Page 1

HP CloudSystem Enterprise and Foundation Software
Configuring
in
Directory Tree
sample
Below is an Active Directory tree sample
that contains
units
unit
“Sales Group” groups as well as
“smith” and “johnson” user accounts. Let’s
consider
belongs to the “Admins Group”
“johnson” is
Directory Services
HP CloudSystem
CloudSystem identity management includes support for
Microsoft Active Directory and OpenLDAP. This white
paper details step-by-step how to set up directory
services in CloudSystem Foundation and Enterprise.
Directory Tree Samples
Two directory tree samples are employed in this white paper. The Directory Tree 1
represents a Microsoft Active Directory tree while the Directory Tree 2 exemplifies an
OpenLDAP tree. Both are detailed in the right side column.
CloudSystem Foundation
Use the CloudSystem Console to manage directory services in CloudSystem Foundation.
Infrastructure administrators can configure directories and associate directory groups to
administrative roles. Create a directory entry using the CloudSystem Console > Settings >
Security > Edit > Directories > Add directory screen.
The CloudSystem Portal and its underlying OpenStack Keystone service are
automatically configured based on the default directory set in the CloudSystem
Console. Cloud administrators can then manage directory users within the directory
service itself, without any other configuration in CloudSystem.
The following sections depict how to set up Microsoft Active Directory and OpenLDAP.
in CloudSystem.
Microsoft Active Directory
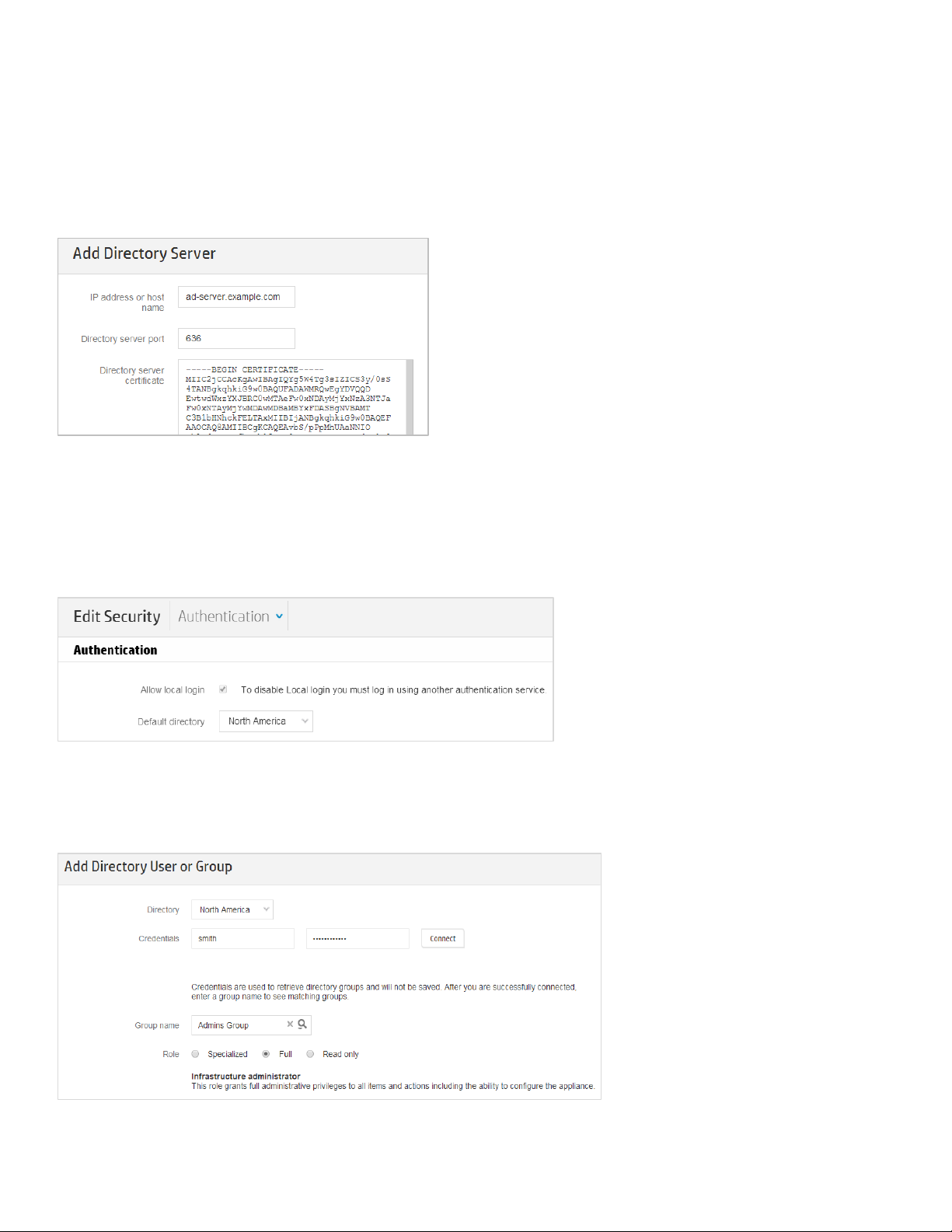
Step 1. Add the directory. Name the directory entry and select the “Active Directory” type.
Enter the search context which consists of user identifier, user search base and base DN
(suffix) as shown below.
Important: Be sure to enter the search context correctly and identically in Foundation
(CloudSystem Console) and Enterprise (Cloud Service Management Console).
1 – Active Directory
hierarchical organizational
. The “North America” organizational
contains the “Admins Group” and
the
that the “smith” user account
while
a member of “Sales Group”.
Figure 1 – Creating the “North America” directory
5900-3794, September 2014
Page 2
Directory Services on CloudSystem
The search context is interpreted as follows:
• User Name/ID: CN
• User search base: OU=North America, OU=Users
• Base DN: DC=example, DC=com
Step 2. Configure the server. Enter an IP address or host name, directory server port and directory
server certificate:
Figure 2 - Configuring a server for the “North America” directory
Step 3. Check and save the settings. On the “Add directory” dialog, enter valid user credentials in the
username and password textboxes. Make sure the user account is located under the
user search base.
Then check the connectivity and save the configuration.
Step 4. Set the default directory. On the “Edit Security” dialog, choose a directory as the default
directory. For example:
Figure 3 – Setting the “North America” as the default directory
Step 5. Add a directory group. Go to CloudSystem Console > User and Groups > Add Directory User or
Group. Connect to a pre-defined directory using a user account. Then select a group from the list and
assign a role to it. For example:
Figure 4 - Assigning the "Admins Group" to the Full Infrastructure administrator role
5900-3794, September 2014
2
Page 3
Directory Services on CloudSystem
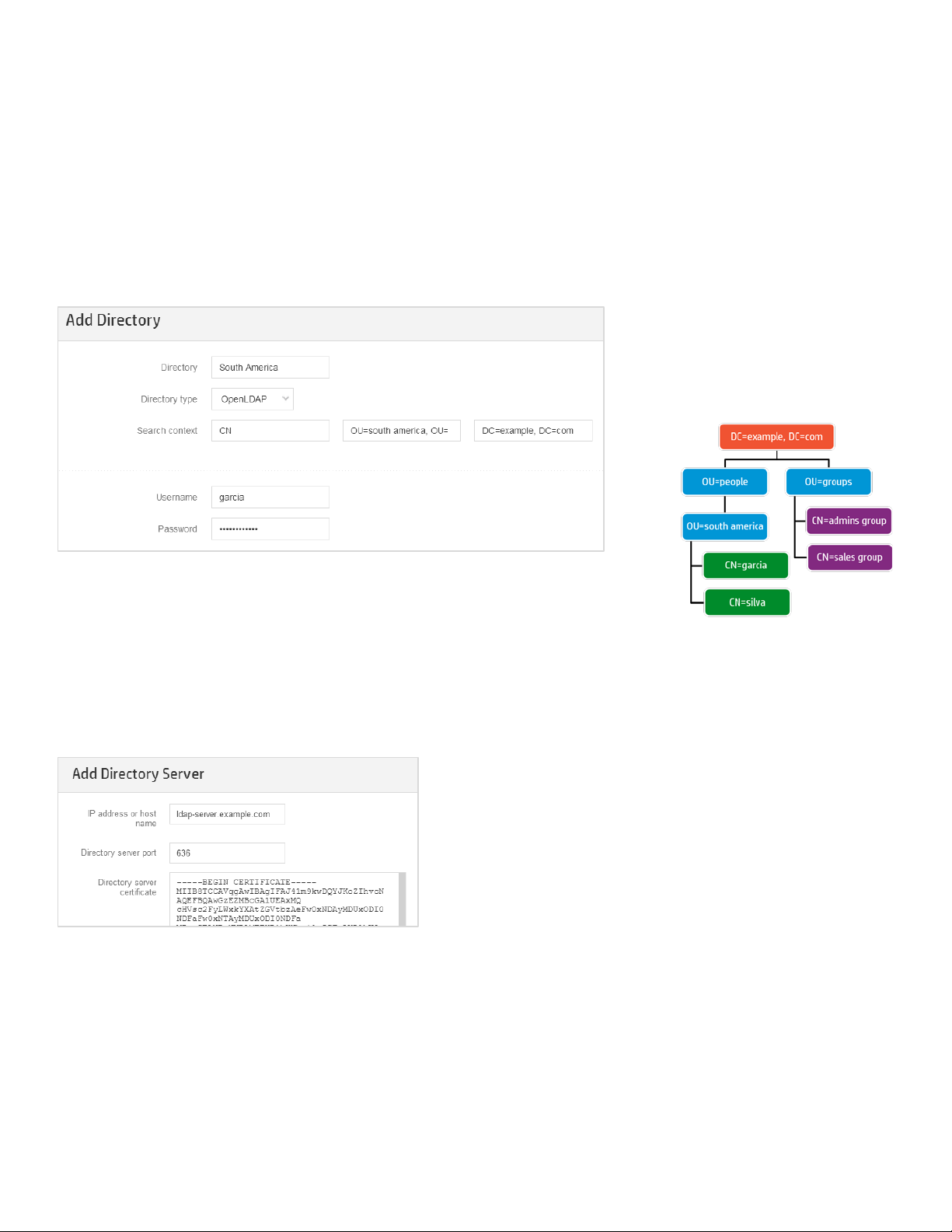
Directory Tree
Below is an OpenLDAP tree sample that
contains
“
contains
accounts. On the other side, the “groups”
organization
and “
“garcia” user account
“admins g
of “s
Active Directory constraints. Below are listed the main constraints in CloudSystem
Foundation for Microsoft Active Directory:
• Directory tree: groups must be located under the user search base
• Directory schema
– Users: supports the “user” objectClass only
– Groups: supports the “group” and “groupOfNames” objectClasses only
OpenLDAP
Step 1. Add the directory. Give a name to the directory entry and select the “OpenLDAP”
type. Then enter the search context which consists of user identifier, user search base
and base DN (suffix) as shown below:
Figure 5 - Creating the “South America” directory
The search context is interpreted as following:
• User Name/ID: CN
• User search base: OU=south america, OU=people
• Base DN: DC=example, DC=com
2 – OpenLDAP sample
tree organizational units. The
south america” organizational unit
“garcia” and “silva” user
al unit holds “admins group”
sales group”. Let’s consider the
belongs to the
roup” while “silva” is a member
ales group”.
Step 2. Configure the server. Enter an IP address or host name, directory server port and
directory server certificate as follows:
Figure 6 - Configuring a server for the “South America” directory
Step 3. Check and save the settings. On the “Add directory” dialog, enter valid user credentials in the
username and password textboxes. Make sure the user account is located under the
user search
base. Then check the connectivity and save the configuration.
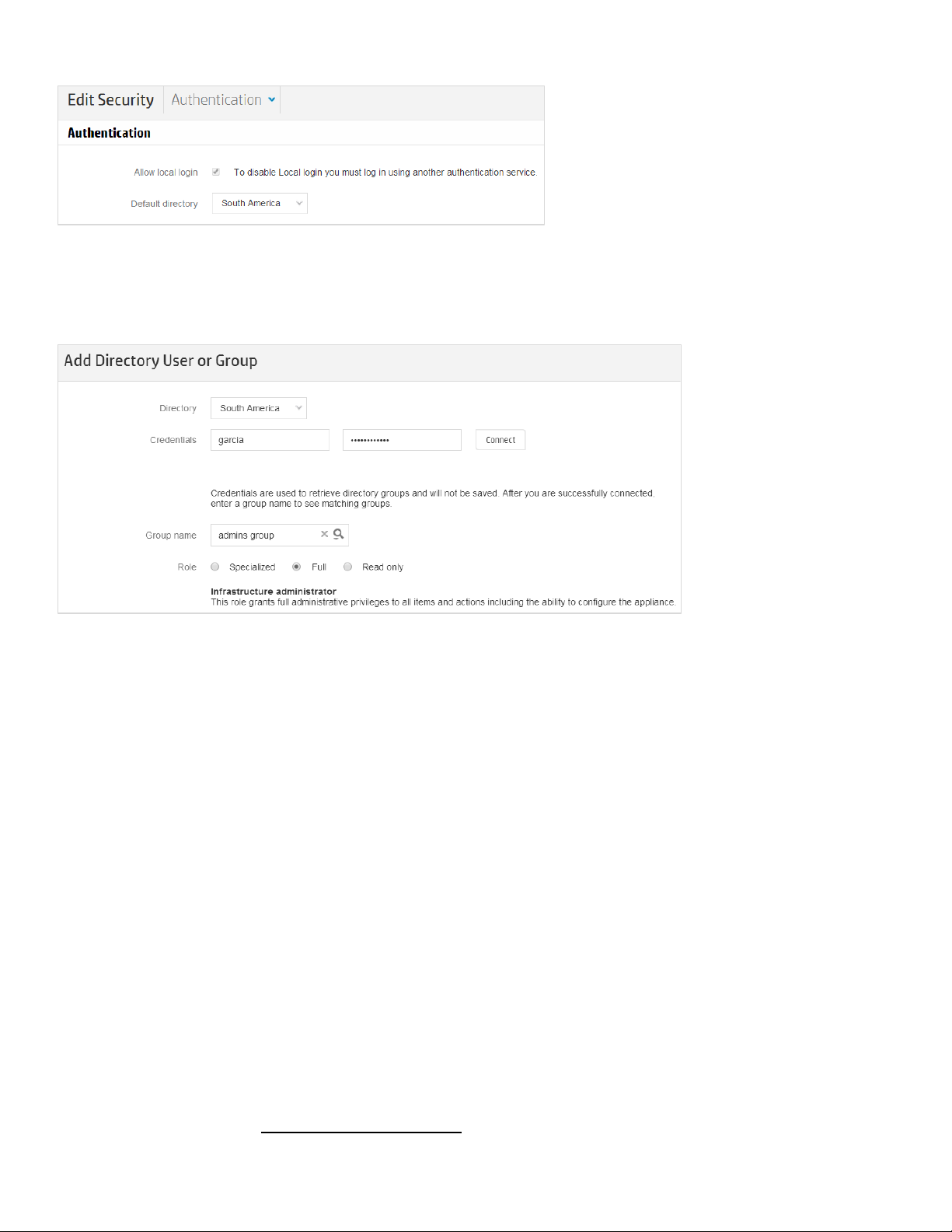
Step 4. Set the default directory. On the “Edit Security” dialog, choose a directory as the default:
5900-3794, September 2014
3
Page 4
Directory Services on CloudSystem
Figure 7 - Setting the “South America” as the default directory
Step 5. Create a directory group. Go to CloudSystem Console > User and Groups > Add Directory User or
Group. Connect to a pre-defined directory using a user account. Then select a group from the list and
assign a role to it. For instance:
Figure 8 - Assigning the "admins group" to the Full Infrastructure administrator role
OpenLDAP constraints. Below are listed the main constraints in CloudSystem Foundation for OpenLDAP:
• Directory tree: groups must be located under the OU=groups from the Base DN
• Directory schema
– Users: supports the “inetOrgPerson” objectClass only
– Groups: supports the “groupOfNames” objectClass only
Summary about User Authorization
In a nutshell, the Foundation user permissions are:
• User accounts from a directory group can log into the CloudSystem Console. Currently only Full
Infrastructure administrator and Read only roles are supported.
• User accounts from the default directory that are assigned to an OpenStack project can log into the
CloudSystem Portal. By default, Full Infrastructure administrators are assigned to the
“administrator” project.
General Constrains
CloudSystem Portal. It is automatically configured based on the default directory and the first server
from the server list. In other words, the CloudSystem Portal does not support multiple directories nor
load balancing servers.
FQDN. Although CloudSystem Console accepts an IP address for the directory server, HP strongly
recommends the usage of FQDN.
Strong certificate validation. By default CloudSystem Foundation does not validate the directory server certificate
in a strict manner. To enable the strong SSL/TLS validation for the CloudSystem Portal, you must export the CA
certificate from the directory server and import it to the Foundation appliance through the appliance console. For
more information, see the “Enabling strong certificate validation in the CloudSystem Portal” appendix in the HP
CloudSystem Administrator Guide at
www.hp.com/go/cloudsystem/docs.
5900-3794, September 2014
4
Page 5

Directory Services on CloudSystem
Directory Tree 1
sample
CloudSystem Enterprise
CloudSystem Enterprise supports the multi-tenancy features in Cloud Service
Automation (CSA). With CSA you can bind Organizations to directory services and then
assign user groups from that directory to be a part of the Organization.
The next sections describe how to configure Microsoft Active Directory and OpenLDAP
in HP CSA. Both assume the “Sales” consumer organization was created previously.
Microsoft Active Directory
Step 1. Configure base AD settings. In the Cloud Service Automation Console, open a
consumer organization and click on the “LDAP” panel. Enter the hostname, port and
optionally check the SSL option for a secure connection. Then set the Base DN, User ID
and password. For instance:
– Active Directory
Figure 9 - Configuring LDAP server information for the “Sales” Organization on AD
Step 2. Configure the user login. Enter the user name attribute, user search base and
optionally check the “Search Subtree” for a recursive lookup. For example:
Figure 10 - Configuring user login for the "Sales" Organization on AD
Notice the search context is identical to CloudSystem Foundation:
• User Name: CN
• User search base: OU=North America, OU=Users
• Base DN: DC=example, DC=com
5900-3794, September 2014
5
Page 6

Directory Services on CloudSystem
Directory Tree 2
Step 3. Save and check the settings. Save the settings and then click on the “Look Up
User” button to search for a regular user.
Step 4. Configure the access control. Click on the “Access Control” panel. Enter name
and DN for a group or organizational unit. For example:
Figure 11 - Assigning the "Sales Group" to the Service Consumer role
OpenLDAP
Step 1. Configure base LDAP settings. In the Cloud Service Automation Console, open a
consumer organization and click on the “LDAP” panel. Enter the hostname, port and
optionally check the SSL option for a secure connection. Then set the Base DN, User ID
and password. For instance:
– OpenLDAP sample
Figure 12 - Configuring LDAP server information for the “Sales” Organization on OpenLDAP
Step 2. Configure the user login. Enter the user name attribute, user search base and
optionally check the “Search Subtree” for a recursive lookup. For example:
5900-3794, September 2014
6
Page 7

Directory Services on CloudSystem
Figure 13 - Configuring user login for the "Sales" Organization on OpenLDAP
Make sure that the search context is identical to CloudSystem Foundation:
• User Name: CN
• User search base: OU=south america, OU=people
• Base DN: DC=example, DC=com
Step 3. Save and check the settings. Save the settings and then click on the “Look Up User” button to search for
a regular user.
Step 4. Configure the access control. Click on the “Access Control” panel. Enter name and DN for the group or
organizational unit. For instance:
Figure 14 - Assigning the "Sales Group" to the Service Consumer role
Summary about User Authorization
Essentially, user accounts from groups or organizational units which are set in the
Organization’s access control can access the respective Marketplace Portal.
General Constraints
Secure connection. The LDAP certificate must be imported to the HP CSA keystore. For more information, see the
“Supported operations on the CloudSystem appliances” appendix in the HP CloudSystem Administrator Guide at
www.hp.com/go/cloudsystem/docs.
Access control. Group or organizational unit must be relative to Base DN.
Learn more about HP CloudSystem
http://www.hp.com/go/CloudSystem and
http://www.hp.com/go/CloudSystem/docs
© Copyright 2014 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. The only
warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein
should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
5900-3794, September 2014
7
 Loading...
Loading...