Netopia 3000 Manual

Software User Guide
Cayman Operating System
Version 6.3
Cayman 3000 series by Netopia
January 2002
Downloaded from www.Manualslib.com manuals search engine

Disclaimers
Copyright © 2002 Netopia, Inc.
All rights reserved, Printed in the USA.
The information in this document is subject to change without notice. The statements, configurations, technical data, and recommendations in this document are believed to be accurate and reliable, but are presented without express or implied warranty. Users must take full responsibility for the applications of any products specified in this document.
Portions of this software are subject to the Mozilla Public License Version 1.1. Portions created by Netscape are copyright 1994-2000 Netscape Communications Corporation. You may obtain a copy of the license at http://www.mozilla.org/MPL/. Software distributed under the License is distributed on an “as is” basis, WITHOUT WARRANTY OF ANY KIND, either express or implied. See the License for the specific language governing rights and limitations under the License.
Portions of this software copyright 1988, 1991 by Carnegie Mellon University. All rights reserved. Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is hereby granted, provided that the above copyright notice and this permission notice appear in supporting documentation, and that the name of Carnegie Mellon University not be used in advertising or publicity pertaining to distribution of the software without specific, written prior permission.
CARNEGIE MELLON UNIVERSITY DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL CMU BE LIABLE FOR ANY SPECIAL, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA, OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE, OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
The information in this document is proprietary to Netopia, Inc.
Trademarks
Cayman Systems is a registered trademark of Cayman Systems, a division of Netopia, Inc. SWIFT-IP, SafetyNet, Zero Configuration, SafeHarbour VPN IPsec Tunnel, and the Cayman Systems logo are trademarks of Netopia, Inc.
Ethernet is a registered trademark of Xerox Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation.
All other trademarks are the property of their respective owners. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Cayman assumes no responsibility with regard to the performance or use of these products.
Statement of Conditions
In the interest of improving internal design, operational function, and /or reliability, Netopia, Inc. reserves the right to make changes to the products described in this document without notice.
Netopia, Inc. does not assume any liability that may occur due to the use or application of the product(s) or network configurations described herein.
Netopia, Inc. Part Number: 6161103-PF-01
Downloaded from www.Manualslib.com manuals search engine

Table of Contents |
|
Disclaimers ........................................................................................................... |
2 |
Table of Contents ................................................................................................ |
3 |
Introduction ......................................................................................................... |
7 |
Section 1 |
|
About Cayman Documentation ............................................................................................ |
7 |
Intended Audience ................................................................................................................. |
7 |
Documentation Conventions ................................................................................................ |
8 |
General .............................................................................................................................. |
8 |
Internal Web Interface ..................................................................................................... |
8 |
Command Line Interface ................................................................................................ |
8 |
Icons ................................................................................................................................... |
9 |
Text .................................................................................................................................... |
9 |
Organization .......................................................................................................................... |
10 |
About Cayman-series Gateways .................................................................... |
11 |
Section 2 |
|
Basic Product Structure ........................................................................................................ |
11 |
What’s New in Version 6.3 ................................................................................................... |
12 |
New Embedded Web Server ........................................................................................ |
12 |
Maintenance Enhancements ......................................................................................... |
12 |
Computer Names ................................................................................................... |
12 |
Updater .................................................................................................................... |
12 |
802.11b Wireless Update ........................................................................................ |
12 |
NIST UTC Reference Signal .................................................................................. |
12 |
Capabilities Roadmap for COS 6.3 ..................................................................................... |
13 |
Overview of Major Capabilities .................................................................... |
14 |
Section 3 |
|
General ................................................................................................................................... |
14 |
Feature Keys ................................................................................................................... |
14 |
Management ................................................................................................................... |
15 |
Embedded Web Server .......................................................................................... |
15 |
Diagnostics .............................................................................................................. |
15 |
Local Area Network ...................................................................................................... |
16 |
DHCP (Dynamic Host Configuration Protocol) Server .................................... |
16 |
DHCP (Dynamic Host Configuration Protocol) Relay Agent ......................... |
16 |
DNS Proxy ............................................................................................................... |
16 |
Wide Area Network ...................................................................................................... |
17 |
DHCP (Dynamic Host Configuration Protocol) Client ..................................... |
17 |
PPPoE (Point-to-Point Protocol over Ethernet) .................................................. |
17 |
Instant-On PPP ........................................................................................................ |
17 |
Static IP Addresses ................................................................................................. |
18 |
IPMaps ..................................................................................................................... |
18 |
Security ............................................................................................................................ |
19 |
Password Protection ............................................................................................... |
19 |
Network Address Translation (NAT) .................................................................. |
19 |
Cayman Advanced Features for NAT ................................................................. |
20 |
Internal Servers ....................................................................................................... |
20 |
Pinholes .................................................................................................................... |
21 |
Default Server ......................................................................................................... |
21 |
3
Downloaded from www.Manualslib.com manuals search engine
Combination NAT Bypass Configuration .......................................................... |
22 |
Security Monitor ..................................................................................................... |
22 |
Event Details ........................................................................................................... |
23 |
IP Source Address Spoofing .......................................................................... |
23 |
Source Routing ................................................................................................. |
23 |
Subnet Broadcast Amplification .................................................................... |
23 |
Illegal Packet Size (Ping of Death) ................................................................ |
23 |
Port Scan ........................................................................................................... |
24 |
Excessive Pings ................................................................................................ |
24 |
Login Failures .................................................................................................. |
25 |
MAC Address Spoofing ................................................................................. |
25 |
BreakWater Basic Firewall .................................................................................... |
26 |
BreakWater Settings ........................................................................................ |
26 |
ClearSailing ..................................................................................................... |
26 |
SilentRunning ................................................................................................. |
26 |
LANdLocked ................................................................................................... |
26 |
VPN IPSec Pass Through ....................................................................................... |
27 |
SafeHarbour VPN IPSec Tunnel ........................................................................... |
28 |
Web-based User Interface ............................................................................... |
29 |
Section 4 |
|
Access the User Interface ..................................................................................................... |
29 |
Open the Web Connection ........................................................................................... |
29 |
Home page ............................................................................................................................. |
30 |
Home page - Information ............................................................................................. |
31 |
Toolbar .................................................................................................................................... |
32 |
Navigating the Web Interface .............................................................................................. |
32 |
Restart ..................................................................................................................................... |
33 |
Help ......................................................................................................................................... |
35 |
Configure ................................................................................................................................ |
36 |
Quickstart ........................................................................................................................ |
36 |
How to Use the Quickstart Page .......................................................................... |
36 |
Setup Your Gateway using a DHCP Connection .............................................. |
37 |
Change Procedure .................................................................................................. |
38 |
Setup Your Gateway using a PPP Connection ................................................... |
40 |
Setup Your Gateway using a Static IP Address ................................................. |
41 |
Configuration Procedure ................................................................................ |
41 |
LAN ................................................................................................................................. |
43 |
WAN ................................................................................................................................ |
44 |
Advanced ........................................................................................................................ |
45 |
Configure Specific Pinholes .................................................................................. |
47 |
Planning for Your Pinholes ............................................................................ |
47 |
Example: A LAN Requiring Three Pinholes ............................................... |
47 |
Pinhole Configuration Procedure ................................................................. |
49 |
Configure the IPMaps Feature .............................................................................. |
52 |
FAQs for the IPMaps Feature ........................................................................ |
52 |
IPMaps Block Diagram ................................................................................... |
54 |
Configure a Default Server ................................................................................... |
56 |
Typical Network Diagram ............................................................................. |
57 |
NAT Combination Application ..................................................................... |
57 |
Security ............................................................................................................................ |
66 |
Create and Change Passwords ............................................................................. |
67 |
Use a Cayman Firewall .......................................................................................... |
69 |
BreakWater Basic Firewall ............................................................................. |
69 |
4
Downloaded from www.Manualslib.com manuals search engine
Configure a SafeHarbour VPN ............................................................................. |
73 |
VPN IPSec Tunnel at the Gateway .............................................................. |
73 |
Parameter Description and Setup ................................................................. |
74 |
IPSec Tunnel Parameter Setup Worksheet .................................................. |
76 |
SafeHarbour Tunnel Setup ............................................................................ |
77 |
Using the Security Monitoring Log ..................................................................... |
80 |
Install ............................................................................................................................... |
83 |
Install Software ....................................................................................................... |
84 |
Updating Your Gateway to COS Version 6.3 .............................................. |
84 |
Install Keys .............................................................................................................. |
93 |
Use Cayman Software Feature Keys .................................................................... |
93 |
Troubleshoot .......................................................................................................................... |
97 |
Perform Troubleshooting on Gateways ....................................................... |
97 |
System Status ....................................................................................................................... |
101 |
Manage a Restricted Number of WAN Users ......................................................... |
101 |
User Status ............................................................................................................. |
101 |
Disconnect Current WAN Users ............................................................................... |
102 |
Exceeding the WAN User Limit ................................................................................ |
103 |
Tour: Command Line Interface .................................................................... |
104 |
Appendix A |
|
Overview .............................................................................................................................. |
104 |
Starting and Ending a CLI Session ................................................................................... |
106 |
Connecting from telnet ............................................................................................... |
106 |
Connecting from the Maintenance Console Port .................................................... |
106 |
Logging In ..................................................................................................................... |
106 |
Ending a CLI Session ................................................................................................... |
107 |
Saving Settings ............................................................................................................. |
107 |
Using the CLI Help Facility ............................................................................................... |
107 |
About SHELL Commands ................................................................................................. |
107 |
SHELL Prompt ............................................................................................................. |
107 |
SHELL Command Shortcuts ...................................................................................... |
107 |
Platform Convention ................................................................................................... |
108 |
SHELL Commands ............................................................................................................. |
108 |
About CONFIG Commands .............................................................................................. |
117 |
CONFIG Mode Prompt ............................................................................................... |
117 |
Navigating the CONFIG Hierarchy .......................................................................... |
117 |
Entering Commands in CONFIG Mode ................................................................... |
118 |
Guidelines: CONFIG Commands .............................................................................. |
118 |
Displaying Current Gateway Settings ...................................................................... |
119 |
Step Mode: A CLI Configuration Technique ........................................................... |
119 |
Validating Your Configuration .................................................................................. |
120 |
CONFIG Commands .......................................................................................................... |
121 |
ATM Settings ................................................................................................................ |
121 |
Bridging Settings .......................................................................................................... |
122 |
DHCP Settings .............................................................................................................. |
123 |
DMT Settings ............................................................................................................... |
124 |
Domain Name System Settings ................................................................................. |
124 |
Ethernet MAC Address Settings ............................................................................... |
124 |
IP Settings ..................................................................................................................... |
125 |
Basic Settings .......................................................................................................... |
125 |
DSL Settings ............................................................................................................ |
125 |
Ethernet Settings ...................................................................................................... |
126 |
5
Downloaded from www.Manualslib.com manuals search engine
Default IP Gateway Settings ................................................................................... |
128 |
WAN-to-WAN Routing Settings ............................................................................ |
129 |
IP-over-PPP Settings ............................................................................................... |
129 |
Static ARP Settings ................................................................................................. |
131 |
Static Route Settings ............................................................................................... |
132 |
WAN Settings .......................................................................................................... |
133 |
IPMaps Settings ............................................................................................................ |
134 |
Network Address Translation (NAT) Default Settings ......................................... |
135 |
Network Address Translation (NAT) Pinhole Settings ......................................... |
135 |
PPPoE Settings ............................................................................................................. |
136 |
Configuring Basic PPP Settings .............................................................................. |
137 |
Configuring Port Authentication ............................................................................. |
138 |
Configuring Peer Authentication ............................................................................. |
140 |
Command Line Interface Preference Settings ......................................................... |
141 |
Port Renumbering Settings ........................................................................................ |
141 |
Security Settings ........................................................................................................... |
142 |
Firewall Settings (for BreakWater Firewall). .......................................................... |
142 |
SafeHarbour IPSec Settings .................................................................................... |
142 |
Internet Key Exchange (IKE) Settings ................................................................ |
144 |
SNMP Settings .............................................................................................................. |
145 |
System Settings ............................................................................................................ |
145 |
Traffic Shaping Settings .............................................................................................. |
147 |
Glossary ............................................................................................................ |
148 |
Appendix B |
|
Index .................................................................................................................. |
158 |
6
Downloaded from www.Manualslib.com manuals search engine

Section 1 |
About Cayman Documentation |
Introduction |
Section 1 |
About Cayman Documentation
Netopia, Inc. provides a suite of technical information for its Cayman-series family of intelligent enterprise and consumer Gateways. It consists of:
•Software User Guide
•Hardware and Installation User Guide
•Dedicated Quickstart booklets
•Specific White Papers
The documents are available in electronic form as Portable Document Format (PDF) files. They are viewed (and printed) from Adobe Acrobat Reader, Exchange, or any other application that supports PDF files.
They are downloadable from Cayman’s website: http://www.cayman.com/
Intended Audience
This guide is targeted to the technical staffs of organizations such as:
•Incumbent Local Exchange Carriers (ILEC)
•Competitive Local Exchange Carriers (CLEC)
•Multiple System Operators (MS0)
•Internet Service Providers (ISP)
These professional staffs include:
•System administrators
•Installation and configuration technicians
•Customer support engineers
They are responsible for planning, deploying, and supporting the Customer Premise Equipment that are the key elements of small business or residential Local Area Networks.
Business and residential subscribers are encouraged to use this guide also.
7
Downloaded from www.Manualslib.com manuals search engine

Section 1 |
Documentation Conventions |
Documentation Conventions
General
This manual uses the following conventions to present information:
Convention (Typeface) Description
|
bold italic |
Menu commands and button names |
|
monospaced |
|
|
bold italic sans serif |
Web GUI page links |
|
terminal |
Computer display text |
|
bold terminal |
User-entered text |
|
Italic |
Italic type indicates the complete titles of |
|
|
manuals. |
Internal Web Interface |
|
|
|
|
|
|
Convention (Graphics) |
Description |
|
|
|
|
dot-dot-dash rounded rect- |
Denotes an “excerpt” from a Web page or |
|
angle or line |
the visual truncation of a Web page |
|
solid rounded rectangle with |
Denotes an area of emphasis on a Web |
|
an arrow |
page |
Command Line Interface |
|
|
Syntax conventions for the Cayman gateway command line interface are as follows:
Convention |
Description |
|
|
straight ([ ]) brackets in cmd line |
Optional command arguments |
curly ({ }) brackets, with values |
Alternative values for an argument are |
separated with vertical bars (|). |
presented in curly ({ }) brackets, with |
|
values separated with vertical bars (|). |
bold terminal type face |
User-entered text |
italic terminal type |
Variables for which you supply your |
face |
own values |
8
Downloaded from www.Manualslib.com manuals search engine

Section 1 |
Documentation Conventions |
BOTH |
Pointing to a CLI command, refers to |
|
both DSL and Ethernet WAN interfaces |
|
for Cayman Gateways |
DSL |
Pointing to a CLI command, refers only |
|
to DSL WAN interface (used with 3220- |
|
H family) |
ENET |
Pointing to a CLI command, refers only |
|
to ENET WAN interface (used with 2E-H |
|
family) |
Icons
Icons used in the guide are:
Icon Description
NOTE Icon:
Requests that you pay particular attention to a specified procedure or piece of information in the text. The NOTE message has a regular type style.
CAUTION Icon:
Suggest you review the referenced details and heed the instructions offered. The CAUTION message has a bold type style.
WARNING Icon:
Demands that you observe the actions given in the text.
The WARNING message has a bold italic type style.
COMPASS Icon:
Points the user to additional information concerning the topic under discussion. The COMPASS message has a regular type style. It is used also to denote a Roadmap table.
Text
The words “Cayman Gateway” and “Gateway” refer to a standard unit from the Netopia Cayman 3000-Series product families.
9
Downloaded from www.Manualslib.com manuals search engine
Section 1 |
Organization |
The expressions “Release 6.3.0” and “R 6.3.0” refer to the most recent generally available Cayman Operating System: COS 6.3.0R0.
Organization
This guide consists of six sections, three appendixes including a glossary, and an index. It is organized as follows:
•Section 1, “Introduction” — Describes the Cayman document suite, the purpose of, the audience for, and structure of this guide. It presents a table of conventions.
•Section 2, “About Cayman Gateways” — Presents a product description and overview of the extensive features of your Cayman gateway including a listing of new capabilities that are included with Cayman
Operating System COS 6.3. A “Roadmap” of features and How To topics is shown.
•Section 3, “Overview of Major Capabilities,” — Itemizes Local Area Network, Wide Area Network, Security, Management, and Software Feature Keys features and functionalities.
•Section 4, “Web-based User Interface,” — Organized in the same way as the web UI is organized. As you go through each section, functions and procedures are discussed in detail.
•Appendix A, “Tour of the Command Line Interface,” — Describes all the current text-based commands for both the SHELL and CONFIG modes. A summary table and individual command examples for each mode is provided.
•Appendix B, “Glossary”
•Index
10
Downloaded from www.Manualslib.com manuals search engine

Section 2 |
Basic Product Structure |
About Cayman-series Gateways Section 2
Basic Product Structure
Units from the Netopia Cayman-series Gateway family are supplied in many configurations. This presents end-users with many alternatives for Wide Area Network (WAN) interfaces and Local Area Network (LAN) interfaces. This is the current product roster that supports COS 6.3:
Cayman |
|
LAN Wired |
LAN Wired |
LAN |
|
WAN Interface |
Wireless |
||||
Model No. |
Ethernet Hub |
Options |
|||
|
Option |
||||
|
|
|
|
||
|
|
|
|
|
|
3220-H |
Full-Rate Discrete Multi- |
Four ports |
|
|
|
|
Tone (DMT) Asynchronous |
10 BaseT |
|
|
|
|
Digital Subscriber Line |
|
|
|
|
|
(ADSL) |
|
|
|
|
3220-H-W11 |
ADSL |
Four ports |
|
802.11b |
|
|
|
10 BaseT |
|
Protocol |
|
3220-H-WRF |
ADSL |
Four ports |
|
HomeRF |
|
|
|
10 BaseT |
|
Protocol |
|
|
|
|
|
|
|
|
|
|
|
|
|
2E |
Ethernet |
One port |
|
|
|
|
|
10 BaseT |
|
|
|
2E-H |
Ethernet |
Eight ports |
|
|
|
|
|
10 BaseT |
|
|
|
2E-H-W11 |
Ethernet |
Eight ports |
|
802.11b |
|
|
|
10 BaseT |
|
Protocol |
|
2E-H-WRF |
Ethernet |
Eight ports |
|
HomeRF |
|
|
|
10 BaseT |
|
Protocol |
|
|
|
|
|
|
|
|
|
|
|
|
|
3445 |
ADSL |
Four ports 10/ |
HPNA |
PCMCIA |
|
|
|
100 Ethernet |
|
802.11b |
|
|
|
|
|
Protocol |
|
3543 |
ADSL |
Four ports 10/ |
|
|
|
|
|
100 Ethernet |
|
|
|
3485 |
Ethernet |
Four ports 10/ |
HPNA |
PCMCIA |
|
|
|
100 Ethernet |
|
802.11b |
|
|
|
|
|
Protocol |
|
3583 |
Ethernet |
Four ports 10/ |
|
|
|
|
|
100 Ethernet |
|
|
11
Downloaded from www.Manualslib.com manuals search engine
Section 2 |
What’s New in Version 6.3 |
What’s New in Version 6.3
The new features for COS 6.3 are:
New Embedded Web Server
Not only is the look and feel different, but the database and the web server engine are new and more flexible.
The design of the new web server is geared to make navigation easier, providing the most commonly used items first. Context-sensitive help is provided.
Maintenance Enhancements
The maintenance enhancements are:
Computer Names
In addition to the IP address, the computer name is now listed in the DHCP lease table and the WAN users table. This allows users to more easily identify the computers in these tables. The computer name is only known if using DHCP to get its IP address.
Updater
This application, Updater Version 1.1, prepares the Gateway for installation of COS 6.3
Updater V 1.1 is required for users running COS 5.6.2 or lower.
For complete details see page 84 of this document.
802.11b Wireless Update
Improved software to support 802.11b wireless base stations response to client requests made after an extended period of LAN inactivity.
NIST UTC Reference Signal
Cayman Gateways acquire the Universal Coordinated Time reference signal from the National Institute of Standards and Technology. This provides date and time information for log entries.
12
Downloaded from www.Manualslib.com manuals search engine

Section 2 |
Capabilities Roadmap for COS 6.3 |
Capabilities Roadmap for COS 6.3
Cayman Gateways support a wide array of features and functionality. This roadmap points you to overview discussions and How To procedures.
Capabilities Roadmap:
Cayman Gateways with COS 6.3
|
Feature |
NewforCOS |
Outline |
Details |
|
|
6.3 |
Page |
|
|
|
|
|
|
General |
|
|
|
|
|
|
|
|
|
|
Software Feature Keys |
Yes |
14 |
93 |
|
|
|
|
|
Management |
|
|
|
|
|
|
|
|
|
|
Embedded Web Server |
Changed |
15 |
29 |
|
|
|
|
|
|
Diagnostics |
|
15 |
99 |
|
|
|
|
|
LAN |
|
|
|
|
|
|
|
|
|
|
DHCP Server |
|
16 |
59 |
|
|
|
|
|
|
DHCP Relay-agent |
|
16 |
59 |
|
|
|
|
|
|
DNS Proxy |
|
16 |
124 |
|
|
|
|
|
WAN |
|
|
|
|
|
|
|
|
|
|
DHCP Client |
|
17 |
123 |
|
|
|
|
|
|
PPPoE |
|
17 |
136 |
|
|
|
|
|
|
Multiple PPPoE Sessions |
Yes |
|
|
|
|
|
|
|
|
Static IP Address |
|
18 |
41 |
|
|
|
|
|
|
IPMaps (Multiple Static IP Addresses) |
Yes |
18 |
52 |
|
|
|
|
|
|
Pinholes |
|
21 |
46 |
|
|
|
|
|
|
User Limits |
Yes |
|
103 |
|
|
|
|
|
Security |
|
|
|
|
|
|
|
|
|
|
Password Protection |
|
19 |
66 |
|
|
|
|
|
|
Network Address Translation (NAT) |
|
19 |
|
|
|
|
|
|
|
Instant-On PPP |
|
17 |
138 |
|
|
|
|
|
|
Security Monitoring Log |
Yes |
22 |
80 |
|
|
|
|
|
|
VPN IPSec Pass Through |
|
27 |
73 |
|
|
|
|
|
|
SafeHarbour VPN IPSec Tunnel |
Yes |
28 |
73 |
|
|
|
|
|
|
BreakWater Basic Firewall |
Yes |
26 |
69 |
13
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
Overview of Major Capabilities |
Section 3 |
This section describes the principal features of Cayman Operating System version 6.3. The information is grouped by usage area.
General
Feature Keys
Certain functionality in this release is controlled through software feature keys. These keys are proprietary files with the following properties:
•They are specific to the serial number of the target unit.
•Once installed, and the Gateway restarted, the desired enhancement is enabled, which then allows full access to:
–Configuration
–Operation
–Maintenance
–Administration
•They will not enable the desired feature on a unit with the wrong serial number.
–They are rejected upon “Restart”, not when the file is downloaded. Enhanced capabilities requiring a feature key include:
•Tiered Operating System
•Security Monitoring Log
•BreakWater Basic Firewall
•SafeHarbour IPSec Tunnel Termination
Many Netopia Cayman-series Gateways ship with particular feature key sets pre-enabled. You can check the feature keys enabled on your Gateway in the System Status web page. See “System Status” on page 101.
14
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
Management
Embedded Web Server
There is no specialized client software required to configure, manage, or maintain your Cayman Gateway. Web pages embedded in the operating system provide access to the following Gateway operations:
•Setup
•System and security logs
•Diagnostics functions
Once you have removed your Cayman Gateway from its packing container and powered the unit up, use any LAN attached PC or workstation running a common web browser application to configure and monitor the Gateway.
Diagnostics
In addition to the Gateway’s visual LED indicators, you access an extensive suite of diagnostic facilities by browsing to the unit.
Two of the facilities are:
•Automated “Multi-Layer” Test
The Run Diagnostics link initiates a sequence of tests. They examine the functionality of the Gateway, from the physical connections (OSI Layer 1) to the application traffic (OSI Layer 7).
•Network Test Tools
Three test tools to determine network reachability are available:
–Ping - tests the “reachability” of a particular network destination by sending an ICMP echo request and waiting for a reply.
–TraceRoute - displays the path to a destination by showing the number of hops and the router addresses of these hops.
–NSLookup - converts a domain name to its IP address and vice versa.
The system log also provides diagnostic information.
Your Service Provider may request information that you acquire from these various diagnostic tools. Individual tests may be performed at the command line. (See Appendix A).
15
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
Local Area Network
DHCP (Dynamic Host Configuration Protocol) Server
DHCP Server functionality enables the Gateway to assign your LAN computer(s) a “private” IP address and other parameters that allow network communication. The default DHCP Server configuration of the Gateway supports up to 253 LAN IP addresses.
This feature simplifies network administration because the Gateway maintains a list of IP address assignments. Additional computers can be added to your LAN without the hassle of configuring an IP address.
DHCP (Dynamic Host Configuration Protocol) Relay Agent
DHCP Relay functionality enables the Gateway to forward a DHCP client request to a specified DHCP Server. This assigned DHCP Server will reply to the request with an IP address and other network parameters.
DNS Proxy
Domain Name System (DNS) provides end users with the ability to look for devices or web sites through the use of names, rather than IP addresses. For websurfers, this technology allows a user to enter the URL (Universal Resource Locator) text string to access a desired website. Each text string identifier has an associated IP address, a series of numbers in the format of xxx.xxx.xxx.xxx (e.g. 147.240.101.006). It is DNS servers that are responsible for this text-to-IP Address translation. DNS Servers, in most cases, are located at Internet Service Provider facilities. They translate domain names into the desired IP address for locating an Internet website by answering DNS requests.
The Cayman DNS Proxy feature allows the LAN-side IP address of the Gateway to be used for proxying DNS requests from hosts on the LAN to the DNS Servers configured in the gateway. This is accomplished by having the Gateway's LAN address handed out as the “DNS Server” to the DHCP clients on the LAN.
The Cayman DNS Proxy only proxies UDP DNS queries, not TCP DNS queries.
16
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
Wide Area Network
DHCP (Dynamic Host Configuration Protocol) Client
DHCP Client functionality enables the Gateway to request an IP address from your Service Provider. DHCP servers on your Service Provider’s network reply to DHCP Client requests and assign the network parameters.
PPPoE (Point-to-Point Protocol over Ethernet)
The PPPoE specification, incorporating the PPP and Ethernet standards, allows your computer(s) to connect to your Service Provider’s network through your Ethernet WAN connection. The Netopia Cayman-series Gateway supports PPPoE, eliminating the need to install PPPoE client software on any LAN computers.
Service Providers may require the use of PPP authentication protocols such as Challenge Handshake Authentication Protocol (CHAP) or Password Authentication Protocol (PAP). CHAP and PAP use a username and password pair to authenticate users with a PPP server.
A CHAP authentication process works as follows:
1.The password is used to scramble a challenge string.
2.The password is a shared secret, known by both peers.
3.The unit sends the scrambled challenge back to the peer.
PAP, a less robust method of authentication, sends a username and password to a PPP server to be authenticated. PAP’s username and password pair are not encrypted, and therefore, sent “unscrambled”.
Instant-On PPP
You can configure your Gateway for one of two types of Internet connections:
•Always On
•Instant On
These selections provide either an uninterrupted Internet connection or an as-needed connection.
While an Always On connection is convenient, it does leave your network permanently connected to the Internet, and therefore potentially vulnerable to attacks.
Cayman's Instant On technology furnishes almost all the benefits of an Always-On connection while providing two additional security benefits:
•Your network cannot be attacked when it is not connected.
17
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
•Your network may change address with each connection making it more difficult to attack.
When you configure Instant On access, you can also configure an idle time-out value. Your Gateway monitors traffic over the Internet link and when there has been no traffic for the configured number of seconds, it disconnects the link.
When new traffic that is destined for the Internet arrives at the Gateway, the Gateway will instantly re-establish the link.
Your service provider may be using a system that assigns the Internet address of your Gateway out of a pool of many possible Internet addresses. The address assigned varies with each connection attempt, which makes your network a moving target for any attacker.
Static IP Addresses
If your Service Provider requires the Cayman Gateway to use Static IP addressing, you must configure your Gateway for it. Dynamically assigned addresses allow a service provider’s customer to install their Gateway without WAN configuration. Static addresses never time out; dynamic addresses time out and will be reassigned.
A static IP address is preferred for setting up and maintaining pinholes through the Cayman Gateway’s NAT security facility.
Your Service Provider may not offer a static IP address option.
IPMaps
IPMaps supports one-to-one Network Address Translation (NAT) for IP addresses assigned to servers, hosts, or specific computers on the LAN side of the Cayman Gateway.
With IPMaps, a Service Provider-assigned static IP address is mapped to a specific internal device. This allows a LAN-located device to appear public without compromising other locally attached devices. The external IP addresses must be on the same subnet.
IPMaps is used for applications such as Web, email, and FTP servers.
See How To: Configure for IPMaps on page 52 for more information.
18
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
Security
Password Protection
Access to your Cayman device is controlled through two access control accounts, Admin or User.
•The Admin, or administrative user, performs all configuration, management or maintenance operations on the Gateway.
•The User account provides monitor capability only.
A user may NOT change the configuration, perform upgrades or invoke maintenance functions.
For the security of your connection, an Admin password must be set on the Cayman unit.
Network Address Translation (NAT)
The Cayman Gateway Network Address Translation (NAT) security feature lets you conceal the topology of a hard-wired Ethernet or wireless network connected to its LAN interface from routers on networks connected to its WAN interface. In other words, the end computer stations on your LAN are invisible from the Internet.
Only a single WAN IP address is required to provide this security support for your entire LAN.
LAN sites that communicate through an Internet Service Provider typically enable NAT, since they usually purchase only one IP address from the ISP.
•When NAT is ON, the Cayman Gateway “proxies” for the end computer stations on your network by pretending to be the originating host for network communications from non-originating networks. The WAN interface address is the only IP address exposed.
The Cayman Gateway tracks which local hosts are communicating with which remote hosts. It routes packets received from remote networks to the correct computer on the LAN (Ethernet A) interface.
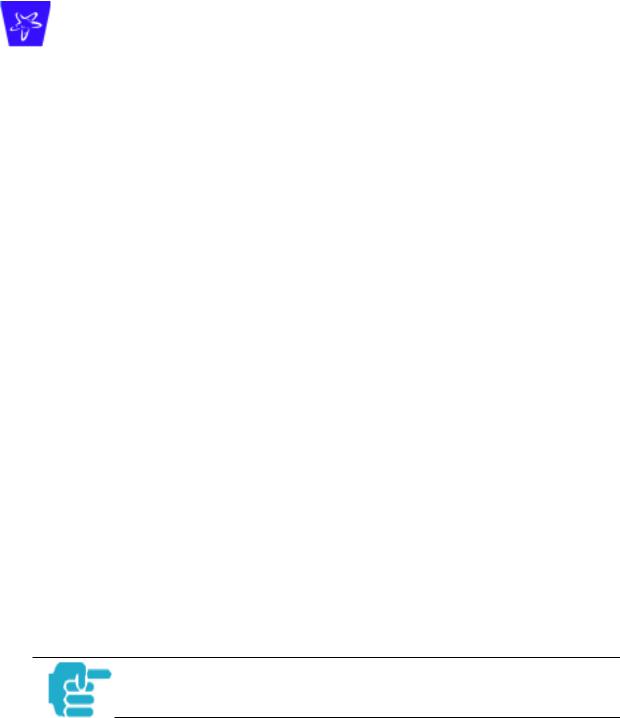
•When NAT is OFF, a Cayman Gateway acts as a traditional TCP/IP router, all LAN computers/devices are exposed to the Internet.
A diagram of a typical NAT-enabled LAN is shown below:
19
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
|
General |
|
|
Dual Ethernet Gateway |
||
Internet |
WAN |
LAN |
|
Ethernet |
Ethernet |
||
|
|||
|
Interface |
Interface |
|
|
NAT |
|
|
Cable |
|
|
|
Modem |
|
|
|
|
|
NAT-protected |
|
|
|
LAN stations |
|
|
Embedded Admin Services: |
|
|
|
HTTP-Web Server and Telnet Server Port |
||
A similar configuration applies to a DSL WAN interface (3220 family).
1.The default setting for NAT is ON.
2.Cayman uses Port Address Translation (PAT) to implement the NAT facility.
3.NAT Pinhole traffic (discussed below) is always initiated from the WAN side.
Cayman Advanced Features for NAT
Using the NAT facility provides effective LAN security. However, there are user applications that require methods to selectively by-pass this security function for certain types of Internet traffic.
Cayman Gateways provide special pinhole configuration rules that enable users to establish NAT-protected LAN layouts that still provide flexible bypass capabilities.
Some of these rules require coordination with the unit’s embedded administration services: the internal Web (HTTP) Port (TCP 80) and the internal Telnet Server Port (TCP 23).
Internal Servers
Related to the pinhole configuration rules is an internal port forwarding facility that enables you to:
•Direct traffic to specific hosts/computers on the LAN side of the Gateway.
•Eliminate conflicts with embedded administrative ports 80 and 23.
20
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
Pinholes
This feature allows you to:
•Transparently route selected types of network traffic using the port forwarding facility.
–FTP requests or HTTP (Web) connections are directed to a specific host on your LAN.
•Setup multiple pinhole paths.
–Up to 32 paths are supported
•Identify the type(s) of traffic you want to redirect by port number.
Common TCP/IP protocols and ports are:
FTP (TCP 21) |
telnet (TCP 23) |
SMTP (TCP 25) |
HTTP (TCP 80) |
SNMP (TCP 161, UDP 161) |
|
See page 47 for How To instructions.
Default Server
This feature allows you to:
•Direct your Gateway to forward all externally initiated IP traffic (TCP and UDP protocols only) to a default host on the LAN.
•Enable it for certain situations:
–Where you cannot anticipate what port number or packet protocol an in-bound application might use.
For example, some network games select arbitrary port numbers when a connection is opened.
–When you want all unsolicited traffic to go to a specific LAN host.
Default Server is not available for traffic inbound via a SafeHarbour IPsec tunnel.
See page 56 for How To instructions.
21
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
Combination NAT Bypass Configuration
Specific pinholes and Default Server settings, each directed to different LAN devices, can be used together.
Creating a pinhole or enabling a Default Server allows inbound access to the specified LAN station. Contact your Network Administrator for LAN security questions.
Security Monitor
The Security Monitor detects security related events including common types of malicious attacks and writes them to a dedicated security log file. You view this log file from either:
•Cayman Web interface
•Text-based command line interface using a telnet or serial port facility
The log provides information useful in identifying a specific type of attack and tracing its origin. The log maintains 100 entries, and requires a manual reset once full. This preserves for troubleshooting purposes the acquired information about specific attacks, their frequency and tracing information.
See page 80 for more information about the Security Monitoring Log.
COS 6.3 Security Monitor software reports the following eight event types:
•IP Source Address Spoofing
•Source Routing
•Subnet Broadcast Amplification
•Illegal Packet Size (Ping of Death)
•Port Scan (TCP/UDP)
•Excessive Pings
•Admin Login Failure
•MAC Address Spoofing
22
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
Event Details
Details on the eight specific event types and the information logged are:
IP Source Address Spoofing
The Gateway checks all incoming packets to see if the IP address attached is valid for the interface the packet is received through. If the address of the packet is not valid for the interface the packet is discarded.
Logged information includes:
IP source address |
IP destination address |
Number of attempts |
Time at last attempt |
IP interface |
|
Source Routing
IP source routing information packets will be received and accepted by the Cayman Gateway. Logging of this activity is provided in the event the source route information has been forged, but appears as valid data.
Logged information includes:
IP source address |
IP destination address |
Number of attempts |
Time at last attempt |
IP interface |
|
Subnet Broadcast Amplification
Distributed DoS (Denial of Service) attacks often use a technique known as broadcast amplification, in which the attacker sends packets to a router’s subnet broadcast address. This causes the router to broadcast the packet to each host on the subnet. These, in turn, become broadcast sources, thereby involving many new hosts in the attack. The Cayman unit detects and discards any packets that would otherwise be transmitted to a subnet broadcast address. The Security Monitoring logs the event.
Logged information includes:
IP source address |
IP destination address |
Number of attempts |
Time at last attempt |
IP broadcast address |
|
Illegal Packet Size (Ping of Death)
The maximum size of an IP packet is 64K bytes, but large packets must usually be fragmented into smaller pieces to travel across a network. Each fragment contains some information that allows the recipient to reassemble all of the fragments back into the original packet. However, the frag-
23
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
mentation information can also be exploited to create an illegally sized packet. Unwary hosts will often crash when the illegal fragment corrupts data outside of the “normal” packet bounds. The Cayman unit will detect and discard illegal packet fragments, and the Security Monitoring software logs the event.
Logged information includes:
IP source address |
IP destination address |
Number of attempts |
Time at last attempt |
Illegal packer size |
|
Port Scan
Port scanning is the technique of probing to determine the list of TCP or UDP ports on which a host, or in our case, a Gateway is providing services. For example, the HTTP service is usually available on TCP port 80. Once hackers have your port list, they can refine their attack by focusing attention on these ports. According to the TCP/IP/UDP standards, a host will return an ICMP (Internet Control Message Protocol) message stating “port unreachable” on all inactive ports. The Security Monitoring software monitors these circumstances, and will log an alert if it appears the cause is the result of someone running a port scan.
Logged information includes:
Protocol type |
IP source address |
Time at last attempt |
Number of ports scanned |
Highest port |
Lowest port |
Port numbers of first 10 ports scanned
Excessive Pings
The PING (Packet InterNet Groper) Utility is used by hackers to identify prospective targets that can be attacked. The Security Monitoring software will record instances where the router itself is pinged by the same host more than ten times.
Logged information includes:
IP source address |
IP destination address |
Number of attempts |
Time at last attempt |
24
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
Login Failures
The Cayman software provides the means for assigning passwords to the Admin or User accounts to control access to the Gateway. Any attempts to login are given three chances to enter a valid password. The Security Monitoring software records instances where the user fails to enter a valid password.
Logged information includes:
IP source address |
Number of attempts |
Attempt count |
Time at last attempt |
MAC Address Spoofing
A MAC (Media Access Control) Address Spoofing Attack can be identified based on the IP-interface where the illegitimate packet came from. If the interface that the spoofed packet arrives on does not have the same MAC address as the legitimate entry in the routing table, then an attack is logged.
Logged information includes:
IP source address |
Number of attempts |
IP interface |
Time at last attempt |
25
Downloaded from www.Manualslib.com manuals search engine

Section 3 |
General |
BreakWater Basic Firewall
BreakWater delivers an easily selectable set of pre-configured firewall protection levels. These settings are readily available for simple implementation through Cayman’s embedded web server interface.
BreakWater provides you and your network with:
•Protection for all LAN users.
•Elimination of firewall management software on individual PC’s.
•Immediate protection through three pre-configured firewall levels.
•Elimination of the complexity associated with developing firewall rules.
See page 69 for How To Configure BreakWater instructions including a table of user tips.
BreakWater Settings
BreakWater Basic Firewall’s three settings are:
ClearSailing
ClearSailing provides protection against network initiated inbound traffic, while securely passing outbound traffic through the Gateway. In conjunction with Network Address Translation, this setting allows authorized remote diagnostic support while protecting against undesired inbound traffic.
SilentRunning
Using this level of firewall protection allows secure transmission of outbound traffic, but disables any attempt for inbound traffic to identify the Gateway. This is the Internet equivalent of having an unlisted number.
LANdLocked
The third option available turns off all inbound and outbound traffic, isolating the LAN and disabling all WAN traffic.
BreakWater Basic Firewall operates independent of the Gateway’s NAT functionality.
26
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
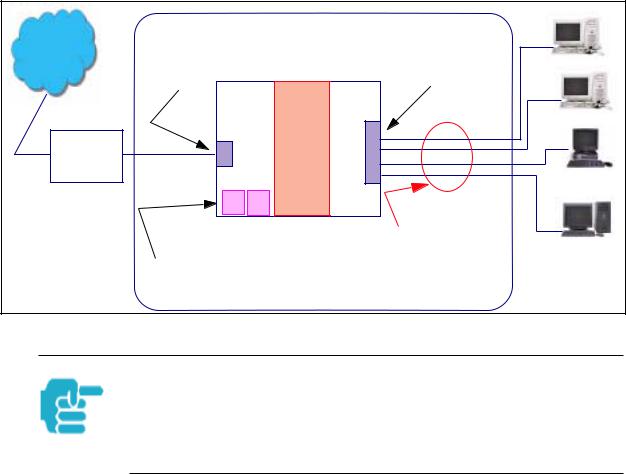
VPN IPSec Pass Through
This Cayman service supports your independent VPN client software in a transparent manner. Cayman has implemented an Application Layer Gateway (ALG) to support multiple PCs running IP Security protocols.
This feature has three elements:
1.On power up or reset, the address mapping function (NAT) of the Gateway’s WAN configuration is turned on by default.
2.When you use your third-party VPN application, the Gateway recognizes the traffic from your client and your unit. It allows the packets to pass through the NAT “protection layer” via the encrypted IPSec tunnel.
3.The encrypted IPSec tunnel is established “through” the Gateway.
A typical VPN IPSec Tunnel pass through is diagrammed below:
Cayman
Gateway
Typically, no special configuration is necessary to use the IPSec pass through feature. This feature may need to be disabled for special VPN clients that are designed to be supported through NAT.
In the diagram, VPN PC clients are shown behind the Cayman Gateway and the secure server is at Corporate Headquarters across the WAN. You cannot have your secure server behind the Cayman Gateway.
When multiple PCs are starting IPSec sessions, they must be started one at atime to allow the associations to be created and mapped.
27
Downloaded from www.Manualslib.com manuals search engine
Section 3 |
General |
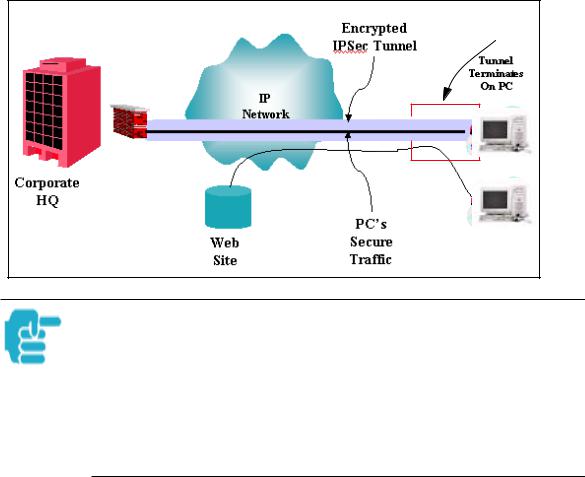
SafeHarbour VPN IPSec Tunnel
SafeHarbour VPN IPSec Tunnel provides a single, encrypted tunnel to be terminated on the Gateway, making a secure tunnel available for all LANconnected Users. This implementation offers the following:
•Eliminates the need for VPN client software on individual PC’s.
•Reduces the complexity of tunnel configuration.
•Simplifies the ongoing maintenance for secure remote access.
A VPN tunnel is a secure link between two networks interconnected over an IP network providing a secure, cost-effective alternative to dedicated leased lines.
SafeHarbour employs VPN standards, including:
•Internet Protocol Security (IPSec) suite, a series of protocols including encryption, authentication, integrity, and replay protection.
•Internet Key Exchange (IKE), a management protocol of IPSec.
Adherence to VPN standards allows seamless interoperability between a Cayman Gateway and another standards-based encryptor. SafeHarbour supports:
•Symmetric encryption protocols DES, 3DES, Blowfish, and CAST
•Hash algorithms MD5 and SHA1
•Diffie-Hellman groups 1, 2, and 5.
Terms are defined in the Glossary and How To sections.
Encrypted IPSec Tunnel |
|
|
“RemoteNetTwo” |
“HQNetOne” |
IP Network |
|
|
Tunnel Terminates |
Tunnel Terminates |
at Standards-based Gateway |
at Cayman Gateway |
SafeHarbour VPN IPSec Tunnel Termination
An important feature of the SafeHarbour VPN IPSec Tunnel is secure encryption of the configured circuit in both directions.
28
Downloaded from www.Manualslib.com manuals search engine

Section 4 |
Access the User Interface |
Web-based User Interface |
Section 4 |
Access the User Interface
Using the embedded Web-based user interface for the Netopia Caymanseries Gateway you can configure, troubleshoot, and monitor the status of your Gateway. For COS Version 6.3 the Web-based UI has been modified:
•To accomodate multiple new features of COS 6.3.
•To make using the entire facility easier.
Open the Web Connection
Once your Gateway is powered up, you can use any recent version of the best-known web browsers that support javascript and Cascading Style Sheets from any LAN-attached PC or workstation.
The procedure is:
Step 1 |
Enter the name or IP address of your Cayman Gateway in the Web browser's |
|
|
|||
|
window and click |
Enter . |
|
|
|
|
|
For example, you would enter http://192.168.1.254 |
if your Cayman Gateway is |
||||
|
using its default IP address. You can enter http://cayman-2e. |
(including the final |
||||
|
period) or http://cayman-dsl. |
if your computer has been configured to obtain its |
||||
|
network configuration from a DHCP server. |
|
|
|||
Step 2 |
If an administrator or user password has been assigned to the Cayman |
|
|
|||
|
Gateway, enter |
Admin |
or User |
as the username and the appropriate |
|
|
|
password and click |
|
OK . |
|
|
|
The Cayman Gateway Home page opens.
If the Gateway is not configured, after logon you will see the Quickstart page.
29
Downloaded from www.Manualslib.com manuals search engine
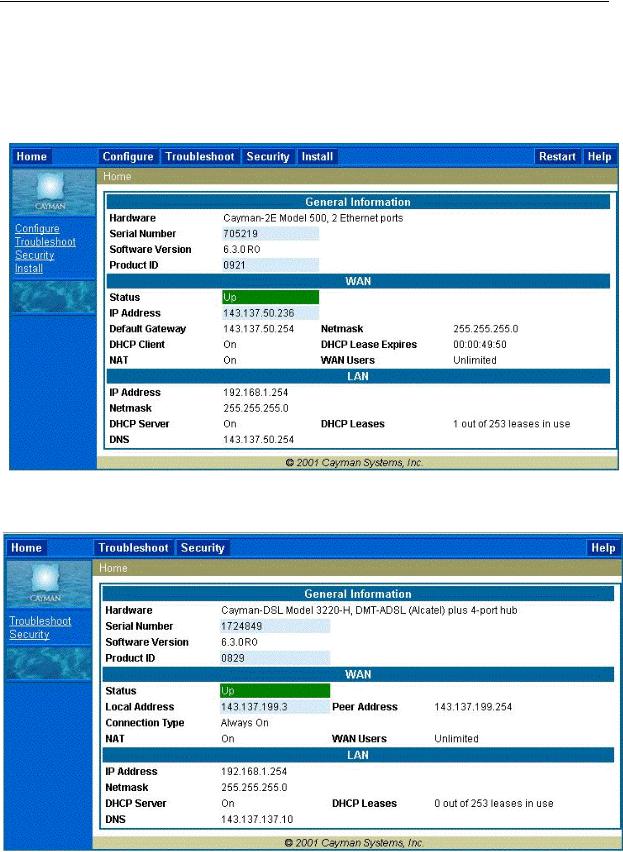
Section 4 |
Home page |
Home page
The Home page is the “dashboard” for your Cayman Gateway. The toolbar at the top provides links to controlling, configuring, and monitoring pages. Critical configuration and operational status is displayed in the center section. If you log on as Admin you see this page.
This example screen is from the Dual Ethernet Gateway.
The Home page differs slightly between DSL and Dual Ethernet Gateways.
Home page - User Mode, DSL Gateway
30
Downloaded from www.Manualslib.com manuals search engine
 Loading...
Loading...