Page 1

Enterprise Operating System
Command Line Interface
User Manual
P/N 620-000134-720
REV A
Page 2
Record of Revisions and Updates
Revision Date Description
620-000134-000 11/2001 Initial release of Manual
620-000134-100 05/2002 Updates for E/OS 2.0
620-000134-200 08/2002 Updates for E/OS 3.0
620-000134-300 09/2002 Updates for E/OS 4.0
620-000134-400 10/2002 Updates for E/OS 4.1
620-000134-500 10/2002 Updates for E/OS 4.1 CD-ROM final
620-000134-600 2/2003 Updates for E/OS 5.1 and EFCM 7.1
620-000134-601 7/2003 Updates for E/OS 5.5
620-000134-700 10/2003 Updates for E/OS 6.0
620-000134-710 12/2003 Updates for E/OS 6.1
620-000134-720 6/2004 Updates for E/OS 6.2
620-000134-730 01/2005 Updates for E/OS 7.0
Copyright © 2001 - 2004 McDATA Corporation. All rights reserved.
Printed December 2004
First Edition
No part of this publication may be reproduced or distributed in any form or by any means, or stored in a
database or retrieval system, without the prior written consent of McDATA Corporation. The information
contained in this document is subject to change without notice. McDATA Corporation assumes no
responsibility for any errors that may appear.
All computer software programs, including but not limited to microcode, described in this document are
furnished under a license, and may be used or copied only in accordance with the terms of such license.
McDATA either owns or has the right to license the computer software programs described in this document.
McDATA Corporation retains all rights, title and interest in the computer software programs.
McDATA Corporation makes no warranties, expressed or implied, by operation of law or otherwise, relating
to this document, the products or the computer software programs described herein. McDATA
CORPORATION DISCLAIMS ALL IMPLIED WARRANTIES OF MERCHANTIBILITY AND FITNESS FOR
A PARTICULAR PURPOSE. In no event shall McDATA Corporation be liable for (a) incidental, indirect,
special, or consequential damages or (b) any damages whatsoever resulting from the loss of use, data or
profits, arising out of this document, even if advised of the possibility of such damages.
©2004 McDATA Corporation. All rights reserved. McDATA, the McDATA logo, McDATA Eclipse,
Fabricenter, HotCAT, Intrepid, Multi-Capable Storage Network Solutions, Networking the World's Business
Data, nScale, nView, OPENready, SANavigator, SANpilot, SANtegrity, SANvergence, SecureConnect and
Sphereon are trademarks or registered trademarks of McDATA Corporation. OEM and Reseller logos are the
ii
Enterprise Operating System Command Line Interface User Manual
Page 3

property of such parties and are reprinted with limited use permission. All other trademarks are the property
of their respective companies. All specifications subject to change.
Enterprise Operating System Command Line Interface User Manual
iii
Page 4

iv
Enterprise Operating System Command Line Interface User Manual
Page 5
Contents
Preface.............................................................................................................................xv
Chapter 1 Introduction
Command Line Interface Overview...............................................1-2
Entering Command Line Interface Commands ...........................1-3
Documentation Conventions...................................................1-3
Navigation Conventions...........................................................1-3
Command Tree...........................................................................1-5
Navigation of the CLI Command Tree.................................1-12
Parameters ................................................................................1-13
Output .......................................................................................1-14
Logging In and Logging Out ........................................................1-14
User Access Rights ..................................................................1-14
Passwords and Secrets ............................................................1-14
login ...........................................................................................1-15
logout.........................................................................................1-16
Using the commaDelim Command..............................................1-17
commaDelim ............................................................................1-17
Handling Command Line Interface Errors .................................1-18
Using the Command Line Interface Help ...................................1-19
Commenting Scripts.......................................................................1-20
ED-5000 Director.............................................................................1-21
Telnet Session...................................................................................1-22
Ethernet Connection Loss.......................................................1-22
Backup and Restoration.................................................................1-23
Chapter 2 CLI Commands
Command Overview........................................................................2-2
Contents
v
Page 6

Contents
New and Changed Commands......................................................2-2
config ..................................................................................................2-5
config.enterpriseFabMode.setState.........................................2-5
config.features.enterpriseFabMode ........................................2-6
config.features.ficonMS............................................................2-6
config.features.installKey.........................................................2-7
config.features.NPIV.................................................................2-8
config.features.openSysMS......................................................2-8
config.features.openTrunking .................................................2-8
config.features.show .................................................................2-9
config.fencing.addPolicy........................................................2-10
config.fencing.addPort............................................................2-10
config.fencing.deletePolicy ....................................................2-11
config.fencing.removePort.....................................................2-12
config.fencing.setParams........................................................2-12
config.fencing.setState ............................................................2-14
config.fencing.show ................................................................2-14
config.fencing.showTypeTable..............................................2-16
config.ficonCUPZoning.addControlHost............................2-16
config.ficonCUPZoning.deleteControlHost ........................2-17
config.ficonCUPZoning.setState ...........................................2-17
config.ficonCUPZoning.show ...............................................2-18
config.ficonMS.setMIHPTO...................................................2-18
config.ficonMS.setState...........................................................2-19
config.ficonMS.show...............................................................2-20
config.ip.ethernet.....................................................................2-20
config.ip.lineSpeed..................................................................2-21
config.ip.show..........................................................................2-21
config.NPIV.maxPortIDs........................................................2-22
config.NPIV.setState ..............................................................2-23
config.NPIV.show ..................................................................2-23
config.openSysMS.setHostCtrlState .....................................2-24
config.openSysMS.setState.....................................................2-24
config.port.blocked..................................................................2-25
config.port.fan..........................................................................2-25
config.port.name......................................................................2-26
config.port.rxCredits...............................................................2-26
config.port.show......................................................................2-27
config.port.showPortAddr.....................................................2-28
config.port.speed.....................................................................2-29
config.port.swapPortByAddr ................................................2-30
config.port.swapPortByNum.................................................2-30
config.port.type........................................................................2-31
vi
Enterprise Operating System Command Line Interface User Manual
Page 7
Contents
config.security ......................................................................... 2-32
config.security.authentication.interface api.outgoing.......2-33
config.security.authentication.interface.api.sequence....... 2-33
config.security.authentication.interface.cli.sequence ........ 2-34
config.security.authentication.interface.eport.outgoing ... 2-34
config.security.authentication.interface.eport.sequence... 2-35
config.security.authentication.interface.nport.outgoing... 2-36
config.security.authentication.interface.nport.sequence... 2-36
config.security.authentication.interface.osms.outgoing ... 2-37
config.security.authentication.interface.osms.setKey ....... 2-38
config.security.authentication.interface.serial.
enhancedAuth ......................................................................... 2-38
config.security.authentication.interface.show.................... 2-39
config.security.authentication.interface.web.sequence..... 2-39
config.security.authentication.port.override ...................... 2-40
config.security.authentication.port.show............................2-41
config.security.authentication.RADIUS.attempts.............. 2-42
config.security.authentication.RADIUS.deadtime............. 2-42
config.security.authentication.RADIUS.deleteServer .......2-43
config.security.authentication.RADIUS.server ..................2-43
config.security.authentication.RADIUS.show.................... 2-44
config.security.authentication.RADIUS.timeout................ 2-45
config.security.authentication.switch.setSecret.................. 2-45
config.security.authentication.user ...................................... 2-46
config.security.authentication.user.add .............................. 2-46
config.security.authentication.user.delete........................... 2-47
config.security.authentication.user.modify ........................ 2-48
config.security.authentication.user.role .............................. 2-49
config.security.authentication.user.show............................ 2-50
config.security.fabricBinding ................................................ 2-51
config.security.fabricBinding.activatePending...................2-53
config.security.fabricbinding.addAttachedMembers........ 2-53
config.security.fabricBinding.addMember ......................... 2-54
config.security.fabricBinding.clearMemList....................... 2-54
config.security.fabricbinding.deactivateFabBind............... 2-55
config.security.fabricBinding.deleteMember...................... 2-55
config.security.fabricBinding.replacePending.................... 2-56
config.security.fabricBinding.showActive .......................... 2-56
config.security.fabricBinding.showPending....................... 2-57
config.security.portBinding................................................... 2-57
config.security.portBinding.bound ...................................... 2-57
config.security.portBinding.show ........................................ 2-58
config.security.portBinding.wwn......................................... 2-59
Contents
vii
Page 8

Contents
config.security.ssh.resetKeys.................................................2-61
config.security.ssh.setState.....................................................2-61
config.security.ssh.show.........................................................2-61
config.security.switchAcl .......................................................2-62
config.security.switchAcl.addRange ....................................2-62
config.security.switchAcl.deleteRange ................................2-63
config.security.switchAcl.setState.........................................2-63
config.security.switchAcl.show.............................................2-64
config.security.switchBinding ...............................................2-64
config.security.switchBinding.addMember ........................2-65
config.security.switchBinding.deleteMember.....................2-66
config.security.switchBinding.setState.................................2-66
config.security.switchBinding.show.....................................2-67
config.snmp.addCommunity.................................................2-68
config.snmp.authTraps...........................................................2-69
config.snmp.deleteCommunity.............................................2-70
config.snmp.setFaMibVersion...............................................2-70
config.snmp.setState ...............................................................2-71
config.snmp.show ...................................................................2-71
config.switch ............................................................................2-72
config.switch.domainRSCN...................................................2-72
config.switch.edTOV...............................................................2-73
config.switch.insistDomainId................................................2-73
config.switch.interopMode....................................................2-74
config.switch.ltdFabRSCN.....................................................2-74
config.switch.prefDomainId..................................................2-75
config.switch.priority..............................................................2-75
config.switch.raTOV ...............................................................2-76
config.switch.rerouteDelay....................................................2-77
config.switch.speed.................................................................2-78
config.switch.show..................................................................2-78
config.switch.zoneFlexPars....................................................2-80
config.switch.zoningRSCN....................................................2-81
config.system.contact..............................................................2-81
config.system.date...................................................................2-82
config.system.description.......................................................2-82
config.system.location ............................................................2-83
config.system.name.................................................................2-83
config.system.show.................................................................2-83
config.zoning............................................................................2-84
config.zoning.activateZoneSet...............................................2-85
config.zoning.addPortMem...................................................2-86
config.zoning.addWwnMem.................................................2-87
viii
Enterprise Operating System Command Line Interface User Manual
Page 9

Contents
config.zoning.addZone ..........................................................2-87
config.zoning.clearZone......................................................... 2-88
config.zoning.clearZoneSet ................................................... 2-88
config.zoning.deactivateZoneSet.......................................... 2-89
config.zoning.deletePortMem............................................... 2-89
config.zoning.deleteWwnMem............................................. 2-90
config.zoning.deleteZone ...................................................... 2-90
config.zoning.renameZone....................................................2-91
config.zoning.renameZoneSet...............................................2-91
config.zoning.replaceZoneSet...............................................2-92
config.zoning.setDefZoneState ............................................. 2-92
config.zoning.showActive..................................................... 2-92
config.zoning.showPending.................................................. 2-93
maint ................................................................................................ 2-95
maint.port.beacon ...................................................................2-95
maint.port.reset ....................................................................... 2-96
maint.system.beacon .............................................................. 2-96
maint.system.clearSysError................................................... 2-97
maint.system.ipl...................................................................... 2-97
maint.system.resetConfig ...................................................... 2-97
maint.system.setOnlineState.................................................2-98
perf ................................................................................................... 2-99
perf.class2................................................................................. 2-99
perf.class3...............................................................................2-100
perf.clearStats ........................................................................ 2-102
perf.errors...............................................................................2-102
perf.link .................................................................................. 2-104
perf.openTrunking.backPressure .......................................2-105
perf.openTrunking.congestionThresh ...............................2-106
perf.openTrunking.lowBBCreditThresh............................ 2-106
perf.openTrunking.setState ................................................. 2-107
perf.openTrunking.show ..................................................... 2-108
perf.openTrunking.unresCongestion.................................2-109
perf.preferredPath................................................................. 2-110
perf.preferredPath.clearPath............................................... 2-110
perf.preferredPath.setPath................................................... 2-111
perf.preferredPath.setState.................................................. 2-112
perf.preferredPath.showPath.............................................. 2-113
perf.preferredPath.showState ............................................. 2-115
perf.thresholdAlerts..............................................................2-116
perf.thresholdAlerts.counter.addAlert.............................. 2-120
perf.thresholdAlerts.counter.addPort................................2-121
perf.thresholdAlerts.counter.removePort......................... 2-122
Contents
ix
Page 10

Contents
perf.thresholdAlerts.counter.setCounter...........................2-123
perf.thresholdAlerts.counter.setParams ............................2-124
perf.thresholdAlerts.counter.show.....................................2-125
perf.threshholdAlerts.counter.showStatisticTable...........2-126
perf.thresholdAlerts.deleteAlert .........................................2-127
perf.thresholdAlerts.setState ...............................................2-127
perf.thresholdAlerts.show ...................................................2-127
perf.thresholdAlerts.throughput.addAlert........................2-129
perf.thresholdAlerts.throughput.addPort .........................2-130
perf.thresholdAlerts.throughput.removePort...................2-131
perf.thresholdAlerts.throughput.setUtilType...................2-132
perf.thresholdAlerts.throughput.setUtilPercentage ........2-133
perf.thresholdAlerts.throughput.setParams .....................2-134
perf.thresholdAlerts.throughput.show..............................2-135
perf.thresholdAlerts.throughput.showUtilTypeTable.....2-135
perf.traffic ...............................................................................2-136
show................................................................................................2-138
show.all...................................................................................2-138
show.auditLog .......................................................................2-139
show.epFrameLog.config.....................................................2-140
show.epFrameLog.filterClassFFrames...............................2-140
show.epFrameLog.setFilterPort ..........................................2-141
show.epFrameLog.noWrap .................................................2-142
show.epFrameLog.wrap.......................................................2-143
show.eventLog.......................................................................2-144
show.fabricLog.noWrap.......................................................2-145
show.fabricLog.wrap............................................................2-146
show.fabric.nodes..................................................................2-148
show.fabric.principal ............................................................2-148
show.fabric.topology ............................................................2-149
show.features .........................................................................2-150
show.fencing.policies............................................................2-150
show.ficonCUPZoning .........................................................2-152
show.ficonMS ........................................................................2-152
show.frus ................................................................................2-153
show.ip.ethernet ....................................................................2-154
show.linkIncidentLog...........................................................2-154
show.loginServer...................................................................2-155
show.nameServer ..................................................................2-156
show.nameServerExt ............................................................2-158
show.NPIV.config .................................................................2-159
show.openSysMS.config.......................................................2-160
show.openTrunking.config..................................................2-161
x
Enterprise Operating System Command Line Interface User Manual
Page 11
Contents
show.openTrunking.rerouteLog.........................................2-162
show.port.config ................................................................... 2-163
show.port.exit........................................................................ 2-164
show.port.info ....................................................................... 2-166
show.port.nodes....................................................................2-167
show.port.opticEDD............................................................. 2-169
show.port.opticInfo .............................................................. 2-170
show.port.profile................................................................... 2-171
show.port.showPortAddr ...................................................2-173
show.port.status.................................................................... 2-174
show.port.technology........................................................... 2-177
show.preferredPath.showPath............................................ 2-178
show.security.fabricBinding................................................2-180
show.security.log .................................................................. 2-181
show.security.portBinding .................................................. 2-182
show.security.switchAcl ...................................................... 2-183
show.security.switchBinding .............................................. 2-184
show.snmp.............................................................................2-185
show.switch ........................................................................... 2-186
show.system........................................................................... 2-188
show.thresholdAlerts.alerts................................................. 2-189
show.thresholdAlerts.log..................................................... 2-192
show.zoning........................................................................... 2-194
Appendix A Error Messages
Appendix B Commands and Corresponding Releases
Glossary
........................................................................................................................g-1
Index ...............................................................................................................................i-1
Contents
xi
Page 12

Contents
xii
Enterprise Operating System Command Line Interface User Manual
Page 13
Tables
1-1 CLI Command Tree Navigation Conventions ......................................... 1-3
1-2 CLI Command Tree ...................................................................................... 1-5
1-3 CLI Command Tree for the ED-5000 Director ........................................ 1-21
2-1 Supported Zoning Configurations ........................................................... 2-85
2-2 Throughput Threshold Alerts ................................................................ 2-118
2-3 Alert Counters ........................................................................................... 2-118
B-1 Commands and Releases ............................................................................. B-1
Table s
xiii
Page 14

Tab les
xiv
Enterprise Operating System Command Line Interface User Manual
Page 15
Preface
This publication is part of the documentation suite that supports the
McDATA® Sphereon™ 3016 Fabric Switch, Sphereon 3032 Fabric
Switch, Sphereon 3216 Fabric Switch, Sphereon 3232 Fabric Switch,
Sphereon 4300 Fabric Switch, Sphereon 4500 Fabric Switch,
Intrepid
®
6064 Director, and Intrepid 6140 Director.
Who Should Use This
Manual
This publication describes the commands that can be entered through
the Command Line Interface (CLI) for the Intrepid
®
6064 Director,
and Intrepid 6140 Director, Sphereon™ 3016 Switch, Sphereon 3032
Switch, Sphereon 3216 Switch, Sphereon 3232 Switch, Sphereon 4300
Switch, and Sphereon 4500 Switch. (A limited number of these
commands are available on the ED-5000 Director.) Access through a
Telnet client is presumed.
This publication is intended for data center administrators and
customer support personnel, who can either enter the commands
manually or write a script containing them. However, the primary
purpose of the Command Line Interface is for scripts written by these
administrators and personnel for use in a host-based scripting
environment. Therefore, this publication presumes that the user is
familiar with:
• Establishing and using a Telnet session
• Using the command line of a terminal
• Writing scripts
• Networking, SAN, and zoning concepts
• McDATA products in the user’s network
Preface
xv
Page 16

Preface
The publications listed in Related Publications provide considerable
information about both concepts and McDATA products.
Organization of This
Manual
This publication is organized as follows:
• Chapter 1, Introduction, provides an introduction and overview of
the Command Line Interface.
• Chapter 2, CLI Commands, describes the Command Line Interface
commands, including their syntax, purpose, and parameters, as
well as examples of their usage and any output that they
generate.
• Appendix A, Error Messages lists and explains error messages that
may appear while using the CLI.
• Appendix B, Commands and Corresponding Releases lists each
command in the CLI and the release in which the command was
added to the CLI.
•The Glossary defines terms, abbreviations, and acronyms used in
this manual.
•An Index is also provided.
Manual Updates Check the McDATA web site at www.mcdata.com for possible
updates or supplements to this manual.
xvi
Related Publications Other publications that provide additional information about the
products mentioned in this manual are:
• Configuration Backup and Restore Utility Installation and User Guide
(958-000370)
• Products in a SAN Environment - Planning Manual (620-000124)
• McDATA ED-5000 Director Element Manager User Manual
(620-000176)
• Intrepid 6064 Director Installation and Service Manual (620-000108)
• Intrepid 6140 and 6064 Directors Element Manager User Manual
(620-000172)
• Intrepid 6140 Director Installation and Service Manual (620-000157)
• E/OSn SNMP Support Manual (620-000226)
• SANpilot User Manual (620-000160)
Enterprise Operating System Command Line Interface User Manual
Page 17

• Sphereon 3016 and 3216 Fabric Switch Element Manager User Manual
(620-000174)
• Sphereon 3016 and 3216 Fabric Switches Installation and Service
Manual (620-000154)
• Sphereon 3032 and 3232 Fabric Switch Element Manager User Manual
(620-000173)
• Sphereon 3032 and 3232 Fabric Switches Installation and Service
Manual (620-000155)
• Sphereon 4300 Fabric Switch Installation and Service Manual
(620-000171)
• Sphereon 4500 Fabric Switch Installation and Service Manual
(620-000159)
• Sphereon 4500 Fabric Switch Element Manager User Manual
(620-000175)
Manual Conventions The following notational conventions are used in this document:
Preface
Convention Meaning
Bold Keyboard keys, buttons and switches on hardware products,
and screen prompts for the Command Line Interface.
Italic
Monospaced
NOTE: A note presents important information that is not hazard-related.
ATTENTION! An attention notice presents important information about
activities that could result in loss of equipment function or loss of data.
Outside book references, names of user interface windows,
buttons, and dialog boxes.
Command syntax, examples of commands, output.
Where to Get Help For technical support, McDATA end-user customers should call the
phone number located on the service label attached to the front or
rear of the hardware product.
For IBM products, contact IBM for technical support, which includes
hardware support, all product repairs, and ordering of spare parts.
Go to:
http://www.ibm.com/servers/storage/support/san/index.html.
Preface
xvii
Page 18

Preface
McDATA’s “Best in Class” Solution Center provides a single point of
contact for customers seeking help with McDATA software products.
The Solution Center will research, explore, and resolve inquiries or
service requests regarding McDATA products and services. The
Solution Center is staffed 24 hours a day, 7 days a week, including
holidays.
NOTE: To expedite warranty entitlement, please have your product serial
number available.
McDATA Corporation
380 Interlocken Crescent
Broomfield, CO 80021
Phone: (800) 752-4572 or (720) 558-3910
Fax: (720) 558-3581
E-mail: support@mcdata.com
NOTE: Customers who purchased the hardware product from a company
other than McDATA should contact that company’s service representative for
technical support.
Forwarding
Publication
Comments
We sincerely appreciate any comments about this publication. Did
you find this manual easy or difficult to use? Did it lack necessary
information? Were there any errors? Could its organization be
improved?
Please send your comments via e-mail, our home page, or FAX.
Identify the manual, and provide page numbers and specific detail.
Thank you.
E-mail: pubsmgr@mcdata.com
Home Page: http://www.mcdata.com
Fax: Technical Communi cation s Manager
(720) 558-8999
Ordering Publications To order a paper copy of this manual, contact your McDATA
representative, or use the contact information listed below.
xviii
Enterprise Operating System Command Line Interface User Manual
Phone: (800) 545-5773 and select the option for information on
McDATA’s complete family of enterprise-to-edge SAN solutions.
Page 19

Preface
Fax: (720) 558-4193
Trademarks The following terms, indicated by a registered trademark symbol (®)
or trademark symbol (™) on first use in this publication, are
trademarks of McDATA Corporation in the United States, other
countries, or both:
Registered Trademarks
Fabricenter
HotCAT
Intrepid
McDATA
OPENready
SANavigator
SANpilot
®
®
®
®
®
®
®
Trademarks
E/OS™
Eclipse™
Fibre Channel Director™
OPENconnectors™
SANvergence™
Sphereon™
SANtegrity®
All other trademarked terms, indicated by a registered trademark
symbol (®) or trademark symbol (™) on first use in this publication,
are trademarks of their respective owners in the United States, other
countries, or both.
Preface
xix
Page 20

Preface
xx
Enterprise Operating System Command Line Interface User Manual
Page 21
1
Introduction
This chapter introduces the Command Line Interface (CLI) and
describes the essentials for using the CLI commands.
• Command Line Interface Overview......................................................1-2
• Entering Command Line Interface Commands....................................1-3
• Logging In and Logging Out..............................................................1-14
• Using the commaDelim Command ....................................................1-17
• Handling Command Line Interface Errors.........................................1-18
• Using the Command Line Interface Help...........................................1-19
• Commenting Scripts...........................................................................1-20
• ED-5000 Director...............................................................................1-21
• Telnet Session......................................................................................1-22
• Backup and Restoration......................................................................1-23
Introduction
1-1
Page 22

Command Line Interface Overview
1
Command Line Interface Overview
The Command Line Interface (CLI) is a feature that provides an
alternative to Graphical User Interface (GUI) and web-based (HTTP)
interface products for director and switch management capabilities.
The CLI can only be used through a Telnet client session in an
out-of-band management environment, using the Ethernet port in the
director or switch. Although the primary use of the CLI is in
host-based scripting environments, the CLI commands can also be
entered directly at a command line. Any hardware platform that
supports the Telnet client software can be used.
The primary purpose of the CLI is to automate management of a
large number of switches with the use of scripts.
Because the CLI is not an interactive interface, no prompts are
displayed to guide the user through a task. If an interactive interface
is needed, use the GUI-based or web-based SAN management
applications instead of the CLI.
1-2
Enterprise Operating System Command Line Interface User Manual
Page 23
Entering Command Line Interface Commands
Entering Command Line Interface Commands
The CLI commands can be entered directly at the command line of a
terminal or coded in a script.
Note that the CLI commands are not case sensitive.
1
Documentation
Conventions
Navigation
Conventions
Throughout this publication, periods are used to separate the
components of a command name. However, the periods cannot be
included when the command is actually entered at the terminal or
coded in a script. (How to enter the commands is explained in
Navigation of the CLI Command Tree on page 1-12.)
Even though the commands cannot be entered with the periods, the
command line prompts do include the periods.
Config.Port>
Basic command line navigation conventions are supported. The
following table includes the asynchronous commands that are
recognized by the CLI.
Table 1-1 CLI Command Tree Navigation Conventions
Character Sequence Common Name Action or Description
<CR> Carriage Return Pass a completed line to the
parser.
<DEL> Delete Backspace one character
and delete the character.
<NL> New Line Pass a completed line to the
<SP> Space Used to separate keywords.
# Pound Sign Used to designate
? Question Mark Provide help information.
“ Quotation Mark Used to surround a single
^A Control-A Position the cursor to the
parser.
comments in a script.
token.
start of the line.
Introduction
1-3
Page 24

Entering Command Line Interface Commands
1
Table 1-1 CLI Command Tree Navigation Conventions (Continued)
Character Sequence Common Name Action or Description
^B Control-B Position the cursor left one
character.
^D Control-D Delete the current character.
^E Control-E Position the cursor to the
end of the line.
^F Control-F Position the cursor right one
character.
^H Control-H Backspace one character
and delete the character.
^I Tab Complete the current
keyword.
^K Control-K Delete to the end of the line.
^L Control-L Redraw the line.
^N Control-N Move down one line in the
command history.
^P Control-P Move up one line in the
command history.
^R Control-R Redraw the line.
^U Control-U Clear the input and reset the
line buffer.
^X Control-X Clear the input and reset the
line buffer.
<ESC>[A Up Arrow Move up one line in the
command history.
<ESC>[B Down Arrow Move down one line in the
command history.
<ESC>[C Right Arrow Position the cursor right one
character.
<ESC>[D Left Arrow Position the cursor left one
character.
1-4
Enterprise Operating System Command Line Interface User Manual
Page 25

Entering Command Line Interface Commands
1
Command Tree
The command tree of the CLI begins from the root. Table 1-2 shows
the CLI command tree. The commands in the four extended branches
(config, maint, perf, and show) are described in Chapter 2, CLI
Commands.
The following commands are not listed in the command tree, but are
globally available and are documented in this chapter:
• login (see login on page 1-15)
•logout (see logout on page 1-16)
• commaDelim (see Using the commaDelim Command on page 1-17)
Table 1-2 shows the command tree hierarchy from the root, reading
from left to right.
Table 1-2 CLI Command Tree
config---------- enterpriseFabMode--- setState
features ----------------- enterpriseFabMode
ficonMS
installKey
NPIV
openSysMS
openTrunking
show
fencing------------------- addPolicy
addPort
deletePolicy
removePort
setParams
setState
show
showTypeT able
ficonCUPZoning------- addControlHost
deleteControlHost
setState
show
ficonMS------------------ setMIHPTO
setState
show
Introduction
1-5
Page 26

Entering Command Line Interface Commands
1
Table 1-2 CLI Command Tree (Continued)
ip-------------------------- ethernet
lineSpeed
show
setHostCtrlState
NPIV--------------------- maxPortIDs
setState
show
openSysMS------------ setState
port ----------------------- blocked
fan
name
rxCredits
show
showPortAddr
speed
swapPortByAddr
swapPortByNum
type
security------------------ authentication---------- interface----------------- api------------------------- outgoing
sequence
cli-------------------------- sequence
eport---------------------- outgoing
sequence
nport---------------------- outging
sequence
osms--------------------- outgoing
setKey
serial--------------------- enhancedAuth
show
web----------------------- sequence
port----------------------- override
show
radius-------------------- attempts
deadtime
deleteServer
server
1-6
Enterprise Operating System Command Line Interface User Manual
Page 27
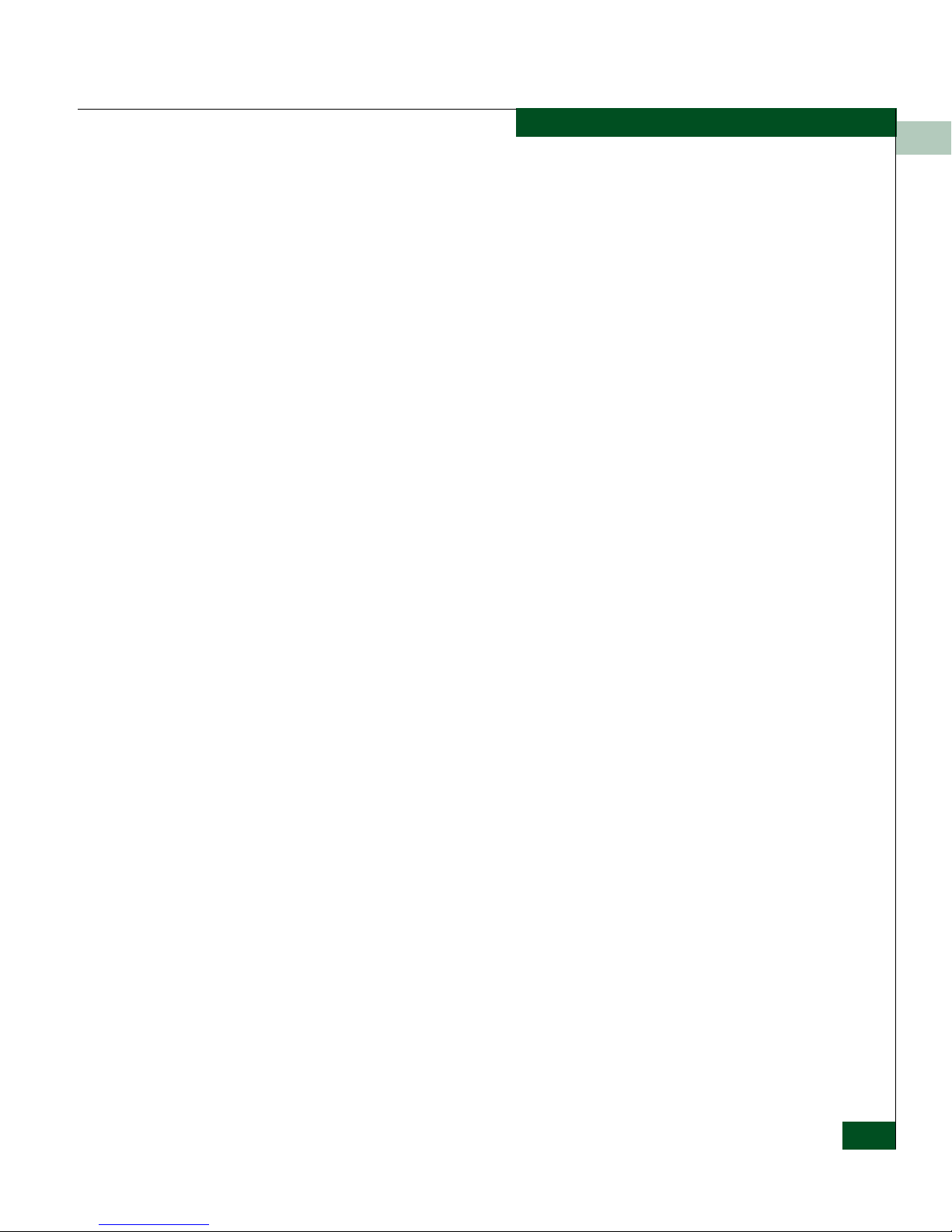
Table 1-2 CLI Command Tree (Continued)
security ----------------- fabricBinding ----------- activatePending
portBinding ------------- bound
ssh------------------------ resetKeys
switchAcl---------------- addRange
switchBinding ---------- addMember
acl ------------------------ addRange
snmp --------------------- addCommunity
Entering Command Line Interface Commands
1
show
timeout
switch-------------------- setSecret
user----------------------- add
delete
modify
role
show
addAttachedMembers
addMember
clearMemList
deactivateFabBind
deleteMember
replacePending
showActive
showPending
show
wwn
setState
show
deleteRange
setState
show
deleteMember
setState
show
deleteRange
setState
show
Introduction
1-7
Page 28

Entering Command Line Interface Commands
1
Table 1-2 CLI Command Tree (Continued)
authTraps
deleteCommunity
setFaMibVersion
setState
show
switch ------------ -- -- -- -- domainRSCN
edTOV
insistDomainId
interopMode
ltdFabRSCN
prefDomainId
priority
raTOV
rerouteDelay
speed
show
zoneFlexPars
zoningRSCN
system ------------------ contact
date
description
location
name
show
zoning ------------------- setDefZoneState
activateZoneSet
deactivateZoneSet
replaceZoneSet
clearZoneSet
addZone
deleteZone
renameZoneSet
addWwnMem
addPortMem
clearZone
deleteWwnMem
1-8
Enterprise Operating System Command Line Interface User Manual
Page 29
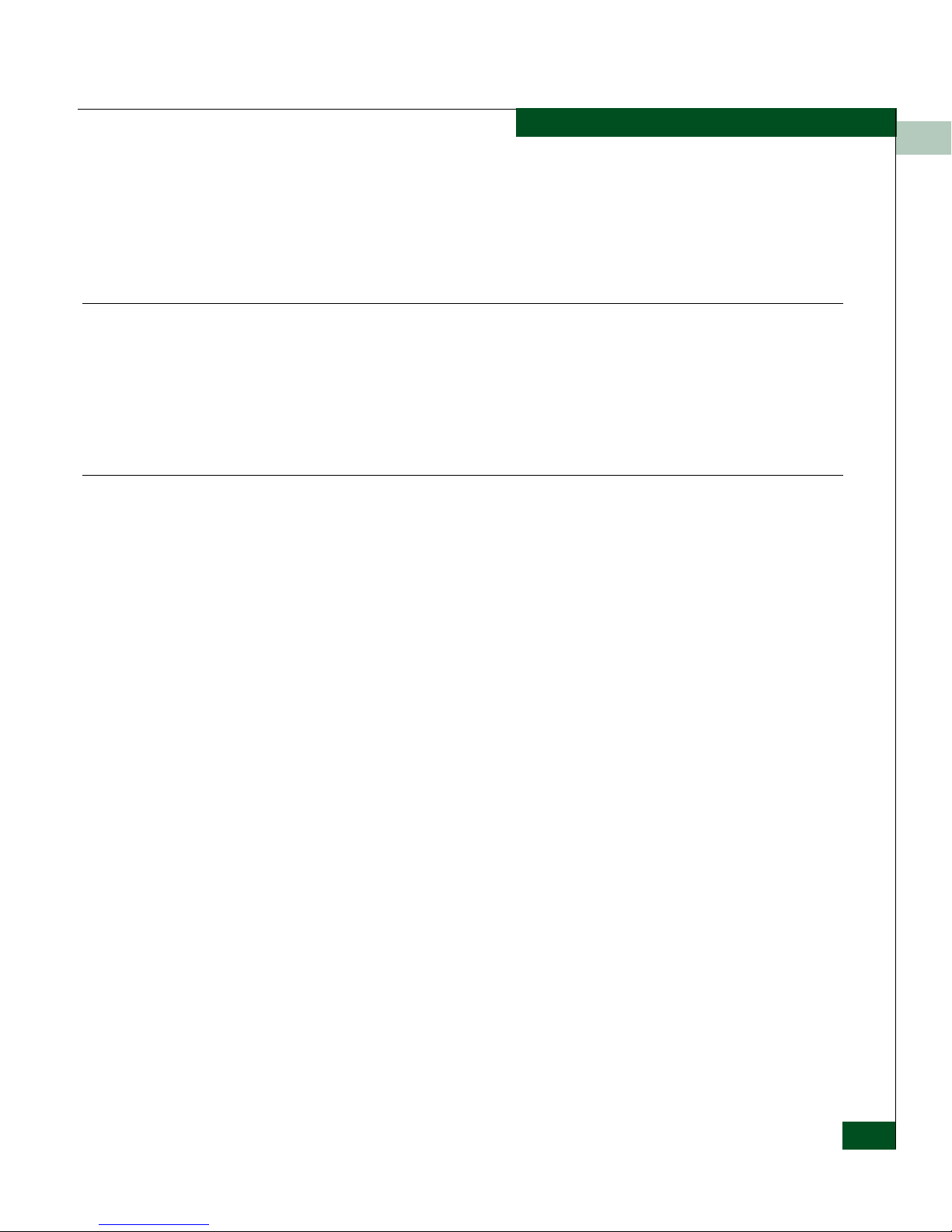
Table 1-2 CLI Command Tree (Continued)
deletePortMem
renameZone
showPending
showActive
maint ---------- port ----------------------- beacon
reset
system ------------------ beacon
clearSysError
ipl
resetConfig
setOnlineState
perf --------- --- class2
class3
clearStats
errors
link
openTrunking ---------- backPressure
congestionThresh
lowBBCreditThresh
setState
show
unresCongestion
preferredPath ---------- clearPath
setPath
setState
showPath
showState
thresholdAlerts -------- counter ------------------ addAlert
deleteAlert
setState
Entering Command Line Interface Commands
1
addPort
removeP ort
setCounter
setParams
show
showStatisticTable
Introduction
1-9
Page 30

Entering Command Line Interface Commands
1
Table 1-2 CLI Command Tree (Continued)
show
throughput -------------- addAlert
addPort
removeP ort
setUtilType
setUtilPercentage
setParams
show
showUtilTypeTable
traffic
show ---------- all
auditLog
epFrameLog----------- config
filterClassFFrames
noWrap
setFilterPort
wrap
eventLog
fabric--------------------- nodes
principal
topology
fabricLog---------------- noWrap
wrap
features
fencing------------------- policies
ficonCUPZoning
ficonMS
frus
ip -------------------------- ethernet
linkIncidentLog
loginServer
nameServer
nameServerExt
NPIV--------------------- config
openSysMS------------ config
1-10
Enterprise Operating System Command Line Interface User Manual
Page 31

Table 1-2 CLI Command Tree (Continued)
openTrunking ---------- config
rerouteLog
port ----------------------- config
exit
info
nodes
opticEDD
opticInfo
profile
showPortAddr
status
technology
preferredPath ---------- showPath
security------------------ fabricBinding
log
log
portBinding
switchAcl
switchBinding
snmp
switch
system
thresholdAlerts-------- alerts
log
zoning
Entering Command Line Interface Commands
1
Note that the commands are shown, with the exception of the zoning
commands, in alphabetical order to make them easier to locate.
Although the commands can be entered in any order, depending on
the results desired, the order shown in Table 1-2, CLI Command Tree,
page 1-5 for the zoning commands is a typical order in which the
zoning commands are entered.
Note that the order in which commands are entered determines the
order in which the show commands display the values. Refer to
Chapter 2, CLI Commands for examples of show commands output.
Introduction
1-11
Page 32

Entering Command Line Interface Commands
1
Navigation of the
CLI Command Tree
Once the administrator or operator logs in and receives the Root>
prompt, the CLI commands are accessed by navigating up and down
the CLI command tree.
To move from the root through the any of the four extended branches,
enter the name of the next branch as shown in Table 1-2, CLI
Command Tree, page 1-5. For example, to use the config.port.name
command to configure the name for port 4 on the switch, this series of
commands is entered:
Root> config
Config> port
Config.Port> name 4 "Sam’s Tape Drive"
At this point, to enter the maint.port.beacon command to set the
beaconing state of port 4, the following series of commands is
entered:
Config.Port> ..
Config> ..
Root> maint
Maint> port
Maint.Port> beacon 4 true
Note that you must return all the way to the root of the tree to
transition to another extended branch. When traversing back to the
root, the name of each branch cannot be used. Instead use the
double-dot command (two periods) to move back towards the root.
Note that only one double-dot command may be entered at a time.
1-12
One approach to making the navigation more concise is to use the
root command to jump directly to the root of the CLI command tree.
The previous example, which shows stepping back to the root with
the double-dot command, is simplified as follows:
Config.Port> root
Root> maint
Maint> port
Maint.Port> beacon 4 true
Another approach to making the navigation more concise is to use
the complete command syntax from the Root> prompt each time. For
example, to issue the config.port.name command and then the
maint.port.beacon command, the commands are entered as follows:
Root> config port name 4 "Sam’s Tape Drive"
Root> maint port beacon 4 true
Enterprise Operating System Command Line Interface User Manual
Page 33

Entering Command Line Interface Commands
As shown in this example, use of the complete command syntax
avoids navigating up and down the branches of the CLI command
tree, and the prompt stays at the root. The use of complete command
syntax is particularly useful when writing scripts.
When coding a script, remember to code the appropriate character
sequences, which are described in Navigation Conventions on page 1-3.
Root> config port name 4 "Sam’s Tape Drive"<CR>
Root> maint port beacon 4 true<CR>
1
Limitation on
Movements
As the commands are entered, they are recorded in a history log.
Note these limitations on movement that result from use of the
history log:
• If a command has more than 60 characters, the command runs,
but the command is not recorded in the history log, and the
position in the tree does not change, as shown in the following
example. Because the command is not recorded in the history, a
subsequent asynchronous command (navigation command)
cannot depend on it.
Root> config zoning addWwnMem TheUltimateZone 10:00:00:00
:C9:22:9B:64
Root>
• Whenever the position in the CLI command tree moves to a new
branch (for example, config to maint, config to config.port, or
config.port to config), the history log is cleared. In this case, any
asynchronous commands (for example, the up-arrow command
<ESC>[A or the up-arrow keyboard symbol) cannot move the
position back towards the root, as shown in this example:
Root> config
Root.Config> port
Root.Config.Port> <ESC>[A
Root.Config.Port>
Parameters
Some command parameters accept character strings that include
spaces. Quotation marks are required when a string includes spaces.
Config.System> location Building_24_Room_16
Config.System> location "Building 24 Room 16"
Introduction
1-13
Page 34

Logging In and Logging Out
1
If spaces are not included in a parameter that accepts a string, the
quotation marks are not required around that string.
To include quotation marks in a string, use the escape character (\)
before the quotation marks.
Config.System> location "Building 24 \"Joe’s PlayLab\""
A null string can be created by using the quotation marks without
any space between them.
Config.System> location ""
Output
All output from the CLI commands is limited to the standard 80
columns supported by most Telnet interfaces. The output is
left-justified.
Logging In and Logging Out
The CLI allows a single Telnet client to be connected to the switch. If a
Telnet client logs out, or if after 15 minutes of inactivity the client’s
access times out, another Telnet client may log in. Also note that the
Telnet client (user) must log in any time the director or switch is
restarted because the current user’s access is lost. Examples of a
restart include an IPL and any power-off situation.
User Access Rights
The CLI supports two user access rights: administrator and operator.
A user who logs in with administrator access rights can use all of the
commands described in this publication. Operator access rights grant
permission to use only the perf and show branches of the CLI
command tree (for example, the perf.traffic and show.system
commands) with the following exceptions: operator rights cannot
access the show.preferredPath, show.security, and
show.thresholdAlerts commands. Operators can also execute the
globally available commands (login, logout, and commaDelim).
Passwords and
Secrets
1-14
Enterprise Operating System Command Line Interface User Manual
Some commands require the user to enter a password or secret before
the command can be executed.
Passwords can be ASCII characters in the range of 32 to 126.
Secrets can be any ASCII character (0-255). Non-printable and
extended ASCII characters can be entered by using a backslash. Two
Page 35

Logging In and Logging Out
hexadecimal characters must follow the backslash. All printable
ASCII characters can be entered using the keyboard or using its
hexadecimal value except for the backslash character. If a backslash
is desired as part of the password its hexadecimal representation
must be used. Spaces are valid, but if they appear at the begging of
the password then they will be ignored. The following are examples
of valid secrets.
simplesecret****
This is an example of a secret that does not use any special characters.
\40\72\A3\F9\12\13\14\15\16\17\18\19\55\33\87\42
This is an example of a secret of length 4 that is configured using the
hexadecimal representation.
a9p\40\40xx\44\88kutfe\89h
This is an example of a secret that has a length of 7 characters that are
composed of a mix using hexadecimal and the printable ASCII
characters.
1
login
Syntax login
Purpose This command allows a Telnet client to connect to the switch.
Description This command allows the user to log in with either administrator or
operator access rights. The default passwords are password.
The login command is called automatically by the CLI each time a
new Telnet session is activated, as well as each time new
administrator access rights are configured.
After the login command is issued, the Username: prompt
automatically displays. After a valid user name is entered, the
Password: prompt automatically displays. After the corresponding
valid password is entered, the Root> prompt displays. At this
prompt the user may enter any of the commands included in
Table 1-2, CLI Command Tree, page 1-5.
When users are prompted to change the password when logging in,
they can enter the default password (password). This will be accepted.
However, at the next login, they will again be required to change the
password, if the default password is still being used. When the user
Introduction
1-15
Page 36

Logging In and Logging Out
1
enters the default password when prompted to change the password,
the data portion of the security log entry for CLI login includes
“password not changed.”
A user name and password can be set by the administrator through
the config.security.authentication.user.add command or through the
config.security.authentication.user.modify command.
The access rights chosen for the CLI are completely independent of
the other product interfaces, for example, SNMP or McDATA product
interfaces.
Parameters This command has no parameters.
Command Examples
logout
Syntax logout
Purpose This command allows a Telnet client to disconnect from the switch.
Description This command logs out the single Telnet client connected to the
Parameters This command has no parameters.
Command Examples
login
Username: Administrator
Password: password
login
Username: Operator
Password: password
switch. This command can be entered at any point in the command
tree.
Root> logout
Config> logout
1-16
Enterprise Operating System Command Line Interface User Manual
Config.Port> logout
Page 37

Using the commaDelim Command
Note that the output examples shown in the other sections of this
publication presume that commaDelim is off.
commaDelim
Syntax commaDelim enable
Purpose This command enables the user to obtain displayed information in
comma-delimited, rather than tabular, format. Tabular format is the
default.
Description This command can be entered at any point in the command tree.
Parameter This command has one parameter
enable Specifies the comma-delineated state for
output. Valid values are true and false. Boolean 1
and 0 may be substituted as values.
Using the commaDelim Command
1
Command Examples
Root> commaDelim true
Config> commaDelim 1
Config.Port> commaDelim false
Output Example Output displayed in commaDelim mode is as follows:
Root> show eventLog
Date/Time,Code,Severity,FRU,Event Data,
04/12/01 10:58A,375,Major,CTP-0,00010203 04050607 08090A0B 0C0D0E0F,
04/12/01 10:58A,375,Major,CTP-0,00010203 04050607 08090A0B 0C0D0E0F,
04/12/01 9:58A,385,Severe,CTP-0,00010203 04050607 08090A0B 0C0D0E0F,
04/11/01 7:18P,395,Severe,CTP-0,00010203 04050607 08090A0B 0C0D0E0F,
Introduction
1-17
Page 38

Handling Command Line Interface Errors
1
Handling Command Line Interface Errors
Two types of errors detected by the CLI are:
• An error associated with the interface. For example, a keyword is
misspelled or does not exist.
Root> confg
Error 234: Invalid Command
• An error associated with fabric or switch issues. For example, a
parameter error is detected by the switch, where port 24 is
entered for a switch that supports only 16 ports.
Root> config port name 24 "Port 24"
Error 218: Invalid Port Number
In either case, the command is ignored. The CLI remains at the point
it was before the command was entered.
The error messages, including error number and error, are listed in
Appendix A, Error Messages.
1-18
Enterprise Operating System Command Line Interface User Manual
Page 39

Using the Command Line Interface Help
The question mark (?) can be used within a command to obtain
certain information:
• If the question mark is used in place of a command keyword, all
the keywords at that level of the CLI command tree display.
Root> config system ?
Command identified
contact - Set the system contact attribute
date - Set the system date and time
description - Set the system description attribute
location - Set the system location attribute
name - Set the system name attribute
show - Display the system configuration
• If the question mark is used at the end of a recognized command,
any parameters for that command display.
Root> config port name ?
- name <portNumber> <portName>
Using the Command Line Interface Help
1
• If the question mark is used after one or more characters of a
keyword, any keywords at that level of the CLI command tree
display.
Root> config s?
security snmp switch system
Introduction
1-19
Page 40

Commenting Scripts
1
Commenting Scripts
The pound sign (#) can be used to add comments in a script file. The
pound sign must be the first character in the line; the CLI ignores
everything after the pound sign in that line. The following lines are
valid:
Root> #Change port 3 to an E_Port<CR>
Root> config port<CR>
config.port> ##################<CR>
config.port> ## Begin Script ##<CR>
config.port> ##################<CR>
The pound sign cannot be used after any other characters (a
command, for example) to start a comment. The following is an
invalid script line:
Root> maint system beacon true # Turn on beaconing<CR>
To correct the previous script line, move the comment either before or
after the line with the command. For example, the following
examples are both valid:
Root> # Turn on beaconing<CR>
Root> maint system beacon true<CR>
Root> maint system beacon true<CR>
Root> # Turn on beaconing<CR>
ATTENTION! Comments of over 200 characters in length may cause
unpredictable system behavior. Limit comments to 200 characters per line.
1-20
Enterprise Operating System Command Line Interface User Manual
Page 41

ED-5000 Director
ED-5000 Director
1
A subset of the CLI commands described in this publication are
available on the ED-5000 Director™. The globally available
commands (login, logout, and commaDelim) are described
previously in this chapter. The following config, maint, and show
commands are described in Chapter 2, CLI Commands.
Table 1-3 CLI Command Tree for the ED-5000 Director
config -------------------- security ----------------- userRights -------------- administrator
operator
show
maint --------------------- system ------------------ resetConfig
show --------------------- ip -------------------------- ethernet
port ----------------------- config
info
status
switch
system
zoning
Introduction
1-21
Page 42

Telnet Session
1
Telnet Session
The CLI can be accessed through a Telnet client session in an
out-of-band management environment, using the Ethernet port in the
director or switch. It can also be accessed using Secure Shell (SSH).
Although the primary use of the CLI is in host-based scripting
environments, the CLI commands can also be entered directly at a
command line. Any hardware platform that supports the Telnet client
software can be used.
NOTE: You can use the Configure option in the GUI-based or web-based
interfaces to enable/disable Telnet access. Telnet access is enabled by default.
Any changes to the enabled state of the Telnet server are retained through
system restarts and power cycles.
Ethernet
Connection Loss
If the Ethernet cable is disconnected from the director or switch
during a Telnet session, one of three scenarios is possible:
• Replace the Ethernet cable before the client connection times out,
and the Telnet session will continue.
• Wait 15 minutes until the client connection times out; then replace
the Ethernet cable and restart the connection.
• If the client connection has already timed out, replace the
Ethernet cable. Open a GUI-based or web-based interface
SAN-management window. Toggle the enabled state of the CLI,
thereby clearing the client connection. Restart the client
connection.
Once the client connection is reestablished, verify your
configuration’s completeness and accuracy.
1-22
Enterprise Operating System Command Line Interface User Manual
Page 43

Backup and Restoration
A standalone Configuration Backup and Restore (CBR) utility is
available for customers that do not use EFCM for backing up and
restoring user configuration data. You can use this utility to backup
and restore configuration data from all switch and director products
running E/OS versions 4.0 and higher. The CBR utility is available for
no charge in the Technical Documents section of the McDATA
website at www.mcdata.com or by contacting your sales
representative or service provider
The procedures for system backup and restoration are documented in
the Configuration Backup and Restore Utility Installation and User Guide
(958-000370), which is also available at www.mcdata.com.
Backup and Restoration
1
Introduction
1-23
Page 44

Backup and Restoration
1
1-24
Enterprise Operating System Command Line Interface User Manual
Page 45

2
CLI Commands
This chapter describes the Command Line Interface (CLI) commands,
including their syntax, purpose, and parameters, as well as examples
of their usage and any output that they generate.
• Command Overview.............................................................................2-2
• New and Changed Commands .............................................................2-2
• config.....................................................................................................2-5
• maint...................................................................................................2-95
• perf ......................................................................................................2-99
• show ..................................................................................................2-138
CLI Commands
2-1
Page 46

Command Overview
2
Command Overview
Most of the commands in this chapter are listed in alphabetical order
to make them easy to locate. Although the commands can be entered
in any order, depending on the results desired (so long as the tree
structure is followed), the order used herein for the zoning
commands follows a typical order of entry. The various show
commands are usually entered at the end of a group of other
commands to verify configuration changes.
New and Changed Commands
The following CLI commands are new for this edition of the
Enterprise Operating System Command Line Interface User Manual:
• config.fencing.addPolicy on page 2-10
• config.fencing.addPort on page 2-10
• config.fencing.deletePolicy on page 2-11
• config.fencing.removePort on page 2-12
• config.fencing.setParams on page 2-12
• config.fencing.setState on page 2-14
• config.fencing.show on page 2-14
• config.fencing.showTypeTable on page 2-16
• config.ficonCUPZoning.addControlHost on page 2-16
• config.ficonCUPZoning.deleteControlHost on page 2-17
• config.ficonCUPZoning.setState on page 2-17
• config.ficonCUPZoning.show on page 2-18
• config.ficonMS.setMIHPTO on page 2-18
• config.ficonMS.show on page 2-20
• config.ip.lineSpeed on page 2-21
• config.NPIV.maxPortIDs on page 2-22
• config.NPIV.maxPortIDs on page 2-22
2-2
Enterprise Operating System Command Line Interface User Manual
• config.NPIV.setState on page 2-23
Page 47

New and Changed Commands
• config.NPIV.show on page 2-23
• config.port.rxCredits on page 2-26
• config.port.show on page 2-27
• config.port.showPortAddr on page 2-28
• config.port.swapPortByAddr on page 2-30
• config.port.swapPortByNum on page 2-30
• config.security.authentication.interface api.outgoing on page 2-33
• config.security.authentication.interface.api.sequence on page 2-33
• config.security.authentication.interface.cli.sequence on page 2-34
• config.security.authentication.interface.eport.outgoing on page 2-34
• config.security.authentication.interface.eport.sequence on page 2-35
• config.security.authentication.interface.nport.outgoing on page 2-36
• config.security.authentication.interface.nport.sequence on page 2-36
2
• config.security.authentication.interface.osms.setKey on page 2-38
• config.security.authentication.interface.osms.outgoing on page 2-37
• config.security.authentication.interface.serial.enhancedAuth on
page 2-38
• config.security.authentication.interface.show on page 2-39
• config.security.authentication.interface.web.sequence on page 2-39
• config.security.authentication.port.override on page 2-40
• config.security.authentication.port.show on page 2-41
• config.security.authentication.RADIUS.deadtime on page 2-42
• config.security.authentication.RADIUS.deleteServer on page 2-43
• config.security.authentication.RADIUS.attempts on page 2-42
• config.security.authentication.RADIUS.server on page 2-43
• config.security.authentication.RADIUS.show on page 2-44
• config.security.authentication.RADIUS.timeout on page 2-45
• config.security.authentication.switch.setSecret on page 2-45
• config.security.authentication.user on page 2-46
CLI Commands
2-3
Page 48

New and Changed Commands
2
• config.security.authentication.user.add on page 2-46
• config.security.authentication.user.delete on page 2-47
• config.security.authentication.user.modify on page 2-48
• config.security.authentication.user.role on page 2-49
• config.security.authentication.user.show on page 2-50
• config.security.switchAcl.addRange on page 2-62
• config.security.switchAcl.deleteRange on page 2-63
• config.security.switchAcl.setState on page 2-63
• config.security.switchAcl.show on page 2-64
• config.security.ssh.resetKeys on page 2-61
• config.security.ssh.setState on page 2-61
• config.security.ssh.show on page 2-61
• config.switch.zoneFlexPars on page 2-80
• perf.thresholdAlerts.show on page 2-127
• show.auditLog on page 2-139
• show.epFrameLog.config on page 2-140
• show.epFrameLog.filterClassFFrames on page 2-140
• show.epFrameLog.noWrap on page 2-142
• show.epFrameLog.wrap on page 2-143
• show.fabric.principal on page 2-148
• show.fabric.topology on page 2-149
• show.fabricLog.noWrap on page 2-145
• show.fabricLog.wrap on page 2-146
• show.fencing.policies on page 2-150
• show.ficonCUPZoning on page 2-152
• show.ficonMS on page 2-152
• show.NPIV.config on page 2-159
• show.openSysMS.config on page 2-160
2-4
Enterprise Operating System Command Line Interface User Manual
• show.port.opticEDD on page 2-169
Page 49

config
config
2
• show.port.opticInfo on page 2-170
• show.port.profile on page 2-171
• show.port.showPortAddr on page 2-173
• show.security.log on page 2-181
• show.security.switchAcl on page 2-183
The config branch of the CLI command tree contains commands that
set parameter values on the switch or director. These values are not
temporary (session) values, but are retained across power cycles.
The commands in the config branch can only be accessed by a user
with administrator level user rights.
CLI commands are activated on the switch immediately, except as
noted.
In general, the config naming commands (except for the
config.zoning commands) use the USASCII character set. All of the
characters in this 128-character set (the first 7-bit subset of the
ISO-8859-1 Latin-1 character set) are valid. Any exceptions are noted
in the specific command descriptions.
config.enterpriseFabMode.setState
Syntax setState enterpriseFabModeState
Purpose This command sets the Enterprise Fabric Mode state for the fabric.
The SANtegrity™ feature key must be installed to activate the
Enterprise Fabric Mode state.
NOTE: The command config.features.enterpriseFabMode on page 2-6 has
functionality that is identical to this command.
Parameters This command has one parameter.
enterpriseFabModeState Specifies whether enterpriseFabMode is
active. Valid values are activate and
deactivate. Boolean 1 and 0 may be
substituted as values.
CLI Commands
2-5
Page 50

config
2
Command Example Root> config enterpriseFabMode setState 1
NOTE: You cannot activate Enterprise Fabric Mode while Open Trunking is
enabled.
config.features.enterpriseFabMode
Syntax enterpriseFabMode enterpriseFabModeState
Purpose This command sets the Enterprise Fabric Mode state for the fabric.
The SANtegrity™ feature key must be installed to activate the
Enterprise Fabric Mode state.
Parameters This command has one parameter.
enterpriseFabModeState Specifies whether enterpriseFabMode is
active. Valid values are activate and
deactivate. Boolean 1 and 0 may be
substituted as values.
Command Example
config.features.ficonMS
Syntax ficonMS ficonMSState
Purpose This command sets the enabled state of the FICON Management
Root> config features enterpriseFabMode 1
NOTE: The command config.enterpriseFabMode.setState on page 2-5 has
functionality that is identical to this command.
Server. The FICON Management Server feature key must be installed
in order to enable the FICON Management Server State. (The
Sphereon 4300 and Sphereon 4500 switches do not accept this
command.)
NOTE: This command is displayed on a Sphereon 3016 and 3216 only if
the feature key is installed.
2-6
Enterprise Operating System Command Line Interface User Manual
Page 51

NOTE: If the FICON Management Server is enabled, the default
management style is the FICON Management Style. The Open Systems
Management Style cannot be used.
Parameters This command has one parameter.
ficonMSState Specifies whether the FICON Management
Server is enabled. Valid values are enable and
disable. Boolean 1 and 0 may be substituted as
values.
config
2
Command Example
config.features.installKey
Syntax installKey featureKey
Purpose This command allows the user to install a feature set that is enabled
Parameters This command has one parameter.
Root> config features ficonMS 1
NOTE: The command config.ficonMS.setState on page 2-19 has functionality
that is identical to this command.
by the provided feature key. The switch can be either offline or online
when this command is executed.
NOTE: If any currently installed features are being removed by the new
feature key, the switch must be offline when the command is given.
featureKey Specifies the key you have received to enable
optional software feature on a specific product.
A feature key is a string of case-sensitive,
alphanumeric ASCII characters.
The number of characters may vary in the
format; however, the key must be entered
exactly, including the hyphens. An example of a
feature key format is XxXx-XXxX-xxXX-xX.
Command Example
Root> config features installKey AaBb-CCdD-eeFF-gH
CLI Commands
2-7
Page 52

config
2
config.features.NPIV
Syntax setState NPIVState
Purpose This command sets the enabled state of the NPIV feature. The NPIV
feature key must be installed in order to enable this feature.
Parameters This command has one parameter.
NPIVState Valid values are enable and disable. Boolean 1 and
0 may be substituted as values.
Command Example
Root> config features NPIV enable
NOTE: The command config.NPIV.setState on page 2-23 has functionality that
is identical to this command.
config.features.openSysMS
Syntax openSysMS openSysMSState
Purpose This command sets the enabled state of the Open Systems
Management Server (OSMS). OSMS is a feature that allows host
control and inband management of the director or switch through a
management application that resides on an open-systems
interconnection (OSI) device.
Parameters This command has one parameter.
osmsState Specifies whether the Open Systems
Management Server is enabled. Valid values are
enable and disable. Boolean 1 and 0 may be
substituted as values.
Command Example
config.features.openTrunking
Syntax openTrunking openTrunkingState
2-8
Enterprise Operating System Command Line Interface User Manual
Root> config features openSysMS 1
NOTE: The command config.openSysMS.setState on page 2-24 has
functionality that is identical to this command.
Page 53

Purpose This command sets the enabled state of the OpenTrunking feature.
The OpenTrunking feature key must be installed in order to enable
open trunking.
Parameters This command has one parameter.
openTrunkingState This parameter can be set to enable or disable
the OpenTrunking feature. Boolean 1 and 0
may be substituted as values.
config
2
Command Example
config.features.show
Syntax show
Purpose This command shows the product feature information configured for
Parameters This command has no parameters.
Command Example
Output The product feature data is displayed as a table that includes the
Root> config features openTrunking 1
NOTE: The command perf.openTrunking.setState on page 2-107 has
functionality that is identical to this command.
this switch.
Root> config features show
following properties.
Installed Feature
Set
The feature set installed using a feature key.
Only installed keys are displayed.
Feature Individual features within each set. In many
State The state of the individual feature. Fabric-wide
cases, there is only one feature within each
feature set.
features are displayed as Active/Inactive.
Features related to the switch are displayed as
Enabled/Disabled.
CLI Commands
2-9
Page 54

config
2
Output Example The output from the config.features.show command displays as
follows.
Installed Feature Set Feature State
------------------------------ ------------------ ----Flex Ports 8 Flex Ports Enabled
SANtegrity Fabric Binding Active
SANtegrity Switch Binding Enabled
SANtegrity Enterprise Fabrics Active
Open Trunking Open Trunking Enabled
NOTE: The command show.features on page 2-150.has functionality that is
identical to this command.
config.fencing.addPolicy
Syntax addPolicy name
Purpose This command configures a new fencing policy and assigns it a name.
The new policy is assigned default settings, which must be changed
before the policy is activated.
Parameters This command has one parameter.
Command Example
config.fencing.addPort
Syntax addPort name portNumber
Purpose This command adds a port to the specified fencing policy.
See config.fencing.setParams on page 2-12 for default settings.
name Specifies the name of the new fencing
policy. This name can consist of any
printable USASCII characters up to a
maximum length of 63 characters. This
name is case-sensitive.
Root> config fencing addPolicy Policy2
NOTE: The maximum number of policies supported is 14.
2-10
Enterprise Operating System Command Line Interface User Manual
Page 55

Parameters This command has two parameters.
name The name of the fencing policy.
portNumber The new port number to add to the
fencing policy, or all, which will add all of
the individual ports to the fencing policy.
Valid values for the port number are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
NOTE: A range of ports is not accepted as a valid input to this command
(e.g., “0-29” is not acceptable).
config
2
The port values can also be substituted with one of the following
keywords that will remove all the ports from the alert, and then use a
specific type of port instead of individual port numbers.
Valid values are:
• eport - This will add all active E ports
NOTE: A fencing policy is not allowed to contain both port types and
individual ports.
Command Example Root> config fencing addPort 24
Root> config fencing addPort eport
config.fencing.deletePolicy
Syntax deletePolicy name
Purpose This command deletes a specified fencing policy. Only disabled
fencing policies can be deleted.
CLI Commands
2-11
Page 56

config
2
Parameters This command has one parameter.
name The name of the fencing policy. You can
also enter all for this argument. This will
delete all of the configured fencing
policies.
Command Example
Root> config fencing deletePolicy Policy1
config.fencing.removePort
Syntax removePort name portNumber
Purpose This command removes a port from the specified fencing policy.
Parameters This command has two parameters.
name The name of the fencing policy.
portNumber The new port number to remove from the
fencing policy, or all, which will remove
all of the individual ports from the
fencing policy.
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
Command Example
config.fencing.setParams
Syntax setParams name typeNumber limit period
Purpose This command sets the type, limit and period values for a specified
2-12
Enterprise Operating System Command Line Interface User Manual
Root> config fencing removePort 24
fencing policy.
Page 57

Parameters This command has four parameters.
name The name of the fencing policy.
typeNumber This must be entered as a number that
corresponds to an entry in the table
shown below.
limit The count of fencing violations that must
occur within the specified period in order
for a port to be automatically disabled.
Acceptable values are in the range of
1-255.
You may also enter default for this
argument, which will set the default limit
value for this fencing policy type.
period The number of seconds in which the
violation count must equal or exceed the
threshold limit in order for a port to be
fenced.
config
2
You may also enter default for this
argument, which will set the default
period for this fencing policy type.
NOTE: The interval value is a fixed length amount of time. This interval is
not a rolling window interval.
Type
Number
Policy Type
Default Limit
Value
Default Period Value
1 Protocol Errors 5 300 seconds
Type
Number Policy Type Limit Value Range Period Value Range
1 Protocol Errors 1 - 255 60 - 1800 seconds
CLI Commands
2-13
Page 58

config
2
Command Example The meaning for each of these inputs can best be described using the
following example sentence:
If ports 0,1, or 2 have more than 5 protocol errors on a single port
within a period of 30 minutes, disable the offending port.
Where:
Port list = 0, 1, 2
Fencing Type = Protocol Errors
Limit = 5
Period = 1800 seconds
config.fencing.setState
Syntax setState name enabledState
Purpose This command sets the enabled state of the specified fencing policy. A
Parameters This command has two parameters.
Command Example
config.fencing.show
Syntax show [name]
Purpose This command displays the settings for fencing policies.
policy cannot be activated if it contains ports that are already
controlled by a different fencing policy of the same type.
name The name of the fencing policy.
enabledState Sets the fencing policy enabled state.
Valid values are enable and disable.
Boolean 1 and 0 values may also be
substituted.
Root> config fencing setState enable
2-14
Enterprise Operating System Command Line Interface User Manual
Page 59

Parameters This command has one optional parameter.
name The name of the fencing policy.
When no parameters are specified, the command will display the
name, type, and state of all policies. If you use the optional
parameter, it will display all the information about the policy.
NOTE: When the name parameter isn't supplied, then only 50 characters of
the names of the policies will be displayed. You will have to enable Comma
Delimited Mode to view the full name.
Command Example Root> config fencing show
Root> config fencing show Policy_1
Output If you do not specify the name parameter, then the output shows the
following information.
config
2
Name The name of the policy. This will be
concatenated to 50 characters in the
summary display. The policy full name
will be shown in comma delim mode.
Ports The ports to which the fencing policy will
be applied
Type The type of the fencing policy.
Limit The number of offenses that are allowed
before a port is disabled.
Period The amount of time that limit of number
of offenses must exceed before a port is
fenced.
State The enabled state of the fencing policy.
Output Example The output from the config.fencing.show command displays as
follows:
Name Type State
------------------------------ ------------------ -----
Default Protocol Error Policy Protocol Error Disabled
Policy_1 Protocol Error Disabled
CLI Commands
2-15
Page 60

config
2
The output from the config.fencing.show Policy_1 command displays
as follows:
Name: Policy_1
Ports: E ports
Type: Protocol Error
Limit: 5
Period: 300 seconds
State: Disabled
config.fencing.showTypeTable
Syntax showTypeTable
Purpose This command displays the table of different fencing types that can
be assigned to a policy. This table is used for reference only.
Parameters This command has no parameters.
Command Example
Root> config fencing showTypeTable
Output Example The output from the config.fencing.showTypeTable command
displays as follows:
Number Fencing Policy Types
--------------------------------1 Protocol Errors
config.ficonCUPZoning.addControlHost
Syntax addControlHost hostNodeWwn
Purpose This command adds a control host to the Control Host List used to
determine the FICON host(s) capable of viewing all ports. This list
overrides the FCZ port visibility mask. The maximum entries in this
list is 8.
Parameters This command has one parameter:
hostNodeWwn The node WWN of the desired control
host, entered in colon-delimited notation
(e.g., 01:02:03:04:05:06:07:08)
2-16
Enterprise Operating System Command Line Interface User Manual
Page 61

Command Example Root> config ficonCUPZoning addControlHost 01:02:03:04:
05:06:07:08
config.ficonCUPZoning.deleteControlHost
Syntax deleteControlHost hostNodeWwn
Purpose This command removes one or all control hosts from the Control
Host List used to determine the FICON host(s) capable of viewing all
ports. This list overrides the FCZ port visibility mask.
Parameters This command has one parameter:
hostNodeWwn The node WWN of the desired control
host, entered in colon-delimited notation
(e.g., 01:02:03:04:05:06:07:08). You can also
enter all to remove the entire list, if no
attached hosts have supervisory
privileges.
config
2
Command Example
Root> config ficonCUPZoning deleteControlHost all
config.ficonCUPZoning.setState
Syntax setState ficonCUPZoningState
Purpose This command sets the enabled state of FICON CUP Zoning. The
FICON Management Server feature key must be installed in order to
enable the FICON CUP Zoning State. (The Sphereon 4300 and
Sphereon 4500 switches do not accept this command.)
NOTE: If the FICON Management Server is enabled, the default
management style is the FICON Management Style. The Open Systems
Management Style cannot be used.
Parameters This command has one parameter.
ficonCUPZoningState Specifies whether the FICON Management
Server is enabled. Valid values are enable
and disable. Boolean 1 and 0 may be
substituted as values.
CLI Commands
2-17
Page 62

config
2
Command Example Root> config ficonCUPZoning setState 1
config.ficonCUPZoning.show
Syntax show
Purpose This command displays the contents of the host control list and the
enabled state of FICON CUP Zoning.
Parameters This command has no parameters.
Command Example
Root> config ficonCUPZoning show
Output The data is displayed as a table that includes the following
information:
FICON CUP
Zoning State
The enabled state of the FICON CUP
Zoning feature
Host Control List List of 0-8 control hosts, displays
“empty” for control host list with no
members.
Output Example The output from the config ficonCUPZoning show command
displays as follows:
FICON CUP Zoning State: Enabled
Host Control List
----------------------01:02:03:04:05:06:07:08
09:0A:0B:0C:0D:0E:0F:00
NOTE: The command show.ficonCUPZoning on page 2-152 has functionality
that is identical to this command.
config.ficonMS.setMIHPTO
Synopsis setMIHPTO timeout
Purpose This command sets the Ficon MS MIHPTO value in seconds. The
2-18
Enterprise Operating System Command Line Interface User Manual
default value is 180 seconds (3 minutes).
Page 63

Parameters This command has one parameter.
timeout Valid values are 15, 30, 45,
60, 120, 180, 240, 300, 360,
420, 480, 540, and 600.
config
2
Command Example
config.ficonMS.setState
Syntax setState ficonMSState
Purpose This command sets the enabled state of the FICON Management
Parameters This command has one parameter.
Root> config ficonms setMIHPTO 180
Server. The FICON Management Server feature key must be installed
in order to enable the FICON Management Server State. (The
Sphereon 4300 and Sphereon 4500 switches do not accept this
command.)
NOTE: This command is displayed on a Sphereon 3016 only if the feature
key is installed.
NOTE: If the FICON Management Server is enabled, the default
management style is the FICON Management Style. The Open Systems
Management Style cannot be used.
ficonMSState Specifies whether the FICON Management
Command Example
Root> config ficonMS setState 1
NOTE: The command config.features.ficonMS on page 2-6 has functionality
that is identical to this command.
Server is enabled. Valid values are enable and
disable. Boolean 1 and 0 may be substituted as
values.
CLI Commands
2-19
Page 64

config
2
config.ficonMS.show
Syntax show
Purpose This command shows the Ficon MS settings
Parameters This command has no parameters.
Command Example
Output The data is displayed as a table that includes the following
Output Example The output from the config ficonMS show command displays as
config.ip.ethernet
Syntax ethernet ipAddress gatewayAddress subnetMask
Purpose This command sets the Ethernet network settings.
Root> config ficonMS show
information:
Ficon MS State The state of the FICON MS feature.
Ficon MIHPTO The FICON MIHPTO value in seconds.
follows:
Ficon MS State: Disabled
Ficon MIHPTO (seconds): 180
ATTENTION! The Telnet connection can be lost when these Ethernet
network settings are changed.
2-20
Enterprise Operating System Command Line Interface User Manual
NOTE: If the IP address is reconfigured, your Telnet client must be
reconnected to the new IP address. A new login will be requested.
Page 65

Parameters This command has three parameters.
ipAddress Specifies the new IP address for the director or
switch. The address must be entered in dotted
decimal format (for example, 10.0.0.0).
gatewayAddress Specifies the new gateway address for the
Ethernet interface. The address must be entered
in dotted decimal format (for example, 0.0.0.0).
subnetMask Specifies the new subnet mask for the Ethernet
interface. The address must be entered in dotted
decimal format (for example, 255.0.0.0).
config
2
Command Example
config.ip.lineSpeed
Synopsis lineSpeed speed duplex
Purpose This command sets the Ethernet line speed
Parameters This command has two parameters. One of the parameters is optional
Command Example
Root> config ip ethernet 10.0.0.0 0.0.0.0 255.0.0.0
depending on the combination.
speed The line speed. Options are auto, 10, or
100. If auto is entered then the optional
duplex should not be entered.
duplex The duplex mode for the connection.
Options are full or half.
Root> config ip lineSpeed 10 half
config.ip.show
Syntax show
Purpose This command shows the LAN configuration.
Parameters This command has no parameters.
Command Example
Root> config ip show
CLI Commands
2-21
Page 66

config
2
Output The LAN configuration data is displayed as a table that includes the
following properties.
IP Address The IP address.
Output Example The output from the config.ip.show command displays as follows.
config.NPIV.maxPortIDs
Syntax maxPortIDs portNumber maxIDs
Purpose This command configures the maximum number of NPIV logins that
Parameters This command has two parameters.
Gateway
The gateway address.
Address
Subnet Mask The subnet mask.
IP Address: 10.0.0.0
Gateway Address: 0.0.0.0
Subnet Mask: 255.0.0.0
are allowed on the specified port.
portNumber Specifies the port number. Valid values
are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
all - applies the maxIDs parameter value
to every port on the product
Command Example Root> config NPIV maxPortIDs 128
2-22
Enterprise Operating System Command Line Interface User Manual
maxIDs Specifies the maximum number of NPIV
logins allowed on the specified port.Valid
values are in the range 1-256.
Root> config NPIV portNumber 60
Page 67

config.NPIV.setState
Syntax setState NPIVEnabledState
Purpose This command sets enabled state of the NPIV feature. The NPIV
Parameters This command has one parameter.
config
2
feature key must be installed in order to enable this feature.
NPIVEnabledState This parameter can be set to enable or disable.
Boolean 1 and 0 values may also be
substituted.
Command Example
config.NPIV.show
Syntax show
Purpose This command displays the current NPIV configuration for all ports.
Parameters This command has no parameters.
Command Example
Output This command displays the following NPIV configuration data:
Root> config NPIV setState enable
Root> config NPIV show
NPIV state The current enabled/disabled state of the NPIV
feature.
Max Allowed NPIV Login Table. A table mapping each port
number on the switch to a corresponding max
number of NPIV logins setting.
Output Example The output from the config.NPIV.show command displays as follows:
NPIV state: Enabled
Port Max Allowed NPIV Logins
---------------------------
110
210
310
40
50
CLI Commands
2-23
Page 68

config
2
6 130
...
NOTE: The command show.NPIV.config on page 2-159 has functionality that
is the same as this command.
config.openSysMS.setHostCtrlState
Syntax setHostCtrlState HostContrlState
Purpose This command sets the enabled state of the Open Systems
Management Server Host Control.
Parameters This command has one parameter:
HostContrlState This parameter can be set to enable or
disable. Boolean 1 and 0 values may also
be substituted.
Command Example
Root> config openSysMS setHostCtrlState enable
config.openSysMS.setState
Syntax setState osmsState
Purpose This command sets the enabled state of the Open Systems
Management Server (OSMS). OSMS is a feature that allows host
control and inband management of the director or switch through a
management application that resides on an open-systems
interconnection (OSI) device.
Parameters This command has one parameter.
osmsState Specifies whether the Open Systems
Command Example
Root> config openSysMS setState 1
Management Server is enabled. Valid values are
enable and disable. Boolean 1 and 0 may be
substituted as values.
2-24
Enterprise Operating System Command Line Interface User Manual
Page 69

config.port.blocked
Syntax blocked portNumber blockedState
Purpose This command sets the blocked state for a port.
Parameters This command has two required parameters.
config
2
NOTE: The command config.features.openSysMS on page 2-8 has functionality
that is identical to this command.
portNumber Specifies the port number. Valid values are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
Command Examples
config.port.fan
Syntax fan portNumber fanOn
Purpose This command sets the fabric address notification (FAN) state for a
blockedState Specifies the blocked state for the port. Valid
values are true and false. Boolean 1 and 0 may be
substituted as values.
Root> config port blocked 4 false
Root> config port blocked 4 0
port (Sphereon 4300 and Sphereon 4500 switches only). This
configuration can be applied to any port regardless of its current
configuration. The FAN value is applied at the time the port is
configured and operated in a loop.
CLI Commands
2-25
Page 70

config
2
Parameters This command has two required parameters.
portNumber Specifies the port number. Valid values are:
0–23 for the Sphereon 4500
fanOn Specifies the FAN state for the port. Valid values
are true and false. Boolean 1 and 0 may be
substituted as values.
Command Example
config.port.name
Syntax name portNumber portName
Purpose This command sets the name for a port.
Parameters This command has two required parameters.
Root> config port fan 4 1
portNumber Specifies the port number. Valid values are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
portName Specifies the name for the port. The port name
must not exceed 24 characters in length.
Command Example
config.port.rxCredits
Syntax rxCredits portNumber numRxCredits
Purpose This command is used to set the number of initial BB Credits for a
2-26
Enterprise Operating System Command Line Interface User Manual
Root> config port name 4 Sam’s tape drive
given port. The number of credits assigned must fall between the
minimum and maximum allowed values for the port.
Page 71

Parameters This command has two required parameters:
portNumber Specifies the port number. Valid values
are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
numBBCredits Specifies the number of Rx BB Credits to
assign the specified port.
For the Sphereon 4300 and Sphereon 4500
the RxCredits per port must be between 2
and 12. The total number of Rx Credits
assigned across all ports must not exceed
the maximum pool size of 150.
For the Intrepid family, the RxCredits per
FPM/UPM port must be between 1 and
60. The RxCredits per XPM port must be
between 4 and 400. There is no pool
limitation.
config
2
Command Example
config.port.show
Syntax show portNumber
Purpose This command displays the current configuration for the specified
Parameters This command has one parameter.
Root> config port rxCredits 8 40
port.
portNumber Specifies the port number. Valid values are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
CLI Commands
2-27
Page 72

config
2
Command Example Root> config port show 4
Output This command displays as a table that includes the following
properties.
Port Number The port number.
Name The configured port name.
Blocked The blocked state. Valid values are true and false.
FAN The fabric address notification (FAN) state. Valid
values are true and false. (Sphereon 4300 and
Sphereon 4500 switches only.)
Type The port type. Valid values are:
•F Port
•E Port
•G Port
• Fx Port (Sphereon 4300 and Sphereon 4500 only)
• Gx Port (Sphereon 4300 and Sphereon 4500 only)
Output Example The output from the config.port.show command displays as follows.
Port Number: 4
Name: Sam’s tape drive
Blocked: false
Type: F Port
Speed: 2 Gb/sec
Rx BB Credits: 12
config.port.showPortAddr
Syntax showPortAddr
Purpose This command displays the port address configuration for all ports.
NOTE: The command show.port.showPortAddr on page 2-173 has functionality
that is the same as this command.
Speed The port speed. Valid values are 1 Gb/sec, 2 Gb/sec,
and Negotiate.
Rx BB Credits The number of configured Rx BB Credits.
2-28
Enterprise Operating System Command Line Interface User Manual
Page 73

Parameters This command has no parameters.
config
2
Command Example
Output The port configuration is shown as a table of properties. The
Output Example
Root> config port showPortAddr
following properties are displayed:
Port The port number
Original Addr The original port address of the port
Current Addr The current port address of the port
Swapped Port Num If the port is swapped with another port,
it will show the port number of the port it
is swapped with.
Port Original Addr Current Addr SwappedPort Num
---- ------------- ------------ ----------------
04 4
15 5
26 7 3
37 6 2
48 8
59 9
6a a
7b b
8c c
...
config.port.speed
Syntax speed portNumber portSpeed
Purpose This command sets the speed for a port. A port can be configured to
operate at 1 Gb/sec, 2 Gb/sec, or a negotiated speed. The port speed
can be set only to 1 Gb/sec if the switch speed is 1 Gb/sec. An
attempt to set the port speed to 2 Gb/sec or to negotiate in a switch
with a 1 Gb/sec switch speed results in an error message.
If the port speed is set to negotiate, the port and the device to which it
is attached negotiate the data speed setting to either 1 Gb/sec or 2
Gb/sec.
CLI Commands
2-29
Page 74

config
2
ATTENTION! Port speed changes temporarily disrupt port data transfers.
Parameters This command has two required parameters.
portNumber Specifies the port number. Valid values are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
portSpeed Specifies the speed of the port. Valid values are
1g, 2g, and negotiate.
Command Examples
Root> config port speed 4 2g
Root> config port speed 6 negotiate
config.port.swapPortByAddr
Syntax swapPortByAddr portAddr1 portAddr2
Purpose This command will swap two ports given the port addresses. The
ports must be offline to perform this operation.
Parameters This command has two required parameters:
portAddr1 Port address, in hexidecimal format, of
portAddr2 Port address, in hexidecimal format, of
Command Example
Root> config port swapPortByAddr 1e 1f
the desired port to be swapped
the desired port to be swapped
config.port.swapPortByNum
Syntax swapPortByNum portNum1 portNum2
2-30
Enterprise Operating System Command Line Interface User Manual
Page 75

Purpose This command will swap two ports given the port numbers. The
ports must be offline to perform this operation.
Parameters This command has two required parameters:
portNum1 Port number, in hexidecimal format, of
the desired port to be swapped
portNum2 Port number, in hexidecimal format, of
the desired port to be swapped
config
2
Command Example
config.port.type
Syntax type portNumber portType
Purpose This command sets the allowed type for a port.
Root> config port swapPortByAddr 1e 1f
A port can be configured as an F_Port, an E_Port, or a G_Port. On a
Sphereon 4300 or Sphereon 4500, a port can also be an Fx_port or
Gx_port.
NOTE: On the Sphereon 4300 Switch, the E_Port, G_Port, and GX_Port
options are not valid, unless the Fabric Capable feature is enabled. For more
information, see the McDATA Sphereon 4300 Switch Installation and Service
Manual (620-000171).
The port configurations function as follows:
• F_Port—cannot be used as an interswitch link, but may attach to a
device with an N_Port.
• E_Port—only other switches may attach to this type of port.
• G_Port—either a device or another switch may attach to this type
• Fx_Port — allows Arbitrated Loop operation in addition to the
• Gx_Port—allows Arbitrated Loop operation in addition to the
of port.
functionality of an F_Port. (Sphereon 4300 and Sphereon 4500
only.)
functionality of an F_Port or an E_Port. (Sphereon 4300 and
Sphereon 4500 only.)
CLI Commands
2-31
Page 76

config
2
Parameters This command has two required parameters.
portNumber Specifies the port number. Valid values are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
portType Specifies the type of the port. Valid values for the
port type are:
eport
fport
gport
fxport (Sphereon 4300 and Sphereon 4500 only)
gxport (Sphereon 4300 and Sphereon 4500 only)
Command Example Root> config port type 4 fport
config.security
The security command on the configuration branch enters the
security configuration branch. All commands under this branch
operate on a particular security attribute.
Some security configuration commands (namely those under the
fabricBinding branch) are different from other CLI commands in that
they are not single action commands that take effect immediately.
These commands implement a rudimentary membership list editor.
A user works on a temporary copy of a membership list in the editor
and can perform actions such as adding or deleting fabric members.
The edited copy can then be activated to the fabric. It should be noted
that not all verification of membership lists can be made in the
pending copy. Therefore, it is possible that a user will build up a
pending membership list definition without errors, but will
encounter errors when saving to the fabric. It should also be noted
that the state of the pending configuration must be set to 'restrict' in
order to make any changes to the (pending) fabric membership list.
2-32
Enterprise Operating System Command Line Interface User Manual
Page 77

config.security.authentication.interface api.outgoing
Syntax outgoing enabledState
Purpose This command determines if outgoing CHAP authentication is used
on all API sessions. If this is enabled, the switch will issue a CHAP
challenge to authenticate all new API connections.
Parameters This command has one parameter:
enabledState This parameter enables and disables
outgoing CHAP authentication for API
sessions. Valid values for this parameter
are enable or disable. Boolean 1 and 0
values may also be substituted.
config
2
Command Example
Root> config security authentication interface api
outgoing enable
config.security.authentication.interface.api.sequence
Syntax sequence method1 [method2]
Purpose This command sets the sequence that the API interface will use to
authenticate. When the preferred method cannot be contacted, the
backup method will be used to authenticate the API session.
Parameters This command has one required parameter, and one optional
parameter:
method1 This sets the preferred method of
authentication. Accepted values are local
or RADIUS.
method2 This optional parameter sets the backup
method of authentication. This backup
method is used when the preferred
method cannot be contacted. Accepted
value is local.
CLI Commands
2-33
Page 78

config
2
NOTE: A preferred method of local and a backup method of RADIUS is not
an accepted combination because the local method can always be contacted.
Command Example Root> config security authentication interface api
sequence RADIUS local
config.security.authentication.interface.cli.sequence
Syntax sequence method1 [method2]
Purpose This command sets the sequence that the CLI interface will use to
authenticate. When the preferred method cannot be contacted, the
backup method will be used to authenticate the CLI login.
Parameters This command has one required parameter, and one optional
parameter:
method1 This sets the preferred method of
authentication for the CLI interface.
Accepted values are local or RADIUS.
method2 This optional parameter sets the backup
method of authentication for the CLI
interface. This backup method is used
when the preferred method cannot be
contacted. Accepted value is local.
NOTE: A preferred method of local and a backup method of RADIUS is not
an accepted combination because the local method can always be contacted.
Command Example Root> config security authentication interface cli
sequence RADIUS local
config.security.authentication.interface.eport.outgoing
Syntax outgoing enabledState
Purpose This command determines if outgoing CHAP authentication is used
on E port connections. If this is enabled, the switch will issue a CHAP
challenge to authenticate the remote end of the ISL.
2-34
Enterprise Operating System Command Line Interface User Manual
Page 79

NOTE: This command requires that the SANtegrity Authentication feature
key be installed.
Parameters This command has one parameter:
enabledState This parameter enables and disables
outgoing CHAP authentication on all
ISLs. Accepted values for this parameter
are enable or disable. Boolean 1 and 0
values may also be substituted.
config
2
Command Example
Root> config security authentication interface eport
outgoing disable
config.security.authentication.interface.eport.sequence
Syntax sequence method1 [method2]
Purpose This command sets the sequence that the E port interface will use to
authenticate. When the preferred method cannot be contacted, the
backup method will be used to authenticate the remote end of the
ISL.
NOTE: This command requires that the SANtegrity Authentication feature
key be installed.
Parameters This command has one required parameter, and one optional
parameter:
method1 This sets the preferred method of
authentication. Accepted values are local
or RADIUS.
method2 This optional parameter sets the backup
method of authentication. This backup
method is used when the preferred
method cannot be contacted. Accepted
value is local.
CLI Commands
2-35
Page 80

config
2
NOTE: A preferred method of local and a backup method of RADIUS is not
an accepted combination because the local method can always be contacted.
Command Example Root> config security authentication interface eport
sequence RADIUS local
config.security.authentication.interface.nport.outgoing
Syntax outgoing enabledState
Purpose This command determines if outgoing CHAP authentication is used
on N port connections. If this is enabled, the switch will issue a
CHAP challenge to authenticate the remote device.
NOTE: This command requires that the SANtegrity Authentication feature
key be installed.
Parameters This command has one parameter:
enabledState This parameter enables and disables
outgoing CHAP authentication on all
ISLs. Accepted values for this parameter
are enable or disable. Boolean 1 and 0
values may also be substituted.
Command Example
Root> config security authentication interface eport
outgoing disable
config.security.authentication.interface.nport.sequence
Syntax sequence method1 [method2]
Purpose This command sets the sequence that the N_port interface will use to
authenticate. When the preferred method cannot be contacted, the
backup method will be used to authenticate the remote end of the
ISL.
NOTE: This command requires that the SANtegrity Authentication feature
key be installed.
2-36
Enterprise Operating System Command Line Interface User Manual
Page 81

Parameters This command has one required parameter, and one optional
parameter:
method1 This sets the preferred method of
authentication. Accepted values are local
or RADIUS.
method2 This optional parameter sets the backup
method of authentication. This backup
method is used when the preferred
method cannot be contacted. Accepted
value is local.
NOTE: A preferred method of local and a backup method of RADIUS is not
an accepted combination because the local method can always be contacted.
Command Example Root> config security authentication interface nport
sequence RADIUS local
config
2
config.security.authentication.interface.osms.outgoing
Syntax outgoing enabledState
Purpose This command determines if outgoing authentication is used on all
OSMS requests. The OSMS key must be configured prior to setting
the outgoing state to enabled.
NOTE: The SANtegrity Authentication feature key must be installed to
configure the OSMS outgoing state.
Parameters This command has one parameter:
enabledState This parameter enables and disables
FCCT authentication. Accepted values
for this parameter are enable or disable.
Boolean 1 and 0 values may also be
substituted.
Command Example
Root> config security authentication interface osms
outgoing 1
CLI Commands
2-37
Page 82

config
2
config.security.authentication.interface.osms.setKey
Syntax setKey
Purpose This command sets the FCCT key that is associated to the single
OSMS username. This username is a static entry in the local
authentication database. This user is not viewable. This command
effectively sets the key that will be used in all OSMS authenticated
requests. This entry in the user database is only used for the OSMS
interface, and cannot be changed.
After issuing this command, you are directed to a password prompt
where the actual 16-byte key is entered. After entering the new secret,
it must be confirmed in the following prompt. After confirmation,
you will be returned to the initial prompt that the command was
executed from. No characters will be echoed back to the screen when
entering a password, or when confirming a password.
NOTE: The SANtegrity Authentication feature key must be installed to
configure the FCCT key.
Parameters This command has no required parameters.
Command Example
Root> config security authentication interface osms
setKey
config.security.authentication.interface.serial.enhancedAuth
Syntax enhancedAuth enhancedAuthState
Purpose This command sets the enhanced serial authentication state.
Enhanced Serial Authentication will require a user to enter a
password when gaining access to the serial port interface.
Parameters This command has one parameter:
enhancedAuthState This parameter enables and disables
enhanced authentication on the serial
port interface. Accepted values for this
parameter are enable or disable. Boolean 1
and 0 values may also be substituted.
2-38
Enterprise Operating System Command Line Interface User Manual
Page 83

Command Example Root> config security authentication serial enhancedAuth
enable
config.security.authentication.interface.show
Syntax show interface
Purpose This command displays the settings in the local authentication
database for a single interface.
NOTE: The SANtegrity Authentication feature key must be installed to view
the eport and nport information, and the OSMS information.
Parameters This command has one parameter.
interface The interface that will be displayed. Valid
values for this parameter are:
cli
web
osms
api
serial
eport
nport.
config
2
Command Example
Root> config security authentication interface show Web
Output Example The output for the config.security.authentication.interface.show
command displays as follows:
Interface: Web
Outgoing: N/A
Incoming: N/A
Sequence: Local, RADIUS
config.security.authentication.interface.web.sequence
Syntax sequence method1 [method2]
Purpose This command sets the sequence that the Web interface will use to
authenticate. When the preferred method cannot be contacted, the
backup method will be used to authenticate the Web login.
CLI Commands
2-39
Page 84

config
2
Parameters This command has one required parameter, and one optional
parameter:
method1 This sets the preferred method of
authentication for the CLI interface.
Accepted values are local or RADIUS.
method2 This optional parameter sets the backup
method of authentication for the CLI
interface. This backup method is used
when the preferred method cannot be
contacted. Accepted value is local.
NOTE: A preferred method of local and a backup method of RADIUS is not
an accepted combination because the local method can always be contacted.
Command Example Root> config security authentication interface cli
sequence RADIUS local
config.security.authentication.port.override
Syntax override portNumber [overrideState]
Purpose This command sets the outgoing override state for a single port. This
setting allows you to override the default outgoing authentication
state for either the E_port or N_port interface. The default setting will
cause the port to use the outgoing state configure for the
corresponding interface (either E_port or N_port).
NOTE: This command requires that the SANtegrity Authentication feature
key be installed.
2-40
Enterprise Operating System Command Line Interface User Manual
Page 85

Parameters This command has one required parameter, and one optional
parameter:
portNumber Specifies the port number. Valid values
are:
0–11 for the Sphereon 4300
0–15 for the Sphereon 3016 and 3216
0–23 for the Sphereon 4500
0–31 for the Sphereon 3032 and 3232
0–63 for the Intrepid 6064
0–127 and 132–143 for the Intrepid 6140
overrideState This parameter sets the outgoing
authentication state for the specified port.
Valid values are enable, disable, or default.
Boolean 1 and 0 values may also be
substituted.
config
2
Command Example
Root> config security authentication port override 138
enable
config.security.authentication.port.show
Syntax show
Purpose This command displays a table displaying the outgoing override
state for each port.
Parameters This command has no parameters.
Command Example
Output This command displays all valid user names in the local database for
Root> config security authentication port show
the specified interface.
Port The port number.
Override State The outgoing authentication override
state.
Output Example The output for the config.security.authentication.port.show
command displays as follows:
CLI Commands
2-41
Page 86

config
2
Port Override State
---- -------------0 Default
1 Default
2 Enable
3 Default
4 Disable
config.security.authentication.RADIUS.attempts
syntax attempts index attempts
Purpose This command configures the number of attempts a packet will be
sent to a RADIUS server if a response is not received before the
timeout. After the transmit attempt limit is reached, the switch will, if
applicable, move on to the next defined RADIUS server. The default
is 3 attempts.
Parameters This command has two required parameters:
index Index of the RADIUS sever (1-3) to
change the transmit attempts value.
attempts The number of transmit attempts. Valid
values are between 1 and 100.
Command Example
Root> config security authentication RADIUS attempts 3 20
config.security.authentication.RADIUS.deadtime
Syntax deadtime minutes
Purpose This command configures the number of minutes a RADIUS server is
marked as “dead”. If a RADIUS server does not respond to an
authentication request, it can be marked as “dead” for a specified
time interval. This may speed up authentication by eliminating
timeouts and retransmissions. If no alternate RADIUS servers are
available (when only one server is configured or when all are marked
dead), then the deadtime is ignored. Deadtime may be 0 to 1440
minutes. The default is 0.
2-42
Enterprise Operating System Command Line Interface User Manual
Page 87

Parameters This command has one required parameter:
minutes The number of minutes a RADIUS server
is marked “dead” before it is contacted
again. Valid values are between 0 and
1440.
config
2
Command Example
Root> config security authentication RADIUS deadtime 120
config.security.authentication.RADIUS.deleteServer
Syntax deleteServer index
Purpose This command removes a RADIUS server from the RADIUS server
list. If you delete a server, and there are servers configured in higher
numbered slots, these servers will be automatically moved up to the
first available slots.
Parameters This command has one required parameter.
index Index of the server to be removed.
Command Example
Root> config security authentication RADIUS deleteServer
3
config.security.authentication.RADIUS.server
Syntax server index [IP:port]
Purpose This command adds or modifies one RADIUS server, at a given
index, that will be used for authentication. Servers are queried in the
order listed, so the primary server must be the first one in the list.
There are three slots available for RADIUS servers. Servers will be
added into the list by the index value. The range is 1 to 3. If a server is
added and there is an empty slot before that server, it will be shifted
up to the empty slot. The IP:port is the IP address and the UDP port
on the RADIUS server.
NOTE: If you want to configure a RADIUS server without a key, you must
specify the key as "". The set of double quotes is an empty string in the CLI.
CLI Commands
2-43
Page 88

config
2
Parameters This command has one required parameter, and two optional
parameters:
index Index of the RADIUS server (1-3) to
add/modify.
IP IP address of the server.
port The UDP port number.
Command Example
Root> config security authentication RADIUS server 3
14.2.114.183:6
config.security.authentication.RADIUS.show
Syntax show
Purpose This command displays the current RADIUS server configuration.
Parameters This command has no parameters.
Command Example
Output This command displays all three configured RADIUS servers.
Root> config security authentication RADIUS show
Deadtime The amount of time a server is marked as
“dead”.
Server The IP address and UDP port of the
configured RADIUS server.
Attempts The number of transmit attempts.
Timeout The timeout value for a server in seconds.
Output Example The output for the config.security.authentication.RADIUS.show
2-44
Enterprise Operating System Command Line Interface User Manual
command displays as follows:
Deadtime: 0
Index IP Address Port Attempts Timeout
----- ------------- ---- ---------- ------1 1.1.1.1 1111 3 2
2 2.2.2.2 2222 3 2
3
Page 89

config.security.authentication.RADIUS.timeout
Syntax timeout index seconds
Purpose This command configures the number of seconds to wait for a
response from the RADIUS server before retransmitting a packet. The
default is 2 seconds.
Parameters This command has two required parameters:
index Index of the RADIUS sever (1-3) to
change the timeout value.
seconds The number of seconds before the
RADIUS server retransmits. Valid values
are between 1 and 1000.
config
2
Command Example
Root> config security authentication RADIUS timeout 3 360
config.security.authentication.switch.setSecret
Syntax SetSecret
Purpose This command sets the CHAP secret that is associated with the
switch. This command effectively sets the secret for the local WWN
username in the local authentication user database. The switch secret
is used for all incoming CHAP challenges on the E port and N port
interfaces.
After issuing this command, you are directed to a “password”
prompt where the actual 16-byte secret is entered. After entering the
new secret, it must be confirmed in the following prompt. After
confirmation, you are returned to the initial prompt that the
command was executed from. No characters will be echoed back to
the screen when entering a password, or when confirming a
password. See Passwords and Secrets on page 1-14 for valid characters.
NOTE: The SANtegrity Authentication feature key must be installed to
configure switch secret.
Parameters This command has no required parameters.
CLI Commands
2-45
Page 90

config
2
Command Example Root> config security authentication switch setSecret
config.security.authentication.user
One of the fundamental concepts of the authentication portion of the
Command Line Interface is that all secured interfaces have
interchangeable users that are stored in a single local authentication
user database. In the past, CLI has supported authorization for only
two username/password pairs (one Administrator-level and another
Operator-level). These two username/password pairs were also
unique to CLI interface. With this release, a CLI user can now
configure multiple users for his own interface, as well as for other
management entities and FC connections. For this reason, the
security.userrights branch of commands has been removed from the
command tree.
config.security.authentication.user.add
Syntax add username interface1 [interface2]
Purpose This command adds a new user to the local authentication database.
Each user can be assigned a combination of interfaces that will
authenticate the new username/password combination. After
executing this command, the user will be moved to a new password
prompt where the user will enter a password; the password must
then be confirmed in next prompt. After confirming the new
password, the user will be returned to the initial prompt. No
characters will be echoed back to the screen when entering a
password, or when confirming a password.
All new users will be assigned a role of “none”; a subsequent “role”
command must be executed to assign a role. Web and CLI users must
be assigned a role before they can access the CLI or Web interfaces.
NOTE: The SANtegrity Authentication feature key must be installed to
configure E port and N port usernames.
Parameters This command has two required parameters, and an additional
password parameter at the prompt after the command.
2-46
Enterprise Operating System Command Line Interface User Manual
Page 91

username The new user name that will be added to
the local authentication database. If the
entered user name already exists in the
user database, an error will be shown.
This parameter can be from 1-23
characters in length for an API, Web or
CLI username. E Port and N Port
usernames must be entered as a standard
colon delimited WWN. All characters in
the printable USASCII character set are
valid with the exception of spaces, single
quotes, and double quotes.
interfaces This is a list of interfaces that will be
assigned to the associated username.
Accepted values for this parameter are:
cli
web
api
eport
nport
config
2
password Sets the password for the new login
NOTE: Currently the only possible combination of multiple interfaces
is (Web and CLI).
Command Example
Root> config security authentication user add
01:2A:3f:4:5:0:0 eport
config.security.authentication.user.delete
Syntax delete username
username. This parameter can be from
1-24 characters in length for a Web or CLI
password. CHAP secrets and FCCT keys
must be exactly 16 bytes long for API,
OSMS, E Port, and N Port interfaces. This
parameter will not be echoed to the
screen. See Passwords and Secrets on
page 1-14 for valid characters.
CLI Commands
2-47
Page 92

config
2
Purpose This command deletes an entry from the local authentication
database. Both the Web and CLI interfaces must have at least one
valid username with an “Administrator” role.
Parameters This command has one parameter:
username A valid username in the local
authentication database.
Command Example
Root> config security authentication user delete
01:2A:3f:4:5:0:0
config.security.authentication.user.modify
Syntax modify username interface1 [interface2]
Purpose This command modifies an existing user in the local authentication
database. The user password and the combination of interfaces can be
modified with this command. After executing this command, you are
prompted to enter a password, similar to behavior of the user.add
command.
The role of a user will remain the same unless the currently assigned
role is invalid for the new combination of interfaces. If the role is no
longer valid for an interface combination, the role will be changed
back to “none”. At least one username with an “Administrator” role
must exist in the user database at all times for both the Web and CLI
interfaces.
NOTE: The SANtegrity Authentication feature key must be installed to
configure E port and N port usernames.
2-48
Enterprise Operating System Command Line Interface User Manual
Page 93

Parameters This command has two required parameters, and an additional
password parameter at the prompt after the command:
username The existing user name whose fields will
be modified in the local authentication
database. If the entered user name does
not exist in the user database, an error
will be shown. This parameter can be
from 1-23 characters in length for an API,
Web or CLI username. E Port and N Port
usernames must be entered as a standard
colon delimited WWN. All characters in
the printable USASCII character set are
valid with the exception of spaces, single
quotes, and double quotes.
interfaces This is a list of interfaces that will be
assigned to the associated username.
Accepted values for this parameter are:
cli
web
api
eport
nport.
config
2
password Sets the password for the existing
username. This parameter can be from
1-24 characters in length for a Web or CLI
username. CHAP secrets must be exactly
16 bytes long for API, OSMS, E Port, and
N Port interfaces. This parameter will not
be echoed to the screen. See Passwords and
Secrets on page 1-14 for valid characters.
NOTE: Currently the only possible combination of multiple interfaces is
(Web and CLI) or (E port or N port).
Command Example Root> config security authentication user modify
01:2A:3f:4:5:0:0 nport
config.security.authentication.user.role
Syntax role username privilegeLevel
CLI Commands
2-49
Page 94

config
2
Purpose This command sets the role value that is associated to an existing
username. The role value can either be set to an administrator or an
operator. This value defaults to “none” when the user is first added to
the database. This value must be changed for all new CLI and Web
users before they will be allowed access to their respective interfaces.
Parameters This command has two required parameters:
username A valid Web or CLI username in the local
authentication database.
privilegeLevel This parameter assigns the privilege level
to a username. Currently only Web and
CLI users can be assigned a role value.
This parameter must be either
administrator or operator.
Command Example
Root> config security authentication user role
01:2A:3f:4:5:0:0 administrator
config.security.authentication.user.show
Syntax show interface
Purpose This command displays a single interface from the local
authentication database.
Parameters This command has one optional parameter:
interface The interface that will be displayed.
Accepted values for this parameter are:
cli
web
api
eport
nport.
Command Example
Output Example The output for the config.security.authentication.user.show
2-50
Enterprise Operating System Command Line Interface User Manual
Root> config security authentication user show web
command displays as follows:
Interface: Web
Page 95

Username Interfaces Role
----------- ----------- -------------
johndoe_1223 Web,CLI Administrator
ewsOperator Web Operator
Operator Web,CLI Operator
config.security.fabricBinding
Fabric Binding functionality, provided by the SANtegrity Binding
feature, allows you to bind the switch or director to specified fabrics
so that it can communicate only with those fabrics. With Fabric
Binding enabled, the product can communicate only with fabrics that
are included in the Fabric Binding Membership List (FBML).
Using Fabric Binding, you can allow specific switches to attach to
specific fabrics in the SAN. This provides security from accidental
fabric merges and potential fabric disruption when fabrics become
segmented because they cannot merge.
config
2
Fabric Binding
Commands
Fabric Binding
Membership
Terminology
The config.security.fabricBinding commands function in a different
way from most CLI commands, which are single action commands
that take effect immediately. Most of the Fabric Binding commands
affect a temporary copy of an FBML in the work area, which is called
the Pending FBML. When this temporary copy, the pending list, is
activated to the fabric, it is called the Active FBML.
ATTENTION! One factor to consider, when using CLI commands to view
and configure Fabric Binding settings, is that the SANpilot
change Fabric Binding status and FBMLs, if it is used at the same time as the
CLI.
®
interface can
Because not all the verification of the Pending FBML can occur on the
temporary copy in the work area, it is possible, however unlikely, that
the copy of the list encounters no errors until the list is activated to
the fabric.
NOTE: A Sphereon 4300 Switch cannot participate in a fabric, unless the
Fabric Capable feature is enabled. For more information, see the McDATA
Sphereon 4300 Switch Installation and Service Manual (620-000171).
Two types of FBMLs are configured using the CLI:
CLI Commands
2-51
Page 96

config
2
• Active FBML: When fabric binding is active, the active FBML is
the list of fabric members with which the product is allowed to
communicate. If fabric binding is disabled, this list is empty.
• Pending FBML: A list used to configure an FBML before it is
made active on the product. Changes to the pending FBML are
not implemented in the fabric until they are saved and activated
using the config.security.fabricBinding.activatePending command as
documented on page 2-53.
The following terms apply to the switches and directors that are part
of the FBMLs:
• Local: The switch or director product that you are configuring.
This is a required FBML member.
• Attached: A switch or director that is currently in a fabric with the
local product. Any switch and director that is attached is a
required FBML member.
• Unattached: A switch or director that is not currently in a fabric
with the local product. These switches and directors are
unattached if they have been added manually to the pending
FBML, or if they segmented from the local fabric.
Enable/Disable and
Online State Functions
In order for Fabric Binding to function, specific operating parameters
and optional features must be enabled. Also, there are specific
requirements for disabling these parameters and features when the
director or switch is offline or online. Be aware of the following:
• Because switches are bound to a fabric by World Wide Name
(WWN) and domain ID, the Insistent Domain ID option in the
Configure Switch Parameters dialog box is automatically enabled if
Fabric Binding is enabled. You cannot disable Insistent Domain
ID while Fabric Binding is active and the switch is online.
• If Fabric Binding is enabled and the switch is online, you cannot
disable Insistent Domain ID.
• If Fabric Binding is enabled and the director is offline, you can
disable Insistent Domain ID, but this will disable Fabric Binding.
• You cannot disable Fabric Binding if Enterprise Fabric Mode is
enabled. However, if Enterprise Fabric Mode is disabled, you can
disable Fabric Binding.
NOTE: Fabric Binding can be disabled when the switch is offline.
2-52
Enterprise Operating System Command Line Interface User Manual
Page 97

config.security.fabricBinding.activatePending
Syntax activatePending
Purpose This command activates the fabric binding configuration contained in
the pending work area to the fabric. The Pending FBML becomes the
Active FBML, and fabric binding is made functional.
NOTE: This command takes effect immediately. The CLI verifies the list
before activating it to the fabric.
Parameters This command has no parameters.
config
2
Command Example
Root> config security fabricBinding activatePending
config.security.fabricbinding.addAttachedMembers
Syntax addAttachedMembers
Purpose This command adds all the current members of the fabric to the
Pending FBML. If a fabric member's domain ID or WWN already
exists in the list, it is not added.
Parameters This command has no parameters.
Command Example
Root> config security fabricbinding addAttachedMembers
CLI Commands
2-53
Page 98

config
2
config.security.fabricBinding.addMember
Syntax addMember wwn domainId
Purpose This command adds a new member to the Pending FBML in the
fabric binding work area. The number of entries is limited to the
maximum available domain IDs for the fabric, which is 239.
NOTE: Changes from this command are not activated to the fabric until the
activatePending command is issued.
Parameters This command has two parameters:
wwn Specifies the world wide name (WWN) of the
member to be added to the Pending FBML. The
value of the WWN must be in colon-delimited
hexadecimal notation (for example,
AA:00:AA:00:AA:00:AA:00).
domainId The domain ID of the member to be added to
the Pending FBML. Valid domain IDs range
from 1 to 239.
Command Example
Root> config security fabricBinding addMember
AA:99:23:23:08:14:88:C1 2
config.security.fabricBinding.clearMemList
Syntax clearMemList
Purpose This command clears the Pending FBML in the working area.
Members that are attached remain in the list, because the Pending
FBML must contain all attached members to become active.
NOTE: This information is not saved to the fabric until the activatePending
command is issued. When the list is cleared, the CLI automatically adds the
managed switch to the Pending FBML.
Parameters This command has no parameters.
Command Example
2-54
Enterprise Operating System Command Line Interface User Manual
Root> config security fabricBinding clearMemList
Page 99

config.security.fabricbinding.deactivateFabBind
Syntax deactivateFabBind
Purpose This command deactivates the active FBML on the fabric. The Active
FBML is erased when this command is executed.
NOTE: This command takes effect immediately in the fabric.
Parameters This command has no parameters.
config
2
Command Example
Root> config security fabricbinding deactivateFabBind
config.security.fabricBinding.deleteMember
Syntax deleteMember wwn domainId
Purpose This command removes a member from the Pending FBML in the
fabric binding work area. The local member and attached members
cannot be deleted from the list.
NOTE: Changes are not activated to the fabric until the activatePending
command is issued.
Parameters This command has two parameters:
wwn Specifies the WWN of the member to be
removed from the Pending FBML. The value of
the WWN must be in colon-delimited
hexadecimal notation (for example,
AA:00:AA:00:AA:00:AA:00).
domainId The domain ID of the member to be removed
from the Pending FBML. Valid domain IDs
range from 1 to 239.
Command Examples
Root> config security fabricBinding deleteMember
AA:99:23:23:08:14:88:C1
Root> config security fabricBinding deleteMember 2
CLI Commands
2-55
Page 100

config
2
config.security.fabricBinding.replacePending
Syntax replacePending
Purpose This command replaces the Pending FBML with the fabric binding
configuration that is currently loaded on the fabric.
Parameters This command has no parameters.
Command Example
Root> config security fabricBinding replacePending
config.security.fabricBinding.showActive
Syntax showActive
Purpose This command displays the fabric binding configuration (active
FBML) saved on the fabric. It performs the same function as
show.security.fabricBinding on page 2-180.
Parameters This command has no parameters.
Output This command displays the following fabric binding configuration
data:
Domain ID The domain ID of the FBML member. Valid
WWN The world wide name (WWN) of the FBML
Attachment
Status
domain ID's range from 1 to 239.
member in colon-delimited hexadecimal
notation.
Indicates whether the FBML member is Local,
Attached, or Unattached. For more information,
see Fabric Binding Membership Terminology on
page 2-51.
Output Example The output from the config.security.fabricBinding.showActive
2-56
Enterprise Operating System Command Line Interface User Manual
command displays as follows.
Domain 1 (20:30:40:50:60:70:8F:1A) (Local)
Domain 3 (00:11:22:33:44:55:66:77) (Unattached)
Domain 2 (88:99:AA:BB:CC:DD:EE:FF) (Attached)
Domain 14 (11:55:35:45:24:78:98:FA) (Attached)
 Loading...
Loading...