Page 1

INTUITY™ Messaging Solutions
Enhance d-Li st Application
Release 1.0
585-310-575
Comcode 107975674
Issue 1
July 1997
Page 2

Copyright 1997, Lucent Te chnologies
All Rights Reserved
Printed in U.S.A.
Notice
Every effort was made to ensure that the information in this book was
complete and accurate at the ti me of printing. However, inf or m ation
is subjec t to change.
Your Responsibility for Your System’s Security
Toll fraud is the unauthorized use of your telecommunications system
by an unauthorized party, for example, per s ons other than your com-
pany’s emplo yee s, age nts, sub con trac tor s, or per so ns worki ng on your
company’s behalf. Note that th ere may be a risk of toll f r aud as s ociated with your telecommunications system and, if toll fraud occurs, it
can result in substantial additional charges for your telecommunications services.
You and you r system manager are responsi ble for the security of your
system, such as progra mming and configuring you r equipment to prevent unauthorized use. The system manager is also responsible for
reading all installation, instruction, and system administration documents provided with this product in order to fully understand the features that can introduce ri s k of toll fraud and the steps that can be
taken to re duce that risk. Lucent Technologies does not warra nt that
this product is immune from or will prevent unauthorized use of common-carri er telecommunication ser vices or facilities accessed thr ough
or connected to it. Luce nt Tec hno lo gi es will not be respo nsible for
any charges that result from s uch unauthor ized use.
Lucent Technologies Fraud Intervention
If you suspect that you are being vict imi zed by tol l fraud and you need
technical s upport or assistance, call Technical Service Center Toll
Fraud Interventio n Hotlin e at 1 800 643-2 353 .
Federal Communications Commission Statement
Part 15: Class A Statement. This equipment has been tested an d
found to comply with the limits for a Class A digital device, pursuant
to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interfer ence when the equi pment is
operated in a commercial environment. This equipment generates,
uses, and can radiate radio-frequency energy and, if not install ed and
used in accor dance with the instructions, may cause harmful int erference to radio communications. Operation of this equipm ent in a residential area is likely to cause harmful interference, in which case the
user will be required to correct the interference at his own expense.
Canadian Department of Communications (DOC)
Interference I nformation
This digital ap pa r a t u s do es no t ex c e ed the Cla s s A li m i ts f or r a dio
noise emissi ons set out in t he radio interference regulations of the
Canadian Depar tment of Communications.
ésent Appareil Nomé riqu e n’émet pas de brui ts r adioélectr iq ues
Le Pr
épassant les limites applicables aux appareils numériques de la class
d
éscrites dans le reglement sur le brouillage radio é l ectrique édicté
A pr
par le minist
Trademarks
See the preface of this document.
Ordering Information
Call: Lucent Technologies Publications Cent er
Write: Lucent Technologies Publications Cent er
Order: Document No. 585-310-575
For additional documents, refer to the section in “About This Document” entitled “Related Resou rc es .”
You can be placed on a standing order list for this an d other documents you may nee d. Standing order will enab le you to autom ati cally
receive update d versions of individual documents or document sets ,
billed to account information that you provide. For more information
on standing orders, or to be put on a li s t to receive future is s ues of thi s
document, contact the Luce nt Technologies Publications Center.
Comments
To comment on this document, return the comment card at the front of
the document.
Acknowledgment
This document was prepared by the Product Documentation Development, Lucent Technologies , Denver, CO and Co lumbus, OH.
ére des Communications du Canada.
Voice 1 800 457 -1 235 International Vo ice 317 361-5353
Fax 1 800 457-1764 International Fax 317 361-5355
P.O. Box 4100
Crawfordsv ille, IN 47933
Comcode 107975674
Issue 1, July 1997
Part 68: Network Registration Number. This equipment is registered with the FCC in accordance with Part 68 of the FCC Rules. It is
identified by FCC registratio n numb er xxx.
Part 68: Answer-Supervision Signaling. Allo win g th is eq ui pme n t t o
be operated in a manner that does not provide proper answer-supervision signaling is in viola tio n of Part 68 R ules. This eq uip men t ret urns
answer-supervision s ignals to the public switched network when :
• Answered by the called station
• Answered by the attendant
• Routed to a recorded announcement that can be administered
by the CPE user
This equipment returns answer-supervision signals on all DID calls
forwarded back to the public switched telephone network. Per m issible exceptions are:
• A call is unanswered
• A busy tone i s re ceived
• A reorder tone is received
Page 3
Contents
About This Book
■ Purpose v
■ Intended Audiences v
■ Trademarks and Service Marks vi
■ Related Resources viii
■ How to Comment on This Book viii
1 Enhanc e d-List A pplicat io n
■ Overview 1
Audience 1
What You Should Know 1
■ Enhanced-List Application 2
■ What ELA Can Do for You 2
■ ELA Administration 3
Basic Concep t s 3
Planning with Professional Services 3
Things to Consider 4
2 Installation
■ Overview 9
■ Installing the Software 9
■ Rebooting the System 11
3 Administering AUDIX for ELA
■ Overview 13
■ Activating ELA 14
■ Verifying that ELA is Enabled 14
Issue 1 July 1997 i
Page 4
Contents
■ Increasing the Number of Mailing
Lists Allowed on the System 15
■ Defining an ELA Class of Service 16
■ Setting Up ELA and Shadow Mailbox
Community IDs 19
Things to Consider 19
Before You Begin 20
ELA Community ID 20
Shadow Mailbox Community ID 22
■ Administering TCP/IP 23
Before You Begin 23
■ Setting Up IMAPI Sessions for
Trusted Server Access 26
■ Defining Two ELA Trusted Servers 28
Before You Begin 28
4 Administering ELA for AUDIX
■ Overview 33
■ Defining the AUDIX server and
Administering Access 33
Before You Begin 33
■ Guidelines for Naming Enhanced Lists 37
■ Creating Enhanced Lists 38
Guidelines for Selecting Enhanced-List Members 41
Adding Members to Enhanced Lists 41
Adding/Deleting Mem bers to an Enhanced List 43
■ Deleting an Enhanced List 46
■ Recording Names for Enhanced Lists 48
■ Testing INTUITY Enhanced Lists 48
5 Preventative Maintenance and Troubleshooting
■ Overview 51
ii Issue 1 July 1997
Page 5
Contents
■ Checking the Administrator’s Log 51
■ Checking the Delivery Failure Log 52
■ Delivery Failure Codes 54
■ Troubleshooting ELA 55
6 Alarms
■ Overview 59
■ DELIVTS Resource Type 59
■ REGISTRY Reso urce Type 61
■ SHADOW Resource Type 62
■ EL — Enhanced-List Application 65
IN Index
Issue 1 July 1997 iii
Page 6

Contents
iv Issue 1 July 1997
Page 7
About This Book
Purpose
This book contains instructions for installing and administrating the
Enhanced-List Application (ELA) on an I
Intended Audiences
This book is intended primarily for the on-site technical personnel who are
responsible for installing and configuring the system and performing initial
administration and acceptance testing. Second ary audienc es include the
following from Lucent:
■ Field support — Technical Service Organiza tion (TSO)
■ Helpline personnel
■ Factory assemble, load, and test (ALT) personnel
■ Provisioning project managers — Sales and Technical Resource Center
(STRC)
This book assumes that the primary users of this book have completed the
NTUITY AUDIX Administration training course.
I
NTUITY™ AUDIX
®
R4 system.
Issue 1 July 1997 v
Page 8

About This Book
Trademarks and Service Marks
The following trademarked products are mentioned in books in the Lucent INTUITY
document set:
■ AT™ is a trademark of Hayes Microcomputer Products, Inc.
■ AUDIX
■ cc:Mail
Development Corporation.
■ COMSPHERE
Paradyne Corp.
■ CONVERSANT
Lucent Technologies™.
■ DEFINITY
■ DMS-100™ is a trademark of Northern Telecom Limited.
■ Dterm™ is a trademark of NEC Telephones, Inc.
■ Equinox™ is a trademark of Equinox Systems, Inc.
■ 5ESS
®
is a registered trademark of Lucent Technologies™.
®
is a registered trademark of cc:Mail, a subsidiary of Lotus
®
is a registered trademark of Lucent Technologies™
®
Voice Information System is a registered trademark of
®
is a registered trademark of Lucent Technologies™.
®
is a registered trademark of Lucent Technologies™.
■ INTUITY™ is a trademark of Lucent Technologies™.
■ Lotus Notes
®
is a registered trademark of Lotus Development
Corporation.
■ MEGAPORT™ is a trademark of Equinox Systems , Inc.
■ MEGAPLEX™ is a trademark of Equinox Systems, Inc.
■ Meridian™ is a trademark of Northern Telecom Limited.
■ MERL IN L EGEND
■ Microcom Networking Protocol
®
is a registered trademark of Lucent Technologies™.
®
is a registered trademark of Microcom,
Inc.
■ Microsoft
■ MS
■ MS-DOS
■ Mitel™ is a trademark of Mitel Corporation.
■ NEAX™ is a trademark of NEC Telephone, Inc.
■ NEC
■ Netware
■ Netware
■ Northern Telecom
®
is a registered trademark of Microsoft Corporation.
®
is a registered trademark of Microsoft Corporation.
®
is a registered trademark of Microsoft Corporation.
®
is a registered trademark of NEC Telephone, Inc.
®
is a registered trademark of Novell, Inc.
®
Loadable Module™ is a registered trademark of Novell, Inc.
®
is a registered trademark of Northern Telecom
Limited.
vi Issue 1 July 1997
Page 9

Trademarks and Service Marks
■ Novell
■ Parady n e
■ Phillips
■ Rolm
■ SL-1™ is a trademark of Northern Telecom Limited.
■ softFAX
■ SUPERSET™ is a trademark of Mitel Corporation.
■ SX-100™ is a trademark of Mitel Corporation.
■ SX-200™ is a trademark of Mitel Corporation.
■ SX-2000™ is a trademark of Mitel Corporation.
■ Telephony OneStip™ is a trademark of Lotus Development Corporation.
■ TMI™ is a trademark of Texas Micro Systems, Inc.
■ UNIX
■ Voice Bridge
®
is a registered trademark of Novell, Inc.
®
is a registered trademark of Lucent Technologies™.
®
is a registered tradema rk of Ph illi ps Sc re w C ompany.
®
is a registered trademark of International Business Machines.
®
is a registered trademark of VOXEM, Inc.
®
is a registered trademark of UNIX Systems Laboratories, Inc.
®
is a registered trademark of Voice Technologies Group,
Inc.
■ VOXEM
■ VT100™ is a trademark of Digital Equipment Corporation.
®
is a registered trademark of VOXEM, Inc.
■ Windows™ is a trademark of Microsoft Corporation.
Issue 1 July 1997
vii
Page 10

About This Book
Related Resources
If you need help with basic administrative procedures, see the
Messaging Solutions Release 4 Administration
How to Comment on This Book
We are always interested in your suggestions for improving this book. Please
complete and return the reader comment card that is located behind the title
page.
If the reader comment card has been removed, send your comments to:
Lucent Technologies
Product Documentation
Room 22-2H15
11900 North Pecos Street
Denver, Colorado 80234
Alternatively, you can fax your comments to:
Lucent I
(303) 538-1741
Please be sure to mention the name and order number of this book.
NTUITY Writing Team
I
NTUITY
book, 585-310-564.
™
viii Issue 1 July 1997
Page 11
Enhanced-List Application
Overview
This chapter describes the Enhanced-List Application (ELA) on an INTUITY™
®
AUDIX
Release 4 system.
1
Audience
Read this book if you are the AUDIX system administrato r respon si b le fo r the
configuration and maintenance of an I
What You Should Know
The procedures in this chapter assume you know basic Lucent INTUITY
commands and navigation, such as logging in and out of the system, the
difference between the VM and SA logins, command prompt function and usage,
and how to move from field-to-field within a screen or window.
If you are not familiar with Lucent I
I
NTUITY
Messaging Solutions Release 4 Administration
NTUITY AUDIX Release 4 system.
NTUITY system basics, please read Chapter 1 i n
before you continue.
Issue 1 July 1997 1
Page 12
Enhanced-List Application
Enhan c e d-List Applica tion
The Enhanced-List Application (ELA) greatly expands your business’ capability
to deliver messages to large numbers of recipients. A single enhanced list can
contain 1500 addresses and you – the system administrator – can create up to
100 such lists. Enhanced lists can be nested (or embedded) in each other, that
is, a list (containing 1500 addresses) can be a member contained in another list.
By doing so, your users can record a message, address it to the parent
enhanced list, and send it to nearly 150,000 people – just as easily as if the
message were being sent to a person 1 desk away.
All users administered in AUDIX (including e-mail and remote users) can send
messages to the recipients on enhanced lists, or you can administer your system
to only allow selected users in your AUDIX network access to the enhanced lists.
ELA has the following characteristics:
■ Up to 1500 recipients can be contained in an enhanced list (compared to
250 addresses in a standard AUDIX mailing list.)
■ Up to 100 enhanced lists can be created on an INTUITY AUDIX machine
■ Nesting (embedding an enhanced list within another Enhanced List)
enables a total recipient population of nearly 150,000
■ Changes in an enhanced list propagate to all lists that refer to the
changed list
■ Access to enhanced lists from anywhere within the AUDIX network
(standard AUDIX mailing lists are only accessible to those users with
mailboxes on the same machine as the lists)
■ Delivery to local and remote AUDIX users, administered e-mail users, and
remote AMIS pre-administered users
■ Cross-domain delivery from an e-mail trusted server to AUDIX. This
enables administered e-mail users to access the Enhanced Lists
What ELA Can Do for You
ELA can:
■ Distribute messages to a targeted audience.
You can create a list of people that you send messages to frequently.
Then, you can send them all the same message by entering one
enhanced-list address.
■ Centralize messages into one AUDIX mailbox.
First select one office as your primary location. Then create an enhanced
list at each secondary location that has, as its only member, the number of
your primary office location. When a mailbox at a secondary location
receives a message, ELA puts it into the mailbox for the primary office.
2 Issue 1 July 1997
Page 13
ELA Adminis t r ation
■ Forward messages to support staff automatically.
If you often forward incoming messages, you can create an enhanced-list
mailbox that automatically forwards messages to your staff. Your staff can
review the messages and then respond to them as they normally would.
ELA Administra t ion
Only the system administrator (sa) login can administer enhanced lists.
Basic Concepts
To understand ELA, you first need to understand some concepts and
terminology, such as
A
trusted server
NTUITY AUDIX that uses its own login and password to launch an IMAPI session
I
and access AUDIX mailboxes. The ELA software, acting as a trusted server, can
access and manipulate an AUDIX message just as the AUDIX application does.
is a computer or a software application in a domain outside of
trusted servers
and
domains
.
For the purposes of ELA, a
applica tio n . I
NTUITY AUDIX voice/fax mail messaging is one domain, and ELA is
domain
another domain. The two domains are linked together to allow messages to be
distributed between domains.
For a complete discussion and definition of trusted server and domain, see your
I
NTUITY
Messaging Solutions Release 4 Administration
Planning with Professional Services
ELA is a separately purchasable feature that incurs a Right-to-Use (RTU) fee.
ELA requires some solid planning to ensure your system makes effective use of
the feature. You can contract with Professional Services to work with you to plan
and administer ELA, or you can do the planning and administration yourself
using ELA worksheets that your account representative provides. In either case,
the result of that planning is comp leted ELA wo rk sheet s that you will us e as you
proceed to implement ELA.
ELA also requires some AUDIX Administration, as well as administration of the
ELA server itself.
is a logical boundary defined by the
book.
Issue 1 July 1997
3
Page 14

Enhanced-List Application
This administration can be divided as follows:
AUDIX Administration:
■ Contact Professional Services (or your account representative, if you did
not contract with Professional Services) to have ELA installed.
■ Contact Professional Services (or your account representative, if you did
not contract with Professional Services) to have ELA activated.
■ Verify that ELA is enabled for your system.
■ Increase the number of mailing lists AUDIX allows on the system.
■ Define an ELA Class of Service.
■ Set up ELA and shadow mailbox Community IDs.
■ Administer TCP/IP on the AUDIX server.
■ Define two ELA trusted servers to the AUDIX server and administer
access (including the surrounding security requirements).
■ Set up IMAPI sessions for ELA server access to AUDIX.
ELA Adminis t r ation:
■ Define the AUDIX server to the ELA servers and administer access.
■ Select shadow mailbox extension.
■ Create and administer the Enhanced List(s).
■ Record a name for the enhanced list (optional).
The next section highlights the planning considerations for implementing ELA.
Administration procedures begin with "Installing the Software" on page 2-9.
Things to Con s id er
ELA is a powerful messaging tool that can distribute large quantities of
messages. The following section discusses various planning considerations that
should be addressed to ensure effective implementation and use of ELA.
ELA Message Delivery
We recommend that you schedule delivery for large enhanced lists during
off-peak hours.
ELA can deliver up to 100 messages a minute. However, during peak traffic
hours, your system also processes other user-generated messages. ELA
intentionally slows delivery of messages to large enhanced lists during peak
traffic so your system can continue to process these other messages.
4 Issue 1 July 1997
Page 15

ELA Adminis t r ation
Hardware/Software Requirements
ELA runs on the same machine as AUDIX.
■ ELA must be installed on a Lucent INTUITY R4.2-4 or higher machine. If
your site has an earlier release, contact your Lucent service representative
to obtain the necessary upgrade. ELA is not available for pre-R4 Lucent
NTUITY systems.
I
■ MAP/40s machines require 64k of RAM.
LAN Impact
If your configuration includes a LAN, planning ELA implementation should
involve your PC/LAN administrator(s) to ensure that AUDIX and the network are
not adversely affected. The amount of LAN traffic on your system from ELA
messages could increase if ELA will be sending messages for delivery to an
e-mail or Message Manager recipient or to TCP/IP-networked remote machines.
If none of these are valid for your site, ELA will not cause any LAN traffic.
I
See Chapter 6 in your
book:
NTUITY
Messaging Solutions Release 4 Administra tion
■ If your site has e-mail, to calculate some initial traffic estimates
■ If your site has Message Manager, to calculate some initial traffic
estimates
Remote Message Impact
If your site is networked, estimate the increase in the amount of remote traffic by
first determining the percent of current traffic that is remote and calculating the
number of messages/minute that percent represents. When ELA is actively
sending messages, add that number of messages to the traffic estimate for
remote message delivery.
NOTE:
For typical applications of ELA, the increase in messaging traffic can be
negligible.
Issue 1 July 1997
5
Page 16

Enhanced-List Application
Port Usage Impact
Voice port usage increases as recipients retrieve messages sent by ELA. Plan for
the increase with Professional Services when you purchase ELA. Refer to the
worksheets that were compiled at the time of the purchase to determine the port
usage impact.
You should monitor your system to determine if your Grade of Service (GOS) falls
below acceptable levels. If that happens frequently, particularly during the peak
busy hour, contact your Lucent account representative to purchase more ports, if
necessary. For more information about GOS and monitoring your system , see
I
NTUITY
your
Messaging Solutions Release 4 Administra tion
NOTE:
If, in its application, ELA degrades service, you might suggest that those
users with access to enhanced lists schedule delivery of ELA messages for
off-peak hours, for example, at 10:00 p.m. or 4:00 a.m. That way, delivery of
messages will not conflict with other user-g enerat ed traff ic.
Security
book.
Securing a system that allows access from another domain involves a 2-pronged
approach. You must consider security from both an internal and an external
perspective. External security involves administration to prevent access from an
unauthorized source, such as an e-mail or AMIS-Analog message originator that
decides to send “mail bombs” to an Enhanced List. Internal security focuses on
preventing, or recovering from, damage if a breach occurs, for example, a virus
is transmitted in a message component such as an attached software file.
For an in-depth discussion and definition of such terms as
domain
, see your
I
NTUITY
Messaging Solutions Release 4 Administration
trusted server
and
book.
External Security
A new option — the trusted server — has been introduced in this release. The
ELA application runs as a trusted server, making requests of the AUDIX server,
via IMAPI, to distribute messages to designated recipients. The trusted server is
empowered to do anything to an ELA mailbox that an AUDIX user can do.
To prevent unauthorized access to AUDIX from an external source such as a
trusted server, system administrators have two levels of security at their disposal:
■ Trusted server password
■ IMAPI password
The trusted server password is administered on both the AUDIX server and on
the trusted server. The trusted server must use this password when it connects to
AUDIX.
6 Issue 1 July 1997
Page 17

ELA Adminis t r ation
The IMAPI password is an optional, secondary level of security used to prevent
an unauthorized source external to AUDIX from starting an IMAPI session. We
strongly recommend
If you choose to administer an IMAPI password, we recommend that you change
it on a regular basis, for example, monthly. (If you have set your administrator’s
password to age automatically, the system prompts you to change your
password. You can use this prompt to remind you to change the IMAPI password
as well.)
NOTE:
If you change an IMAPI password in AUDIX, all trusted servers must be
administered with the new IMAPI password. For example, if your I
AUDIX R4 supports an e-mail server, the e-mail administrator must also
administer the e-mail trusted server to reflect the new IMAPI password.
In addition to trusted server security, there is the possibility that an administered
e-mail or remote AMIS Analog user could use an ELA mailbox in an unauthorized
manner. One example is to send “mail bombs” to an Enhanced List. Mail bombs
are harassing messages that do not serve your business needs, and impose
unnecessary traffic on your system. ELA mailboxes are no more vulnerable to
unauthorized use than other voice mailboxes. However, the impact on system
performance can be many times greater than the potential for harassment when
sending messages to an individual mailbox. Sending to an enhanced list that
forwards a message to 1500 recipients will obviously have much farther reaching
consequences than that of a handful of messages sent to individual mailboxes.
that you take advantage of this extra protection.
NTUITY
To prevent unauthorized access to an ELA mailbox from an external source such
as e-mail users or remote AMIS Analog users, you can place those users in a
community with sending restrictions. See:
■ "Setting Up ELA and Shadow Mailbox Community IDs" on page 3-19 for
information about administering ELA community sending restrictions
■ “Setting Up Community Sending Restrictions” in Chapter 3 of your
Messaging Solutions Administration
guide for information about the
I
NTUITY
implications of administering Community IDs
Internal Security
INTUITY AUDIX R4 allows the transmission of 2 new message components, text
(originating from Message Manager or e-mail) and binary file attachments
(software files, such as a spreadsheet or word processing file). With these new
components come new security considerations, namely, the inadvertent delivery
of a virus that may be embedded in a file attachment. This can occur in any
system that supports the delivery of software files. While the AUDIX machine
Issue 1 July 1997
7
Page 18

Enhanced-List Application
cannot be infected with viruses embedded in these software files, client
machines may become infected when a user launches the applic ation
associated with the software file.
!
CAUTION:
ELA does not perform any virus detection. Your company should evaluate
the security risks of file attachments carefully and make provisions for virus
detection software on PCs running Message Manager or an e-mail
application supported by I
At a minimum, you should advise your users that file attachments should be
detached (not launched) and scanned for viruses before use.
IMAPI Session Requirements
An IMAPI session is invoked when an e-mail trusted server, Message Manager,
or the ELA trusted server needs to communicate with the AUDIX server. The
AUDIX server must have a sufficient number of IMAPI sessions administered to
provide adequate access for all IMAPI requests. Additionally, the ELA server
must be registered as an AUDIX trusted server.
NTUITY
AUDIX R4.
Shadow Mailbox
The shadow mailbox is a special mailbox that ELA uses to distribute messages.
The use of a shadow mailbox prevents replies to ELA-delivered messages from
being sent back to the entire Enhanced List. However, you can administer
enhanced lists such that recipients can reply to the person who originally sent
the message. The shadow mailbox must belong to a community that cannot
receive messages.
8 Issue 1 July 1997
Page 19
Installation
Overview
This chapter describes how to install ELA on a Lucent INTUITY R4.2 or higher
system.
2
Insta lling th e So ftware
The ELA package is provided on a tape labeled
To install ELA on a Lucent I
1. Log in to the Lucent I
2. Starting from the main menu, select:
> Customer/Services Administration
>System Management
>UNIX Management
>Software Install
The system displays the Software Install menu (Figure 2-1).
Enhanced-List Application
NTUITY R4.2 or higher system:
NTUITY system using craft or tsc.
.
Issue 1 July 1997 9
Page 20

Installation
Figure 2-1. Software Install Menu
3. Insert the tape labeled
Enhanced-List Application
into the tape drive.
4. Select:
> Tape drive
The system displays the message:
Insert a tape into the Tape Drive.
Type [go] when ready
or [q] to quit: (default: go)
5. Press to go ahead with the install.
ENTER
The system displays the message:
Installation in progress. Do not remove the tape.
The following packages are available:
1 ELA Enhanced List Application Package
Select package(s) you wish to process (or ‘all’ to
process all packages). (default: all) [?, ??, q].
NOTE:
If you receive a device open failure messag e, the tape was
after
inserted
you selected Tape Drive or the system did not see
the tape. In that case, complete step a through step d below.
10 Issue 1 July 1997
a. Enter q
The system displays the Software Install menu (Figure 2-1).
b. Remove the tape from the tape drive.
c. Re-insert the tape into the tape drive.
d. Repeat step 4 and step 5.
Page 21
Rebooting the System
6. Press to select all.
ENTER
The system installs the software and displays several status messages.
When the software installation is complete, the system displays the
message:
Installation of Enhanced List Application Package
was successful.
Insert a tape into the Tape Drive.
Type [go] when ready
or [q] to quit: (default: go)
7. Remove the tape from the tape drive and re-insert the back-up tape.
8. Enter q
9. Press (F6) repeatedly to return to the main menu.
CANCEL
10. Continue with the next procedure, ‘‘Rebooting the System’’.
Rebootin g the System
Rebooting is a 2-step process. First the voice system must be stopped, and then
the machine can be rebooted. To stop the voice system:
1. Starting from the main menu, select:
> Customer/Services Administration
> System Management
> System Control
>Stop Voice System
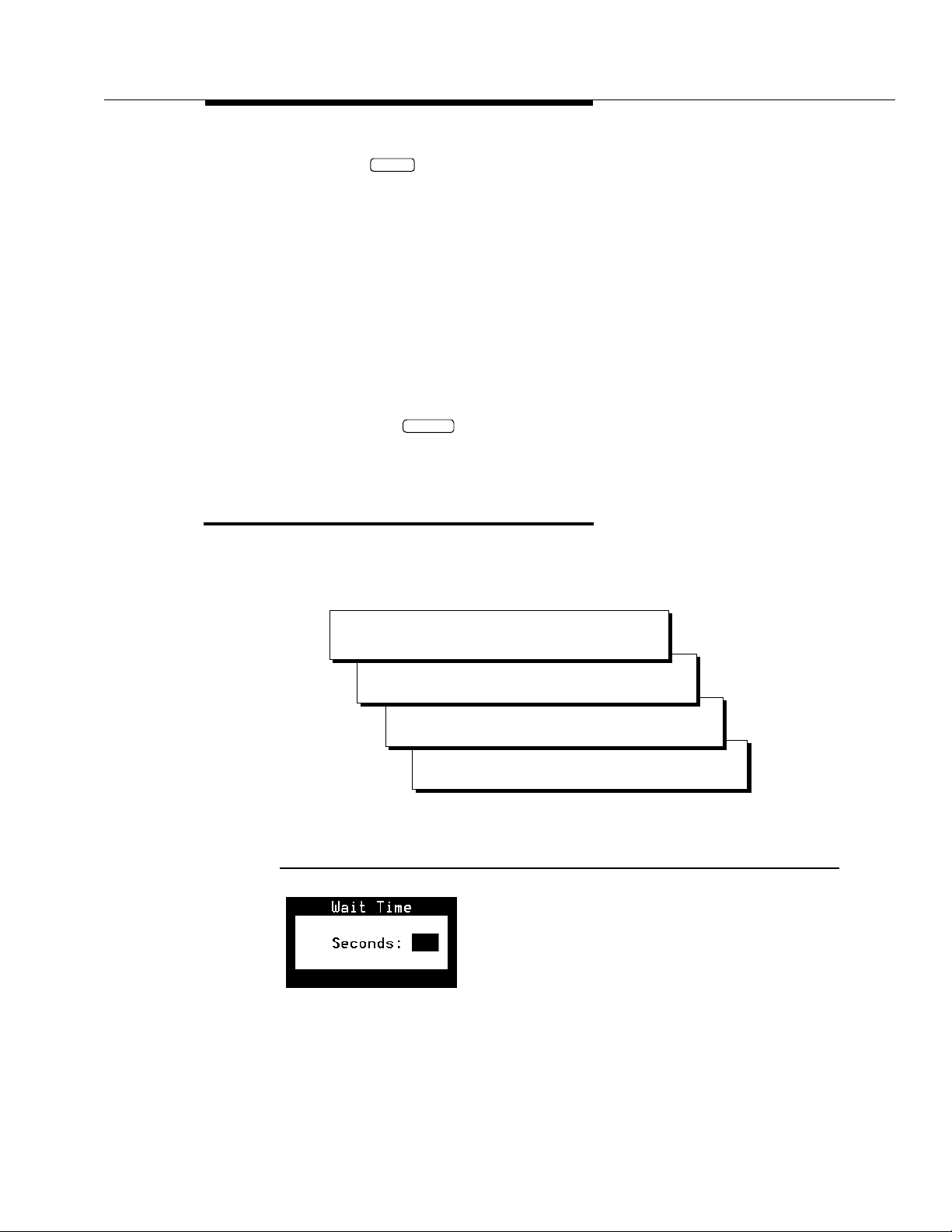
The system displays the Wait Time window (Figure 2-2).
Figure 2-2. W a it Time Window
2. Enter 60 in the Seconds: field to have the system wait one minute for
calls in progress to finish before stopping the voice system.
Issue 1 July 1997
11
Page 22
Installation
3. Press (F3) .
SAVE
The system stops the voice system and displays the a series of status
messages. When the voice system has stopped, the system displays the
message:
The Voice System has stopped.
Press Enter to Continue.
4. Press .
5. Press (F6) .
ENTER
CANCEL
The system displays the System Control window.
6. Select
>Shutdown System
The system displays the Wait Time window (Figure 2-2).
7. Enter 0 (zero) to indicate you would like an immediate shutdown.
8. Press (F3) .
SAVE
The system displays the following message:
Shutdown started.
When the system is completely shut down, the system displays the
message.
The system is down.
Press Ctrl-Alt-Del to reboot your computer.
9. Make sure that there is no diskette in the diskette drive.
10. Press .
CONTROL ALT DEL
The system performs a power-on self test (POST). The screen lists various
hardware components and the status of the tests performed on those
components.
When the reboot is complete, the system displays the following prompt:
Startup of the Voice System is complete.
Console Login:
12 Issue 1 July 1997
Page 23

Administering AUDIX for ELA
Overview
To define the ELA server and functionality to AUDIX:
■ Contact Professional Services (or your account representative, if you did
not contract with Professional Services) to have ELA installed.
3
■ Contact Professional Services (or your account representative, if you did
not contract with Professional Services) to have ELA activated.
■ Verify that ELA is enabled for your system.
■ Increase the number of mailing lists AUDIX allows on the system.
■ Define an ELA Class of Service.
■ Set up ELA and shadow mailbox Community IDs.
■ Administer TCP/IP on the AUDIX server.
■ Define two ELA trusted servers to the AUDIX server and administer
access (including the surrounding security requirements).
■ Set up IMAPI sessions for ELA server access to AUDIX.
Depending on what services your business purchased from Professional
Services during the planning phase for ELA, some of the following procedures
I
NTUITY
may already be done. See your
Administration
book.
Messaging Solutions Release 4
Issue 1 July 1997 13
Page 24

Administering AUDIX for ELA
Activatin g ELA
After the ELA installation is complete, contact your Professional Services (or your
account representative, if you did not contract with Professional Services). The
technician from the remote support center w ill acce ss your system remotely and
activate the ELA feature.
When the remote support center has activated the ELA feature, continue with the
next procedure.
NOTE:
You must log off the system and log back on to get enhanced lists to
display as an option on the Lucent I
Verifying that ELA is Enabled
1. Log into the Lucent INTUITY system using sa.
NTUITY main menu.
The system should display the Lucent I
Enhanced-List Manager as a menu option (Figure 3-1).
Figure 3-1. L uc ent INTUITY Main Menu for Release 4 (with ELA)
2. If Enhanced-List Manager does not display on the main menu, select:
> Customer/Services Administration
> Feature Options
NTUITY main menu with
The system displays the Feature Options window.
14 Issue 1 July 1997
Page 25

Increas ing t h e N umber of Mailin g L ists A llo we d o n the
System
3. Ensure the following fields are set to ON:
■ Enhanced List Application
■ TCP/IP Administration
4. If either of these fields is OFF, and you purchased/installed ELA, call the
support center to request that the features be enabled for your Lucent
NTUITY platform.
I
5. Press (F6) to exit this window.
CANCEL
Increasin g the Number of Ma il ing
Lists Allowed on the System
The following task contains instructions for the fields that relate directly to ELA.
See “Field Definitions: System-Parameters Limits Screen” in Chapter 3 of your
I
NTUITY
Messaging Solutions Administration
and to understand their implications.
To administer AUDIX system limits to support ELA:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> AUDIX Administration
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
change system-parameters limits ch sys li
The system displays the System-Parameters Limits screen.
guide for complete field descriptions
3. Tab to the Lists, Total Entries: field and enter 200000.
4. The Lists/Subscriber field has a default value of 100. If this setting
has changed, enter a value of 15 or greater.
If the default value has not changed, skip this step.
5. The Recipients/Lists field has a default value of 250. If this setting
has changed to less than the default, enter a value of 250.
If the default value has not changed, skip this step.
NOTE:
If there was an administra tive reason f or reduc ing the value in this
field, your system may not be able to support ELA. Review your
system configuration and business needs to determine the
implication of returning this setting to 250.
Issue 1 July 1997
15
Page 26

Administering AUDIX for ELA
6. Press (F3) to save the information in the system database.
ENTER
The cursor returns to the command line, and the system displays the
message Command Successfully Completed.
7. Continue with the next procedure or enter exit to leave AUDIX
Administration.
Defining an ELA C la s s of Servic e
The following task contains instructions for the fields that directly relate to ELA.
The other fields should be admi niste re d to supp ort all capab ilities tha t you
anticipate using, that is, maximum call answer length, announcement set, etc.
I
NTUITY
See your
explanations of the other fields on these screens, and their implications.
NOTE:
ELA can take up to 12 hours to show the changes you make to subscriber
information in I
Before you begin the following p rocedure, ensure t hat you have an unused Class
of Service that you can define for ELA. We recommend that you use a COS that is
between 2 and 11. (Customers often use COS 1 as their default Class of Service).
Messaging Solutions Release 4 Administration
NTUITY AUDIX.
book for
To administer a COS for ELA:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> AUDIX Administration
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
change cos
where
COS_number
COS_number
ch cos
COS_number
is the unique Class of Service you would like to use
for ELA. For example, enter ch cos 10.
The system displays the Class of Service screen (Figure 3-2).
16 Issue 1 July 1997
Page 27

Defining an ELA Class of Service
Figure 3-2. Class of Service Screen, Page 1; Defining a Class of Service for ELA
3. Although not required, we recommend that you change the name of the
COS to be more descriptive , fo r ex ampl e , e nte r ELA in th e Name: field.
NOTE:
You should write down the CO S num ber. You will need it later when
you administer the ELA server.
4. If you would like ELA to be able to distribute call answer messages, enter
call-answer in the Type: field (under PERMISSIONS:). Otherwise, enter
none.
NOTE:
If you administer your system such that ELA mailboxes are to be
accessible only by direct addressing and later decide you would like
some ELA mailboxes with call answer capability, you do not need to
create two Classes of Service. Administer the ELA COS to be call
answer, but only administer the ELA mailbox extension as a number
on the switch if/when you decide to allow call answer messages to
be distributed to the members of that Enhanced List.
5. Enter y in following fields (under PERMISSIONS):
■ Priority Messages?
■ Fax? (If you have purchased fax)
■ Trusted Server Access?
6. Press (F7) . The system displays page 2 (Figure 3-3).
NEXTPAGE
Issue 1 July 1997
17
Page 28

Administering AUDIX for ELA
1
Figure 3-3. Subsc ri ber C l ass of Se rv ic e Para m et e rs Sc re en, Pa ge 2; Ena bl ing ELA on a
COS Basis
7. Enter the following information:
■ 14 in the Retention Times (days), New: field. (This setting
acts as a safety measure, should ELA encounter an operational
problem, and cannot send messages for a couple of days.)
■ 14 in the Retention Times (days), Old: field. (Ordinarily,
there are no old or unopened messages. ELA will forward
old/unopened messages in the event service is interrupted.)
■ 14 in the Retention Times (days), Unopened: field.
(The same explanation holds true for this field, as well.)
■ nudaf in the Outgoing Mailbox, Category Order: field
■ 0 in the Retention Times (days), File Cab: field
■ 1 in the Delivered/Nondeliverable: field
■ 6 in the Maximum Mailing Lists: field
■ 1500 in the Total Entries in all Lists: fiel d
■ 32767 in the Mailbox Size, Maximum Length: field
NOTE:
Administer the other fields to be consistent with the
messaging needs of your business.
18 Issue 1 July 1997
Page 29
Setting Up ELA and Shadow Mailbox Community IDs
8. Press (F3) to save the information in the system database.
ENTER
The cursor returns to the command line, and the system displays the
message Command Successfully Completed.
9. Continue with the next procedure or enter exit to leave AUDIX
Administration.
Setting Up ELA and Shad ow Mailbox
Community IDs
The following task contains instructions that directly relate to ELA. “Setting Up
Community Sending Restrictions” in Chapter 3 of your
Solutions Administration
Commun ity ID s in more detail.
Things to Con s id er
ELA mailing lists are a powe rful messagin g t oo l that all users in your AUDIX
network can access. However, should your business needs indicate differently,
you can control who can use the enhanced lists by administering community
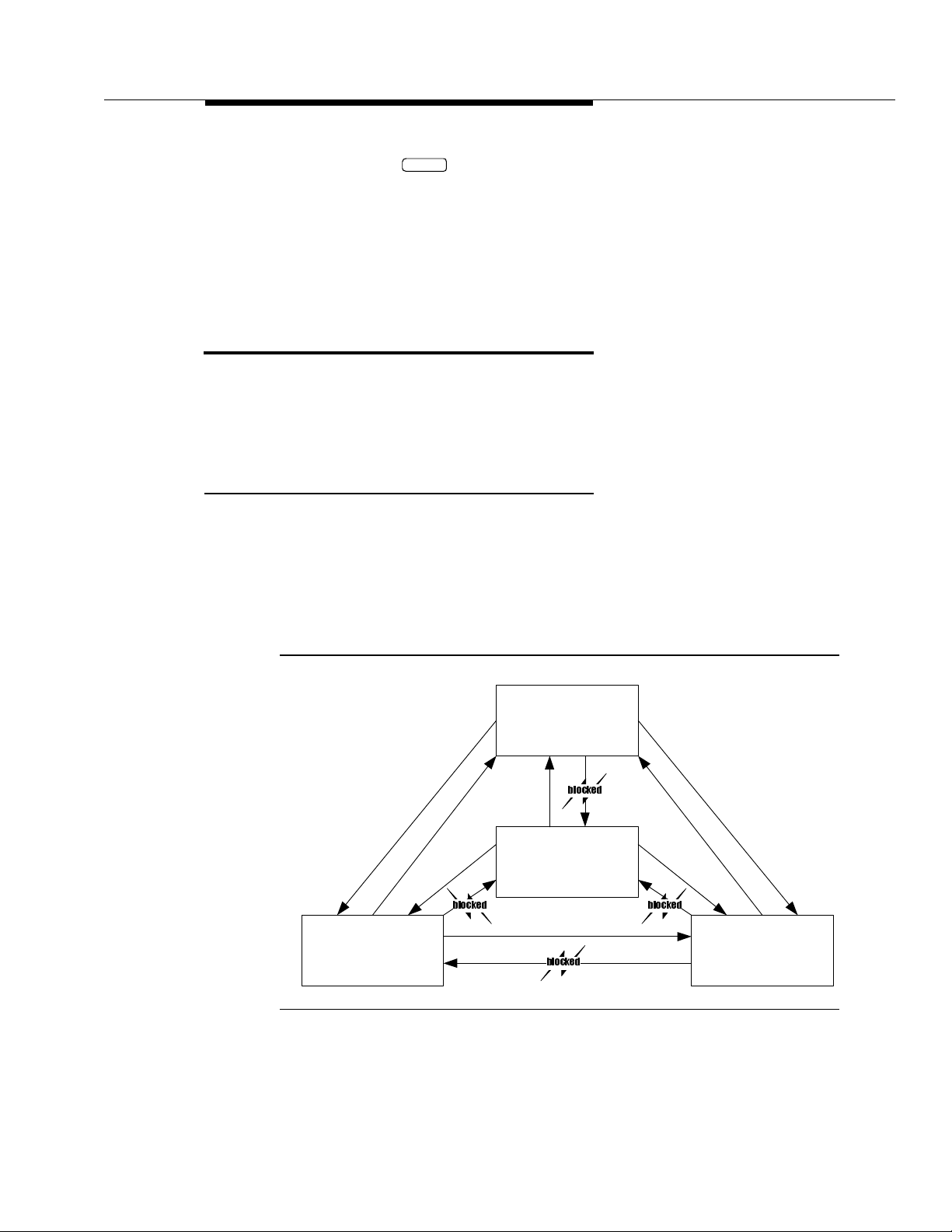
sending restrictions. Figure 3-4 illustrates a typical application of sending
restrictions for ELA and this application of sending restrictions is used as a basis
for the following discussion.
guide discusses the purpose and implementat ion of
I
NTUITY
Messaging
Community 9
Subscribers with enhanced
list privileges
BLOCKED
Community 11
ELA Shadow Mailbox
BLOCKEDBLOCKED
Community 10
Enhanced-List Mailboxes
BLOCKED
Community 1
General Subscribers
Figure 3-4. Example of Communities Administered for use with ELA
Issue 1 July 1997
19
Page 30

Administering AUDIX for ELA
Let’s say you set up the enhanced-list mailbox community to be Community 10.
Community 10 is given permission to send to all other communities (except the
shadow mailbox community). Then, you set up a special user community,
Community 9, and administer Community 9 to send to all communities (except
the shadow mailbox community). Only users you would like to have access to the
enhanced lists are placed into Community 9. All other users would not be able to
send a message to the ELA mailbox.
Additionally, you must set up a shadow mailbox community ID, for example
Community 11. The shadow mailbox community ID is administered such that
messages can be sent to any community, but messages cannot be received
from any other community. You do this so replies from pre-Release 4 Lucent
NTUITY machines or from DEFINITY AUDIX and AUDIX R1 machines do not go to
I
the shadow mailbox.
Also, you w ill ha v e to administe r the re st o f yo ur user populatio n to be long to a
community restricted from sending messages to the enhanced-list mailbox
community, for example, the default Community 1.
NOTE:
If your AUDIX system is networked with other Lucent INTUITY systems, all
enhanced-list mailbox community sending restrictions must be consistently
applied throughout the system, that is, the same Community ID numbers
administered with the same restrictions. In particular, the shadow mailbox
community must not be accessible by any other commun ity on any
machine in the network.
Before You Begin
Before you begin the following procedure, use the display system-parameters
sending restrictions
at least two Communities that you can use for ELA (4 communities are needed if
you are going to implement a special community for selected users with access
to ELA mailboxes.)
ELA Comm u n ity ID
To set up sending an ELA Community ID:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> AUDIX Administration
command in AUDIX administration and ensure that you have
20 Issue 1 July 1997
Page 31

Setting Up ELA and Shadow Mailbox Community IDs
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
change system-parameters sending-restrictions ch sy s
The system displays the Sending Restrictions screen (Figure 3-5).
Example administr ation for:
Users w/ access to ELA in Comm ID = 9*
Enhanced List Mailbox Comm ID = 10
Shadow Mailbox Comm ID = 11
Default User Comm ID = 1*
* Optional administration unless you are limiting
user access to Enhanced Lists
This is required, but can use a
different Comm ID # (see step 4).
This is required, but can use a
different Com m ID # (see step 5).
Figure 3-5. Sending Restrictions Screen
3. Enter y in the Activate Restrictions? field.
4. Leave all fields
blank (horizontally) that correspond to the (sender)
Community ID that you’ve assigned to ELA, and leave all fields
(vertically) that correspond to the (recipient) Community ID you’ve
assigned for users who will have access to the Enhanced Lists. (If all
users are to have access to Enhanced Lists, the recipient communi ty will
be the default user community — usually community 1.)
Following the example discussed under "Things to Consider" on page
3-19, Sender Community 9 would be blank (horizontally from left to right)
and Recipient Community 10 would be blank (vertically from top to
bottom).
5. If all users are to have access to Enhanced Lists, skip this step.
Enter an r in the field that corresponds to the intersection between the
(recipient) ELA Community ID and the (sender) community to which the
rest of the user population belongs. This prevents those who do not have
blank
Issue 1 July 1997
21
Page 32

Administering AUDIX for ELA
access to enhanced lists from sending a message to an Enhanced List.
Following the example discussed under "Things to Consider" on page
3-19, there would be an r in the field corresponding to the intersection
between Sender Community 1 (the default user community) and Recipient
Community 10 (the Enhanced List Mailbox Community).
Shadow Mailbox Community ID
6. Enter an r in all (recipient community) fields in the column that
corresponds to the Community ID that you’ve assigned to the shadow
mailbox. This prevents messages from being sent into the shadow
mailbox.
Following the example discussed under "Things to Consider" on page
3-19, Recipient Community 11 would contain r’s (vertically from top to
bottom).
7. Press (F3) to save the information in the system database.
ENTER
The system displays the message Command Successfully
Completed, and the cursor returns to the command line.
8. Continue with the next procedure or enter exit to leave AUDIX
Administration.
NOTE:
You must now use the Change Subscriber or Change COS screen to
assign your users to either the community that does not have access to
Enhanced Lists, or to the special community that does have access. If you
used your default user community (Community 1) as the community that
does not have access, then you only have to administer those selected
individuals who will belong to the new special community with access to
Enhanced Lists.
22 Issue 1 July 1997
Page 33

Administering TCP/IP
Administering TCP/ IP
If your system is already connected to the LAN, you can skip this procedure.
However, you need to know the IP Address to administer the trusted server, so —
even if your system is already networked — perform step 1 of t his p rocedure and
write down your system’s IP address.
TCP/IP is a set of protocols that links computers across a wide variety of
networks. TCP/IP must be administered for the ELA trusted server to
communicate with AUDIX.
Before You Begin
You will need to know the:
■ Network IP address
■ Host Identifier (AUDIX server name)
■ Subnet mask
■ Gateway Identifier (ID) to administer TCP/IP
Your PC/LAN system administrator should have this information.
!
CAUTION:
Administering TCP/IP requires that you stop and restart the voice
messaging software. Plan to do this procedure at a time when your
business can tolerate some down time on your AUDIX system.
To administer TCP/IP Networking:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> Networking Administration
> TCP/IP Administration
The system displays the TCP/IP Administration window (Figure 3-6).
Issue 1 July 1997
23
Page 34

Administering AUDIX for ELA
TAB
Figure 3-6. TCP/IP Administration Window; Administering TCP/IP for
Enhanced-List Application (ELA)
2. Enter the AUDIX server name in the UNIX Machine Name: field. This
name should be listed on the
can obtain this name from your PC/LAN administrator. This is a
case-sensitive field, so capital letters must be typed as capitals, and
lowercase letters as lowercase.
NOTE:
This name must be the same as the local machine name specified
on the Local Machine Administration screen. It cannot start with a
number and cannot contain any embedded spaces, for example,
denver 1 is not allowed, but denver_1 is allowed.
Installation Information worksheet, or you
3. Enter the IP (Internet Protocol) address in the IP Address: field and
press . This is the Lucent I
NTUITY system’s address. Your PC/LAN
system administrator should have this information.
If your system is not connected to a LAN, enter any number in the format
w.x.y.z, where each letter is a number, 0 to 255.
NOTE:
Write this IP address down, as you will need it when you administer
the ELA trusted server later in this section.
4. Enter the subnet mask in the Subnet Mask: field.
The subnet mask is used to determine which bytes of the IP address
specify the network and host addresses. This is an optional field. If there is
no entry for this field on your worksheet, leave the field blank. The system
will automatically use a default.
NOTE:
The default value may conflict with your LAN configuration. Check
with your PC/LAN system administrator to ensure compatibility.
24 Issue 1 July 1997
Page 35
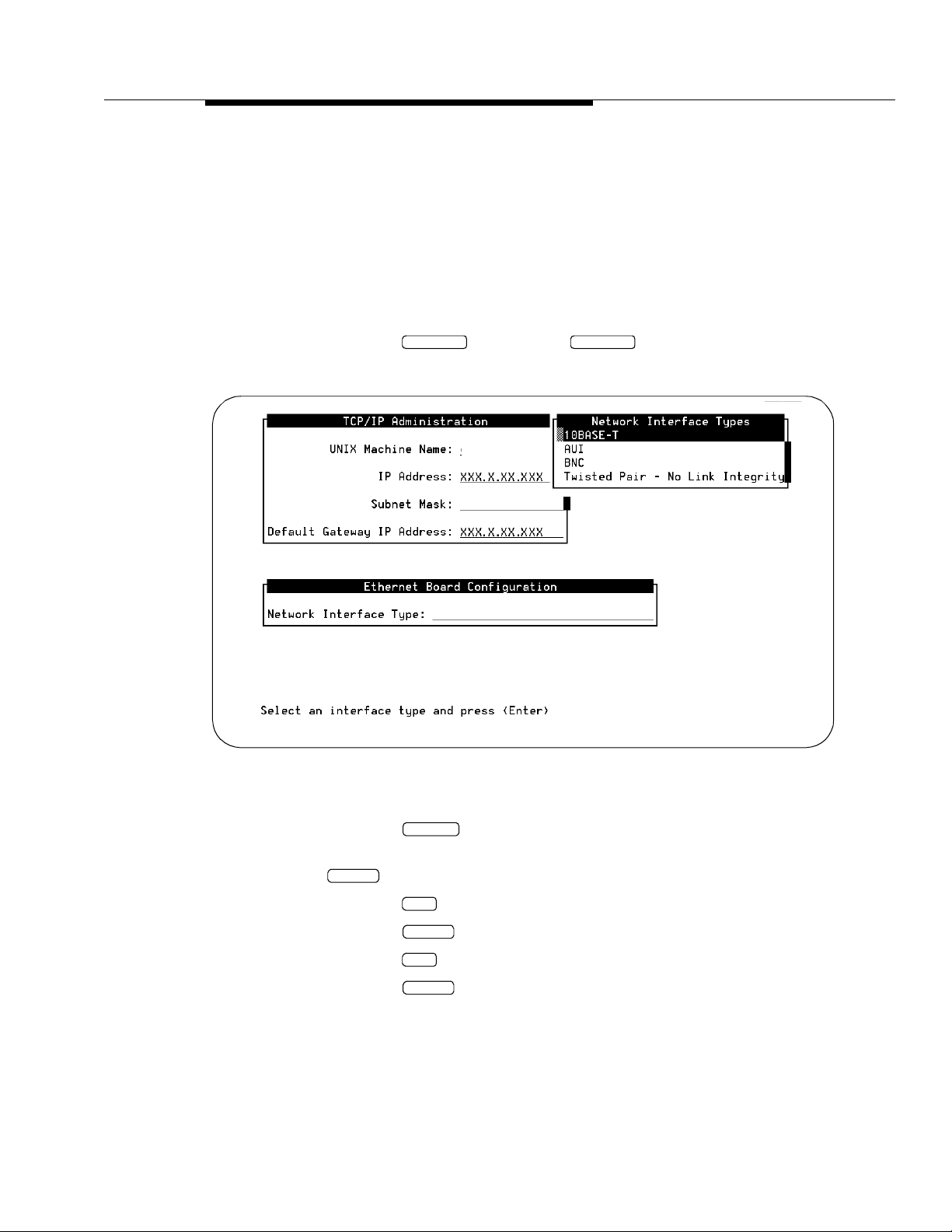
Administering TCP/IP
5. Enter the de fau l t gat ew a y IP a ddre s s in the Default Gateway IP
Address: field.
The default gateway IP address is the address of the gateway router that
serves to connect to addresses on other LANs. This field is left blank if the
Lucent I
the same LAN.
If your system is not connected to a LAN, enter the number you made up
for step 3.
NTUITY system will only be communicating with other machines on
6. Press (F8) and then (F2) . The system displays the
CHG-KEYS BRD CNFG
Ethernet Board Configuration window (Figure 3-7).
denver1
Figure 3-7. Ethern et Bo ar d C onfi gu r at io n Win do w ; Ad m in ist eri ng TCP/IP for
Enhanced-List Application (ELA)
7. Press (F2) to display a list of the network interface types.
CHOICES
8. Highlight the network interface type to be used on this system and press
RETURN
9. Press (F3) to save the Ethernet Board configuration.
10. Press (F6) twice.
11. Press (F3) to save the TCP/IP administration values.
12. Press (F6) repeatedly to return to the main menu.
. Your PC/LAN system administrator should have this information.
SAVE
CANCEL
SAVE
CANCEL
13. Continue with the next procedure.
Issue 1 July 1997
25
Page 36

Administering AUDIX for ELA
NOTE:
The changes to your system will not take effect until you reboot your
I
NTUITY
system. See your
book for instructions.
Messaging Solutions Release 4 Administra tion
Setting Up IMAPI Sessions for
Trusted Server Access
Whenever a trusted server accesses an AUDIX mailbox, it uses an IMAPI
session. IMAPI is the software that allows access to I
Depending on what I
sessions simultaneously, some of which you need to set for trusted server use.
NOTE:
IMAPI sessions cannot be reserved for use by ELA. The following
procedure administers the maximum number of IMAPI sessions you will
allow trusted servers to use simultaneously, but does not guarantee that an
IMAPI session will be available. You should monitor ELA trusted server
activity to see if trusted server requests for IMAPI sessions are frequently
being denied because all sessions are in use (see your
Solutions Release 4 Administration
more IMAPI sessions.
NTUITY model you purchased, there can be up to 96 active
NTUITY AUDIX mailboxes.
I
NTUITY
Messaging
book). If so, you may need to purchase
To set IMAPI sessions for trusted server use:
1. Starting from the main menu, select:
> AUDIX Administration
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
change system-parameters imapi-options ch sy i
The system displays the System-Parameters IMAPI-Options screen
(Fi gur e 3-8).
26 Issue 1 July 1997
Page 37

Setting Up IMAPI Sessions for Trusted Server Access
n
n
Figure 3-8. System-Parameters IMAPI-Options Screen, Page 1; Setting IMAPI Sessions
for Truste d Serv er Ac ces s
NOTE:
The following contain instructions for the fields that directly relate to ELA.
See your
Messaging Solutions Release 4 Administra tion
book. for
I
NTUITY
complete field descriptions and to understand their implications.
3. In the Maximum Simultaneous Sessions: field enter 2 more than the
current value. (For example, if the field currently reads 30, enter 32.)
This number includes sessions for users who are logged into their
mailboxes using Message Manager or an e-mail application supported by
NTUITY AUDIX R4, if applicable, and cannot exceed the value in the
I
Total Sessions Purchased field.
4. In the Simultaneous Sessions Available for Trusted Server
Access: field enter 2 more than the current value. (For example, if the
field currently reads 2, enter 4.)
The maximum value for this field is 4 for MAP/40s and MAP/40 or
6 for MAP/100.
5. Enter 5 in the IMAPI Session Timeout: field.
6. Enter 5 in the Trusted Server Session Timeout: fiel d.
7. Enter y in the Message Transfer? field.
Issue 1 July 1997
27
Page 38

Administering AUDIX for ELA
8. Press (F3) to save this information to the system database.
The cursor returns to the command line, and the system displays the
message Command Successfully Completed.
9. Continue with the next procedure or enter exit to leave AUDIX
Administration.
ENTER
Defining Two ELA T rusted Ser vers
The ELA software runs as two separate trusted servers. For the ELA servers to
communicate with the I
AUDIX system. The installation worksheets you received from your account
represent a t iv e w ill ha v e the exact nam es for the ELA trusted ser v er s. H o we v er ,
for the purposes of this document, the first ELA trusted server will be referred to
administrative server
as the
.
server
A request from ELA to send a message to an AUDIX mailbox involves invoking an
IMAPI session and locking the ELA mailbox. A server that uses IMAPI to access
an AUDIX mailbox is known as a trusted server.
!
SECURITY ALERT:
The procedures in this section include setting a password the trusted
server must use to access AUDIX. There is a secondary layer of security (in
addition to a trusted server password) that you can administer. This
additional layer of security involves setting a separate IMAPI password that
the trusted serv er must use before the syst em will all ow an IMAPI sessi on to
be invoked.
NTUITY AUDIX server, they must be defined to the INTUITY
and the second ELA trusted server as the
delivery
While administration of this additional password is optional, it is strongly
recommended.
Administration
Before You Begin
Before adding the ELA trusted server to the system, you will need the following
information:
■ Two unique 1- to 10-printable character server names for the ELA trusted
servers. These server names must be unique, not only from each other,
but from all other machines in the network (including fax call delivery
machines). Use the li ma and li tr commands to view all machines
currently in your network.
Additionally, the server names must comply with the guidelines for naming
machines your
book for complete information on naming conventions).
28 Issue 1 July 1997
See your
book.
I
NTUITY
I
NTUITY
Messaging Solutions Release 4
Messaging Solutions Release 4 Administration
Page 39
Defining Two ELA Trusted Servers
■ The TCP/IP address for the AUDIX server (see page 3-23).
You will perform this procedure twice, first for the ELA administrative server, and
then for the ELA delivery server. To add the ELA trusted servers to the I
AUDIX server:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> AUDIX Administration
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
add trusted-server ad tr
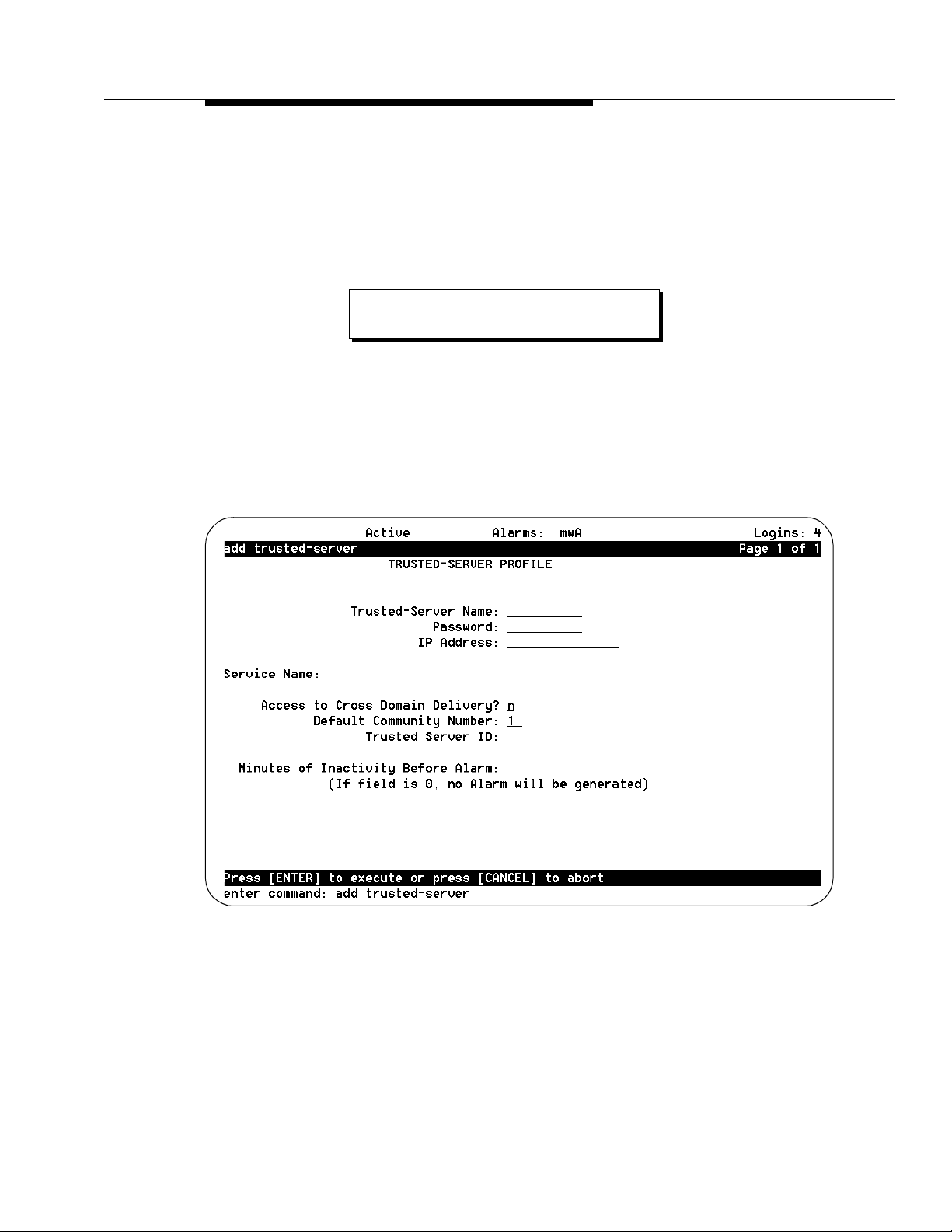
The system displays the Trusted-Server Profile screen (Figure 3-9).
NTUITY
(To see a list of existing trusted servers enter
drmid10
li tr at the command line.)
Figure 3-9. Trusted- Server Prof ile Screen; Defin ing a Trusted Serve r to the Lucent
NTUITY System
I
Issue 1 July 1997
29
Page 40

Administering AUDIX for ELA
3. In the Trusted-Server Name: field, enter a name for the first ELA trusted
server. (See the Note below for tips on trusted server names.)
This name must be a unique 1- to 10-printable character entry.
Additionally, this name cannot start with a number and cannot contain any
embedded spaces, for example, denver 1 is not allowed, but denver_1 is
allowed. (Use the li tr and li ma commands to view existing names and
ensure that you are not using a name that is already assigned.)
NOTE:
You must administer two ELA trusted servers. The installation
worksheets should have the ELA trusted server names. If not, we
recommend that you use names that are descriptive enough that you
can tell them apart, for example, enter the first ELA trusted server
name as ela_admin and, when you add the second ELA trusted
server, use ela_deliv.
4. Enter a 5- to 10-alphanumeric password that the trusted server must use
to log on to the AUDIX server. As you type, your keystrokes display, but
will appear as a series of asterisks (
5. Enter the TCP/IP address of this Lucent I
each letter is a number, 0 to 255. (See page 3-23 for information how to
determine your system’s IP address.)
) after you save.
*
NTUITY in the form w.x.y.z, where
6. Enter Enhanced-List Application in the Service Name: field. Type
exactly as listed, including the hyphen and capitalization.
Every ELA serv er w ill ha v e the same servi ce na m e . (Fo r exa mple, if you
have two ELA servers, they will have separate trusted server names, but
the same serv i ce na me.)
7. Enter n in the Cross-Domain Delivery? field.
8. For the administrative ELA trusted server (ela_admin), enter 0 in the
Minutes of Inactivity Before Alarm: field.
For the delivery ELA trusted server (ela_deliv), enter 255 in the Minutes
of Inactivity Before Alarm: field
9. Press (F3) to save the information in the system database.
ENTER
The cursor returns to the command line, and the system displays the
message Command Successfully Completed.
10. You must now add the delivery ELA server. Return to step 2, and repeat
this procedure, ensuring that you use a unique name for the delivery
trusted server, that is, do not use the name of the ELA trusted server you
just added.
30 Issue 1 July 1997
Page 41

Defining Two ELA Trusted Servers
11. Do you want to administer an IMAPI password?
■ If yes, follow the procedures for setting the IMAPI password in your
I
NTUITY
Messaging So lut ions Release 4 Administra tio n
proceeding to the next section.
■ If no, go to Chapter 4 to Administer ELA, or enter exit to leave
AUDIX Administration.
book before
Issue 1 July 1997
31
Page 42

Administering AUDIX for ELA
32 Issue 1 July 1997
Page 43
Administer ing ELA for AU DIX
Overview
Now that the AUDIX syst em knows abou t the ELA t rusted server s, you can do the
initial administration of the ELA system. To make ELA fully functional, you must:
4
■ Define the AUDIX server to ELA and administer access
■ Create enhanced lists
■ Add members to enhanced lists
■ Record a name for the enhanced lists (optional)
Defining the AUDIX server and
Administering Access
To allow communication between ELA and AUDIX, you must perform some initial
ELA administration.
Before You Begin
To administer the ELA server, you will need to know the:
■ The sa or vm password
■ IMAPI password (Optional, see your
4 Administration
■ ELA administrative trusted server name and password (see page 3-28)
■ ELA delivery trusted server name and password (see page 3-28)
book)
I
NTUITY
Messaging Solutions Release
■ A currently unused extension to use as the shadow mailbox
Issue 1 July 1997 33
Page 44

Administering ELA for AUDIX
■ Enhanced-list mailbox and shadow mailbox Community IDs (see page
3-20)
■ ELA Class of Service (see page 3-16)
To administer the ELA server:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> Enhanced-List Manager
> Set Up Enhanced-List System Data
The Set Up Enhanced-List System Data window displays (Figure 4-1).
Figure 4-1. Set Up Enhanced-List System Data Window
2. Complete the fields in this window using the information in Table 4-1.
34 Issue 1 July 1997
Page 45

Defining the AUDIX server and Administering Access
Table 4-1. Field Definitions: Set Up Enhanced-List System Data Window
Field Name Description/Pro cedure
System Login:
Valid Input
sa, vm
System Password:
Valid Input
6- to 8-alphanumer ic
characters
IMAPI Passwor d :
Valid Input
0- to 8-alphanumer ic
characters
:
:
:
Enter sa (system administrator login) or vm (voice mail
administrator login).
NOTE:
Administrat ors using the vm login cannot administer
enhanced lists or ELA tr usted servers. This field allows
ELA to log into AUDIX
Enter your sa or vm administration password.
The ELA server uses this passwor d to perf orm AUDIX
administration functions, such as adding or deleting an
enhanced-list mailbox.
If you decided to require that trusted servers use an IMAPI
password, enter the IMAPI password you administered in
AUDIX.
Some AUDIX functions do not require passwords.
■ If a password is required, then the one you enter here must
match that password exactly.
■ If a password is not required, you can delete any existi ng
password as follows:
1. Open the Set Up Enhanced-List System Data window.
2. Enter some characters into the
3. Press until all the characters you entered have
4. Press (F3) to save your changes.
Backspace
been deleted.
SAVE
.
IMAPI Password: field.
Administrative Trusted-Serve r
Name:
Valid Input
1- to 10-alphanu meric
characters
:
Enter the Administrative trusted ser ver name that you
administered in AUDIX.
This name should be listed on the Installa ti on Information
worksheet. This fi eld is case-sensitive, so capital let ters must be
typed as capitals, and lowercase letters as lowercase.
This name cannot start wit h a numbe r and cannot contain any
embedded spaces, for example, denver 1 is not allowed, but
denver_1 is allowed.
NOTE:
The ELA trusted server must be added in AUDIX before
you can complete this procedure
.
Continued on next page
Issue 1 July 1997
35
Page 46

Administering ELA for AUDIX
Table 4-1. Field Definitions: Set Up Enhanced-List System Data Window —
Field Name Description/Procedure
Password:
Valid Input
5- to 10-alphanu me ri c
characters
Delivery Trusted-Server Name:
Valid Input
1- to 10-alphanu me ri c
characters
:
:
Enter the Administrative trusted ser ver password (see
page 3-30).
Enter the name of the delivery trusted server that you
administered in AUDIX. (This is the second ELA trusted server
you added.)
This name should be listed on the
worksheet. This fi eld is case-sensitive, so capital letters must be
typed as capitals, and lowercase letters as lowercase.
This name cannot start wit h a numbe r and cannot contain any
embedded spaces, for example, denver 1 is not allowed, but
denver_1 is allowed.
Installa ti on Information
NOTE:
The delivery t rusted server must be added in AUDIX
Password:
Valid Input
1- to 15-alphanu me ri c
characters
SHADOW MAILBOX
ATTRIBUTES
Mailbox Extension:
Valid Input
3- to 10-numeric characters
:
:
before you can complete this procedure
Enter the delivery tr usted server password.
Enter the
!
extension to be use d for the shadow mailbox.
WARNING:
This mailbox must NOT currently exist in AUDIX and must
not be translated on the switch.
.
Continued
SHADOW MAILBOX
ATTRIBUTES
Community ID:
Valid Input
a number from 2 to 15
:
36 Issue 1 July 1997
When the system validates this form, ELA automat ically creates
a shadow mailbox.
Enter the number of the community assigned to the shadow
mailbox. This canno t be the same number as the enhanced-l ist
mailb o x Community ID .
The shadow mailbox communi ty must be administered to be
able to send messages to all other communities, but to not be
able to receive message s from any other community. See
"Setting Up ELA and Shadow Mailbox Com mu nity IDs" on
page 3-19.
Continued on next page
Page 47

Guidelines for Naming Enhanced Lists
Table 4-1. Field Definitions: Set Up Enhanced-List System Data Window —
Field Name Description/Pro cedure
DEFAULT ENHANCED-LIST
MAILBOX ATTRIBUTES
Class of Service:
Valid Input
a number from 2 to 11
DEFAULT ENHANCED-LIST
MAILBOX ATTRIBUTES
Community ID:
Valid Input:
a number from 1 to 15
:
Enter the number of the COS assigned to the enhanced-list
mailbox and the shadow mailbox.
ELA uses this COS number when you create n ew enhanced lis ts.
Enter the number of the community assigned to the
enhanced-list mailbox. This cannot be the same number as the
shadow mailbox Community ID.
The enhanced-list mailbox community must be administered to
be able to send messages to all other communities and re ceive
messages from the comm unit y(ies ) cont aining use rs wit h access
to enhanced lists. See "Setting Up ELA and Shadow Mailbox
Community IDs" on page 3-19.
Continued on next page
3. Press (F3) to save the ELA server information to the system
SAVE
database.
The system displays the message “Successfully Updated!” an d asks
you to press F1 acknowledge the message.
Continued
4. Press (F1) .
ACKNOWLG MESSAGE
The system redisplays the Enhanced List Manager menu.
5. Continue with the next procedure or press (F6) repeatedly to
return to the main menu.
Guideline s fo r Na mi ng Enhanced Lists
We recommend that you use the following guidelines when you name an
enhanced list. These guidelines can help prevent users from inadvertently
sending their messages to the enhanced list, instead of to a person.
■ Do not use embedded spaces in the name. If you would like a list to be
called Marketing Department, type it
■ Avoid naming an enhanced list after a person. INTUITY Message Manage r
does not differentiate between an enhanced list and a person’s name.
Examples of names to avoid:
— Jane_Doe
— Doe_Jane
CANCEL
Marketing_Department_LIst.
Issue 1 July 1997
37
Page 48
Administering ELA for AUDIX
■ Give enhanced lists names that reflect an organization or a function.
Include the word
Examples:
— Marketing_Dept_List
— Maxfield_List
— Western_District_Salesforce_List
list
.
■ If you want all enhanced lists to be grouped together, put the word
Examples:
— List_Marketing_Dept
— List_Maxfield
— List_Western_District_Salesforce
■ Begin the name with the number 1.
Example: 1_McDonnell_List
Users can reach the enhanced-list mailbox through Numbers Addressing
as well as Names Addressing. Since there are no letters associated with
keypad , users will be less lik e l y to ina dv er t e nt ly select the wrong
1
address.
Creating Enhance d Lists
To create an enhanced list and add members:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> Enhanced-List Manager
list
first.
> Administer Enhanced-Lists
The system displays the Administer Enhanced-Lists window (Figure 4-2).
38 Issue 1 July 1997
Page 49

Creating Enhanced Lists
Figure 4-2. Administer Enha nced-Lists Window
2. Press (F4) .
NEW E-LIST
The system displays the New Enhanced-List window (Figure 4-3).
Figure 4-3. New Enhanced-List Window
3. Complete the fields in this window using the information in Table 4-2.
Issue 1 July 1997
39
Page 50
Administering ELA for AUDIX
Table 4-2. Field Definitions: New Enhanced List Window
Field Name Description/Procedure
List Name:
Valid Input
1- to 29-alphanu me ri c
characters
Extension:
Valid Input
a 3- to 10-numeric characters
Password:
Valid Input
5- to 15-numeric characters
Permit Reply to Send er?:
Valid Input
y = yes (default)
n = no
Class of Service:
Valid Input
a number from 2 to 11
:
:
:
:
:
Enter a name for the list. Use the "Guideli nes for Naming
Enhanced Lists" on page 4-37.
Enter the local extensi on for the list m ailbox. This ext ension must
comply with your system dia l plan. ELA cre ates a mailbo x at this
extension aut om atically, if one does not already exist.
Be sure that those users administered to have access to the list
mailbox kno w this extension.
Enter th e pa ss w o rd fo r th is li s t ma ilb o x.
This password is for administrati ve purposes only. Users who
send messages to the ELA mailbox for distri bution do not use a
password.
No entry is requi red if you want t o allo w a recipient of a m essage
that is sent to an enhanced list to reply to the originator of the
message. To reply, both the recipient and the enhanced list
must be on an
Enter n (o) if you would not like recipients to reply to an
ELA-deliver ed m essage.
No entry is required.
The default val ue in this field is the ELA COS number you
administered on the Set Up Enhanced-Lists System Data
window (see page 4-35).
INTUITY AUDIX R4.1 or higher.
Community ID:
Valid Input
a number from 1 to 15
:
4. Press (F3) to save this information in the system database.
The cursor displays in the Administer Enhanced Lists window on the line
that shows the list you just entered. (If you have more than one list, the
new list is placed in line alphabetically with the other lists).
40 Issue 1 July 1997
No entry is required.
The default val ue in this field is the ELA Community ID you
administered on the Set Up Enhanced-Lists System Data
window (see page 4-35).
Continued on next page
SAVE
Page 51

Creating Enhanced Lists
Guidelines for Selecting Enhanced-List Members
The following subscribers can be members of an enhanced list:
■ Local and remote subscribers. These memb ers can be other enhanced
lists.
■ Call delivery numbers, including fax machines
■ E-mail subscribers who are serviced by other trusted servers, including
Lotus Integrated Messaging
■ AMIS pre-administered subscribers
The following cannot be members of an enhanced list:
■ Public or private subscriber-owned lists
■ AMIS-casual addresses
■ Broadcast mailboxes
Adding Members to Enhanced Lists
To add member names, extensions, and network (e-mail) addresses to a new
enhanced list, perform the following tasks. Start on the Administer Enhanced
Lists window.
1. Press (F5) .
OPEN E-LIST
The system displays the Enhanced-List Membershi p for Listname
(listextension) window (Figure 4-4).
Issue 1 July 1997
41
Page 52

Administering ELA for AUDIX
Figu re 4-4. Enhanced List Membership for Listname Window
2. Press (F4) .
ADD MEMBER
The system displays the Add Member data entry window (Figure 4-5).
Figure 4-5. Add Member Window; Adding Members to an Enhanced List
3. Enter one of the following:
■ The user’s name as it appears in the AUDIX system. This name can
be another enhanced list.
■ The user’s extension.
This extension can be the extension for
another enhanced list.
■ The user’s network (e-mail) address in the format dictated by the
e-mail system, for example, username@trusted_servername
42 Issue 1 July 1997
Page 53

Creating Enhanced Lists
4. Press (F3) to save this information in the system database.
SAVE
NOTE:
The Entries: field at the top of the Administer Enhanced-Lists
window increments each time you add a new member to the list.
5. Repeat Step 3 and Step 4 to continue adding member names, extensions,
and e-mail addresses.
NOTE:
We recommend that you print a copy of the completed list to your
system printer, if available. You can use this printout to search
multiple lists for duplicate names or potential loops with a
synchronized e-mail system. Additionally, should you inadvertently
delete an enhanced list, you would have a source from which to
recreate the enhanced list. (The system’s nightly data backup also
saves ELA setup data, list s, a nd memberships.)
6. Review the Administer Enhanced-Lists window. If you want to change or
delete any information you just entered:
a. Press .
CANCEL
The Enhanced List Membership window displays.
b. Select the member name you want to change or delete.
c. Press (F7).
DELETE MEMBER
d. Go to Step 2 to re-enter member information, or go to Step 7 to
continue.
7. When you have finished adding member names to this enhanced list,
press (F6) repeatedly to return to the main menu.
CANCEL
Adding/Deleting Members to an Enhanced List
To change data for a member of an enhanced list, such as the name or
telephone extension, make the change in AUDIX as described under your
Messaging Solutions Release 4 Administration
reflected in all enhanced lists that contain that member.
To add or delete the members of an existing enhanced list:
1. Starting from the main menu (Figure 3-1 on page 3-14), select:
> Enhanced-List Manager
> Administer Enhanced-Lists
I
NTUITY
book. The change is automatically
Issue 1 July 1997
43
Page 54

Administering ELA for AUDIX
OPEN E–LIST
The system displays the Administer Enhanced-Lists window (Figure 4-2).
The names of your enhanced lists display in the window (along with other
desc r iptive data).
2. Using the arrow keys, select the list you would like to add members to. If
the list is not on the visible page, select the list by one of the following
means:
■ Press until the desired list displays. Use the arrow keys to
NEXTPAGE
highlight the list you would like to edit.
■ Press (F8) . An Actions menu displays. Select Find
List and press . Enter the name or extension of the list you
would like to add or change and press (F3) . The Administer
ACTIONS
ENTER
FIND
Enhanced-Lists window will re-display with the specified list
highlighted.
3. Press (F5) .
The system displays the Enhanced-List Membershi p for Listname
(listextension) window (Figure 4-6). The member names of the selected list
display in the window. Accompanying each name is an extension number
or network (e-mail) address and other descriptive data.
Figure 4-6. Enhanced-List Membership for Listname (listextension) Window
At this point you can:
■ Add new members to the list (Step 4)
■ Find a member of a list (Step 5)
44 Issue 1 July 1997
Page 55

Creating Enhanced Lists
■ Delete a member from the list (Step 6)
■ Print the list to your system printer (Step 7)
Adding a Member
4. Press (F4) .
The system displays the Add Member data entry window (Figure 4-5 on
page 4-42).
Finding a Member
5. To find a member name in a list:
ADD MEMBER
a. Enter one of the following:
■ The user’s name as it appears in the AUDIX system
■ The user’s extension
■ The user’s network (e-mail) address in the format dictated by
the e-mail system, for example ,
username@trusted-servername
b. Press (F3) to save this information in the system database.
SAVE
c. Continue entering names/extensions/e-mail addresses until all new
members have been added.
d. Press (F6) to return to the Administer Enhanced List
CANCEL
window or proceed to Step 7 to print a copy of the list.
a. Press (F8) .
ACTIONS
An Actions menu displays.
b. Select Find Member and pr es s .
ENTER
c. Enter the name or extension of the person or list you would like to
find and press (F3) .
FIND
The Enhanced-Lists Membership window re-displays with the
specified person or list highlighted.
Issue 1 July 1997
45
Page 56

Administering ELA for AUDIX
Deleting a Member
6. To delete a member:
a. Locate the member name to be deleted. See ‘‘Finding a Member’’
above.
b. Press (F7) .
The system displays the confirmation message:
DELETE MEMBER
CONFIRM: Deleting
c. Enter y
The Enhanced-List Membership window redisplays.
d. Continue with Step 7 to print a copy of the list.
Printing an Enhanced List
7. Press (F8) . An Actions menu displays.
a. Select Print List Membership and press .
The system displays the message “Printing List Membership
for
system printer.
b. Press (F1) .
The system redisplays the Actions menu.
c. Proceed to Step 8.
8. When you have finished, press (F6) repeatedly to return to the
main men u .
Name= List Extension/Address=
Listname
Listextension
Enter y to continue, n to abort.
ACTIO NS
Listname (listextension
ACKNOWLG MESSAGE
)” and sends the list to the
CANCEL
ENTER
Deleti ng an Enhanc e d List
To delete an existing enhanced list:
1. From the main menu, select:
> Enhanced-List Manager
> Administer Enhanced-Lists
The system displays the Administer Enhanced-Lists window (Figure 4-2
on pa g e 4-39).
46 Issue 1 July 1997
Page 57

Deleting an Enhanced List
2. Use the arrow keys to highlight the line that represents the list you want to
delete. If the list to be deleted does not appear on the visible page, select
the list by one of the following means.
■ Press until the desired list displays. Use the arrow keys to
highlight the list you would like to delete.
■ Select (F8) . An Actions menu displays. Select Find
List and press . Then enter the name or telephone
extension of the list you would like to delete and press (F3) .
The Administer Enhanced-Lists window will re-display with the
specified list highlighted.
3. Press (F7) .
The system displays the Confirm Deletion of Enhanced-List window
(Fi gur e 4-7).
NEXTPAGE
ACTIONS
ENTER
FIND
DELETE E-LIST
Figure 4-7. Confirm Deletion of Enhanced-List Window
4. Do you want to delete the associated AUDIX mailbox?
■ If yes, go to Step 5.
■ If no, enter n. To create a new enhanced list, see page 4-37.
5. Press (F3) to delete the enhanced list.
DELETE
AUDIX deletes the mailbox and all information in it, including any
enhanced-list members or messages.
The system displays the message “Deleted
listextension
(
) Enhanced List” and asks you to press F1
Listname
acknowledge the message.
6. Press (F1) .
ACKNOWLG MESSAGE
The system redisplays the Administer Enhanced-Lists window.
7. Press (F6) repeatedly to return to the main menu.
CANCEL
Issue 1 July 1997
47
Page 58
Administering ELA for AUDIX
Recording Names for Enhanced Lists
Once you have established an enhanced list, is a good idea to record a name for
the list. That way, users will hear a meaningful name for the list when they send a
message to an enhance- list mailbox for distribution. However, you need to
record the name using an administrative recording session.
To record a name for an enhanced list:
1. From a touch-tone telephone, log in as an administrator.
2. Press .
9
The system prompts with “To record names, press 4.”
NOTE:
If you get an error message, open the Class of Service screen for the
administrator’s extension and change the Announcement
Control? field to y. Then start again.
3. Press .
4
The system prompts with “Please enter the extension and pound sign.”
4. Enter the extension for the enhanced-list mailbox.
The system prompts with “When finished recording, press pound to
approve or 1 to edit your message. Record at the tone.”
5. After the tone, speak the name of the list.
6. Press .
#
7. Repeat Steps 4 through 6 to record additional names.
8. Press *r to return to the main menu.
!
CAUTION:
You should also record a name for the Shadow mailbox, using the
same procedure. Use a name such as, “Mailing list - Do not reply.”
That way, anyone who inadvertently enters the Shadow mailbox
extension, will not to try to send a message to it or to reply to a
message from it.
Testing INTUITY Enhanced Lists
1. Perform the administration outlined below, including:
■ "Installing the Software " on pa ge 2-9
■ "Activating ELA" on page 3-14
■ "Increasing the Number of Mailing Lists Allowed on the System" on
page 3-15
48 Issue 1 July 1997
Page 59

Testing INTUITY Enhanced Lists
■ "Defining an ELA Class of Service" on page 3-16
■ "Setting Up ELA and Shadow Mailbox Community IDs" on
page 3-19
■ "Administering TCP/IP" on page 3-23
■ "Setting Up IMAPI Sessions for Trusted Server Access" on
page 3-26
■ "Defining Two ELA Trusted Servers" on page 3-28 (You must have
two available, unused extensions, one for the shadow mailbox and
one for the enhanced-list mailbox)
2. Using the procedures in the Installation manual specific to your platform,
set up two test users and test telephones.
3. Using the procedures in the Installation manual specific to your platform,
use the test-1 telephone to create and send a voice mail message to the
ELA mailbox. Record the following or a similar test message and then
enter the address for the enhanced-list mailbox:
“This is a test ELA message for I
NTUITY AUDIX.”
4. Hang up the test-1 telephone to disconnect.
5. Verify that the MWIs for the test users’ telephones activate and that the test
users received the message. (See the Installation manual specific to your
platform.)
6. Delete the test messages. (See the Installation manual specific to your
platform.)
7. Delete the test users. (See the Installation manual specific to your
platform.)
Issue 1 July 1997
49
Page 60

Administering ELA for AUDIX
50 Issue 1 July 1997
Page 61

Preventative Maintenance and Troubleshooting
Overview
This section describes how to check for system alarms relating to ELA and how
to diagnose common application and end-user problems.
5
Checkin g the Administ ra tor’s Log
The system warns you of potential administrative problems with ELA by
displaying a minor and warning message (Alarms: w or Alarms: m) on the
AUDIX Administration status line when it logs an administration event. Check the
status line (at the top of the AUDIX Administration screen) at least once a day.
Other events besides those generated by ELA create administrative log entries,
but you can view ELA-specific events. You should do this on a regular basis to
monitor ELA performance. To view ELA-specific log entries:
1. Starting from the main menu, select:
> AUDIX Administration
2. At the enter command: prompt, enter either:
Full Command Version Short Command Version
display administrators-log di ad
The system displays the Administrator’s Log screen.
3. Enter the starting date and time.
4. Enter EL in the Application: field.
Issue 1 July 1997 51
Page 62

Preventative Maintenance and Troubleshooting
5. Press (F3) to display the alarm entries.
6. Examine the displayed entries. See the
SAVE
Solutions Release 4 Alarm and Log Messages,
events and alarms, and associated repair procedures.
7. Take whatever corrective action is necessary.
8. Enter exit at the enter command: prompt to exit AUDIX administration.
Checking the Del ivery Failure Log
The delivery failure log contains entries for all failed deliveries, along with
descriptive data regarding cause for the failure and other information. Check this
log to monitor ELA and system performance and if a user complains that
messages are not being delivered.
To view the delivery failure log:
1. Starting from the main menu, select:
> Enhanced List Manager
>View E-List Delivery Failure Log
Lucent I
NTUITY
™ Messaging
585-310-566 for a list of
The system displays the Delivery Failure Log window (Figure 5-1).
Figure 5-1. Delivery Failure Log Window
Table 5-1 explains the log entries in the report.
52 Issue 1 July 1997
Page 63

Checking the Delivery Failure Log
Table 5-1. Field Definitions: Enhanced-List Delivery Failure Log
Window
Field Name Description/Procedure
Date The calendar date t he delivery failure occurred
Time The time that delive ry f ailure occurred
Message Originator The address of the user who sent the message to the enhanced
list for dis tr ib u tio n
The address is in the format address@machine where
can be the telephone extension or the network (e -mail) address.
The system truncates addresses th at are longer than 21
characters.
Parent List The list (mailbox) to which a user originally addressed the
message
Child List The last list mailbox a message reached prior to message
deliv ery failure
Failed Recipient The name of the recipi ent to whi ch AUDIX att em pted to s end the
ELA message. If no name is administered, this field is blank.
address
Failed Address The address to which AUDIX attempted to send the ELA
message
The address is in the format address@machine where
can be the telephone extension or the network (e -mail) address.
The system truncates addresses th at are longer than 21
characters.
Failure Reason This is descriptive text indicating the reason the delivery failure
occurred, such as
Transmi ss io n Pr oblems.
Full Mailbox, Un su pp or te d Media, or
address
Continued on next page
2. Press (F8) to send a copy of this report to the system printer, if
PRINT
you have a printer available.
3. Press (F6) repeatedly to return to the main menu.
Issue 1 July 1997
53
Page 64

Preventative Maintenance and Troubleshooting
Delivery Fail u re Cod es
Delivery failure logs contain the following codes:
Table 5-2. Delivery Failure Codes
Reason of Failure Description
Full mailbox The recipient has a full mailbox.
Could not locate ELA could not locate the reci pient.
Transmission probs Transmission difficulties occurr ed.
Permission deni ed The message contains feat ures ELA can not recogniz e.
Permission is denied.
Sending restriction Delivery denied because of sending restrictions
Login annc exist s The login announcement already exists.
AMIS wrong number This is the wrong number for this AMIS analog recipient.
Too many AMIS xmits Too many transmission attempts fo r AMIS analog
resulted in a transmit-attempt exception.
AMIS unknown return AMIS returned the message with out i dentifying a reason.
misc internal fail Miscellaneous i nternal delivery failure
AMIS longer > 8 minutes The AMIS message is longer than eight minutes.
Unsupported media The message contains media that ELA does not support
for this particular system or subscriber.
Pvt to unsup remote Private messages were not delivered to unsupported
remote systems.
Message too large The voice component of the message is too large for the
remote system.
Continued on next page
54 Issue 1 July 1997
Page 65

Troubleshooting ELA
Troubl eshooting ELA
Table 5-3 lists questions users ask the system administrator and suggested
remedies to commonly encountered system problem s.
Table 5-3. User Questions or System Functionality Symptoms
Question/Symptom Possibl e Ca u se Answer/Suggested Rem ed y
During an upgrade fail ure,
installer/administrator
cannot differentiate
between AUDIX mailboxes
and ELA mailboxes.
“I try to reply to a message
I got, but I get a system
message that I can’t.”
“I am gettin g m u ltiple
copi es of the sa m e
message.”
You inadvertently delete
the shadow mailbox.
Message was sent to
an enhanced list that
did not permit “Reply
to Sender.”
Community IDs for t he
user or recipient
incorrectly
administered
Recipient is not on a
Lucent I
NTUITY system
or is on a pre-R4
system.
Recipient is on more
than one list.
Use the li cos command from AUDIX
Administration to determine the ELA
Class(es) of Service. Use the li su
command and note the extension(s) of all
mailboxes with the applicable COS.
■ Administer the enhanced list to allow
Reply to Sender, if appropriate.
■ Educate your users about ELA
functional it y.
Administer Communit y IDs for user or
recipient, if appropriate.
Upgrade system to Lucent I
NTUITY R4.2_4
or higher.
■ ELA does not check nested l ists to see
if the same name appea rs in more t han
one place. Print out a copy of your
enhanced lists and remove duplicates ,
if possible.
■ Educate your users about ELA
functional it y.
ELA raises a warning alarm. Any messages
waiting in the delivery “queue” is lost.
Re-enter the shadow extension on the Set
Up Enhanced-List System Data window
and then press (F3)
SAVE
.
Continued on next page
Issue 1 July 1997
55
Page 66
Preventative Maintenance and Troubleshooting
Table 5-3. User Questions or System Functionality Symptoms —
Continued
Question/Symptom Possibl e Cause Answer/Suggeste d Re m ed y
Recipient claims s/he did
not get an ELA message.
■ Mailing list not
current
■ Subscriber’s
mailbox not
administered
correctly
■ System delivery
failure
Check the mailing list for the recipient’s
name. Administer, if necessary.
■ Check the Subscriber screen for the
affected user. Look at the Mai lbox siz e.
Put user i n a COS with a l arger mailbo x,
if necessary.
■ Check the List Measurements
Subscriber Day scr een for the affected
user. Look at the available mailbox
space. Advise the user to del ete
unneeded messages and gre etings, if
appropriate.
■ Check that Community ID is correct.
System delivery failures can arise from
many sources.
■ Check the Delivery Failure Log (see
"Checking the Delivery Failure Log" on
page 5-52).
■ Check the Administrator’s Log for
related alarms . If an alarm warrants
further action, see
Lucent I
Messaging Solutions Release 4 Alarm
and Log Messages,
■ Verify network capabilities with your
585-310-566.
PC/LAN administrator.
NTUITY
An enhanced-lis t mem ber
keeps disappeari ng from
Enhanced Lists.
“I can’t send a message t o
an enhanced-list mailbox.”
56 Issue 1 July 1997
■ Sending
Restrictions not
consistent ac ross
machines
System feature to
delete nonadministered re mo te
users is active.
User belongs to a
community with
sending restrictions
administered.
Administer Community IDs for all Lucent
I
NTUITY machines, if approp riate.
■ From AUDIX Administration, enter
ch sys fe. Access page 4 and change
the
Even if on Mailing List?
field to n.
■ Re-administer the remote user.
Consider whether to change this user’s
community ID to allow her/him to use
Enhanced Lists.
Continued on next page
Page 67

Troubleshooting ELA
Table 5-3. User Questions or System Functionality Symptoms —
Continued
Question/Symptom Possibl e Ca u se A nswer/Sugg e ste d R em ed y
“Everyone else seemed to
have received their
enhanced-list message.
I got mine much later.”
You inadvertently delete an
Enhanced List.
User mailbox full Check the List Measurements Subscriber
Day screen for the affected user. Look at
the available mailbox space. Advise the
user to delete unneeded messages and
greetings, if a ppropri ate or c onsider putt ing
the user in a COS with a larger mailbox.
Enhanced list was
very large.
Networking problem s
between originator
system and recipient
system.
Remember that ELA ‘thr ottles’ traffic during
periods of heavy user traffic. Inform user
that it message d elivery to a large recipient
population does ta ke ti m e.
Perform networking troubleshooting. See
Lucent I
Networking,
information.
There are 2 ways to restore an Enhanced
List:
NTUITY
Messaging Solutions Digital
585-310-567 for more
■ Re-enter the names on the list.
■ Restore the data from the previous
night’s tape backup.
!
WARNING:
There is no way to selectively restore
only enhanced list s fr om the backup
tape. Your syst em will lose all
incremental administration data fr om
the point of backup. Use thi s me thod
only if you are sure the busi ness can
tolerate the lo ss of recent
administrat ion.
Continued on next page
Issue 1 July 1997
57
Page 68

Preventative Maintenance and Troubleshooting
58 Issue 1 July 1997
Page 69

Alarms
Overview
The following alarms are associated with the Enhanced-List Application.
6
DELIVTS Resourc e Ty pe
Alarm Code: 1
Event ID: ELA-delivts01
Alarm Level: Warning
Description: Trusted-server data lost, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter all
field information.
■ Restore data from the most recent backup of system data. See Chapter 3,
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
Issue 1 July 1997 59
Page 70

Alarms
Alarm Code: 2
Event ID: ELA-delivts02
Alarm Level: Warning
Description: Trusted-server data partially lost, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter all
■ Restore data from the most recent backup of system data. See Chapter 3,
Alarm Code: 3
field information.
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
Event ID: ELA-delivts03
Alarm Level: Warning
Description: Trusted-server data corrupt, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter all
■ Restore data from the most recent backup of system data. See Chapter 3,
Alarm Code: 4
Event ID: ELA-delivts04
Alarm Level: Warning
Description: Trusted-server data no longer valid.
field information.
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
Repair Action:
1. In AUDIX, enter ch tr
60 Issue 1 July 1997
administrative_trusted_server_name
.
Page 71

REGISTRY Resource Type
2. Verify/administer the screen information, as required.
3. Repeat for the delivery trusted server.
4. Enter ch imapi and verify/administer as required.
5. When complete, enter the correct information in the Set Up Enhanced-List
System Data window.
REGISTRY Resource Type
Alarm Code: 1
Event ID: ELA-registry01
Alarm Level: Warning
Description: E-list registry lost, re-enter or restore. The ELA software has
detected that registry database has disappeared.
Repair Action:
1. Re-administer the registry:
2. If the alarm persists, restore system data from the nightly backup. See
Alarm Code: 2
Event ID: ELA-registry02
Alarm Level: Minor
Description: Unable to write updated E-list registry.
Repair Action:
a. Go to the Administer Enhanced-Lists window.
b. Use (F4) NEW E-LIST to re-enter the name of each Enhanced List,
one at a time. (The individual members do not need to be
re-entered.)
Lucent I
See
Administration,
Chapter 3, “Common System Procedures,” in your maintenanc e book for
instructions about restoring data. If you would prefer to have assistance
with this restore, contact your remote maintenance center.
NTUITY
™ Messaging So lutions R ele ase 4
585-310-564 for more detailed procedures.
This alarm requires intervention from the remote maintenance center.
Issue 1 July 1997
61
Page 72

Alarms
SHADOW Resource Type
Alarm Code: 1
Event ID: ELA-shadow01
Alarm Level: Warning
Description: Shadow mailbox data lost, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter the
shadow mailbox extension and community ID. If a shadow mailbox exists
at the extension ent e red, the system displays a system prompt to that
effect. If a shadow mailbox does not exist at the extension entered, a new
mailbox will be created.
■ Restore data from the most recent backup of system data. See Chapter 3,
Alarm Code: 2
Event ID: ELA-shadow02
Alarm Level: Warning
Description: Shadow mailbox corrupt, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter the
■ Restore data from the most recent backup of system data. See Chapter 3,
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
shadow mailbox extension and community ID. If a shadow mailbox exists
at the extension ent e red, the system displays a system prompt to that
effect. If a shadow mailbox does not exist at the extension entered, a new
mailbox will be created.
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
62 Issue 1 July 1997
Page 73

SHADOW Resource Type
Alarm Code: 3
Event ID: ELA-shadow03
Alarm Level: Warning
Description: Shadow mailbox data corrupt, re-enter or restore.
Repair Action:
There are two recovery methods:
■ Access the Set Up Enhanced-List System Data window and re-enter the
shadow mailbox extension and community ID. If a shadow mailbox exists
at the extension entered, the system displays a system prompt to that
effect. If a shadow mailbox does not exist at the extension entered, a new
mailbox will be created.
■ Restore data from the most recent backup of system data. See Chapter 3,
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
Alarm Code: 4
Event ID: ELA-shadow04
Alarm Level: Warning
Description: Shadow mailbox does not allow trusted-server access.
Repair Action:
1. In AUDIX, enter ch cos
2. Verify that the Trusted Server Access? field is set to y
3. Enter di sub
4. Verify the Class of Service field is the appropriate cos. If it is, call
Alarm Code: 5
Event ID: ELA-shadow05
Alarm Level: Warning
Description: Shadow mailbox does not exist at expected extension.
ELA_Class_of_Service_Name/Number
shadow_mailbox_extension
1-800-56 AUDIX for help.
Issue 1 July 1997
63
Page 74

Alarms
Repair Action:
Access the Set Up Enhanced-List System Data window and re-enter the shadow
mailbox extension and community ID. If a shadow mailbox exists at the extension
entered, t h e s ystem displays a system prompt to th a t effect. If a shadow mailbox
does not exist at the extension entered, a new mailbox will be created.
Alarm Code: 6
Event ID: ELA-shadow06
Alarm Level: Warning
Description: The shadow mailbox is full of messages for recipients who
NOTE:
If you wish to move the shadow mailbox to a new extension, only use the
Set Up Enhanced-List System Data window.
have full mailboxes. ELA cannot deliver these messages
until the recipients make space in their mailboxes. Also,
AUDIX can take up to two weeks to determine that a
message is undeliverable and to generate a log entry for a
delivery failure.
Repair Action:
You can correct single instances of this problem by deleting messages from the
shadow mailbox. To access the shadow mailbox:
1. In AUDIX Administration enter ch su
mailbox.
2. At the Subscriber screen, enter a new password in the Password: field.
Remember this password for step 5 below.
3. Press (F3) to save the password.
4. At the enter command: enter exit
5. Use Message Manager to log into the shadow mailbox.
6. Open the Outgoing folder and delete messages that have been
rescheduled for delivery to full mailboxes. Keep deleting messages until
the shadow mailbox is less than 50 percent full.
We recommend that you make a list of the recipients whose mailboxes are
full, so you can ask them to delete at least half of their messages. (You
cannot use AUDIX to make this request, because it cannot deliver
messages until the mailboxes have more room.)
7. Log out of the shadow mailbox.
ENTER
extension
for the enhanced-list
64 Issue 1 July 1997
Page 75
EL — Enhanced-List Application
If you regularly get this alarm, the following questions can help you evaluate how
your business uses ELA:
■ Do your subscribers use large enhanced lists too frequently? Are they
being used for trivial or non-business purposes?
■ Are subscriber mailboxes too small? Should you increase mailbox space
or purchase more hours for storage?
■ Is the ELA class-of-service correct? (Check the value in the Mailbox
Size (seconds), Maximum: field on the Class of Service screen, Page
2. Is the ELA class-of-service assigned to the shadow mailbox?
■ Are the intervals for rescheduling delivery on the System Parameters
Features screen appropriate?
EL — Enhanced-List Application
The following administrator’s log messages and repair actions apply to the
Enhanced-List Application.
Event ID: ELA-badreca01 through ELA-badreca12
Description: Bad record deleted from E-List registry. Check for missing
lists. (exte ns ion)
ELA detected a corrupt record and took the following action:
■ If the message displays an extension, ELA deleted its
record.
■ If the message does not display an extension, ELA could not
determine the extension of the corrupt record and deletes
the record.
Repair Procedure:
There are two recovery methods:
■ Go to the Administer Enhanced-Lists window and note any lists that may
be missing.
Use (F4) NEW E-LIST to re-enter each missing Enhanced List, one at a
time. If ELA reports that an AUDIX mailbox already exists for a given
extension, and the reported data match those of the missing list, answer
‘y’ to confirm the change of the existing mailbox into an enhanced-list
mailbox.
■ Restore data from the most recent backup of system data. See Chapter 3,
“Common System Procedures,” in your maintenance book for instructions
about restoring data. If you would prefer to have assistance with this
restore, contact your remote maintenance center.
Issue 1 July 1997
65
Page 76

Alarms
Event ID: ELA-lostlock01 through ELA-lostlock10
Description: Messages to an enhanced list could not be delivered
because someone was logged into the shadow mailbox.
Repair Procedure:
No one should ever be logged into the shadow mailbox. However. if someone is,
change the password for the shadow mailbox as follows:
1. In AUDIX Administration enter ch su
mailbox.
2. At the Subscriber screen, enter a new password in the Password: field.
3. Press (F3) to save the password.
ENTER
Event ID: ELA-no_members
Description: ELA received a message for delivery to an Enhanced List,
Repair Procedure:
Perhaps you forgot to add the members to the Enhanced List, or perhaps
the enhanced list is no longer necessary. Go to the Administer
Enhanced-Lists window and do one of the following:
■ Highlight the list and use (F5) OPEN E-LIST to enter members into
the Enhanced List.
■ Use (F7) DELETE E-LIST to delete the Enhanced Lists.
See
Lucent I
585-310-564 for more detailed procedures.
extension
for the enhanced-list
but the enhanced list did not contain any members. In
such a case, ELA will delete the message.
NTUITY
Messaging Solutions Release 4 Administrati on,
Event ID: ELA-nestvioltn
Description: An enhanced list contains more than 20 nested lists.
66 Issue 1 July 1997
For example, enhanced list 1 contains enhanced list 2 as
one of its members. Inside enhanced list 2 is Enhanced
List 3. Enhanced list 3 contains yet another enhanced list
as one of its members, and so on.
Page 77

EL — Enhanced-List Application
Repair Procedure:
Evaluate list membership hierarchy and delete unnecessary nes ting so that ELA
can handle delivery of the message. See
Release 4 Administration,
Event ID: ELA -l oop v ioltn
Description: There are two enhanced lists that refer to each other. For
Repair Procedure:
Go to the Administer Enhanced-Lists window.
1. Use (F5) OPEN E-LIST to open one of the indicated Enhanced
Lists.
2. Search for the extension of the other Enhanced List.
Lucent I
585-310-564 for procedures.
example, enhanced list 1 contains enhanced list 2 as a
member, and enhanced list 2 contains enhanced list 1 as
a member.
NTUITY
Messaging Solutions
3. Use (F7) DELETE E-LIST to delete the Enhanced List.
Lucent I
See
585-310-564 for more detailed procedures.
Event ID: ELA-mboxlock01
Description: An enhanced-list mailbox does not have trusted server
Repair Procedure:
1. In AUDIX, enter ch cos
2. Verify that the Trusted Server Access? field is set to y
3. Enter ch su
4. Verify the Class of Service field is the appropriate cos.
See
Lucent I
585-310-564 for more detailed procedures.
Event ID: ELA-chkrestrct
Description: A message was found in the shadow mailbox.
NTUITY
Messaging Solutions Release 4 Administrati on,
access.
ELA_Class_of_Service_Nam e/N umb er
Enhanced_List_mail box_extension
NTUITY
Messaging Solutions Release 4 Administrati on,
Repair Procedure:
1. In AUDIX, enter ch sys se
Issue 1 July 1997
67
Page 78

Alarms
2. Verify that the shadow mailbox belongs to a community that cannot
receive messages.
NOTE:
The sending restrictions must be identical on all machines in the
NTUITY AUDIX network. Check the sending restrictions on all
I
machines.
Lucent I
See
585-310-564 for more detailed procedures.
Event ID: ELA-shadow07
Description: Shadow mailbox space gridlock caused no ELA service for
Repair Procedure:
See the procedure for SHADOW Resource Type, "Alarm Code: 6" on page 6-64.
Event ID: ELA-delivts05
Description:
The trusted server that delivers ELA messages cannot access
AUDIX. The message shows the amount of elapsed time (in 30
minute increments) since ELA has stopped providing service.
When the time elapsed exceeds the value in the Minutes of
Inactivity Before Alarm: field on the Trusted-Server Profile
screen, AUDIX generates a minor alarm (event ID: SERVER0900,
resource type SERVER, alarm code 900.)
NTUITY
Messaging Solutions Release 4 Administrati on,
longer than number hours.
Number
minutes with session resources unavailable for
delivery trusted server.
Repair Procedure:
1. Open the System Parameters IMAPI-Options s creen.
2. Is the value in the Simultaneous Sessions Available for
Trusted Server Access: field at least 2?
■ If yes, go to step 3.
■ If no, change the value.
3. Determine if the AUDIX server is so overloaded that it has no resources
available for ELA. Some questions to ask are:
■ How many trusted servers are on the network?
■ What are their activity cycles?
68 Issue 1 July 1997
Page 79
Index
IN
A
administering, 34
AUDIX
, 3
COS
, 16
LAN
, 23
TCP/IP
, 23
administrator’s log
alarms
, 51
ELA-badreca01 through ELA-badreca12
ELA-chkrestrct
ELA-delivts01
ELA-delivts02
ELA-delivts03
ELA-delivts04
ELA-delivts05
ELA-loopvioltn
ELA-lostlock01 through ELA-lostlock10
ELA-mboxlock01
ELA-nestvioltn
ELA-no_members
ELA-registry01
ELA-registry02
ELA-shadow01
ELA-shadow02
ELA-shadow03
ELA-shadow04
ELA-shadow06
ELA-shadow07
AMIS users
AUDIX
administering
administering system limits
mailboxes
mailing lists
server name
, 51
, 67
, 59
, 60
, 60
, 60
, 68
, 67
, 67
, 66
, 66
, 61
, 61
, 62
, 62
, 63
, 63
, 64
, 68
, 2
, 3
, 15
, 3, 28
, 2
, 24
, 65
, 66
E
ELA
activating
administering COS
alarms
characteris tics
community IDs
delivery failure codes
domains
enhanced lists
hardware requirements
installation
LAN administration
logs
mailboxes
mailing lists
passwords
planning for
ports
sending restrictions
shadow mailbox
software requi rements
traffic
troubleshoot ing
trusted servers
virus detection
ELA server
administering
e-mail
enhanced lists
deleting
members
naming
testing
, 14
, 16
, 51, 59
, 2
, 19, 21, 36, 37, 40
, 3
, 38
, 9
, 5, 23
, 51
, 6, 7, 17
, 19
, 36
, 3
, 6
, 19
, 8, 19, 22, 36
, 5
, 55
, 3, 8, 23, 26, 28, 35
, 8
, 34
, 34
, 6
, 38
, 46
, 41
, 38
, 48
H
hardware requir em ents, 5
, 54
, 5
, 5
C
community IDs, 19, 21, 36, 37, 40
COS, administering
, 16, 37, 40
D
deliv e ry failure,52
codes
, 54
domains
, 3
I
IMAPI
passwords
sessions
installation
rebooting the system
IP addresses
, 7, 28, 35
, 3, 8, 26
, 9
, 23
, 11
Issue 1 July 1997 69
Page 80

Index
L
LAN administration, 5, 23
logs
, 51
delive ry fa ilu r e
, 52
M
mailboxes, 6, 7, 17, 28
mailing lis t s
AUDIX
messaging traf fic
, 19
, 2
, 5
P
passwords, 6, 28, 36
IMAPI
, 35
list mailbox
system
ports
, 6
, 40
, 35
trusted servers
defini tio n
IMAPI sessions
IP addresses
names
security
, 28
, 3
, 35
, 6, 8
V
virus detect ion, 8
virus prevent ion
, 26
, 23
, 6
R
rebooting the system, 11
S
security
e-mail
, 6
external access
passwords
trusted servers
virus prevention
service degradation, ports and
shadow mailbox
software requirements
system limits, AUDIX
system parameters
system passwords
, 6
, 6
, 6
, 6
, 8, 19, 22, 36
, 5
, 15
, 1
, 35
T
TCP/IP, admini stering, 23
testing enhanced lists
troubleshooting
, 48
, 55
, 6
70 Issue 1 July 1997
 Loading...
Loading...