PGP Desktop User's Guide

The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement.
Version 10.2.1. Last updated: April 2012.
Legal Notice
Copyright (c) 2012 Symantec Corporation. All rights reserved.
Symantec, the Symantec Logo, PGP, Pretty Good Privacy, and the PGP logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners.
The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any.
THE DOCUMENTATION IS PROVIDED"AS IS"AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE.
The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. “Commercial Computer Software and Commercial Computer Software Documentation”, as applicable, and any successor regulations. Any use, modification, reproduction release, performance, display or disclosure of the Licensed Software and Documentation by the U.S. Government shall be solely in accordance with the terms of this Agreement.
Symantec Corporation
350 Ellis Street
Mountain View, CA 94043
Symantec Home Page (http://www.symantec.com)
Printed in the United States of America.
10 9 8 7 6 5 4 3 2 1
Contents
About PGP Desktop 10.2 for Windows |
1 |
What's New in PGP Desktop Version 10.2 for Windows |
1 |
Using this Guide |
3 |
“Managed” versus “Unmanaged” Users |
3 |
Conventions Used in This Guide |
3 |
Who Should Read This Document |
4 |
About PGP Desktop Licensing |
4 |
Licensing PGP Desktop for Windows |
4 |
Checking License Details |
5 |
If Your License has Expired |
6 |
Technical Support |
7 |
Contacting Technical Support |
8 |
Licensing and registration |
8 |
Customer service |
8 |
Support agreement resources |
9 |
PGP Desktop Basics |
11 |
|
|
PGP Desktop Terminology |
11 |
PGP Product Components |
11 |
Terms Used in PGP Desktop |
12 |
Conventional and Public Key Cryptography |
13 |
Using PGP Desktop for the First Time |
14 |
Installing PGP Desktop |
17 |
|
|
Before You Install |
17 |
System Requirements |
17 |
Citrix and Terminal Services Compatibility |
18 |
Installing and Configuring PGP Desktop |
19 |
Installing the Software |
19 |
Upgrading the Software |
19 |
Licensing PGP Desktop |
21 |
Running the Setup Assistant |
21 |
Uninstalling PGP Desktop |
22 |
Moving Your PGP Desktop Installation From One Computer to Another |
22 |
The PGP Desktop User Interface |
25 |
|
|
Accessing PGP Desktop Features |
25 |
The PGP Desktop Main Screen |
26 |
Using the PGP Tray Icon |
27 |
Using Shortcut Menus in Windows Explorer |
28 |
Using the Start Menu |
29 |
PGP Desktop Notifier alerts |
30 |
PGP Desktop Notifier for Messaging |
30 |
PGP Desktop Notifier for Disk features |
32 |
Enabling or Disabling Notifiers |
33 |

ii Contents
Viewing the PGP Log |
34 |
Working with PGP Keys |
35 |
|
|
Viewing Keys |
35 |
Creating a Keypair |
36 |
Passwords and Passphrases |
38 |
Protecting Your Private Key |
38 |
Protecting Keys and Keyrings |
39 |
Backing up Your Private Key |
40 |
What if You Lose Your Key? |
40 |
Distributing Your Public Key |
40 |
Placing Your Public Key on a Keyserver |
41 |
Including Your Public Key in an Email Message |
42 |
Exporting Your Public Key to a File |
42 |
Copying from a Smart Card Directly to Someone’s Keyring |
43 |
Getting the Public Keys of Others |
43 |
Getting Public Keys from a Keyserver |
43 |
Getting Public Keys from Email Messages |
44 |
Working with Keyservers |
44 |
Using Master Keys |
46 |
Adding Keys to the Master Key List |
46 |
Deleting Keys from the Master Key List |
47 |
Managing PGP Keys |
49 |
Examining and Setting Key Properties |
49 |
Working With Photographic IDs |
50 |
Managing User Names and Email Addresses on a Key |
51 |
Importing Keys and X.509 Certificates |
52 |
Using the Import Certificate Assistant |
53 |
Importing X.509 Certificates Included in S/MIME Email Messages |
54 |
Changing Your Passphrase |
54 |
Deleting Keys, User IDs, and Signatures |
55 |
Disabling and Enabling Public Keys |
55 |
Verifying a Public Key |
56 |
Signing a Public Key |
57 |
Revoking Your Signature from a Public Key |
58 |
Granting Trust for Key Validations |
59 |
Working with Subkeys |
59 |
Using Separate Subkeys |
61 |
Viewing Subkeys |
61 |
Creating New Subkeys |
62 |
Specifying Key Usage for Subkeys |
62 |
Revoking Subkeys |
63 |
Removing Subkeys |
64 |
Working with ADKs |
64 |
Adding an ADK to a Keypair |
64 |
Updating an ADK |
65 |
Removing an ADK |
65 |
Working with Revokers |
65 |
Appointing a Designated Revoker |
66 |
Revoking a Key |
66 |

Contents iii
Splitting and Rejoining Keys |
67 |
Creating a Split Key |
67 |
Rejoining Split Keys |
68 |
If You Lost Your Key or Passphrase |
69 |
Reconstructing Keys with PGP Universal Server |
70 |
Creating Key Reconstruction Data |
70 |
Reconstructing Your Key if You Lost Your Key or Passphrase |
72 |
Protecting Your Keys |
73 |
Securing Email Messages |
75 |
|
|
How PGP Desktop Secures Email Messages |
75 |
Incoming Messages |
76 |
Verifying Signatures on Incoming Messages |
77 |
Understanding Annotations on Incoming Messages |
79 |
Outgoing Messages |
79 |
Securing Sent Items on IMAP Email Servers |
79 |
Sending MAPI Email with Microsoft Outlook |
80 |
Using the Sign and Encrypt Buttons in Microsoft Outlook |
81 |
Using Offline Policy |
82 |
Services and Policies |
83 |
Viewing Services and Policies |
84 |
Creating a New Messaging Service |
85 |
Editing Messaging Service Properties |
88 |
Disabling or Enabling a Service |
89 |
Deleting a Service |
89 |
Multiple Services |
90 |
Troubleshooting PGP Messaging Services |
90 |
Creating a New Security Policy |
92 |
Regular Expressions in Policies |
96 |
Security Policy Information and Examples |
97 |
Working with the Security Policy List |
101 |
Editing a Security Policy |
101 |
Editing a Mailing List Policy |
102 |
Deleting a Security Policy |
105 |
Changing the Order of Policies in the List |
106 |
PGP Desktop and SSL |
106 |
Key Modes |
108 |
Determining Key Mode |
109 |
Changing Key Mode |
109 |
Viewing the PGP Log |
110 |
Securing Instant Messaging |
113 |
About PGP Desktop Instant Messaging Compatibility |
113 |
Instant Messaging Client Compatibility |
114 |
About the Keys Used for Encryption |
114 |
Encrypting your IM Sessions |
115 |
Viewing Email with PGP Viewer |
117 |
|
|
Overview of PGP Viewer |
117 |

iv Contents
Compatible Email Clients |
118 |
Opening an Encrypted Email Message or File |
118 |
Copying Email Messages to Your Inbox |
119 |
Exporting Email Messages |
120 |
Specifying Additional Options |
120 |
Specifying Options in PGP Viewer |
121 |
Security Features in PGP Viewer |
121 |
Protecting Disks with PGP Whole Disk Encryption |
123 |
|
|
About PGP Whole Disk Encryption |
124 |
How does PGP WDE Differ from PGP Virtual Disk? |
125 |
Licensing PGP Whole Disk Encryption |
125 |
Using PGP Remote Disable and Destroy |
126 |
Prepare Your Disk for Encryption |
127 |
Supported Disk Types |
128 |
Supported Keyboards |
129 |
Supported Input Method Editors (IME) |
131 |
Ensure Disk Health Before Encryption |
131 |
Calculate the Encryption Duration |
131 |
Maintain Power Throughout Encryption |
132 |
Run a Pilot Test to Ensure Software Compatibility |
132 |
Determining the Authentication Method for the Disk |
133 |
Passphrase and Single Sign-On Authentication |
133 |
Public Key Authentication |
134 |
Token-Based Authentication |
134 |
Trusted Platform Module (TPM) Authentication |
134 |
Setting Encryption Options |
135 |
Partition-Level Encryption |
136 |
Preparing a Smart Card or Token to Use For Authentication |
136 |
Using PGP Whole Disk Encryption Options |
139 |
Encrypting a Disk or Partition |
140 |
Supported Characters for PGP WDE Passphrases |
141 |
Encrypting the Disk |
142 |
Encountering Disk Errors During Encryption |
144 |
Using a PGP WDE-Encrypted Disk |
145 |
Authenticating at the PGP BootGuard Screen |
145 |
Selecting Keyboard Layouts |
150 |
Using PGP WDE Single Sign-On |
152 |
Prerequisites for Using Single Sign-On |
152 |
Encrypting the Disk to Use Single Sign-On |
152 |
Multiple Users and Single Sign-On |
153 |
Logging in with Single Sign-On |
153 |
Changing Your Passphrase With Single Sign-On |
153 |
Displaying the Windows Login dialog box |
154 |
Maintaining the Security of Your Disk |
154 |
Getting Disk or Partition Information |
154 |
Adding Other Users to an Encrypted Disk or Partition |
155 |
Deleting Users From an Encrypted Disk or Partition |
156 |
Changing User Passphrases |
156 |
Re-Encrypting an Encrypted Disk or Partition |
157 |
If you Forgot Your Passphrase |
158 |
Backing Up and Restoring |
159 |

Contents v
Uninstalling PGP Desktop from Encrypted Disks or Partitions |
160 |
Working with Removable Disks |
160 |
Encrypting Removable Disks |
160 |
Using Locked (Read-Only) Disks as Read-Only |
161 |
Moving Removable Disks to Other Systems |
162 |
Reformatting an Encrypted Removable Disk |
162 |
Using PGP WDE in a PGP Universal Server-Managed Environment |
162 |
PGP Whole Disk Encryption Administration |
163 |
Creating a Recovery Token |
164 |
Using a Recovery Token |
164 |
Recovering Data From an Encrypted Drive |
165 |
Creating and Using Recovery Disks |
165 |
Decrypting a PGP WDE-Encrypted Disk |
167 |
Special Security Precautions Taken by PGP Desktop |
168 |
Passphrase Erasure |
168 |
Virtual Memory Protection |
168 |
Hibernation vs Standby |
168 |
Memory Static Ion Migration Protection |
168 |
Other Security Considerations |
169 |
Using the Windows Preinstallation Environment |
169 |
Using PGP Whole Disk Encryption with IBM Lenovo ThinkPad Systems |
169 |
Using PGP Whole Disk Encryption with the Microsoft Windows XP Recovery Console |
170 |
Using PGP Virtual Disks |
173 |
|
|
About PGP Virtual Disks |
173 |
Creating a New PGP Virtual Disk |
174 |
Viewing the Properties of a PGP Virtual Disk |
177 |
Finding PGP Virtual Disks |
177 |
Using a Mounted PGP Virtual Disk |
178 |
Mounting a PGP Virtual Disk |
178 |
Unmounting a PGP Virtual Disk |
179 |
Compacting a PGP Virtual Disk |
179 |
Re-Encrypting PGP Virtual Disks |
180 |
Working with Alternate Users |
181 |
Adding Alternate User Accounts to a PGP Virtual Disk |
181 |
Deleting Alternate User Accounts from a PGP Virtual Disk |
181 |
Disabling and Enabling Alternate User Accounts |
182 |
Changing Read/Write and Read-Only Status |
182 |
Granting Administrator Status to an Alternate User |
183 |
Changing User Passphrases |
183 |
Deleting PGP Virtual Disks |
184 |
Maintaining PGP Virtual Disks |
184 |
Mounting PGP Virtual Disk Volumes on a Remote Server |
184 |
Backing up PGP Virtual Disk Volumes |
185 |
Exchanging PGP Virtual Disks |
185 |
The PGP Virtual Disk Encryption Algorithms |
186 |
Special Security Precautions Taken by PGP Virtual Disk |
186 |
Passphrase Erasure |
186 |
Virtual Memory Protection |
187 |
Hibernation |
187 |
Memory Static Ion Migration Protection |
187 |
Other Security Considerations |
187 |

vi Contents
Creating and Accessing Mobile Data with PGP Portable |
189 |
|
|
Creating PGP Portable Disks |
189 |
Creating a PGP Portable Disk from a Folder |
190 |
Creating a PGP Portable Disk from a Removable USB Device |
190 |
Creating Read/Write or Read-Only PGP Portable Disks |
192 |
Accessing Data on a PGP Portable Disk |
192 |
Changing the Passphrase for a PGP Portable Disk |
193 |
Unmounting a PGP Portable Disk |
194 |
Using PGP NetShare |
195 |
|
|
About PGP NetShare |
195 |
PGP NetShare Roles |
197 |
Integrating with Symantec Data Loss Prevention |
198 |
Licensing PGP NetShare |
199 |
Authorized User Keys |
200 |
Using a Group Key |
200 |
Establishing a PGP NetShare Admin (Owner) |
201 |
"Blacklisted" and "Whitelisted" Files, Folders, and Applications |
201 |
“Blacklisted” and Other Files You Cannot Protect |
201 |
"Blacklisted" and "Whitelisted" Folders Specified by PGP Universal Server |
202 |
Application-based Encryption and Decryption Bypass Lists |
202 |
Working with Protected Folders |
203 |
Choosing the Location for a Protected Folder |
204 |
Creating a New PGP NetShare Protected Folder |
205 |
Using Files in a PGP NetShare Protected Folder |
207 |
Unlocking a Protected Folder |
208 |
Determining the Files in a Protected Folder |
209 |
Adding Subfolders to a Protected Folder |
209 |
Checking Folder Status |
209 |
Copying Protected Folders to Other Locations |
210 |
Working with PGP NetShare Users |
211 |
Adding a PGP NetShare User |
211 |
Changing a User's Role |
212 |
Deleting a User from a Protected Folder |
213 |
Importing PGP NetShare Access Lists |
214 |
Working with Active Directory Groups |
214 |
Setting up PGP NetShare to Work with Groups |
215 |
Adding an Active Directory Group to a Protected Folder |
215 |
Refreshing Groups |
216 |
Decrypting PGP NetShare-Protected Folders |
216 |
Re-Encrypting a Folder |
217 |
Clearing a Passphrase |
218 |
Protecting Files Outside of a Protected Folder |
218 |
Backing Up PGP NetShare-Protected Files |
220 |
Accessing PGP NetShare Features using the Shortcut Menu |
220 |
PGP NetShare in a PGP Universal Server-managed Environment |
221 |
Accessing the Properties of a Protected File or Folder |
221 |
Using the PGP NetShare Menus in PGP Desktop |
222 |
The File Menu |
222 |
The Edit Menu |
223 |

Contents vii
The NetShare Menu |
223 |
Using PGP Zip |
225 |
|
|
Overview |
225 |
Creating PGP Zip Archives |
226 |
Encrypting to Recipient Keys |
228 |
Encrypting with a Passphrase |
229 |
Creating a PGP Self-Decrypting Archive (SDA) |
231 |
Creating a Sign Only Archive |
232 |
Opening a PGP Zip Archive |
234 |
Opening a PGP Zip SDA |
234 |
Editing a PGP Zip Archive |
235 |
Verifying Signed PGP Zip Archives |
236 |
Shredding Files with PGP Shredder |
239 |
Using PGP Shredder to Permanently Delete Files and Folders |
239 |
Shredding Files using the PGP Shredder Icon on Your Desktop |
240 |
Shredding Files From Within PGP Desktop |
240 |
Shredding Files in Windows Explorer |
241 |
Using the PGP Shred Free Space Assistant |
241 |
Scheduling Free Space Shredding |
242 |
Storing Keys on Smart Cards and Tokens |
245 |
|
|
About Smart Cards and Tokens |
245 |
Compatible Smart Cards |
246 |
Recognizing Smart Cards |
248 |
Examining Smart Card Properties |
248 |
Generating a PGP Keypair on a Smart Card |
249 |
Copying your Public Key from a Smart Card to a Keyring |
250 |
Copying a Keypair from Your Keyring to a Smart Card |
251 |
Wiping Keys from Your Smart Card |
252 |
Using Multiple Smart Cards |
252 |
Setting PGP Desktop Options |
255 |
Accessing the PGP Options dialog box |
255 |
General Options |
256 |
Keys Options |
258 |
Master Keys Options |
260 |
Messaging Options |
261 |
Proxy Options |
263 |
PGP NetShare Options |
266 |
Disk Options |
267 |
Notifier Options |
270 |
Advanced Options |
272 |

viii Contents
Working with Passwords and Passphrases |
275 |
|
|
Choosing whether to use a password or passphrase |
275 |
The Passphrase Quality Bar |
276 |
Creating Strong Passphrases |
277 |
What if You Forget Your Passphrase? |
278 |
Using PGP Desktop with PGP Universal Server |
279 |
Overview |
279 |
For PGP Administrators |
280 |
Manually binding to a PGP Universal Server |
281 |
Using PGP Desktop with IBM Lotus Notes |
283 |
About Lotus Notes and MAPI Compatibility |
283 |
Using PGP Desktop with Lotus Notes |
283 |
Sending email to recipients inside your Lotus Notes organization |
283 |
Sending email to recipients outside your Lotus Notes organization |
284 |
Binding to a PGP Universal Server |
284 |
Pre-Binding |
285 |
Manual Binding |
285 |
Notes Addresses |
285 |
Notes Client Settings |
286 |
The Notes.ini Configuration File |
286 |
Using Lotus Notes Native Encryption |
286 |
Index |
289 |
|
|

1 |
About PGP Desktop 10.2 for Windows |
|
|
|
|
|
PGP Desktop is a security tool that uses cryptography to protect your data against |
|
|
unauthorized access. |
|
|
PGP Desktop protects your data while being sent by email or by instant messaging (IM). |
|
|
It lets you encrypt your entire hard drive or hard drive partition (on Windows |
|
|
systems)—so everything is protected all the time—or just a portion of your hard drive, |
|
|
via a virtual disk on which you can securely store your most sensitive data. You can use |
|
|
it to share your files and folders securely with others over a network. It lets you put any |
|
|
combination of files and folders into an encrypted, compressed package for easy |
|
|
distribution or backup. Finally, use PGP Desktop to shred (securely delete) sensitive |
|
|
files—so that no one can retrieve them—and shred free space on your hard drive, so |
|
|
there are no unsecured remains of any files. |
|
|
Use PGP Desktop to create PGP keypairs and manage both your personal keypairs and |
|
|
the public keys of others. |
|
|
To make the most of PGP Desktop, you should be familiar with PGP Desktop |
|
|
Terminology (on page 11). You should also understand conventional and public-key |
|
|
cryptography, as described in Conventional and Public Key Cryptography (on page 13). |
|
|
In This Chapter |
|
|
What's New in PGP Desktop Version 10.2 for Windows ........................................... |
1 |
|
Using this Guide .............................................................................................................. |
3 |
|
Who Should Read This Document ................................................................................ |
4 |
|
About PGP Desktop Licensing ....................................................................................... |
4 |
|
Technical Support ........................................................................................................... |
7 |
What's New in PGP Desktop Version 10.2 for Windows
Building on Symantec Corporation’s proven technology, PGP Desktop 10.2 for Windows includes numerous improvements and the following new and resolved features.
What's New in PGP Desktop 10.2.1
PGP NetShare
PGP NetShare can be integrated with Symantec Data Loss Prevention to provide automatic encryption of files without end-user intervention. A Data Loss Prevention administrator defines policies and rules that define the parameters for identifying sensitive files and provide credentials for the encryption. The integration is accomplished using an endpoint client-side plug-in. Files under consideration for sensitive content can be data in motion (DIM) or data at rest (DAR). For more information, see the chapter on PGP NetShare in the PGP Desktop User's Guide.

2About PGP Desktop 10.2 for Windows
What's New in PGP Desktop Version 10.2 for Windows
What's New in PGP Desktop 10.2.0
General
Certificate enrollment. If you have an existing smart card or certificate, you can now enroll to your PGP Universal Server using the certificate. This provides an additional way to enroll, in addition to email and LDAP enrollment. Applies to new users or users who need to re-enroll only. PGP Desktop for Windows only.
Certificate SSO. After enrolling to a PGP Universal Server, once you encrypt your disk you can then use your smart card at the PGP BootGuard screen for single sign-on directly into Windows. PGP Desktop for Windows only.
Windows 2008 with Terminal Services. Windows 2008 Terminal Services (SP1 and SP 2) and Windows 2008 Terminal Services R2 (SP 1) have been added as system requirements for Citrix and Terminal Services environments. Refer to "Citrix and Terminal Services Compatibility" in the PGP Desktop for Windows release notes for more information.
Additional smart card readers. Added compatibility with Dell E6510/E6410 Broadcom smart card readers for post-boot authentication. PGP Desktop for Windows only.
Symantec identity branding. The user interface and all user assistance (including help and user’s guides) have been rebranded to include the Symantec logo and colors. All product names remain the same. PGP Desktop for Windows and PGP Desktop for Mac OS X.
Messaging
Symantec PGP Viewer for iOS. A separate application for the iPhone and iPad that you use to read encrypted email messages on your iOS mobile device. Available at no cost through the Apple App Store. Requires integration with PGP Universal Server to manage keys.
Microsoft Outlook 2010. PGP Desktop is now compatible with Microsoft Outlook 2010 64-bit. PGP Desktop for Windows only.
PGP NetShare
PGP NetShare group keys. A single key that is shared by a group of users and is used to encrypt or decrypt PGP NetShare-protected files and folders. The single group key reduces the overhead associated with encrypting a file/folder to a large number of keys. Any member of the group associated with the key can access protected folders/files encrypted to that group key. Group membership for the group key is controlled by your PGP Universal Server administrator and is used with Active Directory. PGP Desktop for Windows only.
PGP Whole Disk Encryption
User name and domain in PGP BootGuard. If you are using PGP Desktop in a PGP Universal Server-managed environment, your administrator can now require that you authenticate at PGP BootGuard with your user name and domain (on Windows systems) or user name (on Mac OS X systems). The PGP BootGuard screen displays fields for you to enter your user name, domain, and passphrase.
Intel PROset. Improved compatibility with Intel PROset software and single sign-on with PGP Whole Disk Encryption. PGP Desktop for Windows only.
Smart card readers. Added compatibility with Dell E6510/E6410 Broadcom smart card readers for pre-boot authentication. PGP Desktop for Windows only.

About PGP Desktop 10.2 for Windows |
3 |
Using this Guide |
|
Using this Guide
This Guide provides information on configuring and using the components within PGP
Desktop. Each chapter of the guide is devoted to one of the components of PGP Desktop.
“Managed” versus “Unmanaged” Users
A PGP Universal Server can be used to control the policies and settings used by components of PGP Desktop. This is often the case in enterprises using PGP software. PGP Desktop users in this configuration are known as managed users, because the settings and policies available in their PGP Desktop software are pre-configured by a PGP administrator and managed using a PGP Universal Server. If you are part of a managed environment, your company may have specific usage requirements. For example, managed users may or may not be allowed to send plaintext email, or may be required to encrypt their disk with PGP Whole Disk Encryption.
Users not under the control of a PGP Universal Server are called unmanaged or standalone users.
This document describes how PGP Desktop works in both situations; however, managed users may discover while working with the product that some of the settings described in this document are not available in their environments. For more information, see
Using PGP Desktop with PGP Universal Server (on page 279).
Features Customized by Your PGP Universal Server Administrator
If you are using PGP Desktop as a "managed" user in a PGP Universal Server-managed environment, there are some settings that can be specified by your administrator. These settings may change the way features are displayed in PGP Desktop.
Disabled features. Your PGP Universal Server administrator can enable or disable specific functionality. For example, your administrator may disable the ability to create PGP Zip archives, or to create PGP NetShare protected folders (on Windows systems).
When a feature is disabled, the control item in the left side is not displayed and the menu for that feature is not available. The graphics included in this guide depict the default installation with all features enabled. The PGP Desktop interface may look different if your administrator has customized the features available.
Customized BootGuard. If you are using PGP Desktop in a PGP Universal Server-managed environment, your PGP administrator may have customized the PGP Whole Disk Encryption BootGuard screen to include additional text or a custom image such as your organization's logo. The graphics included in this guide depict the default installation. Your actual login screen may look different if your administrator has customized the screen.
Conventions Used in This Guide
Notes, Cautions, and Warnings are used in the following ways.

4About PGP Desktop 10.2 for Windows Who Should Read This Document
Notes: Notes are extra, but important, information. A Note calls your attention to important aspects of the product. You will be able to use the product better if you read the Notes.
Cautions: Cautions indicate the possibility of loss of data or a minor security breach. A Caution tells you about a situation where problems could occur unless precautions are taken. Pay attention to Cautions.
Warnings: Warnings indicate the possibility of significant data loss or a major security breach. A Warning means serious problems are going to happen unless you take the appropriate action. Please take Warnings very seriously.
Who Should Read This Document
This document is for anyone who is going to be using the PGP Desktop for Windows software to protect their data.
About PGP Desktop Licensing
A license is used within the PGP software to enable the functionality you purchased, and sets the expiration of the software. Depending on the license you have, some or all of the PGP Desktop family of applications will be active. Once you have entered the license, you must then authorize the software with Symantec Corporation, either manually or online.
There are three types of licenses:
Evaluation: This type of license is typically time-delimited and may not include all PGP Desktop functionality.
Subscription: This type of license is typically valid for a subscription period of one year. During the subscription period, you receive the current version of PGP software and all upgrades and updates released during this period.
Perpetual: This type of license allows you to use PGP Desktop indefinitely. With the addition of the annual Software Insurance policy, which must be renewed annually, you also receive all upgrades and updates released during the policy term.
Licensing PGP Desktop for Windows
To license PGP Desktop
Do one of the following:
If you are a managed user, you are most likely already using a licensed copy of PGP Desktop. Check your license details as described in Checking License Details (on page 5). If you have questions, please contact your PGP administrator.
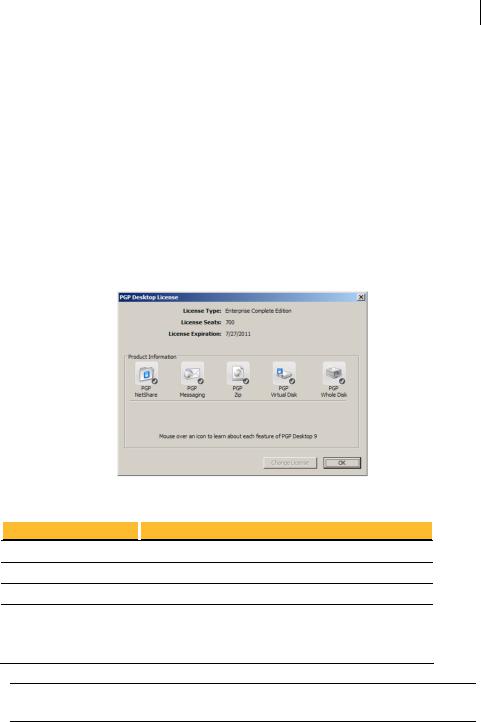

6About PGP Desktop 10.2 for Windows About PGP Desktop Licensing
To authorize PGP Desktop for Windows
If you purchased PGP Desktop, you received an order confirmation with licensing information.
1Double-click the PGP Desktop icon in the System Tray.
2Select Help > License. The PGP Desktop License dialog box is displayed.
3Click Change License. The PGP Licensing Assistant dialog box is displayed.
4Type the Name and Organization exactly as specified in your order confirmation.
5Type the email address you want to assign to the licensing of the product.
6Type the email address again to confirm it.
7Click Next.
8Do one of the following:
Type your 28-character license number in the provided fields (for example, DEMO1-DEMO2-DEMO3-DEMO4-DEMO5-ABC).
Note: To avoid typing errors and make the authorization easier, copy the entire license number, put the cursor in the first “License Number” field, and paste. Your license number will be correctly entered into all six “License Number” fields.
To use PGP Desktop without a license, select Use without a license and disable most functionality. The only feature of PGP Desktop you can use without a license is PGP Zip and Keys.
9Click Next to authorize.
10When PGP is authorized, the features enabled by your license will be displayed. Click Next, and then click Finish to complete the process.
Resolving License Authorization Errors
If you receive any error messages while authorizing your software, the ways to resolve this issue vary based on the error message. For more information, go to the Symantec Knowledgebase (http://www.symantec.com/business/support/index?page=home) and search for HOWTO42066, "HOW TO: License PGP Desktop 10."
,
If Your License has Expired
If your PGP Desktop license has expired, you will receive a PGP License Expiration message when you launch PGP Desktop. See the following sections for information on how an expired license affects the functionality of PGP Desktop.
PGP Desktop Email
Outgoing email messages are no longer sent encrypted.

About PGP Desktop 10.2 for Windows |
7 |
Technical Support |
|
PGP NetShare
PGP NetShare protected folders can be accessed however the protected files remain encrypted. (To view the encrypted files, manually decrypt the folders and files.)
New PGP NetShare protected folders cannot be created.
Files moved into a protected folder are not encrypted.
Keys cannot be added or removed from PGP NetShare protected folders.
PGP Remote Disable and Destroy
When the disk is encrypted with PGP WDE and PGP RDD with Intel AT is activated, the disk remains encrypted and PGP RDD with Intel AT remains activated after the license expiration date.
PGP Virtual Disk
PGP Virtual Disks are still accessible in Read-Only mode. Read-Only allows data to be copied from a PGP Virtual Disk, however no data can be copied to a PGP Virtual Disk.
PGP Whole Disk Encryption
Any fixed disks that have been encrypted with PGP Desktop using an evaluation license are automatically decrypted 90 days after the expiration of the evaluation.
Technical Support
Symantec Technical Support maintains support centers globally. Technical Support’s primary role is to respond to specific queries about product features and functionality. The Technical Support group also creates content for our online Knowledge Base. The Technical Support group works collaboratively with the other functional areas within Symantec to answer your questions in a timely fashion. For example, the Technical Support group works with Product Engineering and Symantec Security Response to provide alerting services and virus definition updates.
Symantec’s support offerings include the following:
A range of support options that give you the flexibility to select the right amount of service for any size organization
Telephone and/or Web-based support that provides rapid response and up-to-the-minute information
Upgrade assurance that delivers software upgrades
Global support purchased on a regional business hours or 24 hours a day, 7 days a week basis
Premium service offerings that include Account Management Services
For information about Symantec’s support offerings, you can visit our Web site at the following URL:

8About PGP Desktop 10.2 for Windows Technical Support
www.symantec.com/business/support/
All support services will be delivered in accordance with your support agreement and the then-current enterprise technical support policy.
Contacting Technical Support
Customers with a current support agreement may access Technical Support information at the following URL:
www.symantec.com/business/support/
Before contacting Technical Support, make sure you have satisfied the system requirements that are listed in your product documentation. Also, you should be at the computer on which the problem occurred, in case it is necessary to replicate the problem.
When you contact Technical Support, please have the following information available:
Product release level
Hardware information
Available memory, disk space, and NIC information
Operating system
Version and patch level
Network topology
Router, gateway, and IP address information
Problem description:
Error messages and log files
Troubleshooting that was performed before contacting Symantec
Recent software configuration changes and network changes
Licensing and registration
If your Symantec product requires registration or a license key, access our technical support Web page at the following URL:
www.symantec.com/business/support/
Customer service
Customer service information is available at the following URL:
www.symantec.com/business/support/
Customer Service is available to assist with non-technical questions, such as the following types of issues:
Questions regarding product licensing or serialization
Product registration updates, such as address or name changes
General product information (features, language availability, local dealers)
About PGP Desktop 10.2 for Windows |
9 |
Technical Support |
|
Latest information about product updates and upgrades
Information about upgrade assurance and support contracts
Information about the Symantec Buying Programs
Advice about Symantec's technical support options
Nontechnical presales questions
Issues that are related to CD-ROMs or manuals
Support agreement resources
If you want to contact Symantec regarding an existing support agreement, please contact the support agreement administration team for your region as follows:
Asia-Pacific and Japan |
customercare_apac@symantec.com |
Europe, Middle-East, Africa |
semea@symantec.com |
North America, Latin America |
supportsolutions@symantec.com |

2 |
PGP Desktop Basics |
|
|
|
|
|
This section describes the PGP Desktop terminology and provides some high-level |
|
|
conceptual information on cryptography. |
|
|
In This Chapter |
|
|
PGP Desktop Terminology........................................................................................... |
11 |
|
Conventional and Public Key Cryptography ............................................................. |
13 |
|
Using PGP Desktop for the First Time ....................................................................... |
14 |
PGP Desktop Terminology
To make the most of PGP Desktop, you should be familiar with the terms in the following sections.
PGP Product Components
PGP Desktop and its components are described in the following list. Depending on your license, you may not have all functionality available. For more information, see About PGP Desktop Licensing (see "Licensing PGP Desktop for Windows" on page 4).
PGP Desktop: A software tool that uses cryptography to protect your data against unauthorized access. PGP Desktop is available for Mac OS X and Windows.
PGP Messaging: A feature of PGP Desktop that automatically and transparently supports all of your email clients through policies you control. PGP Desktop accomplishes this using a new proxy technology; the older plug-in technology is also available. PGP Messaging also protects many IM clients, such as AIM and iChat (both users must have PGP Messaging enabled).
PGP Whole Disk Encryption: Whole Disk Encryption is a feature of PGP Desktop that encrypts your entire hard drive or partition (on Windows systems), including your boot record, thus protecting all your files when you are not using them. You can use PGP Whole Disk Encryption and PGP Virtual Disk volumes on the same system. On Windows systems, you can protect whole disk encrypted drives with a passphrase or with a keypair on a USB token for added security.
PGP NetShare: A feature of PGP Desktop for Windows with which you can securely and transparently share files and folders among selected individuals. PGP NetShare users can protect their files and folders simply by placing them within a folder that is designated as protected.
PGP Keys: A feature of PGP Desktop that gives you complete control over both your own PGP keys, and the keys of those persons with whom you are securely exchanging email messages.

12PGP Desktop Basics
PGP Desktop Terminology
PGP Virtual Disk volumes: PGP Virtual Disk volumes are a feature of PGP Desktop that let you use part of your hard drive space as an encrypted virtual disk. You can protect a PGP Virtual Disk volume with a key or a passphrase. You can even create additional users for a volume, so that people you authorize can also access the volume. The PGP Virtual Disk feature is especially useful on laptops, because if your computer is lost or stolen, the sensitive data stored on the PGP Virtual Disk is protected against unauthorized access.
PGP Shred: A feature of PGP Desktop that lets you securely delete data from your system. PGP Shred overwrites files so that even file recovery software cannot recover them.
|
PGP Viewer: Use PGP Viewer decrypt, verify, and display messages outside |
|
the mail stream |
PGP Zip: A feature of PGP Desktop that lets you put any combination of files and folders into a single encrypted, compressed package for convenient transport or backup. You can encrypt a PGP Zip archive to a PGP key or to a passphrase.
PGP Universal: A tool for enterprises to automatically and transparently secure email messaging for their employees. If you are using PGP Desktop in a PGP Universal Server-managed environment, your messaging policies and other settings may be controlled by your organization’s PGP administrator.
PGP Global Directory: A free, public keyserver hosted by Symantec Corporation. The PGP Global Directory provides quick and easy access to the universe of PGP keys. It uses next-generation keyserver technology that queries the email address on a key (to verify that the owner of the email address wants their key posted) and lets users manage their own keys. Using the PGP Global Directory significantly enhances your chances of finding a valid public key of someone to whom you want to send secured messages. PGP Desktop is designed to work closely with the PGP Global Directory.
Terms Used in PGP Desktop
Before you use PGP Desktop, you should be familiar with the following terms:
Decrypting: The process of taking encrypted (scrambled) data and making it meaningful again. When you receive data that has been encrypted by someone using your public key, you use your private key to decrypt the data.
Encrypting: The process of scrambling data so that if an unauthorized person gets access to it, they cannot do anything with it. The data is so scrambled, it’s meaningless.
Signing: The process of applying a digital signature to data using your private key. Because data signed by your private key can be verified only by your public key, the ability to verify signed data with your public key proves that your private key signed the data and thus proves the data is from you.
Verifying: The process of proving that the private key was used to digitally sign data by using that person’s public key. Because data signed by a private key can only be verified by the corresponding public key, the fact that a particular public key can verify signed data proves the signer was the holder of the private key.
PGP Desktop Basics |
13 |
Conventional and Public Key Cryptography
Keypair: A private key/public key combination. When you create a PGP “key”, you are actually creating a keypair. As your keypair includes your name and your email address, in addition to your private and public keys, it might be more helpful to think of your keypair as your digital ID—it identifies you in the digital world as your driver’s license or passport identifies you in the physical world.
Private key: The key you keep very, very private. Only your private key can decrypt data that was encrypted using your public key. Also, only your private key can create a digital signature that your public key can verify.
Caution: Do not give your private key, or its passphrase, to anyone! And keep your private key safe.
Public key: The key you distribute to others so that they can send protected messages to you (messages that can only be decrypted by your private key) and so they can verify your digital signature. Public keys are meant to be widely distributed.
Your public and private keys are mathematically related, but there’s no way to figure out your private key if someone has your public key.
Keyserver: A repository for keys. Some companies host keyservers for the public keys of their employees, so other employees can find their public keys and send them protected messages. The PGP Global Directory (https://keyserver.pgp.com) is a free, public keyserver hosted by Symantec Corporation.
Smart cards and tokens: Smart cards and tokens are portable devices on which you can create your PGP keypair or copy your PGP keypair. Creating your PGP keypair on a smart card or token adds security by requiring possession of the smart card or token in order to encrypt, sign, decrypt, or verify. So even if an unauthorized person gains access to your computer, your encrypted data is secure because your PGP keypair is with you on your smart card or token. Copying your PGP keypair to a smart card or token is a good way to use it away from your main system, back it up, and distribute your public key. Smart cards and tokens are not available for key storage when used with PGP Desktop for Mac OS X.
Conventional and Public Key Cryptography
Conventional cryptography uses the same passphrase to encrypt and decrypt data. Conventional cryptography is great for data that isn’t going anywhere (because it encrypts and decrypts quickly). However, conventional cryptography is not as well suited for situations where you need to send encrypted data to someone else, especially if you want to send encrypted data to someone you have never met.
Public-key cryptography uses two keys (called a keypair) for encrypting and decrypting. One of these two keys is your private key; and, like the name suggests, you need to keep it private. Very, very private. The other key is your public key, and, like its name suggests, you can share it with the general public. In fact, you’re supposed to share.
Public-key cryptography works this way: let’s say you and your cousin in another city want to exchange private messages. Both of you have PGP Desktop. First, you both need to create your keypair: one private key and one public key. Your private key you keep secret, your public key you send to a public keyserver like the PGP Global Directory (keyserver.pgp.com), which is a public facility for distributing public keys. (Some companies have their own private keyservers.)

14PGP Desktop Basics
Using PGP Desktop for the First Time
Once the public keys are on the keyserver, you can go back to the keyserver and get your cousin’s public key, and she can go to the keyserver and get yours (there are other ways to exchange public keys; for more information, see Working with PGP Keys (on page 35)). This is important because to send an encrypted email message that only your cousin can decrypt, you encrypt it using your cousin’s public key. What makes this work is that only your cousin’s private key can decrypt a message that was encrypted using her public key. Even you, who have her public key, cannot decrypt the message once it has been encrypted using her public key. Only the private key can decrypt data that was encrypted with the corresponding public key.
Your public and private keys are mathematically related, but there’s no feasible way to figure out someone’s private key if you just have a public key.
Using PGP Desktop for the First Time
Symantec Corporation recommends the following procedure for getting started with
PGP Desktop:
1Install PGP Desktop on your computer.
If you are a corporate user, your PGP administrator may have specific installation instructions for you to follow or may have configured your PGP installer with certain settings. Either way, this is the first step.
2Let the Setup Assistant be your guide.
To help you get started, after you install PGP Desktop and reboot your computer, the Setup Assistant is displayed. It assists with:
Licensing PGP Desktop
Creating a keypair—with or without subkeys (if you do not already have a keypair).
Publishing your public key on the PGP Global Directory.
Enabling PGP Messaging
Giving you a quick overview of other features.
If your PGP Desktop installer application was configured by a PGP administrator, the Setup Assistant may perform other tasks.
3Exchange public keys with others.
After you have created a keypair, you can begin sending and receiving secure messages with other PGP Desktop users (once you have exchanged public keys with them). You can also use the PGP Desktop disk-protection features.
Exchanging public keys with others is an important first step. To send them secure messages, you need a copy of their public key, and to reply with a secure message, they need a copy of your public key. If you did not upload your public key to the PGP Global Directory using the Setup Assistant, do so now. If you do not have the public key for someone to whom you want to send messages, the PGP Global Directory is the first place to look. PGP Desktop does this for you—when you send email, it finds and verifies the keys of other PGP Desktop users automatically. It then encrypts your message to the recipient public key, and sends the message.
4Validate the public keys you get from untrusted keyservers.

PGP Desktop Basics |
15 |
Using PGP Desktop for the First Time
When you get a public key from an untrusted keyserver, try to make sure that it has not been tampered with, and that the key really belongs to the person it names. To do this, use PGP Desktop to compare the unique fingerprint on your copy of someone’s public key to the fingerprint on that person’s key (a good way to do that is by telephoning the key’s owner and having them read you the fingerprint information so that you can compare it). Keys from trusted keyservers like the PGP Global Directory have already been verified.
5Start securing your email, files, and instant message (IM) sessions.
After you have generated your keypair and exchanged public keys, you can begin encrypting, decrypting, signing, and verifying email messages and files. The secure IM chat session feature generates its own keys automatically, so you can use this feature even before you generate your keypair. The only requirement is that you must be chatting with another PGP Desktop user for the chat session to be secured.
6Watch for information boxes from the PGP Desktop Notifier feature to appear.
As you send or receive messages, or perform other PGP Desktop functions, the PGP Desktop Notifier feature displays information boxes that appear in whichever corner of the screen you specify. These PGP Notifier boxes tell you the action that PGP Desktop took, or will take. After you grow familiar with the process of sending and receiving messages, you can change options for the PGP Notifier feature—or turn it off.
7After you have sent or received some messages, check the logs to make sure everything is working correctly.
If you want more information than the Notifier feature displays, the PGP Log provides detailed information about all messaging operations.
8Modify your messaging policies, if necessary.
Email messages are sent and received—automatically and seamlessly—if PGP Desktop messaging policies are configured correctly. If your message recipient has a key on the PGP Global Directory the default PGP Desktop policies provide opportunistic encryption. Opportunistic encryption means that, if PGP Desktop has what it needs (such as the recipient's verified public key) to encrypt the message automatically, then it does so. Otherwise, it sends the message in clear text (unencrypted). The default PGP Desktop policies also provide optional forced encryption. This means that, if you include the text “[PGP]” in the Subject line of a message, then the message must be sent securely. If verified keys cannot be found, then the message is not sent, and a Notifier box alerts you.
9Start using the other features in PGP Desktop.
Along with its messaging features, you can also use PGP Desktop to secure the disks that you work with:
Use PGP Whole Disk Encryption to encrypt a boot disk, disk partition (on Windows systems), external disk, or USB thumb drive. All files on the disk or partition are secured — encrypted and decrypted on the fly as you use them. The process is completely transparent to you.
Use PGP Virtual Disk to create a secure “virtual hard disk.” You can use this virtual disk like a bank vault for your files. Use PGP Desktop or Windows Explorer or the Mac OS X finder to unmount and lock the virtual disk, and your files are secure, even if the rest of your computer is unlocked.
Use PGP Zip to create compressed and encrypted PGP Zip archives. These archives offer an efficient way to transport or store files securely.

16PGP Desktop Basics
Using PGP Desktop for the First Time
Use PGP Shredder to delete sensitive files that you no longer need. PGP Shredder removes them completely, eliminating any possibility of recovery.
Use PGP NetShare to share files and folders securely and easily among any number of people—with maximum access control.

3 |
Installing PGP Desktop |
|
|
|
|
|
This section describes how to install PGP Desktop onto your computer and how to get |
|
|
started after installation. |
|
|
In This Chapter |
|
|
Before You Install.......................................................................................................... |
17 |
|
Installing and Configuring PGP Desktop................................................................... |
19 |
|
Uninstalling PGP Desktop ........................................................................................... |
22 |
|
Moving Your PGP Desktop Installation From One Computer to Another............ |
22 |
Before You Install
This section describes the minimum system requirements for installing PGP Desktop on your Windows computer.
System Requirements
Note: In order to continue to improve our products and deliver more sophisticated features and performance, we have added support of the Microsoft Windows 7 operating systems in PGP Desktop 10.0. As a result, we are ending PGP Desktop support for Microsoft Windows 2000 Professional and Microsoft Windows 2000 Server & Advanced Server beginning with PGP Desktop 10.1.
Before you begin the installation, verify that your system meets these minimum requirements:
PGP Desktop can be installed on systems running the following versions of Microsoft
Windows operating systems:
Windows XP Professional 32-bit (Service Pack 2 or 3), Windows XP Professional 64-bit (Service Pack 2), Windows XP Home Edition (Service Pack 2 or 3), Microsoft Windows XP Tablet PC Edition 2005 SP2, Windows Vista (all 32and 64-bit editions, including Service Pack 2), Windows 7 (all 32and 64-bit editions, including Service Pack 1), Windows Server 2003 (Service Pack 1 and 2).
The above operating systems are supported only when all of the latest hot fixes and security patches from Microsoft have been applied.
Note: PGP Whole Disk Encryption (PGP WDE) is not compatible with other third-party software that could bypass the PGP WDE protection on the Master Boot Record (MBR) and write to or modify the MBR. This includes such off-line defragmentation tools that bypass the PGP WDE file system protection in the OS or system restore tools that replace the MBR.

18Installing PGP Desktop Before You Install
PGP Whole Disk Encryption on Windows Servers
PGP Whole Disk Encryption (WDE) is supported on all client versions above as well as the following Windows Server versions:
Windows Server 2003 SP 2 (32and 64-bit editions); Windows Server 2008 64-bit SP 1 and 2; Windows Server 2008 R2 64-bit
VMWare ESXi4 (supported Microsoft Windows Servers operating in a virtual environment)
For additional system requirements and best practices information, go to the the
Symantec Knowledgebase (http://www.symantec.com/business/support/index?page=home) and search for TECH149613, "PGP Whole Disk Encryption on Windows Servers".
PGP Whole Disk Encryption on Tablet PCs
PGP Whole Disk Encryption is supported on Tablet PCs that meet the following additional requirements:
Dell Latitude XT1 and XT2 Tablet PC Touch Screen Laptops (undocked)
1024 x 768 x 16 screen display running SVGA mode
Optional physical keyboard
Hardware Requirements
512 MB of RAM
64 MB hard disk space
For information on compatible email, instant messaging, and anti-virus software, see the PGP Desktop10.2 for Windows Release Notes.
Citrix and Terminal Services Compatibility
PGP Desktop for Windows has been tested with the following terminal services software:
Citrix Presentation Server 4.0
Citrix Metaframe XP
Windows 2003 Terminal Services
Windows 2008 Terminal Services (SP1 and SP 2)
Windows 2008 Terminal Services R2 (SP 1)
The following features of PGP Desktop for Windows are available in these environments, as specified:
Email encryption is fully supported.
PGP Zip functionality is fully supported.
PGP Shred functionality is fully supported.
PGP NetShare is fully supported.
 Loading...
Loading...