
Version 7 . 0
April 2006
Intellisync Mobile Suite
Secure Gateway Administrator’s Guide

PUBLISHED BY:
Nokia Enterprise Solutions
200 North Point Center East, Suite 600
Alpharetta, GA 30022
Copyright © 2006 Nokia. All rights reserved worldwide. Nokia and Nokia Connecting People are registered
trademarks of Nokia Corporation. Intellisync and Intellisync logo are trademarks of Nokia Corporation. Other
trademarks mentioned are the property of their respective owners. Nokia operates a policy of continuous
development. Therefore we reserve the right to make changes and improvements to any of the products described in
this document without prior notice. No part of this publication may be reproduced, transmitted, transcribed, stored in
a retrieval system, or translated into any human or computer language in any form or by any means without the
express written permission of:
Nokia Enterprise Solutions
Information Development
200 North Point Center East, Suite 600
Alpharetta, GA 30022
This publication is provided as is without warranty of any kind, express or implied, including, but not limited to, the
implied warranties of merchantability, fitness for a particular purpose, or non-infringement.
This publication could include technical inaccuracies or typographical errors. Changes are made periodically to the
information herein. These changes will be incorporated in new editions of the publication. Nokia may make
improvements and/or changes at any time to the product(s) and/or the program(s) described in this publication.
Synchrologic, Mobile Suite, RealSync, and Intellisync are tradem arks of Nokia Corporation.
Acrobat Reader® Copyright 1987–2006 Adobe Systems Incorporated. All rights reserved. Adobe and Acrobat are
trademarks of Adobe Systems Incorporated which may be registered in certain jurisdictions.
3Com, Palm Computing, and HotSync are registered trademarks, and Palm Pilot, Palm III, Palm OS, the Palm
Computing platform logo, and all Palm logos are trademarks of Palm Computing, Inc., 3Com Corporation, or its
subsidiaries.
Certicom, movian, movianCrypt, movianVPN, and SSL Plus are trademarks and/or registered trademarks of
Certicom Corp.
Domino and Notes are trademarks, and Lotus and Lotus Notes are registered trademarks of Lotus Development
Corporation.
InstallShield is a registered trademark of InstallShield Corporation.
Microsoft, Word, Excel, Access, ActiveSync, Visual Basic, Visual C++, and Windows are either registered
trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Netscape is a registered trademark of Netscape Communications Corporation.
SecurID is a registered trademark, and RSA Security is a trademark of RSA Security Inc.
Sun is a registered trademark and iPlanet is a trademark of Sun Microsystems, Inc.
All terms mentioned in this book that are known to be trademarks or service marks have been appropriately
capitalized. Nokia cannot attest to the accuracy of this information. Use of a term in this book should not be regarded
as affecting the validity of any trademark or servicemark.
All other trademarks or registered trademarks are the property of their respective owners.

Contents
1 Installing Secure Gateway
Overview ......................................................................................................................... 1-2
Recommended Secure Gateway configuration................................................................ 1-2
Installing the Secure Gateway......................................................................................... 1-4
Setting up a Secure Gateway cluster ............................................................................... 1-7
Installing a Secure Gateway cluster.......................................................................... 1-7
2 Configuring the Secure Gateway
Using the Secure Gateway Admin Console .................................................................... 2-2
Configuring the Secure Gateway properties file ............................................................. 2-3
Authentication and encryption.................................................................................. 2-3
Debugging and logging............................................................................................. 2-4
HTTP server.................................................... .......................................................... 2-4
Secure Gateway cluster configuration ...................................................................... 2-5
Web tunneling....................................................................... ..... ............................... 2-5
Configuring Secure Gateway to route HTTP requests.................................................... 2-6
Configuring Secure Gateway for SSL............................................................................. 2-8
3 Troubleshooting Secure Gateway
Troubleshooting Secure Gateway issues......................................................................... 3-2
Intellisync Mobile Suite Secure Gateway Administrator’s Guide iii

CHAPTER
1
Installing Secure Gateway
This chapter contains instructions for installing the Secure Gateway
and provides a diagram of the recommended configuration.
Overview ............................................................................1-2
Recommended Secure Gateway configuration ..................1-2
Installing the Secure Gateway............................................1-4
Setting up a Secure Gateway cluster ..................................1-7
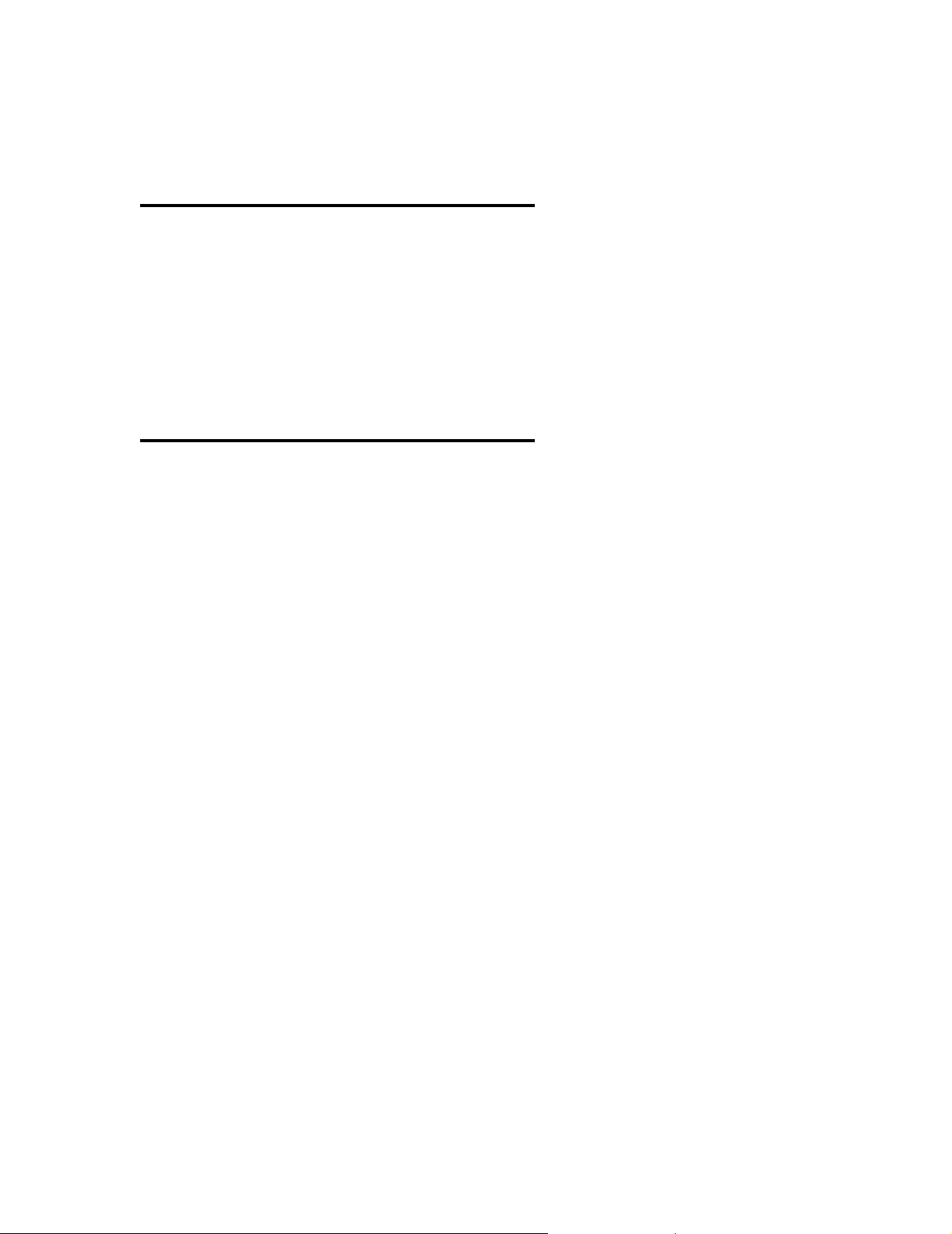
Overview
Your company policy may dictate how you deploy Nokia’s technology within
your network configuration. There are several configuration options available;
however, Nokia recommends the configuration described in this chapter using a
demilitarized zone (DMZ), or screened subnet. The DMZ is a computer or small
subnetwork that sits between a trusted internal network, such as a corporate
private LAN, and an untrusted external network, such as the public Internet.
Recommended Secure Gateway configuration
Nokia recommends using the Secure Gateway configuration within your network.
The Secure Gateway offers secure and scalable communications between mobile
devices and servers and consists of an HTTP listener and communications
services.
Installing Secure Gateway
Overview
The Secure Gateway intercepts the HTTP requests from mobile devices to the
Intellisync Mobile Suite server and can route the requests in three ways:
z Push requests through TCP/IP port 3102
z Sync requests through ports 80 and 443
z Web requests through ports 80 and 443
The following diagram illustrates the recommended configuration for the Secure
Gateway. In this scenario, all Intellisync Mobile Suite components and enterprise
servers are behind the corporate inner firewall.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–2
Recommended Secure Gateway Configuration
Installing Secure Gateway
Recommended Secure Gateway configuration
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–3
Installing Secure Gateway
Installing the Secure Gateway
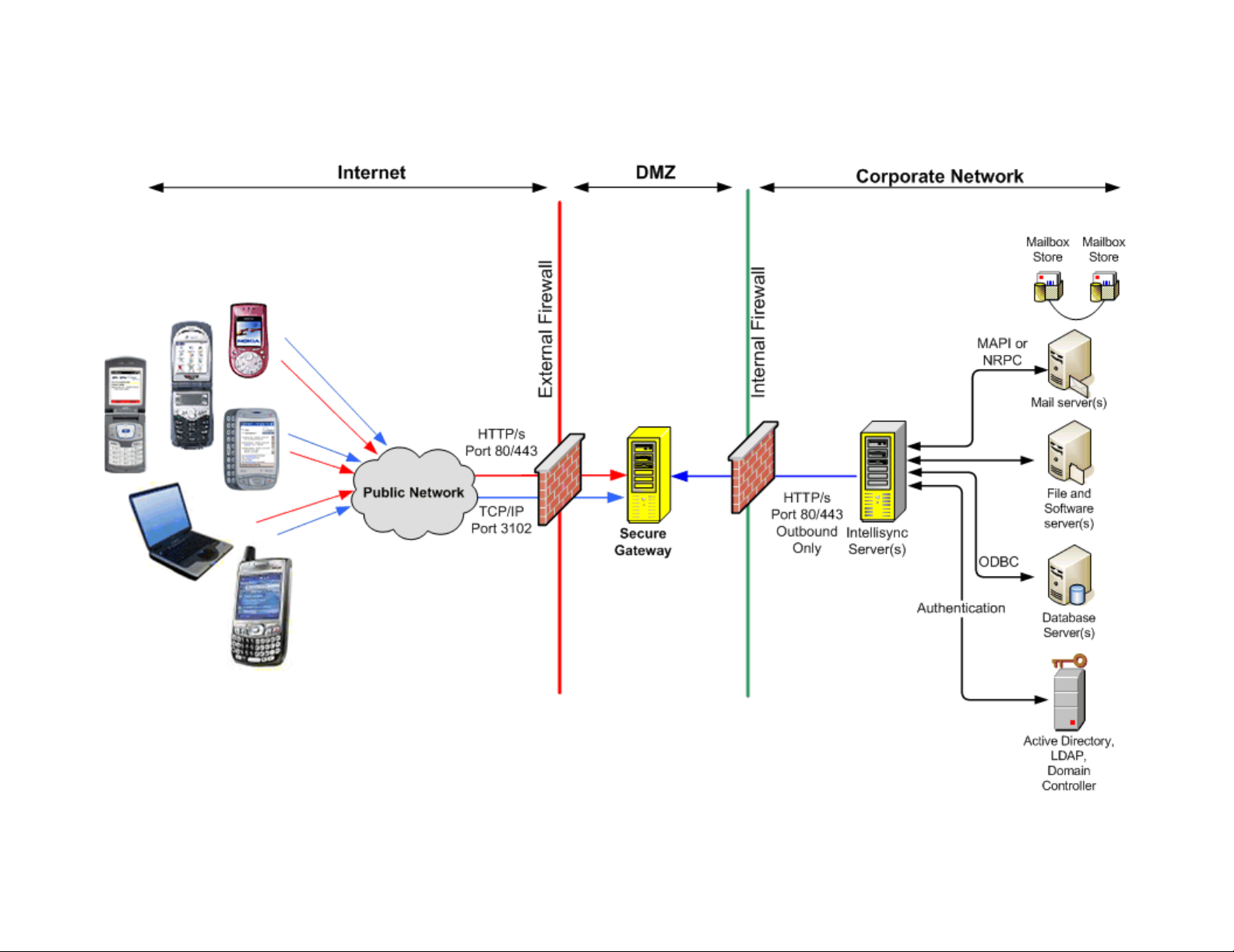
The following table shows the default port settings. Your port settings may be
different depending on your network configuration.
Table 1: Default ports for communication from devices
Communication Protocol Default Port
HTTP
z Sync traffic
z Web tunneling
HTTPS
z Sync traffic
z Web tunneling
TCP/IP
z Push traffic
Installing the Secure Gateway
To install and configure the Secure Gateway, follow these steps:
1. From the installation source folder, doub le-click the setup.exe file. The Secure
Gateway Setup starts and prepares the wizard application for the installation.
2. On the Secure Gateway Welcome screen, click Next. The Destination Folder
screen appears.
3. T o install to a location other than the default folder, click Change. Otherwise,
click Next. The Secure Gateway Service User screen appears.
4. Complete the following fields:
Username. Enter the name for the specified user.
Password. Enter the password for the specified user.
5. Click Next. A confirmation screen appears.
6. Click Install. The installation program installs the Secure Gateway
components into the specified location. When the installation is complete, the
InstallShield Wizard Completed screen appears.
7. Click Finish. The Secure Gateway wizard closes.
80 (configurable)
443 (configurable)
3102 (configurable)
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–4
Installing Secure Gateway
Installing the Secure Gateway
After the installation, you must specify the name of the Secure Gateway computer
on the Intellisync Mobile Suite server. To do so, complete the following steps:
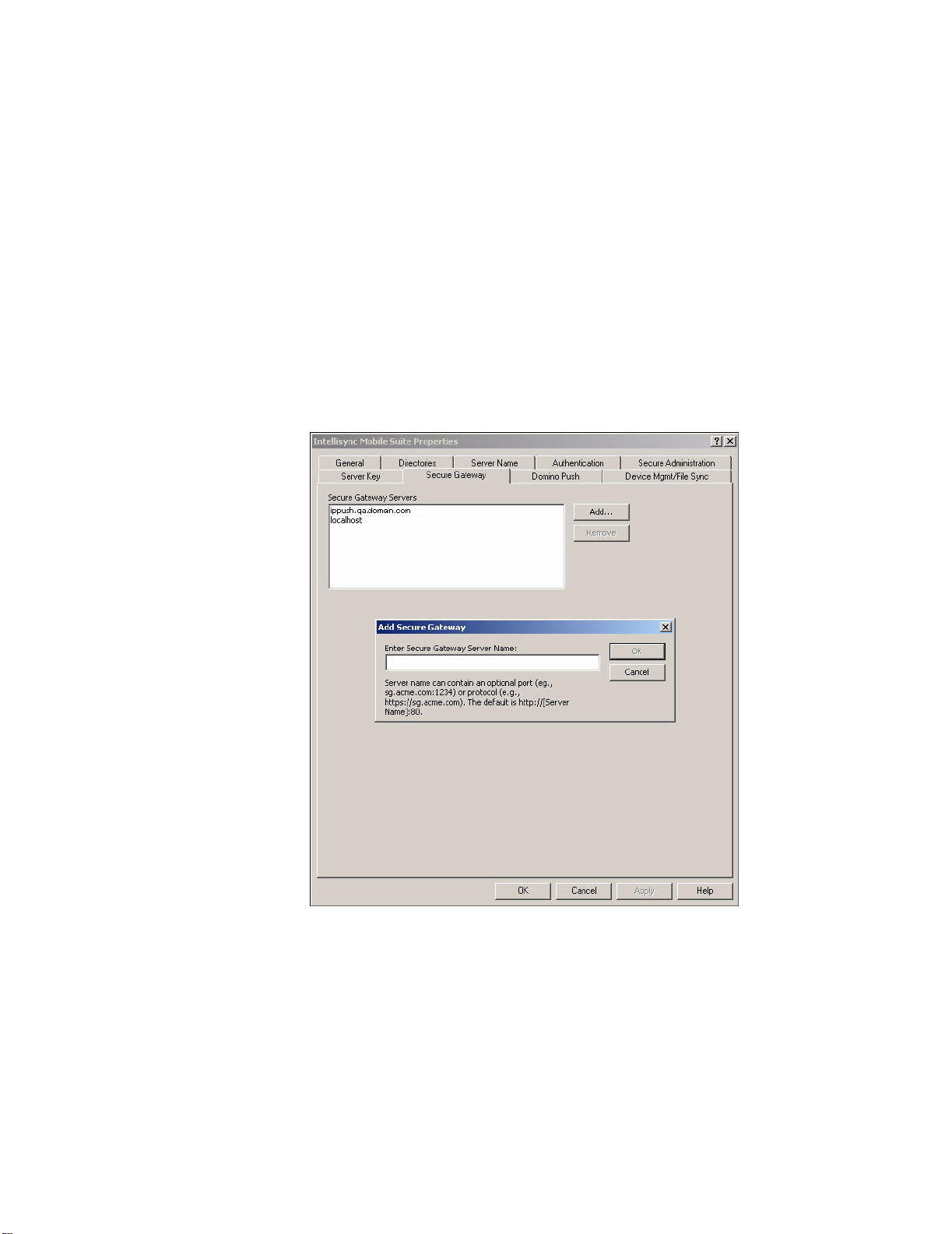
1. From the Windows Start menu on the Intellisync Mobile Suite server, choose
Programs, Intellisync Mobile Suite, and then choose Admin Console. The
Intellisync Mobile Suite control appears.
2. Select Intellisync Mobile Suite in the console tree.
3. From the Action menu, choose Properties. The Intellisync Mobile Suite
Properties dialog box appears.
4. Click the Secure Gateway tab. The Secure Gateway panel appears.
5. Click Add. The Add Secure Gateway dialog box appears.
6. Enter the name or IP address of the Secure Gateway server in the field and
click OK. The Secure Gateway dialog box closes, and the server name
appears in the Secure Gateway Servers field.
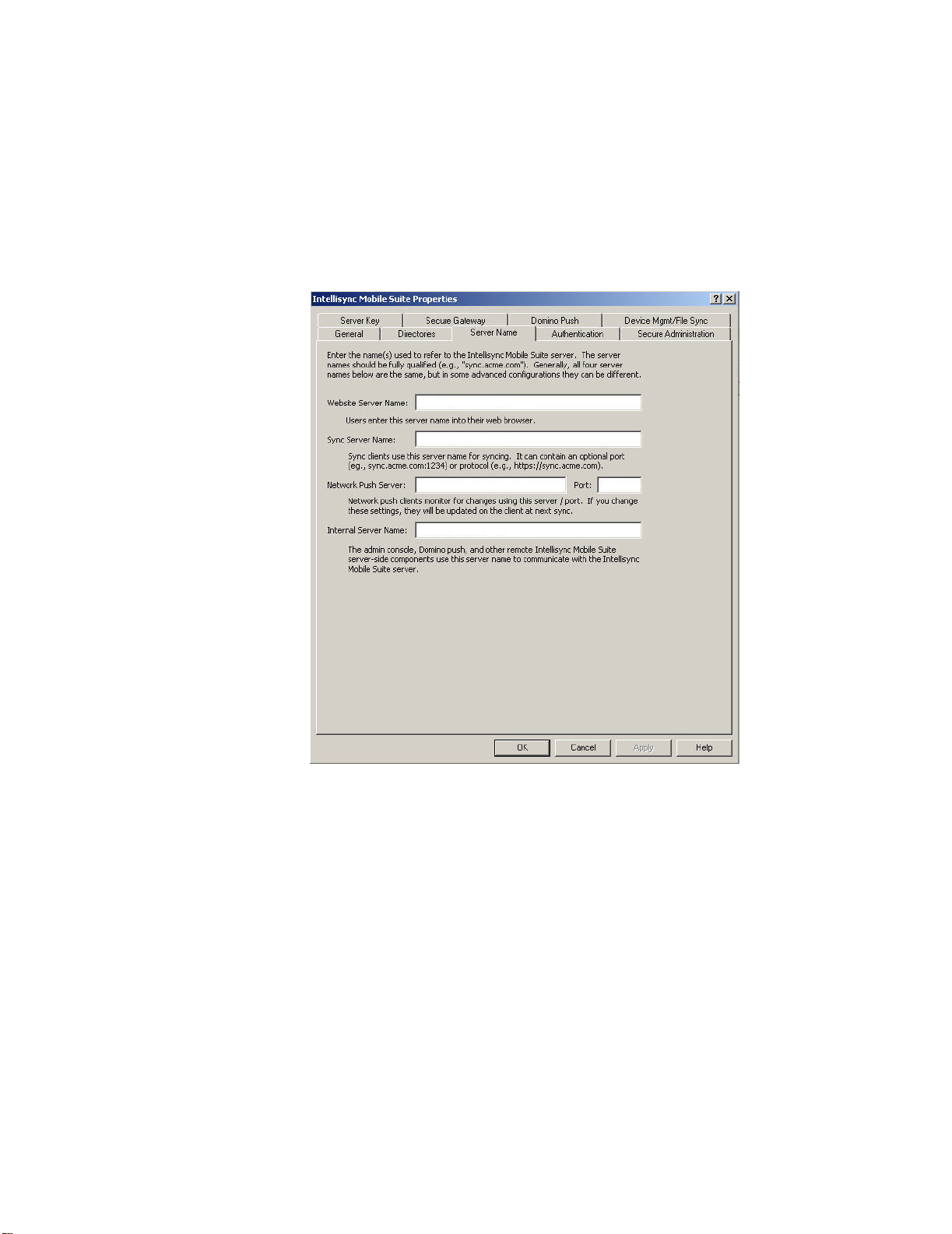
7. Click the Server Name tab.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–5
Installing Secure Gateway
Installing the Secure Gateway
8. Enter the Secure Gateway server name in the following fields:
z Website Server Name
z Sync Server Name
z Network Push Server (this applies only to the IMS server)
9. Click OK. The Intellisync Mobile Suite Properties dialog box closes and the
Secure Gateway Admin Console appears.
10. Restart the Intellisync Mobile Suite service for your changes to take effect.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–6

Setting up a Secure Gateway cluster
You can set up multiple Secure Gateways in a cluster. A Secure Gateway cluster
can provide redundancy to decrease the probability of system downtime in case
one Secure Gateway server should fail.
Installing a Secure Gateway cluster
1. Install Secure Gateway on the additional server(s) you want to add to the
cluster. Refer to “Installing the Secure Gateway” on page 1-4 for installation
steps.
2. Choose a fault-tolerant location to store a shared path since other Secure
Gateway servers in the cluster will access this location.
3. This shared path will contain a file, sgsharedprop.properties, which contains
the cluster server names. This file is automatically created after you have
added each server(s) to the cluster.
Setting up a Secure Gateway cluster
Installing Secure Gateway
Modifying the securegateway.properties file
After you install Secure Gateway on each server, you must modify the
securegateway.properties file on each server. To do so, complete the following
steps:
1. From the C:\Program Files\SecureGateway\CommSvr\conf directory, open
the securegateway.properties file.
2. Define the Secure Gateway shared path for the cluster by entering the
following property:
SecureGatewaySharedPropertiesPath=\\\\<DNS hostname or IP
address>\\<drive>\\<path>\\
This path is the fault-tolerant location for the shared properties file.
3. Restart the Secure Gateway server. If the shared properties file does not exist,
it is automatically created in the shared path.
4. Repeat steps 1-3 for each server in the cluster.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–7

Setting up a Secure Gateway cluster
Installing Secure Gateway
Adding Secure Gateway servers to the cluster
To add the servers to the Secure Gateway cluster, complete the following steps:
1. From the shared properties path, open the sgsharedprop.properties file.
2. Define the Secure Gateway cluster servers by entering the following property
fore each server:
SecureGatewayAddress<1-N>=<DNS hostname or IP address>
3. Restart the Secure Gateway service on each server in the cluster.
A locked copy of the shared properties file is loaded on each server in the
cluster.
If you are setting up a cluster outside of the shared network, you must copy
the sgsharedprop.properties to each server. Any changes to the
sgsharedprop.properties file will have to be manually updated on each server.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 1–8

CHAPTER
2
Configuring the Secure
Gateway
This chapter offers information for configuring the Secure Gateway
after installation.
Using the Secure Gateway Admin Console ....................2-2
Configuring the Secure Gateway properties file.............2-3
Configuring Secure Gateway to route HTTP requests....2-6
Configuring Secure Gateway for SSL.............................2-8

Using the Secure Gateway Admin Console
Using the Secure Gateway Admin Console
The Secure Gateway Admin Console is a management utility located on the
Secure Gateway server. To access the Secure Gateway Admin Console, enter the
following URL or enter
z http://localhost/sgadmin/admin.html or localhost/sgadmin
sgadmin from a local server:
Configuring the Secure Gateway
Secure Gateway Admin Console
The Secure Gateway Admin Console allows the following:
z Enterprise Info. Shows enterprise servers currently connected to the Secure
Gateway.
z Set Admin Credentials. Sets up the administrator user name and password to
access the Secure Gateway.
z Set SSL Certificate Info. Configures an SSL certificate for Secure Gateway
including SSL key name and SSL key password.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–2

Configuring the Secure Gateway properties file
Configuring the Secure Gateway
Configuring the Secure Gateway properties file
You can manage your Secure Gateway configuration using the
securegateway.properties file. With this file, you can configure authentication,
logging, HTTP server, Web tunneling, and properties. When you modify the
securegateway.properties file, you must restart the Secure Gateway service for
changes to take effect.
Authentication and encryption
The following properties define and manage authentication and encryption for
Secure Gateway (default values shown):
Property Description
WebAuthenticationType=1 Sets Secure Gateway authentication type.
Set value to 0 (zero) for no challenge. Set
value to 1 for basic challenge.
WebCommonDomainName= Shares authentication session credentials
for multiple DNS names. If this property is
not set, every DNS name is challenged. For
example, test.acme.com and
test2.acme.com would use
WebCommonDomainName=acme.com.
Used in conjunction with
WebAuthenticationType when property is
set to 1 (basic challenge).
AdminForceSecureConnection=0 Forces Secure Admin Console requests to
be SSL when value is set to 1.
AdminTimeoutMinutes=15 Defines how long a browser-authenticated
administrator session (Secure Admin
Console) can remain inactive before it
expires and re-authenticates.
EncryptMobileGatewayConnection=0 Turns on another layer of AES encryption
between Mobile Gateway and Secure
Gateway servers. Set value to 1 if Secure
Gateway server is outside the corporate
firewall. Regardless of this setting, all
communication between the IMS server to
devices is always encrypted.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–3

Debugging and logging
The following properties define and manage debugging and audit logging for
Secure Gateway (default values shown):
Property Description
LoggingLevel=0 Sets debugging logging for Secure
SecureGatewayLogExpirationDays=8 Specifies the number of days to keep logs
Configuring the Secure Gateway properties file
Configuring the Secure Gateway
Gateway. Logging will appear in a file
<secure_gateway_mm_dd_yyyy_n.log>
located in the default installation log
directory. The Secure Gateway server
automatically picks up the change in two
minutes. LoggingLevel property can be set
from 1 (basic information) to 10 (detailed
information).
before deletion.
HTTP server
The following properties define and manage HTTP server settings for Secure
Gateway (default values shown):
Property Description
HttpIPAddress= Defines th e IP address to listen for HTTP
HttpPort=80 Defines the port to listen for HTTP
SecureGatewayPort=80 Defines the port to listen for TCP
HttpSSLPort=443 Defines the port to listen for HTTPS
connections. Defaults to all IP addresses for
server.
connections (includes Mobile Gateway
servers and devices). Set to zero (0) to not
listen.
connections from Mobile Gateway servers.
connections (includes Mobile Gateway
servers and devices). Set to zero (0) to not
listen.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–4

Configuring the Secure Gateway properties file
Secure Gateway cluster configuration
The following properties define and manage settings for a Secure Gateway cluster
configuration (default values shown):
Property Description
SecureGatewaySharedPropertiesPath= Defines the path of the
sgsharedprops.properties file. Used for
Secure Gateway clusters.
For more information on Secure Gateway clusters, refer to “Installing a Secure
Gateway cluster” on page 1-7.
Web t unneling
Secure Gateway acts as an authenticated reverse-proxy and enables you to route
HTTP requests to the Mobile Gateway behind the firewall. These requests are
then mapped to the correct destination by the Mobile Gateway and sent. This
setup works only in the single enterprise model.
Configuring the Secure Gateway
The following properties define and manage Web tunneling settings for a Secure
Gateway (default values shown):
Property Description
WebTunnelingSupported=1 Allows tunneling of Web requests to the
Mobile Gateway for dispatching.
GALLookupTunnelingSupported=1 Allows tunneling of global address list (GAL)
lookup Web requests to the Mobile Gateway
for dispatching. Used in conjunction with the
WebTunnelingSupported property. Set this
property to 0 (zero) to disallow all Web traffic
except GAL lookup when the
WebTunnelingSupported property value is
set to 1.
WebInactiveMinutes=60 Defines how long a browser-authenticated
session can remain inactive before it expires
and re-authenticates.
SyncMLWebTunnelingSupported=1 Handles HTTP(S) SyncML requests
differently than other Web requests. Set this
value to zero (0) for SyncML device
requests to be routed to the default Web
handler.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–5

Configuring Secure Gateway to route HTTP requests
Configuring the Secure Gateway
Property Description
SyncMLDenyAccess=0 Allows SyncML requests as
unauthenticated. Set value to 1 to disallow
SyncML requests. Used in conjunction with
the SyncMLWebTunnelingSupported
property. To block SyncML access, set value
to 1 when SyncMLWebTunnelingSupported
property value is set to 1.
SyncMLForceSecureConnection=0 Forces SyncML requests to be SSL when
value set to 1. Used in conjunction with the
SyncMLWebTunnelingSupported property
when value is set to 1.
Configuring Secure Gateway to route HTTP requests
If you want to use the Secure Gateway to route HTTP requests through the
firewall, you must define routing destinations.
Routing destinations are entered on the Mobile Gateway diagnostic page. These
destinations control how the requests are interpreted and where the requests
should be delivered.
To access the Mobile Gateway diagnostic page, complete the following steps:
1. From the Intellisync Mobile Suite Admin Console, launch WebAdmin.
2. Enter the Administrator name and password, and then click Login.
3. Enter the URL http://localhost/admin/diag/, and then click the Mobile
Gateway link. The Mobile Gateway System Info and Diagnostics page
appears.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–6

Configuring Secure Gateway to route HTTP requests
Configuring the Secure Gateway
Routing destinations can be defined two ways. The first is DNS-based, where
each different destination has its own unique DNS name. The second is URLbased, where the request URL is examined and the request is routed based on the
folder names in the URL.
By default, if the routing destination is SSL, and the certificate is not trusted, the
Mobile Gateway will return an error to the Secure Gateway and to the Web
browser.
You can set the following property to override this error:
Property Description
WebRoutingAllowUnknownSSLCertifications Overrides a SSL routing destination
and processes the request.
To set this property enter the following:
WebRoutingAllowUnknownSSLCertifications = 1
DNS routing destinations
WebDNSRouting[uniqueNumber]=source,destination
is defined as the following:
source is the Secure Gateway DNS address
–
–
destination is defined as [protocol]address[:port]
Examples:
WebDNSRouting1=webpim.securegateway.com,localhost:8840
webpim.securegateway . com routes to http://localhost:8840
WebDNSRouting2=intranet.securegateway.com,intranet
intranet.securegateway.com routes to http://intranet:80
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–7
Configuring the Secure Gateway
Configuring Secure Gateway for SSL
URL routing destinations
WebURLRouting[uniqueNumber]=source,destination,flag
is defined as the following:
source is the first folder in the URL
–
–
destination is defined as [protocol]address[:port]
–
flag is used for specifying this is a virtual folderName and the name
should be stripped from the URL before being routed
Examples:
WebURLRouting1=/,http://localhost:8840,0
http://www.securegateway.com/ routes to http://localhost
WebURLRouting2=en,http://localhost:8840,0
http://www.securegateway.com/en/login.asp routes to http://localhost/en/login.asp
WebURLRouting3=intranet,http://intranet,1
http://www.securegateway.com/intranet routes to http://intranet
Configuring Secure Gateway for SSL
SSL support is available in Secure Gateway and provides a default key file;
however, you can override this value by using a provided keytool Java utility,
which enables you to administer public/private key pairs and associated
certificates. The keytool utility stores the keys and certificates in a keystore. The
default implements the keystore as a file. It protects private/public keys with a
password. These properties help configure Secure Gateway for SSL.
When you define your keystore file, you can generate a Certification Signing
Request (CSR). With this CSR, you can obtain a digital certificate from a
Certification Authority (CA), such as Verisign. After you have created your
keystore file, you can use the Secure Gateway Admin Console to insert the
encrypted values into the securegateway.properties file.
For more information about Java Key and Certification Management keytool,
refer to http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html
for documentation.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–8

Configuring the Secure Gateway
Configuring Secure Gateway for SSL
To configure Secure Gateway for SSL, complete the following steps:
Create a keystore file
1. Generate the keystore file by running the keytool utility with the following
parameters where <name>.key is a the keystore file you define:
C:\Program Files\Secure Gateway\jre1.5.0_01\bin\keytool -genkey -keyalg
RSA -alias <Web server nam e> -keystore <name>.key
2. Enter your keystore password, and then enter the information at the following
prompts:
– What is your first and lastname?
– What is the name of your organizational unit?
– What is the name of your organization?
– What is the name of your City or Locality?
– What is the name of your State or Province?
– What is the two-letter country code for this unit?
3. Confirm the information entered by entering “Yes” at the prompt.
4. Enter the password for <Web server name>, or press return if this password is
the same as your keystore password.
Generate a CSR
1. Generate a CSR. Run the keytool utility located with the following
parameters where <name>.csr is the name of the CSR (for sending to a CA):
C:\Program Files\Secure Gateway\jre1.5.0_01\bin\keytool -certreq -alias
<Web server name> -keyalg RSA -file <name>.csr -keystore <name>.key.
2. Send the CSR file to a CA via e-mail. The CA authenticates the certificate
requestor and returns a .cer file, a digitally signed certificate, via e-mail.
Import the digital certificate
1. Import the .cer file. Run the keytool utility with the following parameters
where <name>.cer is the digital certificate received from the CA:
C:\Program Files\Secure Gateway\jre1.5.0_01\bin\keytool -import -alias
<Web server name>-trustcacerts -file <name>.cer -keystore <name>.key
2. Enter your keystore password at the prompt. The .cer file imports and a
confirmation message appears.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–9

Configuring the Secure Gateway
Configuring Secure Gateway for SSL
3. Verify yo ur certificat e. Run the keytool utility with the following parameters
where <name>.key is the filename you define:
C:\Program Files\Secure Gateway\jre1.5.0_01\bin\keytool -list -v -alias <Web
server name>-keystore <name>.key
4. Enter keystore password and verify the digital certificate, which includes
owner, issuer, serial number, and certificate fingerprints.
Configure the SSL properties for Secure Gateway
1. Place the keystore file into the following directory or the location of your
securegateway.properties file.
C:\Program Files\Secure Gateway\Commsvr\conf
2. Log in to the Secure Gateway Admin Console by entering the following URL
or entering
/localhost/sgadmin/admin.htm
3. Select the Set SSL Certification Info link.
4. Enter the key file name (information located in the commsvr/conf directory).
5. Enter the password, and then enter it again in the Repeat Password field.
6. Select Save. The properties are added to the securegateway.properties file
with the values encrypted.
7. Restart the Secure Gateway service.
sgadmin from a local server:
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 2–10

CHAPTER
3
Troubleshooting Secure
Gateway
This chapter contains helpful hints for troubleshooting Secure
Gateway issues.
Troubleshooting Secure Gateway issues.........................3-2

Troubleshooting Secure Gateway issues
Troubleshooting Secure Gateway issues
This section provides steps to follow to help identify, isolate, and resolve sync or
push related issues with Intellisync Mobile Suite and Secure Gateway.
Verify server name values and connections
1. From the Windows Start menu on the Intellisync Mobile Suite server, choose
Programs, Intellisync Mobile Suite, and then choose Admin Console. The
Intellisync Mobile Suite control appears.
2. Select Intellisync Mobile Suite in the console tree.
3. From the Action menu, choose Properties. The Intellisync Mobile Suite
Properties dialog box appears.
4. Click the Server Name tab.
5. Verify that Sync Server Name and Network Push Server are set to the external
DNS/IP address that resolves to the Secure Gateway server. (To view
information on the Secure Gateway server, click the Secure Gateway tab.)
6. Click OK.
7. From the Intellisync Mobile Suite server, use Telnet to verify you can connect
to the Secure Gateway.
8. From a computer connected to the Internet, use Telnet to verify you can
connect to the following:
– <SyncServerName> 80
– <NetworkPushServer> 3102
9. Install the Intellisync Mobile Suite client on a test device and the verify that
the Sync Server Name value and Network Push Server value are correct.
Troubleshooting Secure Gateway
Verify network configuration on Intellisync server(s)
1. Add all IP addresses bound to all NICs to the hosts file, resolving to the
hostname.
2. Add any IP addresses for Secure Gateway servers to the hosts file, resolving
to the hostname (only required if the hostname was specified in the Intellisync
Mobile Suite Admin Console).
3. If possible, verify and set the Speed and Duplex values for all NICs.
4. Verify that "ipconfig /all" returns correct and expected values.
5. Verify that "netstat -a" returns correct and expected values.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 3–2

Troubleshooting Secure Gateway
Troubleshooting Secure Gateway issues
Verify network configuration on Secure Gateway server(s)
1. Add all IP addresses bound to all NICs to the hosts file, resolving to the
hostname.
2. Remove all registered DNS server entries on all NICs.
3. Disable the "Register this connection's addresses in DNS" setting on all NICs.
4. Remove all registered WINS server entries on all NICs.
5. Disable the "Enable LMHOSTS lookup" setting on all NICs.
6. Set the "NetBIOS" setting to "Disable NetBIOS over TCP/IP" on all NICs.
7. Verify that "ipconfig /all" returns correct and expected values.
8. Verify that "netstat -a" returns correct and expected values.
Verify firewall router configuration
1. Verify that any nodes (usually firewalls and load balancers) between the
Internet and the Secure Gateway server allow idle connections on port 80 and
3102 to stay active for longer than 15 minutes.
2. Verify that no IDS or packet inspection devices modify data on port 80 or
3102.
Test network connections
1. From a computer connected to the Internet, use a browser to verify you can
access the Intellisync Mobile Suite Web site.
2. From a test device, use the browser to verify you can access the Intellisync
Mobile Suite Web site.
3. Run SocketLife on the Secure Gateway server and verify that a Palm device
can consistently connect to port 80 and 3102 with a Seed Time value of 1, 5
and 15. You can obtain a copy of the SocketLife program from Intellisync
Technical Support.
Intellisync Mobile Suite Secure Gateway Administrator’s Guide 3–3
 Loading...
Loading...