Novell ZENWORKS 10 Retirement Reference
Novell®
www.novell.com
AUTHORIZED DOCUMENTATION
Discovery, Deployment, and Retirement Reference
ZENworks® 10 Configuration Management SP3
novdocx (en) 16 April 2010
10.3
March 30, 2010
ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

Legal Notices
Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation, and
specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose.
Further, Novell, Inc., reserves the right to revise this publication and to make changes to its content, at any time,
without obligation to notify any person or entity of such revisions or changes.
Further, Novell, Inc., makes no representations or warranties with respect to any software, and specifically disclaims
any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc.,
reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to
notify any person or entity of such changes.
Any products or technical information provided under this Agreement may be subject to U.S. export controls and the
trade laws of other countries. You agree to comply with all export control regulations and to obtain any required
licenses or classification to export, re-export or import deliverables. You agree not to export or re-export to entities on
the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws.
You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. See the
Novell International Trade Services Web page (http://www.novell.com/info/exports/) for more information on
exporting Novell software. Novell assumes no responsibility for your failure to obtain any necessary export
approvals.
novdocx (en) 16 April 2010
Copyright © 2007-2010 Novell, Inc. All rights reserved. No part of this publication may be reproduced, photocopied,
stored on a retrieval system, or transmitted without the express written consent of the publisher.
Novell, Inc.
404 Wyman Street, Suite 500
Waltham, MA 02451
U.S.A.
www.novell.com
Online Documentation: To access the latest online documentation for this and other Novell products, see
the Novell Documentation Web page (http://www.novell.com/documentation).

Novell Trademarks
For Novell trademarks, see the Novell Trademark and Service Mark list (http://www.novell.com/company/legal/
trademarks/tmlist.html).
Third-Party Materials
All third-party trademarks are the property of their respective owners.
novdocx (en) 16 April 2010

novdocx (en) 16 April 2010
4 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

Contents
About This Guide 9
Part I Device Discovery 11
1 Basic Concepts 13
1.1 Discovery Methods. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
1.2 IP and LDAP Discovery Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
1.3 IP Discovery Technologies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
1.4 LDAP Discovery Technology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
1.5 Advertised Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
1.6 Discovered Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
1.7 Deployable Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
novdocx (en) 16 April 2010
2 Discovering Devices By Using IP Addresses 23
2.1 Configuring Discovery Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
2.2 Designating a Discovery and Deployment Proxy Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
2.3 Creating an IP Discovery Task. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
3 Discovering Devices in LDAP Directories 35
4 Importing Devices from CSV Files 41
5 Advertised Discovery 43
5.1 Configuring the Advertised Discovery Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
5.2 Discovering Advertised Devices. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
6 Viewing or Updating Device Details 47
Part II ZENworks Adaptive Agent Deployment 49
7 Basic Concepts 51
7.1 Deployment Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
7.2 Deployment Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
7.3 Adaptive Agent Versus Inventory-Only Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
8 Managing Deployment Packages 55
8.1 Package Types and Architectures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
8.2 Default System Packages Versus Custom Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
8.3 Customizing Packages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
8.4 Rebuilding Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
8.4.1 Rebuilding the Default Packages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Contents 5

8.4.2 Rebuilding the Custom Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
9 Registering Devices 61
9.1 What Happens During Registration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
9.2 Creating Registration Keys and Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
9.2.1 Creating a Registration Key. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
9.2.2 Creating a Registration Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
9.3 Modifying the Device Naming Template Used During Registration . . . . . . . . . . . . . . . . . . . . . 69
9.4 Enabling Dynamic Renaming of Devices During Registration . . . . . . . . . . . . . . . . . . . . . . . . . 70
9.4.1 Enabling the Setting at the Management Zone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
9.4.2 Enabling the Setting for a Device Folder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
9.5 Disabling the Use of Registration Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
9.6 Manually Registering a Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
9.6.1 Performing an Initial Registration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
9.6.2 Reregistering a Device with an Additional Registration Key . . . . . . . . . . . . . . . . . . . 74
9.7 Unregistering a Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
10 Deploying the ZENworks Adaptive Agent 77
novdocx (en) 16 April 2010
10.1 Coexisting with the ZENworks Desktop Management Agent . . . . . . . . . . . . . . . . . . . . . . . . . 77
10.2 Customizing the Agent Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
10.2.1 Customizing Features before Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
10.2.2 Customizing Features after Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
10.3 Changing the Target Installation Directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
10.4 Using a Task to Deploy the Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
10.4.1 Prerequisites for Deploying to a Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
10.4.2 Deploying to a Discovered Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
10.4.3 Deploying to a Non-Discovered Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
10.5 Manually Deploying the Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
10.6 Tasks to be Performed After Deploying the Agent on Citrix Servers . . . . . . . . . . . . . . . . . . . . 97
10.7 Uninstalling the Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
11 Deploying the ZENworks Adaptive Agent to Linux Devices 99
12 Deploying the Inventory-Only Module 101
12.1 Downloading the Module from a ZENworks Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
12.2 Installing on Linux/UNIX . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
12.3 Installing on NetWare . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
12.4 Installing on Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
12.5 Installing on Macintosh OS X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
6 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

Part III Device Removal and Retirement 107
13 Deleting Devices from Your ZENworks System 109
14 Retiring or Unretiring Devices 111
Part IV Appendixes 115
A Viewing the Predefined Reports 117
B Schedules 119
B.1 Now . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.2 No Schedule. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.3 Date Specific . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.3.1 Start Dates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.3.2 Run Event Every Year . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.3.3 Select When Schedule Execution Should Start. . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
B.3.4 Use Coordinated Universal Time (UTC) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
B.4 Recurring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
B.4.1 Days of the Week . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
B.4.2 Monthly . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
B.4.3 Fixed Interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
novdocx (en) 16 April 2010
C Configuring NMAP for ZENworks 123
D Troubleshooting Discovery, Deployment, and Retirement 125
E Documentation Updates 131
E.1 March 30, 2010: SP3 (10.3) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Contents 7

novdocx (en) 16 April 2010
8 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

About This Guide
novdocx (en) 16 April 2010
This Novell ZENworks 10 Configuration Management Discovery, Deployment, and Retirement
Reference helps you add devices to your ZENworks
ZENworks Adaptive Agent or Inventory Only Module to the devices. It also helps you install the
ZENworks Adaptive Agent to a Linux device in order to make the device a ZENworks Satellite.
The information in this guide is organized as follows:
Part I, “Device Discovery,” on page 11
Part II, “ZENworks Adaptive Agent Deployment,” on page 49
Part III, “Device Removal and Retirement,” on page 107
Part IV, “Appendixes,” on page 115
Audience
This guide is intended for anyone who will configure and manage a ZENworks system.
Feedback
We want to hear your comments and suggestions about this manual and the other documentation
included with this product. Please use the User Comments feature at the bottom of each page of the
online documentation, or go to the Novell
documentation/feedback.html) and enter your comments there.
®
Documentation Feedback site (http://www.novell.com/
®
Management Zone and then install the
Additional Documentation
ZENworks 10 Configuration Management is supported by other documentation (in both PDF and
HTML formats) that you can use to learn about and implement the product. For additional
documentation, see the ZENworks 10 Configuration Management documentation (http://
www.novell.com/documentation/zcm10/index.html).
Documentation Conventions
In Novell documentation, a greater-than symbol (>) is used to separate actions within a step and
items in a cross-reference path.
®
A trademark symbol (
trademark.
When a single pathname can be written with a backslash for some platforms or a forward slash for
other platforms, the pathname is presented with a backslash. Users of platforms that require a
forward slash, such as Linux*, should use forward slashes as required by your software.
, TM, etc.) denotes a Novell trademark. An asterisk (*) denotes a third-party
About This Guide 9

novdocx (en) 16 April 2010
10 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

I
Device Discovery
novdocx (en) 16 April 2010
The following sections provide information and instructions to help you add devices to your
®
ZENworks
database. After a device is added to the database, a ZENworks Server can
automatically deploy the ZENworks Adaptive Agent to the device.
Chapter 1, “Basic Concepts,” on page 13
Chapter 2, “Discovering Devices By Using IP Addresses,” on page 23
Chapter 3, “Discovering Devices in LDAP Directories,” on page 35
Chapter 4, “Importing Devices from CSV Files,” on page 41
Chapter 5, “Advertised Discovery,” on page 43
Chapter 6, “Viewing or Updating Device Details,” on page 47
Device DiscoveryI11

novdocx (en) 16 April 2010
12 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

1
Basic Concepts
novdocx (en) 16 April 2010
1
Device discovery is the process of adding workstation and server information to the Novell®
ZENworks
Adaptive Agent from a ZENworks Server to the devices. The following sections provide
information to help you understand the discovery terminology and concepts:
Section 1.1, “Discovery Methods,” on page 13
Section 1.2, “IP and LDAP Discovery Tasks,” on page 13
Section 1.3, “IP Discovery Technologies,” on page 13
Section 1.4, “LDAP Discovery Technology,” on page 19
Section 1.5, “Advertised Devices,” on page 19
Section 1.6, “Discovered Devices,” on page 19
Section 1.7, “Deployable Devices,” on page 21
®
database so that you can use that information to automatically deploy the ZENworks
1.1 Discovery Methods
There are four discovery methods you can use:
IP discovery: Use the ZENworks discovery engine to collect information about devices on
your network. The engine uses various protocols and standards (WMI, WinAPI, MAC Address,
NMAP, ZENworks, SNMP, SSH) to discover and collect information from devices that you
identify through IP address ranges.
LDAP directory discovery: Use the ZENworks discovery engine to search Novell
eDirectory
search and the filter to use for the search.
CSV import: Import device information from a comma-separated values (CSV) file. At the
minimum, the file must contain the IP address or DNS name for each device.
Advertised discovery: Use the ZENworks discovery engine to collect information about
devices that have the ZENworks preagent installed.
TM
or Microsoft* Active Directory* for device objects. You specify the contexts to
®
1.2 IP and LDAP Discovery Tasks
IP and LDAP discoveries are performed through discovery tasks. You create a discovery task in
ZENworks Control Center. LDAP discovery requires Novell eDirectory
Directory* to search for devices.
TM
or Microsoft* Active
1.3 IP Discovery Technologies
The ZENworks discovery engine can utilize a variety of different technologies for IP-based
discoveries. When more than one technology is used, the discovery engine initiates a discovery
request for each technology. This is done for each target IP address. For example, if you use MAC
Address, SNMP, and WMI, the discovery engine creates three requests for each target IP address.
Basic Concepts
13

The requests are queued and the discovery engine processes five requests at a time until no requests
remain. Five requests is the default. You can change the default if necessary (see Section 2.1,
“Configuring Discovery Settings,” on page 23) or override the settings in the discovery task.
Using fewer discovery technologies reduces the time required to complete the discovery task but
might also reduce the amount of information received.
By default, the MAC Address, SSH, WinAPI, and ZENworks technologies are enabled; the SNMP,
WMI, and NMAP technologies are disabled. You can change the default if necessary; see
Section 2.1, “Configuring Discovery Settings,” on page 23.
If more than one technology request returns information for a discovered device, the information is
merged together. In the case of conflicting information, the discovery process chooses the “best”
information. If a high priority discovery technology is successful and returns the information, then
the other lower priority discovery technologies are aborted for better performance. For example, if
WinAPI or WMI is successful, then MAC address and NMAP technologies are aborted.
IP discovery tasks require the following information:
The range of IP addresses for the devices you want discovered.
The credentials required for the SSH, WMI, WinAPI, and SNMP discovery technologies to
retrieve information from devices. The NMAP, MAC Address, and ZENworks technologies do
not require credentials.
Not all technologies use the same credentials, and all devices might not have the same
credentials, so you might need to specify multiple credentials to cover all targeted devices and
to utilize all discovery technologies. For example, WMI and WinAPI require Windows
credentials, and SNMP requires SNMP credentials.
The schedule for running the task. You can schedule it to run immediately or at a specified date
and time. Optionally, you can choose to not set a schedule, in which case the task is not run
until you manually initiate it or schedule a time.
The ZENworks Server that you want to run the task.
novdocx (en) 16 April 2010
14 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
The following table provides detailed information about the IP discovery technologies:
Table 1-1 IP Discovery Technologies
novdocx (en) 16 April 2010
IP Discovery
Technology
WMI
(Windows
Management
Instrumentation)
Functionality Requirements Prerequisites
WMI is the infrastructure
for management data
and operations on
Windows-based
operating systems.
Discovery issues a
remote request to the
WMI service on the
devices identified by the
IP-based discovery task
to obtain information.
Retrieves the OS type
and version, MAC
address, Network
Adapters, and CPU
details of the device.
For more information on
WMI, see the MSDN
Web site (http://
msdn.microsoft.com/enus/library/
aa384642(VS.85).aspx).
Because WMI is a
Windows-specific
technology, the
requests generated
from a ZENworks
Server running on
Linux must be routed
to a Windows Proxy
for processing. For
more information,
see Section 2.2,
“Designating a
Discovery and
Deployment Proxy
Server,” on page 26.
Microsoft Windows
Management Instrumentation
Service to be installed and
running on the target
Windows device.
Credentials of an
administrator account on the
target device should be
specified as Windows
credentials in the discovery
task. This is required for
connecting to the WMI
Service.
To authenticate by using the
Windows credentials, set the
value of the Network access:
Sharing and security model
for local accounts Local
Security setting to Classic local users authenticate as
themselves. For more
information on how to
configure the Local Security
settings, see “Enabling
Classic File Sharing” on
page 83.
Since the Remote WMI
connection establishes a
RPC connection with the
target Windows device, the
TCP ports 139 and 445 must
be allowed by the Windows
Firewall of the target device
for the WMI discovery
technology. For more
information on how to open
these ports, see “Enabling
File and Printer Sharing
through Windows Firewall” on
page 82.
Basic Concepts 15

novdocx (en) 16 April 2010
IP Discovery
Technology
WinAPI Issues a request to the
Functionality Requirements Prerequisites
registry on the devices
identified by the IP-based
discovery task to retrieve
the OS type and version,
and CPU details.
Because WinAPI is a
Windows-specific
technology, the
requests generated
from a ZENworks
Server running on
Linux must be routed
to a Windows Proxy
for processing. For
more information,
see Section 2.2,
“Designating a
Discovery and
Deployment Proxy
Server,” on page 26.
Microsoft Remote Registry
Service to be installed and
running on the target
Windows device.
Credentials of an
administrator account with
read privileges on the
Windows registry of the target
device should be specified as
Windows credentials in the
discovery task. This is
required for connecting to the
Remote Registry Service.
The File and Printer Sharing
for Microsoft Networks option
must be enabled. For more
information, see “Enabling
File and Printer Sharing for
Microsoft Networks” on
page 81.
To authenticate by using the
Windows credentials, set the
value of the Network access:
Sharing and security model
for local accounts Local
Security setting to Classic local users authenticate as
themselves. For more
information on how to
configure the Local Security
settings, see “Enabling
Classic File Sharing” on
page 83.
Since the Remote Registry
connection establishes a
RPC connection with the
target Windows device, the
TCP ports 139 and 445 must
be allowed by the Windows
Firewall of the target device.
For more information on how
to open these ports, see
“Enabling File and Printer
Sharing through Windows
Firewall” on page 82. If the
target device is in a different
subnet than the Windows
Proxy or the Primary server
running the task, then the
scope of the Firewall
exception should include
them.
16 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
novdocx (en) 16 April 2010
IP Discovery
Technology
MAC Address Retrieves the MAC
NMAP Uses NMAP (Network
Functionality Requirements Prerequisites
Address of the
discovered device. Uses
ping
and
arp
the
(Address Resolution
Protocol) commands to
map the IP addresses of
the devices identified by
the IP-based discovery
task to their associated
MAC addresses.
The MAC Address
discovery gets only the
MAC address of the
device and does not give
any OS information.
Mapper) to retrieve the
OS type and version
details of the devices
identified by the IP-based
discovery task.
IMPORTANT: NMAP has
certain known limitations.
For more information on
these limitations, see the
NMAP Web site (http://
www.nmap.org).
For the
successful, the target devices
must reside in the same
network as the ZENworks
Server that performs the
discovery request.
For the
successful, the incoming
ICMP echo requests (ping)
must be enabled on the
device, and the ICMP echo
requests and echo responses
must be allowed on the
network.
arp
command to be
ping
command to be
NMAP must be installed on
the ZENworks Server that is
processing the discovery
request.
NMAP is freely available from
InSecure.org (http://
www.insecure.org). For more
information on how to
configure NMAP for
ZENworks, see Appendix C,
“Configuring NMAP for
ZENworks,” on page 123.
Basic Concepts 17

novdocx (en) 16 April 2010
IP Discovery
Technology
ZENworks Issues a request to the
Functionality Requirements Prerequisites
ZENworks Adaptive
Agent or ZENworks
preagent on the devices
identified by the IP-based
discovery task. If the
device has the ZENworks
Adaptive Agent, the
agent responds with the
OS type and version,
MAC Address, Network
Adapters, CPU,
managed device GUID,
Management Zone
GUID, Management
Zone name, Adaptive
Agent version, disk
space, and memory
details. If the device has
the ZENworks preagent
installed, the preagent
responds with the OS
type, CPU, disk space,
memory, and the GUID
details that should be
used to register the
device in the
Management Zone.
The preagent is only installed
on OEM devices or on
devices whose registration
was removed from the zone.
SNMP Issues a request to the
SNMP service on the
devices identified by the
IP-based discovery task.
SNMP versions 2 and 1
are supported, with
SNMP version 2 tried
first. Retrieves the OS
type and version, MAC
address, Network
Adapters, and CPU
details.
Because the
discovery process
uses a Windowsbased SNMP
technology, requests
generated from a
ZENworks Server
running on Linux
must be routed to a
Windows Proxy for
processing. For more
information, see
Section 2.2,
“Designating a
Discovery and
Deployment Proxy
Server,” on page 26.
To query a device using
SNMP, the device must have
SNMP enabled.
The SNMP community string
must be specified as a SNMP
credential in the Discovery
Task.
SNMP uses the UDP Port
161. The firewall must be
configured to allow access
through this port.
18 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

novdocx (en) 16 April 2010
IP Discovery
Technology
SSH Uses the SSH protocol to
Functionality Requirements Prerequisites
To query a device using SSH,
communicate with the
SSH server on the
devices identified by the
IP-based discovery task.
Depending on the device
OS (Linux or NetWare),
the device retrieves the
OS type, OS or Kernel
version, CPU, Network
Adapters, and memory
details.
the device should have SSH
enabled, and the username
and password must be
specified as General or Linux
credentials in the Discovery
task.
1.4 LDAP Discovery Technology
For LDAP discoveries, the ZENworks discovery engine issues an LDAP request to the LDAP
server. The LDAP request contains the LDAP server name, LDAP port, credentials, the context or
group to search, and whether or not to recursively search subcontainers or subgroups.
Device objects that are found are queried for well-known attributes (dnsHostName,
OperatingSystem, wmNameDNS, wmNameOS, and so forth) to attempt to determine the OS
version and DNS name of the device. If the request specifies a recursive search, the context is
searched for well-known container objects. For each container object found, a new LDAP request is
created for the container object and appended to the search context of the current request.
LDAP discovery tasks require the following information:
The connection information (address and port) for the LDAP server.
The credentials required for reading information from the LDAP directory.
The directory contexts to search for devices.
The schedule for running the task. You can schedule it to run immediately or at a specified date
and time. Optionally, you can choose to not set a schedule, in which case the task is not run
until you manually initiate it or schedule a time.
The ZENworks Server that you want to run the task.
1.5 Advertised Devices
The ZENworks discovery engine allows you to discover devices that have the ZENworks preagent
installed, such as OEM devices or devices whose registration was removed from the Management
Zone. Only those devices that have the preagent installed respond to an advertised discovery;
devices that have the ZENworks Adaptive Agent do not respond to an advertised discovery.
1.6 Discovered Devices
As devices are discovered, they are added to the ZENworks database and listed in the appropriate
device type folder in the Discovered panel on the Discovered Devices page.
Basic Concepts 19
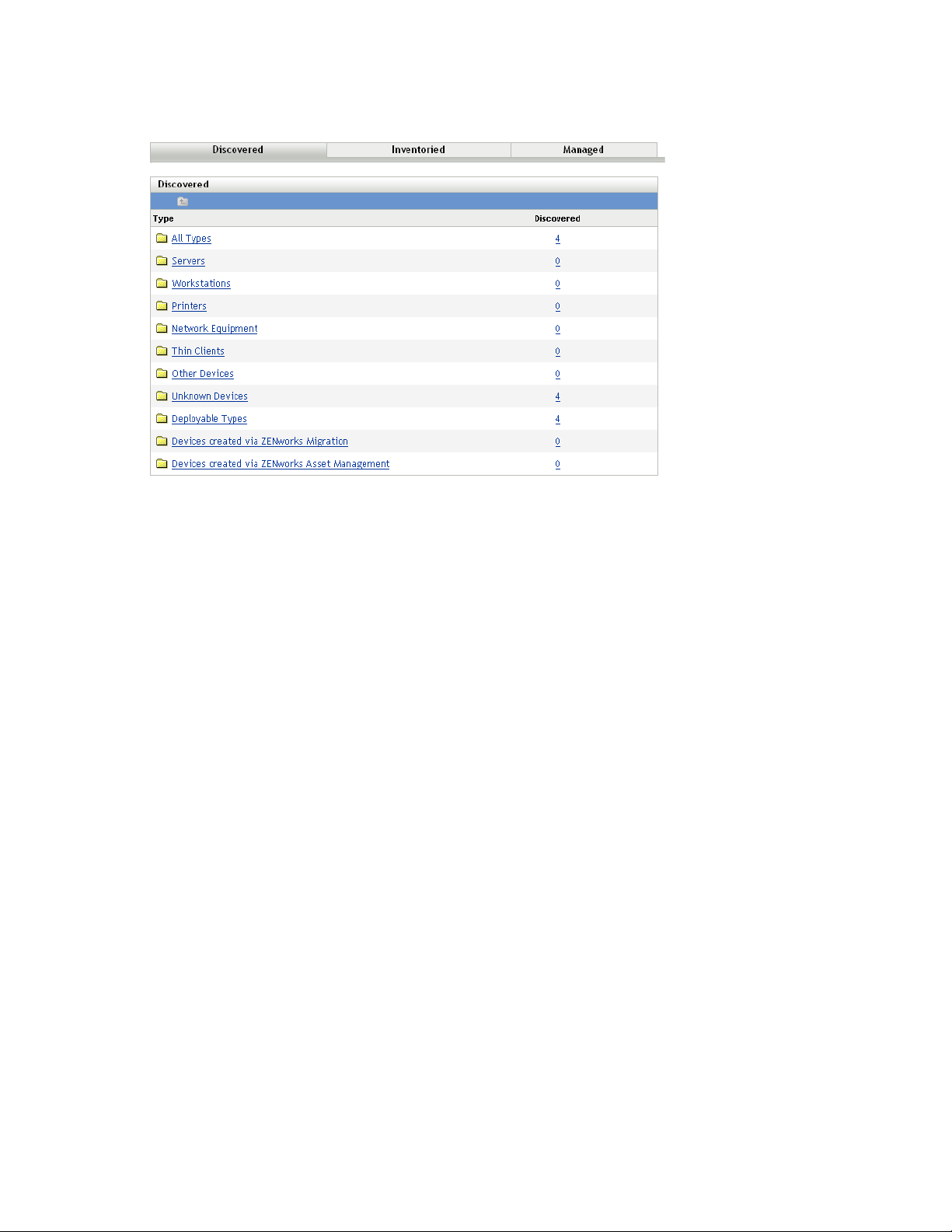
Figure 1-1 Discovered panel (Devices tab > Discovered page)
novdocx (en) 16 April 2010
Each discovered device is categorized by type.
All Types: All discovered devices, regardless of type.
Servers: All discovered devices that have been identified as servers.
Wor kstatio ns: All discovered devices that have been identified as workstations.
Printers: All discovered devices that have been identified as printers. ZENworks does not
manage printers; therefore, you cannot deploy the ZENworks Adaptive Agent to them.
Network Equipment: All discovered devices that have been identified as network equipment.
This incudes such devices as routers. ZENworks does not manage network equipment;
therefore, you cannot deploy the ZENworks Adaptive Agent to network equipment.
Thin Clients: All discovered devices that have been identified as thin clients.
Other Devices: All discovered devices that have been identified but don’t fit into one of the
other categories. This category includes devices that already have the ZENworks Adaptive
Agent installed.
Unknown Devices: All discovered devices whose operating system cannot be identified. The
devices might be listed as unknown because the firewall configuration of the device may block
the usage of discovery technologies, or invalid credentials are provided to the discovery
technology. You can deploy the ZENworks Adaptive Agent to these devices if you can
manually ensure that the agent is supported on these devices. For more information on list of
supported devices, see “Managed Device Requirements” in ZENworks 10 Configuration
Management Installation Guide.
Deployable Types: All discovered devices that have been identified as types to which you can
deploy the ZENworks Adaptive Agent.
Devices Created Via ZENworks Migration: All devices that were migrated from ZENworks
7 through the ZENworks Migration utility.
Devices Created Via ZENworks Asset Management: All devices that were migrated from
ZENworks Asset Management through the ZENworks Asset Management Migration utility.
20 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
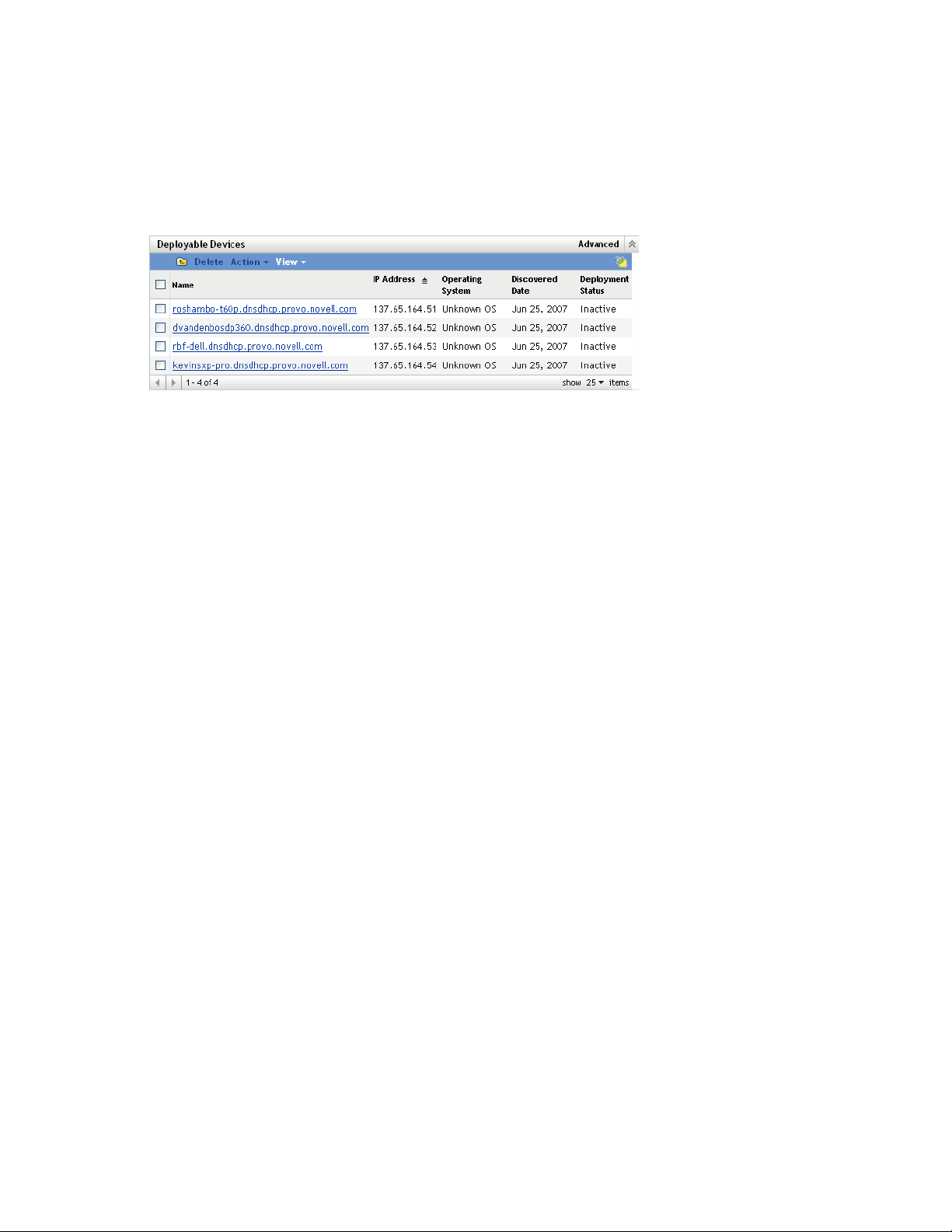
1.7 Deployable Devices
Devices that meet the requirements for the ZENworks Adaptive Agent are displayed in ZENworks
Control Center in the Deployable Devices panel on the Deployment page.
Figure 1-2 Deployable Devices panel (Deployment tab)
Using this panel, you can deploy the Adaptive Agent to devices, remove them from the ZENworks
database, or ignore them by filtering them out of the list.
novdocx (en) 16 April 2010
Basic Concepts 21

novdocx (en) 16 April 2010
22 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
2
Discovering Devices By Using IP
novdocx (en) 16 April 2010
Addresses
You can perform an IP-based discovery of your network to add devices to your ZENworks®
database. With an IP discovery, the ZENworks Server uses a set of technologies (WMI, WinAPI,
MAC Address, NMAP, ZENworks, SNMP, SSH) to discover as much information about the target
devices as possible. The target devices are determined by the IP address range you specify.
Section 2.1, “Configuring Discovery Settings,” on page 23
Section 2.2, “Designating a Discovery and Deployment Proxy Server,” on page 26
Section 2.3, “Creating an IP Discovery Task,” on page 27
2.1 Configuring Discovery Settings
IP discoveries use the following configuration settings that can be modified, if necessary:
Number of discoveries that can be processed concurrently (default is 5)
IP subnets or address ranges that are to be excluded from the discovery
Discovery technologies that are used (the default is LDAP, MAC Address, WinAPI,
ZENworks, and SSH)
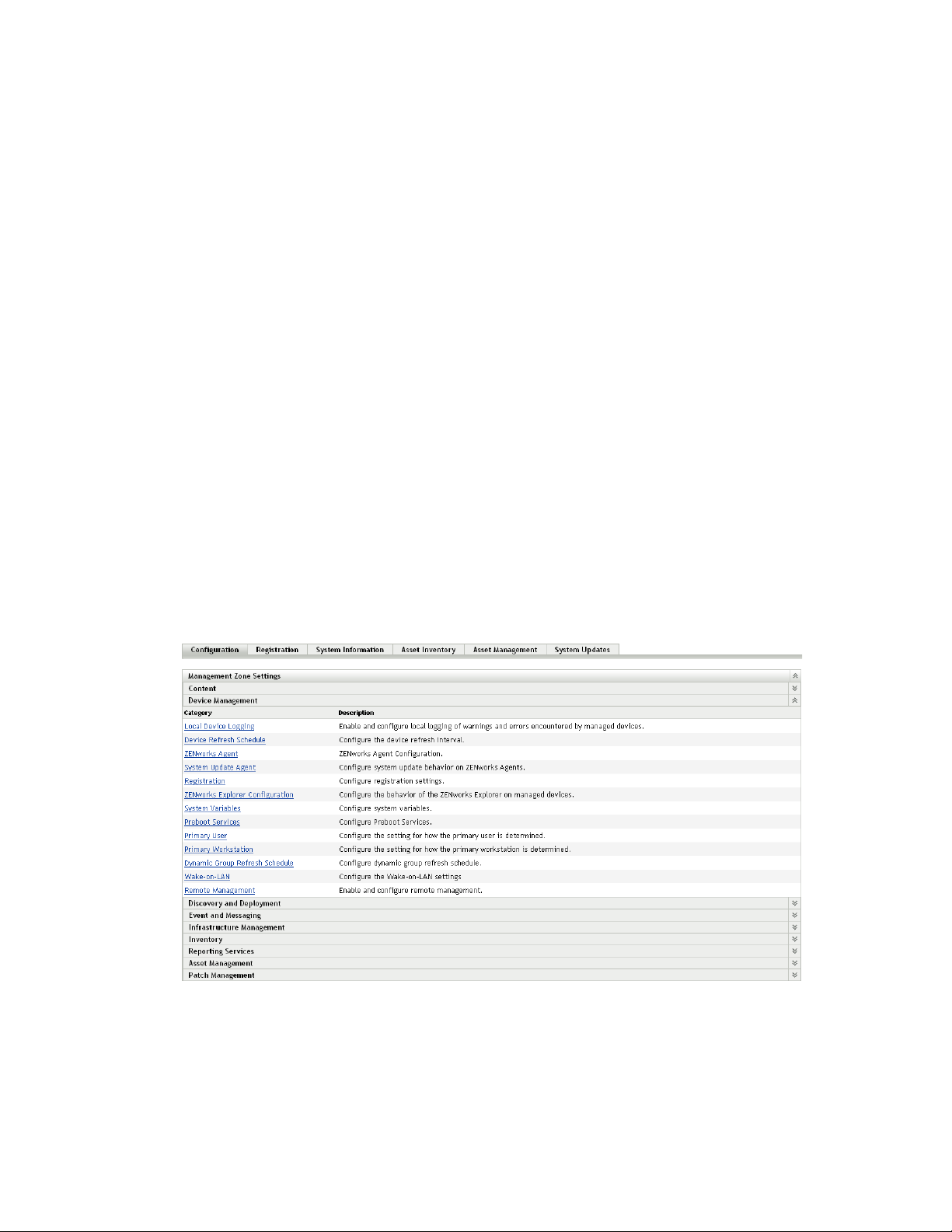
1 In ZENworks Control Center, click the Configuration tab.
2
2 In the Management Zone Settings panel, click Discovery and Deployment, then click the
Discovery option.
Discovering Devices By Using IP Addresses
23
novdocx (en) 16 April 2010
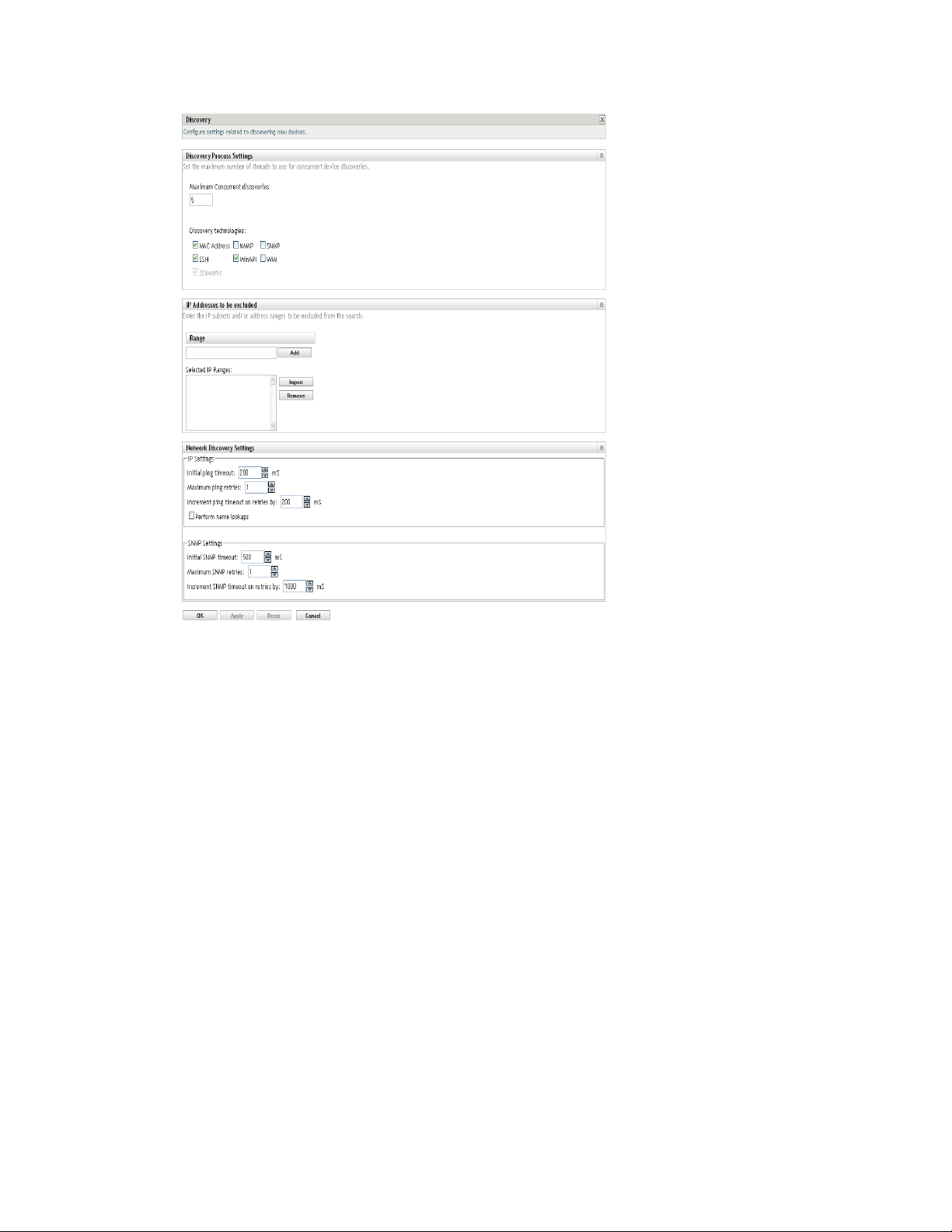
3 In the Discovery Process Settings panel, modify the following settings as necessary:
Maximum Concurrent Discoveries: A discovery task consists of one or more discovery
requests. For IP-based discovery tasks, a request is created for each discovery technology and
each IP address in the specified range. Therefore, if you use six technologies to discover 10 IP
addresses, 60 requests are created. For LDAP-based discovery tasks, a request is created for
each context or group to be searched.
You use this field to specify the maximum number of discovery requests that the ZENworks
Server can process at one time. A smaller number eases the traffic load on the network but
requires more time to complete the discovery task; you should use a smaller number if you
schedule discovery tasks during peak network load times. A larger number has the opposite
effect; heavier traffic load with less time to complete the task.
For more information on the IP discovery process, see Section 1.3, “IP Discovery
Technologies,” on page 13.
Discovery Technologies: The discovery process can utilize a variety of different technologies.
When more than one technology is used, the discovery process initiates a discovery request for
each technology, with all technology requests running simultaneously. This is done for each
target IP address. For example, if you use MAC Address, SNMP, and WMI, the discovery
process creates three requests for each target IP address. The requests are queued and run
according to the Maximum Concurrent Discoveries setting.
If more than one technology request returns information for a discovered device, the
information is merged together. In the case of conflicting information, the discovery process
chooses the “best” information.
24 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference

Using fewer discovery technologies reduces the time required to complete the discovery task
but might also reduce the amount of information received.
For detailed information about each technology, see Section 1.3, “IP Discovery Technologies,”
on page 13.
4 In the IP Addresses to be Excluded panel, specify the IP subnets or address ranges to be
excluded from the discovery.
NOTE: All the discovery tasks inherit the IP address ranges specified at the Management Zone
level. If the IP address range is specified at a task level, the combined ranges of the
Management Zone and discovery task are excluded from the discovery.
You can manually add the IP addresses to be excluded or import the IP addresses to be
excluded from a CSV file.
To manually add the IP address to be excluded:
1. In the Range field, enter the IP address range in one of the following formats:
xxx.xxx.xxx.xxx: Standard dotted-decimal notation for a single address. For
example,
123.45.167.100.
novdocx (en) 16 April 2010
xxx.xxx.xxx.xxx - xxx.xxx.xxx.xxx: Standard dotted-decimal notation for a range of
addresses. For example,
123.45.167.100 - 123.45.167.125
.
xxx.xxx.xxx.xxx/n: Standard CIDR (Classless Inter-Domain Routing) notation. With
CIDR, the dotted decimal portion of the IP address is interpreted as a 32-bit binary
number that has been broken into four 8-bit bytes. The number following the slash (/
n) is the prefix length, which is the number of shared initial bits, counting from the
left side of the address. The /n number can range from 0 to 32, with 8, 16, 24, and 32
being commonly used numbers. For example,
addresses that start with
123.45.167
. When you add the IP address range to the
123.45.167.100/24
matches all IP
Selected IP Ranges list (see the next step), it is automatically expanded to show the
range of addresses in dotted-decimal notation.
2. To add the IP address range to the Selected IP Ranges list, click Add.
To use a CSV list to import an IP address to be excluded:
1. In the Selected IP Ranges list, click Import.
The Import CSV File dialog box is displayed.
2. Click Browse to browse for and select a file that contains a comma-separated or
columnar list of IP addresses.
3. Click OK.
5 In the Network Discovery Settings panel, modify the following settings as necessary:
IP Settings: These settings apply when using the WMI and SNMP discovery technologies.
Initial ping timeout: Specifies how long the discovery technology waits for a response to
an ICMP query (ping).
Maximum ping retries: Specifies the number of times a ping is repeated before giving
up.
Increment ping timeout on retries by: Adds the specified amount of time to each retry.
For example, if the initial ping timeout is 200 milliseconds, the maximum ping retries is 3,
and the increment is 200 milliseconds, the first retry timeout is 400, the second retry
timeout is 600, and the third retry timeout is 800.
Discovering Devices By Using IP Addresses 25

Perform name lookups: Uses a reverse lookup to associate the target IP address with a
DNS name. Deselect this option if you do not want the DNS name discovered.
SNMP Settings: These settings apply when using the SNMP discovery technology.
Initial SNMP timeout: Specifies how long the discovery technology waits for a response
to an SNMP query before assuming that the packet is lost.
Maximum SNMP retries: Specifies the number of times an SNMP query is repeated
before giving up.
Increment SNMP timeout on retries by: Adds the specified amount of time to each
retry. For example, if the initial SNMP timeout is 500 milliseconds, the maximum SNMP
retries is 3, and the increment is 1000 milliseconds, the first retry timeout is 1500, the
second retry timeout is 2500, and the third retry timeout is 3500.
6 Click OK to save the changes.
2.2 Designating a Discovery and Deployment Proxy Server
ZENworks Servers running on Linux cannot perform discovery tasks that use Windows-specific
technologies such as WMI and WinAPI. Linux servers also cannot perform deployment of
ZENworks Adaptive Agents to Windows devices, as deployment uses Windows-specific
technologies. In order to enable the execution of discovery and deployment tasks by Linux
ZENworks Servers, you can designate a managed Windows device in your zone to function as a
discovery and deployment proxy server. The managed device can be either a Windows server or
workstation.
novdocx (en) 16 April 2010
When a Linux ZENworks Server receives a discovery task that includes Windows-specific
technologies, it processes the non-Windows discovery technologies and offloads the Windowsspecific technologies to the proxy. The proxy performs the discoveries and returns the results to the
Linux ZENworks Server. The deployment task is totally offloaded to the Windows Proxy.
If you have only Linux servers in your environment, you must first manually install ZENworks
Adaptive Agent on a Windows device by downloading the agent from
https://IP_address_of_the_ZENworks_Server/zenworks-setup
as a proxy for discovery and deployment tasks.
To designate a proxy:
1 In ZENworks Control Center, click the Configuration tab.
, then designate the device
26 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
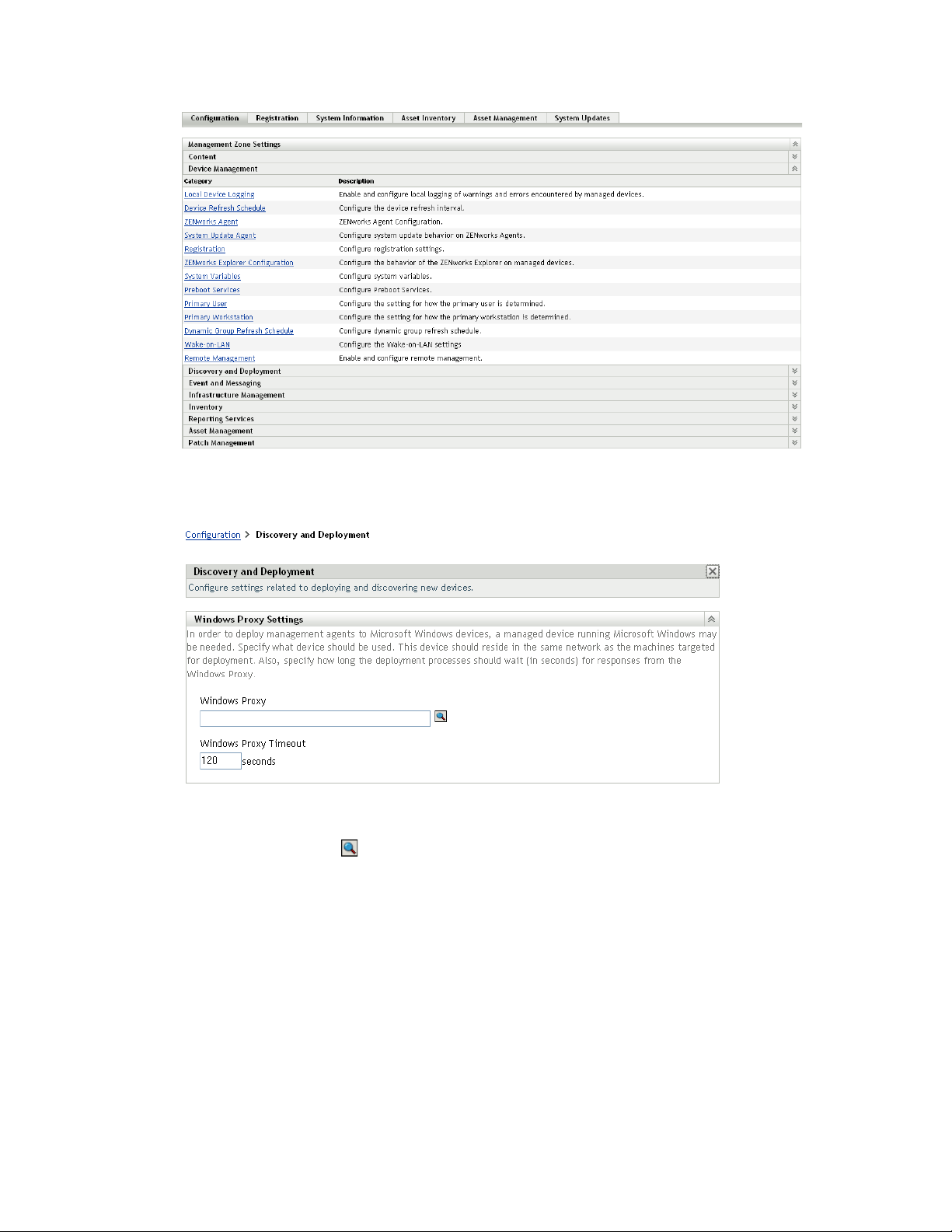
novdocx (en) 16 April 2010
2 In the Management Zone Settings panel, click Discovery and Deployment, then click the
Windows Proxy option.
3 Fill in the following fields:
Windows Proxy: Click to browse for and select the managed Windows device (server or
workstation) on which you want to perform discovery tasks on behalf of Linux-based
ZENworks Servers.
Windows Proxy Timeout: Specify the number of seconds you want the ZENworks Server to
wait for a response from the Windows Proxy. Any responses received after the specified
timeout period are discarded.
4 Click OK to save the changes.
2.3 Creating an IP Discovery Task
You use the Create New Discovery Task Wizard to create and schedule the tasks used by ZENworks
Servers to discover devices on your network and add them to the ZENworks database.
Discovering Devices By Using IP Addresses 27
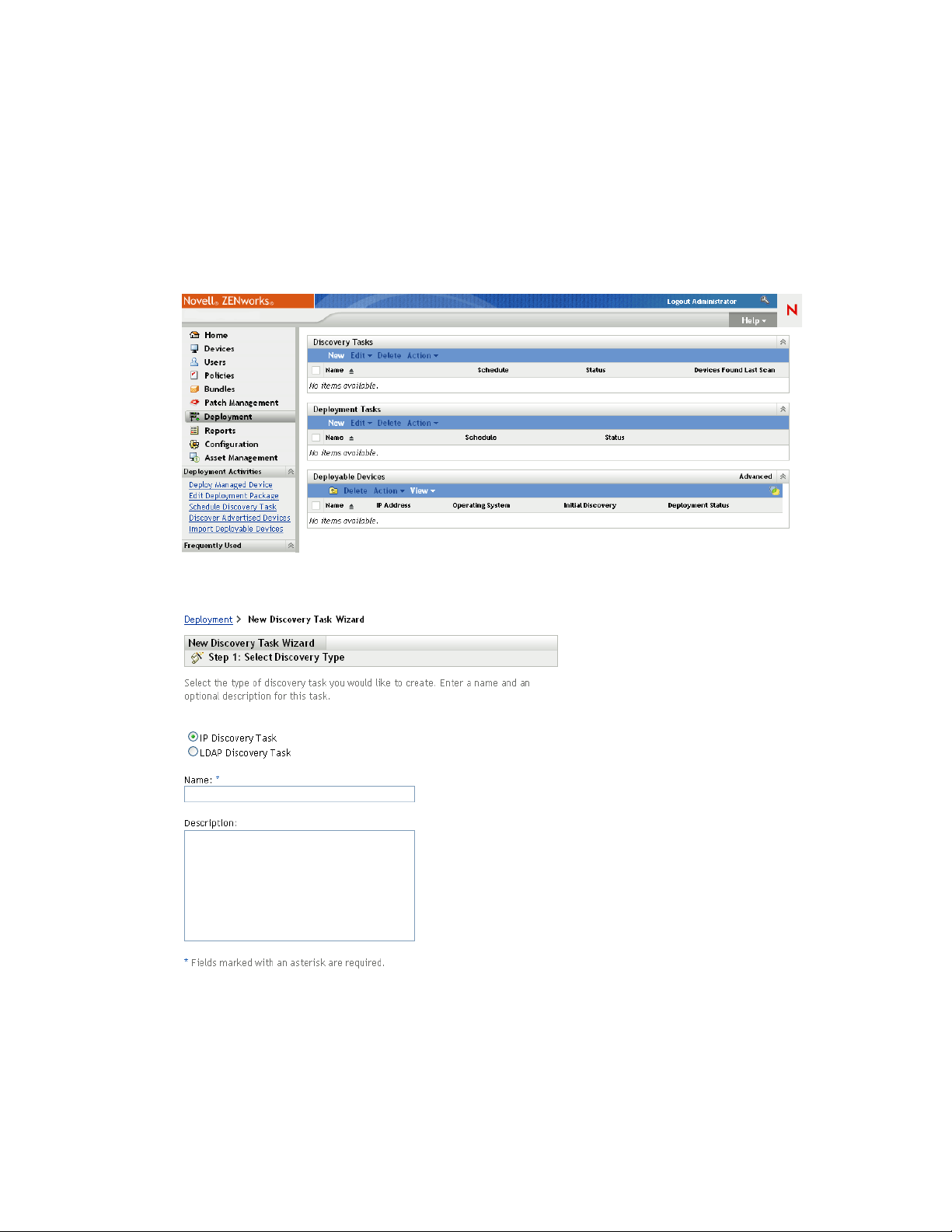
When a discovery task runs, the ZENworks Server creates a discovery request for each IP address
and discovery technology (WMI, WinAPI, MAC Address, NMAP, ZENworks, SNMP, SSH) used.
For example, if you specify one IP address and use all seven discovery technologies, the ZENworks
Server initiates seven discovery requests. Therefore, the more IP addresses you specify and the more
discovery processes you use, the longer the discovery task takes to complete. For fastest results, you
should create tasks that target smaller ranges of IP addresses and, if possible, assign different
ZENworks Servers to process the tasks.
1 In ZENworks Control Center, click the Deployment tab.
novdocx (en) 16 April 2010
2 In the Discovery Tasks panel, click New to launch the New Discovery Task Wizard.
3 Complete the wizard by using information from the following table to fill in the fields.
28 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
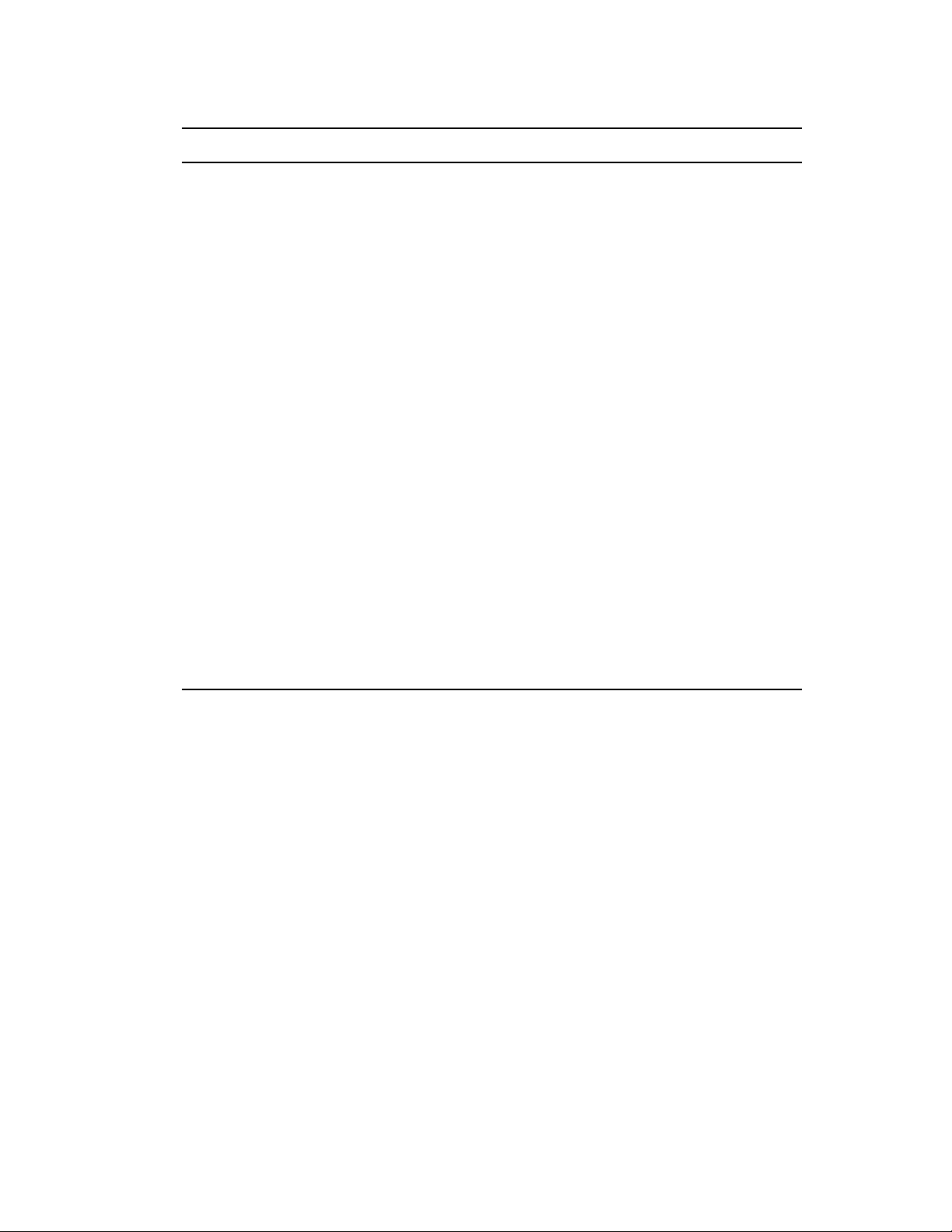
Wizard Page Details
Select Discovery Type page Select IP Discovery Task.
Specify a name for the task. The name cannot include any of the
following invalid characters: / \ * ? : " ' < > | ` % ~
novdocx (en) 16 April 2010
Discovery Settings page >
Override Zone Discovery
Settings field
Discovery Settings page >
Discovery Technologies
Chose whether to override the discovery settings configured at the
Management Zone.
If you want to configure the settings on a device folder or a device,
you must select Override Zone Discovery Settings before you can
modify the settings.
The discovery process can utilize a variety of different technologies.
When more than one technology is used, the discovery process
initiates a discovery request for each technology, with all technology
requests running simultaneously. This is done for each target IP
address. For example, if you use MAC Address, SNMP, and WMI,
the discovery process creates three requests for each target IP
address. The requests are queued and run according to the
Maximum Concurrent Discoveries setting.
If more than one technology request returns information for a
discovered device, the information is merged together. In the case
of conflicting information, the discovery process chooses the “best”
information.
Using fewer discovery technologies reduces the time required to
complete the discovery task but might also reduce the amount of
information received.
For more information about each technology, see Section 1.3, “IP
Discovery Technologies,” on page 13.
Discovering Devices By Using IP Addresses 29

Wizard Page Details
novdocx (en) 16 April 2010
Enter IP Discovery Settings
page > Range field
To specify a range of IP addresses for the discovery task:
1. In the Range field, specify an IP address range using one of
the following formats:
xxx.xxx.xxx.xxx: Standard dotted-decimal notation for a
single address. For example, 123.45.167.100.
xxx.xxx.xxx.xxx - xxx.xxx.xxx.xxx: Standard dotted-decimal
notation for a range of addresses. For example,
123.45.167.100 - 123.45.167.125.
xxx.xxx.xxx.xxx/n: Standard CIDR (Classless Inter-Domain
Routing) notation. With CIDR, the dotted decimal portion of the
IP address is interpreted as a 32-bit binary number that has
been broken into four 8-bit bytes. The number following the
slash (/n) is the prefix length, which is the number of shared
initial bits, counting from the left side of the address. The /n
number can range from 0 to 32, with 8, 16, 24, and 32 being
commonly used numbers. For example, 123.45.167.100/24
matches all IP addresses that start with 123.45.167. When you
add the IP address range to the Selected IP Ranges list (see
the next step), it is automatically expanded to show the range
of addresses in dotted-decimal notation.
You are recommended to specify an IP address range that
does not contain more than 50,000 devices. A task that has a
large IP address range does not get started. For more
information, see the troubleshooting scenario “Discovery task
remains in a pending state if it has a large IP address range”
on page 128.
2. To add an IP address range to the Selected IP Ranges list,
click Add.
3. (Optional) To exclude the IP subnets or address ranges from
the discovery, click Exclude.
The Excluded Addresses dialog box is displayed.
For more information on how to exclude the IP subnets or
address ranges, see “Enter IP Discovery Settings page >
Excluded Addresses dialog box” on page 31.
4. To add additional ranges, repeat Step 1 and Step 2.
30 ZENworks 10 Configuration Management Discovery, Deployment, and Retirement Reference
 Loading...
Loading...