Page 1

M4200 and M4300 Series ProSAFE Managed Switches
CLI Command Reference Manual
Software Version 12.0.2
February 2018
202-11585-04
350 East Plumeria Drive
San Jose, CA 95134
USA
Page 2
M4200 and M4300 Series ProSAFE Managed Switches
Support
Thank you for purchasing this NETGEAR product. You can visit www.netgear.com/support to register your product, get help,
access the latest downloads and user manuals, and join our community. We recommend that you use only official NETGEAR
support resources.
Conformity
For the current EU Declaration of Conformity, visit http://kb.netgear.com/app/answers/detail/a_id/11621.
Compliance
For regulatory compliance information, visit http://www.netgear.com/about/regulatory.
See the regulatory compliance document before connecting the power supply.
Trademarks
© NETGEAR, Inc., NETGEAR and the NETGEAR Logo are trademarks of NETGEAR, Inc. Any non-NETGEAR trademarks are
used for reference purposes only.
Revision History
Publication
Part Number
202-11585-05 February 2018 Updated the sections as follows:
202-11585-03 January 2017 Updated the sections as follows:
202-11585-02 July 2016 Added the following sections and chapter:
202-11585-01 December 2015 Initial publication of this manual.
Publish Date Comments
• Removed the logging persistent command.
• Changed the description for the command in aaa authentication dot1x
default.
• Various defaults in Chapter 7, Switching Commands.
• Corrections to Chapter 15, Power over Ethernet Commands.
• Cloud Managed Commands
• Application Commands
• Chapter 12, Data Center Commands
In addition, added, removed, and changed multiple commands throughout the
manual.
2
Page 3

Contents
Chapter 1 About the NETGEAR Managed Switch Software
Chapter 2 Using the Command-Line Interface
Chapter 3 Software Modules
Scope. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Product Concept . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Command Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Command Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Common Parameter Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
unit/slot/port Naming Convention. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Using the No Form of a Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Executing Show Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
CLI Output Filtering. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Command Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Command Completion and Abbreviation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
CLI Error Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
CLI Line-Editing Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Using CLI Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Access the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Chapter 4 Stacking Commands
Dedicated Port Stacking Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Stack Port Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Stack Firmware Synchronization Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Nonstop Forwarding Commands for Stack Configuration. . . . . . . . . . . . . . . . . . 46
Chapter 5 Management Commands
Configure the Switch Management CPU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
CPU Queue Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Management Interface Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
IPv6 Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Console Port Access Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Telnet Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Secure Shell Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Management Security Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Management Access Control List Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
3
Page 4

M4200 and M4300 Series ProSAFE Managed Switches
Hypertext Transfer Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Access Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
User Account Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Per-Command Authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Exec Authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
SNMP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
RADIUS Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
TACACS+ Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Configuration Scripting Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Prelogin Banner, System Prompt, and Host Name Commands. . . . . . . . . . . . . 159
OpenFlow Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Cloud Managed Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Application Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Chapter 6 Utility Commands
AutoInstall Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
CLI Output Filtering Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
Dual Image Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
System Information and Statistics Commands . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Switch Services Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Logging Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Email Alerting and Mail Server Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
System Utility and Clear Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Simple Network Time Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Time Zone Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
DHCP Server Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
DNS Client Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
IP Address Conflict Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Serviceability Packet Tracing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Support Mode Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 310
Cable Test Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
Power Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
USB commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
sFlow Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
Switch Database Management Template Commands . . . . . . . . . . . . . . . . . . . . 323
Green Ethernet Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 326
Remote Monitoring Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 335
Statistics Application Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 350
Chapter 7 Switching Commands
Port Configuration Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Spanning Tree Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368
Loop Protection Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 401
VLAN Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 404
Switch Port Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 416
Double VLAN Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 421
4
Page 5

M4200 and M4300 Series ProSAFE Managed Switches
Private VLAN Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .424
Voice VLAN Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Provisioning (IEEE 802.1p) Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 430
Asymmetric Flow Control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 430
Protected Ports Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
Private Group Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 434
GARP Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 436
GVRP Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438
GMRP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 440
Port-Based Network Access Control Commands. . . . . . . . . . . . . . . . . . . . . . . . 442
802.1X Supplicant Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 463
Storm-Control Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 467
Link Dependency Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 476
Link Local Protocol Filtering Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 478
MRP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 479
MMRP Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 480
MVRP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 484
Port-Channel/LAG (802.3ad) Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 487
Port Mirroring Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 507
Static MAC Filtering Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 511
DHCP L2 Relay Agent Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 515
DHCP Client Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 522
DHCP Snooping Configuration Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 523
Dynamic ARP Inspection Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 533
MVR Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .540
IGMP Snooping Configuration Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 548
IGMP Snooping Querier Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 557
MLD Snooping Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 562
MLD Snooping Querier Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .570
Port Security Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 575
LLDP (802.1AB) Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 580
LLDP-MED Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 589
Denial of Service Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 597
MAC Database Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 607
ISDP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 610
Interface Error Disabling and Auto Recovery Commands . . . . . . . . . . . . . . . . . 617
UniDirectional Link Detection Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 620
Link Debounce Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 623
Chapter 8 Routing Commands
Address Resolution Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 626
IP Routing Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 632
Routing Policy Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 658
Router Discovery Protocol Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 668
Virtual LAN Routing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 672
Virtual Router Redundancy Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . 675
DHCP and BootP Relay Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 685
IP Helper Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 687
5
Page 6

M4200 and M4300 Series ProSAFE Managed Switches
Open Shortest Path First Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 695
General OSPF Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 695
OSPF Interface Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 715
IP Event Dampening Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 721
OSPF Graceful Restart Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 723
OSPFv2 Stub Router Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 726
OSPF Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 728
Routing Information Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 749
ICMP Throttling Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 757
Chapter 9 Captive Portal Commands
Captive Portal Global Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 761
Captive Portal Configuration Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 766
Captive Portal Status Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 775
Captive Portal Client Connection Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . 777
Captive Portal Interface Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 780
Captive Portal Local User Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 782
Captive Portal User Group Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 789
Chapter 10 IPv6 Commands
Tunnel Interface Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 792
Loopback Interface Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 794
IPv6 Routing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 795
OSPFv3 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 832
Global OSPFv3 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 832
OSPFv3 Interface Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 849
OSPFv3 Graceful Restart Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 854
OSPFv3 Stub Router Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 858
OSPFv3 Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 859
DHCPv6 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 876
DHCPv6 Snooping Configuration Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . 887
Chapter 11 Quality of Service Commands
Class of Service Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 900
Differentiated Services Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 907
DiffServ Class Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 908
DiffServ Policy Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 917
DiffServ Service Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 924
DiffServ Show Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 925
MAC Access Control List Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 931
IP Access Control List Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 940
IPv6 Access Control List Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 956
Time Range Commands for Time-Based ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . 965
Auto-Voice over IP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 967
iSCSI Optimization Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 972
6
Page 7

M4200 and M4300 Series ProSAFE Managed Switches
Chapter 12 Data Center Commands
Priority-Based Flow Control Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 980
Chapter 13 IP Multicast Commands
Multicast Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .985
DVMRP Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 992
PIM Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 997
Internet Group Message Protocol Commands . . . . . . . . . . . . . . . . . . . . . . . . .1015
IGMP Proxy Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1023
Chapter 14 IPv6 Multicast Commands
IPv6 Multicast Forwarder. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1030
IPv6 PIM Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1034
IPv6 MLD Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1049
IPv6 MLD-Proxy Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1057
Chapter 15 Power over Ethernet Commands
About PoE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1064
PoE Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1064
Chapter 16 Switch Software Log Messages
Core. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1076
Utilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1078
Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1081
Switching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1084
QoS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1092
Routing/IPv6 Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1093
Multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1095
Stacking. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1100
Technologies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1101
O/S Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1103
Command List
7
Page 8
1. About the NETGEAR Managed
Switch Software
The purpose of the NETGEAR managed switch software is twofold:
• Assist attached hardware in switching frames, based on Layer 2, 3, or 4 information
contained in the frames.
• Provide a complete device management portfolio to the network administrator.
This chapter contains the following sections:
• Scope
• Product Concept
Note: For more information about the topics covered in this manual, visit the
support website at netgear.com/support.
Note: Firmware updates with new features and bug fixes are made
available from time to time at downloadcenter.netgear.com. Some
products can regularly check the site and download new firmware, or
you can check for and download new firmware manually. If the
features or behavior of your product does not match what is
described in this guide, you might need to update your firmware.
1
8
Page 9

M4200 and M4300 Series ProSAFE Managed Switches
Scope
The NETGEAR managed switch software encompasses both hardware and software
support. The software is partitioned to run in the following processors:
• CPU. This code runs the networking device management portfolio and controls the
overall networking device hardware. It also assists in frame forwarding, as needed and
specified. This code is designed to run on multiple platforms with minimal changes from
platform to platform.
• Networking device processor. This code does the majority of the packet switching,
usually at wire speed. This code is platform dependent, and substantial changes might
exist across products.
Product Concept
Fast Ethernet and Gigabit Ethernet switching continues to evolve from high-end backbone
applications to desktop switching applications. The price of the technology continues to
decline, while performance and feature sets continue to improve. Devices that are capable of
switching Layers 2, 3, and 4 are increasingly in demand. The NETGEAR managed switch
software provides a flexible solution to these ever-increasing needs.
The exact functionality provided by each networking device on which the NETGEAR
managed switch software runs varies depending upon the platform.
The NETGEAR managed switch software includes a set of comprehensive management
functions for managing both the software and the network. You can manage the NETGEAR
managed switch software by using one of the following three methods:
• Command-line interface (CLI)
• Simple Network Management Protocol (SNMP)
• Web-based
About the NETGEAR Managed Switch Software
9
Page 10

2. Using the Command-Line Interface
The command-line interface (CLI) is a text-based way to manage and monitor the system. You
can access the CLI by using a direct serial connection or by using a remote logical connection
with telnet or SSH.
This chapter describes the CLI syntax, conventions, and modes. It contains the following
sections:
• Command Syntax
• Command Conventions
• Common Parameter Values
• unit/slot/port Naming Convention
• Using the No Form of a Command
• Executing Show Commands
• CLI Output Filtering
2
10
Page 11

M4200 and M4300 Series ProSAFE Managed Switches
Command Syntax
A command is one or more words that might be followed by one or more parameters.
Parameters can be required or optional values.
Some commands, such as show network and clear vlan, do not require parameters.
Other commands, such as network parms, require that you supply a value after the
command. You must type the parameter values in a specific order, and optional parameters
follow required parameters. The following example describes the network parms
command syntax:
Format network parms ipaddr netmask [gateway]
• network parms is the command name.
• ipaddr and netmask are parameters and represent required values that you must enter
after you type the command keywords.
• [gateway] is an optional keyword, so you are not required to enter a value in place of
the keyword.
This command line reference manual lists each command by the command name and
provides a brief description of the command. Each command reference also contains the
following information:
• Format shows the command keywords and the required and optional parameters.
• Mode identifies the command mode you must be in to access the command.
• Default shows the default value, if any, of a configurable setting on the device.
The show commands also contain a description of the information that the command shows.
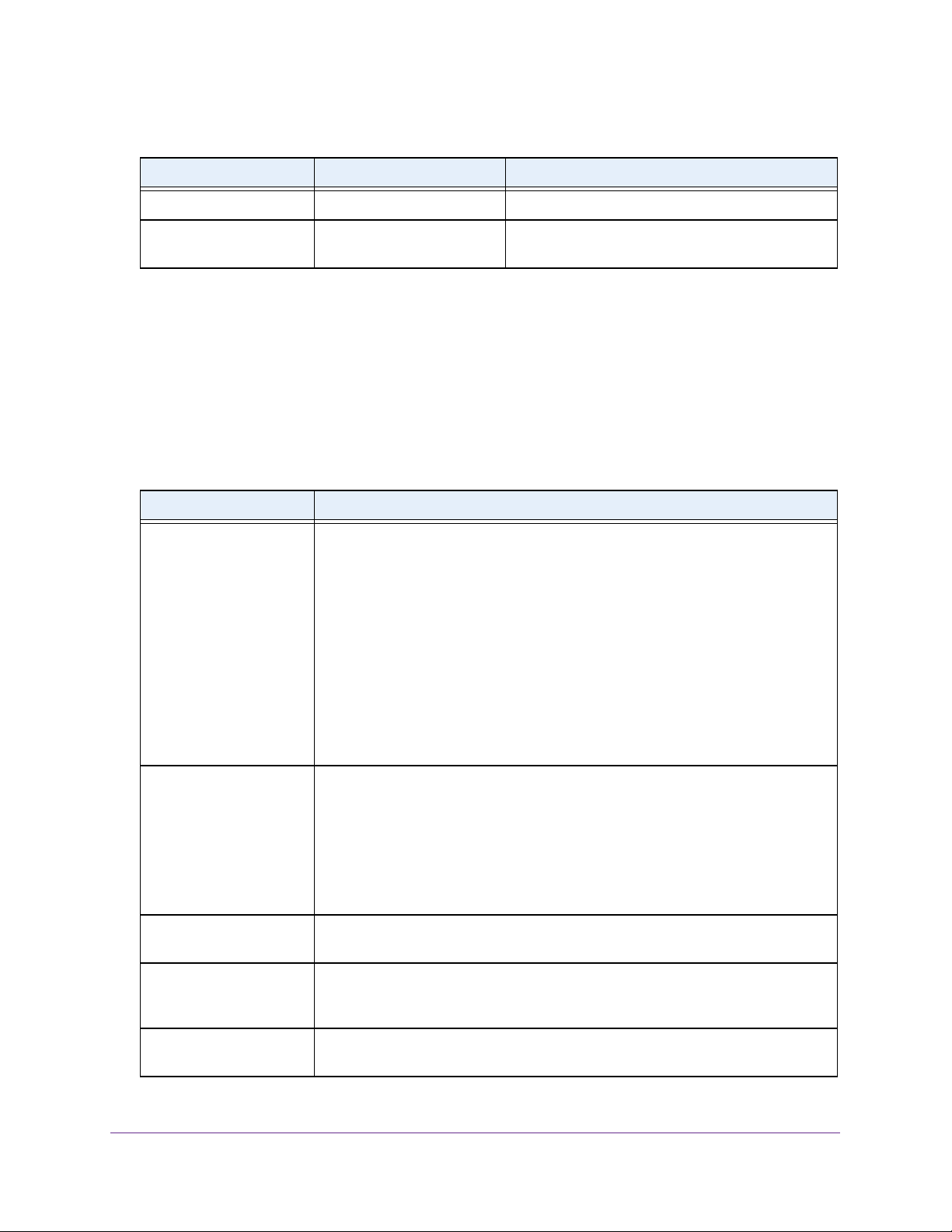
Command Conventions
The parameters for a command might include mandatory values, optional values, or keyword
choices. Parameters are order-dependent. The following table describes the conventions this
document uses to distinguish between value types.
Table 1. Parameter Conventions
Symbol Example Description
italic font value or [value] Indicates a variable value. You must replace the
italicized text, which can be placed within curly
brackets or square brackets, with an appropriate
value, which might be a name or number.
[ ] square brackets [keyword] Indicates an optional parameter.
{ } curly braces {choice1 | choice2} Indicates that you must select a parameter from the
list of choices.
Using the Command-Line Interface
11
Page 12
M4200 and M4300 Series ProSAFE Managed Switches
Table 1. Parameter Conventions (continued)
Symbol Example Description
| Vertical bars choice1 | choice2 Separates the mutually exclusive choices.
[{ }] Braces within
square brackets
[{choice1 | choice2}] Indicates a choice within an optional element. This
format is used mainly for complicated commands
Common Parameter Values
Parameter values might be names (strings) or numbers. To use spaces as part of a name
parameter, enclose the name value in double quotes. For example, the expression “System
Name with Spaces” forces the system to accept the spaces. Empty strings (““) are not valid
user-defined strings. The following table describes common parameter values and value
formatting.
Table 2. Parameter Descriptions
Parameter Description
ipaddr This parameter is a valid IPv4 address. You can enter the IP address in the
following formats:
• a (32 bits)
• a.b (8.24 bits)
• a.b.c (8.8.16 bits)
• a.b.c.d (8.8.8.8)
In addition to these formats, the CLI accepts decimal, hexadecimal and octal
formats through the following input formats (where n is any valid hexadecimal, octal
or decimal number):
• 0xn (CLI assumes hexadecimal format.)
• 0n (CLI assumes octal format with leading zeros.)
• n (CLI assumes decimal format.)
ipv6-addr This parameter is a valid IPv6 address. You can enter the IP address in the
following formats:
• FE80:0000:0000:0000:020F:24FF:FEBF:DBCB
• FE80:0:0:0:20F:24FF:FEBF:DBCB
• FE80::20F24FF:FEBF:DBCB
• FE80:0:0:0:20F:24FF:128:141:49:32
For additional information, refer to RFC 3513.
Interface or
unit/slot/port
Logical Interface Represents a logical slot and port number. This is applicable in the case of a
Character strings Use double quotation marks to identify character strings, for example, “System
Valid slot and port number separated by a forward slash. For example, 0/1
represents slot number 0 and port number 1.
port-channel (LAG). You can use the logical unit/slot/port to configure the
port-channel.
Name with Spaces”. An empty string (“”) is not valid.
Using the Command-Line Interface
12
Page 13
M4200 and M4300 Series ProSAFE Managed Switches
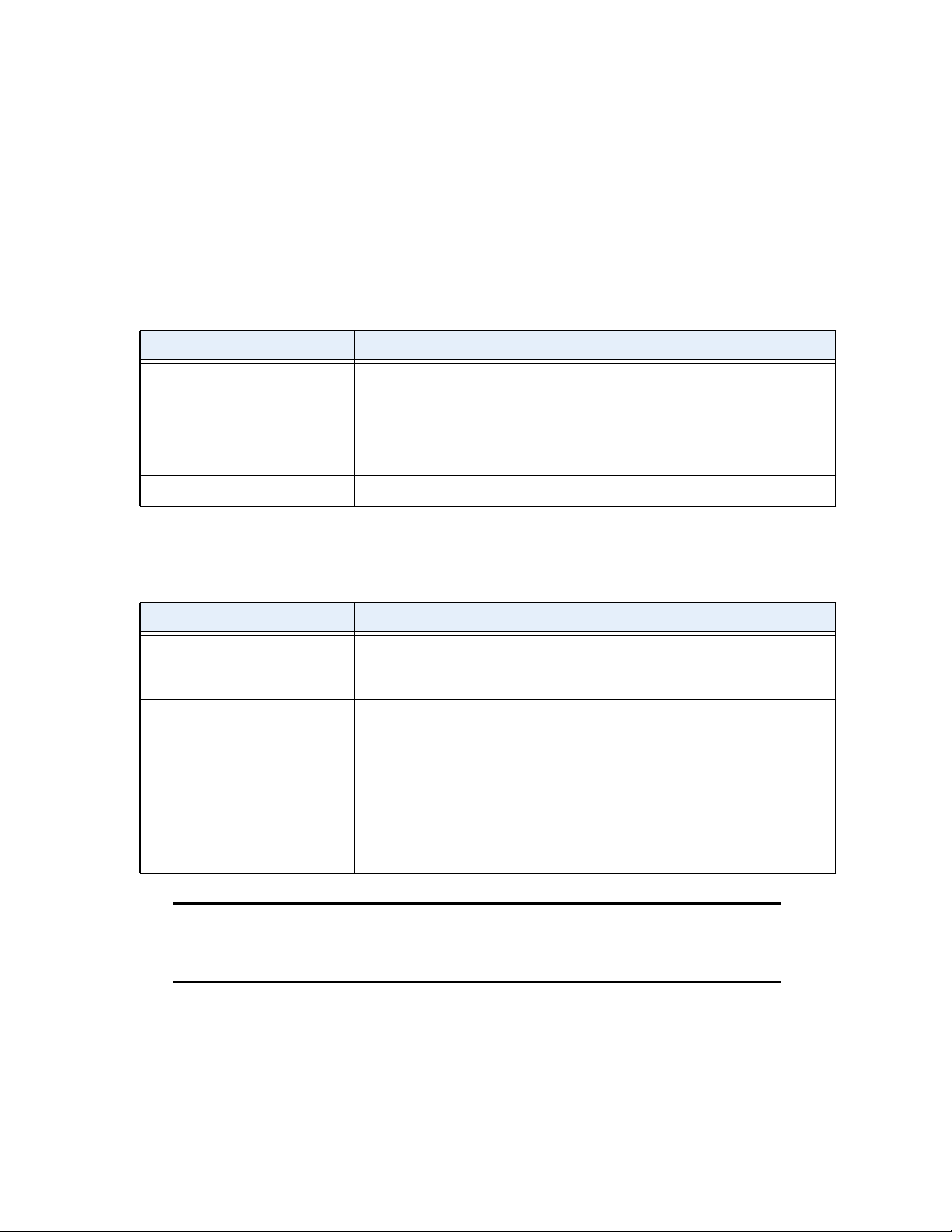
unit/slot/port Naming Convention
The switch references physical entities such as cards and ports by using a
unit/slot/port naming convention. The switch also uses this convention to identify
certain logical entities, such as port channel interfaces.
The slot number has two uses. In the case of physical ports, it identifies the card containing
the ports. In the case of logical and CPU ports it also identifies the type of interface or port.
Table 3. Type of Slots
Slot Type Description
Physical slot numbers Physical slot numbers begin with zero, and are allocated up to the maximum
number of physical slots.
Logical slot numbers Logical slots immediately follow physical slots and identify port-channel
(LAG) or router interfaces. The value of logical slot numbers depend on the
type of logical interface and can vary from platform to platform.
CPU slot numbers The CPU slots immediately follow the logical slots.
The port identifies the specific physical port or logical interface being managed on a given
slot.
Table 4. Type of Ports
Port Type Description
Physical Ports The physical ports for each slot are numbered sequentially starting from one.
For example, port 1 on slot 0 (an internal port) for a switch is 1/0/1, port 2 is
1/0/2, port 3 is 1/0/3, and so on.
Logical Interfaces Port-channel or Link Aggregation Group (LAG) interfaces are logical
interfaces that are only used for bridging functions.
VLAN routing interfaces are only used for routing functions.
Loopback interfaces are logical interfaces that are always up.
Tunnel interfaces are logical point-to-point links that carry encapsulated
packets.
CPU ports CPU ports are handled by the driver as one or more physical entities located
on physical slots.
Note: In the CLI, loopback and tunnel interfaces do not use the
unit/slot/port format. To specify a loopback interface, you use
the loopback ID. To specify a tunnel interface, you use the tunnel ID.
Using the Command-Line Interface
13
Page 14

M4200 and M4300 Series ProSAFE Managed Switches
Using the No Form of a Command
The no keyword is a specific form of an existing command and does not represent a new or
distinct command. Almost every configuration command has a no form. In general, use the
no form to reverse the action of a command or reset a value back to the default. For example,
the no shutdown configuration command reverses the shutdown of an interface. Use the
command without the keyword no to reenable a disabled feature or to enable a feature that is
disabled by default. Only the configuration commands are available in the no form.
Executing Show Commands
All show commands can be issued from any configuration mode (Global Configuration,
Interface Configuration, VLAN Configuration, etc.). The show commands provide information
about system and feature-specific configuration, status, and statistics. Previously, show
commands could be issued only in User EXEC or Privileged EXEC modes.
CLI Output Filtering
Many CLI show commands include considerable content to display to the user. This can
make output confusing and cumbersome to parse through to find the information of desired
importance. The CLI Output Filtering feature allows the user, when executing CLI show
display commands, to optionally specify arguments to filter the CLI output to display only
desired information. The result is to simplify the display and make it easier for the user to find
the information the user is interested in.
The main functions of the CLI Output Filtering feature are:
• Pagination Control
- Supports enabling/disabling paginated output for all show CLI commands. When
disabled, output is displayed in its entirety. When enabled, output is displayed
page-by-page such that content does not scroll off the terminal screen until the user
presses a key to continue. --More-- or (q)uit is displayed at the end of each page.
- When pagination is enabled, press the return key to advance a single line, press q or
Q to stop pagination, or press any other key to advance a whole page. These keys
are not configurable.
Note: Although some NETGEAR Managed Switch show commands already
support pagination, the implementation is unique per command and
not generic to all commands.
• Output Filtering
- “Grep”-like control for modifying the displayed output to only show the user-desired
content.
- Filter displayed output to only include lines containing a specified string match.
Using the Command-Line Interface
14
Page 15

M4200 and M4300 Series ProSAFE Managed Switches
- Filter displayed output to exclude lines containing a specified string match.
- Filter displayed output to only include lines including and following a specified string
match.
- Filter displayed output to only include a specified section of the content (for example,
“interface 0/1”) with a configurable end-of-section delimiter.
- String matching should be case insensitive.
- Pagination, when enabled, also applies to filtered output.
The following shows an example of the extensions made to the CLI show commands for
the Output Filtering feature.
(NETGEAR Switch) #show running-config ?
<cr> Press enter to execute the command.
| Output filter options.
<scriptname> Script file name for writing active configuration.
all Show all the running configuration on the switch.
interface Display the running configuration for specificed interface
on the switch.
(NETGEAR Switch) #show running-config | ?
begin Begin with the line that matches
exclude Exclude lines that matches
include Include lines that matches
section Display portion of lines
For new commands for the feature, see CLI Output Filtering Commands on page 184.
Using the Command-Line Interface
15
Page 16

3. Software Modules
3
NETGEAR managed switch software consists of flexible modules that can be applied in various
combinations to develop advanced Layer 2/3/4+ products. The commands and command modes
available on your switch depend on the installed modules. Additionally, for some show
commands, the output fields might change based on the modules included in the NETGEAR
managed switch software.
The NETGEAR managed switch software suite includes the following modules:
• Switching (Layer 2)
• Routing (Layer 3)
• IPv6 routing
• Multicast
• Quality of Service
• Management (CLI, Web UI, and SNMP)
• IPv6 Management
Allows management of the switch through an IPv6 address without requiring the IPv6
Routing package in the system. The management address can be associated with the
network port (front-panel switch ports), a routine interface (port or VLAN) and the Service
port.
• Secure Management
16
Page 17
M4200 and M4300 Series ProSAFE Managed Switches
Command Modes
The CLI groups commands into modes according to the command function. Each of the
command modes supports specific commands. The commands in one mode are not
available until you switch to that particular mode, with the exception of the User EXEC mode
commands. You can execute the User EXEC mode commands in the Privileged EXEC
mode.
The command prompt changes in each command mode to help you identify the current
mode. The following table describes the command modes and the prompts visible in that
mode.
Note: The command modes available on your switch depend on the software
modules that are installed. For example, a switch that does not support
BGPv4 does not have the BGPv4 Router Command Mode.
Table 5. CLI Command Modes
Command Mode Prompt Mode Description
User EXEC Switch> Contains a limited set of commands to view
basic system information.
Privileged EXEC Switch# Allows you to issue any EXEC command,
enter the VLAN mode, or enter the Global
Configuration mode.
Global Config Switch (Config)# Groups general setup commands and
permits you to make modifications to the
running configuration.
VLAN Config Switch (Vlan)# Groups all the VLAN commands.
Interface Config Switch (Interface
unit/slot/port)#
Switch (Interface Loopback id)#
Switch (Interface Tunnel id)#
Switch (Interface unit/slot/port
(startrange)-unit/slot/port
(endrange)#
Manages the operation of an interface and
provides access to the router interface
configuration commands.
Use this mode to set up a physical port for a
specific logical connection operation.
Use this mode to manage the operation of a
range of interfaces. For example the prompt
may display as follows:
Switch (Interface 1/0/1-1/0/4) #
Switch (Interface lag
lag-intf-num)#
Switch (Interface vlan vlan-id)# Enters VLAN routing interface configuration
Software Modules
17
Enters LAG Interface configuration mode for
the specified LAG.
mode for the specified VLAN ID.
Page 18
M4200 and M4300 Series ProSAFE Managed Switches
Table 5. CLI Command Modes (continued)
Command Mode Prompt Mode Description
Line Console Switch (config-line)# Contains commands to configure outbound
telnet settings and console interface
settings, as well as to configure console
login/enable authentication.
Line SSH Switch (config-ssh)# Contains commands to configure SSH
login/enable authentication.
Line Telnet Switch (config-telnet)# Contains commands to configure telnet
login/enable authentication.
AAA IAS User
Config
Mail Server Config Switch (Mail-Server)# Allows configuration of the email server.
Policy Map Config Switch (Config-policy-map)# Contains the QoS Policy-Map configuration
Policy Class Config Switch(Config-policy-class-map)# Consists of class creation, deletion, and
Class Map Config Switch (Config-class-map)# Contains the QoS class map configuration
Ipv6_Class-Map
Config
Router OSPF
Config
Router OSPFv3
Config
Router RIP Config Switch (Config-router)# Contains the RIP configuration commands.
BGP Router Config Switch (Config-router)# Contains the BGP4 configuration
Switch (Config-IAS-User)# Allows password configuration for a user in
the IAS database.
commands.
matching commands. The class match
commands specify Layer 2, Layer 3, and
general match criteria.
commands for IPv4.
Switch (Config-class-map)# Contains the QoS class map configuration
commands for IPv6.
Switch (Config-router)# Contains the OSPF configuration
commands.
Switch (Config rtr)# Contains the OSPFv3 configuration
commands.
commands.
Route Map Config Switch (config-route-map)# Contains the route map configuration
commands.
IPv6 Address
Family Config
Peer Template
Config
MAC Access-list
Config
Switch (Config-router-af)# Contains the IPv6 address family
configuration commands.
(Config-rtr-tmplt)# Contains the BGP peer template
configuration commands.
Switch (Config-mac-access-list)# Allows you to create a MAC Access-List and
to enter the mode containing MAC
Access-List configuration commands.
Software Modules
18
Page 19
M4200 and M4300 Series ProSAFE Managed Switches
Table 5. CLI Command Modes (continued)
Command Mode Prompt Mode Description
TACACS Config Switch (Tacacs)# Contains commands to configure properties
for the TACACS servers.
DHCP Pool
Config
DHCPv6 Pool
Config
Stack Global
Config Mode
ARP Access-List
Config Mode
Support Mode Switch (Support)# Allows access to the support commands,
Switch (Config dhcp-pool)# Contains the DHCP server IP address pool
configuration commands.
Switch (Config dhcp6-pool)# Contains the DHCPv6 server IPv6 address
pool configuration commands.
Switch (Config stack)# Allows you to access the Stack Global
Config Mode.
Switch (Config-arp-access-list)# Contains commands to add ARP ACL rules
in an ARP Access List.
which should only be used by the
manufacturer's technical support personnel
as improper use could cause unexpected
system behavior and/or invalidate product
warranty.
The following table explains how to enter or exit each mode.
Table 6. CLI Mode Access and Exit
Command Mode Access Method Exit or Access Previous Mode
User EXEC This is the first level of access. To exit, enter logout.
Privileged EXEC From the User EXEC mode, enter
enable.
To exit to the User EXEC mode, enter exit or
press Ctrl-Z.
Global Config From the Privileged EXEC mode, enter
configure.
VLAN Config From the Privileged EXEC mode, enter
vlan database.
Software Modules
19
To exit to the Privileged EXEC mode, enter
exit, or press Ctrl-Z.
To exit to the Privileged EXEC mode, enter
exit, or press Ctrl-Z.
Page 20
M4200 and M4300 Series ProSAFE Managed Switches
Table 6. CLI Mode Access and Exit (continued)
Command Mode Access Method Exit or Access Previous Mode
Interface Config From the Global Config mode, enter:
interface unit/slot/port
From the Global Config mode, enter:
interface loopback id
From the Global Config mode, enter:
interface tunnel id
From the Global Config mode, enter:
interface
unit/slot/port(startrange)-
unit/slot/port(endrange)
From the Global Config mode, enter:
interface lag lag-intf-num
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
From the Global Config mode, enter:
interface vlan vlan-id
Line Console From the Global Config mode, enter
line console.
Line SSH From the Global Config mode, enter
line ssh.
Line Telnet From the Global Config mode, enter
line telnet.
AAA IAS User
Config
Mail Server Config From the Global Config mode, enter
Policy-Map
Config
Policy-Class-Map
Config
From the Global Config mode, enter
aaa ias-user username name.
mail-server address.
From the Global Config mode, enter
policy-map.
From the Policy Map mode enter class. To exit to the Policy Map mode, enter exit. To
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
return to the Privileged EXEC mode, enter
Ctrl-Z.
Class-Map
Config
From the Global Config mode, enter
class-map, and specify the optional
keyword ipv4 to specify the Layer 3
protocol for this class. See class-map on
page 909 for more information.
Software Modules
20
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
Page 21
M4200 and M4300 Series ProSAFE Managed Switches
Table 6. CLI Mode Access and Exit (continued)
Command Mode Access Method Exit or Access Previous Mode
VPC From Global Config mode, enter vpc. To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
Ipv6-Class-Map
Config
Router OSPF
Config
Router OSPFv3
Config
Router RIP
Config
BGP Router
Config
Route Map Config From the Global Config mode, enter
IPv6 Address
Family Config
From the Global Config mode, enter
class-map and specify the optional
keyword ipv6 to specify the Layer 3
protocol for this class. See class-map on
page 909 for more information.
From the Global Config mode, enter
router ospf.
From the Global Config mode, enter
ipv6 router ospf.
From the Global Config mode, enter
router rip.
From the Global Config mode, enter
router bgp asnumber.
route-map map-tag.
From the BGP Router Config mode,
enter address-family ipv6.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
Peer Template
Config
MAC Access-list
Config
TACACS Config From the Global Config mode, enter
DHCP Pool
Config
DHCPv6 Pool
Config
From the BGP Router Config mode,
enter template peer name to create
a BGP peer template and enter Peer
Template Configuration mode.
From the Global Config mode, enter
mac access-list extended name.
tacacs-server host ip-addr,
where ip-addr is the IP address of the
TACACS server on your network.
From the Global Config mode, enter
ip dhcp pool pool-name.
From the Global Config mode, enter
ip dhcpv6 pool pool-name.
Software Modules
21
o exit to the Global Config mode, enter exit. T o
return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
To exit to the Global Config mode, enter exit.
To return to the Privileged EXEC mode, enter
Ctrl-Z.
Page 22
M4200 and M4300 Series ProSAFE Managed Switches
Table 6. CLI Mode Access and Exit (continued)
Command Mode Access Method Exit or Access Previous Mode
Stack Global
Config Mode
ARP Access-List
Config Mode
Support Mode From the Privileged EXEC mode, enter
From the Global Config mode, enter
stack.
From the Global Config mode, enter arp
access-list.
support.
Note: The support command is
available only after you issued the
techsupport enable command.
To exit to the Global Config mode, enter the
exit command. To return to the Privileged
EXEC mode, enter Ctrl-Z.
To exit to the Global Config mode, enter the
exit command. To return to the Privileged
EXEC mode, enter Ctrl-Z.
To exit to the Privileged EXEC mode, enter
exit, or press Ctrl-Z.
Command Completion and Abbreviation
Command completion finishes spelling the command when you type enough letters of a
command to uniquely identify the command keyword. Once you have entered enough letters,
press the SPACEBAR or TAB key to complete the word.
Command abbreviation allows you to execute a command when you have entered there are
enough letters to uniquely identify the command. You must enter all of the required keywords
and parameters before you enter the command.
CLI Error Messages
If you enter a command and the system is unable to execute it, an error message appears.
The following table describes the most common CLI error messages.
Table 7. CLI Error Messages
Message Text Description
% Invalid input detected at
'^' marker.
Command not found / Incomplete
command. Use ? to list
commands.
Ambiguous command Indicates that you did not enter enough letters to uniquely identify the
Indicates that you entered an incorrect or unavailable command. The
carat (^) shows where the invalid text is detected. This message also
appears if any of the parameters or values are not recognized.
Indicates that you did not enter the required keywords or values.
command.
Software Modules
22
Page 23
M4200 and M4300 Series ProSAFE Managed Switches
CLI Line-Editing Conventions
The following table describes the key combinations you can use to edit commands or
increase the speed of command entry. You can access this list from the CLI by entering
from the User or Privileged EXEC modes.
Table 8. CLI Editing Conventions
Key Sequence Description
DEL or Backspace Delete previous character.
Ctrl-A Go to beginning of line.
Ctrl-E Go to end of line.
Ctrl-F Go forward one character.
Ctrl-B Go backward one character.
Ctrl-D Delete current character.
help
Ctrl-U, X Delete to beginning of line.
Ctrl-K Delete to end of line.
Ctrl-W Delete previous word.
Ctrl-T Transpose previous character.
Ctrl-P Go to previous line in history buffer.
Ctrl-R Rewrites or pastes the line.
Ctrl-N Go to next line in history buffer.
Ctrl-Y Prints last deleted character.
Ctrl-Q Enables serial flow.
Ctrl-S Disables serial flow.
Ctrl-Z Return to root command prompt.
Tab, <SPACE> Command-line completion.
Exit Go to next lower command prompt.
? List available commands, keywords, or parameters.
Software Modules
23
Page 24

M4200 and M4300 Series ProSAFE Managed Switches
Using CLI Help
Enter a question mark (?) at the command prompt to display the commands available in the
current mode.
(NETGEAR Switch) >?
enable Enter into user privilege mode.
help Display help for various special keys.
logout Exit this session. Any unsaved changes are lost.
password Change an existing user’s password.
ping Send ICMP echo packets to a specified IP address.
quit Exit this session. Any unsaved changes are lost.
show Display Switch Options and Settings.
telnet Telnet to a remote host.
Enter a question mark (?) after each word you enter to display available command keywords
or parameters.
(NETGEAR Switch) #network ?
ipv6 Configure IPv6 parameters for system network.
javamode Enable/Disable.
mac-address Configure MAC Address.
mac-type Select the locally administered or burnedin MAC
address.
mgmt_vlan Configure the Management VLAN ID of the switch.
parms Configure Network Parameters of the device.
protocol Select DHCP, BootP, or None as the network config
protocol.
If the help output shows a parameter in angle brackets, you must replace the parameter with
a value.
(NETGEAR Switch) #network parms ?
<ipaddr> Enter the IP Address.
none Reset IP address and gateway on management interface
If there are no additional command keywords or parameters, or if additional parameters are
optional, the following message appears in the output:
<cr> Press Enter to execute the command
You can also enter a question mark (?) after typing one or more characters of a word to list
the available command or parameters that begin with the letters, as shown in the following
example:
(NETGEAR Switch) #show m?
mac mac-addr-table mac-address-table
mail-server mbuf monitor
Software Modules
24
Page 25

M4200 and M4300 Series ProSAFE Managed Switches
Access the CLI
You can access the CLI by using a direct console connection or by using a telnet or SSH
connection from a remote management host.
For the initial connection, you must use a direct connection to the console port. You cannot
access the system remotely until the system has an IP address, subnet mask, and default
gateway. You can set the network configuration information manually, or you can configure
the system to accept these settings from a BootP or DHCP server on your network. For more
information, see Management Interface Commands on page 56.
Software Modules
25
Page 26
4. Stacking Commands
This chapter describes the stacking commands.
Note: Stacking commands are supported on the M4300 series switches only.
This chapter contains the following sections:
• Dedicated Port Stacking Commands
• Stack Port Commands
• Stack Firmware Synchronization Commands
• Nonstop Forwarding Commands for Stack Configuration
The commands in this chapter are in two functional groups:
• Show commands. Display switch settings, statistics, and other information.
4
• Configuration commands. Configure features and options of the switch. For every
configuration command, there is a show command that displays the configuration setting.
Note: The Primary Management Unit is the unit that controls the stack.
26
Page 27
M4200 and M4300 Series ProSAFE Managed Switches
Dedicated Port Stacking Commands
This section describes the commands you use to configure dedicated port stacking.
stack
Use this command to set the mode to Stack Global Config.
Default None
Format stack
Mode Global Config
member (Stack Global Config)
Use this command to add a switch to a stack. The unit is the switch identifier of the switch
to be added to the stack. The switchindex is the index into the database of the supported
switch types, indicating the type of the switch being preconfigured. The switchindex is a
32-bit integer. You issue this command on the Primary Management Unit.
Default None
Format member unit switchindex
Mode Stack Global Config
Note: You can obtain the switch index by issuing the show supported
switchtype command in User EXEC mode.
no member
Use this command to remove a switch from a stack. The unit is the switch identifier of the
switch to be removed from the stack. You issue this command on the Primary Management
Unit.
Format no member unit
Mode Stack Global Config
switch priority
Use this command to configure the ability of a switch to become the Primary Management
Unit. The unit is the switch identifier. The value is the preference parameter that lets you
specify the priority of one backup switch over another. The range for priority is 1 to 15. The
switch with the highest priority value becomes the Primary Management Unit if the active
Primary Management Unit fails. The switch priority defaults to the hardware management
Stacking Commands
27
Page 28
M4200 and M4300 Series ProSAFE Managed Switches
preference value 1. Switches without the hardware capability to become the Primary
Management Unit are not eligible for management.
Default Enabled
Format switch unit priority value
Mode Global Config
switch renumber
Use this command to change the switch identifier for a switch in the stack. The oldunit is
the current switch identifier on the switch whose identifier is to be changed. The newunit is
the updated value of the switch identifier. When you issue the command, the switch is
configured with the configuration information for the new switch, if any. The old switch
configuration information is retained, however the old switch becomes operationally
unplugged. You issue this command on the Primary Management Unit.
Note: If the management unit is renumbered, the running configuration is no
longer applied (that is, the stack functions as if the running
configuration is cleared).
Default None
Format switch oldunit renumber newunit
Mode Global Config
movemanagement (Stack Global Config)
Use this command to move the Primary Management Unit functionality from one switch to
another. The fromunit is the switch identifier on the current Primary Management Unit. The
tounit is the switch identifier on the new Primary Management Unit. When you issue the
command, the entire stack (including all interfaces in the stack) is unconfigured and
reconfigured with the configuration on the new Primary Management Unit. After the reload is
complete, you must perform all stack management capability on the new Primary
Management Unit. To preserve the current configuration across a stack move, issue the
copy system:running-config nvram:startup-config command in Privileged
EXEC mode before performing the stack move. A stack move causes all routes and layer 2
addresses to be lost. You issue this command on the Primary Management Unit. The system
prompts you to confirm the management move.
Note: The movemanagement command does not perform nonstop
forwarding (NSF). To move the management unit to the backup unit,
issue the initiate failover command instead. For more
information, see initiate failover (for stack configuration) on page 49.
Stacking Commands
28
Page 29
M4200 and M4300 Series ProSAFE Managed Switches
Default None
Format movemanagement fromunit tounit
Mode Stack Global Config
standby
Use this command to configure a unit as a Standby Management Unit (STBY). The unit
number is the unit number that must become the Standby Management Unit. The unit
number must be a valid unit number.
Default None
Format standby unit number
Mode Stack Global Config
Note: The Standby Management Unit cannot be the current Management
Unit. The Standby unit must be a management-capable unit.
no standby
Use this command to let the switch run the auto Standby Management Unit.
Format no standby
Mode Stack Global Config
slot (for stack configuration)
Use this command to configure a slot in the system. The unit/slot is the slot identifier of
the slot. The cardindex is the index into the database of the supported card types,
indicating the type of the card that is being preconfigured in the specified slot. The
cardindex is a 32-bit integer. If a card is present in the slot that is unconfigured, the
configured information is deleted and the slot is reconfigured with default information for the
card.
Default None
Format slot unit/slot cardindex
Mode Global Config
Note: You can obtain the card index by issuing the show supported
cardtype command in User EXEC mode.
Stacking Commands
29
Page 30
M4200 and M4300 Series ProSAFE Managed Switches
no slot
Use this command to remove configured information from an existing slot in the system.
Format no slot unit/slot cardindex
Mode Global Config
Note: You can obtain the card index by issuing the show supported
cardtype command in User EXEC mode.
set slot disable (for stack configuration)
Use this command to configure the administrative mode for a specified slot or for all slots. If
you specify all, the command is applied to all slots, otherwise the command is applied to the
slot that is identified by unit/slot.
If a card or other module is present in the slot, the administrative mode is applied to the
contents of the slot. If the slot is empty , the administrative mode is applied to any module that
is inserted into the slot. If a card is disabled, all the ports on the device are operationally
disabled and shown as “unplugged” on management screens.
Default None
Format set slot disable [unit/slot | all]
Mode Global Config
no set slot disable
Use this command to remove the administrative mode for a specified slot or for all slots. If
you specify all, the command removes the administrative mode from all slots, otherwise the
command removes the administrative mode from the slot that is identified by unit/slot.
If a card or other module is present in the slot, the administrative mode removes the
configuration from the contents of the slot. If the slot is empty, the administrative mode
removes the configuration from any module inserted into the slot. If a card is disabled, all the
ports on the device are operationally disabled and shown as “unplugged” on management
screens.
Format no set slot disable [unit/slot | all]
Mode Global Config
Stacking Commands
30
Page 31

M4200 and M4300 Series ProSAFE Managed Switches
set slot power (for stack configuration)
Use this command to configure the power mode for a specified slot or for all slots and allows
power to be supplied to the cards that are located in the slots. If you specify all, the
command is applied to all slots, otherwise the command is applied to the slot that is identified
by unit/slot.
Use this command when you install or remove cards. If a card or other module is present in
the slot, the power mode is applied to the contents of the slot. If the slot is empty, the power
mode is applied to any card inserted into the slot.
Default None
Format set slot power [unit/slot | all]
Mode Global Config
no set slot power
Use this command to remove the power mode for a specified slot or for all slots and prohibits
power from being supplied to the cards that are located in the slots. If you specify all, the
command prohibits power to all slots, otherwise the command prohibits power to the slot that
is identified by unit/slot.
Use this command when you install or remove cards. If a card or other module is present in
the slot, power is prohibited to the contents of the slot. If the slot is empty , power is prohibited
to any card inserted into the slot.
Format no set slot power [unit/slot | all]
Mode Global Config
reload (for stack configuration)
Use this command to reset the entire stack or the identified unit. The unit is the switch
identifier. The system prompts you to confirm that you want to reset the switch.
Default None
Format reload [unit]
Mode User EXEC
stack-status sample-mode
Use this command to configure the global status management mode and, as an option, the
sample size. The mode and sample size parameters are applied globally to all units in the
stack. The default sampling mode of the operation is cumulative, which tacks the sum of the
received time stamp offsets cumulatively. You can also select the history sampling mode,
which tracks the history of the received timestamps.
Stacking Commands
31
Page 32

M4200 and M4300 Series ProSAFE Managed Switches
The sample size indicates the maximum number of samples that must be kept. The range for
the number value for max-samples is from 100 to 500.
Note: The stack-status sample-mode command is implemented as
part of a serviceability functionality and therefore not expected to be
persistent across reloads. The configuration is not visible in the
running configuration under any circumstances. When you issue the
command, the configuration is applied to all the members that are part
of the stack. After you issue the command, the configuration is not
applied to new members that you add to the stack.
Default The default for sampling mode is cumulative.
The default for max-samples is 300.
Format stack-status sample-mode {cumulative | history} [max-samples
number]
Mode Stack Global Config
Command example:
The following command sets the sampling mode to cumulative:
(NETGEAR Switch) #configure
(NETGEAR Switch) (Config)#stack
(NETGEAR Switch) (Config-stack)# stack-status sample-mode cumulative
Command example:
The following command sets the sampling mode to history and the sample size to the default.
(NETGEAR Switch) #configure
(NETGEAR Switch) (Config)#stack
(NETGEAR Switch) (Config-stack)#stack-status sample-mode history
Command example:
The following command sets the sampling mode to history and sample size to 100.
(NETGEAR Switch) #configure
(NETGEAR Switch) (Config)#stack
(NETGEAR Switch) (Config-stack)#stack-status sample-mode history max-samples 100
Stacking Commands
32
Page 33

M4200 and M4300 Series ProSAFE Managed Switches
show slot
Use this command to display information about all the slots in the system or about a specific
slot.
Format show slot [unit/slot]
Mode User EXEC
Privileged EXEC
Term Definition
Slot The slot identifier in the unit/slot format.
Slot Status The slot is empty, full, or has encountered an error
Admin State The slot administrative mode is enabled or disabled.
Power State The slot power mode is enabled or disabled.
Configured Card
Model Identifier
Pluggable Cards are pluggable or non-pluggable in the slot.
Power Down Indicates whether the slot can be powered down.
The model identifier of the card preconfigured in the slot. The model identifier is a
32-character field used to identify a card.
If you supply a value for unit/slot, the following additional information displays:
Term Definition
Inserted Card
Model Identifier
Inserted Card
Description
Configured Card
Description
The model identifier of the card inserted in the slot. The model identifier is a
32-character field used to identify a card. This field is displayed only if the slot is
populated.
The card description. This field is displayed only if the slot is populated.
The card description of the card preconfigured in the slot.
show stack-status
Use this command to display the stack unit’s received heartbeat message timings and the
dropped or lost statistics for the specified unit.
Use the following optional keywords to specify the command output:
• number. The output displays for a specific unit in the stack. The value for number can be
from 1 to 8.
• all. The output displays for all units in the stack.
Use the optional keyword clear to remove the statistics of the stack heartbeat message.
Stacking Commands
33
Page 34

M4200 and M4300 Series ProSAFE Managed Switches
Format show stack stack-status [number | all] [clear]
Mode Privileged EXEC
Term Definition
Current The time at which the heartbeat message was received.
Average The average time of the heartbeat messages that were received.
Min The minimum time of the heartbeat messages that were received.
Max The maximum time of the heartbeat messages that were received.
Dropped The number of heartbeat messages that were dropped or lost.
Command example:
This example dumps the stack unit heartbeat status information of the specified unit:
(NETGEAR Switch) #show stack-status
Stack Unit 1 Status
Sampling Mode: Cumulative Summing
-------------------------------------Unit Current Average Min Max Dropped
--------------------------------------
show supported cardtype (for stack configuration)
Use this command to display information about all card types or specific card types that are
supported in the switch.
Format show supported cardtype [cardindex]
Mode User EXEC
If you do not supply a value for cardindex, the following output displays:
Term Definition
Card Index (CID) The index in the database for the supported card types. This index is used when you
preconfigure a slot.
Card Model
Identifier
The model identifier for the supported card type.
Stacking Commands
34
Page 35

M4200 and M4300 Series ProSAFE Managed Switches
If you supply a value for cardindex, the following output displays:
Term Definition
Card Type The 32-bit numeric card type for the supported card.
Model Identifier The model identifier for the supported card type.
Card Description The description for the supported card type.
show switch
Use this command to display information about all units in the stack or about a single unit if
you specify the unit value. For units that lack a matching stack template ID and can therefore
not join the stack, the switch status is shown as “STM Mismatch.”
Format show switch [unit]
Mode Privileged EXEC
Term Definition
Switch The unit identifier assigned to the switch.
If you do not specify a value for unit, the following information displays:
Term Definition
Management
Status
Preconfigured
Model Identifier
Plugged-In Model
Identifier
Switch Status The switch status. Possible values for this state are: OK, Unsupported, Code
Indicates whether the switch is the Primary Management Unit, a stack member, or the
status is unassigned.
The model identifier of a preconfigured switch ready to join the stack. The model
identifier is a 32-character field that is assigned by the device manufacturer to identify
the device.
The model identifier of the switch in the stack. The model identifier is a 32-character
field that is assigned by the device manufacturer to identify the device.
Mismatch, Config Mismatch, or Not Present.
A mismatch indicates that a stack unit is running a different firmware version, Switch
Database Management (SDM) template, or configuration than the management unit.
The SDM Mismatch status indicates that the unit joined the stack, but is running a
different SDM template than the management unit. This status is temporary; the stack
unit automatically reloads using the template that is running on the stack manager. If a
Stacking Firmware Synchronization operation is in progress, the status is shown as
Updating Code.
Code Version The detected version of code on the switch.
Stacking Commands
35
Page 36

M4200 and M4300 Series ProSAFE Managed Switches
Command example:
(NETGEAR Switch) #show switch
Management Standby Preconfig Plugged-in Switch Code
SW Switch Status Model ID Model ID Status Version
--- ---------- --------- ------------- ------------- ------------- ----------1 Stack Mbr Platform v1 Platform v1 STM Mismatch 10.17.15.8
2 Mgmt Sw Platform v2 Platform v2 OK 10.17.15.8
If you specify a value for unit, the following information displays:
Term Definition
Management
Status
Hardware
Management
Preference
Admin
Management
Preference
Switch Type The 32-bit numeric switch type.
Model Identifier The model identifier for this switch. The model identifier is a 32-character field that is
Switch Status The switch status. Possible values are OK, Unsupported, Code Mismatch, Config
Switch Description The switch description.
Expected Code
Version
Detected Code
Version
Detected Code in
Flash
Indicates whether the switch is the Primary Management Unit, a stack member, or the
status is unassigned.
The hardware management preference of the switch. The hardware management
preference can be disabled or unassigned.
The administrative management preference value assigned to the switch. This
preference value indicates how likely the switch is selected as the Primary
Management Unit.
assigned by the device manufacturer to identify the device.
Mismatch, or Not Present.
The expected firmware version.
The version of firmware that is running on this switch. If the switch is not present and
the data is from the preconfiguration, the firmware version is None.
The version of the firmware that is currently stored in flash memory on the switch. The
firmware executes after the switch is reset. If the switch is not present and the data is
from the preconfiguration, the firmware version is None.
SFS Last Attempt
Status
Stack Template ID The ID of the stack template. For example: 3.
Stack Template
Description
Up Time The system up time.
The stack firmware synchronization status in the last attempt for the specified unit.
The stack template description. For example: v1 and v2 Mix.
Stacking Commands
36
Page 37

M4200 and M4300 Series ProSAFE Managed Switches
Command example:
(Netgear Switch) #show switch 1
Switch............................ 1
Management Status................. Management Switch
Hardware Management Preference.... Unassigned
Admin Management Preference....... Unassigned
Switch Type....................... 0xd6064004
Preconfigured Model Identifier.... M4300-52G-PoE+
Plugged-in Model Identifier....... M4300-52G-PoE+
Switch Status..................... OK
Switch Description................ M4300-52G-PoE+ ProSafe 48-port Copper 1G PoE+ L3
Switch with 2-port 10G Copper and 2-port 10G Fiber
Detected Code in Flash............ 12.0.0.2
CPLD version...................... 0x1
SFS Last Attempt Status........... None
Serial Number..................... 4G115B5UF0026
Up Time........................... 2 days 3 hrs 24 mins 33 secs
show supported switchtype (for stack configuration)
Use this command to display information about all supported switch types or about a specific
switch type.
Format show supported switchtype [switchindex]
Modes User EXEC
Privileged EXEC
If you do not supply a value for switchindex, the following output displays:
Term Definition
Switch Index (SID) The index in the database of supported switch types. This index is used when you
preconfigure a member to be added to the stack.
Model Identifier The model identifier for the supported switch type.
Management
Preference
Code Version The firmware load target identifier of the switch type.
If you supply a value for switchindex, the following output displays:
The management preference value of the switch type.
Term Definition
Switch Type The 32-bit numeric switch type for the supported switch.
Stacking Commands
37
Page 38

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
Model Identifier The model identifier for the supported switch type.
Switch Description The description for the supported switch type.
Stack Port Commands
This section describes the commands you use to view and configure stack port information.
stack-port
Use this command to set stacking for a specified port to either stack or ethernet mode.
Default stack
Format stack-port unit/slot/port {ethernet | stack}
Mode Stack Global Config
show stack-port
Use this command to display summary stack-port information for all interfaces.
Format show stack-port
Mode Privileged EXEC
For each interface:
Term Definition
Unit The unit number.
Interface The slot and port numbers.
Configured Stack
Mode
Running Stack
Mode
Link Status The status of the link.
Stack or Ethernet.
Stack or Ethernet.
Link Speed The speed (in Gbps) of the stack port link.
Stacking Commands
38
Page 39

M4200 and M4300 Series ProSAFE Managed Switches
show stack-port counters
Use this command to display summary data counter information for all interfaces.
Use the following optional keywords to specify the command output:
• number. The output displays for a specific unit in the stack. The value for number can be
from 1 to 8.
• all. The output displays for all units in the stack.
Format show stack-port counters [number | all]
Mode Privileged EXEC
Term Definition
Unit The unit number.
Interface The slot and port numbers.
Tx Data Rate The trashing data rate in megabits per second on the stacking port.
Tx Error Rate The platform-specific number of transmit errors per second.
Tx Total Error The platform-specific number of total transmit errors since power-up.
Rx Data Rate The received data rate in megabits per second on the stacking port.
Rx Error Rate The platform-specific number of received errors per second.
Rx Total Errors The platform-specific number of total received errors since power-up.
Link Flaps The number of up and down events for the link since the system bootup.
This example shows the stack ports and associated statistics of unit 2.
(NETGEAR Switch) #show stack-port counters 2
------------TX------------------- ------------RX-------------- -------
Data Error Data Error
Rate Rate Total Rate Rate Total Link
Unit Interface (Mb/s) (Errors/s) Errors (Mb/s) (Errors/s) Errors Flaps
---- ----------- ---------- ----------- ---------- -------- ---------- -------- -------
2 0/53 0 0 0 0 0 0 0
2 0/54 0 0 0 0 0 0 0
2 0/55 0 0 0 0 0 0 0
2 0/56 0 0 0 0 0 0 0
Stacking Commands
39
Page 40

M4200 and M4300 Series ProSAFE Managed Switches
show stack-port diag
Note: This command is intended only for field application engineers (FAEs)
and developers.
Use this command to display front panel stacking diagnostics for each port. An FAE can
advise on the necessity to run this command and capture this information. In verbose mode,
the statistics and counters for RPC, transport, CPU, and transport RX/TX modules are
displayed.
Use the following optional keywords to specify the command output:
• number. The output displays for a specific unit in the stack. The value for number can be
from 1 to 8.
• all. The output displays for all units in the stack.
Format show stack-port diag [number | all] [verbose]
Mode Privileged EXEC
Term Definition
Unit The unit number.
Interface The slot and port numbers.
Diagnostic Entry1 80 character string used for diagnostics.
Diagnostic Entry2 80 character string used for diagnostics.
Diagnostic Entry3 80 character string used for diagnostics.
TBYT Transmitted bytes.
TPKT Transmitted packets.
TFCS Transmitted FCS error frame counter.
TERR Transmitted error (set by system) counter
RBYT Received bytes.
RPKT Received packets.
RFCS Received FCS error frame counter.
RFRG Received fragment counter.
RJBR Received jabber frame counter.
RUND Received undersized frame counter.
ROVR Received oversized frame counter.
RUNT Received RUNT frame counter.
Stacking Commands
40
Page 41

M4200 and M4300 Series ProSAFE Managed Switches
Command example:
This example displays the stack ports and associated statistics of specified unit or all units.
(NETGEAR Switch) #show stack-port diag 1
1 - 0/53:
RBYT:27ed9a7b RPKT:bca1b TBYT:28a0739e TPKT:c93ee
RFCS:0 RFRG:0 RJBR:0 RUND:0 RUNT:0
TFCS:0 TERR:0
1 - 0/54:
RBYT:8072ed RPKT:19a66 TBYT:aecfb80 TPKT:66e4d
RFCS:6e RFRG:4414 RJBR:0 RUND:c19 RUNT:af029b1
TFCS:0 TERR:0
1 - 0/55:
RBYT:0 RPKT:0 TBYT:ae8 TPKT:23
RFCS:0 RFRG:0 RJBR:0 RUND:0 RUNT:0
TFCS:0 TERR:0
1 - 0/56:
RBYT:0 RPKT:0 TBYT:ae8 TPKT:23
RFCS:0 RFRG:0 RJBR:0 RUND:0 RUNT:0
TFCS:0 TERR:0
Command example:
This example displays a dump of the RPC, Transport (ATP, Next Hop, and RLink), and CPU
Transport Rx/Tx module statistics for Unit 2.
(NETGEAR Switch) #show stack-port diag 2 verbose
----------------------------------------HPC RPC statistics/counters from unit..2
-----------------------------------------
Registered Functions........................... 58
Client Requests.............................. 0
Server Requests................................ 0
Server Duplicate Requests...................... 0
Server Replies................................. 0
Client Remote Tx............................... 0
Client Remote Retransmit Count................. 0
Tx without Errors.............................. 0
Tx with Errors................................. 0
Rx Timeouts.................................... 0
Rx Early Exits................................. 0
Rx Out of Sync................................. 0
No Buffer...................................... 0
Collect Sem Wait Count......................... 0
Stacking Commands
41
Page 42

M4200 and M4300 Series ProSAFE Managed Switches
Collect Sem Dispatch Count..................... 0
-------------------------------------
RPC statistics/counters from unit..2
-------------------------------------
Client RPC Requests Count...................... 3
Client RPC Reply Count......................... 0
Client RPC Fail to xmit Count.................. 0
Client RPC Response Timedout Count............. 3
Client RPC Missing Requests.................... 0
Client RPC Detach/Remove Count................. 0
Client RPC Current Sequence Number............. 3
Server RPC Request Count....................... 0
Server RPC Reply Count......................... 0
Server RPC Processed Transactions.............. 0
Server RPC Received Wrong Version Req.......... 0
Server RPC No Handlers......................... 0
Server RPC Retry Transmit Count................ 0
Server RPC Repetitive Tx Errors................ 0
-------------------------------------
ATP statistics/counters from unit..2
-------------------------------------
Transmit Pending Count......................... 2
Current number of TX waits..................... 2
Rx transactions created........................ 145
Rx transactions freed.......................... 145
Rx transactions freed(raw)..................... 0
Tx transactions created........................ 290
BET Rx Dropped Pkts Count...................... 0
ATP Rx Dropped Pkts Count...................... 0
Failed to Add Key Pkt Count.................... 0
Source Lookup Failure Count.................... 0
Old Rx transactions Pkts drop Count............ 0
Nr of CPUs found in ATP communication.......... 2
-----------------------------------------------
CPU Transport statistics/counters from unit..2
-----------------------------------------------
State Initialization........................... Done
Rx Setup....................................... Done
Tx Setup....................................... Done
Tx CoS[0] Reserve.............................. 100
Tx CoS[1] Reserve.............................. 100
Tx CoS[2] Reserve.............................. 100
Tx CoS[3] Reserve.............................. 100
Stacking Commands
42
Page 43

M4200 and M4300 Series ProSAFE Managed Switches
Tx CoS[4] Reserve.............................. 60
Tx CoS[5] Reserve.............................. 40
Tx CoS[6] Reserve.............................. 20
Tx CoS[7] Reserve.............................. 0
Tx Pkt Pool Size............................... 200
Tx Available Pkt Pool Size..................... 198
Tx failed/error Count.......................... 0
Rx Pkt Pool Size............................... 8
-----------------------------------------Next Hop statistics/counters from unit..2
------------------------------------------
State Initialization........................... Done
Component Setup................................ Done
Thread Priority................................ 100
Rx Priority.................................... 105
Local CPU Key.................................. 00:24:81:d0:0f:c7
MTU Size....................................... 2048
Vlan Id........................................ 4094
CoS Id......................................... 7
Internal Priority for pkt transmission......... 7
Rx Pkt Queue Size.............................. 256
Tx Pkt Queue Size.............................. 64
Rx Pkt Dropped Count........................... 0
Tx Failed Pkt Count............................ 0
--------------------------------------RLink statistics/counters from unit..2
---------------------------------------
State Initialization........................... Done
L2 Notify In Pkts.............................. 0
L2 Notify In Pkts discarded.................... 0
L2 Notify Out Pkts ............................ 0
L2 Notify Out Pkts discarded................... 0
Linkscan In Pkts............................... 0
Linkscan In Pkts discarded..................... 0
Linkscan Out Pkts ............................. 0
Linkscan Out Pkts discarded.................... 0
Auth/Unauth In Callbacks....................... 0
Auth/Unauth In Callbacks discarded............. 0
Auth/Unauth Out Callbacks...................... 0
Auth/Unauth Out Callbacks discarded............ 0
RX Tunnelling In Pkts.......................... 0
RX Tunnelling In Pkts discarded................ 0
RX Tunnelling Out Pkts......................... 0
RX Tunnelling Out Pkts discarded............... 0
OAM Events In.................................. 0
Stacking Commands
43
Page 44

M4200 and M4300 Series ProSAFE Managed Switches
OAM Events In discarded........................ 0
OAM Events Out................................. 0
OAM Events Out discarded....................... 0
BFD Events In.................................. 0
BFD Events In discarded........................ 0
BFD Events Out................................. 0
BFD Events Out discarded....................... 0
Fabric Events In............................... 0
Fabric Events In discarded..................... 0
Fabric Events Out.............................. 0
Fabric Events Out discarded.................... 0
Scan Add Requests In........................... 0
Scan Del Requests In........................... 0
Scan Notify(Run Handlers) Out.................. 0
Scan Notify(Traverse Processing)............... 0
show stack-port stack-path
Use this command to display the route that a packet takes to reach its destination. This
command lets you display the stack path to see if an error or packets loss occurs.
Use the following optional keywords to specify the command output:
• source-unit. The output displays for a specific source unit in the stack. The value for
source-unit can be from 1 to 8.
• all. The output displays for all units in the stack.
• destination-unit. The output displays for a specific source unit in the stack. The
value for destination-unit can be from 1 to 8.
Format show stack-port stack-path [source-unit | all] [destination-unit]
Mode Privileged EXEC
Stack Firmware Synchronization Commands
Stack firmware synchronization (SFS) provides an automatic mechanism to synchronize the
firmware on all stack members whose firmware version differs from the version running on
the stack manager. This operation can result in either an upgrade or downgrade of firmware
on the mismatched stack member. However, this operation does not attempt to synchronize
the stack to the latest firmware in the stack.
Stacking Commands
44
Page 45

M4200 and M4300 Series ProSAFE Managed Switches
boot auto-copy-sw (for stack firmware synchronization)
Use this command to enable stack firmware synchronization.
Default Disabled
Format boot auto-copy-sw
Mode Privileged EXEC
no boot auto-copy-sw
Use this command to disable stack firmware synchronization.
Format no boot auto-copy-sw
Mode Privileged EXEC
boot auto-copy-sw trap (for stack firmware synchronization)
Use this command to send SNMP traps related to stack firmware synchronization.
Default Enabled
Format boot auto-copy-sw trap
Mode Privileged EXEC
no boot auto-copy-sw trap
Use this command to disable sending SNMP traps related to stack firmware synchronization.
Format no boot auto-copy-sw trap
Mode Privileged EXEC
boot auto-copy-sw allow-downgrade (for stack firmware synchronization)
Use this command to enable downgrading of the firmware version on the stack member if the
firmware version on the manager is older than the firmware version on the member.
Default Enabled
Format boot auto-copy-sw allow-downgrade
Mode Privileged EXEC
Stacking Commands
45
Page 46

M4200 and M4300 Series ProSAFE Managed Switches
no boot auto-copy-sw allow-downgrade
Use this command to prevent downgrading of the firmware version on the stack member if
the firmware version on the manager is older than the firmware version on the member.
Format no boot auto-copy-sw allow-downgrade
Mode Privileged EXEC
show auto-copy-sw (for stack firmware synchronization)
Use this command to display the stack firmware synchronization configuration status.
Format show auto-copy-sw
Mode Privileged EXEC
Term Definition
Synchronization Shows whether the SFS feature is enabled.
SNMP Trap Status Shows whether the stack sends traps for SFS events
Allow Downgrade Shows wether the stack manager is permitted to downgrade the firmware version of a
stack member.
Nonstop Forwarding Commands for Stack Configuration
You can describe a switch in terms of three semi-independent functions: the forwarding
plane, the control plane, and the management plane. The forwarding plane forwards data
packets. The forwarding plane is implemented in hardware. The control plane is the set of
protocols that determines how the forwarding plane must forward packets, which data
packets can be forwarded, and where the data packets must be forwarded to.
Application software on the management unit functions as the control plane. The
management plane is also application software that runs on the management unit and that
provides interfaces, allowing you to configure and monitor the device.
Nonstop forwarding (NSF) allows the forwarding plane of stack units to continue to forward
packets while the control and management planes restart as a result of a power failure,
hardware failure, or software fault on the management unit.
You can also manually initiate a nonstop forwarding failover by issuing the initiate
failover command. If the management unit fails, traffic flows that enter and exit the stack
through physical ports on a unit other than the management unit continue with at most a
subsecond interruption.
To prepare the backup management unit for a failover, applications on the management unit
continuously checkpoint (that is, forward) information to the backup unit. Changes to the
running configuration are automatically copied to the backup unit. MAC addresses stay the
same across a nonstop forwarding failover so that neighbors do not need to relearn them.
Stacking Commands
46
Page 47

M4200 and M4300 Series ProSAFE Managed Switches
When a nonstop forwarding failover occurs, the control plane on the backup unit starts from a
partially-initialized state and applies the checkpointed (that is, forwarded) information. While
the control plane is initializing, the stack cannot react to external changes, such as network
topology changes. When the control plane is fully operational on the new management unit,
the control plane ensures that the hardware state is updated as necessary . The control plane
failover time depends on the size of the stack, the complexity of the configuration, and the
speed of the CPU.
The management plane restarts when a failover occurs. Management connections must be
reestablished.
For NSF to be effective, adjacent networking devices must not reroute traffic around the
restarting device.
The switch uses three protocol techniques to prevent traffic from being rerouted:
• A protocol can distribute a part of its control plane to stack units so that the protocol can
give the appearance that it is still functional during the restart. Spanning tree and port
channels use this technique.
• A protocol can enlist the cooperation of its neighbors through a technique known as
graceful restart. OSPF uses graceful restart if it is enabled (see “IP Event Dampening
Commands on page 721).
• A protocol can simply restart after the failover if neighbors react slowly enough that they
do not detect the outage. The IP multicast routing protocols are a good example of this
behavior.
To take full advantage of nonstop forwarding, layer 2 connections to neighbors must be
configured over port channels that span two or more stack units and layer 3 routes must be
configured over ECMP routes with next hops over physical ports on two or more units. The
hardware can quickly move traffic flows from port channel members or ECMP paths on a
failed unit to a surviving unit.
nsf (Stack Global Config)
Use this command to enable nonstop forwarding on the stack. When nonstop forwarding is
enabled, if the management unit of a stack fails, the backup unit takes over as the master
without clearing the hardware tables of any of the surviving units. Data traffic continues to be
forwarded in hardware while the management functions initialize on the backup unit.
NSF is enabled by default on platforms that support it. You can disable NSF to redirect the
CPU resources that are consumed by data checkpointing (that is, data forwarding).
If a unit that does not support NSF is connected to the stack, NSF is disabled on all stack
members. If a unit that does not support NSF is disconnected from the stack, all other units
do support NSF, and NSF is administratively enabled, NSF operation resumes.
Default Enabled
Format nsf
Mode Stack Global Config
Stacking Commands
47
Page 48

M4200 and M4300 Series ProSAFE Managed Switches
no nsf
Use this command to disable nonstop forwarding on the stack.
Format no nsf
Mode Stack Global Config
show nsf (for stack configuration)
Use this command to display global and per-unit information for the nonstop forwarding
configuration on the stack.
Format show nsf
Mode Privileged EXEC
Term Definition
NSF Administrative
Status
NSF Operational Status Indicates whether NSF is enabled on the stack.
Last Startup Reason The type of activation that caused the software to start the last time:
Time Since Last
Restart Time
Restart in progress Indicates whether a restart is in progress.
Warm Restart Ready Indicates whether the system is ready to perform a nonstop forwarding failover
Copy of Running
Configuration to
Backup Unit: Status
Indicates whether nonstop forwarding is administratively enabled or disabled. The
default is Enabled.
• “Power-On” means that the switch rebooted. A reboot can be caused by a
power cycle or an administrative “Reload” command.
• “Administrative Move” means that someone issued the movemanagement
command for the stand-by manager to take over.
• “Warm-Auto-Restart” means that the primary management card restarted
because of a failure, and the system executed a nonstop forwarding failover.
• “Cold-Auto-Restart” means that the system switched from the active manager
to the backup manager and was unable to maintain user data traffic. This is
usually caused by multiple failures occurring in a short period.
The time since the current management unit became the active management unit.
from the management unit to the backup unit.
Indicates whether the running configuration on the backup unit includes all
changes made on the management unit. Displays as Current or Stale.
Time Since Last Copy The time when the running configuration was last copied from the management
unit to the backup unit.
Stacking Commands
48
Page 49

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
Time Until Next Copy The number of seconds until the running configuration is copied to the backup
unit. This line only appears when the running configuration on the backup unit is
Stale.
NSF Support (Per Unit
Status Parameter)
Indicates whether a unit supports NSF.
initiate failover (for stack configuration)
Use this command to force the backup unit to take over as the management unit and perform
a “warm restart” of the stack. On a warm restart, the backup unit becomes the management
unit without clearing its hardware tables (on a cold restart, hardware tables are cleared).
Applications apply checkpointed data (that is, forwarded data) from the former management
unit. The original management unit reboots. If the system is not ready for a warm restart, for
example because no backup unit was elected or one or more members of the stack do not
support nonstop forwarding, the command fails with a warning message.
The movemanagement command (see movemanagement (Stack Global Config) on
page 28) also transfers control from the current management unit. However, the hardware is
cleared and all units reinitialize.
Default None
Format initiate failover
Mode Stack Global Config
show checkpoint statistics (for stack configuration)
Use this command to display general information about the checkpoint service operation.
Format show checkpoint statistics
Mode Privileged EXEC
Term Description
Messages
Checkpointed
Bytes
Checkpointed
Time Since
Counters Cleared
Checkpoint
Message Rate
Average
The number of checkpoint messages that are transmitted to the backup unit.
Range: Integer. Default: 0
The number of bytes transmitted to the backup unit. Range: Integer. Default: 0
The number of days, hours, minutes and seconds since the counters were reset to
zero. The counters are cleared when a unit becomes manager or when you issue the
clear checkpoint statistics command.
Range: Time Stamp. Default: 0d00:00:00
The average number of checkpoint messages per second. The average is computed
over the period since the counters were cleared. Range: Integer. Default: 0
Stacking Commands
49
Page 50

M4200 and M4300 Series ProSAFE Managed Switches
Term Description
Last 10-second
Message Rate
Average
Highest 10-second
Message Rate
The average number of checkpoint messages per second in the last 10-second
interval. This average is updated once every 10 seconds. Range: Integer. Default: 0
The highest rate recorded over a 10-second interval since the counters were cleared.
Range: Integer. Default: 0
Command example:
(Switch)#show checkpoint statistics
Messages Checkpointed.....................6708
Bytes Checkpointed........................894305
Time Since Counters Cleared...............3d 01:05:09
Checkpoint Message Rate Average...........0.025 msg/sec
Last 10-second Message Rate Average.......0 msg/sec
Highest 10-second Message Rate............8 msg/sec
clear checkpoint statistics (for stack configuration)
Use this command to clear the statistics for the checkpointing process.
Format clear checkpoint statistics
Mode Privileged EXEC
Stacking Commands
50
Page 51

5. Management Commands
This chapter describes the management commands.
The chapter contains the following sections:
• Configure the Switch Management CPU
• CPU Queue Commands
• Management Interface Commands
• IPv6 Management Commands
• Console Port Access Commands
• Telnet Commands
• Secure Shell Commands
• Management Security Commands
• Management Access Control List Commands
• Hypertext Transfer Protocol Commands
5
• Access Commands
• User Account Commands
• SNMP Commands
• RADIUS Commands
• TACACS+ Commands
• Configuration Scripting Commands
• Prelogin Banner, System Prompt, and Host Name Commands
• OpenFlow Commands
• Cloud Managed Commands
• Application Commands
The commands in this chapter are in one of three functional groups:
• Show commands. Display switch settings, statistics, and other information.
• Configuration commands. Configure features and options of the switch. For every
configuration command, there is a show command that displays the configuration setting.
• Clear commands. Clear some or all of the settings to factory defaults.
51
Page 52

M4200 and M4300 Series ProSAFE Managed Switches
Configure the Switch Management CPU
To manage the switch over the web management interface or Telnet, you must assign an IP
address to the switch management CPU. You can accomplish this task through CLI
commands or you can use the ezconfig tool, which simplifies the task. The tool lets you
configure the following settings:
• The administrator user password and administrator-enable password
• The management CPU IP address and network mask
• The system name and location information
The tool is interactive and uses questions to guide you through the configuration steps. At the
end of the configuration session, the tool lets you save the information. To see which
information was changed by the ezconfig tool after a configuration session, issue the show
running-config command.
ezconfig
This command sets the IP address, subnet mask, and gateway of the switch. The IP address
and the gateway must be on the same subnet.
Format ezconfig
Mode Privileged EXEC
(NETGEAR Switch) #ezconfig
EZ Configuration Utility
-------------------------------Hello and Welcome!
This utility will walk you thru assigning the IP address for the switch
management CPU. It will allow you to save the changes at the end. After
the session, simply use the newly assigned IP address to access the Web
GUI using any public domain Web browser.
Admin password is not defined.
Do you want to assign the admin password (password length must be in range of 8-64
characters) (Y/N/Q)? y
Enter new password:********
Confirm new password:********
The 'enable' password required for switch configuration via the command
line interface is currently not configured.
Do you want to assign it (password length must be in range of 8-64 characters) (Y/N/Q)?
y
Enter new password:********
Management Commands
52
Page 53

M4200 and M4300 Series ProSAFE Managed Switches
Confirm new password:********
Current IPv4 Management Interface: vlan 1
Do you want to set new Management VLAN ID (Y/N/Q)?y
VLAN ID: 1
Assigning an IPv4 address to your switch management
Current IPv4 Address Configuration
---------------------------------Management VLAN ID: vlan 1
IPv4 Address Assignment Mode: None
IPv4 Address: 0.0.0.0
Subnet Mask: 0.0.0.0
Gateway: 0.0.0.0
Routing Mode: Enable
IPv4 address is not assigned. What do you want to do?
C - Configure IPv4 address manually.
D - Assign IPv4 address for the switch using DHCP Mode(current IPv4 address will be
lost).
N - Skip this option and go to the next question.
Q - Quit.
? - Help.
(C/D/N/Q/?)? c
IPv4 Address: 192.168.1.1
Network Mask: 255.255.255.0
Gateway: 192.168.254
Incorrect input! Gateway must be a valid IP address.
Try again (Y/N/Q)? y
Gateway: 192.168.1.254
Do you want to enable global routing (Y/N)?y
Current IPv6 Management Interface: (not configured)
Do you want to set new IPv6 Management VLAN ID (Y/N/Q)?y
VLAN ID: 1
Assigning management IPv6 address.
Current IPv6 Address Configuration
---------------------------------IPv6 Address: fe80::abd:43ff:fe71:73c0/64
IPv6 Current state: TENT
Address DHCP Mode: Disabled
Address Autoconfigure Mode: Disabled
EUI64 : Enabled
Management Commands
53
Page 54

M4200 and M4300 Series ProSAFE Managed Switches
Routing Mode: Enable
IPv6 address has been assigned manually. What do you want to do?
C - Add IPv6 address.
D - Assign IPv6 address for the switch using DHCP Mode.
A - Assign IPv6 address for the switch using Auto Mode.
N - Skip this option and go to the next question.
Q - Quit.
? - Help.
(C/D/A/N/Q/?)? c
IPv6 Address: 2001:1::1
IPv6 Prefix-length: 64
IPv6 EUI64 flag (Y/N): n
IPv6 Gateway: 2001:1::fffe
Current Out of Band(service port) IPv4 Address Configuration
-------------------------------IP Address Assignment Mode: DHCP
IP Address: 172.26.2.104
Subnet Mask: 255.255.255.0
Default Router: 172.26.2.1
IPv4 address will be assigned automatically by the DHCP server in your network. You
can disable DHCP mode and use static(fixed) IPv4 address. If fixed IPv4 Address Mode
is selected, DHCP Protocol Mode will be disabled, and you will be prompted to
set the values for the four fields above.
Do you want to assign IPv4 address manually? (Y/N/Q/?) y
IPv4 Address: 172.26.2.1
Network Mask: 255.255.255.0
Gateway: 172.26.2.254
Current Out of Band(Serviceport) IPv6 Address Configuration
-------------------------------Service port IPv6 Address Mode: None
IPv6 Administrative Mode: Enabled
Service port IPv6 Address Mode autoconfigure: Disabled
IPv6 Address: fe80::abd:43ff:fe71:73be/64
Service port IPv6 address gateway:
EUI Flag: False
IPv6 address has been assigned manually. What do you want to do?
A - Assign IPv6 address for the switch using Auto Mode.
D - Assign IPv6 address for the switch using DHCP Mode.
G - Assign IPv6 Gateway.
Management Commands
54
Page 55

M4200 and M4300 Series ProSAFE Managed Switches
C - Add IPv6 address.
N - Skip this option and go to the next question.
Q - Quit.
? - Help.
(A/D/G/C/N/Q/?)? c
Current Management Interface Configuration
-------------------------------Management Interface: L3 Management VLAN
Current management interface is L3 Management VLAN. What do you want to do?
O - Change to Out of Band port(service port).
V - Change to L3 Management VLAN.
N - Skip this option and go to the next question.
Q - Quit.
? - Help.
(O/V/N/Q/?)?n
Assigning System Name, System Location and System Contact to your switch management
Current Configuration
-------------------------------System Name:
System Location:
System Contact:
Do you want to assign switch name and location information? (Y/N/Q)
CPU Queue Commands
You can send all packets with a specified destination address to a higher priority queue (5)
than the default queue for data packets and unicast packets to the CPU.
ip cpu-priority
This command sends all packets with a specified destination IPv4 address to a higher priority
queue (5) than the default queue for data packets and unicast packets to the CPU.
Format ip cpu-priority ip-address
Mode Privileged EXEC
Management Commands
55
Page 56

M4200 and M4300 Series ProSAFE Managed Switches
no ip cpu-priority
This command removes all packets with a specified destination IPv4 address from the higher
priority queue.
Format no ip cpu-priority ip-address
Mode Privileged EXEC
ipv6 cpu-priority
The command allows all packets with a specified destination IPv6 address into a higher
priority queue (5) than the default queue for data packets and unicast packets to the CPU.
Format ip cpu-priority ipv6-address
Mode Privileged EXEC
no ipv6 cpu-priority
This command removes all packets with a specified destination IPv6 address from the higher
priority queue.
Format no ip cpu-priority ipv6-address
Mode Privileged EXEC
Management Interface Commands
This section describes the commands you use to configure a logical IPv4 interface for
management access.
enable (Privileged EXEC access)
This command gives you access to the Privileged EXEC mode. From the Privileged EXEC
mode, you can configure the network interface.
Format enable
Mode User EXEC
Management Commands
56
Page 57

M4200 and M4300 Series ProSAFE Managed Switches
do (Privileged EXEC commands)
This command executes Privileged EXEC mode commands from any of the configuration
modes.
Format do Priv Exec Mode Command
Mode • Global Config
• Interface Config
• VLAN Config
• Routing Config
Command example:
The following is an example of the do command that executes the Privileged Exec command
script list in Global Config Mode.
(NETGEAR Switch) #configure
(NETGEAR Switch)(config)#do script list
Configuration Script Name Size(Bytes)
-------------------------------- ----------backup-config 2105
running-config 4483
startup-config 445
3 configuration script(s) found.
2041 Kbytes free.
ip management
Use this command to create an IPv4 management interface, enable DHCP on the IPv4
management interface, delete a previous IPv4 management interface, and set the source
interface for all applications, including RADIUS, TACACS, DNS, SNTP, SNMP, and SysLog.
Default vlan 1
Format ip management {vlan number | port unit/slot/port} {dhcp | ipaddr
{prefix-length | subnet-mask}}
Mode Global Config
Management Commands
57
Page 58

M4200 and M4300 Series ProSAFE Managed Switches
ip management source-interface
Use this command to specify the source IP address for all applications, including RADIUS,
TACACS, DNS, SNTP, SNMP, and SysLog.
For the loopback keyword, you can enter a number between 0 and 7.
Default vlan 1
Format ip management source-interface {serviceport | vlan number | port
unit/slot/port | loopback number}
Mode Global Config
no ip management
Use this command to reset the IPv4 management interface to the default settings.
Format no ip management
Mode Global Config
serviceport ip
This command sets the IP address, the netmask, and the gateway of the network
management port. You can specify the none option to clear the IPv4 address and mask and
the default gateway (that is, reset each of these values to 0.0.0.0).
Format serviceport ip {ipaddr netmask [gateway] | none}
Mode Privileged EXEC
serviceport protocol
This command specifies the network management port configuration protocol. If you modify
this value, the change is effective immediately. If you use the
periodically sends requests to a BootP server until a response is received. If you use the
parameter, the switch periodically sends requests to a DHCP server until a response is
received. If you use the
none parameter, you must configure the network information for the
switch manually.
Format serviceport protocol {none | bootp | dhcp}
Mode Privileged EXEC
bootp parameter, the switch
dhcp
Management Commands
58
Page 59

M4200 and M4300 Series ProSAFE Managed Switches
serviceport protocol dhcp
This command enables the DHCPv4 client on a Service port. If the client-id optional
parameter is given, the DHCP client messages are sent with the client identifier option.
Default none
Format serviceport protocol dhcp [client-id]
Mode Privileged Exec
There is no support for the no form of the command serviceport protocol dhcp
client-id. To remove the client-id option from the DHCP client messages, issue the
command serviceport protocol dhcp without the client-id option. The command
serviceport protocol none can be used to disable the DHCP client and client-id
option on the interface.
Command example:
(NETGEAR Switch) # serviceport protocol dhcp client-id
mac management address
This command sets locally administered MAC addresses. The following rules apply:
• Bit 6 of byte 0 (called the U/L bit) indicates whether the address is universally
administered (b'0') or locally administered (b'1').
• Bit 7 of byte 0 (called the I/G bit) indicates whether the destination address is an
individual address (b'0') or a group address (b'1').
• The second character, of the twelve character macaddr, must be 2, 6, A or E.
A locally administered address must have bit 6 On (b'1') and bit 7 Off (b'0').
Format mac management address macaddr
Mode Privileged EXEC
mac management type
This command specifies whether the switch uses the burned in MAC address or the
locally-administered MAC address.
Default burnedin
Format mac management type {local | burnedin}
Mode Privileged EXEC
Management Commands
59
Page 60

M4200 and M4300 Series ProSAFE Managed Switches
no network mac-type
This command resets the value of MAC address to its default.
Format no mac management type
Mode Privileged EXEC
show ip management
This command displays configuration settings that are associated with the switch
management interface. The management interface is the logical interface that is used for
in-band connectivity with the switch over any of the switch front panel ports. The
configuration parameters that are associated with the switch management interface do not
affect the configuration of the front panel ports through which traffic is switched or routed. The
management interface is always considered to be up, whether or not any member ports are
up. Therefore, the output of the show ip management command always shows interface
status as up.
Format show ip management
Modes • Privileged EXEC
• User EXEC
Term Definition
Interface Status The management interface status; it is always considered to be up.
IP Address The IP address of the interface. The factory default value is 0.0.0.0.
Subnet Mask The IP subnet mask for this interface. The factory default value is 0.0.0.0.
Default Gateway The default gateway for this IP interface. The factory default value is 0.0.0.0.
IPv6 Administrative Mode Whether enabled or disabled.
IPv6 Address/Length The IPv6 address and length.
IPv6 Default Router The IPv6 default router address.
Burned In MAC Address The burned- in MAC address used for in-band connectivity.
Locally Administered MAC
Address
You can configure a locally administered MAC address for in-band connectivity. This
configuration requires the following:
• The MAC Address Type must be set to Locally Administered.
• Enter the address as 12 hexadecimal digits (6 bytes) with a colon between bytes.
• Bit 1 of byte 0 must be set to a 1 and bit 0 to a 0. That is, byte 0 must contain the
xxxx xx10 mask.
• The MAC address must be unique.
We recommend that you use the MAC address that is the numerically smallest MAC
address of all ports that belong to the bridge. When concatenated with dot1dStpPriority ,
a unique Bridge Identifier is formed, which is used in the Spanning Tree Protocol.
Management Commands
60
Page 61

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
MAC Address Type The MAC address that must be used for in-band connectivity. The choices are the
burned in or the Locally Administered address. The factory default is to use the burned
in MAC address.
DHCPv6 Client DUID The DHCPv6 client’s unique client identifier. This row is displayed only when the
configured IPv6 protocol is DHCP.
IPv6 Autoconfig Mode Whether IPv6 Stateless address autoconfiguration is enabled or disabled.
DHCP Client Identifier The client identifier is displayed in the output of the command only if DHCP is enabled
with the client-id option on the management interface.
Command example:
(NETGEAR Switch) #show ip management
IPv4 Interface Status.......................... Up
IPv4 Management Interface...................... vlan 1
IP Address..................................... 169.254.100.100
Subnet Mask.................................... 255.255.255.0
Method......................................... DHCP
Routing Mode................................... Enable
Default Gateway................................ 0.0.0.0
Source Interface............................... vlan 1
Burned In MAC Address.......................... DC:EF:09:D3:2D:48
Locally Administered MAC address............... 00:00:00:00:00:00
MAC Address Type............................... Burned In
IPv6 Management Interface is not Configured.
show serviceport
This command displays service port configuration information.
Format show serviceport
Mode • Privileged EXEC
• User EXEC
Term Definition
Interface Status The network interface status. It is always considered to be up.
IP Address The IP address of the interface. The factory default value is 0.0.0.0.
Subnet Mask The IP subnet mask for this interface. The factory default value is 0.0.0.0.
Default Gateway The default gateway for this IP interface. The factory default value is 0.0.0.0.
Management Commands
61
Page 62

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
IPv6 Administrative Mode Whether enabled or disabled. Default value is enabled.
IPv6 Address/Length The IPv6 address and length. Default is Link Local format.
IPv6 Default Router TheIPv6 default router address on the service port. The factory default value is an
unspecified address.
Configured IPv4 Protocol The IPv4 network protocol being used. The options are bootp | dhcp | none.
Configured IPv6 Protocol The IPv6 network protocol being used. The options are dhcp | none.
DHCPv6 Client DUID The DHCPv6 client’s unique client identifier. This row is displayed only when the configured
IPv6 protocol is dhcp.
IPv6 Autoconfig Mode Whether IPv6 Stateless address autoconfiguration is enabled or disabled.
Burned in MAC Address The burned in MAC address used for in-band connectivity.
DHCP Client Identifier The client identifier is displayed in the output of the command only if DHCP is enabled with
the client-id option on the service port.
Command example:
The following example displays output for the service port:
(Netgear switch) #show serviceport
Interface Status............................... Up
IP Address..................................... 10.230.3.51
Subnet Mask.................................... 255.255.255.0
Default Gateway................................ 10.230.3.1
IPv6 Administrative Mode....................... Enabled
IPv6 Prefix is ................................ fe80::210:18ff:fe82:640/64
IPv6 Prefix is ................................ 2005::21/128
IPv6 Default Router is ........................ fe80::204:76ff:fe73:423a
Configured IPv4 Protocol ...................... DHCP
Configured IPv6 Protocol ...................... DHCP
DHCPv6 Client DUID ............................ 00:03:00:06:00:10:18:82:06:4C
IPv6 Autoconfig Mode........................... Disabled
Burned In MAC Address.......................... 00:10:18:82:06:4D
DHCP Client Identifier......................... 0NETGEAR-0010.1882.160C
Management Commands
62
Page 63

M4200 and M4300 Series ProSAFE Managed Switches
IPv6 Management Commands
IPv6 management commands allow a device to be managed via an IPv6 address in a switch
or through IPv4 routing (that is, independent from the IPv6 routing package). For
Routing/IPv6 builds of NETGEAR Managed Switch software, dual IPv4/IPv6 operation over
the service port is enabled. NETGEAR Managed Switch software provides capabilities such
as the following”
• Static assignment of IPv6 addresses and gateways for the service/network ports.
• The ability to ping an IPv6 link-local address over the service/network port.
• Using IPv6 management commands, you can send SNMP traps and queries via the
service/network port.
• The user can manage a device via the network port (in addition to a Routing Interface or
the Service port).
ipv6 management
Use this command to create an IPv6 management interface, enable IPv6 and DHCPv6 on
the management interface, and delete a previous IPv6 management interface, if there was
any. (The switch does not provide a default IPv6 management interface.)
Format ipv6 management {vlan number | port unit/slot/port} {autoconfig |
dhcp | prefix prefix-length}
Mode Global Config
no ipv6 management
Use this command to reset the IPv6 management interface to the default settings, that is,
remove the IPv6 management interface. (The switch does not provide a default IPv6
management interface.)
Format no ipv6 management
Mode Global Config
serviceport ipv6 enable
Use this command to enable IPv6 operation on the service port. By default, IPv6 operation is
enabled on the service port.
Default enabled
Format serviceport ipv6 enable
Mode Privileged EXEC
Management Commands
63
Page 64

M4200 and M4300 Series ProSAFE Managed Switches
no serviceport ipv6 enable
Use this command to disable IPv6 operation on the service port.
Format no serviceport ipv6 enable
Mode Privileged EXEC
serviceport ipv6 address
Use the options of this command to manually configure IPv6 global address, enable/disable
stateless global address autoconfiguration and to enable/disable dhcpv6 client protocol
information on the service port.
Note: Multiple IPv6 prefixes can be configured on the service port.
no serviceport ipv6 address
Use the command no serviceport ipv6 address to remove all configured IPv6
prefixes on the service port interface.
Use the command with the address option to remove the manually configured IPv6 global
address on the network port interface.
Use the command with the autoconfig option to disable the stateless global address
autoconfiguration on the service port.
Use the command with the dhcp option to disable the dhcpv6 client protocol on the service
port.
Format no serviceport ipv6 address {address/prefix-length [eui64] | autoconfig |
dhcp}
Mode Privileged EXEC
serviceport ipv6 gateway
Use this command to configure IPv6 gateway information (that is, default routers information)
for the service port.
Note: Only a single IPv6 gateway address can be configured for the service
port. There may be a combination of IPv6 prefixes and gateways that are
explicitly configured and those that are set through auto-address
configuration with a connected IPv6 router on their service port interface.
Management Commands
64
Page 65

M4200 and M4300 Series ProSAFE Managed Switches
Format serviceport ipv6 gateway gateway-address
Mode Privileged EXEC
Parameter Description
gateway-address Gateway address in IPv6 global or link-local address format.
no serviceport ipv6 gateway
Use this command to remove IPv6 gateways on the service port interface.
Format no serviceport ipv6 gateway
Mode Privileged EXEC
serviceport ipv6 neighbor
Use this command to manually add IPv6 neighbors to the IPv6 neighbor table for the service
port. If an IPv6 neighbor already exists in the neighbor table, the entry is automatically
converted to a static entry . Static entries are not modified by the neighbor discovery process.
They are, however, treated the same for IPv6 forwarding. Static IPv6 neighbor entries are
applied to the hardware when the corresponding interface is operationally active.
Format serviceport ipv6 neighbor ipv6-address macaddr
Mode Privileged EXEC
Parameter Description
ipv6-address The IPv6 address of the neighbor or interface.
macaddr The link-layer address.
no serviceport ipv6 neighbor
Use this command to remove IPv6 neighbors from the IPv6 neighbor table for the service
port.
Format no serviceport ipv6 neighbor ipv6-address macaddr
Mode Privileged EXEC
Management Commands
65
Page 66

M4200 and M4300 Series ProSAFE Managed Switches
show serviceport ipv6 neighbors
Use this command to displays information about the IPv6 neighbor entries cached on the
service port. The information is updated to show the type of the entry.
Default None
Format show serviceport ipv6 neighbors
Mode Privileged EXEC
Field Description
IPv6 Address The IPv6 address of the neighbor.
MAC Address The MAC Address of the neighbor.
isRtr Shows if the neighbor is a router. If TRUE, the neighbor is a router; if FALSE, it is not a router.
Neighbor State The state of the neighbor cache entry. The possible values are: Incomplete, Reachable, Stale,
Delay, Probe, and Unknown.
Age The time in seconds that has elapsed since an entry was added to the cache.
Type The type of neighbor entry. The type is Static if the entry is manually configured and Dynamic if
dynamically resolved.
Command example:
(NETGEAR Routing) #show serviceport ipv6 neighbors
Neighbor Age
IPv6 Address MAC Address isRtr State (Secs) Type
-------------------------------- ----------------- ----- --------- ------ ------FE80::5E26:AFF:FEBD:852C 5c:26:0a:bd:85:2c FALSE Reachable 0 Dynamic
ping ipv6
Use this command to determine whether another computer is on the network. Ping provides
a synchronous response when initiated from the CLI and Web interfaces. To use the
command, configure the switch for network (in-band) connection. The source and target
devices must have the ping utility enabled and running on top of TCP/IP. The switch can be
pinged from any IP workstation with which the switch is connected through the default VLAN
(VLAN 1), as long as there is a physical path between the switch and the workstation. The
terminal interface sends three pings to the target station. Use the ipv6-address or
hostname parameter to ping an interface by using the global IPv6 address of the interface.
The argument unit/slot/port corresponds to a physical routing interface or VLAN
routing interface. The vlan keyword and vland-id parameter are used to specify the VLAN
ID of the routing VLAN directly instead of in the unit/slot/port format. The vlan-id parameter
is a number in the range of 1–4093.
Management Commands
66
Page 67

M4200 and M4300 Series ProSAFE Managed Switches
You can utilize the ping or traceroute facilities over the service or network ports when using
an IPv6 global address ipv6-global-address or hostname. Any IPv6 global address or
gateway assignments to these interfaces causes IPv6 routes to be installed such that the
ping or traceroute request is routed out the service or network port properly. When
referencing an IPv6 link-local address, you must specify the interface keyword with either
the unit/slot/port argument, vlan keyword and vland-id argument, or
serviceport keyword.
Use the optional size keyword and datagram-size parameter to specify the size of the
ping packet.
Default The default count is 1.
The default interval is 3 seconds.
The default size is 0 bytes.
Format ping ipv6 {ipv6-global-address | hostname | {interface {unit/slot/port | vlan
vland-id | serviceport} link-local-address} [size datagram-size]}
Mode Privileged EXEC
User Exec
ping ipv6 interface
Use this command to determine whether another computer is on the network. To use the
command, configure the switch for network (in-band) connection. The source and target
devices must have the ping utility enabled and running on top of TCP/IP. The switch can be
pinged from any IP workstation with which the switch is connected through the default VLAN
(VLAN 1), as long as there is a physical path between the switch and the workstation. The
terminal interface sends three pings to the target station. You can use a loopback, network
port, service port, tunnel, VLAN, or physical interface as the source.
The argument unit/slot/port corresponds to a physical routing interface or VLAN
routing interface. The vlan keyword and vland-id parameter are used to specify the VLAN
ID of the routing VLAN directly instead of in the unit/slot/port format. The vlan-id
parameter is a number in the range of 1–4093. Use the optional size keyword and
datagram-size parameter to specify the size of the ping packet.
Format ping ipv6 interface {unit/slot/port | vlan vland-id | loopback loopback-id |
serviceport | tunnel tunnel-id} {link-local-address link-local-address |
ipv6-address} [size datagram-size]
Modes Privileged EXEC
User Exec
Management Commands
67
Page 68

M4200 and M4300 Series ProSAFE Managed Switches
Console Port Access Commands
This section describes the commands you use to configure the console port. You can use a
serial cable to connect a management host directly to the console port of the switch.
configure
This command gives you access to the Global Config mode. From the Global Config mode,
you can configure a variety of system settings, including user accounts. From the Global
Config mode, you can enter other command modes, including Line Config mode.
Format configure
Mode Privileged EXEC
line
This command gives you access to the Line Console mode, which allows you to configure
various Telnet settings and the console port, as well as to configure console login/enable
authentication.
Format line {console | telnet | ssh}
Mode Global Config
Term Definition
console Console terminal line.
telnet Virtual terminal for remote console access (Telnet).
ssh Virtual terminal for secured remote console access (SSH).
Command example:
((NETGEAR Switch)(config)#line telnet
(NETGEAR Switch)(config-telnet)#
serial baudrate
This command specifies the communication rate of the terminal interface. The supported
rates are 1200, 2400, 4800, 9600, 19200, 38400, 57600, 115200.
Default 9600
Format serial baudrate {1200 | 2400 | 4800 | 9600 | 19200 | 38400 | 57600 | 115200}
Mode Line Config
Management Commands
68
Page 69

M4200 and M4300 Series ProSAFE Managed Switches
no serial baudrate
This command sets the communication rate of the terminal interface.
Format no serial baudrate
Mode Line Config
serial timeout
This command specifies the maximum connect time (in minutes) without console activity. A
value of 0 indicates that a console can be connected indefinitely. The time range is 0 to 160.
Default 5
Format serial timeout 0-160
Mode Line Config
no serial timeout
This command sets the maximum connect time (in minutes) without console activity.
Format no serial timeout
Mode Line Config
set sup-console
This command allows access to the full CLI from any member. By default, the master is
allowed full CLI access. You can move full CLI access among the members, but at any time,
only one member can access the management CLI. You can issue the command on the
member or backup unit. After the console is transferred to the backup unit or to a member
unit, access to the full CLI on the master is disabled to avoid multiple simultaneous CLI
inputs. You can restore full access on the master by entering the command at the master
serial port.
Note: If you enter the command while the master is already allowed full CLI
access, the command does not take effect.
Format set sup-console
Mode Privileged EXEC
Management Commands
69
Page 70

M4200 and M4300 Series ProSAFE Managed Switches
show serial
This command displays serial communication settings for the switch.
Format show serial
Modes • Privileged EXEC
• User EXEC
Term Definition
Serial Port Login Timeout
(minutes)
Baud Rate (bps) The default baud rate at which the serial port will try to connect.
Character Size (bits) The number of bits in a character. The number of bits is always 8.
Flow Control Whether Hardware Flow-Control is enabled or disabled. Hardware Flow Control is always
Stop Bits The number of Stop bits per character. The number of Stop bits is always 1.
Parity The parity method used on the Serial Port. The Parity Method is always None.
The time, in minutes, of inactivity on a serial port connection, after which the switch will close
the connection. A value of 0 disables the timeout.
disabled.
Telnet Commands
This section describes the commands you use to configure and view Telnet settings. Y ou can
use Telnet to manage the device from a remote management host.
ip telnet server enable
Use this command to enable Telnet connections to the system and to enable the Telnet
Server Admin Mode. This command opens the Telnet listening port.
Default enabled
Format ip telnet server enable
Mode Privileged EXEC
no ip telnet server enable
Use this command to disable Telnet access to the system and to disable the Telnet Server
Admin Mode. This command closes the Telnet listening port and disconnects all open Telnet
sessions.
Format no ip telnet server enable
Mode Privileged EXEC
Management Commands
70
Page 71

M4200 and M4300 Series ProSAFE Managed Switches
ip telnet port
Use this command to configure the TCP port number on which the Telnet server detects
requests. The number argument can be a port number in the range from 1 to 65535.
Default 23
Format ip telnet port number
Mode Privileged EXEC
no ip telnet port
Use this command to reset the TCP port number on which the Telnet server detects requests
to the default of 23.
Format no ip telnet port
Mode Privileged EXEC
telnet
This command establishes a new outbound Telnet connection to a remote host. The host
must be a valid IP address or host name. Valid values for port should be a valid decimal
integer in the range of 0 to 65535, where the default value is 23. If debug is used, the current
Telnet options enabled is displayed. The optional line parameter sets the outbound Telnet
operational mode as linemode where, by default, the operational mode is character mode.
The localecho option enables local echo.
Format telnet {ip-address | hostname} port [debug] [line] [localecho]
Modes • Privileged EXEC
• User EXEC
transport input telnet
This command regulates new Telnet sessions. If enabled, new Telnet sessions can be
established until there are no more sessions available. An established session remains
active until the session is ended or an abnormal network error ends the session.
Note: If the Telnet Server Admin Mode is disabled, Telnet sessions cannot
be established. Use the ip telnet server enable command to
enable Telnet Server Admin Mode.
Default enabled
Format transport input telnet
Mode Line Config
Management Commands
71
Page 72

M4200 and M4300 Series ProSAFE Managed Switches
no transport input telnet
Use this command to prevent new Telnet sessions from being established.
Format no transport input telnet
Mode Line Config
transport output telnet
This command regulates new outbound Telnet connections. If enabled, new outbound Telnet
sessions can be established until the system reaches the maximum number of simultaneous
outbound Telnet sessions allowed. An established session remains active until the session is
ended or an abnormal network error ends it.
Default enabled
Format transport output telnet
Mode Line Config
no transport output telnet
Use this command to prevent new outbound Telnet connection from being established.
Format no transport output telnet
Mode Line Config
session-limit
This command specifies the maximum number of simultaneous outbound Telnet sessions.
The number argument can be a number in the range from 0–5. A value of 0 indicates that no
outbound Telnet session can be established.
Default 5
Format session-limit number
Mode Line Config
no session-limit
This command sets the maximum number of simultaneous outbound Telnet sessions to the
default value.
Format no session-limit
Mode Line Config
Management Commands
72
Page 73

M4200 and M4300 Series ProSAFE Managed Switches
session-timeout (Line Config)
This command sets the Telnet session time-out value. The time-out value unit of time is
minutes and is specified by the minutes argument in the range 1–160 minutes.
Default 5
Format session-timeout minutes
Mode Line Config
no session-timeout
This command sets the Telnet session timeout value to the default. The timeout value unit of
time is minutes.
Format no session-timeout
Mode Line Config
telnetcon maxsessions
This command specifies the maximum number of Telnet connection sessions that can be
established. The number argument can be a number in the range from 0–5. A value of 0
indicates that no Telnet connection can be established.
Default 5
Format telnetcon maxsessions number
Mode Privileged EXEC
no telnetcon maxsessions
This command sets the maximum number of Telnet connection sessions that can be
established to the default value.
Format no telnetcon maxsessions
Mode Privileged EXEC
telnetcon timeout
This command sets the Telnet connection session time-out value. A session is active as long
as the session has not been idle for the value set. The time-out value unit of time is minutes
and is specified by the minutes argument in the range 1–160 minutes.
Note: When you change the time-out value, the new value is applied to all
active and inactive sessions immediately. Any sessions that have been
idle longer than the new time-out value are disconnected immediately.
Management Commands
73
Page 74

M4200 and M4300 Series ProSAFE Managed Switches
Default 5
Format telnetcon timeout minutes
Mode Privileged EXEC
no telnetcon timeout
This command sets the Telnet connection session timeout value to the default.
Note: Changing the time-out value for active sessions does not become
effective until the session is accessed again. Also, any keystroke
activates the new time-out duration.
Format no telnetcon timeout
Mode Privileged EXEC
show telnet
This command displays the current outbound Telnet settings. In other words, these settings
apply to Telnet connections initiated from the switch to a remote system.
Format show telnet
Modes • Privileged EXEC
• User EXEC
Term Definition
Outbound Telnet
Login Timeout
Maximum Number
of Outbound Telnet
Sessions
Allow New
Outbound Telnet
Sessions
The number of minutes an outbound Telnet session is allowed to remain inactive before being
logged off.
The number of simultaneous outbound Telnet connections allowed.
Indicates whether outbound Telnet sessions will be allowed.
Management Commands
74
Page 75

M4200 and M4300 Series ProSAFE Managed Switches
show telnetcon
This command displays the current inbound Telnet settings. In other words, these settings
apply to Telnet connections initiated from a remote system to the switch.
Format show telnetcon
Modes • Privileged EXEC
• User EXEC
Term Definition
Remote Connection Login
Timeout (minutes)
Maximum Number of
Remote Connection
Sessions
Allow New Telnet
Sessions
Telnet Server Admin
Mode
Telnet Server Port The port number on which the Telnet server can detect requests.
This object indicates the number of minutes a remote connection session is allowed to remain
inactive before being logged off. May be specified as a number from 1 to 160. The factory
default is 5.
This object indicates the number of simultaneous remote connection sessions allowed. The
factory default is 5.
New Telnet sessions will not be allowed when this field is set to no. The factory default value
is yes.
States whether the Telnet Server Admin Mode is enabled or disabled.
Secure Shell Commands
This section describes the commands you use to configure Secure Shell (SSH) access to the
switch. Use SSH to access the switch from a remote management host.
Note: The system allows a maximum of 5 SSH sessions.
ip ssh
Use this command to enable SSH access to the system. (This command is the short form of
the ip ssh server enable command.)
Default disabled
Format ip ssh
Mode Privileged EXEC
Management Commands
75
Page 76

M4200 and M4300 Series ProSAFE Managed Switches
ip ssh port
Use this command to configure the TCP port number on which the Secure Shell (SSH) server
detects requests. The number argument can be a port number in the range from 1 to 65535.
Default 22
Format ip ssh port number
Mode Privileged EXEC
no ip ssh port
Use this command to reset the TCP port number on which the SSH server detects requests
to the default of 22.
Format no ip ssh port
Mode Privileged EXEC
ip ssh protocol
This command is used to set or remove protocol levels (or versions) for SSH. Either SSH1
(1), SSH2 (2), or both SSH 1 and SSH 2 (1 and 2) can be set.
Default 2
Format ip ssh protocol [1] [2]
Mode Privileged EXEC
ip ssh server enable
This command enables the IP secure shell server. No new SSH connections are allowed, but
the existing SSH connections continue to work until timed-out or logged-out.
Default enabled
Format ip ssh server enable
Mode Privileged EXEC
no ip ssh server enable
This command disables the IP secure shell server.
Format no ip ssh server enable
Mode Privileged EXEC
Management Commands
76
Page 77

M4200 and M4300 Series ProSAFE Managed Switches
sshcon maxsessions
This command specifies the maximum number of SSH connection sessions that can be
established. The number argument can be a number in the range from 0–5. A value of 0
indicates that no ssh connection can be established. The range is 0 to 5.
Default 5
Format sshcon maxsessions number
Mode Privileged EXEC
no sshcon maxsessions
This command sets the maximum number of allowed SSH connection sessions to the default
value.
Format no sshcon maxsessions
Mode Privileged EXEC
sshcon timeout
This command sets the SSH connection session timeout value, in minutes. A session is
active as long as the session has been idle for the value set. The time-out value unit of time
is minutes and is specified by the minutes argument in the range 1–160 minutes.
Changing the timeout value for active sessions does not become effective until the session is
re accessed. Also, any keystroke activates the new time-out duration.
Default 5
Format sshcon timeout minutes
Mode Privileged EXEC
no sshcon timeout
This command sets the SSH connection session time-out value, in minutes, to the default.
Changing the time-out value for active sessions does not become effective until the session
is re accessed. Also, any keystroke activates the new time-out duration.
Format no sshcon timeout
Mode Privileged EXEC
Management Commands
77
Page 78

M4200 and M4300 Series ProSAFE Managed Switches
show ip ssh
This command displays the ssh settings.
Format show ip ssh
Mode Privileged EXEC
Term Definition
Administrative
Mode
Protocol Level The protocol level may have the values of version 1, version 2 or both versions 1 and version 2.
SSH Sessions
Currently Active
Max SSH Sessions
Allowed
SSH Timeout The SSH timeout value in minutes.
Keys Present Indicates whether the SSH RSA and DSA key files are present on the device.
Key Generation in
Progress
This field indicates whether the administrative mode of SSH is enabled or disabled.
The number of SSH sessions currently active.
The maximum number of SSH sessions allowed.
Indicates whether RSA or DSA key files generation is currently in progress.
Management Security Commands
This section describes commands you use to generate keys and certificates, which you can
do in addition to loading them as before.
crypto certificate generate
Use this command to generate a self-signed certificate for HTTPS. The generated RSA key
for SSL has a length of 1024 bits. The resulting certificate is generated with a common name
equal to the lowest IP address of the device and a duration of 365 days.
Format crypto certificate generate
Mode Global Config
no crypto certificate generate
Use this command to delete the HTTPS certificate files from the device, regardless of
whether they are self-signed or downloaded from an outside source.
Format no crypto certificate generate
Mode Global Config
Management Commands
78
Page 79

M4200 and M4300 Series ProSAFE Managed Switches
crypto key generate rsa
Use this command to generate an RSA key pair for SSH. The new key files will overwrite any
existing generated or downloaded RSA key files.
Format crypto key generate rsa
Mode Global Config
no crypto key generate rsa
Use this command to delete the RSA key files from the device.
Format no crypto key generate rsa
Mode Global Config
crypto key generate dsa
Use this command to generate a DSA key pair for SSH. The new key files will overwrite any
existing generated or downloaded DSA key files.
Format crypto key generate dsa
Mode Global Config
no crypto key generate dsa
Use this command to delete the DSA key files from the device.
Format no crypto key generate dsa
Mode Global Config
Management Access Control List Commands
You can use a management Access Control List (ACL) to help control access to the switch
management interface. A management ACL can help ensure that only known and trusted
devices are allowed to remotely manage the switch via TCP/IP. Management ACLs are only
configurable on IP (in-band) interfaces, not on the service port.
When a management ACL is enabled, incoming TCP packets initiating a connection (TCP
SYN) and all UDP packets are filtered based on their source IP address and destination port.
When the management ACL is disabled, incoming TCP/UDP packets are not filtered and are
processed normally.
management access-list
This command creates a management ACL. The management ACL name can be up to
32 alphanumeric characters. Executing this command enters into access-list configuration
Management Commands
79
Page 80

M4200 and M4300 Series ProSAFE Managed Switches
mode, from which you must define the denied or permitted access conditions with the deny
and permit commands. If no match criteria are defined the default is to deny access (deny).
If you reenter to an access-list context, new rules are entered at the end of the access list.
Format management access list name
Mode Global Config
no management access-list
This command deletes a management ACL identified by the name parameter.
Format no management access list name
Mode Global Config
permit ip-source
This command sets permit conditions for the management access list based on the source IP
address of a packet. Optionally, you can specify a subnet mask, service type, priority, or a
combination of these for the rule. Each rule requires a unique priority. Use this command in
Management access-list configuration mode.
Format permit ip-source ip-address [mask {mask | prefix-length}] [service service]
[priority priority]
Mode Management access-list configuration
Parameter Definition
ip-address The source IP address.
mask The network mask of the source IP address.
prefix-length Specifies the number of bits that comprise the source IP address prefix. The prefix length must be
preceded by a forward slash (/).
service Indicates the service type: telnet, ssh, http, https, or snmp.
priority The priority for the rule.
permit service
This command sets permit conditions for the management access list based on the access
protocol. Each rule requires a unique priority. Use this command in Management access-list
configuration mode.
Format permit service service [priority priority]
Mode Management access-list configuration
Management Commands
80
Page 81

M4200 and M4300 Series ProSAFE Managed Switches
Parameter Definition
service Indicates the service type: telnet, ssh, http, https, or snmp.
priority The priority for the rule.
permit priority
This command assigns a permit priority to the rule. Each rule requires a unique priority. Use
this command in Management access-list configuration mode.
Format permit priority priority
Mode Management access-list configuration
deny ip-source
This command sets deny conditions for the management access list based on the source IP
address of a packet. Optionally, you can specify a subnet mask, service type, priority, or a
combination of these for the rule. Each rule requires a unique priority. Use this command in
Management access-list configuration mode.
Format deny ip-source ip-address [mask {mask | prefix-length}] [service service]
[priority priority]
Mode Management access-list configuration
Parameter Definition
ip-address The source IP address.
mask The network mask of the source IP address.
prefix-length Specifies the number of bits that comprise the source IP address prefix. The prefix length must be
preceded by a forward slash (/).
service Indicates the service type: telnet, ssh, http, https, or snmp.
priority The priority for the rule.
deny service
This command sets deny conditions for the management access list based on the access
protocol. Each rule requires a unique priority. Use this command in Management access-list
configuration mode.
Format deny service service [priority priority]
Mode Management access-list configuration
Management Commands
81
Page 82

M4200 and M4300 Series ProSAFE Managed Switches
Parameter Definition
service Indicates the service type: telnet, ssh, http, https, or snmp.
priority The priority for the rule.
deny priority
This command assigns a deny priority to the rule. Each rule requires a unique priority. Use
this command in Management access-list configuration mode.
Format deny priority priority
Mode Management access-list configuration
management access-class
This command activates the configured management ALC and restricts management
connections within the management ACL. The name parameter is the name of the existing
management ACL. You cannot update or remove a management ACL when it is active.
Format management access-class name
Mode Global Config
no management access-class
This command disables a management ACL.
Format no management access-class
Mode Global Config
show management access-list
This command displays information about the configured management ALC.
Format show management access-list [name]
Mode Privileged EXEC
Field Definition
List Name The name of the management ACL
List Admin Mode The administrative mode of the management ACL. To activate a management ACL, enter the
management access-class command (see management access-class on page 82).
Packets Filtered The number of packets filtered by the management ACL
Rules The rules that are included in the ACL.
Management Commands
82
Page 83

M4200 and M4300 Series ProSAFE Managed Switches
Command example:
(NETGEAR Switch) #show management access-list
List Name...................................... mgmtacl
List Admin Mode................................ Disabled
Packets Filtered............................... 0
Rules:
permit ip-source 192.168.2.10 mask 255.255.255.255 service ssh priority 1
permit ip-source 192.168.2.182 mask 255.255.255.255 service ssh priority 2
permit ip-source 192.168.2.23 mask 255.255.255.255 service ssh priority 3
NOTE: All other access is implicitly denied.
show management access-class
This command displays information about the configured management ALC.
Format show management access-class
Mode Privileged EXEC
Field Definition
List Name The name of the management ACL
List Admin Mode The administrative mode of the management ACL. To activate a management ACL, enter the
management access-class command (see management access-class on page 82).
Packets Filtered The number of packets filtered by the management ACL
Command example:
(NETGEAR Switch) #show management access-class
List Name...................................... mgmtacl
List Admin Mode................................ Disabled
Packets Filtered............................... 0
Hypertext Transfer Protocol Commands
This section describes the commands you use to configure Hypertext Transfer Protocol
(HTTP) and secure HTTP access to the switch. Access to the switch by using a W eb browser
is enabled by default. Everything you can view and configure by using the CLI is also
available by using the web.
Management Commands
83
Page 84

M4200 and M4300 Series ProSAFE Managed Switches
ip http accounting exec, ip https accounting exec
This command applies user exec (start-stop/stop-only) accounting list to the line methods
HTTP and HTTPS.
Note: The user exec accounting list should be created using the command
aaa accounting on page 117.
Format ip {http | https} accounting exec {default | listname}
Mode Global Config
Parameter Description
http or https The line method for which the list needs to be applied.
default The default list of methods for authorization services.
listname An alphanumeric character string used to name the list of accounting methods.
no ip http/https accounting exec
This command deletes the authorization method list.
Format no ip {http | https} accounting exec {default | listname}
Mode Global Config
ip http authentication
Use this command to specify authentication methods for http server users. The default
configuration is the local user database is checked. This action has the same effect as the
command ip http authentication local. The additional methods of authentication
are used only if the previous method returns an error, not if it fails. To ensure that the
authentication succeeds even if all methods return an error, specify none as the final method
in the command line.
For example, if none is specified as an authentication method after radius, no
authentication is used if the RADIUS server is down.
Default local
Format ip http authentication method1 [method2...]
Mode Global Config
Management Commands
84
Page 85

M4200 and M4300 Series ProSAFE Managed Switches
Parameter Description
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
Command example:
The following example configures http authentication:
(NETGEAR Switch)(config)# ip http authentication radius local
no ip http authentication
Use this command to return to the default.
Format no ip http authentication
Mode Global Config
ip https authentication
Use this command to specify authentication methods for https server users. The default
configuration is the local user database is checked. This action has the same effect as the
command ip https authentication local. The additional methods of authentication
are used only if the previous method returns an error, not if it fails. To ensure that the
authentication succeeds even if all methods return an error, specify none as the final method
in the command line. For example, if none is specified as an authentication method after
radius, no authentication is used if the RADIUS server is down.
Default local
Format ip https authentication method1 [method2...]
Mode Global Config
Parameter Description
local Uses the local username database for authentication.
none Uses no authentication.
radius Uses the list of all RADIUS servers for authentication.
tacacs Uses the list of all TACACS+ servers for authentication.
Management Commands
85
Page 86

M4200 and M4300 Series ProSAFE Managed Switches
Command example:
The following example configures http authentication:
(NETGEAR Switch)(config)# ip https authentication radius local
no ip https authentication
Use this command to return to the default.
Format no ip https authentication
Mode Global Config
ip http server
This command enables access to the switch through the Web interface. When access is
enabled, the user can login to the switch from the Web interface. When access is disabled,
the user cannot login to the switch's Web server. Disabling the Web interface takes effect
immediately. All interfaces are affected.
Default enabled
Format ip http server
Mode Privileged EXEC
no ip http server
This command disables access to the switch through the Web interface. When access is
disabled, the user cannot login to the switch's Web server.
Format no ip http server
Mode Privileged EXEC
ip http secure-server
This command is used to enable the secure socket layer for secure HTTP.
Default disabled
Format ip http secure-server
Mode Privileged EXEC
Management Commands
86
Page 87

M4200 and M4300 Series ProSAFE Managed Switches
no ip http secure-server
This command is used to disable the secure socket layer for secure HTTP.
Format no ip http secure-server
Mode Privileged EXEC
ip http port
Use this command to configure the TCP port number on which the HTTP server detects
requests. The number argument can be a port number in the range from 1 to 65535.
Default 80
Format ip http port number
Mode Privileged EXEC
no ip http port
Use this command to reset the TCP port number on which the HTTP server detects requests
to the default of 80.
Format no ip http port
Mode Privileged EXEC
ip http session hard-timeout
This command configures the hard time-out for unsecure HTTP sessions. The time-out value
unit of time is hours and is specified by the hours argument in the range 1–168 hours.
Configuring this value to zero will give an infinite hard-time-out. When this time-out expires,
the user will be forced to reauthenticate. This timer begins on initiation of the web session
and is unaffected by the activity level of the connection.
Default 24
Format ip http session hard-timeout hours
Mode Privileged EXEC
no ip http session hard-timeout
This command restores the hard time-out for un-secure HTTP sessions to the default value.
Format no ip http session hard-timeout
Mode Privileged EXEC
Management Commands
87
Page 88

M4200 and M4300 Series ProSAFE Managed Switches
ip http session maxsessions
This command limits the number of allowable unsecure HTTP sessions. The number
argument specifies the number of sessions in the range of 0–16. Zero is the configurable
minimum.
Default 16
Format ip http session maxsessions number
Mode Privileged EXEC
no ip http session maxsessions
This command restores the number of allowable un-secure HTTP sessions to the default
value.
Format no ip http session maxsessions
Mode Privileged EXEC
ip http session soft-timeout
This command configures the soft time-out for un-secure HTTP sessions. The time-out value
unit of time is minutes and is specified by the minutes argument in the range 1–60 minutes.
Configuring this value to zero will give an infinite soft-time-out. When this time-out expires the
user will be forced to reauthenticate. This timer begins on initiation of the Web session and is
restarted with each access to the switch.
Default 5
Format ip http session soft-timeout minutes
Mode Privileged EXEC
no ip http session soft-timeout
This command resets the soft time-out for un-secure HTTP sessions to the default value.
Format no ip http session soft-timeout
Mode Privileged EXEC
ip http secure-session hard-timeout
This command configures the hard time-out for secure HTTP sessions. The time-out value
unit of time is hours and is specified by the hours argument in the range 1–168 hours. When
this time-out expires, the user is forced to reauthenticate. This timer begins on initiation of the
Web session and is unaffected by the activity level of the connection. The secure-session
hard-time-out can not be set to zero (infinite).
Management Commands
88
Page 89

M4200 and M4300 Series ProSAFE Managed Switches
Default 24
Format ip http secure-session hard-timeout hours
Mode Privileged EXEC
no ip http secure-session hard-timeout
This command resets the hard time-out for secure HTTP sessions to the default value.
Format no ip http secure-session hard-timeout
Mode Privileged EXEC
ip http secure-session maxsessions
This command limits the number of secure HTTP sessions. The number argument specifies
the number of sessions in the range of 0–16. Zero is the configurable minimum.
Default 16
Format ip http secure-session maxsessions number
Mode Privileged EXEC
no ip http secure-session maxsessions
This command restores the number of allowable secure HTTP sessions to the default value.
Format no ip http secure-session maxsessions
Mode Privileged EXEC
ip http secure-session soft-timeout
This command configures the soft time-out for secure HTTP sessions. The time-out value
unit of time is minutes and is specified by the minutes argument in the range 1–60 minutes.
Configuring this value to zero will give an infinite soft-time-out. When this time-out expires,
you are forced to reauthenticate. This timer begins on initiation of the Web session and is
restarted with each access to the switch. The secure-session soft-time-out can not be set to
zero (infinite).
Default 5
Format ip http secure-session soft-timeout minutes
Mode Privileged EXEC
Management Commands
89
Page 90

M4200 and M4300 Series ProSAFE Managed Switches
no ip http secure-session soft-timeout
This command restores the soft time-out for secure HTTP sessions to the default value.
Format no ip http secure-session soft-timeout
Mode Privileged EXEC
ip http secure-port
This command is used to set the SSL port where port can be 1025-65535 and the default is
port 443.
Default 443
Format ip http secure-port portid
Mode Privileged EXEC
no ip http secure-port
This command is used to reset the SSL port to the default value.
Format no ip http secure-port
Mode Privileged EXEC
ip http secure-protocol
This command is used to set protocol levels (versions). The protocol level can be set to
TLS1, SSL3 or to both TLS1 and SSL3.
Default SSL3 and TLS1
Format ip http secure-protocol [SSL3] [TLS1]
Mode Privileged EXEC
show ip http
This command displays the http settings for the switch.
Format show ip http
Mode Privileged EXEC
Term Definition
HTTP Mode (Unsecure) The unsecure HTTP server administrative mode.
Java Mode The java applet administrative mode which applies to both secure and un-secure web
connections.
Management Commands
90
Page 91

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
Maximum Allowable HTTP
Sessions
HTTP Session Hard Timeout The hard timeout for un-secure http sessions in hours.
HTTP Session Soft Timeout The soft timeout for un-secure http sessions in minutes.
HTTP Mode (Secure) The secure HTTP server administrative mode.
Secure Port The secure HTTP server port number.
Secure Protocol Level(s) The protocol level may have the values of SSL3, TSL1, or both SSL3 and TSL1.
Maximum Allowable HTTPS
Sessions
HTTPS Session Hard
Timeout
HTTPS Session Soft
Timeout
Certificate Present Indicates whether the secure-server certificate files are present on the device.
Certificate Generation in
Progress
The number of allowable un-secure http sessions.
The number of allowable secure http sessions.
The hard timeout for secure http sessions in hours.
The soft timeout for secure http sessions in minutes.
Indicates whether certificate generation is currently in progress.
Access Commands
Use the commands in this section to close remote connections or to view information about
connections to the system.
disconnect
Use the disconnect command to close HTTP, HTTPS, Telnet or SSH sessions. Use all to
close all active sessions, or use session-id to specify the session ID to close. To view the
possible values for session-id, use the show loginsession command.
Format disconnect {session_id | all}
Mode Privileged EXEC
show loginsession
This command displays current Telnet, SSH and serial port connections to the switch. This
command displays truncated user names. Use the show loginsession long command
to display the complete usernames.
Format show loginsession
Mode Privileged EXEC
Management Commands
91
Page 92

M4200 and M4300 Series ProSAFE Managed Switches
Term Definition
ID Login Session ID.
User Name The name the user entered to log on to the system.
Connection From IP address of the remote client machine or EIA-232 for the serial port connection.
Idle Time Time this session has been idle.
Session Time Total time this session has been connected.
Session Type Shows the type of session, which can be HTTP, HTTPS, telnet, serial, or SSH.
show loginsession long
This command displays the complete user names of the users currently logged in to the
switch.
Format show loginsession long
Mode Privileged EXEC
Command example:
(NETGEAR Switch) #show loginsession long
User Name
-----------admin
test1111test1111test1111test1111test1111test1111test1111test1111
User Account Commands
This section describes the commands you use to add, manage, and delete system users.
The switch provides two default users: admin and guest. The admin user can view and
configure system settings, and the guest user can view settings.
Note: You cannot delete the admin user. There is only one user allowed with
read/write privileges. You can configure up to five read-only users on the
system.
aaa authentication login
Use this command to set authentication at login. The default and optional list names created
with the command are used with the aaa authentication login command. Create a list
by entering the aaa authentication login list-name method command, where
list-name is any character string used to name this list. The method argument identifies
the list of methods that the authentication algorithm tries, in the given sequence.
Management Commands
92
Page 93

M4200 and M4300 Series ProSAFE Managed Switches
The additional methods of authentication are used only if the previous method returns an
error, not if there is an authentication failure. To ensure that the authentication succeeds
even if all methods return an error, specify none as the final method in the command line.
For example, if none is specified as an authentication method after radius, no
authentication is used if the RADIUS server is down.
If you configure local as the first method in the list, the switch tries no other methods.
Default • defaultList. Used by the console and only contains the method none.
• networkList. Used by telnet and SSH and only contains the method local.
Format aaa authentication login {default | list-name} method1 [method2...]
Mode Global Config
Parameter Definition
default Uses the listed authentication methods that follow this argument as the default list of methods when
a user logs in.
list-name Character string of up to 15 characters used to name the list of authentication methods activated
when a user logs in.
method1...
[method2...]
At least one from the following:
• enable. Uses the enable password for authentication.
• line. Uses the line password for authentication.
• local. Uses the local username database for authentication.
• none. Uses no authentication.
• radius. Uses the list of all RADIUS servers for authentication.
• tacacs. Uses the list of all TACACS servers for authentication.
Command example:
(NETGEAR Switch)(config)# aaa authentication login default radius local enable none
no aaa authentication login
This command returns to the default.
Format aaa authentication login {default | list-name}
Mode Global Config
aaa authentication enable
Use this command to set authentication for accessing higher privilege levels. The default
enable list is enableList. It is used by console, and contains the method as enable
followed by none.
A separate default enable list, enableNetList, is used for Telnet and SSH users instead of
enableList. This list is applied by default for Telnet and SSH, and contains enable
followed by deny methods. In NETGEAR Managed Switch, by default, the enable password
Management Commands
93
Page 94

M4200 and M4300 Series ProSAFE Managed Switches
is not configured. That means that, by default, Telnet and SSH users will not get access to
Privileged EXEC mode. On the other hand, with default conditions, a console user always
enter the Privileged EXEC mode without entering the enable password.
The default and optional list names created with the aaa authentication enable
command are used with the enable authentication command. Create a list by entering
the aaa authentication enable list-name method command where list-name
is any character string used to name this list. The method argument identifies the list of
methods that the authentication algorithm tries in the given sequence.
The user manager returns ERROR (not PASS or FAIL) for enable and line methods if no
password is configured, and moves to the next configured method in the authentication list.
The method none reflects that there is no authentication needed.
The user will only be prompted for an enable password if one is required. The following
authentication methods do not require passwords:
• none
• deny
• enable (if no enable password is configured)
• line (if no line password is configured)
See the examples below.
1. aaa authentication enable default enable none
2. aaa authentication enable default line none
3. aaa authentication enable default enable radius none
4. aaa authentication enable default line tacacs none
Examples 1 and 2 do not prompt for a password, however because examples 3 and 4 contain
the radius and tacacs methods, the password prompt is displayed.
If the login methods include only enable, and there is no enable password configured, then
NETGEAR Managed Switch does not prompt for a user name. In such cases, NETGEAR
Managed Switch only prompts for a password. NETGEAR Managed Switch supports
configuring methods after the local method in authentication and authorization lists. If the
user is not present in the local database, then the next configured method is tried.
The additional methods of authentication are used only if the previous method returns an
error, not if it fails. To ensure that the authentication succeeds even if all methods return an
error, specify none as the final method in the command line.
Use the command show authorization methods on page 99 to display information about the
authentication methods.
Note: Requests sent by the switch to a RADIUS or TACACS server include
the username $enabx$, in which x is the requested privilege level.
The login user ID is also sent to a TACACS+ server.
Management Commands
94
Page 95

M4200 and M4300 Series ProSAFE Managed Switches
Default default
Format aaa authentication enable {default | list-name} method1 [method2...]
Mode Global Config
Parameter Description
default Uses the listed authentication methods that follow this argument as the default list of methods, when
using higher privilege levels.
list-name Character string used to name the list of authentication methods activated, when using access
higher privilege levels. Range: 1-15 characters.
method1
[method2...]
Specify at least one from the following:
• deny. Used to deny access.
• enable. Uses the enable password for authentication.
• line. Uses the line password for authentication.
• none. Uses no authentication.
• radius. Uses the list of all RADIUS servers for authentication.
• tacacs. Uses the list of all TACACS+ servers for authentication.
Command example:
The following example sets authentication to access higher privilege levels:
(NETGEAR Switch)(config)# aaa authentication enable default enable
no aaa authentication enable
Use this command to return to the default configuration.
Format no aaa authentication enable {default | list-name}
Mode Global Config
aaa authorization
Use this command to configure command and exec authorization method lists. This list is
identified by default or a user-specified list-name. If tacacs is specified as the
authorization method, authorization commands are notified to a TACACS+ server. If none is
specified as the authorization method, command authorization is not applicable. A maximum
of five authorization method lists can be created for the commands type.
Note: The local method is not supported for command authorization.
Command authorization with RADIUS functions only if the applied
authentication method is also RADIUS.
Management Commands
95
Page 96

M4200 and M4300 Series ProSAFE Managed Switches
Format aaa authorization {exec | commands} {default | list-name} method1
[method2…]
Mode Global Config
Term Definition
exec Provides authorization for user EXEC terminal sessions.
commands Provides authorization for all user-executed commands.
default The default list of methods for authorization services.
list-name Character string used to name the list of authorization methods.
method1 [method2…] Use either tacacs or radius for authorization purpose.
no aaa authorization
This command deletes the authorization method list.
Format no aaa authorization {exec | commands} {default | <list-name>}
<method1> [<method2>…]
Mode Global Config
Per-Command Authorization
When authorization is configured for a line mode, the user manager sends information about
an entered command to the AAA server. The AAA server validates the received command,
and responds with either a PASS or FAIL response. If approved, the command is executed.
Otherwise, the command is denied and an error message is shown to the user. The various
utility commands such as tftp, ping, and outbound telnet should also pass command
authorization. Applying the script is treated as a single command apply script, which also
goes through authorization. Startup-config commands applied on device boot-up are not an
object of the authorization process.
The per-command authorization usage scenario is this:
1. Configure Authorization Method List
aaa authorization commands listname tacacs radius none
2. Apply AML to an Access Line Mode (console, telnet, SSH)
authorization commands listname
3. Commands entered by the user will go through command authorization via TACACS+ or
RADIUS server and will be accepted or denied.
Management Commands
96
Page 97

M4200 and M4300 Series ProSAFE Managed Switches
Exec Authorization
When exec authorization is configured for a line mode, the user may not be required to use
the enable command to enter Privileged EXEC mode. If the authorization response indicates
that the user has sufficient privilege levels for Privileged EXEC mode, then the user bypasses
User EXEC mode entirely.
The exec authorization usage scenario is as follows:
1. Configure Authorization Method List
aaa authorization exec listname method1 [method2....]
2. Apply AML to an Access Line Mode (console, telnet, SSH)
authorization exec listname
3. When the user logs in, in addition to authentication, authorization will be performed to
determine if the user is allowed direct access to Privileged EXEC mode.
Format aaa authorization {commands | exec} {default | list-name} method1 [method2]
Mode Global Config
Parameter Description
commands Provides authorization for all user-executed commands.
exec Provides exec authorization.
default The default list of methods for authorization services.
list-name Alphanumeric character string used to name the list of authorization methods.
method TACACS+, RADIUS, Local, and none are supported.
(NETGEAR Switch) #
(NETGEAR Switch) #configure
(NETGEAR Switch) (Config)#aaa authorization exec default tacacs+ none
(NETGEAR Switch) (Config)#aaa authorization commands default tacacs+ none
no aaa authorization
This command deletes the authorization method list.
Format no aaa authorization {commands | exec} {default | list-name}
Mode Global Config
Management Commands
97
Page 98

M4200 and M4300 Series ProSAFE Managed Switches
authorization commands
This command applies a command authorization method list to an access method (console,
telnet, ssh). For usage scenarios on per command authorization, see the command aaa
authorization on page 95.
Format authorization commands [default | list-name]
Mode Line console, Line telnet, Line SSH
Parameter Description
commands This causes command authorization for each command execution attempt.
no authorization commands
This command removes command authorization from a line config mode.
Format no authorization {commands | exec}
Mode Line console, Line telnet, Line SSH
Command example:
(NETGEAR Switch) (Config)#line console
(NETGEAR Switch) (Config-line)#authorization commands list2
(NETGEAR Switch) (Config-line)#
(NETGEAR Switch) (Config-line)#exit
authorization exec
This command applies a command authorization method list to an access method so that the
user may not be required to use the enable command to enter Privileged EXEC mode. For
usage scenarios on exec authorization, see the command aaa authorization on page 95.
Format authorization exec list-name
Mode Line console, Line telnet, Line SSH
Parameter Description
list-name The command authorization method list.
Management Commands
98
Page 99

M4200 and M4300 Series ProSAFE Managed Switches
no authorization exec
This command removes command authorization from a line config mode.
Format no authorization exec
Mode Line console, Line telnet, Line SSH
authorization exec default
This command applies a default command authorization method list to an access method so
that the user may not be required to use the enable command to enter Privileged EXEC
mode. For usage scenarios on exec authorization, see the command aaa authorization on
page 95.
Format authorization exec default
Mode Line console, Line telnet, Line SSH
no authorization exec default
This command removes command authorization from a line config mode.
Format no authorization exec default
Mode Line console, Line telnet, Line SSH
show authorization methods
This command displays the configured authorization method lists.
Format show authorization methods
Mode Privileged EXEC
Command example:
(NETGEAR Switch) #show authorization methods
Command Authorization List Method
-------------------------- -------------------------------------dfltCmdAuthList tacacs none
list2 none undefined
list4 tacacs undefined
Line Command Method List
------------ -----------------------------Console dfltCmdAuthList
Telnet dfltCmdAuthList
SSH dfltCmdAuthList
Management Commands
99
Page 100

M4200 and M4300 Series ProSAFE Managed Switches
Exec Authorization List Method
----------------------- -------------------------------------dfltExecAuthList tacacs none
list2 none undefined
list4 tacacs undefined
Line Exec Method List
------------ -----------------------------Console dfltExecAuthList
Telnet dfltExecAuthList
SSH dfltExecAuthList
enable authentication
Use this command to specify the authentication method list when accessing a higher
privilege level from a remote telnet or console.
Format enable authentication {default | list-name}
Mode Line Config
Parameter Description
default Uses the default list created with the aaa authentication enable command.
list-name Uses the indicated list created with the aaa authentication enable command.
Command example:
The following example specifies the default authentication method to access a higher
privilege level console:
(NETGEAR Switch)(config)# line console
(NETGEAR Switch)(config-line)# enable authentication default
no enable authentication
Use this command to return to the default specified by the
Format no enable authentication
Mode Line Config
enable authentication command.
username (Global Config)
Use the username command in Global Config mode to add a new user to the local user
database. The default privilege level is 1. Using the encrypted keyword allows the
administrator to transfer local user passwords between devices without having to know the
passwords. When the password parameter is used along with encrypted parameter, the
Management Commands
100
 Loading...
Loading...