Page 1
1
User Manual
( WAP-8123)
HW: V1
UM: V1. 0
Page 2
2
Default Settings
IP Address
192.168.188.253
Password
admin
WiFi SSID
LevelOne 2.4G / LevelOne 5.8G
Password
66666666
Attention:
Check box contents:
1. Screw Kit
2. RJ45 Network Cable
3. Quick Installation Guide
4. Resource CD (User Manual, QIG)
Warning:
Page 3

3
Contents
CHAPTER 1 HARDWARE AND OPERATION MODE INSTRUCTION…………..........5
1.1 Hardware Description……………………………………………………………………………………………………..5
1.2 Installation Description…………………………………………………………………………………………………….6
1.3 Way to supply power for this device……………………………………………………………………………………..6
1.4 Operation Mode description and usage…………………………………………………………………………………7
CHAPTER 2 LOGIN…………………………………………………………………………………………………9
CHAPTER 3 WEB GUI INTERFACE SETTING…………………………………..........................11
3.1 WIZARD…………………………………………………………………………………………………………………..13
3.2 Gateway Mode…………………………………………………………………………………………………………...13
3.2.1 – Static IP setting in Gateway Mode…………………………………………………………………………………..14
3.2.2 – PPPoE(ADSL) setting in Gateway Mode……………………………………………………………………………15
3.2.3 – DHCP setting in Gateway Mode……………………………………………………………………………………..17
3.3 Repeater Mode…………………………………………………………………………………………………………..19
3.4 WISP Mode……………………………………………………………………………………………………………….22
3.5 AP Mode & Wireless Analyzer………………………………………………………………………………………..25
CHAPTER 4 ADVANCED SETTING……………………………………………………………………..28
4.1 Device Status………………………………………………………………………………………………………………28
4.1.1 – Status…………………………………………………………………………………………………………28
4.1.2 – 2.4G Wireless Status……………………………………………………………………………………..28
4.1.3 – 5.8G Wireless Status……………………………………………………………………………………..29
4.1.4 – LAN Status…………………………………………………………………………………………………………….29
4.2 2.4G Wiress……………………………………………………………………………………………………………....30
4.2.1 – 2.4G Basic Settings……………………………………………………………………………………………………30
4.2.2 – 2.4G Virtual AP………………………………………………………………………………………………………...29
4.2.3 – 2.4G Access Control…………………………………………………………………………………………………..31
4.3 5.8G Wiress……………………………………………………………………………………………………………....34
4.3.1 – 5.8G Basic Settings……………………………………………………………………………………………………34
4.3.2 – 5.8G Virtual AP………………………………………………………………………………………………………...35
4.3.3 – 5.8G Access Control…………………………………………………………………………………………………..35
CHAPTER 5 Enable the status of Repeater Mode or AP Mode……………39
5.1 Network…………………………………………………………………………………………………………………...39
5.1.1 – LAN Settings…………………………………………………………………………………………………………...39
5.1.2 – VLAN…………………………………………………………………………………………………………………....41
5.2 Management……………………………………………………………………………………………………………..42
5.2.1 – System Time…………………………………………………………………………………………………………...42
5.2.2 – Logs……………………………………………………………………………………………………………………..44
5.2.3 – Upgrade Firmware…………………………………………………………………………………………………….44
5.2.4 – System………………………………………………………………………………………………………………….45
5.2.5 – User (change the password for Log in)……………………………………………………………………………..45
CHAPTER 6 Enable the status of Gateway Mode or WISP Mode…………………..46
6.1 Network…………………………………………………………………………………………………………………...46
6.1.1 – LAN Settings…………………………………………………………………………………………………………...46
6.1.2 – VLAN…………………………………………………………………………………………………………………....47
6.1.3 – WAN Settings……………………………………………………………………………………………………….....48
6.1.4 – WAN advanced settings………………………………………………………………………………………….......49
6.2 Firewall…………………………………………………………………………………………....................................50
Page 4

4
6.2.1 – IP/Port Filtering…………………………………………………………………………….......................................50
6.2.2 – MAC Filtering……………………………………………………………………………..........................................51
6.2.3 – URL Filtering……………………………………………………………………………...........................................54
6.2.4 – Port Forwarding……………………………………………………………………………......................................55
6.2.5 – DMZ Host……………………………………………………………………………...............................................55
6.3 Management……………………………………………………………………………………………………………..57
6.3.1 – System Time…………………………………………………………………………………………………………...57
6.3.2 – DDNS settings…………………………………………………………………………………………………………59
6.3.3 – QoS…………………………………………………………………………………………......................................60
6.3.4 – Logs…………………………………………………………………………………………………………………….60
6.3.5 – Upgrade Firmware…………………………………………………………………………………………………….61
6.3.6 – System………………………………………………………………………………………………………………….61
6.3.7 – User (change the password for Log in)……………………………………………………………………………..62
APPENDIX A LICENSE STATEMENT / GPL CODE STATEMENT……………………..63
Page 5
5
Chapter 1 Hardware and Operation mode Instruction
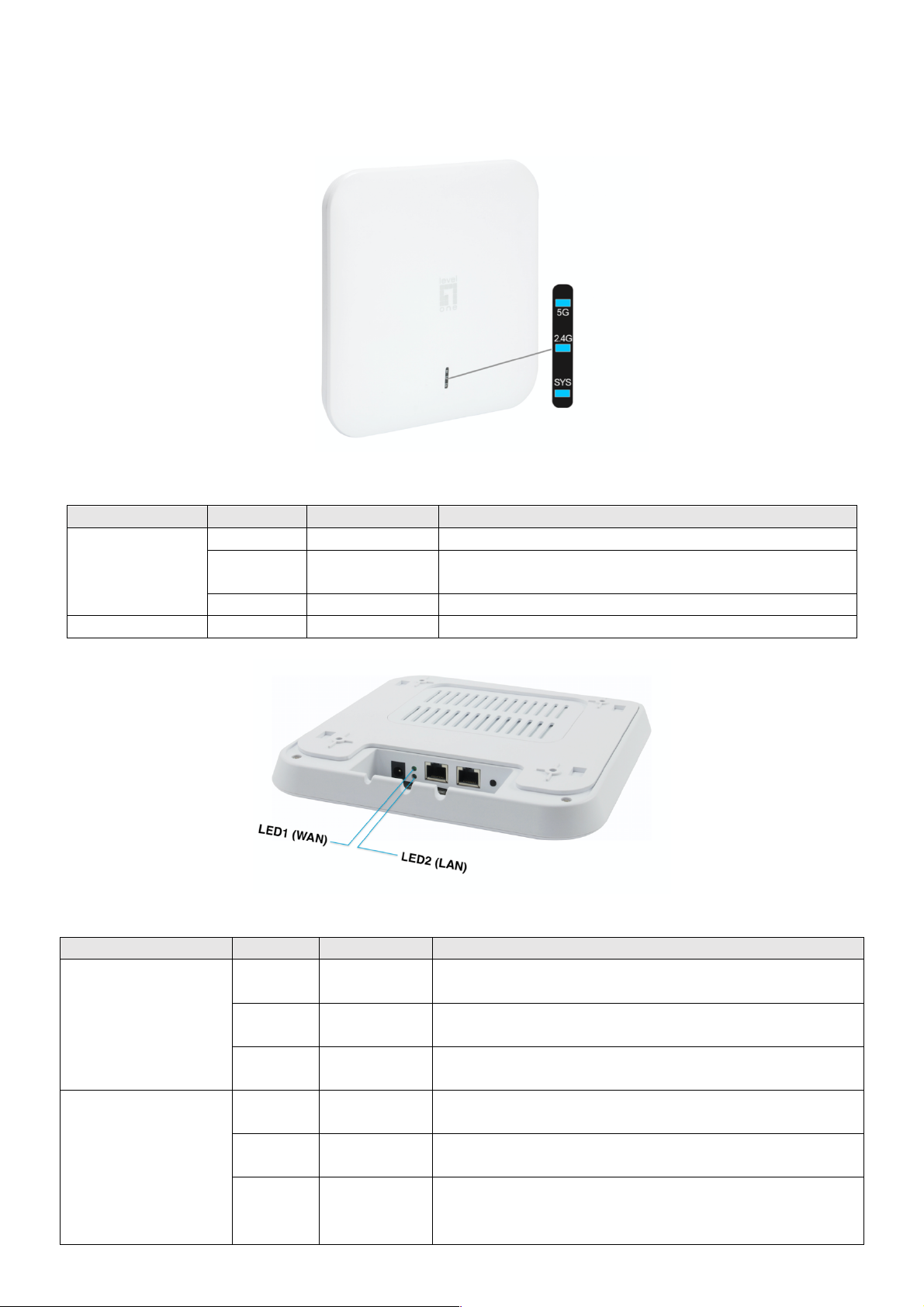
LED
Color
Status
Description
LAN
(10/100/1000Mbps
RJ45 Ports)
Green
Fast
Blinking
The port is transmitting/receiving packets
Green
Solow
Blinking
On LAN is connected
--
Off
The port has no active network cable connected,
or it is not established a link to connected device.
WAN
(10/100/1000Mbps
RJ45 Ports)
Green
Fast
Blinking
The port is transmitting/receiving packets
Green
Solow
Blinking
On WAN is connected
--
Off
The port has no active network cable connected,
or it is not established a link to connected device.
LED indicator
Color
Status
Description
SYS
Blue
On
Device Startup state
Blue
Off
Device Startup state is completed, SYS goes
out and the WIFI blue light flashes.
Blue
Fast Blinking
Reset to Defaults
2.4G / 5G
Blue
Blinking
WIFI SSID Broadcast ON
LED i ndicator:
▲ Front View of the WAP-8123
▲ Rear View of the WAP-8123
Page 6

6
LED/Button/Interface
Description
RESET
(Reset to Default)
With the AP powered on, press the Reset button
for 8~10 seconds until the Signal Strength LED
blink faster than ever. The AP will restart itself
and reset the device to factory default settings.
LAN port
(10/100/1000Mbps RJ45 port)
The LAN port is used to connect to network
devices, such as a switch or PC / NB
WAN
/ PoE port
(10/100/1000Mbps RJ45 port)
The WAN/POE port is used to connect to
network devices, such as a POE switch OR
POE adapter to power the device
( IEEE802.3at ) 48 VDC.
( PoE adapter unit is to be ordered separately )
DC IN
12V/1.5A DC input Power Adapter
Note: Adapter unit is to be ordered separately
1.1
AP Interface:
Page 7
7
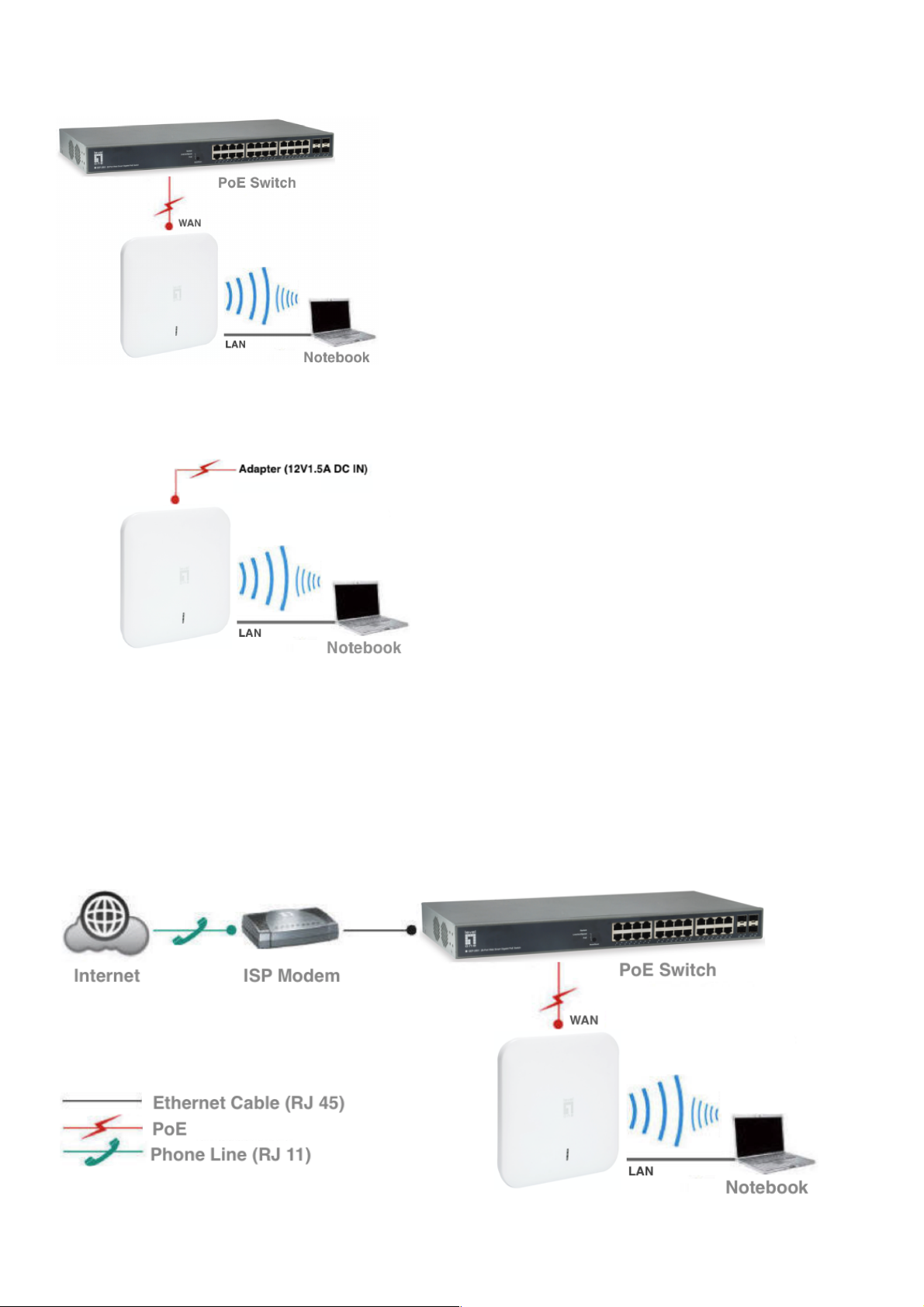
1.3 Way to supply power for this device :
1. PoE Power supply : pls make sure the PoE switch comply with IEEE 802.3at standard.
2. The WAN port connects to the POE adapter (48V DC).
Note: Adapter unit is to be ordered separately
1.4 Operation Mode description and usage:
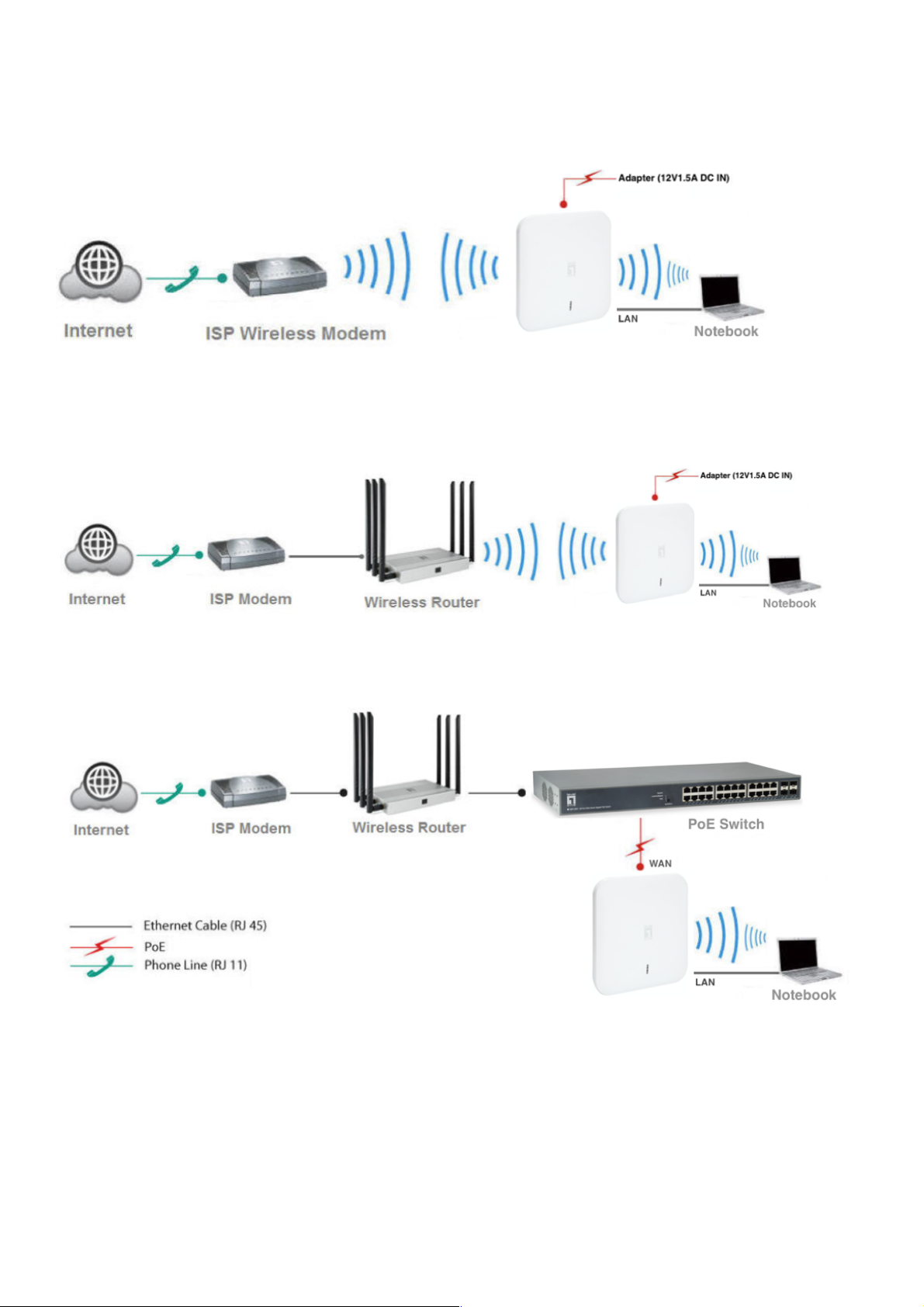
There are four operation mode : Gateway mode , Repeater mode , WISP Mode, AP Mode .
l Gateway mode: Connect to the ISP Modem through the cable network to connect to the
Internet and use with 3 types of Internet access (PPPoE , DHCP, Static IP)
Page 8
8
l WISP mode: Receive ISP Modem Wireless network and select one of them Internet access
method (PPPoE, DHCP, static IP) .
( Note: Adapter unit is to be ordered separately )
l Repeater mode: The WAP-8123 can bridge and extend the existing WiFi signal in this
operation mode . ( Note: Adapter unit is to be ordered separately )
l AP Mode: Please Make sure that the upper device has a router, Only after confirming can
use AP Mode
Page 9
9
Chapter 2 Login
The necessary information about log in is displayed on the sticker of the product, including the URL, User Name
and Pass Word
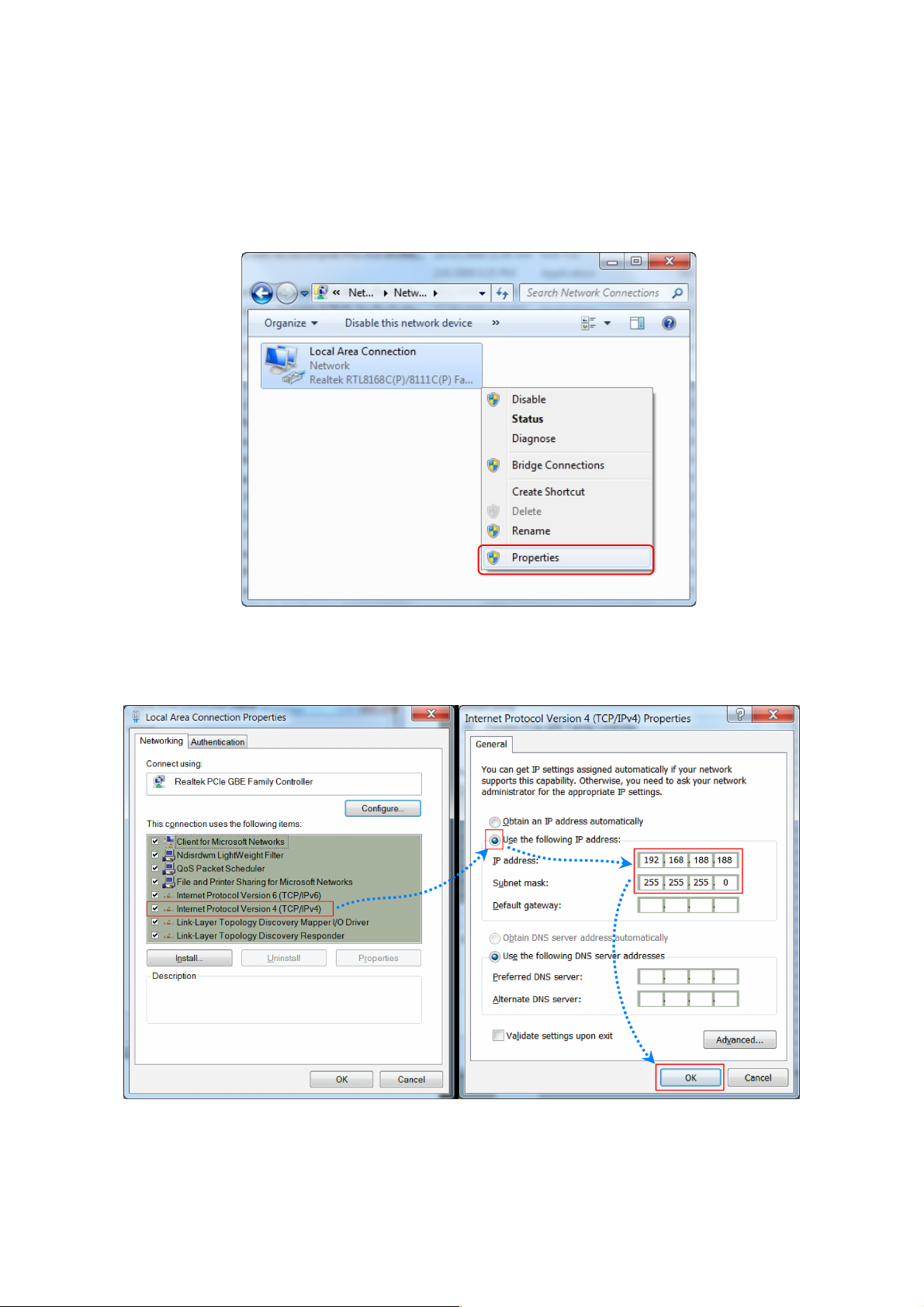
1.Connect the Ceiling AP with computer
2.Configure the PC’s local connection IP address as 192.168.188.X (X is number from 2 to 252), subnet
255.255.255.0, follow P1 and P2 to finish.
mask is
▲ P1 Setting of computer’s IP address
▲ P 2 Setting of computer’s IP address
Page 10
10
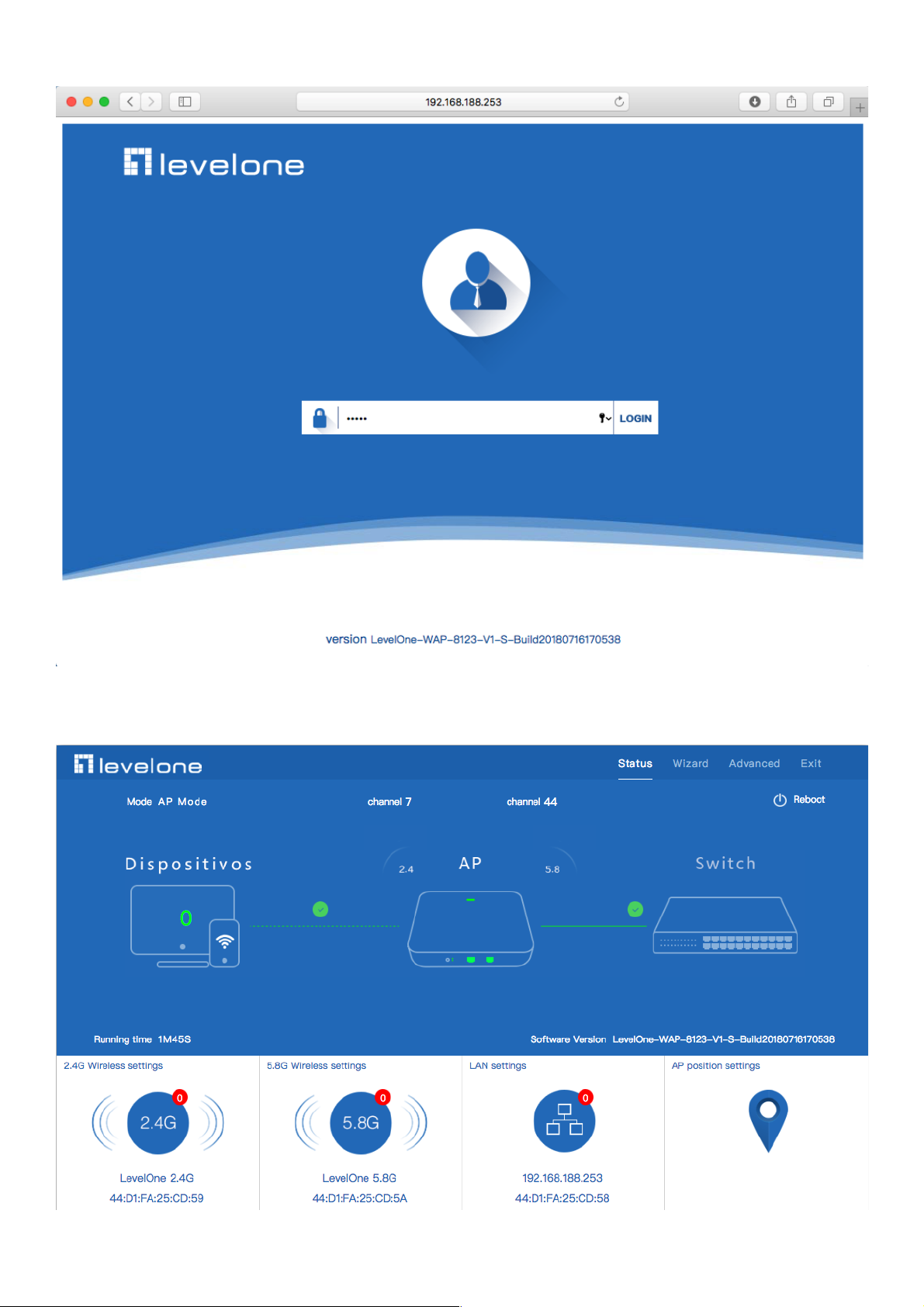
3.Input 192.168.188.253 into browser, then pop up the login page, the default login password: admin, then login,
4.After login, This page will show the Wireless AP’s default operation mode, channel, connection status, CPU usage,
Wireless settings, LAN Setting, Wireless AP’s Location, hardware/firmware version.
Page 11
11
Chapter 3 WEB GUI interface Setting
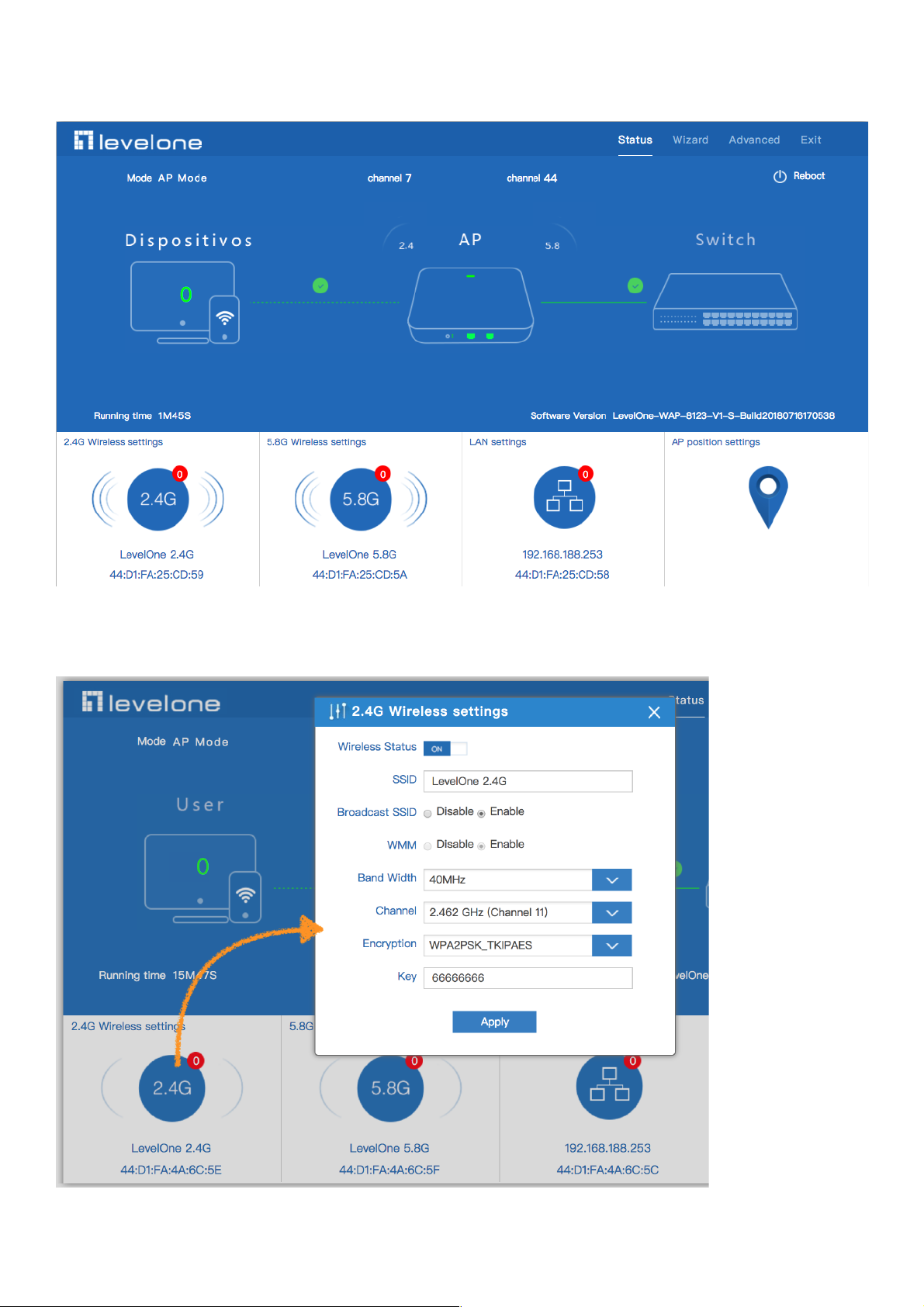
1.Then in Wireless Setting, GUI configuration page showed as below:
2.Then in Wireless Setting, GUI configuration page showed as below:
User can configure the SSID, password, band width, channel here, then Apply to finish.
Page 12
12
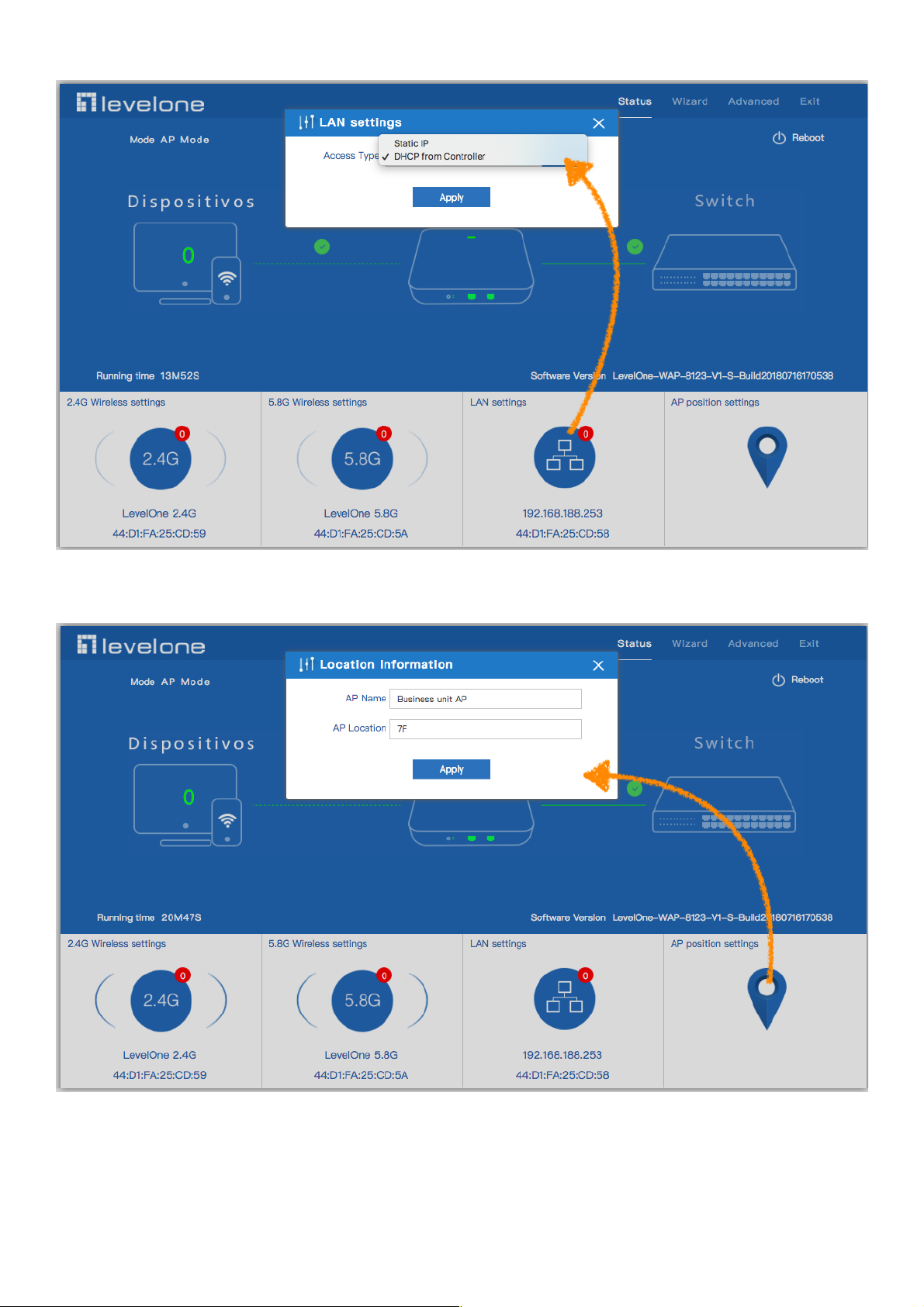
3.LAN Setting to configure the Static IP or DHCP from Controller
4.AP location setting: can mark where the AP set up, and AP name
Page 13
13
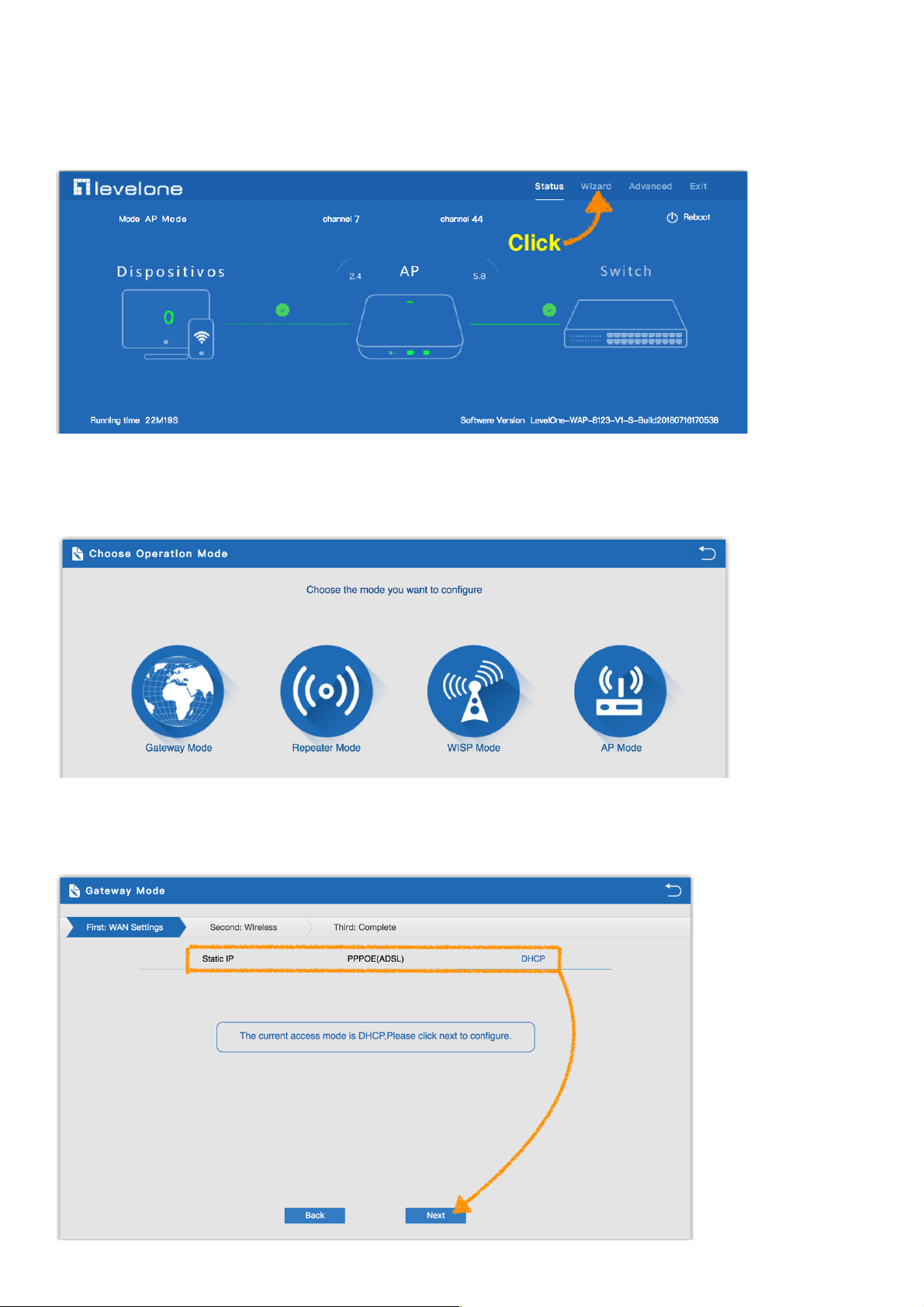
3.1 Wizard :
1.Click Wizard in Status page, will pop up following page to configure the operation mode and there are
explanation for each operation mode for better application.
2.Wizard: It instruct users to configure wireless AP’s operation mode based on needs: there are four operation mode
including gateway, repeater, WISP, Wireless AP. Please confirm the operation mode first before configuration
starting.
3.2 Gateway Mode:
Before Click Gateway mode, confirm your internet will be static IP, PPPoE, or DHCP:
Then will pop up following picture after click it, Please choose the right WAN setting mode, then click next to continue.
Page 14

14
3.2.1 Static IP setting in Gateway Mode :
1. Sample Static IP mode setting method, then click next to continue.
(Please contact with ISP for correct IP address and DNS address)
2. Wireless Setting in Gateway Mode (static IP) , Click Next
3. Please wait for the configuration to finish
Page 15
15
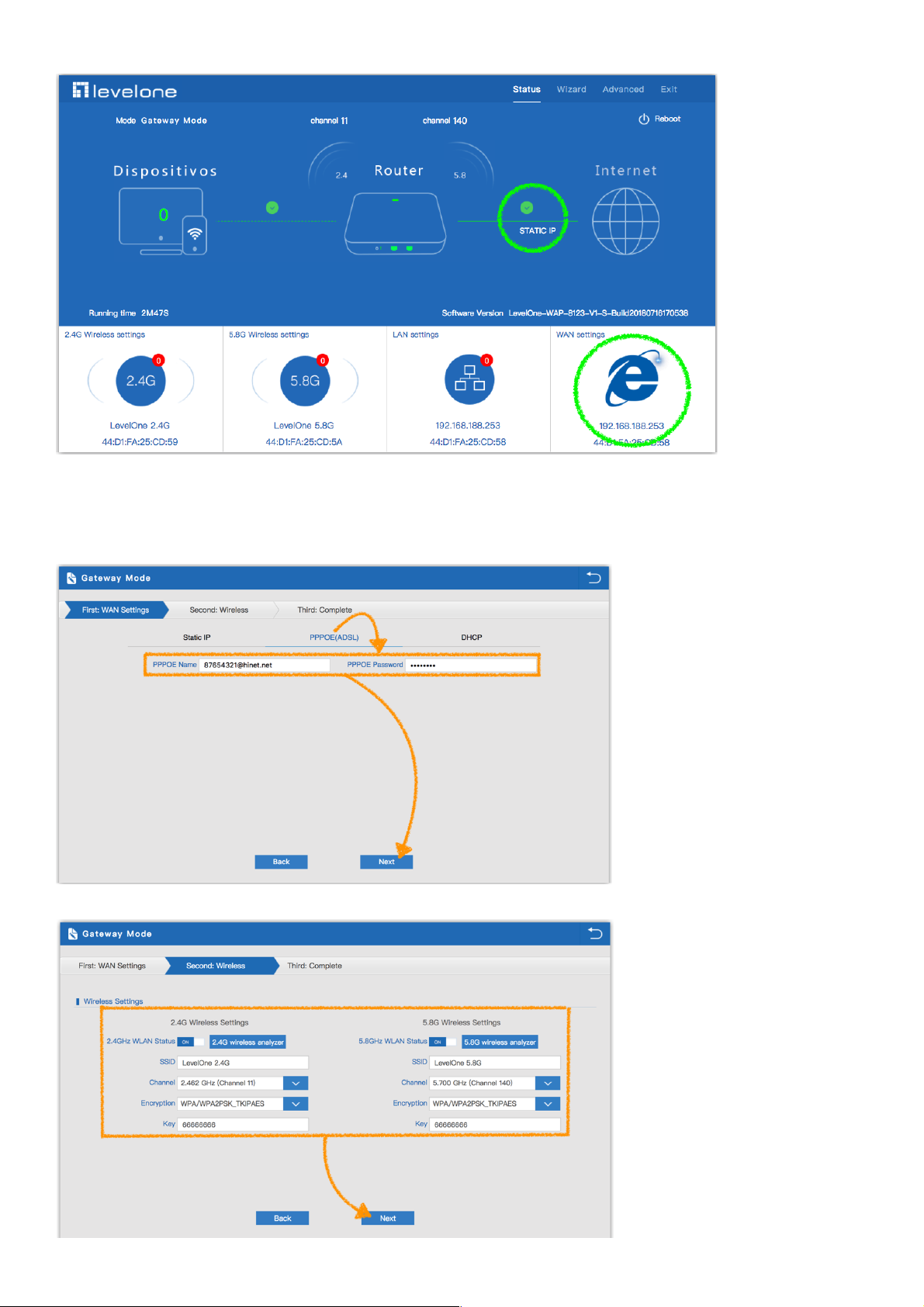
4. Please log in again ,This page will show the connection Static IP status
3.2.2 PPPoE(ADSL) setting in Gateway Mode :
1. Sample PPPoE mode setting method, then click next to continue.
(Please contact with ISP for correct PPPoE Name and Password)
2. Wireless Setting in Gateway Mode (PPPoE), Click Next
Page 16

16
3. Please wait for the configuration to finish
4. Please log in again ,This page will show the connection PPPoE status
Page 17
17
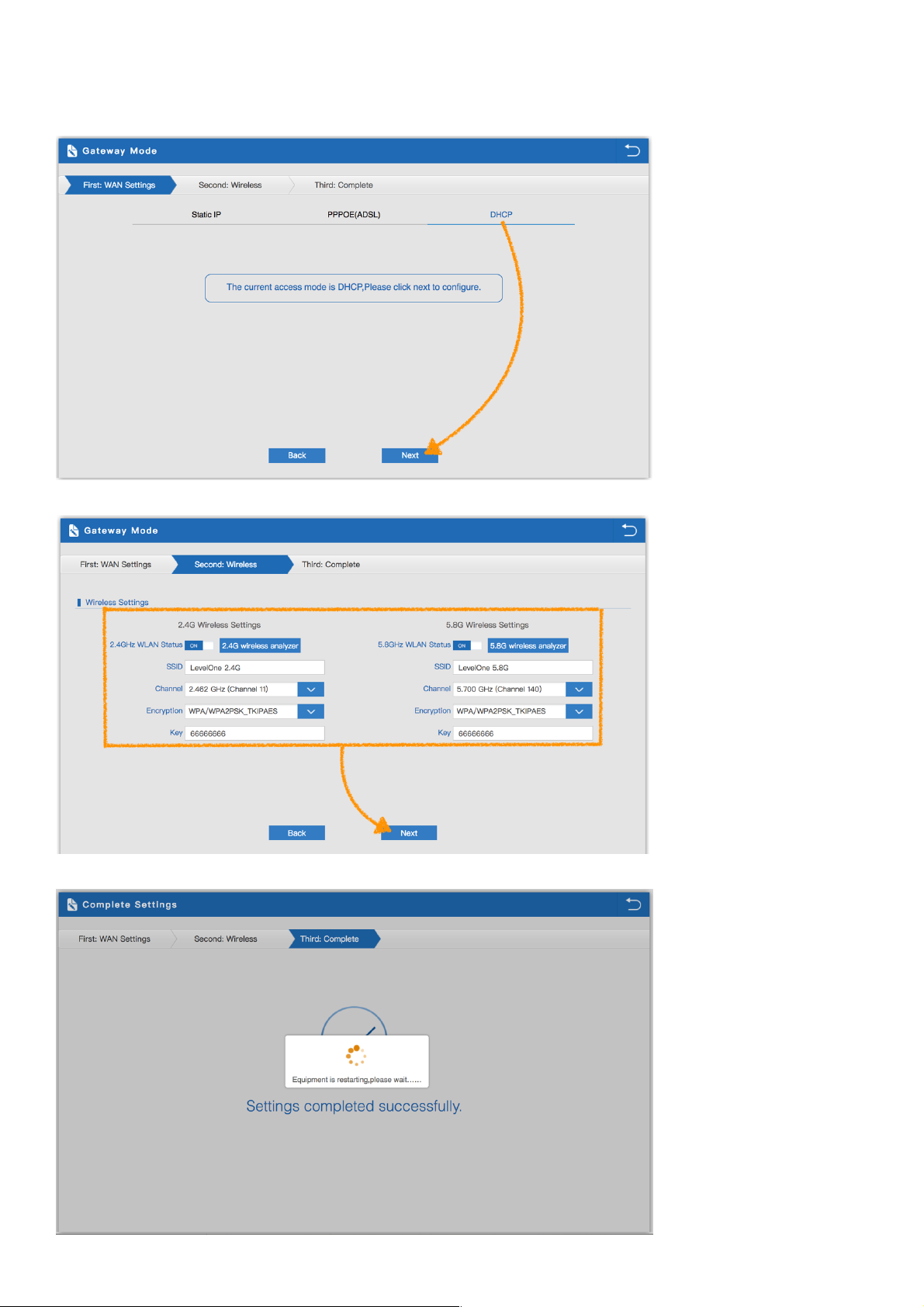
3.2.3 DHCP setting in Gateway Mode :
1. Sample DHCP mode setting method, then click next to continue.
(Please contact with ISP for correct IP address and DNS address. )
2. Wireless Setting in Gateway Mode (DHCP), Click Next
3. Please wait for the configuration to finish
Page 18
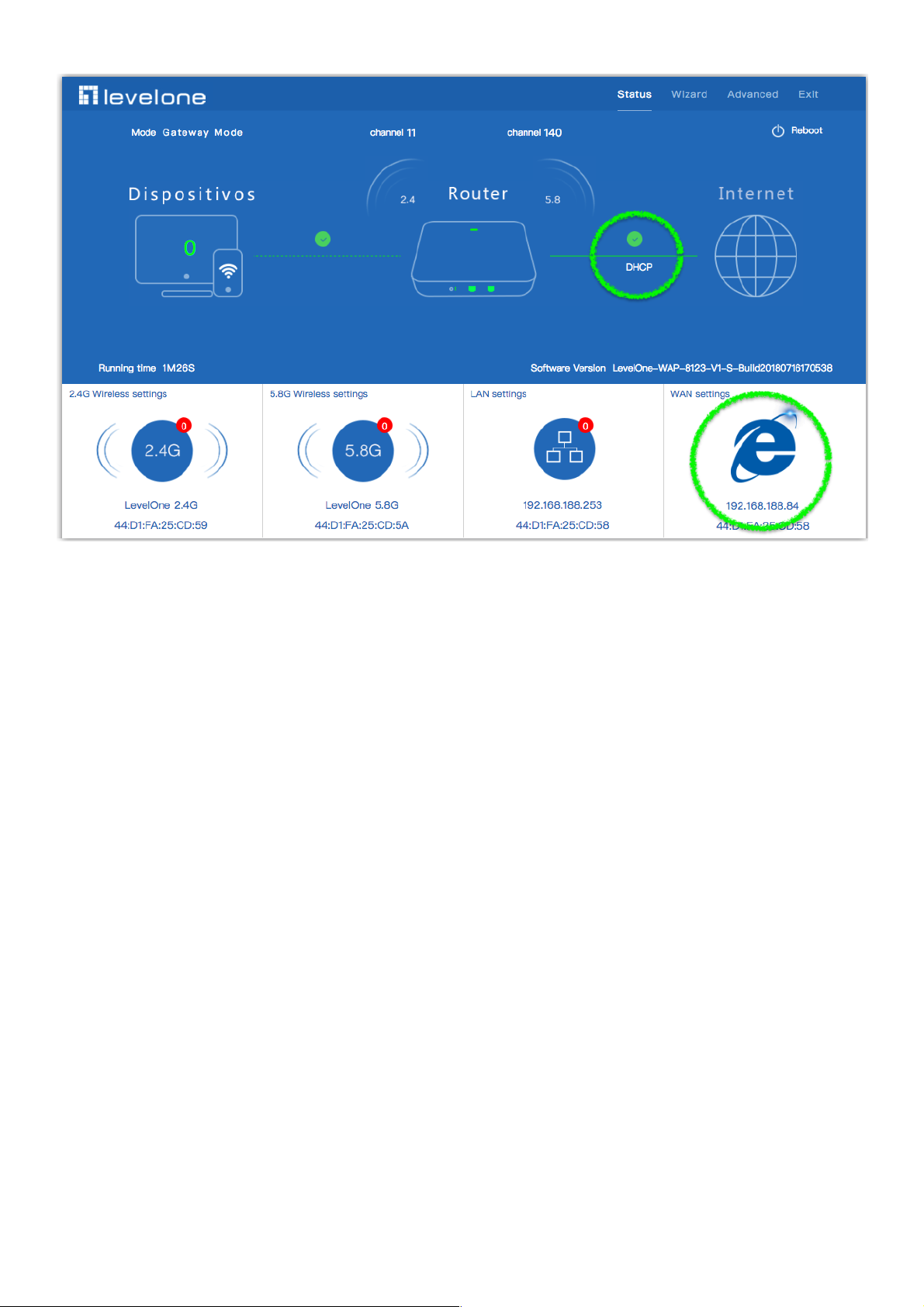
18
4. Please log in again ,This page will show the connection DHCP status
Page 19

19
3.3 Repeater mode :
1.Can choose to relay the front-end 2.4G or 5.8G wireless signal to extend the wireless signal range.
Select the AP’s SSID want to bridge, take “wireless 2.4G” for example, then input the AP’s key, click Scan AP
2.Please select WIFI SSID to connect
Page 20
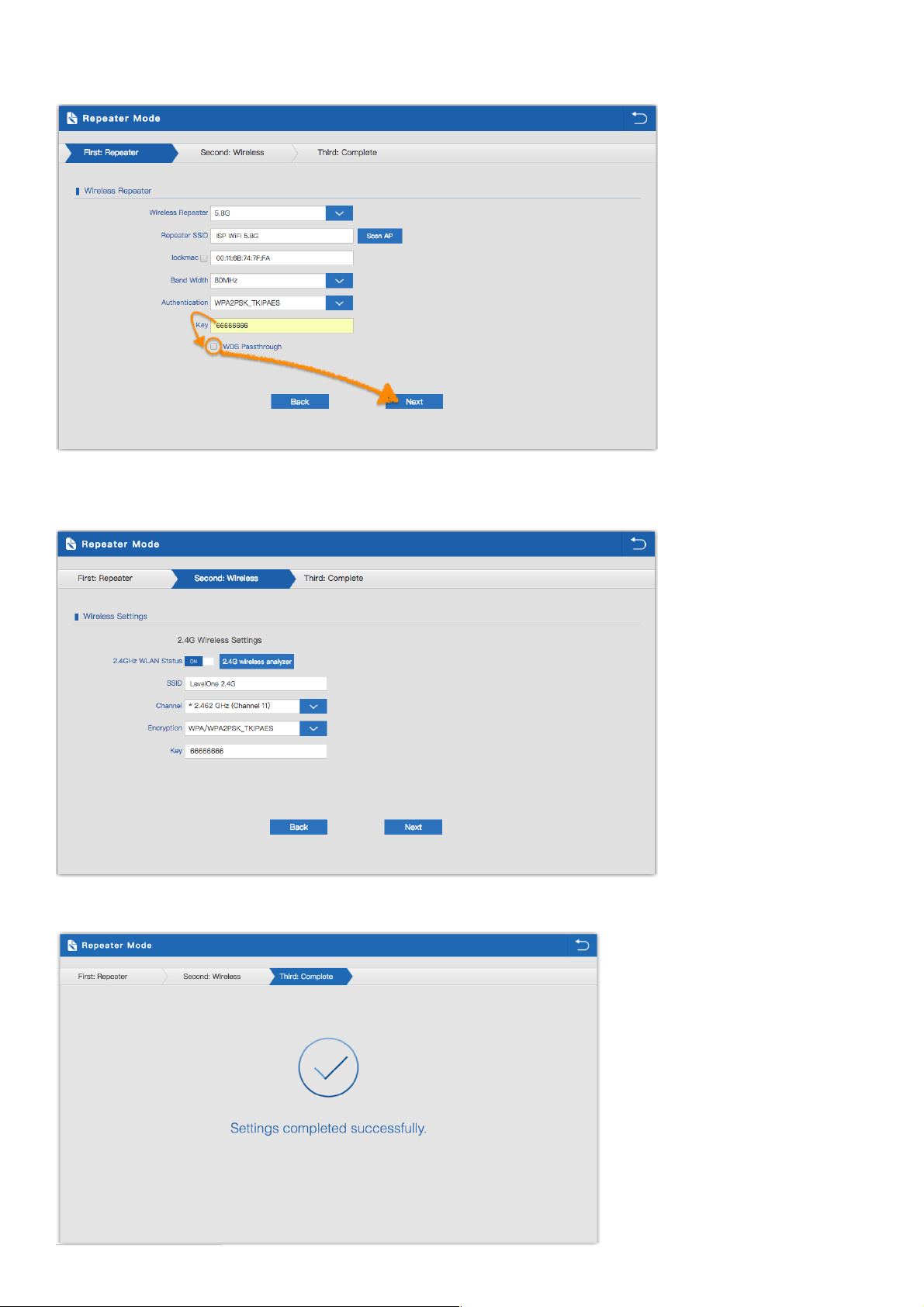
20
3. Enter the WIFI SSID password to be linked, When click Next.
Suggestion: If the upper wireless device is not the same model (WAP-8123), Don't click to WDS Passthrough.
4. If choose to relay the front-end 5.8G wireless signal to extend the wireless signal range. Can choose to enable or
disable the 2.4G wireless broadcast of the WAP-8123 itself.
5.Click Return button, will back to Status, show Repeater mode data, show fail or success
Page 21

21
6. Check WIFI Repeater mode data. If choose to relay the front-end 5.8G wireless signal to extend the wireless signal
range. In wifi repeater operation mode, WAP-8123 the default is 5.8G SSID disable.
7.Click Status button
8. Check WIFI Repeater mode data
Page 22
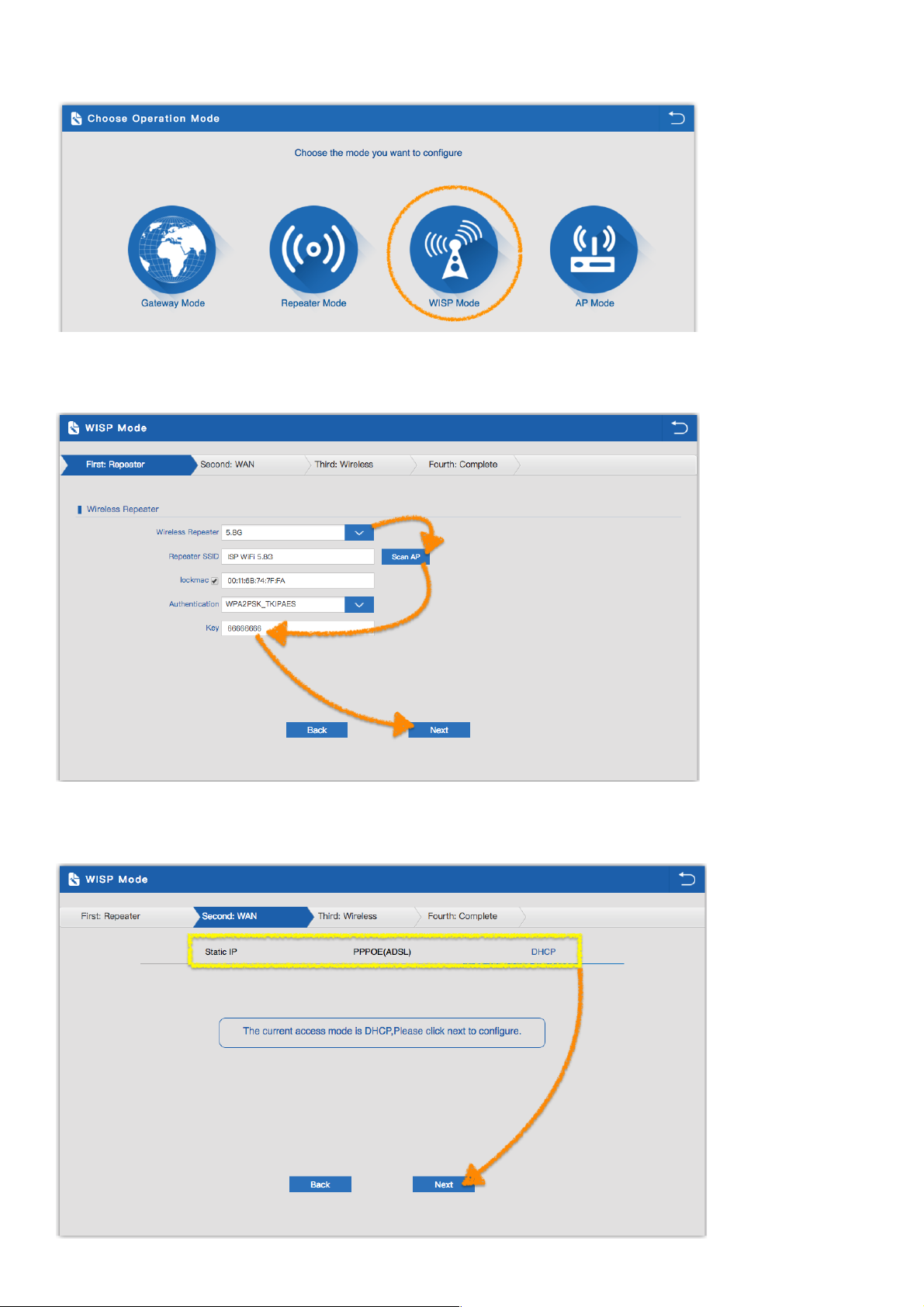
22
3.4 WISP Mode:
1.Select the AP’s SSID want to bridge, take “wireless 5.8G” for example,
then input the AP’s key, click Scan AP. Enter the WIFI SSID password to be linked, When click Next
2.Before Click WISP Mode, confirm your ISP WIFI will be static IP, PPPoE, or DHCP:
Then will pop up following picture after click it, Please choose the right WAN setting mode,then click next to continue.
Page 23

23
3.Take DHCP for example.
4. Configure the SSID and password AP going to broadcast.
5.Click Return button, will back to Status, show WISP mode data, show fail or success
Page 24

24
6.Check WISP Mode Status show fail or success
7. Check WISP Mode data for WAN Status , Check IP address that is received by DHCP .
8.Check WISP Mode Status data
Page 25

25
3.5 AP mode & Wireless analyzer :
1.To make the WAP-8123 work in some clear channel, user can click wireless analyzer at first. Look for
Unoccupied channel, then Wireless performance will be more stable. Picture showed as below.
2. Wireless analyzer Look for Unoccupied channel (2.4GHz)
Page 26

26
3. Wireless analyzer Look for Unoccupied channel (5.8GHz)
4. Set the wireless data, AP Location info as required, then click next to continue and enter into LAN setting.
After LAN setting, complete the AP mode configuration and back to Status.
5.Set according to environmental requirements.
Page 27

27
6.Demo Static IP setting
7. Check AP Mode Status show fail or success.
Page 28

28
Chapter 4 Advanced Setting
4.1 Device Status
4.1.1 Status:
l Mainly to check the wireless AP’s firmware version, hardware version, uptime info.
4.1.2 2.4G W ireless Status:
l Show wireless AP’s SSID, MAC address for WiFi, Channel, Encryption, Client List info.
Page 29

29
4.1.3 5.8G Wireless Status:
l Show wireless AP’s SSID, MAC address for WiFi, Channel, Encryption, Client List info.
4.1.4 LAN Status:
l Check wireless AP’s IP address, Subnet Mask, LAN MAC address and other info showed in following picture
Page 30

30
4.2 2.4G Wireless
4.2.1 2.4G Basic Settings :
l Mainly to configure the wireless SSID, password, band width ,encryption, channel, Multi SSID.
4.2.2 2.4G Virtual AP :
l There are 3 virtual AP in 2.4G wireless, if need enable multi SSIDs, then users can configure it showed in
following picture:
Page 31

31
4.2.3 2.4G Access Control :
1. Allow or deny the users access into this wireless AP based on MAC address.
2. Allow all the users access into this wireless AP
Page 32

32
3. Only users who have joined the MAC address list can access the wireless AP.
The following is a demonstration of teaching . Add the user MAC address in the list to the access control list
4. After the user's MAC address is added to the access control list, Click Apply.
After setting is completed, it will start to allow users access to this wireless AP function
Page 33

33
5. Users who have joined the MAC address list are denied access to the wireless AP.
The following is a demonstration of teaching . Add the user MAC address in the list to the access control list
6. After the user's MAC address is added to the access control list, Click Apply.
After setting is completed, it will start to deny users access to this wireless AP function
Page 34

34
7. In this page, will show the regional, mode, RF Power, Max user access...
4.3 5.8G Wireless
4.3.1 5.8G Basic Settings :
l Mainly to configure the wireless SSID, password, band width ,encryption, channel, Multi SSID.
Page 35

35
4.3.2 5.8G Virtual AP :
l There are 3 virtual AP in 5.8G wireless, if need enable multi SSIDs, then users can configure it showed in
following picture:
4.3.3 5.8G Access Control :
1. Allow or deny the users access into this wireless AP based on MAC address.
Page 36

36
2. Allow all the users access into this wireless AP
3. Only users who have joined the MAC address list can access the wireless AP. The following is a demonstration of
teaching . Add the user MAC address in the list to the access control list
Page 37

37
4. After the user's MAC address is added to the access control list, Click Apply. After setting is completed, it will
start to allow users access to this wireless AP function
5. Users who have joined the MAC address list are denied access to the wireless AP. The following is a
demonstration of teaching . Add the user MAC address in the list to the access control list
Page 38

38
6. After the user's MAC address is added to the access control list, Click Apply. After setting is completed, it will start
to deny users access to this wireless AP function
7. In this page, will show the regional, mode, RF Power, Max user access...
Remark : In Regional, the default is Debug, which including the frequency of 5.180GHz to 5.825GHz, but some local
laws will prohibit this, so, pls strictly abide by local laws and by cautious in using them.
Page 39

39
CHAPTER 5 Enable the status of Repeater Mode or AP Mode
5.1 Network
5.1.1 LAN Settings:
1. Can choose two kinds of usage modes (Static IP, DHCP for Controller) which can be selected according to the
current network architecture environment.
2. Use DHCP for Controller mode, please confirm that the current network architecture has IP address allocation.
3. Click Apply, Wait for DHCP Controller Mode is Enable, please wait about 20~30 seconds.
Page 40

40
4. The following example for Static IP Mode
5. Sample Static IP mode setting method, then click Apply to continue.
(Please contact with ISP for correct IP address, Subnet MasDNS address)
6. Click Apply, Wait for Static IP Mode is Enable, please wait about 40~50 seconds.
Page 41

41
5.1.2 VLAN :
l Please confirm before you can use ,Need support IEEE 802.1Q and VLAN Tagging Managed Switch, Specify
WiFi SSID for WAP-8123 , corresponding to the VLAN-ID (3-4094).
Page 42

42
5.2 Management
5.2.1 System Time :
1. Click on Sync with Host to automatically update to the current Time.
2. Confirm that System Time is correctly refreshed to the current time, Click Apply
3. Enable System for update to the current Time, please wait about 30~50 seconds.
Page 43

43
4. Define the system reboot time(0:00~23:00)
5.Can choose every day or every five days or every 10 days , System Reboot Automatically.
6. Enable Define the system reboot time, please wait about 30~50 seconds.
Page 44

44
5.2.2 Logs :
l In Logs part, you can copy the running history of the device to consult the engineers when you have any trouble
5.2.3 Upgrade Firmware :
l Allows you to browse the new firmware in your computer and upgrade. Please do not power off the device during
upgrade. ( Note : The update firmware is recommended to use the connection RJ45 Network Cable update .
Not recommended to use the wireless connection method to update the firmware.)
Page 45

45
5.2.4 System :
l You are able to backup the current configuration to your PC and restore by applying the configuration file
from your PC. And you can Reset and Reboot the device with just one click
5.2.5 User :
l Management and change the password for Log in
Page 46

46
CHAPTER 6 Enable the status of Gateway Mode or WISP Mode
6.1 Network
6.1.1 LAN Settings :
1. Set the specified device retention IP for easy management. The following is a demonstration of teaching .
2.Click Choice
Page 47

47
3.Add the user MAC address in the list to the access control list . Completed the reserved IP settings
6.1.2 VLAN :
l Please confirm before you can use ,Need support IEEE 802.1Q and VLAN Tagging Managed Switch, Specify
WiFi SSID or WAN/LAN Port for WAP-8123 , corresponding to the VLAN-ID (3-4094).
Page 48

48
6.1.3 WAN Settings :
1. Please check with the ISP first how to access the Internet , The following is a demonstration of Static IP teaching .
2.The following is a demonstration of PPPoE teaching .
Page 49

49
3.The following is a demonstration of DHCP teaching .
6.1.4 WAN advanced settings:
l Internet security does not recommend enable Ping Access on WAN to prevent interested people from knowing
the real IP address
Page 50

50
6.2 Firewall
6.2.1 IP/Port Filtering :
1.Factory default value is Disable, Can be set to whitelist or blacklist. The following will begin to introduce how to set
the enable function
2.Black List : IP Address that can be specified as a separate or range , and then specifies the port range (1~65535)
and protocol(TCP/UDP) .
Page 51

51
3.White List : IP Address that can be specified as a separate or range , and then specifies the port range
(1~65535) and protocol(TCP/UDP) , which is set as the status of the allow.
6.2.2 MAC Filtering :
1.Factory default value is disable, Can be set to whitelist or blacklist. The following will begin to introduce how to set
the enable function
Page 52

52
2.Black List : Scan specified mode or manual input mode to set, you can block the specified MAC address to connect
to the Internet, leaving only link Regional network function.
3.Click Choice
4. Added specified MAC address , Click Apply
Page 53

53
5.White List : Scan specified mode or manual input mode is set to allow the specified MAC address to connect to the
Internet
6.Click Choice
7.Added specified MAC address , Click Apply
Page 54

54
6.2.3 URL Filtering :
1.Factory default value is disable, Can be set to Black List. The following will begin to introduce how to set the enable
Black List function
2.Black List : Can set the URL refuse to access the list , making all devices unable to connect to the list of websites
Page 55

55
6.2.4 Port Forwarding
l The scan specified mode or manual input mode is set to allow the specified internal IP address of the External /
External port so that other users can connect from the remote network to the WAP-8123 internal network
equipment (ex: NAS , IP camera)
l After the setting is completed, the real fixed IP address or DDNS mode can be used to remotely connect to the
NAS inside the WAP-8123
(ex: Remote user page input http://111.250.96.135:2020 Port Forwarding to NAS IP address:192.168.188.197:80)
6.2.5 DMZ Host
1.Factory default value is disable . The following will begin to introduce how to set the enable DMZ Host function
Page 56

56
2.When enabled, will independent a non-military block for this ip address device.
Note : This device will be directly exposed on the Internet, there will be some risk
Page 57

57
6.3 Management
6.3.1 System Time :
1.Get time from NTP server can only be available under Gateway and WISP Mode. Before sync with host, please
select your Time zone. Auto restart : Define the system reboot time(0:00~23:00) , Can choose every day or every
five days or every 10 days , System Reboot Automatically.
2.Can set up the required NAT Server
Page 58

58
3.Can add NTP Server yourself (ex: Hinet NTP Server)
Page 59

59
6.3.2 DDNS settings :
1.Factory default value is disable
2. For users no apply for an ISP fixed IP address, only Floating real IP address , you can also connect to the network
device in WAP-8123 through the DDNS service.
Page 60

60
6.3.3 QoS :
l Can manually specify the IP address range of the device to limit the upload and download
6.3.4 Logs :
l In Logs part, you can copy the running history of the device to consult the engineers when you have any trouble
Page 61

61
6.3.5 Upgrade Firmware :
l Allows you to browse the new firmware in your computer and upgrade. Please do not power off the device during
upgrade.
6.3.6 System :
You are able to backup the current configuration to your PC and restore by applying the configuration file from
your PC. And you can Reset and Reboot the device with just one click
Page 62

62
6.3.7 User :
l Management and change the password for Log in
Page 63

63
Appendix A LICENSE STATEMENT / GPL CODE STATEMENT
This product resp. the here (http://global.level1.com/downloads.php?action=init) for downloading
offered software includes software code developed by third parties, including software code
subject to the GNU General Public License Version 2 (“GPLv2”) and GNU Lesser General Public
License 2.1 („LGPLv2.1“).
WRITTEN OFFER FOR GPL/LGPL SOURCE CODE
We will provide everyone upon request the applicable GPLv2 and LGPLv2.1 source code files via
CDROM or similar storage medium for a nominal cost to cover shipping and media charges as
allowed under the GPLv2 and LGPLv2.1. This offer is valid for 3 years. GPLv2 and LGPLv2
inquiries: Please direct all GPL and LGPL inquiries to the following address:
Digital Data Communications GmbH
Zeche-Norm-Str. 25
44319 Dortmund
Deutschland
Phone: +49 231 9075 - 0
Fax: +49 231 9075 - 184
Email:support@level1.com
Web: www.level1.com
NO WARRANTY
This program is distributed in the hope that it will be useful, but
WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR
PURPOSE. See the GNU General Public License for more details. IN
NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED
TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER
PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM
AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
Page 64

64
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR
INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR
LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE
OF
THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS),
EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF
THE POSSIBILITY OF SUCH DAMAGES.
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but
changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom
to share and change it. By contrast, the GNU General Public License is
intended to guarantee your freedom to share and change free software--
to make sure the software is free for all its users. This General Public
License applies to most of the Free Software Foundation's software and
to any other program whose authors commit to using it. (Some other
Free Software Foundation software is covered by the GNU Lesser
General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price.
Our General Public Licenses are designed to make sure that you have
the freedom to distribute copies of free software (and
charge for this service if you wish), that you receive source code or can
Page 65

65
get it if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to
deny you these rights or to ask you to surrender the rights. These
restrictions translate to certain responsibilities for you if you distribute
copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or
for a fee, you must give the recipients all the rights that you have. You
must make sure that they, too, receive or can get the source code. And
you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2)
offer you this license which gives you legal permission to copy, distribute
and/or modify the software.
Also, for each author's protection and ours, we want to make certain that
everyone understands that there is no warranty for this free software. If
the software is modified by someone else and passed on, we want its
recipients to know that what they have is not the original, so that any
problems introduced by others will not reflect on the original authors'
reputations.
Finally, any free program is threatened constantly by software patents.
We wish to avoid the danger that redistributors of a free program will
individually obtain patent licenses, in effect making the program
proprietary. To prevent this, we have made it clear that any patent must
be licensed for everyone's free use or not licensed at all.
Page 66

66
The precise terms and conditions for copying, distribution and
modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND
MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the
copyright holder saying it may be distributed under the terms of this General Public License. The
"Program", below, refers to any such program or work, and a "work based on the Program"
means either the Program or any derivative work under copyright law: that is to say, a work
containing the Program or a portion of it, either verbatim or with modifications and/or translated
into another language. (Hereinafter, translation is included without limitation in the term
"modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by this License;
they are outside its scope. The act of running the Program is not restricted, and the output
from the Program is covered only if its contents constitute a work based on the Program
(independent of having been made by running the Program). Whether that is true
depends on what the Program does.
1.You may copy and distribute verbatim copies of the Program's source code as you
receive it, in any medium, provided that you conspicuously and appropriately publish on
each copy an appropriate copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty; and give any other
recipients of the Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your
option offer warranty protection in exchange for a fee.
2.You may modify your copy or copies of the Program or any portion of it, thus forming a
work based on the Program, and copy and distribute such modifications or work under
the terms of Section 1 above, provided that you also meet all of these conditions:
Page 67

67
a)
You must cause the modified files to carry prominent notices stating that you
changed the files and the date of any change.
b)
You must cause any work that you distribute or publish, that in whole or in part
contains or is derived from the Program or any part thereof, to be licensed as a whole at
no charge to all third parties under the terms of this License.
c)
If the modified program normally reads commands interactively when run, you must
cause it, when started running for such interactive use in the most ordinary way, to print or
display an announcement including an appropriate copyright notice and a notice that
there is no warranty (or else, saying that you provide a warranty) and that users may
redistribute the program under these conditions, and telling the user how to view a copy of
this License. (Exception: if the Program itself is interactive but does not normally print such
an announcement, your work based on the Program is not required to print an
announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that
work are not derived from the Program, and can be reasonably considered independent
and separate
works in themselves, then this License, and its terms, do not apply to those sections when
you distribute them as separate works. But when you distribute the same sections as part
of a whole which is a work based on the Program, the distribution of the whole must be on
the terms of this License, whose permissions for other licensees extend to the entire whole,
and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work
written entirely by you; rather, the intent is to exercise the right to control the
distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program
(or with a work based on the Program) on a volume of a storage or distribution medium
does not bring the other work under the scope of this License.
3.You may copy and distribute the Program (or a work based on it, under Section 2) in
object code or executable form under the terms of Sections 1 and 2 above provided that
you also do one of the following:
Page 68

68
we use this doubled UL to get the sub-sections indented, while making the bullets as
unobvious as possible.
a)
Accompany it with the complete corresponding
machine-readable source code, which must be distributed under the terms of Sections
1 and 2 above on a medium customarily used for software interchange; or,
b)
Accompany it with a written offer, valid for at least three years, to give any third party,
for a charge no more than your cost of physically performing source distribution, a
complete
machine-readable copy of the corresponding source code, to be distributed under the
terms of Sections 1 and 2 above on a medium customarily used for software
interchange; or,
c)
Accompany it with the information you received as to the offer to distribute
corresponding source code. (This alternative is allowed only for noncommercial
distribution and only if you received the program in object code or executable form with
such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making
modifications to it. For an executable work, complete source code means all the source
code for all modules it contains, plus any associated interface definition files, plus the
scripts used to control compilation and installation of the executable. However,
as a special exception, the source code distributed need not include anything that is
normally distributed (in either source or binary form) with the major components
(compiler, kernel, and so on) of the operating system on which the executable runs,
unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a
designated place, then offering equivalent access to copy the source code from the
same place counts as distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4.You may not copy, modify, sublicense, or distribute the Program except as expressly
provided under this License. Any attempt otherwise to copy, modify, sublicense or
Page 69

69
distribute the Program is void, and will automatically terminate your rights under this
License. However, parties who have received copies, or rights, from you under this
License will not have their licenses terminated so long as such parties remain in full
compliance.
5.You are not required to accept this License, since you have not signed it. However,
nothing else grants you permission to modify or distribute the Program or its derivative
works. These actions are prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the Program), you indicate
your acceptance of this License to do so, and all its terms and conditions for copying,
distributing or modifying the Program or works based on it.
6.Each time you redistribute the Program (or any work based on the Program), the
recipient automatically receives a license from the original licensor to copy, distribute or
modify the Program subject to these terms and conditions. You may not impose any
further restrictions on the recipients' exercise of the rights granted herein. You are not
responsible for enforcing compliance by third parties to this License.
7.If, as a consequence of a court judgment or allegation of patent infringement or for any
other reason (not limited to patent issues), conditions are imposed on you (whether by
court order, agreement or otherwise) that contradict the conditions of this License, they do
not excuse you from the conditions of this License. If you cannot distribute so as to satisfy
simultaneously your obligations under this License and any other pertinent obligations,
then as a consequence you may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by all those who
receive copies directly or indirectly through you, then the only way you could
satisfy both it and this License would be to refrain entirely from distribution of the
Program.
If any portion of this section is held invalid or unenforceable under any particular
circumstance, the balance of the section is intended to apply and the section as a whole is
intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property
right claims or to contest validity of any such claims; this section has the sole purpose of
protecting the integrity of the free software distribution system, which is implemented by
public license practices. Many people have made generous contributions to the wide range
Page 70

70
of software distributed through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing to distribute software
through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed
to be a consequence of the rest of this License.
8.If the distribution and/or use of the Program is restricted in certain countries either by
patents or by copyrighted interfaces, the original copyright holder who places the Program
under this License may add an explicit geographical distribution limitation
excluding those countries, so that distribution is permitted only in or among countries not
thus excluded. In such case, this License incorporates the limitation as if written in the
body of this License.
9.The Free Software Foundation may publish revised and/or new versions of the General
Public License from time to time. Such new versions will be similar in spirit to the present
version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version
number of this License which applies to it and "any later version", you have the option of
following the terms and conditions either of that version or of any later version published
by the Free Software Foundation. If the Program does not specify a version number of this
License, you may choose any version ever published by the Free Software Foundation.
10.If you wish to incorporate parts of the Program into other free programs whose
distribution conditions are different, write to the author to ask for permission. For software
which is copyrighted by the Free Software Foundation, write to the Free Software
Foundation; we sometimes make exceptions for this. Our decision will be guided by the
two goals of preserving the free status of all derivatives of our free software and of
promoting the sharing and reuse of software generally.
NO WARRANTY
11.BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO
Page 71

71
WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE
LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT
HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT
WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT
NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS TO THE QUALITY
AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM
PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION.
12.IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW
OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER
PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED
ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL,
INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR
INABILITY TO USE THE
PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES
OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS),
EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS How to Apply These Terms
to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the
public, the best way to achieve this is to make it free software which everyone can
redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start
of each source file to most effectively convey the exclusion of warranty; and each file
should have at least the "copyright" line and a pointer to where the full notice is found.
One line to give the program's name and an idea of what it does.
Page 72

72
Copyright (C) yyyy name of author
This program is free software; you can redistribute it and/or modify it under the terms of the
GNU General Public License as published by the Free Software Foundation;
either version 2
of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY;
without even the implied warranty of MERCHANTABILITY or FITNESS FOR A
PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if
not, write to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA
02110-1301, USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this
when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author Gnomovision comes with
ABSOLUTELY NO WARRANTY; for details type `show w'.This is free software, and
you are welcome to redistribute it under certain conditions; type `show c' for details.
The hypothetical commands `show w' and `show c' should show the appropriate parts of
the General Public License. Of course, the commands you use may be called something
other than `show w ' and `show c '; they could even be mouse-clicks or menu
items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your school, if any,
to sign a "copyright disclaimer" for the program, if necessary. Here is a sample; alter the
names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision'
(which makes passes at compilers) written by James Hacker.
signature of Ty Coon, 1 April 1989 Ty Coon,
President of Vice
This General Public License does not permit incorporating your program into proprietary
programs. If your program is a subroutine library, you may consider it more useful to
permit linking proprietary applications with the library. If this is what you want to do, use
the GNU Lesser General Public License instead of this License.
Page 73

73
Notification of Compliance
Europe - EU Declaration of Conformity
For complete DoC please visit
http://global.level1.com/downloads.php?action=init
GPL License Agreement
GPL may be included in this product, to view the GPL license agreement goes to
http://download.level1.com/level1/gpl/GPL.pdf
For GNU General Public License (GPL) related information, please visit
http://global.level1.com/downloads.php?action=init
 Loading...
Loading...