Page 1

Parallels® Power Panel
User's Guide
Copyright © 1999-2011 Parallels Holdings, Ltd. and its affiliates. All rights reserved.
Page 2

V
V
A
X
X
V
A
ISBN: N/A
Parallels Holdings, Ltd.
c/o Parallels International GMbH.
Parallels International GmbH
ordergasse 49
CH8200 Schaffhausen
Switzerland
Tel: + 49 (6151) 42996 - 0
Fax: + 49 (6151) 42996 - 255
Copyright © 1999-2011 Parallels Holdings, Ltd. and its affiliates. All rights reserved.
Parallels, Coherence, Parallels Transporter, Parallels Compressor, Parallels Desktop, and Parallels Explorer are registered
trademarks of Parallels Software International, Inc. Virtuozzo, Plesk, HSPcomplete, and corresponding logos are
trademarks of Parallels Holdings, Ltd. The Parallels logo is a trademark of Parallels Holdings, Ltd.
This product is based on a technology that is the subject matter of a number of patent pending applications.
irtuozzo is a patented virtualization technology protected by U.S. patents 7,099,948; 7,076,633; 6,961,868 and having
patents pending in the U.S.
Plesk and HSPcomplete are patented hosting technologies protected by U.S. patents 7,099,948; 7,076,633 and having
patents pending in the U.S.
Distribution of this work or derivative of this work in any form is prohibited unless prior written permission is obtained from
the copyright holder.
pple, Bonjour, Finder, Mac, Macintosh, and Mac OS are trademarks of Apple Inc.
Microsoft, Windows, Microsoft Windows, MS-DOS, Windows NT, Windows 95, Windows 98, Windows 2000, Windows
P, Windows 2003 Server, Windows Vista, Windows 2008, Microsoft SQL Server, Microsoft Desktop Engine (MSDE),
and Microsoft Management Console are trademarks or registered trademarks of Microsoft Corporation.
Linux is a registered trademark of Linus Torvalds.
Red Hat is a registered trademark of Red Hat Software, Inc.
SUSE is a registered trademark of Novell, Inc.
Solaris is a registered trademark of Sun Microsystems, Inc.
Window System is a registered trademark of X Consortium, Inc.
UNIX is a registered trademark of The Open Group.
IBM DB2 is a registered trademark of International Business Machines Corp.
SSH and Secure Shell are trademarks of SSH Communications Security, Inc.
MegaRAID is a registered trademark of American Megatrends, Inc.
PowerEdge is a trademark of Dell Computer Corporation.
eComStation is a trademark of Serenity Systems International.
FreeBSD is a registered trademark of the FreeBSD Foundation.
Intel, Pentium, Celeron, and Intel Core are trademarks or registered trademarks of Intel Corporation.
OS/2 Warp is a registered trademark of International Business Machines Corporation.
Mware is a registered trademark of VMware, Inc.
ll other marks and names mentioned herein may be trademarks of their respective owners.
Page 3

Contents
Introduction ...............................................................................................................6
About Parallels Power Panel ............................................................................................. 7
About This Guide .............................................................................................................. 8
Organization of This Guide ......................................................................................................8
Documentation Conventions ................................................................................................... 9
Getting Help....................................................................................................................10
Feedback........................................................................................................................11
Getting Started With Parallels Power Panel........................................................... 12
Logging in....................................................................................................................... 13
Parallels Power Panel Interface Overview ........................................................................14
Customizing Parallels Power Panel Interface ......................................................................... 17
Using Parallels Power Panel Desktop .............................................................................. 18
Customizing Parallels Power Panel Desktop.......................................................................... 19
Virtual Environment Operations .............................................................................20
Starting, Stopping, and Restarting Virtual Environment....................................................21
Virtual Environment Statuses........................................................................................... 22
Managing Virtual Environment Files and Folders ..............................................................24
Creating Folder...................................................................................................................... 25
Creating Text File................................................................................................................... 25
Editing Text File ..................................................................................................................... 25
Uploading File to Virtual Environment..................................................................................... 26
Copying Files and Folders Inside Virtual Environment ............................................................ 26
Moving Files and Folders Inside Virtual Environment.............................................................. 26
Editing File or Folder Properties ............................................................................................. 27
Working With Containers................................................................................................. 27
Changing Container Root/Administrator Password................................................................ 27
Reinstalling Container............................................................................................................ 28
Repairing Container............................................................................................................... 30
Backing Up and Restoring Container..................................................................................... 31
Updating Container Software ................................................................................................ 35
Resources Overview..............................................................................................................36
Page 4

Contents
Managing Container Applications .......................................................................................... 37
Working With Virtual Machines ........................................................................................ 41
Changing Virtual Machine Administrative password............................................................... 41
Reinstalling Virtual Machine ................................................................................................... 42
Resources Overview..............................................................................................................42
Managing Container Services and Processes .......................................................43
Managing Container Services.......................................................................................... 44
Managing Services in Linux ................................................................................................... 45
Managing Services in Windows ............................................................................................. 48
Managing Container Processes....................................................................................... 50
Managing Container Firewall ...........................................................................................52
Selecting Mode ..................................................................................................................... 53
Configuring Firewall in Normal Mode ..................................................................................... 54
Adding Access Rule in Normal Mode .................................................................................... 55
Building Input Chain .............................................................................................................. 56
Building Output Chain ...........................................................................................................58
Building Forward Chain ......................................................................................................... 59
Adding Rule in Advanced Mode ............................................................................................ 60
Editing Rule in Advanced Mode............................................................................................. 60
Control Panels for Containers.......................................................................................... 61
Managing Plesk Control Panel............................................................................................... 61
Logging in to Confixx Control Panel....................................................................................... 64
Using SSH to Connect to Container ...................................................................................... 65
Using Remote Desktop Connection to Access Container...................................................... 67
Managing Virtual Machine Services and Processes ..............................................68
Viewing System Processes .............................................................................................68
Control Panels for Virtual Machines ................................................................................. 69
Using VNC to Connect to Virtual Machine ............................................................................. 70
Using Remote Desktop ......................................................................................................... 71
SSH Connection to Virtual Machine....................................................................................... 72
4
Page 5

Contents
Monitoring Operations and Viewing Logs ..............................................................74
Viewing History of Container Status Changes.................................................................. 75
Viewing Alerts Log ..........................................................................................................76
Viewing Traffic Log.......................................................................................................... 77
Viewing Task Details .......................................................................................................78
Viewing Error Details .......................................................................................................79
Troubleshooting ......................................................................................................80
Services Inaccessibility.................................................................................................... 81
Elusive Problems............................................................................................................. 82
Login Problems............................................................................................................... 83
File Problems .................................................................................................................. 83
Index ........................................................................................................................84
5
Page 6

C HAPTER 1
Introduction
Parallels Power Panel is a flexible and easy-to-use administration tool designed for managing
a single Container or a virtual machine via a web browser.
In This Chapter
About Parallels Power Panel......................................................................................7
About This Guide ......................................................................................................8
Getting Help..............................................................................................................10
Feedback..................................................................................................................11
Introduction
Page 7

Introduction
About Parallels Power Panel
The Parallels Power Panel functionality provides you with the ability to manage your virtual
environment - Containers and virtual machines, which are functionally identical to isolated
standalone servers, with their own IP addresses, processes, files, their own users databases,
configuration files, applications, etc. - with the help of any standard Web browser on any
platform. Parallels Power Panel allows you to manage virtual environment residing on physical
server running the Windows 2003 Server and Linux operating systems, or bare metal physical
server with Parallels Server Bare Metal installed. Main principles of the Parallels Power Panel
operation for the operating systems are very similar. However, there are some features
peculiar to only Windows 2003 Server or Linux. In case of differences between the two
versions, the steps written specifically for the Windows version are marked with the
and the steps for the Linux version - with the
A list of supported browsers is given below:
• Internet Explorer 8.x and 9.x for Windows
icon.
icon
• Mozilla Firefox 8.x for all platforms
• Safari 5.x for Mac OS
Although other browsers will most likely work, only those listed above have been extensively
tested for compatibility with Parallels Virtual Automation.
Currently, you are able to manage your virtual environments in the following ways:
• Start, stop, or restart the virtual environment;
Mount and unmount the Container in the repair mode;
•
Reinstall the Container;
•
• Back up and restore the Container;
• Change the virtual environment root/Administrator password;
• Start, stop, or restart certain services inside the virtual environment;
• View the list of virtual environment processes and send them signals;
• View the current resources consumption and resources overusage alerts;
• View logs and monitors for the virtual environment;
• Customize the Parallels Power Panel interface;
• Connect to the Container by means of various control panels; (p. 61)
• Connect to the virtual machine by means of various control panels (p. 69);
• etc.
7
Page 8

Introduction
Note: Hereinafter, the root/Administrator denotation is used to identify the main user in the Linux
and Windows operating systems, respectively.
About This Guide
This guide is aimed at a wide range of users who are new to Parallels Power Panel or just
want to make sure they are doing everything right.
The present document is just as easy to use, as the product itself. However, we also provide
complete information about the structure and peculiarities of the guide in the following topics.
Organization of This Guide
The Parallels Power Panel User's Guide consists of the following sections
• The Introduction chapter (p. 6) provides basic information about the product and this
guide.
• The Getting Started With Parallels Power Panel chapter (p. 12) provides information
on logging in to Power Panel and organizing your work.
• The Virtual Environment Operations chapter (p. 20) provides information on managing
virtual environments, such as creating, cloning, configuring, starting/stopping, reinstalling,
repairing, backing up, etc.
• The Managing Container Services and Processes chapter (p. 43) provides information
on managing Container services, firewall system and control panels.
• The Managing virtual Machine Services and Processes chapter (p. 68) provides
information on managing virtual machine services and control panels.
• The Monitoring operations and Viewing logs chapter (p. 74) provides information on
virtual environment resource consumption.
• The Troubleshooting chapter (p. 80) lists most common problems you might encounter
during Parallels Virtual Automation operations and the ways to solve them.
8
Page 9

Documentation Conventions
Before you start using this guide, it is important to understand the documentation
conventions used in it.
The table below presents the existing formatting conventions:
Formatting Conventions Type of information Example
Introduction
Special Bold
Italics
Monospace
Preformatted
Monospace Bold
Key+Key Key combinations for which the
Items you must select, such as
menu options, command buttons
or items in a list.
Titles of chapters, sections and
subsections.
Used to emphasize the
importance of a point, to
introduce a term or to designate a
command line placeholder, which
is to be replaced with a real name
or value.
The names of commands, files
and directories.
On-screen computer output in
your command line sessions;
source code in XML, C++, or
other programming languages.
What you type as contrasted with
on-screen computer output.
user should press and hold down
one key and then press another.
Go to the Resources tab.
Read the Basic Administration chapter.
These are the so-called EZ templates.
To destroy a Container, type vzctl
destroy ctid.
Use vzctl start to start a Container.
Saves parameters for Container
101
# rpm -V virtuozzo-release
Ctrl+P, Alt+F4
Besides the formatting conventions, you should also know about the document organization
convention applied to Parallels documents: chapters in all guides are divided into sections,
which, in turn, are subdivided into subsections. For example, About This Guide is a section,
and Documentation Conventions is a subsection.
9
Page 10

Introduction
Getting Help
Parallels Virtual Automation offers several options for accessing necessary information:
Parallels Virtual Automation documentation
• Parallels Virtual Automation Administrator's Guide. This document contains
extensive information about the product, its usage and troubleshooting. To access the
PDF version of the document, go to the Support link in the left pane and then click
the Downloads pane. You can download any document of the Parallels Virtual
Automation documentation bundle from the Parallels website.
• Parallels Virtual Automation Installation Guides for Linux/Bare Metal and
Windows. These documents contain extensive information on system requirements
for physical computers and instructions how to install Parallels Virtual Automation
components on them.
• Getting Started With Parallels Virtual Automation. This document contains the
basic information how to install, launch and manage Parallels Virtual Automation.
• Parallels Power Panel User's Guide. This document contains extensive information
about the Power Panel application.
• Parallels Virtual Automation 4.6 Agent XML API Reference. This document is a
complete reference on all Parallels Virtual Automation configuration files and physical
server command-line utilities.
• Parallels Virtual Automation Agent Programmer's Guide. This is a task-oriented
guide that provides information on all Parallels Virtual Automation configuration files
and physical server command-line utilities.
The documentation is available for download from the Parallels official website
http://www.parallels.com/products/pva46/resources/.
Context-sensitive help
You can open a help page for the current screen by clicking the Help link in the right upper
corner.
Parallels Website
Parallels website http://www.parallels.com/products/pva/resources/. Explore the Support
web page that includes product help files and the FAQ section.
Parallels Knowledge Base
10
Page 11

Introduction
Parallels Knowledge Base http://kb.parallels.com. This online resource comprises valuable
articles about using the Parallels Virtual Automation, Parallels Virtuozzo Containers and
Parallels Server Bare Metal products.
Feedback
If you spot a typo in this guide, or if you have thought of a way to make this guide better, we
would love to hear from you!
The ideal place for your comments and suggestions is the Parallels documentation feedback
page (http://www.parallels.com/en/support/usersdoc/).
11
Page 12

Getting Started With Parallels Power Panel
Getting Started With Parallels Power Panel
The chapter provides the information on how to log in to Power Panel and explains what
interface elements you may face and how to use them in the most effective way.
Page 13

Getting Started With Parallels Power Panel
Logging in
To log in to your virtual environment, use the IPv4 or IPv6 address (or hostname) and TCP
port of your virtual environment proper. Your provider should inform you of the IP address (or
hostname) and TCP port to enter in the address line of your browser and of the credentials
(user name and password) to use to log in to the virtual environment.
There are two possible ways to log in to your virtual environment:
1 Enter virtual environment administrator credentials: the user name (root for a Linux-
based virtual environment and Administrator for a virtual environment run on
Windows) and the password your provider has given you.
2 Enter admin as the user name and the password of the Plesk admin user. This is
possible only if the Plesk control panel is installed inside your virtual environment and your
provider has entitled you to do so.
Your provider may supply you with the credentials of the Plesk admin user for you to use
the benefits of the Plesk control panel in your virtual environment management. If you have
logged in to your virtual environment using the virtual environment IP address and the TCP
port of Plesk (by default, it is 8443), and the Plesk control panel is not installed in your virtual
environment, you will be asked to install it after you have logged in to the virtual environment.
To do this, follow any of the links on the Plesk main menu in the left part of the displayed
window. You will be warned with a message saying that Plesk is not installed in your virtual
environment and offering you to install it. To complete the installation, you should follow the
instructions on the screen. After you have successfully installed the Plesk control panel in
your virtual environment, you can proceed with the normal course of work.
In either case, once you have connected to the virtual environment, you are recommended
to:
1 Change your root/Administrator password at once by following the Change password
link in the left pane of the Parallels Power Panel page.
2 Provide a valid email address on the Parallels Power Panel configuration page to be able
to log in to Parallels Power Panel if you forget your password. In case, you are unable to
reach your virtual environment due to password-related problems, you can follow the
Forgot your password? link on the login page, which requests you to enter your user
name and the email address provided on the Parallels Power Panel configuration page.
On filling in these fields you will receive a URL at the email address entered informing you
how to change your password.
Also, be aware that when you log in to the Container for the first time in Parallels Power
Panel, the process of updating Container's packages is being executed in order to prepopulate list of applications installed on the Container and to check possible available
updates. This process should not be interrupted. Once the process is successfully
completed, the Container will be accessible in Power Panel without any delays.
13
Page 14
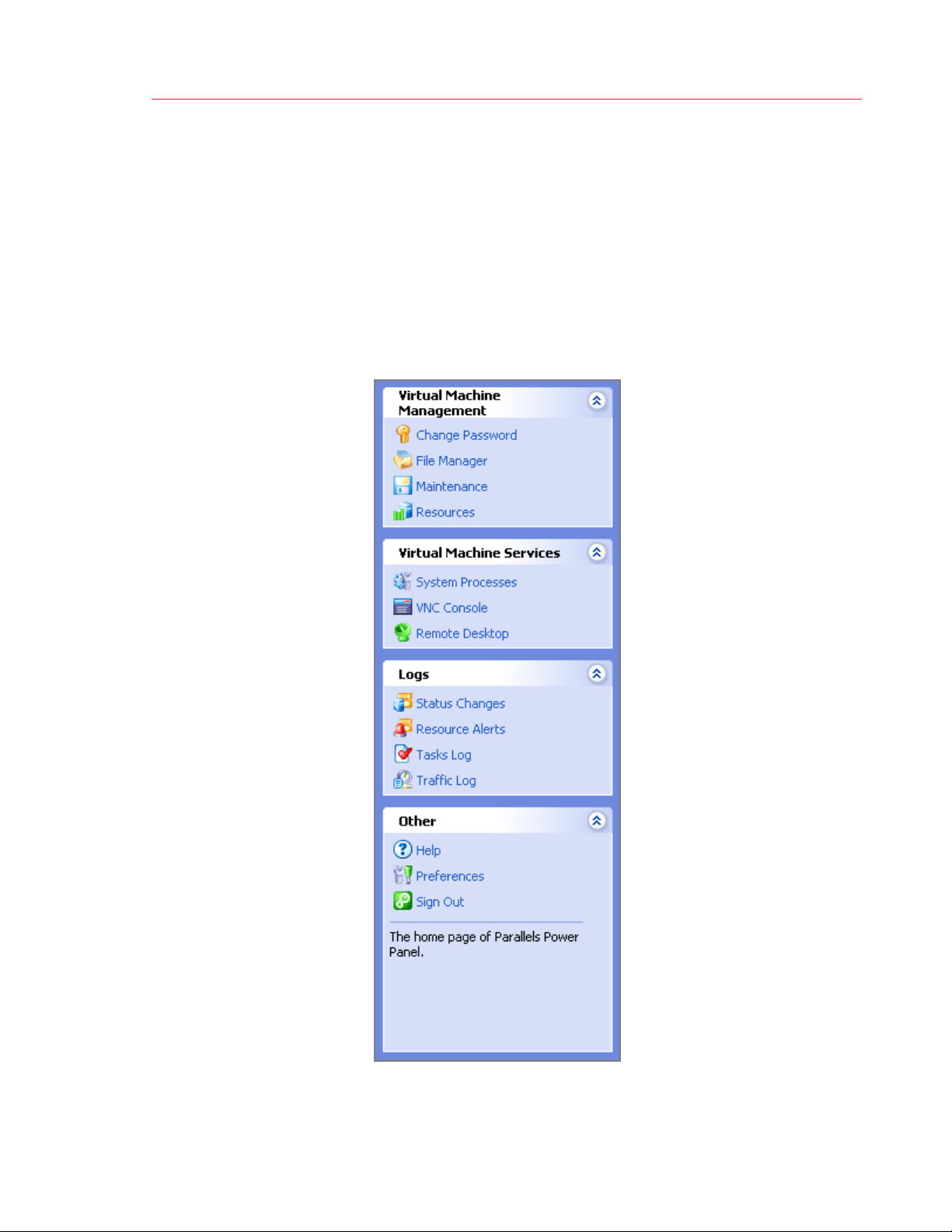
Getting Started With Parallels Power Panel
Parallels Power Panel Interface Overview
The Parallels Power Panel interface has been designed for the virtual environment
administrator to quickly perform all possible tasks through an intuitive navigation system.
All Parallels Power Panel pages have a menu on the left, a toolbar and a status bar on top,
and the content part in the middle. If Parallels Power Panel is integrated in the Plesk control
panel, the Parallels Power Panel menu will be replaced with the Plesk menu. The Parallels
Power Panel menu looks like this:
14
Page 15
Getting Started With Parallels Power Panel
Bear in mind, that depending on whether you manage a Container or a virtual machine via the
Power Panel application, the section names may differ.
It provides links to Parallels Power Panel pages where you can perform various tasks. The
description of the corresponding page is displayed at the bottom of the menu. All links are
gathered into four groups: Container/Virtual Machine Management, Container/Virtual
Machine Services, Logs, and Other, the names of the first three groups being links
themselves. When performing a particular task, you may first click the name of the group to
open the corresponding dashboard and then choose a task, or you may select the task at
once on the menu under the corresponding group.
The links on the menu do the following:
Link Description
Container or Virtual Machine
Management
Change Password Opens the page for changing the virtual environment root/administrator
File Manager Opens the File Manager page where you can view a list of files and
Maintenance
Resources Opens the page where you can learn the current consumption of the
Applications (p. 37) Container-related. Opens the page that lists the installed applications and
Packages (p. 39) Container-related. Opens the page that lists software packages for this
Control Panels (p. 62) Container-related. Opens the page that allows you to download and install
Container or Virtual Machine
Services
Opens the Management dashboard of a Container or a virtual machine
where you can learn more about various management tasks and perform
any of them.
password.
directories and perform all the essential file operations.
Opens the page where you can manage your Container backups,
recover the original template files of your Container if something has gone
wrong, or
command line checks and fixes.
hardware resources by your Container.
shows their statuses.
Container.
Plesk Control Panel on the Container.
Opens the Service Management dashboard, which lets you learn more
about various service management tasks and perform any of them.
start your Container in the so-called repair mode to perform
System Services Container-related. Opens a list of principal services inside your virtual
environment with the opportunity to start, stop, restart any of them and to
control their behavior on the virtual environment startup.
System Processes
Firewall
The Plesk control panel
Opens a list of processes running inside your virtual environment with the
opportunity to send various signals to any of them.
Opens your firewall current settings.
This link is displayed only if the Plesk application template is installed in the
virtual environment being managed. It opens the Plesk control panel login
window.
15
Page 16

Getting Started With Parallels Power Panel
Confixx control panel
VNC Console (p. 70) Opens a VNC console for connecting to your virtual machine.
Remote Desktop
SSH Connection
Logs Opens the Logs dashboard where you can learn more about various logs
Status Changes Opens a list of status changes your virtual environment has recently
Resource Alerts Opens a list of alerts of your virtual environment overusing any hardware
Tasks Log Opens a list of actions you have recently performed in Parallels Power Panel
Traffic Log Opens the page where you can view your traffic statistics for a specified
Help Opens this help system.
Preferences Opens the page where you can customize the Parallels Power Panel
This link is displayed only if the Confixx application template is installed in
the Container being managed. It opens the Confixx control panel login
window.
Opens a Remote Desktop session for connecting to your virtual environment
via RDP.
Opens a ssh terminal window for connecting to your virtual environment via
SSH.
available for your virtual environment and view any of them.
undergone.
resources or coming close to the usage limits imposed on it.
with the current virtual environment.
period in the past.
interface.
Sign out Following this link logs you out of Parallels Power Panel.
The toolbar is to be found on every Parallels Power Panel screen to allow you to easily
perform the operations most frequently required in the course of virtual environment
management with the help of the Start, Stop, Restart, Backup and New buttons.
16
Page 17

Getting Started With Parallels Power Panel
C HAPTER 2
Customizing Parallels Power Panel Interface
Clicking the Preferences link on the Parallels Power Panel left menu opens the Parallels
Power Panel interface configuration page where you can set a number of parameters related
to the Parallels Power Panel interface. The options provided on the Configure page are the
following:
Option Description
Interface Language As Parallels Power Panel is localized into a number of languages, this drop-down
menu lets you choose the default interface language for Parallels Power Panel.
This setting affects the language of both your current Parallels Power Panel
session, and all future sessions if User Default is chosen as the interface language
on the Parallels Power Panel login screen.
Local Time Zone This setting affects the date and time information found on such Parallels Power
Panel pages as Status Changes, Resource Alerts, Actions Log. Choose the
time zone you wish to apply when viewing different kinds of logs.
GUI Elements Style This setting is effective for different types of GUI elements found on different
screens. You may choose a visual mode for them, a textual mode, or a
combination of both.
Interface Skin Here you may choose a suitable interface skin for your Parallels Power Panel
interface. The skin affects such elements as the Parallels Power Panel general
layout (framed or non-framed), icons and images, and the color palette. Parallels
Power Panel does not generate Windows skins, like Vista or XP.
Status Bar Refresh This setting affects the refreshing period of the status bar located at the top of any
Parallels Power Panel page (see Parallels Power Panel Interface Overview (p. 14)).
If you select the Smart Update option, the status bar will be refreshed only when
you follow Parallels Power Panel links, but not more than once per 60 seconds. If
this option is disabled, it means that the chosen interface skin does not use
frames; therefore, it is impossible to reload only part of the page.
Contact Email This field should be filled in with a correct email address to enable the functionality
of restoring the password, should the current user forget it. This email address
pertains to the current user only; other Parallels Power Panel users of the given
Container may fill in this field with other addresses. The link for restoring the
password is located on the Parallels Power Panel login page.
After you decide on the suitable configuration and click the Submit button, the settings will
be remembered for the current browser only. If you change the browser or move to another
computer for working with Parallels Power Panel, the default settings will be used until you
perform a new customization.
Page 18

Getting Started With Parallels Power Panel
Using Parallels Power Panel Desktop
The Desktop allows you to have the most frequently used options at hand, available and
organized in such an individual way that can considerably save your time reaching them. The
Desktop screen displays every time you log in or on clicking on the Virtuozzo logotype. The
Desktop is a remarkably customizable environment the ultimate appearance of which can be
configured on the Customize Desktop page (p. 19).
The Desktop page allows you to exercise the overall control on the virtual environment
activity, state, and configuration.
Virtual Environment Summary
In this section, you can view:
• The current status of the virtual environment.
• The hostname of the physical server where the virtual environment is hosted
• The OS template the virtual environment is based on
• The IP address and the ID number of the virtual environment
Download
Here you can download the Parallels Power Panel documentation from the Parallels web site.
Memo
Here you can leave important information or some memos relevant for you. Just click the Edit
Memo link to type it down and then click the Save Changes link.
Actions
This section contains some useful links, such as the Change Password, Manage System
Processes, Manage Files and some others. Click the Customize Desktop (p. 19) link to
edit the list of links..
If you do not need some of the sections, you can fold them by clicking the triangle element in
the right upper corner of every section.
18
Page 19

Getting Started With Parallels Power Panel
Customizing Parallels Power Panel Desktop
If you clicked the Customize Desktop icon on the Parallels Power Panel toolbar to adapt its
preferences to your current needs, on the Customize Desktop you can use the following
options.
To start with, you can set up your Desktop appearance by placing its items either in two
columns or in any of them in the Desktop Layout subsection: select the item and click the
<< button to move it to the left column or the >> button to move it to the right column. To
further adjust the distribution of the items, use the Up and Down buttons.
Further on, you can write, or edit, anything worth memorizing in the Memo Contents field - if
you want this to be seen on your Desktop, select the Show 'Memo' Section checkbox.
To place to the Desktop an action, select this action in the Available table on the left of the
following section and move it to the Selected table with the >> button. The << button takes
the action selected in the Selected table back to the Available table. You can regulate the
actions position on the Desktop with the Up and Down buttons.
Select the Show 'Actions' Section checkbox to make the actions from the Selected table
appear on your Desktop.
If you select the Show 'Virtual Environment Summary' Section checkbox, the Desktop will
be displaying the summary information on the Container.
Finally, you can decide whether you need to have download links to the Parallels Power Panel
documentation on your Desktop with the help of the Show 'Download' Section checkbox.
19
Page 20

Virtual Environment Operations
C HAPTER 3
Virtual Environment Operations
The common Container or virtual machine operations are accessible in Parallels Power Panel
from the Container/virtual machine Management accordingly.
The following Container operations are available either by following the links under the
Container Management group on the menu or through the links on the Container
Management dashboard itself:
• Changing the Container root/administrator password (the Change Password link);
• Working with Container files and directories (the File Manager link);
• Viewing the current resources consumption (the Resources link);
• Backing up and restoring the Container (the Maintenance link);
Reinstalling the original template files into the Container (the Maintenance link);
•
Mounting and unmounting the Container in the repair mode (the Maintenance link);
•
• Viewing the resource consumption (the Resources link);
• Viewing installed software packages ( the Software Packages link);
• Accessing the Container via various control panels (the Control Panels link);
The following virtual machine operations are available either by following the links under the
Virtual Machine Management group on the menu or through the links on the Container
Management dashboard itself:
• Working with virtual machine files and directories (the File Manager link);
• Backing up and restoring the virtual machine (the Maintenance link);
• Changing the Container root/administrator password (the Change Password link);
• Viewing the resource consumption (the Resources link)
In This Chapter
Starting, Stopping, and Restarting Virtual Environment ............................................. 21
Virtual Environment Statuses .................................................................................... 22
Managing Virtual Environment Files and Folders ....................................................... 24
Working With Containers .......................................................................................... 27
Working With Virtual Machines.................................................................................. 41
Page 21

Virtual Environment Operations
Starting, Stopping, and Restarting Virtual Environment
A virtual environment may be started up, restarted, suspended and shut down like an
ordinary computer. Depending on the virtual environment state, only those operations are
accessible that comply with its current state. For example, a running virtual environment
cannot be started for obvious reasons, and so on. The following virtual environment states
can be characterized as stable:
Status Description
Running The virtual environment is running; therefore, it may only be started or stopped.
Down The virtual environment is stopped; therefore, it may only be started.
Repairing
The virtual environment is being repaired. You cannot perform any action on the virtual
environment until you click the Finish Repair button on the Start Container in Repair
Mode page (p. 30).
Besides these states, during virtual environment operations a virtual environment may be in
one of the transitional states: mounting, starting, stopping, etc. When in a transitional state,
you cannot perform any action on the virtual environment until the operation is finished. The
description of all possible virtual environment statuses is provided in the Physical Server,
Container and Virtual Machine Statuses section.
Click the Start, Stop, Suspend, or Restart button to perform the corresponding action. On
clicking one of these buttons, this action is logged.
If you are managing a virtual environment residing on the physical server with the Linux
operating system installed and wish to stop your virtual environment, bear in mind that there
is a two-minute timeout for the virtual environment shutdown scripts to be executed. If the
virtual environment is not stopped in two minutes, the system forcibly kills all the processes in
the virtual environment. The virtual environment will be stopped in any case, even if it is
seriously damaged. To avoid waiting for two minutes if you are operating a virtual
environment that is known to be corrupt, you may use the Power Off link. It is situated in the
Tasks section of the Container dashboard.
21
Page 22
Virtual Environment Operations
Virtual Environment Statuses
At any point of time, any virtual environment is characterized by a status (or state). A virtual
environment may have five stable statuses and a number of transitional statuses. If the virtual
environment is in one of the stable states, it means that it is likely to continue in this state until
its administrator performs a task that would change its status. If the virtual environment is in
one of the transitional states, it means that it is currently passing from one stable state to
another. During a transition stage, no operation can be performed on the virtual environment
until the transition is finished.
The stable statuses are:
Status Description Possible Actions
down
mounted
running
The virtual environment is stopped and its private area is
unmounted.
The virtual environment private area is initialized and
ready to work, but the virtual environment is not running.
The virtual environment private area is mounted and the
virtual environment is running.
Starting/ repairing/
reinstalling
Starting
Stopping/ restarting/
repairing
suspended
repairing
The virtual environment is stopped and its private area is
unmounted. The difference between the suspended
status and the down status is that the current state of a
suspended virtual environment is written to the
/vz/private/CT_ID/dump/Dump file on the
Hardware Node, and can be quickly restored from
there.
The virtual environment is mounted in the repair mode. Exiting the repair mode.
The transition statuses are:
Status Description
creating
mounting
starting
stopping
restarting
unmounting
destroying
starting-repair
The virtual environment is being created.
The virtual environment is being mounted.
The virtual environment is starting.
The virtual environment is stopping.
The virtual environment is being restarted.
The virtual environment is being unmounted.
The virtual environment is being deleted.
The virtual environment is entering the repair
mode.
Resuming. Restarting,
repairing and reinstalling are
not recommended because
these actions are most likely
to alter the saved state of
the virtual environment.
stopping-repair
22
The virtual environment is quitting the repair
mode.
Page 23
Virtual Environment Operations
setting
migrating
moving
cloning
updating
backing-up
restoring
reinstalling
suspending
resuming
The virtual environment parameters are being
set.
The virtual environment is being migrated.
The virtual environment is being moved.
The virtual environment is being cloned.
The virtual environment is being updated.
The virtual environment is being backed up.
The virtual environment is being restored from
the backup.
The virtual environment is being reinstalled.
The virtual environment is being suspended.
The virtual environment is being resumed from
the suspended state.
23
Page 24
Virtual Environment Operations
Managing Virtual Environment Files and Folders
For a running virtual environment, you can navigate inside the virtual environment directory
structure, list the virtual environment files and directories and perform all essential file
operations on the File Manager page. (
are presented with a list of drives inside the Container. Click a drive (e.g. C:) to see its
contents.) The main information on the directory/drive contents is presented in the form of a
table.
Column Name Description
Type The type of the object: a folder or a file.
Name The name of the directory or file.
Size The size of the file.
Modified The date and time of the last modification of the directory or file.
Container. Right after opening this screen, you
Permissions
User
Group
Actions Hyperlinks for performing certain operations with the directory or file (see below).
Note: If the Container is being repaired (p. 30), the file manager root directory (/) corresponds
to the /repair directory of the temporary Container, in other words, it represents the root
directory of the problem Container, not that of the newly-created one.
The first symbol in this column indicates if this is a directory (the letter d) or not (the
minus sign). The following three symbols designate the permissions that the owner of
the directory/file has on it, then go another three symbols for the permissions of the
users belonging to the group assigned to the directory/file, and the final set of three
symbols denotes the permissions of all the rest. The symbols in each of the set
express consecutively the following permissions: read, write, and execute. The
presence of a letter (correspondingly, r, w, or x) indicates that the permission is given,
and the minus sign - that it is absent.
The owner of the file/directory.
The users' group that has certain permissions on the file/folder. These permissions are
presented by the 5th thru 7th symbols in the Permissions column.
Apart from viewing a list of files and directories with their essential properties, you are able to
perform the following operations:
• Create a new folder in the current directory (p. 25);
• Create a new text file in the current directory (p. 25);
• Edit existing text files (p. 25);
• Upload a file from your local computer to the current virtual environment directory (p. 26);
24
Page 25

Virtual Environment Operations
• Download a file from the current virtual environment directory to your local computer (by
clicking the diskette icon in the Actions column);
• Copy any number of files or folders to another directory inside the virtual environment (p.
26);
• Move any number of files or folders to another directory inside the virtual environment (p.
26);
• Edit the properties of any folder or file (p. 27);
• Remove any number of files or folders by selecting them and following the Remove link.
To perform a certain operation (e.g. copying) on a number of directories or files, tick the
corresponding check boxes. The uppermost check box allows you to select all the directories
and files at once.
Creating Folder
On the Create Folder screen, you can add a new folder and specify its name in the Folder
Name field. Upon finishing the operation, click Create to save the changes. The new folder
will be created in the current directory (designated above the field).
You can access the Create Folder screen from the File Manager section by clicking the
Create Folder button.
Creating Text File
The Create File page allows you to create simple text files directly inside the virtual
environment, without uploading them from your local computer.
In the Specify File section, you should enter the name of the file to be created in the current
directory (this directory is indicated under the page heading) to the Name field and,
optionally, type the text of the file in the Content field. Click Create when you are finished to
create the new file.
Editing Text File
Parallels Virtual Automation allows you to edit any text file inside your virtual environment
directly through the Parallels Virtual Automation interface. The Edit File page can be
accessed by clicking on the right icon in the Actions column for the corresponding text file
on the File Manager page.
This page presents the contents of the file in an editable field. Make your modifications and
click Submit to write a new version of the file.
25
Page 26

Virtual Environment Operations
Uploading File to Virtual Environment
The current version of Parallels Virtual Automation allows you to upload external files to the
virtual environment, up to ten files at a time. The Upload File page is displayed after clicking
the Upload File link on the File Manager page.
Click the Browse button, navigate to the local file you wish to upload and double-click it. The
path to the file will be displayed in the corresponding Specify File field. Another way of
indicating the file is to enter this path manually.
When you click Upload, the files that you have specified will be uploaded to the current
directory inside the virtual environment. For your reference, this directory is indicated above
the Specify File group.
Copying Files and Folders Inside Virtual Environment
The Copy File(s) page, where you can perform the copy operation, gets displayed after you
have selected one or more files and/or folders by ticking the corresponding check boxes on
the File Manager page and clicking Copy.
On the Copy File(s) page, click Select and, in the pop-up window, navigate to the folder
where you want to copy the files and/or folders, check the radio button to the left of it, and
press Select. The path to the target folder will be displayed in the Destination Path field.
Click Copy to begin the copy process.
Moving Files and Folders Inside Virtual Environment
The Move File(s) page, where you can perform the move operation, gets displayed after you
have selected one or more files and/or folders by ticking the corresponding check boxes on
the File Manager page and clicked Move.
On the Move File(s) page, click Select and, in the pop-up window, navigate to the folder
where you want to move the files and/or folders, check the radio button to the left of it, and
press Select. The path to the target folder will be displayed in the Destination Path field.
Click Move to begin the move process.
26
Page 27

Virtual Environment Operations
Editing File or Folder Properties
The page where you can view and edit some properties of a certain file or folder is accessible
by clicking the leftmost icon in the Actions column for the corresponding file or folder on the
File Manager page.
The information is given on the following file or folder general properties, whether editable or
not:
Field Description Editable?
Name The name of the file or folder. Yes.
Path The path to the file or folder inside the virtual
environment.
Size The size of the file. To save the time needed
to open the page, a link is given for a folder to
calculate its overall size.
Modified The date and time of the last modification of
the file or folder.
No. See Moving Files and Folders Inside
virtual environment for information on how
to change the path.
No.
No.
Container. You can also change such file/folder properties as permissions and ownership.
When you click Submit on the Change Properties page, your changes will be applied to the
given file or folder.
Working With Containers
Changing Container Root/Administrator Password
The Change Administrative password page is displayed on clicking the Change Password
link on the Parallels Power Panel menu. Only the root/Administrator password for the current
virtual environment can be changed. You should enter a new root/Administrator password
for the current Container into the fields provided and click Change.
Note that Parallels Power Panel does not check the entered password as to its length and
non-conformity to dictionary entries, so choosing a simple password rests entirely at your
own risk. It is recommended to use a chaotic set of lowercase (a-z) and uppercase (A-Z)
letters, digits (0-9), and punctuation marks as root/administrator password. The following
punctuation marks are allowed: ! “ $ % & , ( ) * + - . / ; : < = > ? [ \ ] ^ _ { | }. The space
character, #, and @ symbols are not allowed. The password should not be less than 5 or
more than 14 characters.
27
Page 28

Virtual Environment Operations
Reinstalling Container
Container reinstallation means recovering the original state of a Container in case you have
unintentionally modified, replaced, or deleted any file that is part of an application or OS
template, and the action has brought about the Container malfunction. The Container
reinstallation process restores these files as they were at the time when the Container was
created or when other applications were added to the Container afterwards, if so.
Reinstallation is likely to bring about some irrevocable changes to your Container, therefore,
to be on the safe side, it is recommended to back up your Container before reinstallation.
Click Next on the Reinstall Container introductory page to review the available options and
to decide whether you really need to reinstall your Container and in what way.
Note: To be reinstalled, each Container has to be stopped. The description of all possible
Container statuses is provided in the Container Statuses section. If it is not stopped, the
corresponding screen will inform you of the fact. In this case follow the Stop Container link in the
Possible Solutions section. Afterwards it is recommended to refresh the page by clicking the
Refresh this page link in the Other possible actions section.
28
Page 29

Virtual Environment Operations
Selecting Reinstallation Type
The page where you should choose the mode of reinstallation is displayed after you click
Next> on the Reinstall Container introductory page. You shall select one of the two
reinstallation options and specify whether to preserve or drop your Container password
database.
When selecting a reinstallation option, bear in mind that there is one thing both options have
in common: the original files of the OS and applications templates are restored in the
Container. Pay attention to the fact that any customization changes you have made to these
files will be lost during the Container reinstallation. In case you have not seriously modified
any system configuration files, reinstalling the original files is likely to solve many problems.
However, you have probably already filled the Container with your personal files. If you are
sure these files cannot cause problems or you need them in your Container, select the first
option - Keep the existing Container contents. In this case, your Container is created anew
with all existing files moved to the
the Container. You shall be sure there is enough disk space to perform this operation,
otherwise, it will fail. Be prepared to move the necessary files from the
c:\reinstall directory to the new existing installation manually. If such files are
numerous, this may prove a tedious task.
/old directory or c:\reinstall directory inside
/old directory or
If you think you have nothing to lose at all, select the second option: Drop the existing
Container contents. Your Container will be erased and recreated from the original
template(s). Naturally, all your personal files will be lost. That is why you should select this
option only if you have no valuable data in your Container or if you have a backup of your
personal files elsewhere.
Pay attention to the Password Options group. The Keep the password database option
retains the information on the Container users and groups. Selecting the Drop the password
database radio button will purge this information altogether and create only the root account
with the password specified in the Set the administrative account password and Retype
the password fields under the radio button. This option may prove useful if your Container
has got a corrupted password database.
When you are done, click Next> to proceed to the Reinstall Container: Final confirmation
page.
Confirming Reinstallation
Finally you shall confirm the reinstallation or give it up. The reinstallation option you have
chosen at the previous step is displayed for you to have a last chance to revise what you are
about to do. Click the Reinstall button to begin the reinstallation process.
Do not forget to start the Container when the operation is complete. To see the current
status of the operation, click the Details link.
29
Page 30

Virtual Environment Operations
Repairing Container
Repairing a Container is another way to solve problems with the Container functioning. In
Parallels Containers terminology, the Container is mounted in the repair mode. This means
that a new Container is temporarily created from scratch with the same network and other
parameters as the broken Container, and the root directory of the broken Container is
mounted as /repair into the newly-created Container. Thereafter, the administrator is
supposed to connect to the new Container via ssh or Parallels Virtual Automation file
manager (p. 24) using the network and login parameters of the broken Container, go to the
/repair directory, and perform one of the following actions:
1 Find the personal data that needs to be saved and copy it to a safe location elsewhere.
Do not copy your personal data directly into your new Container, as it will be destroyed
once you exit the repair mode. After quitting the repair mode, the broken Container can
be reinstalled and the personal data can further be loaded into it from the place where
you have saved them.
2 Identify the source of the problem and manually correct it. This method can be
recommended to advanced Container administrators, as it presupposes some technical
expertise. And it is still recommended to save first your personal data in a safe location,
just in case something goes wrong.
Note: When working inside the Container being repaired by means of the Parallels Virtual
Automation file manager, the file manager root directory (/) corresponds to the /repair directory
of the temporary Container, in other words, it represents the root directory of the problem
Container, not that of the newly-created one.
Clicking the Start Repair button on the Repair Container screen mounts the Container in
the repair mode. It is not necessary to stop the Container beforehand; if the Container is
running at the moment of pressing the Start Repair button, it will be first automatically
stopped. The description of all possible Container statuses is provided in the Container
Statuses section.
When the page is refreshed after pressing the Start Repair button, click the Details link at
the end of the The Container has been scheduled to start in the repair mode message to
see if the repair mode has been successfully entered. Once the Container enters the repair
mode, connect to the new Container via ssh or Parallels Virtual Automation file manager and
do what you deem reasonable inside the Container. After closing your ssh session, click the
Repair link on the Parallels Power Panel menu once again and press the Finish Repair
button to exit the repair mode. After the repair mode is exited, the broken Container starts
running, and you may check the repairing effect.
30
Page 31

Virtual Environment Operations
Backing Up and Restoring Container
Any Container is defined by its operating system files, applications installed, configuration
files, and personal information. Parallels Power Panel allows you to back up all these
components. A regular backing up of the existing Containers is essential for any Container
reliability.
The Maintenance page, which allows you to perform backing up and restoring operations,
opens after you click the Maintenance link on the main menu or selecting the Maintenance
link on the Container Management dashboard accessible after clicking the Container
Management link on the menu. If you already have backups of the given Container, it
displays a table summarizing the backups.
Apart from dealing with Container backups, you may perform the operations that would
guarantee the integrity and overall operability of your Container, that is reinstalling the
Container (the Reinstall Container sub-tab) and mounting the Container in the Repair Mode
(the Repair Mode sub-tab). To open the screen where you can check for, and, if necessary,
download updates for OS and/or application packages in your Container, click the Update
Software button.
Column Name Description
Backed Up The date and time when the backing up was performed.
Size The size of the backup.
Description The additional information on the backup.
Backup Type Denotes if it is a full, incremental, or differential backup. An incremental
backup stores not all the files and settings of the virtual environment at
the given period of time, but only the changes the virtual environment
has undergone since the last backup. A differential backup saves the
data changed after the last full backup.
You can manage your backups on this page in the following ways:
• The New Backup (p. 32) button opens the New Backup screen where you will be able
to back up the current state of your Container, be it running or not. The description of all
possible Container statuses is provided in the Container Statuses section. This option is
available only if you have not reached the maximal number of allowed backups for your
Container. If you have, remove one of the backups first (see below for details). Parallels
Power Panel allows you to place the backup of your Container only onto the physical
server where your Container is hosted.
• The Restore Virtual Environment button restores the Container backup currently
selected in the table. Only one backup should be selected for this operation. The page
opened provides instructions to guide you through the process. The Container will be
restored with all the values overwritten from the backup, including its IP address,
password, application set, etc. The changes in the Container made after the date of this
backup will be lost after the Container has been restored.
31
Page 32

Virtual Environment Operations
Note: If you are using an IP address of your Container to connect to it, you may have to
reconnect to the Container with the IP address retrieved from the backup after the Container is
restored.
• The Remove Backups button removes the Container backup(s) currently selected in the
table. Usually this is done to provide extra space for making new Container backups. Use
the checkbox at the upper left corner to select/deselect all the backups at once.
• If you have reached the limit on the number of Container backups you are allowed to
create, you can make use of the Renew Backup button to renew a Container backup
without having to delete any of your existing Container backups. By default, the oldest
backup is renewed. You can also renew another Container backup by selecting the
checkbox opposite the corresponding backup and clicking on the Renew Backup
button.
• Clicking on a backup date in the table opens the Backup Details (p. 33) page where you
can also restore or remove the corresponding Container backup.
Creating Container Backup
On the New Virtual Environment Backup screen you are supposed to define all the
parameters of the backup operation. This screen is available after you click the New Backup
button on the Backups screen.
In the Backup Description section, enter any commentary you think can be practical for
further backup operations.
(For Containers only) The Exclude section allows you to keep certain files and directories
from backing up:
•
•
Hidden files;
System files;
• Single files or directories. If you do not want to back up a whole directory, type it into the
corresponding field; to add more directories to be excluded from the backup, click the
plus sign.
Warning! If you exclude one or more system or hidden files/folders from the virtual
environment backup (e.g. either the Hidden files or System files checkbox is selected), you'll be
able to restore only separate files from this backup, but not the virtual environment as a whole.
(For Containers only) The Include section allows you to limit the backup process with a
number of selected files or directories inside the virtual environment. In the field provided,
type the absolute path to the file or directory you wish to back up. To include additional files
or directories, click the plus icon to the right of an existing path and enter a new path.
Note: The backup will contain only those files and directories that you have indicated in the
Include section. To back up the whole virtual environment, leave the Include section empty.
32
Page 33

Virtual Environment Operations
Backup Details
The Backup Details page provides general information on the virtual environment backup in
the following table:
Column Name Description
Creation Date
Backup Size
Backup Type
Virtual Environment
IP Address(es)
Backup Node
The date and time when the backing up was performed.
The size of the backup.
Denotes if it is a full, incremental, or differential backup. An incremental backup
stores not all the files and settings of the virtual environment at the given period of
time, but only the changes the virtual environment has undergone since the last
backup. A differential backup saves the data changed after the last full backup.
The name of the backed up virtual environment.
The IP address of the backed up virtual environment.
The hostname of hardware node where the virtual environment was backed up.
If this backup has any description, you can view it in the Backup Description section.
To manage the backup you can use the following options on the Parallels Virtual Automation
toolbar:
• The Restore button restores the virtual environment from the current backup. The
changes in the virtual environment made after the date of this backup will be lost after the
virtual environment has been restored. Mind that you have to confirm restoring the virtual
environment on the Restore Confirmation page to accomplish the process.
• The Browse button (p. 34) allows you to browse the directory structure of the archived
Container backup as if it had been already restored and to restore only the needed files
and folders. Note, that the content of virtual machines backups cannot be browsed.
• The Remove button removes the current virtual environment backup. Usually this is done
to provide extra space for making new virtual environment backups.
33
Page 34

Virtual Environment Operations
Browsing Backup Contents
Parallels Virtual Automation allows you to browse the directory structure of any Container
backup as if this backup had already been restored and restore only the needed files and
folders. The Browse Backup page opens after you follow the Browse button on the Backup
Details page (p. 33).
The content of any directory inside the backup is presented in the table. The first table
column indicates if the object is a directory or a file. The table on the whole provides the
following information:
Column Name Description
Name The name of the directory or file.
Size The size of the file.
Modified The date and time of the last modification of the directory or file.
Permissions
Actions Allows you to download a file to your local computer provided it is not part of an OS or
The standard Linux permissions for the directory or file.
application template.
If you are browsing an incremental Container backup, the information is shown not only on
the files and folders from this backup, but on all the contents of the Container, should it be
restored from this incremental backup. In other words, the backed up Container is always
presented in its integrity and not as a collections of sporadic changes from the incremental
backup.
To restore separate files and folders from the backup to the actual Conatiner, just select them
by ticking the corresponding check boxes in the rightmost column and click the Restore
button.
34
Page 35

Virtual Environment Operations
Updating Container Software
The Update Software page allows you to update the OS and application packages in the
given Container by adding available templates updates (in the case of standard Container
templates) or updating Container packages directly (in the case of Virtuozzo EZ templates).
The Update Software page is available on clicking the Update Container Software link on
the Parallels Virtual Automation toolbar, which becomes visible if you are currently located on
the Application Templates subtab of the Container Software tab.
The page will display the relevant information in one of three ways:
1 If no updated templates for the given Container have been installed on the physical server
or no updated packages are found in the repository, the page just informs you of this fact.
2 If the Container uses standard Virtuozzo templates and one or more updated versions of
the corresponding template(s) are installed on the physical server, you are able to select
an updated version for adding to the Container.
3 If the Container uses Virtuozzo EZ templates and updated packages for the given
Container can be found in the repository, you are able to select the packages that you
wish to update inside the Container.
Two options for customizing the update process are available on clicking the Configure
Updating group:
• The Force software update option tells the system to perform the update even if
unresolved dependencies are met during the process;
• The Jump over several upgrades instead of adding them sequentially option can be
used if two or more sequential updates are found for this or that template.
Click Update to update the templates/packages you have selected for the given Container.
35
Page 36

Virtual Environment Operations
Resources Overview
The Overview subtab summarizes the current CPU, system and disk usage by the Container
in the following table:
CPU Usage This is a positive integer or fractional number that determines the minimal guaranteed
percentage share of the CPU time your Container will receive. For stopped Containers,
this parameter is not available.
Load Average for the CPU usage is the average number of active processes for the
past 1, 5, and 15 minutes, respectively. Value 0.0 means that the CPU is idle, 1.0 that
the CPU is fully used. Value 2.0 denotes that the CPU load exceeds the nominal value by
two times.
Memory Usage This is a cumulative figure presenting the average consumption of a number of critical
memory-related parameters by your Container.
Disk Usage
Disk Space is a total amount of disk space allocated to the Container.
When the space used by the Container hits the soft limit (or reaches
100% on the percent bar), the Container can be allowed additional disk
space up to the hard limit during the grace period.
Disk I/O is a cumulative figure presenting how much of the allowed disk
i/o bandwidth is used by the Container and how much is still available up
to the limit.
The information on the disk and memory usage is organized as follows:
Column Name Description
Resource The name of the resource: memory, disk space, disk i/o bandwidth or disk inodes.
Used Consumed amount of memory, disk size, disk /o resource or the number of inodes.
Free Available amount of memory, disk size, disk /o resource or inodes number.
Total The total amount of memory, disk size, disk /o resource or inodes.
CPU Parameters
For the description of CPU Linux-related commands, refer to the Linux Container
Parameters: CPU section.
For the description of CPU Windows-related commands, refer to the Windows Container
Parameters: CPU section.
36
Page 37

Virtual Environment Operations
Disk Management
For the description of disk Linux-related commands, refer to the Linux Container
Parameters: Disk section.
For the description of disk Windows-related commands, refer to the Windows Container
Parameters: Disk section.
Memory Parameters
For the description of memory Linux-related commands, refer to the Linux Container
Parameters: Memory section.
For the description of memory Windows-related commands, refer to the Windows
Container Parameters: Memory section.
Managing Container Applications
Applications can either be added to the Container by means of the corresponding Virtuozzo
templates or installed in the Container as individual software packages.
Clicking Applications on the Parallels Power Panel menu allows you to do the following:
• view the applications added to the Container as application templates (both EZ and
standard) as well as their up-to-date status.
• if some of the applications are not up to date (i.e. the updated versions of the
corresponding templates or template packages are available on the Hardware Node),
update them by clicking the Update Container Software button on the toolbar.
• add more applications available on the physical server or delete unnecessary ones by
clicking Manage and performing these actions on the screen that opens.
37
Page 38

Virtual Environment Operations
Managing Container Application Templates 03-02-01-03-14
Clicking Applications on the Parallels Power Panel menu and the Manage Applications
button on the screen that opens allows you to manage applications available to the
Container. On this page, you can:
• View the applications already installed in the Container. These applications are listed in
the Installed/Scheduled Applications table in the right part of the page.
• Install new applications to the Container. To add any of the applications from the
Available Applications table to the Container, tick the corresponding checkboxes and
click on the >> button. After that, the applications appear in the Installed/Scheduled
Applications table in the right part of the page. Clicking the Submit button starts the
installation process.
• Delete those applications from the Container that are not needed any more. To remove
any application, tick the corresponding checkbox in the Installed/Scheduled
Applications table and click on the << button. After that, the application appears in the
Available Applications table in the left part of the page. Click the Submit button to start
the deletion process.
Check unresolved dependencies among the selected applications with the help of the
•
Resolve button. To eliminate unresolved dependencies, you can remove one of the
problem applications from the Installed/Scheduled Applications table as explained
above.
Note: Only standard template based Container application dependencies require resolving. If you
are managing a Container based on an EZ template, the Resolve button is not present on the
screen.
38
Page 39

Virtual Environment Operations
Managing Software Packages in EZ Templates Based Container
Parallels Power Panel enables you to install, update and uninstall rpm and deb packages
in Containers based on EZ OS templates. To find out what type of template the Container is
based on, click the General tab and look at the OS Template in the Container Summary
section; if it is Standard, this option is not available for the Container, and if it is EZ you will
find the Manage Software Packages icon on the Container dashboard, on the screen that
opens by the Configuration tab.
Note: The Container you want to manage software packages in has to be running.
Clicking this icon displays the screen where you can obtain the information on the packages
currently installed in the Container in the Installed Packages table, presented as follows:
Column Name Description
Name The name of the package.
Epoch Indicates the version of a deb package or the version of an rpm package in
case the version of the rpm package is not available.
Version The version of an rpm package.
Arch The processor architecture; if the column shows the "noarch" value, the
packet is likely to be either non-executable or contain documentation.
Summary A short description of the package.
Status Shows if there is a fresher version of the package: Up-to-date or Update
Found.
The Installed Packages table displays from 10 up to 80 packages, the default number is 20
and can be changed by clicking 10, 40, or 80 on top of the table. To see the next portion of
packages, click either the number of the page next to the one you are having at the moment,
or next (or last, to view the previous page).
If the status of a package in the Installed Packages table suggests that an update is
available, you can select this package and click the Update link near the table. To update all
those packages that you can see on the page, select the uppermost checkbox and click
Update. If you need to run update for all the packages installed in the Container, do not
select anything - simply click the Update All Packages icon in the Actions section.
To uninstall a package, select it (or select the uppermost checkbox to uninstall all the
packages listed on the page), and click Uninstall.
Virtuozzo can query the repository where the packages for your distribution are stored for
new packages available for downloading and install them in your Container. To connect to
the repository, fetch a list of the packages, see the packages description, download and
install in your Container the packages you need, click the Install Packages icon.
39
Page 40

Virtual Environment Operations
Installing Software Packages in EZ Container
Virtuozzo can connect to your Linux distribution download packages repository to form a
list of packages ready to be downloaded to your host Hardware Node and installed in your
Container. All these operations are available on the Install New Packages screen. To open
this screen, click the Configuration tab on the Container dashboard, then the Software
Packages icon to get the Manage Software Packages screen where you need to click the
Install Packages icon.
Note: A repository can be a place where multiple files are located for distribution over a network,
or a repository can be a location that is directly accessible to the user without having to travel
across a network. Therefore connecting to your repository might involve either going to the web
site repository (e.g. Fedora Core or Red Hat), or to the repository, created on your Hardware
Node. For information on creating a local repository, refer to the Setting Up Repository for EZ
Templates section in the Parallels Virtuozzo Containers Installation Guide.
On the Install New Packages screen you can obtain the following information on the
packages:
Column Name Description
Name The name of the package.
Epoch Indicates the version of a deb package or the version of an rpm package in
case the version of the rpm package is not available.
Version The version of an rpm package.
Arch The processor architecture; if the column shows the "noarch" value, the
packet is likely to be either non-executable or contain documentation.
The Available Packages table can display 10, 20, 40 or 80 packages, the default number is
20 and can be changed by clicking 10, 40, or 80 on top of the table. To see the next portion
of packages, click either the number of the page next to the one you are having at the
moment, or next (or last, to view the previous page).
To install a package, select its checkbox (or the uppermost checkbox, to install all the
packages shown in the table) and click Install.
40
Page 41

Virtual Environment Operations
Managing Container Control Panels
There are a number of control panels that can be installed on the physical server in the form
of templates and added to any Container hosted on that physical server. Among such control
panels are Plesk,
The Control Panels subtab of the Software tab of the Container dashboard provides a
single place for managing all these control panels in this particular Container. It goes without
saying that the control panel template must be installed on the Node for the panel to be
manageable on this screen.
The two major management operations that can be performed here are:
• adding the control panel template to the Container (the Install link), which ensures that
this Container can be managed by the given control panel.
• logging in to the control panel to begin managing the Container with its help (the Login
link). This is possible only if the control panel template has already been added to the
Container.
Sitebuilder, and Confixx.
Note: In the case of the Plesk control panel, the Login link is called Manage and leads to the
screen where you can not only log in to Plesk but also change the Plesk admin password.
Working With Virtual Machines
Changing Virtual Machine Administrative password
The Change Administrative password page is displayed on clicking the Change Password
link on the Parallels Power Panel menu. Only the root/Administrator password for the current
virtual machine can be changed. You should enter a new root/Administrator password for the
current virtual machine into the fields provided and click Change.
Note that Parallels Power Panel does not check the entered password as to its length and
non-conformity to dictionary entries, so choosing a simple password rests entirely at your
own risk. It is recommended to use a chaotic set of lowercase (a-z) and uppercase (A-Z)
letters, digits (0-9), and punctuation marks as root/administrator password. The following
punctuation marks are allowed: ! " $ % & , ( ) * + - . / ; : < = > ? [ \ ] ^ _ { | }. The space
character, #, and @ symbols are not allowed. The password should not be less than 5 or
more than 14 characters.
41
Page 42

Virtual Environment Operations
Reinstalling Virtual Machine
Virtual machine reinstallation means recovering the original state of a virtual machine in case
you have unintentionally modified, replaced, or deleted any file that is part of an application or
OS template, and the action has brought about the Container malfunction. The virtual
machine reinstallation process restores these files as they were at the time when the virtual
machine was created or when other applications were added to the virtual machine
afterwards, if so.
Reinstallation is likely to bring about some irrevocable changes to your virtual machine,
therefore, to be on the safe side, it is recommended to back up your virtual machine before
reinstallation.
Click Reinstall to start the process of reinstallation.
Click Next on the Reinstall Container introductory page to review the available options and
to decide whether you really need to reinstall your Container and in what way.
Note: To be reinstalled, each virtual machine has to be stopped.
Resources Overview
The VM Monitor subpane shows the graphical statistics on CPU, Memory and Disk resource
consumption, i.e how much of the physical server resources this virtual machine consumes.
The data are shown in percentage.
Each of the three resources has its own colour on the chart. If you need to monitor the
changes only for one resource, whatever it is, you can disable the others. Use the Select
Graph subsection.
The chart can reflect the live changes in the resource consumption (choose Live Graph
Type) or show the changes for the defined period (choose History Graph Type). In the
History mode, the chart can include the data for a particular date, month, year or for any
other period of time. To implement the changes, click Apply. the chart will change its
appearance.
The Export Data link allows you save the graphical data in the format of a plain text ( .svs
file) on your computer.
42
Page 43

Managing Container Services and Processes
C HAPTER 4
Managing Container Services and
Processes
Parallels Power Panel allows you to manage services and processes inside virtual
environments in a number of ways by following the corresponding links on the Container
Services or Virtual Machine Services dashboard depending on what virtual environment
you manage via Power Panel. You can:
• Open a list of principal services inside your virtual environment through the System
Services link with the opportunity to start, stop, restart any of them and control their
autostart option.
• Open a list of processes running inside the virtual environment by clicking the System
Processes link with the opportunity to send various signals to any of the processes.
• Log in to the Plesk control panel via the Plesk Panel link in case the corresponding
template is installed in the virtual environment. If the Plesk template is not installed, the
Plesk Panel link is not displayed. Instead you can make use of the Install Plesk link
provided in lieu of the Plesk Panel link to install the Plesk control panel in the Container
this link is available for a virtual environment running the Linux operating system).
(
Log in to the Confixx control panel by choosing the Confixx control panel link in case
•
the corresponding template is installed in the virtual environment. If the template is not
installed, the Confixx control panel link is not displayed. The feature is available for a
Linux-based virtual environment.
Open an ssh terminal window with the help the SSH Connection link for connecting
•
to the virtual environment via SSH. This link is available if you are managing a virtual
environment running the Linux operating system.
•
•
• Open the Sitebuilder application through the Sitebuilder link if the application template is
Open a Remote Desktop terminal window through the Remote Desktop link for
connecting to the Container via RDP (Remote Desktop Protocol). This link is available if
you are managing a virtual environment running Windows 2003 Server.
Open the virtual environment Firewall page through the Firewall link if the virtual
environment you manage runs the Linux OS.
installed on the virtual environment.
In This Chapter
Managing Container Services ................................................................................... 44
Managing Container Processes ................................................................................ 50
Page 44

Managing Container Services and Processes
Managing Container Firewall..................................................................................... 52
Control Panels for Containers ................................................................................... 61
Managing Container Services
The process of managing services inside Container running the Windows operating system
and the Linux operating system varies slightly:
• To learn how to manage services in virtual environment running the Linux operating
system, please see the Managing Services in Linux subsection.
• To learn how to manage services in virtual environment running the Windows operating
system, please see the Managing Services in Windows subsection.
44
Page 45

Managing Container Services and Processes
Managing Services in Linux
The System Services page is displayed after clicking the System Services link on the
Container Services dashboard. The page has two tabs: Standard and Xinetd (p. 46).
The Standard tab is used to view all the services you are running on the Container except for
the xinetd-dependent services. To see the xinetd-dependent services list, click the
Xinetd tab. By default, 20 services are shown for each tab, but you may have more services
displayed by pressing the appropriate link on top of the table. You may also have the System
Services table display only those services that have a particular name or status. On top of
the table, press the Show Search link to display the fields where you can specify the name
or the status of the service you wish to view; then click on the Search link.
The Standard page presents a table reflecting the services inside the Container and
providing the following information:
Column Name Description
Name The system ID of the service executable file.
Status Indicates whether the service is running or not. A green arrow means that the service
is running; a red cross - that it is stopped.
Autostart If there is a green tick in this column, this service is started automatically on the
Container startup; if a red cross - it is not.
You can perform the following actions on any service in the table:
• Stop the service by selecting its checkbox and clicking on the Stop button. Only running
services are subject to this action.
• Restart the service by selecting its checkbox and clicking Restart. Only running services
are subject to this action.
• Start the service by selecting its checkbox and clicking on the Start button. Only stopped
services are subject to this action.
• Enable/disable the autostart feature by clicking the name of the service in the Name
column and opening the Services Details page, where you can manage the option.
Note: If you have just started the Container and opened the Services page, not all the services
may have had enough time to start. Wait a little and refresh the page to update the state of the
services.
45
Page 46

Managing Container Services and Processes
Managing xinetd-Dependent Services
The System Services page is displayed after clicking on the System Services link on the
Container Services dashboard. The page has two tabs: Standard (p. 45) and Xinetd.
The Xinetd tab is used to view all the services you are running on this Container that are
dependent on the xinetd service. To see the other services, click the Standard tab. By
default, 20 services are shown for each tab, but you may have more services displayed by
pressing the appropriate link on top of the table. You may also have the System Services
table display only those services that have a particular name or status. On top of the table,
press the Show Search link to display the fields where you can specify the name or the
status of the service you wish to view; then click on the Search link.
The Xinetd page presents a table reflecting the xinetd-dependent services inside the
Container and providing the following information:
Column Name Description
Name The system ID of the service executable file.
Status Indicates whether the service is enabled or not. A green arrow means that the service
is enabled; a red cross - that it is disabled.
Autostart
If there is a tick in this column, the xinetd service is started automatically on the
Container startup, so is the given service; if a cross - it is not.
You can perform the following actions on any service in the table:
• Enable the service by selecting its checkbox and clicking on the Enable button. Only
disabled services are subject to this action.
• Disable the service by selecting its checkbox and clicking on the Disable button. Only
enabled services are subject to this action.
46
Page 47

Managing Container Services and Processes
Viewing Service Details
The Service Details screen provides the principal information on the given service and lets
you manage it.
The following information is provided:
• The description of the service;
• Whether the service is running or stopped;
• Whether the service is started automatically on the Container startup or not.
You may perform the following actions on any such service:
• Stop the service by clicking the Stop Service button. Only running services are subject to
this action.
• Restart the service by clicking the Restart Service button. Only running services are
subject to this action.
• Start the service by clicking the Start Service button. Only stopped services are subject
to this action.
• Enable/disable the autostart feature by clicking the Enable Autostart/ Disable Autostart
button, correspondingly.
Viewing xinetd-Dependent Service Details
The Service Details screen provides the principal information on the given service and lets
you manage it.
As the service is dependent on the xinetd service, i.e. xinetd is charged with launching the
service when necessary, you can only either enable or disable such a service - depending on
its current state - by clicking the Enable/Disable Service button, correspondingly. Moreover,
the xinetd service must be running to perform any such action; otherwise, the operation will
result in an error. You cannot manage the autostart feature of xinetd-dependent services,
as its value is inherited from the xinetd service.
47
Page 48

Managing Container Services and Processes
Managing Services in Windows
The System Services page is displayed when clicking on the System Services link on
the Parallels Power Panel main menu. It presents the table reflecting those services inside
your Container that you can manage. The table provides the following information:
Column Name Description
Name The name of the service running inside your Container.
Status Indicates whether the service is running or not.
Startup Type Indicates whether:
• The service is started automatically on the Container startup;
• The startup type of the service is set to SERVICE_DISABLED.
Logon as
Indicates the user account (the LocalService account, the
NetworkService account, etc.) that was used to start the service.
You can perform the following operations on any service in the table:
• Stop the service by selecting its checkbox and clicking on the Stop button. Only running
services are subject to this action.
• Restart the service by selecting its checkbox and clicking Restart. Only running services
are subject to this action.
• Start the service by selecting its checkbox and clicking on the Start button. Only stopped
services are subject to this action.
• Open the Services Details page to enable/disable the autostart feature by clicking on the
name of the service in the Name column.
To facilitate working with Container services, you may have the System Services table
display only those services that have a particular name, startup type (automatic, manual,
disabled), are in a certain state (running or stopped), or were started by a certain user. On top
of the table, press the Show Search link to display the fields where you can specify the
parameters your services should meet; then click on the Search link. To view all the services
currently running inside your Container, click on the Show All link to the right of the
parameter fields.
48
Page 49

Managing Container Services and Processes
Viewing Service Details
The Service Management page opened on clicking the name of the service you have
selected on the System Services page allows you to change the startup type of your
Container services:
• Make a service automatically start on the Container startup by selecting Automatic in the
drop-down list of the Startup Type field and clicking on the Submit button.
• Set a service as "manual" meaning that you should start the service manually before it
can be loaded by the operating system and made available for use. To this effect, select
Manual and click on the Submit button.
• Disable a service by selecting Disabled in the drop-down list and clicking on the Submit
button.
Note: Changing the default service settings might prevent key services from running correctly. It is
especially important to use caution when changing the startup type of services that are configured
to start automatically.
In the Dependencies section you can find out what system components depend on the
selected service. You can also view the system components your service depends on, if
there are any. You should always take into account the service dependencies before
changing its settings. This information is very important since if a service is stopped or is not
functioning properly, the dependent services may also be affected.
49
Page 50

Managing Container Services and Processes
Managing Container Processes
The System Processes page is displayed when clicking the Service > System Processes
link. It presents a table reflecting all the running processes inside the Container. The table
provides the following information:
Column Name Description
PID The process ID.
%CPU The percent of the CPU time the process is currently using.
%MEM
Command The command that is used to launch the process.
Nice
Pri The absolute priority of the process assigned to it by the process scheduler. On a Linux
RSS (Resident Segment Size) The size of physical memory the process really uses (in
Stat
Time The total amount of the CPU time the process has used so far.
User The user the process belongs to.
The percent of the RAM size the process is currently using.
The relative priority of the process assigned to it by the user. The negative values mean
that the user has manually increased the priority, the positive values - that they have
decreased it.
physical server, the range is from 0 (the highest priority) to 39 (the lowest priority). The
usual process priority is 30. On a Windows physical server, the range can be from 0
(the highest priority) to 31 (the lowest priority). The usual process priority is 8.
Kilobytes).
The state of the process. The possible states are: R - runnable, on the run queue; S sleeping; T - traced or stopped; D - uninterruptable sleep; Z - defunct, "zombie". If two
letters are shown, the second letter means the following: W - has no resident pages; <
- high-priority process; N - low-priority task; L - has pages locked in memory; s - the
process is a session leader; "+" means the process is in the foreground process group
of its control terminal.
To have the information in the table refreshed automatically with the current values, click the
Enable Autorefresh button. It is worthy to note that only the table on the current page is
refreshed, which takes much less resources in comparison with refreshing the whole Parallels
Virtual Automation page.
Note: The table is available only for a running Container. If the table cannot be accessed, Power
Panel suggests possible actions.
On a Windows physical server, you may select any number of processes by ticking the
check boxes against the corresponding processes (tick the uppermost check box to select
all the processes at once) and end them by clicking the End Process button.
50
Page 51

Managing Container Services and Processes
On a Linux physical server, you may select any number of processes by ticking the check
boxes against the corresponding processes (tick the uppermost check box to select all the
processes at once) and send them a standard signal. Choose the needed signal on the dropdown menu and click the Send Signal button. The following signals can be sent:
• SIGHUP - is a hang-up signal. It is often used to ask a daemon process to re-read its
configuration.
• SIGTERM - sends the termination signal to the process. This is the best way to give the
process a chance for an orderly shutdown and proper data saving. As the process might
be able to catch this signal and stay alive, you may have to make use of the sigkill or
sigint signals.
• SIGCONT - continues the process causing it to resume.
• SIGSTOP - stops (suspends) the process. The process will still be on the task list.
• SIGINT - causes the process to immediately interrupt. The signal is very close to
sigkill, the difference being that, unlike sigkill, it can be caught by the process
and ignored if the process gets out of hand. In this case you should send sigkill to
shut down the process.
• SIGKILL - unconditionally kills the process. Mind that sending sigkill to any process
removes any chance for it to do a tidy cleanup and shutdown, which might have
unfortunate consequences.
51
Page 52

Managing Container Services and Processes
Managing Container Firewall
A firewall is part of your OS and its security. Its main function is to block or permit traffic
between two systems or two parts of a network. The Virtuozzo Containers software has a
built-in firewall that can be managed through both Parallels Power Panel and Parallels Virtual
Automation. Along with - and apart from - the Parallels Power Panel and Parallels Virtual
Automation web interface, the command line is an effective tool to manage a firewall. Here
are the basic principles that make a firewall work.
A firewall applies a control policy over the firewalled system. There are three policies:
• accept the packet: if the packet is accepted, it gains access to the system;
• drop the packet: if the policy is to drop the packet, the packet is denied access to the
system;
• reject the packet: the system does not let the packet in, notifying the sender of the fact;
You can set one of the three policies when creating (p. 60) or editing (p. 60) an access rule in
the advanced mode.
The policies, along with ports and protocols, are chains' attributes. A chain is a list (or a
chain) of rules grouped by the criterion of what type of packets they process. There are three
packets types:
• input;
• output;
• forward.
Therefore we can create three chains - the Input chain, the Output chain and the Forward
chain. The Input chain examines the incoming packets. If there is a rule to process a packet,
the latter is either let in (accept policy) or not (drop/reject policy). Otherwise, the packet is
examined by the next rule. If, finally, there is not any rule to match, the default system policy
is applied. The first rule applied to a packet is the first one on the list that forms a chain.
If a packet is created inside the system, it is sent to the Output chain.
Packets that pass through the system, traverse the Forward chain.
When configuring a firewall, you can change a rule's position on the list, delete a rule from the
list, create, edit and add rules to the list.
To configure the firewall, click on the Firewall link on the Container dashboard.
52
Page 53

Managing Container Services and Processes
Selecting Mode
If you have only just started using the firewall by clicking the Firewall link on the Container
dashboard, the Firewall Setup page is the first one you have displayed.
On the Firewall Setup page, you can choose one of the following modes your firewall
operates in:
• The normal mode. If the security strategy you are planning out does not require a
complicated system of specific rules and all you are going to do is as simple as providing
your system with access to the Internet and the maximum safety, then the best option is
the normal mode. Hence, select the normal mode to configure your firewall using the 8
built-in access rules (p. 54) or to fix the firewall rules settings corrupted either in the
advanced mode or in the normal mode.
• The advanced firewall mode with default policy Accept, or the advanced firewall mode
with default policy Drop. The advanced mode takes more time and experience to
configure, but then there is more flexibility and potential in it to make use of.
Besides, the Firewall Setup page can be reached with the Firewall Setup link from both
advanced and normal mode pages. If so, the choice is quite the same. The only difference is
that in this case the normal mode can also be used as an option if you want to roll back the
changes in the firewall rule(s) settings you have made.
After selecting a mode, click Submit. Click Cancel to return to the previous screen.
53
Page 54

Managing Container Services and Processes
Configuring Firewall in Normal Mode
In the normal mode, the rules you delete or add are called access rules. The Container
access rules are pre-set groups of standard firewall rules. Each access rule refers to a most
widely used service and corresponds to a number of standard firewall rules that ensure the
availability of this service. In the normal mode, each access rule is dealt with as a single
entity. This implies that enabling or disabling an access rule results in enabling or disabling all
the standard firewall rules it corresponds to. By default, 8 preset access rules are active:
1 Access to outer world;
2 DNS server;
3 Internal Services;
4 Mail server;
5 Plesk service;
6 POP3 server;
7 SSH server;
8 WEB server.
The remaining access rules that are not enabled by default can be added on the page, which
you can access by clicking Add Access Rule.
To delete a rule, select one of the check boxes on the right of the screen, click Delete over
the check boxes, and then OK to confirm. To delete all the rules, select the uppermost check
box, click Delete over the check boxes, and then OK to confirm. Note that no access rules
can be permanently deleted from the system. A deleted rule is, in fact, temporarily disabled
and can be enabled back as described on the Adding Access Rule in Normal Mode
subsection (p. 55).
To change the mode, click Firewall Setup.
Note: If this page informs you that you cannot manage firewall on this Container, refer to the
Dealing With Misconfigured Firewall subsection (p. 55).
54
Page 55

Managing Container Services and Processes
Dealing With Misconfigured Firewall
If your firewall has not been configured yet, you will most probably have the page informing
you of the fact. The page can also appear if you did misconfigure your firewall. The common
way to misconfigure a firewall is to add or edit your own specific rules in the advanced mode
and then switch to the normal mode without deleting these rules first.
At this point you will have to decide upon one of two basic strategies: to select the normal
mode or to select the advanced mode:
• select the normal mode to deny all services except those critical to connecting to the
Internet. To select the normal mode, click Switch the firewall back to the normal
mode.
• select the advanced mode to create a rule to permit, deny, or monitor the access to
or from the system for each service you need. If you are going to separately edit each
rule, click Select the advanced firewall mode.
Adding Access Rule in Normal Mode
To open this page, follow the Add Access Rule link on the Firewall page. Here you have
the rules that have not been included into the list of active rules you can see on the Firewall
page. To add a rule here means actually to enable it. To add a rule, select a check box on the
opposite and click Submit - or Cancel if you want to restore the firewall settings prior to the
last action.
55
Page 56

Managing Container Services and Processes
Building Input Chain
To build and edit the Input Chain, select the Input tab. When you click either Advanced
firewall mode with default policy Accept or Advanced firewall mode with default policy
Drop, on the page described in the Selecting mode subsection (p. 53), the first chain of
rules is the Input Chain. The Input Chain is a set of rules for the incoming traffic. If you once
applied Normal firewall mode before selecting Advanced firewall mode with default
policy Accept/Drop, the input chain consists of 13 default rules. If you selected Advanced
firewall mode with default policy Accept/Drop while configuring the Container firewall at
the first time, the input chain has the default system policy access rule only.
Here you can edit, add, delete, enable, disable, filter or change its position in the list of any of
the default rules. In case you need to come back to the original advanced mode settings, the
default rules are:
1 Web server input;
2 SSH server input;
3 Mail server input;
4 POP3 server input;
5 DNS server tcp input;
6 DNS server udp input;
7 All tcp input for hi port allowed;
8 All udp input for hi port allowed;
9 Plesk Panel proxy input;
10 Plesk Panel direct input;
11 Loopback tcp input;
12 Loopback udp input;
13 Default system policy.
Note: If, for some reason, you need to have this rule set back, click Firewall setup and select the
Normal firewall mode radio button.
The table below describes the attributes of the rules in the chain:
Name Description
Name The name of a specific web service this rule applies to.
Policy One of three policies: Accept, Drop or Reject (p. 52).
Protocol One of two protocols used for package transmission - Transmission Control
Protocol (TCP), defined by IETF RFC793 or User Datagram Protocol (UDP),
defined by IETF RFC768.
56
Page 57

Managing Container Services and Processes
Source Address The internal address of the packets (e.g.: IPv4 or IPv6 address, the name of a
network interface, etc.).
Source Port The internal port of the packets.
Destination Address The address where the packets are sent to.
Destination Port The port where the packets are sent to.
Enabled The current status of the rule (Enabled/Disabled). The green circle with a tick
stands for "enabled", the red circle with a cross stands for "disabled".
Move Moving the rule a level up or a level down from its current position.
The default system policy access rule cannot be changed as this rule decides the packet's
destiny - to accept or to drop - when the packet has not any other rule to be processed by.
To edit a rule, click its name in the Name column. To add - or replace - a specific rule, click
New Rule. To disable, enable or delete a rule, select its check box and then click Disable,
Enable or Delete. To move a rule a level up, click
. To move a rule a level down, click .
To filter rules by the policy, the protocol, or the current status, click the Show Search link.
You can have Parallels Virtual Automation display only those parameters you need at the
moment. To show or hide certain columns, click the Select Columns link and select the
parameters you want to be displayed or clear those you do not.
You can also switch to the normal mode by clicking Firewall setup and selecting normal
mode there.
57
Page 58

Managing Container Services and Processes
Building Output Chain
To build and edit the Output Chain, select the Output tab. The output chain regulates the
outbound access. If you once applied Normal firewall mode before selecting Advanced
firewall mode with default policy Accept/Drop, the output chain consists of 13 default
rules. If you selected Advanced firewall mode with default policy Accept/Drop while
configuring the Container firewall at the first time, the output chain has the default system
policy access rule only.
The default rules list is the same as in the Input Chain (p. 56), the only difference being the
output, instead of the input characteristic of the rules. The list of rules on this page is this:
1 Web server output;
2 SSH server output;
3 Mail server output;
4 POP3 server output;
5 DNS server tcp output;
6 DNS server udp output;
7 All tcp output allowed;
8 All udp output allowed;
9 Plesk Panel proxy output;
10 Plesk Panel direct output;
11 Loopback tcp output;
12 Loopback udp output;
13 Default system policy.
The default system policy access rule cannot be changed as this rule decides the packet's
destiny - to accept or to drop - when the packet has not any other rule to be processed by.
If, for some reason, you need to have this rule set back, click Firewall setup and select the
Normal firewall mode radio button.
The attributes of the rules in the chain are described on the Building Input Chain subsection
(p. 56).
58
Page 59

Managing Container Services and Processes
Here you can edit, add, delete, enable, disable, filter or move in the list any or all of the 13
default rules the output chain consists of. To edit a rule, click its name in the name column.
To add a specific rule, click New Rule in the Actions group. To disable, enable or delete a
rule select its check box and then click Disable, Enable or Delete. To move a rule a level up,
click
. To move a rule a level down, click . To filter rules by the policy, the protocol, or the
current status, click the Show Search link. You can have Parallels Virtual Automation display
only those parameters you need at the moment. To show or hide certain columns, click the
Select Columns link and select the parameters you want to be displayed or clear those you
do not.
You can also switch to the normal mode by clicking Firewall Setup and selecting normal
mode there.
Building Forward Chain
To build and edit the Forward chain, select the Forward tab. Unlike the Input and Output
chains, the only default rule the forward chain has is Default system policy. Conceivably,
this one is not to be edited or deleted. Instead, you are free to decide upon any number and
kinds of specific rules to create and add to the Forward chain by clicking on the New Rule
link in the Actions group.
After the number of rules in your Forward chain becomes bigger, you may need to sort them
out. To do that, click the Show Search link and pick the three possible values from the three
drop-down menus: the policy, the port, and the current status of the rule(s). You can have
Parallels Virtual Automation display only those parameters you need at the moment. To show
or hide certain columns, click the Select Columns link and select the parameters you want
to be displayed or clear those you do not. Click
in the chain, or
to relocate it a level down. If two or more rules can be applied to the given
to take a rule a level up its current position
packet, the uppermost rule takes priority.
The attributes of the rules in the chain are described on the Building Input Chain subsection
(p. 56).
To switch to the normal mode of managing the firewall, click Firewall Setup link in the
Actions group.
The default forward chain policy is the policy selected on the Firewall Setup (p. 53) menu.
59
Page 60

Managing Container Services and Processes
Adding Rule in Advanced Mode
To get to this page, click the Add Rule icon on the Input Chain (p. 56), Output Chain (p.
58), or Forward Chain (p. 59) pages. On this page, you can elaborate your own specific rule.
Below are the basics of the advanced mode rules adding:
• the Name field is marked because this field is an obligatory one;
• select one of three policies: Accept, Drop or Reject;
• select one of two protocols for package transmission - Transmission Control Protocol
(TCP), defined by IETF RFC793 or User Datagram Protocol (UDP), defined by IETF
RFC768.
• Source Address and Netmask, Source Port or Port Range, Destination Address and
Netmask and Destination Port or Port Range fields are left to your own discretion, but
in case of an error there is a pink stripe over the field that has to be corrected;
• the standard format for Source/Destination Address and Netmask field is
1.2.3.4/255.255.23.4;
• the standard Port range format is 80-123;
• to enable a rule, select the Enable check box;
• if you are creating this rule for future purposes, clear this box;
• to include the rule into one of three chains, select Input, Output, or Forward on the drop-
down menu;
• on the The rule's position in the chain drop-down menu you are to decide what priority
this rule will have in its chain. There are two options for you to choose between: the
bottom and the top of the chain;
• for the changes you have made to become operational, click Submit, to undo the
changes and return to the previous page, click Cancel.
Editing Rule in Advanced Mode
The main difference here from the operations described in the Adding Rule in Advanced
Mode subsection (p. 60) is that the rules you edit are not those you create as you deem it
expedient. If you edit a rule (with the exception of renaming it), the rule changes and works
differently from the way it did. Before submitting the new settings make sure they meet your
security strategy. Otherwise, click Cancel.
The other detail to be aware of is the possible consequences of changing the initial (default)
firewall settings. If you feel your expertise in the security area permits some future
development, do not change them at all. Applying the changes you are not completely
certain of may decrease your system's security.
60
Page 61

Managing Container Services and Processes
Control Panels for Containers
To manage the Container, you can use the following control panels:
• Plesk Control Panel (p. 61)
• Confixx Control Panel (p. 64)
• SSH connection (p. 65)
• Remote Desktop connection (p. 67)
Managing Plesk Control Panel
There are a number of control panels that can be installed on the physical server in the form
of templates and added to any Container hosted on that physical server. Among such control
panels are Plesk,
The Control Panels menu provides a single place for managing all these control panels in
this particular Container. It goes without saying that the control panel template must be
installed on the Node for the panel to be manageable on this screen.
Sitebuilder, and Confixx.
Tip. If the Control Panel menu does not exist in your Power Panel, it means that your provider
disabled logging in and managing other control panels from this Container.
The two major management operations that can be performed here are:
• adding the control panel template to the Container (the Install link), which ensures that
this Container can be managed by the given control panel.
• logging in to the control panel to begin managing the Container with its help (the Login
link). This is possible only if the control panel template has already been added to the
Container.
Note: In the case of the Plesk control panel, the Login link is called Manage and leads to the
screen where you can not only log in to Plesk but also change the Plesk admin password.
61
Page 62

Managing Container Services and Processes
Installing Plesk
The Install Plesk Control Panels page allows you to install the Plesk control panel in the
Container. This page can be accessed by clicking the Install link on the Control Panels
page, which is displayed if the Plesk template is not installed in the Container. If upon the
Container creation, you specified the Plesk template for Linux (the slm.plesk template) or
for Windows ( the plesk template), you won't need to install Plesk Control Panel and will be
able to log in and work with Plesk.
To install Plesk in a Container, just follow the instructions on the screen to complete the
installation. After you have successfully installed the Plesk Control Panel in the Container, the
Plesk Panel link becomes visible on the Parallels Power Panel menu. Follow this link to start
working in Plesk.
Note: For the Plesk installation to be possible, the Container should be running. Moreover, you
can install Plesk only if authorized to do so by your provider. If you have any problems initializing
the Plesk control panel auto install, seek your provider's help. Mind though that the Plesk auto
install denial may be due to the shortage in your Container resources. To check if this is the case,
you can go to the Viewing Resource Alerts Log page where you'll be informed in the Description
column which parameter has caused the auto install failure. You might have to consider the
possibility of killing some unnecessary memory-demanding process from the Container or ask the
Node administrator to allocate more resources as needed to run Plesk on your Container.
Bare in mind, that to install Plesk Control Panel in a Container, the physical server that hosts
the Container, should have the Plesk application templates installed. When choosing the type
of Plesk template, you should orient at the OS templates that are installed on this physical
server. To learn more information on how to upload OS templates and application templates
on the physical server and then install them in the Container, refer to the Parallels Virtual
Automation Administrator's Guide, the Managing Parallels Containers section.
Working in Plesk Control Panel
When the Plesk control panel is installed inside the Container, you can use the Login to
Plesk link on the Control Panels page to start a Plesk control panel session. A new browser
window with the Plesk control panel is launched and you are able to get straight down to
work there.
To change the Plesk admin password, click the Change Password link on the Plesk
Control Panel page. Setting a new password from time to time is recommended to assure
the maximum security of a Container.
62
Page 63

Managing Container Services and Processes
Changing Plesk Administrator Password
Although logging in to Plesk from Parallels Virtual Automation is performed automatically
and does not require specifying the credentials of the admin user, the Plesk admin user
name and password may be of use for a Parallels Power Panel user willing to directly log in to
the Container via Plesk (p. 13). To maintain the maximum security of the Container, it is
recommended to change occasionally the current password of the admin user. The Change
Plesk Admin Password page opened through the Change Password link on the Plesk
Control Panel page allows you to edit the administrator password.
To set a new password, you need to type it into the New admin password field and then
retype it in the Retype new admin password field below to ensure you have provided a
correct password. The password should be no less than 5 characters and difficult enough to
guess to guarantee the privacy of the Container.
After you have entered a new admin password, press Change to submit the changes made.
Note: If your Plesk version is lower than 7.0.2, the option of changing the admin password is not
provided for Parallels Virtual Automation.
Logging In to Plesk Control Panel
Using the Login to Plesk link on the Plesk control panel page you can open a pop-up
window to start managing the Container via Plesk.
In this window, you should open the Login to Plesk link to start a Plesk control panel
session. A new browser window with the Plesk control panel is launched and you are able to
get straight down to work there.
The logging in to Plesk is performed automatically, you do not need to enter the name and
password of the admin user since you have already been identified by your Parallels Virtual
Automation user credentials.
You might wish to change the Parallels Power Panel user Plesk admin password used to log
in to Parallels Power Panel via Plesk. The Change Plesk Admin Password page allows you
to change the current password of the admin user, which should be done from time to time
to maintain the maximum security of the Container.
Note: If your Plesk version is lower than 7.0.2, the option of changing the admin password is not
provided for Parallels Virtual Automation.
63
Page 64

Managing Container Services and Processes
Logging in to Confixx Control Panel
In case the Confixx control panel is installed inside a Container, the Confixx control panel
icon becomes visible on the Parallels Power Panel menu. You can click this icon to go to the
Confixx control panel login window.
In this window, you should enter your credentials (login and password) into the corresponding
fields and press the Login to Confixx button. You may learn the credentials from your
provider. In case the credentials entered are correct, a new browser window with Confixx
control panel is launched and you can get straight down to work there.
If you select the Save Login data check box, you won't have to type your login and
password again when you later visit this page - the credentials will be filled in automatically. In
this case, the credentials information is stored not on the server, but on the client side (i.e. on
the computer where your browser window is launched).
Note: The Confixx control panel with version below 3.0 is not supported.
64
Page 65

Managing Container Services and Processes
Using SSH to Connect to Container
You can use the Secure Shell (ssh) application to remotely connect to your Container and
work inside its directory tree using standard Linux command line tools. To connect to the
Container by ssh, you should make sure that:
1 You are launching Parallels Virtual Automation in Internet Explorer. SSH connection to the
Container is supported by other browsers only if you have a Java Virtual Machine on your
computer.
2 The Container is running. If it is not, start it on the Start/Stop Container page.
Note: If your Container is running the Windows Server 2003 operating system, please turn to the
Using Remote Desktop Connection to Access Container section (p. 67) to learn to manage
Containers by means of the Remote Desktop Connection application.
The SSH Connection window is opened upon clicking on the Terminal Login icon on the
Parallels Power Panel menu. You are presented with the Login and Password fields where
you should enter the relevant information (root or any other user name you might have
created for this Container and this user's password) to be passed to the ssh server inside
the Container.
After you have filled in these two fields, click the Login button. If you are doing this for the
first time, your browser may display a window like this asking you to install additional
components:
Figure 1: Installing Remote Desktop ActiveX Control
65
Page 66

Managing Container Services and Processes
Note: When connecting to your Container via SSH using a browser other than Internet Explorer,
this window does not appear. The SSH connection through browsers on the Mozilla engine is
provided by the Java technology.
Click Yes in this window and wait for the ssh terminal window to appear, whereupon you get
connected to the Container and may start sending commands to it via ssh.
66
Page 67

Managing Container Services and Processes
Using Remote Desktop Connection to Access Container
You can use Remote Desktop Connection - a standard Windows application - to connect
to the Container by means of the Remote Desktop Protocol (RDP). The feature is available
only for Internet Explorer. It is not supported by other browsers. To connect to the Container
via RDP, you should make sure that the Container is running. If it is not, start it.
Note: If you are managing a Linux-based Container, please turn to the Using SSH to Connect to
Container section (p. 65) to learn to manage the Container by means of Secure Shell.
The Remote Desktop window is opened upon clicking the Remote Desktop icon on the
Parallels Power Panel menu. You are presented with the Login button that you should click
to open a Remote Desktop session. If you are doing this for the first time, your browser may
display a window like this asking you to install additional components:
Figure 2: Installing Remote Desktop ActiveX Control
Click Yes in this window and wait for the Remote Desktop terminal window to appear,
whereupon you will be presented with the Login and Password fields. After entering the
necessary information (Administrator or any other user name you might have created for
this Container and this user's password) in the fields provided, click Enter to get connected
to the Container and start sending commands to it via Remote Desktop.
67
Page 68

Managing Virtual Machine Services and Processes
Managing Virtual Machine Services and
Processes
Viewing System Processes
On the System Processes screen, you can view the list of all the processes running in the
virtual machine and terminate any process or several processes. This screen is available if
you click the System Processes link on the Virtual Machine Services dashboard.
By default, 20 services are shown for each tab, but you may have more services displayed by
pressing the appropriate link on top of the table. You may also have the System Services
table display only those services that have a particular name or status. On top of the table,
press the Show Search link to display the fields where you can specify the name or the
status of the service you wish to view; then click on the Search link.
The table below shows the following information
Column Description
PID The process ID.
%CPU The volume of the CPU (in percentage) that is being
used by the process.
Command The name of the command associated with the running
process.
Pri
RSS The resident portion of shared memory that must stay in
Time The amount of the CPU time used by this command
The priority of the command. If the CPU time is not
enough for the execution of all running command, the
scheduler stat to execute them according to their
priority.
memory at all times (i.e. be resident). In kilobytes (KB).
when it is in the active state.
User The user who initiated the process.
68
Page 69

Managing Virtual Machine Services and Processes
%MEM
NICE
STAT
The memory value that is free.
The priority of the command.
The process state.
If you need to terminate a process or several processes, tick them and click the End
Process button above the table.
To refresh the table with the executed processes information, click the Enable Autorefresh
button.
Control Panels for Virtual Machines
You can manage the virtual machine through various means:
• VNC protocol for Windows and Linux virtual machines (p. 70)
• Remote Desktop connection for Windows virtual machines (p. 71)
• SSH connection for Linux virtual machines (p. 72)
69
Page 70

Managing Virtual Machine Services and Processes
Using VNC to Connect to Virtual Machine
Parallels Virtual Automation allows you to operate the virtual machine via Virtual Network
Computing (VNC). It is a graphical desktop sharing system which remotely controls another
computer. The connection via VNC becomes available if the Remote Display Service is
enabled.
You can enable this option during the virtual machine creation and configure it later in the
virtual machine General Settings screen.
With VNC console, you can connect to a virtual machine residing on a physical server with
Parallels Server Bare Metal software installed.
Note: To establish a remote connection to the virtual machine via VNC, you should have Sun
Java(TM) plugin/JRE installed.
On the virtual machine Console tab, you will see the virtual machine desktop displayed. A
number of additional buttons will help you to work with the virtual machine. These buttons are
described in detail in the following table:
Button Description
Install Tools Clicking this button will initiate the procedure of installing Parallels Tools in
the virtual machine. For the detailed instructions, refer to the Installing
Parallels Tools into Virtual Machine section.
Change CD/DVD ROM Clicking this button will lead you to the screen where you can view and
configure the CD/DVD-ROM image file of the Virtual Machine.
Refresh Display Clicking this button will update the displayed information.
Send Ctrl-Alt-Del
Detach Console Clicking this button will open the virtual machine remote display in a new
Click this button to send the Ctrl-Alt-Del combination to the virtual
machine OS. You can also send this combination by successive pressing
of the keys, if you click the Toggle Sticky Keys button.
browser window.
If you have another program for remote connection to the virtual machine, you can use it as
well. To establish the connection, you will need to specify the IP address of the virtual
machine.
When you create a virtual machine, you should define certain settings to be able to work wit it
remotely via VNC console. So, you should define the IPv4 or IPv6 address of the server
where the virtual machine is hosted and the port that will be used by the virtual machine. For
more information, you can refer to the instructions Creating Virtual Machine section or in
the Changing Virtual Machine Configuration section.
Note that you can easily redefine these settings after the virtual machine creation.
70
Page 71

Managing Virtual Machine Services and Processes
Using Remote Desktop
You can use Remote Desktop Connection - a standard Windows application - to connect
to the virtual machine by means of the Remote Desktop Protocol (RDP). The feature is
available only for Internet Explorer 5.0 or above. It is not supported by other browsers.
Note: If you are managing a Linux-based virtual machine, please turn to the SSH Connection to
Virtual Machine section (p. 72) to learn to manage the virtual machine by means of Secure Shell.
The Remote Desktop window is opened upon clicking on the Remote Desktop icon on the
virtual machine toolbar or dashboard. You are presented with the Login button that you
should click to open a Remote Desktop session. If you are doing this for the first time, your
browser may display a window like this asking you to install additional components:
Figure 3: Installing Remote Desktop ActiveX Control
Click Yes in this window and wait for the Remote Desktop terminal window to appear,
whereupon you will be presented with the Login and Password fields. After entering the
necessary information (Administrator or any other user name you might have created for
this virtual machine and this user's password) in the fields provided, click Enter to get
connected to the virtual machine and start sending commands to it via Remote Desktop.
71
Page 72

Managing Virtual Machine Services and Processes
SSH Connection to Virtual Machine
If you are managing a virtual machine with the Linux operating system installed, you can
use Secure Shell (ssh) to remotely connect to the virtual machine you are operating and work
inside its directory tree using standard Linux command line tools. To connect to the virtual
machine by ssh, you should make sure that you are launching Parallels Virtual Automation in
Internet Explorer 5.0 or above.
Note: If you are managing a virtual machine running Windows 2003 Server, please turn to the
Remote Desktop Connection to Virtual machine section (p. 71) to learn to manage the physical
server by means of the Remote Desktop Protocol.
The Terminal Login window is opened upon clicking on the Terminal Login icon on the
virtual machine toolbar or dashboard. You are presented with the Login and Password fields
where you should enter the relevant information (root or any other user name you might
have created for this virtual machine and this user's password) to be passed to the ssh
server inside the virtual machine.
After you have filled in these two fields, click the Login button. If you are doing this for the
first time, your browser may display a window like this asking you to install additional
components:
Figure 4: Installing Remote Desktop ActiveX Control
Note: When SSH-connecting to your virtual machine using a browser other than Internet Explorer,
this window does not appear. The SSH connection through browsers on the Mozilla engine is
provided by the Java technology.
72
Page 73

Managing Virtual Machine Services and Processes
Click Yes in this window and wait for the ssh terminal window to appear, whereupon you get
connected to the virtual machine and may start sending commands to it via ssh.
73
Page 74

Monitoring Operations and Viewing Logs
C HAPTER 5
Monitoring Operations and Viewing Logs
Parallels Power Panel is able to display four kinds of logs maintained for your virtual
environment:
• Status Changes. This log reflects such changes as starting, stopping, rebooting the
virtual environment, or mounting it in the repair mode. These changes may have been
invoked either through Parallels Power Panel or by other means.
• Resource Alerts. This log reflects those states of your virtual environment when it hits
limits on some hardware resource. To know more about resources, read the Resources
Overview section (p. 36).
• Task Log. This log reflects only those actions related to virtual environment management
that were performed by means of Parallels Power Panel.
• Traffic Log. This log allows you to display your network traffic statistics for a specified
period of time.
You may view all these logs by following the corresponding links from the Logs dashboard.
You can also monitor the Container operations that are either currently under way or have
already been completed by viewing:
Parallels Power Panel also provides specific information in case of an operation failure for you
to learn the error cause(s).
In This Chapter
Viewing History of Container Status Changes............................................................75
Viewing Alerts Log.....................................................................................................76
Viewing Traffic Log....................................................................................................77
Viewing Task Details .................................................................................................78
Viewing Error Details .................................................................................................79
Page 75

Monitoring Operations and Viewing Logs
Viewing History of Container Status Changes
The Status Changes page (accessible by clicking the Status Changes link on the Logs
dashboard) keeps track of all the changes in the status of the virtual environment. These
changes may happen due to the virtual environment routine management via Parallels Power
Panel, or due to the operation of some programs. The three-column table presents the time
when the virtual environment status changed, the old status of the virtual environment, and
the status obtained. By default, 20 records are shown, but you may have more records
displayed by clicking the appropriate link on top of the table. The description of all possible
virtual environment statuses is provided in the Virtual Environment Statuses section.
You may have the Status Changes table display only those log records that have a particular
date and time. On top of the table, click the Show Search link to display the fields where you
can specify the boundaries of the time interval for which you wish to view the log; then click
the Search link.
75
Page 76

Monitoring Operations and Viewing Logs
Viewing Alerts Log
Every time a virtual environment consumes more of a resource than is specified by the limit
on that resource, or is coming close to that limit, an alert is generated and logged. Turn to the
Resources Overview section (p. 36) to know more about the limits for corresponding
resources. You shall pay attention to the problem resource and correct the situation.
The alerts log is shown on the Resource Alerts page available on clicking the Resource
Alerts link on the Logs dashboard.
You may have the Resource Alerts table display only those alerts that have a particular date
or are generated for a definite resource parameter. On top of the table, click the Show
Search link to display the fields where you can specify the boundaries of the time interval or
the resource parameter for which you wish to view the log; then click on the Search link.
The Resource Alerts table provides you with the following data:
Time The date and time when the alert was generated.
Category One of the two alert categories: Resource (alert on a single virtual environment
resource consumption) or Group (alert on the whole Group's resource
consumption).
Details Detailed information on the alert.
Type The alert sign displays the type of alert for the virtual environment. See the
Resources Overview section for more details on the existing alert indicators.
Parameter The type of the virtual environment resource that required the consumption value
alert.
There are certain correspondencies between the alert zone indicators and the alert signs in
the Type column. A green circle with a white tick stands for the green zone, an orange circle
with a white exclamation mark points to the yellow zone, and a red circle with a white
exclamation mark refers to the red zone. Depending on the parameter under alert, you can
learn more about alert zones on the relevant resource type in the CPU Parameters, Memory
Parameters, or Disk Parameters subsections of the Resources Overview section (p. 36).
76
Page 77

Monitoring Operations and Viewing Logs
Viewing Traffic Log
The Traffic Usage page enables you to view the information on all incoming and outgoing
traffic for your virtual environment over a specified time period in the past. This page can be
accessed by clicking the Traffic Log link on the Parallels Power Panel main menu.
To display traffic statistics, you should perform the following operations:
1 In the Show traffic for field, specify the time span for which you wish to see your traffic
by selecting the corresponding duration unit on the drop-down menu. Depending on the
selected unit, the field to the right of the drop-down menu changes and offers you a list of
appropriate values to choose from. The duration units are listed below:
• Day: Click the calendar and specify the exact date (i.e. day, month, and year) for
which you wish to view your network traffic statistics.
• Month: Specify the month and year to display your traffic statistics for.
• Year: Specify the year to display your traffic statistics for.
• Period: Specify the period for which you wish to view your traffic statistics by
selecting the start and end dates on the calendar.
2 In the Traffic class field, specify the traffic accounting classes that will be displayed in the
table.
• All. This option includes all specifically created accounting classes and those traffics
that were not included into any class.
• Other. This option includes only those traffics that do not belong to any specific
accounting class.
• Specific accounting classes. Apart from the All and Other classes, the list shows
the classes created by you for specific needs. You can choose one concrete class to
be displayed in the table. You can create new and view the detailed on the already
existing ones by going to the hosting physical server and clicking the Network tab -->
Traffic subtab.
3 In the Traffic unit field, specify the unit of measurement your traffic statistics will be
displayed in.
4 Click on the Update button to display your traffic statistics for the specified period.
The results will be presented in the following table:
Column Name Description
<Period>
Denotes the specified period. The name of this column depends on the
duration unit selected in the Period field.
77
Page 78

Monitoring Operations and Viewing Logs
Incoming The input traffic statistics (in the selected unit of measurement) during
the specified period. This is the traffic that comes to the virtual
environment from the Internet (e.g. requests from Internet surfers' web
browsers to display a virtual environment website page).
Outgoing The amount of output traffic (in the selected unit of measurement) during
the specified period. This is the traffic that goes out of the virtual
environment to the Internet (e.g. the virtual environment website pages
sent to be displayed in the Internet surfers' web browsers).
The Total row at the bottom of the table summarizes all the incoming and outgoing network
traffic for the specified time span.
Viewing Task Details
The Task Details window is available by clicking the Details link beside any task, be it In
progress, Completed, or Failed.
The Task Details window serves for providing brief and most informative reference on the
operation. The upper table of the window provides you with the task's type, the name of the
virtual environment to which this task is applied, the physical server where the virtual
environment resides, the user who initiated the task, and finally, the task's status.
The lower table consists of the following columns:
Column Name Description
Time The time when a certain operation stage began.
Operation The corresponding utility message.
Status The status of each of the steps the operation the operation consists of- In
progress, Completed, or Failed.
Click Detach to have the message appear in a separated web-browser window.
Click Close to quit the window.
78
Page 79

Monitoring Operations and Viewing Logs
Viewing Error Details
The Error Details page provides specific information in case of an operation failure. When
you are trying to perform an operation and it fails, the corresponding page is refreshed with a
thick red line across the page informing you of the failure and providing the Details link to
learn more about this failure.
This page presents a complete response as to why the operation failed. This response might
help you understand the reason for the failure.
If an operation fails, and a green line is displayed informing that the operation has been
scheduled, it means that the failure occurred after the operation had been scheduled. That is
why it is desirable to always check the status of the scheduled operation by following the
Details link at the right end of the green line to make sure that the operation has been
successfully completed.
79
Page 80

C HAPTER 6
Troubleshooting
Parallels Virtual Automation is an indispensable means for solving various kinds of problems
related to the virtual environment functioning. It is still more flexible due to its ability to work
with not running virtual environments. The common groups of problems lending themselves
readily to be handled by Parallels Power Panel boil down to the following:
• Services inaccessibility;
• Elusive problems.
You can also consult the Network Problems section to try to find out why the virtual
environment is inaccessible by network, and the File Problems section.
Note: The problem situations described in this chapter mainly concern virtual environment with the
Linux operating system installed. However, it can be also of use for those managing the virtual
environments running Windows 2003 Server.
Troubleshooting
In This Chapter
Services Inaccessibility ............................................................................................. 81
Elusive Problems ...................................................................................................... 82
Login Problems ........................................................................................................ 83
File Problems............................................................................................................ 83
Page 81

Troubleshooting
Services Inaccessibility
Various tasks you are accustomed to perform by means of your virtual environment
(accessing your web site or sending email and the like) may fail if the corresponding services
are inaccessible.
Try consecutively the following three steps to determine the reason for this and do away with
it:
1 Check if your virtual environment is running. To this effect, log in to your virtual
environment and look at the status bar to determine if the virtual environment is running or
down. You can also check the status of your virtual environment on the Service
Unavailable screen by clicking the corresponding link provided on this screen. If the
virtual environment is down, click the Start/Stop Container link on the menu and click
the Start Container button. Wait a little for the virtual environment and all the services to
start.
2
Go to the Services page (p. 45) and check the status of the service in question. The
service must be running for the corresponding functionality to be accessible. For
example, psa and mysqld must be running for the Plesk control panel to handle your
requests, httpd - for your web site to function properly, sshd - for the virtual
environment to be accessible by ssh, sendmail - for you to be able to send email,
popa3d - to receive email by the POP3 protocol, etc. You may also try to stop the
iptables service to see if it solves the problem, because some iptables rules might
prevent certain network connections.
3 Go to the Resources page (p. 36) to determine if your virtual environment is short of any
resources. If some of the resources are marked in yellow or red, this is a hazardous
situation that should be resolved immediately.
If the Plesk control panel is installed inside your virtual environment and you are working with
this panel, the Service Unavailable screen may sometimes be displayed when you are trying
to perform this or that Plesk-related operation. This situation is normally handled as described
above. However, in case none of the recommended measures works, you may have to
reinstall the Plesk control panel into the virtual environment, as the Plesk installation might be
corrupted.
81
Page 82

Troubleshooting
Elusive Problems
Sometimes it is hard to determine the exact reason for a problem. The problem might persist
despite any actions undertaken. Such problems call for going back to an earlier state of the
virtual environment with these problems missing. This change-over is usually effected by
means of:
1 Restoring the Container from a working backup;
2 Reinstalling the Container (p. 28);
Note: It is for you to decide which way suits you most. Generally, these two options are
applicable if you can start your Container to copy the valuable information from it. To assure a
safe data saving in the situation where you cannot start the Container, repairing your Container is
the most advisable problem-solving option.
3 Mounting your Container in the repair mode and copying the valuable personal data to a
secure place outside the Container. Using the repair mode is covered in the Repairing
Container section (p. 30).
82
Page 83

Troubleshooting
Login Problems
Problem
Your Container is inaccessible by its hostname or IP address, or you cannot log in as
Administrator/root.
Possible Problems and Solutions
Problems with IP Address and Hostname
Solution 1. If you are using the hostname, try to use the IP address, and vice versa.
Solution 2. A Power Panel is able to connect to the PVA virtual environment using the virtual
environment real hostname or IP address. PVA scans the <virtual_server configuration and
the changes in its configuration due to the IP address. If you manually change the IP address
inside the virtual environment guest OS or renew it with DHCP, Power Panels fails to connect
to the virtual environment until the IP address is updated in the PVA infrastructure by your
provider.
Problems with Credentials
The login operation may fail due to the corrupted credential information. Ask your provider to
change the Administrator/root password for your virtual environment.
Problems with Parallels Tools
A Parallels virtual machine, to be managed via Power Panel, needs to have Parallels Tools
installed inside the guest OS. If Parallels Tools have not been installed, turn to your provider
with the corresponding request.
Problems with Ports
For a successful connection between PVA infrastructure and Power Panel, check that the
4643 port is open.
File Problems
Parallels Power Panel is tuned to not allow giant files to be uploaded to Containers. There is a
maximal file size (e.g. 512 Mb, but it may be any other value) allowed to be uploaded to a
Container. If you need to upload larger files to your Container, you should contact your
service provider.
83
Page 84

Index
Index
B
Backing Up and Restoring Container
backup details - 33
operations on backups - 31
C
Changing Container Password - 27
Confirming Container Reinstallation - 29
Confixx Control Panel
logging in - 64
Container Managing
accessing via RDP - 67
accessing via SSH - 65
backing up - 31
Confirming VE Reinstallation - 29
logging in - 13
rebooting - 21
reinstalling - 28
repairing - 30
restarting - 21
starting - 21
stopping - 21
Container Operations - 20
D
Directories Operations - See Folders
Operations
adding directories - See adding folders
copying directories - See copying folders
creating directories - See creating folder
editing directories properties - See editing
folder properties
moving directories - See moving folders
adding files - 26
copying files - 26
creating text file - 25
editing file properties - 27
editing text file - 25
moving files - 26
Firewall
access rules - 54
chains - 52
editing rules in advanced mode - 60
edting rules in normal mode - 54
general notions - 52
Folders Operations - 24
adding folders - See adding files
copying folders - 26
creating folder - 25
editing folder properties - 27
moving folders - 26
I
Installing Plesk - 62
Introduction - 6
L
Logging In to Confixx Control Panel - 64
Logging In to Container - 13
Logging In to Plesk Control Panel - 63
Logs
alerts log - 76
overview - 74
traffic log - 77
M
Mail - 81
E
Error Details - 79
F
Files Operations - 24
N
Network Problems - 83
O
Operations Monitoring
Page 85

error details - 79
general overview - 74
task details - 78
P
Password
changing root - 27
Plesk Control Panel
installing - 62
logging in - 63
Power Panel Interface Customizing - 17
Processes Managing - 50
R
Reinstalling Container - 28
Remote Desktop Connection - 67
Repairing Container - 30
Resources
monitoring - 36
monitoring resources - 36
Resources Alerts Log - 76
Restarting Container - 21
Index
S
Selecting Reinstallation Type - 29
Services
service details - 47
Services and Processes Managing - 43
Services Inaccessibility - 81
Signals - 50
SSH
connecting to Container - 65
Starting and Stopping Container - 21
T
Task Details Monitoring - 78
Traffic Log - 77
Troubleshooting - 80
W
Website - 81
 Loading...
Loading...