deliver data between your management device (work-station or personal computer) and the system. It
also contains information about port connection options.
This chapter covers the following topics:
Management Access Overview
Key Concepts
Key Guidelines for Implementation
Administration Console Access
Web Management Access
SNMP Access
Standards, Protocols, and Related Reading
3.1 Management Access Overview
The Switch gives you the flexibility to access and manage the Switch using any or all of the following
methods:
An administration console
Web browser interface
An external SNMP-based network management application
The administration console and Web browser interface support are embedded in the Switch software and
are available for immediate use. Each of these management methods has their own advantages. Table
3-1 compares the three management methods.
Method Advantages Disadvantages
Console
Web
‧No IP address or subnet needed
‧Text-based
‧Telnet functionality and HyperTerminal
built into Windows 95/98/NT/2000/ME/XP
operating systems
‧Secure
‧Ideal for configuring the switch remotely
‧Must be near switch or use dial-up
connection
‧Not convenient for remote users
‧Modem connection may prove to be
unreliable or slow
‧Security can be compromised
Browser
‧Compatible with all popular browsers
‧Can be accessed from any location
(hackers need only know the IP address
and subnet mask)
Page 26
‧Most visually appealing ‧May encounter lag times on poor
connections
SNMP
Agent
‧Communicates with switch functions at
the MIB level
‧Based on open standards
Table 3-1 Management Methods Comparison
‧Requires SNMP manager software
‧Least visually appealing of all three
methods
‧Some settings require calculations
‧Security can be compromised
(hackers need only know the
community name)
3.1.1 Administration Console
The administration console is an internal, character-oriented, and command line user interface for
performing system administration such as displaying statistics or changing option settings. Using this
method, you can view the administration console from a terminal, personal computer, Apple Macintosh,
or workstation connected to the switch's console (serial) port.
There are two ways to use this management method: via direct access or modem port access. The
following sections describe these methods. For more information about using the console, refer to
Chapter 5 Command Line Interface Console Management.
3.1.2 Direct Access
Direct access to the administration console is achieved by directly connecting a terminal or a PC
equipped with a terminal-emulation program (such as HyperTerminal) to the Switch console (serial) port.
When using this management method, a null-modem cable is required to connect the Switch to the PC.
After making this connection, configure the terminal-emulation program to use the follo wing parameters:
The default parameters are:
384,00 bps
8 data bits
No parity
1 stop bit
Page 27

You can change these settin gs, if desired, after you log on. This management method is often preferred
because you can remain connected and monitor the system during system reboots. Also, certain error
messages are sent to the serial port, regardless of the interface through which the associated action was
initiated. A Macintosh or PC attachment can use any terminal - emulation program for connecting to the
terminal serial port. A workstation attachment under UNIX can use an emulator such as TIP.
3.2 Web Management
The Switch provides a browser interface that lets you configure and manage the Switch remotely. After
you set up your IP address for the Switch, you can access the Switch's Web interface applications
directly in your Web browser by entering the IP address of the Switch. You can then use your Web
browser to list and manage Switch configuration parameters from one central location, just as if you were
directly connected to the Switch's console port.
Web Management requires either Microsoft Internet Explorer 4.01 or later or Netscape Navigator 4.03 or
later.
3.3 SNMP-Based Network Management
You can use an external SNMP-based application to configure and manage the Switch. This
management method requires the SNMP agent on the Switch and the SNMP Network Management
Station to use the same community string. This management method, in fact, uses two community strings:
the get community string and the set community string. If the SNMP Net-work management Station only
knows the set community string, it can read and write to the MIBs. However, if it only knows the get
community string, it can only read MIBs. The default gets and sets community strings for the Switch are
public.
3.4 Protocols
The Switch supports the following protocols:
Virtual terminal protocols, such as Telnet
Simple Network Management Protocol (SNMP)
3.4.1 Virtual Terminal Protocols
A virtual terminal protocol is a software program, such as Telnet, that allows you to establish a
management session from a Macintosh, a PC, or a UNIX workstation. Because Telnet runs over TCP/IP,
you must have at least one IP address configured on the Switch before you can establish access to it with
a virtual terminal protocol.
Terminal emulation differs from a virtual terminal protocol in that you must connect a
#Note:
terminal directly to the console (serial) port.
Page 28

3.4.2 SNMP Protocol
Simple Network Management Protocol (SNMP) is the standard management protocol for multi-vendor IP
networks. SNMP supports transaction-based queries that allow the protocol to format messages and to
transmit information between reporting devices and data-collection programs. SNMP runs on top of the
User Datagram Protocol (UDP), offering a connectionless-mode service.
3.4.3 Management Architecture
All of the management application modules use the same Messaging Application Programming Interface
(MAPI). By unifying management methods with a single MAP, configuration parameters set using one
method (console port, for example) are immediately displayable by the ot her management methods (for
example, SNMP agent of Web browser).
The management architecture of the Switch adheres to the IEEE open standard. This compliance
assures customers that the Switch is compatible with, and will interoperate with other solutions that
adhere to the same open standard.
Page 29

4. Web Configuration
The WGSD-1022 can be configured through an Ethernet connection, make sure the manager PC must
be set on same the IP subnet address with the Switch. For example, if you have changed the default IP
address of the Switch to 192.168.1.1 with subnet mask 255.255.255.0 via console, then the manager PC
should be set at 192.168.1.x (where x is a number between 1 and 253) with subnet mask 255.255.255.0.
Or you can use the factory default IP address 192.168.1.254 to do the relative configuration on manager
PC. The sceen in Figure 4-1 appears.
Figure 4-1 Web Management via ethernet
Logging on the switch
1. Use Internet Explorer 5.0 or above Web brow ser. Enter the factory-default IP address to access the
Web interface. The factory-default IP Address as following:
http://192.168.1.254
2. When the following login screen appears, the system will ask you to enter the username and
password.
Default User name: admin
Default Password: admin
The login screen in Figure 4-2 appears.
Page 30
Figure 4-2 WGSD-1022 Web Login screen
3. After entering the username and password, the main screen appears as Figure 4-3.
Figure 4-3 Web Main Screen of WGSD-1022
Now, you can use the Web management interface to continue the Switch management or manage the
Switch by console interface.
#Note:
It is recommended to use Internet Explore 6.0 or above to access WGSD-1022.
Page 31

4.1 Main Screen
The Switch provides a Web-based browser interface for configuring and managing the Switch. This
interface allows you to access the Switch using the Web browser of your choice. This chapter describes
how to use the Switch’s Web browser interface to configure and manage the Switch.
Main Functions Menu
Sub Menu
Save Config
Main Screen
Figure 4-1
Via the Web-Management, the administrator can setup the WGSD-1022 by select the functions those
listed in the Main Function. The screen in Figure 4-2 appears.
Figure 4-2 WGSD-1022 Main Funcrions Menu
The following functions can be configured here:
System
Port
VLAN
Spanning Tree
Multicast
QoS
Access Control
Security
SNMP
Manage
Statistics
Save
Page 32

4.2 System
The Setup menus include the tree sub-menus:
Information
IP Config
SNTP
4.2.1 Information
The Information screen provides Device and System Information of the Switch.
Figure 4-3 System Information screen
The page contains the following informations:
• Model Name
• Boot Version
• Firmware Version
• MAC Address
• System Object ID
• System Up Time
• Current Time
The product name of this Switch
The version of boot system currently running on the Switch
The operating system currently running on the Switch
The MAC address of the Switch displays here
Tthe system object identifier is in this field
The time in days, hours and minutes since the last Switch reboot
Specifies the time and date. The format is hour, minute, second,
month, day, year
Page 33

4.2.2 IP Config
The Basic Setup Table include the IP Config (see figure 4-4), which allows you to assign DHCP or static
IP settings to interfaces and assign default gateways. In the IP Config screen, you can set these parts as
below:
The page includes the following fields:
• System Name
• System Location
• System Contact
• Management VLAN
• IP Setting Mode
• Host Name
Type your system name
Type where the Switch is located
Enter the administrative contact person
Where you can select the Management VLAN.
The default Managemanet VLAN is VLAN 1
Where select Static or Dynamic IP address configuration.
The Default Mode is Static
In this field you can enter the DHCP Host Name
Figure 4-4 IP Config screen
• IP Address
• Subnet Mask
Enter the IP address when you want to use a static address.
The default IP Address is 192.168.1.254
Enter the IP subnet mask for the interface.
The factory default value is 255.255.255.0
Page 34

• Gateway
Enter the default gateway for the IP interface.
The factory default value is 0.0.0.0
• DNS Server
Enter the IP Address of the DNS Server. The Domain Name System
(DNS) converts user-defined domain names into IP addresses
4.2.3 SNTP
In the Basic Setup Table, you can see the SNTP (see figure 4-5), by which you can configure the time
settings for the Switch. You can select SNTP Server Time or System Time.
Figure 4-5 SNTP screen
The Time page includes the following fields:
• Use System Time
• Use SNTP Time
• Hours / Minuntes /
Seconds
• Month / Day / Year
Specifies that the system time is not set by an external source but the
Local time settings
Specifies that the system time is set via an SNTP server
Defines the system time. The field format is HH:MM:SS, for example,
21:15:03.
Defines the system date. The field format is Day:Month:Year, for
example, 04 May 2050
Page 35

• Time Zone
The difference between Greenwich Mean Time (GMT) and local time.
For example, the Time Zone Offset for Paris is GMT +1, while the
local time in Taipei is GTM +8
• Daylight Saving
• Time Set Offset
• From
Enables the Daylight Savings Time (DST) on the device based on the
devices location. The possible field values are:
• USA --The device switches to DST at 2 a.m. on the first Sunday
of April, and reverts to standard time at 2 a.m. on the last
Sunday of October.
• European -- The device switches to DST at 1:00 am on the last
Sunday in March and reverts to standard time at 1:00 am on the
last Sunday in October. The European option applies to EU
members, and other European countries using the EU standard.
• Custom -- The DST definitions are user-defined based on the
device locality. If Other is selected, the From and To fields must
be defined.
For non USA and European countries, the amount of time for DST
can be set in minutes. The value range is (1-1440). The default time is
60 minutes
Defines the time that DST begins in countries other than USA or
Europe, in the format DayMonthYear in one field and time in another.
For example, DST begins on the 25th October 2007 5:00 am, the two
fields will be 25Oct07 and 5:00. The possible field values are:
• Date -- The date at which DST begins. The possible field range
is 1-31.
• Month -- The month of the year in which DST begins. The
possible field range is Jan-Dec.
• Year-- The year in which the configured DST begins.
• Time -- The time at which DST begins. The field format is
Hour:Minute, for example, 05:30.
• To
• Recurring
• From
Defines the time that DST ends in countries other than USA or
European in the format DayMonthYear in one field and time in
another. For example, DST ends on the 23rd March 2008 12:00 am,
the two fields will be 23Mar08 and 12:00. The possible field values
are:
• Date -- The date at which DST ends. The possible field range is
1-31.
• Month -- The month of the year in which DST ends. The
possible field range is Jan-Dec.
• Year-- The year in which the config ured DST ends.
• Time -- The time at which DST starts. The field format is
Hour:Minute, for example, 05:30.
Defines the time that DST starts in countries other than USA or
Europe where the DST is constant year to year. The possib le field
values are:
Defines the time that DST begins each year. For example, DST
begins locally every second Sunday in April at 5:00 am. The possible
field values are:
• Day -- The day of the week from which DST begins every year.
Page 36

The possible field range is Sunday-Saturday.
• Week -- The week within the month from which DST begins
every year. The possible field range is 1-5.
• Month -- The month of the year in which DST begins every year.
The possible field range is Jan.-Dec.
• Time -- The time at which DST begins every year. The field
format is Hour:Minute, for example, 02:10.
• To
• SNTP Server IP Address
#Note:
The device supports the Simple Network Time Protocol (SNTP). SNTP assures
accurate network device clock time synchronization up to the millisecond. Time
synchronization is performed by a network SNTP server. SNTP operates only as a
client, and cannot provide time services to other systems.
Defines the recurring time that DST ends each year. For example,
DST ends locally every fourth Friday in October at 5:00 am. The
possible field values are:
• Day -- The day of the week at which DST ends every year. The
possible field range is Sunday-Saturday.
• Week -- The week within the month at which DST ends every
year. The possible field range is 1-5.
• Month --
The month of the year in which DST ends every year.
The possible field range is Jan.-Dec.
• Time -- The time at which DST ends every year. The field format
is Hour:Minute, for example, 05:30.
Enter a user-defined SNTP server IP addresses
Page 37

4.3 Port Configuration
In this field, you can see these parts, such as Port settings, Link aggregation, LACP Config.
4.3.1 Port Settings
To use the port settings screen for setting up each of the Switch’s ports. It shows these parts: port#,
memo, admin control, link status, current speed, duplex mode, MDI/MDIX, Flow control, Phy type, LAG,
PVE (see Figure 4-6):
Figure 4-6 Port Settings screen
The Port Settings screen contains the following fields:
• Port
• Memo
• Admin Control
• Link Status
• Current Speed
Shows the port number. You can click on the Detail button of the
appropriate port (G1, G2) to use an SFP module, and the Detail
button shows the Port Configuration Detail screen, which include port,
description, port type, admin status, current port status ……
Click up the Detail button to make a brief description of the port
When to choose the UP button, the port can be accessed normally, to
choose the Down button, the port will be taken offline
Shows an active connection when you choose the UP button, there is
no active connection or the port has been taken offline by an
Admiinistrator when you choose the Down button
Shows the connection speed of the port and the speed can be
Page 38

configured only when auto-negotiation is disabled on that port
• Duplex Mode
• MDI/ MDIX
• Flow control
• Phy Type
• LAG
• PVE
The port duplex mode, Full (transmission occurs in both directions
simultaneously) or Half (transmission occurs in only one direction at a
time). This mode can be configured only when auto-negotiation is
disabled and port speed is set to 10Mbps or 100Mbps.
It cannot be configured on Link Aggregation Groups (LAGs)
Shows the MDI/MDIX status of the port. To use the MDI setting if the
port is connected to an end station. To use the MDIX setting if the port
is connected to a hub or another switch
Shows the flow control status of the port. It is active when the port
uses Full Duplex Mode
Shows the port type
Shows whether the port is part of a LAG
It bypasses the Forwarding Database and forwards all unicast,
multicast, and broadcast traffic to an uplink when a port is a Private
VLAN Edge (PVE) port, Uplinks can be ports or LAGs
• Edit
It will open the port configuration detail screen
Page 39

Click the Edit button for more detail port configuration.
Port Configuration Detail screen (see figure 4-7)
Figure 4-7 Per Port Configuration detail screen
The Port Configuration screen contains the following fields:
• Port Indicates the number of the port
• Memo Where can be entered by clicking on the Detail button
• Media Type This is the port type
• Admin Status The port can be taken offline by selecting the Down option.
When Up is selected, the port can be accessed normally.
• Operational Status This indicates whether or not the port is active
• Admin Speed
Setting
Change the speed of the port here
Page 40

• Current Port Speed The current speed of the port is displayed he re
• Auto Negotiation You can enabl e or disable the port’s Auto Negotiation feature. If using
an SFP module, Auto Negotiation for the specific port should be set to
disable
• Auto Negotiation
Advertisement
• Back Pressure The Back Pressure feature of the selected port can be enabled or
• Flow Control The Flow Control feature of the selected port can be enabled or
Specifies the capabilities to be advertised by the port. Multiple options
may be selected or Max Capability can be selected to cover all of the
options.
The available options are:
All, which indicates that the port speeds and duplex mode settings
can be accepted.
10 Half, indicates that the port is advertising a 10Mbps half duplex
mode setting.
10 Full, indicates that the port is advertising a 10Mbps full duplex
mode setting.
100 Half, indicates that the port is advertising a 100Mbps half
duplex mode setting.
100 Full, indicates that the port is advertising a 100Mbps full duplex
mode setting.
1000 Full, indicates that the port is advertising a 1000Mbps full
duplex mode setting
disabled
disabled
• MDI/ MDIX • Auto - the port to automatically detect the cable type.
• MDI - if the port is connected to an end station.
• MDIX - if the port is connected to a hub or another switch
• PVE For Gigabit Ethernet switches ONLY. When a port is a Private VLAN
Edge (PVE) port, it bypasses the Forwarding Database and forwards
all unicast, multicast, and broadcast traffic to an uplink. Uplinks can
be ports or LAGs.
Click the Save button to save your changes.
Page 41

4.3.2 Link Aggregation
When you enter the Link Aggregation, you can see these parts (see figure 4-8), such as:
LAG, shows whether the port is part of a LAG.
Figure 4-8 Link Aggregation screen
The Link Aggregation page contains the following fields:
• LAG Indicates the number of the LAG interface. Up to eight LAG interface
can be configured.
• Memo Indicates the description of the LAG ports
• Administrative
Control
• Type The port types that comprise the LAG.
• Link Status Shows an active connection when you choose the UP button, there is
• Speed Shows the connection speed of the port and the speed can be
• Duplex Mode The port duplex mode, Full (transmission occurs in both directions
Up indicates that the port is available and down shows administrator
has taken the port offline. You can click the Save Settings option to
save this option.
no active connection or the port has been taken offline by an
Admiinistrator when you choose the Down button
configured only when auto-negotiation is disabled on that port
simultaneously) or Half (transmission occurs in only one direction at a
time). This mode can be configured only when auto-negotiation is
disabled and port speed is set to 10Mbps or 100Mbps.
• Flow control Shows the flow control status of the port. It is active when the port
Page 42

uses Full Duplex Mode
• LAG Status Shows the current mode of the LAG interface
• Edit
Click the Edit button for more detail port configuration.
Link Aggregation detail configuration
At per-LAG detail configuration page, the administrator can select ports to be the members of the LAG
interface. The screen appears as follow: (See figure 4-9)
It will open the port configuration detail screen
Figure 4-9 Link Aggregation detail screen
Page 43

4.3.3 LACP Config
Aggregated Links can be manually setup or automatically established on the relevant links b y enabling
Link Aggregation Control Protocol (LACP).
Aggregate ports can be linked into link-aggregation port-groups. Each group is comprised of ports with
the same speed, set to full-duplex operation. The LACP screen contains fields for configuring LACP LAG
s (see figure 4-10)
Figure 4-10 LACP configuration screen
The page contains the following fields:
• LACP System Priority
• Port#
• LACP Port Priority
• L ACP Timeout
• Admin Key
Indicates the global LACP priority value. The possible range is 1- 65535
and the default value is 1.
Set the port number which need to timeout and the priority values are
assigned
Where set the LACP priority value for the port and the field range is
1-65535
Administrative LACP timeout. A short or long timeout value can be
selected. Long is the default
A channel will only be formed between ports having the same admin
key , in other words, this only applies to ports located on the same switch
Page 44

4.4 VLAN Configuration
A Virtual LAN (VLAN) is a logical network grouping that limits the broadcast domain. It allows you to
isolate network traffic so only members of the VLAN receive traffic from the same VLAN members.
Basically, creating a VLAN from a switch is logically equivalent of reconnecting a group of network
devices to another Layer 2 switch. However, all the network devices are still plug into the same switch
physically. The WGSD-1022 supports 802.1Q (tagged-based) and GVRP Dynamic VLAN setting in web
management page. In the default configuration, VLAN support is “802.1Q”.
IEEE 802.1Q VLANs
IEEE 802.1Q (tagged) VLAN are implemented on the Switch. 802.1Q VLAN require tagging, which
enables them to span the entire network (assuming all switches on the network are IEEE
802.1Q-compliant).
VLAN allow a network to be segmented in order to reduce the size of broadcast domains. All packets
entering a VLAN will only be forwarded to the stations (over IEEE 802.1Q enabled switches) that are
members of that VLAN, and this includes broadcast, multicast and unicast packets from unknown
sources.
VLAN can also provide a level of security to your network. IEEE 802.1Q VLAN will only deliver packets
between stations that are members of the VLAN. Any port can be configured as either tagging or
untagging. The untagging feature of IEEE 802.1Q VLAN allows VLAN to work with legacy switches that
don't recognize VLAN tags in packet headers. The tagging feature allows VLAN to span multiple
802.1Q-compliant switches through a single physical connection and allows Spanning Tree to be enabled
on all ports and work normally.
Any port can be configured as either tagging or untagging. The untagging feature of IEEE 802.1Q VLAN
allows VLAN to work with legacy switches that don’t recognize VLAN tags in packet headers. The tagging
feature allows VLAN to span multiple 802.1Q-compliant switches through a single physical connection
and allows Spanning Tree to be enabled on all ports and work normally.
Frame Income
Frame Leave
Leave port is tagged Frame remains tagged Tag is inserted
Leave port is untagged Tag is removed Frame remain untagged
Income Frame is tagged Income Frame is untagged
In this field, there are five items, such as Create VLAN, Port setting, Ports to VLAN, VLAN to Ports,
GVRP…
Page 45

4.4.1 Create VLAN
In this table, the information and global parameters for configuring and working with VLAN s will be
provided (see figure 4-11).
Figure 4-11 Create VLAN screen
The page contains the following fields:
Single VLAN
• VLAN ID (2-4094)
• Name
• VLAN ID Range
VLAN Table
The VLAN Table displays a list of all configured VLANs, include the
• VLAN ID,
You can configure the ID number of the VLAN by this item. Up to 256
VLANs can be created. This field is used to add VLANs one at a time.
If you want to add the defined VLAN ID number, you can press the
Add button.
Where shows the user-defined VLAN name
Indicates a range of VLANs configured. To add the defined rang e of
VLAN ID numbers, press the Add Range button
• Name,
• Status
To remove a VLAN, click the Del button.
Page 46

4.4.2 Port Config
In this port setting screen (refer to figure 4-12), the parameters managing ports that are part of a VLAN
will be provided, and you can set the default VLAN ID (PVID). All untagged packets arriving to the device
are tagged by the ports PVID.
Figure 4-12 VLAN Port Setting screen
The page contains the following fields:
• Port# Displays the port number included in the VLAN
• Mode Indicates the port mode. Possible values are:
• General - The port belongs to VLANs, and each VLAN is
user-defined as tagged or untagged (full 802.1Q mode).
• Access - The port belongs to a single untagged VLAN. When a
port is in Access mode, the packet types which are accepted on the
port (packet type) cannot be designated. It is also not possible to
enable/ disable ingress filtering on an access port.
• Trunk - The port belongs to VLANs in which all ports are tagged
(except for an optional single native VLAN).
• Acceptable Frame Type Packet type accepted on the port. Possible values are:
• Admit Tag Only - indicates that only tagged packets are accepted
on the port.
• Admit All - indicates that both tagged and untagged packets are
accepted on the port.
• PVID Assigns a VLAN ID to untagged packets. The possible values are 2 to
4094. VLAN 4095 is defined as per standard and industry practice as
the discard VLAN. Packets classified to the Discard VLAN are dropped
Page 47

• Ingress Filtering Enables or disables Ingress filtering on the port. Ingress filtering
discards packets which do not include an ingress port
• LAG Indicates the LAG to which the VLAN is defined
Port Mode VLAN Membership Frame Leave
Access Belongs to a single untagged VLAN
General
Trunk
Allowed to belongs to multiple untagged
VLANs at the same time
Allowed to belongs to multiple Tagged
VLANs at the same time
(Tag=PVID or Original VID be remained)
( Tag=PVID be removed)
Untagged
Untagged
(Tag=PVID be removed)
Tagged
4.4.3 VLAN Group
The Ports to VLAN screen contains fields for configuring ports to a VLAN. The port default VLAN ID
(PVID) is configured on the Create VLAN screen. All untagged packets arriving to the device are tagged
by the ports PVID. The Ports to VLAN screen contains a Port Table for VLAN parameters for each port.
Ports are assigned VLAN membership by selecting and configuring the presented configuration options,
you can refer to figure 4-13.
Figure 4-13 Ports to VLAN screen
Page 48

The page contains the following fields:
• VLAN
• Access
• Trunk
• General
• Tagged
• Untagged
• Forbidden
• Exclude
Where means the VLAN number
Indicates the port belongs to a single untagged VLAN. When a port is
in Access mode, the packet types which are accepted on the port
cannot be designated. Ingress filtering cannot be enabled/disabled on
an access port.
Which indicates the port belongs to VLANs in which all ports are
tagged, except for one port that can be untagged
Which indicates the port belongs to VLANs, and each VLAN is
user-defined as tagged or untagged (full 802.1Q mode)
Defines the interface as a tagged member of a VLAN. All packets
forwarded by the interface are tagged. The packets contain VLAN
information
Packets forwarded by the interface are untagged
Forbidden ports are not included in the VLAN
Excludes the interface from the VLAN. However, the interface can be
added to the VLAN through GVRP
4.4.4 GVRP Config
GARP VLAN Registration Protocol (GVRP) is specifically provided for automatic distribution of VLAN
membership information among VLAN-aware bridges. GVRP allows VLAN-aware bridges to
automatically learn VLANs to bridge ports mapping, without having to individu ally configure each bridge
and register VLAN membership. The Global System LAG information displays the same field information
as the ports, but represents the LAG GVRP information.
The GVRP screen (refer to 4-14) is divided into two areas, GVRP and GVRP Table. The field definitions
for both areas are the same.
Page 49

Figure 4-14 GVRP configuration screen
The page contains the following fields:
• Set GVRP
• Port#
• State
• Dynamic VLAN
Creation
• Registration
• Update to Table
Enables and disables GVRP on the device
Displays the interface on which GVRP is enabled. Possible field
values are:
Port - indicates the port number on which GVRP is enabled.
LAG - indicates the LAG number on which GVRP is enabled.
When the checkbox is checked, GVRP is enabled on the interface
When the checkbox is checked, Dynamic VLAN creation is enabled
on the interface
When the checkbox is checked, VLAN registration through GVRP is
enabled on the device..
The Update button adds the configured GVRP setting to the table at
the bottom of the screen
Page 50

4.5. Spanning Tree
Spanning Tree Protocol (STP) provides tree topography for any arrangement of bridges. STP also
provides one path between end stations on a network, eliminating loops.
Loops occur when alternate routes exist between hosts. Loops in an extended network can cause
bridges to forward traffic indefinitely, resulting in increased traffic and reducing network efficiency.
The device supports the following Spanning Tr ee versions:
• Classic STP, by which provides a single path between end stations, avoiding and eliminating loops.
• Rapid STP, which detects and uses network topologies that provide faster convergence of the
spanning tree, without creating forwarding loops.
• Multiple STP, which provides full connectivity for packets allocated to any VLAN. Multiple STP is
based on the RSTP. In addition, Multiple STP transmits packets assigned to different VLANs through
different MST regions. MST regions act as a single bridge.
4.5.1 STP Config
The STP Config screen (see figure 4-15) contains parameters for enabling STP on the device.
STP Config Spanning Tree State, which indicates if STP is enabled on the device.
Figure 4-15 STP Config screen
Page 51

The page contains the following fields:
• STP Mode
• BPDU Handling
• Path Cost Default
Values
This indicates the STP mode by which STP is enabled on the device. The
possible field values are:
• Classic STP, where enables Classic STP on the device. This is the
default value.
• Rapid STP, where enables Rapid STP on the device.
• Multiple STP, where enables Multiple STP on the device.
This determines how BPDU packets are managed when STP is disabled
on the port/ device. BPDUs are used to transmit spanning tree
information. The possible field values are:
• Filtering, where filters BPDU packets when spanning tree is disabled
on an interface. This is the default value.
• Flooding, where floods BPDU packets when spanning tree is
disabled on an interface.
This specifies the method used to assign default path costs to STP ports.
The possible field values are:
• Short, specifies 1 through 65,535 range for port path costs.
This is the default value.
• Long, specifies 1 through 200,000,000 range for port path costs. The
default path costs assigned to an interface varies according to the
selected method.
• Priority
• Hello Time
• Max Age
• Forward Delay
Specifies the bridge priority value. When switches or bridges are running
STP, each is assigned a priority. After exchanging BPDUs, the device with
the lowest priority value becomes the Root Bridge.
The port priority value is provided in increments of 4096. For example,
4096, 8192, 12288, etc. The range is 0 to 65535.
The default value is 32768.
This specifies the device Hello Time. The Hello Time indicates the amount
of time in seconds a root bridge waits between configuration messages.
The default is 2 seconds. The range is 1 to 10 seconds.
Where specifies the device Maximum Age Time. The Maximum Age Time
indicates the amount of time in seconds a bridge waits before sending
configuration messages.
The default max age is 20 seconds. The range is 6 to 40 seconds.
This specifies the device forward delay time. The Forward Delay Time
indicates the amount of time in seconds a bridge remains in a listening
and learning state before forwarding packets.
The default is 15 seconds. The range is 4 to 30 seconds.
Page 52

4.5.2 STP Port Config
Network administrators can assign STP Port Config to specific interfaces using the STP Interface
Settings screen (see figure 4-16). The STP Interface Settings page contains the following fields:
Figure 4-16 STP Port Config screen
The page contains the following fields:
• Port# Indicates the port or LAG on which STP is enabled
• Enable STP which indicates if STP is enabled on the port
• Port Fast Indicates if Fast Link is enabled on the port. If Fast Link mode is enabled for a
port, the Port State is automatically placed in the Forwarding state when the port
link is up. Fast Link optimizes the STP protocol convergence. STP convergence
can take 30-60 seconds in large networks.
• Port State Displays the current STP state of a port. If enabled, the port state determines
what forwarding action is taken on traffic. Possible port states are:
• Disabled, indicates that STP is currently disabled on the port. The port
forwards traffic while learning MAC addresses.
• Blocking, where indicates that the port is currently blocked and cannot
forward traffic or learn MAC addresses. Blocking is displayed when Classic
STP is enabled.
• Listening, where indicates that the port is in Listening mode. The port
cannot forward traffic nor can it learn MAC addresses.
• Learning, where indicates that the port is in whose mode. The port cannot
forward traffic, however it can learn new MAC addresses.
Page 53

• Forwarding, the port that can forward traffic and learn new MAC addresses.
• Speed Indicates the speed at which the port is operating
• Path Cost Indicates the port contribution to the root path cost. The path cost is adjusted to a
higher or lower value, and is used to forward traffic when a path being rerouted.
Value Rage : 1-20000000
Default Path Cost - The default path cost of the port is automatically set by the
port speed and the default path cost method. The default values for path costs
are:
- Ethernet - 2000000
- Fast Ethernet - 200000
- Gigabit Ethernet - 20000
• Default Path
Cost
• Priority Indicates priority value of the port. The priority value influences the port choice
• Designated
Bridge ID
• Designated Port
ID
• Designated Cost Where indicates the cost of the port participating in the STP topology. Ports with a
• Forward
Transitions
When selected the default path cost is implemented
when a bridge has two ports connected in a loop. The priority value is between 0
-240. The priority value is provided in increments of 16.
Indicates the bridge priority and the MAC Address of the designated bridge.
Indicates the selected port’s priority and interface.
lower cost are less likely to be blocked if STP detects loops.
This indicates the number of times the port has changed from the Blocking state
to Forwarding state.
Page 54

STP Port status table
Figure 4-17 STP Port status screen
4.5.3 RSTP Port Config
While the classic spanning tree prevents Layer 2 forwarding loops in a general network topology,
convergence can take between 30-60 seconds. This time may delay detecting possible loops, and
propagating status topology changes. Rapid Spanning Tree Protocol (RSTP) detects and uses network
topologies that allow a faster STP convergence without creating forwarding loops (refer to figure 4-18).
Page 55

Figure 4-18 RSTP Port Settings screen
The page contains the following fields:
• Port#
• Role
• Mode
Where displays the port or LAG on which Rapid STP is enabled.
Where indicates the port role assigned by the STP algorithm in order
to provide to STP paths. The possible field values are:
• Root, where provides the lowest cost path to forward packets to
root switch.
• Designated, where indicates that the port or LAG via which the
designated switch is attached to the LAN.
• Alternate, which provides an alternate path to the root switch
from the root interface.
• Backup, which provides a backup path to the designated port
path toward the Spanning Tree leaves. Backup ports occur only
when two ports are connected in a loop by a point-to-point link.
Backup ports also occur when a LAN has two or more
connections connected to a shared segment.
• Disabled, which indicates the port is not participating in the
Spanning Tree.
Where indicates the current Spanning Tree mode. The Spanning Tree
mode is selected in the Global STP screen. The possible field values
are:
• Fast Link
• Port State
• P2P Admin Status
• P2P Oper Statu s
• Classic STP, which indicates that Classic STP is enabled on the
device.
• Rapid STP, which indicates that Rapid STP is enabled on the
device.
• Multiple STP, which indicates that Multiple STP is enabled on
the device.
This indicates if Fast Link is enabled or disabled for the port or LAG. If
Fast Link is enabled for a port, the port is automatically placed in the
forwarding state.
Indicates if RSTP is enabled on the interface.
Indicates if a point-to-point links are established, or permits the device
to establish a point-to-point link. The possible field values are:
• Auto. Point-to-point links are automatically established by the
device.
• Enabled, enables the device to establish a point-to-point link.
• Disabled, where disables point-to-point link.
Indicates the Point-to-Point operating state. To run a migration test,
press Activate next to the Activate Protocol Migration Test field. The
test sends Link Control Protocol (LCP) packets to test if a data link is
enabled.
Page 56

To establish communications over a point-to-point link, the originating PPP first
#Note:
sends Link Control Protocol (LCP) packets to configure and test the data link. After a
link is established and optional facilities are negotiated as needed by the LCP, the
originating PPP sends Network Control Protocols (NCP) packets to select and
configure one or more network layer protocols. When each of the chosen network
layer protocols has been configured, packets from each network layer protocol can
be sent over the link. The link remains configured for communications until explicit
LCP or NCP packets close the link, or until some external event occurs. This is the
actual switch port link type. It may differ from the administrative state.
4.5.4 MSTP Config
MSTP provides differing load balancing scenarios. For example, while port A is blocked in one STP
instance, the same port is placed in the Forwarding State in another STP instance. The MSTP Properties
screen (see figure 4-19) contains information for defining global MSTP settings, region names, MSTP
revisions, and maximum hops.
Figure 4-19 MSTP Properties
Page 57

The page contains the following fields:
• Region Name
• Revision
• Max Hops
• IST Master
Where provides a user-defined STP region name
Where defines unsigned 16-bit number that identifies the revision of
the current MST configuration. The revision number is required as
part of the MST configuration.
The possible field range 0-65535.
Which indicates the total number of hops that occur in a specific
region before the BPDU is discarded. Once the BPDU is discarded,
the port information is aged out. The possible field range is 1-40.
The field default is 20 hops
Where identifies the Spanning Tree Ma ster instance. The IST Master
is the specified instance roo
4.5.5 MSTP Instance Config
MSTP opreation maps VLANs into STP instances (see figure 4-20) Packets assigned to various VLANs
are transmitted along different paths within Multiple Spanning Trees Regions (MST Regions), Regions
are one or more Multiple Spanning Tree bridges by which frames can be transmitted. In configuring MST,
the MST region to which the device belongs is defined. A configuration con sists of the name, revision,
and region to which the device belongs. Network Administrators can define MSTP Instances settings
using the MSTP Instance Settings screen.
Figure 4-20 MSTP Instance Settings screen
Page 58

The page contains the following fields:
• Instance ID
• Included VLAN
• Bridge Priority
• Designated Root
Bridge ID
• Root Port
• Root Path Cost
• Bridge ID
Defines the VLAN group to which the interface is assigned.
Where maps the selected VLAN to the selected instance. Each VLAN
belongs to one instance.
Specifies the selected spanning tree instance device priority. The field
range is 0-61440.
which indicates the ID of the bridge with the lowest path cost to the
instance ID
Where indicates the selected instance’s root port
Indicates the selected instance’s path cost.
Indicates the bridge ID of the selected instance.
• Remaining Hops
Press the VLAN Instance Configuration button, a new window popup. Assgin selected VLAN to specify
MST Instance at the VLAN Instatnce Configuration page. The screen in Figure 4-21 appears.
Indicates the number of hops remaining to the next destination.
Figure 4-21 MSTP VLAN Instance Configuration screen
Page 59

4.5.6 MSTP Interface Settings
Network Administrators can assign MSTP Interface settings using the MSTP Interface Settings screen
(see figure 4-22).
Figure 4-22 MSTP Interfance Settings screen
The MSTP Interface Settings screen contains the following fields:
• Instance ID#
• Port#
• Port State
• Type
Lists the MSTP instances configured on the device. Possible field
range is 0-15.
Indicates the interface for which the MSTP settings are displayed.
The possible field values are two types:
• Port - Specifies the port for which the MSTP settings are
displayed.
• LAG - Specifies the LAG for which the MSTP settings are
displayed.
where indicates whether the port is enabled for the specific instance
Indicates if the port is a point-to-point port, or a port connected to a
hub. The possible field values are:
• Boundary Port, attaches MST bridges to LAN in an outlying
region. If the port is a boundary port, it also indicates whether the
device on the other side of the link is working in RSTP or STP
mode.
• Master Port, where provides connectivity from a MSTP region to
Page 60

the outlying CIST root.
• Internal, indicates the port is an internal port.
• Role
• Interface Priori ty
Indicates the port role assigned by the STP algorithm in order to
provide to STP paths. The possible field values are:
• Root, provides the lowest cost path to forward packets to root
device.
• Designated, indicates the port or LAG via which the designated
device is attached to the LAN.
• Alternate, provides an alternate path to the root device from the
root interface.
• Backup, provides a backup path to the designated port path
toward the Spanning T ree leaves. Backup ports occur only when
two ports are connected in a loop by a point-to-point link.
Backup ports also occur when a LAN has two or more
connections connected to a shared segment.
• Disabled, which indicates the port is not participating in the
Spanning T ree.
Defines the interface priority for specified instance.
The default value is 128.
• Path Cost
• Designated Bridge
ID
• Designated Port ID
• Designated Cost
• Forward Transitions
• Remaining Hops
MSTP Interface status table
The page displays the current MST Interfaces configuration and status.
Indicates the port contribution to the Spanning Tree instance. The
range should always be 1200,000,000.
Where indicates that the bridge ID number that connects the link or
shared LAN to the root.
By which indicates that the Port ID number on the designated bridge
that connects the link or the shared LAN to the root.
Indicates that the default path cost is assigned according to the
method selected on the Spanning Tree Global Settings scree n.
This indicates the number of times the port has changed from the
Forwarding state to Blocking state.
Indicates the hops remaining to the next destination.
Page 61

Figure 4-23 MSTP Interfance configuration screen
Page 62

4.6 Multicast
The Multicast of the Switch
On this field: included IGMP Snooping and Bridge Multicast.
4.6.1 IGMP Snooping
When IGMP Snooping (see figure 4-24) is enabled globally, all IGMP packets are forwarded to the CPU.
The CPU analyzes the incoming packets and determines which ports want to join which Multicast groups,
which ports have Multicast routers generating IGMP queries, which routing protocols are forwarding
packets and Multicast traffic.
Ports requesting to join a specific Multicast group issue an IGMP report, specifying that Multicast group is
accepting members. This results in the creation of the Multicast filtering database.
Figure 4-24 IGMP Snooping screen
The page contains the following fields:
• Set IGMP Snooping
Indicates if IGMP Snooping is enabled or Disabled on the device.
Page 63

• VLAN ID
Specifies the VLAN ID.
• IGMP Status
• Auto Learn
• Host Timeout
• MRouter Timeout
• Leave Timeout
Indicates if IGMP snooping is enabled on the VLAN.
Indicates if Auto Learn is enabled on the device. If Auto Learn is
enabled, the device automatically learns where other Multicast groups
are located.
Enables or disables Auto Learn on the Ethernet device.
Indicates the amount of time host waits to receive a message before
timing out.
The default time is 260 seconds.
Indicates the amount of the time the Multicast router waits to receive a
message before it times out.
The default value is 300 seconds.
Indicates the time the host waits, after requesting to leave the IGMP
group and not receiving a Join message from another station, before
timing out. If a Leave Timeout occurs, the switch notifies the Multicast
device to stop sending traffic. The Leave Timeout value is either
user-defined, or an immediate leave value.
The default timeout is 10 seconds.
#Note:
IGMP Snooping can be enabled only if Bridge Multicast Filtering is enabled.
4.6.2 Bridge Multicast
The Bridge Multicast screen (see figure 4-25) displays the ports and LAGs attached to the Multicast
service group in the Ports and LAGs tables. The Port and LAG tables also reflect the manner in which the
port or LAGs joined the Multicast group. Ports can be added either to existing groups or to new Multicast
service groups.
This screen permits new Multicast service groups to be created, also assigns ports to a specific Multicast
service address group, and included two areas, Configuring Mu lticast and Multicast Table.
Page 64

Figure 4-25 Bridge Multicast screen
The Page contains the following fields:
• Set Bridge Multicast
Filtering
• VLAN ID
• Multicast Address
• Interface
• LAG
The fields are the same for both areas.
The check box allows enable Bridge Multicast Filtering function.
This identifies a VLAN to be configured to a Multicast service.
Identifies the Multicast group MAC address/IP address.
Displays Interface that can be added to a Multicast service.
The configuration options are as follows:
• Static, indicates the port is user-defined.
• Dynamic, indicates the port is configured dynamically.
• Forbidden, forbidden ports are not included the Multicast group,
• None, displays the port is not configured for Multicast service.
Displays LAG that can be added to a Multicast service.
even if IGMP snooping designated the port to join a Multicast
group.
Use the Add to Table button when you want to assigns p orts to a specific Multicast service addr ess
group.
Page 65

Multicast Table
Figure 4-26 Bridge Multicast screen
Example:
Adding Bridge Multicast Addresses
1. Click the check box to enable the Bridge Multicast Filtering.
2. Define the VLAN ID and New Bridge Multicast Address fields.
3. Check a port to Static to join the port to the selected Multicast group.
4. Click “Add to Table” button.
5. Click the “Save” to apply the sttings.
The bridge Multicast address is assigned to the Multicast group, and the device is updated.
Defining Ports to Receive Multicast Service
1. Define the VLAN ID and the Bridge Multicast Address fields.
2. Check and click a port to Static to join the port to the selected Multicast group.
3. Click “Add to Table” button.
4. Click the “Save” to apply the sttings.
5. Select the VLAN ID to check if the entries be added.
The port is assigned to the Multicast group, and the device is updated.
Assigning LAGs to Receive Multicast Service
1. Define the VLAN ID and the Bridge Multicast Address fields.
2. Check and click the LAG to Static to join the port to the selected Multicast group.
3. Click “Add to Table” button.
4. Click the “Save” to apply the sttings.
The LAG is assigned to the Multicast group, and the device is updated.
Page 66

4.7 QoS
Network traffic is usually unpredictable, and the only basic assurance that can be offered is best effort
traffic delivery. To overcome this challenge, Quality of Service (QoS) is applied throughout the network.
This ensures that network traffic is prioritized according to specified criteria, and that specific traffic
receives preferential treatment. And Queue scheduling, 802.1p settings, Dscp Settings, Rate limit, Port
Qos, Policy Qos are provided.
4.7.1 Queue Scheduling
The Queue Setting screen (see figure 4-27) contains fields for defining the QoS queue forwarding types.
Figure 4-27 Quere Setting screen
The page contains the following fields:
• Strict Priority
• WRR
• Queue
• WRR Weight
• % of WRR
This indicates that traffic scheduling for the selected queue is based
strictly on the queue priority.
This indicates that traffic scheduling for the selected queue is based
strictly on the WRR.
Shows the queue for which the queue settings are displayed.
The possible field range is 1 - 4.
Which displays the WRR weights to queues
Default Rate 1:2:4:8
Displays the amount of bandwidth assigned to the queue.
These values are fixed and are not user- defined.
Page 67

Bandwidth
• 6.67%
• 13.33%
• 26.67%
• 53.33%
4.7.2 802.1p Settings
The terms Class of Service (CoS) and QoS are used in the following:
CoS provides varying Layer 2 traffic services. CoS refers to classification of traffic to traffic-classes,
which are handled as an aggregate whole, with no per-flow settings. CoS is usually related to the 802.1p
service that classifies flows according to their Layer 2 priority, as set in the VLAN header. QoS refers to
Layer 2 traffic and above. QoS handles per-flow settings, even within a single traffic class.
The CoS Settings screen (see figure 4-28) contains fields for enabling or disabling CoS. In addition, the
Trust mode can be selected. The Tr ust mode relies on predefined fields within the packet to determine
the egress queue settings. (To configure the Trust Mode, see 4.7.5.)
Figure 4-28 802.1p Settings screen
Page 68

The Page contains the following fields:
• Select QoS Mode
• Class of Service
• Queue
The Restore Defaults button restores the device factory defaults for mapping CoS values to a
forwarding queue.
802.1p Default:
The Table contains the following fields:
This indicates if QoS is enabled on the interface. The possible values
are:
• Disable, disables QoS on the interface.
• Port Qos, enables QoS on the interface.
• Policy Qos, enables the Advanced Mode QoS on the interface.
Specifies the CoS priority tag values, where zero is the lowest and 7
is the highest
Defines the traffic forwarding queue to which the CoS priority is
mapped.
Four traffic priority queues are supported
• Port#
• Default CoS
• Restore Defaults
• LAG
Interface to which the CoS configuration applies
Determines the default CoS value for incoming packets for which a
VLAN tag is not defined. The possible field values are 0-7.
The default CoS is 0
Restores the device factory defaults for mapping CoS values to
forwarding queue.
LAG to which the CoS configuration applies.
Page 69

4.7.3 DSCP Settings
The DSCP Settings screen (see figure 4-29) enables mapping DSCP values to specific queues
Figure 4-29 DSCP Settings screen
The DSCP Settings screen contains the following fields:
• DSCP
• Queue
Indicates the Differentiated Services Code Point value in the incoming
packet.
Maps the DSCP value to the selected queue
Page 70

4.7.4 Rate Limit
The Bandwidth screen (refer to figure 4-30) allows network managers to define the bandwidth settings for
a specified egress interface. Modifying queue scheduling affects the queue settings globally. The
Bandwidth screen is not used with the Service mode, as bandwidth settings are based on services.
Figure 4-30 Rate limit screen
Queue shaping can be based per queue and/or per interface. Shaping is determined by the lower
specified value. The queue shaping type is selected in the Bandwidth screen, include interface, port, LAG,
Rate Limit, Ingress Rate Limit Status, Rate Limit….
The page contains the following fields:
• Port#
• Ingress Rate Limit
Status
• Rate Limit
(62-1000000 Kbps)
Indicates the interface for which the queue shaping information is
displayed. The possible field values are:
• Port, indicates the port for which the bandwidth settings are
displayed.
• LAG, indicates the LAG for which the bandwidth settings are
displayed.
which indicates if rate limiting is defined on the interface
Defines the amount of bandwidth assigned to the interface.
The possible field values are 62-1000000 Kbps.
• Egress Shaping
Indicates if rate limiting is enabled on the interface.
Page 71

Rate on Selected
Port
• Committed
Information Rate
(CIR)
Defines CIR as the queue shaping type.
The possible field value is 64 - 1,000,000 Kbps.
4.7.5 Port Qos
The Port Qos screen (see figure 4-31) contains the following fields:
The page contains the following fields:
• Trust Mode
Displays the trust mode. If a packet’s CoS tag and DSCP tag are
mapped to different queues, the Trust Mode determines the queue to
which the packet is assigned. Possible values are:
• CoS, which sets trust mode to CoS on the device and the CoS
• DSCP, sets trust mode to the DSCP on the device. The DSCP
Figure 4-31 Port Qos screen
mapping determined the packet queue.
mapping determines the packet queue.
Page 72

4.7.6 Policy Qos
Policy Qos (see figure 4-32) provides rules for specifying flow classification and assigning rule actions
that relate to bandwidth management. The rules are based on the Access Control Lists (see Access
Control Tab)
Figure 4-32 Policy Qos screen
MAC A CL s and IP ACLs can be grouped together in more complex structures, called policies. Policies
can be applied to an interface. Policy ACLs are applied in the sequence they appear within the policy.
Only a single policy can be attached to a port.
In advanced QoS mode, ACLs can be applied directly to an interface in the Security -ACL Binding.
However, a policy and ACL cannot be simultaneously applied to an interface.
After assigning packets to a specific queue, services such as configuring output queues for the
scheduling scheme, or configuring output shaping for burst size, CIR, or CBS per interface or per queue,
can be applied.
Out of Profile DSCP Assignments, this button opens up the DSCP Map screen. (see figure 4-33):
Page 73

Figure 4-33 Out of Profile DSCP Assignments screen
The page contains the following fields:
• DSCP In
• DSCP Out
The Policy Settings button opens the Policy Name screen (see figure 4-34):
This displays the DSCP In value.
The value is form 0-63.
This displays the current DSCP out value. A new value can be
selected from the pull-down menu
Page 74

Figure 4-34 Policy Settings screen
The page contains the following fields:
• Policy Name
• Add to List
• Select Policy
• New Policy Name
• Class Map
defines a new Policy name
this button will add the policy to the Policy Name table
which selects an existing Policy by name
which defines a new Policy name
where selects an existing Class Map by name
Page 75

Class Map setting
New Class Map, by which the New Class Map button opens the New Class Map screen (see figure
4-35)
Figure 4-35 Class Map Settings screen
The page contains the following fields:
• Class Map Name
• Preferred ACL
defines a new Class Map name
which indicates if packets are first matched to an IP based ACL or a
MAC based ACL, the possible field values are:
• IP Based ACLs, matches packets to IP based ACLs first, then
matches packets to MAC based ACLs.
Page 76

• MAC Based ACLs, matches packets to MAC based ACLs first,
then matches packets to IP based ACLs.
• IP ACL
• Match
• MAC ACL
Aggregate Policer, where user-defined aggregate policers. The Aggregate Policer button opens the New
Aggregate Policer screen.
Aggregate Policer Setting
New Aggregate Policer screen (see figure 4-36):
Matches packets to IP based ACLs first, and then matches packets to
MAC based ACLs.
Criteria used to match IP addresses and /or MAC addresses with an
ACL’s address. The possible field values are:
• And, both the MAC-based and the IP-based ACL must match a
packet.
• Or, either the MAC-based or the IP-based ACL must match a
packet.
Matches packets to MAC based ACLs and to IP based ACLs
Figure 4-36 Aggregate Policer Settings screen
Page 77

The page contains the following fields:
• Aggregat e Policer
Name
• Ingress Committed
Information Rate
(CIR)
• Ingress Committed
Burst Size (CBS)
• Exceed Action
Where enter a name in this field.
This defines the CIR in bits per second. This field is only relevant
when the Police value is Single.
This defines the CBS in bytes per second. This field is only relevant
when the Police value is Single.
Action assigned to incoming packets exceeding the CIR.
This field is only relevant when the Police value is Single. Possible
values are:
• Drop, which drops packets exceeding the defined CIR value.
• Remark DSCP, where remarks packet’s DSCP values exceeding
the defined CIR value.
• None, forwarding packets exceeding the defined CIR value.
Page 78

4.8 Access Control
An ACL consists of a set of rules which are matched sequentially against a packet. When a packet meets
the match criteria of a rule, the specified rule action (Permit/Deny) is taken and the additional rules are
not checked for a match. On this menu the interfaces to which an ACL applies must be specified, as well
as whether it applies to inbound or outbound traffic. Rules for the ACL are specifi ed/created using the
ACL Rule Configuration menu.
4.8.1 Layer3 Based ACL
The layer3 Based ACL (Access Control List) screen (see figure 4-37) contains information for defining IP
Based ACLs.
Figure 4-37 Layer3-Base ACL screen
The Page contains the following fields:
• ACL Name
• New ACL Name
• Delete ACL
• Action
Displays the user-defined IP based ACLs
Defines a new user-defined IP based ACL
By which deletes the selected ACL
Indicates the action assigned to the packet matching the ACL.
Packets are forwarded or dropped. In addition, the port can be
shutdown, a trap can be sent to the network administrator, or a packet
assigned rate limiting restrictions for forwarding. The options are as
Page 79

follows:
• Permit, by which forwards packets which meet the ACL criteria.
• Deny, which drops packets which meet the ACL criteria.
• Shutdown, where drops packet that meets the ACL criteria, and
disables the port to which the packet was addressed. Ports are
reactivated from the Port Management screen.
• Protocol
• Select from List
By which creates an ACE (Access Control Event) based on a
specific protocol
Where selects from a protocols list on which ACE can be based. The
possible field values are:
• Any, matches the protocol to any protocol.
• EIGRP, which indicates that the Enhanced Interior Gateway
Routing Protocol (EIGRP) is used to classify network flows.
• ICMP, which indicates that the Internet Control Message Protocol
(ICMP) is used to classify network flows.
• IGMP, which indicates that the Internet Group Management
Protocol (IGMP) is used to classify network flows.
• TCP, which indicates that the Transmission Control Protocol is
used to classify network flows.
• OSPF, by which matches the packet to the Open Shortest Path
First (OSPF) protocol.
• UDP, which indicates that the User Datagram Protocol is used to
classify network flows.
• TCP Flags
• Protocol ID to Match, adds user-defined protocols to which
packets are matched to the ACE. Each protocol has a specific
protocol number which is unique. The possible field range is
0-255.
This filters packets by TCP flag. Filtered packets are either forwarded
or dropped. Filtering packets by TCP flags increases packet control,
and network security. The values that can be assigned are:
• Set, which enables filtering packets by selected flags.
• Unset, disables filtering packets by selected flags.
• Don’t care, which indicates that selected packets do not
influence the packet filtering process.
The TCP Flags that can be selected are:
• Urg, indicates the packet is urgent.
• Ack, indicates the packet is acknowledged.
• Psh, indicates the packet is pushed.
Page 80

• Rst, indicates the connection is dropped.
• Syn, indicates request to start a session.
• Fin, indicates request to close a session.
• Source Port
• Destination Port
• Source IP Address
• Wildcard Mask
Defines the TCP/UDP source port to which the ACE is matched. This
field is active only if 800/6-TCP or 800/17-UDP is selected in the
Select from List drop-down menu.
The possible field range is 0 - 65535
Defines the TCP/UDP destination port. This field is active only if
800/6-TCP or 800/17-UDP is selected in the Select from List
drop-down menu.
The possible field range is 0 - 65535
Matches the source port IP address to which packets are addressed
to the ACE
Defines the source IP address wildcard mask. Wildcard masks
specify which bits are used and which bits are ignored.
A wild card mask of 255.255.255.255 indicates that no bit is
important.
A wildcard of 0.0.0.0 indicates that all the bits are important.
For example, if the source IP address 149.36.184.198 and the
wildcard mask is 255.36.184.00, the first eight bits of the IP address
are ignored, while the last eight bits are used.
• Destination IP
Address
• Wildcard Mask
• Match DSCP
• Match IP
Precedence
Use the Add to T able button when you add the configured IP Based ACLs to the IP Based ACL Table at
the bottom of the screen.
Matches the destination port IP address to which packets are
addressed to the ACE
Defines the destination IP address wildcard mask
Matches the packet DSCP value to the ACE. Either the DSCP value
or the IP Precedence value is used to match packets to ACLs.
The possible field range is 0-63
Matches the packet IP Precedence value to the ACE. Either the
DSCP value or the IP Precedence value is used to match packets to
ACLs.
The possible field range is 0-7
Page 81

4.8.2 Layer2 Based ACL
The Layer2 Based ACL screen (see figure 4-38) allows a MAC based ACL to be defined. ACEs can be
added only if the ACL is not bound to an interface.
Figure 4-38 Layer2-Base ACL screen
The Page contains the following fields:
• ACL Name
• New ACL Name
• Delete ACL
• Action
• Source MAC
Address
Displays the user-defined MAC based ACLs
Specifies a new user-defined MAC based ACL name.
By which deletes the selected ACL
Indicates the ACL forwarding action. Possible field values are:
• Permit, by which forwards packets which meet the ACL criteria.
• Deny, drops packets which meet the ACL criteria.
• Shutdown, where drops packet that meet the ACL criteria, and
Matches the source MAC address to which packets are addressed to
the ACE.
disables the port to which the packet was addressed.
• Wildcard Mask
Defines the source IP address wildcard mask. Wildcard masks
specify which bits are used and ignored.
A wild card mask of 255.255.255.255 indicates that no bit is
Page 82

important.
A wildcard of 0.0.0.0 indicates that all the bits are important.
For example, if the source IP address 149.36.184.198 and the
wildcard mask is 255.36.184.00, the first eight bits of the IP address
are ignored, while the last eight bits are used.
• Dest. MAC Address
• VLAN ID
• Ether Type
Use the “Add to T able” button to add the configured MAC Based ACLs to the MAC Based ACL Table at
the bottom of the screen.
Where matches the destination MAC address to which packets are
addressed to the ACE.
Wildcard Mask, which defines the destination IP address wildcard
mask.
Which matches the packet’s VLAN ID to the ACE.
The possible field values are 2 to 4094.
Where specifies the packet’s Ethernet type.
Page 83

4.9 Security
This section is to control the security access of the switch, includes the user access and management
control.
The Security function contains links to the following topics:
• ACL Binding
• RADIUS
• TACACS+
• 802.1x Settings
• Port Security
• Multiple Hosts
• Storm Control
4.9.1 ACL Binding
When an ACL is bound to an interface, all the ACE (Access Control Event) rules that have been defined
are applied to the selected interface. Whenever an ACL is assigned on a port, LAG or, VLAN, flows from
that ingress interface that do not match the ACL are matched to the default rule, which is Drop
unmatched packets. You can refer to figure 4-39.
Figure 4-39 ACL Binding screen
The Page contains the following fields:
• Port#
Indicates the interface to which the ACL is bound. The selection
includes:
Page 84

• Port, indicates port to apply the ACL
• LAG, indicates LAG to apply the ACL
• ACL Name
Use the Add to Table button to add the ACL Binding conf iguration to the ACL Binding Table at the
bottom of the screen.
Indicates the ACL which is bo und to the interface. The selection
includes:
• Layer3 Based ACL
• Layer2 Based ACL
4.9.2 Radius Config
Remote Authorization Dial-In User Service (RADIUS) servers provide additional security for networks.
RADIUS servers provide a centralized authentication method for web access (see figure 4-40).
Figure 4-40 RADIUS screen
The Page contains the following fields:
• IP Address
• Priority
• Authentication Port
The Authentication Server IP address.
Displays the server priority. The possible values are 0-65535, where 1
is the highest value. The RADIUS Server priority is used to configure
the server query order
Identifies the authentication port. The authentication port is used to
verify the RADIUS server authentication.
Page 85

The authenticated port default is 1812
• Number of Retries
• Timeout for Reply
• Dead Time
• Key String
• Source IP Address
Defines the number of transmitted requests sent to RADIUS server
before a failure occurs. The possible field values are 1 - 10.
Three is the default value.
This defines the amount of the time in seconds the device waits for an
answer from the RADIUS server before retrying the query, or
switching to the next server.
The possible field values are 1 - 30.
Three is the default value.
This defines the amount of time (minutes) that a RADIUS server is
bypassed for service requests. The range is 0-2000.
The Dead Time default is 0 minutes.
This defines the default key string used for authenticating and
encrypting all RADIUS communications between the device and the
RADIUS server.
This key must match the RADIUS encryption.
Defines the source IP address that is used for communication with
RADIUS servers.
• Usage Type
Use the Add to T able button when you add the RADIUS configuration to the RADIUS Table at the
bottom of the screen.
Specifies the RADIUS server authentication type. The default value is
Login. The possible field values are:
• Login, indicates that the RADIUS server is used for
authenticating user name and passwords.
• 802.1X, indicates that the RADIUS server is used for 802.1X
authentication.
• All, where indicates that the RADIUS server is used for
authenticating user name and passwords, and 802.1X port
authentication.
Page 86

4.9.3 TACACS+ Config
The device provides Terminal Access Controller Access Control System (TACACS+) client support.
TACACS+ provides centralized security for validation of users accessing the device. TACACS+ provides
a centralized user management system, while still retaining consistency with RADIUS and other
authentication processes. The TACACS+ protocol ensures network integrity through encrypted protocol
exchanges between the device and TACACS+ server. You can refer to figure 4-41.
Figure 4-41 TACACS+ screen
The Page contains the following fields:
• Host IP Address
• Priority
• Source IP Address
• Key String
• Authentication Port
• The Timeout for
Indicates the TACACS+ Server IP address
Displays the order in which the TACACS+ servers are used. The
default is 0
By which displays the device source IP address used for the
TACACS+ session between the device and the TACACS+ server.
This defines the authentication and encryption key for TACACS+
server. The key must match the encryption key used on the
TACACS+ server
Displays the port number through which the TACACS+ session
occurs
This displays the amount of time that passes before the connection
Page 87

Reply
between the device and the TACACS+ server times out.
The field range is 1-30 seconds.
• Status
• Single Connection
Displays the connection status between the device and the TACACS+
server. The possible field values are:
• Connected, there is currently a connection between the device
and the TACACS+ server.
• Not Connected, there is not currently a connection between the
device and the TACACS+ server.
Maintains a single open connection between the device and the
TACACS+ server when selected the Add to List button to add the
TACACS+ configuration to the TACACS+ table at the bottom of the
screen.
Page 88

4.9.4 802.1x settings
Port based authentication enables authenticating system users on a per-port basis via an external
server. Only authenticated and approved system users can transmit and receive data. Ports are
authenticated via the RADIUS server using the Extensible Authentication Protocol (EAP). Refer to
figure 4-42.
Figure 4-42 802.1x setting screen
The Page contains the following fields:
• Enable 802.1x
• Port#
• Status Port Control
• Enable Periodic
Re-authentication
Place a checkmark in the check box to enable 802.1x, authentication
Indicates the port name
This specifies the port authorization state. The possible field values
are as follows:
• Force-Authorized, the controlled port state is set to
• Force-Unauthorized, the controlled port state is set to
Permits immediate port re-authentication. The Setting Timer button
opens the Setting Timer screen to configure ports for 802.1x
functionality.
Force-Authorized (forward traffic).
Force-Unauthorized (discard traffic).
Page 89

4.9.5 Port Security
Work security screen (see figure 4-43) can be increased by limiting access on a specific port only to
users with specific MAC addresses. MAC addresses can be dynamically learned or statically
configured. Locked port security monitors both received and learned packets that are received on
specific ports. Access to the locked port is limited to users with specific MAC addresses. These
addresses are either manually defined on the port, or learned on that port up to the point when it is
locked.
When a packet is received on a locked port, and the packet source MAC address is not tied to that port
(either it was learned on a different port, or it is unknown to the system), the protection mechanism is
invoked, and can provide various options.
Unauthorized packets arriving at a locked port are either:
Forwarded, Discarded with no trap, Discarded with a trap, Cause the port to be shut down.
Figure 4-43 Port Security screen
Locked port security also enables storing a list of MAC addresses in the configuration file. The MAC
address list can be restored after the device has been reset.
Page 90

Disabled ports are activated from the Port Security page.
• Port#
• Lock Interface
• Learning Mode
• Max Entries
Where displays the port or LAG name
Which selecting this option locks the specified interface.
Where defines the locked port type. The Learning Mode field is
enabled only if Locked is selected in the Interface Status field. The
possible field values are:
• Classic Lock, by which locks the port using the classic lock
mechanism. The port is immediately locked,
regardless of the number of addresses that have already been
learned.
• Limited Dynamic Lock, which locks the port by deleting the
current dynamic MAC addresses associated with the port. The
port learns up to the maximum addresses allowed on the port.
Both relearning and aging MAC addresses are enabled.
Specifies the number of MAC addresses that can be learned on the
port. The Max Entries field is enabled only if Locked is selected in the
Interface Status field. In addition, the Limited Dynamic Lock mode is
selected.
The default is 1.
• Action on Violation
• Enable Trap
• Trap Frequency
In order to change the Learning Mode, the Lock Interface must be set to unlocked.
#Note:
Once the mode is changed, the Lock Interface can be reinstated.
Where indicates the action to be applied to packets arriving on a
locked port. The possible field values are:
• Discard, which discards packets from any unlearned source.
This is the default value.
• Forward Normal, forwards packets from an unknown source
without learning the MAC address.
• Discard Disable, which discards packets from any unlearned
source and shuts down the port. The port remains shut down
until reactivated, or until the device is reset.
This enables traps when a packet is received on a locked port.
Which the amount of time (in seconds) between traps.
The default value is 10 seconds
Page 91

4.9.6 Multiple Hosts
The Multiple Hosts screen (see figure 4-44) allows network managers to configure advanced port-based
authentication settings for specific ports and VLANs.
Figure 4-44 Multiple Hosts screen
The Page contains the following fields:
• Port#
• Multiple Hosts
Enable
• Action on Violation
Displays the port number for which advanced port-based
authentication is enabled.
When checked, indicates that multiple hosts are enabled. Multiple
hosts must be enabled in order to either disable the ingress-filter, or to
use port-lock security on the selected port.
This defines the action to be applied to packets arriving in single-host
mode, from a host whose MAC address is not the supplicant MAC
address. The possible field values are:
• Discard, which discards the packets. This is the default value.
• Forward, by which forwards the packet.
• Discard Disable, discards the packets and shuts down the port.
The ports remains shut down until reactivated, or until the device
is reset.
• Enable Traps
• Trap Frequency
When checked, indicates that traps are enabled for Multiple Hosts
Defines the time period by which traps are sent to the host. The Trap
Page 92

Frequency (1-1000000) field can be defined only if multi ple hosts are
disabled.
The default is 10 seconds.
• Status
Where indicates the host status.
4.9.7 Storm control
A BroadcastStorm is a result of an excessive amount of broadc ast messa ges simultaneously transmitted
across a network by a single port. Forwarded message responses are heaped onto the network, straining
network resources or causing the network to time out.
The system measures the incoming Broadcast and Multicast frame rate separately on each port, and
discard frames when the rate exceeds a user-defined rate.
The Storm Control page provides fields for enabling and configuring Storm Control. The screen in Figure
4-45 appears.
Figure 4-45 Storm Control screen
The Page contains the following fields:
• Port#
• Broadcast Control
• Mode
Displays the port number for which storm control is enabled
This indicates whether broadcast packet types are forwarded on the
specific interface.
By which specifies the Broadcast mode currently enabled on the
device. The possible field values are:
• Unknown Unicast, Multicast & Broadcast, counts Unicast,
Multicast, and Broadcast traffic.
Page 93

• Multicast & Broadcast, counts Broadcast and Multicast traffic
together.
• Broadcast Only, counts only Broadcast traffic.
• Rate Threshold
Where the maximum rate (packets per second) at which unknown
packets are forwarded. The range is 70 -100000.
The default value is 3500.
4.10 SNMP
Simple Network Management Protocol (SNMP) provides a method for managing network devices.
Devices supporting SNMP run a local software (agent).
The SNMP agents maintain a list of variables, which are used to manage the device. The variables are
defined in the Management Information Base (MIB). The MIB contains the variables controlled by the
agent. The SNMP protocol defines the MIB specification format, as well as the format used to access the
information over the network.
Access rights to the SNMP agents are controlled by access strings. To communicate with the device, the
Embedded Web Server submits a valid community string for authentication.
4.10.1 Parameters
The Global Parameters screen (see figure 4-46) contains parameters for defining SNMP notification
parameters.
Figure 4-46 Parameter screen
Page 94

The Global Parameter Screen contains the following fields:
• Local Engine ID
• Use Default
• SNMP Notifications
• Authentication
Notifications
Indicates the local device engine ID. The field value is a hexadecimal
string. Each byte in hexadecimal character strings consists of two
hexadecimal digits. Each byte can be separated by a period or a
colon. The Engine ID must be defined before SNMPv3 is enabled. For
stand-alone devices, select a default Engine ID that is comprised of
Enterprise number and the default MAC address.
For a stackable system configure the Engine ID, and verify that the
Engine ID is unique for the administrative domain. This prevents two
devices in a network from having the same Engine ID.
Uses the device generated Engine ID. It’s defined per standard as:
First 4 octets — first bit = 1, the rest is IANA Enterprise number. To
locate the IANA Enterprise number by referring to the V endor website,
or use the show SNMP command using a CLI interface.
The default Engine ID is based on the device MAC address.
which indicates if the device can send SNMP notifications
which indicates if SNMP Authentication failure notification is enabled
on the device
Page 95

4.10.2 Group Profile
The Group Profile screen (see figure 4-47) provides information for creating SNMP groups and assigning
SNMP access control privileges to SNMP groups. Groups allow network managers to assign access
rights to specific device features, or features aspects.
Figure 4-47 Group Profile screen
The page contains the following fields:
• Group Name
• Security Model
• Security Level
Displays the user-defined group to which access control rules are
applied. The field range is up to 30 characters.
Defines the SNMP version attached to the group. The possible field
values are:
• SNMPv1, defined for the group.
• SNMPv2, defined for the group.
• SNMPv3, defined for the group.
Defines the security level attached to the group. Security levels apply
to SNMPv3 only. The possible field values are:
• No Authentication, which indicates that neither the
• Authentication, which authenticates SNMP messages, and
Authentication nor the Privacy security levels are assigned to the
group.
ensures the SNMP messages original is authenticated.
• Privacy
Where encrypts SNMP messages
Page 96

• Operation
Defines the group access rights. The possible field values are:
• Read. The management access is restricted to read-only, and
changes cannot be made to the assigned SNMP view.
• Write. The management access is read-write and changes can
be made to the assigned SNMP view.
• Notify. Sends traps for the assigned SNMP view.
4.10.3 Group Membership
The Group Membership screen (see figure 4-48) provides information for assigning SNMP access control
privileges to SNMP groups.
Figure 4-48 Group Membership
The page contains the following fields:
• User name
• Engine ID
• Group Name
By which provides a user-defined local user list
Indicates either the local or remote SNMP entity to which the user is
connected. Changing or removing the local SNMP Engine ID deletes
the SNMPv3 User Database.
• Local - Indicates that the user is connected to a local SNMP
• Remote - Indicates that the user is connected to a remote SNMP
Contains a list of user-defined SNMP groups. SNMP groups are
defined in the SNMP Group Profile page.
entity.
entity. If the Engine ID is defined, remote devices receive inform
messages
Page 97

• Authentication
Method
Indicates the Authentication method used. The possible field values
are:
• None, that no authentication method is used to authenticate the
port.
• MD5 Password, that port authentication is performed via
HMAC-MD5-96 password authentication.
• SHA Password, that port authentication is performed via
HMAC-SHA-96 password authentication.
• MD5 Key, that port authentication is performed via the
HMAC-MD5 algorithm.
• SHA Key, that port authentication is performed via
HMAC-SHA-96 authentication.
• Password
• Authentication Key
• Pri vacy Key
Use the Add to Table button when you want to add the Group Membership configuration to the
respective table at the bottom of the screen.
Define the local user password. Local user passwords can contain up
to 159 characters.
Define the HMAC-MD5-96 or HMAC-SHA-96 authentication level.
The authentication and privacy keys are entered to define the
authentication key.
If only authentication is required, 16 bytes are defined.
If both privacy and authentication are required, 32 bytes are defined.
Each byte in hexadecimal character strings is two hexadecimal digits.
Each byte can be separated by a period or a colon.
Defines the Privacy Key (LSB).
If only authentication is required, 20 bytes are defined.
If both privacy and authentication are required, 36 bytes are defined.
Each byte in hexadecimal character strings is two hexadecimal digits.
Each byte can be separated by a period or colon.
Page 98

4.10.4 Communities
The Communities screen contains three areas:
• Communities
• Basic Table
• Advanced Table
The screens in Figure 4-49 and 4-50 sppears
Communities
Figure 4-49 Communities configuration screen
The page contains the following fields:
• SNMP Management
Station
• Community String
• Basic
Defines the management station IP address for which the advanced
SNMP community is defined. There are two definition options:
• IP A ddress - Define the management station IP address.
• All - which includes all management station IP addresses.
Defines the password used to authenticate the management station
to the device.
which enables SNMP Basic mode for a selected community and
contains the following fields:
Access Mode - Defines the access rights of the community. The
Page 99

possible field values are:
• Read Only - which indicates management access is restricted to
read-only, and changes cannot be made to the community.
• Read Write - management access is read-write and changes
can be made to the device configuration, but not to the
community.
• SNMP Admin - user has access to all device configuration
options, as well as permissions to modify the community.
View N ame - contains a list of user-defined SNMP views.
• Advanced
Use the Add to Table button when you want to add the Communities configuration to the respective
Table at the bottom of the screen.
Table
Enables SNMP Advanced Mode for a selected community and
contains the following fields:
Group Name - defines advanced SNMP communities group names.
Figure 4-50 Communities table screen
Page 100

The page contains the following fields:
• Management Station
• Community String
• Access Mode
• View Name
• Management Station
• Community String
• Group Name
Displays the management station IP address for which the basic
SNMP community is defined.
Displays the password used to authenticate the management station
to the device.
Where displays the access rights of the community.
Displays the user-defined SNMP view.
Displays the management station IP address for which the basic
SNMP community is defined.
Community String, which displays the password used to authenticate
the management station to the device.
Displays the password used to authenticate the management station
to the device.
Displays advanced SNMP communities group name
4.10.5 Notification Recipient
The Notification Recipient screen (see figure 4-51 and 4-52) contains information for defining filters that
determine whether traps are sent to specific users, and the trap type sent.
Figure 4-51 Notification Recipient
 Loading...
Loading...