Page 1

WGS3-24000
User's Manual
24-Port 10/100/1000Mbps
Layer 3 Managed Ethernet Switch
1
Page 2

Trademarks
Copyright © PLANET Technology Corp. 2007.
Contents subject to which revision without prior notice.
PLANET is a registered trademark of PLANET Technology Corp. All other trademarks belong to their respective owners.
Disclaimer
PLANET Technology does not warrant that the hardware will work properly in all environments and applications, and makes no
warranty and representation, either implied or expressed, with respect to the quality, performance, merchantability, or fitness for
a particular purpose.
PLANET has made every effort to ensure that this User's Manual is accurate; PLANET disclaims liability for any inaccuracies or
omissions that may have occurred.
Information in this User's Manual is subject to change without notice and does not represent a commitment on the part of
PLANET. PLANET assumes no responsibility for any inaccuracies that may be contained in this User's Manual. PLANET makes
no commitment to update or keep current the information in this User's Manual, and reserves the right to make improvements to
this User's Manual and/or to the products described in this User's Manual, at any time without notice.
If you find information in this manual that is incorrect, misleading, or incomplete, we would appreciate your comments and
suggestions.
FCC Warning
This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC
Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated
in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and
used in accordance with the Instruction manual, may cause harmful interference to radio communications. Operation of this
equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the
interference at whose own expense.
CE Mark Warning
This is a Class A product. In a domestic environment, this product may cause radio interference, in which case the user may be
required to take adequate measures.
WEEE Warning
To avoid the potential effects on the environment and human health as a result of the presence of
hazardous substances in electrical and electronic equipment, end users of electrical and electronic
equipment should understand the meaning of the crossed-out wheeled bin symbol. Do not dispose of
WEEE as unsorted municipal waste and have to collect such WEEE separately.
Revision
PLANET 24-Port 10/100/1000Mbps with 4 Gigabit SFP Layer 3 Managed Ethernet Switch User's Manual
FOR MODEL: WGS3-24000
REVISION: 1.1 (May.2007)
Part No. EM-WGS3-24000_v1.1 (2081-A96020-001)
2
Page 3

Table of Contents
1. INTRODUCTION.................................................................................................................. 19
1.1 Packet Contents ............................................................................................................................................................19
1.2 How to Use This Manual................................................................................................................................................19
1.3 Product Feature.............................................................................................................................................................20
1.4 Product Specification.....................................................................................................................................................22
2. INSTALLATION .................................................................................................................... 24
2.1 Product Description .......................................................................................................................................................24
2.1.1 Product Overview..............................................................................................................................................24
2.1.2 Switch Front Panel............................................................................................................................................25
2.1.3 LED Indications.................................................................................................................................................25
2.1.4 Switch Rear Panel ............................................................................................................................................25
2.2 Install the Switch............................................................................................................................................................26
2.2.1 Desktop Installation...........................................................................................................................................26
2.2.2 Rack Mounting..................................................................................................................................................26
2.2.3 Installing the SFP transceiver ...........................................................................................................................27
3. CONFIGURATION ............................................................................................................... 30
3.1 Management Access Overview .....................................................................................................................................30
3.1.1 Administration Console .....................................................................................................................................31
3.1.2 Direct Access ....................................................................................................................................................31
3.2 Web Management .........................................................................................................................................................32
3.3 SNMP-Based Network Management.............................................................................................................................32
3.4 Protocols........................................................................................................................................................................32
3.4.1 Virtual Terminal Protocols .................................................................................................................................32
3.4.2 SNMP Protocol .................................................................................................................................................32
3.4.3 Management Architecture .................................................................................................................................32
4. Web Configuration................................................................................................................ 33
4.1 Main Menu.....................................................................................................................................................................35
4.2 Configure System ..........................................................................................................................................................37
4.2.1 ARP Cache .......................................................................................................................................................37
4.2.2 Inventory Information ........................................................................................................................................38
4.2.3 Configuration ....................................................................................................................................................39
4.2.4 Forwarding Database........................................................................................................................................50
4.2.5 Log....................................................................................................................................................................51
4.2.6 Port ...................................................................................................................................................................57
4.2.7 SNMP ...............................................................................................................................................................64
4.2.9 Statistics............................................................................................................................................................66
4.2.9 System Utilities .................................................................................................................................................74
4.2.10 Trap Management...........................................................................................................................................79
3
Page 4

4.2.11 DHCP Server ..................................................................................................................................................81
4.2.12 SNTP ..............................................................................................................................................................89
4.3 Switching .......................................................................................................................................................................94
4.3.1 VLAN ................................................................................................................................................................94
4.3.2 Protocol-based VLAN .....................................................................................................................................102
4.3.3 Port Security ...................................................................................................................................................104
4.3.4 GARP..............................................................................................................................................................110
4.3.5 IGMP Snooping...............................................................................................................................................11 3
4.3.6 Port Channel...................................................................................................................................................121
4.3.7 Multicast Forwarding Database.......................................................................................................................125
4.3.8 Spanning Tree.................................................................................................................................................128
4.3.9 Class of Service..............................................................................................................................................142
4.4 Security........................................................................................................................................................................143
4.4.1 Port Access Control ........................................................................................................................................146
4.4.2 RADIUS ..........................................................................................................................................................154
4.4.3 TACACS+ .......................................................................................................................................................166
4.4.4 Secure HTTP ..................................................................................................................................................168
4.4.5 Secure Shell ...................................................................................................................................................169
4.5 QoS .............................................................................................................................................................................170
4.5.1 IP Access Control List .....................................................................................................................................170
4.5.2 MAC Access Control List ................................................................................................................................174
4.5.3 ACL Interface Configuration ............................................................................................................................179
4.5.4 Differentiated Services....................................................................................................................................181
4.5.5 Class of Service..............................................................................................................................................191
4.6 Routing ........................................................................................................................................................................197
4.6.1 IP ....................................................................................................................................................................200
4.6.2 VLAN Routing .................................................................................................................................................206
4.6.3 RIP..................................................................................................................................................................209
4.6.4 OSPF ..............................................................................................................................................................217
4.6.5 Router .............................................................................................................................................................244
4.6.6 ARP ................................................................................................................................................................250
4.6.7 BOOTP/DHCP Relay Agent............................................................................................................................254
4.6.8 Router Discovery ............................................................................................................................................256
4.6.9 VRRP..............................................................................................................................................................259
4.7 IP Multicast ..................................................................................................................................................................267
4.7.1 Multicast..........................................................................................................................................................267
4.7.2 IGMP...............................................................................................................................................................274
4.7.3 DVMRP...........................................................................................................................................................281
4.7.4 Mdebug...........................................................................................................................................................290
4.7.5 PIM-DM...........................................................................................................................................................297
4
Page 5

4.7.6 PIM-SM...........................................................................................................................................................301
5. COMMAND STRUCTURE ................................................................................................. 310
5.1 Format .........................................................................................................................................................................310
5.1.1 Command .......................................................................................................................................................310
5.1.2 Parameters .....................................................................................................................................................310
5.1.3 Values .............................................................................................................................................................310
5.1.4 Conventions....................................................................................................................................................311
5.1.5 Annotations ..................................................................................................................................................... 311
6. QUICK START UP .............................................................................................................312
6.1 Quick Starting the Switch.............................................................................................................................................312
6.2 System Info and System Setup ...................................................................................................................................312
7. MODE-BASED CLI ............................................................................................................ 317
7.1 Mode-Based Topology.................................................................................................................................................318
7.2 Mode-based Command Hierarchy...............................................................................................................................319
7.3 Flow of Operation ........................................................................................................................................................321
7.4 "No" Form of a Command............................................................................................................................................322
7.4.1 Support for "No" Form.....................................................................................................................................322
7.4.2 Behavior of Command Help ("?") ....................................................................................................................322
8. CLI Commands: Base ........................................................................................................ 323
8.1 System Information and Statistics Commands ............................................................................................................323
8.1.1 show arp switch ..............................................................................................................................................323
8.1.2 show eventlog.................................................................................................................................................323
8.1.3 show hardware ...............................................................................................................................................324
8.1.4 show interface.................................................................................................................................................324
8.1.5 show interface ethernet...................................................................................................................................325
8.1.6 show logging...................................................................................................................................................329
8.1.7 show mac-addr-table ......................................................................................................................................330
8.1.8 show msglog...................................................................................................................................................330
8.1.9 show running-config ........................................................................................................................................331
8.1.10 show sysinfo .................................................................................................................................................331
8.1.11 snmp-server ..................................................................................................................................................331
8.2 Management VLAN Commands ..................................................................................................................................331
8.2.1 network mgmt_vlan.........................................................................................................................................331
8.3 Dot1P Commands .......................................................................................................................................................332
8.3.1 classofservice dot1pmapping..........................................................................................................................332
8.3.2 show classofservice dot1pmapping ................................................................................................................332
8.3.3 vlan port priority all..........................................................................................................................................332
8.3.4 vlan priority .....................................................................................................................................................332
8.4 LAG/Port-Channel (802.3ad) Commands....................................................................................................................332
8.4.1 port-channel staticcapability ............................................................................................................................332
5
Page 6

8.4.2 show port-channel brief...................................................................................................................................333
8.5 Management Commands ............................................................................................................................................333
8.5.1 bridge aging-time ............................................................................................................................................333
8.5.2 mtu..................................................................................................................................................................334
8.5.3 network javamode...........................................................................................................................................334
8.5.4 network mac-address......................................................................................................................................334
8.5.5 network mac-type............................................................................................................................................334
8.5.6 network parms ................................................................................................................................................335
8.5.7 network protocol..............................................................................................................................................335
8.5.8 remotecon maxsessions .................................................................................................................................335
8.5.9 remotecon timeout ..........................................................................................................................................335
8.5.10 serial baudrate ..............................................................................................................................................336
8.5.11 serial timeout.................................................................................................................................................336
8.5.12 set prompt.....................................................................................................................................................337
8.5.13 show forwardingdb agetime ..........................................................................................................................337
8.7.14 show network................................................................................................................................................337
8.5.15 show remotecon............................................................................................................................................338
8.5.16 show serial....................................................................................................................................................338
8.5.17 show snmpcommunity ..................................................................................................................................338
8.5.18 show snmptrap..............................................................................................................................................339
8.5.19 show trapflags...............................................................................................................................................339
8.5.20 snmp-server community................................................................................................................................340
8.5.21 snmp-server community ipaddr.....................................................................................................................340
8.5.22 snmp-server community ipmask ...................................................................................................................341
8.5.23 snmp-server community mode......................................................................................................................341
8.5.24 snmp-server community ro ...........................................................................................................................341
8.5.25 snmp-server community rw...........................................................................................................................342
8.5.26 snmp-server enable traps .............................................................................................................................342
8.5.27 snmp-server enable traps bcaststorm...........................................................................................................342
8.5.28 snmp-server enable traps linkmode ..............................................................................................................342
8.5.29 snmp-server enable traps multiusers ............................................................................................................343
8.5.30 snmp-server enable traps stpmode...............................................................................................................343
8.5.31 snmptrap.......................................................................................................................................................343
8.5.32 snmptrap ipaddr ............................................................................................................................................344
8.5.33 snmptrap mode.............................................................................................................................................344
8.5.34 telnet .............................................................................................................................................................344
8.6 Device Configuration Commands ................................................................................................................................345
8.6.1 addport............................................................................................................................................................345
8.6.2 auto-negotiate .................................................................................................................................................345
8.6.3 auto-negotiate all ............................................................................................................................................345
6
Page 7

8.6.4 delete interface ...............................................................................................................................................345
8.6.5 deleteport........................................................................................................................................................346
8.6.6 macfilter ..........................................................................................................................................................346
8.6.7 macfilter adddest.............................................................................................................................................346
8.6.8 macfilter adddest all ........................................................................................................................................347
8.6.9 macfilter addsrc...............................................................................................................................................347
8.6.10 macfilter addsrc all ........................................................................................................................................347
8.6.11 monitor session .............................................................................................................................................348
8.6.12 monitor session mode...................................................................................................................................348
8.6.13 port lacpmode ...............................................................................................................................................348
8.6.14 port lacpmode all...........................................................................................................................................349
8.6.15 port-channel..................................................................................................................................................349
8.6.16 port-channel adminmode ..............................................................................................................................349
8.6.17 port-channel linktrap .....................................................................................................................................350
8.6.18 port-channel name ........................................................................................................................................350
8.6.19 protocol group ...............................................................................................................................................350
8.6.20 protocol vlan group .......................................................................................................................................350
8.6.21 protocol vlan group all...................................................................................................................................351
8.6.22 set garp timer join .........................................................................................................................................351
8.6.23 set garp timer join all .....................................................................................................................................352
8.6.24 set garp timer leave ......................................................................................................................................352
8.6.25 set garp timer leave all ..................................................................................................................................352
8.6.26 set garp timer leaveall ...................................................................................................................................353
8.6.27 set garp timer leaveall all ..............................................................................................................................353
8.6.28 set gmrp adminmode ....................................................................................................................................354
8.6.29 set gmrp interfacemode ................................................................................................................................354
8.6.30 set gmrp interfacemode all............................................................................................................................355
8.6.31 set gvrp adminmode .....................................................................................................................................355
8.6.32 set gvrp interfacemode .................................................................................................................................355
8.6.33 set gvrp interfacemode all .............................................................................................................................356
8.6.34 show description ...........................................................................................................................................356
8.6.35 show garp .....................................................................................................................................................356
8.6.36 show gmrp configuration...............................................................................................................................356
8.6.37 show gvrp configuration ................................................................................................................................357
8.6.38 show igmpsnooping ......................................................................................................................................358
8.6.39 show mac-address-table gmrp......................................................................................................................358
8.6.40 show mac-address-table igmpsnooping........................................................................................................358
8.6.41 show mac-address-table multicast................................................................................................................359
8.6.42 show mac-address-table static......................................................................................................................359
8.6.43 show mac-address-table staticfiltering ..........................................................................................................359
7
Page 8

8.6.44 show mac-address-table stats ......................................................................................................................360
8.6.45 show monitor ................................................................................................................................................360
8.6.46 show port ......................................................................................................................................................360
8.6.47 show port protocol.........................................................................................................................................361
8.6.48 show port-channel.........................................................................................................................................361
8.6.49 show storm-control........................................................................................................................................362
8.6.50 show vlan......................................................................................................................................................362
8.6.51 show vlan brief..............................................................................................................................................363
8.6.52 show vlan port...............................................................................................................................................363
8.6.53 shutdown ......................................................................................................................................................364
8.6.54 shutdown all..................................................................................................................................................364
8.6.55 snmp trap link-status .....................................................................................................................................364
8.6.56 snmp trap link-status all ................................................................................................................................364
8.6.57 spanning-tree ................................................................................................................................................365
8.6.58 spanning-tree bpdumigrationcheck ...............................................................................................................365
8.6.59 description ....................................................................................................................................................365
8.6.60 speed ............................................................................................................................................................366
8.6.61 speed all .......................................................................................................................................................366
8.6.62 storm-control broadcast ................................................................................................................................366
8.6.63 storm-control flowcontrol...............................................................................................................................367
8.6.64 vlan ...............................................................................................................................................................367
8.6.65 vlan acceptframe...........................................................................................................................................368
8.6.66 vlan ingressfilter ............................................................................................................................................368
8.6.67 vlan makestatic .............................................................................................................................................368
8.6.68 vlan name .....................................................................................................................................................369
8.6.69 vlan participation ...........................................................................................................................................369
8.6.70 vlan participation all ......................................................................................................................................369
8.6.71 vlan port acceptframe all ...............................................................................................................................369
8.6.72 vlan port ingressfilter all ................................................................................................................................370
8.6.73 vlan port pvid all............................................................................................................................................370
8.6.74 vlan port tagging all.......................................................................................................................................370
8.6.75 vlan protocol group .......................................................................................................................................371
8.6.76 vlan protocol group add protocol...................................................................................................................371
8.6.77 vlan protocol group remove ..........................................................................................................................371
8.6.78 vlan pvid........................................................................................................................................................371
8.6.79 vlan tagging...................................................................................................................................................372
8.7 User Account Management Commands......................................................................................................................372
8.7.1 disconnect.......................................................................................................................................................372
8.7.2 show loginsession...........................................................................................................................................372
8.7.3 show users......................................................................................................................................................372
8
Page 9

8.7.4 users name .....................................................................................................................................................373
8.7.5 users passwd..................................................................................................................................................373
8.7.6 users snmpv3 accessmode ............................................................................................................................374
8.7.7 users snmpv3 authentication ..........................................................................................................................374
8.7.8 users snmpv3 encryption ................................................................................................................................374
8.8 System Utilities............................................................................................................................................................375
8.8.1 clear config .....................................................................................................................................................375
8.8.2 clear counters .................................................................................................................................................375
8.8.3 clear igmpsnooping.........................................................................................................................................375
8.8.4 clear pass .......................................................................................................................................................375
8.8.5 clear port-channel ...........................................................................................................................................375
8.8.6 clear traplog ....................................................................................................................................................376
8.8.7 clear vlan ........................................................................................................................................................376
8.8.8 copy ................................................................................................................................................................376
8.8.9 logout ..............................................................................................................................................................377
8.8.10 ping ...............................................................................................................................................................377
8.8.11 reload ............................................................................................................................................................377
9. CLI COMMANDS: QUALITY OF SERVICE ....................................................................... 378
9.1 CLI Commands: Access Control List.........................................................................................................................378
9.1.1 show ip access-lists ........................................................................................................................................378
9.2 Configuration Commands .........................................................................................................................................378
9.2.1 access-list .......................................................................................................................................................378
9.2.2 ip access-group ..............................................................................................................................................379
9.2.3 ip access-group all ..........................................................................................................................................379
9.3 CLI Commands: Differentiated Services ...................................................................................................................379
9.3.1 diffserv ............................................................................................................................................................381
9.4 Class Commands......................................................................................................................................................381
9.4.1 class-map .......................................................................................................................................................381
9.4.2 class-map rename ..........................................................................................................................................382
9.4.3 match any .......................................................................................................................................................382
9.4.4 match class-map.............................................................................................................................................382
9.4.5 match destination-address mac ......................................................................................................................383
9.4.6 match dstip .....................................................................................................................................................383
9.4.7 match dstl4port ...............................................................................................................................................384
9.4.8 match ip dscp..................................................................................................................................................384
9.4.9 match ip precedence.......................................................................................................................................384
9.4.10 match ip tos ..................................................................................................................................................385
9.4.11 match protocol...............................................................................................................................................385
9.4.12 match source-address mac...........................................................................................................................386
9.4.13 match srcip ...................................................................................................................................................386
9
Page 10

9.4.14 match srcl4port .............................................................................................................................................386
9.4.15 match vlan ....................................................................................................................................................387
9.5 Policy Commands .....................................................................................................................................................387
9.5.1 bandwidth kbps ...............................................................................................................................................387
9.5.2 bandwidth percent...........................................................................................................................................388
9.5.3 class................................................................................................................................................................388
9.5.4 expedite kbps..................................................................................................................................................388
9.5.5 expedite percent .............................................................................................................................................389
9.5.6 mark ip-dscp ...................................................................................................................................................389
9.5.7 mark ip-precedence ........................................................................................................................................390
9.5.8 police-simple...................................................................................................................................................390
9.5.9 police-single-rate.............................................................................................................................................390
9.5.10 police-two-rate ..............................................................................................................................................391
9.5.11 policy-map.....................................................................................................................................................391
9.5.12 policy-map rename .......................................................................................................................................392
9.5.13 randomdrop ..................................................................................................................................................392
9.5.14 shape bps-average .......................................................................................................................................393
9.5.15 shape bps-peak ............................................................................................................................................393
9.6 Service Commands...................................................................................................................................................394
9.6.1 service-policy ..................................................................................................................................................394
9.7 Show Commands......................................................................................................................................................395
9.7.1 show class-map ..............................................................................................................................................395
9.7.2 show diffserv...................................................................................................................................................396
9.7.3 show policy-map .............................................................................................................................................396
9.7.4 show diffserv service.......................................................................................................................................398
9.7.5 show diffserv service brief...............................................................................................................................398
9.7.6 show policy-map interface ..............................................................................................................................399
9.7.7 show service-policy .........................................................................................................................................400
9.8 Rate-Limiting Commands..........................................................................................................................................400
9.8.1 rate-limiting .....................................................................................................................................................400
9.8.2 show rate-limiting ............................................................................................................................................401
10. CLI COMMANDS: SECURITY ......................................................................................... 402
10.1 Security Commands................................................................................................................................................402
10.1.1 authentication login .......................................................................................................................................402
10.1.2 clear dot1x statistics......................................................................................................................................402
10.1.3 clear radius statistics.....................................................................................................................................403
10.1.4 dot1x defaultlogin..........................................................................................................................................403
10.1.5 dot1x initialize ...............................................................................................................................................403
10.1.6 dot1x login ....................................................................................................................................................403
10.1.7 dot1x max-req...............................................................................................................................................403
10
Page 11

10.1.8 dot1x port-control..........................................................................................................................................404
10.1.9 dot1x port-control All .....................................................................................................................................404
10.1.10 dot1x re-authenticate ..................................................................................................................................404
10.1.11 dot1x re-authentication................................................................................................................................404
10.1.12 dot1x system-auth-control...........................................................................................................................405
10.1.13 dot1x timeout ..............................................................................................................................................405
10.1.14 dot1x user ...................................................................................................................................................406
10.1.15 radius accounting mode..............................................................................................................................406
10.1.16 radius server host .......................................................................................................................................406
10.1.17 radius server key.........................................................................................................................................407
10.1.18 radius server msgauth ................................................................................................................................407
10.1.19 radius server primary ..................................................................................................................................407
10.1.20 radius server retransmit ..............................................................................................................................408
10.1.21 radius server timeout ..................................................................................................................................408
10.1.22 show accounting .........................................................................................................................................408
10.1.23 show authentication ....................................................................................................................................409
10.1.24 show authentication users ..........................................................................................................................409
10.1.25 show dot1x..................................................................................................................................................410
10.1.26 show dot1x users........................................................................................................................................411
10.1.27 show radius................................................................................................................................................. 411
10.1.28 show radius statistics ..................................................................................................................................412
10.1.29 show users authentication ..........................................................................................................................413
10.1.30 users defaultlogin........................................................................................................................................413
10.1.31 users login ..................................................................................................................................................413
10.2 Secure Shell (SSH) Commands..............................................................................................................................413
10.2.1 ip ssh ............................................................................................................................................................413
10.2.2 ip ssh protocol ...............................................................................................................................................414
10.2.3 show ip ssh ...................................................................................................................................................414
10.3 HTTP Commands ...................................................................................................................................................414
10.3.1 ip http secure-port .........................................................................................................................................414
10.3.2 ip http secure-protocol ..................................................................................................................................414
10.3.3 ip http secure-server .....................................................................................................................................415
10.3.4 ip http server .................................................................................................................................................415
10.3.5 show ip http...................................................................................................................................................415
10.4 MAC Lock Commands ............................................................................................................................................415
10.4.1 mac-lock .......................................................................................................................................................415
10.4.2 show mac-lock ..............................................................................................................................................416
11. CLI COMMANDS: SWITCHING ....................................................................................... 417
11.1 Spanning Tree Commands......................................................................................................................................417
11.1.1 show spanning-tree .......................................................................................................................................417
11
Page 12

11.1.2 show spanning-tree interface ........................................................................................................................418
11.1.3 show spanning-tree mst detailed...................................................................................................................418
11.1.4 show spanning-tree mst port detailed............................................................................................................418
11.1.5 show spanning-tree mst port summary .........................................................................................................419
11.1.6 show spanning-tree mst summary ................................................................................................................420
11.1.7 show spanning-tree summary .......................................................................................................................420
11.1.8 show spanning-tree vlan ...............................................................................................................................420
11.1.9 spanning-tree ................................................................................................................................................421
11.1.10 spanning-tree configuration name...............................................................................................................421
11.1.11 spanning-tree configuration revision ............................................................................................................421
11.1.12 spanning-tree edgeport ...............................................................................................................................421
11.1.13 spanning-tree forceversion..........................................................................................................................422
11.1.14 spanning-tree forward-time .........................................................................................................................422
11.1.15 spanning-tree hello-time..............................................................................................................................422
11.1.16 spanning-tree max-age ...............................................................................................................................423
11.1.17 spanning-tree mst .......................................................................................................................................423
11.1.18 spanning-tree mst instance .........................................................................................................................424
11.1.19 spanning-tree mst priority............................................................................................................................424
11.1.20 spanning-tree mst vlan................................................................................................................................425
11.1.21 spanning-tree port mode .............................................................................................................................425
11.1.22 spanning-tree port mode all.........................................................................................................................425
12. CLI COMMANDS: Routing ............................................................................................... 426
12.1 Address Resolution Protocol (ARP) Commands........................................................................................................426
12.1.1 arp.................................................................................................................................................................426
12.1.2 no arp............................................................................................................................................................426
12.1.3 ip proxy-arp ...................................................................................................................................................427
12.1.4 no ip proxy-arp ..............................................................................................................................................427
12.1.5 arp cachesize................................................................................................................................................427
12.1.6 no arp cachesize...........................................................................................................................................427
12.1.7 arp dynamicrenew.........................................................................................................................................427
12.1.8 no arp dynamicrenew....................................................................................................................................428
12.1.9 arp purge ......................................................................................................................................................428
12.1.10 arp resptime................................................................................................................................................428
12.1.11 no arp resptime ...........................................................................................................................................428
12.1.12 arp retries....................................................................................................................................................428
12.1.13 no arp retries...............................................................................................................................................428
12.1.14 arp timeout ..................................................................................................................................................429
12.1.15 no arp timeout .............................................................................................................................................429
12.1.16 clear arp-cache ...........................................................................................................................................429
12.1.17 show arp .....................................................................................................................................................429
12
Page 13

12.1.18 show arp brief .............................................................................................................................................430
12.1.19 show arp switch ..........................................................................................................................................431
12.2 IP Routing Commands ............................................................................................................................................431
12.2.2 no routing ......................................................................................................................................................431
12.2.3 ip routing .......................................................................................................................................................431
12.2.4 no ip routing ..................................................................................................................................................432
12.2.6 no ip address ................................................................................................................................................432
12.2.7 ip route..........................................................................................................................................................432
12.2.8 no ip route .....................................................................................................................................................433
12.2.9 ip route default ..............................................................................................................................................433
12.2.10 no ip route default .......................................................................................................................................433
12.2.11 ip route distance..........................................................................................................................................433
12.2.12 no ip route distance.....................................................................................................................................434
12.2.13 ip forwarding ...............................................................................................................................................434
12.2.14 no ip forwarding ..........................................................................................................................................434
12.2.15 ip netdirbcast...............................................................................................................................................434
12.2.16 no ip netdirbcast..........................................................................................................................................434
12.2.17 ip mtu ..........................................................................................................................................................435
12.2.18 no ip mtu .....................................................................................................................................................435
12.2.19 encapsulation..............................................................................................................................................436
12.2.20 show ip brief................................................................................................................................................436
12.2.21 show ip interface.........................................................................................................................................436
12.2.22 show ip interface brief .................................................................................................................................437
12.2.23 show ip route ..............................................................................................................................................438
12.2.24 show ip route summary ...............................................................................................................................439
12.2.25 show ip route preferences...........................................................................................................................439
12.2.26 show ip stats ...............................................................................................................................................440
12.3 Router Discovery Protocol Commands ...................................................................................................................440
12.3.1 ip irdp ............................................................................................................................................................440
12.3.2 ip irdp address ..............................................................................................................................................440
12.3.3 ip irdp holdtime..............................................................................................................................................441
12.3.4 ip irdp maxadvertinterval ...............................................................................................................................441
12.3.5 ip irdp minadvertinterval ................................................................................................................................441
12.3.6 ip irdp preference ..........................................................................................................................................442
12.3.7 show ip irdp...................................................................................................................................................442
12.4 Virtual LAN Routing Commands .............................................................................................................................443
12.4.1 vlan routing ...................................................................................................................................................443
12.4.2 show ip vlan ..................................................................................................................................................443
12.5 Virtual Router Redundancy Protocol Commands....................................................................................................443
12.5.1 ip vrrp (Global Config) ...................................................................................................................................444
13
Page 14

12.5.2 ip vrrp (Interface Config) ...............................................................................................................................444
12.5.3 ip vrrp mode ..................................................................................................................................................444
12.5.4 ip vrrp ip ........................................................................................................................................................444
12.5.5 ip vrrp authentication.....................................................................................................................................445
12.5.6 ip vrrp preempt ..............................................................................................................................................445
12.5.7 ip vrrp priority ................................................................................................................................................446
12.5.8 ip vrrp timers advertise..................................................................................................................................446
12.5.9 show ip vrrp interface stats ...........................................................................................................................446
12.5.10 show ip vrrp ................................................................................................................................................447
12.5.11 show ip vrrp interface ..................................................................................................................................447
12.5.12 show ip vrrp interface brief ..........................................................................................................................448
12.6 DHCP and BOOTP Relay Commands ....................................................................................................................448
12.6.1 bootpdhcprelay cidoptmode..........................................................................................................................448
12.6.2 bootpdhcprelay enable..................................................................................................................................449
12.6.3 bootpdhcprelay maxhopcount .......................................................................................................................449
12.6.4 bootpdhcprelay minwaittime .........................................................................................................................449
12.6.5 bootpdhcprelay serverip................................................................................................................................450
12.6.6 show bootpdhcprelay ....................................................................................................................................450
12.7 Open Shortest Path First (OSPF) Commands ........................................................................................................451
12.7.1 router ospf.....................................................................................................................................................451
12.7.2 enable (OSPF)..............................................................................................................................................451
12.7.3 ip ospf ...........................................................................................................................................................451
12.7.4 1583compatibility ..........................................................................................................................................451
12.7.5 area default-cost (OSPF) ..............................................................................................................................452
12.7.6 area nssa (OSPF).........................................................................................................................................452
12.7.7 area nssa default-info-originate (OSPF) .......................................................................................................452
12.7.8 area nssa no-redistribute (OSPF) .................................................................................................................453
12.7.9 area nssa no-summary (OSPF) ....................................................................................................................453
12.7.10 area nssa translator-role (OSPF)................................................................................................................453
12.7.11 area nssa translator-stab-intv (OSPF).........................................................................................................454
12.7.12 area range (OSPF) .....................................................................................................................................454
12.7.13 area stub (OSPF)........................................................................................................................................454
12.7.14 area stub no-summary (OSPF) ...................................................................................................................455
12.7.15 area virtual-link (OSPF) ..............................................................................................................................455
12.7.16 area virtual-link authentication ....................................................................................................................455
12.7.17 area virtual-link dead-interval (OSPF).........................................................................................................456
12.7.18 area virtual-link hello-interval (OSPF) .........................................................................................................456
12.7.19 area virtual-link retransmit-interval (OSPF).................................................................................................457
12.7.20 area virtual-link transmit-delay (OSPF) .......................................................................................................457
12.7.21 default-information originate (OSPF) ..........................................................................................................457
14
Page 15

12.7.22 default-metric (OSPF) .................................................................................................................................458
12.7.23 distance ospf (OSPF)..................................................................................................................................458
12.7.24 distribute-list out (OSPF).............................................................................................................................458
12.7.25 exit-overflow-interval (OSPF)......................................................................................................................459
12.7.26 external-lsdb-limit (OSPF)...........................................................................................................................459
12.7.27 ip ospf areaid ..............................................................................................................................................459
12.7.28 ip ospf authentication ..................................................................................................................................460
12.7.29 ip ospf cost..................................................................................................................................................460
12.7.30 ip ospf dead-interval....................................................................................................................................460
12.7.31 ip ospf hello-interval ....................................................................................................................................461
12.7.32 ip ospf priority..............................................................................................................................................461
12.7.33 ip ospf retransmit-interval............................................................................................................................461
12.7.34 ip ospf transmit-delay..................................................................................................................................462
12.7.35 ip ospf mtu-ignore .......................................................................................................................................462
12.7.36 router-id (OSPF) .........................................................................................................................................462
12.7.37 redistribute (OSPF) .....................................................................................................................................463
12.7.38 maximum-paths (OSPF) .............................................................................................................................463
12.7.39 timers spf ....................................................................................................................................................463
12.7.40 trapflags (OSPF).........................................................................................................................................464
12.7.41 show ip ospf................................................................................................................................................464
12.7.42 show ip ospf abr..........................................................................................................................................465
12.7.43 show ip ospf area........................................................................................................................................466
12.7.44 show ip ospf asbr........................................................................................................................................467
12.7.45 show ip ospf database ................................................................................................................................467
12.7.46 show ip ospf database database-summary.................................................................................................468
12.7.48 show ip ospf interface .................................................................................................................................469
12.7.49 show ip ospf interface brief .........................................................................................................................470
12.7.50 show ip ospf interface stats.........................................................................................................................471
12.7.51 show ip ospf neighbor .................................................................................................................................473
12.7.52 show ip ospf range......................................................................................................................................474
12.7.53 show ip ospf statistics .................................................................................................................................475
12.7.54 show ip ospf stub table................................................................................................................................475
12.7.55 show ip ospf virtual-link ...............................................................................................................................476
12.7.56 show ip ospf virtual-link brief .......................................................................................................................476
12.8 Routing Information Protocol (RIP) Commands ......................................................................................................478
12.8.1 router rip .......................................................................................................................................................478
12.8.2 enable (RIP)..................................................................................................................................................478
12.8.3 ip rip ..............................................................................................................................................................478
12.8.4 auto-summary...............................................................................................................................................478
12.8.5 default-information originate (RIP) ................................................................................................................479
15
Page 16

12.8.6 default-metric (RIP).......................................................................................................................................479
12.8.7 distance rip....................................................................................................................................................479
12.8.8 distribute-list out (RIP) ..................................................................................................................................480
12.8.9 ip rip authentication .......................................................................................................................................480
12.8.10 ip rip receive version ...................................................................................................................................480
12.8.11 ip rip send version .......................................................................................................................................481
12.8.12 hostroutesaccept.........................................................................................................................................481
12.8.13 split-horizon ................................................................................................................................................481
12.8.14 redistribute (RIP).........................................................................................................................................482
12.8.15 show ip rip...................................................................................................................................................482
12.8.16 show ip rip interface brief ............................................................................................................................483
12.8.17 show ip rip interface ....................................................................................................................................483
13 CLI COMMANDS: IP Multicast ....................................................................................... 485
13.1 Multicast Commands...............................................................................................................................................485
13.1.1 ip mcast boundary.........................................................................................................................................485
13.1.2 ip multicast....................................................................................................................................................485
13.1.3 ip multicast staticroute ..................................................................................................................................486
13.1.4 ip multicast ttl-threshold ................................................................................................................................486
13.1.5 mrinfo............................................................................................................................................................486
13.1.6 mstat .............................................................................................................................................................487
13.1.7 mtrace...........................................................................................................................................................487
13.1.8 show ip mcast ...............................................................................................................................................487
13.1.9 show ip mcast boundary ...............................................................................................................................488
13.1.10 show ip mcast interface ..............................................................................................................................488
13.1.11 show ip mcast mroute .................................................................................................................................489
13.1.12 show ip mcast mroute group .......................................................................................................................489
13.1.13 show ip mcast mroute source .....................................................................................................................490
13.1.14 show ip mcast mroute static........................................................................................................................491
13.1.15 show mrinfo ................................................................................................................................................491
13.1.16 show mstat..................................................................................................................................................491
13.1.17 show mtrace ...............................................................................................................................................492
13.2 Distance Vector Multicast Routing Protocol (DVMRP) Commands.........................................................................493
13.2.1 ip dvmrp ........................................................................................................................................................493
13.2.2 ip dvmrp metric .............................................................................................................................................493
13.2.3 ip dvmrp trapflags .........................................................................................................................................493
13.2.4 show ip dvmrp...............................................................................................................................................494
13.2.5 show ip dvmrp interface ................................................................................................................................494
13.2.6 show ip dvmrp neighbor ................................................................................................................................495
13.2.7 show ip dvmrp nexthop .................................................................................................................................496
13.2.8 show ip dvmrp prune.....................................................................................................................................496
16
Page 17

13.2.9 show ip dvmrp route......................................................................................................................................497
13.3 Internet Group Management Protocol (IGMP) Commands .....................................................................................498
13.3.1 ip igmp ..........................................................................................................................................................498
13.3.2 ip igmp version ..............................................................................................................................................498
13.3.3 set igmp mcrtrexpiretime...............................................................................................................................498
13.3.4 ip igmp last-member-query-count .................................................................................................................499
13.3.5 igmp last-member-query-interval ..................................................................................................................499
13.3.6 ip igmp query-interval....................................................................................................................................499
13.3.7 ip igmp query-max-response-time.................................................................................................................500
13.3.8 ip igmp robustness........................................................................................................................................500
13.3.9 ip igmp startup-query-count ..........................................................................................................................500
13.3.10 ip igmp startup-query-interval......................................................................................................................501
13.3.11 set igmp groupmembershipinterval .............................................................................................................501
13.3.12 set igmp maxresponse ................................................................................................................................502
13.3.13 set igmp mrouter interface ..........................................................................................................................502
13.3.14 set igmp mrouter .........................................................................................................................................502
13.3.15 show ip igmp...............................................................................................................................................503
13.3.16 show ip igmp groups...................................................................................................................................503
13.3.17 show ip igmp interface ................................................................................................................................504
13.3.18 show ip igmp interface membership............................................................................................................505
13.3.19 show ip igmp interface stats........................................................................................................................506
13.4 Protocol Independent Multicast – Dense Mode (PIM-DM) Commands...................................................................507
13.4.1 ip pimdm .......................................................................................................................................................507
13.4.2 ip pimdm mode .............................................................................................................................................507
13.4.3 ip pimdm query-interval.................................................................................................................................507
13.4.4 show ip pimdm ..............................................................................................................................................508
13.4.5 show ip pimdm interface ...............................................................................................................................508
13.4.6 show ip pimdm interface stats.......................................................................................................................508
13.4.7 show ip pimdm neighbor ...............................................................................................................................509
13.4.8 show ip pimdm componenttable....................................................................................................................509
13.5 Protocol Independent Multicast - Sparse Mode(PIM-SM) Commands ....................................................................510
13.5.1 ip pimsm cbsrpreference...............................................................................................................................510
13.5.2 ip pimsm cbsrhashmasklength......................................................................................................................510
13.5.3 ip pimsm crppreference ................................................................................................................................510
13.5.4 ip pimsm message-interval ...........................................................................................................................511
13.5.5 ip pimsm .......................................................................................................................................................511
13.5.6 ip pimsm mode..............................................................................................................................................512
13.5.7 ip pimsm query-interval.................................................................................................................................512
13.5.8 ip pimsm spt-threshold ..................................................................................................................................512
13.5.9 ip pim-trapflags .............................................................................................................................................513
17
Page 18

13.5.10 ip pimsm staticrp.........................................................................................................................................513
13.5.11 ip pimsm register-rate-limit ..........................................................................................................................513
13.5.12 show ip pimsm rphash ................................................................................................................................514
13.5.13 show ip pimsm staticrp................................................................................................................................514
13.5.14 show ip pimsm ............................................................................................................................................514
13.5.15 show ip pimsm componenttable ..................................................................................................................515
13.5.16 show ip pimsm interface .............................................................................................................................515
13.5.17 show ip pimsm interface stats .....................................................................................................................516
13.5.18 show ip pimsm neighbor .............................................................................................................................516
13.5.19 show ip pimsm rp........................................................................................................................................517
13.5.20 show ip pimsm rphash ................................................................................................................................517
14. SWITCH OPERATION ..................................................................................................... 518
14.1 Address Table .........................................................................................................................................................518
14.2 Learning ..................................................................................................................................................................518
14.3 Forwarding & Filtering.............................................................................................................................................518
14.4 Store-and-Forward ..................................................................................................................................................518
14.5 Auto-Negotiation .....................................................................................................................................................519
15. TROUBLE SHOOTING .................................................................................................... 520
APPENDEX A ........................................................................................................................ 521
A.1 Switch's RJ-45 Pin Assignments .................................................................................................................................521
A.2 10/100Mbps, 10/100Base-TX......................................................................................................................................521
GLOSSARY ........................................................................................................................... 523
18
Page 19

1. INTRODUCTION
1.1 Packet Contents
Thank you for purchasing PLANET 24-Port 10/100/1000Mbps wtih 4 shared SFP Layer 3 Managed Switch- WGS3-24000.
Terms of “WGS3-Layer 3 Switch” means the Switches mentioned titled in the cover page of this User’s manual,
i.e.WGS3-24000.
Check the contents of your package for following parts:
▫ The WGS3 Layer 3 Switch x1
▫ CD-ROM user’s manual x1
▫ Quick installation guide x1
▫ 19” rack mounting kit x1
▫ Power cord x1
▫ Rubber feet x 4
▫ RS-232 Console x 1
If any of these are missing or damaged, please contact your dealer immediately, if possible, retain the carton including the
original packing material, and use them against to repack the product in case there is a need to return it to us for repair.
1.2 How to Use This Manual
This User Manual is structured as follows:
Section 2, Installation
The section explains the functions of the Switch and how to physically install the Switch.
Section 3, Configuration
The section contains the information about the software function of the Switch.
Section 4, Web Configuration
The section explains how to manage the switch by Web interface.
Section 5, Command Structure
The section explains how to manage the switch by Console interface..
Section 6, Quick Start Up
Section 7, Mode-Base CLI
Section 8, CLI Command:-Base
Section 9, CLI Command: Quality of Service
Section 10, CLI Command: Security
Section 11, CLI Commands: Switching
Section 12, CLI Commands: Routing
Appendex A
The section contains cable information of the Switch.
In the following section, terms with lower case "switch" means other Ethernet switch devices.
19
Page 20

1.3 Product Feature
Physical Ports
24 RJ-45 ports for 10/100/1000Base-T
4 shared SFP mini-GBIC interfaces ( Shared with Port-12 and Port-24)
One DB9 male/RS-232 console port
One DB9 male/RS-232 console port
One DB9 male/RS-232 console port
Layer 2 Features
Supports auto MDI/MDI-X on all 10/100/1000Base-T ports
The 10/100/1000Base-TX ports support auto-sensing, auto-negotiation
Supports Jumbo frame up to 9KB
Provides wire speed of L2 switching performance
Supports up to 16K MAC address entries
Supports Flow Control
− IEEE 802.1x for Full-Duplex mode
− Back-Pressure Flow Control in Half-Duplex mode
Provides Store-and-Forward forwarding scheme
Provides Broadcast storm protection
Supports IGMP snooping v1, v2
Supports VLAN
− IEEE 802.1Q VLAN
− GARP/GVRP/GMRP
− Up to 4041 VLANs, out of 4041 VLAN IDs
− Protocol-Based VLAN
Supports Spanning Tree Protocol
− STP, IEEE 802.1d
− RSTP, IEEE 802.1w
− MSTP, IEEE 802.1s
Supports Link Aggregation
− up to 8 trunk groups
− up to 8 ports per trunk group
− 802.3ad Link Aggregation and LACP
− Cisco ether-channel (Static Trunk)
Provides Port Mirror (many-to-1)
Routing Features
Supports RIP v1 and v2
Supports OSPF v1/v2
Supports router discovery (IRDP)
20
Page 21

Supports VLAN routing
Supports VRRP
Supports IP routing
Supports route redistribution
Supports route preferences
Multicast
Supports PIM-DM and PIM-SM
Supports DVMRP
Supports IGMP v1/v2/v3
Security
User/Password protected system management
L2/L3/L4 ACL (access control list)
RADIUS client
TACACS client
SSH v1/v2
SSL v3/TLS v1
IEEE 802.1x Port-Based Autentication
Port MAC lock
Quality of Service
IEEE 802.1p based CoS
8 priority queues per port
IP TOS/Precedence based Cos
DSCP based CoS
Policy based DiffServ
Management
Provides 1 male DB9 RS-232C console interface
Supports BOOTP and DHCP for IP address assignment
Supports DHCP relay function
Supports software upload/download via XMODEM or TFTP
Supports configuration upload/download via XMODEM or TFTP
Supports up to three configuration files including factory default
Supports SSH v1/v2 switch management
Supports SSH/SSL/TLS keys download via XMODEM or TFTP
Supports SNTP (Simple Network Time Protocol)
Supports Ping function
Supports telnet function
Supports message/event/error/trap logs
21
Page 22
Supports logging to local file and syslog server
Supports Command Line Interface switch management
Supports Web switch management
Supports SNMP v1, v2c, and v3 switch management
Supports Private Enterprise MIB
Supports RMON groups 1, 2, 3, 9
Supports port mirror (many-to-1)
1.4 Product Specification
WGS3-24000
Product
Hardware Specification
24-Port 10/100/1000Mbps TP with 4-Port mini-GBIC
Layer 3 Managed Ethernet Switch
10/100/1000Base-T Ports
SFP/mini-GBIC slots
Switch Architecture
Switch Fabric
Switch throughput
Address Table
Layer 3 Routing Table
Buffer Memory
Flow Control
LED
Layer 2 function
Management Interface Console. Telnet, SSH, Web, SSL, SNMP
Port configuration
24 RJ-45 Auto-MDI/MDI-X ports
4 SFP interfaces
Store-and-Forward
48Gbps Capacity
35.7Mpps
16K MAC address table with Auto learning function
2048
2Mbits for packet buffer
Back pressure for Half-Duplex
IEEE 802.3x Pause Frame for Full-Duplex
Power, Link/Act, FDX/COL
Port disable/enable. Auto-negotiation 10/100Mbps full and half duplex mode selection. Flow
Control disable / enable. Bandwidth control on each port.
Port Status
VLAN
Port trunking
QoS
IGMP Snooping
Display each port’s speed duplex mode, link status, Flow control status. Auto negotiation
status, trunk status.
IEEE 802.1Q Tagged Based VLAN ,up to 4041 VLAN groups
Support 8 groups of 8-Port trunk
Traffic classification based on Port Number, 802.1p priority, DS/TOS field in IP Packet
Allow to disable or enable.
22
Page 23

IP Routing Protocol
Static Route, RIPv1/v2, OSPFv2,IRDP, VRRP
Multicast Routing
Protocol
Standards Conformance
Regulation Compliance
Standards Compliance
DVMRP, PIM-DM/SM
FCC Part 15 Class A, CE
IEEE 802.3
IEEE 802.3u
IEEE 802.3z
IEEE 802.3ab
IEEE 802.3x
IEEE 802.3ad
IEEE 802.1d
IEEE 802.1w
IEEE 802.1s
IEEE 802.1p
IEEE 802.1Q
10BASE-T
100BASE-TX/100BASE-FX
Gigabit SX/LX
Gigabit 1000T
Flow Control
Port trunk with LACP
Spanning tree protocol
Rapid Spanning tree protocol
Multiple Spanning Tree Protocol
Class of service
VLAN Tagging
23
Page 24
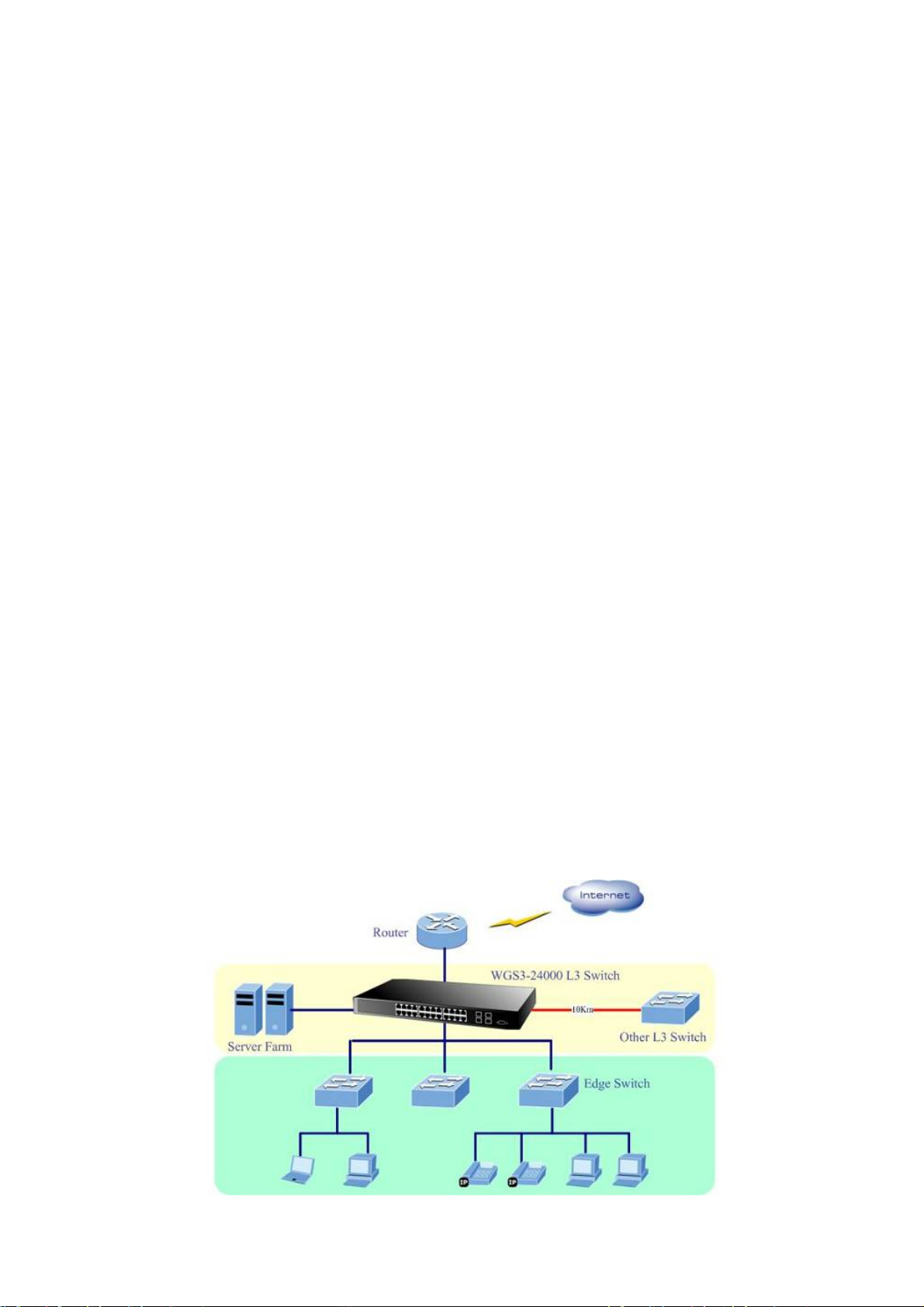
2. INSTALLATION
This section describes the functionalities of the Switch's components and guides how to install it on the desktop or shelf. Basic
knowledge of networking is assumed. Please read this chapter completely before continuing.
2.1 Product Description
The PLANET WGS3-24000 is a 24-Port 10/100/1000Mbps with 4 shared SFP/copper GbE interface Gigabit Ethernet Switch. It
boasts a high performance switch architecture that is capable of providing non-blocking switch fabric and wire-speed throughput
as high as 48Gbps. Its two built-in GbE uplink ports also offer incredible extensibility, flexibility and connectivity to the Core
switch or Servers.
2.1.1 Product Overview
PLANET WGS3-24000 is loaded with powerful traffic management and QoS features to enhance services offered by telcos. It
provides 4 priority queues per port for different types of traffics, allowing administrators to set policies for classified filtering and
rule-based rate limitation. The WGS3-24000 prioritizes applications with WFQ (Weighted Fair Queuing) scheduling algorithm to
allocate more bandwidth to key traffics such as voice transmission, empowering the enterprise to take full advantages of the
limited network resources and guarantee the best performance.
PLANET WGS3-24000 offers comprehensive Access Control List (ACL) for enforcing security to the edge. Its protection
mechanisms comprised of port-based 802.1x user and device authentication. The administrators can now construct highly
secured corporate networks with time and effort considerably less then before.
With its built-in web-based management, the PLANET WGS3-24000 offers an easy-to-use, platform-independent management
and configuration facility. The PLANET WGS3-24000 supports standard Simple Network Management Protocol (SNMP) and
can be managed via any standard-based management software. For text-based management, the WGS3-24000 can also be
accessed via Telnet and the console port. For secure remote management, the WGS3-24000 support SSL and SSH connection
which encrypt the packet content at each session.
24
Page 25
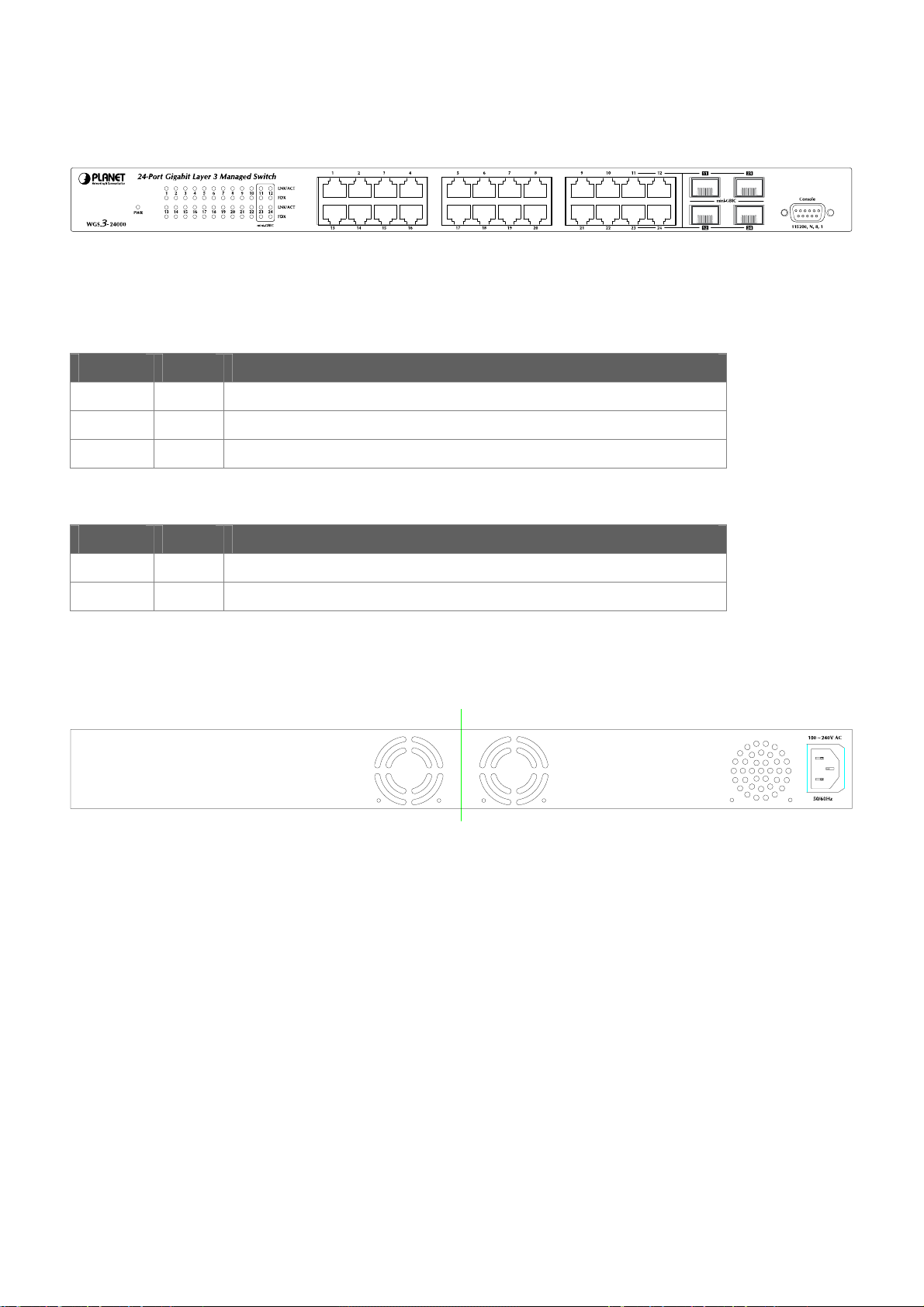
2.1.2 Switch Front Panel
Figure 2-1 shows the front panel of the switch.
Figure 2-1 WGS3-24000 front panel.
2.1.3 LED Indications
Network:
LED Color Function
PWR Green Lights to indicate that the Switch is powered on.
LNK/ACT Green Lights to indicate the link through that port is successfully established.
FDX Green Blink to indicate the switch is actively sending or receiving data over that port.
Gigabit:
LED Color Function
LNK/ACT Green Lights to indicate the link through that port is successfully established.
FDX/COL Green Blink to indicate the switch is actively sending or receiving data over that port.
2.1.4 Switch Rear Panel
Figure 2-2 shows the rear panel of the switch
Figure 2-2 WGS3-24000 rear panel.
Power Notice:
1. The device is a power-required device, it means, it will not work till it is powered. If your networks should active all the time,
please consider using UPS (Uninterrupted Power Supply) for your device. It will prevent you from network data loss or
network downtime.
2. In some area, installing a surge suppression device may also help to protect your switch from being damaged by
unregulated surge or current to the Switch or the power adapter.
25
Page 26

2.2 Install the Switch
This section describes how to install the Ethernet Switch and make connections to it. Please read the following topics and
perform the procedures in the order being presented.
2.2.1 Desktop Installation
To install the Switch on desktop or shelf, please follows these steps:
Step1: Attach the rubber feet to the recessed areas on the bottom of the switch.
Step2: Place the switch on the desktop or the shelf near an AC power source.
Step3: Keep enough ventilation space between the switch and the surrounding objects.
When choosing a location, please keep in mind the environmental restrictions discussed in Chapter
#Note:
Step4: Connect the Switch to network devices.
A. Connect one end of a standard network cable to the 10/100/1000 RJ-45 ports on the front of the Switch
1, Section 4, in Specification.
B. Connect the other end of the cable to the network devices such as printer servers, workstations or routers…etc.
Connection to the Switch requires UTP Category 5 network cabling with RJ-45 tips. For more
#Note:
Step5: Supply power to the switch.
A. Connect one end of the power cable to the switch.
B. Connect the power plug of the power cable to a standard wall outlet.
When the switch receives power, the Power LED should remain solid Green.
information, please see the Cabling Specification in Appendix A.
2.2.2 Rack Mounting
To install the switch in a 19-inch standard rack, please follows the instructions described below.
Step1: Place the switch on a hard flat surface, with the front panel positioned towards the front side.
Step2: Attach the rack-mount bracket to each side of the switch with supplied screws attached to the package.
Figure 2-5 shows how to attach brackets to one side of the switch.
Figure 2-5 Attach brackets to the switch.
26
Page 27
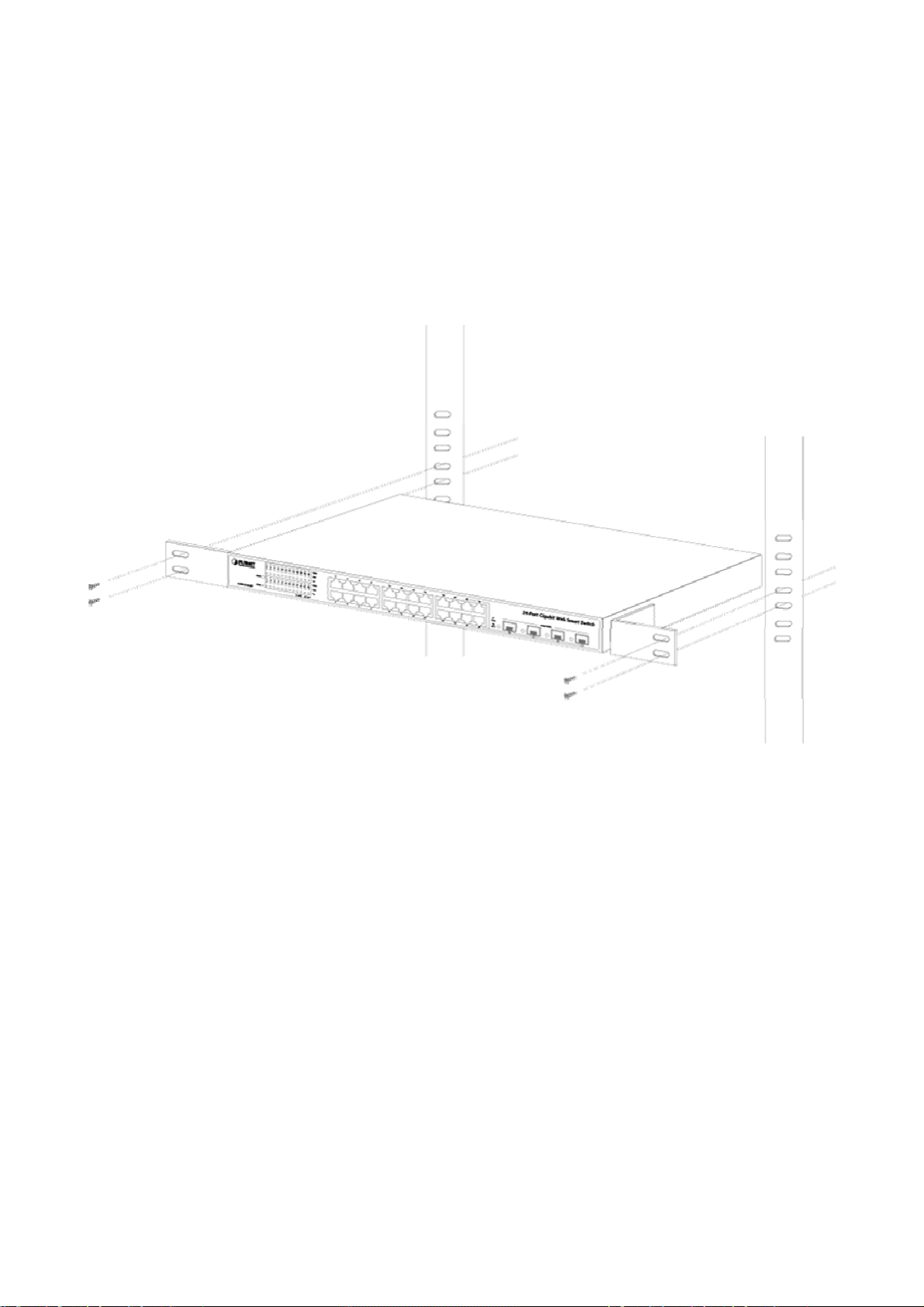
Caution:
You must use the screws supplied with the mounting brackets. Damage caused to the parts by using incorrect screws
would invalidate the warranty.
Step3: Secure the brackets tightly.
Step4: Follow the same steps to attach the second bracket to the opposite side.
Step5: After the brackets are attached to the Switch, use suitable screws to securely attach the brackets to the rack, as shown
in Figure 2-6
Figure 2-6 Mounting the Switch in a Rack
Step6: Proceeds with the steps 4 and steps 5 of session 2.2.1 Desktop Installation to connect the network cabling and supply
power to the switch.
2.2.3 Installing the SFP transceiver
The sections describe how to insert an SFP transceiver into an SFP slot.
The SFP transceivers are hot-pluggable and hot-swappable. You can plug-in and out the transceiver to/from any SFP port
without having to power down the Switch. As the Figure 2-7 appears.
27
Page 28

Figure 2-7 Plug-in the SFP transceiver
Approved PLANET SFP Transceivers
PLANET WGS3-24000 support both single mode and multi mode SFP transceiver. The following list of approved PLANET SFP
transceivers is correct at the time of publication:
■MGB-SX SFP (1000BASE-SX SFP transceiver )
■MGB-LX SFP (1000BASE-LX SFP transceiver )
It recommends using PLANET SFPs on the Switch. If you insert a SFP transceiver that is not
#Note:
Before connect the other switches, workstation or Media Converter.
1. Make sure both side of the SFP transfer are with the same media type, for example: 1000Base-SX to 1000Base-SX,
1000Bas-LX to 1000Base-LX.
2. Check the fiber-optic cable type match the SFP transfer model.
supported, the Switch will not recognize it.
¾ To connect to 1000Base-SX SFP transfer, use the multi-mode fiber cable- with one side must be male duplex LC
connector type.
¾ To connect to 1000Base-LX SFP transfer, use the single-mode fiber cable-with one side must be male duplex LC
connector type.
Connect the fiber cable
1. Attach the duplex LC connector on the network cable into the SFP transceiver.
2. Connect the other end of the cable to a device – switches with SFP installed, fiber NIC on a workstation or a Media
Converter..
3. Check the LNK/ACT LED of the SFP slot on the front of the Switch. Ensure that the SFP transceiver is operating correctly.
4. Check the Link mode of the SFP port if the link failed. Co works with some fiber-NICs or Media Converters, set the Link
mode to “1000 Force” is needed.
Remove the transceiver module
28
Page 29

1. Make sure there is no network activity by consult or check with the network administrator. Or through the management
interface of the switch/converter (if available) to disable the port in advance.
2. Remove the Fiber Optic Cable gently.
3. Turn the handle of the MGB/MFB module to horizontal.
4. Pull out the module gently through the handle.
Figure 2-8 Pull Out the SFP transceiver
Never pull out the module without pull the handle or the push bolts on the module. Direct pull out the
#Note:
module with violent could damage the module and SFP module slot of the device.
29
Page 30

3. CONFIGURATION
This chapter explains the methods that you can use to configure management access to the switch. It describes the types of
management applications and the communication and management protocols that deliver data between your management
device (work-station or personal computer) and the system. It also contains information about port connection options.
This chapter covers the following topics:
▫ Management Access Overview
▫ Key Concepts
▫ Key Guidelines for Implementation
▫ Administration Console Access
▫ Web Management Access
▫ SNMP Access
▫ Standards, Protocols, and Related Reading
3.1 Management Access Overview
The switch gives you the flexibility to access and manage the switch using any or all of the following methods:
▫ An administration console
▫ Web browser interface
▫ An external SNMP-based network management application
The administration console and Web browser interface support are embedded in the switch software and are available for
immediate use. Each of these management methods has their own advantages. Table 3-1 compares the three management
methods.
Method Advantages Disadvantages
Console
Web Browser
y No IP address or subnet needed
y Text-based
y Telnet functionality and HyperTerminal
built into Windows
95/98/NT/2000/ME/XP operating
systems
y Secure
y Ideal for configuring the switch remotely
y Must be near switch or use dial-up connection
y Not convenient for remote users
y Modem connection may prove to be unreliable
or slow
y Security can be compromised (hackers need
SNMP Agent
y Compatible with all popular browsers
y Can be accessed from any location
y Most visually appealing
y Communicates with switch functions at
the MIB level
only know the IP address and subnet mask)
y May encounter lag times on poor connections
y Requires SNMP manager software
y Least visually appealing of all three methods
30
Page 31

y Based on open standards y Some settings require calculations
y Security can be compromised (hackers need
only know the community name)
Table 3-1 Management Methods Comparison
3.1.1 Administration Console
The administration console is an internal, character-oriented, and command line user interface for performing system
administration such as displaying statistics or changing option settings. Using this method, you can view the administration
console from a terminal, personal computer, Apple Macintosh, or workstation connected to the switch's console (serial) port.
There are two ways to use this management method: via direct access or modem port access. The following sections describe
these methods. For more information about using the console, refer to Chapter 4 Command Line Interface Console
Management.
3.1.2 Direct Access
Direct access to the administration console is achieved by directly connecting a terminal or a PC equipped with a
terminal-emulation program (such as HyperTerminal) to the switch console (serial) port.
When using this management method, a null-modem cable is required to connect the switch to the PC. After making this
connection, configure the terminal-emulation program to use the following parameters:
The default parameters are:
▫ 115,200 bps
▫ 8 data bits
▫ No parity
▫ 1 stop bit
You can change these settings, if desired, after you log on. This management method is often preferred because you can
remain connected and monitor the system during system reboots. Also, certain error messages are sent to the serial port,
regardless of the interface through which the associated action was initiated. A Macintosh or PC attachment can use any
terminal-emulation program for connecting to the terminal serial port. A workstation attachment under UNIX can use an
emulator such as TIP.
31
Page 32

3.2 Web Management
The switch provides a browser interface that lets you configure and manage the switch remotely. After you set up your IP
address for the switch, you can access the switch's Web interface applications directly in your Web browser by entering the IP
address of the switch. You can then use your Web browser to list and manage switch configuration parameters from one central
location, just as if you were directly connected to the switch's console port.
Web Management requires either Microsoft Internet Explorer 6.0 or later or Mozilla Firefox 1.5 or later.
3.3 SNMP-Based Network Management
You can use an external SNMP-based application to configure and manage the switch. This management method requires the
SNMP agent on the switch and the SNMP Network Management Station to use the same community string. This management
method, in fact, uses two community strings: the get community string and the set community string. If the SNMP Net-work
management Station only knows the set community string, it can read and write to the MIBs. However, if it only knows the get
community string, it can only read MIBs. The default gets and sets community strings for the switch are public.
3.4 Protocols
The switch supports the following protocols:
▫ Virtual terminal protocols, such as Telnet
▫ Simple Network Management Protocol (SNMP)
3.4.1 Virtual Terminal Protocols
A virtual terminal protocol is a software program, such as Telnet, that allows you to establish a management session from a
Macintosh, a PC, or a UNIX workstation. Because Telnet runs over TCP/IP, you must have at least one IP address configured
on the switch before you can establish access to it with a virtual terminal protocol.
"Note: Terminal emulation differs from a virtual terminal protocol in that you must connect a terminal directly to the console
(serial) port.
3.4.2 SNMP Protocol
Simple Network Management Protocol (SNMP) is the standard management protocol for multi-vendor IP networks. SNMP
supports transaction-based queries that allow the protocol to format messages and to transmit information between reporting
devices and data-collection programs. SNMP runs on top of the User Datagram Protocol (UDP), offering a
connectionless-mode service.
3.4.3 Management Architecture
All of the management application modules use the same Messaging Application Programming Interface (MAPI). By unifying
management methods with a single MAPI, configuration parameters set using one method (console port, for example) are
immediately displayable by the other management methods (for example, SNMP agent of Web browser).
The management architecture of the switch adheres to the IEEE open standard. This compliance assures customers that the
switch is compatible with, and will interoperate with other solutions that adhere to the same open standard.
32
Page 33

4. Web Configuration
The WGS3-24000 can be configured through an Ethernet connection, make sure the manager PC must be set on same the IP
subnet address with the switch. For example, if you have changed the default IP address of the Switch to 192.168.1.1 with
subnet mask 255.255.255.0 via console, then the manager PC should be set at 192.168.1.x (where x is a number between 2
and 254) with subnet mask 255.255.255.0. Or you can use the factory default IP address 192.168.1.254 to do the relative
configuration on manager PC.
Logging on the switch
1. Use Internet Explorer 6.0 or above Web browser. Enter the factory-default IP address to access the Web interface. The
factory-default IP Address as following:
http://192.168.1.254
2. When the following login screen appears, the system will ask you to enter the username and password.
Default User name: admin
Default Password: admin
The login screen in Figure 4-2 appears.
33
Page 34

3. When the following login screen appears, please enter the default username "admin" with password “admin” (or the
username/password you have changed via console) to login the main screen of Switch. The login screen in Figure 4-1
appears.
Figure 4-1 Login screen
Now, you can use the Web management interface to continue the switch management or manage the switch by console
interface.
#Note:
It is recommended to use Internet Explore 6.0 or above to access WGS3-24000.
34
Page 35

4.1 Main Menu
The Switch provides a Web-based browser interface for configuring and managing the Switch. This interface allows you to
access the switch using the Web browser of your choice. This chapter describes how to use the switch’s Web browser interface
to con-figure and manage the switch.
Main Functions Menu
Port Link Status
Main Screen
Help Button
Figure 4-1-1 Main Page
Via the Web-Management, the administrator can setup the WGS3-24000 by select the functions those listed in the Main
Function. The screen in Figure 4-2 appears.
Figure 4-1-2 WGS3-24000 Main Funcrions Menu
Apply Button
35
Page 36

The following functions can be configured here:
System
Switching
Routing
Security
QoS
IP Multicast
System Description
After a successful login, the main screen appears, the main screen displays the port status and a list of System section and the
topics it provide. As showed in Figure 4-2.
。 System Name - Enter the name you want to use to identify this switch. You may use up to 31 alpha-numeric
characters. The factory default is blank.
。 System Location - Enter the location of this switch. You may use up to 31 alpha-numeric characters. The factory
default is blank.
。 System Contact - Enter the contact person for this switch. You may use up to 31 alpha-numeric characters. The
factory default is blank.
Figure 4-1-3 main menu screen
36
Page 37

4.2 Configure System
The System section provides information for configuring system parameters. Under system the following topics are provided to
configure and view the system information:
。 ARP Cache
。 Inventory Information
。 System Loading
。 Configuration
。 Forward Database
。 Log
。 Port
。 SNMP
。 Statistics
。 System Utilities
。 Trap Manager
。 DHCP Server
。 SNTP
4.2.1 ARP Cache
The Address Resolution Protocol (ARP) dynamically maps physical (MAC) addresses to Internet (IP) addresses. This panel
displays the current contents of the ARP cache.
For each connection, the following information is displayed:
。 The physical (MAC) Address
。 The associated IP address
。 The identification of the port being used for the connection
As shows in figure 4-3:
Figure 4-2-1 ARP Cache
37
Page 38

4.2.2 Inventory Information
Use this panel to display the switch's Vital Product Data, stored in non-volatile memory at the factory. The page includes the
following fields:
。 System Description - The product name of this switch.
。 Machine Type - The machine type of this switch.
。 Machine Model - The model within the machine type.
。 Serial Number - The unique box serial number for this switch.
。 FRU Number - The field replaceable unit number.
。 Part Number - The manufacturing part number.
。 Maintenance Level - The identification of the hardware change level.
。 Manufacturer - The two-octet code that identifies the manufacturer.
。 Base MAC Address - The burned-in universally administered MAC address of this switch.
。 Software Version - The release version maintenance number of the code currently running on the switch. For
example, if the release was 1, the version was 2 and the maintenance number was 4, the format would be '1.2.4'.
。 Operating System - The operating system currently running on the switch.
。 Network Processing Device - Identifies the network processor hardware.
。 Additional Packages - A list of the optional software packages installed on the switch, if any. For example,
FASTPATH BGP-4, or FASTPATH Multicast.
Figure 4-2-2 Inventory Information
38
Page 39

4.2.3 Configuration
Use this page to configure the parameters for system management, including the following fields:
。 System Description
。 Switch
。 Network Connectivity
。 Telnet Session
。 Outbound Telnet Client Configuration
。 Serial Port
。 User Account
。 Authentication List Configuration
。 Login Session
。 Authentication List Summary
。 User Login
4.2.3.1 System Description
This page shows the basic system information and is available to define the system name, location and contact person.
Includes the following fields:
。 System Name - Enter the name you want to use to identify this switch. You may use up to 31 alpha-numeric
characters. The factory default is blank.
。 System Location - Enter the location of this switch. You may use up to 31 alpha-numeric characters. The factory
default is blank.
。 System Contact - Enter the contact person for this switch. You may use up to 31 alpha-numeric characters. The
factory default is blank.
。 System Description - The product name of this switch.
。 System Object ID - The base object ID for the switch's enterprise MIB.
。 System IP Address - The IP Address assigned to the network interface.
。 System Up time - The time in days, hours and minutes since the last switch reboot.
。 MIBs Supported - The list of MIBs supported by the management agent running on this switch.
39
Page 40

Figure 4—2-3 System Description
4.2.4.2 Switch Configuration
This page includes the following fields:
。 Broadcast Storm Recovery Mode - Enable or disable this option by selecting the corresponding line on the
pull-down entry field. The factory default is disabled.
。 IEEE 802.3x Flow Control Mode - Enable or disable this option by selecting the corresponding line on the
pull-down entry field. The factory default is disabled.
。 Lag Static Capability Mode - May be enabled or disabled by selecting the corresponding line on the pull-down
entry field. The factory default is disabled.
Figure 4-2-4 Switch Configuration
40
Page 41

4.2.3.3 Network Connectivity
The network interface is the logical interface used for in-band connectivity with the switch via any of the switch's front panel
ports. The configuration parameters associated with the switch's network interface do not affect the configuration of the front
panel ports through which traffic is switched or routed.
Figure 4-2-5 Network Connectivity Configuration
To access the switch over a network you must first configure it with IP information (IP address, subnet mask, and default
gateway). You can configure the IP information using any of the following:
。 BOOTP
。 DHCP
。 Terminal interface via the EIA-232 port
Once you have established in-band connectivity, you can change the IP information using any of the following:
。 Terminal interface via the EIA-232 port
。 Terminal interface via telnet
。 SNMP-based management
。 Web-based management
The page includes the following configurable data:
。 IP Address - The IP address of the interface. The factory default value is 0.0.0.0
。 Subnet Mask - The IP subnet mask for the interface. The factory default value is 0.0.0.0
。 Default Gateway - The default gateway for the IP interface. The factory default value is 0.0.0.0
。 Locally Administered MAC Address - You may configure a locally administered MAC address for in-band
connectivity instead of using the burned-in universally administered MAC address. In addition to entering an
address in this field, you must also set the MAC address type to locally administered. Enter the address as twelve
hexadecimal digits (6 bytes) with a colon between each byte. Bit 1 of byte 0 must be set to a 1 and bit 0 to a 0, i.e.
byte 0 must have a value between x'40' and x'7F'.
。 MAC Address type - Specify whether the burned-in or the locally administered MAC address should be used for
in-band connectivity. The factory default is to use the burned-in MAC address
41
Page 42

。 Network Configuration Protocol Current - Choose what the switch should do following power-up: transmit a
Bootp request, transmit a DHCP request, or do nothing (none). The factory default is DHCP.
。 Management VLAN ID - Specifies the management VLAN ID of the switch. It may be configured to any value in
the range of 1 - 4093. The management VLAN is used for management of the switch. This field is configurable for
administrative users and read-only for other users.
。 Web Mode - Specify whether the switch may be accessed from a web browser. If you choose to enable web mode
you will be able to manage the switch from a web browser. The factory default is enabled.
。 Java Mode - Enable or disable the java applet that displays a picture of the switch at the top right of the screen. If
you run the applet you will be able to click on the picture of the switch to select configuration screens instead of
using the navigation tree at the left side of the screen. The factory default is disabled.
The following data are non-configurable:
。 Burned-in MAC Address - The burned-in MAC address used for in-band connectivity if you choose not to
configure a locally administered address.
。 Network Configuration Protocol Current - Indicates what network protocol was used on the last, or current
power-up cycle, if any.
4.2.3.4 Telnet Session
This page includes the following fields:
Configurable Data
。 Telnet Session Timeout (minutes) - Specify how many minutes of inactivity should occur on a telnet session
before the session is logged off. You may enter any number from 1 to 160. The factory default is 5.
。 Maximum Number of Telnet Sessions - Use the pulldown menu to select how many simultaneous telnet sessions
will be allowed. The maximum is 5, which is also the factory default.
。 Allow New Telnet Sessions - If you set this to no, new telnet sessions will not be allowed. The factory default is
yes.
Figure 4-2-6 Telnet Session Configuration
42
Page 43

4.2.3.5 Outbound Telnet Client Configuration
This page includes the following fields:
Configurable Data
。 Admin Mode - Specifies if the Outbound Telnet service is Enabled or Disabled. Default value is Enabled.
。 Maximum Sessions - Specifies the maximum number of Outbound Telnet Sessions allowed. Default value is 5.
Valid Range is (0 to 5).
。 Session Timeout - Specifies the Outbound Telnet login inactivity timeout. Default value is 5. Valid Range is (1 to
160).
Figure 4-2-7 OutboundTelnet Client Configuration
4.2.3. Remote Session
This page includes the following fields:
。 Remote Login Timeout (minutes) - Specify how many minutes of inactivity should occur on a telnet or SSH
session before the switch logs off. A zero means there will be no timeout. You may enter any number from 0 to 160.
The factory default is 5.
。 Maximum Number of Remote Sessions - Use the pull-down menu to select how many simultaneous telnet or
SSH sessions will be allowed. The maximum is 5, which is also the factory default.
。 Allow New Remote Sessions - If you set this to no, new telnet sessions will not be allowed. The factory default is
yes.
43
Page 44

4.2.3.7 Serial Port
Use this page to define the parameters of console connectivity. The configurable data are:
。 Serial Port Login Timeout (minutes) - Specify how many minutes of inactivity should occur on a serial port
connection before the switch closes the connection. Enter a number between 0 and 160: the factory default is 5.
Entering 0 disables the timeout.
。 Baud Rate (bps) - Select the default baud rate for the serial port connection from the pull-down menu. You may
choose from 1200, 2400, 4800, 9600, 19200, 38400, 57600, and 115200 baud. The factory default is 115200
baud.
And the non-configurable data:
。 Character Size (bits) - The number of bits in a character. This is always 8.
。 Flow Control - Whether hardware flow control is enabled or disabled. It is always disabled.
。 Parity - The parity method used on the serial port. It is always None.
。 Stop Bits - The number of stop bits per character. The value is always 1.
Figure 4-2-8 Serial Port Configuration
44
Page 45

4.2.3.8 User Accounts
By default, two user accounts exist:
。 admin, with 'Read/Write' privileges
。 guest, with 'Read Only' privileges
By default, both of these accounts have blank passwords. The names are not case sensitive.
If you logon with a user account with 'Read/Write' privileges (i.e. as admin) you can use the User Accounts screen to assign
passwords and set security parameters for the default accounts, and to add and delete accounts (other than admin) up to the
maximum of six. Only a user with 'Read/Write' privileges may alter data on this screen, and only one account may be created
with 'Read/Write' privileges.
Selection Criteria
。 User Name Selector - You can use this screen to reconfigure an existing account, or to create a new one. Use this
pull-down menu to select one of the existing accounts, or select 'Create' to add a new one, provided the maximum
of five 'Read Only' accounts has not been reached.
Configurable Data
。 User Name - Enter the name you want to give to the new account. (You can only enter data in this field when you
are creating a new account.) User names are up to eight characters in length and are not case sensitive. Valid
characters include all the alphanumeric characters as well as the dash ('-') and underscore ('_') characters.
。 Password - Enter the optional new or changed password for the account. It will not display as it is typed, only
asterisks(*) will show. Passwords are up to eight alpha numeric characters in length, and are case sensitive.
。 Confirm Password - Enter the password again, to confirm that you entered it correctly. This field will not display,
but will show asterisks (*)
。 Authentication Protocol - Specify the SNMPv3 Authentication Protocol setting for the selected user account. The
valid Authentication Protocols are None, MD5 or SHA. If you select None, the user will be unable to access the
SNMP data from an SNMP browser. If you select MD5 or SHA, the user login password will be used as the
SNMPv3 authentication password, and you must therefore specify a password, and it must be eight characters
long.
。 Encryption Protocol - Specify the SNMPv3 Encryption Protocol setting for the selected user account. The valid
Encryption Protocols are None or DES. If you select the DES Protocol you must enter a key in the Encryption Key
field. If None is specified for the Protocol, the Encryption Key is ignored.
。 Encrypt ion Key - If you selected DES in the Encryption Protocol field enter the SNMPv3 Encryption Key here.
Otherwise this field is ignored. Valid keys are 0 to 15 characters long. The Apply checkbox must be checked in
order to change the Encryption Protocol and Encryption Key.
Non-Configurable Data
。 Access Mode - Indicates the user's access mode. The admin account always has 'Read/Write' access, and all
other accounts have 'Read Only' access.
。 SNMP v3 Access Mode - Indicates the SNMPv3 access privileges for the user account. The admin account
always has 'Read/Write' access, and all other accounts have 'Read Only' access.
45
Page 46

Figure 4-2-9 User Accounts
4.2.3.9 Authentication List Configuration
Use this screen to configure login lists. A login list specifies the authentication method(s) you want used to validate switch or
port access for the users associated with the list. The pre-configured users, admin and guest, are assigned to a pre-configured
list named defaultList, which you may not delete. All newly created users are also assigned to the defaultList until you
specifically assign them to a different list
Selection Criteria
。 Authentication List - Select the authentication login list you want to configure. Select 'create' to define a new
login list. When you create a new login list, 'local' is set as the initial authentication method.
Configurable Data
。 Authentication List Name - If you are creating a new login list, enter the name you want to assign. It can be up to
15 alphanumeric characters long and is not case sensitive.
。 Method 1 - Use the dropdown menu to select the method that should appear first in the selected authentication
login list. If you select a method that does not time out as the first method, such as 'local' no other method will be
tried, even if you have specified more than one method. Note that this parameter will not appear when you first
create a new login list. The options are:
¾ Local- the user's locally stored ID and password will be used for authentication
¾ Radius- the user's ID and password will be authenticated using the RADIUS server instead of locally
¾ Reject- the user is never authenticated
¾ Undefined- the authentication method is unspecified (this may not be assigned as the first method)
。 Method 2 - Use the dropdown menu to select the method, if any, that should appear second in the selected
authentication login list. This is the method that will be used if the first method times out. If you select a method
that does not time out as the second method, the third method will not be tried. Note that this parameter will not
appear when you first create a new login list.
。 Method 3 - Use the dropdown menu to select the method, if any, that should appear third in the selected
authentication login list. Note that this parameter will not appear when you first create a new login list.
46
Page 47

Figure 4-2-10 Authentication List Configuration – Create User
Figure 4-2-11 Authentication List Configuration – DefaultList
4.2.3.10 Login Session
This page shows the information of login session, including:
。 ID - Identifies the ID of this row.
。 User Name - Shows the user name of user made the session.
。 Connection From - Shows the user is connected from which machine.
。 Idle Time - Shows the idle session time.
。 Session Time - Shows the total session time.
47
Page 48

Figure 4-2-12 Login Sessions
4.2.3.11 Authentication List Summary
This page lists the authenticate user, the information fields include:
。 Authentication List - Identifies the authentication login list summarized in this row.
。 Method List - The ordered list of methods configured for this login list.
。 Login Users - The users you assigned to this login list on the User Login Configuration screen. This list is used to
authenticate the users for system login access.
。 802.1x Port Security Users - The users you assigned to this login list on the Port Access Control User Login
Configuration screen - This list is used to authenticate the users for port access, using the IEEE 802.1x protocol.
Figure 4-2-13 Authentication List Summary
48
Page 49

4.2.3.12 User Login
Each configured user is assigned to a login list that specifies how the user should be authenticated when attempting to access
the switch or a port on the switch. After creating a new user account on the User Account screen, you should assign that user to
a login list for the switch using this screen and, if necessary, to a login list for the ports using the Port Access Control User Login
Configuration screen. If you need to create a new login list for the user, you would do so on the Login Configuration screen.
The pre-configured users, admin and guest, are assigned to a pre-configured list named defaultList, which you may not delete.
All newly created users are also assigned to the defaultList until you specifically assign them to a different list.
A user that does not have an account configured on the switch is termed the 'default' or 'non-configured' user. If you assign
the 'non-configured user' to a login list that specifies authentication via the RADIUS server, you will not need to create an
account for all users on each switch. However, by default the 'non-configured user' is assigned to 'defaultList', which by
default uses local authentication.
Selection Criteria
。 User - Select the user you want to assign to a login list. Note that you must always associate the admin user with
the default list. This forces the admin user to always be authenticated locally to prevent full lockout from switch
configuration. If you assign a user to a login list that requires remote authentication, the user's access to the switch
from all CLI, web, and telnet sessions will be blocked until the authentication is complete. Refer to the discussion
of maximum delay in the RADIUS configuration help.
Configurable Data
。 Authentication List - Select the authentication login list you want to assign to the user for system login.
Figure 4-2-14 User Login Configuration
49
Page 50

4.2.4 Forwarding Database
4.2.4.1 Configuration
Use this panel to set the Address Ageing Timeout for the forwarding database.
。 Address Ageing Timeout (s e conds ) - The forwarding database contains static entries, which are never aged out,
and dynamically learned entries, which are removed if they are not updated within a given time. You specify that
time by entering a value for the Address Ageing Timeout. You may enter any number of seconds between 10 and
1000000. IEEE 802.1D recommends a default of 300 seconds, which is the factory default.
Figure 4-2-15 Forwarding Database
4.2.4.2 Search
Use this panel to display information about entries in the forwarding database. These entries are used by the transparent
bridging function to determine how to forward a received frame.
Configurable Data
。 Filter - Specify the entries you want displayed.
¾ Learned: If you choose "learned" only MAC addresses that have been learned will be displayed.
¾ All: If you choose "all" the whole table will be displayed.
。 MAC Address Search - You may also search for an individual MAC address. Enter the two byte hexadecimal
VLAN ID followed by the six byte hexadecimal MAC address in two-digit groups separated by colons, for example
01:23:45:67:89:AB:CD:EF where 01:23 is the VLAN ID and 45:67:89:AB:CD:EF is the MAC address. Then click on
the search button. If the address exists, that entry will be displayed as the first entry followed by the remaining
(greater) MAC addresses. An exact match is required.
50
Page 51

4.2.5 Log
。 Buffered Log Configuration
。 Buffered Log
。 Command Logger Configuration
。 Console Log Configuration
。 Event Log
。 Hosts Configuration
。 Persistent Log Configuration
。 Persistent Log
。 Syslog Configuration
Figure 4-2-16 Forwarding Database Search
4.2.5.1 Buffered Log Configuration
This log stores messages in memory based upon the settings for message component and severity. On stackable systems, this
log exists only on the top of stack platform. Other platforms in the stack forward their messages to the top of stack log.
Configurable Data
。 Admin Status - A log that is "Disabled" shall not log messages. A log that is "Enabled" shall log messages. Enable
or Disable logging by selecting the corresponding line on the pulldown entry field.
51
Page 52

。 Behavior Indicates the behavior of the log when it is full. It can either wrap around or stop when the log space is
filled.
Figure 4-2-17 Buffered Log Configuration
4.2.5.2 Buffered Log
This help message applies to the format of all logged messages which are displayed for the buffered log, persistent log or
console log.
Format of the messages
Messgges logged to a collector or relay via syslog have an identical format of either type
。 <15>Aug 24 05:34:05 STK0 MSTP[2110]: mspt_api.c(318) 237 %% Interface 12 transitioned to root state on
message age timer expiry
-The above example indicates a message with severity 7(15 mod 8) (debug) on a system that is not stack and
generated by component MSTP running in thread id 2110 on Aug 24 05:34:05 by line 318 of file mstp_api.c. This is
the 237th message logged.
Command Buttons
o Refresh - Refresh the page with the latest log entries.
Figure 4-2-18 Buffered Logs
52
Page 53

44.2.5.3 Command Logger Configuration
This page includes the following fields:
Configurable Data
。 Admin Mode - Enable/Disable the operation of the CLI Command logging by selecting the corresponding pulldown
field and clicking Submit.
Figure 4-2-19 Command Logger Configuration
4.2.5.4 Console Log Configuration
This allows logging to any serial device attached to the host.
Configurable Data
。 Admin Status -A log that is "Disabled" shall not log messages. A log that is "Enabled" shall log messages. Enable
or Disable logging by selecting the corresponding line on the pulldown entry field.
。 Severity Filter - A log records messages equal to or above a configured severity threshold. Select the severity
option by selecting the corresponding line on the pulldown entry field. These severity levels have been enumerated
below:
-Emergency (0): system is unusable
-Alert (1): action must be taken immediately
-Critical (2): critical conditions
-Error (3): error conditions
-Warning (4): warning conditions
-Notice(5): normal but significant conditions
-Informational(6): informational messages
-Debug(7): debug-level messages
Figure 4-2-20 Console Log Configuration
53
Page 54

4.2.5.5 Event Log
This allows logging to any serial device attached to the host.
Configurable Data
。 Admin Status -A log that is "Disabled" shall not log messages. A log that is "Enabled" shall log messages. Enable or
Disable logging by selecting the corresponding line on the pulldown entry field.
。 Severity Filter - A log records messages equal to or above a configured severity threshold. Select the severity option
by selecting the corresponding line on the pulldown entry field. These severity levels have been enumerated below:
-Emergency (0): system is unusable
-Alert (1): action must be taken immediately
-Critical (2): critical conditions
-Error (3): error conditions
-Warning (4): warning conditions
-Notice(5): normal but significant conditions
-Informational(6): informational messages
-Debug(7): debug-level messages
Figure 4-2-21 Event Log
4.2.5.6 Hosts Configuration
Figure 4-2-22 Host Configuration
Configurable Data
。 Host - This is a list of the hosts that have been configured for syslog. Select a host for changing the configuration or
choose to add a new hosts from the drop down list.
。 IP Address - This is the ip address of the host configured for syslog.
54
Page 55

。 Port -This is the port on the host to which syslog messages are sent. The default port is 514. The default port is 514.
Specify the port in the text field.
。 Severity Filter -A log records messages equal to or above a configured severity threshold. Select the severity option
by selecting the corresponding line on the pulldown entry field. These severity levels have been enumerated below:
-Emergency (0): system is unusable
-Alert (1): action must be taken immediately
-Critical (2): critical conditions
-Error (3): error conditions
-Warning (4): warning conditions
-Notice(5): normal but significant conditions
-Informational(6): informational messages
-Debug(7): debug-level messages
Non Configurable Data
。 Status -This specifies wether the host has been configured to be actively logging or not.
Command Buttons
。 Submit - Update the switch with the values you entered.
。 Refresh - Refetch the database and display it again starting with the first entry in the table.
。 Delete - Delete a configured host.
4.2.5.7 Persistent Log Configuration
A persistent log is a log that is stored in persistent storage. Persistent storage survives across platform reboots. The first log
type is the system startup log. The system startup log stores the first N messages received after system reboot. The second log
type is the system operation log. The system operation log stores the last N messages received during system operation.
Figure 4-2-23 Persistent Log Configuration
Configurable Data
。 Admin Status - A log that is "Disabled" shall not log messages. A log that is "Enabled" shall log messages. Enable
or Disable logging by selecting the corresponding line on the pulldown entry field.
55
Page 56

。 Severity Filter - A log records messages equal to or above a configured severity threshold. Select the severity
option by selecting the corresponding line on the pulldown entry field. These severity levels have been enumerated
below:
-Emergency (0): system is unusable
-Alert (1): action must be taken immediately
-Critical (2): critical conditions
-Error (3): error conditions
-Warning (4): warning conditions
-Notice(5): normal but significant conditions
-Informational(6): informational messages
-Debug(7): debug-level messages
Command Buttons
。 Submit - Update the switch with the values you entered.
4.2.5.8 Persistent Log
This help message applies to the format of all logged messages which are displayed for the buffered log, persistent log or
console log.
Figure 4-2-24 Persistent Logs
Format of the messages
。 <15>Aug 24 05:34:05 STK0 MSTP[2110]: mspt_api.c(318) 237 %% Interface 12 transitioned to root state on
message age timer expiry
-The above example indicates a user-level message (1) with severity 7 (debug) on a system that is not stack and
generated by component MSTP running in thread id 2110 on Aug 24 05:34:05 by line 318 of file mstp_api.c. This
is the 237th message logged. Messages logged to a collector or relay via syslog have an identical format to the
above message.
Command Buttons
。 Refresh - Refresh the page with the latest log entries.
56
Page 57

4.2.5.9 Syslog Configuration
Figure 4-2-25 Syslog Configuration
Configurable Data
。 Admin Status -For Enabling and Disabling logging to configured syslog hosts. Setting this to disable stops logging to
all syslog hosts. Disable means no messages will be sent to any collector/relay. Enable means messages will be sent
to configured collector/relays using the values configured for each collector/relay. Enable/Disable the operation of the
syslog function by selecting the corresponding line on the pulldown entry field.
。 Local UDP Port This is the port on the local host from which syslog messages are sent. The default port is XXX. The
default port is 514. Specify the local port in the text field.
Non-Configurable Data
。 Messages Relayed - The count of syslog messages relayed.
。 Messages Ignored - The count of syslog messages ignored.
Command Buttons
。 Submit - Update the switch with the values you entered.
Refresh - Refetch the database and display it again starting with the first entry in the table.
4.2.6 Port
4.2.7.1 Configuration
Use this page to configure the parameters of the distinct port.
Selection Criteria
。 Slot.Port - Selects the interface for which data is to be displayed or configured.
Configurable Data
。 STP Mode - The Select the Spanning Tree Protocol Administrative Mode for the port or LAG. The possible values
are:
¾ Enable - select this to enable the Spanning Tree Protocol for this port.
¾ Disable - select this to disable the Spanning Tree Protocol for this port.
。 Admin Mode - Use the pull-down menu to select the Port control administration state. You must select enable if
57
Page 58

you want the port to participate in the network. The factory default is enabled.
。 LACP Mode - Selects the Link Aggregation Control Protocol administration state. The mode must be enabled in
order for the port to participate in Link Aggregation. May be enabled or disabled by selecting the corresponding
line on the pull-down entry field. The factory default is enabled.
。 Physical Mode - Use the pull-down menu to select the port's speed and duplex mode. If you select auto the
duplex mode and speed will be set by the auto-negotiation process. Note that the port's maximum capability (full
duplex and 100 Mbps) will be advertised. Otherwise, your selection will determine the port's duplex mode and
transmission rate. The factory default is auto. The selection when applied against the "All" option in Slot.Port is
applied to all applicable interfaces only.
。 Link Trap - This object determines whether or not to send a trap when link status changes. The factory default is
enabled.
。 Maximum Frame Size - The maximum Ethernet frame size the interface supports or is configured, including
Ethernet header, CRC, and payload. (1518 to 1600). The default maximum frame size is 1518.
Non-Configurable Data
。 Port Type - For normal ports this field will be blank. Otherwise the possible values are:
¾ Mon - the port is a monitoring port. Look at the Port Monitoring screens for more information.
¾ LAG - the port is a member of a Link Aggregation trunk. Look at the LAG screens for more information.
。 Physical Status - Indicates the port speed and duplex mode.
。 Link Status - Indicates whether the Link is up or down.
。 ifIndex - The ifIndex of the interface table entry associated with this port.
Figure 4-2-26 Port Configuration
4.2.6.2 Summary
This screen displays the status for all ports in the box.
58
Page 59

Figure 4-2-27 Port Summary
Selection Criteria
。 MST ID - Select the Multiple Spanning Tree instance ID from the list of all currently configured MST ID's to
determine the values displayed for the Spanning Tree parameters. Changing the selected MST ID will generate a
screen refresh. If Spanning Tree is disabled this will be a static value, CST, instead of a selector.
Non-Configurable Port Status Data
。 Slot.Port - Identifies the port
。 Port Type - For normal ports this field will be blank. Otherwise the possible values are:
¾ Mon - this port is a monitoring port. Look at the Port Monitoring screens for more information.
¾ LAG - the port is a member of a Link Aggregation trunk. Look at the LAG screens for more information.
。 STP Mode - The Spanning Tree Protocol Administrative Mode associated with the port or LAG. The possible
values are:
¾ Enable - spanning tree is enabled for this port.
¾ Disable - spanning tree is disabled for this port.
。 Forwarding State - The port's current state Spanning Tree state. This state controls what action a port takes on
receipt of a frame. If the bridge detects a malfunctioning port it will place that port into the broken state. The other
five states are defined in IEEE 802.1D:
¾ Disabled
¾ Blocking
¾ Listening
¾ Learning
¾ Forwarding
¾ Broken
59
Page 60

。 Port Role - Each MST Bridge Port that is enabled is assigned a Port Role for each spanning tree. The port role will
be one of the following values: Root Port, Designated Port, Alternate Port, Backup Port, Master Port or Disabled
Port.
。 Admin Mode - The Port control administration state. The port must be enabled in order for it to be allowed into the
network. The factory default is enabled.
。 LACP Mode - Indicates the Link Aggregation Control Protocol administration state. The mode must be enabled in
order for the port to participate in Link Aggregation.
。 Physical Mode - Indicates the port speed and duplex mode. In auto-negotiation mode the duplex mode and speed
are set from the auto-negotiation process.
。 Physical Status - Indicates the port speed and duplex mode.
。 Link Status - Indicates whether the Link is up or down.
。 Link Trap - Indicates whether or not the port will send a trap when link status changes.
。 ifIndex - Indicates the ifIndex of the interface table entry associated with this port.
4.2.6.3 Port Mirroring
Use this page to configure the port mirror function.
Figure 4-2-29 Multiple Port Mirroring
Configurable Data
。 Session ID - A session ID or "All Sessions" option may be selected. By default the First Session is selected.
。 Session Mode - Specifies the Session Mode for a selected session ID. By default Session Mode is enabled.
。 Source Port(s) - Specifies the configured port(s) as mirrored port(s). Traffic of the configured port(s) is sent to the
probe port.
。 Destination Port - Acts as a probe port and will recieve all the traffic from configured mirrored port(s). Default value
is blank.
Command Buttons
。 Submit - Send the updated screen to the switch and cause the changes to take effect on the switch.
60
Page 61
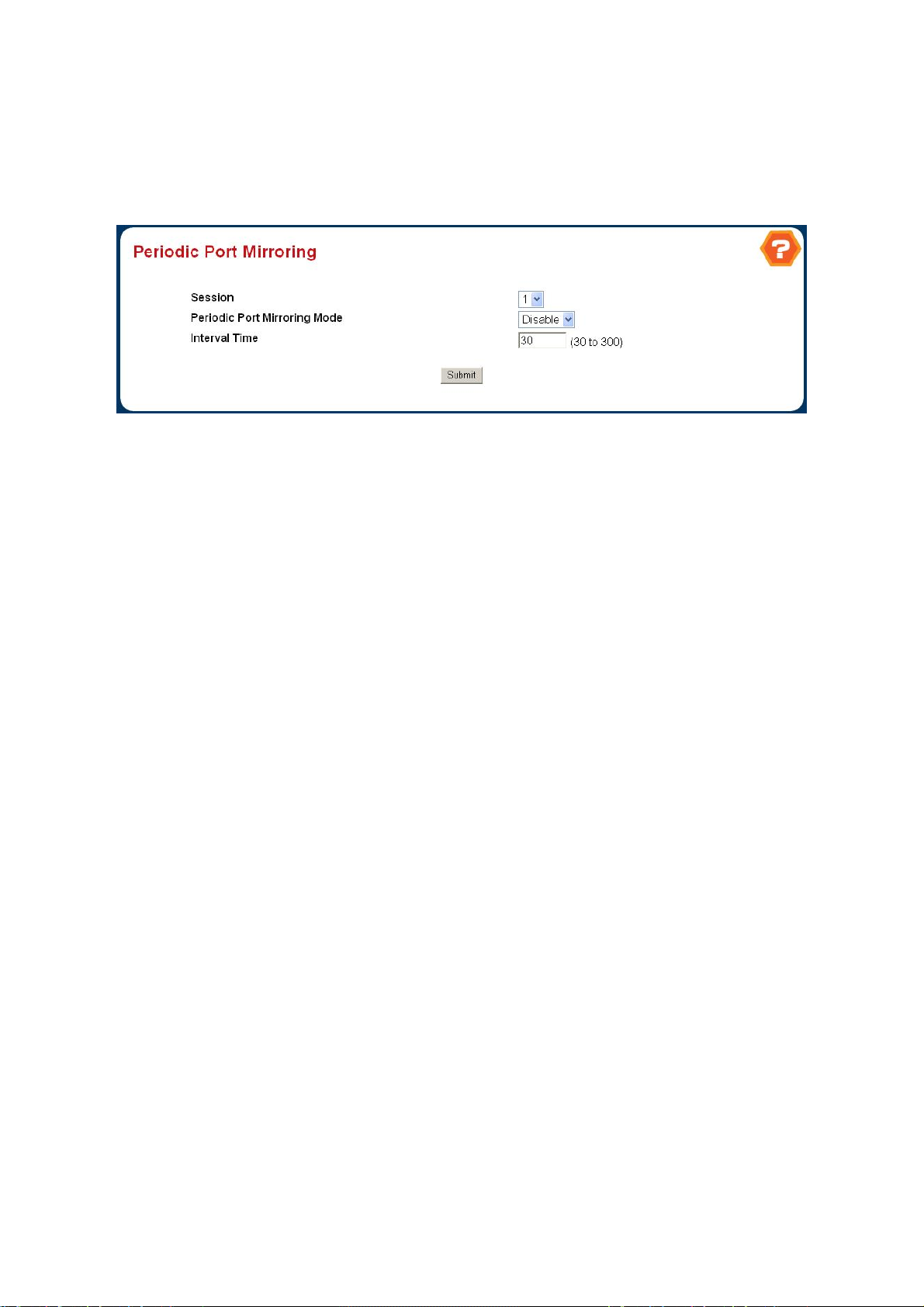
。 Delete - Remove the selected session configuration.
4.2.6.4 Periodic Port Mirroring
Use this page to configure the periodic port mirroring.
Figure 4-2-30 Periodic Port Mirroring
Selection Criteria
。 Session ID - A session ID can be selected. By default the First Session is selected.
Configurable Data
。 Peroidic Port Mirroring Mode - Specifies the Periodic Port Mirroring Mode for a selected session ID. By default
Periodic Port Mirroring Mode is Disabled.
。 Interval Time - Specifies the periodic port mirroring time interval in seconds.Default value is 30. Valid Range is (30
to 300).
Non-Configurable Data
。 Source Port - Specifies the mirrored port. This field is only visible when periodic port mirroring mode is enabled.
Source port changes periodically as per specified Interval Time.
Command Buttons
。 Submit - Send the updated screen to the switch and cause the changes to take effect on the switch.
61
Page 62

4.2.6.5 Double VLAN Tunneling
Use this page to configure the Doubble VLAN Tunneling.
Figure 4-2-31 Double VLAN Tunneling
Selection Criteria
。 Slot/Port - Select the physical interface for which you want to display or configure data. Select 'All' to set the
parameters for all ports to same values.
Configurable Data
。 Mode - This specifies the administrative mode via which Double VLAN Tagging can be enabled or disabled. The
default value for this is Disabled.
。 Customer ID - This is a 12 bit customer ID which will be used as the last 12 bits of the DVlan tag. The valid range for
a customer Id is (0 to 4095). The default customer Id is 0 .
。 EtherType - The two-byte hex EtherType to be used as the first 16 bits of the DVlan tag.
¾ 802.1Q Tag - Commonly used tag representing 0x8100
¾ vMAN Tag - Commonly used tag representing 0x88A8
¾ Custom Tag - Configure the EtherType in any range from (0 to 65535)
Command Buttons
。 Submit - Update the switch with the values on this screen. If you want the switch to retain the new values across a
power cycle, you must perform a save.
62
Page 63

4.2.6.7 Double VLAN Tunneling Summary
Figure 4-2-32 Double VLAN Tunneling Summary
Non-Configurable Data
。 Slot/Port - The physical interface for which data is being displayed.
。 Mode - This specifies the administrative mode via which Double VLAN Tagging can be enabled or disabled. The
default value for this is Disabled.
。 Customer ID - This is the 12 bit customer ID which will be used as the last 12 bits of the DVlan tag. The valid range
for a customer Id is (0 to 4095). The default customer Id is 0 .
。 EtherType - The two-byte hex EtherType to be used as the first 16 bits of the DVlan tag.
¾ 802.1Q Tag - Commonly used tag representing 0x8100
¾ vMAN Tag - Commonly used tag representing 0x88A8
¾ Custom Tag - Configure the EtherType in any range from (0 to 65535)
Command Buttons
Refresh - Refresh the data on the screen with the present state of the data in the switch.
63
Page 64

4.2.7 SNMP
4.2.7.1 Community Configuration
By default, two SNMP Communities exist:
。 private, with 'Read/Write' privileges and status set to enable
。 public, with 'Read Only' privileges and status set to enable
These are well-known communities; you can use this menu to change the defaults or to add other communities. Only the
communities that you define using this menu will have access to the switch using the SNMPv1 and SNMPv2c protocols. Only
those communities with read-write level access will have access to this menu via SNMP.
You should use this menu when you are using the SNMPv1 and SNMPv2c protocol: if you want to use SNMP v3 you should use
the User Accounts menu.
Figure 4-2-33 SNMP Community
Configurable Data
。 SNMP Community Name - You can use this screen to reconfigure an existing community, or to create a new one.
Use this pull-down menu to select one of the existing community names, or select 'Create' to add a new one. A
valid entry is a case-sensitive string of up to 16 characters.
。 Client IP Address - Taken together, the Client IP Address and Client IP Mask denote a range of IP addresses from
which SNMP clients may use that community to access this device. If either (IP Address or IP Mask) value is
0.0.0.0, access is allowed from any IP address. Otherwise, every client's IP address is ANDed with the mask, as is
the Client IP Address, and, if the values are equal, access is allowed. For example, if the Client IP Address and
Client IP Mask parameters are 192.168.1.0/255.255.255.0, then any client whose IP address is 192.168.1.0
through 192.168.1.255 (inclusive) will be allowed access. To allow access from only one station, use a Client IP
Mask value of 255.255.255.255, and use that machine's IP address for Client IP Address.
。 Client IP Mask - Taken together, the Client IP Address and Client IP Mask denote a range of IP addresses from
64
Page 65

which SNMP clients may use that community to access this device. If either (IP Address or IP Mask) value is
0.0.0.0, access is allowed from any IP address. Otherwise, every client's IP address is ANDed with the mask, as is
the Client IP Address, and, if the values are equal, access is allowed. For example, if the Client IP Address and
Client IP Mask parameters are 192.168.1.0/255.255.255.0, then any client whose IP address is 192.168.1.0
through 192.168.1.255 (inclusive) will be allowed access. To allow access from only one station, use a Client IP
Mask value of 255.255.255.255, and use that machine's IP address for Client IP Address.
。 Access Mode - Specify the access level for this community by selecting Read/Write or Read Only from the
pull-down menu.
。 Status - Specify the status of this community by selecting Enable or Disable from the pull-down menu. If you select
enable, the Community Name must be unique among all valid Community Names or the set request will be
rejected. If you select disable, the Community Name will become invalid.
4.2.7.2 Trap Receiver Configuration
This menu will display an entry for every active Trap Receiver.
Figure 4-2-34 SNMP Trap Receiver
。 SNMP Community Name - Enter the community string for the SNMP trap packet to be sent to the trap manager.
This may be up to 16 characters and is case sensitive.
。 IP Address - Enter the IP address to receive SNMP traps from this device. Enter 4 numbers between 0 and 255
separated by periods.
。 Status - Select the receiver's status from the pulldown menu:
。 Enable - send traps to the receiver
。 Disable - do not send traps to the receiver.
65
Page 66

4.2.7.3 Supported MIBS
This is a list of all the MIBs supported by the switch.
。 Name - The RFC number if applicable and the name of the MIB.
。 Description - The RFC title or MIB description.
。 Refresh - Update the data.
Figure 4-2-35 SNMP Supported MIBs
4.2.9 Statistics
4.2.9.1 Switch Detail
This page shows the detail information of the switch, including the following data:
。 ifIndex - This object indicates the ifIndex of the interface table entry associated with the Processor of this switch.
。 Octets Received - The total number of octets of data received by the processor (excluding framing bits but
including FCS octets).
。 Unicast Packets Received - The number of subnetwork-unicast packets delivered to a higher-layer protocol.
。 Multicast Packets Received - The total number of packets received that were directed to a multicast address.
Note that this number does not include packets directed to the broadcast address.
。 Broadcast Packets Received - The total number of packets received that were directed to the broadcast address.
Note that this does not include multicast packets.
。 Receive Packets Discarded - The number of inbound packets which were chosen to be discarded even though
no errors had been detected to prevent their being deliverable to a higher-layer protocol. A possible reason for
discarding a packet could be to free up buffer space.
。 Octets Transmitted - The total number of octets transmitted out of the interface, including framing characters.
。 Packets Transmitted Without Errors - The total number of packets transmitted out of the interface.
。 Unicast Packets Transmitted - The total number of packets that higher-level protocols requested be transmitted
to a subnetwork-unicast address, including those that were discarded or not sent.
。 Multicast Packets Transmitted - The total number of packets that higher-level protocols requested be transmitted
66
Page 67

to a Multicast address, including those that were discarded or not sent.
。 Broadcast Packets Transmitted - The total number of packets that higher-level protocols requested be
transmitted to the Broadcast address, including those that were discarded or not sent.
。 Transmit Packets Discarded - The number of outbound packets which were chosen to be discarded even though
no errors had been detected to prevent their being deliverable to a higher-layer protocol. A possible reason for
discarding a packet could be to free up buffer space.
。 Most Address Entries Ever Used - The highest number of Forwarding Database Address Table entries that have
been learned by this switch since the most recent reboot.
。 Address Entries in Use - The number of Learned and static entries in the Forwarding Database Address Table for
this switch.
。 Maximum VLAN Entries - The maximum number of Virtual LANs (VLANs) allowed on this switch.
。 Most VLAN Entries Ever Used - The largest number of VLANs that have been active on this switch since the last
reboot.
。 Static VLAN Entries - The number of presently active VLAN entries on this switch that have been created
statically.
。 Dynamic VLAN Entries - The number of presently active VLAN entries on this switch that have been created by
GVRP registration.
。 VLAN Deletes - The number of VLANs on this switch that have been created and then deleted since the last
reboot.
。 Time Since Counters Last Cleared - The elapsed time, in days, hours, minutes, and seconds, since the statistics
for this switch were last cleared.
Figure 4-2-36 Switch Detailed Statistics
67
Page 68

4.2.9.2 Switch Summary
。 ifIndex - This object indicates the ifIndex of the interface table entry associated with the Processor of this switch.
。 Broadcast Packets Received - The total number of packets received that were directed to the broadcast address.
Note that this does not include multicast packets.
。 Packets Received With Error - The number of inbound packets that contained errors preventing them from being
deliverable to a higher-layer protocol.
。 Packets Transmitted Without Errors - The total number of packets transmitted out of the interface.
。 Broadcast Packets Transmitted - The total number of packets that higher-level protocols requested to be
transmitted to the Broadcast address, including those that were discarded or not sent.
。 Transmit Packet Errors - The number of outbound packets that could not be transmitted because of errors.
。 Address Entries Currently in Use - The total number of Forwarding Database Address Table entries now active
on the switch, including learned and static entries.
。 VLAN Entries Currently in Use - The number of VLAN entries presently occupying the VLAN table.
。 Time Since Counters Last Cleared - The elapsed time, in days, hours, minutes, and seconds since the statistics
for this switch were last cleared.
Figure 4-2-37 Switch Summary Statistics
68
Page 69

4.2.8.3 Port Detailed
Selection Criteria
。 Slot.Port - Selects the interface for which data is to be displayed or configured.
Non-Configurable Data
。 ifIndex - This object indicates the ifIndex of the interface table entry associated with this port on an adapter.
。 Packets RX and TX 64 Octets - The total number of packets (including bad packets) received or transmitted that
were 64 octets in length (excluding framing bits but including FCS octets).
。 Packets RX and TX 65-127 Octets - The total number of packets (including bad packets) received or transmitted
that were between 65 and 127 octets in length inclusive (excluding framing bits but including FCS octets).
。 Packets RX and TX 128-255 Octets - The total number of packets (including bad packets) received or transmitted
that were between 128 and 255 octets in length inclusive (excluding framing bits but including FCS octets).
。 Packets RX and TX 256-511 Octets - The total number of packets (including bad packets) received or transmitted
that were between 256 and 511 octets in length inclusive (excluding framing bits but including FCS octets).
。 Packets RX and TX 512-1023 Octets - The total number of packets (including bad packets) received or
transmitted that were between 512 and 1023 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Packets RX and TX 1024-1518 Octets - The total number of packets (including bad packets) received or
transmitted that were between 1024 and 1518 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Packets RX and TX 1519-1522 Octets - The total number of packets (including bad packets) received or
transmitted that were between 1519 and 1522 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Packets RX and TX 1523-2047 Octets - The total number of packets (including bad packets) received or
transmitted that were between 1523 and 2047 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Packets RX and TX 2048-4095 Octets - The total number of packets (including bad packets) received or
transmitted that were between 2048 and 4095 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Packets RX and TX 4096-9216 Octets - The total number of packets (including bad packets) received or
transmitted that were between 4096 and 9216 octets in length inclusive (excluding framing bits but including FCS
octets).
。 Octets Received - The total number of octets of data (including those in bad packets) received on the network
(excluding framing bits but including FCS octets). This object can be used as a reasonable estimate of Ethernet
utilization. If greater precision is desired, the etherStatsPkts and etherStatsOctets objects should be sampled
before and after a common interval.
。 Packets Received > 1522 Octets - The total number of packets received that were longer than 1522 octets
(excluding framing bits, but including FCS octets) and were otherwise well formed.
。 Total Packets Received Without Errors - The total number of packets received that were without errors.
。 Unicast Packets Received - The number of subnetwork-unicast packets delivered to a higher-layer protocol.
。 Multicast Packets Received - The total number of good packets received that were directed to a multicast
69
Page 70

address. Note that this number does not include packets directed to the broadcast address.
。 Broadcast Packets Received - The total number of good packets received that were directed to the broadcast
address. Note that this does not include multicast packets.
。 Tot al Packet s Received with MAC Errors - The total number of inbound packets that contained errors preventing
them from being deliverable to a higher-layer protocol.
。 Jabbers Received - The total number of packets received that were longer than 1518 octets (excluding framing
bits, but including FCS octets), and had either a bad Frame Check Sequence (FCS) with an integral number of
octets (FCS Error) or a bad FCS with a non-integral number of octets (Alignment Error). Note that this definition of
jabber is different than the definition in IEEE-802.3 section 8.2.1.5 (10BASE5) and section 10.3.1.4 (10BASE2).
These documents define jabber as the condition where any packet exceeds 20 ms. The allowed range to detect
jabber is between 20 ms and 150 ms.
。 Fragments/Undersize Received - The total number of packets received that were less than 64 octets in length
(excluding framing bits but including FCS octets).
。 Alignment Errors - The total number of packets received that had a length (excluding framing bits, but including
FCS octets) of between 64 and 1518 octets, inclusive, but had a bad Frame Check Sequence (FCS) with a
non-integral number of octets.
。 Rx FCS Errors - The total number of packets received that had a length (excluding framing bits, but including FCS
octets) of between 64 and 1518 octets, inclusive, but had a bad Frame Check Sequence (FCS) with an integral
number of octets
。 Overruns - The total number of frames discarded as this port was overloaded with incoming packets, and could
not keep up with the inflow.
。 Total Received Packets Not Forwarded - A count of valid frames received which were discarded (i.e. filtered) by
the forwarding process.
。 Local Traffic Frames - The total number of frames dropped in the forwarding process because the destination
address was located off of this port.
。 802.3x Pause Frames Received - A count of MAC Control frames received on this interface with an opcode
indicating the PAUSE operation. This counter does not increment when the interface is operating in half-duplex
mode.
。 Unacceptable Frame Type - The number of frames discarded from this port due to being an unacceptable frame
type.
。 Multicast Tree Viable Discards - The number of frames discarded when a lookup in the multicast tree for a VLAN
occurs while that tree is being modified.
。 Reserved Address Discards - The number of frames discarded that are destined to an IEEE 802.1 reserved
address and are not supported by the system.
。 Broadcast Storm Recovery - The number of frames discarded that are destined for FF:FF:FF:FF:FF:FF when
Broadcast Storm Recovery is enabled.
。 CFI Discards - The number of frames discarded that have CFI bit set and the addresses in RIF are in
non-canonical format.
。 Upstream Threshold - The number of frames discarded due to lack of cell descriptors available for that packet's
priority level.
70
Page 71

。 Total Packets Transmitted (Octets) - The total number of octets of data (including those in bad packets)
transmitted on the network (excluding framing bits but including FCS octets). This object can be used as a
reasonable estimate of Ethernet utilization. If greater precision is desired, the etherStatsPkts and etherStatsOctets
objects should be sampled before and after a common interval.
。 Packets Transmitted 1523-2047 Octets - The total number of packets (including bad packets) received that were
between 1523 and 2047 octets in length inclusive (excluding framing bits but including FCS octets).
。 Packets Transmitted 2048-4095 Octets - The total number of packets (including bad packets) received that were
between 2048 and 4095 octets in length inclusive (excluding framing bits but including FCS octets).
。 Packets Transmitted 4096-9216 Octets - The total number of packets (including bad packets) received that were
between 4096 and 9216 octets in length inclusive (excluding framing bits but including FCS octets).
。 Maximum Frame Size - The maximum Ethernet frame size the interface supports or is configured, including
Ethernet header, CRC, and payload. (1518 to 1600). The default maximum frame size is 1518.
。 Total Packets Transmitted Successfully - The number of frames that have been transmitted by this port to its
segment.
。 Unicast Packets Transmitted - The total number of packets that higher-level protocols requested be transmitted
to a subnetwork-unicast address, including those that were discarded or not sent.
。 Multicast Packets Transmitted - The total number of packets that higher-level protocols requested be transmitted
to a Multicast address, including those that were discarded or not sent.
。 Broadcast Packets Transmitted - The total number of packets that higher-level protocols requested be
transmitted to the Broadcast address, including those that were discarded or not sent.
。 Total Transmit Errors - The sum of Single, Multiple, and Excessive Collisions.
。 Tx FCS Errors - The total number of packets transmitted that had a length (excluding framing bits, but including
FCS octets) of between 64 and 1518 octets, inclusive, but had a bad Frame Check Sequence (FCS) with an
integral number of octets
。 Tx Oversized - The total number of frames that exceeded the max permitted frame size. This counter has a max
increment rate of 815 counts per sec at 10 Mb/s.
。 Underrun Errors - The total number of frames discarded because the transmit FIFO buffer became empty during
frame transmission.
。 Total Transmit Packets Discarded - The sum of single collision frames discarded, multiple collision frames
discarded, and excessive frames discarded.
。 Single Collision Frames - A count of the number of successfully transmitted frames on a particular interface for
which transmission is inhibited by exactly one collision.
。 Multiple Collision Frames - A count of the number of successfully transmitted frames on a particular interface for
which transmission is inhibited by more than one collision.
。 Excessive Collision Frames - A count of frames for which transmission on a particular interface fails due to
excessive collisions.
。 Port Membership Discards - The number of frames discarded on egress for this port due to egress filtering being
enabled.
。 STP BPDUs Received - Number of STP BPDUs received at the selected port.
。 STP BPDUs Transmitted - Number of STP BPDUs transmitted from the selected port.
71
Page 72

。 RSTP BPDUs Received - Number of RSTP BPDUs received at the selected port.
。 RSTP BPDUs Transmitted - Number of RSTP BPDUs transmitted from the selected port.
。 MSTP BPDUs Received - Number of MSTP BPDUs received at the selected port.
。 MSTP BPDUs Transmitted - Number of MSTP BPDUs transmitted from the selected port.
。 802.3x Pause Frames Transmitted - A count of MAC Control frames transmitted on this interface with an opcode
indicating the PAUSE operation. This counter does not increment when the interface is operating in half-duplex
mode.
。 GVRP PDUs Received - The count of GVRP PDUs received in the GARP layer.
。 GVRP PDUs Transmitted - The count of GVRP PDUs transmitted from the GARP layer.
。 GVRP Failed Registrations - The number of times attempted GVRP registrations could not be completed.
。 GMRP PDUs Received - The count of GMRP PDUs received from the GARP layer.
。 GMRP PDUs Transmitted - The count of GMRP PDUs transmitted from the GARP layer.
。 GVRP Failed Registrations - The number of times attempted GMRP registrations could not be completed.
。 Time Since Counters Last Cleared - The elapsed time, in days, hours, minutes, and seconds since the statistics
for this port were last cleared.
Figure 4-2-38 Port Detailed Statistic
4.2.8.4 Port Summary
Selection Criteria
。 Slot.Port - Selects the interface for which data is to be displayed or configured.
Non-Configurable Data
。 ifIndex - This object indicates the ifIndex of the interface table entry associated with this port on an adapter.
。 Total Packets Received Without Errors - The total number of packets received that were without errors.
。 Packets Received With Error - The number of inbound packets that contained errors preventing them from being
deliverable to a higher-layer protocol.
72
Page 73

。 Broadcast Packets Received - The total number of good packets received that were directed to the broadcast
address. Note that this does not include multicast packets.
。 Packets Transmitted Without Errors - The number of frames that have been transmitted by this port to its
segment.
。 Transmit Packet Errors - The number of outbound packets that could not be transmitted because of errors.
。 Collision Frames - The best estimate of the total number of collisions on this Ethernet segment.
。 Time Since Counters Last Cleared - The elapsed time, in days, hours, minutes, and seconds since the statistics
for this port were last cleared.
Figure 4-2-39 Port Summary Statistics
4.2.8.5 CPU Statistics
This page shows the system loading information, including the following fields:
Figure 4-2-40 CPU Statistics
Non-Configurable Data
73
Page 74

。 Total Memory - The total RAM memory available with the CPU.
。 Used Memory - The RAM memory already used by CPU.
。 Free Memory - The free memory available with the CPU.
。 % CPU Utilization - % of CPU capacity used over time.
Command Buttons
。 Refresh - Refresh the data on the screen with the present state of the data in the switch.
4.2.9 System Utilities
4.2.9.1 Save All Applied Changes
Saving all applied changes will cause all changes to configuration panels that were applied, but not saved, to be saved, thus
retaining their new values across a system reboot.
Figure 4-2-41 Save All Applied Changes
74
Page 75

4.2.9.2 System Reset
Reboot the switch. Any configuration changes you have made since the last time you issued a save will be lost. You will be
shown a confirmation screen after you select the button.
Figure 4-2-42 System Reset
4.2.9.3 Reset Configuration to Default
Have all configuration parameters reset to their factory default values. All changes you have made will be lost, even if you have
issued a save. You will be shown a confirmation screen after you select the button.
Figure 4-2-43 Reset Configuration to Default
75
Page 76

4.2.9.4 Reset Password to Default
Reset all of the system login passwords to their default values. If you want the switch to retain the new values across a power
cycle, you must perform a save.
Figure 4-2-44 Reset Password to Default
4.2.9.5 Download File To Switch
Use this menu to download a file to the switch.
Configurable Data
。 File Type - Specify what type of file you want to download:
¾ Code - specify code when you want to upgrade the operational flash.
¾ Configuration - specify configuration when you want to update the switch's configuration. If the file has
errors the update will be stopped.
¾ SSH-1 RSA Key File - SSH-1 Rivest-Shamir-Adleman (RSA) Key File
¾ SSH-2 RSA Key PEM File - SSH-2 Rivest-Shamir-Adleman (RSA) Key File (PEM Encoded)
¾ SSH-2 DSA Key PEM File - SSH-2 Digital Signature Algorithm (DSA) Key File (PEM Encoded)
¾ SSL Trusted Root Certificate PEM File - SSL Trusted Root Certificate File (PEM Encoded)
¾ SSL Server Certificate PEM File - SSL Server Certificate File (PEM Encoded)
¾ SSL DH Weak Encryption Parameter PEM File - SSL Diffie-Hellman Weak Encryption Parameter File
(PEM Encoded)
¾ SSL DH Strong Encryption Parameter PEM File - SSL Diffie-Hellman Strong Encryption Parameter File
(PEM Encoded)
The factory default is code.
Note that to download SSH key files SSH must be administratively disabled and there can be no active SSH sessions.
。 TFTP Server IP Address - Enter the IP address of the TFTP server. The factory default is 0.0.0.0.
76
Page 77

。 TFTP File Path - Enter the path on the TFTP server where the selected file is located. You may enter up to 32
characters. The factory default is blank.
。 TFTP File Name - Enter the name on the TFTP server of the file you want to download. You may enter up to 32
characters. The factory default is blank.
。 Start File Transfer - To initiate the download you need to check this box and then select the submit button.
Figure 4-2-45 Download File To Switch
4.2.9.6 Upload File From Switch
Use this menu to upload a configuration or log file from the switch.
77
Page 78

Figure 4-2-46 Upload File from Switch
Configurable Data
。 File Type - Specify the type of file you want to upload. The available options are Configuration, Error Log, System
Trace, and Trap Log. The factory default is Error Log.
。 TFTP Server IP Address - Enter the IP address of the TFTP server. The factory default is 0.0.0.0
。 TFTP File Path - Enter the path on the TFTP server where you want to put the file being uploaded. You may enter
up to 32 characters. The factory default is blank.
。 TFTP File Name - Enter the name you want to give the file being uploaded. You may enter up to 32 characters.
The factory default is blank.
。 Start File Transfer - To initiate the upload you need to check this box and then select the submit button.
4.2.9.7 Ping
Use this screen to tell the switch to send a Ping request to a specified IP address. You can use this to check whether the switch
can communicate with a particular IP station. Once you click the Submit button, the switch will send three pings and the results
will be displayed below the configurable data. If a reply to the ping is not received, you will see No Reply Received from IP
xxx.xxx.xxx.xxx, otherwise you will see Reply received from IP xxx.xxx.xxx.xxx : (send count = 3, receive count = n).
Figure 4-2-47 Ping
Configurable Data
。 IP Address - Enter the IP address of the station you want the switch to ping. The initial value is blank. The IP
Address you enter is not retained across a power cycle.
78
Page 79

4.2.10 Trap Management
4.2.10.1 Trap Flags
Use this menu to specify which traps you want to enable. When the condition identified by an active trap is encountered by the
switch a trap message will be sent to any enabled SNMP Trap Receivers, and a message will be written to the trap log.
Configurable Data
。 Authentication - Enabled or disable activation of authentication failure traps by selecting the corresponding line
on the pull-down entry field. The factory default is enabled.
。 Broadcast Storm Flag - This field will only be displayed if Broadcast storm feature is supported. Enabled or
disable activation of broadcast storm traps by selecting the corresponding line on the pull-down entry field. The
factory default is enabled.
。 Link Up/Down - Enabled or disable activation of link status traps by selecting the corresponding line on the
pull-down entry field. The factory default is enabled.
。 Multiple Users - Enabled or disable activation of multiple user traps by selecting the corresponding line on the
pull-down entry field. The factory default is enabled. This trap is triggered when the same user ID is logged into the
switch more than once at the same time (either via telnet or the serial port).
。 Spanning Tree - Enabled or disable activation of spanning tree traps by selecting the corresponding line on the
pull-down entry field. The factory default is enabled.
Figure 4-2-48 Trap Flags
4.2.10.2 Trap Log
This screen lists the entries in the trap log. The information can be retrieved as a file by using System Utilities, Upload File from
Switch.
Non-Configurable Data
。 Number of Traps since last reset - The number of traps that have occurred since the last time the switch was
79
Page 80

reset.
。 Number of Traps since log last viewed - The number of traps that have occurred since the traps were last
displayed. Displaying the traps by any method (terminal interface display, Web display, upload file from switch etc.)
will cause this counter to be cleared to 0.
。 Log - The sequence number of this trap.
。 System Up Time - The time at which this trap occurred, expressed in days, hours, minutes and seconds since the
last reboot of the switch.
。 Trap - Information identifying the trap.
Figure 4-2-49 Trap Log
80
Page 81

4.2.11 DHCP Server
4.2.11.1 Global Configura tion
Figure 4-2-50 DHCP Server Global Configuration
Configurable Data
。 Admin Mode - Specifies if the DHCP Service is to be Enabled or Disabled. Default value is Disable.
。 Ping Packet Count - Specifies the number of packets a server sends to a Pool address to check for duplication as
part of a ping operation. Default value is 2. Valid Range is (0, 2 to 10). Setting the value to 0 will disable the function.
。 Conflict Logging Mode - Specifies if conflict logging on a DHCP Server is to be Enabled or Disabled. Default value
is Enable.
。 Bootp Automatic Mode - Specifies if Bootp for dynamic pools is to be Enabled or Disabled. Default value is
Disable.
。 Add Excluded Addresses - Specifies the IP addresses that the server should not assign to the client.
¾ From - Specifies the low address in case the user wants to exclude a range of addresses. Specifies the
address to be Excluded in case the user wants to exclude a single address.
¾ To - Specifies the high address in case the user wants to exclude a range of addresses. To exclude a single
addres you may enter the same IP address as specified in From or leave as 0.0.0.0.
。 Delete Excluded Addresses - Lists the Excluded Address ranges with a checkbox against each. One or more
checkbox(es) can be selected (checked) in order to delete the listed Excluded Addresses.
Command Buttons
。 Submit - Sends the updated configuration to the switch. Configuration changes take effect immediately.
81
Page 82

4.2.11.2 Pool Configuration
DHCP Server Pool Configuration
Figure 4-2-51 DHCP Server Pool Configuration
Configurable Data
。 Pool Name* - For a user with readwrite permission, this field would show names of all the existing pools along with
an additional option "Create". When the user selects "Create" another text box "Pool Name" appears where the user
may enter name for the Pool to be created.For a user with readonly permission, this field would show names of the
existing pools only.
。 Pool Name - This field appears when the user with read-write permission has selected "Create" in the Drop Down
list against Pool Name*.Specifies the Name of the Pool to be created. Pool Name can be upto 31 characters in
length.
。 Type of Binding - Specifies the type of binding for the pool.
• Unallocated
• Dynamic
• Manual
。 Network Number - Specifies the subnet number for a DHCP address of a dynamic pool.
。 Network Mask - Specifies the subnet number for a DHCP address of a dynamic pool. Either Network Mask or Prefix
Length can be configured to specify the subnet mask but not both.
。 Prefix Length - Specifies the subnet number for a DHCP address of a dynamic pool. Either Network Mask or Prefix
Length can be configured to specify the subnet mask but not both. Valid Range is (0 to 32)
。 Client Name - Specifies the Client Name for DHCP manual Pool.
82
Page 83

。 Hardware Address - Specifies the MAC address of the hardware platform of the DHCP client.
。 Hardware Address Type - Specifies the protocol of the hardware platform of the DHCP client. Valid types are
ethernet and ieee802. Default value is ethernet.
。 Client ID - Specifies the Client Identifier for DHCP manual Pool.
。 Host Number - Specifies the IP address for a manual binding to a DHCP client. Host can be set only if at least one
among of Client Identifier or Hardware Address is specified. Deleting Host would delete Client Name, Client ID,
Hardware Address for the Manual Pool and set the Pool Type to Unallocated.
。 Host Mask - Specifies the subnet mask for a manual binding to a DHCP client. Either Host Mask or Prefix Length
can be configured to specify the subnet mask but not both.
。 Prefix Length - Specifies the subnet mask for a manual binding to a DHCP client. Either Host Mask or Prefix Length
can be configured to specify the subnet mask but not both. Valid Range is (0 to 32)
。 Lease Time - Can be selected as "Infinite" to specify lease time as Infinite or "Specified Duration" to enter a specific
lease period. In case of dynamic binding infinite implies a lease period of 60 days and In case of manual binding
infinite implies indefinite lease period. Default Value is "Specified Duration".
。 Days - Specifies the Number of Days of Lease Period. This field appears only if the user has specified "Specified
Duration" as the Lease time. Default Value is 1. Valid Range is (0 to 59)
。 Hours - Specifies the Number of Hours of Lease Period. This field appears only if the user has specified "Specified
Duration" as the Lease time. Valid Range is (0 to 1439)
。 Minutes - Specifies the Number of Minutes of Lease Period. This field appears only if the user has specified
"Specified Duration" as the Lease time. Valid Range is (0 to 86399)
。 Default Router Addresses - Specifies the list of Default Router Addresses for the pool. The user may specify upto 8
Default Router Addresses in order of preference.
Figure 4-2-52 DHCP Server Pool Configuration
83
Page 84

。 DNS Server Addresses - Specifies the list of DNS Server Addresses for the pool. The user may specify upto 8 DNS
Server Addresses in order of preference.
。 NetBIOS Name Server Addresses - Specifies the list of NetBIOS Name Server Addresses for the pool. The user
may specify upto 8 NetBIOS Name Server Addresses in order of preference.
。 NetBIOS Node Type - Specifies the NetBIOS node type for DHCP clients.
• b-node Broadcast
• p-node Peer-to-Peer
• m-node Mixed
• h-node Hybrid
。 Next Server Address - Specifies the Next Server Address for the pool.
。 Domain Name - Specifies the domain name for a DHCP client. Domain Name can be upto 255 characters in length.
。 Boot File - Specifies the name of the default boot image for a DHCP client. File Name can be upto 128 characters in
length.
。 Option Code - Specifies the DHCP option code. Valid Range is (1 to 254)
。 Option Ascii - Specifies an NVT ASCII character string.
。 Option Hex - Specifies dotted hexadecimal data. Each byte in hexadecimal character strings is 2 hexadecimal digits.
Each byte can be separated by a colon or white space. A period separates 2 bytes/4 hexadecimal digits.
。 Option IP Address - Specifies the Option IP addresses.
Figure 4-2-53 DHCP Server Pool Configuration
84
Page 85

Command Buttons
。 Submit - Creates/Modifies the Pool Configuration. Sends the updated configuration to the switch. Configuration
changes take effect immediately.
。 Delete - Deletes the Pool. This field is not visible to a user with readonly permission.
#Note:
The network ip address/mask of the switch shall be within the same as ip pool.
4.2.11.3 Pool Options
DHCP Server Pool Options
Selection Criteria
Figure 4-2-54 DHCP Server Pool Options
。 Pool Name - Shows all the existing Pool Names.
Non-Configurable Data
。 Option Code - Specifies the Option Code configured for the selected Pool.
。 Option Type - Specifies the Option Type against the Option Code configured for the selected pool.
• Ascii
• Hex
• IP Address
。 Option Value - Specifies the Value against the Option Code configured for the selected pool.
Configurable Data
。 Delete Option Code - Specifies the Option Code to be deleted for the selected Pool. This field is not visible to a
user with readonly permission.
Command Buttons
。 Delete - Deletes the Option Code for the selected Pool. This field is not visible to a user with readonly permission.
85
Page 86

4.2.11.4 Reset Co nfiguration
DHCP Server Reset Configuration
Figure 4-2-55 DHCP Server Reset Configuration
Selection Criteria
。 Clear - Specifies whether All Dynamic Bindings/Specific Dynamic Binding/All Address Conflicts/Specific Address
Conflict is to be deleted.
。 Clear IP Address - IP Address against the Binding/Address Conflict to be cleared.This field appears only if the user
has selected "Specific Dynamic Binding/Specific Address Conflict" in Clear.
Command Buttons
。 Clear - Clears/Removes the Dynamic Binding/Address Conflict.
4.2.11.5 Bindings Information
DHCP Server Bindings Information
Figure 4-2-56 DHCP Server Bindings Information
Selection Criteria
。 DHCP Binding - Specifies whether information is to be displayed for All/Specific Binding.
。 Binding IP Address - IP Address against the Binding for which information is to be displayed. This field appears
only if the user has selected "Specific Binding" in DHCP Binding.
86
Page 87

Non-Configurable Data
。 IP Address - Specifies the Client's IP Address.
。 Hardware Address - Specifies the Client's Hardware Address.
。 Lease Time - Specifies the Lease time left in Days, Hours and Minutes dd:hh:mm format.
。 Type - Specifies the Type of Binding: Dynamic / Manual.
Command Buttons
。 Submit - Displays information for chosen Bindings.
4.2.11.6 Server Statistics
DHCP Server Statistics
Figure 4-2-57 Server Statistics
Non-Configurable Data
。 Automatic Bindings - Specifies the number of Automatic Bindings on the DHCP Server.
。 Manual Bindings - Specifies the number of Manual Bindings on the DHCP Server.
。 Expired Bindings - Specifies the number of Expired Bindings on the DHCP Server.
。 Malformed Messages - Specifies the number of the malformed messages.
。 DHCPDISCOVER - Specifies the number of DHCPDISCOVER messages received by the DHCP Server.
87
Page 88

。 DHCPREQUEST - Specifies the number of DHCPREQUEST messages received by the DHCP Server.
。 DHCPDECLINE - Specifies the number of DHCPDECLINE messages received by the DHCP Server.
。 DHCPRELEASE - Specifies the number of DHCPRELEASE messages received by the DHCP Server.
。 DHCPINFORM - Specifies the number of DHCPINFORM messages received by the DHCP Server.
。 DHCPOFFER - Specifies the number of DHCPOFFER messages sent by the DHCP Server.
。 DHCPACK - Specifies the number of DHCPACK messages sent by the DHCP Server.
。 DHCPNAK - Specifies the number of DHCPNAK messages sent by the DHCP Server.
Command Buttons
。 Refresh - Refresh the data on the screen to the latest state.
。 Clear Server Statistics - Reset DHCP Server Statistics.
4.2.11.7 Conflicts Information
DHCP Server Conflicts Information
Figure 4-2-58 DHCP Server Conflicts Information
Selection Criteria
。 DHCP Conflict - Specifies whether information is to be displayed for a Specific Address Conflict or for All Address
Conflicts.
。 Conflict IP Address - IP Address of the conflict to be shown. This field appears only if the user has selected
"Specific Address Conflict" in DHCP Conflict.
Non-Configurable Data
。 IP Address - Specifies the IP Address of the host as recorded on the DHCP server.
。 Detection Method - Specifies the manner in which the IP address of the hosts were found on the DHCP Server.
。 Detection Time - Specifies the time when the conflict was detected in N days NNh:NNm:NNs format with respect to
the system up time.
Command Buttons
。 Submit - Displays information about the chosen conflict(s).
88
Page 89

4.2.12 SNTP
4.2.12.1 Global Configuration
Figure 4-2-59 SNTP Global Configuration
Configurable Data
。 Client Mode - Specifies the mode of operation of SNTP Client. An SNTP client may operate in one of the following
modes.
• Disable- SNTP is not operational. No SNTP requests are sent from the client nor are any received SNTP
messages processed.
• Unicast- SNTP operates in a point to point fashion. A unicast client sends a request to a designated server at its
unicast address and expects a reply from which it can determine the time and, optionally the round-trip delay and
local clock offset relative to the server.
• Broadcast - SNTP operates in the same manner as multicast mode but uses a local broadcast address instead of
a multicast address. The broadcast address has a single subnet scope while a multicast address has Internet
wide scope.
Default value is Disable.
。 Port - Specifies the local UDP port to listen for responses/broadcasts. Allowed range is (1 to 65535). Default value is
123.
。 Unicast Poll Interval - Specifies the number of seconds between unicast poll requests expressed as a power of two
when configured in unicast mode. Allowed range is (6 to 10). Default value is 6.
。 Broadcast Poll Interval - Specifies the number of seconds between broadcast poll requests expressed as a power
of two when configured in broadcast mode. Broadcasts received prior to the expiry of this interval are discarded.
Allowed range is (6 to 10). Default value is 6.
89
Page 90

。 Unicast Poll Timeout - Specifies the number of seconds to wait for an SNTP response when configured in unicast
mode. Allowed range is (1 to 30). Default value is 5.
。 Unicast Poll Retry - Specifies the number of times to retry a request to an SNTP server after the first time-out
before attempting to use the next configured server when configured in unicast mode. Allowed range is (0 to 10).
Default value is 1.
Command Buttons
。 Submit - Sends the updated configuration to the switch. Configuration changes take effect immediately.
4.2.12.2 Global Status
Figure 4-2-60 SNTP Global Status
Non-Configurable Data
。 Version - Specifies the SNTP Version the client supports.
。 Supported Mode - Specifies the SNTP modes the client supports. Multiple modes may be supported by a client.
。 Last Update Time - Specifies the local date and time (UTC) the SNTP client last updated the system clock.
。 Last Attempt Time - Specifies the local date and time (UTC) of the last SNTP request or receipt of an unsolicited
message.
。 Last Attempt Status - Specifies the status of the last SNTP request or unsolicited message for both unicast and
broadcast modes. If no message has been received from a server, a status of Other is displayed. These values are
appropriate for all operational modes.
90
Page 91

• OtherNone of the following enumeration values.
• SuccessThe SNTP operation was successful and the system time was updated.
• Request Timed OutA directed SNTP request timed out without receiving a response from the SNTP server.
• Bad Date EncodedThe time provided by the SNTP server is not valid.
• Version Not SupportedTheSNTP version supported by the server is not compatible with the version supported
by the client.
• Server UnsychronizedThe SNTP server is not synchronized with its peers. This is indicated via the 'leap
indicator' field on the SNTP message.
• Server Kiss Of DeathThe SNTP server indicated that no further queries were to be sent to this server. This is
indicated by a stratum field equal to 0 in a message received from a server.
。 Server IP Address - Specifies the IP address of the server for the last received valid packet. If no message has
been received from any server, an empty string is shown.
。 Address Type - Specifies the address type of the SNTP Server address for the last received valid packet.
。 Server Stratum - Specifies the claimed stratum of the server for the last received valid packet.
。 Reference Clock Id - Specifies the reference clock identifier of the server for the last received valid packet.
。 Server Mode - Specifies the mode of the server for the last received valid packet.
。 Unicast Sever Max Entries - Specifies the maximum number of unicast server entries that can be configured on
this client.
。 Unicast Server Current Entries - Specifies the number of current valid unicast server entries configured for this
client.
。 Broadcast Count - Specifies the number of unsolicited broadcast SNTP messages that have been received and
processed by the SNTP client since last reboot.
4.2.12.3 Server Configuration
Configurable Data
Figure 4-2-61 SNTP Server Configuration
91
Page 92

。 Server - Specifies all the existing Server Addresses along with an additional option "Create". When the user selects
"Create" another text box "Address" appears where the user may enter Address for Server to be configured.
。 Address - Specifies the address of the SNTP server. This is a text string of up to 64 characters containing the
encoded unicast IP address or hostname of a SNTP server. Unicast SNTP requests will be sent to this address. If
this address is a DNS hostname, then that hostname should be resolved into an IP address each time a SNTP
request is sent to it.
。 Address Type - Specifies the address type of the configured SNTP Server address. Allowed type is :
• IPV4
Default value is Unknown
。 Port - Specifies the port on the server to which SNTP requests are to be sent. Allowed range is (1 to 65535). Default
value is 123.
。 Priority - Specifies the priority of this server entry in determining the sequence of servers to which SNTP requests
will be sent. The client continues sending requests to different servers until a successful response is received or all
servers are exhausted. This object indicates the order in which to query the servers. A server entry with a
precedence of 1 will be queried before a server with a priority of 2, and so forth. If more than one server has the
same priority then the requesting order will follow the lexicographical ordering of the entries in this table. Allowed
range is (1 to 3). Default value is 1.
。 Version - Specifies the NTP Version running on the server. Allowed range is (1 to 4). Default value is 4.
Command Buttons
。 Submit - Sends the updated configuration to the switch. Configuration changes take effect immediately.
。 Delete - Deletes the SNTP Server entry. Sends the updated configuration to the switch. Configuration changes take
effect immediately.
It is recommended that you research any time server selection to ensure that it can meet your
#Notice:
specific time server requirements. Any NTP time server selection should be evaluated to determine if
the server in question meets your specific time server requirements.
For more detail about the Time Server and Time Server List, please refer to the following URL:
http://ntp.isc.org/bin/view/Servers/WebHome
http://ntp.isc.org/bin/view/Servers/NTPPoolServers
http://support.microsoft.com/kb/262680/en-us
92
Page 93

4.2.12.4 Server Status
Figure 4-2-62 SNTP Server Status
Non-Configurable Data
。 Address - Specifies all the existing Server Addresses. If no Server configuration exists, a message saying "No
SNTP server exists" flashes on the screen.
。 Last Update Time - Specifies the local date and time (UTC) that the response from this server was used to update
the system clock.
。 Last Attempt Time - Specifies the local date and time (UTC) that this SNTP server was last queried.
。 Last Attempt Status - Specifies the status of the last SNTP request to this server. If no packet has been received
from this server, a status of Other is displayed.
• OtherNone of the following enumeration values.
• SuccessThe SNTP operation was successful and the system time was updated.
• Request Timed OutA directed SNTP request timed out without receiving a response from the SNTP
server.
• Bad Date EncodedThe time provided by the SNTP server is not valid.
• Version Not SupportedTheSNTP version supported by the server is not compatible with the version
supported by the client.
• Server UnsychronizedThe SNTP server is not synchronized with its peers. This is indicated via the
'leap indicator' field on the SNTP message.
• Server Kiss Of DeathThe SNTP server indicated that no further queries were to be sent to this server.
This is indicated by a stratum field equal to 0 in a message received from a server.
。 Unicast Server Num Requests - Specifies the number of SNTP requests made to this server since last agent
reboot.
。 Unicast Server Num Failed Requests - Specifies the number of failed SNTP requests made to this server since
last reboot.
93
Page 94

4.3 Switching
This page provides all system operation for configuring VLAN, Port-based VLAN, Spanning Tree, Port Aggregation, and
Multicast Support.
The Switch page contains links to the following topics:
。 VLAN
。 Protocol-based VLAN
。 Filters
。 GARP
。 IGMP Snooping
。 Port Channel
。 Multicast Forwarding Database
。 Spanning Tree
。 Class of Service
。 Port Security
4.3.1 VLAN
VLAN Description
A Virtual Local Area Network (VLAN) is a network topology configured according to a logical scheme rather than the physical
layout. VLAN can be used to combine any collection of LAN segments into an autonomous user group that appears as a single
LAN. VLAN also logically segment the network into different broadcast domains so that packets are forwarded only between
ports within the VLAN. Typically, a VLAN corresponds to a particular subnet, although not necessarily.
VLAN can enhance performance by conserving bandwidth, and improve security by limiting traffic to specific domains.
A VLAN is a collection of end nodes grouped by logic instead of physical location. End nodes that frequently communicate with
each other are assigned to the same VLAN, regardless of where they are physically on the network. Logically, a VLAN can be
equated to a broadcast domain, because broadcast packets are forwarded to only members of the VLAN on which the
broadcast was initiated.
1. No matter what basis is used to uniquely identify end nodes and assign these nodes VLAN
#Notice:
membership, packets cannot cross VLAN without a network device performing a routing
function between the VLAN.
2. The Switch supports IEEE 802.1Q VLAN. The port untagging function can be used to remove
the 802.1 tag from packet headers to maintain compatibility with devices that are tag-unaware.
3. The Switch's default is to assign all ports to a single 802.1Q VLAN named DEFAULT_VLAN.
As new VLAN is created, the member ports assigned to the new VLAN will be removed from
the DEFAULT_ VLAN port member list. The DEFAULT_VLAN has a VID = 1.
IEEE 802.1Q VLANs
IEEE 802.1Q (tagged) VLAN are implemented on the Switch. 802.1Q VLAN require tagging, which enables them to span the
94
Page 95

entire network (assuming all switches on the network are IEEE 802.1Q-compliant).
VLAN allow a network to be segmented in order to reduce the size of broadcast domains. All packets entering a VLAN will only
be forwarded to the stations (over IEEE 802.1Q enabled switches) that are members of that VLAN, and this includes broadcast,
multicast and unicast packets from unknown sources.
VLAN can also provide a level of security to your network. IEEE 802.1Q VLAN will only deliver packets between stations that
are members of the VLAN. Any port can be configured as either tagging or untagging. The untagging feature of IEEE 802.1Q
VLAN allows VLAN to work with legacy switches that don't recognize VLAN tags in packet headers. The tagging feature allows
VLAN to span multiple 802.1Q-compliant switches through a single physical connection and allows Spanning Tree to be
enabled on all ports and work normally.
Any port can be configured as either tagging or untagging. The untagging feature of IEEE 802.1Q VLAN allow VLAN to work
with legacy switches that don’t recognize VLAN tags in packet headers. The tagging feature allows VLAN to span multiple
802.1Q-compliant switches through a single physical connection and allows Spanning Tree to be enabled on all ports and work
normally.
Some relevant terms:
Tagging - The act of putting 802.1Q VLAN information into the header of a packet.
Untagging - The act of stripping 802.1Q VLAN information out of the packet header.
802.1Q VLAN Tags
The figure below shows the 802.1Q VLAN tag. There are four additional octets inserted after the source MAC address. Their
presence is indicated by a value of 0x8100 in the Ether Type field. When a packet's Ether Type field is equal to 0x8100, the
packet carries the IEEE 802.1Q/802.1p tag. The tag is contained in the following two octets and consists of 3 bits of user priority,
1 bit of Canonical Format Identifier (CFI - used for encapsulating Token Ring packets so they can be carried across Ethernet
backbones), and 12 bits of VLAN ID (VID). The 3 bits of user priority are used by 802.1p. The VID is the VLAN identifier and is
used by the 802.1Q standard. Because the VID is 12 bits long, 4094 unique VLAN can be identified.
The tag is inserted into the packet header making the entire packet longer by 4 octets. All of the information originally contained
in the packet is retained.
802.1Q Tag
User Priority CFI VLAN ID (VID)
3 bits 1 bits 12 bits
TPID (Tag Protocol Identifier) TCI (Tag Control Information)
2 bytes 2 bytes
Preamble Destination
Address
Source
Address
VLAN TAG Ethernet
Type
Data FCS
6 bytes 6 bytes 4 bytes 2 bytes 46-1517 bytes 4 bytes
The Ether Type and VLAN ID are inserted after the MAC source address, but before the original Ether Type/Length or Logical
95
Page 96

Link Control. Because the packet is now a bit longer than it was originally, the Cyclic Redundancy Check (CRC) must be
recalculated.
Adding an IEEE802.1Q Tag
Dest. Addr. Src. Addr. Length/E. type Data Old CRC
Original Ethernet
Dest. Addr. Src. Addr. E. type Tag Length/E. type Data New CRC
Priority CFI VLAN ID
New Tagged Packet
Port VLAN ID
Packets that are tagged (are carrying the 802.1Q VID information) can be transmitted from one 802.1Q compliant network
device to another with the VLAN information intact. This allows 802.1Q VLAN to span network devices (and indeed, the entire
network – if all network devices are 802.1Q compliant).
Every physical port on a switch has a PVID. 802.1Q ports are also assigned a PVID, for use within the switch. If no VLAN are
defined on the switch, all ports are then assigned to a default VLAN with a PVID equal to 1. Untagged packets are assigned the
PVID of the port on which they were received. Forwarding decisions are based upon this PVID, in so far as VLAN are
concerned. Tagged packets are forwarded according to the VID contained within the tag. Tagged packets are also assigned a
PVID, but the PVID is not used to make packet forwarding decisions, the VID is.
Tag-aware switches must keep a table to relate PVID within the switch to VID on the network. The switch will compare the VID
of a packet to be transmitted to the VID of the port that is to transmit the packet. If the two VID are different the switch will drop
the packet. Because of the existence of the PVID for untagged packets and the VID for tagged packets, tag-aware and
tag-unaware network devices can coexist on the same network.
A switch port can have only one PVID, but can have as many VID as the switch has memory in its VLAN table to store them.
Because some devices on a network may be tag-unaware, a decision must be made at each port on a tag-aware device before
packets are transmitted – should the packet to be transmitted have a tag or not? If the transmitting port is connected to a
tag-unaware device, the packet should be untagged. If the transmitting port is connected to a tag-aware device, the packet
should be tagged.
Default VLANs
The Switch initially configures one VLAN, VID = 1, called "default." The factory default setting assigns all ports on the Switch to
the "default". As new VLAN are configured in Port-based mode, their respective member ports are removed from the "default."
VLAN and Link aggregation Groups
In order to use VLAN segmentation in conjunction with port link aggregation groups, you can first set the port link aggregation
group(s), and then you may configure VLAN settings. If you wish to change the port link aggregation grouping with VLAN
already in place, you will not need to reconfigure the VLAN settings after changing the port link aggregation group settings.
VLAN settings will automatically change in conjunction with the change of the port link aggregation group settings
96
Page 97

4.3.1.1 VLAN Configuration
802.1Q VLAN Configuration
There are up to 4041 configurable VLAN groups. By default when 802.1Q is enabled, all ports on the switch belong to default
VLAN (VID 1). The default VLAN cannot be deleted.
Understand nomenclature of the Switch
Tagging and Untagging
Every port on an 802.1Q compliant switch can be configured as tagging or untagging.
。 Tagging: Ports with tagging enabled will put the VID number, priority and other VLAN information into the header of all
packets that flow into those ports. If a packet has previously been tagged, the port will not alter the packet, thus keeping
the VLAN information intact. The VLAN information in the tag can then be used by other 802.1Q compliant devices on the
network to make packet-forwarding decisions.
。 Untagging: Ports with untagging enabled will strip the 802.1Q tag from all packets that flow into those ports. If the packet
doesn't have an 802.1Q VLAN tag, the port will not alter the packet. Thus, all packets received by and forwarded by an
untagging port will have no 802.1Q VLAN information. (Remember that the PVID is only used internally within the Switch).
Untagging is used to send packets from an 802.1Q-compliant network device to a non-compliant network device.
Frame Income
Frame Leave
Leave port is tagged Frame remains tagged Tag is inserted
Leave port is untagged Tag is removed Frame remain untagged
Income Frame is tagged Income Frame is untagged
Figure 4-3-1 VLAN Configuration
97
Page 98

Selection Criteria
。 VLAN ID and Name - You can use this screen to reconfigure an existing VLAN, or to create a new one. Use this
pulldown menu to select one of the existing VLANs, or select 'Create' to add a new one.
Configurable Data
。 VLAN ID - Specify the VLAN Identifier for the new VLAN. (You can only enter data in this field when you are
creating a new VLAN.) The range of the VLAN ID is (1 to 4093).
。 VLAN Name - Use this optional field to specify a name for the VLAN. It can be up to 32 alphanumeric characters
long, including blanks. The default is blank. VLAN ID 1 always has a name of 'Default'.
。 VLAN Type - This field identifies the type of the VLAN you are configuring. You cannot change the type of the
default VLAN (VLAN ID = 1): it is always type 'Default'. When you create a VLAN, using this screen, its type will
always be 'Static'. A VLAN that is created by GVRP registration initially has a type of 'Dynamic'. You may use this
pull-down menu to change its type to 'Static'.
。 Participation - Use this field to specify whether a port will participate in this VLAN. The factory default is
'Autodetect'. The possible values are:
。 Include - This port is always a member of this VLAN. This is equivalent to registration fixed in the IEEE 802.1Q
standard.
。 Exclude - This port is never a member of this VLAN. This is equivalent to registration forbidden in the IEEE
802.1Q standard.
。 Autodetect - Specifies that port may be dynamically registered in this VLAN via GVRP. The port will not participate
in this VLAN unless it receives a GVRP request. This is equivalent to registration normal in the IEEE 802.1Q
standard.
。 Tagging - Select the tagging behavior for this port in this VLAN. The factory default is 'Untagged'. The possible
values are:
。 Tagged - all frames transmitted for this VLAN will be tagged.
。 Untagged - all frames transmitted for this VLAN will be untagged.
4.3.1.2 VLAN Status
This page displays the status of all currently configured VLANs.
。 VLAN ID - The VLAN Identifier (VID) of the VLAN. The range of the VLAN ID is (1 to 4093) .
。 VLAN Name - The name of the VLAN. VLAN ID 1 is always named `Default`.
。 VLAN Type - The VLAN type:
¾ Default ( VLAN ID = 1) -- always present
¾ Static -- a VLAN you have configured
¾ Dynamic -- a VLAN created by GVRP registration that you have not converted to static, and that GVRP may
therefore remove
98
Page 99

Figure 4-3-2 VLAN Status
4.3.1.3 VLAN Port Configuration
Selection Criteria
。 Slot.Port - Select the physical interface for which you want to display or configure data. Select 'All' to set the
parameters for all ports to same values.
Configurable Data
。 Port VLAN ID - Specify the VLAN ID you want assigned to untagged or priority tagged frames received on this port.
The factory default is 1.
。 Acceptable Frame Types - Specify how you want the port to handle untagged and priority tagged frames. If you
select 'VLAN only', the port will discard any untagged or priority tagged frames it receives. If you select 'Admit All',
untagged and priority tagged frames received on the port will be accepted and assigned the value of the Port VLAN
ID for this port. Whichever you select, VLAN tagged frames will be forwarded in accordance with the IEEE 802.1Q
VLAN standard. The factory default is 'Admit All'.
。 Ingress Filtering - Specify how you want the port to handle tagged frames. If you enable Ingress Filtering on the
pulldown menu, a tagged frame will be discarded if this port is not a member of the VLAN identified by the VLAN ID
in the tag. If you select disable from the pulldown menu, all tagged frames will be accepted. The factory default is
disable.
。 Port Priority - Specify the default 802.1p priority assigned to untagged packets arriving at the port.
99
Page 100

Figure 4-3-3 VLAN Port Configuration
4.3.1.4 VLAN Port Summary
This page shows the configured VLAN parameters.
。 Slot.Port - The interface.
。 Port VLAN ID - The VLAN ID that this port will assign to untagged frames or priority tagged frames received on
this port.
。 Acceptable Frame Types - Specifies the types of frames that may be received on this port. The options are
'VLAN only' and 'Admit All'. When set to 'VLAN only ', untagged frames or priority tagged frames received on this
port are discarded. When set to 'Admit All', untagged frames or priority tagged frames received on this port are
accepted and assigned the value of the Port VLAN ID for this port. With either option, VLAN tagged frames are
forwarded in accordance to the 802.1Q VLAN specification.
。 Ingress Filtering - When enabled, the frame is discarded if this port is not a member of the VLAN with which this
frame is associated. In a tagged frame, the VLAN is identified by the VLAN ID in the tag. In an untagged frame, the
VLAN is the Port VLAN ID specified for the port that received this frame. When disabled, all frames are forwarded
in accordance with the 802.1Q VLAN bridge specification. The factory default is disabled.
100
 Loading...
Loading...