Page 1

Ethereal User's Guide
V2.0.2 (16376) for Ethereal 0.10.12
Richard Sharpe, NS Computer Software and Services P/L
Ed Warnicke,
Ulf Lamping,
Page 2

Ethereal User's Guide: V2.0.2 (16376) for Ethereal 0.10.12
by Richard Sharpe, Ed Warnicke, and Ulf Lamping
Copyright © 2004-2005 Richard SharpeEd WarnickeUlf Lamping
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU General Public License, Version 2 or any
later version published by the Free Software Foundation.
All logos and trademarks in this document are property of their respective owner.
Page 3

Page 4

Table of Contents
Preface ............................................................................................................................. viii
1. Foreword .............................................................................................................. viii
2. Who should read this document? ................................................................................. ix
3. Acknowledgements .................................................................................................... x
4. About this document ................................................................................................. xi
5. Where to get the latest copy of this document? .............................................................. xii
6. Providing feedback about this document ..................................................................... xiii
1. Introduction ...................................................................................................................... 1
1.1. What is Ethereal? .................................................................................................... 1
1.1.1. Some intended purposes ................................................................................. 1
1.1.2. Features ...................................................................................................... 1
1.1.3. Live capture from many different network media ................................................ 2
1.1.4. Import files from many other capture programs .................................................. 2
1.1.5. Export files for many other capture programs ..................................................... 2
1.1.6. Many protocol decoders ................................................................................. 2
1.1.7. Open Source Software ................................................................................... 2
1.1.8. What Ethereal is not ...................................................................................... 3
1.2. Platforms Ethereal runs on ........................................................................................ 4
1.2.1. Unix ........................................................................................................... 4
1.2.2. Linux ......................................................................................................... 4
1.2.3. Microsoft Windows ....................................................................................... 5
1.3. Where to get Ethereal? ............................................................................................. 6
1.4. A rose by any other name ......................................................................................... 7
1.5. A brief history of Ethereal ......................................................................................... 8
1.6. Development and maintenance of Ethereal ................................................................... 9
1.7. Reporting problems and getting help ..........................................................................10
1.7.1. Website .....................................................................................................10
1.7.2. Wiki ..........................................................................................................10
1.7.3. FAQ ..........................................................................................................10
1.7.4. Mailing Lists ..............................................................................................10
1.7.5. Reporting Problems ......................................................................................11
1.7.6. Reporting Crashes on UNIX/Linux platforms ....................................................11
1.7.7. Reporting Crashes on Windows platforms ........................................................12
2. Building and Installing Ethereal ...........................................................................................14
2.1. Introduction ..........................................................................................................14
2.2. Obtaining the source and binary distributions ...............................................................15
2.3. Before you build Ethereal under UNIX .......................................................................16
2.4. Building Ethereal from source under UNIX .................................................................19
2.5. Installing the binaries under UNIX ............................................................................21
2.5.1. Installing from rpm's under RedHat and alike ....................................................21
2.5.2. Installing from deb's under Debian ..................................................................21
2.6. Troubleshooting during the install on Unix ..................................................................22
2.7. Building from source under Windows ........................................................................23
2.8. Installing Ethereal under Windows ............................................................................24
2.8.1. Install Ethereal ............................................................................................24
2.8.2. Install WinPcap ...........................................................................................25
2.8.3. Update Ethereal ...........................................................................................26
2.8.4. Update WinPcap ..........................................................................................26
2.8.5. Uninstall Ethereal ........................................................................................26
2.8.6. Uninstall WinPcap .......................................................................................27
3. User Interface ..................................................................................................................29
3.1. Introduction ..........................................................................................................29
3.2. Start Ethereal .........................................................................................................30
3.3. The Main window ..................................................................................................31
3.4. The Menu .............................................................................................................33
3.5. The "File" menu .....................................................................................................34
3.6. The "Edit" menu ....................................................................................................37
iv
Page 5

Ethereal User's Guide
3.7. The "View" menu ...................................................................................................39
3.8. The "Go" menu ......................................................................................................42
3.9. The "Capture" menu ...............................................................................................44
3.10. The "Analyze" menu .............................................................................................46
3.11. The "Statistics" menu ............................................................................................48
3.12. The "Help" menu ..................................................................................................50
3.13. The "Main" toolbar ...............................................................................................52
3.14. The "Filter" toolbar ...............................................................................................55
3.15. The "Packet List" pane ..........................................................................................56
3.16. The "Packet Details" pane ......................................................................................57
3.17. The "Packet Bytes" pane ........................................................................................58
3.18. The Statusbar .......................................................................................................59
4. Capturing Live Network Data .............................................................................................61
4.1. Introduction ..........................................................................................................61
4.2. Prerequisites ..........................................................................................................62
4.3. Start Capturing ......................................................................................................63
4.4. The "Capture Interfaces" dialog box ...........................................................................64
4.5. The "Capture Options" dialog box .............................................................................65
4.5.1. Capture frame .............................................................................................65
4.5.2. Capture File(s) frame ....................................................................................67
4.5.3. Stop Capture... frame ....................................................................................67
4.5.4. Display Options frame ..................................................................................68
4.5.5. Name Resolution frame ................................................................................68
4.5.6. Buttons ......................................................................................................68
4.6. Capture files and file modes .....................................................................................69
4.7. Link-layer header type ............................................................................................71
4.8. Filtering while capturing ..........................................................................................72
4.9. While a Capture is running ... ...................................................................................74
4.9.1. Stop the running capture ...............................................................................74
4.9.2. Restart a running capture ...............................................................................75
5. File Input / Output and Printing ...........................................................................................77
5.1. Introduction ..........................................................................................................77
5.2. Open capture files ..................................................................................................78
5.2.1. The "Open Capture File" dialog box ................................................................78
5.2.2. Input File Formats ........................................................................................79
5.3. Saving captured packets ..........................................................................................81
5.3.1. The "Save Capture File As" dialog box ............................................................81
5.3.2. Output File Formats .....................................................................................83
5.4. Merging capture files ..............................................................................................84
5.4.1. The "Merge with Capture File" dialog box ........................................................84
5.5. File Sets ...............................................................................................................86
5.5.1. The "List Files" dialog box ............................................................................86
5.6. Exporting data .......................................................................................................87
5.6.1. The "Export as Plain Text File" dialog box .......................................................87
5.6.2. The "Export as PostScript File" dialog box .......................................................87
5.6.3. The "Export as CSV (Comma Seperated Values) File" dialog box .........................88
5.6.4. The "Export as PSML File" dialog box ............................................................88
5.6.5. The "Export as PDML File" dialog box ............................................................89
5.6.6. The "Export selected packet bytes" dialog box ...................................................90
5.7. Printing packets .....................................................................................................92
5.7.1. The "Print" dialog box ..................................................................................92
5.8. The Packet Range frame ..........................................................................................94
5.9. The Packet Format frame .........................................................................................95
6. Working with captured packets ............................................................................................97
6.1. Viewing packets you have captured ...........................................................................97
6.2. Filtering packets while viewing ............................................................................... 103
6.3. Building display filter expressions ...........................................................................105
6.3.1. Display filter fields ....................................................................................105
6.3.2. Comparing values ...................................................................................... 105
6.3.3. Combining expressions ...............................................................................106
6.3.4. A common mistake .................................................................................... 108
6.4. The "Filter Expression" dialog box .......................................................................... 109
6.5. Defining and saving filters ..................................................................................... 111
v
Page 6

Ethereal User's Guide
6.6. Finding packets .................................................................................................... 113
6.6.1. The "Find Packet" dialog box ....................................................................... 113
6.6.2. The "Find Next" command .......................................................................... 114
6.6.3. The "Find Previous" command ..................................................................... 114
6.7. Go to a specific packet ..........................................................................................115
6.7.1. The "Go Back" command ............................................................................115
6.7.2. The "Go Forward" command ....................................................................... 115
6.7.3. The "Go to Packet" dialog box .....................................................................115
6.7.4. The "Go to Corresponding Packet" command ..................................................115
6.7.5. The "Go to First Packet" command ............................................................... 115
6.7.6. The "Go to Last Packet" command ................................................................ 115
6.8. Marking packets ................................................................................................... 116
6.9. Time display formats and time references ................................................................. 117
6.9.1. Packet time referencing ...............................................................................117
7. Advanced Features .......................................................................................................... 120
7.1. Introduction ........................................................................................................ 120
7.2. Following TCP streams .........................................................................................121
7.2.1. The "Follow TCP stream" dialog box ............................................................121
7.3. Packet Reassembling ............................................................................................ 123
7.3.1. What is it? ................................................................................................123
7.3.2. How Ethereal handles it .............................................................................. 123
7.3.3. Reassembling is disabled by default! ............................................................. 123
7.4. Name Resolution ..................................................................................................124
7.4.1. Ethernet name resolution (MAC layer) ........................................................... 124
7.4.2. IP name resolution (network layer) ................................................................ 124
7.4.3. IPX name resolution (network layer) ............................................................. 125
7.4.4. TCP/UDP port name resolution (transport layer) ..............................................125
8. Statistics ....................................................................................................................... 127
8.1. Introduction ........................................................................................................ 127
8.2. The "Summary" window ........................................................................................128
8.3. The "Protocol Hierarchy" window ........................................................................... 130
8.4. Endpoints ........................................................................................................... 132
8.4.1. What is an Endpoint? .................................................................................. 132
8.4.2. The "Endpoints" window ............................................................................. 132
8.4.3. The protocol specific "Endpoint List" windows ............................................... 133
8.5. Conversations ......................................................................................................134
8.5.1. What is a Conversation? .............................................................................. 134
8.5.2. The "Conversations" window ....................................................................... 134
8.5.3. The protocol specific "Conversation List" windows .......................................... 134
8.6. The "IO Graphs" window ....................................................................................... 135
8.7. Service Response Time ......................................................................................... 137
8.7.1. The "Service Response Time DCE-RPC" window ............................................137
8.8. The protocol specific statistics windows ................................................................... 139
9. Customizing Ethereal ...................................................................................................... 141
9.1. Introduction ........................................................................................................ 141
9.2. Start Ethereal from the command line .......................................................................142
9.3. Packet colorization ............................................................................................... 146
9.4. Control Protocol dissection .................................................................................... 149
9.4.1. The "Enabled Protocols" dialog box .............................................................. 149
9.4.2. User Specified Decodes ..............................................................................151
9.4.3. Show User Specified Decodes ...................................................................... 152
9.5. Preferences .........................................................................................................153
A. Configuration (and other) Files and Folders .........................................................................156
A.1. Windows folders .................................................................................................159
A.1.1. Windows profiles ...................................................................................... 159
A.1.2. Windows NT/2000/XP roaming profiles ........................................................160
A.1.3. Windows temporary folder ......................................................................... 160
B. Protocols and Protocol Fields ........................................................................................... 162
C. Related command line tools ............................................................................................. 163
C.1. Introduction ........................................................................................................ 163
C.2. tcpdump: Capturing with tcpdump for viewing with Ethereal ...................................... 164
C.3. tethereal: Terminal-based Ethereal .........................................................................165
C.4. capinfos: Print information about capture files .......................................................... 166
vi
Page 7

Ethereal User's Guide
C.5. editcap: Edit capture files ..................................................................................... 167
C.6. mergecap: Merging multiple capture files into one .................................................... 170
C.7. text2pcap: Converting ASCII hexdumps to network captures ...................................... 173
C.8. idl2eth: Creating dissectors from Corba IDL files ...................................................... 176
C.8.1. What is it? ............................................................................................... 176
C.8.2. Why do this? ............................................................................................176
C.8.3. How to use idl2eth .....................................................................................176
C.8.4. TODO ..................................................................................................... 177
C.8.5. Limitations ..............................................................................................178
C.8.6. Notes ......................................................................................................178
D. This Document's License (GPL) ........................................................................................ 180
vii
Page 8

Preface
1. Foreword
Ethereal is one of those programs that many network managers would love to be able to use, but
they are often prevented from getting what they would like from Ethereal because of the lack of
documentation.
This document is part of an effort by the Ethereal team to improve the usability of Ethereal.
We hope that you find it useful, and look forward to your comments.
viii
Page 9

Preface
2. Who should read this document?
The intended audience of this book is anyone using Ethereal.
This book will explain all the basics and also some of the advanced features that Ethereal provides.
As Ethereal has become a very complex program since the early days, not every feature of Ethereal
might be explained in this book.
This book is not intended to explain network sniffing in general and it will not provide details about
specific network protocols. A lot of useful information regarding these topics can be found at the
Ethereal Wiki at http://wiki.ethereal.com
By reading this book, you will learn how to install Ethereal, how to use the basic elements of the
graphical user interface (like the menu) and what's behind some of the advanced features that are
maybe not that obvious at first sight. It will hopefully guide you around some common problems
that frequently appears for new (and sometimes even advanced) users of Ethereal.
ix
Page 10
3. Acknowledgements
The authors would like to thank the whole Ethereal team for their assistance. In particular, the au-
thors would like to thank:
• Gerald Combs, for initiating the Ethereal project and funding to do this documentation.
• Guy Harris, for many helpful hints and a great deal of patience in reviewing this document.
• Gilbert Ramirez, for general encouragement and helpful hints along the way.
The authors would also like to thank the following people for their helpful feedback on this docu-
ment:
• Pat Eyler, for his suggestions on improving the example on generating a backtrace.
• Martin Regner, for his various suggestions and corrections.
• Graeme Hewson, for a lot of grammatical corrections.
Preface
The authors would like to acknowledge those man page and README authors for the ethereal
project from who sections of this document borrow heavily:
• Scott Renfro from whose mergecap man page Section C.6, “mergecap: Merging multiple cap-
ture files into one ” is derived.
• Ashok Narayanan from whose text2pcap man page Section C.7, “text2pcap: Converting ASCII
hexdumps to network captures ” is derived.
• Frank Singleton from whose README.idl2eth Section C.8, “idl2eth: Creating dissectors
from Corba IDL files ” is derived.
x
Page 11

Preface
4. About this document
This book was originally developed by Richard Sharpe with funds provided from the Ethereal Fund.
It was updated by Ed Warnicke and more recently redesigned and updated by Ulf Lamping.
It is written in DocBook/XML.
You will find some specially marked parts in this book:
This is a warning!
You should pay attention to a warning, as otherwise data loss might occur.
This is a note!
A note will point you to common mistakes and things that might not be obvious.
This is a tip!
Tips will be helpful for your everyday work using Ethereal.
xi
Page 12

Preface
5. Where to get the latest copy of this document?
The latest copy of this documentation can always be found at: http:/ / www.ethereal.com/ docs/
#usersguide.
xii
Page 13

Preface
6. Providing feedback about this document
Should you have any feedback about this document, please send them to the authors through ethere-
al-dev[AT]ethereal.com.
xiii
Page 14

Preface
xiv
Page 15

Chapter 1. Introduction
1.1. What is Ethereal?
Ethereal is a network packet analyzer. A network packet analyzer will try to capture network pack-
ets and tries to display that packet data as detailed as possible.
You could think of a network packet analyzer as a measuring device used to examine what's going
on inside a network cable, just like a voltmeter is used by an electrician to examine what's going on
inside an electric cable (but at a higher level, of course).
In the past, such tools were either very expensive, proprietary, or both. However, with the advent of
Ethereal, all that has changed.
Ethereal is perhaps one of the best open source packet analyzers available today.
1.1.1. Some intended purposes
Here are some examples people use Ethereal for:
• network administrators use it to troubleshoot network problems
• network security engineers use it to examine security problems
• developers use it to debug protocol implementations
• people use it to learn network protocol internals
Beside these examples, Ethereal can be helpful in many other situations too.
1.1.2. Features
The following are some of the many features Ethereal provides:
• Available for UNIX and Windows.
• Capture live packet data from a network interface.
• Display packets with very detailed protocol information.
• Open and Save packet data captured.
• Import and Export packet data from and to a lot of other capture programs.
• Filter packets on many criteria.
• Search for packets on many criteria.
• Colorize packet display based on filters.
• Create various statistics.
• ... and a lot more!
However, to really appreciate its power, you have to start using it.
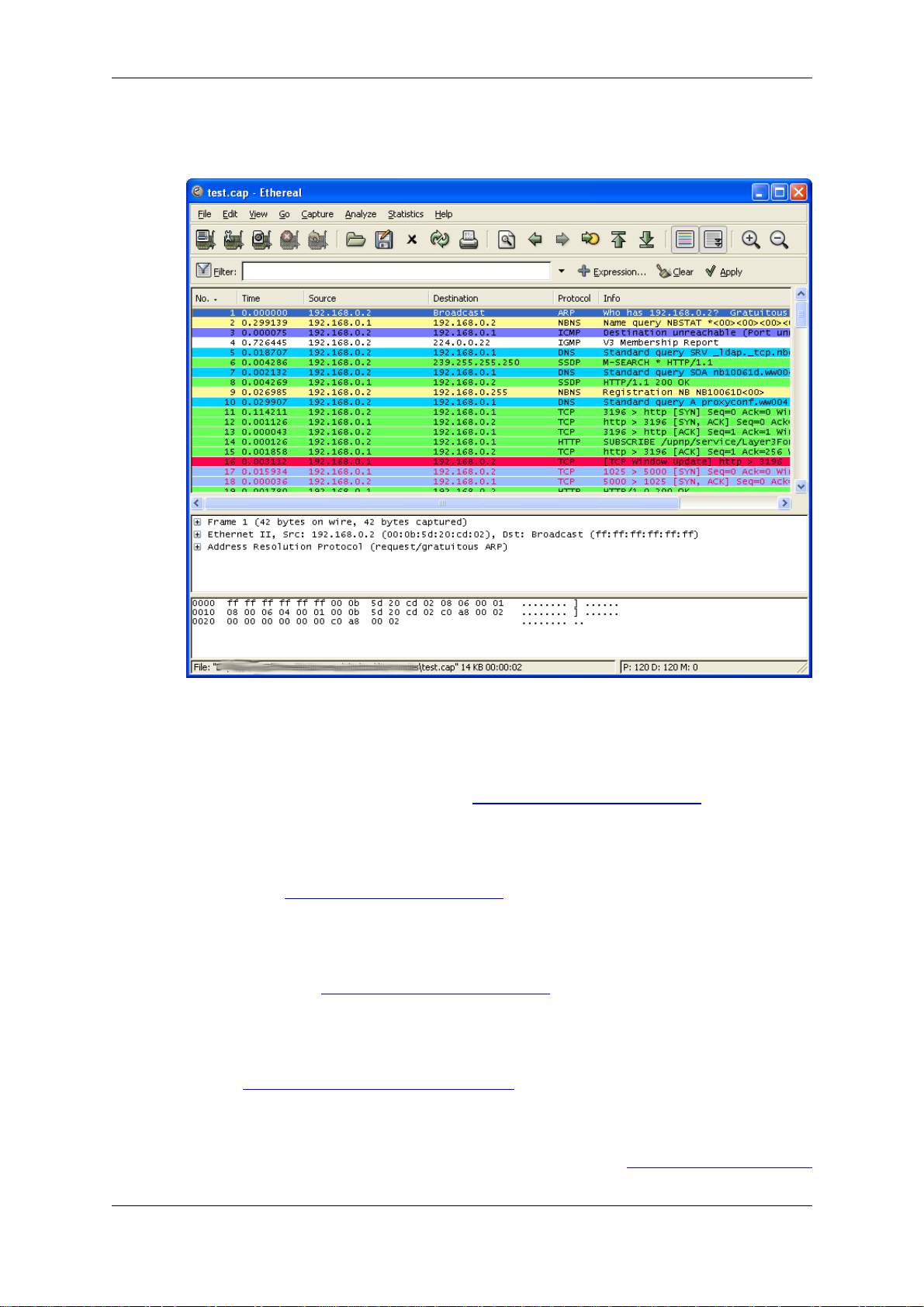
Figure 1.1, “ Ethereal captures packets and allows you to examine their content. ” shows Ethereal
having captured some packets and waiting for you to examine them.
1
Page 16
Introduction
Figure 1.1. Ethereal captures packets and allows you to examine their content.
1.1.3. Live capture from many different network media
Despite its name, Ethereal can capture traffic from network media other than Ethernet. Which media
types are supported, depends on many things like the operating system you are using. An overview
of the supported media types can be found at: http://www.ethereal.com/media.html.
1.1.4. Import files from many other capture programs
Ethereal can open packets captured from a large number of other capture programs. For a list of in-
put formats see Section 5.2.2, “Input File Formats”.
1.1.5. Export files for many other capture programs
Ethereal can save packets captured in a large number of formats of other capture programs. For a list
of output formats see Section 5.3.2, “Output File Formats”.
1.1.6. Many protocol decoders
There are protocol decoders (or dissectors, as they are known in Ethereal) for a great many proto-
cols: see Appendix B, Protocols and Protocol Fields.
1.1.7. Open Source Software
Ethereal is an open source software project, and is released under the GNU General Public Licence
(GPL). You can freely use Ethereal on any number of computers you like, without worrying about
2
Page 17

Introduction
license keys or fees or such. In addition, all source code is freely available under the GPL. Because
of that, it is very easy for people to add new protocols to Ethereal, either as plugins, or built into the
source, and they often do!
1.1.8. What Ethereal is not
Here are some things Ethereal does not provide:
• Ethereal isn't an intrusion detection system. It will not warn you when someone does strange
things on your network that he/she isn't allowed to do. However, if strange things happen, Ethereal might help you figure out what is really going on.
• Ethereal will not manipulate things on the network, it will only "measure" things from it. Ethereal doesn't send packets on the network or do other active things (except for name resolutions, but
even that can be disabled).
3
Page 18

Introduction
1.2. Platforms Ethereal runs on
Ethereal currently runs on most UNIX platforms and various Windows platforms. It requires GTK+,
GLib, libpcap and some other libraries in order to run.
If a binary package is not available for your platform, you should download the source and try to
build it. Please report your experiences to ethereal-dev[AT]ethereal.com.
Binary packages are available for at least the following platforms:
1.2.1. Unix
• Apple Mac OS X
• BeOS
• FreeBSD
• HP-UX
• IBM AIX
• NetBSD
• OpenBSD
• SCO UnixWare/OpenUnix
• SGI Irix
• Sun Solaris/Intel
• Sun Solaris/Sparc
• Tru64 UNIX (formerly Digital UNIX)
1.2.2. Linux
• Debian GNU/Linux
• Gentoo Linux
• IBM S/390 Linux (Red Hat)
• Mandrake Linux
• PLD Linux
• Red Hat Linux
• Rock Linux
• Slackware Linux
• Suse Linux
4
Page 19

1.2.3. Microsoft Windows
Maintained:
• Windows Server 2003 / XP / 2000 / NT 4.0
• Windows Me / 98
Unsupported/Unmaintained (because lack of required libraries):
• Windows CE
• Windows NT / XP Embedded
• Windows 95 is no longer actively maintained by WinPcap, but still may work perfectly
No experiences (fresh versions):
• Windows XP 64-bit Edition
Introduction
• Windows Vista (aka Longhorn)
Please provide your experiences about these fresh versions to: ethereal-dev[AT]ethereal.com.
5
Page 20

Introduction
1.3. Where to get Ethereal?
You can get the latest copy of the program from the Ethereal website: ht-
tp://www.ethereal.com/download.html. The website allows you to choose from among several mir-
rors for downloading.
A new Ethereal version will typically become available every 4-8 weeks.
If you want to be notified about new Ethereal releases, you should subscribe to the ethereal-an-
nounce mailing list. You will find more details in Section 1.7.4, “Mailing Lists”.
6
Page 21

Introduction
1.4. A rose by any other name
William Shakespeare wrote: "A rose by any other name would smell as sweet." And so it is with
Ethereal, as there appears to be two different ways that people pronounce the name.
Some people pronounce it ether-real, while others pronounce it e-the-real, as in ghostly, insubstantial, etc.
You are welcome to call it what you like, as long as you find it useful. The FAQ gives the official
pronunciation as "e-the-real".
7
Page 22

Introduction
1.5. A brief history of Ethereal
In late 1997, Gerald Combs needed a tool for tracking down networking problems and wanted to
learn more about networking, so he started writing Ethereal as a way to solve both problems.
Ethereal was initially released, after several pauses in development, in July 1998 as version 0.2.0.
Within days, patches, bug reports, and words of encouragement started arriving, so Ethereal was on
its way to success.
Not long after that Gilbert Ramirez saw its potential and contributed a low-level dissector to it.
In October, 1998, Guy Harris of Network Appliance was looking for something better than tcpview,
so he started applying patches and contributing dissectors to Ethereal.
In late 1998, Richard Sharpe, who was giving TCP/IP courses, saw its potential on such courses,
and started looking at it to see if it supported the protocols he needed. While it didn't at that point,
new protocols could be easily added. So he started contributing dissectors and contributing patches.
The list of people who have contributed to Ethereal has become very long since then, and almost all
of them started with a protocol that they needed that Ethereal did not already handle. So they copied
an existing dissector and contributed the code back to the team.
8
Page 23
Introduction
1.6. Development and maintenance of Ethereal
Ethereal was initially developed by Gerald Combs. Ongoing development and maintenance of Ethereal is handled by the Ethereal team, a loose group of individuals who fix bugs and provide new
functionality.
There have also been a large number of people who have contributed protocol dissectors to Ethereal,
and it is expected that this will continue. You can find a list of the people who have contributed
code to Ethereal by checking the about dialog box of Ethereal, or at the authors page on the Ethereal
web site.
Ethereal is an open source software project, and is released under the GNU General Public Licence
(GPL). All source code is freely available under the GPL. You are welcome to modify Ethereal to
suit your own needs, and it would be appreciated if you contribute your improvements back to the
Ethereal team.
You gain three benefits by contributing your improvements back to the community:
• Other people who find your contributions useful will appreciate them, and you will know that
you have helped people in the same way that the developers of Ethereal have helped people.
• The developers of Ethereal might improve your changes even more, as there's always room for
improvements. Or they may implement some advanced things on top of your code, which can be
useful for yourself too.
• The maintainers and developers of Ethereal will maintain your code as well, fixing it when API
changes or other changes are made, and generally keeping it in tune with what is happening with
Ethereal. So if Ethereal is updated (which is done often), you can get a new Ethereal version
from the website and your changes will already be included without any effort for you.
The Ethereal source code and binary kits for some platforms are all available on the download page
of the Ethereal website: http://www.ethereal.com/download.html.
9
Page 24
Introduction
1.7. Reporting problems and getting help
If you have problems, or need help with Ethereal, there are several places that may be of interest to
you (well, beside this guide of course).
1.7.1. Website
You will find lot's of useful information on the Ethereal homepage at http://www.ethereal.com.
1.7.2. Wiki
The Ethereal Wiki at http://wiki.ethereal.com provides a wide range of information related to Ethereal and packet capturing in general. You will find a lot of information not part of this user's guide.
For example, there is an explanation how to capture on a switched network, an ongoing effort to
build a protocol reference and a lot more.
And best of all, if you would like to contribute your knowledge on a specific topic (maybe a network protocol you know well), you can edit the wiki pages by simply using your webbrowser.
1.7.3. FAQ
The "Frequently Asked Questions" will list often asked questions and the corresponding answers.
Read the FAQ!
Before sending any mail to the mailing lists below, be sure to read the FAQ, as it will
often answer the question(s) you might have. This will save yourself and others a lot of
time (keep in mind that a lot of people are subscribed to the mailing lists).
You will find the FAQ inside Ethereal by clicking the menu item Help/Contents and selecting the
FAQ page in the upcoming dialog.
An online version is available at the ethereal website: http://www.ethereal.com/faq.html. You might
prefer this online version, as it's typically more up to date and the HTML format is easier to use.
1.7.4. Mailing Lists
There are several mailing lists of specific Ethereal topics available:
ethereal-announce This mailing list will inform you about new program releases, which
ethereal-users This list is for users of Ethereal. People post questions about building
ethereal-dev This list is for Ethereal developers. If you want to start developing a
usually appear about every 4-8 weeks.
and using Ethereal, others (hopefully) provide answers.
protocol dissector, join this list.
You can subscribe to each of these lists from the Ethereal web site: http://www.ethereal.com.
Simply select the mailing lists link on the left hand side of the site. The lists are archived at the Ethereal web site as well.
Tip!
You can search in the list archives to see if someone asked the same question some
time before and maybe already got an answer. That way you don't have to wait until
someone answers your question.
10
Page 25

Introduction
1.7.5. Reporting Problems
Note!
Before reporting any problems, please make sure you have installed the latest version
of Ethereal.
When reporting problems with Ethereal, it is helpful if you supply the following information:
1. The version number of Ethereal and the dependent libraries linked with it, eg GTK+, etc. You
can obtain this with the command ethereal -v.
2. Information about the platform you run Ethereal on.
3. A detailed description of your problem.
4. If you get an error/warning message, copy the text of that message (and also a few lines before
and after it, if there are some), so others may find the place where things go wrong. Please don't
give something like: "I get a warning while doing x" as this won't give a good idea where to
look at.
Don't send large files!
Do not send large files (>100KB) to the mailing lists, just place a note that further data
is available on request. Large files will only annoy a lot of people on the list who are
not interested in your specific problem. If required, you will be asked for further data
by the persons who really can help you.
Don't send confidential information!
If you send captured data to the mailing lists, be sure they don't contain any sensitive
or confidential information like passwords or such.
1.7.6. Reporting Crashes on UNIX/Linux platforms
When reporting crashes with Ethereal, it is helpful if you supply the traceback information (besides
the information mentioned in "Reporting Problems").
You can obtain this traceback information with the following commands:
$ gdb `whereis ethereal | cut -f2 -d: | cut -d' ' -f2` core >& bt.txt
backtrace
^D
$
Note
Type the characters in the first line verbatim! Those are back-tics there!
Note
11
Page 26

Introduction
backtrace is a gdb command. You should enter it verbatim after the first line shown
above, but it will not be echoed. The ^D (Control-D, that is, press the Control key and
the D key together) will cause gdb to exit. This will leave you with a file called
bt.txt in the current directory. Include the file with your bug report.
Note
If you do not have gdb available, you will have to check out your operating system's
debugger.
You should mail the traceback to the ethereal-dev[AT]ethereal.com mailing list.
1.7.7. Reporting Crashes on Windows platforms
The Windows distributions don't contain the symbol files (.pdb), because they are very large. For
this reason it's not possible to create a meaningful backtrace file from it. You should report your
crash just like other problems, using the mechanism described above.
12
Page 27

Introduction
13
Page 28

Chapter 2. Building and Installing Ethereal
2.1. Introduction
As with all things, there must be a beginning, and so it is with Ethereal. To use Ethereal, you must:
• Obtain a binary package for your operating system, or
• Obtain the source and build Ethereal for your operating system.
Currently, only two or three Linux distributions ship Ethereal, and they are commonly shipping an
out-of-date version. No other versions of UNIX ship Ethereal so far, and Microsoft does not ship it
with any version of Windows. For that reason, you will need to know where to get the latest version
of Ethereal and how to install it.
This chapter shows you how to obtain source and binary packages, and how to build Ethereal from
source, should you choose to do so.
The following are the general steps you would use:
1. Download the relevant package for your needs, e.g. source or binary distribution.
2. Build the source into a binary, if you have downloaded the source.
This may involve building and/or installing other necessary packages.
3. Install the binaries into their final destinations.
14
Page 29
Building and Installing Ethereal
2.2. Obtaining the source and binary distributions
You can obtain both source and binary distributions from the Ethereal web site: ht-
tp://www.ethereal.com. Simply select the download link, and then select either the source package
or binary package of your choice from the mirror site closest to you.
Download all required files!
In general, unless you have already downloaded Ethereal before, you will most likely
need to download several source packages if you are building Ethereal from source.
This is covered in more detail below.
Once you have downloaded the relevant files, you can go on to the next step.
Note!
While you will find a number of binary packages available on the Ethereal web site,
you might not find one for your platform, and they often tend to be several versions
behind the current released version, as they are contributed by people who have the
platforms they are built for.
For this reason, you might want to pull down the source distribution and build it, as the
process is relatively simple.
15
Page 30
Building and Installing Ethereal
2.3. Before you build Ethereal under UNIX
Before you build Ethereal from sources, or install a binary package, you must ensure that you have
the following other packages installed:
• GTK+, The GIMP Tool Kit.
You will also need Glib. Both can be obtained from www.gtk.org
• libpcap, the packet capture software that Ethereal uses.
You can obtain libpcap from www.tcpdump.org
Depending on your system, you may be able to install these from binaries, e.g. RPMs, or you may
need to obtain them in source code form and build them.
If you have downloaded the source for GTK+, the instructions shown in Example 2.1, “Building
GTK+ from source” may provide some help in building it:
Example 2.1. Building GTK+ from source
gzip -dc gtk+-1.2.10.tar.gz | tar xvf <much output removed>
cd gtk+-1.2.10
./configure
<much output removed>
make
<much output removed>
make install
<much output removed>
Note!
You may need to change the version number of gtk+ in Example 2.1, “Building GTK+
from source” to match the version of GTK+ you have downloaded. The directory you
change to will change if the version of GTK+ changes, and in all cases, tar xvf - will
show you the name of the directory you should change to.
Note!
If you use Linux, or have GNU tar installed, you can use tar zxvf gtk+-1.2.10.tar.gz.
It is also possible to use gunzip -c or gzcat rather than gzip -dc on many UNIX systems.
Note!
If you downloaded gtk+ or any other tar file using Windows, you may find your file
called gtk+-1_2_8_tar.gz.
You should consult the GTK+ web site if any errors occur in carrying out the instructions in Ex-
ample 2.1, “Building GTK+ from source”.
If you have downloaded the source to libpcap, the general instructions shown in Example 2.2,
16
Page 31

Building and Installing Ethereal
“Building and installing libpcap” will assist in building it. Also, if your operating system does not
support tcpdump, you might also want to download it from the tcpdump web site and install it.
Example 2.2. Building and installing libpcap
gzip -dc libpcap-0.8.3.tar.Z | tar xvf <much output removed>
cd libpcap_0_8_3
./configure
<much output removed>
make
<much output removed>
make install
<much output removed>
make install-incl
<much output removed>
Note!
The directory you should change to will depend on the version of libpcap you have
downloaded. In all cases, tar xvf - will show you the name of the directory that has
been unpacked.
When installing the include files, you might get the error shown in Example 2.3, “Errors while in-
stalling the libpcap include files” when you submit the command make install-incl.
Example 2.3. Errors while installing the libpcap include files
/usr/local/include/pcap.h
/usr/bin/install -c -m 444 -o bin -g bin ./pcap-namedb.h \
/usr/local/include/pcap-namedb.h
/usr/bin/install -c -m 444 -o bin -g bin ./net/bpf.h \
/usr/local/include/net/bpf.h
/usr/bin/install: cannot create regular file \
`/usr/local/include/net/bpf.h': No such file or directory
make: *** [install-incl] Error 1
If you do, simply create the missing directory with the following command:
mkdir /usr/local/include/net
and rerun the command make install-incl.
Under RedHat 6.x and beyond (and distributions based on it, like Mandrake) you can simply install
each of the packages you need from RPMs. Most Linux systems will install GTK+ and GLib in anycase, however, you will probably need to install the devel versions of each of these packages. The
commands shown in Example 2.4, “ Installing required RPMs under RedHat Linux 6.2 and beyond
” will install all the needed RPMs if they are not already installed.
Example 2.4. Installing required RPMs under RedHat Linux 6.2 and beyond
17
Page 32

Building and Installing Ethereal
cd /mnt/cdrom/RedHat/RPMS
rpm -ivh glib-1.2.6-3.i386.rpm
rpm -ivh glib-devel-1.2.6-3.i386.rpm
rpm -ivh gtk+-1.2.6-7.i386.rpm
rpm -ivh gtk+-devel-1.2.6-7.i386.rpm
rpm -ivh libpcap-0.4-19.i386.rpm
Note
If you are using a version of RedHat later than 6.2, the required RPMs have most
likely changed. Simply use the correct RPMs from your distribution.
Under Debian you can install Ethereal using apt-get. apt-get will handle any dependency issues for
you. Example 2.5, “Installing debs under Debian” shows how to do this.
Example 2.5. Installing debs under Debian
apt-get install ethereal
18
Page 33

Building and Installing Ethereal
2.4. Building Ethereal from source under UNIX
Use the following general steps if you are building Ethereal from source under a UNIX operating
system:
1. Unpack the source from its gzip'd tar file. If you are using Linux, or your version of UNIX
uses GNU tar, you can use the following command:
tar zxvf ethereal-0.10.12-tar.gz
For other versions of UNIX, You will want to use the following commands:
gzip -d ethereal-0.10.12-tar.gz
tar xvf ethereal-0.10.12-tar
Note!
The pipeline gzip -dc ethereal-0.10.12-tar.gz | tar xvf - will work here as well.
Note!
If you have downloaded the Ethereal tarball under Windows, you may find that
your browser has created a file with underscores rather than periods in its file
name.
2. Change directory to the Ethereal source directory.
3. Configure your source so it will build correctly for your version of UNIX. You can do this with
the following command:
./configure
If this step fails, you will have to rectify the problems and rerun configure. Troubleshooting
hints are provided in Section 2.6, “Troubleshooting during the install on Unix”.
4. Build the sources into a binary, with the make command. For example:
make
5. Install the software in its final destination, using the command:
make install
19
Page 34

Building and Installing Ethereal
Once you have installed Ethereal with make install above, you should be able to run it by entering
ethereal.
20
Page 35

Building and Installing Ethereal
2.5. Installing the binaries under UNIX
In general, installing the binary under your version of UNIX will be specific to the installation methods used with your version of UNIX. For example, under AIX, you would use smit to install the
Ethereal binary package, while under Tru64 UNIX (formerly Digital UNIX) you would use setld.
2.5.1. Installing from rpm's under RedHat and alike
Use the following command to install the Ethereal RPM that you have downloaded from the Ethereal web site:
rpm -ivh ethereal-0.10.5-0.2.2.i386.rpm
If the above step fails because of missing dependencies, install the dependencies first, and then retry
the step above. See Example 2.4, “ Installing required RPMs under RedHat Linux 6.2 and beyond ”
for information on what RPMs you will need to have installed.
2.5.2. Installing from deb's under Debian
Use the following command to install Ethereal under Debian:
apt-get install ethereal
apt-get should take care of all of the dependency issues for you.
21
Page 36

Building and Installing Ethereal
2.6. Troubleshooting during the install on Unix
A number of errors can occur during the installation process. Some hints on solving these are
provided here.
If the configure stage fails, you will need to find out why. You can check the file config.log in
the source directory to find out what failed. The last few lines of this file should help in determining
the problem.
The standard problems are that you do not have GTK+ on your system, or you do not have a recent
enough version of GTK+. The configure will also fail if you do not have libpcap (at least the required include files) on your system.
Another common problem is for the final compile and link stage to terminate with a complaint of:
Output too long. This is likely to be caused by an antiquated sed (such as the one shipped with Solaris). Since sed is used by the libtool script to construct the final link command, this leads to mysterious problems. This can be resolved by downloading a recent version of sed from http://direct-
ory.fsf.org/GNU/sed.html.
If you cannot determine what the problems are, send mail to the ethereal-dev mailing list explaining your problem, and including the output from config.log and anything else you think is relevant, like a trace of the make stage.
22
Page 37

Building and Installing Ethereal
2.7. Building from source under Windows
It is recommended to use the binary installer for Windows, until you want to start developing Ethereal on the Windows platform.
For further information how to build Ethereal for Windows from the sources, have a look at the Development Wiki: http://wiki.ethereal.com/Development for the latest available development documentation.
23
Page 38

Building and Installing Ethereal
2.8. Installing Ethereal under Windows
In this section we explore installing Ethereal under Windows from the binary packages.
2.8.1. Install Ethereal
You may acquire a binary installer of Ethereal named something like: etherealsetup-x.y.z.exe.
Simply download the Ethereal installer from: http://www.ethereal.com/download.html#releases and
execute it.
Note!
Since Ethereal Version 0.10.12, the WinPcap installer has become part of the
main Ethereal installer, so you don't need to download and install two separate
packages any longer!
2.8.1.1. Command line options
You can simply start the Ethereal installer without any command line parameters, it will show you
the usual interactive installer.
There are some command line parameters available:
• /NCRC disables the CRC check
• /S runs the installer or uninstaller silently with default values. Please note: The silent installer
won't install WinPCap!
• /desktopicon installation of the desktop icon, =yes - force installation, =no - don't install, otherwise use defaults / user settings. This option is available since 0.10.13 an can be useful for a silent installer.
• /quicklaunchicon installation of the quick launch icon, =yes - force installation, =no - don't install, otherwise use defaults / user settings. This option is available since 0.10.13 an can be useful for a silent installer.
• /D sets the default installation directory ($INSTDIR), overriding InstallDir and InstallDirRegKey. It must be the last parameter used in the command line and must not contain any
quotes, even if the path contains spaces.
Example:
ethereal-setup-0.10.13.exe /NCRC /S /desktopicon=yes /quicklaunchicon=no /D=C:\Program Files\Foo
2.8.1.2. Components
Beside the usual installer options like where to install the program, there are several optional components.
Tip!
If you are unsure which settings to select, just keep the default settings.
24
Page 39

Building and Installing Ethereal
The Components (both Ethereal GTK1 and 2 cannot be installed at the same time):
• Etheral GTK1 - Ethereal is a GUI network protocol analyzer.
• Etheral GTK2 - Ethereal is a GUI network protocol analyzer (using the modern GTK2 GUI
toolkit, recommended).
• GTK-Wimp - GTKWimp is the GTK2 windows impersonator (native Win32 look and feel, recommended).
• Tethereal - Tethereal is a command-line based network protocol analyzer.
The dissection extensions for Ethereal and Tethereal:
• Dissector Plugins - Plugins with some extended dissections.
• Tree Statistics Plugins - Plugins with some extended statistics.
• Mate - Meta Analysis and Tracing Engine - user configurable extension(s) of the display filter
engine, see http://wiki.ethereal.com/Mate for details.
• SNMP MIBs - SNMP MIBs for a more detailed SNMP dissection.
The Tools:
• Editcap - Editcap is a program that reads a capture file and writes some or all of the packets into
another capture file.
• Text2Pcap - Text2pcap is a program that reads in an ASCII hex dump and writes the data into a
libpcap-style capture file.
• Mergecap - Mergecap is a program that combines multiple saved capture files into a single output file.
• Capinfos - Capinfos is a program that provides information on capture files.
The Additional Tasks:
• Start Menu Shortcuts - add some start menu shortcuts.
• Desktop Icon - add an Ethereal icon to the desktop.
• Quick Launch Icon - add an Ethereal icon to the Explorer quick launch toolbar.
• Associate file extensions to Ethereal - Associate standard network trace files to Ethereal.
2.8.2. Install WinPcap
Note!
As mentioned above, the Ethereal installer (since version 0.10.12) takes care of
the installation of WinPcap, so usually you don't have to worry about WinPcap at
all!
If you do not have WinPcap installed you will be able to open saved capture files, but you will not
be able to capture live network traffic.
While running, the Ethereal installer detects which WinPcap version is currently installed and will
25
Page 40

Building and Installing Ethereal
install WinPcap, if none or an older version is detected.
More WinPcap info:
• Ethereal related: http://wiki.ethereal.com/WinPcap
• General WinPcap info: http://www.winpcap.org
2.8.2.1. Manual WinPcap Installation
The following is only necessary if you want to try a different version than the one included in the
Ethereal installer, e.g. because a new WinPcap (beta) version was released.
Additional WinPcap versions (including newer alpha or beta releases) can be downloaded from the
following locations:
• The main WinPcap site: http://www.winpcap.org
• The ethereal.com mirror: http://winpcap.mirror.ethereal.com
• The Wiretapped.net mirror: http://www.mirrors.wiretapped.net/security/packet-capture/winpcap
At the download page you will find a single installer exe called something like "auto-installer",
which can be installed under various Windows systems, including 9x/Me/NT4.0/2000/XP.
2.8.3. Update Ethereal
From time to time you may want to update your installed Ethereal to a more recent version. If you
join Ethereal's announce mailing list, you will be informed about new Ethereal versions, see Sec-
tion 1.7.4, “Mailing Lists” for details how to subscribe to this list.
New versions of Ethereal usually become available every 4-8 weeks. Updating Ethereal is done the
same way as installing it, you simply download and start the installer exe. A reboot is usually not required and all your personal settings remain unchanged.
2.8.4. Update WinPcap
New versions of WinPcap are less frequently available, maybe only once in a year. You will find
WinPcap update instructions where you can download new WinPcap versions. Usually you have to
reboot the machine after installing a new WinPcap version.
Warning!
If you have an older version of WinPcap installed, you must un-install it before installing the current version. Recent versions of the WinPcap installer will take care of
this.
2.8.5. Uninstall Ethereal
You can uninstall Ethereal the usual way, using the "Add or Remove Programs" option inside the
Control Panel. Select the "Ethereal" entry to start the uninstallation procedure.
The Ethereal uninstaller will provide several options which things to be uninstalled, the default is to
remove the core components but keep the personal settings, WinPcap and alike.
WinPcap won't be uninstalled by default, as other programs than Ethereal may use it as well.
26
Page 41

Building and Installing Ethereal
2.8.6. Uninstall WinPcap
You can uninstall WinPcap independantly of Ethereal, using the "WinPcap" entry in the "Add or
Remove Programs" of the Control Panel.
Note!
After uninstallation of WinPcap you can't capture anything with Ethereal.
It might be a good idea to reboot Windows afterwards.
27
Page 42

Building and Installing Ethereal
28
Page 43

Chapter 3. User Interface
3.1. Introduction
By now you have installed Ethereal and are most likely keen to get started capturing your first packets. In the next chapters we will explore:
• How the Ethereal user interface works
• How to capture packets in Ethereal
• How to view packets in Ethereal
• How to filter packets in Ethereal
• ... and many other things!
29
Page 44

3.2. Start Ethereal
You can start Ethereal from your shell or window manager.
Tip!
When starting Ethereal it's possible to specify optional settings using the command
line. See Section 9.2, “Start Ethereal from the command line” for details.
Note!
In the following chapters, a lot of screenshots from Ethereal will be shown. As Ethereal runs on many different platforms and there are different versions of the underlying
GUI toolkit (GTK 1.x / 2.x) used, your screen might look different from the provided
screenshots. But as there are no real differences in functionality, these screenshots
should still be well understandable.
User Interface
30
Page 45

User Interface
3.3. The Main window
Lets look at Ethereal's user interface. Figure 3.1, “The Main window” shows Ethereal as you would
usually see it after some packets captured or loaded (how to do this will be described later).
Figure 3.1. The Main window
Ethereal's main window consist of parts that are commonly known from many other GUI programs.
1. The menu (see Section 3.4, “The Menu”) is used to start actions.
2. The main toolbar (see Section 3.13, “The "Main" toolbar”) provides quick access to frequently
used items from the menu.
3. The filter toolbar (see Section 3.14, “The "Filter" toolbar”) provides a way to directly manipu-
late the currently used display filter (see Section 6.2, “Filtering packets while viewing”).
4. The packet list pane (see Section 3.15, “The "Packet List" pane”) displays a summary of each
packet captured. By clicking on packets in this pane you control what is displayed in the other
two panes.
5. The packet details pane (see Section 3.16, “The "Packet Details" pane”) displays the packet se-
lected in the packet list pane in more detail.
6. The packet bytes pane (see Section 3.17, “The "Packet Bytes" pane”) displays the data from the
packet selected in the packet list pane, and highlights the field selected in the packet details
pane.
7. The statusbar (see Section 3.18, “The Statusbar”) shows some detailed information about the
31
Page 46

User Interface
current program state and the captured data.
Tip!
The layout of the main window can be customized by changing preference settings.
See Section 9.5, “Preferences” for details!
32
Page 47

3.4. The Menu
The Ethereal menu sits on top of the Ethereal window. An example is shown in Figure 3.2, “The
Menu”.
Note!
Menu items will be greyed out if the corresponding feature isn't available. For example, you cannot save a capture file if you didn't capture or load any data before.
Figure 3.2. The Menu
It contains the following items:
File This menu contains items to open and merge capture files, save / print / export
capture files in whole or in part, and to quit from Ethereal. See Section 3.5, “The
"File" menu”.
User Interface
Edit This menu contains items to find a packet, time reference or mark one or more
packets, set your preferences, (cut, copy, and paste are not presently implemented).
See Section 3.6, “The "Edit" menu”.
View This menu controls the display of the captured data, including the colorization of
packets, zooming the font, show a packet in a separate window, expand and col-
lapse trees in packet details, .... See Section 3.7, “The "View" menu”.
Go This menu contains items to go to a specific packet. See Section 3.8, “The "Go"
menu”.
Capture This menu allows you to start and stop captures and to edit capture filters. See Sec-
tion 3.9, “The "Capture" menu”.
Analyze This menu contains items to manipulate display filters, enable or disable the dis-
section of protocols, configure user specified decodes and follow a TCP stream.
See Section 3.10, “The "Analyze" menu”.
Statistics This menu contains menu-items to display various statistic windows, including a
summary of the packets that have been captured, display protocol hierarchy statistics and much more. See Section 3.11, “The "Statistics" menu”.
Help This menu contains items to help the user, like access to some basic help, a list of
the supported protocols, manual pages, online access to some of the webpages, and
the usual about dialog. See Section 3.12, “The "Help" menu”.
Each of these menu items is described in more detail in the sections that follow.
Tip!
You can access menu items directly or by pressing the corresponding accelerator keys,
which are shown at the right side of the menu. For example, you can press the Control
(or Strg in German) and the K keys together to open the capture dialog.
33
Page 48

3.5. The "File" menu
The Ethereal file menu contains the fields shown in Table 3.1, “File menu items”.
Figure 3.3. The "File" Menu
User Interface
Table 3.1. File menu items
Menu Item Accelerator Description
Open... Ctrl+O
This menu item brings up the file open dialog box that allows you to load
a capture file for viewing. It is discussed in more detail in Section 5.2.1,
“The "Open Capture File" dialog box”.
Open Recent
This menu item shows a submenu containing the recently opened capture
files. Clicking on one of the submenu items will open the corresponding
capture file directly.
Merge...
This menu item brings up the merge file dialog box that allows you to
merge a capture file into the currently loaded one. It is discussed in more
detail in Section 5.4, “Merging capture files”.
Close Ctrl+W
This menu item closes the current capture. If you haven't saved the capture, you will be asked to do so first (this can be disabled by a preference
setting).
------
34
Page 49

Menu Item Accelerator Description
Save Ctrl+S
This menu item saves the current capture. If you have not set a default
capture file name (perhaps with the -w <capfile> option), Ethereal pops
up the Save Capture File As dialog box (which is discussed further in
Section 5.3.1, “The "Save Capture File As" dialog box”).
Save As... Shift+Ctrl+S
This menu item allows you to save the current capture file to whatever
file you would like. It pops up the Save Capture File As dialog box
(which is discussed further in Section 5.3.1, “The "Save Capture File As"
dialog box”).
-----File Set > List
Files
File Set > Next
File
File Set > Previous File
-----Export > as
"Plain Text"
file...
Export > as
"PostScript"
file...
Export > as
"CSV"
(Comma Separated Values
packet summary) file...
Export > as
"PSML" file...
This menu item allows you to show a list of files in a file set. It pops up
the Ethereal List File Set dialog box (which is discussed further in Sec-
tion 5.5, “File Sets”).
If the currently loaded file is part of a file set, jump to the next file in the
set. If it isn't part of a file set or just the last file in that set, this item is
greyed out.
If the currently loaded file is part of a file set, jump to the previous file in
the set. If it isn't part of a file set or just the first file in that set, this item
is greyed out.
This menu item allows you to export all, or some, of the packets in the
capture file to a plain ASCII text file. It pops up the Ethereal Export dialog box (which is discussed further in Section 5.6.1, “The "Export as
Plain Text File" dialog box”).
This menu item allows you to export the (or some) of the packets in the
capture file to a PostScript file. It pops up the Ethereal Export dialog box
(which is discussed further in Section 5.6.2, “The "Export as PostScript
File" dialog box”).
This menu item allows you to export the (or some) of the packet summaries in the capture file to a .csv file (e.g. used by spreadsheet programs). It
pops up the Ethereal Export dialog box (which is discussed further in
Section 5.6.3, “The "Export as CSV (Comma Seperated Values) File"
dialog box”).
This menu item allows you to export the (or some) of the packets in the
capture file to a PSML (packet summary markup language) XML file. It
pops up the Ethereal Export dialog box (which is discussed further in
Section 5.6.4, “The "Export as PSML File" dialog box”).
User Interface
Note!
If you have already saved the current capture, this menu
item will be greyed out.
Note!
You cannot save a live capture while it is in progress. You
must stop the capture in order to save.
35
Page 50

Menu Item Accelerator Description
Export > as
"PDML" file...
Export > Selected Packet
Bytes...
-----Print... Ctrl+P
-----Quit Ctrl+Q
Ctrl+H
This menu item allows you to export the (or some) of the packets in the
capture file to a PDML (packet details markup language) XML file. It
pops up the Ethereal Export dialog box (which is discussed further in
Section 5.6.5, “The "Export as PDML File" dialog box”).
This menu item allows you to export the currently selected bytes in the
packet bytes pane to a binary file. It pops up the Ethereal Export dialog
box (which is discussed further in Section 5.6.6, “The "Export selected
packet bytes" dialog box”)
This menu item allows you to print all (or some of) the packets in the
capture file. It pops up the Ethereal Print dialog box (which is discussed
further in Section 5.7, “Printing packets”).
This menu item allows you to quit from Ethereal. Ethereal will ask to
save your capture file if you haven't saved it before (this can be disabled
by a preference setting).
User Interface
36
Page 51

3.6. The "Edit" menu
The Ethereal Edit menu contains the fields shown in Table 3.2, “Edit menu items”.
Figure 3.4. The "Edit" Menu
User Interface
Table 3.2. Edit menu items
Menu Item Accelerator Description
Find Packet... Ctrl+F
This menu item brings up a dialog box that allows you to find a packet by
many criteria. There is further information on finding packets in Sec-
tion 6.6, “Finding packets”.
Find Next Ctrl+N
This menu item tries to find the next packet matching the settings from
"Find Packet...".
Find Previous Ctrl+B
This menu item tries to find the previous packet matching the settings
from "Find Packet...".
-----Time Reference
> Set Time Reference (toggle)
Time Reference
> Find Next
Ctrl+T
This menu item set a time reference on the currently selected packet. See
Section 6.9.1, “Packet time referencing” for more information about the
time referenced packets.
This menu item tries to find the next time referenced packet.
37
Page 52

Menu Item Accelerator Description
Time Reference
> Find Previous
Mark Packet
(toggle)
Mark All Packets
Unmark All
Packets
-----Preferences... Shift+Ctrl+P
Ctrl+M
This menu item tries to find the previous time referenced packet.
This menu item "marks" the currently selected packet. See Section 6.8,
“Marking packets” for details.
This menu item "marks" all packets.
This menu item "unmarks" all marked packets.
This menu item brings up a dialog box that allows you to set preferences
for many parameters that control Ethereal. You can also save your preferences so Ethereal will use them the next time you start it. More detail is
provided in Section 9.5, “Preferences”.
User Interface
38
Page 53

User Interface
3.7. The "View" menu
The Ethereal View menu contains the fields shown in Table 3.3, “View menu items”.
Figure 3.5. The "View" Menu
Table 3.3. View menu items
Menu Item Accelerator Description
Main Toolbar
This menu item hides or shows the main toolbar, see Section 3.13, “The
"Main" toolbar”.
Filter Toolbar
This menu item hides or shows the filter toolbar, see Section 3.14, “The
"Filter" toolbar”.
Statusbar
This menu item hides or shows the statusbar, see Section 3.18, “The
Statusbar”.
-----Packet List
This menu item hides or shows the packet list pane, see Section 3.15,
“The "Packet List" pane”.
Packet Details
This menu item hides or shows the packet details pane, see Section 3.16,
“The "Packet Details" pane”.
39
Page 54

Menu Item Accelerator Description
Packet Bytes
This menu item hides or shows the packet bytes pane, see Section 3.17,
“The "Packet Bytes" pane”.
-----Time Display
Format > Time
of Day
Time Display
Format > Date
and Time of
Day
Time Display
Format >
Seconds Since
Beginning of
Capture
Time Display
Format >
Seconds Since
Previous Packet
Name Resolution > Resolve
Name
Name Resolution > Enable
for MAC Layer
Name Resolution > Enable
for Network
Layer
Name Resolution > Enable
for Transport
Layer
Colorize Packet
List
Selecting this tells Ethereal to display time stamps in time of day format,
see Section 6.9, “Time display formats and time references”.
Selecting this tells Ethereal to display the time stamps in date and time of
day format, see Section 6.9, “Time display formats and time references”.
Selecting this tells Ethereal to display time stamps in seconds since beginning of capture format, see Section 6.9, “Time display formats and
time references”.
Selecting this tells Ethereal to display time stamps in seconds since previous packet format, see Section 6.9, “Time display formats and time refer-
ences”.
This item allows you to trigger a name resolve of the current packet only,
see Section 7.4, “Name Resolution”.
This item allows you to control whether or not Ethereal translates MAC
addresses into names, see Section 7.4, “Name Resolution”.
This item allows you to control whether or not Ethereal translates network addresses into names, see Section 7.4, “Name Resolution”.
This item allows you to control whether or not Ethereal translates transport addresses into names, see Section 7.4, “Name Resolution”.
This item allows you to control wether or not Ethereal should colorize
the packet list.
User Interface
Note!
The fields "Time of Day", "Date and Time of Day",
"Seconds Since Beginning of Capture" and "Seconds Since
Previous Packet" are mutually exclusive.
Auto Scroll in
Live Capture
------
Note!
Enabling colorization will slow down the display of new
packets while capturing / loading capture files.
This item allows you to specify that Ethereal should scroll the packet list
pane as new packets come in, so you are always looking at the last packet. If you do not specify this, Ethereal simply adds new packets onto the
end of the list, but does not scroll the packet list pane.
40
Page 55

Menu Item Accelerator Description
Zoom In Ctrl++
Zoom into the packet data (increase the font size).
Zoom Out Ctrl+-
Zoom out of the packet data (decrease the font size).
Normal Size Ctrl+=
Set zoom level back to 100% (set font size back to normal).
Resize All
Columns
-----Expand Sub-
trees
Expand All
Collapse All
-----Coloring
Rules...
-----Show Packet in
New Window
Reload Ctrl-R
Resize all column widths so the content will fit into it.
This menu item expands the currently selected subtree in the packet details tree.
Ethereal keeps a list of all the protocol subtrees that are expanded, and
uses it to ensure that the correct subtrees are expanded when you display
a packet. This menu item expands all subtrees in all packets in the capture.
This menu item collapses the tree view of all packets in the capture list.
This menu item brings up a dialog box that allows you to color packets in
the packet list pane according to filter expressions you choose. It can be
very useful for spotting certain types of packets, see Section 9.3, “Packet
colorization”.
This menu item brings up the selected packet in a separate window. The
separate window shows only the tree view and byte view panes.
This menu item allows you to reload the current capture file.
User Interface
Note!
Resizing may take a significant amount of time, especially
if a large capture file is loaded.
41
Page 56

3.8. The "Go" menu
The Ethereal Go menu contains the fields shown in Table 3.4, “Go menu items”.
Figure 3.6. The "Go" Menu
User Interface
Table 3.4. Go menu items
Menu Item Accelerator Description
Back Alt+Left
Jump to the recently visited packet in the packet history, much like the
page history in a web browser.
Forward Alt+Right
Jump to the next visited packet in the packet history, much like the page
history in a web browser.
Go to Packet... Ctrl-G
Bring up a dialog box that allows you to specify a packet number, and
then goes to that packet. See Section 6.7, “Go to a specific packet” for
details.
Go to Corresponding Packet
-----First Packet
Go to the corresponding packet of the currently selected protocol field. If
the selected field doesn't correspond to a packet, this item is greyed out.
Jump to the first packet of the capture file.
42
Page 57

Menu Item Accelerator Description
Last Packet
Jump to the last packet of the capture file.
User Interface
43
Page 58

User Interface
3.9. The "Capture" menu
The Ethereal Capture menu contains the fields shown in Table 3.5, “Capture menu items”.
Figure 3.7. The "Capture" Menu
Table 3.5. Capture menu items
Menu Item Accelerator Description
Interfaces...
This menu item brings up a dialog box that shows what's going on at the
network interfaces Ethereal knows of, see Section 4.4, “The "Capture In-
terfaces" dialog box”) .
Options... Ctrl+K
This menu item brings up the Capture Options dialog box (discussed further in Section 4.5, “The "Capture Options" dialog box”) and allows you
to start capturing packets.
Start
Immediately start capturing packets with the same settings than the last
time.
Stop Ctrl+E
This menu item stops the currently running capture, see Section 4.9.1,
“Stop the running capture”) .
Restart
This menu item stops the currently running capture and starts again with
the same options, this is just for convenience.
44
Page 59

Menu Item Accelerator Description
Capture Fil-
ters...
This menu item brings up a dialog box that allows you to create and edit
capture filters. You can name filters, and you can save them for future
use. More detail on this subject is provided in Section 6.5, “Defining and
saving filters”
User Interface
45
Page 60

User Interface
3.10. The "Analyze" menu
The Ethereal Analyze menu contains the fields shown in Table 3.6, “Analyze menu items”.
Figure 3.8. The "Analyze" Menu
Table 3.6. Analyze menu items
Menu Item Accelerator Description
Display Fil-
ters...
Apply as Filter
> ...
Prepare a Filter > ...
------
This menu item brings up a dialog box that allows you to create and edit
display filters. You can name filters, and you can save them for future
use. More detail on this subject is provided in Section 6.5, “Defining and
saving filters”
These menu items will change the current display filter and apply the
changed filter immediately. Depending on the chosen menu item, the current display filter string will be replaced or appended to by the selected
protocol field in the packet details pane.
These menu items will change the current display filter but won't apply
the changed filter. Depending on the chosen menu item, the current display filter string will be replaced or appended to by the selected protocol
field in the packet details pane.
46
Page 61

Menu Item Accelerator Description
Enabled Proto-
cols...
Decode As...
User Specified
Decodes...
-----Follow TCP
Stream
Shift+Ctrl+R
This menu item allows the user to enable/disable protocol dissectors, see
Section 9.4.1, “The "Enabled Protocols" dialog box”
This menu item allows the user to force Ethereal to decode certain packets as a particular protocol, see Section 9.4.2, “User Specified Decodes”
This menu item allows the user to force Ethereal to decode certain packets as a particular protocol, see Section 9.4.3, “Show User Specified De-
codes”
This menu item brings up a separate window and displays all the TCP
segments captured that are on the same TCP connection as a selected
packet, see Section 7.2, “Following TCP streams”
User Interface
47
Page 62

User Interface
3.11. The "Statistics" menu
The Ethereal Statistics menu contains the fields shown in Table 3.7, “Statistics menu items”.
Figure 3.9. The "Statistics" Menu
All menu items will bring up a new window showing specific statistical information.
Table 3.7. Statistics menu items
Menu Item Accelerator Description
Summary
Show information about the data captured, see Section 8.2, “The "Sum-
mary" window”.
Protocol Hierarchy
Conversations
Endpoints
IO Graphs
Display a hierarchical tree of protocol statistics, see Section 8.3, “The
"Protocol Hierarchy" window”.
Display a list of conversations (traffic between two endpoints), see Sec-
tion 8.5.2, “The "Conversations" window”.
Display a list of endpoints (traffic to/from an address), see Section 8.4.2,
“The "Endpoints" window”.
Display user specified graphs (e.g. the number of packets in the course of
time), see Section 8.6, “The "IO Graphs" window”.
48
Page 63

Menu Item Accelerator Description
-----Conversation
List
Endpoint List
Service Response Time
-----ANSI
GSM
H.225...
ISUP Message
Types
MTP3
RTP
SCTP
SIP
VoIP Calls...
WAP-WSP...
-----BOOTP-DHCP
HTTP
ISUP Messages
ONC-RPC Programs
TCP Stream
Graph
Display a list of conversations, obsoleted by the combined window of
Conversations above, see Section 8.5.3, “The protocol specific "Conversa-
tion List" windows”.
Display a list of endpoints, obsoleted by the combined window of Endpoints above, see Section 8.4.3, “The protocol specific "Endpoint List"
windows”.
Display the time between a request and the corresponding response, see
Section 8.7, “Service Response Time”.
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
HTTP request/response statistics, see Section 8.8, “The protocol specific
statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
See Section 8.8, “The protocol specific statistics windows”
User Interface
49
Page 64

User Interface
3.12. The "Help" menu
The Ethereal Help menu contains the fields shown in Table 3.8, “Help menu items”.
Figure 3.10. The "Help" Menu
Table 3.8. Help menu items
Menu Item Accelerator Description
Contents F1
This menu item brings up a basic help system.
Supported Protocols
Manual Pages
> ...
Ethereal Online > ...
-----About Ethereal
This menu item brings up a dialog box showing the supported protocols
and protocol fields.
This menu item starts a Web browser showing one of the locally installed
html manual pages.
This menu item starts a Web browser showing the chosen webpage from:
http://www.ethereal.com.
This menu item brings up an information window that provides some information on Ethereal, such as the plugins, the used folders, ...
50
Page 65

User Interface
Note!
Calling a Web browser might be unsupported in your version of Ethereal. If this is the
case, the corresponding menu items will be hidden.
Note!
If calling a Web browser fails on your machine, maybe because just nothing happens
or the browser is started but no page is shown, have a look at the webbrowser setting
in the preferences dialog.
51
Page 66

User Interface
3.13. The "Main" toolbar
The main toolbar provides quick access to frequently used items from the menu. This toolbar cannot
be customized by the user, but it can be hidden using the View menu, if the space on the screen is
needed to show even more packet data.
As in the menu, only the items useful in the current program state will be available. The others will
be greyed out (e.g. you cannot save a capture file if you haven't loaded one).
Figure 3.11. The "Main" toolbar
Table 3.9. Main toolbar items
Toolbar
Icon
------
Toolbar Item Corresponding
Menu Item
Interfaces... Capture/Inter-
faces...
Options... Capture/Options...
Start Capture/Start
Stop Capture/Stop
Restart Capture/Restart
Open... File/Open...
Save As... File/Save As...
Description
This item brings up the Capture Interfaces List dialog box
(discussed further in Section 4.3, “Start Capturing”).
This item brings up the Capture Options dialog box
(discussed further in Section 4.3, “Start Capturing”) and allows you to start capturing packets.
This item starts capturing packets with the options form the
last time.
This item stops the currently running live capture process
Section 4.3, “Start Capturing”).
This item stops the currently running live capture process and
restarts it again, for convenience.
This item brings up the file open dialog box that allows you
to load a capture file for viewing. It is discussed in more detail in Section 5.2.1, “The "Open Capture File" dialog box”.
This item allows you to save the current capture file to
whatever file you would like. It pops up the Save Capture
File As dialog box (which is discussed further in Sec-
tion 5.3.1, “The "Save Capture File As" dialog box”).
Close File/Close
Note!
If you currently have a temporary capture file,
the Save icon will be shown instead.
This item closes the current capture. If you have not saved
the capture, you will be asked to save it first.
52
Page 67

User Interface
Toolbar
Icon
------
Toolbar Item Corresponding
Menu Item
Reload View/Reload
Print... File/Print...
Find Packet... Edit/Find Packet...
Go Back Go/Go Back
Go Forward Go/Go Forward
Go to Packet... Go/Go to Packet...
Go To First
Packet
Go/First Packet
Description
This item allows you to reload the current capture file.
This item allows you to print all (or some of) the packets in
the capture file. It pops up the Ethereal Print dialog box
(which is discussed further in Section 5.7, “Printing
packets”).
This item brings up a dialog box that allows you to find a
packet. There is further information on finding packets in
Section 6.6, “Finding packets”.
This item jumps back in the packet history.
This item jumps forward in the packet history.
This item brings up a dialog box that allows you to specify a
packet number to go to that packet.
This item jumps to the first packet of the capture file.
------
------
------
Go To Last Pack-etGo/Last Packet
Colorize View/Colorize
Auto Scroll in
Live Capture
Zoom In View/Zoom In
Zoom Out View/Zoom Out
Normal Size View/Normal Size
Resize Columns View/Resize
Capture Filters... Capture/Capture
Display Filters... Analyze/Display
View/Auto Scroll
in Live Capture
Columns
Filters...
Filters...
This item jumps to the last packet of the capture file.
Colorize the packet list (or not).
Auto scroll packet list while doing a live capture (or not).
Zoom into the packet data (increase the font size).
Zoom out of the packet data (decrease the font size).
Set zoom level back to 100%.
Resize columns, so the content fits into them.
This item brings up a dialog box that allows you to create and
edit capture filters. You can name filters, and you can save
them for future use. More detail on this subject is provided in
Section 6.5, “Defining and saving filters”.
This item brings up a dialog box that allows you to create and
edit display filters. You can name filters, and you can save
them for future use. More detail on this subject is provided in
Section 6.5, “Defining and saving filters”.
53
Page 68

User Interface
Toolbar
Icon
------
Toolbar Item Corresponding
Menu Item
Coloring Rules... View/Coloring
Rules...
Preferences... Edit/Preferences
Help Help/Contents
Description
This item brings up a dialog box that allows you color packets in the packet list pane according to filter expressions you
choose. It can be very useful for spotting certain types of
packets. More detail on this subject is provided in Sec-
tion 9.3, “Packet colorization”.
This item brings up a dialog box that allows you to set preferences for many parameters that control Ethereal. You can
also save your preferences so Ethereal will use them the next
time you start it. More detail is provided in Section 9.5,
“Preferences”
This item brings up help dialog box.
54
Page 69

User Interface
3.14. The "Filter" toolbar
The filter toolbar lets you quickly edit and apply display filters. More information on display filters
is available in Section 6.2, “Filtering packets while viewing”.
Figure 3.12. The "Filter" toolbar
• The leftmost button labeled "Filter:" can be clicked to bring up the filter construction dialog, described in Figure 6.8, “The "Capture Filters" and "Display Filters" dialog boxes”.
• The left middle text box provides an area to enter or edit display filter strings, see Section 6.3,
“Building display filter expressions” . A syntax check of your filter string is done while you are
typing. The background will turn red if you enter an incomplete or invalid string, and will become green when you enter a valid string. You can click on the pull down arrow to select a previously-entered filter string from a list. The entries in the pull down list will remain available
even after a program restart.
Note!
After you've changed something in this field, don't forget to press the Apply button
(or the Enter/Return key), to apply this filter string to the display.
Note!
This field is also where the current filter in effect is displayed.
• The middle button labeled "Add Expression..." opens a dialog box that lets you edit a display filter from a list of protocol fields, described in Section 6.4, “The "Filter Expression" dialog box”
• The right middle button labeled "Clear" resets the current display filter and clears the edit area.
• The rightmost button labeled "Apply" applies the current value in the edit area as the new display filter.
Note!
Applying a display filter on large capture files might take quite a long time!
55
Page 70

User Interface
3.15. The "Packet List" pane
The packet list pane displays all the packets in the current capture file.
Figure 3.13. The "Packet List" pane
Each line in the packet list corresponds to one packet in the capture file. If you select a line in this
pane, more details will be displayed in the "Packet Details" and "Packet Bytes" panes.
While dissecting a packet, Ethereal will place information from the protocol dissectors into the
columns. As higher level protocols might overwrite information from lower levels, you will typically see the information from the highest possible level only.
For example, let's look at a packet containing TCP inside IP inside an Ethernet packet. The Ethernet
dissector will write its data (such as the Ethernet addresses), the IP dissector will overwrite this by
its own (such as the IP addresses), the TCP dissector will overwrite the IP information, and so on.
There are a lot of different columns available. Which columns are displayed can be selected by preference settings, see Section 9.5, “Preferences”.
The default columns will show:
• No. The number of the packet in the capture file. This number won't change, even if a display
filter is used.
• Time The timestamp of the packet. The presentation format of this timestamp can be changed,
see Section 6.9, “Time display formats and time references”.
• Source The address where this packet is coming from.
• Destination The address where this packet is going to.
• Protocol The protocol name in a short (perhaps abbreviated) version.
• Info Additional information about the packet content.
There is a context menu (right mouse click) available, see details in Figure 6.3, “Pop-up menu of
"Packet List" pane”.
56
Page 71

User Interface
3.16. The "Packet Details" pane
The packet details pane shows the current packet (selected in the "Packet List" pane) in a more detailed form.
Figure 3.14. The "Packet Details" pane
This pane shows the protocols and protocol fields of the packet selected in the "Packet List" pane.
The protocols and fields of the packet are displayed using a tree, which can be expanded and collapsed.
There is a context menu (right mouse click) available, see details in Figure 6.4, “Pop-up menu of
"Packet Details" pane”.
Some protocol fields are specially displayed.
• Generated fields Ethereal itself will generate additional protocol fields which are surrounded by
brackets. The information in these fields is derived from the known context to other packets in
the capture file. For example, Ethereal is doing a sequence/acknowledge analysis of each TCP
stream, which is displayed in the [SEQ/ACK analysis] fields of the TCP protocol.
• Links If Ethereal detected a relationship to another packet in the capture file, it will generate a
link to that packet. Links are underlined and displayed in blue. If double-clicked, Ethereal jumps
to the corresponding packet.
57
Page 72

User Interface
3.17. The "Packet Bytes" pane
The packet bytes pane shows the data of the current packet (selected in the "Packet List" pane) in a
hexdump style.
Figure 3.15. The "Packet Bytes" pane
As usual for a hexdump, the left side shows the offset in the packet data, in the middle the packet
data is shown in a hexadecimal representation and on the right the corresponding ASCII characters
(or . if not appropriate) are displayed.
There is a context menu (right mouse click) available, see details in Figure 6.5, “Pop-up menu of
"Packet Bytes" pane”.
Depending on the packet data, sometimes more than one page is available, e.g. when Ethereal has
reassembled some packets into a single chunk of data, see Section 7.3, “Packet Reassembling”. In
this case there are some additional tabs shown at the bottom of the pane to let you select the page
you want to see.
Figure 3.16. The "Packet Bytes" pane with tabs
Note!
The additional pages might contain data picked from multiple packets.
The context menu (right mouse click) of the tab labels will show a list of all available pages. This
can be helpful if the size in the pane is too small for all the tab labels.
58
Page 73

3.18. The Statusbar
The statusbar displays informational messages.
In general, the left side will show context related information, while the right side will show the cur-
rent number of packets.
Figure 3.17. The initial Statusbar
This statusbar is shown while no capture file is loaded, e.g. when Ethereal is started.
Figure 3.18. The Statusbar with a loaded capture file
The left side shows information about the capture file, its name, its size and the elapsed time while it
was being captured.
User Interface
The right side shows the current number of packets in the capture file. The following values are displayed:
• P: the number of captured packets
• D: the number of packets currently being displayed
• M: the number of marked packets
Figure 3.19. The Statusbar with a selected protocol field
This is displayed if you have selected a protocol field from the "Packet Details" pane.
Tip!
The value between the brackets (in this example arp.opcode) can be used as a display
filter string, representing the selected protocol field.
59
Page 74

User Interface
60
Page 75

Chapter 4. Capturing Live Network Data
4.1. Introduction
Capturing live network data is one of the major features of Ethereal.
The Ethereal capture engine provides the following features:
• Capture from different kinds of network hardware (Ethernet, Token Ring, ATM, ...).
• Stop the capture on different triggers like: amount of captured data, captured time, captured
number of packets.
• Simultaneously show decoded packets while keep on capturing.
• Filter packets, reducing the amount of data to be captured, see Section 4.8, “Filtering while cap-
turing”.
• Capturing into multiple files while doing a long term capture, and in addition the option to form
a ringbuffer of these files, keeping only the last x files, useful for a "very long term" capture, see
Section 4.6, “Capture files and file modes”.
The capture engine still lacks the following features:
• Simultaneous capturing from multiple network interfaces (however, you can start multiple instances of Ethereal and merge capture files later).
• Stop capturing (or doing some other action), depending on the captured data.
61
Page 76

4.2. Prerequisites
Setting up Ethereal to capture packets for the first time can be tricky.
Tip!
A comprehensive guide "How To setup a Capture" is available at: ht-
tp://wiki.ethereal.com/CaptureSetup.
Here are some common pitfalls:
• You need to have root / Administrator privileges to start a live capture.
• You need to choose the right network interface to capture packet data from.
• You need to capture at the right place in the network to see the traffic you want to see.
• ... and a lot more!.
Capturing Live Network Data
If you have any problems setting up your capture environment, you should have a look at the guide
mentioned above.
62
Page 77

Capturing Live Network Data
4.3. Start Capturing
One of the following methods can be used to start capturing packets with Ethereal:
• You can get an overview of the available local interfaces using the " Capture Interfaces"
dialog box, see Figure 4.1, “The "Capture Interfaces" dialog box”. You can start a capture from
this dialog box, using (one of) the "Capture" button(s).
• You can start capturing using the " Capture Options" dialog box, see Figure 4.2, “The
"Capture Options" dialog box”.
• If you have selected the right capture options before, you can immediately start a capture using
the " Capture Start" menu / toolbar item. The capture process will start immediately.
• If you already know the name of the capture interface, you can start Ethereal from the command
line and use the following:
ethereal -i eth0 -k
This will start Ethereal capturing on interface eth0, more details can be found at: Section 9.2,
“Start Ethereal from the command line”.
63
Page 78

Capturing Live Network Data
4.4. The "Capture Interfaces" dialog box
When you select "Interfaces..." from the Capture menu, Ethereal pops up the "Capture Interfaces"
dialog box as shown in Figure 4.1, “The "Capture Interfaces" dialog box”.
Warning!
As the "Capture Interfaces" dialog is showing live captured data, it is consuming a lot
of system ressources. Close this dialog as soon as possible to prevent excessive system
load.
Note!
This dialog box will only show the local interfaces Ethereal knows of. As Ethereal
might not be able to detect all local interfaces, and it cannot detect the remote interfaces available, there could be more capture interfaces available than listed.
Figure 4.1. The "Capture Interfaces" dialog box
Description The interface description provided by the operating system.
IP The first IP address Ethereal could resolve from this interface. If no address
could be resolved (e.g. no DHCP server available), "unknown" will be displayed.
If more than one IP address could be resolved, only the first is shown
(unpredictable which one in that case).
Packets The number of packets captured from this interface, since this dialog was opened.
Will be greyed out, if no packet was captured in the last second.
Packets/s Number of packets captured in the last second. Will be greyed out, if no packet
was captured in the last second.
Stop Stop a currently running capture.
Capture Start a capture on this interface immediately, using the settings from the last cap-
ture.
Prepare Open the Capture Options dialog with this interface selected, see Section 4.5,
“The "Capture Options" dialog box”.
Close Close this dialog box.
64
Page 79

Capturing Live Network Data
4.5. The "Capture Options" dialog box
When you select Start... from the Capture menu (or use the corresponding item in the "Main" toolbar), Ethereal pops up the "Capture Options" dialog box as shown in Figure 4.2, “The "Capture Op-
tions" dialog box”.
Figure 4.2. The "Capture Options" dialog box
Tip!
If you are unsure which options to choose in this dialog box, just try keeping the defaults as this should work well in many cases.
You can set the following fields in this dialog box:
4.5.1. Capture frame
Interface This field specifies the interface you want to capture on. You
can only capture on one interface, and you can only capture
65
Page 80

Capturing Live Network Data
on interfaces that Ethereal has found on the system. It is a
drop-down list, so simply click on the button on the right
hand side and select the interface you want. It defaults to the
first non-loopback interface that supports capturing, and if
there are none, the first loopback interface. On some systems,
loopback interfaces cannot be used for capturing (loopback
interfaces are not available on Windows platforms).
This field performs the same function as the -i <interface>
command line option.
IP address The IP address(es) of the selected interface. If no address
could be resolved from the system, "unknown" will be shown.
Link-layer header type Unless you are in the rare situation that you need this, just
keep the default. For a detailed description, see Section 4.7,
“Link-layer header type”
Buffer size: n megabyte(s) Enter the buffer size to be used while capturing. This is the
size of the kernel buffer which will keep the captured packets,
until they are written to disk. If you encounter packet drops,
try increasing this value.
Capture packets in promiscuous
mode
Note
This option is only available on Windows platforms.
This checkbox allows you to specify that Ethereal should put
the interface in promiscuous mode when capturing. If you do
not specify this, Ethereal will only capture the packets going
to or from your computer (not all packets on your LAN segment).
Note
If some other process has put the interface in
promiscuous mode you may be capturing in
promiscuous mode even if you turn off this option
Note
Even in promiscuous mode you still won't necessarily see all packets on your LAN segment,
see http:/ / www.ethereal.com/ faq#promiscsniff
for some more explanations.
Limit each packet to n bytes This field allows you to specify the maximum amount of data
that will be captured for each packet, and is sometimes referred to as the snaplen. If disabled, the default is 65535,
which will be sufficient for most protocols. Some rules of
thumb:
• If you are unsure, just keep the default value.
• If you don't need all of the data in a packet - for example,
if you only need the link-layer, IP, and TCP headers - you
might want to choose a small snapshot length, as less
66
Page 81

Capturing Live Network Data
• If you don't capture all of the data in a packet, you might
Capture Filter This field allows you to specify a capture filter. Capture fil-
ters are discussed in more details in Section 4.8, “Filtering
while capturing”. It defaults to empty, or no filter.
You can also click on the button labelled Capture Filter, and
Ethereal will bring up the Capture Filters dialog box and allow you to create and/or select a filter. Please see Section 6.5,
“Defining and saving filters”
4.5.2. Capture File(s) frame
An explanation about capture file usage can be found in Section 4.6, “Capture files and file modes”.
CPU time is required for copying packets, less buffer
space is required for packets, and thus perhaps fewer
packets will be dropped if traffic is very heavy.
find that the packet data you want is in the part that's
dropped, or that reassembly isn't possible as the data required for reassembly is missing.
File This field allows you to specify the file name that will be
used for the capture file. This field is left blank by default. If
the field is left blank, the capture data will be stored in a temporary file, see Section 4.6, “Capture files and file modes” for
details.
You can also click on the button to the right of this field to
browse through the filesystem.
Use multiple files Instead of using a single file, Ethereal will automatically
switch to a new one, if a specific trigger condition is reached.
Next file every n megabyte(s) Multiple files only: Switch to the next file after the given
number of byte(s)/kilobyte(s)/megabyte(s)/gigabyte(s) have
been captured.
Next file every n minute(s) Multiple files only: Switch to the next file after the given
number of second(s)/minutes(s)/hours(s)/days(s) have
elapsed.
Ring buffer with n files Multiple files only: Form a ring buffer of the capture files,
with the given number of files.
Stop capture after n file(s) Multiple files only: Stop capturing after switching to the next
file the given number of times.
4.5.3. Stop Capture... frame
... after n packet(s) Stop capturing after the given number of packets have been
captured.
... after n megabytes(s) Stop capturing after the given number of
byte(s)/kilobyte(s)/megabyte(s)/gigabyte(s) have been captured. This option is greyed out, if "Use multiple files" is selected.
67
Page 82

Capturing Live Network Data
... after n minute(s) Stop capturing after the given number of
second(s)/minutes(s)/hours(s)/days(s) have elapsed.
4.5.4. Display Options frame
Update list
of packets
in real
time
Automatic
scrolling in
live capture
Hide capture info
dialog
This option allows you to specify that Ethereal should update the packet list pane in
real time. If you do not specify this, Ethereal does not display any packets until you
stop the capture. When you check this, Ethereal captures in a separate process and
feeds the captures to the display process.
This option allows you to specify that Ethereal should scroll the packet list pane as
new packets come in, so you are always looking at the last packet. If you do not specify this, Ethereal simply adds new packets onto the end of the list, but does not scroll
the packet list pane. This option is greyed out if "Update list of packets in real time"
is disabled.
If this option is checked, the following capture info dialog will be hidden.
4.5.5. Name Resolution frame
Enable MAC name resolution This option allows you to control whether or not Ethereal
translates MAC addresses into names, see Section 7.4, “Name
Resolution”.
Enable network name resolution This option allows you to control whether or not Ethereal
translates network addresses into names, see Section 7.4,
“Name Resolution”.
Enable transport name resolution
This option allows you to control whether or not Ethereal
translates transport addresses into protocols, see Section 7.4,
“Name Resolution”.
4.5.6. Buttons
Once you have set the values you desire and have selected the options you need, simply click on
OK to commence the capture, or Cancel to cancel the capture.
If you start a capture, Ethereal allows you to stop capturing when you have enough packets captured, for details see Section 4.9, “While a Capture is running ...”.
68
Page 83

Capturing Live Network Data
4.6. Capture files and file modes
While capturing, the underlying libpcap capturing engine will grab the packets from the network
card and keep the packet data in a (relatively) small kernel buffer. This data is read by Ethereal and
saved into the capture file(s) the user specified.
Different modes of operation are available when saving this packet data to the capture file(s).
Tip!
Working with large files (several 100 MB's) can be quite slow. If you plan to do a long
term capture or capturing from a high traffic network, think about using one of the
"Multiple files" options. This will spread the captured packets over several smaller
files which can be much more pleasant to work with.
Note!
Using Multiple files may cut context related information. Ethereal keeps context information of the loaded packet data, so it can report context related problems (like a
stream error) and keeps information about context related protocols (e.g. where data is
exchanged at the establishing phase and only referred to in later packets). As it keeps
this information only for the loaded file, using one of the multiple file modes may cut
these contexts. If the establishing phase is saved in one file and the things you would
like to see is in another, you might not see some of the valuable context related information.
Tip!
Information about the folders used for the capture file(s), can be found in Appendix A,
Configuration (and other) Files and Folders.
Table 4.1. Capture file mode selected by capture options
"File" option "Use multiple
files" option
- - - Single temporary
foo.cap - - Single named file foo.cap
foo.cap x - Multiple files,
foo.cap x x Multiple files,
"Ring buffer
with n files" option
Mode Resulting filename(s) used
etherXXXXXX (where
file
continuous
ring buffer
XXXXXX is a unique number)
foo_00001_20040205110102.cap
,
foo_00002_20040205110102.cap
, ...
foo_00001_20040205110102.cap
,
foo_00002_20040205110102.cap
, ...
Single temporary file A temporary file will be created and used (this is the default).
After the capturing is stopped, this file can be saved later under a user specified name.
Single named file A single capture file will be used. If you want to place the
69
Page 84

Capturing Live Network Data
new capture file to a specific folder, choose this mode.
Multiple files, continuous Like the "Single named file" mode, but a new file is created
and used, after reaching one of the multiple file switch conditions (one of the "Next file every ..." values).
Multiple files, ring buffer Much like "Multiple files continuous", reaching one of the
multiple files switch conditions (one of the "Next file every
..." values) will switch to the next file. This will be a newly
created file if value of "Ring buffer with n files" is not
reached, otherwise it will replace the oldest of the formerly
used files (thus forming a "ring").
This mode will limit the maximum disk usage, even for an
unlimited amount of capture input data, keeping the latest
captured data.
70
Page 85

Capturing Live Network Data
4.7. Link-layer header type
In the usual case, you won't have to choose this link-layer header type. The following paragraphs
describe the exceptional cases, where selecting this type is possible, so you will have a guide what
to do:
If you are capturing on an 802.11 device on some versions of BSD, this might offer a choice of "Ethernet" or "802.11". "Ethernet" will cause the captured packets to have fake Ethernet headers;
"802.11" will cause them to have IEEE 802.11 headers. Unless the capture needs to be read by an
application that doesn't support 802.11 headers, you should select "802.11".
If you are capturing on an Endace DAG card connected to a synchronous serial line, this might offer
a choice of "PPP over serial" or "Cisco HDLC"; if the protocol on the serial line is PPP, select "PPP
over serial", and if the protocol on the serial line is Cisco HDLC, select "Cisco HDLC".
If you are capturing on an Endace DAG card connected to an ATM network, this might offer a
choice of "RFC 1483 IP-over-ATM" or "Sun raw ATM". If the only traffic being captured is RFC
1483 LLC-encapsulated IP, or if the capture needs to be read by an application that doesn't support
SunATM headers, select "RFC 1483 IP-over-ATM", otherwise select "Sun raw ATM".
If you are capturing on an Ethernet device, this might offer a choice of "Ethernet" or "DOCSIS". If
you are capturing traffic from a Cisco Cable Modem Termination System that is putting DOCSIS
traffic onto the Ethernet to be captured, select "DOCSIS", otherwise select "Ethernet".
71
Page 86

Capturing Live Network Data
4.8. Filtering while capturing
Ethereal uses the libpcap filter language for capture filters. This is explained in the tcpdump man
page, which can be hard to understand, so it's explained here to some extent.
Tip!
You will find a lot of Capture Filter examples at ht-
tp://wiki.ethereal.com/CaptureFilters.
You enter the capture filter into the Filter field of the Ethereal Capture Options dialog box, as shown
in Figure 4.2, “The "Capture Options" dialog box”. The following is an outline of the syntax of the
tcpdump capture filter language. See the expression option at the tcpdump manual page for details:
http://www.tcpdump.org/tcpdump_man.html.
A capture filter takes the form of a series of primitive expressions connected by conjunctions (and/
or) and optionally preceded by not:
[not] primitive [and|or [not] primitive ...]
An example is shown in Example 4.1, “ A capture filter for telnet than captures traffic to and from a
particular host ”.
Example 4.1. A capture filter for telnet than captures traffic to and from a
particular host
tcp port 23 and host 10.0.0.5
This example captures telnet traffic to and from the host 10.0.0.5, and shows how to use two primitives and the and conjunction. Another example is shown in Example 4.2, “ Capturing all telnet
traffic not from 10.0.0.5”, and shows how to capture all telnet traffic except that from 10.0.0.5.
Example 4.2. Capturing all telnet traffic not from 10.0.0.5
tcp port 23 and not host 10.0.0.5
XXX - add examples to the following list.
A primitive is simply one of the following:
[src|dst] host <host> This primitive allows you to filter on a host IP address or
name. You can optionally precede the primitive with the
keyword src|dst to specify that you are only interested in
source or destination addresses. If these are not present, packets where the specified address appears as either the source or
the destination address will be selected.
ether [src|dst] host <ehost> This primitive allows you to filter on Ethernet host addresses.
72
Page 87

Capturing Live Network Data
You can optionally include the keyword src|dst between the
keywords ether and host to specify that you are only interested in source or destination addresses. If these are not
present, packets where the specified address appears in either
the source or destination address will be selected.
gateway host <host> This primitive allows you to filter on packets that used host
as a gateway. That is, where the Ethernet source or destination was host but neither the source nor destination IP address
was host.
[src|dst] net <net> [{mask
<mask>}|{len <len>}]
[tcp|udp] [src|dst] port <port> This primitive allows you to filter on TCP and UDP port
less|greater <length> This primitive allows you to filter on packets whose length
ip|ether proto <protocol> This primitive allows you to filter on the specified protocol at
This primitive allows you to filter on network numbers. You
can optionally precede this primitive with the keyword
src|dst to specify that you are only interested in a source or
destination network. If neither of these are present, packets
will be selected that have the specified network in either the
source or destination address. In addition, you can specify
either the netmask or the CIDR prefix for the network if they
are different from your own.
numbers. You can optionally precede this primitive with the
keywords src|dst and tcp|udp which allow you to specify that
you are only interested in source or destination ports and TCP
or UDP packets respectively. The keywords tcp|udp must appear before src|dst.
If these are not specified, packets will be selected for both the
TCP and UDP protocols and when the specified address appears in either the source or destination port field.
was less than or equal to the specified length, or greater than
or equal to the specified length, respectively.
either the Ethernet layer or the IP layer.
ether|ip broadcast|multicast This primitive allows you to filter on either Ethernet or IP
broadcasts or multicasts.
<expr> relop <expr> This primitive allows you to create complex filter expressions
that select bytes or ranges of bytes in packets. Please see the
tcpdump man page at http:/ / www.tcpdump.org/ tcp-
dump_man.html for more details.
73
Page 88

Capturing Live Network Data
4.9. While a Capture is running ...
While a capture is running, the following dialog box is shown:
Figure 4.3. The "Capture Info" dialog box
This dialog box will inform you about the number of captured packets and the time since the capture
was started. The selection which protocols are counted cannot be changed.
Tip!
This Capture Info dialog box can be hidden, using the "Hide capture info dialog" option in the Capture Options dialog box.
4.9.1. Stop the running capture
A running capture session will be stopped in one of the following ways:
1. Using the " Stop" button from the Capture Info dialog box .
74
Page 89

Capturing Live Network Data
Note!
The Capture Info dialog box might be hidden, if the option "Hide capture info
dialog" is used.
2. Using the menu item "Capture/ Stop".
3. Using the toolbar item " Stop".
4. Pressing the accelerator keys: Ctrl+E.
5. The capture will be automatically stopped, if one of the Stop Conditions is exceeded, e.g. the
maximum amount of data was captured.
4.9.2. Restart a running capture
A running capture session can be restarted with the same capture options than the last time, this will
remove all packets previously captured. This can be useful, if some uninteresting packets are captured and there's no need to keep them.
Restart is a convenience function and equivalent to a capture stop following by an immediate capture start. A restart can be triggered in one of the following ways:
1. Using the menu item "Capture/ Restart".
2. Using the toolbar item " Restart".
75
Page 90

Capturing Live Network Data
76
Page 91

Chapter 5. File Input / Output and Printing
5.1. Introduction
This chapter will describe input and output of capture data.
• Open/Import capture files in various capture file formats
• Save/Export capture files in various capture file formats
• Merge capture files together
• Print packets
77
Page 92

File Input / Output and Printing
5.2. Open capture files
Ethereal can read in previously saved capture files. To read them, simply select the menu or toolbar
item: "File/ Open". Ethereal will then pop up the File Open dialog box, which is discussed in
more detail in Section 5.2.1, “The "Open Capture File" dialog box”.
Note!
You can also use drag-and-drop to open a file, by simply dropping the desired file
from your file manager onto Ethereal's main window. However, drag-and-drop is not
available/won't work in all desktop environments.
If you didn't save the current capture file before, you will be asked to do so, to prevent data loss (this
behaviour can be disabled in the preferences).
In addition to its native file format (libpcap format, also used by tcpdump/WinDump and other libpcap/WinPcap-based programs), Ethereal can read capture files from a large number of other packet
capture programs as well. See Section 5.2.2, “Input File Formats” for the list of capture formats Ethereal understands.
5.2.1. The "Open Capture File" dialog box
The "Open Capture File" dialog box allows you to search for a capture file containing previously
captured packets for display in Ethereal. Figure 5.1, “The "Open Capture File" Dialog box” shows
an example of the Ethereal Open File Dialog box.
Note
Ethereal uses the open dialog box from the version of the GTK+ toolkit that it's using.
This dialog was completely redesigned in GTK version 2.4. Depending on the installed
GTK version, your dialog box might look different. However, as the functionality remains almost the same, much of this description will work with your version of Ethereal.
Figure 5.1. The "Open Capture File" Dialog box
78
Page 93

File Input / Output and Printing
With this dialog box, you can perform the following actions:
1. The "+ Add" button allows you to add a directory, selected in the right-hand pane, to the favorites (bookmarks?) list. Those changes are persistent.
2. The "- Remove" button allows you to remove a selected directory from that list again (the items
like: "Home", "Desktop", and "Filesystem" cannot be removed).
3. Select files and directories with the list boxes.
4. View file preview information (like the filesize, the number of packets, ...), while browsing the
filesystem.
5. Specify a display filter with the Filter button and filter field. This filter will be used when opening the new file. Clicking on the Filter button causes Ethereal to pop up the Filters dialog box
(which is discussed further in Section 6.2, “Filtering packets while viewing”).
6. Specify which name resolution is to be performed for all packets by clicking on one of the "Enable name resolution" check buttons. Details about name resolution can be found in Sec-
tion 7.4, “Name Resolution”.
7. Click the Open button to accept your selected file and open it. If Ethereal doesn't recognize the
capture format, it will grey out this button.
8. Click the Cancel button to go back to Ethereal and not load a capture file.
You can also change the display filter and name resolution settings later while viewing the packets.
However, for very large capture files it can take a significant amount of extra time changing these
settings later, so it might be a good idea to set at least the filter in advance here.
5.2.2. Input File Formats
79
Page 94

File Input / Output and Printing
The following file formats from other capture tools can be opened by Ethereal:
• libpcap, tcpdump and various other tools using tcpdump's capture format
• Sun snoop and atmsnoop
• Shomiti/Finisar Surveyor captures
• Novell LANalyzer captures
• Microsoft Network Monitor captures
• AIX's iptrace captures
• Cinco Networks NetXray captures
• Network Associates Windows-based Sniffer and Sniffer Pro captures
• Network General/Network Associates DOS-based Sniffer (compressed or uncompressed) cap-
tures
• AG Group/WildPackets EtherPeek/TokenPeek/AiroPeek/EtherHelp/PacketGrabber captures
• RADCOM's WAN/LAN Analyzer captures
• Network Instruments Observer version 9 captures
• Lucent/Ascend router debug output
• HP-UX's nettl
• Toshiba's ISDN routers dump output
• ISDN4BSD i4btrace utility
• traces from the EyeSDN USB S0
• IPLog format from the Cisco Secure Intrusion Detection System
• pppd logs (pppdump format)
• the output from VMS's TCPIPtrace/TCPtrace/UCX$TRACE utilities
• the text output from the DBS Etherwatch VMS utility
• Visual Networks' Visual UpTime traffic capture
• the output from CoSine L2 debug
• the output from Accellent's 5Views LAN agents
• Endace Measurement Systems' ERF format captures
• Linux Bluez Bluetooth stack hcidump -w traces
Note!
It may not be possible to read some formats dependent on the packet types captured.
Ethernet captures are usually supported for most file formats, but other packet types
(e.g. token ring packets) may not be possible to read from all file formats.
80
Page 95

File Input / Output and Printing
5.3. Saving captured packets
You can save captured packets simply by using the Save As... menu item from the File menu under
Ethereal. You can choose which packets to save and which file format to be used.
5.3.1. The "Save Capture File As" dialog box
The "Save Capture File As" dialog box allows you to save the current capture to a file. Figure 5.2,
“The "Save Capture File As" dialog box” shows an example of this dialog box.
Note
Ethereal uses the open dialog box from the version of the GTK+ toolkit that it's using.
This dialog was completely redesigned in the GTK version 2.4. Depending on the installed GTK version, your dialog box might look different. However, as the functionality remains almost the same, much of this description will work with your version of
Ethereal.
Figure 5.2. The "Save Capture File As" dialog box
81
Page 96

File Input / Output and Printing
With this dialog box, you can perform the following actions:
1. Type in the name of the file you wish to save the captured packets in, as a standard file name in
your file system.
2. Select the directory to save the file into.
3. Select the range of the packets to be saved, see Section 5.8, “The Packet Range frame”
4. Specify the format of the saved capture file by clicking on the File type drop down box. You
can choose from the types, described in Section 5.3.2, “Output File Formats”.
Note!
Some capture formats may not be available, depending on the packet types captured.
Tip!
You can convert capture files from one format to another by reading in a capture
82
Page 97

File Input / Output and Printing
file and writing it out using a different format.
5. Use "Browse for other folders" to browse files and folders in your file system.
6. Click on the Save button to accept your selected file and save to it. If Ethereal has a problem
saving the captured packets to the file you specified, it will display an error dialog box. After
clicking OK on this error dialog box, you can try again.
7. Click on the Cancel button to go back to Ethereal and not save the captured packets.
5.3.2. Output File Formats
The following file formats can be saved by Ethereal, so other capture tools can read the capture data
from:
• libpcap (tcpdump)
• Novell LANalyzer
• Network Associates Sniffer
• Sun snoop
• Microsoft Network Monitor
• Visual Networks Visual UpTime traffic
• Accellent 5Views
• Networks Instruments Observer version 9
• HP-UX's nettl
Other protocol analyzers may require that the file has a certain suffix in order to read
the files you generate with Ethereal, e.g.:
".DMP" for Tcpdump/libpcap
".CAP" for Network Associates Sniffer Windows
83
Page 98

File Input / Output and Printing
5.4. Merging capture files
Sometimes you need to merge several capture files into one. For example this can be useful, if you
have captured simultaneously from multiple interfaces at once (e.g. using multiple instances of Ethereal).
Merging capture files can be done in three ways:
• Use the menu item "Merge" from the "File" menu, to open the merge dialog, see Figure 5.3,
“The "Merge with Capture File" dialog box”. This menu item will be disabled, until you have
loaded a capture file.
• Use drag-and-drop to drop multiple files on the main window. Ethereal will try to merge the
packets in chronological order from the dropped files into a newly created temporary file. If you
drop only a single file, it will simply replace a (maybe) existing one.
• Use the mergecap tool, which is a command line tool to merge capture files. This tool provides
the most options to merge capture files, see Section C.6, “mergecap: Merging multiple capture
files into one ”.
5.4.1. The "Merge with Capture File" dialog box
This dialog box let you select a file to be merged into the currently loaded file.
Note!
If your current data wasn't saved before, you will be asked to save it first, before this
dialog box is shown.
Figure 5.3. The "Merge with Capture File" dialog box
84
Page 99

File Input / Output and Printing
Prepend packets to existing file Prepend the packets from the selected file before the currently
loaded packets.
Merge packets chronologically Merge both the packets from the selected and currently
loaded file in chronological order.
Append packets to existing file Append the packets from the selected file after the currently
loaded packets.
All other controls will work the same way as in the "Open Capture File" dialog box, see Sec-
tion 5.2.1, “The "Open Capture File" dialog box”.
85
Page 100

File Input / Output and Printing
5.5. File Sets
When using the "Multiple Files" option while doing a capture, the capture data is spreaded over several capture files, called a file set. Ethereal tries to find the files matching the same filename pattern
than the currently loaded file. This will only work, if all the files of the file set are located in the
same directory.
As it can become tedious to work with a file set by hand, Ethereal provides some features in the
"File" menu to handle these file sets in a more convenient way:
• The List Files dialog box will list the files Ethereal has recognized as being part of the current
file set.
• Next File opens the next file in the file set.
• Previous File opens the previous file in the file set.
XXX - add icons from the menu
5.5.1. The "List Files" dialog box
XXX - add screenshot
Each line contains information about a file of the file set:
• Filename the name of the file
• Created the creation time of the file
• Last Modified the last time the file was modified
• Size the size of the file
The last line will contain info about the currently used directory where all of the files in the file set
can be found.
The content of this dialog box is updated each time a capture file is opened/closed.
If you click on the radio button to the left of the line, the corresponding capture file will be opened.
The Close button will, well, close the dialog box.
86
 Loading...
Loading...