Page 1

IBM TotalStorage™Network Attached Storage 300
Model 326
User’s Reference
Release 2.5
GA27-4276-02
Page 2
Note
Before using this information and the product it supports, be sure to read the general information in “Appendix A. Notices” on
page 127.
First Edition (June 2002)
This edition applies to Release 2.5 of the IBM 5195 TotalStorage Network Attached Storage 300 (Model 326, product
number 5195–326) and to all subsequent releases and modifications until otherwise indicated in new editions.
Order publications through your IBM representative or the IBM branch office servicing your locality. Publications are
not stocked at the address below.
IBM welcomes your comments. A form for reader’s comments is provided at the back of this publication. If the form
has been removed, you may address your comments to:
International Business Machines Corporation
Design & Information Development
Department CGF
PO Box 12195
Research Triangle Park, NC 27709–9990
U.S.A.
You can also submit comments on the Web at www.ibm.com/networking/support/feedback.nsf/docsoverall.
When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any
way it believes appropriate without incurring any obligation to you.
© Copyright International Business Machines Corporation 2002. All rights reserved.
US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract
with IBM Corp.
Page 3

Contents
Figures ...........................vii
Tables ............................ix
About this book ........................xi
Who should read this book .....................xi
Frequently used terms ......................xi
Publications ..........................xi
Descriptions of the Model 326 publications ..............xii
Hardcopy publications shipped with the Model 326 ...........xii
Related publications ......................xii
Web sites ...........................xii
Chapter 1. Introduction ......................1
Roadmap for setting up and configuring the Model 326 ..........3
Cluster setup requirements .....................6
Chapter 2. Configuration and administration tools ...........9
Using a keyboard, monitor, and mouse for setup and configuration ......9
Summary of configuration and administration tools ............9
Terminal Services and the IBM NAS Administration Console ........12
Installing Terminal Services ...................12
Connecting to the desktop through Terminal Services ..........12
IBM NAS Administration console .................13
Determining who is using the network-attached storage .........13
IBM Advanced Appliance Configuration Utility..............13
Initial network adapter selection and connection to the IAACU ......14
IAACU Agent ........................15
IAACU Console........................15
Universal Manageability Services ..................21
System requirements .....................21
Starting UM Services .....................22
Windows 2000 for Network Attached Storage..............23
Telnet Server support ......................24
SNMP support .........................24
Chapter 3. Getting started ....................25
Methods for setting up the Model 326 ................25
Installing the IBM Advanced Appliance Configuration Utility........25
Accessing Universal Manageability Services .............26
Initial setup and configuration ...................26
Setting the date and time ....................27
Setting up the network .....................27
Chapter 4. Setting up storage ...................29
Direct-managed method for managing the 5191 RAID Storage Controller . . . 29
Starting Enterprise Management ..................31
Starting Subsystem Management ..................32
Changing storage-subsystem host type ...............32
Renaming storage subsystems ..................32
Creating arrays and logical drives .................32
Creating arrays and LUNs under the Storage Manager Application .....32
Expanding the LUN ......................33
© Copyright IBM Corp. 2002 iii
Page 4

Formatting the logical drives ...................35
Chapter 5. Completing networking, clustering, and storage access setup 37
Networking setup ........................37
Configuring the interconnect (private) network adapter .........37
Configuring the public local area connection .............38
Verifying network connectivity and names resolution ..........39
Checking or changing the network binding order ...........39
Joining a node to a domain ....................40
Cluster setup .........................40
Configuring clusters .......................41
Configuring cluster state and properties ...............41
Setting up cluster resource balancing ...............42
Setting up failover .......................42
Creating users ........................43
Defining UNIX users and groups .................43
Creating clustered file shares (CIFS and NFS) ............47
Powering off and powering on the Model 326.............49
Recovering from a corrupted Quorum drive .............50
Before you add software ... ....................51
Chapter 6. Managing and protecting the network and storage ......53
IBM Director ..........................53
Dependencies ........................54
Hardware requirements .....................54
Director extensions ......................55
Naming conventions ......................55
Web-based access ......................55
Disaster recovery .......................56
Software distribution ......................56
Real-time diagnostics .....................57
Rack Manager and inventory enhancements .............57
Dynamic NAS groups .....................58
NAS Web UI task .......................58
Electronic Service Agent (eSA) ..................58
Predictive Failure Analysis ....................59
For more information......................59
NAS Backup Assistant ......................59
Restoring using the NT Backup panel ...............60
Persistent Images ........................61
Global Settings ........................62
Volume Settings .......................62
Persistent Images .......................62
Schedules .........................63
Restore Persistent Images ...................64
Disaster Recovery.......................64
Granting user access to persistent image files ............68
PSM notes .........................68
Microsoft Services for UNIX and NFS Support .............72
Configuring Server for NFS ...................73
Antivirus protection .......................75
Chapter 7. Managing adapters and controllers ............77
Managing Fibre Channel host bus adapters ..............77
Enabling communication between system management adapters ......78
Enabling ISMP to RSA communication on a single machine .......80
iv Model 326 User’s Reference
Page 5

Using the ISMP and RSA ....................80
Enabling Ethernet adapter teaming .................81
Intel adapters ........................81
Alacritech 10/100 Quad-Port Ethernet adapter ............82
PRO/1000 XT Server adapter ..................83
Adding a second IBM 5191 RAID Storage Controller Model 0RU ......83
RAID mirroring .........................84
Memory notes .........................84
Adding more engine memory to increase performance .........84
Using the Recovery CD-ROM if you have added more processor memory 84
Chapter 8. Troubleshooting....................85
IBM 5187 Network Attached Storage Model 6RZ ............85
Engine diagnostic tools overview .................85
Identifying problems using LEDs .................86
Engine troubleshooting charts..................89
Power problems .......................91
Recovering BIOS .......................92
Replacing the battery .....................93
Adapter troubleshooting and diagnostics ...............96
Troubleshooting the integrated Ethernet adapter ...........96
Troubleshooting the Gigabit Ethernet SX adapter ...........100
Troubleshooting the Alacritech 10/100 Quad-Port Ethernet adapter ....101
Troubleshooting the PRO/1000 XT Server adapter ..........102
Troubleshooting the ServeRAID-4Lx ...............103
Troubleshooting the SCSI HVD 3570 adapter ............107
Testing the Fibre Channel host adapter with FAStT MSJ ........108
Testing the Integrated System Management Processor .........109
Testing the Remote Supervisor Adapter ..............110
Testing SCSI adapters .....................111
IBM 3534 Fibre Channel Hub Model 1RU ...............111
Hub diagnostics .......................112
IBM 5191 RAID Storage Controller Model 0RU (storage controller) .....113
Replacing hot-swap drives ...................116
IBM 5192 Storage Unit Model 0RU (storage unit) ............118
Chapter 9. Using the Recovery and Supplementary CDs ........123
Using the Recovery Enablement Diskette and Recovery CD ........123
Using the Supplementary CD ...................125
Appendix A. Notices ......................127
Trademarks..........................128
Appendix B. Getting help, service, and information ..........129
Service support ........................129
Before you call for service ....................130
Getting customer support and service ................130
Getting help online: www.ibm.com/storage/support ..........130
Getting help by telephone ...................131
Appendix C. Purchasing additional services ............133
Warranty and repair services ...................133
Appendix D. Engine POST and diagnostic program messages .....135
Power-on self-test (POST) ....................135
POST beep code descriptions ..................135
Contents v
Page 6

POST beep codes ......................137
POST error messages .....................140
Event/error logs .......................145
Diagnostic program messages...................145
Text messages .......................146
Starting the diagnostic programs .................146
Viewing the test log......................148
Diagnostic error message tables .................148
Appendix E. Setup procedures and diagnostics for the Fibre Channel Hub 155
General information .......................155
Isolating a system fault ....................155
Removing power .......................155
Service actions for error messages ................155
Setting up partnering with the 3534 Fibre-managed hubs .........155
Setting IP Address of Fibre Hub and Fibre Switch ...........156
Running diagnostics on the hub ..................157
Attaching to the serial port while the hub is off ............157
Attaching to the serial port while the hub is on ............158
Running diagnostics from a Telnet session on the Ethernet .......158
Diagnostic tests during POST ..................158
Diagnostic commands ......................159
Diagnostic command descriptions .................160
Error messages ........................165
Action codes and recommended actions ..............165
Diagnostic error message formats ................165
Error message tables .....................165
Appendix F. Fast!UTIL options ..................171
Configuration settings ......................171
Host adapter settings .....................171
Selectable boot settings ....................172
Restore default settings ....................172
Raw NVRAM data ......................172
Advanced adapter settings ...................172
Extended Firmware Settings ..................174
Scan Fibre Channel Devices ...................175
Fibre Disk Utility ........................175
Loopback Data Test ......................176
Select Host Adapter ......................176
Appendix G. Customer Replaceable Unit (CRU) list ..........177
Appendix H. Adapter placement tables ...............181
Glossary of terms and abbreviations ...............203
Index ............................221
vi Model 326 User’s Reference
Page 7

Figures
1. File share dependencies ............................47
2. Diagnostics panel LEDs ............................88
3. Boot block jumper location ...........................93
4. Battery removal ...............................95
5. Battery replacement..............................95
© Copyright IBM Corp. 2002 vii
Page 8

viii Model 326 User’s Reference
Page 9

Tables
1. Networking information worksheet for the public connection ...............7
2. Summary of configuration and administration tools for the Model 326 ...........10
3. Example of local area connection names and network adapter IP addresses .........39
4. Persistent image global settings .........................62
5. Persistent image volume settings .........................62
6. ISMP compared to the RSA ...........................79
7. Power supply LEDs ..............................87
8. Descriptions of light-path diagnostics LEDs .....................89
9. Engine troubleshooting symptoms and actions ....................90
10. Power error messages.............................91
11. Integrated Ethernet adapter troubleshooting chart ...................97
12. 10/100 PCI Ethernet adapter troubleshooting chart ..................98
13. Gigabit Ethernet SX adapter troubleshooting chart ..................100
14. Alacritech 10/100 Quad-Port Ethernet adapter LED definitions..............101
15. PRO/1000 XT Server adapter troubleshooting chart .................102
16. ServeRAID-4Lx problems and actions.......................106
17. SCSI HVD 3570 adapter troubleshooting chart ...................108
18. HUB front panel LED status indicators ......................111
19. Hub POST tests...............................112
20. Hub offline and online tests ..........................113
21. Storage controller troubleshooting ........................113
22. Storage unit troubleshooting table ........................118
23. Supplementary CD directories .........................126
24. IBM Web sites for help, services, and information ..................129
25. POST beep codes ..............................137
26. POST no-beep codes ............................139
27. POST error messages ............................140
28. Diagnostic error messages...........................148
29. Hub POST diagnostic tests ..........................158
30. Hub action codes ..............................165
31. Hub diagnostic error messages .........................166
32. Hub system error messages ..........................169
33. Host adapter settings .............................171
34. Advanced adapter settings ...........................172
35. Extended firmware settings ..........................174
36. RIO operation modes.............................174
37. Connection options .............................174
38. 5186-36U Rack ...............................177
39. 5197–6RZ Engine ..............................177
40. 5191–0RU RAID Storage Controller .......................178
41. 5192–0RU Storage Unit ............................178
42. 3534–1RUHub...............................179
43. One-adapter configuration ...........................181
44. Two-adapter configuration ...........................181
45. Three-adapter configuration ..........................182
46. Four-adapter configuration ...........................184
47. Five-adapter configuration ...........................189
© Copyright IBM Corp. 2002 ix
Page 10

x Model 326 User’s Reference
Page 11

About this book
This book provides information necessary to configure and administer the IBM 5195
TotalStorage Network Attached Storage 300, Model 326.
Hereafter, the IBM 5195 TotalStorage Network Attached Storage 300, Model 326, is
referred to as the Model 326.
Who should read this book
This book is for Model 326 administrators.
The Model 326 administrator should have experience in at least the following skills,
or have access to personnel with experience in these skills:
v Microsoft
v Networking and network management
v Disk management
v SAN management
v General technologies of the product (such as Microsoft Cluster Service, Services
for UNIX
v Critical business issues (such as backup, disaster recovery, security)
Frequently used terms
®
Windows®and Windows Advanced Server
®
, storage, RAID, and so on)
Publications
This document contains certain notices that relate to a specific topic. The caution
and danger notices also appear in the multilingual Safety Information on the
Documentation CD that came with the appliance. Each notice is numbered for easy
reference to the corresponding notices in the Safety Information.
The following terms, used within this document or within the Safety Information,
have these specific meanings:
Term Definition in this document
Attention These notices indicate possible damage to programs, devices, or
data. An attention notice is placed just before the instruction or
situation in which damage could occur.
Caution These notices indicate situations that can be potentially hazardous
to you. A caution notice is placed just before descriptions of
potentially hazardous procedure steps or situations.
Danger These notices indicate situations that can be potentially lethal or
extremely hazardous to you. A danger notice is placed just before
descriptions of potentially lethal or extremely hazardous procedure
steps or situations.
Notes These notices provide important tips, guidance, or advice.
The latest versions of the following product publications are available in softcopy at:
http://www.ibm.com/storage/support/nas
© Copyright IBM Corp. 2002 xi
Page 12

Descriptions of the Model 326 publications
The Model 326 library consists of the following publications:
v Hardware Installation Guide
This book describes hardware physical specifications, electrical specifications,
cabling, environmental specifications, and networking specifications for installing
the Model 326.
v User’s Reference
This book describes such operational and administrative activities as:
– Using the configuration utilities
– Administering the Model 326
– Troubleshooting
– Using the Recovery and Supplementary CDs
Hardcopy publications shipped with the Model 326
The following publications are shipped in hardcopy and are also provided in
softcopy (PDF) form at:
http://www.ibm.com/storage/support/nas
v IBM 5195 TotalStorage Network Attached Storage 300 Installation Guide,
GA27-4275
v Release Notes
This document provides any changes that were not available at the time this
book was produced.
Note that the User’s Reference is provided in softcopy only.
Related publications
The following publications contain additional information about the Model 326:
v Network Attached Storage 300 Installation Guide GA27–4275
v Network Attached Storage 300 Service Guide GA27–4277
v UM Services User’s Guide (on the Documentation CD that came with the
appliance)
Additional information on Universal Manageability Services, IBM Director, and
Advanced System Management is located on the Documentation CD that came with
the appliance.
Web sites
The following Web site has additional and up-to-date information about the Model
326:
v http://www.ibm.com/storage/nas/
A highly recommended Web site: for the latest troubleshooting guidance and
symptom-fix tip information, go to the IBM support Web site at:
v http://www.ibm.com/storage/support/nas
This site contains additional information, gathered from field experience, not
available when this document was developed.
xii Model 326 User’s Reference
Page 13

Chapter 1. Introduction
This appliance offers a storage solution for both Windows, UNIX, and UNIX-like
environments, including mixed Windows-UNIX environments that enable Windows
and UNIX clients and servers to share the same Fibre Channel storage. With the
Model 326 integrated storage appliance, your enterprise will gain a scalable,
network-attached storage device that delivers state-of-the-art systems management
capabilities and task-optimized operating system technology. The Model 326
provides your enterprise with increased performance, storage capacity, and
functionality.
This appliance has been developed for workgroup or department environments with
file-serving requirements across Windows and UNIX clients, e-business, and
numerous applications. In addition, this device supports Ethernet LAN environments
with large or shared end-user workspace storage, remote running of executables,
remote user data access, and personal data migration.
This new machine replaces the IBM 5195 Model 325. Enhancements provided by
the Model 326 include:
v Greater granularity in configuring storage size
v Twice the maximum storage size
v More options in configuring Ethernet connections
v More options for tape backup
The Model 326 is a two-node appliance server and features:
v One Rack 36U (with two Power Distribution Units)
v Two engines (IBM 5187 Network Attached Storage Model 6RZ), each with:
– Dual 1.133 GHz processors
– 1 GB memory
– Two redundant 270-watt power supplies
– Fibre Channel adapter
– Four high-performance PCI adapter slots for plugging in optional 10/100 and
Gigabit Ethernet, Fibre Channel, and management adapters. (Communication
between the two engines takes place through an integrated 10/100 Mbps
Ethernet port on each engine’s planar board.)
v Two Fibre Channel hubs
v One Fibre Channel RAID storage controller (with a minimum of three and up to
ten 36.4 or 73.4 GB hot-swappable hard disk drives)
v Optional storage:
– An additional RAID storage controller
– Maximum of seven storage expansion units, each populated with three to ten
36.4 or 73.4 GB hot-swappable hard disk drives
v A 1GB memory upgrade
v Optional adapters:
– Single-port 10/100 Ethernet adapter
– Quad-port 10/100 Ethernet adapter
– Gigabit Ethernet adapter
– ServeRAID-4Lx adapter
– Remote Supervisor Adapter
– Dual-port Fibre Channel Host-Bus Adapter
© Copyright IBM Corp. 2002 1
Page 14

In addition, the Model 326 provides clustering and failover protection with its two
nodes. This high-availability design helps protect against appliance failure and
increases uptime to provide continuous access to data.
Note: Throughout this book, information about the Model 326 node and engine
applies to both its nodes and engines.
The preloaded software is based on the Windows Powered OS operating system,
which is very similar to Microsoft
®
Windows®2000 Advanced Server. Preloaded
software includes:
Microsoft Windows 2000 for Network Attached Storage
Enables remote administration of the appliance using a Web-based
graphical user interface (GUI).
Microsoft Cluster Service
Provides clustering support and failover.
Microsoft Windows Terminal Services
Enables remote administration of the appliance using its Windows desktop.
Microsoft Services for UNIX
Provides file access to UNIX and UNIX-based clients and servers through
the Network File System (NFS) protocol. Note that the Model 326 supports
Linux and other platforms that employ NFS.
IBM Director Agent and Universal Manageability Server Extensions
Provides system management support based on industry standards (in
conjunction with the IBM Director console application as well as other
management software).
IBM Advanced Appliance Configuration Utility agent
Supports management through the IBM Advanced Appliance Configuration
Utility console application (supports aggregate Web-based management of
all of your IBM appliances).
IBM FAStT Storage Manager for Windows 2000
Provides RAID configuration management for the external RAID controllers
and storage expansion units.
ServeRAID Manager RAID Configuration and Monitoring
Provides configuration tools and RAID management of the ServeRAID-4Lx
adapter.
IBM FAStT Management Suite Java (MSJ)
Provides diagnostics for the Fibre Channel adapters.
Intel PROSet II
Provides diagnostics for the Intel Ethernet adapters.
®
Alacritech
SLICuser
Provides diagnostics for the quad-port Ethernet adapter.
®
Columbia Data Products
Persistent Storage Manager (PSM)
Provides 250 persistent images of customer data and enables full online
backup of system with Microsoft’s backup applications.
®
Tivoli
Storage Manager Client
Provides data backup and archive support (in conjunction with Tivoli
Storage Manager Server).
2 Model 326 User’s Reference
Page 15
Roadmap for setting up and configuring the Model 326
A suggestion for first-time users...
Your understanding of the Model 326 and your ability to use it will be greatly
enhanced if you first proceed to the NAS Setup Navigator tutorial.
The NAS Setup Navigator is a distillation of the tasks you will need to
complete to set up and configure the Model 326 and get it up and running.
The Navigator not only presents information on functions and features -- such
as clustering -- but also allows you to enable the functions and features.
After you have become familiar with the Model 326, you can refer to this book
for more details.
The following roadmap presents the requirements and instructions for setting up
and configuring the Model 326. Following these directions and referring to the
appropriate sections of this book will help you in this task.
Prerequisites
v A domain controller must exist on the network and a login ID must be
defined for each node to log on. Each node must join the same domain.
v All Windows shared disks must be defined as basic. Windows 2000
dynamic disks are not supported.
v A Quorum drive must be available to both nodes and have the same
drive letter on each node.
v All disks shared between the two cluster nodes must have the same
drive letter.
v All shared storage must be defined as NTFS and be on primary
partitions.
v Compression cannot be enabled on any disk partition.
v Each node must have one private and one public adapter.
Cluster setup requirements
See “Cluster setup requirements” on page 6.
Configuration and administration tools
The Model 326 is a network-attached storage appliance that has several
different methods of configuration depending on your environment.
First, determine how you will manage the device. You can manage the
Model 326 in “headless” mode or with a keyboard, display, and mouse
directly attached to each node. See “Using a keyboard, monitor, and mouse
for setup and configuration” on page 9 for information on managing this
device using a keyboard, display, and mouse. For “headless” management
of the Model 326, you can use one of the following tools:
v Terminal Services, for remote configuration and management from
another device on the network
v Universal Manageability Services (UMS) for management through a Web
browser
v Windows 2000 for NAS, a Web-based GUI for those not familiar with the
Windows desktop
v IBM Advanced Appliance Configuration Utility (IAACU) for setup and
configuring multiple devices or other appliances on a single network
Chapter 1. Introduction 3
Page 16

After you determine how you will manage the Model 326, you can begin
setup and configuration of the device.
For more information on configuration and administration tools, see
“Chapter 2. Configuration and administration tools” on page 9.
Step 1 - Initial network setup
Configure both nodes to enable access over the network. The general steps
to do this are given below. More details are given in “Chapter 3. Getting
started” on page 25.
1. Use Dynamic Host Configuration Protocol (DHCP) or static addressing
to set up one public network connection in each node.
a. If you are operating with a keyboard, display, and mouse, set up a
public network connection to access the device.
b. If you are operating in a headless environment, use one of the
following methods:
v If DHCP is installed and the IP address requested can be
determined, you can use DHCP for initial setup, but you should
change this address to static later in the configuration.
v If you have multiple appliances or cannot determine the DHCP
address, you can install the IAACU utility to identify appliances
and define IP addresses. The tool will also allow you to set static
addresses.
2. Complete the steps in “Setting the date and time” on page 27 and
“Setting up the network” on page 27.
Step 2 - Define shared storage and setup partitions
The Model 326 comes with preconfigured shared storage spanning nine
disks. The storage is formatted as an array, at RAID-level 5, consisting of
the following logical unit numbers (LUNs):
v A LUN of 500 MB, for the Quorum drive (drive letter G)
v A second LUN, composed of the remaining space and used as a shared
drive with one built-in hot spare
To use this default, preconfigured storage, validate all storage areas and
determine that the drive letters are the same on each node.
Otherwise, from one of the two nodes, define all storage arrays using
Storage Manager and then set up Windows partitions as defined in
“Chapter 4. Setting up storage” on page 29.
Attention: When you set up the shared storage, you must configure the
storage on one node only. During the setup of shared storage, leave the
joining node powered off.
Step 3 - Complete network setup and cluster installation
1. Power on either node. (This becomes the first node.)
2. Set up the first node:
a. Networking setup
See “Networking setup” on page 37. Note the cautionary statement
at the beginning of that section.
b. Domain setup
See “Joining a node to a domain” on page 40.
4 Model 326 User’s Reference
Page 17

3. Power off the first node.
4. Power on the other node (the joining node).
5. Set up the joining node:
a. Networking setup
See “Networking setup” on page 37.
b. Shared storage setup
For the joining node, the only part of this step that you must
complete is assigning drive letters on the shared storage; make sure
that the drive letters are the same as those on the first node.
Also, if you have trouble with the Fibre Channel connection, you can
use the steps in “Testing the Fibre Channel host adapter with FAStT
MSJ” on page 108 to diagnose the problem.
c. Domain setup
See “Joining a node to a domain” on page 40.
d. Power off the joining node.
6. Power on the first node and complete “Cluster setup” on page 40.
7. Power on the joining node and complete “Cluster setup” on page 40.
For more information on network setup and cluster installation, see
“Chapter 5. Completing networking, clustering, and storage access setup”
on page 37.
Step 4 - Cluster administration
At this point you can add users, file shares, and complete other
configuration tasks to improve operations of the Model 326 in a cluster
environment.
1. Add users (see “Creating users” on page 43).
2. Add file shares (see “Creating clustered file shares (CIFS and NFS)” on
page 47). Note that you must configure Server for NFS before NFS file
sharing can be used.
For more information on cluster administration, see “Configuring clusters” on
page 41.
Step 5 - Additional functions
Additional functions are available for backup, persistent images, and adding
more storage areas. It is recommended that after you complete the setup
and configuration procedures, you use the Persistent Storage Manager
Disaster Recovery option (“Disaster Recovery” on page 64) or other method
to back up the system configuration in the event of a failure.
Also, it is imperative to use the system shutdown procedure described
in “Powering off and powering on the Model 326” on page 49 to ensure
system integrity.
For more information, see “Chapter 6. Managing and protecting the network
and storage” on page 53.
Chapter 1. Introduction 5
Page 18

Cluster setup requirements
Before you configure the Model 326 nodes for clustering, ensure that the following
requirements are met:
Network requirements
v A unique NetBIOS cluster name.
v You will need at least seven static IP addresses: five for the node and
cluster setup, and two for each file share served by the cluster. A formula
for the number of static IP addresses is:5+(2xnumber_of_file shares).
The IP addresses required for node and cluster setup are:
– At least three unique, static IP addresses for the public network: one
for each node (for client access through the PCI NIC adapter) and
one for the cluster itself (the administration IP address).
Table 1 on page 7 shows a summary of the networking information
necessary for the public connection.
– Two static IP addresses for the cluster interconnect on a private
network or crossover, through the onboard Ethernet adapter. The
default IP addresses for the private network adapters are 10.1.1.1 for
the first node in the cluster, and 10.1.1.2 for the node that joins the
cluster. (The top node in the Model 326 is considered the first node,
and the bottom node is considered the joining node.)
Notes:
1. If you are not the system administrator, contact that person for the
applicable IP addresses.
2. Each node in a cluster must join the same domain and be able to
access a Primary Domain Controller (PDC) and DNS server, but it is not
required that the nodes log into the domain.
3. Each node in the cluster must have at least two network adapters: at
least one for the public network and the other for the private
interconnect.
Shared disk requirements
Powering off and powering on the Model 326
6 Model 326 User’s Reference
v All shared disk arrays and devices, including the quorum disk, must be
physically attached to a shared storage bus.
v All shared disks must be configured as basic (not dynamic) disks.
v All shared disks must have the same drive letter on each node.
v All partitions on these disks must be formatted with NTFS.
v All partitions on these disks must also be Primary Partitions.
v Compression must not be enabled.
The clustering function requires special considerations when you need to
power off and power on the Model 326. See “Powering off and powering on
the Model 326” on page 49 for details.
Page 19
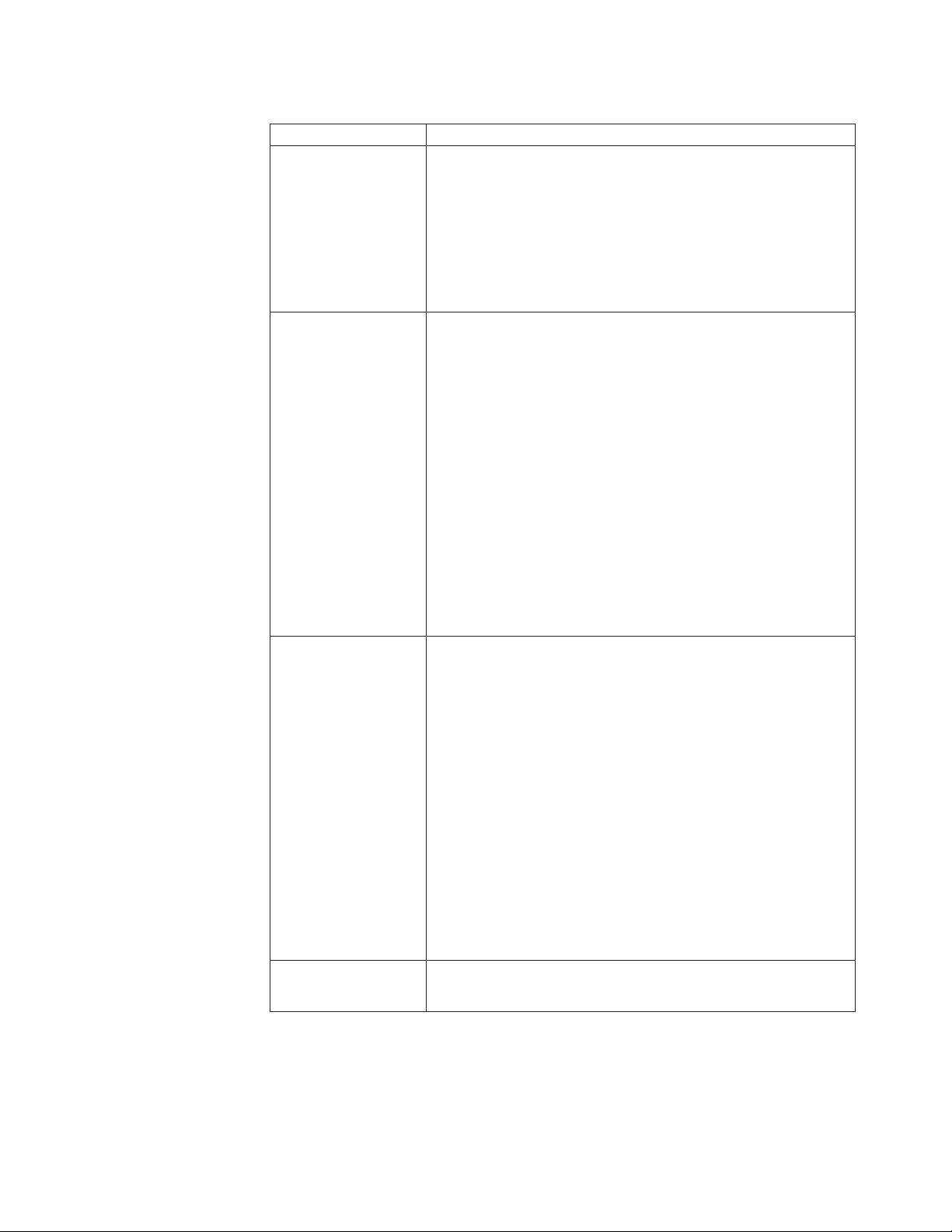
Table 1. Networking information worksheet for the public connection
Cluster component Information needed
Cluster
Cluster name:
IP address:
Subnet mask:
First node
Joining node
Computer name (example: IBM5195–23H1234):
IP address:
Subnet mask:
Gateway:
Preferred DNS:
WINS server (optional):
Computer name:
IP address:
Subnet mask:
Domain to join
Gateway:
Preferred DNS:
WINS server (optional):
Domain name:
Chapter 1. Introduction 7
Page 20

8 Model 326 User’s Reference
Page 21
Chapter 2. Configuration and administration tools
Attention
Changing the preloaded software configuration of this product, including
applying or installing unauthorized service packs or updates to preinstalled
software, or installing additional software products that are not included in
either the preloaded image or on the Supplementary CD, might not be
supported and could cause unpredictable results. For updated compatibility
information, refer to the IBM web site:
http://www.storage.ibm.com/nas
To correct problems with a preloaded software component, back up your user
and system data. Then, use the Recovery CD to restore the preloaded
software image.
The Model 326 appliance comes with the following configuration programs that you
can use to configure and administer the appliance:
v Terminal Services Client
v IBM Advanced Appliance Configuration Utility (IAACU)
v Universal Manageability Services
v Windows 2000 for Network Attached Storage
This chapter describes these tools in general and then in detail.
Using a keyboard, monitor, and mouse for setup and configuration
It is highly recommended that you directly attach a keyboard, monitor, and mouse to
the Model 326 when performing these tasks:
v Initially setting up and configuring the device
v Changing or adding to RAID arrays (for example, adding a new array with
Storage Manager, adding a new RAID controller, or adding a storage expansion
unit)
v Troubleshooting the device
Summary of configuration and administration tools
There are several ways to set up and administer the Model 326. Table 2 on page 10
suggests which tool to use for specific functions, but does not list all options or
combinations. The administrator’s training level or preferences might determine an
alternate approach from that suggested in the table.
© Copyright IBM Corp. 2002 9
Page 22
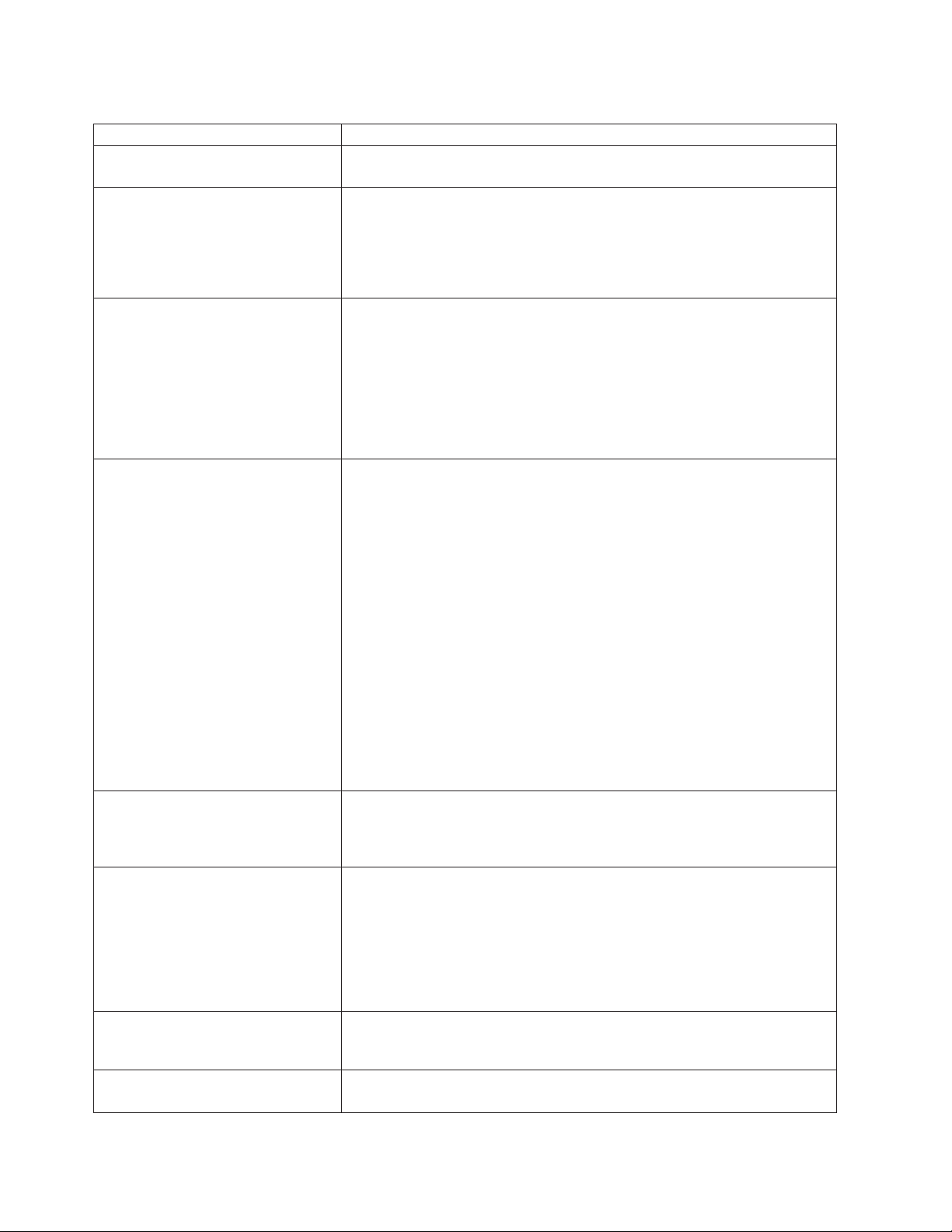
Table 2. Summary of configuration and administration tools for the Model 326
Administration tool Main functions
Windows Domain Controller (not NAS
appliance)
IBM Advanced Appliance
Configuration Utility (IAACU)
Users and user groups can be defined and authenticated by the Windows
Domain Controller, although this is not required.
Access a headless Model 326 node, particularly for the initial setup of the
network connectivity. (Alternatively, you can attach a keyboard, mouse,
display to each node of the Model 326.) IAACU enables you to:
v Set time, date, and initial network connectivity parameters
v Access to Windows 2000 for NAS GUI, Terminal Services (NAS Desktop),
and Universal Manageability Services
Windows 2000 for NAS GUI Provides ease-of-use administration, but not all the capabilities of Terminal
Services and IBM NAS Administration. The GUI enables you to:
v Configure networking connectivity, private (for clustering) and public LAN
connections
v Create and format logical drives
v Join domains
v Set up access permissions and disk quotas for CIFS, NFS, HTTP, FTP,
and Novell
®
NetWare®shares
v Use Persistent Storage Manager
IBM NAS desktop and IBM NAS
Admin program, through a Terminal
Services session or a
directly-connected keyboard and
monitor
Provides in-depth administration of all aspects of Model 326. Provides all of
the Windows 2000 for NAS GUI functions above, plus the ability to:
v Use NAS Backup Assistant, or NT Backup and Restore wizard
v Learn detailed inventory information about hardware, OS, and so on, using
Universal Manageability Services
v RAID configuration through Storage Manager:
– Create RAID arrays and LUNs
– Add additional RAID or storage enclosure after initial purchase
– Rename storage subsystems
v Cluster administration:
– Set up cluster
– Define failover for each volume
– Manually fail over cluster resources
– Set up cluster resource balancing by assigning preferred node
v Diagnose system problems:
– Check Ethernet adapters using PROSet II and 10/100 Quad-Port
Ethernet adapter using SLICuser
– Check Fibre Channel card using FAStT MSJ
– Check RAID subsystem using Storage Manager
Disaster Recovery Restores a previously saved PSM image of the system partition to a failed
machine. This restores all configuration information on the failed node. You
create the recovery boot diskette from the PSM tools in the Windows for
2000 NAS GUI.
Recovery CD Set Reinstalls the software to the original state as shipped on the machine;
however, does not restore configuration information (configuration changes
you applied to the original shipped configuration are lost). You must first boot
with the Recovery Enablement Diskette, and then reboot with the Recovery
CD. To create the Recovery Enablement Diskette, run
enablement_disk_x.y.exe (where x.y are the version number of the disk),
located on the Supplementary CD. You will be prompted to insert a blank disk
into drive a:.
Integrated System Management
Configures the ISMP that is integrated on the engine planar board.
Processor (ISMP) configuration
program
Remote Supervisor Adapter (RSA)
Configures the optional RSA.
configuration program
10 Model 326 User’s Reference
Page 23

Terminal Services Client
The Terminal Services Client, when installed on a workstation that is
attached to the same network as the Model 326, enables you to remotely
administer the appliance using the Model 326 desktop. If you are familiar
with administrative tasks using a Windows desktop, you can use Terminal
Services.
See “Terminal Services and the IBM NAS Administration Console” on
page 12 for more information.
IBM Advanced Appliance Configuration Utility (IAACU)
The IBM Advanced Appliance Configuration Utility (IAACU) aids in setting
up and reconfiguring the network configuration on your appliances. The
IAACU agent works with the IAACU Console to automatically detect the
presence of appliances on the network.
After the appliance is detected by the IAACU Console, you can use the
IAACU to:
v Set up and manage the network configuration for the appliance, including
assigning the IP address, default gateway, network mask, and DNS
server to be used by the appliance. (See the note in “Setting up the
network” on page 27, regarding the Ethernet adapter that is integrated on
the planar board.)
v Start Universal Manageability Services on the appliance, enabling you to
perform advanced systems-management tasks.
See “IBM Advanced Appliance Configuration Utility” on page 13 for more
information.
Universal Manageability Services
Universal Manageability Services (UM Services) provides point-to-point
remote management of client systems using a Web browser. Use UM
Services to:
v Learn detailed inventory information about your computers, including
operating system, memory, network cards and hardware.
v Track your computers with features such as power management, event
log, and system monitor capabilities.
v Integrate with Tivoli Enterprise, Tivoli NetView
Unicenter, Microsoft SMS, and Intel
®
In addition, you can link to Windows 2000 for Network Attached Storage
and Terminal Services from UM Services.
See “Universal Manageability Services” on page 21 for more information.
Windows 2000 for Network Attached Storage
The Model 326 provides a Web-based GUI, Microsoft Windows 2000 for
Network Attached Storage (Windows 2000 for NAS). Using Windows 2000
for NAS, you navigate through administrative task categories by clicking the
appropriate tabs and then selecting a task from that category.
®
, Computer Associates
LANDesk Management Suite.
See “Windows 2000 for Network Attached Storage” on page 23 for more
information.
Chapter 2. Configuration and administration tools 11
Page 24

Terminal Services and the IBM NAS Administration Console
If you are familiar with Windows operating systems, you can use Terminal Services.
In some cases, you must use Terminal Services to complete administrative tasks.
You can access Terminal Services in two ways:
1. Through the UM Services browser, as described in step 3 on page 23.
2. By using the Terminal Services Client software.
Installing Terminal Services
To use the Terminal Services Client, complete the following steps to install it on the
remote workstation and connect to the Model 326 appliance:
1. Insert the Supplementary CD into the workstation CD-ROM drive.
2. Select Start → Run.
3. In the Open field, type (with quotation marks)
"x:\Terminal Services Client\Disk 1\setup.exe"
where x is the drive letter assigned to the CD-ROM drive.
4. Click OK to begin the Terminal Services Client Setup program.
5. Accept the defaults in each window that opens or refer to the Microsoft
Windows documentation for more instructions.
6. When the Terminal Services Client Setup program completes, ensure that the
workstation has network-connectivity to the NAS appliance so that you can
administer the appliance.
Connecting to the desktop through Terminal Services
To connect to Terminal Services from your workstation, do the following:
1. Click Start → Programs → Terminal Services → Terminal Services Client.
2. In the Server field, select the computer name of the appropriate Model 326. If
that Model 326 is not listed, enter the IP address or the computer name of the
Model 326. The computer name is predefined as IBM5195-xxxxxxx, where
xxxxxxx is the serial number located in the lower right corner of the bezel on the
front of the appliance. If you have changed the computer name from the
predefined value, use that name instead.
Note: Although you can do so, it is recommended that you not change the
default computer name to avoid the chance of propagating
misidentification through the system. And, if you are using IBM Director
to manage your appliance, and you change the default name, the default
name continues to appear in IBM Director.
3. For Size, select a screen size in which the Model 326 desktop will appear. It is
recommended that you choose a size other than full screen.
4. Click Connect to start the Terminal Services Client session. A user login window
appears.
5. Log in. Type Administrator in the Username field, type password in the
Password field, and then click OK to log in. After you log in, you can begin
using Terminal Services Client to configure and manage the Model 326, as if a
keyboard, mouse, and monitor were directly attached to it. The Model 326
desktop contains a shortcut, titled IBM NAS Admin, to a special console, the
IBM NAS Administration console.
12 Model 326 User’s Reference
Page 25
IBM NAS Administration console
The IBM NAS Administration console includes all the standard functions provided by
the standard Computer Management console available on any Windows 2000
desktop, plus the following functions specific to the Model 326:
v Cluster Administration (see “Configuring clusters” on page 41)
v Storage Manager (see “Chapter 4. Setting up storage” on page 29)
v These advanced functions (see “Chapter 6. Managing and protecting the network
and storage” on page 53):
– Advanced System Management Integrated Adapter and Remote Supervisor
Adapter
– FAStT MSJ
– NAS Backup Assistant
– Persistent Storage Manager
Determining who is using the network-attached storage
Occasionally, you might want to know who is using the network-attached storage.
To determine this information:
1. Start a Windows Terminal Services session from the administrator’s console to
the Model 326.
2. Click the IBM NAS Admin icon on the desktop.
3. In the left pane, click File Systems → Shared Folders → Sessions.
4. The users currently using the storage are displayed. To close those sessions,
use a right-click. Before you close a session, notify the user that you are going
to close the session by clicking Start → Programs → Accessories → Command
Prompt, and then issuing the net send hostname messagetext command.
IBM Advanced Appliance Configuration Utility
Note: Although you can do so, it is recommended that you not change the default
computer name of your NAS appliance to avoid the chance of propagating
misidentification through the system. Also, The IBM Advanced Appliance
Configuration Utility depends on the original name to function.
The IBM Advanced Appliance Configuration Utility (IAACU) helps you to set up and
reconfigure the network configuration on the Model 326 appliance, as well as other
IBM appliances. The IAACU agent, preinstalled on the Model 326 appliance, works
with the IAACU Console, a Java-based application that is installed on a
network-attached system. You can use the IAACU as a systems-management
console to automatically detect the presence of Model 326 appliances on the
network. After the Model 326 appliance is detected by the IAACU Console, use the
IAACU to set up and manage the appliance’s network configuration, including
assigning the IP address, default gateway, network mask, and DNS server to be
used by the appliance. You can also use the IAACU to start Universal Manageability
Services (UM Services) on the appliance, enabling you to perform more advanced
systems-management tasks.
For networks that are not currently running DHCP servers, the IAACU is useful for
automatically configuring network settings for newly added appliances, such as the
Model 326.
However, networks with DHCP servers will also benefit from using the IAACU
because it enables you to reserve and assign the appliance IP address in an
orderly, automated fashion. Even when you use DHCP and do not reserve an IP
Chapter 2. Configuration and administration tools 13
Page 26

address for the appliance, you can still use the IAACU to discover appliances and
to start UM Services Web-based systems management.
Notes:
1. The IAACU configures and reports the TCP/IP settings of the first adapter
(excluding the integrated Ethernet controller that is used for the interconnection
of the two engines) on each appliance. The “first” adapter is defined by its
position: if there is an adapter in slot 2, it is the first adapter; if there is an
adapter in slot 3, it is the first adapter.
Be sure to connect the first adapter to the same physical network as your
systems-management console. You can do this in one of two ways:
v Manually configure the network adapter to be on the same subnetwork as the
systems-management console.
v Create a Family that assigns the network adapter to the same subnetwork as
the systems-management console. See “Using Families and Groups in the
Tree View” on page 17 for more details. Note that the values for Min IP
address, Max IP address, Subnet Mask, and Default Gateway must be in the
same range that the IAACU is configured.
2. The IAACU must be running to configure newly installed appliances
automatically.
3. The system running the IAACU Console automatically maintains a copy of its
database (ServerConfiguration.dat) in the Advanced Appliance Configuration
Station installation directory. To remove previous configuration data, close the
IAACU, delete this file, and then restart the utility. This deletes all previously
configured Families. However, the IAACU will automatically discover connected
appliances and their network settings.
Initial network adapter selection and connection to the IAACU
Unlike the limited number of network adapter placement options in the previous
release, in this release there are an increased number of network adapter types
and/or locations from which you can connect. Assuming you have a keyboard and
monitor attached, perform the following steps to take into account the new adapter
placement options:
1. Decide which adapter will be used to connect to the IAACU, and connect the
appropriate cable type.
2. Open the Network and Dial-up Connections panel. (From the desktop, right-click
My Network Places, and select Properties.)
3. Determine the connection name of the adapter you have selected to use. Move
the mouse cursor over the adapter name, and a description of the adapter type
will appear. If this is inconclusive, right-click the adapter, and select Properties.
Under the General tab, click the Configure button. The line which contains the
location information will provide the adapter’s slot location. For example,
Location 1 means the adapter is in PCI slot number 1. Close the adapter
properties panel.
4. On the Network and Dial-up Connections menu bar, select Advanced and then
Advanced Settings. From the Connections menu, select the adapter’s
connection name. Then using the down arrow, move the selection down to the
next-to-last position in the list. (The last entry in the list should be the remote
access connections, shown as the telephone icon.) Save your changes by
clicking OK.
5. The IAACU will now detect the appliance using the adapter you have just
enabled.
14 Model 326 User’s Reference
Page 27

IAACU Agent
IAACU Console
The IAACU agent is preinstalled on the Model 326 appliance.
After you connect the Model 326 to your network, the IAACU agent automatically
reports the appliance serial number and type, the MAC address of its onboard
Ethernet controller, and whether DHCP is in use by the appliance. Furthermore, it
reports the host name, primary IP address, subnet mask, primary DNS server
address, and primary gateway address if these are configured on the system.
Note: The IAACU agent periodically broadcasts the appliance IP settings. To
prevent the service from broadcasting this data periodically, stop the
iaaconfig service.
The IAACU Console is a Java application that you install on one system in your
network for use as a systems-management console. For information on how to
install the IAACU Console, see Table 23 on page 126.
Note: The IAACU creates a private database that is specific to the IP subnetwork
to which it is attached. Therefore, do not install it on more than one
systems-management console residing on the same IP subnetwork.
The IAACU Console enables you to:
v Automatically discover Model 326 appliances, as well as other IBM appliances
that run the IAACU agent and are attached to the same physical subnet as the
IAACU Console.
v Use a GUI-based application to configure the appliance network settings.
Use the IAACU to assign network parameters such as IP addresses, DNS and
gateway server addresses, subnet masks, and host names.
v Group discovered appliances into function-specific Families. Appliances are
added to a Family based on the appliance type. Appliances that perform the
same function appear in the same Family.
v Start UM Services Web-based systems-management console.
Launch UM Services on your appliances and perform advanced
systems-management tasks on a selected appliance with a single mouse click.
The IAACU Console is divided into two panes:
v The Tree View Pane
The Tree View Pane, located on the left side of the IAACU Console window,
presents a list of all discovered Model 326 appliances and includes any Families
you have previously defined. The Tree View Pane also includes groups for
appliances that do not fit any of the defined Families, that were not configured
using the IAACU, or that have IP addresses that conflict with other devices on
your network. When you click any item in the Tree View, information about that
item (and any items that are nested below that item in the tree view) appears in
the Information Pane.
v The Information Pane
The Information Pane, located on the right side of the IAACU Console, displays
information about the item that is currently selected in the Tree View Pane. The
information that appears in the Information Pane varies depending on the item
that is selected. For example, if you select the All Appliances item from the Tree
View Pane, the Information Pane displays configuration information (IP settings,
Chapter 2. Configuration and administration tools 15
Page 28

host name, serial number, and so on) about each of the Model 326 appliances
that have been discovered by the IAACU Console. However, if you select a
Family, the Information Pane displays information about the Family settings for
the selected Family.
The IAACU Console also features the following menus:
File Use the File menu to import or export the IAACU Console configuration
data, to scan the network, or to exit the program.
Family
Use the Family menu to add or delete Families, or to move Families up or
down in the tree view.
Appliance
Use the Appliance menu to remove a previously discovered appliance from
a Family or group, and to add an appliance to the first matching Family in
the tree view.
Help Use the Help menu to display product information.
Discovering Model 326 Appliances
Any Model 326 appliance, or other IBM appliance, that is running and is connected
to the same subnet as the system running the IAACU Console is automatically
discovered when you start the IAACU Console. Discovered appliances appear in
the IAACU Console tree view (in the left pane of the IAACU Console window). Each
appliance appears in two locations in the tree view:
v Every discovered appliance is listed in the tree view under All Appliances.
v Each discovered appliance also appears in one of the following sections of the
tree view:
– In a Family
If the discovered appliance fits the requirements of a Family, it will
automatically appear as part of a Family.
Notes:
1. If a discovered appliance fits the requirements of more than one Family, it
is automatically added to the first appropriate Family that is listed in the
tree view, starting from the top of the tree. For information on how to move
appliances between families, see “Using Families and Groups in the Tree
View” on page 17.
2. If the Model 326 cannot be discovered by the IAACU console, check the
IP and subnet addresses of the Model 326 and the computer that is
running the IAACU console.
– In the Orphaned Appliances group
If the discovered appliance does not fit a previously configured Family, it is
placed in the Orphaned Appliances group.
– In the Orphaned Externally Configured Appliances group
Appliances that are running the IAACU agent, but that have a network
configuration that was not set by the IAACU agent or console, will appear in
the Orphaned Externally Configured Appliances group. If an appliance is
contained in the Orphaned Externally Configured Appliances group, you can
use the Adopt By First Matching Family function to add it to a previously
defined Family. For more information, see “Using the Adopt by First Matching
Family function” on page 19.
16 Model 326 User’s Reference
Page 29

Using Families and Groups in the Tree View
Families are important elements of the IAACU. They specify the parameters that the
IAACU uses to automatically categorize discovered appliances and to configure
them with the appropriate network settings. Family rules are defined solely by
appliance type or purpose. Each Family can contain only one type of appliance.
The only way to automatically apply predetermined network settings to newly
installed and discovered appliances is to create and use Families.
Appliances that match the rules criteria for a Family group can be automatically
configured to use predefined network settings. A Family can be configured to allow
appliances to use DHCP to configure their IP settings, or can be defined to
automatically assign IP settings (such as primary gateway and DNS server
addresses, assigning an IP address from a specified IP address range, and
specifying a subnet mask). Host names for discovered appliances can also be
defined so that they are allocated using either a prefix or appliance serial number.
The IAACU is not the only way to configure network settings. For example, network
settings can be configured using Terminal Services for Windows or by attaching a
keyboard and mouse to the appliance and using Windows Control Panel. If the
appliance network settings have been configured by a method other than using the
IAACU, the appliance will be discovered by the IAACU and it will be added to an
appropriate Family, if one exists. Appliances that have been configured using a
method other than the IAACU for which no appropriate family exists will appear in
the Orphaned Externally Configured Appliances group.
The Tree View Panel contains the following items:
v All Appliances
Every discovered appliance is listed in the tree view under All Appliances.
v Families
The Families group in the Tree View Pane shows all Families that have been
defined, with appliances that have already been assigned to each Family nested
beneath the Family name in the tree view. Families are defined by appliance
purpose, so all appliances that appear in a given family are of the same type. If
you select a Family from the Tree View Pane, a description of the Family and the
rules that are used to define the selected Family appear in the Information Pane.
If you select an appliance from a Family in the Tree View Pane, the selected
appliance network settings appear in the Information Pane.
If you are not using DHCP, the IAACU automatically assigns one IP address per
appliance, using available addresses within the range defined in the Family rules.
When the IP address range for the Family has been exhausted, the IAACU
automatically searches for other Families that have rules matching the appliance
being configured. If a matching Family with an available address is found, the
appliance will automatically be assigned to the Family that has available IP
addresses. This enables you to define multiple Families, each of which uses a
set of noncontiguous IP address ranges.
When an appliance is discovered on the network, the IAACU automatically
searches all previously defined Families, starting with the first Family listed in the
Families tree view and moving downward. Appliances are automatically added to
the first defined Family that matches the appliance purpose. Therefore, the order
in which Families appear is important. To adjust this search order, right-click a
Family and then select Move Up or Move Down to adjust its position within the
Families list.
v Orphaned Appliances
Chapter 2. Configuration and administration tools 17
Page 30

Any discovered appliances that have been configured using the IAACU but that
do not meet the rules for any existing Family are automatically added to the
Orphaned Appliances group.
v Orphaned Externally Configured Appliances
Any discovered appliance that has been configured without using the IAACU tool
and that does not meet the rules for any existing Family is automatically added to
the Orphaned Externally Configured Appliances group. Appliances configured
without the IAACU that meet the rules for any existing Family are automatically
added to the matching Family.
To add an Orphaned Externally configured Appliance to an appropriate Family
that was created after the orphaned appliance was discovered, right-click the
orphaned appliance and select Adopt by First Matching Family. For more
information, see “Using the Adopt by First Matching Family function” on page 19.
Note: The IAACU does not change manually configured network settings of
discovered appliances. If the manually configured IP and Subnet
addresses fit an existing Family, the IAACU will place that appliance into
that Family, but does not change any other settings (such as host name,
DNS, or gateway addresses).
v Conflicting Network Addresses
Any discovered appliance that has the same IP address as a previously
discovered appliance will be listed in the Conflicting Network Addresses group.
Creating a Family
To create a Family:
1. Select Create Family from the Family menu.
The IAACU Family Setup window opens.
2. Select Appliance Family Rules.
The Appliance Family Rules determine what purpose an appliance must serve
to be included in the Family. Select one of the following values:
v IBM TotalStorage NAS Appliances
v IBM xSeries 130 and 135
3. Type the name that will be used for this Family in the Family Name field.
4. Specify network resources to be used by members of the Family.
You can use the IAACU to assign network resources for members of this
Family, or you can use a DHCP server to assign network resources.
v To use the IAACU to assign network resources, clear the Use DHCP check
box and fill in the following fields:
18 Model 326 User’s Reference
Min IP Address
The lowest IP address in a range of IP addresses that can be
assigned to an appliance that is a member of this Family.
Max IP Address
The highest IP address in a range of IP addresses that can be
assigned to an appliance that is a member of this Family.
Subnet Mask
The subnet mask value that will be used by appliances that are
members of this Family.
Default Gateway
The IP address of the default gateway that will be used by appliances
that are members of this Family (optional).
Page 31

DNS The IP address of the DNS server that will be used by appliances
that are members of this Family (optional).
v To use a DHCP server to assign network resources, select the Use DHCP
check box. This allows a DHCP server on your network to assign an IP
address and subnet mask and to specify the default gateway address and
address of the DNS server that will be used by appliances that are members
of this Family.
5. Select a Host Name Assignment Type.
The Host Name Assignment Type enables you to automatically specify a Host
Name that members of this Family will use. You can select one of the following
Host Name Assignment Types:
No Allocation
Assigns no preconfigured host name format to appliances that are
members of this Family.
Use Serial Number
Uses the serial number of the discovered appliance as a host name for
the appliance.
Use Prefix Name
Uses a user-specified prefix, along with an incremental number for each
appliance, for the host name of each appliance that is a member of this
Family. Type the prefix in the Host Name Prefix field.
6. Click Finish to save this Family.
Removing Appliances from Families
Use the Remove Appliance function to delete an appliance from the IAACU Console
database and view panel. Removing an appliance that is no longer in use allows
the IP address that was assigned to the appliance to be allocated to another
appliance. You can also remove an appliance from a family and then rescan the
network to add it to an appropriate Family that appears higher in the Tree View
pane.
To remove an appliance, right-click the appliance, and then select Remove
Appliance from the pop-up menu.
v If the IAACU cannot communicate with the selected appliance (because, for
example, it has been removed from the network or has failed), the appliance is
removed immediately.
v If the IAACU can communicate with the selected appliance, you are prompted to
confirm removal of the appliance before the appliance removal task is completed.
This helps prevent accidental removal of an active and functional appliance.
Using the Adopt by First Matching Family function
Use this function to:
v Add an Orphaned Externally Configured Appliance to an appropriate Family.
Appliances that have been configured without using the IAACU tool and that do
not meet the rules for any existing Family are automatically added to the
Orphaned Externally Configured Appliances group. If, after the orphaned
appliance is discovered, you create a Family that is appropriate for the orphaned
appliance, right-click the orphaned appliance and select Adopt by First
Matching Family to move the appliance from the Orphaned Externally
Configured Appliances group to the newly created Family.
v Move an appliance from one Family to another appropriate Family that occurs
higher in the list of previously defined Families. If there is more than one
appropriate Family for a newly discovered appliance, it automatically appears in
Chapter 2. Configuration and administration tools 19
Page 32

the first appropriate Family in the list of Families. If you want to move a
discovered appliance from one appropriate Family to another appropriate Family:
1. Right-click the Family that you want the appliance moved to.
2. Select Move Up in List to move the selected Family up in the list of families.
Repeat steps 1 and 2 until the Family that you want to add the appliance to
appears above the Family that currently contains the appliance.
3. Right-click the appliance that you want to move to another Family and then
select Adopt by First Matching Family.
20 Model 326 User’s Reference
Page 33

Universal Manageability Services
Universal Manageability Services (UM Services) is a Windows application that
functions as both a stand-alone management tool for the system it is installed on
and a client to IBM Director.
As a Director Client, it receives and sends information to the Director Server as
controlled from the IBM Director Console.
As a stand-alone tool, it provides a Web-browser based interface and a Microsoft
Management Console (MMC) interface, where you can view the system status,
perform certain management tasks and configure alerts.
The Universal Manageability Services (UM Services) GUI enhances the local or
remote administration, monitoring, and maintenance of IBM systems. UM Services
is a lightweight client that resides on each managed computer system. With UM
Services, you can use a Web browser and UM Services Web console support to
inventory, monitor, and troubleshoot IBM systems on which UM Services is
installed.
This “point-to-point” systems-management approach, in which you use a Web
browser to connect directly to a remote-client system, enables you to effectively
maintain IBM systems without requiring the installation of additional
systems-management software on your administrator console.
In addition to point-to-point systems-management support, UM Services also
includes support for UM Services Upward Integration Modules. These modules
enable systems-management professionals who use any supported
systems-management platform (including Tivoli Enterprise, CA Unicenter TNG
Framework, and Microsoft Systems Management Server [SMS]) to integrate
portions of UM Services into their systems-management console. Because it was
designed to use industry-standard information-gathering technologies and
messaging protocols, including Common Information Model (CIM), Desktop
Management Interface (DMI), and Simple Network Management Protocol (SNMP),
UM Services adds value to any of these supported workgroup or enterprise
systems-management platforms.
You can use UM Services to perform the following tasks:
v View detailed information about your computers, including operating system,
memory, network cards, and hardware.
v Track your computers with features such as power management, event log, and
system monitor capabilities.
v Upwardly integrate with Tivoli Enterprise, Tivoli Netview, Computer Associates
Unicenter, Microsoft SMS, and Intel LANDesk Management Suite.
Complete documentation on how to use UM Services is included on the
Documentation CD that came with the appliance.
System requirements
The UM Services client is preinstalled on the Model 326 appliance. However, you
must have a Web browser installed on your systems-management console. It is
recommended that you set Microsoft Internet Explorer 5.x (or later) as the default
browser.
Chapter 2. Configuration and administration tools 21
Page 34

Notes:
1. You must install the optional Java Virtual Machine (VM) support to access a
client system running UM Services.
2. If you reinstall Internet Explorer after installing UM Services, you must reapply
the Microsoft VM update. The UM Services client requires Microsoft VM Build
3165 or later. Download the latest Microsoft VM from www.microsoft.com/java
3. If you install UM Services before you install MMC 1.1 (or a later version), you
will not have an icon for Microsoft Management Console in the IBM Universal
Manageability Services section of the Start menu.
Starting UM Services
You can use IAACU or Terminal Services Client to configure the network setting
remotely, or you can attach a keyboard and mouse to your appliance and configure
the Network settings using the Windows Control Panel. After you have configured
the network settings for your appliance, you are ready to use UM Services.
To start UM Services:
1. Start a Web browser and then, in the Address or Location field of the browser,
type:
http://ip_address:1411
where ip_address is the IP address of the Model 326, and then press Enter.
Or, type:
http://computer_name:1411
where computer_name is the computer name of the Model 326. The computer
name is predefined as: IBM5195-xxxxxxx, where xxxxxxx is the serial number
located in the lower right corner of the bezel on the front of the appliance.
If you have changed the computer name from the predefined value, use that
name instead. A user log in window appears.
2. Type Administrator in the User Name field, and type password in the Password
field. You can leave the Domain field blank. Make sure the “Save this password
in your password list” check box is not selected, and then click OK.
Note: To ensure system security, change the Administrator password from
“password” to something else. After you do, or if you create another user
in the Administrator group in the future, use your new
username/password combination instead of the default
username/password combination.
The first time you connect, you might be prompted to install XML and Swing
components. Follow the on-screen instructions to install these components and
then close and restart Internet Explorer before you proceed.
You are now connected to the Model 326 through UM Services. In addition to
the standard UM Services functionality, the appliance includes functionality for
administering the appliance, available from the Appliances tab in the left pane of
the UM Services browser. The default view (in the right pane of the UM
Services browser) when you connect to the appliance is Windows 2000 for
NAS. The other selectable view in the Appliance tab is Windows 2000 Terminal
Services, which displays a Terminal Services Web Connection page.
22 Model 326 User’s Reference
Page 35

3. To start Windows 2000 for NAS, click Administer this server appliance in the
right pane of the UM Services browser. To connect to the Model 326 and
manage it as though you were running Terminal Services Client from the
desktop, select Terminal Services in the Appliance tab of the UM Services
browser, and then follow the instructions for connecting to the Model 326 using
Terminal Services described in “Terminal Services and the IBM NAS
Administration Console” on page 12.
Launching UM Services from the configuration utility
You can use the IAACU to launch UM Services on the Model 326 appliances.
Note: The selected appliance must be running Universal Manageability (UM)
Services as a UM Services client. Also, the systems-management console
(the system that is running the IAACU Console) must use a Web browser
that is supported for use with UM Services. If you have not used UM
Services from this system, you must install several plug-ins before
proceeding.
To use the IAACU Console to start UM Services on an appliance:
1. Click the appliance in the IAACU Console Tree View Pane.
When you select the appliance from the tree view, information about the
selected appliance appears in the Information Pane.
2. Click the Start Web-Based Management button.
Your default Web browser starts, loading the UM Services browser
automatically.
3. Log in to the UM Services browser. Refer to Step 2 on page 22 for login
instructions.
For more information on using UM Services to manage your appliances, see the
Universal Manageability Services User’s Guide, included on the Documentation CD
that came with the appliance.
Windows 2000 for Network Attached Storage
While you can perform most administrative tasks using Windows 2000 for NAS, you
must use Terminal Services Client for some advanced tasks. See “Terminal
Services and the IBM NAS Administration Console” on page 12 for more
information.
Task categories available to you through Windows 2000 for NAS include:
v Status
v Network
v Disks
v Users
v Shares
v Maintenance
v Controller
To start Windows 2000 for NAS, use one of these methods:
v UM Services, described in step 3.
v Web browser, by entering http://ip_address:8099 or http://computer_name:8099
and then logging on to the Model 326.
Chapter 2. Configuration and administration tools 23
Page 36

v Model 326 desktop while using Terminal Services Client and starting a browser.
You can access online help for Windows 2000 for NAS in two ways:
1. Click the Help button at the top of any Web page. This displays a table of
contents that you can navigate to find help for any Windows 2000 for NAS task.
2. Click the question mark (?) button at the top of any Web page. This displays
context-sensitive help for the task you are currently performing.
Telnet Server support
CAUTION:
When you Telnet to another machine, your user name and password are sent
over the network in plain, unencrypted, text.
The Model 326 includes Telnet server capability. The Telnet server provides limited
administrative capability. This can be useful in cases where you need to remotely
administer the Model 326, but do not have access to a Windows-based workstation
(from which you could remotely administer the appliance through a supported Web
browser or Terminal Services Client).
To access the Model 326 from any Telnet client, specify the IP address or host
name of the Model 326, then log in using an ID and password (defined on the
Model 326) with administrative authority. From the command line, you can issue
DOS-like commands (such as dir and cd), and some UNIX-like commands (such
as grep and vi). You can launch some applications, but only character-mode
applications are supported.
SNMP support
By default, the Telnet server is disabled. To enable the Telnet server, from the
Windows 2000 for NAS user interface, go to the Network task group, then select
Telnet. On the Telnet Administration Configuration page, select the Enable Telnet
access to this appliance check box. If you do not require Telnet access to the Model
326, then it is recommended that you leave the Telnet server disabled.
Support for the Simple Network Management Protocol (SNMP) is enabled. To
manage the Model 326 from an SNMP-capable management application, you must
install the management information base (MIB) files for various components of the
Model 326 on the management application workstation, so that the application can
recognize those SNMP elements (values, alerts, and so on) supported by the
components.
24 Model 326 User’s Reference
Page 37

Chapter 3. Getting started
This chapter gives details to set up the initial communication to the Model 326 to
enable setup and configuration. These instructions refer specifically to a base
configuration as shipped and do not cover the setup of additional storage units,
which can be purchased separately.
Note: You must follow these procedures for both nodes.
Methods for setting up the Model 326
The following sections detail how to set up the Model 326. You must first ensure
that the network recognizes the new appliance. Which method you should use
depends on several conditions:
v In “headless” mode (without a keyboard, monitor, and mouse directly attached to
the unit), use one of the following methods:
– IBM Advanced Appliance Configuration Utility
If you have multiple appliances or cannot determine the DHCP address, install
the IAACU to identify appliances and define IP addresses. The tool also
allows you to set static addresses.
If you are using this method, proceed with “Installing the IBM Advanced
Appliance Configuration Utility”.
– Windows Terminal Services
If DHCP is installed and the IP address requested can be determined, use this
method for initial setup, but you should change the address to static later in
the configuration. This condition is most appropriate when using Windows
Terminal Services for operation of the Model 326.
If you are using this method, proceed with “Initial setup and configuration” on
page 26.
v The use of a keyboard, display, and mouse is most appropriate when there is a
single or few appliances in the network and you use static setup and definition.
If you are using this method, proceed with “Initial setup and configuration” on
page 26.
Installing the IBM Advanced Appliance Configuration Utility
These instructions assume that you have installed and powered on the appliance
according to the installation guide procedures. You are now ready to install the
IAACU Console application from the Supplementary CD.
Install the Advanced Appliance Configuration console application from the
Supplementary CD onto a Windows NT 4.0 or Windows 2000 workstation that is
attached to the same IP subnetwork to which the appliance is attached.
Note: The IAACU creates a private database that is specific to the IP subnetwork
to which it is attached. Therefore, do not install it on more than one systems
management console residing on the same IP subnetwork.
For information on how to install the IAACU Console, see Table 23 on page 126.
After you install the Advanced Appliance Configuration console application, the
following steps will take you to the point where you can administer the appliance.
© Copyright IBM Corp. 2002 25
Page 38

1. Start the Advanced Appliance Configuration console application by clicking its
icon.
2. On the left pane of the Advanced Appliance Configuration console, select the
appliance to administer. Initially, the appliance name is IBM5195-serial number;
the serial number is located in the lower right corner of the bezel on the front of
the appliance.
3. Click the Start Web Management button to start the Universal Manageability
(UM) Services browser. This will open a separate Web browser window.
4. Proceed to “Accessing Universal Manageability Services”.
For more information on the IAACU, see “IAACU Console” on page 15.
Accessing Universal Manageability Services
1. You will be prompted to authenticate with the administrative user name
(“Administrator”) and password (initially “password,” but you can change it later;
note that the password is case-sensitive, but the user name is not).
If this is the first time you have accessed the UM Services browser (on any
appliance) from this workstation, you will also be prompted to install the Swing
and XML Java libraries in your Web browser. You can download these libraries
from the Model 326 through the network link.
2. The UM Services browser starts. In the left pane, Microsoft Windows 2000 for
Network Attached Storage is automatically selected on the Appliance tab. In the
right pane, Windows 2000 for Network Attached Storage starts.
3. Again, you are prompted to authenticate with the administrative user name and
password.
4. Click Administer this server appliance to bring up the Microsoft Windows
2000 for Network Attached Storage GUI.
5. You are now ready to begin administering the appliance. Details for this task are
described in “Initial setup and configuration”.
Initial setup and configuration
This section provides details on the initial setup and configuration of the Model 326.
Note that if you are administering the Model 326 without a keyboard, monitor, and
mouse (“headless” mode), you can use one of two methods:
v Terminal Services, which provides full administrative function. (See “Terminal
Services and the IBM NAS Administration Console” on page 12.)
v Windows 2000 for Network Attached Storage, which provides a subset of the full
administrative function in Terminal Services. (See “Windows 2000 for Network
Attached Storage” on page 23.)
In general, you administer the appliance by adjusting information contained in the
following task groups:
Note: In this example, you access the task groups through the Windows 2000 for
Network Attached Storage Web-based GUI.
v “Setting the date and time” on page 27
v “Setting up the network” on page 27
26 Model 326 User’s Reference
Page 39

Although you can modify multiple appliance and network attributes in each task
group, the information given here is the minimum you need to know to administer
the appliance and network.
You can find more information on administration elsewhere in this book and in the
online help.
You can access these task groups in one of three ways:
1. Click the Home tab and then select the task group link.
2. Click the top tab associated with that task group.
3. Click the Back button on the browser until you arrive Home and then select the
task group link.
Setting the date and time
To change the date and time, click Date and Time. (Remember that you can also
access all of these task groups by clicking the titled tabs at the top of the page.)
The Set Date and Time page appears, allowing you to adjust information as
necessary.
Setting up the network
Note: All appliances have an initial default user name of “administrator” and
password of “password.”
As part of the Network task group, you can change the administrator password and
(optionally) you can configure the properties of each network interface that resides
on the appliance.
To change the administrator password, click Change Administrator Password.
The Change Administrator Password page appears, allowing you to change the
password. Note the warning on the page that any information that you enter can be
viewed by others on the network. To prevent others from seeing your information,
set up a secure administration Web site as described in the online help.
To change IP addresses, click on Interfaces. The Network Adapters on Server
Appliance page appears. Use this page primarily to change IP addresses from
dynamic (DHCP, which is the system default) to static.
Note: During the initial setup, you should configure the nonplanar Ethernet adapter
only. The Model 326 engine uses the Ethernet adapter that is integrated on
the planar board as the interconnect private network for clustering.
If you want to use an Ethernet adapter other than the default Ethernet
adapter (in slot 2) as the network interface to be attached to the subnet, then
you can change the order of precedence later with the Windows Networking
Properties option. The order of precedence for the initial configuration is: PCI
slot 2, then PCI slot 3.
Note that you might need to enable some of the Model 326 NIC connections,
because the NICs in slots 1, 3, and 4 are not enabled. During initial setup,
the IAACU first looks for a 10/100 adapter in slot 2, which is enabled by
default. If there is no adapter in slot 2, the IAACU looks for a Gigabit adapter
card in slot 3 and it should be enabled. If the Gigabit adapter card is not
Chapter 3. Getting started 27
Page 40

enabled, right-click the adapter icon to enable it. After the initial setup, you
can then enable all other NIC interfaces installed.
You must modify the adapter by completing the IP task (to modify IP configurations)
and then choosing one or more of the following tasks, as appropriate:
v DNS (to modify DNS configurations)
v WINS (to modify WINS configurations)
v HOSTS (to modify host configurations)
28 Model 326 User’s Reference
Page 41

Chapter 4. Setting up storage
This chapter gives details for setting up and configuring the Model 326 storage.
The Model 326 has a preconfigured shared storage RAID configuration on the first
IBM 5191 RAID Storage Controller. The storage is formatted as an array, at
RAID-level 5, consisting of the following LUNs:
v A LUN of 500 MB, for the Quorum drive (drive letter G). The Quorum drive is
used by Microsoft Cluster Service to manage clustered resources.
Note: See “Recovering from a corrupted Quorum drive” on page 50 in the event
of a power loss to both nodes or a hardware failure that corrupts Quorum
data.
v A second LUN, composed of the remaining space and used as a shared drive
with one built-in hot spare.
You can use this preconfigured storage, or delete it and configure new storage. If
the preconfigured storage meets your requirements, you can proceed with
“Chapter 5. Completing networking, clustering, and storage access setup” on
page 37. If you delete it, you must complete the steps in this chapter.
Note: When you set up the shared storage with Storage Manager, you must
configure the storage on one node only. During the setup of shared storage,
leave the joining node powered off.
To configure the storage, use the IBM FAStT Storage Manager (Storage Manager).
With Storage Manager, you can configure and manage the DASD mounted in the
IBM 5191 RAID Storage Controller Model 0RU (storage controller) and IBM 5192
Network Attached Storage Storage Unit Model 0RU (storage unit) enclosures.
Storage Manager provides a GUI for managing storage subsystems. It features two
main windows:
Enterprise Management Use this window to add, remove, and monitor the
storage subsystem within the management domain.
Subsystem Management Use this window to manage individual storage
subsystem components.
You manage the storage subsystems through the Fibre Channel I/O path between
the engines and the RAID controllers (host-agent method). The Storage Manager
software is installed on both engines, allowing you to manage the storage
subsystems from a Terminal Services session open on either node’s engine.
Direct-managed method for managing the 5191 RAID Storage Controller
The Storage Manager Application provides two methods for managing storage
subsystems: the host-agent managed method and the direct-managed method. The
Model 326 comes preconfigured with the host-agent management method, as
described in “Starting Enterprise Management” on page 31. You can use the
direct-managed method when an alternate management path is required (for
example, during a failure of the host-agent management path).
© Copyright IBM Corp. 2002 29
Page 42

With this method, you can use the Storage Manager client software to manage the
storage subsystem directly over the network through each controller’s Ethernet
connection. To manage a controller directly, you need:
v A Windows 2000 client computer connected to the local Ethernet network.
v Storage Manager client software. The Storage Manager client software package
can be downloaded from the NAS 5195 Model 326 download Web page using
the following URL:
http://ssddom02.storage.ibm.com/techsup/nas/nasdown.nsf/fToolProdView/KUGPJE9903P?
Openform
v DHCP server connected to the local Ethernet network.
v One Ethernet cable for each storage-subsystem controller in the 5191 RAID
Storage Controller to connect to the local Ethernet network. (One dual storage
subsystem controller 5191 RAID Storage Controller is equivalent to two Ethernet
cables; two dual storage-subsystem controller 5191 RAID Storage Controller
Units are equivalent to four Ethernet cables.)
v Ethernet hub or switch.
To install and configure using the direct-managed method:
1. Install the SM client software on the Windows 2000 client computer (not Node A
or Node B).
2. Connect each storage-subsystem controller in the 5191 RAID Storage Controller
to an existing Ethernet network using Ethernet cables. A separate stand-alone
diagnostic network can be created by connecting the SM client computer, DHCP
computer and all storage subsystem controllers to an Ethernet hub.
3. Start Storage Manager. The Enterprise Management window appears and a
pop-up window indicates that it is not configured to monitor any devices. Select
Yes to have it search for subsystems.
If the subsystems do not appear, then the IP address assigned to each
storage-subsystem controller in the 5191 RAID Storage Controller must be identified
so it can be input into the Storage Manager Application. To identify the IP
addresses:
1. Record the Ethernet MAC addresses of each storage-subsystem controller in
the 5191 RAID Storage Controller Unit. The MAC address is located on a label
directly under the RJ-45 Ethernet port on the rear of each storage-subsystem
controller; for example, a MAC address could appear as 10-11-12-13-14-15.
2. On the DHCP server, locate the IP addresses (either two or four) that were
assigned to the MAC addresses of the storage-subsystem controllers.
3. From the Storage Manager Enterprise Management window, select Edit → Add
Device and add the IP addresses that were assigned to the storage-subsystem
controllers.
The storage can now be managed using the external Ethernet connection
regardless of the state of the Node A and Node B engines.
30 Model 326 User’s Reference
Page 43

Starting Enterprise Management
The Enterprise Management window is the first window to open when you start the
Storage Manager Application. Use Enterprise Management to:
v Add and discover the storage subsystem you want to manage.
v Provide a comprehensive view of all storage subsystems in your management
domain.
v Perform batch storage-subsystem management tasks using the Script Editor.
Use the following procedure to start the Enterprise Management window. Perform
these steps on one node, and then bring up the other node to validate the input.
1. Select Start → IBM NAS Admin.
2. Click NAS Management → Storage → NAS Utilities → IBM FAStT Storage
Manager Client. The client software starts, displaying the Enterprise
Management window and the Confirm Initial Automatic Discovery window.
Note: The Enterprise Management window can require up to five minutes to
open. No wait indicator (such as an hourglass) is displayed.
3. Select Yes to begin an initial automatic discovery of hosts and storage
subsystems attached to the local subnetwork on which the management station
is installed. If you do not want to perform the initial automatic discovery, select
No. You must add the device manually to the Storage Manager Application.
The software sends a broadcast message across the local subnetwork where
the management station is installed. It discovers host-agent-managed storage
subsystems if the hosts that provide network management connections to the
storage subsystems respond to the broadcast. The software discovers
direct-managed storage subsystems if the controllers in those storage
subsystems respond to the broadcast message.
Note: The Enterprise Management window can require up to 1 minute to
refresh after an initial automatic discovery.
To stop the automatic discovery operation, close the Enterprise Management
window.
When the initial automatic discovery is complete, you can see all hosts and
storage subsystems attached to the local subnetwork.
If you do not see all hosts and storage subsystems, perform these steps:
a. Check the hardware and connections for possible problems (refer to the
hardware documentation for specific procedures).
b. Refer to the Enterprise Management, online, help topic about discovering
storage subsystems.
If any device has a status of Unresponsive, use the software to remove the
device from the management domain and then add it again. Refer to the
Enterprise Management online help for instructions on removing and adding
devices.
If the storage subsystem is managed directly but is attached to a host with the
host-agent software installed and running, the storage subsystem might be
duplicated in the device tree after an automatic discovery. In this case, you can
remove the duplicate storage-management icon from the device tree using the
remove-device option in the Enterprise Management window.
Chapter 4. Setting up storage 31
Page 44

Starting Subsystem Management
The Subsystem Management window enables you to manage selected subsystems.
Use the following procedure to open a Subsystem Management window for a
selected storage subsystem:
1. In the Enterprise Management window, select a storage subsystem.
2. Select Tools → Manage Device. The software displays the Subsystem
Management window for the selected storage subsystem.
Note: Using the open Subsystem Management window, you can manage only
the selected storage subsystem. However, you can open multiple
Subsystem Management windows to manage other storage subsystems.
Changing storage-subsystem host type
Changing the host type modifies settings on the 5191 RAID Storage Controller to
support the operating system and environment. Use the open Subsystem
Management window to change this setting:
1. Select Storage Subsystem → Change → Default Host Type.
2. From the New Host type drop-down menu, select Windows 2000 Clustered,
then select OK.
3. Continue with “Renaming storage subsystems”.
Renaming storage subsystems
When you start Storage Manager for the first time, the storage subsystems are
unnamed. To rename them, use the Subsystem Management window. Refer to the
renaming storage subsystems topic in the Subsystem Management online help. The
help topic provides detailed instructions for renaming storage subsystems. As a
security precaution, it is recommended that you protect the storage subsystems with
a password.
Creating arrays and logical drives
To create an array or logical drive, perform the following procedure:
1. Highlight a storage subsystem in the Enterprise Management window and select
Tools → Manage Device.
2. Select Configure → Create Array/Logical Drive to create all of your planned
arrays and logical drives on this storage subsystem.
3. Repeat the arrays/logical drive configuration for each storage subsystem
connected to the cluster.
Note: If you add or delete any other logical drives, you must make them known
to the other node in a cluster configuration.
4. Go to “Creating arrays and LUNs under the Storage Manager Application”.
Creating arrays and LUNs under the Storage Manager Application
Note: It takes approximately 48 minutes per 50 GB for drives to initialize.
When you begin this procedure, all nonallocated drives appear as Unconfigured
Capacity in one large drive pool showing the total unconfigured capacity. To create
arrays and LUNs:
1. Right-click Unconfigured Capacity.
32 Model 326 User’s Reference
Page 45

2. Select Create Array.
3. Select either Automatic or Manual, depending on your requirements. Automatic
mode chooses drives across different enclosures connected to that particular
storage controller, which spreads the array bandwidth and increases
redundancy.
Note: In this procedure, it is recommended that the arrays are not RAID-0.
If you are using the preset factory configuration, the first logical drive is
configured as the 500-MB Quorum drive. Configure the second logical drive with
the remainder of the space on the array.
If you are creating a customized configuration on the 5191 RAID Storage
Controller, ensure that you create a 500-MB Quorum drive on a RAID-5 array.
Create another logical drive using the remaining space on that RAID-5 array.
Create additional arrays using the rest of the unconfigured capacity until all of
the arrays are created and initializing. (This process will take place automatically
in the background.)
Note: You will see notifications that new hardware has been found, and you will
be asked whether you want to restart your computer. Do not restart your
computer at this point.
Finally, you will see a message that Windows 2000 has finished installing
new devices, and you will be asked whether you want to restart you
computer. Again, do not restart your computer at this point. Leave this
message in the foreground until the array initialization completes.
4. Once the initialization for all arrays completes, restart the system.
5. Continue with “Formatting the logical drives” on page 35.
Expanding the LUN
LUN expansion is enabled by the DiskPart command line utility. Using DiskPart, you
can dynamically expand an existing logical drive into unallocated space that exists
in a LUN.
Note that you cannot use DiskPart to dynamically expand an existing LUN in array.
You can do this only with array/LUN management software such as ServeRAID or
Storage Manager Application.
To expand a LUN, use the following two DiskPart commands:
select This command focuses on (selects) the volume that you want to expand.
extend
The format of the command and its options are
select volume[=n/l]
You can specify the volume by either index, drive letter, or mount point
path. On a basic disk, if you select a volume, the corresponding partition is
put in focus. If you do not specify a volume, the command displays the
current in-focus volume.
This command extends the current in-focus volume into contiguous
unallocated space. The unallocated space must begin where the in-focus
partition ends. The format of the command and its options are
extend [size=n]
Chapter 4. Setting up storage 33
Page 46

where size is the size of the extension in MB.
Note that if the partition had been formatted with the NTFS file system, the file
system is automatically extended to occupy the larger partition, and data loss does
not occur. However, if the partition had been formatted with a file system format
other than NTFS, the command is unsuccessful and does not change the partition.
DiskPart blocks the extension of only the current system or boot partition.
Several other commands that are useful when you expand the LUN are:
assign
Use this command to assign a letter or mount point to the current selected
(in-focus) partition. If you do not specify a drive letter, the next available
drive letter is assigned. If the letter or mount point is already in use, an
error is generated.
You can use this command to change the drive letter that is associated with
a removable drive. The drive letter assignment is blocked on the system,
boot, or paging volumes. You cannot use this command to assign a drive
letter to an OEM partition or any globally unique identifier (GUID) partition
table (GPT) partition, other than the Msdata partition.
The format of the command and its options are:
assign [letter=l] or [mount=path]
convert
You can use several commands to convert disks. The format and options
for each of the commands are:
convert mbr
convert gpt
convert dynamic
convert basic
convert mbr sets the partitioning style of the current disk to master boot
record (MBR). The disk can be a basic disk or a dynamic disk but the disk
must not contain any valid data partitions or volumes.
convert gpt sets the partitioning style of the current disk to GPT. The disk
may be a basic or a dynamic disk but it must not contain any valid data
partitions or volumes. This command is valid only on Itanium
™
-based
computers; it can be unsuccessful on x-86-based computers.
convert dynamic changes a basic disk into a dynamic disk. The disk can
contain valid data partitions.
convert basic changes an empty dynamic disk to basic.
list You can use several commands to display summaries of disk configuration.
The format for each of the commands is:
list disk
list partition
list volume
list disk displays summary information about each disk in the computer.
The disk with the asterisk (*) has the current focus. Only fixed disks (for
example, IDE or SCSI) or removable disks (for example, 1394 or USB) are
listed. The removable drives are not displayed.
34 Model 326 User’s Reference
Page 47

list partition displays information about each partition on the in-focus disk.
list volume displays information about each volume in the computer.
Formatting the logical drives
Note the following restrictions when formatting logical drives:
1. Disk 0 (the internal hard disk drive) is an 18-GB drive, preformatted into two
partitions: a 6-GB partition (label System, drive letter C) and a 12-GB partition
(label MAINTENANCE, drive letter D). Do not reformat or repartition these
partitions. Doing so could delete important data and seriously impair the
functioning of your system.
2. Do not upgrade any disks to dynamic. Only basic disks are supported for
clustering. In addition, all partitions used for clustering must be primary
partitions.
3. Do not use drive letter F as a volume drive letter. This drive letter is reserved for
Persistent Storage Manager (PSM)-based backup using NAS Backup Assistant.
Using the preset factory configuration
1. After rebooting, open IBM NAS Admin and select Disk Management (Local),in
the Storage folder.
2. At the Write Signature and Upgrade Disk Wizard, click Cancel.
3. Right-click the Unknown disk on the bottom right, and select Write Signature.
4. Check all the boxes to write a Disk Signature to all disks that will be accessed
by the Cluster Server (all disks in the view).
5. On the unformatted drive:
a. Right-click and select Create Partition and click Next.
b. Select Primary Partition and click Next.
c. Select the entire disk size and click Next (preferred method).
d. Choose a drive letter for this volume.
e. Enter the following properties:
v File System of NTFS
v Volume Label of Drive_x, where x is the letter of this volume.
Note: For the Quorum drive, label the volume Quorum Disk.
f. Click Next.
Do not enable disk compression. Select Finish.
6. Format all other drives, but do not enable compression. Use all space available
for each drive for each logical drive assigned by the operating system.
At this point, you have completed shared-storage setup. You can now continue with
“Chapter 5. Completing networking, clustering, and storage access setup” on
page 37.
Customizing the factory configuration
1. After rebooting, open IBM NAS Admin and select Disk Management (Local) in
the Storage folder.
2. The Write Signature and Upgrade Disk Wizard opens. Click Cancel.
3. Right-click Disk 1 and select Write Signature.
4. Write Signature to all disks that will be accessed by the Cluster Server (all disks
in view).
5. On the Quorum drive:
a. Right-click and select Create Partition and click Next.
Chapter 4. Setting up storage 35
Page 48

b. Select Primary Partition and click Next.
c. Select the entire disk size and click Next.
d. Select Drive Letter as G
e. Enter the following properties:
v File System of NTFS
v Volume Label of Quorum Disk
f. Click Next.
Do not enable disk compression, and select Finish.
6. Format all other drives, but do not enable compression. Use all space available
for each drive for each logical drive assigned by the operating system. Assign
drive letter H for the second drive (the first user-data volume), and so on.
You have completed shared storage setup. You can now continue with “Chapter 5.
Completing networking, clustering, and storage access setup” on page 37.
36 Model 326 User’s Reference
Page 49

Chapter 5. Completing networking, clustering, and storage access setup
Note: Before proceeding with the steps in this chapter, configure the shared
storage using the Storage Manager application. See “Chapter 4. Setting up
storage” on page 29 for details.
The Model 326 uses Microsoft Cluster Server (MSCS) software to provide clustering
technology for your storage. Clustering ensures availability of the storage,
regardless of individual component failure.
After installing the clustering function, you can use Cluster Administration to set up
the failover function. Then, if a node or a node’s component were to fail, the Model
326 detects the failure and begins a failover process in less than 10 seconds, and
completes the process within 60 seconds. Failover/Failback includes Active/Active
support for the CIFS and NFS protocols.
Active/Active support is available for HTTP and FTP. See the online cluster
administration guide for this procedure.
Novell NetWare and Apple Macintosh shares are available on both nodes, but not
through clustering services. If either node fails, the shares become unavailable until
the node is brought back up.
This chapter gives the details for installing and initially configuring MSCS on the
Model 326. Administrative concepts and procedures are provided in the online help
and at the following Web sites:
v www.microsoft.com/windows2000/library/technologies/cluster/default.asp
v www.microsoft.com/ntserver/support/faqs/clustering_faq.asp
v http://support.microsoft.com/default.aspx?scid=kb;EN-US;q248025
Networking setup
Attention: Before you install cluster services on the first node, make sure that the
joining node is powered off. This is required to prevent corruption of data on the
shared storage devices. Corruption can occur if both nodes simultaneously write to
the same shared disk that is not yet protected by the clustering software.
Configuring the interconnect (private) network adapter
To configure the interconnect (private) network adapter, perform the following steps
on both nodes. The Private connection is the “heartbeat” interconnect for the
cluster.
1. Right-click My Network Places and then select Properties.
2. Select the network connection that uses the IBM Netfinity 10/100 Ethernet
Adapter.
3. Right-click the adapter icon and click Properties.
4. Click Configure, select the Advanced tab, and verify that the following
characteristics are set:
Link speed and Duplex 100 Mbps / Full Duplex
5. Click OK.
6. If prompted to restart the node, select No.
© Copyright IBM Corp. 2002 37
Page 50

7. In the Properties panel for the IBM 10/100 Adapter connection, select Internet
Protocol (TCP/IP) from the components section, and click Properties.
8. The default IP addresses should be:
v 10.1.1.1 for the first node
v 10.1.1.2 for the joining node
If they are not, it is recommended that you set them to those values.
9. Ensure a Subnet Mask of 255.255.255.0.
10. Click Advanced, and select the WINS tab.
11. Select the Disable NetBIOS over TCP/IP radio button.
12. Click OK.
13. Select Yes at the prompt to continue using an empty Primary WINS address.
14. Click OK on the Internet Protocol (TCP/IP) Properties panel.
15. Click OK on the Local Area Connection Properties (Private) panel.
16. Rename the connection to Private.
Configuring the public local area connection
Note: While the public network adapter’s IP address can be automatically obtained
if a DHCP server is available, this is not recommended for cluster nodes. It
is strongly recommended that you set static IP addresses for all network
adapters in the cluster. If IP addresses are obtained through DHCP, access
to cluster nodes could become unavailable if the DHCP server goes down.
To configure each public local area connection, perform the following steps on each
node:
1. Right-click My Network Places, then click Properties.
2. Select a Local Area Connection.
When you perform this step, the connection that uses the IBM 10/100 Adapter is
the private connection. The other active connection is the public connection.
Use that other active connection for this step and the next step.
3. To rename the connection, click Rename, and then type (for example) Public 1,
and press Enter. Ensure that local area connection names are unique.
When you perform these renaming steps for the joining node, ensure that the
local area connection name for each physically connected network is identical
on each server. See Table 3 on page 39 for a further example.
4. Use the networking information in Table 1 on page 7 to enter the networking
addresses:
a. Right-click My Network Places.
b. Click Properties.
c. Right-click the Public icon, and then click Properties.
d. Select Internet Protocol (TCP/IP).
e. Click Properties, select Use the following IP address:, and enter the
addresses for the IP, subnet mask, default gateway, and preferred DNS
server.
5. If needed, configure the DNS, WINS, HOSTS, or whichever method you will be
using for names resolution. To view this information, click the Advanced button
on the Properties window.
6. Click OK on each panel to return to the Properties window.
38 Model 326 User’s Reference
Page 51

Do not place paired adapters on the same IP network unless you are going to use
adapter teaming or adapter load balancing.
Verifying network connectivity and names resolution
Verify network connectivity and names resolution after you have installed clustering
on the joining node.
To verify that the private and public networks are communicating properly:
1. Click Start → Run, type cmd in the text box, and click OK to bring up an
MS-DOS prompt.
2. Type ping ipaddress where ipaddress is the IP address for the corresponding
network adapter in the other node, and press Enter.
For example, assume that the IP addresses are set as follows:
Table 3. Example of local area connection names and network adapter IP addresses
Node Local area connection name Network adapter IP address
1 Private 10.1.1.1
1 Public 1 192.168.1.12
1 Public 2 192.168.2.12
2 Private 10.1.1.2
2 Public 1 192.168.1.13
2 Public 2 192.168.2.13
In this example, you would type ping 192.168.1.12 and ping 192.168.2.12 for the
first node, and you would type ping 192.168.1.13 and ping 192.168.2.13 for the
joining node. You can do this from any machine that is physically connected to the
network of each node.
To view the addresses, use the ipconfig command on each node:
1. Click Start → Run, type cmd in the text box, and click OK to bring up an
MS-DOS prompt.
2. Type ipconfig /all and press Enter. IP information should appear for all network
adapters in the machine.
Checking or changing the network binding order
The clustering function requires the following binding order:
v Private
v Public 1
v Public 2
v
.
.
.
The top-most connection is first in the binding order. Typically, this is the most
frequently used network adapter.
To check the binding order and change it:
1. From the desktop, right-click My Network Places and then select Properties.
2. Select Advanced Settings from the Advanced menu.
3. Reorder the position of the adapters by selecting them, then pressing the up or
down arrow keys, then clicking OK.
Chapter 5. Completing networking, clustering, and storage access setup 39
Page 52

If prompted to restart, click No. If you change the binding order, you do not have to
reboot until after you join the node to the domain.
Joining a node to a domain
All nodes in the cluster must be members of the same domain and be able to
access a Primary Domain Controller (PDC) and a DNS Server.
Note: The administrator must have a valid domain account on the PDC.
1. Right-click My Computer, and click Properties.
2. Click Network Identification. The System Properties dialog box displays the full
computer name and workgroup or domain.
3. Click Properties and perform these steps to join a domain:
a. Select the Domain radio button.
b. Type the name of your domain and click OK.
c. When prompted, enter the Administrator user ID and password and click
OK.
4. Close the System Properties window.
5. Restart the node, and proceed with “Cluster setup”.
After the computer restarts, it is recommended that you do not log in to the
domain. If you do, you will see the Windows 2000 Configure Your Server
window. Click the I will configure this server later radio button, and then click
the Next button. On the next window, clear the Show this screen at startup
check box and click Finish.
Cluster setup
At this step, you have completed the cluster installation steps on each node and are
ready to set up the cluster.
Perform the following steps:
1. To begin setting up the cluster on the node, open IBM NAS Admin, then the
Cluster Tools folder, and click the Cluster Setup icon.
2. At the prompt, verify that you have completed the steps that precede this
cluster setup step. If you have, click the Continue button.
3. If this is the first node, click the First Node button. If this is the joining node,
go to Step 12 on page 41 and continue from there.
4. The Cluster Information panel appears. Enter the data for the following fields
(some of this data comes from Table 1 on page 7):
v Administrator ID and password
Note: The ID and password are any valid user ID and password with
administrator privileges on the domain.
v Domain name
v Cluster name
v Cluster IP address
v Subnet mask
v Quorum drive (select from the pulldown menu)
5. After you enter the data, click Continue.
6. Verify the information. If it is correct, click Yes to start the configuration.
Configuration takes a few minutes.
40 Model 326 User’s Reference
Page 53

7. If you are prompted to select a user account, enter the user name and
password for the domain account that you want the cluster service to use.
8. If you are prompted to select a disk on which to store cluster checkpoint and
log files, do the following:
a. Select the disk on which the Quorum is located (for instance, G, if this is
b. Click Finish at the Cluster Information panel.
9. Cluster configuration completes for the first node.
10. Power on the joining node. (You will join this node to the cluster.)
11. Go to “Networking setup” on page 37.
12. In the Cluster Setup wizard, click Joining Node.
13. In the First Node Information panel, enter the name of the first node.
14. If prompted to confirm the Administrator name and password, enter that
information and click Finish.
You will see a message that configuration takes a few minutes. When configuration
completes, the Cluster Administration function starts.
You have now completed cluster setup.
Configuring clusters
what you specified earlier) and click Next.
This section contains procedures to assist you in configuring basic cluster functions.
It is assumed that the cluster installation procedures in “Cluster setup” on page 40
have completed without errors, and both cluster nodes are running.
It is recommended that you review the Cluster Administration Guide, located in the
IBM NAS Admin in the Cluster Tools folder, before continuing with the following
steps.
Configuring cluster state and properties
You must complete the following steps to reset the size of the logfile and set the
priority and purpose of the private network.
1. Select Cluster Administration, located in IBM NAS Admin, in the Cluster Tools
folder.
If prompted for a cluster name, enter the name of the cluster, and then click
Open.
2. The cluster name appears in the left panel. Click the cluster name to see the
status of the cluster nodes in the right pane. The state of both nodes should be
“Up”.
3. Right-click the cluster name and select Properties.
a. Select Quorum Disk, and change the Reset quorum log at: field from 64 KB
to 4096 KB.
b. Select Network Priority to view all networks acknowledged by the cluster
server, then select the private network connection and move it to the top for
cluster communication priority by clicking the Move Up button.
This provides internal communication to the private network before attempts
are made to communicate over any public networks that are installed. Do
not change the communication options for the public network adapters as
they should support both network and cluster traffic.
Chapter 5. Completing networking, clustering, and storage access setup 41
Page 54

4. Open the properties for the private network and select Internal cluster
communication only (private network) to ensure that no client traffic will be
placed on the private network.
5. Click Apply, OK, and then OK.
Setting up cluster resource balancing
When you configure cluster resources, you should manually balance them on the
disk groups to distribute the cluster resource functions between the two nodes. This
allows for a more efficient response time for the clients and users accessing these
resources.
To set up cluster resource balancing:
1. Select a disk group and bring up its Properties panel by right-clicking it.
2. Click the General tab.
3. Click the Modify button to the right of the Preferred owners: field.
4. In the Available nodes pane, select a node and click the → button to move the
node to the Preferred Owners pane.
5. Complete Steps 1 through 4 for each disk group.
Each disk group has a preferred owner so that, when both nodes are running, all
resources contained within each disk group have a node defined as the owner of
those resources. Even though a disk group has a preferred owner, its resources
can run on the other node in the cluster following a failover. If you restart a cluster
node, resources that are preferentially owned by the restarted node failback to that
node when the cluster service detects that the node is operational, and provided
that the defined failover policy allows this to occur. If you have not defined the node
as the preferred owner for the resources, then they do not failback to the node.
Note: You must reboot before you can see changes made to the cluster resource
Setting up failover
The failover of resources under a disk group on a node enables users to continue
accessing the resources if the node goes down. Individual resources contained in a
group cannot be moved to the other node; rather, the group it is contained in is
moved. If a disk group contains a large number of resources and any one of those
resources fails, then the whole group will failover according to the group’s failover
policy.
The setup of the failover policies is critical to data availability.
To set up the failover function:
1. Open the Properties panel for the disk group.
2. Select the Failover tab to set the Threshold for Disk Group Failure.
3. Select the Failback tab to allow, or prevent, failback of the disk group to the
balancing.
For example, if a network name fails, clustering services attempts to failover the
group 10 times within six hours, but if the resource fails an eleventh time, the
resource remains in a failed state and administrator action is required to correct
the failure.
preferred owner, if defined.
42 Model 326 User’s Reference
Page 55

In allowing failback of groups, there is a slight delay in the resources moving from
one node to the other. The group can also be instructed to allow failback when the
preferred node becomes available or to failback during specific off-peak usage
hours.
Each resource under each disk group has individual resource properties. The
properties range from restart properties, polling intervals to check if a resource is
operational, to a timeout to return to an online state. The default settings for these
properties are selected from average conditions and moderate daily use.
Creating users
The creation of users is performed through normal procedures. Users do not need
to be created exclusively for use on the cluster resources. You must define
properties of the resources for users to access the resources within the domain
policies. All user-accessible cluster resources have the same properties as standard
Microsoft Windows resources, and should be set up following the same policies.
Note: If your storage will be accessed by UNIX or UNIX-based clients and servers,
continue with “Defining UNIX users and groups”. The Model 326 is on a
Windows domain and inherits those Windows users, eliminating the need to
define local Windows users and groups. Also, shares are created in the
clustering setup.
Defining UNIX users and groups
This section describes how to set up UNIX users and groups to access the Model
326 storage through the Network File System (NFS) protocol.
“Microsoft Services for UNIX and NFS Support” on page 72 has more information
on Services for UNIX and NFS.
Support for NFS is provided in the Model 326 by a preloaded and preconfigured
software component, Microsoft Services for UNIX. The levels of NFS supported by
Services for UNIX, and in turn the Model 326, are NFS Versions 2 and 3. Any client
or server that is using an NFS software stack supporting NFS Version 2 or NFS
Version 3, regardless of the operating system, can connect to the Model 326 and
access its storage through NFS.
You administer NFS file shares and other attributes with standard Windows
administration tools, including those provided as part of the IBM NAS desktop and
the Microsoft Windows 2000 for NAS user interface. Additional configuration of the
User Name Mapping component of Services for UNIX, which maps the UNIX user
name space to the Windows user name space, is required to support NFS security.
You can define a local UNIX name space on the Model 326 by configuring the
Server for PCNFS component of Services for UNIX. Alternately, you can point
Services for UNIX to an existing Network Information Service (NIS) domain that
defines the UNIX name space. In both cases, you must configure the User Name
Mapping component to map the UNIX name space that you select to the Windows
name space, because file shares and individual file and directory permissions on
the Model 326 are defined in the context of the Windows name space.
To define a local UNIX name space, continue with “Using a local UNIX name
space” on page 44. To use a UNIX name space defined on a NIS domain, continue
with “Using the UNIX name space on an NIS domain” on page 45.
Chapter 5. Completing networking, clustering, and storage access setup 43
Page 56

Using a local UNIX name space
You should have to perform this procedure only once. You might have to add more
groups and users in the Server for PCNFS page if you add more users and groups
to your UNIX environment and Model 326 or Windows domain at a later time.
1. Open the IBM NAS Administration console by double-clicking the IBM NAS
Admin icon on the NAS desktop.
2. In the left pane, expand File Systems, then expand Services for UNIX.
3. In the left pane, click Server for NFS.
4. In the right pane, in the Computer name: field, enter localhost.
5. In the left pane, click Server for PCNFS.
6. In the right pane, click Groups.
7. On the Groups page, you must add the groups from your UNIX host to which
all of your UNIX users belong. You must know both the group name and the
group ID (GID) number. This information can be found in the /etc/group file on
most UNIX systems.
As an example, on an AIX system, in the following line from an /etc/group file,
the fields are separated by a colon (:). The first field (“staff”) is the group
name; the third column (“1”) is the GID:
staff:!:1:pemodem,ipsec,netinst,protcs
To add a group, enter the group name and GID number in the Group name
and Group number (GID) fields, and then click New.
8. When you have finished adding groups, click Apply.
9. Click Users.
10. On the Users page, you must add all of the UNIX users who will be accessing
and storing files on the Model 326 through an NFS share. For each user, you
need to know the Windows user name, the UNIX user name, the primary
group, and the user ID (UID) number. This information can be found in the
/etc/passwd and /etc/group files on most UNIX systems.
As an example, on an AIX system, in the following line from an /etc/passwd
file, the fields are separated by a colon (:). The first field (“user1”) is the user
name; the third field (“3135”) is the UID, and the fourth field (“1”) is the GID of
the user’s primary group. This will correspond to a line in the /etc/group file,
where you can find the primary group name corresponding to the GID.
user1:!:3135:1:User 1:/home/user1:/bin/ksh
11. When you finish adding users, click Apply.
12. In the left pane, click User Name Mapping.
13. In the right pane, select Personal Computer Network File System (PCNFS).
14. In the Password file path and name field, type
15. In the Group file path and name field, type
16. Click Apply.
17. Click Maps.
44 Model 326 User’s Reference
To add a user, click New, enter the required information, and then click OK.
c:\winnt\system32\drivers\etc\passwd.
c:\winnt\system32\drivers\etc\group.
On the Maps page, you can configure simple maps or advanced maps.
Configure simple maps if the Windows user name and UNIX user name is the
same for each UNIX user to be mapped, and the Windows group name and
UNIX group name is the same for each UNIX group to be mapped. Otherwise,
you should configure advanced maps.
Page 57

18. To configure simple maps, select Simple maps and continue with Step 20 .
19. To configure advanced maps, clear the Simple maps check box and continue
with Step 21.
20. Under the Simple maps check box, select the Windows domain name (the
domain to which you joined the Model 326 earlier in this chapter) from the
drop-down list, then continue with Step 22.
21. Under Advanced maps, do the following:
a. Define user mappings as follows:
1) Click Show user maps.
2) Select the Windows domain name (the domain to which you joined the
Model 326 earlier in this chapter) from the drop-down list.
3) Click Show Windows Users to display all of the Windows user names
in the Windows domain you selected.
4) Click Show UNIX Users to display all of the UNIX user names in the
NIS domain you selected.
5) Enter a Windows user name, or select one from the list of Windows
user names.
6) Enter a UNIX user name to be mapped to the Windows user name you
specified, or select one from the list of UNIX user names.
7) Click Add to add the mapping between the UNIX user name and
Windows user name to the list of maps.
8) If multiple Windows user names are mapped to one UNIX user name,
select one Windows user name to be the primary user name. Select
the mapping corresponding to the primary user name from the list of
maps, and then click Set Primary.
b. Define group mappings as follows:
1) Click Show group maps.
2) Select the Windows domain name (the domain to which you joined the
Model 326 earlier in this chapter) from the drop-down list.
3) Click Show Windows Groups to display all of the Windows group
names in the Windows domain you selected.
4) Click Show UNIX Groups to display all of the UNIX group names in
the NIS domain you selected.
5) Enter a Windows group name, or select one from the list of Windows
group names.
6) Enter a UNIX group name to be mapped to the Windows group name
you specified, or select one from the list of UNIX group names.
7) Click Add to add the mapping between the UNIX group name and
Windows group name to the list of maps.
8) If multiple Windows group names are mapped to one UNIX group
name, select one Windows group name to be the primary group name.
Select the mapping corresponding to the primary group name from the
list of maps, and then click Set Primary.
22. Click Apply.
Using the UNIX name space on an NIS domain
The following procedure applies whether your NIS server is UNIX-based or
Windows-based (implemented as a Windows domain controller running Microsoft
Server for NIS).
1. Open the IBM NAS Administration console by double-clicking the IBM NAS
Admin icon on the NAS desktop.
2. In the left pane, expand File Systems, then expand Services for UNIX.
3. In the left pane, click Server for NFS.
Chapter 5. Completing networking, clustering, and storage access setup 45
Page 58

4. In the right pane, in the Computer name: field, enter localhost.
5. In the left pane, click User Name Mapping.
6. In the right pane, select Network Information Services (NIS), then click Maps.
On the Maps page, you can configure simple maps or advanced maps.
Configure simple maps if the Windows user name and UNIX user name is the
same for each UNIX user to be mapped, and the Windows group name and
UNIX group name is the same for each UNIX group to be mapped. Otherwise,
you should configure advanced maps.
7. To configure simple maps, select Simple maps and continue with Step 9.
8. To configure advanced maps, clear the Simple maps check box and continue
with Step 10.
9. Under the Simple maps check box, do the following:
a. Select the Windows domain name (the domain to which you joined the
Model 326 earlier in this chapter) from the drop-down list.
b. In the NIS domain field, enter the NIS domain name. You can also enter
the name of a specific NIS server in the NIS server field.
c. Continue with Step 11 on page 47.
10. Under Advanced maps, do the following:
a. Define user mappings as follows:
1) Click Show user maps.
2) Select the Windows domain name (the domain to which you joined the
Model 326 earlier in this chapter) from the drop-down list.
3) In the NIS domain field, enter the NIS domain name. You can also
enter the name of a specific NIS server in the NIS server field.
4) Click Show Windows Users to display all of the Windows user names
in the Windows domain you selected.
5) Click Show UNIX Users to display all of the UNIX user names in the
NIS domain you selected.
6) Enter a Windows user name, or select one from the list of Windows
user names.
7) Enter a UNIX user name to be mapped to the Windows user name you
specified, or select one from the list of UNIX user names.
8) Click Add to add the mapping between the UNIX user name and
Windows user name to the list of maps.
9) If multiple Windows user names are mapped to one UNIX user name,
select one Windows user name to be the primary user name. Select
the mapping corresponding to the primary user name from the list of
maps, and then click Set Primary.
b. Define group mappings as follows:
1) Click Show group maps.
2) Select the Windows domain name (the domain to which you joined the
Model 326 earlier in this chapter) from the drop-down list.
3) In the NIS domain field, enter the NIS domain name. You can also
enter the name of a specific NIS server in the NIS server field.
4) Click Show Windows Groups to display all of the Windows group
names in the Windows domain you selected.
5) Click Show UNIX Groups to display all of the UNIX group names in
the NIS domain you selected.
6) Enter a Windows group name, or select one from the list of Windows
group names.
7) Enter a UNIX group name to be mapped to the Windows group name
you specified, or select one from the list of UNIX group names.
46 Model 326 User’s Reference
Page 59

8) Click Add to add the mapping between the UNIX group name and
Windows group name to the list of maps.
9) If multiple Windows group names are mapped to one UNIX group
name, select one Windows group name to be the primary group name.
Select the mapping corresponding to the primary group name from the
list of maps, and then click Set Primary.
11. Click Apply.
Creating clustered file shares (CIFS and NFS)
Note: For HTTP and FTP clustering setup and file sharing, refer to the information
at the following URL:
http://support.microsoft.com/default.aspx?scid=kb;EN-US;q248025
The creation of file shares on a cluster involves dependencies on a physical disk, a
static IP address, and a network name. These dependencies allow resources that
are defined to the same disk group to move as a group. The dependencies also
assure necessary access for the given resource.
Note: You must configure Server for NFS before NFS file sharing can be used.
See “Configuring Server for NFS” on page 73 for details.
Figure 1 illustrates the file share dependencies. Descriptions of the diagram
components follow the figure.
File share
Network name
(Virtual server name)
IP
(Physical LAN connection)
Figure 1. File share dependencies
Physical disk
The base resource in which to store user data. It is not dependent on any
other resources except the physical disk that it defines. The disk resource
must also have the same drive letters on both nodes so that the definitions
of resources that depend on it do not change if the resource is moved to
the other node.
Static IP address
A virtual address that binds onto an existing IP address on one of the
cluster’s public networks. This IP address provides access for clients and is
not dependent on a particular node, instead a subnet that both nodes can
access. Because this address is not the physical adapter’s permanent
address, it can bind and unbind to its paired adapter on the same network
on the other node in the cluster. You can create multiple IP addresses using
the Cluster Administrator on the same physical network.
Physical disk
Chapter 5. Completing networking, clustering, and storage access setup 47
Page 60

Note: Note that the cluster IP Address should not be used for file shares.
That address is reserved to connect to and manage the cluster
through the network that it is defined on.
Network name
An alternate computer name for an existing named computer. It is physically
dependent on an IP address on one of the public networks. When a disk
group contains an IP address resource and a network name, it is a virtual
server and provides identity to the group, which is not associated with a
specific node and can be failed over to another node in the cluster. Users
access the groups using this virtual server.
In the creation of a basic file share that is publicized to the network under a single
name, you must set it up to be dependent on the physical disk and network name
in the same disk group you are creating the file share in. The network name is
dependent on the IP address, so do not add that to the dependency list. You can
set the share permissions and advanced share resources also.
Users will access the cluster resources using \\<network_name>\<fileshare_name>.
Clustered file share creation example
An example of how to create a clustered file share follows. For this example,
assume that you are creating a file share in Disk Group 2.
1. Create the IP address resource:
a. Right-click Disk Group 2, and select New → Resource.
b. Enter an IP address name, for example ipaddr2, and change the resource
type to IP Address.
c. Select Run this resource in a separate Resource Monitor and click Next.
d. A list of possible owners appears, and both nodes should remain as
assigned. Click Next.
e. There are no resource dependencies on this panel, so click Next.
f. Enter your TCP/IP parameters. This will be the first virtual IP address. The
value in the Network field identifies to the system the network on which the
address is located. Click Finish to create the resource.
g. Right-click the resource and select Bring online.
2. Create the network-name resource:
a. Right-click Disk Group 2, and select New → Resource.
b. Enter the virtual server name to use (for example, NN2), select Network
Name as the resource type, and click Next.
c. Both nodes are possible owners. Click Next.
d. Add the IP address you created as a resource dependency in Step 1 and
click Next.
e. Type the virtual server name, NN2, into the Network Name Parameters field
and click Finish.
f. It takes a few moments to register the virtual server name with your name
server. After this completes, bring the resource online.
3. Create the CIFS or NFS file share resource:
a. Right-click Disk Group 2 and select New → Resource.
b. Enter a file share name (for example, FS2) and select either File Share or
NFS Share.
c. Both nodes are possible owners. Click Next.
48 Model 326 User’s Reference
Page 61

d. Add the resource dependencies for the physical disk and network name that
the file share will use and click Next.
e. Enter the share name of FS2 and the path to the disk in this group, either
drive or subdirectory. You can then set:
v For CIFS shares properties:
– User Limit
– Permissions
– Advanced File Share
v For NFS shares properties:
– Permissions
– Share
A note on anonymous access: When you create an NFS share, it is
strongly recommended that you not disable anonymous access to
avoid client-connection problems. See “Enabling Server for NFS” on
page 75 for more details.
f. Click Finish to create the resource.
g. Right-click the resource and select Bring online.
Powering off and powering on the Model 326
The clustering function requires special considerations when you need to power off
and power on the Model 326. This section gives the details for those
considerations.
Powering off the Model 326 when clustering is active
1. Make note of the order in which you shut down the nodes.
You shut the nodes down one at a time, and in the powering on procedure you
start the nodes in the opposite order in which you powered them off.
2. On the node that you want to shut down last (the second node), click Cluster
Administration, located in IBM NAS Admin, in the Cluster Tools folder. If
prompted for a cluster name, enter the name of the cluster, and then click
Open. Make sure that all resources are in the online state.
3. With all clustered resources in the online state, on the node that you want to
shut down first (the first node), go to Start → Shut Down and select Shut down
from the drop-down menu. Click OK.
4. On the second node, in Cluster Administrator, wait for all resources to failover to
that node and return to the online state.
5. When all resources are in the online state, and the first node has shut down, on
the second node go to Start → Shutdown and select Shut down from the
drop-down menu. Click OK.
6. When both nodes have shut down, power off each 5191 RAID Storage
Controller by pressing the two power switches located on the rear of the unit.
7. Power off all 5192 Network Attached Storage Storage Units and 3534 Managed
Hubs.
8. You can power down any network hubs or switches that are used exclusively by
the Model 326. If they are used by other network attached devices, do not
power these off.
9. You can also power off any Uninterruptible Power Supplies (UPS) that regulate
power for the Model 326, provided that no other equipment that you want to
keep powered on is plugged into the same UPS.
Chapter 5. Completing networking, clustering, and storage access setup 49
Page 62

Powering on the Model 326 when clustering is active
1. Power on any UPS that you powered off in the powering off procedure, and
allow it to return to normal operation.
2. Power on any network hubs or switches that you powered off in the powering off
procedure.
3. Power on all 5192 Network Attached Storage Storage Units and 3534 Managed
Hubs. Give the 3534 Managed Hubs about three minutes to start up.
4. Power on each 5191 RAID Storage Controller. After about three to four minutes,
the storage controllers will have completed their startup routine. You can verify
this by making sure that for each drive in the storage controller and for each
drive in the storage unit, the status LED (on the top front of the drive) is solid
green (not blinking) for at least five seconds.
5. Power on the node that you shut down last in the powering off procedure.
6. After the node comes up, start Cluster Administrator on that node and make
sure that all resources are in an online state or shortly return to that state.
7. If no problems exist and all clustered resources are online, power on the node
that you shut down first in the powering off procedure. Each resource for which
that node is the preferred owner will fail back to that node and return to an
online state.
Recovering from a corrupted Quorum drive
Clustering relies on data stored on the Quorum disk to maintain resource
synchronization between the two nodes in the cluster. In the event of a power loss
to both nodes or a hardware failure that corrupts the Quorum data, the cluster
service might not start, leading to the following event log error:
Event ID: 1147
Source: ClusSvc
Description: The Microsoft Clustering Service encountered a fatal error.
The Quorum drive data must be available so the cluster service can confirm that
the cluster configuration on the local node is up to date. If it cannot read the log,
the cluster service does not start to prevent the loading of old configuration data.
To restore the Quorum disk, a Microsoft Windows Backup utility backup of the
System State of the boot drive (C:) of one node must be available. Backing up the
entire boot drive also saves the System State. Backing up the System State
automatically saves the Quorum log and other cluster files.
A Microsoft tool is needed as part of the Quorum restore procedure. This tool is
called Clusrest.exe and can be downloaded from the Microsoft Web site at the
following URL:
http://download.microsoft.com/download/win2000platform/clusrest/1.0/NT5/ENUS/clusrest.exe
The Quorum restore procedure involves restoring the system state and cluster state
to the node followed by execution of the Clusrest.exe tool. Upon completion of the
restore, the node should rejoin the cluster and return to normal operation.
1. Restore the entire boot drive of the node if needed. Otherwise, restore the
System State to the node.
2. Ensure that the cluster service is stopped on the other node.
50 Model 326 User’s Reference
Page 63

3. Restore the Quorum/cluster information to that node by selecting to restore at
least the system state. This creates a temporary folder under the Winnt\Cluster
folder called Cluster_backup.
4. Run the Clusrest.exe tool to rebuild the Quorum drive. The tool moves the
cluster information from the node’s boot drive to the Quorum drive.
5. After you complete the process and the cluster service has started successfully
on the newly restored node, restart the cluster service on the other node.
Notes:
1. If you do not follow this process, and another node with a more current
database takes ownership of the Quorum before you update the database from
the restored node, the restore does not work.
2. Restoring a Quorum rolls the cluster back in time to the backup date. There are
impacts to performing this operation that include loss of data. You should
perform this operation only when it is absolutely necessary.
Before you add software ...
You have now completed networking and clustering setup and administration, and
the Model 326 is at a point where you can install software on it. But before you do,
it is recommended that you take advantage of the Persistent Storage Manager
(PSM) disaster recovery function, detailed in “Disaster Recovery” on page 64.
The PSM disaster recovery function enables you to restore the system drive from a
single image, without having to go through the entire recovery procedure and then
additionally having to restore a system drive backup. So, if any software you install
creates unresolvable problems for your system, you can regain the stable system
you had before you installed the software.
Chapter 5. Completing networking, clustering, and storage access setup 51
Page 64

52 Model 326 User’s Reference
Page 65

Chapter 6. Managing and protecting the network and storage
This chapter describes the additional administrative functions that you can use to
manage and protect the network and storage on the Model 326.
The following functions are available:
v “IBM Director”, accessed through Start → Programs
v “NAS Backup Assistant” on page 59, accessed through IBM NAS Admin
v “Persistent Images” on page 61, accessed through the Windows 2000 for
Network Attached Storage user interface
v “Microsoft Services for UNIX and NFS Support” on page 72
IBM Director
Note: This section presents an overview of IBM Director functions. For more
detailed information, consult the Director User’s Guide on the Documentation
CD.
IBM Director is a systems-management solution that helps administrators manage
single or large groups of IBM and non-IBM devices, NAS appliances, and
workstations.
All of the functionality of IBM Director is contained in a simple GUI that enables
single-click and drag-and-drop commands. IBM Director can manage up to 5,000
clients depending on configuration density. Powerful remote management functions
include:
v Sophisticated discovery of network components
v Scheduled asset (hardware and software) inventories with persistent storage of
data
v Proactive problem notification and tools for problem resolution
v Hardware system component monitors and thresholds to trigger alerts of
impending problems
v Alert management with automated actions, manual intervention, or both
v Process scheduling to automate wide-scale client software maintenance (clean
up temp files, restart tasks, backups, and so on) according to any timetable
v Help desk and routine maintenance functions such as remote control and file
transfer
v Extensive security and authentication
IBM Director consists of three main components:
v Management Server
v Agent
v Console
The Management Server is a centralized systems manager and is the core of the
IBM Director product. Management data, the server engine, and the management
application logic reside there. Install the IBM Director Management Server on a
dedicated server that has high-availability features. When installed on a Windows
2000 server or Windows NT 4.0 server system in the managed environment, the
Management Server provides the management application logic and persistent data
© Copyright IBM Corp. 2002 53
Page 66

Dependencies
storage of management information using an SQL database. The Management
Server maintains a database of all Director Agents and their inventory. All alerts
from the agents flow to the management server, which also acts as a central point
of configuration for Event Action Plans and System Tasks.
The Agent resides on the NAS Appliances and other systems that IBM Director
manages. IBM Director recognizes two types of managed systems: native agents
(IBM Director Agent installed) and nonnative agents (SNMP agent installed). The
Agent comes preinstalled on all IBM NAS appliances. It runs as a service that is
automatically started at boot time. IBM Director Agent provides valuable information
to IBM Director management server and other supported management applications.
In addition to its native interface with the Director Management Console, it provides
point-to-point remote management of client systems through a Web browser
window.
You perform administrative tasks at the Console. It is a Java application that serves
as the user interface to the Director-managed environment. The console provides
comprehensive hardware management using a single click or drag-and-drop
operation. You can install the Console on a machine at a remote location from the
server. Consoles are not licensed, so you can distribute them freely among
unlimited number of machines. In addition, there is no limit to the number of IBM
Director Consoles that can connect into the Management Server.
The IBM Director 3.1 Agent (the version included in this release) must be managed
by an IBM Director 3.1 Management Server. If your Management Server is running
an earlier version of IBM Director (V2.2 or earlier), then you must upgrade it to
ensure proper operation. This includes Director Consoles as well. The IBM Director
3.1 Management Server contains an Agent software distribution package that you
can use to upgrade pre-version 3.1 Agents. This allows easy and automated
upgrading of the entire system to version 3.1. You can check the version of IBM
Director Agent running on a NAS appliance by issuing: http://<system_name>:411/
on a local Web browser.
Hardware requirements
It is highly recommended that you install the IBM Director Server on a server
separate from the IBM NAS appliance. The IBM Director Server running on an IBM
NAS appliance will significantly reduce its performance. The server must meet
these minimum requirements:
Hardware vendor Must be IBM. The management tools of IBM
CPU A 733 MHz PIII processor is recommended.
Memory 512 MB RAM is recommended. During idle times,
Disk Because the Management Server software requires
54 Model 326 User’s Reference
Director and Director Extensions require IBM
equipment.
Standard PII processors can be functional, but
these processors might not be sufficient during
heavy usage.
while using the standard JET database, the
Management Console can consume 300+ MB
RAM. The number of managed agents, active
consoles, and amount of alerts being processed
increases the amount of memory needed.
Page 67

All IBM NAS products exceed the minimum hardware requirements for operating an
IBM Director Agent.
Director extensions
A portfolio of advanced management tools for IBM-specific hardware is provided by
IBM Director as a set of optional enhancements. These tools integrate into IBM
Director and provide management capabilities from a single console with a
consistent look and feel. These extensions are provided as part of the preinstalled
IBM Director Agent on the IBM NAS appliances:
v Management Processor
v Assistant Capacity Manager
v Cluster Systems Management
v Rack Manager
v ServeRAID Manager
v Software Rejuvenation
v Systems Availability
only 250 MB, and the JET database has a
maximum size of 1 GB, 9 GB of disk space is
sufficient. Usea4GBpartition for the operating
system (including the swap file).
To use these extensions, you must load them on the IBM Director Management
Server during installation.
Naming conventions
All IBM Director Agents have a Director system name that it is known by the
Management Server and Consoles. This Director System Name is defaulted to the
computer name during the NAS appliance preinstallation process
system name does not have to be the same as the computer name. The Director
system name is displayed on the IBM Director Console to identify the NAS
Appliance under the Group Contents column. You can optionally change the
Director System Name on an agent using the following procedure:
1. Open a command prompt window and enter the following IBM Director Agent
command to open the GUI interface:
twgipccf.exe
2. Type the new Director System Name and click OK.
The change takes place immediately.
Note: You might need to delete the NAS appliance from the Group Contents and
Web-based access
IBM Director Agent uses an Apache Web Server for Web-based access. All traffic,
even logon, is certificate-based encrypted. The Web server requires two ports. One
port (411) accepts non-SSL HTTP requests and automatically redirects to the
second port (423), which handles SSL requests.
have it rediscover the appliance by its new name.
1
. The Director
1. Although you can do so, it is recommended that you not change the default computer name to avoid the chance of propagating
misidentification through the system. And, if you are using IBM Director to manage your appliance, and you change the default
name, the default name continues to appear in IBM Director.
Chapter 6. Managing and protecting the network and storage
55
Page 68

Disaster recovery
It is important to provide adequate backup for key IBM Director Management Server
files for restoration purposes. It is recommended that you regularly back up the IBM
Director Management Server so that you can recover it in the event of a server
disaster. You need to save customizations that you make to the IBM Director,
including event action-plans, schedules, thresholds, and so on. Several commands
are provided with IBM Director to accomplish this task:
twgsave
twgrestore
This command saves the complete settings to a directory named
Director.save.#, where # shows the number of backups (for example, the
third backup of the server will be saved in directory Director.save.3). You
must stop the IBM Director Management Server service to execute this
command. The command supports the following options:
twgsave -s
where the optional parameter -s specifies that software distribution
packages not be saved. This helps reduce the size of the backup files.
This command restores the saved data from an IBM Director Management
Server. Do not attempt to use this restore feature to replicate an IBM
Director Server. The command supports the following options:
twgrestore -t directory
twgreset
Software distribution
The Software Distribution task enables you to import and silently distribute
predefined software distribution packages to an IBM Director Client system. These
packages are prepared by IBM for IBM NAS products and include software fixes
and release updates only. This includes upgrading the IBM Director client itself.
where the optional parameter -t specifies that the data is restored, but
server ID and system name is not restored, and directory is where the
saved data resides. IBM Director Management Server cannot be running
when this command is issued.
This command resets the Director Server system to the status after
installing. You can use it if you want to clear all tables in the database and
erase the system ID files. This command can be helpful to make sure that
after a restore only the data from the saved directory will be in the Director
System. The command supports the following options:
twgreset -d -i
Where -d means to clear the tables in the database, and -i means to erase
the unique identification files for the system. You can save and restore data
only when the Director Support Program and service are stopped. Agents
running on IBM NAS appliances do not need to be explicitly backed up
because the NAS recovery CD provides this feature. Applying the Recovery
CD will reinstall the IBM Director Agent.
The basic delivery is a single file package that is signed with a unique IBM NAS
key. Only IBM can create the signed packages that can be used by the IBM
Director Software Distribution tool.
56 Model 326 User’s Reference
Page 69

Software distribution using IBM Director can be deployed to a single IBM Director
client, all IBM Director clients, or some combination in between. The administrator
has complete control over which IBM Director clients receive any given package. By
default, software distribution packages automatically install themselves immediately
following delivery to the IBM client. Delivery of the package can be done manually
or scheduled for a later, more convenient time.
Real-time diagnostics
Real-time diagnostics provides nondisruptive testing of the agent. This is an add-in
provided automatically on all IBM NAS appliances, but you must also install it on
the IBM Director Management Server and Console. When installed, this function
appears in the Tasks column with the name Diagnostics.
To use Real-time diagnostics:
1. From the IBM Director Console, in the Tasks column, select Diagnostics. Then,
drag and drop Diagnostics onto the system that you want to diagnose.
2. In the Component field, select the component to test.
3. In the Action field, select the action for the component.
4. Click Start Action.
5. The action results are displayed in the Results window.
6. You can then highlight the text, right-click the mouse, and copy and paste the
results into a text editor.
Some results might require that you take specific action. For details on correcting a
failed device, consult the documentation that comes with the NAS appliance.
You can also run all tests by selecting All Components for the Component, and All
Non-Destructive Actions for the Action. Depending on the number and size of
hard disks present, this full test suite can take considerable time to complete. Even
though this is a nondisruptive diagnosis, testing might impact performance.
Rack Manager and inventory enhancements
The Rack Manager task has been updated to include all of the IBM NAS
components. A new component category, NAS, includes all of the IBM NAS
appliance engines. All IBM NAS appliances are automatically discovered by the
Rack Manager task for drag-and-drop rack construction. The following component
categories have been updated to include the new IBM NAS appliance components:
Racks Includes the new component, NAS Rack Model 36U
Storage
Includes these new components:
v NAS Storage Expansion Unit Model 0RU
v NAS Storage Expansion Unit Model 1RU
Fibre Channel
Includes these new components:
v NAS 8-port Fibre Channel Hub Model 1RU
v NAS Raid Storage Controller Model EXP
v NAS Raid Storage Controller Model 0RU
v NAS Raid Storage Controller Model 2RU
v NAS Raid Storage Controller Model EXU
NAS Is a new component category that includes these components:
v NAS 100 Engine Model R12
Chapter 6. Managing and protecting the network and storage 57
Page 70

Dynamic NAS groups
Dynamic NAS groups are an IBM Director Management Server enhancement made
specifically for IBM NAS appliances. You must install this enhancement on the IBM
Director Management Server as well as all IBM Director Consoles. You can add
dynamic NAS groups to the IBM Director Server and Consoles by downloading the
InstallShield extension from the IBM Web site and invoking the executable file. This
will create a new Group on all consoles that represent IBM NAS appliances in the
managed network.
Dynamic groups are automatically populated and maintained based on queries to
the database. These dynamic NAS groups must be added after the IBM Director
Management Server has been installed on a dedicated server. IBM NAS appliances
appear under the Groups column in the IBM Director Management Server. The
Group Contents column will then contain all the IBM NAS devices that have been
discovered on the network.
v NAS 100 Engine Model R18
v NAS 200 Engine Model 200
v NAS 200 Engine Model 201
v NAS 200 Engine Model 225
v NAS 200 Engine Model 226
v NAS 200i Engine Model 100
v NAS 200i Engine Model 110
v NAS 300 Engine Model 5RZ
v NAS 300 Engine Model 6RZ
v NAS 300G Engine Model 5RY
v NAS 300G Engine Model 6RY
NAS Web UI task
NAS Web UI is an IBM Director Management Server enhancement made
specifically for managed networks containing IBM NAS appliances. Install NAS Web
UI on the IBM Director Management Server and all IBM Director Consoles to create
a new task called IBM NAS Appliances with a subtask named Launch UI Web.
You can apply this new Console task to a NAS machine, causing a Web browser to
be automatically launched with a URL pointing to the Web UI on the target NAS
machine. The port specified in the URL is port 8099, which invokes Windows 2000
for NAS.
Electronic Service Agent (eSA)
Electronic Service Agent optionally resides on the customer’s system and works in
tandem with IBM Director to monitor events and securely transmit data to IBM on a
periodic, customer-definable timetable.
This monitor watches system inventory, hardware error logs and performance
information, and, if the server is under a service agreement or within warranty
period, automatically reports hardware problems to IBM. IBM will either contact the
customer or send out a replacement part before it fails, based on a PFA alert
received for a component under warranty. Information collected through this Service
Agent is available to IBM service support representatives while they are answering
or diagnosing problems. With early knowledge about potential problems, IBM can
provide proactive service, assisting in maintaining higher availability and
performance.
58 Model 326 User’s Reference
Page 71

The eSA agent must be installed on all IBM NAS appliances that you want to
participate in this service. You can download the software from the following URL:
www.pc.ibm.com/qtechinfo/MIGR-4L4QVC.html
Predictive Failure Analysis
Predictive Failure Analysis (PFA) provides advanced notification of a pending failure
so that corrective action can be taken to avoid unplanned downtime. The PFA alerts
are sent to IBM Director, where a wide variety of Event Action Plans can be
established, such as automatically notifying the administrator through e-mail, or
executing tasks in response to the alert. When used in conjunction with the IBM
electronic service agent, the PFA alerts are routed to an IBM support person, who
responds to the customer about the alert. The alerts can also be forwarded to other
management packages.
For more information
For more information on IBM Director, consult its user’s manual contained on the
Documentation CD.
NAS Backup Assistant
The NAS Backup Assistant is a preloaded utility that helps you create and schedule
backup batch files, and maintain log files. It can be used for backing up either the
Model 326 operating system or user data.
If you want to back up selected folders, you can use NT Backup without the NAS
Backup Assistant (which backs up an entire volume). However, if you use NT
Backup, it is recommended that you select and back up the copy of the files in a
previous persistent image, rather than the original data itself. When selecting the
files for the NT Backup operation, you must select the specific folders in the
persistent image. If you select the entire group of persistent images, the files in
those images will not be selected for backup. For more information about persistent
images see “Persistent Images” on page 61.
Because NAS Backup Assistant only creates and launches scripts, and is not a
comprehensive backup application, it does not support interactive error messages.
To check status of jobs, you must either view the Backup Logs or view the Windows
Event Viewer.
You invoke the NAS Backup Assistant by clicking the IBM NAS Admin desktop icon
to open the IBM NAS Administration console. Select Backup and Restore to
expand that tree, then select IBM NAS Backup Assistant. Once you select this
option, a logon prompt appears. Log on as a user who has backup operator
privileges (an Administrator or backup Administrator). If a logon prompt does not
appear, right-click the IBM NAS Backup Assistant link, and select refresh. Once
you log on, the main panel appears.
The four tabs on the main panel are:
Backup Operations
The main window where you create and schedule backup batch jobs.
Two backup methods you can select in the Backup Operations window are
the standard NT Backup method and the Persistent Storage Manager
(PSM) Persistent Image method. A standard NT Backup operation backs up
only those files on the drive that are not in use. To guarantee a complete
Chapter 6. Managing and protecting the network and storage 59
Page 72

backup image using this method, you must ensure that no users are
accessing any files on the drive, so this method is useful only for offline
backup.
To do a complete online backup that includes files that are in use, choose
the PSM Persistent Image backup method. This method creates a
persistent image (mapped as an unused drive letter on the system), backs
up a copy of that persistent image, and then deletes the original persistent
image (drive letter). For more information about persistent images see
“Persistent Images” on page 61.
Scheduled Jobs
Displays a list of backup batch jobs that you scheduled.
Backup Logs
Displays a list of log files for each backup that has run.
Displayed Logs
Displays the text contained in the log files that you can select from the
Backup Logs tab.
All of the options on each tab are described in detail in the online help. To access
the online help:
1. Click the IBM NAS Admin icon.
2. Expand the Backup and Restore directory.
3. Select IBM NAS Backup Assistant Help.
4. Log in.
Restoring using the NT Backup panel
Note: If you are restoring a backup that you created using Persistent Images in the
NAS Backup Assistant, the NT Backup file (*.BKF) was created for the
persistent image virtual drive letter instead of the original drive letter. For
example, if you selected drive C for backup, a persistent image was created
on the next available drive letter in the system, and that drive was backed up
instead of drive C. If you do not remember the original drive letter, you can
view the backup log files in NAS Backup Assistant. The top section of the log
file gives you the original drive letter, and the bottom section gives you the
persistent image drive letter. When you have the original drive letter, perform
the procedure below.
To restore backups, use the following procedure:
1. Click the Restore using NT Backup link in the Backup and Restore section of
the IBM NAS Admin console to open the backup GUI.
2. Click Restore Wizard, then click Next. You are asked what you want to
restore.
3. Select the appropriate media that you are restoring from.
4. If you are restoring from tape, expand the backup media pool name, and then
double-click the media (this will normally be named media created on {date -
time}. This action will read the set list from the tape.
If you are restoring a file, select Tools → Catalog a backup file, then click
Browse and find the backup file (.BKF) created for this backup.
5. Click OK. You will now have a Media created on {date - time} listed under file.
60 Model 326 User’s Reference
Note: If you do not know the .BKF file name, refer to the backup log in NAS
Backup Assistant.
Page 73

6. Click the plus sign (+) to the left of this media to see the set list. You might be
7. Select the files and directories to restore.
8. Select Alternate Location from the Restore files to: pull-down.
9. In the alternate location window, select the root directory of the original backup
10. To change restore options, select Tools from the menu bar at the top of the
11. After you select the files or directories for restore, the alternate location, and
12. At the prompt, confirm that you want to begin the restore. Click the Advanced
Persistent Images
A persistent image is a copy you make of one or more file system volumes at a
specific time. You can use the Persistent Images function to restore a file or volume
to the state it was in at the time you created the persistent image. Persistent
images are maintained in a way that minimizes the storage required to keep
multiple copies of the volume. This is done by using a copy-on-write technique that
uses, for each volume, an area of pre-allocated storage (the PSM cache file) that
keeps only those data blocks which have been written since the time you made a
persistent image of the volume.
prompted to enter the path to the file you want to catalog; if so, select the
same file that you just imported. This will build a set list.
drive letter you determined (see the note on page 60).
window, and then select Options. Refer to NT Backup online help (see
Restore files from a file or a tape) for use of these options.
options, click the Start Restore button.
button to select advanced options (see the NT Backup online help for details),
then click OK to begin the restore.
Persistent Storage Manager (PSM) allows you to create and preserve images of the
Model 326 drives. You can take a persistent image immediately or schedule
persistent images as one-time events or regularly repeated events.
You can access the PSM tasks in the Disks/Persistent Storage Manager task group
within the Windows 2000 for Network Attached Storage user interface in one of two
ways:
v Open the IBM NAS Admin console on the appliance desktop and select
Persistent Storage Manager. This automatically launches the Windows 2000 for
Network Attached Storage user interface and brings up the Disks/Persistent
Storage Manager page containing the PSM tasks.
v Start the Windows 2000 for Network Attached Storage user interface directly.
Once you create a persistent image, it appears as a directory on the original drive.
Access rights and permissions from the original drive are inherited by the persistent
image. Persistent images are used in the same way as conventional drives.
However, unlike conventional drives, persistent images are records of the content of
the original drive at the time you created the persistent image. Persistent images
are retained following shutdown and reboot.
There are six PSM tasks in the Disks/Persistent Storage Manager group:
v Global Settings
v Volume Settings
v Persistent Images
v Schedules
v Restore Persistent Images
Chapter 6. Managing and protecting the network and storage 61
Page 74

Global Settings
Volume Settings
v Disaster Recovery
Each of these tasks are described in the following sections. More detailed
descriptions and instructions for each of the control panels and topics are covered
in the online help.
On this panel, you can configure the persistent image system attributes shown in
Table 4.
Table 4. Persistent image global settings
Attribute Default value
Maximum number of persistent images 250
Inactive period 5 seconds
Inactive period wait timeout 15 minutes
This panel displays statistics for each volume, such as total volume capacity, free
space, and cache file size and usage. You can also select any volume and
configure volume-specific PSM attributes for that volume, as shown in Table 5.
Table 5. Persistent image volume settings
Attribute Default value
Cache-full warning threshold 80 percent full
Cache-full persistent image deletion threshold 90 percent full
Cache size 15 percent (of the total volume
capacity)
Note: You cannot change the cache size for a volume while there are persistent
Persistent Images
This panel lists all of the persistent images that exist on all volumes. On this panel
you can:
v Create a new persistent image immediately (without scheduling it through the
images on that volume (the Cache size combo box will be disabled). You
must delete all persistent images on the volume before changing the cache
size for that volume.
Schedules panel). When you create the persistent image, you can specify
properties for the persistent image, including:
Volume(s) The persistent image can contain a single
volume or multiple volumes. To select multiple
volumes, hold down the Ctrl key while clicking
the volumes. For multi-volume persistent images,
a virtual directory containing data for a volume
appears under the persistent image directory in
the top level of each volume in the persistent
image (the name of the persistent image
directory is configured in the Global Settings
panel).
62 Model 326 User’s Reference
Page 75

Name You can name the persistent image. This
becomes the name of the virtual directory
containing the persistent image, underneath the
persistent image directory in the top level of the
volume (the name of the persistent image
directory is configured in the Global Settings
panel).
Read-only or read-write A persistent image is read-only by default, so no
modifications can be made to it. However, you
can set the persistent image to read-write, which
permits you to modify it. When a persistent
image is written, the modifications made are also
persistent (they survive a reboot of the system).
Changing a persistent image from read-write to
read-only resets the persistent image to its state
at the time you took the persistent image, as
does selecting Undo Writes for a read-write
persistent image from the Persistent Images
panel.
Retention value A persistent image can be given a relative
retention value or weight. This is important when
PSM needs to delete some persistent images for
a volume because the capacity of the cache file
for that volume has reached a certain threshold,
as described later in this section. If the volume
cache file completely fills, then all persistent
images for that volume are deleted regardless of
the retention values. By default, a new persistent
image is assigned a “Normal” retention value
(there are other higher and lower values which
can be selected).
v Delete an existing persistent image.
v Modify properties of an existing persistent image, including read-only or
read-write, and retention value.
Schedules
Use this panel to schedule persistent images to be taken at specific times (this is
independent of the scheduled backup function through NAS Backup Assistant
described earlier). Each PSM schedule entry defines a set of persistent images to
be taken starting at a specified time and at a specified interval, with each image
having the set of properties defined in the entry. This allows you to customize
scheduled persistent images on a per-volume basis. For instance, you could set a
persistent image for one volume to occur every hour, and for another volume to
occur only once a day.
The set of properties you define are the same properties described in the Persistent
Images panel description assigned above; when you define these properties, all
persistent images created according to this schedule entry will be given those
properties. Once a scheduled persistent image is created, certain properties of that
persistent image can be modified through the Persistent Images panel,
independently of other persistent images created according to the schedule.
After you create a schedule entry, it appears in the list of scheduled persistent
images. Subsequently, you can modify the properties of an existing entry, such as
Chapter 6. Managing and protecting the network and storage 63
Page 76

start time, repetition rate, the volume(s), and so on. For a schedule, you can name
the persistent images based on a pattern you configure. The following format
specifiers allow you to customize variable portions of the name:
%M 3-letter month
%D Day
%Y Year
%h Hour in 12-hour format
%s Second
%i Instance
%a AM/PM
%H Hour in 24-hour format
%W Day of week (M, T, W ...)
%w 3-letter day of week (Mon, Tue, Wed ...)
%% Percent sign
As an example, the name pattern %w_%M_%D_%Y_%h_%m_%a would produce
the persistent image name Mon_Apr_1_2002_10_47_AM.
Restore Persistent Images
On this panel, you can select an existing persistent image and quickly restore the
volume contained in the image back to the state it was in at the time the selected
persistent image was taken. This is useful if you need to recover an entire volume,
as opposed to just a few files. This volume restore function is available for the data
volumes, but not the system volume.
Disaster Recovery
PSM provides a disaster recovery solution for the system drive. This extends the
volume restore function of PSM to provide disaster recovery in the event that the
system drive is corrupted to the point where the file system is corrupt, or the
operating system is unbootable. Note that while disaster recovery is also supported
through the Recovery CD-ROM and backup and restore capability, it is a two-step
process. In contrast, the method supported by PSM allows you to restore the
system drive from a single image, without having to go through the entire recovery
procedure and then additionally having to restore a system drive backup.
Use the Disaster Recovery panel to schedule and create backup images of the
system drive, and to create a bootable diskette which will allow you to restore the
system drive from a backup image (located on the maintenance partition, or
network drive). The remainder of this section provides additional information on how
to perform backup and recovery operations for the Model 326.
Note: Restoration of a PSM backup image over the network is not supported for
the Gigabit Ethernet Adapter. If you have only Gigabit Ethernet adapters
installed, it is recommended that you perform PSM backup of each node to
its maintenance partition (D: drive), which would allow you to recover if the
system volume is corrupt and/or unbootable. Should the hard disk drive fail
completely, you would need to use the Recovery CD as described in
“Chapter 9. Using the Recovery and Supplementary CDs” on page 123 to
restore the node to its original (factory) configuration.
Backing up the system drive
The Disaster Recovery panel lists status information for backup operations, both
scheduled and immediate, as well as buttons for starting and stopping a backup
operation, for configuring backup, and for creating a recovery diskette.
64 Model 326 User’s Reference
Page 77

Click the Modify Settings button to open the Disaster Recovery Settings page.
Modify the settings for backup as you desire. Do not include spaces in the Backup
name field. When you have modified the settings, click the OK button to save the
changes.
On the Disaster Recovery page, click the Start Backup button to begin the backup.
The backup process will first create a persistent image of the system drive (C:),
named System Backup. Then, it will create the backup images from that persistent
image, and then delete that persistent image when the backup operation is
complete.
Creating a PSM recovery diskette
You will now create a bootable PSM recovery diskette which, when used to boot up
the node, will use the backup location settings you configured on the Disaster
Recovery Settings page to locate the backup image and restore it to the system
drive of the node.
1. Insert a blank, formatted diskette in the diskette drive of the node.
2. On the Disaster Recovery page, click Create Disk.
3. Click OK on the Create Recovery Disk page. The diskette drive LED will turn off
when the creation is complete. The diskette creation should take no more than
two minutes.
4. The utility makes the disk DOS-bootable. From a command prompt, either
through the desktop of the node itself (with the diskette still in the diskette drive
of the node), or on another system with the diskette in its diskette drive, type
a:\fixboot.exe and answer the prompts.
Note: When you run fixboot.exe on the diskette, the diskette remains bootable
unless you reformat it; if you later erase files on the diskette, you do not
need to run fixboot.exe again.
5. Remove the diskette from the appropriate diskette drive. Label the diskette
appropriately and keep it in a safe place.
You can create additional copies of the diskette using the above procedure for each
new copy.
Note: If you change the backup location or logon settings using the Disaster
Recovery Settings page, you must rebuild the PSM recovery diskette(s) for
that node to reflect the new settings for that node.
Static IP addressing
If you do not have a DHCP server on your network, and you must access a backup
image that is only accessible through the network (for example, no backup image is
located on the maintenance partition [D: drive] of the node to be recovered), then
you must configure the recovery diskette so that it will use a static IP address and
subnet mask when accessing the network.
On the PSM recovery diskette, edit the file a:\net_sets.bat. Set the IPAddress and
SubnetMask environment variables as follows:
1. Uncomment the two lines that begin with rem (comment lines) by removing the
rem from the beginning of both lines.
2. For each line, what follows the equals sign (=) is an IP address expressed as a
set of four space-separated numbers (an IP address without the dots [.]).
Change the SubnetMask value to match the subnet mask your network uses.
Chapter 6. Managing and protecting the network and storage 65
Page 78

Change the IPAddress value to match the IP address you want to assign to the
node, during the recovery operation. Do not insert dots between the numbers
(octets) in either value.
As an example, here is how the lines would look for a node using IP address
192.168.1.200, and subnet mask 255.255.255.0:
set SubnetMask=255 255 255 0
set IPAddress=192 168 1 200
If you later want to reconfigure the recovery diskette to use DHCP to obtain an IP
address instead of static IP addressing, you must reinsert rem in front of the
SubnetMask and IPAddress lines to disable static IP addressing, as follows (based
on the previous example):
REM set SubnetMask=255 255 255 0
REM set IPAddress=192 168 1 200
Specifying multiple 10/100 Ethernet adapters
If the Model 326 has more than one 10/100 Ethernet adapter (per node), then you
must configure the PSM recovery diskette to target the 10/100 Ethernet adapter to
be used for disaster recovery over the network. On the PSM recovery diskette, edit
the file a:\net_sets.bat, and add the following line:
set SLOT=slotvalue
where slotvalue is one of the following, depending on the PCI slot (on the rear of
the node) in which the targeted 10/100 Ethernet adapter is installed:
0x0027 For the integrated Ethernet adapter
0x0001 For PCI slot 1
0x0022 For PCI slot 2
0x0023 For PCI slot 3
0x0044 For PCI slot 4
0x0045 For PCI slot 5
Restoring the system drive using the PSM recovery diskette
To restore the system drive from a backup image created through the PSM Disaster
Recovery panel as described above, you must use a PSM recovery diskette created
through the Disaster Recovery panel. If you did not create a PSM recovery diskette,
you must use the Recovery CD as described in “Chapter 9. Using the Recovery and
Supplementary CDs” on page 123 to restore the system drive to its original (factory)
configuration.
To restore the system drive:
1. Set the write-protection tab of the PSM recovery diskette to the write-protect
position. This prevents accidental initiation of the recovery process (by booting
the node with the PSM recovery diskette in the diskette drive).
2. Insert the PSM recovery diskette in the diskette drive of the node, and restart
the node.
3. The recovery process begins. The PSM recovery diskette software locates the
first backup image it can find, based on the backup locations specified when the
diskette was created. When it locates a backup image, it begins restoring the
system drive from the image. During the restore operation, the hard disk drive
LED (on the front right of the node’s hard disk drive) will flash green or stay
nearly solid green; this indicates write activity to the system volume.
Note: If the hard-disk drive LED stays off for at least 10 minutes since you
restarted the node, then there is a problem with the recovery procedure
66 Model 326 User’s Reference
Page 79

and it will not be able to restore the system volume from a backup
image. Should this occur, you will need to restore the system drive as
described in “Chapter 9. Using the Recovery and Supplementary CDs” on
page 123.
4. When the restore operation completes, the hard disk drive LED turns off, and a
short song will play periodically (every 15 seconds). Remove the diskette, set
the write-protection tab back to the write-enabled position, and reinsert the
diskette. The log file RESULTS.HTM will be written to the diskette; this log file
can be viewed with any Web browser to examine the results of the restore
operation.
5. When the log file is written, another song will play (continuously). Remove the
diskette and restart the node. If the restore was successful, the node will come
back up in the state it was in at the time you created the backup image used for
the recovery operation.
Note: The persistent image that was created on the system drive (named
System Backup) by the backup process is restored by the restore
process as it is preserved in the backup image. It is recommended that
you now delete that persistent image as it is no longer needed. On the
Persistent Images panel, select the persistent image named System
Backup on drive C: from the list of persistent images, then click Delete,
then click OK on the Delete Persistent Image panel that appears.
If the restore was unsuccessful, then you must use the Recovery CD as described
in “Chapter 9. Using the Recovery and Supplementary CDs” on page 123.
Rebuilding the maintenance partition
If this is a new hard drive or if the Maintenance (D:) partition is unusable, you must
rebuild the Maintenance partition by performing the following steps:
1. Start Disk Management on the node. You can do this in one of two ways:
v Start a Terminal Services session to the node, then click the IBM NAS
Admin icon, and then from the IBM NAS Administration console that
appears, select Computer Management, then Disk Management.
v Start a Windows 2000 for NAS user interface session to the node, then select
Disks and Volumes, then select Disks, and then provide your Administrator
user name and password when prompted.
2. In the Disk Management window, right-click the unallocated area of Disk 0, and
then click Create Partition.
3. In the Create Partition wizard, click Next and select Primary Partition.
4. Click Next and select D: as the drive letter.
5. Click Next and select FAT32 as the file system and change the drive label to
Maintenance.
6. Click Finish to close the wizard.
The partition will then be formatted. When formatting is complete, the status of the
partition should appear as Healthy, and the other properties should appear as:
v Name: Maintenance
v Drive letter: D:
v File system: FAT32
Chapter 6. Managing and protecting the network and storage 67
Page 80

Granting user access to persistent image files
You can give end-users access to files in the persistent images. For example, this
would be helpful to a user who has accidentally corrupted a file and needs to get an
uncorrupted copy of that file.
To enable end-user access to persistent image files:
1. Go into Terminal Services.
2. Click the My Computer icon.
3. Select the volume on which you want to enable persistent image access.
4. Go into the persistent images directory and right-click the mouse on the
selected persistent image mount point, select Sharing, then specify sharing as
appropriate. If you want to enable the same access to all persistent images on
the volume, right-click the persistent images directory (from the top level of the
volume), select Sharing, and then specify sharing as appropriate.
Note: The share settings are maintained in a persistent image. Therefore, granting
access to all end-users only permits those users to access files and
directories within the persistent image that they had permission to access
originally on the actual drive.
PSM notes
v You can take and keep a maximum of 250 persistent images at one time. These
can be taken on local drives, or drives on the external storage that are logically
local.
On various panels, such as the New Persistent Image Schedule panel, the Keep
the last: field indicates the number of persistent images. The total number of
persistent images that you enter in these fields does not override the maximum
number of persistent images that you set in the Global Settings panel. For
example, if the maximum number of persistent images is 10, and you enter
numbers in other fields that add up to greater than 10, only 10 persistent images
will be taken.
v You cannot take a persistent image of the maintenance drive (D:). Hence, you
will not see it as a choice in either the New Persistent Image Schedule panel or
the Create Persistent Image panel. Do not take a persistent image of the
clustering Quorum disk. See “Recovering from a corrupted Quorum drive” on
page 50 for information on how to recover from a corrupted Quorum drive.
v PSM stores the cache file for each drive on the drive itself. The first persistent
image created on a particular drive will require a significant amount of time
because the PSM cache file must be created (pre-allocated) for that drive.
The time required for creation depends on the configured size of the cache file
(15 percent of the total drive size by default). Creation takes roughly three to four
minutes per gigabyte. For example, a 10-GB cache file would require 30 to 40
minutes to create. You should create a persistent image for a drive before
scheduling any persistent images for that drive, to build the cache file. You may
then delete the persistent image that you just created if you do not need to keep
it.
After the creation of the first persistent image on a volume, future persistent
images on that volume will complete faster.
v The default size of the cache file per drive is 15 percent of the total drive
capacity.
In most cases, that should be sufficient. However, it is possible that it will not be
enough to maintain the number of persistent images you want to keep
68 Model 326 User’s Reference
Page 81

concurrently on the drive, given the amount of file-write activity to the drive. PSM
automatically takes action to prevent the cache file from overflowing, because if
that occurred, PSM would be forced to automatically delete all persistent images
on the drive (when it cannot keep track of changes made to the drive, it cannot
maintain a valid persistent image).
PSM takes the following actions as the cache file usage approaches a full
condition:
– When the cache file usage exceeds the warning threshold (configured in the
PSM Volumes panel for the drive; the default value is 80 percent), PSM
generates a warning message to the system event log (viewable through the
Windows 2000 Event Viewer in the IBM NAS Admin console), and to the alert
log in the Microsoft Windows 2000 for Network Attached Storage user
interface. The name of the source for the message is psman5. Additionally,
while the cache file usage is above the warning threshold, PSM prohibits any
attempt to create a new persistent image, and logs error messages (to the
system log and alert log). The text of the error message that is logged in the
system event log (from psman5)is“A persistent image could not be created
due to error 0xe000102b”.
– When the cache file usage exceeds the automatic deletion threshold (also
configured in the PSM Volumes panel for the drive; the default value is 90
percent), PSM automatically selects a persistent image on the volume and
deletes it to reduce the cache file usage. It selects the persistent image with
the lowest retention value (as described in “Persistent Images” on page 62). If
more than one persistent image has the same (lowest) retention value, then
the oldest image will be selected for deletion. If this deletion does not reduce
the cache file usage below the automatic deletion threshold, then it will
continue to select and delete persistent images until the cache file usage is
reduced below the automatic deletion threshold. For each deletion, PSM
generates an error message to the system event log and to the Windows
2000 for Network Attached Storage alert log indicating that a persistent image
was deleted.
You should periodically check the system event log or Windows 2000 for Network
Attached Storage alert log to ensure that the cache file usage is not consistently
high, forcing existing persistent images to be deleted and preventing new
persistent images from being created. If the cache file usage is high, you can
increase the size of the cache file using the PSM Volumes page. However,
because dynamic cache file resizing is not supported in this release, you must
delete all persistent images currently on that volume first.
v When a shared volume is failed over from one engine in the Model 326 to the
other engine, the persistent images for that volume move with the volume. The
Persistent Images panel on a particular engine will display only those persistent
images which are on volumes that the engine owns at a point in time. If
persistent images are scheduled for a volume, on a particular engine, a
scheduled persistent image is created only as long as that engine owns the
volume at the time the scheduled persistent image is to occur.
To ensure that a scheduled persistent image will take place regardless of which
engine owns the volume, you must do the following:
1. Use the Schedules panel to create the schedule on the engine that currently
owns the volume.
2. Use the Cluster Administrator to move the disk group that contains the
volume to the other engine. You can only create or edit a schedule for a
volume on the engine that currently owns the volume. If an engine does not
Chapter 6. Managing and protecting the network and storage 69
Page 82

own the volume, you cannot select the volume when creating a new schedule
through the New Persistent Image Schedule panel (under Schedules).
3. Use the Schedules panel on the other engine to create the same schedule
that you created on the original engine, with all of the same parameters (start
time, frequency, number to keep, and so on).
4. Use the Cluster Administrator to move the disk group that contains the
volume back to the original engine.
v Volume restore of the system volume (C: drive) is not supported. If you attempt
to restore a persistent image containing the system volume, the restore operation
will not take place.
v Volume restore of a data volume might require a reboot of the node. You will be
notified by the Restore Persistent Images panel whether a reboot is required
after a restore operation is initiated.
v When you restart the Model 326 (“restart” in this case means that with both
nodes down, the node that was shut down last is restarted first so that it initially
owns all of the shared data volumes), Persistent Storage Manager (PSM) takes
two actions:
1. Loading
2. Mapping
During loading, PSM loads existing persistent images from the cache files on
each of the volumes. The loading time depends on the amount of cache data
there is to read. Cached data is used by PSM to maintain the persistent images,
and the more cache data there is, the longer it takes to load the persistent
images, and thus the longer it might take the Model 326 to become fully
operational after a restart.
During mapping, PSM makes the loaded persistent images accessible through
the file system by mounting each of them as a virtual volume underneath the
persistent images directory on the real volume for which the persistent image
was created. Mapping takes place five minutes after the real volume has been
mounted. The mapping time varies with the number of persistent images, as well
as the size of the volume.
As an example, suppose that on your Model 326, you defined a 1 TB volume
with 50 percent of the volume allocated to the cache (500 GB cache), and that
you had 20 persistent images on the volume, using 100 GB (20 percent) of the
cache (based on the write activity to the volume since the first persistent image
was created). You would observe an increase in the Model 326 startup time of
roughly 3 minutes, 20 seconds over what it would be without any persistent
images on the volume. Then, once the Model 326 has become fully operational,
all 20 persistent images would become accessible within another 18 minutes
(including the five minutes that PSM waits after the volume comes up to begin
the mapping).
When a volume is failed over between nodes, then PSM must perform persistent
image loading and mapping on the node to which the volume is moving, just as it
does when the “first node” is restarted.
In the failover scenario, loading must take place before the volume can be
brought online on the node (when the clustered disk resource is shown as being
Online in Cluster Administrator). Then, as in the restart case, mapping begins five
minutes after the volume comes online.
70 Model 326 User’s Reference
Page 83

Microsoft Cluster Server, which controls the disk resource failover, waits a certain
period, called the pending timeout, for the disk to come online. (During the
loading phase, the disk resource is shown as being in Online Pending state.)
With a default value of 180 seconds (3 minutes) for the pending timeout, this
time interval might be exceeded because of the time it takes to load the
persistent images on the volume. If this occurs, the delay might cause Cluster
Server to mark the disk as Failed and to not be available to either Model 326
node. Other dependent resources (IP addresses, network names, file shares, and
so on) might also fail.
For this reason, it is recommended that you increase the pending timeout value
for all clustered resources to 1200 seconds (20 minutes). To do this, open
Cluster Administrator, select Resources from the left pane to display all clustered
resources in the right pane, and then for each resource listed in the right pane:
1. Right-click the resource name and select Properties.
2. Select the Advanced tab.
3. Change the Pending timeout value to 1200 (seconds).
4. Click Apply, then click OK.
v PSM imposes a limit of 1 terabyte (TB) of cached data, across all volumes on the
Model 326. For this reason, you should ensure that the total configured size of all
cache files on the Model 326 is not greater than 1 TB.
You can do this by accessing Persistent Storage Manager, then going to the
Volume Settings page, and making sure that the total of all values in the Cache
Size column is 1 TB or less. (You can access Persistent Storage Manager
through the Persistent Storage Manager link on the IBM NAS Admin console on
the Model 326 desktop, or by starting the Windows 2000 for Network Attached
Storage user interface and then selecting Disks, then Persistent Storage
Manager.)
If the total is greater than 1 TB, you should reduce the size of the cache on one
or more of the volumes by selecting the volume from the list, then clicking
Configure, then selecting a smaller value from the “Cache size” drop-down list
and clicking OK.
Note: You cannot change the size of the cache on a volume that has persistent
images. You must delete all persistent images on the volume before
changing the cache size. You should try to reduce the cache size on a
volume that has no persistent images, if possible, before deleting any
persistent images.
If more than 1 TB of cache is configured on the Model 326, the following can
occur (note that a volume for which a persistent image has never been created is
considered to have a cache size of zero, regardless of how large its cache is
configured to be):
– When the Model 326 is restarted, PSM prevents a volume from being
mounted on the file system (prevents it from being accessible) if that volume’s
PSM cache would increase the total size of all cache files (on all volumes
mounted to that point) above 1 TB, and an error message is written to the
system event log. The event source is psman5, and the text of the error
message is:
There is insufficient memory available.
– When a volume is failed over between nodes, then PSM running on the “new”
node will behave as it would if the volume were being mounted during a
restart: if that volume’s PSM cache would increase the total size of all cache
files on that node above 1 TB, then PSM blocks the mount and writes the
Chapter 6. Managing and protecting the network and storage 71
Page 84

“insufficient memory available” error message to the system event log. (This
will also cause the failover to fail, which means that either the volume will try
to come online on the “original” node if it is up, or just simply fail to come
online at all.)
– If you increase the size of any cache such that the total cache size of all
volumes on the Model 326 becomes greater than 1 TB, and if you do not
restart the Model 326 after you change the cache size, then no persistent
images can be created on the volume for which the cache size increase was
made. An attempt to create a persistent image on that volume will cause an
error message to be written to the system event log. The event source is
psman5, and the text of the error message is:
There is insufficient memory available.
v If you delete the last persistent image on a volume, and then immediately
attempt to create a new persistent image on that volume, the creation of the new
persistent image might fail, and an error message will be written to the system
event log.
The event source is psman5, and the text of the error message is:
A persistent image could not be created due to error 0xc0000043.
This message is generated because when PSM is reinitializing the PSM cache
file on a particular volume (after you delete the last persistent image on that
volume), a new persistent image cannot be created. If this error occurs, wait for a
few minutes, and then try to create the persistent image again.
v If you use the Windows Powered Disk Defragmenter to attempt to defragment a
volume containing persistent images, the volume will not be defragmented. If you
select the volume and click the Defragment button, the Disk Defragmenter will
run on the volume and then indicate that the volume was successfully
defragmented. However, the Analysis display will appear the same as it did
before you clicked Defragment, which indicates that defragmentation did not
take place. You can defragment volumes without persistent images.
Attention: The recovery process invalidates persistent images and leaves them in
an inconsistent state. So, if you plan to use the Recovery CD, it is recommended
that you first delete all persistent images to ensure a clean reload of the system
software. For more information on using the Recovery CD, see “Chapter 9. Using
the Recovery and Supplementary CDs” on page 123.
Microsoft Services for UNIX and NFS Support
Support for the Network File System (NFS) is provided in the Model 326 by a
preloaded and preconfigured software component, Microsoft Services for UNIX. The
levels of NFS supported by Services for UNIX, and in turn the Model 326, are NFS
Versions 2 and 3. Any client workstation that supports NFS Version 2 or NFS
Version 3, regardless of the operating system, should be able to connect to the
Model 326 and access its storage as defined by the Model 326 administrator.
To administer NFS file shares and other attributes, use standard Windows
administration tools, including those provided as part of the IBM NAS desktop, and
the Microsoft Windows 2000 for NAS user interface. To support NFS security, you
must perform additional configuration of the User Name Mapping component of
Services for UNIX, which maps the UNIX user name space to the Windows user
name space.
72 Model 326 User’s Reference
Page 85

Consult the online documentation for Services for UNIX for more information on
configuring User Name Mapping. To view the online documentation for Services for
UNIX on the Model 326 (either node can be used):
1. From the Model 326 desktop, click the IBM NAS Admin icon.
2. On the left pane of the IBM NAS Admin console, expand File Systems.
3. Expand Services for UNIX.
4. Select any of the items that appear under Services for UNIX.
5. Click anywhere on the right pane of the IBM NAS Admin console, then press
the F1 key to bring up the online documentation for Services for UNIX in a
separate window.
Configuring Server for NFS
This section describes how to configure Server for NFS.
Services for UNIX is installed on every IBM NAS machine. Additional installation is
required only when the NAS is installed into a Windows domain. If the NAS is
installed as part of a Windows 2000 domain, you must install the Server for NFS
Authentication module on the domain controllers. This module is on the
Supplementary CD.
User and group identification
You can enumerate UNIX users and groups by using one of two methods: get the
data from an NIS server, or from local copies of the UNIX passwd and group files. If
you use an NIS server, no special preparation is necessary. If local files are used,
you must copy them to the NAS machine and possibly modify their format for use
by the User Name Mapping function, as described in “Preparing local copies of
passwd and group”.
Preparing local copies of passwd and group: If you will be using an NIS server,
go to “Creating Windows users and groups” on page 74. If you are using local files
instead of NIS, you must import these files to the NAS and prepare them as follows.
Obtain copies of the UNIX passwd and group files. Copy them into directories on
the NAS machine as:
c:\winnt\system32\drivers\etc\passwd
and
c:\winnt\system32\drivers\etc\group
Next, delete all special users and groups, leaving just the actual users and groups
that will be used in accessing files. An example of a special user is root, usually,
and UID numbers from 0 to 99 are generally reserved for system accounts and
should not be mapped.
Services for UNIX supports a limited syntax in the passwd file. In particular, it
seems to work best when the second field of each line — the password field — is
filled in with a random 13-character string. This need not have anything to do with
the user’s password, so a string such as 0123456789012 is acceptable. Some
UNIX systems use shadow passwords and fill in this field with a meaningless token
value such as x or !, and you will need to change this.
Finally, if this is a clustered NAS, copy these finished files to the same location on
the other node. Both nodes must have the same files for the system to failover
properly.
Chapter 6. Managing and protecting the network and storage 73
Page 86

Creating Windows users and groups
Using the IBM NAS Admin, under the Users and Groups folder, create Windows
accounts corresponding to the UNIX accounts. Note that a potential problem at this
point is the practice in some UNIX systems of defining a UNIX group for each UNIX
user using the same name as the user’s name. Windows does not allow the
creation of groups with the same name as users.
To map these groups, it is necessary to adopt a naming convention to apply to all
these group names. So for a user named alpha, you might have a group named
g_alpha on the NAS that corresponds to the group alpha in UNIX. The naming
convention must be selected so as not to conflict with any existing user or group
names. Introducing a naming convention creates the need for an advanced map in
User Name Mapping, as described in “User Name Mapping”.
For best results, it is necessary to replicate the UNIX group membership among the
mapped users and groups on the NAS by adding the mapped users to the mapped
groups. You can add Windows users to Windows groups using the IBM NAS Admin
Users and Groups folder.
User Name Mapping
Note: This section supplements other information on User Name Mapping in this
book.
Decide where the User Name Mapping server will run. If the NAS is a single-node
product, the server runs on the NAS. For a clustered NAS, User Name Mapping
clustering is recommended, so User Name Mapping can run on both nodes and
failover as needed.
When you have decided where the User Name Mapping server will run, complete
the following steps.
Note that you will need to click the Apply button to effect changes to the settings.
1. Specify the enumeration source.
In the IBM NAS Admin, follow this path, Services for UNIX → User Name
Mapping → Configuration. Then click Network Information Service (NIS) if
you will use an NIS server, or specify where the local files reside.
User Name Mapping rereads its enumeration source on a schedule. By default,
this occurs once a day. You can reset the refresh period. To force User Name
Mapping to reread the enumeration source, you can click Synchronize Now on
the Configuration panel.
Note: If maps do not seem to synchronize, you might need to stop and restart
User Name Mapping. You can do this through the GUI, or by the
commands:
net stop mapsvc
net start mapsvc
2. Define maps.
Simple maps provide automated mapping between UNIX and Windows users
(and groups) with the same names. This is recommended. You can enable
simple maps by following this path User Name Mapping → Maps and clicking
Simple Maps.
To create advanced maps for users and groups, on the Maps panel, click Show
User Maps or Show Group Maps and then fill in the appropriate fields.
74 Model 326 User’s Reference
Page 87

Enabling Server for NFS
To enable Server for NFS, you need to specify where User Name Mapping is
running.
To specify where User Name Mapping is running, follow this path, Services for
UNIX → User Name Mapping, and then enter the server name that is running User
Name Mapping in the Computer Name field. For a cluster, this entry must be the
clustered name or IP address, not that of an individual node.
When planning an NFS installation, consider which machines you want to have
particular access-levels to NFS shares. Each class of access should be captured by
defining a separate client group.
v To define a client group, click Services for UNIX → Client Groups, enter the
group name in the Group Name field, then click New.
v To add members to a client group, select a group name from the current groups
list, then click Advanced and enter the name of a client (a valid computer name).
v A note on anonymous access: It is strongly recommended that you not disable
anonymous access. If a client presents a UID that is not recognized, Server for
NFS can still grant that client a very limited form of access as a special nobody
user. This is known as anonymous access, and you can enable or disable on a
per-share basis. This anonymous user will have very limited access to resources
on the NAS: it has only the permissions that are granted to the Everybody group
in Windows, which corresponds to the other (or world) bits in a POSIX
permissions mode.
Allowing anonymous access is not a security risk, so disabling it might provide a
false sense of security. (The real security risk is to grant everyone access to
resources that should be protected.) And disabling anonymous access has one
severe consequence: it is so unexpected by NFS clients that they may not be
able to connect as NFS V3 clients at all, and may instead downgrade the
connection to use the NFS V2 protocol.
Antivirus protection
You can perform antivirus scanning of Model 326 storage from clients having the
appropriate access permissions. Also, you can install Norton AntiVirus Version 7.5
or later on the Model 326 engine using standard Windows 2000 software installation
procedures.
Depending on configuration options, antivirus scanning might use substantial CPU
or disk resources. Therefore, you should carefully select the scanning options and
schedule.
Chapter 6. Managing and protecting the network and storage 75
Page 88

76 Model 326 User’s Reference
Page 89

Chapter 7. Managing adapters and controllers
This chapter describes the functions that you can use to manage various adapters
and controllers installed in the Model 326.
The following functions are available:
v “Managing Fibre Channel host bus adapters”, accessed through the IBM NAS
Admin
v “Enabling communication between system management adapters” on page 78
v “Enabling Ethernet adapter teaming” on page 81
v “Adding a second IBM 5191 RAID Storage Controller Model 0RU” on page 83
Managing Fibre Channel host bus adapters
The FAStT MSJ diagnostic utility allows you to manage and control Fibre Channel
host bus adapters. With FAStT MSJ, you can:
v Retrieve and display general information about the adapters
v Request and display the real-time statistics of adapters
v Diagnose operations on the adapters and attached devices
v Display the NVRAM parameters of adapters (note that you cannot change the
parameters)
v Monitor alarms and indications of the adapters
The primary purpose of FAStT MSJ in the Model 326 is to obtain diagnostic
information about the Fibre Channel connections.
To use FAStT MSJ:
1. Start FAStT MSJ by double-clicking the IBM NAS Admin icon.
2. Under the NAS Management icon, double-click Storage, then NAS Utilities.
3. Select FAStT MSJ.
4. Once the FAStT MSJ opens:
v If you are connected locally with a monitor, keyboard, and mouse, select
localhost, then click Connect.
v If you are connected through Terminal Services, enter the host name or IP
address of the machine you are connected to through Terminal Services, then
click Connect.
For further details on FAStT MSJ, see the online help.
“Appendix F. Fast!UTIL options” on page 171 provides detailed configuration
information for advanced users who want to customize the configuration of the
FAStT Host Adapter board and the connected devices, using Fast!UTIL to make
changes.
© Copyright IBM Corp. 2002 77
Page 90

Enabling communication between system management adapters
The two types of system management adapters are2:
v The Integrated System Management Processor (ISMP) integrated on the planar
board of each engine of the Model 326
Provides basic operational status about key engine components, such as its
processors, power supplies, fans, and so on.
v An optional Remote Supervisor Adapter (RSA) that can connect to up to twelve
of the ISMPs
Allows you to connect through a LAN or modem from virtually anywhere for
extensive remote management. The RSA works in conjunction with the ISMP of
the Model 326 and an interconnect cable that connects multiple engines to the
ISMP. Remote connectivity and flexibility with LAN capability is provided by
Ethernet connection. Along with ANSI terminal, Telnet, and IBM Director, the RSA
enables more flexible management through a Web browser interface.
To use either adapter, and for more information, see “Using the ISMP and RSA” on
page 80.
Table 6 on page 79 provides a summary of the features of the ISMP and the RSA.
The light-path diagnostics LED status that is available through the ISMP includes:
v Power-supply failure
v Insufficient power for power-supply redundancy
v Exceeded power-supply capabilities
v Non-maskable interrupt occurred
v Over heating
v Fan failure
v Memory error
v Microprocessor failure
v PCI-bus error
v VRM failure
v Planar SCSI failure for system disk or internal tape drive (if any)
Remote status includes information on power supply voltages, voltage-regulator
module (VRM) readings, temperatures of system components, system power status,
power-on hours, fan status, and system state.
2. A third might be referred to in some of the documentation that came with your system, but that adapter is not used in the Model
326.
78 Model 326 User’s Reference
Page 91

Table 6. ISMP compared to the RSA
Feature ISMP RSA
Location On planar board Separate PCI adapter option
Light-path diagnostics Remotely reports on Remotely reports on
LED status of engine Remotely reports on Remotely reports on
LED status of HDD in
No No
engine
Remote update of
Yes Yes
system BIOS
Remote update of ISMP
No Yes
BIOS
Immediate remote power
Yes Yes
on/off
Controlled remote power
No Yes
on/off using the OS
Remote POST (including
No Yes
all POST message ids)
Remote access to
No Yes
engine vital product data
(VPD) and serial number
Multiple login IDs No Yes
TELNET interface overIPNo Yes (through a LAN
connection)
Web-browser interface
No Yes
over IP
Forwarding of SNMP
traps
Yes, to the RSA Yes (through a LAN
connection)
Automated server restart Yes Yes
Remote Alerts No Yes
Configuration By DOS utility By DOS utility/serial ports
Aggregate from other
No Yes
ISMP processors
Chapter 7. Managing adapters and controllers 79
Page 92

Enabling ISMP to RSA communication on a single machine
You must follow one of two methods to enable communication between the ISMP
and the RSA on a single machine:
v Using a single ISMP interconnect cable (with dual RJ-11 plugs):
1. Connect one end of the internal ISMP interconnect cable to the J-54
connector on the system board.
2. Connect the other end (the RJ-11 socket) of the internal ISMP interconnect
cable to the knockout slot on the back panel of the machine until it locks into
place.
3. Connect one connector on the ISMP interconnect cable to the RJ-11 socket
you just installed on the back panel (in step 2).
4. Connect the other connector to the RJ-11 socket on the RSA.
v Using two ISMP interconnect cables (each with a single RJ-11 plug):
1. Connect one end of the internal ISMP interconnect cable to the J-54
connector on the system board.
2. Connect the other end (with the RJ-11 socket) of the internal ISMP
interconnect cable to the knockout slot on the back panel of the machine until
it locks into place.
3. Connect the first ISMP interconnect cable to the RJ-11 socket that you just
installed on the back panel (in step 2).
4. Connect the second ISMP interconnect cable to the RJ-11 socket on the
RSA.
5. Connect the two ISMP interconnect cables with a single Category 5 Ethernet
cable (by plugging one end of the Ethernet cable into the “black box” on the
first ISMP interconnect cable, and the other end into the “black box” on the
second ISMP interconnect cable).
Using the ISMP and RSA
The documentation CD that came with your system contains additional information
and software for the ISMP and the RSA. To use the ISMP, complete the following
steps:
1. Consult the ISMP user’s manual and the README file that is located on the
documentation CD for additional information.
2. Run the executable to create a bootable floppy disk. The executable is located
in:
C:\IBM\ASMP\UPDATES\32P0303.EXE
3. Boot each node of the Model 326 with the bootable floppy disk to configure the
ISMP.
To use the RSA, complete the following steps:
1. Consult the RSA user’s manual and the README file that is located on the
documentation CD.
2. Run the executable to create a bootable floppy disk. The executable is located
in:
C:\IBM\ASMP\UPDATES\33P2474.EXE
3. Boot each node of the Model 326 with floppy disk created in the previous step
to configure the RSA.
80 Model 326 User’s Reference
Page 93

Enabling Ethernet adapter teaming
This section describes how to enable adapter teaming on the Ethernet adapters.
Intel adapters
The Intel Ethernet adapters (Gigabit Ethernet SX and 10/100 Ethernet) that you
install in the PCI slots of the Model 326 nodes support adapter teaming. The 10/100
adapter can also team with the integrated onboard 10/100 Intel Ethernet controller
on the engine. With adapter teaming, two or more PCI Ethernet adapters can be
physically connected to the same IP subnetwork and then logically combined into
an adapter team. Such a team can support one of the following functional modes:
Adapter Fault Tolerance (AFT)
Only one adapter in the team is fully active on the Ethernet network (for
example, sending and receiving data) at any point in time, while the other
adapters are in standby mode (receiving data only). If that adapter detects
a link failure or fails completely, another adapter in the team automatically
and rapidly takes over as the active adapter, and all Ethernet traffic being
handled by the failing adapter is seamlessly switched to the new active
adapter, with no interruption to network sessions (for example, file transfers)
in progress at the time of the failover.
Adapter Load Balancing (ALB)
All adapters in the team are active, increasing the total transmission
throughput over the common IP subnetwork. If any adapter in the team fails
(link failure or complete failure), the other adapters in the team continue to
share the network transmission load, although total throughput is
decreased. Load balancing is only supported for adapter teams consisting
of only one type of adapter; different types of adapters cannot be combined
in a load-balancing team.
Fast Etherchannel (FEC)
FEC is a proprietary technology developed by Cisco. With FEC, you can
create a team of two to four ports on an adapter to increase transmission
and reception throughput. The FEC might also be referred to as load
balancing, port aggregation, or trunking. When you configure this feature,
the adapter ports comprising the FEC team or group create a single
high-speed, fault-tolerant link between the engine and the Ethernet switch
sharing one IP address. With FEC, fault tolerance and load balancing is
provided for both outbound and inbound traffic, unlike other load-balancing
schemes that only balance outbound traffic.
Note: FEC requires an Ethernet switch with FEC capability. The FEC
implementation on the 4-port 10/100 Ethernet adapter does not
support the optional Port Aggregation Protocol (PAgP) feature of
FEC-capable Ethernet switches.
802.3ad
802.3ad is an IEEE industry-standard similar to Cisco’s FEC/Gigabit
Etherchannel (GEC). 802.3ad requires an Ethernet switch with 802.3ad
capability.
Note: It is strongly recommended that you configure adapter teaming before you
set up Microsoft Cluster Server (MSCS) clustering, as described in
“Chapter 5. Completing networking, clustering, and storage access setup” on
page 37
Chapter 7. Managing adapters and controllers 81
Page 94

page 37. Additionally, for each team you configure on one node, you must
configure an identical team (same type of team, same set of adapters, and
so on) on the other node.
To configure adapter teaming, use Intel PROSet II, which is preloaded on the Model
326, as follows:
1. Physically connect the adapters that you want to team to the same IP
subnetwork.
2. Access the Model 326 desktop by directly attaching a keyboard, mouse, and
monitor, or over the network by starting Terminal Services on another
workstation (see “Terminal Services and the IBM NAS Administration Console”
on page 12).
3. From the Model 326 desktop, go to the Start menu, then select Settings, then
select Control Panel.
4. Double-click the Intel PROSet II icon in the Control Panel to start Intel PROSet
II. You will see a list of all adapters for each slot and type supported under
Network Components.
5. Under Network Components, you will see a list of resident and non-resident
adapters for each slot and type supported. Drivers are preset for all supported
adapter configurations but will be loaded only for resident adapters.
6. Identify which adapters you are going to team. Left-click the adapter under
Network Components, and select one of the adapters that will be part of the
teaming.
7. Right click the adapter, select Add to Team, then select Create New Team....
8. Select the type of team to create.
9. Select the adapters to add to the team from the list, and then select Next.
10. Verify that these settings are correct, and then select Finish.
11. Perform Steps 1 through 10 for the other node.
This procedure creates a device named Intel Advanced Network Services Virtual
Adapter. It also binds all network protocols that were bound to the physical adapters
that were added to the team to this virtual adapter, and unbinds those protocols
from the physical adapters. If you delete the team, the settings will return to the
state prior to creating the team.
For complete help on adapter teaming, from Intel PROSet II, click Network
Components, and then select Help from the Help menu.
Note: The integrated Ethernet controller on each Model 326 node is dedicated to
the clustering interconnection between it and another node and cannot be
used for teaming.
Alacritech 10/100 Quad-Port Ethernet adapter
The Quad-Port 10/100 Ethernet adapter supports FEC and 802.3ad across the four
ports on the adapter.
To configure it:
1. Click on Control Panel.
2. Select Network and Dial-Up.
3. Select Adapter.
4. Select Properties.
82 Model 326 User’s Reference
Page 95

5. Select Alacritech SLIC Team Configurator.
6. Select New Team.
PRO/1000 XT Server adapter
This adapter supports several teaming functions that you can configure using the
PROSet configuration utility. This adapter can also team with the integrated onboard
10/100 Intel Ethernet controller on the engine. Specific teaming modes supported
across multiple instances of this adapter are AFT, ALB, FEC/GEC, and 802.3ad.
Adding a second IBM 5191 RAID Storage Controller Model 0RU
This section gives details to follow when you have added a second RAID controller
and need to add a new logical drive or create an array in the unconfigured storage.
Attention: Before proceeding with these steps, note the special considerations
described in “Powering off and powering on the Model 326” on page 49.
To add a second IBM 5191 RAID Storage Controller Model 0RU, you must
power-off one node, and restart the other node. It is recommended that you do the
following procedure during non-peak operation hours.
1. Install the RAID storage controller:
a. Attach a keyboard, monitor, and mouse to the node you will power-down
first.
b. Mount the RAID storage controller into a rack.
c. Attach fibre-channel cables and power cables.
d. Power-down the node (see “Powering off and powering on the Model 326”
on page 49). Make sure that you note which node you power-down in this
step.
e. Power-on the unit. Wait for all drive lights to become solid green.
f. Restart the node (see “Powering off and powering on the Model 326” on
page 49).
g. On the node that is powered on, go into Storage Manager 7, right-click the
host name and select Rescan.
h. Once the node finds the device, it appears under the host name along with
the existing unit.
i. Right-click the new device and select Manage.
j. Create the new array(s) and logical drive(s) (see “Creating arrays and logical
drives” on page 32). Do not restart the node until all the arrays have finished
initializing.
k. After the array(s) have finished initializing, restart the node.
l. The node will install the new devices, and then you must start Disk
Management.
m. Create the logical partitions, format, assign drive letters and label disk(s). To
do this, use the procedure described in “Formatting the logical drives” on
page 35.
n. Power down the node, and continue with Step 2.
2. On the other node:
a. Power on the other node. It will find new devices.
b. Restart the system.
c. Upon restart, start Disk Management.
Chapter 7. Managing adapters and controllers 83
Page 96

RAID mirroring
d. Assign drive letters to the newly found disks and partitions, making sure the
drive letters match those on the other node.
e. Start the Cluster Administrator.
f. Create a new disk group under the cluster name.
g. On the new disk group name, right-click and select New → Resource.
h. Enter the Disk and the drive letter to assign to this disk group; for example,
Disk M:.
i. For the Resource Type, select Physical Disk and click Next.
j. Make sure that both nodes are selected as possible owners and click Next.
k. Under Parameters, use the drop-down menu to select the new disk drive
you want to manage using the Cluster Server and select Finish.
l. Bring the resource online.
3. Perform Steps 2f through 2l for any additional disk drives, placing new disks into
new disk groups.
4. Power-on the first node and wait for resources to come online. You can then
create additional resources, dependencies, and failover policies.
The Model 326 hardware has a RAID-1 mirroring option using the IBM ServeRAID
4Lx adapter. The System and Maintenance partitions are mirrored using two 18 GB
hard drives to provide increased reliability and failover capability. This RAID option
has a stripe size of 8K.
Memory notes
The following sections contain information on adding memory.
Adding more engine memory to increase performance
You can enhance the performance of the Model 326 in an NFS environment by
adding more RAM to its processor. To do this:
1. Purchase two 512M memory DIMMs for each of the two engines as a field
upgrade by ordering 5187-5RZ Feature Code 0007 from your IBM
representative.
2. Follow the instructions in Chapter 3, section “Replacing memory modules,” of
the Installation Guide.
3. Before rebooting the appliance, attach a keyboard and display directly to the
rear connectors of the product. During the first IPL, you will have to read and
answer questions about the additional memory you have installed.
Using the Recovery CD-ROM if you have added more processor memory
If you have installed more processor memory, and later use the Recovery CD-ROM
(see “Chapter 9. Using the Recovery and Supplementary CDs” on page 123), you
will have to attach a keyboard and display and answer questions about the
additional memory that you have installed.
84 Model 326 User’s Reference
Page 97

Chapter 8. Troubleshooting
This chapter provides basic troubleshooting information to help you resolve some
common problems that might occur with the Model 326 components. These
components are:
v IBM 5187 Network Attached Storage Model 6RZ (engine) (see “IBM 5187
Network Attached Storage Model 6RZ”)
v IBM Ethernet and Fibre Channel network adapters (see “Adapter troubleshooting
and diagnostics” on page 96)
v IBM 3534 Fibre Channel Hub Model 1RU (hub) (see “IBM 3534 Fibre Channel
Hub Model 1RU” on page 111)
v IBM 5191 RAID Storage Controller Model 0RU (storage controller) (see “IBM
5191 RAID Storage Controller Model 0RU (storage controller)” on page 113)
v IBM 5192 Storage Unit Model 0RU (storage unit) (see “IBM 5192 Storage Unit
Model 0RU (storage unit)” on page 118)
If you cannot locate and correct the problem using the information in this section,
refer to “Appendix B. Getting help, service, and information” on page 129 for more
information.
For the latest troubleshooting guidance, symptom fixes, and tips, go to the IBM
support Web site at:
www.ibm.com/storage/support/nas
This site contains additional information, gathered from field experience, not
available when this document was developed.
IBM 5187 Network Attached Storage Model 6RZ
This section gives troubleshooting information for the IBM 5187 Network Attached
Storage Model 6RZ (engine).
Note: The information in this section must be applied to both engines in the Model
326. As an example, when the text reads, “The engine has light-emitting
diodes (LEDs) to help you identify problems,” this means that each engine in
the Model 326 has LEDs which require your attention.
As another example, the information contained in “Engine troubleshooting
charts” on page 89 applies to each of the two engines.
Engine diagnostic tools overview
The following tools are available to help you identify and resolve hardware-related
problems:
Note: If you need to remove the engines for inspection, do so one at a time:
remove an engine, inspect it, and put it back; then remove the other engine,
inspect it, and put it back.
v POST beep codes, error messages, and error logs
The power-on self-test (POST) generates beep codes and messages to indicate
successful test completion or the detection of a problem.
© Copyright IBM Corp. 2002 85
Page 98

POST error messages and descriptions are given in “Appendix D. Engine POST
and diagnostic program messages” on page 135.
v Diagnostic programs and error messages
The diagnostic programs are stored in upgradable read-only memory (ROM) on
the system board. These programs are the primary method of testing the major
components of the Model 326 engine. See “Diagnostic program messages” on
page 145 for more information.
v Light-path diagnostics
The engine has light-emitting diodes (LEDs) on its system board to help you
identify problems. These LEDs are part of the light-path diagnostics that are built
into the Model 326 engine. By following the path of lights, you can quickly identify
the type of system error that occurred. See “Light-path diagnostics” on page 88
for more information.
v Networking adapter diagnostic tools
– Intel PROSet II
See “Testing the Ethernet adapters with Intel PROSet II” on page 99.
– FAStT MSJ
See “Testing the Fibre Channel host adapter with FAStT MSJ” on page 108
v Troubleshooting charts
These charts list problem symptoms, along with suggested steps to correct the
problems. See “Engine troubleshooting charts” on page 89 for more information.
v Support
You can register with the following support site to subscribe to e-mail notification
of new technical tips and frequently asked questions, obtain downloads, and join
forum discussions:
www.ibm.com/storage/support/nas
Identifying problems using LEDs
The LEDs are part of the light-path diagnostics built into the Model 326 engine. The
LEDs help you identify the type of system error that occurred. See the following
sections for more information.
Power supply LEDs
The AC and DC power LEDs on the power supply provide status information about
the power supply.
Table 7 on page 87 describes the AC and DC power LEDs.
Note: The minimum configuration required for the DC good light to come on is:
v Power supply
v Power backplane
v System board (with pins 2 and 3 on J23 extension cable connected
together to bypass the power switch).
86 Model 326 User’s Reference
Page 99

Table 7. Power supply LEDs
AC Good
LED
Off Off No power to system
On Off Standby mode or DC
DC Good
LED
Description FRU/action
or AC problem.
problem.
1. Check AC power to system.
2. Power supply
1. Check system board cable
2. Remove the adapters and
3. Power supply
4. Power backplane
5. System board
On On Power is OK. N/A
connectors J32, J33, and J35.
Move jumper on J32’s extension
cable to pins 2-3 to bypass
power control. If the DC Good
LED comes on, press
Ctrl+Alt+Delete. Watch the
screen for any POST errors.
Check the System Event/Error
Log for any listed problems. If
the system powers up with no
errors:
a. Power switch assembly
b. System board
disconnect the cables and power
connectors to all internal and
external devices. Power-on the
system. If the DC Good LED
comes on, replace the adapters
and devices one at a time until
you isolate the problem.
Chapter 8. Troubleshooting 87
Page 100

Light-path diagnostics
You can use the light-path diagnostics built into the Model 326 engine to identify the
type of system error that occurred. Any LEDs that are illuminated remain illuminated
during a shutdown as long as the AC power source is good and the power supplies
can supply +5V DC current to the Model 326 engine. This feature helps you isolate
the problem, if an error causes the Model 326 engine to shut down. See “Light-path
diagnostics”.
Diagnostics panel
You can use the light path diagnostics to quickly identify the type of system error
that occurred. The diagnostics panel is under the “wind tunnel”. Any LEDs that are
On remain On when the Model 326 engine shuts down as long as the AC power
source is stable and the power supplies can provide +5V DC current. This feature
helps isolate the problem if an error causes the Model 326 engine to shut down.
Figure 2 shows the LEDs on the diagnostics panel on the system board. You must
remove the top cover to view the LEDs.
See “Light-path diagnostics” for information on identifying problems using these
LEDs.
MEM
PS1
CPU
PS2
PCI A
PS3
PCI B
NON
PCI C
OVER
VRM
NMI
DASD
TEMP
SP
FAN
REMIND
Figure 2. Diagnostics panel LEDs
Light-path diagnostics
Table 8 on page 89 describes the light-path diagnostics LEDs. The system error
LED is turned on when an error is detected. If the system error LED (an amber “!”
on the lower right corner) is on, remove the cover and check the diagnostic panel
LEDs. Table 8 on page 89 is valid only when the system error LED is on.
Notes:
1. If a diagnostic panel LED is on and the information LED panel system error LED
is off, there is probably an LED problem. Run LED diagnostics.
2. Check the System Error Log for additional information before replacing a FRU.
3. The DIMM error LEDs, processor error LEDs, and VRM error LEDs turn off
when the system is powered off.
88 Model 326 User’s Reference
 Loading...
Loading...