Huawei EG860, EG860-D61, EG860-C71 User Manual

EG860
V200R003C00
User Guide
Issue
Date 2015-04-10
HUAWEI TECHNOLOGIES CO., LTD.
02

Copyright © Huawei Technologies Co., Ltd. 2015. All rights reserved.
No part of this document may be reproduced or transmitted in any form or by any means without prior written
consent of Huawei Technologies Co., Ltd.
Trademarks and Permissions
and other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd.
All other trademarks and trade names mentioned in this document are the property of their respective holders.
Notice
The purchased products, services and features are stipulated by the contract made between Huawei and the
customer. All or part of the products, services and features described in this document may not be within the
purchase scope or the usage scope. Unless otherwise specified in the contract, all statements, information,
and recommendations in this document are provided "AS IS" without warranties, guarantees or representations
of any kind, either express or implied.
The information in this document is subject to change without notice. Every effort has been made in the
preparation of this document to ensure accuracy of the contents, but all statements, information, and
recommendations in this document do not constitute a warranty of any kind, express or implied.
Huawei Technologies Co., Ltd.
Address: Huawei Industrial Base
Bantian, Longgang
Shenzhen 518129
People's Republic of China
Website: http://www.huawei.com
Email: support@huawei.com
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
i
EG860
User Guide
Introduction
This document describes hardware, functions, networking, installation, configurations, and
operation and maintenance (O&M) information of an EG860.
Product Version
About This Document
About This Document
This document (guide) is intended for EG860 in the following models:
Product Name Product Version
EG860-C71 V200R003C00
EG860-D61
Intended Audience
This document is intended for:
l System engineers
l Product engineers
Organization
1 Change History
Updates between document issues are cumulative. Therefore, the latest document issue contains
all updates made in previous issues.
2 Introduction
This section describes functions, networking, and technical specifications of an EG860.
3 Hardware
This section describes hardware components and cables of an EG860.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
ii

EG860
User Guide
About This Document
4 Installation
This chapter describes how to install an EG860.
5 Configuration
Data configuration for EG860 can be performed by using WebUI or by auto-configuration.
6 Maintenance
This chapter describes how to maintain an EG860.
7 Reference
This chapter describes how to use the Web network management system (NMS).
8 Alarm Reference
This chapter describes possible alarms related to EG860, and how to handle them.
9 Glossary
This table provides the related glossary for reference.
Conventions
Symbol Conventions
The symbols that may be found in this document are defined as follows.
Symbol Description
Indicates an imminently hazardous situation which, if not
avoided, will result in death or serious injury.
Indicates a potentially hazardous situation which, if not
avoided, could result in death or serious injury.
Indicates a potentially hazardous situation which, if not
avoided, may result in minor or moderate injury.
Indicates a potentially hazardous situation which, if not
avoided, could result in equipment damage, data loss,
performance deterioration, or unanticipated results.
NOTICE is used to address practices not related to personal
injury.
Calls attention to important information, best practices and
tips.
NOTE is used to address information not related to personal
injury, equipment damage, and environment deterioration.
General Conventions
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
iii

EG860
User Guide
About This Document
The general conventions that may be found in this document are defined as follows.
Convention Description
Times New Roman Normal paragraphs are in Times New Roman.
Boldface Names of files, directories, folders, and users are in
boldface. For example, log in as user root.
Italic Book titles are in italics.
Courier New
Examples of information displayed on the screen are in
Courier New.
Command Conventions
The command conventions that may be found in this document are defined as follows.
Convention Description
Boldface The keywords of a command line are in boldface.
Italic Command arguments are in italics.
[ ] Items (keywords or arguments) in brackets [ ] are optional.
{ x | y | ... } Optional items are grouped in braces and separated by
vertical bars. One item is selected.
[ x | y | ... ] Optional items are grouped in brackets and separated by
vertical bars. One item is selected or no item is selected.
{ x | y | ... }
*
Optional items are grouped in braces and separated by
vertical bars. A minimum of one item or a maximum of all
items can be selected.
[ x | y | ... ]
*
Optional items are grouped in brackets and separated by
vertical bars. Several items or no item can be selected.
GUI Conventions
The GUI conventions that may be found in this document are defined as follows.
Convention Description
Boldface Buttons, menus, parameters, tabs, window, and dialog titles
are in boldface. For example, click OK.
> Multi-level menus are in boldface and separated by the ">"
signs. For example, choose File > Create > Folder.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
iv
EG860
User Guide About This Document
Keyboard Operations
The keyboard operations that may be found in this document are defined as follows.
Format Description
Key Press the key. For example, press Enter and press Tab.
Key 1+Key 2 Press the keys concurrently. For example, pressing Ctrl+Alt
+A means the three keys should be pressed concurrently.
Key 1, Key 2 Press the keys in turn. For example, pressing Alt, A means
the two keys should be pressed in turn.
Mouse Operations
The mouse operations that may be found in this document are defined as follows.
Action Description
Click Select and release the primary mouse button without moving
the pointer.
Double-click Press the primary mouse button twice continuously and
quickly without moving the pointer.
Drag Press and hold the primary mouse button and move the
pointer to a certain position.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
v

EG860
User Guide
Contents
Contents
About This Document.....................................................................................................................ii
1 Change History..............................................................................................................................1
2 Introduction....................................................................................................................................5
2.1 Product Functions...........................................................................................................................................................6
2.2 Network Networking......................................................................................................................................................6
2.3 Technical Specifications.................................................................................................................................................8
2.4 Product Security...........................................................................................................................................................14
2.4.1 Network Security.......................................................................................................................................................14
2.4.2 Application Security..................................................................................................................................................15
2.4.2.1 Wireless Security....................................................................................................................................................15
2.4.2.2 OM Security...........................................................................................................................................................15
2.4.2.2.1 User Authentication and Access Control.............................................................................................................15
2.4.2.2.2 OM System Security............................................................................................................................................16
2.4.2.2.3 Digital Signature of Software..............................................................................................................................17
2.5 Certification Information..............................................................................................................................................18
3 Hardware.......................................................................................................................................19
3.1 EG860 Hardware..........................................................................................................................................................20
3.1.1 Appearance................................................................................................................................................................20
3.1.2 Front Panel.................................................................................................................................................................20
3.1.3 Indicators...................................................................................................................................................................22
3.1.4 Ports...........................................................................................................................................................................23
3.2 EG860 Cables...............................................................................................................................................................23
3.2.1 PoE Cable..................................................................................................................................................................23
3.2.2 Power Cable...............................................................................................................................................................25
3.2.3 PGND Cable..............................................................................................................................................................26
4 Installation....................................................................................................................................28
4.1 Site Preparations...........................................................................................................................................................29
4.2 Installation Preparations...............................................................................................................................................30
4.3 Installation Procedure...................................................................................................................................................32
4.3.1 Mounting an EG860 on a Pole..................................................................................................................................32
4.3.1.1 Mounting EG860 Equipment on a Pole..................................................................................................................34
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
vi

EG860
User Guide
4.3.1.2 Connecting Cables to an EG860 Mounted on a Pole.............................................................................................39
4.3.2 Mounting an EG860 on a Wall..................................................................................................................................47
4.3.2.1 Mounting EG860 Equipment on a Wall.................................................................................................................48
4.3.2.2 Connecting Cables to an EG860 Mounted on a Wall.............................................................................................52
4.4 Checking Installation....................................................................................................................................................61
Contents
5 Configuration...............................................................................................................................64
5.1 Onsite Configuration (WebUI).....................................................................................................................................65
5.1.1 Log in to the WebUI..................................................................................................................................................65
5.1.2 Configuring Basic Data.............................................................................................................................................65
5.1.3 Configuring Transmission Data.................................................................................................................................66
5.1.4 Configuring Dedicates Bearers..................................................................................................................................73
5.2 Remote Configuration (Auto-configuration) ...............................................................................................................73
6 Maintenance.................................................................................................................................76
6.1 Preparations for Site Maintenance................................................................................................................................77
6.2 Powering on/off an EG860...........................................................................................................................................77
7 Reference.......................................................................................................................................79
7.1 Status............................................................................................................................................................................80
7.1.1 Internet.......................................................................................................................................................................80
7.1.2 LAN...........................................................................................................................................................................80
7.1.3 WLAN.......................................................................................................................................................................81
7.2 General Settings............................................................................................................................................................82
7.2.1 SIM Card Settings.....................................................................................................................................................82
7.2.2 Internet Settings.........................................................................................................................................................82
7.2.3 DHCP Settings...........................................................................................................................................................84
7.2.4 WLAN Settings.........................................................................................................................................................85
7.2.5 WLAN Multi-SSID...................................................................................................................................................85
7.2.6 WLAN Access Restrictions.......................................................................................................................................86
7.2.7 Internet MTU.............................................................................................................................................................87
7.2.8 Routing......................................................................................................................................................................87
7.2.9 Dedicated Context.....................................................................................................................................................88
7.2.10 IGMP Management.................................................................................................................................................89
7.2.11 L2TP Settings..........................................................................................................................................................90
7.2.12 FTP Settings............................................................................................................................................................90
7.2.13 Security access Settings...........................................................................................................................................91
7.3 Security Settings...........................................................................................................................................................91
7.3.1 Firewall General........................................................................................................................................................91
7.3.2 MAC Filtering...........................................................................................................................................................92
7.3.3 IP Filtering.................................................................................................................................................................93
7.4 NAT Settings................................................................................................................................................................94
7.5 QoS Management.........................................................................................................................................................95
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
vii

EG860
User Guide Contents
7.6 VPN..............................................................................................................................................................................96
7.7 System..........................................................................................................................................................................98
7.7.1 Device Information....................................................................................................................................................98
7.7.2 Reset..........................................................................................................................................................................98
7.7.3 Backup & Recovery...................................................................................................................................................98
7.7.4 Upgrade.....................................................................................................................................................................99
7.7.5 Password Change.......................................................................................................................................................99
7.7.6 Password Complexity..............................................................................................................................................100
7.7.7 Password security Settings......................................................................................................................................101
7.7.8 Date & Time............................................................................................................................................................101
7.7.9 Diagnosis.................................................................................................................................................................101
7.7.10 Log.........................................................................................................................................................................103
7.7.11 Device Switch........................................................................................................................................................103
7.7.12 Bandinfo Number Configuration...........................................................................................................................104
7.7.13 Work Frequency....................................................................................................................................................104
7.7.14 SIM Configuration.................................................................................................................................................105
7.7.15 Alarm Configuration..............................................................................................................................................105
7.8 Logout.........................................................................................................................................................................107
8 Alarm Reference........................................................................................................................108
8.1 ALM-50001 Lan state................................................................................................................................................109
8.2 ALM-50002 High Temperature..................................................................................................................................110
8.3 ALM 50003-RadioSignal Weak.................................................................................................................................111
9 Glossary.......................................................................................................................................113
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
viii
EG860
User Guide
02 (2015-04-10)
1 Change History
1 Change History
Updates between document issues are cumulative. Therefore, the latest document issue contains
all updates made in previous issues.
01 (2015-03-24)
This is the second release of the V200R003C00 version.
Compared with issue V200R003C00 01, the documentation does not contain any new
information.
Compared with issue V200R003C00 01, the documentation includes the following changes:
Topic Change Description
l 5.1.3 Configuring Transmission Data
l 7.2.2 Internet Settings
Compared with issue V200R003C00 01, the documentation does not delete any information.
This is the first release of the V200R003C00 version.
Compared with issue V200R003C00 Draft C, the documentation does not contain any new
information.
Compared with issue V200R003C00 Draft C, the documentation includes the following changes:
Modified the displayed information for
enabling Routing Behind MS.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1
EG860
User Guide
1 Change History
Topic Change Description
l 2.3 Technical Specifications
l 3.1.3 Indicators
l 4.3.1 Mounting an EG860 on a Pole
l 5.2 Remote Configuration (Auto-
configuration)
l 7.2.3 DHCP Settings
l 7.2.10 IGMP Management
l 7.7.10 Log
l 7.7.15 Alarm Configuration
Compared with issue V200R003C00 Draft C, the documentation deletes the following
information.
Reference > General Settings > WLAN WPS
Draft C (2014-12-01)
This is the Draft C release of the V200R003C00 version.
Optimized the content.
Compared with issue V200R003C00 Draft B, the documentation does not contain any new
information.
Compared with issue V200R003C00 Draft B, the documentation includes the following changes:
Topic Change Description
l 4.2 Installation Preparations
l 4.3.1 Mounting an EG860 on a Pole
l 5.1.1 Log in to the WebUI
l 7.2.4 WLAN Settings
l 7.7.9 Diagnosis
l 7.7.11 Device Switch
Compared with issue V200R003C00 Draft B, the documentation does not delete any
information.
Draft B (2014-11-11)
Optimized the content.
This is the Draft B release of the V200R003C00 version.
Compared with issue V200R003C00 Draft A, the documentation does not contain any new
information.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
2
EG860
User Guide 1 Change History
Compared with issue V200R003C00 Draft A, the documentation includes the following
changes:
Topic Change Description
l 3.2.1 PoE Cable
l 5.1.1 Log in to the WebUI
l 5.2 Remote Configuration (Auto-
configuration)
l 7.2.12 FTP Settings
l 7.2.13 Security access Settings
Compared with issue V200R003C00 Draft A, the documentation does not delete any
information.
Draft A (2014-10-30)
This is the Draft A release of the V200R003C00 version.
Compared with issue V200R002C00 05, the documentation includes the following new
information:
l 2.4 Product Security
l 7.2.12 FTP Settings
Optimized the content.
l 7.2.13 Security access Settings
l 7.2.11 L2TP Settings
l 7.5 QoS Management
l 7.6 VPN
l 7.7.6 Password Complexity
l 7.7.7 Password security Settings
l 7.7.13 Work Frequency
Compared with issue V200R002C00 05, the documentation includes the following changes:
Topic Change Description
2.1 Product Functions Modified the main function of EG860.
2.3 Technical Specifications Modified the technical specifications of
EG860.
5.1.1 Log in to the WebUI Modified the default password of WebUI.
5.1.3 Configuring Transmission Data Added the configuration steps for L2TP.
7.2.1 SIM Card Settings Modified the steps for setting SIM card.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
3
EG860
User Guide 1 Change History
Topic Change Description
7.7.9 Diagnosis Deleted the Tmsi information query. Added
the configuration of WAN ICMP function.
7.7.11 Device Switch Added the configuration of Antenna status
parameter.
7.7.14 SIM Configuration Deleted the default value of PLMN.
l 5.2 Remote Configuration (Auto-
Optimized the content.
configuration)
l 7.1.1 Internet
l 7.1.2 LAN
l 7.1.3 WLAN
l 7.2.2 Internet Settings
l 7.2.3 DHCP Settings
l 7.2.4 WLAN Settings
l 7.2.5 WLAN Multi-SSID
l 7.2.7 Internet MTU
l 7.7.5 Password Change
Compared with issue V200R002C00 05, the documentation deletes the following information.
Reference>FTP Management
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
4

EG860
User Guide 2 Introduction
2 Introduction
About This Chapter
This section describes functions, networking, and technical specifications of an EG860.
2.1 Product Functions
An EG860, as a data service device on the Internet of Things (IoT), is used in a long term
evolution (LTE) network to upload or download user data. It provides data service (in route
mode), security service (firewall/NAT), and equipment maintenance and management. NAT is
short for Network Address Translation.
2.2 Network Networking
An EG860 is a wireless broadband access terminal that serves as a major device in a wireless
Internet of Things (IoT) data private network. It can be installed indoors or outdoors.
2.3 Technical Specifications
The technical specifications of an EG860 cover mechanical, power, surge protection,
performance, antenna, and environment specifications.
2.4 Product Security
EG860 security includes network security and application security. Application security includes
wireless security and OM security.
2.5 Certification Information
This section describes the certification that EG860 has passed.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
5

EG860
User Guide
2.1 Product Functions
An EG860, as a data service device on the Internet of Things (IoT), is used in a long term
evolution (LTE) network to upload or download user data. It provides data service (in route
mode), security service (firewall/NAT), and equipment maintenance and management. NAT is
short for Network Address Translation.
Background Information
A wireless data private network is an important part of IoT infrastructures. The wireless data
private network is based on the wired government private network and requires base stations
and access fibers as supplements. It provides secure and reliable channels for transmitting,
converging, processing, and distributing sensor messages of various IoT applications. The
wireless data private network uses unified standards for receiving sensor messages and is capable
of identity authentication and secure transmission to meet the requirements for operating security
and emergency management of a metro IoT.
2 Introduction
Functions
IoT is about to introduce a new wave in the information industry following computers, Internet,
and mobile communications.
A wireless data private network has the following attractions:
l Provides a unified, secure, omnipresent, and standard channel for transmitting sensor
messages applicable to service and emergency management of a city.
l Avoids repeated construction of sensor networks.
l Reduces the cost of constructing IoT applications, fully utilizes limited frequency
resources, and ensures information security.
An EG860 provides the following functions:
l Software management: bandwidth, software upgrading, wireless backhaul, dual tunnels,
virtual SIM card, physical SIM card, multicast, static routing, routing behind MS, L2TP
tunnel, QoS, data service encryption, and status management.
l Configuration management: auto-configurable commissioning and configuration
management. The NMS manages an EG860 using the TR069 protocol, including
configuration delivery from the NMS to an EG860, software upgrade, status and
performance monitoring, log collection, alarm management, and health check.
l O&M: web-based local maintenance and performance statistics.
l Fault management: alarm, connectivity diagnosis, and log management.
2.2 Network Networking
An EG860 is a wireless broadband access terminal that serves as a major device in a wireless
Internet of Things (IoT) data private network. It can be installed indoors or outdoors.
A government private network is a wired MAN that runs over existing optical cables and
SDH or MSTP networks at the physical layer and adopts MPLS VPN architecture at the IP
layer, to isolate different types of services that coexist over the same network.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
6
EG860
User Guide 2 Introduction
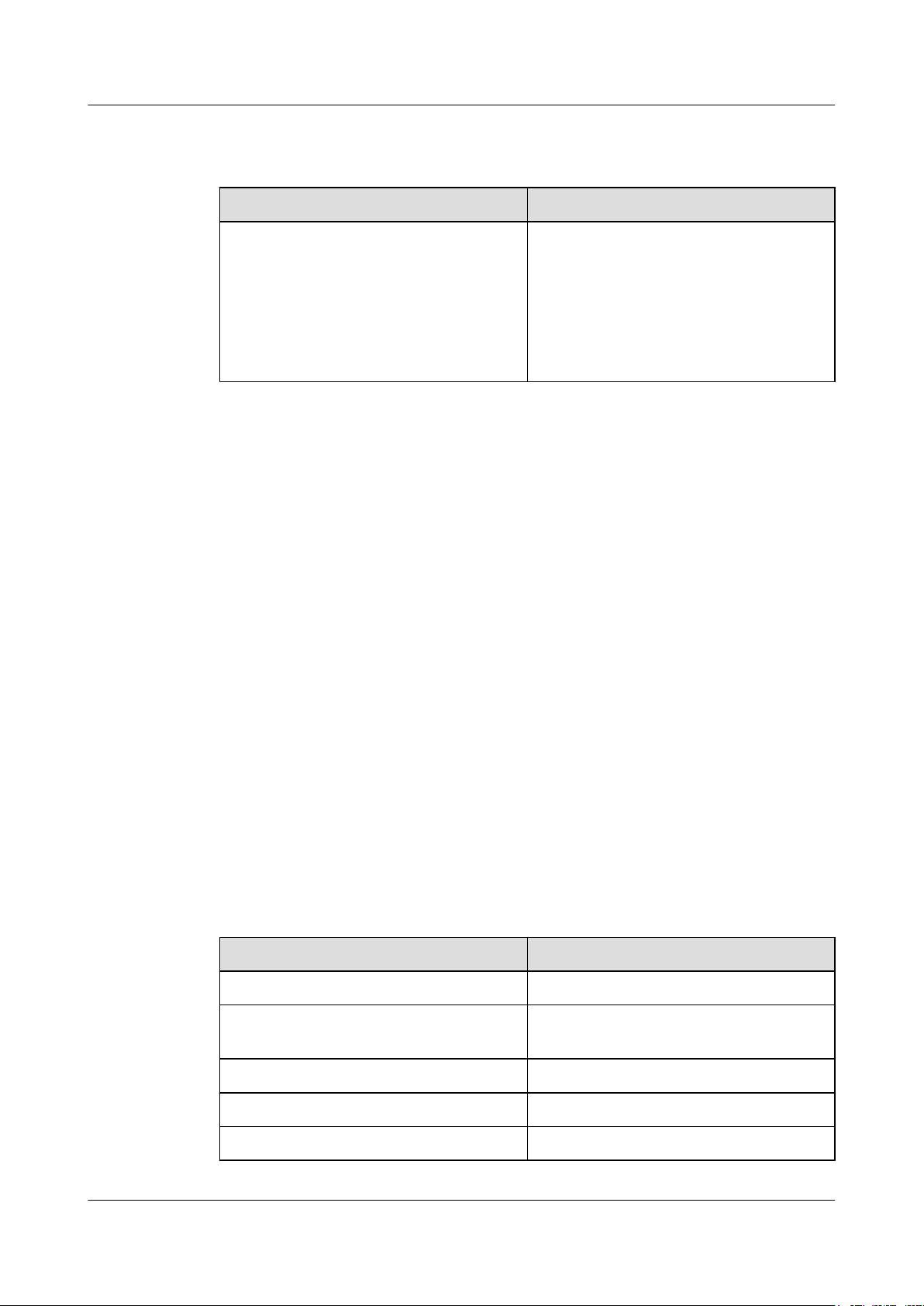
A government private network covers agencies, offices, and business units regardless of size
within a municipality. The integrated network is shown as Figure 2-1.
Figure 2-1 A government integrated network
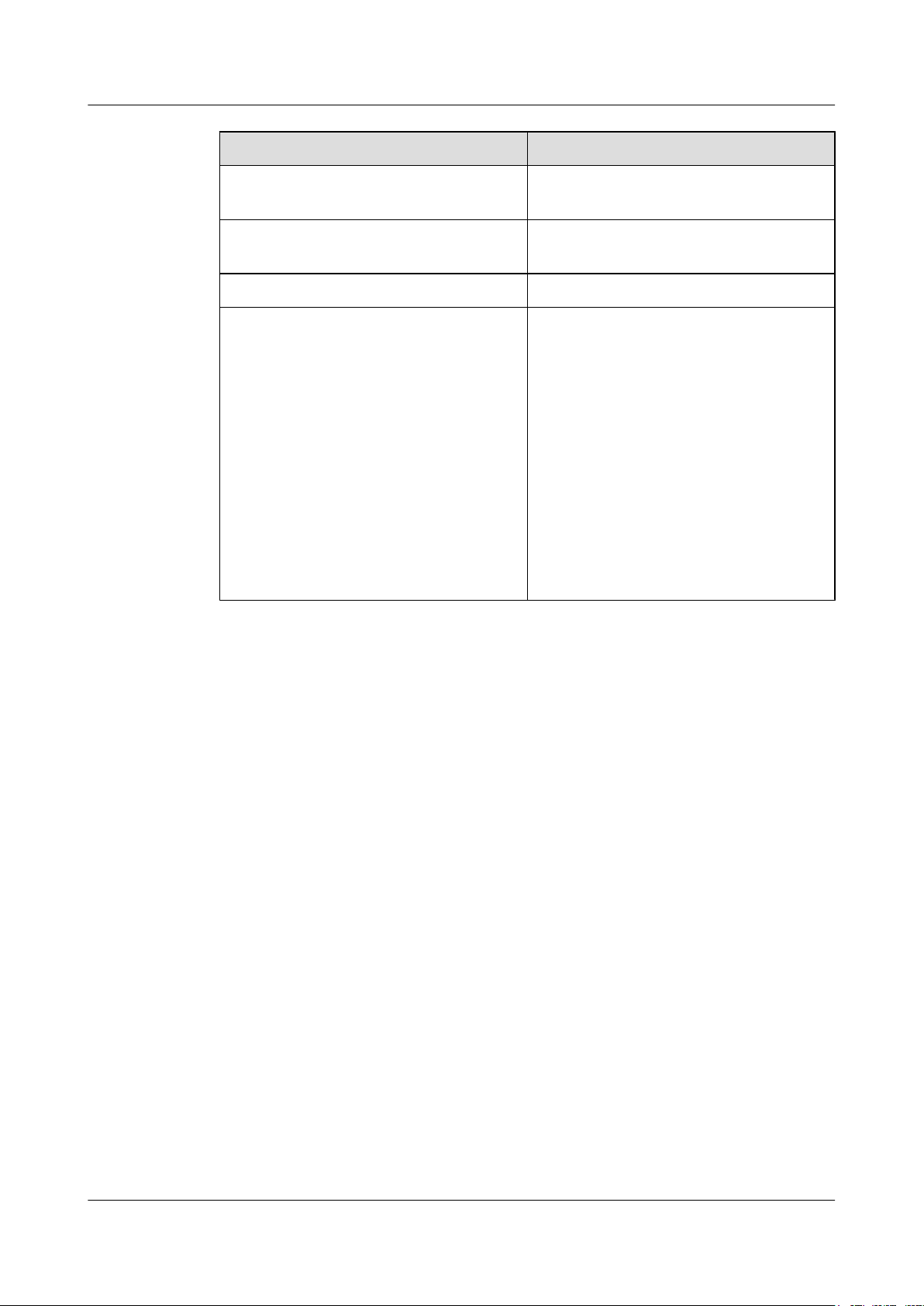
The networking of wireless networks is shown as Figure 2-2.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
7
EG860
User Guide
2 Introduction
Figure 2-2 The networking of wireless networks
An EG860 operates on an LTE network. Data from a sensor travels through a FE port of the
EG860 and, after being encapsulated to IPv4 packets by the EG860, is transferred to backend
servers.
NOTE
Personal information will be anonymized to protect user privacy.
2.3 Technical Specifications
The technical specifications of an EG860 cover mechanical, power, surge protection,
performance, antenna, and environment specifications.
Mechanical specifications
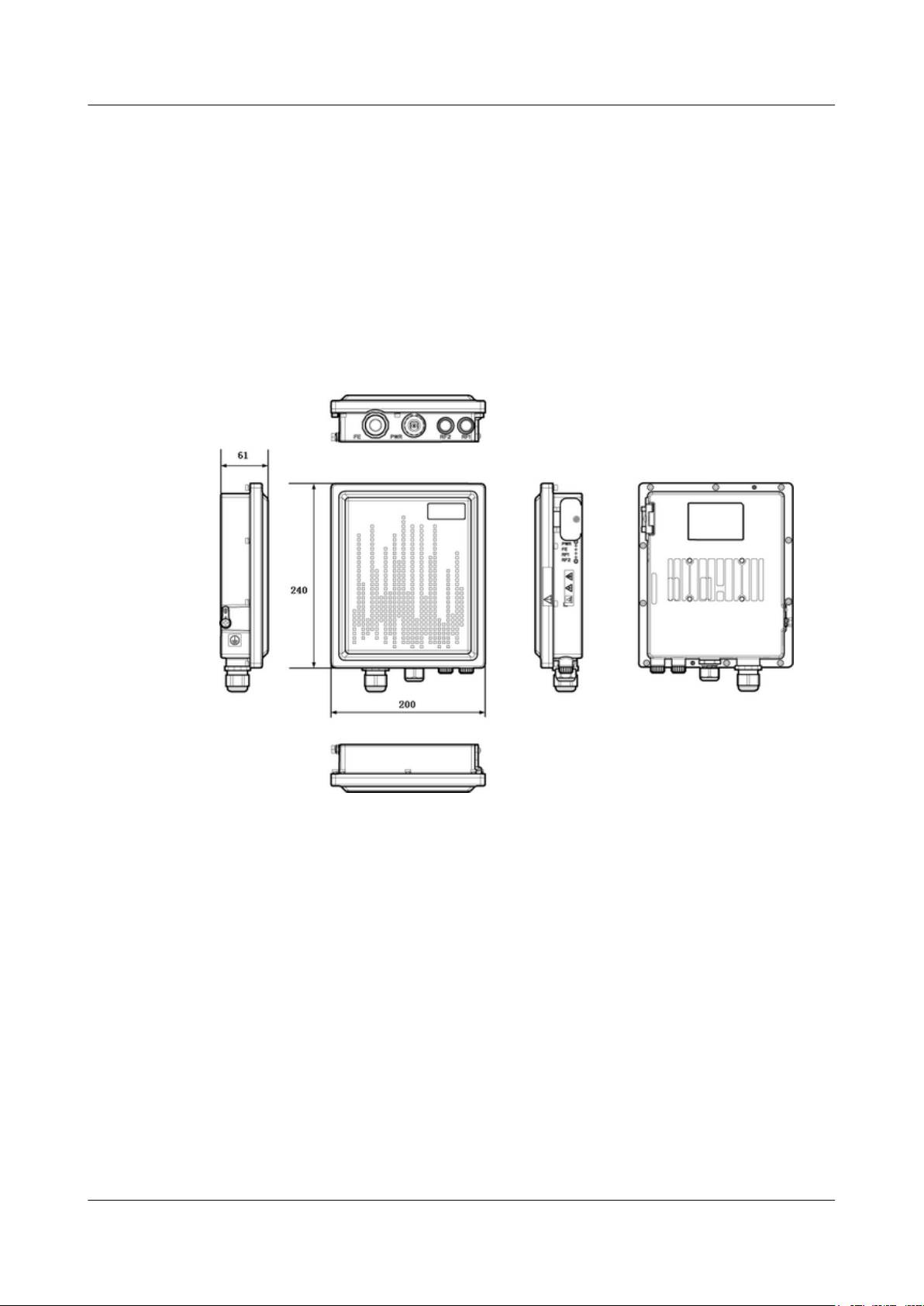
Table 2-1 lists the mechanical specifications of an EG860.
Table 2-1 Mechanical specifications
Dimension Weight
240 mm (H) x 200 mm (W) x 61 mm (D)
≤ 2 kg
Electrical specifications
Table 2-2 lists the electrical specifications of an EG860.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
8
EG860
User Guide 2 Introduction
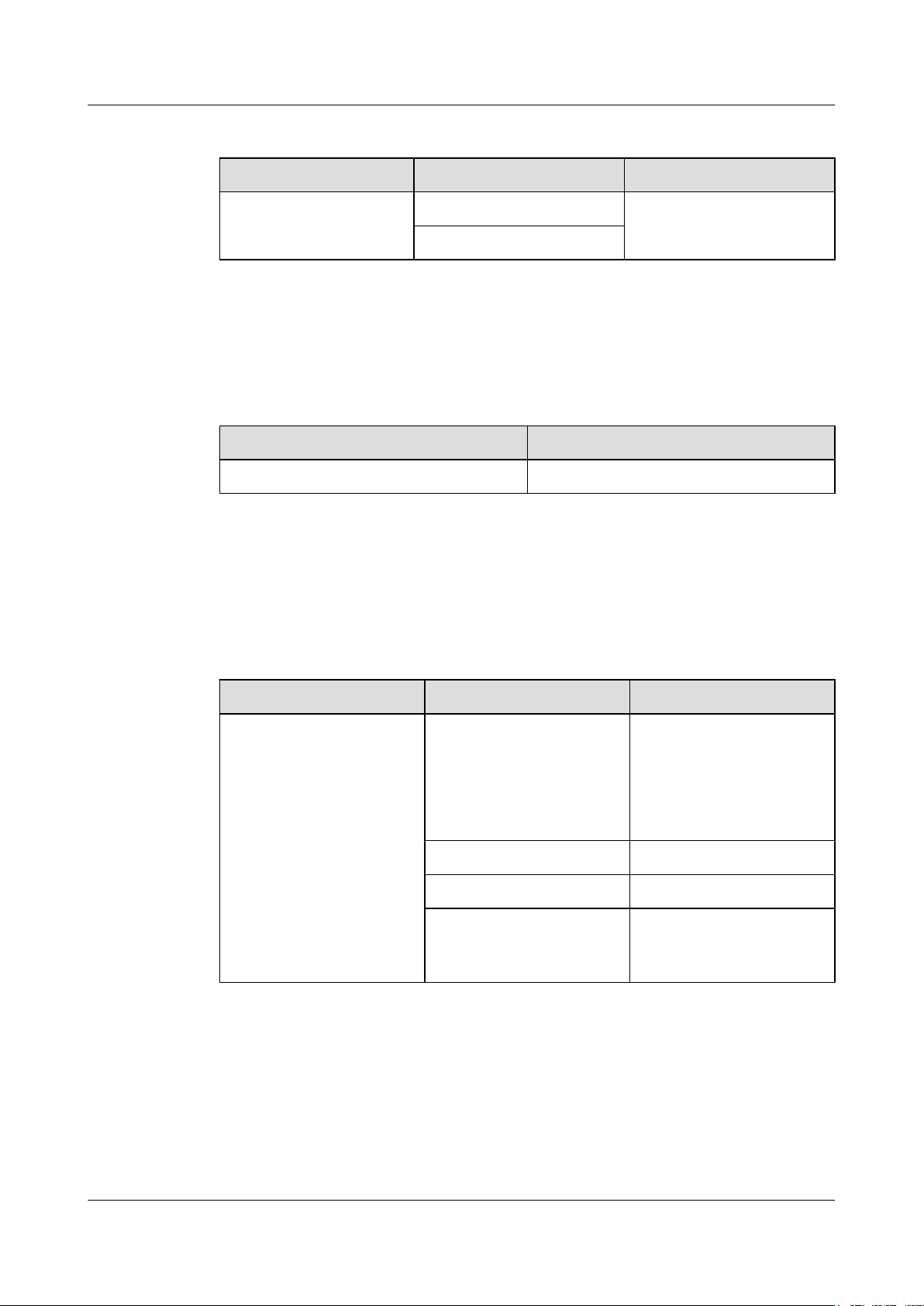
Table 2-2 Electrical specifications of an EG860
Equipment Rated voltage Power
EG860 24 V DC (PWR) Maximum power
-48 V DC (POE)
consumption: 30 W
Surge Protection Specifications
Table 2-3 lists the surge protection specifications of the EG860.
Table 2-3 Surge protection specifications
Port Surge Protection Specifications
Power and signal ports 1,000 V
Specifications
Table 2-4 and Table 2-5 list the radio frequency (RF) specifications of an EG860-C71 and
EG860-D61 respectively.
Table 2-4 RF specifications of EG860-C71
Mode Item Description
LTE Frequency 1447 MHz-1467 MHz
1785 MHz-1805 MHz
832 MHz-862 MHz (uplink)/
791 MHz-821 MHz
(downlink)
Carrier configuration 5 MHz/10 MHz/20 MHz
Maximum transmit power 23 dBm±2 dBm
Output frequency spectrum
template and stray
specifications
3GPP TS 36.101-compliant
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
9

EG860
User Guide 2 Introduction
Mode Item Description
Receiver sensitivity
l 1.8G and 1.4G
– -92dBm/20MHz
– -95dBm/10MHz
– -98dBm/5MHz
l 800M
– -88dBm/20MHz
– -92dBm/10MHz
– -95dBm/5MHz
Blocking 3GPP TS 36.101-compliant
Wi-Fi Working mode IEEE 802.11b/g/n: 2.4 GHz
Output power IEEE 802.11b: <16dBm
IEEE 802.11g: <15dBm
IEEE 802.11n: <13dBm
Receiver sensitivity
IEEE 802.11b: ≤-76
dBm@11Mbps
IEEE 802.11g: ≤-65
dBm@54Mbps
IEEE 802.11n: ≤-75
dBm@54Mbps
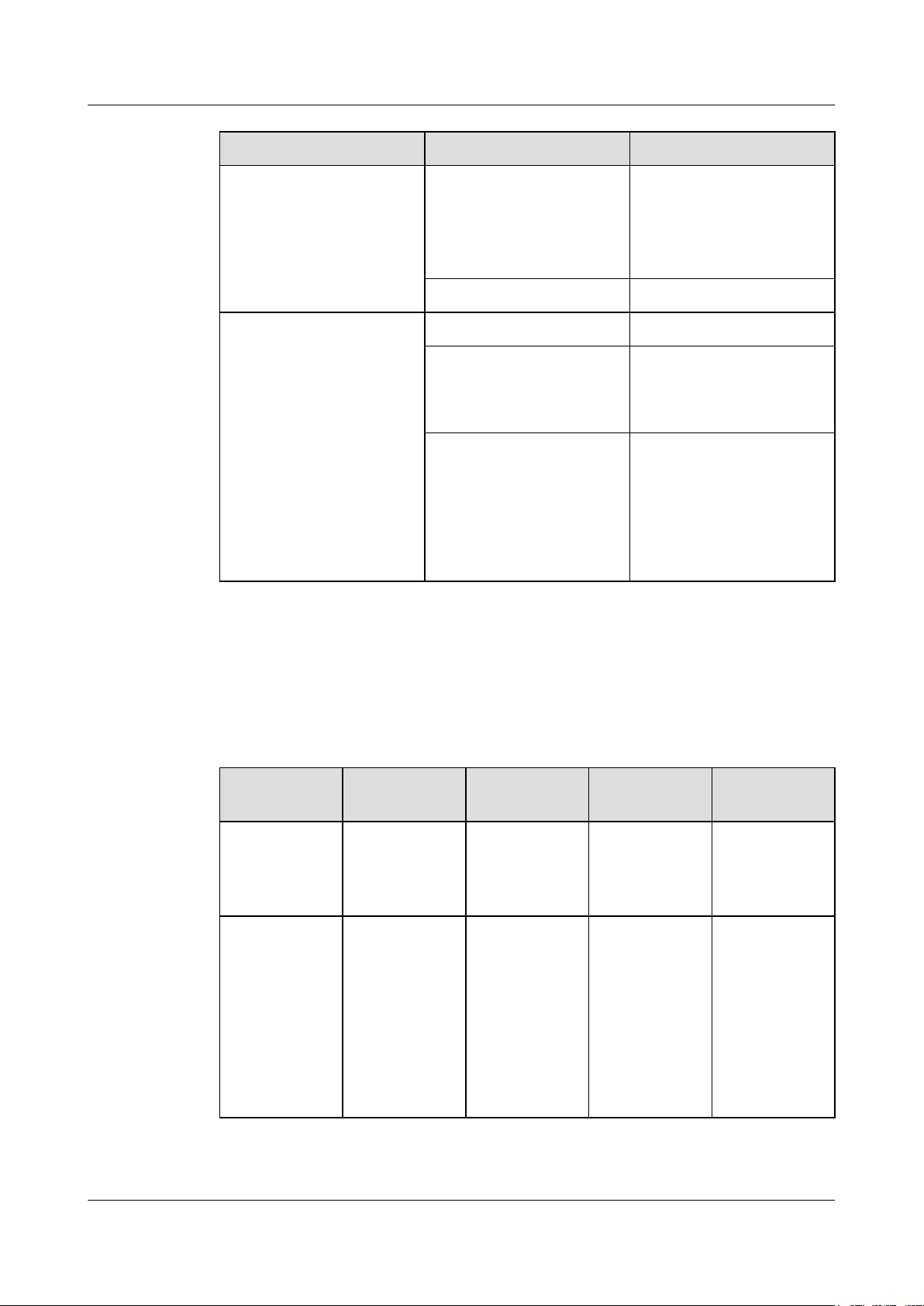
Table 2-5 RF specifications of EG860-D61
Mode Item Description
TD-LTE Frequency 380MHz~450MHz
Carrier configuration In the fixed topology: 3MHz/
5MHz/10MHz/20MHz
In the vehicle-mounted
communications system:
5MHz/10MHz/20MHz
Maximum transmit power 25 dBm±2 dBm
Output frequency spectrum
3GPP TS 36.101-compliant
template and stray
specifications
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
10
EG860
User Guide 2 Introduction
Mode Item Description
Receiver sensitivity -92dBm/20MHz
-95dBm/10MHz
-98dBm/5MHz
-100.2dBm/3MHz
Blocking 3GPP TS 36.101-compliant
Wi-Fi Working mode IEEE 802.11b/g/n: 2.4 GHz
Output power IEEE 802.11b: <16dBm
IEEE 802.11g: <15dBm
IEEE 802.11n: <13dBm
Antenna Specifications
Table 2-6 and Table 2-7 list the antenna specifications of an EG860-C71 and EG860-D61
respectively.
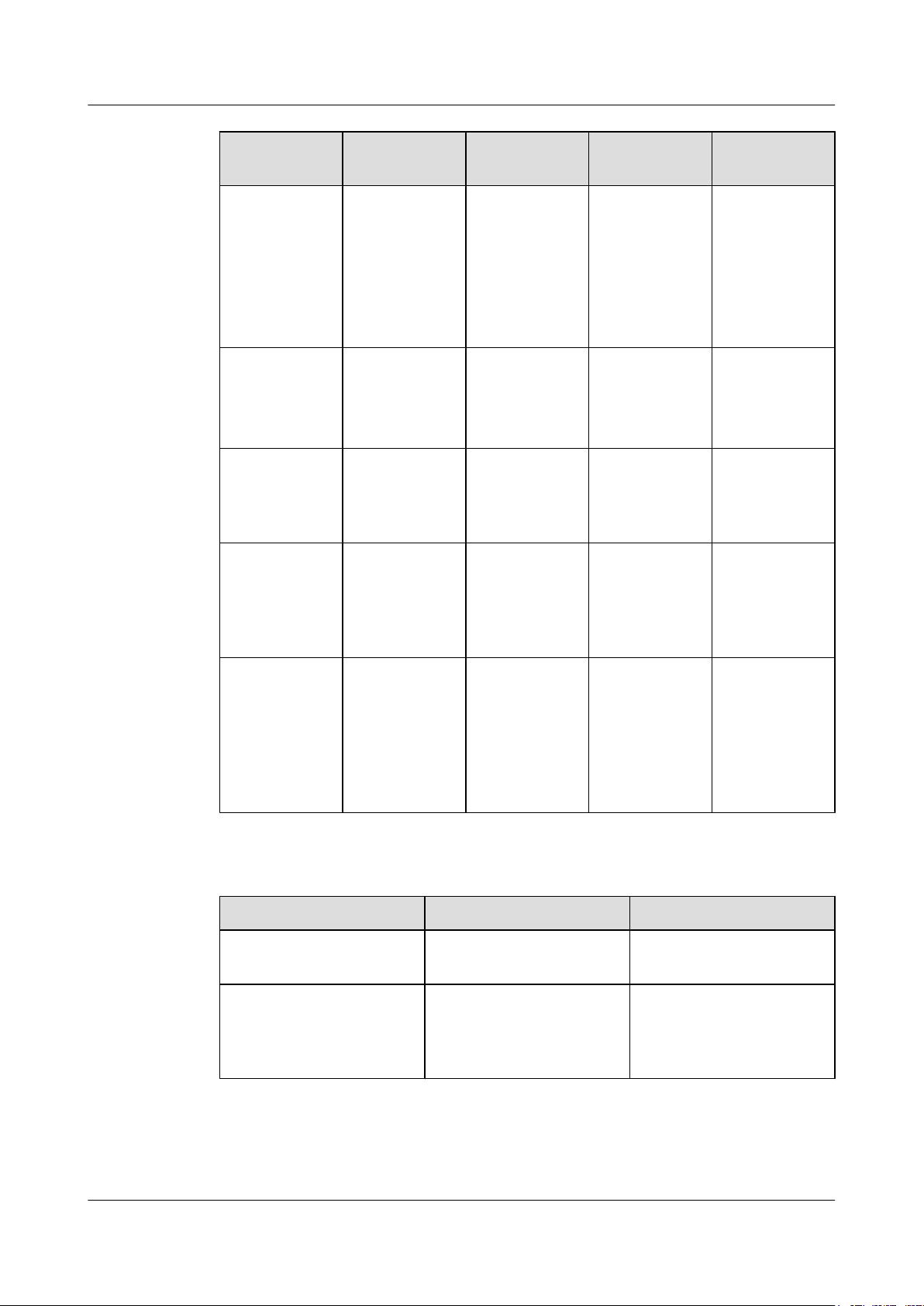
Table 2-6 Antenna specifications of EG860-C71
Item
Mode Built-in
Receiver sensitivity
LTE Antenna
(1.4G)
directional
antenna or
external antenna
LTE Antenna
(1.8G)
Built-in
directional
antenna or
external antenna
IEEE 802.11b: ≤-76
dBm@11Mbps
IEEE 802.11g: ≤-65
dBm@54Mbps
IEEE 802.11n: ≤-75
dBm@54Mbps
LTE Antenna
(800M)
External
antenna
Wi-Fi
Antenna
Built-in
omnidirectional
antenna
Frequency Built-in
directional
antenna:
1447MHz~146
7MHz
External
antenna:
1350MHz~150
0MHz
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Built-in
directional
antenna:
17857MHz~18
05MHz
External
antenna:
1710MHz~188
0MHz
760MHz~870MHz2400MHz~250
0MHz
11
EG860
User Guide 2 Introduction
LTE Antenna
Item
(1.4G)
Gain Built-in
directional
antenna: ≥
7.5dBi
External
antenna: ≥5dBi
Directivity
diagram
Horizontal
plane: > 75
vertical plane: >
60
Isolation
≥20dB ≥20dB
between built-in
LTE directional
antennas
Isolation
None None None
between built-in
Wi-Fi
omnidirectional
antennas
LTE Antenna
(1.8G)
Built-in
directional
antenna: ≥
7.5dBi
External
antenna: ≥
10dBi
Horizontal
plane: > 75
vertical plane: >
60
LTE Antenna
(800M)
Wi-Fi
Antenna
≥5dBi ≥2dBi
OmnidirectionalOmnidirectiona
l
None None
≥20dB
Isolation
>35dB >35dB None >35dB
between built-in
LTE directional
antennas and
built-in Wi-Fi
omnidirectional
antennas
Table 2-7 Antenna specifications of EG860-D61
Item LTE Antenna (400M) Wi-Fi Antenna
Mode External antenna Built-in omnidirectional
antenna
Frequency 380MHz~410MHz/
2400MHz~2500MHz
410MHz~440MHz/
440MHz~450MHz/
380MHz~450MHz
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
12

EG860
User Guide
2 Introduction
Item LTE Antenna (400M) Wi-Fi Antenna
Gain
Directivity diagram Omnidirectional Omnidirectional
Isolation between built-in
LTE directional antennas
Isolation between built-in
Wi-Fi omnidirectional
antennas
Isolation between built-in
LTE directional antennas
and built-in Wi-Fi
omnidirectional antennas
Environment Specifications
l 380MHz~410MHz/
≥ 2 dBi
410MHz~440MHz/
440MHz~450MHz:≥3.5
dBi
l 380MHz~450MHz:≥1.5
dBi
None None
None
≥20dB
None
Table 2-8 lists the operating environment specifications of an EG860.
Table 2-8 Operating environment specifications
Item Description
Temperature
-40℃~+50℃
Relative humidity 5%~95%
Temperature change rate
0.5℃/min
Atmospheric pressure 62 kPa~106 kPa
Altitude
Air flow rate
≤ 3,000 m
≤ 50 m/s
Rainfall intensity 6 mm/min
Rainwater temperature
+5℃
Sand 1000 mg/m³
Earthquake intensity VIII or higher
Table 2-9 lists the storage environment specifications of an EG860.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
13

EG860
User Guide
2 Introduction
Table 2-9 Storage environment specifications
Item Description
Temperature
Relative humidity 10%~100%
Temperature change rate
Atmospheric pressure 62 Kpa~106 Kpa
Air flow rate
2.4 Product Security
EG860 security includes network security and application security. Application security includes
wireless security and OM security.
2.4.1 Network Security
EG860 network security uses Secure Sockets Layer (SSL) and Hypertext Transfer Protocol
Secure (HTTPS).
SSL
-40℃~+70℃
1 ℃/min
≤ 55 m/s
HTTPS
The SSL protocol is a security connection technology for the server and client. It provides a
confidential, trusted, and identity-authenticating connection to two application layers. SSL is
regarded as a standard security measure and has been widely applied to web services.
l Identity authentication
Identity authentication checks whether a communication individual is the expected object.
SSL authenticates servers and clients based on digital certificates and user/password.
Clients and servers have their own identifiers. The identifiers are numbered by the public
key. To verify that a user is legitimate, SSL requires digital authentication during data
exchange in the SSL handshake procedure.
l Connection confidentiality
Data is encrypted before transmission to prevent data from being hacked by malicious users.
SSL uses encryption algorithms to ensure the connection confidentiality.
l Data integrity
Any tampering on data during transmission can be detected. SSL establishes a secure
channel between the client and the server so that all the SSL data can reach the destination
intact.
For the EG860, the OM TCP applications can use SSL. HTTP over SSL is generally called
HTTPS. HTTPS is used for connections between the NMS/WebUI and EG860. SSL also uses
the digital certificate mechanism.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
14

EG860
User Guide
HTTPS provides secure HTTP channels. HTTPS is HTTP to which SSL is added, and SSL
ensures the security of HTTPS.
2.4.2 Application Security
EG860 application security includes wireless security and OM security.
2.4.2.1 Wireless Security
EG860 wireless security includes authentication, air-interface data encryption, and integrity
protection.
For details, see Security Feature Manual.
2.4.2.2 OM Security
OM security includes user authentication, access control, OM system security, and software
digital signature.
2 Introduction
2.4.2.2.1 User Authentication and Access Control
User authentication and access control are implemented for users to be served by the EG860.
The objective of authentication is to identify users and grant the users with proper permission.
The objective of access control is to specify and restrict the operations to be performed and the
resources to be accessed by the users.
User Account Management
Local user account management involves modification and query of local user accounts.
Information about a local user account includes user name and user description. To improve
system security, the following security requirements must be satisfied:
l Password security policies
– The password must contain 8 to 32 characters
– The password must contain at least two character types and must not contain three or
more than three consecutively same characters
– The password must not contain the account name or its reversion
– Maximum number of failed password attempts
– Threshold of consecutive password modification failures
– Duration after which a locked password can be automatically unlocked
l Password usage rules
– Users must enter passwords twice when changing passwords, and the passwords entered
cannot be copied.
– Users can change their own passwords. The old password must be verified when it is
changed.
– User accounts are locked when the number of consecutive password failures reaches a
specified threshold.
l Password storage and transmission rules
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
15

EG860
User Guide
2 Introduction
– Passwords are encrypted and are stored locally.
l Default account management
– By default, the admin user is able to perform all operations except for the functions
related to the TR069 protocol on the system. The acs user only can control the
authentication between eOMC910 and EG860.
l User names and passwords
Table 2-10 describes the user names and default passwords for an EG860.
Table 2-10 User names and passwords
User Name Default Password Description
admin 4GCPE@TD A user that accesses the
EG860 by using the Web
management interface.
acs 4GCPE@TD An eOMC910 user that
performs operations on the
EG860.
NOTICE
l To enhance system security, users need to change the passwords periodically,
preventing brute-force cracking.
l The password of the acs user must be changed on both the eOMC910 and the EG860.
User Login Management
The login types supported by NEs include local user login, and machine-machine authentication
and certificate authentication for NMS access. All login types must be authenticated before
communications. In addition, the following security requirements must be satisfied:
l Identity check mechanism
– Identity check based on accounts and passwords
– Automatic logins by programs for machine-machine accounts
2.4.2.2.2 OM System Security
OM system security includes software integrity check.
In the original procedure for releasing and using the software, the software integrity is ensured
by using cyclic redundancy check (CRC). CRC can only prevent data loss during transmissions.
If data is tampered with during transmissions, a forged CRC value will be regarded as valid by
the CRC. Therefore, the receive end cannot rely on the CRC to ensure the consistency between
the received data and the original data, adversely affecting the reliability and security for the
software.
Software integrity protection implements the Hash algorithm or adds a digital signature to
software (including mediation layers and configuration files) when releasing software, and then
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
16
EG860
User Guide
uploads software to the target server or device. When a target device downloads, loads, or runs
software, the target device performs the Hash check or authenticates the digital signature. By
doing so, software integrity protection ensures end-to-end software reliability and integrity.
Software integrity protection helps detect viruses or malicious tampering in a timely manner,
preventing insecure or virus-infected software from running on the device.
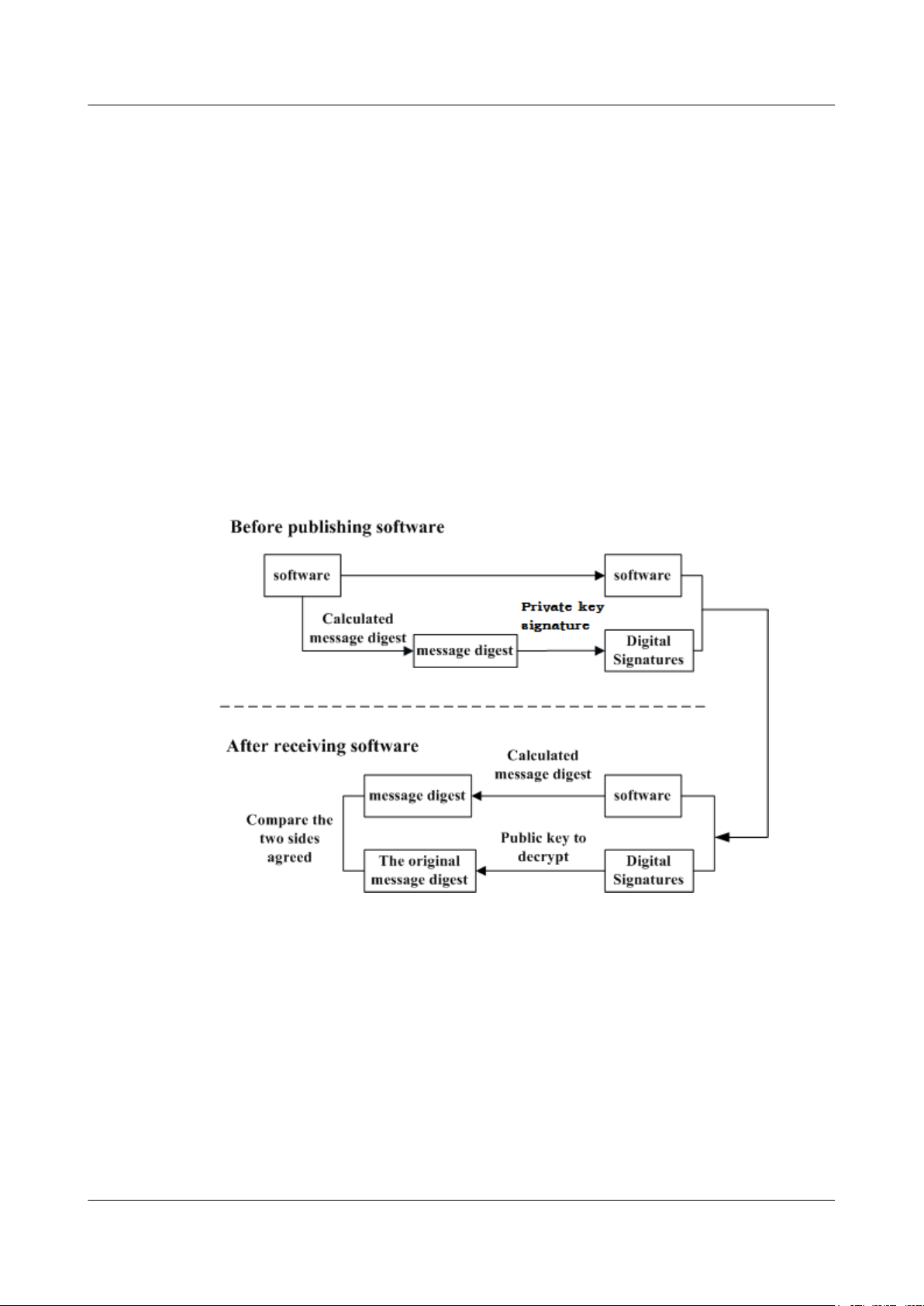
2.4.2.2.3 Digital Signature of Software
A digital signature of software is used to identify the software source. It ensures the integrity
and reliability of software.
When software is released, its digital signature is delivered with the software package. After the
software package is downloaded to an NE, the NE verifies the digital signature of the software
package before using it. If the digital signature passes the verification, the software is intact and
reliable. If the verification fails, the software package is invalid and cannot be used. Figure
2-3 illustrates the principles of a software digital signature.
Figure 2-3 Digital signature of software
2 Introduction
l Before a software package is released, all files in the software package are signed with
digital signatures. That is, after a message digest is calculated for all files in the software
package, the message digest is digitally signed using a private key.
l After a software package with a digital signature is loaded to an NE through a media such
as the software release platform, the NE first verifies the digital signature of the software
package. That is, the NE uses a public key to decrypt the digital signature and obtain the
original message digest. Then, the NE recalculates the message digest and compares the
new message digest with the original one.
– If the two message digests are the same, the software package passes the verification
and can be used.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
17

EG860
User Guide 2 Introduction
– If the two message digests are different, the software package fails the verification and
cannot be used.
The public key used to decrypt digital signatures is stored in the secure storage area of an NE
and cannot be queried or exported.
2.5 Certification Information
This section describes the certification that EG860 has passed.
Table 2-11 describes the certification that EG860 has passed.
Table 2-11 Certification that EG860 has passed
Certification Name Description
Conformite Europende (CE) Products with the CE marking comply with
the electromagnetic compatibility directive
(89/336/EEC) and low voltage directive
(73/23/EEC) issued by European
Commission. The CE marking is a mandatory
conformity mark for products placed on the
European market.
Restriction of the use of certain hazardous
substances (RoHS)
RoHS restricts the use of certain hazardous
materials in the manufacturing of electronic
and electrical equipment, in consideration of
human health and environmental protection.
RoHS is enforced in each member state of the
European Union.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
18

EG860
User Guide 3 Hardware
3 Hardware
About This Chapter
This section describes hardware components and cables of an EG860.
3.1 EG860 Hardware
This section describes the exterior, front panel, indicators, and ports of an EG860.
3.2 EG860 Cables
This section describes the cables of an EG860, including power over Ethernet (PoE) cables,
power cables and protection ground (PGND) cables.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
19
EG860
User Guide
3.1 EG860 Hardware
This section describes the exterior, front panel, indicators, and ports of an EG860.
3.1.1 Appearance
The exterior of an EG860 provides you a fair idea of major components.
Figure 3-1 shows the exterior of an EG860.
Figure 3-1 EG860 exterior (unit: mm)
3 Hardware
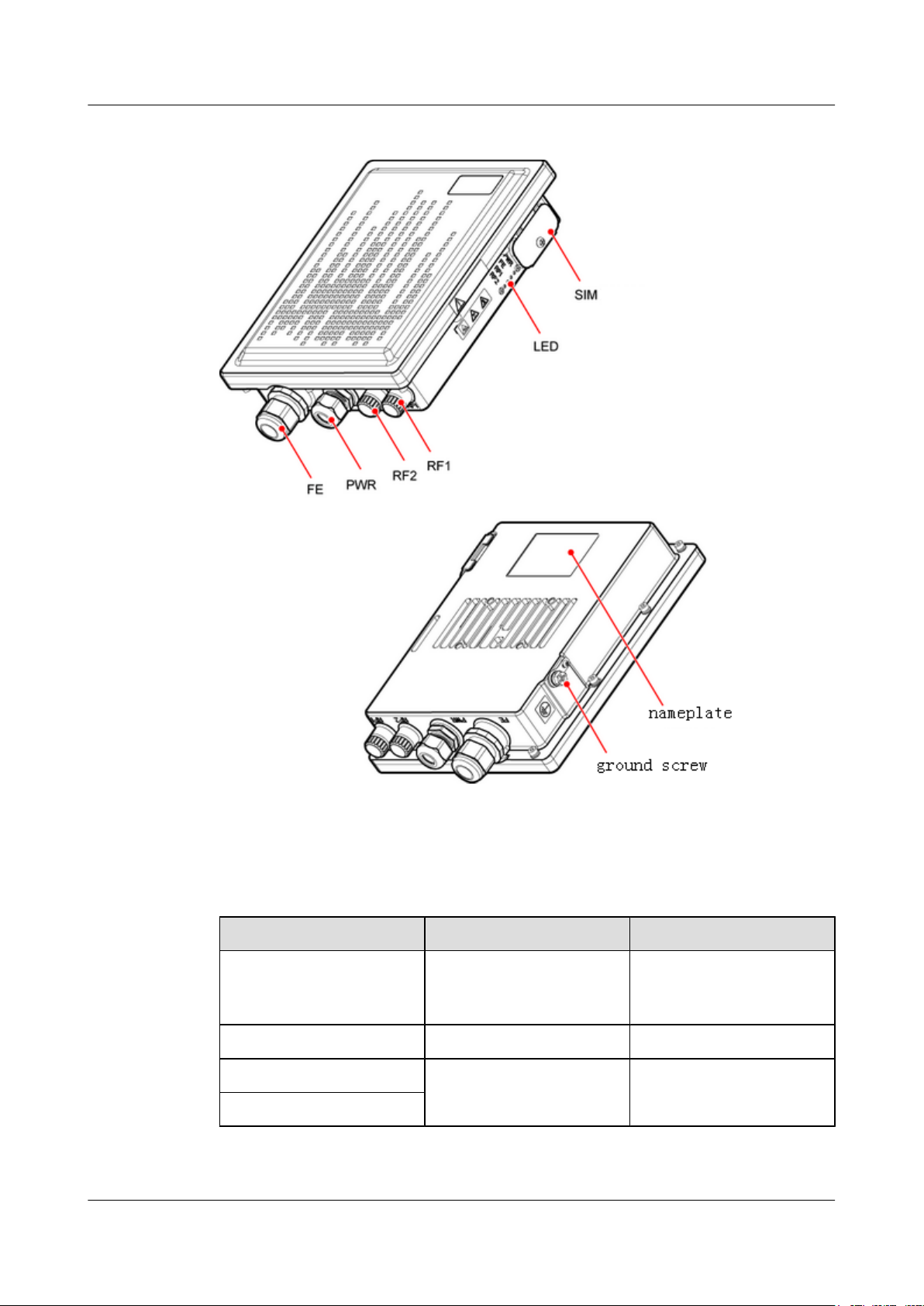
3.1.2 Front Panel
An EG860 has an FE port, a power port, external antenna ports, subscriber identity module (SIM)
card window, indicators, a nameplate, and a ground screw on its front panel.
Figure 3-2 shows the front panel of an EG860.
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
20
EG860
User Guide 3 Hardware
Figure 3-2 EG860 front panel
Table 3-1 provides port description for the front panel.
Table 3-1 Ports of the EG860 front panel
Item Port Description
FE Data service port Receives/Transmits data
PWR Power port Connects to a power supply.
RF1 External antenna port Connects to an external
RF2
Issue 02 (2015-04-10) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
services and supplies power
to an EG860.
antenna.
21
 Loading...
Loading...