Page 1

HP A-IMC Firewall Manager
Configuration Guide
Part number: 5998-2267
Document version : 6 P W 101-20110805
Page 2

Legal and notice information
© Copyright 2011 Hewlett-Packard Development Company, L.P.
No part of this documentation may be reproduced or transmitted in any form or by any means without
prior written consent of Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS
MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained
herein or for incidental or consequential damages in connection with the furnishing, performance, or use
of this material.
The only warranties for HP products and services are set forth in the express warranty statements
accompanying such products and services. Nothing herein should be construed as constituting an
additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Page 3

Contents
Overview ······································································································································································ 1
Introduction to HP A-IMC Firewall Manager··················································································································1
What HP A-IMC Firewall Manager can do ···················································································································1
Installation and uninstallation······································································································································ 2
Installing the firewall manager ········································································································································2
Registering the firewall manager·····································································································································2
Uninstalling the firewall manager ···································································································································3
System management···················································································································································· 4
Device management ·························································································································································4
Managing devices····················································································································································4
Managing batch import········································································································································ 18
Managing device groups ····································································································································· 18
Managing events··················································································································································· 20
Managing device access templates ···················································································································· 22
Managing the device software database··········································································································· 24
Managing deployment tasks ································································································································ 26
Operator management·················································································································································· 27
Managing operators············································································································································· 27
Managing operation logs····································································································································· 29
Changing your login password ··························································································································· 30
System configuration······················································································································································ 31
Configuring system parameter····························································································································· 31
Configuring management ports ··························································································································· 31
Configuring the mail server·································································································································· 32
Managing filters ···················································································································································· 33
Managing LDAP servers ······································································································································· 35
Managing log retention time································································································································ 37
Monitoring the disk space ···································································································································· 37
Managing subsystems··········································································································································· 39
Firewall management ················································································································································42
Attack events monitoring ··············································································································································· 42
Snapshot of events ················································································································································ 42
Recent events list···················································································································································· 44
Device monitoring ················································································································································· 45
Event analysis ································································································································································· 45
Event overview······················································································································································· 45
Event details ··························································································································································· 47
Report exporting management····························································································································· 49
Event auditing································································································································································· 51
Inter-zone access log auditing ·····························································································································52
Abnormal traffic log auditing······························································································································· 52
Blacklist log auditing············································································································································· 53
Operation log auditing········································································································································· 53
Other log auditing················································································································································· 54
NAT log auditing··················································································································································· 55
MPLS log auditing ················································································································································· 55
Security policy management········································································································································· 56
i
Page 4

Security zones························································································································································ 56
Time ranges···························································································································································· 58
Services ·································································································································································· 60
IP addresses ··························································································································································· 65
Interzone rules························································································································································ 72
Interzone policies ·················································································································································· 76
Interzone policy applications ······························································································································· 80
Firewall device management ········································································································································ 83
Managing firewall devices··································································································································· 83
Viewing device statistics ······································································································································· 85
Managing the device configuration database··································································································· 85
Managing deployment tasks ································································································································ 91
SSL VPN auditing ·······················································································································································93
Comprehensive analysis················································································································································ 93
Online users ··························································································································································· 93
Online users trends················································································································································ 94
Daily user statistics ················································································································································ 94
Device monitoring ················································································································································· 95
SSL VPN log auditing ···················································································································································· 96
User access records auditing ······························································································································· 96
Operation log auditing········································································································································· 96
Resource access auditing ·····································································································································97
Authentication failure auditing····························································································································· 97
Configuration example 1 ··········································································································································99
Network requirements ···················································································································································99
Configuration procedure ··············································································································································· 99
Adding devices to the firewall manager············································································································· 99
Configuration example 2 ······································································································································· 101
Network requirements ·················································································································································101
Configuration procedures ···········································································································································101
Configuring the firewall device··························································································································101
Configuring the Firewall Manager ····················································································································102
Configuring intrusion detection in firewall and sending logs to Firewall Manager·····································103
Verification····································································································································································107
Firewall logs and Firewall Manager analysis ··································································································107
Support and other resources ·································································································································· 111
Contacting HP ······························································································································································ 111
Subscription service ············································································································································111
Related information······················································································································································111
Documents····························································································································································111
Websites·······························································································································································111
Conventions ··································································································································································112
Index ········································································································································································ 114
ii
Page 5

Overview
Introduction to HP A-IMC Firewall Manager
HP A-IMC Firewall Manager is a powerful system for comprehensive analysis and centralized
management of firewall devices. It is an important component of the HP A-Intelligent Management
Center (A-IMC).
The Firewall Manager allows you to manage and control all HP firewall devices in your network. It
features great scalability, visual realtime event monitoring, comprehensive security event analysis such as
attack analysis, and rich reports, enabling you to learn the network security status at any time.
In addition, the Firewall Manager provides the Security Socket Layer (SSL) VPN log auditing function for
you to analyze SSL VPN users and monitor firewall devices. SSL VPN is an emerging VPN technology
based on HTTPS, and provides a measure of security for remote access to the intranet.
Together with HP firewall devices, the Firewall Manager provides you with visual, all-around, powerful
network security protection.
What HP A-IMC Firewall Manager can do
As a powerful, efficient firewall management system, the Firewall Manager supports centralized
management and realtime monitoring of firewall devices throughout the network, implements collection
and comprehensive analysis of attack event information, enables log auditing, and provides kinds of
visual, detailed reports. From the all-around reports, you can see the history security status as well as the
security trends of the network easily.
The Firewall Manager presents the following key features:
• Visual realtime monitoring, which can help you detect network attacks in time.
• Perfect comprehensive analysis and rich statistics reports, which can reduce your analysis time.
• Fine log auditing, allowing you to track events.
• Friendly and easy-to-use interface, allowing easy deployment.
1
Page 6

Installation and uninstallation
Installing the firewall manager
The software and hardware requirements of the Firewall Manager are as follows:
• Hardware: P4 2.0 CPU or above, 1.5G memory or more, 80G disk or more.
• Operating system: Windows 2003 Server (recommended) or Windows XP, installed with the
up-to-date patches.
• Browser: IE 6.0 or above
To install HP A-IMC Firewall Manager, you only need to run the executable file install.exe, which is under
the installation directory, and click Next repeatedly as prompted.
CAUTION:
After finishing installation, you must restart the operating system.
Registering the firewall manager
In the address bar of the browser, enter http://localhost/ to open the login page. The default login
username and password are admin and admin1 respectively.
CAUTION:
The last character of the password is digit 1.
When you log in to the Firewall Manager for the first time, you will see the license information page and
such a prompt: You haven’t registered. Please register to use the system normally. You can obtain a
formal license, and register your license by following this procedure:
1. From the navigation tree, select License Application under License Management to enter the license
application page. The system automatically generates a host ID for license application, as shown
in
Figure 1. Perform operations as prompted to obtain a license file.
Figure 1 Generate a host ID
2. From the navigation tree, select License Registration under License Management to enter the
license registration page, as shown in
click Apply to complete registration. The suffix of a license file is lic.
Figure 2. Click Browse to select the license file and then
2
Page 7
Figure 2 Register your license
After seeing the acknowledgement page, you can use the Firewall Manager to configure devices and
perform other operations.
CAUTION:
HP A-IMC Firewall Manager is shipped with a trial license that is effective within one month, which is
saved in a license file named A-IMC Firewall Manager Evaluation License.lic. Before you get a formal
license, you can use the trial license to register.
Uninstalling the firewall manager
To uninstall HP A-IMC Firewall Manager, follow these steps:
1. On the Windows desktop, click Start and then select All Programs > Firewall Manager > Uninstall
Firewall Manager to enter the uninstall page.
2. Click Uninstall, and then click Next repeatedly as prompted.
3. Restart the operating system.
4. Remove all files and subdirectories under the Firewall Manager installation directory (C:\Program
Files\Firewall Manager, for example) and the installation directory itself, if any.
CAUTION:
During the uninstallation process, no system data backup operation is performed and all data is
removed.
If you need the system data, backup the data before uninstalling the Firewall Manager.
3
Page 8

System management
The system management component is mainly used to configure the firewall devices to be managed by
the Firewall Manager.
To access the system management component, select the System Management tab. Then, you can
perform:
•
Device management
Operator management
•
System configuration
•
• License management
The license management function allows you to apply for, register, and view a license. The license
mechanism is used for enterprise identity authentication.
Device management
The device management module allows you to perform the following tasks:
Managing devices
•
Managing batch import
•
Managing device groups
•
Managing events
•
Managing device access templates
•
Managing the device software database
•
Managing deployment tasks
•
Managing devices
Device management
After completing device group and template configuration, you can add devices to be managed. Only
after you add devices to the system component successfully, can you add the devices to the firewall
component to collect statistics on and analyze attack information. The device management page allows
you to add and delete devices. The device list shows the details of all managed devices, and provides the
links for you to export configurations and connect to the devices through web or Telnet.
1. Configuration guide
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, showing the basic information of all devices
added successfully to the Firewall Manager.
4
Page 9
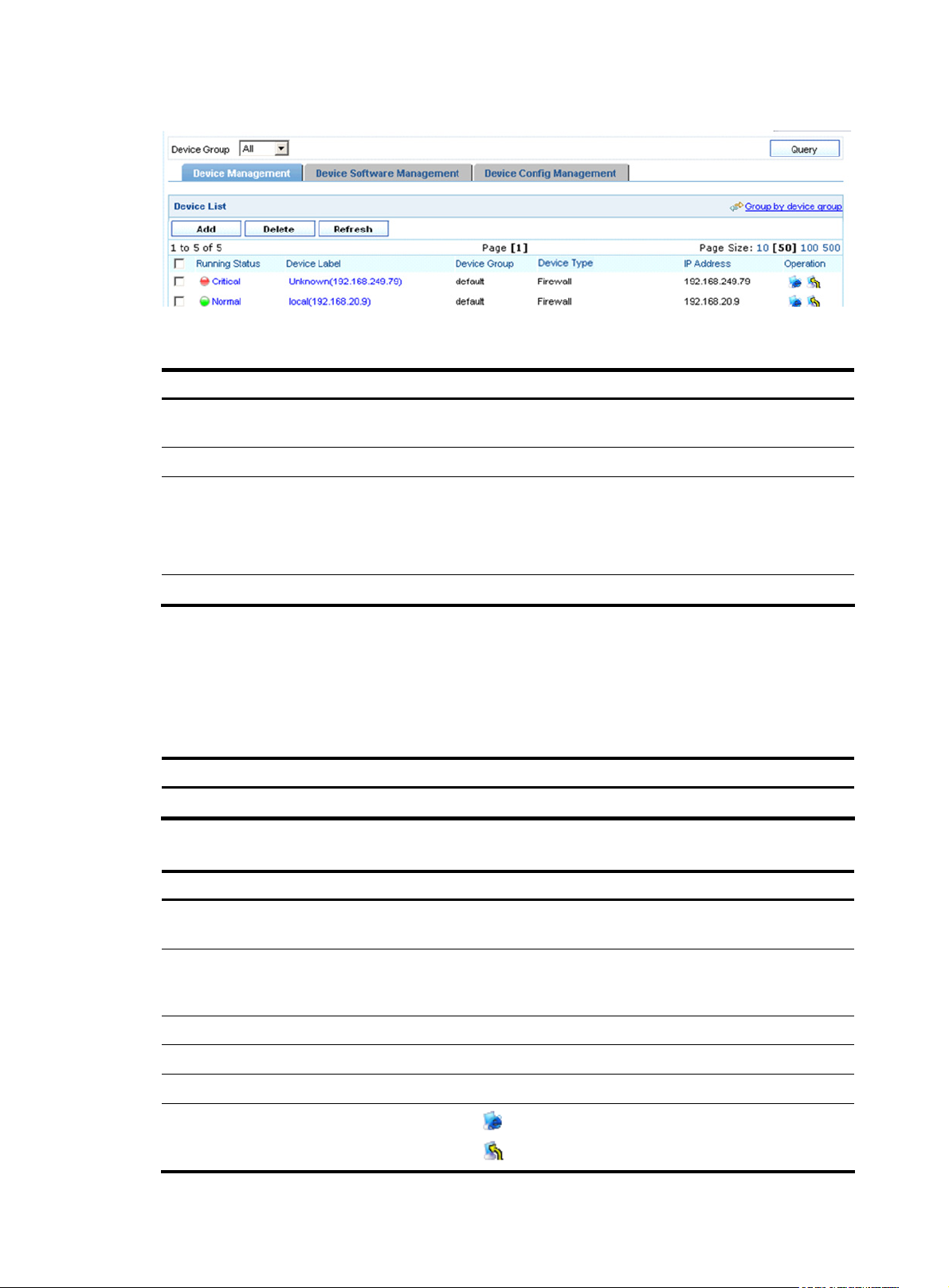
Figure 3 Device management page
Table 1 Device management functions
Function Description
Device list
Adding a device Allows you to add devices to be managed.
Deleting devices
Refreshing device information Allows you to obtain the up-to-date device information.
2. Device list
Allows you to view details about devices, export configurations, and
connect to the devices through web or Telnet.
Allows you to delete devices from the list of managed devices.
Follow these steps:
1. Select the check boxes before the devices to be deleted.
2. Click Delete.
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Figure 3. Table 3 describes the fields
of the device list.
Table 2 Device query option
Option Description
Device Group
Select a device group to list all devices in the device group.
Table 3 Fields of the device list
Field Description
Running Status
Device Label
Device Group
Device Model
IP Address
Operation
Status of the device. You can click the link to view the event list of the
device. For more information, see “
Name and IP address of the device. You can click the link to view the
details of the device and modify the relevant information. For more
information, see “
Device group to which the device belongs
Model of the device
IP address of the device
Device information.”
Managing events.”
• Click the icon of a device to open the web console for the device.
• Click the icon of a device to telnet to the device.
5
Page 10
Return to Device management functions.
3. Adding a device
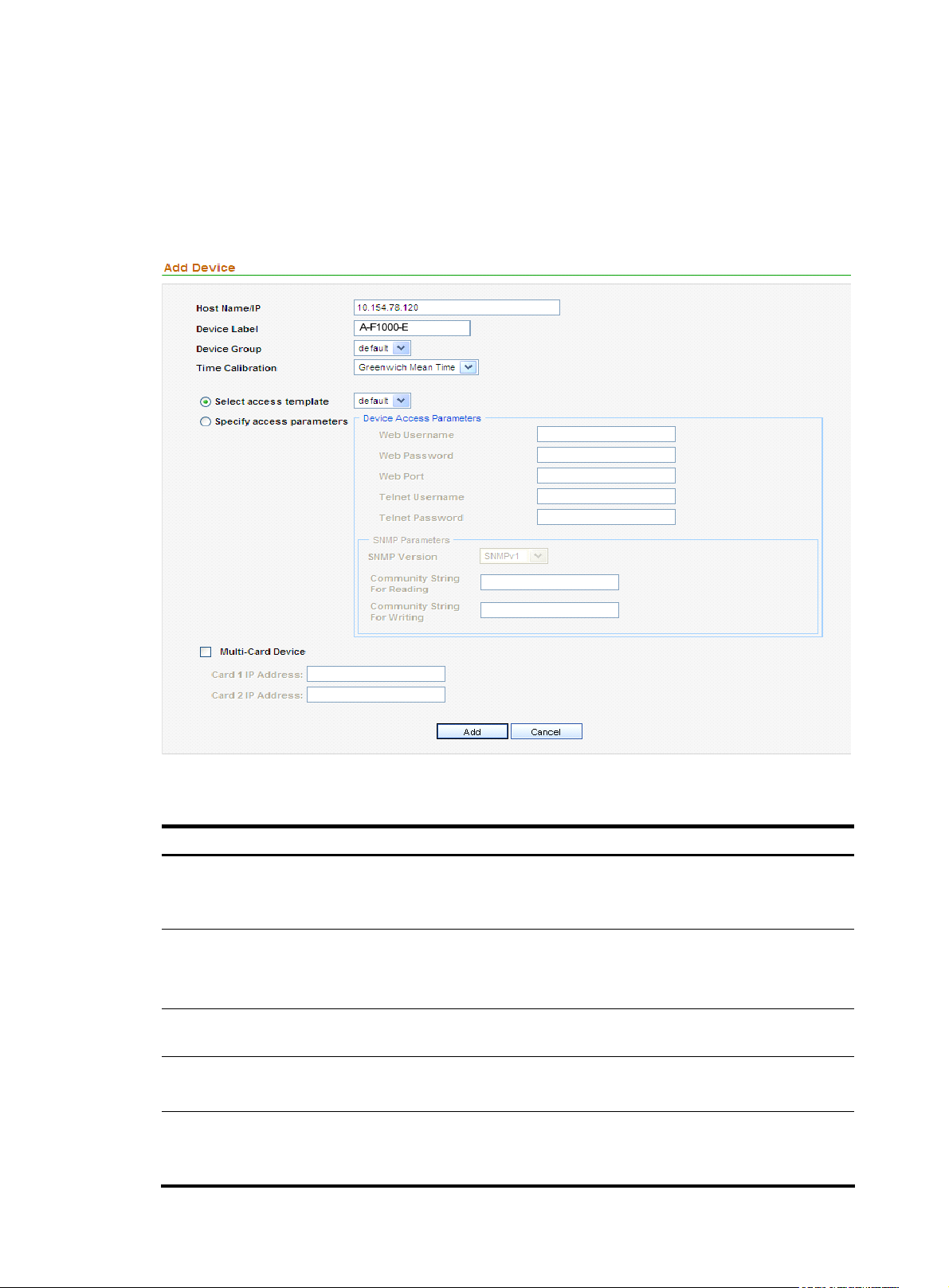
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
device, as shown in
Figure 4 and Table 4.
Figure 3. Then, click Add to add a
Figure 4 Add a device
Table 4 Device configuration items
Item Description
Required
Host Name/IP
Device Label
Device Group
Time Calibration
Select access template
Specify access parameters
Type the name or IP address of the device to uniquely identify the device
in the system.
Required
Type a label for the device, which can be used as an alias of the device.
The device label can comprise up to 20 characters.
Select a device group for the device. By default, the device group named
default is selected.
Required
Select a time mode for the device.
Required. Select either of them.
If you select Select access template, select a template from the following
drop-down list. By default, the template named default is selected.
6
Page 11
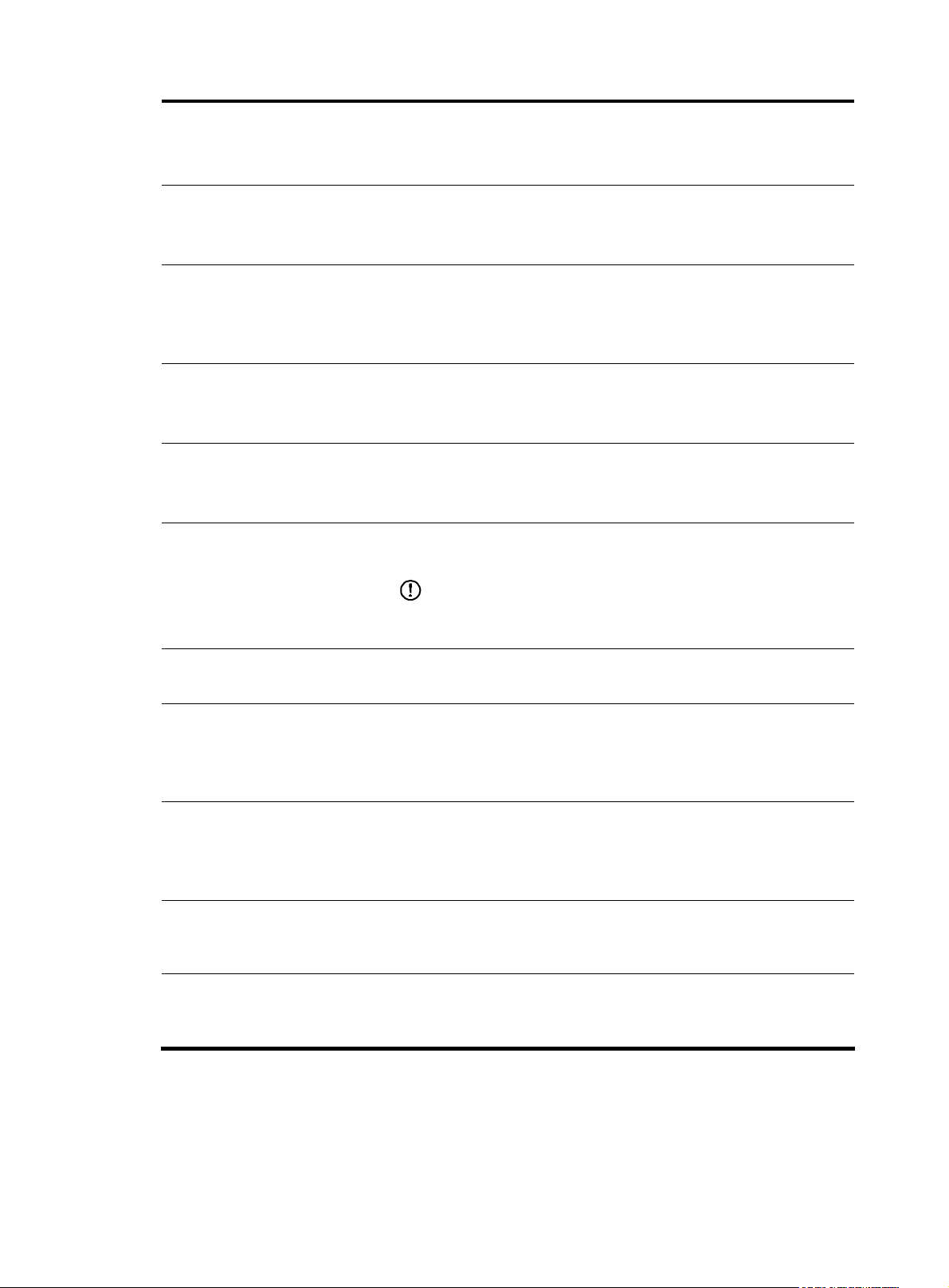
If you select Specify access parameters, specify the access parameters,
including Web Username, Web Password, Web Port, Telnet Username,
Telnet Password, SNMP Version, Community String for Reading, and
Web Username
Web Password
Web Port
Telnet Username
Telnet Password
SNMP Version
Community String for Writing.
Required
Specify the username for managing the device through web.
The username can comprise up to 20 characters.
Required
Specify the password for managing the device through web.
The strength of the password must meet the password strength
requirements of the device.
Optional
Specify the port of the device to be connected with the network.
The port number must be an integer in the range from 0 to 65535.
Optional
Specify the username for telneting to the device.
The username can comprise up to 20 characters.
Optional
Specify the password for telneting to the device.
IMPORTANT:
The strength of the password must meet the password strength requirements
of the device.
Required
Select an SNMP version, which can be SNMPv1, SNMPv2, or SNMPv3.
Community String for Reading
Community String for Writing
Authentication Username
Authentication Protocol
Required
Specify the SNMP read community string to be used for communication
with the device.
The string can comprise up to 20 characters.
Required
Specify the SNMP write community string to be used for communication
with the device.
The string can comprise up to 20 characters.
Required for SNMPv3
Specify the authentication username to be used for communication with
the device.
Required for SNMPv3
Specify the authentication protocol to be used for communication with the
device.
7
Page 12
Required when you select the authentication protocol HMAC-MD5 or
Password
Encryption Protocol
Password
SMAC-SHA.
Specify the authentication password to be used for communication with
the device.
Required when you select the authentication protocol HMAC-MD5 or
SMAC-SHA.
Specify the encryption protocol to be used for communication with the
device.
Required when you select the encryption protocol CBS-DES or AES-128.
Specify the encryption password to be used for communication with the
device.
Optional
Configure the cards in the device.
Multi-Card Device
IMPORTANT:
• You can specify the card 1 IP address, card 2 IP address, or both.
• The input IP address must be in the dotted decimal notation, such as
192.168.0.35.
Return to Device management functions.
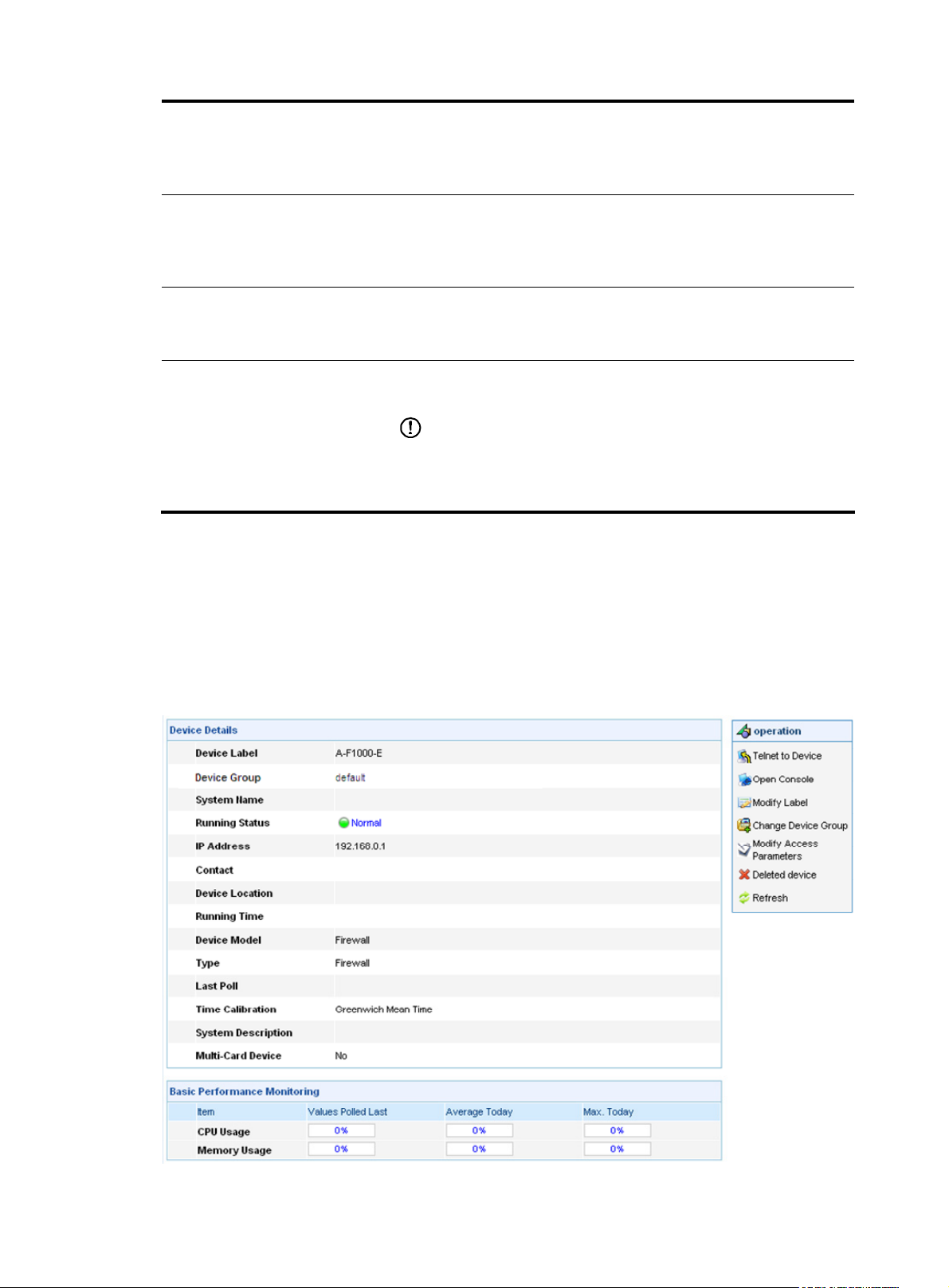
4. Device information
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Figure 3. Then, you can click the
device label link of a device to display the details of the device and modify the information of the device,
as shown in
Figure 5.
Figure 5 Device information
8
Page 13

Device software management
Device software refers to the software that a firewall device runs to provide services. It can be regarded
as the operating system of the device.
The device software management function provides you with the software information of the firewall
devices and allows you to perform a series of operations to the software of firewall devices, including
deploying software to devices and backing up the software of devices. The device software list also
displays the device type, the current software version, and the latest available new software version.
1. Configuration Guide
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Software Management tab to bring up the device software management page, as shown in
Table 5 describes the device software management functions and Table 6 describes the fields of the
device software list.
Figure 6 Device software management page
Figure 3. Then, select the Device
Figure 6.
Table 5 Device software management functions
Function Description
Deploying software to devices Allows you to deploy software to devices as required.
Backing up the software of devices
Refreshing device information Allows you to obtain the up-to-date device information.
Allows you to backup the software of selected devices to the device
software database.
Table 6 Fields of the device software list
Field Description
Device Label
Device Group
Device Type
Current Version
Latest Version
2. Deploying software to devices
Device name and IP address. You can click the link to view details about
the device and modify the configuration.
Device group to which the device belongs
Model of the device
Current software version of the device
Latest software version available for the device. This version information
comes from the software database.
This software deployment function allows you to deploy main boo t file to devices. O n the device software
management page, click Deploy Device Software to enter the software deployment page, as shown in
Figure 7. Table 7 describes the software deployment configuration items. You can deploy software to
9
Page 14
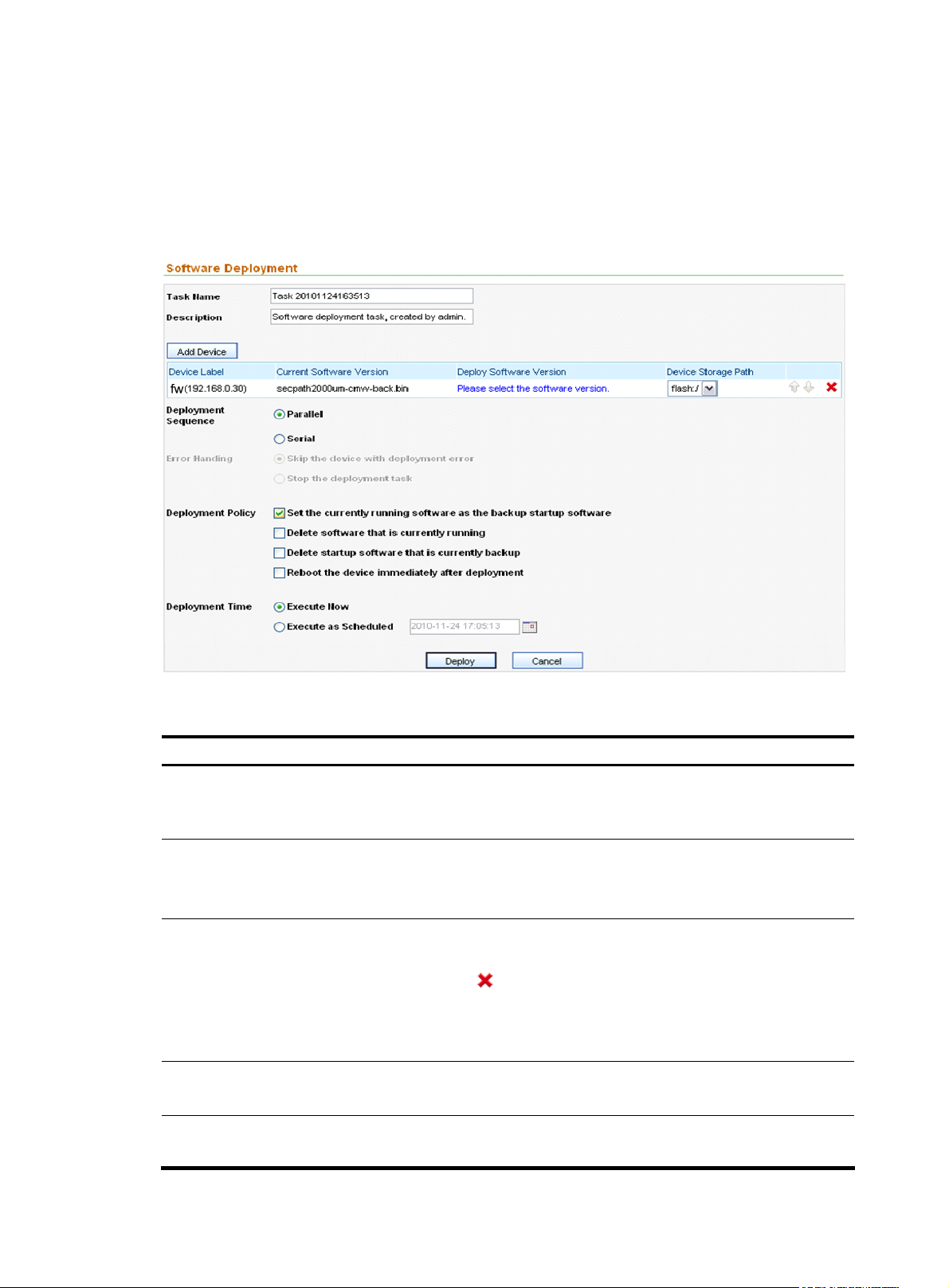
multiple devices at a time. You can specify deployment parameters, such as the deployment sequence,
policy, time, and error handling mode. A successfully created software deployment task is listed in the
deployment task management module.
How many boot files can be stored on a device depends on the device's disk space. Generally, two files,
one main boot file and one backup boot file, are stored on the device.
Figure 7 Deploy software to devices
Table 7 Software deployment configuration items
Item Description
Required
Task Name
Description
Add Device
Deploy Software Version
Deployment Sequence
Type the name of the deployment task. By default, it consists of the word Task,
a string indicating the current time, and a space in between.
Required
Type a description for the task.
The description must not contain these characters: ' " < > & % : ; / \
Click this button to add a device to which you want to deploy a software
version. You can add multiple devices.
You can click the icon of a device to remove it from the list.
Select a location from the Device Storage Path drop-down list to specify where
the software should be saved on the device. Generally, the root directory of the
CF card is selected.
Required
Click the link in this column to select the software version to be deployed.
Required
Select a deployment mode to deploy the software to the devices in parallel
10
Page 15
(Parallel) or one by one (Serial).
Error Handling
Deployment Policy
When the deployment sequence is serial, the icons
adjusting the sequence.
Required when the deployment mode is Serial.
Specify the error handling scheme to be used when a deployment error occurs.
Required
Select the actions to be taken after deploying the software selected in the Deploy
Software Version column.
are configurable for
• Set the currently running software as the backup startup
software—Specifies secpath1000fe-cmw520-b5002.bin as the main startup
software and the current running software as the backup startup software.
• Delete software that is currently running—Specifies
secpath1000fe-cmw520-b5002.bin as the main startup software and
deletes the current running software from the device.
• Delete startup software that is currently backup—Specifies
secpath1000fe-cmw520-b5002.bin as the main startup software, deletes the
backup startup software from the device, and leaves the current running
software on the device.
• Reboot the device immediately after deploying—Specifies
secpath1000fe-cmw520-b5002.bin as the main startup software, leaves all
software files stored on the device, and reboots the device. After the device
reboots, secpath1000fe-cmw520-b5002.bin is the current running software
of the device.
Deployment Time Specify the execution time of the deployment task.
NOTE:
You must select a software version for the Deploy Software Version field before deploying software to
devices.
Return to Device software management functions.
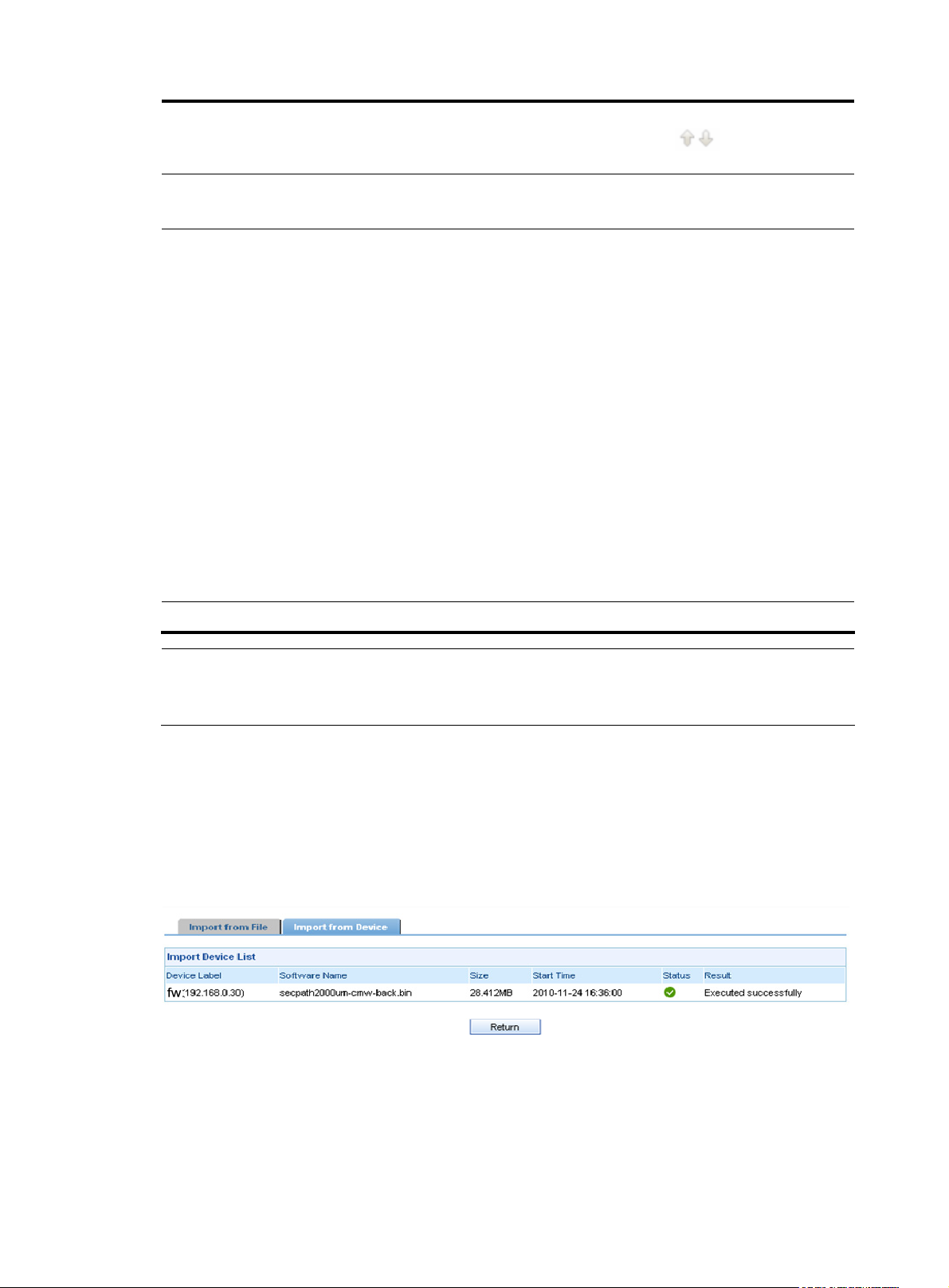
3. Backing up the software of devices
On the device software management page, select devices and then click Backup Device Software to
back up the software of the selected devices. The Import from Device page appears with the operation
results, as shown in
Figure 8. Table 8 describes the fields of the software backup result list.
Figure 8 Software backup result
If the backup operation fails, the system shows the reasons. The software backup files are stored in the
software database.
11
Page 16
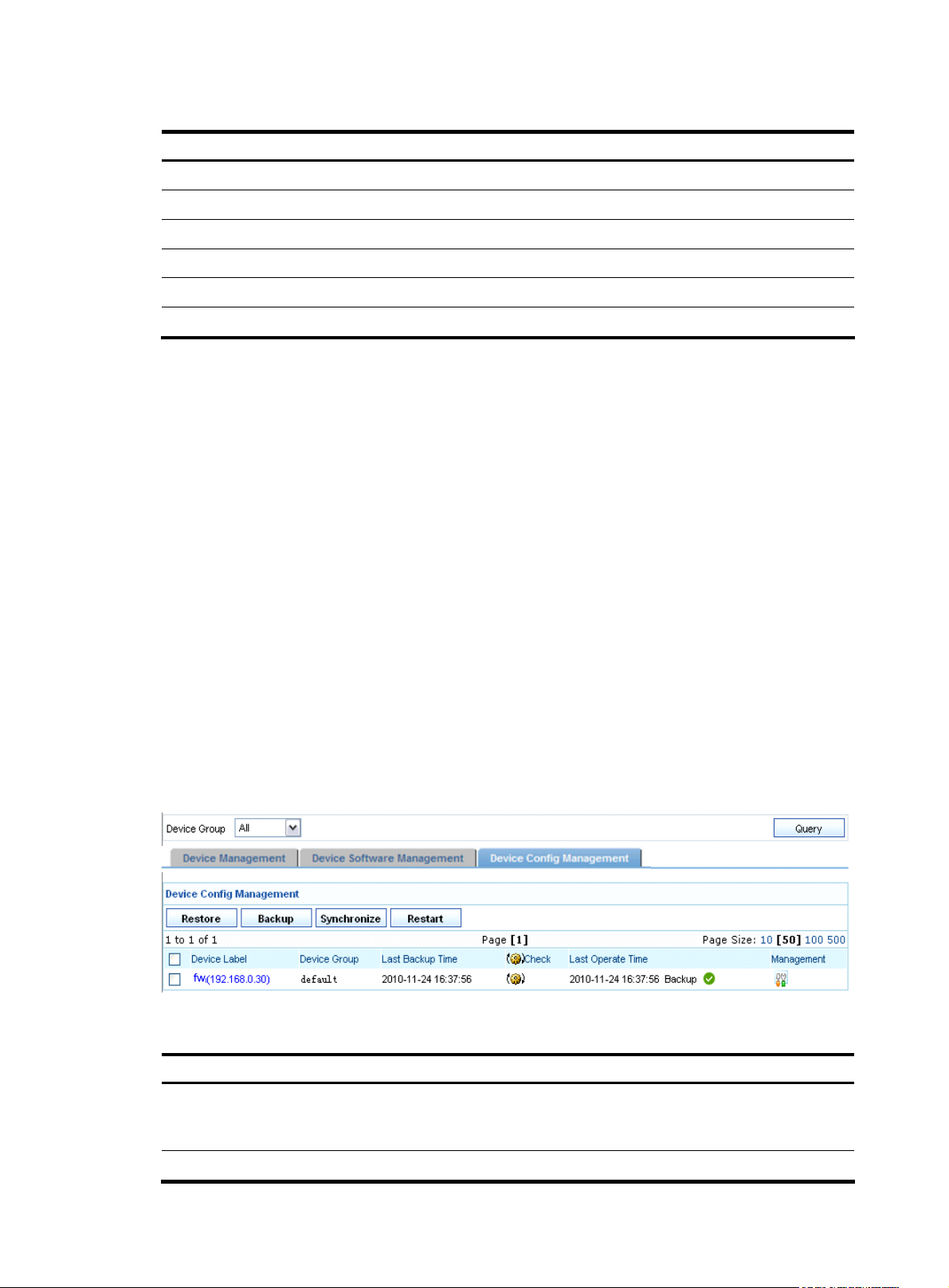
Table 8 Fields of the software backup result list
Field Description
Device Label
Software Name
Size
Start Time
Status
Result Description of the operation result or failure reason
Return to Device software management functions.
Device config management
The device configuration management function allows you to manage configuration files of devices. A
configuration file records the configurations users have made on the device. The configuration file is used
by the device to filter traffic passing through.
A configuration file can be a startup configuration file or a running configuration file. The startup
configuration file refers to the configuration file that a device keeps and will use at next boot. The running
configuration file refers to the configuration currently used by a device, which you can save to the device
as a file, and once saved, becomes the startup configuration file.
The device configuration management function supports setting baseline versions for devices, managing
the running versions and startup versions of devices, and deploying configuration files to devices.
Device name and IP address
Name of the software backed up
Size of the backup file for the software
Start time of the backup operation
Result of the backup operation
1. Configuration guide
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Config Management tab to enter the device configuration management page, as shown in
Figure 3. Then, select the Device
Figure 9.
Table 9 describes the device configuration management functions and Table 10 describes the fields of
the device configuration management list.
Figure 9 Device configuration management page
Table 9 Device configuration management functions
Function Description
Allows you to back up the running configuration file and/or the
Backing up configuration files
startup configuration file of a device. Backup files are identified by
labels and version numbers.
Restoring a configuration file
Allows you to restore the startup and/or backup configuration file of
12
Page 17
a device to another version.
Synchronizing configurations
Restarting devices Allows you to restart devices.
Allows you to deploy new configuration settings to devices to make
them take effect.
Table 10 Fields of the device configuration management list
Field Description
Device Label
Device Group Device group to which the device belongs
Last Backup Time Time of the last configuration file backup operation
Last Operate Time Time of the last configuration file operation
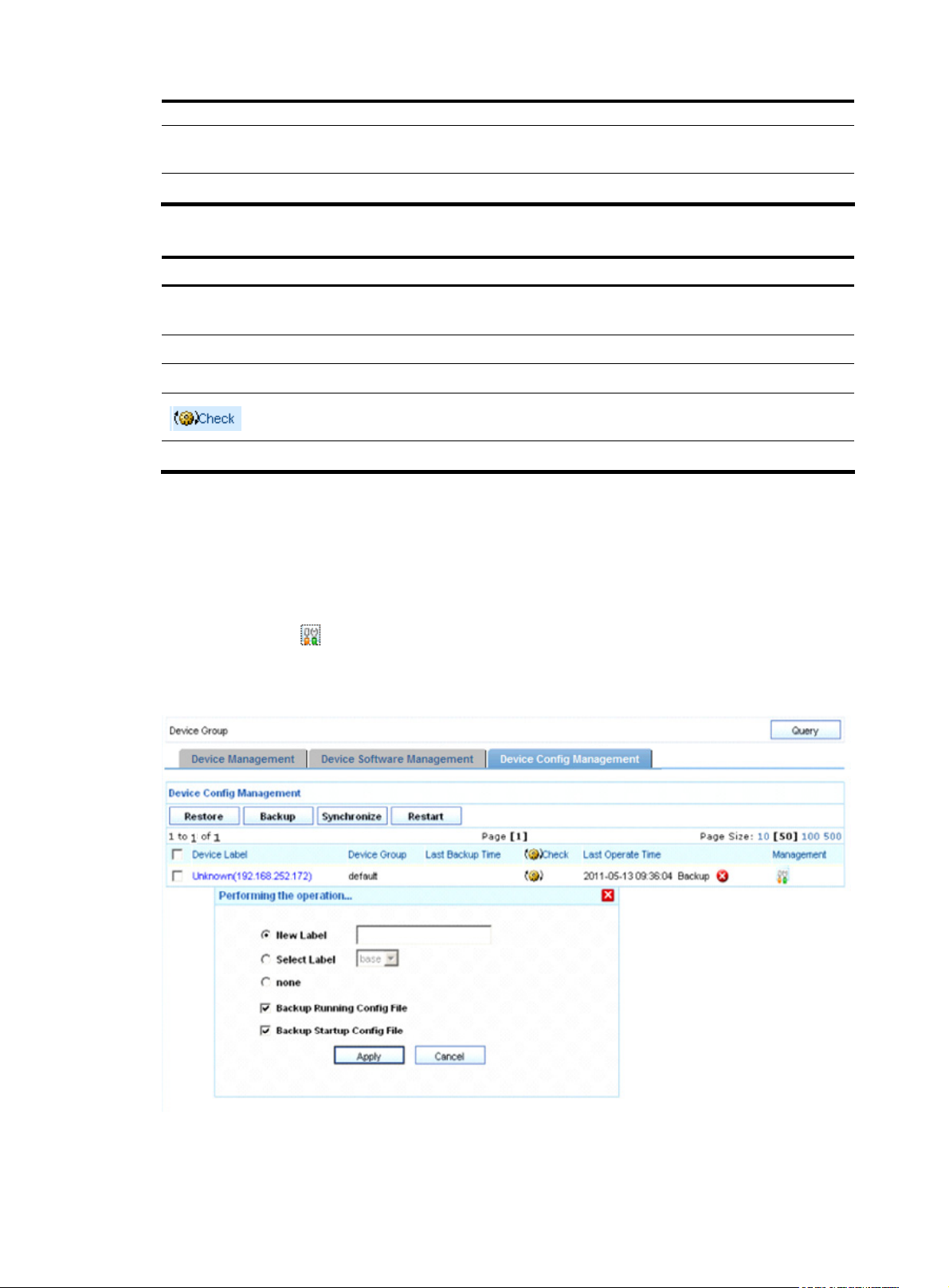
2. Backing up configuration files
Device name and IP address. You can click the link to view details about the device
and modify the configuration.
Check whether the current configuration of the device is consistent with that last
backed up.
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Figure 3. Then, select the Device
Config Management tab to enter the device configuration management page. Select a device by
selecting the check box and click Backup to bring up the backup configuration page, as shown in
Figure
10. A backup file is uniquely identified by a version number that is assigned by the system. After a file is
backed up, click the
icon in the Management column of a device to view the detailed information of
the backup configuration files.
Figure 10 Backup configuration files
Return to Device configuration management functions.
13
Page 18
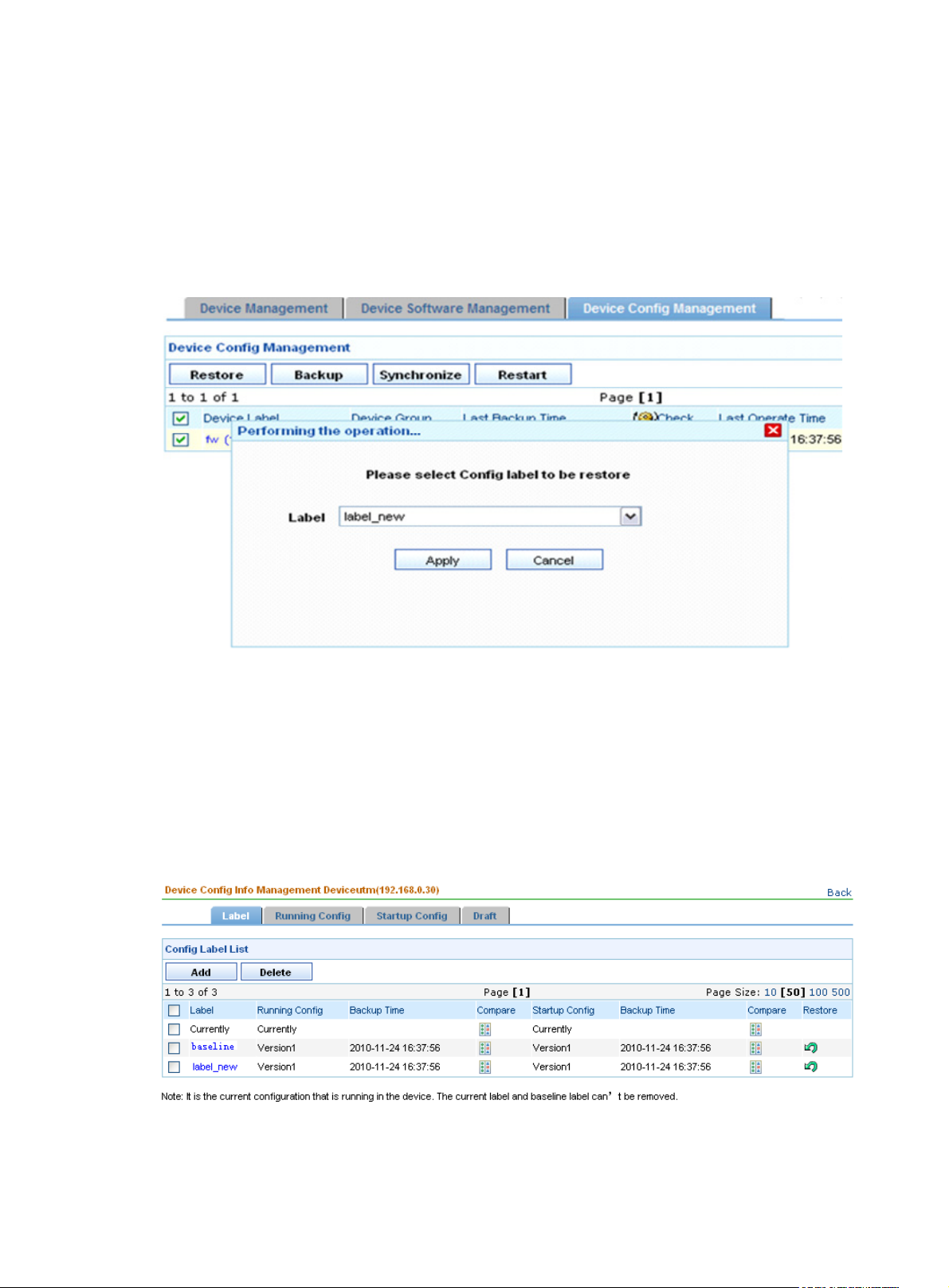
3. Restoring a configuration file
From the navigation tree of the system management component, select Device List under Device
Management. The device management page appears, as shown in
Config Management tab to enter the device configuration management page, as shown in
Select a device and click Restore to bring up the restoration configuration page, as shown in
Figure 3. Then, select the Device
Figure 9.
Figure 11.
Select a startup configuration file and/or running configuration file by their labels and click Apply to
specify the files as the startup and/or running configuration files for the device.
Figure 11 Restore configuration files
Return to Device configuration management functions.
4. Device configuration information management
On the device configuration management list, you can click the icon in the Management column of a
device to bring up the configuration information management page of the device, as shown in
Figure 12.
Table 11 describes the tabs on the device configuration information management page and the functions
provided on the tabs.
Figure 12 Device configuration information management interface
14
Page 19
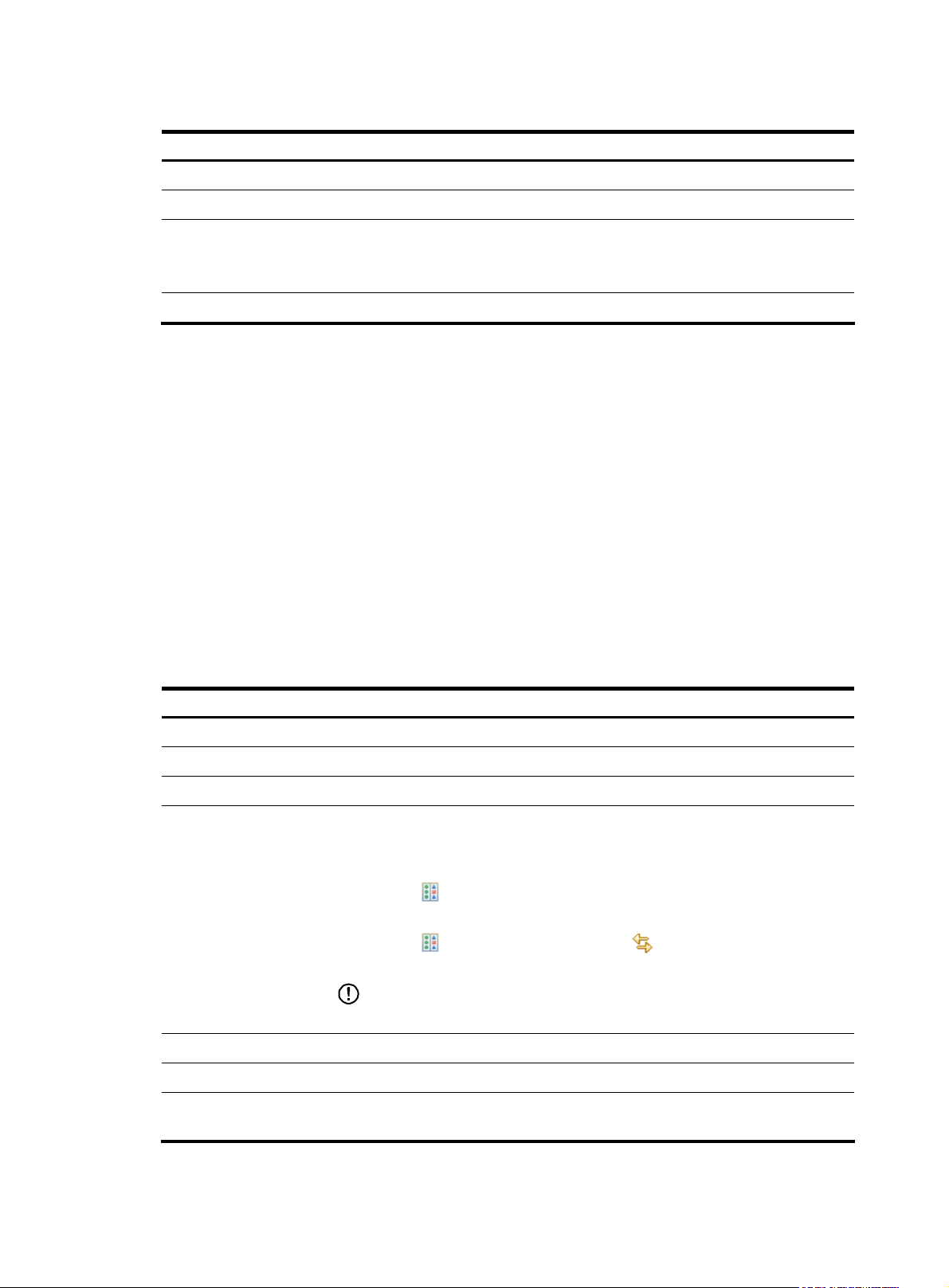
Table 11 Tabs on the device configuration information management page and functions provided
Tab Description
Label A label represents a configuration file of a device. .
Running Config Allows you to perform operations on running configuration files of different versions.
Allows you to view, back up, and delete the current startup configuration file of a
Startup Config
Draft Allows you to manage drafts for a device.
5. Label
device.
The functions are the similar to those for management of running configuration files.
A label is used to indicate the backup running and/or startup configuration files of a device.
On the device configuration management list, you can click the icon in the Management column of a
device to bring up the configuration information management interface of the device, as shown in
Figure
12.
The Label tab allows you to:
• Add and delete labels.
• View the information of the backup configuration file, such as version number and backup time. A
backup file is uniquely identified by a version number assigned by the system.
• Compare two configuration files to find the differences.
• Click the restoration icon to set the startup configuration file and/or running configuration file of a
label as the startup configuration file and/or running configuration file for the device.
Table 12 Fields of the configuration label list
Field Description
Label Label of a startup configuration file and/or running configuration file.
Running Config Version number of the running configuration file associated with the label.
Backup Time Time when the running configuration file is backed up.
Allows you to compare two configuration files including the drafts to find the
differences.
Follow these steps:
3. Click the
Compare
Startup Config Version number of the startup configuration file associated with the label.
file on the left side of the comparison page.
4. Click the
the right side of the comparison page, as shown in Figure 13.
IMPORTANT:
The running configuration file does not support the xml format.
icon of a file and select Compare as Left from the men u to plac e the
icon of another file and select Compare To to place the file on
Backup Time Time when the startup configuration file is backed up.
Restore
Allows you to set the configuration file(s) identified by the label as the startup
configuration file and/or running configuration file for the device.
15
Page 20
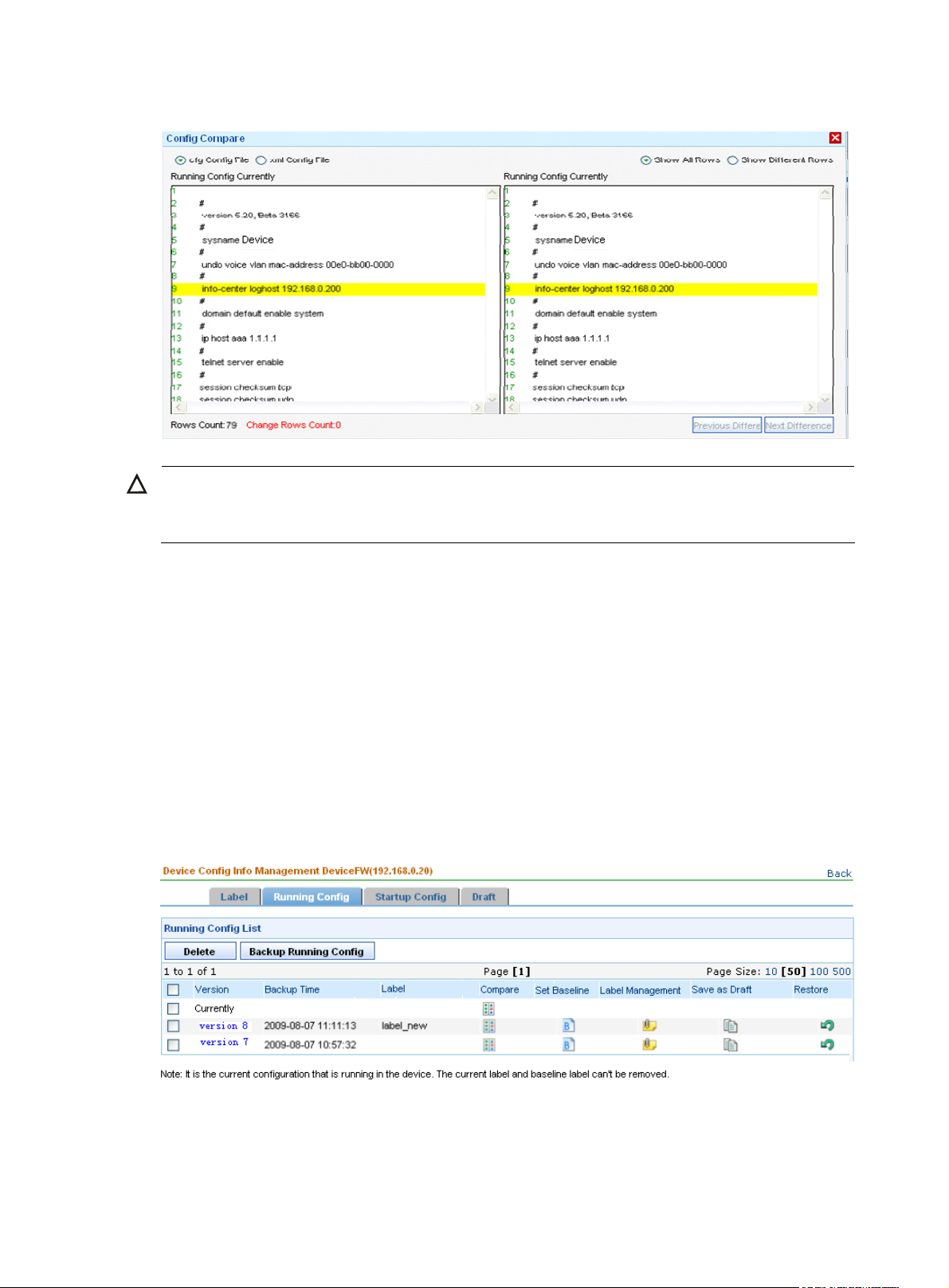
Figure 13 Compare two configuration files
CAUTION:
The label Currently indicates the configuration file is currently used by the device and the label Baseline
indicates the baseline version. Configuration files with any of these labels cannot be deleted.
Return to Tabs on the device configuration information management page and functions provided.
6. Running Config
On the device configuration management list, you can click the icon in the Management column of a
device to bring up the configuration information management interface of the device, as shown in
Figure
12. Then, click the Running Config tab to enter the running configuration file management page, as
shown in
Figure 14.
The Running Config tab allows you to:
• View, back up, restore and delete a running configuration file.
• Specify the running configuration as the baseline or save it as a draft.
• Compare two configuration files to find the differences.
Figure 14 Running configuration file list
16
Page 21
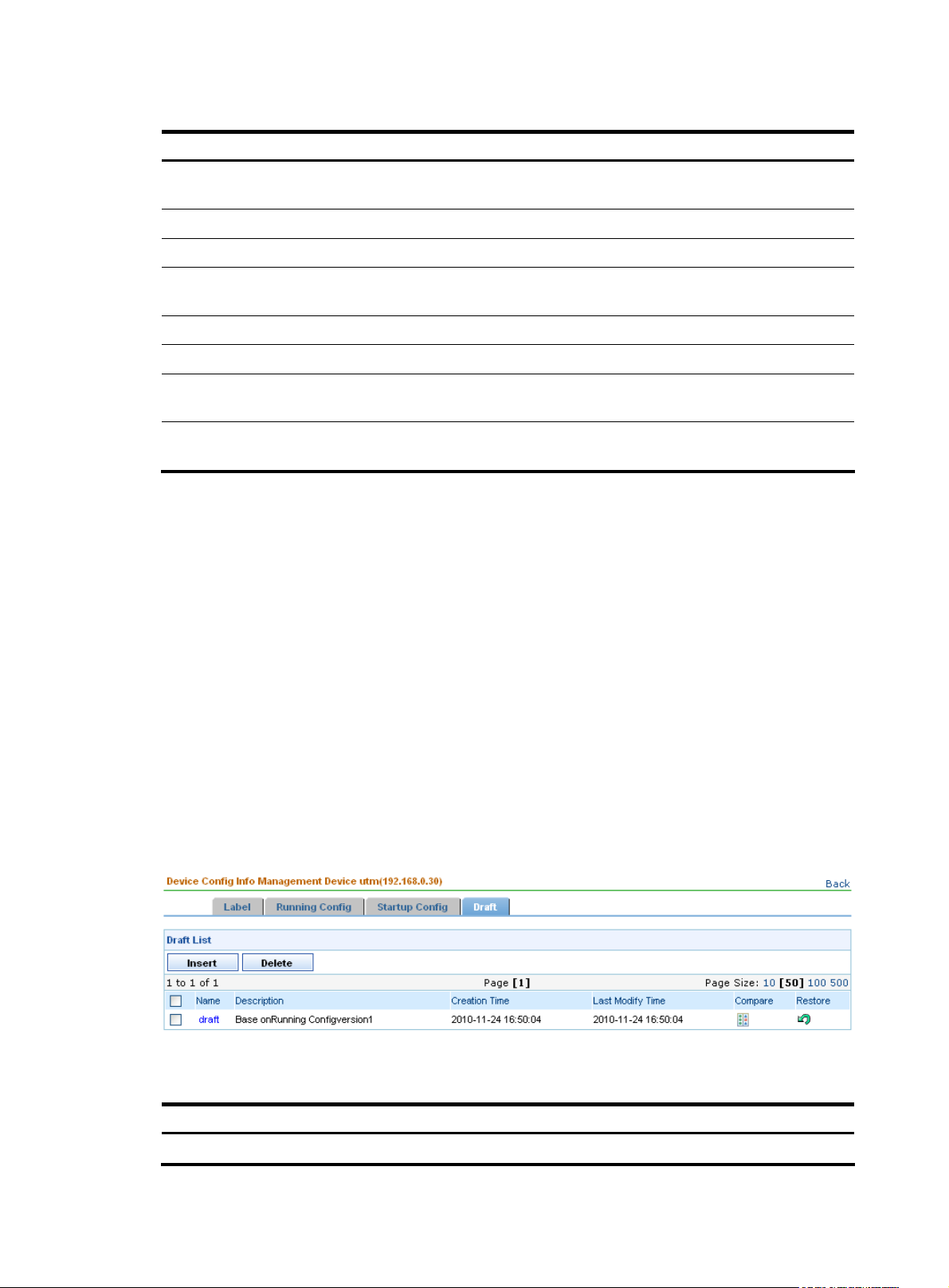
Table 13 Fields of the running configuration list
Field Description
Version
Backup Time Time when the running configuration file is backed up.
Label Label for this version.
Compare
Set Baseline Allows you to set the running configuration file as the baseline.
Label Management Allows you to re-label the running configuration file.
Save as Draft
Restore
Uniquely identifies the running configuration file. The version number is assigned
automatically by the system for each backup file.
Allows you to compare two configuration files including the drafts to find the
differences.
Allows you to save the running configuration file as a draft, and then edit the
content of the draft.
Allows you to set the configuration file identified by the version as the running
configuration file for the device.
Return to Tabs on the device configuration information management page and functions provided.
7. Draft
You can save a configuration file as a draft, or create a new draft.
On the device configuration management list, you can click the icon in the Management column of a
device to bring up the configuration information management interface of the device, as shown in
12. Then, click the Draft tab to enter the draft management page, as shown in
Figure 15. You can
Figure
customize a configuration file and apply it to the device.
The Draft tab allows you to:
• Edit a configuration file and save it as a draft.
• Add and delete drafts.
• Click the restoration icon to replace the contents of the draft with the current startup or running
configuration file.
• Compare a draft with itself, another draft, or any configuration file to find the differences.
Figure 15 Draft list
Table 14 Fields of the draft list
Field Description
Name Name of the draft.
17
Page 22
Description Remarks on the draft.
Creation Time Time when the draft is created.
Last Modify Time Last time when the draft is modified.
Compare Allows you to compare the draft with a configuration file to find the differences.
Allows you to set the draft as the configuration file for the device.
Restore
IMPORTANT:
Do not set a draft as the startup configuration file.
Return to Tabs on the device configuration information management page and functions provided.
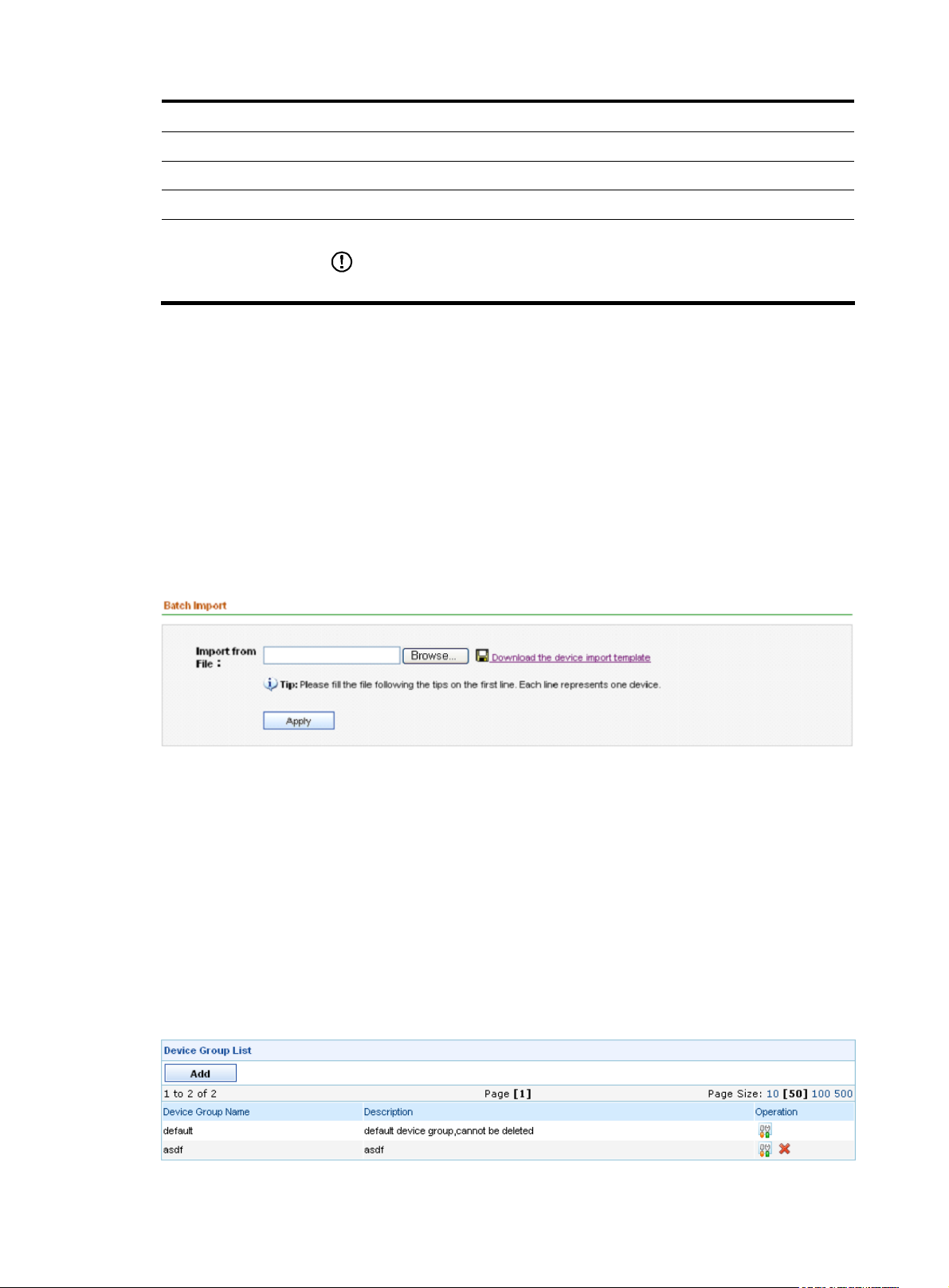
Managing batch import
The batch import function allows you to add devices to the A-IMC Firewall Manager in batches by using
a batch import file.
Configuration guide
From the navigation tree of the system management component, select Batch Import under Device
Management. The batch import page appears, as shown in
import file, and then click Apply.
Figure 16. Click Browse to select the batch
Figure 16 Batch import of devices
Managing device groups
The device group management function allows you to add, modify, and delete device groups. When you
add devices later, you can group devices into device groups so that you can manage and collect statistics
on users, devices, and IP addresses by device group.
Configuration guide
From the navigation tree of the system management component, select Device Group List under Device
Management. The device group management page appears, as shown in
the device group management functions.
Figure 17 Device group management page
Figure 17. Table 15 describes
18
Page 23
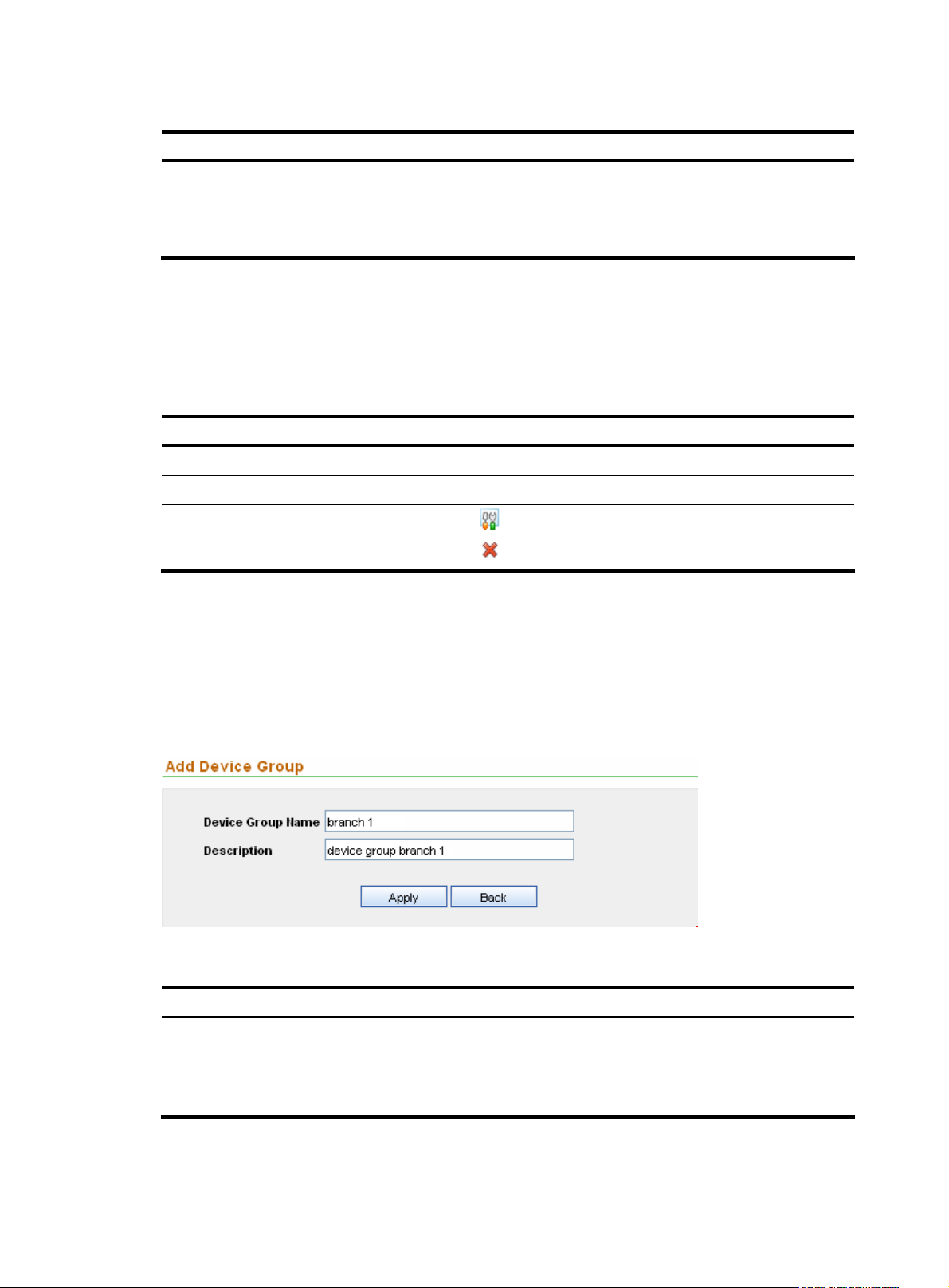
Table 15 Device group management functions
Function Description
Device group list
Adding a device group
Device group list
From the navigation tree of the system management component, select Device Group List under Device
Management. The device group management page appears, as shown in
groups are displayed on the page.
Table 16 Fields of the device group list
Field Description
Device Group Name
Description
Operation
Return to Device group management functions.
Adding a device group
Allows you to view details about device groups and modify and delete
device groups.
Allows you to add a device group and configure the device group name
and description.
Figure 17. Details of all device
Name of the device group
Description of the device group
• Click the icon of a device group to modify the device group.
• Click the icon of a device group to delete the device group.
From the navigation tree of the system management component, select Device Group List under Device
Management to enter the device group management page. Then, click Add to add a device group as
shown in
Figure 18 and Table 17.
Figure 18 Add a device group
Table 17 Device group configuration items
Item Description
Required
Device Group Name
Type a name for the device group.
The device group name can comprise up to 40 characters and must not contain
these characters: ” < > ’ & % : ; / \
19
Page 24
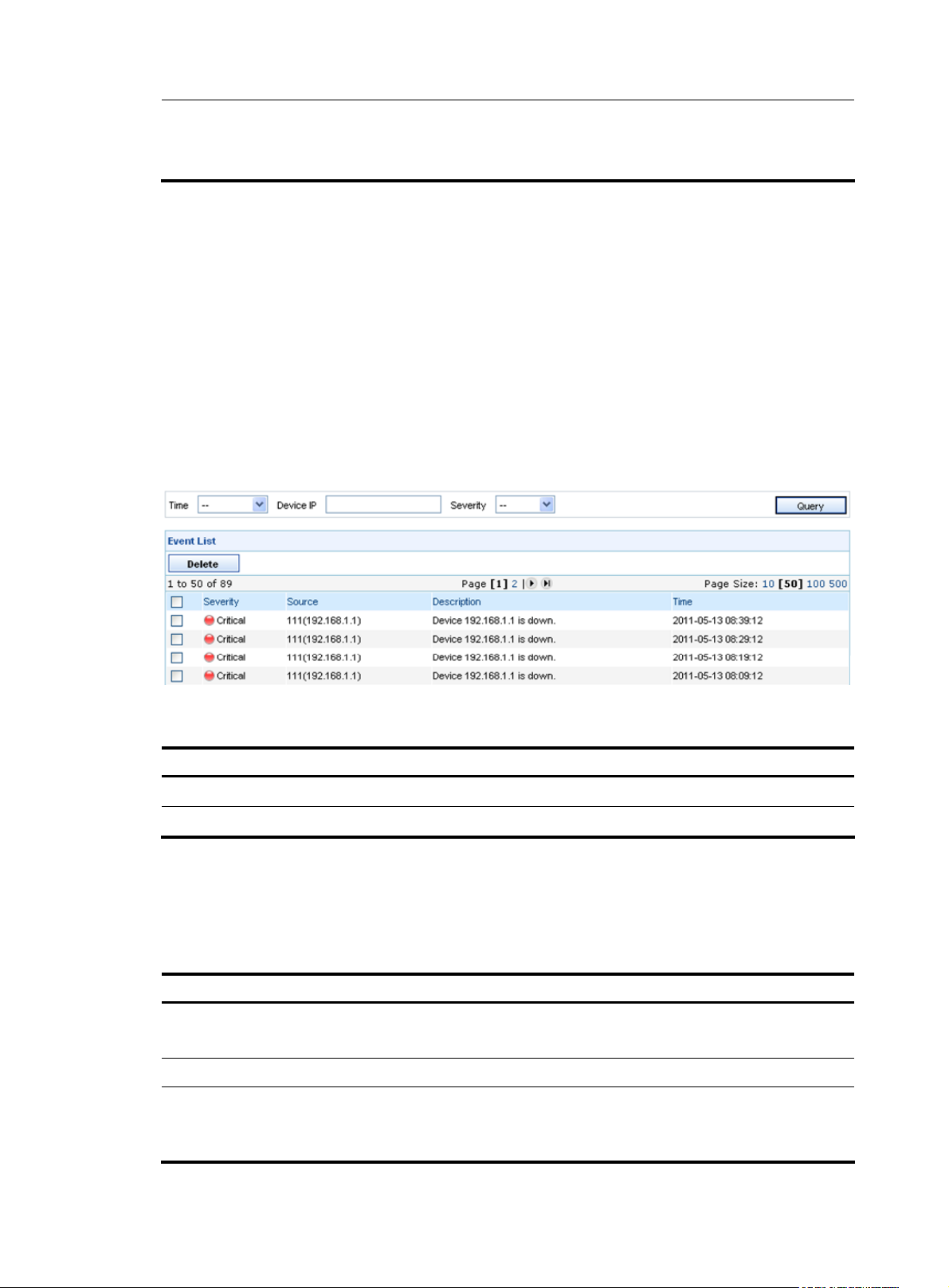
Description
Return to Device group management functions.
Managing events
Configuration guide
The event management function records the operations on managed devices and logs the events,
allowing you to track the status of devices.
From the navigation tree of the system management component, select Events under Device Management.
The device event list page appears by default, as shown in
Table 18 describes the device management functions.
Figure 19 Device event list page
Optional
Type a description for the device group.
The description can comprise up to 40 characters.
Figure 19.
Table 18 Event management functions
Function Description
Device event list Allows you to view details about device events.
Device interface event list Allows you to view details about device interface events.
Device event list
Table 19 describes the device event query options. You can use any combination of the options to query
for the device events of interest.
Table 19 Device event query options
Option Description
Time
Device IP
Severity
Select the time period during which the device events occurred.
By default, the value of this option is --, which means any time.
Type the IP address of the device, in dotted decimal notation.
Select the severity level of the device events.
Severity levels in descending order are critical, major, minor, and
warning. By default, the value of this option is --, which means all levels.
20
Page 25
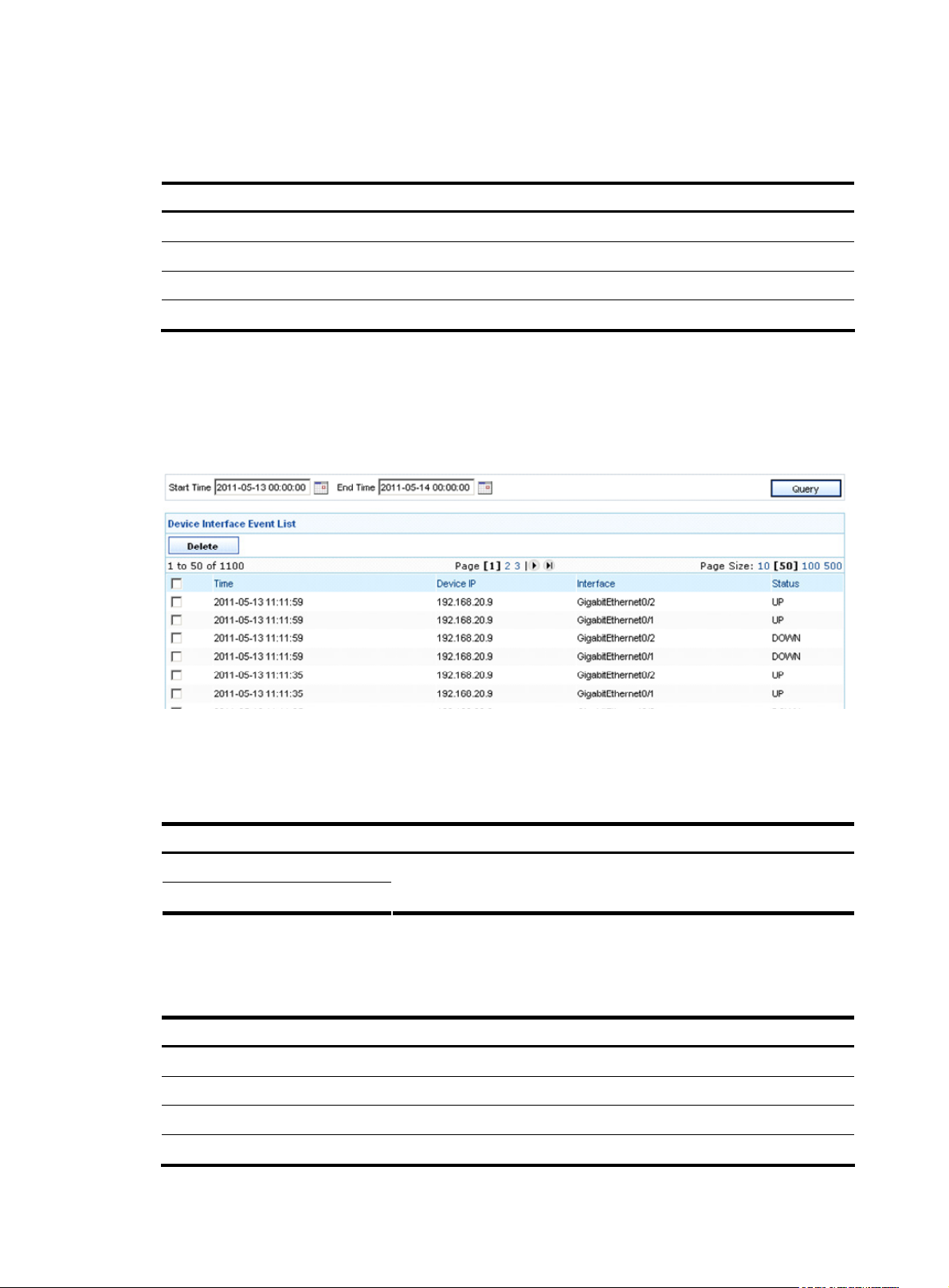
Table 20 describes the fields of the device event list. You can select the check boxes before events and
then click Delete to delete the events.
Table 20 Fields of the device event list
Field Description
Severity
Source
Description
Time
Device interface event list
Select the Device Interface Event List tab to enter the device interface event list page, as shown in Figure
20.
Figure 20 Device interface event list
Severity level of the device event
Label and IP address of the device that is the source of the device event
Description of the device event
Time when the device event occurred
Table 21 describes the event query options. You can use any combination of the options to query for the
events of interest.
Table 21 Device interface event query options
Option Description
Start Time
End Time
Select the time period during which the device interface events occurred.
Table 22 describes the fields of the device interface event list. You can select the check boxes before
events and then click Delete to delete the events.
Table 22 Fields of the device interface event list
Field Description
Time
Device IP IP address of the device in the device interface event
Interface Interface in the device interface event
Status Status of the device interface event
Time when the device interface event occurred
21
Page 26
Managing device access templates
The device access template management function allows you to configure information such as the device
login password.
Configuration guide
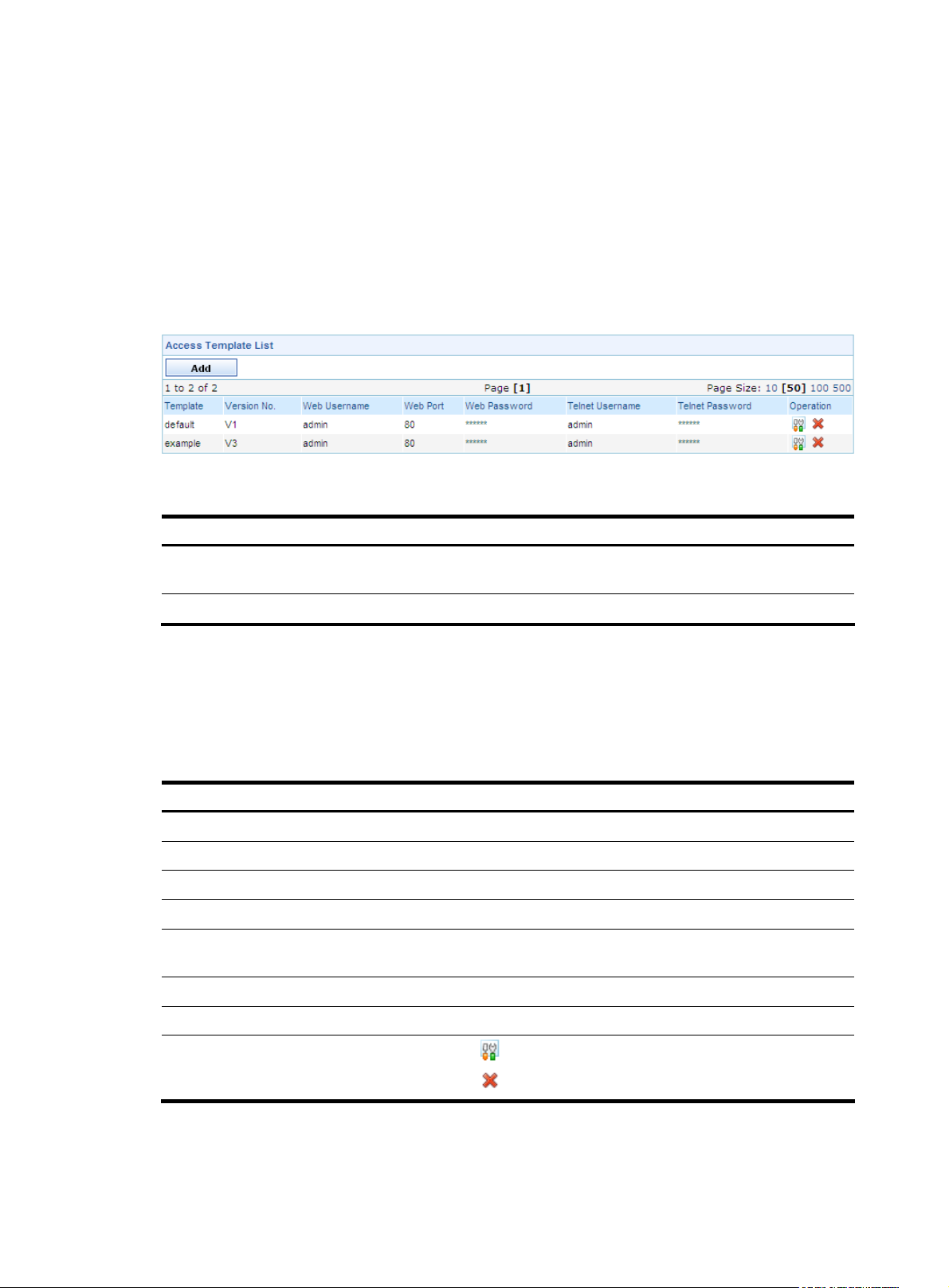
From the navigation tree of the system management component, select Access Template List under Device
Management. The access template management page appears, as shown in
describes the template management functions.
Figure 21 Access template management page
Table 23 Template management functions
Function Description
Figure 21. Table 23
Template list
Adding a template Allows you to add templates.
Template list
From the navigation tree of the system management component, select Access Template List under Device
Management. The access template management page appears, as shown in
access templates are displayed on the page.
Table 24 Fields of the template list
Field Description
Template
Version No.
Web Username
Web Port
Web Password
Telnet Username
Telnet Password
Allows you to view details about access templates and modify and delete
templates.
Figure 21. Details of all
Name of the template
Version of the template
Username for managing the device through web
Port of the device providing web access service
Password for managing the device through web, displayed as a string of
asterisks (*)
Username for telneting to the device
Password for telneting to the device, displayed as a string of asterisks (*)
Operation
• Click the icon of a template to modify the template.
• Click the icon of a template to delete the template.
Return to Template management functions.
22
Page 27
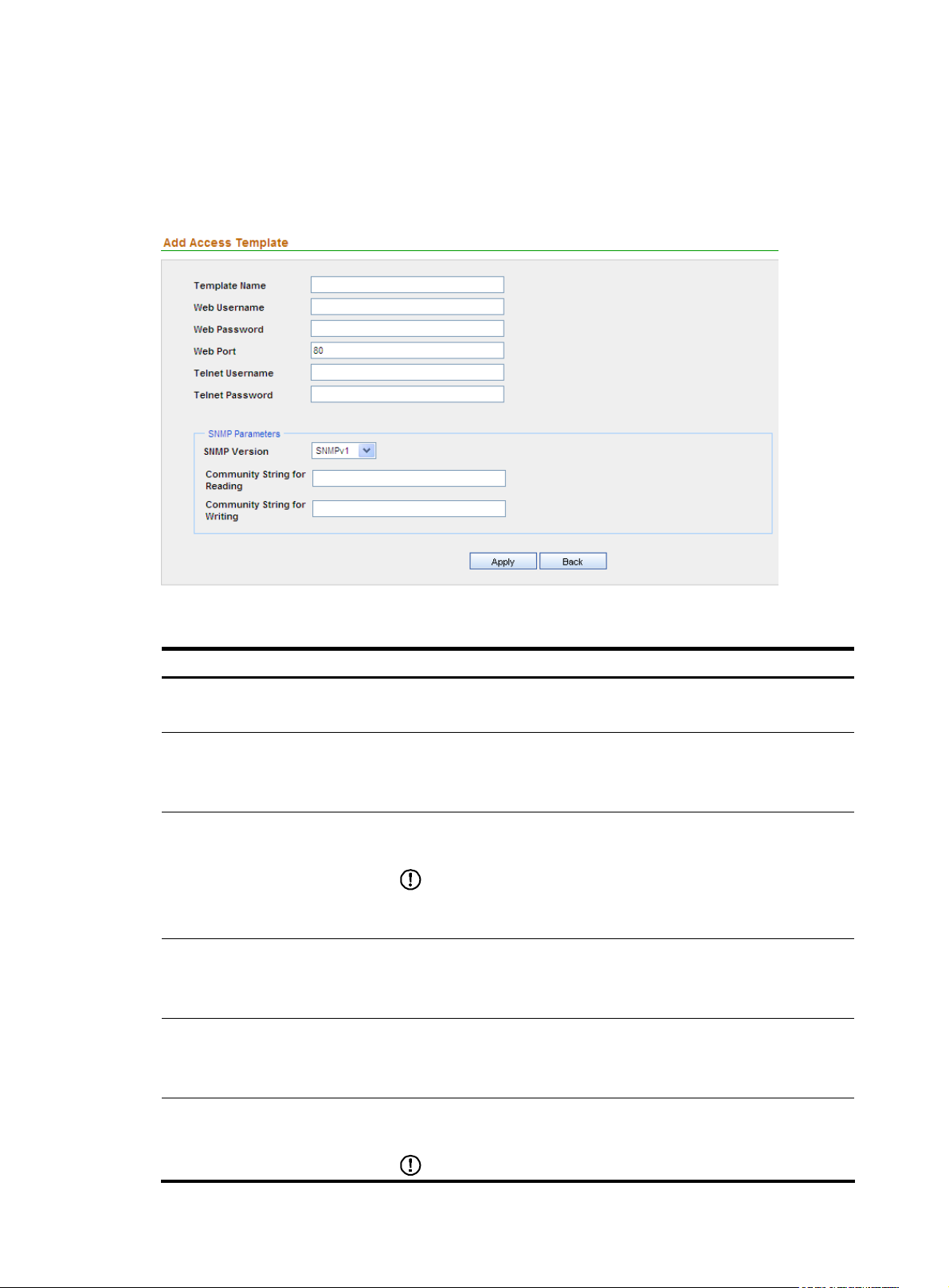
Adding a template
From the navigation tree of the system management component, select Access Template List under Device
Management to enter the access template management page. Then, click Add to add a template as
shown in
Figure 22 Add a template
Figure 22 and Table 25.
Table 25 Template configuration items
Item Description
Template Name
Web Username
Web Password
Web Port
Telnet Username
Required
Type a name for the template, a string of 1 to 20 characters.
Required
Specify the username for managing the device through web.
The username can comprise up to 20 characters.
Required
Specify the password for managing the device through web.
IMPORTANT:
The strength of the password must meet the password strength requirements
of the device.
Required
Specify the port of the device providing web access service.
Port 80 is the default.
Optional
Specify the username for telneting to the device.
The username can comprise up to 20 characters.
Telnet Password
Optional
Specify the password for telneting to the device.
IMPORTANT:
23
Page 28

The strength of the password must meet the password strength requirements
of the device.
SNMP Version
Community String for Reading
Community String for Writing
Authentication Username
Authentication Protocol
Password
Required
Select an SNMP version, which can be SNMPv1, SNMPv2, or SNMPv3.
Required
Specify the SNMP read community string to be used for communication
with the device. It can be a string of up to 20 characters.
Required
Specify the SNMP write community string to be used for communication
with the device. It can be a string of up to 20 characters.
Required for SNMPv3
Specify the authentication username to be used for communication with
the device.
Required for SNMPv3
Specify the authentication protocol to be used for communication with the
device.
Required when you select the authentication protocol HMAC-MD5 or
SMAC-SHA.
Specify the authentication password to be used for communication with
the device.
Required when you select the authentication protocol HMAC-MD5 or
Encryption Protocol
Password
SMAC-SHA.
Specify the encryption protocol to be used for communication with the
device.
Required when you select the encryption protocol CBS-DES or AES-128.
Specify the encryption password to be used for communication with the
device.
Return to Template management functions.
Managing the device software database
The device software database is used to save all device software. It allows you to import device software
to the database from files or devices, and deploy software to devices.
Configuration guide
From the navigation tree of the system management component, select Device Software Database under
Device Management to enter the device software database page, as shown in
describes the device software database functions,
option, and
Table 28 describes the fields of the device software database list.
Table 27 describe the device software database query
Figure 23. Table 26
24
Page 29

Figure 23 Device software database page
Table 26 Device software database functions
Function Description
Importing device software Allows you to import device software from a file or from a device.
Allows you to remove software that is no longer in use.
Deleting device software
Deploying software to device Allows you to deploy software to devices.
Follow these steps:
1. Select the check box before software names.
2. Click Delete.
Table 27 Device software database query option
Option Description
Software Name Specify the name of the software.
Table 28 Fields of the device software database list
Field Description
Software Name Name of the software file
Declaration Remarks on the software
Import Time Time when the software is imported
Size Size of the software file
Check
Rename Allows you to rename the software file.
Export Allows you to export the software to a local place
Deployment Allows you to deploy the software to devices.
Importing device software
Allows you to check whether the exported software is consistent with the
device software.
From the navigation tree of the system management component, select Device Software Database under
Device Management to enter the device software database page, as shown in
Import to bring up the device software import page, as shown in
Figure 24. You can import device
Figure 23. Then, click
software from a file or from devices:
• To import device software from a file, specify the source and destination files.
• To import device software from devices, specify the devices.
25
Page 30
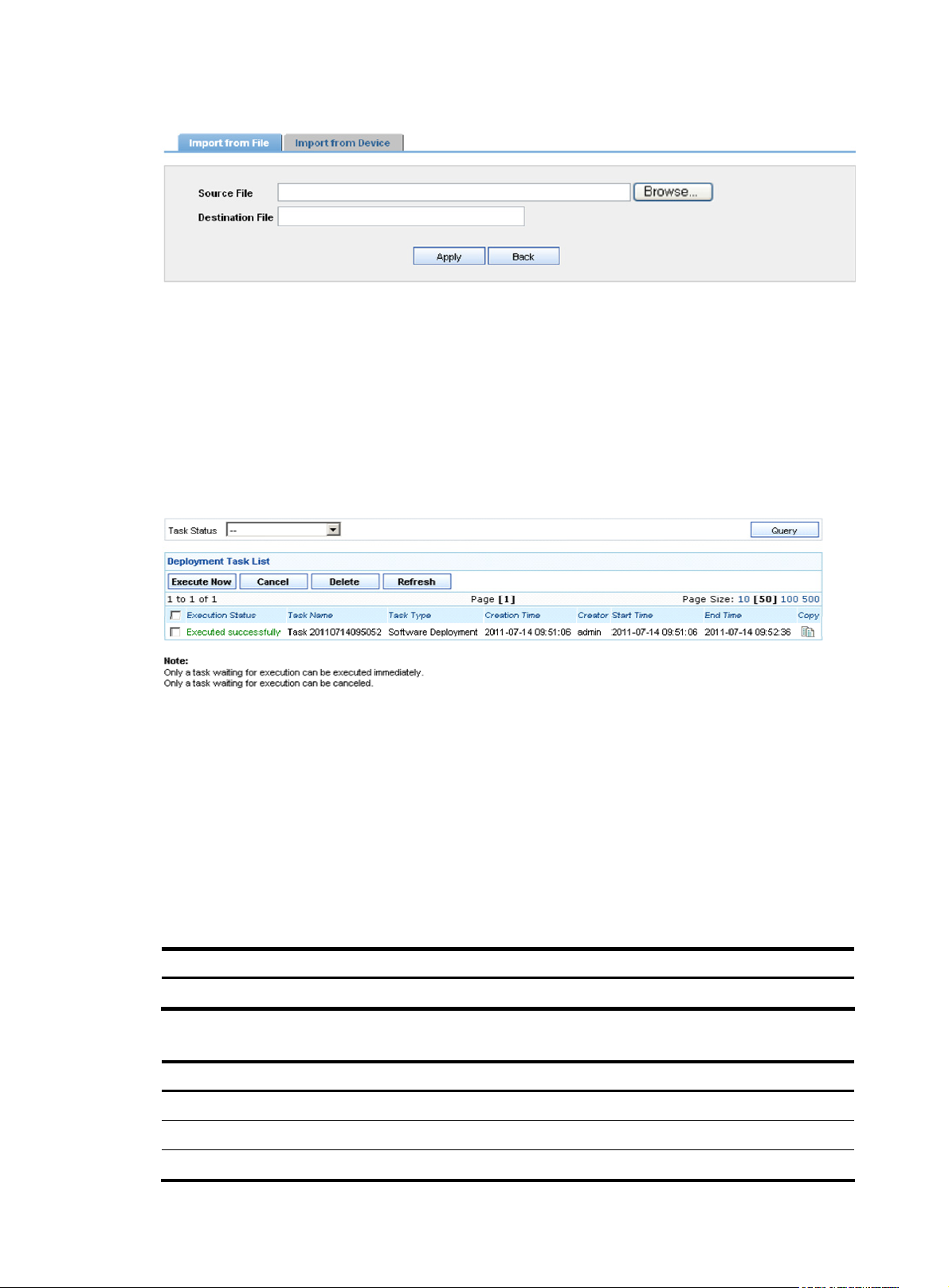
Figure 24 Device software import page
Managing deployment tasks
This function allows you to view all deployment task information.
Configuration guide
From the navigation tree of the system management component, select Deploy Task under Device
Management to enter the deployment task list page, as shown in
Figure 25 Deployment task list
Figure 25.
On the deployment task list, you can:
• Execute deployment tasks immediately.
• Cancel deployment tasks.
• Delete deployment tasks.
• Refresh the deployment task information.
Table 29 describes the deployment task query option and Table 30 describes the fields of the
deployment task list.
Table 29 Deployment task query option
Option Description
Task Status Select a state to list all deployment tasks in the state.
Table 30 Fields of the deployment task list
Field Description
Execution Status Current status of the deployment task
Task Name Name of the deployment task
Task Type Type of the deployment task
26
Page 31

Creation Time Time when the deployment task is created
Creator Creator of the deployment task
Start Time Time when the deployment task starts
End Time Time when the deployment task ends
Copy Allows you to create a deployment task based on the selected one.
Operator management
The operator management function allows you to manage operators and operation logs, and to change
operator passwords.
Managing operators
This function allows you to manage the rights of web users. There are three user levels: common operator,
system administrator, and super administrator. A higher level operator has all the rights of operators of
a lower level.
Table 31 User levels and the rights
Table 31 describes the rights of the three user levels.
User level Rights
Common operator
(visitor level)
System administrator
(monitoring level)
Super administrator
(management level)
Configuration guide
From the navigation tree of the system management component, select Operators under Operator
Management. The operator management page appears, as shown in
Figure 26 Operator management page
• Use the Ping tool
• Cannot perform any configuration
• Use the Ping tool
• View configuration information except for user information
• View log information except for operation logs
• Perform configurations except for user configuration, operation logging
configuration,managing device groups, batch import, access template
management,System Parameter,Management Ports,Mail server,LDAP Server
Management,Log Retention Time,disk monitoring,subsystem
management,license management
• View all configurations
• View all logs
• Perform all configurations
Figure 26.
27
Page 32

Table 32 Operator management functions
Function Description
Operator list
Adding an operator Allows you to add operators.
Operator list
From the navigation tree of the system management component, select Operators under Operator
Management. The operator management page appears, as shown in
Table 33 Fields of the operator list
Field Description
Login Name
Role
Last Login Time
Managed Device Groups
Authentication Mode Authentication mode of the operator
Operation
Allows you to view details about operators, modify operator information,
and delete operators.
Figure 26.
Username used by the operator at login
Operation level of the operator
Last time when the operator logged in
Device groups for which the operator has operation rights
• Click the icon of an operator to modify the operator’s information.
• Click the icon of an operator to delete the operator.
Return to Operator management functions.
Adding an operator
From the navigation tree of the system management component, select Operators under Operator
Management to enter the operator management page. Then, click Add to enter the page for adding an
operator, as shown in
Figure 27 Add an operator
Figure 27. Table 34 describes the operator configuration items.
28
Page 33

Table 34 Operator configuration items
Item Description
Login Name
Login Password
Confirm Password
Role
Manage Device Group
Authentication Mode
Type a name for the operator, a string of up to 40 characters.
Specify a password for the operator to use at login.
The password must comprise 6 to 20 alphanumeric characters, and its strength
must meet the password strength requirements of the device.
Type the password again, which must be the same as that for Login Password. If
the two are not the same, an error message will appear, telling you that they must
be identical.
Select an operation level for the operator.
Specify which device groups the operator can manage.
Select an authentication mode for the operator.
Available authentication modes include local authentication and LDAP
authentication. If you select LDAP authentication, you must also select an LDAP
server.
Return to Operator management functions.
Managing operation logs
Configuration guide
Operation logs reflect what operators have done after login. A super administrator can view operations
logs, query logs by different conditions, and delete logs.
From the navigation tree of the system management component, select Operation Logs under Operator
Management. The operation log management page appears, as shown in
Figure 28. Table 35
describes the operation log query options. You can use any combination of the options to query for the
logs of interest.
Figure 28 Operation log management page
Table 35 Operation log query options
Option Description
Operator
Gateway IP
Operation Result
Specify the operator whose logs you are interested in.
Type the IP address of the gateway.
Select the operation result of the operations.
By default, the value of this option is --, which means both the succeeded and
failed operations.
29
Page 34

Table 36 Fields of the operation log list
Field Description
Operator
IP Address
Time
Operation
Result
Details
Name of the operator
IP address of the PC used by the operator to log in
Time when the operation occurred
What the operator did
Whether the operation succeeded or failed
Operation details
Changing your login password
This function allows you to change your login password.
From the navigation tree of the system management component, select Password under Operator
Management to enter the page for changing your login password, as shown in
describes the configuration items for changing your password.
Figure 29 Change your login password
Figure 29. Table 37
Table 37 Configuration items for changing your password
Item Description
Required
Old Password
New Password
Confirm Password
Type the current password.
The password must be an alphanumeric string of 6 to 20 characters.
Required
Type the new password.
The password must be an alphanumeric string of 6 to 20 characters.
Required
Type the new password again.
This password must be exactly the same as that for New Password.
30
Page 35

System configuration
Configuring system parameter
Configure the system parameter to allow non-SNMP devices in the system.
Configuration guide
From the navigation tree of the system management component, select System Parameter under System
Config. The system parameter configuration page appears, as shown in
for the parameter and click Apply.
Figure 30 System parameter setting
Figure 30. Select the check box
Configuring management ports
This module allows you to specify the Firewall Manager background ports for receiving various logs from
devices.
Configuration guide
From the navigation tree of the system management component, select Management Ports under System
Config. The management ports configuration page appears, as shown in
the management port configuration items.
Figure 31 Management port configuration page
Figure 31. Table 38 describes
Table 38 Management port configuration items
Item Description
NAT Logs Port
Required
31
Page 36

Type the port for receiving NAT logs.
The port number must be in the range from 1 to 65534.
Required
Syslog Port
NetStream V9 Logs Port
Type the port for receiving syslogs.
The port number must be in the range from 1 to 65534.
Required
Type the port for receiving NetStream V9 logs.
The port number must be in the range from 1 to 65534.
Configuring the mail server
This module allows you to configure the mail server information, so that the system emails alarm
information to the specified server.
Configuration guide
From the navigation tree of the system management component, select Mail Server under System Config.
The mail server configuration page appears, as shown in
configuration items.
Figure 32. Table 39 describes the mail server
Figure 32 Configure the mail server
Table 39 Mail server configuration items
Item Description
Required
SMTP Mail Server IP
Type the IP or domain name of the mail server.
The domain name can comprise up to 100 characters.
Require authentication
Username
Optional
Specify whether the mail server authenticates the identities of users trying to
access.
Optional
32
Page 37

Type the username for identity authentication on the mail server.
The password can comprise up to 80 characters.
Password
Sender’s Mail Address
Managing filters
A filter is used to filter the information of IPS devices to present only information that you are interested in
through reports.
By configuring filters, you can specify filtering conditions flexibly.
Configuration guide
From the navigation tree of the system management component, select Filter Management under System
Config. The filter management page appears, as shown in
management functions.
Figure 33 Filter management page
Optional
Type the password for identity authentication on the mail server.
Required
Type the mail address of the sender.
Figure 33. Table 40 describes the filter
Filter list
Table 40 Filter management functions
Function Description
Filter list Allows you to view details about filters and modify filter settings.
Adding a filter Allows you to add a filter.
Allows you to delete filters that are no longer in use.
Deleting filters
Follow these steps:
1. Select the check boxes before the filters to be deleted.
2. Click Delete.
From the navigation tree of the system management component, select Filter Management under System
Config. The filter management page appears, as shown in
Figure 33.
Table 41 Fields of the filter list
Field Description
Filter Name
Name of the filter
Filter Description
Device
Description of the filter
Device that the system collects statistics on
33
Page 38

Field Description
Operation
Return to Filter management functions.
Adding a filter
From the navigation tree of the system management component, select Filter Management under System
Config to enter the filter management page. Then, click Add to enter the page for adding a filter, as
shown in
Figure 34 Add a filter
Click the icon of a filter to modify the settings of the filter.
Figure 34. Table 42 describes the filter configuration items.
Table 42 Filter configuration items
Item Description
Required
Filter Name
Filter Description
Device
Source IP
Destination IP
Source Port
Type a name for the filter.
The filter name can comprise up to 40 characters.
Optional
Type a description for the filter.
The description can comprise up to 50 characters.
Optional
Select the devices that you want the system to collect statistics on.
Optional
Specify the source IP addresses that you want the system to collect statistics on.
Optional
Specify the destination IP addresses that you want the system to collect statistics on.
Optional
34
Page 39

Specify the source ports that you want the system to collect statistics on.
Destination Port
Protocol
Event
CAUTION:
Optional
Specify the destination ports that you want the system to collect statistics on.
Optional
Select the protocols that you want the system to collect statistics on.
Optional
Specify the events that you want the system to collect statistics on.
The configuration items given in the previous table can be used to define query conditions. For example,
you can enter source IP address 1.1.1.1 to search for data with the source IP address being 1.1.1.1, or
enter source IP address 1.1.1.1 and select the Invert selection check box to search for data whose source
IP address is not 1.1.1.1.
Return to Filter management functions.
Managing LDAP servers
This function allows you to configure LDAP servers. Then, you can select LDAP authentication to verify the
operator’s username and password when they log in to the Firewall Manager system.
Configuration guide
From the navigation tree of the system management component, select LDAP Server Management under
System Config. The LDAP server management page appears, displaying all LDAP servers.
Figure 35 LDAP server management page
Table 43 LDAP server management functions
Function Description
LDAP server list Allows you to view details about LDAP servers and modify LDAP server settings.
Adding an LDAP server Allows you to add an LDAP server.
Deleting LDAP servers
LDAP server list
The LDAP server list is on the LDAP server management page, as shown in Figure 35.
Allows you to delete one or more LDAP servers from the system.
35
Page 40

Table 44 Fields of the LDAP server list
Field Description
Server Name
Server IP Address IP address of the LDAP server
Server Version
Operation
Import Users The device does not support importing users.
Return to LDAP server management functions.
Adding an LDAP server
From the navigation tree of the system management component, select LDAP Server Management under
System Config. Click Add to add an LDAP server, as shown in
Figure 36 Add an LDAP server
Name of the LDAP server
Version information of the LDAP server
Click the
icon of a LDAP server to modify the settings of the filter.
Figure 36 and Table 45.
Table 45 LDAP server configuration items
Item Description
Server Name
Server Version
Server IP
Server Port
Admin DN
Required
Type a name for the LDAP server.
Required
Select an LDAP server version.
Required
Type an IP address for the LDAP server.
Required
Type a port number for the LDAP server.
Required
Type the administrator DN for the LDAP server.
36
Page 41

Admin Password
Username Attribute
Base DN
Required
Type the administrator password for the LDAP server.
Required
Type a username attribute for the LDAP server.
Required
Type a base DN for the LDAP server.
Return to LDAP server management functions.
Managing log retention time
This function allows you to configure the period of time during which the system keeps the firewall logs
and SSL VPN logs for query.
Configuration guide
From the navigation tree of the system management component, select Log Retention Time under System
Config. The log retention time configuration page appears, as shown in
days that the system keeps the firewall logs and SSL VPN logs and then click Apply.
Figure 37 Log retention time configuration page
Figure 37. Set the number of
Monitoring the disk space
This function provides the usage statistics of the disk space under the system installation directory. It
allows you to set the minimum free disk space, so that an alarm is generated whenever the free disk
space is less than the threshold. You can also specify an email address so that the system sends
generated alarms to the mail box. This function helps reduce data loss due to lack of disk space.
Configuration guide
From the navigation tree of the system management component, select Disk Monitoring under System
Config. The disk space alarm configuration page appears, as shown in
set the disk space alarm threshold, so that the system issues an alarm whenever the free disk space is less
than the threshold.
Figure 38. On the page, you can
37
Page 42

Figure 38 Disk space alarm configuration page
Table 46 Alarm configuration items of the disk space for logs
Item Description
Required
Warning Disk Space
Set the minimum free disk space required. An alarm is generated once the
actual free disk space is lower than this value.
Optional
Send a report by email
Selecting the check box will make the system send generated alarms to the
specified mail box.
You can also select the Residual Disk Monitoring tab to view the disk space usage information in the last
three hours, 36 hours, and 36 days, and the remaining disk space per day, or select the Detail tab to
view disk space usage statistics of function modules, as shown in
Figure 39.
38
Page 43

Figure 39 Free disk space monitoring page
Managing subsystems
The subsystem management allows you to manage and monitor multiple Firewall Managers effectively.
By adding different systems as the subsystems, you can access these subsystems by simply clicking their
URL links instead of entering the URLs, usernames and passwords repeatedly.
Configuration guide
From the navigation tree of the system management component, select Subsystem Management under
System Config to enter subsystem configuration page, as shown in
fields of the subsystem list.
Figure 40. Table 47 describes the
39
Page 44

Figure 40 Subsystem information
Table 47 Fields of the subsystem list
Field Description
Server IP IP address of the server for the subsystem.
Port Port for connecting to the subsystem.
User Name Username for logging in to the subsystem.
Password Password for logging in to the subsystem.
Link URLs of the subsystem. Click a link to log in to the subsystem.
Adding a subsystem
From the navigation tree of the system management component, select Subsystem Management under
System Config. Click Add to enter the page for adding a subsystem, as shown in
describes the configuration items for adding a subsystem
Figure 41 Add a subsystem
Table 48 Configuration items for adding a subsystem
Item Description
Figure 41. Table 48
Server IP
Server Port
Required
Type the IP address for the subsystem.
Required
Type the port of the subsystem. It defaults to port 80.
40
Page 45

Required
User Name
Password
Type the username for logging in to the subsystem.
The username can comprise up to 40 characters.
Required
Specify the password for logging in to the subsystem.
The password must comprise 6 to 20 alphanumeric characters,
41
Page 46

Firewall management
The Firewall Manager enables centralized management of firewall devices in the network, centralized
event collection and analysis, realtime monitoring, event snapshot, comprehensive analysis, event details,
and log auditing. It provides abundant reports, which can be exported periodically.
To access the firewall management component, select the Firewall tab. Then, you can perform:
•
Attack events monitoring
Event analysis
•
Event auditing
•
Security policy management
•
Firewall device management
•
Attack events monitoring
The firewall management component supports centralized monitoring of security events. It can collect
and report attack events in real time, and provide the snapshot information based on firewall devices and
events.
Snapshot of events
The event snapshot presents the attack protection information in the last hour, including the time, total
number of events, blocked events count, source addresses and destination addresses, as well as event
types. Besides, it provides the TopN list of attack events, attack destination IP addresses and ports, attack
sources, and attack protocols, helping you track the latest security status of the network in an intuitive
way.
Configuration guide
From the navigation tree of the firewall management component, select Snapshot of Events under Events
Monitor to enter the event snapshot page, as shown in
Figure 42.
42
Page 47

Figure 42 Snapshot of events
Table 49 Event snapshot query options
Option Description
Select a device, a device group, or All devices from the Device drop-down list. The
system will display the relevant event information. All devices and device groups that
are under your management will appear in the drop-down list.
Device
IMPORTANT:
• Selecting a device group: Specifies all devices in the device group.
• Selecting a device name: Specifies the single device.
Top
Statistics Time
Select a value in the Top drop-down list to specify the number of records to be displayed
in the graphs and lists.
Period of time during which the statistics were collected. The snapshot statistics time is
the last hour.
Table 50 Fields in the event snapshot lists
Field Description
Attack Event
Destination IP
Destination Port
Source IP
Protocol
Attack protection statistics lists, including the event name/destination IP
address/destination port/source IP address/protocol of the attack
Event Count Count of events
Percentage Percentage of the events
43
Page 48

• In the Detail column of a TopN list, you can click the icon of an attack event to enter the attack
event details page. For more information, see “
Recent events list
The firewall management component presents firewall attack events not only through graphs but also in
a table list. The recent events list presents you the attack events occurred during the last hour, including
the device IP address, the event’s time, source IP address, destination IP address, event description,
protocol, source port, and destination port. It also supports events query by different filters.
Configuration guide
From the navigation tree of the firewall management component, select Recent List under Events Monitor.
The recent events page appears, listing the attack events that occurred during the last hour. as shown in
Figure 43. Table 51 describes the query option of the list. Table 52 describes the fields of the event list.
Figure 43 List of recent attack events
Event details.”
Table 51 Query option description
Option Description
Filter Select a filter from the drop-down list to display specific events.
Table 52 Fields of the recent events list
Field Description
Time Time when the event occurred
Device IP IP address of the firewall device
Source IP Source IP address of the attack packets
Destination IP Destination IP address of the attack packets
Event Description of the event
Protocol Name Protocol of the attack packets
Source Port Source port of the attack packets
Destination Port Destination port of the attack packets
44
Page 49

Device monitoring
In addition to the attack event information of the entire network, the firewall management component
also allows you to view the attack event information of every firewall device.
Configuration guide
From the navigation tree of the firewall management component, select Device Monitoring under Events
Monitor to enter the device monitoring page, as shown in
protection information in the last hour by device, including the total number of events, number of blocked
events, number of source/destination IP addresses, and number of destination ports.
Figure 44 Device monitoring
In the list, you can:
Figure 44. The page presents the attack
• Click the
page of the device. For more information, see “
• Click the
the device. For more information, see “
The firewall management component features comprehensive analysis and statistics reports, through
which you can evaluate the network security status in real time, and take attack prevention measures
accordingly.
icon in the Snapshot column of a firewall device to enter the attack event snapshot
icon in the Details column of a firewall device to enter the attack event details page of
Event analysis
Event overview
The system supports comprehensive analysis of attack events, including:
• Attack event trend analysis during a day, week, month, and a customized period
• TopN statistics reports by event, destination IP address, source IP address, destination port, and
protocol. You can export the reports.
Configuration guide
From the navigation tree of the firewall management component, select Event Overview under Event
Analysis. The attack event trend page appears by default, as shown in
to view attack event trend analysis during a day, week, month, or a customized period of time. This page
shows a trend graph comparing the counts of blocked attack events and the other attack events as well
as a trend graph of attack events by severity level. Under the trend graphs is a list showing the detailed
attack event statistics, including the number of events, number of blocked events, and number of events
of each severity level.
Snapshot of events.”
Event details.”
Figure 45. This page allows you
45
Page 50

Figure 45 Attack event overview
Table 53 Query options on the attack event overview page
Option Description
Select a device, a device group, or All devices from the Device drop-down list. The
system will display the relevant event information. All devices and device groups that
are under your management will appear in the drop-down list.
IMPORTANT:
Device
• If you select a device group, the system will display the event information
(matching the filter) of all firewall devices in the device group in the specified
statistics duration.
• If you select a device name, the system will display the event information
(matching the filter) of the firewall device in the specified statistics duration.
Filter Select a filter from the drop-down list to filter attack events.
Duration
Time
Select the statistics duration. You can select Day, Week, or Month, or select
Customize to specify a statistics duration.
Select the statistics time, whose value range varies with the statistics duration
selected.
Besides the attack event trend graphs, the system also provides contrast graphs of the Top 10 attack
events, attacked IP addresses, attacker IP addresses, attacked ports, and attack protocols, as shown in
Figure 46.
46
Page 51

Figure 46 Top 10 attack events contrast graph
You can click the link to export all the analysis reports that the event overview function
provides.
CAUTION:
Logs are aggregated at 3 o’clock every day. When you query event information of the current month, the
system displays only the data collected from the first day of the month to the day before the current day.
Event details
The Firewall Manager provides the powerful query function, which helps you quickly find the desired
security event information from history data of months.
Configuration guide
From the navigation tree of the firewall management component, select Event Details under Event
Analysis to enter the attack event details page, as shown in
attack events by event name, type, severity, source IP, destination IP, destination port, and protocol to
view the event details.
of the attack event details list.
Figure 47. This page allows you to query
Table 54 describes the event details query options. Table 55 describes the fields
47
Page 52

Figure 47 Attack event details
Table 54 Event details query options
Option Description
Select a device, a device group, or All devices from the Device drop-down list. The system
will display the relevant event information. All devices and device groups that are under
your management will appear in the drop-down list.
Device
IMPORTANT:
• If you select a device group, the system will display the event information (matching the
filter) of all firewall devices in the device group in the specified statistics duration.
• If you select a device name, the system will display the event information (matching the
filter) of the firewall device in the specified statistics duration.
Filter Select a filter from the drop-down list to filter attack events.
Duration
Time Select the statistics time, whose value range varies with the statistics duration selected.
Event Select an attack event type to query the specified type of attack events
Protocol Select the attack protocol. The default is --, which means any protocol.
Severity Select the attack severity. The default is --, which means any severity.
Src IP Specify the attack source IP address.
Dest IP Specify the attack destination IP address.
Dest Port Specify the attack destination port.
Select the statistics duration. You can select Day, Week, or Month, or select Customize to
specify a statistics duration.
Grouping by
Select a grouping mode. The system supports seven grouping modes: None, Event, Src IP,
Dest IP, Src IP and Dest IP, Dest Port, and Protocol.
48
Page 53

g
Table 55 Fields of the attack event details list
Field Description
Time Time when the attack event occurred
Src IP Attack source IP address
Dest IP Attack destination IP address
Event Name of the event
Dest Port Attack destination port
Protocol Protocol used by the attack
Event Count Number of events that occurred at the time
CAUTION:
Lo
s are aggregated at 3 o’clock every day. When you query event information of the current month, the
system displays only the data collected from the first day of the month to the day before the current day.
Report exporting management
This function is for exporting reports periodically. You can specify the report export period, filter, template,
and notification mode to define a report export task. Then, the system will automatically export reports
according to your configuration. You may specify to send a generated reports file to an Email box or
download the reports file from the system.
Configuration guide
From the navigation tree of the firewall management component, select Event Export Tasks under Event
Analysis to enter the repor t expor t task management page, as shown in
report tasks by specifying a report period and/or filter.
Figure 48 Report export task management page
Table 56 Query options of the report export task list
Option Description
Figure 48, where you can query
Select the export interval, which can be Day, Week, Month, Year or All. The
Period
Filter Select a filter to filter the report export tasks.
system will display export tasks with the export interval being the one you
selected.
49
Page 54

Table 57 Fields of the report export task list
Field Description
Report Task Name of the report export task
Creation Time Time when the task was created
Period Reports export interval specified in the export task
Send Mail Whether the report export file is to be sent to the specified mail box.
Generate Report
Click the
the file creation time. These files have the same suffix, which is xls. Click a
report file’s name link to export the file.
icon of a task to display all generated report files of the task and
• Click the icon of a task to enter the task modification page, where you
can modify the task.
Operation
• Click the icon of a task to test whether the task can function. If the test
succeeds, the system generates a report file based on data of the current
day. The filename starts with test.
Table 58 Report export task management functions
Function Description
Report export file list
Adding a report export task Allows you to add a report export task.
Deleting report export tasks
Allows you to view the detailed information of all report export tasks, and
modify and test a report export task.
Allows you to delete report export tasks.
Follow these steps:
1. Select the check boxes before the tasks to be deleted.
2. Click Delete.
Report export file list
From the navigation tree of the firewall management component, select Event Export Tasks under Event
Analysis to enter the report export task management page, as shown in
a task to display all generated report files of the task and the file creation time. These files have the same
suffix, which is xls. Click a report file’s name link to export the file.
Figure 49 Report export file list
Table 59 Fields of the report export file list
Field Description
Filename Name of the report export file
Creation Time Time when the report export file was created
Figure 48. Click the icon of
50
Page 55

Return to Report export task management functions.
Adding a report export task
From the navigation tree of the firewall management component, select Event Export Tasks under Event
Analysis to enter the report export task management page, as shown in
enter the page for adding a report export task, as shown in
configuration items of a report export task.
Figure 50 Add a report export task
Figure 48. Then, click Add to
Figure 50. Table 60 describes the
Table 60 Configuration items of a report export task
Item Description
Required
Task Name
Period
Filter
Template
Notification Mode
Specify the name of the task.
The name can comprise up to 40 characters.
Required
Specify the export interval, which can be Day, Week, Month, or Year. The
default is Day.
Optional
Specify the data to be included in the file by selecting a filter.
Required
Specify the template for exporting reports. Only one template is available at
present.
Optional
Specify the Email box, to which the export file will be sent.
Return to Report export task management functions.
Event auditing
The event auditing function allows you to audit abnormal traffic logs, blacklist logs, operation logs, NAT
logs, inter-zone access control logs, MPLS logs, and other logs. It also supports exporting up to 10,000
entries of logs. If there are more than 10,000 log entries, only the first 10,000 entries will be exported.
51
Page 56

The event auditing function does not support cross-day query. If the query period spans a day or the
query start time is later than the end time, the end time will automatically change to 23:59 of the same
day as the start time.
Inter-zone access log auditing
Configuration guide
From the navigation tree of the firewall management component, select Inter-Zone Access Logs under
Event Auditing to enter the inter-zone access log auditing page, as shown in
A zone is a set consisting of one or more network segments. Inter-zone access logs are logs recorded by
the firewall device when network segments of security zones are attacked. Inter-zone access log auditing
is for analysis of such logs. Each log records the time when the attack occurred, the attack's source zone,
destination zone, source IP:port, destination IP:port, attack protection rule ID, protocol, and action taken
by the system, helping you know about the inter-zone access status of the network.
Figure 51 Inter-zone access log auditing
Figure 51.
Abnormal traffic log auditing
Configuration guide
From the navigation tree of the firewall management component, select Abnormal Traffic Logs under
Event Auditing to enter the abnormal traffic log auditing page, as shown in
logs in order of time, with the most recent log at the top. Each log records the time, source IP, and
destination IP of the abnormal traffic, reason for giving the alarm, severity, and ratio of each protocol
used by the abnormal traffic.
Abnormal traffic log auditing allows you to query abnormal traffic logs by source IP, destination IP,
reason, severity level, time, and device group, helping you analyze traffic for abnormal behaviors.
Figure 52. This page lists the
52
Page 57

Figure 52 Abnormal traffic log auditing
Blacklist log auditing
Configuration guide
From the navigation tree of the firewall management component, select Blacklist Logs under Event
Auditing to enter the blacklist log auditing page, as shown in
Blacklist filters packets by source IP address. It can effectively filter out packets from a specific IP address.
The blacklist log auditing page lists the blacklist logs of HP firewalls. Each log records the log time,
source IP address, reason to add the address to the blacklist, as well as the blacklist entry’s severity level,
hold time of the log entry, and operation mode, helping you know the blacklist status of the network.
Figure 53.
Figure 53 Blacklist log auditing
Operation log auditing
Configuration guide
From the navigation tree of the firewall management component, select Operation Logs under Event
Auditing to enter the operation log auditing page, as shown in
of time, with the most recent log at the top. Each log records the operation’s time, username, IP address
of the PC used to access the system, operation performed, and alarm severity level.
Figure 54. This page lists the logs in order
Operation log auditing allows you to query operation logs by username, user IP, operation, severity level,
time, and device group, helping you know the information of login users and track the users’ operations.
53
Page 58

Figure 54 Operation log auditing
Other log auditing
Configuration guide
From the navigation tree of the firewall management component, select Other Logs under Event Auditing
to enter the page for auditing other logs, as shown in
with the most recent log at the top. Each log records the log time, content, and alarm severity level.
Figure 55. The page lists the logs in order of time,
You can query the logs by content, device group, severity level, and time, so as to get an idea of other
logs.
Figure 55 Other log auditing
54
Page 59

NAT log auditing
Configuration guide
From the navigation tree of the firewall management component, select NAT Logs under Event Auditing
to enter the NAT log auditing page, as shown in
log records the source IP:port and destination IP:port before and after network address translation, as
well as the NAT session start time and end time.
Figure 56 NAT log auditing
Figure 56. The page lists NAT logs of HP firewalls. Each
MPLS log auditing
Configuration guide
From the navigation tree of the firewall management component, select MPLS Logs under Event Auditing
to enter the MPLS log auditing page, as shown in
records such information as source IP address and source port, destination IP address and port, VPN ID,
time, and byte count.
MPLS log auditing allows you to query MPLS logs by source IP, destination IP, source port, destination
port, VPN ID, labels, start time, and end time, helping you know the information of MPLS logs.
Figure 57. This page lists MPLS logs in detail. Each log
55
Page 60

NOTE:
Figure 57 MPLS log auditing
If the IP address/port number is null in the database, NA will be displayed
Security policy management
This function allows you to configure security policies for the firewall devices, so that the devices can
automatically identify and filter network traffic that travel through the devices. More specifically, this
function allows you to configure a series of rules to match packets between a source security zone and
a destination security zone, and permit or drop the matched packets.
Security zones
Configuration guide
From the navigation tree of the firewall management component, select Security Zones under Security
Policy Management to enter the security zone management page, as shown in
describes the security zone management functions available on the page.
Figure 58 Security zone management page
in the IP address or port field.
Figure 58. Table 61
Table 61 Security zone management functions
Function Description
Security zone list Allows you to view the detailed information of all security zones.
56
Page 61

Adding a security zone Allows you to add a security zone.
Importing security zones from a
device
Deleting security zones
CAUTION:
• Security zones Local, Trust, DMZ, and Untrust are system predefined security zones and cannot be
deleted.
• Security zones that have been referenced cannot be deleted.
Security zone list
The security zone list is on the security zone management page, as shown in Figure 58. Table 62
describes the fields of the list.
Table 62 Fields of the security zone list
Field Description
Security Zone Name of the security zone
Allows you to import security zones from a device.
Allows you to delete security zones.
Follow these steps:
1. Select the check boxes before the security zones to be deleted.
2. Click Delete.
Device Device that is configured with the security zone
Referenced Whether the security zone is referenced or not
Operation
Return to Security zone management functions.
Adding a security zone
From the navigation tree of the firewall management component, select Security Zones under Security
Policy Management to enter the security zone management page, as shown in
enter the Add Security Zone page, type a name for the security zone, and click Add.
Figure 59 Add a security zone
Click the
icon to delete the security zone.
Figure 58. Click Add to
57
Page 62

Table 63 Security zone configuration item
Item Description
Security Zone
Type a name for the security zone.
A security zone name cannot contain any of these characters: ^'<>&:;"/\
Return to Security zone management functions.
Importing security zones from a device
From the navigation tree of the firewall management component, select Security Zones under Security
Policy Management to enter the security zone management page, as shown in
from Device to enter the Import Security Zone from Device page, select a device, and click OK.
Figure 60 Import security zones from a device
CAUTION:
Available devices are those added in the device management module of the firewall management
component.
Figure 58. Click Import
Return to Security zone management functions.
Time ranges
Configuration guide
From the navigation tree of the firewall management component, select Time Ranges under Security
Policy Management to enter the time range management page, as shown in
describes the functions available on the page.
Figure 61 Time range management page
Table 64 Time range management functions
Function Description
Figure 61. Table 64
Time range list Allows you to view the detailed information of all time ranges.
Adding a time range Allows you to add a time range.
58
Page 63

Deleting a time range
Time range list
The time range list is on the time range management page, as shown in Figure 61. Figure 62 describes
the fields of the list.
Table 65 Fields of the time range list
Field Description
Name Name of the time range
Description Time periods that the time range covers
Referenced Whether the time range is referenced by a security policy or not
Operation
Return to Time range management functions.
Adding a time range
From the navigation tree of the firewall management component, select Time Ranges under Security
Policy Management to enter the time range management page, as shown in
the Add Time Range page, configure the time range as described in
Allows you to click the
Click the
icon to delete the time range.
icon of a time range to delete the time range.
Figure 61. Click Add to enter
Table 66, and click Add.
Figure 62 Add a time range
Table 66 Time range configuration item
Item Description
Required
Name
Type a name for the time range.
The name can't be null and can't contain any of these characters: ? < > \" %
' & #.
Required
Specify the time periods during which a security policy that references the time
Time Range
range take effect.
A time period can be periodic or absolute:
• Periodic—Select the start time and end time for the periodic time period,
59
Page 64

Return to Time range management functions.
Services
Configuration guide
From the navigation tree of the firewall management component, select Services under Security Policy
Management. The predefined service management page appears, as shown in
describes the functions of the tabs.
Figure 63 Service management page
and then select the days of the week during which the time period applies.
By default, the periodic time period is from 0:0 to 24:0 every day.
• Absolute—Select the start time and end time for the absolute time period.
By default, the absolute time period is a 24-hour period starting from the full
hour of the current time. An absolute time range takes effect only once.
Figure 63. Table 67
Table 67 Service management functions
Function Description
Predefined services Allows you to view the detailed information of all predefined services.
User-defined services Allows you to manage user-defined services.
Service groups Allows you to manage service groups.
Predefined services
The predefined services are displayed by default when you select Services under Security Policy
Management. See
68 describes the fields of the service list.
Table 68 Fields of the predefined service list
Field Description
Name Name of the service
Figure 63. You can view predefined services but cannot delete or modify them. Table
60
Page 65

Protocol Protocol used by the service
Protocol Parameters Parameters configured for the protocol
Return to Service management functions.
User-defined services
From the navigation tree of the firewall management component, select Services under Security Policy
Management. Click the User-Defined Services tab to enter the user-defined service management page,
as shown in
Figure 64 User-defined service management page
Table 69 Fields of the user-defined service list
Figure 64. Table 69 describes the fields of the service list.
Field Description
Name Name of the user-defined service
Description Descriptive information about the user-defined service
Protocol Protocol used by the user-defined service
Protocol Parameters Parameters configured for the protocol
Referenced Whether the user-defined service is referenced or not
Operation
Click the
icon to modify the service.
To add a user-define service, click Add on the user-defined service management page to enter the Add
User-Defined Service page and configure the service as described in
Table 70.
61
Page 66

Figure 65 Add a user-defined service
Table 70 User-defined service configuration items
Item Description
Required
Type a name for the user-defined service.
Name
Description
Valid characters for the name: letters, digits, underscores (_), periods (.),
slashes (/), and hyphens (-), where underscores can’t appear at the beginning
or end of the name.
Optional
Type some descriptive information for the user-defined service.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens
(-), where underscores can’t appear at the beginning or end of the name.
Required
Configure the protocol information for the user-define service.
Select TCP, UDP, ICMP or Others.
• If you select TCP, specify the source port and the destination port, in the
range 0 to 65535.
Protocol
• If you select UDP, specify the source port and the destination port, in the
range 0 to 65535.
• If you select ICMP, specify the protocol type and the code, in the range 0 to
255.
• If you select Others, type the protocol number, in the range 0 to 255 except
1, 6, and 17.
62
Page 67

To delete user-defined services, select them and click Delete on the user-defined service management
page.
Return to
Service groups
From the navigation tree of the firewall management component, select Services under Security Policy
Management. Click the Service Groups tab to enter the service group management page, as shown in
Figure 66. Table 71 describes the fields of the service group list.
Figure 66 Service group management page
Table 71 Fields of the service group list
Field Description
Name Name of the service group
Member Services in the service group
Description Descriptive information about the service group
Service management functions.
Referenced Whether the service group is referenced or not
Operation
Click the
icon to modify the service group.
To add a service group, click Add on the service group management page to enter the Add Service
Group page and configure the service group as described in
Table 72.
63
Page 68

Figure 67 Add a service group
Table 72 Service group configuration items
Item Description
Required
Name
Description
Type a name for the service group.
Valid characters for the name: letters, digits, underscores (_), periods (.), slashes (/),
and hyphens (-), where underscores can’t appear at the beginning or end of the name.
Optional
Type some descriptive information for the service group.
Valid characters for the description: letters, digits, blank spaces, colons (:), underscores
(_), commas (,), periods (.), exclamatory marks (!), and hyphens (-), where underscores
can’t appear at the beginning or end of the name.
Required
Add services to the service group.
• Available services are listed in the left box, including all predefined services and
Service
user-defined services. The right box lists the services to be added to the service group.
• You can select one or more services in the left box and then click Add>> to add them
to the right box. You can also select one or more services in the right box and click
<<Remove to remove them from the right box to the left box.
To delete service groups, select them and click Delete on the service group management page.
Return to
Service management functions.
64
Page 69

IP addresses
Configuration guide
From the navigation tree of the firewall management component, select IP Addresses under Security
Policy Management to enter the IP address management page, as shown in
describes the functions of the tabs.
Figure 68 IP address management page
Figure 68. Table 73
Table 73 IP address management functions
Function Description
Host addresses Allows you to manage all host addresses in the system.
Address ranges Allows you to manage all address ranges in the system.
Subnet addresses Allows you to manage all subnet addresses in the system.
IP address groups Allows you to manage all IP address groups in the system.
Host addresses
From the navigation tree of the firewall management component, select IP Addresses under Security
Policy Management. The host address list is on the lower part, as shown in
the fields of the list.
Table 74 Fields of the host address list
Field Description
Name Name of the host address
IP Addresses All IP addresses for the host address
Figure 68. Table 74 describes
Description Descriptive information about the host address
Referenced Whether the host address is referenced or not
Operation
Click the
icon to modify the IP addresses for the host address.
To add a host address, click Add on the host address management page to enter the Add Host Address
page and configure the host address as shown in
Table 75.
65
Page 70

Figure 69 Add a host address
Table 75 Host address configuration items
Item Description
Required
Type a name for the host address.
Valid characters for the name: letters, digits, underscores (_), periods (.),
Name
Description
IP Address
slashes (/), and hyphens (-), where underscores can’t appear at the beginning
or end of the name.
IMPORTANT:
The name must be unique in the system. It cannot be the same as the name of an
existing host address, address range, subnet address, or IP address group.
Optional
Type some descriptive information for the host address.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens
(-), where underscores can’t appear at the beginning or end of the name.
Required
Specify IP addresses for the host address.
• Input an IP address and click Add next to the text box to add the IP address
to the IP addresses list. You can also select an IP address on the list and click
Delete to remove the IP address from the list.
• The IP addresses must be in dotted decimal notation.
To delete host addresses, select them and click Delete on the host address management page.
Return to
IP address management functions.
66
Page 71

Address ranges
From the navigation tree of the firewall management component, select IP Addresses under Security
Policy Management. Click the Address Ranges tab to enter the address range management page, as
shown in
Figure 70 Address range management page
Table 76 Fields of the address range list
Field Description
Name Name of the address range
Address Range Specific address range
Figure 70. Table 76 describes the fields of the address range list.
Excluded Addresses Excluded addresses in the address range
Description Descriptive information about the address range
Referenced Whether the address range is referenced or not
Operation
Click the
icon to modify the address range.
To add an address range, click Add on the address range management page to enter the Add Address
Range page and configure the range as shown in
Figure 71 and Table 77.
Figure 71 Add an address range
67
Page 72

Table 77 Address range configuration items
Item Description
Required
Type a name for the address range.
Valid characters for the name: letters, digits, underscores (_), periods (.),
Name
Description
Address Range
slashes (/), and hyphens (-), where underscores can’t appear at the beginning
or end of the name.
IMPORTANT:
The name must be unique in the system. It cannot be the same as the name of an
existing host address, address range, subnet address, or IP address group.
Optional
Type some descriptive information for the address range.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens
(-), where underscores can’t appear at the beginning or end of the name.
Required
Set the start IP address and end IP address of the address range.
The IP addresses must be in dotted decimal notation.
Excluded Addresses
To delete address ranges, select them and click Delete on the address range management page.
Return to
Subnet addresses
From the navigation tree of the firewall management component, select IP Addresses under Security
Policy Management. Click the Subnet Addresses tab to enter the subnet address management page, as
shown in
Figure 72 Subnet address management page
Required
Specify the IP addresses to be excluded from the address range.
• Input an IP address and click Add next to the text box to add the IP address
to the excluded IP addresses list. You can also select an IP address on the list
and click Delete to remove the IP address from the list.
• The IP addresses must be in dotted decimal notation.
IP address management functions.
Figure 72. Table 78 describes the fields of the subnet address list.
Table 78 Fields of the subnet address list
Field Description
Name Name of the subnet address
68
Page 73

Subnet Subnet address and mask
Excluded Addresses Addresses excluded from the subnet
Description Descriptive information about the subnet address
Referenced Whether the subnet address is referenced or not
Operation
Click the
icon to modify the subnet address.
To add a subnet address, click Add on the subnet address management page to enter the Add Subnet
Address page and configure the subnet address as shown in
Figure 73 and Table 79.
Figure 73 Add an subnet address
Table 79 Subnet address configuration items
Item Description
Required
Type a name for the subnet address.
Valid characters for the name: letters, digits, underscores (_), periods (.),
Name
Description
IP Address Required
slashes (/), and hyphens (-), where underscores can’t appear at the beginning
or end of the name.
IMPORTANT:
The name must be unique in the system. It cannot be the same as the name of an
existing host address, address range, subnet address, or IP address group.
Optional
Type some descriptive information for the subnet address.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens
(-), where underscores can’t appear at the beginning or end of the name.
69
Page 74

Specify a subnet address.
The IP address must be in dotted decimal notation.
Wildcard
Excluded Addresses
To delete subnet addresses, select them and click Delete on the subnet address management page.
Return to
IP address groups
From the navigation tree of the firewall management component, select IP Addresses under Security
Policy Management. Click the IP Address Groups tab to enter the IP address group management page,
as shown in
Figure 74 IP address group management page
Required
Select a wildcard mask for the subnet address.
Required
Specify the IP addresses to be excluded from the subnet.
• Input an IP address and click Add next to the text box to add the IP address
to the excluded IP addresses list. You can also select an IP address on the list
and click Delete to remove the IP address from the list.
• The IP addresses must be in dotted decimal notation.
IP address management functions.
Figure 74. Table 80 describes the fields of the IP address group list.
Table 80 Fields of the IP address group list
Field Description
Name Name of the IP address group
Member Names of the members in the IP address group
Description Descriptive information about the IP address group
Referenced Whether the IP address group is referenced or not
Operation
Click the
icon to modify the IP address group.
To add an IP address group, click Add on the IP address group management page to enter the Add IP
Address Group page and configure the IP address group as shown in
Figure 75 and Table 81.
70
Page 75

Figure 75 Add an IP address group
Table 81 IP address group configuration items
Item Description
Required
Type a name for the IP address group.
Valid characters for the name: letters, digits, underscores (_), periods (.), slashes (/),
Name
Description
and hyphens (-), where underscores can’t appear at the beginning or end of the name.
IMPORTANT:
The name must be unique in the system. It cannot be the same as the name of an existing
host address, address range, subnet address, or IP address group.
Optional
Type some descriptive information for the IP address group.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens (-), where
underscores can’t appear at the beginning or end of the name.
Required
Add members to the IP address group.
• Available members are listed in the left box, including all added IP addresses. The
Member
right box lists the members to be added to the IP address group.
• You can select one or more members in the left box and then click Add>> to add
them to the right box. You can also select one or more members in the right box and
click <<Remove to remove them from the right box to the left box.
To delete IP address groups, select them and click Delete on the IP address group management page.
Return to
IP address management functions.
71
Page 76

Interzone rules
Configuration guide
From the navigation tree of the firewall management component, select Interzone Rules under Security
Policy Management to enter the interzone rule management page, as shown in
describes the functions available on the page.
Figure 76 Interzone rule management page
Figure 76. Table 82
Table 82 Interzone rule management functions
Function Description
Interzone rule list Allows you to view all interzone rules in the system.
Adding an interzone rule Allows you to add an interzone rule.
Deleting interzone rules
Interzone rule list
From the navigation tree of the firewall management component, select Interzone Rules under Security
Policy Management. The interzone rule list is at the lower part. See
interzone rules in the system.
the fields of the interzone rule list.
Table 83 Interzone rule query options
Option Description
Allows you to delete interzone rules.
Follow these steps:
3. Select the check boxes before the interzone rules to be deleted.
4. Click Delete.
IMPORTANT:
Interzone rules that are referenced cannot be deleted.
Figure 76. This list includes all
Table 83 describes the interzone rule query options and Table 84 describes
Src Zone Query interzone rules by source zone.
Dest Zone Query interzone rules by destination zone.
Action Query interzone rules by filtering action.
Src IP Query interzone rules by source IP.
72
Page 77

Dest IP Query interzone rules by destination IP.
Time Range Query interzone rules by time range.
Policy Query interzone rules by policy.
Status Query interzone rules by status (enabled, disabled, or both)
Referenced Query interzone rules by reference status (referenced, not referenced, or both)
Table 84 Fields of the interzone rule list
Filed Description
Src Zone Source zone of the interzone rule
Dest Zone Destination zone of the interzone rule
ID of the interzone rule
When you create an interzone rule, the system automatically assigns an ID to the
ID
Src IP Source IP address of the interzone rule
rule according to the number of existing rules for the source zone and destination
zone pair, starting from 0. For example, the first rule created for the source zone
Trust and the destination zone DMZ is numbered 0, the second rule created for the
same source zone and destination zone pair is numbered 1.
Dest IP Destination IP address of the interzone rule
Service All services of the interzone rule
Time Range Time range during which the interzone rule takes effect
Action Filtering action of the interzone rule
Description Descriptive information about the interzone rule
Status Whether the interzone rule is enabled or disabled
Logging Whether logging is enabled for the interzone rule
Referenced Whether the interzone rule is referenced or not
Policy
Operation
Return to Interzone rule management functions.
Adding an interzone rule
From the navigation tree of the firewall management component, select Interzone rules under Security
Policy Management. Click Add to enter the Adding an interzone rule page and configure the rule as
shown in
Figure 77 and Table 85.
Policies that the interzone rule is in.
You can click a policy name to enter the page for managing the policy's rules. See
“
Rule management.”
• Click the icon to modify the interzone rule.
• Click the icon to copy the interzone rule.
73
Page 78

Figure 77 Add an interzone rule
Table 85 Interzone rule configuration items
Item Description
Src Zone
Dest Zone
Description
Required
Select a source zone for the interzone rule.
Required
Select a destination zone for the interzone rule.
Optional
Type some descriptive information for the interzone rule.
Valid characters for the description: letters, digits, blank spaces, colons (:),
underscores (_), commas (,), periods (.), exclamatory marks (!), and hyphens (-),
where underscores can’t appear at the beginning or end of the name.
74
Page 79

Required
Add source IP addresses for the interzone rule.
• Available IP addresses are listed in the left box. The right box lists the source
IP addresses to be added to the interzone rule.
Src IP
• You c an sel ect one or more item s in the l eft box and then click Add>> to add
them to the right box. You can also select one or more items in the right box
and click <<Remove to remove them from the right box to the left box.
• If you do not add any IP address to the right box, the interzone applies to
any source IP address.
Required
Add destination IP addresses for the interzone rule.
• Available IP addresses are listed in the left box. The right box lists the
destination IP addresses to be added to the interzone rule.
Dest IP
• You c an sel ect one or more item s in the l eft box and then click Add>> to add
them to the right box. You can also select one or more items in the right box
and click <<Remove to remove them from the right box to the left box.
• If you do not add any IP address to the right box, the interzone applies to
any destination IP address.
Required
Add services for the interzone rule.
• Available services are listed in the left box. The right box lists the services to
be added to the interzone rule.
Service
• You c an sel ect one or more item s in the l eft box and then click Add>> to add
them to the right box. You can also select one or more items in the right box
and click <<Remove to remove them from the right box to the left box.
• If you do not add any service to the right box, the interzone applies to any
service.
Policy
Action
Time Range
Enable logging
Required
Add policies to which you want to add the interzone rule. You can add a rule
to multiple policies when you create the rule, or add it to a policy on the
policy’s rule management page.
• Available policies are listed in the left box. The right box lists the policies to
be added for the interzone rule.
• You c an sel ect one or more item s in the l eft box and then click Add>> to add
them to the right box. You can select one or more items in the right box and
click <<Remove to remove them from the right box to the left box.
Required
Select a filtering action for the interzone rule. It can be Permit or Deny.
Optional
Specify the effective time for the interzone rule.
You can select a time range for the rule. If you do not select a time range, the rule
takes effect at any time.
Optional
Select this option to enable the syslog function for the interzone rule.
By default, this option is not selected.
75
Page 80

Enable this rule
Continue to add another rule
Return to Interzone rule management functions.
Interzone policies
Configuration guide
From the navigation tree of the firewall management component, select Interzone Policies under Security
Policy Management to enter the interzone policy management page, as shown in
describes the functions available on the page.
Figure 78 Interzone policy management page
Optional
Select this option to enable the interzone rule.
By default, this option is not selected.
Optional
Select this option to add another rule after finishing this rule.
By default, this option is not selected.
Figure 78. Table 86
Table 86 Interzone policy management functions
Function Description
Interzone policy list Allows you to view all interzone policies in the system.
Adding an interzone policy Allows you to add an interzone policy.
Deleting interzone policies
Interzone policy list
From the navigation tree of the firewall management component, select Interzone Policies under Security
Policy Management. The interzone policy list is at the lower part of the page, as shown in
Table 87 describes the fields of the list.
Allows you to delete interzone policies.
Follow these steps:
1. Select the check boxes before the interzone policies to be deleted.
2. Click Delete.
IMPORTANT:
• Interzone policies that have been applied cannot be deleted.
• Interzone polices named default and corporate are system predefined
policies and cannot be deleted.
Figure 78.
76
Page 81

Table 87 Fields of the interzone policy list
Filed Description
Policy Name Name of the interzone policy
Description Descriptive information about the interzone policy
Device Name of the device to which the interzone policy is deployed
Referenced Whether the interzone policy is referenced or not
Rules
Return to Interzone policy management functions.
Adding an interzone policy
From the navigation tree of the firewall management component, select Interzone policies under Security
Policy Management. Click Add to enter the Adding Interzone Policy page and configure the policy as
shown in
Figure 79 Add an interzone policy
Table 88 Interzone policy configuration items
Figure 79 and Table 88.
Click the icon to enter the page for managing the policy’s rules (see “Rule
management”).
Item Description
Name
Description
Return to Interzone policy management functions.
Rule management
From the navigation tree of the firewall management component, select Interzone policies under Security
Policy Management. Click the
shows the rule management page of the policy default.
Required
Type a name for the interzone policy.
The name cannot contain any of these characters: ^'<>&:;"/\
Optional
Type some descriptive information for the interzone policy.
icon of a policy to enter the policy’s rule management page. Figure 80
Table 89 describes the fields of the rule list.
77
Page 82

Figure 80 Rule management page
Table 89 Fields of the policy’s rule list
Filed Description
ID of the interzone rule
When you create an interzone rule, the system automatically assigns an ID to the
ID
Src Zone Source zone of the interzone rule
rule according to the number of existing rules for the source zone and destination
zone pair, starting from 0. For example, the first rule created for the source zone
Trust and the destination zone DMZ is numbered 0, the second rule created for the
same source zone and destination zone pair is numbered 1.
Dest Zone Destination zone of the interzone rule
Src IP Source IP address of the interzone rule
Dest IP Destination IP address of the interzone rule
Service All services of the interzone rule
Time Range Time range during which the interzone rule takes effect
Description Descriptive information about the interzone rule
Action Filtering action of the interzone rule
Status Whether the interzone rule is enabled or disabled
Logging Whether logging is enabled for the interzone rule
Sort
Details/Modify
Click the
the same source zone and destination zone. See “
Click the
icon to change the position of the interzone rule among the rules for
Sorting interzone rules.”
icon to enter the interzone rule list and modify the interzone rule.
To add more interzone rules to the policy, click Add on the policy’s rule management page. A page as
shown in
Figure 81 appears, showing all rules that have been created for the same source zone and
destination zone pair but are not in the policy. Select the rules you want to add to the policy and click
Add.
78
Page 83

Figure 81 Add interzone rules to the policy
Return to Interzone policy management functions.
Sorting interzone rules
On an interzone policy’s rule management page, you can click the icon of a rule to change the
position of the rule among the policy’s rules for the same source zone and destination zone. For example,
on the page shown in
82, select after, select rule 1 from the drop-down list, and click Apply to move rule 0.
result.
Figure 80, you can click the ic on of rule 0 to bring up the page shown in Figure
Figure 83 shows the
Figure 82 Move rules 0
Figure 83 Policy’s rule list after sorting the order
Return to Fields of the policy’s rule list.
79
Page 84

Interzone policy applications
Configuration guide
From the navigation tree of the firewall management component, select Apply Interzone Policy under
Security Policy Management to enter the interzone policy application management page, as shown in
Figure 84. Table 90 shows the functions available on the page.
Figure 84 Interzone policy application management
Table 90 Interzone policy application management functions
Function Description
Interzone policy application list Allows you to view all interzone policy applications in the system.
Applying interzone policies Allows you to apply an interzone policy to devices.
Applied rules list
Redeploying a policy Allows you to redeploy an interzone policy to devices.
Interzone policy application list
From the navigation tree of the firewall management component, select Apply Interzone Policy under
Security Policy Management. The interzone policy application list is at the lower part of the page. See
Figure 84. Table 91 describes the policy application query options and Table 92 describes the fields of
the policy application list.
Table 91 Interzone policy application query options
Option Description
Device Query interzone policy applications by device.
Policy Query interzone policy applications by policy.
Table 92 Fields of the interzone policy application list
Allows you to manage the interzone rules deployed on the specified
device.
Field Description
Device Label Name and IP address of the device to which the interzone policy is applied
Device Group Device group that the device is in
Name of the policy applied to the device
Policy Name
You can click the policy name link to manage the policy’s rules (see “
management”).
80
Rule
Page 85

g
Application Result Application result of the interzone policy
Displays the security zones that are covered by some of the policy’s rules but not
Remarks
configured on the device. Rules that cover these security zones will not be deployed to
the device.
Operation
Return to Interzone policy application management functions.
Applying interzone policies
From the navigation tree of the firewall management component, select Apply Interzone Policy under
Security Policy Management. Select a device and click Apply. The interzone policy application page
appears, as shown in
the policies to the right box, and click Apply.
Figure 85 Apply policies to the device
• Click the icon to apply policies to t he device (see ”Applying interzone policies”)
• Click the icon to view the rules applied to the device (see “Applied rules list”).
Figure 85. Select the policies to be applied from the left box, click Add>> to add
CAUTION:
The left box lists the available policies. The right box lists the policies to be applied to the device. Leavin
the right box blank means to delete all interzone policies on the device.
Applied rules list
From the navigation tree of the firewall management component, select Apply Interzone Policy under
Security Policy Management. Click the
86 shows the rules applied to device 192.168.0.30.
describes the fields of the rule list.
icon of a device to view the rules applied to the device. Figure
Table 93 describes the query options and Table 94
81
Page 86

Figure 86 List of rules applied to a device
Table 93 Applied rule list query options
Option Description
Src Zone Query interzone rules by source zone.
Dest Zone Query interzone rules by destination zone.
Action Query interzone rules by filtering action.
Src IP Query interzone rules by source IP.
Dest IP Query interzone rules by destination IP.
Time Range Query interzone rules by time range.
Policy Query interzone rules by policy.
Status Query interzone rules by status (enabled or disabled)
Table 94 Fields of the interzone rule list
Filed Description
Src Zone Source zone of the interzone rule
Dest Zone Destination zone of the interzone rule
ID of the interzone rule
When you create an interzone rule, the system automatically assigns an ID to the rule
ID
Src IP Source IP address of the interzone rule
Dest IP Destination IP address of the interzone rule
Service All services of the interzone rule
according to the number of existing rules for the source zone and destination zone
pair, starting from 0. For example, the first rule created for the source zone Trust and
the destination zone DMZ is numbered 0, the second rule created for the same source
zone and destination zone pair is numbered 1.
Time Range Time range during which the interzone rule takes effect
Action Filtering action of the interzone rule
Description Descriptive information about the interzone rule
Status Whether the interzone rule is enabled or disabled
Logging Whether logging is enabled for the interzone rule
82
Page 87

Policies that the interzone rule is in.
Policy
You can click a policy name to enter the page for managing the policy's rules. See
“
Rule management.”
Return to Interzone policy application management functions.
Firewall device management
Managing firewall devices
With the management right on devices, you can add or delete devices, view the detailed information of
the devices, and change the device groups and labels of the devices.
If the system cannot discover some firewall devices automatically, you need to add these firewall devices
to the firewall management component manually so that the Firewall Manager can collect and display
the attack event statistics and event auditing information of these devices.
Configuration guide
From the navigation tree of the firewall management component, select Device Management under
Device Management to enter the device management page, where the managed firewall devices are
listed, as shown in
Figure 87.
Figure 87 Firewall device management page
On the firewall device management page, you can view information about a firewall, or add or delete
a firewall.
Table 95 describes the functions in detail.
Table 95 Firewall management functions
Function Description
Firewall device list Allows you to view information about the current firewall devices.
Adding firewall devices
Deleting devices
Allows you to add the firewall devices managed in the system
management component to the firewall management component.
Allows you to delete firewall devices.
Follow these steps:
1. Select the check box before the firewall devices that you want to delete
in the firewall device list.
2. Click Delete.
83
Page 88

Firewall device list
From the navigation tree of the firewall management component, select Device Management under
Device Management. The firewall device list is at the lower part of the page. See
describes the fields of the list.
Table 96 Query options on the firewall device management page
Option Description
Device IP Query a firewall device by its IP address.
Figure 87. Table 97
Query a firewall device by its label.
Device Label
Table 97 Fields of the firewall device list
Field Description
Device Label
Device IP IP address of the device
Device Group Device group where the device resides
Operation
Return to Firewall management functions.
Adding firewall devices
This function is used to add firewall devices to the firewall management component. You can add only
firewall devices that are under your management.
IMPORTANT:
The label you input here must not include the parentheses and IP address.
For example, if the device label is wxsh (10.154.78.120), input only wxsh.
Device name and IP address. You can click the link to view the detailed
information of the device and modify the device settings. For more
information, see “
Device information.”
• Click the icon of a device to log in to open the web console of the
device.
• Click the icon of a device to telnet to the device.
From the navigation tree of the firewall management component, select Device Management under
Device Management to enter the device management page. Then, click Add to enter the page for adding
firewall devices, as shown in
Figure 88.
Figure 88 Add firewall devices
Select the check boxes before the devices that you want to add to the firewall management component,
and then click Add. The firewall device management page appears, indicating that the devices are
successfully added.
84
Page 89

Return to Firewall management functions.
Viewing device statistics
The device statistics function can collect statistics on devices by day, week, and month. You can select the
statistics period as needed and view the statistics report, which provides statistics on each firewall device,
including the total number of events, number of blocked events, destination IP address count, source IP
address count, and destination port count.
Configuration guide
From the navigation tree of the firewall management component, select Device Statistics under Device
Management to enter the device statistics page, as shown in
Figure 89 Device statistics
Figure 89.
Table 98 Device statistics query options
Option Description
Duration
Time
You can click the icon in the Analysis column of a device to enter the attack event analysis page.
This page provides the detailed attack statistics data where you can view the detailed attack statistics in
different ways. See “
Event overview” for details.
Select the statistics duration. You can select Day, Week, or Month, or
select Customize to specify a statistics duration.
Select the statistics time, whose value range varies with the statistics
duration selected.
Managing the device configuration database
The system provides a centralized configuration segment management interface, where there are a set of
pre-defined configuration segments. You can customize your own configuration segments based on these
pre-defined segments, and modify, copy, delete, export, or deploy the custom configuration segments.
You can also import configuration files from devices and modify them to quickly create new configuration
segments that satisfy your requirements.
Configuration guide
From the navigation tree of the firewall management component, select Device Configuration Database
under Policy Management to enter the device configuration segment management page, as shown in
Figure 90. On this page, you can query configuration segments by filename and file type, add, modify,
or delete configuration segments, import configuration segment from a local file, or import a
configuration file from a device.
85
Page 90

Figure 90 Device configuration segment management page
Table 99 Configuration segment management functions
Function Description
Configuration segment list Allows you to view information about all configuration segments.
Adding a configuration segment Allows you to add a configuration segment.
Importing a configuration
segment
Deleting configuration segments
Refreshing configuration
segments
Importing configuration segments
from device
Configuration segment list
The configuration segment list is on the configuration segment management page, as shown in Figure
90.
Table 100 Fields of the configuration segments list.
Allows you to import a configuration segment from a locally saved file.
On the configuration segment management page, click the Import button.
Allows you to selected configuration segments.
On the configuration segment management page, select the configuration
segments that you want to delete and click the Delete button.
Allows you to refresh the configuration segments list.
On the configuration segment management page, click the Refresh button.
Allows you to import the running configuration file from a device.
Field Description
Filename Name of the configuration segment file
File Type Type of the configuration segment file
Creation Time Creation date and time of the configuration segment
86
Page 91

Description Detailed description of the configuration segment
Operation
Return to Configuration segment management functions.
Adding a configuration segment
To add a configuration segment, click Add on the configuration segment management page to enter the
Add Configuration Segment page, as shown in
type a description, and add and edit configuration commands that comply with the configuration file
syntax requirements. Finally, click Add to create the configuration segment.
Figure 91 Add a configuration segment
• Click the icon of a configuration segment to rename the configuration
segment file.
• Click the icon of a configuration segment to modify the description and
configurations of the segment.
• Click the icon of a configuration segment to copy the segment.
• Click the icon of a configuration segment to export the segment.
• Click the icon of a configuration segment to configure a deployment task
for the segment (see “Deploying a configuration segment”).
Figure 91. Then, select the file type, specify a filename,
87
Page 92

y
Table 101 Configuration segment configuration items
Item Description
File Type
Filename
Description
Configurations
Required
Select the configuration segment type, cfg or xml.
Required
Type a filename for the configuration segment.
A filename must be unique in the system. Leading spaces and ending spaces in the
filename will be removed and the filename cannot contain any of these characters:
'"<>&%:;/\
Optional
Type some descriptive information for the configuration segment.
Required
Type the contents of the configuration segment.
Return to Configuration segment management functions.
Importing configuration segments from device
On the configuration segment management page, click Import from Device to import the running
configuration file of a device.
Select a device, select the file type, specify a filename and a description, and click Import to import the
running configuration file of the device. After the import operation completes successfully, a
configuration segment by the name you specified will appear in the configuration segments list. Later,
you can modify the content of the segment as desired.
Figure 92 Import the running configuration file of a device
CAUTION:
• Available devices are those added in the device management module of the firewall management
component.
• The imported configuration file will be saved with the specified filename in the system. You must specif
the filename and the filename must not be used by any existing file. Leading spaces and ending spaces
in the filename will be removed and the filename cannot contain any of these characters: '"<>&%:;/\
Return to Configuration segment management functions.
88
Page 93

Deploying a configuration segment
On the configuration segments list, click the icon of a configuration segment to configure a
deployment task for the segment, as shown in
1. Select devices—Click Add Device and select the devices you want to deploy the configuration
segment to, and then click Next.
Figure 93 Select the devices you want to deploy the configuration segment to
Figure 93.
2. Configure parameters—Type the SNMP version and community string and click Next.
Figure 94 Configure parameters
3. Configure deployment task attributes as shown in Figure 95 and click Next.
89
Page 94

Figure 95 Configure deployment task attributes
4. Confirm your configuration. You can click the icon in the device list to view the configuration
content to be deployed. To modify your configuration, click Previous. Check that everything is OK
and click Finish.
Figure 96 Confirm your configuration
Return to Configuration segment management functions.
90
Page 95

Managing deployment tasks
Configuration guide
From the navigation tree of the firewall management component, select Deployment Tasks under Policy
Management to enter the deployment task management page, as shown in
can select a task status to display all deployment tasks in the status, select tasks to execute them
immediately, or cancel, delete, or modify tasks.
Figure 97 Deployment task management page
Figure 97. On this page, you
Table 102 Deployment task management functions
Function Description
Deployment task list Allows you to view information about all deployment tasks.
Executing deployment tasks
immediately
Canceling deployment tasks
Deleting deployment tasks
Deployment task list
From the navigation tree of the firewall management component, select Deployment Tasks under Policy
Management. The deployment task list is at the lower part of the page. See
describes the fields of the list.
Allows you to execute selected deployment tasks.
On the configuration segment management page, select the deployment
tasks that you want to execute and click the Execute Now button.
Only a task waiting for execution can be executed immediately.
Allows you to cancel selected deployment tasks.
On the configuration segment management page, select the deployment
tasks that you want to cancel and click the Cancel button.
Only a task waiting for execution can be canceled.
Allows you to delete deployment tasks.
Follow these steps:
1. Select the check boxes before the deployment tasks to be deleted.
2. Click Delete.
Figure 97. Table 103
91
Page 96

Table 103 Fields of the deployment task list
Field Description
Execution Status Execution status of the task
Task Name Name of the task
Task Type Type of the task
Creation Time Creation date and time of the task
Creator Administrator who created the task
Start Time Time when the task started.
End Time Time when the task ended.
Modify
Details
The Modify icon
modify task attributes such as the description, deployment sequence, error
handling mode, and deployment time.
The Details icon brings you to the details page of a task.
brings you to the task modification page, where you can
92
Page 97

SSL VPN auditing
As Virtual Private Network (VPN) is much cheaper and more flexible to use than leased lines, more and
more companies are establishing VPNs over public networks such as the Internet, so as to allow
employees working at home or traveling on business, employees of branch offices, and partners to
access the internal networks. SSL VPN is an emerging VPN technology, and has been widely used for
secure remote web-based access. For example, it can allow remote users to access the corporate network
securely.
The SSL VPN auditing component supports analyzing and auditing operations of SSL VPN users. It also
provides realtime monitoring of online users and history records, helping you understand SSL VPN usage
and the network security.
To access the SSL VPN auditing component, select the SSL VPN Auditing tab. Then, you can perform:
•
Comprehensive analysis
SSL VPN log auditing
•
Comprehensive analysis
The comprehensive analysis function provides information of online users, online user trend, daily user
statistics and device monitoring for you to understand what SSL VPN users have done during their access
to the internal network. You can export and save the reports as an Excel file.
Online users
The online user statistics function displays the SSL VPN users that are currently accessing the internal
network. This list presents the username, user IP address, virtual IP address, login time, online duration,
operation that the user has performed, and resources the user has accessed. It also supports flexible
online user query.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select Online Users under Comprehensive
Analysis to enter the online user list page, as shown in
Figure 98 Online user list
Figure 98.
93
Page 98

Online users trends
The online user trend graph displays the number of online SSL VPN users during a day, week, month, or
a customized period of time.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select Online Users Trends under
Comprehensive Analysis to enter the online user trend analysis page, where the online user trend graph
is listed, as shown in
the audit time, online user count, and a link for you to view the user information.
Figure 99 Online user trend
Figure 99. Under the trend graph is a list showing the online user statistics, including
Daily user statistics
The daily user statistics function presents you the counts of login times of SSL VPN users, user operations,
and resources that users have accessed every day during a period of time.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select Daily User Statistics under
Comprehensive Analysis to enter the daily user statistics page, as shown in
graph is a list showing the detailed daily user trend statistics, including the time, user login times, number
of user operations, and number of resources that the users have accessed.
Figure 100. Under the trend
94
Page 99

Figure 100 Daily user statistics
NOTE:
The User Count field shows the count of login times on that day.
Device monitoring
In addition to the SSL VPN user statistics of the entire network, the SSL VPN auditing component also
allows you to view SSL VPN access statistics by firewall device and log in to a device as an administrator
or user.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select Device Monitoring under
Comprehensive Analysis to enter the device monitoring page, as shown in
the daily SSL VPN access information by device, including the IP address of the device, maximum daily
user login times, maximum daily operations, and maximum daily resource access operations.
In addition, you can:
• Click the
• Click the
Figure 101 Device monitoring
icon in the Admin Login column of a device to lo g in to the device as an ad ministrator.
icon in the User Login column of a device to log in to the device as a user.
Figure 101. The page presents
95
Page 100

SSL VPN log auditing
The SSL VPN log auditing function allows you to audit user access records, operation logs, resource
accesses, and authentication failures. You can also export and save the reports as an Excel file.
User access records auditing
The user access records display details about the access information of SSL VPN users, such as the
username, IP address of the SSL VPN user, virtual IP address, login time, logout time, online duration, IP
address of the firewall device, number of user operations, and number of accessed resources. It also
supports flexible user access records query.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select User Access Records under Log
Auditing to enter the user access records page, as shown in
Figure 102 User access record auditing
Figure 102.
Operation log auditing
The operation log auditing allows you to audit operations of SSL VPN system operators based on the
information of username, executed operation and related parameters, operation time, and IP address of
the firewall device. It also supports flexible operation log query.
Configuration guide
From the navigation tree of the SSL VPN auditing component, select Operation Log Auditing under Log
Auditing to enter the operation log auditing page, as shown in
Figure 103.
96
 Loading...
Loading...